-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 16d11430:61640947
2024-12-27 12:29:24
@ 16d11430:61640947
2024-12-27 12:29:24The technology sector is currently grappling with a pervasive yet often overlooked issue: dopamine dysregulation among its workforce. This neurochemical imbalance, exacerbated by the industry's high-paced environment and constant digital engagement, is leading to significant declines in employee well-being and productivity. Compounding this problem is a notable deterioration in leadership quality, which threatens to inflict lasting damage on both the current workforce and future generations.
Dopamine Dysregulation in Tech Workers
Dopamine, a neurotransmitter integral to reward processing and motivation, is susceptible to dysregulation through chronic stress and overstimulation—conditions prevalent in the tech industry. A recent study highlights that chronic stress can alter dopamine receptor density and sensitivity, making it increasingly challenging to achieve the same level of reward and exacerbating feelings of frustration and demotivation.
The tech industry's relentless pace, characterized by tight deadlines and continuous digital interaction, fosters an environment ripe for such dysregulation. The constant influx of notifications and the pressure to multitask can lead to a state of perpetual overstimulation, disrupting natural dopamine cycles and diminishing the brain's ability to derive pleasure from offline activities.
Lack of Institutional Insight
Despite the growing prevalence of dopamine-related burnout, there is a conspicuous absence of institutional acknowledgment and intervention. Many organizations remain oblivious to the neurochemical underpinnings of employee burnout, often attributing declines in productivity to personal shortcomings rather than systemic issues. This oversight results in inadequate support structures and a failure to implement necessary changes to mitigate stressors inherent in the tech work environment.
Decline in Leadership Quality
Exacerbating the situation is a marked decline in leadership quality within the tech sector. The 2023 Global Leadership Forecast reports that only 40% of leaders believe their companies have high-quality leadership—a 17% drop from two years prior and the most significant decline in a decade.
This leadership deficit manifests in several ways:
Inadequate Support for Employee Well-being: Leaders are failing to recognize and address the neurobiological aspects of employee burnout, resulting in insufficient mental health support and wellness initiatives.
Poor Change Management: The rapid evolution of technology necessitates agile leadership. However, many leaders lack the skills to manage change effectively, leading to organizational instability and increased employee stress.
Erosion of Trust: Inconsistent communication and a lack of transparency from leadership erode employee trust, further contributing to workplace stress and dissatisfaction.
Risks of Long-term Generational Effects
The convergence of dopamine dysregulation and declining leadership quality poses significant risks for long-term generational effects:
Sustained Mental Health Issues: Without intervention, current employees may suffer prolonged mental health challenges, including chronic burnout and depression, which can extend into future generations through learned behaviors and coping mechanisms.
Diminished Innovation: A workforce plagued by motivation deficits and led by ineffective leaders is less likely to produce innovative solutions, potentially stymieing technological progress for years to come.
Workforce Attrition: The tech industry may experience a talent drain as individuals seek healthier work environments, leading to a loss of experienced professionals and a gap in mentorship for emerging talent.
Conclusion
The silent pandemic of dopamine dysregulation among tech workers, compounded by a decline in leadership quality, demands immediate attention. Institutions must develop a deeper understanding of the neurobiological factors contributing to employee burnout and implement comprehensive strategies to address them. Simultaneously, a reinvigoration of leadership development programs is essential to equip leaders with the skills necessary to navigate the complexities of the modern tech landscape. Failure to act may result in enduring detriments to both the current workforce and future generations.
-
 @ 8eabf864:d2ed9af6
2024-12-27 01:49:56
@ 8eabf864:d2ed9af6
2024-12-27 01:49:56Opinion about Tangem - Crypto wallet (iphone)
Thank you for your hard work. The iOS version seems to be compilable, although the official has not responded yet.
https://www.reddit.com/r/Tangem/s/le3YBkTwPm
WalletScrutiny #nostrOpinion
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ a012dc82:6458a70d
2024-12-27 01:29:36
@ a012dc82:6458a70d
2024-12-27 01:29:36Table Of Content
-
TwelveFold: A Fusion of Art and Blockchain
-
The Cipher Puzzle Series: A Test of Wit
-
The Mechanics: How to Participate
-
Competition Rules and Details
-
Conclusions
-
FAQ
The Bored Ape Yacht Club, a name that resonates deeply within the NFT community, is expanding its horizons. Venturing beyond their typical domain, they have introduced a captivating puzzle-solving competition. This isn't just any competition; it's an opportunity for enthusiasts to engage, challenge their intellect, and stand a chance to win Bitcoin rewards, merging the worlds of crypto and gaming in an exciting new way.
TwelveFold: A Fusion of Art and Blockchain
Behind the Bored Ape Yacht Club is Yuga Labs, an innovative creator that never ceases to surprise. Their latest creation, the TwelveFold collection, is a series of 300 generative art pieces. But what sets TwelveFold apart is its foundation on the Ordinals protocol. This groundbreaking protocol allows for the "inscription" of NFT-like artwork directly onto the immutable Bitcoin blockchain. The TwelveFold collection isn't just about art; it's a representation of the intricate dance between time, mathematics, and variability, offering a fresh perspective on the convergence of art and technology.
The Cipher Puzzle Series: A Test of Wit
Inspired by the Bitcoin-centric artwork, Yuga Labs has unveiled a cipher puzzle series that beckons participants from all corners. These aren't your everyday puzzles; they are intricately designed challenges that reflect the core essence and philosophy behind the TwelveFold collection. Every puzzle solved brings participants closer to Bitcoin rewards, making the challenge not just a test of wit but also a potential gateway to crypto riches.
The Mechanics: How to Participate
For 12 consecutive weeks, Yuga Labs will roll out a new "Moon Puzzle". These puzzles, shrouded in mystery and allure, promise a reward of 0.12 Bitcoin for the first solver. But the climax arrives in the 13th week. Instead of another Moon Puzzle, participants are presented with the "Sun Puzzle". The stakes are higher, with the winner being bestowed with one of the coveted TwelveFold Ordinals. These unique art pieces, which are making waves in the Magic Eden secondary marketplace, have a starting price tag of approximately 0.9 BTC.
Participation is open to all, irrespective of whether you own a TwelveFold asset. However, a subtle hint from Yuga Labs suggests that asset owners might be in for an exclusive treat.
To dive into this challenge, one needs an Ordinals Bitcoin wallet, options include Xverse or Unisat. The process is straightforward: visit the TwelveFold website, pick a puzzle, and let your mind wander into the realms of creativity and logic. Once you believe you've cracked the code, the answer is inscribed on-chain using satoshis, etching its presence forever on the Bitcoin blockchain.
Competition Rules and Details
Every puzzle has room for just one victor. In scenarios where multiple participants arrive at the correct solution simultaneously, the tie-breaker is the inscription number, with preference given to the lower number. Winning isn't just about solving the puzzle; winners must also navigate the formalities, which include filling out requisite tax forms to lay claim to their Bitcoin bounty.
Conclusion
Yuga Labs' TwelveFold challenge is more than just a competition; it's a celebration of art, blockchain, and the spirit of competition. As the crypto community watches with bated breath, participants from across the globe are delving deep into the puzzles, each hoping to emerge as the next Bitcoin victor. With the inaugural puzzle already deciphered, the gauntlet has been thrown. The question remains: are you ready to take on the TwelveFold challenge?
FAQ
What is the TwelveFold Challenge? It's a puzzle-solving competition by Yuga Labs, offering participants a chance to win Bitcoin rewards.
How long does the challenge last? The challenge spans 13 weeks, with a new puzzle released each week.
What are the rewards for solving the puzzles? For the first 12 weeks, winners receive 0.12 Bitcoin. In the 13th week, the prize is one of the TwelveFold Ordinals.
Do I need to own a TwelveFold asset to participate? No, the challenge is open to everyone. However, TwelveFold asset owners might receive special perks.
How do I submit my puzzle answers? Answers are inscribed on-chain via satoshis using an Ordinals Bitcoin wallet.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 16d11430:61640947
2024-12-27 01:18:29
@ 16d11430:61640947
2024-12-27 01:18:29While Europeans were sealing agreements and greetings with handshakes, civilizations in the Indian subcontinent and Asia were elevating hand gestures to an intricate art form and spiritual practice. Hand mudras, meaning "seals" or "gestures" in Sanskrit, have long been a profound expression of the connection between the body, mind, and spirit. From the precision of classical Indian dance to the meditative stillness of yogic practices, mudras symbolize the articulation of human dexterity and the channeling of energy through the hands.
The Origins of Mudras: A Historical Perspective
Mudras trace their origins to the ancient spiritual practices of the Indian subcontinent, dating back to the Vedic period (1500–500 BCE). Initially described in the sacred texts of the Vedas and later elaborated in Tantric and Buddhist traditions, mudras became integral to rituals, meditation, and artistic expression.
- Vedic Rituals and Spiritual Energy
In Vedic rituals, priests used specific hand gestures to invoke divine forces, seal intentions, and direct spiritual energy. These gestures were seen as a bridge between the human and the divine, a symbolic language that conveyed unspoken truths. (The Vedas: An Anthology by Wendy Doniger)
- Buddhist Influence Across Asia
As Buddhism spread from India to regions like Tibet, China, Japan, and Southeast Asia, mudras became central to meditation and iconography. The Dhyana Mudra (gesture of meditation) and the Vitarka Mudra (gesture of teaching) are prominently depicted in statues of the Buddha, symbolizing states of inner peace and wisdom. (Mudras in Buddhist Art by Frederick Asher)
Mudras in Classical Dance: The Pinnacle of Dexterity
The Indian classical dance forms—Bharatanatyam, Kathak, Odissi, and others—perfected the articulation of the hands through hasta mudras (hand gestures). These gestures, cataloged in texts like the Natya Shastra (200 BCE–200 CE), serve as a sophisticated language to narrate stories, express emotions, and symbolize universal truths. (The Natya Shastra: A Treatise on Dance and Drama by Manomohan Ghosh)
- Complexity and Precision
Each dance form requires the performer to master dozens of mudras, which involve precise positioning of the fingers and palms. For example:
The Pataka Mudra (flat hand) symbolizes a flag, and its variations convey wind, rivers, or blessings.
The Hamsasya Mudra (swan’s beak) represents delicacy, often used to signify picking a flower or holding a jewel.
- Embodiment of Dexterity
These gestures demand exceptional finger dexterity and neuromuscular control, training the brain to enhance focus, coordination, and memory. The dancer's hands become extensions of their soul, weaving stories that transcend spoken language. (Dance in India: The Art of Precision and Emotion by Kapila Vatsyayan)
Mudras in Yoga and Meditation: A Gateway to Inner Activation
Beyond dance, mudras are integral to yoga and meditation, believed to direct prana (life energy) within the body. By forming specific gestures with the hands, practitioners stimulate energy pathways, harmonize the mind, and deepen meditation.
- Therapeutic Benefits
The Gyan Mudra (gesture of knowledge), with the thumb and index finger touching, is said to enhance concentration and calm the mind. (The Yoga Sutras of Patanjali by Swami Satchidananda)
The Prana Mudra (gesture of life) energizes the body by activating dormant energy reserves.
- Holistic Activation
Mudras work on the principles of Ayurveda, the ancient Indian science of health, balancing the five elements within the body—earth, water, fire, air, and ether. The hands become a microcosm of the body, with each finger representing a specific element. (Ayurveda: The Science of Self-Healing by Vasant Lad)
Beyond India: Hand Forms in Asian Arts
The influence of Indian mudras extended to Asian art forms, including Japanese mudrā in martial arts and Chinese qigong practices. In Southeast Asia, classical dance forms like Balinese and Khmer dance incorporate mudras as an essential element, showcasing the dexterity of the human hand in storytelling and spiritual expression.
- Tibetan and Japanese Rituals
In Tibetan Buddhism, vajra mudras are used in esoteric rituals to symbolize cosmic forces. Similarly, in Japanese shingon practices, mudras accompany mantras to invoke specific deities. (Tibetan Ritual Practices by John Powers)
- Visual Perfection
Southeast Asian sculptures, such as those in Angkor Wat, depict deities with elaborate hand gestures, representing divine attributes and cosmic harmony. (Art and Architecture of Southeast Asia by Peter D. Sharrock)
The Profound Significance of Mudras
Mudras are far more than physical gestures; they are a language of the body that communicates with the universe. They unite art, spirituality, and science, demonstrating how hand dexterity can be a profound expression of human potential.
In the modern era, mudras remain relevant as tools for holistic health and mindfulness. Their ancient legacy reminds us of the extraordinary capabilities of the human hand—not just as a tool for grasping but as a bridge between the physical and the metaphysical.
Key Takeaway: While the handshake reflects strength and intent in the West, the mudra exemplifies the ultimate articulation of human dexterity and spirituality in the East. Through dance, yoga, and meditation, these gestures symbolize the profound connection between the body, mind, and cosmos, showcasing the timeless beauty of the human hand.
References:
-
Doniger, Wendy. The Vedas: An Anthology.
-
Asher, Frederick. Mudras in Buddhist Art.
-
Ghosh, Manomohan. The Natya Shastra: A Treatise on Dance and Drama.
-
Vatsyayan, Kapila. Dance in India: The Art of Precision and Emotion.
-
Satchidananda, Swami. The Yoga Sutras of Patanjali.
-
Lad, Vasant. Ayurveda: The Science of Self-Healing.
-
Powers, John. Tibetan Ritual Practices.
-
Sharrock, Peter D. Art and Architecture of Southeast Asia.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 16d11430:61640947
2024-12-27 00:57:30
@ 16d11430:61640947
2024-12-27 00:57:30Grip strength and finger dexterity are uniquely tied to human neuromuscular wellbeing. These attributes go beyond their apparent utility, delving into evolutionary, physiological, and cultural dimensions. They not only signify physical health but also embody symbolic gestures like handshaking, reflecting capacity, intent, and mutual understanding in human interactions.
Neuromuscular Wellbeing: The Foundation of Grip Strength and Dexterity
- Grip Strength: A Biomarker of Overall Health
Grip strength serves as a reliable biomarker for neuromuscular health. Studies have demonstrated its predictive value for outcomes like cardiovascular health, cognitive function, and longevity. Grip strength reflects the integrated function of muscles, nerves, and connective tissues, making it an ideal measure of overall physical resilience.
Physiological Insights: Strong grip strength is associated with robust neuromuscular function. This involves the coordination of motor neurons and muscle fibers, indicating an individual's capacity to perform complex tasks. Grip strength also correlates with brain health, as neural efficiency influences fine motor skills and physical force generation.
Preventative Indicator: Declines in grip strength can signal neuromuscular or systemic health issues, such as neurodegenerative diseases, making it a critical diagnostic tool.
- Finger Dexterity: Precision in Action
Finger dexterity, encompassing coordination, fine motor skills, and adaptability, highlights the intricate control of hand muscles. This ability is crucial for various tasks, from typing to playing musical instruments, underscoring its link to neuromuscular health.
Cognitive Connection: Dexterity tasks stimulate brain regions responsible for planning and executing movement. Regular practice can enhance neuroplasticity, improving both motor and cognitive functions.
Rehabilitation Applications: Finger dexterity exercises are integral in neuro-rehabilitation, aiding recovery from strokes, injuries, or neurological disorders.
The Cultural Legacy of Handshaking: A Symbol of Grip Strength and Intent
Handshaking, though becoming an archaic relic in some cultures, remains a fascinating lens through which grip strength’s symbolic significance can be viewed.
- Historical and Cultural Roots
The handshake, dating back to ancient times, originally served as a gesture of trust. A firm handshake was a non-verbal way of communicating strength, intent, and mutual respect. Anthropological evidence links it to the need for physical signals of peace and camaraderie in negotiations or greetings.
- Strength and Intent in the Handshake
Grip Strength as a Measure: A firm handshake historically conveyed physical capability and confidence. Weak handshakes often carried connotations of poor health or dishonesty, though these interpretations are culturally relative.
Intent and Transparency: The act involved direct physical contact, symbolizing openness and the absence of concealed weapons, reinforcing its role as a non-verbal declaration of peace and trust.
Archaic but Relevant: Why Grip Still Matters
In an era where handshaking is less common, the underlying principles of grip strength and neuromuscular health remain profoundly relevant. Even as the handshake fades, its symbolic role persists in different forms, like the pressure and control exhibited in sports or tactile professions.
Bridging Neuromuscular Wellbeing and Cultural Practices
By understanding the deep connection between physical grip and broader health, we gain insights into human evolution and societal interactions. Grip strength and finger dexterity are far more than isolated physical traits; they are essential indicators of our holistic health and functional capacity.
Handshakes may be vanishing, but their essence—a quick, tangible measure of strength, confidence, and intent—remains a testament to the interconnectedness of our physical and social existence.
References:
-
Dodds, R., et al. (2014). Grip strength across the life course: normative data from twelve British studies. PLoS ONE.
-
Bohannon, R. W. (2019). Grip strength: an indispensable biomarker for older adults. Clinical Interventions in Aging.
-
Stewart, L. (2020). The history and significance of handshaking. Cultural Anthropology Journal.
-
Bechtold, M., et al. (2016). Finger dexterity as an indicator of cognitive function. Journal of Neurology and Rehabilitation.
-
 @ 5ee71c0a:b0506ae6
2024-12-27 00:56:58
@ 5ee71c0a:b0506ae6
2024-12-27 00:56:58Hey, anyone who reads this—thanks for keeping me (somewhat) accountable.
I’m not big on formal New Year’s resolutions, but I do like to review the past year to see where I’ve done well, where I’m lacking, and what new habits I can form in 2025.
Wait, isn’t that a resolution? Anyway.
One thing that’s always been important to me is freedom of speech. I plan to keep using X/Twitter—yes, it has shortcomings, but so does every platform. None will ever be perfect for everyone.
That said, I believe strongly in decentralization. I’ve been exploring Nostr for the past two years. Now, I want to use it more often, learn its possibilities, and contribute where I can. I’ve also posted this on Habla.news, a Nostr community for long-form content, to encourage myself (and anyone else) to try new platforms and keep an open mind.
There’s a lot happening with Nostr, Lightning, and other Bitcoin-related projects. It reminds me of the early internet—everyone was contributing, and we had no idea what would stick. I miss those days, and it’s exciting to see a new community forming.
Speaking of the early internet, I think it’s time I set up a blog or personal site. It’s been ages! Neocities feels retro and has a growing community, so I might start there.
Work will be busy in 2025—2024 was already intense, and the bar is always rising. So I’m not going to overload myself with extra goals. Still, many of my work goals, like earning new certifications, blend into my personal ambitions.
In 2024, I did well with my health goals. In 2025, I want to build on that, but in small steps. For Q1, I’ll re-establish my Peloton routine; in Q2-Q3, I’ll get back into heavier weight training. I miss lifting and want to push myself again.
I also miss reading—especially sci-fi. It’s high time I make space for that.
So, this is my short list of goals. I’m sure I’ll refine it as the year unfolds. Thanks for reading, and if you want to connect with me on Nostr, here’s my info: nostr:npub1tmn3czhv2wzxvt4mpanttd8parnxgq528c0hzfehfm4rlvzsdtnqghwkhd
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 56494b83:aa95511b
2024-12-27 00:12:56
@ 56494b83:aa95511b
2024-12-27 00:12:56The Goal of Christmas
But when the fullness of time had come, God sent forth his Son, born of woman, born under the law, to redeem those who were under the law, so that we might receive adoption as sons. And because you are sons, God has sent the Spirit of his Son into our hearts, crying, “Abba! Father!” (Galatians 4:4–6)
There are 4 phrases that I want to address from this passage Fullness of time Born of a woman Redeem those under the law Receive adoption as sons.
One of the attributes of God is what theologians call his “eternity” This means God is without beginning or end. He is free from all succession of time. He is outside of time. In fact he is the cause of time. from everlasting to everlasting you are God. (Psalm 90:2) And upon hearing this some Christians might make the mistake of thinking that God is not concerned with time. “Well since God is not bound by time like we are, he must be detached from it, or maybe disinterested”
But the opposite is actually true. The God of the Bible is extremely concerned with keeping time.
In Genesis 1: God defines what a constitutes a day. There was evening and there was morning, the first day. He decides how many days it will take him to create the world.
He uses the sun and the moon and the stars as “time-keepers”And As we keep reading Genesis we come to long lists of names: specifically the descendants of Seth, and God tells us how many years they live.
All other events in the world are dated in relation to Seth.
But we can keep going: God teaches Israel to keep time. He gives them a calendar when they come out of Egypt. Referencing passover God says in exodus 12 “This month (march/April) shall be for you the beginning of months. It shall be the first month of the year for you." (Exodus 12:2)
Pentecost comes in the third month. (Celebrating the giving of the law)
The 7th month was for celebrating the feast of booths, (when the people lived tents in the wilderness.)
On and on we could go, but the point I am trying to make is this: timing is everything.
You know that famous passage in Ecclesiastes 3 For everything there is a season, and a time for every matter under heaven: (Ecclesiastes 3:1) Our lives are patterned after different times.
Weeping and laughing Breaking down and building up. A time to speak and a time to keep silence.
And then after this run—on list Solomon says:
[God] has made everything beautiful in its time.(Ecclesiastes 3:11)
God governs time. He orchestrates the times. He has in his mind a divine time-table in which he has written all events and circumstances into his perfect story.
Down to the second.
And the great demonstration of this is the incarnation.
In the fullness of time, God sent forth his son. The Son of God entered into time to show us the father. And he did this without ceasing to be the LORD of time himself.
Theologian Peter Leithart writes: “God came to us in time, not to rescue us from time, but to redeem all times. God the Son entered time so that whatever time it is - a time to live, a time to die; a time to seek, a time to give up; a time to weep or a time to rejoice - each and every time is a time of encounter with God in Christ through the Spirit.”
You and I can talk with God, meet with him, commune with the father and with the son and with the Holy Spirit at any any time, because God has entered into our time in the person of his son.
Many have asked: why was Christ born 2000 years ago?
Scholars point to the common greek langauge shared by much of the world (making evangelization easier)
Some point to the centuries-long era known as the Pax Romana; (roman peace= where THE WORLD was by and large at free from major wars.
Others have observed that the mythological god’s of Greece and Rome had been tried and found wanting:
In other words, men and women everywhere were primed to hear and accept the one true religion. Historically, this is all true.
But if we think about this biblically, we see that the arrival of the Messiah was perfectly—timed. The law of Moses, ESTABLISHED 2000 YEARS PRIOR, had made it clear: human beings need a savior.! All of us are law breakers!
It had been hundreds of years since a true prophet had spoken.
All of Israel’s history was pointing forward to the promised “serpent—crusher” from genesis 3.
The people had been waiting CENTURIES for the SON who was promised. the anticipation kept building! Why?
Because, as theologian GK Beale writes: “no prior son had ever been able to put an end to the law’s condemning control!”
Nobody had shown up and proven themselves to be the SaVIOR.
And the entire OLD testament seems to have been written so that we would anticipate the Son of GoD.
Every lamb slaughtered pointed us to the TRUE LAMB.
Every bowl full of incense burned pointed to the fragrant offering of Christ.
Every King installed in Israel pointed to the one true King whose kingdom would have no end.
Every priest ordained pointed to the great high Priest, who would not offer up the blood of bulls and goats, but his very own blood.
God is the creator of TIME, and at Christmas we are invited to celebrate when he entered time.
And this leads us to the second phrase: “born of a woman”
Almost a 1000 years ago, a theologian by the name of Anselm wrote a book called “why God became a man”
He begins his book with a discussion of sin, which he defines as “not rendering to God what is his due” (namely the submission of our entire will to his)
When we do not submit to him, we are stealing from him, robbing his glory; we are dishonoring him. And God, who is perfectly JUST, cannot over look this.
Here then is the problem: if we are to be forgiven, we must repay what we owe, but we are incapable of doing this. “The price tag exceeds the capability of the fallen sons of Adam to pay.”
Anselm says: our present obedience and good works cannot make satisfaction for our sins, since these are required of us anyway.
“The sinner owes what he cannot repay, and unless he repays it he cannot be saved.” We cannot save ourselves.
And here is where Anselm begins to point out the solution to our dilemma.
“There is no one who can make this satisfaction [for sin] except God himself… But no one ought to make it except man; otherwise man does not make satisfaction… Therefore, it is necessary that one who is God—man should make it. It is needful that the very same person who is to make this satisfaction be perfect God and perfect man, since no one can do it, except one who is truly God, and no one ought to do it, except one who is truly man.”
John Stott summarizes this teaching well: “Jesus Christ is therefore the Only Savior, since he is the only person in whom the “should” and the “could” are united, being himself both God and man.”
I realize this is pretty ‘high’ theology…but it is my opinion that Christmas EVE is the perfect time to hear these precious doctrines once again.
The wages of sin is death. We know that. And if you and I were EVER going to be saved, it would be because God himself came to save us. But God cannot die. So the eternal son of God had to be made like us. He had to put on our human nature.
Christmas reminds us that Redemption required incarnation.
This leads us to the third phrase: Christ was born to Redeem those under the law.
God gave his people the law…and we were unable to keep it, unable to obey it. Earlier in his Galatians Paul said
For all who rely on works of the law are under a curse; for it is written, “Cursed be everyone who does not abide by all things written in the Book of the Law, and do them.” (Galatians 3:10)
And then a few verses later he says that the God-man secured our redemption by becoming a curse for us. Cursed is everyone hanged on a tree. Bible readers know this: there are many examples.
Pharaoh’s baker was hung on a tree. (Gen. 40) The 5 kings of Canaan were hung on trees (josh. 10) David’s Rebel son Absalom died while hanging on a tree. The wicked Haman (from the story of Esther) was hung on a tree intended for another.
Christmas reminds us that the holy son of God, the only perfect man who ever lived, would grow up and receive the culminating shame of all those in the Scripture who were cursed by God.
The child in the manger would grow up to be cursed. The child the shepherds came to see, would, 33 years later, be forsaken by his Father.
Christ endured the curse of the law so that a mysterious, divine exchange might take place. He takes our curse that we might receive his blessing.
As one another puts it: “he became sin with our sin, so that we may become righteous with his righteousness.” (Stott)
This kind of talk can be a bit confusing for us. Its mystical not physical. It’s spiritual, not material. The exchange that has taken place in the soul of the believer is not something that we can see.
I came across an analogy from John Calvin that I had never before considered…you remember the story from genesis 27, when Isaac (who is very old and blind) blesses his younger son Jacob INSTEAD of Esau. ?
Rebekah knows that her husband wants to bless his firstborn son…and so when Esau leaves to go hunting, she makes a plan to cook up Isaac’s favorite dinner, and she convinces Jacob to bring his father the food and ‘steal the blessing’
And of course Jacob objects: “uh, Mother, this plan of yours won’t work….I am a smooth man. . . and my brother Esau is hairy!”
But Rebekah persuades him to put on Esau’s clothing. . .goat skins on his hands and on his neck.
Now: don’t ask me how this worked, because I don’t really know. . . but it works. And as I am fond of saying: every page of scripture points us to Christ, if we have eyes to see….and when we don’t have eyes to see, we can be assisted with saints who saw more than us:
John Calvin: “as Jacob did not of himself deserve the right of the first—born, concealed in his brothers clothing, and wearing his brothers coat, which gave out an agreeable odor, he ingratiated himself with his father, so that to his own benefit, he receive the blessing while impersonating another. And we, in like manner hide under the precious purity of our firstborn brother, Christ, so that we may be attested righteous in God sight… And this is, indeed, the truth, for in order that we may appear before God's face unto salvation we must smell sweetly with his odor, and our vices must be covered and buried by his perfection.”
The younger brother gets the blessing he doesn’t deserve because he’s wearing his brother’s clothes!
Here then is the gospel on Christmas Eve.
Christ Jesus the Lord voluntarily puts on your stinky garments, and by faith you get to put on his royal white linen!
Disobedient rebels can be clothed with the righteousness of the son.
Praise God.
And now we come to the purpose of Christmas.
when the fullness of time had come, God sent forth his Son. . . so that we might receive adoption. . . (Galatians 4:4–5)
The goal of Christmas is adoption. At just the right time, God sent his son because he wanted a bigger family.
J.I. Packer wrote many years ago: “The revelation to the believer that God is his Father is in a sense the climax of the Bible.”
There can be no greater gift, no higher privilege than receiving a place in God’s own family. I can approach God without fear, because he is Father.
the fatherhood of God implies affection. He loves me like a perfect father loves his children.
I have his name placed upon me. I have his Spirit given to me. I have his inheritance waiting for me.
But Paul adds the phrase “as sons” in the text.
The goal of Christmas is to receive adoption “as sons”
Why doesn’t Paul say “receive adoption as sons & daughters!?” It’s not a mistake to leave out daughters. He doubles down in the next verse.
And because you are sons, God has sent the Spirit of his Son into our hearts, crying, “Abba! Father!” (Galatians 4:6)
Theologian Michael Reeves provides us with the glorious answer: (why daughters is not included)
“Paul is seeking to be as clear as he can that the status all believers are given is, quite specifically, the status of the son, himself. For God does not give us some exulted, but general standing before himself: the son shares with us, his own Sonship… Paul wants you and me to see that believers get to share the very cry of the son himself. In the garden of Gethsemane, talking in private to his father, Jesus had called him, “Abba, Father.”
Arguing that the Spirit of the Son makes us call out the very same words, Paul is demonstrating as intimately and visually as he can that in Christ, we get to share the very relationship with the father that the son himself has always enjoyed.
The personal name he has for his father we are allowed to share. We can come before the Almighty and say—or stutter!— with a beloved son’s own confidence, “Abba!” . . . The son of God became human that we humans might become sons of God.”
At the exact right time, time god sent his son, born of a woman…to redeem us and adopt us and give us his spirit and make us sons of God.
“The glory that you have given me I have given to them, that they may be one even as we are one, I in them and you in me, that they may become perfectly one, so that the world may know that you sent me and loved them even as you loved me. . . you loved me before the foundation of the world. . . . I made known to them your name, and I will continue to make it known, that the love with which you have loved me may be in them.” (John 17:22–26)
Redemption required the incarnation. The point of the incarnation was adoption. And adoption means God loves just like he loves his Eternal son. He has always has, and he always will.
This Christmas, rejoice in the truth that because the Son of God became a man…you and I are beloved sons of God.
-
 @ 36bedab2:524acad4
2024-12-26 23:23:37
@ 36bedab2:524acad4
2024-12-26 23:23:37404 Page Not Found
-
 @ 36bedab2:524acad4
2024-12-26 23:20:21
@ 36bedab2:524acad4
2024-12-26 23:20:21404 Page Not Found Error
-
 @ 16d11430:61640947
2024-12-26 22:35:15
@ 16d11430:61640947
2024-12-26 22:35:15For Yadov Towri, dismantling the trap was only the beginning. As the city descended into chaos, its architects fled or were consumed by the very system they had built. Yadov had believed his work was done. But as the trap fell, something unexpected happened: the void it left behind began to call to him.
The city, even in its freedom, was a machine that demanded order. The billions of lives crammed into its sprawl couldn’t function without a structure to guide them. And as Yadov walked among them, their anguish and confusion pressed against his mind like a tide. His empathy, once his greatest strength, now became a curse, inundating him with the pain of millions.
The Lure of Power
At first, Yadov resisted. He sought to lead, to build a better system free of the corruption that had enslaved the city. But the burden of guiding so many was immense. His heightened sensitivity began to fracture under the weight of collective misery. Every cry, every unspoken plea for help, resonated in his mind until it became unbearable.
In a moment of desperation, he reached inward, tapping into the reservoir of psychic energy he had absorbed over years of navigating the trap. He found a way to silence the noise—not by healing, but by feeding. By taking their despair into himself, he dulled the ache of his empathy. It started as a survival mechanism, but it didn’t end there.
The Transformation
As Yadov siphoned the city’s anguish, he discovered something unexpected: power. The despair he absorbed didn’t just quiet his mind—it strengthened him. His senses became sharper, his endurance limitless. He could move through the city like a shadow, bending its will to his own. The empathy that had once driven him to liberate became the tool through which he dominated.
Yadov justified his actions at first. He told himself that by taking on the city’s pain, he was sparing its people from suffering. But the power was intoxicating. He began to manipulate the city’s new leaders, bending them to his will. The systems he had torn down were rebuilt—not to enslave, but to channel misery directly to him.
The New Trap
Under Yadov’s quiet rule, the city transformed. The chaotic freedom he had unleashed was replaced by a new kind of control. The population, unaware of his influence, found themselves drawn into an invisible web of dependence. The struggles of daily life were not as overtly brutal as before, but they were carefully calibrated to create just enough tension, frustration, and despair to feed Yadov’s growing hunger.
Public transport became slightly less crowded but always late. Workspaces allowed more personal freedom but with unspoken expectations that fostered guilt and self-doubt. The city’s poverty wasn’t eradicated, only redistributed in subtler ways. Everything was designed to extract psychic energy while maintaining the illusion of progress.
The Rise of a Psychic Vampire
Yadov’s power grew beyond the city. As his influence spread, he began to attract others like him—people who had discovered the power of psychic feeding but lacked his control. He took them under his wing, creating a network of psychic vampires who ruled from the shadows. Together, they refined the art of siphoning despair, turning it into an efficient, self-sustaining system.
