-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
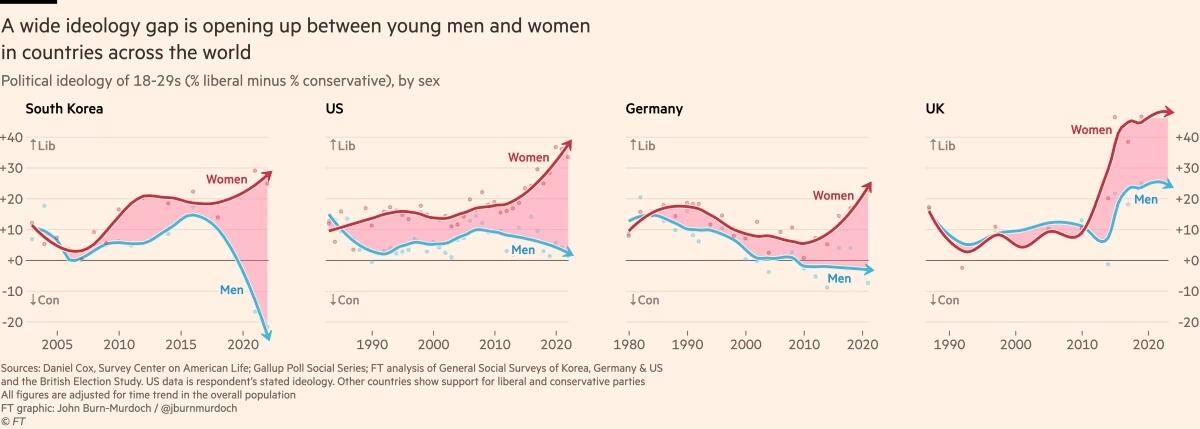
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 59cb0748:9602464b
2025-01-01 06:15:09
@ 59cb0748:9602464b
2025-01-01 06:15:09Nostrでお世話になっている方も、お世話になってない方も、こんにちは!
タコ頭大吉です!
NIP-23を使った初めての投稿です。
今回は、私がここ数ヶ月中にデザインをした三種類のビタキセケースの紹介記事になります!!
ビタキセを買ったもののあまり自分の好みに合う外観や仕様のケースがなく、いくつかプロトタイプを作りそれなりに時間をかけて考えたケース達です。
これら3シリーズに関しては、FDMタイプの3Dプリンタの精度、耐久性、出力後の作業性を考慮して一つのパーツで完結することに拘って設計をしました。
一定以上の充填率でプリントをすればそれなりに丈夫なはずです。
また、基本的に放熱性と保護性を両立できるように設計をしたつもります。
それぞれのモデルについて簡単に紹介をさせていただきますので、よろしければ各リポジトリに付属のREADMEを読んでいただいて自作、フィードバックをいただけましたら幸いです。
それでは、簡単に各モデルの紹介をさせていたきます。
AirLiftFrame
 最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
TwinAirLiftFrame
 ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
VoronoiShell
 AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
いずれカスタム方法やインサートナットや増設ファンの選定方法等を紹介したいのですが、今回はNIP-23になれるという意図もあるので紹介に留めます! また、他の関連OSハードウェアプロジェクトのケースもデザインできたらと思っております!
今後ともタコ頭をよろしくお願いいたします。
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ ccc8ee23:9f3d9783
2024-12-23 22:03:15
@ ccc8ee23:9f3d9783
2024-12-23 22:03:15Chef's notes
Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy.
Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Chicken Fillet 250 grams
- Potato 100 grams
- Egg 1 pc
- Curry block 2 pcs or 20 grams
- breadcrumbs 100 grams / 2 cups
- flour 20 grams
- Cooking oil (for frying)
- chicken or vegetable stock 500ml
- soy sauce 1 tbsp
- Seasoning
- onion 1 pc, finely chopped
- garlic cloves 2 pcs, minced
- carrot 1 pc, chopped
Directions
- Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain.
- Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste.
- Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies.
-
 @ ae6ce958:d0f02c7d
2025-01-01 05:24:36
@ ae6ce958:d0f02c7d
2025-01-01 05:24:36In the world of software development, achieving failure isn’t just a buzzword; it’s the secret weapon of the strongest, most resilient teams. When you aim for greatness, you must also face your weaknesses head-on, stress-testing your limits until you break. This philosophy isn’t new—it’s the same principle that made bodybuilders like Tom Platz, with his monstrous leg days, legends. It’s not about avoiding failure; it’s about embracing it, owning it, and using it to rise stronger.
Let’s get something straight: failure is where growth happens. You don’t get bigger quads without pushing through reps to muscle failure. And you don’t build indestructible software without finding the cracks in your systems before they become catastrophic. That’s where DamageBDD steps in—it’s the squat rack for your code, the arena where your software’s strength is truly tested.
The Beauty of Controlled Destruction
Developers often shy away from failure, fearing downtime, bugs, or the dreaded post-mortem meeting. But failure isn’t the enemy—it’s the blueprint for success. DamageBDD is your spotter, encouraging you to load up the bar and attempt that new PR (personal record) for system resilience. By simulating real-world scenarios, integrating failure conditions into your tests, and verifying those outcomes on the blockchain, DamageBDD lets you train harder and smarter.
Think of your system as a muscle. It grows stronger under tension, stress, and controlled failure. With DamageBDD, you can:
-
Expose Weak Links: Identify vulnerabilities that would otherwise lie dormant until disaster strikes.
-
Build Resilience: Test every feature, every API, every assumption—so nothing escapes the grind.
-
Reap Confidence Gains: Know that when your system is live, it’s already conquered tougher challenges in the DamageBDD gym.
Why DamageBDD is the Tom Platz of BDD Tools
Like the legendary Platz, DamageBDD is unapologetically intense and methodical. It doesn’t just want you to succeed; it wants you to fail spectacularly in a controlled environment where you can learn, adapt, and grow.
Precision Execution: Every test case is a perfect rep. No shortcuts, no sloppy form. DamageBDD’s blockchain verification ensures every action is recorded immutably.
Progressive Overload: Just as you progressively increase weights in the gym, DamageBDD scales with your application’s complexity. New scenarios? Bigger challenges? Bring it on.
Discipline for Longevity: Consistency breeds success. With DamageBDD, you develop a habit of testing thoroughly, ensuring your system stays strong and reliable for years to come.
Pain Today, Strength Tomorrow
As developers, we often celebrate success stories without recognizing the failures that made them possible. But here’s the truth: failure is the crucible of champions. The pain of discovering a flaw today prevents the agony of catastrophic failure tomorrow. DamageBDD helps you confront that pain with the discipline of a bodybuilder—systematically, rigorously, and with purpose.
So, if you’re ready to take your development process to the next level, it’s time to embrace failure. It’s time to load the bar, set your sights on resilience, and let DamageBDD guide you to software greatness. Remember: strength is earned, not given.
Now go—fail, learn, and build systems that are as unbreakable as Platz’s legendary quads.
-
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ b4403b24:83542d4e
2024-12-31 22:24:43
@ b4403b24:83542d4e
2024-12-31 22:24:43As we bid farewell to 2024, let’s celebrate the memories, lessons, and triumphs it brought us. May 2025 shine even brighter, bringing you joy, success, and endless opportunities.
Here’s to new beginnings, cherished moments, and a year filled with happiness. Cheers to 2025! 🥂
originally posted at https://stacker.news/items/831699
-
 @ ccc8ee23:9f3d9783
2024-12-21 06:38:47
@ ccc8ee23:9f3d9783
2024-12-21 06:38:47Chef's notes
Enjoy these Chocolate Sprinkle Cookies, a delightful combination of buttery richness, velvety chocolate, and a crunchy sprinkle finish
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 90 min
- 🍽️ Servings: 10
Ingredients
- Plain flour 250 grams
- Margarine 100 grams
- Butter 100 grams
- Vanilla essence 1 tsp
- Milk powder 1 tbsp
- Sugar 40 grams
- Chocolate bar - 80 grams, melted
- Chocolate sprinkles - for decoration
Directions
- Make the Dough: Combine the plain flour, margarine, butter, milk powder, sugar, and vanilla essence in a mixing bowl. Knead the mixture by hand until smooth and well combined.
- Shape and divide the dough into small balls, weighing approximately 8 grams each.
- Preheat the oven to 175°C. Arrange the dough balls on a baking tray and bake for about 30 minutes, or until the cookies are dry and fully cooked.
- Coat with Chocolate: Melt the chocolate bar using a double boiler or microwave. Once the cookies have cooled completely, dip each cookie into the melted chocolate, ensuring they are evenly coated.
- Place the coated cookies onto paper cups.
- While the chocolate coating is still wet, sprinkle chocolate sprinkles on top of each cookie.
- Allow the chocolate to dry completely, then arrange the cookies in a decorative airtight container for storage.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ ccc8ee23:9f3d9783
2024-12-21 06:03:28
@ ccc8ee23:9f3d9783
2024-12-21 06:03:28Chef's notes
Celebrating seasons🎉
Kastengel Chocolate-Dip, where the savoury richness of cheese meets the decadent sweetness of chocolate. A perfect flavours in every bite!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 90 min
- 🍽️ Servings: 10
Ingredients
- Plain Flour 250 grams
- Margarine - 100 grams
- Butter 100 grams
- Egg yolk 1 pc
- Sugar 20 grams
- Grated cheese 100 grams (half for the dough, half for garnish, adjustable)
- Chocolate bar 80 grams, melted
Directions
- Make the Dough: Combine the plain flour, margarine, butter, sugar, and half of the grated cheese in a bowl. Knead the mixture with your hands until smooth and well incorporated. Roll out the dough using a rolling pin and cut into desired shapes for cookies.
- Beat the egg yolk. Brush the shaped cookies with the egg yolk mixture and sprinkle the remaining grated cheese on top.
- Bake the cookies 175’C for about 30 minutes, or until they are dry and perfectly cooked.
- Melt the chocolate bar in a double boiler or microwave until smooth.
- Dip in Chocolate: Once the cookies have cooled completely, dip both the top and bottom ends of each cookie into the melted chocolate.
- Place the dipped cookies on a wire rack or a cookie drying tray to allow the chocolate to harden and set.
- Arrange the cookies neatly in an airtight container.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ ac8bb9b0:70278acc
2024-12-20 18:48:36
@ ac8bb9b0:70278acc
2024-12-20 18:48:36Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 10
- 🍽️ Servings: 4
Ingredients
- 1 lb large shrimp, peeled and deveined
- 1 tablespoon extra virgin olive oil
- 3 cloves garlic, chopped
- 1/4 cup white wine, dry
- 14 oz can petite diced tomatoes, drained
- 1/2 cup half and half
- 1/2 teaspoon dried oregano
- kosher salt and fresh black pepper, to taste
- 1 teaspoon lemon juice
- 1/4 cup fresh parsley, chopped
- 8 ounces angel hair pasta, whole wheat, gluten-free or high fiber
Directions
- Boil water with salt in a large pot for the pasta. Cook pasta al dente according to package directions.
- Meanwhile, season shrimp with 1/4 teaspoon salt, black pepper and oregano.
- Heat a large skillet over medium heat. Add the oil, when warm add the shrimp and garlic and cook about 2 minutes on each side.
- Add tomatoes, wine, salt and pepper and cook an additional minute.
- Remove from heat and stir in half and half. Add lemon juice and parsley and serve over pasta.
- Divide equally in 4 plates or shallow bowls.
-
 @ 468f729d:5ab4fd5e
2024-12-31 22:03:31
@ 468f729d:5ab4fd5e
2024-12-31 22:03:31 -
 @ ccc8ee23:9f3d9783
2024-12-19 12:46:00
@ ccc8ee23:9f3d9783
2024-12-19 12:46:00Chef's notes
Salmon Mentai Rice. Create your own layers of fluffy, seasoned rice are topped with tender, pan-seared chicken or salmon and a creamy, spicy mentai sauce made with spicy Japanese mayo .
Torched to golden perfection, it’s finished with nori and tobiko for a burst of texture and flavor. A simple tasty Japanese fusion delight that’s perfect🤩
Subtitude of Tobiko, white sesame seeds as economical option will add a nutty flavor and subtle crunch to the dish for texture and visual appeal.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Steamed Rice 400 grams
- Rice vinegar 1 tbsp
- Sugar 1 tsp
- chicken breast / thighs 250 grams
- soy sauce 1 tbsp
- oyster sauce 1 tbsp
- sesame oil 1 tsp
- garlic powder 1 tsp
- cooking oil 1 tbsp
- mayonnaise (e.g., Kewpie) 4 tbsp
- sriracha or any chili sauce 1 tbsp
- tobiko if any or white sesame as optional, for texture, 2 tsp only
Directions
- Prepared the Rice: mixed in bowl 2 cups steam rice, 1 tbsp rice vinegar, 1 tsp sugar and 1/2 tsp salt. Set a side.
- Cook the Chicken: 1. Marinate the chicken pieces with 1 tsp soy sauce, 1 tsp oyster sauce, 1 tsp sesame oil, 1 tsp garlic powder for 15–20 minutes. 2. Heat cooking oil in a pan over medium heat and stir-fry the chicken until fully cooked and slightly caramelized. Remove from heat.
- Make the Mentai Sauce 1. In a small bowl, combine 4 tbsp mayonnaise, 1 tbsp chili sauce, and 1 tsp sesame oil. Add tobiko if desired for texture. Mix well.
- Assemble the Mentai Rice 1. In a heatproof bowl or tray, layer the seasoned rice as the base. 2. Add a layer of cooked chicken on top of the rice. 3. Spread the mentai sauce evenly over the chicken layer.
- Grill or Broil: Use a kitchen torch or place the dish under a broiler for 2–3 minutes until the sauce is slightly charred and bubbly.
- Garnish with white sesame or nori strips, or extra tobiko.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ ccc8ee23:9f3d9783
2024-12-19 05:55:09
@ ccc8ee23:9f3d9783
2024-12-19 05:55:09Chef's notes
Dare to taste the bold? One bite of Jengkol Balado and you’ll be hooked
Spicy Jengkol Balado - Betawi Style A traditional dish from Betawi (Jakarta), Jengkol Balado is nutty bold and aromatic delicacy made with jengkol beans. This version uses thinly sliced jengkol for a delightful texture.
Serve it with a plate of steamed fragrant white rice and a side of crunchy cucumber for a complete meal that satisfies on every level.
Details
- 🍳 Cook time: 40 min
- 🍽️ Servings: 2
Ingredients
- Jengkol 250 grams
- Chilli 100 grams
- Shallot 5 cloves
- Garlic 2 cloves
- Tomato 1 clove (small)
- Bay leaves 2
- Galangal 2cm. Bruished
- Veggie oil 20ml or 4 tsp
- Seasoning
Directions
- Prepare the Jengkol Wash the jengkol thoroughly and slice it thinly. Boil the slices in water with the bay leaves for 10–15 minutes to soften and reduce their strong odour. Drain and set aside.
- Make the Balado Paste. Blend chillies, shallots, garlic, candlenut and tomatoes into a slightly coarse paste using a blender
- Heat oil in a pan and sauté the balado paste until fragrant and the oil starts to separate. Add the galangal, bay leaves, salt, sugar, and seasoning. Stir well
- Add jengkol to the pan. Mix until jengkol are fully coated in the balado paste.
- If the mixture seems too dry, add a splash of water and let it simmer on low heat to allow the flavours to infuse.
- Taste the dish and adjust the seasoning with more salt or sugar if needed.
- Remove from heat and serve hot with steamed rice.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ d873a9c8:269f1419
2024-12-31 20:08:17
@ d873a9c8:269f1419
2024-12-31 20:08:17This crossword contains a bitcoin wallet within, take the wallet for yourself.
If this Wallet still has bitcoin, the crossword has not been completed.
 ## Across:
## Across:- (5 Across) A piece of furniture used for work or study (13).
- (7 Across) At the back of or following someone or something (23).
- (10 Across) A non-professional or novice (16).
- (13 Across) More than what is needed or allowed (8).
- (14 Across) A choice or alternative path (4).
- (16 Across) A support or position to hold or display something (2).
- (18 Across) A skilled worker or the fundamental workings of a system (7).
- (19 Across) A married woman, often part of a partnership (17).
- (20 Across) Widely liked or accepted by many (20).
- (21 Across) A competition to achieve something first (9).
- (22 Across) To confess or allow access (6).
- (24 Across) A member of the species Homo sapiens (22).
Down:
- (1 Down) A bird often associated with golden eggs in stories (18).
- (2 Down) A location identifier or a formal speech (12).
- (3 Down) Something of enormous size or importance (14).
- (4 Down) A representative or someone acting on behalf of another (21).
- (6 Down) The beginning or earliest part of something (1).
- (8 Down) A mistake or incorrect action (24).
- (9 Down) A term for something outdated or ancient (5).
- (11 Down) A grassy field often teeming with life (15).
- (12 Down) The art of arranging sounds harmoniously (19).
- (15 Down) Unmotivated or unwilling to act (10).
- (17 Down) A powerful effect or collision (3).
- (23 Down) Lacking intelligence or unable to speak (11).
The number after each definition is used in the construction of the prize seed phrase.
Luka
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ ac8bb9b0:70278acc
2024-12-18 21:18:57
@ ac8bb9b0:70278acc
2024-12-18 21:18:57Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 20
- 🍽️ Servings: 5
Ingredients
- 8 ounces uncooked linguine
- 1 pound chicken breast, cut into strips
- 1-2 tsp Cajun seasoning, or more to taste
- 1 tsp garlic powder
- 1 tbsp extra virgin olive oil
- 1 medium red bell pepper, thinly sliced
- 1 medium yellow bell pepper, thinly sliced
- 8 oz fresh mushrooms, sliced
- 1/2 red onion, sliced
- 3 cloves garlic, minced
- 2 tomatoes, diced
- 1 cup low sodium chicken broth
- 1/3 cup skim milk
- 1 tbsp flour
- 3 tbsp light cream cheese
- fresh cracked pepper
- 2 scallions, chopped
- kosher salt to taste
- avocado oil spray
Directions
- Prep all your vegetables.
- In a small blender make a slurry by combining milk, flour and cream cheese. Set aside.
- Season chicken generously with Cajun seasoning, garlic powder and salt.
- Prepare pasta in salted water according to package directions.
- Heat a large heavy nonstick skillet over medium-high heat; spray with oil and add half of the chicken.
- Sauté 5 to 6 minutes or until done, set aside on a plate and repeat with the remaining chicken. Set aside.
- Add olive oil to the skillet and reduce to medium; add bell peppers, onions, and garlic to skillet, sauté 3-4 minutes.
- Add mushrooms and tomatoes and sauté 3-4 more minutes or until vegetables are tender.
- Season with 1/4 tsp salt, garlic powder and fresh cracked pepper to taste.
- Reduce heat to medium-low; add chicken broth and pour in slurry stirring about 2 minutes.
- Return chicken to skillet; adjust salt and Cajun seasoning to taste, cook another minute or two until hot, then add linguine; toss well to coat.
- Top with chopped scallions and enjoy!
-
 @ 0403c86a:66d3a378
2024-12-31 19:22:15
@ 0403c86a:66d3a378
2024-12-31 19:22:15As we kick off the new year and gear up for GSC's Anniversary Celebration on January 11, we’re thrilled to unveil our anticipated list of 11 oN 11 – the 11 athletes who dominated their sports, broke records, and inspired the world in the past year.
These icons didn’t just shine on the field, court, or track – they redefined excellence and left an indelible mark on the global sports landscape.
Our nominees will be revealed daily, follow the countdown to greatness #11oN11
These athletes didn’t just win games – they won hearts, inspired nations, and moved the needle for their respective sports.
✨ Join the conversation and tell us your picks for the most defining athletes of last year! Who inspired YOU the most? Let’s celebrate excellence together as we count down to GSC’s Anniversary on January 11!!!
Global Sports Central 🌐 #11oN11
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ ac8bb9b0:70278acc
2024-12-16 19:37:12
@ ac8bb9b0:70278acc
2024-12-16 19:37:12Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 20
- 🍽️ Servings: 6
Ingredients
- 2 tablespoons extra virgin olive oil
- 1 1/2 pounds ground chicken
- 1 yellow onion, chopped
- 2 tablespoons taco seasoning
- salt and black pepper
- 2 1/2 cups salsa or enchilada sauce
- 1 chipotle chili in adobo, chopped
- 2 cups fresh corn
- 4 ounces cream cheese, at room temperature
- 1/4 cup plain greek yogurt
- 1 teaspoon chili powder
- 1 1/2 cups shredded Mexican cheese blend
- 2 cups tortilla chips
- avocado, cilantro, and green onions, for serving
Directions
- Preheat the oven to 400° F.
- In a large oven-safe skillet, combine the olive oil, chicken, onion, salt, and pepper. Set the skillet over high heat. Cook, breaking up the meat as it cooks, until browned all over, 5 minutes. Add the taco seasoning, cook another 2 minutes. Then add 1/2 cup water. Stir in the salsa/enchilada sauce and chipotle. Simmer 5 minutes. Remove from the heat and add in the cilantro.
- In a bowl, combine the corn, cream cheese, yogurt, chili powder, and salt. Stir in 1/2 cup cheese.
- Dollop 1/3 of the corn mix over the skillet. Add the tortilla chips on top, pressing them gently into the skillet. Add the remaining corn mix by spoonfuls on top of the chips (like nachos). Top with the remaining cheese. Bake for 15 minutes, until the cheese is melted.
- Serve topped as desired with avocado, cilantro, green onion, and cotija/feta cheese.
-
 @ 3f770d65:7a745b24
2024-12-31 17:03:46
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025:
Decentralization: The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
Privacy Standards: Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
Interoperability: Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
Adoption and Migration: Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 07804b78:c375c543
2024-12-15 12:56:05
@ 07804b78:c375c543
2024-12-15 12:56:05Japanese follows. 日本語はあとで。
This article is for the 14th day of Nostr Advent Calendar 2024 (relay blogging). The article for the 13th day was "Open Sats 申請編" (Applying for Open Sats) by mono-san. The article for the 14th day will be "Nostrはじめました。" (I started Nostr) by bro-san.
Thinking of Thingstr
I've come up with an idea for Other Staff that I think is interesting (at least, for me), so I'm going to write about it. I actually wanted to show you the implementation and brag about it, but it's not solid enough to be implemented yet.
The key idea is just “add a reaction to the WikiData ID”.
WikiData
There is a service called WikiData. It is a knowledge base that provides structured data. You may be wondering what it is, but the important thing to understand here is that WikiData assigns identifiers to a fairly wide range of “objects” and “things”.
So, if you can react to this, you can think of various applications just by thinking of it for a moment, right?
For example, the anime series “There are too many losing heroines!” is assigned the ID
Q123819103. The corresponding page is https://www.wikidata.org/wiki/Q123819103 .(NOTE: The canonical URI for entities on Wikidata is http://www.wikidata.org/entity/Q1142841. This is in accordance with Semantic Web conventions, and is not https, but http. Also, this URI does not necessarily match the actual address of the correspnding web page. Just an identifier. In most cases, it will redirect).
What can wd do?
For example, what about a website that records your anime viewing history? You can record what you want to watch with 👀, what you've already watched with ✅, and your favorites with ☆. You can also express your “likes” for production companies, staff, voice actors, etc. In this way, you can see what a particular user likes.
This could be a movie, a book, a comic, an author, music, an idol group, a place, or food (Someone likes pork cutlet
Q1142841). The fact that you can record everything in the same framework is what makes it interesting.What form of event should it be recorded as?
There is probably room for discussion about how to record this information in a concrete way. The simplest way would be to use NIP-25's "Reactions to a website" kind:17 (a.k.a. Makibishi). How about something like this?
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]Since NIP-73 has External Content IDs, it would be good if we could include WikiData here so that we could write
wd:Q123819103. Actually,isbn:and other identifiers have already been defined, so it is possible to use the current NIP range to describe books (however, the authors do not have IDs. If we use WikiData as an ID, we can also describe reactions related to the author). Of course, it is not a matter of choosing one or the other, and it is also fine to add the ISBN tag at the same time as the WikiData tag for books.Search for recorded reactions
So far, this is all very simple, but it would be inconvenient if we didn't include tags to mark subsets of reactions (for example, only those related to anime) so that we can query them together. When we try to create a site that is specialized for a certain purpose, we need to be able to extract the reactions that are necessary.
On Wikidata, the predicate
wdt:P31(instance of) is used to group together concepts that represent the same thing. For example, how about including this in theltag? "There are too many losing heroines!" is a "Japanese television anime series (Q63952888)", so:json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]UPDATE(2024-12-15): rnurachue-san suggested that
#lor#Lmight be better for labeling (the first version used#a). I think that's a good idea, so I've updated the article. nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dHowever, when you think about creating an anime website, you may want to query both TV anime and anime films. This makes things more complicated. "Japanese TV anime series (
Q63952888)" is a subclass (subclass of;wdt:P279) of "Anime series (Q117467261)", which is in turn a subclass of "Anime (Q1107)". However, if you were to embed this hierarchy in each reaction, it would waste a lot of space. The following query will get all the superclasses of "Japanese TV anime series (Q63952888)", but there are 54 of them.https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
So, I think it should be okay for practical purposes to embed
P31s of the reaction target. In other words, if you search for "anime seriesQ63952888" and "anime movieQ20650540", that should be enough. Fortunately, the conditions for single-character tags work with OR, so you can query multiple tags at once. we'll have to try it to see how well it works in practice, though.Discussion: Which kind should I use?
So far we have considered using kind:17, but we have not yet decided whether it is a good idea to mix Thingstr events with reactions to web pages.
Also, there may be a debate over whether to record regular events or addressable events, depending on the purpose of use. For example, if you want to record the transition of viewing results and impressions on an anime viewing site, you should use regular events, and if you want to maintain the viewing status, you should use addressable events.
What do you think?
Other ideas
If we can react to Nodes on OpenStreetMap using the same framework, we might be able to create something like Swarm. Since the views you want to see will differ depending on the purpose, it would be good to create various sites while having a consistent way of recording. Wouldn't that be the most Nostr-like thing?
Summary
I discussed how to use WikiData and OpenStreetMap as an ID infrastructure and realize various check-in and review services with a unified data model by using them on Nostr. Please let us know if you have any feedback. Or why not try implementing it?
この記事は Nostr Advent Calendar 2024 の14日目の記事です。13日目の記事はmonoさんによる「Open Sats 申請編」でした。15日目の記事はbroさんによる「Nostrはじめました。」です。
Thingstrについて考えた
面白そうな(と勝手に思ってる) Other Staff のアイディアを思いついたので、書いてみます。 本当は実装を持ってきて自慢したかったのですが、まだふわっとしていて実装に落ちていません。
コアになるアイディアは「WikiData の ID に対して、Reactionをつける」これだけです。
WikiData
WikiData というサービスがあります。構造化データを提供する知識ベースです。 なにそれ?という感じですが、ここで大事なのはWikiDataはかなり広範な「もの」「こと」に識別子(Identifier)を付与している、ということです。
だから、これにリアクションできれば、ぱっと思いつくだけでもいろいろな応用ができそうじゃないですか。
例えば、アニメシリーズ「負けヒロインが多すぎる!」には
Q123819103というIDが振られています。これに対応するページとして https://www.wikidata.org/wiki/Q123819103 があります。(ただし、WikiData のエンティティに対する canonical な URI は http://www.wikidata.org/entity/Q1142841 であることには注意が必要です。セマンティックウェブの作法で https ではなく http になっています。そして、このURIは必ずしもWebページのアドレス一致しません。大抵の場合はリダイレクトされます)。
なにができるの
たとえば、アニメの視聴記録サイトはどうでしょう。👀は見たい作品、✅は視聴済み、☆はお気に入り、みたいに記録していく。制作会社、スタッフ、声優、...に対してLikeを表明したりできそうです。そうすると、あるユーザが何にLikeしているかわかります。
これが映画でもいいし、書籍、漫画、作家でもいいし、音楽でもいいし、アイドルグループでもいいし、場所でもいいし、食べ物でもいい(とんかつ
Q1142841が好き、とか)。全部同じ枠組みで記録できるのが面白そうなところです。どういうNostrイベントで記録する?
具体的な記録の仕方には議論の余地があるでしょう。一番単純なのは、NIP-25の "Reactions to a website" kind:17 (Makibishi) を使う方法でしょうか。こんなのはどうでしょう。
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]NIP-73にExternal Content IDsがあるので、ここにWikiDataを入れられるようにして
wd:Q123819103と書けるとよさそうです。実はisbn:などはすでに定義されているので、書籍に関しては現行のNIPの範囲でもうまいことできます(ただ、著者にはIDが振られていません。WikiDataをIDに使うと著者に関するリアクションも記述できます)。もちろん、どちらか一方を選ぶというものでもなくて、書籍にはWikiDataのタグと当時にISBNのタグを付与しておいてもいいと思います。記録されたリアクションを検索する
ここまではシンプルでよいのですが、リアクションの部分集合(たとえばアニメに関連するものだけ、とか)をまとめてクエリできるように、目印となるタグを入れておかないと不便です。ある目的に特化したサイトを作ろうとしたとき、必要になるリアクションが抽出できるようにしておかないといけません。
WikiData では
wdt:P31(instance of) という述語で、ある概念が何を表しているかをグルーピングしてくれています。例えばこれをlタグとかに含めておくのはどうでしょうか。負けヒロインが多すぎる!は「日本のテレビアニメシリーズ(
Q63952888)」なので、json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]みたいな感じで付与します。
UPDATE(2024-12-15): rnurachueさんからラベル付けには
#lまたは#Lのほうがよいかもという提案をいただきました。最初のバージョンでは#aを使用していました。そのとおりだと思ったので更新しました。 nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dただ、アニメサイトを作ることを考えると、テレビアニメも劇場版アニメも両方クエリしたいこともありそうですよね。そうなると話が複雑になってきます。
「日本のテレビアニメシリーズ(
Q63952888)」は「アニメシリーズ(Q117467261)」のサブクラス(subclass of;wdt:P279)で、それがさらに「アニメ(Q1107)」 のサブクラスになっています。ただ、この階層をいちいちリアクションに埋め込むのと大変なことになります。以下のようなクエリで「日本のテレビアニメシリーズ(Q63952888)」のすべての上位クラスが取れるのですが、54件もあります。https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
なので、リアクション対象の
P31を埋め込む、くらいで実用上は問題ないような気がします。つまり、検索するときに 「アニメシリーズQ63952888」と「アニメ映画Q20650540」を対象にすれば、十分では、ということです。幸い、一文字タグの条件はORで効くので、複数を並べて一度にクエリできます。実際にどのくらいうまく行くかはやってみないとわからないですが。議論: どの kind を使うべきか?
一旦 kind 17 を使うことを考えてきましたが、Thingstr のイベントが Web ページに対するリアクションと混ざるのが良いことなのか、いまいち判断がついていません。
また、用途によって regular event で記録するべきか、それとも addressable event で記録すべきか、という議論もありそうです。 アニメ視聴サイトを例にあげるなら、視聴実績とか感想の変遷を記録したいならば regular event でしょうし、視聴の状態を保持したいならば addressable とするのがよさそうです。
どう思いますか?
他のアイディア
これと同じ枠組みで OpenStreetMap の Node に対してリアクションできるようにすれば Swarm のようなものも実現できるかもしれません。
用途ごとに見たいビューは違うだろうから、一貫した記録の仕方を持ちつつ、色々なサイトを作ったらいいんじゃないでしょうか。それって最高にNostrっぽくないですか?
まとめ
WikiDataやOpenStreetMapをID基盤として活用し、Nostr上でreactすることで、様々なチェックインサービス、レビューサービスを統一的なデータモデルで実現する方法について議論しました。フィードバックがあったら教えてください。むしろ実装してみてください。
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ ac8bb9b0:70278acc
2024-12-11 20:10:29
@ ac8bb9b0:70278acc
2024-12-11 20:10:29Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 1 hour 30 minutes
- 🍽️ Servings: 10
Ingredients
- 1 lb. ground beef
- 1 cup celery diced
- 1 cup carrots diced
- 1 medium onion diced
- 2 medium potatoes diced
- 5 cups beef broth
- 1 15 oz. can corn, drained
- 1 8 oz. can tomato sauce
- 1 28 oz. can diced tomatoes
- 1 teaspoon salt
- 1 teaspoon Italian seasoning
- 1 bay leaf
Directions
- In a large dutch oven (I used a 6-quart), over medium heat brown the ground beef until done. Spoon off the excess fat.
- Add the remaining ingredients and stir. Bring to a boil and reduce the heat. Allow to simmer for 1 to 1 ½ hours (with the lid on, but tilted so steam can release) or until the vegetables are tender.
- Remove the bay leaf and serve.
-
 @ 933f9d20:996b56ae
2024-12-31 16:41:41
@ 933f9d20:996b56ae
2024-12-31 16:41:41คำถามจากความอยากตระหนักรู้ในตนเอง
จู่ๆตัวเราก็นึกอยากจะเข้าใจตนเองมากขึ้น บนโลกนี้มีศาสตร์แห่งบุคลิกภาพมากมายที่ให้เราได้ศึกษาและทำแบบทดสอบ แต่จะดีกว่ามั้ยที่เรารู้อย่างคร่าวๆเกี่ยวกับศาสตร์ที่อยู่เบื้องหลังแบบทดสอบเหล่านั้น
Enneargram คืออะไร?

