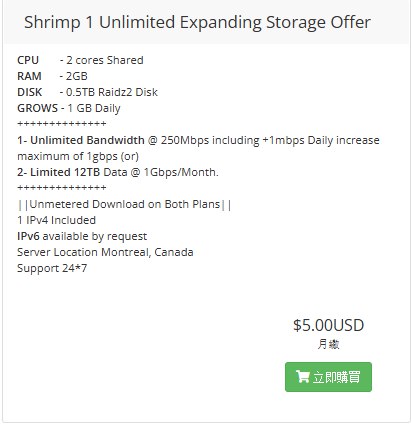
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 592295cf:413a0db9
2024-11-30 08:33:35
@ 592295cf:413a0db9
2024-11-30 08:33:35Week 25 11
Vitor created another social network edit mode. There are countless cases of use. But type threads are possible, small books, Rabbit hole and those who put it more.
nostr:nevent1qvzqqqqqqypzq3svyhng9ld8sv44950j957j9vchdktj7cxumsep9mvvjthc2pjuqyghwumn8ghj7mn0wd68ytnhd9hx2tcqyrewvkqwqt7urn2u9h5tk88vj9p3csl0wt08aqd8kxsngxtdmr0zqmszxds
Nostr Report is missing, was a lot of news, 20 notes in a day.
Some news do not need resonance case, Primal did a good job with trending. Of course is a centralized service. But it was one of the Twitter features, he did it with the top trending hashtags. Now Primal is more focused on DVM smart feed, read, and Discovery. This will bring chaos, as long as you can switch the trend feed with your Algo or DVM Algo. I'm obsessed with these switches 😅
Hostile people can happen along the way, it's not like in Bluesky 😔.
Someone share on Bluesky https://bsky.app/profile/laurenshof.online/post/3lbrsjzobps2u Video is this https://audiovisual.ec.europa.eu/fr/video/I-264553?lg=en
Trying to convince someone for Unanimity, Relay groups are nice, but Unanimity is simpler.
nostr:nevent1qqs9ar5t9xu97nhtwef9ej2y7cklnysf7hgwce7t2wk5axhfdwuq5sqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qmzyp990kgskujdyplzydmd08ft42mkkfg4lzldaap8ng7n2u3kmss8l76e
Game on Nostr on 2025, cool be.
Angor are finally ready, crowdfunding with Nostr and Bitcoin. (alpha test)
nostr:nevent1qvzqqqqqqypzqw4hcggg2f9h68qutp0snsdhux20teljykjmh9rlx78qwnt5a8dlqqstte0g54hfa2cmr63vq4ava7e7wsr483p63tylvut8cvufzs44a0cd6saa3
PR 1600
The name is curated pubblication use kind 30040 e 30041, 30040 Is the envelope and 30041 are chapters or paragraphs. We'll see what's left in a month. There are no big discussions until now. This is the basis to leave it so, if you can improve it without breaking it ok. I think liminal is preparing at least two other NPs. The bottom problem is that there are no "competitor", someone else outside who wants to use this thing. But if there are no one can invent.
You can't do things with others. There's too "bad" people. Keep calm is a toxin environment. Maybe you have to get away a bit.
I was trying to help David but there are no aggregators for neo4j Nostr. Dustin's example, I think it's only worth the DVM. There are two other projects one grain of Oceanslim I saw the video where he explains some things, with Dr. Morales. And the other is Cody's Nostr Relay tray. At least you have all the data in a Relay, and for that Relay you can query, I don't think you find anything significant, maybe you need 100(k) notes to have a good sample. I think I'll make the update. I downloaded two months ago, it worked for a while with Nostrudel, then only with next, lately some problems with next. Cody launched the project with fiatjaf and I think it is also implemented here. In the end, I don't think this answer is useful to David.
Zapview nostr-zap-view The lokuyow project, always attentive to zap lightning and Nostr.
Give a "microsat" to Fiatjaf nostrabia relay
I managed to send a zap from a hex known id, it only works with getalby, so until January 4th. I have to prove if other lnurls have the call.
Something I might have understood about the new version of Nostr_sdk or rust Nostr. Sending messages will be harder. The builder does not support the tag, it breaks almost all the scripts I was writing and to verify them you can do nothing but send to the Relays, I wait a few days if there are news, but I don't think there will be. It is no longer linked to the table of examples so it will not be updated presumably, I would like to continue, as the cli does not come out. That then the cli will be in python 12.. (I'm still in version 3.10.9 of python)
I've seen bulletin proof, posting on Nostr seems interesting, but they need many interactions to have a functioning client. link, stacker news
Nostr nuance, login, Nostr connect, private. (two Notes)
nostr:nevent1qvzqqqqqqypzq77777lz9hvwt86xqrsyf2jn588ewk5aclf8mavr80rhmduy5kq9qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qpqqqqz3757ha8j5xcm7er8kkdc0dgtvmy55dz2t2d7c2tv9h8qm88qlcjsls
nostr:nevent1qvzqqqqqqypzq9eemymaerqvwdc25f6ctyuvzx0zt3qld3zp5hf5cmfc2qlrzdh0qyt8wumn8ghj7ur4wfcxcetjv4kxz7fwvdhk6tcpzpmhxue69uhkummnw3ezumt0d5hsqgz98qckr40flhpyt48fxqjkuf9p4dv245634ygvp6dfu2kt7qk5egqmc4l8
An other microsat to Fiatjaf chronicle relay
Kind 1 was a mistake and many people are realizing it, they are replacing it. Kind 5 now it is only almost to eliminate drafts, here the option is to overwrite.
That's all!!
-
 @ 592295cf:413a0db9
2024-11-16 10:40:22
@ 592295cf:413a0db9
2024-11-16 10:40:22Week 11-11
Lamenting is becoming something I should ask people who complain. Charity bussiness and after sending zap received to those who do not complain...
I started making an RSS feed template. Open an opml file and check the feed. I called this script,Teed.
This morning I saw a bounty from a fiatjaf note, on a rss-feed long form, basic a plugin for an app. But I'm not doing that, of course, I can also publish it as soon as I'm in charge. Maybe I have some opml files and I want to see if these are still active.
Starter pack is not good apparently creates elites and maybe gives you the feeling of not choosing, but that's what people want. Do not choose but have the illusion of choosing.
Toxicity level. high.
P2P stuff, Iroh is a protocol for syncing & moving bytes iroh computer post on Bluesky
Juraj new project
nostr:nevent1qvzqqqqqqypzpk4kccr9csumnwhmpv83ladqc6p88089cx2e5s2c4448ppgl2pakqqsyv4hs424x6c8phks903s595q2lqp5fpwyq7ajwrf00lxev8cfamcvmq23h
Alex Gleason bunker Knox. (Beta) "knox is a new Nostr bunker CLI for running a NIP-46 remote signer and granting credentials to members of your team". Announcing bunker knox article
Local First podcast, web2.5. Something like Nostr but Local P2P, interesting episode. youtube link
Open Secret AI. "OpenSecret is a backend for app developers that turns private encryption on by default." announcment AI
I think users with regard to algorithms do not want ten different feeds to choose from, but that their feed adapts to their choices, training the feed if this makes sense. So the feed is your feed for your choices, respond and train with them.
Pleblab 2, cool "ANNOUNCING TOP BUILDER SEASON 2! " nostr:nevent1qvzqqqqqqypzpmx02p4slzahlf7jlcaspsx57g6uc7kl7cc7dvhlsnqtpn6khjj0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcqyzy9w0frd802hfmrp45jr6dqhf7umqj7s63z0jvhv7hvvkcsqjg0vjwd7q4)
It was the real Guardian, quit 7fqx, we know it's you who want to distract us from number go up. The Guardian has left or wants to leave twitter is looking for alternatives, but how to verify a high profile user on Nostr? Nostr Address is already something but it's not enough.
We sometimes think that there is the money tree somewhere is that they magically appear, when instead the money is in the ground but they are dirty.
If Amethyst doesn't support is others stuff
People are simple, they want an app that works for all devices they have. People are "flutter-system".
A podcast feed xml file
Add to teed, if only i had made that option, meanwhile i saw a new interesting project
An other RSS feed github project
Imagine making a file opml with categories and those are your follow nostriches.
The problem is this does not bring new sap to the social chart is important to you, receive the selected posts and it is fantastic. You can also not use Nostr, if you want to use it as backup is fine. Share opml files? It's okay, but you can also find specific sites and find the best. Update for clients, you have a lot of RSS feeds from clients but update after a few hours so if there is really an emergency you lose. I still need to figure out how to integrate Nostr into RSS feed. Maybe an event to make your lists known.
I saw the event in these pr: nostr verified podcast nip #1465 Add audio track NIP #1043
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46 -
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 0d532801:197a0c30
2024-12-06 05:13:25
@ 0d532801:197a0c30
2024-12-06 05:13:25Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden.
İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım.
Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor.
Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar.
İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu.
Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür.
Büyük bir fırsat ondan faydalanılmasını bekler.
Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce.
İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür.
İnsanlar iletişim kuramadıkları zaman öfkelenir.
İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi.
Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım.
Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda.
-
 @ b2d670de:907f9d4a
2024-12-02 21:24:45
@ b2d670de:907f9d4a
2024-12-02 21:24:45onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 0d532801:197a0c30
2024-12-01 21:27:48
@ 0d532801:197a0c30
2024-12-01 21:27:48
߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
- Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
- Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
- Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
- Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
- İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
- Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 234035ec:edc3751d
2024-12-14 05:12:52
@ 234035ec:edc3751d
2024-12-14 05:12:52America's Fourth Fourth Turning
We can learn much from the Book "The Fourth Turning: An American Prophecy" By William Strauss and Neil Howe. The Book looks back throughout history to identify the cyclical patterns that emerge and establishes archetypes that emerges in the generations as they come of age in these different stages of history.
There are four phases (turnings) that are outlined in the book:
- The High
- The Awakening
- The Unraveling
- The Crisis
The authors identify that America is due for another fourth turning, and I would argue that we are now in the midst of America's Fourth ever fourth turning. The first three being marked by the American Revolution, the Civil War, and the Great Depression- WWII. Today we have been in an increasingly unstable financial, political, and social environment which share eery similarities to the unraveling period of the prior cycles.
I believe that this fourth turning began with the 2008 "Great Financial Crisis" and has been ongoing ever since the fed chose to engage in mass currency devaluation in order to keep the banks solvent. While these actions have delayed the inevitable larger crisis, they will not be able to avoid it. Since 2008 the money supply has grown from roughly $8 Trillion to over $20 Trillion. This massive currency dilution is reflected in increased prices across all sectors but heavily concentrated in scarce desirable assets. As National debt continues to rise and interest expenses balloon, the only way out for the US dollar is massive inflation.
The issue with continued inflation is that it leads to massive societal suffering and unrest. At 2% inflation most individuals aren't aware that they are being stolen from, but as inflation rates start to stick above 10% people start to realize what is really going on. History tells us that as currencies enter into hyper-inflation, the societal fabric begins to fall apart. One does not have to be an anthropologist to look around and realize the massive cultural shifts that we have seen since moving to a fiat standard in 1971 and much faster ever since 2008.
I find it very profound that at the same time that the global financial system began showing cracks, Satoshi Nakamoto introduced the solution to the world. It feels as though this fourth turning is centered around technological innovation in computing, as well as the collapse of an outdated and corrupt financial system. Bitcoin exists at the perfect intersection of these two by utilizing cryptography to empower people to exit the corrupt system and begin to build a superior one on sound foundation. If the crisis of this great fourth turning is centered around the sovereign debt crisis, than Bitcoin becomes the clear answer.
Thriving In The Chaos
Being Born in 2001 I do not have much memory of a pre-2008 world. Being only 7 years old at the time I did not fully grasp the significance of what was going on, but my life has been impacted by it nonetheless.
When the central bank chooses to hold interest rates artificially low, they are effectively driving money into more and more places where it shouldn't actually be. This is usually described as a bubble, which then bursts leaving many financially ruined. Accept for those who the central bank then chooses to bail out by diluting the purchasing power of all the savers.
Much of the Millenial and Gen Z generations feel that they will never reach financial security or be able own a home and retire at a reasonable age. Many of them are saddled with large student loans, credit card debt, and car loans. While much of this is due to personal decision making, we exist in a system today that is designed to extract as much value as possible from each citizen. If you were to take out a loan to go to school, get a job, a mortgage, and a car payment, and used a savings account, you would never become financially free.
People my age have become increasingly unsatisfied with the way that things are, which is why I am so hopeful for a brighter future. While most aren't quite aware of what the true heart of the issue is, they feel that something is deeply wrong. I believe that Bitcoin will be the catalyst for the masses to wake up and stop funding the current system.
Those that lead the way into a new frontier during these fourth turnings come out on the other side in positions of great respect and power. While these next few years will likely difficult, there will be massive opportunity for those who are bold enough to stand for their beliefs and work to propagate them.
-
 @ 94a6a78a:0ddf320e
2024-11-27 19:36:12
@ 94a6a78a:0ddf320e
2024-11-27 19:36:12The backbone of your Nostr experience lies in relays—servers that transmit your notes, zaps, and private messages across the decentralized network. Azzamo offers three specialized relays to suit different user needs, ensuring reliability, performance, and privacy.
1. Free Relay
- URL:
wss://nostr.azzamo.net - Overview: Azzamo’s Free Relay is perfect for newcomers to Nostr. It’s open-access, reliable, and ensures fair use with moderate rate limits.
- Key Features:
- Free to use.
- Notes older than one month are purged daily.
- Accessible gateway for decentralized communication.
2. Paid Relay
- URL:
wss://relay.azzamo.net - Overview: Designed for power users, the Paid Relay offers unmatched performance with 99.9% uptime and low latency.
- Key Features:
- Scalable for heavy users.
- Fewer users for faster, consistent connections.
- Premium support included for paid users.
3. Inbox Relay
- URL:
wss://inbox.azzamo.net - Overview: Never miss a private message again with the Inbox Relay, optimized for secure, spam-free direct messaging.
- Key Features:
- Guaranteed message delivery.
- Optimized for NIP-17 private messages.
- Optimized for NIP-19 group chats.
- Premium users enjoy advanced support.
Why Choose Azzamo Relays?
Life on Nostr is easier with Azzamo relays. They’re fast, reliable, and built to handle whatever you throw at them. The Paid Relay keeps your connections strong, the Inbox Relay makes sure no private message gets lost, and the Free Relay is always there to get you started. Supporting Azzamo by going premium helps keep this decentralized network growing—and you get priority support while you’re at it. Azzamo has your back on Nostr!
🔗 Start now:
- Free Relay:
wss://nostr.azzamo.net - Paid Relay: azzamo.net/pay
- Inbox Relay: azzamo.net/inbox
Support the network and upgrade your experience—add time to your account via the Azzamo Dashboard. Choose Azzamo, and take control of your Nostr journey today!
- URL:
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ e31e84c4:77bbabc0
2024-11-27 11:32:57
@ e31e84c4:77bbabc0
2024-11-27 11:32:57‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
Childhood Lessons
As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny.
Definitions of Security
Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs.
Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis.
When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change.
How Bitcoin Changed Me
The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights.
Here are just a few examples:
Freedom of Expression
Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions.
Adequate Living Standards
Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards.
Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards.
Freedom of Association
Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions.
Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code.
Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power.
Right to Information
The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use.
Personal Context
For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code.
In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon…
A Modern Necessity
These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview:
“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” (https://www.youtube.com/watch?v=K4ciiDyUvUo)
As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society.
The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities.
Bitcoin’s True Security
Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it.
Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections.
Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times.
‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
-
 @ e373ca41:b82abcc5
2024-12-11 11:48:41
@ e373ca41:b82abcc5
2024-12-11 11:48:41There is a nice image in complexity theory: to describe the indirect effects in complex systems, one uses the image of a butterfly whose distant flapping of wings can have much greater effects in a completely different place. In the USA, the balance of power has changed dramatically. Corona policy critics Kennedy and Bhattacharya are to become Secretary of Health and Human Services and head of the NIH, respectively. Every wave, every flapping of wings that comes from the USA will eventually reach Germany. For decades, Germany has only been a recipient of impulses, not a provider of them.
Germany has failed to deal with the corona pandemic in the same manner as it had previously compliantly supported and carried out the madness. But the tsunami of enlightenment from the USA is building up and will eventually reach Germany. A nation in the hands of perpetrators, cover-ups, accomplices and profiteers must once again be liberated from the outside. When will we become an independent country?
First it crumbles, then it erodes quickly
The precursors of the tsunami can be felt everywhere. The first signs of panic are spreading among local coronists. The big row back and “save what can still be saved” is spreading. After the coalition broke down, the FDP suddenly called for a committee of inquiry and Lauterbach's resignation. ARD broadcasts a documentary about vaccination victims; it takes stock after uncritically following the damage to citizens' health for four years. On Hart aber Fair, there was a small pseudo-debate between the coronavirus nomenclature (Lauterbach, Buyx, Hirschhausen) and a few critical mainstream voices around Heribert Prantl.
However, the coronavirus narrative is breaking ever stronger and faster and this is bringing a new dynamic into play. A report by the US House of Representatives now speaks of a laboratory accident as the most plausible cause of coronavirus. The biggest cover-up and obfuscator of this thesis in Germany was Christian Drosten. This view could easily get you banned from social media or get you into professional trouble during coronavirus. The physicist Roland Wiesendanger from the University of Hamburg was labeled a conspiracy theorist and campaigns were initiated against him. A laboratory accident then? Of course, it would now be necessary to explain how an “accident” fits in with the timely implementation of the simulation game “Event 201” or vaccines suddenly pulled out of a hat (developed in January 2020). It has just been revealed that the trucks from Bergamo, which were supposed to transport coffins of alleged corona deaths to crematoria in a convoy of 13 trucks, had apparently only loaded one coffin per truck. It doesn't take much effort for viral images and morbid emotions. The stage of the Corona Theater has been stormed, the stage set exposed as a fake.
Every narrative has a life cycle and Corona's is just coming to an end. The phase of self-destruction is about to begin. The dismantling of the old nomenclature by the stirrup holders and profiteers begins. Christian Drosten is now being publicly criticized for his rash stance on child vaccinations, accusing his colleague of “underhand” behaviour. The Bild newspaper now claims to have discovered that Lauterbach lied. Only now? The Springer publishing house has been a supporter of the pandemic from the very beginning, a representative of corona orthodoxy, only with a semi-critical veneer, a kind of pseudo-opposition in the mainstream. Biontech received a prize from the publisher, and the then editor-in-chief of Bild, Julian Reichelt, fantasized that 20 Biontechs were needed in Germany. Nobody could fail to notice that Karl Lauterbach was fanatical, confused and a permanent liar.
Advertisement:
Are you looking for the easiest way to buy Bitcoin and store it yourself? The RELAI app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees. (no financial advice).

Upgrade your self-custody with hard ware wallets! Check-out the newest Trezor Wallets, browse the shop or book an intro with an expert.
The book of the hour is “Seduced Thinking” by Czeslaw Milosz. The later Nobel Prize winner for literature from Poland described the subjugation of the intellectual caste in Poland by Soviet doctrine in the 1950s. He describes obedience to the system, conformity to orthodoxy, the different types of followers (he calls them Alpha, Beta, Gamma, Delta). The most unimaginable thing for him was that this was “servitude through knowledge”.
Milosz writes:
“There has never been such servitude through knowledge, it was reserved for the twentieth century. My generation was still taught at school that knowledge makes you free.”
Seduced thinking leads to a weighted mind, resulting in a stooped posture and ultimately a broken spine.
High treason against democracy, anyone?
What happened during Corona in Germany was more than a seduction of thought. It was a conspiracy by politicians, a caste of experts, the media, the scientific community and the cultural sector, who actively fought against any form of criticism and sold the health of an entire nation to a group of philanthrocapitalists around Bill Gates & Co. for a large-scale field trial with novel vaccines. As we know today and could have guessed at the time: with disastrous consequences and unforeseeable damage. And all this in the “best democracy of all time”. A better campaign to discredit democracy is hardly possible.
The coronavirus era was a breach of the democratic social contract, the greatest possible delegitimization of the state. A new democracy was created out of the old democracy: “Our democracy”. New institutions were created out of the institutions; the Bundestag was disempowered and a government of experts and councillors was set up, which took a strictly orthodox line. A new people of protectors was elected and critics were silenced. The good citizen was suddenly the obedient citizen. The conspiracy was not the result of collusion, but of incentivization. Everyone was aware of which statement could promote or destroy a career. Everyone made their own decision, chose their own camp. Anyone who wanted to make a pro-government statement, from a no-name expert to an innkeeper who barred unvaccinated people, only had to make it known and they were guaranteed attention through airtime, interviews and reporting. Everyone could get a piece of the cake, but it was a poisoned cake.
The sugar had an immediate effect, but the poison is insidious.
This article first appeared in German by Milosz Matuschek on Freischwebende Intelligenz.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ 21b41910:91f41a5e
2024-11-23 12:00:26
@ 21b41910:91f41a5e
2024-11-23 12:00:26Chef's notes
Based on assorted recipes and refined over time, this round of beef tastes great as a result of the sweet and savory marinade.
Details
- ⏲️ Prep time: 5 minutes (+ 1 day)
- 🍳 Cook time: 20 minutes
Ingredients
- 2 pounds lean beef (may be labeled as London Broil)
- 1/3 cup olive oil
- 1/4 cup soy sauce
- 1/4 cup malt vinegar
- 1/4 cup lemon juice
- 1 tbsp sweetener of choice (honey, molasses, syrup, 4 packets of duck sauce, etc)
- 2 tsp old bay seasoning
- 1 tsp garlic powder
- 1 tsp sea salt
- 1/2 tsp black pepper
Directions
- Day Before: Mix all ingredients except the beef in a bowl to form a marinade. Place the cut of beef in a gallon sized Ziploc bag. Pour marinade over beef, ensure fully covered. Remove any excess air from the bag and seal. Place back in refrigerator for up to 24 hours before cooking.
- Cooking: Bring beef out of refrigerator (still in bag), and allow to rise to room temperature (about 30-40 minutes). Preheat broiler for about 15 minutes (your oven will vary). Broil for about 7-8 minutes on one side, then flip over. Continue broiling for another 7-10 minutes until temperature reads 140°F. Remove from broiler and let rest for 10 minutes before slicing thinly.
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 87730827:746b7d35
2024-11-20 09:27:53
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
KEY TAKEAWAYS
- The Central Bank of Brazil has proposed regulations prohibiting privacy-centric cryptocurrencies like Monero.
- The regulations categorize exchanges into intermediaries, custodians, and brokers, each with specific capital requirements and compliance standards.
- While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens (NFTs) are still ‘deregulated’ in Brazil.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines regulations for virtual asset service providers (VASPs) operating in the country.
In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil.
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
If the BCB’s current rule is approved, exchanges dealing with coins that provide anonymity must delist these currencies or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to prevent criminals from using digital assets to launder money. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
… restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
The Central Bank has identified that removing algorithmic stablecoins is essential to guarantee the safety of users’ funds and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to control all digital assets traded by companies in Brazil. According to the current proposal, the national regulator will have the power to ask platforms to remove certain listed assets if it considers that they do not meet local regulations.
However, the regulations will not include NFTs, real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, other nations are banning Monero in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as Binance have already announced they will delist Monero on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with MiCA regulations.
Data from Chainalysis shows that Brazil is the seventh-largest Bitcoin market in the world.

In Latin America, Brazil is the largest market for digital assets. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ 592295cf:413a0db9
2024-10-26 13:39:00
@ 592295cf:413a0db9
2024-10-26 13:39:00[Week 21-10] I thinks that Saylor is on right, don't trust verify, is bullshit Bitcoin is a financial tool! I think it's good for me to get away from social media once a week. I could do things outside, like walking. Take pictures of the landscape. The weirdest thing is when the alarm calls you up in an hour.
Fiatjaf wants a cache client. I feel like I can do it, I have the set to do it, but nostrudel is no longer working, so it's a little murky. Next nostrudel does not accept changes to settings (It works now!), so maybe i can think something. I want to make a corny chat, test, read this article. Nostr doesn't work with a vpn because relays don't know who you are. jokes aside, some clients have difficulties.
I couldn't take pictures of the landscape if I didn't take the wind blades. Small local controversy.
Missing the point of content creator. Simply for final user, Simply for the creator, new feature, no missing nothing. I'm trying to limit everything to writing for a week. I almost did. Maybe another week can do well.
Meanwhile I updated apps like Amber and Voyager, coracle, nostrmo.
The experiment continues with open vibe following the trending of Nostr. I'm following almost 120 npub. He'll stop, I don't know, possible he's already reached the limit. You still can't block words on the Nostr side of Open, strange thing. The app doesn't count the follow well, still some problem cleaning the cache seems that it doesn't need. After a while open and close and seems updated. I wanted to try open librarian, but I was busy sending fake zap on Nostr. This morning i try and It keeps giving me error 500 when I try to connect to a relay.
I hate when a profile follows everyone indistinctly, why does everyone follow? and in voyage, I read with WoT setting, I probably have to do unfollow. There must be an indication in which not include the followers of this person in the web of trust, I would do it by default if you follow more than 600 people.
WoT on Nostr Visualized post on stackernews
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 599f67f7:21fb3ea9
2024-10-20 11:28:08
@ 599f67f7:21fb3ea9
2024-10-20 11:28:08LNDhub te permite importar fácilmente una billetera en aplicaciones compatibles. Si bien puedes guardar tu billetera Bitcoin Txoko LNbits en tu teléfono como una aplicación web progresiva (PWA), una aplicación nativa como Zeus o BlueWallet ofrece una mejor experiencia de usuario así como un mayor nivel de seguridad. Con Alby, también puedes importar la billetera a la extensión de tu navegador para facilitar los pagos Lightning en la web y para los zaps de Nostr. Por suerte para nosotros, todas estas billeteras hablan un lenguaje común llamado LNDhub.
En esta guía cubriremos cómo importar la billetera a tu navegador y a tu móvil. Si quieres usar tu billetera tanto en el navegador como en tu móvil, empieza con la configuración de Alby, ya que uno de los pasos te permitirá importar fácilmente tu billetera también a Zeus. Pero si sólo te interesa utilizar la billetera en tu móvil, puedes pasar directamente a la sección de Zeus.
Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 es una extensión de navegador que lleva Lightning y Nostr a tu navegador. Utilizando el protocolo WebLN, esta extensión puede detectar facturas LN en paginas web y pagarlas, así como posibilita iniciar sesión en sitios web con Lightning. También puedes fijar presupuestos para tus sitios favoritos de Lightning. Por otro lado también puedes utilizarla para firmar en Nostr utilizando NIP-07, lo cual es mucho más seguro que ingresar tu clave privada en clientes web.
¿Qué necesito?
- Un navegador web que soporte extensiones Chrome o Firefox
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
- (Opcional) Un dispositivo móvil para configurar Zeus
1. Habilita la extensión LNDhub en tu LNbits wallet
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez se haya habilitado, dirígete a la página de extensión de LNDhub.2. Instala la extensión Alby
Dirígete a getalby.com y instala la extensión desde el store de extensiones del navegador. Configura tu contraseña de desbloqueo y guárdala en un lugar seguro.
3. Importar a Alby
 (Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)
(Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)En la siguiente pantalla, elige
Conectary luego eligeLNDhub. Vuelve a tu extensión LNDhub y copia la URL de conexión. Pégala en el campoURI de exportación de LNDhub. Pulsa continuar. ¡Ahora deberías haber estado conectado a tu billetera de LNbits con LNDhub!💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). Le dan a Alby diferentes permisos para interactuar con tu cartera de LNbits.
- La URL de factura te permite crear facturas y recibir pagos
- La URL de administración también te permite enviar pagos
4. Configurar Zeus con Alby (opcional)

Ahora que ya has conectado tu LNbits con Alby, también puedes importarlo de una manera sencilla a Zeus con Alby. Abre la extensión, haz cilc en el nombre de tu billetera y navega a la configuración de la cuenta. En
Wallet Settings>Generalse encuentra la opción de conectar tu billetera móvil. Al pulsar conectar, se mostrará un código QR para escanear desde Zeus.Si no tienes instalada Zeus con anterioridad, dirígete a zeusln.app y descarga la aplicación de Zeus para tu sistema operativo móvil.
Una vez tengas descargado Zeus, entra en
Configuración>Añadir un nuevo nodo. Aquí puedes escanear el código QR que te muestra Alby para importar la billetera.Voilà! Ahora tienes el poder de Lightning al alcance de la mano ¿Ya te sientes como un dios?
Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf es una formidable aplicación de código abierto que permite conectar tu propio nodo a tu dispositivo movil. Es compatible con todas las principales implementaciones de nodos Lightning, como LND, CLN y Eclair, así como conexiones a través de Tor y clearnet. Recientemente también han anunciado su propio LSP (Lightning Service Provider).
¿Qué necesito?
- Teléfono Android o iOS
- Otro dispositivo en el que puede acceder a tu billetera LNbits (para mostrar el código QR para escanear)
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
1. Descarga Zeus
Puedes descargar la aplicación Zeus para tu sistema operativo aquí.
2. Habilita la extensión LNDhub en tu billetera LNbits
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez habilitada, abre la pagina de la extensión LNDhub.3. Importar a Zeus
Ve a
Configuración>Añadir un nuevo nodo en Zeus.Escanea la cartera que quieras instalar.
💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). - La URL de la factura te da permiso para generar facturas y recibir pagos. - La URL de administración también te permite enviar pagos.
Una vez que hayas escaneado el código QR, todos los campos en Zeus deberían rellenarse automáticamente. También puedes añadir un apodo para tu billetera.

¡Ahora puedes guardar la configuración del nodo y controlar la billetera desde tu teléfono!
Extra
Zeus también ofrece funciones interesantes como temas personalizados, conversiones de precios, modo acechador y verificación biométrica. Estos temas están más allá del alcance de esta guía, ¡juega en la aplicación y descubre todas esas características por ti mismo!
-
 @ 0461fcbe:35a474dd
2024-11-12 17:58:48
@ 0461fcbe:35a474dd
2024-11-12 17:58:48On Nostr, I am running several marketing accounts for my projects: Ditto, The Mostr Bridge, and Cobrafuma. But I want other people to be able to post from those accounts. In fact, I want to hire a "social media manager" someday (for when my wife is not available 😂).
This is a pretty basic need for social media, but of course on Nostr it isn't basic at all, because private keys have nuclear potential if leaked. Even if you trust the person, a small mistake could be disastrous.
To solve this, we need a bunker.
What is a bunker?
A bunker (aka "remote signer") allows you to store your keys on your computer, but give others access. Once the other person is granted access, they can send commands to your computer like
sign_eventandget_public_key, and your computer will perform those operations without needing to expose the actual key.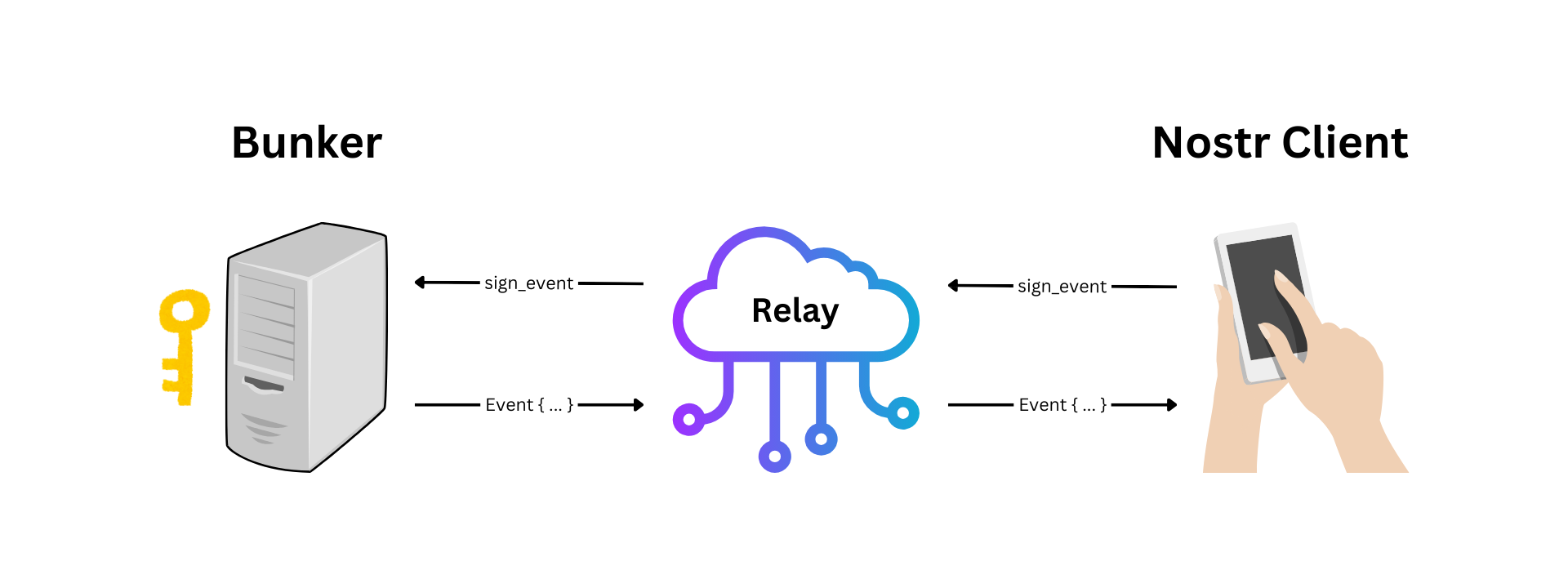
In reality the UX is not so technical. Your bunker generates a unique URI containing the connection details, and the other person pastes it into the login screen. Everything else happens automatically.
As for the running the bunker, you can run it on a VPS, a laptop, an old computer in your house, a Raspberry Pi, or even an Android phone.
The first bunker was an Android app called Nostr Connect. This lead to the creation of nsecBunker (a hosted service), nsec.app (a bunker that runs inside your web browser), and Amber (another Android app).
These days nsec.app and Amber are the only ones being actively developed, but due to running in restricted environments (web and Android respectively), they don't offer the level of 24/7 reliability I wanted in a bunker. If you are a single user managing your own keys I still recommend Amber, but for doling out credentials to your team, you might want knox.
Introducing Knox
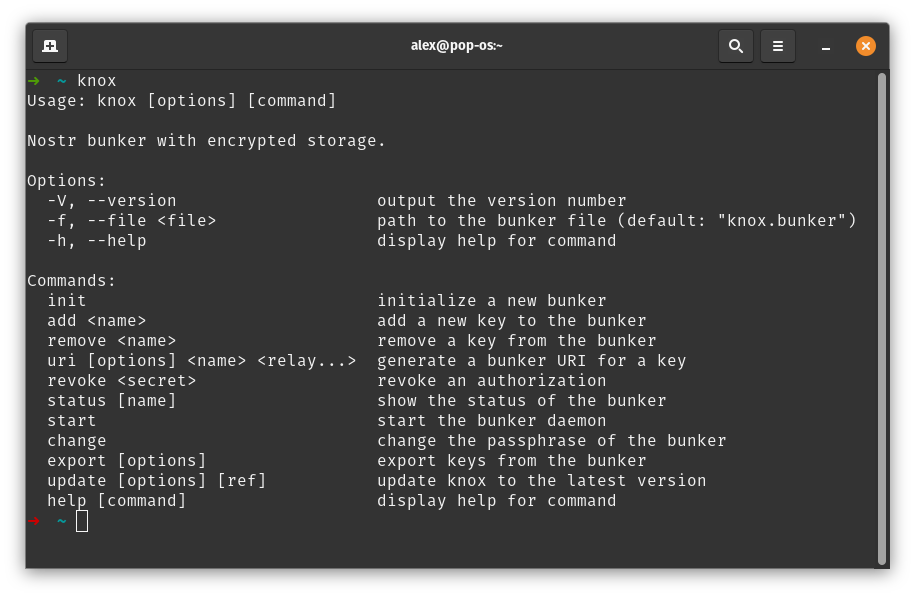
knox is a command-line tool that manages keys, generates bunker URIs, and runs a bunker server. It is still beta software, but I am using it successfully today to post on Ditto.
knox is inspired by the wonderful
nak bunkercommand, which almost solved my problem but has no way to store credentials. So I created my own command-line bunker that you can run again and again.
Most notably, knox introduces a portable
.bunkerfile format for storing keys and connection details. It's encrypted with a password, which you have to type every time you want to add or remove keys, generate new URIs, and when you start the bunker.With knox you can have one bunker file, or many. It is loosely inspired by the KeePass
.kbdxidea.knox is written in TypeScript, but it's available as a precompiled executable on Linux, MacOS, and Windows thanks to
deno compile.Getting Started
To install knox, I've prepared a simple setup script that will detect your OS and install the knox command in your path:
sh curl https://dl.soapbox.pub/install/knox.sh | shYou can also grab a precompiled binary if you don't want to run the script.
Commands
Once installed, run
knoxto see a list of supported commands. It should look something like this:``` Usage: knox [options] [command]
Nostr bunker with encrypted storage.
Options: -V, --version output the version number -f, --file
path to the bunker file (default: "knox.bunker") -h, --help display help for command Commands: init initialize a new bunker add
add a new key to the bunker remove remove a key from the bunker uri [options] generate a bunker URI for a key revoke revoke an authorization pubkey [options] show the public key of a secret key status [name] show the status of the bunker start start the bunker daemon change change the passphrase of the bunker export [options] export keys from the bunker update [options] [ref] update knox to the latest version help [command] display help for command ``` Run
knox initto create a new bunker file. Then useknox add alex(replace with your own name) to add a key, thenknox uri alexto get a connection string. Finally, runknox startto start the bunker.While the bunker is running, you can continue to run commands like
knox addandknox uriin another tab, and the bunker will detect the file changes and automatically refresh.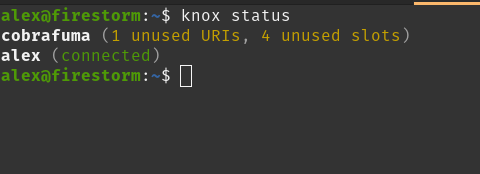
Another good one is
knox status, which shows a list of keys and whether any of their URIs are being utilized.knox status <key>can show the individual connections for a specific key, andknox revoke <secret>can revoke an individual connection.Bunker Where?
knox needs internet connectivity to connect to relays, but it does not need to expose any ports to the outside world, so the ideal place might be on a desktop computer in your living room. This might be considered more secure than a VPS in a datacenter, depending on your circumstances.

