-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ bbb5dda0:f09e2747
2024-12-14 13:58:25
@ bbb5dda0:f09e2747
2024-12-14 13:58:25What is it about travel that makes us so addicted to it? Chasing the high of the next view, the next location. Is travel always the same as travel? I think certainly not. Is travel valuable? Then what about it provides the value. Because it's different when someone from the same country goes to that attraction, vs when you come from the other side of earth to see it. What do you gain?
Up until now travel for me has been stillness with nature, and even within the more social trips like SEC-03 I appreciate the ability to be alone and stare at the waves for hours on end. As I'm doing while typing this. Travel changes over time, as it changes you. It's not about seeing more rockfaces anymore, it's about seeing the details in just one of them. The subtle hints to a far and violent past that formed these layers of rock, now exposed for us to be seen and appreciated.
If only we did that more and not just running to so many of these places without appreciating them. Destroying the exact thing we want to see in the process. I really hope mass tourism will come to an end along with the 'social' media that created it. I ended up at a beautiful beach the other day, it came with a freaking waterfall and I saw at least a dozen people only taking basically a photoshoot of themselves or their (girl)friends for 15-30 minutes straight. It doesn't really annoy me but it just makes me wonder, do they actually notice their surroundings and are they actually enjoying the places they go to? I just hope their minds work different from mine and that they actually are enjoying themselves by doing that. As far as mass-tourism goes I wouldn't mind if we replace it with mass-wandering, to places not on the top 10's, not filled with chic hotels and resorts. Just the places that welcome you but won't live to serve you, that is what travel is to me.
I've been taking less pictures over time, the ones I take are mostly because I appreciate the composition, especially after watching the same view for over an hour, and suddenly spotting a new detail that I hadn't noticed before. Anyway, I don't even know where I'm going with this, I just felt the need to write down these thoughts...
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46 -
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 0d532801:197a0c30
2024-12-06 05:13:25
@ 0d532801:197a0c30
2024-12-06 05:13:25Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden.
İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım.
Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor.
Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar.
İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu.
Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür.
Büyük bir fırsat ondan faydalanılmasını bekler.
Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce.
İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür.
İnsanlar iletişim kuramadıkları zaman öfkelenir.
İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi.
Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım.
Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda.
-
 @ e373ca41:b82abcc5
2024-12-11 11:48:41
@ e373ca41:b82abcc5
2024-12-11 11:48:41There is a nice image in complexity theory: to describe the indirect effects in complex systems, one uses the image of a butterfly whose distant flapping of wings can have much greater effects in a completely different place. In the USA, the balance of power has changed dramatically. Corona policy critics Kennedy and Bhattacharya are to become Secretary of Health and Human Services and head of the NIH, respectively. Every wave, every flapping of wings that comes from the USA will eventually reach Germany. For decades, Germany has only been a recipient of impulses, not a provider of them.
Germany has failed to deal with the corona pandemic in the same manner as it had previously compliantly supported and carried out the madness. But the tsunami of enlightenment from the USA is building up and will eventually reach Germany. A nation in the hands of perpetrators, cover-ups, accomplices and profiteers must once again be liberated from the outside. When will we become an independent country?
First it crumbles, then it erodes quickly
The precursors of the tsunami can be felt everywhere. The first signs of panic are spreading among local coronists. The big row back and “save what can still be saved” is spreading. After the coalition broke down, the FDP suddenly called for a committee of inquiry and Lauterbach's resignation. ARD broadcasts a documentary about vaccination victims; it takes stock after uncritically following the damage to citizens' health for four years. On Hart aber Fair, there was a small pseudo-debate between the coronavirus nomenclature (Lauterbach, Buyx, Hirschhausen) and a few critical mainstream voices around Heribert Prantl.
However, the coronavirus narrative is breaking ever stronger and faster and this is bringing a new dynamic into play. A report by the US House of Representatives now speaks of a laboratory accident as the most plausible cause of coronavirus. The biggest cover-up and obfuscator of this thesis in Germany was Christian Drosten. This view could easily get you banned from social media or get you into professional trouble during coronavirus. The physicist Roland Wiesendanger from the University of Hamburg was labeled a conspiracy theorist and campaigns were initiated against him. A laboratory accident then? Of course, it would now be necessary to explain how an “accident” fits in with the timely implementation of the simulation game “Event 201” or vaccines suddenly pulled out of a hat (developed in January 2020). It has just been revealed that the trucks from Bergamo, which were supposed to transport coffins of alleged corona deaths to crematoria in a convoy of 13 trucks, had apparently only loaded one coffin per truck. It doesn't take much effort for viral images and morbid emotions. The stage of the Corona Theater has been stormed, the stage set exposed as a fake.
Every narrative has a life cycle and Corona's is just coming to an end. The phase of self-destruction is about to begin. The dismantling of the old nomenclature by the stirrup holders and profiteers begins. Christian Drosten is now being publicly criticized for his rash stance on child vaccinations, accusing his colleague of “underhand” behaviour. The Bild newspaper now claims to have discovered that Lauterbach lied. Only now? The Springer publishing house has been a supporter of the pandemic from the very beginning, a representative of corona orthodoxy, only with a semi-critical veneer, a kind of pseudo-opposition in the mainstream. Biontech received a prize from the publisher, and the then editor-in-chief of Bild, Julian Reichelt, fantasized that 20 Biontechs were needed in Germany. Nobody could fail to notice that Karl Lauterbach was fanatical, confused and a permanent liar.
Advertisement:
Are you looking for the easiest way to buy Bitcoin and store it yourself? The RELAI app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees. (no financial advice).

Upgrade your self-custody with hard ware wallets! Check-out the newest Trezor Wallets, browse the shop or book an intro with an expert.
The book of the hour is “Seduced Thinking” by Czeslaw Milosz. The later Nobel Prize winner for literature from Poland described the subjugation of the intellectual caste in Poland by Soviet doctrine in the 1950s. He describes obedience to the system, conformity to orthodoxy, the different types of followers (he calls them Alpha, Beta, Gamma, Delta). The most unimaginable thing for him was that this was “servitude through knowledge”.
Milosz writes:
“There has never been such servitude through knowledge, it was reserved for the twentieth century. My generation was still taught at school that knowledge makes you free.”
Seduced thinking leads to a weighted mind, resulting in a stooped posture and ultimately a broken spine.
High treason against democracy, anyone?
What happened during Corona in Germany was more than a seduction of thought. It was a conspiracy by politicians, a caste of experts, the media, the scientific community and the cultural sector, who actively fought against any form of criticism and sold the health of an entire nation to a group of philanthrocapitalists around Bill Gates & Co. for a large-scale field trial with novel vaccines. As we know today and could have guessed at the time: with disastrous consequences and unforeseeable damage. And all this in the “best democracy of all time”. A better campaign to discredit democracy is hardly possible.
The coronavirus era was a breach of the democratic social contract, the greatest possible delegitimization of the state. A new democracy was created out of the old democracy: “Our democracy”. New institutions were created out of the institutions; the Bundestag was disempowered and a government of experts and councillors was set up, which took a strictly orthodox line. A new people of protectors was elected and critics were silenced. The good citizen was suddenly the obedient citizen. The conspiracy was not the result of collusion, but of incentivization. Everyone was aware of which statement could promote or destroy a career. Everyone made their own decision, chose their own camp. Anyone who wanted to make a pro-government statement, from a no-name expert to an innkeeper who barred unvaccinated people, only had to make it known and they were guaranteed attention through airtime, interviews and reporting. Everyone could get a piece of the cake, but it was a poisoned cake.
The sugar had an immediate effect, but the poison is insidious.
This article first appeared in German by Milosz Matuschek on Freischwebende Intelligenz.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 234035ec:edc3751d
2024-12-14 05:12:52
@ 234035ec:edc3751d
2024-12-14 05:12:52America's Fourth Fourth Turning
We can learn much from the Book "The Fourth Turning: An American Prophecy" By William Strauss and Neil Howe. The Book looks back throughout history to identify the cyclical patterns that emerge and establishes archetypes that emerges in the generations as they come of age in these different stages of history.
There are four phases (turnings) that are outlined in the book:
- The High
- The Awakening
- The Unraveling
- The Crisis
The authors identify that America is due for another fourth turning, and I would argue that we are now in the midst of America's Fourth ever fourth turning. The first three being marked by the American Revolution, the Civil War, and the Great Depression- WWII. Today we have been in an increasingly unstable financial, political, and social environment which share eery similarities to the unraveling period of the prior cycles.
I believe that this fourth turning began with the 2008 "Great Financial Crisis" and has been ongoing ever since the fed chose to engage in mass currency devaluation in order to keep the banks solvent. While these actions have delayed the inevitable larger crisis, they will not be able to avoid it. Since 2008 the money supply has grown from roughly $8 Trillion to over $20 Trillion. This massive currency dilution is reflected in increased prices across all sectors but heavily concentrated in scarce desirable assets. As National debt continues to rise and interest expenses balloon, the only way out for the US dollar is massive inflation.
The issue with continued inflation is that it leads to massive societal suffering and unrest. At 2% inflation most individuals aren't aware that they are being stolen from, but as inflation rates start to stick above 10% people start to realize what is really going on. History tells us that as currencies enter into hyper-inflation, the societal fabric begins to fall apart. One does not have to be an anthropologist to look around and realize the massive cultural shifts that we have seen since moving to a fiat standard in 1971 and much faster ever since 2008.
I find it very profound that at the same time that the global financial system began showing cracks, Satoshi Nakamoto introduced the solution to the world. It feels as though this fourth turning is centered around technological innovation in computing, as well as the collapse of an outdated and corrupt financial system. Bitcoin exists at the perfect intersection of these two by utilizing cryptography to empower people to exit the corrupt system and begin to build a superior one on sound foundation. If the crisis of this great fourth turning is centered around the sovereign debt crisis, than Bitcoin becomes the clear answer.
Thriving In The Chaos
Being Born in 2001 I do not have much memory of a pre-2008 world. Being only 7 years old at the time I did not fully grasp the significance of what was going on, but my life has been impacted by it nonetheless.
When the central bank chooses to hold interest rates artificially low, they are effectively driving money into more and more places where it shouldn't actually be. This is usually described as a bubble, which then bursts leaving many financially ruined. Accept for those who the central bank then chooses to bail out by diluting the purchasing power of all the savers.
Much of the Millenial and Gen Z generations feel that they will never reach financial security or be able own a home and retire at a reasonable age. Many of them are saddled with large student loans, credit card debt, and car loans. While much of this is due to personal decision making, we exist in a system today that is designed to extract as much value as possible from each citizen. If you were to take out a loan to go to school, get a job, a mortgage, and a car payment, and used a savings account, you would never become financially free.
People my age have become increasingly unsatisfied with the way that things are, which is why I am so hopeful for a brighter future. While most aren't quite aware of what the true heart of the issue is, they feel that something is deeply wrong. I believe that Bitcoin will be the catalyst for the masses to wake up and stop funding the current system.
Those that lead the way into a new frontier during these fourth turnings come out on the other side in positions of great respect and power. While these next few years will likely difficult, there will be massive opportunity for those who are bold enough to stand for their beliefs and work to propagate them.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a39d19ec:3d88f61e
2024-12-14 14:42:26
@ a39d19ec:3d88f61e
2024-12-14 14:42:26This week's practical 3d print is a simple catch all tray.

Catch all tray
As for most of the useful prints I show you in this series I printed it a long time ago and can't find the link to the design file. I am pretty sure it's from Thingiverse though.
What it does
It perfectly serves as a central place for the things I commonly need when I go out. So I don't need to search for them.
What I like about the design is, that it catches all things from my pockets i.e. key, lighter, earpods, slide wallet and more when I come home. But not the dust and dirt. It falls throught the holes in tray.