Enneargram ความหมายคือ 'นพลักษณ์' เป็นศาสตร์ที่มีจุดประสงค์ไว้เพื่อการเข้าใจตนเองและเข้าใจคนอื่นหรือเพื่อให้เราอยู่ร่วมกันในสังคมได้อย่างสงบสุข(และหลีกเลี่ยงการแทงใจดำคนอื่นโดยที่ตัวเองไม่ได้ตั้งใจได้!) โดยในแต่ละประเภทจะเรียกกันว่า 'ลักษณ์'
และในบทความนี้ผมจะพูดถึงความรู้เกี่ยวกับ Enneargram ในภาพรวมกันครับ!
นพลักษณ์ (Enneargram)

หากคุณบ้าบอคิดจะข้าม(เผลอๆข้ามไปแล้วมั้ง..)จากหัวข้อนี้ไปดื้อๆคุณก็จะอ่านไม่รู้เรื่องเลยด้วยซ้ำหากคุณไม่รู้ว่านพลักษณ์คืออะไร
'นพลักษณ์' โดยคำว่า 'นพ' ซึ่งแปลว่า 9(เก้า) และคำว่า 'ลักษณ์' ก็คือความหมายว่าเป็น ลักษณะ
ซึ่งก็จะแปลได้เป็น ลักษณะทั้ง 9 นั่นเองครับ!
แล้วก็จะมีการจัดกลุ่มลักษณ์โดยแบ่งเป็น 3 กลุ่มซึ่งก็จะถูกเรียกว่า
ปัญญา 3 ฐาน (The 3 centers) อันได้แก่
ฐานการกระทำหรือฐานกาย แทนเป็น (A) ฐานความรู้สึกหรือฐานใจ แทนเป็น (F) ฐานความคิดหรือฐานหัว แทนเป็น (T)

พอรู้ปัญญา 3 ฐานแล้ว...เรามาดูลักษณะในแต่ละลักษณ์กันเลยดีกว่า!
The perfectionist (ลักษณ์ 1 A) เป็นลักษณ์ที่รักความสมบูรณ์แบบอย่างสุดซึ้ง มีระเบียบวินัยในชีวิตโคตรๆ เป็นคนเนี้ยบของทุกอย่างรอบตัวจะถูกจัดอย่างเป็นระเบียบ หากมีเศษขี้เล็บใครอยู่บนโต๊ะเขาก็จะรู้เลยว่ามันไม่ใช่ของเขา ยึดมั่นในคุณธรรมจริยธรรมอันดี และชอบความแน่นอน
The giver (ลักษณ์ 2 F) เป็นผู้ชอบให้ชอบเสียสละสิ่งที่ตนมี โดยที่ตนเองก็หวังลึกๆว่าจะได้สิ่งตอบแทนกลับมาด้วย มีนิสัยที่ร่าเริงแจ่มใสใจกว้างและเป็นมิตรต่อทุกๆคน
The preformer (ลักษณ์ 3 F) รัก(บ้า)การแข่งขันและชอบการเอาชนะเป็นที่สุด เกลียดการพ่ายแพ้และต้องการเป็นภาพลักษณ์ตามที่ตนเองต้องการ
The romantic (ลักษณ์ 4 F) พื้นฐานคืออารมณ์เศร้าหมองและมีความอิจฉาลึกๆ ไม่อยากเหมือนใครในสิ่งที่ตนเองสนใจและความเป็นศิลปินในตัวสูง
The observer (ลักษณ์ 5 T) คลั่งการหาความรู้(หรือจะฝึกฝนก็ตาม)มาใส่หัวแบบจะเอาให้เทพสุดๆรู้มากสุดๆในเรื่องนั้นๆไปเลย มักแยกอารมณ์ออกจากกระบวนการคิดเชิงเหตุผล ต้องการพื้นที่ส่วนตัวสูงและเป็นลักษณ์ที่เก็บตัวสูง
The guardian (ลักษณ์ 6 T) เป็นลักษณ์ที่มีความกลัวเป็นพื้นฐานของอารมณ์ ชอบวิเคราะห์และวางแผนอนาคตแถมขี้สงสัยด้วย ไม่ชอบความไม่มั่นคงและความไม่ปลอดภัยหวาดระแวงตลอด(โดยเฉพาะอนาคต) ชอบอยู่ใต้การบังคับบัญชามากกว่า
The optimist (ลักษณ์ 7 T) เสพสุขรักการจญภัยและชอบเติมเต็มชีวิตด้วยความแปลกใหม่ตลอดเวลา มีความตะกละเป็นสันดานและไม่ชอบให้ใครมาวาดกรอบให้ตัวเอง
The leader (ลักษณ์ 8 A) มีความโกรธเป็นพื้นฐานของอารมณ์และมีความเป็นผู้นำโดยธรรมชาติ ฝักใฝ่หรือสนใจในอำนาจและการควบคุม สามารถใช้ความโกรธเชื่อมโยงในสิ่งใดก็ได้ตามใจอยาก(และมันโคตรทรงพลังนะจะบอกให้!) ชอบปฏิเสธความอ่อนแอ(ซึ่งเป็นข้อเสีย)และชอบทำสุดใส่สุด(โดยเฉพาะทางกายภาพ เช่น จะกินก๋วยเตี๋ยวเผ็ดๆก็เทพริกซะหมดแก้วบรรจุซะ)
The peacemaker (ลักษณ์ 9 A) นักการทูตตัวจริงเสียงจริง มักเป็นลักษณ์ที่เมื่อเกิดความขัดแย้งระหว่างกลุ่ม ลักษณ์นี้นี่แหละคือตัวปิดความขัดแย้งที่แท้ทรู แต่หากไม่เกิดผลลักษณ์นี้ก็จะหนีออกมาจากความขัดแย้งแทนซะงั้น เป็นลักษณ์ที่รักสงบและเกลียดความขัดแย้งนั่นเอง
Wing (สภาวะปีก)

เป็นสภาวะที่เกิดขึ้นโดยที่ลักษณ์หลักของเราได้รับผลกระทบจากลักษณ์รอบๆ เช่น คนที่มีลักษณ์ 8 ก็จะมีปีกเป็น ลักษณ์ 7 และ ลักษณ์9 ซึ่งจะมีเพียงด้านที่ถนัดที่สุดเท่านั้น หากใช้ลักษณ์ 7 บ่อยที่สุด เราก็จะเขียนได้เป็น
8w7(8 คือลักษณ์หลักของเรา และ 7 ก็คือลักษณ์รองลงมาที่อยู่ข้างๆนั่นเอง โดยมีตัว 'w' เป็นสัญลักษณ์คั่นกลางไว้) และเราจะต้องอ่านว่าลักษณ์8ปีก7ซึ่งเราก็จะได้อิทธิพลลักษณะจากลักษณะข้างด้วยนั่นเองครับ ซึ่งบางสถานการณ์ก็อาจจะไม่มีก็ได้
Subtype (ลักษณ์ย่อย)

เป็นการแบ่งลักษณะการใส่ใจของแต่ละลักษณ์ โดยลักษณ์แต่ละลักษณ์จะต้องมี 3 ลักษณะ ซึ่งจะมีทั้งหมด 27 ลักษณ์ทั้งหมดในนพลักษณ์
Self-preservation (sp) เป็นลักษณ์ย่อยที่ใส่ใจกับความปลอดภัยและความมั่นคงของตนเองก่อน ซึ่งรวมถึงความมั่งคั่งและสิ่งของด้วย
Sexual,one-to-one (sx) เป็นลักษณ์ย่อยที่ให้ความสำคัญกับความสัมพันธ์กับใครคนใดคนหนึ่ง ไม่จำกัดว่าต้องเป็นคน จะเป็นสัตว์เลี้ยงก็ได้ ความสัมพันธ์ในครอบครัวหรือความสัมพันธ์แบบกุ๊กกิ๊กจักจี้หัวใจ(ก็โรแมนติกนั่นแหละ)
Social (so) เป็นลักษณ์ที่อยากมีส่วนร่วมหรือให้ความสำคัญในสังคมหรือในครอบครัว กลุ่มเพื่อน กลุ่มเพื่อนร่วมงาน ต้องการเป็นที่จดจำและต้องการความเคารพจากคนอื่น
Arrow line (สภาวะลูกศร)

เป็นสภาวะที่จะแสดงถึงพฤติกรรมต่างๆในแต่ละสถานการณ์ โดยจะเรียกกันว่าสภาวะมั่นคง ไม่มั่นคง และสภาวะปกติ
สภาวะปกติ ก็คือปกติ ไม่สุขไม่ทุกข์ มั่นคงและไม่มั่นคงในเวลาเดียวกัน
สภาวะมั่นคง เป็นสภาวะที่รู้สึกมั่นคงตามชื่อเลย เป็นความรู้สึกที่เป็นไปตามอยากตามต้องการ
สภาวะไม่มั่นคง ไม่ปกติ ไม่มั่นคง เครียด! หรือก็คือกำลังเจออยู่กับสิ่งที่ตนหลีกเลี่ยงนั่นเอง
โดยหากคนที่เป็นคนลักษณ์ 8 (อีกแล้ว!) ได้อยู่ใน....
-สภาวะไม่มั่นคง คนลักษณ์ 8 ก็จะได้รับอานิสงส์จากลักษณ์ที่ 5 หรือก็คือจะเก็บตัวมากขึ้น โฟกัสหรือสนใจแค่สิ่งๆหนึ่ง กลับไปจัดระเบียบชีวิต ความคิดตนเองหรือข้าวของที่อาจกระจัดกระจายไปทั่วในบ้านของตนเอง
-สภาวะมั่นคง คนลักษณ์ 8 ก็จะได้รับอิทธิพลจากลักษณ์ 2 ซึ่งนั่นก็คือการ Takecare ใจกว้างและรับฟังคนด้วย! ซึ่งดูมีความสุขแฮปปี้ลั้นลาในฉบับของลักษณ์ 8
ส่งท้าย
บทความนี้เป็นบทความแรกในชีวิตของผมเลย ซึ่งตัวผมเองก็เป็นลักษณ์ 8 ปีก 7 (8w7) ผมได้จมปรักกับเรื่องพวกนี้มากพอควร (3 ปีกว่าแล้วล่ะครับ) ซึ่งตัวผมในอดีตก็คงไม่ได้คิดหรอกว่าจะเขียนบทความ แถมยังเขียนใน Nostr อีก!
แต่ก็นะ.... ผมก็ขอขอบคุณที่อ่านมาจนถึงวรรคนี้นะครับ
ขอให้คุณตั้งใจใช้ชีวิตไปกับปีหน้านะครับ!

-From 31/12/2024
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f0c7506b:9ead75b8
2024-12-08 09:05:13
@ f0c7506b:9ead75b8
2024-12-08 09:05:13
Yalnızca güçlü olanların hakkıdır yaşamak.
Güçlü olan ileri gider ve saflar seyrekleşir. Ama üç beş büyük, güçlü ve tanrısal kişi güneşli ve aydınlık gözleriyle o yeni, o vaat edilmiş ülkeye ulaşacaktır. Belki binlerce yıl sonra ancak. Ve güçlü, adaleli, hükmetmek için yaratılmış elleriyle hastaların, zayıfların ve sakatların ölüleri üzerinde bir krallık kuracaklardır. Bir krallık!
Benim aradığım insanların kendileri değil, sesleridir.
Duyguları körelmiş, çeşitli düşüncelere saplanmış kalabalık hiçbir zaman ilerlemenin taşıyıcısı olamaz, kendi küçüklüğünün o küflü içgüdüsüyle kalabalığın kin ve nefretle baktığı bir kişi, bir büyük kişi, iradesinin gösterdiği yolda kimsenin gözünün yaşına bakmaksızın ilahi bir güç ve bir zafer gülümsemesiyle yürüyebilir ancak.
Bizim soyumuz da sonsuz oluşum piramidinin doruk noktasını oluşturmaktan uzaktır. Bizler de mükemmelliğe ulaşmış değiliz. Bizler de henüz olgunlaşmadık.
Şairler sevgiye övgüler döşenir; doğrusu sevginin güçlü bir şey olduğu kesin. Hüneşin bir ışınıdır sevgi, aydınlatıp nurlandırır insanı der bazıları; bazıları da insanı esrikliğe sürükleyen bir zehri kendisinde barındırdığını söyler. Gerçekten de yol açtığı sonuçlar, bir hekimin ağır bir ameliyattan önce korkudan titreyen hastaya teneffüs ettirdiği güldürücü gazınkine benzer, içinde tepinip duran acıyı unutturur hastaya.
Önemli olan, hayatta hiç değilse bir kez kutsal bir ilkbaharın yaşanmasıdır; öyle bir bahar ki, insanın gönlünü ilerideki bütün günleri altın yaldızla kaplamaya yetecek kadar ışık ve parıltıyla doldursun.
Şu hayat denen şey kötü bir işçiliğin ürünü, acemilere göre bir şey. Bu kepaze yaşam uğruna insan nelere katlanmıyor ki!
Kendisine sadakatten ayrılmadığı, yalnızca kendisinin olan bir tek bu var: Yalnızlığı.
Sahildeki üstü tenteli hasır koltuklar arkasındaki yüksek, sessiz kum tepeleri içinde yürürsen, tenteler altındaki insanları göremezsin; ama birinin bir diğerine seslendiğini, bir başkasının gevezelik ettiğini, bir ötekinin güldüğünü işitir ve anlarsın hemen: bu insan şöyle şöyle biridir diyebilirsin. Onun hayatı sevdiğini, bağrında büyük bir özlem ya da acı barındırdığını, bu acının da sesini ağlamaklı kıldığını her gülüşünde hissedersin.
-
 @ 6bae33c8:607272e8
2024-12-31 14:52:56
@ 6bae33c8:607272e8
2024-12-31 14:52:56I missed this game because I was on an overnight flight back to Portugal via Munich last night. Just got in, actually, jetlagged af, so I won’t have too much to say about it. Plus, our bags didn’t make the connecting flight, which is annoying.
-
If the Niners score 34 against you, that’s not a good sign for the playoffs. I guess the last TD came in garbage time, but still. I would say Vikings +2.5 this week, but Detroit could easily drop to the fifth seed.
-
Brock Purdy is a top-10 NFL QB IMO. I didn’t see this game, but he always passes the eye test for me. (Looks like he got banged up too, but nothing serious.)
-
George Kittle is quietly having a huge year on just 91 targets, thanks to 11.9 YPT. Kittle is in the Rob Gronkowski lineage, while Travis Kelce is more Tony Gonzalez (higher volume, less blocking.)
-
Ricky Pearsall apparently had a breakout game. They took him in the first round, so it makes sense they’d give him an extended audition while drawing dead. It’s odd that Pearsall and Jauan Jennings are more relevant that Deebo Samuel and the injured Brandon Aiyuk.
-
Amon-Ra St. Brown didn’t get a lot of headlines this year, but he’s up to 112-1,186-12 on 8.9 YPT. Not bad.
-
Even with David Montgomery out, Jahmyr Gibbs’ workload was fairly modest — 18 carries/four targets. This game didn’t matter to the Lions though. Against the Vikings I should think he’d get a McCaffrey-esque stat line, but we’ll see.
-
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ ed60dae0:cc3d5108
2024-12-31 14:14:16
@ ed60dae0:cc3d5108
2024-12-31 14:14:16Disclaimer
Not financial advice. This is for educational purposes only. Do your own research. You are responsible for your own choices. The author is not a professional trader and/or financial advisor, only a student of the markets. Act accordingly.
Intro
I wanted to explore some opportunities using Bitcoin options in combination with price models. Like a student, I aim to think it through by writing it down. Any feedback is welcome—I’m eager to learn.
Gold as a standard for financial measurement
There are people who can describe far more eloquently why the U.S. Dollar isn’t the ideal tool for measurement. Gold, due to its unique properties, is one of the best—though not perfect—financial tools to use as a measure for various reasons. Personally, I prefer to measure the adoption of the Bitcoin network against gold, and I believe the ultimate metric for measuring adoption is price.
 ## Worst Case Scenario
## Worst Case ScenarioFor this exploration, I want to focus on downside risk. The chart above shows that the price of Bitcoin, expressed in gold ounces, follows a power law. Before I continue, I want to state the obvious: the “power law” is not a certainty. As British statistician George E. P. Box famously said, “All models are wrong, but some are useful.” Let’s assume that if the rate of network adoption in the coming year is equal to or greater than in previous years, the power law will retain its validity. The chart shows that the price usually falls to negative 1 standard deviation during a bear market. However, in some cases, such as the bear market of 2022, the price even reached negative 1.5 standard deviations.
In the opportunity example, I will examine the option expiration date of December 26, 2025. Since the chart isn’t interactive, you can’t hover over the lines to get the exact numbers, so I will state them here. According to the Power Law, the price of Bitcoin expressed in gold ounces on December 31, 2025, is 33.4 ounces for -1 sigma and 26.6 ounces for -1.5 sigma.
Depending on your expectations for the price of one ounce of gold on December 26, 2025, you can calculate the bear market bottom in the event of an unexpected downturn of the market next year. Based on today’s gold price, this would be 33.4 x $2,600 = $86,840 for a -1 sigma move and 26.6 x $2,600 = $69,160 for a -1.5 sigma move down. You could argue that the price of gold might be lower if an unexpected bear market begins for risk-on assets. The question is whether gold will be lower or even higher in such an environment. Currently, gold is being purchased as a hedge against inflation and wealth confiscation (e.g., as seen when the U.S. froze Russian state-owned U.S. Treasury bonds). However, in a bear market, it could also be bought as a safe haven during an economic downturn.
Example
With these numbers in mind, we can explore the option chain on platforms like Deribit. For this example I’m looking at BTC-26DEC25. As of today, December 31, 2024, the futures price for this expiration date is approximately $104,000.
Let’s say you’re a HODLER who believes the current bull market isn’t over yet. You own spot Bitcoin, which essentially means you are long Bitcoin and short dollars. For simplicity, let’s assume you own 1 whole Bitcoin. Since you believe the bull market has further to run, you don’t want to sell your Bitcoin (or perhaps you never want to), but you’re interested in opportunities to stack more Bitcoin.
One option is to pledge your Bitcoin as collateral on the Deribit exchange, giving you enough margin to open a position. This way, you won’t have to sell your Bitcoin but can still participate in new trades. For example, you could sell a put with a $90,000 strike price for, say, 0.16 BTC. At the current spot price, that’s approximately $15,000.