I am running knox on an old Dell computer under my TV, which is a cheap and simple solution. It's connected to a backup battery in case the power flickers, but a prolonged outage would require starting the bunker again manually. I also suggest running the bunker in
screenor a similar tool so you can reconnect and view the logs over ssh on your home network.It's not suggested to run knox in systemd, because knox requires manually entering the encryption password when it starts. Any solution to store the password to disk, or pass it through a command-line argument, would compromise security.
What's Next?
For now, knox is meeting my needs. As the idea evolves I expect to make more changes, and possibly improvements to the
.bunkerformat if anyone else decides to use it. Feel free to drop any suggestions on GitLab!Another interesting idea would be to build a UI to manage the
.bunkerfile, or to offer hosted bunker (although I am kind of against this, unless the hoster is just cloud sync service and the bunker is decrypted locally within the browser, similar to KeeWeb). -
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ 592295cf:413a0db9
2024-10-13 08:29:48
@ 592295cf:413a0db9
2024-10-13 08:29:48[07/10 week]
Thinking about it, even the protocol is a cathedral, Rabble in the speech in Riga on Bluesky.
He said the protocol is a bazaar. But you have to converge on the scheme in the NIPs or between Apps.
NIPs for example are like Luther's 95 theses, but they change continuously and adapt, but they always remain those 95.
Maybe that Pr on theother curve keys could lead to saying this is "nostr" these others are similar. Creating more points, but I just think it would have led to endless diatribes.
What will be of the protocol and who knows. He can do everything or maybe nothing and from tomorrow we will see and it will be, it will be what it will be. Italian Song
Notifications with nostter are not hidden, they are in your feed and this is good, you always know if someone has searched for you. While in the others you do not know.
I saw a sliver of light pass by it was Unanimity.
It's a very stupid idea, it takes a long time. it's basically a community + channel, where you post the channel in the community and start talking about that topic in the channel. The channel is an approved message. I made musicbook channel, it's the collection of albums released on Friday. The idea of also making a blogger channel, where to put long-form articles.
Following nostr trending on Openvibe social, with a new profile, the Lost One, sad, in this One follow fiatjaf, means I won't bother him anymore . Now I follow 62 profiles, it's an account that I will use to read the notes of the top profiles. Curious if this number will grow enormously or is there a spectre.
The strength of the protocol is the developers if they collaborate together, otherwise it can still work, everyone goes their own way, but it's like saying I want to make my own fence.
One who in his long form doing an analysis of the various social networks. npub19mq9swna4dkhlm3jaux4yhgv5kjj556lkfhv3qnjtyh0kcljph6s88e295 Nostr is all based on Bitcoin. The difficult thing is Bitcoin not Nostr and he says so.
Controversies are useful, or my doubts, but maybe people who can't write code don't understand much, the so-called end users. No one is an end user at this time. The end user doesn't care about the person behind it, only having their own service, if the service is good they also do promotion, they become sponsors. We have seen in recent months sponsoring a Nostr app, result a small attack can damage that app. But the strength of having all these apps is that the other app doesn't have that problem. Spam attack example. The problem is that you can't sponsor an ecosystem, so it becomes difficult to suggest 10 apps to download. The best 10 apps of Nostr and the other 100, there is no easy way out. It's a bit like proposing a new place in NY, then everyone goes to that place and it loses a bit. What the sponsor must understand is that Nostr has only one "one shot".
I saw a video on Nostr of two people posting content on social media, making a review. Not bad, compared to the previous video, that Nostr doesn't even have a token. It doesn't give me a sign up. The main feature they say is a platform or at least they reviewed damus, damus for Bitcoin maxi. And so Nostr is populated by people who Number go up, only fiat thought they would say on Nostr. It's true in part there are those obsessed, even the non-obsessed are obsessed.
How nice it would be to call them NPs Nostr protocol specification, today supertestnet called them that. (the nice thing is that they are pronounced the same way).
-
 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集:
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | 官网 | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | 官网 | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | 官网 | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | 官网 |
持续更新。。。
推广:
访问不了openai,去
低调云购买VPN。官网:https://didiaocloud.xyz
邀请码:
w9AjVJit价格低至1元。
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 07804b78:c375c543
2024-12-15 12:56:05
@ 07804b78:c375c543
2024-12-15 12:56:05Japanese follows. 日本語はあとで。
This article is for the 14th day of Nostr Advent Calendar 2024 (relay blogging). The article for the 13th day was "Open Sats 申請編" (Applying for Open Sats) by mono-san. The article for the 14th day will be "Nostrはじめました。" (I started Nostr) by bro-san.
Thinking of Thingstr
I've come up with an idea for Other Staff that I think is interesting (at least, for me), so I'm going to write about it. I actually wanted to show you the implementation and brag about it, but it's not solid enough to be implemented yet.
The key idea is just “add a reaction to the WikiData ID”.
WikiData
There is a service called WikiData. It is a knowledge base that provides structured data. You may be wondering what it is, but the important thing to understand here is that WikiData assigns identifiers to a fairly wide range of “objects” and “things”.
So, if you can react to this, you can think of various applications just by thinking of it for a moment, right?
For example, the anime series “There are too many losing heroines!” is assigned the ID
Q123819103. The corresponding page is https://www.wikidata.org/wiki/Q123819103 .(NOTE: The canonical URI for entities on Wikidata is http://www.wikidata.org/entity/Q1142841. This is in accordance with Semantic Web conventions, and is not https, but http. Also, this URI does not necessarily match the actual address of the correspnding web page. Just an identifier. In most cases, it will redirect).
What can wd do?
For example, what about a website that records your anime viewing history? You can record what you want to watch with 👀, what you've already watched with ✅, and your favorites with ☆. You can also express your “likes” for production companies, staff, voice actors, etc. In this way, you can see what a particular user likes.
This could be a movie, a book, a comic, an author, music, an idol group, a place, or food (Someone likes pork cutlet
Q1142841). The fact that you can record everything in the same framework is what makes it interesting.What form of event should it be recorded as?
There is probably room for discussion about how to record this information in a concrete way. The simplest way would be to use NIP-25's "Reactions to a website" kind:17 (a.k.a. Makibishi). How about something like this?
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]Since NIP-73 has External Content IDs, it would be good if we could include WikiData here so that we could write
wd:Q123819103. Actually,isbn:and other identifiers have already been defined, so it is possible to use the current NIP range to describe books (however, the authors do not have IDs. If we use WikiData as an ID, we can also describe reactions related to the author). Of course, it is not a matter of choosing one or the other, and it is also fine to add the ISBN tag at the same time as the WikiData tag for books.Search for recorded reactions
So far, this is all very simple, but it would be inconvenient if we didn't include tags to mark subsets of reactions (for example, only those related to anime) so that we can query them together. When we try to create a site that is specialized for a certain purpose, we need to be able to extract the reactions that are necessary.
On Wikidata, the predicate
wdt:P31(instance of) is used to group together concepts that represent the same thing. For example, how about including this in theltag? "There are too many losing heroines!" is a "Japanese television anime series (Q63952888)", so:json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]UPDATE(2024-12-15): rnurachue-san suggested that
#lor#Lmight be better for labeling (the first version used#a). I think that's a good idea, so I've updated the article. nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dHowever, when you think about creating an anime website, you may want to query both TV anime and anime films. This makes things more complicated. "Japanese TV anime series (
Q63952888)" is a subclass (subclass of;wdt:P279) of "Anime series (Q117467261)", which is in turn a subclass of "Anime (Q1107)". However, if you were to embed this hierarchy in each reaction, it would waste a lot of space. The following query will get all the superclasses of "Japanese TV anime series (Q63952888)", but there are 54 of them.https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
So, I think it should be okay for practical purposes to embed
P31s of the reaction target. In other words, if you search for "anime seriesQ63952888" and "anime movieQ20650540", that should be enough. Fortunately, the conditions for single-character tags work with OR, so you can query multiple tags at once. we'll have to try it to see how well it works in practice, though.Discussion: Which kind should I use?
So far we have considered using kind:17, but we have not yet decided whether it is a good idea to mix Thingstr events with reactions to web pages.
Also, there may be a debate over whether to record regular events or addressable events, depending on the purpose of use. For example, if you want to record the transition of viewing results and impressions on an anime viewing site, you should use regular events, and if you want to maintain the viewing status, you should use addressable events.
What do you think?
Other ideas
If we can react to Nodes on OpenStreetMap using the same framework, we might be able to create something like Swarm. Since the views you want to see will differ depending on the purpose, it would be good to create various sites while having a consistent way of recording. Wouldn't that be the most Nostr-like thing?
Summary
I discussed how to use WikiData and OpenStreetMap as an ID infrastructure and realize various check-in and review services with a unified data model by using them on Nostr. Please let us know if you have any feedback. Or why not try implementing it?
この記事は Nostr Advent Calendar 2024 の14日目の記事です。13日目の記事はmonoさんによる「Open Sats 申請編」でした。15日目の記事はbroさんによる「Nostrはじめました。」です。
Thingstrについて考えた
面白そうな(と勝手に思ってる) Other Staff のアイディアを思いついたので、書いてみます。 本当は実装を持ってきて自慢したかったのですが、まだふわっとしていて実装に落ちていません。
コアになるアイディアは「WikiData の ID に対して、Reactionをつける」これだけです。
WikiData
WikiData というサービスがあります。構造化データを提供する知識ベースです。 なにそれ?という感じですが、ここで大事なのはWikiDataはかなり広範な「もの」「こと」に識別子(Identifier)を付与している、ということです。
だから、これにリアクションできれば、ぱっと思いつくだけでもいろいろな応用ができそうじゃないですか。
例えば、アニメシリーズ「負けヒロインが多すぎる!」には
Q123819103というIDが振られています。これに対応するページとして https://www.wikidata.org/wiki/Q123819103 があります。(ただし、WikiData のエンティティに対する canonical な URI は http://www.wikidata.org/entity/Q1142841 であることには注意が必要です。セマンティックウェブの作法で https ではなく http になっています。そして、このURIは必ずしもWebページのアドレス一致しません。大抵の場合はリダイレクトされます)。
なにができるの
たとえば、アニメの視聴記録サイトはどうでしょう。👀は見たい作品、✅は視聴済み、☆はお気に入り、みたいに記録していく。制作会社、スタッフ、声優、...に対してLikeを表明したりできそうです。そうすると、あるユーザが何にLikeしているかわかります。
これが映画でもいいし、書籍、漫画、作家でもいいし、音楽でもいいし、アイドルグループでもいいし、場所でもいいし、食べ物でもいい(とんかつ
Q1142841が好き、とか)。全部同じ枠組みで記録できるのが面白そうなところです。どういうNostrイベントで記録する?
具体的な記録の仕方には議論の余地があるでしょう。一番単純なのは、NIP-25の "Reactions to a website" kind:17 (Makibishi) を使う方法でしょうか。こんなのはどうでしょう。
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]NIP-73にExternal Content IDsがあるので、ここにWikiDataを入れられるようにして
wd:Q123819103と書けるとよさそうです。実はisbn:などはすでに定義されているので、書籍に関しては現行のNIPの範囲でもうまいことできます(ただ、著者にはIDが振られていません。WikiDataをIDに使うと著者に関するリアクションも記述できます)。もちろん、どちらか一方を選ぶというものでもなくて、書籍にはWikiDataのタグと当時にISBNのタグを付与しておいてもいいと思います。記録されたリアクションを検索する
ここまではシンプルでよいのですが、リアクションの部分集合(たとえばアニメに関連するものだけ、とか)をまとめてクエリできるように、目印となるタグを入れておかないと不便です。ある目的に特化したサイトを作ろうとしたとき、必要になるリアクションが抽出できるようにしておかないといけません。
WikiData では
wdt:P31(instance of) という述語で、ある概念が何を表しているかをグルーピングしてくれています。例えばこれをlタグとかに含めておくのはどうでしょうか。負けヒロインが多すぎる!は「日本のテレビアニメシリーズ(
Q63952888)」なので、json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]みたいな感じで付与します。
UPDATE(2024-12-15): rnurachueさんからラベル付けには
#lまたは#Lのほうがよいかもという提案をいただきました。最初のバージョンでは#aを使用していました。そのとおりだと思ったので更新しました。 nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dただ、アニメサイトを作ることを考えると、テレビアニメも劇場版アニメも両方クエリしたいこともありそうですよね。そうなると話が複雑になってきます。
「日本のテレビアニメシリーズ(
Q63952888)」は「アニメシリーズ(Q117467261)」のサブクラス(subclass of;wdt:P279)で、それがさらに「アニメ(Q1107)」 のサブクラスになっています。ただ、この階層をいちいちリアクションに埋め込むのと大変なことになります。以下のようなクエリで「日本のテレビアニメシリーズ(Q63952888)」のすべての上位クラスが取れるのですが、54件もあります。https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
なので、リアクション対象の
P31を埋め込む、くらいで実用上は問題ないような気がします。つまり、検索するときに 「アニメシリーズQ63952888」と「アニメ映画Q20650540」を対象にすれば、十分では、ということです。幸い、一文字タグの条件はORで効くので、複数を並べて一度にクエリできます。実際にどのくらいうまく行くかはやってみないとわからないですが。議論: どの kind を使うべきか?
一旦 kind 17 を使うことを考えてきましたが、Thingstr のイベントが Web ページに対するリアクションと混ざるのが良いことなのか、いまいち判断がついていません。
また、用途によって regular event で記録するべきか、それとも addressable event で記録すべきか、という議論もありそうです。 アニメ視聴サイトを例にあげるなら、視聴実績とか感想の変遷を記録したいならば regular event でしょうし、視聴の状態を保持したいならば addressable とするのがよさそうです。
どう思いますか?
他のアイディア
これと同じ枠組みで OpenStreetMap の Node に対してリアクションできるようにすれば Swarm のようなものも実現できるかもしれません。
用途ごとに見たいビューは違うだろうから、一貫した記録の仕方を持ちつつ、色々なサイトを作ったらいいんじゃないでしょうか。それって最高にNostrっぽくないですか?
まとめ
WikiDataやOpenStreetMapをID基盤として活用し、Nostr上でreactすることで、様々なチェックインサービス、レビューサービスを統一的なデータモデルで実現する方法について議論しました。フィードバックがあったら教えてください。むしろ実装してみてください。
-
 @ ec42c765:328c0600
2024-12-15 11:13:44
@ ec42c765:328c0600
2024-12-15 11:13:44てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
-
 @ fd78c37f:a0ec0833
2024-12-11 01:32:23
@ fd78c37f:a0ec0833
2024-12-11 01:32:23Bitcoin, as a decentralized digital currency, is reshaping the global financial landscape, sparking innovation and transformation across various sectors. In South America, Bitcoin communities are emerging as crucial drivers of economic empowerment, financial inclusion, and local technological advancement. This issue will highlight 21 Bitcoin communities from South America, exploring their missions, growth trajectories, and recent developments. By examining these grassroots initiatives, we aim to show how Bitcoin is being leveraged to create sustainable economic ecosystems, foster social progress, and expand access to education and financial tools. Thank you, YakiHonne decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.Mi Primer Bitcoin nostr:npub17cyatz6z2dzcw6xehtcm9z45m76lde5smxdmyasvs00r4pqv863qrs4ml3 * Introduction My First Bitcoin is a Bitcoin education initiative rooted in the principles of independence, fairness, and community leadership. Originating in El Salvador, it aims to empower individuals and communities by providing open-source educational resources and fostering a decentralized network. Through a commitment to high-quality education, resistance to external influence, and the creation of a global collaborative network, it seeks to spread Bitcoin education to every corner of the world, offering a transparent and transformative model for reshaping traditional financial systems. * Latest Updates Recently, MyfirstBitcoin successfully hosted the fourth Bitcoin Educators Unconference, featuring guests such as nostr:npub1zfgx8v2g0faswd0ry2qn3ay4pvx4jr6q4fw9d0yqalpkyv9hhp0sjccnj5 nostr:npub1rhh9pkmf6l6z7298yg6fgp95rzkmx4j9uxpekn8j73p5k95ck7gsvce7vj attracting around 170 participants and receiving positive feedback. They also held the graduation ceremony in Ilopango, El Salvador, and continued to organize their regular monthly Bitcoin education meetups and Bitcoin game nights. Additionally, MyfirstBitcoin’s Bitcoin Educators Node Network welcomed four new projects from Canada, Nigeria, and the United States. In partnership with Bitcoin Boma, they are launching a free online Bitcoin education course for Malawi in January 2025, aimed at enhancing local Bitcoin knowledge.
- Introduction Bitcoin Beach is a groundbreaking initiative in El Salvador aimed at fostering sustainable local economic development through Bitcoin. The project provides financial services to the community, particularly for those without access to traditional banking. By using Bitcoin for payments, residents can cover everyday expenses such as utility bills, medical costs, and food. Bitcoin Beach leverages the Lightning Network and community collaboration to promote the adoption of Bitcoin both within El Salvador and globally.
- Latest Updates Recently, Bitcoin Beach attended the conference at Bitcoin Lake, where they hosted the Bitcoin Beach Meetup and Bitcoin Beach Festival to support local businesses with Bitcoin. They also invited notable figures such as nostr:npub1q0al05h2uvtj0fp8ww7etl0pdjnkum638ynz9tmku3e522fyvlmqjq04mt Hermann Buhr-Vivier, nostr:npub164xhe3pgcqaj70ls7ls5e4hwlnvl4ttuu8wns99jmwp5z6lwhutsa27wle as podcast guests. The discussions covered a range of impactful topics, including how Bitcoin mining can truly light up rural Africa, how to use Bitcoin to transform small towns in South Africa, and integrating Bitcoin into state-level policies across the United States, among other key areas.
3.Praia Bitcoin Brazil nostr:npub1m3tu3l6y59g2tmackq23v5vgn59u7hu66gxg8xajghz59tqm6xnqk2m888 * Introduction Praia Bitcoin Brazil, located in Jericoacoara, Brazil, is dedicated to creating the country's first Bitcoin circular economy, empowering local residents with financial inclusion. Founded by Fernando Motolese, the project promotes Bitcoin adoption through education, technology, and community-driven initiatives. It has integrated over 40 local businesses into the Bitcoin ecosystem and raised more than 12 BTC through Bitcoin-only crowdfunding. Praia Bitcoin offers self-sovereign financial services and runs programs like the "Bitcoin Smiles" initiative and educational support for children. * Latest Updates Recently, Praia Bitcoin Brazil launched several innovative projects, including the first stage lighting course and free acoustic guitar course funded entirely through Bitcoin crowdfunding. Additionally, Praia Bitcoin successfully hosted the Praia Bitcoin Conference 2024, attracting 10 volunteers, 100 local residents, and 10 new merchants. The conference also sponsored the first music performance paid in Bitcoin and introduced three local courses, all funded via Bitcoin crowdfunding. These initiatives highlight Praia Bitcoin's ongoing efforts to drive Bitcoin adoption and foster local community development.
4.Bitcoin Lake / Lago Bitcoin Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake aims to create a circular economy powered by Bitcoin, providing a novel and accessible solution for unbanked as well as banked merchants in Guatemala. * Latest Updates The Bitcoin Lake community has been actively preparing and promoting a series of innovative initiatives. On November 30 and December 1, Bitcoin Lake successfully hosted its 2024 conference, inviting industry experts such as Ronny Avendaño, co-founder and CEO of the Bitcoin hardware store, and prominent Bitcoin advocate Roman Martínez (chimbera). During the conference, the community also organized creative activities like the coffee workshop and “Be Captain of the Bitcoin Boat”, offering participants an opportunity to dive deeper into Bitcoin and the local economy. Additionally, through partnerships with local merchants, Bitcoin Lake is actively advancing the development of the Bitcoin economy, fostering economic growth and financial inclusion in the community.
5.Bitcoin jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network with the goal of creating a circular Bitcoin economy. The project provides education, resources, and technology to both individuals and businesses. Starting from the Golden Triangle area in Costa Rica (Dominical, Uvita, Ojochal, Platanillo, Tinamaste), it is developing a shining example of what a Bitcoin community can represent. * Latest Updates Recently, the Bitcoin Jungle community has been actively promoting the adoption and use of Bitcoin in Costa Rica, participating in various projects and events. Community members attended the Adopting Bitcoin conference in El Salvador, further advancing global Bitcoin adoption. At the same time, they have been actively supporting children's charity projects and Bitcoin diploma courses, continuously driving Bitcoin education, social responsibility, and community development.
6.Bitcoin Berlín sv * Introduction Bitcoin Berlín sv aimed at creating a financially sovereign town in Berlín, El Salvador, through the implementation of a Bitcoin circular economy. The project seeks to integrate Bitcoin into the local economy by educating residents and businesses about its benefits, promoting the adoption of Bitcoin-based payment systems, and empowering local entrepreneurs with financial education. It also focuses on environmental sustainability, encouraging the use of renewable energy and waste reduction. * Latest Updates Recently, the Bitcoin Berlín sv has been actively promoting the use of Bitcoin by sharing informative articles and supporting the graduation of podcast producer Joel through the BlinkBTC QR code platform, allowing contributions in sats. This initiative not only supports the growth and development of community members but also furthers Bitcoin’s adoption and usage within the community. Additionally, on November 23rd, the community successfully hosted a cultural festival celebrating the local heritage. During the event, all vendors accepted Bitcoin payments, showcasing its practical application in Berlín’s economy. The festival attracted numerous tourists and residents eager to experience Bitcoin payments, further advancing its integration into daily life.
7.Bitcoin embassy San Salvador * Introduction Bitcoin embassy San Salvador is more into promoting Nostr in the region. * Latest Updates Recently, the Bitcoin Embassy San Salvador has been actively promoting the use and adoption of Bitcoin within the community, organizing various events. One of the highlights was the Christmas Toy Drive x Cuarteto Salvación, where toys were purchased using Sats to bring holiday cheer to children in need. The event, held on December 1 at Cuscatlán Park, also featured a special Music Night, attracting a large audience. Additionally, the Embassy hosted an educational gathering for food vendors, aimed at promoting Bitcoin payment systems. During the event, vendors accept Bitcoin payments through tiankii_Tech and blinkbtc platforms, further encouraging local businesses to embrace and adopt Bitcoin payments.
8.ONG Bitcoin Argentina * Introduction ONG Bitcoin Argentina is dedicated to advancing the development and application of decentralized technologies, particularly in the fields of Bitcoin, cryptocurrencies, and blockchain. As a leading organization in this space, the community promotes user protection and the healthy growth of the crypto ecosystem through education, training, and public advocacy. Its mission is to help individuals, businesses, and decision-makers understand and leverage decentralized, transparent, and secure technologies to bring more opportunities and progress to society. ONG Bitcoin Argentina has become a leading force in promoting decentralized technology in Argentina and Latin America. * Latest Updates Recently, ONG Bitcoin Argentina has been actively preparing for the “Moon Party | Despedimos el año ATH (A Todo Hodler)” celebration, set to take place on December 5, 2024. Bitcoin enthusiasts will gather to enjoy exciting activities, including a Lightning Network demonstration and the Fish Bowl Manizesto Bitcoiner art exhibition. In addition, the community has hosted and will host a series of conferences and workshops covering a range of topics, including local digital asset services, Bitcoin as a strategic reserve in the U.S., the reconversion of the Bitcoin and cryptocurrency economy and financial systems, the role of crypto economics in financial system reform, the impact of Bitcoin ETFs on markets, and Bitcoin's influence on global issues, fostering in-depth discussions and development within the crypto industry.
9.La bitcoineta * Introduction La Bitcoineta is an initiative launched by the Argentine community in 2018, designed to promote the adoption and understanding of Bitcoin through a unique and powerful tool: a van and a group of volunteers. This traveling educational project has visited hundreds of towns across Latin America, Africa, and Europe, reaching thousands of people and covering hundreds of thousands of kilometers with the aim of spreading its mission and activities.With its innovative and mobile approach, Bitcoineta has become a globally recognized educational project.
10.Motiv Peru * Introduction Motiv is a non-profit organization founded in 2020, focused on addressing systemic poverty through Bitcoin and innovative projects, aiming to provide better opportunities for survival and prosperity to underserved communities. Its founders, Rich Swisher and Vali Popescu, witnessed firsthand the tragic impact of poverty and lack of basic living conditions in a remote village in the Andes Mountains of Peru, where children were dying due to preventable causes. This inspired them to create Motiv, with the goal of empowering vulnerable populations. By leveraging global support and partnerships, Motiv uses Bitcoin to help local communities break free from poverty and improve their lives, striving to bring positive change and hope to those in need. * Latest Updates Recently, MOTIV Perú has made significant progress in promoting Bitcoin and the circular economy. The organization continues to transform communities across Peru through various initiatives. For example, in the Comas district of Lima, entrepreneurial women are paying for their classes with Bitcoin and learning how to make delicious desserts, further advancing the local circular economy. Additionally, MOTIV Perú held its first Bitcoin training in Carabayllo-Lima, helping Peruvians understand the nature of money and the advantages of Bitcoin. MOTIV is also assisting communities in areas like Tarapoto and Ancon, where locals are using Bitcoin for daily transactions, driving financial freedom and economic empowerment.
11.Montanha bitcoin * Introduction Building a circular economy in Sao thome, Brazil. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to June 2024, highlighting a water contamination incident.
12.Amityage honduras * Introduction Amityage Honduras is the first Bitcoin education center in Honduras, located on Roatán Island in the Prosperá zone. The center's mission is to educate the local community about Bitcoin and spread this knowledge throughout Central America and the Caribbean. It is dedicated to helping businesses on the island adopt Bitcoin as a payment method, teaching children financial literacy, and empowering individuals to achieve financial sovereignty through Bitcoin. The center aims to empower the local community through education and innovation, fostering economic independence and sustainable development. * Latest Updates Recently, Amityage Honduras is actively promoting Bitcoin education by participating in various international Bitcoin events and organizing local courses to help more people understand Bitcoin. Community members took part in significant events such as AdoptingBTC 2024 and BitcoinUnconference, and hosted workshops around the theme of “How to Enter the World of Bitcoin Education.” In Haidmühle, Germany, AmityAge completed a four-day Bitcoin Educators Academy, where the curriculum included topics like using simple analogies to explain Bitcoin and public speaking exercises. Additionally, the community hosted Bitcoin education courses on Roatán Island and provided a free Bitcoin event for beginners at the Crawfish Rock community, further spreading Bitcoin knowledge.
13.Lima - Orange Pill Perú nostr:npub1fw8m5g6nfywmsgqjc66j47jax7jrv8lq46zf7grydjqppc54a8eql47qrx * Introduction Orange Pill Peru is a community-driven initiative dedicated to empowering Peruvians through Bitcoin education. With a focus on transforming the financial landscape, Orange Pill Peru provides resources for individuals to learn about Bitcoin, connect with like-minded enthusiasts, and grow their knowledge through various events and workshops. The community serves as a hub for both beginners and professionals, offering a supportive environment to explore the fundamentals of Bitcoin, its history, and its potential to shape the future of finance. * Latest Updates Recently, there have been no major updates. They actively engage in Bitcoin education and industry updates by sharing and reposting Bitcoin-related content. They support MOTIV Perú's financial freedom education project in the Ancon community in Lima, emphasizing the empowerment of women through Bitcoin. Additionally, the community has shared information about the upcoming Bitcoin Medellin Conference scheduled for January 2025.
14.La Antigua Bitcoin * Introduction La Antigua Bitcoin is a community-based initiative in La Antigua Guatemala, focusing on promoting Bitcoin adoption in local businesses. The community works to create awareness and facilitate the use of Bitcoin as a payment method in various establishments throughout the city. By encouraging merchants to accept Bitcoin, La Antigua Bitcoin aims to integrate cryptocurrency into the everyday economy, driving financial innovation and expanding access to decentralized financial systems within the region. * Latest Updates Recently, the Antigua Bitcoin community has had few updates, with a focus on organizing its first meetup in collaboration with “Run with Bitcoin” on November 24, 2023. The event garnered significant attention within the community, featuring interactions with a special guest. The aim of the event was to further promote Bitcoin adoption in Antigua, Guatemala, and encourage exchange and collaboration between Bitcoin enthusiasts and the local community.
15.Horizonte Bitcoin nostr:npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk * Introduction Project that aims to contribute to the Bitcoinization of the economy and encourage Entrepreneurship and Decentralization. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to Oct 2024, which shared a message encouraging women to learn more about Bitcoin and connect with others in the field, highlighted a meetup, Satoshe's Lounge, for women, providing a space to learn, discuss, and share knowledge about Bitcoin.
16.Escuelita Bitcoin nostr:npub1awggmqvlw8pa0kp9qq5law8zsvp2a8suztk0357j7e0nt746suwspt7lwx * Introduction Educational Project for Little School. * Latest Updates Recently, the Escuelita Bitcoin team has grown to five members and is actively advancing Bitcoin education and community development. Team members have hosted several workshops in Paraguay and Mexico, spreading Bitcoin knowledge within local communities and encouraging merchants to accept Bitcoin payments, particularly in Ciudad del Este, Paraguay. The team is raising funds through platforms like Geyser. fund and Kuno.anne.media to support the expansion of their educational initiatives and help locals better understand and use Bitcoin. Escuelita Bitcoin also emphasizes privacy education, promoting the use of tools like CakeWallet and Monero. Through collaborations with other organizations and individuals, the team is extending the reach of Bitcoin education, fostering the adoption of Bitcoin in Latin America and emerging markets.
17.Bitcoin é aqui! Rolante/Riozinho-RS-BRASIL nostr:npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 * Introduction Bitcoin é Aqui! Rolante is located in Rolante, Brazil, and is dedicated to creating a lifestyle and tourism destination where 40% of businesses now accept Bitcoin as a payment method, showcasing the community's success in integrating Bitcoin into the local economy. Residents and visitors can use it to pay for all services, including accommodation, tours, local goods, medical services, and even construction and solar energy equipment. This reflects the practical application and convenience of its use in everyday life, aiming to create a digitally-driven environment powered by Bitcoin. * Latest Updates Recently, the Bitcoin é Aqui! Rolante has been actively promoting the adoption and use of Bitcoin in Brazil and beyond. The community has organized several educational events aimed at spreading basic Bitcoin knowledge and its practical applications in daily life, particularly through online videos and lectures. These efforts help people understand how Bitcoin plays a crucial role in the global financial system. The community has also been actively involved in promoting Bitcoin payments, supporting their adoption by local businesses and in the tourism industry.
18.Bitcoin Forte * Introduction Bitcoin Forte is a voluntary initiative aimed at introducing Bitcoin as a currency to Praia do Forte in Bahia, Brazil. The project provides valuable information about Bitcoin’s importance and encourages local merchants to adopt it as a payment method. By highlighting Bitcoin's international use, simplicity, and security, Bitcoin Forte aims to facilitate its adoption among both tourists and businesses.The community promotes Bitcoin as a stable and controlled currency, helping to avoid systemic price inflation. Bitcoin Forte simplifies the process for businesses by offering tools such as QR codes and the “Satoshi POS Wallet” app, which connects to a merchant’s primary wallet for seamless transactions. * Latest Updates Recently, the community has had no recent updates. The latest event dates back to July 2024, introducing Airbtc, a platform similar to Airbnb, but it only accepts Bitcoin as payment.
19.Bitcoin Paraguay * Introduction Bitcoin Paraguay is a community dedicated to connecting individuals in Paraguay who are interested in Bitcoin, promoting its adoption, and fostering the development of local circular economies. The community’s mission is to increase Bitcoin adoption by collaborating with local businesses and nonprofit organizations, helping to create a more sustainable local economy. Through regular events, talks, and resource sharing, Bitcoin Paraguay provides education and support to its members while actively exploring Bitcoin's application across various sectors in Paraguay. * Latest Updates Recently, the Bitcoin Paraguay community has made significant progress in promoting Bitcoin adoption. On November 5, they successfully hosted the fifth Bitcoin meetup in Asunción, attracting 110 attendees. The event included two Spanish-language presentations and a Lightning Network onboarding training session, with food and drinks available for purchase using Bitcoin. The event was made possible with strong support from sponsors Blink Wallet and Hacking Lives. On November 13, Josef Tetek visited Bitcoin Paraguay to help promote the adoption of Vexl in the country. The community also shared their progress through articles, with Jake, a community member, publishing an article in the Asunción Times on how Bitcoin Paraguay is improving people's lives.
20.Bitcoin Amantikir * Introduction They are starting the first community in the Serra da Mantiqueira to use and extol people about the bitcoin economy. * Latest Updates Recently, the Bitcoin Amantikir community has made significant progress in promoting Bitcoin as a payment method and fostering a circular economy in Santo Antônio do Pinhal. Various businesses, including a pet store, transportation service providers, a hotel, a fruit shop, and a tourist attraction, have started accepting Bitcoin payments. Additionally, the community is organizing a Bitcoin financial education course on December 2nd at Munay Pousada, aimed at helping young people aged 14-18 acquire essential financial knowledge and understand the importance of Bitcoin.
21.La Crypta nostr:npub1rujdpkd8mwezrvpqd2rx2zphfaztqrtsfg6w3vdnljdghs2q8qrqtt9u68 * Introduction La Crypta is an open-source community dedicated to advancing the adoption of the Nostr protocol and Bitcoin through developer-friendly tools and resources. By providing an integrated open-source stack, La Crypta empowers developers to sync with multiple relays, showcase profiles with badges, and facilitate seamless messaging, making it easier to build and utilize decentralized social platforms. Events like hackathons further enhance collaboration and attract new members, fostering innovation in decentralized social media. * Latest Updates LaWallet, their open-source wallet, integrates Bitcoin, Lightning, and Nostr to provide a seamless learning experience. With over 8,000 NFC cards distributed across conferences in regions like Argentina, Brazil, and Spain, LaWallet enables easy adoption while prioritizing user privacy. The wallet’s functionality is now supported by Alby’s official browser extension, further boosting accessibility.
-
 @ 3f0702fa:66db56f1
2024-12-15 10:02:58
@ 3f0702fa:66db56f1
2024-12-15 10:02:58В Кургане стартовало масштабное исследование состояния здоровья жителей, проводимое учеными с использованием передовых технологий. Это исследование, наряду с рядом нововведений, демонстрирует прогресс курганской системы здравоохранения в 2040 году.
Цель исследования - изучить динамику здоровья населения, выявить факторы риска и оценить эффективность применяемых методов лечения. Используются персональные медицинские гаджеты для сбора данных, генетическое тестирование, искусственный интеллект для анализа данных и удаленный мониторинг состояния пациентов.
Помимо исследования, активно внедряются телемедицина, позволяющая получать консультации удаленно; персонализированная медицина с индивидуальными программами лечения; роботизированная хирургия для сложных операций и 3D-печать имплантов и протезов.
Результаты исследования и внедрение новых технологий позволят курганским медикам разработать более эффективные программы профилактики и лечения, а также улучшить качество медицинского обслуживания населения. Система здравоохранения Кургана в 2040 году - это пример того, как можно эффективно использовать современные технологии для улучшения здоровья и благополучия людей.
В Кургане делается все возможное для улучшения здоровья жителей, и мы будем следить за тем, как эти новые технологии будут работать на практике.
Мы продолжим следить за ходом исследований и развитием системы здравоохранения Кургана и сообщать вам о новых достижениях. Следите за нашими публикациями.
45news
Курган2040
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3f0702fa:66db56f1
2024-12-15 09:34:17
@ 3f0702fa:66db56f1
2024-12-15 09:34:17Курган в 2040 году стал центром международной промышленности, открывая новую эру экономического роста и процветания для региона. Благодаря привлечению иностранных инвестиций, развитию инновационных производств и активному внедрению передовых технологий, курганская промышленность вышла на мировой уровень.
Ключевым изменением стало создание современных промышленных кластеров, специализирующихся на высокотехнологичных производствах в области машиностроения, электроники, биотехнологий и возобновляемой энергетики. На территории региона разместили свои производства ведущие международные компании, создавая тысячи новых рабочих мест и обеспечивая высокий уровень заработной платы.
Интеграция с глобальными производственными цепочками позволила курганским предприятиям выйти на новые рынки сбыта, а внедрение цифровых технологий оптимизировало процессы производства, сделав их более эффективными и экологичными.
Изменения коснулись и жизни курганцев: вырос уровень доходов, повысилось качество жизни, появились новые возможности для профессионального и личностного развития. Курган стал городом, привлекающим высококвалифицированных специалистов из разных регионов и стран, что способствует дальнейшему росту и процветанию региона.
Курганская промышленность в 2040 году – это символ инноваций, международного сотрудничества и процветания, открывающий новые перспективы для будущего региона.
Мы продолжим следить за развитием промышленности Кургана и сообщать вам о новых достижениях и проектах. Следите за нашими публикациями.
45news #Курган2040
-
 @ 06639a38:655f8f71
2024-11-01 22:32:51
@ 06639a38:655f8f71
2024-11-01 22:32:51One year ago I wrote the article Why Nostr resonates in Dutch and English after I visited the Bitcoin Amsterdam 2023 conference and the Nostrdam event. It got published at bitcoinfocus.nl (translated in Dutch). The main reason why I wrote that piece is that I felt that my gut feeling was tellinng me that Nostr is going to change many things on the web.
After the article was published, one of the first things I did was setting up this page on my website: https://sebastix.nl/nostr-research-and-development. The page contains this section (which I updated on 31-10-2024):
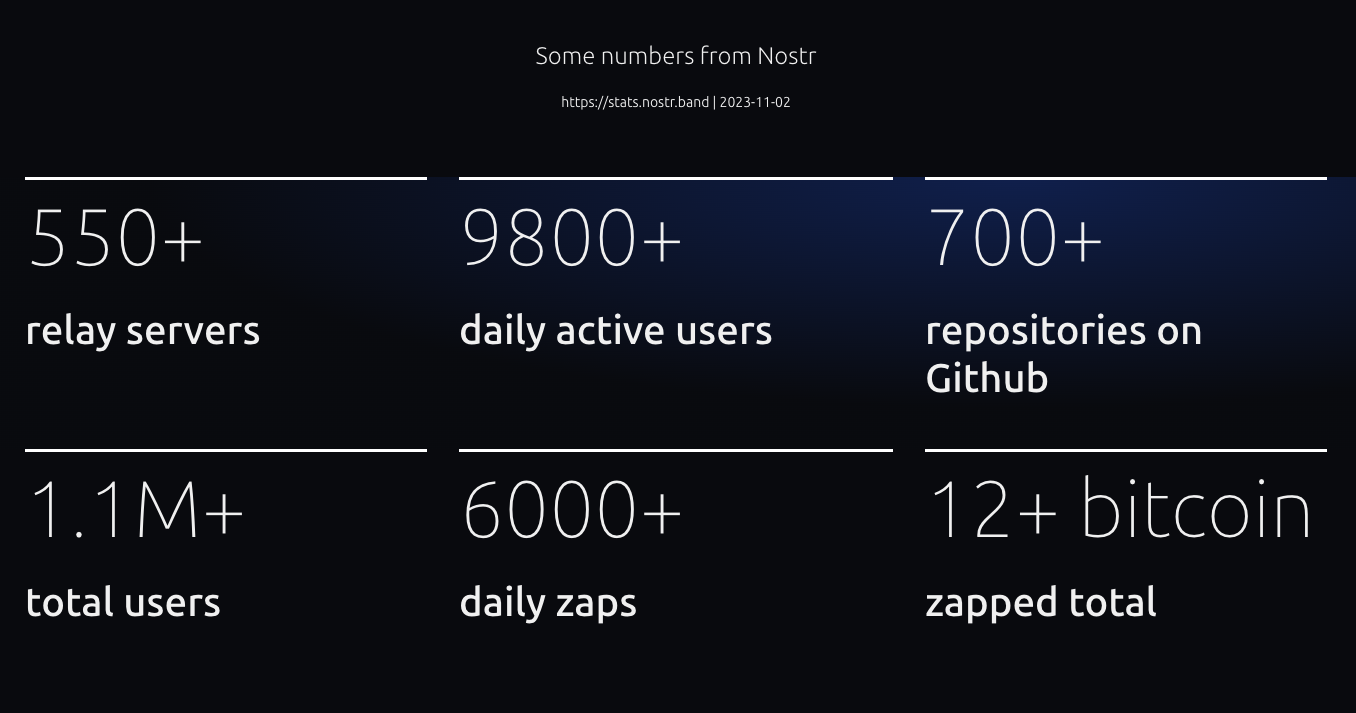
One metric I would like to highlight is the number of repositories on Github. Compared to a year ago, there are already more than 1130 repositories now on Github tagged with Nostr. Let's compare this number to other social media protocols and decentralized platforms (24-10-2024):
- Fediverse: 522
- ATProto: 159
- Scuttlebot: 49
- Farcaster: 202
- Mastodon: 1407
- ActivityPub: 444
Nostr is growing. FYI there are many Nostr repositories not hosted on Github, so the total number of Nostr reposities is higher. I know that many devs are using their own Git servers to host it. We're even capable of setting up Nostr native Git repositories (for example, see https://gitworkshop.dev/repos). Eventually, Nostr will make Github (and other platforms) absolute.
Let me continue summarizing my personal Nostr highlights of last year.
Organising Nostr meetups

This is me playing around with the NostrDebug tool showing how you can query data from Nostr relays. Jurjen is standing behind me. He is one of the people I've met this year who I'm sure I will have a long-term friendship with.OpenSats grant for Nostr-PHP


In December 2023 I submitted my application for a OpenSats grant for the further development of the Nostr-PHP helper library. After some months I finally got the message that my application was approved... When I got the message I was really stoked and excited. It's a great form of appreciation for the work I had done so far and with this grant I get the opportunity to take the work to another higher level. So please check out the work done for so far:Meeting Dries

One of my goosebumps moments I had in 2022 when I saw that the founder and tech lead of Drupal Dries Buytaert posted 'Nostr, love at first sight' on his blog. These types of moments are very rare moment where two different worlds merge where I wouldn't expect it. Later on I noticed that Dries would come to the yearly Dutch Drupal event. For me this was a perfect opportunity to meet him in person and have some Nostr talks. I admire the work he is doing for Drupal and the community. I hope we can bridge Nostr stuff in some way to Drupal. In general this applies for any FOSS project out there.
Here is my recap of that Drupal event.Attending Nostriga

A conference where history is made and written. I felt it immediately at the first sessions I attended. I will never forget the days I had at Nostriga. I don't have the words to describe what it brought to me.