3dprint #3ddruck #3dprinting
-
 @ bd32f268:22b33966
2024-12-14 14:06:06
@ bd32f268:22b33966
2024-12-14 14:06:06O título deste texto dá-nos uma pergunta retórica, isto é, uma interrogação com uma resposta evidente. Para que não restem dúvidas a resposta evidente seria, um enfático e inequívoco sim. Sim, o mal existe. Contudo, nos dias que correm muitas pessoas aparentam duvidar da existência do mal.
Creio que em verdade não será tanto uma dúvida sincera, porque de facto ninguém consegue sustentar uma visão de mundo sem ter alguma ideia do que é o mal. Penso que será mais uma tentativa de fazer apologética do mal, disfarçada de uma certa ingenuidade. O que quero dizer é que as pessoas que apregoam que o mal não existe sabem perfeitamente que existe, no entanto é conveniente negá-lo para que daí não decorra um julgamento sincero das suas atitudes. A definição objetiva destas coisas pode ser-nos difícil porque implica que nos vejamos de uma forma mais clara e honesta quando usamos de uma medida objetiva.
Ao desviarmos a atenção destes factos, tentamos de alguma forma justificar a nossa corrupção moral. Dizemos adágios populares como: “cada cabeça sua sentença”; isto para esconder um facto incontornável que é a universalidade do mal. Significa isto que o mal quando nasce é para todos, assim como o bem. Não é lógico nem racional defender que a pedofilia é um mal na nossa cultura mas que nas outras culturas não é assim tão mau. Se é um mal é-o naturalmente para a humanidade. Por outro lado defender que as leis morais são exclusivas para um determinado grupo de humanos é concorrer para a ideia de casta social ou diferença na essência do humano.
Um outro esquema que nos leva a considerar que o mal é relativo é o facto de ignorarmos de onde provém a definição de mal. É porventura frequente que imbuídos do espírito da democracia ocidental julguemos que a possível definição de mal vem da convenção social, ou seja, daquilo que a maior parte das pessoas acredita ser o mal. Contudo, facilmente percebemos que não é assim, que a definição de mal não provém de convenção social mas que depende de condições preternaturais. Há uma intemporalidade no mal que não depende da época ou da convenção social.
Penso que a analogia com a física pode ajudar-nos a perceber melhor estas realidades. Não há uma lei da gravidade diferente para a pessoa A e para a pessoa B, a lei é exatamente a mesma no entanto os corpos movem-se a diferentes velocidades e altitudes portanto sentem-na de formas diferentes.
No ramo da psicologia vejo infelizmente um problema sério que se pretende com a excessiva utilização da linguagem terapêutica para falar sobre o mal. É muitíssimo frequente ver uma tentativa de patologizar todos os males. Não negando que o distúrbio psíquico pode estar presente na pessoa que comete um mal, inclusive um mal grave, isso não significa que em muitos casos não haja um assentimento consciente e deliberado da pessoa àquela atitude. Esta linguagem terapêutica levam-nos por vezes a romantizar o mal, e a procurar narrativas que o tornam numa novela sentimental onde a pessoa é sempre rotulada como uma vítima das circunstâncias contextuais, basta vermos o exemplo do marxismo que assim a determina.
Nesta ideologia a pessoa comete crimes porque é pobre e foi vetada a uma exclusão social, como se não fosse possível à pessoa pobre seguir um caminho de retidão moral. O filme Joker ilustra bem este aspeto novelesco da romantização do mal. Neste filme a personagem principal, um psicopata degenerado, é retratado como um doente mental que procura fazer “justiça” assassinando inocentes e destruindo património. Devido à pueril noção de agência, responsabilidade individual, e livre arbítrio o mal é quase tratado como uma caminho único, como se a personagem estivesse predestinada aquele mal.
 > Joaquin Phoenix - Joker 2019
> Joaquin Phoenix - Joker 2019São muitos os esquemas á nossa volta que além de dissimularem o mal, tentando indicar a sua inexistência, o promovem como sendo um bem. São muitas as mensagens contraditórias que promovem o exercício da vontade humana como um imperativo moral. São também frequentes as apologias à tolerância e empatia para com o mal. Contudo, isto é absurdidade. Como teremos ordem e paz sem combater os males? Como teremos espaço para a virtude quando tudo estiver tomado pelo mal ? Precisamos de filtrar este ruido para perceber de forma mais objetiva qual é a verdadeira face do mal.
-
 @ b2d670de:907f9d4a
2024-12-02 21:24:45
@ b2d670de:907f9d4a
2024-12-02 21:24:45onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ 141daddd:1df80a3f
2024-12-14 11:11:10
@ 141daddd:1df80a3f
2024-12-14 11:11:10This is a random post to try out Reads on Nostr.
For years, I had been waiting for the moment when stability hits my life: a stable place to live, a stable occupation or project, a stable headspace, for that matter. But it never came. And I realize now that it never will.
Since childhood my life has been a constant change of domicile, education facilities, etc. I was bron in one place, raised in another, changed 3 kindergartens and 4 schools. Then another move to study in a big city, a move abroad, a comeback and now again... It seems that the average change-stability cycle lasts around 2 years. It seems that the average change-stability cycle lasts around 2 years.
It's no wonder that I start feeling stale and bored when life becomes routine, repetitive: my nature rejects it. For a long time, I thought this constant change was a bug and I longed stability, especially seeing many people become extremely successful by doing the same thing year after year. That it's a feature is a recent revelation. Or, to be precise, it's both a bug and a feature, a two-sided coin like everything in this life.
Need to quit a job? Move to another city? Start a company or shut one down? Hire or fire someone? Conceive another child? These life-altering decisoins don't come easy to many people. As a matter of fact, some are totally paralized in life because they're afraid to make a change. But not me. Change is in my blood. The fact that the future is unknown is exciting to me, not scary.
And so far, it's worked well. Sure, impulsive decisions often cause unintended consequences and mistakes, but this is exactly how I learn, this is my modus operandi. I don't read instructions — I act.
Wow, this guy likes talking about himself!
The post is not about me. I just feel that there are many more people with a similar mindset, cultivated this way for various reasons, but even more people whose lives are too stagnant. So I want to say to them: just go for it. The worst and most extreme thing that can happen to you is death. But even that is not so bad: life-long inaction means you're already walking dead, and that is much worse.
-
 @ 2fb77d26:c47a6ee1
2024-12-08 21:08:02
@ 2fb77d26:c47a6ee1
2024-12-08 21:08:02****Der Staat geriert sich als Bewahrer von Demokratie und Menschenrechten, als singuläres Modell zur Aufrechterhaltung gesellschaftlicher Ordnung. Dabei haben die Strukturen supranationaler »Global Governance« das Konzept Nationalstaat längst obsolet gemacht. Und auch ein Blick auf das Handeln des Machtapparats Staat lässt begründete Zweifel an dessen öffentlicher Darstellung aufkommen – denn das Kerngeschäft eines jeden Staates besteht aus Unterdrückung, Raub und Mord. **
Mein exklusiver Beitrag für die zweite GEGENDRUCK, die 224 Seiten umfasst, am 15.10.2024 veröffentlicht wurde und unter www.gegendruck.eu bestellt werden kann. Nur durch die Unterstützung von analogen Formaten dieser Art wird aus der Gegenwart eine Vergangenheit, die man in der uns drohenden Zukunft noch zu rekonstruieren vermag. * Original mit Quellen: www.regenauer.press/blog/regieren-ist-ok*
»Wenn das Volk die Regierung fürchtet, haben wir Tyrannei. Wenn die Regierung das Volk fürchtet, haben wir Freiheit« – soll Thomas Jefferson, einer der Gründerväter der USA, dereinst festgehalten haben. Wer sich also in Anbetracht des Status quo noch nicht ganz si-cher ist, mit welchem Herrschaftssystem ihn die kriegslüsterne Biosicherheitsdoktrin der Postmoderne beglückt, mag in Jeffersons Worten entsprechende Inspiration finden. Denn mit Demokratie hat die ohrenbetäubende Kakofonie von Stil-, Rechts- und Sinnbrüchen selbstverständlich nichts zu tun. Die verblassende Pluralismussimulation der zurückliegen-den Dekaden mausert sich zu dem, was mental mobile Staatstheoretiker, Historiker, Philoso-phen, Journalisten und Aktivisten seit langem erwarten – einer offen kriminellen Terrorherr-schaft. Selten war klarer als jetzt: Regieren ist organisierte Kriminalität.
Folgt man Thomas Hobbes und Friedrich Nietzsche, ist der Staat ein »Ungeheuer«. Wäh-rend Hobbes diesen Umstand durchaus goutierte, fand Nietzsche ihn abstoßend. Und zwar zurecht. Denn die repressiven Züge, die das Staatskonzept seit der frühen Neuzeit kenn-zeichnen, sind inhärenter Bestandteil der Politikproduktion. Egal, welche Ideologie ein Staat vertritt, seinen Souveränitätsanspruch kann er nur mit Gewalt durchsetzen. Nach außen mit Krieg, nach innen mit dem auf konstant interpretationsoffener werdenden Gesetzen basieren-den Gewaltmonopol. Im Rahmen seiner Halbwertszeit durchläuft jedes Herrschaftskonstrukt vergleichbare Zyklen. Ist ein Staat gegründet, eine Regierung ausgerufen, institutionalisiert sie das favorisierte politische Modell – Demokratie, Sozialismus, Konservatismus, Libera-lismus, et cetera – und vereinnahmt ihre Untertanen mit Indoktrination, Zugeständnissen und moderater Autonomie. Doch Macht korrumpiert. Und macht gierig. Vor allem in repräsenta-tiven Systemen wie der korporatisierten Sozialdemokratie, wo Einfluss einen monetären Wert darstellt.
Die Folge: Lobbyismus, Korruption, Lagerbildung, Grabenkämpfe und Obszönitäten. Einer Phase relativer Freiheit und Prosperität folgt so bald eine mehr oder weniger harsche »Ent-differenzierung« (Wolfgang Merkel, 2010) – also die Auflösung alter Strukturen, Funktio-nen und Integrationsmechanismen. Die herrschenden »Machteliten« (C. Wright Mills, 1956) grenzen sich nach zwei Seiten ab. Auf der einen von regimetreuen Bewahrern des ursprüng-lichen Konzepts, den Konservativen, auf der anderen von den Gegnern »progressiver« Re-formen. Reformen, von denen zumeist die von wachsender staatlicher Machtfülle benachtei-ligte Bevölkerung betroffen ist. Diese zahlt natürlich auch die Zeche. Rechtsprechung und Medien passen sich diesem zusehends autoritären Umfeld an, um ihre Daseinsberechtigung nicht einzubüßen. Mit dem Implementierungsgrad solcher Reformprojekte aus dem Elfen-beinturm, in der Regel begleitet von ausufernder Bürokratie, wachsen die Widerstände dage-gen. Aus Autokratie wird Totalitarismus. »Erst ist es ein Polizeistaat, dann kommen die Aufstände«. Die »Mistgabeln« (Nick Hanauer, 2014). Aus der Vogelperspektive betrachtet sind es stets die gleichen zivilisatorischen Prozesse. Seit Jahrhunderten. In allen Systemen. Offen ist nur, wie brutal der Staat vorgehen muss, um sich an der Macht zu halten – und wie lange es dauert, bis die Arroganz der wenigen dennoch an der Macht der vielen erstickt.
Denn schlussendlich fällt jedes Imperium. Das lehrt die Geschichte. Hat das System den Zenit überschritten, fällt ob der grotesken Machtexzesse und Schizophrenitäten auch den konformistischsten Etatisten auf, dass die politmediale Schmierenkomödie nichts mehr mit der Realität des eigenen Lebens zu tun hat. Gewalt greift Raum. Psychische Gewalt – und physische. Demnach hat nun zweifelsohne auch der vermeintlich liberale Rechtsstaat der von supranationalen Verordnungen diktierten Gegenwart sein finales Entwicklungsstadium er-reicht: Die Tyrannei.