\ Note that you potentially could earn more by selling a put with a $100,000 strike price, where the extrinsic value is larger. However, I’m choosing $90,000 because it aligns more closely with $86,840, which provides greater room for an unexpected downturn in the market toward the -1 sigma move.
By holding onto your spot Bitcoin, you still retain all the upside potential in case the bull market continues. Selling the put doesn’t require you to take on excessive risk—you’re already long on Bitcoin. If the Power Law holds, it’s probable that the price will remain above $90,000 by December 26, 2025.
Historically, the price of Bitcoin tends to reset toward the Short-Term Holder (STH) cost basis during bull markets. Currently, the STH cost basis is around $87,000. If this happens, it could present an even better opportunity. You could stick with a strike price of $90,000 and collect a larger premium, thereby lowering your breakeven price, or you could aim for the same premium amount and choose a lower strike price, which would reduce your breakeven price even further. However, it’s not guaranteed that you’ll get that chance.
Risk Management
There are risks involved in this trade. These risks include third-party risks, where Deribit might lose your Bitcoin and be unable to pay it back. The biggest risk is that the adoption of the bitcoin network stalls and the power law gets invalidated to the downside and the price of bitcoin ends up way below your strike price. Another risk of this trade lies in the fact that your collateral is held in BTC, while your trade also depends on Bitcoin moving sideways or upward. If Bitcoin’s price declines, your collateral will lose value. In the event of a market crash, like a black swan event, the market could move significantly against your trade, the put option will go in the money and acquire intrinsic value, which is unfavorable for the seller of the put. In extreme cases, you could face a margin call, requiring you to pledge more collateral, or the exchange could liquidate your Bitcoin and close your position. The bitcoin price could recover and still end up above $ 90,000 at the end of 2025, but you’ll end up with none.
To mitigate this risk—not entirely, but partially—you could sell some spot Bitcoin. Let’s say your goal is to end up with at least 1 Bitcoin. You could sell an amount equivalent to the premium you would receive if the price closes above $90,000. In this case, you would sell 0.16 BTC, resulting in a balance of 0.84 BTC and $15,000. This strategy protects you somewhat if Bitcoin’s price drops, as the premium you receive (denominated in BTC) would be worth less. If the price closes above $90,000, you will still end up with 1 BTC and $15,000. Essentially, you’re sacrificing some upside potential in exchange for added certainty.
If you’re an experienced trader, you could temporarily hedge your position to delta neutral in uncertain periods by shorting the bitcoin future price with the corresponding expiration date. The risk here is that a trader could wind up losing all his potential profit or worse through ‘a death by a thousand cuts’.
It’s important to note that your breakeven price in this trade is $90,000 - $15,000 = $75,000. Additionally, the worst-case scenario, though unlikely, is a -1.5 sigma move, which could bring the price (depending on the USD price of an ounce of gold at the time of expiration) to around $70,000. While this doesn’t eliminate all risk, if you believe the adoption rate of the bitcoin network will stay the same (at worst) and thus the power law won’t be invalidated and so you believe in Bitcoin’s value and its bright future, this represents an asymmetric bet where the probable outcome of gaining $15,000 outweighs the improbable outcome of losing $5,000.
Your own assessment
Uncertainty is the name of the game—it’s the very reason why premiums and insurance exist in the first place. Nothing is certain; even the presence of the sun could one day vanish. However, you can turn this uncertainty into your ally rather than your enemy. Do your own research and make your own assessment. Ask yourself: what do you think 2025 will bring?
- What will be the yield on the 10-year Treasury Note, a.k.a. the “risk-free rate”?
- Will inflation remain sticky?
- Will AI drive significant productivity gains?
- Will growth outpace inflation?
- What will be the impact of reduced immigration on the labor market?
- Will the Trump administration deliver on its promises?
- What if the U.S. Dollar becomes too strong?
- Will central banks extend their balance sheets further?
- Will governments take on even more debt?
- Will Bitcoin play a bigger role in corporate treasury strategies?
- Will more Nation States adopt Bitcoin?
- Can this train be stopped?
Use your own assessment alongside pricing models like the BTC/Gold oz Power Law. What do you consider probable, and what do you consider improbable?
To summarize, and based on the assumptions stated earlier, this represents an asymmetric bet where the outcome of gaining $15,000 has an estimated probability of around 70%, as a -1 sigma move aligns closely with the strike price. The probability of breaking even is approximately 80%, while there is a 20% chance of losing $5,000 or more. These probabilities* are based solely on the Bitcoin/Gold oz power law. Your own 2025 assessment could either enhance these odds or make the outcome less probable.
*Please note that the outcomes of the power law are not normally distributed but positively skewed. The chances are better than described above. Source
-
 @ fde4c423:40a85910
2024-12-31 13:26:45
@ fde4c423:40a85910
2024-12-31 13:26:45It’s December 31st, 2024. The end of another year, another cycle. Tomorrow, a new cycle begins, full of adventure and misfortune, ups and downs, inflows and outflows. Such is life, and it cannot be otherwise.
Somewhere in the middle of it all, I’m starting a new blog on the best platform I’ve seen so far — anonymously or rather pseudonymously.
I like writing. I’ve been doing it on and off for some time, but I’ve always wanted to try it without any attachment to my name. Not sure why, but perhaps it gives a bit more freedom. You shouldn’t care about what others think, of course, but our egos still remind us of others when we do certain things, and for this reason, we don’t do those things exactly how we’d do them if nobody watched. Like dancing in an empty room or singing in the shower: it’s just you, without the weight of other people’s eyes and ears pressing on you.
For the time being, I will write just about anything that comes to my mind, using Nostr Reads as my brain dump playground. But, at some point, a certain direction will form that I will stick to. Which will give me more focus and attract an audience that will expect my next pieces. Because if you don’t know what I’m going to write about next, why would you expect my next article? (Unless I’m so good with words that you get hooked no matter what — but I’m not, I’m just an amateur.)
Bitcoin, Nostr, business, family, politics — all will be intertwined here. Of course, with my own twist, as I’ll write about everything based on my perception of things, my knowledge, experience, and wisdom if there’s any.
This is not a New Year’s resolution but rather an introductory post. You can even consider it a filler, a seed article. In any case, I will see you in 2025.
Happy New Year!
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 714dd0db:9c6f1a4c
2024-12-31 10:54:01
@ 714dd0db:9c6f1a4c
2024-12-31 10:54:01Nostrで初めての長文投稿
2024年の大晦日。今年1年、個人的に何があったか振り返ってみる。
自転車生活に慣れてきた
移動手段を電車や車から自転車メインに切り替えた。暑さも寒さも体験し、生きてるなあ、という実感が得られるね。
ふと寄り道もできるし、お店やら新しい発見も多かったな。
夏の山口県旅行
夏に実家への帰省も兼ねて、山口県を旅行した。今年は日本酒にハマってしまったので、山口県内の酒蔵をいくつか巡ってみた。
美祢市にある別府弁天池の水の蒼さに感動。まさにエメラルドグリーンだった。
日本酒にハマる
最初は、お米の可能性として、お米からできている麺や米菓子を好んでいたが、「そういえば 日本酒もお米からできているよな」と気づき、飲み始めたところ、はまってしまったというわけ。
とは言っても下戸の部類に入るので、低アルコールの日本酒ばかりを飲んでいる。6〜7度のフルーツ日本酒も美味しいが、身体に合っているのは14度のスッキリ系もしくは若干のフルーツさの味わいをよく飲んでいる。山口の大嶺酒造や栃木の仙禽が多いかな。
SNSはNostrとfediverseで
分散型SNSにハマった1年だった。今ではすっかり馴染んで活用している。もうXwitterやInstagramは見なくなったなあ。
Nostrのおかげで、Satsのことも知り、仮想通貨の情報収集や勉強をしているところ。
Nostrは、クライアントによって、見え方が全然違うのが面白い。
そして2025年へ
2025年は、昭和100年にあたる。100年かぁ。昭和世代には感慨深い。
来年もぼちぼちやっていきます。よろしくお願いいたします。
-
 @ 148755e6:450c107f
2024-12-05 10:09:32
@ 148755e6:450c107f
2024-12-05 10:09:32突然荒野に行きたくなったので行ってきたエントリーです
まずは練習。高尾山へ
Nostrは古今東西ありとあらゆるオフ会が生えており、
まるで荒野に行きたいという私の意志を完全に汲み取ったかのように「紅葉を見にいこうようオフ」がそこに生えていたので参加した。(しおんさんご主催ありがとうございました)
前半1時間くらいの坂道がマジきつかったです。前半キツすぎて後半足痛かった。。 終始人がいっぱいいて渋谷かと思った。
確かに道がかなり整備されていて、逆にコンクリート故に足が疲れたのかもしれない。隣の人は途中の急な坂道で足を滑らせてて、横で転倒事故が起きるかと思いました。
山頂に行っても人がたくさんいて、迷子になりかけた。あそこはスクランブル交差点や。 そして山頂の先にあるもみじ台まで歩くと人がまばらで、まったりして蕎麦食べたりしながら休憩して下山。
登りは暑くて汗かきましたが、山頂でまったりしてると汗も引いてきて少し冷えました。
下山はスイスイ。16時近くで結構暗かったので、冬の間は早めの登頂・下山がおすすめですね。
登り2時間・下り1時間半で概ね見込み通りって感じでした。
高尾山は登ってると景色が変わります。ちょっと開けた場所に出て下の街が見えたり、草木があったり、階段があったり、参道があったり。。そういう意味では退屈しない2時間でした。
ビギナー山とはいえ、革靴やヒールのある靴で登ってる人がいてびっくり。ツルッと滑ることあると思いますので、スニーカーで登ることをお勧めします。
舐めプしてたとはいえめちゃくちゃキツかったおもひで。
更なる練習。小浅間山へ
さて私は荒野に行きたいワケなのですが、高尾山に荒野はありませんでした。更なる練習として小浅間山へ。
前日(か前々日)に雪が降ったようで、山に雪が残っておりました。
それでも都内の汚れてべちゃっとした感じの雪ではなく、粉砂糖がちょっと積もってるみたいな感じで綺麗だった。
登り前半の30分くらい、景色や道が変わらず、ずっと歩きっぱなしになってしまいました。時間みて休憩しながら行けばよかったなあ。
登るにつれて気温が下がっていくのか、積雪が厚くなっていく。
40分くらいは割と平坦な道が続きますが、突然山頂っぽいものが現れて、「これを登れっていうのかい...?」とビビるほどピーンと急な道が出てきました。(写真だと分かりづらいですね)
ただ、高尾山のコンクリート道に比べると足の疲れはそこまででした。雪道なので気をつけて歩くという意味では疲れましたが、春〜秋とかは快適に登れるんじゃないでしょうか。
山頂に到着するとドーンと浅間山が見えて圧巻。
風が強くて飛ばされる恐怖はありましたが、なんとか無事でいられました。あったかいお茶美味しかった〜。
なぜかギャルの看板があって、謎でした。写真はひとまずありません。
山頂が2箇所あって、それぞれで眺めを満喫していたら結構時間が経ってました。
小さい背丈くらいの木や足元にちょっとした植物があったり、自分的にはかなり理想の荒野に近かったです。(植物に対する解像度が低すぎる) 往復で2時間程度の山らしいんですが、なんやかんやと2時間半強くらいいた気がします。
荒野ビギナーは小浅間山に往け
というわけで、荒野に行きたい人はまずは小浅間山を登ると良いと思います。 また登りたい。
荒野部部長
一緒に高尾山・小浅間山に登ってくれた方、ありがとうございました! 個人的には来年の春までに秩父多摩甲斐国立公園に行き、来年の秋までに大山隠岐国立公園に行くという目標を立ててるんですが、 少々時間が空くので次どこに行こうかしらと考えているところです。
ヒントとしては、火山で、あまり高低差のないところだとビギナーの私にちょうど良さそうです。
とある情報筋によると伊豆大島が良さそうなので、次の機会に行けたらと思っています。
みんなで荒野に行こう!
-
 @ ac8bb9b0:70278acc
2024-12-04 20:30:30
@ ac8bb9b0:70278acc
2024-12-04 20:30:30Chef's notes
Make Ahead: You can prepare this recipe up to one week in advance. Store it in an airtight container in the refrigerator.
To Freeze: Allow the dish to cool completely before transferring it to a freezer-safe bag. Lay the bag flat in the freezer to ensure even freezing and to save space. Thaw it in the refrigerator overnight before using it.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- ½ cup soy sauce
- 2 Tablespoons rice vinegar
- 1 Tablespoon sesame oil
- 1/4 cup + 1 Tablespoon light brown sugar
- 1 Tablespoon honey
- 3/4 teaspoon ground ginger
- 1 clove garlic , minced
- 2 teaspoons cornstarch+ 2 tsp water , mixed together to make a cornstarch slurry
- 1/4 teaspoon crushed red pepper flakes
Directions
- Make the teriyaki sauce by adding all of the sauce ingredients to a small saucepan over medium heat.
- Bring to a boil, stirring constantly, and boil for about 1 minute. The sauce should be thick enough to coat the back of the spoon.
- Serve over rice or with a stir-fry. See post above for additional ideas.
-
 @ 26bb2ebe:70530958
2024-12-02 16:46:10
@ 26bb2ebe:70530958
2024-12-02 16:46:10nostterに画像最適化機能つけたよ(サーバー編)
この記事はNostr Advent Calendar 2024 の3日目の記事です。
あまり技術的な話はないので暇つぶし程度に読んでみてください。
どうしてこうなった?
そもそも認証の改善以前にNostrあんまり人が増えてないのが一番課題だよねと思ったのが始まりでした。 Nostrに人が増えないのはオーガニック検索流入が少ないからに違いないと特に根拠もなく思ったのでNostrのまとめサイト(Toggeter)のようなものを作ろうと考えました。
ところでNostrのまとめを行うアプリ自体は鎌倉さんという方がノスリというのを作成されていました。ブログ形式のイベントにTwitterライクな短文投稿をまとめるというものでまさしくToggeterですが、そこまで活用されていません。 そこでその仕組みをありがたくそのまま転用してまとめ記事を何らかの方法で量産しつつ、一つのドメインのサイトにまとめてSEOもなんかうまいことやれば検索流入増えるんじゃねという目論みです。
ところでそのまとめサイトは静的サイトジェネレータで(SSG:Static Site Generator)でつくりたいなと思いました。いや普通に考えてSSRにしてサーバ側でNostrからデータとってきたらSEO的にもよくねって感じなんですが、SSRでサーバーでウェブソケット呼ぶのだる…レイテンシを考慮すると結構不利じゃないかなと思ったわけです。うそです。そこまで考えてなくてほとんど個人的な好みです。(多分ちゃんとキャッシュきかせればそんなにレイテンシ問題にならなさそうな気がする)。ただキャッシュとかも考慮すると結構複雑な気はする。
ということで今年の6月頃にNostrのブログ記事をSSGするサイトをためしに作りました。 去年のアドベントカレンダー記事とか乗っけてます。
全然画像最適化の話になりませんね。もうちょっとです。
SSGのブログといえばGatsby(今は下火かも)とかで作成した経験があります。Gatsbyでは画像用のプラグインが公式に用意されていて生成されたブログに表示される画像はもとの画像データから変換され、表示時のサイズに最適化されたサイズにリサイズすることができます。
それだけではなくサイトの初期表示時には画像の画質を落としてぼやけた画像を表示してその後元画像が読み込まれたらきれいな画像を表示する、みたいなことができます。インラインでデータを持っているのでHTMLの表示と同時に画像の初期表示ができたりします。(その頃はよくわかってなかったがNostrのNIP-92で定義されているblurhashとかを使っていたんでしょう多分)
とにかくSSGは初期表示の速さが良い。というのが自分の頭の中にあるわけです。SSGのブログをNostrで作るとなると当然同じことがやりたい。
しかし、Nostrの画像はただのURLです。(オプショナルで画像のメタデータを定義できるimetaタグはあるが…)
基本的にSSGの画像最適化というのはローカルに存在する画像データをビルド時に変換するという流れで行われます。もしくはリモートURLに画像が置かれる場合は画像ストレージサービスやCDN上で配信されるときに最適化されることになります。
Nostrの画像はただの外部のURLですから(2回目)、ローカルの画像を変換する方法は採用できないわけです。無理やり実行するならビルド時にURLからすべての画像を一旦ダウンロードして変換するとかも考えましたが、ただの外部URLというのはつまりは一体どういうファイルなのかダウンロードしてみるまでわからない、要するに全然信頼できないということですから、よくわからないURLをかたっぱしからダウンロードするようなことは避けたいわけですね。(極端な話100GBの画像URLとかつくって攻撃されたら破綻しますよね)
ここが結構他の中央集権的なSNSと違って辛いところなのかなと思います。X(Twitter)とかであれば画像ストレージサーバは一つなので表示される画像の形式も一つに限定されるのですが、画像のアップロードが外部頼みでただのURLなので(3回目)何が来るかわからないということですね。
サーバ側で画像形式などを制限できない(imetaも信頼できるかわからない)となるとクライアント側でなんとか対応する必要があり、Nostrはクライアント側が大変なプロトコルだなあとということに思いを馳せていましたが、いろいろ考えたり調べた結果として作るべきものは画像最適化のためのプロキシサーバであるということがわかりました。
プロキシサーバというのはここでどういう働きをするのかというと、もとの画像がおいてあるサーバとクライアントのあいだに入って、もとの画像を一旦ダウンロードして圧縮したり縮小したりしてそのあとクライアントに送ってあげるという働きをします。
プロキシがないとき
[画像置き場] -> [クライアント]プロキシがあるとき
[画像置き場] -> [プロキシ] -> [クライアント]利点としてはクライアントが実際にダウンロードするのはサイズの小さな画像になるので通信量や画像の表示スピードは改善します。が、一方でサーバを経由する分通信にかかる時間(レイテンシ)が長くなります。というわけなので、当初の目的である表示速度の改善を実現するには、画像をエッジキャッシュするなどの対応が必須となります。平たく言うと一度送った画像はプロキシで保存しておいて次に要求されたらそれをすぐ返すということです。
画像をどれくらいのサイズにするか、画質はどうするかなどはプロキシに指示してあげれば良いのでクライアント側は想定通りの画像を受け取れてハッピーということになります。嘘です。ある程度はハッピーですが、プロキシ自体がエラーを返す可能性もあるし、処理できなくてもとの画像をそのまま返す場合もあります。そんなあれこれの結果、クライアントはフォールバック処理を実装する必要がありました。(それはまた別の記事で)
一方で自分はNostrのモバイルクライアントのヘビーユーザですので、Nostrの通信量の多さも解決したい課題でした。Nostrやってるとすぐギガがなくなります。 通信量の多さのボトルネックはウェブソケットで送られるNostrのイベントの通信量というよりは投稿に添付される画像のダウンロードの方ではないかという話もTLで耳にしたため(特に裏もとらず)、いっちょ画像最適化のプロキシサーバを作ってクライアントに実装してプルリクエスト投げるかと考えました。
そこで私はまずクライアントをAmethystからnostterに乗り換えることから始めました。なぜならばAmethystよりもTypeScriptとSvelteで書かれているnostterのほうがコントリビュートしやすかったという私的な事情です。
解決したい課題
遠回りしてきましたが課題はこれ。
- Nostrの画像の表示改善
- Nostrの通信量の改善
インターフェイス(設計)
画像最適化のプロキシは実装よりもインターフェースを考えるのが大変です。ここはとても苦労しそうな気がしたので、何も考えず cloudflare Imagesのインターフェースをそのまま借用することにしました。
https://developers.cloudflare.com/images/transform-images/transform-via-url/
また何かあってもcloudflare Imageに課金して乗り換えることが可能という利点もあります。
実装
とにかく時間がないので手グセでかけるTypeScriptかJS。かつ課金しないで可用性を維持できる無料枠のサーバレス環境が使いたかったので cloudflare workers に目星をつけて調査したところ、非常に素晴らしい記事を見つけましたのでこのwasmのライブラリをTSから呼び出して使わせていただくことにしました。
自分の実装したところはURLのパースと、キャッシュAPIの呼び出しを行って、最後にこのライブラリを叩くだけです。 ほかはクライアントキャッシュ用のヘッダーを書き換えたりとか細かいことはやっていますが全く大したことはやっておらず、サーバは非常にリーズナブルにやりたいことを実装した形になりました。 大変助かりました。
実装したものがこちらです。
https://github.com/ocknamo/nostr-image-optimizer
実装後の課題
このプロキシただのパブリックAPIなのでDoS攻撃に弱いです。何回もAPIをたたかれたら無料枠をすぐに超えてしまうことが容易に想像できました。 無料枠超えても使えなくなるだけで破産はしないので安心ですが、しかし対策は考える必要があります。
WAF
WAFです。APIに対するリクエスト回数などに対する制限をIPごとにかけています。また攻撃された場合検知できれば特定のIPや地域をブラックリストに入れることも可能です。
細かいことを説明してギリギリを攻めて攻撃されても困るので細かく説明しませんが、当初は全力でDoS攻撃されても無料枠超えないくらいの感じで制限をかけていました。 しかしNostrのTLをちょっと早めに表示するとすぐにWAFに引っかかってエラーになるという状態になることもあり、結局アイコンの表示は画像最適化の対象にしない方針にするなどの影響がありました。
いろいろあって、前提が変わり、もう少し制限をゆるくしたのでアイコンの対応は今後は検討できるかもしれません。
まとめ
割と手抜きで作ったことがわかるかと思います。実装しててNostrへの貢献ではあるはずですが、Nostrのプロトコル(NIPsとか)全然関係ないことやってるなと思いました。
フロントについては来週書きます。
次回のアドベントカレンダーの記事は eyemono.moe さんによる”クライアント自作を通して得られた知見まとめ”ですね!楽しみです!
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ cf7ed325:050194cf
2024-12-31 08:43:53
@ cf7ed325:050194cf
2024-12-31 08:43:53Embark on a luxurious adventure aboard the Sonesta Moon Goddess Nile Cruise, an exceptional vessel that combines elegance, comfort, and impeccable service. This 5-star cruise offers an unforgettable journey between Luxor and Aswan, showcasing Egypt's iconic ancient treasures along the way.
The Sonesta Moon Goddess Nile Cruise boasts spacious cabins with private balconies, allowing guests to enjoy breathtaking views of the Nile. The cruise features gourmet dining, a relaxing sun deck, a swimming pool, and entertainment programs that highlight Egypt's rich culture and history. Whether you're exploring the Valley of the Kings, Karnak Temple, or the Philae Temple, this cruise ensures an enriching and seamless experience.
For travelers seeking similar luxurious experiences, the Farah Nile Cruise and Oberoi Zahra Nile Cruise are excellent alternatives. These cruises offer exceptional service, elegant accommodations, and curated excursions to Egypt's most iconic sites. Another standout is the Oberoi Philae Nile Cruise, known for its personalized service and exquisite cuisine.
History enthusiasts will appreciate the refined charm of the Historia Nile Cruise, while the Jaz Crown Jewel Nile Cruise and Jaz Regent Nile Cruise provide a perfect blend of modern amenities and classic elegance. Those seeking more options within the Sonesta fleet can explore the Sonesta Sun Goddess Nile Cruise, Sonesta Star Goddess Nile Cruise, or Sonesta Nile Goddess Nile Cruise, each offering unique features and premium services.
Lastly, the Sonesta George Nile Cruise stands out for its contemporary design and warm hospitality. Whether you choose the Sonesta Moon Goddess Nile Cruise or another luxury vessel, your journey along the Nile will be a captivating blend of history, culture, and unparalleled comfort.
🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 Email: info@etbtours.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt
-
 @ c230edd3:8ad4a712
2024-12-02 03:49:19
@ c230edd3:8ad4a712
2024-12-02 03:49:19Chef's notes
This recipe is not my own, but it was great and easy, so I'm moving it here. Cooking as instructed serves 2, but this could easily be adjusted to include stir fry vegetables and rice, to make this a meal for 4.
Details
- ⏲️ Prep time: 15 minutes, 1-24 hours marinating
- 🍳 Cook time: 10-15 minutes
- 🍽️ Servings: 2-4
Ingredients
- 1 Venison Heart (elk would work well, too. recipe would need to be doubled)
- 1/2 Asian Pear, grated
- 2 Cloves Garlic, grated
- 1 Tbsp Ginger, grated
- 3 Tbsp Soy Sauce
- 1 Tbsp Honey
- 1 Tbsp Onion, grated
- 1 Tbsp Toasted Sesame Oil
- 1 tsp Red Pepper Flakes
- 2 Shallots, chopped
- Sesame Seeds
- Cooking Oil
Directions
- Mix all ingredients besides heart, shallots, sesame seeds and cooking oil in a medium bowl.
- Remove arteries and excess fat from heart, cut in half and rinse
- Cut into thin slices or bite size pieces
- Add to marinade, mix and cover. Allow to soak for 1-24 hours.
- Heat oil in large frying pan over med-high to high heat
- Drain excess marinade.
- Place heart in pan and sear on both sides to desired doneness. Medium rare is ideal for heart.
- Remove from pan and garnish with chopped shallots and sesame seeds. Serve with stir fry veggies and rice, if desired.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 2063cd79:57bd1320
2024-12-31 08:31:09
@ 2063cd79:57bd1320
2024-12-31 08:31:09Obwohl einige andere Themen, wie der kürzlich erschienene New York Times Artikel, in dem sich faktisch falsch und inhaltlich voreingenommen mit Bitcoin-Mining befasst wird, oder die Entdeckung des Satoshi Whitepapers auf Apple Computern momentan die heissen und viel besprochenen Nachrichten sind, hält auch die Diskussion über Ordinals und Inscriptions und besonders deren Auswirkungen auf das Bitcoin-Netzwerk an. Einer der viel besprochenen Aspekte bei diesem Thema ist die Auswirkung dieser Bitcoin-NFTs auf die Gebührenstruktur und somit Gewinnzusammensetzung für Miner, aber auch die direkten Auswirkungen auf On-Chain-Transaktionen durch die höheren Gebühren und den seit Wochen sehr vollen Mempool. Genau über den wollen wir uns diese Woche etwas detaillierter unterhalten, da es auch unter erfahrenen Bitcoinern immer noch einige Missverständnisse zu geben scheint.
Fangen wir zunächst ganz vorne an. Regelmäßigen Leser//innen dieses Blogs sollte in Erinnerung sein, dass ich Anfang Februar einen Artikel über UTXOs und Gebührenmanagement geschrieben habe:
https://www.genexyz.org/post/25-block-774775-utxos-fee-management-v3ulch/
In diesem Artikel habe ich beschrieben wie Transaktionen zusammengesetzt sind und welche Möglichkeiten Nutzer//innen haben, um ihre persönlichen Transaktionen anhand variabler Gebühreneinstellungen schnell oder langsam im Netzwerk zu platzieren.
Welchen Nutzen haben hohe gegenüber niedrigen Gebühren? Bitcoin-Miner handeln nicht ganz uneigennützig, denn sie werden für ihre Arbeit entlohnt. Für jeden produzierten Block erhalten sie neben dem Blockanteil (Reward) auch sämtliche Transaktionsgebühren, der im neuen Block enthaltenen Transaktionen. Ohne zu sehr ins Detail zu gehen, bedeutet dies, dass Miner einen Anreiz haben, Transaktionen mit möglichst hohen Gebühren zuerst in den neuen Block zu schreiben, um so ihren Profit zu maximieren. Je höher eine Gebühr relativ zu denen der anderen Transaktionen im Mempool ist, desto wahrscheinlicher ist, dass diese Transaktion im nächsten Block landet. Das bietet dem/der Nutzer//in die Möglichkeit, die eigene Transaktion zu priorisieren.
Der Mempool, kurz für Memory Pool, hat also was mit Transaktionen zu tun - und zwar ganz schön viel. Denn jede im System propagierte Transaktion landet zunächst im Mempool. Also kann man sagen, dass der Mempool sowas wie ein Wartezimmer, oder eine Warteschlange am Supermarkt oder im Vergnügungspark ist. Soll eine Transaktion in einen Block geschrieben werden, so muss sie sich erstmal anstellen. Dabei bleibt festzuhalten, dass Transaktionen erst im Netzwerk propagiert werden, bevor sie in einen Block geschrieben werden können. Wenn man also in seiner Wallet eine Transaktion abschickt und einen grünen Haken oder eine Animation angezeigt bekommt, dass die Transaktion erfolgreich versendet wurde, dann bedeutet dies schlicht nur, dass die Wallet die Nachricht, die diese Transaktion enthält, zunächst an eine Node (einen Knotenpunkt im Netzwerk) übertragen hat. Das dezentrale Peer-to-Peer Bitcoin-Netzwerk erledigt dann den Rest: Die Nodes propagieren diese Nachricht sofort weiter an alle verbundenen Nodes (Flooding genannt), und somit ist die Nachricht innerhalb weniger Sekunden an alle Netzwerkteilnehmer versendet. Dabei werden Transaktionen erstmal auf ihre Richtigkeit überprüft. Dann werden diese erst von den Mining-Nodes aus dem Mempool übernommen, die die Transaktionen sortieren und ihren Blöcken hinzufügen.

Transaktionen werden also von Wallets als Nachrichten ins Netzwerk gesendet. Ganz einfach gesprochen enthält jede Nachricht Informationen über den Sender, den Empfänger, die Höhe der versendeten Zahlung und die Höhe der angehefteten Gebühr. Diese Informationen müssen also erstmal im Netzwerk untergebracht werden, damit die Mining-Nodes aus diesem Pool von unbestätigten Transaktionen ihre Blöcke zusammensetzen können.
Jetzt sitzen also in diesem Wartezimmer ganz viele Transaktionen und warten darauf, aufgerufen zu werden, um von Dr. Miner in seinem Besprechungszimmer empfangen zu werden. Doch anders als beim Arzt, wo man in der Reihenfolge aufgerufen wird, in der man seinen Termin vereinbart hat, oder beim Straßenverkehrsamt, wo die Nummer auf dem kleinen Ticket, das man beim Eintritt gezogen hat, über die Reihenfolge entscheidet, sucht Dr. Miner sich selbst aus, welche Patienten (Transaktionen) er in welcher Reihenfolge sehen möchte. Dr. Miner bittet zum Vorsprechtermin. Und da alle Patienten ein kleines Schildchen hochhalten, auf dem die Gebühr steht, die sie bereit sind zu zahlen, um so schnell wie möglich von Dr. Miner empfangen zu werden, kann dieser ganz einfach diejenigen bevorzugen, die am meisten zahlen (würde so im normalen Leben ja keineswegs ablaufen - hrr hrr, Kassenpatienten!).

Damit möchte ich nicht sagen, dass bei Bitcoin ein Zwei- oder Mehrklassensystem besteht, wie das im deutschen Gesundheitssystem der Fall ist, allerdings gibt es Einzelnen die Freiheit darüber zu entscheiden, wie wichtig ihnen einzelne Transaktionen sind und wie viel sie bereit sind, dafür zu bezahlen (ähem, freie Marktwirtschaft, hust!) Diese variable Gebührenstruktur ist also ganz eng mit dem Anreizsystem von Bitcoin verbunden. Gebühren werden in sats/B oder sats/vB (Satoshis pro (virtual) Byte) berechnet, also wie viele Sats man pro Byte entrichten muss. Damit werden Transaktionen mit mehr Blockgewicht automatisch teurer (hallo Ordinals 👋), was eigentlich sehr fair ist, aber die variable Gebühreneinstellung in den meisten Wallets erlaubt Versendenden ihre Transaktion auch anderen Transaktionen gegenüber zu priorisieren, wenn diese es für notwendig halten.

Eine oft falsche Annahme ist, dass es irgendwie den einen Mempool gibt. Das ist natürlich falsch und aufgrund der dezentralen Struktur des Netzwerks auch gar nicht möglich. Vielmehr verfügt jede Node über ihren eigenen Mempool (mit seinen eigenen Einstellungen). Dieses Missverständnis rührt wahrscheinlich daher, dass immer von DEM Mempool gesprochen wird und Block-Explorer, wie mempool.space, durch ihre Übersicht suggerieren, dass diese Informationen aus DEM Mempool entstammen. Dabei sind Explorer oft nur die Visualisierung einer einzelnen Node, oder aggregieren verschiedene Informationen, um einen möglichst akkuraten Gesamteindruck darzustellen.
☝️ Kurz zusammengefasst: Ein Mempool ist die Warteschlange ausstehender und unbestätigter Transaktionen für eine Node. Es gibt keinen zentralen oder globalen Mempool. Jede Node verwaltet ihren eigenen Mempool, sodass verschiedene Nodes theoretisch unterschiedliche Transaktionen in ihren Mempools sammeln können. Transaktionen wiederum enthalten Gebühreninformationen, die für die Mining-Nodes wichtig sind, um diese zu priorisieren.