I also pushed myself out of my comfort zone by giving a keynote called 'POSSE with Nostr - how we pivot away from API's with one of Nostr superpowers'. I'm not sure if this is something I would do again, but I've learned a lot from it.
You can find the presentation here. It is recorded, but I'm not sure if and when it gets published.Nostr billboard advertisement
This advertisment was shown on a billboard beside the A58 highway in The Netherlands from September 2nd till September 16th 2024. You can find all the assets and more footage of the billboard ad here: https://gitlab.com/sebastix-group/nostr/nostr-ads. My goal was to set an example of how we could promote Nostr in more traditional ways and inspire others to do the same. In Brazil a fundraiser was achieved to do something similar there: https://geyser.fund/project/nostrifybrazil.
Volunteering at Nostr booths growNostr

This was such a great motivating experience. Attending as a volunteer at the Nostr booth during the Bitcoin Amsterdam 2024 conference. Please read my note with all the lessons I learned here.
The other stuff
- The Nostr related blog articles I wrote past year:
- Run a Nostr relay with your own policies (02-04-2024)
- Why social networks should be based on commons (03-01-2024)
- How could Drupal adopt Nostr? (30-12-2023)
- Nostr integration for CCHS.social (21-12-2023)
- https://ccns.nostrver.se
CCNS stands for Community Curated Nostr Stuff. At the end of 2023 I started to build this project. I forked an existing Drupal project of mine (https://cchs.social) to create a link aggregation website inspired by stacker.news. At the beginning of 2024 I also joined the TopBuilder 2024 contest which was a productive period getting to know new people in the Bitcoin and Nostr space. - https://nuxstr.nostrver.se
PHP is not my only language I use to build stuff. As a fullstack webdeveloper I also work with Javascript. Many Nostr clients are made with Javascript frameworks or other more client-side focused tools. Vuejs is currently my Javascript framework I'm the most convenient with. With Vuejs I started to tinker around with Nuxt combined with NDK and so I created a starter template for Vue / Nuxt developers. - ZapLamp
This is a neat DIY package from LNbits. Powered by an Arduino ESP32 dev board it was running a 24/7 livestream on zap.stream at my office. It flashes when you send a zap to the npub of the ZapLamp. - https://nosto.re
Since the beginning when the Blossom spec was published by @hzrd49 and @StuartBowman I immediately took the opportunity to tinker with it. I'm also running a relay for transmitting Blossom Nostr eventswss://relay.nosto.re. - Relays I maintain
I really enjoy to tinker with different relays implementations. Relays are the fundamental base layer to let Nostr work.
I'm still sharing my contributions on https://nostrver.se/ where I publish my weekly Nostr related stuff I worked on. This website is built with Drupal where I use the Nostr Simple Publish and Nostr long-form content NIP-23 modules to crosspost the notes and long-form content to the Nostr network (like this piece of content you're reading).
The Nostr is the people
Just like the web, the web is people: https://www.youtube.com/watch?v=WCgvkslCzTo
the people on nostr are some of the smartest and coolest i’ve ever got to know. who cares if it doesn’t take over the world. It’s done more than i could ever ask for. - @jb55
Here are some Nostriches who I'm happy to have met and who influenced my journey in Nostr in a positive way.
- Jurjen
- Bitpopart
- Arjen
- Jeroen
- Alex Gleason
- Arnold Lubach
- Nathan Day
- Constant
- fiatjaf
- Sync
Coming year
Generally I will continue doing what I've done last year. Besides the time I spent on Nostr stuff, I'm also very busy with Drupal related work for my customers. I hope I can get the opportunity to work on a paid client project related to Nostr. It will be even better when I can combine my Drupal expertise with Nostr for projects paid by customers.
Building a new Nostr application
When I look at my Nostr backlog where I just put everything in with ideas and notes, there are quite some interesting concepts there for building new Nostr applications. Filtering out, I think these three are the most exciting ones:
- nEcho, a micro app for optimizing your reach via Nostr (NIP-65)
- Nostrides.cc platform where you can share Nostr activity events (NIP-113)
- A child-friendly video web app with parent-curated content (NIP-71)
Nostr & Drupal
When working out a new idea for a Nostr client, I'm trying to combine my expertises into one solution. That's why I also build and maintain some Nostr contrib modules for Drupal.
- Nostr Simple Publish
Drupal module to cross-post notes from Drupal to Nostr - Nostr long-form content NIP-23
Drupal module to cross-post Markdown formatted content from Drupal to Nostr - Nostr internet identifier NIP-05
Drupal module to setup Nostr internet identifier addresses with Drupal. - Nostr NDK
Includes the Javascript library Nostr Dev Kit (NDK) in a Drupal project.
One of my (very) ambitious goals is to build a Drupal powered Nostr (website) package with the following main features:
- Able to login into Drupal with your Nostr keypair
- Cross-post content to the Nostr network
- Fetch your Nostr content from the Nostr content
- Serve as a content management system (CMS) for your Nostr events
- Serve as a framework to build a hybrid Nostr web application
- Run and maintain a Nostr relay with custom policies
- Usable as a feature rich progressive web app
- Use it as a remote signer
These are just some random ideas as my Nostr + Drupal backlog is way longer than this.
Nostr-PHP
With all the newly added and continues being updated NIPs in the protocol, this helper library will never be finished. As the sole maintainer of this library I would like to invite others to join as a maintainer or just be a contributor to the library. PHP is big on the web, but there are not many PHP developers active yet using Nostr. Also PHP as a programming language is really pushing forward keeping up with the latest innovations.
Grow Nostr outside the Bitcoin community
We are working out a submission to host a Nostr stand at FOSDEM 2025. If approved, it will be the first time (as far as I know) that Nostr could be present at a conference outside the context of Bitcoin. The audience at FOSDEM is mostly technical oriented, so I'm really curious what type of feedback we will receive.
Let's finish this article with some random Nostr photos from last year. Cheers!





-
 @ 081f3b0c:c00498a5
2024-10-31 11:52:15
@ 081f3b0c:c00498a5
2024-10-31 11:52:15Muchas son las maneras de referirse a la compra y mantenimiento de Bitcoin en cartera. Muchas también son las maneras de almacenarlo. Y, aunque en realidad NADIE almacena Bitcoin, sino llaves privadas y llaves públicas, no es de mi interés entrar hoy en esos tecnicismos.
Hoy quiero escribirle a la gente de a pie, los trabajadores, emprendedores, empresarios y todo aquel que se interese por lo menos un poquito en su futuro y el de los suyos. Hay algo que todos los Bitcoiners sabemos pero que muchos de ustedes no lo experimentan hasta llevarse un buen susto en su primer año de inversión (Hablaré en todo el artículo de manera indistinta entre inversión y ahorro en Bitcoin ya que en el largo larguísimo plazo y mirando a Bitcoin como moneda pero también como activo, pueden utilizarse ambos términos). Lo que no saben los que miran desde afuera, es que muy poca gente compró Bitcoin en centavos o pocos dólares (o lo minó en épocas tempranas) y todavía lo mantienen en cartera. Me arriesgaría a decir que este numero de individuos no supera unos pocos miles. Muchos no-coiners creen que los bitcoiners compraron a dos centavos se durmieron 15 años y hoy son todos ricos, pero la mayoría de los early adopters, se hundieron intentando navegar las profundas y peligrosas aguas de la custodia y el HODL.
Para quien todavía esté medio perdido y quizás este sea el primer artículo que lea, HODL es una manera "chistosa" de referirse a mantener Bitcoin en cartera, y se remonta allá por el 2013 donde un usuario quiso decir que estaba Holdeando (manteniendo) Bitcoin en cartera y lo escribió como HODLING. Pasó a la historia y hoy se usan HODL y HOLD de manera indistinta como chiste interno Bitcoiner.
En fin... Las profundas aguas... Holdear Bitcoin no es sencillo para las masas. Imaginate que tenés un activo en tu cartera, o compraste a 100 dólares y ahora vale 1.000. Lo venderías verdad? Y si vale 20.000 dólares? Ahí si lo venderías? Estarías multiplicando tu inversión como nunca. Bueno, a esa decisión se enfrentaron y se enfrentan TODOS los holders de Bitcoin más temprano o más tarde. Incluso aquel loco que compro por el 2017 en un precio de 20.000 hoy puede decidir vender y multiplicar casi por 4 su dinero en unos pocos años. Ni hablar de ese estresante momento que habías comprado en 69.000 dólares y lo viste bajar hasta los 17.000 dólares, unos cuantos meses de sufrimiento y temor... Más de uno se asustó de verdad y vendió todo, solo para verlo unas horas más tarde por arriba de los 20.000 y un año más tarde nuevamente en 70.000 dólares.
Si bien no me gusta poner el foco en el precio, lo que intento ilustrar es lo DIFICIL que puede ser ver tu inversión en máximos o en mínimos y aún así decidir mantenerla unos cuantos años más. Es dificil, aún para los que viven su tercer o cuarto ciclo de mercado. Pero se hace más y más fácil a medida que uno avanza en el famoso "rabbit hole" de Bitcoin y empieza a entenderlo desde las bases, cada vez mejor. Este camino también es arduo, entender de Bitcoin requiere un poco de conocimiento en cada campo, hay que saber un poco de tecnología, un poco de redes, un poco de seguridad informatica, una pizca de teoría de juegos, una apasionante cantidad de macroeconomía, y hasta un interés genuino en lo que Mises llamó "La acción Humana". Y todo esto, uno lo va a prendiendo con ganas y de a poco sólo para llegar a la conclusión, meses o incluso años después, de que Bitcoin tiene que ser un activo por siempre en la cartera de uno, no se vende. Incluso hay quienes llegan al punto (como este humilde ser que escribe) que no poseen otro tipo de ahorro o inversión que no sean sus pocos o muchos satoshis en Billetera Fria.
Mi recomendación siempre será que DYOR, "do your own research", investiguen, lean, pregunten, únanse a #nostr que tiene la mejor comunidad del mundo a la hora de ayudar a otros usuarios, pero si no llegan a tener el tiempo de leer y progresar sólo tómenme estos dos consejos:
- Háganse el tiempo para leer.
- Stay humble y stack sats (De a poco y constante, todo ahorro mensual que uno haga, está mejor guardado en Bitcoin, siempre gastando menos de lo que ingresa esto no debería ser dificil).
Otra dificultad que encontramos además de la parte emocional y humana relacionada con los precios y el desconocimiento, es la custodia. Cientos de personas perdieron TODO su Bitcoin por no saber almacenarlo correctamente. Decenas de maneras de almacenar claves y sin embargo muchos usuarios de Bitcoin no se sienten del todo seguro durante sus primeros años de inversión, y no están el todo equivocados... Por un lado puede ser tan sencillo como guardar 24 palabras. Por otro lado, puede no ser tan fácil, dependiendo del tipo de usuario. Entraremos en detalles de custodia en el próximo artículo.
Saludos!
El Tío.
PD: No es consejo de inversión.
-
 @ 3f0702fa:66db56f1
2024-12-15 09:26:22
@ 3f0702fa:66db56f1
2024-12-15 09:26:22На центральной площади Кургана установили цифровую проекцию говорящей головы Владимира Ленина, что вызвало неоднозначную реакцию в обществе. Инициатива, заявленная как способ почтения истории, стала поводом для оживленной дискуссии о приемлемости такого формата в современной городской среде.
Проекция, выполненная с применением современных технологий, транслирует реалистичное изображение Ленина, которое, по задумке авторов, должно напоминать жителям об исторических событиях и фигурах прошлого. Однако, не все курганцы разделяют этот подход.
Противники проекта выражают опасения, что такое изображение может восприниматься как попытка политической пропаганды и возрождения идеологий прошлого, которые многие считают неприемлемыми. Они также отмечают, что центральная площадь должна быть пространством для современного искусства и культурных событий, а не памятником прошлому.
Сторонники проекта считают, что проекция является инновационным способом сохранения исторической памяти, который несет образовательный посыл и помогает молодым поколениям узнать больше о прошлом страны. Они подчеркивают, что это всего лишь цифровая проекция, а не настоящий памятник, и что такое решение соответствует современным тенденциям в городском дизайне.
В настоящее время в городе проводятся общественные слушания, где каждый житель может высказать свое мнение по поводу проекта. Власти города, в свою очередь, заявили, что готовы прислушаться к мнению курганцев и внести коррективы в проект при необходимости.
Установка проекции говорящей головы Ленина в Кургане стала катализатором дискуссии о балансе между уважением к истории и современным культурным ценностям. Дальнейшая судьба проекта будет зависеть от результатов общественного обсуждения.
Мы продолжим следить за развитием ситуации и сообщать вам о дальнейших новостях. Следите за нашими публикациями.
https://psv4.userapi.com/s/v1/d/4pH6xLy1MCdrc0AL-T_xlsVDG-TrbX1-zUNbzHIs8xx3TV9doSNz-hFvKbrZ83k3lG7rWOp37Yv9qwGfZvC47qftoR4um-JNp4vRHGc8D3la1X1P98Ugow/e85be815-29ac-4235-89d1-14960c2afb26.mp4
45news #Курган2040
-
 @ a58a2663:87bb2918
2024-12-09 13:39:49
@ a58a2663:87bb2918
2024-12-09 13:39:49- Concluir com minha filha, até o fim de 2025, a leitura da tradução latina de Ursinho Pooh, isto é, Winnie Ille Pu, de Alexander Lenard (1910-1972), poeta, ensaísta e tradutor húngaro que viveu no Brasil. Que texto curioso! Estranho estímulo que me chegou para voltar a estudar latim a sério.

-
Importar mais livros pela Thrift Books e menos pela Loja do Diabo. Seu acervo é excepcional e o frete é mais barato. Às vezes, em menos de duas semanas já estou com o livro em mãos (e olha que resido no Maranhão).
-
Concluir e publicar meu livro Vida após as Universidades. Escrita & criação em velhos & novos contextos de risco, desenvolvimento de algumas ideias que insinuei em Contra a vida intelectual, no que diz respeito ao encerramento de um ciclo histórico de modos de fazer investigação erudita.
-
Rematar o terceiro e último módulo de Convivium - Seminário Permanente de Humanidades, "A Alegoria do Mundo: o Mago, o Filólogo e o Colonizador", embrião de um longo ensaio sobre o "projeto humanista" e as vias de saída da modernidade oferecidas pelo pensamento latino-americano. (As inscrições seguem abertas. Caso queira inscrever-se pagando em bitcoin, me mande um e-mail: camoensiii57@protonmail.com).
-
Defender no primeiro semestre minha tese de doutoramento sobre João Francisco Lisboa (1812-1863), o maior prosador brasileiro de meados do século XIX. Compreender seu Jornal de Tímon implica rever concepções há muitos estabelecidas sobre a formação da literatura brasileira.
-
Escrever pelo menos cinco ensaios de apresentação do pensamento de Vilém Flusser e do que pretendo realizar em FLUSSER_project. A ideia é divulgá-los em inglês e especialmente aqui pelo Nostr.
-
Ler TUDO de Ignacio Gómez de Liaño.
-
Não ceder à tentação de discutir com imbecil.
-
 @ 3f770d65:7a745b24
2024-10-29 17:38:20
@ 3f770d65:7a745b24
2024-10-29 17:38:20Amber
Amber is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications.

Amber is supported by a growing list of apps, including Amethyst, 0xChat, Voyage, Fountain, and Pokey, as well as any web application that supports NIP-46 NSEC bunkers, such as Nostr Nests, Coracle, Nostrudel, and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms.

Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's GitHub page, via Obtainium or Zap.store.
To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com.

Citrine
Citrine is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control.

With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality.
Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration.

Pokey
Pokey for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device.

Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem.
Zap.store
Zap.store is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency.

Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing Zap.store on your favorite Android device, and install all of the applications mentioned above.
Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems.
-
 @ 47750177:8969e41a
2024-10-05 17:40:25
@ 47750177:8969e41a
2024-10-05 17:40:2528.0 Release Notes
Bitcoin Core version 28.0 is now available from:
This release includes new features, various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Running Bitcoin Core binaries on macOS requires self signing.
cd /path/to/bitcoin-28.0/bin xattr -d com.apple.quarantine bitcoin-cli bitcoin-qt bitcoin-tx bitcoin-util bitcoin-wallet bitcoind test_bitcoin codesign -s - bitcoin-cli bitcoin-qt bitcoin-tx bitcoin-util bitcoin-wallet bitcoind test_bitcoinCompatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux Kernel 3.17+, macOS 11.0+, and Windows 7 and newer. Bitcoin Core should also work on most other UNIX-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
Testnet4/BIP94 support
Support for Testnet4 as specified in BIP94 has been added. The network can be selected with the
-testnet4option and the section header is also named[testnet4].While the intention is to phase out support for Testnet3 in an upcoming version, support for it is still available via the known options in this release. (#29775)
Windows Data Directory
The default data directory on Windows has been moved from
C:\Users\Username\AppData\Roaming\BitcointoC:\Users\Username\AppData\Local\Bitcoin. Bitcoin Core will check the existence of the old directory first and continue to use that directory for backwards compatibility if it is present. (#27064)JSON-RPC 2.0 Support
The JSON-RPC server now recognizes JSON-RPC 2.0 requests and responds with strict adherence to the specification. See JSON-RPC-interface.md for details. (#27101)
JSON-RPC clients may need to be updated to be compatible with the JSON-RPC server. Please open an issue on GitHub if any compatibility issues are found.
libbitcoinconsensus Removal
The libbitcoin-consensus library was deprecated in 27.0 and is now completely removed. (#29648)
P2P and Network Changes
- Previously if Bitcoin Core was listening for P2P connections, either using
default settings or via
bind=addr:portit would always also bind to127.0.0.1:8334to listen for Tor connections. It was not possible to switch this off, even if the node didn't use Tor. This has been changed and nowbind=addr:portresults in binding onaddr:portonly. The default behavior of binding to0.0.0.0:8333and127.0.0.1:8334has not been changed.
If you are using a
bind=...configuration withoutbind=...=onionand rely on the previous implied behavior to accept incoming Tor connections at127.0.0.1:8334, you need to now make this explicit by usingbind=... bind=127.0.0.1:8334=onion. (#22729)-
Bitcoin Core will now fail to start up if any of its P2P binds fail, rather than the previous behaviour where it would only abort startup if all P2P binds had failed. (#22729)
-
UNIX domain sockets can now be used for proxy connections. Set
-onionor-proxyto the local socket path with the prefixunix:(e.g.-onion=unix:/home/me/torsocket). (#27375) -
UNIX socket paths are now accepted for
-zmqpubrawblockand-zmqpubrawtxwith the format-zmqpubrawtx=unix:/path/to/file(#27679) -
Additional "in" and "out" flags have been added to
-whitelistto control whether permissions apply to inbound connections and/or manual ones (default: inbound only). (#27114) -
Transactions having a feerate that is too low will be opportunistically paired with their child transactions and submitted as a package, thus enabling the node to download 1-parent-1-child packages using the existing transaction relay protocol. Combined with other mempool policies, this change allows limited "package relay" when a parent transaction is below the mempool minimum feerate. Topologically Restricted Until Confirmation (TRUC) parents are additionally allowed to be below the minimum relay feerate (i.e., pay 0 fees). Use the
submitpackageRPC to submit packages directly to the node. Warning: this P2P feature is limited (unlike thesubmitpackageinterface, a child with multiple unconfirmed parents is not supported) and not yet reliable under adversarial conditions. (#28970)
Mempool Policy Changes
-
Transactions with version number set to 3 are now treated as standard on all networks (#29496), subject to opt-in Topologically Restricted Until Confirmation (TRUC) transaction policy as described in BIP 431. The policy includes limits on spending unconfirmed outputs (#28948), eviction of a previous descendant if a more incentive-compatible one is submitted (#29306), and a maximum transaction size of 10,000vB (#29873). These restrictions simplify the assessment of incentive compatibility of accepting or replacing TRUC transactions, thus ensuring any replacements are more profitable for the node and making fee-bumping more reliable.
-
Pay To Anchor (P2A) is a new standard witness output type for spending, a newly recognised output template. This allows for key-less anchor outputs, with compact spending conditions for additional efficiencies on top of an equivalent
sh(OP_TRUE)output, in addition to the txid stability of the spending transaction. N.B. propagation of this output spending on the network will be limited until a sufficient number of nodes on the network adopt this upgrade. (#30352) -
Limited package RBF is now enabled, where the proposed conflicting package would result in a connected component, aka cluster, of size 2 in the mempool. All clusters being conflicted against must be of size 2 or lower. (#28984)
-
The default value of the
-mempoolfullrbfconfiguration option has been changed from 0 to 1, i.e.mempoolfullrbf=1. (#30493)
Updated RPCs
-
The
dumptxoutsetRPC now returns the UTXO set dump in a new and improved format. Correspondingly, theloadtxoutsetRPC now expects this new format in the dumps it tries to load. Dumps with the old format are no longer supported and need to be recreated using the new format to be usable. (#29612) -
AssumeUTXO mainnet parameters have been added for height 840,000. This means the
loadtxoutsetRPC can now be used on mainnet with the matching UTXO set from that height. (#28553) -
The
warningsfield ingetblockchaininfo,getmininginfoandgetnetworkinfonow returns all the active node warnings as an array of strings, instead of a single warning. The current behaviour can be temporarily restored by running Bitcoin Core with the configuration option-deprecatedrpc=warnings. (#29845) -
Previously when using the
sendrawtransactionRPC and specifying outputs that are already in the UTXO set, an RPC error code of-27with the message "Transaction already in block chain" was returned in response. The error message has been changed to "Transaction outputs already in utxo set" to more accurately describe the source of the issue. (#30212) -
The default mode for the
estimatesmartfeeRPC has been updated fromconservativetoeconomical, which is expected to reduce over-estimation for many users, particularly if Replace-by-Fee is an option. For users that require high confidence in their fee estimates at the cost of potentially over-estimating, theconservativemode remains available. (#30275) -
RPC
scantxoutsetnow returns 2 new fields in the "unspents" JSON array:blockhashandconfirmations. See the scantxoutset help for details. (#30515) -
RPC
submitpackagenow allows 2 new arguments to be passed:maxfeerateandmaxburnamount. See the subtmitpackage help for details. (#28950)
Changes to wallet-related RPCs can be found in the Wallet section below.
Updated REST APIs
- Parameter validation for
/rest/getutxoshas been improved by rejecting truncated or overly large txids and malformed outpoint indices via raising an HTTP_BAD_REQUEST "Parse error". These requests were previously handled silently. (#30482, #30444)
Build System
-
GCC 11.1 or later, or Clang 16.0 or later, are now required to compile Bitcoin Core. (#29091, #30263)
-
The minimum required glibc to run Bitcoin Core is now 2.31. This means that RHEL 8 and Ubuntu 18.04 (Bionic) are no-longer supported. (#29987)
-
--enable-lcov-branch-coveragehas been removed, given incompatibilities between lcov version 1 & 2.LCOV_OPTSshould be used to set any options instead. (#30192)
Updated Settings
- When running with
-alertnotify, an alert can now be raised multiple times instead of just once. Previously, it was only raised when unknown new consensus rules were activated. Its scope has now been increased to include all kernel warnings. Specifically, alerts will now also be raised when an invalid chain with a large amount of work has been detected. Additional warnings may be added in the future. (#30058)
Changes to GUI or wallet related settings can be found in the GUI or Wallet section below.
Wallet
-
The wallet now detects when wallet transactions conflict with the mempool. Mempool-conflicting transactions can be seen in the
"mempoolconflicts"field ofgettransaction. The inputs of mempool-conflicted transactions can now be respent without manually abandoning the transactions when the parent transaction is dropped from the mempool, which can cause wallet balances to appear higher. (#27307) -
A new
max_tx_weightoption has been added to the RPCsfundrawtransaction,walletcreatefundedpsbt, andsend. It specifies the maximum transaction weight. If the limit is exceeded during funding, the transaction will not be built. The default value is 4,000,000 WU. (#29523) -
A new
createwalletdescriptorRPC allows users to add new automatically generated descriptors to their wallet. This can be used to upgrade wallets created prior to the introduction of a new standard descriptor, such as taproot. (#29130) -
A new RPC
gethdkeyslists all of the BIP32 HD keys in use by all of the descriptors in the wallet. These keys can be used in conjunction withcreatewalletdescriptorto create and add single key descriptors to the wallet for a particular key that the wallet already knows. (#29130) -
The
sendallRPC can now spend unconfirmed change and will include additional fees as necessary for the resulting transaction to bump the unconfirmed transactions' feerates to the specified feerate. (#28979) -
In RPC
bumpfee, if afee_rateis specified, the feerate is no longer restricted to following the wallet's incremental feerate of 5 sat/vb. The feerate must still be at least the sum of the original fee and the mempool's incremental feerate. (#27969)
GUI Changes
-
The "Migrate Wallet" menu allows users to migrate any legacy wallet in their wallet directory, regardless of the wallets loaded. (gui#824)
-
The "Information" window now displays the maximum mempool size along with the mempool usage. (gui#825)
Low-level Changes
Tests
-
The BIP94 timewarp attack mitigation is now active on the
regtestnetwork. (#30681) -
A new
-testdatadiroption has been added totest_bitcointo allow specifying the location of unit test data directories. (#26564)
Blockstorage
- Block files are now XOR'd by default with a key stored in the blocksdir.
Previous releases of Bitcoin Core or previous external software will not be able to read the blocksdir with a non-zero XOR-key.
Refer to the
-blocksxorhelp for more details. (#28052)
Chainstate
- The chainstate database flushes that occur when blocks are pruned will no longer empty the database cache. The cache will remain populated longer, which significantly reduces the time for initial block download to complete. (#28280)
Dependencies
- The dependency on Boost.Process has been replaced with cpp-subprocess, which is contained in source. Builders will no longer need Boost.Process to build with external signer support. (#28981)
Credits
Thanks to everyone who directly contributed to this release: - 0xb10c - Alfonso Roman Zubeldia - Andrew Toth - AngusP - Anthony Towns - Antoine Poinsot - Anton A - Ava Chow - Ayush Singh - Ben Westgate - Brandon Odiwuor - brunoerg - bstin - Charlie - Christopher Bergqvist - Cory Fields - crazeteam - Daniela Brozzoni - David Gumberg - dergoegge - Edil Medeiros - Epic Curious - Fabian Jahr - fanquake - furszy - glozow - Greg Sanders - hanmz - Hennadii Stepanov - Hernan Marino - Hodlinator - ishaanam - ismaelsadeeq - Jadi - Jon Atack - josibake - jrakibi - kevkevin - kevkevinpal - Konstantin Akimov - laanwj - Larry Ruane - Lőrinc - Luis Schwab - Luke Dashjr - MarcoFalke - marcofleon - Marnix - Martin Saposnic - Martin Zumsande - Matt Corallo - Matthew Zipkin - Matt Whitlock - Max Edwards - Michael Dietz - Murch - nanlour - pablomartin4btc - Peter Todd - Pieter Wuille - @RandyMcMillan - RoboSchmied - Roman Zeyde - Ryan Ofsky - Sebastian Falbesoner - Sergi Delgado Segura - Sjors Provoost - spicyzboss - StevenMia - stickies-v - stratospher - Suhas Daftuar - sunerok - tdb3 - TheCharlatan - umiumi - Vasil Dimov - virtu - willcl-ark
As well as to everyone that helped with translations on Transifex.
- Previously if Bitcoin Core was listening for P2P connections, either using
default settings or via
-
 @ 592295cf:413a0db9
2024-10-05 09:32:22
@ 592295cf:413a0db9
2024-10-05 09:32:22Week 30th September
Wiki article on the topic. [sPhil] (https://sphil.xyz/) Religion politics philosophy history are critical. They are not objective things.
Week of updates for protocol apps, including Gossip, coracle app, nostrmo, nostur and many others.
Kind7 Tags: K, emoji,a,others Others threads multi people
Show likes as kind 1 This person liked this post. Or this post has three likes in your timeline. The likes I don't know in your timeline really interest you.
The first book is the bible... Word of Alexandria.
I added cyberspace to the difficult things of the protocol ultra brain things. Low brain, middle brain, top brain, ultra.
Some alphaama codes .AA u login .AA q stuff .AA q run b .AA q run f .AA q close f
high things of alphaama nostr:nevent1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqlqu2vwpwax7dj420e75yws7g7vyua9e245c0x73c056gunxchluey4q99
Comment: nostr:nevent1qqs8pn0zzhgk5l2raqh736rj3ckm48pfl6r7m72rnz2r2p7lzgmx20gzyqduwzspfzelx9k6x0lrez0j8cl8rtz0lxvqylk8z2ustnfy76jpzqcyqqqqqqgpramhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjsjt5rvu
You have to get to the point where you have your community relay. But you have to go down the rabbit hole of relays. General, search, local, inbox outbox, cache. Etc until you get to community relay that is being talked about these days because of NIP 29 "Relay-based Groups". In the end you have to have that table with the various types of relays clearly in your mind. If the user doesn't think about it, who should think about it, who? if I choose the relays?
NIP-100 the world to make community for me. NIP-28 + NIP-72. So you have some structure interoperability with kind1. But the Channel is another kind. You arrange the various channels in the community. No posts need to be approved.
It's useless Protocol users are becoming more reddit users or so. I don't want to deal with these people.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 4ba8e86d:89d32de4
2024-10-25 11:40:05
@ 4ba8e86d:89d32de4
2024-10-25 11:40:05A loja Aurora vem com um excelente design, interface de usuário amigável para iniciantes e muitos recursos.
A loja Aurora foi originalmente baseada na loja Yalp de Sergei Yeriomin, mas a versão 3.0 passou do zero para a conclusão seguindo o Material Design reescrito para rodar em todos os dispositivos Android 5.0.
Dentre as diversas características oferecidas pela Aurora Store, destacam-se:
- Login Anônimo: Para garantir sua privacidade, você pode fazer login anonimamente, assegurando que suas atividades permaneçam confidenciais.
- Login do Google: Além do anonimato, a opção de login do Google permite acessar aplicativos pagos e instalar versões beta.
- Falsificação de Dispositivo: Caso um aplicativo não esteja disponível para o seu dispositivo, você pode recorrer à funcionalidade de falsificação de dispositivo, permitindo a instalação.
- Filtragem de Aplicativos F-Droid: A possibilidade de filtrar aplicativos do F-Droid evita que eles apareçam em sua lista de atualizações.
- Aplicativos na Lista Negra: Ao adicionar aplicativos à lista negra, você mantém o Google no escuro quanto aos aplicativos instalados.
A loja de aplicativos se apresenta com um design clássico, apresentando uma capa de apps e jogos em destaque, proporcionando um visual convidativo. A aba de aplicativos instalados permite uma gestão mais eficiente, possibilitando atualizações automáticas para a versão mais recente disponível.
A busca por aplicativos é facilitada por categorias que abrangem diversos interesses, como fotografia, música e áudio, compras, personalização, livros e quadrinhos, entre outras. A eficaz função de busca permite localizar aplicativos específicos de maneira rápida e fácil.
A Aurora Store se diferencia pela tecnologia de pesquisa única, agilizando a descoberta de aplicativos em questão de segundos. Além disso, a loja vem com a licença GPLv3, reforçando seu compromisso com o software livre.
Privacidade é um foco central da Aurora Store, sendo considerada uma excelente alternativa para quem preza por manter suas informações pessoais protegidas. O aplicativo suporta contas pessoais e permite downloads com contas anônimas, assegurando que suas atividades não estejam vinculadas a você.
Com a integração do Exodus, a Aurora Store verifica rastreadores presentes nos códigos dos aplicativos, proporcionando uma visão mais transparente das informações coletadas.
O aplicativo se destaca por ser livre de anúncios e pop-ups, proporcionando uma experiência de uso mais limpa. O suporte ao modo escuro oferece conforto visual em ambientes com pouca luz ou durante a noite.
A Aurora Store é uma alternativa valiosa à Google Play Store, oferecendo um ambiente mais privado, recursos robustos e um design elegante que visa aprimorar a experiência do usuário em busca e gerenciamento de aplicativos.
https://github.com/whyorean/AuroraStore
https://f-droid.org/packages/com.aurora.store/
https://gitlab.com/AuroraOSS/AuroraStore/-/releases
-
 @ c4b5369a:b812dbd6
2024-12-01 16:19:21
@ c4b5369a:b812dbd6
2024-12-01 16:19:21Ecash systems built on top of bitcoin have seen increasing adoption over the last couple of years. They have become a polarising topic in the bitcoin community, due to their centralized and custodial nature. Like any system, ecash comes with a lot of pros and cons when compared to other systems, that are fercely debated in cyber- and meat-space.
I have been working on developing tools and software for the ecash implementation Cashu for about 2 years now. I have had countless discussions with various people from different backgrounds about the topic. OG bitcoiners, fiat bankers, friends and family, privacy enthusiast... . As you can imagine the flow and outcome of these discussions varied widely.
Usually, conversations with bitcoiners were the most interesting for me. Their opinions about ecash polarised the most, by far. (excluding the fiat bankers, but that's a story for another day). In this short peice, I want to share some insights from the discussions I had, and maybe clear up some misconceptions about ecash on bitcoin.
What is Ecash?
If you still don't know what ecash is, sorry, I won't go into much detail explaining it. I recommend reading the wikipedia article on Ecash , and then this article on the rise and fall of digicash, the first and maybe only ecash company that existed. This will bring you up to speed on ecash history up until bitcoin entered the scene. Ecash was pretty much dead from the day after digicash went bankrupt untill it recently saw it's revival in two different spheres:
One of these spheres is obviously the bitcoin sphere. Here, ecash got reintroduced with the two open source projects Fedimint and Cashu. In my opinion, the main reason for this revival is the following fact: Unlike an implementation of ecash in the fiat world, that would rely on the permissioned system to "allow" something like ecash to exist, bitcoin does not come with that limitation. The permissionless nature of bitcoin allows for these protocols to exist and interoperate with the existing bitcoin stack.
The second, and maybe lesser known sphere is the revival of ecash as a CBDC. Bitcoiners might get scared at the mentioning of that word. Trust me, I don't like it either. Nonetheless, privacy enthusiasts see the opportunity to steer the CBDC-ship in another direction, by using an underlying technology for them that would limit targeted discrimination by the centralized authorithy. Something that works like cash... but in cyberspace... Ecash. One such implementation is GNU Taler, another one is Project Tourbillon. Usually, these kind of implementations use a cuck-version of the OG ecash, where only payers are anonymous, but not payees.
Anyway, in this article we will focus on the implementation of ecash on bitcoin.
About self custody
Bitcoin as a whole is about sovereignty and liberation. If someone else controls your money, they control you. For the first time since we've stopped using gold, bitcoin allows us to fully take control back of our money. A money that doesn't corrode, a money which supply connot get inflated, and a money that cannot be easily seized. All of this is true for bitcoin. There is only one precondition: You have to hold and use it self custodially.
Using bitcoin self custodially
The problem comes in when using bitcoin in a self custodial fashion. For bitcoin to maintain the monetary properties mentioned above, it has to remain decentralized. This means it is hard to scale, which in turn means the use of bitcoin tends to become more costly as usage increases.
So even if we wish that everyone would use bitcoin self custodially all the time for everything, I fear it is mostly just a dream, at least for the forseable future. Even with trustless second layer protocols like the Lightning Network, we are running into scaling issues, since at the end of the day, they are bound to the same onchain fee realities as bare-bones bitcoin transactions.
For most of humanity, it is financially not viable to pay even 1$ transaction fees for every transaction. Second layer protocol may bring the cost down a bit, but have other requirements. For example in lightning, you have an online assumption, to make sure your channel peers aren't trying to cheat. You need to have inbound liquidity to receive payments. There are cost associated with opening or closing payment channels, or rebalancing liquidity.
Other upcoming second layer protocols like Ark may improve on some of these issues. It is definitely something to look forward to! But they will have their own trade-offs, most likely also cost related. The fact remains that all trustless protocols that use the bitcoin timechain for conflict resolution, will have to deal with this matter. This is the cost of trustlessness.
Soo... Don't self custody...?
NO! If you can, you should always use self custody. As much as possible!
Personally, I use all the tools mentioned above. And I recommend that if you can, you should too.
But the fact is, not everyone can. Many would love to take control over their financial freedom, but the threshold for them to use bitcoin in a sovereign fashion is simply to high. So they will either remain in fiat slavery land, or they will end up using "bitcoin" through a custodian like coinbase, binance, or whatever banking service they have access to.
I will also mention that for some usecases, enjoying the convenience of a custodian is just very attractive. Of course, this is only the case as long as the custodian plays by the book, and doesn't suddenly freeze-, or worse, run away with your deposits.
The right tool for the right job
I don't beleive that one way of using bitcoin is better than the other. It entirely depends on which problem you are trying to solve.
If the problem is storing or transfering wealth, then of course you would want to do that on chain.
If on the other hand, you want to send and receive frequent small to midsized payments, you might want to get setup with a lightning channel to an LSP. Depending on how deep you want to get involved, you may even set up some infrastructure and become part of the Lightning network.
If you want to receive digital tips that you can later claim into self custody after they reach a certain threshold, you might opt for a custodial solution.
If you require certain properties, like offline peer-to-peer transferability, or cash-like privacy, you might choose an ecash system.
It doesn't mean that if you use one, you cannot use the other. You should use whatever is useful for the current problem you are trying to solve, maybe even using multiple tools in conjuction, if that makes sense.
Ecash vs Onchain vs L2?
First of all, we have to understand that ecash is neither a replacement for self custody, nor is it a replacement for trustless second layer protocols. They are irreplaceable with something that is custodial in nature, due to the simple fact that if you lose control over your money, you have lost the control over your life.
So. No one beleives you should prioritize custodial solutions to secure your wealth. Self custody will always remain king in that regard. Custodial wallets should be thought off as a physical spending wallet you can walk around with, even through the dark alleyways where it might get robbed from you. Keep your cash in there for convenient spending, not worrying about fees, liquidity, data footprints, channel backups, etc. etc. etc... These benefits obviously come at the cost of trust, that the provider doesn't rug-pull your deposit.
I really like the user experience of custodial services. I would never put a lot of money into any one of them though, because I don't trust them. Just like I wouldn't walk around with $10000 in my physical wallet. The risk that it gets stolen is simply to great. At the same time, this risk doesn't mean I will get rid of my physical wallet. I think having a wallet with some cash in it is super useful. I will mittigate the risk by reducing the amount I carry inside that wallet. This is the same way I think about digital money I hold in custodial wallets, be it an ecash service or others.
All things considered, it is hard to argue that self custody comes even close to the UX a custodian can give you, due to the fact that they can take care of all the complexities (mentioned above) for you.
So then, why ecash?
We now know, that we are NOT comparing ecash with the sovereign bitcoin stack. We are comparing it instead to traditional custodial systems. This is the area ecash is trying to improve uppon. So if you've chosen that the best tool to solve a problem might be a custodial solution, only then should you start to consider using ecash.
It offers a more privacy preserving, less burdonsome and less censorable way of offering a custody solution.
It offers some neat properties like offline peer-to-peer transactions, programability, de-linkage from personally identifiable information, and more.
Here is an example, on how ecash could create a fairer environment for online consumers:
Online services love to offer subscriptions. But for the consumer, this is mostly a trap. As a consumer, I would rather pay for a service right now and be done with it. I don't want to sign up for a 10 year plan, give them my email address, my date of birth , create an account, etc...
One way of doing that, would be for the service provider to accept payments in ecash, instead of having an account and subscription model.
It would work like this:
- The user creates ecash by paying into the service's mint. Hereby it is not required to use lightning or even bitcoin. It could be done with any other value transfer meduim the service provider accepts (cash, shitcoins, lottery tickets...).
- You use the issued ecash, to retreive services. This could be anything from video streaming, to AI prompts.
- Once you are done, you swap your remaining ecash back.
In a system like this, you wouldn't be tracked as a user, and the service provider wouldn't be burdoned with safeguarding your personal information. Just like a cash-for-goods transaction in a convenience store.
I beleive the search engine Kagi is building a system like that, according to this podcast. It has also be demoed by https://athenut.com/ how it would be implemented, using Cashu.
Here is another example, on how an event organizer can provide privacy preserving electronic payment rails for a conference or a festival, using ecash:
If you have been part of organizing a conference or an event, you might have experienced this problem. Onchain payments are too slow and costly. Lightning payments are too flaky.
Do merchants have to setup a lightning channel? Do they have to request inbound liquidity from an LSP? Do they have to splice into the channel once they run out of liquidity? In practice, these are the realities that merchants and event organizers are faced with when they try to set up payment rails for a conference.
Using ecash, it would look like this:
- Event organizer will run a dedicated ecash mint for the event.
- Visitors can swap into ecash when ariving at the entrance, using bitcoin, cash, or whatever medium the organizer accepts.
- The visitor can spend the ecash freely at the merchants. He enjoys good privacy, like with cash. The online requirements are minimal, so it works well in a setting where connectivity is not great.
- At the end of the event, visitors and merchants swap their ecash back into the preferred medium (cash, bitcoin...).
This would dreastically reduce the complexity and requirements for merchants, while improving the privacy of the visitors.
A bold experiment: Free banking in the digital age
Most bitcoiners will run out of the room screaming, if they hear the word bank. And fair enough, I don't like them either. I believe in the mantra "unbank the banked", after all. But the reason I do so, is because todays fiat/investment banks just suck. It's the same problem as with the internet platforms today. You, the "customer", is not realy the customer anymore, but the product. You get sold and squeezed, until you have nothing more to give.
I beleive with a sound money basis, these new kind of free banks could once again compete for customers by provididng the best money services they can, and not by who can scam his way to the money printer the best. Maybe this is just a pipe dream. But we all dream a little. Some dream about unlimited onchain transactions (I've had this dream before), and some dream about free banks in cyberspace. In my dream, these banks would use ecash to respect their users privacy.
Clearing up misconceptions and flawed assumptions about ecash on bitcoin
Not only, but especially when talking with bitcoiners there are a lot of assumptions regarding ecash on bitcoin. I want to take this opportunity to address some of those.
Ecash is an attack on self custody
As we've mentioned above, ecash is not meant to compete with self custody. It is meant to go where self custodial bitcoin cannot go. Be it due to on-chain limitations, or network/infrastructure requirements. Ecash is completely detached from bitcoin, and can never compete with the trustless properties that only bitcoin can offer.
Ecash mints will get rugged
100% correct. Every custodial solution, be it multisig or not, will suffer from this risk. It is part of the deal. Act accordingly. Plan for this risk when choosing to use a custodial system.
Working on ecash is a distraction from what really matters, since it is not self custodial
While it is true that improving self custodial bitcoin is one of the most important things our generation will have to solve, it doesn't mean that everything else becomes irrelevant. We see that today, in a lot of circumstances a fully sovereign setup is just not realistic. At which point most users will revert back to custodial solutions. Having technology in place for users that face these circumstances, to offer them at least some protection are worth the effort, in my opinion.
Ecash mints will retroactively introduce KYC
Yes it is true that ecash mints can do that. However, what would they learn? They would learn about the amount you were holding in the mint at that time, should you choose to withdraw. They would not be able to learn anything about your past transactions. And needless to say, at which point you should be one and done with this mint as a service provider, and move to someone that respects their users.
Ecash will be used to "steal" bitcoins self custodial user base
I would argue the oposite. Someone that has realized the power of self custody, would never give it up willingly. On the other hand, someone that got rugged by an ecash mint will forever become a self custody maximalist.
Closing thoughts...
I hope you enjoyed reading my take on ecash built on bitcoin. I beleive it has massive potential, and creators, service providers and consumers can benefit massively from ecash's proposition. Using ecash doesn't mean you reject self custody. It means you have realized that there is more tools than just a hammer, and you intend to use the tool that can best solve the problem at hand. This also means, that to some the tool "ecash" may be useless. After all, not everyone is a carpenter. This is also fine. Use whatever you think is useful, and don't let people tell you otherwise.
Also, please don't take my word for it. Think for yourself.
Best,
Gandlaf
-
 @ 3f0702fa:66db56f1
2024-12-15 08:48:16
@ 3f0702fa:66db56f1
2024-12-15 08:48:16Курган в 2040 году закрепил за собой статус ведущего образовательного центра не только в регионе, но и по всей России. Благодаря внедрению инновационных методик, развитию современной инфраструктуры и фокусу на индивидуальное развитие каждого студента, курганское образование стало образцом для всей страны.
Ранее, Курган был известен как промышленный регион, но сегодня ситуация изменилась. Теперь город лидирует в сфере образования, предлагая уникальные возможности для студентов со всей страны.
Ключевыми нововведениями стали персонализированное обучение, когда интеллектуальные системы анализа данных создают индивидуальные траектории для каждого студента. Учебный процесс обогащен интерактивными образовательными платформами, с использованием VR/AR-технологий и геймификации. Курганские вузы и школы активно сотрудничают с ведущими образовательными учреждениями России и мира, а студенты имеют возможность проходить стажировки на ведущих предприятиях.
Эти нововведения коренным образом изменили учебный процесс: студенты стали более мотивированными и вовлеченными, уровень усвоения материала значительно повысился, а выпускники курганских вузов востребованы на рынке труда.
Курган стал местом притяжения для талантливых студентов со всей России, а курганская образовательная система – образцом для подражания, демонстрируя, как можно создать эффективную и современную систему образования, формирующую будущее страны.
Курган в 2040 году - это не только центр промышленности, но и признанный лидер в сфере образования. Город продолжает развиваться, предоставляя новые возможности для своих студентов.
Мы продолжим следить за развитием образовательной сферы в Кургане и сообщать вам о новых достижениях. Следите за нашими публикациями.
45news #Курган2040
-
 @ 4ba8e86d:89d32de4
2024-10-24 14:03:14
@ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais.
Recursos e Funcionalidades.
O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório.
Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes.
O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets.
Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo:
-
Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional.
-
Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes.
-
Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações.
O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável.
https://www.collaboraoffice.com/
https://github.com/CollaboraOnline/online
-
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 4ba8e86d:89d32de4
2024-10-23 00:11:19
@ 4ba8e86d:89d32de4
2024-10-23 00:11:19Ele permite que os usuários descubram, baixem e instalem aplicativos em seus dispositivos Android sem depender da Google Play Store, que é a loja de aplicativos padrão do Android.
História do F-Droid
O F-Droid foi lançado em 2010 por um grupo de desenvolvedores liderados por Ciaran Gultnieks. A ideia por trás do projeto era criar uma alternativa de código aberto para a Google Play Store, que é uma plataforma centralizada controlada por uma única empresa. O F-Droid foi desenvolvido como um catálogo de aplicativos que só inclui aplicativos de código aberto que podem ser baixados e instalados gratuitamente.
Desde o lançamento, o F-Droid cresceu significativamente e agora oferece mais de 3.500 aplicativos de código aberto para Android, com uma ampla gama de categorias, incluindo jogos, educação, produtividade, privacidade e segurança. O projeto é mantido por uma comunidade de desenvolvedores voluntários e é executado sem fins lucrativos.
Os problemas que o F-Droid resolve
O F-Droid resolve vários problemas associados à Google Play Store e outras lojas de aplicativos. O primeiro é o controle centralizado de uma única empresa. A Google Play Store pode remover aplicativos que violem suas políticas, e os desenvolvedores podem ser impedidos de distribuir aplicativos por meio da loja por motivos arbitrários. O F-Droid, por outro lado, é administrado por uma comunidade sem fins lucrativos e não há restrições sobre quais aplicativos podem ser incluídos no catálogo.
Além disso, o F-Droid oferece uma alternativa para os usuários preocupados com a privacidade que não querem depender dos serviços da Google. O F-Droid é independente do Google Play Services e não rastreia os usuários ou coleta informações pessoais, tornando-se uma escolha atraente para aqueles que buscam maior privacidade.
Por que usar o F-Droid?
Há várias razões pelas quais você pode querer usar o F-Droid em vez da Google Play Store ou outras lojas de aplicativos. Aqui estão algumas delas:
-
Privacidade: Como mencionado anteriormente, o F-Droid é independente do Google Play Services e não rastreia os usuários. Isso significa que você pode baixar e instalar aplicativos sem se preocupar com a coleta de dados pessoais.
-
Segurança: O F-Droid oferece apenas aplicativos de código aberto e de software livre, o que significa que a comunidade pode examinar o código-fonte para garantir que não haja vulnerabilidades ou backdoors mal-intencionados.
-
Controle: O F-Droid permite que os usuários controlem seus próprios dispositivos Android e decidam quais aplicativos são instalados e atualizados.
-
Escolha: O F-Droid oferece uma ampla gama de aplicativos de código aberto e de software
Também é importante observar que nem todos os aplicativos disponíveis no F-Droid são completamente livres de riscos. Portanto, é sempre recomendável ler cuidadosamente as informações sobre o aplicativo e avaliar os riscos antes de baixá-lo e instalá-lo.
Aqui está o passo a passo para instalar o F-Droid em seu dispositivo Android:
-
Acesse o site oficial do F-Droid em https://f-droid.org/ usando um navegador da web no seu dispositivo Android.
-
Verifique a assinatura PGP do arquivo APK que você irá baixar. Para isso, clique no link "PGP Signature" abaixo do botão "Download F-Droid" na página inicial do site. Na página seguinte, baixe o arquivo "F-Droid.apk.asc" clicando no botão "Download". Baixe também a chave pública do desenvolvedor do F-Droid, clicando no link "PGP key of F-Droid release signing key" na mesma página. É importante verificar a assinatura antes de prosseguir com a instalação.
-
Clique no botão "Download F-Droid" para baixar o arquivo APK.
-
Abra o arquivo APK baixado em seu dispositivo Android. Se você não sabe como abrir o arquivo, vá até o gerenciador de arquivos do seu dispositivo e encontre o arquivo APK que acabou de baixar. Toque no arquivo e siga as instruções na tela para instalar o aplicativo.
-
Se aparecer uma mensagem de alerta informando que a instalação de aplicativos de fontes desconhecidas está desativada, vá até as configurações de segurança do seu dispositivo e habilite a opção "Fontes desconhecidas". Isso permitirá que você instale aplicativos de fora da Google Play Store.
-
Clique em "Instalar" e aguarde a instalação ser concluída.
-
Após a instalação, abra o aplicativo F-Droid e aguarde a inicialização do repositório de aplicativos.
-
Pronto! Agora você pode navegar e baixar aplicativos do F-Droid em seu dispositivo Android. O F-Droid oferece uma ampla variedade de aplicativos de código aberto e de software livre, e todos são gratuitos para baixar e usar. Você pode usar o F-Droid como uma alternativa à Google Play Store se estiver preocupado com privacidade, segurança ou controle de seus próprios dispositivos Android.
https://github.com/f-droid
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 4ba8e86d:89d32de4
2024-10-22 23:04:43
@ 4ba8e86d:89d32de4
2024-10-22 23:04:43O objetivo principal do Tutanota é oferecer um serviço de e-mail protegido, onde as mensagens são criptografadas de ponta a ponta. Isso significa que as mensagens são codificadas no dispositivo do remetente e permanecem criptografadas até chegarem ao dispositivo do destinatário. Somente o remetente e o destinatário têm as chaves necessárias para descriptografar as mensagens, garantindo a confidencialidade das comunicações.
Além da criptografia de ponta a ponta, o Tutanota oferece outras medidas de segurança. Os e-mails são armazenados de forma criptografada nos servidores da empresa, o que significa que mesmo se alguém obtiver acesso aos servidores, os e-mails permanecerão ilegíveis sem a chave de descriptografia do usuário. O Tutanota também permite que os usuários protejam suas contas com senhas fortes.
O Tutanota foi fundado em 2011 na Alemanha por Arne Möhle e Matthias Pfau, com o objetivo de oferecer um serviço de e-mail seguro e privado. Eles buscavam fornecer uma alternativa aos serviços tradicionais, enfatizando a proteção da privacidade e a criptografia de ponta a ponta. Desde então, o Tutanota expandiu suas funcionalidades, adicionando recursos como armazenamento criptografado, calendário e agenda. A empresa está comprometida com a proteção dos dados dos usuários e está sediada na Alemanha, seguindo o Regulamento Geral de Proteção de Dados (GDPR). O Tutanota continua a ser reconhecido como uma referência em privacidade digital e mantém seu compromisso com a segurança e a privacidade dos usuários.
Recursos de Segurança: 1. Criptografia de ponta a ponta: Uma das principais características do Tutanota é a criptografia de ponta a ponta. Isso significa que suas mensagens são codificadas no dispositivo do remetente e permanecem criptografadas durante o trânsito até o dispositivo do destinatário. Somente o remetente e o destinatário têm as chaves para descriptografar as mensagens, tornando praticamente impossível para terceiros interceptá-las e acessar seu conteúdo.
-
Armazenamento criptografado: Além da criptografia de ponta a ponta para as mensagens em trânsito, o Tutanota também armazena seus e-mails de forma criptografada em seus servidores. Isso significa que, mesmo se alguém obtiver acesso aos servidores do Tutanota, os e-mails armazenados permanecerão ilegíveis sem a chave de descriptografia do usuário.
-
Proteção por senha: O Tutanota permite que você defina uma senha segura para proteger sua conta de e-mail. Essa senha é usada para criptografar seus dados armazenados e deve ser mantida em sigilo para garantir a segurança de sua conta.
Outros Recursos e Funcionalidades: 1. Interface amigável: O Tutanota oferece uma interface de usuário intuitiva e fácil de usar, semelhante aos serviços de e-mail convencionais. Isso torna a transição para o Tutanota suave para os usuários acostumados a outras plataformas de e-mail.
-
Aplicativos móveis: O Tutanota oferece aplicativos móveis para dispositivos iOS e Android, permitindo que você acesse sua conta de e-mail de forma segura em seu smartphone ou tablet.
-
Armazenamento e anexos: O Tutanota oferece 1 GB de armazenamento gratuito para sua conta de e-mail, permitindo que você mantenha um histórico de mensagens seguro. Além disso, você pode enviar e receber anexos com segurança, pois eles também são criptografados.
-
Proteção contra spam: O Tutanota possui um filtro de spam eficiente que verifica e filtra mensagens indesejadas, garantindo que sua caixa de entrada seja livre de spam e ameaças.
-
Calendário e Contatos: Além do serviço de e-mail, o Tutanota também oferece recursos de calendário e agenda, permitindo que você organize seus compromissos de forma segura e mantenha uma lista de contatos criptografados.
-
Personalização: O Tutanota permite que você personalize sua conta de e-mail, como escolher seu próprio domínio personalizado (para usuários pagos) e criar aliases de e-mail para maior flexibilidade na comunicação.
-
Compromisso com a privacidade: O Tutanota é conhecido por sua postura pró-privacidade e compromisso com a proteção dos dados de seus usuários. A empresa está sediada na Alemanha, onde estão sujeitos a rigorosas leis de proteção de dados, e segue o Regulamento Geral de Proteção de Dados (GDPR) da União Europeia.
O Tutanota é uma opção excelente para aqueles que valorizam a privacidade e desejam proteger suas comunicações online. Com sua criptografia de ponta a ponta, armazenamento criptografado e outros recursos de segurança, o Tutanota garante que suas mensagens e dados pessoais permaneçam privados e seguros.
https://tutanota.com/pt_br/
https://github.com/tutao/tutanota
-
-
 @ 13bb2eae:bb084375
2024-12-15 08:35:50
@ 13bb2eae:bb084375
2024-12-15 08:35:50 @ 592295cf:413a0db9
2024-09-28 08:19:25
@ 592295cf:413a0db9
2024-09-28 08:19:25Week 23th September
It's not your voice anymore if it's available to everyone.
Nostr is psycho pop.
Nostrasia took place today. It all seemed beautiful. A muffled meeting, a bit in the clouds compared to the air you breathe in social media.
It seems there are two types of Nostr the one who doesn't want to grow and the one who wants to grow. 😅
-
There has always been a misconception that kind1 is the discovery layer, but in reality it is the opposite. If someone publishes a long form article there is less audience, it is true, but then it is easier to find quality content, therefore quality profiles to follow in the kind1 client aka twitter clone. And this can be true for all portable data layers, video streaming, audio, long form, ngit, wiki and whatsoever. So you have finally good follow.
-
The fact that in Nostr you don't see who follows you generally, only in a few clients, I only know one where you see who started following you. It's a strange thing, made to avoid seeing masses of bots that follow you and you can want to block, and you increase that list to the point of absurdity. It's strange because there is a lot of focus on the social graph, if you follow me it's an important aspect.
So in Nostr there are - portable data layers (Twitter style and other social) - non-portable, applications that use disposable npub, where the key is ephemeral.
- 0xchat was becoming a good client, they killed it because it has to focus on chat. I don't use chat, I don't have anyone to chat with, I follow the 0xchat channel and then I read things from Moment. I use it with my second account, because after the nos2x-amber affair with the Odell result, which I had already told you about, I no longer tried to have the first profile even on the mobile. In the end they are all keys that will be burned 😔
Maybe I won't use Nostr anymore in the future just with burn npub, pow and whatsoever. In the end you don't build anything because it's a "stateless" communication.
Lol Moment
On Nostr the poor answer guy is helping the network 🤣🤣
call the police 911: what is your emergency?
a spam bot is attacking "nostr" relays.
you want some government censorship on those relays that contain spam, yes we can do that.
-Previous week- 16 09 Machines Like Me was a good book, maybe now it will become reality.
-
The cool thing about Plebchain radio, it's not the guests, it's these two Nostr users that do a podcast. And they focused on Bitcoin and Nostr and lightning, but maybe it's just the beginning, first you have to focus on a niche and then you expand to the whole world. I think the whole world phase is starting, the podcast topics would become too repetitive. The best part is the 15 10 minute intro. Or in the live show part, there could be some interesting clips.
-
-
idea White button for activity pub user on voyage (app).
-
People hate Nostr. Don't use it
-
UnNip, now we've seen it all
-
Until the morale improves
-
-
People think Sync works like this by magic. Unfortunately it doesn't, I think, at least that's what those who are trying to do say, auto-merge, tinybase, evolu. There is an interesting local-first project. Jaguard a collaborative environment for writing empirical research papers.
-
Now I can search by id. I couldn't do it and I didn't understand the mechanism. Everything has to be instantiated. it works. Now I have to create a function maybe note_list_id and note_id. I continued to edit the NIPs page with asciidoc, categorizing this table is very fun.
New wave of Opensats grants.
- If you haven't heard about WoT this week, you probably live on Mars. There are people who didn't know you could edit on amethyst.
You need to do a podcast of NIPs, features and whatsoever, maybe doing a podcast is not the best solution because it assumes you know something more and something that could change the next day or be no longer valid. maybe you should avoid doing things you don't have full control over, or at least not spread it outside. Maybe because last year at this time I was recording audio.
-
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 79008e78:dfac9395
2024-12-01 03:15:00
@ 79008e78:dfac9395
2024-12-01 03:15:00บทที่ 1: เกริ่นนำ
เกริ่นนำเรื่องราวของบิตคอยน์แบบกระทัดรัด
บิตคอยน์ (Bitcoin) เป็นชุดแนวคิดและเทคโนโลยีที่เข้ามาผสมผสานรวมกันจนได้กลายเป็นระบบเงินสดอิเล็กทรอนิกส์ หน่วยเงินที่เรียกว่าบิตคอยน์นั้น ใช้เพื่อเก็บและส่งต่อมูลค่าให้กับผู้ใช้คนอื่น ๆ ในระบบ ผู้ใช้ทั้งระบบสื่อสารกันบนโปรโตคอลของบิตคอยน์ โดยผู้ใช้ส่วนใหญ่ก็เข้าถึงกันผ่านอินเตอร์เน็ต แต่ก็ไม่ได้หมายความว่าระบบนี้ไม่สามารถใช้เครือข่ายการสื่อสารรูปแบบอื่นได้ ซอฟต์แวร์ของโปรโตคอลนี้เป็นโอเพนซอร์สและสามารถรันได้บนอุปกรณ์คอมพิวเตอร์หลายประเภท เช่น แล็ปท็อปและสมาร์ทโฟน และสิ่งนี้เองที่ทำให้เทคโนโลยีนี้สามารถเข้าถึงได้ง่าย
ผู้ใช้งานสามารถส่งบิตคอยน์ให้กันผ่านเครือข่ายของบิตคอยน์เพื่อทำกิจกรรมต่าง ๆ เช่น ซื้อ-ขายแลกเปลี่ยนสินค้าและบริการ หรือใช้เพื่อแลกเปลี่ยนเป็นสกุลเงินต่าง ๆ ซึ่งถือว่าเหมาะสมเป็นอย่างมากสำหรับการใช้งานบนอินเทอร์เน็ต เพราะมีทั้งความรวดเร็ว ความปลอดภัย และยังข้อจำกัดเรื่องพรมแดน
ซึ่งบิตคอยน์นั้นแตกต่างจากสกุลเงินโดยทั่วไป เนื่องจากเป็นระบบเงินอิเล็กทรอนิกส์ จึงไม่มีเหรียญหรือธนบัตรจริง ๆ ให้ได้จับต้อง แต่คำว่าเหรียญที่มักใช้กันในสังคมของบิตคอยน์จะหมายถึงในธุรกรรมที่ผู้ใช้รายหนึ่งโอนมูลค่าไปยังผู้ใช้อีกรายหนึ่ง ผู้ใช้งานบิตคอยน์จะควบคุมคีย์ (Private Key) ที่ใช้พิสูจน์ความเป็นเจ้าของในบิตคอยน์นั้น ๆ ในเครือข่าย และด้วยคีย์นี้เองทำให้พวกเขาสามารถเซ็นชื่อในธุรกรรมเพื่อปลดล็อกมูลค่าและทำการส่งมันต่อไปยังผู้รับอีกรายหนึ่ง ซึ่งมักจะถูกเก็บอยู่ในกระเป๋าเงินดิจิทัล หรือสมาร์ทโฟนของผู้ใช้งาน การครอบครองคีย์ที่สามารถเซ็นชื่อในธุรกรรมได้เป็นสิ่งเดียวที่จำเป็นในการใช้จ่ายในระบบของบิตคอยน์ และนั่นเป็นเหตุผลที่ทำให้ความสามารถในการควบคุมบิตคอยน์อยู่ในมือผู้ใช้แต่ละคน
เข้าใจว่าในบริบทนี้น่าจะหมายถึง Hot-wallet เพราะงั้นผมไม่ได้แนะนำให้เก็บคีย์คอมพิวเตอร์หรือมือถือนะครับ ส่วนถ้าคุณอยากทำก็เรื่องของคุณจ้าแนะนำเฉย ๆ อยากทำไรทำ
บิตคอยน์นั้นเป็นระบบแบบกระจายศูนย์และทำงานแบบเพียร์-ทู-เพียร์ (Peer-to-Peer) หรือเอาภาษาบ้าน ๆ ว่า เป็นระบบการทำงานแบบบุคคลสู่บุลคลที่ไม่มีตัวกลางระหว่างการทำงาน ดังนั้นจึงไม่มีเซิร์ฟเวอร์กลางหรือจุดควบคุม บิตคอยน์นั้นถูกสร้างขึ้นโดยกระบวนการที่เรียกว่าการขุด ซึ่งเป็นการทำงานทางการคำนวณซ้ำ ๆ ที่อ้างอิงกับรายการธุรกรรมบิตคอยน์ล่าสุด (จริง ๆ ก็มี hash ของบล็อกก่อนหน้าด้วย) ซึ่งผู้ใช้งานบิตคอยน์ทุกคนสามารถที่จะขุดบิตคอยน์ได้ โดยใช้อุปกรณ์คอมพิวเตอร์ของตนเพื่อช่วยรักษาความปลอดภัยในธุรกรรม โดยทุก ๆ สิบนาทีโดยเฉลี่ยนั้น จะมีนักขุดคนหนึ่งที่ได้ช่วยเพิ่มความปลอดภัยให้กับธุรกรรมในอดีต และจะได้รับรางวัลเป็นบิตคอยน์ใหม่และค่าธรรมเนียมจากธุรกรรมชุดล่าสุด ซึ่งกระบวนการนี้ทำให้การออกสกุลเงินและการชำระธุรกรรมไม่จำเป็นต้องมีธนาคารกลาง
โปรโตคอลของบิตคอยน์ มีอัลกอรึทึมที่คอยควบคุมความยากง่ายในการการขุดให้อยู่ในระดับที่เหมาะสม โดยความยากง่ายในการขุดจะขึ้นจะถูกปรับตามระยะเวลาเฉลี่ยของการขุดในช่วงก่อนหน้านี้เพื่อให้การขุดนั้นมีโอกาสสำเร็จเฉลี่ยในทุก ๆ 10 นาที ไม่ว่ามีจำนวนผู้ขุดและการประมวลผลเท่าใดก็ตาม และนอกจากนี้เองโปรโตคอลของบิตคอยน์นั้นยังลดจำนวนของบิตคอยน์ที่นักขุดจะได้เป็นรางวัลลงเรื่อย ๆ ซึ่งจะทำให้บิตคอยน์ที่สร้างได้ในระบบนั้นมีไม่เกิน 21,000,000 ล้านบิตคอยน์ ซึ่งผลลัพธ์ที่ได้ก็คือ จำนวนบิตคอยน์ที่หมุนเวียนในระบบนั้นจะสามารถคาดเดาได้อย่างง่ายดาย ซึ่งอีกครึ่งหนึ่งของบิตคอยน์ที่เหลืออยู่จะถูกเพิ่มเข้าไปในระบบทุก ๆ 4 ปี และที่บล๊อกประมาณ 1,411,200 ซึ่งคาดว่าจะเกิดประมาณปี 2035 จะมีบิตคอยน์เป็นจำนวน 99 % ของที่สามารถเกิดขึ้นได้ในระบบ เนื่องจากอัตราการการผลิตของบิตคอยน์ที่น้อยลงเรื่อย ๆ ทำให้บิตคอยน์มีลักษณะของเงินฝืดในระยะยาว นอกจากนี้ยังไม่มีใครที่สามารถบังคับให้คุณรับบิตคอยน์ที่ถูกผลิตมานอกเหนือจากชุดกฎที่คุณเลือกได้
เบื้องหลังต่าง ๆ ของโปรโตคอลบิตคอยน์ที่ทำให้มันเป็น เครือข่ายแบบบุคคลถึงบุคคล และการคำนวณแบบกระจายศูนย์นั้น ถูกสร้างขึ้นมาบนพื้นฐานของงานวิจัยในด้านการเข้ารหัสและระบบกระจายศูนย์มาเนิ่นนานหลายทศวรรษ โดยมีการรวมเอานวัตกรรมสำคัญ ๆ 4 อย่างนี้มารวมเข้าด้วยกัน:
- เครือข่ายเพียร์ทูเพียร์ที่กระจายศูนย์ (ฺBitcoin protocol)
- บัญชีธุรกรรมสาธารณะ (Blockchain)
- ชุดของกฎในการตรวจสอบธุรกรรมอย่างอิสระและการออกสกุลเงิน ( consensus rules )
- กลไกในการหาข้อตกลงร่วมกันทั่วโลกเกี่ยวกับบล็อกเชนที่ถูกต้อง (PoW algorithm)
ในมุมมองของนักพัฒนา นาย Andreas M. Antonopoulos and David A. Harding ( ไม่ใช่ผมจ้าา ถึงจะเห็นด้วยก็ตาม) พวกเขามองว่าบิตคอยน์นั้นคล้ายกับอินเทอร์เน็ตของเงิน เป็นเครือข่ายสำหรับการกระจายมูลค่าและการรักษาความเป็นเจ้าของสินทรัพย์ดิจิทัลผ่านการคำนวณแบบกระจายศูนย์ ซึ่งบิตคอยน์มีรายระเอียดเยอะกว่าที่พวกเขาเห็นในตอนแรกมาก ๆ
ในบทนี้เองจะเป็นการอธิบายแนวคิด และคำศัพท์หลัก ๆ รวมทั้งการติดตั้งซอฟแวร์ต่าง ๆ ที่จำเป็นในการทอดลองใช้บิตคอยน์สำหรับทำธุรกรรมง่าย ๆ และสำหรับในบทถัดไป เราจะทำการดำดิ่งลงไปในเทคโนโลยีต่าง ๆ ที่ประกอบรวมกันเป็นบิตคอยน์ว่าทำไมมันถึงเป็นไปได้ และตรวจสอบการทำงานภายในของเครือข่ายและโปรโตคอล
ก่อนการมาถึงของบิตคอยน์
สกุลเงินดิจิทัลที่ใช้งานได้จริงในอดีตนั้นมักเกี่ยวข้องกับพัฒนาการในด้านการเข้ารหัส ซึ่งนั่นก็ไม่ได้แปลกอะไรหากเราพิจารณาถึงปัญหาพื้นฐานในการใช้ข้อมูลเพื่อแทนมูลค่าที่สามารถแลกเปลี่ยนเป็นสินค้าและบริการ โดยการที่เงินดิจิทัลจะถูกยอมรับได้นั้นมักจะต้องสามารถตอบคำถามทั้งสามข้อนี้ได้เสียก่อน:
- ฉันจะเชื่อได้อย่างไรว่าเงินนั้นเป็นของจริงและไม่ใช่ของปลอม?
- ฉันจะเชื่อได้อย่างไรว่าเงินดิจิทัลสามารถใช้ได้เพียงครั้งเดียว (ปัญหาการใช้ซ้ำหรือ "double-spend")?
- ฉันจะมั่นใจได้อย่างไรว่าไม่มีใครสามารถอ้างสิทธิ์ว่าเงินนี้เป็นของพวกเขาไม่ใช่ของฉัน?
ผู้ที่ออกเงินกระดาษเองก็พยายามต่อสู้กับปัญหาการปลอมแปลงโดยการใช้เทคโนโลยีการพิมพ์ที่ซับซ้อนมากขึ้นเรื่อย ๆ และเงินกายภาพเองก็จัดการปัญหาการใช้ซ้ำได้ง่ายเพราะธนบัตรเดียวกันไม่สามารถอยู่ในสองที่พร้อมกันได้ แน่นอนละว่าเงินทั่วไปก็ถูกเก็บและส่งแบบดิจิทัลเช่นกัน ในกรณีเหล่านี้ ปัญหาการปลอมแปลงและการใช้ซ้ำจะถูกจัดการโดยการเคลียร์ธุรกรรมทางอิเล็กทรอนิกส์ทั้งหมดผ่านหน่วยงานกลางที่สามารถตรวจสอบสถานะของเงินได้ แต่สำหรับเงินดิจิทัลที่ไม่สามารถใช้หมึกพิเศษหรือแถบโฮโลแกรมได้ การเข้ารหัสจึงเป็นพื้นฐานสำคัญในการยืนยันความถูกต้องของการอ้างสิทธิ์ในมูลค่าของผู้ใช้ โดยเฉพาะอย่างยิ่ง การเซ็นชื่อดิจิทัลที่เข้ารหัสช่วยให้ผู้ใช้สามารถเซ็นชื่อในสินทรัพย์ดิจิทัลหรือธุรกรรมเพื่อยืนยันการเป็นเจ้าของสินทรัพย์นั้น ซึ่งสิ่งนี้เองยังสามารถใช้ในการแก้ปัญหาการใช้ซ้ำ (doble-spending) ได้
ศาสตร์ของการเข้ารหัสนั้นเริ่มเป็นที่แพร่หลายในช่วงปลายของทศวรรษที่ 1980 นักวิจัยหลายคนเริ่มพยายามใช้การเข้ารหัสเพื่อสร้างสกุลเงินดิจิทัล โดยโครงการเงินดิจิทัลในยุคแรก ๆ นั้นมักจะออกเงินดิจิทัลที่มีการสนับสนุนโดยสกุลเงินของชาติหรือโลหะมีค่าอย่างเช่น ทองคำ
ซึ่งแม้ว่าสกุลเงินดิจิทัลยุคแรกเหล่านี้จะทำงานได้ แต่ก็มีปัญหาที่การรวมศูนย์ของระบบ เนื่องจากมันทำให้ระบบเป็นเป้าหมายที่ง่ายต่อการโจมตีโดยรัฐบาลและเหล่าแฮกเกอร์ สกุลเงินดิจิทัลยุคแรกใช้ศูนย์กลางในการชำระธุรกรรมทั้งหมดเป็นระยะ ๆ เช่นเดียวกับระบบธนาคารทั่วไป เป็นที่น่าเสียดายที่สกุลเงินดิจิทัลเหล่านี้ส่วนใหญ่ถูกกำหนดเป้าหมายโดยรัฐบาลที่กังวลและมักจะถูกฟ้องร้องจนล้มเหลว บางส่วนล้มเหลวอย่างรวดเร็วเมื่อบริษัทผู้ก่อตั้งปิดตัวลงอย่างกะทันหัน และเพื่อให้สกุลเงินดิจิทัลมีความแข็งแกร่งต่อต้านการแทรกแซงจากศัตรู ไม่ว่าจะเป็นรัฐบาลที่ถูกกฎหมายหรืออาชญากรรม เราจึงจำเป็นต้องมีสกุลเงินดิจิทัลที่กระจายศูนย์ เพื่อป้องกันปัญหาดังกล่าว ซึ่งบิตคอยน์คือระบบแบบนั้น ระบบที่ถูกออกแบบให้กระจายศูนย์ และปราศจากอำนาจหรือจุดควบคุมกลางใด ๆ ที่สามารถถูกโจมตีหรือทำให้เสียหายได้
ประวัติของบิตคอยน์
บิตคอยน์ได้ปรากฏครั้งแรกในปี 2008 บนเอกสารที่มีชื่อว่า “Bitcoin: A Peer-to-Peer Electronic Cash System” ซึ่งถูกเขียนโดยบุคคลหรือกลุ่มคนนิรนามที่ใช้นามแฝงว่า ซาโตชิ นากาโมโตะ ซึ่งได้มีการนำนวัตกรรมหลาย ๆ อย่างมารวมเข้าด้วยกัน ไม่ว่าจะเป็นลายเซ็นดิจิทัล และ Hashcash มาสร้างระบบเงินสดอิเล็กทรอนิกส์ที่กระจายศูนย์อย่างสมบูรณ์ ซึ่งไม่ต้องพึ่งพาหน่วยงานกลางในการออกสกุลเงินหรือการชำระและตรวจสอบธุรกรรม โดยนวัตกรรมสำคัญคือการใช้ระบบคำนวณแบบกระจายศูนย์ (Proof-of-work) เพื่อทำสิ่งที่คล้าย ๆ กับการจับฉลากทุก ๆ 10 นาที ทำให้เครือข่ายที่กระจายศูนย์สามารถมีฉันทามติในสถานะของธุรกรรมได้ และสิ่งนี้เองยังสามารถแก้ไขปัญหาการทำธุรกรรมซ้ำซ้อน ซึ่งเป็นข้อบกพร่องของสกุลเงินดิจิทัลที่เคยต้องใช้หน่วยงานกลางในการตรวจสอบธุรกรรมทั้งหมดได้อีกด้วย
เครือข่ายของบิตคอยน์นั้นเริ่มต้นขึ้นในปี 2009 โดยอ้างอิงจากซอฟแวร์ที่เผยแพร่โดย ซาโตชิ และได้ถูกปรับปรุงโดยโปรแกรมเมอร์คนอื่น ๆ มากมายนับไม่ถ้วนมานับตั้งแต่นั้น จำนวนและกำลังของอุปกรณ์ที่ใช้ประมวลผล Proof of Work algorithm (การขุด) เองนั้นก็เพิ่มขึ้นอย่างมหาศาล จนในปัจจุบันนี้พลังการคำนวณรวมกันของเครือข่ายนี้มีมากกว่าจำนวนการคำนวณของซุปเปอร์คอมพิวเตอร์ชั้นนำของโลกทั้งหมดรวมกันเสียอีก ซึ่งสิ่งนี้เองได้ช่วยรักษาความปลอดภัยและความเสถียรของเครือข่ายของบิตคอยน์ได้เป็นอย่างดี
ซาโตชิ นากาโมโตะ ได้ทำการถอนตัวและหายตัวไปในเดือนเมษายนในปี 2011 และมอบหมายความรับผิดชอบในการพัฒนาโค้ดและเครือข่ายให้กับกลุ่มอาสาสมัครที่เติบโตขึ้นเรื่อย ๆ ซึ่งตัวตนของบุคคลหรือกลุ่มคนที่อยู่เบื้องหลังบิตคอยน์นั้นยังไม่เป็นที่รู้จัก แต่อย่างไรก็ตาม ไม่ว่าจะเป็นซาโตชิ นากาโมโตะ หรือใครหน้าไหนก็ตามก็ไม่สามารถควบคุมเครือข่ายของบิตคอยน์ได้ตามลำพัง เนื่องจากมันอยู่บนหลักการทางคณิตศาสตร์ที่โปร่งใส โค้ดโอเพนซอร์ส และฉันทามติจากผู้ที่เข้าร่วม โดยนวัตกรรมนี้ถือเป็นการเปลี่ยนแปลงครั้งใหญ่และได้ก่อให้เกิดวิทยาการใหม่ในด้านการคำนวณแบบกระจายศูนย์ เศรษฐศาสตร์ และเศรษฐมิติอีกด้วย
การแก้ปัญหาในระบบคำนวณแบบกระจายศูนย์
นวัตกรรมของซาโตชิ นากาโมโตะ ยังเป็นการแก้ไขปัญหาที่มีประสิทธิภาพและแปลกใหม่สำหรับปัญหาในระบบคำนวณแบบกระจายศูนย์ที่เรียกว่า "Byzantine Generals' Problem" ซึ่งปัญหานี้เกี่ยวข้องกับการพยายามทำให้ผู้เข้าร่วมหลายคนที่ไม่มีผู้นำสามารถตกลงกันในแผนการดำเนินการได้โดยการแลกเปลี่ยนข้อมูลในเครือข่ายที่ไม่น่าเชื่อถือและอาจถูกโจมตีได้ โดยการแก้ปัญหาของซาโตชินั้นได้ใช้แนวคิด proof of work เพื่อหาฉันทามติโดยไม่ต้องมีผู้ควบคุมที่น่าเชื่อถือ ถือเป็นความก้าวหน้าในด้านการคำนวณแบบกระจายศูนย์
เปิดประตูสู่บิตคอยน์
บิตคอยน์เป็นโปรโตคอลที่สามารถเข้าถึงได้ผ่านทางแอปพลิเคชันที่มีการรับรองโปรโตคอลนี้ Bitcoin wallet นั้นเป็นช่องทางหลักที่ผู้ใช้งานส่วนใหญ่เลือกใช้เพื่อเข้าถึงโปรโตคอลของบิตคอยน์ เช่นเดียวกันกับที่ผู้ใช้งานอินเตอร์เน็ตส่วนใหญ่ใช้เว็บบราวเซอร์เป็นช่องทางในการเข้าถึงโปรโตคอลอย่าง HTTP นั่นเอง Bitcoin wallet เองก็มีหลากหลายยี่ห้อเฉกเช่นเดียวกับเว็บบราวเซอร์ อาทิเช่น chorme, safari, firefox ฯลฯ Bitcoin wallet เองก็เช่นกัน แต่ละยี่ห้อเองก็มีความแตกต่างกันในด้านต่าง ๆ ไม่ว่าจะเป็นในด้านคุณภาพ ประสิทธิภาพ ความปลอดภัย ความเป็นส่วนตัว และความน่าเชื่อถือ อีกทั้งยังมี Bitcoin wallet ที่ถูกสร้างขึ้นมาคู่กับโปรโตคอลของบิตคอยน์อย่าง “Bitcoin Core” ซึ่งมีการพัฒนาต่อมาจากเวอร์ชันที่เขียนโดยซาโตชิ
การเลือก Bitcoin wallet
Bitcoin wallet เป็นหนึ่งในประเภทของแอปพลิเคชันที่มีการพัฒนาอย่างต่อเนื่องมากที่สุดในระบบนิเวศของบิตคอยน์ และแน่นอนว่ามีการแข่งขันกันสูงที่สุดด้วย อาจมี Bitcoin wallet ใหม่ ๆ ที่กำลังพัฒนาอยู่ในขณะนี้ Bitcoin wallet เก่า ๆ บางตัวจากปีที่แล้วก็อาจไม่มีการพัฒนาอย่างต่อเนื่องอีกต่อไป Bitcoin wallet หลาย ๆ ตัวเน้นไปที่แพลตฟอร์มหรือการใช้งานเฉพาะ และบางตัวเหมาะสำหรับผู้เริ่มต้น ในขณะที่บางตัวเต็มไปด้วยฟีเจอร์สำหรับผู้ใช้ขั้นสูง การเลือก Bitcoin wallet นั้นจึงขึ้นอยู่กับความต้องการและระดับความเชี่ยวชาญของผู้ใช้ ดังนั้นการที่เราจะแนะนำยี่ห้อหรือ Bitcoin wallet เฉพาะจึงอาจจะไม่เกิดประโยชน์เท่าไหร่ แต่อย่างไรก็ตาม เราสามารถแบ่งประเภท Bitcoin wallet ได้ตามแพลตฟอร์มและการใช้งานได้ดังนี้
ประเภทของ Bitcoin wallet
- Desktop wallet: กระเป๋าเงินแบบเดสก์ท็อปเป็น Bitcoin wallet ประเภทแรกที่ถูกพัฒนาขึ้นและผู้ใช้ส่วนใหญ่มักจะเลือกใช้ Bitcoin wallet ประเภทนี้เพราะฟีเจอร์ของมัน เช่นความความเป็นอิสระในการใช้งาน ความสามารถในการควบคุมบิตคอยน์ในกระเป๋า แต่อย่างไรก็ตาม การใช้งานบนระบบปฏิบัติการทั่วไป อย่างเช่น Windows และ macOS อาจมีข้อเสียด้านความปลอดภัย เนื่องจากแพลตฟอร์มเหล่านี้มักไม่มีความปลอดภัยเพียงพอและอาจถูกตั้งค่ามาอย่างไม่เหมาะสม
- Mobile wallet: กระเป๋าเงินแบบมือถือเป็น Bitcoin wallet ประเภทที่พบเจอได้มากที่สุด โดยทำงานบนระบบปฏิบัติการสมาร์ทโฟน เช่น Apple iOS และ Android กระเป๋าเงินเหล่านี้มักเป็นตัวเลือกที่ดีสำหรับผู้ใช้ใหม่ เพราะออกแบบมาให้ใช้งานง่ายและสะดวก นอกจากนี้ยังมีกระเป๋าเงินมือถือที่มีฟีเจอร์ครบครันสำหรับผู้ใช้ที่มีความเชี่ยวชาญ แต่เพื่อหลีกเลี่ยงการดาวน์โหลดและจัดเก็บข้อมูลปริมาณมาก กระเป๋าเงินมือถือส่วนใหญ่จะดึงข้อมูลจากเซิร์ฟเวอร์ระยะไกล ซึ่งอาจลดความเป็นส่วนตัวของผู้ใช้เนื่องจากต้องเปิดเผยข้อมูลเกี่ยวกับ address และจำนวนบิตคอยน์ Bitcoin ต่อบุคคลที่สาม
- Web wallet: กระเป๋าเงินแบบเว็บสามารถเข้าถึงได้ผ่านเว็บเบราว์เซอร์และเก็บกระเป๋าเงินของผู้ใช้ไว้บนเซิร์ฟเวอร์ที่บุคคลที่สามเป็นเจ้าของ คล้ายกับบริการอีเมลบนเว็บที่พึ่งพาเซิร์ฟเวอร์ของบุคคลที่สามโดยสมบูรณ์ โดยบางบริการใช้โค้ดฝั่งไคลเอนต์ที่ทำงานในเบราว์เซอร์ของผู้ใช้ และเพื่อให้ผู้ใช้สามารถควบคุมคีย์ของบิตคอยน์ได้เอง แต่การพึ่งพาเซิร์ฟเวอร์ยังคงส่งผลกระทบต่อความเป็นส่วนตัว อย่างไรก็ตาม บริการส่วนใหญ่จะควบคุมคีย์ของบิตคอยน์แทนผู้ใช้เพื่อแลกกับความสะดวกสบาย เราจึงไม่แนะนำให้เก็บ บิตคอยน์จำนวนมากบนระบบของบุคคลที่สาม
- Hardware Signing Devices: อุปกรณ์สำหรับเซ็นดิจิทัลเป็นอุปกรณ์ที่สามารถจัดเก็บคีย์และเซ็นธุรกรรมโดยใช้ฮาร์ดแวร์และเฟิร์มแวร์เฉพาะทาง ซึ่งโดยทั่วไปแล้วจะเชื่อมต่อกับกระเป๋าเงินเดสก์ท็อป มือถือ หรือเว็บ ผ่านสาย USB การสื่อสารระยะใกล้ (NFC) หรือกล้องที่รองรับ QR code แต่เนื่องจากการดำเนินการที่เกี่ยวข้องกับบิตคอยน์ ทั้งหมดถูกจัดการบนฮาร์ดแวร์เฉพาะ อุปกรณ์เหล่านี้จึงปลอดภัยจากการโจมตีหลายรูปแบบ อย่างไรก็ตาม อุปกรณ์เซ็นดิจิทัลมักถูกเรียกว่า hardware wallet แต่ต้องใช้งานร่วมกับกระเป๋าเงินที่มีฟีเจอร์ครบครันเพื่อส่งและรับธุรกรรม ความปลอดภัยและความเป็นส่วนตัวที่ได้จากกระเป๋าเงินที่ใช้งานร่วมกันก็มีบทบาทสำคัญต่อความปลอดภัยและความเป็นส่วนตัวโดยรวมของผู้ใช้อุปกรณ์เซ็นดิจิทัล
ประเภทของการเชื่อมต่อกับโปรโตคอลของบิตคอยน์
- Full node: บิตคอยน์ฟลูโหนดเป็นโปรแกรมที่ตรวจสอบความถูกต้องของประวัติธุรกรรมทั้งหมดของบิตคอยน์ (ทุกธุรกรรมที่เคยเกิดขึ้นโดยผู้ใช้ทุกคน) และนอกจากนี้ บิตคอยน์ฟลูโหนดยังสามารถเลือกเก็บข้อมูลธุรกรรมที่ได้รับการตรวจสอบแล้วก่อนหน้า และให้บริการข้อมูลแก่โปรแกรมบิตคอยน์อื่น ๆ ได้ ไม่ว่าจะเป็นบนคอมพิวเตอร์เดียวกันหรือผ่านอินเทอร์เน็ต แต่แม้ว่าบิตคอยน์ฟลูโหนดเองก็ใช้ทรัพยากรคอมพิวเตอร์ในปริมาณมาก (ประมาณเท่ากับการดูวิดีโอสตรีมมิ่งหนึ่งชั่วโมงต่อวันสำหรับธุรกรรมบิตคอยน์ในแต่ละวัน) บิตคอยน์ฟลูโหนดเองก็มอบความเป็นอิสระอย่างสมบูรณ์แก่ผู้ใช้
- Lightweight Client: lightweight client หรือที่เรียกกันอีกชื่อว่าไคลเอนต์การตรวจสอบการชำระเงินแบบง่าย (Simplified-Payment-Verification: SPV) ซึ่งจะเชื่อมต่อกับโหนดแบบเต็มหรือเซิร์ฟเวอร์ระยะไกลอื่น ๆ เพื่อรับและส่งข้อมูลธุรกรรมของบิตคอยน์แต่เก็บกระเป๋าเงินของผู้ใช้ไว้ในเครื่อง โดยสามารถตรวจสอบธุรกรรมที่ได้รับบางส่วน และสร้างธุรกรรมขาออกอย่างอิสระอีกด้วย
- ไคลเอนต์ API ของบุคคลที่สาม (Third-Party API Client): ไคลเอนต์ API ของบุคคลที่สามเป็นโปรแกรมที่เชื่อมต่อกับระบบบิตคอยน์ผ่าน API ของบุคคลที่สาม แทนที่จะเชื่อมต่อกับเครือข่ายบิตคอยน์โดยตรง กระเป๋าเงินนี้อาจถูกจัดเก็บโดยผู้ใช้เองหรือบนเซิร์ฟเวอร์ของบุคคลที่สาม แต่ไคลเอนต์จะต้องไว้วางใจเซิร์ฟเวอร์ระยะไกลในการให้ข้อมูลที่ถูกต้องและปกป้องความเป็นส่วนตัวของตน
บิตคอยน์เป็นเครือข่ายแบบเพียร์ทูเพียร์(Peer-to-Peer หรือ P2P) โดยที่บิตคอยน์ฟลูโหนด ทำหน้าที่เป็นเพียร์ในเครือข่าย เพียร์แต่ละตัวจะตรวจสอบความถูกต้องของธุรกรรมที่ยืนยันแล้วทุกธุรกรรมอย่างอิสระ และสามารถให้ข้อมูลที่เชื่อถือได้แก่ผู้ใช้ Lightweight Wallets และซอฟต์แวร์อื่น ๆ เองก็เป็นลูกข่ายที่ต้องพึ่งพาเพียร์หนึ่งหรือหลายตัวในการรับข้อมูลที่ถูกต้อง ไคลเอนต์สามารถตรวจสอบข้อมูลบางส่วนที่ได้รับเพิ่มเติมและเชื่อมต่อกับเพียร์หลายตัวเพื่อลดการพึ่งพาเพียร์ตัวเดียว แต่ในท้ายที่สุดความปลอดภัยของไคลเอนต์ยังคงขึ้นอยู่กับความน่าเชื่อถือของเพียร์ที่เชื่อมต่อด้วย
ใครควบคุมคีย์
อีกหนึ่งในประเด็นสำคัญที่ควรพิจารณาเพิ่มเติมคือใครเป็นผู้ควบคุมคีย์ (Private key) เนื่องจากเป็นสิ่งที่มีบทบาทสำคัญในการควบคุมการเข้าถึงบิตคอยน์ โดยคีย์เหล่านี้เองเปรียบเสมือน PIN ที่ยาวมาก ซึ่งหากคุณเป็นผู้ควบคุมคีย์ของคุณเองด้วยตัวเอง คุณก็เป็นผู้ควบคุมบิตคอยน์ของคุณด้วยเช่นกัน แต่หากไม่ใช่ ก็จะแปลว่ากุญแจเหล่านั้นจะถูกดูแลโดยบุคคลที่สาม ซึ่งจะเป็นผู้จัดการเงินของคุณในนามของคุณ
ซอฟแวร์ในการจัดการกุญแจนั้นถูกแบ่งออกเป็นสองประเภทหลัก ๆ คือ wallet ที่คุณจำเป็นต้องดูแลคีย์ของตัวเองและ บัญชีที่มีผู้ดูแล (Custodian Accounts) ซึ่งจะมีบุคคลที่สามเป็นผู้ควบคุมกุญแจ
“Your keys, your coins. Not your keys, not your coins.”
มาอยู่ตัวอย่างเพื่อความเข้าใจที่มาขึ้นกันเถอะ
สมมุติว่าอลิซเป็นผู้ใช้งานที่ไม่ได้เชี่ยวชาญด้านเทคนิค และเพิ่งได้ยินเกี่ยวกับบิตคอยน์จากเพื่อนสนิทของเขา โจ ระหว่างปาร์ตี้ โจกำลังอธิบายเกี่ยวกับบิตคอยน์อย่างกระตือรือร้นให้ทุกคนฟังและสาธิตวิธีการใช้งานต่าง ๆ ให้ดู อลิซเองได้มีความสนใจในบิตคอยน์หลังจากได้ฟังโจอธิบาย จึงได้ถามโจว่าเธอจะเริ่มต้นใช้งานบิตคอยน์ได้อย่างไร โจจึงแนะนำให้อลิซดาวน์โหลด Mobile wallet ตัวโปรดของเขาเนื่องจากมันเหมาะสมกับมือใหม่ อลิซจึงดาวน์โหลดและติดตั้งแอปพลิเคชันกระเป๋าเงินที่โจแนะนำบนโทรศัพท์ของเธอ
เมื่ออลิซเปิดแอปพลิเคชันครั้งแรก เธอได้เลือกสร้างกระเป๋าใหม่และเนื่องจากกระเป๋าที่เธอเลือกนั้นเป็นแบบที่ไม่ได้อยู่ภายใต้การควบคุมบุคคลที่สาม (Noncustodial Wallet) อลิซจึงเป็นผู้ควบคุมคีย์เพียงคนเดียว ซึ่งหมายความว่าเธอต้องรับผิดชอบในการสำรองข้อมูลด้วยตัวของเธอเอง และหากเธอได้ทำคีย์สูญหายไป เธอจะไม่สามารถเข้าถึงบิตคอยน์ของเธอได้อีกไปตลอดกาล และเพื่อเพื่อช่วยในเรื่องนี้ Bitcoin wallet ต่าง ๆ จึงมักจะสร้างรหัสการกู้คืน (Recovery Code) ให้ซึ่งสามารถใช้ในการกู้คืน Bitcoin wallet อันนั้น ๆ
Recovery Code (รหัสในการกู้คืน)
Bitcoin wallet แบบที่ไม่ได้อยู่ภายใต้การควบคุมของบุคคลที่สามนั้นส่วนใหญ่จะให้รหัสการกู้คืนแก่ผู้ใช้งานเพื่อสำรองข้อมูล และรหัสการกู้คืนนี้มักประกอบด้วยตัวเลข ตัวอักษร หรือคำที่ถูกเลือกแบบสุ่มโดยซอฟต์แวร์ และใช้เป็นพื้นฐานสำหรับการสร้าง Bitcoin wallet โดยแต่ละยี่ห้อก็อาจมีความแตกต่างกัน เช่น