»Seht uns nur an. Alles ist verdreht, alles steht Kopf. Ärzte zerstören Gesundheit, Anwälte zerstören Gerechtigkeit, Psychiater zerstören Verstand, Wissenschaftler zerstören Wahr-heit, Massenmedien zerstören Information, Religionen zerstören Spiritualität und Regierun-gen zerstören die Freiheit.« (Michael Ellner)
Neu ist das alles nicht. Nur die Darreichungsformen und Machtinstrumente von Herrschaft wandeln sich über die Jahrhunderte. Die disziplinierenden Kontrollmechanismen zur Subor-dination der Massen professionalisieren sich im Rahmen des technologischen Fortschritts. So wirkt der Panoptismus der Postmoderne vor allem deshalb monströs, weil unser Gehirn evolutionär nicht darauf eingestellt ist. Es ist der Militarisierung von Information im Dauer-feuer multimedialer Infantilisierungspropaganda in den wenigsten Fällen gewachsen. Wer versucht, dieser omnipräsenten Pervertierung von Realität mit tradierten Denk- und Hand-lungsmustern zu begegnen, geht unter.
Nicht umsonst klagt der »Widerstand« in weiten Teilen über Erschöpfungszustände, Ver-schleiß, Burnout und Depression. Genau da soll er in Augen des Staatskonzeptes sein – am Ende. Aufgerieben. Entmutigt. Ohnmächtig. Dabei wäre gerade Humor das Patentrezept, um auch düsteren Zeiten ein erfülltes Leben abzugewinnen. Ein freies Leben. Denn frei wird man nicht, frei ist man – oder eben nicht. Freiheit ist eine Geisteshaltung, kein organisatori-sches Problem.
»Unsere Gesellschaft wird von Wahnsinnigen mit wahnsinnigen Zielen geführt. (…) Und ich denke, ich werde als Wahnsinniger eingesperrt, wenn ich das zum Ausdruck bringe. Das ist das Verrückte daran.« (John Lennon)
In diesem Lichte betrachtet nimmt es also kaum Wunder, dass das primäre Ziel der regieren-den Kaste darin besteht, die Bevölkerung in Angst, Armut, Abhängigkeiten und Agonie zu halten. Selbstbestimmte, selbstbewusste Individuen hätten nämlich nicht nur die Zeit, son-dern auch die mentale Kapazität und die Mittel, das Ponzi-Schema des polit-finanziellen Komplexes intellektuell wie organisatorisch zu durchdringen. Dementsprechend ist das Staatskonzept auch nicht darauf ausgelegt, das Individuum zu fördern. Es dient der Imple-mentierung eines konformistischen Kollektivismus. Die Massen sollen sich um die Flagge scharen. Wer kritische Fragen stellt und sich der Polonaise der Gutgläubigen verweigert, gilt als Landesverräter.
Doch nicht nur die vermeintlichen Häretiker sind Opfer staatlicher Willkür und Gewaltherr-schaft. Jeder Bürger stellt per se eine potenzielle Gefahr für die Machthaber dar. Dement-sprechend agiert das »Ungeheuer« Staat. Es führt einen konstanten – mehr oder weniger vernichtenden – Krieg gegen die eigene Bevölkerung. Welche Waffen in diesem Gefecht zum Einsatz kommen, erläutert ein von Wikileaks am 13. Juni 2008 veröffentlichtes Ge-heimdokument der US-Armee vom 20. September 1994. Titel: »Foreign Internal Defense Tactics, Techniques, and Procedures for Special Forces«. Zu Deutsch: Taktiken, Techniken und Verfahren zur internen Verteidigung im Ausland für Spezialeinheiten. Julian Assange nannte es einmal »das wichtigste Dokument, das Wikileaks je veröffentlichte«. Aus gutem Grund. Denn während der Titel des 219 Seiten umfassenden Strategiepapiers darauf abstellt, dass es sich um Arbeitsanweisungen für Spezialeinheiten handelt, die im Ausland operieren, sind die beschriebenen Methoden der asymmetrischen Kriegsführung genau jene, unter de-nen – neben dem Rest der Welt – auch die amerikanische Bevölkerung leidet.
Die US-Armee beschreibt im Detail, wie die verdeckt operierenden Kräfte Regierungen ab-setzen, Oppositionsgruppen infiltrieren, die Bevölkerung manipulieren und Kriege initiieren sollen. Auf Gesetze, Moral oder Kollateralschäden wird dabei keine Rücksicht genommen. Primäres Ziel – koste es, was es wolle – ist die Durchsetzung der Pax Americana im Zielge-biet. Ein paar Zitate verdeutlichen, wie das »Ungeheuer« dabei vorgeht.
»Aufstände sind nicht einfach zufällige politische Gewalt; sie sind gezielte politische Gewalt. Sie erfordern eine Führung, die Vision, Richtung, Anleitung, Koordination und organisato-rische Kohärenz bietet. Die Anführer der Aufständischen müssen ihre Sache dem Volk be-kannt machen und die Unterstützung der Bevölkerung gewinnen. (…) Ihre Ausbildung, ihr Hintergrund, ihre Familie, ihre sozialen Verbindungen und Erfahrungen prägen ihr Den-ken und die Art und Weise, wie sie ihre Ziele erreichen. Diese Faktoren prägen auch ihre Herangehensweise an die Problemlösung.« (S. 13)
»Die Ideologie von Gruppen innerhalb der Bewegung kann auf unterschiedliche Ansichten über strategische Ziele hinweisen. Gruppen können ideologische Konflikte haben, die gelöst werden müssen, bevor ein Gegner daraus Kapital schlagen kann. Die Ideologie kann wahr-scheinliche Ziele und Taktiken nahelegen. Sie beeinflusst stark die Wahrnehmung der Um-gebung durch den Aufständischen. Diese Wahrnehmung der Umgebung wiederum prägt die organisatorischen und operativen Methoden der Bewegung.« (S. 14)
»Wenn eine Situation explosiv ist, kann fast jedes Ereignis als auslösendes Ereignis dienen. Das richtige Timing kann auch in kurzer Zeit eine Flut von Ereignissen hervorrufen, sodass es schwierig ist, ein einzelnes Ereignis als die Handlung zu bezeichnen, die den Kampf aus-gelöst hat. Daher kann es hilfreicher sein, eine Reihe von Handlungen als auslösendes Er-eignis zu betrachten. Auslösende Ereignisse können historisch sein – und die Aufständi-schen erinnern die Bevölkerung an das Ereignis. Diese Technik befreit den Aufständischen davon, auf ein geeignetes Ereignis zu warten.« (S. 18)
»Oft sind es die Armen, die im Krieg kämpfen. CSDF-Programme (CSDF: Civilian Self-Defense Force) bieten der wohlhabenden Klasse die Möglichkeit, direkt und persönlich am Kampf gegen Gesetzlosigkeit und Aufstände beteiligt zu sein. Geschäftsleute und Fachleute beteiligen sich an CSDF aus einem Gefühl der bürgerlichen Pflicht, aus Stolz und aus der Notwendigkeit, ihr Vermögen zu schützen. Ihre aktive Beteiligung verleiht dem Programm Glaubwürdigkeit, stärkt die Legitimität der Regierung und verringert Klassenkonflikte. Wohlhabendes Personal kann bei der Ausstattung seiner Einheiten mithelfen. Es darf ihnen jedoch nicht gestattet sein, den Teilnehmern ein Gehalt zu zahlen.« (S. 128)
»PSYOP-Personal oder in PSYOP ausgebildete SFOD-Mitglieder (SFOD: Special Forces Operational Detachment) erleichtern die Zusammenarbeit zwischen der lokalen Bevölke-rung und dem HN-Militär (HN: Host Nation). Wenn qualifiziertes oder fähiges HN-Personal verfügbar ist, arbeitet das US-Personal durch sie. CSDF-Elemente müssen in der Anwendung von PSYOP geschult werden, um die Bevölkerung über die Vorteile zu informie-ren, die sie durch die Zusammenarbeit mit ihnen erzielen. PSYOP-Themen müssen sich an nationale und/oder fiktive Themen halten, um eine einheitliche Politik darzustellen. Es ist entscheidend, dass PSYOP zunächst an die lokale Bevölkerung gerichtet wird, um ihre Un-terstützung der Aufständischen zu beenden und ihre Akzeptanz und Zusammenarbeit für das CSDF-Programm zu gewinnen. (…) PSYOP kann die Mission unterstützen, indem es die aufständischen Kräfte bei neutralen Gruppen diskreditiert, Zwietracht unter den Auf-ständischen selbst sät und Überläuferprogramme unterstützt. Spaltungsprogramme führen zu Zwietracht, Desorganisation, niedriger Moral, Subversion und Überläufern innerhalb der aufständischen Kräfte. Wichtig sind auch nationale Programme, um Aufständische mit Angeboten von Amnestie und Belohnungen auf die Seite der Regierung zu ziehen. Die Motive für eine Kapitulation können von persönlichen Rivalitäten und Bitterkeit bis hin zu Desillusi-onierung und Entmutigung reichen. Druck seitens der Sicherheitskräfte hat Überzeugungs-kraft. (…) Alle Agenten werden genau beobachtet und diejenigen, die nicht zuverlässig sind, werden abgelöst. Wenige, zielgerichtete, zuverlässige Agenten sind besser und wirtschaftli-cher als viele schlechte. (…) Sicherheitskräfte können Einzelpersonen aus der Bevölkerung dazu bringen, Informanten zu werden. Sicherheitskräfte nutzen verschiedene Motive (Staatsbürgersinn, Patriotismus, Angst, Strafvermeidung, Dankbarkeit, Rache oder Eifer-sucht, finanzielle Belohnungen) als überzeugende Argumente. Sie nutzen die Zusicherung des Schutzes vor Repressalien als Hauptanreiz.« (S. 139, ff)
Zusammengefasst: Die Reichen bezahlen, sorgen für Stimmung und Glaubwürdigkeit, die politische Klasse passt die Vorgehensweise an lokale Strukturen, herrschende Ideologien, Demoskopie und Kommunikationsprozesse an – und die Armen werden zum Sterben an die Front geschickt. Und das sind nur kurze Einblicke in ein über 200 Seiten starkes Handbuch zum Krieg gegen die Zivilbevölkerung, die in Augen des Hegemon offenkundig nichts ande-res als Verfügungsmasse und Kanonenfutter ist. Man möchte Julian Assange beipflichten: Dieses Dokument erklärt nicht nur, warum unsere Gesellschaften, die Wirtschaft und das moralische Koordinatensystem des Homo sapiens in Auflösung begriffen sind – die Skru-pellosigkeit der im Detail beschriebenen Methoden lässt einem das Blut in den Adern gefrie-ren. Selbst nach auszugsweiser Lektüre muss man konstatieren: Nietzsche hatte Recht. Der Staat ist ein eiskaltes Ungeheuer.