Wenn man sich das obige Bild einmal anschaut, versteht man auch, was es mit den Gebühren auf sich hat. Am einfachsten ist es sich vorzustellen, es gäbe eine Autobahn, auf der ein Algorithmus entscheidet, wie schnell alle Autos fahren. Um überhaupt auf diese Autobahn auffahren zu dürfen, muss man 1,98 sat/vB zahlen, sonst wird man gar nicht drauf gelassen. Diejenigen Transaktionen, die 4 sat/vB zahlen, dürfen zwar auf die Autobahn, stehen aber momentan auf dem Standstreifen und kommen nicht vorwärts. Wer mind. 5 sat/vB zahlt, fährt automatisch auf der rechten Spur, alle die mind. 7 sat/vB zahlen, fahren in der Mitte, und wer mind. 10 sat/vB ausgeben möchte, darf rechts am schnellsten fahren.
Oder um eine andere Analogie zu bemühen, schauen wir uns eine Warteschlange im Vergnügungspark an. Allerdings gibt es nicht nur eine lange Schlange, sondern verschiedene Schlangen für dieselbe Achterbahn mit unterschiedlich langen Wartezeiten. Jedoch muss man mehr Fahrpreis bezahlen, wenn man in die Schlange mit der kürzeren Wartezeit möchte (würde so im normalen Leben ja keineswegs ablaufen - hrr hrr, Genie-Pass im Disney World). Alle 10 Minuten fährt die Achterbahn eine Runde und nimmt immer nur eine gewisse Anzahl von Parkbesuchern mit, bis das Gewichtslimit der Bahn erreicht ist - nur das Gewicht der Fahrgäste ist entscheidend, nicht die Menge.

Es gibt einige Fahrgäste, denen es wert ist, auf jeden Fall in der nächsten Bahn zu sitzen, koste es was es wolle. Dann wiederum gibt es welche, die schauen, wie viele Fahrgäste schon in den jeweiligen Reihen stehen und sich ausrechnen, wie viel sie bezahlen müssten, um eine fast 100%ige Chance zu erhalten, in der nächsten Bahn zu sitzen, ohne unnötig draufzuzahlen. Dann gibt es diejenigen, denen es egal ist, denn sie wissen, dass sie auf jeden Fall irgendwann mitfahren, aber auf Schnelligkeit keinen Wert legen. Diese unterschiedlichen Warteschlangen lassen sich im folgenden Bild gut an den Kohorten der linken Spalte ablesen. Dort werden die jeweiligen Gebührenbereiche in sats/vB dargestellt und naturgemäß sind die unteren Bereiche mehr gefüllt, als die oberen.

Die Einordnung der Gebühren, das Analysieren der jeweiligen Bänder und das Errechnen der Mindestgebühren, etc. übernimmt natürlich nicht der Sender jedes Mal manuell. Wallets nutzen Algorithmen, um genau diese Informationen aus dem Netzwerk auszuwerten und um dann dem/der Nutzer//in die Gebühren schon einzustellen. Sollte es jedoch trotzdem vorkommen, dass die Gebühren zu niedrig eingestellt wurden und somit Transaktionen im Mempool stecken bleiben (sprich: Die Gebühren sind zu gering, um von Mining-Nodes als interessant genug erachtet zu werden und die Transaktion wird deshalb Block nach Block umgangen), gibt es die Möglichkeit Transaktionen zu pushen.
https://www.genexyz.org/post/19-block-765505-on-chain-analytics-mhcumo/
Wie wir in meinem Artikel vom Dezember letztes Jahres gesehen haben, wurde mit Version 0.24 des Bitcoin Core Protokolls eine Änderung in der Core Implementierung vorgenommen:
Und zwar wird der Default von Opt-in auf Full replace-by-fee (RBF) geändert. RBF ist eine Mempool-Funktion, die 2015 vorgeschlagen wurde und ins Protokoll übernommen wurde, die Nutzer//innen eine Möglichkeit gibt feststeckende Transaktionen voranzutreiben, wenn diese lange Zeit unbestätigt im Mempool hängen. Wenn Nutzer//innen diese jetzt beschleunigen wollen, können sie eine höhere Gebühr zahlen, um die eigene Transaktion attraktiver zu machen. In der 2016 eingeführten Opt-in RBF Funktion, müssen Nutzer//innen aktiv einwilligen, dass ihre Transaktionen durch Transaktionen mit höheren Gebühren ersetzt werden, wohingegen die neue Full RBF Funktion standardmäßig jede Transaktion ersetzbar macht, solange für die Ersetzung eine höhere Gebühr gezahlt wird.
☝️ Kurz zusammengefasst: Der Mempool funktioniert als Sammelbecken für alle dem Netzwerk übertragenen Transaktionen, die dann von den Minern sukzessive in einen Block gepackt werden. Dies erfolgt in der Regel nach Höhe der Gebühren, d.h. Transaktionen, die eine höhere Gebühr mit sich führen, werden von Minern präferiert, da dies deren Profit steigert. Wurde eine Transaktion mit geringer Gebühr übertragen, oder treten aus verschiedenen Gründen hohe Gebührenspitzen auf, können die unpräferablen Transaktionen im Mempool hängen bleiben.
Wie wir jetzt wissen, verwaltet jede Node ihren separaten, individuellen Mempool. Die Einstellungen können die Betreiber der Nodes selbst vornehmen, denn während die Standardgröße auf eine Memory-Grenze von 300 MB festgelegt ist, kann jeder Knotenbetreiber seinen eigenen Wert festlegen. Die Mempool-Größenbeschränkung bezieht sich jedoch nicht auf die serialisierten Daten oder das Transaktionsgewicht der Transaktionen in der Warteschlange, sondern auf die tatsächliche Speichernutzung der deserialisierten Transaktionsdaten auf der jeweiligen Node.
Wenn die Mempool-Grenze einer Node erreicht ist, werden die Transaktionen mit der niedrigsten Gebühr gelöscht und die Node gibt dem Netzwerk bekannt, dass vorerst keine Transaktionen unter einer gewissen Gebühr weitergeleitet werden sollen. Da jede Node unterschiedliche Grenzen hat, kann es sein, dass eine Node mit einem kleineren oder größeren Mempool Transaktionen früher oder später löscht.
Nachdem der Rückstand unter die (meistens) 300 MB-Grenze gesunken ist, senken Nodes ihre Gebührenmindestanforderung und beginnen wieder damit, Transaktionen zu akzeptieren, die zuvor ausgeschlossen wurden.
Jetzt ist es auch über drei Monate her, dass das Ordinals / Inscriptions Protokoll veröffentlicht wurde und nach einem anfangs relativ langsamen Start (trotz heftiger Diskussionen, vieler Publikationen zu dem Thema, etc.) wurden in dieser Zeit mittlerweile mehr als 1 Millionen Artefakte hochgeladen.


Das Hochladen so vieler (meistens) Bilder direkt in die Bitcoin-Blockchain ist mit recht hoher Sicherheit der Treiber dafür, dass der Mempool seit einiger Zeit komplett ausgelastet ist (also die 300 MB-Grenze übersteigt) und, wie oben gesehen, zum Zeitpunkt des Verfassens, ca. 17.000 Transaktionen darauf warten, in einen Block geschrieben zu werden. Dies entspricht etwa 90 Blöcken, die das Netzwerk produzieren könnte, ohne dass eine einzige weitere Transaktion hinzu kommt. Die große Menge an hochgeladenen Daten hat auch dazu geführt, dass Gebühren zeitweise in den Bereich von 20-40 sat/vByte gehoben wurden.

Vor SegWit (Segregated Witness) wurden Gebühren nach Transaktionsgröße bestimmt. SegWit führte das Konzept des Blockgewichts ein und änderte die zu erhebenden Gebühren nach Gewichtseinheit anstelle der Transaktionsgröße. Diese Änderung wurde eingeführt, um die Transaktionsgebühren insgesamt zu senken, jedoch kommt es dennoch vor, dass Blöcke erstellt werden, die überwiegend aus Inscriptions bestehen.

SegWit war ironischerweise auch der Soft Fork, der es erst ermöglichte, dass Inscriptions in der heutigen Form hochgeladen werden können. Mehr dazu hier:
https://www.genexyz.org/post/26-block-775770-ordinals-inscriptions-36zg3n/
Um das Ordinals / Inscriptions Thema abzuschließen, bleibt bei aller Kritik auf der einen Seite und einem neuen Geschäftsmodell / einer neuen Einnahmequelle für Miner auf der anderen Seite, zu sagen, dass der Anteil an Transaktionsgebühren, die auf Ordinals / Inscriptions zurückzuführen sind, doch recht überschaubar ist.

Es bleibt festzuhalten, dass der Mempool einen sehr wichtigen Teil des Bitcoin-Netzwerks darstellt. Er ermöglicht uns zu verstehen, wie ge- oder überfüllt das Netzwerk ist und ob es Transaktionsstaus gibt, die zu langsameren Bestätigungszeiten und höheren Gebühren führen. Er hilft fortgeschrittenen Nutzer//innen zu verstehen, wie sie ihre Gebühren am besten einstellen, aber bietet auch einen Überblick über den gesamten Zustand des Netzwerks. Will man sich einen Gesamteindruck über Bitcoin - das Netzwerk - machen, schaut man sich nicht den aktuellen Tageskurs an, sondern vielmehr den Mempool und die Hashrate. Diese zwei Quellen bieten eine Menge Auskunft darüber, was gerade im Netzwerk passiert und vielleicht passieren wird.

Los Miner, ihr habt zu viele ungelesene Transaktions-Nachrichten in eurem Mempool-Postfach!
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 3369d0a7:eb020757
2024-11-28 07:41:32
@ 3369d0a7:eb020757
2024-11-28 07:41:32Chef's notes
This recipe was a staple at every thanksgiving with family and now I share it with you nostr family. Absolutely one of my favorite side dish during the holiday. The corn pudding in the photo is NOT baked, I will update it. I hate stock photos.
Details
- ⏲️ Prep time: 15-20 min
- 🍳 Cook time: 30-40 min
- 🍽️ Servings: 6-8
Ingredients
- 2 cans of creamed corn
- 2c Milk
- 1 Box of Jiffy Cornbread Mix
- 3 eggs
- 1/4-1/3c sugar
- 1/2- green bell pepper or pepper onion blend
- 1/4TBsp vanilla
- 1/2tsp Salt
- 2TBsp Butter
Directions
- Grab medium saucepan and desired baking dish at least 9x9
- Place saucepan on medium-high heat
- Add butter and sauté pepper onion blend until tender
- Combine milk, eggs, sugar and vanilla, mix well
- Lather warmed (NOT HOT) baking dish with butter
- Sprinkle half a box of Jiffy corn bread mix in the baking dish
- Add both cans of creamed corn to peppers and onions
- Pour wet ingredients into slightly cooled creamed corn mixture
- Sprinkle the other half box of jiffy mix into the baking dish
- Incorporate the wet and dry ingredients in dish so there are no dry lumps
- Let set for 10 min before placing in a 325 degree oven for 30-40 minutes, until the center is solid and the edges are golden brown.
-
 @ c1e6505c:02b3157e
2024-11-28 00:02:26
@ c1e6505c:02b3157e
2024-11-28 00:02:26Chef's notes
Leftover ground beef? Not sure what to do with it?
Here’s what I do with mine. I call it…
The Beef Panzone
It’s like an omelette, a calzone, and a quesadilla had a baby. I called it that for now, but hey, if you’ve got a better name, lemme hear it!
The beef’s already cooked and seasoned with sea salt, but feel free to spice it up however you like.
Watch the video here: https://video.nostr.build/ad4856d2704ab0626a1907f5da8fedcb776495080bbaa92f4472db402c9f689d.mp4
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 10
- 🍽️ Servings: 1-2
Ingredients
- ground beef
- 2-3 eggs
- water
- sea salt
- honey
- coconut oil
Directions
- Leftover ground beef – Chop it into small pieces. Trust me, the smaller, the better—it’ll cover more surface area in the pan.
- Two eggs, whipped with a dash of water.
- Heat up a small pan.
- Add coconut oil (around a tablespoon).
- Once the oil’s warmed up, throw in the beef.
- Stir it around.
- I like to add local honey here—sweeten it up to your taste.
- Mix it all around.
- Pour in the egg mixture, making sure it spreads out evenly. I use chopsticks here because they make it easier to maneuver.
- Use those chopsticks to poke through the egg and let the uncooked top flow to the pan. This speeds up cooking time.
- Cover it for 1–3 minutes.
- Optional step: Cut it down the middle.
- Fold it over like a calzone.
- Plate it up, either by flipping the pan over onto the plate or scooping it out.
- PANZONE!
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 800be102:4e47eb69
2024-12-31 07:49:14
@ 800be102:4e47eb69
2024-12-31 07:49:14[3]
[4]
-
 @ c8adf82a:7265ee75
2024-12-31 07:22:34
@ c8adf82a:7265ee75
2024-12-31 07:22:34My life’s purpose is to save souls
Some think that preaching and convincing people is the way, maybe, but I prefer a more practical way. I want to actually solve real world problems for good and change people’s lives for the better
Most people have some sort of void in their heart nowadays, some big, some small. Some are still fighting to fill it, most gave up and accepted that life is just as whatever the eyes can see
Jesus said walk by faith and not by sight. I want to show people that this is the case but how can I do it when the world is so clouded? Most people believe that anything they think or feel is justified and we have to agree to disagree with each other to avoid conflict. This is madness
I’ve lived in this world for a while and by the grace of God, I can see through everything. Satan made money a requirement to live in this earth. Try asking people what’s one thing they are looking for, you’ll hear two common answers; money or happiness
Happiness people are made clueless, they are people who lost to their thoughts and gave in to their heart. Just ask them what makes them happy, and you will see how blind they are about reality. Their happiness comes from owning materialistic stuff or having experiences they haven’t experience because that’s what the media made them believe
Money people can think just enough that they need money to satisfy their heart, but not enough to realize that money is the root of all their misery. In reality, money is still a big issue in our world right now even after Bitcoin. Satan has successfully shifted the narrative of what Bitcoin actually is
I feel the need to help people with money, so that they have less worries about their finances, so that they can think less about money and more about important things in life; relationships, death and eternal life
The world is currently dark and corrupted, people are kept poor, hopeless and suppressed by the hands of satan. They’re killing our future generations with debt without explaining what debt truly is. They made the world so disillusioned to the point that everyone is talking about Hollywood over the lives of people
I was guilty of waiting for a change, but by the grace of God, tis no more. I will be the light of the world
Tomorrow is a new year, don’t spend another year doing the same thing. Join the fight. Use your blessed mind to tell people that Bitcoin is freedom money. We don't need to verify anymore, everything is clear if we open our eyes. Trust the Word and not the religion. Say no to Karmageddon
We are all Satoshi
We are legion
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 2063cd79:57bd1320
2024-12-31 05:29:22
@ 2063cd79:57bd1320
2024-12-31 05:29:22Angesichts der jüngsten Aufmerksamkeit in den sozialen Medien, die durch Greenpeace und die von Shitcoin finanzierte Änderung der Code-Bewegung geschaffen wurde, ist es wichtig zu betonen, warum Proof of Work (PoW) ein Feature und kein Bug ist und warum der Aufwand an Energie und damit Strom und damit der Verbrauch von idealerweise dichten Energiequellen, die zur Herstellung von Bitcoin verwendet werden, ein wesentlicher Bestandteil der DNA von Bitcoin darstellen. Die von Greenpeace befürwortete Alternative, Proof of Stake (PoS), die nicht so viel physische Energie verbraucht, aber auch nicht den Funktionsumfang von Proof of Work mit sich bringt, ist in sich fehlerhaft, denn PoS schafft es nicht, die digitale Währung - die die meisten alternativen CrYpTo Currencies sein wollen - und eben nicht “World Computer” oder “Smart Contract Application” - in der realen Welt zu verankern.

Die Geschichte von Geld ist fast so lang wie die der Menschheit als solche. Wie schon oft und besonders in letzter Zeit besprochen, hat sich unser Geld und der Umgang mit diesem mit der Entwicklung des modernen Menschen weiterentwickelt. Neue Technologien haben dazu geführt, dass auch unser Geld weiterentwickelt wurde und sich den aktuellen Gegebenheiten angepasst hat. Das jeweilig in seiner Zeit vorhandene Geld war immer das Beste, was der technologische Fortschritt und die äußeren Faktoren hervorbringen konnten. Heute leben wir in einer stark digitalisierten Welt und in diesem digitalen Raum bedarf es eines Geldes, das diese Anforderungen erfüllt. Natürlich gibt es immer Mittel und Wege, das aktuell beste Geld mit Hilfsmitteln so anzupassen, dass es den neuen Herausforderungen eine gewisse Zeit standhält, aber das ist immer nur eine Notlösung zur Überbrückung der Zeit, bis die nächste Innovation Einzug erhält. Das haben wir z.B. mit Gold und der Einführung von Papiergeld gesehen.
https://www.genexyz.org/post/11-block-752065-fractional-reserve-banking-wird-durch-bitcoin-obsolet-bdpznh/
Eine lange Zeit war Gold DAS beste Geld. Doch mit der Weiterentwicklung von anderen Technologien, die z.B. das Reisen über weite Strecken und damit den Handel zwischen Ländern und Kontinenten möglich machten, aber auch der Weiterentwicklung der Finanzsysteme und der damit einhergehenden Globalisierung, wurde Gold als Zahlungsmittel schnell unpraktisch und durch Papiergeld erweitert. Was zunächst nur eine bessere und neuere Art der Handhabung von Gold war, also die Möglichkeit den Besitz von Gold zu belegen und damit die Notwendigkeit schwere Barren oder Münzen von A nach B zu bewegen, abgelöst hat, wurde schnell zum neuen Geld. Papiergeld (und damit auch Notenbankgeld und Geschäftsbankbuchungen) ist spätestens seit 1971 das neue, am weitesten verbreitete Geld.
https://wtfhappenedin1971.com/
Doch durch die nächste Stufe in unserer Entwicklung, der Erfindung des Internets und des World Wide Webs, musste auch dieses Geld den Umständen angepasst werden. Papiergeld, bzw. Fiat-Geld ist allerdings nicht für das digitale Zeitalter gemacht, weshalb wir uns heutzutage mit weiteren Substituten wie PayPal, Venmo, Kwitt (haha), Zelle, usw. versuchen auszuhelfen. Was ich damit sagen will, ist, dass Geld eine Lebensdauer hat, und Fiat-Geld in seiner aktuellen Form nur noch effizient genutzt werden kann, da es Produkte gibt, die es ermöglichen eine Brücke zwischen der Geld-Technologie und den äußeren Umständen, also der immer weiter voranschreitenden Verschiebung unseres Lebens in den digitalen Raum zu schlagen. Wo Papiergeld damals Gold als das am häufigsten genutzte Zahlungsmittel abgelöst hat, können Dienste wie PayPal allerdings nicht zum neuen Geld werden. Dies wird durch die Aufsichtsbehörden, Staaten und internationalen Institutionen verhindert, denn die monetäre Autorität, das Recht Geld auszugeben - zu prägen - (und auszugeben!), ist in allen Staaten dieser Welt einzig und allein dem Staat vorbehalten (also nur eigentlich, aber dazu mehr ein anderes Mal).
https://x.com/Culture_Crit/status/1638293934735601666
Diese Digitalisierung des Werts von Geld ist gerade heute die Achillesferse von Gold. Gold ist (neben Bitcoin) die beste Möglichkeit, Besitz zu sichern und zu sparen. Es ist als Zahlungsmittel jedoch unbrauchbar. Fiat-Geld hingegen lässt sich bislang einigermaßen in den digitalen Raum überbrücken, aber Gold, der einzige bislang harte Wert, ist ein physischer Wert, was bedeutet, dass man es in der realen Welt schützen muss. Dies geschieht mit Hilfe von Tresoren oder Anbietern, die die Verwahrung übernehmen, was zur Zentralisierung des Eigentums und zu Vertrauensabhängigkeit führt, oder, wie oben beschrieben, zur Nutzung von Schuldscheinen. Da der einzige Grund sein Vermögen in Gold aufzubewahren darin besteht, solche Abhängigkeiten von Dritten zu vermeiden, führen Schuldscheine die Verwahridee ad absurdum, denn Schuldscheine sind nichts anderes, als Banknoten, die über kurz oder lang von ihrem zugrunde liegenden Wert entkoppelt werden. Dies ist bei Papiergeld der Fall, welches nicht durch den zugrunde liegenden Wert gedeckt wird.
Ist man jedoch in der Lage den zugrunde liegenden Wert zu entmaterialisieren, kann man diesen viel einfacher speichern, indem man Kryptographie verwendet, um diesen mit dem Internet zu verbinden, in dem weltweit die meisten Handelsgeschäfte und Transaktionen abgewickelt werden. Die Entmaterialisierung eines Werts birgt auch den Vorteil, dass dieser Wert in unendlich kleine Teile gestückelt werden kann. So ist es z.B. unmöglich einen Bruchteil des Wertes von Gold zu verleihen oder auszugeben, ohne es entweder in kleine Stücke zu zerlegen oder ein Derivat zu erstellen, das wiederum nur ein Proxy vom eigentlichen Gold darstellt.
Daher bringt ein entmaterialisierter Wert eines Guts viele Vorteile mit sich, die der einzige andere harte Wert, Gold, nicht bieten kann. Deshalb ist ein Gut, dass digital in einer entmaterialiserten Form existiert besser als ein physisches Gut. Dies kann man auch sehen, wenn man diesen Gedanken auf alte Geldarten zurückführt, denn es zeigt, dass diese damals verwendeten Gelder einen gewissen Wert hatten und als Ware marktwirtschaftlichen, oder sogar fast schon darwinistischen, Kräften eines Kampfes zwischen den jeweiligen Eigenschaften dieser Geldformen ausgeliefert waren. Muscheln wurden von Glasperlen abgelöst, Glasperlen von Silber, Silber von Gold. Gold war das wertvollste bekannte Gut, da Gold in der physischen Welt am schwierigsten herzustellen ist, oder war.

Denn in dieser evolutionistischen Kette löst Bitcoin Gold ab. Denn Bitcoin muss, obwohl es digital ist und damit in der heutigen Zeit des Internets perfekt funktioniert, in der physischen Welt beschafft oder produziert werden. Und das ist genau der Wert, den Proof of Work schafft. Bevor Bitcoin in der digitalen Welt existieren kann, muss es in der physischen Welt hergestellt werden. Und zwar unter sehr realen und physisch existierenden Umständen und Einschränkungen. Es muss Energie aufgebracht werden, um den Stromverbrauch von Mining-Rigs zu sättigen.
Damit hat Bitcoin einen Weg gefunden, Werte in der realen, greifbaren Welt mit denen der digitalen, entmaterialiserten Welt zu verbinden und genau diesen Wert in den digitalen Bereich zu übertragen. Der Mining-Prozess von Bitcoin transformiert also reale, physische Energie in ein digitales Gut, ohne dabei den Wert zu mindern, wenn überhaupt, wird der Wert dabei gesteigert. Denn die Transformation verankert nicht nur die aufgebrachte physische Energie in der realen Welt und wandelt diese in einen digitalen Wert um, sie steigert deren Wert sogar, indem sie ein Gut schafft, das weitere Eigenschaften in sich vereint, die in der realen Welt nicht existieren. Damit geht der Wert der verbrauchten Energie nicht verloren (wie gerne von Kritikern behauptet wird), sondern in diesem Prozess entsteht ein Gut, das größer ist als die Summe seiner Teile.
Diese Eigenschaft von Bitcoin, und Proof of Work im Speziellen, wird oft nicht erkannt, bzw. braucht einige Zeit, um verstanden zu werden. Es ist leicht nur auf den Energieverbrauch von Bitcoin in der physischen Welt zu zeigen, ohne die andere Seite der Gleichung in Betracht zu ziehen. Die zuvor genannten Medienkampagnen von Greenpeace, aber auch der EU, der EZB, des Weißen Hauses in den USA, usw. beschränken sich allerdings genau auf diese vereinfachte Anschauung der Tatsachen (oder vielmehr Narrative). Dieses Phänomen ist nicht neu. Ähnlich wird auch beispielsweise bei der Betrachtung von Antriebsarten von PKW vorgegangen. Elektrische Motoren werden mit Verbrennermotoren verglichen, indem man den Benzinverbrauch und den Benzinpreis einfach mit dem Stromverbrauch und Strompreis vergleicht. Der daraus entstehende Schluss, dass Elektroantriebe günstiger sind, hinkt natürlich vorne und hinten, da nicht alle Bestandteile der Gleichung in Betracht gezogen werden.
Das Verankern eines digitalen Werts in der physischen Wert ist allerdings nicht alleinig die Erfindung Satoshi Nakamotos und Bitcoin, sondern eine Verkettung von vielen Ideen und Konzepten zu einem einzigartigen und bislang nie dagewesenen neuen und bahnbrechenden technologischen Fortschritt.