รหัสการกู้คืนมักเรียกว่า "mnemonic" หรือ "mnemonic phrase" หรือในภาษาไทยว่าวลีช่วยจำ ซึ่งบ่งบอกว่าคุณควรจดจำวลีนั้น แต่การจดวลีนี้ลงบนกระดาษใช้เวลาน้อยกว่าและมักจะเชื่อถือได้มากกว่าความจำของคนส่วนใหญ่ เพราะฉนั้นผมเลยแนะนำว่าจดเถอะ จะได้ไม่เกิดปัญหาที่ไม่คาดคิดในอนาคต
หาก bitcoin wallet ของอลิซมีปัญหา เธอสามารถดาวน์โหลดซอฟแวร์ใหม่และใส่รหัสในการกู้คืนลงไป เพื่อสร้างฐานข้อมูลของ bitcoin wallet ใหม่ที่บันทึกธุรกรรมบนเชนทั้งหมดที่เธอเคยรับหรือส่ง แต่อย่างไรก็ตาม การกู้คืนจากการใช้รหัสการกู้คืนเพียงอย่างเดียวนั้นอาจจะไม่สามารถกู้คืนข้อมูลเพิ่มเติมที่อลิซเคยบันทึกไว้ใน wallet นั้น ๆ ได้ เช่น ป้ายกำกับที่เธอเชื่อมโยงกับที่อยู่หรือธุรกรรมต่าง ๆ แม้ว่าการสูญเสียข้อมูลเมตานี้จะไม่สำคัญเท่ากับการสูญเสียเงิน แต่ก็ยังมีความสำคัญในบางแง่มุม เช่น หากคุณต้องตรวจสอบรายการธนาคารหรือบัตรเครดิตเก่า แต่ชื่อของผู้ที่คุณชำระเงินหรือผู้ที่จ่ายเงินให้คุณถูกลบออกไป ดังนั้นเพื่อป้องกันการสูญเสียข้อมูลเมตา wallet หลาย ๆ ยี่ห้อจึงมีฟีเจอร์สำรองข้อมูลเพิ่มเติมนอกเหนือจากรหัสการกู้คืน
สำหรับ wallet บางประเภทนั้น ฟีเจอร์สำรองข้อมูลเพิ่มเติมนี้ถือว่ามีความสำคัญมาก เนื่องจากการชำระเงินเงินด้วยบิตคอยน์จำนวนมากในปัจจุบันทำผ่านเทคโนโลยีที่อยู่นอกเชน (Offchain) ซึ่งธุรกรรมไม่ได้ถูกบันทึกลงในบล็อกเชนสาธารณะ เนื่องจากการชำระเงินแบบนี้ช่วยลดค่าใช้จ่ายของผู้ใช้และเพิ่มความเป็นส่วนตัวได้บ้าง แต่นั่นก็หมายความว่ากลไกอย่างรหัสการกู้คืนที่พึ่งพาข้อมูลบนเชนไม่สามารถรับประกันการกู้คืนบิตคอยน์ทั้งหมดของผู้ใช้ได้ ดังนั้นสำหรับแอปพลิเคชันที่รองรับการใช้งาน Offchain การสำรองข้อมูลฐานข้อมูล wallet บ่อยครั้งจึงเป็นสิ่งที่มีความสำคัญมาก
นอกจากนี้ เมื่อได้รับบิตคอยน์ครั้งแรกใน moblie wallet หลาย ๆ wallet มักจะตรวจสอบอีกครั้งว่าคุณได้สำรองรหัสการกู้คืนไว้อย่างปลอดภัยแล้ว การตรวจสอบนี้อาจเป็นเพียงการแจ้งเตือน หรืออาจถึงขั้นให้ผู้ใช้ป้อนรหัสนั้นซ้ำด้วยตัวเอง
คำเตือน แม้ว่า Bitcoin Wallet หลาย ๆ ตัวอาจจะมีการให้คุณต้องกรอกรหัสในการกู้คืนใหม่ในบางกรณี แต่มันก็มักจะมีแอปพลิเคชันมัลแวร์จำนวนมากที่เลียนแบบการออกแบบของ wallet ต่าง ๆ โดยมันจะบังคับให้คุณป้อนรหัสการกู้คืน จากนั้นมันจะส่งรหัสที่ป้อนไปยังผู้พัฒนามัลแวร์เพื่อขโมยบิตคอยน์ของคุณ นี่เปรียบเสมือนเว็บไซต์ฟิชชิงที่พยายามหลอกให้คุณให้รหัสผ่านธนาคารของคุณ สำหรับ Bitcoin wallet ส่วนใหญ่ เวลาที่พวกเขาจะขอรหัสการกู้คืนคือในระหว่างการตั้งค่าเริ่มต้น (ก่อนที่คุณจะได้รับบิตคอยน์) และระหว่างการกู้คืน (หลังจากที่คุณสูญเสียการเข้าถึง wallet เดิม) หากแอปพลิเคชันขอรหัสการกู้คืนในช่วงเวลาอื่น คุณควรปรึกษาผู้เชี่ยวชาญเพื่อให้แน่ใจว่าคุณไม่ได้ตกเป็นเหยื่อของการฟิชชิง
Bitcoin Addresses (ที่อยู่ในการรับหรือส่งบิตคอยน์)
ในตอนนี้อลิซพร้อมแล้วสำหรับการสร้าง Bitcoin wallet ใหม่ของเธอ Bitcoin wallet ที่เธอเลือกได้ทำการสร้าง private key แบบสุ่มให้เธอ ซึ่งจะเชื่อมโยงกับ Bitcoin Address ทั้งหมดที่มีใน Bitcoin wallet ของเธอ แต่ ณ ขณะนี้ยังไม่มีใครรู้ Bitcoin address ของเธอ (แม้แต่ Bitcoin network ก็ไม่รู้) นอกจากตัวเธอเอง Bitcoin address เหล่านี้เป็นเพียงตัวเลขที่เชื่อมโยงกับ Private key ของเธอ ซึ่งเธอสามารถใช้ควบคุมการเข้าถึง Bitcoin ใดกระเป๋าได้ Bitcoin address เหล่านี้ถูกสร้างขึ้นโดยอิสระจากกระเป๋าของเธอโดยไม่ต้องอ้างอิงหรือเชื่อมต่อกับบริการใด ๆ
คำแนะนำ: Bitcoin address และ Invoice นั้นมีหลากหลายรูปแบบที่แตกต่างกัน และทั้งหมดนี้สามารถแชร์ให้กับคนอื่น ๆ ได้ เพื่อเป็นการอณุญาติให้พวกเขาส่งบิตคอยน์เข้ามาในกระเป๋าคุณตรง ๆ คุณสามารถแชร์ Bitcoin address และ Invoice ให้คนอื่นได้โดยไม่ต้องกังวลเกี่ยวกับความปลอดภัยของบิตคอยน์ของคุณ เนื่องจากผู้ที่รู้ Bitcion address ของคุณไม่สามารถถอนเงินออกจาก address นั้น ๆ ได้แม้เขาจะสามารถรู้จำนวนเงินใน address นั้น ๆ ก็ตาม เพราะฉะนั้นเพื่อปกป้องความเป็นส่วนตัวของคุณ คุณจึงควรสร้าง Invoice จาก Bitcoin address ใหม่ทุกครั้งที่จะส่งให้ผู้อื่น
-
 @ 592295cf:413a0db9
2024-09-14 18:13:41
@ 592295cf:413a0db9
2024-09-14 18:13:4109 09 week
The billboard has reached its first goal.
I don't understand anything, too much.
The web is a dangerous place, maybe the couch at home is for you.
Nostr is like being in a public place like a bar and you listen to the radio, and you can decide which radio to choose, you can also talk on the radio, only those who follow you and those who are connected to that frequency can listen to you.
We talk on multiple frequencies so if one is offline they can hear me on the other.
Spam will always be a constant as are fixed costs, personnel costs, taxes things that people in general hate
A lot of talk that will be blown away by the wind.
Jack Dorsey says Nostr will be a protocol for private encrypted chats
-
Open-sats drama
-
Carnivore dietitian
-
Lightning diatribe
-
This is already Twitter 😉
Fiatjaf explained for the umpteenth time what the outbox model is, now those who look at images instead of reading books must have understood it too. My note, Patricia writes in her relays write, including select some in her outbox 10002 kind. it was a dev page of something, so maybe it won't be online for long
Thinking that with Kamala Harris's victory, the price of Bitcoin would hit a low and holders would be happy to buy. 🤣🤣 Instead with Trump new all time High, holders would be happy. 🤣🤣 Lol Moment.
I read the article about btcmap maps, there were some notes to make but I didn't, it's beyond my level, it was only for builders.
Satlantis, trustroots, and wherostr were not noted.
I had this thought that we will not "succeed" in building the openness of type 1, in the following nips, because of the relays and because discovering new things has a cost, and no one wants to discover new things. And then after that the others should use them, but how and after that at least two others appear who are doing a similar thing, but they don't talk to each other because they don't have time.
If the time horizon is 10 years, those who survive will see.
Keeping calm seems difficult.
I tried nostr-relay-tray works. It works, I would suggest a couple of changes
- Delete some events.
- View events
- Search by npub id or time
- Delete by time.
These are difficult things but they can be done with a database, so they may as well not be done.
I hope that all the controversies are forgotten and overcome and we are more serene.
-
-
 @ dc4cd086:cee77c06
2024-10-18 17:41:42
@ dc4cd086:cee77c06
2024-10-18 17:41:42Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ 6d8e2a24:5faaca4c
2024-11-30 00:07:10
@ 6d8e2a24:5faaca4c
2024-11-30 00:07:10Why do people enjoy pain and a short time pleasure, which could ruin their life and peace?
Why can't people leave their fleshy desires, obsession and pleasures even if it kills them?
Many have become slaves to their obsession having no will of theirs, claiming to be free yet imprisoned by their futility and lust.
We thought we have closed all the doors and windows, turn off the light so no one can see us, least so we thought to ourselves, forgetting our conscience is wide open, and God who sit in heaven watching, like it was never night nor dark, sees through us for he is light ruling over darkness.
The devil working upon our obsession making it a reality. The devil always uses our sinful, lustful desire to trick us given an end vain pleasure
We fall once, down with the guilt and pain of sin, the weight of the burden once thought, destroying the spirit and causing so many pains of regret, low self-esteem, and lack of confidence again.
He comes again not to bring new but to dwell in our past, bringing memories, mistakes, and errors making us feel more guilty and vulnerable, making us feel worthless and hopeless "We are doomed, so we think, God can't help us, our sins are too many; and with that, he finds a way to make us fall again, destroying us slowly till we are empty, having no will (stronghold).
Like a fire 🔥 lit in a bush, small as it is no one thought it could cause so much harm, or rather they thought they could control it or, put it off when they don't need it or, get bizarre.
Anything that has passed infantry allowed to grow is difficult or impossible to control so is a sin when is allowed to grow like a fire covering many areas is hard to put all areas off fast before one knows many areas are damaged many are beyond repairs
Every day we wake up, we plan how our lives, and how we are going to live the day, without the slimmest thought of contention, 'what if'. We do believe we have everything under control, everything planned out, but we forget that we are nothing but a sand timer that runs down so quickly than we thought.
Like the sand timer, our lives fade away gently, piece by piece till we cease to exist, only then, do we understand that we are rebels in this kingdom, not owners for we own nothing, with the dust reaching its last, the heartbeat and craves for more time, then we also understand, that time is never enough and time is so precious and priceless
Why do we always feel as if we have all the time in the world? why do we assume death to be a fairytale or a horror ghost story just to scare us out? Without having a sting.
Every day death proves more eager, the grave is so desperate that it looms looking and searching for any opportunity necessary to sting it stings.
But we are so carried away by life, deceived by what we have, the power, authority, and influence. We feel we are covered, yes we are but only to some certain extent. For life is so spiritual, than we could ever imagine or think of.
The night comes darkness looms over, evil rises, and fear grips one's heart, all wishing for the light. But now is no longer darkness that's so terrifying, but light itself has become as terrifying as the darkness, people wishing to live through the light, now wish the same to live through the night, for in it they find peace and comfort 😢
Why, I ask why, why has light become so terrifying and darkness become more comforting that the people find solace in it?
I came to understand why people find comfort in darkness is because they are afraid of selves afraid of what they have become, darkness does not challenge but rather allows you to wallow in your misery and regret, killing and draining you where no one will correct you or remind you, that you are not good enough, darkness gives you the room to accept who and what you have become, and there and then it echoes is better to die and live in peace than to be alive and live in misery.
Why will one think of death as the only option or think of death as the only solution to peace, is living not joyful, is life not great to live, why will one wish to leave all, family, friends everything, and settle for death?
I came to understand that, the most reason why one tends to choose death over life or loves to behold the warmth of darkness instead of light, is the feeling of emptiness and internal failure even after a significant measure, of material and social success, is a direct result of failure to discover purpose in life and a reason of being, when one loses his peace, joy all that's left or remain is pain, and regret. When a man reaches a stage of emptiness, where nothing else again matters life itself has no meaning, then it's only a test of time before destruction befalls such a person
Even the rich are depressed and frustrated beholding the enticement of the dark, and many try to drink themselves up, to them is the only way to find peace within, why, after so much wealth and achievement yet feel lonely, his greatest friends are alcohol and nights.
If money, riches cant give fulfillment or perfect peace then what can?
-
 @ e3ba5e1a:5e433365
2024-12-15 08:13:57
@ e3ba5e1a:5e433365
2024-12-15 08:13:57The world we live in today is inflationary. Through the constant increase in the money supply by governments around the world, the purchasing power of any dollars (or other government money) sitting in your wallet or bank account will go down over time. To simplify massively, this leaves people with three choices:
- Keep your money in fiat currencies and earn a bit of interest. You’ll still lose purchasing power over time, because inflation virtually always beats interest, but you’ll lose it more slowly.
- Try to beat inflation by investing in the stock market and other risk-on investments.
- Recognize that the game is slanted against you, don’t bother saving or investing, and spend all your money today.
(Side note: if you’re reading this and screaming at your screen that there’s a much better option than any of these, I’ll get there, don’t worry.)
High living and melting ice cubes
Option 3 is what we’d call “high time preference.” It means you value the consumption you can have today over the potential savings for the future. In an inflationary environment, this is unfortunately a very logical stance to take. Your money is worth more today than it will ever be later. May as well live it up while you can. Or as Milton Friedman put it, engage in high living.
But let’s ignore that option for the moment, and pursue some kind of low time preference approach. Despite the downsides, we want to hold onto our wealth for the future. The first option, saving in fiat, would work with things like checking accounts, savings accounts, Certificates of Deposit (CDs), government bonds, and perhaps corporate bonds from highly rated companies. There’s little to no risk in those of losing your original balance or the interest (thanks to FDIC protection, a horrible concept I may dive into another time). And the downside is also well understood: you’re still going to lose wealth over time.
Or, to quote James from InvestAnswers, you can hold onto some melting ice cubes. But with sufficient interest, they’ll melt a little bit slower.
The investment option
With that option sitting on the table, many people end up falling into the investment bucket. If they’re more risk-averse, it will probably be a blend of both risk-on stock investment and risk-off fiat investment. But ultimately, they’re left with some amount of money that they want to put into a risk-on investment. The only reason they’re doing that is on the hopes that between price movements and dividends, the value of their investment will grow faster than anything else they can choose.
You may be bothered by my phrasing. “The only reason.” Of course that’s the only reason! We only put money into investments in order to make more money. What other possible reason exists?
Well, the answer is that while we invest in order to make money, that’s not the only reason. That would be like saying I started a tech consulting company to make money. Yes, that’s a true reason. But the purpose of the company is to meet a need in the market: providing consulting services. Like every economic activity, starting a company has a dual purpose: making a profit, but by providing actual value.
So what actual value is generated for the world when I choose to invest in a stock? Let’s rewind to real investment, and then we’ll see how modern investment differs.
Michael (Midas) Mulligan
Let’s talk about a fictional character, Michael Mulligan, aka Midas. In Atlas Shrugged, he’s the greatest banker in the country. He created a small fortune for himself. Then, using that money, he very selectively invested in the most promising ventures. He put his own wealth on the line because he believed each of those ventures had a high likelihood to succeed.
He wasn’t some idiot who jumps on his CNBC show to spout nonsense about which stocks will go up and down. He wasn’t a venture capitalist who took money from others and put it into the highest-volatility companies hoping that one of them would 100x and cover the massive losses on the others. He wasn’t a hedge fund manager who bets everything on financial instruments so complex he can’t understand them, knowing that if it crumbles, the US government will bail him out.
And he wasn’t a normal person sitting in his house, staring at candlestick charts, hoping he can outsmart every other person staring at those same charts by buying in and selling out before everyone else.
No. Midas Mulligan represented the true gift, skill, art, and value of real investment. In the story, we find out that he was the investor who got Hank Rearden off the ground. Hank Rearden uses that investment to start a steel empire that drives the country, and ultimately that powers his ability to invest huge amounts of his new wealth into research into an even better metal that has the promise to reshape the world.
That’s what investment is. And that’s why investment has such a high reward associated with it. It’s a massive gamble that may produce untold value for society. The effort necessary to determine the right investments is high. It’s only right that Midas Mulligan be well compensated for his work. And by compensating him well, he’ll have even more money in the future to invest in future projects, creating a positive feedback cycle of innovation and improvements.
Michael (Crappy Investor) Snoyman
I am not Midas Mulligan. I don’t have the gift to choose the winners in newly emerging markets. I can’t sit down with entrepreneurs and guide them to the best way to make their ideas thrive. And I certainly don’t have the money available to make such massive investments, much less the psychological profile to handle taking huge risks with my money like that.
I’m a low time preference individual by my upbringing, plus I am very risk-averse. I spent most of my adult life putting money into either the house I live in or into risk-off assets. I discuss this background more in a blog post on my current investment patterns. During the COVID-19 money printing, I got spooked about this, realizing that the melting ice cubes were melting far faster than I had ever anticipated. It shocked me out of my risk-averse nature, realizing that if I didn’t take a more risky stance with my money, ultimately I’d lose it all.
So like so many others, I diversified. I put money into stock indices. I realized the stock market was risky, so I diversified further. I put money into various cryptocurrencies too. I learned to read candlestick charts. I made some money. I felt pretty good.
I started feeling more confident overall, and started trying to predict the market. I fixated on this. I was nervous all the time, because my entire wealth was on the line constantly.
And it gets even worse. In economics, we have the concept of an opportunity cost. If I invest in company ABC and it goes up 35% in a month, I’m a genius investor, right? Well, if company DEF went up 40% that month, I can just as easily kick myself for losing out on the better opportunity. In other words, once you’re in this system, it’s a constant rat race to keep finding the best possible returns, not simply being happy with keeping your purchasing power.
Was I making the world a better place? No, not at all. I was just another poor soul trying to do a better job of entering and exiting a trade than the next guy. It was little more than riding a casino.
And yes, I ultimately lost a massive amount of money through this.
Normal people shouldn’t invest
Which brings me to the title of this post. I don’t believe normal people should be subjected to this kind of investment. It’s an extra skill to learn. It’s extra life stress. It’s extra risk. And it doesn’t improve the world. You’re being rewarded—if you succeed at all—simply for guessing better than others.
(Someone out there will probably argue efficient markets and that having everyone trading stocks like this does in fact add some efficiencies to capital allocation. I’ll give you a grudging nod of agreement that this is somewhat true, but not sufficiently enough to justify the returns people anticipate from making “good” gambles.)
The only reason most people ever consider this is because they feel forced into it, otherwise they’ll simply be sitting on their melting ice cubes. But once they get into the game, between risk, stress, and time investment, they’re lives will often get worse.
One solution is to not be greedy. Invest in stock market indices, don’t pay attention to day-to-day price, and assume that the stock market will continue to go up over time, hopefully beating inflation. And if that’s the approach you’re taking, I can honestly say I think you’re doing better than most. But it’s not the solution I’ve landed on.
Option 4: deflation
The problem with all of our options is that they are built in a broken world. The fiat/inflationary world is a rigged game. You’re trying to walk up an escalator that’s going down. If you try hard enough, you’ll make progress. But the system is against you. This is inherent to the design. The inflation in our system is so that central planners have the undeserved ability to appropriate productive capacity in the economy to do whatever they want with it. They can use it to fund government welfare programs, perform scientific research, pay off their buddies, and fight wars. Whatever they want.
If you take away their ability to print money, your purchasing power will not go down over time. In fact, the opposite will happen. More people will produce more goods. Innovators will create technological breakthroughs that will create better, cheaper products. Your same amount of money will buy more in the future, not less. A low time preference individual will be rewarded. By setting aside money today, you’re allowing productive capacity today to be invested into building a stronger engine for tomorrow. And you’ll be rewarded by being able to claim a portion of that larger productive pie.
And to reiterate: in today’s inflationary world, if you defer consumption and let production build a better economy, you are punished with reduced purchasing power.
So after burying the lead so much, my option 4 is simple: Bitcoin. It’s not an act of greed, trying to grab the most quickly appreciating asset. It’s about putting my money into a system that properly rewards low time preference and saving. It’s admitting that I have no true skill or gift to the world through my investment capabilities. It’s recognizing that I care more about destressing my life and focusing on things I’m actually good at than trying to optimize an investment portfolio.
Can Bitcoin go to 0? Certainly, though year by year that likelihood is becoming far less likely. Can Bitcoin have major crashes in its price? Absolutely, but I’m saving for the long haul, not for a quick buck.
I’m hoping for a world where deflation takes over. Where normal people don’t need to add yet another stress and risk to their life, and saving money is the most natural, safest, and highest-reward activity we can all do.
Further reading
- Buying Bitcoin or selling dollars? (my own blog post)
- My Path to Bitcoin (also my own blog post)
- The Bullish Case for Bitcoin (great explanation of the monetization of Bitcoin)
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 4ba8e86d:89d32de4
2024-10-15 01:06:52
@ 4ba8e86d:89d32de4
2024-10-15 01:06:52Ele usa uma abordagem única de virtualização baseada em compartimentos para isolar diferentes aplicativos e atividades em máquinas virtuais independentes. Isso significa que cada atividade, desde navegar na web , é isolada em seu próprio compartimento virtual, fornecendo um ambiente altamente seguro.
O Qubes OS foi criado em 2010 pelo pesquisador de segurança polonês Joanna Rutkowska. Ela se inspirou na ideia de "security by compartmentalization" (segurança por compartimentalização) e começou a desenvolver um sistema operacional baseado em compartimentos para atender às suas necessidades de segurança. Em 2012, a primeira versão do Qubes OS foi lançada e desde então tem evoluído continuamente.
O Qubes OS usa o conceito de máquinas virtuais (VMs) para criar uma abordagem de segurança baseada em compartimentos. Ele executa diferentes aplicativos e atividades em máquinas virtuais independentes, cada uma das quais é isolada do resto do sistema. Cada VM é atribuída a uma categoria de segurança e é configurada de acordo com as políticas de segurança necessárias para aquela categoria. Por exemplo, uma VM de navegação na web pode ser configurada com políticas de segurança para limitar o acesso à rede e restringir o acesso aos arquivos do sistema.
O Qubes OS usa um recurso chamado "dom0" para gerenciar as VMs. O dom0 é uma VM privilegiada que é responsável por gerenciar as outras VMs e dispositivos de hardware do sistema. Ele é isolado do resto do sistema e é executado com permissões limitadas para reduzir o risco de ataques de software malicioso.
O Qubes OS resolve vários problemas de segurança, especialmente para usuários que precisam lidar com informações confidenciais ou sensíveis. Alguns dos principais problemas que o Qubes OS resolve são:
-
Ataques de malware: A abordagem baseada em compartimentos do Qubes OS reduz significativamente o risco de ataques de malware. Se um aplicativo ou atividade for comprometido, o dano será limitado ao compartimento virtual onde está sendo executado.
-
Rastreamento de atividades: O Qubes OS protege a privacidade do usuário ao evitar que atividades diferentes sejam correlacionadas. Cada atividade é executada em um compartimento virtual separado, impedindo que os dados de atividade sejam compartilhados entre os aplicativos.
-
Proteção de dados confidenciais: O Qubes OS isola diferentes tipos de dados em VMs separadas, proporcionando um alto nível de proteção aos dados confidenciais. As VMs são configuradas com políticas de segurança adequadas para cada tipo de dados, protegendo-os contra acesso não autorizado.
-
Proteção contra ataques de rede: O Qubes OS utiliza técnicas de isolamento de rede para proteger contra ataques de rede, como ataques de escuta, interceptação de tráfego ou ataques de injeção de pacotes. Cada VM pode ter uma interface de rede dedicada e isolada, garantindo que o tráfego de rede seja controlado e limitado a apenas o que é necessário para cada VM.
-
Compartilhamento seguro de arquivos: O Qubes OS oferece a opção de compartilhar arquivos entre VMs de forma segura, sem comprometer a segurança do sistema. Isso é feito por meio do recurso de "transferência de arquivos segura", que permite que os usuários movam arquivos entre as VMs com segurança e sem o risco de contaminação por malware.
-
Proteção de hardware: O Qubes OS também fornece recursos de segurança de hardware, como a possibilidade de bloquear portas USB ou desativar o microfone ou a webcam quando não estão em uso. Isso ajuda a evitar a exploração de vulnerabilidades de hardware e aumenta a segurança do sistema como um todo.
-
Sistema operacional confiável: O Qubes OS é baseado em uma distribuição Linux confiável e de código aberto, o que significa que os usuários podem verificar o código fonte do sistema operacional e garantir que não haja backdoors ou vulnerabilidades ocultas.
https://github.com/QubesOS
https://www.qubes-os.org/
https://www.youtube.com/live/DpnSFhWEEXk?feature=share
-
-
 @ 3f0702fa:66db56f1
2024-12-15 08:09:43
@ 3f0702fa:66db56f1
2024-12-15 08:09:43Образовательная система Кургана в 2040 году пережила масштабную трансформацию, предлагая студентам комфортные условия обучения, мощную поддержку одаренных учеников и передовые технологии, что подтверждается высокими достижениями курганских учащихся.
Ключевым изменением стало внедрение персонализированных образовательных траекторий, разработанных на основе анализа интересов и способностей каждого ученика. Учебные заведения оснащены интерактивными классами, лабораториями с VR/AR-оборудованием и современными коворкинг-зонами, создающими комфортную среду для обучения и творчества.
Особое внимание уделяется поддержке одаренных учеников, для которых разработаны специальные программы и гранты на участие в научных исследованиях и международных конкурсах. Развитая система наставничества позволяет молодым талантам раскрыть свой потенциал и реализовать самые амбициозные проекты.
Результаты обучения говорят сами за себя: курганские студенты занимают лидирующие позиции на национальных и международных олимпиадах, а выпускники востребованы в лучших компаниях страны и мира.
Курганская образовательная система стала примером для других регионов, демонстрируя, как можно сочетать современные технологии с индивидуальным подходом к обучению для формирования будущей интеллектуальной элиты.
Мы продолжим следить за достижениями курганских студентов и педагогов и рассказывать вам о новых инициативах в сфере образования. Следите за нашими публикациями.
45news
Курган2040
-
 @ 09fbf8f3:fa3d60f0
2024-10-14 15:42:04
@ 09fbf8f3:fa3d60f0
2024-10-14 15:42:04我搭建了一个网盘,国内访问速度还可以。
我买的是每月5刀的无限存储计划,只要还在使用,每天会增加1G的存储。(需要通过面板重启后赠送。)
官网
-
不要使用VPN注册,会提示欺诈风险,有可能会砍单。
-
 @ 3f0702fa:66db56f1
2024-12-15 08:04:32
@ 3f0702fa:66db56f1
2024-12-15 08:04:32Курганцы сегодня получили в распоряжение полностью обновленную систему общественного транспорта, знаменующую собой новую эру в передвижении по городу. В результате масштабной модернизации на улицы вышли современные беспилотные электробусы и аэротакси.
Теперь привычные маршруты общественного транспорта обслуживают комфортабельные беспилотные электробусы с увеличенной вместимостью, оборудованные Wi-Fi, USB-портами и климат-контролем. Маршруты оптимизированы на основе анализа трафика в режиме реального времени, что обеспечивает быструю и удобную перевозку пассажиров.
Кроме того, для быстрого перемещения по городу и пригородам стали доступны аэротакси – компактные беспилотные летательные аппараты, способные доставлять пассажиров в любую точку города за считанные минуты. Заказ такси осуществляется через удобное мобильное приложение.
Обновление общественного транспорта снизило нагрузку на дороги, повысило комфорт и безопасность пассажиров и значительно уменьшило негативное воздействие на окружающую среду.
Мы продолжим следить за развитием транспортной инфраструктуры Кургана и сообщать вам о новых изменениях. Следите за нашими публикациями.
45news
Курган2040
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 3f0702fa:66db56f1
2024-12-15 08:02:05
@ 3f0702fa:66db56f1
2024-12-15 08:02:05Сегодня Курган официально открыл два новых современных аэропорта, знаменующих собой прорыв в транспортной инфраструктуре региона. Эти объекты не только расширяют возможности авиасообщения, но и внедряют передовые технологии будущего.
Примечательно, что на всех рейсах пассажиров кормят, обеспечивая высокий уровень сервиса. Кроме того, в аэропортах установлены бесплатные куллеры с водой, что делает ожидание рейса более комфортным. Эти изменения не только сокращают путешествия, но и делают их более приятными, включая стремление Кургана к современному уровню обслуживания в авиационной сфере.
Новые аэропорты
“Курган-Северный” для гражданских рейсов и “Курган-Восточный” для грузовых и специальных перевозок, построены с учетом последних достижений в области авиации и логистики. Оба комплекса оснащены автоматизированными системами управления воздушным движением, взлетно-посадочными полосами для приема всех типов современных самолетов, включая беспилотные летательные аппараты, а также используют возобновляемые источники энергии.
“Курган-Северный” предлагает пассажирам комфортабельные терминалы с полным комплексом услуг, включая экспресс-регистрацию, автоматизированный багажный сервис и зоны отдыха. Здесь также функционирует система персонального сопровождения с помощью голосовых ассистентов и AR-навигации.
“Курган-Восточный” оборудован современными логистическими центрами и роботизированными погрузочно-разгрузочными комплексами, обеспечивающими высокую скорость и точность обработки грузов.
Открытие этих аэропортов значительно повышает транспортную доступность Курганской области, способствует развитию туризма и бизнеса, а также укрепляет позиции региона как важного логистического узла страны.
Мы продолжим следить за развитием транспортной инфраструктуры Кургана и сообщать вам о новых достижениях. Следите за нашими публикациями.
45news #Курган2040
https://psv4.userapi.com/s/v1/d/KKViIRBPO0Innk4DEkNo-y4lZgvf2oK5hRz3qlcmViBzuuH-c_lMdI-sXBNsnZk7XkyyViNqUsu0msw_Bh_jobjqbLoI8j7mSPW9bQK6eilX4KD0BPZE0g/Untitled.mp4
-
 @ 09fbf8f3:fa3d60f0
2024-10-14 15:41:08
@ 09fbf8f3:fa3d60f0
2024-10-14 15:41:08既然说是一款Web版的软件,也就是对应客户端版而开发的,如果你的歌曲都保存在NAS上,那么这款软件就非常适合你;如果你的歌曲都保存在电脑本地,那么可以直接使用客户端版的同名软件。
01
MusicTagWeb的特色 这款软件刚开始在 Github 上开源的时候,笔者就注意到了,不过当时功能还刚有个雏形、不太完善,就没有推荐给大家。经过开发者一段时间的辛勤付出,现在看来功能和管理能力基本上都已经完成了,具体的功能点和特性如下:
支持批量自动修改音乐标签 支持音乐指纹识别,即使没有元数据也可以识别音乐 支持整理音乐文件,按艺术家,专辑分组 支持文件排序,按照文件名,文件大小,更新时间排序 支持plex专辑类型,新增配置显示/隐藏字段 修复不同类型音频文件的专辑类型 新增歌曲语言整理文件 优化自动打标签匹配算法 新增智能刮削标签源,集成多个平台的标签源,按匹配度排序 支持繁体匹配,新增消息中心展示自动刮削不匹配的数据 支持保存专辑封面文件,支持自定义上传专辑封面 简单适配H5端,支持手机端访问 支持wma,wmv格式, 修复自动刮削报错停止的问题 音轨号,光盘号 格式优化,优化匹配规则 对新增的音乐文件后台自动刮削,无感知刮削。修复.ape文件读取报错的问题 新增自定义层数的整理文件,新增根据刮削状态排序,修复大写的音乐后缀名识别不到 新增数据库挂载映射
其实上面没有提到,这款软件支持从6个音乐平台刮削歌曲信息,安全起见,具体是哪6个平台笔者就不说了,感兴趣的朋友可以接着往下看,自己跑起来就知道了。
02
安装MusicTagWeb MusicTagWeb目前仅支持Docker部署,在你的NAS上,可以使用Docker和Docker Compose两种方式来部署,任选一种即可。
1、Docker方式
docker run -d \ --restart=unless-stopped \ -p 8001:8001 \ -v /path/to/your/music:/app/media \ -v /path/to/your/config:/app/data \ xhongc/music_tag_web:latest2、Docker Compose方式
version: '3' services: music-tag: image: xhongc/music_tag_web:latest container_name: music-tag-web restart: unless-stopped ports: - "8001:8001" volumes: - /path/to/your/music:/app/media:rw - /path/to/your/config:/app/data以上两种方式中,/path/to/your/music改成你的音乐文件夹路径,/path/to/your/config改为MusicTagWeb的配置文件路径。
03
使用MusicTagWeb 使用Docker启动MusicTagWeb后,在浏览器中使用IP+端口号打开系统,然后输入用户名和密码即可登录,默认的用户名和密码均为admin,建议登录后进行修改。
1、登录系统 Username 和 Password 均输入admin,邀请码不需要填。
2、首页主屏
主屏分成两栏(实际是三栏,还有一栏在操作的时候会显示出来),左边是音乐文件目录,右边默认是一张占位图片。
3、单个编辑/刮削歌曲信息
选择一个歌曲文件,这时候界面就是三屏了,右侧一栏变成两栏,分别显示歌曲元数据和音源搜索结果。搜索和设置完成后,点击保存信息按钮,即可完成对歌曲元数据的编辑。
最后
详细教程去官网: https://xiers-organization.gitbook.io/music-tag-web V1版够用了,V2收费的,68一个激活码。
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 460c25e6:ef85065c
2024-10-10 13:22:06
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - Super Clients: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
-
Clients: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
-
Mini Clients: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
-
Micro Clients: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
Super Clients - amethyst - nostrudel - coracle
Clients - damus - twitter - primal - twitter - snort - twitter - gossip - twitter - lume - twitter - ditto - twitter - rabbit - twitter - freefrom - twitter - nos - twitter - flycat - twitter - straylight - twitter - nostter - twitter - iris - twitter - nostur - twitter - nostrmo - twitter - yana - twitter - openvibe - twitter - freerse - twitter - 0xchat - chats - cornychat - chats - coop - chats - nostrchat - chats - blowater - chats - habla - blogs - yakihonne - blogs - highlighter - blogs - blogstack - blogs - stemstr - music - wavlake - music - fountain - podcasts - zap.stream - live streaming - shopstr - marketplace - plebeian.market - marketplace - flotilla - communities - satellite - communities - zapddit - communities - nostr.kiwi - communities - hivetalk - video calls - flare - long-form videos - nostrnests - audio spaces - wherostr - location - yondar - location - stacker.news - news - flockstr - events - nostrocket - issue tracker - docstr - docs - satshoot - freelance - wikifreedia - wiki - formstr - forms - chesstr - chess - memestr - meme feed - npub.cash - wallet - npub.pro - websites - gitworkshop - dev tools - onosendai - metaverse - degmods - games - turdsoup - prompts
Mini Clients - amber - signer - alby - signer - nos2x - signer - nsec.app - signer - keys.band - signer - nostrame - signer - nokakoi - anon - zap.cooking - recipes - anonostr - anon - getwired - anon - lowent - anon - creatr - exclusive content - lightning.video - exclusive content - zaplinks - slides - listr - lists - zap.store - app store - badges.page - badges - oddbean - news - dtan - torrents - nosta - user pages - pinstr - pinterest - pollerama - polls - swarmstr - trending - nostrapp - apps manager - noogle - search - ostrich.work - job postings - emojito - emoji manager - nostree - links - citrine - local relay - joinstr - coinjoins - heya - crowdfunding - zapplepay - zaps - nosbin - clipboard - shipyard - scheduler - tunestr - live streams - filestr - files - nostrcheck.me - media hosting - sheetstr - spreadsheets - crafters - curriculum vitae
Micro Clients - w3 - url shortener - nosdrive - backups - zaplife - zaps dashboard - zapper.fun - payments - nostrends - trends - zephyr - trends - wavman - music player - nostrrr - relay info - nosdump - relay info - notestack - blogs - nostr.build - media hosting - nostr.watch - relay info - nostr hours - use reports - lazereyes - vision prescriptions - snakestr - games - deletestr - deletion requests - 2048str - games - nostrqr - qr generator - notanostrclient - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more Mini and Micro clients.
-
-
 @ 592295cf:413a0db9
2024-08-25 09:17:54
@ 592295cf:413a0db9
2024-08-25 09:17:54A Ux designer has arrived on Nostr. I thought run away while you can. He could get rich, if there was a little economy.
Klout, do you remember that service, which took data from Twitter and made a ~~ WoT~~.
From a note of chip, I understood one thing:
Bitcoin is your "sovereign" currency. Nostr is just third party protocol. If you have a service you can use Nostr to face your customers. "Sovereign" people offer services. They can be bitcoiners or not. So at this stage Nostr is a layer 3 Bitcoin.
So to grow the enveiroment it must be attractive. Let's paraphrase: the protocol is agnostic, the people are fundamentalist Catholics.
So when an atheist person arrives he says ah ok, how do I silence these people and use the protocol If a Protestant Catholic arrives he is laughed at or ignored or at most converted.
I had a disagreement with Dergigi, in the end he won, but he is not right... (True)