Doch was ist der Staat? War es früher das klar erkenntliche Machtvehikel von Monarchen, Imperatoren, Familiendynastien und Klerus, erweckt das Staatskonzept der jüngeren Neuzeit gerne den Eindruck, es hätte sich von dieser Despotie der wenigen gelöst, stünde für sich, auf einem Fundament des Volkswillens, der sich in Verfassungen, Gesetzen und Wahlen widerspiegelt. Weit gefehlt. Auch die »Global Governance« von heute ist nichts anderes als Despotismus. Weithin kontrolliert von den gleichen Bankenkartellen, Familien, Unterneh-men und Organisationen, die seit Generationen den Lauf der Welt bestimmen. Die Regenbo-gen emanierende Pluralismussimulation der Postmoderne verbirgt diesen Umstand nur bes-ser. Sie tyrannisiert indirekt. Köpfe werden nicht mehr abgeschlagen, sondern gewaschen. Exakt so, wie es die angloamerikanischen Vordenker dieses Systems im ausgehenden 19. Jahrhundert insinuierten. Siehe Carroll Quigley, Tragedy and Hope, 1966, Kapitel »The Fu-ture in Perspective«, Seite 1247:
»Das Argument, dass die beiden Parteien entgegengesetzte Ideale und politische Ansichten vertreten sollten, eine vielleicht rechts, die andere links, ist eine törichte Idee, die nur für doktrinäre und akademische Denker akzeptabel ist. Stattdessen sollten die beiden Parteien nahezu identisch sein, sodass das amerikanische Volk die Schurken bei jeder Wahl raus-werfen kann, ohne dass es zu tiefgreifenden oder umfassenden politischen Veränderungen kommt. Die politischen Pläne, die für Amerika lebenswichtig und notwendig sind, sind nicht länger Gegenstand großer Meinungsverschiedenheiten, sondern nur noch in Einzelheiten des Verfahrens, der Priorität oder der Methode umstritten.«
Sodass nach Scheindebatten, Empörungsmanagement und Abstimmungen nicht vom allge-meinen Kurs abgewichen werden muss. Was Quigleys elitäre Zirkel – er war bis zur Veröf-fentlichung von Tragedy and Hope einer von ihnen und unterstützte ihre Ideen – für die Rückführung der 13 US-Kolonien sowie die moderne Expansion des britischen Empire vor-sahen, ist heute zentrales Element der wertewestlichen Fassadendemokratie. Symptombe-sprechung, Lippenbekenntnisse, Emotionsamplituden, »Der Dritte Weg« – »wo soziale Ge-rechtigkeit und Markt miteinander versöhnt werden sollen« – und auch nach der x-ten Wahl bleibt alles beim Alten. Ob Berlin, Brüssel, London, New York, Beirut oder Peking: Ein Potemkin’sches Dorf. Denn wir leben längst in der Idealvorstellung von Benito Mussolini, der den perfekten Faschismus als Korporatismus bezeichnete und als symbiotische Fusion der Macht von Staat und Konzernen verstand. Als »Public Private Partnership«.
»Benito Mussolini hat der modernen Sparpolitik den Weg bereitet und die Arbeiterbewe-gung unterdrückt. Liberale Ökonomen im In- und Ausland bewunderten ihn dafür«, schrieb man bei Jacobin am 6. März 2023. So zeitigt das Staatskonzept dieser Tage die gleichen ver-heerenden Folgen wie die Herrschaftskonstrukte der Vergangenheit. Vertikale Durchlässig-keit begrenzt, das Volk manipuliert, ausgebeutet und gegängelt. Anstelle von Arbeitslagern, Schlägertrupps und Exekutionskommandos machen heute Algorithmen die Drecksarbeit. Sonst hat sich kaum etwas geändert.
Stand heute leben nach Angaben von Oxfam weltweit knapp fünf Milliarden mehr Men-schen in Armut als vor 2020. Das sind die ärmsten 60 Prozent der Menschheit. Zusammen haben sie circa 20 Milliarden US-Dollar verloren. Das Gesamtvermögen der reichsten Deut-schen wuchs im gleichen Zeitraum von 89 auf 155 Milliarden US-Dollar – ein Zuwachs von 73,85 Prozent. Die 148 größten Konzerne der Welt konnten zwischen Juni 2022 und Juni 2023 circa 1,8 Billionen Dollar an Gewinnen verzeichnen – ein Anstieg von 52,5 Prozent gegenüber dem Durchschnitt der Jahre 2018 bis 2021. Der Reingewinn stieg gegenüber die-sem Zeitraum um 20 Prozent auf 700 Milliarden Dollar. Und die fünf reichsten Menschen der Welt haben ihr Vermögen seit 2020 verdoppelt. Wer vom Nachhaltigkeitskorporatismus profitiert, dürfte damit geklärt sein.
Der Normalbürger dagegen kämpft gegen steigende Steuern, Inflation und anziehende Ener-giekosten. In einem luftabschnürenden Korsett von Verträgen, Verpflichtungen und Ver-bindlichkeiten gefangen, bleibt weder Zeit noch Geld für ein Leben in Würde. Der angepass-te Regenbogendemokrat wird geboren, indoktriniert, ausgebeutet und dann bestattet. Indivi-duelle Entfaltung ist in diesem Lebensentwurf von der Stange nicht vorgesehen. Die leitme-dialen Podiumsdiskussionen um Work-Life-Balance, Gendersprache und feministische Au-ßenpolitik klingen in den Ohren der buckelnden Arbeiterklasse – und auch für weite Teilen des schwindenden Mittelstandes – wie blanker Hohn. Das Habitat des Mediazän, das nicht selten den Eindruck erweckt, man lebe in einer fehlerhaft programmierten Simulation, zwingt seinen Bewohner immer häufiger dazu, sich existenziellen Problemen zu stellen: Unterkunft, Nahrung, Fortpflanzung. Überleben.
Noch bezahlt er Jahreslizenzen für Cloud-Software, Netflix für Filme und Streamingdienste für Musik, die er früher erwarb und dann einfach besaß. Noch geht er wählen und entschei-det brav zwischen Pest und Cholera, um vier weitere Jahre nicht die Hoffnung zu verlieren. Noch glaubt, ignoriert oder kommentiert er leidensfähig die intelligenzbeleidigenden Lügen-gebilde, die als Realität vermarktet werden.
Mithin erstaunlich. Denn nicht erst seit der Corona-Krise belegen nackte Zahlen, dass der Mensch in diesem System nicht nur beraubt und unterdrückt, sondern auch als Versuchska-ninchen für den pharmakologisch-finanziellen Komplex missbraucht wird. Nürnberger Ko-dex hin oder her. Während Robert Koch vor der Schaffung dieses vermeintlichen Bollwerks für die körperliche Unversehrtheit noch ungestraft Menschenversuche in seinen kolonialen Konzentrationslagern durchführen durfte, ist das Thema seit Ende des Zweiten Weltkrieges tabu. Gesetzlich eliminiert. Angeblich. Doch bereits in den 1940er Jahren infizierte der US-Gesundheitsdienst Gefängnisinsassen und psychisch kranke Personen mit Syphilis-Erregern. Von 1946 bis 1949 weiteten die USA das Programm auf Guatemala aus und machten sich zusätzlich über Soldaten und Prostituierte her. Das Echo der angelsächsisch geprägten Eugeniklehre hallte im fortgeführten Rassismus nach.
»Schockierende Fälle wie der Tod der 49 Kinder nach Medikamententests in einem indi-schen Krankenhaus sind in der Geschichte der Medizin nichts Neues: In den USA wurde Farbigen zu Studienzwecken von 1932 bis 1972 die Syphilis-Therapie verweigert.« (SZ, Das Verbrechen von Tuskegee, 11. Mai 2010)
Am 20. September 1950 spritzte die US-Marine vor der Küste San Franciscos Mikroben in die Troposphäre, um zu testen, welche Effekte ein Angriff mit Biowaffen auf die damals 800.000 Einwohner der Stadt haben würde. 1953 startete die CIA das MK-Ultra-Programm, in dessen Rahmen abertausenden ahnungsloser Menschen LSD verabreicht wurde. Zwei Jahre später nahm »Project Whitecoat« – Projekt Weißkittel – seine Arbeit auf. Die bestand im Verlauf der folgenden 20 Jahre darin, Menschenversuche mit Hasenpest, Typhus, Gelb-fieber und Milzbrand durchzuführen. Und Ende der 60er testeten die amerikanischen Streit-kräfte Nervengas an den eigenen Soldaten. Der SPIEGEL schrieb diesbezüglich am 10. Juli 2013:
»11. Oktober, 16:25 Uhr, 26 Stunden nach Testbeginn. Kleine blutende Anomalien am lin-ken Bein festgestellt. Subjekt behauptet, es habe seinen Rasierer fallen gelassen und sich dabei ins Bein geschnitten – doch so war es nicht. Er habe seine Sommersprossen damals für Käfer gehalten, sagt Rochelle: »Die krabbelten überall unter meiner Haut herum«. Den Betreuern habe er nichts davon erzählt, es sei ihm peinlich gewesen: »Ich habe meine Ra-sierklinge genommen und versucht, die Käfer aus meiner Haut zu schneiden.« Er war längst nicht mehr selbst dazu in der Lage, die Experimente zu stoppen. Damit war die Ein-verständniserklärung Makulatur. So wie Frank Rochelle ergeht es in Edgewood mehr als 7.800 US-Soldaten; im ganzen Land sind es rund 100.000. Systematisch haben Militär und Geheimdienste die eigenen Leute seit Ende des Ersten Weltkriegs Giften, Gasen, Drogen und Psycho-Kampfstoffen ausgesetzt, darunter LSD, Sarin, Senfgas, BZ, VX, Barbiturate, Amphetamine, Chlorpromazin und immer so weiter. Nachsorgeuntersuchungen? Fehlan-zeige. Erst nach fast sechs Jahrzehnten stoppt das US-Parlament die Menschenversuche im Jahr 1975.«
Ebenfalls bis weit in die 70er hinein injizierte man US-Gefängnisinsassen Pestizide und Herbizide. Mindestens 2.600 Menschen wurden derartigen Versuchen unterzogen. Natürlich musste auch die Atombombe am lebenden Objekt getestet werden. Sowohl Frankreich als auch Großbritannien, die ehemalige Sowjetunion oder die USA schickten Menschen auf die Testgelände. Viele von ihnen segneten danach relativ rasch das Zeitliche. Bis heute kämpfen Bewohner der entsprechenden Landstriche um Entschädigungen, weil sie ihre Krebserkran-kungen der im Umland von Testgebieten gestreuten Strahlung zuschreiben. In den 70ern machte sich der Journalist Paul Jacobs auf eigene Faust daran, die Geschichte der Betroffe-nen zu dokumentieren – um 1978 selbst an Krebs zu sterben. Selbst vor Versuchen an Kin-dern schreckte das »Ungeheuer« nie zurück, wie wiederum der SPIEGEL in Ausgabe 45 vom 2. November 1986 ausführt:
»Dwayne winkte seiner Mutter zu, sie lächelte zurück, dann schloss sich die schwere Eisen-tür hinter dem todkranken Kind. Seit drei Jahren wurde Dwayne Sexton am Strahleninstitut des Atomforschungszentrums Oak Ridge im Bundesstaat Tennessee gegen Leukämie be-handelt. Er hatte eine qualvolle Knochenmark-Transplantation sowie etliche Runden von Chemotherapie hinter sich. Alles war vergeblich geblieben. Als letztes Mittel wollten die Ärz-te nun versuchen, mit massiver Bestrahlung die Krebszellen im Knochenmark des Kindes zu zerstören. Dass diese Methode riskant und – zur damaligen Zeit, 1968 – auch wenig er-probt war, teilten die Ärzte den Eltern des Kindes mit. Was sie aber verschwiegen, war, dass sie auch im Auftrag der amerikanischen Weltraumbehörde NASA arbeiteten. Sie soll-ten herausfinden, wieviel Strahlung Astronauten im All aushalten würden, ohne krank zu werden. Für die von der NASA bestellte Untersuchung erprobten die Ärzte an ihren Patien-ten, so hieß es in einem ihrer Berichte, verschiedene »therapeutische Szenarien, die aus Strahlenmengen im All abgeleitet wurden«. Im Klartext: Nicht allein medizinische Erwä-gungen zum Wohl des Patienten setzten die Höhe der Strahlendosis fest, sondern auch die Bedürfnisse der NASA. In diesem Sinn waren die Patienten lebende Versuchskaninchen.«
Mindestens 23.000 US-Amerikaner wurden von Militäreinrichtungen und Gesundheitsbe-hörden vorsätzlich verstrahlt. Zu Forschungszwecken. »Kalter Krieg gegen US-Bevölkerung« nannte es die taz am 24. Oktober 1994.
