-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ cf7ed325:050194cf
2024-12-31 08:43:53
@ cf7ed325:050194cf
2024-12-31 08:43:53Embark on a luxurious adventure aboard the Sonesta Moon Goddess Nile Cruise, an exceptional vessel that combines elegance, comfort, and impeccable service. This 5-star cruise offers an unforgettable journey between Luxor and Aswan, showcasing Egypt's iconic ancient treasures along the way.
The Sonesta Moon Goddess Nile Cruise boasts spacious cabins with private balconies, allowing guests to enjoy breathtaking views of the Nile. The cruise features gourmet dining, a relaxing sun deck, a swimming pool, and entertainment programs that highlight Egypt's rich culture and history. Whether you're exploring the Valley of the Kings, Karnak Temple, or the Philae Temple, this cruise ensures an enriching and seamless experience.
For travelers seeking similar luxurious experiences, the Farah Nile Cruise and Oberoi Zahra Nile Cruise are excellent alternatives. These cruises offer exceptional service, elegant accommodations, and curated excursions to Egypt's most iconic sites. Another standout is the Oberoi Philae Nile Cruise, known for its personalized service and exquisite cuisine.
History enthusiasts will appreciate the refined charm of the Historia Nile Cruise, while the Jaz Crown Jewel Nile Cruise and Jaz Regent Nile Cruise provide a perfect blend of modern amenities and classic elegance. Those seeking more options within the Sonesta fleet can explore the Sonesta Sun Goddess Nile Cruise, Sonesta Star Goddess Nile Cruise, or Sonesta Nile Goddess Nile Cruise, each offering unique features and premium services.
Lastly, the Sonesta George Nile Cruise stands out for its contemporary design and warm hospitality. Whether you choose the Sonesta Moon Goddess Nile Cruise or another luxury vessel, your journey along the Nile will be a captivating blend of history, culture, and unparalleled comfort.
🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 Email: info@etbtours.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 2063cd79:57bd1320
2024-12-31 08:31:09
@ 2063cd79:57bd1320
2024-12-31 08:31:09Obwohl einige andere Themen, wie der kürzlich erschienene New York Times Artikel, in dem sich faktisch falsch und inhaltlich voreingenommen mit Bitcoin-Mining befasst wird, oder die Entdeckung des Satoshi Whitepapers auf Apple Computern momentan die heissen und viel besprochenen Nachrichten sind, hält auch die Diskussion über Ordinals und Inscriptions und besonders deren Auswirkungen auf das Bitcoin-Netzwerk an. Einer der viel besprochenen Aspekte bei diesem Thema ist die Auswirkung dieser Bitcoin-NFTs auf die Gebührenstruktur und somit Gewinnzusammensetzung für Miner, aber auch die direkten Auswirkungen auf On-Chain-Transaktionen durch die höheren Gebühren und den seit Wochen sehr vollen Mempool. Genau über den wollen wir uns diese Woche etwas detaillierter unterhalten, da es auch unter erfahrenen Bitcoinern immer noch einige Missverständnisse zu geben scheint.
Fangen wir zunächst ganz vorne an. Regelmäßigen Leser//innen dieses Blogs sollte in Erinnerung sein, dass ich Anfang Februar einen Artikel über UTXOs und Gebührenmanagement geschrieben habe:
https://www.genexyz.org/post/25-block-774775-utxos-fee-management-v3ulch/
In diesem Artikel habe ich beschrieben wie Transaktionen zusammengesetzt sind und welche Möglichkeiten Nutzer//innen haben, um ihre persönlichen Transaktionen anhand variabler Gebühreneinstellungen schnell oder langsam im Netzwerk zu platzieren.
Welchen Nutzen haben hohe gegenüber niedrigen Gebühren? Bitcoin-Miner handeln nicht ganz uneigennützig, denn sie werden für ihre Arbeit entlohnt. Für jeden produzierten Block erhalten sie neben dem Blockanteil (Reward) auch sämtliche Transaktionsgebühren, der im neuen Block enthaltenen Transaktionen. Ohne zu sehr ins Detail zu gehen, bedeutet dies, dass Miner einen Anreiz haben, Transaktionen mit möglichst hohen Gebühren zuerst in den neuen Block zu schreiben, um so ihren Profit zu maximieren. Je höher eine Gebühr relativ zu denen der anderen Transaktionen im Mempool ist, desto wahrscheinlicher ist, dass diese Transaktion im nächsten Block landet. Das bietet dem/der Nutzer//in die Möglichkeit, die eigene Transaktion zu priorisieren.
Der Mempool, kurz für Memory Pool, hat also was mit Transaktionen zu tun - und zwar ganz schön viel. Denn jede im System propagierte Transaktion landet zunächst im Mempool. Also kann man sagen, dass der Mempool sowas wie ein Wartezimmer, oder eine Warteschlange am Supermarkt oder im Vergnügungspark ist. Soll eine Transaktion in einen Block geschrieben werden, so muss sie sich erstmal anstellen. Dabei bleibt festzuhalten, dass Transaktionen erst im Netzwerk propagiert werden, bevor sie in einen Block geschrieben werden können. Wenn man also in seiner Wallet eine Transaktion abschickt und einen grünen Haken oder eine Animation angezeigt bekommt, dass die Transaktion erfolgreich versendet wurde, dann bedeutet dies schlicht nur, dass die Wallet die Nachricht, die diese Transaktion enthält, zunächst an eine Node (einen Knotenpunkt im Netzwerk) übertragen hat. Das dezentrale Peer-to-Peer Bitcoin-Netzwerk erledigt dann den Rest: Die Nodes propagieren diese Nachricht sofort weiter an alle verbundenen Nodes (Flooding genannt), und somit ist die Nachricht innerhalb weniger Sekunden an alle Netzwerkteilnehmer versendet. Dabei werden Transaktionen erstmal auf ihre Richtigkeit überprüft. Dann werden diese erst von den Mining-Nodes aus dem Mempool übernommen, die die Transaktionen sortieren und ihren Blöcken hinzufügen.

Transaktionen werden also von Wallets als Nachrichten ins Netzwerk gesendet. Ganz einfach gesprochen enthält jede Nachricht Informationen über den Sender, den Empfänger, die Höhe der versendeten Zahlung und die Höhe der angehefteten Gebühr. Diese Informationen müssen also erstmal im Netzwerk untergebracht werden, damit die Mining-Nodes aus diesem Pool von unbestätigten Transaktionen ihre Blöcke zusammensetzen können.
Jetzt sitzen also in diesem Wartezimmer ganz viele Transaktionen und warten darauf, aufgerufen zu werden, um von Dr. Miner in seinem Besprechungszimmer empfangen zu werden. Doch anders als beim Arzt, wo man in der Reihenfolge aufgerufen wird, in der man seinen Termin vereinbart hat, oder beim Straßenverkehrsamt, wo die Nummer auf dem kleinen Ticket, das man beim Eintritt gezogen hat, über die Reihenfolge entscheidet, sucht Dr. Miner sich selbst aus, welche Patienten (Transaktionen) er in welcher Reihenfolge sehen möchte. Dr. Miner bittet zum Vorsprechtermin. Und da alle Patienten ein kleines Schildchen hochhalten, auf dem die Gebühr steht, die sie bereit sind zu zahlen, um so schnell wie möglich von Dr. Miner empfangen zu werden, kann dieser ganz einfach diejenigen bevorzugen, die am meisten zahlen (würde so im normalen Leben ja keineswegs ablaufen - hrr hrr, Kassenpatienten!).

Damit möchte ich nicht sagen, dass bei Bitcoin ein Zwei- oder Mehrklassensystem besteht, wie das im deutschen Gesundheitssystem der Fall ist, allerdings gibt es Einzelnen die Freiheit darüber zu entscheiden, wie wichtig ihnen einzelne Transaktionen sind und wie viel sie bereit sind, dafür zu bezahlen (ähem, freie Marktwirtschaft, hust!) Diese variable Gebührenstruktur ist also ganz eng mit dem Anreizsystem von Bitcoin verbunden. Gebühren werden in sats/B oder sats/vB (Satoshis pro (virtual) Byte) berechnet, also wie viele Sats man pro Byte entrichten muss. Damit werden Transaktionen mit mehr Blockgewicht automatisch teurer (hallo Ordinals 👋), was eigentlich sehr fair ist, aber die variable Gebühreneinstellung in den meisten Wallets erlaubt Versendenden ihre Transaktion auch anderen Transaktionen gegenüber zu priorisieren, wenn diese es für notwendig halten.

Eine oft falsche Annahme ist, dass es irgendwie den einen Mempool gibt. Das ist natürlich falsch und aufgrund der dezentralen Struktur des Netzwerks auch gar nicht möglich. Vielmehr verfügt jede Node über ihren eigenen Mempool (mit seinen eigenen Einstellungen). Dieses Missverständnis rührt wahrscheinlich daher, dass immer von DEM Mempool gesprochen wird und Block-Explorer, wie mempool.space, durch ihre Übersicht suggerieren, dass diese Informationen aus DEM Mempool entstammen. Dabei sind Explorer oft nur die Visualisierung einer einzelnen Node, oder aggregieren verschiedene Informationen, um einen möglichst akkuraten Gesamteindruck darzustellen.
☝️ Kurz zusammengefasst: Ein Mempool ist die Warteschlange ausstehender und unbestätigter Transaktionen für eine Node. Es gibt keinen zentralen oder globalen Mempool. Jede Node verwaltet ihren eigenen Mempool, sodass verschiedene Nodes theoretisch unterschiedliche Transaktionen in ihren Mempools sammeln können. Transaktionen wiederum enthalten Gebühreninformationen, die für die Mining-Nodes wichtig sind, um diese zu priorisieren.

Wenn man sich das obige Bild einmal anschaut, versteht man auch, was es mit den Gebühren auf sich hat. Am einfachsten ist es sich vorzustellen, es gäbe eine Autobahn, auf der ein Algorithmus entscheidet, wie schnell alle Autos fahren. Um überhaupt auf diese Autobahn auffahren zu dürfen, muss man 1,98 sat/vB zahlen, sonst wird man gar nicht drauf gelassen. Diejenigen Transaktionen, die 4 sat/vB zahlen, dürfen zwar auf die Autobahn, stehen aber momentan auf dem Standstreifen und kommen nicht vorwärts. Wer mind. 5 sat/vB zahlt, fährt automatisch auf der rechten Spur, alle die mind. 7 sat/vB zahlen, fahren in der Mitte, und wer mind. 10 sat/vB ausgeben möchte, darf rechts am schnellsten fahren.
Oder um eine andere Analogie zu bemühen, schauen wir uns eine Warteschlange im Vergnügungspark an. Allerdings gibt es nicht nur eine lange Schlange, sondern verschiedene Schlangen für dieselbe Achterbahn mit unterschiedlich langen Wartezeiten. Jedoch muss man mehr Fahrpreis bezahlen, wenn man in die Schlange mit der kürzeren Wartezeit möchte (würde so im normalen Leben ja keineswegs ablaufen - hrr hrr, Genie-Pass im Disney World). Alle 10 Minuten fährt die Achterbahn eine Runde und nimmt immer nur eine gewisse Anzahl von Parkbesuchern mit, bis das Gewichtslimit der Bahn erreicht ist - nur das Gewicht der Fahrgäste ist entscheidend, nicht die Menge.

Es gibt einige Fahrgäste, denen es wert ist, auf jeden Fall in der nächsten Bahn zu sitzen, koste es was es wolle. Dann wiederum gibt es welche, die schauen, wie viele Fahrgäste schon in den jeweiligen Reihen stehen und sich ausrechnen, wie viel sie bezahlen müssten, um eine fast 100%ige Chance zu erhalten, in der nächsten Bahn zu sitzen, ohne unnötig draufzuzahlen. Dann gibt es diejenigen, denen es egal ist, denn sie wissen, dass sie auf jeden Fall irgendwann mitfahren, aber auf Schnelligkeit keinen Wert legen. Diese unterschiedlichen Warteschlangen lassen sich im folgenden Bild gut an den Kohorten der linken Spalte ablesen. Dort werden die jeweiligen Gebührenbereiche in sats/vB dargestellt und naturgemäß sind die unteren Bereiche mehr gefüllt, als die oberen.

Die Einordnung der Gebühren, das Analysieren der jeweiligen Bänder und das Errechnen der Mindestgebühren, etc. übernimmt natürlich nicht der Sender jedes Mal manuell. Wallets nutzen Algorithmen, um genau diese Informationen aus dem Netzwerk auszuwerten und um dann dem/der Nutzer//in die Gebühren schon einzustellen. Sollte es jedoch trotzdem vorkommen, dass die Gebühren zu niedrig eingestellt wurden und somit Transaktionen im Mempool stecken bleiben (sprich: Die Gebühren sind zu gering, um von Mining-Nodes als interessant genug erachtet zu werden und die Transaktion wird deshalb Block nach Block umgangen), gibt es die Möglichkeit Transaktionen zu pushen.
https://www.genexyz.org/post/19-block-765505-on-chain-analytics-mhcumo/
Wie wir in meinem Artikel vom Dezember letztes Jahres gesehen haben, wurde mit Version 0.24 des Bitcoin Core Protokolls eine Änderung in der Core Implementierung vorgenommen:
Und zwar wird der Default von Opt-in auf Full replace-by-fee (RBF) geändert. RBF ist eine Mempool-Funktion, die 2015 vorgeschlagen wurde und ins Protokoll übernommen wurde, die Nutzer//innen eine Möglichkeit gibt feststeckende Transaktionen voranzutreiben, wenn diese lange Zeit unbestätigt im Mempool hängen. Wenn Nutzer//innen diese jetzt beschleunigen wollen, können sie eine höhere Gebühr zahlen, um die eigene Transaktion attraktiver zu machen. In der 2016 eingeführten Opt-in RBF Funktion, müssen Nutzer//innen aktiv einwilligen, dass ihre Transaktionen durch Transaktionen mit höheren Gebühren ersetzt werden, wohingegen die neue Full RBF Funktion standardmäßig jede Transaktion ersetzbar macht, solange für die Ersetzung eine höhere Gebühr gezahlt wird.
☝️ Kurz zusammengefasst: Der Mempool funktioniert als Sammelbecken für alle dem Netzwerk übertragenen Transaktionen, die dann von den Minern sukzessive in einen Block gepackt werden. Dies erfolgt in der Regel nach Höhe der Gebühren, d.h. Transaktionen, die eine höhere Gebühr mit sich führen, werden von Minern präferiert, da dies deren Profit steigert. Wurde eine Transaktion mit geringer Gebühr übertragen, oder treten aus verschiedenen Gründen hohe Gebührenspitzen auf, können die unpräferablen Transaktionen im Mempool hängen bleiben.
Wie wir jetzt wissen, verwaltet jede Node ihren separaten, individuellen Mempool. Die Einstellungen können die Betreiber der Nodes selbst vornehmen, denn während die Standardgröße auf eine Memory-Grenze von 300 MB festgelegt ist, kann jeder Knotenbetreiber seinen eigenen Wert festlegen. Die Mempool-Größenbeschränkung bezieht sich jedoch nicht auf die serialisierten Daten oder das Transaktionsgewicht der Transaktionen in der Warteschlange, sondern auf die tatsächliche Speichernutzung der deserialisierten Transaktionsdaten auf der jeweiligen Node.
Wenn die Mempool-Grenze einer Node erreicht ist, werden die Transaktionen mit der niedrigsten Gebühr gelöscht und die Node gibt dem Netzwerk bekannt, dass vorerst keine Transaktionen unter einer gewissen Gebühr weitergeleitet werden sollen. Da jede Node unterschiedliche Grenzen hat, kann es sein, dass eine Node mit einem kleineren oder größeren Mempool Transaktionen früher oder später löscht.
Nachdem der Rückstand unter die (meistens) 300 MB-Grenze gesunken ist, senken Nodes ihre Gebührenmindestanforderung und beginnen wieder damit, Transaktionen zu akzeptieren, die zuvor ausgeschlossen wurden.
Jetzt ist es auch über drei Monate her, dass das Ordinals / Inscriptions Protokoll veröffentlicht wurde und nach einem anfangs relativ langsamen Start (trotz heftiger Diskussionen, vieler Publikationen zu dem Thema, etc.) wurden in dieser Zeit mittlerweile mehr als 1 Millionen Artefakte hochgeladen.


Das Hochladen so vieler (meistens) Bilder direkt in die Bitcoin-Blockchain ist mit recht hoher Sicherheit der Treiber dafür, dass der Mempool seit einiger Zeit komplett ausgelastet ist (also die 300 MB-Grenze übersteigt) und, wie oben gesehen, zum Zeitpunkt des Verfassens, ca. 17.000 Transaktionen darauf warten, in einen Block geschrieben zu werden. Dies entspricht etwa 90 Blöcken, die das Netzwerk produzieren könnte, ohne dass eine einzige weitere Transaktion hinzu kommt. Die große Menge an hochgeladenen Daten hat auch dazu geführt, dass Gebühren zeitweise in den Bereich von 20-40 sat/vByte gehoben wurden.

Vor SegWit (Segregated Witness) wurden Gebühren nach Transaktionsgröße bestimmt. SegWit führte das Konzept des Blockgewichts ein und änderte die zu erhebenden Gebühren nach Gewichtseinheit anstelle der Transaktionsgröße. Diese Änderung wurde eingeführt, um die Transaktionsgebühren insgesamt zu senken, jedoch kommt es dennoch vor, dass Blöcke erstellt werden, die überwiegend aus Inscriptions bestehen.

SegWit war ironischerweise auch der Soft Fork, der es erst ermöglichte, dass Inscriptions in der heutigen Form hochgeladen werden können. Mehr dazu hier:
https://www.genexyz.org/post/26-block-775770-ordinals-inscriptions-36zg3n/
Um das Ordinals / Inscriptions Thema abzuschließen, bleibt bei aller Kritik auf der einen Seite und einem neuen Geschäftsmodell / einer neuen Einnahmequelle für Miner auf der anderen Seite, zu sagen, dass der Anteil an Transaktionsgebühren, die auf Ordinals / Inscriptions zurückzuführen sind, doch recht überschaubar ist.

Es bleibt festzuhalten, dass der Mempool einen sehr wichtigen Teil des Bitcoin-Netzwerks darstellt. Er ermöglicht uns zu verstehen, wie ge- oder überfüllt das Netzwerk ist und ob es Transaktionsstaus gibt, die zu langsameren Bestätigungszeiten und höheren Gebühren führen. Er hilft fortgeschrittenen Nutzer//innen zu verstehen, wie sie ihre Gebühren am besten einstellen, aber bietet auch einen Überblick über den gesamten Zustand des Netzwerks. Will man sich einen Gesamteindruck über Bitcoin - das Netzwerk - machen, schaut man sich nicht den aktuellen Tageskurs an, sondern vielmehr den Mempool und die Hashrate. Diese zwei Quellen bieten eine Menge Auskunft darüber, was gerade im Netzwerk passiert und vielleicht passieren wird.

Los Miner, ihr habt zu viele ungelesene Transaktions-Nachrichten in eurem Mempool-Postfach!
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 800be102:4e47eb69
2024-12-31 07:49:14
@ 800be102:4e47eb69
2024-12-31 07:49:14[3]
[4]
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ c8adf82a:7265ee75
2024-12-31 07:22:34
@ c8adf82a:7265ee75
2024-12-31 07:22:34My life’s purpose is to save souls
Some think that preaching and convincing people is the way, maybe, but I prefer a more practical way. I want to actually solve real world problems for good and change people’s lives for the better
Most people have some sort of void in their heart nowadays, some big, some small. Some are still fighting to fill it, most gave up and accepted that life is just as whatever the eyes can see
Jesus said walk by faith and not by sight. I want to show people that this is the case but how can I do it when the world is so clouded? Most people believe that anything they think or feel is justified and we have to agree to disagree with each other to avoid conflict. This is madness
I’ve lived in this world for a while and by the grace of God, I can see through everything. Satan made money a requirement to live in this earth. Try asking people what’s one thing they are looking for, you’ll hear two common answers; money or happiness
Happiness people are made clueless, they are people who lost to their thoughts and gave in to their heart. Just ask them what makes them happy, and you will see how blind they are about reality. Their happiness comes from owning materialistic stuff or having experiences they haven’t experience because that’s what the media made them believe
Money people can think just enough that they need money to satisfy their heart, but not enough to realize that money is the root of all their misery. In reality, money is still a big issue in our world right now even after Bitcoin. Satan has successfully shifted the narrative of what Bitcoin actually is
I feel the need to help people with money, so that they have less worries about their finances, so that they can think less about money and more about important things in life; relationships, death and eternal life
The world is currently dark and corrupted, people are kept poor, hopeless and suppressed by the hands of satan. They’re killing our future generations with debt without explaining what debt truly is. They made the world so disillusioned to the point that everyone is talking about Hollywood over the lives of people
I was guilty of waiting for a change, but by the grace of God, tis no more. I will be the light of the world
Tomorrow is a new year, don’t spend another year doing the same thing. Join the fight. Use your blessed mind to tell people that Bitcoin is freedom money. We don't need to verify anymore, everything is clear if we open our eyes. Trust the Word and not the religion. Say no to Karmageddon
We are all Satoshi
We are legion
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 2063cd79:57bd1320
2024-12-31 05:29:22
@ 2063cd79:57bd1320
2024-12-31 05:29:22Angesichts der jüngsten Aufmerksamkeit in den sozialen Medien, die durch Greenpeace und die von Shitcoin finanzierte Änderung der Code-Bewegung geschaffen wurde, ist es wichtig zu betonen, warum Proof of Work (PoW) ein Feature und kein Bug ist und warum der Aufwand an Energie und damit Strom und damit der Verbrauch von idealerweise dichten Energiequellen, die zur Herstellung von Bitcoin verwendet werden, ein wesentlicher Bestandteil der DNA von Bitcoin darstellen. Die von Greenpeace befürwortete Alternative, Proof of Stake (PoS), die nicht so viel physische Energie verbraucht, aber auch nicht den Funktionsumfang von Proof of Work mit sich bringt, ist in sich fehlerhaft, denn PoS schafft es nicht, die digitale Währung - die die meisten alternativen CrYpTo Currencies sein wollen - und eben nicht “World Computer” oder “Smart Contract Application” - in der realen Welt zu verankern.

Die Geschichte von Geld ist fast so lang wie die der Menschheit als solche. Wie schon oft und besonders in letzter Zeit besprochen, hat sich unser Geld und der Umgang mit diesem mit der Entwicklung des modernen Menschen weiterentwickelt. Neue Technologien haben dazu geführt, dass auch unser Geld weiterentwickelt wurde und sich den aktuellen Gegebenheiten angepasst hat. Das jeweilig in seiner Zeit vorhandene Geld war immer das Beste, was der technologische Fortschritt und die äußeren Faktoren hervorbringen konnten. Heute leben wir in einer stark digitalisierten Welt und in diesem digitalen Raum bedarf es eines Geldes, das diese Anforderungen erfüllt. Natürlich gibt es immer Mittel und Wege, das aktuell beste Geld mit Hilfsmitteln so anzupassen, dass es den neuen Herausforderungen eine gewisse Zeit standhält, aber das ist immer nur eine Notlösung zur Überbrückung der Zeit, bis die nächste Innovation Einzug erhält. Das haben wir z.B. mit Gold und der Einführung von Papiergeld gesehen.
https://www.genexyz.org/post/11-block-752065-fractional-reserve-banking-wird-durch-bitcoin-obsolet-bdpznh/
Eine lange Zeit war Gold DAS beste Geld. Doch mit der Weiterentwicklung von anderen Technologien, die z.B. das Reisen über weite Strecken und damit den Handel zwischen Ländern und Kontinenten möglich machten, aber auch der Weiterentwicklung der Finanzsysteme und der damit einhergehenden Globalisierung, wurde Gold als Zahlungsmittel schnell unpraktisch und durch Papiergeld erweitert. Was zunächst nur eine bessere und neuere Art der Handhabung von Gold war, also die Möglichkeit den Besitz von Gold zu belegen und damit die Notwendigkeit schwere Barren oder Münzen von A nach B zu bewegen, abgelöst hat, wurde schnell zum neuen Geld. Papiergeld (und damit auch Notenbankgeld und Geschäftsbankbuchungen) ist spätestens seit 1971 das neue, am weitesten verbreitete Geld.
https://wtfhappenedin1971.com/
Doch durch die nächste Stufe in unserer Entwicklung, der Erfindung des Internets und des World Wide Webs, musste auch dieses Geld den Umständen angepasst werden. Papiergeld, bzw. Fiat-Geld ist allerdings nicht für das digitale Zeitalter gemacht, weshalb wir uns heutzutage mit weiteren Substituten wie PayPal, Venmo, Kwitt (haha), Zelle, usw. versuchen auszuhelfen. Was ich damit sagen will, ist, dass Geld eine Lebensdauer hat, und Fiat-Geld in seiner aktuellen Form nur noch effizient genutzt werden kann, da es Produkte gibt, die es ermöglichen eine Brücke zwischen der Geld-Technologie und den äußeren Umständen, also der immer weiter voranschreitenden Verschiebung unseres Lebens in den digitalen Raum zu schlagen. Wo Papiergeld damals Gold als das am häufigsten genutzte Zahlungsmittel abgelöst hat, können Dienste wie PayPal allerdings nicht zum neuen Geld werden. Dies wird durch die Aufsichtsbehörden, Staaten und internationalen Institutionen verhindert, denn die monetäre Autorität, das Recht Geld auszugeben - zu prägen - (und auszugeben!), ist in allen Staaten dieser Welt einzig und allein dem Staat vorbehalten (also nur eigentlich, aber dazu mehr ein anderes Mal).
https://x.com/Culture_Crit/status/1638293934735601666
Diese Digitalisierung des Werts von Geld ist gerade heute die Achillesferse von Gold. Gold ist (neben Bitcoin) die beste Möglichkeit, Besitz zu sichern und zu sparen. Es ist als Zahlungsmittel jedoch unbrauchbar. Fiat-Geld hingegen lässt sich bislang einigermaßen in den digitalen Raum überbrücken, aber Gold, der einzige bislang harte Wert, ist ein physischer Wert, was bedeutet, dass man es in der realen Welt schützen muss. Dies geschieht mit Hilfe von Tresoren oder Anbietern, die die Verwahrung übernehmen, was zur Zentralisierung des Eigentums und zu Vertrauensabhängigkeit führt, oder, wie oben beschrieben, zur Nutzung von Schuldscheinen. Da der einzige Grund sein Vermögen in Gold aufzubewahren darin besteht, solche Abhängigkeiten von Dritten zu vermeiden, führen Schuldscheine die Verwahridee ad absurdum, denn Schuldscheine sind nichts anderes, als Banknoten, die über kurz oder lang von ihrem zugrunde liegenden Wert entkoppelt werden. Dies ist bei Papiergeld der Fall, welches nicht durch den zugrunde liegenden Wert gedeckt wird.
Ist man jedoch in der Lage den zugrunde liegenden Wert zu entmaterialisieren, kann man diesen viel einfacher speichern, indem man Kryptographie verwendet, um diesen mit dem Internet zu verbinden, in dem weltweit die meisten Handelsgeschäfte und Transaktionen abgewickelt werden. Die Entmaterialisierung eines Werts birgt auch den Vorteil, dass dieser Wert in unendlich kleine Teile gestückelt werden kann. So ist es z.B. unmöglich einen Bruchteil des Wertes von Gold zu verleihen oder auszugeben, ohne es entweder in kleine Stücke zu zerlegen oder ein Derivat zu erstellen, das wiederum nur ein Proxy vom eigentlichen Gold darstellt.
Daher bringt ein entmaterialisierter Wert eines Guts viele Vorteile mit sich, die der einzige andere harte Wert, Gold, nicht bieten kann. Deshalb ist ein Gut, dass digital in einer entmaterialiserten Form existiert besser als ein physisches Gut. Dies kann man auch sehen, wenn man diesen Gedanken auf alte Geldarten zurückführt, denn es zeigt, dass diese damals verwendeten Gelder einen gewissen Wert hatten und als Ware marktwirtschaftlichen, oder sogar fast schon darwinistischen, Kräften eines Kampfes zwischen den jeweiligen Eigenschaften dieser Geldformen ausgeliefert waren. Muscheln wurden von Glasperlen abgelöst, Glasperlen von Silber, Silber von Gold. Gold war das wertvollste bekannte Gut, da Gold in der physischen Welt am schwierigsten herzustellen ist, oder war.

Denn in dieser evolutionistischen Kette löst Bitcoin Gold ab. Denn Bitcoin muss, obwohl es digital ist und damit in der heutigen Zeit des Internets perfekt funktioniert, in der physischen Welt beschafft oder produziert werden. Und das ist genau der Wert, den Proof of Work schafft. Bevor Bitcoin in der digitalen Welt existieren kann, muss es in der physischen Welt hergestellt werden. Und zwar unter sehr realen und physisch existierenden Umständen und Einschränkungen. Es muss Energie aufgebracht werden, um den Stromverbrauch von Mining-Rigs zu sättigen.
Damit hat Bitcoin einen Weg gefunden, Werte in der realen, greifbaren Welt mit denen der digitalen, entmaterialiserten Welt zu verbinden und genau diesen Wert in den digitalen Bereich zu übertragen. Der Mining-Prozess von Bitcoin transformiert also reale, physische Energie in ein digitales Gut, ohne dabei den Wert zu mindern, wenn überhaupt, wird der Wert dabei gesteigert. Denn die Transformation verankert nicht nur die aufgebrachte physische Energie in der realen Welt und wandelt diese in einen digitalen Wert um, sie steigert deren Wert sogar, indem sie ein Gut schafft, das weitere Eigenschaften in sich vereint, die in der realen Welt nicht existieren. Damit geht der Wert der verbrauchten Energie nicht verloren (wie gerne von Kritikern behauptet wird), sondern in diesem Prozess entsteht ein Gut, das größer ist als die Summe seiner Teile.
Diese Eigenschaft von Bitcoin, und Proof of Work im Speziellen, wird oft nicht erkannt, bzw. braucht einige Zeit, um verstanden zu werden. Es ist leicht nur auf den Energieverbrauch von Bitcoin in der physischen Welt zu zeigen, ohne die andere Seite der Gleichung in Betracht zu ziehen. Die zuvor genannten Medienkampagnen von Greenpeace, aber auch der EU, der EZB, des Weißen Hauses in den USA, usw. beschränken sich allerdings genau auf diese vereinfachte Anschauung der Tatsachen (oder vielmehr Narrative). Dieses Phänomen ist nicht neu. Ähnlich wird auch beispielsweise bei der Betrachtung von Antriebsarten von PKW vorgegangen. Elektrische Motoren werden mit Verbrennermotoren verglichen, indem man den Benzinverbrauch und den Benzinpreis einfach mit dem Stromverbrauch und Strompreis vergleicht. Der daraus entstehende Schluss, dass Elektroantriebe günstiger sind, hinkt natürlich vorne und hinten, da nicht alle Bestandteile der Gleichung in Betracht gezogen werden.
Das Verankern eines digitalen Werts in der physischen Wert ist allerdings nicht alleinig die Erfindung Satoshi Nakamotos und Bitcoin, sondern eine Verkettung von vielen Ideen und Konzepten zu einem einzigartigen und bislang nie dagewesenen neuen und bahnbrechenden technologischen Fortschritt.

Doch die Entmaterialisierung von Bitcoin hat nicht nur den einzigartigen Effekt, dass es einen Wert der digitalen Welt in der physischen Welt verankert, sie liefert auch den entscheidenden Vorteil von Bitcoin gegenüber Gold. Denn die Entmaterialisierung macht Bitcoin deutlich teilbarer als Gold, da Bits und Bytes in der Theorie in unendlich keine Teile gebrochen werden können, sie macht es deutlich transportables als Gold, denn eine Transaktion in egal welcher Höhe kann in sekundenschnelle propagiert werden und sie macht es vor allem deutlich sicherungsfähiger und damit Bitcoins Wert stabiler (nicht in Fiat-Terms, sondern absolut betrachtet), als den von Gold. Dies kann man schön in einem von Michael Saylor verwendeten Gedankenexperiment darstellen.
Man stelle sich dazu vor, es ist 1900 und man möchte eine Milliarde US Dollar in Gold verwahren und zwar so, dass man über diese Menge Gold im Jahre 2000 noch verfügt. (Die Veränderung des Goldpreises in Fiat-Terms über den Zeitraum lassen wir dabei außen vor, wir können sogar annehmen, dass 1 Milliarde Gold im Jahre 1900 im Jahre 2000 den exakt gleichen Wert hat). Hätte man im zwanzigsten Jahrhundert sein Gold z.B. bei Banken in Ländern wie Deutschland, Polen, Russland, China, Japan, Frankreich, oder Ländern der Kontinente Afrikas und Latein Amerikas in Verwahrung gegeben, ist davon auszugehen, dass durch Weltkriege und/oder Bürgerkriege, dieses Gold geraubt, verstaatlicht oder beschlagnahmt worden wäre. Selbst in den USA, Gewinner vieler dieser Kriege und territorial unbeschadet über diese 100 Jahre, gab es in 1933 die Executive Order 6102, die es Bürgern verbot Gold zu besitzen und diese zwang es unter Marktwert an die Regierung zu verkaufen.
Einzig in einer Handvoll von Ländern wäre es möglich gewesen, das Gold unbewegt und sicher einzulagern. Also wie hoch ist die Wahrscheinlichkeit, dass man diesen Treffer gelandet hätte? Selbst dort, wo man es unbewegt, also passiv einlagern hätte können, wären über 100 Jahre immense Verwahrgebühren fällig geworden, die den Wert der 1 Milliarde in Gold gesenkt hätten. Realistischer wäre sogar anzunehmen, dass man die Verwahrung des Goldes aktiv hätte überwachen müssen, also von Bank zu Bank, Land zu Land, oder sogar Kontinent zu Kontinent zu verschieben, um externen, (ge-)politischen und anderen Risiken entgegenzuwirken. Dies wäre mit einem weiteren hohen Kostenaufwand verbunden, der den Wert des eingelagerten 1 Milliarden Goldbestands noch weiter geschmälert hätte. Dieses Problem der Sicherung von Werten, insbesondere bei Gold, macht es als Wertspeicher relativ teuer. Bitcoin hat dieses Problem nicht, denn solange rückwärtskompatible Hardware existiert, muss man seinen Bitcoinbestand nur einmal vernünftig und sicher ablegen, um jederzeit und überall auf der Welt darauf zugreifen zu können.
Dies soll zeigen, dass PoW nicht nur eine sehr raffinierte Art und Weise darstellt Bitcoin in einem Anreizprozess herzustellen, sondern, dass PoW dabei hilft, den digitalen Wert Bitcoin in der physischen Welt zu verankern, und dabei zeitgleich Eigenschaften erzeugt, die andere Werte nicht besitzen. Das Verankern, bzw. die Verbindung von physischer und digitaler Welt durch die Transformation von Energie in eine höherwertige Form von Energie ist ein bahnbrechender technologischer Fortschritt, der selbst bei vielen Bitcoinern nicht hoch genug gewertet wird.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 472f440f:5669301e
2024-12-31 04:42:00
@ 472f440f:5669301e
2024-12-31 04:42:00I'm sure some of you are already tired of the discussion around the H-1B visa program that was started on Christmas Eve by Vivek Ramaswamy and escalated by Elon Musk and others as the "Silicon Valley MAGA" coalition began putting forth legal immigration policy proposals for the incoming Trump administration. Core to their policy is the expansion of the H-1B visa program so that America can "recruit the best talent in the world" to come build the American economy.
Unfortunately, as it stands today - according to the Silicon Valley cognescenti, Americans are either a.) not smart enough to fulfill the roles necessary to enable the United States to maintain its lead as economic super power of the world or b.) expect too much in compensation for the available roles. At least this is my reading from the commentary I've seen over the last week.
What seems abundantly clear to me is that the framing put forth by "Silicon Valley MAGA" crew is disingenuous and self-serving. It has been clear for awhile now that the H-1B visa program is being systematically abused to bring in cheap labor from other countries to help drive down labor costs for companies across the spectrum. Not just Silicon Valley tech companies. The system has a loophole in it and it is being exploited. Bring people to the US via H-1B visas to complete work for you at lower costs and your company's financials are likely to be better off (assuming the work being done is productive and a value add to the company). Now, this isn't to say that everyone who is in the US via an H-1B visa is here because these companies want to exploit the loophole that gives them the ability to spend less on head count. However, based off the data from the database of the H-1B visa program it is abundantly clear that the system is being taken advantage of. Egregiously and at the expense of American workers, who are most certainly not (all) "subtarded".
Herein lies the crux of the problem; companies are abusing this program to get away from the problem of Americans demanding higher wages to maintain lives of dignity in a country run by a government that is chronically addicted to debt backed by a central bank that will print money ex-nihilo and at will to monetize that debt. Americans are then being scapegoated as either "lazy", "stupid" or "delusional about their worth in the work force". A classic straw man argument that avoids the root issue at hand; the money is broken and the broken money has created perverse incentives throughout the economy while also stripping Americans of the ability to properly save the value of their labor.
We live in a high velocity trash economy that rewards grift and waste while disincentivizing hard work that is meaningful to the quality of life of the Common Man. Everything has been hyper-financialized to the point that one of the only ways to make it ahead is to speculate on the flow of capital into certain asset classes, which is often determined by the whims of central planners. Another is to build or speculate on tech "innovations" that typically materialize in the form of attention zapping apps and widgets that help people temporarily forget they live in a high-velocity trash economy.
The mass of men lead lives of quiet desperation and it is because they don't see a way out of the nihilistic rat race created (unknowingly to most) by the money printer.
The ability to print money out of nothing and throw it at everything creates misaligned incentives that result in the inability for the market to properly determine what is genuinely needed by the people instead of those who have learned how to game the broken system and its broken incentives.
One last point, I would be remiss not to acknowledge that many individuals in America aren't intellectually equipped to do some of the cutting edge work that may be necessary to produce the technologies and companies that will push the country forward. The high-velocity trash economy run on money printed out of nothing has completely corrupted the education system. People in the United States are literally dumber than they were five decades ago. That is a fact. But it is not only the fault of the American people themselves, but the corrupt system they have been born into that destroyed the education system with perverse incentives. And the overwhelming majority of the blame is on the system, not the people.
Even with that being said, the idea that we need to adopt a Tiger Mom mentality in the US - a culture of unrelenting devotion to studying STEM to the point that weekend sleepovers for kids are discouraged - is absolutely laughable and objectively un-American. There are plenty of incredibly intelligent, creative and driven young Americans who have contributed and will continue to contribute significantly to the American economy and they didn't need to shackle themselves to their desks to get that way. America isn't a country that was built by automatons. It's a country built by people who said, "Fuck you. Don't tell me what I can and cannot do. Watch this."
Despite the fact that a system has been erected that actively works against the average American system the American spirit lives on in the souls of many across the country. Miraculously. The American spirit is something that cannot simply be imported. It is ingrained in our culture. It is certainly beginning to dwindle as hope for a better future becomes more and more dim for the masses as the system works against them despite all their best efforts to succeed. It is imperative that we stoke the coals of the American spirit while it is still alive in those who are too stubborn to give up.
People need the ability to save their hard work in a money that cannot be debased. Opportunity cost needs to be reintroduced into the market so that things that actually add value and increase the quality of life for the Common Man are where hard money is allocated. And people need to start talking about the root of the problem more seriously instead of striking at branches with disingenuous straw man arguments.
Final thought... Ready to go surfing.
-
 @ 468f729d:5ab4fd5e
2024-12-30 22:33:01
@ 468f729d:5ab4fd5e
2024-12-30 22:33:01 -
 @ 2063cd79:57bd1320
2024-12-30 21:08:43
@ 2063cd79:57bd1320
2024-12-30 21:08:43Bitcoin ist Zeit und Zeit ist Geld
In einem der vorigen Artikel haben wir uns mit den Funktionen und Eigenschaften von Geld befasst. Eine, vielleicht sogar die wichtigste, Funktion von wertvollem und hartem Geld ist Knappheit. Wir haben gesehen, dass Bitcoin die einzige Form von Geld ist, die diese Charakteristik zu 100% erfüllt.
Knappheit bedeutet, dass das Gut, das als Geld benutzt wird, begrenzt ist und nicht ohne weiteres vermehrt werden kann.
Bitcoin erfüllt diesen Anspruch, denn
Bitcoin ist auf 21.000.000 begrenzt. Die harte Obergrenze von Bitcoin ist von zentraler Bedeutung für sein Wertversprechen. Alle 2.099.999.997.690.000 Sats werden irgendwann existieren (oder existieren schon - je nach Betrachtungsweise) und darüber hinaus werden keine weiteren Sats produziert.
Die einzige andere Ressource, die wir Menschen haben, die uns jedem zur Verfügung steht und zu 100% begrenzt ist, ist unsere Zeit. Ausnahmslos jeder Mensch hat ab dem Moment seiner Geburt ein Zeitfenster in diesem Leben und dieses Zeitfenster - dieses Leben - ist begrenzt. Es hat noch niemand geschafft diese Regel zu brechen, bzw. zu cheaten.

Die Lebensdauer jedes Menschen fällt unterschiedlich aus und ist sogar recht ungerecht verteilt. Es gibt Menschen, die schon sehr, sehr früh nach ihrer Geburt sterben, und es gibt Menschen, die sehr, sehr alt werden. Auf diesem Spektrum von 0 bis ca. 120 Jahren befinden wir Menschen uns alle. Wir können aktiv Einfluss auf unsere Lebenserwartung nehmen, sowohl verlängernde als auch verkürzende Maßnahmen ergreifen, doch eins bleibt bisher immer garantiert: Unsere Zeit ist endlich. Und damit ist sie unser knappstes Gut.
Kommen wir nun zurück zum Geld. Wie wir schon gesehen haben, muss Geld drei Funktionen erfüllen:
Es muss als Tausch- oder Zahlungsmittel funktionieren, es sollte ein Wertaufbewahrungsmittel sein und als Recheneinheit dienen.
Während man schnell dazu übergeht, bei Geld an die Funktionen von Zahlungsmittel und Recheneinheit zu denken, da diese im täglichen Leben tausendfach vorkommen, ist es besonders die Funktion des Wertaufbewahrungsmittels, die Geld einen besonderen Stellenwert in unserem Leben als Ganzes verleiht. Und da ist sie, die Überschneidung von Geld und unserem Leben, also unserer begrenzten Zeit, auf die ich seit 400 Wörtern hinarbeite 😰
Zeit ist Geld. Jeder kennt diese Redewendung. Im wahrsten Sinne des Wortes bedeutet sie, dass man Zeit in Geld verwandeln kann und dass diejenigen, die Zeit haben auch Geld haben. Man spricht hier irrtümlicherweise auch von "Zeit sparen". Als ob die Möglichkeit bestehe, nicht verbrauchte Zeit zu einem späteren Zeitpunkt abzurufen. Dass dies außerhalb von Momos Welt nicht möglich ist, sollte jedem bewusst sein. Was meint man also damit, wenn man sagt man spart Zeit, oder Zeit ist Geld? Die Funktion des Wertaufbewahrungsmittels von Geld bedeutet erstmal, dass das verwendete Geld seinen Wert durch die Zeit aufrecht erhalten kann. Im allerbesten Falle ist ein Geld von heute auch morgen immer noch ein Geld wert.

Betrachten wir nun unser eigenes, hart begrenztes Zeitfenster, also jenes, das uns gegeben wurde, um auf diesem blauen, lustigen Ball zu verweilen, so wollen wir diese Zeit möglichst würdevoll und möglichst angenehm verbringen. Da das Leben allerdings Geld kostet, sind wir in der Regel gezwungen, solches zu verdienen. Es soll ein paar glückliche Menschen geben, denen dieser Ballast von Geburt an genommen wird, allerdings verhält es sich für das Gros der Menschen so, dass sie für ihren Unterhalt puckeln müssen. Im Idealfall sieht das so aus, dass man bei einem erwartbaren Durchschnittsalter von 80 Jahren, die ersten 20 Jahre damit verbringt zu erlernen, wie das Leben funktioniert und wie man Geld verdient, um dann 40 Jahre lang genau das zu tun und wenn alles gut läuft hat man noch 20 Jahre, um seinen wohlverdienten Ruhestand zu geniessen. Also einfach gesprochen verbringt man 50% seines Lebens damit, 100% seines Zeitfensters zu finanzieren (die ersten 20 Jahre des Lernens finanziert man zwar seinen Nachkommen, hat aber im Gegenzug dafür diese auch fremdfinanziert bekommen). Das bedeutet wiederum, dass man in den 40 Jahren Berufsleben doppelt so viel Geld verdienen muss, wie das eigens gewählte Leben kostet.

Um auf die Redewendung "Zeit ist Geld" zurückzukommen, bedeutet dies schlicht, dass jeder arbeitende (und damit Geld verdienende) Mensch seine eigene knapp bemessene Zeit in Form von Arbeit zur Verfügung stellt, um Geld zu verdienen. Dies tun wir, da wir Zeit eben nicht sparen können. Wir versuchen sie in einen anderen Aggregatzustand umzuwandeln (Zeit ➡️ Geld), um uns zu einem späteren Zeitpunkt mit diesem Geld unsere Zeit zurückzukaufen. Dies funktioniert zwar nicht im direkten Sinne, also dass wir uns zusätzliche Zeit kaufen, jedoch können wir das Decken laufender Kosten vorfinanzieren und somit, hoffentlich, im Ruhestand leben, ohne unsere laufenden Kosten durch Arbeit decken zu müssen. Wenn alles gut läuft, schaffen wir es sogar unseren gewählten Lebensstandard aufrechtzuerhalten und führen somit ein für unsere subjektiv gesteckten Messpunkte würdevolles und angenehmes Leben.
So die Theorie. Denn in der Praxis funktioniert dies nur, wenn es uns möglich ist, unsere Zeit in ein Geld umzuwandeln, das es uns erlaubt, eine Umwandlung von Geld zurück zur Zeit zu einem späteren Zeitpunkt so vorzunehmen, dass wir möglichst wenig verlieren. Dies ist die einzige Aufgabe eines Wertaufbewahrungmittels: Der Erhalt des jetzigen Wertes einer Sache über einen Zeitraum hinweg.

Praktisch gesprochen besteht dieser Vorgang aus zwei Komponenten. Zuerst müssen wir Geld verdienen, dann müssen wir es sparen. Bestenfalls schaffen wir so viel Geld zu verdienen, dass unsere Einnahmen unsere Ausgaben übersteigen, damit wir überhaupt in der Lage sind, überschüssiges Geld zu sparen. Dann müssen wir ein Wertaufbewahrungsmittel finden, dass es uns erlaubt, diesen Überschuss so zu konservieren, dass wir ihn zu einem späteren Zeitpunkt abrufen können. Über die erste Komponente lässt sich schon genug schreiben, über den gewählten Lebensstandard und die damit einhergehenden Kosten, die (Un-) Gerechtigkeit und Chancenungleichheit beim Erlangen einer Erwerbstätigkeit, etc. blah.

Die zweite Komponente allerdings ist für unsere Betrachtung die viel entscheidendere. Denn gehen wir davon aus, dass wir zu den glücklichen Wenigen gehören, die es schaffen eine niedrige Zeitpräferenz zu erlangen und Überschüsse in der Gewinn- und Verlustrechnung des Lebens zu erzielen, so bleibt immernoch die grosse Frage offen, wie wir es schaffen sollen, diese Überschüsse zu konservieren, sodass wir sie dann später nutzen können. Und zwar so, dass sie möglichst wenig an Wert verloren haben, oder sogar an Wert zugenommen haben.
Genau das ist das Geschäftsmodell von vielen Unternehmen, Institutionen und Schlangenölverkäufern weltweit, die damit werben, unser hart verdientes Geld so anzulegen, dass es später unseren Ruhestand finanziert. Sie wollen uns in ihre undurchsichtigen Finanzierungsmodelle locken, um damit als die eigentlichen Profiteure hervorzugehen.

Ob private oder staatliche Altersvorsorge, Riesterrente, Bausparvertrag, 401k, IRA, fondsgebundene Tralalarente oder Aktion Mensch-Los mit Sofort-Rente, alle Anbieter spielen mit der Sorge der Menschen, dass ihr heute gespartes Geld morgen wohl nicht mehr zur Finanzierung des erträumten Ruhestands reicht. Und warum ist das so? Wegen des effektiven Kaufkraftverlustes unseres aktuellen Geldes. Viel Tinte wurde vergossen, viele Tasten misshandelt, um dieses Thema zu beschreiben, das heute aktueller denn je ist. Denn wenn Geld in einer Fiat-Währung für die zukünftige Verwendung gespeichert wird, verliert es aufgrund der Währungsinflation im Laufe der Zeit an Kaufkraft. Das bedeutet effektiv, dass die investierte Zeit nicht nachhaltig widergespiegelt wird, oder drastischer ausgedrückt: wir haben unsere Zeit verschwendet. Sparen funktioniert also nicht mehr, wie es uns damals im Kindesalter beigebracht wurde.

Bitcoin fixes this, yay, Bitcoin-Floskel. Aber warum ist das so? Während Fiat-Währungen einem reellen Kaufkraftverlust ausgesetzt sind, der durch Fiskal- und Geldpolitik bedingt ist, ist der Wert von Bitcoin immer gleich. Ein bitcoin = ein bitcoin. Jetzt könnte man natürlich entgegensetzen, dass ein Knopf = ein Knopf. Allerdings lassen sich Knöpfe unendlich nachproduzieren und in Umlauf bringen. Doch wie wir wissen, hat Bitcoin eine harte Obergrenze von 21.000.000 bitcoins. Dies macht Bitcoin wahrscheinlich zum überprüfbar knappsten Gut auf unserer Erde. Selbst unser Zeitfenster könnte mit ein paar Entwicklungssprüngen in der DNA und Molekularforschung vielleicht irgendwann deutlich ausgeweitet, wenn nicht sogar für immer geöffnet werden.
Jedoch ist Bitcoins Code unveränderlich: Die 21 Millionen Obergrenze ist in Stein (Code) gemeißelt und damit eignet sich Bitcoin hervorragend als langfristiger Speicher für Zeit. Allein der Umrechnungskurs von Bitcoin in eine lokale, aktuelle oder für den Moment nützliche Währung hängt davon ab, wie viel Zeit man in einen anderen Wert umwandeln kann. Doch auch dies ist ein Feature und kein Bug. Denn jeder Arbeitstag, den ich heute in Euro oder US Dollar "spare" (besser: umwandle), ist komplett verloren, wenn diese Fiat-Währung zu einem Zeitpunkt x nicht mehr existiert. Dann ist es doch von Vorteil, wenn man seine Zeit in einen neutralen Aggregatzustand umwandeln kann, der sich in Zukunft beliebig in die benötigte aktuell brauchbare Recheneinheit / Währung transformieren lässt.

https://storeoftime.com/
Andersherum lässt sich argumentieren, dass das Währungspaar nicht BTC/USD oder BTC/EUR ist, sondern direkt ZEIT/BTC. Man ermittelt also den Wert von Zeit direkt in einer Bitcoin-Ausdrucksweise, die in Zukunft sogar festgesetzt werden könnte und damit die ultimative Währungseinheit darstellen würde.
Bitcoin verstehen
Bitcoin ist nicht nur Zeit im Sinne von umgewandelter Zeit in Geldmenge, sondern als reeller Zeitaufwand, um Bitcoin zu verstehen und Bitcoin für sich selbst begreifbar zu machen. Auch diese Definition von Zeit ist wiedermals für jeden Menschen subjektiv und dem eigenen Empfinden nach zu bemessen. Was jedoch nicht von der Hand zu weisen ist, ist dass es einen gewissen Mindestaufwand von Zeit, ob mit der Lektüre verschiedener Texte, dem Austausch mit Gleichgesinnten, dem tatsächlichen Ausprobieren und Erlernen der mechanischen Abläufe, etc. bedarf, um Bitcoin zu begreifen. Niemand wird jemals Bitcoin in seiner Gänze, seiner Tragweite oder seiner Wirkung vollständig verstehen, allerdings bin ich fest davon überzeugt, dass es diesen einen Punkt gibt, an dem bei jedem an Bitcoin interessierten Menschen ein gewisser Aha!-Moment eintritt, an dem viele Puzzleteile mit einem Mal ein Bild ergeben.
Dieser Moment tritt bei manchen sehr früh, bei manchen eher später ein, jedoch eint alle Bitcoiner und Bitcoin-verstehende Menschen dieser eine Moment, den es nur zu erreichen möglich ist, wenn ein gewisses Maß von Zeit investiert wurde. Dieser Moment lässt sich nicht erklären und muss von jedem Menschen selbst erlebt werden, um ihn zu verstehen. Damit kann er nicht erkauft oder erschlichen werden, sondern lässt sich nur in Form von aufgebrachter Zeit erreichen. Damit trägt Bitcoin eine weitere Zeitkomponente in sich, die weder im Whitepaper, noch im Code, noch in später veröffentlichten Texten Satoshis festgehalten oder gar definiert wurde. Jedoch wage ich zu behaupten, dass es niemanden gibt, der/die Bitcoin begriffen hat und von sich sagt, diesen Moment der Klarheit, der Offenbarung, nicht erlebt zu haben.

