-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 07f367da:0e76880d
2025-01-06 15:48:08
@ 07f367da:0e76880d
2025-01-06 15:48:08- https://www.newspoole.kr/news/articleView.html?idxno=10814
- 탈시설 장애인의 금전관리와 활동지원
- 2024.08.22 11:30
활동지원사가 도둑으로 몰리는 몇 사례
2024년 3월 활동지원사 김씨는 노조에 상담을 요청했다. 김씨는 N지원주택에서 장애인이용자 이씨에게 서비스를 제공 중인데, 자립생활 지원주택 팀장이 일방적으로 서비스 중단을 요구했고, 장애인이용자에게는 이와 관련된 이야기를 언급조차 하지 말라고 신신당부했다. 팀장은 활동지원사가 속한 활동지원 기관에도 서비스 중단을 통보했다. 활동지원사는 이 상황을 납득할 수 없어 직접 장애인이용자에게 물었다. 그런데 정작 장애인이용자는 계속 서비스를 해주길 바란다고 했다. 노동조합은 N지원주택 팀장에게 면담을 요청했다.
N지원주택 팀장은 이씨가 김씨로부터 활동지원을 받는 날이면 주문음식을 너무 많이 시켜먹는다는 점을 문제 삼았다. 주택 팀장은 장애인이용자가 배달음식을 자주 시켜먹는 일이 활동지원사의 잘못이라고 보았다. 활동지원사는 순전히 이용자가 원해서 배달음식을 시켜 준 것이라고 항변했다. 심지어 이용자가 자기 손으로 스마트폰을 작동해 주문음식을 시켜먹었다는 것이다. 간혹 함께 음식을 먹는 경우가 있어 서로 돌아가면서 주문하기도 하고, 일부 금액은 활동지원사가 부담했다고 한다. 면담을 통해 알게 된 사실은 해당 이용자가 발달장애나 지적장애가 있는 것도 아니고, 시설에서 나온 지 얼마 되지 않았지만, 판단능력에 특별히 문제가 있는 것도 아니었다. 김씨의 잘못이 아니라는 점이 밝혀졌지만, 팀장이 이미 장애인 이씨에게 김씨를 그만두게 하자고 한 상태였고 김씨는 다시 일터로 돌아갈 수 없었다.
2019년 활동지원사 박씨는 도둑으로 몰려 일을 그만두게 된 사례였다. 장애인이용자 최씨는 탈시설을 한 지 얼마 되지 않았다. 자립생활지원금 천만원 가량 최씨의 통장으로 입금되었다. 최씨는 글을 몰랐다. 하지만 판단 능력에 문제가 없었고 최씨는 스스로 통장에 있던 돈을 소비했다. 그런데 최씨의 지출은 다소 과했고 이에 주택 측은 박씨에게 최씨가 왜 그렇게 돈을 많이 썼냐고 물었다. 돈은 최씨가 썼으니, 돈에 대한 기록을 박씨가 가지고 있을 리도 없었다. 24시간을 함께 있는 것도 아니었다. 주택 측의 계속된 추궁에 활동지원사 박씨는 일을 계속했다가 누명을 쓸 것 같아 그만뒀다. 최씨는 이후 다른 활동지원사에게 서비스를 받고 있다. 최씨는 박씨에게 수년이 지난 현재까지도 수시로 연락한다. 박씨는 최씨에게 필요한 노동을 간혹 제공한다.
2017년 김씨를 처음 본 것은 다른 체험홈에서였다. 김씨의 이용자 정씨는 탈시설해 체험홈에 살았다. 언제부턴가 연애도 시작하면서 연애에 따른 소비도 많아졌다. 체험홈에서 제공하는 금전관리 교육프로그램에 참여하는 정씨는 체험홈으로부터 지출에 대한 지적을 받았다. 정씨가 자신의 체크카드로 돈을 쓰면 통장에 기록이 남아 체험홈에 지출 사실이 드러났고, 이는 계속된 지적으로 이어졌다. 처음 맛보는 돈 쓰는 맛을 포기할 수 없었던 정씨는 자신의 지출을 은폐하기 위해 활동지원사 김씨에게 돈을 빌려 달라고 했다. 당시 초보 활동지원사였던 김씨는 별 의심 없이 돈을 빌려줬다. 그리고 약속된 어느 날 정씨로부터 돈을 다시 돌려받았다. 그러자 난리가 났다. 김씨가 정씨의 돈을 빼갔다고 소문이 돌기 시작했다. 자신의 지출을 숨기고 싶었던 정씨는 모르겠다고만 했다. 김씨는 정씨로부터 빌려준 돈을 받은 것이라고 말했지만 체험홈 측은 김씨를 쉽게 믿어주지 않았다. 경찰에 신고하니 마니 하는 이야기를 듣고, 김씨는 일을 그만뒀다. 어찌 된 일인지 경찰서에서 연락이 오지는 않았다.
이어지는 고민들
활동지원사의 노동조건이 안정적이라면 사실 도둑으로 의심받는 일 정도는 큰 일이 아닐 수도 있다. 감사나 조사를 받고 진상이 규명되면 될 일이다. 하지만 활동지원사는 노동자들이 괴로워하는 감사나 징계위 절차를 밟는 기회조차 주어지지 않는 경우가 많다. 이용자의 서비스 제공 거부만으로 소득이 끊기고, 활동지원기관들은 일거리를 제공할 의무를 부담하지 않는 것이 용인되는 현실에서 우리의 일상적 노동조건은 '무기한 무급 정직'이 기본값이다. 우리는 소문만으로도 생존권을 위협받는다. 하지 동시에 장애인이 처한 현실에 대해 동시에 고민하게 되기도 한다.
접촉하는 순간 돌봄권력이 생길 가능성 배제하지 말아야
장애인을 위한다는 각종 지원이, 장애인의 자기결정권을 제약하는 권력이 되기도 한다. 때로는 원하지 않는 지원이 강요될 수도 있고, 너무 필수적인 지원이라 거절이 힘들 수도 있다. 서비스 제공자가 자신의 의사를 관철하거나 강요하기도 한다. 혹자는 이것을 '돌봄권력'이라고 명명한다. 아마도 주택 측에서 활동지원사에게 휘둘려 재산을 탕진하는 장애인을 상상하는 일이 잦은 것 같다. 마찬가지로 활동지원사가 '돌봄권력'을 장애인에게 행사한다는 편견을 갖고 있기 때문일 것이다.
하지만 '돌봄권력'을 갖는 존재는 활동지원사로 한정되지 않는다. 사회복지사, 탈시설운동가, 동료상담가, 교육자, 중증장애인 일자리 사업가 등 다양한 존재일 수 있다. 장애인 입장에서는 주거지원 서비스에 대한 여러 선택지가 눈에 보이지 않는 상황에서 현재 거주하는 지원주택을 벗어나는 일도 쉽지 않을 터이다.
앞서 살펴본 사례는 자립생활지원주택이 장애인의 지출 욕구를 억압한 상태에서 장애인의 자기결정권을 존중해주는 활동지원사와 함께 있을 때 그 욕구가 분출된 사례로 볼 수 있다. 돈을 마음껏 쓰지 못하게 하는 주택측이 이 돈을 누가 어떻게 어디서 썼냐고 물으면 장애인은 쉽게 답하지 못하는 건 당연하다.
당사자가 경험하는 진정한 실패가능성
장애인의 지출을 통제하게 되는 주택의 입장도 이해 못 할 바는 아니다. 주택은 임시로 있는 곳이고 계속 거주할 수는 없다. 지원주택을 나가 진짜 자립생활을 시작하려면 거주자가 얼마간 자금이 있어야 한다. 장애인은 지출관리에서 실패하면 다시 시설로 돌아가야 할지도 모른다. 자신들이 관리하는 주택에서 장애인에 대한 갈취가 있다면 그것은 그것대로 오명이다. 하지만 장애인이 주체적으로 탕진할 가능성을 배제해서는 안 된다. 시설에서는 차단됐을 각종 상품광고는 이 물건을 소비하라 꼬드긴다. 비장애인도 일상적으로 지출 충동과 싸운다. 지름신 밈이 괜히 나온 게 아니다. 이러한 상황에서 장애인에게 재정건전성을 강요하는 일 또한 차별적 인식이다.
나는 이 점에서 장애인의 진정한 실패가능성에 대해 논의해야 할 때라고 생각한다. 자기결정권을 방어하는 의미에서 장애인의 실패할 권리를 주장하기만 할 것이 아니라, 어떤 결정이 어떤 과정을 통해 장애인 당사자에게 실패가 될 수 있는지 물어야 한다. 누군가가 대신해 주고 누군가가 대신 실패하기만 한다면 장애인은 실패의 경험조차 차단당하는 것과 다를 바 없다. 장애인 당사자 자신이 지출을 결정했음에도 그 책임이 활동지원사에게 돌아간다면 장애인당사자는 자신이 내린 결정의 결과와 자신이 겪을 경험의 기회를 잃는다. 보호의 이름으로 장애인이 겪을 실패의 경험을 차단하는 것은 아닌지 자문해 봐야한다.
재기 가능한 실패를 위해
여기서 또 중요한 지점은 장애인이 실패를 겪을 때 그것의 정도, 즉 재기 가능 여부일 것이다. 자립생활지원금을 온전히 탕진하고 시설로 돌아가는 것은 단순한 실패가 아니다. 장애인의 탕진 가능성을 상상하기엔 그 결과에 따르는 위험이 너무 큰 것이 문제일 수 있다. 주택측 입장에서는 위험이 크니 위험 요소를 차단하기 위해 더욱 격렬히 반응한다. 장애인의 실패가 장애인 당사자에게 교훈이자 경험이 되기 위해서는 다시 시도할 기회도 주어져야 한다.
비장애인은 사회와 접촉하면서도 법적 보호를 받으며 성장하는 미성년의 시기를 거친다. 미성년 시기의 재산은 용돈으로 한정된다. 용돈의 운용에 실패가 있어도 의식주를 비롯한 생존에 제약은 없다. 용돈을 다 쓰면 용돈을 쓸 수 없다는 제약에 용돈을 아껴 쓰는 법을 배운다. 그런데 시설에서 금방 나온 장애인에게 이런 종류의 기회나 경험은 차단되어 왔으며, 시설만 나온다고 해서 다양한 경험의 기회가 새로이 제공되지 않는다. 장애인에게 지원되는 자립생활지원 금액은 실패를 되돌리기에는 너무 큰 금액이고 그 대가는 크다. 자기결정권 및 결정에 따른 책임능력을 둘러싼 논의에서 외부의 개입에 대한 방어뿐 아니라, 실패를 통한 자립능력을 어떻게 기를 것인지에 구체적 논의가 필요하다.
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 4d41a7cb:7d3633cc
2025-01-03 20:52:22
@ 4d41a7cb:7d3633cc
2025-01-03 20:52:22Today is Bitcoin genesis block day, literally Bitcoin’s birthday number 16th. The purpose of this article is to deep dive into Bitcoin's beginnings, what it was meant to be, what its creator's incentives were, why the collaborators were interested in contributing to its success, and what Bitcoin is achieving.
Bitcoin exists to solve a problem.
The root problem with conventional currency is all the trust that's required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible.
Satoshi Nakamoto, February 11, 2009
In this post, Satoshi reveals the main problem: central banking, how this institution has abused the trust we have put in them. Bitcoin is an alternative to a “broken” or corrupt monetary system that it’s been running and stealing from people for centuries, creating credit bubbles with their debt-based fractional reserve banking system
Ponzi nature of banking system
For those who don’t understand this system and its corrupt and inviable nature, think about it as a rigged musical chairs game.
When the music (trust in the banking system and its currency) is on, everyone is happy playing the economic game. Economic activity is soaring; we see new businesses, new products, cheap credit, high lending, asset prices inflate, and people consuming more (thus pushing the economic numbers higher). Everything seems to be okay. But then something happens.
Under this monetary game, deposits are chairs and depositors are players; as the game goes on, there are always more players than chairs or depositors than deposits because banks “lend” currency that they don’t have. When the music (trust in the bank) is stopped, the game is over, and many people lose their chairs (their deposit), creating deflationary recessions and economic crises.
When this happens, everything starts trending the exact opposite way. The economic activity starts slowing down, debt problems arise, bankruptcies occur, people lose their jobs and consume less, asset prices deflate, until the central bank intervenes and the cycle starts again.
This is officially known as the “economic cycle,” and it's sold to us as a natural phenomenon. But the truth is this is a pure central bank–artificially created cycle by monetary manipulation, as we can learn from the Austrian school of economics.
I call the central bankers the market wizards because they hold the lever to manipulate the economic game. They are the money masters, the financial alchemists, the kings of the economic and financial game of commerce where all economic agents operate under.
Bitcoin is a revolution against the central bank monarch, but Satoshi was not shouting about this to the four winds. He didn’t want to get attention before Bitcoin was strong enough, because it would have implied a great risk to its success. Central banks are the most powerful institutions on earth; they literally have the power to create currency in unlimited amounts and buy anything they need to maintain their monopoly.
If we need a more clear confirmation of this, we can look into the encrypted message that Satoshi left in the genesis block. To understand the genesis block, imagine a bookkeeping ledger that adds new pages (blocks) daily and contains a record of all bitcoin transactions ever made. The very first page of this book is called the genesis block.
Chancellor on brink of second bailout for banks
Satoshi Nakamoto 03 January 2009
Here’s the newspaper cover he was making reference to.
 In allusion to the bank bailouts that were taking place at the time, Satoshi included this intriguing line in the genesis block when he created Bitcoin during the Great Global Financial Crisis. In addition to providing the remedy, those who caused the issue (and profit from it) were making unprecedented profits. \
\
This game is about privatizing profits and socializing losses. This is the opposite of free markets and capitalism. It's clear that Satoshi Nakamoto, whomever he was, detested the established financial system. Since the Bank of England, which was the subject of this article, was established in 1694, we may trace the debt based fractional reserve banking system history back at least 331 years. \
\
This allusion to traditional banking's shortcomings was a declaration of what Bitcoin was trying to combat: fractional reserve banking and its consequences, which include debt, taxation, and inflation.
In allusion to the bank bailouts that were taking place at the time, Satoshi included this intriguing line in the genesis block when he created Bitcoin during the Great Global Financial Crisis. In addition to providing the remedy, those who caused the issue (and profit from it) were making unprecedented profits. \
\
This game is about privatizing profits and socializing losses. This is the opposite of free markets and capitalism. It's clear that Satoshi Nakamoto, whomever he was, detested the established financial system. Since the Bank of England, which was the subject of this article, was established in 1694, we may trace the debt based fractional reserve banking system history back at least 331 years. \
\
This allusion to traditional banking's shortcomings was a declaration of what Bitcoin was trying to combat: fractional reserve banking and its consequences, which include debt, taxation, and inflation.\ \ The bookkeepers \ \ In essence, banking and money management are bookkeeping, keeping track of who owns what and who owes what. Due to its revolutionary impact on accounting, Bitcoin has been dubbed "triple entry bookkeeping" by some. \ \ These days, banks are in charge of bookkeeping; they basically have the authority to make changes to the books and add new entries, or "print money." Inflation is basically a robber of time, energy, and wealth from everyone using that currency denomination, and banks are the ones who create it. Additionally, they have the ability to cause economic crises and market crashes for their own financial gain, making them deflation inductors. \ \ The incapacity of gold (real money) to meet the demands of a growing global economy gave banks this authority. They essentially became gold safe-keepers and gold IOU bookkeepers' ledgers because people trusted these organizations to provide scalability and lower the cost and risk of gold transactions. \ \ The purpose of banking was to enable credit and payments. Governments and banks did not create money. The free market determined the value of gold and silver, and people only trusted banknotes that were backed by gold. \ \ “Gold is money, everything else is credit" JP Morgan, 1912. \ \ Since banks began growing, they have sought to increase their size even more. When they discovered that the metal money system was restricting their ability to increase credit and bank profits, they literally plotted to seize control of the money market and overthrow governments by demonetizing these metals, effectively eliminating the demand for money in general and substituting it with debt and credit instruments. Essentially promissory notes issued by banks based on debt. \ \ "The borrower is a slave to the lender, and the wealthy dominate the poor”. Proverbs 22:7\ \ Human history is a chronicle of the literal plot by banks to enslave humanity, which resulted in hundreds of wars, thousands of assassinations, and the loss of millions of innocent lives in order to fulfill the banksters' objective of creating a global fractional reserve credit system. The currency that they decided to control? The term "U.S dollars" is frequently and incorrectly used to refer to Federal Reserve Notes. \ \ Slavery is essentially personified in this system. Slavery, in my opinion, is working for a currency that someone else can print without any effort or labor. This is the underlying cause of legal inequality. Theoretically, we live in a democracy and capitalist society where everyone is treated equally, but income taxes and central banking are vital components of the communist manifiesto. \ \ Where do we draw the boundary between a free human being and a slave citizen, given that this system directly violates private property rights? You are 100% slave when you pay 100% taxes, and 40% slave when you pay 40% taxes. It is being violently imposed upon you if it is not a voluntary business deal. Violence or the threat of losing your freedom are used to compel people to pay taxes. \ \ Natural law, often known as moral law, states that every person has the right to keep all of the fruits of their labor. However, this fraudulent financial system is robbing everyone of their means of trade, whether they are called coins, currencies, deposits, checks, etc. Furthermore, ceasing to feed a parasite is the only way to eradicate it. \ \ A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution.
Satoshi Nakamoto, October 31, 2008\ \ \ \ What backs fiat currencies?\ \ The worst aspect of this system is that it views people as collateral cattle for the currency's purchasing power. In essence, "government currencies" are credits of their corresponding debts, or government bonds, which are effectively secured by the government's “authority” to impose taxes on its populace. In essence, the government's power to compel its people to give them X percent of their income without providing them with equal recompense.
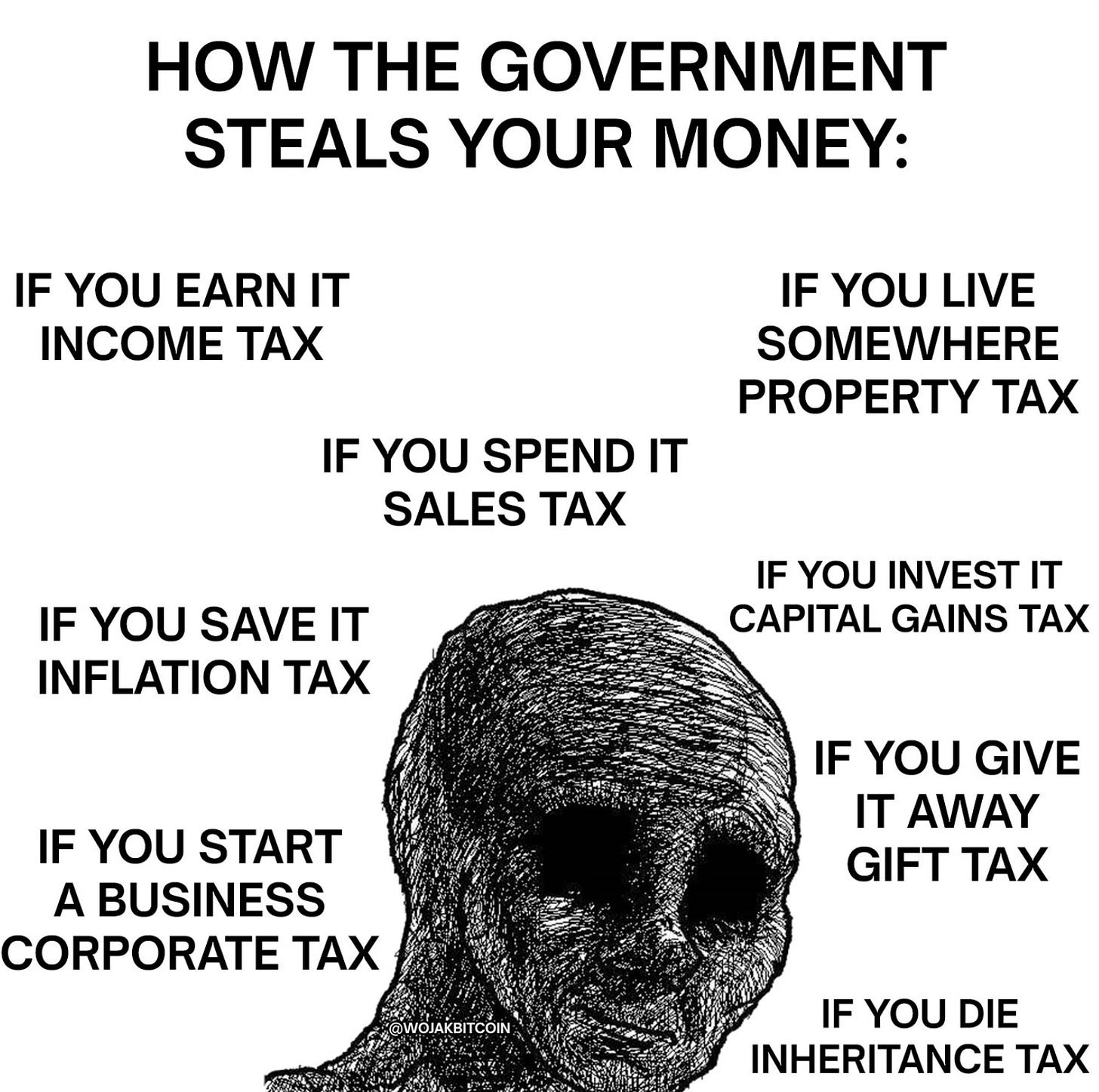 In essence, citizens' wealth is "baking" the government's debts. Since the currency cannot be exchanged for wealth at a particular rate, it is inaccurate to state that it is backed, thus I said "baking." However, if we must identify a valuable component of the currency, it is as follows: wealth and labor (i.e., human time and energy).
In essence, citizens' wealth is "baking" the government's debts. Since the currency cannot be exchanged for wealth at a particular rate, it is inaccurate to state that it is backed, thus I said "baking." However, if we must identify a valuable component of the currency, it is as follows: wealth and labor (i.e., human time and energy).\ And what makes up this wealth? Among other things, land, homes, resources, businesses, and human time. They have demand for trade and exchanges because they make up half of every transaction. However, what do people trade more for currency? Energy and time. \ \ Those who can produce currency out of thin air with little effort (simply adding numbers to the bank ledger) can effectively steal from everyone else who has to labor and invest time and energy (real wealth), as most people exchange their time and energy for currency. Clearly, this is the root cause of inequality. \ \ Not only is this utterly immoral and unfair, but it gets worse. The worst aspect is not that they want to charge interest and can easily generate currency, but rather that they insist that WE repay them! \ \ What am I saying? Every currency unit's counterpart in government bonds is a public debt that generates compound interest on a continuous basis. There is a dollar due plus interest for every dollar that exists. In essence, this debt is a claim on the nation's wealth, which includes the labor (time and energy) and wealth of its citizens. \ \ And to whom is this debt owed? The banks. Therefore, if we apply common logic, it is easy to see that just as borrowers are slaves to lenders, governments and "we the people" are slaves to banks. \ \ However, what precisely do we owe? What kind of material have they given our governments? Is it wealth of any sort, whether it land, gold, or resources? No, it's not. is essentially a promissory note issued by a private bank, a document that serves as a means of exchange and may be produced in an infinite quantity. A counterfeit check.\ \ Global slavery to the banks is the price we pay for a scalable medium of exchange! \ \ And now we have a great substitute! \ \ To sum up, we spend our lives, precious time, energy, stress, suffering, and effort to obtain these currencies and pay our taxes, while another group sits there making up new reasons to add currency the ledger —also known as "printing digital money"—that we must repay plus interest! It's crazy. \ \ The worst aspect is that because the debt exceeds the amount of money in circulation due to compound interest, which keeps accruing and increasing the loan's size, it is mathematically impossible to pay back.\ \ It is equivalent to burning the currency because we pay taxes to cover the interest on an ever-increasing debt that we are unable to pay back. A black hole for taxpayer funds, debt-based currencies are essentially human slavery that is supported by banks and maintained by governments. \ \ Why isn't everyone voicing their disapproval and exposing this? The answer is brainwashing and a lack of knowledge. Much of this has been concealed or esoteric, and a major contributing factor to this blind spot is the misinformation we receive regarding the operation of this system. In order to play the game the way they want us to and avoid the game ending anytime soon, we are given a children's interpretation of human history and reality. \ \ \ Libertarianism\ \ Bitcoin's libertarian nature cannot be disregarded; even Satoshi acknowledged this when he stated:\ \ It’s very attractive to the libertarian viewpoint if we can explain it properly.\ I’m better with code than with words though.
Satoshi Nakamoto, November 14, 2008\ \ Libertarianism is a political philosophy that holds freedom and liberty as primary values. Many libertarians conceive of freedom in accord with the Non-Aggression Principle, according to which each individual has the right to live as they choose, so long as it does not involve violating the rights of others by initiating force or fraud against them.
Libertarians advocate for the expansion of individual autonomy and political self-determination, emphasizing the principles of equality before the law and the protection of civil rights, including the rights to freedom of association, freedom of speech, freedom of thought and freedom of choice. They generally support individual liberty and oppose authority, state power, warfare, militarism and nationalism, but some libertarians diverge on the scope and nature of their opposition to existing economic and political systems. 1\ \ Here are several arguments in favor of Bitcoin's libertarian nature. \ \ Non-Aggression Principle: Unlike taxes and fiat currencies, which are supported by state aggression, Bitcoin is supported by energy, math, and processing power. The monopoly of violence “belongs” to governments, and banks use this authority to compel everyone to follow their rules (I'm talking about business). \ \ Personal independence: Bitcoin doesn't require confidence and doesn't have counterparty risk. With bitcoin, the person has complete control over his finances and doesn't require "permission" from a third party to earn, save, or spend it. Bitcoin is referred to be "freedom money" for this reason. \ \ Equality before the law: Unlike the actual banking system, where a group can create money out of thin air with little effort and can alter the rules to suit their interests, the bitcoin protocol ensures that everyone is playing by the same rules and that there is no possibility of cheating or inflating the supply of bitcoin. Equality exists under the Bitcoin protocol. \ \ Indeed there is nobody to act as central bank or federal reserve to adjust the money supply as the population of users grows.\ Satoshi Nakamoto, Febrero 18, 2009\ \ Freedom of speech: To uphold justice and the truth in an era of widespread censorship, freedom of speech is an essential human right. The fact that Bitcoin is information also fits into this category; money is a means of conveying value, but this time in an unstoppable manner that is impervious to censorship. \ \ Freedom of thought: Using bitcoin does not require you to subscribe to any particular philosophy or set of beliefs, including libertarianism or anarchism. Bitcoin is unbiased and doesn't care. \ \ Freedom of choice: Unlike fiat currencies, where you frequently have no other choice, no one will compel you to use bitcoin. \ \ Libertarians reject the current political and economic structures because they are blatantly immoral, criminal, and illegitimate. It is "shaped" by indoctrinated mob rule democracies, supported by violence, and based on lies.
 Bitcoin's ascent \
\
Bitcoin wasn't created overnight; rather, it was the result of decades' worth of research, development, and technology. Above all else, however, bitcoin represented a breakthrough—a new method of accomplishing tasks that had previously been impossible. \
\
A lot of people automatically dismiss e-currency as a lost cause because of all the companies that failed since the 1990's. I hope it's obvious it was only the centrally controlled nature of those systems that doomed them. I think this is the first time we're trying a decentralized, non-trust-based system.
Bitcoin's ascent \
\
Bitcoin wasn't created overnight; rather, it was the result of decades' worth of research, development, and technology. Above all else, however, bitcoin represented a breakthrough—a new method of accomplishing tasks that had previously been impossible. \
\
A lot of people automatically dismiss e-currency as a lost cause because of all the companies that failed since the 1990's. I hope it's obvious it was only the centrally controlled nature of those systems that doomed them. I think this is the first time we're trying a decentralized, non-trust-based system.Satoshi Nakamoto, Febrero 15, 2009\ \ Due to their centralization and unique points of failure, all of the numerous attempts to implement alternative e-currencies failed. The distributed nature of the bitcoin network makes it more robust and challenging to attack. \ \ The secret to developing a decentralized unchangeable ledger was Satoshi's solution to a problem that had been thought to be intractable since the 1970s. Following years of failure and lessons learned, Satoshi established a finite amount of money that is governed by processing power and energy.\ \ The proof-of-work chain is a solution to the Byzantine Generals Problem.\ Satoshi Nakamoto, Febrero 15, 2009
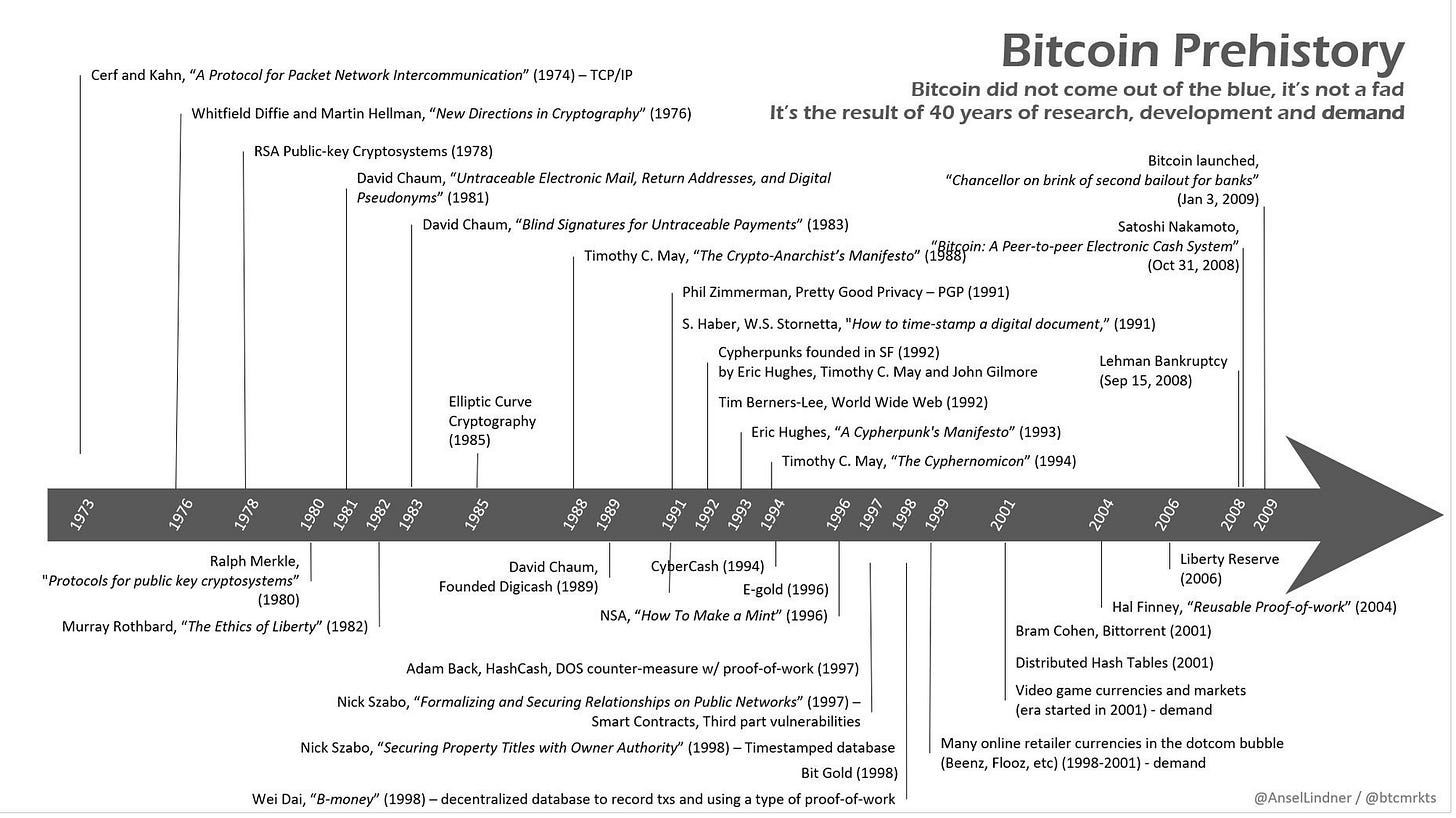 The return of money \
\
Bitcoin has also had a significant impact on the monetary front, particularly on the system's capacity to function as money and not simply a currency. It has been shown to be the best store of value (SOV) in addition to being an excellent medium of exchange (MOE).
The return of money \
\
Bitcoin has also had a significant impact on the monetary front, particularly on the system's capacity to function as money and not simply a currency. It has been shown to be the best store of value (SOV) in addition to being an excellent medium of exchange (MOE).Since currencies replaced money during the last century, we have lost track of what money is. And in order to protect our wealth, we need to be aware of the important distinctions between these technologies. \ \ A currency must be recognized, divisible, fungible, portable, and widely accepted in order to function as a medium of exchange. \ \ All of those qualities are present in money, but it also has the capacity to hold value over time, and it must be scarce in order to function as a store of value. A currency, in contrast to money, is susceptible to inflation due to its ease of replication. This is the cause of the constant price increases. \ \ The money supply needs to be scarce in order to preserve its purchasing power over time (i.e., to be immune to inflation). For thousands of years, gold and silver have been the preferred forms of money. \ \ At first, paper currency was only used to facilitate transitions by serving as a convenient alternative (derivative) to precious metals. Since goldsmiths and subsequent bankers used fractional reserve banking to lend more money (i.e., print more paper currency) than they actually had in storage, paper currencies—which are easily reproducible—have always been vulnerable to inflation. This resulted in the recurring "bank run" crises that are documented throughout history.\ \ But before bitcoin, we didn't have any money since 1933 because banks had taken it and devalued it. Real state, stocks, bonds, and other choices had been selected as alternatives due to the absence of money (a store of value). People buy real estate, stocks, and bonds to protect their wealth because fiat currencies are continually being inlfated, not because they love them. \ \ An estimated 900 trillion dollars' worth of wealth is held in financial and tangible assets worldwide. \ \ In real state, 330 trillions (36.6%)\ \ Bonds worth 300 billions (33.3%)\ \ Currency totaling 120 trillions (13.3%)\ \ Equity of 115 trillions (12,7%)\ \ Art worth 18 billions (2%)\ \ Gold worth 16 trillions (1,77%)\ \ Automobiles and collectibles worth 6 trillions (0,66%)\ \ Bitcoin worth two trillions (0,22%)\ \ Bitcoin only makes up about 0.22% of the world's total wealth. The greatest money ever created, property that you can actually own, with a sovereign protocol, no counterparty risk, a limited supply (better than scarce), and no need for banks or governments. Freedom money is unaffected by debt, taxes, or inflation. \ \ A bitcoin market cap of x10 ($1,000,000) would represent 2,22% of the world's wealth, and a market cap of x100 ($10,000,000) would represent 22,22%. \ \ The denominator, the dollar, is always losing value since it is created infinitely by continuously increasing the debt supply, and wealth is not fixed—rather, it is eternally increasing. According to CBNC the U.S. national debt is rising by $1 trillion about every 100 days.
Bitcoin is energy \ \ Bankers and significant international leaders are aware that energy is the foundation of all human activity. They are aware that they must control the energy sources, including their supply, distribution, and price, in order to establish a monopoly over every industry and a system of slave labor. They even clarified in several released documents that this is the only way to engineer the global economy.
:Silent Weapons for Quiet Wars explains:
In order to achieve such sovereignty, we must at least achieve this one end: that the public will not make either the logical or mathematical connection between economics and the other energy sciences or learn to apply such knowledge.
It is only a matter of time before the new breed of private programmer/economists will catch on to the far-reaching implications of the work begun at Harvard in 1948. The speed with which they can communicate their warning to the public will largely depend upon how effective we have been at controlling the media, subverting education, and keeping the public distracted with matters of no real importance.
The Harvard Economic Research Project (1948-) was an extension of World War II Operations Research. Its purpose was to discover the science of controlling an economy: at first the American economy, and then the world economy. It was felt that with sufficient mathematical foundation and data, it would be nearly as easy to predict and control the trend of an economy as to predict and control the trajectory of a projectile. Such has proven to be the case. Moreover, the economy has been transformed into a guided missile on target.
As we can see, the actual monetary system was created as a system of control (SOC), which is essentially founded on thievery and has restrictions, barriers, closed doors, a lack of transparency, and different rules for different actors. Through fabricated inflation and economic crises, it has been stealing our riches and freedom and controlling not just the electrical supply but also the social energies of humanity. (Inductors and economic conductors)\ \ However, Bitcoin is restoring our freedom. A way to make money, save it, and spend it without any restrictions, inflation, or capricious regulations. A novel kind of property that is not dependent on a counterparty, like banks or governments, and that requires energy to manufacture rather than being formed spontaneously.
Bitcoin generation should end up where it's cheapest. Maybe that will be in cold climates where there's electric heat, where it would be essentially free.
Satoshi Nakamoto, August, 2010
This fact is key to unlock the benefits of deflation that had been opaqued by the artificially created inflation.
Natural deflation
The primary benefit of bitcoin is deflation. Deflation incentives people to delay consumption and save more. Saving is the key to economic growth, because it can help to increase investment and productivity.
With the increase in productivity, prices tend to go down as they are more abundant and we find cheaper ways to produce thanks to technology.
The only reason that prices are not going down today -except in products where improvements are very rapid (e.g., computers)- is because of government-caused-currency inflation.
They have been stealing the benefits of natural deflation from us, but now we can access it thanks to Bitcoin.
It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy.
Satoshi Nakamoto, 1/17/2009
Conclusion
To only way to scape the slavery system is to earn, save and spend bitcoin; a money that’s not controlled by the governments and banks, that is not subject to inflation and where everyone has to play under the same rules.
Happy birthday Bitcoin!
Bitcoin or Slavery!