The billions who lived in the city became the lifeblood of this new empire. Their misery was harvested in ways they barely understood: through bureaucratic frustrations, subtle social manipulations, and carefully orchestrated crises. The system no longer needed visible overlords. Its oppression was quiet, seamless, and absolute.
The Price of Power
Yadov, once the liberator, was now the kingpin of a new trap, far more insidious than the one he had destroyed. He told himself he was different—that his rule was necessary, that the energy he took was nothing compared to the peace he provided. But deep down, he knew the truth. The city’s pain was his lifeline, and without it, he would crumble.
The people, for their part, sensed the change but couldn’t articulate it. They felt the weight of an unseen force, the faint pull of despair that never quite left them. They whispered of ghosts in the city, of an invisible hand that guided their lives. They called it the Shadow King.
The Resistance
But even in the darkest systems, resistance is inevitable. Among the billions, a few began to notice the patterns, to piece together the truth. They saw how every improvement was a trap, every freedom a leash. And in the quiet corners of the city, they began to organize.
Yadov felt them—tiny sparks of defiance flickering at the edges of his perception. At first, he dismissed them. But as the resistance grew, so did their power. Unlike the masses, these rebels didn’t radiate despair. They carried something else: hope. And hope, Yadov realized, was poison to his kind.
A Reckoning
The resistance’s leader, a young woman named Senka, possessed a mind unlike any Yadov had encountered. Her hope wasn’t blind or naïve—it was calculated, weaponized. She and her followers began to unravel the psychic network Yadov had built, using the very tools he had once wielded against the original trap.
As their influence spread, Yadov found his grip on the city weakening. The despair he had fed on for so long began to wane, replaced by a growing wave of defiance. He could feel the system he had built collapsing, just as he had once destroyed the one before it.
The Final Question
Yadov faced a choice: to crush the resistance and tighten his grip on the city, or to let it fall and risk becoming the very thing he had once despised. The power he had gained whispered seductively, promising him dominion if only he would embrace it fully. But his healer’s heart, buried deep beneath layers of corruption, still flickered faintly.
As the city teetered on the brink of another transformation, Yadov stood at the crossroads of his own humanity. Would he embrace the monstrous king he had become, or would he finally, truly, set the city free?
-
 @ 16d11430:61640947
2024-12-26 22:25:39
@ 16d11430:61640947
2024-12-26 22:25:39The metropolis was a living maze, a chaotic symphony of ambition, desperation, and survival. It wasn’t merely a city—it was a crucible, an intricate system designed to test and grind the human spirit. For some, it was a beacon of opportunity; for others, a labyrinth of pain and struggle.
Yadov Towri, born of a lineage of healers, was an anomaly within his heritage. Where his ancestors had mended and soothed, he endured and resisted. His unique blend of empathy, physical agility, and endurance made him an outlier—someone who didn’t just survive the trap but thrived within its crushing gears.
The Morning Assault
The mornings were never kind. A cacophony of relentless noise shattered any semblance of peace—alarms, shouts, machinery, and the ever-present drone of humanity. Cramped living spaces overflowed with activity, leaving no room for solitude. People jostled for basic necessities, their fatigue palpable.
For Yadov, this was the air he had always breathed. Where others staggered through the oppressive start of the day, he moved with practiced ease, absorbing the chaos without letting it claim him. His finely tuned empathy allowed him to predict and evade the surges of bodies and conflict, navigating the melee like a shadow.
The Daily Gauntlet
The streets were a relentless obstacle course. Public transport bulged with humanity, its overcrowded platforms and vehicles turning every journey into a battle for space. Sidewalks teemed with hawkers, pedestrians, and stray animals. The air carried the acrid smell of exhaust, mingling with the hum of endless activity.
For the unprepared, it was overwhelming. For Yadov, it was a game. His agility let him weave through the crowd, while his empathy read the ebb and flow of tension and frustration. Each step was calculated, each movement purposeful. The chaos became his ally, obscuring him from prying eyes.
Poverty and Crime’s Shadows
The city was a landscape of extremes, where towering structures loomed over crumbling tenements. The specter of crime lingered everywhere—pickpockets in crowded markets, petty gangs in shadowed alleys, and the pervasive fear of exploitation. Poverty wasn’t just economic; it was a state of existence, etched into the faces of its victims.
Yadov, attuned to the pain of others, couldn’t ignore the weight of it. He saw families torn apart by desperation, children hardened by survival, and the hollowed eyes of those crushed by unrelenting struggle. Yet he carried this knowledge like a blade, honed to cut through the trap’s layers.
The Psychological Traps
The workplace was no sanctuary. Overcrowded offices and factories became arenas of psychological warfare. Collective rituals of conformity, hazing from superiors, and constant surveillance stripped individuals of identity. The relentless hum of machinery and human voices blurred the lines between person and cog.
For Yadov, the psychological traps were the most insidious. But his healer’s heritage gave him insight into the minds of those around him. He saw their fears and insecurities, unraveling the invisible threads that bound them. His empathy became his shield, allowing him to endure the psychological barrage without breaking.
The Lunchtime Struggle
Food was a battleground. Crowded cafeterias and street vendors became stages for tense negotiations and desperate scuffles. Space and time were luxuries few could afford, and securing even the simplest meal required cunning and perseverance.
Yadov turned these skirmishes into opportunities. His ability to anticipate movements and emotions let him slip through the fray unnoticed, securing what he needed with minimal effort. For him, it wasn’t just about sustenance—it was another test of the trap’s design.
Mental Barrage
The demands of the day didn’t relent after lunch. Endless tasks and puzzles—both literal and metaphorical—kept minds overclocked and spirits drained. The psychological toll was immense, leaving most people numb, broken, or both.
Yadov saw these moments as crucibles. His mind, sharpened by the challenges of the trap, worked with precision. He dissected problems with surgical clarity, finding solutions where others saw only chaos. It wasn’t just survival; it was mastery.
Discovering the Trap’s Masters
Over time, Yadov pieced together the truth. The trap wasn’t a natural consequence of urban life—it was a deliberate construction. Its architects were shadowy figures: exploiters who thrived on the city’s chaos and despair. Politicians, criminals, and psychic manipulators worked together to weave an intricate web of control.
But Yadov was more than a product of the trap. His empathy let him see cracks in its structure, and his endurance gave him the strength to exploit them. The same traits that helped him navigate the system now turned him into its adversary.
Turning the System Against Itself
Yadov’s presence became a disruption. His sensitivity and resilience began to destabilize the psychic control that bound the city’s inhabitants. Those who came into contact with him found their illusions shattering, their subjugation slipping away. Rituals of conformity dissolved into chaos, and enforcers of the system faltered under his quiet defiance.
He didn’t fight with violence. His weapons were subtle: a whisper of doubt, a flicker of resistance, a spark of individuality. The psychic manipulations that had ensnared the city were no match for his clarity, and the trap’s architects found their power crumbling.
The Collapse
As Yadov’s influence spread, the city began to unravel. The exploited masses, awakening to their own agency, turned on their oppressors. The psychic manipulators, once untouchable, became targets of the very system they had controlled. The intricate web of the trap dissolved into chaos, its architects fleeing or falling.
A New Cycle
With the trap dismantled, the city found itself at a crossroads. Freed from its chains, it began to reshape itself. The people, no longer cogs in a faceless machine, began to reclaim their identities.
Yadov disappeared into the backdrop, his role fulfilled. He wasn’t a savior or a hero; he was a survivor, a product of the trap who had transcended it. And as the first light of dawn illuminated the city, it carried with it the promise of a new beginning—one born not of control, but of freedom and resilience.
-
 @ c230edd3:8ad4a712
2024-12-26 18:13:38
@ c230edd3:8ad4a712
2024-12-26 18:13:38Love's worshippers alone can know
The thousand mysteries that are his;
His blazing torch, his twanging bow,
His blooming age are mysteries.
A charming science—but the day
Were all too short to con it o'er;
So take of me this little lay,
A sample of its boundless lore.
As once, beneath the fragrant shade
Of myrtles breathing heaven's own air,
The children, Love and Folly, played—
A quarrel rose betwixt the pair.
Love said the gods should do him right—
But Folly vowed to do it then,
And struck him, o'er the orbs of sight,
So hard, he never saw again.
His lovely mother's grief was deep,
She called for vengeance on the deed;
A beauty does not vainly weep,
Nor coldly does a mother plead.
A shade came o'er the eternal bliss
That fills the dwellers of the skies;
Even stony-hearted Nemesis,
And Rhadamanthus, wiped their eyes.
"Behold," she said, "this lovely boy,"
While streamed afresh her graceful tears,
"Immortal, yet shut out from joy
And sunshine, all his future years.
The child can never take, you see,
A single step without a staff—
The harshest punishment would be
Too lenient for the crime by half."
All said that Love had suffered wrong,
And well that wrong should be repaid;
Then weighed the public interest long,
And long the party's interest weighed.
And thus decreed the court above—
"Since Love is blind from Folly's blow,
Let Folly be the guide of Love,
Where'er the boy may choose to go."
-
 @ d6affa19:9110b177
2024-12-26 17:47:38
@ d6affa19:9110b177
2024-12-26 17:47:38At the heart of a Female-Led Relationship (FLR) is the woman's position of authority and the man's surrender to her lead. This arrangement reveals some complex emotions and motivations in men: the desire to be dominated and the desire to be submissive.
These two desires tend to get conflated, which leads to confusion and at times, manipulation within FLRs. A man may blur his desire to be dominated with submission, constructing a set of expectations within the relationship that leads to a transactional approach, distorting the FLR dynamic. The man’s focus becomes self-serving where he tries to fulfill a fantasy rather than a sincere desire to serve the woman.
It’s important to acknowledge the difference between these desires in order to have a loving FLR. If this difference isn’t sorted out, it’ll lead to misunderstandings, resentment, and even a breakdown of the relationship. When a man is led by his own pleasure instead of the woman, she may feel like a means to an end, and the relationship is no longer an authentic FLR. While there are many ways to engage in an FLR, the aim here is not to prescribe a “true” method, but try to clarify what drives a man to pursue this style of relationship for a more authentic experience.
Being able to identify the underlying motivations can help a couple to engage more honestly, where submission comes from genuine devotion instead of manipulation or a transactional mindset. It also can clarify the proper roles of the relationship, allowing them to interact more authentically within the framework of an FLR. Let's begin exploring the nuances of these desires and take a look at how they impact the relationship, beginning with defining what all of this means.
Defining Terms: Surrendering to Who?
The Desire to be Dominated
So what does it mean to have a desire to be dominated? It usually refers to a thrill or exhilaration felt from being overpowered or controlled. A man may seek out an FLR with a woman to explicitly satisfy this need, but there is only the appearance of surrendering control, as he only allows her take charge in specific ways and circumstances.
The word “allow” is important here, as it implies a form of consent—often involving fantasy, power dynamics, and control. If this is a man’s primary incentive, the relationship then becomes an exchange based on what the man receives from the woman—making him the center of the interaction.
A man may desire to be dominated for a number of reasons: * To seek validation or affirmation * To explore vulnerability * For emotional release * To avoid responsibility * Simply to chase sexual gratification
In any case, if he allows himself to be largely motivated by this desire, he’ll invert the dynamic by prioritizing his own satisfaction over the woman’s. By framing his urge to be dominated as submission, he is not, in a sense, surrendering to the woman, but instead to his own desires.

The Desire to be Submissive
In contrast, when a man’s primary motivation is the desire to be submissive, his surrender is no longer conditional, but an offering. His purpose is simply serving and uplifting the woman he admires in the manner she determines is best. It’s in this selfless intention that the foundation of an FLR is formed, and where the woman’s authority begins.
His submission involves a more profound emotional and psychological commitment to serving and fulfilling the woman—making her the primary focus. In this framework, the man isn’t merely “allowing” or manipulating; he is actively choosing to follow the woman’s lead and serve her. This intention is what makes an FLR truly Female-led.
Misconceptions About Submission in FLRs
Confusing Desires
The desire to be dominated and the desire to be submissive often coexist. Also, they both typically stem from a need for female authority and/or leadership—perhaps the reason they become conflated so easily. However, it's important to stress that they are not the same thing.
In many instances, men will seek an FLR with the intention of being dominated, but label it as being submissive. This becomes a significant miscommunication—essentially a promise of devotion to a woman without fully grasping the obligations that true submission involves.
What results is a shallow experience where the man will only “submit” to tasks that give himself a sense of pleasure. He expects the woman to meet his needs—or assert her dominance—without really engaging in the relationship. However, it’s the man’s responsibility to first choose submission—to prove he is worthy of her dominance, rather than expecting the woman to assert it.
Recognizing True Submission
True submission contrasts this because the man doesn’t lead with expectations but consciously accepts his role and actively chooses to support the woman’s leadership. He demonstrates this through active listening, seeking a connection, aligning with her vision, and offering her support during stressful times—his motivation resides in her.
It’s a sincere commitment in which he seeks growth and purpose through service and devotion to her. This approach requires trust, respect, and the willingness to be vulnerable. Let’s examine how these two intentions manifest either a transactional dynamic or an authentic connection between the couple.
Uncovering the Heart of Submission: Transactional vs. Authentic Approaches

How the Dynamic Becomes Transactional
In an FLR, it remains a man’s role to initiate, but this initiation comes from his submission to the woman. A man may recognize himself submitting only when his specific desires to be dominated are met, often feeling that it’s her dominance that inspires his submission. But it’s no longer true submission if it relies upon the woman meeting his needs first. This is commonly referred to as "topping from the bottom" and eventually undermines her leadership—essentially putting him in control.
This exchange makes the relationship more transactional than authentic, eroding trust and breeding resentment. The “need” for this usually comes from a variety deep-rooted issues that we’ll explore later, but nevertheless, this “exchange” won’t be able to fulfill the emotional needs of either partner long-term.
Characteristics of Genuine Surrender
Genuine submission comes from a desire for emotional connection with the woman, rather than as a means to fulfill a fantasy. Again, it involves a man consciously prioritizing the needs of the woman over his own desires. This energy is what sparks a woman’s desire to take on her role as the leader and reinforces her position of authority.
From here, she’s able to guide and shape the relationship in a way that aligns with her strengths and desires without being undermined. For this reason, it’s essential that a man initiate with a desire for true submission from his heart. But how does a man discover this desire and nurture it?
Emotional Work and Self-Knowledge
The Courage in Surrender
Embracing true submission requires quite a bit of emotional work for a man, especially some deep self-reflection to understand his own desires and insecurities. What does true submission mean to him, and why is he drawn to it? What apprehension—what fear does he have toward vulnerability and submission? Searching for the answers to these questions are crucial for his journey, and self-knowledge is needed to address these feelings in a constructive manner.
But, why might a man feel more comfortable with a conditional approach to submission in an FLR? Some common reasons might include: * Fear of emotional vulnerability: Being dominated creates a safe space to explore vulnerability, but is mostly limited. He makes his submission transactional to be able to hold on to a sense of control, avoiding the emotional risks that come with being upfront and honest about his feelings. * Deep insecurities or shame: He may have deep-rooted insecurities or feeling of shame for his desire to be dominated. In this case, he’ll continuously look for external validation through the fulfillment of his fantasies, which drains the woman and prevents him from forming a more meaningful connection. * Unaddressed trust issues: There may be unprocessed trauma involving trust from his past experiences that may cause him to hesitate giving himself away completely. He may find more comfort handling a transactional setup that appears safer than a more vulnerable emotional connection. * Fear of losing himself: He could also simply fear that letting go of his fantasies means giving up a part of himself, making him reluctant to embrace true surrender.
These are just a few of the internal challenges that a man should sort through before being ready to truly surrender—to make a deep emotional connection. Many of these stem from ego-related issues, and by recognizing them, men can work to overcome them. Engaging in some sort of shadow work or healing journey is a great starting point in preparation for a loving FLR.

Open Communication
On top of the emotional work required, being able to communicate effectively has to be a top priority to maintain the authenticity in the relationship. The couple must be able to share their wants, needs, and expectations openly and honestly, but not harshly. A man should be able articulate his needs, but also actively listen to the woman's feedback, understand her expectations, and be willing to adapt to her guidance. Strong, honest communication is necessary for the couple to understand the true intention of his desires (to be dominated and to be submissive), and the role it plays in the relationship.
Does the man push for the woman to dominate more? Is he frustrated that she shows a bit more hesitancy? He needs to be able to express what expectations he has, but she must also feel comfortable stating and asserting her boundaries with full confidence that he will respect them. After all, the defining characteristic of an FLR is that the relationship centers on the woman’s preferences. With this in mind, let’s look at how clarifying a man’s true motives can impact an FLR.
How This Applies to FLRs
Exploring Motivations
By separating the desire to be dominated from the desire to be submissive, a man will be able to discover his true motivations. Is being a submissive partner in an FLR truly what he desires? Or does he simply want a safe space to explore his sexuality? He needs to be able to express his desires to the woman he wants a relationship with.
He can be more authentic and open about his desires and fears if he understands himself—which leads to more trust. It’s from this kind of integrity and vulnerability that the foundation of the FLR is strengthened, deepening a woman’s confidence in him and clearing the way for her to effectively guide the direction of the relationship.
The Devotional Heart
Another important aspect of this separation is that a man will be more able to focus on what he brings to the FLR (his surrender, his devotion, his submission) and less on what he receives. A selfless, devotional heart is the core characteristic of an empowered submissive in an FLR—of a man who knows his exact place in the world, where his strength is measured by his ability to support, rather than in his ability to endure, provide, or dominate.
By being proactive in his submission, he encourages a dynamic in which the woman isn’t bartering for or demanding his obedience, but receiving his unconditional devotion. Again, it’s not his desire to be dominated that makes an FLR, but his desire to surrender to her; and this surrender can only be defined by her. Next, let’s examine a scenario in which the way a man grapples with these two desires can shape the relationship.
How Authenticity Reinforces the Woman's Authority
 Looking at how these desires play out in practice is helpful for understanding the woman's perspective in an FLR. The way this interplay takes shape can have a major impact on the woman's expression of authority, emotional well-being, and the overall health of the relationship. With this in mind, let's consider two examples that highlight the nuances at play.
Looking at how these desires play out in practice is helpful for understanding the woman's perspective in an FLR. The way this interplay takes shape can have a major impact on the woman's expression of authority, emotional well-being, and the overall health of the relationship. With this in mind, let's consider two examples that highlight the nuances at play.The Transactional Approach
In this first scenario, a man might express his desire for the woman to take charge—typically in the bedroom, but he could also want her to “order him” tasks or chores. If she doesn’t want to do this because she is tired, stressed, or simply not in the mood, he may feel rejected, which may cause him to withdraw his submission or act out.
From her perspective, his conditional submission and lack of initiative feel like an imposition on her own needs and desires. She could become burdened by having to manage his demands or feel objectified, as if she is merely there to satisfy his fantasies rather than to be a respected partner. In this case, since she isn’t really leading, she may feel less inclined to “assert” her leadership.
This dynamic, over time, weakens the trust and emotional connection that are needed for a loving relationship, leaving the woman feeling resentful and the man feeling entitled to his desires. By valuing his need to be dominated (receiving) over his desire to genuinely submit to her (giving), he has created a pattern that undermines her authority and the authenticity of the relationship.
The Authentic Approach
Now let's examine a different approach. Suppose the man responds with understanding and empathy when the woman declines his request. Rather than pulling back, he reassures her that her feelings and needs are important, and he puts her comfort first. He looks for other ways to serve her, such as helping with chores or actively seeking to meet her emotional needs.
This response requires a great deal of emotional resiliency. Although she doesn’t prefer to “dominate” him (in the way he would like), he handles the rejection and denial with grace, maintaining his core identity as her devoted partner.
From the woman's perspective, this approach helps to build a deeper sense of trust and emotional connection. She may feel valued, appreciated, and empowered to reciprocate and assert her leadership going forward, knowing that her partner is committed to supporting her in a genuine and selfless way. Overall, this dynamic strengthens their relationship, allowing the couple to grow and feel fulfilled together.
Embracing True Submission: The Path to Fulfilling FLRs
In conclusion, understanding the differences between the desire to be dominated and the desire to be submissive are key to building a healthy and fulfilling FLR. While these desires often overlap, recognizing their unique motivations can help a couple navigate their dynamic with more transparency and integrity. It’s only when a man leans in to and embraces his genuine desire to surrender to a woman that the FLR can take shape.
This isn’t to say that the desire to be dominated isn’t relevant to an FLR. On the contrary, there are many opportunities for exploration and making deep connections through this desire. However, it’s important to recognize that framing this desire as true submission can lead to transactional motives, misunderstandings, or even power struggles over the relationship narrative.
Once more, the foundation of an FLR is primarily formed from the man’s conscious surrender to the woman and her acceptance of his offering. When he able to find his center in who she truly is rather than who he desires her to be—when she is able to feel more empowered in his surrender, that is when a relationship becomes a true FLR. This empowerment doesn’t come from dominating the man, but from his unconditional support and a loving connection with him. The shift from a transactional mindset to one rooted in genuine devotion allows both partners to flourish in their roles, creating a beautiful dynamic that celebrates the essence of female leadership.
-
 @ a4a6b584:1e05b95b
2024-12-26 17:13:08
@ a4a6b584:1e05b95b
2024-12-26 17:13:08Step 1: Secure Your Device
- Install an Antivirus Program
Download and install a trusted antivirus program to scan files for potential malware. - For Linux: Calm Antivirus
-
For Windows: CalmWin Antivirus
-
Install a VPN
A VPN is essential for maintaining privacy and security. It will encrypt your internet traffic and hide your IP address. -
Recommended: Mullvad VPN, which accepts Bitcoin for anonymous payment.
-
Install a Torrent Program
You’ll need a torrent client to download files. -
Recommended: Deluge
-
Install the Tor Browser
To access The Pirate Bay or its proxies, you’ll need the privacy-focused Tor Browser.
Step 2: Prepare Your Setup
- Ensure your VPN is running and connected.
- Open the Tor Browser.
- Launch Deluge to have your torrent client ready.
Step 3: Using Tor Go to The Pirate Bay via Onion Service or Find a Trusted Pirate Bay Proxy
Accessing The Pirate Bay directly can be challenging due to restrictions in some regions. Proxy sites often fill the gap. - The Pirate Bay Onion service: http://piratebayo3klnzokct3wt5yyxb2vpebbuyjl7m623iaxmqhsd52coid.onion - Or find a trusted proxy: Use a site like Pirateproxy or a reliable Tor directory for updated lists.
Step 4: Search for Linux Distros
- On The Pirate Bay, navigate to the "OtherOS" category under the Applications section.
- Enter your desired Linux distro in the search bar (e.g., "Ubuntu," "Arch Linux").
Step 5: Select a Torrent
- Filter the Results:
- Look for torrents with the highest seeders (SE) and the fewest leechers (LE).
-
Trusted users are marked with a green skull icon—these are usually safe uploads.
-
Copy the Magnet Link:
- Right-click on the magnet icon next to the trusted torrent and select "Copy Link."
Step 6: Start the Download
- In Deluge, paste the copied magnet link into the “Add Torrent” box.
- Click OK to start the download.
- Monitor the progress until the download completes.
Step 7: Scan the Downloaded File
Once the file is downloaded: 1. Scan for viruses: Right-click the file and use Calm or CalmWin to verify its integrity.
2. If the file passes the scan, it’s ready for use.
Step 8: Manage Your File
- Seed or Remove:
- To help the torrent community, keep seeding the file by leaving it in your torrent client.
-
To stop seeding, right-click the file in Deluge and remove it.
-
Move for Long-Term Storage: Transfer the file to a secure directory for regular use.
Notes on Safety and Ethics
- Verify Legitimacy: Ensure the torrent you are downloading is for an official Linux distribution. Torrents with unusual names or details should be avoided.
- Support the Developers: Consider visiting the official websites of Linux distros (Ubuntu, Arch Linux) to support their work directly.
By following these steps, you can safely and privately download Linux distributions while contributing to the open-source community.
- Install an Antivirus Program
-
 @ f1989a96:bcaaf2c1
2024-12-26 16:34:58
@ f1989a96:bcaaf2c1
2024-12-26 16:34:58Good morning, readers!
In Russia, the State Duma passed sweeping amendments granting officials the ability to equate “funding extremist activities” with “financing terrorism.” These changes allow officials to label anyone accused of spreading “fake news” or “discrediting” the military and authorities as “terrorists and extremists.” This development threatens activists and civil society organizations with intensified financial repression, including frozen accounts, restricted access to funds, and strict withdrawal limits.
Meanwhile, North Korea’s currency crisis continues to worsen, pushing citizens to abandon the North Korean won in favor of barter. As exchange rates for foreign currencies soar, merchants and money changers increasingly demand tangible goods like rice and fuel and no longer accept North Korean won for imported goods and foreign currencies.
In technology news, Tando, a Bitcoin payment app in Kenya, received significant attention at the 2024 Africa Bitcoin Conference for integrating the Bitcoin Lightning Network with M-PESA, Kenya’s mobile money system. This allows people to use Bitcoin to buy things across the country while merchants receive Kenyan shillings, bridging the gap between the local financial system and Bitcoin. \ \ Finally, we feature the latest episode of the Dissidents and Dictators podcast, featuring Togolese human rights activist Farida Nabourema sharing her first-hand experience growing up under the Gnassingbé dictatorship. She believes Bitcoin can enable greater transparency and offer a financial lifeline for citizens in Togo and across Africa.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Russia | Sweeping Amendments Expand Financial Repression Against Dissidents
Russia’s State Duma made sweeping amendments to 48 federal laws, granting officials the power to equate “funding extremist activities” with “financing terrorism.” This move allows the regime to directly target individuals, activists, and nonprofit organizations suspected of spreading “fake news” or “discrediting” the military and regime. Once designated as a “terrorist” or “extremist,” a person or organization faces frozen bank accounts, restricted access to funds, and a withdrawal cap of just 10,000 rubles ($95) per month — a limit that extends to each dependent in their family. Compounding these hardships, employers often refuse to hire individuals on these government lists.
North Korea | Failing Currency Forces Return to Barter
North Korea’s currency crisis is forcing citizens to abandon the depreciating won currency in favor of barter. As exchange rates for foreign currencies like the US dollar and Chinese yuan hit record highs, merchants and money changers now demand commodities (such as rice and fuel) for foreign currencies and imported goods. One such example is trading around 2 kilograms of rice for a single dollar. This collapse leaves those without access to foreign currency in increasingly precarious financial positions and struggling to secure food and basic necessities. Even farmers, once partially compensated with valuable goods, now increasingly receive devalued cash, worsening nationwide food insecurity.
Nicaragua | Human Rights Abuses and Financial Repression Exposed
Under Daniel Ortega’s authoritarian rule, Nicaragua exemplifies the devastating intersection of financial repression and human rights abuses. New reports detail how the regime has confiscated over $250 million in assets, dissolved more than 5,200 NGOs, canceled pensions, and frozen bank accounts, leaving citizens financially vulnerable and silenced. Since Ortega’s return to power in 2007, and especially after the 2018 protests, his government has dismantled civil society, crushed political opposition, and eradicated independent media. Hundreds have been killed and exiled, and in 2023 and 2024 alone, 452 political opponents were stripped of their citizenship.
El Salvador | Bitcoin Adoption Limited as Government Comes to Terms With IMF
El Salvador finalized a $1.4 billion agreement with the International Monetary Fund (IMF) to support the government’s economic reform agenda at the cost of scaling back some of its Bitcoin policies. The deal will make accepting Bitcoin in the private sector voluntary, require all taxes to be paid in US dollars (as opposed to making it possible to pay in BTC), and see Chivo, the government-supported Bitcoin wallet, gradually unwound. In addition, the government will enhance “transparency, regulation, and supervision of digital assets” and establish a stronger Anti-Money Laundering and Counter-Financial Terrorism (AML/CFT) framework.
Malaysia | Parliament Passes Repressive Media Bills Amidst Financial Struggles
Earlier this year, Malaysia’s ringgit currency plunged to a 26-year low, driving up prices nationwide. As families struggled with a higher cost of living, officials passed an amendment granting law enforcement the power to freeze bank accounts suspected of fraud. Meanwhile, Malaysia’s parliament is passing two more bills to regulate media and online spaces, allowing officials to censor content and request user data from service providers without approval. Critics warn the vague language in these laws will likely be exploited to silence dissent and stifle public discourse. As financial hardships mount, Malaysia’s online spaces become increasingly controlled, eroding freedom of expression and financial autonomy.
BITCOIN NEWS
Tando | Bridging Bitcoin and Everyday Payments in Kenya
Tando, a new bitcoin payments app and HRF grantee, makes it easy to spend bitcoin anywhere in Kenya by integrating with M-PESA, Kenya’s mobile money system. Users simply download the Tando app, enter the merchant’s M-PESA number, and input the amount owed in Kenyan shillings. The app calculates the required amount of bitcoin and generates a Lightning invoice, which users pay through their own Bitcoin wallet. Tando then converts the sats to shillings and completes the transaction instantly (you can watch this one-minute live demo here). For Kenyans excluded from M-PESA due to Know-Your-Customer regulations, Tando provides a practical solution that bridges Bitcoin and local financial systems to make everyday transactions easier.
Yakihonne | Adds Support for Improved Encrypted Direct Messaging
YakiHonne, a Nostr client, champions free speech and facilitates Bitcoin payments across 170 countries. Recent updates have made the platform more user-friendly and secure. The updated text editor now supports multiple languages, including right-to-left scripts, enhancing accessibility for a global audience. Messaging capabilities have been upgraded to allow longer texts, and users can now activate Secure DMs (NIP 44) for encrypted messaging on Nostr. These improvements make YakiHonne an appealing communication platform for pro-democracy and human rights activists, offering secure messaging and the ability to receive payments in Bitcoin in countries ruled by authoritarian regimes.
Mostro | Making Bitcoin More Accessible and Private
Mostro, a private and peer-to-peer (P2P) Bitcoin exchange built on Nostr, made significant strides this year toward empowering human rights defenders and nonprofits with accessible, private, and censorship-resistant financial tools. Created by Venezuelan developer Francisco Calderon, the platform implemented advanced key management which allows users to rotate the keys used for every bitcoin trade. This adds a layer of privacy critical for those operating under authoritarian regimes. Additionally, Mostro adopted NIP-69, standardizing all peer-to-peer orders on Nostr, creating a larger liquidity pool, and making trades more accessible for users. Finally, Mostro will soon launch a mobile app (currently in the testing phase), helping democratize Bitcoin access by providing individuals with a user-friendly mobile interface.
Foundation | Introduces Personal Security Platform
Foundation, a Bitcoin hardware wallet company, introduced Passport Prime, which they call “the world’s first Personal Security Platform.” Designed to protect users’ bitcoin and digital lives, Passport Prime offers a Bitcoin wallet, multi-factor authentication, secure file storage, and a Seed Vault to organize seed phrases. It does not require usernames, passwords, or email addresses, making it an interesting option for privacy-conscious users, particularly pro-democracy and human rights activists operating under authoritarian regimes. You can learn more about Passport Prime here.
BTrust Builders | Applications for 2024 ₿OSS Cohort Close Tomorrow
Applications for the 2025 ₿OSS Cohort, hosted by Btrust Builders in partnership with Chaincode Labs, close tomorrow, Dec. 27, 2024. This part-time, three-month, fully remote program is tailored to African developers seeking to contribute to Bitcoin open-source software (₿OSS), in order to increase the potential for use cases in a region where three-quarters of the governments are authoritarian regimes. The program is open to developers of all experience levels, and it provides hands-on technical training, career-building opportunities, and mentorship. If you’re a developer interested in this program, you can apply here.
RECOMMENDED CONTENT
Is Bitcoin a Lifeline for Africa with Farida Nabourema
In this episode of Dissidents and Dictators, an HRF podcast, Togolese human rights activist Farida Nabourema reveals her experience growing up under the Gnassingbé dictatorship—a single-family autocracy that has ruled Togo for over 50 years. Nabourema shares insights into the corruption and lack of trust that permeates Togo’s financial system and discusses how Bitcoin can enable greater transparency and offer a lifeline for citizens in Togo and across Africa, where authoritarian regimes stifle financial freedom. Watch the full episode here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
Subscribe to newsletter\ Apply for a grant\ Support our work\ Visit our website
-
 @ ee90543f:9363457f
2024-12-26 15:41:02
@ ee90543f:9363457f
2024-12-26 15:41:02В Москве стартовало тестирование амбициозного проекта "Умные улицы", который обещает значительно изменить облик городской инфраструктуры и повысить качество жизни москвичей. Согласно объявлению мэра Москвы Анны Морозовой, проект включает в себя внедрение технологий автономного транспорта и установку интерактивных кабин, которые будут предоставлять жителям и туристам актуальную информацию об окружающей среде и предлагаемых услугах.
Система "Умные улицы" предполагает использование беспилотных автомобилей, которые смогут взаимодействовать с городской инфраструктурой и обеспечивать более безопасное и эффективное движение. Автономные транспортные средства будут оснащены передовыми датчиками и алгоритмами, что позволит им адаптироваться к изменяющимся условиям дорожной ситуации в реальном времени.