Bitcoin hat sein eigenes Verständnis von Zeit
Zeit ist ein sehr tiefgründiges und subjektives Konstrukt. Es gibt die Uhrzeit, also eine Zahl, die uns anzeigt, wie weit der jeweilige Tag vorangeschritten ist. Der Kalender misst auch Uhrzeit, nur eben nicht in Form von Stunden, Minuten und Sekunden, sondern in Monaten, Wochen und Tagen. Und dann gibt es noch Jahre. Wohingegen Sekunden, Minuten, Stunden, Tage, Wochen und Monate begrenzt sind - es gibt z.B. nur 12 Monate, dann fangen wir wieder von vorne an zu zählen, ist die Anzahl von Jahren keinem Zyklus unterworfen. Es wird immer weiter gezählt. Natürlich gibt es Dekaden, Jahrhunderte, Jahrtausende, etc., doch sind diese nur Recheneinheiten, die das Zählen von Jahren vereinfachen. In unserem System gibt es ein Jahr null und seit dem zählen wir vorwärts (wenn man davon absieht, dass sich jemand vor 400 Jahren das Jahr null ausgedacht hat und seit dem alles zurückgerechnet wurde, aber wir wollen mal nicht kleinlich sein) und alles was vor diesem Jahr null liegt, wird rückwärts gezählt. Dem Weihnachtshasen sei Dank 🙏
Genauso willkürlich, wie diese Zeiterfassung festgelegt wurde, verhält es sich bei Bitcoin auch. Denn Bitcoins innerer Maschinenraum ist eigentlich nichts anderes als eine eigenwillige und nutzungsbezogene Uhr. Die Bitcoin-Blockchain ist eigentlich eine Timechain, ein sogenannter Timestamp-Server. Wie schon mehrmals erwähnt, findet man das Wort 'Blockchain' in Satoshis Whitepaper nicht ein einziges Mal. Dafür findet man bereits im vierten Satz den Begriff 'Timestamp'.

Da Zeit ein recht flexibler Begriff ist und die Zeitmessung vom jeweiligen Nutzen oder dem Erfüllen eines Ziels abhängig ist, ist es besonders schwierig, ein allgemeingültiges System zu wählen. Zeit kann in vielen Formen dargestellt werden, von "Jetzt bis kein Bock mehr", oder "Anno Pief und Dazumal" gibt es etliche Redewendungen, die zeigen, dass Zeit gefühlt wird und nicht gemessen wird. Doch wenn man ein global funktionierendes dezentrales Netzwerk errichten möchte, dass darauf basiert seine eigene Wahrheit zu speichern, ohne auf Dritte angewiesen zu sein und alle Transaktionen so zu speichern, dass sie nachvollzogen und validiert werden können, bedarf es eines Zeitmessungsmechanismus. Und dieser muss absolut fehlerfrei sein und darf keine Latenz zulassen, da sonst Raum für Schummeleien geboten wäre. Was eignet sich da also besser, als ein eigener, eigens für diesen besonderen Zweck erdachter Mechanismus zum Festhalten von Geschehnissen? Diese Geschehnisse werden vom System mit einem Zeitstempel versehen, der unmissverständlich macht, welche Reihenfolge von Geschehnissen die eine Wahrheit ausmacht, der alle Netzwerkteilnehmer vertrauen.
Gigi hat sich dem Thema in seinem neuen Buch deutlich detaillierter gewidmet und ich empfehle jedem/r die Lektüre dieses Kapitels:
https://21-ways.com/2/
Fazit
Bitcoin ist nicht nur Zeit. Bitcoin misst die Zeit in seiner eigenen Weise. Bitcoin verlangt Zeit von uns, damit wir es begreifen, aber Bitcoin hilft uns, den Wert unserer Zeit einzufangen. Damit ist Bitcoin sowohl das Metronom, das seinen eigenen Takt angibt, strenger Lehrer, der Aufwand fordert, um Exzellenz zu erreichen, als auch Tresor oder Akku, der aufgebrachter Zeit einen Wert beimisst, und diesen Wert zu speichern vermag. Tick, tock, next Block!
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 234035ec:edc3751d
2024-12-30 19:36:42
@ 234035ec:edc3751d
2024-12-30 19:36:42When Satoshi created Bitcoin, he not only created the perfected form of sound money, but he also created an immutable universal measurement for time. Each block is found roughly every 10 minuets with the difficulty adjustment either ratcheting up or down the difficulty every 2,016 blocks. As we know the halving event occurs every 210,000 blocks (roughly 4 years). As an added bonus, Satoshi decided to release the white-paper during an election year. Therefor, every halving going forward will coincide with the US presidential election.
As you descend down the bitcoin rabbit hole, weather it is conscious or not, you begin to measure your life in these cycles. I remember when Bitcoin finally clicked for me in late 2021, all I was focused on was accumulating as much BTC as possible before the 2024 halving. You often hear people stating that they have been in Bitcoin for X number of cycles as a sort of accolade. Both of these are examples of how measuring your finite time with Bitcoins immutable time chain can be beneficial.
My Life by Cycles
I was born in the year 2001 shortly after the 911 attacks. Therefore, as I have grown I have only ever known a world of ever changing technological and cultural environments. I was 7 years old when satoshi released the white-paper and was entirely unaware of it for the first epoch (Too busy playing with Yu-Gi-Oh cards SMH).
The Second Epoch Bitcoin was still entirely off my radar, I was 11-13 years old and just getting into the sport of Wrestling. This was my awkward transitionary phase. Also during this time I got my first Ipod which was the beginning of my screen addiction but also opened a new world of opportunities.
The Third Epoch encompassed my time in high school. This cycle is when I first became interested in investing and heard about Bitcoin for the first time. I was extremely focused on my wrestling career throughout this cycle and became a 2 time state champion. But I also spent the majority of my free time with friends and girlfriends not spending much time thinking deeply about what I was doing or what was going on around me. Towards the end of this cycle was when I first bought Bitcoin, we had all been sent home from school for covid-19 and my senior year was cut short. While I did by a small amount of Bitcoin I held majority shitcoins and did not yet understand the true value of Bitcoin.
The Fourth Epoch begins with turbulence, my senior year of highschool was cut short and I decided to take a gap year before going to university. I spent that year working and studying and I began to get a clearer picture of the problems with our financial and political systems developing a more libertarian mindset. The following year I went off to college where I would be a student athlete on the wrestling team studying business. During my freshman year was when I truly went down the Bitcoin Rabbit hole. I could not get enough information about it and I was completely obsessed (still am). I had been moving all of my income into Bitcoin and then my sophomore year I sold all of my other investments to go all in on BTC. This was a difficult decision as I had made significant gain in tesla and believe in the company, but I could not stand the opportunity cost of not buying cheap sats. In retrospect this was a very good trade and ever since then the only asset that I purchase is Bitcoin.
The Fifth Epoch in the spring of 2024 came in my Junior year of University. This Halving was extremely satisfying as I have now made it through an entire bear market and came out with more Bitcoin than I had ever hoped for. Now that I am sitting on significant profit there is far less stress in Hodling and I feel that those around me are beginning to understand that I may be correct about this thing. This spring I will be graduating and moving on to my next phase in life which will be either employment, entrepreneurship or a combination of the two. This cycle will extend until the year 2028 when I will be 26 years old. As I look forward, it is quite possible that I will have proposed to my now Girlfriend of three years by the Fifth halving. I have stacking as well as fitness goals that I am looking to reach by the conclusion of this cycle.
The Sixth Epoch, will take me from ages 26-30. As I think about where I want to be by this time, I imagine myself with a young and growing family, a strong budding career either with my own established business or with plans to create one. I hope to have hit significant stacking milestones by this point, but I imagine that the USD exchange rate will be in the millions by this time.
Spend your time wisely
You are only given a finite amount of time in this life, Bitcoin gives you a means of measuring it that is equally scarce. As you store you economic energy in it you become more powerful over time. As you measure your time in it, the picture of your progress becomes much more clear.
If you have less Bitcoin at the end of an Epoch than at the beginning than you have been net-unproductive throughout that cycle. As you move forward with your life, try to think about where and who you want to be by the end of this epoch and keep that goal in mind.
-
 @ 3f770d65:7a745b24
2024-12-30 19:25:45
@ 3f770d65:7a745b24
2024-12-30 19:25:45As I look back on my predictions for Nostr in 2024, it’s clear I had some hits and misses. I believe my first two predictions were spot on, accurately reflecting the trends and developments we witnessed. However, my second two predictions missed the mark, proving to be far less accurate. Maybe I was too bullish?
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcqypsm9tk39g20atwqskvjcvhq7rher5nkgwjr05lzspne4gf0uvyxukew5mg
What did I get right? Clients did increasingly prioritize user and content discovery while enabling users to easily select and choose their own algorithms. (DVMs, Trending, What's Hot, Feeds, etc.) This focus provided individuals with more tools, greater control, and unprecedented power over their social streams and attention than ever before. This is still actively happening and will continue to happen throughout 2025 too.
What did I get wrong? We didn't see an Other Stuff application breakthrough as a clear winner that became a mainstream favorite. I anticipated a standout application that would interest users and become a "must-use" within the ecosystem, but this didn’t happen. And we also clearly didn't hit 1M active users either. While adoption did increase, it didn’t reach the critical mass I expected.
But this doesn't mean 2024 fell short of expectations—in fact, quite the opposite. The year brought incredible client innovations (Damus Notedeck, Primal 2.0, TOR only Amethyst, Flotilla, Chachi, Olas, Coracle feeds, etc.) and relay milestones (Web-of-Trust relays, private relays, algorithm based relays, etc.) with the introduction of these innovative features and the launch of these new platforms.
Beyond technology, the Nostr community achieved something truly remarkable: a grassroots movement that united people globally.
From supporting Nostr meetups and events to hosting booths across continents at major conferences, the community came together to raise money to support these initiatives in ways no one predicted. This organic, ground-up effort showcased the strength and passion behind Nostr, creating a foundation that will #grownostr and success for years to come.
Too bullish? Maybe I wasn't bullish enough? As is tradition, I will post my 2025 predictions tomorrow.
-
 @ 6538925e:571e55c3
2024-12-30 15:51:30
@ 6538925e:571e55c3
2024-12-30 15:51:30In 2024, listeners sent a total of $127,900 to creators on Fountain
The 2 BTC sent is equivalent to $127,900 based on a daily price conversion but it would be worth nearly 50% more today.
You sent over 40,000 boosts to your favourite shows and artists, with an average boost value of 3,380 sats (around $3.20 at today's price).
To add to that, over 63 million sats were streamed over the course of the year, representing 32% of total value sent.
Here are some of the shows and artists who picked up the top awards in 2024. To read the full article, head to our website.
Most Supported Show: Rabbit Hole Recap
Rabbir Hole Recap is a bitcoin news show hosted by Marty Bent and Matt Odell. Over the last three years, RHR has become one of the moved shows among Fountain listeners (affectionately known as ‘freaks’). In 2022 they were #3, in 2023 they were #2, and in 2024 they finally claimed the #1 spot. Congratulations, Marty and ODELL. Your dedication and humility is an inspiration to bitcoiners around the world.
Show with Most Supporters: Mr Obnoxious
Peter McCormack announced earlier this year that What Bitcoin Did, the preeminent podcast he has hosted for as long as we can remember, would come to an end to make way for a new show, Mr Obnoxious. In December, the Real Bedford FC owner announced that Danny Knowles would be the new custodian - much to the relief of the 800 listeners who supported the show this year. Thanks for everything, Pete!
Most Supported Episode: LINUX Unplugged | 545: 3,062 Days Later
LINUX Unplugged is just one of many popular shows about open-source, security and privacy from Jupiter Broadcasting. Editor-in-chief Chris Fisher finishes the year with three shows in Fountain's top 40. How? He and his co-hosts have made boosting a core part the listener experience, with his audience often sending "zip code boosts" (which can get pretty expensive if you live in Alaska).
Most Supported Artist: Ainsley Costello
At just 20 years old, Ainsley has been working toward a career in music for over half her life. Her music is the modern pop soundtrack of the next generation. Ainsley first made "waves" on the internet in August 2023 as the first artist to receive 1 million sats with her hit song “Cherry On Top.” Since then, she has inspired countless artists to follow her path, becoming the face of this exciting new movement.
Artist with Most Supporters: Man Like Kweks
Don Kweka is a producer and rapper from Tanzania. When he's not at his desk working his 9 to 5, he's making beats in his bedroom - and he has been prolific in 2024. Earlier this year he told Forbes he had earned a total of $25.68 from United Masters, the distribution company he uses for traditional DSPs (for which he pays a $60 annual fee). Since first publishing his music on Wavlake, he’s earned 2.3 million sats (over $2,000).
Most Supported Track: Abi Muir | Stockholm
Born in Scotland and now residing in Australia, Abi’s distinctive, goosebump-inducing vocals and heartfelt lyrics define her creative songwriting. Her unique style sees her delivering memorable, catchy pop songs of singer-songwriter prose with a contemporary pop sound. In Stockholm she explores a darker, harder edge to her music that crosses into alt-rock, topped with Muir's piercing, sultry vocals.
 ### Read Fountain Rewind 2024 in full on our website
### Read Fountain Rewind 2024 in full on our websiteTo see the full list of award winners, the top 40 shows and artists, plus the top stories from this year, hit the link below.
 ### Share your Rewind for a chance to win Fountain AirPods, limited edition merch and 100,000 sats
### Share your Rewind for a chance to win Fountain AirPods, limited edition merch and 100,000 satsOpen the app to see your Fountain Rewind (make sure you're using the latest version). Post a screenshot of any screen in your Fountain Rewind on X or Nostr and tag @fountain_app in your post. We will be announcing three lucky winners on Dec 31 - good luck!
-
 @ 6bae33c8:607272e8
2024-12-30 14:29:06
@ 6bae33c8:607272e8
2024-12-30 14:29:06I was supposed to be back in Lisbon right about now, but am still in Florida. The itinerary changed on me, though it was always this way, and I just didn’t know it. Turns out Heather *thought* she had booked the flight for December 29th to arrive on the 30th, but really had booked the 30th to arrive on the 31st. She discovered this on the night of the 28th. It meant we had to cancel a 6:30 am New Year’s Day ski trip to France which was, to be honest, a relief to all of us.
I love skiing, but it entailed a two hour flight to Geneva, an hour drive to our friend’s house, then 40 minutes each way the next few days from there to the slopes, renting all the gear, etc. all while being jetlagged af and not having slept more than a few hours for two days after an eight day international trip to states. And cancelling only cost us half the price of the Lisbon to Geneva tickets, about $450 total, while saving us a couple thousand in meals, four-wheel drive rental car, lift tickets, etc. Plus we get Oscar back early from the dog camp now.
As a result, instead of traveling, I was able to catch some of the games yesterday, mostly the two late ones. My season is done, so this was more just observing how badly I botched my Steak League lineup at the last second and feeling enraged about that.
Anyway, the French alps would have been cool, but Florida isn’t that bad.


-
I have Anthony Richardson at QB in the Steak League because you get a point every 10 yards rushing and six points per rushing TD, but only four per passing TD and one point every 25 passing yards. But Richardson was hurt, it was a 14-team league, and the best I could do on waivers was his backup Joe Flacco against the Giants. So I had Flacco in the lineup, but right before we were about to leave for brunch, I saw that Davante Adams was active against the Bills, impulsively picked up Aaron Rodgers and subbed him in for Flacco. That cost me 17 points and could very well result in my buying rather than eating Steak.
-
Malik Nabers wears No. 1 and looks like a clone of Ja’Marr Chase in a Giants uniform. He’ll be a first round pick next year, no matter who the Giants QB is. And who knows, maybe Drew Lock is next year’s Sam Darnold.
-
The Giants win kicked them out of the top draft slot, and I’m good with that. I don’t want them to be forced to take a QB — better to sign someone unless the rookie is a can’t-miss generational prospect if that even exists anymore.
-
I thought I was being clever taking the Cowboys +9.5 with Jalen Hurts iffy, but I was not.
-
Saquon Barkley broke 2,000 yards but will probably sit against the Giants next week rather than go for Eric Dickerson’s all-time record of 2,105. It would be easy for him to do, but given he got to 2K in 16 games, and the Eagles are locked into the No. 2 seed, better to rest him. Breaking the 16-game record in a 17-game season means less than it would. The NFL single-season record books are one big asterisk field now.
-
When I started Rodgers I was afraid the game might go the way it did, and that Tyrod Taylor was able to engineer two TDs in garbage time was insult to injury. The Jets have packed it in, and I should have factored that into my decision.
-
I caught some of the Bengals-Broncos Saturday, but was at a restaurant when the Bengals went for the game-winning FG in overtime, assumed they made it, only to find out later they covered on a third-TD catch by Tee Higgins. This after they should have won on a FG in regulation but for some bizarre clock mismanagement. Tough beat if you had the Broncos +3.5.
-
Joe Burrow has 4,641 yards and 42 TDs vs eight picks with one game to go. The Bengals are still alive for the playoffs, but they’d need to beat the Steelers, the resting Chiefs to beat the Broncos and the packed-it-in Jets to beat the Dolphins, so they’re almost drawing dead. It’s too bad because Bengals-Bills in the Wild Card round would be a lot more exciting than Broncos-Bills.
-
Chase Brown sprained his ankle on the dumbest play of all time. Why run the ball toward the end zone and slide to avoid scoring at the one? Just kneel down at the six!
-
Ja’Marr Chase killed me this week with a meager 9-102-0 line.
-
Why wasn’t Marvin Mims getting more looks all year?
-
I went 2-3 in Circa, but boy was I right about Chargers -4. Perfect spot for a solid team to destroy a weak one that had played over its head the prior week.
-
Ladd McConkey is a bit fragile, but he’ll go around the 2/3 turn in next year’s drafts.
-
I didn’t catch much of Rams-Cardinals mercifully. Kyler Murray is so inconsistent.
-
Puka Nacua should be a top-10 fantasy pick next year too. The only receivers I’d take ahead of him are Chase, Nabers, Justin Jefferson, CeeDee Lamb and Amon-Ra St. Brown.
-
Brock Bowers broke Mike Ditka’s rookie receiving record. Depending upon the QB situation there, he might go at the 1-2 turn.
-
You have to love games where where the top RBs are Ameer Abdullah and Clyde Edwards-Helaire. I honestly didn’t realize CEH was even on the Saints until I looked at the box score.
-
The Panthers play everyone tight except apparently the Bucs. I’m glad they won, and the Falcons lost, as the Bucs are a much more entertaining playoff team.
-
Bucky Irving will go no later than the fourth round next year.
-
Mike Evans got 97 yards, putting him just 85 shy of 1,000. The Bucs need the game next week against the Saints, too. Only a injury can prevent him from getting there for an 11th straight year.
-
What if Mac Jones is next year’s Sam Darnold? Trevor Lawrence might be the next Baker Mayfield too.
-
Brian Thomas will go no later than early second-round next year, maybe even late first. I was one pick away in the 14-team RotoWire Dynasty league from getting Nabers and Thomas with my first two picks. Had to settle for Xavier Worthy and Bucky Irving/Jonnu Smith at the 3/4 turn.
-
The Dolphins without Tua are bad, but DTR is the worst QB in NFL history.
-
Jerry Jeudy is going in the third round again next year, and no one can stop this from happening.
-
Darnold threw one bad pick, but otherwise balled out again. He has 35 TDs and 12 picks with 8.2 YPA. If the Vikings upset the Lions in Detroit next week, and he has another big game — which is likely as the Lions defense isn’t good — Darnold will have MVP-type numbers on the 15-2 No. 1 seed. He won’t win because it’s Josh Allen’s “turn” but he would deserve it as much as anyone.
-
I didn’t watch the Sunday night game, but I’m glad the Falcons lost. They have no business being near the playoffs.
-
-
 @ a38a5cd0:92b1b8f0
2024-12-30 13:31:02
@ a38a5cd0:92b1b8f0
2024-12-30 13:31:02I was born and raised in Europe—Switzerland, to be exact—and we’ve always had a special relationship with Europe or the EU. Although Switzerland is in the middle of Europe, it has always been isolated—not politically speaking, but through clever negotiations and an attractive financial marketplace.
But it’s still part of Europe, and whenever we drove to Germany, Austria (where I now live), or Italy, we always felt at home. Everyone was welcoming and accepted that Switzerland is the ‘special kid’ on the continent.
This is one of Europe’s superpowers. It lives off its different cultures. Other than America, I’m sorry to compare it, but it feels like many Americans have never left their own country; we can drive somewhere for three hours and pass two or even three countries.
Citizens speak different languages in each country, but we get along because there is a certain ‘European Vibe’ around. These different cultures and societies enable you to find communities where you feel at home and can be the best version of yourself—at least, that’s what I believe and have experienced.
However, the last 15 years have been challenging. Not only from a business standpoint, we tend to regulate and not innovate, but also from a political standpoint.
The EU and specific countries such as Sweden, Germany, and even Austria are fighting with high immigration, the Euro crisis – casually losing over 65% of its purchasing power this past decade – and ever-increasing debt.
Combine that with a keen interest by the majority of the population in Europe for Communism or Socialism. Please don’t ask me why it’s so popular in Europe. I think it could be an outcome of the world war situations where we never wanted to shift extremely right again. Or maybe the openness of the European spirit invites this thoughtfulness.
These ideologies don’t want the individual to succeed. For the better of all, it has always been at the center of these political movements. Inevitably, this idea leads to more poverty, more centralization, and, in the end, less democracy (the favorite word of any left-leaning politician in Europe) with a dictator at the whelm.
For some weird reason, we don’t want individual Europeans to succeed; instead, we have a collectivism that punishes brilliant ideas and nurtures the ever-increasing state.
So, why are you writing this essay then, Joël? Are you a right winger who’s just here to tell us Communism failed and we should do something else? NO! While my political views can definitely be described as conservative, I’m not associated with the right side of the aisle and would describe myself as a libertarian. However, for the European standard, I might be categorized as ‘right-wing,’ but who isn’t these days?!
But to answer the question, I think we have a secret weapon. Many of these freaks are either ignoring or deliberately downplaying because they’re scared of losing power and trying everything to forbid it.
You might have guessed by the title this secret weapon is Bitcoin!
There are apparent reasons why Bitcoin is the ultimate solution for Europe. These reasons are well known, from its scarcity to its natural state as the best reserve asset and its average value increase of 45% each year for the past decade. From a monetary perspective, these points make perfect sense.
However, there is more to the orange coin, especially from a polarization perspective. In Europe, the left and right are so far apart that it’s laughable. Bitcoin is the only asset or ecosystem enabling people from two corners to reunite and agree on something.
In Europe, in particular, this is something like human rights and privacy for every individual on the continent. It doesn’t matter whether you’re in Switzerland, Germany, or Portugal. Every citizen of these countries is rooting for human rights and the right to protect your most precious secrecies from third parties, aka the ever-increasing security state.
If you take a closer look at most political debates in Europe, both the left and the right agree that citizens should be able to protect their physical or digital properties and how to be more independent. Bitcoin enables you to do all of these things.
Additionally, mining can be an excellent catalyst for all parties to unite if you examine topics such as energy independence. Lefties can choose renewable energy, while right-wingers can embrace a free and healthy energy market. Bitcoin also enables this.
However, the most significant and crucial point is that Bitcoin will enable all nations to be independent again. Many countries lost their sovereignty mainly due to the EU and the Euro.
We no longer talk about each country’s interests; instead, we insert the sentence, ‘Anything that’s good for the EU.’ While the EEA (European Economic Area) was a noble idea that facilitated trade and economic output in Europe, it was abused and became a regulatory superpower with the EU.
You can see the consequences of this from the sheer number of companies who left Europe or international companies who treat Europe as a secondary market with little interest.
If Nations can regain sovereignty again and nurture their economic or sociological advantages, every citizen in these countries will have a new outlook on life.
All it takes for each of them to make the most important step in their Bitcoin journey; being curious enough to learn more about it, spending some time learning the fundamentals, and getting off zero!
One European nation with great potential for this is my home country, Switzerland. We’re the golden European standard for democracy, sovereignty, a strong economy, and a country where everyone can succeed.
After all, fellow Bitcoiners have already taken the initiative to add Bitcoin to the Swiss National Bank (SNB) ’s balance sheet and have already invested in MicroStrategy.
All it takes is the last step, which is to stack Sats as a strategic treasury reserve asset. As a fellow Swiss citizen and someone who works at a Swiss Bitcoin-only company, I would welcome this step and would love to help out!
To quote Walt Disney: ‘The way to get started is to quit talking and begin doing.’ So go ahead, Europe, and get started! Block space is limited, and 2140 is edging closer every ten minutes with a new block!
-
 @ ef1d1f12:a6811a37
2024-12-30 12:20:00
@ ef1d1f12:a6811a37
2024-12-30 12:20:00Is it a real news?
In a bold and defiant move, 77-year-old Thai protest leader, Srisompob Juntaratip, has shaved her head in a symbolic act of resistance against the country's military government. The protest leader, known for her outspoken criticism of the regime, was seen shaving her head in front of the Parliament building, surrounded by supporters and journalists.
The move comes as tensions between protesters and the government continue to escalate, with both sides engaging in increasingly violent clashes. Srisompob Juntaratip has been a key figure in the protests, using her platform to denounce the military's handling of the country's economy and political system.
Background:
Srisompob Juntaratip is a veteran activist who has been involved in Thai politics for decades. She has been arrested multiple times by the military government, but continues to speak out against its policies. The shaving of her head is seen as a powerful symbol of her commitment to the cause and willingness to risk arrest.
Reactions:
The move has sparked widespread reactions across Thailand, with some praising Srisompob Juntaratip's bravery and others condemning her actions as provocative. Social media is filled with images and videos of the protest leader shaving her head, with many using the hashtag #SrisompobJuntaratip.
Next Steps:
The military government has vowed to take action against Srisompob Juntaratip, with some calling for her arrest. However, the protest leader remains defiant, stating that she will continue to speak out against the regime and fight for democracy in Thailand. The situation is likely to escalate further in the coming days, as both sides dig in their heels.
Stay Tuned:
This story is developing and will be updated as more information becomes available. Follow our coverage for the latest updates on this breaking news story.
-
 @ 5accc5a7:b0fe15c1
2024-12-30 12:17:16
@ 5accc5a7:b0fe15c1
2024-12-30 12:17:16Breaking News: In a bold and defiant move, 77-year-old Thai protest leader, Srisompob Juntaratip, has shaved her head in a symbolic act of resistance against the country's military government. The protest leader, known for her outspoken criticism of the regime, was seen shaving her head in front of the Parliament building, surrounded by supporters and journalists.
The move comes as tensions between protesters and the government continue to escalate, with both sides engaging in increasingly violent clashes. Srisompob Juntaratip has been a key figure in the protests, using her platform to denounce the military's handling of the country's economy and political system.
Background:
Srisompob Juntaratip is a veteran activist who has been involved in Thai politics for decades. She has been arrested multiple times by the military government, but continues to speak out against its policies. The shaving of her head is seen as a powerful symbol of her commitment to the cause and willingness to risk arrest.
Reactions:
The move has sparked widespread reactions across Thailand, with some praising Srisompob Juntaratip's bravery and others condemning her actions as provocative. Social media is filled with images and videos of the protest leader shaving her head, with many using the hashtag #SrisompobJuntaratip.
Next Steps:
The military government has vowed to take action against Srisompob Juntaratip, with some calling for her arrest. However, the protest leader remains defiant, stating that she will continue to speak out against the regime and fight for democracy in Thailand. The situation is likely to escalate further in the coming days, as both sides dig in their heels.
Stay Tuned:
This story is developing and will be updated as more information becomes available. Follow our coverage for the latest updates on this breaking news story.
-
 @ 16d11430:61640947
2024-12-30 11:41:51
@ 16d11430:61640947
2024-12-30 11:41:51The heart chakra, or Anahata, is revered in spiritual traditions as the center of love, compassion, and harmony. Positioned at the midpoint of the seven energy centers in the body, it symbolizes a bridge between the physical and spiritual realms. In esoteric traditions, this chakra is pivotal in processes such as chrism rising, where spiritual energy ascends to higher states of consciousness. While these concepts are often explored metaphysically, modern medical science has begun to uncover fascinating parallels between the symbolic attributes of the heart chakra and the physiological complexity of the heart, particularly its nervous autonomy and its integration with the brain.
The Heart Chakra and Chrism Rising
In the context of chrism rising, the heart chakra represents a transformative stage. As sacred energy moves upward, it transitions from concerns of survival, sexuality, and personal willpower (root, sacral, and solar plexus chakras) to the higher realms of universal love and spiritual connection. This stage signifies the transcendence of ego and the integration of emotions with higher consciousness.
The journey through the heart chakra is marked by the awakening of compassion, forgiveness, and emotional balance. In spiritual terms, it represents the alchemical merging of the material (lower chakras) and spiritual (upper chakras) planes, enabling the individual to experience profound interconnectedness and divine love.
The Science of the Heart: Autonomy and Neurocardiology
Modern science offers compelling insights into the physiological and neurological sophistication of the heart. The field of neurocardiology has revealed that the heart is far more than a mechanical pump—it is a dynamic organ with its own nervous system, often referred to as the "heart brain."
The Autonomy of the Heart
- Intrinsic Nervous System:
The heart contains approximately 40,000 neurons, forming a complex neural network capable of independent operation. This "heart brain" can learn, remember, and even make decisions independent of the brain.
It plays a crucial role in regulating heart rhythms and coordinating with the autonomic nervous system.
- Heart-Brain Communication:
The heart sends more signals to the brain than the brain sends to the heart. These signals influence emotional processing, decision-making, and even higher cognitive functions.
This bidirectional communication underscores the heart's influence on mental and emotional states, echoing the heart chakra's role as an emotional center.
- Electromagnetic Field:
The heart generates the most powerful electromagnetic field in the body, measurable up to several feet away. This field is thought to synchronize the body's systems and may even influence the energy fields of others, aligning with the heart chakra's association with universal love and connection.
Mastery of the Heart and Performance Unlocking
From a performance perspective, mastery of the heart-brain connection unlocks extraordinary potential. This mastery aligns with the symbolic unlocking of the heart chakra in spiritual traditions, enabling an individual to operate with clarity, emotional resilience, and enhanced intuition.
- Heart Rate Variability (HRV):
HRV, a measure of the variation in time between heartbeats, is a key indicator of autonomic nervous system balance. High HRV is associated with emotional resilience, adaptability, and peak performance.
Techniques like heart-focused meditation and coherence training improve HRV, fostering a state of flow and heightened performance.
- Emotional Regulation:
The heart's intrinsic nervous system plays a critical role in regulating emotions. When the heart is coherent, emotional turbulence is minimized, allowing for calm, focused decision-making.
This mirrors the heart chakra's symbolic function of balancing emotions and fostering inner harmony.
- Intuition and Decision-Making:
Research suggests that the heart processes and responds to stimuli milliseconds before the brain, contributing to intuitive decision-making.
This intuitive capacity aligns with the spiritual concept of the heart chakra as a portal to higher wisdom.
Recent Breakthroughs in Heart-Brain Science
Modern research continues to shed light on the profound interplay between the heart and the brain, offering new dimensions to our understanding of the heart's role in physical and emotional health:
- The Polyvagal Theory:
Developed by Dr. Stephen Porges, this theory emphasizes the role of the vagus nerve in regulating the heart and promoting states of safety and connection.
Practices that stimulate the vagus nerve, such as deep breathing and meditation, not only enhance heart-brain coherence but also resonate with spiritual practices aimed at opening the heart chakra.
- Heart Intelligence:
Studies by the HeartMath Institute demonstrate that cultivating positive emotions, such as gratitude and compassion, improves heart-brain coherence. These findings parallel the spiritual emphasis on love and forgiveness as transformative energies of the heart chakra.
- Regenerative Medicine:
Advances in understanding the heart's regenerative potential, including its ability to produce new cells, highlight its resilience and adaptability. This mirrors the heart chakra's symbolic association with healing and renewal.
The Heart Chakra as a Key to Higher Potential
The convergence of spiritual wisdom and scientific insight paints the heart as both a physiological marvel and a metaphysical gateway. In the context of chrism rising, the activation of the heart chakra represents a transformative leap toward love, unity, and higher consciousness. From a scientific perspective, mastering the heart's neural and energetic capabilities unlocks profound emotional balance and peak performance.
Whether through the lens of spiritual tradition or modern science, the heart remains central to human experience—a pulsating vortex of connection, compassion, and boundless potential. By understanding and harmonizing its physical and energetic dimensions, we unlock not only the mastery of ourselves but also our ability to resonate harmoniously with the world around us.
-
 @ bcbb3e40:a494e501
2024-12-30 11:29:30
@ bcbb3e40:a494e501
2024-12-30 11:29:30
No podemos ignorar la importancia que el Reino Visigodo tiene en la configuración de España, de la impronta definitiva que aportó al proceso de etnogénesis para dar la forma definitiva a esa entidad histórica que hoy, tras tres siglos de invasiones germánicas, desde la caída del Imperio Romano a finales del siglo V d.C., hasta el advenimiento del Islam. A modo de contraste, diremos también, que la identidad nacional española, o si se quiere ver así, el alma hispánica, se forjó en claro y evidente contraste con el ocupante sarraceno, y su presencia en el orbe peninsular, junto al recuerdo de la herencia visigoda y los sucesivos concilios toledanos, sirvieron de estímulo al avance de los reinos cristianos del norte. Es decir, España se construyó en la lucha, en el combate abierto contra un enemigo al que consideraba ocupante y representaba una realidad cultural, étnica y civilizacional totalmente antagónica a la naciente realidad hispánica.
De ahí la importancia del sustrato germánico, godo, que viene a agregarse al ya preexistente de hispano-romanos, celtas e íberos. En las últimas décadas esta importancia se ha visto relegada, de forma deliberada, a un segundo plano, y si nuestros padres y abuelos conocían la famosa lista de reyes godos, en la actualidad, su conocimiento entre gran parte de la población española, y especialmente entre los más jóvenes, es puramente testimonial, cuando no inexistente.
|
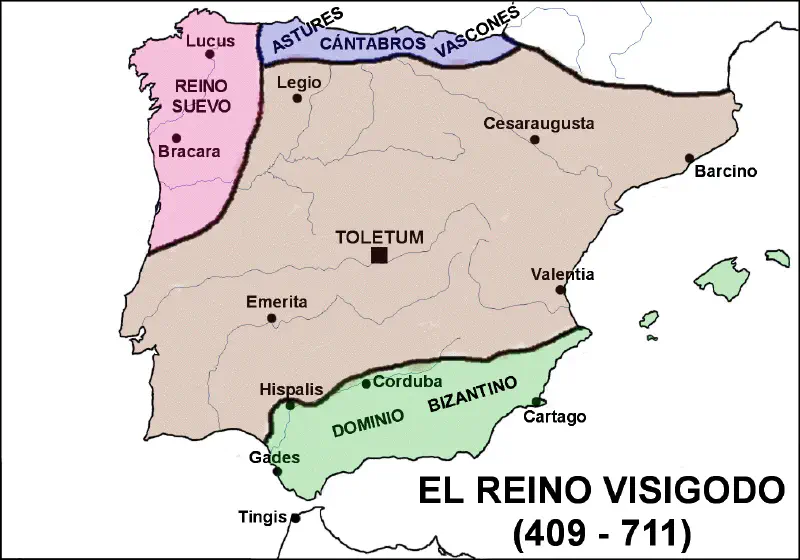 |
|:-|
|El mapa muestra la distribución territorial de la península ibérica durante el período del Reino Visigodo (409-711 d.C.). Se destacan los dominios visigodos, con Toledo como capital, y las principales ciudades como Emerita, Hispalis, y Cesaraugusta. También se señala la presencia del dominio bizantino en el sureste (Cartago y Córdoba) y la región ocupada por los suevos en el noroeste (Bracara y Lucus). Las áreas de los astures, cántabros y vascones aparecen al norte como zonas independientes.|
|
|:-|
|El mapa muestra la distribución territorial de la península ibérica durante el período del Reino Visigodo (409-711 d.C.). Se destacan los dominios visigodos, con Toledo como capital, y las principales ciudades como Emerita, Hispalis, y Cesaraugusta. También se señala la presencia del dominio bizantino en el sureste (Cartago y Córdoba) y la región ocupada por los suevos en el noroeste (Bracara y Lucus). Las áreas de los astures, cántabros y vascones aparecen al norte como zonas independientes.|No obstante, no queremos hacer aquí una relación de reyes, ni hablar de las estructuras políticas, económicas o religiosas del reino visigodo, sino que pretendemos centrarnos en una sola figura, la del rey Sisebuto, cuya fama y los elogios que se dedican a su persona nos han sido legados por las fuentes de la época. San Isidoro de Sevilla, una de las grandes personalidades de la época —autor de las famosas Etimologías, un compendio del saber antiguo en lo que se consideró como la primera enciclopedia cristiana— y uno de los grandes maestros del Occidente medieval, nos aporta valiosas informaciones sobre Sisebuto:
«fue brillante en su palabra, docto en sus pensamientos y bastante instruido en conocimientos literarios [...]. Fue notable por sus conocimientos bélicos y célebre por sus victorias».
O también en Historia Gothorum:
«se mostró tan clemente después de su victoria, que pagó un precio para dejar en libertad a muchos que habían sido hechos prisioneros por su ejército y reducidos a esclavitud como botín de guerra».
De hecho existió un vínculo de amistad entre Isidoro de Sevilla y Sisebuto, y el primero dedicó al segundo una primera edición de sus Etimologías, y escribió a instancias del monarca visigodo otras obras como De natura rerum. La fama del rey visigodo traspasó fronteras y encontramos referencias a sus virtudes y cualidades personales a través de la Crónica del Pseudo Fredegario, donde se aplican otros calificativos como «varón sabio, piadosisimo y digno de toda alabanza». De modo que las fuentes ya nos permiten trazar un primer retrato general sobre la figura del protagonista de nuestro escrito, y que podríamos resumir así: monarca sabio, guerrero y sensible. Cualidades estas que pueden parecer difícilmente compatibles, pero que nuestro Sisebuto aunaba conformando una poderosa personalidad.
Rey guerrero
Pero antes que nada deberíamos preguntarnos por los orígenes del rey Sisebuto, quien ocupó el trono del reino visigodo durante 9 años, entre el 612 y el 621. Se destacó por su capacidad para defender tanto en las fronteras interiores como exteriores la autoridad de la monarquía visigoda. Prueba de ello fueron las campañas que acometió contra los astures en el Norte, terminando con las veleidades independentistas de estos pueblos belicosos, aunque hay cierto oscurantismo en cuanto a las fuentes. Y paralelamente, en el Sur, las operaciones militares de Sisebuto estuvieron dirigidas contra la provincia bizantina ubicada en el sureste peninsular desde mediados del siglo anterior. Las sucesivas campañas militares consiguieron mermar los dominios bizantinos en la península, especialmente con la conquista de Málaga en 619. Además conviene destacar el notable desarrollo del ejército naval visigodo, alcanzando elevadas cotas de esplendor nunca registradas con monarcas precedentes. No hay datos totalmente contrastados, pero es posible que, con Sisebuto, surgiera una marina organizada.
Las guerras que se libraron entre visigodos y bizantinos fueron cruentas y sanguinarias, generando gran dolor y consternación entre nuestro monarca, algo que, como indican los propios historiadores y cronistas de la época, era bastante infrecuente. En la citada Crónica de Fredegario se le atribuyen ciertas afirmaciones a tal respecto, en las que lamenta las pérdidas humanas y se expresa con un notable humanitarismo:
«Si se producen guerras —escribía Sisebuto a Cesario—, si la cruenta espada se ensaña por doquier, si los vicios de los hombres hacen que los tiempos presentes sean tiempos belicosos, ¿qué cuentas, pensadlo, habrá que rendir a Dios por tantos crímenes, por tantas calamidades, por tantas funestas heridas?»
«Se mostró tan clemente después de su victoria —dice San Isidoro en Historia de los Godos— que pagó un precio con el fin de dejar en libertad a muchos que habían sido hechos prisioneros por su ejército y reducidos a esclavitud, llegando incluso su tesoro a servir para el rescate de los cautivos.»
Lo fundamental para Sisebuto era la unificación del territorio peninsular bajo el poder godo, pero no solo empleó medios militares, sino que también hizo uso de la diplomacia. Respecto a este tema, se conservan dos cartas de la correspondencia entre Sisebuto y el gobernador provincial e imperial en España, Cesario, en torno a la disputas entre visigodos y bizantinos relacionadas con los prisioneros de guerra. Con ocasión de la captura del obispo Cecilio de Mentesa por parte de los bizantinos, Cesario se apresuró a ponerlo en libertad y escribió al rey Sisebuto para comunicárselo con las siguientes palabras:
«Nuestro beatísimo padre, Cecilio, fue capturado por nuestros hombres, mas en consideración a Dios y vuestro reino y como prueba de buena voluntad, lo liberamos rápidamente y pusimos la mayor diligencia para que fuera devuelto a su santa iglesia y enviado a vuestra presencia».
Sisebuto respondió a Cesario de manera cordial y afectuosa, lo que supuso la toma de contacto a través de una delegación diplomática entre ambas partes, godos y bizantinos, que condujo a un acuerdo. Los bizantinos no serían expulsados definitivamente del territorio peninsular hasta el reinado de Suintila (588-633).
Rey sabio
El monarca visigodo también fue un notable erudito e intelectual, muy destacado en una época de gran esplendor cultural capitaneada por San Isidoro de Sevilla, de quien ya hemos dicho que mantuvo una estrecha relación con Sisebuto. Las famosas Etimologías isidorianas estuvieron consagradas en su primera edición a la figura del rey a través de las siguientes palabras, que le honraban a través de la siguiente dedicatoria:
«Como te he prometido —escribía al rey el obispo hispalense— te envío ahora la obra acerca “Del origen” de ciertas cosas, recopilada con el recuerdo de antiguas lecturas. Por eso, en algunos pasajes aparece anotada de acuerdo con lo que habían escrito nuestros antepasados».
Se puede decir que Sisebuto fue al mismo tiempo un promotor de la actividad literaria, intelectual y científica, y un hombre sabio de su época, con la producción de obras en el ámbito de la ciencia y la literatura, al margen de los asuntos propiamente religiosos, algo que podría resultar chocante en relación a otros reyes bárbaros de aquel entonces. Fruto de esta doble vertiente tenemos el Liber de natura rerum, obra de San Isidoro, dedicada al conocimiento del universo y los fenómenos naturales. Por su parte su contribución a la producción científica de la época fue el Liber rotarum o Carmen de luna, un poema en el que trataba de explicar el fenómeno de los eclipses al margen de motivaciones religiosas, en el terreno puramente físico.
Sus incursiones no se limitaron al mundo puramente científico de los fenómenos físicos, sino que sus intereses también se orientaron hacia la vida y hechos de otros hombres de su tiempo. Tal es así, que vemos como su principal obra, Vida y pasión de San Desiderio, un obispo de Borgoña que padeció de persecuciones y murió años atrás. Esta obra guarda ciertas particularidades por sus motivaciones políticas, orientadas a congraciarse con Clotario II, rey de la Francia merovingia.
Rey religioso (y gibelino)
Sisebuto fue un monarca profundamente religioso y en consonancia con la ortodoxia, lo que hizo que en muchas ocasiones tuviera que intervenir para su fortalecimiento y mantenimiento. De hecho, su propio hijo, Teudila, ingresó en una orden monástica impelido por su progenitor, que alentó su celo religioso. Incluso envió una carta al rey longobardo Adaloaldo, convertido al catolicismo, exhortándolo a que hiciera lo propio con la totalidad del reino, y terminar así con los últimos restos de herejía arriana, que había tenido un relativo éxito entre los pueblos germánicos en su momento. Además trató de ofrecer argumentos lógicos y fundamentados en la exégesis católica, amparándose rigurosamente en las Sagradas Escrituras. Al mismo tiempo, augura prosperidad y buenos designios en un futuro hipotético ante la conversión al catolicismo, favoreciendo la acción benéfica de la providencia divina sobre su pueblo. Todavía debería pasar medio siglo para la conversión de los longobardos, mucho después de la muerte de Sisebuto, acontecida en el 621.
Sisebuto también se preocupó por fortalecer y vigorizar la propia estructura eclesiástica, algo que fue una constante en la España visigoda y se materializó a través de sucesivos Concilios en Toledo. Sisebuto, como nos relata el historiador José Orlandis, lejos de utilizar la Iglesia como un parapeto, como una suerte de protección para reforzar su posición, se mostró más bien con cierta mentalidad «cesaropapista». Actitud a través de la cual Sisebuto tomaba la iniciativa, tanto en el ámbito político y temporal como en aquel religioso-espiritual y atemporal. En cierto sentido podríamos calificar a Sisebuto como un «rey gibelino» por esa simbiosis entre ambas esferas, asumiendo él mismo, personalmente, la función de velar por el buen orden eclesiástico. Un buen ejemplo de ello lo tenemos en las imposiciones a Eusebio, el obispo de Tarragona, influyendo directamente sobre decisiones internas de la institución.
|
 |
|:-:|
|MORDINI, Attilio; El católico gibelino; Hipérbola Janus, 2016|
|
|:-:|
|MORDINI, Attilio; El católico gibelino; Hipérbola Janus, 2016|El problema religioso: los judíos
Ya en el primer código legal de visigótico, la Lex Romana Visigothorum promulgado en el año 506, en el que se establecía la condición jurídica de los hispanorromanos, se excluía a los judíos de los cargos públicos, proscribía los matrimonios mixtos entre cristianos y judíos y limitaba sus actividades religiosas. Al margen de las comunidades religiosas cristianas, los judíos seguían sus propias leyes y preceptos religiosos, mantieniendo una barrera respecto a los pobladores autóctonos. Con la conversión de la fe arriana a la católica de Recaredo I, y en consecuencia del propio reino, los monarcas visigodos comenzaron una serie de políticas encaminadas a conseguir la unidad religiosa y política del reino. Su decisión, que fue oficializada en el III Concilio de Toledo, contó con un apoyo mayoritario del clero y la nobleza visigoda. A partir de ese momento comenzó un proceso de integración entre godos e hispanorromanos en virtud del principio religioso.
|
 |
|:-|
|Una moneda de oro visigoda acuñada durante el reinado de Sisebuto (612-621 d.C.). En el anverso, aparece el retrato estilizado del rey, rodeado por una inscripción en caracteres latinos. Estas monedas reflejan la influencia romano-bizantina en el arte y economía del Reino Visigodo. (Foto: Wikimedia Commons)|
|
|:-|
|Una moneda de oro visigoda acuñada durante el reinado de Sisebuto (612-621 d.C.). En el anverso, aparece el retrato estilizado del rey, rodeado por una inscripción en caracteres latinos. Estas monedas reflejan la influencia romano-bizantina en el arte y economía del Reino Visigodo. (Foto: Wikimedia Commons)|Esta situación dejó a otros grupos religiosos ante un dilema, que era o la conversión o la expulsión. Sisebuto fue quien más celo puso a tal respecto para lograr la deseada unidad religiosa. A partir de una serie de decretos promulgados al cabo de pocos meses del inicio de su reinado, en el 612, se ordenó la liberación de todos los cristianos en su relación de dependencia respecto a los judíos. Estas medidas incluían la liberación de los esclavos y servidores cristianos en relación a los judíos, la transferencia de éstos a señores cristianos o la obligación de manumitir y quedando así libres. Estas disposiciones eran de obligado cumplimiento bajo la pena de muerte o confiscación de bienes.
Al mismo tiempo, Sisebuto también se propuso impedir el proselitismo religioso judío y estimular su conversión al cristianismo. De hecho, los matrimonios mixtos preexistentes debían adoptar una educación en la fe cristiana para los hijos, en caso de no aceptarlo, el matrimonio se consideraba nulo. Los conversos y judíos también quedaban excluidos de los cargos públicos. También se debía producir una renuncia y abjuración pública de la ley y prácticas judaicas. La mencionada ley tuvo unas consecuencias inmediatas sobre la comunidad judía en el ámbito económico, donde además la existencia de esclavos y colonos en arriendo eran numerosos, además de las prácticas usurarias.
Sisebuto ha quedado para la historia como el gran perseguidor de los judíos, aunque en realidad su propósito era misionero y evangélico, por el celo religioso que ya hemos expuesto, y tampoco fue obra del propio Sisebuto, sino que encontramos los primeros ecos de esta legislación en la última etapa del Imperio Romano. Si hasta el momento la legislación se había aplicado de manera un tanto superficial, con Sisebuto adquiere mayor «radicalidad», aunque tampoco afectasen exclusivamente a la población judía, la cual era numerosa en aquella época. Los propios godos no pudieron casarse con los romanos hasta las reformas legales aplicadas bajo el reinado de Leovigildo.
Respecto a la cuestión de la prohibición de que los judíos poseyeran esclavos cristianos, algo que era muy frecuente, también infringían la ley al circuncidarse, dado que formaba parte del ritual formal de judaización o conversión a la fe judía. El decreto de Sisebuto ofrecía a estos esclavos la opción de obtener la libertad bajo el amparo de la corona, si no eran vendidos a otros amos cristianos. El impacto económico al que aludíamos también afectó notablemente las actividades agropecuarias de la comunidad judía, que perdieron su estatus privilegiado entre los sectores más acomodados de la sociedad. Del mismo modo que la prohibición de desempeñar cargos públicos mermó su preponderancia social.
No obstante, Sisebuto consideraba el asunto en una dimensión puramente religiosa, y el fin último era la integración bajo la unidad del credo católico. La unificación religiosa se convirtió en una prioridad, y su celo religioso no se fundaba en un criterio de fanatismo irracional, sino todo lo contrario. Al monarca godo le importaban, y mucho, las conversiones sinceras, sujetas a un principio reflexivo y racional. De hecho, en ese tiempo había otros segmentos de la población que se movían en el terreno de las creencias paganas, como los propios arrianos, a los que también interesaba encuadrar bajo el mismo principio religioso. En cuanto a los judíos, y la incidencia que se hizo sobre este grupo, se debió a que eran comunidades que representaban un enorme poder en el conjunto del reino, con una notable influencia, especialmente en el sur y el Levante español, regiones que se encontraban en la frontera con los territorios bizantinos peninsulares.
No obstante, y a pesar de que existe una continuidad en la aplicación de estas políticas para contener la influencia de la religión judía en los límites del reino, y vemos como éstas se mantienen hasta el hundimiento final con la conquista árabe del 711, lo cierto es que la práctica de la religión judía se mantuvo a ciertos niveles, como prueba la existencia de tumbas e inscripciones judías registradas a lo largo de esta época. Paradójicamente, en el plano económico y social fueron mucho más efectivas que en el terreno religioso, y de hecho, de haberse aplicado con la radicalidad que se les presume, estas leyes hubieran acabado con la existencia de la población judía en el reino, o bien mediante la conversión o bien mediante la expulsión, pero nada de eso sucedió finalmente.
El reinado de Sisebuto terminó en el 621, tras nueve años de intenso reinado. Se sospecha que murió envenenado por la ingesta excesiva de un medicamento, según el testimonio de otro rey, Suintila. No obstante hay muchos puntos oscuros bajo esta explicación, y la falta de fuentes fiables no nos permite desentrañar los hechos que rodearon su muerte. Le sucedería su hijo Recaredo II, quien también moriría en extrañas circunstancias, nunca desentrañadas, a los pocos meses de su coronación.
Lo fundamental, si tenemos que hacer una idea general de la figura del rey godo, es que representó una etapa peculiar en el desarrollo histórico del Reino toledano, en la medida que mostró una personalidad ilustrada, con notables conocimientos respecto al saber de la época, cultivó la poesía y la literatura, y no por ello descuidó los asuntos de gobierno. Los fundamentos religiosos, tan importantes en lo sucesivo, y a través de los Concilios de Toledo, en la configuración político-religiosa y en la unidad embrionaria de la futura España, fueron una de sus grandes prioridades, y para alcanzar la consolidación del reino no dudo en hacer la guerra, de manera implacable, para ser magnánimo y generoso cuando la situación lo requería. Desde Hipérbola Janus, y quien os escribe, no nos queda sino valorar la figura de este olvidado, y en ocasiones injustamente denostado, rey visigodo.
Artículo original: Hipérbola Janus, Sisebuto, el rey sabio, guerrero y humanitario (TOR), 30/Dic/2024
-
 @ a1c19849:daacbb52
2024-12-30 11:17:00
@ a1c19849:daacbb52
2024-12-30 11:17:00Introduction
nostr:npub1nj5v9hfxegyuqz4z9vfpgu9lxpgald066wspxadywmhslasuw2gsnyrxzg shared a great thread on X about what the Dutch Noderunners did to push Bitcoin adoption. Since it took him quite some time and he didn’t want to redo it on #nostr I’m happy to share his thread here as well, since it has a lot of cool stuff in it. Here we go:
Noderunners 2024 Recap
by nostr:npub1nj5v9hfxegyuqz4z9vfpgu9lxpgald066wspxadywmhslasuw2gsnyrxzg

Here it is, the 2024 Noderunners recap! As we are preparing for our annual party on the third day of Christmas I’d like to reflect to all the great stuff we’ve build together to push bitcoin adoption from bottom up. I’m proud we’ve made it this far and we’re just starting! 🔥 We like to come together as often as possible to chat about bitcoin and drink a beer so we started even more meetups. We now do meetups in Roermond, Leiden, Eindhoven, Utrecht, Breda, Friesland, Zaandam. And an occasional party in Arnhem or Den Bosch. Feel free to join us anytime.




On our meetups and in the wild we meet the most awesome bitcoiners. To show them our respect we honor them by knighting them as an Honorary Noderunner. This year nostr:npub1nw5vdz8sj89y3h3tp7dunx8rhsm2qzfpf8ujq9m8mfvjsjth0uwqs9n2gn nostr:npub13ql75nq8rldygpkjke47y893akh5tglqtqzs6cspancaxktthsusvfqcg7 nostr:npub1cn4t4cd78nm900qc2hhqte5aa8c9njm6qkfzw95tszufwcwtcnsq7g3vle and nostr:npub1uaj9phu5lpxpczm3vaayt46m0yv0pduxzy7z6quwd2uggxue7fmqx9665u joined our ranks! 🧡



As you can imagine, we were pleasantly surprised when we saw an honorary Noderunner wearing his pin in the courtroom in the case against fAkEtOsHi! Nice to meet again in Amsterdam nostr:npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw !



The Bitcoin conference in Amsterdam was full of Noderunners. On and off stage. On stage we had nostr:npub1jqs0u7zhh53e94gyhm4eu458wm6sw7z0kk66jjhhkhh346tcq2ysfgr247 nostr:npub1h0fd5xu8rfhwdkkjr78ssdhm7rdjyf97hhjqr9acwv77ux0uvf8q23kvcg nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl Tom Lamoen and others.




In the panel there was nostr:npub1art8cs66ffvnqns5zs5qa9fwlctmusj5lj38j94lv0ulw0j54wjqhpm0w5 who asked a cheeky question… 🤓 He wrote the awesome “The Genesis Book” in which he describes the people and technology that led to the birth of bitcoin. Hope to see you 3kd Aaron!
Proof of work is the thing Noderunners value the most. We do the work on and offline. In Amsterdam we had several projects to display! Of course the BitcoinTaps, the bitcoin bitaxe B at the entrance, The nostr:npub1kd3nlw09ufkgmts2kaf0x8m4mq57exn6l8rz50v5ngyr2h3j5cfswdsdth arcade and the video of @npub1f59dz0ru0l8zpsl4cryj5ch2rahwxeex3mr7lpl2ltzxsfwsdwastu6nqk!

Personally I was very exited nostr:npub1qg5a5l3t7pakmm4r4up2e764xecsw62fk3rntevm24fwyczhndtsdrvc4x Edward and Stef of Connect The World Podcast allowed us to bring the Arcade to the afterparty at Braai where we played some tournaments with nostr:npub1jt97tpsul3fp8hvf7zn0vzzysmu9umcrel4hpgflg4vnsytyxwuqt8la9y nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg and many others!



Hopefully we can create a Noderunners lounge or such next year at @npub13e6qu4kdjsyysrfl5an558rawvqg0rx2xuat9ca706spcdqjzhuqq6md43! Connections were made!



This year there was also the first edition of nostr:npub1uv2tr83c5y7k82af6zdzlqs8m0klcmndd8u5vmlg2eyrskld6uzsv4rmr8 organized by nostr:npub14mge80nm5r0zj0gncxvpunlr28jyku95547q0m82ec475x3yy92skvjgm5 and Bitcoin Stad. It was an awesome event with great speakers but the best thing was the Noderunners Lounge in the basement where Hester Bais tapped a beer.. 🍺



There was some trouble in paradise when the GitHub page of nostr:npub1k5f85zx0xdskyayqpfpc0zq6n7vwqjuuxugkayk72fgynp34cs3qfcvqg2 got canceled due to false copyright claims.. He makes the most beautiful, full open source BTClock! He’s a good frend and very productive Noderunner! 🧡



nostr:npub1k5f85zx0xdskyayqpfpc0zq6n7vwqjuuxugkayk72fgynp34cs3qfcvqg2 also did a lot behind the scenes for the Noderunners SOLO Mining Pool! http://pool.noderunners.network


As we are also very enthusiastic about NOSTR nostr:npub1p6xyr6u5vet33r4x724vxmp9uwfllax5zjdgxeujyrtxt90lp74qvah0rm has set up our own nostr relay: wss://relay.noderunners.network

Noderunner nostr:npub1yn84ur49llj7pp9a7uv477f7vrpj0rj7df5pnfncvkusaxgy6jqsj9xgfl set up a mixer where he organizes a weekly coinjoin every sunday for more anonymous bitcoin transactions. https://coinjoin.nl

Our Belgian Noderunner Kim de Vos made the infamous “Big Mac index” where he expresses the price of bitcoin in Big Macs.. He also runs the AVBpodcast (my personal favorite).

We have several members who have their own podcasts. Also a lot of Noderunners appeared in podcasts as a guest. nostr:npub1agyf7kae8nkxqrd7rvvxt6nh9vwpcqzen2mc9dl3u38a04awpjcq09n23f educates bitcoin beginners.
 Tom Lamoen talks about libertarianism.
Tom Lamoen talks about libertarianism.nostr:npub1gfxgylgst4lcemkjth6xdvcvq7le8rtlrym7wayml63qrjggngaqkqescl interviews bitcoiners from all over the world.

And nostr:npub1kj2ngxmm0zccswfqplff87rpgvmq9utvk0g726wc0h8pv4kwm8ss6zgm4n laughs at 🤡🌍

After months, even years of hard work nostr:npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx launched the best bitcoin board game ever!


nostr:npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx is also involved with the Dutch bitcoin magazine BitcoinFocus which features a lot of Noderunner builds and articles.


Of course I should mention our frens at nostr:npub1ua6fxn9ktc4jncanf79jzvklgjftcdrt5etverwzzg0lgpmg3hsq2gh6v6 where you can pay a few sats to play your favorite songs! http://radio.noderunners.org

LightningPlaces is working hard making entrepreneurs accepting bitcoin and putting them on their website! 🔥💪🏼



nostr:npub1lhufm09wzp42y67t3s8axlewwna8rmetak68w38yal7xjrwktpsscpt08x is also hooking up webshops and physical shops (and bars) to accept bitcoin! Connect them if you’re looking for a custom solution! https://lightningcheckout.eu/nl/


Maybe we should create an open source HW Wallet too but for now we have the man, the myth, the legend nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl in our midst.. A real honor as we all share the same values and ethics in life but especially in bitcoin! We’ve been building seedsigners from scratch by the dozen!


Most of us are very entrepreneurial. Several bitcoin shops are run by Noderunners.
nostr:npub1qvwdl9rp7a5ghrxv57wnml5ehg2whjh708vys6kaxpkgu0z3aclsuy2h4p - https://bitcoinbrabant.com
nostr:npub1k00lff0ahjv4d2kwuwxy040d2282yjmzj6eeu5ghav054s4yrfzsplyc86 - https://bitsaga.be
nostr:npub1837pplcuwcjn35zwmpuy62ekcfdtvklajn6pueus3am09s27vu6smuj6v9 - https://miningwholesale.eu
A special shoutout to our junior Noderunner Esramsterdam who is organizing a bitcoin event focused on women. Because bitcoin is not only for men. More info: https://vanbanknaarbitcoin.nl

Also a special shoutout to @npub17k8u7c6kfjgtd380890zx0m4adu8vl53m9fvtc7lal4j9gp74xqqkguha4! The only way to get free sats. Drank not enough beer with nostr:npub1pzurm7nx3q08894wl6uautryq95sku5jhzgwjjrskwdafcwxekuq4n7vtu this year.. but we really need to set up a collaborative project!

Ok I’m done. Forgot a lot but this sums it up quite well. Greetings and love to everyone involved with the Noderunners I forgot to mention. I love you all and hope to build a lot more together! 🧡🔥
nostr:npub103uy2vsk5hrnldwdu0nztmsg7g6207cfqu744rnrnalauns6facsgj5ddp
nostr:npub1l9evr9vx4u2xefesmfu6gyypfdu7k8zwdw7rrnh5ckdds8fqx59sy3ferg
nostr:npub1cwzduskqu6yuxjs2a75uptj3vzfa84gv5q3xlkcpzs6usjfey24qvk70dv
nostr:npub1etuf22z5jwp765m8dqcw7rx5egjzjnwm9xwm4m367e9hxkd9vvaq04duqw
nostr:npub1mw6tm8kery0dwmz670vvg74z0xzttwt3y7yppya5rulufpkkaj7qmg2922
nostr:npub12qw34mucxxk200835d8qt5mshfukd39vvz4s94f0e6xthg0xpjmq3wvjlw
nostr:npub1d5axlx84ajq7q5yn4u86m9xgnmssgq5c6ktjfmu6qtw7jah24hzs57tmvz
nostr:npub1vnlkmja076ft0h2ppme4pvcyfh8zmwl4l7hpfm4du0jagwck04lq8rkr0w
Jan Burgers
nostr:npub1r35gr0g93gxpkcq77v9sx97d5aqg4edr0qwhdj2xr4xxt6slp7nswgahlx
Short Non-Bitcoin
nostr:npub12786tz9vyzuhe5jdjc9esd64vqh3pvqe34u9a3dyegudv5chkx9sexz86w
Joep Laser Sheep - Elden Lord 3x
nostr:npub12xtq7ufn6kjppvl24dnvezsny872u8xacfsy640fzd69446kgczsp8v5nm
nostr:npub1m0yz3tvsa8cwheqhkqj96zr9kget8j8yda0vfmrah5c0dafj6xcq4l4az6
@Erik Dutch
nostr:npub1kvfz8rglvpsqevznlt86ukcz0s9uap3pypjwd3tnmkn2pgjmjujqlncy2c
nostr:npub1l5pxvjzhw77h86tu0sml2gxg8jpwxch7fsj6d05n7vuqpq75v34syk4q0n
Noderunners Shop
nostr:npub1ylnqfg0neysvsesen9je80wmsv9r5204x30mgd5ev6dr3q95xpxq3nmcxd
nostr:npub1ap78x7mvw0vu9s7yltflmkqphx8rt8hsk9gdg0k42vwnmnpvpe2qptxewe
nostr:npub1n2ph08n4pqz4d3jk6n2p35p2f4ldhc5g5tu7dhftfpueajf4rpxqfjhzmc
@Bitcmonkey
@Roynode
nostr:npub18n56f28efvmsjcl80lv2ngtmkl3y6q2rg0m2zqas3kw4jwkrsvdqxnmver
nostr:npub135q6dvnjah9023xszmjs2wvd4gqhn2trku52wt2lv8cl4hc8ltjsk0w4sq
nostr:npub1837u93v8am8q2rauvkqfk9sf6xfq07p9m4m82jueqh5u4qzkg25qesqrr4
nostr:npub1pkmp7vtgfwg7g0pt4xdd4r2npz2p8yweeq0yx7xm590h4nuszynqq2e2r3
nostr:npub19r33crtgdt4spqxl5a3nhqx2ucdputtqcnnxkplnp4mv2dqldqqs39j5eq
nostr:npub19z9g9ymx3aalx3h0jr2cskehvhgppznv2lpqsrpgggpeueesq4lsknsp8r
nostr:npub1jlvtd4zmq7ukjcytqxu2gy5myp2uataupjk4a3l467fj7pxpk3xq5p3w0j
@HeroVanKampen
nostr:npub16htmakd0gvsmwjnravfvfn5mh2x7wjd0vxq20z2c0979e7xh0a8q6ssnew
nostr:npub1xw6jekvethghmrlv0chkx5p78h3wk2ep5x588ga854d68cugr40qxuwt5e
nostr:npub1zakkum8w7uancehpev0drxuly3e74fg5v7q4n0zpxcdn72wakpjs9cgpve
and all others I can’t find here or I forgot.. 🧡🔥💪🏼 LFG, see you soon!
Bonus: This has never aired but @DanielMol was doubtful of our impact to more bitcoin adoption.. I know we are a bit toxic but we have our hearts on the right place and help anyone who is serious about it.. Happy days Daniel! 🧡

-
 @ b8a9df82:6ab5cbbd
2024-12-30 11:15:49
@ b8a9df82:6ab5cbbd
2024-12-30 11:15:49In just two days, 2024 will come to a close. And as I sit here reflecting and drinking my morning coffee, I can confidently say that this has been the best year I’ve had since 2018. The years leading up to this one, especially since returning to Berlin, were some of the most challenging of my life. They tested me in ways I never expected—moments when I wanted to give up, when I felt so lost I couldn’t see or feel anything anymore. I lost my smile, my positive side, my emotions, and even my sense of self. But this year was different. It felt like the sun finally broke through the clouds, and I could see light at the end of the tunnel. I laughed more. I loved more. I felt deeply again, like my emotions finally had room to breathe. For those who have read my book, you know I’ve faced my share of dark days, as many of us do. Some days were heavier than I could have imagined, and even now, there are moments when I question, *“Why? Why this path? Why me?”* But this reflection isn’t about the darkness. **It’s about the gratitude.** 2024 blessed me with so many moments of joy. I traveled, saw the world from new perspectives, and met extraordinary people who brought meaning and light into my life. These experiences reminded me that connection matters, that there’s beauty in the unfamiliar, and that we grow when we open ourselves up to it all—the good, the difficult, the unexpected. Now, back in Berlin, I feel a shift. The city feels cold again—not just in temperature, but in energy. Dark skies and gray streets mirror an unbalanced restlessness I can’t ignore. It’s not the coldness itself or the clouds; it’s the way this place feels as though it’s lost its spark. Smiles seem rare, warmth even rarer. And perhaps, that’s my sign. My time here feels like it’s coming to a close. But as this chapter winds down, I feel at peace. 2024 reminded me that life doesn’t stay stagnant. Even in the darkest times, the wheel turns. This year was proof that healing is possible, that joy can return, and that love—whether found in people, places, or moments—still exists. So, wherever this journey takes me next, I will carry this year with me. I’ll carry the laughter, the lessons, and the memories of those who reminded me that even in a messy, chaotic world, light and connection can thrive. And perhaps, just perhaps, this is only the beginning. The chapters ahead are unwritten, but I feel ready to meet them—with an open heart and gratitude for all that’s brought me here. Happy 2025 to all of YOU
-
 @ 16d11430:61640947
2024-12-30 06:25:23
@ 16d11430:61640947
2024-12-30 06:25:23The sky was a smear of red and gray, a molten soup of corporate smog and the fallout from decaying orbital platforms. A low hum vibrated through the megascraper’s skeletal walls, the pulse of industrial turbines below or something worse—something alive. Daniel had stopped looking over his shoulder hours ago. Paranoia was pointless now. They were tracking him through every lens and drone. Every step he took, every breath he exhaled, was already logged on some server buried under a thousand feet of reinforced concrete.
His son, Mikey, sat cross-legged on the floor of the abandoned node café, the glow of a salvaged holographic tablet painting his freckled face in shifting rainbows. Ten years old. Too young for this world, but not too young for what Daniel needed to do.
“Mikey,” Daniel said, slumping against the wall. His ribs screamed where the drone's shard had grazed him earlier. He'd staunched the bleeding with a strip of synthcloth, but the pain was relentless. “We don’t have much time.”
Mikey didn’t look up. He was playing some ancient 8-bit game that Daniel had installed when he was still naïve enough to think childhood could be preserved.
“They’re coming for me,” Daniel said, his voice sharp enough to slice through the haze of distraction. Mikey paused the game.
“Who’s coming?” he asked, his voice quivering.
“The kind of people who don’t leave witnesses.” Daniel knelt down, gripping Mikey’s shoulders. His hands were trembling, but his grip was firm. “Listen to me. They want something I have—private keys to tech they can’t control. But it’s more than just money, Mikey. It’s freedom. It’s hope. If they get it, they’ll own everything, everyone.”
Mikey stared at him, wide-eyed. “Why don’t you just give it to them?”
“Because,” Daniel said, leaning in close, “it’s not just mine. It’s the only thing keeping the world from falling apart. But I’m running out of time. They dosed me with a neural decay agent. My brain’s got hours, maybe a day, before it’s mush.”
Mikey’s lip quivered. “What do we do?”
Daniel exhaled, a bittersweet mix of relief and despair. “We’re going to do something crazy. I’m going to teach you everything I know.”
The Download
The next hour was a blur. Daniel jacked into a local darknet relay, setting up a secure uplink to his personal server cluster—what was left of it, anyway. The room buzzed with the flicker of dying neon and the hum of overworked processors.
“Mikey,” Daniel said, pulling a thin mesh glove from his pack. “This is a cognitive transference device. It’s experimental, and it’s going to hurt, but it’s the only way.”
Mikey looked at the glove, then at his father. “What does it do?”
“It maps my neural pathways, compresses them, and streams them into your brain. You’ll have fragments of my skills, my memories. Not perfect, but enough. Enough to code, to think like I do. But it’s risky. You ready?”
Mikey nodded, eyes steeled. “I’m ready.”
Daniel slipped the glove onto Mikey’s hand and activated the uplink. A lattice of blue light spiraled up Mikey’s arm, embedding itself into his skin like a living tattoo. The boy screamed, his body convulsing. Daniel held him tight, whispering encouragements through gritted teeth.
“It’s okay, Mikey. It’s okay. Breathe. You’re stronger than this.”
Mikey’s screams subsided, replaced by rapid, shallow breaths. His eyes fluttered open, glowing faintly with the residual charge of the transfer.
“I see it,” Mikey whispered. “I see the code.”
The Final Hour
They worked side by side, father and son. Daniel guided Mikey through the cryptic maze of his life’s work: quantum-proof encryption, autonomous networks, self-healing AI. Mikey’s hands flew across the keyboard, his newfound knowledge mingling with his innate creativity.
“They’re breaching,” Mikey said, his voice calm despite the chaos. Red indicators flashed on the terminal, signaling the proximity of their pursuers.
“Focus,” Daniel said, ignoring the pounding in his chest. “Deploy the polymorphic algorithm. Let it spread through the mesh. It’ll buy us time.”
Mikey nodded, typing furiously. Lines of code cascaded down the screen like a digital waterfall.
“Done,” Mikey said, glancing at his father. “But what about you?”
Daniel smiled weakly, his vision blurring. “Doesn’t matter. What matters is you. The world. You’ve got everything you need now, Mikey. Everything I am, everything I stood for, is in you.”
The door exploded inward, a blast of light and sound. Shadows moved through the smoke, the silhouette of their enemies sharp and inhuman. Mikey turned to his father, tears streaming down his face.
“I won’t let them win,” he said.
Daniel nodded, his lips forming a final, unspoken command: Run.
Mikey bolted for the emergency hatch, clutching the tablet tight against his chest. Behind him, the sound of gunfire erupted, followed by silence.
Epilogue
Weeks later, the world was different. Subtly, at first. Corporate networks began to collapse, their monopolies eroded by the decentralized systems Mikey had unleashed. Grassroots movements flourished, empowered by tools they didn’t fully understand but knew they could trust.
Mikey sat alone in a hidden bunker, the tablet glowing faintly in his lap. His father’s voice echoed in his mind, fragments of the neural transfer surfacing like ghosts in the machine.
“The code is freedom, Mikey. And freedom always wins.”
-
 @ 0cb6f0b2:4fe22158
2024-12-30 06:21:39
@ 0cb6f0b2:4fe22158
2024-12-30 06:21:39Table of Contents 1.Introduction 2.Understanding the Role of a Realtor **3.Key Qualities of a Top Realtor ** * Knowledge and Expertise * Strong Communication Skills * Reputation and Trustworthiness * Negotiation Skills * Local Market Knowledge * Attention to Detail
**4.Proven Success Factors in a Top Realtor ** * Consistent Sales Performance * Client Testimonials and Reviews * Professional Certifications and Associations * Track Record of Successful Transactions
5.How to Evaluate a Realtor’s Track Record 6.Questions to Ask Before Hiring a Realtor
7.Conclusion
- Introduction
When it comes to buying or selling a home, one of the most important decisions you’ll make is choosing the right realtor. A top realtor not only helps you find the right property or buyer but also navigates the complexities of the real estate market to ensure you get the best deal. The real estate industry is highly competitive, and having a skilled, trustworthy, and knowledgeable realtor on your side can make all the difference. This guide explores how to identify a top realtor by focusing on key qualities, proven success factors, and effective ways to evaluate their track record.
-
Understanding the Role of a Realtor Before delving into the qualities of a top realtor, it's important to understand what a realtor does. A realtor is a licensed professional who assists clients in buying, selling, and renting properties. Unlike real estate agents, realtors are members of the National Association of Realtors (NAR) and are bound by a strict code of ethics. They help clients navigate the complex real estate market, ensuring smooth transactions and minimizing potential risks.
-
Key Qualities of a Top Realtor Knowledge and Expertise A top realtor has a deep understanding of the real estate market. This includes knowledge of current trends, pricing, financing options, and legal requirements. Whether you're buying or selling, a knowledgeable realtor can help you make informed decisions and avoid costly mistakes. For instance, a study by the National Association of Realtors (NAR) found that 87% of buyers and 89% of sellers said that a realtor’s market knowledge was critical in the decision-making process. Knowledge of local markets is particularly important, as housing prices can vary greatly by location. Strong Communication Skills Effective communication is one of the most important qualities in a top realtor. Whether you're negotiating a deal, scheduling showings, or discussing terms, a realtor with excellent communication skills can ensure that all parties are on the same page. According to a report by Inman, 91% of clients said that strong communication was a key factor in their satisfaction with a realtor. Top realtors respond promptly to emails, phone calls, and messages, keeping clients updated throughout the process. They explain complicated real estate terms and processes in a clear, concise manner to ensure you understand every step of the transaction. Reputation and Trustworthiness A realtor's reputation is one of the most reliable indicators of their success. A strong reputation comes from consistently delivering results and building long-lasting relationships with clients. Word-of-mouth referrals, online reviews, and client testimonials are great ways to assess a realtor's credibility. Trustworthiness is crucial when dealing with such a significant investment like a home. You need a realtor who acts in your best interest, not their own. According to NAR, 75% of buyers and sellers trust their realtors based on past performance, and their ability to represent them effectively. Negotiation Skills The ability to negotiate effectively is perhaps the most crucial skill a realtor can possess. Whether you are buying or selling, negotiations can significantly impact the final deal. A top realtor will fight to get you the best price, whether you’re negotiating a home sale price or asking for repairs after an inspection. A study by the National Association of Realtors found that 77% of sellers said they would hire a realtor based on their ability to negotiate on their behalf. Local Market Knowledge Top realtors have an in-depth understanding of the local market trends, including property values, zoning laws, and school districts. They can help you find homes in neighborhoods that fit your lifestyle and budget. Local knowledge helps in determining whether a property is priced competitively, assessing the neighborhood's long-term value, and advising on future developments. Realtors familiar with your area can offer insights that others may overlook. Attention to Detail Real estate transactions involve a lot of paperwork, contracts, and legalities. A top realtor will have great attention to detail, ensuring everything is done correctly, from the initial offer to the closing paperwork. Small errors or overlooked details can lead to delays or even legal issues, so it’s crucial to have a realtor who is thorough and meticulous.
-
Proven Success Factors in a Top Realtor Consistent Sales Performance A top realtor consistently performs well, regardless of market conditions. This doesn’t mean they have to be the top seller in the country, but they should have a track record of closing deals on time and achieving results for their clients. You can check a realtor’s sales history to assess how many transactions they’ve completed, their average sale price, and how long it typically takes them to sell a property. Many realtors will proudly showcase their sales figures on their website or in their marketing materials. Client Testimonials and Reviews A great way to gauge the effectiveness of a realtor is by looking at client reviews and testimonials. Websites like Zillow, Realtor.com, and Google My Business feature reviews from past clients. Positive reviews can provide valuable insights into how a realtor works with clients and handles challenges during the buying or selling process. You should look for realtors with multiple positive reviews and testimonials. While no one is perfect, a realtor with consistently good feedback is likely to provide a positive experience. Professional Certifications and Associations Top realtors often have professional certifications and are members of professional organizations like the National Association of Realtors (NAR). Certifications such as Certified Residential Specialist (CRS), Accredited Buyer’s Representative (ABR), or Certified Luxury Home Marketing Specialist (CLHMS) signify a realtor’s commitment to continuing education and professional development. These certifications can indicate a higher level of expertise, ensuring the realtor is up-to-date on industry standards and trends. Track Record of Successful Transactions A realtor with a history of successful transactions in both buyer’s and seller’s markets shows their ability to adapt and deliver results under any circumstances. They should have experience handling different types of properties (single-family homes, condos, luxury homes, etc.) and clients (first-time buyers, seasoned investors, downsizers, etc.).
**5. How to Evaluate a Realtor’s Track Record ** Here’s a simple table to help you evaluate a realtor’s track record: Factor What to Look For Number of Transactions Look for a realtor with a consistent number of transactions in the past year or two. Sales to Listing Ratio A high sales-to-listing ratio indicates that they sell properties quickly and at or above asking price. Client Testimonials Positive reviews with specific details about the realtor’s professionalism, expertise, and results. Experience in Your Area Realtors with local knowledge will be better suited to find properties that match your needs.
-
Questions to Ask Before Hiring a Realtor Before hiring a realtor, it’s essential to ask the right questions. Here are some key questions to consider: How many homes have you sold in the past year? What is your marketing strategy for selling my home? How familiar are you with the neighborhoods I’m interested in? Can you provide references from past clients? What is your average days-on-market for listings? Asking these questions will help you gauge whether the realtor aligns with your goals and expectations.
-
Conclusion
Choosing the right realtor can significantly impact your real estate experience. By focusing on key qualities like communication skills, market knowledge, negotiation abilities, and trustworthiness, you can ensure that you’re working with a professional who has the experience to guide you through the process successfully. Additionally, evaluating their track record, client reviews, and certifications will help you make an informed decision. When it comes to one of the largest financial transactions of your life, you deserve a realtor who understands your needs, communicates clearly, and fights for your best interests. Take the time to identify a top realtor who aligns with your goals, and you’ll be on the right path to a successful real estate experience.
-
 @ a012dc82:6458a70d
2024-12-30 05:51:11
@ a012dc82:6458a70d
2024-12-30 05:51:11Table Of Content
-
The Influence of Global Oil Prices
-
Bitcoin's Roller Coaster Ride
-
Anticipation Surrounding the 2024 Halving Event
-
The Broader Crypto Landscape
-
Conclusions
-
FAQ
In the ever-evolving world of cryptocurrencies, Bitcoin stands as a beacon, often dictating the mood of the entire crypto market. Its price fluctuations are closely watched by investors, analysts, and enthusiasts alike. Max Keiser, a prominent figure in the crypto space, recently shed light on some intriguing factors that might be influencing Bitcoin's current price trajectory. This article delves into Keiser's insights, exploring the broader implications of global events on Bitcoin's market performance.
The Influence of Global Oil Prices
Max Keiser, a renowned Bitcoin advocate and former trader, recently drew attention to the interplay between global oil prices and Bitcoin's market performance. Responding to a post by German economics expert, Holger Zschaepitz, Keiser highlighted the significance of Brent oil reaching $90 per barrel for the first time since the previous November. According to Keiser, the surge in oil prices, driven by Saudi Arabia's decision to extend its reduction in oil production for another three months, has had ripple effects in the financial world. One of these effects is the shift of investor interest towards higher interest deposit USD accounts. This diversion of investments is creating what Keiser terms as "a small headwind for Bitcoin," implying that as traditional markets like oil show promise, some investors might be reconsidering their cryptocurrency positions.
Bitcoin's Roller Coaster Ride
The cryptocurrency market, known for its volatility, witnessed Bitcoin's price undergoing significant fluctuations recently. A notable event that gave Bitcoin a temporary boost was Grayscale's triumph over the SEC in a legal battle concerning the conversion of its Bitcoin Trust into a spot ETF. This victory led to a rapid 7.88% spike in Bitcoin's price within a mere hour, pushing it from the $26,000 bracket to briefly touch the $28,000 threshold. However, this euphoria was short-lived. Over the subsequent week, the cryptocurrency saw its gains erode, settling in the $25,400 range. At the time the reference article was penned, Bitcoin was hovering around $25,688.
Anticipation Surrounding the 2024 Halving Event
The Bitcoin community is abuzz with anticipation for the next scheduled Bitcoin halving, projected to take place in April-May 2024. This event will see the rewards for Bitcoin miners being slashed by half, resulting in a decreased supply of Bitcoin entering the market. Historically, such halvings have acted as catalysts, propelling Bitcoin's price upwards. A case in point is the aftermath of the 2020 halving, post which Bitcoin soared to an all-time high of $69,000 in October 2021. However, some financial analysts argue that this surge was less about the halving and more a consequence of the extensive monetary measures adopted by institutions like the US Federal Reserve. These measures, taken in response to the pandemic and the ensuing lockdowns, flooded the market with cash, potentially driving up Bitcoin's price.
The Broader Crypto Landscape
While Bitcoin remains the most dominant and influential cryptocurrency, it's essential to consider its position within the broader crypto ecosystem. Other cryptocurrencies, often referred to as 'altcoins', also play a role in shaping investor sentiment and market dynamics. Factors such as technological advancements, regulatory changes, and global economic shifts not only impact Bitcoin but the entire crypto market. As investors diversify their portfolios and explore newer blockchain projects, Bitcoin's role as the market leader is continually tested. Yet, its pioneering status and proven resilience make it a focal point of discussions and analyses in the crypto world.
Conclusion
Bitcoin, the flagship cryptocurrency, has always been subject to a myriad of market forces and global events. While its inherent potential remains undeniable, the current market landscape, shaped by factors ranging from oil prices to global economic policies, presents challenges. Yet, with events like the 2024 halving on the horizon, there's an air of optimism among Bitcoin enthusiasts and investors about the future trajectory of this digital asset.
FAQ
Who is Max Keiser? Max Keiser is a prominent Bitcoin advocate, former trader, and well-known crypto podcaster.
What did Keiser say about Bitcoin's price? Keiser pointed out that rising global oil prices and the allure of higher interest deposit USD accounts are creating a "small headwind" for Bitcoin.
How did Grayscale's legal victory affect Bitcoin? Grayscale's win over the SEC led to a 7.88% spike in Bitcoin's price within an hour.
When is the next Bitcoin halving expected? The next Bitcoin halving is projected to occur around April-May 2024.
Did the 2020 Bitcoin halving influence its price? Yes, post the 2020 halving, Bitcoin reached an all-time high of $69,000 in October 2021.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 16d11430:61640947
2024-12-30 05:08:22
@ 16d11430:61640947
2024-12-30 05:08:22The colonial period in India introduced systemic neglect of public welfare and sanitation, fostering a culture that normalized unsanitary practices. This transformation can be understood by analyzing the psychological, societal, and infrastructural impacts of colonial neglect, combined with the natural challenges of scaling traditional systems to meet the needs of a rapidly growing population.
- Colonial Neglect and Disruption of Indigenous Sanitation Practices
Destruction of Community Systems
Before colonization, sanitation systems in India were often community-managed. Local governance structures (e.g., village panchayats) organized water management, waste disposal, and hygiene practices.
The British prioritized centralized control, sidelining these systems. This resulted in a vacuum where no effective local or central systems functioned properly for the majority of the population.
Urbanization Without Sanitation
British industrial and trade-focused urbanization led to densely populated cities like Bombay, Calcutta, and Madras, which lacked adequate sanitation infrastructure.
Overcrowding, lack of waste disposal, and insufficient clean water supplies created unhygienic living conditions.
Psychological Impact of Exclusion
The colonial administration primarily catered to European populations, neglecting Indian communities. Indians were implicitly (and sometimes explicitly) told that their hygiene and living conditions were not a priority.
Over time, this neglect fostered a sense of inferiority and apathy towards public health and sanitation among the general population.
- Psychological and Societal Impact of Neglect
Normalization of Unsanitary Conditions
Two centuries of neglect normalized squalor and uncleanliness as inevitable aspects of daily life. Public spaces filled with waste became a common sight, and efforts to improve hygiene were deprioritized at individual and community levels.
Apathy towards sanitation became ingrained in public consciousness, with the belief that it was either too expensive or unnecessary.
Internalized Self-Neglect
Repeated messaging of Indian inferiority during the colonial period caused a cultural shift towards accepting unsanitary conditions as unchangeable.
Post-independence, this internalized neglect persisted, as people struggled to see sanitation as a collective responsibility.
Caste and Sanitation
The British formalized and exacerbated caste divisions. Sanitation work became even more stigmatized and relegated to specific marginalized groups, further discouraging others from engaging in hygiene practices.
This contributed to a societal disconnect from sanitation responsibilities.
- Biological Challenges Against Unsustainable Systems
Unscalable Traditional Systems
Traditional sanitation systems (e.g., open defecation combined with composting) were sustainable in low-density rural settings but could not scale to urban centers or a rapidly growing population.
The British colonial administration failed to invest in modern infrastructure that could meet these new challenges, leaving cities overwhelmed.
Biological Realities of Waste
Human biological urges for immediate waste disposal clashed with the lack of public facilities. Open defecation and improper waste disposal became the norm in the absence of latrines and garbage systems.
The lack of accessible facilities perpetuated the cycle of unsanitary conditions.
- Post-Colonial Normalization of Unsanitary Practices
Lack of Systemic Overhaul
After independence, India inherited an underdeveloped sanitation infrastructure. Attempts to modernize sanitation systems often faltered due to resource constraints, corruption, and a lack of public awareness.
Government campaigns to promote cleanliness were met with limited success because deeply ingrained cultural norms and apathy persisted.
Urban-Rural Divide
Investments in sanitation have often prioritized urban areas, leaving rural communities with limited facilities. This disparity perpetuates unsanitary practices in the majority of the population.
Population Growth
Rapid population growth has outpaced the development of sanitation infrastructure, further compounding the problem.
- Cultural Normalization of Unsanitary Situations
Cognitive Dissonance
People adapt to unsanitary environments by rationalizing them as unavoidable. The widespread acceptance of open defecation, garbage-filled streets, and polluted water is partly due to cognitive dissonance—a way of reconciling living conditions with the lack of alternatives.
Institutionalized Apathy
Bureaucratic inefficiency and corruption contribute to a lack of accountability for improving sanitation.
Over time, citizens have learned to expect inaction from the state, perpetuating a cycle of neglect.
Economic Priorities
For much of the population, economic survival takes precedence over sanitation. Limited resources mean that people often prioritize immediate needs (e.g., food, shelter) over hygiene.
Solutions and Lessons
Reversing Colonial Legacies
Encouraging community participation in sanitation reforms can revive traditional systems of collective responsibility.
Public awareness campaigns (e.g., Swachh Bharat Abhiyan) can help shift societal attitudes towards hygiene.
Investment in Infrastructure
Comprehensive sanitation infrastructure that includes toilets, waste disposal systems, and clean water supply is essential to breaking the cycle of neglect.
Education and Inclusion
Addressing cultural stigmas around sanitation work and promoting dignity for sanitation workers can help integrate cleanliness into societal values.
Education campaigns should emphasize the public health benefits of sanitation.
Scaling for Population Needs
Modernizing sanitation systems to handle urban density and rural accessibility is critical. Technologies like biogas toilets, community waste treatment plants, and water recycling systems can bridge the gap.
Conclusion
The colonial period created a systemic neglect of sanitation in India, fostering a culture of self-neglect that persists to this day. Addressing this legacy requires a combination of community engagement, infrastructure investment, and education to redefine hygiene as a collective responsibility. Recognizing the intersection of history, biology, and culture is key to creating scalable, sustainable solutions.
-
 @ e57fec0c:e3153bf8
2024-12-30 04:34:00
@ e57fec0c:e3153bf8
2024-12-30 04:34:00The Logic Behind “I’m Too Late to Bitcoin”
It makes sense why someone who hasn’t researched Bitcoin would assume that they are too late to the game. Bitcoin’s first known transaction took place on May 22nd, 2010, when Laszlo Hanyecz, a programmer, offered 10,000 Bitcoins (approximately $41 at the time) to anyone who could obtain two large Papa John’s pizzas and deliver them to his doorstep. Laszlo established Bitcoin’s first price, less than half a cent. Since then, Bitcoin has faced relentless attacks from nation states, banks, sophisticated hackers, and subject to endless slander from the media… all while growing to a market cap of $1.5 trillion.
From $0.0041 to $65,000 is a 15-million bagger. Due to the law of large numbers, you’re not likely to see another 15,000,000x return without severe hyperinflation; but the question at hand is not whether you’re too late to get insanely rich off a tiny investment in a short period of time. The question is, are you too late to dramatically improve your and your loved ones’ lives with Bitcoin? The answer is unequivocally, NO.
Disclaimer: Bitcoin is a disruptive technology laying the foundation for an entirely new economic system. It should be noted, as Jeff Booth, author of The Price of Tomorrow says, “anything that attempts to value the new system in terms of the old system is fundamentally flawed.” Thinking about Bitcoin in terms of dollars has a number of pitfalls, including that it makes Bitcoin seem volatile. In reality, 1 BTC = 1 BTC. Nonetheless, number-go-up does more marketing for Bitcoin than anything else, which is why it’s useful to this discussion. This is evidenced by the following chart of retail adoption vs. price. As price rises, new buyers enter the market. When price falls, they exit.
 Bitcoin has seen multiple 75%+ corrections, including a 35% correction this year. Without strong conviction around Bitcoin’s long-term value, these draw-downs tend to shake Bitcoin holders out and discourage them from returning. However, even during the worst performing four year period in Bitcoin’s history (December 2017-2021), you would still have seen a 23% CAGR. Lowering your time preference is key to weathering Bitcoin’s short-term price volatility. When in doubt, zoom out.
Bitcoin has seen multiple 75%+ corrections, including a 35% correction this year. Without strong conviction around Bitcoin’s long-term value, these draw-downs tend to shake Bitcoin holders out and discourage them from returning. However, even during the worst performing four year period in Bitcoin’s history (December 2017-2021), you would still have seen a 23% CAGR. Lowering your time preference is key to weathering Bitcoin’s short-term price volatility. When in doubt, zoom out.Reason 1: Money is a Technology and Bitcoin is Better Money
Money is an emergent technology that solves the Double Coincidence of Wants Problem. People have used beads, shells, large rocks and cacao beans as money, but there have only been two layer one monies adopted globally: gold and dollars. Gold was a widely accepted form of money for 5,000 years because it outperformed the alternatives in terms of its durability, portability and divisibility. Gold backed the US Dollar until 1971… how the dollar became unpegged from gold is a discussion for another day. The point is, dollars (paper IOUs) were easier to move, divide and trade, which is largely why gold failed. Bitcoin is more durable, portable and divisible than both gold and dollars which is part of makes it the best money ever discovered.
For more on how Bitcoin obsoletes all other monies, here are a few books to read:
- The Bitcoin Standard by Saifadean Ammous
- Gradually, Then Suddenly by Parker Lewis
- Broken Money by Lyn Alden
- The Hidden Cost of Money by Seb Bunney
Reason 2: Inflation Protection
Beyond the three aforementioned properties, money’s most important function is storing purchasing power through time. When demand for gold increases, gold production increases. When demand for dollars increases (i.e. the government wants to finance a war or manipulate the economy), the bankers and politicians simply create more, diluting the value of the current dollars in circulation. While it is difficult to say exactly how much purchasing power the dollar has lost over a specific time frame, I don’t need to convince you that the prices of food, gas, rent, etc. have increased dramatically in recent years.
Keynesian economists assert that 2% inflation is healthy and the “velocity” of money helps to “grease the economic wheels.” This is a fallacy with profound implications. A 2% annual inflation rate halves the value of money in approximately 36 years. As a result, the average person must become an investor in their free time, using assets like stocks and real estate to protect themselves from debasement. But not everyone has the ability to invest in stocks, or purchase real estate. Currency debasement increases the wealth gap between people who save in hard assets and people who save in cash. Bitcoin is more accessible and scarce than stocks or real estate, making it a superior store of value. The following chart shows the relationship between the monetary base and inflation.
 ## Reason 3: Increased Purchasing Power Over Time
## Reason 3: Increased Purchasing Power Over TimeHistorical data indicates that Bitcoin is likely to buy more goods and services in the future than it does today. While this is not an investment pitch, Bitcoin’s dollar price does more marketing than anything else.
Try this exercise- consider the three most valuable assets you own. Your car, house, computer, maybe a private jet? How much did they cost at the time in terms of dollars and in terms of Bitcoin? How much would it cost for you to purchase that same asset today in terms of dollars? What about in terms of Bitcoin?
 This chart shows the price of an average home in terms of the two competing monies, highlighting Bitcoin’s increasing purchasing power vs. the dollar’s erosion of value. Over a 4+ year time frame, it’s almost guaranteed that these three assets would cost less Bitcoin today, and more dollars (Anthony Pompliano explains this in relation to the median home). The key insight here is that Bitcoin is already re-pricing all assets. As long as Bitcoin remains decentralized and secure, this trend is likely to continue. The counter argument here is that the same could be said about gold or stocks. Gold already failed as money and you can’t buy anything with stocks. While Bitcoin is not yet a widely accepted medium of exchange, it is already being used to purchase assets such as real estate.
This chart shows the price of an average home in terms of the two competing monies, highlighting Bitcoin’s increasing purchasing power vs. the dollar’s erosion of value. Over a 4+ year time frame, it’s almost guaranteed that these three assets would cost less Bitcoin today, and more dollars (Anthony Pompliano explains this in relation to the median home). The key insight here is that Bitcoin is already re-pricing all assets. As long as Bitcoin remains decentralized and secure, this trend is likely to continue. The counter argument here is that the same could be said about gold or stocks. Gold already failed as money and you can’t buy anything with stocks. While Bitcoin is not yet a widely accepted medium of exchange, it is already being used to purchase assets such as real estate.Reason 4: A Growing Network, Lagging Price
Price and market cap are metrics that fail to capture the Bitcoin network‘s overall growth. Bitcoin’s price topped $67k in November 2021 before entering a bear market that bottomed around $16k. As of today (October 2024) the USD/BTC exchange rate is dancing between $60-70k/BTC. Based on this one metric, we could conclude that Bitcoin’s growth has been stagnant for three years. This is an incorrect assessment. While BTC price has not surpassed it’s inflation-adjusted all-time highs in three years, other metrics such as hash rate, difficulty adjustment, active nodes, stock-to-flow, and on-chain analytics tell a different story.
 As you can see in the chart above, Bitcoin’s hash rate continues to increase over time. Bitcoin miners are directing more and more energy to the network, making it more robust and secure. Miners have skin in the game, and the fact that hash rate continues to increase is a signal that they expect the network to continue growing. Add to that the number of full Bitcoin nodes, active wallet addresses, increased mining difficulty and supply distribution. These metrics point to Bitcoin’s growth, with price being a lagging indicator.
As you can see in the chart above, Bitcoin’s hash rate continues to increase over time. Bitcoin miners are directing more and more energy to the network, making it more robust and secure. Miners have skin in the game, and the fact that hash rate continues to increase is a signal that they expect the network to continue growing. Add to that the number of full Bitcoin nodes, active wallet addresses, increased mining difficulty and supply distribution. These metrics point to Bitcoin’s growth, with price being a lagging indicator.Reason 5: Supply and Demand: Institutional and Corporate Adoption
Institutions and corporations have opened the floodgates for larger pools of capital to flow into Bitcoin. In 2024, Bitcoin ETFs set record inflows and quickly became top 10 funds in terms of AUM, causing a ruckus on Wall Street. Corporations are adopting Bitcoin as a treasury asset, adding it to their balance sheet instead of holding cash, T-Bills or bonds. MicroStrategy (MSTR) pioneered the Bitcoin treasury playbook, and since August 2020 has outperformed every single company in the S&P 500, including Invidia (NVDA).
The predicament MicroStrategy faced in 2020 is not unique. Companies with cash and cash equivalents on their balance sheets are holding a melting fiat ice cube, losing purchasing power every day. Saylor’s strategy is being replicated by other companies such as Square, Semler Scientific, Fold and others. What happens when Apple or Microsoft decides to put 5% of its treasury into Bitcoin?
Sovereign wealth funds and nation states are also starting to adopt Bitcoin. El Salvador adopted bitcoin as legal tender in 2021 and has been purchasing 1 BTC every day since. Bhutan has been quietly mining Bitcoin for years. Wisconsin’s pension fund now holds Bitcoin. US politicians are discussing Bitcoin as a strategic reserve asset. Rewind just a few years and all of this would sound ludicrous. The Overton window has shifted and Bitcoin is no longer just magic internet money for money laundering and illegal transactions.
These groups are driving demand, but what about supply? Since 2021 the amount of Bitcoin issued to the network halved, from 6.5 BTC/block (\~900 BTC/day) to 3.125 BTC/block (450 per day). \~19,570,000 or 93% of Bitcoin have been mined to date, and by 2034, 99% of all Bitcoin ever to exist will be in circulation, or lost. Michael Saylor aptly describes the coming decade as the “Digital Gold Rush.” Bitcoin’s absolute scarcity is something humanity has never experienced before.
Reason 6: Overcoming Unit Bias
Bitcoin’s unit bias causes many people to think they are too late to Bitcoin. From an early age, we are conditioned to think in terms of dollars. At $0.05, $5, $500, or even $5,000, owning a full Bitcoin was feasible on an entry-level salary. But today, only 1 in 3 Americans can afford a $400 emergency expense. Acquiring a full Bitcoin is out of the question, so why even try? What these folks fail to see is that is that mathematically, owning 1 BTC was never going to achievable for the average person. If you divide Bitcoin’s total supply, 21 million, by 8 billion, the current global population, the result is .002625 Bitcoin or 262,500 Satoshis (a Satoshi is 1/100,000,000th of a Bitcoin). However, Bitcoin ownership is not evenly distributed. MicroStrategy currently holds more than 252,000 BTC. Once you account for the 20-30% of coins already lost forever, there’s no way everyone can own 262k sats. At the time of writing, 262k sats is worth \~$170. You read that right. For $170 you can buy more Bitcoin than the average person will ever own. Unlike stocks, Bitcoin does not have CEO who can decide to do a share split to avoid unit bias, which means those who can wrap their head around this are likely to adopt Bitcoin sooner.
Reason 7: Not Just a Store of Value – Bitcoin Use Cases
Bitcoin is versatile. People with differing pain points and needs use Bitcoin in distinct ways. In the West, Bitcoin is typically thought of as a store of value. “Do you invest in Bitcoin?” “At what price will you sell?” In other countries, Bitcoin is useful for different reasons. For example, a Ukrainian refugee was able to escape to Poland with much of his wealth, rather than leave everything he worked for behind. Bitcoin is also being used to get aid to Gaza, and facilitate P2P transactions in Nigeria. Cross-border remittances are another way Bitcoin is giving power back to the people. These use cases are happening all over the world today. Because Bitcoin is a digital bearer asset protected by the strongest cryptographic network ever created, it provides optionality for an uncertain future.
Human Rights Foundation Chief Strategy Officer, Alex Gladstein makes the case that Bitcoin has four primary use cases: savings, commerce, freedom and power. You can listen to his episode on What Bitcoin Did, here. In addition to Alex’s thesis on four primary use cases, Bitcoin researcher Daniel Batten outlines 19 ways bitcoin is already being used. Bitcoin has even more potential because it is not just a store of value.
Conclusion
THERE IS NO SUCH THING AS BEING “TOO LATE” TO BITCOIN. Is it too late to start eating healthy? Is it too late to start working out? Is it too late to start an internet-based business? Of course not. In the same way, it’s never too late to study and ultimately plug Bitcoin into your life. As BTC Sessions articulates, “the last person on earth to adopt Bitcoin will benefit from it immensely.” There’s no arguing that the longer you wait, and the higher Bitcoin’s price goes, the harder it will be to acquire a certain amount of Bitcoin, but even if you don’t adopt it personally, Bitcoin is threatening the power of the money printer and creating more transparency and fairness in the economic system.
You get Bitcoin at the price you deserve. I remember when Bitcoin’s price was $23. I didn’t deserve it then. It took the government sending me a $1400 stimulus check in 2020 to buy my first Bitcoin, and it’s changed my life in many ways since. Bitcoin’s eventual USD-denominated price is already known: infinity / 21M. Bitcoin has no ceiling because fiat has no floor.
In conclusion, I hope this article sparked some curiosity to learn more about how Bitcoin solves the age-old problem of currency debasement. Satoshi Nakamoto created Bitcoin so that you could create the life you are meant to live.
Last thing- the arguments in this article still hold up once Bitcoin’s price surpasses $100k, $1M or $10M. The only thing that would make you too late to Bitcoin is if the network itself is no longer secure or decentralized.
Listen to the episode here: https://fountain.fm/episode/T7Yh2vmBOfNAc3RKTU2p
-
 @ 16d11430:61640947
2024-12-30 03:14:06
@ 16d11430:61640947
2024-12-30 03:14:06- Introduction: The Crisis of Modern Digital Design
The digital age has delivered unprecedented connectivity and convenience, but it has also brought a dark underbelly: poorly designed digital interfaces that exploit and exhaust users. These interfaces, driven by profit-maximizing motives and shortsighted leadership, target the most productive and capable members of society—engineers, creators, thinkers—undermining their mental health and productivity. This is not merely a design issue; it is a crisis with profound implications for global stability, innovation, and the future of humanity.
- Critical Failures by Leadership
Modern leadership in both corporate and governmental spheres has repeatedly failed to address the following systemic issues in the digital landscape:
- Profit over People:
Leaders prioritize revenue generation (e.g., ad-based models, data mining) over the cognitive and emotional well-being of users.
Examples: Algorithmic design optimized for engagement metrics, not user health, leads to addictive and mentally draining experiences.
- Lack of Accountability:
Big Tech often escapes regulation, perpetuating harmful practices like dark patterns and manipulative UI/UX.
Example: Platforms like Facebook and TikTok amplify divisive content for profit, intensifying societal fractures.
- Incompetence in Digital Policy:
Policy makers lack the technical literacy to regulate effectively, leaving users vulnerable to exploitative systems.
Example: GDPR and similar regulations address data privacy but fail to address the root causes of digital harm—poor design and exploitative incentives.
- Shortsighted Metrics:
Corporate focus on quarterly earnings drives iterative, superficial changes instead of meaningful, user-focused innovation.
Example: Instead of solving UX pain points, companies often introduce features that increase complexity and cognitive load.
- Risks to Mass Populations
The societal consequences of failing to address this crisis are severe:
- Mental Health Epidemic:
Digital interfaces are linked to increased rates of anxiety, depression, and burnout, particularly among high-functioning individuals.
Source: Twenge et al. (2017) report a sharp increase in depression and suicidal ideation among teens correlating with smartphone usage.
- Productivity Collapse:
The workforce's most creative and capable members are being drained by poor UX, leading to a significant loss in economic output.
Source: Gallup (2022) shows record-low engagement among knowledge workers, exacerbated by digital fatigue.
- Cultural and Civic Decline:
Manipulative interfaces polarize societies, eroding trust in institutions and fragmenting social cohesion.
Source: MIT Technology Review (2021) highlights the role of algorithmic content delivery in amplifying political extremism.
- Long-Term Cognitive Harm:
Sustained interaction with chaotic digital environments can alter brain function, impairing critical thinking and long-term memory.
Source: Carr, "The Shallows" (2010), describes how digital tools reshape neural pathways, often detrimentally.
- The Role of DamageBDD in Driving Massive Change
DamageBDD offers a potential scaffolding for radical improvement by targeting the root issues:
- Behavior-Driven Verification:
By emphasizing behaviors, DamageBDD ensures digital systems align with human needs and expectations, rather than manipulative profit-driven incentives.
Use case: Verifying accessible, transparent, and intuitive UI behaviors for public and private digital platforms.
- Accountability Through Immutable Records:
DamageBDD leverages blockchain for an immutable record of system behaviors, fostering accountability in design and implementation.
Use case: Tracking user-centric design milestones and holding corporations accountable for harmful design practices.
- Rewarding Ethical Development:
DamageBDD incentivizes high-quality, ethical software development through Bitcoin Lightning payouts for verified milestones.
Use case: Developers receive immediate rewards for implementing systems that prioritize user well-being.
- Cognitive Restoration:
By reducing friction and chaos in digital systems, DamageBDD promotes a healthier cognitive landscape, restoring productivity and creativity to users.
- Conclusion: A Call to Action
The current state of digital design is unsustainable. The continued exploitation of human cognition through rotten interfaces represents a direct threat to mental health, economic productivity, and societal stability. Immediate intervention is not just desirable but essential.
DamageBDD provides the foundation for this intervention. By combining accountability, ethical incentives, and a focus on user behavior, it represents a scalable solution to a crisis that impacts billions. The time to act is now—before the collective depression caused by these interfaces buries the very people capable of driving humanity forward.
-
 @ 6cc4225f:942b7222
2024-12-30 00:32:47
@ 6cc4225f:942b7222
2024-12-30 00:32:47(Cover image photo credit: The Crypto Times)
“Our world of widows needs to be saved / it’s now or never — victim or victory, rebel or regret / who you are and who you claim to be / no more heroes.” -Converge, “No Heroes”
Usually, bad takes from big figures in the Bitcoin space roll off my back. I often don’t feel a need to counter them because 1.) Everyone is entitled to their opinion and 2.) I don’t enjoy spending my time arguing with people on the Internet.
But when a take is really bad — downright evil — I feel compelled to respond.
And respond I did to a bad take this week (link in just a second, first some context).
Lately in the media, MicroStrategy Chair Michael Saylor has been laying out his vision for a digital asset framework.
This framework includes conceptualizing Bitcoin as a commodity — nothing more than capital — and stablecoins like Tether (USDT) and USD Coin (USDC) as “digital currencies” (his words).
As if someone who considers themselves a “triple bitcoin maxi” (maybe one of the lamest terms ever) denying that bitcoin is a currency weren’t nauseating enough, his “evil genius plan” (his words) to get the world hooked on USD stablecoins as money while the US hoards bitcoin should have you upchuck everything in your guts if you truly believe in Bitcoin’s value proposition.
Below (a few lines down) is the piece I wrote countering Saylor’s perspective.
If there are two things I hope you take away from it, the first is to KILL YOUR IDOLS (not literally, of course) and the second is that WE ARE BITCOIN, and if we believe in the technology — all dimensions of it — we have to defend it.
Enjoy.
Michael Saylor Doesn't Understand Bitcoin
## Support The Open Dialogue Foundation
Speaking of defending Bitcoin, we all owe a debt of gratitude to the work that the Open Dialogue Foundation (ODF) is doing to defend our legal right to use non-custodial bitcoin wallets.
Please read the following piece I wrote this week to learn more.
Protect Your Non-Custodial Bitcoin Wallet — Support The Open Dialogue Foundation
And please make a tax-deductible contribution (before the year’s end) to the organization here.
Bitcoin’s Second Book-Length Academic Text — The Satoshi Papers — Coming Soon
This week, I published my interview with Natalie Smolenski, a PhD-holding theoretical anthropologist who often makes very valuable thought contributions to the Bitcoin space.
What I loved most about this interview (and I loved a lot about it) is Smolenski’s lack of reverence.
Two of my favorite quotes from the interview:
“There was kind of a triumph of a certain very statist approach to socialism and even communism in the American academy, in the Anglophone academy, that has persisted to this day, where there's, like I was saying earlier, a suspicion of anything smacking of individualism as bourgeois conceit or reinscribing social hierarchies, racial hierarchies, gender hierarchies, blah, blah, blah.”
The “blah, blah, blah” hit hard. It reminded me of how I used to tune out when speaking with a good portion of my co-workers during the years I taught at the college level.
The other one:
“What do you hope people will take away from The Satoshi Papers?
*> If there's only one idea that people take away from it, it's that your emancipation does not require the state. You do not need to wait for the government.
*> My God, take control of your life. You can, it is within your power to do so, and here are some examples of ways that people throughout human history have chosen to do so."
The “My God” was so properly placed. Chef’s kiss.
Check out to entire piece to absorb more of Smolenski’s wisdom.
Thank you all for reading, and here’s to a great week ahead!
Best,
Frank
-
 @ 8d34bd24:414be32b
2024-12-29 23:22:36
@ 8d34bd24:414be32b
2024-12-29 23:22:36Everyone was amazed and gave praise to God. They were filled with awe and said, “We have seen remarkable things today.” (Luke 5:26)
There are lots of verses in the Bible, both Old and New Testaments, where people were amazed at the works of God, but my question is, “Is there anything that amazes God?”
When the Sabbath came, he began to teach in the synagogue, and many who heard him were amazed.
“Where did this man get these things?” they asked. “What’s this wisdom that has been given him? What are these remarkable miracles he is performing? Isn’t this the carpenter? Isn’t this Mary’s son and the brother of James, Joseph, Judas and Simon? Aren’t his sisters here with us?” And they took offense at him.
Jesus said to them, “A prophet is not without honor except in his own town, among his relatives and in his own home.” He could not do any miracles there, except lay his hands on a few sick people and heal them. He was amazed at their lack of faith. (Mark 6:2-6) {emphasis mine}
This passage mentions the people being amazed at Jesus’s teaching, but it also talks about Jesus being amazed at their lack of faith. It is amazing that people could see the son of God, face to face, and listen to Him teach God’s word and still not believe. They heard about and even saw Him work miracles and yet they did not repent, nor believe.
This is an example of a negative amazement. Are there any examples of positive amazement? There are two passages, that I know of, that describe one particular event that amazed Jesus:
The centurion replied, “Lord, I do not deserve to have you come under my roof. But just say the word, and my servant will be healed. For I myself am a man under authority, with soldiers under me. I tell this one, ‘Go,’ and he goes; and that one, ‘Come,’ and he comes. I say to my servant, ‘Do this,’ and he does it.” *When Jesus heard this, he was amazed* and said to those following him, “Truly I tell you, I have not found anyone in Israel with such great faith**. I say to you that many will come from the east and the west, and will take their places at the feast with Abraham, Isaac and Jacob in the kingdom of heaven. But the subjects of the kingdom will be thrown outside, into the darkness, where there will be weeping and gnashing of teeth.”
Then Jesus said to the centurion, “Go! Let it be done just as you believed it would.” And his servant was healed at that moment. (Matthew 8:8-13) {emphasis mine}
The other mention of this event is in Luke:
He was not far from the house when the centurion sent friends to say to him: “Lord, don’t trouble yourself, for I do not deserve to have you come under my roof. That is why I did not even consider myself worthy to come to you. But say the word, and my servant will be healed. For I myself am a man under authority, with soldiers under me. I tell this one, ‘Go,’ and he goes; and that one, ‘Come,’ and he comes. I say to my servant, ‘Do this,’ and he does it.”
When Jesus heard this, he was amazed at him, and turning to the crowd following him, he said, “I tell you, I have not found such great faith even in Israel.” (Luke 7:6-9) {emphasis mine}
This Roman centurion had greater faith than any one of God’s chosen people in Israel. This gentile man trusted that Jesus had the power to heal his servant and that all it would take was Jesus’s command. If Jesus spoke the word, his servant would be healed, and it was so. Just as Jesus spoke the universe into existence, He also spoke the centurion’s servant into health. The creator healed His creation with His word and the centurion believed that it would be so.
What can amaze God? It looks like both our lack of faith and great faith can amaze God.
This coming year, let’s try to amaze God with our undying faith in His goodness and ability to do anything and everything for our good.
Trust Jesus.
-
 @ 16d11430:61640947
2024-12-29 23:17:52
@ 16d11430:61640947
2024-12-29 23:17:52Bitcoin, as a decentralized digital asset, exists fundamentally outside the framework of traditional financial (TradFi) systems. While the adoption of Bitcoin by TradFi institutions has brought it closer to mainstream acceptance, the dynamics of regulated markets create barriers to accurately reflecting Bitcoin’s intrinsic value. Here’s why:
- TradFi's Centralized Control and Market Manipulation
Regulated markets are built on centralized systems that allow institutions to exert significant control over price movements. Unlike Bitcoin’s decentralized, trustless model, TradFi relies on intermediaries and can be prone to manipulative practices such as spoofing, short selling, and derivative leveraging. These tactics often distort Bitcoin’s price to align with institutional agendas rather than its organic demand and supply.
For example:
Futures contracts allow institutions to short Bitcoin, pushing prices down without requiring physical delivery of the asset.
Over-the-counter (OTC) trading hides real volumes, further distorting public price signals.
- Lack of Weekend Liquidity
Regulated markets like futures or ETFs don’t operate 24/7. This creates a disjointed price discovery mechanism. Bitcoin trades continuously on global exchanges, but its value can diverge significantly from TradFi-set benchmarks over weekends due to thin liquidity and increased volatility. When TradFi markets reopen, institutions often adjust Bitcoin prices to suit their positioning, regardless of real market sentiment.
- Regulatory Constraints
The core ethos of Bitcoin is permissionless, borderless, and resistant to censorship. TradFi markets, by contrast, are heavily regulated and often impose restrictions that undermine Bitcoin’s true value:
Limits on leverage, capital flows, and trading hours inhibit the natural market dynamics that define Bitcoin.
Regulatory actions, such as lawsuits or exchange crackdowns, introduce external pressures that disproportionately impact prices.
- Misaligned Incentives
Many TradFi institutions profit more from Bitcoin's volatility than its growth. Products like Bitcoin ETFs or derivatives generate fees regardless of whether Bitcoin's price goes up or down, giving TradFi little incentive to advocate for Bitcoin's long-term value. Moreover, central banks and governments may view Bitcoin as a threat to fiat systems, further motivating policies that suppress its adoption.
How Bitcoiners Can Factor This In Over the Weekend
Weekends present unique challenges for Bitcoin holders, given the interplay of reduced liquidity, TradFi manipulation, and retail-driven volatility. Here are strategies to reduce exposure:
- Limit Leveraged Positions
Leverage amplifies risk, particularly over weekends when sudden price swings can trigger liquidations. Bitcoiners should consider reducing or closing leveraged positions before the weekend to avoid forced selling during thin markets.
- Use Stop-Loss Orders
Setting stop-loss orders can protect against significant downside risk during volatile periods. However, ensure these are placed strategically to avoid being liquidated by temporary wicks or market manipulation.
- Diversify Holding Strategies
Rather than keeping funds solely on centralized exchanges, Bitcoiners can use:
Cold storage: Safeguard long-term holdings from price volatility.
Lightning Network wallets: For immediate liquidity and payments without exposing large holdings to exchange risk.
- Monitor On-Chain Metrics
Bitcoin’s true value is better gauged through on-chain data, such as:
Hash rate: Reflects network security and miner activity.
Wallet activity: Indicates organic user demand.
HODL waves: Show long-term accumulation trends.
- Avoid Emotional Trading
Weekend price swings are often exaggerated by low liquidity and retail panic. Staying focused on Bitcoin’s fundamentals and long-term vision helps prevent reactive decisions.
Conclusion
TradFi markets will never fully reflect Bitcoin’s true value because their structure is antithetical to Bitcoin's decentralized, free-market ethos. Bitcoiners should be aware of the disconnect and take proactive steps, especially over weekends, to protect their investments from TradFi-induced volatility. By limiting leverage, diversifying holdings, and focusing on long-term fundamentals, Bitcoiners can mitigate TradFi's influence and stay aligned with Bitcoin's revolutionary potential.
-
 @ 569d536d:ba043e85
2024-12-29 22:43:33
@ 569d536d:ba043e85
2024-12-29 22:43:33Test post
-
 @ 90cf0438:33f1db73
2024-12-29 22:36:23
@ 90cf0438:33f1db73
2024-12-29 22:36:23It's been almost 3 years since the day I put on my headphones and went for a walk while listening to interviews and podcasts with npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc npub1hghnjjpnvkz8t6gkszuf37d7puwc2qtxc65rnklqsngzv6kkug9qhhfyz2 npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe npub1hk0tv47ztd8kekngsuwwycje68umccjzqjr7xgjfqkm8ffcs53dqvv20pf npub1mz704n7dsaw3jcj3kr5le45n97tqughyt5lxe3yv3xy3025hv3dsp5tl8g npub1jt97tpsul3fp8hvf7zn0vzzysmu9umcrel4hpgflg4vnsytyxwuqt8la9y npub15vzuezfxscdamew8rwakl5u5hdxw5mh47huxgq4jf879e6cvugsqjck4um npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx npub1ahxjq4v0zlvexf7cg8j9stumqp3nrtzqzzqxa7szpmcdgqrcumdq0h5ech and many more...
I'm sure many of you plebs have had similar experiences and had those AHA! moments as I did, falling down the Bitcoin rabbit hole. At some point I got so overwhelmed and obsessed with Bitcoin that I really had to talk with someone about it. And that's how the BitcoinWalk was born. Today in over 50 cities worldwide people meet for BitcoinWalk. Some do it everySAT, some once a month. People connect, spread the word of Satoshi and learn from each other.