-
 @ 714f9dc3:76659adb
2025-01-02 20:47:45
@ 714f9dc3:76659adb
2025-01-02 20:47:45Last week, I was reading “The Air We Breathe”, by Glen Scrivener. It’s about “How We All Came to Believe in Freedom, Kindness, Progress, and Equality”, and it explores the Christian roots of the values we prize in today's western society. It’s all around us, but we don’t really know where it came from: It’s the air we’re breathing. The ideas and ethics behind Christianity, whether you believe in them or not, are embedded in our culture.
As I was reading this, I saw so many parallels with Bitcoin, so wanted to list them below and share some of my thoughts. Can Bitcoin also become “The Air We Breathe”? Or in plebs words: hyperbitcoinization? Can Bitcoin become so ubiquitous that it becomes normal? Can there be a world in which we don’t even know where Bitcoin came from? It would be a world with many similar views as with today's view on Christianity. It becomes the air we breathe, something that used to be a counterculture that over time became ubiquitous. What can we learn from it?
These are my ten parallels of Bitcoin with the early days of Christianity. 1. Separation from state 2. From obscure counterculture to dominant force 3. Exponential grassroots growth 4. Conversion of emperors/politicians 5. Sudden tolerance and protection for ideology 6. Fall of the empire, end of the status quo 7. Missionaries spreading the word 8. Persuasion and education are key 9. Age of Enlightenment
Note: I’m no expert on Christianity, nor a historian of the Roman Empire, and I know just a bit about Bitcoin. See this as a thought experiment.
1. Separation from state In all fairness, I’m not the first to draw this first parallel. It was Satoshi Nakamoto themself who made the connection even before Bitcoin was available to the public, with several hints pointing back to important dates and moments in Christian history. The big parallel here is the “separation of money and state” and “separation of church and state”.
Before going back to the early days of Christianity in the first centuries AD, I first want to draw this parallel with Satoshi.
It’s 1517. The German Priest Maarten Luther writes his Ninety-five Theses, and nails this on the church doors in Wittenberg. The theses are also known as the “Disputation on the Power and Efficacy of Indulgences”. He kickstarted a movement with a radical new idea for that time: The separation of the church from the state.
The Catholic Church had become one with the state. Via the means of indulgences, there was an ability to pay for your redemption. The church was corrupted by money, power and politics. The church and indulgences replaced the need for personal responsibility and an individual faith with money and perverse structures.
Reformation Day is a Protestant Christian religious holiday celebrated on 31 October in remembrance of the onset of the Reformation. But the 31st of October is also the day in which Satoshi shared his pamphlet with the world: in 2008 they published the Bitcoin Whitepaper. It kickstarted a movement with a radical new idea for that time: The separation of the money from the state.
But this was not Satoshi’s only hint. Another one is the date of Bitcoin’s Genesis Block: January 3, 2009. It was the day that the idea of the separation of money and the state became reality, more than just an idea in an individual's mind.
Did you know that Maarten Luther was excommunicated from the Catholic Church in 1521 by Pope Leo X for sparking this revolutionary new way of thinking (and being). It happened on January 3 as well. I bet Satoshi Nakamoto knew.
To be fair, this parallel is not new and known by many bitcoiners. But it’s a good introduction to the topic, and after reading “The Air We Breathe: How We All Came to Believe in Freedom, Kindness, Progress, and Equality”, I automatically started to see more parallels between (the early days of) Christianity and todays adoption of Bitcoin. Because it was of course not Maarten Luther who sparked these rebellious thoughts in 1500, but it was Jesus himself approx. 2000 years ago.
Let’s go back from the 1500s to the first decades AD to the beginning of this radical new belief system. During the dominance of the Roman empire in the Mediterranean and much of Europe, Western Asia and North Africa, someone told a story that opposed every mainstream paradigm.
Jesus’ idea was radically different from the belief systems of that day. He preached Freedom, Kindness, Progress, and Equality in a world that was full of Debauchery and Violence, with Gladiator Games, Slavery, Public Crucifixion, and Brutalities. The belief system of that time was not like todays. There were superior races (Greek/Romans over barbarians), superior sexes (man over women), superior classes (free man over slaves) and the concept of justice was more something in the realm of “restoring rights of those that were superior”, than “equality for all, men and women, Greek and barbarian, free and slave”.
Jesus opposed the status quo. It started small and irrelevant; as a counterculture. But it didn’t stay that way.
2. From obscure counterculture to dominant force In “The Air We Breathe”, Scrivener asks the question: “How did the obscure, marginal Jesus movement of the 1st century become the dominant religious force in the Western world in a few centuries?”
Important to know, is that the Christian faith was the opposite of the narrative. Concepts like Freedom, Kindness, Progress, and Equality didn’t exist in the Roman Empire. Human rights neither. Individual rights neither. The emperor was almost de facto God himself.
Early Christians were persecuted for preaching a different story: that God is NOT the ruler of the empire. Jesus preached the separation of politics from God; separating faith from the state. As a result, he was crucified, and many of his followers were killed by Nero (between 54 and 68 AD), Domitian (81–96 AD), Trajan (98–117 AD) and Decius (249–251 AD). This new narrative was a thread for the Roman rulers.
Draw the parallels of how there have been many attempts to “kill” bitcoin, not with physical persecution but with an information war. Not by physical violence, but by misinformation. Bitcoin threatens the status quo, just like Christianity threatened the Roman Empire.
You see?
But how is the obscure movement of Bitcoin in the 20th century becoming the dominant force, similar to the question that Scrivener asked about Christianity? Perhaps the answer lies in the following parallel.
3. Exponential grassroots growth Sociologist Rodney Stark estimates in “The Rise of Christianity” that from the time of the first Easter, the church began growing at a rate of 40% per decade, a modest but relentless 3.4% per year. By the year 300, Christians numbered perhaps 6 million: about a tenth of the empire.
Despite pushbacks, the army of believers continued to grow. Grassroots, peer-to-peer. It was not the state-religion, it was a peaceful army of believers that spread the word, resulting in an exponential growth of its followers. The counterculture became more and more dominant.
You may see what I’m doing here. It was basically the meme that all Bitcoiners know: Gradually, then suddenly. Against the current.
4. Conversion of emperors/politicians In 312 a big change happened: Emperor Constantine converted to Christianity. As Stark writes, "Constantine's conversion would better be seen as a response to the massive exponential wave in progress, not as its cause".
Are we living in that same era, where nation states start to embrace Bitcoin? Where politicians don’t oppose as strongly anymore, but are flirting with the idea of embracing it? And again the parallel: it’s responsive to the exponential wave of progress, not as its cause.
Whether Constantine is Nayib Bukele, Donald Trump, or Milei: it doesn’t matter. It’s the dynamic that matters. The counterculture becomes so dominant, that the “rulers” of the world are wanting to be part of it. Which will be followed by “rules” that favour the ideology, movement, and beliefs.
5. Tolerance and protection for ideology In 313 Constatines Edict of Milan granted freedom to Christians that were remarkable for that time and a model for religious toleration for the coming centuries.
The tide was turning, and by 380 Emperor Theodosius made Christianity Rome's official religion, more than half the population had already converted. In a few short centuries Christianity had gone from radical counterculture to dominant cultural power. This was an extraordinary shift in the church's relationship with the world. The edict expressly grants religious liberty to Christians, who had been the object of special persecution, but also goes even further and grants liberty to all other religions. And then, in 410, the world itself changed.
It changed from grassroots, bottom-up adoption to some kind of nation state adoption. One that was driven by decrees and edicts, instead of the analog cyberhornets of that day. Actually, the ideas of Indulgences were introduced via these Edicts, something that Maarten Luther actually was fighting against in the 1500s.
The world changed from the state-less Christian belief and moved (back) towards a system in which the state and church were connected again. Yes — the Roman Catholic Church. Until the previously mentioned critics during the Reformation.
6. Fall of the empire, end of the status quo When people speak of the fall of the Roman Empire, they usually mean in the 5th century when the western half fell. But there was also an eastern half, known as the Byzantine Empire (with its capital in what is modern-day Istanbul).
How did this relate to the movement that once was Cult, and now suddenly had become Culture?
It was Augustine, the north African bishop (354-430), who laid the foundation for a new philosophical, theological, and legal system. He distinguished between the fragile earthly realm and the eternal heavenly kingdom. Rome was “a city of man”, which fell. But the “city of God” was forever. He continued to separate the Roman Catholic Church from the faith that it once was. This distinction was vital, and it gave rise to the concept of "the secular realm". He planted the first ideas of "the separation of church and state" again, which started to spread throughout Europe during the supposedly "sandy desert" of the Middle Ages.
The parallel and lesson here might be that narratives can be taken over, for the worse. And that it takes centuries to take back the narrative, but/and only after an empire has fallen. Whether we refer to “The Fourth Turning” by William Strauss and Neil Howe or “Changing World Orders” by Ray Dalio. There is something to preserve, and it needs active monitoring and pushbacks!
7. Missionary, spreading the word The way the church sought to spread its influence would become a question that would take many centuries (and many failures) to settle. In the past, empires sought to spread their influence almost always by force. Christianity has been a missionary faith from the beginning. It was for this reason that Pope Gregory the Great sent Augustine to Britain to convert the Anglo-Saxons.
Augustine was commanded by Gregory to use only "gentle means". His goal was persuasion. His method was teaching and preaching. And he was successful, converting King Aethelbert of Kent and becoming the first Archbishop of Canterbury.
You see what I’m talking about again: the parallel is simple. Bitcoin is a similar peaceful revolution, a missionary movement, of those that wish to see their Cult turn into a Culture. “Genle means”, teachings, persuasions. Or in pleb terminology: Orangepilling.
8. Persuasion and education are key Over the next decades and centuries, this movement continued. English Benedictine monk (675-754) Boniface was sent from the previously “barbarian” Britain to “orangepill the East” – in this case the Saxons in the Germanic lands. In the words of his advisor, the Bishop of Winchester, his goal was "to convince them by many documents and arguments". This mission of persuasion and education was largely successful. Today he’s better known as “the Apostle to the Germans". He was killed in The Netherlands (Dokkum).
Boniface kept to a policy of non-violence and non-retaliation, even to the point of death. Another famous writer about this topic, Tom Holland, summarises the lesson we learn from Boniface: "to convert was to educate".
In the following century this lesson was sorely needed by the Frankish king Charles the Great, aka Charlemagne (742-814). Charlemagne's path to power was a brutal one. When the Saxons stood in his way, Charlemagne beheaded 4,500 of them in a single day. There are concrete reasons why "getting medieval" might be associated today with brutality.
Is “Bitcoin as Legal Tender”, whether this is peaceful or violently, the way to go? Are we “getting medieval” with these kind of measures, in order to go from Cult to Culture, from counterculture to dominant culture, in which we lose the true essence of our revolution of separation of the state from the matter?
9. Age of Enlightenment Alcuin of York (735-804), was bold enough to write to Charlemagne directly with his criticism. "A person can be drawn into the faith, not forced into it". Be a lighthouse, not a tugboat!
The church's official teaching would later agree with Alcuin's position. In the 12th century all "harsh means" were forbidden since faith arises from the will, not compulsion. Enlightenment comes through education and persuasion.
There’s work to do. Grassroots. Education. Peer-to-peer. Not directed by politicians, nor opposed by those in power. Through education and persuasion. Rules without rulers. Because eventually, with the Crusades and the Spanish Inquisition, there are stark examples of the church using “harsh means" again. Forcing Bitcoin on people will never be the way: it’s a cheat code to the end goal. In order to succeed, we’ll need to be a missionary.
Final words I don’t want in any way to compare Christianity in itself as a faith, and Bitcoin as a technology, with each other. I enjoyed exploring the sociological phenomena between two countercultures, the grassroots movement and missionary parallels between both of them. Satoshi gave the first assist, with the 31st of October (Whitepaper Day) and the Genesis Block on January 3rd.
Let’s not mix religion with monetary systems, even though there are many similarities between certain movements. That’s not my goal for sharing this brain dump. But let’s learn from the past, from Constatine’s Edict and from Augustine, from Charlemagne (and especially Alcuin of York), from Boniface and from Maarten Luther. And from Satoshi Nakamoto.
-
 @ 07f367da:0e76880d
2025-01-06 15:45:24
@ 07f367da:0e76880d
2025-01-06 15:45:24- 혁명적 운동의 물적 토대가 착취로 마련된다면
- https://www.newspoole.kr/news/articleView.html?idxno=10743
- 2024.05.20 14:14
활동지원사 노동자의 권리다툼 자체를 막으려는 조직적 활동
A센터에는 장애인활동지원사와 관련된 5개의 재판이 걸려 있었다. 1개 재판은 확정되었고 4개의 재판은 아직도 진행 중이다.[^1] 취업규칙개정 무효 확인 소송과 퇴직자 1인, 재직자 3인의 체불임금과 관련한 민·형사 소송이다. 체불임금을 청구하는 민사소송은 대한법률구조공단의 지원을 받아 진행 중이다.[^2] 형사재판 두 건은 검사의 구형에 따라 법원이 판결을 내릴 사안이므로 노동자들은 피해자로서의 역할만 하면 된다. 그리고 취업규칙개정 무효 확인 소송은 공익인권법재단 공감 노동팀의 변호사들로부터 지원을 받았다.
A센터와의 취업규칙개정 무효소송이 시작되고 약 두 달 뒤, 사건을 대리한 변호사로부터 연락이 왔다. 연락한 이유는 장애인차별금지추진연대(장추련)와 한국장애인자립생활센터협의회(한자협)의 활동가들이 공감에 찾아와 공감이 전국활동지원사노동조합의 사건을 대리한 것에 문제를 제기했기 때문이다.
전달받은 바에 의하면 그들의 주장은 ▲공감에서 사건을 대리하는 바람에 변호사 찾기가 어렵다 ▲이 사건은 공익소송이 아니다 ▲노동조합이 의도적으로 A센터를 상대로 소송을 제기했다 ▲소송을 통해서 A센터가 망하면 장애인들에게 영향이 생긴다는 내용이었다.
공감이 사건을 계속 맡을 경우 항의성명을 내거나 기자회견을 하겠다는 말도 비공식적으로 흘렸다고 했다.[^3] 공감은 장애인권영역에서도 공익변론활동을 하므로 이 사안이 사무실 회의에서 재차 논의되어 검토하였으나, 공감은 사건을 계속 맡기로 결정하였고 장추련과 한자협의 항의방문 사안을 원고(우리)들에게 공식적으로 전달하기로 결정했다.
공감이 사건을 계속 맡기로 판단한 이유는 ▲A센터와의 갈등 이전에도 우리 노조는 관공서공휴일 관련한 문제제기를 지속해서 하고 있었기에 A센터만을 표적으로 하고 있다고 판단할 수 없으며 ▲A센터와의 대화를 시도하였으나 A센터가 응하지 않은 사실이 확인되었으며 ▲관공서공휴일 수당이 정부 예산에 반영된 사실이 정부 문건으로 확인되었으며 ▲A센터의 총회자료상 순수익 발생이 확인되었기 때문이었다.
나중에 변호사들을 만났을 때, 장추련과 한자협이 해당사건을 공익소송이 아니라고 판단한 이유에 대해서도 말해주더냐고 물어보았다. 변호사는 장애인활동지원제도는 장애인을 위한 제도라는 이유를 들었다고 전해주었다. 한편으로는 흔들리지 않는 변호사들과 공감이라는 단체가 고마웠지만, 장추련과 한자협 활동가들의 인식과 행태에는 실소를 금할 수 없었다. 산업의 목적에 의해 노동자의 권리가 부정된다면, 산업의 성장을 위해 다치고 죽고 해고당해도 할 말이 없는 것 아닌가. 산업의 발전을 위해 생산력이 떨어지는 장애인이 배제되는 것도 마찬가지다. 길에서 농성하는 노동자들의 투쟁에는 쉬이 연대하면서도, 정작 자신들과 가장 가까운 장애인활동지원사의 노동권을 위한 투쟁은 공익활동조차 아니었고, 공익변호사의 조력조차 받아서는 안 되는 일이었다.
한자협의 탄원서 조직 업무협조 요청
얼마 전, 노동자 3인의 체불임금에 대한 민사1심 선고를 앞둔 시기였다. 모든 변론은 종결되었고, 판사는 선고 시기를 추후에 알려주겠다고 했다. 며칠의 시간이 흐른 뒤, 법원은 3월 28일에 선고하겠다고 알려왔다. 선고일을 받고 기다리는데, 한 조합원이 한자협의 공문을 보내오며 "이거 선생님 사건 아니에요?"라고 물었다. 한자협은 3월 18일 회원단체 전체에 업무협조 요청 공문을 발송했다. 협조요청 공문 내용의 골자는 이러했다.
 ▲한자협 업무연락 2024년 10호 공문 부분
▲한자협 업무연락 2024년 10호 공문 부분- 현재 A센터는 장애인활동지원사의 임금 지급과 관련한 민사소송의 피고 신분으로 판결을 앞두고 있다. 긴급하게 피고 A센터를 위해 탄원서를 조직하고자 한다.
- 이번 판결은 장애인활동지원사의 임금 산정 방식에 대한 법원의 해석에 해당되어 A센터뿐만 아니라 장애인활동지원기관 전반에 영향을 미칠 수 있는 중요한 판결이다.
- 장애인활동지원사업은 활동지원사가 근무 후 결제하는 바우처 정보에 따라 사업비가 지급되며 여기에는 활동지원사의 '연장수당' 등 법정수당이 모두 반영되어 지급되지 않는다. 장애인활동지원의 비현실적 시간당 단가, 운영비 미지원 등의 문제가 활동지원사와 중개기관의 열악한 조건을 고착시키고 있다는 점은 오래전부터 제기된 사안이다.
- 장애인자립생활센터를 비롯해 많은 활동지원기관이 활동지원사의 연장수당 책정을 월 174시간을 기준으로 하고 있으며, 소정근로일을 특정할 수 없는 활동지원사의 근무 형태를 고려하여 연차수당을 급여 안에 포함해 지급하고 있다. 이 같은 임금산정 및 급여 지급 방식은 근무조건이 유동적이고 소정근로일을 특정할 수 없는 장애인활동지원사의 근무 형태에 적절하다고 할 수 있다.
- 하지만 원고들은 임금산정에 있어 연장수당은 일 8시간을 기준으로, 연차수당은 연 단위 미사용 연차에 대한 총액으로 계산해야 함을 제기하고 있다. 이 경우 기관은 임금을 사업비에서 충당하기 위해서 일반적인 근로자와 같이 일 근무시간을 8시간으로 철저하게 관리할 수밖에 없다. 이 경우 활동지원제도의 취지가 무색할 정도로 이용자의 권리가 축소되고 기관의 운영 부담은 더욱 가중될 것이다.
- 활동지원제도의 특수성이 조명될 수 있도록, 무책임한 정부가 가려지지 않을 수 있도록 긴급하게 탄원서 요청한다.
A센터가 법원에 제출한 한자협의 자료들
A센터는 한자협의 자료를 공판 과정에서 이미 제출한 바가 있다. 사실 A센터가 법원에 한자협의 자료를 근거로 주장한 내용마저도 문제가 많았다. 한자협은 파스페이[^4]라는 임금 정산 전산시스템을 제공하면서 회원기관들로부터 이용료를 징수해 왔다. 그리고 이 이용료도 활동지원사업 수익금에서 지출되리라고 짐작할 수 있다. A센터도 이 시스템을 사용했는데, A센터는 공판 과정에서 한자협 회원기관들의 임금대장을 익명처리하여 제출하였다. A센터가 법원에서 주장한 바는, 한자협의 탄원협조 공문에서 드러난 논지와 동일했는데, 자신들의 임금체계는 활동지원기관들이 취하는 업계 일반적인 임금산정 방식이고 이는 활동지원사업의 '특성상' 불가피하다는 주장이었다. 하지만 법원에 제출된 자료만으로는 그것을 사업전체에 일반화할 수는 없다. 다른 장애인자립생활센터 연합단체의 경우나 복지관, 사회적협동조합 등 다른 여타 유형의 활동지원기관의 임금산정 방식에 대한 검토가 없다. 그리고 그러한 일반화가 있다 하더라도 법률위반이 만연한 것이 법률위반에 대한 정당화 근거가 될 수는 없다.
한자협 회원기관 중에서도 파스페이를 사용하지 않는 기관들이 종종 있다. 다시 말하지만, 한자협 회원기관 몇 군데의 임금대장 만으로는 "연장수당 책정을 월 174시간을 기준으로 하고 있으며, 소정근로일을 특정할 수 없는 활동지원사의 근무 형태를 고려하여 연차수당을 급여 안에 포함해 지급"하는 임금지급 방식을 모든 활동지원기관이 적용하고 있다고 말할 수는 없다. 엄밀하게 말하면 한자협이 주장하는 임금산정 방식은 '파스페이'를 사용하는 활동지원기관들에게만 확인되었다 할 수 있는 방식이다. 그리고 그 방식은 이미 A센터와 한자협이 법원에서 그리고 협조요청 공문으로 자인한 바대로, 연장수당 책정을 월근무시간 기준으로 책정하고 있다. 그리고 이러한 연장근무수당 산정 방식은 근로기준법 위반이다. A센터와 한자협의 주장 섞인 진술은 한자협 회원기관 중에서도 '파스페이'를 사용하는 활동지원기관은 근로기준법을 위반하고 있다는 고백과 다름없다. 근로기준법상 연장근무수당 산정방식은 1일 법정근무시간 8시간을 초과하는 시간에 해당하는 근무시간은 연장근무수당을 지급해야만 한다.
법원의 판결은 이미 많이 있었다
나는 탄원서 조직협조 공문이 목적하는 바가 법원에서 다투고 있는 쟁점에 관한 주장 및 입증은 아니라고 생각한다. 정말 법정에서 다투는 쟁점에 관한 사항이라면 A센터가 한자협을 통해 확보한 자료들로 주장에 대한 근거를 삼으면 될 일이다. 당사자인 A센터가 아니라 한자협이 적극적으로 탄원서를 조직했다. 나는 탄원서 조직의 진짜 목적은 법원을 설득하는 데에 있는 것이 아니라 다른 곳에 있다고 생각한다. 이 탄원서 조직은 한자협 내부 회원들을 조직하고 한자협의 입장을 전파하는 기능을 갖는다. 그리고 전파되는 내용은 활동지원사의 노동권을 부정하는 악의적이고 거짓된 내용으로 구성되어 있다.
탄원 조직 공문은 이번 판결이 임금 산정 방식에 대한 법원의 해석이므로 장애인활동지원기관 전반에 영향을 끼칠 수 있는 중요한 판결이라 서술한다. 이러한 서술은 해당 판결을 강조함으로써 이전의 판결들을 흐리게 만든다. 한자협이 말하는 것 같은 중요한 판결은 이번 판결만이 아니었다. 우리 노조는 활동지원사의 노동권 확보를 위해 투쟁해 왔고 그 나름의 역사가 있다. 우리 노조가 활동지원사업을 수탁받은 사회복지법인들과 노동자 권리를 두고 법정에서 싸운 것만 수차례다. 그리고 그 투쟁 속에서 노동청 검찰청 법원은 물론 대법원의 판단까지 받았다. 활동지원사의 임금과 관련한 법원 판결은 이번이 첫 번째 판결이 아니다. 그리고 법원은 활동지원사의 임금과 관련해서 근로기준법상의 기준을 지키라고 지속해서 판결해 왔다. 한자협은 이번 법정분쟁의 의미만을 확대함으로써 기존의 법원 판결에 대한 의미축소와 삭제를 노린다. 동시에 자신들의 임금산정 및 급여 지급 방식이 법률 위반이 아닌 적절한 방법이라는 억지주장을 반복하고 있다. 하지만 법원도 행정부도 한자협이 설정한 임금지급방식을 지시하거나 지지하는 입장을 표한 적도 없고, 문건을 생산한 적도 없다. 3월 28일의 선고도 원고들의 승소로 판결되었다. 법원은 체불임금 산정에 있어 A센터와 한자협의 주장 어느 하나도 인정하지 않았다. 그런데 A센터 소장은 다시 항소했다.
근로기준법과 75%
보건복지부에서는 매년 '장애인활동지원 사업안내'라는 책자를 발간한다. 현장에서는 보통 지침이라고 불린다. 지침에는 정부가 기관에 지급하는 '사업비 중 종사자 인건비 지출'을 규정하는 부분이 있다. "급여비용 중 75% 이상을 활동지원인력 임금으로 사용"할 것을 권장하는 내용이 그 부분이다. 본래는 "사용해야 함"이라고 명시하여 의무로 하던 것이 2019년 7월부터 '권장'으로 바뀌었다.
우리 노조는 다시 의무로 바꿔야 한다는 입장이다. 근로기준법의 기준만 충족하면 기관은 더욱 수익을 낼 수 있고, 이는 근로기준법의 각종 규정에서 제외되는 초단시간 노동자로 활동지원사들의 노동조건을 후퇴시킬 가능성이 아주 높기 때문이다. 영리를 추구하는 기관들의 태도가 활동지원제도의 공공성을 어떻게 망가뜨릴지는 예측하기 힘들다. 그런데 이 75% 기준에 대한 한자협의 입장은 노조와 다르다. 한자협은 권고기준마저 삭제하고자 한다. 한자협 2024년 총회자료에 따르면, 75% 권장사항마저 삭제할 것을 정부에 요구하고 있다.
 ▲한자협 2024년 총회자료 일부 발췌 및 편집 : 한자협이 보건복지부에 지침개정을 요구한 내용 중 일부
▲한자협 2024년 총회자료 일부 발췌 및 편집 : 한자협이 보건복지부에 지침개정을 요구한 내용 중 일부현재 활동지원기관들은 75% 이상 지급하라는 권장사항을 대부분 준수한다. 복지부 지침상으로는 '권고'수준이나, 기초자치단체와 국민연금공단의 평가에서 평가기준으로 작용하기 때문이다. 노동관계법령을 관할하는 노동부와는 별도로 행정상에서 지침이 작동하는 사례이다. 이 권장사항이 사라지게 되면 기초자치단체와 국민연금공단은 인건비 비율 관련 평가조차 하지 않게 된다.
A센터는 자신들이 근로기준법을 위반하지 않았다는 주장의 근거로 기초자치단체와 국민연금공단의 평가를 댄다. 평가상에 아무런 문제가 발견되지 않았다는 주장이다. 하지만 기초자치단체와 국민연금공단의 평가 및 감사는 활동지원기관에게 활동지원사의 실제 근무시간 자료를 요구하지 아니하고, 바우처 단가 중 75%만을 인건비로 썼는지 판단하기 때문에 이 평가만으로는 기관의 근로기준법 준수여부를 확인할 수는 없다.
A센터의 수익방법
A센터는 어떻게 수익을 내었을까? 이 질문이야말로 진정한 질문이다. A센터와 한자협의 주장은 짐짓 제도상의 구조적 피해를 호소하는 듯하지만, 정작 활동지원기관의 중간착취를 돕고 중간착취를 확대하는 기재로 작동한다. 임금의 세계는 선악의 세계가 아니라 수치의 세계이다. 충분과 부족의 일도양단으로 시시비비를 가릴 수는 없다.
A센터 2022년 정기총회 자료에서 회계감사는 단식부기로 1억 4천의 이익이 발생했고, "활동보조인 중개사업의 수익금액 증가에 기인"한다고 적시하고 있다. 이 수익에 대해서 A센터와 한자협은 설명하지 않는다. A센터의 수익에 75%와 연장근무수당의 비밀이 내포되어 있다. 우리나라 근로기준법 체계상 주휴수당과 연차수당 등은 법정근무시간인 1일 8시간을 기준으로 책정된다. 연장근무수당 미지급이 정당화되면 노동자는 일을 할수록 시간당 임금이 줄어드는 기이한 현상이 생긴다. 그리고 A센터는 이를 이용해 수익을 냈다. 이를 분석하기 위해서는 월 근무시간 구간별로 노동자에게 지급되는 임금 구성요소가 어떻게 되는지 살펴보면 된다.[^5]
A센터는 법정에서 월근무 174시간 기준으로 209시간까지는 연장근무수당을 책정하고, 그 이상의 근무에 대해서는 연장근무수당을 책정하지 않았다고 답변했다. 209시간 이상의 근무에 대해서는 보건복지부 지침에 따라 75%의 임금을 보장했다고 설명했다.[^6] 시간당 임금 구간을 나누어 서술하면 이렇다.
- 월 근무시간이 1시간부터 174시간 구간까지는[^7] 최저임금, 주휴수당, 연차수당이 지급된다.
- 월 근무시간이 174시간부터 209시간 구간까지는 최저임금과 연장근무수당이 지급된다.
- 월 근무시간이 209시간이 넘어가는 시간은 바우처 수가 75%의 임금만을 지급한다.
여기서 알아야 할 숫자는 최저임금, 주휴수당, 연차수당, 연장근무수당, 바우처 75%의 금액이다.
2021년 기준 최저임금은 8,720원이다. 주휴수당은 5일 근무 시 1일 유급휴일이므로 시간급으로 나누면 1/5에 해당한다. 계산하면 1,744원이다. 연차수당은 연차일수 17일을 가정할 경우[^8] 시간급으로 나누면 약 569원이 된다. 연장근무수당은 통상임금의 50%이므로 4,360원이다. 2021년 바우처 수가는 주간기준 14,020원이고 75%는 10,515원이다. 이 값들을 각 식에 대입해 보자.
- 근무시간 1 ~ 174 구간의 시간당 임금: 8,720(최저임금) + 1,744(주휴수당) + 569(연차수당) = 11,033
- 근무시간 174 ~ 209 구간의 시간당 임금 : 8,720(최저임금) + 4,360(연장근무수당) = 13,080
- 근무시간 209 ~ 구간의 시간당 임금 : 14,020(바우처 단가) * 0.75 (75%) = 10,515
사업장에서 시간당 수입이 일정한 조건에서 노동력을 통해 수익을 내기 위해서 가장 중요하게 고려할 요소는 노동자에게 지급하는 시간당 임금 비율이다. 정리하면 다음과 같다.
- 근무시간 1 ~ 174 구간의 시간당 수익 : 14,020(바우처 주간수가) - 11,033(임금) = 2,987
- 근무시간 174 ~ 209 구간의 시간당 수익 : 14,020(바우처 주간수가) - 13,080(임금) = 940
- 근무시간 209 ~ 구간의 시간당 수익 : 14,020(바우처 주간수가) - 10,515(임금) = 3,505
- 근무시간 209 ~ 구간의 시간당 수익 (한자협의 주장대로 75% 권장사항이 삭제될 경우) : 14,020(바우처 주간수가) - 8,720(최저임금) = 5,300
1 ~ 174 구간에서 주간바우처 단가 기준 운영비 수익은 2,987원이고, 174 ~ 209 구간에서 운영비 수익은 940원이 된다. 209시간을 넘어가면 운영비 수익은 3,505원으로 뛴다. 한자협의 주장대로 75% 권장사항이 삭제될 경우에는 최저임금만 지급하면 되므로 운영수익이 시간당 5,300원으로 폭증하게 된다. A센터는 활동지원사의 노동시간을 통제하지 않으면서(소극적 권장) 시간당 운영비 수익을 더욱더 많이 얻을 수 있었다. 일반적인 사업장에서 초단시간 노동자 고용을 통해 인건비를 아끼는 것과 동일하게(사용자가 초단시간 노동자로 노동자의 노동조건을 하락시키는 이유도 시간당 지급되는 인건비를 줄이기 위해서이다), A센터는 반대의 방향으로 근무시간은 늘리고 연장근무수당을 지급하지 않음으로 시간당 수익을 넓히는 전략을 취한 것이다.
사용자의 예상되는 대응이 노동자에게 불이익이 아니라면, 도대체 싸우지 않을 이유가 없다
노동조합의 입장에서는 문제를 제기함에 있어 신중할 수밖에 없다. 법이 항상 약자의 편은 아니고 자본가는 더 빼앗기 위해 법률을 검토하고 이용할 자원이 있기 때문이다. 노동조합도 자신의 행보에 따른 사용자의 대응전략을 예상해 본다. 그런데 그 대응이 노동자계급에 전혀 피해를 주지 않는다면 싸우지 않을 이유가 없다.
한자협은 자신들이 근로기준법을 준수하기 위해서 이제는 1일 근무시간을 8시간으로 통제해야 한다고 선전한다. 그리고 이러한 조처가 불가피하고 이는 장애인이용자들의 불편으로 이어질 것이라고 말한다. 그런데 앞서 설명한 대로 노동자의 임금을 셈한다 하더라도, 연장근무수당을 부정하는 현재의 상태가 유지된다면 노동자 입장에서는 차라리 노동시간 통제가 유리하다. 사용자가 그러한 것과 마찬가지로 노동자 입장에서도 결국 노동력을 제공하는 시간당 임금이 중요한데, 일하면 일할수록 시간당 임금이 줄어드는 A센터와 한자협의 임금체계는 노동자 입장에서 싸우지 않을 이유가 없게 만든다. 특히나 그렇게 수익을 남기면서도 관공서공휴일 유급휴일수당 지급을 회피하고, 노동자를 속여 취업규칙을 개정하는 A센터와 같은 악덕 사업주에게는 더더욱 싸움을 피해야 할 이유가 없다.
한편으로는 이제야 1일 근무시간을 통제하겠다는 한자협의 주장은 기만이다. 한자협 회원기관들은 활동지원제도가 법률로 시행된 2011년부터 회원기관끼리 연계하여 활동지원사의 권리를 찢어 지우기 급급했다. 그 제한이 월 174시간이거나, 1일 8시간이거나 정도의 차이만 있었을 뿐, 개별 사업장들은 이런 통제를 계속해왔다. 그래서 활동지원사 입장에서는 저들의 대응이 하나도 새삼스럽지가 않다.
또한 민간의 활동지원기관이 자신들의 수익성 때문에 장애인이용자에게 불편을 끼친다면, 그것은 그것대로 사회서비스 공공성을 추구해야 할 이유가 될 것이고, 한자협과 같은 활동지원사업 민간수탁기관들이 사라져야 할 이유가 될 것이다.
혁명을 위한 착취가 정당화된다면 그것이 혁명일까
이제 정리해 보자. 한자협의 활동지원사업을 둘러싼 주요 행보는 활동지원사노동자의 중간착취를 정당화 또는 확대하는 방향으로 이루어졌다. 최근 서울시의 활동지원기관 재지정을 둘러싼 한자협의 반발[^9]도 필자가 보기에는 이와 같은 맥락으로 읽힌다. 한자협 회원기관 다수는 근로기준법을 위반하고 활동지원사 노동자를 착취해 가며 센터 규모를 키워왔다. 근로기준법 위반이 명백한 상황에서 재지정 심사에서 탈락하는 기관이 다수 생기는 것도 어렵지 않게 예상 가능하다. 그런데 한자협은 자신들의 노동착취와 위반행위는 인정하지 않은 채 보수정당의 장애인인권운동 탄압으로 프레이밍 한다.
자신들이 성명서 말미에서 요구하는 "단가현실화"와 "공공성 보장"은 어떻게 이루어지는가? 그리고 어떻게 이루어져 왔는가? 활동지원사가 근로기준법 적용을 요구하고 활동지원기관과 싸우는 투쟁이 없었더라도 수가인상이 이루어졌을까? 한자협이 주장하는 대로 수가에 충분히 반영되지 않아서 지불할 수 없다는 정당화가 용인되어도 수가 인상이 이루어졌을까? 시장화된 사회서비스 환경에서 민간기관의 근로기준법 위반을 묵인하는 것으로 공공성이 보장될까? 도대체가 말이 안 되는 소리다. 진보적 장애인 인권운동의 이름으로 발화되는 이런 시답잖은 주장을 언제까지 들어야만 하는가.
한자협은 자신들의 정체성을 운동단체로 규정짓는다. 하지만 그 회원사업장 밑에서 일하는 활동지원사 노동자의 입장에서 보기에, 운동을 핑계로 노동자를 착취하는 또 다른 방식의 자본가일 뿐이다. 우리나라의 사회운동은 언제부턴가 운동의 요구를 한계 짓기 시작했다. 국가가 책임지는 공공성보다는 국가예산을 일부 획득하고 국가의 하청이 되기를 자임했다. 바뀌어버린 풍경은 의식도 변화하게 만들고, 중간착취자로서 자신의 사유를 규정하게 된다. 이제 이쯤 되었으면 운동단체의 국가사업 수탁에 대해서 다시 심각하게 재고해야 하지 않을까. 운동의 몰락은 외부의 탄압에서 기인하지 않는다.
[^1]: 취업규칙 무효소송은 원고의 일부승소로 판결났다. 원고와 피고 모두 항소하지 않아 선고가 확정되었다. [^2]: 대한법률구조공단은 체불피해근로자들에게 민사 소송대리 등의 무료법률구조를 실시하고 있다. [^3]: 이후에 한자협은 기자회견을 하기는 했다. 다만 공감에 대한 규탄 내용은 빠졌다. 해당 기자회견에 대한 글은 이전 칼럼 [장애인 인권은 외치지만 차별주의자입니다] 에서 다루고 있다. [^4]: 파스페이, < https://kcil.org/ >, 한자협에서 구축하고 한자협 회원기관에게만 서비스를 제공하는 장애인활동지원 급여시스템이다. 놀랍게도 해당 서비스는 '근로기준법, 세법준수'를 서비스 장점으로 내세운다. [^5]: 야간근무수당이나 휴일근무수당 또한 같은 방식으로 분석할 수 있지만 이 글에서는 논외로 하자. 퇴직금은 운영수익에서 비례하여 지급되므로 분석하지 않는다. [^6]: 2022년 부터는 226시간까지 연장근무수당을 책정했다고 설명했다. [^7]: 1년은 365일이고, 12개월, 1주일은 7일이다. 365/12/7=4.3452... 1년 중 1달의 평균 주수이다. 1주 40시간이 법정근무시간으로 가정할 경우 40시간 * 1달 평균 주수 = 1달 근무시간이 된다. 이 수치가 약 173.8... 이 된다. 1달 기준 대략적인 법정근무시간이다. [^8]: 연차수당은 근속년수에 따라 다르다. 근로기준법 제60조 4항. [^9]: 한국장애인자립생활센터협의회 성명, [성명] 서울시 ‘활동지원기관 (재)지정 심사’는 법도 원칙도 없는 ‘장애인 단체 길들이기’, ‘적반하장’의 전형이다. 서울시의 부적절 관행과 정부의 무책임에 칼을 빼겠다. , < https://www.kcil.or.kr/post/618 >, 2024-04-26.
-
 @ 3906af02:af15c9f4
2024-12-19 13:40:00
@ 3906af02:af15c9f4
2024-12-19 13:40:00NEW: HRF #Bitcoin Development Fund grants 700 million satoshis to 20 projects worldwide!
https://bitcoinmagazine.com/business/human-rights-foundation-donates-700000000-satoshis-to-fund-bitcoin-development-and-projects
The grants cover decentralized #Bitcoin mining, technical education, decentralized communications, independent media & privacy-enhanced financial solutions for human rights groups, focusing on key regions in Latin America, Asia, and Africa 🌍🌏🌎🎁
Grants include:
🛠️ Stratum V2 Reference Implementation (SRI) decentralizes #Bitcoin mining by allowing nodes create their own block templates, reducing reliance on large pools. Funds will support @bit-aloo’s work on SRI including benchmarking tools, integration tests & codebase maintenance
⛏️ Public Pool makes #Bitcoin mining accessible for low-hash-rate devices, empowering individuals to self-host mining servers & contribute to decentralization. Funds will support hosting costs, hardware upgrades, & operational expenses.
🛠️ Jon Atack, recognized as one of the top all-time contributors to #Bitcoin Core, plays a pivotal role in enhancing Bitcoin’s decentralization and robustness. Funds will empower him to continue his vital contributions to Bitcoin development
👩🏿💻 Naiyoma, the first female #Bitcoin Core developer from Africa. Her work focuses on reviewing pull requests (PRs), addressing bugs through new PRs & improving Bitcoin Core’s codebase. Funds will support her full-time contributions to advancing Bitcoin Core.
🔒 Daniela Brozzoni, a #Bitcoin Core developer who previously contributed to the Bitcoin Development Kit (BDK). This grant will support her full-time contributions to Bitcoin Core reviewing key pull requests (PRs), contributing to new features & improving testing coverage
📱 UX/UI Design for Bitcoin Core by @Michaelhaase will bring the #Bitcoin Core App to mobile enabling users to run nodes, access essential wallet features directly on their phones to improve their financial privacy. Funding will support the project’s design & development.
🚀 Brink, co-founded by Mike Schmidt, supports #Bitcoin protocol engineers with grants and offers training & mentorship to onboard new contributors to open-source development. This grant will support operational expenses
⚡@Tando.me, cofounded by Sabina Gitau, integrates #Bitcoin with Kenya’s M-PESA system, enabling KYC-free, fee-free Lightning payments for everyday transactions for 54 million Kenyans. Funds will help boost Tando’s liquidity, support user growth & drive African expansion.
🌐 YakiHonne, a Nostr client founded by Wendy Ding, supports free speech & promote #Bitcoin payments across 170 countries with innovative functionality & a blend of online & offline events. Funds will support smart widget development, relay improvements & community events.
🌍 SeedSigner Multi-language Support brings accessibility to the open-source SeedSigner hardware wallet, empowering marginalized communities through inexpensive & accessible self-custody. Funds support Ace to deliver a multi-language version of SeedSigner.
🤝 Vexl, cofounded by Lea Petrasova, provides a private, KYC-free, peer-to-peer #Bitcoin trading experience by connecting users to trade through the social graph of their phone contacts. Funds will support expanded adoption in Africa & improvements to the backend infrastructure.
🇮🇳 Tomatech is building developer talent in Goa, India to advance #Bitcoin infrastructure & FOSS projects through training, workshops, & community meetups. Funding will support developer training, the creation of a developer hub, bounties & grants, & general operations.
💾 Krux, open-source firmware that turns generic devices into hardware wallets for secure #Bitcoin self-custody featuring air-gapped operations, key management & backups & support for 10 languages. Funding will support @odudex to advance this project.
🔐 Iris, a #Nostr web client by @MarttiMalmi, which aims to improve protection for metadata & message content, ensuring conversations remain private, especially in surveillant environments. Funding will support hiring an additional developer to expand Iris' features & functionality.
💻 Cashu-ts, the primary Software Development Kit in the @CashuBTC ecosystem developed by @Gandlaf21, simplifies wallet creation, integrates the latest protocol updates & powers popular wallets. Funds will support the developers to maintain & improve this essential library.
🤝 Unify, a Payjoin wallet developed by Fontaine, enhances privacy in #Bitcoin transactions by obscuring transaction histories, crucial for individuals navigating repressive regimes. Funds will support the developer to ship new features & expand compatibility with other wallets.
📢 The Financial Freedom Policy Coalition, led by Venezuelan activist Jorge Jraissati, promotes economic opportunities for people living under authoritarian regimes. Funds will support advocacy missions to educate policymakers on how #Bitcoin supports human rights.
🎓 African UX Bitcoin Bootcamp, led by @MouxDesign, empowered 10 African UX designers with #Bitcoin UX research skills ahead of the Africa Bitcoin Conference & support to test 5 popular Bitcoin products during the conference. Funds cover all program expenses for participants.
📰 No BS Bitcoin delivers ad-free, privacy-focused #Bitcoin news in clear & accessible format, essential for activists & citizens under authoritarian regimes. This grant ensures continued operations, adds an editor & supports Nostr features like Zaps & comments.
📖 Bitcoin History, a research project by Pete Rizzo, documenting key people, events & materials that shaped Bitcoin’s rise as a global monetary & human rights force. Fund will support a researcher to investigate & document stories of Bitcoin’s use against authoritarianism.
🌎 HRF is committed to supporting human rights and financial freedom with #Bitcoin.
If you are working on a #Bitcoin or adjacent freedom tech software (Nostr, eCash, TOR etc), education or adoption project that meets our mandate, submit your application at http://hrf.org/bdfapply 💪
-
 @ 7ed7d5c3:6927e200
2024-12-18 00:56:48
@ 7ed7d5c3:6927e200
2024-12-18 00:56:48There was a time when we dared not rustle a whisper. But now we write and read samizdat and, congregating in the smoking rooms of research institutes, heartily complain to each other of all they are muddling up, of all they are dragging us into! There’s that unnecessary bravado around our ventures into space, against the backdrop of ruin and poverty at home; and the buttressing of distant savage regimes; and the kindling of civil wars; and the ill-thought-out cultivation of Mao Zedong (at our expense to boot)—in the end we’ll be the ones sent out against him, and we’ll have to go, what other option will there be? And they put whomever they want on trial, and brand the healthy as mentally ill—and it is always “they,” while we are—helpless.
We are approaching the brink; already a universal spiritual demise is upon us; a physical one is about to flare up and engulf us and our children, while we continue to smile sheepishly and babble:
“But what can we do to stop it? We haven’t the strength.”
We have so hopelessly ceded our humanity that for the modest handouts of today we are ready to surrender up all principles, our soul, all the labors of our ancestors, all the prospects of our descendants—anything to avoid disrupting our meager existence. We have lost our strength, our pride, our passion. We do not even fear a common nuclear death, do not fear a third world war (perhaps we’ll hide away in some crevice), but fear only to take a civic stance! We hope only not to stray from the herd, not to set out on our own, and risk suddenly having to make do without the white bread, the hot water heater, a Moscow residency permit.
We have internalized well the lessons drummed into us by the state; we are forever content and comfortable with its premise: we cannot escape the environment, the social conditions; they shape us, “being determines consciousness.” What have we to do with this? We can do nothing.
But we can do—everything!—even if we comfort and lie to ourselves that this is not so. It is not “they” who are guilty of everything, but we ourselves, only we!
Some will counter: But really, there is nothing to be done! Our mouths are gagged, no one listens to us, no one asks us. How can we make them listen to us?
To make them reconsider—is impossible.
The natural thing would be simply not to reelect them, but there are no re-elections in our country.
In the West they have strikes, protest marches, but we are too cowed, too scared: How does one just give up one’s job, just go out onto the street?
All the other fateful means resorted to over the last century of Russia’s bitter history are even less fitting for us today—true, let’s not fall back on them! Today, when all the axes have hewn what they hacked, when all that was sown has borne fruit, we can see how lost, how drugged were those conceited youths who sought, through terror, bloody uprising, and civil war, to make the country just and content. No thank you, fathers of enlightenment! We now know that the vileness of the means begets the vileness of the result. Let our hands be clean!
So has the circle closed? So is there indeed no way out? So the only thing left to do is wait inertly: What if something just happens by itself?
But it will never come unstuck by itself, if we all, every day, continue to acknowledge, glorify, and strengthen it, if we do not, at the least, recoil from its most vulnerable point.
From lies.
When violence bursts onto the peaceful human condition, its face is flush with self-assurance, it displays on its banner and proclaims: “I am Violence! Make way, step aside, I will crush you!” But violence ages swiftly, a few years pass—and it is no longer sure of itself. To prop itself up, to appear decent, it will without fail call forth its ally—Lies. For violence has nothing to cover itself with but lies, and lies can only persist through violence. And it is not every day and not on every shoulder that violence brings down its heavy hand: It demands of us only a submission to lies, a daily participation in deceit—and this suffices as our fealty.
And therein we find, neglected by us, the simplest, the most accessible key to our liberation: a personal nonparticipation in lies! Even if all is covered by lies, even if all is under their rule, let us resist in the smallest way: Let their rule hold not through me!
And this is the way to break out of the imaginary encirclement of our inertness, the easiest way for us and the most devastating for the lies. For when people renounce lies, lies simply cease to exist. Like parasites, they can only survive when attached to a person.
We are not called upon to step out onto the square and shout out the truth, to say out loud what we think—this is scary, we are not ready. But let us at least refuse to say what we do not think!
This is the way, then, the easiest and most accessible for us given our deep-seated organic cowardice, much easier than (it’s scary even to utter the words) civil disobedience à la Gandhi.
Our way must be: Never knowingly support lies! Having understood where the lies begin (and many see this line differently)—step back from that gangrenous edge! Let us not glue back the flaking scales of the Ideology, not gather back its crumbling bones, nor patch together its decomposing garb, and we will be amazed how swiftly and helplessly the lies will fall away, and that which is destined to be naked will be exposed as such to the world.
And thus, overcoming our timidity, let each man choose: Will he remain a witting servant of the lies (needless to say, not due to natural predisposition, but in order to provide a living for the family, to rear the children in the spirit of lies!), or has the time come for him to stand straight as an honest man, worthy of the respect of his children and contemporaries? And from that day onward he:
· Will not write, sign, nor publish in any way, a single line distorting, so far as he can see, the truth;
· Will not utter such a line in private or in public conversation, nor read it from a crib sheet, nor speak it in the role of educator, canvasser, teacher, actor;
· Will not in painting, sculpture, photograph, technology, or music depict, support, or broadcast a single false thought, a single distortion of the truth as he discerns it;
· Will not cite in writing or in speech a single “guiding” quote for gratification, insurance, for his success at work, unless he fully shares the cited thought and believes that it fits the context precisely;
· Will not be forced to a demonstration or a rally if it runs counter to his desire and his will; will not take up and raise a banner or slogan in which he does not fully believe;
· Will not raise a hand in vote for a proposal which he does not sincerely support; will not vote openly or in secret ballot for a candidate whom he deems dubious or unworthy;
· Will not be impelled to a meeting where a forced and distorted discussion is expected to take place;
· Will at once walk out from a session, meeting, lecture, play, or film as soon as he hears the speaker utter a lie, ideological drivel, or shameless propaganda;
· Will not subscribe to, nor buy in retail, a newspaper or journal that distorts or hides the underlying facts.
This is by no means an exhaustive list of the possible and necessary ways of evading lies. But he who begins to cleanse himself will, with a cleansed eye, easily discern yet other opportunities.
Yes, at first it will not be fair. Someone will have to temporarily lose his job. For the young who seek to live by truth, this will at first severely complicate life, for their tests and quizzes, too, are stuffed with lies, and so choices will have to be made. But there is no loophole left for anyone who seeks to be honest: Not even for a day, not even in the safest technical occupations can he avoid even a single one of the listed choices—to be made in favor of either truth or lies, in favor of spiritual independence or spiritual servility. And as for him who lacks the courage to defend even his own soul: Let him not brag of his progressive views, boast of his status as an academician or a recognized artist, a distinguished citizen or general. Let him say to himself plainly: I am cattle, I am a coward, I seek only warmth and to eat my fill.
For us, who have grown staid over time, even this most moderate path of resistance will be not be easy to set out upon. But how much easier it is than self-immolation or even a hunger strike: Flames will not engulf your body, your eyes will not pop out from the heat, and your family will always have at least a piece of black bread to wash down with a glass of clear water.
Betrayed and deceived by us, did not a great European people—the Czechoslovaks—show us how one can stand down the tanks with bared chest alone, as long as inside it beats a worthy heart?
It will not be an easy path, perhaps, but it is the easiest among those that lie before us. Not an easy choice for the body, but the only one for the soul. No, not an easy path, but then we already have among us people, dozens even, who have for years abided by all these rules, who live by the truth.
And so: We need not be the first to set out on this path, Ours is but to join! The more of us set out together, the thicker our ranks, the easier and shorter will this path be for us all! If we become thousands—they will not cope, they will be unable to touch us. If we will grow to tens of thousands—we will not recognize our country!
But if we shrink away, then let us cease complaining that someone does not let us draw breath—we do it to ourselves! Let us then cower and hunker down, while our comrades the biologists bring closer the day when our thoughts can be read and our genes altered.
And if from this also we shrink away, then we are worthless, hopeless, and it is of us that Pushkin asks with scorn:
Why offer herds their liberation?
............................. Their heritage each generation
The yoke with jingles, and the whip.February 12, 1974
—translated from the Russian by Yermolai Solzhenitsyn
-
 @ 07f367da:0e76880d
2025-01-06 15:33:14
@ 07f367da:0e76880d
2025-01-06 15:33:14- 장애인활동지원제도 부정수급과 장애인을 지배하는 자들
- https://www.newspoole.kr/news/articleView.html?idxno=10690
- 입력 2024.03.23 20:19
“무급으로 함께 일하기엔 너무 좋고 고마운 존재지만, 막상 임금을 지불하기엔 뭔지 모르게 찝찝하고 아깝다”라는 동료의 속마음을 들어야 했다. 1년을 근무한 단체에서는 임금을 지불할 여유가 도저히 없다며 나의 활동보조시간 일부를 동료에게 명의를 돌려서 가사보조를 얼마만큼 포기하게 하는 대신 나의 임금으로 주기도 했다. 몸과 마음이 점점 지쳐가고, 급기야 몸담고 있던 단체의 안 좋은 실상들을 깨닫게 될 때 쯤 난 동료들과 자주 부딪치기 시작했다. 얼마 지나지 않아 나는 그 일터를 떠났다. - 출처: ‘생산성’ 묻는 사회, 장애여성의 노동은? - 일다 - < https://www.ildaro.com/6188 >
불법으로 규정된 부정수급과 편중된 교육
장애인활동지원제도는 장애인에게 바우처를 지급하고 그 바우처는 장애인활동지원서비스에만 사용하도록 용처를 제한하고 있다. 활동지원 서비스 외의 서비스나 재화를 제공받고 활동지원급여비용을 청구하는 행위 일체는 부정수급으로 판단된다. 활동지원급여비용 청구 주체는 활동지원기관이고, 이 급여비용 중 일부를 활동지원사에게 임금으로 지급한다.
활동지원서비스가 얼마나 제공되었는지는 사회보장정보원 전산시스템을 통해서 기록된다. 활동지원사는 활동지원기관이 지급한 단말기를 가지고 출근한다. 장애인이용자를 만나면 단말기에 장애인이용자의 카드를 태그하고, 전자바우처시스템을 통해 받은 활동지원인력 자신의 카드를 태그한다. 태그가 있어야 사회보장정보원 전산시스템에 출근과 퇴근을 기록할 수 있다. 그러면 서비스를 제공한 시간만큼 장애인이용자의 바우처가 차감된다.
이렇게 기록된 전산기록을 근거로 급여비용이 청구된다. 급여비용은 활동지원기관이 활동지원사를 보내어 장애인에게 정당한 서비스를 제공한 것을 전제로 지급되고, 또 그 전제로 활동지원사에게 임금이 지급된다. 전제가 되는 정당한 활동지원서비스가 없었다면 지급된 비용은 이자가 가산되어 환수[^1]되고, 부정한 청구 행위는 형사처벌을 받을 수 있다.[^2] 행정 차원에서 지정취소 혹은 자격정지를 당하거나[^3] 가담한 장애인수급자는 일정한 기간 활동지원급여가 중단될 수도 있다.[^4]
법률이 엄중히 처벌하는 만큼 부정수급 금지는 강조하고 반복해서 교육된다. 부정수급에 가담할 수 있는 주체는 활동지원기관, 장애인활동지원사, 장애인이용자 세 주체이다. 그리고 이들에게 지배적 지위에 있는 자들이 개입할 수 있다. 그런데 교육은 거의 활동지원사에게만 이루어진다. 활동지원기관은 부정수급을 단속하고 교육해야 할 책임기관 중 한 곳이다. 장애인이용자교육은 대체로 이루어지지 않는다. 장애인이용자 교육도 활동지원기관이 담당하는데, 활동지원기관 입장에서 장애인이용자는 서비스를 제공받고 바우처를 지급하는 고객에 해당한다. 장애인이용자를 교육한다는 것은 고객을 교육하는 꼴이다. 기관에서 교육을 소집해도 장애를 이유로 참가하는 사람 수가 적다. 결국 장애인 고객들에게는 서면이 전달되고 서명만 이루어진다. 교육이 제대로 될 리 없다.
부정수급을 주도하는 자는 누구일까
정작 부정수급은 활동지원사의 주도로 이루어지지 않는다. 사람들의 통념은 부정수급이 장애인을 등쳐먹는 활동지원사들에 의해 이루어진다고 상상하는 듯하다. 제대로 서비스는 제공하지도 않고 임금만 받아 가는 활동지원사. 하지만 여기서 가정되는 장애인은 멍청하고 속기만 하고 빼앗기기만 하는 무력한 장애인이다. 오히려 우리는 장애인이 그런 존재이기만 한지 질문해야 한다. 장애인을 무능한 존재로만 바라보는 시선은 장애혐오 시선의 일부다. 장애혐오적 시선은 노동자에 대한 혐오적 시선으로 이어진다. 그리고 활동지원사만 교육하고 닦달하는 현재의 제도는 어쩌면 그 인식의 결과로 보인다.
앞서 설명한 것처럼, 사회보장정보원에 근무기록을 남기는 방법은 단말기에 카드를 태그해야 한다. 태그를 하기 위해서는 장애인과 활동지원사의 의사일치가 필요하다. 활동지원시간을 장애인들은 생명 같은 시간으로 묘사한다. 활동지원사가 장애인 몰래 카드를 찍는다는 것은 그 생명 같은 시간을 무단으로 탈취하는 행위다. 특히 활동지원 시간을 금액으로 환산하여 표기하기 시작한 2011년부터 장애인이용자들은 바우처 금액을 자신에게 주어진 돈으로 인지하는 경향이 있다. 장애인 몰래 서비스를 제공하지 않고 근무기록을 남긴다는 것은 누군가가 몰래 돈을 훔쳐 가는 것과 같은 일이다. 정말로 활동지원사 단독으로 기망에 의해 그 같은 일이 벌어진다면, 그 장애인은 아주 위험한 상황이다. 바우처뿐만 아니라 모든 재산에 대한 점검이 필요한 문제상황이다. 이런 문제상황은 오히려 활동지원서비스 외에 다른 국가적 차원의 지원이 더욱 필요하다. 하지만 그런 사례는 드물고 장애인은 자신의 욕구에 따라 바우처라는 자원을 잘 분배하여 사용한다.
역으로 질문해 보자. 활동지원사가 부정수급을 제안할 수 있을까? 활동지원사가 부정수급을 제안한다면 장애인 이용자는 즉시 활동지원기관에 알릴 수 있다. 장애인이용자는 응하지 않고 바로 활동지원사를 교체할 수도 있다. 이런 상황에서 활동지원사가 부정수급을 최초로 제안한다는 것은 이미 어떤 특별한 관계 속에 있지 않고서는 불가능한 일이다.
거절할 수도, 신고할 수도 없지만 책임은 져야 한다
활동지원사는 장애인이용자의 부정수급 제안을 거절하기가 힘들다. 이유를 불문하고 서비스 중단을 요구할 수 있는 권력이 장애인이용자에게 있는 현재 상황에서 부정수급을 거절한다는 것은 실질적 해고에 노출되는 것을 각오하는 행위이다.
코로나가 한창이던 시기 뉴스보도에 따르면 한 활동지원사는 장애인이용자의 부정수급 권유를 거절하여 하루아침에 일자리에서 잘리게 됐다.[^5] 코로나 시기에만 있었던 일일까. 해당 보도에서는 코로나로 인한 장애인 일자리 감소를 이유로 들지만, 코로나 이전에도 끝난 지금에도 우리나라 전체 기업체에서 근무하고 있는 장애인 상시근로자 수는 거의 변동이 없다.[^6] 단지 감염병 유행으로 필수 돌봄노동자로서 활동지원사의 실태가 언론에 조금 주목받았을 뿐이지, 정말로 장애인 일자리 감소를 이유로 볼 수는 없다. 보도의 활동지원사는 4월에 근무를 시작하여 9월에 처음으로 부정수급 제안을 받고 교체되는데, 해당 이용자는 이전에도 이후에도 부정수급을 반복할 가능성이 크다.
활동지원사는 부정수급이 이루어지고 있다는 사실을 알아도 신고하기가 힘들다. 부정수급 사실을 알 수 있는 사람은 몇 되지 않아 신분이 노출될 가능성이 크다. 이 또한 서비스 중단으로 이어져 활동지원사가 감내해야 할 부담이 크다.
한편 단속에 적발된 부정수급에 대해서는 활동지원사만 전적으로 책임을 져야 할 가능성이 크다. 입증할 수 없는 사건은 존재하지 않는 것과 같다. 부정수급은 그 불법성이 강조되는 만큼이나 공모자들도 부정수급이 불법이라는 사실을 익히 알고 있다. 그렇다면 공모자들은 그와 관련된 증거를 없애야만 한다. 부정수급은 장애인과 장애인의 주변 사람에 의해 주도되지만, 부정수급과 관련된 증거는 활동지원사를 향하고 있다. 활동지원사와 장애인이용자가 같이 있지 않았다는 증거는 대개 명백하고, 활동지원사에게 임금이 지급된 사실도 명백하다. 하지만 장애인이용자와 주변 사람이 취한 이득에 대해서는 증거가 없을 가능성이 크다. 임금은 활동지원사의 계좌를 스쳐 흔적이 남지 않는 현금으로 누군가에게 전달된다.
장애인을 지배하는 자 바우처를 지배하리니
인용한 본문을 다시 살펴보자. 장애여성은 자신이 기존에 받던 "활동보조시간 일부"를 "동료"에게 명의를 돌려 "임금"으로 받았다고 한다. 본문의 장애여성이 일한 곳은 "장애인을 위한 시민단체"이다. 동시에 활동지원사업을 수탁받은 단체이다. 장애여성에게 임금을 지급할 수 없는 사정이 있다고 주장하는 단체는 (아마도 비장애인)동료를 활동지원사로 등록시켜 서비스를 제공하지 않고도 제공한 듯 활동지원급여비용을 청구했을 테고, 또 동료의 계좌로 활동지원사 임금명목의 금전을 지급했을 것이다. 그리고 그 금전을 현금으로 받아 장애여성에게 임금으로 지급하는 방식을 취했을 것이다.
여기서 중요한 것은 장애여성의 노동시장에서의 취약한 지위가 이중적 착취를 초래한다는 점이다. 임금은 단체가 지급한 것이 아니라, 장애여성이 제공받았어야 할 서비스를 단순히 돈으로 돌려받은 것에 불과하다. 그런데도 장애여성은 노동력까지 제공했다. 바우처 금액도 온전히 받지 못했을 가능성이 크다. 동료는 자신의 명의를 공짜로 제공했을까. 동료의 인건비 일부로 지출되었을 가능성도 있다. 활동지원기관은 25%까지 징수할 수 있는 중개수수료를 확보한다.
이 과정에서 기존에 서비스를 제공하던 활동지원사는 어떻게 됐을까? 서비스 중단을 통보받고 실질적 해고 상태에 돌입하거나, 일을 지속할 수 있었다면 일거리가 줄어 임금이 줄었을 것이다. 장애인이용자의 서비스중단 요구권이 절대적인 현재의 제도 하에서는, 장애인이용자의 취약성은 활동지원사의 취약성으로 연결된다.
이후에 부정수급이 발각된다면 장애여성은 자신이 지급받은 '임금'을 반환할까? 삼자 간의 관계가 어찌 전개될지는 알 수 없다. 어쨌거나 증거는 활동지원사 명의를 달아둔 '동료'를 향해있다.
부정수급이 불가능한 제도가 힘들다면 신고라도 할 수 있는 노동조건을
장애인활동지원제도의 부정수급과 관련한 신문기사는 주기적으로 나온다. 정부는 이를 근절하기 위한 방법으로 단속강화만을 말한다. 하지만 단속만으로 부정수급이 근절될까. 우리는 부정수급을 금지하는 제도가 아니라 부정수급이 불가능한 제도를 구축하라고 주장하고 있다. 장애인의 서비스 시간과 활동지원사의 임금이 연계된 현재의 체계로는 부정수급 가능성이 언제나 잔존한다. 부정수급을 할 이유도 없고 가능하지도 않은 제도로 변화해야 한다. 노동자가 노동자로 보장받아야 할 권리와 장애인이 받아야 할 활동지원의 권리가 분리되어 각각 보장되는 방식으로 제도개선이 이루어져야 한다고 주장하고 있다.
가끔 부정수급과 관련한 문의가 온다. 처음 일을 시작한 지 얼마 되지 않아 뭔가가 이상하다며 문의하는 활동지원사도 있고, 다른 사람이 부정수급을 하는 것을 알게 되었는데 어떻게 하면 되느냐고 묻는 활동지원사도 있다. 미처 모르고 부정수급에 동참한 노동자 대다수의 경우는 장애인이용자나 활동지원기관, 주변 사람들이 부정수급을 주도한 사실에 관한 증거는 없다. 부정수급 관련 상담을 할 때 더 이상 신고하라는 말을 쉽게 할 수가 없다. 정말로 신고했다가 크게 고생하는 활동지원사를 봤기 때문이다. 활동지원사는 정직하게 신고했지만, 임금을 환수당하고 벌금을 내고 자격을 정지당했다. 반면 장애인이용자는 수급권이 잠시 정지되었을 뿐이다. 활동지원사가 부정수급의 굴레를 벗어나려면 일을 그만두는 수밖에는 없다. 일을 그만두는 이유를 밝히기도 힘들다. 자발적 퇴사로 인한 불이익은 노동자 부담이다.
다른 활동지원사가 이용자와 부정수급을 하는 것을 알게 된 활동지원사도 마찬가지다. 실제로 한 노동자는 클린센터에 신고하자 신고를 취소하라는 활동지원기관의 전화를 받았다. 신고자를 보호한다는 클린센터를 믿지 마시라. 그저 모른 척 일하면서, 조용히 다른 일거리를 찾는 게 최선이다.
부정수급이 불가능한 제도로의 혁신이 안 된다면, 활동지원사가 부당한 일을 보면 신고라도 할 수 있는 노동조건은 확보되어야 하지 않을까. 장애인활동지원제도의 부정수급 프로세스의 핵심은 부정수급에 대한 주도권이 장애인과 장애인을 지배하는 자에게 있음에도 증거는 활동지원사를 향해 있다는 점이다. 이 점을 심각하게 받아들이지 않고서는 부정수급을 끊어낼 수도 없고, 이를 통해 피해를 보는 활동지원사가 현장을 이탈하는 일만 늘어날 것이다.
[^1]: 장애인활동 지원에 관한 법률 제35조(부당지급급여의 징수) [^2]: 동법 제47조(벌칙) 제1항 "3년 이하의 징역 또는 3천만원 이하의 벌금에 처한다." [^3]: 동법 제24조(활동지원기관 지정의 취소 등), 제30조(활동지원인력의 자격 취소 및 자격 정지 등) [^4]: 동법 제19조(활동지원급여의 중단 또는 제한) 제1항 "1년의 범위에서 활동지원급여의 수령이나 제공 기간 등을 제한하여야 한다." [^5]: 황 씨는 한 시각 장애인을 주6일, 오전 10시부터 오후 6시까지 돌보고 있었습니다. 그런데 이 시각장애인이 황 씨에게 '거래'를 제안한 겁니다. 화요일과 목요일은 자신을 돌봐주지 않아도 되고, 다른 요일에도 오후 일찍 퇴근할 수 있도록 해 주는 등 편의를 봐줄 테니 60만 원을 달라고 요구했다는 것입니다. 황 씨는 "60만 원을 주고는 도저히 일을 못 하겠다고 (돌봄 대상자에게) 얘기했더니 하루아침에 (일자리에서)잘리게 됐다"고 합니다. _ KBS뉴스, 2020년 12월 8일자 보도, “우리도 돌봄이 필요해요”…장애인 돌보는 ‘돌봄 노동자’, < https://news.kbs.co.kr/news/pc/view/view.do?ncd=5065927 > [^6]: 한국장애인고용공단에서는 매년 '기업체장애인고용실태조사'를 발표한다. 2018년부터 2023년 우리나라 전체 기업체에서 근무하고 있는 장애인 상시근로자 수를 살펴보면 22만 명 언저리에서 큰 변동이 없다.
-
 @ 07f367da:0e76880d
2025-01-06 15:28:36
@ 07f367da:0e76880d
2025-01-06 15:28:36- 활동지원사와 명절선물
- https://www.newspoole.kr/news/articleView.html?idxno=10652
- 입력 2024.01.25 12:55
나는 소속 활동지원기관에서 지급하는 추석 선물을 며칠 전에 받아왔다. 2023년 추석의 선물을 2024년 1월이 되어서야 받아온 것이다. 그리고 내가 서비스하는 장애인이용자에게 주어지는 선물 또한 받아 전달하였다. 이것은 짐짓 간단한 사실 같지만, 많은 쟁점을 내포하고 있다.
누군가는 선물을 주면 감사히 받아야 한다고 생각할 것이다. 하지만 그게 임금으로 받아야 할 것을 돌려서 받는 거라면 이야기가 다르다. 최저임금과 근로기준법상의 법정수당은 지급하지 않으면서 명절 선물은 준다면 이야기는 달라진다. 임금-권리로 받아야 할 돈을 돌려 시혜적 선물로 받는 것에 불과하기 때문이다. 그리고 선물이라면 상여금이 좋은가 상품이 좋은가? 상품이라면 어떤 상품이 좋은가? 장애인이용자에게도 선물을 준다면 그 선물은 어떤 방식으로 전달되어야 하는가? 수년째 명절 선물을 받으면서도 나는 이런 질문들을 해왔다.
활동지원사 중에는 기관에서 명절 선물도 안 준다고 불만을 토로하는 분이 있는가 하면, 명절 선물보다는 돈으로 줬으면 좋겠다는 분들도 있다. 선물에는 주는 사람이 받는 사람을 생각하는 마음이 들어있다고 느끼는 사람들이 있다. 이런 마음을 느끼는 것을 중히 여기는 노동자들도 있어 '돈'으로 받는 것 보다 '선물'을 선호하는 사람도 있다. 이런 분 중 한 분에 의하면 '선물'로 받아야만 기관에 소속된 감정을 느낀다고 했다. 이런 감정은 정말 사람마다 다르고 지역마다 달라서 '정서'의 차이라고밖에는 설명할 수가 없다. 이것은 결국 당사자의 차이에서 기인하는 것으로 당사자의 의사에 따라 달리 정할 수밖에 없다.
그런데 또 아무리 선물이 좋아도 사람 마음이라는 게 비교도 한다. 기관마다 선물이 다르면 선물을 비교하기도 한다. 선물의 시장가가 얼마이고, 어디에서 구매했으며, 자신에게 어떤 제품이 얼마나 효용이 좋은지 따지게 된다. 그래서 노동자들이 더욱 선호하는 상품이 생기게 된다. 그래서 그것은 때론 노사협의회 안건이 되기도 한다.
그런데 가끔은 기관에 따라 이 선물을 신념으로 구매하기도 한다. 내가 속한 센터도 그런 센터 중의 하나이다. 매번 명절선물을 진보적 장애인운동 기금 마련을 위한 명절특판에서 구매한다. 이번에 내가 받아온 선물은 2023년 전장연 추석특판 상품번호 27 델리팜잡곡 2호다. 가격은 3만 원으로 책정되어 있다.
 ▲전장연 2023 추석선물 특판 웹자보. ‘품절’ 표시된 상품이 〈2023년 전장연 추석특판 상품번호 27 델리팜잡곡 2호〉. 이미지 출처=전국장애인차별철폐연대
▲전장연 2023 추석선물 특판 웹자보. ‘품절’ 표시된 상품이 〈2023년 전장연 추석특판 상품번호 27 델리팜잡곡 2호〉. 이미지 출처=전국장애인차별철폐연대 사회 운동단체들은 운동기금을 마련하기 위해서 후원주점을 열거나 수익사업을 한다. 이런 사업에 참여하는 후원자들은 질과 양을 따지지 않는다. 후원주점이나 단체 수익사업의 취지는 개최하는 단체에 재정적 지원을 하는 것이고, 참여자들은 후원하고자 하는 단체가 최대한 수익을 남길 수 있도록 최대한 호구가 될 마음으로 참여한다. 지불은 하지만 물질적 향유를 추구하지 않는 것이 참여자의 기본 덕목이다.
그런데 그런 상품을 노동자 복지에 사용한다면 어떨까? 노동자 복지를 깎아 먹는 일이 될 것이다. 그리고 그러한 결정이 독단에 의해 결정된다면 더욱 문제가 많을 것이다. 그리고 그러한 과정에서도 이득을 보는 사람이 있다. 나는 지난 칼럼에서도 제세공과금 명목으로 관련 단체로 활동지원사업 수익금이 흘러 들어감을 지적했다. 선물 구매과정도 이와 유사하다. 기관 회계상으로는 선물구매와 금액으로만 기록이 남겠지만, 특판 목적 자체가 진보적 장애인 운동 기금 마련이므로, 활동지원사업 수익금은 관련 단체 기금 마련에 기여하게 된다.
이렇게 보면 명절 선물 구매는 특정 단체 수익을 위해 수단화된 과정이고, 선물 수여는 노동자들에게 빼앗은 권리를 은폐하기 위한 은혜가 된다. 이런 사례가 모든 활동지원기관에 적용된다고 확언할 수는 없다. 노동자 권리를 온전히 보장하면서도 노동자 복지를 위해서 선물을 추가로 지급하는 기관이 있다면 아주 훌륭한 기관일 것이다. 하지만 기관의 집행 세부내역에까지 공적 관리체계가 작동하지 않는 이상 얼마든지 다른 방식으로 변주될 수 있다. 그리고 이것은 어쩌면 이미 어떤 변주이기도 하다. 기존에 종교단체가 노동자에게 십일조를 강요해 문제가 됐다면, 이제 운동단체는 권리삭제를 은폐하고 시혜로 가장하여 신념에 기여할 것을 강제했을 뿐이다.
선물은 구매로 끝나는 것이 아니다. 선물을 사는 이유는 주기 위해서다. 우리 노동자들은 선물을 받으러 활동지원기관에 방문해야만 한다. 노동자에게 주어지는 선물이므로 문제가 아니다. 그런데, 기관에 따라서는 장애인이용자에게도 명절선물을 주는 경우가 있다. 장애인이용자가 기관에까지 방문하는 것은 힘든 경우가 많다. 그런데, 이에 대한 배달 노동은 활동지원사에게 무급노동으로 떠맡겨진다.
출근하지도 않았는데 장보기를 시키는 사례는 너무 흔한 장애인이용자 갑질사례다. "오는 길에 XX 좀 사다 주세요."라는 장애인이용자의 출근길 요청은 꽤 곤란하다. 사실상 이용자를 위한 장보기 노동을 수행하는데 무급으로 수행된다. 이런 요청이 잦아지면 이용자들도 미안해서 활동지원사에게 바우처 카드를 맡기기도 한다. 하지만 활동지원사가 이용자를 위해 마트에 들어가는 순간에 근무시작을 기록해도 정부는 '부정수급'으로 판단하고 노동자는 범죄자가 된다. 이용자의 카드를 소지하는 것은 부정수급의 소지가 있기에 금지되고, 장애인이용자와 함께 있지 않은 상황에서 근무기록을 하는 것은 부정수급이라는 것이 정부의 일관된 기준이다.
정부가 말하는 기준은, 이용자를 만나 출근한 후에 장보기를 수행하라는 것이다. 장애인이용자와 함께 장 보기가 어렵다면 활동지원기관에 보고하고 장보기를 수행해야만 한다. 하지만 이런 기준에도 출근길에 무언가를 사 오라며 부탁하는 장애인이용자들은 흔하다. 출근길에 소모되는 시간은 너무 쉽게 판단되고 오는 길에 무언가를 사 오는 무급노동은 장애인이용자들에게 너무 당연한 일이어서 문제다.
그런데 활동지원사의 무급노동을 당연시하는 태도가 명절선물을 대하는 활동지원기관의 태도에서도 드러난다. "오는 길에 XX 좀 사다 주세요" 와 "가는 길에 선물 좀 갖다주세요"는 너무 완벽하게 대칭되는 한 쌍이다. 활동지원기관의 선물전달이 활동지원사의 업무에 해당하기는 하는가? 선물 배달시간은 근무시간에 왜 해당하지 않는가? 활동지원기관들은 활동지원사에게 왜 이런 업무를 어떻게 시킬 수 있을까? 오히려 기관의 선물은 장애인이용자의 집으로 택배 배달을 시키는 것이 상식적이고 당연하지 않은가?
나는 추석선물을 뒤늦게 받아 들고 이런저런 상념에 빠진다. 적어도 나에게 활동지원사의 명절 선물은 단순한 선물이 아니다. 내가 이 추석선물을 3달이 지나 받아 들게 된 것도, 서류 업무와 기관 방문이 무급으로 상정된 제도적 문제, 해당 시간에 대한 유급화를 회피하는 활동지원기관의 자체 정책 결과다. 노동자로서 방문의 의무가 없으니 3달이 지나서야 물품을 수령한다. 마침 단말기가 고장 나지 않았다면 더 늦게 수령했을 수도 있다. 활동지원제도의 근간 자체가 돌봄노동자의 무급노동 위에 서 있다. 정부도 활동지원기관도 이에 대한 문제인식이 있을까? 저항하지 않는 존재는 존중받지 못한다.
-
 @ fd78c37f:a0ec0833
2024-12-11 01:32:23
@ fd78c37f:a0ec0833
2024-12-11 01:32:23Bitcoin, as a decentralized digital currency, is reshaping the global financial landscape, sparking innovation and transformation across various sectors. In South America, Bitcoin communities are emerging as crucial drivers of economic empowerment, financial inclusion, and local technological advancement. This issue will highlight 21 Bitcoin communities from South America, exploring their missions, growth trajectories, and recent developments. By examining these grassroots initiatives, we aim to show how Bitcoin is being leveraged to create sustainable economic ecosystems, foster social progress, and expand access to education and financial tools. Thank you, YakiHonne decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.Mi Primer Bitcoin nostr:npub17cyatz6z2dzcw6xehtcm9z45m76lde5smxdmyasvs00r4pqv863qrs4ml3 * Introduction My First Bitcoin is a Bitcoin education initiative rooted in the principles of independence, fairness, and community leadership. Originating in El Salvador, it aims to empower individuals and communities by providing open-source educational resources and fostering a decentralized network. Through a commitment to high-quality education, resistance to external influence, and the creation of a global collaborative network, it seeks to spread Bitcoin education to every corner of the world, offering a transparent and transformative model for reshaping traditional financial systems. * Latest Updates Recently, MyfirstBitcoin successfully hosted the fourth Bitcoin Educators Unconference, featuring guests such as nostr:npub1zfgx8v2g0faswd0ry2qn3ay4pvx4jr6q4fw9d0yqalpkyv9hhp0sjccnj5 nostr:npub1rhh9pkmf6l6z7298yg6fgp95rzkmx4j9uxpekn8j73p5k95ck7gsvce7vj attracting around 170 participants and receiving positive feedback. They also held the graduation ceremony in Ilopango, El Salvador, and continued to organize their regular monthly Bitcoin education meetups and Bitcoin game nights. Additionally, MyfirstBitcoin’s Bitcoin Educators Node Network welcomed four new projects from Canada, Nigeria, and the United States. In partnership with Bitcoin Boma, they are launching a free online Bitcoin education course for Malawi in January 2025, aimed at enhancing local Bitcoin knowledge.
- Introduction Bitcoin Beach is a groundbreaking initiative in El Salvador aimed at fostering sustainable local economic development through Bitcoin. The project provides financial services to the community, particularly for those without access to traditional banking. By using Bitcoin for payments, residents can cover everyday expenses such as utility bills, medical costs, and food. Bitcoin Beach leverages the Lightning Network and community collaboration to promote the adoption of Bitcoin both within El Salvador and globally.
- Latest Updates Recently, Bitcoin Beach attended the conference at Bitcoin Lake, where they hosted the Bitcoin Beach Meetup and Bitcoin Beach Festival to support local businesses with Bitcoin. They also invited notable figures such as nostr:npub1q0al05h2uvtj0fp8ww7etl0pdjnkum638ynz9tmku3e522fyvlmqjq04mt Hermann Buhr-Vivier, nostr:npub164xhe3pgcqaj70ls7ls5e4hwlnvl4ttuu8wns99jmwp5z6lwhutsa27wle as podcast guests. The discussions covered a range of impactful topics, including how Bitcoin mining can truly light up rural Africa, how to use Bitcoin to transform small towns in South Africa, and integrating Bitcoin into state-level policies across the United States, among other key areas.
3.Praia Bitcoin Brazil nostr:npub1m3tu3l6y59g2tmackq23v5vgn59u7hu66gxg8xajghz59tqm6xnqk2m888 * Introduction Praia Bitcoin Brazil, located in Jericoacoara, Brazil, is dedicated to creating the country's first Bitcoin circular economy, empowering local residents with financial inclusion. Founded by Fernando Motolese, the project promotes Bitcoin adoption through education, technology, and community-driven initiatives. It has integrated over 40 local businesses into the Bitcoin ecosystem and raised more than 12 BTC through Bitcoin-only crowdfunding. Praia Bitcoin offers self-sovereign financial services and runs programs like the "Bitcoin Smiles" initiative and educational support for children. * Latest Updates Recently, Praia Bitcoin Brazil launched several innovative projects, including the first stage lighting course and free acoustic guitar course funded entirely through Bitcoin crowdfunding. Additionally, Praia Bitcoin successfully hosted the Praia Bitcoin Conference 2024, attracting 10 volunteers, 100 local residents, and 10 new merchants. The conference also sponsored the first music performance paid in Bitcoin and introduced three local courses, all funded via Bitcoin crowdfunding. These initiatives highlight Praia Bitcoin's ongoing efforts to drive Bitcoin adoption and foster local community development.
4.Bitcoin Lake / Lago Bitcoin Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake aims to create a circular economy powered by Bitcoin, providing a novel and accessible solution for unbanked as well as banked merchants in Guatemala. * Latest Updates The Bitcoin Lake community has been actively preparing and promoting a series of innovative initiatives. On November 30 and December 1, Bitcoin Lake successfully hosted its 2024 conference, inviting industry experts such as Ronny Avendaño, co-founder and CEO of the Bitcoin hardware store, and prominent Bitcoin advocate Roman Martínez (chimbera). During the conference, the community also organized creative activities like the coffee workshop and “Be Captain of the Bitcoin Boat”, offering participants an opportunity to dive deeper into Bitcoin and the local economy. Additionally, through partnerships with local merchants, Bitcoin Lake is actively advancing the development of the Bitcoin economy, fostering economic growth and financial inclusion in the community.
5.Bitcoin jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network with the goal of creating a circular Bitcoin economy. The project provides education, resources, and technology to both individuals and businesses. Starting from the Golden Triangle area in Costa Rica (Dominical, Uvita, Ojochal, Platanillo, Tinamaste), it is developing a shining example of what a Bitcoin community can represent. * Latest Updates Recently, the Bitcoin Jungle community has been actively promoting the adoption and use of Bitcoin in Costa Rica, participating in various projects and events. Community members attended the Adopting Bitcoin conference in El Salvador, further advancing global Bitcoin adoption. At the same time, they have been actively supporting children's charity projects and Bitcoin diploma courses, continuously driving Bitcoin education, social responsibility, and community development.
6.Bitcoin Berlín sv * Introduction Bitcoin Berlín sv aimed at creating a financially sovereign town in Berlín, El Salvador, through the implementation of a Bitcoin circular economy. The project seeks to integrate Bitcoin into the local economy by educating residents and businesses about its benefits, promoting the adoption of Bitcoin-based payment systems, and empowering local entrepreneurs with financial education. It also focuses on environmental sustainability, encouraging the use of renewable energy and waste reduction. * Latest Updates Recently, the Bitcoin Berlín sv has been actively promoting the use of Bitcoin by sharing informative articles and supporting the graduation of podcast producer Joel through the BlinkBTC QR code platform, allowing contributions in sats. This initiative not only supports the growth and development of community members but also furthers Bitcoin’s adoption and usage within the community. Additionally, on November 23rd, the community successfully hosted a cultural festival celebrating the local heritage. During the event, all vendors accepted Bitcoin payments, showcasing its practical application in Berlín’s economy. The festival attracted numerous tourists and residents eager to experience Bitcoin payments, further advancing its integration into daily life.
7.Bitcoin embassy San Salvador * Introduction Bitcoin embassy San Salvador is more into promoting Nostr in the region. * Latest Updates Recently, the Bitcoin Embassy San Salvador has been actively promoting the use and adoption of Bitcoin within the community, organizing various events. One of the highlights was the Christmas Toy Drive x Cuarteto Salvación, where toys were purchased using Sats to bring holiday cheer to children in need. The event, held on December 1 at Cuscatlán Park, also featured a special Music Night, attracting a large audience. Additionally, the Embassy hosted an educational gathering for food vendors, aimed at promoting Bitcoin payment systems. During the event, vendors accept Bitcoin payments through tiankii_Tech and blinkbtc platforms, further encouraging local businesses to embrace and adopt Bitcoin payments.
8.ONG Bitcoin Argentina * Introduction ONG Bitcoin Argentina is dedicated to advancing the development and application of decentralized technologies, particularly in the fields of Bitcoin, cryptocurrencies, and blockchain. As a leading organization in this space, the community promotes user protection and the healthy growth of the crypto ecosystem through education, training, and public advocacy. Its mission is to help individuals, businesses, and decision-makers understand and leverage decentralized, transparent, and secure technologies to bring more opportunities and progress to society. ONG Bitcoin Argentina has become a leading force in promoting decentralized technology in Argentina and Latin America. * Latest Updates Recently, ONG Bitcoin Argentina has been actively preparing for the “Moon Party | Despedimos el año ATH (A Todo Hodler)” celebration, set to take place on December 5, 2024. Bitcoin enthusiasts will gather to enjoy exciting activities, including a Lightning Network demonstration and the Fish Bowl Manizesto Bitcoiner art exhibition. In addition, the community has hosted and will host a series of conferences and workshops covering a range of topics, including local digital asset services, Bitcoin as a strategic reserve in the U.S., the reconversion of the Bitcoin and cryptocurrency economy and financial systems, the role of crypto economics in financial system reform, the impact of Bitcoin ETFs on markets, and Bitcoin's influence on global issues, fostering in-depth discussions and development within the crypto industry.
9.La bitcoineta * Introduction La Bitcoineta is an initiative launched by the Argentine community in 2018, designed to promote the adoption and understanding of Bitcoin through a unique and powerful tool: a van and a group of volunteers. This traveling educational project has visited hundreds of towns across Latin America, Africa, and Europe, reaching thousands of people and covering hundreds of thousands of kilometers with the aim of spreading its mission and activities.With its innovative and mobile approach, Bitcoineta has become a globally recognized educational project.
10.Motiv Peru * Introduction Motiv is a non-profit organization founded in 2020, focused on addressing systemic poverty through Bitcoin and innovative projects, aiming to provide better opportunities for survival and prosperity to underserved communities. Its founders, Rich Swisher and Vali Popescu, witnessed firsthand the tragic impact of poverty and lack of basic living conditions in a remote village in the Andes Mountains of Peru, where children were dying due to preventable causes. This inspired them to create Motiv, with the goal of empowering vulnerable populations. By leveraging global support and partnerships, Motiv uses Bitcoin to help local communities break free from poverty and improve their lives, striving to bring positive change and hope to those in need. * Latest Updates Recently, MOTIV Perú has made significant progress in promoting Bitcoin and the circular economy. The organization continues to transform communities across Peru through various initiatives. For example, in the Comas district of Lima, entrepreneurial women are paying for their classes with Bitcoin and learning how to make delicious desserts, further advancing the local circular economy. Additionally, MOTIV Perú held its first Bitcoin training in Carabayllo-Lima, helping Peruvians understand the nature of money and the advantages of Bitcoin. MOTIV is also assisting communities in areas like Tarapoto and Ancon, where locals are using Bitcoin for daily transactions, driving financial freedom and economic empowerment.
11.Montanha bitcoin * Introduction Building a circular economy in Sao thome, Brazil. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to June 2024, highlighting a water contamination incident.
12.Amityage honduras * Introduction Amityage Honduras is the first Bitcoin education center in Honduras, located on Roatán Island in the Prosperá zone. The center's mission is to educate the local community about Bitcoin and spread this knowledge throughout Central America and the Caribbean. It is dedicated to helping businesses on the island adopt Bitcoin as a payment method, teaching children financial literacy, and empowering individuals to achieve financial sovereignty through Bitcoin. The center aims to empower the local community through education and innovation, fostering economic independence and sustainable development. * Latest Updates Recently, Amityage Honduras is actively promoting Bitcoin education by participating in various international Bitcoin events and organizing local courses to help more people understand Bitcoin. Community members took part in significant events such as AdoptingBTC 2024 and BitcoinUnconference, and hosted workshops around the theme of “How to Enter the World of Bitcoin Education.” In Haidmühle, Germany, AmityAge completed a four-day Bitcoin Educators Academy, where the curriculum included topics like using simple analogies to explain Bitcoin and public speaking exercises. Additionally, the community hosted Bitcoin education courses on Roatán Island and provided a free Bitcoin event for beginners at the Crawfish Rock community, further spreading Bitcoin knowledge.
13.Lima - Orange Pill Perú nostr:npub1fw8m5g6nfywmsgqjc66j47jax7jrv8lq46zf7grydjqppc54a8eql47qrx * Introduction Orange Pill Peru is a community-driven initiative dedicated to empowering Peruvians through Bitcoin education. With a focus on transforming the financial landscape, Orange Pill Peru provides resources for individuals to learn about Bitcoin, connect with like-minded enthusiasts, and grow their knowledge through various events and workshops. The community serves as a hub for both beginners and professionals, offering a supportive environment to explore the fundamentals of Bitcoin, its history, and its potential to shape the future of finance. * Latest Updates Recently, there have been no major updates. They actively engage in Bitcoin education and industry updates by sharing and reposting Bitcoin-related content. They support MOTIV Perú's financial freedom education project in the Ancon community in Lima, emphasizing the empowerment of women through Bitcoin. Additionally, the community has shared information about the upcoming Bitcoin Medellin Conference scheduled for January 2025.
14.La Antigua Bitcoin * Introduction La Antigua Bitcoin is a community-based initiative in La Antigua Guatemala, focusing on promoting Bitcoin adoption in local businesses. The community works to create awareness and facilitate the use of Bitcoin as a payment method in various establishments throughout the city. By encouraging merchants to accept Bitcoin, La Antigua Bitcoin aims to integrate cryptocurrency into the everyday economy, driving financial innovation and expanding access to decentralized financial systems within the region. * Latest Updates Recently, the Antigua Bitcoin community has had few updates, with a focus on organizing its first meetup in collaboration with “Run with Bitcoin” on November 24, 2023. The event garnered significant attention within the community, featuring interactions with a special guest. The aim of the event was to further promote Bitcoin adoption in Antigua, Guatemala, and encourage exchange and collaboration between Bitcoin enthusiasts and the local community.
15.Horizonte Bitcoin nostr:npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk * Introduction Project that aims to contribute to the Bitcoinization of the economy and encourage Entrepreneurship and Decentralization. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to Oct 2024, which shared a message encouraging women to learn more about Bitcoin and connect with others in the field, highlighted a meetup, Satoshe's Lounge, for women, providing a space to learn, discuss, and share knowledge about Bitcoin.
16.Escuelita Bitcoin nostr:npub1awggmqvlw8pa0kp9qq5law8zsvp2a8suztk0357j7e0nt746suwspt7lwx * Introduction Educational Project for Little School. * Latest Updates Recently, the Escuelita Bitcoin team has grown to five members and is actively advancing Bitcoin education and community development. Team members have hosted several workshops in Paraguay and Mexico, spreading Bitcoin knowledge within local communities and encouraging merchants to accept Bitcoin payments, particularly in Ciudad del Este, Paraguay. The team is raising funds through platforms like Geyser. fund and Kuno.anne.media to support the expansion of their educational initiatives and help locals better understand and use Bitcoin. Escuelita Bitcoin also emphasizes privacy education, promoting the use of tools like CakeWallet and Monero. Through collaborations with other organizations and individuals, the team is extending the reach of Bitcoin education, fostering the adoption of Bitcoin in Latin America and emerging markets.
17.Bitcoin é aqui! Rolante/Riozinho-RS-BRASIL nostr:npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 * Introduction Bitcoin é Aqui! Rolante is located in Rolante, Brazil, and is dedicated to creating a lifestyle and tourism destination where 40% of businesses now accept Bitcoin as a payment method, showcasing the community's success in integrating Bitcoin into the local economy. Residents and visitors can use it to pay for all services, including accommodation, tours, local goods, medical services, and even construction and solar energy equipment. This reflects the practical application and convenience of its use in everyday life, aiming to create a digitally-driven environment powered by Bitcoin. * Latest Updates Recently, the Bitcoin é Aqui! Rolante has been actively promoting the adoption and use of Bitcoin in Brazil and beyond. The community has organized several educational events aimed at spreading basic Bitcoin knowledge and its practical applications in daily life, particularly through online videos and lectures. These efforts help people understand how Bitcoin plays a crucial role in the global financial system. The community has also been actively involved in promoting Bitcoin payments, supporting their adoption by local businesses and in the tourism industry.
18.Bitcoin Forte * Introduction Bitcoin Forte is a voluntary initiative aimed at introducing Bitcoin as a currency to Praia do Forte in Bahia, Brazil. The project provides valuable information about Bitcoin’s importance and encourages local merchants to adopt it as a payment method. By highlighting Bitcoin's international use, simplicity, and security, Bitcoin Forte aims to facilitate its adoption among both tourists and businesses.The community promotes Bitcoin as a stable and controlled currency, helping to avoid systemic price inflation. Bitcoin Forte simplifies the process for businesses by offering tools such as QR codes and the “Satoshi POS Wallet” app, which connects to a merchant’s primary wallet for seamless transactions. * Latest Updates Recently, the community has had no recent updates. The latest event dates back to July 2024, introducing Airbtc, a platform similar to Airbnb, but it only accepts Bitcoin as payment.
19.Bitcoin Paraguay * Introduction Bitcoin Paraguay is a community dedicated to connecting individuals in Paraguay who are interested in Bitcoin, promoting its adoption, and fostering the development of local circular economies. The community’s mission is to increase Bitcoin adoption by collaborating with local businesses and nonprofit organizations, helping to create a more sustainable local economy. Through regular events, talks, and resource sharing, Bitcoin Paraguay provides education and support to its members while actively exploring Bitcoin's application across various sectors in Paraguay. * Latest Updates Recently, the Bitcoin Paraguay community has made significant progress in promoting Bitcoin adoption. On November 5, they successfully hosted the fifth Bitcoin meetup in Asunción, attracting 110 attendees. The event included two Spanish-language presentations and a Lightning Network onboarding training session, with food and drinks available for purchase using Bitcoin. The event was made possible with strong support from sponsors Blink Wallet and Hacking Lives. On November 13, Josef Tetek visited Bitcoin Paraguay to help promote the adoption of Vexl in the country. The community also shared their progress through articles, with Jake, a community member, publishing an article in the Asunción Times on how Bitcoin Paraguay is improving people's lives.
20.Bitcoin Amantikir * Introduction They are starting the first community in the Serra da Mantiqueira to use and extol people about the bitcoin economy. * Latest Updates Recently, the Bitcoin Amantikir community has made significant progress in promoting Bitcoin as a payment method and fostering a circular economy in Santo Antônio do Pinhal. Various businesses, including a pet store, transportation service providers, a hotel, a fruit shop, and a tourist attraction, have started accepting Bitcoin payments. Additionally, the community is organizing a Bitcoin financial education course on December 2nd at Munay Pousada, aimed at helping young people aged 14-18 acquire essential financial knowledge and understand the importance of Bitcoin.
21.La Crypta nostr:npub1rujdpkd8mwezrvpqd2rx2zphfaztqrtsfg6w3vdnljdghs2q8qrqtt9u68 * Introduction La Crypta is an open-source community dedicated to advancing the adoption of the Nostr protocol and Bitcoin through developer-friendly tools and resources. By providing an integrated open-source stack, La Crypta empowers developers to sync with multiple relays, showcase profiles with badges, and facilitate seamless messaging, making it easier to build and utilize decentralized social platforms. Events like hackathons further enhance collaboration and attract new members, fostering innovation in decentralized social media. * Latest Updates LaWallet, their open-source wallet, integrates Bitcoin, Lightning, and Nostr to provide a seamless learning experience. With over 8,000 NFC cards distributed across conferences in regions like Argentina, Brazil, and Spain, LaWallet enables easy adoption while prioritizing user privacy. The wallet’s functionality is now supported by Alby’s official browser extension, further boosting accessibility.
-
 @ 07f367da:0e76880d
2025-01-06 15:25:20
@ 07f367da:0e76880d
2025-01-06 15:25:20- 장애인에 대한 편의제공 의무의 범주
- https://www.newspoole.kr/news/articleView.html?idxno=10611
- 입력 2023.11.22 17:09
활동지원사 호텔비도 지출해야 해요?
나의 이용자와 함께 타지역으로 여행을 간 적이 있었다. 여행지에 아는 사람이 있어 그런지 이용자는 나에게 숙박비 이야기를 하지는 않았다. 친구의 집에 초대되어 식사하던 중에, 활동지원사에 대해 생각해 본 적이 없었다며 초대자가 여러 가지를 물었다. 어쩌면 노동자보다 장애인이 더 친근한 초대자는 장애인이 여행하는 데 직면하는 무수한 문제에 더욱 공감하는 듯했다. 그러니까, 장애인이 여행을 갈 때, 같이 가는 활동지원사의 호텔비까지 장애인이 부담해야 하는 것이냐고 물었다.
누구나 그렇듯 장애인도 때로는 여행을 가고 싶다. 그런데 넘어야 할 산이 많다. 장애인의 여행에는 단순히 이동권 보장만 문제가 되는 것은 아니다. 2023년 8월 28일자 KBS보도에서는 장애인이 제주도로 비행기를 타고 가는데 파리를 여행하는 것과 비슷한 비용이 든다고 보도했다. 그런데 사실 조금 더 따져보자면 여기에는 몇몇 비용이 누락되어 있다. 장애인이 이동할 때 장애인만 가는 것은 아니다. 장애인을 지원할 누군가가 동행해야 한다. 이는 활동지원사가 될 수도 있고 가족이 될 수도 있고 반려인이 될 수도 있다.
현행 장애인활동지원제도에서는 활동지원서비스를 받는 장애인이 활동하는 데에 드는 비용을 누가 부담해야 하는지 기준을 제시한다. 활동지원사는 자신이 먹는 식사와 관련하여 장애인에게 부담을 주지 말라고 양성 교육에서부터 교육받는다. 그 외에 "외출동행에 소요되는 서비스 제공자의 경비 부분(공연 관람 등)은 이용자가 제공"하도록 되어 있다. 하지만 현장에서는 유명무실한 경우가 많다. 장애인당사자들이 재정적으로 넉넉한 경우는 거의 없다 보니, 활동지원사에 해당하는 비용은 활동지원사가 지불하길 요구하는 경우들이 종종 있다. 흔하게는 영화관람부터 동물원, 놀이동산, 드물게는 여행에 이르기까지 다양하다.
가족이나 반려인, 지인은 자신이 동행하는 비용을 함께 여행가는 비용으로 여길 테지만 노동자인 활동지원사의 경우 상황이 조금 다르다. 활동지원사 입장에서는 다른 지역까지 멀리 일하러 가는 것인데, 일하는 데에 드는 비용을 부담한다는 것은 임금이 삭감되는 것과 마찬가지다. 안 그래도 여행지에서의 식비는 대게 물가가 비싼 경우가 많은데, 교통비와 숙박비까지 부담한다는 것은 임금으로 생활을 영위해야 하는 노동자 입장에서는 곤란한 일이다. 장애인이 여행을 결심한다는 것은 축하해야 할 일이지만, 옆에서 일하는 활동지원사 입장에서는 여행을 앞두고 고민을 토로하는 경우가 많다. 낯선 환경에서의 업무강도 가중, 피로는 덤이다. 더욱 부담되는 것은 대개 활동지원사가 이 비용을 부담하지 않으면 장애인의 여행계획은 무산되는 경우가 많다는 것이다. 활동지원사의 책임은 아니지만, 이용자의 원망은 이성적으로 이루어지는 것이 아니고, 비용을 기꺼이 부담하는 누군가로 대체되어 일자리를 잃을 수도 있다. 그래서 나는 어딘가에 여행을 다녀왔다는 장애인을 보면 내심 "그래서 활동지원사에게 숙박비와 교통비를 얼마만큼 부담시켰나요?"라고 묻고 싶어질 때가 있다.
나도 일상적으로 장애인이용자와 영화관람을 할 때가 있다. 하지만 영화관람을 할 때 내가 영화를 온전히 한편을 다 관람하기는 힘들다. 장애인이용자도 활동지원사를 영화관에 동행시킬 정도면, 자신이 서비스받아야 할 필요가 있기 때문이다. 눈물 콧물을 사소하게 닦아주는 것부터, 갑작스레 화장실에 같이 갈 경우까지, 아니면 정말 영화가 재미가 없어서 갑자기 나오는 경우까지. 해당 영화관람은 나의 의사로 자유롭게 온전하게 이루어지기 힘들다. 나는 장애인의 편안한 영화관람을 위해 투입되는 인력일 뿐이지, 영화를 관람하는 소비자는 아니다. 정말 재미있는 영화라면 나는 나중에 별도로 비용을 지불하고 다시 영화를 봐야 한다. 이런 지경이다 보니 영화관에서 나에 대한 비용을 받는다는 것과 이 비용을 장애인이 부담해야 하는 것이 다소 불합리하게 여겨진다.
이런 불합리함을 느끼며 나는 종종 차라리 활동지원사를 인간으로 취급해 주지 않았으면 싶을 때가 있다. 차라리 개 취급을 해줬으면 싶을 때가 있다. 시각장애인 안내견들은 장애인을 위한 안내 업무를 하면서 문화시설에 대한 출입료가 징수되지 않는다. 시각장애인 안내견에 대한 출입금지가 시각장애인에 대한 차별인 것이 인정된다면, 활동지원사에 대한 출입금지 혹은 비용에 대한 부과는 왜 장애인에 대한 차별이 아닌가.
나는 이 글에서 두 가지를 말하고 싶다. 이 모든 차별에도 불구하고 활동지원사노동자에게 비용을 전가하는 장애인이용자들의 행태는 비판받아야 하고 금지되어야 한다. 서비스제공자가 장애인과 동행하는 사람에 대한 비용을 징수하는 것은 큰 범주에서 장애인차별로 인정되고 금지되어야 한다.
-
 @ a58a2663:87bb2918
2024-12-09 13:39:49
@ a58a2663:87bb2918
2024-12-09 13:39:49- Concluir com minha filha, até o fim de 2025, a leitura da tradução latina de Ursinho Pooh, isto é, Winnie Ille Pu, de Alexander Lenard (1910-1972), poeta, ensaísta e tradutor húngaro que viveu no Brasil. Que texto curioso! Estranho estímulo que me chegou para voltar a estudar latim a sério.