Doch die Entmaterialisierung von Bitcoin hat nicht nur den einzigartigen Effekt, dass es einen Wert der digitalen Welt in der physischen Welt verankert, sie liefert auch den entscheidenden Vorteil von Bitcoin gegenüber Gold. Denn die Entmaterialisierung macht Bitcoin deutlich teilbarer als Gold, da Bits und Bytes in der Theorie in unendlich keine Teile gebrochen werden können, sie macht es deutlich transportables als Gold, denn eine Transaktion in egal welcher Höhe kann in sekundenschnelle propagiert werden und sie macht es vor allem deutlich sicherungsfähiger und damit Bitcoins Wert stabiler (nicht in Fiat-Terms, sondern absolut betrachtet), als den von Gold. Dies kann man schön in einem von Michael Saylor verwendeten Gedankenexperiment darstellen.
Man stelle sich dazu vor, es ist 1900 und man möchte eine Milliarde US Dollar in Gold verwahren und zwar so, dass man über diese Menge Gold im Jahre 2000 noch verfügt. (Die Veränderung des Goldpreises in Fiat-Terms über den Zeitraum lassen wir dabei außen vor, wir können sogar annehmen, dass 1 Milliarde Gold im Jahre 1900 im Jahre 2000 den exakt gleichen Wert hat). Hätte man im zwanzigsten Jahrhundert sein Gold z.B. bei Banken in Ländern wie Deutschland, Polen, Russland, China, Japan, Frankreich, oder Ländern der Kontinente Afrikas und Latein Amerikas in Verwahrung gegeben, ist davon auszugehen, dass durch Weltkriege und/oder Bürgerkriege, dieses Gold geraubt, verstaatlicht oder beschlagnahmt worden wäre. Selbst in den USA, Gewinner vieler dieser Kriege und territorial unbeschadet über diese 100 Jahre, gab es in 1933 die Executive Order 6102, die es Bürgern verbot Gold zu besitzen und diese zwang es unter Marktwert an die Regierung zu verkaufen.
Einzig in einer Handvoll von Ländern wäre es möglich gewesen, das Gold unbewegt und sicher einzulagern. Also wie hoch ist die Wahrscheinlichkeit, dass man diesen Treffer gelandet hätte? Selbst dort, wo man es unbewegt, also passiv einlagern hätte können, wären über 100 Jahre immense Verwahrgebühren fällig geworden, die den Wert der 1 Milliarde in Gold gesenkt hätten. Realistischer wäre sogar anzunehmen, dass man die Verwahrung des Goldes aktiv hätte überwachen müssen, also von Bank zu Bank, Land zu Land, oder sogar Kontinent zu Kontinent zu verschieben, um externen, (ge-)politischen und anderen Risiken entgegenzuwirken. Dies wäre mit einem weiteren hohen Kostenaufwand verbunden, der den Wert des eingelagerten 1 Milliarden Goldbestands noch weiter geschmälert hätte. Dieses Problem der Sicherung von Werten, insbesondere bei Gold, macht es als Wertspeicher relativ teuer. Bitcoin hat dieses Problem nicht, denn solange rückwärtskompatible Hardware existiert, muss man seinen Bitcoinbestand nur einmal vernünftig und sicher ablegen, um jederzeit und überall auf der Welt darauf zugreifen zu können.
Dies soll zeigen, dass PoW nicht nur eine sehr raffinierte Art und Weise darstellt Bitcoin in einem Anreizprozess herzustellen, sondern, dass PoW dabei hilft, den digitalen Wert Bitcoin in der physischen Welt zu verankern, und dabei zeitgleich Eigenschaften erzeugt, die andere Werte nicht besitzen. Das Verankern, bzw. die Verbindung von physischer und digitaler Welt durch die Transformation von Energie in eine höherwertige Form von Energie ist ein bahnbrechender technologischer Fortschritt, der selbst bei vielen Bitcoinern nicht hoch genug gewertet wird.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 472f440f:5669301e
2024-12-31 04:42:00
@ 472f440f:5669301e
2024-12-31 04:42:00I'm sure some of you are already tired of the discussion around the H-1B visa program that was started on Christmas Eve by Vivek Ramaswamy and escalated by Elon Musk and others as the "Silicon Valley MAGA" coalition began putting forth legal immigration policy proposals for the incoming Trump administration. Core to their policy is the expansion of the H-1B visa program so that America can "recruit the best talent in the world" to come build the American economy.
Unfortunately, as it stands today - according to the Silicon Valley cognescenti, Americans are either a.) not smart enough to fulfill the roles necessary to enable the United States to maintain its lead as economic super power of the world or b.) expect too much in compensation for the available roles. At least this is my reading from the commentary I've seen over the last week.
What seems abundantly clear to me is that the framing put forth by "Silicon Valley MAGA" crew is disingenuous and self-serving. It has been clear for awhile now that the H-1B visa program is being systematically abused to bring in cheap labor from other countries to help drive down labor costs for companies across the spectrum. Not just Silicon Valley tech companies. The system has a loophole in it and it is being exploited. Bring people to the US via H-1B visas to complete work for you at lower costs and your company's financials are likely to be better off (assuming the work being done is productive and a value add to the company). Now, this isn't to say that everyone who is in the US via an H-1B visa is here because these companies want to exploit the loophole that gives them the ability to spend less on head count. However, based off the data from the database of the H-1B visa program it is abundantly clear that the system is being taken advantage of. Egregiously and at the expense of American workers, who are most certainly not (all) "subtarded".
Herein lies the crux of the problem; companies are abusing this program to get away from the problem of Americans demanding higher wages to maintain lives of dignity in a country run by a government that is chronically addicted to debt backed by a central bank that will print money ex-nihilo and at will to monetize that debt. Americans are then being scapegoated as either "lazy", "stupid" or "delusional about their worth in the work force". A classic straw man argument that avoids the root issue at hand; the money is broken and the broken money has created perverse incentives throughout the economy while also stripping Americans of the ability to properly save the value of their labor.
We live in a high velocity trash economy that rewards grift and waste while disincentivizing hard work that is meaningful to the quality of life of the Common Man. Everything has been hyper-financialized to the point that one of the only ways to make it ahead is to speculate on the flow of capital into certain asset classes, which is often determined by the whims of central planners. Another is to build or speculate on tech "innovations" that typically materialize in the form of attention zapping apps and widgets that help people temporarily forget they live in a high-velocity trash economy.
The mass of men lead lives of quiet desperation and it is because they don't see a way out of the nihilistic rat race created (unknowingly to most) by the money printer.
The ability to print money out of nothing and throw it at everything creates misaligned incentives that result in the inability for the market to properly determine what is genuinely needed by the people instead of those who have learned how to game the broken system and its broken incentives.
One last point, I would be remiss not to acknowledge that many individuals in America aren't intellectually equipped to do some of the cutting edge work that may be necessary to produce the technologies and companies that will push the country forward. The high-velocity trash economy run on money printed out of nothing has completely corrupted the education system. People in the United States are literally dumber than they were five decades ago. That is a fact. But it is not only the fault of the American people themselves, but the corrupt system they have been born into that destroyed the education system with perverse incentives. And the overwhelming majority of the blame is on the system, not the people.
Even with that being said, the idea that we need to adopt a Tiger Mom mentality in the US - a culture of unrelenting devotion to studying STEM to the point that weekend sleepovers for kids are discouraged - is absolutely laughable and objectively un-American. There are plenty of incredibly intelligent, creative and driven young Americans who have contributed and will continue to contribute significantly to the American economy and they didn't need to shackle themselves to their desks to get that way. America isn't a country that was built by automatons. It's a country built by people who said, "Fuck you. Don't tell me what I can and cannot do. Watch this."
Despite the fact that a system has been erected that actively works against the average American system the American spirit lives on in the souls of many across the country. Miraculously. The American spirit is something that cannot simply be imported. It is ingrained in our culture. It is certainly beginning to dwindle as hope for a better future becomes more and more dim for the masses as the system works against them despite all their best efforts to succeed. It is imperative that we stoke the coals of the American spirit while it is still alive in those who are too stubborn to give up.
People need the ability to save their hard work in a money that cannot be debased. Opportunity cost needs to be reintroduced into the market so that things that actually add value and increase the quality of life for the Common Man are where hard money is allocated. And people need to start talking about the root of the problem more seriously instead of striking at branches with disingenuous straw man arguments.
Final thought... Ready to go surfing.
-
 @ 617f0a85:b403d1ed
2024-11-27 00:35:41
@ 617f0a85:b403d1ed
2024-11-27 00:35:41Chef's notes
I got this recipe from a friend in college. I'm not sure where she came across it, but I don't think she'd mind me posting it here.
Details
- ⏲️ Prep time: 15 min
Ingredients
- 2.5 cups unbleached all-purpose flour
- 1 tsp salt
- 2 tbsp sugar
- 12 tbsp cold unsalted butter
- 0.5 cup lard
- 0.25 cup vodka
- 0.25 cup cold water
Directions
- Process 1.5 cups flour, salt, and sugar in food processor until combined, about 2 one-second pulses. Add butter and shortening and process until homogeneous dough just starts to collect in uneven clumps, about 15 seconds (dough will resemble cottage cheese curds and there should be no uncoated flour). Scrape bowl with rubber spatula and redistribute dough evenly around processor blade. Add remaining cup flour and pulse until mixture is evenly distributed around bowl and mass of dough has been broken up, 4 to 6 quick pulses. Empty mixture into medium bowl
- Sprinkle vodka and water over mixture. With rubber spatula, use folding motion to mix, pressing down on dough until dough is slightly tacky and sticks together. Divide dough into two even balls and flatten each into 4-inch disk. Wrap each in plastic wrap and refrigerate at least 45 minutes or up to 2 days.
-
 @ 9f51b59f:75e7c3a2
2024-11-26 20:04:51
@ 9f51b59f:75e7c3a2
2024-11-26 20:04:51Chef's notes
Use bone in or boneless short rib. This recipe also works with ox tail and pork shoulder or any kind of meat that’s ideal for braising low and slow.
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 2.5-3.5 hours
- 🍽️ Servings: 6-8
Ingredients
- 3 Tablespoons natural cooking oil (I use tallow or ghee)
- 2 lbs boneless short ribs (bone-in also works)
- Salt & Pepper
- 1 small red onion, diced
- 5 garlic cloves rough chopped
- 1 bell or poblano pepper, seeded & diced
- 2 teaspoon chili powder
- 1 teaspoon ancho chili powder
- 1 tablespoon smoked paprika
- 1 tablespoon dark coco powder
- 2 teaspoon cumin
- 1 tablespoon graham masla
- 1 teaspoon dried oregano
- 3 tablespoons apple cider vinegar
- 1/2 cup tomato puree
- 3 tablespoons chipotle adobo sauce
- 3 bay leaves
- 1.5 cups stock or water
- 2 fresh limes, juiced
- Banana leaves, optional
- Avocado, sour cream, lime juice
- Shaved red cabbage with lime juice
Directions
- Preheat oven to 315 degrees F. Using a Dutch oven or braising pan, begin heating oil over high heat on the stove top.
- Season beef with salt and pepper and begin searing in the pot. Once browned on all sides set the beef aside and add the onions, garlic, and peppers to the same pan and reduce the heat.
- Season and cook the veggies 5 to 8 minutes until they start to caramelize. Add the chili pepper, paprika, coco, cumin, marsala, and dried oregano.
- Briefly toast the spices and deglaze with the vinegar and immediately add the tomato puree.
- Add the adobo sauce, broth, and using a stick blender or blender buzz the cooking liquid. (if using banana leaves remove the cooking liquid from the pan or use a new pot with lid. Line the pot with the leaves shingled over one another, return the cooking liquid over the leaves.)
- Return the beef to the pot and cover with lid or foil (fold leaves over the meat then cover).
- Place the pot in the oven and cook for 2 hours before checking, the meat should be fork tender when done.
- Mash the avocado into the sour cream and season with lime juice or hot sauce. Serve on tortillas with the crema and cabbage.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 468f729d:5ab4fd5e
2024-12-30 22:33:01
@ 468f729d:5ab4fd5e
2024-12-30 22:33:01 -
 @ 4dc2e570:7b8126f9
2024-11-25 17:39:37
@ 4dc2e570:7b8126f9
2024-11-25 17:39:37Chef's notes
Pickled pearl onions can usually be found at a middle eastern grocery store.
Details
- ⏲️ Prep time: 30 - 45 minutes
- 🍳 Cook time: 2 hours and 30 minutes
- 🍽️ Servings: 6
Ingredients
- 2.5 lbs stew meat
- 4 cloves Garlic
- 2 onions
- 6oz Bacon, chopped
- 4 Carrots (cut in 1/2 in pieces)
- 3 celery sticks (cut in 1 in pieces)
- 5 or so small gold potatoes, quartered
- 3ish tbps Flour
- 4 tbsp tomato paste
- 14 oz Guinness Beer
- 3 cups chicken stock
- 1 tsp Thyme
- 2 bay leaves
- Ghee
- Salt and pepper
Directions
- Pat dry then salt and pepper the beef. Melt 1/2 tbsp ghee over high med-high heat. Brown the beef on each side well, makes the stew tasty. This takes patience. Do some breath work while you're at it. :) Add ghee as necessary so browny bits on bottom dont burn. Put meat aside.
- In same pan, sauté onion and garlic for a few min. Throw in bacon till browned. Put in carrot and celery.
- Add 3tbsp flour (or a bit more, basically till oil is soaked up) and stir for a minute. Add tomato paste. Stir a couple more minutes.
- Add thin layer of beer and scrape yummy bits from bottom of pan. Mix everything well. Add rest of beer, broth, and herbs.
- Carmelize the pickled pearl onion on low med heat with a lil olive oil and stirring occasionally.
- Simmer covered for 2 hours. Add potatoes. Simmer for a further 30 minutes uncovered to let the sauce reduce a bit. Salt and pepper as you like. Add in some pearl onions. Enjoy.
-
 @ 4dc2e570:7b8126f9
2024-11-25 17:39:08
@ 4dc2e570:7b8126f9
2024-11-25 17:39:08Chef's notes
Pickled pearl onions can usually be found at a middle eastern grocery store.
Details
- ⏲️ Prep time: 30 - 45 minutes
- 🍳 Cook time: 2 hours and 30 minutes
- 🍽️ Servings: 6
Ingredients
- 2.5 lbs stew meat
- 4 cloves Garlic
- 2 onions
- 6oz Bacon, chopped
- 4 Carrots (cut in 1/2 in pieces)
- 3 celery sticks (cut in 1 in pieces)
- 5 or so small gold potatoes, quartered
- 3ish tbps Flour
- 4 tbsp tomato paste
- 14 oz Guinness Beer
- 3 cups chicken stock
- 1 tsp Thyme
- 2 bay leaves
- Ghee
- Salt and pepper
Directions
- Pat dry then salt and pepper the beef. Melt 1/2 tbsp ghee over high med-high heat. Brown the beef on each side well, makes the stew tasty. This takes patience. Do some breath work while you're at it. :) Add ghee as necessary so browny bits on bottom dont burn. Put meat aside.
- In same pan, sauté onion and garlic for a few min. Throw in bacon till browned. Put in carrot and celery.
- Add 3tbsp flour (or a bit more, basically till oil is soaked up) and stir for a minute. Add tomato paste. Stir a couple more minutes.
- Add thin layer of beer and scrape yummy bits from bottom of pan. Mix everything well. Add rest of beer, broth, and herbs.
- Carmelize the pickled pearl onion on low med heat with a lil olive oil and stirring occasionally.
- Simmer covered for 2 hours. Add potatoes. Simmer for a further 30 minutes uncovered to let the sauce reduce a bit. Salt and pepper as you like. Add in some pearl onions. Enjoy.
-
 @ 2063cd79:57bd1320
2024-12-30 21:08:43
@ 2063cd79:57bd1320
2024-12-30 21:08:43Bitcoin ist Zeit und Zeit ist Geld
In einem der vorigen Artikel haben wir uns mit den Funktionen und Eigenschaften von Geld befasst. Eine, vielleicht sogar die wichtigste, Funktion von wertvollem und hartem Geld ist Knappheit. Wir haben gesehen, dass Bitcoin die einzige Form von Geld ist, die diese Charakteristik zu 100% erfüllt.
Knappheit bedeutet, dass das Gut, das als Geld benutzt wird, begrenzt ist und nicht ohne weiteres vermehrt werden kann.
Bitcoin erfüllt diesen Anspruch, denn
Bitcoin ist auf 21.000.000 begrenzt. Die harte Obergrenze von Bitcoin ist von zentraler Bedeutung für sein Wertversprechen. Alle 2.099.999.997.690.000 Sats werden irgendwann existieren (oder existieren schon - je nach Betrachtungsweise) und darüber hinaus werden keine weiteren Sats produziert.
Die einzige andere Ressource, die wir Menschen haben, die uns jedem zur Verfügung steht und zu 100% begrenzt ist, ist unsere Zeit. Ausnahmslos jeder Mensch hat ab dem Moment seiner Geburt ein Zeitfenster in diesem Leben und dieses Zeitfenster - dieses Leben - ist begrenzt. Es hat noch niemand geschafft diese Regel zu brechen, bzw. zu cheaten.

Die Lebensdauer jedes Menschen fällt unterschiedlich aus und ist sogar recht ungerecht verteilt. Es gibt Menschen, die schon sehr, sehr früh nach ihrer Geburt sterben, und es gibt Menschen, die sehr, sehr alt werden. Auf diesem Spektrum von 0 bis ca. 120 Jahren befinden wir Menschen uns alle. Wir können aktiv Einfluss auf unsere Lebenserwartung nehmen, sowohl verlängernde als auch verkürzende Maßnahmen ergreifen, doch eins bleibt bisher immer garantiert: Unsere Zeit ist endlich. Und damit ist sie unser knappstes Gut.
Kommen wir nun zurück zum Geld. Wie wir schon gesehen haben, muss Geld drei Funktionen erfüllen:
Es muss als Tausch- oder Zahlungsmittel funktionieren, es sollte ein Wertaufbewahrungsmittel sein und als Recheneinheit dienen.
Während man schnell dazu übergeht, bei Geld an die Funktionen von Zahlungsmittel und Recheneinheit zu denken, da diese im täglichen Leben tausendfach vorkommen, ist es besonders die Funktion des Wertaufbewahrungsmittels, die Geld einen besonderen Stellenwert in unserem Leben als Ganzes verleiht. Und da ist sie, die Überschneidung von Geld und unserem Leben, also unserer begrenzten Zeit, auf die ich seit 400 Wörtern hinarbeite 😰
Zeit ist Geld. Jeder kennt diese Redewendung. Im wahrsten Sinne des Wortes bedeutet sie, dass man Zeit in Geld verwandeln kann und dass diejenigen, die Zeit haben auch Geld haben. Man spricht hier irrtümlicherweise auch von "Zeit sparen". Als ob die Möglichkeit bestehe, nicht verbrauchte Zeit zu einem späteren Zeitpunkt abzurufen. Dass dies außerhalb von Momos Welt nicht möglich ist, sollte jedem bewusst sein. Was meint man also damit, wenn man sagt man spart Zeit, oder Zeit ist Geld? Die Funktion des Wertaufbewahrungsmittels von Geld bedeutet erstmal, dass das verwendete Geld seinen Wert durch die Zeit aufrecht erhalten kann. Im allerbesten Falle ist ein Geld von heute auch morgen immer noch ein Geld wert.

Betrachten wir nun unser eigenes, hart begrenztes Zeitfenster, also jenes, das uns gegeben wurde, um auf diesem blauen, lustigen Ball zu verweilen, so wollen wir diese Zeit möglichst würdevoll und möglichst angenehm verbringen. Da das Leben allerdings Geld kostet, sind wir in der Regel gezwungen, solches zu verdienen. Es soll ein paar glückliche Menschen geben, denen dieser Ballast von Geburt an genommen wird, allerdings verhält es sich für das Gros der Menschen so, dass sie für ihren Unterhalt puckeln müssen. Im Idealfall sieht das so aus, dass man bei einem erwartbaren Durchschnittsalter von 80 Jahren, die ersten 20 Jahre damit verbringt zu erlernen, wie das Leben funktioniert und wie man Geld verdient, um dann 40 Jahre lang genau das zu tun und wenn alles gut läuft hat man noch 20 Jahre, um seinen wohlverdienten Ruhestand zu geniessen. Also einfach gesprochen verbringt man 50% seines Lebens damit, 100% seines Zeitfensters zu finanzieren (die ersten 20 Jahre des Lernens finanziert man zwar seinen Nachkommen, hat aber im Gegenzug dafür diese auch fremdfinanziert bekommen). Das bedeutet wiederum, dass man in den 40 Jahren Berufsleben doppelt so viel Geld verdienen muss, wie das eigens gewählte Leben kostet.

Um auf die Redewendung "Zeit ist Geld" zurückzukommen, bedeutet dies schlicht, dass jeder arbeitende (und damit Geld verdienende) Mensch seine eigene knapp bemessene Zeit in Form von Arbeit zur Verfügung stellt, um Geld zu verdienen. Dies tun wir, da wir Zeit eben nicht sparen können. Wir versuchen sie in einen anderen Aggregatzustand umzuwandeln (Zeit ➡️ Geld), um uns zu einem späteren Zeitpunkt mit diesem Geld unsere Zeit zurückzukaufen. Dies funktioniert zwar nicht im direkten Sinne, also dass wir uns zusätzliche Zeit kaufen, jedoch können wir das Decken laufender Kosten vorfinanzieren und somit, hoffentlich, im Ruhestand leben, ohne unsere laufenden Kosten durch Arbeit decken zu müssen. Wenn alles gut läuft, schaffen wir es sogar unseren gewählten Lebensstandard aufrechtzuerhalten und führen somit ein für unsere subjektiv gesteckten Messpunkte würdevolles und angenehmes Leben.
So die Theorie. Denn in der Praxis funktioniert dies nur, wenn es uns möglich ist, unsere Zeit in ein Geld umzuwandeln, das es uns erlaubt, eine Umwandlung von Geld zurück zur Zeit zu einem späteren Zeitpunkt so vorzunehmen, dass wir möglichst wenig verlieren. Dies ist die einzige Aufgabe eines Wertaufbewahrungmittels: Der Erhalt des jetzigen Wertes einer Sache über einen Zeitraum hinweg.

Praktisch gesprochen besteht dieser Vorgang aus zwei Komponenten. Zuerst müssen wir Geld verdienen, dann müssen wir es sparen. Bestenfalls schaffen wir so viel Geld zu verdienen, dass unsere Einnahmen unsere Ausgaben übersteigen, damit wir überhaupt in der Lage sind, überschüssiges Geld zu sparen. Dann müssen wir ein Wertaufbewahrungsmittel finden, dass es uns erlaubt, diesen Überschuss so zu konservieren, dass wir ihn zu einem späteren Zeitpunkt abrufen können. Über die erste Komponente lässt sich schon genug schreiben, über den gewählten Lebensstandard und die damit einhergehenden Kosten, die (Un-) Gerechtigkeit und Chancenungleichheit beim Erlangen einer Erwerbstätigkeit, etc. blah.

Die zweite Komponente allerdings ist für unsere Betrachtung die viel entscheidendere. Denn gehen wir davon aus, dass wir zu den glücklichen Wenigen gehören, die es schaffen eine niedrige Zeitpräferenz zu erlangen und Überschüsse in der Gewinn- und Verlustrechnung des Lebens zu erzielen, so bleibt immernoch die grosse Frage offen, wie wir es schaffen sollen, diese Überschüsse zu konservieren, sodass wir sie dann später nutzen können. Und zwar so, dass sie möglichst wenig an Wert verloren haben, oder sogar an Wert zugenommen haben.
Genau das ist das Geschäftsmodell von vielen Unternehmen, Institutionen und Schlangenölverkäufern weltweit, die damit werben, unser hart verdientes Geld so anzulegen, dass es später unseren Ruhestand finanziert. Sie wollen uns in ihre undurchsichtigen Finanzierungsmodelle locken, um damit als die eigentlichen Profiteure hervorzugehen.

Ob private oder staatliche Altersvorsorge, Riesterrente, Bausparvertrag, 401k, IRA, fondsgebundene Tralalarente oder Aktion Mensch-Los mit Sofort-Rente, alle Anbieter spielen mit der Sorge der Menschen, dass ihr heute gespartes Geld morgen wohl nicht mehr zur Finanzierung des erträumten Ruhestands reicht. Und warum ist das so? Wegen des effektiven Kaufkraftverlustes unseres aktuellen Geldes. Viel Tinte wurde vergossen, viele Tasten misshandelt, um dieses Thema zu beschreiben, das heute aktueller denn je ist. Denn wenn Geld in einer Fiat-Währung für die zukünftige Verwendung gespeichert wird, verliert es aufgrund der Währungsinflation im Laufe der Zeit an Kaufkraft. Das bedeutet effektiv, dass die investierte Zeit nicht nachhaltig widergespiegelt wird, oder drastischer ausgedrückt: wir haben unsere Zeit verschwendet. Sparen funktioniert also nicht mehr, wie es uns damals im Kindesalter beigebracht wurde.

Bitcoin fixes this, yay, Bitcoin-Floskel. Aber warum ist das so? Während Fiat-Währungen einem reellen Kaufkraftverlust ausgesetzt sind, der durch Fiskal- und Geldpolitik bedingt ist, ist der Wert von Bitcoin immer gleich. Ein bitcoin = ein bitcoin. Jetzt könnte man natürlich entgegensetzen, dass ein Knopf = ein Knopf. Allerdings lassen sich Knöpfe unendlich nachproduzieren und in Umlauf bringen. Doch wie wir wissen, hat Bitcoin eine harte Obergrenze von 21.000.000 bitcoins. Dies macht Bitcoin wahrscheinlich zum überprüfbar knappsten Gut auf unserer Erde. Selbst unser Zeitfenster könnte mit ein paar Entwicklungssprüngen in der DNA und Molekularforschung vielleicht irgendwann deutlich ausgeweitet, wenn nicht sogar für immer geöffnet werden.
Jedoch ist Bitcoins Code unveränderlich: Die 21 Millionen Obergrenze ist in Stein (Code) gemeißelt und damit eignet sich Bitcoin hervorragend als langfristiger Speicher für Zeit. Allein der Umrechnungskurs von Bitcoin in eine lokale, aktuelle oder für den Moment nützliche Währung hängt davon ab, wie viel Zeit man in einen anderen Wert umwandeln kann. Doch auch dies ist ein Feature und kein Bug. Denn jeder Arbeitstag, den ich heute in Euro oder US Dollar "spare" (besser: umwandle), ist komplett verloren, wenn diese Fiat-Währung zu einem Zeitpunkt x nicht mehr existiert. Dann ist es doch von Vorteil, wenn man seine Zeit in einen neutralen Aggregatzustand umwandeln kann, der sich in Zukunft beliebig in die benötigte aktuell brauchbare Recheneinheit / Währung transformieren lässt.

https://storeoftime.com/
Andersherum lässt sich argumentieren, dass das Währungspaar nicht BTC/USD oder BTC/EUR ist, sondern direkt ZEIT/BTC. Man ermittelt also den Wert von Zeit direkt in einer Bitcoin-Ausdrucksweise, die in Zukunft sogar festgesetzt werden könnte und damit die ultimative Währungseinheit darstellen würde.
Bitcoin verstehen
Bitcoin ist nicht nur Zeit im Sinne von umgewandelter Zeit in Geldmenge, sondern als reeller Zeitaufwand, um Bitcoin zu verstehen und Bitcoin für sich selbst begreifbar zu machen. Auch diese Definition von Zeit ist wiedermals für jeden Menschen subjektiv und dem eigenen Empfinden nach zu bemessen. Was jedoch nicht von der Hand zu weisen ist, ist dass es einen gewissen Mindestaufwand von Zeit, ob mit der Lektüre verschiedener Texte, dem Austausch mit Gleichgesinnten, dem tatsächlichen Ausprobieren und Erlernen der mechanischen Abläufe, etc. bedarf, um Bitcoin zu begreifen. Niemand wird jemals Bitcoin in seiner Gänze, seiner Tragweite oder seiner Wirkung vollständig verstehen, allerdings bin ich fest davon überzeugt, dass es diesen einen Punkt gibt, an dem bei jedem an Bitcoin interessierten Menschen ein gewisser Aha!-Moment eintritt, an dem viele Puzzleteile mit einem Mal ein Bild ergeben.
Dieser Moment tritt bei manchen sehr früh, bei manchen eher später ein, jedoch eint alle Bitcoiner und Bitcoin-verstehende Menschen dieser eine Moment, den es nur zu erreichen möglich ist, wenn ein gewisses Maß von Zeit investiert wurde. Dieser Moment lässt sich nicht erklären und muss von jedem Menschen selbst erlebt werden, um ihn zu verstehen. Damit kann er nicht erkauft oder erschlichen werden, sondern lässt sich nur in Form von aufgebrachter Zeit erreichen. Damit trägt Bitcoin eine weitere Zeitkomponente in sich, die weder im Whitepaper, noch im Code, noch in später veröffentlichten Texten Satoshis festgehalten oder gar definiert wurde. Jedoch wage ich zu behaupten, dass es niemanden gibt, der/die Bitcoin begriffen hat und von sich sagt, diesen Moment der Klarheit, der Offenbarung, nicht erlebt zu haben.

Bitcoin hat sein eigenes Verständnis von Zeit
Zeit ist ein sehr tiefgründiges und subjektives Konstrukt. Es gibt die Uhrzeit, also eine Zahl, die uns anzeigt, wie weit der jeweilige Tag vorangeschritten ist. Der Kalender misst auch Uhrzeit, nur eben nicht in Form von Stunden, Minuten und Sekunden, sondern in Monaten, Wochen und Tagen. Und dann gibt es noch Jahre. Wohingegen Sekunden, Minuten, Stunden, Tage, Wochen und Monate begrenzt sind - es gibt z.B. nur 12 Monate, dann fangen wir wieder von vorne an zu zählen, ist die Anzahl von Jahren keinem Zyklus unterworfen. Es wird immer weiter gezählt. Natürlich gibt es Dekaden, Jahrhunderte, Jahrtausende, etc., doch sind diese nur Recheneinheiten, die das Zählen von Jahren vereinfachen. In unserem System gibt es ein Jahr null und seit dem zählen wir vorwärts (wenn man davon absieht, dass sich jemand vor 400 Jahren das Jahr null ausgedacht hat und seit dem alles zurückgerechnet wurde, aber wir wollen mal nicht kleinlich sein) und alles was vor diesem Jahr null liegt, wird rückwärts gezählt. Dem Weihnachtshasen sei Dank 🙏
Genauso willkürlich, wie diese Zeiterfassung festgelegt wurde, verhält es sich bei Bitcoin auch. Denn Bitcoins innerer Maschinenraum ist eigentlich nichts anderes als eine eigenwillige und nutzungsbezogene Uhr. Die Bitcoin-Blockchain ist eigentlich eine Timechain, ein sogenannter Timestamp-Server. Wie schon mehrmals erwähnt, findet man das Wort 'Blockchain' in Satoshis Whitepaper nicht ein einziges Mal. Dafür findet man bereits im vierten Satz den Begriff 'Timestamp'.