»Zwischen 1950 und 1972 finanzierte das Pentagon außerdem fünf klinische Studien über die Aufnahmefähigkeit des menschlichen Körpers von Strahlen, um Aussagen über die psy-chologischen wie biologischen Folgen von Atomexplosionen zu erhalten. Die Versuchsper-sonen waren größtenteils in Armut lebende Schwarze. (…) Bei einem anderen Experiment mussten Soldaten auf Fässern mit radioaktivem Material herumfahren, um zu prüfen, ob ihre Autos sie vor den Strahlen schützten. In Hanford im US-Bundesstaat Washington setz-ten die Militärs absichtlich eine nukleare Wolke frei, um die Verlagerung der Wolke zu un-tersuchen. Aufgrund einer plötzlichen Änderung der Wetterlage fielen die radioaktiven Teil-chen auf einem 300 Kilometer langen und 60 Kilometer breiten Gebiet nieder (…). (jW, 29. August 1997)
Der Umgang mit der indigenen Bevölkerung wirft kein besseres Licht auf die Vereinigten Staaten. Von fünf bis sieben Millionen Ureinwohnern im Jahr 1500 waren im Jahr 1900 noch 237.000 übrig. Ob Hungersnöte, Sklavenarbeit, Massaker, Umsiedlungen oder »Boar-ding Schools« – Umerziehungsinternate: Die aus Großbritannien eingereisten Siedler verüb-ten einen Genozid an den indigenen Stämmen. Nachdem die mageren Reste der stolzen Indi-anervölker in Reservate gepfercht worden waren, suchte der Staat deren Fortpflanzung mit-tels Zwangssterilisation zu verhindern. Mehr als 60.000 Indigene wurden im 20. Jahrhundert einer solch abscheulichen Behandlung unterzogen. Darüber hinaus war das Eugenik-Programm der USA, das erst 1981 endgültig eingestellt wurde, Grundlage für die Rassen-lehre des deutschen NS-Regimes.
Ähnlich ging man in Kanada vor. Seit den 1920er Jahren wurden dort tausende indigene Frauen zwangssterilisiert – bis heute – obwohl die entsprechenden Gesetze mittlerweile ab-geschafft wurden. Die tagesschau vermeldet dazu am 10. März 2024:
»Die Worte des weißen Arztes haben sich Liz (…) ins Gedächtnis gebrannt: »Es ist besser, du stimmst der Abtreibung zu. Denn wir werden dir dieses Baby wegnehmen. So oder so«. Die damals 17-jährige Kanadierin vom indigenen Volk der Anishinabe wagt es nicht, zu widersprechen. Verängstigt sitzt sie Ende der 1970er-Jahre im Behandlungsraum der Indi-an Clinic in der Provinz Ontario, einer Klinik, in der Indigene behandelt werden, damit sie an die sogenannte Zivilisation angepasst werden. (…) Die alleinerziehende Mutter sei nicht in der Lage, für ein weiteres Kind zu sorgen. Der Arzt will ihr deshalb die Eileiter abbinden und sie dadurch sterilisieren. (…) Erst Jahre später wird ihr klar: Sie ist nicht allein. Zehn-tausende indigene Frauen sind in Kanada seit den 1920er-Jahren im Einklang mit der Eu-genik-Gesetzgebung gegen ihren Willen sterilisiert worden. Und obwohl es diese Gesetze nicht mehr gibt, geschieht es bis heute, weiß Senatorin Yvonne Boyer im Kongress in Otta-wa (…). Noch immer ist Zwangssterilisation kein Tatbestand im kanadischen Strafgesetz-buch. (…) Vergangenes Jahr wurde in den Nordwest-Territorien ein Arzt bestraft, weil er 2019 eine Inuit-Frau gegen ihren Willen unfruchtbar gemacht hat. Er verlor seine Lizenz – für fünf Monate.«
Dass sich nicht nur das angloamerikanische Empire für Eugenik begeisterte, zeigt die Ein-richtung des ersten rassenbiologischen Instituts in Schweden im Jahr 1921. Zwischen 1935 und 1976 wurden dort circa 62.000 Menschen zwangssterilisiert. Die offiziellen Begrün-dungen für die Eingriffe reichten von »Mischling« über »Alkoholismus« bis zu »dämlich« und »religiös«. Sprich: Reine Willkür unter dem Deckmantel der Wissenschaft. Legalisiert vom schwedischen Staat.
Heute begegnen uns die staatlich organisierten Eugenik-Programme unter wohlklingenden Labels wie Bioethik, reproduktive Gesundheit, biosoziale Forschung und Bevölkerungspoli-tik. Seit 1954 finden die von den Vereinten Nationen (UN) organisierten Weltbevölkerungs-konferenzen statt. Die letzte im November 2019 in Nairobi (Kenia). Was bei diesen Konfe-renzen besprochen wird, lässt sich anhand eines Artikels des GUARDIAN vom 15. April 2012 oder eines Beitrags von C-Fam (Center for Family and Human Rights) erahnen:
»Großbritannien hat 166 Millionen Pfund (268 Millionen Dollar) für ein Regierungspro-gramm in Indien gespendet, das arme Frauen und Männer zwangssterilisiert. Die britische Hilfsorganisation nannte die Notwendigkeit, dem Klimawandel durch Bevölkerungsreduzie-rung zu begegnen, als Hauptgrund für die Finanzierung des missbräuchlichen indischen Programms (…). Verpfuschte Operationen verursachten Qualen, Blutungen und Todesfäl-le. In einer von der britischen Regierung ins Visier genommenen Region verblutete die 35-jährige Frau eines armen Arbeiters, die mit Zwillingen schwanger war. Einige Frauen, die während der Schwangerschaft sterilisiert wurden, erlitten Fehlgeburten. Einige wurden mit weniger als acht Dollar und einem Sari bestochen, anderen wurde mit dem Verlust ihrer Lebensmittelkarten gedroht. Manchen wurde gesagt, die Operationen dienten der allgemei-nen Gesundheitsfürsorge, und sie erfuhren den wahren Zweck erst zu spät. Kliniken erhiel-ten Prämien für mehr als dreißig Operationen pro Tag. Nichtstaatliche Mitarbeiter wurden für jede Person bezahlt, die sie zu einer Operation überredeten. Ein Chirurg, der in einem Schulgebäude arbeitete, führte in zwei Stunden 53 Operationen durch – ohne qualifiziertes Personal, fließendes Wasser oder Mittel zum Reinigen der Geräte. Berichte der indischen Regierung aus den Jahren 2006 und 2009 warnten vor Problemen mit dem Programm. Dennoch empfahl ein Bericht des britischen Ministeriums für internationale Entwicklung aus dem Jahr 2010 die weitere Unterstützung des Programms mit der Begründung, dass eine Reduzierung der Bevölkerungszahl die Treibhausgase senken würde. (…) Sterilisation ist die häufigste Methode der Familienplanung, die in Phase II des indischen Programms für Reproduktions- und Kindergesundheit eingesetzt wird, das 2005 mit britischer Finanzie-rung begann. Trotz der Enthüllungen im ersten Jahr hat Großbritannien keine Bedingungen an seine Finanzierung geknüpft. (…) Im Juli wird Großbritannien zusammen mit der Bill & Melinda Gates Stiftung einen Familienplanungsgipfel in London ausrichten. Ziel der Veran-staltung ist es, beispielloses politisches Engagement und Ressourcen von Entwicklungslän-dern, Gebern, dem privaten Sektor, der Zivilgesellschaft und anderen Partnern zu generie-ren, um den Familienplanungsbedarf von Frauen in den ärmsten Ländern der Welt bis 2020 zu decken, erklärte das britische Ministerium für internationale Entwicklung. Melinda Gates hielt kürzlich eine Rede, in der sie behauptete, dass die Hilfe bei der Empfängnisver-hütung nichts mit Bevölkerungskontrolle oder Zwangssterilisationsprogrammen zu tun ha-be.« (C-Fam, 2. Mai 2012)
»Familienplanungsbedarf«? Dass solche Programme nichts mit »Bevölkerungskontrolle« zu tun haben, ist eine infame Lüge. Schon die von Julian Huxley verfasste Grundsatzschrift der UNESCO von 1946 spricht davon, dass Eugenik wieder salonfähig gemacht werden muss. »Das Undenkbare wenigstens wieder denkbar machen«, nannte Huxley es damals. So muss auch die ungezügelte Massenmigration als Waffe im mittlerweile allgegenwärtigen Kampf der Kulturen verstanden werden. Dabei ist allerdings nicht die Migration selbst das Problem – denn auch die Migranten sind Opfer dieser Agenda – sondern der jeweilige Auslöser für diese Zuwanderungsströme. Die verarmten, verzweifelten, traumatisierten, mit falschen Ver-sprechungen gelockten und als Spaltpilz missbrauchten Menschen für die Symptome des wertwestlichen Neokolonialismus verantwortlich zu machen, greift zu kurz.
Die chaotischen Zustände auf deutschen, britischen, schwedischen und französischen Stra-ßen sind kein Zufall, sondern gewollt. Das belegt ein Strategiepapier der Vereinten Nationen, das am 21. März 2000 publiziert wurde. Titel des Dokuments: »Replacement Migration: Is it A Solution to Declining and Ageing Populations?« Übersetzt: »Ersatzmigration: Ist sie eine Lösung für schrumpfende und alternde Bevölkerungen?«. Auf 177 Seiten erläutert die Stu-die, wie Frankreich, Großbritannien, Deutschland, Italien, Japan oder Russland zurückge-hende Geburtenraten durch massenhafte Zuwanderung kompensieren sollen. Auf den Seiten 32 und 33 liest man diesbezüglich:
»Abbildung 1 zeigt einen standardisierten Vergleich der Zuwanderungsströme pro Million Einwohner (Stand: 2000). Aus diesem Vergleich geht hervor, dass im Verhältnis zur Lan-desgröße die Zahl der Einwanderer, die im Zeitraum 2000-2050 pro Jahr benötigt wird, um den Bestand der Bevölkerung im erwerbsfähigen Alter zu erhalten (Szenario IV), mit 6.500 Einwanderern auf eine Million Einwohner in Italien am höchsten ist, gefolgt von Deutschland mit 6.000 Einwanderern pro Jahr auf eine Million Einwohner. Von den in die-sem Bericht untersuchten Ländern und Regionen benötigten die Vereinigten Staaten mit et-wa 1.300 Einwanderern auf eine Million Einwohner die geringste Zahl von Einwanderern, um einen Rückgang ihrer Bevölkerung im erwerbsfähigen Alter zu verhindern.«
»Die Zahl der Einwanderer, die notwendig ist, um ein Schrumpfen der Bevölkerung im er-werbsfähigen Alter auszugleichen, übersteigt diejenige, die einen Rückgang der Gesamtbe-völkerung ausgleichen würde, um ein Erhebliches. Ob solche höheren Einwanderungszah-len zu den Optionen gehören, die den Regierungen zur Verfügung stehen, hängt zum großen Teil von den sozialen, wirtschaftlichen und politischen Verhältnissen des jeweiligen Landes beziehungsweise der jeweiligen Region ab.«
Wer also annimmt, dass die Destabilisierungskriege und Raubzüge der NATO-Hegemonie nur dem Zwecke dienten, missliebige Regierungen auszutauschen und der Rohstoffe eines Landes habhaft zu werden, liegt offenkundig falsch. Wenn das wertewestliche Imperium irgendwo Demokratie abwirft, hat es dabei auch die strategischen Ziele globaler Bevölke-rungskontrolle im Blick. Migration als Waffe – gerichtet gegen beide involvierten Parteien. Demnach kann man sich nur wünschen, dass die Gewaltausbrüche zwischen einheimischer Bevölkerung und Migranten in den verschiedenen EU-Ländern rasch ein Ende nehmen und sich die von Verzweiflung herrührende Wut beider Parteien auf das eigentliche Problem fo-kussiert: Die herrschende Kaste und ihr gesichtsloses Imperium supranationaler Organisati-onen.