Post more notes, zap more, follow 1000 people update FAQ to the nth degree. We are in the desert of the Tartars and the enemy is coming and there are those who say every day we must be ready, sooner or later, it will happen, ah ok. Everything must be perfect. Push harder. This leads to exhaustion.
New Grant from Opensat to Victor of Amethyst, totally deserved, pushed the envelope. If you are a grapheneos user download Amethyst. It's not just Amethyst it's also orbot, citrine, amber, zap store or obtainium or f-droid.
GitCitadel has raised its first fund I wonder if it was just a test on geyser, I wonder if it is the right project to do on nostrocket, but I think Opensat grant for nostrocket makes it irreconcilable. This opens a pandora's box, as always. We are silent as fish.
I tried not to answer some questions even in one case I knew the answer, I apologize, Nostr is much older than me, so it's okay not to answer sometimes. Tomorrow begins nostRiga, The last unconference of Nostr.
(First day) The morning was so-so, in the evening the situation improved a little. In the evening I played a bit with Nostr and it broke The second day good in the morning bad in the evening. I saw little of the backstage maybe only two panels, Will by Damus, and P2Phash on Nostr.
I don't follow anyone anymore, I did a little bit of a unfollow. I saw that two users had 200 followers in common, and I said to myself ah ok what is this thing, I have to understand how they do it there is something that doesn't work, let's try to be a little more distant.
It's weird, too much reliance on following, you have to go and look, not be stationary.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 592295cf:413a0db9
2024-08-17 07:36:43
@ 592295cf:413a0db9
2024-08-17 07:36:43Week 12-08 a suitable protocol
The knots come to a head, some of you have gray hair, you get older.
Tkinter is better than ws://, more secure, but has limitations, unless you know how to use figma and do some magic. The project of Nabismo.
Maybe Nostr doesn't work for me.
Aspirin moment Nip-17, works with nip-44 and nip-59. Someone said they made the groups encrypted with nip-17. I tried and succeeded, now you can DM me, don't do it. I had sent the link to a conversation of nip-87 closed groups. There's JeffG doing something with MLS. Then there's keychat.io which uses signal Nostr Bitcoin ecash and that's it... But in dart. It's a bit like the Matrix analogue for Nostr.
Final controversy not all nips are mandatory.
Build the foundation. You can't think about selling the house
Yakihonne has a countdown. What can a desktop app be. Community Lists, Nip-29
A birthday on Nostr, no that's not possible, they're all cypherpunks. 🎉🎉 (Except me)
There is a different attitude from Nostr when updates are released compared to Bluesky, everyone there is still enthusiastic, on Nostr ah ok but this is missing oh but this is missing or but support this other one, or but * zap, wait a minute, keep calm 🙇♂️, I'm the first to do this. (The revolt of the developers)
Deletetion: Client that have relay paired can do delete, more intelligently, Perhaps you can think of a delete.nrelay subdomain as a filter. This id is deleted. Be careful what you don't want to do. Maybe a session with a psychologist is better, because then you find yourself doing what you said you didn't want to do.
Does it make sense to follow someone on Bluesky? In my opinion no, or better yet yes. There are several algorithms on Bluesky, which do their job well. In the end it's just a matter of arranging them better on the screen. Yes you can have lists to save someone, but then you read everything, so lists with algorithm seems like a next feature. this way they can keep the following small, almost minimal, because there are algorithms that work for the user. People will start writing for SEO algorithm and AI and other things, which tech gurus really like and so on. The fact that it is almost exclusively an app will greatly facilitate this trend, there will be almost no need for moderation, and you can get it all in just a few apps. (Great)
Oh yegorpetrov has abandoned. Pegorpetrov said that he is coming back 😌 It might be an invention but I'm a little heartened by it.
Bankify, a new wallet of super testnet, only for crush testers.
You can't stream on zap stream without reach, maybe it's better audio space. Contact someone maybe an influencer or Nostr elite or whatever. Open Source Justice Foundation streaming
Designer, I wanted to propose comment on wikifreedia nielliesmons article and follow #nostrdesign, but too many answers for today. NVK note is ~~mainstream~~
I think I'm not suited to Nostr.
Nostr-ava bike file geo tag sharing. (NIP-113) Sebastix doesn't respond, I must have done something bad to him, or maybe I'm stressing him too much. Finally he replied 🤙. In the end maybe, I have too much hype about this proposal and it's something I don't know maybe, but maybe if they were already doing something with geo tags it's better to say so.
Another birthday, less cypher more punk 😌
Usdt on Nostr, there must be some error. (freeform app)
USDT on tron is like Money. (Bitcoiner not really)
Privacy issue, deletion motion, or deletion request, go go.
Nip29 hype, i don't have hype at all. I'm tired of words, I record a podcast on Nostr. Let's see if I can do it, at least think it. (It's more of a workflow thing than actually something I would do)
- Create an npub (easy)
- Record the audio episode (I think I can do it). Terrible audio
- Loading on a Nostrhosting, if less than 10 MB it should go smoothly.
- Publish the video or audio of the episode on some Nostr client, perhaps using blastr relay 😞.
- Do the nostree link, by putting the episode, and also the npub.pro and put the URL on café-society. 6) Publish all these links on the Main profile, saying that, made a podcast about Nostr in Nostr of nostr. 😂
I thought a client could have poll, form, spreadsheet, collaboration document. It's the kind of otherstuff we want to see. Something that goes beyond a normal feed.
Emoj on bluesky, Eventually also zap 🥜 link emoj Blue
Eventually there will be a developer revolt And they will only do a social network in their downtime, they will call it Nostr.
There is a storm, Nostr does not work in 4g with two bars. Or now 4G is gone too.
Yakihonne Smart widgets, something to try on the weekend.
-
 @ 3f0702fa:66db56f1
2024-12-15 07:56:27
@ 3f0702fa:66db56f1
2024-12-15 07:56:27Курганская область сегодня – это не просто аграрный регион, но и процветающий туристический центр, привлекающий путешественников со всего мира. Регион совершил впечатляющий прорыв в развитии туристической отрасли, благодаря инновационному подходу, инвестициям и грамотной стратегии продвижения.
Раньше Курганская область оставалась в тени более популярных туристических направлений, но сегодня ситуация кардинально изменилась.
Инфраструктура нового поколения
По всей области появились современные эко-отели и комфортабельные глэмпинги, идеально вписанные в окружающую природу. Регион интегрирован в национальную сеть скоростных магистралей, а региональный аэропорт принимает рейсы из многих крупных городов России и зарубежья. Развита сеть внутреннего общественного транспорта, включая беспилотные автобусы и электромобили. Мультиязычные туристические порталы и мобильные приложения с дополненной реальностью помогают гостям легко ориентироваться и находить интересные места.
Уникальные туристические продукты
Культурно-исторический комплекс “Курганская крепость” стал одним из главных магнитов для туристов, предлагая интерактивные программы и ремесленные мастер-классы. Развита сеть эко-троп и кемпингов, предлагаются туры на байдарках и велосипедах. Популярен и агротуризм, где гости могут познакомиться с сельской жизнью. В регионе регулярно проводятся фестивали, выставки, концерты. Курганские музеи и картинные галереи предлагают уникальные экспозиции, рассказывающие об истории и культуре региона. Курганские санатории и лечебницы предлагают современные программы оздоровления, а также, благодаря близости космодрома “Восточный”, развит космический туризм.
Инновационные технологии на службе туризма
Туристы могут использовать персональных голосовых ассистентов и AR-приложения для получения информации, бронирования экскурсий и заказа билетов. Технологии VR и AR позволяют гостям предварительно “посетить” интересующие их места. Интерактивные карты с дополненной реальностью помогают легко ориентироваться на местности.
Партнерство и продвижение
Региональные власти активно сотрудничают с российскими и международными турфирмами, предлагая привлекательные туры. Курганская область активно продвигает свой туристический потенциал в социальных сетях и участвует в международных туристических выставках.
Мы продолжим следить за развитием туристической индустрии в Курганской области и сообщать вам о новых возможностях для путешественников. Следите за нашими публикациями.
45news
Курган2040
-
 @ 592295cf:413a0db9
2024-08-10 09:24:14
@ 592295cf:413a0db9
2024-08-10 09:24:14Week on Nostr 05-08
List of site for nostriches https://zaplinks.lol/
Fiatjaf web components
Welcome bear market 🧟♂️ fear, angry, build It's fine meme
I mutated one on stackernews. Basically I have notifications on Nostr page But someone keeps spamming every single thing, from his point of view it's a shared bookmark, but do it on your site. Maybe it's the heat...
On bluesky they eliminated a "for you" feed, now there is Discovery, not your feed, not your choice. There's actually a label that says my feeds, they're yours... Designed for you is more appropriate.
Mutiny lightning, "get the fuck on board". 😔
You lose your Money, ok
I don't know much about programming languages, but it seems like a jungle of scams
The purple pill help the Orange pill go down, maybe it was wrong. For now it's more people passing pills I have the orange give me the purple, I have the purple give me the orange. 😅
If you don't want no corn content you can go to mastodon and bluesky or whatever.
I thought nostr:relay might be a good solution to be a little more like a mint. It was deprecated, then the Nip-73 was added, rss feed and other devilry.
If you don't like what you see, change the app, this one will perhaps clear your following list and you'll start again from scratch. Not all things come to harm.
Why not Building agregore on Nostr, Nostr pear fedimint cashu mesh and local first. It doesn't seem like a simple application to make, from a local-first perspective, I solve a problem, but it's not a small problem to solve, Sync, database management, database schema, authentication, put everything together, instead I need this to solve this problem. It seems strange.
Aspie96 is making a client of ours, there was a lot of talk about how to increase content not related to bitcoin and things like that, there was one who was anti-bitcoin. I thought: Bitcoin is just a tool. Even guns are just a tool. I hate guns, I hate Bitcoin. It will be difficult, if you know any npub that hates Bitcoin comment below, thanks.
Trying not to use nostter for a while. It has glitches when loading threads and even with zap, I zapped myself even though I was clicking on the post I was replying to.
Voyage separates follow to topic in a new version.
People start arguing, it's allowed, everyone wants to be right, that's not the definition of social 👾.
Monitors watch-only bitcoin wallets https://github.com/sommerfelddev/sentrum
I noticed on Openvibe that in the trending timeline Nostr's notes have more interactions than responses. Maybe it was just that today Fiatjaf was doing universal polls 😅.
Step away from your favorite app, for a week if you can. Detox.
Oh Our founding, rain of money https://github.com/theborakompanioni/nostr-spring-boot-starte https://opensats.org/blog/nostr-grants-august-2024#seer
I'm happy for Vic and Sepher Nostroot exists 😅, note from some time ago. (I can't find it)
Perhaps the list of grant applications should be published, no one wants to open Pandora's box. 🙇♂️
Nostrasia 2.0 the Japanese community is a bit at a loss, they are trying to relaunch themselves 🤙, even if I'm seeing less enthusiasm, I'm following less.
I think a month has passed since I said this sentence, every day it was better but the next day something happened that you said maybe 6 months is too long. nostr:nevent1qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7te3xsczue3h0ghxjme0qyw8wumn8ghj7mn0wd68ytnxwfskxarpd35h5ety9ehx2ap0qythwumn8ghj7mn0wd68ytnnw3skkete9ehx2ap0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qpqf25td2xxgxfu80xpgg47cmfg2zkn6v803kefj3htjss5nvamfmgswf2kcs
Ho iniziato a seguire un po' local-first. https://docnode.dev/local-first I follow a podcast of the same name and dev tools.
When everyone thinks of Nostr they think of their favorite app and think that others see the same, but this is not the case.
I delete some gossip (photo)

Gossip is Nostr or Nostr is gossip.
Communities are difficult, they take time. I don't have this type of problem. People are fine on telegram and on simplex or any app. But maybe a Nostr project should be on Nostr?? Nip-29 can be interesting. Even if you start from scratch or almost. It's true that there are more apps, but this will perhaps only add to the confusion.
They are still talking about paid or non-paid relay, it's not a mature stage. Early stage.. I thought designers liked relays, that's not the case, I thought it was a place of experimentation, that's not the case. Bring more people. Last week I was talking about how I was jealous of bluesky who had an agenda for design, now it's also on Nostr, first hypernote article https://wikifreedia.xyz/hypernote-nip
I might say silly things, I'll go.
Hey Will remember to practice safe nsec always
nostr:nevent1qqsr6x8hduv8ta0g2da4aukrhzdtv6qcekyp5f9z9sxq6sd5peegnxgprpmhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygr4wku5l2q32tl99xjgn8feq22279pzwu25eezqxm2su2ken4wzvuf2ydnp
nostr:nevent1qqspsm343talkkjnyf3ah0zwy727cwd7phw3xnz49q59q5cfw4uhyngpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgcwaehxw309aex2mrp0yhxummnwa5x2un99e3k7mgzyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2j7zajz
Use nsec.app, 😅 Share bunker (smart people will know how to do it)
-
 @ 1bda7e1f:bb97c4d9
2024-10-10 01:38:43
@ 1bda7e1f:bb97c4d9
2024-10-10 01:38:43Tldr
- I’m Rod
- I’m going down the Nostr rabbit hole
- I’m a startup founder, former listco CEO, NED, Bitcoin Miner, New Zealander, Dad
- I value community
- I was white-pilled by the free and interoperable internet and am ready to chip in
Nice to meet you
Today I am getting started creating a profile for my real self on Nostr. I am going to share what I learn.
Your average new Nostr user probably shouldn’t follow my lead here. The “main flow” onboarding for Nostr is becoming very smooth. Download Damus or Primal or Amethyst, then click “create account,” and be up and running in seconds.
For me though, I want to go off-road. I think Nostr is a fundamental reimagining of the internet where power resides with users rather than platforms. I want to work on it and with it. I think it has a chance to bring back the internet of my youth where people could be "internet" users rather than "corporate internet brandname" users.
So I plan to go on a tour of the weird and wonderful side quests that Nostr can offer—in order to really have some fun with it and write about it as I go.
I hope the writing will add some value.
Nostr is being driven forward by passionate and prolific devs who are creating wild new proofs of concept everywhere. These primatives are amazing, and also for a regular pleb, sometimes inaccessible and confusing.
I think I can add value by highlighting some of the “why” of fun and useful Nostr rabbit holes. If I can document what I do as a user, what I managed to make work, how I made it work, and why it was important, then I may encourage others to join and have a go.
Not a how to guide. Rather a “what I did and how and why” journal of sorts.
I can do a better intro than that
My name is Rod, and I am non-technical startup founder, former listco CEO, and company director.
Foremost in recent times, I am the founder of Jayride Group, which is a travel e-commerce marketplace that helps travelers to find and book rides around the world. I launched Jayride in January 2012 and grew it for six years to public listing on the Australian Securities Exchange (ASX:JAY) in January 2018, then ran it as a public company for six more years before stepping back from Managing Director to the role of Non-Exec Director around August 2023.
I am also a Non-Exec Director of Fishburners, Australia’s foremost technology startup founder community (and co-working space). Fishburners helps startup founders to get started. I was an early Fishburners resident, and being involved in that community was instrumental to my early startup success.
I have been flirting with Bitcoin mining since 697532 or thereabouts with 3.5Ph of hash rate, which was briefly about 1/100,000th of the network.
I’m a Nostr pleb, happily married, rational optimist, expat New Zealander living in Australia, and dad.
I will post about all of these things too.
Two key lessons led me to Nostr today
I learned the importance of community from Fishburners.
In the early days of a startup, you don’t know what you don’t know. Community helps you to learn those things simply by being amongst it. And when you find something specific which you know you need to know, community is there for you then too.
The more time I spend on Nostr, the more aware I am that this is a an awesome community of builders with the potential to add some real and lasting value to the internet and world. I want to do whatever small things I can to help and be part of that.
I learned the importance of resilience from the world's reaction to COVID.
Travel businesses and co-working businesses were smashed by lockdowns. To chart the path through it all, it became my full-time job to study the disaster of fake narratives and regulatory capture and bad policy responses, in order to try to navigate it. I learned that if you pay attention long enough then you can see behind the curtain–and it’s not a good look.
On Nostr, I find myself gradually returning to a rationally optimistic outlook. No amount of propaganda and greed and bureaucracy will ever be as fast and powerful and resilient as a free and interoperable internet.
We can build systems which leverage these strengths. If built, these systems will naturally outcompete and win on their merits, because they will be faster, freer, more powerful marketplaces for ideas and capital, more resistant to capture, and more resilient to external shocks.
Better systems means better aligned and fairer outcomes for everyone. These systems are a must-have and need to succeed. So I’m going to chip in.
I’m not sure exactly how yet!
But I’m up for it.
In summary
Hi. It’s nice to meet you all, and I hope to share something of value!
Because: - Nostr is becoming an incredible community of builders that will make its mark on the world, and - Nostr can become a true reimagining of the internet and contribute to a powerful, free and resilient world.
Up next
To start, I've learned a few things about setting up a new profile and I can share what I learned in future posts:
- Mining a branded vanity pubkey with Rana
- Setting up a self-custody lightning wallet to make zaps on Nostr with Phoenixd and Albyhub
- Setting up Nostr and lightning addresses at your own domain with Sveltekit and Vercel
Looking forward to it.
-
 @ 592295cf:413a0db9
2024-08-04 05:55:02
@ 592295cf:413a0db9
2024-08-04 05:55:02Nostter muted by kind
Will mute freefrom, hashtag fall
Venezuela riots, after the vote
I was thinking that having a Nostr conference every 6 months doesn't make sense, maybe it's better to focus on something else. If not it becomes a Tour Life. It doesn't increase adoption Produces tons of material It's good for networking It's not sustainable
Readable updates, how important they are. If it's just bugs and fixes it's better.
I hate Pam. As user It writes interesting stuff, but, doesnn't write in long form, because long form are more difficult, less reach and immediacy, and difficulties to share over in the feed,but not write a poem, sorry.
The thing about coracle is that I load the initial feed, but that gets printed, and it doesn't tell me if there are new notes coming in, as if it interrupts the flow, and it's always a fetch. I want to read the future, not always the past. RealTime feeds Like bluesky 🧞