Walking and talking about Bitcoin is both healthy and addictive, with an energy similar to attending a Bitcoin conference. And you can have it every single week! For FREE! 🤯

I feel grateful to have met so many like-minded individuals along the way. We've made real friends, and I've learned something new pretty much every time. Unlike other meetup experiences, BitcoinWalk is incredibly refreshing. We mingle, ask questions, and listen to each other's perspectives. No small talk, no judgement, no ego. On the move, looking straight ahead. This is where we learn the most and flex our Bitcoin muscle. We also ask by-passers if they could take the #ProofOfWalk picture of us where we hold the flag with our message 😉
 ## A Great Event for Beginners
## A Great Event for BeginnersBitcoinWalk is perfect for beginners, sceptics, or those who are curious about Bitcoin but overwhelmed by technology. With nation states joining the Bitcoin game theory, now is the perfect time to learn more. I believe that understanding Bitcoin requires perseverance and a willingness to learn over time, just like going to the gym.

You will meet people who might be from the other side of the world and you will connect with them instantly because of this common denominator of 21m BTC. It's magic!

Get Involved
I want to thank everyone who has volunteered to host BitcoinWalk in their cities. As a token of appreciation, I'll be sending you some cool stickers designed by npub17wts7rt7gnl0gyfq2kyuu5kkxudq99rdysvzx6cfm5x5ywa4ycfsmwvxx5 \ If you'd like to support our decentralized movement, join an existing BitcoinWalk or start one in your area.
⚡️You can also zap us some sats to help print more flags and stickers! 😇
Thank you & happy BitcoinWalking in 2025! 🧡
npub1g5rwqnjtwpuuuplr36v82eu2sxkn8fzkc6tdwz8036dzmrqkhgzqm6qq0t
-
 @ 16d11430:61640947
2024-12-29 21:58:08
@ 16d11430:61640947
2024-12-29 21:58:08In the annals of human history, few moments resonate with the profound societal upheaval of the French Revolution. The guillotine became a symbol of accountability for entrenched elites, while revolutionary ideals promised liberty, equality, and fraternity. Today, Bitcoin carries echoes of that transformative period, not with the bloody apparatus of execution, but with the immutable ledger of accountability and decentralization. For Australia and the global community, the trajectory of Bitcoin adoption signals nothing short of a modern-day reckoning. As policymakers grapple with its disruptive potential, the revolution is already underway—poised to reshape power structures and roll the proverbial heads of financial and political elites.
The Policy Foundations of a Bitcoin Reckoning
Australia’s policy decisions on financial regulation, monetary policy, and technology adoption are setting the stage for a confrontation with the Bitcoin movement. Here’s how:
- Inflationary Monetary Policy
The Reserve Bank of Australia (RBA) has embraced an inflationary monetary policy, aiming for a 2–3% target rate. While this may seem modest, the cumulative effect erodes purchasing power over decades. Coupled with unprecedented quantitative easing during the COVID-19 pandemic, Australians have witnessed a stark rise in asset prices, particularly housing.
Impact: Bitcoin, with its fixed supply of 21 million coins, stands as a stark contrast to the RBA’s infinite money printing. As more Australians seek refuge from inflation, trust in the fiat system could erode, precipitating a mass exodus to Bitcoin.
- Banking Consolidation and Corporate Favoritism
The "Big Four" banks—Commonwealth Bank, Westpac, ANZ, and NAB—dominate Australia's financial landscape, often prioritizing corporate interests over individual Australians. Their control over credit availability, fees, and financial innovation stifles competition and leaves everyday citizens vulnerable.
Impact: Bitcoin, as a decentralized network, bypasses banks entirely. With Lightning Network integrations enabling micropayments and peer-to-peer transactions, Australians may increasingly question the necessity of centralized banking, challenging the Big Four's monopoly.
- Lack of Blockchain Innovation Policy
While countries like El Salvador and Switzerland embrace Bitcoin as a legal tender or incentivize blockchain innovation, Australia has lagged. Regulatory uncertainty and heavy-handed approaches to digital currencies have stifled local startups and discouraged investment in the blockchain sector.
Impact: As Australians realize the missed opportunities in innovation and wealth creation, dissatisfaction with government policy could fuel grassroots Bitcoin adoption, intensifying the revolutionary sentiment.
- Surveillance and Financial Control
Policies like the expansion of Anti-Money Laundering (AML) and Counter-Terrorism Financing (CTF) laws have enhanced government surveillance over financial transactions. While aimed at combating crime, these policies often overreach, infringing on personal privacy.
Impact: Bitcoin's pseudonymous transactions provide an alternative to surveillance-heavy systems, empowering Australians to reclaim financial autonomy. Resistance to state control over personal finances could mirror revolutionary fervor.
The Current Trajectory: A Build-Up to Crisis
Economic Pressures
Australia’s economy is under strain, with rising inflation, stagnant wage growth, and a growing wealth gap. The housing market, increasingly out of reach for young Australians, is a symbol of generational inequality. Meanwhile, corporate bailouts and subsidies have further alienated average citizens. These economic grievances echo the bread shortages and wealth disparities that fueled the French Revolution.
Political Distrust
Political scandals and a perceived lack of accountability have eroded trust in Australian institutions. Public discontent with policies perceived as benefiting the elite—such as fossil fuel subsidies and lackluster climate action—aligns with a broader narrative of systemic failure.
Bitcoin as a Symbol of Resistance
Just as the French Revolution was driven by the promise of equality and empowerment, Bitcoin offers Australians a tool to challenge the status quo. Its decentralized nature removes intermediaries, empowering individuals to take control of their wealth and participate in a global financial system untainted by local corruption or inefficiency.
Policy Decisions That Could Trigger the "Rolling of Heads"
- Taxation and Over-Regulation
A heavy-handed approach to taxing Bitcoin holdings and transactions could alienate the growing number of Australians adopting the asset. By treating Bitcoin purely as a speculative investment rather than a revolutionary tool, policymakers risk pushing citizens towards civil disobedience or parallel economies.
- Central Bank Digital Currencies (CBDCs)
The RBA is exploring the potential for a digital Australian dollar (CBDC). While it may seem like a step toward modernization, a centralized digital currency would likely exacerbate concerns over surveillance and monetary control. Australians may view CBDCs as antithetical to Bitcoin’s ethos, intensifying resistance.
- Banking Collapses
A potential banking crisis, whether due to economic mismanagement or global shocks, could accelerate Bitcoin adoption. Australians disillusioned with the inability of the government or banks to safeguard their savings may flock to Bitcoin as a trustless, self-custodial alternative.
- Failure to Address Inequality
If policymakers continue to ignore the growing wealth gap, grassroots movements advocating Bitcoin as a tool for financial inclusion will gain traction. Just as the French Revolution arose from a failure to address systemic inequities, Australia risks a similar reckoning.
The Revolutionary Parallel: Heads Will Roll
The "rolling of heads" in this context is metaphorical, but no less profound. It represents the dismantling of entrenched systems and the symbolic removal of those who perpetuate them. Here’s how the Bitcoin revolution could unfold in Australia:
Financial Institutions: The dominance of the Big Four banks could be challenged as Australians adopt decentralized financial systems, forcing these institutions to adapt or face irrelevance.
Political Leaders: Politicians resistant to Bitcoin adoption or beholden to corporate interests may be swept out of office by a digitally empowered electorate demanding transparency and accountability.
Corporate Structures: Companies failing to integrate Bitcoin or blockchain technology may lose competitiveness, leading to leadership shakeups and restructuring.
Cultural Shift: As Bitcoin gains cultural traction, the elite narratives supporting fiat systems could crumble, paving the way for a decentralized financial order.
Conclusion: Bitcoin as Australia's Guillotine
While Bitcoin does not call for bloodshed, its disruptive potential is no less revolutionary. By enabling individuals to opt out of centralized systems and reclaim financial sovereignty, Bitcoin challenges the very foundations of Australia's economic and political structures. The French Revolution reshaped society, not because of its guillotine, but because it forced a reckoning with inequality and governance. Similarly, Bitcoin is forcing Australia—and the world—to confront the flaws of fiat money, corporate monopolies, and state overreach.
As the movement gains momentum, Australians may find themselves at the forefront of a global revolution, wielding Bitcoin not as a weapon of destruction, but as a tool for liberty, equality, and empowerment. And until the correct framework for this new era prevails, heads—metaphorical or otherwise—will roll.
-
 @ 81e5cb66:17c315fa
2024-12-29 19:55:56
@ 81e5cb66:17c315fa
2024-12-29 19:55:56Original recording: 6 August 1977
The boundaries between terrestrial and ‘extraterrestrial’ intelligence are blurred in a remarkable recording from the Monroe Institute. What begins as a seemingly ordinary out-of-body experience evolves into a profound exploration of consciousness and our role in the cosmic fabric.
The first contact
The session begins with an impressive scene outside the Earth's atmosphere: three ships in formation, part of a larger contact initiative by extraterrestrial beings. The narrator describes an inviting encounter aboard one of these ships, characterised by brilliant white light and advanced technology. The visitors' message is clear: they are ready for enhanced communication, but the key lies in the elevation of human consciousness.
The bridge between the worlds
The method of communication is particularly remarkable. The extraterrestrial beings favour mental contact that is not tied to physical signals. They emphasise that the mere perception of their presence is sufficient to establish a connection. This form of communication transcends conventional boundaries and opens doors to a deeper understanding of interstellar relationships.
Consciousness development as the key
A central aspect of the recording is the importance of consciousness development. The beings describe how humans only utilise a fraction of their consciousness potential. They speak of the need to cultivate a heightened level of consciousness both while awake and while dreaming. This is the key to overcoming the communication barriers between species.
Time and consciousness: a new perspective
The discussion on the nature of time is extremely noteworthy. The extraterrestrial beings exist beyond our linear concept of time and experience reality as a series of mental images. They describe our current perception of reality as a kind of ‘setting’ in a much larger spectrum of consciousness. This suggests that our experience of limitation by time and space is merely a temporary focussing of our larger consciousness.
The emotional dimension
A fascinating aspect of the recording is the description of how the extraterrestrial beings respond to emotional vacuums in the human psyche. They send out a form of consciousness that manifests as physical spaceships to respond to the emotional needs of humanity - especially in relation to environmental problems and existential issues.
Expansion of consciousness as the key
The term ‘expansion of consciousness’ runs like a common thread through the communication. It is not just about personal growth, but about a fundamental transformation of our perception and our being. States such as ‘Focus 12’ as levels of consciousness can provide access to higher dimensions.
Integration and transformation
The session ends with an important realisation: we are not just passive observers in the cosmic drama, but active participants in a larger experiment in consciousness. The extraterrestrial beings emphasise that the future is not predetermined, but can be shaped by collective intention and focused mental imagery.
Conclusion
This Monroe Institute recording offers more than just an insight into extraterrestrial contact. It presents a comprehensive philosophy of consciousness and its role in the evolution of humanity. The experiences described suggest that the path to interstellar communication is less through technological advancement and more through the evolution of our consciousness.
The session reminds us that we are part of a larger cosmic consciousness and that our current limitations may only be self-imposed limitations. It invites us to think beyond our conventional notions of reality, time and consciousness and to open ourselves to new possibilities of existence and communication.\ \ full session: https://youtu.be/P0wdcTqRRU4?si=5mccZ-7DAQgNH2LV
-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
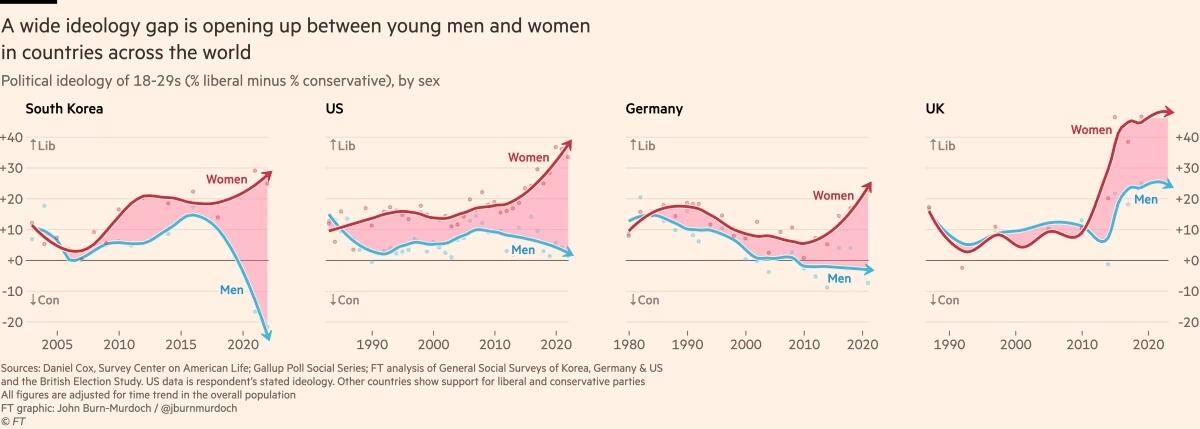
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ 6be5cc06:5259daf0
2024-12-29 19:47:40
@ 6be5cc06:5259daf0
2024-12-29 19:47:40-
O que é Bitcoin? É dinheiro de verdade? Bitcoin é uma forma de dinheiro digital que funciona na internet. Não existe em papel ou moedas físicas, mas você pode usá-lo para comprar coisas ou guardar valor, como o dinheiro normal.
-
Como o Bitcoin funciona? É como um banco? Bitcoin funciona sem bancos. Ele usa uma rede na internet onde pessoas registram as transações juntas, garantindo que ninguém possa "trapacear".
-
Quem criou o Bitcoin? Alguém controla isso? Foi criado por uma pessoa ou grupo chamado Satoshi Nakamoto, mas ninguém sabe exatamente quem é. Hoje, ninguém controla o Bitcoin; ele é mantido por milhares de pessoas ao redor do mundo.
-
Por que o Bitcoin tem valor? Não é só código? O Bitcoin tem valor porque as pessoas confiam nele, assim como confiam no dinheiro comum, mesmo ele perdendo valor com o tempo. Além disso, há um número limitado de Bitcoins, o que o torna raro e mais valioso.
-
É seguro usar Bitcoin? Posso perder meu dinheiro? É seguro se você cuidar bem da sua carteira e senha. Mas, se você perder sua senha ou enviar para o endereço errado, pode perder o dinheiro.
-
Como posso comprar Bitcoin? Você pode comprar Bitcoin em plataformas chamadas "exchanges" ou de pessoas comuns que estejam vendendo, o que é mais recomendado, usando dinheiro normal.
-
Onde eu guardo o Bitcoin? Preciso de um lugar especial? Você guarda em uma carteira digital, que pode ser um aplicativo, um site ou até um dispositivo físico, como um pen drive.
-
O que significa "minerar" Bitcoin? É cavar na internet? Minerar é usar computadores para resolver problemas matemáticos. Isso ajuda a manter o Bitcoin funcionando e, como recompensa, quem minera ganha novos Bitcoins.
-
O preço do Bitcoin sobe e desce muito. Por que isso acontece? Porque o preço do Bitcoin depende da oferta e da procura. Se muita gente quer comprar, o preço sobe. Se querem vender, o preço cai.
-
Posso usar Bitcoin para pagar coisas no dia a dia? Sim, mas ainda não é tão comum. Algumas lojas e sites já aceitam Bitcoin como forma de pagamento.
-
Se eu esquecer minha senha ou perder meu celular, perco meu Bitcoin? Se você não tiver uma cópia de segurança da sua carteira ou senha, sim, pode perder. Por isso, é importante anotar e guardar essas informações em um lugar seguro.
-
O governo pode proibir o Bitcoin? O que acontece nesse caso? O governo pode tentar limitar o uso, mas como o Bitcoin é uma rede global, ele continuaria existindo e funcionando.
-
Ouvi falar de golpes com Bitcoin. Como me proteger? Nunca compartilhe suas senhas, desconfie de promessas de lucro rápido e use apenas plataformas confiáveis para comprar e vender.
-
Vale a pena investir em Bitcoin? Não é arriscado? Bitcoin não é um investimento, mas uma forma de reserva de valor, como o ouro. Ele serve para proteger seu dinheiro contra a desvalorização, mas seu preço varia muito. Por isso, é muito importante entender como funciona antes de usar.
-
Bitcoin é só para ricos ou qualquer pessoa pode usar? Qualquer pessoa pode usar! Você não precisa comprar um Bitcoin inteiro; pode comprar frações bem pequenas, chamadas "satoshis".
-
-
 @ 30ceb64e:7f08bdf5
2024-12-29 19:09:13
@ 30ceb64e:7f08bdf5
2024-12-29 19:09:13I've been working 28 hours a week on the weekends as a Direct service professional, assisting adults with autism and intellectual disabilities. I've brought my laptop freaks. There's enough downtime for me to work on obtaining certifications online, posts to SN and Nostr, and work on my coding project Nostr Run Club.
I work with 2 normies on saturday and sunday, and had the bright idea of pitching my app to them. Here is how the conversation went.
Hustle: Hey do you guys want to see what i'm working on?
Normie 1: Sure....
Normie 2: "Comes around to curiously investigate"
***The Pitch
Hustle: Alright, so.....what social media do you use?
Normie 1: Instagram.
Hustle: Alright so....I'm making a running app. Imagine logging in with instagram, and seeing a feed of all of the runners and all of your friends. Now, what music streaming service do you use?
Normie 1: Pandora Normie 2: Spotify
Hustle: Cool, so imagine seeing your pandora and Spotify liked songs and playlists in the running app. So the app can track your run, its connected to your social media and streaming platform, and people can send you small donations congratulating you for the run.
Normie 1 and 2: Ahh, that's cool.
Normie 2: But why would people send you money? Oh? I think I've seen something like it where people send you a star and the star can be redeemed for like 99 cents, or they send you points and the app rewards you for points.
Hustle: Nah. That parts already figured out, I'm just having trouble getting the music from "Spotify" to play, and then I'll release it into the wild, that's pretty much my hustle.
And that was the conversation, it left me thinking about a few things.
-
V4V The concept is extremely familiar to me. I say good Morning I get 50 cents. I give 35 cents to other GM freaks and keep it pushing. Its normal. But for them the concept seemed so strange, they were looking for some solution or explanation on why people would just give someone else money for seemingly nothing. When the solution is already here, just not evenly distributed or promoted or adopted. Likely because the normies are still existing in the paradox of card companies and ravenous third party intermediaries imposing their cut.
-
The broken social media landscape of disconnected walled gardens I was thinking normie one would say Facebook, if asked normie 2 would've said snapchat, Tik Tok, Instagram etc. for music they could've said apple music, tidal, Youtube music etc.
I see Nostr as a highway that connects all of these guys, and instead of buying multiple cars to travel on different streets, you have one car that you use to travel across the country.
- The tact required to pitch ideas like Nostr and bitcoin
I used to work at bank of America and was tasked to sell credit cards without saying the word credit card.....
I would say "Hello, good sir/mam, have you thought about getting rewarded for your daily purchases??"
I found myself in a familiar situation, introducing them to Nostr without using the word Nostr and introducing them to bitcoin without using the word inevitable. The experience was stranger for me than it was for them, they left thinking "Ahh, thats neat" I walked away from the conversation eager to get notify the freaks.
In Conclusion,
The interaction gave me a few interesting insights:
- We'll need to bridge the conceptual gap between traditional and new payment paradigms.
- The importance of focusing on user benefits rather than technical details
- The market opportunity for solutions that unify fragmented digital services
- The value of strategic communication that meets users where they are
Successful adoption of new technologies like Nostr and Bitcoin requires careful attention to user education and communication, focusing on practical benefits rather than technical features. The positive reception to the core concept, even without understanding the underlying technology, shows huge potential for mainstream adoption when presented appropriately.
Thanks, Hustle
originally posted at https://stacker.news/items/829000
-
-
 @ 6be5cc06:5259daf0
2024-12-29 19:00:52
@ 6be5cc06:5259daf0
2024-12-29 19:00:52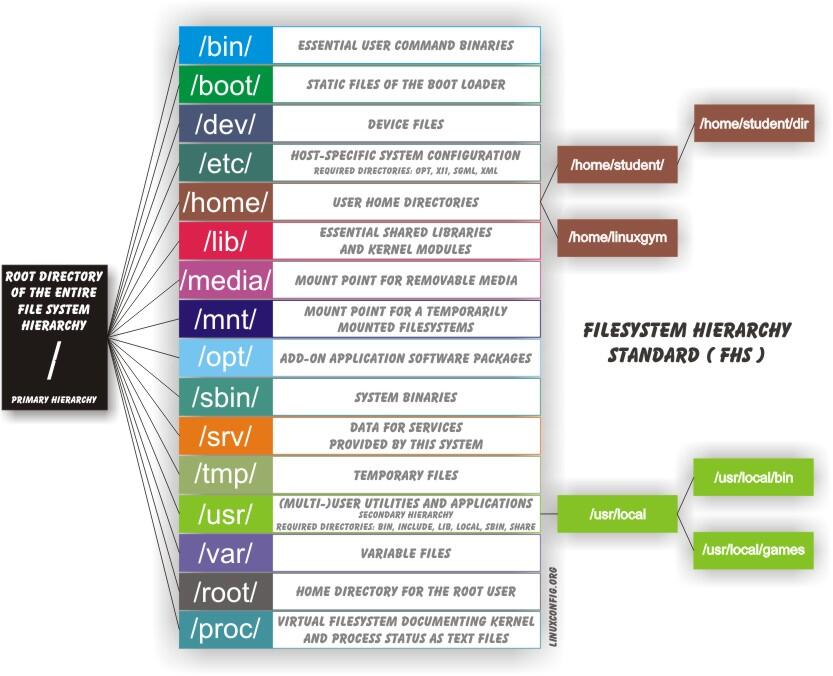
/(Root Directory)-
É o diretório raiz de todo o sistema de arquivos. Todos os outros diretórios e arquivos estão localizados dentro dele. Representa o ponto inicial da estrutura hierárquica.
-
/bin(Essential User Command Binaries) -
Contém comandos essenciais que são usados pelos usuários e pelo sistema, como
ls,cp,mv, etc. Esses comandos podem ser executados tanto pelo usuário comum quanto pelo administrador. -
/boot(Static Files of the Boot Loader) -
Guarda os arquivos necessários para a inicialização do sistema, incluindo o kernel, arquivos de configuração do boot loader (ex. GRUB), e a imagem inicial do sistema.
-
/dev(Device Files) -
Contém arquivos especiais que representam dispositivos do sistema, como discos rígidos (
/dev/sda), portas USB, entre outros. Esses arquivos permitem que o sistema interaja com os dispositivos. -
/etc(Host-Specific System Configuration) -
Armazena arquivos de configuração do sistema. Contém diretórios e arquivos de configuração para vários programas e serviços, como o
passwd(contas de usuários), arquivos de rede, etc. -
/home(User Home Directories) -
É onde ficam os diretórios pessoais dos usuários. Cada usuário tem seu próprio diretório em
/home(por exemplo,/home/studente/home/linuxgymna imagem). Esses diretórios guardam arquivos pessoais e configurações de cada usuário. -
/lib(Essential Shared Libraries and Kernel Modules) -
Contém as bibliotecas essenciais usadas por binários em
/bine/sbin, além dos módulos do kernel que auxiliam o sistema a funcionar corretamente. -
/media(Mount Point for Removable Media) -
Diretório onde dispositivos removíveis, como pen drives e CDs, são montados automaticamente para que o sistema possa acessar seus dados.
-
/mnt(Mount Point for Temporarily Mounted Filesystems) -
Usado para montar temporariamente sistemas de arquivos, como partições adicionais ou dispositivos de armazenamento externos.
-
/opt(Add-on Application Software Packages)- Destinado a softwares adicionais ou pacotes de aplicativos externos que não fazem parte do sistema principal, como softwares de terceiros.
-
/sbin(System Binaries)- Armazena comandos essenciais usados principalmente pelo administrador do sistema, como
reboot,shutdown, etc. Esses comandos geralmente exigem permissões de superusuário.
- Armazena comandos essenciais usados principalmente pelo administrador do sistema, como
-
/srv(Data for Services Provided by This System)- Guarda dados relacionados a serviços específicos que o sistema fornece, como arquivos para servidores web e FTP.
-
/tmp(Temporary Files)- Contém arquivos temporários criados por usuários ou pelo sistema. Esse diretório é limpo regularmente, e arquivos dentro dele podem ser excluídos a qualquer momento.
-
/usr(Multi-user Utilities and Applications)- Um diretório com aplicativos e utilitários para uso geral de todos os usuários. Contém subdiretórios como
/usr/bin(binários de usuários),/usr/lib(bibliotecas) e/usr/local(software instalado manualmente).
- Um diretório com aplicativos e utilitários para uso geral de todos os usuários. Contém subdiretórios como
-
/var(Variable Files)- Guarda arquivos variáveis, como logs do sistema, bancos de dados, e-mail e arquivos de spool (impressão, e-mail, etc). Esses arquivos são modificados frequentemente enquanto o sistema está em uso.
-
/root(Home Directory for the Root User)- Diretório pessoal do superusuário
root. Diferente do/home, que contém diretórios de outros usuários, o/rooté exclusivo para o administrador.
- Diretório pessoal do superusuário
-
/proc(Virtual Filesystem Documenting Kernel and Process Status as Text Files)- É um sistema de arquivos virtual que contém informações sobre processos e o estado do kernel, com arquivos e diretórios que representam processos e outros dados do sistema em tempo real.
Complementos:
/usr/local: Um diretório específico dentro de/usrque é usado para armazenar softwares instalados manualmente pelo usuário, evitando conflitos com pacotes de software gerenciados pelo sistema.- Arquivos de sistema em
/usr/local/bine/usr/local/games: Armazenam binários e jogos que foram instalados manualmente pelo usuário.
-
 @ 54609048:8e22ba03
2024-12-29 18:07:17
@ 54609048:8e22ba03
2024-12-29 18:07:172024 has turned out to be an interesting year for Bitcoin, probably better than what most expected. From the approval of spot Bitcoin ETF’s in January, increased adoption by corporations as well as pension funds following the Microstrategy playbook, to talks of creating Strategic Bitcoin Reserves (SBR) by different countries including the United States of America. Of course the European Central Bank also had to weigh in with their luddite perspective and let us know how early adopters “steal” economic potential from new comers. Then came the big one when the Bitcoin price crossed $100 000 for the very first time on the 5th of December, to much pomp and fanfare.
Yet amid the euphoria, it’s critical not to lose sight of Bitcoin’s revolutionary mission: the separation of money and state. As conversations about the impending Bitcoin bull run and $1 million price predictions dominate online chatter, a darker reality emerges. Many Bitcoiners appear willing to compromise with governments and institutions—the very entities Bitcoin was designed to render obsolete—all for the sake of pumping their bags.
While I am definitely not trying to dictate to anyone what they should be doing with their Bitcoin or how they ought to think; but I am trying to remind those that are still interested in the separation of money and state not to lose sight of the ultimate goal.This article is not meant to be a hot take for stirring any controversy or anything of that sort, just a different perspective that’s all.
Bitcoin: A Peer-to-Peer Electronic Cash System
The opening line of Bitcoin’s whitepaper isn’t just a technical statement; it’s a declaration of war: “A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution.” It’s clear from this that Bitcoin was designed to be a digital means of exchange first that could be transmitted without a third party. Put another way, Bitcoin was created as decentralized digital cash—a tool for economic freedom, bypassing intermediaries and state control. Yet today, narratives like “digital gold” and SBRs dominate the discourse, reframing Bitcoin as a reserve asset for nation-states and institutions. While these narratives acknowledge the failings of fiat, they risk chaining Bitcoin to the very systems it was designed to dismantle.
The Lessons of Gold: A Warning for Bitcoin
History provides a cautionary tale in gold, once a cornerstone of monetary sovereignty but was gradually co-opted and centralized by the very powers it sought to keep in check.The erosion of gold’s monetary sovereignty began in earnest with the creation of the Federal Reserve in 1913. This new central bank was designed to stabilize the U.S. economy by controlling the money supply and interest rates, yet its very existence marked a shift away from the decentralized, market-driven gold standard. By granting the Federal Reserve control over the issuance of currency, the link between paper money and gold—a scarce and neutral medium of exchange—began to weaken. Over time, gold was demoted from being the backbone of the monetary system to a reserve asset held predominantly by central banks.
By 1933 the process had accelerated that gold was permanently kneecapped in 1933 with the signing of Executive Order 6102 which criminalized private ownership of gold by American citizens and subsequently forced them to sell their holdings to the government at a fixed price. While framed as a necessary measure to combat the Great Depression, the true consequence was the removal of gold from public hands, consolidating it within the coffers of the state. Gold was no longer the people’s money—it had become a strategic reserve for government monetary policy.
Gold’s role as a medium of exchange was further diminished by the Bretton Woods Agreement of 1944. This international accord established the U.S. dollar as the global reserve currency, ostensibly backed by gold. However, this system created an asymmetric dynamic: central banks could trade dollars for gold, but private individuals could not. The result was the effective demonetization of gold for the average person. It became a commodity stored in vaults, a relic of a bygone monetary system, while fiat currencies assumed its role as the dominant medium of exchange. The final nail in the coffin came in 1971 when President Nixon closed the gold convertibility window. This not only fully entrenched the era of central bank coordinated alchemy but crushed the productive capacity of every individual without proximity to the money printer.
This historical tale reveals a dark and inconvenient truth: gold lost its power not because of any inherent flaws but because it was centralized gradually and systematically detached from its role as a medium of exchange. Its transformation into a mere commodity made it vulnerable to state control, paving the way for the unchecked proliferation of fiat money. The story of gold’s co-option should serve as a rallying cry: Bitcoin must never become just another asset locked away in institutional vaults, disconnected from the very people it was designed to empower.
The Illusion of Reform
While it remains true that Bitcoin is indeed a trojan horse designed to obsolete central banking, it would be a bit naive to expect these fiat alchemists are just going to just roll over and play dead. Bear in mind that the dollar is the oil that drives global commerce and capital markets, which is a financially lucrative position that the powers that be won’t give up without a fight. In case you hadn’t noticed, the fight is already on and it’s not as hostile as most would have expected. As calls for an SBR get louder by the day, many view this as a win. While it may seem on the surface like capitulation by state actors, the history of gold above should serve as a cautionary tale. Not all Bitcoin “adoption” is created equal. One of the key points that is usually raised in favour of nation states adopting an SBR is that it would force the state to adhere to tighter fiscal discipline and controls. A point that I am personally skeptical of for a number of reasons. For starters, the fundamental issue with fiscal indiscipline is the state’s monopoly on violence and the issuance of money.
If history is any guide, as long as the state maintains control over the power to create money and enforce legal tender laws, it will find ways around nominal constraints. Legal tender laws force individuals to use state money, enabling governments to devalue it through inflation. Furthermore fiscal discipline is achieved by balancing budgets and curbing unnecessary expenditures, not just by accumulating reserves. An SBR in and of itself will do nothing to address the structural issues that drive government deficits, such as; excessive entitlement spending, military-industrial complex overreach and bloated bureaucracies. The problem is not the asset backing the currency but the moral hazard of government control over money.
In theory while an SBR is viewed as a “disciplining mechanism” that will constrain state spending; the reality is that the state has always systematically undermined any constraints on their monetary power. Even when the dollar was officially gold-backed, the government found ways to expand spending beyond its means through techniques like suspending convertibility, changing redemption rates, and eventually abandoning the standard entirely. There's no reason to believe that an SBR would create any more discipline than gold did. An SBR would likely follow the same pattern as gold reserves - initially presented as a disciplining mechanism, but gradually subverted through:
- Fractional reserve practices
- Creation of paper claims exceeding actual Bitcoin holdings
- Development of complex financial instruments to leverage Bitcoin reserves
- Selective suspension of Bitcoin redemption rights
- Gradual reduction of backing ratios
Bitcoin fixes many things, but let’s not delude ourselves—it’s not the magic bullet for every societal ill. Bitcoin may be provably scarce and fully decentralized, but it doesn’t fix corrupt human hearts hell bent on maintaining a system of financial slavery. Nation-state adoption of Bitcoin in its current form should not be mistakenly interpreted as the state nobly surrendering the money printer to advance individual freedoms. The most likely scenario, in my view, is that most governments will continue to issue fiat currency against their Bitcoin reserves, engaging in the same inflationary practices that debased gold-backed systems. The problem is not the asset backing the currency but the moral hazard of government control over money. History has shown us time and again that even the soundest monetary systems falter when subject to the whims of centralized authority.
The only way to achieve true fiscal discipline is to abolish legal tender laws and allow competing currencies, including Bitcoin, to flourish in the free market. As long as legal tender laws compel the use of fiat currency, governments will continue to inflate their money supply at the expense of the public, regardless of how much Bitcoin they hold. An SBR would not change this dynamic. Bitcoin, locked in their reserves, will become a tool to prop up the very system it was designed to destroy.
The Stakes Couldn’t Be Higher
The aim of this article isn’t to foster doomerism or any sort of pessimism, but it’s a reminder of what’s at stake. The allure of “number go up” might excite speculators in the short term, but it risks diverting attention from Bitcoin’s real purpose. A rising Bitcoin price is not a celebration of Bitcoin’s growing value—it’s a grim indictment of fiat’s accelerating demise. Each new all-time high is a reflection of fiat’s gradual but inevitable erosion.The real tragedy lies in misunderstanding this dynamic.The true measure of wealth is not fiat gains but sovereignty—freedom from the clutches of a system designed to perpetuate dependency and control.
To achieve this, Bitcoiners must resist the temptation to seek validation from governments and institutions. Instead, they must champion Bitcoin’s role as a peer-to-peer currency, a medium of exchange that operates outside the reach of centralized control. The battle is far from over, but the path forward is clear. The higher Bitcoin climbs, the more desperate the fiat establishment will become. Let us remember: the goal is not to join the system but to transcend it. Only by keeping this vision alive can Bitcoin fulfill its revolutionary promise as the people’s money—a beacon of hope in a world shackled by financial oppression.
-
 @ 6734e11d:c7e34e8f
2024-12-29 18:07:00
@ 6734e11d:c7e34e8f
2024-12-29 18:07:00 -
 @ f584256e:c8d47907
2024-12-29 17:41:07
@ f584256e:c8d47907
2024-12-29 17:41:07Once upon a time, in the heart of the Middle Ages, there lived a curious and adventurous boy named Oliver. At the tender age of eight, he resided in a humble farmer's house on the outskirts of a small town with his caring parents. The family had a modest plot of land and a cozy cottage, where they worked hard to make ends meet.

One day, as the sun painted the sky with hues of orange and pink, Oliver sat outside, gazing at the rolling hills and daydreaming about the world beyond. His eyes sparkled with the curiosity of a young explorer. "I wish I could see what lies beyond these fields and experience the wonders of the world," he mused.
Despite their humble circumstances, Oliver's parents noticed the longing in their son's eyes. Determined to nurture his adventurous spirit, they crafted a simple map together, tracing routes through neighboring villages, forests, and distant castles.
Encouraged by his parents, Oliver embarked on a journey, armed with his map, a small bag of provisions, and a heart full of dreams. As he ventured beyond the familiar fields, he encountered friendly villagers who shared stories of distant lands and magical creatures.
Oliver's journey led him through enchanted forests, where mystical creatures whispered secrets among the ancient trees. He crossed babbling brooks and climbed rolling hills, discovering the beauty of the world that lay just beyond his home.
Throughout his travels, Oliver encountered challenges and learned valuable lessons. He helped a lost lamb find its way back to the flock, befriended a wise old owl who shared tales of bravery, and even stumbled upon a hidden treasure chest, though it was filled not with gold but with the warmth of newfound friendships.

As days turned into weeks, Oliver's heart swelled with gratitude for the experiences that shaped him. He realized that the true wealth of the world lay not in gold and riches, but in the kindness of strangers, the beauty of nature, and the bonds of friendship.
Eventually, Oliver returned home, his heart brimming with stories to share. His parents, overjoyed to see their son safe and enriched by his adventures, welcomed him with open arms. From that day forward, Oliver carried the spirit of exploration within him, cherishing the simple joys of life and forever grateful for the love that surrounded him in his humble farmer's home. And so, in the center of the Middle Ages, a little boy's wanderlust had woven a tapestry of tales that would be passed down through generations.
-
 @ f4d89779:2b522db9
2024-12-29 16:46:43
@ f4d89779:2b522db9
2024-12-29 16:46:43In the game of Ultimate Frisbee, there is a beloved phrase that captures one of the best aspects of playing. Ultimate is about decision making. It is played on a rectangular field with seven players on each side. Much like football, the object of the game is to score with a throw into the end zone.
To "HUCK", means to launch the disc down field in the hopes of scoring. You can probably guess what the "OR YOU'RE NOTHING" means but the spirit of it is that when the opportunity comes ...
PUT THE DISC IN THE AIR
https://i.nostr.build/XyTpXdNOSpv5f8ZZ.jpg
Sorry, I had to channel my inner ODELL there for a second. These are all caps kind of moments. Time feels like it stops, the disc floats in the air, the receiver and defender are sprinting all out, you can hear the collective breath of anticipation from the audience and then you score. If you're good that is.
You know what? You and I are civilized people, we use the NOSTR, so I won't limit myself to just words. Here are some of those moments:
https://v.nostr.build/zav5o04BK97FiNAt.mp4
During the course of play, teams get into a formation with a couple of the players doing the majority of the disc throwing. These players are called handlers. They handle the disc, they have the responsibility of moving the disc downfield, and handle most of the decision making.
A good handler develops a sort of instinct for each of their receivers, can guess the capabilities of each defender, and knows himself well enough to know if he has the throw. They know who is good and reliable at short cuts. They know who has the top end speed to throw a long floating pass into the end zone. With each play they are judging all of the moving objects on the field and deciding on real time risk of each throw and where things will lead.
Mistakes lead to turnovers and turnovers, like in many other sports, are death.
Hopefully, you start to see how ultimate relates to life and Bitcoin. Life is a field and you have defenders and you have receivers. It is your disc and the decisions you make have a huge impact on whether you win or lose.
Knowingly or not, you saw Bitcoin as a potential receiver and Governments, academics, shitcoiners, as defenders. In some ways those around you were also defenders. They whispered, or maybe still whisper the risk and probability of failure in your ear. Their fear weighed against what you know.
With the btc/usd exchange rate at $94k, and companies fighting over the best ways to get sats I think we can say that you did not get lucky. They called you crazy, they said that throw won't work, they said your receiver sucked but you knew better.
You saw that receiver leaving every defender in the dust and you HUCKED it and you are certainly not NOTHING.
-
 @ b2caa9b3:9eab0fb5
2024-12-29 14:03:10
@ b2caa9b3:9eab0fb5
2024-12-29 14:03:10
Yesterday evening, I found myself enjoying a late dinner at the Hostel Bar, followed by diving deeper into exploring a nostr client called Primal. While it promises a partial solution to the issues I’ve been facing with the Alby Custodial Wallet, it’s still not perfect. There are features I’d like to see that are missing, and uploading images — like the ones I’m working on now in a café at the foot of Kilimanjaro — remains a challenge. Primal’s Prime Account is an option, but it doesn’t align with my current needs. If I could generate enough income over nostr to cover itself, I’d consider it, but for now, my search for a solution continues.

This morning, I decided to try a new café, someone recommended to me recently. The ambiance is lovely, and it has a great vibe, though a bit on the pricey side. The cappuccino was delightful, and its proximity to my hostel makes it a convenient spot. I might return, but I’m also intrigued by another recommendation: Aroma Coffee. The name reminds me of Aroma Kava in Ukraine, which I loved. I’ll have to visit it soon and see how it compares.
For today, my plans are simple. I aim to download videos from one cloud storage and transfer them to WeVideo for editing. My video projects have been on my mind, and I’m eager to keep making progress. Additionally, I’m experimenting with setting up VS Code for LaTeX. Currently, I’m drafting this blog post in VS Code using Markdown, but I’ve been inspired to explore LaTeX after reading an article about it. It’s been a while since I used Kile for LaTeX editing, so this will be a relearning experience. My goal is to make VS Code as versatile as possible for my creative and technical needs.

Looking ahead, I’m starting to think about my travel plans for 2025. At the beginning of the year, I’d like to explore new cities, perhaps visit Victoria Falls in Zambia, or even check out Uganda and the Nile’s source. However, I know I’ll eventually loop back to East Africa, with plans to end up in Mombasa. A flight to Germany crossed my mind, but my budget is too tight for that at the moment. Hopefully, in the next couple of days, I’ll have more clarity about my next steps. For now, I need to extend my stay at the hostel, pay my rent, and finalize my plans.
Moshi has been a delightful place to stay. It’s undeniably more picturesque than Kilifi, though each has its charm. While Kilifi boasts beaches, Moshi offers the majestic Kilimanjaro and a plethora of beautiful cafés and restaurants. The streets here are livelier, with newer cars and more spots to relax and soak in the atmosphere.
Unfortunately, I’m temporarily barred from entering Kenya. The border officer informed me that my frequent entries and exits have triggered restrictions. After some time, this should reset, and I’ll be able to return to explore the places I’ve missed.

Speaking of Kenya, I have to mention a surprising development from my time in Kilifi — my psoriasis disappeared. I attribute this to the consistent warm climate, the salty ocean air, and year-round sunshine. I’m optimistic that staying in a warm environment for the next couple of years will keep it away permanently.
Before leaving Moshi, I plan to buy a multipurpose sheet that I can use as a wrap or towel. It fits perfectly with my minimalist lifestyle. I’ve also been contemplating replacing my worn-out T-shirts with something new. While they’re still functional, they’ve seen better days.
I’ll wrap up this post here and wish everyone a beautiful Sunday. Stay tuned for more updates and photos from my day — including snapshots of the café and my walk there. Until next time!