Wahrlich – die Liste an staatlich organisierten, legitimierten, orchestrierten und geduldeten Gräueltaten ließe sich beliebig lange fortführen. Je nachdem, wie weit man zurückzublicken gedenkt. Viele dieser Verbrechen sind Teil der offiziellen Geschichtsschreibung. Jeder weiß es. Dennoch führt dieses Wissen um die Skrupellosigkeit eines im Kern faschistoiden Sys-tems erstaunlicherweise bis heute nicht dazu, dass sich die Menschheit auf andere Formen des Zusammenlebens, der Verwaltung und Organisation einigt. Noch immer sehnen sich die Massen nach Führung, zentraler Steuerung und Ikonen, die ihnen ein besseres Leben ver-sprechen. Dabei belegt die Zivilisationsgeschichte mehr als eindrücklich, dass es sich um leere Versprechen handelt, dass die Hoffnung auf den edlen Ritter, die rettende Wahl oder eine bessere Zukunft reine Illusion ist. Der Machtapparat Staat dient nur einem einzigen Zweck – dem Erhalt des Machtapparats.
Es bedarf demnach auch keiner Diskussion um marginale Optimierungen des herrschenden Systems. Denn wer nur Symptome behandelt, wird die Ursache der Krankheit nicht eliminie-ren. Es bedarf der konstruktiven Debatte darüber, wie dieses System in Gänze zu ersetzen ist.
Dabei gilt es, eigene Narrative zu entwickeln. Geschichten. Vorstellungen von einer freiheit-lich organisierten Zukunft. Von einem lebenswerten morgen. Für eine Zeit nach dem »Un-geheuer«. Wir brauchen Ideen, von denen wir nachfolgende Generationen begeistern kön-nen. Und damit ist nicht die technische Verbesserung des Smartphones oder eine neue App gemeint, sondern eine Utopie. Denn gegen etwas zu sein, ist einfach. Für etwas zu sein, da-gegen nicht.
So engagieren wir uns längst nicht mehr nur für den Erhalt der Meinungsfreiheit, sondern für die Bewahrung des freien Willens. Denn was im Namen des Staates – »im Namen des Volkes« – und damit im Namen jener Menschen, die den Staat durch Wahl oder Duldung legitimieren, geschah, geschieht und geschehen wird, kann kein emotional gesundes Mitglied unserer Spezies wirklich wollen.
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ dfe02069:d3e2fa29
2024-12-07 14:51:36
@ dfe02069:d3e2fa29
2024-12-07 14:51:36-
Gerade wird Anthony Fauci in öffentlichen Anhörungen zerlegt. Gleichzeitig (und trotzdem) greift die WHO nach mehr Macht. Wann kommen unsere Untersuchungsausschüsse?
-
Die RKI-Files bringen sämtliche Corona-Gewissheiten des Mainstreams zum Implodieren. Gleichzeitig steigt eine neue (alte) Vogelgrippe aus dem Tiefschlaf wieder auf, sogar Impfungen sind schon da.
-
Die EU-Kommissionspräsidentin Ursula von der Leyen will die Europäer nun gegen Desinformation "impfen". Wie gut die letzten von ihr propagierten Impfungen funktionierten, konnte man bei AstraZeneca sehen, das im März vom Markt genommen wurde. Für den Rest konstatierte zuletzt der Telegraph, dass die Impfungen zu einer Übersterblichkeit geführt hätten. Oh Wunder der späten Erkenntnis...Wie viel Schaden kann man als Politiker heute eigentlich anrichten, bis man zur Verantwortung gezogen wird?
-
Hinzu kommt natürlich noch die in Deutschland obligatorische Frage, ob ein Lied von Gigi d`Agostino nun rechtsextremistisch ist (so wie alle, die es hören) um ja nicht darüber nachdenken zu müssen, ob afghanische Messerstecher nun das Land eher bereichern oder gefährden.
Und das war irgendwie gerade mal eine Woche.
Das lauter werdende Kriegsgeheul und die geistige Mobilmachung ist da noch gar nicht erwähnt; auch nicht, dass Hunter Bidens Laptop („aus der Hölle"), nun doch keine Verschwörungstheorie ist, findet das FBI. Facebook löschte derartige Berichte während des letzten Wahlkampfs von seiner Plattform.
Wir leben gerade im Mahlstrom der Ereignisse. Diesen Mahlstrom kennzeichnet, dass gleichzeitig so viele wichtige Ereignisse parallel passieren, dass jedes Ereignis wie eine Ablenkung vom anderen wirkt. Wenn alles gleich wichtig zu sein scheint, zerstäubt sich die Aufmerksamkeit jedoch und keines der (wichtigen) Ereignisse bekommt dann noch die gebührende Aufmerksamkeit. Es kann also in einer solchen Zeit viel passieren, ohne dass dem Großteil bewusst wird, dass sich Gewichtiges tut. Die Ereignisse kommen stoßweise, übersprungsartig, fast\ übertölpelnd, als gäbe es ein Art Vorwärts-Panik. Will man so der Welle der Aufarbeitung entgehen? Überführten Gaunern glaubt die Welt bei der nächsten „Pandemie" ja vielleicht etwas weniger.
Stand und Zukunft dieser Publikation
Neue Zeiten erfordern neue Weichenstellungen.
Und ich will auch hier mit Ihnen ehrlich sein. Die Zeiten für kritische Information werden härter, auch bei mir kommen die ersten Ausläufer davon an. Als lesergestützte Publikation bin ich relativ frei, aber auch nicht gänzlich unabhängig, denn ich bin ja auf Sie (allein) angewiesen. Bei anderen kritischen Substack-Autoren machte Stripe (der Zahlungsanbieter) erste Probleme. Bei mir häuft sich die Anzahl Abonnenten, deren Zahlungen von Banken abgewiesen werden. Bin ich auf einer schwarzen Liste? Für mich bedeutet das bisher vor allem administrativen Mehraufwand. Die Publikation selbst erfreut sich stetig wachsender Beliebtheit und ich danke allen, die mich unterstützen, einfach schon für den Akt selbst, unabhängig von der Summe. Leider ist es immer noch ein geringer Prozentsatz gegenüber den Frei-Abonnenten.
Um meinen Aktionsradius und meine Unabhängigkeit in diesen Zeiten zu festigen, denke ich schon seit geraumer Zeit über weitere Schritte nach. Die Substack-Autorin Bari Weiss hat zum Beispiel eine Reihe von Mäzenen um sich geschart, um eine finanzielle Basis für die Entwicklung Ihrer\ Publikation zu haben. Doch direkte größere Geldgeber will ich aus verschiedenen Gründen nicht, es bedeutet zwangsläufig die Gefahr des Einflusses anderer. Ich bin zu dem Entschluss gekommen, dass es am besten für alle wäre, einen oder mehrere Werbepartner/Sponsoren mit ins Boot zu holen, die zur Ausrichtung des Blogs passen und mein publizistisches Angebot im Idealfall ergänzen. Wer kritisch, wahrheitsliebend, der Freiheit und Selbstbestimmung des Einzelnen verpflichtet, aufklärerisch und mutig, thematisch schmerzfrei und antizensorisch eingestellt ist, passt zu mir. Ich könnte so weiterhin einen Großteil meiner Artikel frei zugänglich halten, eine kleine Redaktion aufbauen und meine Palette an Projekten erweitern. Ein „werbefreies" Medium wäre ich dann nicht mehr, aber streng genommen bin ich das jetzt auch schon nicht, da ich die Bitcoin-App Relai empfehle (und Bücher rezensiere, also auch bewerbe). Sagen Sie mir gerne, wie Sie darüber denken. Bisher bin ich ein 1-Mann Betrieb, der alles selbst macht: recherchieren, schreiben, Vertrieb, Marketing, Abo-Abteilung, Leserbriefredaktion, Back-Office. Mit den ersten Interessenten bin ich bereits im Gespräch. Sie sind eine Firma und haben Interesse am Thema Sponsoring/Werbung? Schreiben Sie mich gerne an: kontakt\@idw-europe.org.
Liebe Inserenten, hier könnte Ihre Werbung stehen! Liebe Leser: Wenn Sie mich von Werbepartnern fernhalten wollen, lassen Sie gerne ein Abo oder eine Spende da! Das geht auch per Überweisung, Bitcoin oder PayPal: kontakt\@idw-europe.org
Stand des Pareto-Projekts
Mit dem Pareto-Projekt baue ich mit einem Team von Entwicklern an einer neuartigen Publikationsplattform, für die einige aus Ihrem Kreise auch gespendet haben, herzlichen Dank hierfür. Pareto soll eine neue zensurresistente Publikationsplattform sein, die jeder nutzen kann, egal ob Text, Video oder Podcast. Wir bauen auf dem Netzwerk von Nostr auf, d.h., die Inhalte werden nicht auf klassischen Servern gespeichert, sondern in dezentralen Nostr-Knotenpunkten. Dadurch gibt es keinen zentralen Angriffspunkt mehr, und Zensur hat keine Chance.
In den letzten Wochen ist viel passiert, was ich bisher, aufgrund von Lesereisen und immer neuen Entwicklungen, noch nicht kommuniziert habe.
-
In den letzten Monaten haben unser CTO Muharem und ich das Projekt bei interessierten Kreisen vorgestellt, zum Beispiel auf der Bitcoin-Konferenz in Madeira sowie auf der Crypto Mountain Conference in Davos (nein, hat gar nichts mit dem WEF zu tun).
-
Wir haben einen Businessplan für Investoren erstellt und unser Team erweitert.
-
Derzeit arbeiten wir an einem Prototyp, den wir in den nächsten drei Monaten finalisieren wollen.
-
Gerade bauen wir einen Github auf, haben uns bei Nostr für ein Accelerator-Programm beworben und in der kommenden Woche knüpfe ich auf der Bitcoin Konferenz in Prag weitere Kontakte in die Community (sorry für die Anglizismendichte, das muss im Start-up-Sprech so sein).
-
Aufruf: Für den Prototypen suchen wir kurzfristig auf zunächst freiwilliger Basis Entwickler und Tester. Sie fühlen sich angesprochen? Schreiben Sie mich gerne an: kontakt\@idw-europe.org. Wir können aus Spenden gerade nur kleine Aufwandsentschädigungen zahlen, bei guter Chemie ist eine weitere Zusammenarbeit gut vorstellbar. Gerne Erfahrung mit Nostr/Lightning. Sonst: Erfahrung in Typescript/Javascript für Frontend; Entwickler für backend; Erfahrung mit peertube, glossomdrive, nostr relay wären ideal. Proposal und Prototype Spec können wir zur Verfügung stellen. Kontakt\@idw-europe.org
Sie wollen uns anderweitig unterstützen? Spenden für die Entwicklung des Prototyps sind weiterhin sehr willkommen (links in CHF/rechts EURO)

Ich bleibe für Sie ansonsten weiter am Ball, auch in den Sommermonaten, und danke für die Unterstützung meiner Arbeit sowie die zahlreichen erbaulichen und mutmachenden Signale, die Sie mir senden. Zuletzt durfte ich eine Reihe von Interviews führen. Bei Interesse schauen Sie gerne rein.