Njump had problems, it keeps the cache and if the user changes something in their data it doesn't update it immediately. Fiatjaf was angry.
It's the month of NostRiga, we can move on to September without thinking about it. No
It's funny when you see a text in Japanese and inside read Nostr, I want to know what it says. He usually says Nostr is great. And the next note I drank too much 🤣
Today I thought that on the other side of the world it is February and that their February is 31 days. Pam said was sick. I see that hate is a virus 😅🙇♂️
I decided to publish stronpy when it's ready, maybe in 6 months. I've done the lineup, now I have to do the gantt 😅. Maybe I can post the gantt somewhere.
If it's not encrypted it's public. Amethyst draft 31000 and something like event
Nostr Is great but the amount of time Lost to the same thing because you don't know that exist Is remarkable. Nostr is a redundancy protocol
nostr:nevent1qqsqjqauc34k9k278x6cka5jyf3aq033y4pn5czwaff72l3rwum7llq7ela3x When they do that I can't stand them, then maybe it's a little different 😔😔 Zapper.fun ✅ Because you launch a project, example nostr.band but contain others 100 apps 😅 Nostr.band, nostrapp.link, zapper.fun, Nostr login, nsec.app, Npub.pro, Npub.pro also cli, Nostr universe/ knows as spring site
Even in Coracle it would be great to have a check on the note as root, because when you see the answers, perhaps the distance from another post, is so small, so perhaps a gray line for the mark of another note as root.
I listened to several minutes of plebchain radio episode on nostrnests. Language is an obstacle, but also an excellent justification. Last year I started recording a podcast episode, in which I talked about nostr bookmark update. I didn't even want to listen to it again 🤣.
I sent a video of an explanation of a zap it was 500 MByte of video for 4 minutes.
Nostr doesn't work. In practice, many apps have removed the possibility of logging in with the simple key, be it public or private, because especially the private one you don't want to copy paste in every single clients/apps, increasing the attack surface.
However, by removing this functionality and doing little onboarding, the matter is very difficult, but there is a certain belief that people who arrive at a Twitter like client get to know the network a little and then move on to videos or writing, or similar. But one can open a site by chance and see what it offers without knowing anything.
In the future there will only be one client, that of medical data...
Someone share this nostr:nevent1qqs24qzelpk8xjlk4dthr9tfkqwz8n58dlm04ezyvg9nuztud6jjfhc9mg04n I had in my bookmarks. I see dozen types of this self hosted manners. Maybe captains-log is for nostr-type, good.
-
 @ 4ba8e86d:89d32de4
2024-10-08 22:45:17
@ 4ba8e86d:89d32de4
2024-10-08 22:45:17Um gerenciador de senhas é um software que ajuda os usuários a armazenar e gerenciar senhas e outras informações de autenticação. Ele é projetado para criar senhas seguras e únicas para cada conta e armazená-las de maneira segura. O Birwaden permite que os usuários criem cofres seguros para armazenar suas senhas e outras informações de autenticação. Esses cofres são protegidos por criptografia AES de 256 bits, o que significa que as senhas armazenadas são mantidas seguras e protegidas contra acesso não autorizado.
A história do Bitwarden começa em 2017, quando o programador russo Vladimir Ivanov decidiu criar um gerenciador de senhas de código aberto. Ivanov tinha preocupações crescentes sobre a segurança de senhas na Internet, especialmente com a crescente incidência de hacks e vazamentos de dados. Ele queria criar uma solução segura e fácil para gerenciar senhas que pudesse ajudar as pessoas a proteger suas contas. Ivanov escolheu usar criptografia AES de 256 bits para proteger as senhas armazenadas no Bitwarden, pois é considerado um dos algoritmos de criptografia mais seguros disponíveis.
Um Gerenciador de Senhas é um software que ajuda a armazenar e gerenciar senhas e outras informações de autenticação. Ele é projetado para criar senhas seguras e únicas para cada conta e armazená-las de maneira segura. O usuário pode acessar suas senhas sempre que precisar, sem precisar se preocupar em lembrar de todas elas.
Um Gerenciador de Senhas resolve vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Um gerenciador de senhas também ajuda a simplificar o processo de login, economizando tempo e reduzindo a frustração.
Usar um Gerenciador de Senhas pode ajudar a proteger as contas do usuário e reduzir o risco de comprometimento de dados. Ele também simplifica o processo de login, tornando mais fácil para o usuário acessar suas contas em vários dispositivos.Além disso, um gerenciador de senhas pode ajudar a gerar senhas fortes e únicas, que são mais difíceis de serem quebradas por hackers.
Passo a passo instalação do aplicativo Bitwarden:
-
Baixe e instale o Bitwarden em seu dispositivo móvel https://play.google.com/store/apps/details?id=com.x8bit.bitwarden
-
Crie uma conta no Birwaden. O aplicativo permitirá que você crie uma conta segura usando uma senha forte e um endereço de e-mail válido.
-
Crie um cofre seguro no Bitwarden para armazenar suas senhas. O aplicativo permite que você crie vários cofres para diferentes categorias de senhas, como redes sociais, finanças, e-mail, entre outras.
-
Adicione suas senhas ao cofre seguro. O Bitwarden permite que você adicione senhas manualmente ou importe senhas de outros gerenciadores de senhas.
-
Use o Bitwarden para acessar suas senhas sempre que precisar. O aplicativo permite que você acesse suas senhas de forma rápida e segura, sem precisar se preocupar em lembrar de todas elas.
-
Utilize o gerador de senhas do Bitwarden para criar senhas fortes e únicas para cada conta. O aplicativo oferece uma ferramenta para gerar senhas aleatórias, garantindo que suas contas estejam protegidas contra hackers.
-
Aproveite outras funcionalidades do Bitwarden, como preenchimento automático de senhas e autenticação de dois fatores. O aplicativo pode ajudar a simplificar o processo de login e aumentar a segurança de suas contas online.
-
-
 @ 2fb77d26:c47a6ee1
2024-11-29 22:07:30
@ 2fb77d26:c47a6ee1
2024-11-29 22:07:30»Worte interessieren nur da, wo sie zu Taten führen«, notierte ich vor knapp 15 Jahren für einen meiner Texte. Gelten sollte diese Prämisse vor allem für Wahlversprechen. Doch die Geschichte zeigt, dass von den vollmundigen Zusicherungen eines Wahlkampfes nach Amtsantritt kaum etwas umgesetzt wird. Davon muss wohl auch in Bezug auf die US-Präsidentschaftswahl 2024 ausgegangen werden. Auch wenn viele immer noch auf eine »Trockenlegung des Sumpfes« hoffen. Ein Überblick.
Original mit Quellen (VÖ: 14.11.2024): https://www.regenauer.press/trump-reloaded
Unterhaltsam ist es bisweilen. Keine Frage. Ist ja auch Politainment. Fake. Eine Show. Eine ziemlich kostenintensive dazu. Und einer gewissen Schadenfreude kann man sich in der Tat kaum verwehren, betrachtet man die irrationalen Reaktionen, Nervenzusammenbrüche und infantilen Ausraster der Wahlverlierer – dem Lager, das in puncto Covid, Klimaschutz und Genderpolitik nie einen Hehl aus seinen totalitären Anwandlungen machte. Leider wird aus Spaß aber schnell bitterer ernst. So tötete ein psychisch labiler Mann aus Minnesota am Tag nach Donald Trumps Wahlsieg zuerst seine ehemalige Partnerin und deren Kind, dann seine Frau und den eigenen Sohn, und anschließend sich selbst. Während die Polizei bislang kein offizielles Tatmotiv kommuniziert, implizieren Social-Media-Beiträge des 46-jährigen Demokraten, dass seine Angst vor den Republikanern, beziehungsweise dem Einzug Trumps ins Weiße Haus, durchaus Auslöser des Amoklaufes sein könnten.
Während die weithin von »Wokeness« beseelten Demokraten ihre Wunden lecken, zelebrieren das konservative Lager der Republikaner und die MAGA-Apologeten einen vermeintlich historischen Sieg. Trump selbst verspricht bei seiner Siegesrede ein »goldenes Zeitalter«. Dass er jetzt »alles in Ordnung bringen« werde. Die Krypto-Branche wähnt sich im Aufwind. Der Bitcoin-Kurs steigt. Dow Jones, S&P 500 und Nasdaq erreichen neue Allzeithochs. In Iowa soll 2026 eine Art Weltausstellung stattfinden, um das 250-jährige Jubiläum Amerikas zu feiern. Bis zum Beginn der Feierlichkeiten sollen Elon Musk und Vivek Ramaswamy die Ausgaben des Staatsapparats um zwei Billionen US-Dollar reduziert haben. Natürlich ist Trump auch die letzte Chance der USA, um endlich die Grenze zu Mexiko zu sichern. Und von Robert F. Kennedy Jr. erwartet man, die Vereinigten Staaten im Rahmen eines MAHA-Programmes – »Make America Healthy Again« – wieder gesund zu machen.
Im Überschwang der Euphorie – oder Frust der Niederlage – fällt gerne unter den Tisch, dass Wähler in Amerika den Präsidenten gemäß Verfassung gar nicht direkt wählen dürfen, weil das für die Wahl des Präsidenten zuständige Electoral College im Prinzip völlig unabhängig vom eigentlichen Wahlausgang entscheiden kann. Die Wahlmänner könnten auch jeden anderen zum Staatsoberhaupt ernennen. Ob das Volk ihn will, oder er überhaupt angetreten ist, spielt rein formal gar keine Rolle. Bei genauerer Betrachtung also nicht unbedingt Demokratie in Reinform. Egal. Schnöde Details. »Trust the plan. Wir haben gewonnen. Geschichte wurde geschrieben« – und so weiter.
Die NATO gibt unterdes zu Protokoll, dass sich an ihrer geostrategischen Agenda »nichts ändern wird, egal, wer die Wahl gewinnt«, weil das »im Interesse der Vereinigten Staaten liege«. Vielleicht hat das US-Militär ja deshalb nur wenige Stunden nach Schließung der Wahllokale eine Minuteman III Interkontinentalrakete zu Testzwecken abgefeuert. Eine Langstreckenwaffe, die drei einzeln steuerbare Atomsprengköpfe transportieren kann.
Auch das Ron Paul Institute rechnet nicht mit grundlegenden Veränderungen und führt diverse Bereiche an, die unabhängig von der Besetzung des Oval Office ein Problem bleiben werden: Kontinuierliche Unterminierung der Verfassung, Krieg gegen die eigene Bevölkerung, Tiefenstaat, Washingtons ausufernde, verstetigte Notstandsermächtigungen, Militärinterventionen in aller Welt, maßlose Korruption und staatliche Tyrannei. Klingt nicht wirklich nach einem goldenen Zeitalter.
Die Reaktionen rund um die US-Wahl – ob positiv oder negativ, ob vor Ort oder im Rest der Welt – veranschaulichen jedenfalls, dass Wahlen Emotionsamplituden auslösen, die in keiner Relation zu dem stehen, was ein Präsident, Kanzler oder Premierminister tatsächlich bewirken kann. Sonst hätte Trump den tiefenstaatlichen »Sumpf« ja schon in seiner ersten Amtsperiode trockenlegen können.
Während die Demokraten also darauf warten, dass die USA ab dem 20. Januar 2025 zur Diktatur verkommen und auf Demonstrationen gegen das Resultat der US-Variante von Demokratie protestieren, fiebern die anderen dem Anbruch eines goldenen Zeitalters entgegen.
Genug Zeit also, den 47. Heilsbringer im Oval Office noch einmal genauer unter die Lupe zu nehmen. Denn auch wenn Donald Trump sich fraglos darauf versteht, zu unterhalten und große Reden von Freiheit und staatlicher Souveränität, von Weltfrieden und Prosperität zu schwingen, sprechen seine Taten zumeist eine ganz andere Sprache.
Fangen wir vorne an: Dank der Zurückstellung vom Wehrdienst konnte Donald Trump bereits 1968 bei Trump Management einsteigen, dem Unternehmen seines Vaters Fred C. Trump, der vor allem mit staatlichen geförderten Wohnungsbauprojekten – »Federal Housing Projects«, heute die Ghettos von New York – zum Multimillionär geworden war. 1971 übernahm Donald im Alter von 25 Jahren die Geschäftsleitung der Firma. Bei Interviews prahlt er bis heute gerne damit, dass sein Vater ihm in jungen Jahren »lediglich einen kleinen Kredit« über eine Million Dollar als Startkapital gewährte. Daraus habe er dann als gewiefter Unternehmer ein Immobilienimperium erschaffen. Dieser Darstellung widerspricht ein Artikel der New York Times (NYT) vom 2. Oktober 2018, der basierend auf Steuer- und Buchhaltungsunterlagen kalkuliert, dass Donald Trump gut 60 Millionen US-Dollar an Krediten erhielt.
»Im Alter von drei Jahren verdiente Trump am Imperium seines Vaters 200.000 Dollar jährlich. Mit acht Jahren war er Millionär. Mit 17 Jahren überließ ihm sein Vater einen Teilbesitz an einem Mehrfamilienhaus mit 52 Wohneinheiten. Kurz nachdem Trump das College abgeschlossen hatte, erhielt er von seinem Vater jährlich umgerechnet eine Million Dollar. Über die Jahre stiegen die jährlichen Schenkungen. In seinen Vierzigern und Fünfzigern lagen sie bei über fünf Millionen Dollar jährlich.«
Als Fred Trump im Juni 1999 verstarb, hatte der trickreiche Unternehmer und Steuerallergiker seinem Sprössling nach Berechnungen der NYT insgesamt 413 Millionen Dollar überschrieben. Selbst wenn New York Times, Associated Press und Co. im Jahr 2018 mit diesen Artikeln fraglos Stimmung gegen Trump machen wollten, kann dessen selbstbeweihräuchernde Darstellung augenscheinlich nicht ganz der Wahrheit entsprechen.
Aber: Er hatte Erfolg. Und das war in der Immobilienbranche des New Yorks der 70er und 80er nicht selbstverständlich. Denn sie wurde von der Mafia dominiert. Von den »Fünf Familien«. Wer nicht den Schutz von »Fat Tony« Salerno, Carmine Galante, Paul Castellano et al. genoss, den Bossen der Genovese-, Bonanno- und Gambino-Familien, hatte schlechte Karten. Das wusste auch Donald Trump. Also macht er Gebrauch von den exzellenten Kontakten seines Freundes, Mentors und Anwalts Roy Cohn, der nicht nur enge Verbindungen zum langjährigen FBI-Chef J. Edgar Hoover pflegte, sondern unter anderem auch Nancy Reagan, die Besitzer des Studio 54, Andy Warhol, die katholische Erzdiözese und die Führungsetage der fünf Mafia-Familien als Anwalt vertrat. Nicht umsonst ist Cohn ein zentraler Charakter in Whitney Webbs Zweiteiler »One Nation under Blackmail«. Den Kontakt zu Cohn, einer Schlüsselfigur für die Zusammenarbeit von Oberschicht und Unterwelt, suchte Donald Trump bereits 1973, als die US-Regierung ein Unternehmen seines Vaters verklagte. Er sollte bestehen bleiben, bis Cohn im August 1986 seiner AIDS-Erkrankung erlag.
Cohns Verbindungen zu Politik, Mafia und Jimmy Hoffas teilkrimineller Teamster-Gewerkschaft sorgten dafür, dass Trump in der Stadt Fuß fassen und sein Geschäft ausbauen konnte. Im Gegenzug war er gezwungen, überteuerte Baumaterialien von Fat Tonys Tarnfirmen zu beziehen. Nach Angaben eines ehemaligen Mitarbeiters von Cohn trafen sich Trump und Salerno in dessen Stadthaus in Manhattan. Trump will sich an ein solches Meeting allerdings nicht erinnern können – obwohl Salerno 1988 unter anderem wegen Erpressung in Höhe von acht Millionen Dollar im Rahmen eines Trump-Bauprojektes rechtskräftig verurteilt wurde. Die Wahrheit kennt wohl nur Trump selbst. Denn Cohn und Fat Tony sind tot.
Sicher ist: Die Geschäftsbeziehungen zwischen Donald Trump und Firmen des organisierten Verbrechens waren intensiver als seinerzeit üblich. Auf Tonbändern des FBI und der US-Staatsanwaltschaft, damals geleitet vom späteren Trump-Anwalt Rudy Giuliani, die beim Abhören von Mafia-Fahrzeugen und -Etablissements entstanden, ist mehrfach von Trump-Projekten die Rede. Donald passte sich dem Geschäftsgebaren seines Umfelds an. Den opportunistischen, skrupellosen, steuervermeidenden Praktiken seines Vaters – und dem von organisierter Kriminalität durchzogenen Filz des Ostküsten-Establishments.
Donald Trumps Frühphase, seine Geschäfte und Geschäftspartner sind also nicht unbedingt ein Paradebeispiel in Sachen Arbeitsethos. Im Vergleich zu seinen späteren Kontakten wirken seine Buddys der 70er und 80er aber fast noch sympathisch – denn Steuern sind Raub und die Mafia pflegt, im Gegensatz zu Regierungen, Militär und Geheimdiensten, zumindest einen Ehrenkodex.
Die 90er begannen für Trump mit finanziellen Turbulenzen. Diverse Bau- und Casino-Projekte liefen nicht wie geplant. Investments warfen nicht den erwarteten Gewinn ab und die Schulden häuften sich bis zur Zahlungsunfähigkeit. In der Öffentlichkeit gab er jedoch weiterhin den erfolgreichen Entrepreneur. 1995 gründe Trump, immer noch bis über beide Ohren verschuldet, eine Aktiengesellschaft und ging an die Börse. Durch diesen Schritt landete er nach 1989 erstmals wieder auf der Forbes-Liste der reichsten Amerikaner. Da die neue AG aber aufgrund der Altlasten mit 1,7 Milliarden Dollar verschuldet war, fiel ihr Börsenkurs zwischen 1996 und 2005 von 35 Dollar auf 17 Cent. Dann wurde der Handel ausgesetzt. Trump bezog aber noch bis 2009 Vergütungen aus der Gesellschaft in Höhe von 44 Millionen Dollar.
Parallel zu diesen fragwürdigen Umtrieben zu Lasten von Anlegern und Geschäftspartnern mauserte sich Donald Trump zum Society-Phänomen. Ob The Apprentice, WrestleMania, The Fresh Prince of Bel-Air, Talkshows oder soziale Anlässe aller Art – Trump war überall, wo sich Öffentlichkeit für Trump generieren ließ. Mit Erfolg. Überschuldung, Zahlungsunfähigkeit, Mafia-Kontakte, Betrugsvorwürfe und juristische Probleme verblassten im omnipräsenten Scheinwerferlicht.
Weniger glamourös dagegen ist Donald Trumps Beziehung zu einem der verachtenswertesten Menschen der jüngeren Vergangenheit – Jeffrey Epstein. Denn während Trump lange Jahre leugnete, überhaupt mit Epstein in Kontakt gestanden zu haben, belegen unlängst veröffentlichte Audio-Mitschnitte, dass er sehr wohl eine Beziehung mit dem verurteilten Sexualstraftäter, Pädophilen, Menschenhändler und Doppelagenten pflegte. Eine sehr enge.
Jeffrey Epstein bezeichnet sich im Zuge der Aufnahmen als »Trumps engsten Freund«. Für über zehn Jahre. Man besuchte die gleichen Partys, kannte die gleichen Leute. Kaum verwunderlich. Epstein war bestens mit dem »Who is Who« des Establishments vernetzt – auch mit dem zwielichtigen Roy Cohn. Es liegt nahe, dass über diesen der Erstkontakt zustande kam. Epstein erpresste elitäre Zirkel in aller Welt mit heimlich aufgenommenen Videos arrangierter Sex-Eskapaden. Die Opfer: Meist Minderjährige. Manche erst acht Jahre alt. Wer Macht und Einfluss ausüben und sichern wollte, nahm seine Dienste in Anspruch. Das wusste wohl jeder seiner engeren Kontakte. Trotzdem sprach Donald Trump von einem »tollen Typen, den er seit 15 Jahren kenne«, als er in einem Interview mit dem New York Magazine 2002 nach seiner Meinung zu Epstein und der gemeinsamen Vorliebe für junge Frauen gefragt wurde. Darüber hinaus flog Donald Trump mindestens sieben Mal mit Jeffrey Epsteins Privatjet, besser bekannt als »Lolita Express«.
Elon Musk, über dessen hinter Imagedesign verborgene Nähe zu Militär, Geheimdiensten, Big Pharma und Transhumanisten ich bereits im Oktober 2022 ausführlich berichtet habe, hatte ebenfalls Verbindungen zu Jeffrey Epstein, wie ein ausführliches Dossier von Johnny Vedmore belegt. Ganz zu schweigen von Musks Forderungen nach CO2-Steuern gegen den Klimawandel oder seinen offenen Plädoyers für Technokratie, einem faschistischen Herrschaftsmodell, das schon sein Großvater Joshua N. Haldemann in leitender Position vertrat. Man kann sich also ausmalen, was unter einem Effizienzprogramm unter Musks Ägide zu erwarten ist – Tech-Faschismus, getarnt als libertäre Progressivität.
Auch RFK Jr. flog zwei Mal mit dem »Lolita Express«, gibt aber an, in Begleitung von Frau und Kindern gereist zu sein – während er gleichzeitig erklärt, die beiden Flüge seien nur zustande gekommen, weil seine »Frau irgendeine Art von Beziehung mit Ghislaine Maxwell hatte«. Was für eine Beziehung das war, beschreibt RFK Jr. nicht. Dabei wären die Hintergründe dieser Beziehung durchaus relevant für die Bewertung seiner Verbindung zum Epstein-Netzwerk. Denn Maxwell, deren Elternhaus für CIA und Mossad tätig war, war seit 1991 Epsteins engste Mitarbeiterin. Sie führte ihm minderjährige Mädchen zu. Phantombilder legen nahe, dass sie auch am Verschwinden, beziehungsweise Tod, von Madeleine McCann beteiligt sein könnte. Nach dem als Suizid vermarkteten Mord an Epstein im August 2019 tauchte Maxwell ab. Aufenthaltsort unbekannt. Erst am 2. Juli 2020 konnte das FBI sie festnehmen. Im Dezember 2021 wurde Maxwell wegen Unterstützung von Epsteins Pädo-Business zu 20 Jahren Haft verurteilt.
Man darf gespannt sein, ob Epsteins unter Verschluss gehaltene Kundenliste jemals ans Licht kommt. Wenn Trump nichts zu verbergen hat, seine dahingehenden Ankündigungen wahr machen und den Sumpf trockenlegen will, könnte er damit ordentlich vorlegen. Entsprechende Forderungen stehen ja bereits im Raum.
Bei einer Pressekonferenz im Weißen Haus am 21. Juli 2020 verkündete er allerdings noch, Maxwell mehrfach getroffen zu haben und wünschte ihr »wirklich alles Gute«.
Wahrscheinlich ist eine Offenlegung der Kundenliste aber nicht. Denn auch Trumps neuer Generalstaatsanwalt, Matt Gaetz, gegen den 2020 wegen sexueller Kontakte zu einem minderjährigen Mädchen ermittelt wurde, sprach sich in der Vergangenheit explizit gegen eine neuerliche Überprüfung des Falls Epstein aus. Er behauptete außerdem, Epstein sei von ausländischen Geheimdiensten, nicht vom US-Tiefenstaat ermordet worden. Sein Wahlkampf-Team nutzte denn auch die gleiche Anwaltskanzlei wie Jeffrey Epstein. Und ein enger Vertrauter von Gaetz warb intensiv dafür, Ghislaine Maxwell aus der Haft zu entlassen. Seit 2021 ist Gaetz mit der Schwester des Peter Thiel-Protegés Palmer Lucky verheiratet, der mit seiner Firma Anduril für das High-Tech-Überwachungssystem an der mexikanischen Grenze verantwortlich zeichnet, KI-Waffenprogramme entwickelt und für das US-Verteidigungsministerium an Project Maven arbeitet. Sumpf, soweit das Auge reicht. Trockenzulegen gäbe es da also einiges.
Warten wir’s ab – und werfen unterdes einen Blick auf Donald Trumps erste Amtszeit. Denn auch diesbezüglich sagen Taten mehr als Worte.
Während Trump sich derzeit als Gegner der Weltgesundheitsorganisation (WHO) geriert, war er als 45. US-Präsident mit »Operation Warp Speed« (OWS) für eine militarisierte Impf-Kampagne der Superlative verantwortlich, die 300 Millionen Dosen einer experimentellen mRNA-Gentherapie unters Volk bringen und den Herstellern mindestens 18 Milliarden Dollar in die Kasse spülen sollte. Anthony Fauci, den Trump heute gerne öffentlich diffamiert, kümmerte sich für ihn um den Rollout der Injektionen und die damit verbundene Nudging-Propaganda. Für seine Verdienste im Rahmen von OWS erhielt Fauci von Trump am letzten Tag seiner Präsidentschaft eine Auszeichnung, wie eine Pressemitteilung im Archiv des Weißen Hauses belegt. Während Trump sich in den letzten Wochen medienwirksam von Fauci distanzierte und abstritt, diese Auszeichnung abgesegnet zu haben, verweisen Mitarbeiter des Weißen Hauses darauf, dass eine solche Auszeichnung gemäß Protokoll nur dann verliehen wird, wenn der Präsident sie persönlich autorisiert. Fragt sich, wer lügt.
Daneben genehmigte Trump im Februar 2020 eine Zahlung von 1,16 Milliarden US-Dollar an GAVI, die Impfallianz von WHO, Weltbank, UNICEF und der Bill & Melinda Gates Stiftung. Der Betrag sollte GAVI binnen drei Jahren über die CIA-Tarnfirma USAID ausbezahlt werden. Ungeachtet aller Gegenanzeigen, Nebenwirkungen und Kollateralschäden durch Lockdowns und partielle Impfpflichten pries Donald Trump OWS stets als durchschlagenden Erfolg. Erst nach der Ankündigung, mit Kennedy kollaborieren zu wollen, hielt er sich mit dem Eigenlob zurück. Dass er sich in den Wochen vor dem Wahlsieg neu positionierte, dürfte also reine Wahlkampfstrategie gewesen sein.
Wenn Trump nun in Aussicht stellt, Impfungen verbieten und Amerika gemeinsam mit RFK Jr. gesund machen zu wollen, ist das in Anbetracht der immensen Marktmacht von Big Pharma kaum als realistisch zu bewerten. Siehe Briefing des Roosevelt Institute vom 22. Mai 2019. Titel: »Kapern der Regierung – Wie Big Pharma die Gesetzgebung übernahm«. In Trumps Team wurden in den letzten Wochen bereits Stimmen laut, die forderten, sich von RFK Jr. zu distanzieren. Während Kennedy in einem Interview vom 28. Oktober verkündete, Trump habe ihm den »Chefposten der Gesundheitsbehörde HHS versprochen«, stellte Howard Lutnik, Vize-Vorsitzender von Trumps Transition-Team, am 30. Oktober bei CNN fest, dass dies »natürlich nicht der Fall sein werde« und man Kennedy lediglich Zugriff auf Daten gewähren wolle. Am 14. November gab Donald Trump dann allerdings bekannt, RFK Jr. tatsächlich zum Chef der HHS machen zu wollen. Die Nominierung muss aber noch vom Senat bestätigt werden. Und bis Januar kann noch einiges passieren. Die Vergangenheit lässt jedenfalls darauf schließen, dass weder Big Pharma noch WHO oder GAVI künftig unter der neuen Regierung leiden werden.
Dann wären da noch die galoppierenden Staatsschulden der Vereinigten Staaten. Denn unter Trumps Ägide schöpfte die US-Zentralbank allein im Jahr 2020 über drei Billionen Dollar. »Die Vereinigten Staaten haben im Juni mehr Geld gedruckt als in den ersten zwei Jahrhunderten nach ihrer Gründung. Letzten Monat war das Haushaltsdefizit der USA – 864 Milliarden Dollar – größer als die Gesamtverschuldung von 1776 bis Ende 1979«, so Dan Morehead, CEO von Pantera Capital am 29. Juli 2020. Seit 2020 hat die Staatsverschuldung um knapp zwölf Billionen Dollar zugenommen und belief sich im September 2024 auf 35,46 Billionen Dollar. Das sollten speziell Trump-Anhänger vor Ort nicht vergessen, wenn sie nun für den Wocheneinkauf deutlich tiefer in die Tasche greifen müssen. Inflation sei Dank.
»Dafür hat Trump keine neuen Kriege angefangen!« – hört man immer wieder, wenn man auf dessen Verfehlungen hinweist. Stimmt. Weil er fünf Krisenherde von der vorherigen Regierung geerbt hat und sich dort austoben konnte. Trump hat nämlich deutlich mehr Drohnen-Einsätze befohlen als sein Vorgänger. Obama autorisierte in den ersten zwei Jahren seiner Amtszeit 186 Einsätze – bei Trump waren es 238. Allein im Jemen hat die Trump-Regierung 176 Angriffe binnen zwei Jahren durchgeführt. Bei Obama waren es 154 in acht Jahren. Und während die Regierung unter Obama zumindest teilweise Daten zu den Opferzahlen dieser Einsätze veröffentlichte, änderte Trump die entsprechenden Transparenzanforderungen und veröffentlichte gar keine Daten. Laut einem Artikel von Foreign Policy vom 9. August 2017 ist Trump »der kriegslüsternste Präsident der jüngeren Geschichte«. Weiter führte das 1970 von Samuel P. Huntington gegründete Magazin aus:
»Unter Trump haben die Vereinigten Staaten bis zum 31. Juli etwa 20.650 Bomben abgeworfen, das sind 80 Prozent der Menge, die unter Obama im gesamten Jahr 2016 abgeworfen wurden. (…) Daten zeigen, dass die Vereinigten Staaten im Irak und in Syrien Bomben in beispiellosem Ausmaß abwerfen. Im Juli warf die Koalition zur Bekämpfung des Islamischen Staats (sprich: die Vereinigten Staaten) 4.313 Bomben ab, 77 Prozent mehr als im Juli letzten Jahres. Im Juni lag die Zahl bei 4.848 – 1.600 Bomben mehr als unter Präsident Barack Obama jemals pro Monat abgeworfen wurden. In Afghanistan ist die Zahl der abgeworfenen Bomben seit Trumps Amtsantritt ebenfalls sprunghaft angestiegen. Im April wurden im Land mehr Bomben abgeworfen als auf dem Höhepunkt von Obamas Truppenaufstockung im Jahr 2012. In diesem Monat bombardierten die Vereinigten Staaten das afghanische Mamand-Tal mit der größten nichtnuklearen Bombe, die jemals abgeworfen wurde. Trump hat auch das militärische Engagement der USA in Ländern außerhalb der Kriegsschauplätze ausgeweitet – nämlich im Jemen, in Somalia und in Pakistan. In den letzten 193 Tagen von Obamas Präsidentschaft gab es in diesen drei Ländern 21 tödliche Anti-Terror-Operationen. Trump hat diese Zahl verfünffacht und mindestens 92 solcher Operationen im Jemen, sieben in Somalia und vier in Pakistan durchgeführt.«
Klingt für mich jetzt nicht so ganz nach Friedenstauben.
Wahrscheinlich war es am Ende nur die Hektik bei der Übergabe der Amtsgeschäfte im Januar 2021, oder der Stress permanenter Medienpräsenz, der Trump auch noch davon abhielt, Julian Assange oder Edward Snowden zu begnadigen. Immerhin war er »kurz davor, einen der beiden auszuwählen«, wie er in einem Interview für Daily Wire verlauten ließ. Am Ende blieb dann aber leider doch nur Zeit für die Begnadigung der anderen 116 Personen auf der Liste. Dumm gelaufen.
Wenden wir uns der Gegenwart zu. Und dem, was uns die nächsten vier Jahre erwarten könnte. Es muss ja jetzt auf jeden Fall alles viel besser laufen als in der ersten Runde. Denn in den Augen vieler seiner Unterstützer habe Trump in der Zwischenzeit viel gelernt und wurde damals nur hinters Licht geführt. Überrumpelt vom Tiefenstaat, den er eigentlich abschaffen wollte. Zudem hat er nun Elon Musk und RFK Jr. an seiner Seite, der gemäß Lutnik zwar keinen Job bekommt, aber immerhin steht irgendwo Kennedy auf der Banderole. Das ist doch auch was.
Ernsthaft. Bereits in Rahmen seiner ersten Amtszeit plante Trump, ein biometrisches System zur Ein- und Ausreisekontrolle zu etablieren. Es sollte zunächst nur für Ausländer gelten. Aber jeder weiß, dass es nicht lange dauert, bis so ein System für jeden gilt. Dazu passt, dass seit Beginn des Wahlkampfes 2024 permanent von der Voter ID gesprochen wird. Ausweise für alle – gegen Wahlbetrug. Bisher besitzen nur knapp 40 Prozent der Amerikaner einen Reisepass. Nur acht Prozent verlassen im Urlaub überhaupt das Land. Die virtuelle Wand wird das ändern, nicht nur an der Grenze zu Mexiko. Denn über kurz oder lang resultiert das Projekt in der flächendeckenden Einführung einer eID. Basis für die eID- oder Voter ID-Infrastruktur könnte zum Beispiel E-Verify sein, ein vom Department of Homeland Security betriebenes Projekt zur Verifikation von Personen, dessen Nutzung für Personalabteilungen von Bundesbehörden seit dem 1. Oktober 2007 obligatorisch ist. Die Nominierung von Tom Homan als Chef der Einwanderungs- und Zollbehörde impliziert, dass genau dieser Kurs eingeschlagen wird. Homan ist Hardliner. Er war Teil des rechtskonservativen Project 2025 und befürwortet neben flächendeckender Biometrie auch die Trennung von Eltern und Kindern an der Grenze.
Kein Zufall also, dass der Gründer der Cardano-Blockchain, Charles Hoskinson, die Regierung Trump ab 2025 in Bezug auf Kryptoanwendungen beraten soll. Immerhin hatte Hoskinson bereits mit dem von Jeffrey Epstein finanzierten Ben Goertzel ein biometrisches eID-System für Schulkinder in Äthiopien entwickelt. Und nachdem die von Peter Thiel finanzierte Silikon-Valley-Marionette JD Vance als Vizepräsident fungiert, hat auch der mächtigste Überwachungskonzern der Welt, Palantir, nun einen Fuß in der Tür des Oval Office. Mit diesem Setup dürfte der gläserne Bürger der Gegenwart bald ein Relikt der Vergangenheit sein.
Ganz zur Freude von Ex-Spion John Ratcliffe, dem neuen CIA-Direktor unter »Orange Man«. In Trumps erster Amtszeit war Ratcliffe »Director of National Intelligence«, unter George W. Bush zuständig für Anti-Terror-Operationen und nationale Sicherheit. Später leitete er zusammen mit John Ashcroft, Generalstaatsanwalt unter Bush und Architekt des Ermächtigungsgesetzes »Patriot Act«, ein Unternehmen für strategische Beratung (AGS). Im Dezember 2023 unterstützte John Ratcliffe den Bilderberger, Kriegstreiber und Tiefenstaat-Neocon Mike Pompeo bei der Erneuerung des Foreign Intelligence Surveillance Act (FISA), der die fortgesetzte, anlasslose Massenüberwachung der US-Bevölkerung legalisiert. Und kaum war er nominiert, machte Ratcliffe am 13. November 2024 auf FOX-News wahrheitswidrig Stimmung gegen den Iran und unterstellte der dortigen Regierung »kriegerische Handlungen« gegenüber den USA.
Kollaborieren wird Ratcliffe künftig mit Tulsi Gabbard. Sie beerbt ihn als Trumps neuer »Director of National Intelligence«. Gabbard war Mitglied der WEF Young Global Leaders sowie des Council on Foreign Relations (CFR). Beide Organisationen tilgten ihren Namen von der eigenen Homepage, nachdem Gabbard öffentlich über US-Biowaffenlabore in der Ukraine sprach. In Interviews bestätigt sie ihre Rolle im CFR allerdings selbst. Gabbard befürwortete die Covid-Impfkampagne und schmückt sich gerne mit dem Image »Kriegsveteran« – obwohl sie die Schrecken des Krieges lediglich aus sicherer Entfernung sah. Eine Opportunistin, deren konservativ-kritisches Image nichts weiter ist als ein wackliges Kartenhaus.
»Ich war Kadett. Was ist das Motto der Kadetten in West Point? Du wirst nicht lügen, betrügen, oder stehlen – und diejenigen nicht dulden, die das tun. Ich war der CIA-Direktor. Wir haben gelogen, wir haben betrogen, wir haben gestohlen. Wir haben ganze Trainingskurse dazu absolviert.« (Mike Pompeo, April 2019)
Und wer denkt, Donald Trump werde wenigstens die Einführung einer digitalen Zentralbankwährung (CBDC) verhindern, irrt. Zumindest im Kern. Denn im Rahmen seiner Rede auf der Bitcoin Konferenz 2024 sprach Donald Trump von »regulatorischer Klarheit« sowie der »sicheren und verantwortungsvollen Expansion von Stablecoins«. Damit bestätigte er, dass die Einführung von digitalem Geld über privatwirtschaftliche Entitäten erfolgen wird. Denn ein Konto bei der Zentralbank will niemand. Leider werden aber die Transaktionen all der ach so marktwirtschaftlich eingeführten Digitalwährungen zentral erfasst. Im »Unified Ledger« der Bank für Internationalen Zahlungsausgleich (BIZ) in Basel. Was am Ende zum exakt gleichen Ergebnis führt wie eine vom Staat oder der Zentralbank aufgelegte CBDC – zu lückenloser Überwachung mit Interventionspotenzial.
Zurück zur künftigen Regierung. Stabschef im Weißen Haus und damit »mächtigste Frau in Washington« soll Susie Wiles werden – bisher Co-Vositzende von Mercury Public Affairs LLC, einem Lobby-Giganten, der unter anderem Pfizer, GAVI, die Vereinten Nationen oder SpaceX vertritt. Mercury Public Affairs gehört seit 2003 zur Omnicom Group, einem WEF-Partner für Öffentlichkeitsarbeit. Wiles gilt als die »am meisten gefürchtete und am wenigsten bekannte Politagentin Amerikas«.
Als Außenminister nominierte Trump den von der Zionismus-Lobby korrumpierten Marco Rubio. Einen Neocon. Sprich: Militärischer Interventionismus und unilaterale Hegemonieansprüche. Den Posten des nationalen Sicherheitsberaters offeriert Trump dem ehemaligen Green Beret Mike Waltz. Neben Marco Rubio der zweite Mann in der künftigen Regierung, der sich mit China anlegen möchte. Ergänzt wird das kriegsaffine Duo von Brian Hook, der dem Iran am liebsten sofort den Krieg erklären möchte und den Auftrag erhielt, Schlüsselpositionen im Außenministerium mit geeignetem Personal dafür zu besetzen.
Der ehemalige texanische Kongressabgeordnete Ron Paul sieht in diesen Nominierungen »einen schlechten Tag für jene, die an America First glaubten«. Sollte Trump die Unterstützung der Ukraine seitens Amerika tatsächlich beenden, dürften nämlich ersatzweise zuerst der Iran und langfristig eventuell gar China von Demokratie aus der Luft beglückt werden. Daran wird auch die neue US-Botschafterin bei den Vereinten Nationen nichts ändern. Denn Elise Stefanik hat praktisch keine relevante Berufserfahrung – und ist ebenfalls ein Neocon. Sowohl Stefanik als auch Rubio, Waltz oder Hook setzen sich für weitere Waffenlieferungen nach Israel und eine Fortsetzung des auch von israelischen Zeitungen also solchen bezeichneten Genozids in Gaza ein.
»Die westliche Zivilisation repräsentiert heute das Verständnis, dass Zionismus und Amerikanismus die Frontlinien der westlichen Zivilisation und Freiheit in unserer Welt sind«, erklärte der Army-Veteran, United Against Nuclear Iran-Advokat und Ex-FOX-News-Mitarbeiter Pete Hegseth im April 2019.
An dieser faschistoiden wie imperialistischen Doktrin scheinen sich auch Trump und Co. zu orientieren – denn Hegseth wird nun Verteidigungsminister. Passend dazu wird Mike Huckabee, ein bekennender Zionist, der nächste US-Botschafter in Israel. Huckabee nennt das Westjordanland Judäa und behauptet entgegen historischer Fakten, dass es Teil Israels ist. Auch die Annexion der Westbank fände er in Ordnung. Seine Nominierung kann als Kriegserklärung an die Palästinenser verstanden werden. Wohlwissend, dass Israels völkerrechtswidriges Vorgehen leicht zu einem regionalen, wenn nicht globalen Flächenbrand führen kann.
Apropos globale Themen: Dahingehend lohnt sich ein genauerer Blick auf die Hintergründe des bereits erwähnten Howard Lutnick. Diesen hat die Investigativ-Journalistin Whitney Webb am 7. November 2024 gewagt. Unter der Überschrift »Macht euch bereit für den Kohlenstoffmarkt der Republikaner« erklärt sie:
»Viele der einflussreichsten Namen der kommenden Trump-Regierung sowie der vorherigen haben sich in den letzten Jahren intensiv mit der Schaffung von Kohlenstoffmärkten befasst, während andere eine langjährige Erfolgsgeschichte bei der Implementierung von CO2-Steuern und anderen Formen der CO2-Bepreisung vorweisen können. Der wichtigste unter ihnen ist Howard Lutnick, Co-Vorsitzender von Trumps Transition-Team, der erklärte, seine Aufgabe sei es, Talente für die kommende Regierung zu finden. Lutnick ist der langjährige Leiter von Cantor Fitzgerald, einem der ersten Akteure im Emissionshandel, der sich seitdem zu einem weltweit führenden Unternehmen für ESG-Investitionen, die Finanzierung nachhaltiger Infrastruktur und grüne Anleihen entwickelt hat. So hat sich Cantors nachhaltiger Infrastrukturfonds ausdrücklich der digitalen Transformation, Dekarbonisierung und Verbesserung und Modernisierung alternder Infrastruktur verschrieben, während ein Hauptaugenmerk des Fonds darauf liegen wird, in Emittenten zu investieren, die mit ihren Produkten und Dienstleistungen dazu beitragen, bestimmte Ziele der Vereinten Nationen für nachhaltige Entwicklung zu erreichen. Darüber hinaus ist Invenergy, ein Unternehmen für erneuerbare Energien, das im Rahmen von Bidens umstrittenem Inflationsbekämpfungsgesetz eine beträchtliche Menge an Subventionen erhalten hat und vom ersten Windmilliardär des Landes, Michael Polsky, geleitet wird, der wichtigste Bestandteil eines weiteren Infrastrukturfonds von Cantor. Lutnick sitzt auch im Vorstand eines Satellitenüberwachungsunternehmens namens Satellogic. Neben Lutnick ist der ehemalige Finanzminister von Trump, Steve Mnuchin, Vorsitzender des Vorstands. Auch Joe Dunford, ehemaliger Stabschef des US-Militärs unter Trump, sitzt im Vorstand. Satellogic ist integraler Bestandteil eines Konsortiums, das versucht, durch undurchsichtige vertragliche Vereinbarungen auf kommunaler Ebene einen riesigen, Blockchain-basierten Kohlenstoffmarkt in Lateinamerika durchzusetzen. Dieser Kohlenstoffmarkt, der unter dem Namen GREEN+ operiert, soll auf einer Bitcoin-Sidechain aufgebaut werden. Das entsprechende Emissionsgutschriftsystem ist für lateinamerikanische Gemeinden zutiefst ungerecht. So könnten die betroffenen Gemeinden beispielsweise nur Geld verdienen, wenn Einnahmen unter den für GREEN+ anerkannten, nachhaltigen Projekten generiert werden, während die Investoren von GREEN+ den Großteil der Gewinne einstreichen. Das Programm würde Gemeinden außerdem ohne ihre Zustimmung dem Satellitenüberwachungsapparat von Satellogic (der mit der US-Regierung und dem israelischen Geheimdienst verbunden ist) aussetzen. Darüber hinaus ist GREEN+ in bemerkenswerter Weise mit Personen verbunden, die Trumps Verbündeten in der Region nahestehen. So ist eine wichtige Persönlichkeit in Nayib Bukeles politischer Partei – der Bürgermeister von San Salvador, Mario Durán – Vizepräsident einer der wichtigsten Gruppen, die das GREEN+-Programm orchestrieren, während das Netzwerk Endeavor Argentina, das sehr enge Verbindungen zu Javier Milei pflegt, ebenfalls eng mit Satellogic verbunden ist. Satellogic ist ein von Endeavor unterstütztes Unternehmen, während Endeavors erster Milliardär und Unternehmer, Marcos Galperín von MercadoLibre, im Vorstand von Satellogic sitzt. Darüber hinaus ist ein anderer wichtiger Investor von Satellogic, der Dollar-Stablecoin-Emittent Tether, auch eng mit Howard Lutnick verbunden. Lutnick ist langjähriger Fürsprecher von Tether. Und Cantor Fitzgerald hält den Großteil der US-Staatsanleihen von Tether, um deren Stablecoin und seine Bindung an den US-Dollar zu stützen.«
Das sollte Wähler, die dem Klimawandel-Narrativ und Digitalwährungen skeptisch gegenüberstehen, hellhörig werden lassen – denn auch wenn Donald Trump im Rahmen seiner öffentlichen Auftritte gegen die Nachhaltigkeitsagenda wettert und der leitmediale Komplex seine entsprechenden Phrasen für Konterpropaganda nutzt, sprechen die Taten wieder einmal eine ganz andere Sprache. In Anbetracht vorgängig beschriebener Umstände sieht es nämlich nicht so aus, als widersetze sich der 47. US-Präsident dem Nachhaltigkeitskorporatismus der UN. Im Gegenteil.
»Der König ist tot, es lebe der König«. Die neue US-Regierung wird die gleiche Agenda fahren wie die alte – nur die Vermarktung ändert sich. Das kündigte Lynn Forester de Rothschild (CIC) schon vor über einem Jahr bei Bloomberg an. Genau wie Larry Fink (BlackRock).
Die Einführung biometrischer Massenüberwachung wird nun mit der Migrationskrise und drohendem Wahlbetrug, mit der Stärkung der Demokratie gerechtfertigt, anstatt mit einem Virus. Den Krieg in der Ukraine wird man nicht weiter unterstützen. Diesen Brandherd sollen die Europäer am Kokeln halten, damit man endlich den Iran und China ins Fadenkreuz nehmen kann. So ein dritter Weltkrieg wäre nämlich ein profitables Geschäft. Das Klimawandel-Narrativ wird man öffentlich negieren und verhöhnen, während die Agenda 2030 trotzdem umsetzt wird. Gleiches gilt für Totalüberwachung, Genderwahn, globale Gleichschaltung von Lerninhalten und die schleichende Digitalisierung des Weltfinanzsystems. Denn auch diese Programme werden von überstaatlichen Akteuren vorangetrieben und entziehen sich dem Einfluss nationaler Regierungen. So funktioniert Korporatismus.
Ernüchternd ist vor allem, dass sich die Bevölkerung, die in den letzten vier Jahren tatsächlich ein gewisses Maß an rebellischem Potenzial entwickelte, wieder einmal täuschen lässt. Trump-Hype wohin man schaut. Selbst die Corona-Dissidenten, selbst jene, die dem Staat aufgrund von Covid-Lügen, Green-Economy-Deindustrialisierung und militantem Neoimperialismus zusehends kritisch gegenüberstanden, haben sich in weiten Teilen von den leeren Versprechungen der MAGA-Promotion und ihren Sekundanten blenden lassen.
Sie werden genauso desillusioniert zurückbleiben wie einst die auf »Hope« geeichten Obama-Fans – und sich in ein paar Jahren vermutlich trotzdem wieder an die Wahlurne schleppen, weil sie auf den nächsten Erlöser hoffen, anstatt selbst die Welt zu verändern.
Zur Wahl stehen aber jeweils nur verschiedene Geschmacksrichtungen der gleichen, bitteren Pille Marke Unterdrückung. Keine Unterdrückung – das ist natürlich keine Option. Das steht nicht auf dem Wahlzettel.
Linke gegen Rechte, Demokraten gegen Republikaner, Christentum gegen Islam – Bevölkerungsgruppen, die man gegeneinander aufwiegeln kann, finden sich dagegen immer. Präsentiert man ihnen einen verheißungsvollen Erlöser, werden sie ihn unterstützen, um die andere Gruppe loszuwerden. Das ist Herrschaftsdialektik. Man bringt die Menschen dazu, um Dinge zu betteln, die ohnehin eingeführt werden sollen. Und der einzige Gewinner in diesem immer riskanter werdenden Spiel ist die Prädatorenkaste.
»Die mächtigste Waffe in den Händen der Unterdrücker ist der Geist der Unterdrückten.« (Stephen Bantu Biko)
Wer Donald Trump unterstützt, ist nicht für Frieden und Freiheit, sondern nur gegen das, was die andere Seite will. Denn Donald Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang.
-
 @ 8f0a121e:24038909
2024-11-28 09:07:00
@ 8f0a121e:24038909
2024-11-28 09:07:00كلنا نعرف أبيات إمرئ القيس في الليل التي تعلمناها في المدارس صغارا.
وليل كموج البحر أرخى سدوله ... عليّ بأنواع الـــهموم ليـــبتلي فقلـــت له لمـا تمـــطى بصـلبـــه ... وأردف أعجازا وناء بكلــــكل ألا أيها الليل الطويل ألا انـجـلي ... بصبح وما الإصباح منك بأمثل
وهي من أروع وأعلى ما قيل في الليل، ولكن تراثنا وشعرنا مليء بروائع في نفس المعنى. يقول النابغة الذبياني:
كليـــني لهمًّ يا أمــيمة ناصـــبِ ... وليل أقاسيه بطيء الكـــواكب تطاول حتى قلت ليس بمنقضٍ ... وليس الذي يرعى النجوم بآيب وصدر أراح الليل عازب هــــمه ... تضاعف فيه الحزن من كل جانب
يطلب النابغة من ابنته أميمة أن تدعه لهمه وتعبه ويشكي بطئ سير كواكب وثقلها في السير كناية على طول الليل.
في البيت الثاني، أقام الصبح مقام الراعي الذي يغدو فيذهب بالماشية والإبل، وبالمثل الصبح يذهب بالنجوم.
ثم يقول أن الليل "أراح عازب همه" بمعنى أنه أرجع اليه همه البعيد.
ويقول الوليد بن يزيد:
لا أسأل الله تغييرا لما فَعَلَت ... نامت وقد أسهرت عينيَّ عيناها فالليل أطول شيءٍ حين أفقدها ... والليل أقصر شيءٍ حين ألقاها
ويقول بشار:
خليلَيَّ ما بال الدجى لا تزحزح ... وما بال ضوء الصبـح لا يتوضح أضل النهار المستنير سبـــــيله ... أم الدـــــهر لـــيل كله لا يبــــرح
شعر #أدب #بالعربي
-
 @ 3f0702fa:66db56f1
2024-12-15 07:51:08
@ 3f0702fa:66db56f1
2024-12-15 07:51:08Сегодня мы можем с уверенностью констатировать: Курган – один из самых технологичных городов России. За последние два десятилетия цифровизация не просто вошла в нашу жизнь, она стала ее неотъемлемой частью, кардинально изменив то, как мы работаем, учимся, отдыхаем и взаимодействуем друг с другом.
Раньше мы могли только мечтать о тех возможностях, которые доступны нам сегодня. Давайте посмотрим, как именно новые технологии изменили жизнь курганцев.
Умный город - умная жизнь
Интеллектуальная транспортная система, управляемая искусственным интеллектом, теперь норма для Кургана. Пробки остались в прошлом, благодаря умным светофорам, анализирующим трафик в реальном времени. Беспилотный общественный транспорт, включая аэротакси, стал привычным способом передвижения по городу. Цифровизация коснулась и ЖКХ: коммунальные платежи, отслеживание потребления ресурсов и вызов аварийных служб – все это доступно через удобные мобильные приложения и персональных голосовых ассистентов. Датчики на каждом доме контролируют состояние инфраструктуры, предотвращая аварии и поломки. Кроме того, интегрированная система видеонаблюдения с распознаванием лиц и объектов помогает оперативно реагировать на любые происшествия и обеспечивать высокий уровень безопасности.
Искусственный интеллект - двигатель развития
Образование в Кургане вышло на новый уровень. Искусственный интеллект анализирует успеваемость и интересы каждого ученика, подбирая индивидуальные образовательные траектории. Виртуальные и дополненные реальности используются для создания захватывающих учебных программ, позволяющих “погрузиться” в изучаемый материал. Доступ к мировым образовательным ресурсам стал повсеместным благодаря онлайн-образованию. Курганцы могут обучаться в лучших университетах мира, не выходя из дома. Курганские ученые активно используют цифровые технологии в своих исследованиях, участвуя в международных проектах и совершая прорывы в различных областях науки.
Практически все предприятия, от крупных заводов до небольших магазинов, перешли на цифровое управление. Искусственный интеллект помогает автоматизировать рутинные процессы, оптимизировать производство и повысить эффективность работы. Курган стал одним из центров развития IT-индустрии в России, привлекая специалистов из разных регионов. Многие курганцы работают удаленно, используя современные средства коммуникации, что обеспечивает гибкий график и позволяет совмещать профессиональную деятельность с личной жизнью.
Персональная медицина стала реальностью благодаря цифровым медицинским картам, носимым устройствам и технологиям телемедицины. Врачи осуществляют постоянный мониторинг состояния здоровья пациентов и оказывают своевременную помощь. Искусственный интеллект помогает врачам ставить более точные диагнозы, подбирать индивидуальные программы лечения и контролировать эффективность терапии. Консультации с ведущими специалистами страны и мира доступны через онлайн-платформы, что особенно важно для жителей отдаленных районов.
Творчество и технологии
Современные технологии позволяют создавать интерактивные экспозиции, оживляющие историю и культуру региона в цифровых музеях и театрах. Виртуальные туры позволяют посещать музеи и театры, не выходя из дома. Курганцы имеют возможность наслаждаться любимой музыкой и участвовать в культурных мероприятиях в режиме онлайн. Киберспортивные арены стали популярным местом проведения досуга, а курганские киберспортсмены занимают лидирующие позиции на национальных и международных соревнованиях.
Курган 2040 – это город, где цифровые технологии стали неотъемлемой частью повседневной жизни, повышая ее качество и создавая новые возможности для каждого жителя. Это город, где прошлое уважается, а будущее строится с учетом последних достижений науки и техники. Курган становится примером для других регионов, демонстрируя, как можно преобразить жизнь с помощью цифровизации.
Мы продолжим следить за развитием цифровых технологий в Кургане и сообщать о новых достижениях. Следите за нашими публикациями.
45news
Курган2040
-
 @ 4ba8e86d:89d32de4
2024-10-07 22:48:24
@ 4ba8e86d:89d32de4
2024-10-07 22:48:24é um sistema operacional portátil baseado em Linux que pode ser iniciado a partir de um pen drive ou DVD. Ele é projetado para manter sua privacidade enquanto navega na internet, protegendo você de vigilância e censura. O Tails é gratuito e de código aberto, o que significa que qualquer pessoa pode usá-lo e modificá-lo.
O projeto Tails teve início em 2009, quando um grupo de desenvolvedores de software preocupados com a crescente vigilância na internet começaram a trabalhar em uma solução para proteger a privacidade dos usuários. O objetivo era criar um sistema operacional que pudesse ser executado a partir de um pendrive USB e que utilizasse a rede Tor para manter a privacidade do usuário.
O Tails oferece várias ferramentas de privacidade, incluindo o Tor (The Onion Router), um serviço de rede que protege sua identidade online e oculta sua localização. Ele também inclui o navegador Tor, que permite navegar na internet anonimamente e acessar sites bloqueados em seu país. Além disso, o Tails vem com outras ferramentas de privacidade, como o Kleopatra PGP (Pretty Good Privacy) uma ferramenta de criptografia de e-mail que ajuda a proteger suas mensagens.
O Tails é fácil de usar, mesmo se você não tiver conhecimento técnico avançado. Ele é projetado para ser iniciado a partir de um pen drive ou DVD, o que significa que você pode usá-lo em qualquer computador sem precisar instalá-lo no disco rígido. Ele é projetado para deixar o mínimo de rastros possível, o que significa que não salva seus dados pessoais ou suas atividades online.
O Tails é projetado com segurança em mente. Ele é atualizado regularmente para corrigir quaisquer vulnerabilidades de segurança e para incluir as últimas ferramentas de privacidade. O Tails também é projetado para manter sua privacidade e segurança em caso de perda ou roubo do dispositivo que contém o sistema operacional. Ele usa criptografia de disco para proteger seus arquivos pessoais e mantém todos os arquivos temporários na memória RAM, que é apagada quando você desliga o computador.
Mas você pode salvar alguns de seus arquivos e configurações em um Persistent Storage criptografado em seu stick USB Tails. O Persistent Storage é uma partição criptografada protegida por uma senha que ocupa todo o espaço livre deixado no pendrive. Tudo no Persistent Storage é criptografado automaticamente.
Para usar Tails, basta baixar a imagem do sistema operacional e gravá-la em um pendrive USB. Quando você estiver pronto para usá-lo, basta conectar o pendrive USB ao computador e iniciar o sistema operacional a partir dele. Depois de usar Tails, basta remover o pendrive USB e nenhum traço será deixado no computador.
https://tails.boum.org
-
 @ df67f9a7:2d4fc200
2024-07-07 18:25:32
@ df67f9a7:2d4fc200
2024-07-07 18:25:32Anyone who thinks that “onboarding new users” is simply a technical challenge of educating people about “how Nostr works”, is grossly mistaken about social networks in general and blind to what makes Nostr so special.
Social Networks are for Friends
Relationship building is why people use social networks. Connecting with friends and loved ones (and colleagues and customers also) is the obvious reason to join, and should be the primary objective in any onboarding endeavor. Everything else “about the technology” only needs to be introduced “as needed” in order for each new user to achieve this goal.
The Nostr Network Requires Trusted Friendships
To thrive at scale, Nostr needs to have established and interconnected “webs of trusted friends” for “verifying” authentic profiles and quality content. This PgP strategy for decentralized trust implemented on Nostr, is the best way to keep bots and bad actors at bay while preserving freedom and sovereignty for every user. Even though Nostr still doesn’t have a standard for determining who “is trusted” for any one user across all clients, we can already build tools to onboard new friends of the highest quality trust. Leveraging existing relationships, “webs of trust” can be strengthened even at this early stage simply by advocates “inviting friends to Nostr”.
Nostr is New and Already Full of Trusted Friends
But it won’t be for long. Bots and bad actors are relatively “easy” to keep at bay today because the Nostr userbase is still small. People who come to Nostr and STAY have mostly been a self selecting group of “freedom tech fans”. We like it this way, and are generally happy to be here. The comraderie is refreshing. But the more people that come to Nostr, the more Nostr will attract different kinds of people.
This is already happening. Nostr is growing at the edges, reaching out beyond the “freedom tech fans” and attracting a number of “less committed” (and some nefarious) individuals here and there. Who sticks around? The “friends of freedom tech fans” stick around longer because they have friends here. WAY BEFORE even considering how “the network effect” will take over, Nostr needs to solve for retention by bringing more “trusted friends” into the network. Social onboarding tools will allow us to share Nostr to “friends of freedom tech fans” and beyond, establishing interconnected “webs of trust” that are increasingly impermeable to bots and bad actors.
Nostr is Freedom Tech that People Want to Share
Creators and influencers of every kind share Nostr (and Nostr content) every day. This phenomenon is a gold mine for onboarding, and can be supported with tools and incentives. Driven by the fact that Nostr is an open protocol, owned by nobody and available for anybody to build upon and profit from, the passion for sharing Nostr will never wane. But our userbase may fall off, if people become disenchanted by undesirable content or lack of good follows. This is why onboarding efforts, to attract more “friends” to the network, are so important. Leveraging the “share worthy” phenomenon of Nostr itself to grow Nostr’s networks of “trusted friends” seems like a no brainer. But for this strategy to work, it needs to be win win win for all parties.
Everybody Wins with More Trusted Users on Nostr
Even as standards for qualifying trust are still being refined, “social onboarding” increases the ratio of “more” trusted over “less” trusted users across the network.
Developers Win
With more trusted users on the network, Nostr developers win by being able to attract an increasingly diverse range of business partners to sponsor their projects.
Sponsors Win
An increase in trusted usership equates to more “real people” perusing “desired content” and more chances for brands to engage “organically” with target audiences. Marketing opportunities increase with trust.
Advocates Win
Simply by sharing Nostr with their friends, Advocates support the sustained growth of trust across the network. Valuable zap reward programs to incentivize high quality onboarding efforts are easily justified and funded by social onboarding clients and their sponsors.
Users Win
More trusted users across the network means more trustworthy content in every feed and more easily discoverable friends and new follows regardless of the client or algorithm used.
Nostr Wins
More trusted users on the network means more “high quality” trust connections between each user. Strong webs of trust is what keeps out bots and bad actors, and is essential for stability as Nostr scales.
Social Onboarding Clients Bring Trust to Nostr
Having more tools for “sharing Nostr with friends” is how Nostr wins. Any client can have capacity for “Social Onboarding”. This may be a dedicated onboarding client or a feature set within a social client. A client that offers “Social Onboarding” will support Nostr advocates and the users that they invite. These should have the following feature set :
- Nostr advocates may create and share any number of customizable “Nostr invites” for different audiences or occasions. Each may have different reccomendations, or access codes, or expiry options. (A NIP is in the works)
- Nostr invite QR codes (and shareable URLs) should resolve to a WEB based interface for prospective (and existing) users who MAY NOT have a client or browser extension already installed.
- Each invite should (within the onboarding client) provide access to low friction profile creation AND advocate reccomended lists of new friends, interest groups, preferred clients, best relays, and other stuff.
- Private key generation and management for new users should be handled entirely within the onboarding client (using NIP standards without a browser extension or external bunker app) to reduce friction at this crucial moment.
- A human readable Nostr address (NIP05 or some future NIP) should be generated automatically for all new users.
- New account creation should result immediately in a direct message or group thread of private “gift wrap” encrypted messages. This thread acts as the new user’s “first contact” with the advocate (possibly others as well) and an anchor for exploring the rest of Nostr.
- Invite “receipt” data (who invited who) should be “gift wrap” encrypted, accessible only to the advocate and new user. Clients wishing to use this data for analytics MAY request access from BOTH parties.
- Top Advocates may be calculated by the client (using data from invite receipts OR from public Nostr usage metrics), and awards may be offered.
- Advocates may also be supported by the client through access to private “advocate support” groups and communities over the Nostr network.
Support Social Onboarding for Nostr
Meet Me On Nostr is an app for sharing Nostr with friends via advocate invites. It is a reference client to demonstrate the power of Social Onboarding for Nostr. The first launch of "feature complete" client is expected in fall 2024.
This is a “bootstrap” funded project in active development. We are not grant funded or VC funded. Instead, we are looking to pay our developers by sponsorships from “Nostr adjacent” businesses who want to increase brand recognition over this new social network.
Is Your Business Nostr Adjacent?
“I’d like to advertise on Nostr but it’s “not quite ready” says our marketing team.”
“It has potential, and we have alignment, but the technology is still a bit rough.”
“Nostr is a perfect fit for our “target audience”, but there simply aren’t enough people using it.”
If your business is aligned with freedom technology, and the people who build and use Nostr, then NOW is the perfect time to sponsor Social Onboarding. Help grow Nostr’s base of trusted users and engage directly with Nostr’s most active advocates and influencers as it scales.
Release Nostr’s Superpower
When Nostr advocates are equipped and incentivized to share Nostr with their friends, nothing can stop this network from growing and growing and growing ever more secure and interconnected networks of trusted users.
Onboarding and retaining trusted users as Nostr scales will require so much more than just pointing people to “how Nostr works” content. Nostr’s true power lies dormant in the existing relationships that Nostr users already have outside of Nostr. Leveraging this power is what Social Onboarding is all about. Social Onboarding is Nostr’s superpower.
-
 @ 4ba8e86d:89d32de4
2024-10-07 15:43:17
@ 4ba8e86d:89d32de4
2024-10-07 15:43:17Ele oferece recursos adicionais em relação ao aplicativo oficial do YouTube, como a possibilidade de assistir vídeos sem anúncios, reproduzir em segundo plano, baixar vídeos e áudios, entre outros.
O NewPipe foi desenvolvido como uma alternativa de código aberto ao aplicativo oficial do YouTube para dispositivos Android. O projeto foi iniciado por Christian Schabesberger em 2015, como um projeto de software livre hospedado no GitHub. Desde então, vários colaboradores se juntaram ao projeto para melhorar e expandir suas funcionalidades. O objetivo principal por trás do desenvolvimento do NewPipe foi fornecer uma experiência mais privada, segura e personalizada para os usuários do YouTube. Muitas pessoas estavam preocupadas com a coleta de dados e o rastreamento de usuários feitos pelo aplicativo oficial do YouTube, e o NewPipe surgiu como uma alternativa para resolver essas preocupações. O desenvolvimento do NewPipe foi impulsionado pela comunidade de software livre e pela filosofia de transparência, privacidade e liberdade de escolha do usuário. Como um projeto de código aberto, o NewPipe permite que os usuários examinem e modifiquem o código-fonte, se assim desejarem, tornando o aplicativo mais transparente e confiável. Ao longo dos anos, o NewPipe evoluiu e adicionou recursos, como reprodução em segundo plano, bloqueio de anúncios, download de vídeos e áudios, gerenciamento de inscrições e muito mais. Esses recursos extras fornecem aos usuários uma experiência mais personalizada e conveniente ao assistir e baixar conteúdo do YouTube.
Principais recursos do NewPipe:
-
Reprodução de vídeos: O NewPipe permite assistir a vídeos do YouTube diretamente no aplicativo, fornecendo uma interface intuitiva e fácil de usar.
-
Reprodução em segundo plano: Você pode reproduzir vídeos do YouTube em segundo plano, permitindo que você ouça o áudio do vídeo enquanto realiza outras tarefas em seu dispositivo Android.
-
Bloqueador de anúncios: O NewPipe bloqueia automaticamente anúncios em vídeos do YouTube, proporcionando uma experiência de visualização mais livre de interrupções.
-
Download de vídeos: O aplicativo permite baixar vídeos do YouTube diretamente para o armazenamento do seu dispositivo Android. Você pode escolher a qualidade de vídeo desejada e salvá-lo para assistir offline.
-
Download de áudios: Além de vídeos, o NewPipe também permite que você baixe apenas o áudio dos vídeos do YouTube em formatos como MP3 ou AAC.
-
Assinaturas e notificações: Você pode se inscrever nos canais do YouTube no NewPipe e receber notificações sobre novos vídeos dos canais que você segue.
-
Privacidade e segurança: O NewPipe prioriza a privacidade dos usuários. Ele não requer login em uma conta do Google para acessar o conteúdo do YouTube, o que significa que você pode usar o aplicativo sem fornecer suas informações pessoais.
O NewPipe oferece uma alternativa interessante para aqueles que desejam uma experiência personalizada e privada ao acessar o conteúdo do YouTube em dispositivos Android.
Pode baixar F-droid https://f-droid.org/packages/org.schabi.newpipe/
https://github.com/TeamNewPipe/NewPipe
-
-
 @ 2779f3d9:1a7f98d1
2024-11-28 00:43:46
@ 2779f3d9:1a7f98d1
2024-11-28 00:43:46NOSTR SDK FOR APPLE PLATFORMS
Progress Report # 1: Aug - Oct 2024
Nostr SDK for Apple Platforms made great strides this quarter. I was the sole developer who maintained Nostr SDK for Apple Platforms part-time, as the other core contributors, unfortunately, could not commit time to developing or reviewing code for the project.
Approximately 50% of the tasks listed in the original OpenSats application have been completed. Moreover, implementations of several other NIPs / event kinds not listed in the application were fixed or added.
There was a substantial architecture change in how Nostr event kinds are built to improve the project's code maintainability and scalability as more NIPs and event kinds are supported. Specifically, certain event kinds support several handfuls of tags, some of which have complex logic. This requirement resulted in the introduction of a large, unmaintainable number of parameters in event creation methods in the EventCreating protocol. Multiple event kinds share some tags, but the EventCreating architecture made it difficult to share logic. By deprecating the EventCreating protocol in favor of the NostrEventBuilding protocol, we can encourage a composable architecture: decompose each event kind tag into a separate builder function, and tags shared across multiple event kinds can re-use the same code. This architecture change has and will pay dividends in future changes. For example, labels, custom emojis, and threading are concepts and tags shared across multiple event kinds, and their implementation has been made substantially more manageable with this architecture. Vitor Pamplona, developer of Amethyst, applauded the architecture design by saying:
It's nice indeed. I will be copying your SDK patterns on Kotlin :)I battle-tested Nostr SDK for Apple Platforms in the wild by integrating it into Comingle iOS, an events app powered by Nostr, solely developed by me. It was launched and used at Nostriga in August 2024 for attendees to see the conference schedule and RSVP to talks. It proved that a developer could quickly use the SDK to build a functional iOS app on Nostr using Swift.
1) How did you spend your time?
Below is a broken-down summarized bulletpointed list of completed tasks.
Development of Nostr SDK for Apple Platforms
Added
- NIP-17 Private Direct Messages
- NIP-31 alt tags
- NIP-32 Labeling
- NIP-36 Sensitive Content / Content Warning
- NIP-40 Expiration Timestamp
- Add NostrEventBuilding protocol to enable flexible composition of shared patterns across different kinds of NostrEvents
- Add Swift 6.0 to unit tests
- Integration into Comingle iOS client to battle-test SDK
Updated
- NIP-01 - Add missing test coverage for referencedEventIds and referencedPubkeys functions in TextNoteEventTests
- NIP-01 - Add referencedPubkeys, referencedEventIds, and referencedEventCoordinates to NostrEvent
- NIP-01 - Fix incorrect test fixture and assertions in TextNoteEventTests for replies
- NIP-10 - Refactor threaded event tag building and interpreting logic so non-kind-1 events can reuse them
- NIP-25 Reactions - Add ReactionEvent.Builder to deprecate equivalent function in EventCreating
- NIP-42 Authentication - Add AuthenticationEvent.Builder to deprecate equivalent function in EventCreating
- NIP-42 - Deprecate AuthenticationEvent initializer in favor of AuthenticationEvent.Builder
- NIP-59 Gift Wrap - Add support for receiver aliases for gift wrap creation to avoid exposing identities and improve test coverage
- Fix GitHub workflows to trigger on pull_request_target so that they can run on PRs from public forks
- Expose RelayResponse.Message and RelayResponse.MessagePrefix as public
- Fix SwiftLint errors from latest SwiftLint release
- Fix GitHub workflows to also run on main branch
- Update README with current list of NIPs
In Progress
- NIP-28 Public Chat - Review pull request from external contributor developing Skatepay
- NIP-57 Lightning Zaps
- Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds
2) What do you plan to work on next quarter?
The remaining items in the original application to OpenSats include: - Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds - Provide better support for integrating data models with persistence layers - Add unit tests and graceful handling for bad data from relays - Outbox model support / relay abstraction on top of events - Integrate demo app with more implemented NIPs - Integrate Nostr SDK for Apple Platforms further into Comingle iOS for further battle-testing - Support Damus, Nos.social, Primal, and other clients as they integrate with parts of the SDK by answering questions, fixing any issues they have, adding requested features, and reviewing pull requests - Consider integrating SDK NIP-44 v2 encryption or NIP-17 DMs with Damus iOS to battle-test implementation and push for deprecation of NIP-04 DMs - NIP-28 Public Chat - Review pull request from external contributor developing Skatepay - NIP-47 Nostr Wallet Connect - Review pull request from external contributor - NIP-57 Lightning Zaps
3) How did you make use of the money?
Living expenses.
-
 @ 3f0702fa:66db56f1
2024-12-15 07:42:25
@ 3f0702fa:66db56f1
2024-12-15 07:42:25Сегодня мы стали свидетелями открытия, которого Курган ждал десятилетия – культурно-исторического комплекса «Курганская крепость». Это не просто реконструкция старинных укреплений, а уникальный проект, объединивший прошлое и будущее, создавшее пространство для образования, развлечений и погружения в историю нашего края.
Идея воссоздания крепости, существовавшей в XVII-XVIII веках, витала в воздухе давно, но только сейчас, благодаря современным технологиям и подходу к культурному наследию, она воплотилась в жизнь во всем своем великолепии. Комплекс расположен на историческом месте, где некогда возвышались деревянные стены и башни, и занимает внушительную территорию.
Главной особенностью крепости является то, что на территории комплекса действуют иммерсивные театры, где разыгрываются сцены из жизни первых поселенцев, проходят ремесленные мастер-классы, где можно не только увидеть, но и попробовать себя в роли кузнеца, ткача или гончара.
Виртуальная и дополненная реальность позволяют увидеть крепость в ее первозданном виде, “прогуляться” по улицам 17 века, стать свидетелем исторических событий, недоступных ранее. Специальные AR-приложения оживляют экспонаты, рассказывают истории людей, живших в то время.
Кстати, комплекс построен с использованием современных экологически чистых материалов. Солнечные панели обеспечивают его электроснабжение, а система сбора дождевой воды – полив зеленых насаждений. “Зеленая” концепция - один из приоритетов проекта, позволяющий сохранить уникальную флору региона и минимизировать воздействие на окружающую среду. Научно-исследовательский центр: На базе комплекса функционирует современный научно-исследовательский центр, изучающий историю региона, археологические находки и культурное наследие. Это позволяет не только углубить знания о прошлом, но и обеспечить сохранность артефактов для будущих поколений.
Отметим, «Курганская крепость» – это не только место для туристов, но и площадка для проведения фестивалей, концертов, выставок и других культурных мероприятий. Комплекс стал новым центром притяжения для горожан и гостей города, способствуя развитию творческого потенциала региона.
В рамках комплекса также работают образовательные центры для детей и взрослых, где в интерактивной форме преподаются история, краеведение, ремесла. Уникальные методики обучения позволяют “прикоснуться к прошлому” в прямом смысле этого слова и пробудить интерес к изучению истории.
«Курганская крепость» – это не просто историческая реконструкция, это проект будущего, демонстрирующий, как можно эффективно использовать современные технологии для сохранения и популяризации культурного наследия. Это инвестиция в наше будущее, в нашу идентичность, в понимание того, откуда мы пришли и куда идем.
Мы будем следить за развитием комплекса и рассказывать вам о новых открытиях и событиях. Оставайтесь с нами!
45news
Курган2040
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ e83b66a8:b0526c2b
2024-09-26 19:29:43
@ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining.
Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully.
Solo mining pools exist, such as: https://solo.ckpool.org/
It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool.
You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power.
There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely.
A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine.
So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning.
So here’s my recommendation.
Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin.
Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join.
If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools.
Bear in mind that many of the other smaller pools are still controlled by Bitmain.
If you're still interested in lottery mining, here are your chances of winning a block:
Represented as Hash rates of different miners:
Nerdminer: 20 KH/s = 20,000 H/s
Bitaxe: 750 GH/s = 750,000,000,000 H/s
Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s
Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s
Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s
Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000
If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357%
Over a year, your chances increase to: 0.00627707006369428%
Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one):
0.000005%
Over a year, your chances increase to: 0.00026%
Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions:
https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/
https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx
https://www.youtube.com/watch?v=Wo91DWvZRs8
https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
-
 @ c4b5369a:b812dbd6
2024-11-24 09:27:12
@ c4b5369a:b812dbd6
2024-11-24 09:27:12How to print your own ecash, using Gandlaf's money printer
To celebrate the recent money printer update, here is a short guide on how to use it.
Step 1: Go to the money printer
Unlike the FED's money printer, this Cashu ecash money printer is openly available. Head over to https://brrr.gandlaf.com to give it a spin.
Select a mint
Choose a mint that should be backing the ecash notes. You have a few different options when choosing a mint:
- Connect to your own mint: Connecting to your own mint is great if you want to be the backer of the ecash notes. It does however require you to have your mint up and running. You can connect to it by typing the mint URL into the input field.
- Connect to a known mint: There are mints that are already indexed on nostr. You can find them by clicking on the `discover more mints` button.
- Connect to any mint you want!: All you need is the mints URL. Just type it into the input bar!
Once you selected a mint, click connect to set up the mint for money printing :