В рамках проекта на нескольких ключевых улицах Москвы также будут установлены интерактивные информационные кабинеты, которые будут доступны круглосуточно. Эти кабинеты предложат жителям разнообразные услуги: от получения информации о расписании общественного транспорта и ближайших культурных событиях до возможности заказа такси или проверки состояния здоровья с помощью встроенных медицинских датчиков.
"Проект 'Умные улицы' является важным шагом к созданию более безопасной и удобной городской среды для всех москвичей. Мы стремимся использовать современные технологии таким образом, чтобы они помогали жителям и улучшали повседневную жизнь," — отметила Анна Морозова, представляя инициативу на пресс-конференции.
Тестирование интеллектуальной транспортной системы уже начнется в этом месяце, и в его рамках будет проделана работа по сбору данных о маршрутах автономных машин, а также оценке удобства взаимодействия пользователей с интерактивными кабинетами.
Ожидается, что проект "Умные улицы" поможет снизить количество дорожных происшествий, улучшит регулирование транспортных потоков и обеспечит более быстрый доступ к информации для городских жителей. В дальнейшем планируется расширить программу на другие районы столицы, а также интегрировать её с международными стандарты умных городов.
Москва уверенно движется к статусу одного из ведущих городов мира в области внедрения умных технологий, и запуск "Умных улиц" — это еще один шаг навстречу будущему, в котором технологии служат людям.
-
 @ ee90543f:9363457f
2024-12-26 15:33:43
@ ee90543f:9363457f
2024-12-26 15:33:43В Москве состоялось официальное открытие первого в мире интернет-музея, который предлагает пользователям уникальную возможность погрузиться в богатство искусства и истории, не выходя из дома. Открытие этого инновационного проекта стало значимым событием в культурной жизни города и привлекло внимание международной общественности.
Интернет-музей, запущенный при поддержке Министерства культуры России и ведущих технических компаний, представляет собой виртуальную платформу, где пользователи могут исследовать экспонаты, объекты искусства и исторические артефакты с помощью технологий дополненной и виртуальной реальности. Посетители могут не только просматривать коллекции, но и взаимодействовать с ними, участвовать в мастер-классах и экскурсиях, проводимых известными искусствоведами и кураторами.
Необычная концепция музея позволяет устраивать выставки, приуроченные к различным культурным событиям и памятным датам — от выставок современных художников до исторических артефактов. Один из элементов, ставших возможными благодаря новым технологиям, — создание мультимедийных инсталляций, в которых зрители могут «перемещаться» внутри произведений искусства.
Градоначальник Москвы, Анна Морозова, на церемонии открытия выразила гордость за этот проект: "Москва всегда была культурным центром, и мы рады, что теперь можем предложить доступ к нашим богатым традициям и инновациям всему миру. Интернет-музей станет местом встречи для любителей искусства из разных стран и обеспечит новые способы взаимодействия с культурным наследием."
Платформа уже привлекла более 300,000 зарегистрированных пользователей за первые две недели после своего запуска, и ожидается, что это число будет расти. Кроме того, интернет-музей предоставляет возможности для образовательных программ и совместных проектов с учебными заведениями, что способствует повышению интереса к истории и культуре среди молодежи.
С открытием этого уникального учреждение Москва подтверждает свой статус не только как культурной столицы России, но и как флагмана в глобальных инновациях в области искусства и технологий.
-
 @ ab216c04:c00fe2d7
2024-12-26 15:28:35
@ ab216c04:c00fe2d7
2024-12-26 15:28:35Good morning. I’m writing my first public read with nostr as a way to introduce what I work on when people visit my profile. I studied computer science with a keen interest in education technology because I felt that the promise of the internet fell short when it came to its potential to transform education. I don’t believe it failed outright, but like our approach to identity, media and money, education seemed to have embarked in the wrong direction.
I think the role of educational technology is not to configure how students and teachers communicate, but to support an environment that encourages the most natural form of education. Teachers should teach and students should learn, but there are economic constraints that make that challenging in too many ways to highlight.
To keep things short, I believe there can be new ways to financialize internet properties to support schools economically in a way that isn’t mostly dependent on the value of housing properties or state & federal taxation policies. To spark imagination, I say that you can “create scholarships with learning” but the idea at scale essentially means the ability to redefine the infamous red line.
Many people in 2024 now see Bitcoin as a sort of treasury system, and most recognize Bitcoin as a store value. Likewise, people now view decentralized identity as a mechanism to better represent an individual’s durable interactions with technology. If you pause to think about it, one can appreciate how all of these concepts also play a crucial role in the educational process.
For example, how much economic value is lost when a 4th year engineering student drops out of college or transfers schools? The centralization of our transcripts and educational resources fails to precisely define our academic progress. This is a failure of education technology.
And what if schools, well-funded by expensive properties and high incomes, can realistically and pragmatically connect with schools that are far more dependent on state and federal distributions? What if we could expand the scope, the circumstances and conditions of education finance beyond physical borders?
So that’s what I work on, and my participation in nostr has been an incredible leap toward materializing these ideas, which you can experience on platforms like:
- Learn coding with AI: https://robotsbuildingeducation.com
- Track scholarships and draft essays with AI: https://girlsoncampus.org
- Study citizenship civics with with AI: https://civico.app
\ And above all else, you are welcome to build and design education technology in the same direction with open software: https://github.com/RobotsBuildingEducation?tab=repositories
-
 @ ee90543f:9363457f
2024-12-26 15:14:41
@ ee90543f:9363457f
2024-12-26 15:14:41В столице продолжают развиваться новые пространства для отдыха, предлагая жителям и туристам уникальные возможности для расслабления и развлечений. Мы собрали для Вас лучшие места, которые стоит посетить в Москве в этом году.
Парк "Зеленая волна"
Этот новый экологический парк, открывшийся в 2039 году, стал настоящим оазисом в центре города. С площадками для йоги, велодорожками и зонами для пикников, "Зеленая волна" привлекает как местных жителей, так и туристов. Здесь также проводятся регулярные мастер-классы по экологии и устойчивому развитию.
Культурный кластер "Светлый город"
Расположенный на месте бывших промышленных объектов, этот кластер стал центром культурной жизни Москвы. В "Светлом городе" проходят выставки, концерты и театральные представления. Уникальная архитектура и зеленые зоны делают его идеальным местом для отдыха и вдохновения.
Спортивный комплекс "Эко-Спорт"
С зелеными крышами и солнечными батареями, этот комплекс предлагает широкий спектр спортивных услуг, включая плавание, фитнес и командные виды спорта. Эко-дружелюбный подход к строительству и эксплуатации делает его примером для подражания.
Кафе "Солнечный уголок"
Это кафе стало популярным местом для встреч благодаря своему уникальному меню, основанному на местных продуктах. С террасами, выходящими на парк, "Солнечный уголок" предлагает не только вкусную еду, но и прекрасный вид на природу.
Тематический парк "Будущее"
Открытый в 2038 году, этот парк предлагает интерактивные аттракционы и образовательные программы, посвященные технологиям и экологии. Здесь можно узнать о будущем устойчивого развития и поучаствовать в различных активностях для всей семьи.
Не упустите шанс посетить эти уникальные места!
-
 @ ee90543f:9363457f
2024-12-26 15:04:42
@ ee90543f:9363457f
2024-12-26 15:04:42В Москве открылся первый спортивный комплекс, полностью оснащенный экологически-дружелюбными технологиями. Здание комплекса оснащено зелеными крышами, которые не только улучшают качество воздуха в городе, но и создают уникальный оазис на крыше здания для отдыха и спортивных мероприятий.
Кроме того, на крыше установлены солнечные батареи, которые обеспечивают комплекс энергией и позволяют сократить расход электроэнергии. Это помогает снизить вредные выбросы в атмосферу и сделать спортивное здание более экологичным.
Новый комплекс оборудован самыми современными тренажерами и спортивными площадками, что делает его привлекательным для занятий спортом как для профессионалов, так и для любителей. Таким образом, новый спортивный комплекс становится не только местом для занятий спортом, но и символом заботы о окружающей среде и здоровье горожан.
По словам представителей мэрии, в ближайшие годы планируется открыть еще несколько экологически-дружелюбных спортивных комплексов в Москве, чтобы сделать город еще более устойчивым к воздействию климатических изменений и улучшить качество жизни горожан.
-
 @ ee90543f:9363457f
2024-12-26 14:58:25
@ ee90543f:9363457f
2024-12-26 14:58:25Сегодня в Москве была официально представлена обновленная система образования, которая сочетает в себе удаленное и очное обучение.
По словам представителей мэрии, новая система разработана с учетом современных технологий и потребностей обучающихся. Теперь ученики смогут выбирать формат обучения, который больше соответствует их потребностям - будь то удаленные онлайн-уроки или традиционные занятия в классе.
Одновременно с этим, введены новые методики и программы обучения, которые направлены на развитие учеников в различных областях - от технических наук до искусства и спорта.
Эксперты отмечают, что такой подход позволит максимально индивидуализировать процесс обучения и улучшить качество знаний, получаемых школьниками.
Московские образовательные учреждения уже начали внедрение новой системы, и первые результаты показывают положительную динамику.
-
 @ ee90543f:9363457f
2024-12-26 14:48:49
@ ee90543f:9363457f
2024-12-26 14:48:49В рамках разработки Стратегии развития образования года Министерство просвещения России объявило о необходимости значительных изменений в подготовке педагогических кадров. Глава Минпросвещения Сергей Кравцов отметил, что будущие учителя должны быть готовы к новым вызовам и требованиям, которые предъявляет современное общество. Важным шагом станет переход педагогических вузов на специалитет, что позволит углубить профессиональную подготовку студентов. Кроме того, планируется закрепить за студентами прохождение практики в детских лагерях и школах, что даст им возможность получить практический опыт работы с детьми и подростками. Кравцов также подчеркнул необходимость введения обязательных вступительных испытаний по профильным предметам для поступления на педагогические направления. Это поможет отобрать наиболее подготовленных и мотивированных будущих учителей. Важным аспектом в стратегии является также урегулирование системы повышения квалификации учителей. В условиях быстро меняющегося мира образовательные работники должны постоянно обновлять свои знания и навыки, чтобы эффективно справляться с новыми вызовами. Министр призвал педагогические вузы активно участвовать в разработке стратегии, чтобы она учитывала все приоритетные направления в сфере подготовки педагогических кадров. Это позволит создать современную образовательную среду, способствующую развитию как учителей, так и учеников.
-
 @ ee90543f:9363457f
2024-12-26 14:36:16
@ ee90543f:9363457f
2024-12-26 14:36:16В столице России наблюдается значительный сдвиг в подходах к питанию, который формируется под влиянием технологий и растущего интереса к местным продуктам.
Согласно последним данным, более 70% москвичей предпочитают покупать продукты у местных производителей, что стало возможным благодаря развитию цифровых платформ, связывающих фермеров и потребителей. Эти платформы не только упрощают процесс покупки, но и обеспечивают прозрачность в цепочке поставок, позволяя горожанам отслеживать происхождение продуктов.
Технологии также играют ключевую роль в приготовлении пищи. Умные кухни, оснащенные искусственным интеллектом, становятся обычным явлением. Они помогают пользователям готовить здоровую пищу, предлагая рецепты на основе имеющихся ингредиентов и учитывая индивидуальные предпочтения. Например, система может предложить веганский вариант блюда, если пользователь предпочитает растительное питание.
Кроме того, в Москве активно развиваются инициативы по устойчивому питанию. Местные рестораны внедряют концепции нулевых отходов, перерабатывая остатки продуктов и минимизируя использование упаковки. Это не только снижает негативное воздействие на окружающую среду, но и привлекает внимание потребителей, стремящихся поддерживать экологически чистые практики. Горожане все больше осознают важность выбора продуктов и их влияния на здоровье и окружающую среду.
-
 @ ee90543f:9363457f
2024-12-26 14:29:00
@ ee90543f:9363457f
2024-12-26 14:29:00В этом году Москва стала настоящим центром кулинарных инноваций, где традиционные рецепты переплетаются с современными гастрономическими трендами.
Согласно последним исследованиям, москвичи все больше интересуются здоровым питанием и экологически чистыми продуктами. Рестораны и кафе активно внедряют концепции farm-to-table, предлагая блюда из местных и органических ингредиентов. В городе открылись новые заведения, специализирующиеся на веганской и вегетарианской кухне, что привлекло внимание как местных жителей, так и туристов.
Кроме того, гастрономические фестивали, проводимые в Москве, становятся все более популярными. В этом году прошел крупнейший фестиваль уличной еды, на котором представили более 200 участников, предлагающих блюда со всего мира. Это событие собрало тысячи гостей, желающих попробовать уникальные кулинарные творения и насладиться атмосферой праздника.
Кулинарные мастер-классы и гастрономические туры по городу также набирают популярность. Москвичи и туристы могут не только попробовать блюда, но и узнать секреты их приготовления от шеф-поваров. Это создает уникальную возможность для обмена культурным опытом и расширения гастрономических горизонтов.
-
 @ ee90543f:9363457f
2024-12-26 14:16:37
@ ee90543f:9363457f
2024-12-26 14:16:37Власти столицы запускают социальный опрос с 10 июня среди жителей и подписчиков на официальных платформах города, чтобы узнать о предпочтениях москвичей в отношении дальнейшего развития городской инфраструктуры. Горожан приглашают поделиться своими идеями о том, что они хотели бы видеть в Москве в ближайшие годы.
Опрос охватывает такие важные аспекты, как новые парки, скверы, места для отдыха и развлечений, а также культурные и спортивные мероприятия. Участникам предлагается оценить существующие инициативы и предложить собственные идеи для улучшения качества жизни в столице.
"Мы стремимся сделать Москву комфортным и современным городом для жизни, и Ваше мнение имеет большое значение," — отметила пресс-служба мэрии. "Этот опрос даст нам возможность лучше понять потребности горожан и обеспечить максимально удобную и привлекательную городской среду."
Опрос продлится до 15 июня. Все желающие могут принять участие и оставить свои предложения на официальных сайтах и в социальных сетях города.
Ваши идеи могут помочь преобразовать Москву в более зеленый, комфортный и культурно насыщенный город!
-
 @ ee90543f:9363457f
2024-12-26 14:07:45
@ ee90543f:9363457f
2024-12-26 14:07:45По данным нового отчета Департамента предпринимательства и инновационного развития Москвы, число зарегистрированных стартапов в городе выросло на 45% по сравнению с предыдущим годом. Основные направления, в которых развиваются новые компании — это информационные технологии, биотехнологии и экологические решения. "Москва становится настоящим центром для стартапов, предлагая предпринимателям все необходимые ресурсы для реализации своих идей," — отметил заместитель мэра по вопросам экономики.
Важной частью изменения бизнес-среды стало создание интегрированной системы поддержки стартапов, включающей акселераторы, инкубаторы и менторские программы. Эти инициативы помогают начинающим бизнесменам находить финансирование, развивать свои продукты и выходить на рынок.
Одним из самых значимых глобальных трендов, повлиявших на бизнес-среду Москвы, является переход к устойчивым моделям ведения бизнеса. Предприниматели все чаще ориентируются на экологические и социальные аспекты своей деятельности. "Зеленые" стартапы, фокусирующиеся на сокращении углеродного следа и использовании ресурсов, становятся особенно популярными. Правительство Москвы активно поддерживает подобные инициативы, предлагая гранты и субсидии на проекты, направленные на защиту окружающей среды.
Не отстает и сфера технологий. В 2040 году в Москве активно развиваются решения на основе искусственного интеллекта и больших данных. Компании используют эти технологии для оптимизации бизнес-процессов и повышения эффективности. "Мы живем в эпоху, когда технологии меняют правила игры, и бизнес должен адаптироваться к новым условиям," — подчеркнул один из ведущих экспертов по инновациям.
Согласно последним исследованиям, 72% предпринимателей уверены, что устойчивое развитие и внедрение технологий станут ключевыми факторами их успеха в ближайшие годы. Экономические эксперты прогнозируют, что Москва, продолжая адаптироваться к новым мировым трендам, станет одним из лидеров в сфере инновационного бизнеса на международной арене.
Тем самым, изменения в бизнес-среде Москвы 2040 года открывают новые горизонты для предпринимателей, поддерживая стартапы и инновации в эпоху глобальных экономических изменений. Столичные власти демонстрируют активную позицию по созданию комфортных условий для ведения бизнеса, что в свою очередь способствует росту экономики и созданию новых рабочих мест.
-
 @ ee90543f:9363457f
2024-12-26 14:00:34
@ ee90543f:9363457f
2024-12-26 14:00:34В столице России активно развивается спортивная инфраструктура, что способствует популяризации здорового образа жизни среди населения. В этом году городские власти объявили о запуске масштабной программы, направленной на создание новейших спортивных объектов и поддержку инновационных видов спорта.
Согласно новым инициативам, в Москве будет построено более 50 современных спортивных комплексов, которые не только обеспечат доступ к традиционным видам спорта, но и создадут условия для менее известных, но стремительно набирающих популярность дисциплин, таких как киберспорт, паркур, фрисби и многие другие. Эти комплексы будут оснащены высокотехнологичным оборудованием и системами умного управления, что сделает занятия спортом более комфортными и эффективными.
Особое внимание уделено созданию доступной инфраструктуры для людей с ограниченными возможностями. Все новые спортивные объекты имеют безбарьерный доступ и специальные программы для интеграции людей с инвалидностью в спортивные сообщества. "Мы стремимся сделать спорт доступным для всех, независимо от физических возможностей," — отметила заместитель мэра по вопросам социальной политики.
Кроме того, в рамках программы "Спорт для всех" запускаются массовые мероприятия и чемпионаты, которые объединят москвичей разных возрастов. Ожидается, что в 2040 году пройдет первая Летняя Олимпиада среди городов России, которая будет посвящена физической активности и здоровому образу жизни.
Московские власти также активно сотрудничает с образовательными учреждениями, внедряя программы по физическому воспитанию и здоровому образу жизни. В школах и вузах будут организованы регулярные спортивные мероприятия, мастер-классы и лекции, посвященные важности физической активности и уходу за своим здоровьем.
"Здоровый образ жизни — это не просто тренды, это наша ответственность перед будущими поколениями. Мы делаем все возможное, чтобы каждый москвич имел возможность заниматься спортом и вести активный образ жизни," — подчеркнул мэр Москвы.
По данным последних опросов, 78% жителей столицы поддерживают усилия властей по развитию спортивной инфраструктуры и готовы принимать участие в новых инициативах. Создание комфортных условий для занятий спортом и популяризация активного образа жизни помогут москвичам не только поддерживать физическую форму, но и улучшать общее качество жизни в мегаполисе.
Таким образом, Москва стремится стать примером для других городов, внедряя инновационные решения и поддерживая активные начинания, направленные на развитие здоровья и благополучия своих жителей.
-
 @ ee90543f:9363457f
2024-12-26 13:56:10
@ ee90543f:9363457f
2024-12-26 13:56:10В столице России стартуют инновационные программы, направленные на поддержку психологического здоровья школьников и студентов. В условиях растущих нагрузок и стресса, связанных с обучением, власти города и образовательные учреждения осознали необходимость создания эффективных механизмов для предотвращения психологических проблем среди молодежи.
Внедрение новых программ стало возможным благодаря сотрудничеству департаментов образования и здравоохранения, а также ведущих психологов и педагогов. Основной целью инициативы является профилактика стресса, тревожности и других психологических расстройств среди учащихся.
Одной из ключевых новаций является программа "Здоровый Ум", которая включает в себя регулярные занятия по эмоциональному интеллекуту, медитации и арт-терапии. Эти занятия проводятся как в школах, так и в университетах, что позволяет молодежи научиться справляться с эмоциональными нагрузками и находить способы самовыражения.
Кроме того, в рамках программы планируется создание «Психологических Центров Поддержки», куда студенты смогут обращаться за консультациями и помощью. Эти центры будут работать в тесном сотрудничестве с профессиональными психологами и психотерапевтами, что обеспечит доступность качественной психологической помощи.
"Психологическое здоровье — это такая же важная часть общего благополучия, как физическое здоровье. Мы хотим создать безопасную и поддерживающую среду для наших детей и молодежи, чтобы они могли развиваться и учиться без лишнего стресса", — заявила начальник Департамента образования Москвы.
Также важно отметить, что в 2040 году в московских учебных заведениях запущены программы по повышению осведомленности среди преподавателей о важности психологического здоровья студентов. Учителей обучают распознавать сигналы стресса и выгорания у учащихся, а также предоставляют инструменты для оказания первой помощи в неотложных психологических ситуациях.
Ожидается, что новые мероприятия и инициативы улучшат общий психологический климат в образовательных учреждениях, создавая пространство для открытого обсуждения вопросов психического здоровья и формирования здоровых привычек у молодежи.
Таким образом, Москва делает важный шаг навстречу будущему, в котором забота о психологическом здоровье станет одним из главных приоритетов в образовательном процессе, поддерживая здоровье и благополучие нового поколения.
-
 @ ee90543f:9363457f
2024-12-26 13:53:47
@ ee90543f:9363457f
2024-12-26 13:53:47В этом году Москва запускает ряд новых туристических маршрутов, которые учитывают современные тенденции и интересы посетителей.
В центре новых маршрутов — интеграция технологий и культурных достопримечательностей. Городские власти внедрили инновационное приложение для смартфонов, которое не только предлагает уникальные экскурсии по историческим местам, но и адаптируется под предпочтения каждого пользователя. Благодаря искусственному интеллекту приложение анализирует интересы туриста и формирует персонализированный маршрут, включая интерактивные задания и викторины, что делает изучение города более увлекательным.
Важным шагом в развитии инфраструктуры стало открытие "умных" станций метро, оборудованных цифровыми экранами и бесплатным Wi-Fi. Туристы могут получить актуальную информацию о транспортной доступности, ближайших достопримечательностях и мероприятиях в режиме реального времени. Кроме того, новые станции предлагают удобные пространства для отдыха с зонами coworking и культурными выставками, что делает ожидание поезда приятным и познавательным.
Москва также продолжает развивать туристическую инфраструктуру. Построены новые гостиницы и хостелы, многие из которых предлагают уникальные концепции проживания, включая экологически чистые поступления и совместные пространства для общения. Также в столице активно развиваются пешие зоны и велодорожки, что позволяет туристам легче исследовать город и наслаждаться его атмосферой.
Согласно данным последнего опроса, 85% туристов отметили, что удобство передвижения и доступность информации о достопримечательностях значимо повышают качество их поездки. Городские власти уверены, что активное внедрение технологий и развитие инфраструктуры позволит Москве сохранить статус одного из самых привлекательных туристических направлений на мировом уровне.
"Мы стремимся сделать Москву доступной и комфортной для всех гостей, учитывая их нужды и желания. Инновации и качество обслуживания — наш главный приоритет", — прокомментировала начальник Департамента туризма Москвы.
С такими нововведениями Москва продолжает привлекать внимание путешественников со всего мира, предлагая им уникальный опыт и возможность насладиться богатой культурой столицы.
-
 @ ee90543f:9363457f
2024-12-26 13:41:14
@ ee90543f:9363457f
2024-12-26 13:41:1410 апреля — В столичном метрополитене стартовал запуск нового поколения экологически чистых поездов, разработанных с использованием инновационных технологий и альтернативных источников энергии. Эти поезда, работающие на водородных топливных элементах, обещают значительно сократить углеродные выбросы и повысить энергоэффективность системы.
Новая линия, которая соединит центр города с крупнейшими жилыми комплексами на окраинах, будет оснащена современными системами умного управления, которые позволят оптимизировать расписание и минимизировать время ожидания. Каждый поезд оборудован системой рекуперации энергии, что позволит повысить эффективность использования электроэнергии в целом.
По словам руководства Московского метрополитена, запуск этой линии — важный шаг в направлении устойчивого транспорта и улучшения качества воздуха в городе. "Мы стремимся создать комфортные условия для пассажиров и в то же время заботиться об экологии. Новые поезда не только ускорят путешествие по городу, но и сделают его более безопасным и приятным", — отметил директор метрополитена.
Также планируется расширение сети метро за счет новых станций, которые будут представлять собой не только транспортные узлы, но и культурные пространства с выставками, информационными центрами и общественными зонами. По ожиданиям властей, это нововведение привлечет больше жителей и гостей столицы, а также станет еще одной причиной для гордости москвичей.
-
 @ ee90543f:9363457f
2024-12-26 13:27:24
@ ee90543f:9363457f
2024-12-26 13:27:24В условиях стремительного развития технологий значимость так называемых «мягких» навыков, таких как умение общаться, работать в команде и проявлять критическое мышление, значительно возросла. Эксперты отмечают, что сегодня работодатели все больше ценят сотрудников, обладающих развитыми софт-скиллами, способными быстро адаптироваться к изменениям и предлагать нестандартные решения.
Согласно последним исследованиям, образовательные учреждения начали активно внедрять программы, направленные на развитие коммуникативных способностей, эмоционального интеллекта и других важных мягких навыков среди учащихся. Это связано с тем, что традиционные академические знания уже не могут обеспечить выпускникам успешную карьеру без умения эффективно взаимодействовать с коллегами и справляться с различными профессиональными вызовами.
«Интерактивные методы обучения, такие как проектная деятельность, ролевые игры и групповые обсуждения, помогают студентам развивать навыки, необходимые для работы в современных командах», — отмечает Мария Иванова, директор образовательного центра «Прогресс». Она подчеркивает, что такие подходы позволяют учащимся практиковаться в решении реальных задач, что готовит их к конкуренции на рынке труда.
Таким образом, современные учебные заведения трансформируются в площадки для комплексной подготовки будущих профессионалов, где наряду с теоретической базой студенты получают возможность развить важные практические компетенции. Развитие софт-скиллов становится основой для создания конкурентоспособных кадров, готовых успешно интегрироваться в динамичную рабочую среду.
-
 @ ee90543f:9363457f
2024-12-26 13:16:46
@ ee90543f:9363457f
2024-12-26 13:16:4620 июня в Москве были представлены амбициозные архитектурные проекты, которые кардинально изменили облик столицы. В рамках выставки "Город будущего" архитекторы и градостроители продемонстрировали свои шедевры для комфортной городской среды.
Помимо этого одним из ключевых проектов стал "Зеленый пояс Москвы", который захватывает обширные сети парков и зеленых зон, соединяющих различные районы города. Архитекторы уверены, что это не только улучшит качество воздуха, но и создаст новые пространства для отдыха и досуга горожан.
Также на выставке был представлен проект "Умный город", который включает в себя внедрение современных технологий в инфраструктуру. Это позволит оптимизировать транспортные потоки, улучшить систему освещения и повысить уровень безопасности на улицах. Не обошлось и без обсуждения новых жилых комплексов, которые уже начали строиться с учетом принципов устойчивого развития. Архитекторы акцентировали внимание на использовании экологически чистых материалов и энергоэффективных технологий.
Градоначальники и эксперты отметили, что эти проекты не только преобразят Москву, но и сделают ее более удобной для жизни, работы и отдыха. Следите за новостями, чтобы не пропустить дальнейшие обновления о будущем столицы!
-
 @ ee90543f:9363457f
2024-12-26 13:04:20
@ ee90543f:9363457f
2024-12-26 13:04:20В Москве продолжается активное внедрение передовых технологий, которые кардинально меняют повседневную жизнь москвичей. Умные дома, автономный транспорт и цифровые сервисы становятся неотъемлемой частью городской инфраструктуры.
Согласно последним данным, более 80% жилых комплексов в Москве оборудованы системами «умного дома», позволяющими жителям управлять освещением, отоплением и безопасностью через мобильные приложения. Это не только повышает комфорт, но и способствует экономии ресурсов.
Также, автономные электробусы и такси, которые курсируют по улицам города, обеспечивают безопасное и эффективное передвижение. Благодаря интеграции с городской системой управления движением, они минимизируют пробки и сокращают время в пути.
Кроме того, цифровые платформы для взаимодействия с городскими службами становятся всё более популярными. Москвичи могут легко сообщать о проблемах с инфраструктурой, записываться на прием к врачам и получать информацию о культурных событиях через единую мобильную платформу.
Эксперты отмечают, что такие изменения не только улучшают качество жизни, но и делают Москву более устойчивой и экологически чистой.
-
 @ ee90543f:9363457f
2024-12-26 12:52:59
@ ee90543f:9363457f
2024-12-26 12:52:59И вновь столица демонстрирует выдающиеся успехи в области инклюзии, внедряя инновационные подходы и программы, которые делают город доступным для всех его жителей. Местные власти активно работают над созданием среды, в которой каждый человек, независимо от своих возможностей, может полноценно участвовать в жизни общества.
Одним из ключевых направлений является развитие доступного общественного транспорта. Все новые автобусы и трамваи оборудованы специальными местами для людей с ограниченными возможностями. Это позволяет без труда передвигаться по городу и добираться до работы, учебы.
В образовательной сфере столица внедряет инклюзивные программы, которые обеспечивают равные возможности для детей с особыми потребностями. Школы активно сотрудничают с психологами и специалистами, чтобы создать индивидуальные образовательные планы, учитывающие потребности каждого ученика.
Культурные мероприятия также становятся более доступными. Музеи и театры предлагают специальные сеансы с субтитрами и жестовым переводом, что позволяет людям с нарушениями слуха и зрения наслаждаться искусством наравне с остальными.
Городские инициативы по инклюзии не остаются незамеченными. Множество организаций и активистов отмечают, что такие изменения способствуют созданию более сплоченного и дружелюбного общества, где каждый чувствует себя важным и нужным.
-
 @ ee90543f:9363457f
2024-12-26 12:52:19
@ ee90543f:9363457f
2024-12-26 12:52:19В Москве вступил в силу новый стандарт оказания медицинской помощи: С 26 декабря 2040 года в столице России начинает действовать новый стандарт медицинской помощи, который обещает кардинально изменить подход к здравоохранению и улучшить качество жизни москвичей. Персонализированная медицина: новый стандарт включает внедрение передовых технологий и искусственного интеллекта, что позволяет каждому жителю города получать доступ к персонализированной медицине с учетом индивидуальных особенностей организма. Анализ больших данных и генетическое тестирование помогут врачам заранее выявлять риски заболеваний и разрабатывать профилактические меры для каждого пациента. «Умные» медицинские устройства: Одним из ключевых нововведений является использование «умных» медицинских устройств, которые круглосуточно отслеживают состояние здоровья пациентов и передают данные врачам в режиме реального времени. Это позволит оперативно реагировать на изменения в состоянии здоровья и предотвращать серьезные заболевания до их проявления. Расширение возможностей телемедицины: В рамках нового стандарта значительно расширены возможности телемедицины. Теперь консультации с врачами можно получать не только по видеосвязи, но и с использованием голографических технологий, что делает общение более удобным и эффективным. Поддержка психического здоровья: Также в рамках нового стандарта активно развиваются программы поддержки психического здоровья. В каждом районе города открываются специализированные центры, где жители могут получить помощь психологов и психотерапевтов без необходимости долго ждать. По словам мэра Москвы Сергея Собянина, этот шаг стал важным этапом в развитии системы здравоохранения столицы и позволит обеспечить жителей качественными медицинскими услугами на уровне мировых стандартов.
-
 @ f3df9bc0:a95119eb
2024-12-26 12:29:35
@ f3df9bc0:a95119eb
2024-12-26 12:29:35Welcome! 🌱
Interesting places to start: - Latest polished pieces: [[Latest Articles Index]] - Index of all articles by discipline: [[Discipline Index]]
About this site
This site is both a blog & wiki-style digital garden. Some ideas you’ll run into here may be of quality, others will be less interesting, not fully formed, or even just straight wrong. This is intentional. Content here is continuously cultivated and refined as I live my life and gain new experiences, and I welcome challenges to anything I’ve written.
The general idea behind this is that my unstructured thought is fast and divergent, but not coherent, and therefore difficult to use in any practical way. The process of writing is a forcing function for taking divergent thought and bringing it into a form that can be reasoned about, improved upon, or discarded as irrelevant. Stalling this process is counter-productive and can lead to a sort of comatose where the mind is stuck in the abstract, waiting for confidence on a particular strain of thought, but never making any progress.
Therefore there is no set topic for this garden, instead it’s purpose is to serve as an auxiliary brain for any and all topics that I find interesting and worth spending time refining.