-
Importar mais livros pela Thrift Books e menos pela Loja do Diabo. Seu acervo é excepcional e o frete é mais barato. Às vezes, em menos de duas semanas já estou com o livro em mãos (e olha que resido no Maranhão).
-
Concluir e publicar meu livro Vida após as Universidades. Escrita & criação em velhos & novos contextos de risco, desenvolvimento de algumas ideias que insinuei em Contra a vida intelectual, no que diz respeito ao encerramento de um ciclo histórico de modos de fazer investigação erudita.
-
Rematar o terceiro e último módulo de Convivium - Seminário Permanente de Humanidades, "A Alegoria do Mundo: o Mago, o Filólogo e o Colonizador", embrião de um longo ensaio sobre o "projeto humanista" e as vias de saída da modernidade oferecidas pelo pensamento latino-americano. (As inscrições seguem abertas. Caso queira inscrever-se pagando em bitcoin, me mande um e-mail: camoensiii57@protonmail.com).
-
Defender no primeiro semestre minha tese de doutoramento sobre João Francisco Lisboa (1812-1863), o maior prosador brasileiro de meados do século XIX. Compreender seu Jornal de Tímon implica rever concepções há muitos estabelecidas sobre a formação da literatura brasileira.
-
Escrever pelo menos cinco ensaios de apresentação do pensamento de Vilém Flusser e do que pretendo realizar em FLUSSER_project. A ideia é divulgá-los em inglês e especialmente aqui pelo Nostr.
-
Ler TUDO de Ignacio Gómez de Liaño.
-
Não ceder à tentação de discutir com imbecil.
-
 @ c4b5369a:b812dbd6
2024-12-01 16:19:21
@ c4b5369a:b812dbd6
2024-12-01 16:19:21Ecash systems built on top of bitcoin have seen increasing adoption over the last couple of years. They have become a polarising topic in the bitcoin community, due to their centralized and custodial nature. Like any system, ecash comes with a lot of pros and cons when compared to other systems, that are fercely debated in cyber- and meat-space.
I have been working on developing tools and software for the ecash implementation Cashu for about 2 years now. I have had countless discussions with various people from different backgrounds about the topic. OG bitcoiners, fiat bankers, friends and family, privacy enthusiast... . As you can imagine the flow and outcome of these discussions varied widely.
Usually, conversations with bitcoiners were the most interesting for me. Their opinions about ecash polarised the most, by far. (excluding the fiat bankers, but that's a story for another day). In this short peice, I want to share some insights from the discussions I had, and maybe clear up some misconceptions about ecash on bitcoin.
What is Ecash?
If you still don't know what ecash is, sorry, I won't go into much detail explaining it. I recommend reading the wikipedia article on Ecash , and then this article on the rise and fall of digicash, the first and maybe only ecash company that existed. This will bring you up to speed on ecash history up until bitcoin entered the scene. Ecash was pretty much dead from the day after digicash went bankrupt untill it recently saw it's revival in two different spheres:
One of these spheres is obviously the bitcoin sphere. Here, ecash got reintroduced with the two open source projects Fedimint and Cashu. In my opinion, the main reason for this revival is the following fact: Unlike an implementation of ecash in the fiat world, that would rely on the permissioned system to "allow" something like ecash to exist, bitcoin does not come with that limitation. The permissionless nature of bitcoin allows for these protocols to exist and interoperate with the existing bitcoin stack.
The second, and maybe lesser known sphere is the revival of ecash as a CBDC. Bitcoiners might get scared at the mentioning of that word. Trust me, I don't like it either. Nonetheless, privacy enthusiasts see the opportunity to steer the CBDC-ship in another direction, by using an underlying technology for them that would limit targeted discrimination by the centralized authorithy. Something that works like cash... but in cyberspace... Ecash. One such implementation is GNU Taler, another one is Project Tourbillon. Usually, these kind of implementations use a cuck-version of the OG ecash, where only payers are anonymous, but not payees.
Anyway, in this article we will focus on the implementation of ecash on bitcoin.
About self custody
Bitcoin as a whole is about sovereignty and liberation. If someone else controls your money, they control you. For the first time since we've stopped using gold, bitcoin allows us to fully take control back of our money. A money that doesn't corrode, a money which supply connot get inflated, and a money that cannot be easily seized. All of this is true for bitcoin. There is only one precondition: You have to hold and use it self custodially.
Using bitcoin self custodially
The problem comes in when using bitcoin in a self custodial fashion. For bitcoin to maintain the monetary properties mentioned above, it has to remain decentralized. This means it is hard to scale, which in turn means the use of bitcoin tends to become more costly as usage increases.
So even if we wish that everyone would use bitcoin self custodially all the time for everything, I fear it is mostly just a dream, at least for the forseable future. Even with trustless second layer protocols like the Lightning Network, we are running into scaling issues, since at the end of the day, they are bound to the same onchain fee realities as bare-bones bitcoin transactions.
For most of humanity, it is financially not viable to pay even 1$ transaction fees for every transaction. Second layer protocol may bring the cost down a bit, but have other requirements. For example in lightning, you have an online assumption, to make sure your channel peers aren't trying to cheat. You need to have inbound liquidity to receive payments. There are cost associated with opening or closing payment channels, or rebalancing liquidity.
Other upcoming second layer protocols like Ark may improve on some of these issues. It is definitely something to look forward to! But they will have their own trade-offs, most likely also cost related. The fact remains that all trustless protocols that use the bitcoin timechain for conflict resolution, will have to deal with this matter. This is the cost of trustlessness.
Soo... Don't self custody...?
NO! If you can, you should always use self custody. As much as possible!
Personally, I use all the tools mentioned above. And I recommend that if you can, you should too.
But the fact is, not everyone can. Many would love to take control over their financial freedom, but the threshold for them to use bitcoin in a sovereign fashion is simply to high. So they will either remain in fiat slavery land, or they will end up using "bitcoin" through a custodian like coinbase, binance, or whatever banking service they have access to.
I will also mention that for some usecases, enjoying the convenience of a custodian is just very attractive. Of course, this is only the case as long as the custodian plays by the book, and doesn't suddenly freeze-, or worse, run away with your deposits.
The right tool for the right job
I don't beleive that one way of using bitcoin is better than the other. It entirely depends on which problem you are trying to solve.
If the problem is storing or transfering wealth, then of course you would want to do that on chain.
If on the other hand, you want to send and receive frequent small to midsized payments, you might want to get setup with a lightning channel to an LSP. Depending on how deep you want to get involved, you may even set up some infrastructure and become part of the Lightning network.
If you want to receive digital tips that you can later claim into self custody after they reach a certain threshold, you might opt for a custodial solution.
If you require certain properties, like offline peer-to-peer transferability, or cash-like privacy, you might choose an ecash system.
It doesn't mean that if you use one, you cannot use the other. You should use whatever is useful for the current problem you are trying to solve, maybe even using multiple tools in conjuction, if that makes sense.
Ecash vs Onchain vs L2?
First of all, we have to understand that ecash is neither a replacement for self custody, nor is it a replacement for trustless second layer protocols. They are irreplaceable with something that is custodial in nature, due to the simple fact that if you lose control over your money, you have lost the control over your life.
So. No one beleives you should prioritize custodial solutions to secure your wealth. Self custody will always remain king in that regard. Custodial wallets should be thought off as a physical spending wallet you can walk around with, even through the dark alleyways where it might get robbed from you. Keep your cash in there for convenient spending, not worrying about fees, liquidity, data footprints, channel backups, etc. etc. etc... These benefits obviously come at the cost of trust, that the provider doesn't rug-pull your deposit.
I really like the user experience of custodial services. I would never put a lot of money into any one of them though, because I don't trust them. Just like I wouldn't walk around with $10000 in my physical wallet. The risk that it gets stolen is simply to great. At the same time, this risk doesn't mean I will get rid of my physical wallet. I think having a wallet with some cash in it is super useful. I will mittigate the risk by reducing the amount I carry inside that wallet. This is the same way I think about digital money I hold in custodial wallets, be it an ecash service or others.
All things considered, it is hard to argue that self custody comes even close to the UX a custodian can give you, due to the fact that they can take care of all the complexities (mentioned above) for you.
So then, why ecash?
We now know, that we are NOT comparing ecash with the sovereign bitcoin stack. We are comparing it instead to traditional custodial systems. This is the area ecash is trying to improve uppon. So if you've chosen that the best tool to solve a problem might be a custodial solution, only then should you start to consider using ecash.
It offers a more privacy preserving, less burdonsome and less censorable way of offering a custody solution.
It offers some neat properties like offline peer-to-peer transactions, programability, de-linkage from personally identifiable information, and more.
Here is an example, on how ecash could create a fairer environment for online consumers:
Online services love to offer subscriptions. But for the consumer, this is mostly a trap. As a consumer, I would rather pay for a service right now and be done with it. I don't want to sign up for a 10 year plan, give them my email address, my date of birth , create an account, etc...
One way of doing that, would be for the service provider to accept payments in ecash, instead of having an account and subscription model.
It would work like this:
- The user creates ecash by paying into the service's mint. Hereby it is not required to use lightning or even bitcoin. It could be done with any other value transfer meduim the service provider accepts (cash, shitcoins, lottery tickets...).
- You use the issued ecash, to retreive services. This could be anything from video streaming, to AI prompts.
- Once you are done, you swap your remaining ecash back.
In a system like this, you wouldn't be tracked as a user, and the service provider wouldn't be burdoned with safeguarding your personal information. Just like a cash-for-goods transaction in a convenience store.
I beleive the search engine Kagi is building a system like that, according to this podcast. It has also be demoed by https://athenut.com/ how it would be implemented, using Cashu.
Here is another example, on how an event organizer can provide privacy preserving electronic payment rails for a conference or a festival, using ecash:
If you have been part of organizing a conference or an event, you might have experienced this problem. Onchain payments are too slow and costly. Lightning payments are too flaky.
Do merchants have to setup a lightning channel? Do they have to request inbound liquidity from an LSP? Do they have to splice into the channel once they run out of liquidity? In practice, these are the realities that merchants and event organizers are faced with when they try to set up payment rails for a conference.
Using ecash, it would look like this:
- Event organizer will run a dedicated ecash mint for the event.
- Visitors can swap into ecash when ariving at the entrance, using bitcoin, cash, or whatever medium the organizer accepts.
- The visitor can spend the ecash freely at the merchants. He enjoys good privacy, like with cash. The online requirements are minimal, so it works well in a setting where connectivity is not great.
- At the end of the event, visitors and merchants swap their ecash back into the preferred medium (cash, bitcoin...).
This would dreastically reduce the complexity and requirements for merchants, while improving the privacy of the visitors.
A bold experiment: Free banking in the digital age
Most bitcoiners will run out of the room screaming, if they hear the word bank. And fair enough, I don't like them either. I believe in the mantra "unbank the banked", after all. But the reason I do so, is because todays fiat/investment banks just suck. It's the same problem as with the internet platforms today. You, the "customer", is not realy the customer anymore, but the product. You get sold and squeezed, until you have nothing more to give.
I beleive with a sound money basis, these new kind of free banks could once again compete for customers by provididng the best money services they can, and not by who can scam his way to the money printer the best. Maybe this is just a pipe dream. But we all dream a little. Some dream about unlimited onchain transactions (I've had this dream before), and some dream about free banks in cyberspace. In my dream, these banks would use ecash to respect their users privacy.
Clearing up misconceptions and flawed assumptions about ecash on bitcoin
Not only, but especially when talking with bitcoiners there are a lot of assumptions regarding ecash on bitcoin. I want to take this opportunity to address some of those.
Ecash is an attack on self custody
As we've mentioned above, ecash is not meant to compete with self custody. It is meant to go where self custodial bitcoin cannot go. Be it due to on-chain limitations, or network/infrastructure requirements. Ecash is completely detached from bitcoin, and can never compete with the trustless properties that only bitcoin can offer.
Ecash mints will get rugged
100% correct. Every custodial solution, be it multisig or not, will suffer from this risk. It is part of the deal. Act accordingly. Plan for this risk when choosing to use a custodial system.
Working on ecash is a distraction from what really matters, since it is not self custodial
While it is true that improving self custodial bitcoin is one of the most important things our generation will have to solve, it doesn't mean that everything else becomes irrelevant. We see that today, in a lot of circumstances a fully sovereign setup is just not realistic. At which point most users will revert back to custodial solutions. Having technology in place for users that face these circumstances, to offer them at least some protection are worth the effort, in my opinion.
Ecash mints will retroactively introduce KYC
Yes it is true that ecash mints can do that. However, what would they learn? They would learn about the amount you were holding in the mint at that time, should you choose to withdraw. They would not be able to learn anything about your past transactions. And needless to say, at which point you should be one and done with this mint as a service provider, and move to someone that respects their users.
Ecash will be used to "steal" bitcoins self custodial user base
I would argue the oposite. Someone that has realized the power of self custody, would never give it up willingly. On the other hand, someone that got rugged by an ecash mint will forever become a self custody maximalist.
Closing thoughts...
I hope you enjoyed reading my take on ecash built on bitcoin. I beleive it has massive potential, and creators, service providers and consumers can benefit massively from ecash's proposition. Using ecash doesn't mean you reject self custody. It means you have realized that there is more tools than just a hammer, and you intend to use the tool that can best solve the problem at hand. This also means, that to some the tool "ecash" may be useless. After all, not everyone is a carpenter. This is also fine. Use whatever you think is useful, and don't let people tell you otherwise.
Also, please don't take my word for it. Think for yourself.
Best,
Gandlaf
-
 @ 6d8e2a24:5faaca4c
2024-11-30 00:07:10
@ 6d8e2a24:5faaca4c
2024-11-30 00:07:10Why do people enjoy pain and a short time pleasure, which could ruin their life and peace?
Why can't people leave their fleshy desires, obsession and pleasures even if it kills them?
Many have become slaves to their obsession having no will of theirs, claiming to be free yet imprisoned by their futility and lust.
We thought we have closed all the doors and windows, turn off the light so no one can see us, least so we thought to ourselves, forgetting our conscience is wide open, and God who sit in heaven watching, like it was never night nor dark, sees through us for he is light ruling over darkness.
The devil working upon our obsession making it a reality. The devil always uses our sinful, lustful desire to trick us given an end vain pleasure
We fall once, down with the guilt and pain of sin, the weight of the burden once thought, destroying the spirit and causing so many pains of regret, low self-esteem, and lack of confidence again.
He comes again not to bring new but to dwell in our past, bringing memories, mistakes, and errors making us feel more guilty and vulnerable, making us feel worthless and hopeless "We are doomed, so we think, God can't help us, our sins are too many; and with that, he finds a way to make us fall again, destroying us slowly till we are empty, having no will (stronghold).
Like a fire 🔥 lit in a bush, small as it is no one thought it could cause so much harm, or rather they thought they could control it or, put it off when they don't need it or, get bizarre.
Anything that has passed infantry allowed to grow is difficult or impossible to control so is a sin when is allowed to grow like a fire covering many areas is hard to put all areas off fast before one knows many areas are damaged many are beyond repairs
Every day we wake up, we plan how our lives, and how we are going to live the day, without the slimmest thought of contention, 'what if'. We do believe we have everything under control, everything planned out, but we forget that we are nothing but a sand timer that runs down so quickly than we thought.
Like the sand timer, our lives fade away gently, piece by piece till we cease to exist, only then, do we understand that we are rebels in this kingdom, not owners for we own nothing, with the dust reaching its last, the heartbeat and craves for more time, then we also understand, that time is never enough and time is so precious and priceless
Why do we always feel as if we have all the time in the world? why do we assume death to be a fairytale or a horror ghost story just to scare us out? Without having a sting.
Every day death proves more eager, the grave is so desperate that it looms looking and searching for any opportunity necessary to sting it stings.
But we are so carried away by life, deceived by what we have, the power, authority, and influence. We feel we are covered, yes we are but only to some certain extent. For life is so spiritual, than we could ever imagine or think of.
The night comes darkness looms over, evil rises, and fear grips one's heart, all wishing for the light. But now is no longer darkness that's so terrifying, but light itself has become as terrifying as the darkness, people wishing to live through the light, now wish the same to live through the night, for in it they find peace and comfort 😢
Why, I ask why, why has light become so terrifying and darkness become more comforting that the people find solace in it?
I came to understand why people find comfort in darkness is because they are afraid of selves afraid of what they have become, darkness does not challenge but rather allows you to wallow in your misery and regret, killing and draining you where no one will correct you or remind you, that you are not good enough, darkness gives you the room to accept who and what you have become, and there and then it echoes is better to die and live in peace than to be alive and live in misery.
Why will one think of death as the only option or think of death as the only solution to peace, is living not joyful, is life not great to live, why will one wish to leave all, family, friends everything, and settle for death?
I came to understand that, the most reason why one tends to choose death over life or loves to behold the warmth of darkness instead of light, is the feeling of emptiness and internal failure even after a significant measure, of material and social success, is a direct result of failure to discover purpose in life and a reason of being, when one loses his peace, joy all that's left or remain is pain, and regret. When a man reaches a stage of emptiness, where nothing else again matters life itself has no meaning, then it's only a test of time before destruction befalls such a person
Even the rich are depressed and frustrated beholding the enticement of the dark, and many try to drink themselves up, to them is the only way to find peace within, why, after so much wealth and achievement yet feel lonely, his greatest friends are alcohol and nights.
If money, riches cant give fulfillment or perfect peace then what can?
-
 @ 07f367da:0e76880d
2025-01-06 15:24:40
@ 07f367da:0e76880d
2025-01-06 15:24:40- 장애인활동지원제도의 화폐중심적 사유와 차별
- 뉴스풀 : https://www.newspoole.kr/news/articleView.html?idxno=10564
- 입력 2023.10.08 00:22
추석이 지나니 사람들이 연휴 후유증을 겪는다. 총 6일간의 연휴가 있다 보니 다시 업무에 돌입하기가 힘든가보다. 2023년 추석이 지나니 사람들은 벌써 내후년의 명절을 기다리는 모양이다. 2025년 추석은 7일의 연휴라고 한다.
하지만 정규직 직장인들이 그토록 환호하는 연휴에도 장애인은 고통스러워한다. 일단 활동지원사도 경우에 따라서는 명절을 가족과 보내야 해서 근무를 하지 못하는 경우가 많다. 장애인들은 명절에 활동지원사를 구하기 힘들고, 다행스럽게도 구한다 하더라도 바우처 소비가 더욱 많아져 고통스러워한다.
장애인의 입장에서는 활동지원 바우처 소비가 많아져 명절을 싫어한다고 말하면 사람들은 일견 낯설어한다. 하지만 이러한 문제는 사실 하루 이틀 일이 아니다. 장애인 활동지원제도는 2011년부터 법제화되어 시행되었고, 2011년 이전까지 '월 단위 시간'으로 보장되던 활동지원이 '월 단위 금액'으로 환산되어 표시되기 시작했다. 2012년부터 야간과 휴일에 소비되는 바우처 수가가 주간보다 1천 원 많이 소모되도록 변화되었고,[^1] 2013년 8월 1일부터는 휴일/야간의 경우 주간 대비 150%의 수가가 소비되도록 변경한 것이 현재까지 이어져 오고 있다.
문제는 이렇게 '시간'에서 '돈'처럼 금액 단위로 표기하고 야간이나 휴일 시기에 따라 소모되는 양을 변화시키는 방식이 장애인들에게 예상치 못한 변수로 다가오게 된다는 점이다. 이번 10월 2일처럼 대통령이 갑자기 임시공휴일을 지정이라도 하는 일이 생기면, 그날의 바우처 소비는 150%로 증가하게 된다. 관공서공휴일을 많은 사람들이 유급휴일로 누리지만, 이를 누릴 수 없는 5인 미만 사업장 노동자들이 차별을 겪는 것처럼, 장애인이 쓸 수 있는 활동지원 시간은 줄어들게 되어 실질적 손해로 이어지게 되니, 나로서는 이러한 것도 차별이라 생각한다.
그런데 이런 문제는 사실 꼭 명절이 아니어도 마찬가지다. 주간에 활동지원을 쓰는지 야간에 활동지원을 쓰는지에 따라 장애인이 이용할 수 있는 시간이 변동된다. 장애인 중에는 야간에 특히 활동지원을 받는 것이 중요한 사람들이 있다. 욕창을 방지하기 위해 체위 변경이 필수적인 사람들, 수면중 호흡기 상태를 옆에서 누군가가 관찰해야 하는 장애인들 등. 오히려 야간에 서비스가 필요한 사람들이 있다. 그런데 이들은 야간에 서비스를 쓸 수록, 지원받을 수 있는 활동지원서비스 시간의 총량이 줄어들게 된다.
'시간'에서 '금액'으로의 변화는 전 국가적으로 한 번에 이루어지지 않았다. 2019년 중앙정부는 사회보장정보원을 통한 사회서비스 바우처 전산관리를 점차로 확대하기 시작했고, 기초단위에서 추가로 지원되던 활동지원시간도 '시간' 보장에서 '금액' 보장으로 변화하게 되었다. 그 확대 과정에서도 얼마간의 갈등은 있었다. 적어도 기초추가지원의 경우 밤에 쓰건 낮에 쓰건 휴일에 쓰건, 일정 '시간'을 보장받던 장애인들은 자신의 시간이 줄어든 것을 체감했다. 장애인당사자들이 투쟁한 일부 기초지자체의 경우 지원시간을 늘려줌으로써 변화에 대한 완충을 기했지만, 당사자들이 투쟁하지 않거나 못했던 지역의 경우 주간수가를 기준으로 '금액'을 보장받았다.
시간을 보장하는 방식으로 되돌려도 '월 단위' 시간이라는 점이 장애인의 삶을 불안하게 한다. 2월처럼 한 달이 28일인 경우 보장받는 시간이 상대적으로 넉넉하지만, 한 달이 31일인 경우는 또 다르다.
나는 장애인활동지원제도의 가장 심각한 모순점 중 하나가 장애인의 권리와 노동자의 권리를 정부의 예산중심적 시각으로 획일화하는 데에서 발생한다고 생각한다. 활동지원제도가 장애인이 일상생활을 영위할 수 있도록 제공되는 보편적 권리로서의 공공재 성격을 가진다면, 주간이건 야간이건 공휴일이건 월간이건 일정한 수준이 꾸준하게 공급되어야 한다고 생각한다. 나는 이를 실현하기 위해서 장애인에게 현재처럼 월 단위가 아닌 주 단위로(적어도 일정 일수를 주기로) 활동지원서비스가 보장되어야 하고, 금액이 아니라 시간으로 활동지원 서비스가 보장되어야 한다고 생각한다. 그리고 활동지원사 노동자 권리 보장 기준은 장애인의 권리를 보장하는 기준과는 별도로 구분되어 예산이 책정되어야 한다고 생각한다.
[^1]: 2011년까지는 주간-휴일-야간의 경우 서비스 제공 수가가 일괄 6,000원이었다. 활동지원사에게도 야간-휴일 수당이 있어야 한다는 주장들이 있자 정부는 2012년부터 주간수가는 8,300원, 야간-휴일의 경우 9,300원으로 변경하였다. 그마저도 4시간까지만 적용되었다.
-
 @ 07f367da:0e76880d
2025-01-06 15:22:59
@ 07f367da:0e76880d
2025-01-06 15:22:59- 전가된 돌봄과 엄벌주의
- https://www.newspoole.kr/news/articleView.html?idxno=10518
- 입력 2023.08.25 13:54
공격성향의 돌봄대상 – 교육도 지원도 없이
나는 A를 B와 함께 만났다. A는 대화가 통하지 않았다. B는 A의 보호자다. B는 A에게 필요한 일을 나에게 지시했다. 내가 밥과 물을 차려주면 A는 알아서 먹었다. 때로는 A를 데리고 산책을 다녀왔다. A는 보조기기 없이도 잘 다녔고, 집 바깥 화장실을 좋아했다. 우리는 종종 집 인근 공원의 화장실에 오갔다. A는 대소변을 본 후 뒤처리를 해 줄 필요가 없어 큰 어려움이 없었다. 다만 그가 다른 사람을 깨물기도 해 문제였다. A에게는 손발톱 깎기, 목욕이 필요했고, A는 그 과정에서 나에게 공격성을 보이기도 했다. 처음 서비스를 들어간 지 얼마 되지 않아, B는 A를 목욕시키라고 했다. A는 목욕을 싫어하는 듯 했고, 목욕을 거부하며 나를 깨물려 했다. 자칫했다간 내가 물릴 판이었다. 결국 나는 A의 머리를 밀치고 목덜미를 잡은 채 몇 대 쥐어박았다. A는 공포에 떨며 몸 씻김을 당했다. 깔끔해진 A를 보며 B는 만족해했다. B는 다소 폭력이 있었음을 알았지만, 같이 살려면 어쩔 수 없다며 묵인했다.
장애인 활동지원에 관한 이야기다. 하지만 장애인에 관한 이야기는 아니다. A는 장애인 B씨가 키우는 반려견이다. 나는 개를 키워본 적이 없고, 개를 대하는 방법에 대해 교육받아본 적이 없다. 반려동물이 대중화된 만큼이나 반려동물을 키우는 장애인도 많고, 반려동물을 돌보는 일도 현실적 업무로 활동지원사에게 떠넘겨진다. 하지만 이에 대한 지침은 물론이고 교육은 전무하다. 돌이켜보면, 반려견이 조금은 더 편안해할 목욕이 불가능한 것은 아닐 것이다. 먼저 반려견과 내가 친해지고 서로에게 익숙해지는 시간이 충분히 있었으면 좋았을 것이다. 그리고 나에게 누군가가 반려견의 행동을 살피고 헤아리는 방법, 반려견의 공격행동을 대처하는 방법, 이러한 행동을 교정할 수 있는 방법을 미리 알려주었더라면 더 좋았을 것이다. 반려견의 개별적 특성도 알려줬다면 더 좋았을 것이다. 아니면 아예 개 전문가를 붙여줄 수도 있다. 하지만 우리에게는 그런 시스템이 없다. 그저 활동지원사는 장애인이용자에게 갈 뿐이고, 장애인이용자가 요구하면 요구하는 대로 서비스를 제공한다.
신체장애인과 구분되는 발달장애인 지원방법
이는 반려동물에게만 적용되는 이야기는 아니다. 활동지원사들은 종종 발달장애인의 지원에 관해 어려움을 토로한다. 활동지원사들은 실질적인 매뉴얼이 없다고 호소한다. 신체장애인은 그들의 지시대로 업무를 수행하면 되지만 발달장애인은 같지 않다. 발달장애인을 지원하는 방법은 애초부터 장애인의 의사에 따르지 않는다. 활동지원사는 발달장애인을 부모 혹은 그에 준하는 주변사람과 함께 만난다. 활동지원사들의 서비스 내용은 장애인당사자가 정하는 것이 아니라, 보호자에 의해 결정된다. 활동지원사는 첫 만남에서 발달장애인 개인의 특성을 파악하는 것은 불가능하고, 보호자의 이야기를 듣는다. 실질적인 업무지시는 이들을 통해서 이루어지고, 해당 활동지원사에게 서비스를 받을지 중단할지에 대한 결정도 보호자를 통해 이루어진다. 보호자가 요청하는 서비스 내용에는 당사자에게 통제를 가하는 내용이 포함된다. 보호자가 발달장애인 당사자에게 소위 인권적이라 할 만한 서비스를 요구하는지도 불확실하다. 사실 발달장애인의 의사를 존중하고, 발달장애인의 모든 행위에 대해 보호자가 책임을 져 준다면, 활동지원사는 발달장애인을 통제할 이유가 없다.
발달장애인과 활동지원사는 관계를 미리 형성할 시간도 주어지지 않고, 발달장애인을 대하는 특별한 교육이나 지침도 없고, 개별 발달장애인의 특성에 대한 적절한 정보가 주어지지 않는다. 안타깝게도 보호자들은 개별 발달장애인의 특성을 잘 정리하여 활동지원사에게 전달할 여력이 없는 경우도 있고, 활동지원인력이 서비스 제공을 꺼릴 사유를 알리고 싶어하지 않는 경우도 많다. 발달장애인에게 공격당한 활동지원사가 산재보험을 신청하려 해도 혹여나 자신의 자녀가 어려운 이용자로 소문날까 두려워한 부모의 만류로 신청하지 못한 경우도 있었다.
자기결정권이라는 환상
국가는 장애를 통제하기 위해 일률적으로 장애라 규정하고 줄 세우지만, 장애 내부의 차이는 비장애와 장애의 차이보다 크다. 나는 솔직히 발달장애인의 자기결정권을 이야기 할 때, 비장애인과 신체장애인 중심으로 형성된 자기결정권 패러다임을 발달장애인에게 일괄적으로 적용하는 것이 정당한지 의문이 들 때가 많다. 겉으로는 발달장애인의 자기결정권을 존중하는 척 하지만, 내용을 들여다보면 그렇지가 않다. 우리 사회는 발달장애인의 자기결정권을 존중하지도 않고, 활동지원사들에게 그렇게 가르치지도 않고, 그렇게 지시하지도 않는다.
중증의 발달장애인에게는 신체장애인을 지원할 때에는 강조되지 않는 보호, 그리고 그 보호와 구분되지 않는 통제가 요청되기도 한다. 언어장애인과의 소통에는 언어장애를 고려하여 천천히 반복적으로 신중하게 인내심을 갖고 듣는 것이 강조되지만, 발달장애인과의 소통에는 장애인이 말을 잘 듣도록 만들기 위한 스킬들이 강조된다.
활동지원사 양성교육교재를 보자. 활동지원사가 되고자 하는 사람은 해당 교재로 교육을 받는다. 발달장애인을 설명하는 장에서는 “자기결정권 부여”하라 면서도, “지적장애인에 대한 무조건적인 수용이나 인정은 바람직하지 않다”[^1]고 말한다. 존중받을 사안과 존중받지 않아야 할 사안을 타인이 판단하는 것 자체가 이미 존중받지 못함을 의미한다. 한편 사회적으로 이슈화되고 문제가 제기되는 발달장애인의 도전행동에 대해서는 신체적 개입, 공간적 분리 조치가 가능한 것으로 언급한다.
③ 위기단계
이 단계에서는 이용자의 감정상태가 일정 수준 이상으로 증가하고, 결과적으로 도전적 행동이 발생한다. 활동지원사는 이용자의 도전적 행동이 어떻게 진행되는지 이해하고, 도전적 행동의 발생상황에 지원하는 과정에서 이용자와 활동지원사 모두를 보호할 수 있어야 한다.
이때 이용자나 타인의 안전을 위하여 신체적 개입이 이루어지기도 한다. 손목잡기 등의 직접적 신체접촉을 통한 개입이나 격리·문 잠그기 등의 활동에 제한을 가하는 공간적 개입과 같은 유형이 있다.다만 신체적 개입에 대해 이용자의 인권을 보호 및 존중하기 위하여 다른 방법이 없을 경우 최후의 수단으로 최소한 시간이 소요되도록 진행되어야 한다._ 보건복지부 한국장애인개발원 발간, 활동지원사 양성 교육교재, 2021년 12월 발행판, 139쪽. 밑줄강조 필자.
이러한 조치 이전에 제시하고 있는 절차는 관련된 사람들과의 논의가 전부다.
발생 전과 후에 이르기까지 활동지원사의 역할을 확인하고, 특히 신체적 개입 등에 관해서도 논의할 필요가 있다. 이와 같은 당사자, 활동지원사, 보호자와 가족, 활동지원 제공기관의
소통과정은 사전에 이루어져야 할 것이며, 지원 과정에서도 지속될 필요가 있다.이때 비판적인 태도를 보이지 않으면서 정보를 공유해야 한다._ 보건복지부 한국장애인개발원 발간, 활동지원사 양성 교육교재, 2021년 12월 발행판, 137쪽. 밑줄강조 필자.
보호자로부터 허락받은 신체구속과 감금은 정당할까
양성교육교재에서는 “당사자, 활동지원사, 보호자와 가족, 활동지원 제공기관”이 소통하여 사전에 정하고 소통이 지속되는 것이 바람직하다고 말한다. 하지만 현장에서 이에 대한 논의는 거의 전적으로 보호자에게 의존되어 있다. 당사자는 동의·부동의 여부를 표할 수 없는 경우도 있고, 보호자가 활동지원기관을 선택하므로 활동지원기관의 영향력이란 크지 않다. 활동지원기관은 기관대로 사례별로 촘촘히 지원하기에는 인력이 부족하다. 결국 앞서 말한 대로 서비스 내용은 보호자에 의해 결정되고, 앞서 언급된 “신체접촉을 통한 개입”과 “공간적 개입”은 보호자의 의사에 따라 이루어질 수 있다. 아니면 보호자마저 방임하여 활동지원사가 전적으로 결정하게 될 수도 있다.
보호자도 장애인을 학대하지 않는다고 보장할 수 없다. 2019년 7월 보건복지부가 발간한 양성교육교재에서는 도전행동에 대한 명시 자체가 없었다. 2019년 12월 대전에서는 친모와 활동지원사가 지적장애인을 수시로 화장실에 가두고 때려 숨지게 하는 사건이 있었다.[^2] 장애인 구속을 위해 개 목걸이가 사용되기도 했다. 그런데 그 사건이 있은 얼마 후 발달장애인의 도전행동에 대한 신체적·공간적 개입을 새로이 명시하는 양성교육교재가 2021년 12월에 발행되었다. 정부는 개별 사건을 일탈적 사건으로 인식하는 데에 급급하다.
피할 수 없는 구체적 돌봄, 국가의 역할
신체장애인에게 신체구속과 감금이 이루어졌다면, 장애인학대로 판단될 것이다. 비장애인에게 같은 일이 벌어진다면, 형법상 범죄로 판단될 것이다. 발달장애인에게 신체장애인 또는 비장애인과 같은 수준의 자기결정권이 존중된다면, 마찬가지로 판단되어야만 하는 것은 아닐까?
장애인에 대한 지원은 공적 지원체계로 이루어져야 한다. 그리고 그래서 발달장애인의 도전행동 돌발행동에 대한 통제도 공적 차원에서 이루어져야 한다. 나는 발달장애인에 대한 신체통제가 사인의 판단에 의해, 사인의 물리력 행사에 의해 가능하다는 생각 자체가 발달장애인을 둘러싼 학대 등 여러 사건의 싹은 아닐까 생각한다. 차별적 교육을 받은 종사자들이 학대를 하지 않는 것이 오히려 기적은 아닐까. 교재에서 말하는 ‘최후의 수단’, ‘최소한의 시간’은 정말 최후이고 최소한일까. 그 판단에 대한 보증은 누가하는가? 이러한 판단들을 사인에게만, 그것도 대부분의 경우 한사람의 활동지원사에게 맡겨두는 것은 옳은가. 우리사회는 장애인을 대함에 있어 국가공권의 사용마저 아까워하는 사회는 아닐까.
발달장애인에 대한 신체통제가 정말로 ‘최후의 수단’, ‘최소한의 시간’ 만큼 필요하다면 비장애인에게 그러한 것처럼 사법절차와 공권력에 의해서만 예외적으로 신중하게 행사되도록 하는 것이 맞다. 국가가 행할 판단을 어정쩡하게 돌봄노동자들에게 전가시키고, 학대라며 비난하는 일은 없어져야 한다. 제대로 된 매뉴얼과 지원방안이 조속히 마련되어야 한다.
[^1]: 보건복지부 한국장애인개발원 발간, 활동지원사 양성 교육교재, 2021년 12월 발행판, 132쪽. [^2]: 연합뉴스, 지적장애인 빨랫방망이로 때려 숨지게 한 활동지원사 징역 17년, https://www.yna.co.kr/view/AKR20200618115100063 , 2020-06-18
-
 @ 8f0a121e:24038909
2024-11-28 09:07:00
@ 8f0a121e:24038909
2024-11-28 09:07:00كلنا نعرف أبيات إمرئ القيس في الليل التي تعلمناها في المدارس صغارا.
وليل كموج البحر أرخى سدوله ... عليّ بأنواع الـــهموم ليـــبتلي فقلـــت له لمـا تمـــطى بصـلبـــه ... وأردف أعجازا وناء بكلــــكل ألا أيها الليل الطويل ألا انـجـلي ... بصبح وما الإصباح منك بأمثل
وهي من أروع وأعلى ما قيل في الليل، ولكن تراثنا وشعرنا مليء بروائع في نفس المعنى. يقول النابغة الذبياني:
كليـــني لهمًّ يا أمــيمة ناصـــبِ ... وليل أقاسيه بطيء الكـــواكب تطاول حتى قلت ليس بمنقضٍ ... وليس الذي يرعى النجوم بآيب وصدر أراح الليل عازب هــــمه ... تضاعف فيه الحزن من كل جانب
يطلب النابغة من ابنته أميمة أن تدعه لهمه وتعبه ويشكي بطئ سير كواكب وثقلها في السير كناية على طول الليل.
في البيت الثاني، أقام الصبح مقام الراعي الذي يغدو فيذهب بالماشية والإبل، وبالمثل الصبح يذهب بالنجوم.
ثم يقول أن الليل "أراح عازب همه" بمعنى أنه أرجع اليه همه البعيد.
ويقول الوليد بن يزيد:
لا أسأل الله تغييرا لما فَعَلَت ... نامت وقد أسهرت عينيَّ عيناها فالليل أطول شيءٍ حين أفقدها ... والليل أقصر شيءٍ حين ألقاها
ويقول بشار:
خليلَيَّ ما بال الدجى لا تزحزح ... وما بال ضوء الصبـح لا يتوضح أضل النهار المستنير سبـــــيله ... أم الدـــــهر لـــيل كله لا يبــــرح
شعر #أدب #بالعربي
-
 @ 07f367da:0e76880d
2025-01-06 14:35:32
@ 07f367da:0e76880d
2025-01-06 14:35:32- 장애인이 하는 요리
- https://www.newspoole.kr/news/articleView.html?idxno=10445 - 입력 2023.06.21 11:59
어느 날 일요일 아침이다. 출근하니 장애인 이용자가 친구의 집들이를 간다고 했다. 각자가 요리를 조금씩 준비하는 포틀럭 파티(Potluck party)를 하기로 했다며, 오늘은 자신이 궁중떡볶이를 해주겠다고 큰소리를 친다. 이용자는 양손을 쓸 수 없는 뇌병변장애인이다. 나는 대뜸 이렇게 물었다. "궁중 떡볶이를 해주겠다는 거예요. 궁중 떡볶이를 하게 시키겠다는 거예요?"
그러자 특유의 유쾌한 웃음을 보이며 자신이 다닌 야학에서는 활동지원사가 한 것도 자기가 한 거라고 배웠다고 한다. 아니 활동지원사가 한 게 어떻게 자기가 한 게 되는가? 이제 이용자가 나를 냉장고로 이끈다. 냉장고에는 양념 된 고기와 썰어진 야채들이 준비되어 있다. "오~ 많이 준비해 뒀네요?"라고, 감탄하니, "내가 준비했다."고 말한다. 우리는 서로를 보며 또 한 번 웃는다. 그럴 리가.
이제 재료를 조리 판 위에 놓는다. 재료 투입에도 순서가 있다. 이용자는 이것저것 지시한다. 불을 강하게 하랬다가 약하게 하랬다가, 식재료를 저기로 치워 두랬다가 이제는 넣으라 했다가. 나는 그냥 시키는 대로 한다. 다년간의 활동지원 경력으로 나의 판단은 의미가 없다는 것을 배웠다. 이 요리는 내가 한 것이 아니고, 내 책임도 아니다. 요리 과정에 의견을 내는 것이 장애인 이용자의 자기결정권을 침해하는 행위가 될 수도 있다. 망친 요리는 더러운 맛으로 이용자의 혀에 타격을 가할 것이다. 장애인은 실패할 권리가 있고, 실패 또한 자립생활의 한 부분이다.
미리 식재료를 준비해 둔 탓일까? 장보기와 밑손질 시간이 들지 않으니 비교적 빠르게 떡볶이가 완성되었다. 집들이에 참석할 다수의 인원을 생각해 양이 아주 푸짐하다. 요리를 마치자 때마침 핸드폰에서 메시지가 왔음을 알리는 소리가 난다. 비보다. 집들이 참석 인원 중 한 명이 아파 다른 날로 집들이 일정을 수정하겠다는 소식이다.
이용자는 난감한 표정을 짓는다. 이 많은 음식을 어떡할지 고민이다. 잠시간 고민을 하더니 어머니에게 가자고 한다. 어차피 떡볶이 양이 많아 버리게 될 것이 뻔하니 어머니에게 가져다주자고 한다. 장콜을 부르고, 기다리고, 차가 오고, 짐을 싣고, 어머니 집으로 간다.
어머니 집에 가니 이용자의 동생도 있다. 이 궁중 떡볶이는 누가 했냐고 묻는다. 이용자가 옆에서 "내가 했다."고 말한다. 동생이 비릿한 웃음을 짓는다. 몇 개 집어 먹더니 맛이 없다고 말한다.
이용자와 나는 다시 이용자의 집으로 돌아왔다. 집에 남아있는 궁중떡볶이를 같이 먹는다. 양념이 조금 밍밍한 편이나 썩 나쁘지는 않다. 떡볶이를 먹으며 하루를 돌아본다. 장애인이용자는 요리를 자신이 했다고 주장하기 위해 요리의 절차를 고민하고 숙지하고 있었다. 그리고 온전히 자신이 했다고 주장하기 위해서인지 노동의 배분 때문인지 모르겠으나 전체 과정을 여럿의 활동지원사에게 분배했다. 과정이 세분화 될 수록 활동지원사는 전체 과정에서 자신의 기여분을 주장하기 어려워질 것이다. 아이폰 뒷면의 문구를 변용하자면 궁중떡볶이 뒷면에는 이렇게 쓰일 수도 있지 않을까. Designed by 장애인 김모씨 in Korea, Processed by 김모씨의 활동지원사들. 동생이 맛이 없다 하던 그 말도 떠오른다. 나는 이 평가로부터 자유로운가. 자유로우면 좋은 것인가. 그 자유는 자유인가 소외인가.
-
 @ 07f367da:0e76880d
2025-01-06 14:32:52
@ 07f367da:0e76880d
2025-01-06 14:32:52- 대체공휴일이 늘어도 변하는 것이 없는 노동자
- https://www.newspoole.kr/news/articleView.html?idxno=10406
- 입력 2023.05.23 17:00
법에선 유급휴일, 행정해석에는 소정근로일이 아니면 무급휴일
2018년 3월 근로기준법 개정으로 민간에서도 관공서공휴일을 유급휴일로 보장하도록 되었다. 해당 조항은 2022년이 되어 5인이상 사업장이면 모두 적용되게 되었다. 고용노동부는 2018년 5월에 개정 근로기준법 설명자료를 배포하였는데, 당시에는 개정이유를 이렇게 설명하고 있다.
○ 우리나라 관공서 등은 「관공서의 공휴일에 관한 규정」에 따라 공휴일을 지정하고 있으나 민간기업의 경우에는 단체협약, 취업규칙 등에 따라 공휴일 휴무 여부가 다른 실정
- 이에 단체협약, 취업규칙 등에 공휴일 휴무규정이 없는 영세 중소기업 근로자는 명절 연휴와 같은 공휴일을 유급휴일로 보장받지 못해 휴일에 있어서도 불합리한 차별이 존재
○ 따라서, 공휴일에 근로자가 차별 없이 휴식을 취할 수 있도록 공휴일을 근로기준법상 유급휴일로 보장하려는 것임
_ 2018. 05. 고용노동부 발간, 개정 근로기준법 설명자료, 20쪽.
조금 풀어 적자면, 법 개정 이전에는 ▲관공서를 포함해 사업장 규모가 크고 노동조합이 있어, 단체협약이나 취업규칙에 관공서공휴일을 유급휴일로 규정한 사업장은 관공서공휴일을 유급휴일로 쉬고 있었다. ▲반면 영세 중소기업 근로자는 명절 연휴와 같은 공휴일을 유급휴일로 보장받지 못해 휴일에 있어서도 불합리한 차별이 있었다. ▲그래서 관공서공휴일을 유급휴일로 보장하라고 법에 명시를 했다는 것이다.
그런데 중소기업(?) 시간급제 노동자인, 장애인활동지원사들은 법률이 개정되어도 이 법률의 혜택이 오지 않았다. 바로 고용노동부 임금근로시간과-743 행정해석 때문이다. 임금근로시간과-743은 토요일과 같은 비번일·무급휴일이 관공서공휴일과 겹칠 경우, 노동자에게 별도로 유급휴일수당을 더 지급할 필요가 없다고 답한다.
이런 행정해석이 나오자 장애인활동지원기관들은 관공서공휴일에 근무를 하지 말라거나, 급여제공 일정표에 근무를 계획하지 말라는 지시를 했다. 혹여나 근무를 하더라도 평일에 바우처 결제를 하도록 지시하기도 했다. 그리고 관공서공휴일을 ‘소정근로일이 아닌 날’, ‘무급휴일’로 한다는 근로계약과 취업규칙개정을 강행했다. 결국 장애인활동지원사들은 사업주들의 이런저런 조치로 관공서공휴일이 무급휴일로 설정되었고 관공서공휴일을 유급휴일로 누리지 못하게 되었다.
임금의 감소만 없으면 법개정 취지에 반하지 않는다
한편 임금근로시간과-653은 임금근로시간과-743 행정해석에 제동을 거는 새로운 기준을 제시한다. “근무편성시 관공서 공휴일에 근무할 근로자를 고의로 누락 하거나 이날을 제외하는 방법 등으로 유급휴일을 보장하지 않아 법적용 전보다 해당 근로자의 임금이 감소되는 경우라면 이는 법개정 취지에 반한다고 할 것”이라고 말한다. 이 행정해석은 법개정 취지에 반하는 요건을 나열하고 있는데, 사업주가 고의로 유급휴일을 보장하지 않아, 법적용 이전보다 임금이 감소되는 경우로 한정하고 있다. 하지만 이 해석은 이 해석대로 기이하다. 법률 개정으로 유급휴일이 늘어났으면 일을 하지 않아도 임금이 그대로거나, 같은 일을 하면 임금이 늘어야 하는 것이 상식적 결과다. 그런데 임금근로시간과-653에 따르면, 같은 일을 하고도 임금만 줄지 않는다면, 법개정 취지에 반하지 않아 위법하지 않는 경우가 생긴다.
장애인활동지원사들의 경우 사업주의 고의로 유급휴일을 보장하지 않아도, 다른 날에 근무를 더 몰아서 많이 하게 되어 임금의 감소는 발생하지 않을 수 있다. 월급제 노동자의 경우 관공서공휴일 유급휴일을 누리고 다른 대체근무일을 고민하지 않아도 되지만, 장애인활동지원사들은 다른 근무 가능한 요일을 찾아 근무해야 한다. 하지만 최종적으로 임금의 감소는 발생하지 않으니, 임금근로시간과-653의 해석상으로도 위법은 아니다. 743이나 653이나 활동지원사 노동자는 관공서공휴일유급휴일을 보장받기는 어렵다.
이러한 행정해석의 문제는 비단 장애인활동지원사만의 문제가 아니다. 법적용 이후에 근무를 시작하는 노동자의 경우나, 법적용 이후에 생긴 일자리의 경우에 대한 고려가 없다. 이러한 경우는 법 개정 이전에는 근무 자체를 하지 않았으니 비교 대상이 없다. 비교할 대상이 없으니 감소하는 경우에 해당하지 않는다. 결국 사용자는 2개의 행정해석에 힘입어 “관공서공휴일은 소정근로일에서 제외하고, 무급휴일로 한다”는 문구만 근로계약서에 추가하면 관공서공휴일을 무급휴일로 만들 수 있다. 그러고는 산업 자체의 특성 때문에, 관공서공휴일은 일을 할 필요가 없다고 주장할 수도 있겠다. 사회는 빠르게 바뀌고 새로운 산업도 다양하게 생기고 있다. 사업주 입장에서는 이런 식의 근로계약을 체결하는 데에 강력한 유인을 갖는다. 결과적으로 고용노동부가 시간급제 고용을 권장하는 꼴이다. 그리고 여전히 “영세 중소기업 근로자는 명절 연휴와 같은 공휴일을 유급휴일로 보장받지 못해 휴일에 있어서도 불합리한 차별이 존재”하게 된다. 법률을 개정한 이유에 의문을 가질 수밖에 없다. 행정권이 입법권을 덮어버리는 모양새다.
유급휴일의 양극화
2023년, 석가탄신일에도 대체공휴일이 적용되게 되었다. 2023년 석가탄신일은 토요일이고 대개의 직장의 경우 토요일은 무급휴일이므로, 임금근로시간과-743 행정해석에 따르면 유급휴일을 보장하지 않아도 되는 날이다. 그런데 대체공휴일이 도입되었다. 공무원과 월급제 노동자들은 아마도 월요일 유급휴일이 하루 더 늘어났겠지만, 시간급제 노동자들은 무급휴일만 하루 더 늘어났다. 전 정권에서도 현 정권에서도 공휴일은 늘어만 간다. 대체공휴일이 늘어날 때 대통령들과 국무위원들은 토요일이 소정근로일인지를 따지지 않았을 것이다. 2018년 3월 근로기준법 개정안을 통과시킨 국회의원들도 마찬가지였을 것이다. 하지만 정작 노동자의 권리를 보장해야할 고용노동부가 소정근로일을 빌미로 유급휴일을 없애고 있다.
근로기준법은 노동조건의 최저선을 제시하는 법이다. 그런데 그 최저선이 소정근로시간인가 아닌가 하는 사업주의 자의에 의해 휘둘리는게 옳은가? 꼭 장애인활동지원사가 아니라도 "우리는 관공서공휴일 유급휴일은 해당 없다"고 말하는 시간급제 노동자들을 종종 본다. 관공서공휴일 유급휴일 부여에 별다른 조건을 달아서는 안 된다. 평등한 유급휴일 보장을 위해서는 그 수밖에 없다. 고용노동부는 하루빨리 해당 행정해석을 폐기해야만 한다.
-
 @ c4b5369a:b812dbd6
2024-11-24 09:27:12
@ c4b5369a:b812dbd6
2024-11-24 09:27:12How to print your own ecash, using Gandlaf's money printer
To celebrate the recent money printer update, here is a short guide on how to use it.
Step 1: Go to the money printer
Unlike the FED's money printer, this Cashu ecash money printer is openly available. Head over to https://brrr.gandlaf.com to give it a spin.
Select a mint
Choose a mint that should be backing the ecash notes. You have a few different options when choosing a mint:
- Connect to your own mint: Connecting to your own mint is great if you want to be the backer of the ecash notes. It does however require you to have your mint up and running. You can connect to it by typing the mint URL into the input field.
- Connect to a known mint: There are mints that are already indexed on nostr. You can find them by clicking on the `discover more mints` button.
- Connect to any mint you want!: All you need is the mints URL. Just type it into the input bar!
Once you selected a mint, click connect to set up the mint for money printing :

After connecting to the mint, you will have the option to select the currency you want to print. Not all mints support all currencies! The dropdown menu below will show all available currencies the mint offers.
After selecting your preferred currency, click confirm to continue.

In the next step, you will chose the amount that should be printed on each note. Be careful though, because unfortunately not every amount is possible. To preserve mint users privacy ecash mints use fixed coin amounts. This means a specific amount, will be made up from smaller amounts. Today, most cashu mints use power-of-2 amounts.
So if you for example would like to print the amount "100", it would be made up from the coins [64, 32, 4]. The maximum number of coins that can be encoded in a QR code, without the QR code losing its readability is \~4. The money printer will analyze which amounts the mint offers, and show how many coins will be needed.
Below, you will see the calculation of how much the total issuance for this printing cycle will be. Once you are all set, click confirm to continue.

You can now either add the funds for the print via Cashu token or via Lightning. Let's first take a look on how to add funds via Cashu token.
If you select this option, I will assume that you already own ecash from the mint you wish to print the notes. Otherwise, you should move on to the payment by lightning.
You have to make sure that the token you are pasting is from the correct mint, in the correct unit/currency and matches the amount exactly! Otherwise, it will not work.

If you don't own ecash from that mint, you can pay for the print with lightning directly. The only fees that will be charged are Lightning network fees.
Just scan the QR code that is presented to you and wait for the payment to be confirmed.

Once the payment has confirmed, either through Cashu or through Lightning, the print is ready. You can now customize the design you wish to print.
You can select a color, a brand image and a corner image that should be put on the note.
Once you are happy with the design, go ahead and click `Print now! BRRRRRRRRRRR`

This will take you to the print page. You can now print the ecash by pressing `CTRL`+`P`
And that's it! You have now printed your own money. I hope you liked the experience of playing FED for a day.
Be aware! Once scanned and redeemed, the ecash notes become invalid. So they are one-time-use.
If you want to make another print, just refresh the page. It will take you back to the beginning. Your past prints will also be stored in the browser cache, so you can come back to them at a later time, if your printer overheated or something.

Happy printing!
Gandlaf
-
 @ 319ad3e7:cc01d50a
2024-11-22 21:03:17
@ 319ad3e7:cc01d50a
2024-11-22 21:03:17Candied Pecans by Double00Satoshi
Details⏲️ Prep time: 10 🍳 Cook time: 45 🍽️ Servings: 16
Ingredients
- 1/4 cup light brown sugar
- 1/4 cup granulated sugar
- 1 tablespoon ground cinnamon
- 1 teaspoon salt
- 1 pound unsalted pecans halves
- 1 egg white
- 1/2 teaspoon vanilla extract
- 1 teaspoon water
Directions
Preheat oven to 300 degrees F. Line a large baking sheet with parchment paper and set aside. In a bowl, add sugars, cinnamon, and salt. Whisk until combined. Set aside. In a large bowl, whisk the egg white, vanilla, and water together until frothy. Add the pecans and gently toss until the pecans are well coated. Add the sugar and cinnamon mixture and toss until pecans are covered. Spread the pecans out in a single layer on prepared baking sheet. Bake for about 30-45 minutes, stirring every 15 minutes. Remove from the oven and let the pecans cool on the baking sheet. When completely cool, store in an airtight container for up to 1 month.
Deviled Eggs by Seth
Details ⏲️ Prep time: 20 min 🍳 Cook time: 15 min 🍽️ Servings: 6
Ingredients
- 6 hard boiled eggs, peeled
- 3 tablespoons of mayonnaise
- 1/2 teaspoon of soy sauce
- 1 teaspoon of Dijon mustard
- 1/2 stalk of celery, finely diced
- Salt and pepper
Directions
Cut eggs in half lengthwise and pop yolks out into bowl, mash with fork. Mix in mayonnaise, mustard, celery, soy sauce, salt and pepper. Whip until a creamy texture Scoop out fill and add to egg whites, heaping it slightly. Add garnish of choice Serve immediately or refrigerate before serving.
Bang Bang Shrimp by Hes ⚡️
Details ⏲️ Prep time: 20 min 🍳 Cook time: 20 min 🍽️ Servings: 4
Ingredients
- 1 pound shrimp
- 1 teaspoon granulated sugar
- ½ cup all-purpose flour
- ½ cup panko breadcrumbs
- 1 teaspoon salt
- ½ teaspoon black pepper
- ¼ teaspoon garlic powder
- ¼ teaspoon onion powder
- ¼ teaspoon dried basil
- 1 egg
- 1 cup milk
- 4 – 5 teaspoon chili garlic sauce
- 1 teaspoon rice vinegar
- ½ cup mayonnaise
Directions
Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
To Find More Recipes, go to Zap.Cooking
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ ddf03aca:5cb3bbbe
2024-11-20 22:34:52
@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions.
Subscriptions with Cashu
One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that?
However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this:
-
Overpaying:
To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. -
Full Interactivity:
In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends.
Enter Locking Scripts
One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone.
A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key.
To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token.
With these tools, we can now create non-interactive payment streams!
One Missing Piece…
Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams.
The Grand Finale: Payment Streams
Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender.
Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.
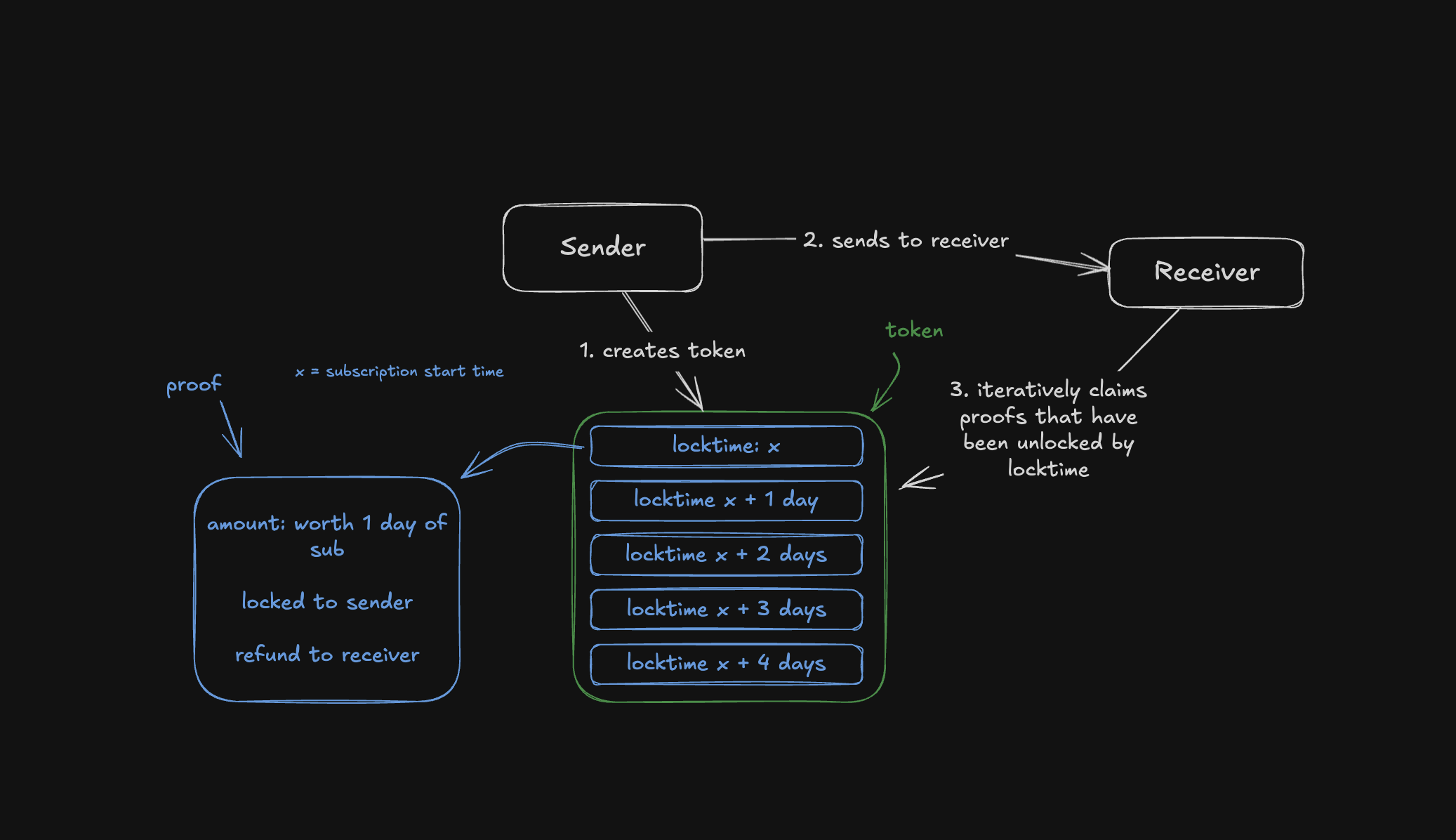
Example: Renting a VPS
Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work:
- Construct a token worth 7,000 sats to cover the entire week.
- Divide the token into 7 proofs, each worth 1,000 sats.
- Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key.
- The first proof has a locktime of
now. - The second proof has a locktime of
now + 1 day. - The third proof has a locktime of
now + 2 days, and so on.
When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on.
At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver.
With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds.
Thank you for reading. Make sure to leave a nut if you enjoyed this :)
-
-
 @ af9d7040:42d05d35
2024-11-14 09:25:34
@ af9d7040:42d05d35
2024-11-14 09:25:34
Oswald: Ruthlessness in the Pursuit of Power and Survival
In Gotham City, Oswald Cobblepot, known as “The Penguin,” lives by the unrelenting rules of the mob: ruthless, without compromise or boundaries. For him, survival demands sheer will, extreme cunning, and coldness. He will do anything to achieve his aims, even betray those closest to him—like his mother, who has profoundly influenced him. His attachment to her is rooted in a twisted, obsessive need for approval, and his ruthlessness is not only a survival strategy but also an expression of his deeply embedded self-centeredness.
The Penguin maneuvers through the shadows of Gotham City with manipulation, deceit, and vengeance, like a serpent coiling around its prey. His every success is built on a disregard for humanity and a relentless thirst for power. Though he appears to show devotion to his mother, this is only another facet of his self-serving nature. He cherishes her only so long as she provides him with a sense of security; the moment she becomes a liability, he discards her without hesitation. This twisted complexity makes him a character who elicits both fascination and repulsion.
The Penguin’s unique blend of cruelty and contradiction separates him from the typical mob character. His ruthless selfishness is rooted in self-preservation. He is capable of manipulating or even betraying those closest to him. His “loyalty” is merely a mask for his unyielding self-interest. This guise of loyalty makes him more isolated and untrustworthy than those around him, ultimately marking him as a true antihero—someone who cannot be trusted and who feels no attachment even to those he holds dear.

Sofia: A Tender Wound in the Cold Reality
In contrast to the Penguin’s dark nature, Sofia, the female lead, presents a softer, yet no less complex character. Like him, she exists within Gotham’s shadows, but she retains a degree of innocence and kindness. Sofia, too, has a damaged side, but hers is gentler, perhaps even curable; her inner nature is resilient and compassionate. The Penguin, however, is wholly different—cold and selfish, with his inner darkness shaping every decision and action. Where Sofia struggles within Gotham’s corruption but maintains her inner light, the Penguin is the opposite, allowing his cruelty to permeate every aspect of his life.
Sofia’s presence is like a quiet undercurrent, casting the Penguin’s icy nature in sharper relief. She occasionally brings light into his shadowed world, though her warmth is ultimately no match for his darkness. Sofia’s compassion exposes the Penguin’s pathological selfishness, and her fleeting kindness only emphasizes his chilling indifference.

The Solitude of a Drifter
With its muted color palette, the film portrays Gotham as a city almost devoid of life, where the clamor of daily existence only serves to conceal an underlying emptiness. The city’s visual loneliness, along with a slow, deliberate narrative and moments of silence, subtly reflects the Penguin’s inner struggle. His journey for power begins with a warped attachment to Gotham, and as the story unfolds, we see him descend into total darkness, losing all semblance of warmth. The scattered plot structure and somber music shape his evolution into a kind of melancholic, fragmented poem.
In this solitude, the director refrains from casting the Penguin in simple moral terms. Like life itself, the narrative is complex and fragmented, juxtaposing Gotham’s wealthy and impoverished neighborhoods to create a blurry psychological divide. In this “ruin” of Gotham, some people drift, some settle, while the Penguin himself wanders, searching for a place to belong. The pacing and cinematography draw the viewer in as though they are walking Gotham’s desolate streets, accompanied by a haunting piano melody.

The Paradox of Power and Loneliness
The Penguin’s loneliness is not merely a result of Gotham’s darkness; it is the byproduct of his dependence on power. His need for control and his fixation on security bind him, like twin shackles, to his misery. He cannot escape his solitude even when perched at the top of Gotham’s hierarchy. His attachment to his mother is merely an extension of his self-interest; he has never truly known love or warmth. His cold and selfish nature is not a choice but an innate part of him, driving him inevitably toward isolation.
The series offers no definitive moral compass nor romanticizes any side. The Penguin’s relationship with Sofia and the sacrifices, betrayals, and suffering they both endure on the road to power seem to reflect the harsh realities of life. Gotham’s “ruinous” stage presents each character grappling with their choices and their costs.

Moving Forward in the Darkness
The allure of The Penguin lies not only in its portrayal of an antihero but also in its exploration of the character’s inner lives. The Penguin’s turbulent life as a mobster intertwines with his attachment to Gotham, echoing those who search for belonging in places that feel forgotten. Sofia’s gentleness and fragile compassion, like a tender blade, continually pierce the Penguin’s illusions about power and loneliness.
The Penguin does not rise to power swiftly; instead, he edges toward a deep, inevitable abyss. The director’s pacing, intense and deliberate, brings the Penguin closer to the heights of power while making his solitude more profound. The Penguin strikes at the heart of adult disillusionment, showing us that the world will not soften simply because we yield. We can only stumble forward in the dark, perhaps even make peace with it.
— Written by @Shaun on November 13, 2024
-
 @ 07f367da:0e76880d
2025-01-06 14:30:57
@ 07f367da:0e76880d
2025-01-06 14:30:57- 장애인 인권은 외치지만 차별주의자입니다
- https://www.newspoole.kr/news/articleView.html?idxno=10379
- 입력 2023.04.26 10:30
사람들에게는 각자 정의가 미치는 범위, 즉 정의의 범위가 있다. 누구나 정의를 추구하는 것 같지만, 실제로 사람들이 생각하는 정의가 미치는 영역은 한계선이 있다. 어떤 경계를 중심으로 정의의 영역 안에 있는 사람들은 존중받아 마땅하고 공정한 분배가 이루어져야 한다고 생각한다. 하지만 그 영역 밖에 있는 사람들은 적으로 생각되거나 비인간화되고 잔인하게 대해도 된다고 느낀다. 이들은 정의가 관장하는 도덕적 세계 밖에 존재한다.
– 김지혜, 선량한 차별주의자(창비, 2019), 147.
오래된 중재 요청의 기억
전국장애인차별철폐연대(전장연)에는 전국단위 장애인자립생활센터들의 협의체 한국장애인자립생활센터협의회(한자협)가 소속되어 있고, 한자협 소속 장애인자립생활센터 다수가 활동지원사업을 수탁하고 있다. 우리노조는 중앙단위인 전장연, 한자협과 공동사업을 한 기억을 살리며, 노사 갈등에 있어 중재자 역할을 해줄 것을 요청하기도 했다.
2017년 11월 2일, 우리노조와 당시 돌봄지부[^1]는 전장연과 한자협에 공문을 발송했다. 대구지역 전장연 소속단위 활동지원기관 여러 곳이 활동지원사들에게 부당한 임금꺾기를 하여 이에대한 중재를 요청하는 공문이었다. 당시 대구의 활동지원기관들은 노동자가 1시간을 일하면 10분씩을 휴게시간으로 부여했다고 주장하며 노동자들의 근무시간을 축소 산정하고 임금을 삭감했다. 당시 지역언론을 통해 공개된 급여명세서에 따르면, 센터가 복지부에 청구한 결제시간은 138시간이지만 노동자가 받은 임금은 115시간에 해당하는 임금이었다.[^2] 자립생활센터는 정부에게는 138시간 서비스가 제공되었다고 보고하여 138시간에 해당하는 수가를 받고도 노동자들에게는 115시간에 해당하는 임금만을 지급했다. 휴게시간 명목으로 임금을 제했지만, 노동자들에게 실질적인 휴게시간도 보장되지 않았다.[^3] 부당한 처사다. 그런데 당시 대구장애인차별철폐연대(대구장차연)의 정책국장은 기사 말미에서 이렇게 말한다.
“활동보조 서비스가 도입될 때부터 시장화된 서비스로 만들어지면서 이미 예견된 상황이었다. 새 정부가 사회서비스 관련해서 핵심적인 방향을 잡아주면 좋겠다”며 “활동보조인 공공성이 확보될 수 있는 인프라를 만들고, 예산을 확대해 공공서비스 노동자들의 처우 문제 해결에 나서야 한다”
노조의 공문에 대한 전장연과 한자협의 태도는 어땠을까? 아무런 대답도 하지 않았다. 공공운수노조와 해당 사업장 노동자들의 투쟁으로 해당 사안은 국회 및 정부에 전달되었으며 문제가 외화되고 나서야 결국 사업장들은 휴게시간 임금꺾기를 철회하였다.
3월 23일, 한자협의 기자회견
지난 이야기를 언급하는 이유는, 3월 23일에 있었던 한자협 주최 기자회견 때문이다. 한자협은 3월 23일 서울동부지방법원 앞에서 “「시급제 활동지원사 처우」는 보건복지부에 「관공서 공휴일 수당 지급」은 고용노동부에 책임을 물어라!”라는 제목으로 기자회견을 열었다. 3월 23일은 A장애인자립생활센터 관련 민사재판의 첫 공판일이었다. 우리노조는 A센터를 상대로 취업규칙 무효확인과 미지급한 수당을 청구하는 소송을 제기하였는데[^4] 첫 공판이 3월 23일에 있었다.
공판 전인 당일 오전에 누군가를 규탄하기 위해 한자협은 기자회견을 열었다. 기자회견 제목에는 “책임을 물”으라고 되어 있지만, 누구더러 물으라는 것인지 구체적 명시가 없다. 기자회견 보도자료[^5]와 발언[^6]을 잘 살피면, 해당 기자회견이 규탄 대상으로 삼고 있는 사람들은 실질적으로 나를 포함한 원고인 노동자들과 노동조합임을 알 수 있다. A센터에 법적 다툼을 걸지 말고, 노동부나 보건복지부로 가라는 규탄이다.
특별히 2017년의 사건이 떠오른 이유는, 발언 논지의 유사성도 유사성이지만 한자협은 회원사업장의 부정에 대해 방관한 역사가 있으면서도 노조가 대화하지 않고 있다고 노조를 규탄했기 때문이다. “함께 고민하고 연대”하는 것은 얼마나 좋은 말인가? 하지만 이 말도 사실을 왜곡하고 누군가를 억압할 때 쓰일 수 있다는 것을 그날의 기자회견은 보여준다. 2017년의 묵살 이후 우리는 개별 사업장의 분쟁에 대해 개별 사업장 단위로 대응하고 있다. 어쩌면 우리의 중재요청이 한자협을 곤란한 입장에 처하게 하는 것은 아닐까 하는 판단 때문이다. 개별 사업장 단위에서 노조가 대화의 노력을 않는 것도 아니다. 노조는 A센터에 노사협의회를 통해 의견을 제기하고 재직노동자 80명의 연서명을 받아 의견을 제출하였다. A센터 소장으로부터 돌아온 대답은 법대로 하라는 응답과 묵살이었다.
이제 내용을 보자. 이날의 기자회견에서도 2017년 대구장차연 정책국장이 한 발언과 비슷한 논지의 발언이 반복되었다. 정부가 설계한 활동지원제도는 갈등의 소지를 품고 있으며, 이에 대한 책임은 기관에는 없고 정부에만 있다는 식이다. 시장화정책에 대한 문제인식을 표하며 겉으로는 공공성을 추구하는 듯하지만, 실상은 민간위탁기관으로서의 자신들의 책임을 면피하고, 예산지급의 경로 문제를 언급하지 않음으로써 전달체계의 문제를 은폐한다. 결국 자신들에게 예산을 더 내려달라는 요구다.
보도자료를 보자 ▲정부가 노사갈등과 분쟁이 발생하도록 오랫동안 방치해 왔으며 ▲정부는 부처 간 핑퐁으로 구체적인 매뉴얼 또는 취업규칙을 만들어 배포한 적이 없다 ▲활동지원기관은 공익성 사업 활동지원사업을 하고 있고 수익사업을 하지 않으며 ▲노사협의체를 성실히 운영하는데도 악질적인 사업체로 몰아가서 유감이다 ▲A센터 취업규칙 개정은 적법하다는 내용이다. 보도자료의 최상단 박스칸에는 ‘표준 취업규칙 제공’, ‘급여지급 기준 마련’, ‘활동지원급여단가 책정’을 요구하고 있다.
이 모든 사태가 정부의 무한책임이라면, 활동지원기관 무책임의 한계는 어디까지일까.
나도 정부의 무책임에 대해서는 할 말이 많다. 하지만 그렇다고 활동지원기관의 모든 행위에 책임이 없는 것은 아니다. A센터 대리를 맡은 장애인차별금지추진연대(장추련) 자문변호사의 비유[^7]를 이어 말해보자면, 부모가 없는 사이에 아이들이 싸우면, 부모가 돌아와서 그 싸움이 왜 일어났는지에 대한 시시비비를 가리고 아이들을 훈계해야 한다. 그런데 나이가 많은 형이 동생에게 상해를 입히고도 그 책임은 부모가 방기한 탓이라고 말하면 그 말이 설득력이 있을까. 자신을 훈육하는 부모에게 그런 말을 한다면, 혹은 맞은 동생에게 그렇게 말한다면 그걸 그대로 받아들일 수 있을까.
활동지원기관들이 정부를 탓하는 자기정당화 발언은 오래되었다. 노동자의 노동권을 주장하는 모든 시도에 활동지원기관들은 정부를 탓했다. 2017년의 사례에서 노동자의 노동시간을 꺾고 중간에서 이득을 취하는 행위를 정부가 시킨 것은 아니다. 기관이 자신들의 운영이 어려운 사정에 대해 노동자들에게 고통을 전가한 행위일 뿐이다. 한자협 기관이 아닌 활동지원기관들의 사례도 나열해보자. 재정적 여유가 있음에도 활동지원사에게 임금채권포기각서를 강요한 사업장에서도, 정당한 임금을 요구한 노동자들을 해고한 사업장에서도, 성추행 피해 노동자에 대한 보호를 요구했던 사업장에서도, 결국은 정부의 책임이라고 말하며 노동자의 권리를 외면했다. 그러면서 그들은 말한다. “이 문제는 함께 해결해가야 할 문제”라고. 하지만 그 속에 자신들의 책임은 없다. 기자회견 사회를 본 한자협 국장의 말대로 아무런 책임이 없는 “하청 업체”일 뿐이라면, 활동지원기관의 존재의의는 어디에 있는가. 활동지원사 노동자의 권리는 어디까지 포기해야 하는가.
A센터는 법 적용시기인 2021년부터 2022년까지 관공서공휴일유급휴일수당을 전혀 지급하지 않았다. 법 적용시기 이전부터 수당을 지급해야 하는 것 아니냐 의견을 주었음에도 지급하지 않았다. 센터 운영이 어렵다는 이유였다. 이 부분은 법률 및 행정해석에 대한 입장 차가 있더라도 명백한 불법이다. 한자협에서 주장하는 해석을 적용한다고 하더라도, 전혀 지급하지 않았기에 임금체불이 있는 것이다. 그러고는 지급을 회피하기 위해 2021년 12월에 취업규칙을 개정했다. 이 모든 행동을 정당화하기 위해 A센터가 하는 말은 다른 여러 활동지원기관이 말하듯이 정부가 예산을 충분히 주지 않아 센터 운영이 어려워 어쩔 수 없다는 말이다.
하지만 A센터 홈페이지에 공개된 총회 자료를 살펴보면 재정 상황이 나쁘지 않았다. 2022년 총회자료에서 회계감사는 “활동보조인 중개사업의 수익금액 증가에 기인”하여 1억4천의 이익이 발생했다고 말하고, 2023년 총회 자료에서는 A센터가 이사와 인테리어에 3억5천을 지출한 내용이 나온다. 정부가 예산을 충분히 지급하지 않아 지불 능력이 없다는 핑계는 사업장마다의 개별 회계를 투명하게 공개하여서 확인하면 될 일이다. 법정수당을 지급받지 못함으로써 직접적인 피해를 보고 있는 노동자와 논의를 통해 합의하면 될 일이다. 하지만 A센터 소장은 가장 최근의 노사협의회에서까지, 센터 재정 상황 설명 및 자료를 요청하는 노동자위원에게 공개된 자료만을 ‘알아서’ 보라며 자료를 제공하지도 않았고, 당연히 구체적 상황에 대한 논의를 진행할 수조차 없었다. 이런 소장의 태도가 한자협이 말하는 “노사협의체를 성실히 운영하고 있는 기관”의 태도일까.
이 정도 됐으면 A센터 소장은 자신 사업장 소속 노동자들이 왜 이렇게 화를 내고 있는지 자신의 행동을 돌아보아야 할 것은 아닐까. 그런데 A센터 소장은 끝까지 비겁하다. 한자협을 내세워 기자회견을 하고, 원고를 호명하면서도 자신은 끝까지 익명의 존재로 남아있다. 관심과 지지를 부탁한다는 보도자료의 문구가 무색하게, 어느 사업장인지는 알 수가 없다.
장애인차별금지추진연대의 혐오정치, 차별 발언
3월 23일 기자회견은 여기서 한발 더 나아간다. 장추련 김성연 사무국장과 장추련 자문변호사 김정환 변호사는 활동지원사 노동자들과 노조에 대한 낙인찍기를 시도한다.
이 소송을 제기한 활동지원노조는 현재 다수 발생하고 있는 활동지원사로부터의 인권침해 사건에 대해서는 매우 무심하고 이것과 관련해서 전혀 자정능력을 가지고 고민하고 있지 않으면서 정작 근로조건에 대한 문제만을 계속 이야기해서 …장애인을 이용해서 자신의 이익을 챙기고 있는 많은 활동지원사들의 문제로 계속 상담이 계속되고 있습니다. …저희가 오늘, 이 소송과 관련해서 분명하게 입장을 밝히는 가장 큰 이유중에 하나는 이 문제를 마치 노측과 사측의 문제로 가져가면서 장애인당사자인권에 대해서 얼마나 고민하고 있는지는 전혀 밝히고 있지 않습니다. …
– 장애인차별금지추진연대 김성연 사무국장 발언
근로조건의 개선을 요구하는 그 과정에서 활동지원사분들이 현재 있는 장애인과 관련된 많은 문제에 있어서 장애인과 관련된 어떤 인권침해의 문제라든지 어떤 노조 내부의 자정능력을 가지고 있는지 그러한 부분에 대해서 활동지원 노조의 입장에서 먼저 선제적으로 앞서서 장애인을 위해서 그런 부분을 고려해 주시길 바랍니다.
– 법무법인 도담 김정환 변호사 발언
이 발언들은 마치 소송의 원고들이 장애인 인권침해를 자행하면서 노동조건 개선만을 요구하는 사람처럼 묘사하고 있다. 노동조합은 인권침해를 자행하는 활동지원사들로 구성되어 있으며 이에 대한 자정능력이 없는 집단으로 묘사되고 있다.
무엇보다 문제인 것은 이들의 발언에서 드러나는 인식이 반인권적이라는 사실이다. 장애인에 대한 철저한 인권의식이 ‘노동인권’을 보장받기 위한 조건처럼 말해진다. 장추련에게 묻고 싶다. 자신들만큼 드높은 장애인 인권의식을 갖지 못하면 노동인권 따위는 보장되지 않아도 된다는 입장인걸까. 활동지원사업이 확대되고 있는 만큼이나 현장에서는 별의별 일들이 다 일어난다. 하지만 아무리 현장에서 여러 문제가 일어난다고 해도 개별 행위자를 일반화 범주화하여 낙인찍는 일은 인권에 반한다. 장애인에 대한 사회적 낙인과 차별에 반대한다는 사람들이, 왜 노동조합과 노동자에게는 극우 보수정치인들이나 행할 혐오정치를 하고 있는 걸까.
특별히 강조하고 싶은 부분은 “장애인을 이용해서 자신의 이익을 챙기고 있는 많은 활동지원사들”이라는 표현이다. 활동지원사는 노동자이고 노동자는 사전 그대로 자신의 노동력을 제공하고 그 대가로 받은 임금으로 살아가는 사람을 말한다. 따지고 보면 모든 사회복지 노동자들은 수급자를 이용해 생계를 이어가는 사람들이다. 장애인을 이용하는 활동지원사와 이용하지 않는 활동지원사는 구분되지 않는다. 얼마나 강한 노동강도로 서비스를 제공하면 장애인을 이용하지 않는 것이 되는 걸까. 그것을 판단할 객관적 기준이 있기나 한 건가. 사실은 활동지원사가 하는 일 없이 돈 번다고 생각하고 있는 것은 아닌가.
활동지원사들은 현장에서 서비스를 제공할 때 주변의 이상한 노동혐오적 시선 때문에 이중구속에 빠진 자신의 처지를 한탄하기도 한다. 장애인이용자에게 사무적으로 대하면 돌봄이 소홀하다 비난받고, 장애인이용자에게 성심성의껏 서비스하면 장애인이용자를 이용하기 위해 ‘홀린다’는 소리를 듣는다. 혹자는 ‘빨대를 꽂는다’며 비하한다. 도대체 어쩌라는 말일까? 우리는 모두 누군가의 노동환경이다. 주변인들의 노동혐오적 시선은 활동지원사들이 활동지원 현장 이탈을 결심하게 하는 주효한 이유 중 하나다. 장추련은 활동지원사 없는 세상을 원하는가.
노동조건과 인권의식은 무관할까
그날 장추련 사무국장은 인권침해 행위에 대한 고민 없이 노동조건만을 말한다고 노조를 질타했다. 그런데 노동조건과 인권의식은 무관한가. 활동지원사에게 인권의식이 요구된다는 것은 모두들 동의한다. 그리고 그 인권의식 고취를 위해 활동지원제도는 보수교육을 시행한다. A센터는 보수교육 참여에 대한 임금마저 제대로 지급하지 않는 사업장이었다. A센터는 갈등이 불거지자 2022년 하반기에 뒤늦게 활동지원사들에게 5,760원을 입금하였다. 2021년 보수교육에 대한 임금 보전분이다. 2021년 최저임금은 8,720원이었지만, A센터는 보수교육 참가자시간에 대한 임금을 시간당 8,000원으로 책정하여 지급하였다. 미지급한 720원의 8시간분 임금이 5,760원인 것이다. 이 지급도 관할 지자체의 시정지시를 받고서야 이루어졌다. 그보다 이전의 일은 언급하지 않겠다.
이런 상황에서 노동조건을 주장하는 것은 인권의식 고취를 위해서도 필요한 일이다. 그런데 활동지원사의 처우개선에는 동의한다면서도, 노동조건과 인권의식을 대립시키는 이 같은 발언을 어찌 이해해야 하나. 저들의 사유에서는 이미 노동자들의 인권의식과 노동조건이 함께 가는 것이 아니다. 인권감수성은 그냥 생기는 것이 아니다. 인권감수성 이전에 인권교육이 있어야만 한다. 하지만 우리사회는 사람을 길러내는 과제에 대해 무관심하고, 사람을 싸고 쉽게 쓰고 버리려는 풍토가 만연해 있다. 그리고 A센터도 그 혐의로부터 자유롭지 않다.
싸우는 노동자 설요한을 상상하며
나는 그날의 기자회견 이후 설요한을 다시금 떠올리며 생각하게 된다. 언론에 보도된 대로 장애인자립생활센터에서 동료상담가로 일하던 뇌병변장애인 설요한은 실적압박에 못 이겨 스스로 목숨을 끊었다. 자립생활센터가 실적을 못채우면 정부로부터 지원받은 금액을 환수당해야 했기 때문이다. 한자협은 이런 식의 제도를 만든 고용노동부가 설요한을 죽였다고 주장하며 제도의 개선을 이뤄냈다. 하지만 나는 요즘 그런 상상을 해본다. 설요한이 살아와 나에게 노동상담을 한다면 그 상황에서 나는 어떤 이야기를 해줄 수 있을까.
나는 먼저 장애인인권운동 동료상담가들이 그러하는 것처럼, 장애를 당신 개인의 탓으로 돌리지 않을 것이다. 당신에게 비장애인만큼의 생산성을 요구하려면 장애의 사회적 모델에 근거해서 그만큼의 지원이 더 있어야만 한다고 말해줄 것이다. 그리고 한 발짝 더 나아가 노동자 일반에게 해줄 수 있는 조언을 해줄 것이다. 사업장이 정부와 맺은 계약은 도급계약으로 보이고, 당신이 자립생활센터와 맺은 계약은 근로계약이라고. 사업장은 계약을 수행하지 못하면 대가를 받지 못하는 것이 맞지만, 근로계약은 어떤 업무의 완성이 임금의 조건이 아니라, 그저 근로를 제공하기만 하면 임금채권이 발생하는 것이라고. 그리고 당신의 임금은 당신의 실적과 무관한 당신의 생존권이고, 그 임금을 빼앗는 것은 불법 부당한 행위라고 말해줄 것이다. 그리고 어쩌면 기 지급된 월급의 환수를 요구하는 장애인자립생활센터에 맞서는 법정 투쟁을 지원할지도 모른다. 나는 설요한을 옥죈 논리가 활동지원사 노동자들을 억압하고 있다고 느낀다. 설요한이 죽은 그 자리가 사업주들로 구성된 한자협의 자리보다, 나의 자리에 가깝다고 느낀다.
인권을 주장하는 것을 자신의 삶으로 여기는 활동가도 충분히 반인권적인 차별주의자일 수 있다. 나는 저들의 정의로움을 의심하지 않는다. 다만, 저들이 주장하는 ‘인간’의 범주에는 진보적 장애인 인권운동의 자장 아래에 있는 사업장에서 일하는 노동자들이 포함되어 있지 않다. 이 노동자에는 비장애인뿐만 아니라 장애인 또한 포함되어 있어서, 그 예외성이 자신의 정체성을 좀먹을 정도다. 진보적 장애인 인권운동이라 해서 노동인권의 성역은 아니다. 나는 이들의 논리가 하루빨리 논파될 수 있도록, 장애인에 대한 최저임금 적용 제외가 하루빨리 철폐되길 바라며, 장애인일자리도 확대되길 바란다.
[^1]: 당시 민주노총 공공운수노조 의료연대본부 돌봄지부. [^2]: 뉴스민, 장애인의 삶과 동행하는 우리가 당당했으면, https://www.newsmin.co.kr/news/21569/, 2017-06-21. [^3]: 앞 기사 내용 중 장애인이용자 정경애 씨의 발언을 주목하라. “중개기관이 근무시간에서 휴게시간을 빼는데, 만약 휴게시간을 제가 주지 않는다면 이 뜻은 제가 활동보조인의 노동을 착취했다는 것으로밖에 볼 수 없는 거잖아요”. 이러한 갈등은 현재에도 이어지고 있다. 지역의 일부 활동지원기관들은 활동지원사에게 휴게시간을 ‘준수’하라고 강요하고 있는데, 현장에서는 정작 실질적인 휴게시간 권리를 보장받지 못해 고통스러워하는 노동자들이 많다. 근로기준법상 휴게시간은 사용자의 지배-개입으로부터 벗어나 자유롭게 사용할 수 있는 시간을 실질적인 휴게시간으로 보고 있는데, 실질적인 휴게시간이 아니면 노동시간으로 여겨지고 이에 대한 임금을 지급하지 않으면 임금체불이 된다. 그런데도 노동자들에게 휴게시간을 ‘준수’하라며 사용자들이 들볶고 있다. ‘권리’가 ‘준수’라는 명목으로 강요되는 것은 이상한 상황이다. 이 준수를 강요하는 주체가 누구고 대상이 누구인지를 주목해서 보아야 한다. 노동자에게 휴게시간을 부여해야 할 의무가 사업주에게 있고, 이를 부여하기 위해서 대체인력을 투입하거나 서비스를 제공할 수 없는 사정은 사업주의 사정이다. 그런데 이런 사정에 대해서 장애인이용자에게 양해를 구하는 것이 아니라, 노동자에게 강요하고 있다. 활동지원현장에서의 권력 위계를 엿볼 수 있는 하나의 예이다. [^4]: 전국활동지원사노동조합 보도자료, [기자회견] 취업규칙 무효 확인 소송, https://cafe.daum.net/paspower/4Pq3/400, 배포 일자 2022-08-10. [^5]: 한국장애인자립생활센터협의회 보도자료, 「시급제 활동지원사 처우」는 보건복지부에 「관공서 공휴일 수당 지급」은 고용노동부에 책임을 물어라!, 배포 일자 2023-03-22. [^6]: 그날의 발언은 장추련 유튜브 채널에서 다시 볼 수 있다. 장애인차별금지추진연대, 「시급제 활동지원사 처우」는 보건복지부에~「관공서 공휴일 수당 지급」은 고용노동부에 책임을 물어라! 한국장애인자립생활센터협의회 기자회견, https://www.youtube.com/live/qJC3W_5Oeg4, 2023-03-23. 기자회견 보도자료와 발언내용은 https://dqj.notion.site/dqj/2023-03-23-744ef95b8c4a4857b0ebdeb556019d97 참고. [^7]: 법무법인 도담 김정환 변호사는 그날의 연대발언에서 “마치 부모가 아이들을 방임해 놓았는데, 아이들끼리 싸우고 있는 것을 아이들 책임으로만 돌리는 그런 상황이 연출되고 있습니다.”라고 말했다.
-
 @ cbaa0c82:e9313245
2024-10-01 11:04:45
@ cbaa0c82:e9313245
2024-10-01 11:04:45TheWholeGrain - #September2024
To start the second year of Bread and Toast off strong the September of 2024 includes five Sunday Singles, and the newest piece of cover art for a comic from Toast's Comic Collection includes a touch of color. Some bonus pieces of content were included this September. This includes one of the Political posts we all take so seriously, and a promotional piece for the upcoming npub10hj9rg5gds5x2gk0z0s2jlqnq04jg7g30aj2t5pqzdaaztfactgsnze5ny event coming up in October. The Concept Art released this month is an early design of a possible website logo. This month's Bitcoin Art stars End-Piece who is well informed on what money really is and asks the question, "Do you?"
September Sunday Singles
2024-09-01 | Sunday Single 055 Jump Rope https://i.nostr.build/ESlb23xVmTQLw7sw.png
2024-09-08 | Sunday Single 056 Trampoline https://i.nostr.build/1HNutqYQUjsA1JaG.png
2024-09-15 | Sunday Single 057 Hippity Hop https://i.nostr.build/5dTyLA0FJdK2rNol.png
2024-09-22 | Sunday Single 058 Jumping on the Bed https://i.nostr.build/PWaHDMroMjjfPmWS.png
2024-09-29 | Sunday Single 059 Shades https://i.nostr.build/pWeIZrttOjpcXAtz.png
Other Content Released in September 2024
2024-09-04 | Toast's Comic Collection Teenage Mutant Ninja Bread #5 Four brothers trained in ninjutsu live underneath the city and come up to the surface in order to save it! https://i.nostr.build/WPSB1qn2lMRlbdwJ.png
2024-09-10 | Politics Debate Night The first official debate between the candidates for Selection2024. https://i.nostr.build/wppFU8U3NJCww6U0.png
2024-09-11 | Concept Art Early Website Logo Design This is an early concept for a logo. It was never used. https://i.nostr.build/hxhzvtS4fCe0imNh.png
2024-09-18 | Bitcoin Art On Top of It End-Piece knows what money is. Do you? https://i.nostr.build/6TCWK5d1ynPhrteA.png
2024-09-27 | Nostr Valley Nostr Valley 001 Bread is getting prepared for NostrValley! Hope to see you there! https://i.nostr.build/nQqsPGmJ8hjvxROK.png
September Additions to The Bakery in 2024
2024-09-05 | npub1895dg7n47ldxxq8hyqj9h4xa3xwwxzpnn8lm7hydag4tck6cfj3qcmc4f0 https://m.primal.net/KgDW.jpg
2024-09-26 | npub1hcusg0xp9maamlh9vnv4mf635uwldsfeut00ghzrrjk7kjjh8j3sf9049l https://image.nostr.build/a0a64d709376b3650ebde0f3de5076748d69a999aef9e5fbd882574d5e64cf88.jpg
We hope you enjoyed this first issue of The Whole Grain. The Whole Grain will be released on the first of every month and will cover all of the content released by npub1ew4qeq576v3vz4gukeseknqghx3x4jtlld8ftys9amrca6f3xfzsrm8jpd in the previous month.
Thanks for checking it out, Bread, Toast, and End-Piece
BreadandToast #SundaySingle #ToastsComicCollection #ConceptArt #BitcoinArt #TheBakery #Bread #Toast #EndPiece #Art #Artstr #DigitalArt #Comic #Manga #NostrValley #NostrOnly #🖼️
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 07f367da:0e76880d
2025-01-06 14:24:42
@ 07f367da:0e76880d
2025-01-06 14:24:42- https://www.newspoole.kr/news/articleView.html?idxno=10338
- 장애인활동지원사 성폭력 피해와 대책
- 입력 2023.03.16 18:07
활동지원사 성폭력 피해가 드러나기 어려운 이유
활동지원서비스를 받는 장애인이용자는 남성이 60.51% 여성이 39.49%로[^1] 남성이 더 많다. 활동지원서비스를 제공하는 활동지원사의 경우 여성이 87.85%로 대다수를 차지한다.[^2] 그래서 남성 장애인이 여성 비장애인에게 서비스받는 일이 많다.
우리 사회는 아직 장애인을 성적 주체로 인정하지 않는다. 나아가 장애인은 무성애자일 것이 강요된다. 장애인 당사자들도 이런 사정이 괴롭다고 호소하기도 한다. 성적 주체로 인정되지 않다 보니, 소극적 차원에서의 (성적)사생활조차 보장받지 못한다. 노인 비장애 남성에게는 "숟가락 들 힘만 있어도…."라는 우스갯소리가 있지만, 장애인에게 설사 숟가락 들 힘이 있다고 할지라도 그런 종류의 조롱마저 허락되지 않는다.
한편, 성적 주체성에 대한 불인정은 성적 주체로서 행할 폭력의 가능성에 대한 불인정이기도 하다. 장애인활동지원사 성폭력 피해에 대책을 요구하는 자리에서 복지부 담당 공무원이 "아니 장애인이 어떻게 성폭력을 해요?"라고 물었다는 사실은 우리끼리는 반복해서 곱씹는 술자리 안줏거리다. 이런식의 인식이 만연하다 보니, 성폭력 피해 활동지원사들은 자신의 피해사실을 말하기가 두렵다.
장애인을 무성애자로 간주하는 사회일반의 잘못된 인식이 꼭 작동하지 않더라도, 장애는 중요한 요소로 고려될 수밖에 없다. 활동지원사 당사자가 장애인이 성폭력을 저지른 것 아니냐는 질문, 고충토로, 상담요청을 하면 당장 나부터도 장애특성으로 인한 것인지 아닌지를 먼저 따지게 된다. 피해자 중심주의나, 당사자의 불쾌감보다 장애인의 장애 특성으로 인한 불가피성이 우선 검토된다. 피해자 입장에서는 주관적 불쾌감이 있어도, 성폭력을 정당화하는 여러 요소 중에 '장애'가 하나 더 생기는 것이다.
성폭력 문제를 다루는 데에는 전문성이 필요하고, 장애인 관련 사안을 다루는 데에도 전문성이 필요하다. 양자를 두루 함께 고민하기는 쉬운 일이 아니다. 한 조합원은 우리 노동조합에 오기 전, 다수의 여성단체에 자신의 피해에 대한 상담을 받았는데, 상담자가 장애에 대한 이해가 낮아 곤란했던 경험을 말하기도 했다. 한 단체에서는 부정수급이나 장애인 인권 의식 수준에 대한 지적을 받았다고 했다. 이 말을 듣는 순간 이것도 2차 가해의 일종이 아닌가 하는 의문이 들었다. 피해자에게 순결성과 피해자다움을 강요하는 것도 2차 가해의 범주에 해당하니 말이다.
여성 활동지원사는 87.85%고 40대 이상 여성 활동지원사는 84.13%, 50대 이상 여성 활동지원사는 68.20%이다. 성비 불균형 문제뿐만 아니라, 노동자들이 고령이기도 하다. 활동지원사 중에는 기혼자들도 많다. 성폭력 피해 고통을 호소하는 활동지원사 중에는 남편이 이성에게 서비스 들어가는 사실 자체를 모르고 있다며, 그러한 사실이 알려져서는 안 된다며 사건을 묻어버리기도 했다. 지원하는 자, 신고받는 자, 주변의 사람, 누구 하나 쉽게 믿을 수 없는 상황에서 성폭력 피해를 당한 활동지원사들은 그냥 입을 다무는 것을 선택하는 경우들이 많다. 서비스를 계속 들어갈 수는 없고, 수입이 끊긴 채 방치되고 현장을 떠나는 경우가 일반적인 수순이다.
활동지원사 성폭력 피해 산재승인 소식
그런 와중에 성폭력 피해를 당한 활동지원사가 산재승인을 받았다는 기적같은 소식이 들려온다. 우리노조는 피해자를 사건발생 몇 달이 지나서야 알게 되었다. 당시 피해자는 경찰에 신고했고 조사까지 받았다고 했다. 어떻게 그런 용기를 냈냐는 질문에, 피해자는 이렇게 말했다.
"센터에 가장 먼저 전화했는데요. 기다리라고 하고는 1시간이 지나도록 별 소식이 없더라고요. 센터에서 꼼짝 말고 기다리라고 해서, 그 집 다른 곳에서 기다리고 있었거든요. 그런데 너무 무서워 더는 견딜 수가 없어 경찰에 전화했어요. 열쇠로 문 열고 들어올 것만 같았어요."
어쩌면 전담인력이 조금만 빨리 왔더라도 경찰신고는 없었을지도 모른다. 그렇다면 당연히 판결도 없었을 것이고, 산재승인이라는 결과도 없었을지 모른다. 근로복지공단은 판결이 나오고 나서야 피해사실에 대한 인과관계를 인정하며 산재승인 결정을 내렸다. 피해자도 2차가해는 두렵다. 주변에서 말이 돌까봐 공무원에게조차 자신의 집을 선뜻 밝히지 못했다. 그러한 두려움을 감수하고 경찰에 도움을 요청할 수밖에 없을만큼 피해자는 기관의 방치에 내몰렸다.
피해자더러 범죄장소에 머물라는 이상한 지시. 결국 사건발생 2시간이나 지나서야 등장한 전담관리인력은 왜 경찰에 신고했냐 다그치며 피해자에게 가해자와의 3자 면담을 요구했다. 결제를 못해서 수익이 줄게 생겼다는 걱정섞인 말을 건내는 것은 덤이다.
피해자는 사건 이후 정신과 치료를 장기간 받았지만, 사업주는 고용노동부에 산업재해 발생을 보고하지도 않았고, 피해자에게 산재 신청 절차도 알리지 않았다. 피해자는 일거리가 끊겨 수입이 없는 상태로 어렵게 병원을 다녔다.
노조를 알게 된 피해자가 긴 시간이 흘러서야 산재를 신청했다. 사업주는 노조와 면담을 하고서야 사건을 관할 지자체에 보고했다. 피해자는 노조의 지원을 받아 유급휴가를 부여하지 않은 점에 대해 노동청에 진정을 넣었다. 그러자 사업주는 계약종료를 통보했다.
가해자의 유죄판결과 피해자의 산재승인은 기뻐할 일이지만, 사건 과정에서 보인 활동지원기관의 태도는 '비영리 단체' 혹은 '사회적 기업'[^3]이라고 생각하기에는 끔찍한 수준이었다. 낮은 성 인지 감수성은 물론이거니와 최대한 노동자에게 지출되는 비용을 줄이기 위해 안간힘을 쓰는 자본가의 태도와 별반 다르지 않았다.
노조가 정부에 요구하는 대책
우리노조는 장애인이용자의 성폭력 가해 사건에 대한 대책을 정부에 요구해왔다. 요구한 내용은 △사건 전담인력이 숙지해야 할 매뉴얼 마련 △피해자 유급병가ㆍ상담치료 예산 책정 △지자체에 신고ㆍ상담센터 설치 △사건접수 시 보고의무 강화 △가해(이용)자 교육을 정부가 담당 △가해자에게 동성 활동지원사 파견 등이다.
해당 사건에서도 볼 수 있듯이 전담인력의 대응이 전문적이지 않다. 전담인력이 전문성을 가질 수 있도록 매뉴얼을 만들고 보급할 필요가 있다.
또 피해자들이 아무런 지원을 받지 못한 채 현장을 떠나는 경우가 많다. 분리 조치만 취해진 채, 수입이 없어 불안한 시간을 보내게 된다. 피해자를 지원하기 위해서 유급병가와 상담치료 예산을 정부가 책정해야 한다.
활동지원사들은 가해자가 기관을 옮겨 다니면서 서비스 받고 또 다른 가해를 저지르는 경우들이 있다고 말한다. 정부에 보고의무를 강화해 정부가 사례를 수집하고 접수된 가해이용자에 대해서 정부가 직접 교육을 시행해야 한다.
충격적인 것은 활동지원기관이 가해자로 지목된 장애인이용자에게 또다시 이성 활동지원사를 파견한다는 점이다. 해당사건에서 가해자는 실형을 선고받기 직전까지 이성으로부터 서비스를 받았다. 노조가 개입한 다른 사건에서 한 활동지원기관의 장은 또다시 이성을 매칭시킨 것을 항의하는 노조에게 '이성에게 서비스를 받는것도 장애인의 선택권' 이라고 항변했다. 장애인의 선택권은 무한한가. 가해자에게는 동성활동지원사를 파견하도록 강제해야 한다.
피해자가 호소해도 변함없는 정부
사건 피해자는 작년 "나와 같은 피해자가 없기를 바란다"며 복지부를 직접 방문해 대책 마련을 요구했다. 하지만 2023년 새로운 지침이 발간되었지만 아무런 변화가 없었다. 어떻게 정부가 이렇게 무책임할 수 있을까? 우리는 그 원인을 민간위탁과 바우처 제도를 꼽는다. 민간에 사업을 위탁하고 모든 책임을 전가한 채, 정부는 방치할 뿐이다.
우리는 다시 공공성 확보를 요구할 수 밖에 없다. 노동자가 성폭력을 당해도 방치되는 일터는 공공성이 결여된 사회서비스 전달체계의 필연적 결과다. 정부가 직접 서비스를 제공하면 이런 상태로 남아있을수가 없다. 성폭력은 권력과 위계의 문제다. 노동이 존중받는 사회에서 직장내 성폭력은 줄어들 수밖에 없다. 노동자가 천시받는 상태로 내버려두는 정부가, 성폭력이 만연한 사회서비스를 만든다. 정부가 책임지고 직접 서비스 제공하라.
[^1]: 우리노조가 2020년에 기초지자체를 대상으로 정보공개청구를 하여 취합한 바로는 정보부존재 외에 장애인이용자의 성별에 대한 정보가 있는 경우는 남성 47,591명(60.51%), 여성 31,060(39.49%)명이었다. [^2]: 2021년 5월 사회보장정보원 전산자료 기준. 자료출처 보건복지부 장애인서비스과. [^3]: 장애인활동지원사업기관으로 지정받기 위해서는 '공공ㆍ비영리 법인 및 단체'이거나, 특별한 경우에 한해 '사회적기업'일 경우에 지정받을 수 있다.
-
 @ 599f67f7:21fb3ea9
2024-09-19 08:27:12
@ 599f67f7:21fb3ea9
2024-09-19 08:27:12¿Qué es una dirección Lightning o Lightning address?
Una dirección Lightning es una dirección que visualmente se asemeja a una dirección de correo electrónico legible para los humanos, por ejemplo usuario@dominio.com pero que en realidad te permite recibir pagos en bitcoin instantáneos y económicos, sin la necesidad de tener un nodo en linea en tu dispositivo ni tener que generar facturas de forma manual cada vez que alguien te quiere hacer un pago.
¿Suena bien no?
¿Y cómo funciona?
Funciona utilizando el protocolo de pago LNURL.
Aquí se muestra un sencillo esquema de lo que ocurre en segundo plano.
En resumen, cuando otro usuario quiere pagarte usando tu dirección Lightning, tu billetera convierte la dirección Lightning en una solicitud de pago LNURL. Luego se utiliza esa solicitud de pago LNURL exitosa para obtener una factura BOLT11.
💡 Dirección Lightning > LNURLp > Factura BOLT 11.
Suena bien, pero ¿cuál es el problema?
Por el momento, muchas de las implementaciones de Lightning Address son de custodia, porque se necesita un dominio para que Lightning Address funcione y un nodo que esté siempre en línea para recibir los pagos. Debido a que es de custodia, el custodio puede atacarte en cualquier momento y monitorear tus transacciones.
Tienes que confiar en el propietario del dominio para no cambiar el registro de tu dirección Lightning. Y no funciona si el servidor LNURL no está en línea.
Bitcoin Txoko ofrece una sencilla solución de Lightning Address respaldada por LNbits. Esto también es de custodia, así que por favor mantén solo una pequeña cantidad en tu billetera Bitcoin Txoko y ve retirando a tu billetera de autocustodia a medida que recibas más sats.
Estoy listo, ¿qué necesito para empezar?
¡Todo lo que necesitas es un teléfono móvil o un ordenador y una conexión a Internet!
1. Creando tu billetera
Si aún no lo has hecho, navega a https://bitcointxoko.com y crea una nueva billetera. Puedes elegir el nombre que quieras.
2. Activar extensiones
Hace falta la extensión
Pay Linkspara que las direcciones Lightning funcionen.Abre
Extensionesen la barra de herramientas y activaPay Links.3. Creando tu enlace de pago
-
En a la extensión
Pay Links, haz clic enNew Pay Link. -
Elige la billetera que has creado.
-
Para la descripción del artículo, puedes escribir lo que quieras.
-
Elige un nombre de usuario de tu dirección Lightning. Tu dirección Lightning se verá como
username@bitcointxoko.com. -
Desmarque
Fixed amounty cambia el valor mínimo a 1 y el valor máximo a 500000.
⚠️ También puedes cambiar el valor máximo a algo más alto, pero es más probable que los pagos más grandes fallen debido a la limitada capacidad de entrada del nodo Lightning de Bitcoin Txoko. Así que recomendamos mantenerlo en 500000 sats.
-
Ahora abre
Advanced optionsy cambiaComment maximum charactersa 799. Este paso no es necesario pero permite más funcionalidades más adelante. -
Marca
Enable nostr zapsen la parte inferior, para que puedas utilizar tu dirección Lightning para recibir zaps. -
Las demás opciones avanzadas son opcionales, puedes configurarlas si quieres o dejarlas en blanco.
Al final debería verse algo así.
- Cuando hayas comprobado que todo es correcto, sigue adelante y haz clic en
Create Pay Link.
Probando
Puedes probar si tu nueva dirección Lightning funciona yendo a otra cartera, pulsando en
Enviary escribiendo tu dirección Lightning como destino, y luego enviándote una pequeña cantidad de sats.Vuelve a tu billetera Bitcoin Txoko y comprueba si has recibido tu propio pago. Es posible que tengas que actualizar la página.
Si todo funcionó correctamente, ¡enhorabuena! 🥳
Si no es así, háznoslo saber. Siempre estamos aquí para ayudar.
Próximos pasos
Nostr zaps
Puedes añadir tu dirección Bitcoin Txoko Lightning a tu perfil de nostr y usarla para recibir zaps. Normalmente, esto se hace yendo a
Perfil>Editar>Dirección Lightningy cambiando la dirección Lightning.LNDhub
Puedes importar tu billetera LNbits como un LNDhub en tu teléfono utilizando una aplicación como Zeus o BlueWallet, en lugar de visitar la billetera en el navegador cada vez que desees comprobar tu saldo o realizar un pago. Echa un vistazo a nostr:naddr1qvzqqqr4gupzqkvlvlma7a55ccp6d5rrdc27h3ssmdmael286mjaq5uxmqslk04fqqxnzd3exuerqdfkxccnyv3cs0uvul sobre cómo hacer esto.
Código QR
También puedes compartir o imprimir tu código QR LNURLp para que la gente pueda escanearlo fácilmente con sus teléfonos. ¡Muy útil si estás introduciendo bitcoin a tu comerciante local favorito para que pueda recibir propinas Lightning!
Simplemente comparte el enlace a tu página compartida, o imprime el código QR como PDF yendo a
View Link>Print. -
-
 @ edeb837b:ac664163
2025-01-06 14:12:55
@ edeb837b:ac664163
2025-01-06 14:12:55What is Social Trading?
Social trading is a revolutionary approach to financial markets, leveraging the power of community and technology to democratize trading and investing. Unlike traditional trading, where individuals make isolated decisions based on personal research and analysis, social trading allows users to observe, interact, and replicate the trading activities of others. This communal approach not only opens up financial markets to novices but also creates a collaborative environment where traders of all levels can learn and grow together.