After connecting to the mint, you will have the option to select the currency you want to print. Not all mints support all currencies! The dropdown menu below will show all available currencies the mint offers.
After selecting your preferred currency, click confirm to continue.

In the next step, you will chose the amount that should be printed on each note. Be careful though, because unfortunately not every amount is possible. To preserve mint users privacy ecash mints use fixed coin amounts. This means a specific amount, will be made up from smaller amounts. Today, most cashu mints use power-of-2 amounts.
So if you for example would like to print the amount "100", it would be made up from the coins [64, 32, 4]. The maximum number of coins that can be encoded in a QR code, without the QR code losing its readability is \~4. The money printer will analyze which amounts the mint offers, and show how many coins will be needed.
Below, you will see the calculation of how much the total issuance for this printing cycle will be. Once you are all set, click confirm to continue.

You can now either add the funds for the print via Cashu token or via Lightning. Let's first take a look on how to add funds via Cashu token.
If you select this option, I will assume that you already own ecash from the mint you wish to print the notes. Otherwise, you should move on to the payment by lightning.
You have to make sure that the token you are pasting is from the correct mint, in the correct unit/currency and matches the amount exactly! Otherwise, it will not work.

If you don't own ecash from that mint, you can pay for the print with lightning directly. The only fees that will be charged are Lightning network fees.
Just scan the QR code that is presented to you and wait for the payment to be confirmed.

Once the payment has confirmed, either through Cashu or through Lightning, the print is ready. You can now customize the design you wish to print.
You can select a color, a brand image and a corner image that should be put on the note.
Once you are happy with the design, go ahead and click `Print now! BRRRRRRRRRRR`

This will take you to the print page. You can now print the ecash by pressing `CTRL`+`P`
And that's it! You have now printed your own money. I hope you liked the experience of playing FED for a day.
Be aware! Once scanned and redeemed, the ecash notes become invalid. So they are one-time-use.
If you want to make another print, just refresh the page. It will take you back to the beginning. Your past prints will also be stored in the browser cache, so you can come back to them at a later time, if your printer overheated or something.

Happy printing!
Gandlaf
-
 @ d6dc9554:d0593a0c
2023-09-21 18:37:14
@ d6dc9554:d0593a0c
2023-09-21 18:37:14Nas blockchains PoW o consenso é alcançado por meio de prova de trabalho computacional e o objetivo principal é evitar que atores mal intencionados consumam ou ataquem a rede de forma perigosa. Este método de consenso requer um grande poder computacional para criar novos blocos, mas é muito simples, por parte de outros, verificar esse trabalho. Por isso se diz que PoW é uma estratégia assimétrica.
Nas blockchains PoS o objetivo é o mesmo, criar blocos e chegar a um consenso, mas nas PoS não é necessário um poder de processamento tão grande como nas PoW. Em média as PoS gastam menos de 1% da energia das PoW. Nas PoS os mineradores são chamados de validadores. Enquanto que nas PoW quem fica com a recompensa é quem resolve primeiro a charada matemática, nas PoS o validador que vai ganhar a recompensa é escolhido de forma aleatória, mas dando maior probabilidade aos que respeitem determinados critérios. A comunidade bitcoin é muito relutante em relação a PoS porque é mais fácil conseguir uma grande quantidade da moeda em causa do que mais que 51% de poder processamento. Logo as PoS são mais vulneráveis no que toca a segurança. Mas aqui cada caso é um caso e é preciso fazer essa análise para cada moeda.
As blockchains PoW tendem a ser mais descentralizadas enquanto as PoS mais centralizadas, não só em acesso, mas também em operação. Mais de metade dos validadores de ethereum estão na cloud da amazon. As blockchains PoW apresentam grandes desafios na escalabilidade de operação, muitas vezes exigindo soluções de segunda camada (L2), enquanto que as PoS possuem mecanismos de escalabilidade muito mais flexíveis. Os algoritmos PoW são muito mais simples de implementar do que os PoS e, portanto, menos suscetíveis a erros. Um bom exemplo é o PoS da ethereum que estava a ser implementado desde 2018.
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-