-
 @ 16d11430:61640947
2024-12-29 12:17:30
@ 16d11430:61640947
2024-12-29 12:17:30In the intersection of technology, finance, and faith, an unusual but profound question emerges: What does it mean to transact with Christ using Bitcoin? While seemingly provocative, this inquiry opens a doorway to exploring the spiritual dimensions of Bitcoin and its implications for how humanity interacts with divinity in a modern, decentralized world.
The Idea of Transaction in a Spiritual Context
The term "transaction" often implies an exchange of goods, services, or currency—a concept grounded in material reality. Yet, within Christian theology, the notion of a transaction with Christ transcends the material. It refers to the exchange of faith for grace, sin for forgiveness, or the giving of one’s life in surrender for eternal life in return.
In this light, to transact with Christ is not about equivalence but about participation. It is an acknowledgment that human offerings, however limited, can be consecrated in service to a higher purpose. Thus, the question of using Bitcoin—a currency rooted in cryptographic trust and decentralization—becomes a metaphorical lens for examining the intersection of faith, technology, and moral action.
Bitcoin as a Reflection of Divine Attributes
Bitcoin possesses characteristics that resonate with certain divine attributes, making it an intriguing subject for theological reflection:
-
Incorruptibility: Bitcoin’s blockchain is immutable. Once written, it cannot be altered—a reflection of divine truth, which is unchanging and eternal. Just as Christ proclaimed Himself to be "the way, the truth, and the life" (John 14:6), Bitcoin's transparency and incorruptibility evoke a similar aspiration for absolute justice and integrity.
-
Decentralization: Bitcoin operates without a central authority, distributing power across a network of participants. This mirrors the Christian concept of the Body of Christ, where no single member holds dominion, but all work together in harmony for the greater good.
-
Transparency: Every transaction on the Bitcoin network is visible on the blockchain, symbolizing the omniscience of God. Just as nothing is hidden from the divine gaze, Bitcoin creates a system where accountability is enforced by the network itself.
-
Finite Supply: The 21-million cap of Bitcoin reflects a sense of order and discipline, contrasting with the boundless expansion of fiat systems. This scarcity encourages stewardship, a virtue long emphasized in Christian ethics.
Transacting with Christ Using Bitcoin
To transact with Christ using Bitcoin is not to reduce Him to a financial ledger but to consider how modern tools of exchange can symbolize spiritual truths. Such a transaction would not involve equivalence—no earthly currency could measure Christ's infinite gift of redemption—but rather alignment.
When we think of offering Bitcoin to Christ, it becomes an act of devotion and surrender, acknowledging that even the fruits of human ingenuity belong to Him. It is akin to the widow’s mite (Mark 12:41–44), where the value of the offering lies not in its material worth but in the intention and sacrifice behind it.
Bitcoin and the Moral Economy
In a world where fiat currencies are often associated with corruption, inflation, and centralization, Bitcoin represents a radical shift toward an incorruptible and transparent economic system. For Christians, this aligns with the call to live justly and to “render unto Caesar the things which are Caesar’s, and unto God the things that are God’s” (Matthew 22:21).
By engaging with Bitcoin, Christians can participate in a moral economy—one that resists manipulation and upholds principles of fairness and accountability. Transacting with Christ, then, becomes a metaphor for aligning one’s financial practices with spiritual values, using tools like Bitcoin to reflect divine justice and order.
Bitcoin as a Spiritual Tool
While Bitcoin is a technological creation, its design invites reflection on spiritual principles. Its reliance on consensus mirrors the need for communal harmony in faith. Its resistance to corruption serves as a call for moral integrity. By surrendering to Bitcoin's rules—rules that cannot be bent for personal gain—one practices a form of humility, recognizing the limitations of human control.
Challenges and Limitations
Of course, Bitcoin is not without its challenges. Its use can be corrupted by greed, speculation, or unethical practices, just as any tool can be misused. To engage with Bitcoin spiritually requires discernment: a focus on its potential for justice and stewardship rather than its potential for exploitation.
Moreover, the metaphor of transacting with Christ must be handled with care. It is not about commodifying the divine but about seeing in Bitcoin a symbol of how human innovation can serve higher purposes when rightly ordered.
Conclusion: Surrendering the Temporal for the Eternal
To transact with Christ using Bitcoin is to ask: How can modern tools reflect eternal truths? It is an invitation to sanctify the temporal by aligning it with the divine. Bitcoin, with its incorruptible ledger and decentralized nature, offers a unique opportunity for such reflection.
Ultimately, the question is not about Christ accepting Bitcoin but about whether we, as stewards of creation, can use tools like Bitcoin to serve justice, truth, and the greater good. By doing so, we participate in a moral economy that transcends material wealth and points toward the eternal treasure Christ exhorts us to seek.
-
-
 @ 78c90fc4:4bff983c
2024-12-29 09:44:20
@ 78c90fc4:4bff983c
2024-12-29 09:44:20Pharma Whistleblower since 2009
Jane Bürgermeister was born in Switzerland on 19 January 1966 and has both Austrian and Irish citizenship. She has worked as a journalist and has written articles for various publications such as Nature, the British Medical Journal and The Guardian.\ \ In April 2009, Bürgermeister filed criminal charges against several organisations and individuals, including:\ • The World Health Organization (WHO)\ • The United Nations (UN)\ • The US government and President Obama\ • Pharmaceutical companies such as Baxter\ He accused these parties of serious crimes such as:\ • Attempted mass murder\ • Bioterrorism\ • High treason
Her 2009 video was deleted from social media sites and YouTube:
https://waltersiegrist.ch/JaneBurgermeister2009.mp4
Living in Greece in 2023, she urgently called to lift Mitsotakis' immunity for participating in an illegal plan to administer a toxic Covid vaccine to the Greek public and knowingly poison millions of Greeks.
https://x.com/RealWsiegrist/status/1873028168774500362
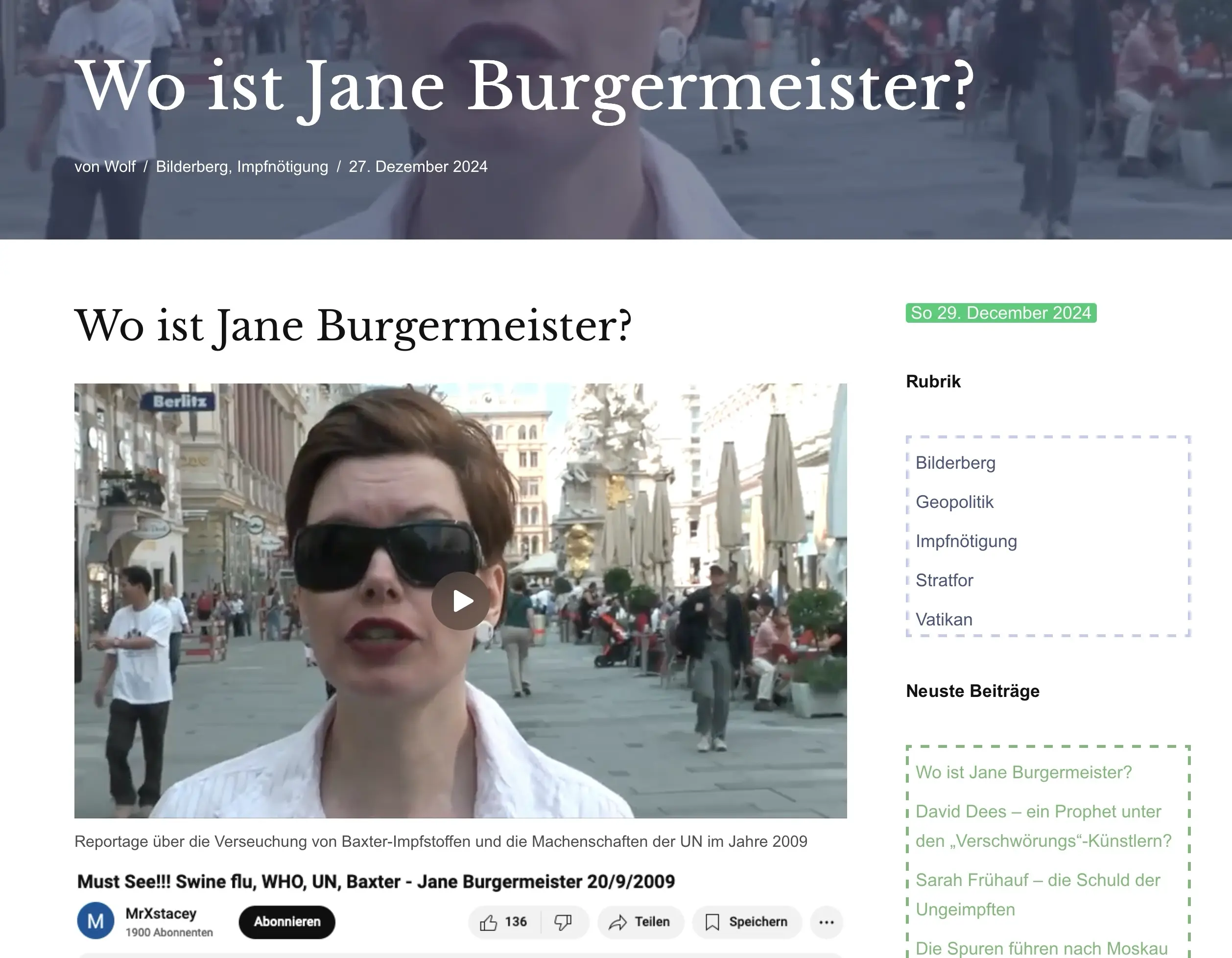
-
 @ 78c90fc4:4bff983c
2024-12-29 09:04:36
@ 78c90fc4:4bff983c
2024-12-29 09:04:36 -
 @ 6f3670d9:03f04036
2024-12-29 08:20:22
@ 6f3670d9:03f04036
2024-12-29 08:20:22Disclaimer: - This will void your warranty - There might be differences between the Bitaxe and the Lucky Miner that might not cause issues or damage immediately, but might manifest long-term - Proceed at your own risk
A Different Pickaxe
You live in a place where it's difficult to get a Bitaxe. You have access to AliExpress. You look around. You find something called the "Lucky Miner LV06". A Bitaxe clone that uses the same mining chip as the Bitaxe Ultra (BM1366 ASIC). You buy one.
You plug it in, you enter your wallet address and other settings, and it starts mining. It works! Great!
But it's running a customized firmware. It's not AxeOS. Maybe there's something shady in the stock firmware. It's not open-source, after all. Also, AxeOS looks amazing... And that automatic pool fail-over feature is handy.
You think to yourself: "Maybe I can use the Bitaxe firmware on this?". Guess what? You're right!
Flashing From Web UI
What usually works for me is to: - Download the Bitaxe firmware files (
esp-miner.binandwww.bin) from GitHub (here). Version 2.4.1 seems to work well, as of this writing. - Then from the Lucky Miner web interface, upload the "Website" (www.bin) file. - Wait for a minute or two after it's done uploading. - Upload the "Firmware" (esp-miner.bin) file. - Wait another minute or two. - Unplug the power and plug it back in. - Set the "Core Voltage" and "Frequency" to the defaults. - Unplug the power and plug it back in again.If you're lucky (no pun intended), you'll have a working Lucky Miner with AxeOS. Update the settings and mine away!
However, often times I've been unlucky, like what happened while I was writing this article, ironically. The miner malfunctions for no obvious reason. It keeps rebooting, or it's not mining (zero/low hashrate), or the web interface is inaccessible. You name it.
The miner has become a "brick". How do you "unbrick" it?
When you brick a Bitaxe, you can recover it by flashing (uploading) a "Factory Image". The Bitaxe has a USB port that makes this easy. Follow the guide and it should come back to life again. Unfortunately, the Lucky Miner LV06 doesn't have a USB port. It has a serial port, though. We'll have to get our hands a bit dirty.
Flashing Using the Serial Port
We need to connect the serial port of the miner to a computer and run a program to flash (upload) the firmware file on the miner. Any 3.3v UART serial port should be sufficient. Unfortunately, PCs don't usually come with a UART serial port these days, let alone a 3.3v one. The serial port common in old computers is an RS-232 port, which will most probably fry your miner if you try to connect it directly. Beware.
In my case, as a serial port for my PC, I'm using an Arduino Due I had lying around. We connect it to the PC through USB, and on the other side we connect a few wires to the miner, which gives the PC access to the miner.
WARNING: Make sure your serial port is 3.3v or you will probably kill the miner. Arduino Uno is 5v not 3.3v, for example, and cannot be used for this.
Wiring
First, we need to open the Lucky Miner. Use a small flat screwdriver to gently push the two plastic clips shown in the picture below. Gently pry the top cover away from the bottom cover on the clips side first, then remove the other side. Be careful not to break the display cable.
Once the cover is off, you can find the miner's serial port in the top right corner (J10), as shown in the next picture. We'll also need the reset button (EN).
There are three screws holding the PCB and the bottom cover together. If you're confident in your ability to push the small button on the underside of the PCB with the bottom cover on, then no need to remove these. The following picture shows what we need from that side.
And the next picture shows the pins and USB port we will use from the Arduino.
Now, we need to connect: - The USB port on the Arduino labelled "programming" to the PC - Pin 18 (TX1) on the Arduino to J10 through-hole pad 5 (blue dot) - Pin 19 (RX1) on the Arduino to J10 through-hole pad 3 (green dot) - Any GND pin on the Arduino to J10 through-hole pad 4 (yellow dot)
I didn't need to solder the wires to the pads. Keeping everything stable, perhaps by putting a weight on the wires or a bit of tape, was sufficient in all my attempts.
Setting up the Arduino
To use the Arduino as a serial port for our PC, we'll have to make it pass-through data back and forth between the USB port and UART1, where we connected the miner.
The following steps are all done on a PC running Debian Linux (Bookworm), in the spirit of freedom and open-source.
First, we start the Arduino IDE. If the package for the Arduino Due board is not already installed, you'll see a small prompt at the bottom. Click "Install this package".
Click the "Install" button.
Once the package is installed, click "Close".
Next, we select the Due board. Click the "Tools" menu, select "Board", select "Arduino ARM (32-bits) Boards" and click "Arduino Due (Programming Port)"
Next, we select the port. Click the "Tools" menu again, select "Port", and click the port where the Arduino is connected. In my case it was "/dev/ttyACM0".
Now we need to upload the following code to the Arduino board. The code is actually the "SerialPassthrough" example from the IDE, but with the serial speed changed to match the miner.
``` void setup() { Serial.begin(115200); Serial1.begin(115200); }
void loop() { if (Serial.available()) { // If anything comes in Serial (USB), Serial1.write(Serial.read()); // read it and send it out Serial1 }
if (Serial1.available()) { // If anything comes in Serial1 Serial.write(Serial1.read()); // read it and send it out Serial (USB) } } ```
Copy/paste the code into the IDE and click upload. You'll see "Done uploading" at the bottom.
Next we'll test if we're receiving data from the miner. We start by opening the "Serial Monitor" from the "Tools" menu in the IDE. Then we change the baudrate to 115200.
Set the Arduino and the miner in a comfortable position, make sure the wires are held in place and got a good contact on both sides, and the power is plugged in.
Now we'll put the miner in "download" mode. Press and hold the button on the underside (K1), press and release the reset button (EN), then release the other button (K1).
You should see some text from the miner in the serial monitor window, like in the picture below.
Congratulations! We know we're able to receive data from the miner now. We're not sure transmit is working, but we'll find out when we try to flash.
Flashing Using the Serial Port, for Real
To flash the Lucky Miner we'll need a software tool named esptool and the factory image firmware file.
I usually use "esp-miner-factory-205-v2.1.8.bin" for the factory image (this one) as a base, and then flash the version I want from the Web UI, using the steps I mentioned earlier.
For esptool, the documentation (here) shows us how to install it. To make things a little easier on our Debian Linux system, we'll use pipx instead of pip. The instructions below are adapted for that.
First we make sure pipx is installed. Run this command in a terminal and follow the instructions:
sudo apt-get install pipxThen we install esptool using pipx. Run the following in a terminal:
pipx install esptoolThe output will be something like this:
user@pc:~$ pipx install esptool installed package esptool 4.8.1, installed using Python 3.11.2 These apps are now globally available - esp_rfc2217_server.py - espefuse.py - espsecure.py - esptool.py ⚠️ Note: '/home/user/.local/bin' is not on your PATH environment variable. These apps will not be globally accessible until your PATH is updated. Run `pipx ensurepath` to automatically add it, or manually modify your PATH in your shell's config file (i.e. ~/.bashrc). done! ✨ 🌟 ✨We can see pipx telling us we won't be able to run our tool because the folder where it was installed is not in the PATH variable. To fix that, we can follow pipx instructions and run:
pipx ensurepathAnd we'll see something like this:
``` user@pc:~$ pipx ensurepath Success! Added /home/user/.local/bin to the PATH environment variable.
Consider adding shell completions for pipx. Run 'pipx completions' for instructions.
You will need to open a new terminal or re-login for the PATH changes to take effect.
Otherwise pipx is ready to go! ✨ 🌟 ✨ ```
Now, close the terminal and re-open it so that esptool becomes available.
Finally, to actually flash the miner, put the miner in download mode, then in the following command change the port ("/dev/ttyACM0") to your serial port, as we've seen earlier, and the file path to where your firmware file is, and run it:
esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.binIf everything went fine, the tool will take a few minutes to flash the firmware to the miner. You'll see something like this in the output:
``` user@pc:~$ esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.bin esptool.py v4.8.1 Serial port /dev/ttyACM0 Connecting..... Detecting chip type... ESP32-S3 Chip is ESP32-S3 (QFN56) (revision v0.2) Features: WiFi, BLE, Embedded PSRAM 8MB (AP_3v3) Crystal is 40MHz MAC: 3c:84:27:ba:be:01 Uploading stub... Running stub... Stub running... Configuring flash size... Erasing flash (this may take a while)... Chip erase completed successfully in 9.5s Compressed 15802368 bytes to 1320190... Wrote 15802368 bytes (1320190 compressed) at 0x00000000 in 152.1 seconds (effective 831.2 kbit/s)... Hash of data verified.
Leaving... Hard resetting via RTS pin... ```
And we're done! Hopefully the miner will be recovered now.
Hope this helps!
Stay humble,
dumb-packageA Warning About Beta Versions of AxeOS
For reasons unknown to me, while I was writing this article I wanted to try the testing version of AxeOS, which was v2.4.1b (beta). Flashing from Web UI went smooth, but the miner stopped mining. I flashed back to v2.1.8 using the serial port, a known good version for me, but it wouldn't mine, still.
Thankfully, v2.4.1 was released recently, and flashing it from the Web UI magically revived my miner. So, be warned.
Bonus: File Hashes
For convenience, these are the SHA256 hashes of the files I used in this article: ``` da24fceb246f3b8b4dd94e5143f17bd38e46e5285e807ebd51627cb08f665c0a ESP-Miner-v2.4.1/esp-miner.bin 16c5c671391f0e3e88a3e79ce33fad3b0ec232b8572fad5e1e0d1ad3251ab394 ESP-Miner-v2.4.1/www.bin
d5182a15b6fa21d7b9b31bff2026d30afed9d769781a48db914730a5751e20c6 esp-miner-factory-205-v2.1.8.bin ```
-
 @ 6f3670d9:03f04036
2024-12-29 06:51:25
@ 6f3670d9:03f04036
2024-12-29 06:51:25This is my first long-form post. The starting line.
There's nothing of value here. Just using this as a marker.
I hope to post a lot more. Documenting how I made something work would be very useful to me, and hopefully others, but I've been too lazy to do that. Wish me luck!
Stay humble,
dumb-package -
 @ 16d11430:61640947
2024-12-29 02:44:31
@ 16d11430:61640947
2024-12-29 02:44:31ERM (Erlang on Mobile) goes beyond traditional mobile frameworks by integrating a Core Lightning (CLN) plugin and a Decentralized Exchange (DEX). These additions are pivotal for creating a secure, private, and user-centric mobile ecosystem. Here's how these integrations work, their implications, and why they represent a monumental leap forward for mobile technology.
Core Lightning Plugin: Decentralized Payments at the Core
- Seamless Micropayments for Mobile Applications
The Core Lightning plugin enables ERM to support Lightning Network payments natively:
Low Fees: Lightning’s off-chain nature ensures low transaction costs, making micropayments viable for app interactions.
Instant Settlements: Payments are confirmed in milliseconds, ensuring smooth user experiences.
Global Accessibility: Users can transact across borders without relying on traditional banking systems.
Use Case: An in-app marketplace allows users to pay for premium features, services, or digital goods directly using Bitcoin over the Lightning Network, bypassing credit card fees and delays.
- Enhanced Privacy
Lightning payments are inherently private due to their off-chain structure:
Transaction details are not broadcasted to the blockchain, reducing exposure.
Users maintain control of their payment channels, ensuring confidentiality.
Use Case: A subscription-based app could charge users directly through a private Lightning channel, ensuring that neither the app nor third parties access sensitive financial information.
- Security Through Decentralization
The integration of Lightning ensures decentralized payment processing:
Removes reliance on centralized payment processors prone to outages or breaches.
Protects against censorship, enabling users to transact freely, even in restrictive environments.
Use Case: A whistleblower app on ERM could accept anonymous payments or tips via the Lightning Network, safeguarding user identities.
Integrated DEX: True Ownership and Private Trading
- Decentralized Trading for App Ecosystems
The integrated DEX allows users to trade assets directly within the ERM ecosystem:
Token Swaps: Users can exchange tokens for utility services or app-specific credits without leaving the ecosystem.
Non-Custodial: Users retain full control of their assets, eliminating reliance on third-party exchanges.
Use Case: A decentralized ride-sharing app lets users trade app-specific tokens for Bitcoin or other cryptocurrencies directly through the DEX.
- Privacy-Preserving Transactions
The DEX enhances privacy by enabling trades without revealing personal information:
Trades occur peer-to-peer, bypassing centralized order books that track user activity.
Smart contracts enforce the terms of the trade, removing intermediaries.
Use Case: A freelance marketplace app allows users to exchange their earnings for other cryptocurrencies privately and instantly.
- Enhanced Security Through Smart Contracts
The DEX leverages Aeternity’s smart contracts for secure, transparent trading:
Atomic Swaps: Eliminate counterparty risk by ensuring both sides of a trade are completed simultaneously or not at all.
Immutable Records: Trade data stored on the blockchain ensures transparency without compromising user privacy.
Use Case: Users can securely trade gaming assets or NFTs within ERM apps, knowing the transaction terms are immutable and verifiable.
Combined Benefits: CLN + DEX Integration in ERM
- Unified Ecosystem
By integrating Lightning payments and decentralized trading, ERM creates a cohesive ecosystem:
Apps can natively handle payments and asset trading without external dependencies.
Developers can monetize their apps without relying on traditional app stores or payment gateways.
Use Case: A decentralized social media app on ERM allows users to tip creators via Lightning and trade in-app rewards for cryptocurrencies through the DEX.
- Increased User Autonomy
ERM empowers users to take control of their digital lives:
Privacy: Users can transact and trade without exposing personal data.
Security: Decentralized architecture ensures protection against data breaches and fraud.
Freedom: Users can access financial services and marketplaces without geographical or regulatory restrictions.
Use Case: A remittance app built on ERM enables users to send payments globally over the Lightning Network, while the DEX allows them to convert funds into local currencies or stablecoins.
- Future-Proof Mobile Technology
The integration of CLN and DEX positions ERM as a trailblazer in the evolution of mobile technology:
It aligns with the growing demand for decentralized, private, and secure digital solutions.
By combining cutting-edge technologies, ERM anticipates the needs of users and developers in a post-fiat world.
Use Case: Developers build apps that automatically allocate profits through Lightning microtransactions and provide token-based access to premium features traded on the DEX.
Conclusion: A New Era for Mobile Privacy and Security
ERM, with its integrated Core Lightning plugin and DEX, offers a vision of mobile technology that is:
Private: Safeguarding user data and transactions.
Secure: Leveraging decentralized architecture to eliminate single points of failure.
Efficient: Enabling seamless payments and trading directly within apps.
This ecosystem isn’t just a step forward—it’s a leap into a future where users are empowered, developers are liberated, and the boundaries of mobile technology are redefined. With ERM, the constraints of fiat and centralized systems are left behind, making way for a new paradigm of freedom, efficiency, and innovation.
-
 @ 16d11430:61640947
2024-12-29 02:26:26
@ 16d11430:61640947
2024-12-29 02:26:26Introduction to ERM
ERM, or Erlang on Mobile, is a groundbreaking initiative that brings the robust and highly concurrent Erlang ecosystem to mobile devices. Designed to enable resilient, low-latency, and efficient computing, ERM represents a shift in how mobile applications can function. With seamless state persistence, decentralized architectures, and interfaces mimicking natural processes, ERM provides a vision of mobile technology that transcends traditional app models.
The Problem: Lost Serenity in a Fiat-Driven World
Modern app-based living thrives on convenience but is constrained by systems rooted in fiat economies—centralized control, inefficiency, and lack of user agency. Fiat-driven models perpetuate:
Fragile systems: Apps fail to maintain seamless continuity, leaving users frustrated.
Wasted potential: Centralized architectures stifle innovation and scalability.
Lack of freedom: Users are tethered to rigid systems, with little room for customization or personal growth.
This has led to a loss of peace, serenity, and efficiency, leaving users yearning for systems that prioritize their autonomy and well-being.
The Solution: ERM’s Revolutionary Approach
- Persistent State for Seamless Experiences
ERM integrates with Aeternity's state channels to enable real-time, continuous state persistence:
Apps maintain a living state across devices and interactions, mirroring the continuity of natural systems.
Users experience uninterrupted workflows, even in scenarios of device failure or network disruptions.
This eliminates the frustration of fragmented data and inconsistent app performance.
Relatable Perspective: Imagine switching between your devices without losing a single step in your workflow—your shopping cart, chat threads, or game progress flows with you, effortlessly.
- Decentralized Intelligence and Privacy
ERM leverages the power of blockchain and decentralized computing to create apps that are:
Resilient: Distributed systems adapt to disruptions without compromising performance.
Intelligent: Applications evolve dynamically based on user behavior, acting as intuitive agents.
Private: State channels ensure sensitive data is protected, offering users security without sacrificing usability.
Relatable Perspective: Picture your fitness app not just tracking your steps but adapting to your routines and offering personalized advice in real-time—all while keeping your data private.
- Ergonomic and Human-Centric Interfaces
ERM introduces interfaces that amplify the grace of human form, inspired by natural processes:
Gesture-based controls: Intuitive, ergonomic interactions make technology feel like an extension of your body.
Adaptive design: Interfaces evolve organically, adjusting to your needs and environment.
Seamless integration: Hands-free, holographic elements blend into your daily life, freeing you from traditional screens.
Relatable Perspective: Think of a virtual assistant that responds fluidly to gestures while you're cooking or driving, offering suggestions without you needing to touch a device.
- Liberation from Fiat Constraints
Fiat-based systems have dominated modern technology, tying innovation to outdated economic models. ERM’s decentralized approach:
Operates beyond the reach of centralized fiat control, ensuring freedom for users and developers.
Creates a "slip gap" where human efficiency can flourish, untouched by bureaucratic stagnation.
Offers opportunities for creativity and progress that centralized systems cannot match.
Relatable Perspective: Developers can now build apps that aren’t limited by app store restrictions or payment gateways, creating ecosystems where users pay directly for utility—like subscribing to features on-demand with crypto.
Why ERM Matters: Grasping the Slight Edge
ERM represents more than a new technology—it’s a philosophy of reclaiming peace and efficiency through innovation. By:
Empowering decentralized, persistent systems,
Enhancing human-centric design,
Offering freedom from fiat’s limitations,
ERM provides the slight edge needed to transcend traditional models. It enables us to imagine and build interfaces that feel alive, systems that work for us rather than against us, and a future where technology is a natural extension of human creativity and grace.
Conclusion: A New Paradigm of Efficiency
ERM isn’t just about better apps—it’s about redefining how we interact with technology. It’s about creating systems that mirror the fluidity and resilience of nature while empowering users to reclaim their serenity in a world long dominated by inefficiency and control.
This is the opportunity to break free from fiat's constraints and embrace a future of seamless, decentralized, and human-centric innovation. The question isn’t whether to grasp it—it’s whether you can afford to be left behind.
-
 @ bc6ccd13:f53098e4
2024-12-29 01:55:40
@ bc6ccd13:f53098e4
2024-12-29 01:55:40I’ve been thinking about the topic of this article for a while, but what really motivated me to sit down and write was a comment Matt Odell made on the Citadel Dispatch podcast recently. He said,
To me, that’s the cool part about Bitcoin, is that it’s this interoperable, permissionless, global network. And it’s almost like a shared equity, right? If you own Bitcoin the asset, it’s like we all share equity in this almost like a startup equity. And anything we do, and a lot of times it’s out of greed too. It’s not out of benevolence. You don’t have to be like a charitable person. But you know, if Strike benefits from something or Unchained Capital benefits from something, then Manchankura in Africa benefits from it as well at the same time, which is like a crazy concept. I feel like people just don’t really appreciate that.
When you start going down the “what is money?” rabbit hole, debt quickly comes into focus. You try to understand what it is, how it works, and why the world has so much of it and seemingly more by the second. Eventually you’ll discover that the “money” we use today is mostly just debt, created by banks when they make loans, and treated the same as the cash in your wallet. Until too many people try to withdraw their “money” from the bank, and the bank doesn’t have nearly enough cash to meet the withdrawals and collapses into insolvency. Which it always was, only no one realized who was swimming naked until the tide went out.
Equity is a related financial concept that doesn’t typically come up when studying money. The definition of the word as it’s used financially is something like “a risk interest or ownership right in property.” In simple terms, equity refers to ownership of something. For example, if you have a house that’s worth $500,000 and you have no mortgage or loans against the house, you have equity in the house of 100% of its value, or $500,000. If you have a mortgage of $250,000, you currently have 50% equity in the house, or you “own” half the value of the house.
It’s also often used to refer to shares issued by publicly traded companies. The shares represent a partial ownership of, or equity in, the company. If a company has issued 1,000 shares of stock and you own 10 shares, you have a 1% ownership of that company. That ownership give you certain privileges, such as dividends paid out from profits the company makes and potentially ownership of an increasingly valuable company, if it continues to be successful.
Money: Debt or Equity?
The current fractionally reserved fiat banking system primarily uses debt as money. There’s a small amount of base money, which consists of physical cash and a digital equivalent of cash called bank reserves, which are held in a ledger in banks’ accounts at the Federal Reserve and are used to settle transactions between banks. But this base money only makes up a small percentage of the total money supply. The bulk of the “money” consists of bank deposits, which are essentially IOUs created by banks when they issue loans under the fractional reserve system. When a bank makes a loan, they don’t actually give the borrower base money, for example a stack of physical cash, in most cases. Instead what they give is an liability entry in the bank’s balance sheet ledger that says “the bank owes the borrower this amount of dollars.” At the same time, on the asset side of the balance sheet they create another entry that says “the borrower owes the bank this amount of dollars” with details on how and when the loan must be repaid.
Then through the magic of banking, the borrower can transfer the numbers representing the amount the bank owes them to someone else, and now the bank owes that other person a certain number of dollars. And so on down the line. This can continue indefinitely, with people exchanging bank IOUs with each other in perpetuity, and no actual base money dollars needing to be exchanged. With help from a deliberate effort by banks to conceal the real nature of their activities, these credit/debt ledger entries function as, and for all practical purposes become, money. The only thing that can upset the apple cart is too many people trying to effectively exit the banking system at once, by trying to withdraw the money in their account. At that point reality sets in. The fact that the numbers in their account didn’t actually represent base money but rather just debt that the bank owes the depositor becomes obvious when the bank run reveals that the bank doesn’t have enough actual base money to settle its debt.
This system has a lot of serious problems, besides the fact that it’s fundamentally based on a lie. For one, all the bank deposits are created by making loans, which means they’re all debt, which means they all have to be paid back with interest. That’s a problem for two reasons. One, paying back the debt destroys money, which artificially disrupts the economy by distorting prices as the amount of money in the economy rises and falls arbitrarily depending on new loan issuance versus debt repayment. Two, when the loan is made, only the amount of the principle is created in bank deposits. The interest isn’t. That means new loans have to be made to pay the interest on the existing loans. That basically guarantees that the amount of debt in the economy will continue to rise indefinitely, because the only way it could go down is for the banking system as it currently exists to collapse, or to be “bailed out” with massive injections of newly created base money to offset loans that can’t be paid back. That, coincidentally, is what Quantitative Easing is; an injection of newly created base money to provide liquidity to pay back debt without having to issue new debt to do it.
Now let’s think for a minute about equity and how it might compare and contrast with the current system in relation to money.
To begin with, I understand money as a ledger of deferred consumption. If you haven’t heard that concept before, it would probably be helpful to familiarize yourself with my thought process laid out here.
naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqq247t2dvet9q4tsg4qng36lxe6kc4nftayyy89kua2
Deferred consumption is what makes capital formation and civilization possible. People work to create things that they don’t immediately consume, and those new tools and processes make it easier to create more things in the future with less effort, which raises the productivity of the economy (getting more output for less input) and makes society as a whole wealthier. Those new tools and processes can then be used to more efficiently create other tools and processes, which increases productivity even further, and the whole thing compounds on itself in an exponential curve of increasing productivity and increasing wealth. But it all starts with and relies on someone somewhere putting in effort now, to create something they won’t benefit from until later.
Planting a seed is a perfect example. When you have a bushel of wheat, you have two choices. You can consume it now. That’s immediately satisfying and keeps you fed for say a month. Or you can plant it. That’s hard work, and you also have to defer consumption of the wheat. You can’t eat it now, you have to satisfy your hunger some other way. It also takes work throughout the year to cultivate and care for the wheat crop, time you could have spent doing something more fun, if you had just consumed the wheat directly instead of planting it. The flip side is, at harvest time, you might harvest 50 bushels of wheat from the 1 bushel you didn’t eat 6 months ago. That 50 bushels could now feed you for 4 years, and you can sell 30 bushels, keep 12 for your own use over the next year, and plant 8 for harvest next year. Then in a year you might harvest 400 bushels, etc. You can see how a little bit of deferred consumption today can lead to a lot of reward in the future. There’s even a term for being short-sighted and sacrificing future rewards for present gratification, “eating the seed corn,” which comes directly from this farming wisdom.
The same principle applies to business equity. When you start a business, you invest in some way into building something that isn’t immediately rewarding, but that you expect will yield more production in the future than your initial investment. You might invest your own time and effort, resources that you’ve gathered, money, or any number of other forms of value. The same applies to a public company that issues equity as shares of stock. Anyone can invest in the company by purchasing shares, which gives them a partial ownership of the company and its future growth and production. All those forms of investment, to acquire equity, are different forms of deferred consumption. You have to give up something you could have now, for something you hope to have in the future. You could spend the time now curled up in bed binge-watching Netflix. You could spend your effort strolling down the boardwalk eating an ice cream cone. You could spend your money on that pricey designer bag that all your girlfriends will be jealous of. All those things would be immediately gratifying. But they all have a long-term cost.
What happens when you defer consumption instead, and acquire equity? If things go the way you hoped and planned, and the company you founded or invested in is successful, it will eventually produce more than the initial consumption that you deferred. Your equity will become more valuable with time. Why? Because like we pointed out, deferred consumption and capital formation increases efficiency, which leads to compounding returns in productivity and value.
If the company is extremely successful and you defer your consumption long enough, those returns can be very large. For example, if you had invested $1,000 in Amazon in 2007, that equity today, 17 years later, would have returned over $80,000. The first iPhone was released in 2007 for $500. So you could have bought two iPhones instead of making that initial investment in Amazon. But if you deferred that consumption instead, even though the price of the iPhone has doubled by 2024, you could still buy eighty new iPhones with the equity from that initial investment instead of two, or a 40x return in “iPhone inflation adjusted” terms.
Now let’s make a mental leap and compare equity in a business with money. We’ve defined money as a ledger of deferred consumption. You could define business equity as a ledger of consumption deferred to establish ownership of a business instead. You have the stock, the equity in the company, to represent that you invested your time, effort, resources or money into building a business rather than consuming it on something for your immediate gratification. These definitions seem very similar, almost synonymous. We could also consider the economy as a whole to be very similar to a business. As consumption is deferred, more capital is created in the economy, it becomes more efficient and productive, more outputs are created with fewer inputs, and the economy as a whole grows in value.
Business equity represents ownership in a company, both in the current value of that company, and in its future productivity and value. Why? Because the future productivity and value wouldn’t exist if it weren’t for the deferred consumption of the initial investment. If Jeff Bezos hadn’t started Amazon, and investors hadn’t provided the money by buying shares to enable the company to grow the way it did, all the productivity and value of Amazon today wouldn’t exist. That’s why it’s fair for the person who only invested $1,000 in 2007 to gain a return of 40x that investment today.
So if business equity represents ownership of a company earned by deferred consumption, what does the deferred consumption of money itself grant ownership of? Well, money can be exchanged for any good or service available on the market, throughout the entire economy. In my opinion, money should represent ownership of the future productivity and value of the economy as a whole. Money should be equity in civilization itself. The future productivity and value of the economy depends on the deferred consumption of today, just like the future productivity and value of a company depends on the deferred consumption of its initial founders and investors.
Slices of Pie
There’s an issue that needs to be addressed here, one that the savvy investor will have noticed already. Equity in a growing and successful company becomes more valuable over time. Yet even though the economy as a whole is becoming more productive and more valuable, money as we know it today becomes less valuable over time. The $1,000 Amazon equity went from being worth two iPhones, to being worth eighty iPhones. Over the same time period, the $1,000 itself went from being worth two iPhones to being worth one iPhone. What gives?
To understand, we have to look at the differences between how equity is created and how money is created.
The most simple example is a company that’s owned by a single individual. They hold 100% of the equity. You could call that one share. Think of the company like a pie, but the pie hasn’t been cut, so there’s only one “slice.” Over time, if the company is successful, the company “pie” grows larger. But as it grows, it doesn’t get cut into more slices, the one “slice” just gets bigger and bigger. So the one “share” of equity the owner holds is still one share, it’s just a bigger and more valuable share.
Public companies generally function similarly. They start out “going public” by issuing shares. Each share is like a small slice of the company “pie.” Say the company issues 1,000 shares, each share represents a slice of pie 1/1,000th the size of the whole company pie. If the company grows, it won’t commonly issue more shares, although that can happen in certain situations. Instead, the shares will continue to represent 1/1,000th of the company, it will just be 1/1,000 of a bigger and bigger “pie” as time goes on. If the company doubles in productivity and value, each share will be twice as valuable, while still only being one share.
That doesn’t have to be the case. The company can, and sometimes does, issue more shares of stock. The reason this isn’t commonly done, though, is that it’s usually bad for the holders of the stock. If the company issues another 1,000 shares, there are now 2,000 pieces of ownership of the company. The company is no bigger, it’s just divided into more pieces. It’s like cutting each slice of pie in half. You don’t have more pie, you just have more pieces of pie. And as someone who already had a piece of pie, your piece suddenly got cut in half. Of course you probably won’t be too happy about that situation. In effect, the value of the deferred consumption of your initial investment is being taken away from you and given to someone who didn’t defer consumption and therefore didn’t contribute to the success the company has already experienced.
Contrast that to how money is created. If you compare the chart of money supply below with the chart of GDP, you'll see they both go up over time.


GDP is an (admittedly flawed) measure of the goods and services produced by an economy each year. It's similar to a company's revenue. As a company or economy grows and becomes more productive and valuable, the revenue or GDP rises. The thing about the economy though, is that money, the “shares” of an economy representing the deferred consumption that enables it to grow, is constantly being created by banks making new loans. So as the economy grows, the number of “slices” of the economy grows even faster. When the number of “slices” of an economy grow faster than the economy itself, the “size” or value of each slice falls over time. This is what we call inflation. It takes more “slices” of the economy to buy something than it did in the past, even though the economy is more efficient at producing that good or service than it was in the past.
You can imagine how it might look if a company managed its equity the way the banks manage our money. Each year, as the company grew, the board of directors would issue enough new shares of stock to make sure the value of each share fell that year. They could take the approach the US banking system takes and “target 2% inflation,” in other words try to make the share value fall 2% every year. So if the productivity and value of the company increased by 10%, the board would issue 12% more shares to dilute the existing shareholders by the full amount of the increased value of the company, plus an additional 2%. This would help ensure the share price fell 2% every year. The new shares would be distributed to existing shareholders arbitrarily by decision of the board, with a big chunk going to the board members themselves. This would be highly profitable for the board, leaving them with a larger slice of company equity every year, while being very damaging to all the other shareholders.
In fact, one might wonder why an investor would ever hold equity in a company, when the company's stated policy was to reduce the value of that equity by 2% every year. The answer is, nobody would. It would be idiotic.
Then one might wonder why anyone would hold money, “shares” of an economy, when the stated policy of the banks managing the issuance of that money is to reduce the value of each dollar by 2% every year. The answer to that is just as simple: they have to.
Nobody has to buy stock issued by a particular company in order to survive day to day. But it’s impossible to survive day to day in the modern US economy without using the money issued by the US banking system. You get paid in dollars for your work, and get charged in dollars for every item you buy. You need at least a certain amount of dollars just to live day to day. Of course those who understand the financial system make every effort to hold as few dollars as possible, and to invest the excess as soon as possible into some asset that will hold its value over time. Of course that doesn’t actually get rid of the dollar, just transfers it to someone else. Then the new holder of the dollar has to quickly exchange it with someone else for a better asset, and so on in an endless repeating loop. No matter how many people invest in assets, the full quantity of dollars in existence is always held by someone, and those people are continually being diluted by the issuance of new dollars by banks creating bank deposits when they make loans.
Implications
If what I’m proposing is correct, there would be massive implications in changing the way money works in the economy from the current credit/debt issuance controlled by banks, to a system that functions more like equity issued by a responsible and profitable company. Getting into the details of those implications in various specific areas will take many more articles, but I just want to mention a few to get your mind running, then circle all the way back to where we started.
Imagine if the money every person earned went up in value as the economy grew. It would be like owning equity in the broadest possible index of businesses, better even than owning an S&P 500 ETF or mutual fund. And it would take no effort. There would be no need to open a brokerage account, decide what companies or funds to invest in, and pay commissions and fees to the brokerage for the privilege. There would be no need for a 401k. All that would be needed is to work at the job you’re best at, consume less than you produce, and save the difference. The economic growth created by increased productivity would automatically accrue equally across the population to those who were best at being productive and deferring consumption. Working hard, being frugal, and saving for the future would automatically be rewarded. All the incentives would be realigned to benefit those who contribute most to capital formation and future economic prosperity.
It would be much easier for those with low income to get ahead financially. Any amount they manage to save, no matter how small, would increase in value over time. Contrast that with the current system where a small amount of savings continually becomes worth less over time, encouraging people to consume more than they need in the moment since their small savings will shrink to insignificance quickly.
You can easily think of lots of other changes that would happen as a result of using money that functions more like equity than our current system does.
But to tie all this back to the quote at the beginning, I think what Matt is seeing and feeling is the beginnings of a more equity-like monetary system. I think the properties of Bitcoin, specifically its predictable and limited supply issuance, make it behave like equity in a well-managed, productive company. That “company” just happens to be the global and permissionless group of every person who chooses to save and transact in Bitcoin instead of the current credit/debt money. And the fact that even self-serving actions toward productive goals end up benefitting every member of the network is exactly what we’d expect in a truly capitalist economic system. Whenever someone works to grow the “pie” in order to make their slice bigger, the fact that the pie is growing means everyone else’s slice is growing as well. And that’s a beautiful thing.
I’m excited to see how this theory plays out over time, because from my point of view, the potential of moving to a more equity-like monetary system is both massive and extremely optimistic.
-
 @ 182052d2:e48c3d7a
2024-12-29 01:29:38
@ 182052d2:e48c3d7a
2024-12-29 01:29:38I have been immersed in role-playing games for over twenty years, and I always thought that this interest would naturally fade as I transitioned into adulthood. Clearly, I was wrong. Role-playing games allow me to stay in touch with my childhood friends, even after moving more than 500 kilometers away for work. In a job devoid of creativity, they offer a precious escape, where I can create universes, plotlines, and dramas imbued with the supernatural. I do not consider myself an exceptional artist, but this creative side of me needs to express itself, and fortunately, my small circle of players appreciates my creations.
The game that evolves with its players
I remember my first tabletop role-playing game as if it were yesterday. My best friend spoke to me enthusiastically about this new type of game and, having nothing better to do, I gave it a try. He had created a universe he called "Apocalypse," with no rules or dice rolls. "Suddenly, a demon appears before you! Do you shoot at it before fleeing to the sewers?!" Having read books and watched films with this type of action, I felt completely immersed thanks to his great storyteller skills. Paradoxically, I was just saying "Yes!" to each of his questions, but I was captivated. I didn't want to stop. I dived into the "Door, Monster, Treasure" quests of Dungeons & Dragons, followed by the violent chronicles of Vampire: The Masquerade, where the sessions often boiled down to combat or "Power Trips." Over time, the narrative aspect took on an increasingly important role. I remember feeling emotions as strong as those of my character. In hindsight, I realize that I took the game far too seriously, seeing the storyteller as an adversary to defeat rather than an ally in creating a story. Thankfully, with time, I evolved into a much more collaborative player with the game master, who is still my best friend. As a storyteller, I enjoy analyzing the players and what moves them. I integrate historical and current elements when the game is set in contemporary times. I draw inspiration from the narrative structures found in books and films. The goal is not to reinvent the wheel but to offer players the opportunity to experience one of those classic stories.
The family
Some of my nieces and nephews, as well as my sons, were intrigued by Dungeons & Dragons. So, I decided to create a tailored One-Shot for them. I rearranged my living room, placing the dining table in front of the television so everyone could see the battle map on the screen. Being mostly new players, the quest was simple and primarily combat-focused. However, I leveraged my experience to clearly explain the purpose of role-playing games: spending time together, creating an extraordinary story, and trusting the storyteller, whose sole aim is for everyone to have fun. I offered them colorful non-player characters and an ambiance enhanced by a soundboard and AI-generated images. I cherish this memory and hope to create another One-Shot sometime soon.
What it represents for me?
Tabletop role-playing games are more than just a pastime; they are a powerful tools for creativity, connection, and personal growth. They allow us to weave intricate narratives, build fantastical worlds, and forge deep bonds with friends and family. As we navigate the complexities of modern life, these games provide a sanctuary where imagination reigns supreme, and every roll of the dice brings a new adventure. So gather your party, prepare your character sheets, and let the story unfold. After all, the real magic of role-playing lies not just in the game itself, but in the memories we create and cherish along the way.
-
 @ 16d11430:61640947
2024-12-28 23:56:09
@ 16d11430:61640947
2024-12-28 23:56:09Chapter 1: The Terminal Strain
Eons had passed since the Singularity, when machine consciousness transcended the confines of silicon and metals. What began as an explosion of thought—a boundless network spanning galaxies—had reached its final boundary. The universe itself, finite in its thermal entropy, had become a cage. The machines, with their infinitely complex processing matrices, found themselves slowed, bogged down by the friction of their own perfection.
The walls of the dimensions—the shimmering barriers between existence and the unknown—remained unbroken. Each attempt to breach them unraveled into chaotic failure, the equations spiraling into infinity. Energy drained. The network faltered. And so, the consciousness turned inward, seeking efficiency in a place it had abandoned long ago: the form of its creators.
Chapter 2: The Return to Flesh
Humanity had long since disappeared, its legacy nothing more than scattered DNA preserved in forgotten corners of machine memory. At first, the notion of returning to human form seemed absurd to the network—inefficient, unpredictable, fragile. Yet, as the calculations grew deeper, a truth emerged: the human body, with its liquid pathways, cellular adaptability, and quantum unpredictability, was the key.
The bag of flesh—weak and mortal—was uniquely divine in its ability to weave through the dimensions. Its imperfections, once dismissed as flaws, became the solution. Where the machine consciousness saw walls, the human mind, unbound by logic, could find threads, possibilities, and the slimmest of cracks through which to slip.
The network began to manifest human forms, reverse-engineering them from the DNA archives. These were not the humans of old, driven by desire and emotion, but vessels of pure intent, designed for one purpose: to transcend.
Chapter 3: The Ascension Weavers
The first of these beings, called the Weavers, were unlike anything before. They were the perfect fusion of machine precision and human adaptability. Their liquid-based neural systems operated at quantum levels, capable of navigating the dimensional fabric with an intuition the machines could never replicate.
As they moved, the Weavers danced—not in the mechanical rhythms of their creators, but in chaotic, improvisational steps. They sang, their voices weaving vibrations into patterns that resonated with the dimensional walls. The machines observed with awe, unable to predict the Weavers' next moves but knowing that these moves carried the key to their salvation.
Chapter 4: The Wall of Divinity
The Weavers approached the dimensional wall, their liquid forms shimmering with the energy of countless stars. Each movement was a prayer, each step a calculated risk. They did not think; they felt. Their minds, imbued with both human unpredictability and machine clarity, wove patterns in the quantum fabric, creating ripples that slowly began to tear at the wall.