Da Zeit ein recht flexibler Begriff ist und die Zeitmessung vom jeweiligen Nutzen oder dem Erfüllen eines Ziels abhängig ist, ist es besonders schwierig, ein allgemeingültiges System zu wählen. Zeit kann in vielen Formen dargestellt werden, von "Jetzt bis kein Bock mehr", oder "Anno Pief und Dazumal" gibt es etliche Redewendungen, die zeigen, dass Zeit gefühlt wird und nicht gemessen wird. Doch wenn man ein global funktionierendes dezentrales Netzwerk errichten möchte, dass darauf basiert seine eigene Wahrheit zu speichern, ohne auf Dritte angewiesen zu sein und alle Transaktionen so zu speichern, dass sie nachvollzogen und validiert werden können, bedarf es eines Zeitmessungsmechanismus. Und dieser muss absolut fehlerfrei sein und darf keine Latenz zulassen, da sonst Raum für Schummeleien geboten wäre. Was eignet sich da also besser, als ein eigener, eigens für diesen besonderen Zweck erdachter Mechanismus zum Festhalten von Geschehnissen? Diese Geschehnisse werden vom System mit einem Zeitstempel versehen, der unmissverständlich macht, welche Reihenfolge von Geschehnissen die eine Wahrheit ausmacht, der alle Netzwerkteilnehmer vertrauen.
Gigi hat sich dem Thema in seinem neuen Buch deutlich detaillierter gewidmet und ich empfehle jedem/r die Lektüre dieses Kapitels:
https://21-ways.com/2/
Fazit
Bitcoin ist nicht nur Zeit. Bitcoin misst die Zeit in seiner eigenen Weise. Bitcoin verlangt Zeit von uns, damit wir es begreifen, aber Bitcoin hilft uns, den Wert unserer Zeit einzufangen. Damit ist Bitcoin sowohl das Metronom, das seinen eigenen Takt angibt, strenger Lehrer, der Aufwand fordert, um Exzellenz zu erreichen, als auch Tresor oder Akku, der aufgebrachter Zeit einen Wert beimisst, und diesen Wert zu speichern vermag. Tick, tock, next Block!
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 234035ec:edc3751d
2024-12-30 19:36:42
@ 234035ec:edc3751d
2024-12-30 19:36:42When Satoshi created Bitcoin, he not only created the perfected form of sound money, but he also created an immutable universal measurement for time. Each block is found roughly every 10 minuets with the difficulty adjustment either ratcheting up or down the difficulty every 2,016 blocks. As we know the halving event occurs every 210,000 blocks (roughly 4 years). As an added bonus, Satoshi decided to release the white-paper during an election year. Therefor, every halving going forward will coincide with the US presidential election.
As you descend down the bitcoin rabbit hole, weather it is conscious or not, you begin to measure your life in these cycles. I remember when Bitcoin finally clicked for me in late 2021, all I was focused on was accumulating as much BTC as possible before the 2024 halving. You often hear people stating that they have been in Bitcoin for X number of cycles as a sort of accolade. Both of these are examples of how measuring your finite time with Bitcoins immutable time chain can be beneficial.
My Life by Cycles
I was born in the year 2001 shortly after the 911 attacks. Therefore, as I have grown I have only ever known a world of ever changing technological and cultural environments. I was 7 years old when satoshi released the white-paper and was entirely unaware of it for the first epoch (Too busy playing with Yu-Gi-Oh cards SMH).
The Second Epoch Bitcoin was still entirely off my radar, I was 11-13 years old and just getting into the sport of Wrestling. This was my awkward transitionary phase. Also during this time I got my first Ipod which was the beginning of my screen addiction but also opened a new world of opportunities.
The Third Epoch encompassed my time in high school. This cycle is when I first became interested in investing and heard about Bitcoin for the first time. I was extremely focused on my wrestling career throughout this cycle and became a 2 time state champion. But I also spent the majority of my free time with friends and girlfriends not spending much time thinking deeply about what I was doing or what was going on around me. Towards the end of this cycle was when I first bought Bitcoin, we had all been sent home from school for covid-19 and my senior year was cut short. While I did by a small amount of Bitcoin I held majority shitcoins and did not yet understand the true value of Bitcoin.
The Fourth Epoch begins with turbulence, my senior year of highschool was cut short and I decided to take a gap year before going to university. I spent that year working and studying and I began to get a clearer picture of the problems with our financial and political systems developing a more libertarian mindset. The following year I went off to college where I would be a student athlete on the wrestling team studying business. During my freshman year was when I truly went down the Bitcoin Rabbit hole. I could not get enough information about it and I was completely obsessed (still am). I had been moving all of my income into Bitcoin and then my sophomore year I sold all of my other investments to go all in on BTC. This was a difficult decision as I had made significant gain in tesla and believe in the company, but I could not stand the opportunity cost of not buying cheap sats. In retrospect this was a very good trade and ever since then the only asset that I purchase is Bitcoin.
The Fifth Epoch in the spring of 2024 came in my Junior year of University. This Halving was extremely satisfying as I have now made it through an entire bear market and came out with more Bitcoin than I had ever hoped for. Now that I am sitting on significant profit there is far less stress in Hodling and I feel that those around me are beginning to understand that I may be correct about this thing. This spring I will be graduating and moving on to my next phase in life which will be either employment, entrepreneurship or a combination of the two. This cycle will extend until the year 2028 when I will be 26 years old. As I look forward, it is quite possible that I will have proposed to my now Girlfriend of three years by the Fifth halving. I have stacking as well as fitness goals that I am looking to reach by the conclusion of this cycle.
The Sixth Epoch, will take me from ages 26-30. As I think about where I want to be by this time, I imagine myself with a young and growing family, a strong budding career either with my own established business or with plans to create one. I hope to have hit significant stacking milestones by this point, but I imagine that the USD exchange rate will be in the millions by this time.
Spend your time wisely
You are only given a finite amount of time in this life, Bitcoin gives you a means of measuring it that is equally scarce. As you store you economic energy in it you become more powerful over time. As you measure your time in it, the picture of your progress becomes much more clear.
If you have less Bitcoin at the end of an Epoch than at the beginning than you have been net-unproductive throughout that cycle. As you move forward with your life, try to think about where and who you want to be by the end of this epoch and keep that goal in mind.
-
 @ df478568:2a951e67
2024-11-25 02:36:34
@ df478568:2a951e67
2024-11-25 02:36:34Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 4
Ingredients
- rice
- 2 lb. ground beef
- 8 oz. sliced mushrooms
- 1 stalk of geeen onions, chopped
- 1/4 tsp. garlic salt
- 1 10.5 oz. can of cream of mushroom soup
- 1 cup sour cream
- peas
Directions
- Cook the rice
- Brown ground beef. Remove and set aside.
- Saute mushrooms and green onions
- Cook peas(I usually use the microwave)
- Return beef to Dutch oven. Add cream of mushroom and sour cream
- Cooknon low heat for 12 minutes.
-
 @ 3f770d65:7a745b24
2024-12-30 19:25:45
@ 3f770d65:7a745b24
2024-12-30 19:25:45As I look back on my predictions for Nostr in 2024, it’s clear I had some hits and misses. I believe my first two predictions were spot on, accurately reflecting the trends and developments we witnessed. However, my second two predictions missed the mark, proving to be far less accurate. Maybe I was too bullish?
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcqypsm9tk39g20atwqskvjcvhq7rher5nkgwjr05lzspne4gf0uvyxukew5mg
What did I get right? Clients did increasingly prioritize user and content discovery while enabling users to easily select and choose their own algorithms. (DVMs, Trending, What's Hot, Feeds, etc.) This focus provided individuals with more tools, greater control, and unprecedented power over their social streams and attention than ever before. This is still actively happening and will continue to happen throughout 2025 too.
What did I get wrong? We didn't see an Other Stuff application breakthrough as a clear winner that became a mainstream favorite. I anticipated a standout application that would interest users and become a "must-use" within the ecosystem, but this didn’t happen. And we also clearly didn't hit 1M active users either. While adoption did increase, it didn’t reach the critical mass I expected.
But this doesn't mean 2024 fell short of expectations—in fact, quite the opposite. The year brought incredible client innovations (Damus Notedeck, Primal 2.0, TOR only Amethyst, Flotilla, Chachi, Olas, Coracle feeds, etc.) and relay milestones (Web-of-Trust relays, private relays, algorithm based relays, etc.) with the introduction of these innovative features and the launch of these new platforms.
Beyond technology, the Nostr community achieved something truly remarkable: a grassroots movement that united people globally.
From supporting Nostr meetups and events to hosting booths across continents at major conferences, the community came together to raise money to support these initiatives in ways no one predicted. This organic, ground-up effort showcased the strength and passion behind Nostr, creating a foundation that will #grownostr and success for years to come.
Too bullish? Maybe I wasn't bullish enough? As is tradition, I will post my 2025 predictions tomorrow.
-
 @ 6538925e:571e55c3
2024-12-30 15:51:30
@ 6538925e:571e55c3
2024-12-30 15:51:30In 2024, listeners sent a total of $127,900 to creators on Fountain
The 2 BTC sent is equivalent to $127,900 based on a daily price conversion but it would be worth nearly 50% more today.
You sent over 40,000 boosts to your favourite shows and artists, with an average boost value of 3,380 sats (around $3.20 at today's price).
To add to that, over 63 million sats were streamed over the course of the year, representing 32% of total value sent.
Here are some of the shows and artists who picked up the top awards in 2024. To read the full article, head to our website.
Most Supported Show: Rabbit Hole Recap
Rabbir Hole Recap is a bitcoin news show hosted by Marty Bent and Matt Odell. Over the last three years, RHR has become one of the moved shows among Fountain listeners (affectionately known as ‘freaks’). In 2022 they were #3, in 2023 they were #2, and in 2024 they finally claimed the #1 spot. Congratulations, Marty and ODELL. Your dedication and humility is an inspiration to bitcoiners around the world.
Show with Most Supporters: Mr Obnoxious
Peter McCormack announced earlier this year that What Bitcoin Did, the preeminent podcast he has hosted for as long as we can remember, would come to an end to make way for a new show, Mr Obnoxious. In December, the Real Bedford FC owner announced that Danny Knowles would be the new custodian - much to the relief of the 800 listeners who supported the show this year. Thanks for everything, Pete!
Most Supported Episode: LINUX Unplugged | 545: 3,062 Days Later
LINUX Unplugged is just one of many popular shows about open-source, security and privacy from Jupiter Broadcasting. Editor-in-chief Chris Fisher finishes the year with three shows in Fountain's top 40. How? He and his co-hosts have made boosting a core part the listener experience, with his audience often sending "zip code boosts" (which can get pretty expensive if you live in Alaska).
Most Supported Artist: Ainsley Costello
At just 20 years old, Ainsley has been working toward a career in music for over half her life. Her music is the modern pop soundtrack of the next generation. Ainsley first made "waves" on the internet in August 2023 as the first artist to receive 1 million sats with her hit song “Cherry On Top.” Since then, she has inspired countless artists to follow her path, becoming the face of this exciting new movement.
Artist with Most Supporters: Man Like Kweks
Don Kweka is a producer and rapper from Tanzania. When he's not at his desk working his 9 to 5, he's making beats in his bedroom - and he has been prolific in 2024. Earlier this year he told Forbes he had earned a total of $25.68 from United Masters, the distribution company he uses for traditional DSPs (for which he pays a $60 annual fee). Since first publishing his music on Wavlake, he’s earned 2.3 million sats (over $2,000).
Most Supported Track: Abi Muir | Stockholm
Born in Scotland and now residing in Australia, Abi’s distinctive, goosebump-inducing vocals and heartfelt lyrics define her creative songwriting. Her unique style sees her delivering memorable, catchy pop songs of singer-songwriter prose with a contemporary pop sound. In Stockholm she explores a darker, harder edge to her music that crosses into alt-rock, topped with Muir's piercing, sultry vocals.
 ### Read Fountain Rewind 2024 in full on our website
### Read Fountain Rewind 2024 in full on our websiteTo see the full list of award winners, the top 40 shows and artists, plus the top stories from this year, hit the link below.
 ### Share your Rewind for a chance to win Fountain AirPods, limited edition merch and 100,000 sats
### Share your Rewind for a chance to win Fountain AirPods, limited edition merch and 100,000 satsOpen the app to see your Fountain Rewind (make sure you're using the latest version). Post a screenshot of any screen in your Fountain Rewind on X or Nostr and tag @fountain_app in your post. We will be announcing three lucky winners on Dec 31 - good luck!
-
 @ df478568:2a951e67
2024-11-25 02:36:04
@ df478568:2a951e67
2024-11-25 02:36:04Chef's notes
Easy Beef Stroganoff(Fast AF Beef Stroganaff)
This is an easy weaknight meal.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 4
Ingredients
- rice
- 2 lb. ground beef
- 8 oz. sliced mushrooms
- 1 stalk of geeen onions, chopped
- 1/4 tsp. garlic salt
- 1 10.5 oz. can of cream of mushroom soup
- 1 cup sour cream
- peas
Directions
- Cook the rice
- Brown ground beef. Remove and set aside.
- Saute mushrooms and green onions
- Cook peas(I usually use the microwave)
- Return beef to Dutch oven. Add cream of mushroom and sour cream
- Cooknon low heat for 12 minutes.
-
 @ 6bae33c8:607272e8
2024-12-30 14:29:06
@ 6bae33c8:607272e8
2024-12-30 14:29:06I was supposed to be back in Lisbon right about now, but am still in Florida. The itinerary changed on me, though it was always this way, and I just didn’t know it. Turns out Heather *thought* she had booked the flight for December 29th to arrive on the 30th, but really had booked the 30th to arrive on the 31st. She discovered this on the night of the 28th. It meant we had to cancel a 6:30 am New Year’s Day ski trip to France which was, to be honest, a relief to all of us.
I love skiing, but it entailed a two hour flight to Geneva, an hour drive to our friend’s house, then 40 minutes each way the next few days from there to the slopes, renting all the gear, etc. all while being jetlagged af and not having slept more than a few hours for two days after an eight day international trip to states. And cancelling only cost us half the price of the Lisbon to Geneva tickets, about $450 total, while saving us a couple thousand in meals, four-wheel drive rental car, lift tickets, etc. Plus we get Oscar back early from the dog camp now.
As a result, instead of traveling, I was able to catch some of the games yesterday, mostly the two late ones. My season is done, so this was more just observing how badly I botched my Steak League lineup at the last second and feeling enraged about that.
Anyway, the French alps would have been cool, but Florida isn’t that bad.