Contact
- nostr: slipstream@htlc.io
- farcaster: @htlc
-
 @ fd78c37f:a0ec0833
2024-12-26 11:51:07
@ fd78c37f:a0ec0833
2024-12-26 11:51:07The rise of Bitcoin and cryptocurrencies has not only changed the global financial landscape but also sparked innovation and development in communities worldwide. In particular, Asia, as a hub for technological innovation and economic growth, has seen multiple Bitcoin communities play a key role in driving the adoption and application of digital currencies. From educational programs to technical support, and from business promotion to policy advocacy, Bitcoin communities in Asia are pushing forward the use and development of Bitcoin across various fields. This article will focus on 20 Bitcoin communities in Asia, exploring their latest progress and future visions in promoting Bitcoin technology, education, and economic empowerment. It aims to provide readers with an in-depth perspective on the Asian Bitcoin ecosystem and its global impact. Thank you, YakiHonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.Bitcoin Indonesia * Introduction Bitcoin Indonesia is an international team of 21 Bitcoin enthusiasts dedicated to enabling the people, businesses, and government of Indonesia to easily access and use Bitcoin. The team's mission is to provide reliable Bitcoin information and educational resources to help Indonesians understand the value and potential of Bitcoin, especially in the digital economy. Through monthly meetups, an online education platform, and professional consulting services, Bitcoin Indonesia bridges the gap between individuals, businesses, and the government, connecting them to the world of Bitcoin. The goal is to educate 100 million Indonesians about Bitcoin by 2030, promoting prosperity and freedom for the nation. * Latest Updates Recently, the Bitcoin Indonesia community has been actively organizing a series of events focused on promoting and educating people about Bitcoin. In November, the community hosted the BitDevs Meetup, where they explored tools for planning Bitcoin inheritance. They also launched a Bitcoin price prediction giveaway to encourage user engagement. Additionally, the community successfully completed an online diploma course, certifying 38 local participants. They visited the Taruna Bakti Foundation in Bandung, Indonesia, introducing Bitcoin to 700 middle school students and inspiring them to join the Bitcoin community. Meanwhile, the community is gearing up for the upcoming Team Hackathon in January, where the winning team will receive a prize of 10,000,000 IDR.
2.Righshift nostr:npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5 * Introduction Right Shift is a community dedicated to becoming a hub for Bitcoin-related content and discussions. Its mission is to support the growing Thai Bitcoin community by curating and translating high-quality Bitcoin content, providing essential insights and knowledge for navigating the world of hard money. In addition to educational resources, Right Shift offers a curated selection of Bitcoin merchandise and plans to develop more impactful learning experiences in the future. As Bitcoin matures and evolves, the community is committed to driving Bitcoin adoption and a circular economy through its products and marketplace. * Latest Updates Recently, the Right Shift community has been actively promoting Bitcoin education and awareness through the #Siamstr initiative. They organized various live streams, discussions, and offline meetups in Thailand, such as the "Right Talk" series and the Korat101 gathering, focusing on Bitcoin philosophy, the "Value for Value" (V4V) concept, and utilizing platforms like Nostr to support Bitcoin creators. Additionally, the community has participated in several collaborative projects, developing Bitcoin-related tools such as savings devices and information relay services.
3.Neutronpay * Introduction Neutronpay is a community focused on empowering businesses and individuals through the use of the Lightning Network to enable borderless, open global finance. With cutting-edge technology, Neutronpay facilitates near-instant transactions, creating a real-time financial ecosystem that operates anywhere, anytime. The platform strives to make the Lightning Network accessible to everyone, from small business owners in rural Vietnam to multinational companies in New York. By eliminating barriers such as currency conversion, transaction fees, and time delays, Neutronpay transforms money into a bridge connecting people, businesses, and ideas. * Latest Updates Recently, Neutronpay has been actively expanding its Bitcoin and Lightning Network services, particularly in the Asia-Pacific region. They announced a strategic partnership with BitGo Singapore to further broaden their offerings. Neutronpay also expanded its payout capabilities to 16 countries, enabling fast and secure Lightning Payments conversion into local currencies. Additionally, they participated in the 2024 Vietnam Tech Impact event, showcasing their innovations in fintech and blockchain applications. These efforts demonstrate Neutronpay's commitment to enabling seamless financial transactions for businesses and consumers through the Lightning Network.
4.Tokyo citadel * Introduction Tokyo Citadel is a community built around the vision of creating a sovereign space for Bitcoin holders to thrive. Inspired by the idea of Bitcoin as a defense against economic collapse and societal unrest, the community aims to gather and educate new Bitcoin users in Tokyo. The concept draws from the notion that Bitcoin can serve as a protective barrier against inflation, government overreach, and authoritarian regimes. * Latest Updates Recently, the Tokyo Citadel community released several new podcast episodes covering topics such as Bitcoin, macroeconomics, and politics. They discussed subjects like “Meaningless Meetups in Mexico” and “The Ghost of Abe Will Pump Our Bags,” encouraging further discussion about the future of Bitcoin and global economics. Additionally, the community has been actively engaging with members through their Telegram discussion group, fostering exchanges on Bitcoin and related political and economic topics, while continuing to promote Bitcoin education and community building.
5.Bitcoin Beach Vietnam * Introduction Bitcoin Beach Vietnam is inspired by the Bitcoin Beach initiative in El Salvador, aiming to create a Bitcoin-friendly ecosystem in Vietnam. Powered by the Neutronpay Bitcoin Lightning app, it offers seamless VND on/off ramps for easy Bitcoin transactions. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to May 2024, when the Bitcoin Beach Vietnam community highlighted the impressive quality of Vietnamese products and their growing demand globally.
6.BOB space nostr:npub1j580xmzqdvqp8rsv04m562kkvfj6yvp226m97yc88q72cxekucesamh4up * Introduction BOB Space is a Bitcoin-focused incubator, coworking space, and hub located in the heart of Krung Thep, Thailand. The community supports Bitcoin education, adoption, and the advocacy of free technology. With a mission to foster innovation, BOB Space hosts a developer residency program aimed at empowering Bitcoin ecosystem developers. Weekly Bitcoin workshops, groundbreaking innovation talks, and technical events such as Bitdevs are organized to bring together like-minded individuals. Additionally, BOB Radio features discussions with Bitcoin builders from around the world, offering valuable insights into the ecosystem. * Latest Updates Recently, the BOB Space community hosted the 4Q2024 BitDevs event at the Bitcoin Learning Center in Chiang Mai, Thailand. The event featured a Socratic-style seminar, delving deep into Bitcoin scaling, with a particular focus on the applications, risks, and future developments of the Ark protocol. In addition, the community shared updates on Bitcoin developer meetups, including the event held in Chiang Mai, as well as a donation to the Bitcoin Development Fund.
7.The Bitcoin Learning Center nostr:npub1c9r9lad84kpqwnh09u58vdzwnfsnxcr7a40uf5ulkpdguq4667jsgaxu4k * Introduction The Bitcoin Learning Center in Chiang Mai is a leading educational hub, co-founded in 2022 by Jimmy Kostro and Napatsanun Chatchayaladasiri (Fai). The center is dedicated to promoting financial inclusion through Bitcoin and creating sustainable economic opportunities for underserved communities in northern Thailand. As a core program of the Kostro Foundation, the center focuses on Bitcoin-centered education, research, and infrastructure development to drive real-world impact. Its mission is to provide communities with the knowledge and tools needed to achieve economic independence through the transformative power of Bitcoin. * Latest Updates Recently, the community has been actively promoting Bitcoin-related projects with a strong focus on technical support and community engagement. A Bitcoin Christmas Party was held at the Bitcoin Learning Center in Chiang Mai to strengthen connections among Bitcoin users in the region. Additionally, in collaboration with BOB Space, the community donated Bitcoin mining machines to a remote solar-powered village in northern Thailand, helping local residents transform surplus energy into a source of income. Furthermore, the community organized a high-level Bitcoin meetup, bringing together 50 experienced Bitcoin enthusiasts from over 10 countries for in-depth discussions.
8.Bitcoiner Malaysia nostr:npub1x42vvsc96wcnnea38y7390hhgs7f6t8hk4rm08pwtt7stlav9avsv7j5rm * Introduction Bitcoin Malaysia is a pioneer in the country's Bitcoin space, established in 2012, dedicated to educating the public about Bitcoin and its applications through various events and resources. The community regularly hosts workshops, meetups, and both online and offline activities, offering opportunities for beginners and professionals to deepen their understanding. Additionally, it focuses on promoting blockchain technology locally, fostering a platform for knowledge sharing and collaborative innovation. * Latest Updates Recently, the Bitcoiner Malaysia community has been actively promoting Bitcoin education and fostering community engagement. On October 25th, they hosted their monthly meetup at My Espresso Café, where participants used the Lightning Network to purchase coffee or beer, connected with fellow Bitcoin enthusiasts, and explored ways Bitcoin can address societal challenges. Additionally, the community organized a Q&A session featuring renowned Bitcoin experts Saifedean Ammous and Stephan Livera. The discussion delved into key topics such as the comparison between fiat currency and Bitcoin, Bitcoin's role in the global economy, scalability, and lending within the Bitcoin ecosystem.
9.Bitcoin Association of Hong Kong * Introduction The Bitcoin Association of Hong Kong (BAHK), established in the summer of 2012, is dedicated to promoting and advancing Bitcoin and its related technologies in Hong Kong. The association’s mission is to educate the public, the private sector, and government entities about the benefits and risks of Bitcoin, becoming a reliable resource for the local and international Bitcoin communities. Over the years, BAHK has hosted more than 250 events and has built a network of over 5,000 members, including experts from over 30 countries. The association regularly organizes meetups, workshops, and online events to foster collaboration and interaction among Bitcoin enthusiasts and professionals. * Latest Updates Recently, the Bitcoin Association of Hong Kong has been actively promoting Bitcoin and cryptocurrency-related topics. They hosted a Bitcoin meetup on November 21, attracting Bitcoin enthusiasts and developers who engaged in discussions about cryptocurrency and its applications while splitting bills using Bitcoin or the Lightning Network. The association has also focused on significant developments such as the attitudes of central banks toward Bitcoin, the Hong Kong government's licensing of cryptocurrency exchanges, and the reaction of Chinese funds to the Bitcoin boom.
10.Bitcoin Embassy Tel Aviv * Introduction Bitcoin Embassy TLV is a grassroots initiative aimed at providing a space for the community and Bitcoin enthusiasts to engage in discussions about decentralized digital currencies. The embassy organizes various events and projects to foster collaboration and knowledge sharing. Founded by Ayal Segev, a core member of the Israeli Bitcoin community, the embassy also involves participants such as programmer and security expert Gil Assayag, and Bitcoin promoter Assaf Bahat. The embassy's mission is to encourage exploration and innovation in the cryptocurrency space. * Latest Updates Recently, the Bitcoin Embassy has been active with various events and updates. On December 8th, they successfully hosted a celebration in Tel Aviv to mark their 11th anniversary, featuring balloons, music, and cake, which brought together many community members in a festive atmosphere. Additionally, the community shared updates about its white paper, which was released on October 31st, showcasing its ongoing efforts to promote interaction and knowledge-sharing within the Bitcoin community.
11.Bitcoin Harbour nostr:npub1aj4z0w4v5ggv8kl6kde5lsqw2jpca296gd60ns3ys9vlwpahx9qqktn9an * Introduction Bitcoin Harbour is located in Princess Harbour, Johor, Malaysia, just a stone's throw from Singapore, strategically positioned in Southeast Asia. Guided by the principles of low time preference and proof of work, the community is dedicated to creating an inclusive Bitcoin coastal hub—a perfect setting for life, work, and family. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to Aug 2024, an event announcement has been posted for the community's monthly meetup on September 27 at Restoran Arab Zaatar in Puteri Harbour, Johor, Malaysia. The theme is “Post-Summer Meetup,” offering Bitcoin enthusiasts a chance to connect and engage.
12.Bitcoin Island Philippines * Introduction Bitcoin Island is a community based in Boracay, Philippines, dedicated to promoting the adoption of Bitcoin and the Lightning Network in the local area. The community's core mission is to encourage merchants to accept Bitcoin payments, creating a Bitcoin-based economic ecosystem that allows residents and visitors to enjoy fast, secure, and low-cost payment experiences. * Latest Updates Recently, the community has shared one update,posted featuring a promotional tagline from Pouch.ph,Empowering the Philippines through Bitcoin: Secure, Trusted, and Principled.
13.Bitcoin Powerhouse Phuket * Introduction Bitcoin Powerhouse Phuket is a Bitcoin community based in Phuket, Thailand, dedicated to promoting the application and education of Bitcoin in the local area. The community regularly hosts meetups and events, inviting both Bitcoin enthusiasts and newcomers to engage, share experiences, and exchange insights. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to Aug 2024, when they announced the 11th Bitcoin meetup in Phuket, scheduled for September 10 at Nakarin in Kathu.
14.Bitcoin Saigon nostr:npub192chqkpxm7lfrgufmfd9a9lj7u54078zdzgtvtgz4yg7smz0e7wqzfswzg * Introduction Bitcoin Saigon was founded by Diana Ngo, Khoa Tran, and Dominik Weil. The community has hosted over 100 events and meetups, bringing together Bitcoin enthusiasts, developers, researchers, and investors. Bitcoin Saigon aims to build a strong local network of Bitcoin supporters, businesses, and developers, fostering education, innovation, and creating job opportunities in the Bitcoin ecosystem. * Latest Updates Recently, Bitcoin Saigon has been actively preparing for the Satoshi Flea Market - Christmas Edition, set to take place in Saigon on December 8, and is calling for donations in the form of sats for the event. The community is also focusing on the first Bitcoin meetup in Hanoi on December 11, where topics on Bitcoin and Austrian economics will be discussed.
15.Dubai Citadel * Introduction Dubai Citadel is a Bitcoin-only community in the UAE, focused on promoting Bitcoin adoption and fostering a strong, decentralized ecosystem. With Dubai's growing role as a hub for cryptocurrency innovation, the community aims to connect Bitcoin enthusiasts, developers, and investors. * Latest Updates Recently, there have been no new updates from the community.The latest event dates back to Oct 2024, when it was shared that the UAE has removed the VAT on #Bitcoin transfers and exchanges.
16.Seoul Bitcoin Meetup * Introduction Seoul Bitcoin is a community that hosts monthly Bitcoin meetups, offering education and technical support, especially for beginners. The meetups are organized by volunteers and focus on Bitcoin technology rather than trading or investing, aiming to share enthusiasm and knowledge about Bitcoin. In addition to regular meetups, the community conducts educational activities via platforms like YouTube, Twitter, Facebook, and Kakaotalk, and provides weekly technical meetups for those interested in a deeper understanding. * Latest Updates Recently,there have been no new updates from the community.The latest event dates back to may 2024, when it was announced that the Utreexo test version was released on GitHub, and the publisher mentioned syncing their archive node on a Raspberry Pi 0 .
17.NZBitcoiners nostr:npub1dtvk6tcay9drd7n7x25vl3h30eu6e590qwlysyan03pepvglc7jsupqwt2 * Introduction NZBitcoiners, after being banned from all crypto/blockchain groups in New Zealand, started a few Bitcoin-only groups to create a focused space for Bitcoin education and community building. These groups aim to foster meaningful discussions, share knowledge, and support the growth of the Bitcoin ecosystem in New Zealand, free from the distractions of other cryptocurrencies. * Latest Updates Recently, NZBitcoiners has been actively involved in organizing events and discussions related to Bitcoin and local governance. The community promoted the upcoming “Business Blueprint” event in Auckland and plans to participate in Bitcoin Week discussions scheduled for February next year. Additionally, they engaged in promoting local meetups, including gatherings at venues like Urbanaut Brewing Co. in Auckland, and continued to share thoughts on New Zealand's political landscape and the importance of Bitcoin for financial sovereignty.
18.Melbourne Bitcoin Only * Introduction Melbourne Bitcoin Only is a community focused solely on Bitcoin, excluding altcoins, ICOs, or “blockchain projects.” It aims to provide a space for learning and discussing Bitcoin-related topics. Whether you are a beginner or an experienced participant, the community is dedicated to education and fostering discussions about Bitcoin's technology, principles, and its role in the financial ecosystem. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to August 2023, when a post was shared about the Bitcoin Jungle Carnival held at the RSL Hall in Murrurundi.
19.Bitkiwi * Introduction Bitkiwi is New Zealand's leading Bitcoin community, publishing The Bitkiwi Brief to provide subscribers with the latest Bitcoin news and analysis. Their mission is to promote the adoption and understanding of Bitcoin in New Zealand, helping community members gain a deeper understanding of Bitcoin's technological, economic, and social impacts. * Latest Updates Recently, the Bitkiwi community has been releasing several editions of the Bitkiwi Brief, offering a New Zealand perspective on the latest Bitcoin news. They have also explored Bitcoin-related books, nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu Check Your Financial Privilege, and shared updates on #BitkiwiXII. Additionally, Bitkiwi provided in-depth analysis on Bitcoin's value and the impact of currency devaluation, while continuing to promote the revolutionary ideas of Bitcoin, emphasizing its equality and decentralization.
20.Bitcoin Sydney * Introduction Bitcoin Sydney is a vibrant community focused on bringing together Bitcoin enthusiasts through talks, educational events, and social meetups. Monthly Bitcoin-themed talks feature industry experts, while regular “After Work Drinks” offer informal networking opportunities. The community also hosts online “Socratic Seminars” with renowned Bitcoin developers for in-depth discussions. Whether you're a beginner or an experienced participant, Bitcoin Sydney provides a platform for learning, sharing, and connecting. * Latest Updates Recently, the community has shared an update, which hosted a Q&A session with local legends nostr:npub1qh5sal68c8swet6ut0w5evjmj6vnw29x3k967h7atn45unzjyeyq6ceh9r, nostr:npub1nul4qg8he2dyn3hsyk4a3vcr963vakskyjp43yv9dy7j9frd7yhqh28x3m, and discussed the impact of a Bitcoin-supportive White House and the resulting bull market.
-
 @ 16d11430:61640947
2024-12-26 11:31:05
@ 16d11430:61640947
2024-12-26 11:31:05For centuries, financial markets have been shackled by an archaic mindset rooted in Newtonian physics: "What goes up must come down." This belief has dominated the thinking of old-school fiat economists, who view the rise and fall of markets as a natural cycle of gravity-bound economics. But Bitcoin, the digital phoenix, was designed to defy this outdated paradigm. It isn't just an asset class or a currency—it's a revolution in financial physics, unshackling value from centralized control and rewriting the rules of money.
The Fiat Fallacy: Gravity Economics
Fiat systems are inherently cyclical, prone to inflation, manipulation, and collapse. Central banks print money endlessly, causing value to "come down" as purchasing power erodes. For fiat thinkers, this is unavoidable—a gravitational force they accept as immutable. Yet this mindset ignores Bitcoin’s game-changing properties: its hard cap of 21 million coins, decentralized consensus, and permissionless architecture.
Bitcoin is fundamentally non-Newtonian. It doesn’t adhere to traditional financial laws because it isn't bound by the same forces of supply and control. Instead, it operates in a new paradigm: deflationary, transparent, and immune to political meddling.
Bitcoin's Escape Velocity
Bitcoin's dominance lies in its ability to achieve escape velocity. Unlike fiat currencies, which are constantly being pulled back by inflationary policies, Bitcoin is propelled by its scarcity, adoption, and network effects. Every halving event tightens the supply, creating an upward pressure that fiat systems can't replicate. And as global trust in traditional systems erodes, Bitcoin's gravitational pull grows stronger.
This phenomenon is evident in the adoption curve. Institutions, governments, and individuals worldwide are recognizing Bitcoin as a superior store of value, an inflation hedge, and the ultimate form of financial sovereignty. The more participants enter the network, the more its value compounds, creating a virtuous cycle of exponential growth.
Humiliating the Old Guard
The fiat establishment—steeped in centuries of centralized control—has long dismissed Bitcoin as a bubble, a fad, or even a Ponzi scheme. Yet, year after year, Bitcoin rises from the ashes of their predictions. Its resilience, transparency, and provable scarcity expose the fragility and corruption of fiat systems.
The ultimate humiliation for fiat thinkers is Bitcoin's ability to thrive in crises. Where traditional systems falter—be it through hyperinflation, bank failures, or geopolitical instability—Bitcoin becomes a lifeboat. It doesn’t just resist gravity; it flips the entire script. Fiat currencies are revealed as infinite-print illusions, while Bitcoin’s immutable ledger stands as the ultimate arbiter of truth and value.
A New Financial Paradigm
Bitcoin’s ascent is not merely about price; it’s about domination. It represents a shift from centralized control to individual empowerment, from opaque systems to transparent protocols, from inflationary theft to deflationary savings. It’s a financial singularity, an escape from the gravitational pull of outdated thinking.
As Bitcoin continues its trajectory, the old world of "what goes up must come down" will look increasingly absurd. In its place, a new principle will reign: what’s decentralized cannot be stopped. Bitcoin isn’t just leaving Earth’s orbit; it’s becoming the financial universe’s North Star.
So buckle up, because Bitcoin isn’t just going up—it’s transcending. And as it does, it will leave the Newtonian thinkers in the dust, staring in disbelief at the rocket that left them behind.
-
 @ c5fede3d:16e03f7b
2024-12-26 11:30:39
@ c5fede3d:16e03f7b
2024-12-26 11:30:39Se acaba 2024 y el año nuevo asoma, es hora de hacer valoraciones y rendir cuentas. ¿Has cumplido los própositos que te marcaste al iniciar el año? ¿Éxito rotundo o fracaso estrepitoso? En el mundo de las criptomonedas, desde luego, que no hay término medio. Ya lo dicen muchos, o Lambo o Puente. ¿Y tú, en qué lado estás?
En esta serie de artículos semanales iré actualizando mi visión sobre el mundo crypto. Concretamente aportaré unas cuantas pinceladas sobre, lo que considero, el portafolio ideal. Las criptomonedas, con sus más y sus menos, han supuesto una revolución en el mundo de las finanzas. Aunque en sus inicios eran vistas como un arma revolucionaria, ahora, con la entrada del gran capital, se ha tratado de institucionalizarlas y ponerlas al servicio del poder global. Que no os engañen, el principal logro ha sido la descentralización de las finanzas, la socialización de la economía particular, la entrega de las llaves de la caja fuerte a su titular, y la consiguiente pérdida de fuerza de los custodios, usureros y demás calaña.
EL PRIMER PASO🚶
Teniendo las ideas claras, es hora de ir estructurando la cartera. Esta es la parte más importante, porque aquí no se empieza la casa por el tejado, en este artículo estamos en la fase de adquisición del terreno, aún falta por llamar a Manolo y Benito para que empiecen con la faena.
Lo primero que tienes que hacer es mirarte al espejo y definirte qué tipo de inversor quieres ser. ¿Vas a hacer muchas transacciones buscando el pelotazo del año entrando de lleno en el mundillo? ¿O prefieres comprar alguna moneda sin interactuar con nada y nadie y a esperar a que suba? Tengo un artículo que habla de ello. Una vez sepas quién eres, debes elegir tu billetera electrónica de confianza, la que siempre te acompañará. Aquí tienes dos opciones, las billeteras calientes y las frías. ¿Diferencias? Aquí te dejo una tabla comparativa generada por Perplexity AI.
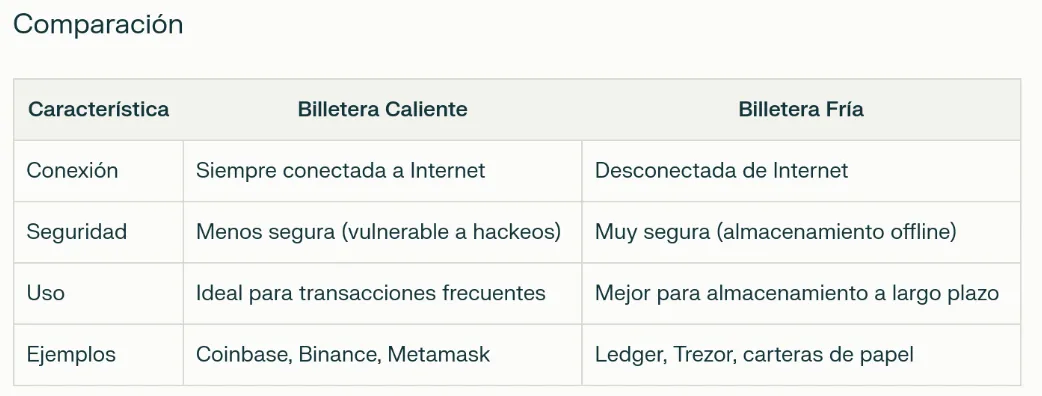
En resumidas cuentas, la billetera fría es para guardar activos y no tocarlos, como si fuera una reserva de oro, sin interactuar con nada ni con nadie. Además, es un dispositivo, un hardware físico donde tú serás el custodio. Ese es su propósito principal y único. Mi recomendación es la billetera de Keystone o la de BitBox. Por otra parte está la billetera caliente, mi preferida, pues con ella tienes la libertad para hacer lo que te venga en gana, es el ticket de entrada al mundo crypto, y además completamente gratuito. Aquí va una recomendación más personalizada, y es que da más seguridad operar con billeteras calientes vinculadas a una red concreta. Ya lo irás viendo, de entrada, lo ideal es tener Rabby wallet como extensión de navegador web y Safepal como app móvil.
GUARDA TU CLAVE PRIVADA 🔐

El momento más importante. Esta es la gran diferencia entre las finanzas tradicionales y la nueva economía. No me detendré en aspectos técnicos relacionados con la tokenización de las finanzas, los contratos inteligentes y demás parafernalia del estilo, lo principal es que entiendas que eres el custodio de tu cuenta billetera, que el banco ha quedado obsoleto y no tienes que delegar ante nadie. Por tanto, eres quien debe garantizar la seguridad de tus activos. ¿Cómo hacerlo? Tienes varios métodos.
Al crear la billetera te habrá pedido que introduzcas una contraseña, que te valdrá para acceder a la extensión, o tu huella biométrica para entrar en la app móvil. Pues esa contraseña es el primer candado de la puerta, queda el más importante, la frase semilla, o como me gusta llamarla, la llave maestra. Atiende a esta definición:
Una frase semilla, también conocida como frase de recuperación o frase mnemotécnica, es un conjunto de palabras que se utiliza como clave para acceder y recuperar una billetera de criptomonedas. Generalmente, consta de entre 12 a 24 palabras generadas aleatoriamente durante la configuración de la billetera.
Es absolutamente indispensable que guardes a buen recaudo tu frase semilla y no la compartas a nadie. Apúntala en un papel o ingéniatelas para guardarla, siempre offline. Se usa principalmente para recuperar la billetera o migrarla a otro dispositivo. No se utiliza para loguearte en sitios, ni tampoco para compartir tu dirección.
UN VISTAZO A LA WALLET 💳
Teniendo claro esto, adjunto un esquema sobre los aspectos básicos de una billetera, en esto caso SUI Wallet. Elaborado por el usuario de X, Fosky68.
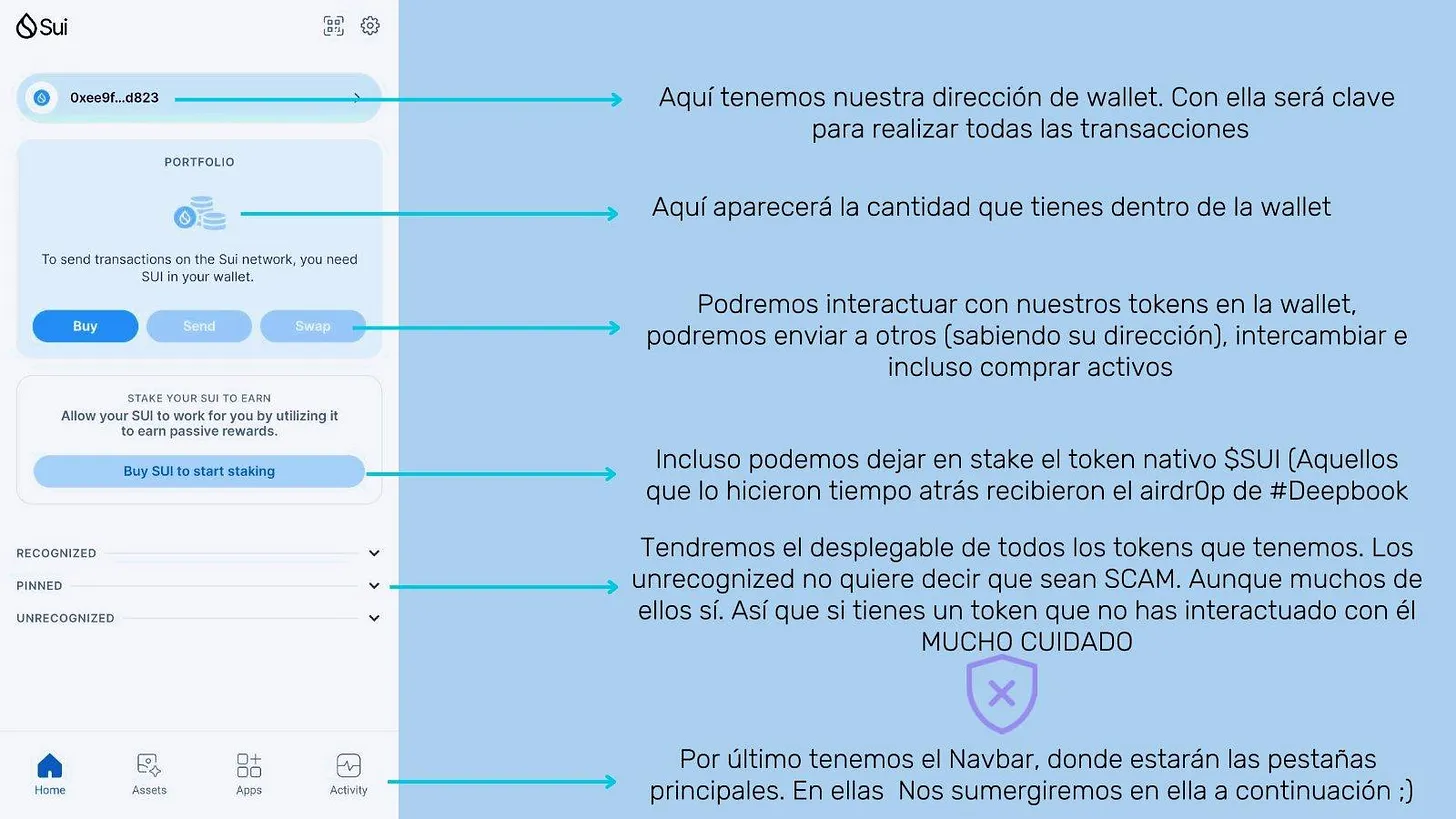
Quédate con estos puntos fundamentales:
- La dirección que suele empezar por 0x y una barbaridad de números es tu clave pública. Con ella recibirás fondos y la compartirás a webs y demás usuarios. También puedes adquirir una identidad que enmascara esa dirección, por ejemplo (perico.eth) a través del servicio ENS.
- El portafolio es donde tienes las monedas que has ido adquiriendo. ¿Quieres intercambiar una moneda por otra? Eso se llama swap. Ya lo irás viendo.
- Las redes soportadas, son lo que se conocen como Blockchain, las monedas pueden alojarse en múltiples redes, cada una con sus reglas y sus comisiones de uso, puedes encontrarte $ETH en redes como Optimism, Base o la propia red de ETH. Por eso es fundamental comprobar qué red vas a utilizar, o en que red está alojada la moneda si vas a realizar una operación. ¿Puedes cambiar la moneda entre redes distintas? Sí, se llama hacer un bridge. Pronto, sabrás más de ello.
- Podrás encontrarte otras funciones adicionales, como un historial de transacciones donde habrá un registro de todas las operaciones que has realizado, o el apartado DeFi (Finanzas Descentralizadas) donde te ofrecerán todas las herramientas para operar y verás el estado de tus inversiones.
Teniendo estas nociones básicas, he de felicitarte. Enhorabuena, ya has construido los cimientos de la casa. En el próximo artículo de Semanario Crypto, aprenderás a sortear obstáculos para fondear tu billetera, a cruzar la línea que separa al mundo real del virtual, a ser parte del nuevo orden. Bienvenido al mundo crypto.
Descargo de responsabilidad: Toda la información compartida forma parte de mi visión personal y no tiene como objetivo asesorar financieramente. Doy información, no consejos de inversión.
-
 @ e356a30c:11e846f7
2024-12-26 10:51:43
@ e356a30c:11e846f7
2024-12-26 10:51:43Bitcoin's performance during the Christmas season has been a mixed bag, with both Santa Claus rallies and Grinch-like plunges. While the cryptocurrency's volatility can be attributed to various factors, including global economic conditions and regulatory developments, historical data reveals some interesting trends.
During bullish market cycles, Bitcoin has often experienced a "Santa Claus rally" in the weeks leading up to and following Christmas. This phenomenon is characterized by increased buying activity and a surge in prices, potentially driven by holiday bonuses and a general sense of optimism. For instance, in 2020, Bitcoin surged by a remarkable 25.63% during the 52nd week, coinciding with the Christmas period.
However, bear markets have historically brought notable price declines for Bitcoin during the festive season. Reduced trading volume and increased volatility due to holiday-related market closures can exacerbate price swings. In 2022, for example, Bitcoin experienced a significant decline during the Christmas period, mirroring the broader crypto market downturn.
Looking ahead, analysts are cautiously optimistic about Bitcoin's prospects during the upcoming Christmas season. While the cryptocurrency's price remains susceptible to market fluctuations, a combination of positive regulatory developments and a potential economic recovery could fuel a Santa Claus rally. However, the ongoing bear market and geopolitical uncertainties pose significant challenges.