Nachdem ich zuletzt erstmals in der Wiener U-Bahn erkannt und angesprochen wurde, will ich in den nächsten Monaten wieder Interviewpause einlegen. Für mich zählen die Inhalte meiner Texte und nicht die Bekanntheit meines Gesichts (erstere altern auch besser).
-
-
 @ 0d532801:197a0c30
2024-12-01 21:27:48
@ 0d532801:197a0c30
2024-12-01 21:27:48
߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
- Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
- Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
- Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
- Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
- İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
- Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.
-
 @ 30e902b3:49c066b2
2024-12-14 10:12:49
@ 30e902b3:49c066b2
2024-12-14 10:12:49Llegó a mis manos en busca de ayuda para volver a sentirse joven.
Se trata de un grabador open reel Berlant Concertone 20-20 de 1955. Aquí el manual original:
https://museumofmagneticsoundrecording.org/images/R2R/Concertone20-20ManualMOMSR.pdf
https://images.app.goo.gl/NcdAaYv2HTCHVnvX9
Como se ve en la imagen no me llegó en las mejores condiciones.
Cuento con vuestra guía para conseguir los repuestos que falten y lograr dejarlo parecido a este:
https://d10j3mvrs1suex.cloudfront.net/s:bzglfiles/u/146088/fbd8aec299456da8f127cd52f7dafcd4be37331b/original/berlant-concertone-tape-recorder.jpg/!!/b%3AW1sic2l6ZSIsInBob3RvIl1d/meta%3AeyJzcmNCdWNrZXQiOiJiemdsZmlsZXMifQ%3D%3D.jpg
Pretendo iniciar con el nuevo año. Voy recopilando ideas y consejos que me compartas. Va a ser necesario restaurar los frentes, contactos, revisar la electrónica y válvulas todo en modo DIY o "a pulmón".
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 94a6a78a:0ddf320e
2024-11-27 19:36:12
@ 94a6a78a:0ddf320e
2024-11-27 19:36:12The backbone of your Nostr experience lies in relays—servers that transmit your notes, zaps, and private messages across the decentralized network. Azzamo offers three specialized relays to suit different user needs, ensuring reliability, performance, and privacy.
1. Free Relay
- URL:
wss://nostr.azzamo.net - Overview: Azzamo’s Free Relay is perfect for newcomers to Nostr. It’s open-access, reliable, and ensures fair use with moderate rate limits.
- Key Features:
- Free to use.
- Notes older than one month are purged daily.
- Accessible gateway for decentralized communication.
2. Paid Relay
- URL:
wss://relay.azzamo.net - Overview: Designed for power users, the Paid Relay offers unmatched performance with 99.9% uptime and low latency.
- Key Features:
- Scalable for heavy users.
- Fewer users for faster, consistent connections.
- Premium support included for paid users.
3. Inbox Relay
- URL:
wss://inbox.azzamo.net - Overview: Never miss a private message again with the Inbox Relay, optimized for secure, spam-free direct messaging.
- Key Features:
- Guaranteed message delivery.
- Optimized for NIP-17 private messages.
- Optimized for NIP-19 group chats.
- Premium users enjoy advanced support.
Why Choose Azzamo Relays?
Life on Nostr is easier with Azzamo relays. They’re fast, reliable, and built to handle whatever you throw at them. The Paid Relay keeps your connections strong, the Inbox Relay makes sure no private message gets lost, and the Free Relay is always there to get you started. Supporting Azzamo by going premium helps keep this decentralized network growing—and you get priority support while you’re at it. Azzamo has your back on Nostr!
🔗 Start now:
- Free Relay:
wss://nostr.azzamo.net - Paid Relay: azzamo.net/pay
- Inbox Relay: azzamo.net/inbox
Support the network and upgrade your experience—add time to your account via the Azzamo Dashboard. Choose Azzamo, and take control of your Nostr journey today!
- URL:
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ fd78c37f:a0ec0833
2024-12-11 01:32:23
@ fd78c37f:a0ec0833
2024-12-11 01:32:23Bitcoin, as a decentralized digital currency, is reshaping the global financial landscape, sparking innovation and transformation across various sectors. In South America, Bitcoin communities are emerging as crucial drivers of economic empowerment, financial inclusion, and local technological advancement. This issue will highlight 21 Bitcoin communities from South America, exploring their missions, growth trajectories, and recent developments. By examining these grassroots initiatives, we aim to show how Bitcoin is being leveraged to create sustainable economic ecosystems, foster social progress, and expand access to education and financial tools. Thank you, YakiHonne decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.Mi Primer Bitcoin nostr:npub17cyatz6z2dzcw6xehtcm9z45m76lde5smxdmyasvs00r4pqv863qrs4ml3 * Introduction My First Bitcoin is a Bitcoin education initiative rooted in the principles of independence, fairness, and community leadership. Originating in El Salvador, it aims to empower individuals and communities by providing open-source educational resources and fostering a decentralized network. Through a commitment to high-quality education, resistance to external influence, and the creation of a global collaborative network, it seeks to spread Bitcoin education to every corner of the world, offering a transparent and transformative model for reshaping traditional financial systems. * Latest Updates Recently, MyfirstBitcoin successfully hosted the fourth Bitcoin Educators Unconference, featuring guests such as nostr:npub1zfgx8v2g0faswd0ry2qn3ay4pvx4jr6q4fw9d0yqalpkyv9hhp0sjccnj5 nostr:npub1rhh9pkmf6l6z7298yg6fgp95rzkmx4j9uxpekn8j73p5k95ck7gsvce7vj attracting around 170 participants and receiving positive feedback. They also held the graduation ceremony in Ilopango, El Salvador, and continued to organize their regular monthly Bitcoin education meetups and Bitcoin game nights. Additionally, MyfirstBitcoin’s Bitcoin Educators Node Network welcomed four new projects from Canada, Nigeria, and the United States. In partnership with Bitcoin Boma, they are launching a free online Bitcoin education course for Malawi in January 2025, aimed at enhancing local Bitcoin knowledge.
- Introduction Bitcoin Beach is a groundbreaking initiative in El Salvador aimed at fostering sustainable local economic development through Bitcoin. The project provides financial services to the community, particularly for those without access to traditional banking. By using Bitcoin for payments, residents can cover everyday expenses such as utility bills, medical costs, and food. Bitcoin Beach leverages the Lightning Network and community collaboration to promote the adoption of Bitcoin both within El Salvador and globally.
- Latest Updates Recently, Bitcoin Beach attended the conference at Bitcoin Lake, where they hosted the Bitcoin Beach Meetup and Bitcoin Beach Festival to support local businesses with Bitcoin. They also invited notable figures such as nostr:npub1q0al05h2uvtj0fp8ww7etl0pdjnkum638ynz9tmku3e522fyvlmqjq04mt Hermann Buhr-Vivier, nostr:npub164xhe3pgcqaj70ls7ls5e4hwlnvl4ttuu8wns99jmwp5z6lwhutsa27wle as podcast guests. The discussions covered a range of impactful topics, including how Bitcoin mining can truly light up rural Africa, how to use Bitcoin to transform small towns in South Africa, and integrating Bitcoin into state-level policies across the United States, among other key areas.
3.Praia Bitcoin Brazil nostr:npub1m3tu3l6y59g2tmackq23v5vgn59u7hu66gxg8xajghz59tqm6xnqk2m888 * Introduction Praia Bitcoin Brazil, located in Jericoacoara, Brazil, is dedicated to creating the country's first Bitcoin circular economy, empowering local residents with financial inclusion. Founded by Fernando Motolese, the project promotes Bitcoin adoption through education, technology, and community-driven initiatives. It has integrated over 40 local businesses into the Bitcoin ecosystem and raised more than 12 BTC through Bitcoin-only crowdfunding. Praia Bitcoin offers self-sovereign financial services and runs programs like the "Bitcoin Smiles" initiative and educational support for children. * Latest Updates Recently, Praia Bitcoin Brazil launched several innovative projects, including the first stage lighting course and free acoustic guitar course funded entirely through Bitcoin crowdfunding. Additionally, Praia Bitcoin successfully hosted the Praia Bitcoin Conference 2024, attracting 10 volunteers, 100 local residents, and 10 new merchants. The conference also sponsored the first music performance paid in Bitcoin and introduced three local courses, all funded via Bitcoin crowdfunding. These initiatives highlight Praia Bitcoin's ongoing efforts to drive Bitcoin adoption and foster local community development.
4.Bitcoin Lake / Lago Bitcoin Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake aims to create a circular economy powered by Bitcoin, providing a novel and accessible solution for unbanked as well as banked merchants in Guatemala. * Latest Updates The Bitcoin Lake community has been actively preparing and promoting a series of innovative initiatives. On November 30 and December 1, Bitcoin Lake successfully hosted its 2024 conference, inviting industry experts such as Ronny Avendaño, co-founder and CEO of the Bitcoin hardware store, and prominent Bitcoin advocate Roman Martínez (chimbera). During the conference, the community also organized creative activities like the coffee workshop and “Be Captain of the Bitcoin Boat”, offering participants an opportunity to dive deeper into Bitcoin and the local economy. Additionally, through partnerships with local merchants, Bitcoin Lake is actively advancing the development of the Bitcoin economy, fostering economic growth and financial inclusion in the community.
5.Bitcoin jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network with the goal of creating a circular Bitcoin economy. The project provides education, resources, and technology to both individuals and businesses. Starting from the Golden Triangle area in Costa Rica (Dominical, Uvita, Ojochal, Platanillo, Tinamaste), it is developing a shining example of what a Bitcoin community can represent. * Latest Updates Recently, the Bitcoin Jungle community has been actively promoting the adoption and use of Bitcoin in Costa Rica, participating in various projects and events. Community members attended the Adopting Bitcoin conference in El Salvador, further advancing global Bitcoin adoption. At the same time, they have been actively supporting children's charity projects and Bitcoin diploma courses, continuously driving Bitcoin education, social responsibility, and community development.
6.Bitcoin Berlín sv * Introduction Bitcoin Berlín sv aimed at creating a financially sovereign town in Berlín, El Salvador, through the implementation of a Bitcoin circular economy. The project seeks to integrate Bitcoin into the local economy by educating residents and businesses about its benefits, promoting the adoption of Bitcoin-based payment systems, and empowering local entrepreneurs with financial education. It also focuses on environmental sustainability, encouraging the use of renewable energy and waste reduction. * Latest Updates Recently, the Bitcoin Berlín sv has been actively promoting the use of Bitcoin by sharing informative articles and supporting the graduation of podcast producer Joel through the BlinkBTC QR code platform, allowing contributions in sats. This initiative not only supports the growth and development of community members but also furthers Bitcoin’s adoption and usage within the community. Additionally, on November 23rd, the community successfully hosted a cultural festival celebrating the local heritage. During the event, all vendors accepted Bitcoin payments, showcasing its practical application in Berlín’s economy. The festival attracted numerous tourists and residents eager to experience Bitcoin payments, further advancing its integration into daily life.
7.Bitcoin embassy San Salvador * Introduction Bitcoin embassy San Salvador is more into promoting Nostr in the region. * Latest Updates Recently, the Bitcoin Embassy San Salvador has been actively promoting the use and adoption of Bitcoin within the community, organizing various events. One of the highlights was the Christmas Toy Drive x Cuarteto Salvación, where toys were purchased using Sats to bring holiday cheer to children in need. The event, held on December 1 at Cuscatlán Park, also featured a special Music Night, attracting a large audience. Additionally, the Embassy hosted an educational gathering for food vendors, aimed at promoting Bitcoin payment systems. During the event, vendors accept Bitcoin payments through tiankii_Tech and blinkbtc platforms, further encouraging local businesses to embrace and adopt Bitcoin payments.