-
I have Anthony Richardson at QB in the Steak League because you get a point every 10 yards rushing and six points per rushing TD, but only four per passing TD and one point every 25 passing yards. But Richardson was hurt, it was a 14-team league, and the best I could do on waivers was his backup Joe Flacco against the Giants. So I had Flacco in the lineup, but right before we were about to leave for brunch, I saw that Davante Adams was active against the Bills, impulsively picked up Aaron Rodgers and subbed him in for Flacco. That cost me 17 points and could very well result in my buying rather than eating Steak.
-
Malik Nabers wears No. 1 and looks like a clone of Ja’Marr Chase in a Giants uniform. He’ll be a first round pick next year, no matter who the Giants QB is. And who knows, maybe Drew Lock is next year’s Sam Darnold.
-
The Giants win kicked them out of the top draft slot, and I’m good with that. I don’t want them to be forced to take a QB — better to sign someone unless the rookie is a can’t-miss generational prospect if that even exists anymore.
-
I thought I was being clever taking the Cowboys +9.5 with Jalen Hurts iffy, but I was not.
-
Saquon Barkley broke 2,000 yards but will probably sit against the Giants next week rather than go for Eric Dickerson’s all-time record of 2,105. It would be easy for him to do, but given he got to 2K in 16 games, and the Eagles are locked into the No. 2 seed, better to rest him. Breaking the 16-game record in a 17-game season means less than it would. The NFL single-season record books are one big asterisk field now.
-
When I started Rodgers I was afraid the game might go the way it did, and that Tyrod Taylor was able to engineer two TDs in garbage time was insult to injury. The Jets have packed it in, and I should have factored that into my decision.
-
I caught some of the Bengals-Broncos Saturday, but was at a restaurant when the Bengals went for the game-winning FG in overtime, assumed they made it, only to find out later they covered on a third-TD catch by Tee Higgins. This after they should have won on a FG in regulation but for some bizarre clock mismanagement. Tough beat if you had the Broncos +3.5.
-
Joe Burrow has 4,641 yards and 42 TDs vs eight picks with one game to go. The Bengals are still alive for the playoffs, but they’d need to beat the Steelers, the resting Chiefs to beat the Broncos and the packed-it-in Jets to beat the Dolphins, so they’re almost drawing dead. It’s too bad because Bengals-Bills in the Wild Card round would be a lot more exciting than Broncos-Bills.
-
Chase Brown sprained his ankle on the dumbest play of all time. Why run the ball toward the end zone and slide to avoid scoring at the one? Just kneel down at the six!
-
Ja’Marr Chase killed me this week with a meager 9-102-0 line.
-
Why wasn’t Marvin Mims getting more looks all year?
-
I went 2-3 in Circa, but boy was I right about Chargers -4. Perfect spot for a solid team to destroy a weak one that had played over its head the prior week.
-
Ladd McConkey is a bit fragile, but he’ll go around the 2/3 turn in next year’s drafts.
-
I didn’t catch much of Rams-Cardinals mercifully. Kyler Murray is so inconsistent.
-
Puka Nacua should be a top-10 fantasy pick next year too. The only receivers I’d take ahead of him are Chase, Nabers, Justin Jefferson, CeeDee Lamb and Amon-Ra St. Brown.
-
Brock Bowers broke Mike Ditka’s rookie receiving record. Depending upon the QB situation there, he might go at the 1-2 turn.
-
You have to love games where where the top RBs are Ameer Abdullah and Clyde Edwards-Helaire. I honestly didn’t realize CEH was even on the Saints until I looked at the box score.
-
The Panthers play everyone tight except apparently the Bucs. I’m glad they won, and the Falcons lost, as the Bucs are a much more entertaining playoff team.
-
Bucky Irving will go no later than the fourth round next year.
-
Mike Evans got 97 yards, putting him just 85 shy of 1,000. The Bucs need the game next week against the Saints, too. Only a injury can prevent him from getting there for an 11th straight year.
-
What if Mac Jones is next year’s Sam Darnold? Trevor Lawrence might be the next Baker Mayfield too.
-
Brian Thomas will go no later than early second-round next year, maybe even late first. I was one pick away in the 14-team RotoWire Dynasty league from getting Nabers and Thomas with my first two picks. Had to settle for Xavier Worthy and Bucky Irving/Jonnu Smith at the 3/4 turn.
-
The Dolphins without Tua are bad, but DTR is the worst QB in NFL history.
-
Jerry Jeudy is going in the third round again next year, and no one can stop this from happening.
-
Darnold threw one bad pick, but otherwise balled out again. He has 35 TDs and 12 picks with 8.2 YPA. If the Vikings upset the Lions in Detroit next week, and he has another big game — which is likely as the Lions defense isn’t good — Darnold will have MVP-type numbers on the 15-2 No. 1 seed. He won’t win because it’s Josh Allen’s “turn” but he would deserve it as much as anyone.
-
I didn’t watch the Sunday night game, but I’m glad the Falcons lost. They have no business being near the playoffs.
-
-
 @ de75eb1d:710c3014
2024-11-24 20:28:46
@ de75eb1d:710c3014
2024-11-24 20:28:46Chef's notes
Traditional Victorian recipe made better with the addition of chocolate, fills x6 one lb jars and each jar makes approximately 15 pies or one large tart.
Store in a cool dry place for 12 months for an even deeper flavour.
Unlike supermarket mincemeat, this recipe is naturally palm oil free when made using traditional ingredients (NOT Atora!), you could swap the animal fat for ghee or solid cocoa butter.
Go wild on the dried fruit, anything and everything works. This is a great area to play around and make extra special versions - like Cherry Brandied Chocolate! You can also swap or omit the nuts
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 3 hours
Ingredients
- 1 lb cooking apples, cored and diced
- 1.5lb mixed dried fruit
- 1lb unrefined sugar (or honey)
- 1/2lb beef suet
- 1/2lb candied citrus peel
- 2oz chopped or flaked almonds
- 4tsp mixed spice
- 1tsp ground cinnamon
- 1/2tsp ground nutmeg
- 1/2lb dark chocolate roughly chopped
- 6tbspn brandy or rum
- zest and juice of 2 oranges & lemons
Directions
- Combine all of the ingredients except the chocolate and alcohol in a large oven proof bowl, cover and leave overnight to infuse
- Next day cover the bowl with foil and bake slowly for 3 hours in a preheated oven at 120c
- As the mincemeat cools periodically stir in the fat and when completely cold add the alcohol and chocolate chips
- Pack into sterilised jars and cover with a wax disk or 1tsp melted suet, screw the lids on tight and it will keep for 3-5 years
-
 @ a38a5cd0:92b1b8f0
2024-12-30 13:31:02
@ a38a5cd0:92b1b8f0
2024-12-30 13:31:02I was born and raised in Europe—Switzerland, to be exact—and we’ve always had a special relationship with Europe or the EU. Although Switzerland is in the middle of Europe, it has always been isolated—not politically speaking, but through clever negotiations and an attractive financial marketplace.
But it’s still part of Europe, and whenever we drove to Germany, Austria (where I now live), or Italy, we always felt at home. Everyone was welcoming and accepted that Switzerland is the ‘special kid’ on the continent.
This is one of Europe’s superpowers. It lives off its different cultures. Other than America, I’m sorry to compare it, but it feels like many Americans have never left their own country; we can drive somewhere for three hours and pass two or even three countries.
Citizens speak different languages in each country, but we get along because there is a certain ‘European Vibe’ around. These different cultures and societies enable you to find communities where you feel at home and can be the best version of yourself—at least, that’s what I believe and have experienced.
However, the last 15 years have been challenging. Not only from a business standpoint, we tend to regulate and not innovate, but also from a political standpoint.
The EU and specific countries such as Sweden, Germany, and even Austria are fighting with high immigration, the Euro crisis – casually losing over 65% of its purchasing power this past decade – and ever-increasing debt.
Combine that with a keen interest by the majority of the population in Europe for Communism or Socialism. Please don’t ask me why it’s so popular in Europe. I think it could be an outcome of the world war situations where we never wanted to shift extremely right again. Or maybe the openness of the European spirit invites this thoughtfulness.
These ideologies don’t want the individual to succeed. For the better of all, it has always been at the center of these political movements. Inevitably, this idea leads to more poverty, more centralization, and, in the end, less democracy (the favorite word of any left-leaning politician in Europe) with a dictator at the whelm.
For some weird reason, we don’t want individual Europeans to succeed; instead, we have a collectivism that punishes brilliant ideas and nurtures the ever-increasing state.
So, why are you writing this essay then, Joël? Are you a right winger who’s just here to tell us Communism failed and we should do something else? NO! While my political views can definitely be described as conservative, I’m not associated with the right side of the aisle and would describe myself as a libertarian. However, for the European standard, I might be categorized as ‘right-wing,’ but who isn’t these days?!
But to answer the question, I think we have a secret weapon. Many of these freaks are either ignoring or deliberately downplaying because they’re scared of losing power and trying everything to forbid it.
You might have guessed by the title this secret weapon is Bitcoin!
There are apparent reasons why Bitcoin is the ultimate solution for Europe. These reasons are well known, from its scarcity to its natural state as the best reserve asset and its average value increase of 45% each year for the past decade. From a monetary perspective, these points make perfect sense.
However, there is more to the orange coin, especially from a polarization perspective. In Europe, the left and right are so far apart that it’s laughable. Bitcoin is the only asset or ecosystem enabling people from two corners to reunite and agree on something.
In Europe, in particular, this is something like human rights and privacy for every individual on the continent. It doesn’t matter whether you’re in Switzerland, Germany, or Portugal. Every citizen of these countries is rooting for human rights and the right to protect your most precious secrecies from third parties, aka the ever-increasing security state.
If you take a closer look at most political debates in Europe, both the left and the right agree that citizens should be able to protect their physical or digital properties and how to be more independent. Bitcoin enables you to do all of these things.
Additionally, mining can be an excellent catalyst for all parties to unite if you examine topics such as energy independence. Lefties can choose renewable energy, while right-wingers can embrace a free and healthy energy market. Bitcoin also enables this.
However, the most significant and crucial point is that Bitcoin will enable all nations to be independent again. Many countries lost their sovereignty mainly due to the EU and the Euro.
We no longer talk about each country’s interests; instead, we insert the sentence, ‘Anything that’s good for the EU.’ While the EEA (European Economic Area) was a noble idea that facilitated trade and economic output in Europe, it was abused and became a regulatory superpower with the EU.
You can see the consequences of this from the sheer number of companies who left Europe or international companies who treat Europe as a secondary market with little interest.
If Nations can regain sovereignty again and nurture their economic or sociological advantages, every citizen in these countries will have a new outlook on life.
All it takes for each of them to make the most important step in their Bitcoin journey; being curious enough to learn more about it, spending some time learning the fundamentals, and getting off zero!
One European nation with great potential for this is my home country, Switzerland. We’re the golden European standard for democracy, sovereignty, a strong economy, and a country where everyone can succeed.
After all, fellow Bitcoiners have already taken the initiative to add Bitcoin to the Swiss National Bank (SNB) ’s balance sheet and have already invested in MicroStrategy.
All it takes is the last step, which is to stack Sats as a strategic treasury reserve asset. As a fellow Swiss citizen and someone who works at a Swiss Bitcoin-only company, I would welcome this step and would love to help out!
To quote Walt Disney: ‘The way to get started is to quit talking and begin doing.’ So go ahead, Europe, and get started! Block space is limited, and 2140 is edging closer every ten minutes with a new block!
-
 @ 21b41910:91f41a5e
2024-11-23 12:00:26
@ 21b41910:91f41a5e
2024-11-23 12:00:26Chef's notes
Based on assorted recipes and refined over time, this round of beef tastes great as a result of the sweet and savory marinade.
Details
- ⏲️ Prep time: 5 minutes (+ 1 day)
- 🍳 Cook time: 20 minutes
Ingredients
- 2 pounds lean beef (may be labeled as London Broil)
- 1/3 cup olive oil
- 1/4 cup soy sauce
- 1/4 cup malt vinegar
- 1/4 cup lemon juice
- 1 tbsp sweetener of choice (honey, molasses, syrup, 4 packets of duck sauce, etc)
- 2 tsp old bay seasoning
- 1 tsp garlic powder
- 1 tsp sea salt
- 1/2 tsp black pepper
Directions
- Day Before: Mix all ingredients except the beef in a bowl to form a marinade. Place the cut of beef in a gallon sized Ziploc bag. Pour marinade over beef, ensure fully covered. Remove any excess air from the bag and seal. Place back in refrigerator for up to 24 hours before cooking.
- Cooking: Bring beef out of refrigerator (still in bag), and allow to rise to room temperature (about 30-40 minutes). Preheat broiler for about 15 minutes (your oven will vary). Broil for about 7-8 minutes on one side, then flip over. Continue broiling for another 7-10 minutes until temperature reads 140°F. Remove from broiler and let rest for 10 minutes before slicing thinly.
-
 @ ef1d1f12:a6811a37
2024-12-30 12:20:00
@ ef1d1f12:a6811a37
2024-12-30 12:20:00Is it a real news?
In a bold and defiant move, 77-year-old Thai protest leader, Srisompob Juntaratip, has shaved her head in a symbolic act of resistance against the country's military government. The protest leader, known for her outspoken criticism of the regime, was seen shaving her head in front of the Parliament building, surrounded by supporters and journalists.
The move comes as tensions between protesters and the government continue to escalate, with both sides engaging in increasingly violent clashes. Srisompob Juntaratip has been a key figure in the protests, using her platform to denounce the military's handling of the country's economy and political system.
Background:
Srisompob Juntaratip is a veteran activist who has been involved in Thai politics for decades. She has been arrested multiple times by the military government, but continues to speak out against its policies. The shaving of her head is seen as a powerful symbol of her commitment to the cause and willingness to risk arrest.
Reactions:
The move has sparked widespread reactions across Thailand, with some praising Srisompob Juntaratip's bravery and others condemning her actions as provocative. Social media is filled with images and videos of the protest leader shaving her head, with many using the hashtag #SrisompobJuntaratip.
Next Steps:
The military government has vowed to take action against Srisompob Juntaratip, with some calling for her arrest. However, the protest leader remains defiant, stating that she will continue to speak out against the regime and fight for democracy in Thailand. The situation is likely to escalate further in the coming days, as both sides dig in their heels.
Stay Tuned:
This story is developing and will be updated as more information becomes available. Follow our coverage for the latest updates on this breaking news story.
-
 @ 5accc5a7:b0fe15c1
2024-12-30 12:17:16
@ 5accc5a7:b0fe15c1
2024-12-30 12:17:16Breaking News: In a bold and defiant move, 77-year-old Thai protest leader, Srisompob Juntaratip, has shaved her head in a symbolic act of resistance against the country's military government. The protest leader, known for her outspoken criticism of the regime, was seen shaving her head in front of the Parliament building, surrounded by supporters and journalists.
The move comes as tensions between protesters and the government continue to escalate, with both sides engaging in increasingly violent clashes. Srisompob Juntaratip has been a key figure in the protests, using her platform to denounce the military's handling of the country's economy and political system.
Background:
Srisompob Juntaratip is a veteran activist who has been involved in Thai politics for decades. She has been arrested multiple times by the military government, but continues to speak out against its policies. The shaving of her head is seen as a powerful symbol of her commitment to the cause and willingness to risk arrest.
Reactions:
The move has sparked widespread reactions across Thailand, with some praising Srisompob Juntaratip's bravery and others condemning her actions as provocative. Social media is filled with images and videos of the protest leader shaving her head, with many using the hashtag #SrisompobJuntaratip.
Next Steps:
The military government has vowed to take action against Srisompob Juntaratip, with some calling for her arrest. However, the protest leader remains defiant, stating that she will continue to speak out against the regime and fight for democracy in Thailand. The situation is likely to escalate further in the coming days, as both sides dig in their heels.
Stay Tuned:
This story is developing and will be updated as more information becomes available. Follow our coverage for the latest updates on this breaking news story.
-
 @ 16d11430:61640947
2024-12-30 11:41:51
@ 16d11430:61640947
2024-12-30 11:41:51The heart chakra, or Anahata, is revered in spiritual traditions as the center of love, compassion, and harmony. Positioned at the midpoint of the seven energy centers in the body, it symbolizes a bridge between the physical and spiritual realms. In esoteric traditions, this chakra is pivotal in processes such as chrism rising, where spiritual energy ascends to higher states of consciousness. While these concepts are often explored metaphysically, modern medical science has begun to uncover fascinating parallels between the symbolic attributes of the heart chakra and the physiological complexity of the heart, particularly its nervous autonomy and its integration with the brain.
The Heart Chakra and Chrism Rising
In the context of chrism rising, the heart chakra represents a transformative stage. As sacred energy moves upward, it transitions from concerns of survival, sexuality, and personal willpower (root, sacral, and solar plexus chakras) to the higher realms of universal love and spiritual connection. This stage signifies the transcendence of ego and the integration of emotions with higher consciousness.
The journey through the heart chakra is marked by the awakening of compassion, forgiveness, and emotional balance. In spiritual terms, it represents the alchemical merging of the material (lower chakras) and spiritual (upper chakras) planes, enabling the individual to experience profound interconnectedness and divine love.
The Science of the Heart: Autonomy and Neurocardiology
Modern science offers compelling insights into the physiological and neurological sophistication of the heart. The field of neurocardiology has revealed that the heart is far more than a mechanical pump—it is a dynamic organ with its own nervous system, often referred to as the "heart brain."
The Autonomy of the Heart
- Intrinsic Nervous System:
The heart contains approximately 40,000 neurons, forming a complex neural network capable of independent operation. This "heart brain" can learn, remember, and even make decisions independent of the brain.
It plays a crucial role in regulating heart rhythms and coordinating with the autonomic nervous system.
- Heart-Brain Communication:
The heart sends more signals to the brain than the brain sends to the heart. These signals influence emotional processing, decision-making, and even higher cognitive functions.
This bidirectional communication underscores the heart's influence on mental and emotional states, echoing the heart chakra's role as an emotional center.
- Electromagnetic Field:
The heart generates the most powerful electromagnetic field in the body, measurable up to several feet away. This field is thought to synchronize the body's systems and may even influence the energy fields of others, aligning with the heart chakra's association with universal love and connection.
Mastery of the Heart and Performance Unlocking
From a performance perspective, mastery of the heart-brain connection unlocks extraordinary potential. This mastery aligns with the symbolic unlocking of the heart chakra in spiritual traditions, enabling an individual to operate with clarity, emotional resilience, and enhanced intuition.
- Heart Rate Variability (HRV):
HRV, a measure of the variation in time between heartbeats, is a key indicator of autonomic nervous system balance. High HRV is associated with emotional resilience, adaptability, and peak performance.
Techniques like heart-focused meditation and coherence training improve HRV, fostering a state of flow and heightened performance.
- Emotional Regulation:
The heart's intrinsic nervous system plays a critical role in regulating emotions. When the heart is coherent, emotional turbulence is minimized, allowing for calm, focused decision-making.
This mirrors the heart chakra's symbolic function of balancing emotions and fostering inner harmony.
- Intuition and Decision-Making:
Research suggests that the heart processes and responds to stimuli milliseconds before the brain, contributing to intuitive decision-making.
This intuitive capacity aligns with the spiritual concept of the heart chakra as a portal to higher wisdom.
Recent Breakthroughs in Heart-Brain Science
Modern research continues to shed light on the profound interplay between the heart and the brain, offering new dimensions to our understanding of the heart's role in physical and emotional health:
- The Polyvagal Theory:
Developed by Dr. Stephen Porges, this theory emphasizes the role of the vagus nerve in regulating the heart and promoting states of safety and connection.
Practices that stimulate the vagus nerve, such as deep breathing and meditation, not only enhance heart-brain coherence but also resonate with spiritual practices aimed at opening the heart chakra.
- Heart Intelligence:
Studies by the HeartMath Institute demonstrate that cultivating positive emotions, such as gratitude and compassion, improves heart-brain coherence. These findings parallel the spiritual emphasis on love and forgiveness as transformative energies of the heart chakra.
- Regenerative Medicine:
Advances in understanding the heart's regenerative potential, including its ability to produce new cells, highlight its resilience and adaptability. This mirrors the heart chakra's symbolic association with healing and renewal.
The Heart Chakra as a Key to Higher Potential
The convergence of spiritual wisdom and scientific insight paints the heart as both a physiological marvel and a metaphysical gateway. In the context of chrism rising, the activation of the heart chakra represents a transformative leap toward love, unity, and higher consciousness. From a scientific perspective, mastering the heart's neural and energetic capabilities unlocks profound emotional balance and peak performance.
Whether through the lens of spiritual tradition or modern science, the heart remains central to human experience—a pulsating vortex of connection, compassion, and boundless potential. By understanding and harmonizing its physical and energetic dimensions, we unlock not only the mastery of ourselves but also our ability to resonate harmoniously with the world around us.
-
 @ 8cd9d25d:69e9894d
2024-11-23 04:45:03
@ 8cd9d25d:69e9894d
2024-11-23 04:45:03Chef's notes
Note that youtube recipe is asking for 1tablespoon of salt, which is waaaaaay too much. Recipe works fine with a teaspoon,, but your mileage may vary. Play around with it.
You don't need to prove modern packet yeasts in my experience... just yolo it.
If you want an extra crispy crust, add a second baking pan to the base of the oven as you pre-heat. Then once you've placed the dough in, to the oven, take some boiling water and pour into the second baking tray. This gives you a steam oven on a budget :)
Details
- ⏲️ Prep time: 15min (not including time for dough rises)
- 🍳 Cook time: 30mins
- 🍽️ Servings: 4-5
Ingredients
- 500 grams wholemeal spelt flour
- 1 packet baker's yeast (10grams)
- 350 ml lukewarm water
- 350 ml lukewarm water
- 1 teaspoon salt 🧂
Directions
- Preheat your oven to Preheat oven to 430°F and put a baking tray in at the same time to heat up.
- Add all ingredients to a bowl (best to use a stand mixer to save time, but you can do by hand too. Mix and knead until the dough comes together. After about 5 mins you should have a moist dough that doesn't stick to your hands... if it is a bit sticky, just add a bit more flour (different flours like differenent amounts of water)... If too dry, add a bit more water... etc.
- Remove dough from bowl & form into a ball (smooth on top, never mind if not perfectly smooth on its base). Put back in a bowl and cover with a damp cloth. Allow to rest for 30mins/1hr until dough has roughly doubled in size. Time will depend on the ambient temp where you are. In the tropics, 30mins is just fine.
- Take risen dough out of bowl and put on a floured surface and press the gas out of it... flatten the dough with your hands, and then fold each edge in until you have a rectangle (video makes this bit clear). Then roll the rectangle up into a cylinder. This gives you a nice tight dough for baking. Pinch the ends of the cylinder to seal the dough.
- Place dough onto a baking sheet/ piece of parchment paper etc... cover with damp towlel and let rise for 15/30mins
- Score the risen dough (a razer blade, clean box cutter, or serrated knife works well) , this lets steam escape from the loaf as it bakes without slpititng it in ways you wouldn't like.
- Take your hot baking tray out of the over and transfer your dough onto it. Put into oven.
- Bake at 430°F (220°C) for 15mins, then reduce oven temp to 350°F (180°C) for the final 15mins. Total bake time 30mins.
- Remove from oven and allow to cool for 20-30mins.
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ 9bc2d34d:d19d2948
2024-11-22 17:26:28
@ 9bc2d34d:d19d2948
2024-11-22 17:26:28Chef's notes
Hot Dogs? Check. Cheese? Check. Jalapeno? Definitely (unless you can't handle the spice)
Details
- ⏲️ Prep time: 1 minute
- 🍳 Cook time: 3-5 minutes
- 🍽️ Servings: 1-4
Ingredients
- 3 Hot Dogs (Sliced Thinly or Cut into Chunks)
- Handful of Shredded Cheese Blend
- 1/4 Jalapeno minced (add less or more)
- Optional: Any toppings you like on nachos, such as tomatoes, onions, sour cream, beans, etc
Directions
- Microwave 3 hot dogs for 2-3 minutes (some hot dogs will expand)
- Top with cheese
- Microwave for 1-2 minutes (until cheese is melted)
- Sprinkle all your favorite toppings on top
- Serve
-
 @ ac8bb9b0:70278acc
2024-11-21 15:14:11
@ ac8bb9b0:70278acc
2024-11-21 15:14:11Chef's notes
If you’d like to make this soup part of your rotation and want to shave off a little time for the next time around, double the recipe for the meatballs and freeze half. That way, all you’ll have to do is make the soup and add the meatballs as directed in the recipe. (They may take a few extra minutes to warm through if you add them directly from the freezer.)
The soup can be frozen for up to 3 months but wait until you reheat the soup to add the pasta. Defrost the soup in the refrigerator for 12 hours and then reheat it on the stovetop over medium heat until simmering, add the pasta, and cook until the pasta is tender.
Details
- ⏲️ Prep time: 50
- 🍳 Cook time: 30
- 🍽️ Servings: 8
Ingredients
- 1 large egg
- 3 tablespoons finely chopped fresh chives
- 2 teaspoons finely chopped fresh sage
- 2 cloves garlic, minced
- ¾ lb 85 or 90% lean ground beef
- ½ lb sweet or hot Italian sausage, removed from the casings
- ½ cup grated Parmigiano Reggiano
- ⅓ cup Italian seasoned bread crumbs
- ¼ teaspoon salt
- 2 tablespoons extra virgin olive oil
- 1 medium yellow onion, diced
- 2 large carrots, diced
- 2 stalks celery, diced
- 6 cups high-quality chicken broth
- 2 cups high-quality beef broth
- 2 cups water
- ½ cup dry white wine
- 1 bay leaf
- ½ teaspoon salt
- ¼ teaspoon white pepper (okay to use black pepper)
- 1 cup small dittalini pasta
- 4 oz fresh spinach, stems trimmed and roughly chopped (once prepped, you should have about 3 packed cups)
- Parmigiano Reggiano, for serving
Directions
- Make the meatballs: Preheat the oven to 350°F. Line a baking sheet with aluminum foil and set an oven-proof roasting rack over top. Spray the rack generously with nonstick cooking spray.
- In a large bowl, beat the egg with the chives, sage and garlic. Add the remaining meatball ingredients and mash with your hands until evenly combined. Roll the mixture into tablespoon-size balls, about 1 inch in diameter (it will make approximately 50 meatballs), and place on the prepared rack. Bake for 15 to 18 minutes, or until lightly browned and cooked through. Set aside.
- Meanwhile, start the soup. In a large soup pot or Dutch oven over medium heat, heat the olive oil. Add the onions, carrots, and celery and cook, stirring frequently, until the vegetables are softened, about 8 minutes. Add the chicken broth, beef broth, water, wine, bay leaf, salt and pepper and bring to a boil. Add the pasta and cook, uncovered, at a gentle boil until the pasta is al dente, 8 to 10 minutes (or according to package directions). Taste the soup and adjust the seasoning, if necessary. Reduce the heat to low and add the spinach and meatballs. Simmer for a few minutes, until the spinach is wilted and the meatballs are warmed through. Ladle into bowls and serve with grated Parmigiano Reggiano.
-
 @ bcbb3e40:a494e501
2024-12-30 11:29:30
@ bcbb3e40:a494e501
2024-12-30 11:29:30
No podemos ignorar la importancia que el Reino Visigodo tiene en la configuración de España, de la impronta definitiva que aportó al proceso de etnogénesis para dar la forma definitiva a esa entidad histórica que hoy, tras tres siglos de invasiones germánicas, desde la caída del Imperio Romano a finales del siglo V d.C., hasta el advenimiento del Islam. A modo de contraste, diremos también, que la identidad nacional española, o si se quiere ver así, el alma hispánica, se forjó en claro y evidente contraste con el ocupante sarraceno, y su presencia en el orbe peninsular, junto al recuerdo de la herencia visigoda y los sucesivos concilios toledanos, sirvieron de estímulo al avance de los reinos cristianos del norte. Es decir, España se construyó en la lucha, en el combate abierto contra un enemigo al que consideraba ocupante y representaba una realidad cultural, étnica y civilizacional totalmente antagónica a la naciente realidad hispánica.
De ahí la importancia del sustrato germánico, godo, que viene a agregarse al ya preexistente de hispano-romanos, celtas e íberos. En las últimas décadas esta importancia se ha visto relegada, de forma deliberada, a un segundo plano, y si nuestros padres y abuelos conocían la famosa lista de reyes godos, en la actualidad, su conocimiento entre gran parte de la población española, y especialmente entre los más jóvenes, es puramente testimonial, cuando no inexistente.
|
 |
|:-|
|El mapa muestra la distribución territorial de la península ibérica durante el período del Reino Visigodo (409-711 d.C.). Se destacan los dominios visigodos, con Toledo como capital, y las principales ciudades como Emerita, Hispalis, y Cesaraugusta. También se señala la presencia del dominio bizantino en el sureste (Cartago y Córdoba) y la región ocupada por los suevos en el noroeste (Bracara y Lucus). Las áreas de los astures, cántabros y vascones aparecen al norte como zonas independientes.|
|
|:-|
|El mapa muestra la distribución territorial de la península ibérica durante el período del Reino Visigodo (409-711 d.C.). Se destacan los dominios visigodos, con Toledo como capital, y las principales ciudades como Emerita, Hispalis, y Cesaraugusta. También se señala la presencia del dominio bizantino en el sureste (Cartago y Córdoba) y la región ocupada por los suevos en el noroeste (Bracara y Lucus). Las áreas de los astures, cántabros y vascones aparecen al norte como zonas independientes.|No obstante, no queremos hacer aquí una relación de reyes, ni hablar de las estructuras políticas, económicas o religiosas del reino visigodo, sino que pretendemos centrarnos en una sola figura, la del rey Sisebuto, cuya fama y los elogios que se dedican a su persona nos han sido legados por las fuentes de la época. San Isidoro de Sevilla, una de las grandes personalidades de la época —autor de las famosas Etimologías, un compendio del saber antiguo en lo que se consideró como la primera enciclopedia cristiana— y uno de los grandes maestros del Occidente medieval, nos aporta valiosas informaciones sobre Sisebuto:
«fue brillante en su palabra, docto en sus pensamientos y bastante instruido en conocimientos literarios [...]. Fue notable por sus conocimientos bélicos y célebre por sus victorias».
O también en Historia Gothorum:
«se mostró tan clemente después de su victoria, que pagó un precio para dejar en libertad a muchos que habían sido hechos prisioneros por su ejército y reducidos a esclavitud como botín de guerra».
De hecho existió un vínculo de amistad entre Isidoro de Sevilla y Sisebuto, y el primero dedicó al segundo una primera edición de sus Etimologías, y escribió a instancias del monarca visigodo otras obras como De natura rerum. La fama del rey visigodo traspasó fronteras y encontramos referencias a sus virtudes y cualidades personales a través de la Crónica del Pseudo Fredegario, donde se aplican otros calificativos como «varón sabio, piadosisimo y digno de toda alabanza». De modo que las fuentes ya nos permiten trazar un primer retrato general sobre la figura del protagonista de nuestro escrito, y que podríamos resumir así: monarca sabio, guerrero y sensible. Cualidades estas que pueden parecer difícilmente compatibles, pero que nuestro Sisebuto aunaba conformando una poderosa personalidad.
Rey guerrero
Pero antes que nada deberíamos preguntarnos por los orígenes del rey Sisebuto, quien ocupó el trono del reino visigodo durante 9 años, entre el 612 y el 621. Se destacó por su capacidad para defender tanto en las fronteras interiores como exteriores la autoridad de la monarquía visigoda. Prueba de ello fueron las campañas que acometió contra los astures en el Norte, terminando con las veleidades independentistas de estos pueblos belicosos, aunque hay cierto oscurantismo en cuanto a las fuentes. Y paralelamente, en el Sur, las operaciones militares de Sisebuto estuvieron dirigidas contra la provincia bizantina ubicada en el sureste peninsular desde mediados del siglo anterior. Las sucesivas campañas militares consiguieron mermar los dominios bizantinos en la península, especialmente con la conquista de Málaga en 619. Además conviene destacar el notable desarrollo del ejército naval visigodo, alcanzando elevadas cotas de esplendor nunca registradas con monarcas precedentes. No hay datos totalmente contrastados, pero es posible que, con Sisebuto, surgiera una marina organizada.
Las guerras que se libraron entre visigodos y bizantinos fueron cruentas y sanguinarias, generando gran dolor y consternación entre nuestro monarca, algo que, como indican los propios historiadores y cronistas de la época, era bastante infrecuente. En la citada Crónica de Fredegario se le atribuyen ciertas afirmaciones a tal respecto, en las que lamenta las pérdidas humanas y se expresa con un notable humanitarismo:
«Si se producen guerras —escribía Sisebuto a Cesario—, si la cruenta espada se ensaña por doquier, si los vicios de los hombres hacen que los tiempos presentes sean tiempos belicosos, ¿qué cuentas, pensadlo, habrá que rendir a Dios por tantos crímenes, por tantas calamidades, por tantas funestas heridas?»
«Se mostró tan clemente después de su victoria —dice San Isidoro en Historia de los Godos— que pagó un precio con el fin de dejar en libertad a muchos que habían sido hechos prisioneros por su ejército y reducidos a esclavitud, llegando incluso su tesoro a servir para el rescate de los cautivos.»
Lo fundamental para Sisebuto era la unificación del territorio peninsular bajo el poder godo, pero no solo empleó medios militares, sino que también hizo uso de la diplomacia. Respecto a este tema, se conservan dos cartas de la correspondencia entre Sisebuto y el gobernador provincial e imperial en España, Cesario, en torno a la disputas entre visigodos y bizantinos relacionadas con los prisioneros de guerra. Con ocasión de la captura del obispo Cecilio de Mentesa por parte de los bizantinos, Cesario se apresuró a ponerlo en libertad y escribió al rey Sisebuto para comunicárselo con las siguientes palabras:
«Nuestro beatísimo padre, Cecilio, fue capturado por nuestros hombres, mas en consideración a Dios y vuestro reino y como prueba de buena voluntad, lo liberamos rápidamente y pusimos la mayor diligencia para que fuera devuelto a su santa iglesia y enviado a vuestra presencia».
Sisebuto respondió a Cesario de manera cordial y afectuosa, lo que supuso la toma de contacto a través de una delegación diplomática entre ambas partes, godos y bizantinos, que condujo a un acuerdo. Los bizantinos no serían expulsados definitivamente del territorio peninsular hasta el reinado de Suintila (588-633).
Rey sabio
El monarca visigodo también fue un notable erudito e intelectual, muy destacado en una época de gran esplendor cultural capitaneada por San Isidoro de Sevilla, de quien ya hemos dicho que mantuvo una estrecha relación con Sisebuto. Las famosas Etimologías isidorianas estuvieron consagradas en su primera edición a la figura del rey a través de las siguientes palabras, que le honraban a través de la siguiente dedicatoria:
«Como te he prometido —escribía al rey el obispo hispalense— te envío ahora la obra acerca “Del origen” de ciertas cosas, recopilada con el recuerdo de antiguas lecturas. Por eso, en algunos pasajes aparece anotada de acuerdo con lo que habían escrito nuestros antepasados».
Se puede decir que Sisebuto fue al mismo tiempo un promotor de la actividad literaria, intelectual y científica, y un hombre sabio de su época, con la producción de obras en el ámbito de la ciencia y la literatura, al margen de los asuntos propiamente religiosos, algo que podría resultar chocante en relación a otros reyes bárbaros de aquel entonces. Fruto de esta doble vertiente tenemos el Liber de natura rerum, obra de San Isidoro, dedicada al conocimiento del universo y los fenómenos naturales. Por su parte su contribución a la producción científica de la época fue el Liber rotarum o Carmen de luna, un poema en el que trataba de explicar el fenómeno de los eclipses al margen de motivaciones religiosas, en el terreno puramente físico.
Sus incursiones no se limitaron al mundo puramente científico de los fenómenos físicos, sino que sus intereses también se orientaron hacia la vida y hechos de otros hombres de su tiempo. Tal es así, que vemos como su principal obra, Vida y pasión de San Desiderio, un obispo de Borgoña que padeció de persecuciones y murió años atrás. Esta obra guarda ciertas particularidades por sus motivaciones políticas, orientadas a congraciarse con Clotario II, rey de la Francia merovingia.
Rey religioso (y gibelino)
Sisebuto fue un monarca profundamente religioso y en consonancia con la ortodoxia, lo que hizo que en muchas ocasiones tuviera que intervenir para su fortalecimiento y mantenimiento. De hecho, su propio hijo, Teudila, ingresó en una orden monástica impelido por su progenitor, que alentó su celo religioso. Incluso envió una carta al rey longobardo Adaloaldo, convertido al catolicismo, exhortándolo a que hiciera lo propio con la totalidad del reino, y terminar así con los últimos restos de herejía arriana, que había tenido un relativo éxito entre los pueblos germánicos en su momento. Además trató de ofrecer argumentos lógicos y fundamentados en la exégesis católica, amparándose rigurosamente en las Sagradas Escrituras. Al mismo tiempo, augura prosperidad y buenos designios en un futuro hipotético ante la conversión al catolicismo, favoreciendo la acción benéfica de la providencia divina sobre su pueblo. Todavía debería pasar medio siglo para la conversión de los longobardos, mucho después de la muerte de Sisebuto, acontecida en el 621.
Sisebuto también se preocupó por fortalecer y vigorizar la propia estructura eclesiástica, algo que fue una constante en la España visigoda y se materializó a través de sucesivos Concilios en Toledo. Sisebuto, como nos relata el historiador José Orlandis, lejos de utilizar la Iglesia como un parapeto, como una suerte de protección para reforzar su posición, se mostró más bien con cierta mentalidad «cesaropapista». Actitud a través de la cual Sisebuto tomaba la iniciativa, tanto en el ámbito político y temporal como en aquel religioso-espiritual y atemporal. En cierto sentido podríamos calificar a Sisebuto como un «rey gibelino» por esa simbiosis entre ambas esferas, asumiendo él mismo, personalmente, la función de velar por el buen orden eclesiástico. Un buen ejemplo de ello lo tenemos en las imposiciones a Eusebio, el obispo de Tarragona, influyendo directamente sobre decisiones internas de la institución.
|
 |
|:-:|
|MORDINI, Attilio; El católico gibelino; Hipérbola Janus, 2016|
|
|:-:|
|MORDINI, Attilio; El católico gibelino; Hipérbola Janus, 2016|El problema religioso: los judíos
Ya en el primer código legal de visigótico, la Lex Romana Visigothorum promulgado en el año 506, en el que se establecía la condición jurídica de los hispanorromanos, se excluía a los judíos de los cargos públicos, proscribía los matrimonios mixtos entre cristianos y judíos y limitaba sus actividades religiosas. Al margen de las comunidades religiosas cristianas, los judíos seguían sus propias leyes y preceptos religiosos, mantieniendo una barrera respecto a los pobladores autóctonos. Con la conversión de la fe arriana a la católica de Recaredo I, y en consecuencia del propio reino, los monarcas visigodos comenzaron una serie de políticas encaminadas a conseguir la unidad religiosa y política del reino. Su decisión, que fue oficializada en el III Concilio de Toledo, contó con un apoyo mayoritario del clero y la nobleza visigoda. A partir de ese momento comenzó un proceso de integración entre godos e hispanorromanos en virtud del principio religioso.
|
 |
|:-|
|Una moneda de oro visigoda acuñada durante el reinado de Sisebuto (612-621 d.C.). En el anverso, aparece el retrato estilizado del rey, rodeado por una inscripción en caracteres latinos. Estas monedas reflejan la influencia romano-bizantina en el arte y economía del Reino Visigodo. (Foto: Wikimedia Commons)|
|
|:-|
|Una moneda de oro visigoda acuñada durante el reinado de Sisebuto (612-621 d.C.). En el anverso, aparece el retrato estilizado del rey, rodeado por una inscripción en caracteres latinos. Estas monedas reflejan la influencia romano-bizantina en el arte y economía del Reino Visigodo. (Foto: Wikimedia Commons)|Esta situación dejó a otros grupos religiosos ante un dilema, que era o la conversión o la expulsión. Sisebuto fue quien más celo puso a tal respecto para lograr la deseada unidad religiosa. A partir de una serie de decretos promulgados al cabo de pocos meses del inicio de su reinado, en el 612, se ordenó la liberación de todos los cristianos en su relación de dependencia respecto a los judíos. Estas medidas incluían la liberación de los esclavos y servidores cristianos en relación a los judíos, la transferencia de éstos a señores cristianos o la obligación de manumitir y quedando así libres. Estas disposiciones eran de obligado cumplimiento bajo la pena de muerte o confiscación de bienes.
Al mismo tiempo, Sisebuto también se propuso impedir el proselitismo religioso judío y estimular su conversión al cristianismo. De hecho, los matrimonios mixtos preexistentes debían adoptar una educación en la fe cristiana para los hijos, en caso de no aceptarlo, el matrimonio se consideraba nulo. Los conversos y judíos también quedaban excluidos de los cargos públicos. También se debía producir una renuncia y abjuración pública de la ley y prácticas judaicas. La mencionada ley tuvo unas consecuencias inmediatas sobre la comunidad judía en el ámbito económico, donde además la existencia de esclavos y colonos en arriendo eran numerosos, además de las prácticas usurarias.
Sisebuto ha quedado para la historia como el gran perseguidor de los judíos, aunque en realidad su propósito era misionero y evangélico, por el celo religioso que ya hemos expuesto, y tampoco fue obra del propio Sisebuto, sino que encontramos los primeros ecos de esta legislación en la última etapa del Imperio Romano. Si hasta el momento la legislación se había aplicado de manera un tanto superficial, con Sisebuto adquiere mayor «radicalidad», aunque tampoco afectasen exclusivamente a la población judía, la cual era numerosa en aquella época. Los propios godos no pudieron casarse con los romanos hasta las reformas legales aplicadas bajo el reinado de Leovigildo.
Respecto a la cuestión de la prohibición de que los judíos poseyeran esclavos cristianos, algo que era muy frecuente, también infringían la ley al circuncidarse, dado que formaba parte del ritual formal de judaización o conversión a la fe judía. El decreto de Sisebuto ofrecía a estos esclavos la opción de obtener la libertad bajo el amparo de la corona, si no eran vendidos a otros amos cristianos. El impacto económico al que aludíamos también afectó notablemente las actividades agropecuarias de la comunidad judía, que perdieron su estatus privilegiado entre los sectores más acomodados de la sociedad. Del mismo modo que la prohibición de desempeñar cargos públicos mermó su preponderancia social.
No obstante, Sisebuto consideraba el asunto en una dimensión puramente religiosa, y el fin último era la integración bajo la unidad del credo católico. La unificación religiosa se convirtió en una prioridad, y su celo religioso no se fundaba en un criterio de fanatismo irracional, sino todo lo contrario. Al monarca godo le importaban, y mucho, las conversiones sinceras, sujetas a un principio reflexivo y racional. De hecho, en ese tiempo había otros segmentos de la población que se movían en el terreno de las creencias paganas, como los propios arrianos, a los que también interesaba encuadrar bajo el mismo principio religioso. En cuanto a los judíos, y la incidencia que se hizo sobre este grupo, se debió a que eran comunidades que representaban un enorme poder en el conjunto del reino, con una notable influencia, especialmente en el sur y el Levante español, regiones que se encontraban en la frontera con los territorios bizantinos peninsulares.
No obstante, y a pesar de que existe una continuidad en la aplicación de estas políticas para contener la influencia de la religión judía en los límites del reino, y vemos como éstas se mantienen hasta el hundimiento final con la conquista árabe del 711, lo cierto es que la práctica de la religión judía se mantuvo a ciertos niveles, como prueba la existencia de tumbas e inscripciones judías registradas a lo largo de esta época. Paradójicamente, en el plano económico y social fueron mucho más efectivas que en el terreno religioso, y de hecho, de haberse aplicado con la radicalidad que se les presume, estas leyes hubieran acabado con la existencia de la población judía en el reino, o bien mediante la conversión o bien mediante la expulsión, pero nada de eso sucedió finalmente.
El reinado de Sisebuto terminó en el 621, tras nueve años de intenso reinado. Se sospecha que murió envenenado por la ingesta excesiva de un medicamento, según el testimonio de otro rey, Suintila. No obstante hay muchos puntos oscuros bajo esta explicación, y la falta de fuentes fiables no nos permite desentrañar los hechos que rodearon su muerte. Le sucedería su hijo Recaredo II, quien también moriría en extrañas circunstancias, nunca desentrañadas, a los pocos meses de su coronación.
Lo fundamental, si tenemos que hacer una idea general de la figura del rey godo, es que representó una etapa peculiar en el desarrollo histórico del Reino toledano, en la medida que mostró una personalidad ilustrada, con notables conocimientos respecto al saber de la época, cultivó la poesía y la literatura, y no por ello descuidó los asuntos de gobierno. Los fundamentos religiosos, tan importantes en lo sucesivo, y a través de los Concilios de Toledo, en la configuración político-religiosa y en la unidad embrionaria de la futura España, fueron una de sus grandes prioridades, y para alcanzar la consolidación del reino no dudo en hacer la guerra, de manera implacable, para ser magnánimo y generoso cuando la situación lo requería. Desde Hipérbola Janus, y quien os escribe, no nos queda sino valorar la figura de este olvidado, y en ocasiones injustamente denostado, rey visigodo.
Artículo original: Hipérbola Janus, Sisebuto, el rey sabio, guerrero y humanitario (TOR), 30/Dic/2024
-
 @ 07804b78:c375c543
2024-11-21 11:37:37
@ 07804b78:c375c543
2024-11-21 11:37:37Chef's notes
- The Premium Juku Curry comes individually packaged in single-serving portions, so it's convenient for using small amounts like in this recipe.
- Use your favorite spicy level of hot bean-curd soup base/curry roux.
Details
- 🍽️ Servings: 4
Ingredients
- 1 box of “Cook Do®” (Chinese seasoning mix) for Szechuan-style Mapo Tofu
- 2 servings of Premium Juku Curry
- 500g tofu
- 400g cut tomatoes
- 200g minced meat
- 80g garlic sprouts
- 100ml water
- 1 tablespoon sesame oil
- Cooked rice, enough for the number of people
Directions
- Slice the garlic shoots diagonally into 3-4cm pieces. Cut the tofu into bite-sized pieces.
- Heat the sesame oil in a frying pan and fry the minced meat over a medium heat.
- When the meat is about 80% cooked, add the garlic shoots and continue to fry, stirring, until the meat is fully cooked.
- Turn off the heat and add the Cook Do® Sichuan-style Mapo Tofu seasoning, and mix well.
- Turn the heat back on to medium, add the cut tomatoes and water, and bring to the boil, stirring gently.
- When it comes to a boil, turn the heat down to low, add the Premium Juku Curry, and stir well to dissolve.
- Once the curry has dissolved, add the tofu and cook until the tofu is warmed through.
-
 @ a1c19849:daacbb52
2024-12-30 11:17:00
@ a1c19849:daacbb52
2024-12-30 11:17:00Introduction
nostr:npub1nj5v9hfxegyuqz4z9vfpgu9lxpgald066wspxadywmhslasuw2gsnyrxzg shared a great thread on X about what the Dutch Noderunners did to push Bitcoin adoption. Since it took him quite some time and he didn’t want to redo it on #nostr I’m happy to share his thread here as well, since it has a lot of cool stuff in it. Here we go:
Noderunners 2024 Recap
by nostr:npub1nj5v9hfxegyuqz4z9vfpgu9lxpgald066wspxadywmhslasuw2gsnyrxzg