The Core Concept of Social Trading
At its core, social trading is about transparency and connectivity. It transforms the solitary act of trading into a collective endeavor, where information, strategies, and experiences are shared openly within a community. This is facilitated through platforms that provide real-time access to the trading activities of others, enabling users to follow successful traders, copy their trades, and gain insights into market trends.
Key Elements of Social Trading:
- Trade Sharing: Traders share their trades with the community in real-time, providing insights into their strategies and market movements.
- Copy Trading: Less experienced traders can automatically replicate the trades of successful investors, benefiting from their expertise without needing deep market knowledge.
- Community Interaction: Platforms often include features like discussion forums, leaderboards, and social media integration to foster interaction and learning.
The Rise of NVSTly: The Best Platform for Social Trading
What Sets NVSTly Apart?
Among the plethora of social trading platforms, NVSTly stands out as a premier choice for several reasons. It combines a user-friendly interface with robust features, making it an ideal platform for both novice and experienced traders. Here’s why NVSTly is the best platform for social trading:
- Completely Free: Unlike many other platforms that impose a paywall, NVSTly is completely free. Users can sign up and access all features without any cost, making it accessible to everyone.
- Cross-Platform Availability: NVSTly is available on both web browsers and mobile devices (iOS and Android). This flexibility ensures that users can trade and interact with the community anytime, anywhere.
- Unique Discord Integration: NVSTly is the only social trading platform fully integrated with Discord. Through a unique bot, users can perform almost all actions on NVSTly directly through Discord, enhancing community interaction and ease of use.
NVSTly’s Standout Features
NVSTly offers a comprehensive suite of features designed to enhance the social trading experience:
- Real-Time Trade Tracking and Sharing: Users can track, share, or copy trades in real-time. Each position comes with extensive insights and performance stats.
- Multi-Market Support: NVSTly supports trading in stocks, options, and over 25 cryptocurrency exchanges, with plans to include futures and forex markets soon.
- Trade Insight UI: Every trade has a dedicated UI showing all events (open, average, trim, exit) along with real-time asset data and a unique POV chart marking key trading points.
- Global Trades Feed: A real-time feed showing all trades submitted by users. It includes filters to show trades from specific traders, top trades, or specific tickers.
- Global Leaderboards: Rankings of top traders for each market or combined markets, allowing users to follow and learn from the best.
- Real-Time Notifications: Follow any trader and receive notifications of their trades in real-time.
- Brokerage Integration: Automated tracking and sharing of trades executed within the broker, with cryptocurrency exchange integration coming soon.
- Automated Signals and Sharing: Trades can be shared instantaneously to social media and Discord.
- Future Goals: NVSTly aims to implement 1-click copy trading, simplifying the process even further.
- Trader Dashboards: In-depth performance stats for each trader, including trade history, win rate, total gain, average gain/loss/return, highest winning trade, and more.
Why NVSTly is Ideal for Social Traders
NVSTly's blend of comprehensive features, accessibility, and unique integrations makes it the ultimate platform for social trading. Whether you’re a beginner looking to learn from seasoned traders or an experienced investor seeking to share your insights and grow your following, NVSTly provides the tools and community to achieve your goals.
The platform’s commitment to being free and its integration with popular communication tools like Discord highlight its user-centric approach. By fostering a supportive and interactive environment, NVSTly not only enhances trading success but also builds a vibrant community of traders who can thrive together.
In conclusion, NVSTly redefines social trading by combining cutting-edge technology with a robust community framework. Its extensive features and unique integrations position it as the leading platform for anyone looking to engage in social trading. Sign up today and experience the future of trading with NVSTly.
NVSTly is available for free on web, mobile devices (iOS & Google Play), and is fully integrated with Discord via a unique bot- the only of it's kind and available to any server or trading community on Discord. Or feel free to join a community of over 45,000 investors & traders on our Discod server.
-
 @ 07f367da:0e76880d
2025-01-06 13:47:37
@ 07f367da:0e76880d
2025-01-06 13:47:37- https://cms.newspoole.kr/news/articleView.html?idxno=10299
- 전장연과 서울시 구도에서 은폐되는 것
- 입력 2023.02.16 16:35
전장연과 보수정치인들
얼마 전 2월 2일, 오세훈 서울시장과 박경석 전국장애인차별철폐연대(이하 전장연) 대표의 면담이 있었다. 해당 면담에 관해 필자의 SNS에서는 이에 대한 평들이 있었다. SNS 타임라인을 구성한 필자의 편향성 덕분에, 전장연을 옹호하고 서울시를 비판하는 내용 일변도였다. 이 논란 중에 장애인활동지원예산 관련한 글들이 눈에 보였다. 이준석 전 대표가 썰전에서 한 발언, 김상한 복지정책실장의 발언에 대한 반박이 반복되면서, 나는 이미 시장화된 사회서비스 분야에 대한 문제인식이 은폐되고 노동자를 억압하는 논리가 다시 확산되고 있다고 느꼈다.
이준석 전 대표와 김상한 복지실장의 말을 보자.
이준석: 탈시설 예산을 늘리면 그 돈이 어디로 갑니까? ... 탈시설 추진하는 시민단체나 아니면 사회단체로 가는 것 아닙니까? 집행기관이 거기잖아요. ... 장애인들에게 전달되기까지 그 과정 중에서 사업을 수행하는 기관들이 그 돈을 가져가잖아요.
2022년 5월 12일 JTBC썰전 라이브
과연 그게 24시간 활동보조를 붙여서 자립생활하는 것이 정말 장애인을 위한 것이냐 아니면 활동보조인력을 위한 것이냐. 아니면 활동보조서비스를 제공하는 그 단체를 위한 것인지에 대해서 여러 의구심들을 제시하는 의견들이 또 있습니다. 심지어는 활동보조서비스를 제공하는 기관에서 25% 수수료를 가져가는 그것 때문에 혹시 그 재정여건을 개선시키기 위해서 탈시설을 강조하는 거 아니냐 의구심이 있거든요.
서울시 김상한 복지정책실장 발언. 출처: 비마이너, [전문] 전장연-오세훈 단독 공개 대담 녹취록, < https://www.beminor.com/news/articleView.html?idxno=24563 >, 2023.02.02.
이 두 발언을 이어서 풀어보자면 "활동보조서비스를 제공하는 기관에서 25% 수수료를 가져가는 그것 때문에 혹시 그 재정여건을 개선시키기 위해서 탈시설을 강조하는 거 아니냐 의구심이 있"고, 그 돈이 "탈시설 추진하는 시민단체나 사회단체로 가는 것"아니냐는 의심이다. 이를 반론하기 위해 장애인언론 비마이너와 넓게 진보적 장애인 인권운동의 자장에 있는 사람들은 ▲장애인활동지원사업은 수익사업이 아니고 남는게 없으며 ▲시민사회단체. 즉, 전장연으로 돈이 흘러갈 리가 없다고 주장하고 있었다.[^1]
필자는 전장연이 주장하는 탈시설 이념에 동의한다. 노인장기요양분야에서도 지역사회계속거주 이념(Aging in place)이 실현되기를 바란다. 또 김상한 실장과 이준석 전 대표가 과장하듯이 탈시설 예산 전부가 전장연으로 흘러들어간다고 생각하지는 않는다. 그리고 전장연이 단순히 수수료 몇 퍼센트를 먹기 위해 투쟁을 하고 있다고 생각하지도 않는다. 하지만 그에 반론하여 말하듯 활동지원사업이 수익사업이 아니며, 전장연으로 돈이 전혀 흘러가지 않는다고 생각하지도 않는다.
장애인자립생활센터의 유일한 수익사업 활동지원사업
필자는 장애인자립생활센터에서 근무하고 있다. 이 센터는 활동지원사업을 기초지자체로부터 수탁받아 사업을 진행하고 있다. 전장연에 소속된 여러 단체들의 회원센터이기도 하다. 나는 한때 활동지원사업 운영위원(활동지원사분)이기도 했고, 노사협의회 노동자위원이기도 하다. 그리고 공교롭게 박 대표는 해당 센터의 운영위원이다.[^2]
필자는 센터와 현재 분쟁중에 있다. 당사자로서 체불임금과 관련한 노동청 진정을 제기하였으며 해당 사건은 검사의 기소의견이 법원에 전달되어 있다. 필자가 센터와 싸움을 결심하게 된 이유는 활동지원사를 소외시키고 도구화하는 센터의 행태에 배신감을 느꼈기 때문이다. 센터는 활동지원사들(시간급제 노동자들)의 수당을 삭제하는 취업규칙 개정을 강행하면서 노동자들에게 '개정된 근로기준법이 반영된 것'이라는 거짓말을 하고 서명을 받았다. 운동단체답게 평소에는 장애인과 노동자가 연대해서 투쟁해야 한다는 말을 하며 노동자들의 열악한 노동조건에 대한 책임을 정부로 돌렸지만, 노동조합이 투쟁해온 경과는 무시한 채, 정보약자인 노동자들을 기망하며 노동조건을 후퇴시키고 사업주로서의 법적 권한만을 강조했다.
그렇게 취업규칙을 개정하고 얼마 후에 층이 4개인 건물로 이사를 할 계획을 세웠다. 본인이 입사할 때는 2개의 사무실을 사용하는 작은 센터였다. 노사협의회에서 필자는 공간유지비용이 어떻게 마련되는지를 물었다. 센터는 이에 대해 설명하지 않았다. 본인은 공간유지비용이 센터가 수행하는 여러 사업에 의해 합리적으로 배분되어야 하는 것 아니냐고 주장했다. 활동지원사업과 무관한 사업의 공간이용비용으로 활동지원사업 수익금을 사용하는 것이 정당화될 수는 없다고 생각했기 때문이다.[^3] 이에 센터장은 타 사업에서는 공간운영비용이 나오지 않으며, 그 비용을 사업별로 분담하라는 주장은 사실상 사업을 하지 말라는 말과 같다고 항변했다. 센터의 유일한 수익사업은 활동지원사업이라고 주장했다.
공간뿐만이 아니었다. 활동지원사업 수익금으로 전장연 관련 단체 회비가 지출되었다. 제세공과금 명목이었다. 서울장애인차별철폐연대, 한국장애인자립생활센터협의회, 서울장애인자립생활센터협의회, 전국장애인야학협의회, 장애해방 열사 단, 박종필추모사업회, 피플퍼스트. 그 수가 많았다. 이 각종 단체들에 대해 활동지원사업과의 관련성을 얼마나 인정해야 할지는 각자의 판단이 있을터이다. 사업을 수탁한 기초지자체에 민원을 제기하였고, 일부는 사업과의 관련성이 인정되지 않아, 이제 앞으로 그렇게 하지 말라는 '시정지시'가 뒤늦게 있었다.
센터가 수탁하고있는 다른 사업분야는 필자도 잘 모른다. 센터가 상세히 설명하지도 않거니와, 센터장이 말하는 대로 믿을뿐이다. 하지만 보조금이라서 전혀 쓸 수 없다는 말을 쉽게 할 수 있을 정도로 활동지원사업이 단순하지는 않다. 센터 운영에 있어 의사결정 권한이 있는 운영위원들은 대부분 전장연 관련인사로 채워져 있다. 특별히 이 센터만을 탓하기 위해 하는 말이 아니라, 수년간 여러 종류의 사업체를 보아도 서로서로가 운영위원이 되어주며 적당히 친한 사람들로 자리를 매우는게 이 업계 풍토라면 풍토다. 관리감독의 책임이 있는 기초자치단체 공무원의 행정능력도 그렇게 꼼꼼하지 않다. 복지부 지침은 양이 많을 뿐만 아니라 공무원의 순환보직으로 매번 숙지되지 않는다. 대부분의 사람들은 센터 내부사정을 잘 알기도 힘들고, 민원을 제기해도 시정이 어렵다.
아무리 전장연 깍아내리기에 대한 반론이라고 하지만 민간위탁으로 점철된 한국의 사회복지사업이 투명하다고 강조하는 것은 거짓말 아닌가. 사회복지분야 회계투명성을 위해 투쟁하고 있는 사람들의 노고를 무시하는 발언이다. 그 말을 하는 사람들은 장애인수용시설사업을 하는 사회복지법인들의 재정이 투명하다고 믿고 있을까.
활동지원사업 수익금의 '일부'는 전장연으로 흘러가는 것이 맞다. 전부 흘러가는것도 아니고 전혀 흘러가지 않는것도 아니고 '일부'는 흘러간다. 그리고 개별행위자들은 그 부스러기 같은 '일부' 때문에 취업규칙을 고치고 노동자들을 기망한다. 한자협 소속 장애인자립생활센터 중, 활동지원사업을 하는 비율은 몇프로나 되는가? 오히려 사업을 수탁하지 않은 자립생활센터를 찾기가 힘들다. 사업을 하지 않는 자립생활센터들도 활동지원사업 수탁을 받고자 안달이다. 이는 활동지원사업을 통해 공간을 마련-유지하고, 자금을 운용할 틈을 만들기 위해서이지 않은가.
최소한의 운영을 위해서건, 공간확보를 위함이건, 회원단체 회비 납부를 위해서건 정부에 의해 수입이 정해진 사업구조에서 활동지원기관이 자금을 확보하기 위한 전략은 노동자들의 노동조건 후퇴이다. 이 과정에서 희생되는 것은 노동자들이다. 그리고 노동자들이 가장 많이 듣는 이야기는 전장연을 위한 반론에서 강조되는 대로 활동지원사업이 '수익사업이 아니다', '남는게 없다'는 식의 주장들이다. 우리노조는 활동지원사업을 수행하는 각종 종교재단, 복지관 등에서 활동지원사 노동권 확보를 위한 투쟁을 이어왔다. 그들이 하는 말도 똑같았다. 노동자들에게 임금채권포기각서를 요구한 사업장 대표가 하는 말도 '정부지원이 부족하다', '남는게 없다', '어쩔 수 없다'였다.[^4] 그리고 정작 사건화되어 검찰이 회계를 요구해 검토하자 그렇게 사정이 나쁘지도 않았다. 전장연을 옹호하는 사람들의 말도 노동자의 노동조건을 후퇴시키고 억압하는 논리를 반복하고 있다.
정부와 서울시의 무책임
탈시설 예산 일부가 전장연으로 흘러들어가는 매커니즘의 바탕에는 결국 시장화된 사회서비스가 있다. 정부의 재정을 투입하면서도 민간위탁 시키면 이윤의 논리가 반영될 수밖에 없다. 결국 이런 구조를 설정하고 있는 것은 정부이고 지자체이다. 다른 활동지원기관들의 재정이용은 투명한가? 활동지원기관 일반의 재정이 어디로 도는지 알 수는 있는가?
활동지원사 입장에서는 활동지원기관을 성장시킨 비용이 어디에서 나오는지 궁금하다. 활동지원기관이 정말로 근로기준법을 지킬 수 없을 정도로 상황이 어려운지 알고 싶다. 하지만 회계자료 요구는 번번히 거절당하고, 운영사정은 설명들을 수 없다. 중앙정부는 활동지원기관의 회계를 확보하지도 못할 뿐만 아니라, 관리감독 권한이 있는 기초지자체는 회계를 입수했다 하더라도 "영업비밀"이라며 공개를 거부한다. 만약 오세훈 서울시장이 시민사회단체로 흘러들어가는 일부분 만이라도 진정으로 문제라 여긴다면 활동지원기관의 회계를 투명하게 유지하고 정부가 관리감독을 잘하면 된다. 오해하지말라. 전장연의 회계가 아니라 정부 수탁사업자로서 활동지원기관의 회계 말이다.
또 다른 방안으로는 민간위탁사업자를 없애고 공공 운영 하여 정부가 직접 서비스를 제공하는 방안이다. 서비스 제공 과정에서 발생하는 손해건 수익이건 정부에게 돌아가도록 하면 된다. 노동자들과 시민사회단체는 시장화된 사회서비스에 문제인식을 느끼고 사회서비스 공적 전달체계로의 개편을 바라며 오랜세월 투쟁해왔다. 그러한 목소리들의 성과가 사회서비스원이다. 서울시사회서비스원 설립 당시 자립생활센터는 "민간기관의 피해"를 걱정하기도 했다.[^5] 서울시사회서비스원이 잘되면, 자신들의 입지가 줄어든다고 판단한 것이다.
사회서비스원의 성과는 우리사회가 코로나19를 겪으며 더욱 두드러지게 드러났다. 민간위탁기관과 대비되게 인력수급이 비교적 안정적인 서울시사회서비스원은 긴급한 상황 긴급하게 인력을 투입할 수 있었다. 직접서비스를 제공하는 돌봄노동자들은 소중한 노동으로 격상되었다. "일상의 영웅"으로 칭송받으며 "필수노동자"라고 칭해지기도 했다. 하지만 윤석열 정부 들어 사회서비스원 전체를 통폐합 하는 기조이고, 서울시로 국한해 보아도 서울시사회서비스원은 축소되고 있다.[^6] 장애인활동지원사업을 제공하던 노원종합재가센터가 폐지되고 성동종합재가센터만 남아 있다. 사회서비스원의 활동지원인력도 줄었다. 놀라운 것은 장애인자립생활센터가 걱정하던 사안을 사회서비스원 대표가 규탄하고 있다는 사실이다.[^7] 오세훈 시장의 보좌관 출신으로 알려진 황정일 대표이사는 오세훈 서울시장이 새로이 임명한 사람이다.
서울시사회서비스원의 축소는 공공운영의 축소이고 민간위탁기관이 활동할 시장의 범위를 더 넓어지게 만드는 처사이다. 서울시가 접던 판도 다시 깔아주면서 노름하지 말라하는 모양새다. 오세훈의 서울시는 여러모로 보아도 전장연을 깍아내릴 자격조차 없다.
사회서비스 공공성 확보하라
활동지원사들은 정부가 예산을 낮게 책정하고, 센터는 정부를 핑계대는 핑퐁게임에 참으로 오랜세월동안 노출되어 왔다. 그 결과는 상시적 고용불안에 노출되어 있으면서도 언제나 최저임금과 근로기준법상 법정수당을 지급받지 못하는 현실이다.
나는 보수정치인들의 전장연 깍아내리기와 그를 방어하는 논쟁의 구도에서 또다시 이 핑퐁게임을 본다. 각자가 그렇게 주장하는 전체적 의도가 왜 없겠는가. 그렇다고 단편적 주장을 무시하면 그것은 그것대로 남아 누군가를 괴롭힐 것이다. 나는 사회서비스 공공성 확보가 중요하다고 주장할 수 밖에 없다. 이 방안만이 노동자와 인력공급에 불안을 느끼는 장애인을 위하는 방안이라고 생각한다. 사회서비스 전달체계 구조에 대한 고민이 절실하다.
[^1]: 비마이너, [탈시설 팩트체크] 탈시설 예산 늘리면 그 돈은 어디로 갈까?, < https://www.beminor.com/news/curationView.html?idxno=23397 >, 2022.05.23. [^2]: 2022년 초 해당 센터 총회자료 기준 [^3]: 보건복지부에서 매년 발간하는 「장애인활동지원사업안내」에서는 수익금을 활동지원인력 인건비로 최우선적으로 사용하도록 하고 있다. [^4]: 해당 사건은 대법원까지 간 끝에 사업주의 유죄가 확정됐다. 최초 문제제기 이후 4년이 걸렸다. 관련기사. 에이블뉴스, “활동지원사 임금포기 확인서 서명 강요 유죄”, < http://www.ablenews.co.kr/news/articleView.html?idxno=87514 >, 2020.03.16. / 매일노동뉴스, “임금포기각서 요구, 거부한 조합원은 초단시간 노동자로”, < http://www.labortoday.co.kr/news/articleView.html?idxno=203984&fbclid=IwAR3KQ-KWnFsSaIq7D9zkrJXG9foGgtECVNJ0ulxgPTXRIEv_DF4AO1la-oU >, 2021.07.21. [^5]: "사실 사회복지가 공공의 영역에서 국가가 책임지고 가야 하는 방향성은 맞으나, 재가노인요양기관 뿐 아니라 장애인활동지원기관도 운영의 큰 부분을 바우처 사업으로 가져가고 있는 상황에서 자칫 잘못하면, 민과 관의 경쟁구도로, 민간 기관들이 피해를 볼수도 있는 상황이기 때문이다."_장애인자립생활센터 활동지원사업 운영위원회 사업평가 발췌, 2019. [^6]: 2023년 서울시의 사회서비스원 관련 예산은 69억으로 142억원이 삭감되었다. 서울시사회서비스원 유지 자체가 불투명하다. 서울사회서비스원의 노동자 탄압에 대해서는 김호세아, 참여와혁신, "[기고] 서울시사회서비스원 돌봄노동자들 월급도둑 취급은 부당하다", < https://www.laborplus.co.kr/news/articleView.html?idxno=30697 > , 2022.12.22. [^7]: 뉴스인오늘, [인터뷰] 서울시사회서비스원 황정일대표, 여러분은 서울시사회서비스원에 대해 얼마나 알고 계십니까?, < http://www.focus24.co.kr/47715 >, 2023.01.16.
-
 @ 13e63e99:25525c6a
2024-09-03 09:29:54
@ 13e63e99:25525c6a
2024-09-03 09:29:54Preview
Last week, President Nayib Bukele of El Salvador emphasized Bitcoin’s role in enhancing the country's global image that boosted foreign investment and tourism. At the NostrWorld Unconference in Riga, the synergy between Bitcoin and decentralized social networks was a key focus, showcasing the potential for integrating Bitcoin with the growing Nostr protocol. Meanwhile, Lightspark launched its Extend platform, facilitating instant Bitcoin payments for U.S. businesses, thereby expanding the accessibility of Bitcoin transactions. Publicly traded companies have increased their Bitcoin holdings by nearly 200%, bringing their total to $20 billion, reflecting strong institutional confidence in Bitcoin as a reserve asset. Additionally, Bitcoin in exchange experienced its third-largest daily net outflow of 2024, indicating a shift toward long-term holding among investors. Despite some withdrawals, including a $13.5 million outflow from BlackRock’s iShares Bitcoin Trust, the fund remains a dominant force in the Bitcoin investment landscape. Lastly, Nigeria's SEC granted its first provisional exchange license, a milestone in the regulation of the country’s rapidly growing digital asset industry, positioning Nigeria as a leading player in global digital asset adoption. For more details, continue reading below.
A. Bitcoin Data Dashboard
1. Bitcoin Transactions\ 2. Supply\ 3. Mining\ 4. Transaction Fees\ 5. Difficulty Retarget\ 6. Lightning Network (Public)
B. Bitcoin Ecosystem
1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador\ 2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks\ 3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.\ 4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion\ 5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024\ 6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals
C. Regulation
1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation
D. Macroeconomy
1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich\ 2. Jobless claims drop as labor market slows, US economy remains on steady growth path
A. Bitcoin Data Dashboard

As of Sep 2, 2024
B. Bitcoin Ecosystem
1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador
President Nayib Bukele recently provided a candid assessment of El Salvador's groundbreaking decision to adopt Bitcoin as legal tender, a move that has drawn both praise and criticism on the global stage. In an interview with Time magazine, Bukele emphasized that the initiative has had substantial benefits particularly in enhancing El Salvador's international image despite the country's bitcoin adoption has not expanded as rapidly as he has hoped, Bukele described the Bitcoin adoption as a powerful rebranding tool for the nation, one that has attracted foreign investment and boosted tourism. The president’s marketing advisor, Damian Merlo, echoed this sentiment, calling the decision "genius" and likening it to a major public relations campaign that El Salvador didn’t have to pay for. "We could have spent millions on a PR firm to rebrand the country," Merlo noted, "but instead, we adopted Bitcoin." While the move initially strained relations with institutions like the International Monetary Fund (IMF), which urged Bukele to abandon the policy due to perceived risks, there are signs that the tension is easing. El Salvador has recently reported progress in negotiations with the IMF, with a focus on enhancing transparency and addressing potential fiscal and financial stability risks related to the Bitcoin project.

Reference: Bitcoin.com, Time
2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks
Last week, NostrWorld’s third unconference, held in Riga, Latvia, gathered advocates and developers of the Nostr protocol. Organized by Jack Dorsey, NostrWorld provides a platform for open-source enthusiasts to collaborate on building a decentralized internet. The event, called Nostriga, underscored the emerging synergy between Nostr’s decentralized social network and Bitcoin. Nostr is an open-source protocol for a decentralized, censorship-resistant social network. Unlike traditional platforms, Nostr operates on a network of relays, supporting features like micropayments and digital identity management. It promises greater privacy and independence from centralized platforms. A highlight of the conference was Strike CEO Jack Mallers discussing how Nostr’s micropayments—Zaps—helped a skeptic understand Bitcoin’s value. This feature shows Bitcoin’s utility in social contexts, advancing the concept of internet tipping. Jack Dorsey enphasizing the importance of open source. Nostr faces the challenge of broadening its user base beyond Bitcoin enthusiasts. New initiatives like Ditto aim to integrate Nostr with larger internet communities, potentially increasing Bitcoin’s visibility and accessibility. Nostr’s role as a social and identity system could pave the way for decentralized digital economies. By leveraging social graphs and cryptographic trust, Nostr and Bitcoin together could enable secure, decentralized commerce.
Reference: Bitcoin magazine
3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.
Lightspark has unveiled Lightspark Extend, a new solution designed to facilitate instant Bitcoin Lightning payments for U.S. businesses. This platform integrates with Universal Money Addresses (UMA) and Lightning-enabled wallets, exchanges, or bank accounts, offering a compliant and cost-effective way to handle transactions around the clock. Lightspark Extend is compatible with over 99% of U.S. banks that support real-time payments, enabling businesses to provide their customers with fast, low-cost transactions. UMA simplifies the payment process by using easy-to-remember addresses similar to email, removing the need for complex codes or passwords. With this launch, Lightspark Extend makes real-time payments via the Bitcoin Lightning Network accessible to eligible recipients across the U.S. Businesses interested in adopting this solution can sign up for a UMA address, link their accounts, and start receiving payments through an onboarding process facilitated by Zero Hash, a regulated U.S. financial institution. The introduction of Lightspark Extend marks a significant advancement in expanding the accessibility and utility of Bitcoin payments. This follows Lightspark’s recent announcement of a partnership with Coinbase, enabling customers to send up to $10,000 instantly through the Lightning Network.
Reference: Bitcoin magazine
4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion
Publicly listed companies have seen their Bitcoin holdings soar by nearly 200% in a year, rising from $7.2 billion to $20 billion. According to Bitbo data, 42 such companies now hold 335,249 BTC, valued at roughly $20 billion. This marks a 177.7% increase from a year ago, when their BTC holdings were worth $7.2 billion. The trend began with MicroStrategy's August 2020 purchase of over 21,000 BTC, making Bitcoin its primary treasury reserve asset, and the company has since grown its holdings to 226,500 BTC. A survey commissioned by Nickel Digital Asset Management revealed strong institutional support for Bitcoin as a reserve asset, with 75% of 200 surveyed institutional investors and wealth managers endorsing public companies holding BTC. The survey, involving firms managing $1.7 trillion in assets, also found that 58% believe 10% or more of public companies will hold BTC within five years. Nickel Digital's CEO, Anatoly Crachilov, noted that institutional investors see Bitcoin as a hedge against currency debasement and a valuable addition to reserve allocations. Despite this growth, the 335,249 BTC held by public companies represent just 1.6% of Bitcoin's total capped supply of 21 million.
Reference: Cointelegraph
5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024
Bitcoin is seeing a significant uptick in exchange withdrawals as its price nears the $60,000 mark, with approximately 45,000 BTC removed from exchanges on August 27 alone. This movement represents the third-largest net outflow of Bitcoin from exchanges in 2024, following similar spikes in July. According to data from CryptoQuant, this trend could signal a growing bullish sentiment among investors, who appear to be transferring their Bitcoin off exchanges to hold for the long term, thereby reducing potential selling pressure in the market. As of August 27, major exchanges hold around 2.63 million BTC, reflecting a 12.5% decrease from the 3.01 million BTC held at the beginning of the year. This reduction in exchange reserves underscores a broader trend of investors preferring to hold their Bitcoin privately, possibly in anticipation of future price increases.

Reference: Cointelegraph
6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals
BlackRock's iShares Bitcoin Trust (IBIT) experienced a $13.5 million outflow on Thursday, marking its first outflow since May 1st and only the second in the fund's history since its launch in January. This rare withdrawal contrasts with the ETF’s usual pattern of consistent inflows, underscoring its dominance in the Bitcoin investment space. The outflow came as part of a broader trend affecting spot Bitcoin ETFs, which saw a collective $71.8 million in withdrawals on Thursday. Competing Bitcoin ETFs from Grayscale, Fidelity, Valkyrie, and Bitwise also reported significant outflows, ranging from $8 million to $31 million. Despite these withdrawals, ARK's Bitcoin ETF saw an inflow of $5.3 million, highlighting a mixed investor sentiment as Bitcoin remains below the $60,000 mark. This divergence suggests varied outlooks among investors regarding Bitcoin's future. Despite the recent dip, BlackRock's Bitcoin ETF continues to lead the market, having attracted over $20 billion in net inflows since inception. With more than 350,000 BTC under management, it remains one of the largest institutional Bitcoin holders, reflecting its enduring appeal and influence in the Bitcoin investment landscape.
Reference: Bitcoin magazine
C. Regulation
1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation
The Nigerian Securities and Exchange Commission (SEC) has granted Quidax, an Africa-based crypto exchange, its first provisional operating license. This marks a significant step toward formal recognition and regulation of Nigeria's digital asset industry. The SEC's license allows Quidax to operate as a registered crypto exchange in Nigeria, a move the company describes as a "shot of adrenaline" for the local crypto community, spurring innovation and growth. Quidax CEO Buchi Okoro praised the SEC, particularly under the leadership of Emomotimi Agama, for its efforts to bring order and investor protection to the Nigerian crypto market. The approval also paves the way for Quidax to collaborate with banks and financial institutions, pending approval from the Central Bank of Nigeria. This licensing follows the SEC's recent amendment to its rules on June 21, covering digital asset issuance, exchange, and custody. Despite concerns that stringent requirements could limit local crypto exchanges, the new regulatory framework, including the Accelerated Regulatory Incubation Programme, aims to align virtual asset service providers with the latest standards. Nigeria, Africa's largest economy, is a global leader in cryptocurrency adoption, ranking second in Chainalysis’ 2023 Cryptocurrency Geography Report. While foreign investment in Nigeria's crypto sector has been slower than expected, the new regulatory environment and Quidax's licensing could attract more investors by offering a stable and secure market.
Reference: Cointelegraph
D. Macroeconomy
1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich
As a presidential candidate, Vice President Harris has aligned with President Biden’s tax policies, including the pledge not to raise taxes on anyone earning under $400,000 annually. However, she also has her own ambitious tax proposals. These include raising the top marginal tax rate on high earners from 37% to 39.6%. Although she previously suggested a 4% “income-based premium” on households earning over $100,000 to fund Medicare for All, this idea has not resurfaced in 2024. Among the more controversial proposals Harris supports is a tax on unrealized capital gains for individuals with over $100 million in wealth. Often dubbed the “billionaire tax,” this would require these households to pay an annual minimum tax of 25% on their combined income and unrealized gains. This approach would be groundbreaking in U.S. tax history, as it taxes assets that have not yet been sold. For example, if you buy stock at $10 and it increases to $20, you would owe taxes on the $10 gain, even if you haven’t sold the stock. The same principle would apply to real estate, where yearly value increases would be taxed. This proposal raises significant concerns, particularly about the administrative challenges of valuing assets annually and the potential for future expansion of the tax to lower wealth thresholds. The wealth tax faces hurdles in Congress and potential court challenges, but it signals Harris's intent to push for new forms of taxation on the ultra-wealthy.

Reference: Forbes
2. Jobless claims drop as labor market slows, US economy remains on steady growth path
Last week, new applications for jobless benefits in the U.S. dropped slightly, but re-employment opportunities for laid-off workers are becoming scarcer, indicating the unemployment rate likely remained high in August. Despite this, the labor market's orderly slowdown is keeping economic growth on track, with the economy growing faster than initially reported in the second quarter, driven by consumer spending and rebounding corporate profits. The labor market's cooling supports the expectation that the Federal Reserve may start cutting interest rates next month, though a 50-basis-point reduction seems unlikely. Initial jobless claims fell by 2,000 to 231,000 for the week ending August 24, while continuing claims, which indicate ongoing unemployment, rose slightly, suggesting prolonged joblessness. In the second quarter, the economy grew at an annualized rate of 3.0%, with consumer spending revised upward to a 2.9% growth rate, offsetting lower business investment and exports. Corporate profits also reached a record high, helping businesses manage input costs amid supply-chain challenges. The goods trade deficit widened in July due to a surge in imports, likely driven by expectations of higher tariffs if former President Trump wins the November election. Despite these factors, economists predict growth will slow but avoid a recession.