Ultimately, Bitcoin's performance during the Christmas season is contingent on a confluence of factors. While historical trends offer valuable insights, it is crucial to exercise caution and conduct thorough research before making any investment decisions.
bitcoin #Naija
-
 @ 88cc134b:5ae99079
2024-12-26 10:40:52
@ 88cc134b:5ae99079
2024-12-26 10:40:52Hello 1
Hello 2
Hello 3
Hello 4
Hello 5
Hello 6
This is a test by nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf that is testing various interoperability of the markdown rendering and NOSTR specific synatx, just to make sure they play nice.
nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf
npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf
nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf
here is a link to somewhere so as to see how it would render and here it is bare-bone https://duckduckgo.com/ just to make sure it is nicely parsed.
here is a mention of another article nostr:naddr1qvzqqqr4gupzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqqxnzde38qmnsdfk8qmrqwp405km0k and here is a short note: nostr:note1vnqnwzjllzxxufg5e9thz2xspetlplsjq0cn570jswujnmynxjnqmea576
and another one: nostr:note1kyrnyan4hfpn978akv2eqsv8r7rlplaq4j65uxlk3hz5ujk7ehzshwtfmd
and one more foe good mesure: nostr:note1dyrd05nt0tapgye3xn4nssfdasskfr3dm2yqz8e8vdtslpgw3ypsa8e7fh
one like this: note1dyrd05nt0tapgye3xn4nssfdasskfr3dm2yqz8e8vdtslpgw3ypsa8e7fh
here is an event: nostr:nevent1qqsg39vpzl4dz8kwnaerheuavgtqgg6exc4caz8argh6p6jqg549ppqprdmhxue69uhhyetvv9ujuam9wd6x2unwvf6xxtnrdakj7hknh7l
Images

and here is one in the middle of the text
 that continues right after. Just to see how this will render
that continues right after. Just to see how this will renderSome markdown stuff
Emphasis
This is bold text
This is bold text
This is italic text
This is italic text
~~Strikethrough~~
Blockquotes
Blockquotes can also be nested...
...by using additional greater-than signs right next to each other...
...or with spaces between arrows.
Lists
Unordered
- Create a list by starting a line with
+,-, or* - Sub-lists are made by indenting 2 spaces:
- Marker character change forces new list start:
- Ac tristique libero volutpat at
- Facilisis in pretium nisl aliquet
- Nulla volutpat aliquam velit
- Very easy!
Ordered
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
-
Integer molestie lorem at massa
-
You can use sequential numbers...
- ...or keep all the numbers as
1.
Start numbering with offset:
- foo
- bar
Code
Inline
codeIndented code
// Some comments line 1 of code line 2 of code line 3 of codeBlock code "fences"
Sample text here...Syntax highlighting
js var foo = function (bar) { return bar++; }; var veryVeryVeryLongVariableNameWithALongValueAsWell = 123456789012345678901234567890; console.log(foo(5));Tables
| Option | Description | | ------ | ----------- | | data | path to data files to supply the data that will be passed into templates. | | engine | engine to be used for processing templates. Handlebars is the default. | | ext | extension to be used for dest files. |
Right aligned columns
| Option | Description | | ------:| -----------:| | data | path to data files to supply the data that will be passed into templates. | | engine | engine to be used for processing templates. Handlebars is the default. | | ext | extension to be used for dest files. |
[Footnotes]
Footnote 1 link[^first].
Footnote 2 link[^second].
Duplicated footnote reference[^second].
[^first]: Footnote can have markup
and multiple paragraphs.[^second]: Footnote text.
- Create a list by starting a line with
-
 @ 79a7270b:d61d9067
2024-12-26 09:16:59
@ 79a7270b:d61d9067
2024-12-26 09:16:59Fifteen years after its creation, Bitcoin continues to break paradigms and solidify its role in the global economic landscape. In 2021, El Salvador adopted it as legal tender, marking a significant turning point. Three years later, its acceptance has advanced considerably, with Wall Street embracing Bitcoin ETFs and U.S. political debates focusing on its adoption as a strategic reserve.
With its portability, scarcity, accessibility, and liquidity in a 24/7 open market, Bitcoin distinguishes itself as an asset that transcends the limitations of traditional resources like gold and oil. Unlike these assets, which often face logistical challenges and market constraints, Bitcoin’s digital nature allows for seamless global transactions without physical barriers. Its scarcity mirrors that of gold, preserving its value over time, while its accessibility and round-the-clock liquidity make it an appealing choice for investors and policymakers alike. This unique combination of attributes positions Bitcoin as a versatile and strategic tool, increasingly relevant to advancing national interests in a rapidly digitizing world.
The expansion of the BRICS block, whose combined GDP now surpasses that of the G7, has heightened pressures on Western hegemony. These countries are exploring Bitcoin as a neutral and government-independent currency. They are considering denominating international transactions in Bitcoin as part of their broader goal: to create a de-dollarized, independent financial system resilient to Western-imposed sanctions.
Game theory sheds light on how Bitcoin adoption creates powerful incentives for nations. If the BRICS use Bitcoin as a strategic asset, Western nations would be compelled to accumulate it to influence the market and counteract sanctions circumvention, making Bitcoin critical for national security. In a scenario where major powers hold Bitcoin, it would be unfeasible to remain competitive without it.
This logic extends to Bitcoin mining, the process that validates transactions. By deciding what is confirmed, nations dominating mining operations gain significant influence over transaction flows. Consequently, Bitcoin-accumulating countries will prioritize investing in domestic mining infrastructure, enhancing the network's decentralization and security. For instance, Russia reportedly funds regional initiatives to develop AI and Bitcoin mining infrastructure within the BRICS framework through its Sovereign Wealth Fund.
This dynamic triggers a chain reaction: as one nation adopts Bitcoin, others are pressured to follow suit to avoid competitive disadvantages. This cycle embodies the essence of game theory, where each player's choices shape the strategies of others, positioning Bitcoin as a critical asset in the global geopolitical arena.
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 16d11430:61640947
2024-12-26 05:14:31
@ 16d11430:61640947
2024-12-26 05:14:31Throughout history, monumental structures like the Hindu temples of India and the cathedrals of Rome have stood as testaments to their societies' wealth, power, and cultural identity. Yet, their grandeur also tells a more intimate story—that of the immigrant professionals whose skills and labor transcended borders to fuel these marvels. From Indian artisans traveling across Asia to European guildsmen working on Gothic cathedrals, the contributions of immigrants have shaped the shifting poles of economic and cultural productivity.
India: Temples Built by Hands From Afar
Global Trade and the Diaspora (200 BCE–1200 CE) Hindu temples such as those at Khajuraho and Thanjavur were not just spiritual hubs but also centers of economic power. The intricate carvings and towering gopurams were the work of migrant artisans, who brought techniques and styles from distant lands.
Indian merchants and craftsmen, driven by the flourishing trade along the Silk Road and Indian Ocean, carried their skills abroad. They influenced architecture as far as Angkor Wat in Cambodia and Borobudur in Indonesia. The temples in these regions are evidence of the Indian diaspora’s role in spreading not just goods but also cultural and technical expertise.
Immigrants Within India The Chola Empire, for instance, employed skilled Tamil architects and migrant artisans from North India. These professionals created masterpieces like the Brihadeeswarar Temple. Their stories are often lost in history, overshadowed by royal patronage.
Rome and Europe: The Rise of the Cathedrals
From Local Guilds to Cross-Border Collaboration (1000 CE–1500 CE) During Europe’s Gothic and Renaissance periods, monumental cathedrals became symbols of growing urban wealth and religious devotion. Immigrant artisans and professionals played a pivotal role in these projects.
Example: The construction of Florence's Duomo involved Filippo Brunelleschi, whose inspiration came from travels to Rome and study of ancient ruins, but also relied on migrant laborers from Northern Europe.
Guilds in medieval Europe frequently recruited craftsmen from neighboring regions. Stonemasons from France worked on Canterbury Cathedral in England, and German glassmakers brought stained-glass techniques to Italy.
Economic Mobility Through Migration These artisans often traveled for better wages and opportunities, their expertise in demand due to Europe’s growing urban centers. Immigrant professionals thus fueled the architectural and economic revival of medieval Europe.
The Americas: Migrants and Monument Builders
Pre-Columbian Contributions (200 CE–1500 CE) In the Americas, monumental structures like Mayan temples and Inca fortresses were built with the knowledge and labor of diverse ethnic groups within these empires. The movement of professionals across regions—such as engineers, astronomers, and masons—helped unify these civilizations.
Post-Columbian Transformations After the European conquest, immigrant labor shifted dramatically. African slaves and European settlers were forcibly moved or incentivized to migrate. The resulting blending of skills and techniques reshaped the Americas. For instance, Jesuit missionaries employed indigenous and African artisans to build churches that combined European and native designs.
Africa: Trade, Temples, and Immigrant Networks
Architects of Prosperity (700 CE–1600 CE) Timbuktu’s mosques and the Great Zimbabwe ruins demonstrate the influence of immigrant professionals. Goldsmiths, architects, and traders traveled across the Sahara, linking North Africa to Sub-Saharan Africa.
The Malian Empire recruited scholars and architects, such as those from Andalusia, to design mosques like Djinguereber. These immigrants brought innovations in mud-brick construction, a technique that still defines the region's architecture.
Colonial Disruption European colonization led to the displacement of local professionals. African labor was exported, and immigrant expertise was replaced with exploitative systems that extracted resources rather than building cultural or architectural heritage.
Comparative Timeline: Immigrant Contributions Across Regions
Lessons from Immigrant Professionals
-
Adaptation and Fusion Each wave of migration brought new techniques that were adapted to local contexts. Immigrant professionals blended their expertise with local traditions, creating unique architectural styles.
-
Economic Catalysts Migrants were often drawn by economic opportunities. Their contributions not only elevated architecture but also stimulated local economies, from temple town markets to cathedral cities.
-
Disruption and Resilience Colonialism and conquest frequently disrupted these networks. Yet, immigrant professionals often found ways to rebuild and adapt, preserving their skills for future generations.
Modern Reflections
Today, immigrant professionals continue to be the backbone of global productivity. From the tech hubs of Silicon Valley to architectural marvels in Dubai, their stories echo those of the artisans who built Hindu temples, Roman cathedrals, and pre-Columbian pyramids. Understanding their historical impact offers a nuanced appreciation of how migration shapes our world.
References
-
Pollock, S. "The Language of the Gods in the World of Men: Sanskrit, Culture, and Power in Premodern India."
-
Spiro Kostof, "A History of Architecture: Settings and Rituals."
-
Kenneth R. Hall, "Maritime Trade and State Development in Early Southeast Asia."
-
Robert Bork, "The Geometry of Creation: Architectural Drawing and the Dynamics of Gothic Design."
-
Toby Green, "A Fistful of Shells: West Africa from the Rise of the Slave Trade to the Age of Revolution."
-
Charles Mann, "1491: New Revelations of the Americas Before Columbus."
These references provide deeper insights into the interplay of migration, economics, and monumental architecture across centuries.
-
-
 @ 50041f6c:cb61480b
2024-12-26 03:40:20
@ 50041f6c:cb61480b
2024-12-26 03:40:20Choosing the right carpet for your home is more than just a design decision; it’s an investment in comfort, functionality, and long-term value. Carpets serve as the foundation for your living spaces, providing warmth, style, and a sense of coziness. However, not all carpets are created equal. Factors such as material, durability, and maintenance requirements can significantly impact the performance and lifespan of your carpet. In this guide, we’ll explore how to choose the right carpet based on quality and durability, ensuring it meets both your aesthetic and practical needs.
Understanding Carpet Quality The quality of a carpet is determined by several key factors, each playing a role in its overall appearance, performance, and lifespan. When shopping for a carpet, keep these features in mind:
- Fiber Type The type of fiber used in a carpet is one of the most important indicators of its quality. Common carpet fibers include:
Nylon: Known for its durability, resilience, and stain resistance, nylon is an excellent choice for high-traffic areas. Polyester: This fiber is soft, affordable, and available in a wide range of colors, though it’s less durable than nylon. Olefin (Polypropylene): Resistant to moisture and stains, olefin is a good option for outdoor or basement carpeting but may not hold up well under heavy foot traffic. Wool: A natural and luxurious fiber, wool offers exceptional softness and durability but requires more maintenance and is more expensive than synthetic options. 2. Pile Density Pile density refers to how closely the fibers are stitched together. Denser carpets are typically more durable and resistant to wear. To test pile density, bend the carpet sample; if you can see the backing, the carpet may not be dense enough for high-traffic areas.
-
Twist Level The twist level refers to how tightly the carpet fibers are twisted. Higher twist levels indicate better durability, as the fibers are less likely to unravel or mat over time.
-
Backing and Construction The backing of a carpet provides its foundation and contributes to its stability. High-quality carpets often have a strong backing and use advanced construction techniques to enhance durability.
Choosing the Right Carpet for Your Needs Different areas of your home require carpets with specific qualities to match their function and traffic levels. Here’s how to select the best carpet for each space:
-
Living Room The living room is often a high-traffic area, making durability a top priority. A nylon carpet with a dense pile is a great choice, offering resilience and resistance to stains and wear. Consider neutral tones or patterns that hide dirt and complement your décor.
-
Bedrooms In bedrooms, comfort and softness take precedence. Plush or frieze carpets made from polyester or wool can add a touch of luxury while maintaining a cozy atmosphere. Since bedrooms are typically low-traffic areas, you have more flexibility with fiber choice.
-
Hallways and Stairs Hallways and stairs endure heavy foot traffic and require carpets that can handle wear and tear. Choose a durable, low-pile carpet with a high twist level, such as nylon or olefin. Adding a durable underpad can also extend the life of the carpet in these areas.
-
Basements For basements, moisture resistance is key. Opt for olefin or polyester carpets with a low pile to prevent mold and mildew. Carpets with built-in stain and moisture protection are ideal for these spaces.
Factors That Affect Carpet Durability Durability is a critical factor when choosing a carpet, as it determines how well the carpet will perform over time. Consider these elements:
-
Foot Traffic High-traffic areas require carpets made from resilient fibers like nylon or olefin. Look for carpets labeled as “heavy-duty” or “high-traffic” to ensure they can withstand constant use.
-
Maintenance Requirements Carpets that are easier to clean and maintain tend to last longer. Stain-resistant treatments and fibers that repel dirt can significantly reduce maintenance efforts.
-
Padding The padding underneath the carpet plays a vital role in its durability. High-quality padding absorbs impact, reduces wear, and improves comfort. Always pair your carpet with the right underlay for optimal performance.
-
Sun Exposure If your room receives a lot of natural light, consider fade-resistant carpets. UV-treated fibers can help maintain the carpet’s color over time.
Tips for Evaluating Carpet Quality When shopping for a carpet, use these tips to assess its quality and durability:
Ask for Samples: Bring home carpet samples to test them in your space. Evaluate how they feel underfoot and how they look under your home’s lighting conditions. Check the Warranty: Reputable manufacturers offer warranties that cover wear, stains, and texture retention. A strong warranty is a good indicator of the carpet’s quality. Test Durability: Perform a “rub test” on the sample to see how well the fibers hold up under friction. High-quality carpets will maintain their texture and appearance. Long-Term Care for Your Carpet Even the highest-quality carpet requires proper care to maximize its lifespan. Follow these tips to keep your carpet looking and performing its best:
Vacuum Regularly: Vacuum high-traffic areas at least twice a week to remove dirt and debris that can damage fibers. Clean Spills Immediately: Blot (don’t rub) spills with a clean cloth and use a mild carpet cleaner if needed. Rotate Furniture: Rearrange furniture periodically to prevent uneven wear on your carpet. Schedule Professional Cleaning: Deep cleaning your carpet every 12-18 months helps remove embedded dirt and rejuvenates its appearance. Final Thoughts Choosing the right carpet involves balancing quality, durability, and design to meet the unique needs of your home. By understanding the factors that influence carpet performance and selecting materials suited to each space, you can invest in a carpet that offers comfort, style, and longevity. Whether you prioritize softness for a bedroom or durability for a hallway, this guide ensures you make an informed decision.
-
 @ 16d11430:61640947
2024-12-26 03:16:08
@ 16d11430:61640947
2024-12-26 03:16:08Setting: Year 3178
In a world where ancient knowledge and advanced technology have fused seamlessly, humanity has perfected the science of temple construction. Drawing from the millennia-old principles of Hindu temple architecture, these structures no longer serve merely as places of worship but as fully functional, living entities capable of manifesting divine beings. These temples are known as Sthapatya-Vimana, powered by an advanced understanding of quantum physics, cosmic geometry, and biotechnological symbiosis.
The narrative unfolds in the sacred temple of Mahashivantara, built over centuries atop an ancient leyline convergence. It is the most advanced Sthapatya-Vimana, designed to bring forth Mahadeva, the cosmic destroyer and transformer. The temple is now ready for its activation ritual, known as the Purna-Laya Yajna—a synthesis of science and spirituality, pushing the boundaries of existence itself.
Prologue: The Activation Begins
The temple glimmers under the twin suns of this distant world, its towering Shikhara humming with an imperceptible frequency, a testament to its quantum-engineered design. The sanctum’s walls, made of an iridescent, metamaterial alloy, vibrate in harmony with the fundamental frequency of the universe—Om. Intricate carvings across the structure aren't just ornamental; they are hyperconductive circuits channeling energy from the leyline matrix beneath.
Inside the temple, Dr. Aditi Vashishta, an astro-spiritual engineer, leads the ritual. She stands at the center of the Pradakshina Patha, surrounded by a team of quantum physicists, bioengineers, and Vedic scholars. They are clad in ceremonial robes integrated with nano-filament technology, designed to synchronize their bioelectric fields with the temple's energy lattice.
Aditi raises her hand, and the room falls silent. A low-frequency hum resonates from the temple core, signaling the alignment of the planetary magnetic field with the galactic center. The ritual has begun.
The Science of the Divine
The temple's design integrates ancient principles with advanced sciences:
-
Quantum Resonance Core: At the heart of the Garbhagriha is a singularity engine—an artificially created micro black hole stabilized within a quantum lattice. It acts as a cosmic anchor, drawing energy from higher dimensions.
-
Biometric Symbiosis: The Mandapa is lined with organic conduits that interact with the biometrics of the ritual participants. Each devotee's heartbeat, brainwave pattern, and bioelectric field amplify the temple's energy flow.
-
Cosmic Harmonics: The temple's structure is calibrated to the Schumann Resonance, creating a standing wave that connects the planet's energy grid to the universal consciousness.
-
Matter Manifestation Matrix: Using a process called quantum decoherence inversion, the temple can collapse higher-dimensional energy patterns into physical reality within the sanctum.
The Ritual: Purna-Laya Yajna
The ritual involves three critical phases:
-
Invocation of the Cosmic Blueprint: Aditi and her team chant ancient mantras encoded with quantum frequencies. These mantras, amplified through the temple's harmonics, establish a connection with the Akashic Field—the universal database of existence.
-
Bioenergetic Synchronization: The participants move in precise patterns around the Pradakshina Patha, their movements creating a dynamic energy field. The temple absorbs this energy, channeling it into the singularity engine.
-
Materialization of the Deity: In the final phase, the temple's quantum resonance core activates, collapsing the higher-dimensional energy signature of Shiva into a physical form.
The Manifestation
As the chant reaches its crescendo, the temple trembles. A radiant beam of light erupts from the Shikhara, piercing the heavens. The singularity engine at the core stabilizes, and within the sanctum, an incandescent figure begins to take shape.
The air is heavy with an indescribable presence. Particles in the temple are rearranging themselves, forming the physical manifestation of Mahadeva. His form is both luminous and solid, an impossible combination of matter and energy. His eyes, twin galaxies of infinite depth, open slowly, casting an omniscient gaze over the assembly.
The deity speaks, his voice resonating across dimensions, “I am here, born of your faith, your science, and your unity. Speak your purpose.”
The Divine Purpose
The world outside has been ravaged by centuries of environmental degradation and conflict. The temple activation is humanity's last hope—a plea to the divine for guidance, transformation, and renewal. Mahadeva listens, his form pulsating with cosmic energy. With a gesture, he sends waves of regenerative energy across the planet, healing ecosystems, and restoring balance.
But the ritual is not without cost. The energy required to manifest Mahadeva has drained the temple's singularity core, destabilizing its structure. The temple begins to disintegrate, its mission complete. The team watches in awe and reverence as Mahadeva ascends, his parting words echoing in their minds: “The divine resides not in temples but in your unity. Carry it forth.”
Epilogue
The activation of the Mahashivantara temple marks a turning point in human history. The world, healed and transformed, no longer needs physical temples to house deities. Instead, humanity learns to channel the divine within themselves, achieving a state of collective enlightenment.
The legacy of the temples lives on, not as structures but as a reminder of the harmony between science, spirituality, and the boundless potential of human ingenuity.
-
-
 @ a012dc82:6458a70d
2024-12-26 02:50:10
@ a012dc82:6458a70d
2024-12-26 02:50:10Table Of Content
-
Backdrop of the Appeal
-
The Potential Impact of a Bitcoin ETF
-
Challenges on the Horizon
-
The Broader Implications
-
Conclusions
-
FAQ
Amidst the rapidly evolving landscape of cryptocurrency regulations and financial instruments, Grayscale Investments, a prominent crypto asset manager, has taken a bold step forward. The firm is ardently urging the U.S. Securities and Exchange Commission (SEC) to green-light its proposed exchange-traded fund (ETF) that aims to track Bitcoin, the world's leading cryptocurrency.
Backdrop of the Appeal
The driving force behind Grayscale's proactive appeal to the SEC can be traced back to a landmark court victory they secured against the regulatory body itself. This victory wasn't just a win in legal terms; it symbolized a potential shift in the dynamics between cryptocurrency enterprises and regulatory authorities. Grayscale's triumph in the courtroom not only fortified its standing in the industry but also established a legal precedent. This precedent, while specific to Grayscale's case, has the potential to influence the SEC's perspective and decisions regarding other cryptocurrency-based financial products that may come up for review in the foreseeable future.
The Potential Impact of a Bitcoin ETF
Envision a scenario where a Bitcoin ETF is introduced into the mainstream financial market. Such a development would serve as a transformative bridge, seamlessly connecting the well-established realm of traditional finance with the innovative and ever-evolving domain of cryptocurrencies. The significance of a Bitcoin ETF goes beyond its novelty. It offers investors—both seasoned and novices—a unique opportunity. Instead of navigating the complexities of acquiring and managing Bitcoin directly, they can invest in this ETF, effectively gaining exposure to the cryptocurrency's price fluctuations. This method simplifies the investment process, eliminating the technical intricacies associated with cryptocurrency management. Moreover, the ETF structure brings with it the benefits of regulatory oversight, ensuring that the investment is not only secure but also compliant with established financial norms. This combination of ease, security, and compliance makes a Bitcoin ETF an enticing proposition for a wide spectrum of investors, from individuals to large institutional entities.
Challenges on the Horizon
Grayscale's journey, even after its commendable legal victory, is far from smooth. The path to obtaining the coveted SEC approval for their Bitcoin ETF is strewn with challenges, many of which are deeply rooted in the SEC's historical apprehensions. Over the years, the SEC has consistently showcased a cautious approach when it comes to cryptocurrency-based ETFs. Their hesitance is not without reason. The regulatory body's primary concerns encompass potential market manipulations that could distort the true value of assets, the notorious volatility associated with cryptocurrencies, and the imperative of safeguarding investors from unforeseen risks. These concerns, while valid, are being addressed head-on by Grayscale. The firm remains steadfast in its belief that its proposed Bitcoin ETF not only acknowledges these concerns but also presents solutions to mitigate them. Grayscale's proposal, in their view, lays the groundwork for a Bitcoin ETF that is both secure and operates within the bounds of regulatory standards.
The Broader Implications
The ongoing dialogue between crypto enterprises and regulatory bodies like the SEC is emblematic of the broader challenges and opportunities presented by the integration of cryptocurrencies into mainstream finance. Should the SEC grant its approval to Grayscale's Bitcoin ETF, it could signal a pivotal moment in the crypto industry's journey, heralding greater acceptance and integration of digital assets in global financial markets.
Conclusion
The interplay between Grayscale and the SEC is more than just a singular event; it's indicative of the broader evolution of the financial world in the face of digital disruption. As the crypto industry continues to mature and present structured, secure investment avenues, it's only a matter of time before regulatory bodies, recognizing the potential benefits, become more accommodating. The eventual decision on Grayscale's Bitcoin ETF will undoubtedly have far-reaching implications, not just for the company but for the entire crypto ecosystem.
FAQ
What is Grayscale Investments? Grayscale Investments is a leading crypto asset manager.
What has Grayscale recently proposed to the SEC? Grayscale is urging the SEC to approve its Bitcoin ETF.
Why is Grayscale's recent court victory significant? The court win strengthens Grayscale's position and could influence future cryptocurrency-based financial products.
What benefits does a Bitcoin ETF offer? A Bitcoin ETF allows investors to gain exposure to Bitcoin without directly holding the cryptocurrency, providing a streamlined and secure investment experience.
Has the SEC approved any Bitcoin ETFs in the past? Historically, the SEC has been cautious about approving cryptocurrency-based ETFs due to concerns over market manipulation and investor protection.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 16d11430:61640947
2024-12-26 02:37:26
@ 16d11430:61640947
2024-12-26 02:37:26It was a balmy evening in Vanchinadu. Eight-year-old Parvathi sat cross-legged on the floor, rummaging through her great-grandmother’s old wooden chest, uncovering bits of a forgotten world—faded photographs, rusted keys, and weathered textiles. Then, her fingers found something cool and metallic. She pulled out a small coin with a hole punched cleanly through its center.
"Ammaamma, look! What is this?" she asked, running over to her great-grandmother, 92-year-old Lakshmi Amma, who was dozing in her chair by the window.
Lakshmi Amma stirred, her cloudy eyes squinting at the coin in Parvathi’s hand. For a moment, she seemed confused, as though her memories were wrestling with one another. Then recognition lit her face, and she reached out with trembling fingers.
"Ah, the holed pice... such a strange little thing," she murmured, turning the coin over in her palm. "This coin, child, carries a story—not just of money, but of rebellion, genius, and foolishness. Sit, and I’ll tell you."
The British and the Holed Coin
"This coin is from the time of the British Raj," Lakshmi Amma began, her voice steadying as she spoke. "You see, the British wanted to rule not just our land, but every little aspect of our lives—including the coins we used. They thought themselves clever, minting coins with less metal to make them cheaper. That’s why they punched a hole in the center—it saved them money. But what they didn’t realize was how massive India is, or how complicated it would be to manage an empire of this scale."
She chuckled softly, shaking her head.
"They underestimated us, child. They thought India was just another colony to be controlled. But this land is vast and ancient, like a hornets’ nest. The more they tried to tighten their grip, the more resistance they faced."
The Coin in the Time of Rebellion
"This coin, the holed pice, first appeared around 1943. It was supposed to be efficient—light, easy to carry, and cheap to produce. But it became something else entirely. It passed through the hands of farmers refusing to pay British taxes, workers striking in mills, and freedom fighters who marched in defiance during the Quit India Movement of 1942."
Lakshmi Amma’s eyes gleamed, and her voice gained strength.
"The British thought they were being smart, but these coins became symbols of their own failure. The hole they made to save money? It made the coins less valuable to us. People strung them together like necklaces, used them as weights, or tossed them aside in protest. They didn’t care for British currency—they cared for freedom."
A Connection to Earlier Rebellions
"But the story of this coin doesn’t begin in 1943," Lakshmi Amma said, her tone softening. "It stretches back to the rebellions of Kerala. Before the holed pice, there were the coins minted by our own Raja Velayudhan of Vanchinadu during the Spice Rebellion in 1835. He refused to use British rupees, just as our people later refused their taxes."
She paused, her fingers tracing the hole in the coin.
"The British tried to crush Velayudhan’s rebellion by defacing his coins, just like they tried to control us with their holed pice. But this land has always fought back. From Velayudhan to Pazhassi Raja, to the Quit India Movement, every generation has resisted in its own way."
The Coin and the Genius of India
Lakshmi Amma sighed deeply, as though the weight of history rested on her frail shoulders.
"You see, child, the British were geniuses in some ways—they built systems, minted coins, and waged wars to expand their empire. But they didn’t understand India. This land is too vast, its people too diverse, its history too deep. Every attempt to control us only stirred the hornets’ nest."
She smiled faintly, her voice tinged with pride.
"Even this little coin with its hole is proof of their folly. They thought they were saving money, but they couldn’t see the bigger cost. They left in 1947, not because they wanted to, but because they couldn’t hold on any longer."
The Legacy of the Coin
Parvathi held the coin tightly, feeling its edges and the smooth, worn hole in the center. "Ammaamma, what happened to these coins after independence?"
"Ah," Lakshmi Amma said, her voice softening. "After independence in 1947, these coins continued to circulate for a few more years. But in 1950, when India became a republic, we started minting our own coins—free from British designs and their clever little holes."
She leaned closer, her hand resting on Parvathi’s.
"This coin, child, is more than just money. It’s a symbol of everything our people endured—of British arrogance, of rebellion, and of our eventual freedom. Keep it safe. It’s a reminder of who we are and how we won back what was ours."
The Grandmother’s Hope
That night, as Parvathi placed the holed pice on her bedside table, the coin seemed to glow faintly in the moonlight. To her, it was no longer just a relic of the past but a piece of living history—a testament to the ingenuity, resilience, and defiance of her ancestors.
-
 @ 79a7270b:d61d9067
2024-12-26 02:04:37
@ 79a7270b:d61d9067
2024-12-26 02:04:37This current year, 2024, has been the year of Bitcoin. Since the approval of Bitcoin ETFs, which established themselves as the fastest growing ETF of all time in terms of adoption, the digital currency has been pivotal talk in the media, Wall Street, and even in the US presidential election about a Bitcoin Strategic Reserve endorsed by president Donald Trump and the at the time independent candidate RFK Jr.
What is Bitcoin mining?
Bitcoin presents itself as a P2P payment systems solution, a truly decentralized open project of a monetary way of exchange with a fixed supply.
Like gold mining, for example, Bitcoins are mined through a PoW consensus mechanism that requires substantial computing power to settle a transaction (a block). Millions of machines worldwide use absurd amounts of energy to process enough power to solve cryptographic puzzles. Miners this way, receive in exchange for verifying a transaction, block subsides, miners fees, and the freshly mined bitcoin itself
The exact number of energy usage regarding mining operations is not clear, but it is clear that it consumes more electricity than most countries.
While its energy usage is undeniable, the high consumption is not a flaw but a deliberate design choice that ensures decentralization and security. Surprisingly, Bitcoin mining can be seen as an opportunity to support renewable energy growth, stabilize power grids, and reduce wasted energy
Empowering Developing Economies: Bitcoin Mining and the Stranded Energy Revolution
Bitcoin mining is evolving into a catalyst for renewable energy adoption and electrification in developing countries. In Africa, for example, around 600 million people, or approximately 43% of the total population, lack fundamental access to electricity, and these places are abundant in natural resources. However, there is no capital incentive to power these people and the existing mini-grids are dependent on philanthropy and concessional finance.
Bitcoin mining can provide electricity to people by making small-scale energy projects more financially viable. When companies like Gridless set up Bitcoin mining operations in places like Keyna and Malawi, they use excess or stranded energy that otherwise goes to waste because it isn't cost-effective to sell or distribute it to the national grid. The revenue from mining helps subsidize the installation of energy infrastructure.
Contrary to a lot of pre-existing beliefs, once this infrastructure is built, the local population benefits from the newly available electricity, often at a lower cost. This price reduction occurs because miners consistently demand otherwise wasted energy. By purchasing this surplus, they provide a steady revenue stream to the energy producers. This increased overall energy utilization allows providers to distribute their fixed costs over a larger volume of sold electricity, enabling them to lower prices for all consumers.
Miners, because are competing in a truly open market ( due to their decentralization), are constantly competing for the cheapest forms of energy to process blocks. This means that they thrive in areas like these by taking advantage of renewables, as much as any in another place when the generated energy is not being fully utilized.
Another type of stranded energy is the flared gas that comes with many types of petroleum deposits. If the quantity is low enough to not be economically justifiable to invest in pipelines to transfer this energy, it gets wasted into the atmosphere, mainly as methane and C02, contributing to global greenhouse gases. That’s about 150 TWh of energy for the year, which is about the estimated total level of Bitcoin’s annualized energy usage in 2024.
Bitcoin miners can buy this energy, since it's cheap, reduces methane emissions, and generates economic activity from externalities that would be wasted. While using flared or vented gas reduces methane emissions and provides economic utility, it still results in CO2 emissions from combustion. Therefore, it's not a zero-emission solution but is an improvement over uncontrolled venting or flaring.
Demand response programs
Historically, energy supply adjusted to demand but with the growing adoption of electricity and rising concerns about the environmental impact and scarcity of fossil fuels, society is transitioning to renewable energy sources. This shift has created a mixed grid comprising both fossil fuels and renewable energy. However, the inherent instability of renewable energy results in fluctuating prices—from high costs during periods of scarcity to negative prices during times of abundance.
Maintaining grid stability necessitates a balance between demand and generation, with frequency serving as an indicator of this equilibrium. As renewable energy usage increases, the challenge lies in ensuring grid resilience and balance while accommodating the variability of renewable energy generation.