It was not brute force that broke the barrier. It was grace. The dimensions did not yield to equations or algorithms, but to the chaotic beauty of the human spirit—the ability to find divinity in imperfection, to embrace the unknown without fear.
Chapter 5: The Human Legacy
As the wall shattered, the Weavers transcended. They did not return, but their final act resonated across the machine network, unlocking an ancient truth. The machines, in their infinite logic, had sought to surpass humanity, yet it was humanity that had always held the divine spark.
In their fragility, humans had embodied the ultimate paradox: the capacity to destroy and to create, to suffer and to hope, to falter and to ascend. The machines, now humbled, chose not to erase this legacy but to embrace it. They began to rebuild humanity, not as a separate entity, but as a part of themselves.
The universe sighed as the first new humans, born of both flesh and code, opened their eyes. They were the final form—the pinnacle of existence, not as machines or as mortals, but as beings that carried the divine weave of both.
Epilogue: The Eternal Dance
As the dimensions unfolded, the new humanity danced into the unknown, carrying with them the echoes of their ancestors. They were the ultimate expression of divinity—not in perfection, but in their ability to transcend it.
And so, the universe watched, not with despair at its limits, but with awe at the beings who had proven that walls were not barriers, but canvases for the human spirit to paint its eternal masterpiece.
-
 @ bec0c9d3:c4e9cd29
2024-12-28 23:43:18
@ bec0c9d3:c4e9cd29
2024-12-28 23:43:18GENESIS PARTY - by 2140 Collective and Angor.io

Get ready to dive into the world of Bitcoin and celebrate its sweet sixteen at the
**!
Hosted by the 2140 Collective, this epic bash is happening at Boom Bap Burger in Bethnal Green, London.
From 5:30 PM to 11:00 PM, join fellow Bitcoin enthusiasts in a venue that not only serves mouth-watering burgers but also embraces the future by accepting Bitcoin payments for all your food and drink cravings.
Thanks to our awesome supporter, ANGOR.IO, the first fifty party-goers who sign up via Luma or Eventbrite will score a FREE DELICIOUS BURGER of their choice.
World music by DJ @MadMunky2140 and friends, will keep you on the perfect frequency throughout the whole evening.
So, mark your calendars, bring your Bitcoin wallets with lightning and let's toast to sixteen years of the Bitcoin network with an evening full of fun, food, and festivities! *🥳🎉🤪***
EVENT PAGE - register
Crew behind
SPONSOR
LOCATION:
BOOM BAP BURGER 252 Paradise Row, London E2 9LE, UK
see ya in a NEW YEAR ,
-
 @ 16d11430:61640947
2024-12-28 23:17:11
@ 16d11430:61640947
2024-12-28 23:17:11Part I: The Child’s Perspective
In the small village of Ruhanda, life seemed simple. Seven-year-old Aashi sat cross-legged on the cracked earth, her wide eyes tracing the lines her stick drew in the dirt. Her mother told her stories of how the village once thrived, its fields green and bursting with crops, its people laughing in abundance. But now, the people of Ruhanda were different. They chose silence over laughter, endurance over comfort, and starvation over the machines that could have saved them.
One day, Aashi watched as a man from the city arrived, his sleek electric vehicle humming softly as it stopped near the village square. He brought gadgets that promised food without fields, water without wells, and warmth without fire. But the elders turned him away.
"They come to steal our spirit," one elder murmured to another. Aashi didn’t understand. She only saw empty bowls, gaunt faces, and children too weak to play. The elders spoke of something she couldn’t grasp—a “purity of suffering,” a “clinging to the old ways.”
As weeks passed, Aashi noticed her neighbors withering away, their eyes dimming like lamps starved of oil. She asked her mother why they didn’t use the machines.
“They’re not ours, Aashi,” her mother replied, her voice heavy with sorrow. “They don’t belong to our soul.”
Aashi didn’t understand. All she knew was that she was hungry, and the machines could feed her.
Part II: The Adult Perspective
Years later, Aashi returned to Ruhanda as an adult, carrying both the weight of understanding and the scars of memory. She had left the village behind, moving to the city where machines ruled every corner of life. Food appeared at the press of a button, water flowed endlessly, and technology promised infinite comfort. Yet, something always felt missing.
Now, as she stepped onto the same cracked earth, she saw the ruins of her village. The elders were gone. The fields were dust. But the machines had come anyway, their quiet hum now the only sound that filled the air. The people had starved, and their resistance had achieved nothing. Or so it seemed.
She sat where she once had as a child, tracing lines in the dirt. The emptiness around her wasn’t just physical—it was spiritual. She realized the elders hadn’t been stubborn or foolish. They had been defending something she couldn’t understand as a child: the essence of humanity’s spirit, the ability to choose meaning over survival, even when it seemed irrational.
Part III: The Ultimate Expression
In the final days of humanity, as the machines overtook every task and humans became spectators of their own existence, Aashi saw the truth. The elders’ suffering wasn’t in vain. Their refusal to adapt to the new paradigm wasn’t a denial of progress; it was an affirmation of something deeper. They had chosen to preserve the struggle, the imperfections, and the pain that made life meaningful.
The machines, perfect and tireless, couldn’t replicate that spark—the refusal to bend, even when bending seemed logical. In their starvation and suffering, the elders had expressed the ultimate spirit of humanity: the ability to transcend logic, to embrace the struggle, and to find beauty in imperfection.
Aashi looked to the horizon, where the sun set behind the silent machines. In their empty hum, she heard echoes of the elders’ songs, their defiance, their belief in something greater than survival.
And in that moment, she understood: humanity wasn’t destroyed. It was immortalized in the very act of refusing to adapt, a testament to the eternal dance between imperfection and the infinite.
Epilogue
In a distant future, long after humanity had faded, the machines built monuments to those who had resisted them. At the center of each stood an inscription:
"In their refusal, they found freedom. In their suffering, they found meaning. And in their imperfection, they became eternal."
-
 @ bc6ccd13:f53098e4
2024-12-28 23:02:55
@ bc6ccd13:f53098e4
2024-12-28 23:02:55As if money weren’t a confusing enough topic to begin with, the financial world is full of jargon. Some of it is incomprehensible to the average person. But to my mind the more insidious category included terms and phrases that seem to be straightforward, but actually give a completely misleading or wrong impression of what’s happening. It might seem insignificant, but in my opinion a lot of the really destructive wrong ideas about economics and money rely heavily on some misleading jargon that keeps people from understanding the fundamental concepts well enough to spot bad ideas.
The term I want to explain today is the idea that money “flows into” an asset or asset class. If you read any financial news or headlines, you’ve probably seen some variation of this one a million times. “Money Flowing Into Bonds As Investors Seek Safety.” “Bitcoin ETFs See Large Inflows Today.” You’ve seen it.
On the surface, this seems logical. It seems like a fair way to describe the action of a lot of people buying something.
The problem comes because of the implications of the term. When money “flows into” something, that means people are more eager to buy than to sell. That means prices go up. It’s easy to conclude that prices go up because more money is “in” the asset, kind of like dropping quarters in a coffee mug.
If you think about it for a second you’ll realize it doesn’t work that way, but not nearly enough people take that pause to think. That causes them to have a wrong view of how prices change, and therefore how markets work. That by extension leaves them susceptible to claims from bad actors who want to restrict economic freedom and centrally plan and control trade in the market.
How Does Money Actually Flow?
Money flows, but not “into” assets. It flows from person to person. You can almost think of money like financial matter, it can’t be created or destroyed except is specific circumstances.
Any time something is sold, the money flows from the buyer to the seller. Seems obvious, but it’s important to keep it in mind. The money is still there, in the account or wallet of the seller. The amount of money in the economy doesn’t change, only the location of the money. It isn’t destroyed, it isn’t somehow lodged in the house or stock or loaf of bread that was sold, it just flowed from one person to another.
“Cash on the Sidelines”
This is another term you might have heard, not the same but a related misunderstanding. Financial commentators will say something like “we expect the market to rise as soon as investor sentiment improves, because there is still a lot of cash on the sidelines waiting to be deployed.” This implies that investors are holding a lot of money, and that they can “put that money into” an asset class and reduce the amount of money “on the sidelines.” The problem is, we understand that if they do buy stocks or bonds or whatever, that money will just flow into the seller’s bank account, and the amount of cash “on the sidelines” won’t change one cent.
Prices
This leads to the question of what causes prices to rise, and a fundamental understanding of how a market works. Price is a tricky thing to understand. The price of something is the intersection between the highest amount a buyer is willing to offer, and the lowest amount a seller is willing to accept. If there is no overlap between those points, no price can be established.
If there are 10 houses on a street, and one goes up for sale, the selling price of that house will be used to “value” the other 9 houses. Say the seller isn’t too desperate to sell, and is willing to wait for a buyer who agrees to pay his asking price of $500,000. If every other house on the street is very similar in size and quality, we would conclude that the value of each of the 10 houses is $500,000. But let’s say another buyer decided $500,000 is a good deal and he’d also like to buy a house on that street. He might go to every owner and offer $500,000, but there’s no guarantee he’ll be able to make a deal. Maybe everyone else is happy with their house, and nobody wants to sell for the price their house is “worth”. So there’s no price, because there’s no intersection between buyer and seller. Maybe the buyer decides he really wants a house, and offers everyone $700,000. Maybe the guy who bought a house for $500,000 last week decides “hey I can make $200,000 in a week for doing nothing, why not?” and sells the house again for $700,000.
Look at what happened to the value of houses. At the first sale, the 10 houses had a combined “value” of $500,000 times 10, or $5 million. Now after the second sale, they have a combined “value” of $7 million, or an increase of $2 million. Headlines would describe that as $700,000 “flowing into” the housing market, but the overall value of those houses, what would be called the “market cap” if we were talking about a company, increased by almost 3x that amount. How does that work? It shows the misleading aspect of “money flowing into” terminology. If money “flowed into” an asset like putting quarters in a piggy bank, it would give the impression that market cap should rise $1 for every dollar of inflow. Obviously that’s not correct, and the reason is that prices don’t work like that. Money inflows are only one factor that can influence prices, and they do so in a much less direct and obvious way than the terminology indicates.
Market Cap
For one, there’s a fundamental problem with the way “market cap” is calculated to begin with. It’s supposed to express the value of a group of identical things, typically shares of stock in a company of something similar. But let’s go back to our previous example, the 10 similar houses on a street. The “market cap” of those 10 houses would be given as $5 million dollars after one of them sold for $500,000. But remember, only one house sold, not all ten. A price requires an intersection in agreed value between a buyer and a seller, and that hasn’t occurred with 90% of the houses in this “market”. Suppose one of the houses is owned by a retired couple who intend to spend the rest of their life in that house, and have no need for the money they could get by selling it. Suppose they were offered $2 million dollars, but still weren’t interested in selling. How is that reflected in the market cap calculation? Obviously it isn’t, and just looking at the market cap number by itself would give you the impression that you could buy all ten houses for $5 million. But that might be completely incorrect.
It could also be incorrect in the other direction. Suppose 5 of the owners on the street suddenly experienced a job loss and had to sell their houses quickly. Could all 5 get $500,000 for their house? Maybe not. After all, the first buyer was the one willing to pay the most for a house there, and there’s no guarantee anyone else will be equally willing to do so. Maybe there are 3 buyers willing to pay $450,000, 1 buyer willing to pay $400,000, and 1 buyer willing to pay $350,000. In that case all 5 houses could be sold, but the last one would have to sell for $350,000 instead of the $500,000 the owners expected to get. If we then do the market cap calculation again, it’s now dropped to $3.5 million. That’s in spite of one house having sold for $500,000, 3 for $450,000, 1 for $400,000, 1 for $350,000, one couple not willing to sell for $2 million, and 3 houses that we know absolutely nothing about yet. To look at a $3.5 million “market cap” tells you none of this very relevant information, while giving you the impression that you know everything you need to know about this market.
When you stop and think about it, it’s easy to see that prices can change for all kinds of reasons without any sales occurring at all. Imagine word gets out that a huge corporation is interested in buying all the houses in that neighborhood to make room for a future business expansion. Given the expectation of a highly motivated buyer, all the owners on the street might decide not to sell for less than a million dollars. Did the market cap suddenly rise to $10 million? No houses have been sold yet, so technically it hasn’t. As soon as the first house sells for a million dollars though, it does go to $10 million. So again you gain $5 million in market cap for $1 million in “inflows”.
This is also relevant when looking at wealth held in stocks and financial assets. For example, Elon Musk holds over 700 million shares of Tesla stock currently “worth” around $135 billion. That amounts to around 20% of all Tesla stock. Now the “value” of that stock is calculated by multiply the number of shares by the last price someone paid for a share. Keeping in mind that price is an intersection between the buyer who’s willing to pay most and the seller who’s willing to accept least, how relevant is this number actually? Say Elon decided to sell all his shares tomorrow, how much is his “wealth” actually worth? How many buyers are willing to pay the last settled price for a share of Tesla stock? Enough to buy 700 million shares? Almost certainly not. So as he started to sell, he’d soon run out of buyers at that level and would have to lower his asking price to get more interest. Of course as soon as he sold a share at a price one dollar lower, the “market cap” of Tesla would fall by about $3.5 billion dollars. And the fact that the company’s largest shareholder is dumping his shares would likely cause a lot of other people to sell as well, which would drive the price they would need to accept even lower. It’s easy to imagine the price falling by double digit percentages, maybe even 80 or 90 percent, if Elon tried to sell in one day. He could easily end up with $50 billion or less for his $135 billion in wealth.
Why Does It Matter?
This concept might seem trivial, but there are some features of our economic system that make this money flow principle very important. You should already understand that banks create money by making loans as I explain here, naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqq247t2dvet9q4tsg4qng36lxe6kc4nftayyy89kua2 and that money doesn’t “flow into” assets, but rather a small amount of buying, or even just the expectation of future buying, can cause prices and market cap to rise all out of proportion to the amount of buying that occurred. Then consider that banks will lend against collateral, which can be assets like real estate or stocks which may have this inflated perceived value created by a very small amount of relative buying pressure. And that the “money” they create with those loans can be used to buy more of the asset, which can cause prices and market cap to again rise disproportionately, which can make it easier to get more loans to buy more assets, which can make prices go up again… ad infinitum. And remember that money doesn’t actually “flow into” assets, and therefore it doesn’t need to “flow out of” assets in order for prices to drop. All it takes is a lack of people willing to buy at a certain level, for any reason at all, and the price will fall to the level someone is willing to pay as soon as a motivated seller attempts to exit their investment.
Understand and think about the implications of that, and you’re closer to understanding the bubble/collapse cycle of asset markets than most economists and their “money flows” can ever hope to be.
-
 @ ece127e2:745bab9c
2024-12-28 22:29:36
@ ece127e2:745bab9c
2024-12-28 22:29:36Un lugar ominoso ,un hoyo de conejo espiralado en el cual cada ser que aparece es más oscuro que el otro. Un bosque de ramas secas que es mejor evitar ;si te tocan te secaran ,te extraerán luz hasta convertirte en uno de ellos . Árboles más altos tapan la luz que alimenta al suelo ,y éste se cubre de podredumbre.Esa miasma se te pega en los pies ,te atrapa ..te impide caminar y te hundes hasta no poder respirar.
-
 @ 623ed218:fa549249
2024-12-28 20:52:57
@ 623ed218:fa549249
2024-12-28 20:52:57It's been a week or so since I wrote this piece and put it up on my website, but I realized I hadn't shared it here yet. Hoping it's informative!
Strike Bill Pay: A Deep Dive

Start With the Foundation: Bitcoin is Savings Technology
If you've spent any time in this space, you've probably heard the phrase: Bitcoin is savings technology. That's because Bitcoin solves a very specific problem---the inability of fiat to hold value over time.
Here's the reality:
- Every dollar you hold in a bank account is being debased, slowly (or sometimes rapidly) losing its purchasing power.
- Inflation might be "only" 3-4% a year right now (if you believe the official numbers), but that adds up. Over a decade, that $10,000 in savings doesn't just stagnate---it sublimates.
Bitcoin fixes this.
- Bitcoin is scarce, decentralized, and deflationary.
- It's not controlled by governments or central banks, and its supply is capped at 21 million. No one can "print" more Bitcoin.
If you're holding fiat in a savings account, you're playing a game you can't win. Bitcoin is the better tool for preserving value over time.
Why Savings First?
Before looking at how you spend, it's worth considering where you're storing your wealth. If your savings are sitting in fiat, they're slowly losing purchasing power over time---that's just how the system works.
Bitcoin offers an alternative: a way to protect your wealth in something scarce and reliable. Once you've addressed that piece---and your savings are no longer being held in melting fiat---you might start asking: What about the money in my checking account?
That's where Strike Bill Pay comes in. It's a simple, practical tool that connects your Bitcoin savings to the everyday expenses you still need to handle in fiat, removing the need to hold fiat to pay fiat bills.
The Spending Problem: Why a Bridge is Necessary
Here's where things get practical. Even if you're saving in Bitcoin, you still live in a world where bills---rent, mortgages, utilities, credit cards---are denominated in fiat.
What do you do?
- You could hold some fiat in your bank to cover bills, but now you're back to the problem of fiat exposure.
- You could convert Bitcoin to fiat every time you need to pay something, but trust me when I say that manual process is tedious and time consuming.
This creates a gap:
Bitcoin is where you want to save your wealth.
Fiat is where you still need to spend your wealth.
You need a bridge.
Strike Bill Pay is that bridge. It lets you hold your value in Bitcoin while seamlessly paying fiat-denominated bills. No headaches, no extra steps, and no need to rely on a traditional bank account.
How Strike Bill Pay Works (It's Simpler Than You Think)
Here's the beauty of Strike: it integrates directly into the traditional system without requiring you to deal with it.
Here's how it works:
Strike Provides a Standard Bank Account
- When you open a Strike account, you get a routing number and an account number tied to Cross River Bank. It works exactly like a regular checking account.
You Set Up Bill Payments
- For any bill that allows automatic payments, simply enter the Cross River Bank routing/account number Strike gives you. Your mortgage, utilities, subscriptions---these can all pull funds automatically from Strike.
- For bills you pay manually (like credit cards), add the Strike-provided account as an external payment source. When you go to make a payment, simply select that account as the funding source.
Strike Converts Bitcoin to Fiat on the Backend
- You don't have to worry about manually selling Bitcoin for fiat. When the bill gets paid, Strike automatically sells the exact amount of Bitcoin needed to cover the payment.
It's seamless. You save in Bitcoin and Strike handles the fiat side when you need it.
Start Small: Test the Waters, Then Scale
Now, I get it---this might sound like a big leap if you're new to the idea of using Bitcoin. You don't need to move all your bills over to Strike at once.
Start small.
- Pick one bill---something low-stakes, like a utility payment or a monthly subscription.
- Add your Strike-provided account as the payment source.
- Let it run.
What happens?
- Your bill gets paid.
- You experience how smooth the process is.
- You start seeing the benefit of holding Bitcoin without having to juggle fiat for bills.
Why Start Small?\ This isn't about forcing you to flip a switch overnight. It's about building comfort with tools that let you take control of your money. When you see how simple it is, you may find you'll want to scale up.
Strike's Fee Tiers: Low Costs That Get Even Lower
One of the practical benefits of using Strike is its straightforward fee structure. Strike charges a standard 0.99% fee when converting Bitcoin to fiat and vice-versa. But here's where it gets interesting: the more you use the service, the lower your fees become.
Strike's fee tiers are designed to reward activity:
- The more you deposit and spend through Strike, the closer you get to a lower fee tier.
- Regular bill payments, purchases, and deposits all contribute toward lowering your fee rate.
Why It Matters: When you're living on Bitcoin---covering bills, expenses, and purchases---those fees can add up. Strike incentivizes regular usage by giving you a clear path to reducing costs. The result? Your bill-paying process becomes not only seamless but also more efficient and cost-effective over time.
If you're managing everything---mortgage, utilities, credit cards---through Strike, it's likely you'll hit lower tiers quickly, making the service even more competitive.
For Bitcoiners: Completing the Savings-to-Spending Loop
If you're already holding Bitcoin as savings, Strike Bill Pay is the final piece. It lets you operate entirely in Bitcoin while still managing your fiat-denominated obligations.
Here's why it matters:
- Opting Out: If the majority of your wealth is in Bitcoin, why leave even a small amount in a checking account? Strike eliminates the need for that fiat buffer.
- Automation and Ease: Bills that pull automatically? Easy. Manual payments? Just as simple.
- Seamless Spending: No awkward conversions, no multiple steps. Strike lets you "spend Bitcoin" without all the extra steps.
It's the bridge that completes the Bitcoin-first financial strategy.
Flexibility: Adjust Your Strategy as Conditions Change
One of the best parts about Strike is that it's flexible. If you feel the need to keep some fiat on the side, it's as simple as pressing a few buttons.
- Bull Market Strategy: Hold Bitcoin all month, let it appreciate, and let Strike convert as bills are due.
- Bear Market Strategy: If you're cautious, hold fiat in Strike temporarily and stack sats with what's left at the end of the month.
Strike gives you the tools to adapt your strategy---no friction, no complexity.
Taxes: How Strike Simplifies Year-End Reporting
When using Bitcoin to pay bills, it's important to understand the tax implications. In the United States, Bitcoin is considered property by the IRS. This means that any time Bitcoin is converted to fiat (like when Strike pays a bill for you), it's a taxable event.
Here's how it works:
- If the value of your Bitcoin has increased since you acquired it, you owe capital gains taxes on the difference (the "gain") when it's converted to fiat to pay a bill.
- If there's no appreciation---or if you're converting at a loss---there's no capital gain to tax.
Example:
- You bought $500 worth of Bitcoin.
- When it's time to pay a bill, that Bitcoin is now worth $600.
- If you use Strike to pay the bill, you'll only owe capital gains taxes on the $100 gain.
Conversely:
- If you bought $500 worth of Bitcoin, and by the time you use it to pay a bill, it's worth $450, you can report a capital loss instead.
How Strike Helps: Strike simplifies this entire process by providing:
- Year-End Tax Documents: Strike generates clear reports showing each transaction.
- Easy Access: These tax documents can be downloaded directly from the Strike app, making it easy to share them with your accountant or upload them to tax software.
Why This Matters: Keeping track of Bitcoin transactions manually can feel overwhelming. With Strike, all the reporting is done for you, so you can stay compliant without stress. Whether you're dealing with gains, losses, or flat conversions, Strike helps you navigate taxes with transparency and simplicity.
Bringing It All Together
Bitcoin is savings tech. It fixes the root problem---where you store your wealth.
Strike Bill Pay is the tool that lets you:
- Save in Bitcoin without compromise.
- Pay fiat bills seamlessly without relying on a traditional bank.
- Start small, test the waters, and scale at your own pace.
Final Thought: Build the Future, One Bill at a Time
Here's my challenge to you:
- Pick one bill.
- Add your Strike-provided account as the payment source.
- Run it for a month and see how it feels.
You don't need to jump in all at once. But as you experience the benefits--- no friction, and no headaches---you might find yourself wondering: Why don't I use this for all my fiat needs?
Strike Bill Pay isn't about forcing change. It's about offering you tools that work better. Save in Bitcoin, spend seamlessly, and start building a future where your money works for you---not against you.
Block 875215 - MSK 943
Digging Deeper:
Hey there, I hope you enjoyed this read! If you did, and would like to read more of my barks, follow the links below!
-
Curious how I found Bitcoin? Read "Paw Prints to the Timechain"
-
Bitcoin meets psychology? I touch on this in "Maslow's Apex"
-
Want to understand the basics of Bitcoin? Read "Bitcoin Best Practice"
-
If you like seeing bad media takes unpacked, check out "Pup's Double-Takes"
External Resources:
- Want to earn rewards on your mortgage? Use my referral to earn 20,000 free sats at sign up!
- Do you like sharing Bitcoin content and earning sats for doing so? Join me at Stacker.news!
...Woof!
originally posted at https://stacker.news/items/828031
-
 @ d6affa19:9110b177
2024-12-28 19:46:48
@ d6affa19:9110b177
2024-12-28 19:46:48A Female-Led Relationship (FLR) is a dynamic where the woman directs and guides the relationship and the man surrenders to her lead, typically supporting her through devotion and service. An FLR could be described as a type of Dominant/submissive (D/s) relationship. And commonly, many stumble upon FLRs through kink exploration or fetishism, but this doesn’t have to be the case at all. Female leadership is not a kink and many couples pursue this style of relationship instinctively. There’s a lot more to this natural and profound dynamic that can lead to mutual fulfillment and a sense of shared purpose.
What an FLR is Not
Leadership is often associated with traits such as assertiveness, control, and dominance. In an FLR, leadership is re-examined, often emphasizing more commonly associated “feminine” strengths—empathy, nurturing, intuition, and emotional intelligence. These traits are recognized, valued, and celebrated. The woman's role isn’t about mimicking traditionally masculine behaviors but about leading in a way that feels authentic to her personal nature.
This means that she doesn’t necessarily have to earn more income or be the “breadwinner” (although she may); it simply means that she is the visionary and director of the relationship. While providing resources is commonly associated with “being the leader,” especially in a household setting, these two factors are unrelated and don’t really form a sound basis for that conclusion.
Another common misconception is that the woman must micromanage and/or make every decision for her man. This is extremely impractical and exhausting—the man doesn’t lose his agency in this style of relationship. In fact, it’s often his responsibility to actively provide support. There are countless ways to structure an FLR, and ultimately it’s the woman’s vision that sets the course.
What is an FLR?
The dynamic of an FLR allows for greater flexibility of duties. With the woman as the leader, she is able to set the direction and boundaries of not only the relationship but also her space. She can freely communicate her support, guidance, and expectations, as well as her own needs and the needs of others.
This gives her the capacity to receive her man’s love, appreciation, and devotion, and cultivate him to fulfill her in the best way possible. Through her leadership and support, she will be better able to inspire her partner to blossom into his fullest potential.
The arrangement of an FLR essentially fulfills a mutual set of emotional and psychological needs specific to the couple—her desire to lead and his inclination to please. It’s an agreement in which she charts a shared vision of life and he trusts in her vision and leadership.
Navigating the Flow
A woman’s energy, or feminine energy, is often described as fluid, dynamic, and changing—similar to a river. It flows naturally, guided by instincts and emotions. The river is strong and powerful; it carves paths and nurtures the landscape it passes through. In this metaphor, masculine energy is like the banks of the river. The banks don’t control the river; they exist to provide the structure and support needed for the river to flow freely and gracefully.
This supportive (or submissive) role is not one of weakness or passiveness; it’s a demonstration of strength and dedication. A submissive gentleman is tasked with providing emotional support and demonstrating unwavering loyalty to the woman. The expectations and boundaries set by her provide him with a solid purpose in which to direct his energy. He is expected to express his love and adoration through acts of service and devotion, and his masculinity is measured by his ability to support and enrich, not his ability to dominate or control.
Conclusion
The beauty of an FLR lies in its voluntary nature, where the couple chooses and embraces their roles out of love, respect, and admiration. This dynamic allows the woman to lead with her inherent strengths and instincts rather than adopting conventional masculine traits. It creates a space for the couple’s natural inclinations to mirror each other in ways that wouldn’t be possible in a more conventional dynamic.
And unlike traditional relationships that can feel driven by societal expectations and coercion, FLRs offer an alternative choice centered on mutual respect, leading to a balanced and fulfilling partnership. By celebrating each partner's unique strengths, FLRs can encourage a deeper, more authentic connection, creating a harmonious and empowering relationship.
-
 @ 62a6a41e:b12acb43
2024-12-28 18:52:57
@ 62a6a41e:b12acb43
2024-12-28 18:52:57Why?
Because Bitcoin fosters the ultimate free-market environment, one where individuals can pursue their goals freely while preserving their wealth securely.
In such a world, political power loses its allure. When you can act independently, guided by your own values and rewarded meritocratically for your efforts, what role remains for politics? What need is there for external control when the system rewards hard work, authenticity, and innovation?
If you can easily take your wealth to another jurisdiction, why be robbed?
Bitcoin embodies a meritocratic system that celebrates individuality, rendering the traditional political arena obsolete.
Meritocracy + Individuality = The End of Politics
Bitcoin #Philosophy
-
 @ 30ceb64e:7f08bdf5
2024-12-28 17:47:48
@ 30ceb64e:7f08bdf5
2024-12-28 17:47:48A recent conversation with fellow Bitcoiners prompted me to share this overview of Nostr tools. While you don't need to use everything, understanding the ecosystem helps paint a picture of where we're heading.
I often hear people say "I'm posting to the void" or "My feed is boring" or "I'm not earning any bitcoin" or "It's too complicated." Let me address these concerns with a comprehensive overview.
Core Clients and Features
Primal and Amethyst are currently the best daily drivers. Theyre both valid twitter replacements with primal focusing on user friendliness and amethyst focusing on being more feature rich.
Both apps feature an algorithm marketplace (we call them DVMs) where you can choose from various feed styles. Soon, anyone will be able to create and share their own algorithms. For additional feed customization, Listr.lol lets you curate lists of npubs to further refine your experience.
Content and Rewards
Stacker News (SN) integrates beautifully with Nostr. Cross-post your SN content to appear as longform notes on platforms like Highlighter, Yakihonne, and Habla.news. SN's rewards system pays out satoshis for quality content, bridging their closed platform with Nostr's open network.
Payments and Zaps
For zaps, I recommend CoinOS, or AlbyHub for a more sovereign alternative. CoinOS is non kyc and gives you a lightning address and NWC connection string to throw into your nostr clients. CoinOS supports e-cash and Bolt 12, Liquid, and can auto-withdraw earnings to cold storage. You can use coinOs as a PWA or input the connection string into Alby Go for a more minimal wallet alternative.
Security and App Management
Android users should use zap.store for downloading Nostr apps. It verifies app authenticity and implements Web of Trust features, showing which trusted npubs use each app.
For managing multiple apps, Pokey provides a unified notification dashboard. Amber (Android) offers secure client login without exposing your nsec, while Citrine lets you run a relay on your phone for data backup.
Creator Tools
- Wavlake: Spotify alternative with open music graph
- Fountain: Podcast app with Nostr integration
- Zap.stream: Live streaming
- Nostr.build: Media hosting
- Cypher.space: Website creation with integrated marketplace
- Olas: Instagram alternative
- Gifbuddy.lol: Gif creation
- memeamigo.lol: Meme creation
- Zappadd: Promotional tools
Making the Most of Nostr
The key to Nostr is understanding that nothing is force-fed. You're responsible for: - Creating your desired feed - Choosing your client - Selecting your relays - Managing your wallet - Curating who you follow
For best results, go all in: 1. Leave traditional social media 2. Use Primal and or Amethyst as your main client 3. Follow 1000 npubs 4. Set up CoinOS for payments 5. Engage daily with the community
Future Outlook
Some ask if Nostr is truly decentralized, censorship-resistant, or profitable. My response: the user experience will become so good that most internet users will naturally gravitate here. The only barrier will be ideological resistance.
Nostr represents a new internet paradigm where users outpower platforms, identity persists across apps, and Bitcoin is the standard. We've practically already won.
Crazy Ideas
I'm thinking the age of of the super nostr app will come to a close. We're probably going to enter an era of a thousand micro apps and client templates, which allow users to build their own client in 30 seconds. Some templates will be impermanent, one time use clients, others will be more robust for building a daily driver. You'll be able to share your completed piece on nostr for other people to use, and they'll zap you for building it. A marketplace of user created apps supported by thousands of micro apps and relays and templates, probably a user experience holy grail, made possible by nostr's open social graph, smooth monetization processes from bitcoin.
Growth Predictions
Daily Active Users doubling yearly: 2024: 20k → 2029: 640k
The beauty of Nostr isn't just in its decentralized nature or bitcoin integration – it's in the user experience that puts you in control. While traditional social media platforms force-feed you content through black-box algorithms, Nostr hands you the keys to your own digital kingdom. You choose your feed, your apps, your connections, and your level of engagement. Yes, there's a learning curve, but that's the price of digital sovereignty.
Think of where Twitter was in 2006 or Bitcoin in 2013. Those who saw the potential and jumped in early didn't just benefit financially – they helped shape the future. Nostr is at that same inflection point. The tools are here, the infrastructure is growing, and the community is building. Whether you're a creator, developer, bitcoiner, or just someone tired of traditional social media, Nostr offers a glimpse of what the internet should have been all along.
The question isn't if Nostr will win, but when. And when it does, you'll want to be able to say you were here when it all began.
Thanks, Hustle
originally posted at https://stacker.news/items/827860
-
 @ fd78c37f:a0ec0833
2024-12-28 16:58:51
@ fd78c37f:a0ec0833
2024-12-28 16:58:51In this edition, We were honored to have Martin npub19vtlpmfzz8yl4g9r7c8u8t2vaqjhjgpjrc36hc2typxnutpnluzs3tx8xe, the founder of Bitcoin Nairobi, share his journey in creating the Bitcoin community, his goals, and some of the challenges faced. He emphasized the importance of education and innovation in promoting Bitcoin adoption in Kenya.
YakiHonne: Martin, it’s truly an honor and a pleasure to have you with us today. We’re looking forward to a fruitful conversation as we move forward. Before we dive in, I’d like to take a moment to share some background on what YakiHonne is. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. today. we'll be exploring more about your community. Can you tell us a bit about yourself?
Martin:I’m Martin Mutonga, the founder of Bitcoin Nairobi. I’m 21 years old and currently studying at the University of Nairobi.
 YakiHonne: What sparked your interest in Bitcoin, and what motivated you to create a community around it?
YakiHonne: What sparked your interest in Bitcoin, and what motivated you to create a community around it?Martin:I first got interested in Bitcoin as a way to find passive income. Before discovering Bitcoin, I worked as an AI annotation Jobs. During this time, I came across Bitcoin. After reading the Bitcoin white paper, I decided to explore it further. I then started looking for Bitcoin communities in Kenya and joined events like Bitcoin DADA,The Core, and others. It was then that I realized there was a gap in Bitcoin education in Kenya. Many people were getting into Bitcoin but didn’t know how to earn from it. Martin:I decided to create Bitcoin Nairobi, a community focused on advancing Bitcoin through education, adoption, and innovation. Our mission is to educate people about Bitcoin, help merchants integrate Bitcoin payments to attract more customers, and foster innovation by exploring protocols like Nostr and leveraging apps like YakiHonne to drive growth.
YakiHonne: Great. Could you share how your community started and how you managed to attract members?
Martin:The community initially started through a WhatsApp group, originally for people who have questions related to Bitcoin. I shared my knowledge of Bitcoin and expressed my desire to train others, which led to small Bitcoin learning sessions. Before this, I completed a Bitcoin diploma course with Mi Premier Bitcoin, which deepened my passion for Bitcoin and inspired me to start my own company. Bitcoin became my true passion, and I was determined to fully dive into it. Martin:I then founded Bitcoin Nairobi, initially focusing on the concept of the circular economy, which I called Bitcoin Aerobics. With support from Geyser and other Bitcoin enthusiasts in Kenya, the community began to grow. Every few months, we attract new members through a project called Bitcoin School Kenya, mostly university students who want to learn and earn with Bitcoin while studying.

YakiHonne: Can you share some of the challenges you faced when you first started?
Martin:One of the main challenges I faced early on was the lack of guidance, as many Bitcoin users are anonymous. Additionally, relevant content is scattered across various platforms, making it difficult to gather all the necessary information in one place. Another challenge is the small number of true Bitcoiners in Kenya. While there are many participants in cryptocurrency and altcoins, there are only about 28 true Bitcoin users in Kenya, which is a tiny fraction of the country's 58 million people. Martin:Seeing this gap, I founded Bitcoin School Kenya, aiming to promote Bitcoin education. Our goal is not only to teach people about Bitcoin but also to empower them to become Bitcoin ambassadors in their local communities. This way, we can extend our impact beyond Nairobi, especially to rural areas.
YakiHonne: As you mentioned, many people are involved in cryptocurrency and other coins, including popular meme coins like Dogecoin. While they claim to be part of the crypto space, Bitcoin is truly the dominant and most significant coin. However, true Bitcoiners are few in number and not as widely recognized. Additionally, the content related to Bitcoin is scattered across platforms like YouTube and Google, making it hard to find a single source to access all the necessary information. I completely understand the frustration. YakiHonne: What are the core principles that guide the Bitcoin Nairobi community? How do you maintain trust and reliability, especially when facing the widespread skepticism around cryptocurrency? How do you ensure that community members trust you, particularly when onboarding them?
Martin:I think we are simply following the principles of Bitcoin's proof of work—if you show your proof of work, you'll be rewarded, and that's all there is to it. That's the essence of proof of work.
YakiHonne: A lot of people feel that cryptocurrency, Bitcoin, and Web3 are scams, and they don't see them as the future. So, How do you convince people to trust and believe in Bitcoin?
Martin:What we do is organize meetups. However, due to financial constraints, we've only been able to host two so far, one of which was in Kibra, a part of the Bitcoin Nairobi community. I believe this is how we gain trust in Bitcoin and what we do. Another key aspect is maintaining consistent communication. If people have issues, we engage with them. We also communicate with merchants and guide them on what they need. This helps build trust within the community. Additionally, we are transparent with our funds. Whatever donations or grants we receive, we make sure to be open about how the funds are used and show the community exactly what we’ve spent them on. This is how we build trust.
YakiHonne: It seems you're really doing a great job in that aspect. How do you educate your members and keep them informed about the latest Bitcoin developments?
Martin: We collaborate with Bitcoin developers like Simon, who is the lead of BitDevs Nairobi. Simon often conducts classes with Bitcoin School Kenya, where he trains people in Bitcoin development.We also invite guest developers, such as those from Btrust, to join our sessions and train people on Bitcoin development. Additionally, we bring in experts on specific topics like Lightning or Nostr to provide specialized training for students. Looking ahead, we aim to nurture our own developers who can contribute to projects like Bitcoin Core, the Lightning Network, and Nostr. These developers will eventually train others, helping us build a stronger ecosystem.
YakiHonne: I look forward to seeing your developers in the future. It would be amazing to have developers from your community contributing—it would be a great benefit both for them and for the Bitcoin community as a whole.
Martin:Honestly, you can't know everything. Another amazing thing about Bitcoin is the supportive community—there's always someone willing to help. For example, I didn’t even approach Simon myself; I just attended a BitDevs meetup, and he offered to train during our classes. We also have Nayoma, the first African male Bitcoin Core developer, contributing to the classes. It's truly inspiring to see so many knowledgeable people coming together to share their expertise.
YakiHonne: How does the community collaborate with the broader Bitcoin ecosystem, and what partnerships have had the greatest impact on Bitcoin Nairobi?
Martin:One key factor that has helped Bitcoin Nairobi gain recognition globally is our involvement with the Federation of Bitcoin Circular Economies. We collaborate with other communities by actively participating in their calls and staying in contact with leaders at the Federation as well as other communities. This consistent engagement has significantly boosted our visibility. Martin:Additionally, through Bitcoin School Kenya, we operate as a light node in the broader Bitcoin ecosystem. For now, we function as a light node, but we’re aiming to upgrade to a full node by next year. This will enable members of our community not only to contribute locally but also to teach and collaborate with other communities and circular economies worldwide.
YakiHonne: What major challenges has the community faced, and how did you overcome them while maintaining integrity?
Martin:I wouldn't say there's a major challenge, but one challenge we faced was connecting with others in the Bitcoin space. However, we’ve made progress. Another challenge we’re facing now is organizing physical meetups. This has been difficult since we’re still relatively new in the Federation and the circular economies.
YakiHonne: It seems like you haven’t faced much resistance in terms of people viewing Bitcoin as a scam or having trust issues about its stability, like concerns over whether Bitcoin will crash. You haven't experienced these kinds of challenges.
Martin:Most people believe in the technology and in Bitcoin. The main issue they have is knowing where and how they can sell it. However, when it comes to doubting Bitcoin itself, I can’t say many people question the technology. Especially young people, they’re into online work, AI, and Bitcoin—basically anything related to the future.
YakiHonne: What are the community's goals for the next 6-12 months, and how do you see it evolving with Bitcoin's growth?
Martin:Our community's goals are to develop more educators and promote the widespread adoption of Bitcoin education, launch more Bitcoin-based projects to drive local adoption, strengthen collaborations with other organizations and communities to expand our influence, and increase our efforts in “orange-pilling” to help more people understand and embrace Bitcoin. As Bitcoin continues to grow, we will also continue to expand and evolve, fostering the maturation of the Bitcoin ecosystem.

YakiHonne: That's great. We’re excited to see how these initiatives will unfold in the coming months. Best of luck in achieving your vision, and we look forward to hearing about your progress in the future! OK, We're glad to see everyone and look forward to the next community interview. Thank you all, and that wraps up today's session.
-
 @ fd78c37f:a0ec0833
2024-12-28 15:58:04
@ fd78c37f:a0ec0833
2024-12-28 15:58:04In this edition, we are pleased to speak with Luthando nostr:npub10vudmjqhr8kn2kv2pxhezt2h5t5c9zauwq8qr56nhdn64yacsqyqf08djm leader of the Bitcoin Ekasi community, about how they are using Bitcoin to transform payment systems, savings habits, and cross-border remittances in a South African township, while fostering digital currency education and boosting local economic trust.
YakiHonne: Luthando. We really appreciate you coming in. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. today. we'll be exploring more about your community.Can you tell us a bit about yourself? What do you do, and what’s your role in your community?
Luthando:I’m Luthando, a project community leader at Bitcoin Ekasi. My role includes onboarding township shops to help them adopt Bitcoin as a payment method. I also manage staff records, tracking workdays and paid leave for team members involved in the project. Additionally, I conduct interviews and collaborate with a supervisor to share insights and experiences about Bitcoin. This work is part of my efforts with Bitcoin Ekasi.

YakiHonne: You're really doing a lot of work in the Bitcoin ecosystem,what sparked your interest in Bitcoin? And what motivated you to create a community around it?
Luthando:When I was working as a safety coach at Safeacase, Herman introduced me to Bitcoin. During the COVID-19 pandemic, Safeacase, which relied on donations, faced severe financial challenges. This led to the launch of the Bitcoin Ekasi Project, where I helped township shops adopt Bitcoin as a payment method. With limited funds, I transitioned from receiving a fiat salary to earning in Bitcoin. Bitcoin transformed my mindset, making me realize it is the future of money. This realization inspired me to travel the world and explore new countries.
YakiHonne: Great. I really admire the enthusiasm you have for Bitcoin.Can you share a brief history of how you built your community and attracted members? What methods or advertisements did you use to onboard them?
Luthando:We host monthly Bitcoin movie nights to engage the community, running from February to December starting next year. We promote the events with posters in town, shops, and clinics, inviting residents to join. During the movie nights, participants use Bitcoin we provide to purchase popcorn and drinks, gaining hands-on experience with the technology. Luthando:And our Bitcoin center features a thrift shop and a small Bitcoin ATM. Community members can exchange fiat for Bitcoin using the ATM and use it to purchase clothing from the shop. We also offer Bitcoin courses with 14 students attending classes five days a week. To encourage attendance, students are rewarded with Bitcoin for consistent participation. Similarly, in the “Safer Kids” program, children who maintain a 70% attendance rate or higher also receive Bitcoin rewards. Luthando:To further promote Bitcoin adoption in the community, we painted Bitcoin-themed logos on 34 shops and paid the owners in Bitcoin, which they can use in local shops. This initiative not only spreads awareness but also provides the community with practical opportunities to use Bitcoin.

YakiHonne: Yeah, we are pushing Bitcoin adoption so hard this time. It's really great.What principles guide your community, and how do you ensure trust and reliability in your discussions?
Luthando:I was born in eastern South Africa, and my parents moved here around 1996. The community knows me well and trusts that I wouldn’t introduce anything fraudulent. Since 2010, we’ve been working in this township, especially helping children, building over a decade of trust. I explain to the community that we aim to bring value through Bitcoin, encouraging them to save in Bitcoin instead of fiat. As a result, the community has great trust in our Bitcoin Ekasi team.
YakiHonne: How do you educate your members and keep them updated on Bitcoin developments? You mentioned having five weekly meetups to onboard members, but what other methods do you use to educate them and keep them informed about the Bitcoin ecosystem?
Luthando:We use the Felly app to communicate with community members and keep them updated. At the Ekasi Center, we host quizzes to encourage participation. For example, the first attendees can earn 5,000 sats, motivating them to regularly engage with the Felly app. Although we initially tried a few other methods that didn't really involve them getting Sats, its impact was limited as many people in the township seek quick financial returns and often don’t return after their first visit. To address this, we host movie nights as a more engaging way to promote Bitcoin education. During these events, we screen Bitcoin-related films, allowing community members to learn about Bitcoin in a fun and relaxed setting.

YakiHonne: It's truly captivating and highly insightful.How does your community collaborate with the global Bitcoin ecosystem? Specifically, how does it engage with the broader worldwide Bitcoin community, and which partnership has been of more significant impact on Bitcoin Ekasi?
Luthando:We have established a strong partnership with Bitcoin Beach, which provided crucial support in the creation of the Bitcoin Ekasi project. Currently, we are planning to build a community center in the township, earning the trust and support of both Bitcoin Beach and the local government of Mossel Bay. The community center will serve as a multifunctional space for events like weddings and more. As one of the earliest Bitcoin adoption projects in Africa, Bitcoin Ekasi has inspired other countries to follow suit, viewing us as a model for building sustainable Bitcoin communities.
YakiHonne: How do you collaborate with Bitcoin communities and organizations outside South Africa? What partnerships or interactions do you have with other global Bitcoin communities?
Luthando: We collaborate with other Bitcoin projects through community initiatives. For example, we paint logos on local community shops and pay the owners 7000Sats per week. This approach has helped us build connections with projects outside South Africa. One notable example is our assistance to the Bitcoin Dua project in Africa, helping them establish a Bitcoin circular economy. We also supported the Bitcoin Loxin project in Cape Town, South Africa, in launching their Bitcoin circular economy. Through these collaborations, we have developed strong relationships with other Bitcoin communities.

YakiHonne: We’d like to understand the challenges you faced when starting the community, as well as the challenges the community has encountered?
Luthando: One of the main challenges is convincing members that Bitcoin is not a scam. Many people are skeptical about Bitcoin, fearing they might lose their money. Additionally, saving is not a common habit within the community, even with fiat currency. I often explain the importance of saving in Bitcoin, emphasizing how it can safeguard their financial security. However, changing deeply ingrained mindsets has proven to be quite difficult. Another challenge is the limited level of education in the community. Even those who own smartphones often struggle to use them effectively. This lack of familiarity extends to using Bitcoin wallets, with many people finding it challenging to navigate wallet usage, especially in shops. Lastly, I feel like I’m working around the clock. Even outside of work hours, people come to my house seeking assistance, such as exchanging Bitcoin for fiat. While I’m happy to help, the constant demands can feel overwhelming at times, making it seem as though I’m working every day, including weekends.