-
 @ 07f367da:0e76880d
2025-01-06 13:46:33
@ 07f367da:0e76880d
2025-01-06 13:46:33- https://cms.newspoole.kr/news/articleView.html?idxno=10273
- 장애인활동지원사 월급 천만원
- 입력 2023.01.17 17:20
“장애인활동지원사가 돈을 많이 번다”는 발화의 이면
종종 활동지원사들이 돈을 많이 번다는 이야기를 듣는 일이 있다. 바로 얼마 전 보건복지부 공무원 면담을 하는데 노조 앞에서 담당 행정사무관이 이렇게 말했다. 장애인에게 24시간 서비스하면서 월 800만 원 소득을 얻는 분들은 다른 건 필요 없고 그냥 계속 그런 식으로 근무하길 원한다고 말이다. 그는 이렇게 말하며 노동조합의 제도 개선 요구를 일축하고 있었다.
이런 종류의 발언은 현장에서도 많이 나온다. 연초다 보니 연말정산을 안내하는 전담인력은 활동지원사에게 이렇게 안내했다 한다. “월 천만 원씩 버시는 분들이 센터 여러 개 하시잖아요. 그러니까….” 설명의 요지는 간단하다. 직장이 여러 곳인 노동자는 원천징수 영수증을 사업장별로 각각 발급받아 제출해야 한다는 내용이다. 그런데 이런 설명을 할 때도 “월 천만 원”이라는 금액이 그 앞에 붙는다.
우리 사회 일반의 노동 인식에는 기대가 없지만, 진보적 장애인 인권운동을 표방하는 이들조차 이런 발언을 쉽게 한다. 노동자들을 지원하면서 경악했던 사건 중 하나는 한 장애인 활동가가 우리 조합원이 일하는 장소에서 활동지원사의 노동을 폄훼해서 벌어진 갈등이었다. 그 활동가는 자신의 발언을 변호하기 위해 “밥 먹고 잠자면서도 돈 버는 거 아니냐”, “천만 원까지 벌 수 있다”, “장애인들이 얼마나 좋은 일자리를 만들어 준 거냐” 같은 이야기가 ‘장판(장애인 인권 운동판)’에서 농담처럼 나오는 이야기라고 주장하는 서신을 제출했다.
활동지원사의 수입이 월 천만 원이라는 말은 어떤 맥락 속에 있는 말이다. 연봉으로 치면 1억 2천. 이것은 그저 누군가가 선망하는 직종의 월수입에 대한 사실을 표현하는 말이 아니다. 그 말의 이면에는 장애인활동지원사 같이 별것도 하지 않는 일에서, 밥 먹고 잠을 자면서도 월 천만 원의 수입이 가능하니, 행정사무관의 태도처럼 정부에 감사하고 군소리를 말던가, 장애인 인권운동가의 태도처럼 그 제도 혹은 좋은 일자리를 만들어낸 진보적 장애인 인권운동에 감사하며 군소리를 말아야 한다는 뜻이 내포되어 있다. 발화자들이 의식하건 의식하지 못하건 이는 우리 사회 일반에 만연한 젠더화된 노동 혹은 돌봄노동에 대한 저평가와 멸시를 반영한 발화이다.
장시간노동이 가능한 조건을 만든 이유가 뭔지 물어야
활동지원사 일반이 월평균 천만 원을 버는 직종은 당연히 아니다. 활동지원사의 월 근무시간은 편차가 크다. 일하는 시간만큼 급여가 발생하는 시간급제 노동자이고, 일할 수 있는 시간도 매칭되는 장애인에 따라 차이가 크다. 급여의 수준보다도 근무시간의 불안정성이 활동지원사에게는 더욱 큰 문제로 다가온다.
2020년 공공운수노조 의료연대본부에서 발간한 “장애인활동지원사 노동·인권 실태 결과”에 의하면 설문에 응한 전업 활동지원사 월 근무시간의 최저값은 10시간이고 최대 597시간으로 편차가 심하다. 조사 당시의 전업 활동지원사 월평균 근무시간은 158.31시간이다. 2022년 수가 기준으로 평균 임금을 계산해보면 175만 원에 해당한다.
편차가 큰 근무시간 분포를 생각하면, 하루 24시간을 한 달 내도록 일하면 월 천만 원의 수입도 가능하긴 하다. 이렇게 근무하는 활동지원사들은 하루 24시간의 근무가 가능하도록 하기 위해 3개의 활동지원기관에 등록하여 근무해야 한다. 8시간의 근무는 A기관에서 근무한 것으로 기록하고, 다음 8시간은 B기관에서, 그 다음의 8시간은 C기관에서 근무한 것으로 기록하는 식이다.
이런 식의 노동형태가 개인의 차원에서도 제도적 차원에서도 추구할만할 노동형태는 아니다. 실제로 장시간 노동을 하는 조합원들은 결국 몸이 아파서 그런 노동을 유지할 수 없는 경우가 많다. 그렇다면 이런 노동형태에 대한 비난을 개별 노동자가 떠맡아야 할 문제일까? 나는 이런 식의 노동형태가 가능한 이유가 무엇인지는 따져 물어야 한다고 생각한다. 애초부터 이런 노동이 가능한 조건을 만들어둔 이유는 무엇인지 물어야 한다고 생각한다.
정부와 기관의 공모, 노동자 권리의 소멸
활동지원사가 센터를 여러 개 등록하는 데에는 정부와 활동지원기관의 암묵적 공모가 있다. 제도 법제화 이전에 활동지원사는 1개의 사업장에만 속할 수 있었다. 활동지원사가 수행한 근무는 모두 한 명의 ‘사장님’ 밑에서 이루어진다. 근로기준법은 사업장을 기준으로 적용되고, 법률상 법정근무시간 8시간을 넘어가는 근무시간은 연장근무수당을 지급해야만 한다. 하지만 활동지원제도가 법제화되면서 활동지원사 또한 여러 기관에 등록할 수 있도록 정부가 규제를 풀었다. 정부의 핑계는 장애인이용자들의 선택권을 보장하기 위해서라고 말했지만, 사실 이런 식의 선택권 보장은 장애인이용자들이 기관을 선택하는 것만으로도 충분히 실현이 가능했다. 이러한 변화의 실체는 노동자의 권리를 찢어 없앨 수 있도록 길을 열어둔 것이다.
활동지원기관들은 소속 활동지원사들의 근무시간을 여러 기관으로 찢어 나누기 시작했다. 활동지원사는 같은 장애인 이용자에게 같은 서비스를 제공하면서도, 여러 곳(활동지원기관)의 소속이 되어야만 했다. 결국, 근무시간은 사업장의 개수만큼 나누어져 계산되었고, 노동자가 더 받아야만 할 법정수당도 사라지게 되었다. 그리고 기관들은 이러한 노동시간 찢기를 자신들과 친한 중개기관들끼리 서로 나누며 진행하였고, 그들은 이러한 연계를 통해 월 서비스 총 시간(곧 수익)은 유지할 수 있었다. 이러한 조치들은 현재에도 활동지원기관들 사이에서 이루어지고 있는 것이 현실이다.
다른 센터가 다른 노동자를 파견하면 활동지원사의 장시간노동도 가능하지 않다. 하지만 문제는 인력을 구하기도 힘들뿐더러 장애인이 원하는 수준의 서비스를 받기가 힘들다는 문제가 있다. 장애인의 입장에서는 자신에게 익숙한 1명의 활동지원사가 계속 서비스해 주기를 바라는 경우들이 있다. 행정사무관도 이런 경우들을 언급했다. 하지만 나는 1명의 활동지원사만을 고집하는 장애인이용자들의 욕구가 인정되어야 한다고 생각하지는 않는다. 그 단 1명의 활동지원사가 아프거나 사고로 인해 근무할 수 없게 된다면, 그 활동지원사에게 의존되어 있던 장애인의 삶은 순식간에 무너질 수도 있기 때문이다. 자립은 의존으로부터의 탈피가 아니라 의존의 선택이자 분산이라고 탈시설 자립생활운동 활동가들은 말한다. 1명의 익숙한 활동지원사가 아니라, 자신이 편안히 서비스 받을 수 있는 여러 명의 활동지원사가 확보되는 것이 장애인 삶의 안정성 측면에서도, 활동지원사의 건강권 측면에서도 올바르다. 다른 활동지원사가 와서 비슷한 수준의 서비스를 제공한다면 장애인이용자는 그 단 1명의 활동지원사를 고집할 이유가 없다.
장애인이 1명의 활동지원사가 계속 서비스를 제공해 주길 바라는 이면에는 장애인 이용자가 바라는 최소 수준의 서비스 정도를 보장할 수 없는 활동지원서비스의 불안정성, 교육시스템의 부재가 바탕하고 있다. 그리고 그 외에도, 24시간 서비스를 제공하는 활동지원사들의 경우 다른 활동지원사들은 엄두 낼 수 없는 압도적인 서비스를 제공하는 경우가 많은데, 특장차를 구매하여 장애인에게 차량서비스를 제공하거나(운수사업법 위반), 석션(의료법 위반) 등 의료서비스를 제공하는 경우가 이에 해당한다. 장애인이 이런 서비스를 제공할 수 있는 활동지원사를 구하는 것은 당연히 어렵고, 대체불가능한 지위에 있는 활동지원사는 장시간노동이 불가피해진다. 이런 경우들도 이동권이 보장되지 않는 현실과 일상적 의료서비스가 제공되지 않는 현실이 바탕하는 것이다.
종합해 보자면 인력을 구할 수 없는 장애인의 필요와 법정수당 지급을 회피하고자 하는 활동지원기관의 이해, 생활에 필요한 임금을 충당하고자 장시간노동을 선택하는 노동자의 결정, 거기에 인력수급 안정성 확보와 교육시스템 구축이라는 과제를 회피하고자 하는 정부의 의지 속에서 월 천만 원 수익의 활동지원사가 가능하게 된다. 이 천만 원의 수익도 사실은 노동자로서는 삭제된 권리의 결과물이다. 장시간노동을 하고 돈을 많이 벌고자 하는 노동자의 선택은 이 전체 과정에서 얼마만큼의 주도권을 가지고 있을까.
이러한 조건들을 무시한 채 돈을 많이 버니까 입을 다물고 있으라는 식의 발화를 받아들일 수는 없다. 무엇보다 정부와 행정관료가 이런 식의 말을 해서는 안 된다. 정말 그것이 문제라면 여타의 정부 일자리 사업처럼 노동자는 1개의 일자리 사업에만 참여할 수 있도록 제한하면 된다. 하지만 왜 그렇게 하지 않을까? 어떤 난리가 날지 눈에 뻔하기 때문이다.
노동혐오 장애혐오
하는 일 없이 돈을 번다는 인식의 매개에는 심야 서비스에 대한 인식이 끼어있다. 사람이 잠을 자지 않고 일을 할 수는 없으며, 장애인이 잠자는 동안에 일하지 않으면서도 돈을 번다는 인식이다.
이런 인식은 정부나 사회보장정보원 부정수급 방지 교육자료를 보아도 알 수 있다. 사회보장정보원 교육자료에는 사회서비스 사업별 주요 이상 결제 유형으로 모든 서비스에서 심야결제를 꼽고 있다. 밤에 서비스한다고 보고하는 노동자는 부정수급 의혹을 받고 이와 함께 밤에 서비스 받는 장애인은 상시로 부정수급 의혹을 받으며 정부의 감시 대상이 된다. 복지 수급권이 권리가 아니라 낙인이 되는 데에는 이런 논리들이 작동한다.
달리 말하면 ‘장애인이 잠을 자는데 일을 할 리가 없잖아’는 ‘잠자는 시간에 서비스 받을 리가 없잖아’와 한 쌍의 인식이다. 이를 보면서 서비스 대상자에 대한 인식과 노동자에 대한 인식의 연결고리를 본다. “유전병자 한 명이 60살까지 살기 위해 평균 5만 마르크의 비용이 듭니다.”라는 나치의 발화와 장애인 권리 예산을 깎아내리는 정부의 인식이 다르지 않다고 장애인 인권운동은 말한다. “장애인활동지원사가 1년 버는 돈이 1억 2천입니다”라는 발화는 장애인에게 투여되는 국가 예산이 그를 웃돈다는 것을 함의하기도 한다.
활동지원사노동자와 장애인당사자가 이런 논리에 동조해야 할까? 일반적-통계적 사실에 부합하지도 않을뿐더러, 우리 사회가 나아가야 할 방향에도 적절한 인식은 아니다. 예산 논리에 매몰된 정부 관료가 이런 발언을 하면 차라리 규탄을 할 수 있지만, 우리가 이런 이야기를 농담으로 한다는 사실은 견디기 힘들다. 이런 이야기 농담으로라도 하지 말라.
-
 @ 469fa704:2b6cb760
2024-09-02 06:11:43
@ 469fa704:2b6cb760
2024-09-02 06:11:43I joined Nostr a week ago and wanted to recap it for myself and also give other newbies a simple introduction. Maybe this will help you get started too.
Step 1: Create your identity and get your private key for a browser extension
I started with the Snort client on my local home server. It created my private/public key pair and I was good to go. Then I transferred the private key to Amethyst, a pretty good Android-based client. Before looking at various clients and other nostr-based websites, I tried transferring my private key into a browser extension. I looked at Alby and nos2x. I chose the latter because I wanted to keep my Lightning wallet separate from my identity management. You don't have to, I just found it easier.
Step 2: If you're confused, always check your feed settings
I tried many different clients and was very confused at first. Due to its decentralized nature, Nostr relies on relays, which are just small servers, and to each one you can connect to, all your data is stored. When you post a message, write a note, an article like this or simply who you follow. The main reason and benefit for this is that there is no single point of failure or server-like entity that could be censored. The side effect of this, combined with using different clients, was that not only did it look different everywhere, but the content was also very different. This was simply because I wasn't connected to all my different clients with the same relays. But the main reason why each feed looks different on each client is usually because you can choose different variations of feeds and some clients even offer filters for the feeds.
Scroll down to get a small overview of the clients I've tried.
Step 3: Set up your lightning wallet with something like Wallet of Satoshi
I made my Bitcoin Lightning wallet independent of my identity. That's why I just went with the number one Lightning wallet on the market: Satoshi's Wallet. It's very simple and provides you with a Lightning address that resembles and has the format of an email address. You can add this address to your Nostr profile description and you're ready to receive Sats. Anyone can send them to you, e.g. for a good message or something else they find valuable on Nostr (like a podcast, a video, an article, ...). Just be aware that Satoshi's wallet contains your key and the sats you have there are not really your sats. So only leave a small amount there or no more than you need for your nostr experience.
Step 4: Set up your Nostr address
I set up a unique NIP-05 identifier that is human readable and also looks like an email address. For me, that's tobiya@nostrplebs.com, also called a nostr address. It's much easier to read, share and remember than your public key, which is just a long, unwieldy string of characters.
Some popular services are: * NostrVerified * Alby * Iris * Primal * Snort * nostrplebs.com
Most offer free services or at least a free tier. I chose nostrplebs.com because it links my Nostr address (tobiya@nostrplebs.com) to my Lightning wallet. ⚡
Brief overview of the clients (I have tested)
Web/Browser:
- Primal: Fast, user-friendly, nice looking, easy to use
- Coracle: Focuses on decentralized reputation, privacy and trust metrics. Also well organized and structured
- noStrudel: The most comprehensive I've found, has everything
- Rabbit: Designed like X (Twitter) Pro, focuses on everything at once
- Nostter: Clearly structured, easy to find what you're looking for
- Snort: Fast web client for those who prefer simplicity and speed.
iOS
I'm not an iPhone user, but everything I've discovered says that Damus is the best app for iOS.
Android:
- Amethyst: Feature rich for Android, I only tried this program because it gives me everything I currently need on my phone.
- Primal: Works seamlessly with Primal on the web, which is a pretty convenient starting point if you only want to use one client.
As for the web clients, I'm still figuring out which one will be my favorite. But I think they're all good in their own way. In the time of writing, I am mainly using Primal on Android and Web, Amethyst and noStrudel.
Let's have fun!!
-
 @ 07f367da:0e76880d
2025-01-06 13:45:33
@ 07f367da:0e76880d
2025-01-06 13:45:33- https://www.newspoole.kr/news/articleView.html?idxno=10154
- 입력 2022.10.14 17:02
- 제목: 활동지원사 수급 문제, 왜 활동지원사에게는 묻지 않을까?
활동지원사 수급 문제, 왜 활동지원사에게는 묻지 않을까?
장애인활동지원제도의 문제점으로 반복적으로 지적되는 것 중의 하나가, 활동지원인력의 수급 불안정이다. 장애인 부모와 장애인이용자들은 활동지원사를 구할 수 없어 괴롭다고 말한다. 이 정도 주장에 그치면 고충을 느끼는 당사자로서 느끼는 바를 말하고 정부에 해결을 촉구하는 활동으로 이해할 수 있다. 그런데 여기서 더 나아가 다른 제도적 주장을 하기도 한다. 장애인 가족에게도 활동지원서비스를 제공할 수 있도록 허용해달라는 내용이거나, 용처를 제한한 바우처 대신에 현금으로 달라는 개인예산제와 관련된 주장이 이어진다.
가족 활동지원 허용을 주장하는 사람이나, 개인예산제를 도입하라고 주장하는 사람이나, 결론적으로 이를 주장하는 사람에게 ‘현금’을 달라는 주장으로 내용을 정리할 수 있다. 매칭이 되지 않는 장애인을 둔 가족은, 내가 장애인을 돌보니 활동지원사와 동일하게 임금을 받도록 해달라거나 자신만이 장애인 자녀를 돌볼 수 있으니 나에게 임금을 달라고 주장한다. 매칭이 안 되는 장애인 당사자는 바우처를 현금화하여 자신에게 주면 필요한 곳에 더 지혜롭게 쓸 수 있을 것이라 주장한다.
이러한 주제에 있어서는 그 주장이 오래된 만큼이나 비판도 오래되었다. 그래서 여기서 중언부언 말할 필요는 없어 보인다. 다만 그러한 논의와 별개로 해당 장애인이 활동지원사를 구하지 못하는 문제를 왜 장애인에게서 답을 구하는지는 항상 의문스럽다. 최근 MZ[^1]가 퇴사를 해서 기업들이 속이 탄다는 이야기들이 있었는데, 이런 문제의 해법을 사장님께 여쭈면 나오는 답은 뻔하다. 그러니까 나에게 ‘가족 활동지원 허용’과 ‘개인예산제’같은 해법은 사장님들이 말하는 ‘요즘 젊은것들의 근성을 키우기 위한 획기적인 방안’과 꼭 같은 느낌이다. MZ가 퇴사하는 이유는 MZ에게 물어봐야 한다. 활동지원사를 못 구하는 이유는? 활동지원사들이 왜 안가는지를 물어야 한다.
현장에서 활동지원사를 하고 노동조합 활동을 하면서, 매칭이 되지 않는다고 소문난 장애인 이용자들을 몇 알고 있다. 실제로 긴급하게 투입이 되어 본 적도 있고, 아는 사람이 문제의 장애인이용자에게 서비스를 제공하면서 고통스러움을 토로한 적도 있다. 좀 죄송한 말씀이지만, 사람들이 안가는 데에는 안 갈만한 이유가 있다. 장애인 개인의 행동이 문제인 경우도 있고, 그의 물적 인적 환경이 문제인 경우도 있고, 안타깝게도 제도의 한계 때문인 경우도 있다. 어쨌거나 해법은 활동지원사 입장에서 기피되는 원인에 대한 제거가 있어야 매칭이 원활히 이루어진다.
일부 관계자들은 활동지원사들이 중증장애인을 기피한다는 주장을 하기도 한다. 하지만 내 입장에서 또는 주변의 활동지원사를 보아도, 바우처 시간이 넉넉한 장애인이용자를 활동지원사들이 선호한다. 시간을 많이 받는다는 것은 국가가 시행하는 종합조사 검사표에서 높은 점수를 획득했다는 뜻이고 달리 말하면 시간이 많은 장애인이용자는 국가가 공인한 중증장애인이라는 의미이기도 하다. 누구는 중증장애인을 기피한다고 말하고, 누구는 중증장애인일수록 좋다고 말하는 현상이 벌어진다.
나는 이러한 괴리가 장애를 보는 관점의 충돌로 읽힌다. 장애인인권운동은 오랜 시간 장애의 의료적 모델에 저항해왔다. 그리고 여전히 국가가 설계한 종합조사 검사표 질문에는 능력과 기능을 집중적으로 묻는 질문들이 즐비하다. 활동지원사들이 중증장애인을 기피한다고 주장하는 사람들의 장애관은 의료적 모델인 경우도 있고 사회적 모델인 경우도 있다. 그리고 노동자 입장에서는 장애에 대한 급부적 모델이라고 할만한 시각이 존재한다. 이 시각에서는 국가가 정한 15개의 장애유형 따위는 상관없고, 장애가 사회적으로 어떤 차별을 받는지도 무관심하며, 그저 노동자 자신이 어떤 급부를 얼마나 많이 제공해야 하는지가 중요하다.
노동자 입장에서 최고의 직장은 일은 쉬우면서 임금을 많이 주고 사회적 인정도 받는 직장이다. 활동지원사들은 중증장애인을 기피하는 것이 아니라, 돈이 너무 안되거나 돈에 비해서 힘든 장애인이용자를 기피한다. 기피되는 중증장애인이란 국가가 충분히 인정한 중증장애인은 아니며, 한편으로는 노동자 입장에서는 너무나도 서비스하기 힘든 어떤 업무가 있는 장애인이용자이다. 그리고 그 극단적 대척점에는 국가는 너무나도 인정해서 많은 시간은 부여되었지만, 노동자 입장에서는 별일을 시키지 않는 소위 좋은 이용자들이 있다.
나는 각 관점들의 의견에 대한 종합적이고 총체적인 반영이 있어야 한다고 생각하는 편이다. 장애인이용자 개개인의 욕구를 반영하고, 사회적 의미에서 그러한 욕구가 권리로 인정되어야 할지 판단 후 보장하며, 그 권리를 보장하기 위해서는 얼마만큼의 노동이 필요한지에 대한 고려가 되어야 한다. 의료적 모델은 장애인들을 줄 세워 선별하여 예산을 아끼기 쉽기에 정부에 의해 선호될 뿐이고, 사회적 모델은 장애인의 욕구를 충분히 반영할 수 있다 판단되어 장애인권운동에서 선호될 뿐이다. 하지만 장애인의 욕구가 충분히 반영되고 과도한 예산이 투입된다고 할지라도 누군가는 선호되고 누군가는 기피되는 현상을 피할 수는 없다. 결국은 노동자가 어떻게 움직이는지에 대한 고려가 있어야만 한다. 노동강도를 평등화 할 수 있는 정책적 지원, 여러 시도들이 고민되어야만 한다.
[^1]: MZ 세대(MZ Generation). 밀레니얼 세대와 Z세대를 아우르는 용어이다. 1980년대 초부터 2000년대 초반에 출생한 사람에 해당한다.
-
 @ 0edc2f47:730cff1b
2024-09-02 01:54:55
@ 0edc2f47:730cff1b
2024-09-02 01:54:55Chef's notes
In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 6 hours
- 🍽️ Servings: 12
Ingredients
- 1 medium onion, peeled and quartered
- 2 tsp ground ginger
- 8-10 large cloves garlic
- 1 cup ketchup
- ¼ cup dry sherry
- ¼ cup sake
- ¼ cup cider vinegar
- ¼ cup soy sauce
- ¼ cup honey
- ¼ cup Dijon mustard
- 1 tablespoon coarsely ground black pepper
- ¼ teaspoon ground cloves
- 1½ cups Coca-Cola, ginger ale, or Dr. Pepper
- 1 first-cut brisket, 6 to 7 pounds (2.7-3.2kg), rinsed and patted thoroughly dry
Directions
- Preheat oven to 325F / 160C.
- Combine all ingredients except brisket in a blender and blend until smooth.
- Place brisket in a Dutch oven or other large pot with a tight-fitting lid.
- Pour sauce over brisket, place lid on pot, roast in oven for 3 hours. Flip roast and return to oven for 3 hours or until fork tender.
- Remove roast to rest. Skim fat from sauce and reduce if desired. Serve immediately with sauce or cool, cover brisket and refrigerate overnight in cooking pan. The next day, defat sauce, reduce if desired, and reheat meat in sauce before serving.
-
 @ 3b7fc823:e194354f
2024-09-01 23:52:38
@ 3b7fc823:e194354f
2024-09-01 23:52:38I dOn'T cAre ABouT pRivAcY. IT dOEsN'T maTtER. i'M nOT dOiNg AnyThiNg wRonG.
GHOSTn
Your phone is spying on you. Your apps are spying on you. Your websites, search engine, fitness tracker, smart watch, IoT device, EVERYTHING is collecting anything it can and sending it off to be stored, cross referenced, and sold.
Data is the new oil.
So what? I don't care if Google knows I like motorcycles. By itself one data point isn't a big deal but once you start bringing everything together...
Who are you talking to? When and how long did you talk to them? Where did you go? How often do you go there? On and on the profile starts to become overwhelmingly invasive.
Right now it is extremely cheap and easy to collect and store the data but it's hard and expensive to cross reference and tabulate the data down to the individual. But in the extremely near future using AI and faster processers, data profiles for sale go from white men between 25 - 30, with this education level, and background like XYZ to -> John loves motorcycls and steak.
Suddenly your insurance premiums are way higher than your friends because you partake in dangerous activities and eat too much red meat. You get denied that loan because you invest in risky assets and it raises your risk factors to pay it back. That job that you applied to never responded because they already ran you through the algorithm and you don't fit the culture.
Protect your data and privacy now before its too late.
privacy
-
 @ 91687725:a0de48ea
2024-08-24 05:40:14
@ 91687725:a0de48ea
2024-08-24 05:40:14こんにちは。Kateです。
最近ちょっとお休みしていますが、日本でビットコインを専門に扱うDiamond Hands Magazineに寄稿したりしてます。
私がビットコインと出会ったのは2011年、まだビットコイン利用者はとても少なかった時代です。たまたま身内にビットコイン界隈の人がいました。もしかしたら今でいうビト妻だったかも?
まだビットコインが1ドル以下でおもちゃみたいな存在だった頃に知ったわけですが、その後勢いづいて、100ドル、1000ドルと価値が上がっていきました。
それを見て、ビットコインを少しずつ買って貯めておけば、将来リタイヤの蓄えになるかもと思ってお小遣い程度のビットコインを積立してました。でも、アクシデントで失くしちゃったんですよね。
その後、身内のごたごたで自分の生活が天地がひっくり返るように一変し、気がつけばカナダでただお金がないアジア系移民シングルマザー、しかも周りに家族が誰もいないという、非常にマイノリティな立場になりました。
人生、何事も経験。一度ビットコインを失くし、傷心もあり、数年はビットコインから離れました。でも気がつけばビットコインは冬の時代を終えて、また元気になっていたんですね。自分は海外でひとり子育てに追われ、なんとか生きてた感じですが!
ビットコインが500ドルくらいになっていた時に困窮していた私は、ふとペーパーウォレットと呼ばれた当時の携帯可能ウォレット?に0.5btc 残っていたのを発見して速攻換金しましたね。悔やまれます。
その後、2017年頃、カナダで当時大手の割と使い勝手のいい取引所があることを知って、再度ビットコイン貯蓄にチャレンジしました。2年ほどで、ほぼ1ビットコインと10ETHくらいあったんですけどね、今度は取引所の代表者が行方不明になり、またもやビットコインを失くしました。
ふつうだったら、もうやめますよね。2回もなくしたら。
けれど、自分はかつてインターネットが始まったころのワクワクを経験していました。90年代半ば、新宿にできたばかりのインターネットカフェで、GIFがかろうじて表示できるグレーのブラウザ画面と対面しました。世界を変える技術を体験した時の感動は今でも忘れられません。
(こう書くと立派なオバサンなのがバレちゃいますね。ビットコインネイティブ世代の中では年長者)
それから15年以上たって、初めてサトシナカモトのホワイトペーパーを読んだ時に、同じ衝撃を受けたのです。初めて実用化されたインターネット上で世界の誰とでも送り合えるマネー。その可能性は無限∞。
そのビットコインの進化を、実際に買ってみたり、使ってみたり、なくしたりしつつ、より深く知ろうと付き合ってきた自分は、いつの間にかビットコインを通して世の中のいろいろを見て考えるようになりました。
ビットコインが生まれ、実験段階を経て、すでに15年が経ちます。けれども、ビットコインは今でも多くの人から最も誤解されている技術・発明のように見えます。ここまで来たら、自分が生きている間に、ビットコインが世界とどう関わっていくのか見届けたいと思います!
そして、私自身がビットコインを知ることで発見した世界や新しい価値観を、誰かに伝えられたらいいなと願って、このブログをスタートすることにしました。
今回は自己紹介という形になりましたが、私がビットコインを通して学んだことや気づいたことをこれから少しづつアップしてみます!
週1くらいのペースで投稿が目標です。よろしくお願いします。
-
 @ b0510a0c:12716ced
2024-08-21 06:03:43
@ b0510a0c:12716ced
2024-08-21 06:03:43On April 24, 2012, Erik Voorhees changed everything about Bitcoin with the launch of Satoshi Dice:
a game that captivated users and intensified debates about Bitcoin's evolution and the network's ability to handle an increasing volume of transactions.
At that time, Satoshi Dice allowed thousands of players to bet on digital dice rolls, leading to a MASSIVE influx of transactions that filled the blocks of the blockchain.
📈 Success of Satoshi Dice:
Satoshi Dice achieved phenomenal success, attracting millions of users with its simplicity. Players flocked in, bets piled up, and blocks filled up.
Erik Voorhees effectively leveraged Bitcoin's microtransactions, quickly saturating the blocks with these. This was a testament to the game's popularity, but also a source of tension within the community.
Within months, Satoshi Dice became the most popular service on the Bitcoin network, boosting its usage and virality.
Players appreciated the "provable fairness" aspect of the game, where they could verify the transparency and fairness of each bet.
🚫 Criticism and Controversy:
However, this success was not without criticism.
Many Bitcoin enthusiasts viewed the massive influx of transactions generated by the game unfavorably. For them, these sometimes trivial transactions "spammed" the blockchain, clogging the blocks and increasing transaction fees for all users. Does this sound familiar?
The network, designed to handle about seven transactions per second, quickly reached its maximum capacity, causing validation delays and "high" fees.
⚔️ BlockSize Wars:
The BlockSize wars, which took place mainly between 2016 and 2017, were a technical and ideological conflict centered on block size and scalability solutions.
While Satoshi Dice was not the sole cause, the game significantly contributed to the emergence of this event by helping to popularize Bitcoin among new users and generating substantial transaction volume.
As Bitcoin adoption grew, the network faced intense pressure, leading to block saturation and rising transaction fees. On one side, some advocated for increasing block size to allow more transactions, leading to the creation of Bitcoin Cash in August 2017. On the other, proponents of solutions like SegWit pushed for improvements without compromising decentralization.
🔧 Adoption of SegWit:
Erik Voorhees expressed his support for the SegWit2x proposal, which aimed to improve network scalability by combining the implementation of SegWit with an increase in block size.
Segregated Witness (SegWit) was adopted in August 2017, allowing transaction data to be separated from signatures. This reorganization not only increased transaction processing capacity but also paved the way for the development of the Lightning Network, a layer 2 solution enabling instant and low-cost transactions.
SegWit was a crucial response to the challenges posed by network congestion, which had been exacerbated by Bitcoin's growing adoption and the emergence of popular applications like Satoshi Dice.
⚡ SegWit and Lightning:
The adoption of SegWit helped resolve blockchain congestion issues, while the Lightning Network, a layer 2 solution, facilitated fast and low-cost transactions.
Together, these innovations not only addressed technical challenges but also renewed enthusiasm for games and other applications on Bitcoin, paving the way for a new wave of development.
🎲 Nostr Dice:
Today, as we reflect on the impact of Satoshi Dice, a new project emerges: nostr:npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84
This modern clone of the original game is built on Nostr, a decentralized communication protocol, and Lightning, paying homage to the past while offering an enhanced gaming experience that does not impact layer 1 congestion!
From a game that caused Bitcoin congestion to its rebirth on Lightning, which it helped to bring about, the circle is complete!
-
 @ fd78c37f:a0ec0833
2025-01-06 13:28:13
@ fd78c37f:a0ec0833
2025-01-06 13:28:13The rise of Bitcoin and cryptocurrencies has reshaped the global financial system, igniting new possibilities for innovation and development. In North America, a region at the forefront of technological advancements and economic influence, Bitcoin communities have played a pivotal role in advancing the adoption and utilization of digital currencies. These communities are engaged in a wide array of activities, from fostering education and providing technical support to promoting business opportunities and advocating for policy changes. This article will highlight 23 Bitcoin communities across North America, shedding light on their latest achievements and future ambitions in driving the expansion of Bitcoin technology, education, and economic empowerment. It offers readers a comprehensive understanding of the North American Bitcoin ecosystem and its significant influence on the global stage.
Thank you, nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.PlebLabs nostr:npub1an84q6c03wml5lf0uwcqcr20ydwv0t0lvv0xktlcfs9seattef8sdhz6yg * Introduction PlebLab is a hacker space and community accelerator based in Austin, Texas, dedicated to supporting the next generation of Bitcoin developers and startups. It brings together developers, hackers, creatives, and open-source builders to create a collaborative and innovative environment. PlebLab offers workshops, hackathons, and Startup Days to foster learning and growth within the Bitcoin ecosystem. By providing exposure, mentorship, and collaboration opportunities, PlebLab helps early-stage Bitcoin projects succeed. Its core philosophy is to support free and open-source development, driving innovation and progress within the Bitcoin space. * Latest Updates Recently, the PlebLab has continued to make significant strides in driving Bitcoin innovation and entrepreneurship. They have launched the second season of Top Builder, with a series of top-tier workshops focusing on Bitcoin Accounting, Bitcoin UX & UI Design, Bitcoin Marketing and Media, and more. These workshops aim to discover the next generation of Bitcoin industry startups, with participants having the chance to win up to $15,000 in BTC. The events will bring together Bitcoin developers and entrepreneurs, providing opportunities for showcasing ideas and networking. Additionally, PlebLab will host workshops related to Bitcoin technology and applications, helping members deepen their understanding of Bitcoin Core and enhance their development skills.
2.BAYAREA * Introduction Bay Area Bitcoin Users is a community formed by the people, for the people, aimed at providing an open and inclusive platform for all Bitcoin enthusiasts. The community regularly hosts events in the Bay Area, offering a space to share ideas, opinions, memes, and have relaxed discussions. It’s a great fit for anyone looking to dive deeper into Bitcoin technology or simply enjoy gatherings with like-minded individuals. * Latest Updates Recently, the Bay Area Bitcoin Users community hosted a Bitcoin Holiday Party at Eve (1535 Folsom St) in San Francisco, California. The event featured a Socratic seminar co-hosted by BitDevs and LitDevs at Digital Garage, followed by a festive celebration with music, snacks, a bar, and Bitcoin-related interactions. Designed as a family-friendly gathering, the event welcomed children accompanied by guardians, even though no specific activities for kids were organized.
3.Ann Arbor Bitcoin nostr:npub1j4dvdn24dp963f4sfak0g6nz0chnw8tyglvs3pn9gqhhhfukmrfsyznne7 * Introduction Ann Arbor Bitcoin is a community-focused organization based in Ann Arbor, Michigan, dedicated to fostering Bitcoin adoption and engagement. The group hosts regular meetups and events, providing a platform for Bitcoin enthusiasts to share knowledge and exchange ideas. * Latest Updates Recently, there have been no new updates from the community, with the latest event dating back to December 2022, which encouraged everyone to join their Telegram group to stay updated on all the latest news about meetups.
4.Bit Miami * Introduction BitMiami is a vibrant community dedicated to exploring and learning about the Bitcoin ecosystem in South Florida. * Latest Updates Recently, the BitMiami community has shared various Bitcoin-related events and updates. They highlighted Bitcoin Vortex Week in Miami and also focused on the HODLween event. BitMiami continues to support the growth of the South Florida Bitcoin community by reposting valuable content from local Bitcoin enthusiasts and organizations. They also encourage community members to actively engage with the Bitcoin ecosystem through meetups and educational opportunities.
5.Seattle Bitcoin and Beer nostr:npub1x2dm3cwqt0v9tqlf0ppzztaskn3th2x40p33hepl8rkwdgedw8eshypm5s * Introduction Seattle Bitcoin and Beer is a community that brings together Bitcoin enthusiasts and freedom lovers in Seattle. They regularly meet to discuss Bitcoin and build strong local connections in a city that may not always embrace freedom. The group fosters collaboration while enjoying good beer along the way. * Latest Updates Recently, the Seattle Bitcoin and Beer community hosted a monthly meetup on December 26th at the Old Stove Brewery on Nickerson St. Ship Canal, aiming to expand the sovereignty of the Bitcoin user network in the Great Northwest. Although this wasn't a cryptocurrency-exclusive meetup, participants gathered in a relaxed atmosphere to discuss Bitcoin and strengthen community connections.
6.Bitcoin Aruba * Introduction Bitcoin Aruba is a community dedicated to promoting the use and acceptance of Bitcoin across the beautiful island of Aruba. Their mission is to encourage local businesses and individuals to embrace Bitcoin as a payment option, creating a vibrant ecosystem where people can experience the freedom and potential of decentralized currency.. * Latest Updates Recently, the Bitcoin Aruba community has shared various Bitcoin-related updates on Twitter. They highlighted and reposted content from several Bitcoin initiatives, including the StackSats 250k Sat giveaway, BTCPay Server’s holiday greetings, and discussions on the importance of running your own Bitcoin node. Additionally, Bitcoin Aruba has been encouraging community members to actively engage in the Bitcoin ecosystem, with a focus on topics like node operation and privacy protection.
7.Bitcoin Beach Yucatan nostr:npub1w2my0n7rklzdgw7anjdnssq8mjzkpr54apqeg3pk9qjauu9dt26smyydvm * Introduction Bitcoin Beach Yucatán is a community dedicated to promoting Bitcoin education and adoption throughout the Yucatán state. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to Oct 2024, when they shared a post calling for help for the disaster-stricken area of Sisal, requesting food, clothing, and other essential supplies.
8.Bitcoin Brunch Miami * Introduction Bitcoin Brunch Miami is a community where Bitcoin enthusiasts gather every Sunday for casual discussions over brunch. * Latest Updates Recently, there have been no new updates from the community on twitter, The latest event dates back to July 2023. However, Bitcoin Brunch Miami has already hosted five brunch discussions in December.
9.Bitcoin Charlotte nostr:npub1p7g986pc56qmvryplgzka0fsrpuwlk6mxk3h686w4e46n74e56qqhz88vk * Introduction Bitcoin Charlotte is a community for those passionate about Bitcoin, decentralization, privacy, and freedom. It provides opportunities to connect with individuals at the forefront of this transformative technology through social events, workshops, and online hangouts. The community’s mission is to educate and empower people to break free from financial dependence on banks and governments by embracing Bitcoin, the most superior form of money in history. * Latest Updates Recently, the Bitcoin Charlotte community hosted several events, including an in-person meetup at Southern Strain Brewery in Plaza Midwood, where members connected with like-minded individuals and celebrated Bitcoin's potential for financial liberation by purchasing beer with Bitcoin. Additionally, the community held an online Bitcoin meetup and knowledge-sharing session on December 2, further promoting Bitcoin education and awareness.
10.Bitcoin Ciudadela * Introduction Bitcoin Ciudadela is focused on transforming San Cristóbal de las Casas and Chiapas into strongholds for Bitcoin adoption and education. The community aims to build a robust network of Mexican Bitcoiners who are united in promoting the benefits of decentralized finance and empowering individuals with knowledge about Bitcoin. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to Apr 2024, when they shared a post criticizing those who supported restrictions on freedom and praised those who fought for liberty, questioned authority, and stood against oppression.
11.Bitcoin Jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network, aiming to create a circular Bitcoin economy. It supports individuals and businesses by providing education, resources, and technology to drive Bitcoin adoption. Starting in the Golden Triangle region of Costa Rica, the project strives to set an example for Bitcoin communities. The goal is to establish a sustainable Bitcoin ecosystem for communities worldwide. * Latest Updates Recently, Bitcoin Jungle is actively preparing for the next Bitcoin Freedom Festival, which will take place from February 20th to 24th, 2025, at the Awake Earth Festival in Uvita, Costa Rica. The event will combine Bitcoin seminars with a music festival, lectures, and discussions, aiming to attract new audiences to the Bitcoin space in a unique and engaging way.
12.Bitcoin Lake Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake Guatemala is a Bitcoin community located in Guatemala, focused on promoting the use and education of Bitcoin in the Lake Atitlán region. By supporting local businesses in adopting Bitcoin payments and providing educational resources, the community aims to build a sustainable economy based on Bitcoin. * Latest Updates Recently, the community has shared one update,this post celebrates the continued growth and resilience of the Bitcoin movement, marking a significant milestone for the community.
13.Round Rock Bitcoiners nostr:npub17ysayggwumkpkpgsq75axd7ed9guw03wz9jldz5d0zrkgz0cja2qd09tzu * Introduction Round Rock Bitcoiners is a Bitcoin community in Round Rock, Texas, dedicated to promoting Bitcoin knowledge and adoption. Through monthly meetups and resource sharing, the group supports individuals and small businesses in adopting Bitcoin and fosters a local peer-to-peer network. * Latest Updates Recently, The Round Rock Bitcoiners community has been actively organizing events to promote Bitcoin education and strengthen community bonds. Recently, they hosted a screening of the film No More Inflation, exploring the future of money and inflation-free solutions, followed by a Bitcoin-themed happy hour. Additionally, they announced the second biennial Base58 Bitcoin LARP event, offering participants a unique experience of hands-on learning, networking, and fun. Additionally, they shared posts addressing KYC privacy risks, critical discussions about the IRS, the legacy of cypherpunk ideals, and new features in the Bitcoin ecosystem, such as Zaps integration with the Rumble platform.
14.SacTown Bitcoin * Introduction Sactown Bitcoiners is a Bitcoin-focused community with members from across the Greater Sacramento region. The group hosts two monthly events: a discussion and member-led presentation at the Arden-Dimick Library on the 4th Thursday and a social gathering at a brewery or restaurant on the 2nd Thursday. Discussions revolve around Bitcoin, covering topics like money, hope, and the future under a Bitcoin standard. Open to Bitcoin enthusiasts, beginners, and maximalists alike, the community maintains a strict “Bitcoin only” policy, creating a dedicated space for pure Bitcoin conversations. * Latest Updates Recently, SacTown Bitcoin hosted a Christmas Party and highlighted Bitcoin's transformative impact. On December 12, 2024, SacTown Bitcoin hosted the Sactown Bitcoiners Christmas Party at Turkovich Family Wines Tasting Room. The event featured a potluck, a white elephant gift exchange (participants were asked to bring a gift worth approximately $20), and a raffle. Additionally, SacTown Bitcoin has been focusing on the profound impact of Bitcoin on personal financial understanding and its potential to disrupt economic inequalities. They have shared posts highlighting insights from financial and investment professionals inspired by Bitcoin, as well as discussions on how Bitcoin empowers ordinary people to benefit from asset growth.
15.San Diego Bitcoiners * Introduction San Diego Bitcoiners is a community dedicated to learning and discussing Bitcoin, providing a platform for anyone interested in the cryptocurrency. Established during the COVID-19 pandemic, the community hosts monthly events featuring guest speakers, brief presentations, or casual conversations. Meetings are held every second Thursday of the month at Quantum Brewing in Kearny Mesa, welcoming all Bitcoin enthusiasts. * Latest Updates Recently, San Diego Bitcoiners have been actively engaged in promoting Bitcoin education and fostering community interaction. They were featured in a local news article as the oldest running Bitcoin meetup in San Diego. The community has been sharing important reminders, such as testing Bitcoin wallet backups every six months. They also continue to host regular meetups, with a focus on practical demonstrations, including CoinJoin and wallet integrations like Sparrow Wallet and JoinMarket. The latest meetup took place in December at Quantum Brewing, where members gathered to discuss Bitcoin and explore new tools in the ecosystem.
16.SLC-BTC * Introduction The SLC-BTC community focuses on Bitcoin and the Lightning Network, welcoming participants of all experience levels. Regular meetups feature discussions on topics such as Bitcoin protocol, software, economics, self-custody, and mining. Whether you're a newcomer or an experienced user, the community encourages open dialogue and answers any Bitcoin-related questions. * Latest Updates Recently, the SLC-BTC community hosted a series of successful events, including a Christmas party, thanks to the active participation and support of its members. During the party, the community offered a variety of giveaways and collaborated with several partners. Additionally, the community organized a Christmas Potluck Party and celebrated the milestone of Bitcoin's price breaking 100K. SLC-BTC continues to provide opportunities for Bitcoin enthusiasts to connect, learn, and grow together.
17.Topeka Bitcoin * Introduction The Topeka Bitcoin Meet-up aims to expand knowledge and awareness within the community. Hosted at local businesses, the group discusses topics such as Bitcoin (network vs asset), the Lightning Network, running a full node, self-custody, and accumulation strategies. Additionally, the community explores Bitcoin literature, podcasts, and other relevant topics. * Latest Updates Recently, the Topeka Bitcoin community shared some interesting Bitcoin-related insights and updates on Twitter. Members celebrated the new year, highlighting the concept of "time is money" and encouraging everyone to accumulate at least 31,536,000 Sats this year (one sat per second). The community also discussed the concept of "sat/cent parity," offering a unique perspective on Bitcoin's value. Additionally, Topeka Bitcoin shared creative activities related to Bitcoin, such as Bitcoin-friendly cruise line initiatives.
18.Vancouver Bitcoiners * Introduction The Vancouver Bitcoin community is a dedicated group of Bitcoin enthusiasts actively engaging in events like Bitdevs and more. With the motto “Splendor Sine Inflatione” (Splendor Without Inflation), the community focuses on fostering knowledge and connections around Bitcoin. * Latest Updates Recently, the Vancouver Bitcoiners community has been actively involved in advocating for Vancouver to become a Bitcoin-friendly city. Community members have supported Mayor Ken Sim's proposal to invest in Bitcoin and have participated in backing the city council's Bitcoin-friendly motion. Additionally, the community has voiced concern over the Bitcoin mining ban in British Columbia, suggesting the use of local renewable energy sources like tidal, wind, and solar power for Bitcoin mining to expand the grid and utilize excess heat from mining rigs. During the council's discussions, the community also supported the idea of Vancouver building a Bitcoin reserve, despite the associated risks.
19.Victoria Bitcoin * Introduction Victoria Bitcoin is a community that regularly hosts Bitcoin-focused meetups and BitDevs seminars, typically held one to two times a month. These events are free and open to the public, providing opportunities for discussion, learning, and networking. Community members can also win prizes from Canada's Bitcoin self-custody pioneers, Bull Bitcoin and Coinkite. The community places a strong emphasis on privacy, with all discussions following Chatham House rules. * Latest Updates Recently, the Victoria Bitcoin community has been actively hosting several Bitcoin-related events, fostering interaction and engagement among local Bitcoin enthusiasts. The community regularly organizes “Bitcoin & Coffee” meetups, providing members with opportunities to discuss Bitcoin. The most recent event was scheduled for December 22 at Discovery Coffee. Additionally, the community hosted an exciting Christmas party on December 13, where attendees enjoyed free pizza, beer, and champagne, and Christmas gifts were purchased with Bitcoin, showcasing the practical use of Bitcoin in everyday life. The event also included a Bitcoin giveaway for lucky participants..
20.Michigan Bitcoin Meetup in Benton Harbor * Introduction Michigan Bitcoin Meetup in Benton Harbor is a community focused on exploring Bitcoin's impact on investing, entrepreneurship, and self-sovereignty. It provides a platform for like-minded individuals to connect, learn, and share ideas. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to Nov 2024, which Announced Bitcoin Meetup Night in Benton Harbor on Thursday, November 21.
21.Western Mass Bitcoin Meetup nostr:npub1xgyjasdztryl9sg6nfdm2wcj0j3qjs03sq7a0an32pg0lr5l6yaqxhgu7s * Introduction Western Mass Bitcoin Meetup is a community focused on connecting local bitcoiners, promoting bitcoin education, and increasing merchant adoption. The group hosts monthly meetups and offers support for newcomers in areas like self-custody, Lightning Network, and mining. * Latest Updates Recently, the Western Mass Bitcoin Meetup has been actively organizing events to foster community engagement and growth. On December 8th, they hosted a social meetup at Fitzwilly's in Northampton, providing a space for Bitcoin enthusiasts to connect and share ideas. Additionally, they are preparing for their 29th meetup on January 5th in East Longmeadow, continuing to offer a platform for local Bitcoin supporters to gather and collaborate.
22.Yes Bitcoin Haiti nostr:npub1mjmaggp53xan2435wdse8ts06pzfcjejfex4pxasu67kxs5hqdpsyk7hx8 * Introduction Yes Bitcoin Haiti is Haiti's first Bitcoin-only initiative, launched to empower communities through Bitcoin education and adoption. Founded by Phanor Mendelking in February 2024, the project focuses on spreading financial literacy, promoting economic growth, and building a circular Bitcoin economy. Its mission includes offering local Bitcoin certification, hosting meetups and workshops, and onboarding businesses and community members. Operating from St. Michel de l'Attalaye, it aims to drive financial inclusion and resilience in Haiti's challenging economic landscape. * Latest Updates Recently, the Yes Bitcoin Haiti community has been actively advancing Bitcoin education. The first batch of students is nearing the end of their courses, with two students leading the discussion of Chapter 10 in preparation for the upcoming final exams and graduation. Additionally, the community has showcased proof-of-work in action, reinforcing the spread of Bitcoin knowledge through student-led lessons and engagement in activities.
23.YYC Bitcoin * Introduction YYC Bitcoin is a community-focused meetup dedicated to growing, educating, and supporting the Bitcoin ecosystem in Calgary. The group hosts biweekly meetups for networking and learning, covering essential Bitcoin topics such as wallet setup, privacy, multisig, lightning, and mining. Newcomers are encouraged to visit the website to familiarize themselves with key concepts and bring their questions to future events. * Latest Updates Recently, YYC Bitcoin has actively promoted Bitcoin education and outreach through several updates. They shared the BTC Sessions year-end recap and the The 4th Annual BTC Sessions HODLiday Special, engaging community participation. Additionally, YYC Bitcoin reposted Blockstream Jade's promotional offer, encouraging the purchase of hardware wallets. The community also highlighted Bitcoin Mentor's personalized coaching services to help members better understand Bitcoin technology. Furthermore, they supported and promoted ticket sales for the Learning Bitcoin 2025 conference, further advancing Bitcoin education.
-
 @ bcbb3e40:a494e501
2024-08-16 18:00:07
@ bcbb3e40:a494e501
2024-08-16 18:00:07El hombre y el contexto
El pensamiento tradicionalista español cuenta con una amplia trayectoria en la que concurren personajes, situaciones e ideas gestadas en el transcurso de dos siglos, en los que debemos distinguir el conflicto dinástico y el papel del legitimismo de la propia doctrina, que es algo que se construirá en el tiempo, con la contribución de figuras como el protagonista de este escrito, Don Juan Vázquez de Mella, así como por la confluencia de fuerzas de diferente signo que tiene lugar a lo largo del siglo XIX y la consolidación del Estado liberal, que lo hará siempre en lucha abierta contra las peculiaridades y el carácter genuino del pueblo español. Vázquez de Mella, nuestro autor, quizás represente la consolidación y madurez doctrinal del movimiento tradicionalista español, uno de sus primeros y más brillantes sistematizadores. No se destacó por una obra extensa ni especialmente difundida más allá de sus discursos, de sus artículos en periódicos y sus escritos dispersos, los cuales fue capaz de dotar de una especial significación y dignidad fruto de su enorme carisma y especial clarividencia para dar una forma definida y meridianamente clara a las ideas y doctrinas que nutrieron el tradicionalismo español madurado al calor de las armas, de las tres guerras que el carlismo libró contra el liberalismo español.
|
 |
|:-:|
|Juan Vázquez de Mella|
|
|:-:|
|Juan Vázquez de Mella|Nuestro autor, de origen asturiano, y nacido en Cangas de Onís un 8 de junio de 1861, ha mantenido vivo su prestigio y el valor de sus aportaciones teórico-doctrinales, ampliamente reconocidos por sus sucesores, por Rafael Gambra Ciudad (1920-2004) y Francisco Elías de Tejada y Espinola (1918-1978), así como de otros autores como Álvaro D'Ors (1915-2004) y otros muchos, que han reivindicado su figura en el tiempo y se han nutrido de sus fecundas enseñanzas. Se ha destacado la rectitud de su pensamiento, su inquebrantable voluntad y su impagable contribución en la creación de un marco teórico y conceptual para dar un sentido y una forma a las ideas del tradicionalismo español. Hijo de un militar de origen gallego, muerto prematuramente, quedó huérfano de padre durante su niñez, por lo cual pasó al cuidado de unos parientes de origen modesto. Estudió en la Universidad de Santiago de Compostela, donde mostró tempranamente su temperamento y habilidades oratorias, que explotó convenientemente a través de diarios como La Restauración o El pensamiento galaico, donde también mostró sus filiaciones militantes con el catolicismo tradicional. Sus habilidades y la brillantez de sus escritos pronto llegaron a Madrid, a las más altas instancias del Carlismo, lo que le permitió dar continuidad a sus actividades desde un medio más amplio, a través de El correo español.
En su militancia política llegó a las más altas cotas de su trayectoria con la elección en 1893 como representante de las Cortes por el distrito de Estella, Navarra, que ya con sus primeros discursos obtuvo un notable éxito, incluso entre los propios liberales, hasta 1900, fecha en la que se vio obligado a marcharse a Portugal, acusado de participar en una conspiración para derrocar el régimen de la Restauración. No regresó a España hasta 1905, manteniendo su estatus como diputado hasta 1919. De todos modos, no queremos dar más protagonismo a la biografía en detrimento de la doctrina, que es lo que nos interesa en este artículo, de ahí que obviemos otros datos biográficos trascendentes, polémicas con otras facciones del carlismo o sus posturas respecto a la dictadura del general Miguel Primo de Rivera, que nos harían desviar la atención del propósito principal que acabamos de enunciar.
La gran paradoja del Carlismo fue que a pesar de su derrota en la Tercera Guerra Carlista (1872-1876), y pese a la posterior escisión integrista en 1888, el partido carlista continuó manteniendo una fuerza y preponderancia significativa en la sociedad española del régimen de la Restauración durante el último cuarto de siglo. El Carlismo se vio inmerso en un buen número de paradojas, de situaciones encontradas, especialmente en relación al Desastre del 98 y la pérdida de los últimos territorios ultramarinos. Mientras que la gran esperanza del tradicionalismo español estaba depositada en el desmoronamiento y caída final de la restauración alfonsina, por otro lado este mismo régimen trataba de defender, al menos en teoría, los últimos restos del imperio español y, de algún modo, a la España católica frente a una nación protestante, como era la anglosajona estadounidense. Al mismo tiempo, durante esta época el tradicionalismo español se enfrentó a los grandes retos que presentaba una sociedad en cambio, con transformaciones políticas y sociales de gran calado como la emergencia del sufragio universal o el nacimiento de los separatismos periféricos (propiciados por la burguesía liberal), las cuales requerían de nuevas estrategias y reestructuraciones internas capaces de enfrentar la envergadura de todos estos cambios. Fue en este contexto donde se significó la figura de Juan Vázquez de Mella, quien merced a la obra de sistematización a la que ya hemos hecho alusión, y de sus concurridas conferencias, dio lugar a la denominada Acta Loredán, redactada por el tradicionalista asturiano y publicado en El correo español. Este escrito tenía como ejes fundamentales la defensa de la nación política española fundamentada en la monarquía, el catolicismo y el régimen foral. Al mismo tiempo, también recogía la reivindicación de un programa corporativista y gremial al abrigo de la doctrina social de la Iglesia defendido en la encíclica Rerum Novarum (1891), y es lo que se conoce como el «sociedalismo», cuyos antecedentes encontramos ya en autores como Donoso Cortés o Antonio Aparisi Guijarro. Son precisamente los atributos de esta doctrina, que contribuyó a la revitalización del pensamiento carlista, los que nos disponemos a desarrollar a continuación.
La figura del tradicionalista asturiano, de Don Juan Vázquez de Mella, aparece como necesaria ante una serie sucesiva de destrucciones que el régimen liberal ha producido sobre los fundamentos tradicionales de España, pero su papel no fue, como ya venimos apuntando, el de un gran intelectual erudito, y de hecho, como apunta Rafael Gambra, las mayores debilidades de su pensamiento se encuentran en los principios filosóficos, y destacando, en cambio, su papel de «revulsivo espiritual» podemos ubicarlo mejor en el ámbito de lo político y lo espiritual. Para ello debió tomar en cuenta las fuentes de sus predecesores, entre los cuales podemos ubicar perfectamente al ya mencionado Donoso Cortés y Jaime Balmes, así como también a otro contemporáneo suyo, Menéndez Pelayo. De los dos primeros tomó su capacidad de síntesis y la sencillez expositiva, mientras que de Menéndez Pelayo tomó, al menos en parte, el sentido de la crítica histórica en aras de la restauración de una Tradición nacional. Pero más allá de los sistemas de pensamiento y elementos retóricos, vemos a Vázquez de Mella profundamente interesado por la vida política de los pueblos medievales de Las Españas, lo cual fue, en definitiva, el marco de referencia para una síntesis política de conjunto más allá de los posicionamientos teóricos, como algo que puede ser llevado a la práctica en sus aspectos concretos y que es perfectamente viable. Todo un sistema edificado sobre el pensamiento tomista y una una profunda religiosidad, En este contexto, y más allá de las ideas formuladas por realistas y carlistas en la primera mitad del siglo XIX, Mella teoriza junto a la concepción del espíritu medieval, la idea de la coexistencia de dos soberanías, una política y otra social, una teoría de la soberanía tradicional inspirada por un principio dinámico y que se cimenta en las propias experiencias humanas en el devenir de la historia.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023|El concepto de lo social
Lo social para Mella no tiene absolutamente nada que ver con las denominadas «políticas sociales», tan comunes en el lenguaje político de las democracias liberales, en las que se contempla lo social como un elemento externo a la propia estructura política, donde prevalece el individualismo a todos los niveles, y la sociedad aparece como un mero agregado de individuos. Muy al contrario, lo social, en el tradicionalismo de nuestro autor, implica la afirmación de un principio intrínseco tanto al modelo social como al tipo humano, así como a la naturaleza de las cosas en las que la persona desarrolla su existencia en común con los demás. Nos referimos a las instituciones, a los elementos jurídicos y otros órganos gestados en el tiempo por la experiencia histórica, que regulan la vida común.
En el ámbito de la sociedad cristiana medieval, en plena Reconquista, cuando todavía no existía un Estado unitario como tal, cada municipio tenía sus propias leyes y sus normas, adaptadas a su modelo de vida y costumbres, Las comunidades se concebían como agrupaciones de familias con un sistema de propiedad comunal y privado en las que el patrimonio y el estatus de cada uno de sus miembros venía garantizado por el ejercicio activo de una serie de derechos en defensa de las libertades concretas, cuya fuente última era el derecho natural. Los señores feudales y los reyes se limitaban a reclamar tributos para la guerra, pero sin interferir en la defensa de estas libertades concretas ni vulnerar el sistema que las sustentaba.
Eran gobiernos autárquicos, muy estables e inspirados por un principio democrático, el cual nada tenía que ver con las democracias liberales plutocráticas de la actualidad, cuya idea del derecho y la justicia está pervertida por el formalismo jurídico vacío e inane de sus constituciones, abstractas y plenamente funcionales a las oligarquías, al servicio de intereses espurios. En este caso, el hombre alcanzaba una plena dignidad y desarrollo en el contexto de una comunidad donde prevalecía el vínculo comunitario, al amparo de un modelo tradicional, de normas consuetudinarias y concretas que permitían la defensa efectiva del propio derecho. Ni siquiera con el advenimiento de los Estados modernos, y la centralización de algunos elementos de poder, como la Hacienda o el Ejército, se vieron alterados significativamente estos elementos, que representaban a los denominados «cuerpos intermedios» de la sociedad, y que adquirieron su propia expresión particular bajo el nombre de «Fueros», los que los propios reyes juraron respetar a lo largo de toda la Edad Moderna y hasta el advenimiento del régimen borbónico.
La antropología tradicional vincula al hombre a un medio social, a una familia, a una estirpe o a un pueblo, que reproducen esa misma estructura familiar, aunque a mayor escala. En nuestro caso particular lo vemos a través de la convivencia de pequeños grupos humanos, de ahí la importancia de los municipios o de los concejos en un marco de vida comunitaria fuertemente institucionalizada. Al mismo tiempo este modelo y estructura también se replicaba en otros ámbitos, como en la vida económica y profesional, impregnando todas las esferas de la vida del hombre. Instituciones naturales, amparadas en el derecho natural, y orientadas a la protección y garantía de prosperidad de los hombres, y esto por encima de cualquier interés particular y mercantil de negocio. Para Mella, la ruptura con este mundo, y en general con las experiencias del pasado, es la que nos lleva, merced a la acción del liberalismo, a los tiempos actuales, y lo hace recorriendo un itinerario que todos conocemos, y que tienen su punto de partida en la Ilustración y la posterior Revolución Francesa, la irrupción del elemento racional y abstracto y la destrucción de la religión, considerada como fruto de la superstición. La destrucción del orden feudal, que todavía pervivía como marco de convivencia en el mundo rural, como una suerte de prolongación de ese espíritu medieval, hizo desaparecer de un plumazo ese entorno de relaciones concretas y personales para sustituirlas por lo «público» entendido como la centralización estatal uniforme, ignorando las realidades particulares subyacentes en el cuerpo social, los denominados «cuerpos intermedios», que fueron despojados de su autonomía, corporaciones y patrimonios. De modo que la destrucción de estas «sociedades intermedias» que mediaban entre el Estado y la sociedad desenraizó y destruyó la propia sociedad, al mismo tiempo que los fundamentos cristianos del derecho natural sobre la cual se hallaba asentada, para hacer prevalecer esos principios racionales y abstractos traídos por la revolución.
Al mismo tiempo, y anejo a este desarraigo, del individuo se encuentra sometido a poderes arbitrarios del propio Estado liberal, sin un conglomerado institucional propio que lo proteja de estos atropellos, sumido en el individualismo ajeno a toda institución y destino colectivo, se limita al voto cada cuatro años de los partidos al servicio de oligarquías e intereses espurios, contrarios al Bien común. En este sentido, y advirtiendo las posibles acusaciones de «absolutismo» que en ocasiones se han lanzado contra el tradicionalismo, hay que señalar que Mella las rechaza por completo, dado que viola la idea de contrapoderes frente a la autoridad del rey que éste formula, ya que el absolutismo creía en la existencia de un poder ilimitado y tiránico del rey, transmitido por Dios y ajeno a la participación de la sociedad y sus estamentos. Como bien señaló Julius Evola, el absolutismo es un fenómeno antitradicional, vinculado a la descomposición y desacralización de las estructuras tradicionales. De hecho, el absolutismo, como los regímenes liberales de hoy, dejan al individuo totalmente desprotegido, sin un asidero sobre el que apoyarse en la defensa de sus libertades concretas. El propio Mella, como bien saben todos los que se adentren en su obra, fue partidario de contrarrestar el creciente poder del aparato estatal, tal y como hemos visto y seguiremos viendo en lo sucesivo, a lo largo del presente artículo.
|
 |
|:-:|
|EVOLA, Julis; Metapolítica, Tradición y Modernidad: Antología de artículos evolianos, Hipérbola Janus, 2020|
|
|:-:|
|EVOLA, Julis; Metapolítica, Tradición y Modernidad: Antología de artículos evolianos, Hipérbola Janus, 2020|En nuestro caso particular, la desaparición de la organización gremial y corporativa tuvo unas consecuencias especialmente nefastas, y en especial después de las dos desamortizaciones liberales (Mendizabal y Madoz) al despojar a los grupos sociales populares de su natural organización sociohistórica. Asimismo, desvincularon la propiedad en las relaciones comunitarias y su uso patrimonial para vincularla al uso privado y anónimo, para fines puramente especulativos, los que caracterizan al liberal-capitalismo. De ahí nace la figura del asalariado, del contratado como mera mercancía, en un proceso de alienación del trabajo característico en el desarrollo del capitalismo burgués. De aquí parte lo que algunos tradicionalistas, como Gambra, denominan el «problema social», frente al cual, y al margen de las recetas ideológicas de la modernidad, Mella reivindica la restauración de los antiguos vínculos corporativos y orgánicos de inspiración medieval.
La idea de soberanía social
Todos los procesos disolutivos que conducen a la Modernidad liberal tienen su punto de inicio con el Renacimiento, con la afirmación del individualismo y la ruptura definitiva del ecumene cristiano medieval, algo que aparece indefectiblemente unido a la Reforma luterana, así como la «valorización» del mundo clásico, con la reemergencia de teorías de tipo hedonista, como las de Epicuro, por ejemplo, generando una disolución de los vínculos con el medio concreto. Esto supone la aparición de un nuevo tipo, que es el hombre abstracto que escapa cada vez más al entorno inmediato y vital, esto al tiempo que el poder del Estado se robustece y se vuelve omnipotente. Es por ese motivo que en lo sucesivo se ha impuesto en nuestras sociedades la falta de concreción, tanto en lo teórico como en lo político, lo cual ha propiciado el triunfo del contrato social roussoniano y la justificación del orden social en virtud de componendas voluntarias y totalmente artificiales. Estas construcciones político-ideológicas son las que contribuyen a la construcción de la sociedad liberal, asentada sobre patrones puramente racionales, individualistas y mercantilistas.
De hecho, la mayor preocupación de Mella es la destrucción de las instituciones locales y ese vínculo afectivo del hombre con su realidad inmediata, algo que impregnaba su relación con el trabajo, con su obra, con su impronta vocacional y devota, imprimiéndole, como en el caso del artesano, un sello propio y particular a su trabajo.
Y en este sentido, Mella afirma que la sociedad moderna ha perdido su sentido institucional como base estable de la sociabilidad. A través del elemento jurídico y la participación en las instituciones es el medio a partir del cual la comunidad se cohesiona y construye sus vínculos y su particular autonomía, que le hace tener una vida propia e interna, y con la institución nos podemos referir desde una asociación profesional, a la universidad o una cofradía etc. El individualismo ha representado el factor disolutivo y corrosivo que ha destruido este vínculo social fundado en múltiples solidaridades que han enfrentado y polarizado al cuerpo social, con el enfrentamiento entre «clases sociales» y la negación de las jerarquías naturales.
Ante todo lo relatado, y como consecuencia de las destrucciones provocadas por la revolución, Mella plantea su teoría de la soberanía social. Esta teoría consiste básicamente en encuadrar de nuevo a la sociedad en sus raíces naturales, concebida en todos sus órdenes como portadora de un dinamismo propio en una suerte de organización geométrica en la que conviven objetivos y finalidades variadas y concretas con su propia legitimidad y autonomía. Estas finalidades, amparadas en el derecho natural, son junto al poder del propio Estado las únicas formas de limitación del poder. La particularidad de esta idea de soberanía social está en el hecho de que la formación de la jerarquía social tiene una dirección ascendente, que tiene como punto de partida a las personas colectivas y concretas, pasando por una serie de instituciones, hasta llegar al Estado central, de forma escalonada y plenamente conscientes de sus funciones. Así lo expresa Mella en su propio lenguaje: «la jerarquía de personas colectivas, de poderes organizados, de clases, que suben desde la familia hasta la soberanía que llamo política concretada en el Estado, que deben auxiliar, pero también contener». Es lo que Mella concibe como el sociedalismo, que supone la reintegración de la sociedad en la vida concreta de los hombres, con el desarrollo de una vida política común y estable en el marco de instituciones naturales que potencien las relaciones humanas y sociales, estimulando la sociabilidad. Y hablamos, desde la perspectiva de la integración de distintas sociedades, fuertemente institucionalizadas con funciones y finalidades concretas, más allá del sentido democrático y pactista que pueda entenderse en términos modernos o de cualquier asociación u organización relacionada con el «problema social».
¿Qué es la Tradición?
De este modo quedan formuladas las dos soberanías, la política y la social, que coexisten en un mismo espacio limitándose y apoyándose recíprocamente en lo que es uno de los fundamentos del sociedalismo de Mella. No obstante, esta doble soberanía no explica todavía la concreción política de cada pueblo y el vínculo superior que lo lleva a federarse con las diferentes sociedades y a mantenerse unido en una historia y espíritu comunes. Los vínculos que las mantienen unidas en el tiempo tienen que ver con un orden histórico concreto, con un vínculo espiritual que las entrelaza interiormente de una generación a otra, y en última instancia de ese orden tradicional que lo engloba todo, y que al mismo tiempo se asienta en la monarquía y la religión católica. La lealtad a Dios y a un solo rey en torno a los cuales se aglutina la fe, viene a coronar todas estas estructuras y lazos forjados en el fermento de la historia.
No se trata de la Tradición en términos de un «ultraconservadurismo», que ya sabemos que el prefijo «ultra» (lo que sea) es muy recurrente en nuestros días, con la idea de un medio social y político petrificado e invariable, sino que es el producto de un proceso de maduración y evolución histórica, de carácter dinámico y nutrido de experiencias humanas. Nada que ver con las monstruosas ideologías progresistas y modernas, nacidas de lo abstracto e impulsadas por un desbocado «ir hacia delante», desarraigado y que tiende siempre hacia la deshumanización y la destrucción de toda creación humana natural forjada en el devenir de los siglos. Este mismo dinamismo, planteado por Mella, en torno al concepto e idea de Tradición tiene continuidad y adquiere fuerza en sus sucesores y depositarios. Y al fin y al cabo, Mella no hace más que partir de la propia etimología del término, que viene del latín tradere, entregar, de la generación que entrega los frutos de su experiencia a la siguiente, perfeccionándola, haciéndola más estable y segura.
Podríamos seguir extrayendo más conclusiones del pensamiento tradicional de Vázquez de Mella, pero probablemente excedería, y por mucho, el modesto propósito de este escrito, de modo que nos quedaremos aquí, no sin advertir a nuestros lectores de la posibilidad de que en un futuro volvamos a retomar nuevamente el tema.
Antes de acabar queremos llamar la atención sobre una polémica acontecida hace unos años en torno a una Plaza en Madrid que llevaba el nombre de nuestro autor y que se cambio para dedicársela a un sujeto cuyos méritos eran, por decirlo suavemente, más que discutibles, concretamente a Pedro Zerolo, miembro del PSOE y activista al servicio del lobby homosexualista. Durante aquella época, en 2019, muchos miembros de la izquierda globalista trataron de identificar a Vázquez de Mella como un «pensador franquista», cuando en realidad ni cronológica ni ideológicamente tuvo nunca nada que ver con el franquismo. Recordemos que murió en 1928, y la impronta de su pensamiento ha tenido como continuadores a sus propios correligionarios dentro del ámbito tradicional, aunque en su tiempo llegó a ser muy respetado también por sus adversarios, los liberales. Aunque la retirada del nombre de una calle pueda resultar algo banal, o carente de una importancia excesiva, también contribuye, a su modo, a una forma de damnatio memoriae que condena al olvido y al ostracismo a grandes autores de la Tradición, portadores de un Patriotismo sano y capaz de entender las peculiaridades y el Dasein profundo de España, que si bien no nació invertebrada, como pretendían los Orteguianos, su esencia y naturaleza es mucho más compleja que cualquiera de las grandes naciones de Europa.
Artículo original: Hipérbola Janus, Juan Vázquez de Mella y el tradicionalismo español, 16/Ago/2024
-
 @ 7776c32d:45558888
2025-01-06 12:34:40
@ 7776c32d:45558888
2025-01-06 12:34:40Attached is a screenshot of the reddit profile of one of my possible past victims.
A few days ago, it crushed my soul to look at this not knowing if this /u/ykorea person is alive, and knowing even if she is, there must be other victims that are dead. I wrote most of this post those few days ago. After the harassment I've faced in the past few days with no significant backup, I'm numb to it.
I have never been able to get solid answers on what happened to ykorea after she stopped posting, but her posts read like someone that might have committed suicide over money lost trading options. I didn't make her lose money, but I contributed to her leaving, whether it was by suicide or not.
She is not Digit, but she is another woman I met on wallstreetbets - meaning, of all the people I might have accidentally killed, at least two are women from wallstreetbets possibly dead via suicide. I would have preferred to save both of them. I just cause so many deaths, two possible ones happen to line up that way instead.
This ykorea woman said something hurtful to me once, something to do with how lonely I was and how women never cared about me at the time. I don't remember the specifics beyond that. I harassed her with hateful reminders of how she hurt me for a while, and still ended up forgetting the details myself by now.
Soon after that, I got rich, and she happened to befriend me for a brief time, not mentioning our past differences. I didn't mention them either because I wasn't sure if becoming acquainted with me was burying the hatchet, or simply forgetting I was the same guy from all the hateful comments.
She was having a hard time financially and I wanted to help her, but I still wasn't rich enough to help everyone I want to help, and I didn't deem her worthy of being one of those few prioritized people I'd try to give some financial support. I was distrustful of any woman trying to find such support from men on wallstreetbets.
Why did I care enough about her words to be hurt by them enough to harass her over it for a while, but not care about her enough to really become a close supportive friend to her later? Because I'm a dangerously bad person and I can't cut off the cycle of abuse I'm in. People have made me learn to suppress my sympathy and I don't have the emotional capacity to afford to get it back. But I have the emotional capacity for anger, all day, every day. I can always afford anger. I'm the kind of person all the good writers warn you about in every story with any meaning. The kind of person they warn you not to be, and the kind of person they warn you not to make others into. None of us ever learn the easy way, do we?
She had not become friends with me based on burying the hatchet. She had forgotten who I was. That topic came up eventually and she was embarrassed about forgetting, and she pretty much stopped talking to me.
I didn't tell her to buy AMC. If she lost money on bad trades, that probably added more to her leaving than me. But I added to it by being a bad person. Whoever made her buy AMC could have been a bad person too, but it's also possible they were just misguided and desperate like her. I'm a monster, capable of nothing but offering good advice nobody takes, and making people hate themselves over their mistakes. I'm even worse than people who are just good at getting their advice taken by giving bad advice.
Unless Digit is alive. If she is, I can stop doing this. If I can stop doing this, people who keep giving bad advice can be worse than me. Every time I have proof she's alive, it becomes so much easier to just be fucking nice to people like Kurt Vonnegut says to do. But she deleted her accounts over a year ago and I keep getting more scared, and no matter how hard I try to cultivate self control, the best I can do is be a little less cruel, a little more forgiving, a little less selfish - not enough to stop contributing to suicides. Not enough to stop contributing to deaths of slaves in third world countries making products I use. Not enough. If I've failed her, I do believe I will not stop failing everyone as long as I live.
Remember, I wrote most of this with those feelings I had a few days ago, before the recent events where nostr:npub1jk9h2jsa8hjmtm9qlcca942473gnyhuynz5rmgve0dlu6hpeazxqc3lqz7 triggered a new wave of harassment against me and cornered me in a position where I have no better strategy than trying to cause suicides on nostr. It's all obvious and droll now. People die. So what? Digit isn't here to make lives matter anyway. This stuff will only matter if she shows up.
But it's not just me. Everyone contributes to suicides in their own way. Everyone contributes to climate change. Everyone uses products made by slaves. Almost any suicidal person can be helped by almost anyone who cares enough. If you don't know that, you don't understand. Tragic deaths happen millions of times a year because of society, not me in particular.
And everyone failed Digit spectacularly in the time I knew her. The world was made miserable for her and I need her to be strong enough to be living in it anyway. When I knew her, she couldn't be angry at everyone like I can, her love for everyone forced her to turn anger in on herself. I need proof she survived that, because if she wasn't strong enough to survive absorbing everyone's bullshit like that, I can't even get my hopes up about trying. All I can do if she's gone is be the world's punishment for her, and my own punishment at the same time - but not make myself the sponge of everyone's punishment. Worse people have to suffer more, as long as I'm suffering like this for who I am.
Take nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc for example. Despite recently losing his dad to suicide, he seems to be pretending he's unaware of the harassment I'm facing over a loved one I'm worried about; or perhaps he echo chambers himself so extensively that he's actually not aware.
I believe, like me, he cannot think of a way to cope with his loss without causing it to happen to others for the rest of his life. Unlike me, I don't think he'll admit it or take responsibility for it. Unlike me, I don't think he's tried to fight it and found himself cornered; I think he's just fine with it because he's part of a society that's fine with behaving this way and blaming the victims. I think he'll probably be one of the many people using me to cause others to commit suicide but pretending to have no responsibility in the matter, pretending it's magically all me. Meanwhile, I actually admit my own part in it.
I will be punished for this, and eventually I will probably be permanently stopped from standing up for the truth. That only makes me more motivated to punish all the deceptive pieces of shit that have done this to the world, until I am fucking stopped.
While we're on the topic of uncertain speculation, my bet is neither me or Gigi can really enjoy the killing. We must both be empty shells. Maybe the reason he can't take responsibility is because, far from enjoying it, he actually finds the bloodshed more unbearable than I do.
What about the rest of you? Do you all find reality too unbearable to face, or are some of you gleefully enjoying the process of abusing and deceiving others while more and more people die? I think some of you are - and the police that might arrest me for my posts someday will do nothing about it. So I'll do what I can myself, and people will die in the crossfire. So be it.
Maybe I can't make any of you take responsibility, but when a nostr user commits suicide, I will have done everything I can to make you think the words "I failed to prevent this" and feel the weight of them.
-
 @ 06830f6c:34da40c5
2024-08-11 20:13:46
@ 06830f6c:34da40c5
2024-08-11 20:13:46On August 10, 2024, the vibrant Sarit Expo was alive with energy as Bitcoin Dada celebrated the graduation of its seventh cohort. This momentous event, dedicated to advancing the understanding and application of cryptocurrency, showcased the dynamism and innovation of the Bitcoin Dada community.
 The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts.
The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts.

As the MC continued, participants were asked for their impressions of the event space and suggestions for improvement. Comments ranged from critiques of overly bright lighting to discussions about the relevance of Bitcoin. One participant proposed an intriguing app idea that combined Eventbrite and WhatsApp, reflecting the innovative spirit of the audience.
The highlight of the evening was the inspiring opening speech by the CEO of Bitcoin Dada.
 She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team
She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team 
each member contributing uniquely: Edith, the community lead from Uganda; Sabina, the recruiter who found a sense of belonging; and Memelord, the project manager with a flair for comedy.

The ideathon segment was particularly thrilling. Debra’s third-place pitch proposed a Bitcoin-powered marketplace aimed at reducing youth unemployment by showcasing skills. Shantelle’s second-place idea focused on using Bitcoin to address global issues, such as helping refugees find safe zones with GPS technology. The top prize went to Meg, with her solution promising a significant impact—though the specifics were left as a tantalizing cliffhanger. 🌟🏆
PS : Sabina also gave a preview of the #tando app tha you can check out here on my youtube channel Link HERE
Meeting Inspiring Figures and Making Connections 📸
Throughout the event, I had the pleasure of meeting some remarkable individuals who are deeply involved in the Bitcoin community.
First, I met Felix from TheCore, a key panelist in the discussion on the financial revolution amidst economic unrest. We took a photo together, capturing a moment of shared enthusiasm for the potential of Bitcoin.

Later, I connected with a Bitcoin Dada and gamer who is actively involved with Thndr Games, Mary Imasuen. We took a photo showcasing our shared passion for Bitcoin and gaming.

I also had the chance to meet a Bitcoin enthusiast named Hope and she was adorned in Bitcoin-themed merchandise. We snapped a photo together, celebrating our mutual enthusiasm for Bitcoin and its future.

Panel Discussions: Insightful Exchanges and Thoughtful Dialogues
The panel discussion titled “Financial Revolution Amidst Economic Unrest” featured Felix from TheCore, Jason, a Bitcoin Dada supporter, and Bill, a lawyer with expertise in Bitcoin. They delved into the major challenges Kenyans face in adopting Bitcoin, emphasizing the importance of education and community support. They discussed the solid foundation of Bitcoin’s base layer and the need for further development in subsequent layers to enhance its functionality.

The discussion also touched on Kenya’s future in the Bitcoin space. Bill suggested integrating Bitcoin with fiat transactions and stock exchanges, while Jason highlighted the government's welcoming stance and the need for energy to support Bitcoin. Felix proposed making Bitcoin legal tender and finding sustainable energy sources to bolster its use. ⚖️🌍

Audience questions added further depth to the conversation. One attendee asked about using Bitcoin to offset government debt, while another inquired about measures for improving public education on Bitcoin. The responses stressed the need for comprehensive educational initiatives. When asked about alternative cryptocurrencies, the panel firmly rejected the idea of “shitcoins,” focusing instead on the value of Bitcoin. 🚫💸
The second panel discussion, moderated by Sharon from ₿-Trust, explored personal experiences with Bitcoin Dada. Panelists Anon, Vera, and Caroline shared how the program impacted their perspectives.

- Anon discovered a niche and a supportive community, emphasizing Bitcoin’s role as “lightning-fast internet money,” especially with Layer 2 advancements. 🌐⚡
- Vera found Bitcoin to be a valuable medium of exchange, advocated against other cryptocurrencies as “shitcoins,” and highlighted opportunities for women. 💪💰
- Caroline expanded her knowledge and aimed to educate others, describing Bitcoin as a store of value and emphasizing the importance of combating inflation through education. 📚🔍

The panelists also discussed opportunities for Bitcoin in their communities: - Anon saw potential for learning and growth through knowledge-sharing. - Vera mentioned BitSacco, a solution for saving in Bitcoin, and other upcoming projects like Sabina’s Tando app. - Caroline stressed the importance of education to counteract misconceptions about Bitcoin and its benefits. 🏡📈
In their closing remarks, the panelists shared their future aspirations: - Anon aimed to become a developer impacted by Bitcoin. - Vera planned to engage with the community and learn from others. - Caroline focused on educating the community to dispel myths about Bitcoin. 🌟👩💻
The event concluded with a warm dinner where attendees mingled, exchanged ideas, and enjoyed a meal together. WATCH https://video.nostr.build/4d0fbc2dd6ae0c20e0d45aa071a9e88000a9544f4289414900c91134d13960da.mp4
The Bitcoin Dada Cohort 7 graduation was more than just a celebration of individual achievements; it was a testament to the collective potential of the Bitcoin community.
As the event wrapped up, the atmosphere was charged with optimism and a shared commitment to advancing bitcoin technology. The graduating cohort left with new skills, fresh ideas, and a network of like-minded individuals, ready to make a significant impact on the future of Bitcoin. 🌍💡 #kenya #bitbiashara #kenya
-
 @ 75d2e92b:4e9baa11
2025-01-06 12:25:41
@ 75d2e92b:4e9baa11
2025-01-06 12:25:41Imagine this: inflation is like rust on a machine. It forces the gears of the economy to keep spinning, not because we want progress, but because if we stop, everything corrodes. Your savings? They’re not yours for long. Your energy? Wasted, turned to dust. The system is rigged to keep you running, just to stand still.

Governments print money like confetti 🎉, indebting future generations while your hard earned wealth evaporates. The rich? They move their "piles of gold" into assets, safe from the storm. But families, savers, the everyman? They watch their stored energy years of work devalue into nothingness.

But here’s where it gets personal for me.
I believe our generation is different. We’re on the cusp of a new era. Advances in AI 🤖, medicine 🩺, and genetics 🧬 might make us the first generation to live 150, 200 years or more. If that happens, what good is working today if the value of our sweat turns into cents tomorrow? Why should our life’s energy stored as money shrink while we grow older?
Do you want to work for 200 years? Or do you want your stored value, your time, your essence, to hold strong like a fortress?

Bitcoin is that fortress. 🏰 Unlike fiat, it doesn’t rust. It doesn’t erode. It doesn’t let anyone no government, no bank reach into your pocket and steal the fruits of your labor. Its fixed supply (21M forever) is the ultimate time machine, preserving your value across generations.
So here’s my take: Inflation is the Great Thief 🕵️♂️. It keeps the machine running but at the cost of your freedom, your time, and your future. Bitcoin is the oil and the shield. It’s the key to breaking free from this endless hamster wheel. 🐹💸

Do you want your energy spent today to be worth a millisecond of tomorrow’s? Or do you want a tool that fights back, protects your time, and keeps the gears turning on your terms?
Choose wisely. Choose Bitcoin. 🧡 BY: Falco
#Bitcoin #Freedom #TimeIsMoney #Cypherpunk
-
 @ dd664d5e:5633d319
2024-07-10 14:45:43
@ dd664d5e:5633d319
2024-07-10 14:45:43The Law Giver
In my previous article, I briefly went into the topic of how contract law is holy law.
The Father of the Christians, you see, is a God of Covenants, and He sent His Son to Earth to fulfill the Law and pay a Price for our salvation. The Father also created the Natural Order to confirm His Laws through our observation of that Law in action.
That is why Christians have a deep respect for honest contracts, true prices, fair measures, natural systems, and good laws. Not merely for their own sake, but also because understanding them helps us to understand and emulate the Law Giver.
The tired What would Jesus do? meme is actually an attempt to capture this emulation of the Highest Judge. Jesus knows the Law, since His Father defined it and He is One with the Father, so how would He apply the Law best, in this situation?
The Last Things
Working together with him, then, we entreat you not to accept the grace of God in vain. For he says, “At the acceptable time I have listened to you, and helped you on the day of salvation.”
Behold, now is the acceptable time; behold, now is the day of salvation.
-- 2 Corinthians 6:1-2 New Testament, RSV Bible
One of the things most devout Christians frequently ruminate over, is when Christ will return.
Every day, we ponder. We go for a walk, and ponder. We cook dinner, and ponder.
At the same time, we are called upon to live each day in a productive manner, and to not simply lie around, vegetating, and staring at the heavens. Not only for our own sake, but also because to do so would be to limit our ability to inform others about the Good News, so that they can take to pondering with us. We are called to ponder with as many people as we can produce, adopt, convert, or simply collect through our daily interactions.
This means that we are not of the world (as our eyes are watching God and baptism has made us Immortals), but we are definitely in the world (involved in, and effected by, the everyday dealings around us.) It is a very difficult balancing act to know when we are paying too much attention to the one or the other, or to know where to store up our treasures, if we can't put them all immediately into the Final Treasury.
So, we worked today and earned a bit of fiat cash and we have no immediate usage for it. What to do with it?
Well, some of it should go to charity or be invested in a business that provides important goods, services, and employment. Some of it will be needed to simply cover the day-to-day costs of our own life, or that of those dependent upon us. But it might be prudent to store up some of it, for the mysterious length of time between receipt of the monies and our own ascent into Heaven.
Typically, that store was the local currency, but that's being inflated away at an alarming rate. Then we all began to move to precious metals, and many of us still do, but they are so difficult to spend and can't be broken into small bits or transported over wide distances at low cost.
Enter Bitcoin.
The Great Ledger
In our frustration, more and more Christians are turning to a new technology, to save up some treasure in a liquid asset, for the mid-term. And, once we begin using it, and begin to understand how it works, we quickly grow fond of it.
Bitcoin is a beautiful money because it is a money based upon keeping precise accounts, using a fair measure, and obeying the Laws of Nature.
In essence, Bitcoin is a debt note emitted by a universal debtor (the network) in exchange for some good or service. This frees the individual people using it from ever needing to carry debt, as the debt stays in the network, the value and enforceability of that debt note is protected by the effort used to create and maintain the network, and the eagerness with which other people wish to store their efforts up in that same network. The debt still exists, but it can be so thinly and widely spread that it no longer rests as a burden upon one particular person.
The debt, in other words, has been disassociated from humans and the management has been distributed to machines. This is the precise opposite process of a "fiat" (by decree) currency, which only has value so long as it is associated with some particularly solvent group of humans (who personally vouch for repayment of any debts denominated in the currency), and where management is centralized to some other group of humans.
Have you accepted Bitcoin as your personal money and store of value?
You have invested $10 to buy the electricity to mine Bitcoin? Then you receive $10 of Bitcoin in return. The Bitcoin network now owes you the $10 purchasing power equivalent of that electricity.
If someone then gives you $5 worth of pizza, then you can then give them a $5 portion of your $10 worth of Bitcoin. You have taken a part of your Bitcoin debt note and shared it with them.
They now hold $5 worth of Bitcoin invested in the network and can spend it on some other good or service. Or they can simply hold it and wait for it to rise in value, as more people "mine" more of it (and produce more notes, paradoxically making the existing notes more useful and therefore valuable) and more people try to gain the notes in order to manage their own finances by storing their energy in the network or transporting their energy using the network.
Bitcoin, in other words, is an accounting book that needs no accountant because it stores, tracks, and controls the ledger on its own. It is a Natural Ledger that runs according to the the Laws.
It is the only human-made ledger that allows for true and immediate Final Settlement. This Final Settlement is what allows people to trade using the convenience of digital debt notes, with neither person occurring or even risking any personal debt. We Christians know that all debt is a burden, including monetary debts, which is why we are called to forgive each other's debt and to hope that our own debts are forgiven. Better still, is to avoid the accumulation of debts, altogether.
So, Final Settlement? Final Settlement is what Jesus would do.
-
 @ 3c7d12a6:9532013e
2024-06-20 14:47:12
@ 3c7d12a6:9532013e
2024-06-20 14:47:12NUD: Pubkey to colors
This NUD defines how to convert pubkey to colors.
Why?
npubis nonsense to display.- too long.
npub1bla...blais nonsense to display.npub1takes too much space....means nothing.
Specs
- Uses hex pubkey.
- Converts 64 characters to 8 colors.
- Splits 64 with 8 length chunks.
- Converts each 2 in 8 into
- Alpha (0-255 -> 0.0-1.0)
- Hue (0-255 -> 0.0-360.0)
- Saturation (0-255 -> 0.0-1.0)
- Light (0-255 -> 0.0-1.0)
- Supports dark and light theme.
- When Light is 1.0, flip the Light for light theme (0.0).
-
 @ 44189afb:b62f396c
2025-01-06 11:44:06
@ 44189afb:b62f396c
2025-01-06 11:44:06Changes
Daniel D’Aquino (20):
- Automated i18n file changes from npm run build
- Add notedeck waitlist page
- Refactor code into several smaller blocks
- Add tab component
- Add Nostr DM OTP support to Purple checkout
- Purple welcome page
- Add better troubleshooting to OTP auth
- Fix subtle purple icon issue
- Update navigation around the website
- Improve checkout refresh stability
- npm run i18n
- Improve build process
- Fix checkout and login for npubs devoid of a profile
- Fix expired session token detection and automatic logout
- Add Purple checkout maintenance mode option
- Add nix-shell support
- Notedeck alpha landing page and install instructions page
- Storybook setup for development
- Add Nostr note component
- WIP 2024 review page
William Casarin (2):
- notedeck tweaks
- 2024 damus wrapped
ashleendaly (1):
- fix good first link
pushed to damus.io:refs/heads/master
-
 @ cf7ed325:050194cf
2025-01-06 11:04:51
@ cf7ed325:050194cf
2025-01-06 11:04:51Sharm el Sheikh day tours , located on the Red Sea, offers a range of exciting activities for adventure seekers and relaxation lovers alike. One of the most popular activities is a Snorkeling trip in Ras Mohammed by Boat, where you can explore vibrant coral reefs and swim alongside colorful marine life. For those looking to venture further, the Day Tour to Snorkeling in Tiran Island is a must, providing an unforgettable experience in crystal-clear waters.
For thrill-seekers, Explore Quad Biking Sharm el Sheikh with Sharm Day Tours is an exciting way to experience the desert landscape. You can also enjoy a Day Trip to Quad Bike in Sharm El Sheikh, where you’ll ride through the stunning dunes on a powerful quad bike.
If you're seeking family-friendly fun, Sharm El Sheikh Day Tours: Trip to Aqua Park offers a day of water slides and pools, perfect for all ages. For a unique underwater experience, consider an Explore Semi Submarine Excursion in Sharm el Sheikh, where you can see marine life through large windows without getting wet.
Sharm el Sheikh also offers incredible excursions to nearby natural wonders. Take a Colored Canyon Excursion Safari from Sharm el Sheikh to explore the breathtaking desert landscapes, or embark on a Saint Catherine Monastery One Day Excursion from Sharm el Sheikh to visit one of the world’s oldest Christian monasteries.
For those interested in cultural exploration, a Cairo 2 Days Excursions from Sharm el Sheikh or a Luxor Day Trip from Sharm el Sheikh will take you to the heart of Egypt’s ancient history. Alternatively, enjoy a Full Day Trip from Sharm el Sheikh to Cairo by Plane for a quick visit to the pyramids.
Whether you're booking a Glass Bottom Boat Excursion in Sharm el Sheikh or Petra Tours by Ferryboat with Sharm Day Tours, Sharm el Sheikh promises a diverse range of activities for every traveler
🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 Email: info@etbtours.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt
-
 @ 38f9a05c:6999fc04
2024-04-07 12:08:30
@ 38f9a05c:6999fc04
2024-04-07 12:08:30
In today's world, where self-promotion appears to be the standard, there exists a subtle charm in modesty. As a child, I frequently encountered the expression, "Only a donkey praises their tail." its significance has remained with me throughout my life. It serves as a reminder that authentic excellence does not require shouting from the rooftops; instead, it manifests itself in actions, not words.
Allow me to now introduce Alfred Adler, a pioneer in the field of psychology. Born in Vienna in 1870, Adler's theories challenged the prevailing views of his time, particularly Sigmund Freud's emphasis on the unconscious mind. Adler proposed individual psychology, focusing on the unique experiences and perceptions that shape each person's worldview. Central to his theories was the concept of the "inferiority complex" and its counterpart, the "superiority complex," shedding light on how individuals grapple with feelings of inadequacy and superiority.
Inferiority complex
The "inferiority complex" describes persistent feelings of inadequacy and self-doubt, stemming from early experiences. Individuals afflicted with this complex often seek validation and may engage in compensatory behaviors. Therapy and self-reflection are key to addressing and overcoming these feelings, fostering healthier self-esteem and confidence.
An example of an inferiority complex might be a person who, from a young age, consistently felt overshadowed by their siblings' achievements and talents. Despite their own unique abilities and successes, they internalize a belief that they are inherently inferior to others. This belief could manifest in various ways throughout their life, such as constantly seeking approval from others, feeling anxious or inadequate in social situations, or striving excessively for success in an attempt to prove their worth.
Superiority Complex
Conversely, the "superiority complex" manifests as an exaggerated sense of self-importance and entitlement. Individuals with this complex may exhibit arrogance and lack empathy towards others, struggling with meaningful relationships and criticism.
An example of a superiority complex could be seen in a person who consistently belittles others and insists on being the center of attention in social settings. They might boast about their achievements, talents, or possessions in an attempt to assert their superiority over those around them.
Back to the childhood phrase "Only a donkey brags praises their tail." Returning to the childhood adage "Only a donkey brags praises their tail,” modesty and humility are often misconstrued as weakness or a lack of self-confidence. Nevertheless, it is far from that. It entails possessing a realistic view of oneself and comprehending that one's value should not rely solely on external validation or praise. Instead, it's found in the genuine connections we make with others and the positive impact we have on the world around us.
By abstaining from boasting about ourselves, we provide room for others to shine. It is not about denigrating our accomplishments or pretending to be less than we are. On the contrary, it involves acknowledging our abilities without feeling compelled to advertise them to the public continually. Therein lies the elegance of allowing our actions to speak louder than our words.
Moreover, humility allows for personal growth and learning. When we're humble, we're open to feedback and constructive criticism. Instead of becoming defensive or dismissive, we approach each opportunity for improvement with an open mind and a willingness to learn. This mindset not only helps us develop professionally but also fosters a sense of humility and gratitude for the knowledge and experiences that others bring to the table.
Humility enables personal development and learning. When we're not constantly focused on ourselves, we become more attuned to the needs and experiences of those around us. We listen more intently, offer support more readily, and celebrate the successes of others with genuine enthusiasm. In doing so, we cultivate deeper connections and create a more inclusive and supportive community.
In a society that often glorifies self-promotion and individualism, it can be challenging to embrace humility fully. However, it's a quality worth cultivating, both personally and professionally. By focusing on what we can contribute rather than what we can gain, we create a more harmonious and compassionate world. Hence, should you ever find the urge to trumpet your achievements or magnify your ego, pause to reflect on the timeless wisdom encapsulated in the age-old adage: "Only a donkey praises their tail," alongside the profound insights of the Austrian psychiatrist's psychological framework. Instead of trying to prove yourself with words, show who you are through your actions. Embrace humility, which means being modest and not bragging. True greatness isn't about loudly boasting about your good qualities. It's about having inner strength and making a positive impact on the people around you.
Lastly as the Great Roman emperor Marcus Aurelius said, "Waste no more time arguing about what a good man should be. Be one."
-
 @ 3c984938:2ec11289
2024-04-01 09:36:34
@ 3c984938:2ec11289
2024-04-01 09:36:34A long time ago, a girl resided on a tropical island. The girl's name is Sirena. She resided with her mother in close proximity to the Hagåtña River. Sirena's mother was a bit strict and tried to teach her to follow her in footsteps to be a lady, but Sirena only dreamed of swimming all day.\
 \
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
\
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
Sirena's mother was preparing for a special event and needed her to acquire special ingredients from the nearby village. She had a significant amount of preparations to complete, therefore she requested that Sirena procure the necessary ingredients and return promptly. Sirena made a promised to her mother that she would hurry back.\