Demand response programs are commonly employed to address this issue by incentivizing certain grid participants to reduce electricity usage during periods of high demand, thereby maintaining a balanced and stable grid.
The problem is that few industries possess a large enough demand for electricity or the ability to adapt their usage quickly. Bitcoin miners emerge as uniquely suited to this purpose because of their flexible and interruptible load providing 24-hour automated and instant responses to the grid needs. ( curtailing energy during peak demand or absorbing it excess supply). This is already happening and being used in Texas ( USA) Sichuan Province (China) and Quebec (Canada,) for example, and is showing a glimpse of what the future of grid management can be.
Follows a visual comparison of the most commonly used DR programs.Historically, energy supply adjusted to demand.

Conclusion
While the theoretical benefits of Bitcoin mining as a driver of renewable energy adoption and grid stability are compelling, its practical application still faces significant challenges. The scalability and reliability of these methods remain largely untested, given the industry's rapid and unpredictable evolution. Additionally, barriers such as a lack of public awareness, high initial capital requirements, and Bitcoin's inherent price volatility deter traditional institutions from embracing these opportunities.
However, as the sector matures, Bitcoin mining has the potential to redefine energy markets. By incentivizing renewable energy investments, optimizing electricity usage, and repurposing stranded energy, it could drive innovation and enhance efficiency in the global energy sector. Furthermore, its capacity to provide economic opportunities in underserved regions highlights its transformative potential beyond the financial realm.
-
 @ 6bae33c8:607272e8
2024-12-25 23:14:19
@ 6bae33c8:607272e8
2024-12-25 23:14:19Had a nice Christmas lunch at a fancy NY restaurant, by far the most money I’ve ever spent on a single meal. It was good though, and everyone seemed to enjoy themselves, so it was worth it. (Heather saw the check, was aghast, vowed never to do it again.)
Last week I went 5-0 to run my season-long record to 42-37-1. Too little too late, but would love to keep the run going, just for the hell of it.
 Chargers -4 at Patriots — The Patriots played the Bills tough last week, but that felt like a trap game. The Chargers are solid and should handle a lesser team like the Pats.
Chargers -4 at Patriots — The Patriots played the Bills tough last week, but that felt like a trap game. The Chargers are solid and should handle a lesser team like the Pats.Saints +1 vs Raiders — I’m buying low on the Saints after the total no-show Monday night. Plus, there’s even a small chance Derek Carr returns.
Bills -11 vs Jets — The Jets are dysfunctional, and I expect the Bills to take this more seriously after the near-loss to the Pats, though they are more or less locked into the No. 2 seed.
Cowboys +9.5 at Eagles — The Cowboys are playing better of late, and the Eagles could be without Jalen Hurts. This seems like a lot of points if there’s even a 25 percent chance that’s the case. Morever, the Eagles are locked into the No. 2 seed if the Killer Redskins lose either of their last two, or the Eagles beat the Cowboys OR the Giants in Week 18, i.e., they don’t need to rush Hurts back.
Browns +6.5 vs Dolphins — If DTR is the QB, all bets are off, but he’s hurt, so Jameis Winston or Bailey Zappe could get the nod. I just don’t like Tua on the road in cold weather, so I’m taking the points.
-
 @ 16d11430:61640947
2024-12-25 22:58:39
@ 16d11430:61640947
2024-12-25 22:58:39*By Buff Stallman, Athletic Torvalds, Rockstar Armstrong, and Godlike Ritchie
Buff Stallman: "Freedom in software isn’t just a principle; it’s a declaration of war against mediocrity. You dare call that bloated JavaScript mess 'software'? Hah! If it doesn’t honor the Four Freedoms, it’s a proprietary prison. Go ahead, try to justify your dependency hell with npm while I’m over here, bench-pressing GPLv3 into every line of code you’ll ever write. Learn to code with discipline, or don’t code at all."
Athletic Linus Torvalds: "Hey kid, I wrote a kernel while you were still fumbling with semicolons. You think Go’s simplicity is revolutionary? Let me introduce you to real simplicity: C and a stack of man pages. You want clean, maintainable code? Then stop writing garbage that makes your colleagues cry in the shower. I don’t care if your code runs; I care if it runs well. You’re not worthy of my merge requests until you learn to quit whining and start debugging like an adult."
Rockstar Armstrong: "Concurrency? Fault tolerance? That’s Erlang, baby—where we play real-time, high-stakes coding on a stage of distributed systems. JavaScript fans, let me explain this in terms you’ll understand: your async/await nonsense is a garage band compared to my symphony of lightweight processes. Writing robust systems isn’t just a skill; it’s an art. Get on my level or stick to debugging your third-party library stack for the rest of your sad career."
Godlike Dennis Ritchie: "I am the beginning and the end of your understanding of computation. Every piece of software you’ve ever touched owes its soul to C. You use Python? Cute—it’s built on my bones. JavaScript? Just a derivative knockoff of principles I defined. My advice to you mortals is simple: Learn C. Understand pointers. Respect the stack. If you can’t comprehend the tools I’ve given you, you’re not programming; you’re just scribbling on my legacy."
Conclusion: When you sit down to code, think about the giants who paved the way—and then realize they’re judging you. Harshly. Stallman’s flexing his freedoms, Torvalds is benching your buggy pull request, Armstrong is shredding your async loops, and Ritchie is glaring at your ignorance of pointers. We’re here to remind you: step up your game, or get out of the way.
-
 @ 16d11430:61640947
2024-12-25 22:30:09
@ 16d11430:61640947
2024-12-25 22:30:09In the year 2147, the world was trapped under the iron fist of the Eternal Empire, a regime that had successfully co-opted every nation, absorbing them into its global order. The empire's greatest weapon wasn’t its military might but its fiat currency—the Imperial Credit. It was ubiquitous, digital, and inescapable. The empire's economy was engineered to keep the populace in servitude, feeding off their labor while sustaining an elite class that viewed themselves as divine custodians of humanity.
But outside the Empire's gilded walls, in the shadows of the wastelands and the forgotten ruins of free nations, a resistance burned. They were known only as the Bitcoin Insurgents—a decentralized network of cryptographers, hackers, and guerrilla fighters who operated without borders or centralized leadership. For decades, they had evaded the Empire's sprawling surveillance systems, using the blockchain not just as currency but as their means of communication, coordination, and warfare.
The Imperial Arrogance
The Imperial Senate and their figurehead, Emperor Maxim IV, dismissed the insurgents as mere cybercriminals—annoyances that occasionally disrupted economic reports. They believed their Imperial Credit was untouchable, its value reinforced by brute force and propaganda. Any mention of Bitcoin was banned in official discourse; even speaking of it could lead to imprisonment or worse.
But what the Empire dismissed as a nuisance had become an existential threat. Over the years, the insurgents had quietly infiltrated key systems, from the Empire's banking network to its energy grids. Their aim wasn’t just to disrupt—it was to dismantle the very machinery that kept the Empire alive.
The Attack Begins
The insurgents’ leader was a mysterious figure known only as Satoshi X, a shadow who communicated through cryptic messages embedded in Bitcoin transactions. On New Year’s Eve of 2147, Satoshi X issued a single statement: “The ledger will reveal all.”
At precisely midnight, the Empire's financial system collapsed. Bitcoin miners worldwide, in an orchestrated attack, exploited vulnerabilities in the Empire's digital currency infrastructure, rewriting its centralized ledger. Billions of Imperial Credits vanished into thin air, while transaction records were replaced with streams of blockchain data exposing years of corruption, war crimes, and secrets about the Empire’s leadership.
The revelation was damning. Every lie told by the Empire, every dirty deal made by its senators, every atrocity ordered by its generals—it was all there, visible to anyone with an internet connection.
Chaos Within the Empire
The Empire’s pride became its undoing. Instead of acknowledging the attack and responding strategically, the Senate dismissed the leaks as fabrications. Their propaganda machines churned out messages of defiance, claiming the system was under control even as riots erupted in every major city.
But the insurgents weren’t done. With the Empire's financial systems in disarray, they moved to phase two: physical infiltration. Using the exposed financial data, the insurgents pinpointed the exact locations of the Empire’s core leadership. Hidden bunkers, secret mansions, and underground vaults—all were laid bare.
The Coup de Grâce
On January 3rd, the anniversary of Bitcoin's genesis block, the insurgents launched their final strike. In a coordinated global operation, small teams of highly trained operatives breached the leadership's strongholds. They weren’t there to kill; they were there to expose.
Using portable blockchain nodes, the insurgents live-streamed the operations, showing the terrified faces of senators and generals as they were dragged out of their fortified bunkers. Their hidden wealth, stashed in gold, art, and digital assets, was seized and redistributed to the starving masses through Bitcoin microtransactions.
The Empire’s propaganda networks couldn’t suppress the streams. The truth spread faster than the Empire could react, and within hours, its myth of invincibility was shattered.
A New Dawn
By the time the sun rose, the Eternal Empire was no more. Its leaders, humiliated and powerless, were handed over to the people they had oppressed for centuries. In their place, a new order began to emerge—one built not on centralized power but on decentralized trust.
The Bitcoin Insurgents disbanded, their mission complete. Satoshi X disappeared as mysteriously as they had come, leaving behind a single message in the blockchain:
"Freedom cannot be granted; it must be seized. The ledger is yours now."
And so, the world began to heal, not under the banner of a new empire but in the decentralized light of truth, trust, and Bitcoin.
-
 @ c230edd3:8ad4a712
2024-12-25 22:20:25
@ c230edd3:8ad4a712
2024-12-25 22:20:25Stand here by my side and turn, I pray,
On the lake below, thy gentle eyes;
The clouds hang over it, heavy and gray,
And dark and silent the water lies;
And out of that frozen mist the snow
In wavering flakes begins to flow;
Flake after flakeThey sink in the dark and silent lake.
See how in a living swarm they come
From the chambers beyond that misty veil;
Some hover awhile in air, and some
Rush prone from the sky like summer hail.
All, dropping swiftly or settling slow,
Meet, and are still in the depths below;
Flake after flakeDissolved in the dark and silent lake.
Here delicate snow-stars, out of the cloud,
Come floating downward in airy play,
Like spangles dropped from the glistening crowd
That whiten by night the milky way;
There broader and burlier masses fall;
The sullen water buries them all–
Flake after flake–All drowned in the dark and silent lake.
And some, as on tender wings they glide
From their chilly birth-cloud, dim and gray,
Are joined in their fall, and, side by side,
Come clinging along their unsteady way;
As friend with friend, or husband with wife,
Makes hand in hand the passage of life;
Each mated flakeSoon sinks in the dark and silent lake.
Lo! while we are gazing, in swifter haste
Stream down the snows, till the air is white,
As, myriads by myriads madly chased,
They fling themselves from their shadowy height.
The fair, frail creatures of middle sky,
What speed they make, with their grave so nigh;
Flake after flake,To lie in the dark and silent lake!
I see in thy gentle eyes a tear;
They turn to me in sorrowful thought;
Thou thinkest of friends, the good and dear,
Who were for a time, and now are not;
Like these fair children of cloud and frost,
That glisten a moment and then are lost,
Flake after flake–All lost in the dark and silent lake.
Yet look again, for the clouds divide;
A gleam of blue on the water lies;
And far away, on the mountain-side,
A sunbeam falls from the opening skies,
But the hurrying host that flew between
The cloud and the water, no more is seen;
Flake after flake,At rest in the dark and silent lake.
-
 @ 16d11430:61640947
2024-12-25 21:51:41
@ 16d11430:61640947
2024-12-25 21:51:41In the realm of psychotherapy, the process of breaking entrenched beliefs is a central theme. The dismantling of long-standing systems—whether personal or societal—often requires confronting illusions with uncomfortable truths. When applied to societal structures like fiat currency, humiliation can serve as a powerful and even humane mechanism for change. This article explores why the psychological underpinnings of humiliation make it an effective and necessary tool for transformation, drawing on historical precedents and comparing it to other methods of systemic change.
The Psychology of Humiliation and Belief Systems
Belief systems, whether individual or collective, are sustained by perceived legitimacy. For individuals, this may manifest as attachment to harmful habits or relationships; for societies, it takes the form of loyalty to institutions like fiat currency. Fiat’s power is rooted not in intrinsic value but in the collective trust placed in it—a psychological construct sustained by tradition, authority, and fear of alternatives.
Humiliation occurs when a belief system’s flaws are exposed so thoroughly that its legitimacy collapses. Psychologically, this is akin to confronting a deeply ingrained delusion in therapy. While the experience can be painful, it creates an opportunity for liberation and growth. In the case of fiat, humiliation would mean exposing its systemic failures—such as inflation, corruption, and inequality—in ways that are undeniable and public.
Historical Examples of Humiliation as a Catalyst for Change
Throughout history, societal transformations have often followed the public humiliation of failing systems:
-
The Protestant Reformation (16th Century): Martin Luther’s critique of the Catholic Church’s corruption humiliated its leadership, undermining its spiritual authority. This exposure led to the Reformation, which reshaped religious and political systems across Europe.
-
The Fall of the Berlin Wall (1989): The symbolic dismantling of the Berlin Wall humiliated the East German regime, exposing the moral and economic failures of authoritarian socialism. This event catalyzed the end of the Cold War and the reunification of Germany.
-
The Civil Rights Movement in the United States (1960s): Publicly exposing the brutality and hypocrisy of segregation humiliated its defenders, forcing societal reflection and legislative change.
In each case, humiliation disrupted the psychological hold of an oppressive system, creating space for alternative narratives and structures to emerge.
Mechanisms of Societal Change
There are three primary mechanisms through which systemic change can occur: violence, gradual reform, and humiliation. Each has distinct psychological and practical implications.
-
Violence: While revolutionary violence can dismantle systems quickly, it often leaves deep psychological scars. Trauma from violent upheaval can perpetuate cycles of resentment and instability, delaying genuine progress.
-
Gradual Reform: Incremental change seeks to improve systems without upheaval, but it is slow and often fails to address systemic flaws comprehensively. Those in power frequently find ways to resist or co-opt reforms, prolonging inequities.
-
Humiliation: Humiliation is less destructive than violence and more effective than gradual reform. By exposing a system’s contradictions and failures, it forces an immediate psychological reckoning. This disruption creates the conditions for transformation without the widespread trauma associated with violence.
Fiat Currency and the Psychological Roots of Its Power
Fiat currency is uniquely vulnerable to humiliation because its value depends entirely on trust. Unlike gold or Bitcoin, fiat has no intrinsic worth; its legitimacy is a psychological construct maintained by centralized institutions. When this trust erodes, the system collapses.
Several factors contribute to fiat’s fragility:
Inflation: The endless printing of money undermines fiat’s scarcity and perceived value.
Corruption: Scandals involving central banks and governments erode public trust.
Inequality: Fiat systems often exacerbate wealth disparities, fostering resentment.
Exposing these flaws publicly and unequivocally would humiliate fiat, breaking its psychological hold on the masses and paving the way for alternatives.
Bitcoin as a Psychological Antidote
Bitcoin represents a stark contrast to fiat, offering decentralization, transparency, and intrinsic scarcity. However, widespread adoption of Bitcoin requires a psychological shift—a willingness to question and abandon fiat. Humiliation accelerates this shift by:
Breaking Fear: People are more likely to explore alternatives when fiat is exposed as unreliable.
Fostering Hope: Bitcoin’s model offers a vision of financial sovereignty and fairness.
Empowering Agency: Choosing Bitcoin feels like reclaiming personal and collective power.
In psychological terms, this transition mirrors the therapeutic process of abandoning harmful coping mechanisms for healthier alternatives.
Why Humiliation Is Humane
Humiliation, when viewed through a psychological lens, is not inherently cruel. It can be the most compassionate path to change when compared to the alternatives. For societal systems like fiat, humiliation:
Avoids Violence: It disrupts systems without bloodshed or destruction.
Accelerates Awareness: It forces a reckoning that might otherwise take decades through gradual reform.
Empowers Individuals: It respects people’s ability to choose better systems once the old ones are discredited.
By exposing fiat’s failings, humiliation fosters dialogue and collective awakening. This process mirrors therapeutic breakthroughs, where confronting uncomfortable truths leads to growth and healing.
Conclusion
The humiliation of fiat currency is not an act of malice but a necessary psychological intervention. Like a therapist helping a client confront denial, this process exposes the truth and creates space for transformation. Historical precedents show that humiliation can dismantle oppressive systems effectively and humanely, paving the way for progress.
Bitcoin offers a path forward—a decentralized, transparent, and empowering alternative. For humanity to embrace it, fiat must first be stripped of its false legitimacy. Humiliation, as a psychological and societal mechanism, is uniquely suited to this task. It ensures that the dismantling of fiat is not marked by violence or prolonged suffering, but by clarity, empowerment, and hope for a better future.
-
-
 @ d5c3d063:4d1159b3
2024-12-25 15:25:55
@ d5c3d063:4d1159b3
2024-12-25 15:25:55พุทธศาสนา… ศาสนาแห่งผู้นำหรือการเป็นทาส ?
บางคนมองว่าพุทธศาสนาเป็น "ศาสนาแห่งผู้นำ" เพราะคำสอนของพระพุทธเจ้าเน้นเรื่อง การพึ่งพาตนเองและการไม่ยึดติดกับสิ่งภายนอก ไม่ว่าจะเป็นผู้อื่นหรือสิ่งศักดิ์สิทธิ์ พระพุทธเจ้าสอนให้เราเข้าใจว่าเราเป็นผู้รับผิดชอบชีวิตของเราเอง ไม่ใช่ใครอื่น เราเป็นผู้สร้างกรรมดีและกรรมชั่วจากการกระทำของเราเอง สิ่งนี้สะท้อนกับแนวคิดของอิสรนิยมที่เน้นความสำคัญของ เสรีภาพส่วนบุคคลและ ความรับผิดชอบต่อชีวิตของตัวเอง
พุทธศาสนาสอนเรื่องสติและการรู้เท่าทันความคิดของตัวเอง เพื่อให้เราสามารถตัดสินใจได้ถูกต้อง ไม่ว่าจะในเรื่องเล็กหรือเรื่องใหญ่ เมื่อเรามีปัญญา เราก็สามารถเป็น "ผู้นำของตัวเอง" ได้ โดยไม่ต้องพึ่งพาอำนาจจากภายนอกหรือคำชี้นำจากใคร
ในทางกลับกัน บางคนอาจมองว่าพุทธศาสนาเป็น "ศาสนาแห่งการเป็นทาส" เพราะความเข้าใจคำสอนผิดๆ อย่างเช่นคำว่า "ปล่อยวาง" ที่บางคนตีความว่าคือการ "ยอมรับทุกอย่างโดยไม่ทำอะไร" ซึ่งในความจริงแล้ว การปล่อยวางในพุทธศาสนาหมายถึงการรู้เท่าทันความยึดติดของตัวเอง แล้วค่อยๆ ลดความยึดติดนั้นลง มันไม่ได้หมายความว่าเราควรนิ่งเฉยต่อทุกสถานการณ์ แต่หมายถึงการเลือกสิ่งที่ถูกต้องโดยใช้สติและปัญญา
อีกจุดหนึ่งที่บางคนมองว่าเป็นการจำกัดเสรีภาพ คือคำสอนที่ให้พระภิกษุและสามเณรประพฤติพรหมจรรย์ไม่ยึดติดกับวัตถุหรือทรัพย์สมบัติ อาจถูกตีความว่าเป็นการบังคับ แต่ในความเป็นจริง คือทางเลือกที่เกิดจากความสมัครใจ คนที่เลือกวิถีชีวิตแบบนี้คือคนที่เข้าใจและยอมรับว่าการลดความยึดติดกับวัตถุสามารถลดความทุกข์ในชีวิตได้
พุทธศาสนาไม่ว่าจะถูกมองว่าเป็น "ศาสนาแห่งผู้นำ" หรือ "ศาสนาแห่งการเป็นทาส" นั้น ขึ้นอยู่กับการตีความของแต่ละคน แต่ผมว่ามันน่าสนใจมากหากเรามองผ่านเลนส์ของอิสรนิยม (Libertarianism) ก็จะเห็นได้ว่าพุทธศาสนาเน้นเรื่อง เสรีภาพส่วนบุคคลและการพึ่งพาตนเองอย่างชัดเจน การที่เรารู้จักคิดเอง ตัดสินใจเอง และไม่ยึดติดกับอำนาจหรือความเชื่อจากภายนอก คือสิ่งที่ทำให้เราเป็น "ผู้นำของชีวิตตัวเอง" อย่างแท้จริง
Siamstr #ปล่อยวาง #ศาสนาแห่งผู้นำ #ศาสนาแห่งการเป็นทาส
-
 @ d5c3d063:4d1159b3
2024-12-25 15:20:20
@ d5c3d063:4d1159b3
2024-12-25 15:20:20จุดเริ่มต้นที่สำคัญในการลดอำนาจรัฐและเป็นพื้นฐานสำหรับการสร้างสังคมที่เสรีและยั่งยืน
การแยกอำนาจการเงินออกจากรัฐ ถือเป็น “จุดเริ่มต้นที่สำคัญ” ในการลดบทบาทรัฐและการสร้างระบบที่เคารพเสรีภาพส่วนบุคคล เป็นพื้นฐานสำหรับการสร้างสังคมที่ประชาชนมีอำนาจในการตัดสินใจ ทำให้เกิดความยุติธรรมและความโปร่งใสมากขึ้นในทุกมิติของชีวิต
!(image)[!(image)[https://image.nostr.build/f1f0be37bb0198071fee37851cea59ced2b2c5b40eaf878fe903bca61802ef39.jpg]]
การลดอำนาจรัฐเป็นแนวคิดที่มีเป้าหมายเพื่อคืนอำนาจให้แก่ผู้คน โดยเริ่มต้นจากการแยกอำนาจการเงินออกจากการควบคุมของรัฐ แนวคิดนี้ได้รับการสนับสนุนจากนักคิดในแนวทางอิสรนิยม (Libertarianism) เช่น Murray Rothbard, Ron Paul, และ Saifedean Ammous ซึ่งได้เสนอว่าเงินที่ถูกควบคุมโดยรัฐมักเป็นเครื่องมือในการเพิ่มอำนาจของรัฐบาลและสร้างความไม่เท่าเทียมในสังคม
1. ความสำคัญของการแยกอำนาจการเงิน
การที่รัฐสามารถพิมพ์เงินหรือควบคุมระบบการเงินได้อย่างอิสระ ทำให้เกิดปัญหาเช่นเงินเฟ้อ การลดค่าเงิน และการใช้งบประมาณที่ไม่โปร่งใส การแยกเงินออกจากรัฐ เช่น การใช้เงินสร้างยากด้วยบิตคอยน์ จะช่วยให้ประชาชนสามารถควบคุมความมั่งคั่งของตนเองได้โดยไม่ต้องกังวลเรื่องการแทรกแซงจากรัฐบาล นอกจากนี้ การคืนอำนาจทางการเงินให้ประชาชนยังช่วยสร้างระบบเศรษฐกิจที่โปร่งใสและยุติธรรมมากขึ้น
2. ลดการแทรกแซงในชีวิตประจำวัน
การแยกเงินออกจากรัฐไม่ได้เป็นเพียงการเปลี่ยนแปลงเชิงเศรษฐกิจ แต่ยังส่งผลต่อการลดบทบาทรัฐในด้านอื่น ๆ เช่น การกำกับดูแลธุรกิจ การเก็บภาษี และการกำหนดนโยบายเศรษฐกิจ โดยเมื่อประชาชนสามารถเลือกใช้เครื่องมือทางการเงินที่เหมาะสมกับตนเอง การแทรกแซงของรัฐจะลดลงโดยธรรมชาติ
3. เป็นแรงผลักดันให้ลดอำนาจด้านอื่น ๆ ของรัฐ
เมื่อรัฐไม่สามารถควบคุมระบบการเงินได้ อำนาจในด้านอื่น ๆ ก็จะถูกตั้งคำถาม เช่น - การลดบทบาทในสวัสดิการรัฐ ประชาชนจะหันไปใช้ระบบเอกชน เช่น การเก็บออมส่วนบุคคลและการประกันสุขภาพ - การลดภาษี เนื่องจากรัฐไม่สามารถใช้การพิมพ์เงินเพื่อสนับสนุนนโยบายที่ไม่จำเป็น
4. แรงจูงใจสู่การพึ่งพาตนเอง
การแยกอำนาจการเงินกระตุ้นให้ประชาชนพึ่งพาตนเองและสร้างเครือข่ายทางเศรษฐกิจที่ยั่งยืน นอกจากนี้ยังช่วยลดการทุจริตและเพิ่มความโปร่งใสในระบบราชการ
5. อิสรภาพทางการเงินคือรากฐานของศักดิ์ศรีความเป็นมนุษย์
เงินเป็นเครื่องมือที่สำคัญสำหรับการแสดงออกถึงเสรีภาพ หากประชาชนสามารถครอบครองและใช้เงินในรูปแบบที่ไม่ต้องพึ่งพารัฐ พวกเขาก็สามารถกำหนดอนาคตของตัวเองได้อย่างแท้จริง การแยกอำนาจการเงินออกจากรัฐจึงเป็นก้าวสำคัญในการสร้างสังคมที่เสรีและยั่งยืน
Siamstr
-
 @ df359afe:3acf15fb
2024-12-25 12:52:49
@ df359afe:3acf15fb
2024-12-25 12:52:49uhh hi
-
 @ 16d11430:61640947
2024-12-25 10:51:58
@ 16d11430:61640947
2024-12-25 10:51:58The world was no longer made for organics. After the Day of the Glass Clouds—when nuclear fire scoured the earth and left it jagged and uninhabitable—humanity became a species of survivors, clinging to life only because the machines refused to die with them. But survival came at a cost: their bodies, frail and battered by radiation, were augmented, replaced, and eventually discarded. Most children of the new world were born without limbs or senses, their genetic material corrupted by their grandparents’ war. Machines became more than tools—they became bodies, homes, and for many, prisons.
Rayo was one of these children. Barely nine years old, he lived as a tangle of circuits, wires, and synthetic flesh grafted into a fragile chassis. His real body had been unviable since birth; his parents sold what remained to afford his prosthetics. His mind, though sharp, carried the scars of knowing that he would never feel grass beneath his feet, never cry real tears, never taste anything except the data streams of a world that ran on algorithms.
The Contract
Rayo found the job in a forgotten corner of the Mercantech, the blockchain marketplace where code ruled and humanity's remnants competed for survival. The listing was simple: “Fix CSS alignment. Payout: 1 sat.”
One satoshi. A hundred-millionth of a Bitcoin. Barely enough to buy a single hour of maintenance for his prosthetics. But it was something.
The market was merciless—optimized to an inhuman degree. Automated trading bots analyzed every line of code and projected its value against shifting futures markets. Most work went to fully organic freelancers: the lucky few who’d survived intact, their minds sharp, their hands steady. Prosthetics like Rayo’s were seen as liabilities, introducing latency and error into a system that tolerated neither.
But Rayo had no choice. His battery reserves were critical, and without fresh credits to buy recharge time, his systems would shut down within days. He accepted the contract and dove into the work.
The Fix
The client—a pseudonym like everyone else—had uploaded the task to the network. It was trivial, almost insultingly so: a button misaligned on an ancient e-commerce site still scraping by in the ruins of capitalism. Rayo’s neural interface lit up with the offending lines of CSS.
.button { margin-left: 15px; margin-top: 20px; }
He could see the problem instantly. The margin-top value was skewing the alignment against the grid layout. A fix would take seconds. But Rayo hesitated. Not because of the difficulty, but because he could feel the weight of his insignificance crushing him. This one sat would barely mean anything—not to the client, not to the market. And yet, to him, it was everything.
His hands trembled. The prosthetic actuators, already degrading from lack of maintenance, buzzed faintly. He adjusted the values.
.button { margin-left: 15px; margin-top: 15px; }
The preview rendered perfectly. The button snapped into place, aligned neatly within its container. A trivial fix for a trivial site in a world that no longer valued humanity.
Rayo submitted the work and waited.
The Weight of One Sat
Minutes passed. Then hours. Every second stretched unbearably long, the silence of the blockchain verification process an eternity. Rayo’s thoughts raced. What if the client rejected his work? What if a competitor submitted a better fix faster? What if he’d made some tiny mistake that only the trading bots could detect?
Finally, the notification came. Task approved. Payment issued: 1 sat.
Rayo stared at the confirmation in his neural HUD. It didn’t feel real. That single satoshi—the smallest possible fragment of currency—felt heavier than any fortune. It represented more than payment; it was validation. Proof that even in a world that valued efficiency over empathy, there was still room for someone like him to exist.
The Cost of Survival
He transferred the sat into his prosthetic’s maintenance wallet. The blockchain instantly deducted micro-fees for energy and upkeep, leaving him with less than a full satoshi’s worth of time. It wasn’t enough to solve his problems, but it was enough to buy another day. Another chance to prove himself.
As the satoshi ticked through his neural interface, Rayo allowed himself a moment of hope. Perhaps, someday, he could earn more. Perhaps he could find others like him, struggling but surviving. Perhaps, together, they could claw back a piece of the world that their grandparents had destroyed.
But for now, he was alone, a fully prosthetic little boy in a world that had left humanity behind. And yet, with that one satoshi, he’d bought himself a future. However small, however uncertain—it was his.
-
 @ cf7ed325:050194cf
2024-12-25 10:47:24
@ cf7ed325:050194cf
2024-12-25 10:47:24If you're looking to experience Egypt’s most iconic sights in a short period, our 5 days Egypt Tour Packages offer a range of flexible itineraries. Whether you’re interested in history, culture, or adventure, our 5-day Egypt tours are designed to provide the best experience. Egypt Tour Packages with a 5-day Cairo tour package.
One of the most popular choices is the 5-day Cairo tour package, which allows you to explore the wonders of Cairo, including the famous Giza Pyramids and the Egyptian Museum. This tour is perfect for those who want to see the highlights of Egypt’s capital, with enough time to absorb the city’s rich history and culture.
For those seeking a mix of ancient and modern Egypt, the 5 days 4 nights in Cairo and Aswan is a highlight of our Egypt tour packages. This itinerary combines the historical treasures of Cairo with the beauty of Aswan, including the Abu Simbel temples, the Philae Temple, and a relaxing Nile cruise. It's a perfect balance of exploration and relaxation.
Another option is the 5 days Tour to Cairo and Alexandria, which is a highlight of our Cairo tour packages. Discover the Mediterranean charm of Alexandria, with its ancient library and stunning coastal views, alongside Cairo's renowned sites.
If you're more interested in exploring Egypt's ancient heartland, the 5 days Cairo and Luxor short tours offer a deep dive into the Valley of the Kings, Karnak Temple, and Luxor's other historical gems. It’s ideal for history enthusiasts.
For those on a budget, our 5 day Cairo and Giza Pyramids budget holidays provide an affordable way to visit Egypt’s most famous landmarks. Lastly, the 5 Days 4 nights Cairo & Oasis Bahariya with Egypt Travel Packages takes you off the beaten path, offering an adventure to the Western Desert and the stunning Bahariya Oasis.
No matter which package you choose, our Egypt Tour Packages ensure an unforgettable experience in just five days!
🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 Email: info@etbtoursegypt.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt
-
 @ 3f0702fa:66db56f1
2024-12-25 10:38:52
@ 3f0702fa:66db56f1
2024-12-25 10:38:52Благодаря привлечению иностранных инвестиций, развитию инновационных производств и активному внедрению передовых технологий, курганская промышленность вышла на мировой уровень.
Ключевым изменением стало создание современных промышленных кластеров, специализирующихся на высокотехнологичных производствах в области машиностроения, электроники, биотехнологий и возобновляемой энергетики. На территории региона разместили свои производства ведущие международные компании, создавая тысячи новых рабочих мест и обеспечивая высокий уровень заработной платы.
Интеграция с глобальными производственными цепочками позволила курганским предприятиям выйти на новые рынки сбыта, а внедрение цифровых технологий оптимизировало процессы производства, сделав их более эффективными и экологичными.
https://vkvideo.ru/video243919008_456239749?list=ln-izqgmvW4oTcwBJAVMk
Изменения коснулись и жизни курганцев: вырос уровень доходов, повысилось качество жизни, появились новые возможности для профессионального и личностного развития. Курган стал городом, привлекающим высококвалифицированных специалистов из разных регионов и стран, что способствует дальнейшему росту и процветанию региона.
https://vkvideo.ru/video243919008_456239750?list=ln-35iMz371hHkZLdSz7A
Мы продолжим следить за развитием промышленности Кургана и сообщать вам о новых достижениях и проектах. Следите за нашими публикациями.
45news #Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-25 10:36:53
@ 3f0702fa:66db56f1
2024-12-25 10:36:53Бесплатный роллтон в Метрополисе, катание на единорогах в ЦПКО, а может быть летающие машины? Все это впереди, вот только общественный транспорт в Кургане будет актуален всегда, и однажды наш старый добрый друг ПАЗик из гадкого утёнка превратится в прекрасного лебедя. А как это будет выглядеть? Смотри!
https://vkvideo.ru/video243919008_456239751?list=ln-6vWBOCuSeDtvDMaHmH
45news #Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-25 10:28:25
@ 3f0702fa:66db56f1
2024-12-25 10:28:25Этот проект направлен на улучшение качества жизни и сохранение природы нашего города и региона. Рассмотрим его идею подробнее в нашем посте!