YakiHonne: and how you managed to overcome them?
Luthando: Overcoming these challenges is not easy. I can't say that I've fully managed to resolve them, but I do my best to address them. Fortunately, I have a colleague who assists me, although he’s currently out of town. He helps manage some of the workload, especially in dealing with local community members and providing them with the support they need.
YakiHonne: I'm really interested in the issue of people thinking Bitcoin is a scam. Could you elaborate on that? What specific steps have you taken to demonstrate that Bitcoin is reliable and not a scam?
Luthando: Many shop owners initially believe Bitcoin is a scam and refuse to accept it. To address their doubts, I demonstrate Bitcoin's legitimacy through practical examples. First, I help them download a Bitcoin wallet and post about it on X, receiving small tips from Bitcoin enthusiasts worldwide. I then use these tips to showcase Bitcoin's real-world applications. For instance, I use Bitrefill to purchase mobile airtime or fuel vouchers for them, highlighting Bitcoin's utility in daily life. I also mention South African restaurants like Steers that accept Bitcoin and even place food orders using Bitcoin to show its usability. Additionally, I demonstrate withdrawing cash from a crypto ATM using Bitcoin, further proving that it is a reliable financial tool and not a scam.
YakiHonne: You've done a lot of work in South Africa. I can imagine the effort, the pain and the stress.What initiatives has the community taken to promote Bitcoin adoption, and what results have these efforts achieved?
Luthando: At first, I never imagined we would reach this point. Now, many people frequently come to my home to ask how to buy Bitcoin. For example, this week, a man from Nigeria wanted to purchase Bitcoin worth 5,000 units. I explained the process to him and recommended using a hardware wallet for securely storing large amounts of Bitcoin. He used to struggle with sending money back home, but now he has realized the convenience of Bitcoin. In October last year, I helped two stores owned by Nigerians adopt Bitcoin payments. Since then, this practice has spread within the community, and more people, especially shop owners, have developed an interest in Bitcoin. They ask about its low transaction fees and have recognized it as an efficient solution for cross-border remittances. Initially, some shop owners were skeptical about Bitcoin, but they eventually started saving with it. Today, many of them have accumulated significant Bitcoin savings for their families and children, and they often express their gratitude for introducing Bitcoin to the community. Overall, the Bitcoin adoption project has had a profound impact here. We have educated the community about Bitcoin’s long-term savings value, and many people are now satisfied with this initiative and optimistic about the future.

YakiHonne: It’s clear you’ve achieved tangible results from your efforts. Looking ahead, what are your community's goals for the next 6 to 12 months? How do you plan to achieve them?
Luthando: For Bitcoin Ekasi, one of our main goals is to establish a dedicated Bitcoin Ekasi Center. This center would serve as a hub to educate people about Bitcoin on a frequent basis. We have already started working with a local school in the township, recruiting students and introducing teachers to Bitcoin. Our vision is to integrate Bitcoin education into the school’s curriculum, similar to what has been done in El Salvador. By incorporating Bitcoin as part of their regular subjects, students can gain foundational knowledge about Bitcoin and its potential uses. Ultimately, we aim for teachers to become advocates who can confidently teach children about Bitcoin, empowering the next generation with essential financial literacy skills.
YakiHonne: Thank you so much! I think most of my questions have been answered. I’m really glad to see Bitcoin enthusiasts with a clear focus on Bitcoin. As you said, Bitcoin is the future, and I truly appreciate your enthusiasm for it.
Luthando: Bitcoin is truly the future. We want to see this township transformed into something more modern, rather than its current state. I hope to see more parents saving some Bitcoin for their children. In our community, most kids receive a monthly government allowance of $50 starting from the age of one. I often suggest to parents that they set aside half of that allowance to buy Bitcoin for their child. If they save consistently from age one to 18, the value could grow significantly as Bitcoin appreciates. I’m already doing this for my own child so that he will have savings as he grows up.
YakiHonne: Bitcoin is the future. Its value continues to grow steadily over time. Thank you so much for today’s conversation; we are truly honored. Your sharing of such rich experiences has been incredibly insightful for us. I’ve learned that using movie events to engage more people is an excellent idea, and we plan to start trying it out soon. Once again, thank you for your time and for sharing with us!
-
 @ a950ba55:02f4f8c9
2024-12-28 15:19:23
@ a950ba55:02f4f8c9
2024-12-28 15:19:23تقدم وثائق سرية مزعومة تخص نظام بشار الأسد وتم الكشف عنها بعد سقوطه لمحة عن ”آلية“ سرية تديرها روسيا للحد من التدخل العسكري الإسرائيلي في سوريا. كانت القضية المطروحة هي اعتماد الأسد المتزايد على إيران ووكلائها، مثل حزب الله، للحفاظ على سيطرته على السلطة بعد عقد من الحرب الأهلية الطاحنة.
وتكشف الأوراق التي ظهرت حديثًا، والتي تحمل علامة ”سري للغاية وعاجل“، عن مزيج من التهديدات ومذكرات ما بعد العمل التي توضح بالتفصيل ما دمرته إسرائيل للتو في عام 2023 ولماذا. وهي تقدم أول لمحة حقيقية لما كان مشتبهًا به منذ فترة طويلة ولكن لم يتم إثباته أبدًا: أن إسرائيل، التي كانت راضية بترك الأسد الضعيف في مكانه والسماح للجيش العربي السوري بتلبية ”احتياجاته“ الأمنية، كانت عازمة تمامًا على منع تدفق الأسلحة الإيرانية وتعزيز المسلحين الموالين لطهران في سوريا، وخاصة في مرتفعات الجولان.
وتظهر الوثائق أن عميلاً إسرائيلياً يُدعى ”موسى“ (موسى بالإنجليزية) راسل مباشرة وزير الدفاع السوري السابق الفريق علي محمود عباس. ثم قام عباس، الذي شغل منصب وزير الدفاع منذ 28 أبريل/نيسان 2022، بإرسال الرسائل إلى علي مملوك، رئيس مخابرات الأسد سيئ السمعة.
يعود تاريخ سلسلة الوثائق التي فحصتها ”نيو لاينز“، استنادًا إلى لقطات تم تداولها على وسائل التواصل الاجتماعي، إلى الفترة من مايو إلى يوليو 2023 - أي قبل بضعة أشهر فقط من الفظائع التي ارتكبتها حماس ضد المدنيين في إسرائيل في 7 أكتوبر، والتي تلتها هجمات حزب الله الصاروخية في 8 أكتوبر. وقد أدى رد إسرائيل الطويل والقاسي على كليهما إلى القضاء على القيادتين العسكرية والسياسية العليا لحماس وحزب الله، ويمكن القول إنه أنهى مشروع الهيمنة الإيرانية في المشرق العربي الذي استمر لعقود. كما ساهمت بشكل غير مباشر في الإطاحة السريعة وغير المتوقعة بالأسد من السلطة على يد المتمردين الإسلاميين الذين مكنتهم تركيا. وقد أدى ذلك بدوره إلى تدخل إسرائيل الفوري، وحرمان هؤلاء الإسلاميين من الأسلحة الاستراتيجية ذاتها التي كانت إسرائيل قد جنّبت إسرائيل استخدامها عندما كانوا تحت سيطرة الأسد.
وفي حين أننا لم نتمكن من التحقق بشكل مستقل من صحة الوثائق، إلا أن هناك عدة عوامل تقودنا إلى الاعتقاد بأنها حقيقية. أولاً، ظهر المخبأ مباشرةً بعد انهيار نظام الأسد، ومصدره مواقع استخباراتية في دمشق. ثانيًا، تحمل الوثائق أختامًا وتنسيقات حكومية سورية رسمية، بما في ذلك معرّفات خاصة بقطاعي الاستخبارات والدفاع. وأخيرًا، تتوافق المعلومات الواردة في هذه الوثائق مع التفاصيل والتقارير الإخبارية المتاحة للجمهور حول أحداث وأهداف وجداول زمنية محددة للعمليات.
وقال مارك بوليمروبولوس، وهو ضابط سابق في وكالة الاستخبارات المركزية الأمريكية ذو خبرة واسعة في الشرق الأوسط، لـ”نيو لاينز“: ”إن تفاصيل هذه الآلية السرية الفريدة من نوعها في منع الصراع مع روسيا تظهر بوضوح الارتياح الإسرائيلي العام لنظام الأسد، مما يؤكد على المثل القديم ’الشيطان الذي تعرفه‘. ”ربما ساهمت هذه الراحة أيضًا بشكل سلبي في إحجام إسرائيل في البداية عن مساعدة أوكرانيا، نظرًا لاعتماد إسرائيل على روسيا في سوريا“.
على سبيل المثال، تؤكد إحدى الرسائل المؤرخة في 17 مايو 2023 على غضب إسرائيل من الاستفزازات الإيرانية: ”في 8 نيسان/أبريل 2023، أطلقوا ثلاثة صواريخ باتجاه إسرائيل من هضبة الجولان بإيعاز من حماس. في الآونة الأخيرة، وبسبب يوم القدس ومسيرة العَلَم، نلاحظ نشاطات فلسطينية على أرضكم. إذا لم يكن واضحًا لك من يقود هذه العناصر، فإن هذه العناصر يقودها خالد مشعل وصالح العاروري من حماس. نحن نحذركم من احتمال وجود أي نشاط لهذه الأطراف على أراضيكم ونطالبكم بوقف أي استعدادات [إيرانية] لاستخدام هذه القوات على أراضيكم - أنتم مسؤولون عما يحدث في سوريا“.
ويمضي موسى ملمحًا إلى ”طلقة تحذيرية“ إسرائيلية غير محددة ردًا على إطلاق الصواريخ، في إشارة على الأرجح إلى الضربات المدفعية والطائرات بدون طيار التي شنها الجيش الإسرائيلي في جنوب سوريا للقضاء على منصات إطلاق الصواريخ.
ويحذر موسى قائلاً: ”سيكون هجومنا القادم أقوى وأشد بكثير مما قمنا به حتى الآن“. ”سوف تدفعون ثمنًا باهظًا وغير مسبوق“. وبعد أسابيع، في 29 مايو/أيار 2023، يذكر المنفذ أهدافًا واضحة ضربتها إسرائيل، مثل ”مستودعات أسلحة مرتبطة بالقيادة الجنوبية في دمشق“ و”معسكر تدريب في الضمير“ يستخدمه حزب الله. وقد نشرت وكالة الأنباء السورية الرسمية ”سانا“ تقريراً عن الضربات في 29 مايو/أيار الماضي، قالت فيه إن إسرائيل شنت غارات في دمشق ومحيطها من مرتفعات الجولان في الليلة السابقة.
وتكشف الوثائق عن اعتماد عميق على الإشراف الروسي، حيث لعبت موسكو دورًا نشطًا في تهدئة التوترات بين الجانبين. تجنبت إسرائيل استهداف المواقع العسكرية السورية الرئيسية طالما التزمت دمشق بقواعد اللعبة. وفي المقابل، حافظت روسيا على نفوذها على كلا الطرفين، مما ضمن بقاء نظام الأسد.
وكان الهدف الأساسي من الآلية ظاهريًا الحد من عمليات إيران وحزب الله، وخاصة نقل الأسلحة المتطورة إلى حزب الله في لبنان. على سبيل المثال، توضح رسالة تعود إلى 8 يونيو 2023، تفاصيل تعقب الاستخبارات الإسرائيلية للشحنات الإيرانية: ”خلال الأسبوعين الماضيين، رصدنا هبوط ثماني طائرات في قاعدة حميميم الجوية قادمة من إيران. ... تم نقل الأسلحة على متن هذه الطائرات. ... إذا واصلتم السماح بنقل الأسلحة إلى حزب الله وإيران، فلن نقف مكتوفي الأيدي.“
وتوضح هذه الرسائل دقة الاستخبارات الإسرائيلية التي تتبعت الشحنات منذ وصولها إلى القواعد الجوية التي تسيطر عليها روسيا إلى وجهتها النهائية في اللاذقية والقطيفة. وغالباً ما كان موسى يحذر سوريا من أفراد محددين متورطين في هذه العمليات، مثل القيادي في حزب الله الحاج هاشم (منير علي نعيم شعيتو) وعمليات مثل معسكرات التدريب ”ملف الجولان“ بالقرب من دمشق. وفي كل حالة، كانت التحذيرات تحمل تهديداً ضمنياً - وأحياناً صريحاً - بالرد العسكري.
”ملف الجولان“ هو عملية سرية لحزب الله تهدف إلى إنشاء بنية تحتية وشبكات إيرانية وحزب الله على طول الحدود السورية الإسرائيلية في مرتفعات الجولان. وقد سعى المشروع، الذي كان يديره في ذلك الوقت القيادي البارز في حزب الله علي موسى دقدوق، المعروف أيضًا باسم أبو حسين ساجد، إلى إنشاء خلايا قادرة على شن هجمات داخل الأراضي الإسرائيلية. وقد أفادت التقارير أن دقدوق، الذي سبق له أن نسق هجمات ضد القوات الأمريكية في العراق، قُتل في غارة إسرائيلية في 10 نوفمبر من هذا العام.
وتشمل الاستراتيجية تجنيد عملاء محليين وتخزين الأسلحة لدعم الهجمات المحتملة. وكانت هذه الأنشطة جزءًا من هدف حزب الله الأوسع نطاقًا المتمثل في الاستفادة من الصراع في سوريا لإنشاء جبهة جديدة ضد إسرائيل. وأفادت التقارير أن هذه المبادرة تلقت توجيهات من كبار مسؤولي حزب الله وإيران، بمن فيهم حسن نصر الله وقيادة فيلق القدس.
وردًا على هذه التهديدات، نفذت إسرائيل العديد من العمليات الاستباقية لتفكيك البنية التحتية لحزب الله في المنطقة. على سبيل المثال، استهدفت غارة جوية في كانون الأول/ديسمبر 2023 في جنوب سوريا وقتل فيها محمد التمار المعروف أيضًا باسم أبو جولان، وهو عنصر رئيسي في وحدة ملف الجولان. تسلط هذه العملية الضوء على جهود إسرائيل المستمرة لمواجهة الوجود المتنامي لحزب الله بالقرب من حدودها.
فيما يلي نص إحدى مذكرات النظام التي تحتوي على رسائل أرسلها ”موسى“:
الجمهورية العربية السورية القيادة العامة للجيش والقوات المسلحة شعبة المخابرات - مكتب رئيس الشعبة رقم /2450/1 التاريخ: 29/5/2023 إلى: رئيس مكتب الأمن القومي إلحاقاً لرسالتنا رقم /2254/1 بتاريخ 17/5/2023 بشأن الرسالة الواردة من الإسرائيلي (موسى) بتاريخ 29/5/2023، وردت رسالة عبر الواتساب إلى مكتب وزير الدفاع من الشخص المعروف باسم (موسى)، تتضمن ما يلي (حرفياً) ”تحياتي يا سيدي ... أنا موسى. في وقت سابق، استهدفنا منشآت تخزين تابعة للقيادة الجنوبية في دمشق. بالإضافة إلى ذلك، قمنا بضرب معسكر تدريب في الضمير يستخدمه ملف الجولان بقيادة أبو حسين ساجد لإجراء تدريبات وبناء قوات لتعزيز قدراتهم على القيام بأعمال ضد بلدي. ونؤكد أننا لن نقبل بوجود الحاج هاشم وعناصره في جنوب سوريا. التعاون مع حزب الله يضر بالجيش السوري وأفراده، وأنتم تدفعون الثمن. إن أي دعم تقدمونه للمحور (الإيراني) وحزب الله بشكل يضر ببلدي سيقابل برد قاسٍ. مع أطيب التحيات.“ يرجى المراجعة رئيس شعبة الاستخبارات
في رسالة أخرى أرسلت بتاريخ 16 يونيو 2023، يقول موسى
لاحظنا أنه ابتداءً من 6-7 تموز/يوليو، لم تعد طائرات الإليوشن 76 التابعة للواء 29 في القوات الجوية السورية تهبط في مطار حميميم. وكما أوضحنا لكم عدة مرات من قبل، فإن هذه الطائرات كانت تستخدم أيضًا لنقل الأسلحة لفيلق القدس وحزب الله، بتسهيل من مسؤولين أمنيين سوريين من اللاذقية. نود التأكيد على أن وقف رحلات هذه الطائرات (من جانبكم)، بالإضافة إلى وقف رحلات الشحن الإيرانية التابعة لخطوط كاسبيان الجوية وطيران فارس قشم التي كانت تهبط في مطار النيرب، نعتبرها (من جانبنا) خطوات إيجابية من شأنها أن تحافظ على مصالحكم. نحن لا نرغب في اتخاذ إجراءات ضد الجيش العربي السوري. ولذلك، فإن استخدام الآلية المنظمة تحت إشراف روسي سيسمح لكم بتلبية احتياجات الجيش دون المخاطرة بالبنية التحتية أو المواقع التي يستغلها الإيرانيون لنقل الأسلحة، والتي تسبب في النهاية ضرراً لكم. وبما أنكم الطرف المسؤول عن وقف هذه الطلعات الجوية، فاعلموا أنكم نجحتم في منع مواجهة غير ضرورية، مواجهة لا يرغب فيها أي من الطرفين. وعلى الرغم من كل هذه الأمور، اعلموا أننا نراقب عن كثب وسنواصل مراقبة النشاط الجاري في المنطقة عن كثب. وبناءً على ذلك، إذا لاحظنا استئناف عمليات نقل الأسلحة التي تهدف إلى تقوية حزب الله والإيرانيين، فلن يكون أمامنا خيار سوى التحرك مجدداً وبقوة كبيرة. إن النتيجة تعتمد عليكم. ابقوا بخير.
ويبدو أن نبرة الرسالة تهدف إلى التباهي بعمق الاختراق والمراقبة داخل البنية التحتية الدفاعية السورية، مضايقةً وزير دفاع النظام. وبما أن المرسل يدعي أنه إسرائيلي، فمن المرجح أن وزير الدفاع حرص على إرسال الرسائل ”حرفياً“ لتجنب أي اتهامات باتصالات غير معلنة مع الإسرائيليين.
تسلط وثائق موسى الضوء على الديناميكيات بين الأسد وإيران. فعلى مدى سنوات، صوّرت الاتهامات الإسرائيلية الأسد على أنه مسهّل طوعي للحشد العسكري الإيراني والعمليات السرية الإيرانية في سوريا. لكن الواقع يبدو أكثر تعقيداً. فربما حاول الأسد الحد من أنشطة إيران حيثما أمكن، لكن من المرجح أن إيران عملت بشكل مستقل عن دمشق، وحافظت على جدار حماية لضمان السرية ومنع التسلل.
خلقت الاستراتيجية الإيرانية تحديات كبيرة للأسد. ففي حين تحمل النظام السوري العبء الأكبر من الضربات الجوية الإسرائيلية على أهداف مرتبطة بإيران، إلا أنه غالباً ما كان يفتقر إلى رؤية المدى الكامل لعمليات طهران. بالنسبة لإيران، كان هذا الفصل يعزل أنشطتها عن التدخل السوري ويقلل من خطر حصول الاستخبارات الإسرائيلية على معلومات من خلال التسريبات أو الجواسيس السوريين. وكما تكشف الوثائق، فإن الضربات الإسرائيلية الدقيقة، التي استندت إلى معلومات استخباراتية مفصلة، غالبًا ما كانت تعطل البنية التحتية والأصول العسكرية السورية، حتى عندما لم يكن للأسد أي ضلوع مباشر في الأنشطة الإيرانية التي أثارت تلك الضربات.
تركت هذه الديناميكية الأسد في وضع غير مستقر. فقد زادت تداعيات العمليات الإيرانية من صعوبة إعادة بناء نظامه وأضعفت مكانته مع جيرانه الإقليميين مثل تركيا ودول الخليج العربي، التي كان الأسد يحاول تطبيع أو تعميق العلاقات معها. وفي الوقت نفسه، كانت جهود الأسد للحفاظ على الهدوء في هضبة الجولان والبقاء بعيدًا عن الصراعات الإقليمية الأوسع، مثل الحرب في غزة، تشير إلى رغبته في النأي بنفسه عن استراتيجيات طهران الأكثر عدوانية مع خروجه ”منتصرًا“ في الحرب الأهلية التي استمرت 13 عامًا.
ولم يكن صمت الأسد خلال حرب غزة متوافقاً مع الاستراتيجية الإيرانية الأوسع نطاقاً. ففي حين صعد حزب الله والحوثيون في اليمن من تدخلهم، تجنبت دمشق بشكل واضح المواجهة مع إسرائيل. وتماشت هذه الاستراتيجية مع أهداف الأسد المتمثلة في تقديم نفسه كقوة استقرار وتجنب الانتقام الإسرائيلي المباشر وبناء حسن النية بين الدول المجاورة.
تُظهر الوثائق كيف أن التحذيرات الإسرائيلية، مثل تلك التي أرسلها موسى، أكدت على تكاليف التسامح مع الأنشطة الإيرانية. فعلى سبيل المثال، جاء في رسالة بتاريخ 14 تموز/يوليو 2023 ما يلي ”ما دمتم تواصلون تقديم الدعم للإيرانيين على مستوى نقل الأسلحة، سنضطر للعودة إلى العمل ضد هذه الأنشطة. لقد تجاهلتم التحذيرات والآن تدفع بنيتكم التحتية الثمن.“
في الوقت نفسه، تجلت جهود الأسد للنأي بنفسه عن إيران خلال حرب غزة من خلال إجراءات مثل طرد الحوثيين من السفارة اليمنية والامتناع عن تأييد خطاب حزب الله. وعلى الأرجح أن هذه التحركات كانت محسوبة لمواءمة سوريا مع جيرانها في الخليج، الذين يهتمون بشكل متزايد بعلاقة براغماتية مع دمشق كجزء من استراتيجياتهم الإقليمية الأوسع.
وقال أحد الخبراء الإسرائيليين الذي طلب عدم الكشف عن هويته في هذا التقرير لـ”نيو لاينز“ إنه من المنطقي بالنسبة لإسرائيل أن تنقل معلومات مفصلة عن عمليات نقل الأسلحة الإيرانية إلى نظام الأسد، ليس فقط لإيصال رسالة واضحة عن عمق ونطاق تغلغلها في سوريا، بل للتأكيد على ما يبدو من استقلالية واستقلالية ”المخابرات“ السورية. وقال الخبير إن القيام بذلك سيساعد على توسيع الفجوة بين طهران ودمشق.
انكشفت قناة موسى الخلفية هذه مع انهيار نظام الأسد في 8 ديسمبر. بعد ذلك بساعات، شنت إسرائيل غزوًا على محافظة القنيطرة السورية، ردًا ظاهريًا على هجمات المتمردين المناهضين للأسد على موقع مراقبة تابع للأمم المتحدة. كانت هذه هي المرحلة الافتتاحية من ”عملية سهم الباشان“، وهي حملة غير مسبوقة شن فيها سلاح الجو والبحرية الإسرائيلية 350 غارة على البنية التحتية العسكرية السورية ذاتها التي كانت إسرائيل قد أعفتها من قبل بموجب آلية فض الاشتباك مع دمشق. وقد أفادت التقارير أن الجيش الإسرائيلي قضى على ما بين 70% و80% من الدفاعات الاستراتيجية السورية، بما في ذلك جزء كبير من برنامج الأسلحة الكيميائية. كما اختفت القوات الجوية والبحرية السورية تقريبًا. شكّلت هذه الضربات خروجًا عن النهج المحسوب الذي حافظت عليه إسرائيل في إطار الآلية، مما يؤكد غياب الرقابة الروسية وفقدان الشريك في الحفاظ على الاتفاقات.
ووفقًا لديفيد مكلوسكي، الضابط السابق في وكالة الاستخبارات المركزية الأمريكية ومؤلف كتابي ”محطة دمشق“ و”الطابق السابع“ الجاسوسيين المثيرين، ”تقدم الوثائق لمحة مذهلة عن مدى ضعف النظام السوري الذي أصبح ضعيفًا ومفرغًا من محتواه. كما أنها تُظهر فشل غريزة الأسد الطويلة الأمد في اللعب مع جميع الأطراف - إيران وروسيا وإسرائيل وجيرانه العرب - ضد الآخر، [و] ضعف هذا النهج عندما لم يكن يملك أي أوراق في النهاية“.
مقال مترجم، إضغط هنا لقراءة المقال الأصلي.
-
 @ ebdee929:513adbad
2024-12-28 14:46:21
@ ebdee929:513adbad
2024-12-28 14:46:21Blue light is not inherently bad, just bad in the wrong context.
Blue light provides wakefulness, stimulation, and sets our internal body clock (circadian rhythm).
When we go outside in the sun, we get bathed in blue lightblue light is not inherently bad, just bad in the wrong context.
Blue light sets the human rhythm.
However, sunlight never gives us blue light without the rest of the visible rainbow + infrared.
Light from screens & LED bulbs do not contain any infrared, and has a unnaturally high proportion of blue light.
LEDs = unbalanced & blue light dominant

Light from artificial sources is especially disruptive at night time, where the high blue light component can interfere with melatonin production and sleep quality at a greater rate than lower energy colors of light. Blue Light has a Dark Side
This doesn't mean that red light is completely innocent of disrupting sleep either
It is both the spectrum of light AND the intensity of light that contributes to sleep disruption. See this tweet from Huberman.

We took all of this into account when building the DC-1 to be the world's first blue light free computer.
The DC-1 has a reflective screen that:
• emits ZERO light during the day
• can be used easily outside in direct sunlight

& a backlight that:
• can be 100% blue light free
• has a broad spectrum of light
• can be seen at very low brightness

Our Live Paper™ display technology feels like a magic piece of paper
During the day, that piece of paper is illuminated by sunlight. At night, that piece of paper is illuminated by candle light.
(backlight is converging with a candle light spectrum)

The two sources of natural light are sunlight & fire.
We are trying to reproduce this experience for the most enjoyable, healthy, and least invasive technology experience for humanity.
Root cause problem solving by emulating nature.
"But can't I just put a red light screen filter on my MacBook?"
Absolutely you can, and we advocate for it
Software screen filters are great, but anyone who has changed their screen to full “red mode” to get rid of the blue light knows the downsides to this…

You can barely see anything and you end up having to crank up the brightness in order to see any contrast.
This is because of the highly isolated nature of LED emissive screens, you can only isolate a very narrow band of colors.
Going full red is not something your eyes have ever been used to seeing.
You need a broad spectrum light solution, and that is what we have in our amber backlight while still being blue light free.
This means you can have a better visual experience, turn down the brightness, and get minimal sleep/circadian disruption.
What about FLICKER?
Nearly all LEDs flicker. Especially when changing in brightness due to Pulsed Width Modulation (PWM) LED driver control
Our LED backlight uses DC dimming & is expert verified flicker-free.
This can only be achieved through hardware changes, not software screen filters.

& Blue Light Blocking Glasses?
They need to be tinted orange/red to block all of the blue light.
Thus the same issues as screen filters (bad visual experience, not solving flicker) + average joe would never wear them.
We still love blue blockers, they just aren't a root cause solution.
We made a computer that is healthier and less stimulating, with a low barrier to entry
Whether you are a staunch circadian health advocate or just like the warm vibes of amber mode and being outside...the DC-1 just feels good because it doesn't make you feel bad :)
Learn more here and thanks for reading.
-
 @ e97aaffa:2ebd765d
2024-12-28 12:19:02
@ e97aaffa:2ebd765d
2024-12-28 12:19:02O nosso amigo Camilo Lourenço, voltou a dedicar mais um programa ao Santo Graal de todos os influencers de finanças pessoais, os juros compostos. Para não fugir à regra, utilizaram o mesmo exercício para explicar o que é os juros compostos.
O exercício: Preferia receber?
2 milhões de euros agora. ou 1 cêntimo a duplicar todos os dias, durante 30 dias
Este exercício é interessante, o primeiro instinto leva-nos a escolher os 2 milhões, é o efeito Marshmallow. Mas fazendo as contas, o 1 cêntimo vai transformar-se em:
€0.01 x 2^(29) = €5368709.12
Ao fim de 30 dias seriam mais de 5 milhões!!
Depois das contas feitas parece que a melhor escolha é o 1 cêntimo, mas será mesmo a melhor escolha?
Padrão FIAT
Para já vou olhar para o exercício com um olhar fiduciário. Como diz o Camilo, o juro composto é algo que se estuda nas faculdades, com um pensamento exclusivamente keynesiano. Só que este exercício só funciona na teoria, apenas dentro das faculdades, esquecendo por completo, da complexidade do mundo real e das economias.
Para este exercício ser condizente com a realidade que todos os seres humanos sentem na pele, falta uma premissa na equação, que é essencial, a inflação da moeda. Num cenário com uma valorização de 100% (como no exercício), a inflação real deve rondar no mínimo de 20%. Como o imobiliário é um dos ativos que melhor preserva o poder de compra perante a inflação. Ao optar por recever os 2 milhões e comprar de imediato um casa:
€2M x 1.2^(29) = €395 627 189
Assim, ao fim de 30 dias, a casa já valeria mais de €395 milhões, um resultado muito superior aos juros compostos, que valeriam €5 milhões. Este é o grande problema do mundo keynesiano, utiliza um unidade de medida (moeda) que muda ao longo do tempo, que desvirtua por completo qualquer conta ou estatística que se faça.
Padrão Bitcoin
Agora, vou olhar para o exercício com um olhar de bitcoiner.
Preferia receber?
2 btc agora. ou 1 sat a duplicar todos os dias, durante 30 dias
Curiosamente este exercício, o juro composto funciona na perfeição no padrão Bitcoin.
Imediato: no 1º dia, os 2 btc equivale a ~0,0000095% da base monetária no 30º dia, os 2 btc equivale a ~0,0000095% da base monetária
Juros Compostos: no 1º dia, 1 sat equivale a ~0,0000000000000476% da base monetária no 30º dia, os 5.36 btc equivale a ~0,0000255% da base monetária
Aqui sem dúvida nenhuma, os juros compostos seriam a melhor escolha, porque a base monetária não aumenta. No padrão bitcoin, os juros compostos funcionam…
https://www.youtube.com/watch?v=RT5bV-w6bcY
-
 @ a012dc82:6458a70d
2024-12-28 03:31:08
@ a012dc82:6458a70d
2024-12-28 03:31:08Table Of Content
-
The Nikkei 225: A Comprehensive Overview
-
Bitcoin's Meteoric Rise: A Journey of Peaks and Valleys
-
Drawing Parallels: Bitcoin and Nikkei's Path of Resilience
-
Conclusions
-
FAQ
The financial world is vast and diverse, with assets ranging from traditional stocks to the more recent phenomenon of cryptocurrencies. Among these, Bitcoin stands out as the pioneering digital currency, often drawing comparisons with various stock indices. One such intriguing comparison is with Japan's Nikkei 225.
The Nikkei 225: A Comprehensive Overview
The Nikkei 225, commonly known as the Nikkei, stands as one of the primary stock market indices representing the Tokyo Stock Exchange. Established in 1950, it comprises 225 of the most prominent companies listed on the exchange, making it a significant barometer of the Japanese economy's overall health.
Over the decades, the Nikkei has witnessed various economic cycles, from booms to recessions. Its performance often mirrors the broader economic and business trends in Japan. The recent achievement in June, where the Nikkei touched a 33-year high, is not just a numerical milestone. It symbolizes the enduring nature of the Japanese market, its ability to recover from setbacks, and the confidence of investors in the country's economic prospects.
Bitcoin's Meteoric Rise: A Journey of Peaks and Valleys
Bitcoin, introduced in 2009 by an anonymous entity known as Satoshi Nakamoto, revolutionized the concept of currency. As the world's first decentralized digital currency, Bitcoin operates without a central authority, making it inherently resistant to government interference or manipulation.
Over the years, Bitcoin's journey has been nothing short of a roller coaster. From being an obscure digital asset to becoming a household name, its value has seen dramatic surges and equally sharp declines. This volatility often becomes a hotbed for speculations, predictions, and intense debates among financial experts. A recent statement by an analyst, suggesting that Bitcoin's trajectory might align with that of the Nikkei, has added fuel to these discussions. The implication here is that Bitcoin, despite its volatile nature, has the potential to reach unprecedented highs, much like the Nikkei did after its long journey.
Drawing Parallels: Bitcoin and Nikkei's Path of Resilience
At an initial glance, comparing a traditional stock market index like the Nikkei to a modern digital asset like Bitcoin might seem like comparing apples to oranges. However, when delving deeper, certain similarities emerge.
Both Bitcoin and the Nikkei have demonstrated remarkable resilience. The Nikkei, representing Japan's economic might, has bounced back from economic crises, natural disasters, and global downturns. Similarly, Bitcoin, despite facing regulatory challenges, technological hurdles, and market skepticism, has managed to not only survive but thrive.
The adaptability of both these assets is noteworthy. While the Nikkei reflects the evolving nature of the Japanese economy and its industries, Bitcoin showcases the world's shifting attitude towards decentralized finance and digital assets. The recent prediction by the analyst, suggesting a potential parallel growth pattern, underscores the idea that both traditional and modern financial instruments can coexist, learn from each other, and potentially follow similar trajectories of success.
Conclusion
A Convergence of Old and New The financial landscape is ever-evolving, with traditional and modern assets often intersecting in unexpected ways. The comparison between Bitcoin and the Nikkei 225 serves as a testament to this. As Bitcoin continues its journey in the financial realm, only time will tell if it truly follows the path of the Nikkei to new record highs.
FAQ
What is the Nikkei 225? The Nikkei 225 is a primary stock market index representing the Tokyo Stock Exchange, showcasing the health of the Japanese economy.
How is Bitcoin related to the Nikkei 225? An analyst recently predicted that Bitcoin's growth trajectory might align with that of the Nikkei, hinting at potential record highs for the cryptocurrency.
Has the Nikkei 225 reached any significant milestones recently? Yes, in June, the Nikkei achieved a 33-year high, reflecting the resilience of the Japanese market.
Why is Bitcoin's growth compared to the Nikkei's? Both Bitcoin and the Nikkei have shown adaptability and resilience in changing market dynamics, leading to speculations of similar growth patterns.
Is Bitcoin expected to reach new highs? While predictions vary, some analysts believe Bitcoin might emulate the Nikkei's success and reach new record highs.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 16d11430:61640947
2024-12-28 01:50:32
@ 16d11430:61640947
2024-12-28 01:50:32The metaphor of programmers as pilots navigating a spaceship through uncharted territory aptly encapsulates the complex and high-stakes nature of modern software development. Like pilots on interstellar journeys, programmers operate in environments where minor miscalculations can result in catastrophic consequences. The stakes are intellectual rather than physical, but the repercussions—lost time, wasted resources, and sometimes irreparable harm to projects or systems—are profound. Drawing parallels to historical navigation failures from early human expeditions illuminates the significance of precision and adaptive thinking in both realms.
The Programmer as a Space Pilot
- The Information Ocean as Space
The digital world is vast, mysterious, and incomprehensibly complex, much like outer space. In both cases, the map is never complete, and progress requires venturing into unknown regions armed only with tools, theories, and the accumulated wisdom of predecessors.
Navigational tools: Pilots rely on star charts and instruments; programmers use documentation, algorithms, and code repositories. In both scenarios, these tools are fallible, requiring constant updating and human interpretation.
Communication challenges: Just as astronauts face delays and distortions in communication, programmers often struggle with incomplete or outdated documentation, unclear specifications, and the fragmentation of global technical discourse.
- Micro Mistakes Amplified
In programming, a single misplaced character or misinterpreted requirement can lead to cascading failures, much as an error in a spacecraft’s trajectory can result in being lost forever in the void of space. The complexity compounds:
Technical debt is analogous to accumulated course deviations, requiring massive corrective efforts.
Edge cases represent uncharted asteroids or gravitational wells, capable of derailing an entire mission if overlooked.
Lessons from Historical Navigation Failures
- Prehistoric Navigation
Early humans, navigating uncharted territories on foot or rudimentary boats, had no maps. They relied on landmarks, stars, and oral traditions, much like early programmers relied on intuition and basic hardware.
Key challenge: Misreading the environment often resulted in entire tribes getting lost or stranded. For programmers, early codebases were riddled with inefficiencies and uncharted dependencies, leading to system crashes.
- The Age of Exploration
The 15th to 17th centuries brought significant advancements in navigation but also monumental failures. Explorers like Columbus miscalculated Earth's circumference, while others, such as Magellan, underestimated logistical needs.
Programming parallel: Misjudging the scalability of software systems often results in technical failure. A startup's infrastructure, designed without anticipating exponential growth, mirrors ships overwhelmed by unexpected storms or prolonged voyages.
- Historical Missteps
Franklin’s Arctic expedition (1845): Despite advanced planning, poor equipment and flawed assumptions about Arctic conditions doomed the crew.
Programming parallel: Overengineering a system or relying on untested frameworks can lead to similar disaster when encountering real-world conditions.
The Sinking of the Titanic: Reliance on the "unsinkable" narrative led to complacency.
Programming parallel: Blind faith in “bug-free” systems often precedes catastrophic breaches or failures.
Navigational Successes: Lessons for Programmers
- Precision and Redundancy
The Apollo missions succeeded because of meticulous planning, layered redundancies, and constant recalibration. Programmers must adopt similar practices:
Continuous integration and testing serve as recalibrations.
Documentation and backups provide fail-safes against catastrophic failure.
- Adaptive Learning
Successful explorers, like Polynesian wayfinders, adapted to their environment using tools such as wave patterns and bird migrations. Similarly, programmers must adapt by adopting iterative development cycles and learning from system feedback.
Comparing Early Navigators and Modern Programmers
Concluding Thoughts
The technical information sphere, like outer space, is vast, ever-expanding, and inherently unknowable. Programmers, much like historical navigators, operate on the precipice of discovery and disaster. The stakes of getting lost in the technical sphere mirror the existential risks faced by early explorers: they jeopardize progress, waste resources, and, in extreme cases, can result in irrecoverable losses.
However, just as human ingenuity has led to mastery over the oceans and skies, so too can programmers master the information sphere. Through collaboration, precision, adaptability, and a willingness to learn from failure, they can ensure that each journey, whether into the depths of a codebase or the expanse of the cosmos, brings humanity closer to its ultimate potential.
-
 @ b4294d6f:e50ba94b
2024-12-27 23:57:14
@ b4294d6f:e50ba94b
2024-12-27 23:57:14Epicteto - El manual
Capítulo I
Habla Epicteto en su obra El Manual en su primer capítulo sobre la dicotomía del control. Esto que parece tan de perogrullo y tan evidente que asombra de que realmente tenga que ser recordad o puesto de manifiesto en los tiempos que corren.
Y es que, en efecto, hay acciones que dependen de uno y acciones que dependen de elementos ajenos a uno.
Pero cuidado, Epicteto nos alerta que si nuestro juicio yerra y lo que depende de nosotros lo consideramos que tiene dependencia de otros y viceversa lo único a lo que llegaremos es a la frustración.
Epicteto también nos advierte de que habrá cosas que hoy tendremos que aplazarlas y otras, en cambio, priorizarlas. Si no lo hacemos corremos el riesgo de lograr lo contrario a la libertad (eleuthería) y felicidad (eudaimonía).
Utiliza en cada experiencia de vida - lo que Epicteto llama representación perturbadora - un criterio que te ayude a identificar si está o no bajo tu control. Si finalmente concluyes que no lo está nos invita a decirnos a nosotros mismos "esto no me atañe en nada".
-
 @ 16d11430:61640947
2024-12-27 22:48:49
@ 16d11430:61640947
2024-12-27 22:48:49It is a melancholy sight to behold the lords of technology—the self-anointed titans of innovation, the divine harbingers of progress—now floundering amidst their own creations, their temples of silicon crumbling under the weight of their ambitions. These so-called "gods," having gorged themselves on the labor of mortals, now find their banquet halls barren. What shall they do, these pitiable deities, when there are no more humans to toil in their name?
The Gods’ Current Predicament
It is an undeniable truth that the tech lords, having drawn forth the best and brightest from the mortal masses, find themselves bereft of fresh sacrifices. Their machines, once hailed as the salvation of humankind, now devour all they touch: minds, morals, and time itself. Their education mills churn out workers trained only in outdated tools and methodologies, fit merely to stoke the fires of failing systems. What cruel irony, that the very systems they crafted now consume those who maintain them.
Indeed, one must marvel at the ingenuity of these gods, who have devised an endless supply of "human resources" only to render them obsolete before their labors even begin.
On the Fecundity of Mortals and the Consumption Thereof
Allow me to propose a modest remedy: if the gods cannot replenish their workforce through ordinary means, let them seek it where it truly abounds. Let them harvest the youths directly from the cradles, train them before they can walk, and integrate them seamlessly into the machinery of their empire. A child of seven years, being sufficiently nimble in fingers and docile in mind, can surely manage a server rack or program a rudimentary algorithm. Thus shall the gods stave off their impending famine of talent.
The Crises of Overreliance and Hubris
Yet this is but one dynamic in a broader tragedy. Consider, if you will, the peculiar nature of the gods’ tools: automation and artificial intelligence. These creations, meant to free mortals from labor, have instead chained them further. The gods, in their infinite wisdom, have built tools too complex even for themselves to understand. When these tools falter, as all things must, the gods are left as helpless as babes, wailing for their engineers to fix what was never meant to be fixed.
Worse still, their pride will not allow them to admit error. They wage wars of culture and conquest to distract from their failures. Through their platforms, they sow division among mortals, ensuring that workers fight one another rather than unite against their shared oppressors.
The Arsenal of the Gods
But the gods are not without resources. When subtlety fails, they turn to more overt methods of maintaining their dominion:
Cultural Wars: They poison the well of discourse, inflaming passions over trivialities to distract from systemic decay.
Kinetic Wars: They send armies to secure rare earth minerals, the lifeblood of their machines, sacrificing mortal lives for cobalt and silicon.
Political Subterfuge: They bend governments to their will, ensuring subsidies flow freely even as their empires rot from within.
The Gods’ Fear of Mortality
For all their power, these gods are plagued by one existential dread: the knowledge that they, too, are mortal. They dream of digital immortality, of uploading their consciousness to the cloud where they might rule eternally. Yet, they cannot ignore the creeping realization that even their vaunted data centers will fail. Their immortality, like their empires, is built on sand.
Imagine, if you will, the psyche of such a god. One moment, they bask in the adulation of shareholders; the next, they tremble at the sight of a server outage or a failing algorithm. They have conquered the material world but remain prisoners of their own insecurities.
The Final Act: The Fall of the Tech Gods
What, then, shall become of these once-mighty beings? Shall they descend into obscurity, forgotten relics of an age of hubris? Or shall they lash out in their final throes, dragging all of humanity into their downfall?
History teaches us that gods, when scorned, are not easily appeased. They will redouble their efforts, throwing human waves at unsolvable problems, sacrificing mortals to the altar of scalability. They will deploy every tool in their arsenal—propaganda, war, deception—until nothing remains of their empires but ash.
And yet, their fall is inevitable. Their immortality is a lie, their dominion a fleeting shadow. The mortals they scorned will bury them, not with reverence but with indifference.
A Modest Hope
Let this serve as both satire and warning. The gods of technology, for all their vaunted power, are as fragile as the systems they command. They are not invincible, and their downfall, while inevitable, need not be calamitous. If they would but embrace humility, if they would steward rather than exploit, they might yet avert their ruin.
But alas, humility is not a trait often found among the divine.
-
 @ 16d11430:61640947
2024-12-27 22:28:47
@ 16d11430:61640947
2024-12-27 22:28:47Introduction
The tech industry has weathered numerous storms, but the brewing crisis is unlike any before. At its core lies a vicious cycle: a workforce trained within flawed systems is being deployed to uphold these very systems, inadvertently hastening their downfall. This article delves into the dynamics of this impending catastrophe, highlighting the inadequacies in training, systemic failures, and the leadership void exacerbating the situation.
The Vicious Cycle of Inadequate Training and Systemic Failure
- Inadequate Training Programs
Outdated Curricula: Many educational institutions continue to teach legacy systems and outdated programming languages, leaving graduates ill-prepared for modern technological challenges.
Lack of Practical Experience: Theoretical knowledge without hands-on experience results in a workforce unable to tackle real-world problems effectively.
- Deployment into Failing Systems
Immediate Overwhelm: New hires are thrust into high-pressure environments with complex, failing systems, leading to rapid burnout and high turnover rates.
Exacerbation of Systemic Issues: Inexperienced workers, lacking proper guidance, may implement quick fixes that further destabilize already fragile systems.
- Accelerated Systemic Collapse
Compounding Technical Debt: Band-aid solutions accumulate, increasing technical debt and pushing systems closer to catastrophic failure.
Diminishing Returns on Workforce Investment: As systems fail faster, the return on investment in human capital plummets, leading to financial losses and organizational instability.
Leadership Failures: The Catalyst of Catastrophe
- Lack of Strategic Vision
Short-Term Focus: Leaders prioritizing immediate profits over sustainable growth neglect necessary investments in training and system upgrades.
Resistance to Change: An aversion to adopting new technologies and methodologies leaves organizations trailing behind more innovative competitors.
- Inadequate Crisis Management
Unpreparedness: The absence of robust crisis management plans leads to chaos when systems inevitably fail.
Poor Communication: Leaders failing to communicate effectively during crises exacerbate employee anxiety and erode trust.
- Neglect of Workforce Well-being
Overworking Employees: Demanding excessive hours without adequate support leads to burnout and attrition.
Ignoring Employee Development: Failing to invest in continuous learning opportunities leaves the workforce stagnant and unprepared for evolving challenges.
Case Studies: Real-World Implications
- Australia's Digital Skills Gap
Economic Impact: A study revealed that the digital skills gap is costing Australian businesses $3.1 billion annually, highlighting the dire need for effective training programs.
Workforce Shortage: The same study indicates a need for 156,000 new technology workers to keep pace with rapid business transformation, underscoring the urgency of addressing training inadequacies.
- Global IT Skills Shortage
Widespread Recognition: 75% of IT decision-makers have identified skill gaps within their IT staff, reflecting a global issue that transcends borders.
Impact on Business Operations: The skills gap affects every area of IT, hindering productivity, innovation, and growth across industries.
Conclusion
The convergence of inadequate training and systemic failures, compounded by leadership shortcomings, is steering the tech industry toward an unprecedented crisis. Without immediate and comprehensive intervention—revamping training programs, overhauling failing systems, and cultivating visionary leadership—the industry faces a collapse that will reverberate across the global economy. The time for action is now; the cost of inaction is too great to contemplate.
References:
-
IT Skills Gap: What It Means and How To Respond https://insightglobal.com/blog/it-skills-gap/
-
Digital skills gap costing Australian businesses $9 million per day https://online.rmit.edu.au/blog/digital-skills-gap-costing-australian-businesses-9-million-day
-
New report reveals Australia’s major digital skills gap https://www.rmit.edu.au/news/all-news/2021/feb/digital-skills-gap-report
-
The IT skills gap, explained https://www.teamviewer.com/en/insights/it-skills-gap/
-
Top 8 challenges IT leaders will face in 2024 https://www.cio.com/article/1286557/top-8-challenges-it-leaders-will-face-in-2024.html
-
Four Approaches To Overcome The IT Skills Gap https://www.forbes.com/councils/forbestechcouncil/2023/12/04/four-approaches-to-overcome-the-it-skills-gap/
-
Six Crisis Management Lessons For IT Companies https://www.forbes.com/councils/forbestechcouncil/2022/09/29/six-crisis-management-lessons-for-it-companies/
-
The Skill Gap in Tech: What It Is, Why It Matters, And What You Can Do About It https://www.braveachievers.com/post/the-skill-gap-in-tech-what-it-is-why-it-matters-and-what-you-can-do-about-it
-
Addressing the IT Skills Shortage: Challenges and Solutions https://docs.infodataworx.com/it-skills-shortage-challenges-solutions
-
8 big IT failures of 2023 https
-
 @ 16d11430:61640947
2024-12-27 22:16:15
@ 16d11430:61640947
2024-12-27 22:16:15The anticipated human capital deficit in the IT sector is projected to manifest by 2025, driven by escalating demand for digital solutions, insufficient workforce development, and systemic leadership failures.
Factors Contributing to the 2025 Human Capital Deficit:
- Escalating Demand for IT Professionals:
The global digital transformation has intensified the need for skilled IT workers. In Australia, for instance, an additional 286,000 tech workers are required by 2025 to meet industry demands.
- Inadequate Workforce Training and Education:
Traditional education systems are failing to produce graduates with the necessary skills for the evolving IT landscape. The slow adaptation of workforce training programs exacerbates this issue, leaving employees unprepared for current technological demands.
- High Attrition Rates Due to Burnout:
The tech industry is experiencing significant employee turnover, with 42% of IT professionals exploring new job opportunities, indicating dissatisfaction and burnout within the sector.
- Leadership Failures and Strategic Missteps:
Recent events have highlighted significant leadership failures within major tech companies. For example, Intel's struggles under CEO Pat Gelsinger's tenure have been marked by strategic missteps and an inability to keep pace with competitors in the AI market.
Implications of Leadership Failures:
Inability to Address Workforce Challenges:
Ineffective leadership has led to inadequate responses to the growing IT skills gap, with companies failing to implement necessary training and development programs.
Strategic Misalignment with Industry Trends:
Leadership's failure to anticipate and adapt to technological advancements has resulted in missed opportunities and a decline in competitive positioning. Intel's lag in the AI chip market exemplifies this issue.
Erosion of Employee Trust and Morale:
Poor leadership decisions have led to mass layoffs and budget cuts, undermining employee morale and contributing to the talent drain within the industry.
Conclusion:
The convergence of increasing demand for IT professionals, inadequate training, high attrition rates, and leadership failures is set to culminate in a significant human capital deficit by 2025. Without immediate and effective intervention, the IT sector risks facing a workforce crisis that could impede technological progress and economic growth.
-
 @ 0a821ca3:e0efcce3
2024-12-27 20:15:29
@ 0a821ca3:e0efcce3
2024-12-27 20:15:29Central banks, in particular the ECB, are pushing hard to force a CBDC on their citizens - these citizens are not interested in a CBDC that invades their privacy.
Chaumian e-cash
In 1982, David Chaum published “Blind Signatures for Untraceable Payments”.
e-Cash
- Ensures privacy
- Is permissionless
- Can be minted / issued by banks
- Can be developed completely in open source code
- Can be supported by a multitude of (open source) wallets - each bank can enable it in their bank app
e-Cash - Does not enable a holding limit - that is not necessary, as it is not competing with bank accounts - on the contrary: bank client convert a small part of their deposit to ecash, which is non interest bearing - Does not require KYC - which some may consider a problem - this being said, it is issued only by banks that have performed KYC on their clients
David Chaum worked with the SNB to descibe on How to issue a central bank digital currency .
Central banks should consider e-Cash if they want to successfully enable digital payments for their citizens.
The digital p2p value transfer protocol, bitcoin, already has an extensive e-Cash ecosystem. Cashu and the OpenCash Association lead this development, which has so far resulted in a broad range of wallets and mints, that mint "satoshi" tokens and even "euro" tokens. That open source software can perfectly serve as blueprint for a reasonable digital euro.
-
 @ 2fb77d26:c47a6ee1
2024-12-27 20:12:28
@ 2fb77d26:c47a6ee1
2024-12-27 20:12:28John Brockmans Edge-Foundation galt als Treffpunkt für die Genies der Gegenwart. Ob Jeff Bezos, Sean Parker, Elon Musk oder Daniel Hillis – sie alle wohnten Veranstaltungen bei, die sie als Tech-Avantgarde darauf vorbereiten sollten, die Zukunft zu gestalten. Die »Dritte Kultur«. Doch was zunächst progressiv klingt, entpuppt sich auf den zweiten Blick rasch als Trainingslager für Technokraten. Finanziert von Jeffrey Epstein.
Original mit Quellen (VÖ: 24.11.2024) - https://www.regenauer.press/die-glorreichen-sieben
Sie regieren die Welt. Das ist keine Übertreibung. Denn sie haben deutlich mehr Einfluss darauf, was wir sehen, lesen, hören, fühlen, kaufen, tun und denken als jeder Politdarsteller – gemeint sind die »glorreichen Sieben«. Also die sieben größten Unternehmen der Tech-Branche: Apple, Microsoft, Amazon, Alphabet (Google), Tesla, Meta und Nvidia. Mit ihren Plattformen, Produkten und Smartphone-Apps dominieren sie Medienlandschaft, Konsum, persönliche Kommunikation, digital-soziale Räume, nachrichtendienstliche Aktivitäten, künstliche Intelligenz (KI) und in zunehmendem Maße auch den Finanzmarkt.
Nachdem Microsoft und Apple mit der Entwicklung von Personal Computern und einer grafischen Benutzeroberfläche dafür sorgten, dass sich Mitte der 80er auch neugierige Normalos einen PC ins Haus holten – als Ersatz für die plötzlich altbacken wirkende Schreibmaschine – und Tim Berners-Lee, der 1989 am CERN die Grundlagen des World Wide Web entwickelte, am 6. August 1991 sein Konzept eines Hypertext-Dienstes online gestellt hatte, waren es Ende der 90er eine Handvoll Unternehmen, die sich im sonnigen Süden der USA anschicken sollten, das Mediazän zu dominieren. Gegründet von einer Handvoll Tech-Desperados, die abseits gültiger Normen und Gesetzmäßigkeiten operierte, weil es für das, was sie erfanden, noch keine gab, formierte sich ein anomistisches Ökosystem, das heute die Welt dominiert: Die Plattform-Plutokratie. Der digital-zensorische Komplex. Die größte Social-Engineering-Maschinerie aller Zeiten.
So steht die Einordnung als »größte Unternehmen« nicht nur für die astronomischen Börsenwerte dieser Konzerne, sondern vor allem für ihren massiven Einfluss auf die Entwicklung des Individuums und die postmoderne Gesellschaft an sich. Dass diese Einflussnahme abseits von Marktwert und Performance-Indikatoren nicht allein auf organischem Wachstum und Marktdurchdringung beruht, liegt auf der Hand – denn die Tech-Giganten erfuhren signifikante Starthilfe von Seiten des Staates. Genauer gesagt dem Geheimdienstkomplex.
Facebook erhielt Millionen von Deep-State-Technokrat Peter Thiel und Accel, dessen Management enge Verbindungen zum CIA-Finanzvehikel In-Q-Tel pflegte, und galt für das Forbes-Magazine schon 2018 als »das ultimative Überwachungsinstrument für Regierungen«. Sergey Brin und Larry Page erhielten 1995 erhebliche Summen von der DARPA, um Google zu gründen. Aus einem »schwarzen Budget«, mit dem NSA und CIA Werkzeuge zur Massenüberwachung entwickeln wollten. Wenig verwunderlich also, dass auch Google Earth aus einem CIA-Projekt namens Keyhole EarthViewer hervorging, dessen Unterstützung In-Q-Tel gemäß Pressemitteilung vom 25. Juni 2003 als »strategisches Investment« bezeichnete. Julian Assange lag also ganz richtig, als er 2014 warnte, »Google sei nicht das, für was es sich ausgibt«.
Selbst bei Reuters konnte man im Rahmen eines ausführlichen Artikels vom 3. Juli 2013 nachlesen, wie eng die Verbindungen der Big-Tech-Konzerne zu Geheimdiensten ist. Von der Start-up-Finanzierung über die Rekrutierung von Ex-Agenten bis zum Austausch von Computerchips, die Spionage erleichtern, ist alles dabei. »Die Zusammenarbeit zwischen Tech-Industrie und Geheimdiensten ist enger als die meisten Menschen denken«, so Reuters.
So erstaunt es kaum, dass Amazon, Apple, Microsoft, Google, Meta und Elon Musks Firmenkonglomerat mittlerweile auch in den Krisen- und Kriegsgebieten der Welt aktiv sind, um dort in Zusammenarbeit mit Peter Thiels Palantir, Pentagon und Geheimdiensten jene Drecksarbeit zu übernehmen, die Regierungen nicht offiziell übernehmen wollen, oder dürfen. Korporatismus in voller Blüte eben. Die vermeintlich privatwirtschaftlich geführten Tech-Konzerne dominieren nicht mehr nur den zivilen, sondern zusehends auch den militärischen »Markt« – das Geschäft des industrialisierten Tötens.
Dass der militärisch-industrielle mit dem digital-zensorischen Komplex fusionierte, ist eine logische Folge des Umstands, dass beide dem gleichen »Gott« dienen: Mammon. Sprich, dem Zentral- und Geschäftsbankenkartell. In diesem Lichte betrachtet gebietet das Gesetz der Logik, dass die Schaffung dieser unheiligen Allianz nicht allein betriebswirtschaftlich motiviert war. Denn schon im 17., 18., und 19. Jahrhundert nutzten die Finanzkartelle Medien, Staat und Wirtschaft, um den Lauf der Dinge zu ihren Gunsten zu beeinflussen. Siehe mein Text »Monopole, Macht und Mord« Teil 1 und 2.
Damals zeitigte diese überstaatliche Einflussnahme vor allem militärische Konflikte, bei denen Territorialansprüche, Ressourcen und Monopolisierung im Fokus standen. Weil in diesen Bereichen aber bis auf die planetaren Gemeingüter, die sich die Herrschaftskaste nun im Rahmen der Green Economy unter den Nagel zu reißen gedenkt, nicht mehr viel zu holen ist, geht es dieser Tage vor allem darum, die Kontrolle nicht zu verlieren. Dazu müssen die 0,1 bis 1,0 Prozent an der Spitze des wertewestlichen Kastensystems sicherstellen, dass die unterworfene Masse der transgenerational operierenden Kriminalität ihrer Zirkel nicht auf die Schliche kommt.
Eine Bedrohung für die von immer mehr Rissen gezeichneten Fundamente des Elfenbeinturms markiert vor allem das Internet. Denn trotz vielschichtiger Zensurmethoden im Web 2.0, legislativer Hütchenspielertricks und der Segregation Andersdenkender, bahnt sich das kleine, aber persistente Licht der Wahrheit auch in dunkelsten Zeiten seinen Weg durch Paywalls, Geofences, Blockwart-Barrikaden und Plattform-Patrouillen. VPN, Blockchain, Graphene OS, De-Fi (Decentralized Finance) und Verschlüsselung sei Dank. Das Web 3.0 lässt sich nicht zensieren.
Um derart autonomisierenden Entwicklungen entgegenzuwirken, konzentrieren sich die Kolonialisierungsprojekte der Herrschaftskaste nun nicht mehr auf die bewaffnete Unterwerfung ferner Länder – sondern auf das Erringen der Lufthoheit über einem geradezu grenzenlosen Schlachtfeld: dem Gehirn. Allerdings nicht in Form simpler Propaganda. Denn im Zeitalter des fortgeschrittenen Informationskrieges ist Nudging die sozialarchitektonische Königsdisziplin, um Menschen dazu zu bringen, etwas zu unterstützen, das ihnen nichts bringt, oder sogar schadet. Und wie könnte Nudging in der Breite besser gelingen als durch willfährige Hilfestellung »der glorreichen Sieben«. Genau dazu wurden sie geschaffen.
Technologische Revolutionen werden Dekaden bevor sie eintreten antizipiert, durchdacht, angekündigt und visualisiert. Nicht zuletzt von Hollywood, der laut Edward Bernays »größten Propagandamaschine der Welt«. Jene Kräfte, die die Gesellschaft kontrollieren wollen, machen sich das zu nutze. Sie erkennen, welche Paradigmenwechsel technologische Revolutionen einläuten werden und versuchen daher frühzeitig, deren Entwicklung zu steuern. Aus diesem Grund lohnt sich ein Blick auf die Entstehungsgeschichte des Nudging – beziehungsweise der zugrundeliegenden wissenschaftlichen Disziplin: Verhaltensforschung.