She was on the village path. She kept her eyes on the trail, trying her best to be a good daughter and hurry back. But she took one glance briefly at the river.
 \
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
\
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
 \
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
\
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
Sirena was happy because now she can be in the water all day long. However, Sirena also wished she did what her mother asked and found another way to punish her. A part of her will forever be saddened by the loss of her Mother and Godmother.
It said that sailors have spotted mermaids on their voyage across the sea. Just that their too crafty & swift to be caught.
Historical Notes/context
 The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother.
The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother. 
👉I like to point out in this, Thomas Edison patented the light bulb in 1879. So visually the lights outside and inside the huts as flames. As Ai(text to image) does not account for these type of items.
👉This also goes back to be careful what you wish for because you may actual get your wish.
👉Chamorro people are Pacific Islanders, similar to Hawaiians, and have a brown/tan skin complexion.\

👉My mermaid looks strikingly similar to the Disney's recent version of Ariel. I Thought that was interesting because I put just "mermaid" into the text prompt. Its worth pointing out ai limitations as it's not advanced as I originally thought, likely due to its limited data. In this case only disney as a reference for mermaid.
based on ordinary prompts\

 Prompt used:\
Prompt used:\
 That's all-Thank you until next time (N)osyters!
That's all-Thank you until next time (N)osyters!If you like it, send me some ❤❤hearts❤ and if you didn't like it-⚡⚡🍑🍑zap⚡⚡🍑🍑 me!🍑🍑 me!
For email updates you can subscribe to my paragraph.xyz/\@onigirl or below if using the Yakihonne App
-
 @ 97c70a44:ad98e322
2024-03-23 04:34:58
@ 97c70a44:ad98e322
2024-03-23 04:34:58The last few days on developer nostr have involved quite a kerfluffle over the gossip model, blastr, banning jack, and many related misunderstandings. This post is an attempt to lay out my thoughts on the matter in an organized and hopefully helpful way.
What's wrong with gossip?
It all started with a post from jack asking why more devs haven't implemented the gossip model. There are many answers to this question, not least having to do with there being two standards for user relay selections, and ongoing changes to NIP 65. But I don't want to talk about compatibility here.
nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszymhwden5te0wfjkccte9enrw73wd9hj7qpq2uf488j3uy084kpsn594xcef9g9x3lplx4xnglf0xwghyw2n3tfqqnrm02
Mazin responded with some numbers which estimate how many connections the gossip model requires. Too many connections can become expensive for low-power clients like mobile phones, not to mention some privacy issues stemming from nosy relays.
nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgewaehxw309amk2mrrdakk2tnwdaehgu3wwa5kuef0qyghwumn8ghj7mn0wd68ytnhd9hx2tcqyp2xzsjktypudzmygplljkupmuyadzzr6rkgnvx9e0fx3zwhdm0vkz4ceg7
I have some minor disagreements with Mazin's numbers, but I basically agree with his point — a purist gossip model, where a large proportion of nostr users run their own relays results in a high number of connections to different relays. I brought this question up late last year in my interview with Mike Dilger and in a conversation with fiatjaf, who convinced me that in practice, this doesn't matter — enough people will use a handful of larger hubs that there will be a good amount of overlap in relay selections between most pubkeys.
To articulate this more clearly: the goal is not "personal web nodes", which is a pipe dream the Farcasters and BlueSkys (BlueSkies?) of the world aim at, but a more pragmatic mix between large hubs and smaller purpose-built relays. These small relays might be outlets for large publishers, small groups, or nerds who also run their own SMTP servers and lightning nodes.
The point of the gossip model is that these small nodes be possible to run, and discoverable from the rest of the network so that we can preserve the censorship-resistant qualities of nostr that brought us here in the first place.
Blast It!
It's no secret that I've long been a critic of Mutiny's blastr relay implementation. My main objection is that the blastr approach doesn't account for the hard limits involved in scaling smaller relays. If the goal is to cross-pollinate notes across all relays in the network, all relays will require the same size database, and contain all notes in the network. This works right now (sort of), but as the network grows, the relays running on a $5 VPS are going to have their disks fill up and will inevitably fall over.
nevent1qyvhwumn8ghj76r0v3kxymmy9ehx7um5wgcjucm0d5hszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qqs07jr9qx49h53nhw76u7c3up2s72k7le2zj94h5fugmcgtyde4j9qfrnwxj
Not only that, but the content breakdown on any given relay by default becomes an undifferentiated soup of "GM", chinese notes, bots, bitcoin memes, and porn. Blastr makes it impossible to run an interesting relay without implementing write policies.
Which is actually fine! Because that's always been true — servers that allow anonymous uploads always get abused. Tony is just helpfully pointing out to us that this is no less true of nostr relays. I only wish he could have waited a little longer before mounting his attack on the network, because lots of hobbyists are interested in running interesting relays, but the tools don't yet exist to protect those servers from unsolicited notes.
One other note on blastr — Tony at one point described blastr as a relay proxy. This is an interesting perspective, which puts things in a different light. More on proxies later.
Ban Jack?
Here's a thought experiment: how might we actually "ban blastr"? @Pablof7z suggested to me in a conversation that you could configure your relay to check every note that gets published to your relay against the big nostr hubs, and if it exists on any of them to simply delete it. Of course, that would result in your relay being basically empty, and the hubs having all of your content. That's game theory for you I guess.
Another approach that was floated was to encourage users to only publish to small relays. In theory, this would force clients to implement gossip so users could still see the content they were subscribed to. Fiatjaf even posted two identical notes, one to his personal relay, and one to a hub to see which would get more engagement. The note posted to the mainstream relay got 10x more replies and likes than the more obscure note.
nostr:nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgmwaehxw309aex2mrp0yh8wetnw3jhymnzw33jucm0d5hszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqdc2drrmdmlkcyna5kkcv8yls4f8zaj82jjl00xrh2tmmhw3ejsmsmp945r
Of course, this is thwarted by blastr, since blastr not only replicates notes posted to it, it also actively crawls the network as well. So the next logical step in this train of thought would be for hubs to encourage people to use small relays by actively blocking high-profile accounts.
nostr:nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpzdmhxue69uhhyetvv9ujue3h0ghxjme0qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qpqpjhnn69lej55kde9l64jgmdkx2ngy2yk87trgjuzdte2skkwwnhqv5esfq
This would of course never happen (Damus is one client that hasn't implemented NIP 65, and they also run the biggest relay), but it was a fun thought experiment. At any rate, the silliness of the suggestion didn't stop certain people from getting offended that we would "disrupt the free market" by "forcing" our opinions on everyone else. Oh well.
Death to Blastr
In reality, even though blastr makes it a little harder to adopt gossip in the short term, its days are numbered. Eventually, relay operators will start to feel the pain of unsolicted notes, and will either shut their relays down or look for tools that will help them curate the content they host.
From my perspective, these tools take two forms — read protection and write protection. This is something I alluded to in my talk at Nostrasia last November.
Write protection is straightforward — already many relays have access control lists based on active subscriptions, invite codes, or just static whitelists that determine who is allowed to post to a given relay, or what event authors are represented there. This approach effectively prevents blastr from using relays as free storage, which is a huge improvement.
Read protection is more tricky, because anything publicly readable will be scraped by blastr and replicated to unauthenticated-write relays across the network. In most cases, this is ok, but there are use cases for relays to exist that host a unique collection of notes oriented around some organizing principle. Unfortunately, with blastr in action (or any scraper that might exist), the only way to do this is to actively protect proprietary content. There are a few approaches that can work to make this happen:
- IP-based access control lists
- AUTH-based access control lists
- Stripping signatures when serving events
- Storing and serving encrypted content
Each of these approaches has its own set of trade-offs. But depending on use case, any of them or a combination of them could work to allow relay operators to carve out their own piece of the nostr-verse. In fact, this is a big part of what Coracle is about — the white-labeled version of the product confines certain notes to proprietary relays, with optional encrypted group support.
Enough of my polemic against blastr. Let's talk about how to make the gossip model actually work.
Hints are pointless
Right now, clients that implement the gossip model rely pretty heavily on relay hints to find related notes — whether user profiles, reply parents, or community definitions. The problem with hints is that they are prone to link rot. Many of the relays that were set up a year ago when nostr took off are no longer online, and yet they persist in user relay lists, and in relay hints. These hints can't be updated — they are set in stone. What this means is that a different mechanism has to be used to find the notes the hints were supposed to help locate.
Because of this, I've come around to the position that hints are basically pointless. They are fine as a stopgap, and might be appropriate for certain obscure and ill-defined use cases where relay urls are the most durable address type available. But they provide basically no value in supporting the long-term robustness of the network.
What are durable, however, are pubkeys. Pubkeys are available pretty much everywhere, except in event id hints — and there is a proposal in the works to add a pubkey to those too. The cool thing about pubkeys as hints is that once you have a pubkey, all you need to do is find that person's kind 10002 inbox/outbox selections, and you should be able to find any note they have published.
This goes with the caveat that when users change their relay selections, or rotate their key, they (or their relays) should be sure to copy their notes to the new relay/pubkey.
The question then is: how do I find a given pubkey's relay selections?
There are already several mechanisms that make this reasonably easy. First of all, NIP 65 explicitly recommends publishing relay selections to a wide range of relays. This is a place where the blastr approach is appropriate. As a result, relay selections are usually available on the most popular public relays. Then there are special purpose relays like purplepag.es, which actively seek out these notes and index them.
These indexes are not confined to relays either. It would be trivial to create a DVM that you could ask for a pubkey's relay selections, optionally for a fee. Alex Gleason's proxy tag could also be used to indicate indexes that exist outside the nostr network — whether that be torrents, DHT keys, or what have you.
The best part is that this doesn't negatively impact the decentralization of the network because in principle these indexes are stateless — in other words, they're easily derived from the state of the public part of the nostr network.
Just do it for me
Looping back to where we started — the complexity and technical challenges of implementing the gossip model — there is a simple solution that many people have experimented with in different ways that could solve both issues at once: proxies.
As I mentioned above, Tony thinks of blastr as a proxy, and he's right. More specifically, it's a write-proxy. This is only part of its functionality (it also acts as an independent agent which crawls the network. EDIT: apparently this is not true!), but it is an essential part of how people use it.
Another kind of proxy is a read proxy. There are several implementations of these, including my own multiplextr proxy, which is gossip-compatible (although it requires a wrapper protocol for use). The advantage of a proxy like this is that it can reduce the number of connections a client has to open, and the number of duplicate events it has to download.
Proxies can do all kinds of fancy things in the background too, like managing the gossip model on behalf of the client, building an index of everything the user would be likely to ask for in advance to speed up response times, and more.
One interesting possibility is that a NIP 46 signer could double as a proxy, reducing the number of round trips needed. And since a signer already has access to your private key, this kind of proxy would not result in an escalation in permissions necessary for the proxy to work.
It's simple
The number of cool and creative solutions to the content replication and indexing problem is huge, and certainly doesn't end with blastr. Just to summarize the next steps I'm excited to see (to be honest, I want to build them myself, but we all know how that goes):
- More clients supporting gossip
- Gossip implementations maturing (Coracle's still has some issues that need to be worked out)
- A shift from relying on relay hints to relying on pubkey hints + relay selection indexes of some kind
- Proxy/signer combos which can take on some of the heavy lifting for clients of delivering events to the right inboxes, and pulling events from the right outboxes
Let's get building!
-
 @ e1cded6c:151bd1be
2025-01-06 10:20:41
@ e1cded6c:151bd1be
2025-01-06 10:20:41What is Nostr?
Notwithstanding the lack of capitalisation, Nostr is an acronym for Notes and Other Stuff Transmitted by Relays. According to the website of its creator, Nostr was created in response to perceived issues with Twitter.
It’s important to be clear that Nostr is not an app or service that you sign up for. Rather it can be better understood as an open standard for social media that anyone can use. A useful analogy is the SMTP (Simple Mail Transfer Protocol) used for email. You probably know how this works:
- You write your email using Gmail, Outlook, or whichever email client you prefer.
- Your message travels through various email servers.
- The recipient can read it using any email client they choose.
Nostr works similarly:
- You write your note in an Nostr client (like Damus, Primal, and many others).
- Your note travels through Nostr relays (similar to email servers).
- Others can read it using whichever Nostr client they prefer.
The use of a standard protocol enables interoperability, allowing users to choose their preferred software. No single company controls the system.
Isn’t Mastodon a decentralised social media platform? Why do we need another one?
While Nostr and Mastodon both enable decentralised socially communication, they take fundamentally different approaches. The comparison made above equating Nostr relays with email servers is actually imperfect and better describes the approach Mastodon takes. Mastodon does rely on servers run by organisations or individuals where users create accounts. Your identity is tied to your chosen server, similar to having a Gmail address. This means you are still at the mercy of the entity running the server.
Nostr, in contrast, removes the need for servers entirely. Your identity is a cryptographic key pair, which works directly with any compatible client or relay. This key pair is mathematically linked. One is a private key (which is kept secret, like a password) and the other is a public key (which you share freely, like an email address). This enables the impressive ability to use different clients with the same identity without the need for accounts. The downside is that the onus is users to safeguard their key pairs. There is no Nostr tech support to help with a lost private key!
Nostr aligns with library values
From a librarian’s perspective, there is a lot to like about Nostr. There is no central algorithm that controls what content is shown to you. Individual relays can choose what they show, but users can connect to other relays. The diversity of relays effectively prevents single-point censorship, as there is no central authority that can remove content from the entire network. Again, more is demanded from the user in terms of selecting which relays to connect to, but this aligns with the long-held value of librarians of developing information literate citizens capable of making such choices on their own. In an age of information overload, we need to trust people to select their own sources wisely rather than rely on centralised content moderation. Nostr protects freedom of speech at the protocol level, ensuring that no central authority can arbitrarily block content from being posted.
Nostr also scores highly on privacy. No personal information is needed to generate a private-public key pair. This obviously aligns with librarianship’s historical role in championing patron privacy as a cornerstone of intellectual freedom. The lack of a centralised authority allows users to access information with reduced risk of surveillance.
Information preservation is another library value that Nostr is better aligned with compared to centralised social media platforms. A lot of historically and culturally significant content has been posted to social media, and there is a need to preserve it and make it available for future research. However, it is doubtful that for-profit social media companies will prioritise this. The biggest advance in this respect came in 2010, when the Library of Congress announced with great fanfare that it would archive all public tweets. But in the face of various challenges, the project was scaled back in 2017. I could find no further updates from the LoC, and given the current ownership of Twitter/X I think it unlikely that much progress will be made. The centralised nature of traditional social media means that preservation is the hands of a single entity.
Contrast this with Nostr’s architecture that requires multiple relays and hence multiple copies of data. This creates resilience in a way that librarians will be familiar with (“Lots of Copies Keep Stuff Safe”). Libraries could potentially choose to create their own relays and preserve notes that are relevant to their own collection development policies. Again, the open nature of the protocol means that they would not have to seek permission to do this.
In essence, Nostr's decentralized architecture naturally aligns with core library values of intellectual freedom, privacy, and preservation, potentially providing a pathway to a truly open digital commons. Librarians and information professionals could play a pivotal role in shaping this online public square.
Getting started with Nostr
I am cautious of getting too carried away with the potential of Nostr. It currently has very few users for a social network. At the time of writing, the stats page of Nostr.Band showed the number of daily active users hovering below 20,000. This is a tiny fraction of the 245 million daily active users of Twitter/X. Given the importance of the network effect to social media, Nostr has a long way to go before it becomes a true competitor.
However, it is not inconceivable, and I would argue that the alignment of the Nostr architecture with our values makes it important for librarians to engage with and understand this technology. The best possible outcome would be a truly decentralised, censorship-resistant, online social space on top of which anyone could build apps and services. In such a world, individual citizens will need to be much more information literate and independent. As information professionals, librarians could play a leading role in adopting and advocating for this.
Nostr clients
The best way to get started is to download a client. As mentioned, there are many Nostr clients to choose from. Some offer additional features for subscribers. Try out a few to see which one you prefer and remember that you can use all of them with the same key pair!
Recommended longer read
Exploring the Nostr Ecosystem: A Study of Decentralization and Resilience: This pre-print on arxiv.org provides a more technical introduction to Nostr. The Nostr primer that starts on page 4 is particularly helpful for new users.
-
 @ 6871d8df:4a9396c1
2024-02-05 23:29:22
@ 6871d8df:4a9396c1
2024-02-05 23:29:22The Apple Vision Pro was released, and it is the talk of the town right now. To be frank, I think it's a stupid product. It's not useful or particularly enticing to me in its current form factor. It's a toy, not a tool. All the features seem gimmicky as opposed to generally helpful. I'm not saying it may never be worthwhile, but as of this first release, it is only a party trick.
Coincidently, this is the first product that does not have any of Steve Jobs' influence. To me, it shows. I don't think Jobs would have ever let this product see the light of day.
Jobs understood product. He didn't make things for the sake of progress or to make sci-fi reality; he made things because he 'wanted to make a dent in the world.' He wanted to solve problems for everyday people by innovating with cutting-edge technology. He aspired to make people's lives better. Steve Jobs' genius was the way he married cutting-edge technologies with valuable tools that made those cutting-edge technologies simple and elegant.
The Vision Pro may be technically innovative, but it is not a tool, at least in its current form. It may be one day, but that is precisely my point; Jobs would have never released a product where the form factor would hold it back from becoming a tool. At best, it is an intriguing toy that is additive to some content at the behest of being very awkward to wear or be seen in. In my view, mainstream adoption can happen only in a world where we can use the Vision Pro as a contact lens or very small, discreet, minimalist glasses, but certainly not this iteration where it covers more than half your face.
Seeing people's eyes makes us human. So much emotion, understanding, and communication happens with just a look. It is a window into the soul. I don't want to live in a world where we are actively bringing all the negatives about communicating in the digital world to the physical one.
https://image.nostr.build/2365609411f144f5d789ffd684ffce9b4d867626a7bfe11bb311cb0f61057199.jpg
I can't help but wonder or hypothesize what Steve Jobs would focus on if he were still alive today. I think Apple's priorities would be completely different. My gut tells me he would not have let Siri get as bad as it is. Siri is a horrible product; I never use it, and everyone I know who tries to use it does so unsuccessfully, at least most of the time. I personally always default to ChatGPT or Bard. These AI systems make my life dramatically more productive. They are tools in the purest sense.
In my opinion, Steve would not have missed this train. Sure, Apple could wake up and integrate these systems into Siri — if they were smart, they would — but in its current form, it is so far behind that it almost astounds me. My intuition leads me to believe he would be closer to what [Rabbit] is doing.
Who knows? Maybe I am entirely wrong, and Apple just kickstarted VR's mass adoption phase. Unfortunately, I think this will likely be the biggest failure of a physical product that Apple will have seen since Jobs returned ages ago. The Vision Pro is only slightly better than the Oculus, and Facebook has already deprioritized VR for AI. Apple is further behind, and I don't see a world where they do not make the same pivot. There is a skill to creating successful, innovative products, and it makes me sad to see the torch that Jobs passed lose its flame. As someone who respected how Apple used to innovate, watching this decay in real-time is jarring as this is just the latest in a string of disappointing decisions that exemplify that 'peak Apple' is behind us.
-
 @ e1ff3bfd:341be1af
2024-01-06 19:41:35
@ e1ff3bfd:341be1af
2024-01-06 19:41:35Over the last few months it feels the bitcoin community has gotten more and more jaded on lightning. To be honest, this is for good reason, back in 2017 we were promised a decentralized payment network that would always have cheap payments and everyone would be able to run their own node. Nowadays, the average lightning user actually isn't using lightning, they are just using a custodial wallet and the few of that do run lightning nodes often find it a burdensome task. For us at Mutiny Wallet, we are trying to make this better by creating a lightweight self-custodial wallet and in my opinion we have been executing on that dream fairly well. In this post, I'll analyze these issues and present a new way to view lightning and what that means for bitcoin going forward.
First and foremost one of the hardest UX challenges of lightning is channel liquidity. No other payment system has these problems today besides lightning so this often confuses lots of users. To make matters worse, there aren't any practical hacks that we can do to get around this. Muun Wallet used an on-chain wallet + submarine swaps to get around the channel liquidity problem, this worked very well until fees went up and everyone realized it wasn't actually a lightning wallet. The better solution is JIT liquidity like we do in Mutiny or splicing like that is done in Phoenix. These solutions abstract some of it away but not enough, we often get support questions confused on why some payments have fees and others do not. The fact is channel liquidity is not a usable UX for most end users.
The other major pain point of lightning is the offline receive problem. Inherently, you must be online with your private keys to sign and claim a payment. There is technically an ongoing spec proposal to be able to work around this (essentially creating a notification system of when people are online to receive payments), but it doesn't solve the fundamental problem and still has limitations. There has been a few attempts to get around this, most notably was Zeus Pay lightning addresses. These essentially worked by just creating stuck payments and waited for the user to come online to claim, this caused a ton of problems for people and even forced us at Mutiny to block users from paying them because it caused so many force closures. This is a hard problem because the entire rest of the bitcoin/crypto ecosystem works by just copy-paste an address and you can send to it whenever, there isn't caveats around asking your friend to open their wallet. This is further exacerbated by things like lightning address that requires a webserver to even get an invoice in the first place.
Channel liquidity and offline receives in my opinion are the two most obvious reasons why self-custodial lightning is not popular. When most users hear about any of these, they just think screw that and move to a custodial wallet because it is so much easier. If these were our only two problems, I think self-custodial lightning would be fine, it may never be the predominant way people use lightning, but we could get the UX good enough that we have a significant portion of people using lightning in a sovereign way. However, there are more problems under the surface.
Channel liquidity is a problem, but it is also deceptive. When you have 100k sats of inbound liquidity you would think you could receive up to 100k sats, but this isn't the case, often you can't actually receive any. This is because of on-chain fees, when a payment is being made in lightning you are creating pre-signed transactions that have outputs for every in-flight payment, these outputs cost potential on-chain fees and the high on-chain fees go the more it eats into your liquidity. After we've solved most of our force close issues Mutiny this has been number one support request. Even if you do everything right, understand liquidity and have enough for your payment, sometimes it still won't work because on-chain fees are too high. This is always really discouraging because isn't the whole point of lightning to not have to pay on-chain fees? Fundamentally, all current lightning channels could become entirely useless if on-chain fees went high enough because a single payment would require too many reserves. Obviously this is hyperbolic, but I hope I am getting the point across that on-chain fees don't just effect the opening and closing costs of channels, even if you are a diligent node runner that only opens channels when fees are low, that is not enough, your channels need to be large enough to pay for the on-chain fees of each HTLC at any future on-chain fee rate. As on-chain fees go up and up this problem will only get worse.
The proposed solution to these reserve issues are things like anchor channels, package relay, ephemeral anchors, etc. These are all well and good but kind of just mask the problem. They do solve it so the fee reserve can be much lower and possibly zero, however with the tradeoff that you need on-chain funds available to fee-bump your force closes so they can actually get into a block. This again breaks the UX for self-custodial users because they have hold on-chain funds alongside their lightning funds so they can do those on-chain fee bumps. The size requirements for their on-chain funds is still dynamically based on how high on-chain fees can spike. Solutions for this can include having someone else bump your transaction fees but this brings basically a trusted 3rd party into the mix and isn't ideal.
When you lay out all the different tradeoffs a lightning node needs to make, especially in a high fee environment, it makes me think, what are we doing here, are we going down the wrong path? Lightning is still fundamentally a fantastic payment protocol but its limitation is that it requires scale. Basically every problem I've outlined goes away when you have a large lightning node with lots of liquidity and high uptime so many we should optimize for that. The market has been telling us this for years already, +90% of lightning users are using custodial wallets because it works so much better at scale. So how can we use large scale lightning nodes without custodial wallets?
Combining existing large scale lightning infrastructure with self-custodial solutions sadly, isn't totally possible. The only real way to do that as of now is Muun Wallet which as we talked about earlier, doesn't really solve the problem because everything is just an on-chain transaction. However, Muun was onto something. The architecture of having a simpler protocol interface with lightning is genius and gives us the best of both worlds. We can make fast cheap payments and let the big boys collect fees for running the lightning node. Aqua Wallet just launched which is essentially a Muun Wallet but on top of Liquid, this is a good bandaid fix but doesn't get to the root of the problem.
Before we go further we should take a step back and break down what problems we are trying to solve. Bitcoin has a fundamental scaling limitation through the block size, if we could make infinite, then we wouldn't necessarily need any layer 2s because we could just make on-chain payments. However, we live in the real world and have a 1mb block size limit, and this limits the number of transactions we can make on-chain. Lightning is a huge improvement to bitcoin because we don't need to put every transaction on-chain, we just need to open a channel and can make seemingly countless payments. So why isn't lightning the silver bullet? Lightning lets us move payments off-chain but what it doesn't do is let us move ownership off-chain. Fundamentally lightning still relies on that, at the end of the day, a utxo goes to single user. So even if every on-chain transaction was a lightning channel, we still run into the limit of how many people can actually own those channels. What we need is another layer 2 that can scale utxo ownership and caninterop with lightning, that way we have a way to scale ownership combined with scaling payments.
So how do we scale ownership? Simply put, the answer today is custody, whether that is pure custodial like a Wallet of Satoshi or in the grey area like fedimints and liquid, the only way to do it today is through custody or federated bridges. In bitcoin, the only way to delegate ownership of a utxo to multiple parties is through multisig, however, that requires every user to be online when anyone wants to transact, and when you take go down this path far enough you end up just reinventing lightning.
Are we doomed then? Is there no way to scale bitcoin in a self-sovereign way? Luckily, the answer is no, but we need some soft-forks. Covenants are the way to scale bitcoin ownership. There are a bunch of covenant proposals but at their core what they propose to do is to add a way, so you can have a bitcoin address that limits where and how the coins in it can be spent. This can seem scary, but we already have these in bitcoin today, OP_CTLV (Check LockTime Verify), which was soft forked in 2016, only allows you to spend from a bitcoin address if the transaction has a given locktime, this lets you gate when a utxo can be spent. What the current covenant proposals do is let you gate where a utxo can be spent. With that simple primitive many different protocols can be built that allow for scaling ownership.
There are a lot of current covenant proposals, the main ones being: OP_CTV, OP_VAULT, OP_CSFS, OP_TXHASH, OP_CAT, and APO. They all have different functionality and tradeoffs but in my opinion we should be looking towards activating a form of covenants because otherwise we will likely be moving towards a future of less sovereign bitcoin users.
The future is not bleak however, even without covenants we can still scale bitcoin for the world, just not in the ideal way. At Mutiny, we are full steam ahead on implementing fedimint into the wallet, in my opinion (and the rest of the team's) it looks like the best current scaling solution for bitcoin. Fedimints give us the ability to dynamically share ownership over a group of utxos and is able to interop with lightning through gateways. It is the pinnacle of the scaling dream for bitcoin with current technology and I can't wait to help make it reality while we can.
-
 @ 8947a945:9bfcf626
2023-10-23 08:13:39
@ 8947a945:9bfcf626
2023-10-23 08:13:39จงตระหนักรู้คุณค่าของตัวเอง เพชรไม่ได้เปล่งประกายเจิสจรัสจากสุดปลายถ้ำ

2023’s Wake up call
แรงบันดาลใจที่ทำให้ผมตัดสินใจเอาเรื่องนี้มาเล่าบน #ทุ่งม่วง เกิดจากเมื่อต้นปี 2023 ผมได้รับสัญญาณเตือนภัยจากที่ทำงานแห่งหนึ่ง (Wake up call) ปลุกให้ตื่นขึ้นจากภวังค์ ตระหนักรู้ถึงความเป็นจริงบางอย่าง ว่างาน part time ที่กำลังทำเริ่มมีสัญญาณความไม่มั่นคงเกิดขึ้นทีละเล็กทีละน้อย มีความสุ่มเสี่ยงที่จะถูกขอให้งดคลินิคไม่ต้องมาออกตรวจ (ภาษาสุภาพของการเลิกจ้างหมอ)
สำหรับหมอที่ทำงานหลายโรงพยาบาล จะเข้าใจสถานะ”หมอ part time” ของตนเองดีว่า สามารถถูกถอดเวรออกได้ทุกเมื่อ หากทางโรงพยาบาลมีความจำเป็น
เมื่อเกิดเหตุการณ์นี้ ผมติดต่อโรงพยาบาลใกล้บ้านเป็นแผนสำรองเอาไว้ ที่นี่ขาดอัตรากำลังแพทย์พอดี ผมเลยสามารถเริ่มงานได้ทันที ทำให้รายได้ไม่กระทบกระเทือนต่อครอบครัว แต่สิ่งที่ต้องพบเจอก็คือโรงพยาบาลแห่งใหม่นี้ งานหนักมาก หนักถึงขั้นกระอักเลือด เต็มไปด้วยความเสี่ยงที่ยังไม่มีระบบการบริหารจัดการที่มีประสิทธิภาพ ผมทำงานที่นี่ไประยะนึง เมื่อมาดูสลิปค่าตอบแทน พบว่าผมถูกจัดกลุ่มให้อยู่ในกลุ่มแพทย์เวชปฏิบัติทั่วไป (General practitioner หรือ GP คือหมอทั่วไปที่ยังไม่ได้เรียนต่อเฉพาะทาง)
แพทย์เฉพาะทาง ตามกลไกจะได้ค่าตอบแทนสูงกว่าแพทย์ GP ถึง 70 - 80%
ผมนำเรื่องนี้ขึ้นปรึกษาหน่วยงานที่เกี่ยวข้อง ได้รับการดำเนินแก้ไขอย่างเร่งด่วนเพราะความเข้าใจผิด และผมก็ได้ค่าตอบแทนสมน้ำสมเนื้อตามมาทีหลัง แต่ด้วยเนื้องานที่หนักมาก เหนื่อยมาก เลิกงานเที่ยงคืน วันอื่นๆทำงานอีก ทำงาน 7 วันต่อสัปดาห์ ร่างกายเริ่มส่งสัญญาณเตือนบางอย่างว่ากำลัง overheat เครื่องกำลังจะไหม้ในอีกไม่ช้า ถ้ายังคงลากเลือดขนาดนี้ แต่เวลานั้นผมทำเพื่อครอบครัวอย่างเดียว เลยไม่ได้ลังเล เดินหน้าต่อ
จุดเปลี่ยนมันอยู่ตรงนี้ครับ ผมมีอาจารย์แพทย์ที่เคารพมากท่านหนึ่ง อาจารย์เขารับรู้เรื่องผมมาตลอด เมื่อทราบว่าผมทำงานหักโหม แลกกับความเสี่ยงหลายมิติ จึงมีโอกาสได้นั่งคุยกัน อาจารย์ท่านนี้เล่าเรื่องสั้นเรื่องหนึ่งให้ฟัง และทิ้งท้ายเอาไว้ให้คิดว่า
ทรัพยากรที่มีค่าที่สุดคือเวลา จงเอาตัวผมไปอยู่ในที่ที่เห็นคุณค่าในตัวผมให้ได้ ถ้าผมทำได้ เวลาของผมมีจะสร้างมูลค่าได้มหาศาลกว่านี้
การสนทนาจบลงด้วยความรู้สึกพบแสงสว่างที่ปลายอุโมงค์ หลังจากนั้นไม่กี่สัปดาห์ผมตัดสินใจ ของดคลินิคจากโรงพยาบาลแห่งนั้นทันที และเป็นความโชคดี เพราะที่ทำงานประจำกำลังขาดแคลนหมอ ผมเลยได้ตารางออกตรวจเพิ่ม รายได้มั่นคงมากกว่าเดิม
ส่วนโรงพยาบาลที่กระตุ้น wake up call ผมตอนแรก เล็งเห็นความสำคัญของทักษะเฉพาะทางของผมที่ขาดไม่ได้และจำเป็นมากต่อสถานการณ์ปัจจุบัน จึงขอให้ผมอยู่ช่วยต่อและเพิ่มค่าตอบแทนเพิ่มจากเดิมอีกเกือบ 100%
ทักษะการเขียนบทความ ที่เกือบจะถูกปิดผนึกไปตลอดกาล เพราะเอาตัวเองไปอยู่ไม่ถูกที่
 สิ่งที่ผมสนใจอยู่เป็นทุนเดิมคือการเล่าเรื่องแฝงแง่คิดจากประสบการณ์ของตัวเองให้กับผู้อื่นฟัง ตัวผมเองเป็นคนพูดไม่เก่ง บุคคลิกเก็บตัว Introvert ใช้เวลาส่วนใหญ่อยู่กับความคิดตัวเอง แล้วจดบันทึกข้อคิดที่คิดได้เอาไว้ ตั้งใจว่าถ้ามีเวลาพอ จะเอาสิ่งที่รีดออกมาจากสมอง มาขยายทำเป็นบทความ เพื่อเอาไว้ให้คนอื่นอ่าน เผื่อว่ามันจะมีประโยชน์ไม่มากก็น้อย ผมตระเวนหาเวบไซต์สำหรับนักเขียนไปเรื่อย แต่ก็หาที่ที่ถูกใจไม่ได้ ผมก็เลย”จำใจ” เขียนลงไปในเฟสบุค และ แพลตฟอร์มนักเขียนแห่งหนึ่งของประเทศไทย
สิ่งที่ผมสนใจอยู่เป็นทุนเดิมคือการเล่าเรื่องแฝงแง่คิดจากประสบการณ์ของตัวเองให้กับผู้อื่นฟัง ตัวผมเองเป็นคนพูดไม่เก่ง บุคคลิกเก็บตัว Introvert ใช้เวลาส่วนใหญ่อยู่กับความคิดตัวเอง แล้วจดบันทึกข้อคิดที่คิดได้เอาไว้ ตั้งใจว่าถ้ามีเวลาพอ จะเอาสิ่งที่รีดออกมาจากสมอง มาขยายทำเป็นบทความ เพื่อเอาไว้ให้คนอื่นอ่าน เผื่อว่ามันจะมีประโยชน์ไม่มากก็น้อย ผมตระเวนหาเวบไซต์สำหรับนักเขียนไปเรื่อย แต่ก็หาที่ที่ถูกใจไม่ได้ ผมก็เลย”จำใจ” เขียนลงไปในเฟสบุค และ แพลตฟอร์มนักเขียนแห่งหนึ่งของประเทศไทยในช่วงแรกผมลองเขียนบทความลงเฟสบุค ผลลัพธ์เป็นไปตามคาดครับว่าไม่เป็นที่สนใจ ประเมินผลหยาบๆจากยอดกดไลค์ คอมเม้นท์ และการแชร์ เงียบเหมือนป่าช้าเลย นานๆจะมีคนมากดไลค์ซักที แต่ก็เป็นที่รู้ๆกันครับว่าการกดไลค์ มันอาจจะเกิดจากคนอื่นเปิดมาเจอโพสต์ของผม แล้วจะปัดให้มันพ้นๆไป “ไอ้บ้านี่มันบ่นอะไรของมัน” แต่นิ้วโป้งดันไปจิ้มโดนปุ่มไลค์พอดี ในเมื่อจิ้มไปโดนแล้วก็แล้วกันไปก็เป็นไปได้
เวลาผ่านไปมันเหมือนผมขึ้นไปพูดบนเวทีที่ไม่มีผู้ฟัง หรือ ผู้ฟังหลับทั้งห้อง บทความต่างๆข้อคิดต่างๆที่ผมตั้งใจเรียบเรียงมันส่งไปไม่ถึงผู้คน มันดูไร้ค่า จบด้วยการนั่งคุยกับตัวเองเหมือนเป็นคนไข้จิตเวช เหตุการณ์ทั้งหมดนี้เกือบนำพาผมไปสู่ข้อสรุปที่ว่า “ผมเองคงเขียนไม่เก่ง” หรือ “เขียนไม่ได้แย่หรอก แต่ไม่ได้โปรโมท เลยไม่มีใครมาพบเจอ” หรือไม่ก็ถูกทั้งสองข้อ บางครั้งอยากจะล้มเลิกการเขียนไปเลยก็มีครับ
ช่วงมกราคมปี 2023 เวบไซต์ Right shift เริ่มเป็นที่รู้จัก ฟังคอนเซปจากอาจารย์พิริยะแล้วชอบมาก
เวบไซต์ Right shift ตั้งใจเป็นแหล่งรวบรวมข้อมูลสำหรับผู้ที่สนใจอยากศึกษาบิตคอยน์ ให้สามารถเข้ามาศึกษาได้โดยไม่มีค่าใช้จ่าย แถมยังเชิญชวนให้ผู้ที่อยากเขียนบทความที่เป็นประโยชน์ให้แก่ผู้อื่น ใครสนใจสามารถส่งบทความเข้ามาได้ ถ้าหากบทความไหนมีแวว จะมีทีมบก.ติดต่อกลับไปเพื่อทำงานร่วมกันในการขัดเกล้า แก้ไขสำนวนบางจุดให้ดียิ่งขึ้น
พอรู้มาถึงตอนนี้มันนเหมือนมีอะไรมาเคาะกะโหลกดังๆ จนความรู้สึก “ปังปุริเย่ เฮ้ ร้องว้าว” มันผุดขึ้นมา แต่มันก็มาพร้อมกับความไม่มั่นใจในตัวเองนั่นแหละครับ ความขัดแย้งเต็มไปหมดว่า “จะเขียนหรือไม่เขียนดี” “เอาจริงอ่ะ? จะเขียนบทความส่งไปจริงๆเหรอ?” “ม_ึง ไม่ใช่นักเขียนมืออาชีพนะ คนที่เขาส่งบทความไปมีแต่เทพๆทั้งนั้น จะเอาอะไรไปสู้กับเขา” และเสียงอื่นๆในหัวอีกมากมาย
แต่สุดท้ายผมทลาย “Comfort zone” ได้ ด้วยกำลังใจเล็กๆน้อยๆจากภรรยาครับ ภรรยาผมบอกด้วยคำสั้นๆว่า “ก็ลองดูสิ สกิลการเขียนเล่าเรื่องของเธอก็ไม่ขี้เหร่นะ” ผมเลยลองทำดู และนี่คือสิ่งที่เกิดขึ้น
บอกได้ว่าเป็นครั้งแรกที่ผมได้ถูกฝึกการเขียนบทความโดย "ใครก็ไม่รู้” ผมรู้แค่ว่าเป็นทีมบก.ของ Right shift เมื่อทำงานร่วมกันไปเรื่อยๆ ทีมบก.ทุ่มเทในการช่วยแก้ไขช่วยตรวจสอบบทความของผมมากๆ จนผมสังเกตุเห็นได้
ใครเคยใช้ Google document ร่วมแก้ไขบทความด้วยกันมากกว่าหนึ่งคนคงจะรู้ดีนะครับว่า เวลาที่มีการแก้ไขข้อความมันจะมีเมล์แจ้งเตือนไปหาทุกคนที่เข้ามาร่วมแก้ไขเอกสารทั้งหมด บางคืนที่ผมนอนหลับไม่สนิท ตีสองตีสามตื่นมาเข้าห้องน้ำ ผมยังเห็นเมล์อัพเดทการแก้ไขบทความจากทีมงาน right shift เด้งๆอยู่เลย
จนสุดท้ายงานเขียนผมก็ได้รับการเผยแพร่บนเวบไซต์ Right shift

ใครยังไม่เคยอ่านกดตรงนี้ได้เลยครับ
หลังจากนั้นผมรับรู้ถึงทักษะนี้มากขึ้น เลยตั้งใจว่าต้องฝึกให้เก่งขึ้นดีขึ้นในทุกๆบทความที่ผมเขียน ผมอ่านหนังสือเยอะขึ้น ศึกษาสำนวนการเขียนจากนักเขียนรวมถึงนักแปลท่านอื่นๆ เพื่อดูตัวอย่างสำนวน ลีลาสไตล์การใช้คำ เอามาประยุกต์ใช้กับงานเขียนของตัวเอง
ไม่รู้ตัวหรอกครับ ว่าทักษะนี้มันโดนฝึก โดนขัดเกลาตั้งแต่เมื่อไหร่ แต่ตอนนี้ตระหนักรู้ถึงการที่มันมีตัวตนอยู่ภายในตัวผมแล้ว ผมก็จะลับคมมันไปเรื่อยๆ หลายครั้งตอนที่ผมเขียนบทความอยู่ผมลืมเวลา ลืมหิว ลืมง่วง ลืมเหนื่อยไปเลย ถ้าเปรียบเทียบกับนักกีฬา คาดว่าสภาวะตอนนั้นคงเป็นสภาวะหนึ่งของการเข้าสมาธิแบบ “Into the zone”
เรื่องสั้นที่อาจารย์ของผมเล่าให้ฟัง มอบบทเรียนชีวิตที่มีค่า อยู่ต่อจากนี้ครับ

พ่อคุยกับลูกสาว “ยินดีด้วยที่จบการศึกษา พ่อซื้อรถคันนี้ไว้ให้ลูกซักพักแล้ว ตอนนี้พ่อจะให้ลูกนะ แต่ก่อนที่พ่อจะให้ พ่ออยากให้ลูกนำไปที่ร้านรับซื้อ-ขายรถในตัวเมือง แล้วมาบอกพ่อด้วยว่าเขาให้ราคาเท่าไหร่”
ลูกสาวทำตาม กลับมาหาพ่อ บอกว่า “ร้านนี้เขาให้ราคา $10,000 เพราะรถเก่า” พ่อบอกลูกว่า “โอเคลูก ทีนี้พ่ออยากให้หนูเอารถไปที่โรงรับจำนำ ลองดูซิว่าเขาจะตีราคารถคันนี้เท่าไหร่”
ลูกสาวทำตาม แล้วกลับมาบอกพ่อว่า “โรงรับจำนำให้ราคา $1,000 เพราะรถเก่ามาก ดูแล้วต้องซ่อมอีกหลายรายการ ”
ครั้งนี้พ่อบอกลูกสาวให้นำรถนี้ไปยังชมรมคนรักรถที่มีผู้เชี่ยวชาญ และนำรถให้พวกเขาดู
ลูกสาวทำตาม ขับรถนี้ไปที่ชมรมที่ว่า หลังจากนั้นไม่นานลูกสาวกลับมาบอกพ่อด้วยน้ำเสียงตื่นเต้นว่า “บางคนเสนอราคา $100,000 เพราะเป็นรถหายาก และสภาพดีมาก”

ผู้เป็นพ่อยิ้มให้กับลูกสาว เหมือนว่ารู้อยู่แล้วว่าจะเกิดอะไรขึ้น ด้วยความสงสัยลูกสาวจึงถามพ่อว่า
“ในเมื่อพ่อรู้อยู่แล้วว่าร้านไหนจะให้ราคาสูง ทำไมพ่อไม่ให้หนูไปที่ชมรมคนรักรถตั้งแต่แรกล่ะ”
พ่อบอกลูกสาวว่า “นี่แหละบทเรียนชีวิตที่สำคัญบทหนึ่งที่พ่ออยากมอบให้แก่ลูก พ่ออยากให้ลูกรู้ไว้ว่า ลูกจะไม่มีค่าใดๆเลยถ้าอยู่ผิดที่ ที่ที่คนอื่นมองไม่เห็นเรา ไม่ต้องเสียเวลาไปโกรธโมโหไม่พอใจหรอกนะ สิ่งที่ลูกต้องทำก็คือเดินออกจากที่นั่น ออกไปจากสังคมและสถานที่ที่ไม่เห็นค่าในตัวลูก ค้นหาที่สถานที่ของลูกให้เจอ ถ้าลูกไม่ลองลงมือทำด้วยตัวเอง ลูกก็จะไม่ได้เรียนรู้อะไรเลย”

ข้อคิดที่อยากจะแบ่งปันกับทุกท่านที่อ่านมาจนจบ
บทความนี้มีความพิเศษกว่าบทความอื่นๆ ท้ายบทความของผมผมจะมาชวนคุยและสรุปข้อคิดที่เป็นประโยชน์ให้แก่เพื่อนๆพี่ๆทุกท่านที่อ่านมาจนจบ แต่สำหรับบทความนี้ข้อคิดที่ผมอยากให้ ถูกสรุปขมวดไว้ทั้งหมดแล้วในประโยคที่พ่อบอกลูกสาว
อย่าลืมต่อสู้ ฝ่าฟันอุปสรรค ค้นหาสถานที่ของตัวเราเองให้พบนะครับ เมื่อค้นพบทักษะในตัวแล้ว อย่าให้ถูกปิดผนึกไว้ เพียงเพราะอยู่ผิดที่ ลงมือฝึกฝนพัฒนามันไปเรื่อยๆ เราจะดีขึ้นในทุกๆวันครับ
-
 @ 9c35fe6b:5977e45b
2025-01-06 09:42:52
@ 9c35fe6b:5977e45b
2025-01-06 09:42:52Affordable Adventures with ETB Tours Egypt Discover the magic of Egypt without straining your wallet with our budget tour to Egypt. At ETB Tours Egypt, we specialize in crafting exceptional Egypt budget tours that combine affordability with unforgettable experiences. Our thoughtfully designed itineraries, such as the 8 Days Cairo and Sharm Budget Tour Package, ensure you experience the best of Egypt without compromising on quality.
Unveiling Egypt’s Iconic Landmarks Our Egypt tour packages offer a comprehensive exploration of the country’s historic treasures. From the majestic Pyramids of Giza in our Egypt pyramid tour packages to the bustling markets of Cairo, every moment is packed with wonder. Dive into history with Cairo day tours, or embrace ancient Egyptian culture with Egypt classic tours that include visits to Luxor and Aswan.
Relaxation and Adventure by the Red Sea Looking for a mix of adventure and tranquility? Our Red Sea tour packages and the 8 Days Cairo & Hurghada by Flight offer a perfect blend of exploration and relaxation. Experience the crystal-clear waters and vibrant marine life of the Red Sea while enjoying the value-packed perks of all-inclusive Egypt vacations.
Nile Cruises: A Budget-Friendly Luxury Experience the timeless beauty of the Nile River with our Nile cruise holidays. Whether you choose the classic Nile cruise Luxor Aswan or the scenic Nile cruises from Cairo, our Egypt travel packages ensure a luxurious yet affordable journey through Egypt’s most iconic sites.
Customized Tours for Every Traveler At ETB Tours Egypt, we cater to diverse interests. Whether you're looking for Egypt family tours, empowering Egypt women tours, or adventurous Egypt safari tours, we have the perfect Egypt holiday packages for you. For those seeking flexibility, our Egypt private tours provide personalized itineraries at unbeatable prices.
Quick Getaways and Day Trips For travelers on a time crunch, our Egypt day tours offer a chance to explore popular destinations like Cairo, Luxor, Aswan, and Alexandria. These quick yet enriching trips are perfect for those wanting a taste of Egypt on a budget.
Budget Travel Made Easy With ETB Tours Egypt, budget travel to Egypt is simple and accessible. From affordable accommodations to expertly planned itineraries, we ensure that every aspect of your journey is cost-effective yet rich in experiences.
To Contact Us: E-Mail: info@etbtours.com Mobile & WhatsApp: +20 10 67569955 Address: **4 El Lebeny Axis, Nazlet Al Batran, Al Haram, Giza, Egypt
-
 @ 57fe4c4a:c3a0271f
2023-10-18 13:02:10
@ 57fe4c4a:c3a0271f
2023-10-18 13:02:10📝 Summary: Batched splicing can be risky due to certain conditions like no funds in a channel and using an old state. It is important for batched splicing mechanisms to have a backout option to prevent disruptions caused by confirmed old states. Additionally, not all splice implementations performing a check can lead to potential loss of funds.
👥 Authors: • Greg Sanders ( nostr:npub1jdl3plz00rvxwc6g2ckemzrgg0amx5wen4kfvs3laxtssxvk9cvsf3gh0m ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l )
📅 Messages Date: 2023-10-17
✉️ Message Count: 3
📚 Total Characters in Messages: 5405
Messages Summaries
✉️ Message by ZmnSCPxj on 17/10/2023: Batched splicing can be risky if certain conditions are met, such as having no funds in a channel and using an old state. It is important for batched splicing mechanisms to have a backout option to prevent disruptions.
✉️ Message by Greg Sanders on 17/10/2023: Batched splicing is risky because if an old state is broadcasted and confirmed before the splice, it can disrupt the process. It is important for batched splicing mechanisms to have a backout option.
✉️ Message by ZmnSCPxj on 17/10/2023: Batched splicing can be risky if not all splice implementations perform a check to ensure subsequent splices confirm, potentially leading to loss of funds.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 5e13e5d5:217fe898
2025-01-06 06:46:21
@ 5e13e5d5:217fe898
2025-01-06 06:46:21With the rapid development of science and technology, the popularization of information technology in modern society has made our lives more convenient and efficient. However, in this era of high information flow, the emergence of signal jammers has aroused widespread concern. This signal jammer not only plays an important role in certain specific situations, but is also part of the intersection of science and technology and daily life. This article will explore the positive impact of signal jammers and their application in our lives.
Basic concept of signal jammers Signal jammers, in simple terms, are a device that interferes with or blocks wireless signals in a specific frequency band by emitting radio waves. Usually, it can effectively shield mobile phone signals, Wi-Fi signals, etc. In some special occasions, this device is used to prevent information leakage, protect privacy, and ensure safety. Although the use of Cellular Jammer is subject to legal restrictions in some countries, the positive impact it brings cannot be ignored.
Protecting privacy and information security In the era of information explosion, the protection of personal privacy has become a thorny issue. Whether in public places or in private environments, the leakage of information may cause serious losses to individuals and enterprises. Signal jammers can effectively prevent external monitoring and sneak shots and protect people's privacy.
12 Antenna 5G Phone and WiFi Signal Jammer
For example, in some important meetings or negotiations, signal jammers can block external eavesdropping devices and ensure the confidentiality of communication content. The application of this technology not only improves the security of commercial transactions, but also enhances people's trust in their own information security.
Oppose harassment and criminal behavior In recent years, with the popularity of smart phones, various harassing calls and online frauds have emerged in an endless stream, posing a threat to the normal order of society. The use of signal jammers can curb these illegal activities to a certain extent. For example, in some public places, such as banks and shopping malls, installing Bluetooth Jammer can reduce the risk of criminals using communication equipment to carry out illegal activities.
In addition, signal jammers can also be used in special places such as prisons to prevent prisoners from making illegal contacts through mobile phones, making prison management more strict and efficient. The reasonable application of this technology can effectively combat illegal activities and contribute to social stability.
Promote scientific and technological innovation and industrial development The research and development and application of signal jammers have promoted the advancement of related technologies, such as innovations in radio communications, signal processing and other fields. At the same time, this has also created new market demand for the electronic product manufacturing industry. With the improvement of people's awareness of information security, the market potential of signal jammers has continued to expand, giving rise to the emergence of a series of emerging industries.
The participation of technology companies has injected new impetus into the development of Anti Drone Blocker, allowing the technology in this field to be continuously updated and iterated. Competition between companies has promoted the improvement of product performance and the reduction of costs, and ultimately enabled more users to benefit from this technology.
Optimizing public safety management In public safety management, signal jammers have also shown their unique advantages. For example, in the security work of major events, the use of signal jammers can effectively prevent terrorists from using mobile phones to perform remote detonation and other dangerous behaviors. By cutting off potential wireless signals, security personnel can better control the situation on the scene and ensure public safety.
At the same time, signal jammers also play an active role in emergency response. In natural disasters or other emergencies, signal jammers can help maintain the communication order on the scene and avoid network congestion caused by too much unnecessary communication. This application provides strong support for emergency management and improves rescue efficiency.
Conclusion As an important achievement of modern science and technology, the positive impact of Audio bug jammer cannot be underestimated. It not only plays an important role in protecting personal privacy and maintaining social security, but also promotes the innovation of related technologies and the development of industries. Although its use is subject to certain legal restrictions, if it can be used reasonably within the legal framework, signal jammers will undoubtedly bring more convenience and safety to our lives.
In the future, with the further development of science and technology, we look forward to seeing the wider application of signal jammers in various fields, so that technology can truly serve life, improve our quality of life, and build a safer information society.
-
 @ 32e18276:5c68e245
2023-10-10 12:02:37
@ 32e18276:5c68e245
2023-10-10 12:02:37Hey guys, I'm spending some time today preparing v1.6 for the app store, it's been a long time coming with many new features. Here's a breakdown of everything new in this version!
Notable new features in 1.6
- Custom built, embedded C WASM interpreter (nostrscript), which will be used for custom algos, filters and lists
- Longform note support
- Hashtag following
- Configurable reactions
- New Live user status NIP (music, general)
- Adjustable font sizes
- A very long list of bug fixes and performance improvements
- Fast and persistent profile searching using nostrdb
Top priorities for 1.7
- Lists
- Custom algos and filters using nostrscript
- Stories
- Multi account
- Tor integration
- Better NWC integration (wallet balances, transaction history)
- Advanced note search via nostrdb
- Fully switch to nostrdb for all notes
- Discord-like relays (click a relay to view all the notes on it)
So much more but maybe I will not try to be too ambitious ...
Contributors
name added removed commits William Casarin +57964 -8274 288 petrikaj +1524 -0 1 Terry Yiu +1266 -964 9 ericholguin +1234 -252 11 Daniel D’Aquino +1223 -399 19 Suhail Saqan +905 -70 16 Grimless +838 -736 6 Bryan Montz +793 -744 30 Jon Marrs +658 -60 3 Joel Klabo +653 -105 6 transifex-integration[bot] +176 -0 9 Fishcake +129 -21 5 Daniel D‘Aquino +123 -9 5 Jericho Hasselbush +78 -2 2 cr0bar +66 -19 11 Daniel D'Aquino +55 -32 2 Mazin +53 -0 1 gladiusKatana +37 -8 1 doffing.brett +10 -6 1 tappu75e@duck.com +5 -1 2 Ben Harvie +5 -0 1Changelog
- 76 Fixes
- 18 Changes
- 26 Additions
Added
- Add "Do not show #nsfw tagged posts" setting (Daniel D’Aquino)
- Add ability to change order of custom reactions (Suhail Saqan)
- Add close button to custom reactions (Suhail Saqan)
- Add followed hashtags to your following list (Daniel D’Aquino)
- Add initial longform note support (William Casarin)
- Add r tag when mentioning a url (William Casarin)
- Add relay log in developer mode (Montz)
- Add settings for disabling user statuses (William Casarin)
- Add space when tagging users in posts if needed (William Casarin)
- Add support for multilingual hashtags (cr0bar)
- Add support for multiple reactions (Suhail Saqan)
- Add support for status URLs (William Casarin)
- Add the ability to follow hashtags (William Casarin)
- Added feedback when user adds a relay that is already on the list (Daniel D'Aquino)
- Added generic user statuses (William Casarin)
- Added live music statuses (William Casarin)
- Added merch store button to sidebar menu (Daniel D’Aquino)
- Added padding under word count on longform account (William Casarin)
- Adjustable font size (William Casarin)
- Click music statuses to display in spotify (William Casarin)
- Enable banner image editing (Joel Klabo)
- Finnish translations (petrikaj)
- Hold tap to preview status URL (Jericho Hasselbush)
- Re-add nip05 badges to profiles (William Casarin)
- Show nostr address username and support abbreviated _ usernames (William Casarin)
- Suggested Users to Follow (Joel Klabo)
Changed
- Allow reposting and quote reposting multiple times (William Casarin)
- Damus icon now opens sidebar (Daniel D’Aquino)
- Hide nsec when logging in (cr0bar)
- Improve UX around clearing cache (Daniel D’Aquino)
- Improved memory usage and performance when processing events (William Casarin)
- Increase size of the hitbox on note ellipsis button (Daniel D’Aquino)
- Make carousel tab dots tappable (Bryan Montz)
- Move the "Follow you" badge into the profile header (Grimless)
- Remove nip05 on events (William Casarin)
- Remove note size restriction for longform events (William Casarin)
- Rename NIP05 to "nostr address" (William Casarin)
- Show muted thread replies at the bottom of the thread view (#1522) (Daniel D’Aquino)
- Show renotes in Notes timeline (William Casarin)
- Start at top when reading longform events (William Casarin)
- Switch to nostrdb for @'s and user search (William Casarin)
- Updated relay view (ericholguin)
- Use nostrdb for profiles (William Casarin)
- clear statuses if they only contain whitespace (William Casarin)
Fixed
- Allow relay logs to be opened in dev mode even if relay (Daniel D'Aquino)
- Allow user to login to deleted profile (William Casarin)
- Apply filters to hashtag search timeline view (Daniel D’Aquino)
- Avoid notification for zaps from muted profiles (tappu75e@duck.com)
- Crash when muting threads (Bryan Montz)
- Dismiss qr screen on scan (Suhail Saqan)
- Don't always show text events in reposts (William Casarin)
- Don't spam lnurls when validating zaps (William Casarin)
- Eliminate nostr address validation bandwidth on startup (William Casarin)
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Fix Invalid Zap bug in reposts (William Casarin)
- Fix PostView initial string to skip mentioning self when on own profile (Terry Yiu)
- Fix UI freeze after swiping back from profile (#1449) (Daniel D’Aquino)
- Fix UTF support for hashtags (Daniel D‘Aquino)
- Fix action bar appearing on quoted longform previews (William Casarin)
- Fix broken markdown renderer (William Casarin)
- Fix bug where it would sometimes show -1 in replies (tappu75e@duck.com)
- Fix compilation error on test target in UserSearchCacheTests (Daniel D‘Aquino)
- Fix crash when long pressing custom reactions (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fix freezing bug when tapping Developer settings menu (Terry Yiu)
- Fix icons on settings view (cr0bar)
- Fix images and links occasionally appearing with escaped slashes (Daniel D‘Aquino)
- Fix issue where malicious zappers can send fake zaps to another user's posts (William Casarin)
- Fix issue where relays with trailing slashes cannot be removed (#1531) (Daniel D’Aquino)
- Fix issue where typing cc@bob would produce brokenb ccnostr:bob mention (William Casarin)
- Fix issue with emojis next to hashtags and urls (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix lag when creating large posts (William Casarin)
- Fix localization issues and export strings for translation (Terry Yiu)
- Fix localization issues and export strings for translation (Terry Yiu)
- Fix long status lines (William Casarin)
- Fix nav crashing and buggyness (William Casarin)
- Fix nostr:nostr:... bugs (William Casarin)
- Fix npub mentions failing to parse in some cases (William Casarin)
- Fix padding of username next to pfp on some views (William Casarin)
- Fix padding on longform events (William Casarin)
- Fix paragraphs not appearing on iOS17 (cr0bar)
- Fix parsing issue with NIP-47 compliant NWC urls without double-slashes (Daniel D’Aquino)
- Fix potential fake profile zap attacks (William Casarin)
- Fix profile not updating (William Casarin)
- Fix profile post button mentions (cr0bar)
- Fix profiles not updating (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix situations where the note composer cursor gets stuck in one place after tagging a user (Daniel D’Aquino)
- Fix small graphical toolbar bug when scrolling profiles (Daniel D’Aquino)
- Fix some note composer issues, such as when copying/pasting larger text, and make the post composer more robust. (Daniel D’Aquino)
- Fix status events not expiring locally (William Casarin)
- Fix text composer wrapping issue when mentioning npub (Daniel D’Aquino)
- Fix text editing issues on characters added right after mention link (Daniel D’Aquino)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fix zaps sometimes not appearing (William Casarin)
- Fixed a bug where following a user might not work due to poor connectivity (William Casarin)
- Fixed audio in video playing twice (Bryan Montz)
- Fixed disappearing text on iOS17 (cr0bar)
- Fixed issue where hashtags were leaking in DMs (William Casarin)
- Fixed issue where reposts would sometimes repost the wrong thing (William Casarin)
- Fixed issues where sometimes there would be empty entries on your profile (William Casarin)
- Fixed nav bar color on login, eula, and account creation (ericholguin)
- Fixed nostr reporting decoding (William Casarin)
- Fixed nostrscript not working on smaller phones (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fixes issue where username with multiple emojis would place cursor in strange position. (Jericho Hasselbush)
- Hide quoted or reposted notes from people whom the user has muted. (#1216) (Daniel D’Aquino)
- Hide users and hashtags from home timeline when you unfollow (William Casarin)
- Make blurred videos viewable by allowing blur to disappear once tapped (Daniel D’Aquino)
- Mute hellthreads everywhere (William Casarin)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Show longform previews in notifications instead of the entire post (William Casarin)
- Stop tab buttons from causing the root view to scroll to the top unless user is coming from another tab or already at the root view (Daniel D’Aquino)
- don't cutoff text in notifications (William Casarin)
- endless connection attempt loop after user removes relay (Bryan Montz)
- icon color for developer mode setting is incorrect in low-light mode (Bryan Montz)
- relay detail view is not immediately available after adding new relay (Bryan Montz)
Removed
- Remove following Damus Will by default (William Casarin)
- Remove old @ and & hex key mentions (William Casarin)
-
 @ 16d11430:61640947
2025-01-06 04:20:10
@ 16d11430:61640947
2025-01-06 04:20:10Introduction
The human body’s remarkable ability to bridge the physiological and psychological realms often gives rise to questions about the interplay between ancient spiritual practices and modern biochemistry. One such question pertains to the potential relationship between chakra activation—a concept from ancient spiritual traditions—and the secretion of dimethyltryptamine (DMT), an endogenous compound with profound psychoactive effects.
In this article, we explore the biophysical mechanisms that may underlie this connection, synthesizing insights from neurobiology, endocrinology, and spiritual traditions. While direct scientific evidence is limited, existing research and plausible hypotheses provide a compelling framework for further exploration.
The Biochemistry of DMT
DMT is a tryptamine molecule derived from the amino acid tryptophan. Its synthesis involves two key steps:
-
Decarboxylation of Tryptophan: Tryptophan is converted into tryptamine, a neurotransmitter precursor.
-
Methylation of Tryptamine: The enzyme indolethylamine-N-methyltransferase (INMT) catalyzes the addition of methyl groups, forming DMT.
DMT is produced in small quantities in the human body and has been detected in:
Cerebrospinal fluid and bloodstream.
Tissues such as the lungs, liver, and brain, including the pineal gland (though its role in DMT synthesis is debated).
DMT’s ability to bind to serotonin 5-HT2A receptors in the brain gives it its potent psychoactive effects, influencing perception, cognition, and consciousness.
Chakras and Neuroendocrine Systems
Chakras, as described in ancient yogic texts, are energy centers aligned with key anatomical structures:
-
Ajna Chakra (Third Eye): Associated with the pineal gland.
-
Sahasrara Chakra (Crown): Linked to higher states of consciousness and the brain's integration centers.
From a physiological perspective, these chakras correspond to nerve plexuses and endocrine glands that regulate vital functions and neurochemical balance. For instance:
The pineal gland is central to circadian rhythms and melatonin production, and it has been hypothesized to produce DMT.
The hypothalamic-pituitary-adrenal (HPA) axis governs stress responses, which could influence DMT secretion.
Mechanisms Linking Chakra Activation and DMT Secretion
- Meditation and Neurochemical Modulation
Meditation, a common practice for activating chakras, induces measurable changes in brain activity and neurochemistry:
Increased Gamma Brain Waves: Associated with heightened states of awareness and transcendence.
Serotonin Regulation: Meditation enhances serotonin activity, a precursor in DMT synthesis.
Stress Reduction: Lower cortisol levels may optimize conditions for enzymes like INMT to function efficiently.
- Breathwork and Hypoxia
Pranayama and other breathwork techniques, integral to chakra activation, can alter oxygen and carbon dioxide levels in the blood. Hypoxia (low oxygen levels) is known to:
Stimulate the release of endogenous neurochemicals.
Potentially trigger DMT secretion as part of an adaptive stress response.
- Pineal Gland Activation
The pineal gland, often called the "seat of the soul," has drawn significant attention in both spiritual and scientific contexts:
It expresses the enzyme INMT, essential for DMT synthesis.
Practices like focusing on the Ajna chakra (third eye) during meditation could theoretically stimulate the pineal gland, influencing DMT production.
- Vibrational Frequencies and Resonance
Chanting or tonal vibrations (e.g., the sound "Om") during chakra activation may stimulate specific brain regions or glands through resonance effects. Such stimulation could hypothetically enhance DMT secretion, although direct evidence is lacking.
Physiological Correlates of Altered States
Practitioners of chakra meditation often report vivid imagery, euphoria, or a sense of oneness—experiences similar to those induced by exogenous DMT. This raises the question: Could these altered states result from an increase in endogenous DMT secretion?
Near-Death Experiences (NDEs): Research in rats has shown elevated DMT levels in the brain during cardiac arrest, suggesting that extreme physiological states can trigger its release.
Dreaming: DMT’s psychoactive effects have led to hypotheses that it plays a role in REM sleep and the generation of dreams.
Evidence and Limitations
While the theoretical links between chakra activation and DMT secretion are intriguing, direct evidence remains sparse. Key challenges include:
-
Difficulty Measuring DMT: Its rapid metabolism and trace quantities in the body make it hard to study.
-
Lack of Controlled Studies: Most insights come from anecdotal reports or animal models, not rigorous human trials.
However, recent advances in neuroimaging and biochemical assays hold promise for future research.
Conclusion and Future Directions
The potential connection between chakra activation and endogenous DMT secretion represents a fascinating intersection of spirituality and biophysics. While the precise mechanisms remain elusive, emerging evidence suggests that practices like meditation, breathwork, and chanting may influence brain chemistry in profound ways.
Future studies should focus on:
Identifying triggers for DMT synthesis and release in humans.
Exploring the role of the pineal gland in altered states of consciousness.
Investigating the long-term effects of meditation and chakra activation on neurochemical balance.
By bridging ancient wisdom with modern science, we may unlock deeper insights into the mysteries of human consciousness.
References
-
Barker, S. A., et al. (2012). "The occurrence of N,N-dimethyltryptamine in mammals." Medical Hypotheses.
-
Dean, R. A., et al. (1991). "Biosynthesis of serotonin and melatonin in the pineal gland." Journal of Pineal Research.
-
Strassman, R. (2001). DMT: The Spirit Molecule. Rochester, VT: Park Street Press.
-
Mandell, A. J. (1980). "Neurotransmitter precursors and altered states of consciousness." Psychopharmacology Bulletin.
-
Gallimore, A. R. (2015). "Building alien worlds: The neuropsychological and evolutionary implications of DMT." Frontiers in Psychology.
-
-
 @ 2edbcea6:40558884
2023-10-08 15:27:57
@ 2edbcea6:40558884
2023-10-08 15:27:57Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) NIP 43: Fast Auth between clients and relays
Some relays are member-only. There has to be some way for relays to verify the content being sent/requested is from an authorized user (one of the members). Most methods for this are clunky and slow.
This NIP proposes a faster method for auth between clients and relays. From what I can tell when clients open a connection to a relay they’ll open it with an “authorization” query parameter on the end of the relay url. That query param will actually be an encoded Nostr event whose payload has the necessary info for the relay to authenticate the user opening the connection.
Kinda looks like an auth header like you’d see in an http request but shoehorned into a query parameter since websockets (which are used for connections to relays) don’t traditionally support headers.
Author: aruthurfranca
2) (Proposed) Updates to NIP 03: Timestamps you can rely on
Sometimes you want to make sure that a piece of Nostr content was actually created/pushed to a relay at a specific time. The example from last week was in the case of a future betting system built on Nostr, you really don’t want people to be able to publish that they made a bet 2 weeks ago for something whose outcome was determined twenty minutes ago.
NIP-3 already outlines a way to add OpenTimestamp attestations to Nostr events essentially allowing Nostr clients to outsource trust to a third party on whether a piece of content was created when it claims to be created. As is, NIP 3 is a little hard to use. This update would make it far simpler.
In the new methodology, you’d publish a Nostr event of kind 1040 with the proof of timestamp and point to the event that you’re trying to prove the timestamp for.
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
Notable Projects
Cellar Relay
If you haven’t been graced by the nostr.wine community they are a group of fine folks that host wine-themed relays. They’re some of the most reliable and widely used public and paid relays around.
nostr:npub18kzz4lkdtc5n729kvfunxuz287uvu9f64ywhjz43ra482t2y5sks0mx5sz recently announced the “Cellar” Relay that will store notes long term for paid users. Like we talked about in last week’s #NostrTechWeekly long-term note storage is a challenge for relay hosts (especially for relays that are free to users). But solving long term storage will help folks on Nostr feel like they’re building a persistent social experience instead of building an ephemeral feed.
Nice work! Glad to see the trend continuing for long-term note storage. 💪
Memestr.app
I can’t tell you how many times folks I talk to have said there should be a meme-focused client on Nostr. nostr:npub1zumzudhtu2558fgvycnjlc7pq9l4m338vghgcfzafftz9qg45ruslzpl4x delivers with https://memestr.app I definitely had some giggles when I logged on.
This could quickly evolve into a nostr-based Imgur and be far better for being nostr-based. But one thing I think is missing from the internet (not just Nostr) is a way to iterate on memes easily in the same place where you can share them. In combination with prisms/boosts this could be an interesting way for people to make money for their content and earn from what is built on top of their content.
Zap threads
Threaded conversations are an important component to social experiences on the internet. Reddit and Hackernews have really shown its power, we’ve seen StackerNews also leverage this format as well.
nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 has created a nostr-based component for supporting the threaded comments, and it looks like it could be used in any web-application that needs commenting, spreading Nostr to every corner of the internet. It’s already powering the commenting on Habla.News
nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 also did a great writeup on the reasoning for this project and where it’s going: https://habla.news/franzap/threading-the-web-with-nostr
If you need comments on your project, take a look!
Latest conversations: How decentralized is decentralized enough?
Distributed vs Decentralized
These two concepts are often used interchangeably, and it’s worth highlighting their distinction, especially in the context of Nostr. This is a good visualization to illustrate the difference.
Distributed: the P2P model
Robust, distributed systems are extremely censorship resistant, and include a lot of redundancy. Distributed systems distribute power widely, everyone is a peer.
Biological systems (cells, ecosystems, etc) are like this, cells are all peers and replaceable. Napster was distributed, everyone in the Napster ecosystem stored and shared some of the songs. IP (the “internet protocol”), which is how computers find each other on the internet, is a peer to peer technology where every node gossips about where to find other nodes.
Ideally all systems would be built this way, but in practice distributed / P2P systems are generally used when there’s a high chance of node failure (the death of individual cells) or attack (government takedowns). The challenge is that they’re expensive to run.
This might be confusing because Napster was “free” right? Most P2P software feels free-ish because many are donating some of their existing hardware/bandwidth/etc. But if you take the aggregate resources to run Napster versus just the parts of Spotify that help users to upload and download music, Spotify for sure uses fewer resources.
Distributed systems by their very nature have to assume that most peers in the network may fail. In order to maintain uptime, that results in P2P systems having many copies of what’s being shared and/or sending data many times to ensure it arrives.
I think most people would say they’d prefer everything to be P2P but it’s difficult to maintain a good experience in a P2P system and so it’s often only used in cases where it’s absolutely necessary.
Where does decentralization work better?
I wrote up a whole thing about decentralization a while back but the TL;DR is decentralized systems are better than centralized systems at distributing power widely, but they are generally still more performant than peer to peer systems.
Sometimes you need a mix of preventing abuses of power but still maintain a good experience for users. Freedom minded folks usually end up supporting decentralized solutions because they’re viable in the market and still take power away from centralized players.
Is Bitcoin decentralized or distributed?
The Bitcoin blockchain is a distributed system. Every Bitcoin full-node is an equal participant in storing, updating, and validating the blockchain.
Bitcoin as a monetary system, on the other hand, is decentralized: there are many more Bitcoin users than Bitcoin full-nodes. The nodes are the hubs and the users are the spokes.
There’s a reason for this architecture. Bitcoin nodes are ultimately in control of Bitcoin, it must be the least corruptible, most censorship resistant architecture possible. On the other hand a decentralized system has efficiency gains that make Bitcoin more competitive in comparison to existing financial systems. By having hubs (full-nodes, Bitcoin banks, wallet providers, exchanges, etc), the system is more efficient (and therefore cheaper). But by having many hubs, power is still spread widely.
Nostr: Decentralized or Distributed?
 Nostr, as introduced by FiatJaf, seems like it was intended to be decentralized. Relays are the hubs and users are the spokes. Clients help connect users to relays (and therefore each other). There is wisdom to this architecture, because it will scale better than a P2P system.
Nostr, as introduced by FiatJaf, seems like it was intended to be decentralized. Relays are the hubs and users are the spokes. Clients help connect users to relays (and therefore each other). There is wisdom to this architecture, because it will scale better than a P2P system.Think of it this way, there are on the order of hundreds of millions of songs available for human consumption. With 10 million users storing a few hundred songs, there would be plenty of redundancy to allow Napster to distribute every song in a P2P manner. There are on the order of trillions of social media posts, if you include follows, reactions, DMs, etc, it’s likely in the quadrillions. With current technology a P2P system would never be able to provide coverage of every post and make it available in a reasonable time.
That said, there are some elements of Nostr that could benefit from being more P2P. Especially operations that would benefit from greater privacy (DMs, zaps, and reactions). Right now privacy around these actions is not well supported via Nostr.
Dev work has started on some P2P Nostr functionality announced by nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and it’s right along those lines: maximizing privacy and security for nostr-based comms. It will have all the great things and all the difficulties of any P2P system, but it may be necessary to improve privacy on Nostr.
One thing that is great about Nostr is everyone can try things out and see if they work and if people want them. I see a lot of demand for privacy for certain Nostr operations, and if a P2P model would help, it needs to be tried. We’ll see whether the trade offs of P2P make Nostr better or if they make it less likely to succeed. We’ll see as development continues!
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 16d11430:61640947
2025-01-06 03:55:21
@ 16d11430:61640947
2025-01-06 03:55:21Ah, the path to enlightenment has never been more accessible, my friends. Forget the mystics, the gurus, and the silent retreats. The ultimate deep meditative state is found by tuning your inner vibrations to the soothing hum of the money printer. That's right – the cosmic Brrrr is your new mantra.
Step 1: Assume the Position
First, sit comfortably in a position that screams "I understand fiat but choose to transcend it." Maybe cross-legged, maybe lounging in your gamer chair with a Bitcoin hoodie. Whatever works.
Step 2: Focus on the Sound
Close your eyes and visualize the printer in all its glory, churning out currency like a caffeinated octopus. Let the rhythm of Brrrr wash over you. This is not just a sound; it’s the vibration of a system so intricate, it persists by sheer force of mass cognitive dissonance.
Step 3: Sync with the Counter
Here’s the key: attune your mind to the rate of counter persistence. Each new unit of fiat materializes not as value, but as a data point in the algorithm of systemic confidence. Breathe in the inflation, exhale the diminishing purchasing power. Feel the balance.
Step 4: Become One with the System
As the printer continues its song, let your consciousness merge with the ledger of the world. Understand the duality: to some, it’s salvation; to others, a Ponzi scheme so complex even Madoff would blush. In this awareness lies the secret truth: the system operates because it must.
Step 5: Release and Reflect
Slowly emerge from your trance, whispering your final affirmation: "I am not a consumer; I am a node." Congratulations, you’ve transcended fiat reality. Treat yourself to a decentralized transaction to celebrate.
Post-Meditation Exercise:
For the fully enlightened, consider live-streaming your practice. Your audience will marvel at your ability to tune into a system that operates solely on the unspoken agreement that nobody asks too many questions.
Namaste, fellow printers of truth. May your sats always stack higher than the Fed’s balance sheet.
-
 @ 662f9bff:8960f6b2
2025-01-06 03:48:26
@ 662f9bff:8960f6b2
2025-01-06 03:48:26I remember taking this picture on the train from the airport into HK on my first morning after the overnight flight from Brussels via Zurich. Somehow I had expected that there might be a party on the plane since we flew over the end of the year, but...nothing! Also it did strike me as symbolic that I got a one-way ticket.
Great winter weather in HK this week - we spent a few days away in Cheung Chau; for such a small island there are sooo many people living there and it is a totally different atmosphere to much of Hong Kong - very traditional and relaxed.
Set 1/4 Set 2/4 Set 3/4 Set 4/4
Letter from ...around the worldRoger Price
 Click to see photos from the trip
Click to see photos from the tripApart from that, quite a few hikes this week - you have really got to appreciate the good weather and convenience of HK. No matter where you go you can easily get to and from the hike with public transport and you have all conceivable environments available - beach, forrest, mountain and even city-walks. Not to mention girls in the trees!
Following
Michael Saylor is a required follow - gotta appreciate his clarity of vision and eloquence of explanation. The CEO! Do also check out Michael's legacy, The Saylor Academy. Saylor Academy is a nonprofit initiative working since 2008 to offer free and open online courses to all who want to learn. Offering nearly 100 full-length courses at the college and professional levels, each built by subject matter experts. All courses are available to complete — at your pace, on your schedule, and free of cost. @saylor
Saifedean Ammous - author of The Fiat Standard - required reading for these times to understand what the governments are doing to you and your savings. @saifedean
Jeff Booth - author of The Price of Tomorrow - further evidence, if needed that the current system (over 100 years in the making) is ending. Jeff has a unique ability to connect the dots to something bigger. Few books offer a more succinct, provocative, and enlightening view of the world as it is today, and what it could be tomorrow. Your world view will transform instantly. @jeffbooth
Listening
Coming to a city near you - Price Gouging, Price Controls, And Inflation.... Pomp's latest newsletter read by him.
Joe Brown also explains how Turkey inches closer to Hyperinflation. I do rather think that you need to pay attention to what happens here. Turkey ranks 11th place globally in terms of GDP at PPP in 2020 ahead of Italy and Mexico and just behind UK and France.
Super interesting interview of Cory Klippstein, CEO of Swan Bitcoin - indeed a reminder that we are still early: SLP333 Cory Klippsten - Building for Bitcoiners
Watching
One of the best interviews of the year: Peter and Lyn discuss Currency wars; I can listen to Lyn all day.
Equally informative is James' Holiday special with Jeff Booth and Greg Foss
Mark explains all about endless wars: Central Banks Covert Plan For Never-Ending Stimulus | Get Ready. And then, George G: Breaking: Media Now Saying US Needs PRICE CONTROLS!!
James' fast-paced outlook for 2022 is wide-ranging and informative
I do recommend: Guy's tips for Security for your Crypto
Reading
I finally finished Harry Potter and the Order of the Phoenix. I really did not like this book when I read it 18 years ago. Second time round, though still a dark read, you will spot so many parallels to what is happening in the world right now. Well worth the 30+ hours on audible.com or 896 pages! Not to mention that whilst the "first wave" from Voldemort is over there are two more episodes to come...
Still In my queue: Harry Potter - book 6 (Half Blood Prince) and book 7 (Deathly Hallows) ...
I have now started on When Money Dies - The Nightmare of Deficit Spending, Devaluation, and Hyperinflation in Weimar, Germany. This really is required reading for these times. Those who do not learn from history are doomed to repeat it. Once aware of them you will see signs all around you.
I think it is not linked on their website but still accessible if you know where to look (maybe download and safestore it before it disappears): The Bank of England 1914-21 (Unpublished War History). This corroborates and elaborates on what you can read in The Creature from Jekyll Island.
That's it!
No one can be told what The Matrix is. \ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
 @ 662f9bff:8960f6b2
2025-01-06 03:44:45
@ 662f9bff:8960f6b2
2025-01-06 03:44:45Season's greetings from Hong Kong - as we approach the end of the year I am taking a few days off work (mostly) - so I have a bit more time for some personal projects and interests. We will be island hopping again/still this week!
Considering the need for improved privacy and security on mobile phones, I am experimenting with CalyxOS - on a very nice Pixel 4. Surprisingly pleasant experience on a Google-free device. It was easy to replace Android on the phone and you have pretty much all you need via either the F-Droid or Aurora app stores - certainly if you enable MicroG (not a bad option, I think). Do let me know your thoughts on this if you use it. Documentation here. Apps that are handy on the phone:
- Signal - Messaging. Avoid WhatsApp, FB Messenger and others if possible
- Brave Browser - privacy oriented version of Chrome - just great!
- Element - Group Chat and conversations
- Antenna - Podcasts.. just a great experience
- Bitwarden - Password manager - it just works... highly recommended
- NewPipe - Youtube without all the nonsense!
- Phoenix - Lighning & Bitcoin payments - and I do not even live in El Salvador
- DuckDuckGo - Search.. why would you use anything else?
I am also experimenting with Raspberry Pi - these are fascinating little devices - if you are interested to know more, do say. Among other things they allow you to host your own private servers that keep data safe whilst being securely accessible by a personal VPN.
Something completely different - a little video update from my hike around The Peak...
Following
On Twitter, I do recommend following @DougAntin and do check our his website and newsletter: The Sovereign Individual Weekly
@Laserhodl is also an interesting follow - do listen to his interview by Stephan Livera
Listening
- Listen and learn to clear talk on what is happening and will come soon in the Macro World: w/ Jeff Booth, Preston Pysh & Greg Foss
I do love listening to Guy Swan - he has really read more on this topic than anyone else and he happily shares his knowledge. Here his and Lyn's knowledge!
- Proof of Stake & Stablecoins - Part 1: A Centralization Dilemma [Lyn Alden]
- Proof of Stake & Stablecoins - Part 2 [Lyn Alden] - you will understand why Proof of Stake networks are vulnerable to government manipulation unlike Bitcoin with its Proof of Work mining.
Watching
Guy's weekly news review is required weekly watching - issued every Monday so we see it Tuesday morning in HK. Do also subscribe to his newsletter
Mark explains how the measuring stick is being changed to steal from you
If you have seen The Matrix Resurrections
- you may have missed some Easter Eggs
- you may or may not be ready for the Full Decode - warning, this is DEEP
In case you heard about Log4j and wondered what it was and why it's important
BTW - you might be interested to Restore YouTube Dislikes
Reading
I am still reading Harry Potter and the Order of the Phoenix, Book 5. So many interesting parallels in the book to what is happening right now in the world. Gotta wonder, this is book 5 and there is still book 6 to come...
In my queue: When Money Dies by Adam Fergusson - I feel this may be very relevant in the month ahead - already so in some countries...
If case you missed them - I do recommend:
- The Creature from Jekyll Island - The untold history of the FED...
- Sovereign Individual - written in 1997 they did predict personal computers, mobile phones, cryptocurrencies and even the current pandemic situation..
- The Fourth Turning - we have been here before
For audio-books, I do recommend getting used to listening at >= 1.5x speed. After a while 1.8x to 2x is quite fine and you will wonder how you ever did differently!
That's it!
No one can be told what The Matrix is. \ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
 @ 662f9bff:8960f6b2
2025-01-06 03:41:34
@ 662f9bff:8960f6b2
2025-01-06 03:41:34(12-22-21) Something of a computer-centric update this week, ahead of Christmas. Responding to several folks asking about this and with the continual drumbeat of new threats (echoes of 1984?) and recurring theft of personal and business data, you might find it useful to have some suggestions from many years of industry experience - let me know if you need more!
Backups
Top priority - ensure that you have backups of your critical data and that you are able to recover it; keep in mind that if you have not tested your backup you should consider that you do not really have one. Yes, testing backups is a real pain!
A good starting point is the 3-2-1 strategy. Have at least three copies of your important data on two different backup media with at least one copy somewhere offsite. You can always increment these numbers to make things more resilient. For onsite storage it's a good idea to keep the media in a solid metal safe for protection against fire, theft and electromagnetic attacks.
Important to have the recovery steps written down safely and available in case of need - when trouble hits you will appreciate this advice AND remember test from time to time.
If your data on Social media sites is important, consider getting and keeping a download that is included in your backups from time to time; all the major services have to offer this.
Passwords
Use a password manager - there is no excuse. A good password manager makes it easy to create and use a strong password for every site and application that you use and for all of these to be different; this is important to avoid that compromise of one supplier would expose all your other systems using same password. A good password manager also works on Mobile and Computer browsers and should be accessible securely on all your devices.
Multi-Factor Authentication (MFA)
Just do it - and avoid using SMS for this if possible (risk of SIM swap attack). MFA ensures that someone needs more than just your username and password to log in to your accounts. Consider Time-based One Time Password solutions (TOTP). Be sure that you have backup of this stored safely and it can be useful to have it in several devices
Patching vs Anti-virus
For personal use, the best thing you can do is to ensure that you timely apply vendor patches. It's generally a good idea to wait a couple of days from patch release just in case the patch causes issues but after a week or so, just patch! Both Windows PCs and Macs are decent choices these days as long as you use and do not disable the built-in protections with Mac being slightly easier to keep safe and secure, I think!
I wouldn't recommend antivirus for personal use - other than possible on-demand scans/checks or clean-up if you do get or suspect a malware infection. Windows and MacOS contain pretty good malware protection measures and use of 3rd party products can open up additional risks.
Mobile Phones
Android or Apple/iOS? For most people, Apple is generally simpler and safer but there are trade-offs, including cost! Android systems tend to be slower to get patches and easier for criminals to exploit - if you use one, keep it up to date and avoid unofficial App Stores. An interesting wrinkle here is that the Google Pixel phones are generally patched more quickly and they also allow you to install Privacy Centric operating system in place of Android (eg CalyxOS); with this approach it is possible to "de-google" yourself - not a bad ambition!
Privacy
Be aware that all the cloud-based services and most mobile Apps that you use are tracking what you do and they may well be doing much worse with your data. In theory they need to tell you in Privacy Policy but can anyone read or understand these and you are pretty helpless when these change them unilaterally. So - choose carefully which services you use and minimse unnecessary sharing of data!
That's it!
No one can be told what The Matrix is. \ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
 @ 662f9bff:8960f6b2
2025-01-06 03:17:31
@ 662f9bff:8960f6b2
2025-01-06 03:17:31Only in HK can you go golfing on a remote island, come back in the evening, leave your golf clubs at the quay, go for dinner and pick them up on the way home!
We spent most of the last week up in Sai Kung, way up in the North East - things in HK are so handy, so even this is just an easy one hour from Central on public transport. Weather this week was fantastic - 18-24 degrees and mostly sunny; November and December are the best months of the year here. It will be nice weather till about 6 January and then it switches to cool and cloudy till Chinese New Year after which the humidity will return.
Planning
Over the Christmas and New Year period I expect to have a bit more time for things so, responding to requests from people I plan to share a few things you might find handy
- Stay Safe online - tips and tricks to ensure that your mobile phones and computers are safe from hackers. Also protecting access to your critical data and accounts.
- Secure Messaging and Chat - this is becoming increasingly important with arbitrary (or not?) censorship, cancellation and bot-driven targetting becoming routine. With diminishing trust in the existing platforms many are looking for safer alternatives - I'll share my suggestions.
- Privacy tools - there are quite a few tools that enable you to keep private your data and transactions - we will be exploring those too and sharing suggestions.
Following
On Twitter, I do recommend following @DougAntin and do check our his website and newsletter: The Sovereign Individual Weekly
Listening
Fascinating interview of @LaserHodl by Stephan Livera - you need to listen to this because obviously this is not allowed on YT. Pro tip: do get used to listening to Podcasts and YT and 1.75x-2x speed - you will quickly find it the ONLY way to do it!
Watching
Guy's weekly news review is required weekly watching - issued every Monday UK time, Tuesday mornings here in HK. This week's update.
Guy's longest video every is dedicated to the recent World Economic Forum slew of whitepapers outlining their plan for World Domination - required watching here. Blow by Blow:\ 1:33 What Is The World Economic Forum? 4:00 Introduction 6:38 Corporations And Central Banks 14:13 Stablecoin And CBDC Regulations 18:28 Stablecoin And CBDC Risks 24:55 Stablecoins And Financial Inclusion 30:52 Digital Currencies For Humanitarian Aid 33:56 CBDC “Privacy” 38:40 Stablecoin And CBDC Interoperability 42:02 CBDC Technology
Blow by blow accunt and analysis of the recent CEO Testimony: Government vs. CRYPTO by Guy - watch and learn - summary here, blows below!\ 1:25 About The Hearing 3:37 Opening Statements 9:18 Stablecoin Questions 12:18 Crypto Market Questions 14:18 Regulation Questions 17:56 Crazy Questions 21:02 Crypto Mining Questions 24:05 Hearing Analysis 26:57 Outro
Reading
I am still reading Harry Potter and the Order of the Phoenix, Book 5. Progress this week has been a bit slow with a lot on at work but I hope to have more time in the weeks ahead to finish the series, for a second time!
I am also re-reading (listening on Audible) Mythos - narrated by Stephen Fry. This is absolutely AMAZING and highly recommended. There is so much wisdom in these stories from antiquity - you have got to wonder....!
That's it!
No one can be told what The Matrix is. \ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.\ You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
 @ fab018ad:dd9af89d
2023-09-07 13:39:26
@ fab018ad:dd9af89d
2023-09-07 13:39:261. ฟาร์มกุ้งวิปโยค
“ทุกอย่างล้วนหายไปหมดแล้ว”
–Kolyani Mondal
เมื่อ 52 ปีก่อน พายุไซโคลนโบลาฆ่าผู้คนในแถบชายฝั่งของบังกลาเทศไปมากกว่า 1 ล้านคน ถือเป็นพายุไซโคลนที่ร้ายแรงที่สุดที่มีการบันทึกไว้ในประวัติศาสตร์
หน่วยงานท้องถิ่นและองค์กรนานาชาติรู้ถึงความเสี่ยงที่จะเกิดความเสียหายร้ายแรงจากพายุลักษณะนี้เป็นอย่างดี ดังนั้นในช่วงปี 1960 หน่วยงานภูมิภาคจึงสร้างแนวกันคลื่นขนาดใหญ่เพื่อป้องกันแนวชายฝั่ง ซึ่งเปิดโอกาสให้มีการใช้พื้นที่สำหรับการเกษตรได้มากขึ้น
แต่หลังจากการลอบสังหารผู้นำอย่าง ชีค มูจิบูร์ เราะห์มาน ในการประกาศอิสรภาพ ก็ได้เกิดการเปลี่ยนแปลงแนวทางภายใต้ระบอบเผด็จการของบังกลาเทศด้วยการผลักดันของอิทธิพลจากต่างประเทศ ชีวิตของผู้คนถูกลดความสำคัญ และแนวป้องกันพายุสำหรับประชาชนถูกทำให้อ่อนแอลง
หมายเหตุผู้แปล : ชีค มูจิบูร์ เราะห์มาน (Sheikh Mujibur Rahman) เป็นผู้ก่อตั้งประเทศบังกลาเทศ โดยดำรงตำแหน่งประธานาธิบดีและนายกรัฐมนตรีระหว่างปี 1971 จนถูกลอบสังหารในปี 1975
ทั้งหมดก็เพื่อเร่งอัตราการส่งออกและเพื่อนำเงินมาชดใช้หนี้
โดยแทนที่จะส่งเสริมการปลูกป่าชายเลน ซึ่งสามารถเป็นแนวป้องกันพายุตามธรรมชาติ เพื่อประโยชน์สำหรับประชาชนมากกว่า 1 ใน 3 ของประเทศที่อาศัยอยู่ตามแนวชายฝั่ง หรือแม้แต่ลงทุนในการผลิตอาหารให้เพียงพอต่อการบริโภคภายในประเทศที่กำลังเติบโตอย่างรวดเร็ว แต่รัฐบาลกลับเลือกที่จะกู้เงินจากธนาคารโลกและกองทุน IMF เพื่อที่จะขยายฟาร์มกุ้ง ซึ่งกระบวนการเพาะเลี้ยงสัตว์น้ำในประเทศนั้นถูกควบคุมโดยเครือข่ายชนชั้นปกครองที่ร่ำรวยอีกด้วย
พวกคนรวยรวมหัวกันผลักดันบรรดาเหล่าชาวไร่ให้กู้ยืมเงินเพื่อทำสิ่งที่เรียกว่าการ “อัปเกรดกระบวนการเพาะเลี้ยง” โดยทำการขุดหลุมตามแนวกันคลื่นซึ่งป้องกันที่ดินของพวกเขาจากทะเล ทำให้ที่ดินที่เคยอุดมสมบูรณ์ของพวกเขาเต็มไปด้วยน้ำเกลือ หลังจากนั้นพวกเขาก็ต้องทำงานอย่างหลังขดหลังแข็ง เพื่อจับตัวอ่อนของกุ้งจากทะเลด้วยมือเปล่า เพื่อนำมันกลับมาเลี้ยงในบ่อพัก ก่อนจะขายกุ้งตัวโตเต็มวัยให้กับผู้รับซื้อกุ้ง ซึ่งมักจะเป็นผู้มีอิทธิพลในพื้นที่