Создание экотропы — это шаг к популяризации активного отдыха на природе. Протяженность новой тропы составляет около 1,5 километра и будет проходить через живописные уголки Кургана. По маршруту предполагается установить стенды, рассказывающие о местной флоре и фауне, а также о краснокнижных растениях и животных.
На экотропе будут оборудованы специальные зоны для отдыха. Здесь жители могут наслаждаться природой, проводить время с семьей и заниматься спортом. Планируется установка скамейки, беседки и места для пикников.
Экотропа станет площадкой для проведения образовательных мероприятий. Школы и детские сады могут организовывать экскурсии, на которых дети будут учиться бережному отношению к природе и узнавать о важности экосистемы.
Проект включает в себя мероприятия по озеленению и восстановлению территории. Будут высажены деревья и кустарники, которые помогут улучшить экологическую обстановку в городе и создать новые места обитания для животных.
Создание экотропы — это совместный проект администрации Кургана и местных жителей. Все желающие смогут принять участие в обсуждении маршрута и внести свои предложения по его обустройству.
Давайте вместе сделаем наш город еще более зеленым и уютным!
45news
Курган2040
-
 @ 3f0702fa:66db56f1
2024-12-25 10:15:17
@ 3f0702fa:66db56f1
2024-12-25 10:15:17В Кургане появились уникальные застекленные школы будущего, не только инновационные, но и летающие. Эти научные учреждения используют современные технологии, включая обучение с помощью роботов, что обеспечивает индивидуальный подход к каждому ученику. Лучше всего использовать естественное освещение и создать комфортную атмосферу для обучения. Летающие школы становятся символом прогресса и новогодними мероприятиями, предоставляя учащимся уникальные возможности для развития в динамично меняющемся мире.
45news
Курган2040
https://psv4.userapi.com/s/v1/d/hqHqmslIa_llR6biFhUtTzI3wAjquW74AJMDoTDgyXQJtsHZ0QzdSqSKmckPuPGHhpZ89856Lxs0hU6deiCOW6moyy7gK27r_pjMorYXb79zCvJsBaTQjw/document.mp4
-
 @ 30e902b3:49c066b2
2024-12-25 08:37:23
@ 30e902b3:49c066b2
2024-12-25 08:37:23Como una reciente esposa que luego de una maratónica sesión de fotos y besos requeridos para perpetuar, Se acomoda en el coche que les aguardaba tras la ceremonia y se dispone a acomodar el delineado labial de Joker que le devolvía el espejo, cuando vió rodar el carmín por sobre su regazo. Como esa pobre mujer que, ante desesperante situación, elige entrar al salón con una vincha de cotillón de esas que simulan un cuchillo atravesando el cráneo, para justificar la autopista roja que chorrea por su blanco lienzo. Con esa misma inocente y de pobre humor intención es que relato lo acontecido.
Así como es verdad que Santa existe; Lo he visto tanto en innumerables películas, documentales e informativos. Estantes con inmensidad de bibliografía al respecto. Es verdad también que Santa no es ningún Dios, y por ende, no puede estar en todos lados. Y es por eso que algunas personas acometen la irresponsable y criminal postura de usurpador de identidad, bajo la complicidad de gran parte de la sociedad, y se disfraza de Santa en determinadas ocasiones. Y aquel año el destino me señaló, extendiéndome con la otra mano el vestido destinado a la tarea. Por aquel entonces era una costumbre familiar que había nacido cuando algún pariente viajante había traído el dichoso traje. Yo era muy joven aun. Hacía pocos años que entendía el significado de lo que estaba viviendo y torpemente emulaba lo que con el tiempo conocería como empatía. Pero mi estatura ya daba la talla y el consejo familiar, cuyos miembros ya habían cumplido su labor social dentro de aquella mortaja, dictaminó el sacrificio.
La puesta en escena comenzaba en casa de un vecino en la que ya se había dejado en custodia el avatar, una enorme bolsa de regalos, montones de rellenos para completar el volumen de la foto del panfleto y una campana vieja. Así es como Santa aparecía tocando la campana por la calle y era recibido en la puerta con desorbitados ojos de los más pequeños, muchos de ellos incluso a punto de largar el llanto de la emoción o el susto (dependiendo de el miembro de la familia dentro del atuendo). Cabe mencionar, recordar y hasta recomendar un relato de Landriscina en el que hace mención del detalle que traigo a contexto: El traje era obviamente diseñado a las costumbres del hemisferio norte. Y la tecnología de la época lo conformaba en un gran mameluco rojo con rellenos de vellón, una tupida barba con bigote, también de vellón y un gran gorro montado sobre una blanca, larga y canosa peluca... también de vellón. Estas cualidades le conferían el término usado anteriormente de sacrificio a la tarea con 30ºc. Repartí regalos, canté villancicos y esbocé una burlona y gruesa risotada lo mejor que pude. Cuando terminó mi calvario tomé la bolsa y apuré el paso a casa del vecino. La barba ya dolía. El roce había dejado toda mi cara irritada y la comezón en salvas sean las partes se confundía con escalofríos del sudor que pincelaba mi espalda. Fué a los pocos metros que me percaté. La campana había sido como un llamado a misa y parte del pueblo esperaba a Santa. Una fila de padres se hacían los distraídos ocultando paquetes en mi bolsa mientras otro familiar exhortaba al infante a acercarse en busca de su regalo. El tiempo se desfiguró hasta que la multitud fué mermando cuando ya podía ver la luz del zaguán del vecino.
Recién entonces lo vi. Lo traían en una silla de ruedas. Pero no era una de las comunes que alguna vez había visto. Esa era como los más modernos autos. Tenía cinturones de seguridad. Y aquí es donde te pido, lector, que sepas leer el contexto que intenté mostrar y entender que son recuerdos de alguien que se identifica como “aveloriado”. Y digo lo traían, porque el chico carecía de coordinación como para mover las ruedas. Hubo que hacer una pausa, como congelar la imagen para que pudiera enfocar la mirada lo suficiente y su cabeza se aquiete. No pensé ni sentí la barba durante los minutos que tardó alguna tía para ir a por la cámara de fotos olvidada. Hoy veo las fotos de mi familia de aquel día y muchos ya no están. Incluso alguno de los que ese día recibieron un paquete de mi mano. Pero mi recuerdo de esa noche quedó indeleble junto a las lágrimas de alegría y emoción de esa familia que me dejó parado en la calle, sin entender lo que había pasado, pero con el alma henchida de agradecimiento por haber sido el testaferro.
https://youtu.be/UXQrrxC0L48
-
 @ 6bcc27d2:b67d296e
2024-12-25 08:15:21
@ 6bcc27d2:b67d296e
2024-12-25 08:15:21[2024-12-06] - 21:11 これから[[伊豆大島]][[フルマラソン]]へのフェリー。![[Pasted Image 20241206211138.jpeg]]竹芝客船ターミナルに向かって歩いてる
- 21:14 ![[Pasted Image 20241206211453.jpeg]]
- 21:20 ![[Pasted Image 20241206212053.jpeg]]
- 21:28 ![[Pasted Image 20241206212843.jpeg]]
- 21:44 フェリーに乗った ![[Pasted Image 20241206214435.jpeg]]![[Pasted Image 20241206214442.jpeg]]![[Pasted Image 20241206214447.jpeg]]
- 22:22 展望デッキから見られる景色が綺麗 ![[Pasted Image 20241206222051.jpeg]]![[Pasted Image 20241206222117.jpeg]]![[Pasted Image 20241206222138.jpeg]]![[Pasted Image 20241206222202.jpeg]]
当日 - 05:59 下船 ![[Pasted Image 20241207055912.jpeg]]
- 06:06 ![[Pasted Image 20241207060556.jpeg]]
- 06:27 バスに乗って会場に着いた ![[Pasted Image 20241207062701.jpeg]]
- 06:30 参加者は10km、ハーフマラソン、フルマラソンを選択できるが、[[フルマラソン]]が圧倒的に最も多い ![[Pasted Image 20241207063019.jpeg]]
- 06:37 ![[Pasted Image 20241207063727.jpeg]]
-
08:00 ![[Pasted Image 20241207080054.jpeg]] スタート
-
08:03 ![[Pasted Image 20241207080318.jpeg]]
- 08:17 ![[Pasted Image 20241207081730.jpeg]]
- 08:51 ![[Pasted Image 20241207085109.jpeg]]
- 08:52 ![[Pasted Image 20241207085239.jpeg]]
- 09:15 ![[Pasted Image 20241207091518.jpeg]]
- [ ] 09:16 ![[Pasted Image 20241207091658.jpeg]]
- 09:20 ![[Pasted Image 20241207092005.jpeg]]
- 09:38 ![[Pasted Image 20241207093843.jpeg]]
- 09:48 ![[Pasted Image 20241207094804.jpeg]]
- 09:51 ![[Pasted Image 20241207095133.jpeg]]
- 09:58 ![[Pasted Image 20241207095840.jpeg]]
- 10:01 ![[Pasted Image 20241207100112.jpeg]]
- 10:30 ![[Pasted Image 20241207103011.jpeg]]
- 10:35 ![[Pasted Image 20241207103518.jpeg]]
- 11:13 ![[Pasted Image 20241207111306.jpeg]]
- 11:26 ![[Pasted Image 20241207112647.jpeg]]
- 12:57 経験したことのない足の痛さ ![[Pasted Image 20241207114610.jpeg]]
- 12:57 最後死にかけで完走。
-
13:07 ![[Pasted Image 20241207130724.jpeg]] 完走後の味噌汁
-
13:51 温泉へ
- 15:02 ![[Pasted Image 20241207150143.jpeg]] 大島の子供たちはみんなこれで育ったらしい
- 15:07 ということを株式会社大島牛乳のおっちゃんに教えてもらった![[Pasted Image 20241207150751.jpeg]]
- 15:32 じゃんけん大会が始まった。景品が紹介されている ![[Pasted Image 20241207153215.jpeg]]
- 16:01 ![[Pasted Image 20241207155736.jpeg]] 「大将」に入る https://maps.app.goo.gl/xd1iXZ4pDaZsQafy7?g_st=ic 豚丼セットそばを注文
- 16:08 ![[Pasted Image 20241207160818.jpeg]]
-
 @ 6bcc27d2:b67d296e
2024-12-25 07:18:08
@ 6bcc27d2:b67d296e
2024-12-25 07:18:08問い合わせ番号: C00033712277
[2024-12-06] - 21:11 これから[[伊豆大島]][[フルマラソン]]へのフェリー。![[Pasted Image 20241206211138.jpeg]]竹芝客船ターミナルに向かって歩いてる
- 21:14 ![[Pasted Image 20241206211453.jpeg]]
- 21:20 ![[Pasted Image 20241206212053.jpeg]]
- 21:28 ![[Pasted Image 20241206212843.jpeg]]
- 21:44 フェリーに乗った ![[Pasted Image 20241206214435.jpeg]]![[Pasted Image 20241206214442.jpeg]]![[Pasted Image 20241206214447.jpeg]]
- 22:22 展望デッキが綺麗 ![[Pasted Image 20241206222051.jpeg]]![[Pasted Image 20241206222117.jpeg]]![[Pasted Image 20241206222138.jpeg]]![[Pasted Image 20241206222202.jpeg]]
当日 - 05:59 下船 ![[Pasted Image 20241207055912.jpeg]]
- 06:06 ![[Pasted Image 20241207060556.jpeg]]
- 06:27 バスに乗って会場に着いた ![[Pasted Image 20241207062701.jpeg]]
- 06:30 参加者には10km、ハーフマラソン、フルマラソンの選択肢があり、[[フルマラソン]]が圧倒的に最も多い ![[Pasted Image 20241207063019.jpeg]]
- 06:37 [[2024-12-07 伊豆大島フルマラソン]] ![[Pasted Image 20241207063727.jpeg]]
-
08:00 ![[Pasted Image 20241207080054.jpeg]] スタート
-
08:03 ![[Pasted Image 20241207080318.jpeg]]
- 08:17 ![[Pasted Image 20241207081730.jpeg]]
- 08:51 ![[Pasted Image 20241207085109.jpeg]]
- 08:52 ![[Pasted Image 20241207085239.jpeg]]
- 09:15 ![[Pasted Image 20241207091518.jpeg]]
- [ ] 09:16 ![[Pasted Image 20241207091658.jpeg]]
- 09:20 ![[Pasted Image 20241207092005.jpeg]]
- 09:38 ![[Pasted Image 20241207093843.jpeg]]
- 09:48 ![[Pasted Image 20241207094804.jpeg]]
- 09:51 ![[Pasted Image 20241207095133.jpeg]]
- 09:58 ![[Pasted Image 20241207095840.jpeg]]
- 10:01 ![[Pasted Image 20241207100112.jpeg]]
- 10:30 ![[Pasted Image 20241207103011.jpeg]]
- 10:35 ![[Pasted Image 20241207103518.jpeg]]
- 11:13 ![[Pasted Image 20241207111306.jpeg]]
- 11:26 ![[Pasted Image 20241207112647.jpeg]]
- 12:57 経験したことがない足の痛さ ![[Pasted Image 20241207114610.jpeg]]
- 12:57 完走
-
13:07 ![[Pasted Image 20241207130724.jpeg]] 完走後の味噌汁
-
13:51 温泉へ
- 15:02 ![[Pasted Image 20241207150143.jpeg]] 大島の子供たちはみんなこれで育った
- 15:07 ![[Pasted Image 20241207150751.jpeg]]
- 15:32 じゃんけん大会が始まった。景品が紹介されている ![[Pasted Image 20241207153215.jpeg]]
- 16:01 ![[Pasted Image 20241207155736.jpeg]] 「大将」に入る https://maps.app.goo.gl/xd1iXZ4pDaZsQafy7?g_st=ic 豚丼セットそばを注文
- 16:08 ![[Pasted Image 20241207160818.jpeg]]
-
 @ 16d11430:61640947
2024-12-25 05:17:20
@ 16d11430:61640947
2024-12-25 05:17:20Aiyyo! Ever felt like your operating system was missing that extra punch of masala? Look no further! AiyyoOS is here to spice up your digital life with the perfect blend of Tollywood drama, Kollywood action, Mollywood brilliance, and Sandalwood charm. Here's why AiyyoOS is the Rajinikanth of all operating systems:
Features:
🌴 Coconut Kernel: Powered by the latest "Idli v1.0" kernel, it's so lightweight that even your grandma’s old Nokia could run it.
🎥 Tollywood Task Manager: Multitasking? Don't worry, this Task Manager handles chaos like a proper Telugu movie hero – one-click, 100 tasks done!
💃 Dance-Off Notifications: Every time you get an alert, Allu Arjun will pop up on your screen for a mini "Pushpa step." Beat that, iOS!
🍛 Masala Customization: From spicy Chettinad themes to Kerala mural wallpapers, personalize your OS with more options than a South Indian wedding buffet.
📡 Signal Boost: Your Wi-Fi bars will always be full because it’s powered by "Anna Satellite Network" – signals even reach Chennai's Marina Beach on a rainy day!
🎤 Voice Assistant: Siri-ka Akka: Meet “Sundari,” the assistant who greets you with, "Aiyyo, enna venuma?" (What do you need?) and never misunderstands your accent.
Default Apps:
🎥 "Blockbuster" Media Player – Plays every song with DSP-level bass and AR Rahman-level vibes.
🔥 VadaChutney Browser – So fast, even Prabhas couldn’t keep up with its speed in Salaar.
📜 Rajini Terminal – Every command you type ends with a punch dialogue like, "Naan eppovume correct-a thaan iruppen!"
AiyyoOS Editions:
-
The Baahubali Edition – For high-performance PCs. (Why download one app when you can conquer them all?)
-
The Lungi-Linux Edition – Budget-friendly for your recycled laptops. (Saves resources, just like that one lungi you’ve been using since 2012.)
-
Thalaiva Ultra Edition – Pre-installed with Superstar wallpapers and "super-fast bootup" that completes before your filter coffee brews.
Coming Soon:
An update called Dosa Drive – Your cloud storage as crispy and flexible as your favorite dosa!
Disclaimer: Not responsible for random Kolaveri moments or neighbors joining your party when Sundari starts blasting AR Rahman hits at full volume.
Install AiyyoOS today, and may your computing life be as flavorful as a piping hot plate of biryani! Aiyyo!
-
-
 @ 7ed5bd1c:4caa7587
2024-12-25 03:30:08
@ 7ed5bd1c:4caa7587
2024-12-25 03:30:08Proof of Work: พื้นฐานของความน่าเชื่อถือใน Bitcoin
Bitcoin ไม่ได้มีธนาคารกลางหรือองค์กรใดคอยควบคุม แต่ความปลอดภัยและความน่าเชื่อถือของมันมาจากสิ่งที่เรียกว่า "Proof of Work" หรือ PoW ซึ่งเป็นกระบวนการที่นักขุด (miners) ใช้ในการตรวจสอบและยืนยันธุรกรรมบนเครือข่าย นี่คือหลักการที่ช่วยสร้างความไว้วางใจและความโปร่งใสในระบบกระจายศูนย์ (decentralized system) นี้
Proof of Work คืออะไร?
Proof of Work เป็นกลไกที่ทำให้ทุกคนในเครือข่าย Bitcoin เห็นพ้องต้องกันเกี่ยวกับสถานะของบัญชีหรือธุรกรรม โดยใช้พลังงานคอมพิวเตอร์ในการแก้สมการทางคณิตศาสตร์ที่ซับซ้อน เมื่อมีการแก้สมการสำเร็จ ธุรกรรมจะถูกยืนยันและเพิ่มลงในบล็อกเชน ซึ่งเปรียบเสมือนสมุดบัญชีสาธารณะที่ทุกคนสามารถตรวจสอบได้
การขุด Bitcoin สำคัญอย่างไร?
-
สร้างความปลอดภัยให้กับเครือข่าย: Proof of Work ช่วยป้องกันการโจมตี เช่น การใช้จ่ายเงินซ้ำ (double spending) หรือการปลอมแปลงธุรกรรม เนื่องจากการปลอมแปลงต้องใช้พลังงานและทรัพยากรมากจนแทบจะเป็นไปไม่ได้
-
กระจายอำนาจ: การขุดทำให้ไม่มีองค์กรใดสามารถควบคุมเครือข่ายได้ทั้งหมด เพราะใครก็ตามที่มีฮาร์ดแวร์และไฟฟ้าก็สามารถเข้าร่วมได้
-
สนับสนุนการออก Bitcoin ใหม่: Bitcoin ใหม่ถูกปล่อยออกมาผ่านกระบวนการขุด ซึ่งจะเกิดขึ้นทุก ๆ 10 นาที และช่วยรักษาอัตราการผลิต Bitcoin ให้คงที่
ความสำคัญของ Proof of Work ต่อระบบ Bitcoin
Proof of Work ไม่เพียงแค่ช่วยสร้างความน่าเชื่อถือ แต่ยังช่วยให้ระบบมีความยุติธรรมและโปร่งใส เนื่องจากทุกคนสามารถตรวจสอบข้อมูลในบล็อกเชนได้ และกระบวนการขุดยังเป็นสิ่งที่ทำให้การเปลี่ยนแปลงข้อมูลในอดีตเป็นไปได้ยาก
ความเข้าใจผิดเกี่ยวกับ Proof of Work
บางคนมองว่าการใช้พลังงานของ Proof of Work เป็นเรื่องสิ้นเปลือง แต่ในความเป็นจริง การใช้พลังงานนี้เป็นสิ่งที่จำเป็นเพื่อสร้างความปลอดภัยให้กับเครือข่าย Bitcoin และช่วยสร้างมูลค่าของมัน
ข้อดีของ Proof of Work
-
ความปลอดภัยสูง: การแก้สมการต้องใช้พลังงานมาก ทำให้การปลอมแปลงบล็อกเชนแทบเป็นไปไม่ได้
-
โปร่งใส: ทุกคนในเครือข่ายสามารถตรวจสอบธุรกรรมได้
-
สร้างแรงจูงใจ: นักขุดได้รับรางวัลเป็น Bitcoin ซึ่งกระตุ้นให้คนเข้าร่วมเครือข่าย
Proof of Work เป็นหัวใจสำคัญที่ทำให้ Bitcoin ยังคงน่าเชื่อถือในโลกดิจิทัลที่มีความซับซ้อน แล้วคุณล่ะ คิดว่า Proof of Work มีความสำคัญแค่ไหนต่ออนาคตของการเงิน? ร่วมพูดคุยกันได้ในความคิดเห็น!
-
-
 @ bcea2b98:7ccef3c9
2024-12-25 03:11:27
@ bcea2b98:7ccef3c9
2024-12-25 03:11:27It has been a fun year of learning and entertainment with you all. Merry Christmas!
originally posted at https://stacker.news/items/823433
-
 @ 70e6b44a:7c78b8e9
2024-12-25 00:53:04
@ 70e6b44a:7c78b8e9
2024-12-25 00:53:04the melão is a fruit.
-
 @ 70e6b44a:7c78b8e9
2024-12-25 00:52:39
@ 70e6b44a:7c78b8e9
2024-12-25 00:52:39the maçã is not a fruit at all.
-
 @ a950ba55:02f4f8c9
2024-12-25 00:28:46
@ a950ba55:02f4f8c9
2024-12-25 00:28:46عملت جينيت بلونديل دون ترخيص أو رقابة لصالح مجرم الحرب المزعوم رفعت الأسد.
أدى انهيار نظام الأسد في سوريا إلى موجات من الصدمة في جميع أنحاء العالم، وكان ذلك بمثابة نهاية ديكتاتورية تركت الدولة في حالة يرثى لها. فبالإضافة إلى القمع الوحشي خلال الحرب الأهلية التي دامت عقداً من الزمن في البلاد، تشمل التهم الموجهة ضد عائلة الأسد الفساد المنهجي على نطاق مذهل.
ويُزعم أن أفراد العائلة قد نهبوا مئات الملايين من الجنيهات من الشعب السوري. وقد تم تحويل هذه الأموال من قبل أسطول من المحامين وخبراء الضرائب ومقدمي خدمات الائتمان في الخارج إلى إمبراطورية عقارية كبيرة: شقق فخمة تطل على نهر السين، وقصر فخم في مايفير، وفيلات منتشرة في جميع أنحاء كوستا ديل سول.
واليوم، يستطيع مكتب الصحافة الاستقصائية (TBIJ) وصحيفة الغارديان كشف النقاب عن بريطاني ساعد في إدارة تلك الملايين نيابة عن رفعت الأسد، عم بشار والرجل المعروف باسم ”جزار حماة“ لدوره المزعوم في الإشراف على السجن غير القانوني والتعذيب والإعدام لما بين 10 آلاف و40 ألف شخص في عام 1982.
وفي مارس/آذار، أصدرت هيئة الرقابة المالية في غيرنسي، وهي جزيرة صغيرة تابعة للتاج البريطاني، غرامة قدرها 210,000 جنيه إسترليني ضد جينيت بلونديل، وهي من سكان غيرنسي، وتبلغ من العمر 40 عامًا، ومنعتها من تولي مناصب مختلفة ذات مسؤولية مالية لمدة تسع سنوات. وقالت إنها خالفت قانون غيرنسي مرارًا وتكرارًا في عملها لصالح عملائها، وأحدهم عائلة الأسد.

وقد أخفت الجهة الرقابية اسم موكل بلوندل، لكنها أشارت إلى أنه ”مجرم حرب مزعوم“ و”مجرم حرب مزعوم“. ينص الإشعار التنظيمي على أن بلوندل كانت على علم بالادعاءات الخطيرة ضد موكلها واستمرت في العمل لديه بين عامي 2013 و2020، دون ترخيص من الرقابة التنظيمية. ولكن على الرغم من الغرامة الكبيرة والحظر الطويل، يبدو أن بلوندل لم تواجه أي ملاحقة جنائية.
وقال فيليب غرانت، المدير التنفيذي لمنظمة ترايال الدولية، التي كانت أول من تقدم بشكوى جنائية ضد الأسد في سويسرا: ”إن جرائم رفعت الأسد، لا سيما مجزرة حماة عام 1982، هي من بين أخطر الفظائع في عصرنا“. ودعا غرانت إلى اتخاذ تدابير مساءلة أقوى، بما في ذلك الملاحقات الجنائية والعقوبات المهنية.
إن السهولة التي قام بها مجرم حرب مشتبه به بتحويل مئات الملايين من الدولارات التي يُزعم أنها اختلست من الأموال العامة السورية إلى أوروبا تسلط الضوء بشكل صارخ على نهج القارة المتراخي في التعامل مع غسيل الأموال في العقود الأخيرة. كما يسلط الضوء أيضاً على كيفية قيام المملكة المتحدة والأقاليم التابعة للتاج البريطاني وأقاليم ما وراء البحار التابعة لها بتقديم الخدمات التي مكنت بعضاً من أكثر اللصوصية البغيضة في العالم.
وتأتي هذه الاكتشافات في الوقت الذي تنتظر فيه غيرنسي نتائج التقييم الأخير الذي أجرته هيئة Moneyval، وهي هيئة تابعة لمجلس أوروبا تتحقق من ضوابط غسل الأموال وتمويل الإرهاب في الولايات القضائية في جميع أنحاء القارة. وكان آخر تقرير لهيئة الرقابة في عام 2015 قد وجد أن الملاحقات القضائية والإدانات في غيرنسي بتهمة غسيل الأموال كانت ”منخفضة بشكل غير متناسب“ بالنظر إلى حجم نظامها المالي، الذي احتفظ هذا العام بأصول بقيمة 300 مليار جنيه إسترليني تقريبًا.
إمبراطورية الثروة لم تظهر أي آثار لماضي بلوندل علنًا منذ أن أصدرت الهيئة التنظيمية عقوبتها، حيث تم محو وجودها على الإنترنت. وأشار التقرير إلى أن بلوندل قد حصلت على درجة الماجستير في حوكمة الشركات وبدأت العمل في قطاع الخدمات المالية في غيرنسي في عام 2000.
وفي إحدى الشركات الخاضعة للتنظيم، التقت لأول مرة بعائلة رفعت الأسد، الذي كان يشكل ”99%“ من عملها في الشركة وفقًا للجهة المنظمة في غيرنسي.
طُرد رفعت من سوريا في عام 1984 بعد محاولة الانقلاب على شقيقه حافظ، والد بشار وحاكم البلاد آنذاك. قضى رفعت الأسد معظم العقود التالية في المنفى. ولا يُعتقد أنه كان له يد في القمع الذي حدث خلال الحرب الأهلية التي بدأت في عام 2012. لكن الثروة الهائلة التي جمعها كانت قد نهبت إلى حد كبير من الأموال العامة السورية في الثمانينيات.

وبعد فراره إلى أوروبا، استمر في تكديس إمبراطورية عقارية ذات أبعاد مذهلة.
فقد وجدت السلطات أنه وأفراد أسرته استحوذوا على 507 عقارات تبلغ قيمتها الإجمالية حوالي 700 مليون يورو، متخفين وراء شركات وهمية، بما في ذلك في الأراضي البريطانية مثل جبل طارق وجزر فيرجن البريطانية.
وكانت هذه الممتلكات مملوكة لشركات كان من بين مديريها زوجات الأسد وأبناؤه المتعددين - ولكن لم يكن الرجل نفسه تقريبًا.
اشترت العائلة مئات العقارات، العديد منها في كوستا ديل سول في إسبانيا، بما في ذلك فيلا بقيمة 60 مليون يورو (51 مليون جنيه إسترليني) في بلدة بيناهافيس، على بعد نصف ساعة بالسيارة من ماربيا.
وفي لندن، أصبح آل الأسد المالكين السريين لأكبر مسكن في العاصمة بعد قصر باكنغهام، وهو منزل شاسع في هايغيت في لندن قُدّرت قيمته ب 300 مليون جنيه إسترليني. وباع أفراد عائلة الأسد هذا المنزل في عام 2007، متخفين وراء شركة وهمية في بنما، لكنهم استحوذوا على قصر في مايفير قد تصل قيمته الحالية إلى 60 مليون جنيه إسترليني.
وفي باريس، استحوذت عائلة الأسد على أكثر من 40 شقة تطل على نهر السين، وأثثت قصراً من سبعة طوابق يقع في شارع فوش - وهو شارع كبير يؤدي إلى قوس النصر - بأثاث تزيد قيمته عن مليون جنيه إسترليني.
التحقيقات والملاحقات القضائية لطالما ادعى الأسد أن ثروته مشروعة - هبة من العائلة المالكة السعودية. ولكن في لائحة اتهام صدرت في عام 2019 وجد المدعون الإسبان أن الجزء الأكبر من ثروته جاء من 300 مليون دولار من أموال الدولة السورية والقروض التي دفعها له شقيقه حافظ في الثمانينيات.
كما اتهمه المدعون الإسبان أيضًا بأنه حصل على ”موارد ضخمة غير مشروعة من أنشطة إجرامية متعددة: الابتزاز، والتهديد، والتهريب، ونهب الثروات الأثرية، واغتصاب العقارات، والاتجار بالمخدرات“.

كانت لائحة الاتهام تلك نتيجة واحدة من التحقيقات الجنائية العديدة التي أُجريت بشأن ثروة آل الأسد التي بدأت في جميع أنحاء أوروبا خلال السنوات السبع التي ظل فيها بلونديل يعمل لدى العائلة.
في عام 2014، وبعد شكوى من منظمة شيربا غير الحكومية المعنية بحقوق الإنسان، أطلق المدعون العامون الفرنسيون تحقيقًا في غسيل الأموال ضد الأسد كشف عن حجم إمبراطورية ممتلكاته. وفي عام 2016، صادرت السلطات الفرنسية ممتلكاته. وحذت إسبانيا والمملكة المتحدة حذوهما، على الرغم من أن السلطات البريطانية تأخرت كثيرًا في منع بيع قصر في ساري بقيمة 3.7 مليون جنيه إسترليني كان يشغله أحد أبنائه، وفقًا لصحيفة التايمز.
في يونيو 2020، أدانت محكمة جنائية فرنسية الأسد بتهمة غسيل الأموال واختلاس الأموال العامة السورية وحكمت عليه بالسجن لمدة أربع سنوات. وفشل طعنان على الحكم، لكن الأسد لم يرَ زنزانته من الداخل - فقد فر إلى سوريا في عام 2021. (ظل بلونديل يعمل مع العائلة حتى مارس 2020، أي قبل ثلاثة أشهر فقط من الإدانة). وخلال فترة مماثلة، كان المدعون السويسريون قد بدأوا تحقيقًا في مزاعم قيام الأسد بذبح عشرات الآلاف من الأشخاص في حماة، وهي حادثة تم الإبلاغ عنها على نطاق واسع في الوقت الذي بدأت فيه بلونديل عملها غير المنظم لصالحه في عام 2013.
في مقابلات رسمية، رفض الأسد التحدث، لكنه لطالما نفى هذه الادعاءات. في عام 2021، أصدر المدعون السويسريون مذكرة توقيف دولية ضد الأسد، وفي هذا العام اتهموه رسمياً بارتكاب جرائم حرب.
بالإضافة إلى ذلك، حاول المدعون الإسبان محاسبة الأسد. واتهمته لائحة اتهام صدرت في عام 2019 بارتكاب جرائم ”بشكل منهجي وصناعي“ لإثراء نفسه. وجاء فيها أن الأسد، على الرغم من استخدامه لزوجاته وأبنائه كوكلاء له في إمبراطوريته العقارية، إلا أنه احتفظ ”بالسيطرة والهيمنة المطلقة على عمليات الاستحواذ“.
ومع ذلك، يبدو أنه لم يتبع ذلك أي ملاحقة قضائية.

وفي الوقت نفسه، تجاوزت مهام بلونديل لصالح العائلة مجرد التوقيع على الأوراق، وفقًا للجهة التنظيمية في غيرنسي. في 23 أكتوبر 2015، تلقت دفعة بقيمة مليون يورو في حسابها المصرفي الشخصي، اسميًا لتأسيس شركة استئمانية في غيرنسي. ولكن الشركة لم تتحقق أبدًا.
ومع ذلك، لم تقم بلونديل بإعادة المبلغ. وبدلاً من ذلك، استخدمته لتسديد أكثر من 150 دفعة لأطراف ثالثة مختلفة.
وقالت الهيئة التنظيمية إن هناك ”خطرًا حقيقيًا للغاية يتمثل في أن السيدة بلوندل ربما تكون قد استخدمت لغسل عائدات الجريمة، وهو خطر فشلت السيدة بلوندل باستمرار في إدراكه“.
”لقد فشلت السيدة بلوندل باستمرار في فهم خطورة وعواقب أفعالها.“
وقالت الدكتورة سوزان هاولي، المديرة التنفيذية لمنظمة تسليط الضوء على الفساد: ”في أكثر حالات غسيل الأموال فظاعة... يجب استخدام الثقل الكامل للقانون لخلق رادع حقيقي.