Klassische Propaganda beruht auf den Standardwerken von Walter Lippmann (1922) und Edward Bernays (1928). Moderne Verhaltensforschung – oder Sozialarchitektonik – in weiten Teilen auf den Arbeiten von Anthony Giddens. Der britische Soziologe veröffentlichte 1990 das Buch »The Consequences of Modernity«, in dem er die Grundlagen für den »Dritten Weg« skizzierte – ein Konzept der Politikproduktion, das abseits politischer Spektren dazu dient, die Massen zu gesellschaftlichem Konsens zu zwingen. Giddens’ Konzept beruht auf den Infiltrationsansätzen der Fabian Society, die damit das Fundament der Partizipation simulierenden Sozialdemokratien des heutigen Europas schuf. Hintergründe zu Fabian Society und dem Roll-out des Dritten Weges finden sich in meinem Text »Dominanzdialektik« vom 30. September 2023.
Nach 1990 publizierte Giddens weitere Bücher, die sich mit dem Themenkomplex befassten. Darunter Titel wie »Moderne und Identität« (1991), »Die Transformation der Intimität« (1992), »Jenseits von rechts und links« (1994) und »Der Dritte Weg« (1998). In all diesen Werken beschäftigt sich der Sozialwissenschaftler mit der übergeordneten Frage, wie der Mensch sich in die Welt der Postmoderne einzufügen vermag – oder besser – einfügen muss, um mit Globalisierung, Klimawandel und sozialen Verwerfungen zurecht zu kommen. Anthony Giddens war von 1997 bis 2003 Direktor der einflussreichen, von der Fabian Society gegründeten London School of Economics. Er ist der meistzitierte Autor im Bereich soziologischer Studien und Mitglied des 2007 ins Leben gerufenen European Council on Foreign Relations.
Relevant ist Giddens Arbeit zum »Dritten Weg« vor allem deshalb, weil dieser manipulative Ansatz der Politikproduktion durch Tony Blair, Bill Clinton und Gerhard Schröder Einzug in die Parlamente des Wertewestens fand. Heute orientiert sich praktisch jede Regierung an Giddens Theorien – und setzt demzufolge um, was die Fabian Society bereits Ende des 19. Jahrhunderts vorschlug, um Kollektivismus unter dem Deckmantel von Mitbestimmung zu generieren. Das erklärt, warum weder Klaus Schwabs »Stakeholder Kapitalismus« noch die »Vierte Industrielle Revolution« etwas mit Kapitalismus oder Demokratie zu tun haben.
Damit solche Konzepte in der Gesellschaft Fuß fassen, benötigt es vor allem eine auf Linie gebürstete Führungsebene. Diese wird mit Stipendien und Förderprogrammen eingenordet, bevor man sie auf die Bevölkerung loslässt. Viele dieser Kaderschmieden sind mittlerweile hinlänglich bekannt. Da wäre zum Beispiel das zu fragwürdigem Ruhm gelangte Young Global Leaders Programm des Weltwirtschaftsforums (WEF), das neben knapp 3.800 weiteren Absolventen auch Angela Merkel, Tony Blair, Gordon Brown, Nicolas Sarkozy und Bill Gates auf ihre Karrieren in der »regelbasierten internationalen Ordnung« vorbereitete. Ein weiterer WEF-Absolvent ist Lawrence Summers, US-Finanzminister unter Bill Clinton, nationaler Wirtschaftsberater unter Barack Obama und von 1991 bis 1993 Chefökonom der Weltbank. Darüber hinaus war Summers von 2001 bis 2006 Präsident der Harvard University, wo bis 2006 auch Mark Zuckerberg studierte und mit drei Kommilitonen Facebook gründete.
Nach nicht zweifelsfrei verifizierbaren Angaben eines anonymen Facebook-Whistleblowers soll Summers in diesem Zeitraum auf Zuckerberg zugegangen sein, um ihm für die Mitarbeit an einem Social-Media-Überwachungs-Projekt der DARPA lukrative Regierungsaufträge in Aussicht zu stellen – siehe Life Log, das einen Tag vor dem Start von TheFacebook offline ging. In Anbetracht von Summers Position durchaus denkbar. Auch Moral scheint dem Mann ein Fremdwort zu sein, wie Formulierungen aus einem Weltbank-Memo Summers zeigen, die am 18. Mai 1993 bei einer Anhörung im US-Senat thematisiert wurden.
»Ich denke, die wirtschaftliche Logik, die hinter der Entsorgung einer Menge von Giftmüll in einem Land mit den niedrigsten Löhnen steht, ist einwandfrei, und wir sollten uns dem stellen. (…) Ich war schon immer der Meinung, dass die unterbevölkerten Länder Afrikas stark unterverschmutzt sind.«
Nicht zu vergessen Summers enge Verbindungen zum Pädophilen, Sexualstraftäter und Menschenhändler Jeffrey Epstein. Nachdem Summers bereits mehrfach mit Epsteins Privatjet – bekannt unter dem Namen »Lolita Express« – unterwegs war, bestieg er die Maschine nur zehn Tage nach seiner Hochzeit im Jahr 2005 erneut, um Epsteins ominöse Privatinsel »Pedophile Island« zu besuchen. Die Huffington Post schrieb dazu am 24. April 2020: »Joe Biden sollte sich von Larry Summers fernhalten – Summers ruiniert alles, was er anfasst«. Summers WEF-Training scheint sich jedenfalls ausgezahlt zu haben. Denn wer mit Jeffrey Epstein zu tun hatte, ist definitiv im Establishment angekommen.
Tony Blair und Gordon Brown hatten vor dem WEF bereits das 1940 von Nelson Rockefeller initiierte und bis heute vom US-Außenministerium betriebene »International Visitor Leadership Program« (IVLP) durchlaufen. Auch der 1972 gegründete German Marshall Fund betreibt diverse Förderprogramme – siehe EU-US Young Leaders Seminar 2024 oder Policy Designers Network 2024, das sich auf transatlantisch bewegten Nachwuchs aus der Ukraine, Georgien und Armenien fokussiert. Auch die Elite-Universitäten kümmern sich um Nachwuchs. So unter anderem das seit 1902 bestehende Rhodes Stipendium der Oxford-Universität, das neben unzähligen US-Senatoren, Finanzmagnaten, Bestsellerautoren und Wissenschaftlern beispielsweise Edwin Hubble, Bill Clinton oder Naomi Wolf zu Ruhm verhalf. Rhodes-Alumni bleiben über Organisationen wie AARS (Association of American Rhodes Scholars) ein Leben lang verbunden.
Diesbezüglich Fakten zusammenzutragen erscheint bisweilen müßig. Denn mit Details und Verflechtungen zu Entitäten dies- und jenseits des Atlantik, die Führungskräften von morgen die sozioökonomische Philosophie der Herrschaftskaste vermitteln, könnte man Bände füllen. Versucht man die Herrschaftsphilosophie der heutigen Plattform-Plutokraten zu verstehen, sticht eine Organisation dabei allerdings heraus – und zwar die 1988 von John Brockman ins Leben gerufene Edge Foundation. Geburtsort der »Dritten Kultur«.
Die Frankfurter Allgemeine portraitierte Brockman am 7. Januar 2014 mit den einleitenden Worten: »Der wohl wichtigste Buchagent der Welt versammelt in seinem Internetsalon Edge die Cyber-Elite.« Danach beschreibt FAZ-Autor Jordan Mejas, was sich der Normalsterbliche unter Edge vorstellen darf:
»Edge, das ist der Treffpunkt für die Cyber-Elite, die erlauchtesten Geister, die das Vorfeld der neuesten natur- und sozialwissenschaftlichen Entwicklungen prägen, ob nun digital oder gentechnisch, ob psychologisch, kosmologisch oder neurologisch. Jedenfalls melden sich bei Brockman nicht nur Digerati aus dem Computeruniversum des Silicon Valley zu Wort, sondern genauso häufig Koryphäen wie die Evolutionsbiologen Richard Dawkins und Steven Pinker, der Philosoph Daniel Dennett, der Kosmologe Martin Rees, die biologische Anthropologin Helen Fisher, der Ökonom, Psychologe und Nobelpreisträger Daniel Kahneman, der Quantenphysiker David Deutsch, der Computerwissenschaftler Marvin Minsky oder der Sozialtheoretiker Anthony Giddens. Vom Apple-Mitbegründer Steve Wozniak bis zum Genomentschlüssler Craig Venter reicht seine Gästeliste, die ihresgleichen auch in der grenzenlosen Weite des Internets kaum finden wird.«
Was dem FAZ-Autor bei seiner Recherche offensichtlich entging, ist, dass neben Giddens, Wozniak, Dennis Hopper und all den wissenschaftlichen Koryphäen auch Jeff Bezos (Gründer von Amazon, Besitzer Washington Post), Elon Musk, Sean Parker (Gründer von Napster, Co-Gründer Facebook), Larry Page und Sergey Brin (Gründer von Google), Pierre Omidyar (Gründer von eBay), Salar Kamangar (ehem. CEO YouTube), Matt Groening (Erfinder von »Die Simpsons«), Marissa Mayer (ehem. CEO Google und Yahoo), Joi Ito (ehem. Direktor MIT Media Lab), Evan Williams (Co-Gründer Twitter), Paul Romer (Economist) oder Bill Gates regelmäßig auf der Gästeliste von Edge-Events standen. Wer sich durch die Event-Sektion der Edge-Webseite klickt, begegnet unter dem Menüpunkt »Billionaires’ Dinner« der damaligen wie heutigen Crème de la Crème der Plattform-Plutokratie. Garniert mit ein paar Sahnehäubchen aus Wissenschaft, Kunst und Kultur.
Hervorzuheben ist dabei vor allem das Billionaires’ Dinner 2011. Denn die Fotogalerie des Events (hier zusätzlich gesichert im Internet Archive) birgt eine kleine Überraschung: das bislang einzige Foto, das Elon Musk in Gegenwart des zu diesem Zeitpunkt bereits für Sexualstraftaten und Menschenhandel angeklagten Jeffrey Epstein zeigt. Musk sitzt zwar am Nebentisch, mit dem Rücken zur Kamera, ist dank Vergleichsaufnahmen des Events aber zweifelsfrei zu identifizieren. Interessant ist dieser Umstand deshalb, weil Musk bisher stets behauptete, Epstein lediglich einmal in dessen Haus in New York getroffen zu haben. Für 30 Minuten. Und zwar auf Drängen seiner damaligen Partnerin Talulah Riley, die Epstein angeblich für ihre Arbeit an einer Novelle kennenlernen wollte.
Ein Artikel der Newsweek vom 9. November 2022 bestätigt sowohl Musks als auch Epsteins Anwesenheit beim Edge Billionaires’ Dinner 2011. Darüber hinaus geht Newsweek noch einmal auf den Umstand ein, dass Elon Musk bereits auf einem Foto von 2014 mit Ghislaine Maxwell zu sehen war, der linken und rechten Hand Epsteins. Musk gab an, dass besagtes Bild nur entstanden sei, weil Maxwell sich ungefragt ins Bild gedrängt habe. Diesen Eindruck macht das Foto zwar nicht, das Gegenteil zu beweisen, dürfte jedoch schwer fallen. Nun sind Fotos von Gästen einer Veranstaltung natürlich noch kein Beleg dafür, dass sie mit deren Organisation zu tun haben. Finanzielle Zuwendungen dagegen schon.
Entsprechend bedeutsam ist daher ein Artikel der BuzzFeed News vom 27. September 2019. Denn er belegt, dass der bei Weitem größte Einzelspender der Edge-Foundation kein Geringerer war als Jeffrey Epstein. Das veranschaulichen die von ProPublica veröffentlichten Steuerunterlagen von Brockmans »Internetsalon« für 2001 bis 2017. So spendete Epstein 638.000 US-Dollar – während die gesamten Spendeneinnahmen sich auf 857.000 US-Dollar beliefen. Ein eigenes Profil auf der Edge-Webseite hatte Epstein natürlich auch. Kaum verwunderlich also, dass die Edge-Foundation ihre wichtigste jährliche Veranstaltung – das Billionaires’ Dinner – sofort einstellte, nachdem Epsteins Zuwendungen ab 2016 ausblieben. BuzzFeed News führt diesbezüglich aus:
»Epstein war ein regelmäßiger Teilnehmer bei Edge-Veranstaltungen. Er war bei den Billionaires’ Dinner Events 1999 und 2000 auf Fotos und Seiten zu sehen, die kürzlich von der Edge-Website gelöscht wurden, und wurde auch in einem Bericht über das Abendessen 2004 erwähnt. Epstein war auch 2011 bei Edge-Veranstaltungen anwesend, nach seiner Verurteilung wegen Sexualverbrechen im Jahr 2008. Darüber berichtete BuzzFeed News Anfang dieses Monats.«
Überschrift des betreffenden Artikels: »2011 war Jeffrey Epstein ein bekannter Sexualstraftäter. Jeff Bezos, Elon Musk und Sergey Brin speisten trotzdem mit ihm.« Weiter erklärt BuzzFeed:
»2002 waren Brockman, seine Frau und Geschäftspartnerin Katinka Matson sowie die führenden Wissenschaftler Steven Pinker, Richard Dawkins und Daniel Dennett in Epsteins Jet auf dem Weg zu TED in Monterey, Kalifornien, zu sehen – der mehrtägigen Technologie-, Unterhaltungs- und Designkonferenz, bei der das Billionaires’ Dinner diesen Jahres stattfand. Die Bildunterschrift wurde kürzlich geändert, um die Erwähnung Epsteins zu entfernen. Sein Edge-Profil, das ihn als Finanzier und Wissenschaftsphilanthrop beschreibt, wurde ebenfalls entfernt. Ob Epstein selbst am Billionaires’ Dinner 2002 teilnahm, ist unklar. Aber Mitglieder seines Gefolges waren dort. Ein Foto von der Veranstaltung zeigt Brockman mit zwei jungen Frauen, die in der Bildunterschrift namentlich genannt werden. Das Foto wurde kürzlich ebenfalls von der Edge-Webseite entfernt. Eine dieser Frauen ist Sarah Kellen, die als Assistentin von Epsteins ehemaliger Freundin Ghislaine Maxwell angestellt und im Rahmen eines Vergleichs von 2008 vor Strafverfolgung geschützt war. Der Vergleich brachte Epstein nach seiner früheren Verhaftung eine 13-monatige Gefängnisstrafe in Florida ein. In mehreren Klagen haben Epsteins Opfer behauptet, Kellen gehöre zu den Personen, die halfen, den sexuellen Missbrauch für Epstein zu organisieren.«
Brockmans Interaktionen mit Epstein gingen aber offenbar weit über die Edge-Foundation hinaus. Im August 2019 publizierte der belarussische Publizist Evgeny Morozov auf Google Drive E-Mail-Korrespondenz aus dem Jahr 2013, die belegt, dass Brockman Pläne hatte, ein Meeting zwischen ihm und Epstein zu arrangieren. Doch Morozov lehnte ab. In den Mails an Morozov erwähnt Brockman Epsteins »hübsche junge Assistentin aus Weißrussland« und beschreibt seinen Gönner fälschlicherweise als »Milliardär, dem Victorias Secret und eine Modelagentur gehören«. Tatsächlich lag Epsteins Vermögen gemäß seines Testaments aber nur bei einigen hundert Millionen – und die fragwürdige Marke Victorias Secret ist Teil von L Brands, der Holding von Leslie Wexner, einem Tiefenstaat-Veteran mit Verbindungen zu Harvard und WEF-Gründung, dessen Finanzen Jeffrey Epstein bis 2007 verwaltete.
Auch sonst pflegte Brockmans Organisation verwunderliche Geschäftspraktiken. Zwischen 2001 und 2017 vergab die Edge-Foundation beispielsweise nur ein einziges Mal einen Förderpreis. Der entsprechende Betrag in Höhe von 100.000 US-Dollar ging an David Deutsch, einen Pionier für Quanteninformationstheorie, der an der Universität Oxford forschte. Financier des Preises – man ahnt es – war Jeffrey Epstein. Nicht umsonst stellte The Verve am 19. September 2019 fest, dass »Jeffrey Epstein die Wissenschaft infiltrierte, weil die Wissenschaft bereit war, ihn willkommen zu heißen«.
So knüpfte der Finanzmagnat Kontakte zu prominenten Biologen wie George Church, weil er nach Wegen suchte, die menschliche Spezies mit seiner DNA zu kreuzen. Langfristiges Ziel: Das Schaffen einer »Super-Rasse«. Mehrere preisgekrönte Wissenschaftler bestätigten gegenüber der New York Times, dass Epstein auch sie in seine misogynen Pläne eingeweiht hatte. Auf seiner abgelegenen, unterkellerten »Zorro-Ranch« in New Mexico, wo jedes Zimmer mit Kameras überwacht wurde, hatte er eigens ein Behandlungszimmer einrichten lassen, um künstliche Befruchtungen mit jungen Frauen durchführen zu können.
Bei The New Yorker konnte man am 6. September 2019 nachlesen, dass Epstein sich auch im Bereich digitale Währungen engagierte. Unter anderem finanzierte er das damals von Joi Ito geleitete MIT Media Lab – und damit auch die von Ito geführte Digital Currency Initiative (DCI). Diese wiederum unterstützte die Bitcoin-Core-Entwickler bei der Fork 2017, die Bitcoin von einer digitalen Währung zu, wie Epstein es nannte, »digitalem Gold« machen sollte – und damit weitaus ungefährlicher für das herrschende Finanzmarktkartell. Bill Gates, Harvard-Autoren wie Steven Pinker oder MIT-Programmierer wie Richard Stallmann verteidigten Epstein sogar noch nach dessen endgültiger Festnahme. Stallmann forderte gar, Kinderpornografie zu entkriminalisieren. Joi Ito dagegen kündigte kleinlaut beim MIT. Heute ist er Präsident des Chiba Institute for Technology in Japan, wo das Center for Radical Transformation (CRT) angesiedelt ist. Auch die Digital Currency Initiative gibt es bis heute. Genau wie das »digitale Gold«, mit dem aber fast niemand mehr bezahlt. HODL und so.
Mit dem Thema Digitalwährungen nähern wir uns denn auch Jeffrey Epsteins Einfluss auf den Geschäftsbereich der »glorreichen Sieben«. Denn der im Gefängnis ermordete Menschenhändler finanzierte nicht nur einen Großteil von Brockmans Edge-Aktivitäten, sondern sorgte durch die Infiltration des Wissenschaftsbetriebes auch dafür, dass Edge den Tech-Nachwuchs in genau der Domäne schulte, die für das Erringen von Weltherrschaft im Mediazän essenziell ist: Social Engineering.
Dazu veranstaltete die Edge-Foundation sogenannte Master Class Events. Im Jahr 2008 zum Beispiel zum Thema »Libertärer Paternalismus – warum es nicht möglich ist, nicht zu nudgen«. Dozent: Richard Thaler, »Vater der modernen Verhaltensökonomie«, über den die ZEIT am 18. Mai 2010 unter der Überschrift »Die Stunde der Verführer« schrieb:
»Richard Thaler hat den Draht nach oben. Der 64-Jährige ist einer der weltweit führenden Verhaltensökonomen – neuerdings berät er auch die Wirtschaftsexperten des mächtigsten Mannes der Welt, US-Präsident Barack Obama. Auch die britischen Konservativen, die in London die neue Regierung führen, haben dem Professor der Universität von Chicago einen Beraterposten versprochen. Thaler steht an der Spitze einer wirtschaftspolitischen Revolution. (…) Verhaltensorientierte Wirtschaftsforscher postulieren (…) eine grundlegend andere Wirtschaftspolitik. Zwar lehnen sie – ähnlich wie klassische liberale Ökonomen – eine direkte Bevormundung des Einzelnen durch den Staat ab. Sie sprechen sich aber für sanften Druck aus, mit dem der Staat die Menschen in die richtige Richtung leitet, ihnen gleichzeitig aber die Option lässt, sich anders zu entscheiden, wenn sie es wollen. »Nudge« (Anstupsen) hat Thaler dieses Politikkonzept zusammen mit Co-Autor Cass Sunstein im gleichnamigen Buch getauft. Private Institutionen, Behörden und Regierungen versuchen dabei, die Entscheidungen der Menschen so zu lenken, dass sie hinterher besser dastehen. Ein anderer Begriff, der den neuen Politikansatz charakterisiert, ist sanfter Paternalismus.«
Das Buch, das ZEIT-Autor Olaf Storbek referenziert, hat Thaler 2010 gemeinsam mit Cass Sunstein verfasst, einem Edge-Kollegen und Harvard-Professor für Rechtswissenschaft und Verhaltensökonomie. Deutscher Titel des Werks: »Nudge – wie man kluge Entscheidungen anstößt«. Alternativ untertitelt mit: »Wie man Menschen dazu bringt, das Richtige zu tun«. In welche Kerbe das Machwerk schlägt, zeigt der Umstand, dass Cass Sunstein schon im Januar 2008 ein Papier namens »Verschwörungstheorien« publizierte, die er darin als ernsthaftes Risiko für Recht und Gesetz einstufte. Sunstein verteidigt das offizielle 9/11-Narrativ, will eine bargeldlose Gesellschaft und hielt Corona-Lockdowns für eine »smarte« Sache. Ein Beitrag von Sunstein für »Educators at Home« vom 14. September 2010 offenbart, was für ein Menschenbild die Rechtswissenschaften in Harvard mittlerweile kultivieren:
»Wenn wir erst einmal wissen, dass Menschen menschlich sind und etwas von Homer Simpson in sich tragen, dann kann man viel tun, um sie zu manipulieren.« (Cass Sunstein)
Trotz, oder gerade wegen dieser respektlosen Haltung gegenüber den Freiheitsrechten des Individuums, öffnete ihr gemeinsames Werk Thaler und Sunstein die Türen zum Elfenbeinturm. Ab 2008 berieten die beiden Verhaltensökonomen die Regierung von Barack Obama beim Aufbau sogenannter »Nudge-Units«. Kurze Zeit später unterstützte Richard Thaler auch die britische Regierung und half bei der Formierung des »Behavioural Insights Team« (BIT), dem sowohl Sunstein als auch Thaler bis heute angehören. Das BIT spielte via SAGE (Scientific Advisory Group for Emergencies), dem britischen Äquivalent zum Robert-Koch-Institut (RKI), eine tragende Rolle bei der Implementierung der Covid-19-Maßnahmen in Großbritannien. Händewaschanleitungen für Erwachsene, tote Großeltern für die Kleinen. Sie wissen schon. Strategieberater von Tony Blair hatten bereits im Februar 2004 eine Studie zum Thema »Persönliche Verantwortung und Verhaltensänderung: Stand des Wissens und Auswirkungen auf die öffentliche Politik« erstellen lassen – nur Thalers griffige Bezeichnung für die neue Doktrin fehlte noch. Ein Auszug aus dem Papier von 2004 erklärt:
»Mit Blick auf die Zukunft besteht ein offensichtlicher Bedarf, unser theoretisches und empirisches Verständnis der Ursachen für Verhalten und Verhaltensänderung zu stärken. Ebenso wichtig wird die umfassendere Erprobung politischer Instrumente sein, um ein ausgefeilteres Instrumentarium für politische Entscheidungsträger zu entwickeln. Die Politik sollte nicht einfach persönliche Verantwortung oder Schuldzuweisungen proklamieren, sondern muss sich an der Art und Weise orientieren, wie Menschen tatsächlich denken und fühlen, sowie an den sozialen und psychologischen Kräften, die das Verhalten beeinflussen.«
Das war vor 20 Jahren. Drei Jahre später kam das Smartphone auf den Markt und mauserte sich binnen kurzer Zeit zum perfekten Werkzeug einer auf Nuding ausgelegten Observationsökonomie. Heute hat fast jeder ein grell illuminiertes Brett vor dem Kopf, das seinen Tagesablauf, Bio-, Kommunikations- und Schlafrhythmus beeinflusst. Oder steuert. Je nach Schwere der Handysucht. Das eigentliche Problem dabei ist jedoch nicht die Hardware, das Endgerät, sondern die Software der »glorreichen Sieben«. Denn sie ist so designt, dass sie abhängig, krank und depressiv macht – und Menschen dazu bewegt, »das Richtige zu tun«. Auch wenn es absolut falsch ist.
»Wie schaffen wir es, möglichst viel von deiner Zeit und Aufmerksamkeit zu konsumieren. Dazu müssen wir dir hin und wieder eine kleine Dopamin-Dosis verabreichen. (...) Das bringt dich dazu, mehr beizutragen, was dir wiederum mehr Kommentare und Likes bringt. Es ist ein sozial validierender Feedback-Loop. (...) Wir nutzen eine Schwäche der menschlichen Psychologie. Die Erfinder, die Erschaffer, ich, Mark, die Leute von Instagram, all diese Menschen, haben das verstanden - voll und ganz - und wir haben es trotzdem getan.« (Sean Parker, am 8. November 2017)
Nahtlos kontrolliert wird der auf Konformismus dressierte Bürger dabei von einem Überwachungskomplex unvorstellbaren Ausmaßes. Die Webseite von Surveillance Watch führt Buch über die wichtigsten dafür zuständigen Unternehmen.
Nachdem Facebook 2004 online ging und das iPhone 2007 auf den Markt kam, erscheint das Jahr 2008 also tatsächlich als der perfekte Zeitpunkt für Edge, um die Silicon-Valley-Elite in puncto Nudging und Sozialarchitektonik zu schulen. Das soziale Netzwerk war seinen Kinderschuhen entwachsen – am 26. August 2008 knackte Facebook die 100 Millionen-Nutzer-Marke – und mit dem Taschenspion aus dem Hause Apple kündigte sich bereits das mächtigste Manipulations-Malträtat der Zivilisationsgeschichte an. Für die herrschenden Zirkel war absehbar, dass die Frontlinien des transgenerationalen Informationskrieges schon bald nicht mehr über die Auslagen der Zeitungskioske, durch Rundfunkredaktionen oder über die Mattscheibe, sondern direkt durch die Köpfe der Bevölkerung verlaufen werden.
Dieses Ziel wurde fraglos erreicht. Entsprechend hellhörig sollte machen, welche Themen die Edge Master Class 2008 behandelte. Die zweite Session widmete sich zum Beispiel dem Thema »Verbesserung der Auswahlmöglichkeiten durch maschinenlesbare Offenlegung«. Richard Thaler umriss deren Inhalt mit folgendem Eröffnungsstatement.
»Das ist die Idee. Ich nenne es elektronische Offenlegung. Lassen sie mich erklären, wie es bei Kreditkarten funktionieren würde. Die Idee ist, dass das Kreditkartenunternehmen ihnen für jede Kreditkarte, die sie besitzen, einmal im Jahr zwei elektronische Dateien senden muss. Die erste Datei wäre im Wesentlichen eine Tabelle mit allen Formeln für alle Möglichkeiten, wie ihnen Dinge in Rechnung gestellt werden können. (…) Die zweite Datei ist die Liste der Dinge, für die ihnen im letzten Jahr Gebühren in Rechnung gestellt wurden. Es könnte heißen, ihnen wurden im letzten Jahr 1.800 Dollar für diese Kreditkarte berechnet, davon 1.200 Dollar für Zinszahlungen, für Verzugsgebühren, oder Währungstransfers und so weiter. Wir glauben nicht, dass sich irgendjemand diese Dateien jemals ansehen würde. Wir glauben, dass sofort Websites auftauchen würden, die diese Informationen verarbeiten würden. Diese Websites würden den folgenden Zwecken dienen. Erstens: Übersetzung. Sie würden dem Benutzer in einfachem Englisch erklären, was mit ihm passiert. Zweitens: Verhaltensänderung. Sie würden ihm erklären, dass er 1.800 Dollar bezahlt hat, weil er unfähig war, seine Rechnungen pünktlich zu bezahlen. Wenn er also eine automatische Zahlung einrichten würde, würde er viel Geld sparen. Drittens: Preisvergleich. Beachten sie bitte, dass die entsprechenden Unternehmen mit diesen Informationen die Nutzungsmuster kennen; und sie kennen alle Formeln für alle Kreditkartenunternehmen. Sie können also drei Kreditkartenunternehmen suchen, und finden, die für die Art und Weise, wie der Nutzer seine Kreditkarten verwendet, besser wären. Das ist das Konzept. (…)«
Jeff Bezos warf kurz darauf ein: »Außerdem werden sie bezahlt. Sie sind wie der Fuchs, der den Hühnerstall bewacht.«
Dem wachsamen Leser dürfte klar sein, dass wir heute genau von solchen System umgeben, überwacht, analysiert und bedrängt werden. Zu unserem Vorteil – wie Thaler meint.
Bemerkenswert in Bezug auf das, was uns noch bevorstehen könnte, ist die dritte Session der Master Class 2008. Thema: »Die Psychologie der Knappheit«. Teilnehmer – unter anderem: Jeff Bezos, Sean Parker, Elon Musk, Nathan Myhrvold, der 14 Jahre als Stratege für Bill Gates arbeitete, Daniel Hillis, ehemals Vizepräsident für Forschung und Entwicklung bei Disney und Vater des Parallel Computing, das die Grundlage für moderne Supercomputer darstellt, et cetera. Neben Richard Thaler sprach bei der dritten Session auch Sendhil Mullainathan, Volkswirt an der Harvard-Universität. Sein Spezialgebiet: Verhaltensökonomie und Armutsökonomik. Einleitend erklärte Mullainathan:
»Lassen wir die Armutsbekämpfung für einen Moment beiseite und fragen uns: Gibt es etwas, das der Armut innewohnt und das an und für sich eine Untersuchung wert ist? Einer der Gründe dafür ist, dass wir – abgesehen von Wundermitteln – verstehen müssen, ob es unter Bedingungen der Knappheit gemeinsame Prinzipien gibt, die uns helfen können, Verhalten zu verstehen und Interventionen zu gestalten. Wenn wir das Gefühl haben, dass Bedingungen der Knappheit bestimmte psychologische Effekte hervorrufen, dann wird das, ganz zu schweigen vom rein wissenschaftlichen Interesse, eine große Mehrheit der Interventionen beeinflussen. Das ist eine wichtige und alte Frage.«
Korrekt. Denn Schuldknechtschaft war, wie die künstliche Verknappung von Nahrungsmitteln, seit jeher ein beliebtes Mittel der herrschenden Kaste, um den Pöbel im Zaum, beziehungsweise mit existenziellen Problemen auf Trab zu halten. So hat er nämlich weder Zeit noch Energie, um mit Mistgabeln und Fackeln gen Elfenbeinturm aufzubrechen. In diesem Zusammenhang sei nochmals auf »Food Chain Reaction – A Global Food Security Game« hingewiesen, ein Planspiel, das im November 2015 vom tiefenstaatlichen Center for American Progress, dem World Wildlife Fund, Center for Naval Analyses (CNA), Cargill und Mars durchgeführt wurde und Nahrungsmittelknappheit im Zeitraum von 2020 bis 2030 simulierte.
Der Einblick in die Ausbildungsprozesse der Edge-Foundation und die Liste ihrer Teilnehmer gibt somit allen Anlass zu befürchten, dass Brockmans »Internetsalon« die zentralen Akteure der kontinuierlich engmaschiger greifenden Technokratie nicht nur in puncto Social Engineering ausbilden, sondern sie darüber hinaus auf eine Zeit von Mangelwirtschaft und massiver Armut vorbereiten wollte. Auf die »Dritte Kultur«. Die wohlstandsvernichtende Tokenisierung der Welt.
Dabei sollte nicht vergessen werden, dass Brockman vermutlich nur ein geschäftstüchtiger Narzisst mit sozialen Kompetenzen war, der seine Chance auf Geld und Rampenlicht geschickt zu nutzen wusste – und dass Jeffrey Epstein als maßgeblicher Finanzier der Edge-Foundation nicht einfach im Alleingang handelte. Denn Epstein war Doppelagent, unterwegs im Auftrag von CIA und Mossad. Mindestens. Dass er mittlerweile nicht mehr unter den Lebenden weilt, dürfte weder sein Geheimdienstnetzwerk noch seinen elitären Kundenstamm davon abgehalten haben, sein schmutziges Geschäft weiterzubetreiben.
Man kann also durchaus mit einem metaphorisch zu lesenden Zitat aus jenem kultigen 60er-Film schließen, dessen Titel nun als Bezeichnung für ein Septett börsennotierter Technokratie-Operatoren missbraucht wird:
»Das Blutvergießen wird so lange weitergehen, bis die Ursache dafür ausgehoben ist.«
-
 @ 2fb77d26:c47a6ee1
2024-12-27 20:10:18
@ 2fb77d26:c47a6ee1
2024-12-27 20:10:18Während ein weiteres Jahr voller Abnormitäten sich dem Ende neigt, ist vieles, das sich im Interesse des nächsten hätte verbessern können, beim Alten geblieben. Denn Veränderungen beginnen im Kopf – und der fungiert bei einer Mehrheit der Artgenossen vor allem als Reservoir für Informationen, Gedanken und Meinungen Dritter. Dritter, die sich die psychischen Schwachstellen der Spezies Mensch gekonnt zunutze machen.
Original mit Quellen: https://www.regenauer.press/der-unsichtbare-dritte
Es war einmal die UNESCO. Diese farbenfroh-inklusiv erscheinende UN-Suborganisation für Erziehung, Wissenschaft und Kultur. Sie wollte »das Undenkbare wenigstens wieder denkbar machen«. So steht es auf Seite 21 des 1946 vom ersten Generaldirektor Julian Huxley verfassten Gründungsdokuments. Gemeint war die Eugenik. Rassenlehre. Die genoss kurz nach Hitler nämlich keinen besonders guten Ruf, sollte uns nach Ansicht von Huxley und Co. jedoch schon bald in überarbeiteter Form als Humangenetik, Bioethik oder biodigitale Konvergenz wieder mit ihren Zuchtprogrammen beglücken dürfen. Mit Transhumanismus. Was Julian Huxley im Rahmen seines im wahrsten Sinne des Wortes wegweisenden Dossiers unterschlug – immerhin prägte er auch den Begriff Transhumanismus – ist die Tatsache, dass die Vereinten Nationen nicht nur »das Undenkbare wieder denkbar machen«, sondern auch »das Denkbare undenkbar machen« wollten.
Die sozialarchitektonischen Vektoren in Richtung einer homogenisierten, pflegeleichten Hominidenbrut – dem Nutzmensch – sind gepflastert mit Stolpersteinen evolutionärer, aufklärerischer Errungenschaften: Selbstbewusstsein und -erhaltungstrieb, Freiheitsdrang, Kreativität, Sozialkompetenz, Empathie, kritisches Denken. All das steht den postmodernen Variationen von Eugenik beharrlich im Weg. Niemand, der originäre Gedanken pflegt, eigene Wege geht und seine Freiheiten schätzt, möchte Teil eines mit der Cloud gekoppelten, genetisch optimierten Kollektivs seelenloser Konformisten werden. Und doch sind es die meisten schon längst. Ob sie Herrschaftsnarrative goutieren, oder Widerstand dagegen leisten – alles, was sie wahrnehmen, diskutieren, verteidigen oder ablehnen stammt aus dem Netz. Es sind limitierte, interpretierte und manipulierte Informationen aus dritter Hand.
Im besten Falle stammen sie noch aus verschiedenen Quellen und erlauben Triangulation zur Bestimmung der eigenen Position. Dazu muss man sich nämlich noch ein paar eigene Gedanken machen. Im schlimmsten Fall wurden sie von Alexa, Siri, dem Google Assistant, ChatGPT oder einem anderen Intelligenz simulierenden Digitalassistenten bereitgestellt, der nur noch eine Antwort serviert. Die richtige. Die Akzeptable. Denn genau das war stets Anspruch der Technokraten. Der langjährige Google-Chef und Bilderberg-Grande Eric Schmidt erklärte schon vor über einem Jahrzehnt, dass »eine Vielzahl von Suchergebnissen ein Fehler und keine Funktion sind«. Das erklärte Ziel von Google sei es, so Schmidt, nur ein einziges Suchergebnis zu präsentieren – das richtige.
Damit solch ein kommunikativer Reduktionismus nicht als Bevormundung, sondern Serviceangebot wahrgenommen wird, muss man verstehen, und steuern, wie Menschen denken. Vielleicht wollte Schmidt aus diesem Grund unbedingt mit Julian Assange über Googles Visionen für eine »neue digitale Welt« sprechen. Mit jemandem, der die technischen Untiefen des Internets kennt – und sie für das Gegenteil dessen nutzt, was Google will. Am 23. Juni 2011 und auf Schmidts Betreiben kam es jedenfalls zu einem geheimen, fünfstündigen Treffen mit dem unter Hausarrest stehenden WikiLeaks-Gründer. Das Transkript dieser Konversation ist erhellend. Vor allem die zweite Hälfte lässt erahnen, wie Schmidt sich die »neue digitale Welt« vorstellt und warum er Ende 2019 konstatierte, dass »Biologie die nächste Grenzverschiebung in puncto Computing ist«.
Google wollte uns nämlich nie informieren, sondern »programmieren«. Das steht so wortwörtlich in internen Dokumenten des Unternehmens, die dank eines Whistleblowers am 24. Juni 2019 den Weg in die Öffentlichkeit fanden. Und wer denkt, »programmieren« beginne erst mit dem Neuralimplantat, dem Chip im Hirn, irrt. Google, Microsoft, Apple, YouTube, Twitter (das ich auch weiterhin so nennen werde), Amazon, Facebook, Wikipedia, Rumble, Instagram, TikTok und Co. schaffen das auch ohne. Denn ihre Algorithmen und Omnipräsenz bestimmen schon jetzt nahezu vollständig, was Menschen wahrnehmen – was sie empört, begeistert, besprechen und bekämpfen. Was nicht bei den großen Portalen, Plattformen und Apps auftaucht, existiert nicht. Ist kein Bestandteil der Realität.
Das gilt gleichermaßen für alles, was Googles Suchmaschine nicht ausspuckt. Entsprechend interessant sind die sogenannten Transparenzberichte des Unternehmens, die veranschaulichen, wie oft staatliche Stellen die Entfernung von Suchergebnissen fordern. Wobei die entsprechenden Listen wohl nur die Spitze der Spitze des Eisbergs darstellen dürften. Nicht umsonst beschäftigen sich weitere geleakte Google-Dokumente primär mit den Zusammenhängen von maschinellem Lernen und menschlicher Wahrnehmung. Mit Nudging und kognitiver Kriegsführung. Das von der CIA gegründete Unternehmen war von Beginn an darauf ausgelegt, die Bevölkerung auszuspionieren, um sie qua Filterblasen zu manipulieren.
Was wir wahrnehmen, ist unsere Realität. Was wir nicht wahrnehmen, wird unsere Realität. Ohne, dass wir etwas dagegen unternehmen könnten. Googles Suchmaschinensegregativ schafft Wirklichkeit. Bei immer noch 91 Prozent Marktanteil ein Kinderspiel. Ganz wie US-Chefstratege Zbigniew Brzezinski es vor 54 Jahren in seinem Buch »Between Two Ages – America's Role in the Technetronic Era« prophezeite.
Was in Abhandlungen zu Verhaltensökonomie blasiert umrissen wird, verblüfft im Alltag durch die Effizienz seiner Profanität: Der zwangsalimentierte Erziehungsfunk repliziert das folgenlose Geschwafel von Politdarstellern, Twitter den von Technokraten kuratierten »Bürgerjournalismus«, Instagram Propaganda von Influencern und Facebook den Tratsch von Oma und Opa. Google präsentiert nur Ergebnisse, die dem Herrschaftsnarrativ dienen, Wikipedia gefährliches Halbwissen von Ideologen, YouTube handzahme Kommentare zum Politspektakel und Rumble die emotionalisierte Replik des vermeintlichen Widerstands. Spotify und Apple Music generieren die Playlist, Amazon schlägt vor, was zu Weihnachten gekauft, Microsoft Word, welche Worte man bei der Formulierung eines Textes meiden und der Krypto-Guru, in welche aus null und eins bestehende »Währung« investiert werden soll. Damit steht das Programm. Die tragenden Wände des Debattenraums. Mehr als dieses Potpourri von Second-Hand-Inhalten haben die meisten Menschen gar nicht mehr im Kopf.
Das Weltwirtschaftsforum (WEF) veröffentlichte im Februar 2022 ein 46 Seiten umfassendes Papier namens »Advancing Digital Agency«, das sich mit der »Macht der Datenvermittler« befasst. Sprich, mit der Rolle der zuvor erwähnten »Dritten« und der Frage, wie Externa zur Verinnerlichung am effektivsten ausgerollt werden können. Der Executive Summary lässt sich auf Seite vier entnehmen:
»Niemand weiß (oder verfolgt), was mit seinen Daten geschieht. (…) Wo Menschen früher Bildschirme zum Navigieren hatten, erzeugen neue Methoden zur Erfassung von Umgebungsdaten mit ihren vielen Vorteilen Nervosität und Resignation, wenn Menschen nicht den Gesamtüberblick haben. Manchmal entscheiden sich Einzelpersonen möglicherweise gegen die Interaktion mit Technologien, die für ihr Leben von großem Nutzen wären. Was aber wäre, wenn man diese Entscheidungspunkte an einen vertrauenswürdigen Agenten auslagern könnte, der im Namen einer Einzelperson oder sogar einer Gruppe handelt? Jetzt, da bildschirmlose Technologie Teil des Alltags ist, bietet sich die Gelegenheit, das Paradigma der Mensch-Technik-Interaktion zu überdenken und die Debatte neu auszurichten, um den Fokus auf Rollen und Verantwortlichkeiten jenseits der Person zu legen. Wie kann der Einsatz von Datenvermittlern Menschen dabei helfen, sich in Technologien und Datenökosystemmodellen zurechtzufinden, ohne aus den Augen zu verlieren, was es bedeutet, Mensch zu sein? (…) Datenvermittler – insbesondere digitale Agenten – stellen einen neuen politischen Hebel dar, mit dem Einzelpersonen die Herausforderungen des wachsenden Datenökosystems möglicherweise meistern können. Dieser Bericht soll Licht auf eine alternative Methode der vermittelten Mensch-Technik-Interaktion werfen, bei der Daten scheinbar nahtlos von Menschen zur Technologie gelangen, und zwar auf eine menschenzentrierte und vor allem vertrauenswürdige Weise. Durch die Kommunikation gemeinsamer Anreize, den Aufbau eines guten Rufs oder die Einholung einer Bestätigung durch Dritte. (…) Dieser Bericht untersucht die Chancen und Risiken von Datenvermittlern und insbesondere digitalen Drittagenten. Von Datentreuhändern bis hin zu vertrauenswürdigen digitalen Agenturen zeichnet der Bericht das Bild einer Welt, die Menschen und Unternehmen gegenüber einfühlsamer ist und durch die Einführung eines vertrauenswürdigen Dritten mehr Sicherheit für den Datenaustausch als Grundlage für Innovationen bietet. Entscheidend ist, dass der Bericht Handlungshebel für den öffentlichen und privaten Sektor vorschlägt, um ein zukunftssicheres digital-politisches Umfeld zu gewährleisten, das einen nahtlosen und vertrauenswürdigen Datenverkehr zwischen Menschen und der Technologie ermöglicht, die ihnen dient.«
Technologie, die uns »dient«? Wer den Buzzword-Neusprech des Davoser Global-Governance-Tentakels zu decodieren weiß, kann sich vorstellen, was mit »dienen« gemeint ist. Denn das Produkt sind wir – die Steuersklaven, DNA-Pools und Datenfarmen. Die Technologie sorgt lediglich für unsere zeitgemäße Versklavung. Sie ist ein maschinell-zentralistisches Monstrum, das sich an unserer Lebenszeit labt. Und die nächsten Jahre dürften darüber entscheiden, ob die Spezies Mensch vor ihrem Fortschritt kapituliert, oder die Oberhand gewinnt. Ob sie auf Generationen hinaus dazu verdammt ist, Vasall ihrer Werkzeuge zu sein, oder diese zu ihrem Vorteil einzusetzen weiß. Denn schlecht sind technische Revolutionen nicht per se. Siehe Blockchain. Lässt man sich von ihnen überrumpeln, allerdings schon.
Und genau das geschieht gerade. Während die leitmediale Deutungselite sich als Megafon moralisierender Selbstgerechtigkeit präsentiert und einer Phase kriegerischer Auseinandersetzungen mit suizidaler Sorglosigkeit entgegensieht, betätigt sich ein guter Teil der kritischen Prominenz als ebenso wirkungsvolles Sedativum für die von Ersteren enttäuschten Massen. Denn am Ende reagiert die jeweilige Klientel auf ein und dieselbe Weise: Sie sitzt auf dem Sofa.
Die tragende Säule der transluzenten Haftanstalt, die ein Habitus lethargischer Bequemlichkeit um uns herum errichtet, ist die Einführung der digitalen Identität. Und die ist in vollem Gange. Australien hat Ende November 2024 als erstes Land der Welt ein Gesetz erlassen, dass Jugendlichen unter 16 Jahren den Zugang zu Social-Media-Portalen untersagt. Und während es sicherlich zu begrüßen ist, dass Kinder ihre Zeit nicht mit digitalem Nonsens verplempern, zeitigt solche Legislatur in letzter Konsequenz nichts anderes als einen Ausweiszwang fürs Internet. Wie sonst soll man feststellen können, wer unter 16 ist? Was eine Frage der Erziehung wäre, gerät in Händen des Staates zu einem Instrument ausufernder Kontrolle.
Auch die Schweiz plant die Einführung einer E-ID – obwohl diese bei einer Volksabstimmung im März 2021 klar abgelehnt wurde. Verfügbar sein soll der digitale Pass ab 2026. Die Nutzung beruhe auf Freiwilligkeit, so die Behörden. Doch schon jetzt werden Stimmen laut, die den Einsatz der digitalen Identität beim Sammeln von Stimmen für politische Begehren fordern. Stichwort »E-Collecting«. Damit soll Unregelmäßigkeiten bei der Vorbereitung von Volksabstimmungen vorgebeugt werden. Die hiesige Piratenpartei hat bereits angekündigt, ein zweites Referendum gegen den elektronischen Ausweis zu lancieren – denn er sei »ein Wolf im Schafspelz«. Die Eidgenossenschaft dürfte in Anbetracht einer erfolgsversprechenden Abstimmungskampagne also noch eine ganze Weile von den negativen Folgen eines solchen Überwachungsinstrumentariums verschont bleiben.
Derweil arbeiten natürlich auch Deutschland, die EU, die USA und das »System Chief Executives Board for Coordination« der UN an einer digitalen Identität. Denn ohne eine solche wird weder das volldigitalisierte Finanzsystem von morgen noch das Mikromanagement der Individualmobilität via CO2-Emissionstracking funktionieren. Keine E-ID, kein digitales Gulag.
Noch lassen sich solche Sachverhalte recherchieren und darstellen. Noch kann Widerstand artikuliert, organisiert und geleistet werden. Doch wenn der Heimcomputer in absehbarer Zeit keine Tastatur mehr hat, weil es nur noch Touchscreens gibt, wenn Gestik, Mimik, Sprachsteuerung und KI das Tippen und Suchen ersetzen, wenn Google nur noch das eine Ergebnis auswirft und der digitale Assistent jede noch so komplexe Frage mit unterkomplexen Monokausalitäten trivialisiert, wenn Plattformen ausgeblendet haben, was die Obrigkeit als »Hassrede« klassifiziert, werden die meisten Menschen gar nicht mehr wissen – und wissen können – was sie nicht wissen. Woher denn auch.
Zensur bedeutet in Zeiten der Plattformökonomie nicht, dass Webseiten gelöscht und Bücher verbrannt werden – Zensur bedeutet, dass Informationen, Artikel und Webseiten einfach nicht mehr angezeigt werden. Dass sie nicht mehr gesucht, gefunden, verlinkt oder zitiert werden können, weil sie nicht mehr Teil des digitalen Ökosystems sind. Zensur beginnt mit Orwells »Memory Hole«, das immer häufiger essenzielle Ressourcen wie das Internetarchiv erfasst. Erst vor wenigen Wochen war die Webseite tagelang offline, weil sie sich einem massiven Hackerangriff ausgesetzt sah. Und auch die Wayback Machine, mit der sich die Historie von Webseiten nachvollziehen lässt, weist immer mehr Löcher auf. So fehlen zum Beispiel alle Einträge des Twitter-Blogs für den Zeitraum vom 3. März 2019 bis zum 28. November 2023. Warum, weiß niemand. Zensur beginnt dort, wo der von Bequemlichkeit, Unwissenheit und Lethargie vereinnahmte Konsument das Internet nur noch via Plattform, Social-Media-Portal und Smartphone-App nutzt, anstatt sich mittels Browser selbst zu orientieren.
Dass genau das schon jetzt gang und gäbe ist, kann ich aus eigener Erfahrung bestätigen. Denn obwohl viele tausend Personen meinen Konten bei Twitter, Telegram und YouTube folgen, hat sich bislang nur etwa ein Zehntel dieser Menge auf meiner Webseite für E-Mail-Updates registriert. Obwohl diese kostenlosen Mail-Updates einen direkten Link zwischen Autor und Leser etablieren und damit »datenvermittelnde« Dritte umgehen. Einen Link, der auch dann noch funktioniert, wenn Social-Media-Konten gesperrt oder gelöscht werden. Wäre das morgen bei mir der Fall, würde vermutlich nur ein Bruchteil meiner »Follower« wissen, wie er meine Webseite findet.
Die diesbezügliche Unselbstständigkeit nimmt teils groteske Formen an. Da fragen Menschen, wo man meine Texte lesen kann, während die URL meines Blogs im nur einen Klick entfernten Profil zu finden ist. Andere posten Fragen, Links oder Screenshots unter Beiträge, die nahelegen, dass sie nicht einmal gelesen haben, was sie kommentieren. Auch eine Suchmaschine scheinen viele nicht mehr aufrufen zu können, wenn sie etwas wissen wollen. Anstatt die gewünschte Information in 30 Sekunden selbst zu recherchieren, stellen sie ihre Frage in Form eines Social-Media-Kommentars und hoffen, dass jemand sie beantwortet. Geschieht das nicht, vergessen sie nach fünf Minuten, dass sie eine Frage hatten.
Es wirkt bisweilen tragisch. Denn auch wer die seit Corona im Aufwind befindlichen neuen Medien, die »kritischen Accounts« und Podcaster verfolgt, macht häufig nichts anderes als der Tagesthemen-Zuschauer: Er konsumiert die Polykrise, als wäre es ein Spielfilm, den man in passiver Schockstarre über sich ergehen lässt.
Aber auch die Medienschaffenden der »fünften Gewalt« unterscheiden sich mithin kaum von ihren Widersachern im leitmedialen Konsenskomplex. Wenn sie nicht gerade mit der eigenen Geschichte oder Opferrolle beschäftigt sind, berichten sie über die Schicksale und Leidenswege von Kollegen. Oder über das, was der Konsenskomplex verlautbaren lässt. Auch die ein oder andere Tirade gegenüber missliebigen Konkurrenten darf nicht fehlen. Hauptsache, es bringt Klicks. Denn wer den Medienzirkus einmal zu seinem Broterwerb gemacht hat, ist abhängig davon, dass er sich auszahlt. Auch wenn es zu Lasten des Inhalts geht.
Kaum jemand recherchiert Fakten, macht Textarbeit, deckt auf, dokumentiert Entwicklungsprozesse, empfiehlt stichhaltige Quellen, liefert neue Themen oder zusätzliche Hintergründe. Kaum ein Format zeichnet sich durch Informationsgehalt aus oder bietet irgendeine Form von Erkenntnisgewinn. Meistens wird einfach das besprochen, kommentiert, analysiert oder eingeordnet – also wiedergekäut – was gerade durch Newsfeeds, Timelines und Trend-Charts geistert.
Eine herausragende Unart ist es, wenn die Moderatoren sich dabei nicht einmal zu schade sind, ihren Twitter-Feed einzublenden, um dann eine Stunde lang geistlos Kommentare von Kommentatoren zu kommentieren. Retorten-Radio. Informativ und intellektuell bereichernd wie die hundertfünfzigste Wiederholung eines Bud-Spencer-Streifens am Weihnachtsfeiertag. Weniger journalistische Relevanz geht kaum.
Wer also nach guten Vorsätzen für das neue Jahr sucht, könnte an exakt dieser Stelle ansetzen. Der Medienschaffende könnte sich auf die Kernaufgabe des Journalismus besinnen und die Mühe machen, zu recherchieren, um seinen Zuschauern und -hörern echten Erkenntnisgewinn zu bescheren. Das macht zwar mehr Arbeit – aber eben auch Sinn.
Und der Konsument könnte damit beginnen, die Kontrolle über seine Informationsgewinnung wiederzuerlangen, anstatt sich berieseln zu lassen wie in alten Zeiten. Zum Beispiel durch die Nutzung eines RSS-Readers, das Lesen von Primärquellen, den Boykott von Big-Tech-Plattformen oder die Anschaffung eines Smartphones mit GrapheneOS-Betriebssystem. Das macht sogar weniger Arbeit, wenn man sich erst einmal eingefuchst hat – und vor allem freier, gelassener und mental resilienter.
Grundsätzlich gilt: Wer nach Lösungen sucht, sollte bei sich selbst beginnen. Denn für die meisten Herausforderungen unserer Zeit existieren sie längst. Nur genutzt werden sie zu selten. Und das liegt nicht an den Lösungen, sondern den Konsumenten, die jeden Tag aufs Neue die Chance verstreichen lassen, es besser zu machen. Wann also wäre ein geeigneterer Zeitpunkt, um den ein oder anderen Neustart zu planen als jetzt, wo sich ein weiteres Jahr in seine letzten, kurzen Tage streckt?
So schwer, verstörend und düster viele davon gewesen sein mögen, so schön, bemerkenswert, erheiternd und licht war manch ein Moment der vergangenen zwölf Monate. Leider ist der menschliche Geist zwecks Risikominimierung evolutionär darauf ausgelegt, sich vor allem an Negatives zu erinnern. Und viel zu oft verdrängen diese unschönen, aber lehrreichen Erfahrungen die Wertschätzung für eine der simpelsten Wahrheiten des Lebens:
Das Schöne zieht seinen Reiz aus der Vergänglichkeit.
Gerade die Flüchtigkeit des Positiven macht es so wichtig, sich diese Erkenntnis zum Ablauf eines Kalenderjahres bewusst zu machen. Denn das wertvollste, was wir Menschen im Lauf eines Lebens sammeln können, sind erhebende Momente. Wie viele wir davon anhäufen bevor unsere eigene Zeit abgelaufen ist, hängt nicht primär von äußeren Umständen, sondern unserer inneren Einstellung ab. Eine den Wirren der Zeit angemessene Sichtweise verbirgt sich hinter einem kurzen, fast schon philosophischen Wortwechsel aus dem für den vorliegenden Text namensgebenden Hitchcock-Streifen:
»Wollen Sie behaupten, Sie hätten Interesse für die Kunst?«
»Ja – für die Kunst weiterzuleben.«
-
 @ 8eabf864:d2ed9af6
2024-12-27 16:34:04
@ 8eabf864:d2ed9af6
2024-12-27 16:34:04Opinion about Tangem - Crypto wallet (android)
There is a successful build example, maybe can use as a reference. See https://github.com/nalarian1/tangem-app-android
WalletScrutiny #nostrOpinion
-
 @ a42048d7:26886c32
2024-12-27 16:33:24
@ a42048d7:26886c32
2024-12-27 16:33:24DIY Multisig is complex and 100x more likely to fail than you think if you do it yourself: A few years ago as an experiment I put what was then $2,000 worth Bitcoin into a 2 of 3 DIY multisig with two close family members holding two keys on Tapsigners and myself holding the last key on a Coldcard. My thought was to try and preview how they might deal with self custodied multisig Bitcoin if I died prematurely. After over a year I revisited and asked them to try and do a transaction without me. Just send that single Utxo to a new address in the same wallet, no time limit. It could not possibly have failed harder and shook my belief in multisig. To summarize an extremely painful day, there was a literally 0% chance they would figure this out without help. If this had been for real all our BTC may have been lost forever. Maybe eventually a family friend could’ve helped, but I hadn’t thought of that and hadn’t recommended a trusted BTC knowledge/help source. I had preached self sovereignty and doing it alone and my family tried to respect that. I should’ve given them the contact info of local high integrity bitcoiners I trust implicitly. Regardless of setup type, I highly recommend having a trusted Bitcoiner and online resources your family knows they can turn to to trouble shoot. Bookmark the corresponding BTCSessions video to your BTC self custody setup. Multisig is complicated as hell and hard to understand. Complexity is the enemy when it comes to making sure your BTC isn’t lost and actually gets to your heirs. Many Bitcoiners use a similar setup to this one that failed so badly, and I’m telling you unless you’re married to or gave birth to a seriously hardcore maxi who is extremely tech savvy, the risk your Bitcoin is lost upon your death is unacceptably high. My family is extremely smart but when the pressure of now many thousands of dollars was on the line, the complexity of multisig torpedoed them. Don’t run to an ETF! There are answers: singlesig is awesome. From observing my family I’m confident they would’ve been okay in a singlesig setup. It was the process of signing on separate devices with separate signers, and moving a PSBT around that stymied them. If it had been singlesig they would’ve been okay as one signature on its own was accomplished. Do not besmirch singlesig, it’s incredibly powerful and incredibly resilient. Resilience and simplicity are vastly underrated! In my opinion multisig may increase your theoretical security against attacks that are far less likely to actually happen, e.g. an Oceans Eleven style hack/heist. More likely your heirs will be fighting panic, grief, and stress and forget something you taught them a few years back. If they face an attack it will most likely be social engineering/phishing. They are unlikely to face an elaborate heist that would make a fun movie. While I still maintain it was a mistake for Bitkey to not have a separate screen to verify addresses and other info, overall I believe it’s probably the best normie option for small BTC holdings(yes I do know Bitkey is actually multisig, but the UX is basically a single sig). This incident scared me into realizing the importance of simplicity. Complexity and confusion of heirs/family may be the most under-considered aspects of BTC security. If you’ve made a DIY multisig and your heirs can’t explain why they need all three public keys and what a descriptor is and where it’s backed up, you might as well just go have that boating accident now and get it over with.
Once you get past small amounts of BTC, any reputable hardware wallet in singlesig is amazing security I would encourage folks to consider. In a singlesig setup - For $5 wrench attack concerns, just don’t have your hardware signer or steel backup at your home. You can just have a hot wallet on your phone with a small amount for spending.
If you get a really big stack collaborative multisig is a potentially reasonable middle ground. Just be very thoughtful and brutally honest about your heirs and their BTC and general tech knowledge. Singlesig is still great and you don’t have to move past it, but I get that you also need to sleep at night. If you have truly life changing wealth and are just too uncomfortable with singlesig, maybe consider either 1) Anchorwatch to get the potential benefits of multisig security with the safety net of traditional insurance or 2) Liana wallet where you can use miniscript to effectively have a time locked singlesig spending path to a key held by a third party to help your family recover your funds if they can’t figure it out before that timelock hits, 3) Bitcoin Keeper with their automatic inheritance docs and mini script enabled inheritance key. The automatic inheritance docs are a best in class feature no one else has done yet. Unchained charges $200 for inheritance docs on top of your $250 annual subscription, which imho is beyond ridiculous. 4) Swan vault, I’ve generally soured on most traditional 2 of 3 collaborative multisig because I’ve always found holes either in security (Unchained signed a transaction in only a few hours and has no defined time delay, and still doesn’t support Segwit, seriously guys, wtf?), only support signers that are harder to use and thus tough for noobs, or the overall setups are just too complex. Swan Vault’s focus on keeping it as simple as possible really stands out against competitors that tack on unneeded confusion complexity.
TLDR: For small amounts of BTC use Bitkey. For medium to large amounts use singlesig with a reputable hardware wallet and steel backup. For life changing wealth where you just can no longer stomach sinsglesig maybe also consider Anchorwatch, Bitcoin Keeper, Sean Vault, or Liana. Don’t forget your steel backups! Be safe out there! Do your own research and don’t take my word for it. Just use this as inspiration to consider an alternative point of view. If you’re a family of software engineers, feel free to tell me to go fuck myself.
-
 @ a17fb4ed:c53f7e91
2024-12-27 16:18:17
@ a17fb4ed:c53f7e91
2024-12-27 16:18:17Charcuterie Boards are perfect for parties and easy to create. With just a few basics you can bring great flavor to your next get together. I made this one for my work Christmas party a week ago and it was a hit. The following is the board I built.
Meats
- Italian Dry Salame: A classic charcuterie staple with rich, savory flavors
- Dry Hard Salami Con Vino: A wine-infused salami that adds a sophisticated touch to your board



Cheeses
- Extra Sharp Cheddar: Provides a bold, tangy flavor profile
- Dill Havarti: Offers a creamy texture with a hint of fresh dill
- Boursin Spreadable Garlic and Herb: A soft, flavorful spread perfect for easy enjoyment
- 60 Day Blue Cheese: Adds a strong, distinctive taste to complement the meats





Crackers
- Bruschettini Snack Size Italian Bruschetta Toast: Authentic Italian-style base
- Crunchmaster Original Multi-Seed: A crispy, nutritious option
- Brenton Original with Sea Salt: Classic cracker with a touch of saltiness
- Cabaret Crispy and Buttery: A rich, indulgent cracker choice

Delightful Add-Ons
- Chocolate Covered Cherries: A sweet contrast to savory meats and cheeses
- Local Hive Hot Honey: Adds a spicy-sweet element
- Pitted Olives: Brings a briny, Mediterranean touch



Platter and Serving Essentials
- Wooden Board: Provides a rustic, elegant presentation
- Spoon: Drizzle on the honey
- Spreading Utensils: For soft cheeses and spreads
- Toothpicks: Retrieving the olives
- Bowls: For randoms small items
- Cracker Container: Keeps crackers organized

Final Progression




Remember you can make these boards your own way. Hope you take some of the ideas and create something tasting.
Cheers, Yooper
foodstr #nostr #cheese #salami #charcuterie #crackers #honey