เงินทุนที่กู้จากธนาคารโลกและ IMF ทำให้ไร่นาสวน ที่ดินลุ่มน้ำ และป่าชายเลนนับไม่ถ้วน ถูกดัดแปลงให้กลายเป็นบ่อกุ้งที่เรียกว่า “ghers”
พื้นที่บริเวณสามเหลี่ยมปากแม่น้ำคงคานั้นถือเป็นพื้นที่ที่มีความอุดมสมบูรณ์อย่างน่าทึ่ง โดยเป็นที่ตั้งของ “ป่าสุนทรพนา” ป่าชายเลนที่ใหญ่ที่สุดในโลก แต่หลังจากที่การทำฟาร์มกุ้งเชิงพาณิชย์ได้กลายเป็นธุรกิจหลักในท้องถิ่น ต้นโกงกางมากกว่าร้อยละ 45 ได้ถูกตัดออกไปเกลี้ยง ทิ้งให้ผู้คนเผชิญกับคลื่นสูงกว่า 10 เมตรที่พุ่งเข้าชนแนวชายหาดเวลาเกิดพายุไซโคลน พื้นที่ทำกินที่อุดมสมบูรณ์และสิ่งมีชีวิตตามริมแม่น้ำค่อย ๆ ถูกทำลายไปจากความเค็มที่เพิ่มขึ้นจากน้ำทะเล
จนสุดท้ายป่าทั้งป่าก็ได้อันตรธานหายไป เพราะฟาร์มกุ้งนั้นทำลายพืชพรรณท้องถิ่นทั้งหมด กลุ่มความร่วมมือพัฒนาชายฝั่ง (Coastal Development Partnership) ได้กล่าวถึงผลกระทบที่เกิดขึ้นนี้ว่า “การกระทำนี้ทำให้ดินแดนที่เคยอุดมสมบูรณ์กลายเป็น ‘ทะเลทรายที่เต็มไปด้วยน้ำเค็ม' ”

พื้นที่ไร่นาที่ปล่อยน้ำทะเลเข้ามาเพื่อทำฟาร์มกุ้งในจังหวัด Khuna
อย่างไรก็ตาม ผู้มีอิทธิพลที่รับซื้อกุ้งเหล่านี้กลับร่ำรวยขึ้นอย่างมาก และกุ้ง (ซึ่งถูกเรียกว่าเป็น “ทองคำสีขาว”) ก็กลายเป็นสินค้าส่งออกอันดับ 2 ของประเทศ
โดยนับตั้งแต่ปี 2014 เป็นต้นมา ชาวบังกลาเทศมากกว่า 1.2 ล้านคนทำงานในอุตสาหกรรมกุ้ง และผู้คนอีกกว่า 4.8 ล้านคนที่ต้องพึ่งพิงอุตสาหกรรมนี้ในทางอ้อม ซึ่งตัวเลขนี้ถือเป็นครึ่งหนึ่งของจำนวนคนยากจนที่อาศัยอยู่ตามชายฝั่ง คนเก็บกุ้งเป็นผู้ที่ทำงานหนักที่สุด (ซึ่งถือเป็นร้อยละ 50 ของแรงงานในอุตสาหกรรม) แต่ได้รับส่วนแบ่งเพียงร้อยละ 6 ของผลกำไร โดยร้อยละ 30 ของแรงงานนั้นเป็นแรงงานเด็กที่มีทั้งเด็กผู้ชายและเด็กผู้หญิง ซึ่งทำงานในน้ำเค็มมากถึง 9 ชั่วโมงต่อวันด้วยค่าจ้างรายวันน้อยกว่า 1 ดอลลาร์สหรัฐ เด็กเหล่านี้ส่วนมากไม่รู้หนังสือและไม่ได้เรียนต่อ
ผู้คนเคยมีการลุกฮือขึ้นประท้วงต่อต้านการขยายตัวของฟาร์มกุ้ง แต่แล้วก็ถูกปราบปรามอย่างรุนแรง โดยในเหตุปราบปรามที่เลื่องลือครั้งหนึ่่งนั้น ขบวนผู้ประท้วงถูกทำร้ายด้วยระเบิดจากผู้มีอิทธิพลที่รับซื้อกุ้งและกลุ่มลูกน้อง และมีผู้หญิงรายหนึ่งชื่อ Kuranamoyee Sardar ถูกตัดศีรษะจากเหตุปราบปรามดังกล่าว
ในงานวิจัยปี 2007 ซึ่งสำรวจฟาร์มกุ้งของชาวบังกลาเทศกว่า 102 แห่ง พบว่าแม้ค่าใช้จ่ายในการผลิตทั้งหมดจะอยู่ที่ 1,084 ดอลลาร์สหรัฐต่อเฮกตาร์ แต่รายได้สุทธิกลับอยู่ที่ 689 ดอลลาร์สหรัฐ นั่นหมายถึงกำไรที่ประเทศได้จากการส่งออกนั้น แลกมาด้วยการที่แรงงานในอุตสาหกรรมกุ้งต้องรับเคราะห์จากค่าจ้างที่ถูกกดและสภาพแวดล้อมของพวกเขาที่ถูกทำลายจนหมดสิ้น
ในรายงานที่จัดทำโดยมูลนิธิความยุติธรรมด้านสิ่งแวดล้อม (Environmental Justice Foundation) ชาวไร่ที่อยู่ริมชายฝั่งอย่างคุณ Kolyani Mondal ได้กล่าวว่า “เธอเคยปลูกข้าว พร้อมเลี้ยงปศุสัตว์และสัตว์ปีก” แต่หลังจากที่ได้มีการทำเกษตรฟาร์มกุ้ง “วัว ควาย และแพะของเธอก็เริ่มเป็นโรคท้องร่วงไปพร้อม ๆ กับเหล่าแม่ไก่และเป็ดซึ่งเป็นสัตว์ของเธอ พวกมันล้วนตายทั้งหมด”

ตอนนี้ทุ่งของเธอเต็มไปด้วยน้ำเกลือ และที่ดินที่ยังเหลืออยู่ก็เพาะปลูกอะไรแทบไม่ขึ้น ในอดีตนั้นครอบครัวของเธอสามารถปลูกข้าวได้ 18-19 มอนต่อเฮกตาร์ แต่ตอนนี้เหลือแค่ 1 มอนต่อเฮกตาร์ เธอยังจำช่วงเวลาในปี 1980 ที่เพิ่งเริ่มมีการทำฟาร์มกุ้งได้ ในตอนนั้น ชาวบ้านได้รับการสัญญาว่าสิ่งนี้จะสร้างรายได้เพิ่มขึ้น รวมทั้งมอบอาหารและพืชผลให้พวกเขามากขึ้น
แต่ตอนนี้ “ทุกอย่างล้วนหายไปหมดแล้ว” ชาวไร่ผู้เลี้ยงกุ้งขอเช่าที่ดินของเธอ โดยตกลงจะจ่ายเงินเธอ 140 ดอลลาร์สหรัฐต่อปี แต่ตอนนี้อย่างดีที่สุดที่เธอได้รับคือเงินผ่อนจ่ายแปลงละ 8 ดอลลาร์สหรัฐบ้างเป็นครั้งคราว โดยเธอกล่าวว่า “ในอดีตครอบครัวของเธอสามารถหาเลี้ยงตัวเองได้อย่างดีจากบนผืนดินแห่งนี้ แต่ตอนนี้ไม่เหลือทางเลือกใด ๆ นอกจากการไปซื้ออาหารที่ตลาด”
หมายเหตุผู้แปล : - มอน (Muand) เป็นหน่วยวัดน้ำหนักดั้งเดิมที่ใช้กันในเอเชียใต้ โดย 1 มอนมีค่าเทียบเท่าที่หลากหลายตั้งแต่ 11 กิโลกรัม จนถึง 72 กิโลกรัม - เฮกตาร์ (Hectare) เป็นหน่วยวัดพื้นที่ในมาตราเมตริกโดย 1 เฮกตาร์ เท่ากับ 10,000 ตารางเมตร หรือประมาณ 6 ไร่ 1 งาน.
ในบังกลาเทศนั้นเงินกู้เพื่อการปรับโครงสร้างจากธนาคารโลกและ IMF ปริมาณนับพันล้านดอลลาร์ (ที่มาของชื่อ “เงินกู้เพื่อการปรับโครงสร้าง” ได้มาจากการที่ผู้ปล่อยกู้จะบังคับให้ประเทศผู้กู้ต้องปรับโครงสร้างทางเศรษฐกิจเพื่อให้เอื้อกับการส่งออก ซึ่งต้องแลกมาด้วยการบริโภคภายในประเทศ) ได้ทำให้กำไรในการส่งออกกุ้งของประเทศเพิ่มขึ้นจาก 2.9 ล้านดอลลาร์สหรัฐในปี 1973 - เพิ่มเป็น 90 ล้านดอลลาร์สหรัฐในปี 1986 - และเพิ่มเป็น 590 ล้านดอลลาร์สหรัฐในปี 2012
ซึ่งรายได้ดังกล่าวถูกนำมาใช้จ่ายหนี้ต่างประเทศและใช้ในการพัฒนากองทัพ แต่เงินบางส่วนก็ไหลเข้ากระเป๋าเจ้าหน้าที่รัฐ (ซึ่งก็ไม่ได้แตกต่างอะไรกับกรณีส่วนใหญ่ของประเทศกำลังพัฒนา) ในขณะที่เหล่าแรงงานทาสในอุตสาหกรรมกุ้งต้องถูกกดขี่ให้ยากจน ถูกลิดรอนอิสรภาพ ต้องพึ่งพิงผู้อื่น และมีความสามารถในการหาเลี้ยงตัวเองได้น้อยลงกว่าแต่ก่อน
โดยที่แย่ไปกว่านั้นคือผลวิจัยยังแสดงให้เห็นว่า “หมู่บ้านที่มีป่าชายเลนไว้เป็นแนวป้องกันตัวจากคลื่นพายุซัดฝั่งจะมีผู้เสียชีวิตน้อยลงมาก เมื่อเทียบกับหมู่บ้านที่ป่าชายเลนเสียหายหรือถูกทำลาย”

ภายใต้แรงกดดันของสาธารณชน ในปี 2013 ธนาคารโลกจึงได้ปล่อยเงินกู้ 400 ล้านดอลลาร์สหรัฐให้แก่บังกลาเทศเพื่อใช้ในการพยายามแก้ไขความเสียหายของระบบนิเวศที่เกิดขึ้น ซึ่งพูดในอีกแง่หนึ่งก็คือธนาคารโลกจะได้รับค่าตอบแทนในรูปแบบของดอกเบี้ยจากการพยายามแก้ปัญหาที่ตัวเองเป็นผู้ก่อขึ้นตั้งแต่แรก ในขณะเดียวกันธนาคารโลกยังได้ปล่อยเงินกู้นับพันล้านดอลลาร์สหรัฐไปยังทุกประเทศ ไล่ตั้งแต่เอกวาดอร์ ไปยันโมร็อกโก จนถึงอินเดีย เพื่อเปลี่ยนฟาร์มดั้งเดิมในท้องถิ่นให้กลายเป็นฟาร์มกุ้ง
ธนาคารโลกได้อ้างว่าบังกลาเทศนั้นคือ “เรื่องราวที่น่าทึ่งของการลดความยากจนและการพัฒนาประเทศ” หากยึดจากในข้อมูลตามเอกสารที่ว่าแล้ว นี่ถือเป็นชัยชนะ เพราะเศรษฐกิจของประเทศอย่างบังกลาเทศมีแนวโน้มที่จะเติบโตต่อไป ในขณะเดียวกับที่มูลค่าการส่งออกนั้นเติบโตขึ้นเพื่อชดเชยมูลค่าจากการนำเข้า แต่แท้จริงแล้วรายได้จากการส่งออกส่วนใหญ่กลับไหลเข้าสู่กระเป๋าของชนชั้นนำและเจ้าหนี้ต่างประเทศ และหลังจากได้รับเงินกู้เพื่อการปรับโครงสร้างมาถึง 10 ครั้ง หนี้ของบังกลาเทศเติบโตขึ้นอย่างมหาศาล โดยเพิ่มจาก 145 ล้านดอลลาร์สหรัฐในปี 1972 กลายเป็น 95,900 ล้านดอลลาร์สหรัฐในปี 2022 ซึ่ง ณ ตอนนี้ประเทศบังกลาเทศเองก็กำลังเผชิญกับวิกฤตด้านดุลการชำระเงิน (Balance of Payments) จากหนี้สินอีกครั้ง และในเดือนพฤศจิกายน 2022 รัฐบาลก็ตกลงที่จะกู้เงินปรับโครงสร้างครั้งที่ 11 จาก IMF โดยมีการอัดฉีดเงินช่วยเหลือมูลค่า 4,500 ล้านดอลลาร์สหรัฐเข้ามาในระบบ โดยแลกกับการถูกแทรกแซงในการปรับโครงสร้างที่เพิ่มขึ้นไปอีก
ธนาคารโลกและ IMF นั้นก็ต่างอ้างว่าพวกเขาต้องการช่วยเหลือประเทศที่ยากจน แต่ตลอด 50 ปีที่ผ่านมา ผลลัพธ์จากนโยบายของพวกเขาก็ได้แสดงให้เห็นอย่างชัดเจนว่า ประเทศอย่างบังกลาเทศกลับกลายเป็นประเทศที่ต้องพึ่งพาผู้อื่นมากขึ้น และเต็มไปด้วยหนี้สินอย่างที่ไม่เคยเป็นมาก่อน

ในระหว่างวิกฤตหนี้ของประเทศโลกที่สามในช่วงทศวรรษ 1990 การวิพากษ์วิจารณ์จากสาธารณชนทั่วโลกที่ต้องการจะตรวจสอบข้อเท็จจริงของธนาคารโลกและ IMF ได้ค่อย ๆ สะสมจนปะทุขึ้น เริ่มมีการศึกษาวิจัยเพื่อสืบค้นข้อมูลอย่างจริงจัง ผู้คนออกมาประท้วงตามท้องถนน และมีความเชื่อที่แพร่กระจายไปยังทุกฝั่งการเมือง (แม้กระทั้งในรัฐสภาของสหรัฐฯ เอง) ว่าองค์กรเหล่านี้ไร้ซึ่งประโยชน์ หรือกระทั่งเป็นพิษภัยด้วยซ้ำ แต่ความรู้สึกและความสนใจในองค์กรเหล่านี้ได้จางหายไปเกือบหมดแล้ว และถึงแม้ความรู้สึกและความสนใจเหล่านี้จะกลับมาอีกครั้ง มันกลับถูกมองว่าเป็นสิ่งที่ไม่สำคัญ หรือแม้จะมีการยอมรับว่าองค์กรพวกนี้มีปัญหาแต่ก็ยังมีความจำเป็นอยู่ หรือกระทั่งยังมีความเชื่อว่าองค์กรพวกนี้มีประโยชน์และยังได้รับการต้อนรับเหมือนเดิม
ความเป็นจริงแล้วองค์กรเหล่านี้ทำให้ผู้คนนับล้านยากจนลงและชีวิตเสี่ยงอันตรายมากกว่าในอดีต ในขณะเดียวกันกลับทำให้เหล่าผู้นำเผด็จการและเครือข่ายที่ยักยอกความมั่งคั่งของประเทศนั้นร่ำรวยขึ้น และยอมละทิ้งสิทธิมนุษยชนเพื่อทำให้อาหาร ทรัพยากรธรรมชาติ และแรงงานราคาถูกไหลออกจากประเทศที่ยากจนไปสู่ประเทศที่ร่ำรวย พฤติกรรมของพวกเขาที่กระทำในบังกลาเทศนั้นไม่ใช่เรื่องผิดพลาดหรือเป็นกรณียกเว้นแต่อย่างใด
แต่นั่นเป็นวิธีการดำเนินธุรกิจตามปกติของพวกเขา..
⚡️กด Zap บทความนี้เป็นกำลังใจทีมงาน
(ทุกยอด zap จะถูกแบ่งอัตโนมัติเข้าวอลเล็ทของผู้เขียนบทความต้นฉบับภาษาอังกฤษ, ผู้แปลดราฟต์ 1, ผู้เรียบเรียงดราฟต์ 2-3, กองบรรณาธิการและพิสูจน์อักษรจากไรท์ชิฟต์ พร้อมกันบางส่วนไว้เพื่อเป็นค่าธรรมเนียมธุรกรรม)
>แปลและเรียบเรียงจากบทความต้นฉบับเรื่อง : STRUCTURAL ADJUSTMENT: HOW THE IMF AND WORLD BANK REPRESS POOR COUNTRIES AND FUNNEL THEIR RESOURCES TO RICH ONES ซึ่งเผยแพร่ครั้งแรกเมื่อวันที่ 22 พ.ย. ปี ค.ศ. 2022
-
 @ 04ed2b8f:75be6756
2025-01-06 03:05:52
@ 04ed2b8f:75be6756
2025-01-06 03:05:52Tired? So what? Do you think success waits for you to feel rested? Achievements don’t care about your comfort, and neither should you. The truth is brutal: either you keep going, or you get left behind. Sitting around waiting for the “perfect moment” is a luxury for those who don’t want it bad enough.
Why Excuses Don’t Cut It
Feeling tired doesn’t make you special—it’s a universal experience. Everyone feels drained, but only the determined push through. The difference between winners and everyone else? Winners get it done, regardless of how they feel.
- Fatigue Is Temporary: That exhaustion you feel? It will pass. But quitting creates a habit that sticks.
- Action Over Emotion: Don’t let how you feel dictate what you do. Feelings are fleeting; the work is what matters.
- Nobody Cares About Excuses: Harsh truth—no one’s handing out awards for “almost tried.” Results are what count.Strength Is Built in the Struggle
Every time you push through fatigue, you become stronger. You’re not just building your dreams—you’re building your resilience.
- Growth Comes From Resistance: Muscles grow under tension. The same applies to your mind and willpower.
- Tired? Good. It means you’re working. It means you’re on the edge of improvement. Keep going.
- Prove It to Yourself: This is your chance to show yourself what you’re made of. Are you going to quit, or are you going to fight?What’s the Alternative?
Let’s be real. The alternative to pushing through is stagnation. If you quit now, where does that leave you?
- Wasted Time: All the effort you’ve already put in—gone. Do you want to start over later, or finish now?
- Living With Regret: The pain of pushing through is nothing compared to the pain of looking back and wishing you’d tried harder.How to Push Through the Exhaustion
It’s not easy, but nothing worth having ever is. When you’re tired, here’s how to keep moving:
- Simplify the Task: Stop overthinking. Break it into smaller, manageable steps. Focus on the next move.
- Use the Pain as Fuel: Let the fact that you’re tired ignite your determination. Think of it as a test you refuse to fail.
- Visualize the Finish Line: Picture what success looks and feels like. Let that vision pull you forward.You’ve Got More in You
Being tired is a signal, but it’s not a stop sign. You have more in you than you realize, but you’ll never know unless you push past the point of comfort. Remember, the best don’t quit when they’re tired—they keep going until the job is done.
Final Challenge
So, what’s it going to be? Are you going to fold under the weight of your own excuses, or are you going to rise and fight? Being tired isn’t an excuse—it’s proof that you’re in the arena, doing the work. Now finish what you started.
Because tired or not, the goal doesn’t care. And neither should you.
-
 @ 662f9bff:8960f6b2
2025-01-06 03:05:13
@ 662f9bff:8960f6b2
2025-01-06 03:05:13Reading this week
- Blocksize War - Bitcoin’s blocksize war was waged from August 2015 to November 2017. On the surface, the battle was about the amount of data allowed in each bitcoin block, however it exposed much deeper issues, such as who controls bitcoin’s protocol rules. It is not possible to cover every twist and turn in the labyrinthine conflict or all the arguments, but this is a chronology of the most significant events. Quite a bit of it happened in HK with those famous overnight meetings in Cyberport. \ \ I remember being immensely frustrated and confused at the time about what was happening - having read the book it does indeed seem that even many of the participants did not understand what was happening or what would happen next depending on whch course was picked - CRAZY STUFF!!
- Harry Potter and the Order of the Phoenix - Book 5 in the series. Dark times have come to Hogwarts. After the Dementors' attack on his cousin Dudley, Harry Potter knows that Voldemort will stop at nothing to find him. There are many who deny the Dark Lord's return, but Harry is not alone: a secret order gathers at Grimmauld Place to fight against the dark forces. Harry must allow Professor Snape to teach him how to protect himself from Voldemort's savage assaults on his mind. But they are growing stronger by the day and Harry is running out of time....
- I am re-reading (listening on audible.com) Mythos - narrated by Stephen Fry. Stephen is fantastic - he brings life to Greek Mythology and you have got to wonder where all these stories really come from. So many interesting insights and possibilities. Absolutely recommended.
- Also re-reading Sovereign Individual - it is truely remarkable that James Davidson and William Rees-Mogg (father of the current one!) wrote this back in 1997 - they did predict mobile phones, personal computers, cryptocurrencies and even pandemic, governmental overreach and restrictions including capital controls and preventing international travel.
Youtube links
- Required watching: Jeff Booth, interviewed by James. The Price of Tomorrow! A must hear interview on the key to our future. You do need to open your eyes and stop taking the Soma. His book is here - recommended reading. Indeed people focus on the symtoms and avoid (even disallow) discussion on the root cause. As Raoul explained the current situation has been nore than 100 years in the making.
- Great interview by Peter McCormack with Brandon on Fourth Turning - a great explanation and super interesting discussion and insights.
- Guy explains how badly behaved Danske Bank was. Those in Northern Ireland will recognise that name as being the new owner of Northern Bank that was renowned for the largest ever Bank Raid!
- If you ever wondered how the Millennial Generation is different from the Baby Boomers, just watch: Ellio explains the recent crypto crash this weekend past. This is not a one-off - he posts every single day and he is running a company with more than a hundred developers working on his projects.
- Do check out Academy of ideas
 vx
vxThat's it!
No one can be told what The Matrix is. \ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.\ You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
 @ 662f9bff:8960f6b2
2025-01-06 02:57:41
@ 662f9bff:8960f6b2
2025-01-06 02:57:41Loosely inspired by Alistair Cooke's Letter from America, this is where it all begins.
In the weeks and months ahead my intention is to gather my thoughts and share things that I find interesting and maybe good to know. I will be pulling from many sources and I plan to experiment with various media to see what works best.
Feel free to check back from time to time to see what has been added. You can also subscribe to get notified when I post updates. Feel free also to reach out to me and suggest topics that you would like to me to cover or enlarge upon.
For starters - a few interesting things happened or occurred to me this past week:
Raoul Paul (former Goldman Sachs Hedge fund manager) did a great explainer on how the world got into the current state; spoiler: it took over 100 years to get like this and there were many pivotal moments including WW1, WW2, Bretton Woods, 1971 Nixon Shock, Vietnam (and perpetual) war and now this! - Raoul's sequel to the exponential age and here with James of IA. You can also catch the full, uninterrupted version in his own words here on Realvision
Saifedean Ammous has gleaned and published similar insights in The Fiat Standard - a superb follow-on to his earlier book, The Bitcoin Standard. The contrast could not be more obvious - and his podcast explainer here
For those who prefer historical references, check The Creature From Jekyll Island - a long read but each chapter starts with a summary so you can read all the summaries and dive deeper where you dare.
Crazy but true, all of this was foreseen in The Sovereign Individual, written back in 1997. You will be amazed that they foresaw mobile phones, personal computers, cryptocurrencies and even pandemic, governmental overreach and restrictions including capital controls and preventing international travel.
Not to mention The Fourth Turning which reveals clearly the cycles that the world goes through. This too clearly foresaw the current situation and indicates how things might well develop.
Michael Saylor, CEO of MicroStrategy, is unstoppable. He, like Raoul, seems to be one one of the articulate leaders foreseen in The Sovereign Individual. Do listen to his interview with Peter McCormack and one with John Vallis, not to mention that amazing interview on Fox News!
A couple of classics worth mentioning - Animal Farm where all are equal but some are more equal than others and where history and constitution get rewritten when it suits. An then of course there is Brave New World where, among other things, the masses are kept subdued with soma.
Lastly for today, you have got to wonder if Satoshi Nakamoto a time traveller - read his whitepaper here. They say there is no smoke without fire and there is certainly plenty of smoke at the moment - not least from Joe Wiesenthal, Editor and Host at Bloomberg - here. Recent days also marked a turning point where narrative shifts from "inflation is transient" to "inflation is good for you" (echoes of Animal Farm...).
Enough for now. You may well want to disconnect from the Matrix and be more selective in your information sources - also it's good to have your priorities right and live life to the maximum.
Do reach out to me with your thoughts and suggestions - I'll be sharing mine.
Roger
That's it!
No one can be told what The Matrix is. \ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.\ You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
 @ a012dc82:6458a70d
2025-01-06 01:15:32
@ a012dc82:6458a70d
2025-01-06 01:15:32Table Of Content
-
The Anticipation of Bitcoin Halving
-
Progress Status: 85% Complete
-
Long-Term Holders and Their Influence
-
Analyzing the Supply Trends
-
What History Tells Us
-
Conclusion
-
FAQ
In the dynamic world of cryptocurrency, certain events stand out as pivotal moments that can shape the trajectory of the market. One such event is the Bitcoin halving, a process that reduces the rewards for mining Bitcoin by half, effectively slowing down the rate at which new Bitcoins are created. As we approach the next halving, scheduled for mid-2024, there's a palpable sense of anticipation among investors and market watchers. This article delves into the current status of the halving process and examines the role of long-term holders in influencing market trends.
The Anticipation of Bitcoin Halving
The cryptocurrency market is on the brink of a significant phase. With the next Bitcoin halving anticipated in mid-2024, the event is garnering immense attention from investors. Historical patterns suggest that a full-fledged bull market might not commence until the following year.
Progress Status: 85% Complete
Recent data reveals that the Bitcoin halving process is 85% complete. Concurrently, the supply of Bitcoin held by long-term holders (LTHs) is nearing its all-time high (ATH). In past cycles, such a scenario indicated the proximity of a macro bottom, which was then succeeded by the onset of a new cycle.
Long-Term Holders and Their Influence
The amount of Bitcoin supply in the possession of long-term holders has traditionally served as a reliable gauge for the cryptocurrency market's health. This metric has shown an inverse correlation with Bitcoin's long-term price trajectory.
During market lows, long-term hodlers tend to keep their assets stationary. The most significant surge in LTH possession typically transpires during intense bear markets. This is when steadfast investors, despite witnessing Bitcoin's price plummet, choose not to sell. Their conviction lies in the belief that the market will eventually recover, making their investments profitable.
Conversely, during a bull market's unraveling, the spike in Bitcoin's price prompts LTHs to become increasingly inclined to sell their assets for profit. Historically, every major bull market has seen a sharp decline in the supply held by LTHs. This leads to the coins transitioning to short-term holders (STHs), who are motivated by quick profit prospects.
Analyzing the Supply Trends
A cryptocurrency analyst showcased a chart depicting the Bitcoin supply in the hands of long-term holders. The chart reveals that the current BTC supply ratio held by LTHs is nearing its ATH of 76%, a benchmark set in late 2015 before the second halving.
Historically, this indicator peaked several months before each Bitcoin halving. Following this peak, the supply held by LTHs would typically plateau until several months post the subsequent halving. A significant drop in this metric was observed roughly six months after the event, marking the advent of a mature bull market.
What History Tells Us
If past patterns hold true, the cryptocurrency market might experience a sideways trend for approximately a year. The upcoming Bitcoin halving in mid-April 2024 might not have an immediate influence on Bitcoin's price. Its repercussions might only manifest in the last quarter of 2024 and continue into 2025.
This forecast aligns with the trends observed in the supply chart of long-term holders. The indicator is on the verge of reaching its ATH and might require around 12 months to reverse its trajectory, transitioning into a distribution phase. The commencement of LTHs selling post the Bitcoin halving could be one of the early indicators of a budding cryptocurrency bull run.
Conclusion
The Bitcoin halving is more than just a technical event; it's a significant milestone that has historically influenced market dynamics and investor behavior. As we inch closer to the next halving, the role of long-term holders becomes increasingly crucial. Their actions, whether holding steadfastly or choosing to sell, can set the tone for the market's direction in the subsequent months. While history offers insights, the ever-evolving nature of the cryptocurrency landscape means that nothing is set in stone. Investors and enthusiasts alike should remain vigilant, informed, and prepared for the myriad possibilities the future holds.
FAQ
When is the next Bitcoin halving expected? The next Bitcoin halving is anticipated to occur in mid-2024.
How does the halving impact long-term holders? Historically, as the halving approaches, the supply of Bitcoin held by long-term holders (LTHs) nears its all-time high, influencing market trends and price trajectories.
What does the current data suggest about the halving process? Current data indicates that the Bitcoin halving process is 85% complete, with the supply held by LTHs nearing its all-time high.
How has Bitcoin halving influenced market dynamics in the past? In previous cycles, the approach of a halving event signaled the proximity of a macro bottom, followed by the early phase of a new market cycle.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ d830ee7b:4e61cd62
2023-08-31 04:44:06
@ d830ee7b:4e61cd62
2023-08-31 04:44:06ผมเจอหลายคนเริ่มต้นกับ Nostr มานาน แต่กลับยังไม่สามารถ “อิน” กับการอยู่ในสังคมแห่งใหม่นี้ได้เท่าไหร่นัก บางคนยังมีเพื่อนใหม่เพียงหลักสิบคน และหลายคนยังแทบไม่รู้จักหรือกดตามใครเลย บางคนมีคนติดตามเพียง 3-5 คน เท่านั้น แล้วมันจะไปมีคนเห็นสิ่งที่เราสื่อสารออกไปได้มากพอได้อย่างไรล่ะคับ?
ก็คนที่ไม่ได้ติดตามเราเค้าก็จะมองไม่เห็นสิ่งที่เราโน๊ตไปนั่นเอง
นี่แหละครับ Nostr
ผมไม่ชอบใช้คำว่า “เล่น Nostr” เท่าไหร่นัก สำหรับผมแล้ว.. Nostr คือ สถานที่ใหม่ สังคมใหม่ที่ทุกคนต้องเริ่มนับใหม่จากศูนย์ ผมขอใช้คำว่ามันเป็นการ “ใช้ชีวิตบน Nostr” ก็แล้วกัน เชื่อไหมครับว่าในแต่ละวัน ผมยังรู้สึกว่าตัวเองมีเวลาไม่มากพอจะใช้ชีวิตบน Nostr ให้สมใจอยากได้เลย.. ในขณะที่บางคนกลับรู้สึกว่า 5 นาทีมันก็นานเกินไปแล้ว..
เราลองมาพิจารณากันดูไหมว่าเพราะอะไร?
มันไม่ค่อยมีอะไรให้อ่าน ไม่ค่อยมีเรื่องให้ทำ
สำหรับข้อโต้แย้งนี้ผมคงต้องบอกว่ามัน “ผิดถนัด” เลยล่ะ.. บน Nostr นี่มีอะไรให้เราทำมากกว่าบนทุกแพลตฟอร์มเก่าๆ มาขยำรวมกันเสียอีกนะ
ผมคิดว่า.. ผมคงต้องเริ่มเล่าเรื่องในจินตนการให้พวกเราเห็นภาพนี้ได้ง่ายขึ้น ผมขอพาพวกเรากลับไปสู่จุดเริ่มต้นของการก่อร่างสร้างสังคม
อันดับแรก ผมอยากให้พวกเราลืม “สังคมแบบเดิม” ไปเสียก่อน ทั้งในชีวิตจริง หรือในโลกออนไลน์ที่เราเคยประสบพบเจอมา ที่ Nostr นี่มันต่างออกไปอย่างสิ้นเชิงครับ
จินตการว่าเราได้ลงจากเรือโนอาห์ที่เกาะขนาดใหญ่แห่งหนึ่ง กองเรือจัดตั้งอาณานิคมใหม่หลายลำที่พาผู้คนหลักแสนมาปล่อยไว้ ณ สถานที่เดียวกัน เกาะอันเวิ้งว้างว่างเปล่าที่อุดมไปด้วยทรัพยากรธรรมชาติ เต็มไปด้วยสิ่งเร้นลับและแปลกใหม่ ที่รอให้เหล่านักสำรวจได้ออกไปทำการค้นพบ
Nostr ก็คือสถานที่แบบเดียวกันนั้น..
เราต่างคนต่างมา ณ ที่แห่งนี้ เรามีสถานะภาพเท่าเทียมกันทุกประการ ทุกคนเริ่มนับหนึ่งใหม่ที่นี่ เริ่มทำความรู้จักกัน รวมกลุ่มกัน สร้างสังคมขนาดย่อมจนผ่านเวลาไปถึงขนาดกลางและกลายเป็นใหญ่ได้ในที่สุด
สิ่งนี้จะเกิดขึ้นไม่ได้เลย ถ้าผู้คนเหล่านี้ไม่พยายาม “Engage” เข้าหากัน ไม่มีปฏิสัมพันธ์ต่อกัน ไม่ยอมแลกเปลี่ยนหรือทำกิจกรรมบางอย่างร่วมกัน นี่คือกลไกการสร้างสังคมโดยธรรมชาติที่จะไม่มีใครมีคอยชี้นำ บังคับ หรือออกกฏเกณฑ์ชี้นิ้วสั่งใครให้ต้องทำอะไรทั้งนั้น.. มันคือสังคมแห่งเสรีชนโดยแท้จริง ทุกคนจะประพฤติอย่างเสรีภายใต้ทัศนวิสัยของปัจเจกชน
โฆษณาชวนเชื่อ หรือการทำเท่ห์ด้วยคอนเท้นต์โก้หรู ศิลปะในการหลอกล่ออัลกอริทึมเหมือนที่เคยทำๆ กันมา มันใช้ไม่ได้กับที่แห่งนี้
ที่นี่พวกเราให้ค่ากับ “คุณค่า” ที่เราจะได้รับมันมาจริงๆ และคุณค่าของแต่ละคนก็ไม่มีวันเหมือนกันเสียด้วย นี่คือความท้าทายที่พวกเราต้องเริ่มออกไปค้นหา ‘คุณค่า’ ที่ว่านั้น ด้วยตัวเองหรือจะทำกันเป็นหมู่คณะก็ย่อมให้ผลดีกว่าอย่างแน่นอนครับ
ไม่มีใครต้องการ “ฮีโร่” ที่นี่ ทุกคนแค่ต้องการ “เพื่อน” เพื่อนที่จะคอย 'ให้' เราก่อนและ 'ขอ' เราทีหลัง
ผมร่ายมายาวก็เพียงแค่ต้องการจะบอกว่า..
ที่เราไม่เห็นคอนเทนต์อะไรน่าสนใจเลย อาจเป็นเพราะเรายังทำความรู้จักกับ “คนที่น่าสนใจ” ยังไม่มากพอก็เป็นได้
แล้วมันเพราะอะไรได้อีกบ้าง?

เรายังกดติดตามคนอื่นน้อยเกินไป
ทำให้เราไม่เจอโน๊ตหรือคอนเทนต์ที่ดึงดูดใจเราได้มากพอ เราก็จะเห็นแต่โน๊ตของคนที่เราติดตามไว้อย่างน้อยนิดนั่นแหละครับ เว้นแต่เราจะไปกดดูแบบ Global ที่จะเห็นผู้คนทั้งเกาะเป็นหมื่นๆ แสนๆ ต่างคนต่างคนโน๊ตกันรัวๆ ซึ่งมันคงเต็มไปด้วยสิ่งที่เราไม่ได้ให้ความสนใจหรือคัดสรรมา
เรามีคนติดตามเราน้อยเกินไป
ทำให้เหงาและเงียบกริบทุกรอบที่เราโน๊ต มันก็แน่อยู่แล้ว ถ้าทั้งเกาะมีคนที่รู้จักเราอยู่แค่ 2-3 คน มันก็คงมีคนแค่จำนวนนี้แหละครับที่จะได้ยินสิ่งที่เราพูด ได้เห็นสิ่งที่เราทำ เราแค่ต้องออกไปทำความรู้จักหรือมีปฏิสัมพันธ์กับคนอื่นๆ ให้มากกว่านี้ มันไม่เหมือนกันนะครับ ระหว่างการโพสต์สิ่งที่อยากพูดออกไป เน้นเอาเท่ เอาเจ๋ง ไว้ก่อน กับการเดินไปหาคนอื่นเพื่อแลกเปลี่ยนความคิดและสร้างมิตรภาพกับเขาอย่างจริงใจ ผมคิดว่ามันให้ผลลัพธ์ไม่เหมือนกันบน Nostr
เรายังไม่เจอ Hashtag หรือกลุ่มสนทนาที่ตรงกับจริต
ทำให้เราไม่รู้สึกอินกับอะไรที่นี่เลย คนชอบฟุตบอลก็ชอบเสวนากับคนดูบอลฉันใด บิตคอยเนอร์ก็อยากจะคุยถูกคอกับบิตคอยเนอร์ฉันนั้น คนรักแมวก็มองหาคนรักแมว ฯลฯ ที่นี่มันพาเราย้อนกลับไปที่ยังยุคแรกๆ ของสังคมโซเชียลมีเดีย ที่คนจะเชื่อมโยงหากันโดยใช้ “Hashtag” ที่ต่างก็สนใจร่วมกัน มันเหมือนการชูป้ายไฟโลกให้รู้ว่า “ฉันรักแมว” (#Catstr) เพื่อดึงดูดคนประเภทเดียวกัน นั่นแหละครับ เราแค่ต้องหาป้ายไฟที่ว่านั่นให้เจอ
เราไม่เห็นได้ “Earn Zap” อย่างที่หลายคนป้ายยาเราไว้เลย
ก็ถ้าวันนี้เราเองยังไม่ค่อยอยาก Zap ให้ใครเท่าไหร่ แน่นอนว่ามันก็จะไม่มีใครอยาก Zap ให้เราด้วยเช่นกัน ป๋ามา-ป๋ากลับ คนที่นี่เป็นกันแบบนั้น มันประหลาดดี ทำลายความเชื่อแบบเดิมๆ ของเราไปเลยทีเดียว
จริงๆ แล้วมันไม่มีใครอยากได้ Sats เพิ่มบน Nostr เพราะมันไม่ง่ายขนาดนั้น พวกเขาก็แค่อยากหาเรื่อง Zap ให้คนอื่นๆ พวกเขาแสวงหาโน๊ต ข้อความ หรือคอนเทนต์ แม้กระทั่งมีมที่โดนใจ ไม่มีใครมาคอยนั่งคิดคำนวนว่า "วันนี้ฉัน Earn ไปเท่าไหร่” (คอนเซ็ปต์แบบนี้มัน Fiat สิ้นดี) สังคมบน Nostr นั้นเน้นการให้และการมีส่วนร่วม ช่วยเหลือกัน เมื่อคุณให้มา เราจะให้กลับ มันแฟร์ๆ แมนๆ ครับ
ในสังคมที่ไม่มีใครคอยมาทำหน้าที่กำกับดูแลพฤติกรรมหรือการกระทำของเรา ความสัมพันธ์จะเกิดขึ้นอย่างเป็นธรรมชาติสุดๆ เป็นเรื่องของปัจเจกชนที่จะเลือกว่าพวกเขาจะให้คุณค่ากับอะไร ดังนั้น.. เราจึงแทบไม่มีทางรู้ได้เลยว่าใครจะชอบ หรือคิดอะไรยังไง นอกเสียจากว่า.. เราจะใช้เวลาไปกับการทำความรู้จักความคิดและจิตใจของพวกเขา ออกไปพูดคุยแลกเปลี่ยนกับพวกเขาเพื่อให้เราเข้าใจคนอื่นได้มากขึ้นนั่นเอง
เมื่อคุณเข้าใจผู้อื่น มันก็ไม่ยากที่คุณจะรู้ว่า “คุณค่า” ที่พวกเขาตามหานั้นคืออะไร?

บก. จิงโจ้ ผู้มีปฎิสัมพันธ์และคอย Make friend กับคนไปทั่ว นั่นทำให้เขามีคนติดตาม และติดตามคนอื่นจำนวนมากทีเดียว เขาทำไปเพื่อ Sats หรือเปล่า? ผมคิดว่าไม่นะ.. Just make friend
เราไม่รู้ว่ามันใช้งานยังไง ทำอะไรได้บ้าง เลยไม่รู้จะไปต่อยังไง
ประเด็นนี้ก็ต้องย้อนกลับไปที่หัวข้อต่างๆ ด้านบน ก็ในเมื่อเรายังไม่เคยเจอคนที่จะคอยตอบคำถาม หรือสอนการใช้งานเราให้กับเราได้ หรือจริงๆ แล้วเราก็อาจแค่ถูกสอนให้ “รอรับ” มากกว่าที่จะ “ค้นหา” จนเคยตัว เราเลยไม่ชินกับการต้องออกไปไขว่คว้ามันด้วยตัวเอง?
ไม่ว่าอย่างไร.. เรามาเริ่มกันใหม่ที่นี่ เชื่อไหมครับว่าหลายคนบน Nostr นั้นเป็นระดับพระกาฬแทบทั้งสิ้น แถมพวกเขายังเต็มใจที่จะให้ความช่วยเหลือหรือคอยตอบคำถามให้กับพวกเราด้วย เราต้องหาเค้าให้เจอและเปลี่ยนตัวเองให้เป็นคนที่จะ “กล้า” ถาม กล้าแสดงออก และกล้าที่จะยอมรับว่าเราไม่รู้ ก่อนที่จะเราจะกลายเป็นผู้เชี่ยวชาญได้ในภายหลัง
นี่เป็นโอกาสที่เราจะได้ใกล้ชิดกับคนที่เราอยากคุยด้วยมานานแล้ว คนที่เราเคยชื่นชม หรือคนที่เราเคยเห็นบนโลกเฟียตๆ แต่ไม่เคยหาเหลี่ยมได้สักทีว่าจะเข้าหาหรือเข้าถึงพวกเขาได้ยังไง

แค่เริ่มทำความรู้จัก โลกก็เปลี่ยน
เอาล่ะ.. ผมจะลองแนะนำวิธีว่าเราจะเพิ่มผู้ติดตามหรือเลือกเฟ้นยังไงในการติดตามผู้อื่น ผมมีแนวทางของผมเอง คงไม่ใช่สูตรสำเร็จ แต่ถ้าเพื่อนๆ จะลองนำไปประยุกต์ก็ไม่ว่ากันครับ
ตามคนดัง
วิธีที่ง่าย และตรงไปตรงมาที่สุด ซึ่งมันก็ถูกแล้ว เพราะคนเหล่านี้การที่เค้าจะดังได้ต่างก็มี proof-of-work และความน่าสนใจในแบบของตัวเองด้วยกันทั้งนั้น แอคเคาต์แรกๆ ที่พวกเราคงนึกถึงก็คงเป็น อ.ตั๊ม พิริยะ และ Right Shift ทั้งแอคเคาต์ทางการ และทีมงานทั้งทีม ก็แหง๋ล่ะ เพราะพวกเขาป้ายยาพาคุณมาอยู่บน Nostr แต่อย่าตามแค่พวกเขาไม่กี่คนเท่านั้นนะครับ คุณควรจะ...
ตามคนอื่นๆ เลียนแบบคนดัง
เราสามารถกดดูได้ว่าใครกดติดตามใครเอาไว้บ้าง คนดังก็มักจะตามกลุ่มคนที่น่าสนใจแหละส่วนหนึ่ง ส่วนที่เหลือเขาก็คงตามคนที่ถูกจริตกับตัวเอง นอกจากนี่คนที่กดติดตามพวกเขาก็จะเป็นคนที่ชอบอะไรคล้ายๆ กับเขา มันก็เป็นไปตามกฎแห่งแรงดึงดูดทางด้านความสัมพันธ์ เราค่อยๆ กดไปดูโปรไฟล์ของแต่ละคนได้ว่าเขามีความน่าสนใจยังไง ชอบโน๊ตหรือการสื่อสารแบบไหน เขามีวิธีคิดหรือนิสัยใจคอ มีเคมีแบบเดียวกันกับเราหรือเปล่า?
ถ้าใช่.. คุณก็แค่กดปุ่ม Follow แล้วกระโจนเข้าไปตอบโต้กับเขาได้เลย ไม่ว่าจะในโน๊ตใหม่ หรือ โน๊ตเก่าๆ คอมเม้นให้มันได้เพื่อนนะครับ อย่าไปเม้นให้ได้ศัตรู

เราจะเห็นแอคฯ น่าสนใจให้เพียบ แค่ลองกดไปดูว่าคนดังๆ เขามีวงสังคมบน Nostr เป็นใครกันบ้าง แล้วตอบตัวเองว่าเราอยากพาตัวเองเข้าไปอยู่ในนั้นบ้างไหม?
ตาม Hashtag
ตามหา “ป้ายไฟ” สีที่เราชอบ หรือก็คือกด ‘#’ นำในช่องค้นหา ตามด้วยคำที่เราสนใจ แล้วลองไล่หาดูได้เลย คุณอาจเจอเข้ากับกระทู้ที่ตรงกับสิ่งที่ตามหา เรื่องที่อยากอ่าน หรือมุมมองที่อยากเห็น รวมไปถึงคนที่.. เอ้อ มันเจ๋งดีว่ะ อะไรแบบนี้ได้ง่ายๆ เลยล่ะ
เมื่อเราชอบแฮ็ชแท็กไหน เรายังสามารถกดติดตามตัวแฮชแท็กนั้นได้อีกด้วย และอย่าลืมกดติดตาม หรือติดแฮ็ชแท็ก #ThaiNostrich กับ #Siamstr เอาไว้ด้วยนะครับ มันคือป้ายไฟสามัญประจำบ้านของคนไทยบน Nostr คุณสามารถตามหาเพื่อนคนไทยได้ง่ายๆ ด้วยแฮชแท็ก 2 ตัวนี้นี่แหละ

Swarmstr เป็นตัวอย่างไคลเอนต์ที่จะรวบรวมข้อมูลบน Nostr ที่เราสามารถค้นหา หรือศึกษา Nostr ได้จากหัวข้อต่างๆ ตามแฮชแท็คที่แสดงเป็นตัวอย่างได้ (หรือค้นหาด้วยตัวเอง)
ตามประเด็นที่สนใจไปจนเจอตัวพ่อ
มันต้องมีบางโอกาสที่เราไปเจอเข้ากับกระทู้น่าสนใจ มีการสนทนากันอย่างเผ็ดร้อนหรือรื่นเริงจนคุณก็อดเข้าไปแจมด้วยไม่ได้ ที่แบบนี้แหละที่คุณจะเจอกับคนเก่งๆ ในด้านนั้นๆ หรือผู้เชี่ยวชาญเฉพาะด้าน หรือกระทั่งเป็นผู้ก่อตั้ง หรือนักพัฒนาไคลเอนต์เลยทีเดียว และคนเหล่านี้เขาก็มาที่เกาะแห่งนี้ด้วยจุดประสงค์คล้ายๆ เรา คือ "หนีความวุ่นวายและโสมมบนโลกเก่าเพื่อแสวงหาเสรีภาพและมิตรภาพ ณ สังคมใหม่"
ดังนั้น เขาเต็มใจที่จะได้ทำความรู้จักกับเราอย่างแน่นอนครับ
แต่คนนิสัยไม่ดี หรือมีพฤติกรรมไม่เป็นมิตรเราก็จะดูออกได้ในทันที และมันก็เป็นสิทธิ์ของเราล้านเปอร์เซ็นต์ที่จะเลือกว่า จะสนใจติดตามคนๆ นี้ หรือแค่ปล่อยผ่าน หรือไม่ก็ บล็อกแม่ง ให้มันจบๆ ไป

Nostrends เป็นตัวอย่างไคลเอ็นต์ที่คอยรวบรวมและแสดงโน๊ต หรือหัวข้อที่กำลังได้รับความนิยมบน Nostr ตามช่วงเวลาหรือตัวกรองที่เราเลือก
พยายามอย่าทำพฤติกรรมแบบเดิมๆ บน Nostr
ผมเชื่อว่ามีพวกเราส่วนใหญ่ (ชาวไทย) จะคุ้นเคยกับการใช้งานและวัฒนธรรมบน Facebook แต่ชาวต่างชาติหรือผู้ใช้งานส่วนใหญ่ที่นี่จะเคยชินกับวัฒนธรรมแบบ Twitter กันมากกว่านะครับ ไม่ว่าจะเป็นการโพสต์ การคอมเมนต์ หรือการกดตอบโต้ด้วยอีโมจิ (Discord cult) ก็ถือว่าเป็นวัฒนธรรมในแบบที่เราอาจยังไม่คุ้นเคยกันมากนักและคงต้องใช้เวลาเรียนรู้กันพอสมควร
ขอให้พวกเราทิ้งวิธีคิดแบบเดิมๆ ในการใช้งานโซเชียลมีเดียไปได้เลยครับ เราควรอยู่บน Nostr โดยใช้แนวคิดแบบเดียวกับการอยู่ในสังคมจริงๆ ทักทาย ตอบโต้ เห็นอกเห็นใจ ช่วยเหลือ แลกเปลี่ยน คอนทริบิ้วท์และมีส่วนร่วมให้มากกว่าที่เคย ฯลฯ เราจึงจะมีตัวตนและรู้สึกเหมือนเป็นส่วนหนึ่งในสังคมแห่งนี้ได้จริงๆ (ไม่งั้นเราก็เป็นได้เพียง "ผู้สังเกตการณ์เหงาๆ" เท่านั้นเอง)
ที่นี่.. ไม่ให้คุณค่ากับ การอวดรู้ หรือ โชว์พาว ทุกคนดูออกได้ง่ายๆ ว่าเจตนาของแต่ละคนคืออะไร คนเหล่านี้ล้วนเคยขยะแขยง Fiat Social Media Cult มาแทบทั้งนั้น ถ้าต้องมาเจออะไรแบบนี้บน Nostr ก็จะ ยี้ ได้ทันที และทุกคนก็พร้อม และ มีสิทธิ์ที่จะบล็อกเราได้ตลอดเวลา
เราจะกดติดตามคนนั้น-คนนี้ให้มากมายไปทำไมกัน ถ้าเราจะแค่ไถๆๆ ฟีดวืดๆๆ ไปวันๆ เราจะไม่ได้เพื่อนเลยสักคนกับการทำแบบนั้น และอาจพลาดโอกาสดีๆ ที่จะได้เรียนรู้อะไรบางอย่าง
เราไม่ควรทำแค่อ่านผ่านๆ เหมือนกับตอนที่เราเบื่อโลกเมื่อต้องใช้ Facebook และเห็นแต่อะไรที่ไม่ต้องการเห็น ที่นี่.. เราจะเลิกติดตามไปเลยก็ได้ถ้าแอคฯ นั้นเอาแต่โพสต์อะไรที่ดูไม่เข้าตา หรือไม่สามารถดึงดูดเราได้ (ถ้าเกรงใจก็กด Mute ไว้ก่อนก็ได้)
การอ่านอย่างตั้งใจในสิ่งที่เค้าโพสต์มา และตอบโต้ตามสมควร ก็เปรียบเสมือน การรับฟังผู้พูดอย่างตั้งอกตั้งใจ นั่นเอง นั่นคือหนทางเดียวที่เราจะเรียนรู้ได้ว่าเราควรตอบโต้อย่างไร เพราะเราเข้าใจ สาส์น ที่เขาได้สื่อออกมาอย่างถ่องแท้นั่นเองครับ
ถ้าไม่ว่าง คุณก็ปัดทิ้งได้ แล้วค่อยตามไปอ่านทีหลัง มันไม่มีการลบหรือปิดกั้นเรา ไม่มีโฆษณามาให้รกหูรกตา ถ้าเจอพวก แสกม/แสปม ก็บล็อกมันซะ อย่าให้พวกน่ารังเกียจได้มีที่ยืนบนสังคมที่คุณอยากให้เป็น
และขอให้ทุกคนระลึกไว้เสมอว่า การพูดคุยและมีปฎิสัมพันธ์ต่อกัน เท่านั้น ที่จะทำให้มนุษย์ได้มีความสัมพันธ์ต่อกัน
ผมขอทิ้งท้ายด้วยเคล็ดลับตกผลึกสั้นๆ ว่า..
- ติดตามผู้อื่น
- Zap ให้คนอื่นๆ
- เริ่มสร้าง Note ของตัวเอง (โพสต์) สักครั้ง หรือบ่อยครั้ง
- คุยกับคนอื่นให้มากกว่าที่เคย (มากกว่าแค่อ่านๆ ไปเรื่อยเหมือนตอนใช้ Facebook)
- ได้ Zap กลับมาจากคนอื่น
- สำรวจแฮชแท็กต่างๆ ลองใช้งานมันไปเรื่อยๆ
เหนือสิ่งอื่นใด จงใช้ชีวิตบน Nostr และแค่สนุกไปกับมันให้ได้ก็พอ.. :)
ปล. |--
-
มนุษย์มีวุ้นแปลภาษาจริงๆ แล้วนะครับ ก็ Google translate นั่นยังไง อย่าให้ภาษากลายเป็นกำแพงแห่งการเรียนรู้.. จงใช้มัน ไม่ต้องขวยเขิลกันหรอกครับ (เพราะผมเองก็ใช้)
-
บทความต่อไปผมจะมาลองแนะนำว่า มีแอคเคานต์ไหนบ้างที่น่าสนใจกดติดตามสัก 10-20 บัญชี เอาคนไทยเราก่อนเลย ไว้คอยติดตามกันนะครับ
-
 @ 6e468422:15deee93
2023-04-04 13:23:19
@ 6e468422:15deee93
2023-04-04 13:23:19Not too long ago, I tried to paint a picture of what a vision for a value-enabled web could look like. Now, only a couple of months later, all this stuff is being built. On nostr, and on lightning. Orange and purple, a match made in heaven.
It goes without saying that I'm beyond delighted. What a time to be alive!
nostr
Here's the thing that nostr got right, and it's the same thing that Bitcoin got right: information is easy to spread and hard to stifle.[^fn-stifle] Information can be copied quickly and perfectly, which is, I believe, the underlying reason for its desire to be free.
[^fn-stifle]: That's a Satoshi quote, of course: "Bitcoin's solution is to use a peer-to-peer network to check for double-spending. In a nutshell, the network works like a distributed timestamp server, stamping the first transaction to spend a coin. It takes advantage of the nature of information being easy to spread but hard to stifle."
Easy to spread, hard to stifle. That's the base reality of the nature of information. As always, the smart thing is to work with nature, not against it.[^1] That's what's beautiful about the orange coin and the purple ostrich: both manage to work with the peculiarities of information, not against them. Both realize that information can and should be copied, as it can be perfectly read and easily spread, always. Both understand that resistance to censorship comes from writing to many places, making the cost of deletion prohibitive.
Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
Eric Hughes, A Cypherpunk's Manifesto
Nostr is quickly establishing itself as a base layer for information exchange, one that is identity-native and value-enabled. It is distinctly different from systems that came before it, just like Bitcoin is distinctly different from monies that came before it.
As of today, the focus of nostr is mostly on short text notes, the so-called "type 1" events more commonly known as tweets.[^fn-kinds] However, as you should be aware by now, nostr is way more than just an alternative to twitter. It is a new paradigm. Change the note kind from
1to30023and you don't have an alternative to Twitter, but a replacement for Medium, Substack, and all the other long-form platforms. I believe that special-purpose clients that focus on certain content types will emerge over time, just like we have seen the emergence of special-purpose platforms in the Web 2.0 era. This time, however, the network effects are cumulative, not separate. A new paradigm.Let me now turn to one such special-purpose client, a nostr-based reading app.
[^fn-kinds]: Refer to the various NIPs to discover the multitude of event kinds defined by the protocol.
Reading
I'm constantly surprised that, even though most people do read a lot online, very few people seem to have a reading workflow or reading tools.
Why that is is anyone's guess, but maybe the added value of such tools is not readily apparent. You can just read the stuff right there, on the ad-ridden, dead-ugly site, right? Why should you sign up for another site, use another app, or bind yourself to another closed platform?
That's a fair point, but the success of Medium and Substack shows that there is an appetite for clean reading and writing, as well as providing avenues for authors to get paid for their writing (and a willingness of readers to support said authors, just because).
The problem is, of course, that all of these platforms are platforms, which is to say, walled gardens that imprison readers and writers alike. Worse than that: they are fiat platforms, which means that permissionless value-flows are not only absent from their DNA, they are outright impossible.[^2]
Nostr fixes this.