Here it is, the 2024 Noderunners recap! As we are preparing for our annual party on the third day of Christmas I’d like to reflect to all the great stuff we’ve build together to push bitcoin adoption from bottom up. I’m proud we’ve made it this far and we’re just starting! 🔥 We like to come together as often as possible to chat about bitcoin and drink a beer so we started even more meetups. We now do meetups in Roermond, Leiden, Eindhoven, Utrecht, Breda, Friesland, Zaandam. And an occasional party in Arnhem or Den Bosch. Feel free to join us anytime.




On our meetups and in the wild we meet the most awesome bitcoiners. To show them our respect we honor them by knighting them as an Honorary Noderunner. This year nostr:npub1nw5vdz8sj89y3h3tp7dunx8rhsm2qzfpf8ujq9m8mfvjsjth0uwqs9n2gn nostr:npub13ql75nq8rldygpkjke47y893akh5tglqtqzs6cspancaxktthsusvfqcg7 nostr:npub1cn4t4cd78nm900qc2hhqte5aa8c9njm6qkfzw95tszufwcwtcnsq7g3vle and nostr:npub1uaj9phu5lpxpczm3vaayt46m0yv0pduxzy7z6quwd2uggxue7fmqx9665u joined our ranks! 🧡



As you can imagine, we were pleasantly surprised when we saw an honorary Noderunner wearing his pin in the courtroom in the case against fAkEtOsHi! Nice to meet again in Amsterdam nostr:npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw !



The Bitcoin conference in Amsterdam was full of Noderunners. On and off stage. On stage we had nostr:npub1jqs0u7zhh53e94gyhm4eu458wm6sw7z0kk66jjhhkhh346tcq2ysfgr247 nostr:npub1h0fd5xu8rfhwdkkjr78ssdhm7rdjyf97hhjqr9acwv77ux0uvf8q23kvcg nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl Tom Lamoen and others.




In the panel there was nostr:npub1art8cs66ffvnqns5zs5qa9fwlctmusj5lj38j94lv0ulw0j54wjqhpm0w5 who asked a cheeky question… 🤓 He wrote the awesome “The Genesis Book” in which he describes the people and technology that led to the birth of bitcoin. Hope to see you 3kd Aaron!
Proof of work is the thing Noderunners value the most. We do the work on and offline. In Amsterdam we had several projects to display! Of course the BitcoinTaps, the bitcoin bitaxe B at the entrance, The nostr:npub1kd3nlw09ufkgmts2kaf0x8m4mq57exn6l8rz50v5ngyr2h3j5cfswdsdth arcade and the video of @npub1f59dz0ru0l8zpsl4cryj5ch2rahwxeex3mr7lpl2ltzxsfwsdwastu6nqk!

Personally I was very exited nostr:npub1qg5a5l3t7pakmm4r4up2e764xecsw62fk3rntevm24fwyczhndtsdrvc4x Edward and Stef of Connect The World Podcast allowed us to bring the Arcade to the afterparty at Braai where we played some tournaments with nostr:npub1jt97tpsul3fp8hvf7zn0vzzysmu9umcrel4hpgflg4vnsytyxwuqt8la9y nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg and many others!



Hopefully we can create a Noderunners lounge or such next year at @npub13e6qu4kdjsyysrfl5an558rawvqg0rx2xuat9ca706spcdqjzhuqq6md43! Connections were made!



This year there was also the first edition of nostr:npub1uv2tr83c5y7k82af6zdzlqs8m0klcmndd8u5vmlg2eyrskld6uzsv4rmr8 organized by nostr:npub14mge80nm5r0zj0gncxvpunlr28jyku95547q0m82ec475x3yy92skvjgm5 and Bitcoin Stad. It was an awesome event with great speakers but the best thing was the Noderunners Lounge in the basement where Hester Bais tapped a beer.. 🍺



There was some trouble in paradise when the GitHub page of nostr:npub1k5f85zx0xdskyayqpfpc0zq6n7vwqjuuxugkayk72fgynp34cs3qfcvqg2 got canceled due to false copyright claims.. He makes the most beautiful, full open source BTClock! He’s a good frend and very productive Noderunner! 🧡



nostr:npub1k5f85zx0xdskyayqpfpc0zq6n7vwqjuuxugkayk72fgynp34cs3qfcvqg2 also did a lot behind the scenes for the Noderunners SOLO Mining Pool! http://pool.noderunners.network


As we are also very enthusiastic about NOSTR nostr:npub1p6xyr6u5vet33r4x724vxmp9uwfllax5zjdgxeujyrtxt90lp74qvah0rm has set up our own nostr relay: wss://relay.noderunners.network

Noderunner nostr:npub1yn84ur49llj7pp9a7uv477f7vrpj0rj7df5pnfncvkusaxgy6jqsj9xgfl set up a mixer where he organizes a weekly coinjoin every sunday for more anonymous bitcoin transactions. https://coinjoin.nl

Our Belgian Noderunner Kim de Vos made the infamous “Big Mac index” where he expresses the price of bitcoin in Big Macs.. He also runs the AVBpodcast (my personal favorite).

We have several members who have their own podcasts. Also a lot of Noderunners appeared in podcasts as a guest. nostr:npub1agyf7kae8nkxqrd7rvvxt6nh9vwpcqzen2mc9dl3u38a04awpjcq09n23f educates bitcoin beginners.
 Tom Lamoen talks about libertarianism.
Tom Lamoen talks about libertarianism.nostr:npub1gfxgylgst4lcemkjth6xdvcvq7le8rtlrym7wayml63qrjggngaqkqescl interviews bitcoiners from all over the world.

And nostr:npub1kj2ngxmm0zccswfqplff87rpgvmq9utvk0g726wc0h8pv4kwm8ss6zgm4n laughs at 🤡🌍

After months, even years of hard work nostr:npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx launched the best bitcoin board game ever!


nostr:npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx is also involved with the Dutch bitcoin magazine BitcoinFocus which features a lot of Noderunner builds and articles.


Of course I should mention our frens at nostr:npub1ua6fxn9ktc4jncanf79jzvklgjftcdrt5etverwzzg0lgpmg3hsq2gh6v6 where you can pay a few sats to play your favorite songs! http://radio.noderunners.org

LightningPlaces is working hard making entrepreneurs accepting bitcoin and putting them on their website! 🔥💪🏼



nostr:npub1lhufm09wzp42y67t3s8axlewwna8rmetak68w38yal7xjrwktpsscpt08x is also hooking up webshops and physical shops (and bars) to accept bitcoin! Connect them if you’re looking for a custom solution! https://lightningcheckout.eu/nl/


Maybe we should create an open source HW Wallet too but for now we have the man, the myth, the legend nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl in our midst.. A real honor as we all share the same values and ethics in life but especially in bitcoin! We’ve been building seedsigners from scratch by the dozen!


Most of us are very entrepreneurial. Several bitcoin shops are run by Noderunners.
nostr:npub1qvwdl9rp7a5ghrxv57wnml5ehg2whjh708vys6kaxpkgu0z3aclsuy2h4p - https://bitcoinbrabant.com
nostr:npub1k00lff0ahjv4d2kwuwxy040d2282yjmzj6eeu5ghav054s4yrfzsplyc86 - https://bitsaga.be
nostr:npub1837pplcuwcjn35zwmpuy62ekcfdtvklajn6pueus3am09s27vu6smuj6v9 - https://miningwholesale.eu
A special shoutout to our junior Noderunner Esramsterdam who is organizing a bitcoin event focused on women. Because bitcoin is not only for men. More info: https://vanbanknaarbitcoin.nl

Also a special shoutout to @npub17k8u7c6kfjgtd380890zx0m4adu8vl53m9fvtc7lal4j9gp74xqqkguha4! The only way to get free sats. Drank not enough beer with nostr:npub1pzurm7nx3q08894wl6uautryq95sku5jhzgwjjrskwdafcwxekuq4n7vtu this year.. but we really need to set up a collaborative project!

Ok I’m done. Forgot a lot but this sums it up quite well. Greetings and love to everyone involved with the Noderunners I forgot to mention. I love you all and hope to build a lot more together! 🧡🔥
nostr:npub103uy2vsk5hrnldwdu0nztmsg7g6207cfqu744rnrnalauns6facsgj5ddp
nostr:npub1l9evr9vx4u2xefesmfu6gyypfdu7k8zwdw7rrnh5ckdds8fqx59sy3ferg
nostr:npub1cwzduskqu6yuxjs2a75uptj3vzfa84gv5q3xlkcpzs6usjfey24qvk70dv
nostr:npub1etuf22z5jwp765m8dqcw7rx5egjzjnwm9xwm4m367e9hxkd9vvaq04duqw
nostr:npub1mw6tm8kery0dwmz670vvg74z0xzttwt3y7yppya5rulufpkkaj7qmg2922
nostr:npub12qw34mucxxk200835d8qt5mshfukd39vvz4s94f0e6xthg0xpjmq3wvjlw
nostr:npub1d5axlx84ajq7q5yn4u86m9xgnmssgq5c6ktjfmu6qtw7jah24hzs57tmvz
nostr:npub1vnlkmja076ft0h2ppme4pvcyfh8zmwl4l7hpfm4du0jagwck04lq8rkr0w
Jan Burgers
nostr:npub1r35gr0g93gxpkcq77v9sx97d5aqg4edr0qwhdj2xr4xxt6slp7nswgahlx
Short Non-Bitcoin
nostr:npub12786tz9vyzuhe5jdjc9esd64vqh3pvqe34u9a3dyegudv5chkx9sexz86w
Joep Laser Sheep - Elden Lord 3x
nostr:npub12xtq7ufn6kjppvl24dnvezsny872u8xacfsy640fzd69446kgczsp8v5nm
nostr:npub1m0yz3tvsa8cwheqhkqj96zr9kget8j8yda0vfmrah5c0dafj6xcq4l4az6
@Erik Dutch
nostr:npub1kvfz8rglvpsqevznlt86ukcz0s9uap3pypjwd3tnmkn2pgjmjujqlncy2c
nostr:npub1l5pxvjzhw77h86tu0sml2gxg8jpwxch7fsj6d05n7vuqpq75v34syk4q0n
Noderunners Shop
nostr:npub1ylnqfg0neysvsesen9je80wmsv9r5204x30mgd5ev6dr3q95xpxq3nmcxd
nostr:npub1ap78x7mvw0vu9s7yltflmkqphx8rt8hsk9gdg0k42vwnmnpvpe2qptxewe
nostr:npub1n2ph08n4pqz4d3jk6n2p35p2f4ldhc5g5tu7dhftfpueajf4rpxqfjhzmc
@Bitcmonkey
@Roynode
nostr:npub18n56f28efvmsjcl80lv2ngtmkl3y6q2rg0m2zqas3kw4jwkrsvdqxnmver
nostr:npub135q6dvnjah9023xszmjs2wvd4gqhn2trku52wt2lv8cl4hc8ltjsk0w4sq
nostr:npub1837u93v8am8q2rauvkqfk9sf6xfq07p9m4m82jueqh5u4qzkg25qesqrr4
nostr:npub1pkmp7vtgfwg7g0pt4xdd4r2npz2p8yweeq0yx7xm590h4nuszynqq2e2r3
nostr:npub19r33crtgdt4spqxl5a3nhqx2ucdputtqcnnxkplnp4mv2dqldqqs39j5eq
nostr:npub19z9g9ymx3aalx3h0jr2cskehvhgppznv2lpqsrpgggpeueesq4lsknsp8r
nostr:npub1jlvtd4zmq7ukjcytqxu2gy5myp2uataupjk4a3l467fj7pxpk3xq5p3w0j
@HeroVanKampen
nostr:npub16htmakd0gvsmwjnravfvfn5mh2x7wjd0vxq20z2c0979e7xh0a8q6ssnew
nostr:npub1xw6jekvethghmrlv0chkx5p78h3wk2ep5x588ga854d68cugr40qxuwt5e
nostr:npub1zakkum8w7uancehpev0drxuly3e74fg5v7q4n0zpxcdn72wakpjs9cgpve
and all others I can’t find here or I forgot.. 🧡🔥💪🏼 LFG, see you soon!
Bonus: This has never aired but @DanielMol was doubtful of our impact to more bitcoin adoption.. I know we are a bit toxic but we have our hearts on the right place and help anyone who is serious about it.. Happy days Daniel! 🧡

-
 @ ac8bb9b0:70278acc
2024-11-20 16:28:11
@ ac8bb9b0:70278acc
2024-11-20 16:28:11Chef's notes
Optional: Creamy Cilantro-Basil Ranch: In a blender, blend 1/2 cup plain Greek yogurt or sour cream, 1/3 cup mayo, 2 tablespoons buttermilk, 1 cup fresh cilantro, 1/2 cup fresh basil, 1/4 cup fresh chopped chives, 2 teaspoons Worcestershire, 1 teaspoon garlic powder, 1 teaspoon onion powder, 1/4 teaspoon cayenne, and a pinch each of kosher salt and black pepper. Blend until creamy.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 15
Ingredients
- 4 (4-6 ounce) salmon filets, cut into bite-size chunks
- 6 tablespoons extra virgin olive oil
- 1 teaspoon smoked paprika
- salt and black pepper
- 1 bunch asparagus, ends trimmed
- 1/2 cup honey
- 2-3 tablespoons hot sauce
- 1-3 teaspoons cayenne pepper
- 3/4 teaspoon chipotle chili powder
- 1/2 teaspoon garlic powder
- 1/2 teaspoon onion powder
- 3-4 cups cooked rice
- 2 avocados, diced
- 1 serrano or jalapeño, sliced
- 1/2 cup fresh cilantro, chopped
- 2 tablespoons chopped fresh dill
- 1/2 cup crumbled feta cheese
- 2 tablespoons extra virgin olive oil
- 1 tablespoon lemon juice
- 1/3 cup toasted seeds, pumpkin, sesame, sunflower, etc.
Directions
-
- Preheat the oven to 450° F.
-
- On a baking sheet, toss the salmon pieces with 3 tablespoons olive oil, paprika, salt, and pepper. Arrange in a single layer. On the other side of the pan, add the asparagus. Toss with 1 tablespoon olive oil, salt, and pepper. Roast 10-15 minutes or until the salmon is just undercooked to your liking.
-
- Meanwhile, make the hot honey. In a sauce pot, warm together the honey, hot sauce, cayenne, chili powder, onion powder, and garlic powder, plus a pinch of salt.
-
- Spoon some of the hot honey over the salmon. Switch the oven to broil and broil until lightly charred and crispy. Spoon over additional hot honey, to your taste.
-
- To make the avocado salsa. Combine avocados, serrano or jalapeño, cilantro, dill, feta cheese, extra virgin olive oil, lemon juice, and toasted seeds in a bowl and season with salt, gently tossing.
-
- Arrange the salmon and asparagus over bowls of rice. Top with salsa.
-
 @ ac8bb9b0:70278acc
2024-11-20 16:25:18
@ ac8bb9b0:70278acc
2024-11-20 16:25:18Details
- ⏲️ Prep time: 25
- 🍳 Cook time: 20
- 🍽️ Servings: 6
Ingredients
- 1 tablespoon extra virgin olive oil
- 1 medium yellow onion chopped (about 1 1/2 cups)
- 2 teaspoons kosher salt, divided
- 3 tablespoons red curry paste
- 2 tablespoons grated fresh ginger (from a 3-inch piece)
- 3 medium cloves garlic, minced (about 1 tablespoon)
- 4 cups lower-sodium vegetable broth
- 1 1/2 pounds butternut squash, cut into 1 1/2-inch cubes (from 2 [20-ounce] package)
- 1 15.5-ounce can unsweetened coconut milk, well stirred
- 2 tablespoons fresh lime juice (from 1 or 2 limes)
- 6 tablespoons crushed salted peanuts
- Chopped fresh cilantro and crushed red pepper (optional), for serving
Directions
- Heat oil in a large pot over medium. Add onion and 1/2 teaspoon salt; cook, stirring often, until onion starts to brown, 6 to 7 minutes.
- Add curry paste, ginger, and garlic; cook, stirring, until fragrant, about 1 minute. Add broth and 1 teaspoon salt, scraping up browned bits from bottom of pot. Stir in squash. Bring to a simmer over medium-high. Cover and reduce heat to low; simmer until squash is tender, 12 to 15 minutes.
- Remove from heat. Stir in coconut milk, lime juice, and remaining 1/2 teaspoon salt. Use an immersion blender to process until smooth. (Or transfer to a blender, cover with lid, and remove center piece. Place a towel over opening. Process until smooth.)
- Serve sprinkled with peanuts, cilantro, and, if using, crushed red pepper.
-
 @ ac8bb9b0:70278acc
2024-11-19 19:49:52
@ ac8bb9b0:70278acc
2024-11-19 19:49:52Chef's notes
This recipe is SO easy. We simply mix herbs and spices in a small dish. Add the chicken legs to a large, gallon-sized ziptop bag and add the olive oil. Seal the bag and roll those legs around for a minute to distribute the oil evenly on all the chicken. Then, open the bag, pour in the seasonings, close the bag and do the shake thing. Take a minute or so to do this and massage the chicken to really get that seasoning well distributed.
Seasoning chicken legs in a ziptop bag Set aside for a minute and preheat your oven to 425°(F) and line a baking sheet with aluminum foil. Give the foil a good spray with non-stick cooking spray. This is important as the chicken will stick without it.
Now take the chicken out of the bag and place on the foil lined sheet. Then into the oven it goes for 40 minutes.
Recipe for oven baked chicken legs After 40 minutes the chicken will be a beautiful golden color and the inside will be at least 165°(F) when checked with an instant read thermometer. In fact, it will probably be closer to 185-195°(F) which is exactly what we want!
Pro Tip: Chicken Legs are Better at 185-195°(F)! The rule of cooking chicken to a minimum internal temperature of 165°F has been well-established for quite some time. However, when it comes to darker meat portions such as chicken legs, thighs, or the entire leg quarter, exceeding this temperature is often encouraged for optimal results! When heated to around 185°F, the collagens within the meat begin to break down, contributing to the juiciness and “fall-off-the-bone” tenderness that we cherish so much in dark poultry meat.
Check out this great article by America’s Test Kitchen regarding “overcooking” chicken drumsticks and thighs.
Let Rest and Serve Carefully remove the chicken to a plate or platter and let it rest for 5 minutes before serving.
Recipe for oven baked chicken legs Can this recipe be doubled? It sure can. You can even triple or quadruple this recipe! Simply adjust the ingredients accordingly. The cook time will still be 40 minutes, just be sure to not crowd the chicken too much on the pan. Keep the legs from touching and always keep in a single layer.
Give it a kick Want to give the chicken legs a little heat? Add a ½ teaspoon of cayenne pepper and even a teaspoon of crushed red pepper flakes. You can also deepen the flavor by using smoked paprika instead of regular paprika.
Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 40
- 🍽️ Servings: 2-3
Ingredients
- 6 chicken legs
- 2 tsp paprika
- 1.5 tsp kosher salt
- 1 tsp onion powder
- 1 tsp garlic powder
- 1 tsp rosemary, dried
- 1 tsp parsley flakes
- ½ tsp ground black pepper
- ½ tsp ground mustard
- 1 tbls olive oil
Directions
- Preheat oven to 425°(F)
- Pat chicken legs dry with a paper towel and trim any excess skin
- Place chicken legs in a large ziptop bag and add olive oil. Close bag and shake to coat chicken well with the oil.
- Add seasoning mix to bag, close and shake to get chicken well coated with seasoning.
- Line a baking sheet with foil and spray with non-stick cooking spray.
- Place chicken legs on baking sheet and place on middle rack of oven for 40 minutes, turning halfway.
- Chicken must have internal temperature of at least 165°(F), but 185-195°(F) is ideal for best results.
- Let rest for several minutes before serving.
-
 @ b8a9df82:6ab5cbbd
2024-12-30 11:15:49
@ b8a9df82:6ab5cbbd
2024-12-30 11:15:49In just two days, 2024 will come to a close. And as I sit here reflecting and drinking my morning coffee, I can confidently say that this has been the best year I’ve had since 2018. The years leading up to this one, especially since returning to Berlin, were some of the most challenging of my life. They tested me in ways I never expected—moments when I wanted to give up, when I felt so lost I couldn’t see or feel anything anymore. I lost my smile, my positive side, my emotions, and even my sense of self. But this year was different. It felt like the sun finally broke through the clouds, and I could see light at the end of the tunnel. I laughed more. I loved more. I felt deeply again, like my emotions finally had room to breathe. For those who have read my book, you know I’ve faced my share of dark days, as many of us do. Some days were heavier than I could have imagined, and even now, there are moments when I question, *“Why? Why this path? Why me?”* But this reflection isn’t about the darkness. **It’s about the gratitude.** 2024 blessed me with so many moments of joy. I traveled, saw the world from new perspectives, and met extraordinary people who brought meaning and light into my life. These experiences reminded me that connection matters, that there’s beauty in the unfamiliar, and that we grow when we open ourselves up to it all—the good, the difficult, the unexpected. Now, back in Berlin, I feel a shift. The city feels cold again—not just in temperature, but in energy. Dark skies and gray streets mirror an unbalanced restlessness I can’t ignore. It’s not the coldness itself or the clouds; it’s the way this place feels as though it’s lost its spark. Smiles seem rare, warmth even rarer. And perhaps, that’s my sign. My time here feels like it’s coming to a close. But as this chapter winds down, I feel at peace. 2024 reminded me that life doesn’t stay stagnant. Even in the darkest times, the wheel turns. This year was proof that healing is possible, that joy can return, and that love—whether found in people, places, or moments—still exists. So, wherever this journey takes me next, I will carry this year with me. I’ll carry the laughter, the lessons, and the memories of those who reminded me that even in a messy, chaotic world, light and connection can thrive. And perhaps, just perhaps, this is only the beginning. The chapters ahead are unwritten, but I feel ready to meet them—with an open heart and gratitude for all that’s brought me here. Happy 2025 to all of YOU
-
 @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
Directions
- The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
- Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.



