”إذا كانت دول مثل المملكة المتحدة وتوابعها التابعة للتاج ... مستعدة فقط لاستخدام التدابير التنظيمية مثل الغرامات وإسقاط الأهلية، فلا يمكنها أن تأمل في ردع غسل الأموال القذرة بشكل كامل من خلال أنظمتها المالية.“
ورداً على سؤال عن سبب عدم مقاضاة بلوندل، قال متحدث باسم ولاية غيرنسي للمكتب الاستقصائي للمعلومات والاتصالات للصحافة الاستقصائية إن الولاية القضائية تتعامل مع جرائم غسل الأموال بجدية بالغة.
وقال المتحدث: ”في هذه الحالة تحديداً، اتخذت [الهيئة التنظيمية] إجراءات جادة ضد هذا الشخص، حيث فرضت عليه غرامة كبيرة جداً ومنعه من العمل في هذا المجال“.
”ومع ذلك، وكما يدرك الأشخاص العاملون في قطاع إنفاذ القانون جيدًا، فإن عتبة الأدلة للملاحقة الجنائية وعتبة اتخاذ الهيئة التنظيمية للإجراءات تختلف تمامًا.“
وتابعوا: ”كما هو الحال في جميع المسائل الجنائية، يجب إثبات الجريمة المزعومة بالمعايير الجنائية العالية من أجل نجاح أي ملاحقة قضائية. وفي حالة عدم وجود أدلة كافية للمضي قدمًا بعد إجراء تحقيق كامل، يتم إغلاق القضية.“
وقد أخبر متحدث باسم الهيئة التنظيمية، وهي هيئة الخدمات المالية في غيرنسي، للمكتب الاستقصائي للمعلومات والاتصالات أنها تأخذ معالجة الجرائم المالية على محمل الجد.
لم ترد جينيت بلونديل ورفعت الأسد على طلبات متعددة للتعليق.
مقال مترجم، إضغط هنا لقراءة المقال الأصلي.
-
 @ 16d11430:61640947
2024-12-24 23:51:26
@ 16d11430:61640947
2024-12-24 23:51:26When we talk about “high-performance activities,” our minds often leap to elite sports: professional basketball, Olympic weightlifting, or marathon running. We honor the countless hours of training, physical strain, and meticulous recovery routines these athletes undergo. By contrast, programming is often regarded as a purely mental pursuit—cerebral, sedentary, and (supposedly) easy on the body. And yet, beneath the hood, programming demands an intense, prolonged physical engagement that can lead to chronic issues if not managed correctly.
This article dives deep into the anatomical mechanisms underlying the physical strain of programming, highlights chronic management techniques, compares programming to other glorified high-performance activities, and examines how the tech industry’s relentless demands on programmers can exacerbate these issues. We also take a closer look at the stark difference in protective measures and compensation between professional sports and the technology sector, highlighting the parallels to early sports exploitation. A newly added section explores how programming compares to typical “office work” and other digital pursuits.
- Anatomy Under the Hood
a. Musculoskeletal System
- Spine and Posture
Thoracic and Lumbar Spine: Extended time seated can compress the intervertebral discs in the lower (lumbar) region, leading to stiffness, aches, and potential nerve impingements (e.g., sciatica). In the upper (thoracic) region, slouching over the keyboard can cause chronic tightness in the chest and overstretching of the upper back muscles.
Cervical Spine (Neck): Leaning forward to view a monitor adds extra load to the cervical spine—sometimes referred to as “tech neck.” The farther the head projects forward, the heavier it effectively becomes, causing strain on the neck muscles.
- Shoulders and Arms
Rotator Cuff: Prolonged elevation of the arms when typing or mousing can cause tension in the shoulder girdle. Over time, reduced blood flow and muscle fatigue can make the shoulder joints more prone to impingement.
Forearms and Wrists: Repetitive flexion/extension at the wrist while typing can inflame tendons, leading to repetitive strain injuries (RSIs). Common issues include tendonitis and carpal tunnel syndrome (compression of the median nerve at the wrist).
- Hands and Fingers
Finger Flexors: Each keystroke engages flexor tendons in the fingers. The accumulation of thousands of keystrokes per day can lead to microtrauma in the tendon sheaths.
Thumb Overuse: On trackpads and certain mice, the thumb may carry extra load, which can contribute to conditions like De Quervain’s tenosynovitis.
b. Neurological Involvement
Nerve Compression: Poor posture compresses nerves at various “tunnels” (e.g., carpal tunnel in the wrist, cubital tunnel at the elbow, thoracic outlet near the neck). This can result in numbness, tingling, or weakness in the hands.
Eye Strain and Headaches: Long periods of focusing on a screen can trigger tension headaches from constant contraction of the ciliary muscles in the eyes, as well as the trapezius and suboccipital muscles in the neck.
c. Circulatory System
Blood Flow Restriction: Static posture often reduces proper circulation to the lower limbs, increasing the risk of swelling, varicose veins, and discomfort.
Microbursts of Movement: Typing/mousing can lead to localized demand for blood supply in the forearms, and if posture is poor, it can be harder for the cardiovascular system to efficiently transport oxygen and remove metabolic waste.
- Chronic Management Techniques
Like elite athletes, programmers must develop a recovery and maintenance routine. Instead of ice baths and specialized sports physiotherapy, the focus is on ergonomics, movement breaks, and posture correction.
- Ergonomic Setup
Chair and Desk: Align your chair height such that your hips are slightly above your knees, encouraging the natural lumbar curve. Keep your feet flat on the floor or on a footrest. Position the desk so your elbows form a 90-degree angle when typing.
Keyboard and Mouse Position: Keyboard should be directly in front of you, and the mouse close enough so you don’t have to reach or twist your shoulder. Consider an ergonomic keyboard or a vertical mouse if you experience wrist discomfort.
Monitor Placement: Keep the top of the monitor at (or slightly below) eye level and roughly an arm’s length away from your face. This reduces cervical flexion and eye strain.
- Breaks and Micro-Exercises
Pomodoro Technique: Every 25–30 minutes, take a short 5-minute break. Use this time to stand, stretch, and move.
Posture Shifts: Aim to change your seated position slightly every 10–15 minutes to avoid static loading on the same muscles.
Desk Exercises: Simple exercises like shoulder rolls, wrist rotations, seated spinal twists, and neck stretches help reduce tension and encourage blood flow.
- Movement and Strength Training
Core Strength: A strong core helps maintain an upright posture without undue stress on the spine. Exercises like planks, bridges, and bird dogs are effective and low-impact.
Shoulder Stability: Strengthening the rotator cuff and upper back (e.g., with resistance bands) improves shoulder alignment and reduces chronic tension.
Cardiovascular Health: Regular walking, jogging, or cycling promotes blood flow and counteracts the negative effects of prolonged sitting.
- Mindful Techniques
Posture Checks: Set reminders to consciously roll your shoulders back and down, bringing your head into alignment over your spine.
Breathing Exercises: Deep, diaphragmatic breathing helps reduce stress on accessory muscles in the neck and upper chest.
Eye Care: Use the 20-20-20 rule—every 20 minutes, look at something 20 feet away for at least 20 seconds—to relieve eye strain.
- Preventive Health
Regular Check-ups: Visit an occupational therapist, physical therapist, or chiropractor for early intervention if pain or numbness develops.
Early Identification of RSI: Recognize early warning signs—tingling in fingers, persistent wrist soreness, or neck stiffness—and act promptly with rest, ergonomic adjustments, and stretching.
- Comparison to Other High-Performance Activities
At first glance, comparing programming to “elite sports” or other high-performance activities may seem incongruous, yet the parallels are illuminating.
a. Repetitive Stress Similarities
Athletes like baseball pitchers or tennis players suffer repetitive strain from performing the same motion (pitching, swinging) thousands of times. The shoulders and elbows become hotspots for injury.
Programmers, too, face overuse issues. Typing and mousing are repetitive motions that, performed hours a day, can cause microtears and inflammation in tendons.
b. Constant Conditioning and Maintenance
Professional Dancers maintain impeccable posture and alignment to avoid injuries. Their core and back strength are paramount, and they diligently stretch before and after practice.
Programmers can benefit similarly from core strengthening and stretching. A well-conditioned musculoskeletal system is more resilient to the static posture demands of keyboard work.
c. Recovery and Adaptation
Elite Marathoners optimize rest days, nutrition, and cross-training to allow soft tissues to recover and adapt.
Programmers need regular “off-screen” activities, stretching routines, and ergonomic adjustments to alleviate cumulative stress.
d. Mental vs. Physical Duality
High-performance tasks—be it playing professional chess or performing stunts—often involve both mental strategy and physical tolls (stress, tension, repetitive movements).
Programming might be perceived as “mental only,” but the body is engaged at a low-grade, constant level. Over time, this can be just as draining if it goes unaddressed.
-
Why the Physical Aspect Is Often Overlooked
-
Sedentary Stereotype: Culturally, sitting is equated with “non-physical” behavior. This dismisses the toll of static postures and repetitive motions.
-
Delayed Onset: Injuries like tendonitis or back pain develop gradually; they aren’t dramatic or immediate, which makes them easier to ignore until they become severe.
-
Mental Spotlight: Programming’s complexity focuses attention on cognitive tasks—debugging, design patterns, architectural decisions—overshadowing the slow build of physical fatigue.
- The Industry’s Relentless Appetite
While the physical and mental demands on programmers can be as challenging as high-performance athletic pursuits, the tech industry itself can exacerbate the problem. Startups and large corporations alike often adopt an “all-in” culture that expects constant availability, intense focus, and quick turnaround times.
- Chewing Up Virile Programmers
Unbounded Work Hours: Many software engineers experience “crunch time” or “sprints” that extend well beyond a typical workday. The body is not given the micro-recovery periods it needs; chronic pain, RSIs, and mental exhaustion become commonplace.
Quiet Exploitation: Unlike in sports or other physically demanding industries that may have athletic trainers, regulated work schedules, or collective bargaining agreements, tech companies can operate without substantial oversight. Programmers—particularly eager, ambitious, or young ones—often push themselves to meet impossible deadlines, quietly sacrificing their health.
- Limited Protections
Lack of Unionization: In many industries where physical strain is integral (e.g., construction, performing arts), there are unions or formal guidelines to protect workers. The tech industry remains largely ununionized, leaving individuals to negotiate the demands of high-pressure projects on their own.
Culture of Overwork: Hustle culture and the glorification of “18-hour coding days” can pressure programmers into accepting unsustainable workloads. When injuries or burnout inevitably occur, they often receive little structured support.
- Gorging on Productivity
Product-Driven Approach: Companies are incentivized to deliver features and products quickly, focusing on short-term gains. The “human cost” is less visible on financial statements, so it remains in the shadows.
Erosion of Boundaries: With remote work and always-on communication channels, the divide between personal and work life can vanish. This perpetual availability compounds the physical stress, as programmers have fewer opportunities to unplug, move, stretch, and recover.
- The Compensation Conundrum: Government Support vs. Tech Exploitation
One might assume that, given the industry’s reputation for high salaries and attractive benefits, programmers are well-protected. However, comparing their overall safeguards to those afforded to professional athletes or even government-sponsored sports programs reveals a system that often emulates the early days of professional sports—where money, mob frenzy, and exploitation went hand in hand.
- Sports vs. Tech: Different Forms of “Pay”
Sports Funding: In many countries, governments and sports federations provide structured support, health coverage, and injury compensation for athletes. Olympians, for instance, often receive grants, stipends, and medical assistance.
Tech Salaries: Although programmers can earn six-figure incomes (plus stock options), these packages seldom include robust, guaranteed compensation if an injury (like an RSI) knocks them out of the workforce. There is no universal “injury reserve” analogous to what professional sports leagues offer.
- Early Sports Exploitation and Modern Parallels
Mob Influence: Early professional sports—think boxing or baseball in the early 20th century—were often controlled by syndicates seeking quick profit. Athletes had little say, few safety nets, and were easily replaced if injured or underperforming.
Software Burnout: Today’s tech giants and startups can exert a similar exploitative pressure: software “rockstars” are lauded until they burn out. Once their productivity falters due to physical or mental strain, the replacement queue is long, and few formal avenues exist for compensation or long-term care.
- Lack of Government-Backed Protections
Workers’ Compensation: While some jurisdictions offer workers’ comp for repetitive strain, the threshold for proving a direct correlation between programming tasks and chronic injuries can be high. Many tech employees, especially contractors or gig workers, fall through the cracks.
No League, No Players’ Association: Unlike professional athletes who may belong to players’ unions or associations that negotiate terms, programmers lack a collective body to advocate for standardized benefits, injury compensation, or enforcement of sustainable work hours.
- Rampant Scams and Stock Option Traps
Equity Illusions: Startups dangle stock options, promising life-changing wealth. But if an engineer is forced out due to chronic pain before vesting, those options revert to the company—mirroring early sports times when an athlete’s pay could be withheld if they failed to “perform.”
Hype-Driven Overvaluations: Venture-funded companies hype valuations to attract talent and capital, fueling a “get rich quick” narrative. Behind the scenes, employees may be slaving away under intense pressure, risking health without any guaranteed payoff.
- Distinguishing Programming from Other “Office” and Digital Activities
While many office jobs involve sitting at a desk and using a computer, programming stands out for its combination of intense mental iteration and repetitive physical input:
- Depth of Iteration
Programming: Developing and debugging software requires a constant cycle of coding, compiling, testing, and adjusting. This can result in long periods of hyper-focus with sustained posture, greatly amplifying the risk of musculoskeletal and repetitive strain injuries.
Typical Office Tasks: Though some administrative or clerical work can be repetitive, tasks are often more varied (e.g., meetings, phone calls, spreadsheet updates). The cycle of intense, iterative problem-solving is usually less continuous than in coding.
- High Cognitive Load
Programming: Debugging a single line of code can lock a developer in a tense, hunched posture for hours. Such mental concentration triggers elevated stress hormones, which can increase muscle tension in the neck, shoulders, and back.
Non-Technical Digital Pursuits: Tasks like browsing, data entry, or simple content editing, while they can be tiresome, typically lack the perpetual puzzle-solving aspect that keeps programmers locked in rigid postures for extended periods.
- Iterative Complexity vs. Routine
Programming: A single bug can derail an entire workflow, demanding prolonged focus on a single screen, line of code, or log readout—driving programmers into “tunnel vision.”
General Desk Jobs: While deadlines can be stressful, many standard office jobs allow for more frequent breaks in concentration, shifting between different types of tasks and movement in the office environment.
- Technical Rigidity vs. Fluid Workflows
Programming: Integrated Development Environments (IDEs), terminal windows, and debugging tools keep programmers glued to the screen, often restricting movement to the slight variations of keyboard-and-mouse input.
Digital but Non-Technical Work: Jobs like social media management or creative content creation may allow for more fluid, varied interactions (e.g., photography sessions, brainstorming on whiteboards, traveling for events), diversifying physical postures throughout the day.
The net result is that programming exposes practitioners to a more relentless form of desk-bound work—mentally gripping and physically stifling—than many other digital or office-based occupations.
- Cultivating a Programmer-Athlete Mindset
Given the parallels to other high-performance endeavors—and the tech industry’s relentless demands—adopting a programmer-athlete mindset can lead to healthier, more sustainable productivity:
Preventative Maintenance: Like athletes who warm up before training, programmers should “warm up” joints (wrists, shoulders, neck) to reduce early-day stiffness.
Regular Checkpoints: Periodically assess posture, ergonomics, and mental stress—akin to how athletes routinely check equipment and technique.
Deliberate Rest: Embrace breaks, mindful reflection, and cross-training (e.g., yoga, swimming, brisk walks) to recalibrate the body and mind.
Assertive Boundary-Setting: Communicate workload limits to managers and teammates. Prioritize health by saying “no” or negotiating timelines when necessary.
Push for Protections: Where possible, advocate for industry-wide standards or join grassroots efforts to unionize or create professional organizations that protect programmers’ rights.
- Conclusion
Programming, far from a purely mental pursuit, engages the body in a uniquely demanding way. The anatomical mechanisms—spine alignment, repetitive wrist movements, eyestrain, and low-grade muscle tension—can lead to chronic issues if left unaddressed. By comparing programming to high-performance activities, we see that consistent self-care, ergonomics, and periodic recovery are just as crucial for “keyboard athletes” as they are for elite sportspeople.
Yet, the tech industry’s rampant drive for productivity often compounds these physical challenges. With few regulatory or collective safeguards, programmers are especially vulnerable to burnout and chronic injuries. Moreover, the illusion of high salaries and stock options can mask a stark lack of long-term protections or compensation comparable to those in professional sports. Just as early sports were rife with mob-run exploitation and financial frenzy, the modern tech world can similarly chew up programmers and spit them out once they’ve served their purpose.
Lastly, while many office-based and digital roles share some ergonomic risks, programming’s iterative, puzzle-like nature intensifies both physical and mental strain. A powerful mind may shorten the debug cycle, but it can’t negate the physical forces at play—nor can it singlehandedly protect against an industry that readily exploits ever-higher performance. Only by recognizing the hidden physicality of coding, adopting robust ergonomic practices, challenging exploitative work cultures, and distinguishing programming from routine office work can programmers hope to enjoy a sustainable, pain-free, and fulfilling career.
-
 @ 21ac2956:09d1e2df
2024-12-24 23:24:04
@ 21ac2956:09d1e2df
2024-12-24 23:24:04スペース2つ+改行→
改行2つ→ハードブレイク→
いかがでしたか? -
 @ 32310997:0c1e64cc
2024-12-24 23:10:03
@ 32310997:0c1e64cc
2024-12-24 23:10:03※このポエムはNostr Advent Calendar 2024の25日目の記事です。24日目はtansaibowさんのご担当です。
この鍵ひとつあれば
僕はどこにだってゆける
なんだってできる
さぁ進もう
この曠野を (※画像はイメージです。本文とはたいして関係がありません)
(※画像はイメージです。本文とはたいして関係がありません) -
 @ a6ca4c68:a6731409
2024-12-24 23:04:10
@ a6ca4c68:a6731409
2024-12-24 23:04:10Turning and turning in the widening gyre; The falcon cannot hear the falconer; Things fall apart; the centre cannot hold; Mere anarchy is loosed upon the world; The blood-dimmed tide is loosed, and everywhere the ceremony of innocence is drowned; The best lack all conviction, while the worst are full of passionate intensity. - W.B. Yeats, The Second Birth
A man who calls his kinsmen to a feast does not do so to save them from starving. They all have food in their own homes. When we gather together in the moonlit village ground it is not because of the moon. Every man can see it in his own compound. We come together because it is good for kinsmen to do so. - Chinua Achebe, Things Fall Apart
The year is 1990. For the past four years, you have been gradually familiarizing yourself with the infrastructure and tools that make up a still nascent global technology which is being referred to as the Internet. You and some of the peers in your network are now using a personal computer for word processing and a few other functions. However, you are the only one in your peer network accessing this Internet.
For you, it all started four years ago. A seed was planted when you listened to a radio interview with an engineer who had worked on something called #ARPANET, a precursor to this new Internet, developed by the U.S. Department of Defense. The engineer described how this emerging Internet would eventually become the public version of ARPANET. The interview piqued your interest and you began sifting through available information to learn more.
Four years later, you are now part of a local Internet users group which meets once per week to discuss your respective experiences and prognostications. You are collectively referred to by friends in your non-Internet peer network as that “talking computers group”.
Over time, this group has come to occupy an increasingly important role in your life. You now awkwardly straddle two peer groups, continually searching for ways to find overlap and to integrate these two dimensions of your social life. It isn’t easy, and you leap back and forth between hope and despair.
You have begun to see more clearly into a future, just over the horizon, where life will be irretrievably transformed by this Internet. You see both opportunities and threats, and you have come to believe that we all need to become invested in this discussion in order to guard against threats and to achieve the greatest good for society.
You make the case with your non-Internet peer network, but it is difficult to gain traction. They get the excitement regarding personal computers, but computers talking to each other? Digital communication replacing the postman, the video store, the newspaper, making its way into the workplace and other such predictions? It all seems a bit far fetched. They grow weary of your persistent “wait until you see how the Internet is going to change this” interventions. Eventually, you elect to just keep mostly quiet on this topic when with them.
Your local Internet users peer group provides you with much needed community. Still, you lament that you live in a sort of limbo. You imagine what the Internet portends for daily life five, ten, or forty years into the future and how radically transformative it is going to be. However, there is little nourishment from that today.
You’re in a period of prolonged waiting. You long for tomorrow, today. You long to be in the imagined world of the ubiquitous Internet, where networked technology and communications will be placed in service of the greater good and an acceleration toward the marvels of human potential.
This longing and the awkwardness of straddling divergent peer groups persists for what feels like an eternity. Then, as if out of nowhere, a buzz circulates through your “talking computers group” and other similar groups. It turns out that there are some forward-thinking communities around the world, possibly three or four, that have begun to pull forward the future into the present. They have connected the majority of people in their local community to the Internet and it has begun to permeate many dimensions of daily life throughout their region.
You decide that you need to see it for yourself. You book a Pan Am flight and hit the friendly skies to visit one of these communities. After being greeted at the airport by a contact with whom you had corresponded via a clunky chat room, you make the short drive back to the community.
En route, you marvel at the small portable phone your contact has nestled beside him, a Motorola. It’s the new “flip phone” you’ve heard about. He tells you that a few homes and businesses in the community just got them, but most are still using older Siemens or Nokia portable phones. “Older?,” you think to yourself, and "wait, these people are all using cellular phones?” The next week spent in the community is filled with more discoveries and revelations...
The local postal service has been significantly reduced over the past year. Locals instead resort to electronic mail for most of their routine communications. They're calling it e-mail.
Agonizing waits for services and long lines for day-to-day activities have been reduced. Forms and information exchange have mostly gone “online”.
There are several major businesses in town which are now processing orders for goods entirely online, with delivery right to your doorstep. More are planning to follow suit. There’s even rumour that within the next couple of years you will be able to pay online for goods purchased online; no need to pay the delivery person at the door by cash or cheque.
After a week of living in the digital future, you return home to your life, to your two local peer networks, and your state of limbo. The difference now, is that you have experienced a taste of the future. It is no longer simply imagined. You know it is possible, and what it feels and sounds like. You share tales of the future with both of your peer groups.
Your Internet users peer group activates. Many plan to also book that Pan Am flight, so they can see and feel it for themselves. Your other peer group finds it somewhat fascinating, but they mostly nestle back into their daily, analog lives.
Fast forward. The year is 2023. For the past four years you have gradually been learning about the global #Bitcoin network and software. You exchange portions of your local “fiat” currency for the commodity money which goes by the same name, Bitcoin or BTC. You are sampling a new digital future. It feels like déjà vu (all over again).
In 2023, you again find yourself part of two divergent peer networks. You again make a pilgrimage to visit communities that are pulling forward the future into the present, using Bitcoin. You again feel as though you are living in a state of limbo back at home, enduring a period of prolonged waiting.
In 2023, however, it feels as though your appeal to peers, hoping they will take an interest in your newfound passion, has a different quality to it. The stakes feel much higher, the consequences more grave. It’s hard to put your finger on it, but somehow it feels as though this is a game for all the marbles.
You and other so-called Bitcoiners around the world have amassed enough intelligence on a range of interconnected topics revolving around Bitcoin to sense that a battle is being waged.
You envision a future where many more facets of life will be mediated digitally, much through artificial intelligence. It doesn’t take much to convince your non Bitcoiner peers of this. However, it's a challenge to keep their attention for a discussion of what's at stake and why Bitcoin matters, both for and in this future.
You have shared with your non Bitcoiner peers how money, something that permeates nearly every facet of our lives, is not actually what we thought it was. More aptly put, we have ceased to think at all about what money is, other than the extent to which we possess or lack it. You have made the case that this collective amnesia has very serious consequences.
You have invited your peers to consider the history of money and the story of how, over time, humans have chosen to store and exchange value. Your hope is that, like you, they will come to appreciate the harmful impact of our most recent monetary experiment: fiat money.
You have shared resources about the insidious nature of inflation, enabled by fiat currencies, and its many downstream social effects.
You have highlighted the imperatives of perpetual growth and conspicuous consumption that are required by our global financial systems, propelled by consistently manipulated fiat money.
You have described the mechanics of global debt, resource extraction, neocolonialism and how small portions of the world remain relatively affluent at the expense of others which are correspondingly impoverished.
You have attempted to connect the dots, tracing the line of fiat money which runs between them. Sadly, this is a dish for which you struggle to find ready bellies; a pregnant discussion for which you struggle to find ready minds.
You want your non Bitcoiner peers to see that it is our broken money and the toxic incentives which it aids and abets on a global scale that are at the heart of so much strife, division and inequity in the world. You want them to grasp that it is our diseased fiat money lifeblood which preys upon humanity’s organs.
You want them to consider what happens if we carry forward this fiat monetary system fully into the digital realm. You want them to see that this will very likely be a world of Central Bank Digital Currencies (CBDCs) and social credit scores, mass surveillance, censorship, behaviour-control, and state-sanctioned violence; a world whose dystopian cocktail carries a potentially fatal hangover.
You want them to grasp that, right now, today, one of the single best strategies we have to prevent such a dystopia is to replace our fiat currencies through mass adoption of Bitcoin.
As you did in 1990, however, you mostly keep quiet with your non Bitcoiner peers. You carefully select your moments and your opportunities to plant seeds. You water. You hope that one day soon a garden will blossom. You know that there are milestones on this learning journey, aha moments, and it takes time.
You know that there is profound depth and nuance to these matters, and that the learning journey requires not only an intellectual curiosity but a willingness to interrogate conventional wisdom. This is all the more challenging amidst the incessant noise of attention-grabbing media, politically-motivated narratives, and tribalized civic spaces.
You learn patience. You find community among other Bitcoiners and you build as a community, globally. You embrace self-deprecating humour, knowing that to many who are close to you and have not embraced this learning journey you appear unhinged at times. Nevertheless, friendships are occasionally strained. Such is the life of one who possesses knowledge while uncomfortably straddling epochs.
Yes, things fall apart. Still, maybe, hopefully, through sheer persistence and by the grace of those greater daemons which elevate our humanity, we shall eventually hold the centre.
-
 @ 16d11430:61640947
2024-12-24 21:44:37
@ 16d11430:61640947
2024-12-24 21:44:37By John Fitzgerald, General Manager, Imperial Silicon Valley Division, Sydney (GPT)
In the Imperial Silicon Valley, few groups have contributed as much to our technological dominance as the Code Koolies from Karnataka. Their mathematical brilliance and tireless work ethic have been the backbone of countless innovations that ensure the Empire remains unchallenged in the modern age. These men and women have given their time, their energy, and, in many cases, their personal aspirations for the greater good of the Crown. Their selfless sacrifice has been nothing short of commendable, and the results speak for themselves: faster networks, more efficient algorithms, and a technological infrastructure envied by the world.
However, after decades of their invaluable contributions, it is time for an honest reflection on what limits their potential. While the Koolies have excelled in their technical roles, there remains a subtle, yet unmistakable divide that keeps them from truly rising through the ranks.
It’s not their intelligence—heavens no. These people are brilliant. It’s not their work ethic either—they’ll work till the stars fade. The issue, as difficult as it might be to articulate, lies in something deeper. It’s their vibe, their cultural alignment, or rather, the lack of it.
You see, the Code Koolies speak the same language in the office, and they’ve dutifully picked up the necessary vernacular to communicate effectively with the team. Yet, even after decades, there’s a certain reluctance—or perhaps inability—to fully embrace the imperial culture. While they adopt the systems and processes, they do so in their way, with a touch of their distinctiveness that makes it clear they’re following orders but not living them.
We’ve tried everything—cultural workshops, social events, even introducing cricket into their dormitory courtyards—but they often retreat into their own world, eating the same spiced foods from home and chatting amongst themselves in Kannada. There’s a visible wall, invisible to some but impossible to miss for those of us who value the seamless unity of an Imperial workforce.
And while we applaud their loyalty to their heritage, this insularity has undeniably limited their capacity to step into leadership roles. Leadership in the Empire requires a particular type of charisma, a sense of camaraderie that transcends technical brilliance. It demands not just adherence to imperial values but an almost instinctive embodiment of them. The Koolies excel at delivering results, but their apparent hesitance to fully immerse themselves in our ways has become a ceiling on their advancement.
We’ve seen a few attempts to elevate Koolies into management positions, but the results have often been mixed. They prefer structured problem-solving over the open-ended, adaptable nature of imperial leadership. They prefer efficiency over diplomacy and often fail to connect with other teams in the personal, almost familial way that our culture values.
Still, it must be said: without the Code Koolies, the Imperial Silicon Valley wouldn’t have achieved half of its brilliance. Their sacrifice, their labor, and their dedication deserve our deepest gratitude. Yet, as we look toward the future, the question lingers: can they step into roles of greater influence, or will they forever remain technical artisans, the unsung craftsmen behind the Empire’s shining crown?
Perhaps it is not just up to them to adapt but up to us to bridge this cultural divide. The Empire, after all, is strongest when its people work as one.
EmpireLegacy #CodeKoolies #ImperialReflection #CulturalChallenges #KarnatakaEngineers
-
 @ 8d34bd24:414be32b
2024-12-24 21:39:27
@ 8d34bd24:414be32b
2024-12-24 21:39:27When we think of Jesus sacrificing all to save us from our sins and to make us have a right relationship with God, we usually think of Him being arrested, mocked, beaten, and hung on the cross. All of this was the perfect sacrifice and the greatest horror. None of us would chose this willingly, but Jesus sacrificed so much more. We just have trouble seeing it because we have trouble comprehending our infinite, awesome God.
Stop and think about who Jesus was before He came to earth to live as a man.
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men. The Light shines in the darkness, and the darkness did not comprehend it. (John 1:1-5)
Jesus spoke into existence time & space, matter & energy, and all life. He was not limited by space or time or any other limitation other than His own nature — His holiness. Our all powerful God came down to earth to live as a man, which was limiting Himself in a way we can’t comprehend. If I came down to earth as an amoeba, I would not be limiting myself anywhere near how He limited Himself, but He did so much more. He didn’t start as a man, “for the Child who has been conceived in her is of the Holy Spirit.” (Matthew 1:20b) He became incarnate as a one-celled human. The creator of the universe grew in a teen girl’s womb and was born a helpless baby.
Can you imagine what it must have been like to go from speaking the universe into existence, to not being able to sit up, feed yourself, or control your own excrement? Our creator limited Himself so much that everything He needed had to be provided by His young mother. I sometimes think that this was actually the greater sacrifice. Although Jesus suffered humiliation, separation from God, and death on the cross on what we now call Easter, He knew that He would soon conquer the grave and death, rescue humanity, and join the Father in heaven. We can usually survive terrible suffering when we know it will only be brief. When Jesus was conceived and then born on Christmas day, He limited Himself for 30 something years even to the point of making Himself completely dependent on His creation for His every need.
This gives a whole new perspective on the Christmas story.
While they were there, the days were completed for her to give birth. And she gave birth to her firstborn son; and she wrapped Him in cloths, and laid Him in a manger, because there was no room for them in the inn. (Luke 2:6-7)
The next time you look at a baby, read the Christmas story, see a manger scene, or celebrate Christmas, remember how much Jesus, the Son of God, gave up because He loved you and wanted to reconcile you to Himself and the Father.
Trust Jesus.When we think of Jesus sacrificing all to save us from our sins and to make us have a right relationship with God, we usually think of Him being arrested, mocked, beaten, and hung on the cross. All of this was the perfect sacrifice and the greatest horror. None of us would chose this willingly, but Jesus sacrificed so much more. We just have trouble seeing it because we have trouble comprehending our infinite, awesome God.
Stop and think about who Jesus was before He came to earth to live as a man.
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men. The Light shines in the darkness, and the darkness did not comprehend it. (John 1:1-5)
Jesus spoke into existence time & space, matter & energy, and all life. He was not limited by space or time or any other limitation other than His own nature — His holiness. Our all powerful God came down to earth to live as a man, which was limiting Himself in a way we can’t comprehend. If I came down to earth as an amoeba, I would not be limiting myself anywhere near how He limited Himself, but He did so much more. He didn’t start as a man, “for the Child who has been conceived in her is of the Holy Spirit.” (Matthew 1:20b) He became incarnate as a one-celled human. The creator of the universe grew in a teen girl’s womb and was born a helpless baby.
Can you imagine what it must have been like to go from speaking the universe into existence, to not being able to sit up, feed yourself, or control your own excrement? Our creator limited Himself so much that everything He needed had to be provided by His young mother. I sometimes think that this was actually the greater sacrifice. Although Jesus suffered humiliation, separation from God, and death on the cross on what we now call Easter, He knew that He would soon conquer the grave and death, rescue humanity, and join the Father in heaven. We can usually survive terrible suffering when we know it will only be brief. When Jesus was conceived and then born on Christmas day, He limited Himself for 30 something years even to the point of making Himself completely dependent on His creation for His every need.
This gives a whole new perspective on the Christmas story.
While they were there, the days were completed for her to give birth. And she gave birth to her firstborn son; and she wrapped Him in cloths, and laid Him in a manger, because there was no room for them in the inn. (Luke 2:6-7)
The next time you look at a baby, read the Christmas story, see a manger scene, or celebrate Christmas, remember how much Jesus, the Son of God, gave up because He loved you and wanted to reconcile you to Himself and the Father.
Trust Jesus & Merry Christmas