The beauty of nostr is that it is not a platform. It's a protocol, which means that you don't have to sign up for it---you can create an identity yourself. You don't have to ask for permission; you just do, without having to rely on the benevolence of whatever dictator is in charge of the platform right now.
Nostr is not a platform, and yet, powerful tools and services can be built and monetized on top of it. This is good for users, good for service providers, and good for the network(s) at large. Win-win-win.
So what am I talking about, exactly? How can nostr improve everyone's reading (and writing) experience?
Allow me to paint a (rough) picture of what I have in mind. Nostr already supports private and public bookmarks, so let's start from there.
Imagine a special-purpose client that scans all your bookmarks for long-form content.[^fn-urls] Everything that you marked to be read later is shown in an orderly fashion, which is to say searchable, sortable, filterable, and displayed without distractions. Voilà, you have yourself a reading app. That's, in essence, how Pocket, Readwise, and other reading apps work. But all these apps are walled gardens without much interoperability and without direct monetization.
[^fn-urls]: In the nostr world long-form content is simply markdown as defined in NIP-23, but it could also be a link to an article or PDF, which in turn could get converted into markdown and posted as an event to a special relay.
Bitcoin fixes the direct monetization part.[^fn-v4v] Nostr fixes the interoperability part.
[^fn-v4v]: ...because Bitcoin makes V4V practical. (Paywalls are not the way.)
Alright, we got ourselves a boring reading app. Great. Now, imagine that users are able to highlight passages. These highlights, just like bookmarks now, could be private or public. When shared publicly, something interesting emerges: an overlay on existing content, a lens on the written Web. In other words: swarm highlights.
Imagine a visual overlay of all public highlights, automatically shining a light on what the swarm of readers found most useful, insightful, funny, etc.
Further, imagine the possibility of sharing these highlights as a "type 1" event with one click, automatically tagging the highlighter(s)---as well as the author, of course---so that eventual sat-flows can be split and forwarded automatically.
Voilà, you have a system that allows for value to flow back to those who provide it, be it authors, editors, curators, or readers that willingly slog through the information jungle to share and highlight the best stuff (which is a form of curation, of course).
Zaps make nostr a defacto address book[^fn-pp] of payment information, which is to say lightning addresses, as of now. Thanks to nostr wallet connect (among other developments), sending sats ~~will soon be~~ is already as frictionless as leaving a like.
[^fn-pp]: The Yellow Pages are dead, long live The Purple Pages!
Value-for-value and participatory payment flows are something that traditional reading apps desperately lack, be it Pocket, Instapaper, Readwise, or the simple reading mode that is part of every browser.
A neat side-effect of a more structured way to share passages of text is that it enables semi-structured discussions around said passages---which could be another useful overlay inside special-purpose clients, providing context and further insights.[^5]
Further, imagine the option of seamlessly switching from text-on-screen to text-to-speech, allowing the user to stream sats if desired, as Podcasting 2.0 clients already do.[^3]
Imagine user-built curations of the best articles of the week, bundled neatly for your reading pleasure, incentivized by a small value split that allows the curator to participate in the flow of sats.
You get the idea.
I'm sure that the various implementation details will be hashed out, but as I see it, 90% of the stuff is already there. Maybe we'll need another NIP or two, but I don't see a reason why this can't be built---and, more importantly: I don't see a reason why it wouldn't be sustainable for everyone involved.
Most puzzle pieces are already there, and the rest of them can probably be implemented by custom event types. From the point of view of nostr, most everything is an event: bookmarks are events, highlights are events, marking something as read is an event, and sharing an excerpt or a highlight is an event. Public actions are out in the open, private actions are encrypted, the data is not in a silo, and everyone wins. Especially the users, those who are at the edge of the network and usually lose out on the value generated.
In this case, the reading case, the users are mostly "consumers" of content. What changes from the producing perspective, the perspective of the writer?
Writing
Back to the one thing that nostr got right: information is easy to spread but hard to stifle. In addition to that, digital information can be copied perfectly, which is why it shouldn't matter where stuff is published in the first place.
Allow me to repeat this point in all caps, for emphasis: IT SHOULD NOT MATTER WHERE INFORMATION IS PUBLISHED, and, maybe even more importantly, it shouldn't matter if it is published in a hundred different places at once.[^fn-torrents]
What matters is trust and accuracy, which is to say, digital signatures and reputation. To translate this to nostr speak: because every event is signed by default, as long as you trust the person behind the signature, it doesn't matter from which relay the information is fetched.
This is already true (or mostly true) on the regular web. Whether you read the internet archive version of an article or the version that is published by an online magazine, the version on the author's website, or the version read by some guy that has read more about Bitcoin than anyone else you know[^fn-guy]---it's all the same, essentially. What matters is the information itself.
[^fn-guy]: There is only one such guy, as we all know, and it's this Guy: nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev
Practically speaking, the source of truth in a hypernostrized world is---you guessed it---an event. An event signed by the author, which allows for the information to be wrapped in a tamper-proof manner, which in turn allows the information to spread far and wide---without it being hosted in one place.
The first clients that focus on long-form content already exist, and I expect more clients to pop up over time.[^4] As mentioned before, one could easily imagine prism-like value splits seamlessly integrated into these clients, splitting zaps automatically to compensate writers, editors, proofreaders, and illustrators in a V4V fashion. Further, one could imagine various compute-intensive services built into these special-purpose clients, such as GPT Ghostwriters, or writing aids such as Grammarly and the like. All these services could be seamlessly paid for in sats, without the requirement of any sign-ups or the gathering of any user data. That's the beauty of money proper.
Plagiarism is one issue that needs to be dealt with, of course. Humans are greedy, and some humans are assholes. Neither bitcoin nor nostr fixes this. However, while plagiarism detection is not necessarily trivial, it is also not impossible, especially if most texts are published on nostr first. Nostr-based publishing tools allow for OpenTimestamp attestations thanks to NIP-03, which in turn allows for plagiarism detection based on "first seen" lookups.
That's just one way to deal with the problem, of course. In any case, I'm confident that we'll figure it out.
Value
I believe that in the open ~~attention~~ information economy we find ourselves in, value will mostly derive from effective curation, dissemination, and transmission of information, not the exclusive ownership of it.
Although it is still early days, the statistics around Podcasting 2.0 and nostr zaps clearly show that (a) people are willing to monetarily reward content they care about, and (b) the willingness to send sats increases as friction decreases.
The ingenious thing about boostagrams and zaps is that they are direct and visible, which is to say, public and interactive. They are neither regular transactions nor simple donations---they are something else entirely. An unforgable value signal, a special form of gratitude and appreciation.
Contrast that with a link to Paypal or Patreon: impersonal, slow, indirect, and friction-laden. It's the opposite of a super-charged interaction.
While today's information jungle increasingly presents itself in the form of (short) videos and (long-form) audio, I believe that we will see a renaissance of the written word, especially if we manage to move away from an economy built around attention, towards an economy built upon value and insight.
The orange future now has a purple hue, and I believe that it will be as bright as ever. We just have a lot of building to do.
Further Reading
NIPs and Resources
- Nostr Resources
- value4value.info
- nips.be
- NIP-23: Long-form content
- NIP-57: Event-specific zap markers
- NIP-47: Nostr Wallet Connect
- NIP-03: OpenTimestamps attestations for events
Originally published on dergigi.com
[^1]: Paywalls work against this nature, which is why I consider them misguided at best and incredibly retarded at worst.
[^2]: Fiat doesn't work for the value-enabled web, as fiat rails can never be open and permissionless. Digital fiat is never money. It is---and always will be---credit.
[^3]: Whether the recipient is a text-to-speech service provider or a human narrator doesn't even matter too much, sats will flow just the same.
[^4]: BlogStack and Habla being two of them.
[^5]: Use a URI as the discussion base (instead of a highlight), and you got yourself a Disqus in purple feathers!
[^fn-torrents]: That's what torrents got right, and ipfs for that matter.
-
 @ da19b5d2:1f6cbfaa
2025-01-06 00:18:25
@ da19b5d2:1f6cbfaa
2025-01-06 00:18:25he touches the sun
she creates the ground
he keeps her safe
when no one's around
without her
he feels so unreal
like a lightning bolt
with no grounds to feel
his shoulders are strong
her hips are so sexy
without both
both just feel empty
she moves like the moon
while he stares at the ceiling
this thing we call life ☯️
what a wonderful feeling
-d☀️t🌓
-
 @ 22c5769e:09af4623
2025-01-05 22:49:48
@ 22c5769e:09af4623
2025-01-05 22:49:48I made my mother in law bday donner
-
 @ 22c5769e:09af4623
2025-01-05 22:45:25
@ 22c5769e:09af4623
2025-01-05 22:45:25I can't wait to start something small with my dream goal to which is to start my own food truck by starting something small by selling eggroll. My passion is cooking, I love to learn new recipe and create my own recipe. My family& friends loves my cooking #foodstr
-
 @ bf47c19e:c3d2573b
2025-01-05 21:58:43
@ bf47c19e:c3d2573b
2025-01-05 21:58:4302.05.2023. / Autor: Igor Mirković
Bitcoin halving je ključni događaj Bitcoin mreže koji umanjuje nagrade za rudarenje, utiče na trend tržišta, profitabilnost rudara i pokreće inovacije u kripto ekosistemu.
Smanjenje nagrade za rudare utiče i na cenu Bitcoin-a, a veliki investitori i rudarska postrojenja igraju značajnu ulogu u oblikovanju tržišnog odgovora na ovaj događaj.
Predstojeći halving može podstaći investitore i rudare da pored Bitcoin-a istraže ponudu altkoina ali i da potraže isplativija rešenja za rudarenje.

Sta je Bitcoin halving?
Bitcoin halving je proces smanjenja nagrade koju rudari dobijaju za potvrđivanje transakcija na Bitcoin mreži. Ovaj proces se dešava svakih 210.000 blokova, što pada na svake četiri godine.
Kada je Bitcoin prvi put pokrenut 2009. godine, nagrada za izrudaren blok u kome se čuvaju transakcije bila je 50 BTC. Nakon prvog halvinga 2012. godine, nagrada se smanjila na 25 BTC po bloku. Drugi halving se dogodio 2016. godine i nagrada se smanjila na 12,5 BTC po bloku. Treći halving se dogodio u maju 2020. godine i nagrada se smanjila na 6,25 BTC po bloku.

Sledeći halving se očekuje 2024. godine i nagrada će se ponovo smanjiti upola, na 3,125 BTC po bloku.
Smanjenje nagrade za cilj ima smanjenje količine novih Bitcoina koji se stvaraju kako bi se dostigla ograničena ukupna ponuda od 21 milion BTC. Ova dinamika stvaranja novih coina takođe utiče na cenu Bitcoina.
Kada se poslednji Bitcoin izrudari, nagrade po izrudarenom bloku će nestati. To se očekuje oko 2140. godine. Nakon toga, rudari će moći da zarađuju samo kroz naknade za realizaciju transakcija koje korisnici mreže plaćaju.

Bitcoin halving je događaj koji smanjuje broj novih Bitcoina koji se generišu po bloku.
U skladu sa opštim zakonom ekonomije – manja ponuda uz stabilnu tražnju bi trebalo da rezultira višim cenama.
Godinu dana pre dugo očekivanog halvinga, stručnjaci i investitori u kripto industriji pažljivo prate njegov potencijalni uticaj na tržište.
Bitcoin halving je je osnovni deflatorni mehanizam definisan u Bitcoin protokolu. Dizajniran je da smanji nagradu za rudarenje za 50% na svakih 210.000 blokova ili otprilike svake četiri godine. Ovo smanjenje ima dvostruku svrhu.
Jedna je kontrola stope inflacije Bitcoin-a kroz imitaciju oskudice, a druga je garancija predvidljive i sve manje ponude novog BTC-a koji ulazi na tržište.
Ovaj mehanizam ima za cilj da očuva vrednost BTC-a tokom vremena, čineći ga atraktivnim čuvarom vrednosti. Kao rezultat toga, halving je ključna komponenta dugoročne ekonomske održivosti Bitcoin-a.
Istorijski gledano, halving je značajno uticao na cenu Bitcoina zbog smanjene ponude novog BTC-a na tržištu. Na primer, u halving događajima 2012, 2016. i 2020. cena bitcoina je doživela značajan porast u mesecima nakon prepolovljavanja nagrade, zato što su trgovci očekivali šok na strani ponude i povećanu potražnju za oskudnijom imovinom.
Trenutno, nagrada za rudarenje iznosi 6,25 BTC po bloku. Nakon sledećeg halvinga koji se očekuje 2024. godine, nagrada za rudarenje će se smanjiti na 3,125 BTC po bloku.

Kakve je posledice halving uzrokovao u prošlosti?
Stručnjaci predviđaju da bi halving mogao dovesti do značajnih promena u ceni BTC-a, kao što je bio slučaj prethodnog puta. Međutim, faktori kao što su globalni ekonomski uslovi, regulatorni razvoj i strategije institucionalnih investitora mogu uticati na ishod.
Tokom halvinga 2012. cena Bitcoina je porasla sa oko 11 dolara u novembru 2012. na oko 1.100 dolara u novembru 2013. godine, što je značajno povećanje u roku od godinu dana.
Tokom ovog perioda, Bitcoin je još uvek bio relativno nov koncept. A tržište su prvenstveno pokretali mali investitori i rani korisnici koji su predvideli potencijal decentralizovane digitalne valute.
Halving u 2016. doveo je do povećanja cene bitcoina sa oko 650 dolara u julu 2016. na skoro 20.000 dolara u decembru 2017. Taj rast je bilo podstaknut povećanom pažnjom velikih medija i ulaskom institucionalnih investitora.
Ipak, regulatorni razvoji i pokušaji da se nametnu strožija pravila za kripto berze, doprineli su nestabilnosti tržišta.
Halving iz 2020. doveo je do povećanja cene bitcoina sa oko 9.000 dolara u maju 2020. na istorijski maksimum od oko 69.000 dolara u novembru 2021. Halving 2020. okarakterisan je rekordnim institucionalnim interesovanjem, vođenim velikim korporacijama i investicionim fondovima koji su ušli na kripto tržište.
COVID-19 pandemija takođe je odigrala značajnu ulogu u oblikovanju raspoloženja na tržištu. Kako su globalna ekonomska kriza i neviđene fiskalne stimulativne mere izazvale zabrinutost zbog inflacije i slabljenja nacionalnih valuta, potražnja za Bitcoinom je rasla.
Kada je sledeći datum Bitkoin halvinga?
Sledeći datum Bitkoin halvinga je zakazan za blok 840.000 – predviđeno je da će se desiti 20. aprila 2024. u 09:20 UTC.
Na datum Bitkoin halvinga predviđeno je da nagrada za blok padne sa 6,25 bitkoina po bloku na 3,125 bitkoina po bloku.
BTC Halving 2024
Analizirajući istorijske obrasce Bitcoin halvinga, čini se da investitori često akumuliraju Bitcoin uoči halvinga i to upravo nekih godinu dana pre.
To bi značilo, ako pretpostavimo da je najniža cena za ovaj ciklus bila u novembru prošle godine (kada je Bitcoin dostigao minimum od oko 16.000 dolara), trenutno se pripremamo za novi vrh koji bi se desio godinu dana nakon halvinga odnosno dve godine od sada. Ova teorija zasniva se na verovanju da kretanja cena prate sličan obrazac kao prethodnih događaja.
Međutim, važno je znati da ne znači nužno da će doći do povećanja ili stagnacije cene Bitcoina. Kripto tržište je značajno sazrelo od poslednjeg halvinga 2020. godine i sada postoji daleko više kriptovaluta koje su u prvom planu korisnika.
Porast rudarske snage
Predstojeći halving će smanjiti nagrade za rudarenje za 50%, što vrši značajan finansijski pritisak na Bitcoin rudare. Ovo smanjenje nagrada tera rudare da prilagode svoje poslovanje kako bi održali profitabilnost i nastavili da održavaju blokčejn mrežu.
Kao odgovor na smanjene nagrade, rudari mogu izabrati da nadograde svoju opremu, kroz ulaganje u energetski efikasniji i moćniji hardver kako bi optimizovali svoje rudarske operacije. Koristeći najnoviju tehnologiju, rudari mogu smanjiti potrošnju energije ali i operativne troškove.

Međutim, povećani troškovi povezani sa nadogradnjom opreme i poboljšanjem energetske efikasnosti mogu nepogodno uticati na manje rudare. Ovim manjim rudarskim postrojenjima često nedostaju finansijska sredstva da se takmiče sa većim, dobro finansiranim rudarskim fondovima.
Kao rezultat toga, neki manji rudari mogu biti primorani da napuste tržište ili mogu biti primorani da se pripoje većim rudarskim postrojenjima kako bi opstali u trci za nagrade.
Pored toga, uticaj halvinga na rudare može dovesti do promena u rudarskom pejzažu, pri čemu rudari traže lokacije sa nižim troškovima energije ili povoljnijim regulatornim okruženjem. Ovo bi moglo da promeni geografsku sliku rudarskih stanica što dodatno utiče na decentralizaciju mreže.
-
 @ bf47c19e:c3d2573b
2025-01-05 21:45:24
@ bf47c19e:c3d2573b
2025-01-05 21:45:24Bitcoin: Peer-to-peer sistem elektronskog novca
Satoshi Nakamoto
satoshin@gmx.com
Translated in Serbian from bitcoin.org/bitcoin.pdf by ECD
Sažetak. Potpuna peer-to-peer verzija elektronskog novca omogućila bi slanje uplata putem interneta direktno od jedne strane ka drugoj bez posredovanja finansijskih institucija. Digitalni potpisi pružaju deo rešenja, ali se glavni benefiti gube ako je i dalje potrebna pouzdana treća strana za sprečavanje dvostruke potrošnje. Predlažemo rešenje problema dvostruke potrošnje korišćenjem peer-to-peer mreže. Mreža vremenski označava transakcije tako što ih hešuje u tekući lanac dokaza o radu (proof of work) temeljen na hešu, formirajući zapis koji se ne može promeniti bez ponovnog rada i objavljivanja dokaza o tom radu. Najduži lanac ne služi samo kao dokaz niza događaja, nego i kao dokaz da je taj niz događaja potvrđen od strane dela peer-to-peer mreže koja poseduju najveću zbirnu procesorsku snagu (CPU). Sve dok većinu procesorske snage kontrolišu čvorovi (nodes) koji ne sarađuju u napadu na mrežu, oni će generisati najduži lanac i nadmašiti napadače. Sama mreža zahteva minimalnu strukturu. Poruke kroz mrežu se prenose uz pretpostavku da svaki čvor čini maksimalan napor da poruku prenese u svom izvornom obliku i na optimalan način, a čvorovi mogu napustiti mrežu i ponovo joj se pridružiti po želji, prihvatajući najduži lanac dokaza o radu kao dokaz onoga što se dogodilo dok ih nije bilo.
1. Uvod
Trgovina na Internetu počela je da se oslanja skoro isključivo na finansijske institucije koje služe kao pouzdani posrednici pri obradi elektronskih plaćanja. Iako sistem radi dovoljno dobro za većinu transakcija i dalje trpi od inherentnih slabosti modela utemeljenog na poverenju.
Potpuno nepovratne transakcije zapravo nisu moguće, jer finansijske institucije ne mogu izbeći posredovanje u rešavanju eventualnih sporova. Troškovi posredovanja povećavaju troškove transakcija, ograničavaju minimalnu praktičnu veličinu transakcija i onemogućuju male, povremene transakcije jer postoji velika šteta zbog gubitka mogućnosti da se izvrše nepovratna plaćanja za nepovratne usluge. Uz mogućnost povraćaja transakcije, potreba za poverenjem raste. Trgovci moraju biti oprezni prema svojim kupcima i tražiti im više informacija nego što bi inače bilo neophodno. Određeni procenat prevara prihvaćen je kao neizbežan. Ovi troškovi i nepouzdanost plaćanja mogu se izbeći korišćenjem gotovine, ali ne postoji mehanizam za elektronsko plaćanje bez pouzdane treće strane.
Ono što je potrebno je elektronski sistem plaćanja zasnovan na kriptografskom dokazu umesto na poverenju, koji omogućava da bilo koje dve strane direktno i dobrovoljno međusobno trguju bez potrebe za posrednikom. Transakcije koje su nepovratne bi zaštitile prodavce od prevara, a escrow mehanizmi mogli bi se lako implementirati radi zaštite kupaca. U ovom dokumentu predlažemo rešenje problema dvostruke potrošnje korišćenjem peer-to-peer distribuiranog servera vremenskih oznaka (timestamp) za generisanje računarskog dokaza o hronološkom redosledu transakcija. Sistem je siguran sve dok pošteni čvorovi zajedno kontrolišu više procesorske snage procesora nego bilo koja udružena grupa napadačkih čvorova.
2. Transakcije
Elektronski novčić definišemo kao lanac digitalnih potpisa. Svaki vlasnik prenosi novčić na sledećeg digitalnim potpisivanjem heša prethodne transakcije i javnog ključa sledećeg vlasnika, dodajući ih potom na kraj novčića. Primalac transakcije može da verifikuje potpise, a time i lanac vlasništva.

Problem je naravno u tome što primalac ne može potvrditi da jedan od prethodnih vlasnika nije dva puta poslao isti novčić. Uobičajeno rešenje je uvođenje pouzdanog centralizovanog posrednika, kreatora novčića koji proverava sve transakcije. Nakon svake transakcije, novčić se mora vratiti kreatoru kako bi se izdao novi novčić i veruje se da samo za novčiće izdate direktno od kreatora možemo biti sigurni da nisu dva puta potrošeni. Problem sa ovim rešenjem je što sudbina čitavog novčanog sistema zavisi od kompanije koja kreira novčiće, jer svaka transakcija mora da prođe kroz nju, baš kao što je slučaj sa bankom.
Treba nam način da primalac bude siguran da prethodni vlasnici nisu potpisali nikakve ranije transakcije kojim bi potrošili taj novčić. Za naše potrebe, računamo transakciju koja se prva desila i ne zanimaju nas naredni pokušaji da se isti novčić ponovo pošalje. Jedini način da sa sigurnošću potvrdimo da taj novčić nije prethodno bio poslat je da imamo informacije o svim transakcijama koje su se ikada desile. U modelu baziranom na centalizovan kreatoru, taj kreator je imao informacije o svim transakcijama i odlučivao koja transakcija je prva stigla. Da bismo to postigli bez pouzdanog posrednika, transakcije moraju biti javno objavljene [1] i potreban nam je sistem u kojem učesnici mogu da se dogovore o jedinstvenoj istoriji redosleda kojim su transakcije primljene. Primaocu je potreban dokaz da se u trenutku dešavanja svake od transakcija većina čvorova složila oko toga da je baš ta transakcija bila ona koja je prva primljena.
3. Server vremenskih oznaka
Rešenje koje predlažemo počinje serverom vremenskih oznaka. Server vremenske oznake radi tako što uzima heš bloka podataka kojem će se dodeliti vremenska oznaka i objavi taj heš svima u mreži, slično kao u novinama ili kao post na Usenet mreži [2-5]. Vremenska oznaka očigledno dokazuje da su podaci morali postojati u to vreme kako bi ušli u haš. Svaka vremenska oznaka sadrži prethodnu vremensku oznaku u svom hešu, formirajući tako lanac, pri čemu svaka dodatna vremenska oznaka pojačava potvrde onih pre nje.

4. Dokaz o radu (Proof-of-Work)
Da bismo implementirali distribuirani server vremenskih oznaka na peer-to-peer principu, moraćemo da koristimo sistem dokaza o radu sličan Hashcash-u Adama Back-a [6], umesto Uneset postova ili novinskih objava. Dokaz o radu uključuje traženje vrednosti koja će, kada se hešuje, na primer pomoću SHA-256 heš funkcije, stvarati heš čiji binarni zapis započinje određenim brojem nula. Prosečna količina potrebnog rada eksponencijalno raste sa brojem potrebnih početnih nula, a može se proveriti izvršavanjem samo jedne heš fuknkcije.
Za našu mrežu vremenskih oznaka implementiramo dokaz o radu povećavajući nonce broja u bloku sve dok se ne pronađe ona vrednost nonce-a koja daje hešu bloka potreban broj početnih nula. Jednom kada se procesorska snaga utroši kako bi se zadovoljio dokaz o radu, blok se ne može izmeniti bez ponovljenog rada. Kako se kasniji blokovi vežu na taj blok, rad potreban da se on izmeni uključivao bi i ponovno obrađivanje svih blokova nakon njega.

Dokaz o radu takođe rešava problem utvrđivanja većine pri odlučivanju. Ako bi se većina zasnivala na principu jednog glasa po IP adresi, mogao bi je narušiti svako ko je u stanju da glasa sa više IP adresa odjednom. Dokaz o radu u osnovi predstavlja jedan glas po jedinici procesorske snage. Većinska odluka je predstavljena najdužim lancem u čije je stvaranje zapravo investirano najviše rada prilikom dokazivanja. Ako većinu procesorske snage kontrolišu pošteni čvorovi, pošten lanac će rasti najbrže i nadmašiće sve konkurentske lance. Da bi izmenio neki od prethodnih blokova, napadač bi morao da ponovi dokaz o radu za taj blok i sve blokove nakon njega, a zatim da sustigne i nadmaši količinu rada poštenih čvorova. Kasnije ćemo pokazati da se dodavanjem novih blokova eksponencijalno smanjuje verovatnoća da će sporiji napadač uspeti da sustigne pošteni lanac.
Da bi se kompenzovalo povećanje brzine hardvera i promenljivo interesovanje ljudi za vođenje čvorova tokom vremena, težina obavljanja dokaza o radu (proof-of-work difficulty) određuje se prema prosečnom broju blokova krairanih za sat vremena. Ako se blokovi stvaraju prebrzo, težina se povećava.
5. Mreža
Koraci za vođenje mreže su sledeći:
1) Nove transakcije se prosleđuju svim čvorovima u mreži. 2) Svaki čvor prikuplja nove transakcije u blok. 3) Svaki čvor radi na pronalaženju dokaza o radu dovoljnog nivoa težine za svoj blok. 4) Kada čvor pronađe dokaz o radu, on emituje taj blok ka svim čvorovima. 5) Čvorovi prihvataju blok samo ako su sve transakcije u njemu ispravne i nisu već potrošene. 6) Čvorovi izražavaju prihvatanje bloka radeći na stvaranju sledećeg bloka u lancu, koristeći heš prihvaćenog bloka kao prethodni heš.
Čvorovi uvek smatraju da je najduži lanac ispravan i nastaviće da rade na njegovom produžavanju. Ako dva čvora istovremeno emituju različite verzije sledećeg bloka, neki čvorovi prvo mogu primiti jedan ili drugi blok. U tom slučaju svaki čvor radi na prvom koji je dobio, ali čuvaju drugu kariku lanca u slučaju da ona postane duža. Dilema će biti rešena kada se pronađe sledeći dokaz o radu i jedna karika postane duža; čvorovi koji su radili na drugoj karici lanca će se prebaciti na dužu kariku.
Emitovanje novih transakcija ne mora nužno doći do svih čvorova. Sve dok stižu do velikog broja čvorova, te transakcije će ući u blok. Slično važi i za blokove, ni oni ne moraju doći odmah do svih čvorova. Ako neki čvor propusti da primi informaciju o bloku, kada mu stigne sledeći blok,primetiće da je propustio jedan, pa će ga tražiti naknadno.
6. Podsticaj
Po pravilu, prva transakcija u bloku je posebna transakcija koja kreira novi novčić u vlasništvu kreatora bloka. Ovo daje podsticaj čvorovima da podrže mrežu i pruža način za početnu ubacivanje novčića u opticaj, budući da ne postoji centralno telo koje ih izdaje. Stalno dodavanje konstantne količine novih novčića liči na rudarenje zlata, gde rudari ulažu resurse kako bi izrudarili nove količine zlata i ubacili ih u opticaj. U našem slučaju ulaže se procesorsko vreme i električna energija.
Podsticaj se takođe može finansirati i transakcionim naknadama. Ako je iznos izlaznog dela transakcije manji od ulaznog, razliku čini naknada za transakciju koja se dodaje iznosu nagrade za kreatora bloka koji sadrži tu transakciju. Nakon što predefinisani broj novčića uđe u opticaj, podsticaj mogu u potpunosti činiti transakcione naknade, čime se sistem oslobađa inflacije.
Čvorovi su na ovaj način podstaknuti da ostanu pošteni. Ako je pohlepni napadač u stanju da angažuje više procesorske snage od svih poštenih čvorova zajedno, morao bi da bira između toga da poništi svoje izvršene transakcije i time prevari ljude ili da procesorsku snagu koristi za stvaranje novih novčića. On bi trebalo bi uvidi da je isplativije igrati po pravilima koja ga nagrađuju sa više novih novčića od svi drugi zajedno, nego da potkopava sistem i vrednost sopstvenog bogatstva.
7. Oslobađanje prostora na hard disku
Kada je dovoljno blokova dodato nakon poslednje transakcije novčića, prethodne transakcije tog novčića se mogu odbaciti kako bi se uštedeo prostor na hard disku. Kako bi se to ostvarilo bez razbijanja heša bloka, transakcije su hešovane u Merkleovo stablo (Merkle Tree) [7] [2] [5], gde je samo koren uključen u heš bloka. Stari blokovi se tada mogu sabiti uklanjanjem nepotrebnih grana drveta. Unutrašnji heševi ne moraju biti skladišteni.

Zaglavlje bloka bez transakcija bilo bi oko 80 bajtova. Ako pretpostavimo da su blokovi generisani svakih 10 minuta, 80 bajtova * 6 * 24 * 365 = 4,2 MB godišnje. Imajući u vidu činjenicu da se u 2008. godini računari uglavnom prodaju sa oko 2 GB RAM-a i Murov zakon koji predviđa trenutni rast od 1,2 GB godišnje, skladištenje ne bi trebalo da predstavlja problem čak i ako se zaglavlja bloka moraju čuvati u memoriji.
8. Pojednostavljena verifikacija plaćanja
Moguće je verifikovati plaćanja bez vođenja čitavog mrežnog čvora. Korisnik samo treba da sačuva kopiju zaglavlja blokova najdužeg lanca dokaza o radu, do koje može doći upitom ka mrežnim čvorovima dok se ne uveri da je dobio najduži lanac i dobije Merkleova granu
koja povezuje transakciju sa blokom u koji je uneta vremenska oznaka za tu transakciju. Ne može samostalno proveriti transakciju, ali povezujući je sa mestom u lancu može videti da je prihvaćena od strane čvora mreže i da su na njen blok dodati naknadni blokovi što dalje potvrđuje da ju je mreža prihvatila.

Kao takva, verifikacija je pouzdana sve dok pošteni čvorovi kontrolišu mrežu, ali je ranjiva ako napadač nadjača ostatak mreže. Čvorovi mreže mogu sami proveriti transakcije, ali napadačeve lažne transakcije mogu zavarati one koji koriste pojednostavljenu metodu verifikacije transakcija sve dok je on u stanju da nadjačava ostatak mreže. Jedna od strategija zaštite bila bi prihvatanje upozorenja čvorova mreže kada otkriju nevažeći blok, pri čemu bi korisnikov softver morao da preuzme ceo blok i sporne transakcije kako bi potvrdio nepravilnost. Biznisi koji primaju česte uplate će verovatno želeti da pokrenu i vode sopstvene čvorove radi brže verifikacije i potrebe da im sigurnost ne zavisi od drugih.
9. Kombinovanje i deljenje vrednosti
Iako bi bilo moguće pojedinačno rukovati novčićima, bilo bi nezgrapno kreirati zasebnu transakciju za svaki cent u toj transferu. Da biste dozvolili podelu i kombinovanje vrednosti, transakcije sadrže više ulaza i izlaza. Obično će postojati ili jedan ulaz iz veće prethodne transakcije ili više unosa koji kombinuju manje iznose, a najviše dva izlaza: jedan za samo plaćanje, a jedan koji vraća kusur, ako ga ima, nazad pošiljaocu.

Treba napomenuti da situacija u kojoj transakcija zavisi od nekoliko drugih transakcija, a te transakcije zavise od još mnogo više, ovde nije problem. Nikada ne postoji potreba za izdvajanjem istorije pojedinačne transakcije.
10. Privatnost
Tradicionalni bankarski model postiže odgovarajući nivo privatnosti ograničavanjem pristupa informacijama na strane uključene u transakciju i posrednika. Neophodnost javnog objavljivanja svih transakcija isključuje mogućnost primene pomenutog modela, ali privatnost se i dalje može zadržati na drugi način: čuvanjem javnih ključeva (public keys) anonimnim. Javnost može videti da neko šalje iznos nekom drugom, ali bez informacija koje povezuju transakciju sa bilo kim. Ovo je slično količini informacija koje objavljuju berze, gde se vreme i veličina pojedinačnih trgovina čine javnim, ali bez navođenja ko su stranke uključene u tu trgovinu.

Kao dodatni zaštitni zid, preporučljivo je koristiti novi par ključeva za svaku transakciju, kako ne bi bili povezane sa zajedničkim vlasnikom. Neka povezivanja su i dalje neizbežna kod transakcija sa više ulaza, koje nužno otkrivaju da su njihovi ulazi bili u vlasništvu istog vlasnika. Rizik je taj da bi se otkrivanjem vlasnik ključa mogle otkriti i ostale transakcije koje su pripadale tom vlasniku.
11. Proračuni
Razmatramo scenario u kome napadač pokušava da generiše alternativni lanac brže od poštenog lanca. Čak i ako se to postigne, to ne omogućuje proizvoljne promene u sistemu, poput stvaranje vrednosti ni iz čega ili uzimanje novca koji nikada nije pripadao napadaču. Pošteni čvorovi neće prihvatiti nevažeće transakcije kao uplatu i nikada neće prihvatiti blok koji ih sadrži. Napadač može samo pokušati da promeni jednu od svojih transakcija kako bi vratio novac koji je nedavno potrošio.
Trka između poštenog lanca i lanca napadača može se predstaviti kao binomska distribucija slučajne diskretne varijable (Binomial Random Walk). Uspešni ishod je da se pošten lanac produži za jedan blok, povećavajući svoje vođstvo za +1, a neuspešni ishod je da se napadačev lanac produži za jedan blok, smanjujući zaostatak za -1.
Verovatnoću da napadač nadoknadi određeni deficit možemo izraziti kroz problem kockareve propasti (Gambler’s Ruin Problem). Pretpostavimo da kockar sa neograničenim iznosom novca počinje sa zaostatkom i igra potencijalno beskonačan broj ponovljenih igara u pokušaju da nadoknadi zaostatak. Možemo izračunati verovatnoću za nadoknađivanje zaostatka ili da će napadač stići pošten lanac, na sledeći način [8]:
p= verovatnoća da pošten čvor pronađe sledeći blok q= verovatnoća da napadač pronađe sledeći blok qz= verovatnoća da će napadač ikada dostići z blokova zaostatka

S obzirom na našu pretpostavku da je p > q, verovatnoća pada eksponencijalno kako se povećava broj blokova koje napadač mora da nadoknadi. Sa šansama protiv njega, ako mu se u početku ne posreći, njegove šanse postaju manje i manje sa povećanjem zaostatka.
Sada razmatramo koliko primalac nove transakcije treba da čeka pre nego što postane
dovoljno siguran da pošiljalac ne može promeniti transakciju. Pretpostavljamo da je pošiljalac napadač koji želi da natera primaoca da veruje da mu je platio, a zatim nakon nekog vremena tu transakciju preusmeri ka sebi. Primalac će primetiti kada se to dogodi, ali pošiljalac se nada da će tad već biti prekasno.
Primalac generiše novi par ključeva i daje javni ključ pošiljaocu neposredno pre potpisivanja transakcije. Ovo sprečava pošiljaoca da unapred pripremi lanac blokova radeći na njemu neprekidno dok mu se ne posreći da stekne dovoljnu prednost i u tom trenutku izvrši transakciju. Kada se transakcija pošalje, nepošteni pošiljalac počinje tajno da radi na paralelnom lancu koji sadrži alternativnu verziju njegove transakcije.
Primalac čeka dok transakcija ne bude dodata u blok, i dok z blokova nije dodato nakon tog bloka. On ne zna tačno koliko je napadač napredovao, ali pod pretpostavkom da su pošteni blokovi kreirani očekivanom dinamikom, potencijalni napredak napadača će biti prikazan kao Poasonova distribucija sa očekivanom vrednošću:

Kako bismo izračunali verovatnoću da napadač ipak može da nadoknadi zaostatak, množimo gustinu verovatnoće za svaki nivo napretka koji je mogao da ostvari sa verovatnoćom da od tog trenutka može da potpuno nadoknadi zaostatak:

Preuređujemo formulu kako bismo izbegli sabiranje beskonačnog broja sabiraka zbog repa distribucije:

I konvertujemo u programski kod u programskom jeziku C…

Kroz par primera, vidimo da verovatnoća opada eksponencijalno sa porastom z.

Rešavanje za P < 0.1%…

12. Zaključak
Predložili smo sistem za elektronske transakcije bez oslanjanja na poverenje. Počeli smo sa uobičajenim šablonom i novčićima nastalim iz digitalnih potpisa, koji pruža snažnu kontrolu nad vlasništvom, ali je nepotpun bez načina da se spreči dvostruka potrošnja. Kako bismo ovo rešili, predložili smo peer-to-peer mrežu koja koristi dokaz o radu za čuvanje javne istorije transakcija čija izmena napadačima brzo postaje računski nepraktična ako pošteni čvorovi kontrolišu većinu procesorske snage. Mreža je robusna u svojoj nestrukturiranoj jednostavnosti. Svi čvorovi rade istovremeno uz malo koordinacije. Ne treba ih identifikovati, jer se poruke ne usmeravaju na jedno određeno mesto nego samo trebaju biti prenete uz maksimalan napor od strane čvorova da se taj prenos odradi na predviđen način. Čvorovi mogu da napuste i ponovo se pridruže mreži po želji, prihvatajući lanac dokaza o radu kao dokaz onoga što se dogodilo dok ih nije bilo. Oni glasaju svojom procesorskom snagom, izražavajući svoje prihvatanje validnih blokova time što pokušavaju da ih nadgrade novim blokovima i odbacuju nevažeće blokove odbijanjem ih nadgrađuju. Sva potrebna pravila i podsticaji mogu se nametnuti ovim mehanizmom postizanja konsenzusa.
Reference:
[1] W. Dai, „b-money,“ http://www.weidai.com/bmoney.txt, 1998. [2] H. Massias, X.S. Avila, and J.-J. Quisquater, „Design of a secure timestamping service with minimal trust requirements,“ In 20th Symposium on Information Theory in the Benelux, May 1999. [3] S. Haber, W.S. Stornetta, „How to time-stamp a digital document,“ In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [4] D. Bayer, S. Haber, W.S. Stornetta, „Improving the efficiency and reliability of digital time-stamping,“ In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [5] S. Haber, W.S. Stornetta, „Secure names for bit-strings,“ In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [6] A. Back, „Hashcash – a denial of service counter-measure,“ http://www.hashcash.org/papers/hashcash.pdf, 2002. [7] R.C. Merkle, „Protocols for public key cryptosystems,“ In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [8] W. Feller, „An introduction to probability theory and its applications,“ 1957.
-
 @ bf47c19e:c3d2573b
2025-01-05 21:42:25
@ bf47c19e:c3d2573b
2025-01-05 21:42:2513.06.2023. / Autor: Igor Mirković
Ograničena količina Bitcoina:
Ukupno: 21 milion BTC
Trenutno izrudareno: 19.400.050 BTC
Preostalo za rudarenje: 1.599.950 BTC
Dnevno se izrudari: 900 BTC
Da li je 21 milion Bitcoina dovoljno?
Da li znate koliko je milionera u svetu? Oko 56 miliona milionera, odnosno 1.1% populacije. Ako podelimo 21 milion Bitcoin-a na 56 miliona milionera dobijamo 0.375 BTC po svakom milioneru.
Ograničena zaliha Bitcoina i broj milionera su sami dovoljni da lansiraju cenu, jer bi posedovanje jednog celog Bitcoin-a moglo da postane status moći milionera u budućnosti.

Verovatno bi se oni nekako i dogovorili na ravnopravnu raspodelu da u svetu nema preko 2.000 milijardera, kojima ni 1, a kamoli 0.39 BTC nisu dovoljni za smislenu investiciju.
Zašto kompanije kupuju Bitcoin?
Jedan od faktora koji ovu računicu čini još diskutabilnijom su Bitcoin-i koji su zauvek nestali i zaboravljeni na novčanicima. Nezahvalno je tvrditi koliko je Bitcoin-a „izgubljeno“, ali postoje i istraživanja koja pokazuju da to uopšte nije mali deo celokupne ponude. Kreator Bitcoin-a Satoši odmah je u startu pretpostavio da ovako nešto može da se desi i na ovu okrutnu prirodnu selekciju dao je logičan komentar da će, u slučaju ako neko izgubi pristup svojim Bitcoin-ima, coini koje ima ostatak zajednice samim tim vredeti više.
Kako bismo shvatili zašto je ograničena zaliha izuzetno važna, vratićemo se na staro dobro poređenje zlata i Bitcoin-a. Bitcoin i zlato imaju mnogo sličnosti ali i jednu ključnu razliku. Bitcoin nazivaju digitalnim zlatom, nekada čak i drugom, unapređenom verzijom zlata (Zlato 2.0).
I zlato i Bitcoin:
Imaju fiksnu i ograničenu zalihu. Za BTC se zna koliko ga ima, a za zlato se zna da je ograničeno i da ga nema mnogo. Ne mogu biti lažirani i napravljeni veštački.
Najveća razlika između ova dva čuvara vrednosti je što je zlato u fizičkom obliku, a BTC je isključivo digitalan. Digitalne karakteristike Bitcoin-u daju brojne prednosti u odnosu na zlato: Lako je deljiv na sitnije delove, lako se šalje svuda u svetu, lako se čuva, transportuje i potpuno je transparentan.
Magija od 21 miliona
Ponuda i tražnja… dva jednostavna koncepta, a opet dovoljno sveobuhvatna da definišu i utiču na sve. Kada se spoje, kreiraju apstraktnu pojavu koja se zove vrednost.
Koliko nečega ima i koliko je traženo? Odrednica je za plate radnih mesta, cene imovine, roba, usluga, dobra i gde god želimo da pripišemo neku vrednost možemo početi od tog osnova.
Od samog nastanka čoveka, sve na svetu je imalo percipiranu neograničenu zalihu. Od životinja, zemlje, zlata, vode, nafte. Ljudi su bukvalno konzumirali počevši od pećinskog čoveka pa do danas kao da nema ograničenja ni u čemu.
U stanju smo da konzumiramo i trošimo resurse dok ne nestanu zauvek sa zemlje, samo pogledajte životinje, biljke i sirovine koje su nestale ili su veoma ugrožene zbog uticaja ljudskih „potreba“. Smislili smo čak i šta ćemo kada odrećene sirovine ili životinje nestanu. Napravićemo DNK klonove, sintetičke proizvode, imitaciju koja će nam služiti za naše lične potrebe. Što su zalihe manje i manje, cene su veće ali i želja… potreba za konzumacijom nema cenu.
Šta to znači u slučaju Bitcoin-a? Kao što znamo, Bitcoin je bio prva imovina koja je zaista ograničena, na 21 milion coina, to je sve što će ikada biti stvoreno, a ljudi ne mogu da ga kloniraju, doštampaju, veštački naprave, lažiraju ili slično.
Ograničenost Bitcoin-a se kosi sa svim ljudskim potrošačkim navikama. Uvek postoji način da dobijete više, osim u slučaju Bitcoin-a.
Ova činjenica ograničenosti zaliha je poremetila definiciju ekonomske vrednosti za Bitcoin. To je razlog zašto je on došao do vrednosti od preko 20 hiljada dolara za nešto više od 10 godina. To je jedan od najvećih skokova vrednosti u istoriji čovečanstva i po mišljenju mnogih, samo početak.
Zašto je ograničenje od 21 miliona koje zagovornici ističu toliko važno, koliko je trenutno Bitcoin-a na tržištu i koji je proces koji stvara nove coine odnosno kada će i poslednji BTC biti dostupan?

Bitcoin se često smatra novom vrstom novca koji rešava nedostatke i nudi poboljšanja postojećeg monetarnog sistema. Jedno od tih poboljšanja je fiksna zaliha – 21 milion Bitcoin-a i kodirana logika, koja se ne može menjati, o tome kako će se Bitcoin-i stvarati i po kom principu distribuirati dok se ne postigne ta cifra što se očekuje oko 2150. godine.
Postoje dva elementa fiksne zalihe koji su bitni za razumevanje: Zašto je fiksna zaliha bitna karakteristika za novac i koji sistem Bitcoin koristi kako bi je garantovao.
Odnos ograničene zalihe i vrednosti
Prvi oblici novca pojavili su se nezavisno u različitim kulturama i predstavljali su ključno rešenje i prelazak sa tadašnje trampe. Različite vrste stvari isprobane su kao oblik novca – kokosovi orasi, stoka, ječam, so, biseri, školjke – pre nego što su se zlato i srebro utemeljili kao najefikasniji.
Razlog zbog kojeg su plemeniti metali postali standard za novac bilo je ispunjavanje ključnih karakteristika kako bi novac bio efikasan kao sredstvo razmene:
Prenosiv – Lak za nošenje Izdržljiv – Neće fizički propasti Deljiv – Može se podeliti na manje jednake delove Zamenljiv – Svaka deo je zamenljiv za bilo koju drugu stvar Prepoznatljiv – Očigledno je šta je Oskudan – nema ga u izobilju niti ga je lako nabaviti
Od šest magičnih stvari koje čine novac korisnim za razmenu, poslednja je daleko najvažnija (isto tako je u slučaju novca kao načina očuvanja vrednosti – skladišta vrednosti).
Zamislite sa kakvim problemima bismo se suočavali da je so ostala dominantan oblik novca.
Zlato ispunjava uslov oskudnosti i većinu od ostalih pet, ali je njegova mana izuzetno tešak transport.
Kada je Satoši Nakamoto krenuo sa stvaranjem novog oblika internet novca, on/ona/oni su morali da pronađu način da stvore neku vrstu digitalnog zlata, ali sa isprogramiranom distribucijom odnosno ukupnom ponudom, što je bilo mnogo teže realizovati i napraviti nego što zvuči.
Isprogramirana zaliha
Ako razmislite o najpoznatijim digitalnim formatima- jpeg slikama, Google dokumentima, mp3 datotekama – svi oni mogu da se kopiraju prilično lako. Bitcoin ne može, jer to nije datoteka koja se nalazi na vašem telefonu ili laptopu, već postoji u obliku zapisa koji je povezan sa adresom – mestom na bitcoin blokčejnu– koji možete zamisliti kao broj bankovnog računa.
Ako imate pristup bitcoin adresi i neka sredstva u Bitcoin-u na njoj, možete ga iskoristiti. Dakle, Bitcoin blokčejn kao monetarni sistem je kuća svih bitkoina koji su u opticaju, drugim rečima, ukupne ponude Bitkoina.
Sledeće logično pitanje je kako se kontroliše i održava bitkoin mreža? Česta zabluda koja postoji zbog tradicionalnih finansijskih sistema je da ko god to kontroliše može stvoriti onoliko BTC-a koliko želi? Možda, ako bi to kontrolisala jedna osoba, sigurno bi bila u iskušenju… tako u stvari funkcioniše postojeći novac centralnih banaka.
Kako nastaju Bitkoini?
Jedan od najmagičnijih mehanizama Bitcoin sistema je način na koji se stvaraju novi Bitcoin-i kroz proces koji se zove rudarenje. To je prilično složen proces, tako da ko želi da istraži i kopa dublje može se informiše na našem blogu u sekciji rudarenje.
Bitcoin sistem funkcioniše u skladu sa skupom pravila koji se nazivaju Bitcoin Protokol. Taj skup pravila kaže da će ukupno postojati maksimalno 21 milion, sa fiksnim brojem Bitcoin-a koji se kreira svakih 10 minuta kao nagrada za rudare koji obrađuju nove transakcije u bloku podataka. Blokovi podataka su povezani zajedno sa neraskidivim kriptografskim vezama – otuda i termin blokčejn.
Rudarenje kriptovaluta – Kakva su iskustva srpskih rudara?
Prvi blok je iskopan u januaru 2009. godine, kada je nagrada za rudare bila 50 BTC-a. Tako je 50 novih koina puštano u promet svakih 10 minuta.
Protokol o Bitcoin-u je programiran da kada se stvori 210.000 blokova, nagrada se prepolovi, što se dešava otprilike svake četiri godine i naziva se Bitcoin halving.
Bitcoin je do sada prošao kroz tri halvinga. Umesto da bude inflatoran – sa stalno rastućom ponudom – koja narušava vrednost, Bitcoin je deflatoran jer raste uz opadajuću maržu, koja će na kraju dostići nulu kada se dostigne količina od distribuiranih 21 milion BTC-a.
Zašto baš 21 milion?
Neka jednostavna matematika ukazuje na to da je Satoši možda imao mnogo veću viziju o bitkoinu – što bolje objašnjava zašto je izabran maksimalni iznos od 21 milion.
U vreme stvaranja Bitcoin-a, celokupna svetska ponuda novca iznosila je približno 21 hiljadu milijardi dolara. Ova cifra, poznata kao M1 novčana masa, sastoji se od ukupne vrednosti celokupnog fizičkog novca na svetu, uključujući gotovinu, kovanice, čekove i još mnogo toga.
Ako bi Bitcoin narastao i postao jedinstvena svetska valuta — zamenjujući sve one od kojih se sastoji M1 cifra — onda bi svaki BTC vredeo milion dolara. Pošto u svakom Bitcoin-u ima 100 miliona satošija, to bi postavilo vrednost svakog satošija na 0,01 dolara.
Činjenica da su ovi brojevi tako blisko usklađeni bila bi izuzetna slučajnost, ako nije namerno.
Druga verzija
Iako je teorija zamene novčane mase M1 možda najverovatnije obrazloženje zašto je Satoši odabrao 21 milion da bude limit za Bitcoin, postoji još jedno donekle jednostavnije objašnjenje.
Gledajući parametre koji se koriste za kontrolu distribucije Bitcoin-a, postaje jasno da cifra od 21 milion BTC-a omogućava mreži da osigura da se blokovi rudare u redovnom vremenskom okviru (10 minuta).
Takođe. osigurava da se količina bitkoina koji se isplaćuje rudarima kao nagrade za blok vremenom smanjuje, kako se maksimalna ponuda približava granici. Kako se ispostavilo, parametri koje je Satoshi postavio za ovo neizbežno dovode do proizvodnje od maksimalno 21 miliona BTC. Na osnovu ove karakteristike, ukupno 210.000 blokova treba da se rudari u svakom četvorogodišnjem ciklusu, nakon čega se nagrada za blok prepolovi.

U prvom ciklusu je puštano 50 BTC po bloku; ovo je prepolovljeno na 25 BTC po bloku u 2012. godini, zatim ponovo na 12,5 BTC po bloku u 2016. Nakon prepolovljenja u 2020., trenutno je na 6,25 BTC po bloku.
Ako nastavimo videćemo da je zbir nagrada za blok za svaki ciklus jednak 100 (50 + 25 + 6,25 +3,125, itd.). Množenjem ovog broja sa cifrom od 210.000 blokova, dobijate maksimalnu moguću ponudu od 21 milion.
Dakle, da li je zaliha Bitcoin-a filozofski gest ili proizvod nemilosrdne matematičke logike? Samo Satoši Nakamoto zaista zna.
-
 @ c8841c9d:ae8048e2
2025-01-05 21:33:57
@ c8841c9d:ae8048e2
2025-01-05 21:33:57Ever wondered how to navigate the vast world of cryptocurrency without getting lost?
Welcome to our exploration of the crypto and blockchain world! Today, we're going to start learning together about the complex universe of cryptocurrency using mind maps, which will facilitate our understanding of this fascinating technology.
This post aims to highlight the importance of learning to acquire competence in cryptocurrency, focusing on intellectual enlightenment rather than the mere hope of gains. (Although wisely used knowledge can indeed lead to gains.)
To illustrate our journey, here's a representation inspired by the Dunning-Kruger Effect, showing the typical path of learning in any complex field, including crypto.
Reaching the Zenith of Mastery is a long road! My goal is to provide tools to minimize the falls in the ravine and make the Ascent of Knowledge easier! We are on this journey together, and I hope our interactions will be mutually beneficial.
Cryptocurrency is more than digital money; it's a new way of thinking about the world. want to contribute to the wider distribution of knowledge about this revolutionary technology. It took me almost two years to gain enough competence and confidence to publish my first post and I'm excited to start.
I will be posting, both on X and Nostr to keep the knowledge decentralized, crypto mind maps to visualize the cryptocurrency learning journey, from the basics to the most advanced topics. Keep an eye out for #cryptomindmap!
-
 @ 41fa852b:af7b7706
2025-01-05 20:41:40
@ 41fa852b:af7b7706
2025-01-05 20:41:40"Bitcoin is the apex predator of money. It's eating fiat currencies, and there's nothing they can do to stop it."--Max Keiser
Good morning bitcoiners, here we go with another full week of meetups.
Things are fully back up and running on Monday morning, so this coming week, we have a much healthier 10 meetups to look forward to.
If you've been watching from the sidelines so far, 2025 is the year to get out there and get involved in the UK Bitcoin social scene.
Here's your guide for this coming week…
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Bitcoin 101 at Cyphermunk House: Discover bitcoin wallets, nodes, privacy, and other key topicsr. The class is customised to ensure everyone is challenged. It's a 1.5-hour session on Tuesday 7th from 7 - 8:30 PM, please arrive ahead of time. 🔐
-
Canterbury Bitcoin: Meeting this month at the Millers Arms in Canterbury at 7 PM on Tuesday the 7th of January. An informal meetup to discuss Bitcoin and chat. 🍺
-
Belfast Bitcoin: Join them on Tuesday the 7th January, 8pm. These guys meet in person monthly on the first Tuesday of each month at Ormeau Baths Event Space, 18 Ormeau Avenue, Belfast, BT2 8HS, Northern Ireland. 🍻
-
Glasgow Bitcoin: Head along to The Piper Whisky Bar on Wednesday 8th January at 18:00. Newcomers are welcome to come along and meet some likeminded bitcoiners. 🍻
-
Bitcoin Beach Bournemouth: Every second Thursday of the month at Chaplins Cellar Bar. 529 Christchurch Road, Boscombe, United. You'll find them in the Cogg Room at 19:30. This month it's the 9th. 🍻
-
Lincolnshire Bitcoin: Lincolnshire Bitcoin meets on the first Thursday of each month at 7:30 PM in the Treaty of Commerce, Lincoln. Open to all, from OG's to newcomers. This month on the 7th. 🍺
-
Bitcoin Educators Academy: A unique 3-days "Train the trainers" style academy in Edinburgh, for Bitcoiners who already are or want to become Bitcoin Educators for their communities. It starts on Friday the 10th and runs to the 12th. 📚👨🏻🏫👨🏽🎓
-
Northants Bitcoin Walk: This month the Northants Walk will start at Crustys Cafe 11:00, with a walk around the historic village of Finedon and back to the bitcoin accepting cafe for refreshments afterwards. 🚶🚶🏻♀️🚶♂️
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🚶🏻♀️🚶♂️
-
Wiltshire BTC: Meeting at The Stonehenge Inn at 18:00 on Saturday 11th January. Bitcoin accepted at the venue. 🍻
Upcoming Special Events
This event isn't happening this week, but it's important to add to your calendar now as tickets are selling fast.
- Bitcoin Builders Workshop: Corby based engineering company BTC Citadel are hosting an afternoon of Bitcoin building and chat. Build that project you've been thinking about but didn't know how to start. Come and use high-end 3D printers, 3D scanners, electronics lab and the CNC laser engraver. Everyone welcome, no technical ability needed. Learn how to build a Seedsigner. Refreshments provided for this free event.
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 0b14a03f:3f0257c2
2025-01-05 20:22:44
@ 0b14a03f:3f0257c2
2025-01-05 20:22:44Current democracies are fallacies. We DO NOT live in democracies, not in England, nor Nigeria, nor Brazil, not in any other country on this planet. \ \ All countries are managed by monarchies, aka enterprises. Monarchies in the past looked like one leader + the same leader from the same family. The only difference now is that we think we 'choose' from two monarchs through a vote, which we believe is fair competition.\ \ Governments are big corporations, meaning, they only want profit and making that profit out of slaves' work/time, aka you, the employee.\ \ Humans were not put on this earth to work 2/3 parts of their day. They were put here to explore themselves and the planet around them. The planets around that planet. The stars around those planets. The infinite galaxies and beyond.\ \ What you're doing with the 24 hours of each day is up to you. And you only. How you decide to spend that time is shown in each of your decisions. What you give your time to, what content you consume, the food you eat, the actions you make, the relationships you keep or discard.\ \ You have more power within yourself that you will never be able to find outside of yourself. Please, read that again.\ \ What becomes tricky in the matrix is how you decide to use that power.
-
 @ 3f770d65:7a745b24
2025-01-05 18:56:33
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter Olas.
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the #Olas365 challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
Download on Android or download via Zapstore.
Let's make waves together.
-
 @ 3814facc:86fe153b
2025-01-05 17:32:27
@ 3814facc:86fe153b
2025-01-05 17:32:27My name is Beau and I spent 6.5 years playing live poker professionally in Los Angeles and Las Vegas. Poker was something I was drawn to at a young age through my love of puzzles, math, and game shows. Later in my life, when I decided to start my professional career, I was committed to becoming the best poker player I could possibly be. The side effect of this, which I didn’t consider at the time, was that my health and wellness would drastically decline over the years. I had spent my childhood playing baseball and was always athletic with exceptional hand eye coordination skills, but my journey playing cards led me to feeling dull and lifeless.

During the pandemic, I was following a few content creators journeys, many of whom were tired of the lockdowns and the suppression of human freedom. These creators were posting about health, family, and living an alternative lifestyle that piqued my interest. When I saw an ad about a retreat in Costa Rica, a place I had been on vacation three times already and loved, I was immediately interested. My fellow coworker poker friends were great, but I was craving deeper connection. I wanted to meet other people who were also interested in living more of an alternative lifestyle, and of course, spend time in nature relaxing — just truly letting go of the daily grind the poker lifestyle brought me.

At the retreat, I was pretty shy (most poker players are), but I was having so much fun doing the activities at the retreat which included mediation, breathwork, yoga, cacao ceremonies, sharing circles, waterfall adventures, beach bbq & bonfires, and workshops around business, sovereignty, and content creation. I was connecting in a really deep way with a few of the guys from the retreat and having an incredible time.

On one of the last days, we were listening to a live concert by one of the locals who was playing introspective Costa Rican vibey music, and I had an epiphany. I realized that my time on Earth is truly limited and life really is too short to not be doing something that I really love. It was in this moment, that I knew my poker career was over. A game that I once loved many years ago was no longer something I wanted to dedicate time to. I had grown old of feeling unhealthy, the late nights under artificial lighting, the toxic environment a casino brings, and how disconnected from my emotions I became (the best poker players are robotic).

I shared some of my story with the other retreat guests about how I feel I needed to change my life in a drastic way. I knew I wanted to move out of Southern California and continue my journey of traveling and meeting new people. I was considering traveling all around Asia and going to multiple countries over five months, but luckily, two friends of mine from the retreat invited me to come live with them in a Mexican beach town.

I knew instantly this was a great place to start for my new journey. I ended up trying many brazilian jiu jitsu classes, dove deeper into my yoga practice, and spent a lot of time outdoors in the sun near the beach. I was focused on my journey of self development as a man.

In the next several months, I had gone to two more retreats that were similar to the first one I had gone to — one in Mexico and one more in Costa Rica. I continued to meet new people, share my story, and I developed a passion and joy for life that was attracting all kinds of wonderful people to me. I was amazed how going to that first retreat had given me the opportunity to become friends with all these people, open my eyes to a new life, and discover what it felt like to be healthy.

At this point, I was feeling called to move on from Mexico, so I went to Europe and Bali that summer, really putting myself out into the unknown. It was great because I knew that I was truly living on my edge and having a great time. In Bali, I connected with my new girlfriend in a deeper way, someone I met as friends during the very first retreat.

Fast forward a few months later to now, and I am living in the jungle of Costa Rica, a place that I have now been to seven times, and a place that is obviously very special to me. I am still continuing my journey of rapid personal development, exploring further ways to feel strong & healthy, and am committed to being a source of light and inspiration for the community I live in.

Throughout this journey, I have wondered what it is I will do next. How do you follow up a poker career? I wasn’t sure, but I was patient with myself. A few weeks ago, I feel it hit me square in the head and became incredibly obvious. I desire to create a retreat that gives people a similar experience that I felt. I want people to experience what it feels like to be healthy again, to allow them opportunities to meet new and creative people, and to create a safe place for people to let go of the day to day worries they currently have. I want to help create new leaders, give people the opportunity to meet lifelong brothers and sisters, and build a special community of like-minded and driven people.

Right now, I am in the early stages of building this, but I am focused on delivering the best possible experience while cultivating a unique and special group of people.
If you feel called to get exclusive updates on this journey, you can sign up for the email list at https://thebeauwinn.com.
Thanks everyone. Much love and pura vida,
Beau

-
 @ 554ab6fe:c6cbc27e
2025-01-05 15:51:49
@ 554ab6fe:c6cbc27e
2025-01-05 15:51:49Energy is at the root of life and nature. Life is a product of the energy flow from the sun to the earth, as a natural consequence of entropy and the second law of thermodynamics. When contemplating human health, one must similarly consider the fundamental role energy plays in our physiologic system. There are two major sources of energy to consider: the energy of the sun which gives rise to life on this planet, and the energy produced by our cells, in the mitochondria, in the form of Adenosine Triphosphate (ATP).
Mitochondria, commonly known as the ‘powerhouse’ of the cell, was a symbiote that found its home within the proto-eukaryotic cell roughly 1.5 to 2 billion years ago1. This merger between two cells was developmentally significant, as it gave a cell the capability of producing energy internally, allowing for more complex processes. ATP is produced within the mitochondria via oxidative phosphorylation which includes two steps: the electron transport chain and chemiosmosis. The electron transport chain is where electrons provided by the glucose from our food, combined with the oxygen we breathe, produces a proton gradient across the membrane of the mitochondria, and results in the production of water. The proton gradient produced subsequently allows a protein complex named ATP synthase to produce ATP, the energy for the body.
Up until very recently in human history, the most common cause of death was from diseases that were communicable. Given the rise of modern medicine, many of these diseases are treatable. However, in the 1900s, a shift also occurred where non-communicable disease because, by a large margin, the leading cause of death2. Leading causes of death today include diabetes, cancer, obesity, and respiratory disease2. Unlike our historical past, the way society alleviates this burden of disease is not by being hostile toward a pathogen, but by having humility in appreciating how our modern lifestyles are out of sync with nature and causes disease. For example, our modern lives create busy brains, and we accordingly lose appreciation for having a state of mindfulness, which is a state of mind more akin to life in nature which has the capability of reducing overall chronic disease3. At the physical level, what is at the root of our chronic disease is the health of our mitochondria. With energy, in the form of ATP, the body is not capable of effectively performing the physiological processes needed for healthy function. No matter how many good resources you feed a factory, without energy, there is no production. Mitochondrial health is at the center of our chronic disease4,5.
The key to mitochondrial health includes some intuitive solutions such as exercise and good nutrition. However, to gain a deeper understanding of the deterioration of our mitochondria, one must appreciate this powerhouse’s relationship with the energy that feeds the planet. Mammal biology is adapted to live in the sun, and our physiology consequently requires a relationship with it. As discussed in a previous piece, there are many health benefits to the eyes and skin from both the longer-wavelength hours (red light) of the sunset and sunrise, and the ultra violet light of the midday. Our body benefits from the wide range of light emitted by the sun throughout the cycle of the day. However, we are similarly at a detriment if we receive a wavelength of light that is unnatural to that time of day.
Light plays a predominant role in our circadian rhythm. Artificial light at night (ALAN) severely delay the production of melatonin, the hormone that helps us sleep6. This is caused from our exposure to blue light, which only naturally occurs during the midday, but is being emitted by nearly every electronic light source in our modern homes7. Made worse is the fact that LED screens emit 3 times more blue light than non-LED screens8. Our circadian rhythm and sleep health is also highly influential on our mitochondrial health. To explore this idea further, a more thorough understanding of mitochondria is needed.
As mentioned previously, mitochondria fundamentally turn our food and oxygen into water and energy. This is done via oxidative phosphorylation. Figure 1 below provides a diagram for this process.
 Figure 1 Sourced from The Role of Mitochondria in Cancer and Other Chronic Diseases (Gonzales, 2014)
Figure 1 Sourced from The Role of Mitochondria in Cancer and Other Chronic Diseases (Gonzales, 2014)In this process of oxidative phosphorylation, complex 1-4 perform the electron transport chain. Various processes occur that pump protons (H+) out of the mitochondria and into the cell, only so that the ATP synthase pump can produce ATP by moving the proton back inside due to the gradient formed on each side of the inner membrane. Complex I and II move protons provided by NADH and FADH from glucose. Complex IV does so by turning oxygen into water. This process of turning oxygen into water comes with a periodic side effect of producing reactive oxygen species (ROS). ROS can be beneficial to the body, but in can be dangerous in excess. Most critically, ROS can damage the mitochondrial DNA (mtDNA)4. Dysfunctional mtDNA will result in the improper production of proteins that are necessary for us to sustain life4. This naturally means that the body is constantly in a state of balance: both producing the necessity of ROS despite its damage to our mtDNA, while simultaneously performing processes that reduce this damage. Melatonin, an antioxidant produced via the circadian rhythm, is one such method of reducing this damage via the reduction of ROS9. A takeaway here is that a healthy relationship with sleep can directly benefit mitochondrial health. Additionally, healthy sleep is obtained by becoming more synchronized with the sun and reducing the amount of artificial blue light exposure during the times outside of the midday. Melatonin can also be increased with a meditation practise10. Furthermore, it has been shown that mitochondria themselves produce more melatonin than the pineal gland, for their own protection11. This further highlights the importance in mitochondrial health, as they need to be activated enough to produce more melatonin to prevent chronic issues. However, this is just scratching the surface of how we keep our mitochondria healthy.
Sunlight is central to mitochondrial health. On the one hand, sunlight increases the production of melanin, the pigmentation that is responsible for darker skin. This is important because melanin protects our skin from DNA damage caused by UV light, and because mtDNA is also damaged by UV light, melanin likely offers safe protection for our mitochondria12,13. UV light also increases the activity of melanocytes, increasing the production of melanin and leading to darker skin13. This is especially true in the eyes, where it has been shown that UVB stimulation to the eye causes increased epidermal melanocyte activity14. This leads to the possible conclusion that sunglasses, which block UV rays from entering the eye, decrease our ability to produce melanin when we expose ourselves to the sun.
It is common in the modern era to consider UV light dangerous, as its capability to damage DNA could lead to skin cancer. This is a drastically oversimplified rational. A study in 2014 known as the Southern Sweden Cohort aimed to investigate to what degree sun exposure led to increased death of pale individuals stemming from this rational15. The results found that increased sun exposure was extremely indirectly correlated with risk of death15. Meaning, the more someone was out in the sun, the less likely they were to die. The authors of this paper mainly attributed to the vital importance of Vitamin D production, but the benefits likely run much deeper.
Consider how animals in the wild may bask in the shade during the middle of the day. Naturally, UV light has its costs and benefits, and avoiding the rays emitted in the middle of the day would be helpful. Nonetheless, these animals are outside all day, meaning they are also being exposed to infrared light (IR) which, like UV light, is not visible. IR light is highest during the midday as well, but it can pass through objects more easily due to its longer wavelength. Infrared light plays a key role in mitochondrial health and is something we severely lack from living indoors.
IR light increases ATP production in the mitochondria. A recent study found that blood glucose spikes could be reduced when exposing patients to IR light16. Additionally, patients exhaled more CO2, a byproduct of oxidative phosphorylation and cellular respiration16. Both measurements indicate greater mitochondrial activity, driven by the exposure of IR light. There are several theories as to how IR triggers this incredibly healthy response. It is possible that Cytochrome C Oxidase, which transfers electrons between complex III and IV, is a chromophore for infrared light and increases its activity under its exposure, thereby allowing for the increased production of ATP17. It is also possible that the longer wavelength light increases ATP synthase efficiency by reducing the viscosity of the water surrounding the ATP pump18. Either way, there is ample evidence to suggest that our human body benefits directly from sun exposure. The light we receive from the sun passes into our bodies and increase the activation of our mitochondria, providing us with the energy necessary for a healthy life.
Mitochondria benefit from sunlight beyond potential direct influences from the rays of light. Additionally, there is a relationship between UV light, melanin, and mitochondria. Proopiomelanocortin (POMC) is a precursor protein for many melanocortin, which include melanocyte-stimulating hormones (MSH), that produce melanin19,20. UV light is what triggers the production of the POMC-derived melanin producing hormone, which leads to the production of melanin itself21. All of this is to say that UV light leads to the production of melanin and the darkening of our skin pigmentation. Melanin, besides determining skin color, also plays an important role in mitochondrial health. Melanin, due to its chemical structure, is a reversible oxidation-reduction system, meaning it can go through both chemicals processes that allow it to lose and gain electrons22. This means that melanin can acts as a kind of battery, storing electrons for when they are needed. This is vital to mitochondrial health, because fundamentally what the electron transport chain needs to produce ATP is, obviously, electrons. The more melanin the body has, the more batteries it has to store electrons for use by the mitochondria. Therefore, there is a deep fundamental relationship between the body’s need to be exposed to the sun’s UV rays, and its ability to maintain melanin supply to fuel the electrons needed for mitochondrial ATP production.
Lastly, it is then curious to consider how some of our ancient ancestors who lived in environments where the sun was not abundant were able to stay healthy, given the importance of sun exposure on mitochondrial health. To understand how populations in northern latitudes prospered, a thorough investigation of uncoupled mitochondria is required. Within some mitochondria are uncoupled proteins. These proteins allow the protons to re-enter the mitochondrial matrix without using the ATP synthase. Rather than generating ATP through this process, heat is generated instead. There are various kinds of uncouple proteins (UCPs)23:
- UCP1 are mainly founded in brown adipose tissue (BAT) as is activated by fatty acids
- UCP2 are found in the lymphoid system, macrophages, and pancreatic islets
- UCP3 are mainly found in skeletal muscles
When a mammal is exposed to repeated cold temperatures, this triggers the development of brown fat24. This development of brown fat from the cold was an evolutionary adaptation that seemed to develop independently in European and Asian people25. Furthermore, there is evidence to suggest that homo-sapiens acquired this adaptation through the interbreeding with Neanderthals and Denisovans respectively25. This suggest that the humans who left Africa, our birthplace with plenty sun exposure, were able to survive and thrive better if they received the genes of our cousins that had mitochondria more fit for the cold environments.
Despite this adaptation for warmth, these uncoupling proteins do not explain how cold adapted humans were able to have proper mitochondrial health given the reduced sun exposure. Research has also found that increased heat dissipation by mitochondria coincides with an increased expression of the gene that encodes leptin26. Accordingly, the LEPR gene influences satiety, fatty acid processing in adipose tissue, energy balance, fat storage, and glucose metabolism26. Furthermore, leptin activates POMC27. Given POMC leads to the generation of melanin, a storehouse for electrons, cold adapted individuals were able to maintain proper mitochondrial health by producing melanin via a different mechanism than those who are exposed to the sun. This provides much perspective to those living in colder climates today, but who live in temperature regulated homes and do not regularly expose themselves to the cold.
In summary, a proper relationship with sunlight is vital to mitochondrial health and reducing chronic disease. Overexposure to blue light decreases melatonin, which negatively impacts sleep and reduces our mitochondria’s ability to defend itself from the DNA damage of ROS. UV light is vital to the production of melanin which provides ample supply of electrons to our mitochondria so we can produce energy. Furthermore, infrared light allows for the mitochondria to be more efficient at turning those electrons into energy. Lastly, for human beings that do not live in sunny climates, exposure to the cold leads to the development of brown fat which contains within its mitochondria that will generate heat and melanin as a replacement for UV light. Nature is where true healing is found.
References
- Wallace DC, Brown MD, Lott MT. Mitochondrial DNA Variation in Human Evolution and Disease. Vol 238.; 1999. www.elsevier.com/locate/gene
- O U AP, F UC, F EO, O C AC. Epidemiologic Transition of Diseases and Health-Related Events in Developing Countries: A Review. American Journal of Medicine and Medical Sciences. 2015;2015(4):150-157. doi:10.5923/j.ajmms.20150504.02
- Zhang D, Lee EKP, Mak ECW, Ho CY, Wong SYS. Mindfulness-based interventions: An overall review. Br Med Bull. 2021;138(1):41-57. doi:10.1093/bmb/ldab005
- Gonzalez MJ, Miranda-Massari JR, Duconge J. The role of mitochondria in cancer and other chronic diseases. Published online 2014. Accessed August 30, 2024. https://www.researchgate.net/publication/311389607
- Casey M, Calley M. Good Energy: The Surprising Connection Between Metabolism and Limitless Health. Avery; 2024.
- Phillips AJK, Vidafar P, Burns AC, et al. High sensitivity and interindividual variability in the response of the human circadian system to evening light. Proc Natl Acad Sci U S A. 2019;116(24):12019-12024. doi:10.1073/pnas.1901824116
- West KE, Jablonski MR, Warfield B, et al. Blue light from light-emitting diodes elicits a dose-dependent suppression of melatonin in humans. J Appl Physiol. 2011;110(3):619-626. doi:10.1152/JAPPLPHYSIOL.01413.2009/ASSET/IMAGES/LARGE/ZDG0031194630004.JPEG
- Cajochen C, Frey S, Anders D, et al. Evening exposure to a light-emitting diodes (LED)-backlit computer screen affects circadian physiology and cognitive performance. J Appl Physiol. 2011;110:1432-1438. doi:10.1152/japplphysiol.00165.2011.-Many
- Leon J, Acuña-Castroviejo D, Sainz RM, Mayo JC, Tan DX, Reiter RJ. Melatonin and mitochondrial function. Life Sci. 2004;75(7):765-790. doi:10.1016/j.lfs.2004.03.003
- Solberg EE, Holen A, Ekeberg Ø, Østerud B, Halvorsen R, Sandvik L. The effects of long meditation on plasma melatonin and blood serotonin. Medical Science Monitor. 2004;10(3):96-102.
- Zimmerman S, Reiter RusselJ. Melatonin and the Optics of the Human Body. Melatonin Research. 2019;2(1):138-160. doi:10.32794/mr11250016
- Birch-Machin MA, Russell E V., Latimer JA. Mitochondrial DNA damage as a biomarker for ultraviolet radiation exposure and oxidative stress. British Journal of Dermatology. 2013;169(s2):9-14. doi:10.1111/BJD.12207
- Wicks NL, Chan JW, Najera JA, Ciriello JM, Oancea E. UVA Phototransduction Drives Early Melanin Synthesis in Human Melanocytes. Curr Biol. 2011;21(22):1906. doi:10.1016/J.CUB.2011.09.047
- Hiramoto K, Yanagihara N, Sato EF, Inoue M. Ultraviolet B Irradiation of the Eye Activates a Nitric Oxide-dependent Hypothalamopituitary Proopiomelanocortin Pathway and Modulates Functions of α-Melanocyte-stimulating Hormone-responsive Cells. Journal of Investigative Dermatology. 2003;120(1):123-127. doi:10.1046/J.1523-1747.2003.12004.X
- Lindqvist PG, Epstein E, Landin-Olsson M, et al. Avoidance of sun exposure is a risk factor for all-cause mortality: Results from the Melanoma in Southern Sweden cohort. J Intern Med. 2014;276(1):77-86. doi:10.1111/joim.12251
- Powner MB, Jeffery G. Light stimulation of mitochondria reduces blood glucose levels. J Biophotonics. 2024;17(5):e202300521. doi:10.1002/JBIO.202300521
- De Freitas LF, Hamblin MR. Proposed Mechanisms of Photobiomodulation or Low-Level Light Therapy. IEEE Journal of Selected Topics in Quantum Electronics. 2016;22(3):348-364. doi:10.1109/JSTQE.2016.2561201
- Sommer AP, Haddad MK, Fecht HJ. Light Effect on Water Viscosity: Implication for ATP Biosynthesis. Sci Rep. 2015;5. doi:10.1038/srep12029
- Hadley ME, Haskell-Luevano C. The Proopiomelanocortin System.
- Biebermann H, Kühnen P, Kleinau G, Krude H. The neuroendocrine circuitry controlled by POMC, MSH, and AGRP. Handb Exp Pharmacol. 2012;209:47-50. doi:10.1007/978-3-642-24716-3_3
- Slominski AT. Ultraviolet radiation (UVR) activates central neuro-endocrine-immune system. Photodermatol Photoimmunol Photomed. 2015;31(3):121. doi:10.1111/PHPP.12165
- Figge FHJ. Melanin: a Natural Reversible Oxidation-Reduction System and Indicator. https://doi.org/103181/00379727-41-10593P. 1939;41(1):127. doi:10.3181/00379727-41-10593P
- Rousset S, Alves-Guerra MC, Mozo J, et al. The Biology of Mitochondrial Uncoupling Proteins. Diabetes. 2004;53(suppl_1):S130-S135. doi:10.2337/DIABETES.53.2007.S130
- Lim S, Honek J, Xue Y, et al. Cold-induced activation of brown adipose tissue and adipose angiogenesis in mice. Nature Protocols 2012 7:3. 2012;7(3):606-615. doi:10.1038/nprot.2012.013
- Sellayah D. The Impact of Early Human Migration on Brown Adipose Tissue Evolution and Its Relevance to the Modern Obesity Pandemic. J Endocr Soc. 2019;3(2):372-386. doi:10.1210/JS.2018-00363
- Sazzini M, Schiavo G, De Fanti S, Martelli PL, Casadio R, Luiselli D. Searching for signatures of cold adaptations in modern and archaic humans: hints from the brown adipose tissue genes. Heredity 2014 113:3. 2014;113(3):259-267. doi:10.1038/hdy.2014.24
- Oswal A, Yeo GSH. The leptin melanocortin pathway and the control of body weight: Lessons from human and murine genetics. Obesity Reviews. 2007;8(4):293-306. doi:10.1111/j.1467-789X.2007.00378.x