8.ONG Bitcoin Argentina * Introduction ONG Bitcoin Argentina is dedicated to advancing the development and application of decentralized technologies, particularly in the fields of Bitcoin, cryptocurrencies, and blockchain. As a leading organization in this space, the community promotes user protection and the healthy growth of the crypto ecosystem through education, training, and public advocacy. Its mission is to help individuals, businesses, and decision-makers understand and leverage decentralized, transparent, and secure technologies to bring more opportunities and progress to society. ONG Bitcoin Argentina has become a leading force in promoting decentralized technology in Argentina and Latin America. * Latest Updates Recently, ONG Bitcoin Argentina has been actively preparing for the “Moon Party | Despedimos el año ATH (A Todo Hodler)” celebration, set to take place on December 5, 2024. Bitcoin enthusiasts will gather to enjoy exciting activities, including a Lightning Network demonstration and the Fish Bowl Manizesto Bitcoiner art exhibition. In addition, the community has hosted and will host a series of conferences and workshops covering a range of topics, including local digital asset services, Bitcoin as a strategic reserve in the U.S., the reconversion of the Bitcoin and cryptocurrency economy and financial systems, the role of crypto economics in financial system reform, the impact of Bitcoin ETFs on markets, and Bitcoin's influence on global issues, fostering in-depth discussions and development within the crypto industry.
9.La bitcoineta * Introduction La Bitcoineta is an initiative launched by the Argentine community in 2018, designed to promote the adoption and understanding of Bitcoin through a unique and powerful tool: a van and a group of volunteers. This traveling educational project has visited hundreds of towns across Latin America, Africa, and Europe, reaching thousands of people and covering hundreds of thousands of kilometers with the aim of spreading its mission and activities.With its innovative and mobile approach, Bitcoineta has become a globally recognized educational project.
10.Motiv Peru * Introduction Motiv is a non-profit organization founded in 2020, focused on addressing systemic poverty through Bitcoin and innovative projects, aiming to provide better opportunities for survival and prosperity to underserved communities. Its founders, Rich Swisher and Vali Popescu, witnessed firsthand the tragic impact of poverty and lack of basic living conditions in a remote village in the Andes Mountains of Peru, where children were dying due to preventable causes. This inspired them to create Motiv, with the goal of empowering vulnerable populations. By leveraging global support and partnerships, Motiv uses Bitcoin to help local communities break free from poverty and improve their lives, striving to bring positive change and hope to those in need. * Latest Updates Recently, MOTIV Perú has made significant progress in promoting Bitcoin and the circular economy. The organization continues to transform communities across Peru through various initiatives. For example, in the Comas district of Lima, entrepreneurial women are paying for their classes with Bitcoin and learning how to make delicious desserts, further advancing the local circular economy. Additionally, MOTIV Perú held its first Bitcoin training in Carabayllo-Lima, helping Peruvians understand the nature of money and the advantages of Bitcoin. MOTIV is also assisting communities in areas like Tarapoto and Ancon, where locals are using Bitcoin for daily transactions, driving financial freedom and economic empowerment.
11.Montanha bitcoin * Introduction Building a circular economy in Sao thome, Brazil. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to June 2024, highlighting a water contamination incident.
12.Amityage honduras * Introduction Amityage Honduras is the first Bitcoin education center in Honduras, located on Roatán Island in the Prosperá zone. The center's mission is to educate the local community about Bitcoin and spread this knowledge throughout Central America and the Caribbean. It is dedicated to helping businesses on the island adopt Bitcoin as a payment method, teaching children financial literacy, and empowering individuals to achieve financial sovereignty through Bitcoin. The center aims to empower the local community through education and innovation, fostering economic independence and sustainable development. * Latest Updates Recently, Amityage Honduras is actively promoting Bitcoin education by participating in various international Bitcoin events and organizing local courses to help more people understand Bitcoin. Community members took part in significant events such as AdoptingBTC 2024 and BitcoinUnconference, and hosted workshops around the theme of “How to Enter the World of Bitcoin Education.” In Haidmühle, Germany, AmityAge completed a four-day Bitcoin Educators Academy, where the curriculum included topics like using simple analogies to explain Bitcoin and public speaking exercises. Additionally, the community hosted Bitcoin education courses on Roatán Island and provided a free Bitcoin event for beginners at the Crawfish Rock community, further spreading Bitcoin knowledge.
13.Lima - Orange Pill Perú nostr:npub1fw8m5g6nfywmsgqjc66j47jax7jrv8lq46zf7grydjqppc54a8eql47qrx * Introduction Orange Pill Peru is a community-driven initiative dedicated to empowering Peruvians through Bitcoin education. With a focus on transforming the financial landscape, Orange Pill Peru provides resources for individuals to learn about Bitcoin, connect with like-minded enthusiasts, and grow their knowledge through various events and workshops. The community serves as a hub for both beginners and professionals, offering a supportive environment to explore the fundamentals of Bitcoin, its history, and its potential to shape the future of finance. * Latest Updates Recently, there have been no major updates. They actively engage in Bitcoin education and industry updates by sharing and reposting Bitcoin-related content. They support MOTIV Perú's financial freedom education project in the Ancon community in Lima, emphasizing the empowerment of women through Bitcoin. Additionally, the community has shared information about the upcoming Bitcoin Medellin Conference scheduled for January 2025.
14.La Antigua Bitcoin * Introduction La Antigua Bitcoin is a community-based initiative in La Antigua Guatemala, focusing on promoting Bitcoin adoption in local businesses. The community works to create awareness and facilitate the use of Bitcoin as a payment method in various establishments throughout the city. By encouraging merchants to accept Bitcoin, La Antigua Bitcoin aims to integrate cryptocurrency into the everyday economy, driving financial innovation and expanding access to decentralized financial systems within the region. * Latest Updates Recently, the Antigua Bitcoin community has had few updates, with a focus on organizing its first meetup in collaboration with “Run with Bitcoin” on November 24, 2023. The event garnered significant attention within the community, featuring interactions with a special guest. The aim of the event was to further promote Bitcoin adoption in Antigua, Guatemala, and encourage exchange and collaboration between Bitcoin enthusiasts and the local community.
15.Horizonte Bitcoin nostr:npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk * Introduction Project that aims to contribute to the Bitcoinization of the economy and encourage Entrepreneurship and Decentralization. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to Oct 2024, which shared a message encouraging women to learn more about Bitcoin and connect with others in the field, highlighted a meetup, Satoshe's Lounge, for women, providing a space to learn, discuss, and share knowledge about Bitcoin.
16.Escuelita Bitcoin nostr:npub1awggmqvlw8pa0kp9qq5law8zsvp2a8suztk0357j7e0nt746suwspt7lwx * Introduction Educational Project for Little School. * Latest Updates Recently, the Escuelita Bitcoin team has grown to five members and is actively advancing Bitcoin education and community development. Team members have hosted several workshops in Paraguay and Mexico, spreading Bitcoin knowledge within local communities and encouraging merchants to accept Bitcoin payments, particularly in Ciudad del Este, Paraguay. The team is raising funds through platforms like Geyser. fund and Kuno.anne.media to support the expansion of their educational initiatives and help locals better understand and use Bitcoin. Escuelita Bitcoin also emphasizes privacy education, promoting the use of tools like CakeWallet and Monero. Through collaborations with other organizations and individuals, the team is extending the reach of Bitcoin education, fostering the adoption of Bitcoin in Latin America and emerging markets.
17.Bitcoin é aqui! Rolante/Riozinho-RS-BRASIL nostr:npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 * Introduction Bitcoin é Aqui! Rolante is located in Rolante, Brazil, and is dedicated to creating a lifestyle and tourism destination where 40% of businesses now accept Bitcoin as a payment method, showcasing the community's success in integrating Bitcoin into the local economy. Residents and visitors can use it to pay for all services, including accommodation, tours, local goods, medical services, and even construction and solar energy equipment. This reflects the practical application and convenience of its use in everyday life, aiming to create a digitally-driven environment powered by Bitcoin. * Latest Updates Recently, the Bitcoin é Aqui! Rolante has been actively promoting the adoption and use of Bitcoin in Brazil and beyond. The community has organized several educational events aimed at spreading basic Bitcoin knowledge and its practical applications in daily life, particularly through online videos and lectures. These efforts help people understand how Bitcoin plays a crucial role in the global financial system. The community has also been actively involved in promoting Bitcoin payments, supporting their adoption by local businesses and in the tourism industry.
18.Bitcoin Forte * Introduction Bitcoin Forte is a voluntary initiative aimed at introducing Bitcoin as a currency to Praia do Forte in Bahia, Brazil. The project provides valuable information about Bitcoin’s importance and encourages local merchants to adopt it as a payment method. By highlighting Bitcoin's international use, simplicity, and security, Bitcoin Forte aims to facilitate its adoption among both tourists and businesses.The community promotes Bitcoin as a stable and controlled currency, helping to avoid systemic price inflation. Bitcoin Forte simplifies the process for businesses by offering tools such as QR codes and the “Satoshi POS Wallet” app, which connects to a merchant’s primary wallet for seamless transactions. * Latest Updates Recently, the community has had no recent updates. The latest event dates back to July 2024, introducing Airbtc, a platform similar to Airbnb, but it only accepts Bitcoin as payment.
19.Bitcoin Paraguay * Introduction Bitcoin Paraguay is a community dedicated to connecting individuals in Paraguay who are interested in Bitcoin, promoting its adoption, and fostering the development of local circular economies. The community’s mission is to increase Bitcoin adoption by collaborating with local businesses and nonprofit organizations, helping to create a more sustainable local economy. Through regular events, talks, and resource sharing, Bitcoin Paraguay provides education and support to its members while actively exploring Bitcoin's application across various sectors in Paraguay. * Latest Updates Recently, the Bitcoin Paraguay community has made significant progress in promoting Bitcoin adoption. On November 5, they successfully hosted the fifth Bitcoin meetup in Asunción, attracting 110 attendees. The event included two Spanish-language presentations and a Lightning Network onboarding training session, with food and drinks available for purchase using Bitcoin. The event was made possible with strong support from sponsors Blink Wallet and Hacking Lives. On November 13, Josef Tetek visited Bitcoin Paraguay to help promote the adoption of Vexl in the country. The community also shared their progress through articles, with Jake, a community member, publishing an article in the Asunción Times on how Bitcoin Paraguay is improving people's lives.
20.Bitcoin Amantikir * Introduction They are starting the first community in the Serra da Mantiqueira to use and extol people about the bitcoin economy. * Latest Updates Recently, the Bitcoin Amantikir community has made significant progress in promoting Bitcoin as a payment method and fostering a circular economy in Santo Antônio do Pinhal. Various businesses, including a pet store, transportation service providers, a hotel, a fruit shop, and a tourist attraction, have started accepting Bitcoin payments. Additionally, the community is organizing a Bitcoin financial education course on December 2nd at Munay Pousada, aimed at helping young people aged 14-18 acquire essential financial knowledge and understand the importance of Bitcoin.
21.La Crypta nostr:npub1rujdpkd8mwezrvpqd2rx2zphfaztqrtsfg6w3vdnljdghs2q8qrqtt9u68 * Introduction La Crypta is an open-source community dedicated to advancing the adoption of the Nostr protocol and Bitcoin through developer-friendly tools and resources. By providing an integrated open-source stack, La Crypta empowers developers to sync with multiple relays, showcase profiles with badges, and facilitate seamless messaging, making it easier to build and utilize decentralized social platforms. Events like hackathons further enhance collaboration and attract new members, fostering innovation in decentralized social media. * Latest Updates LaWallet, their open-source wallet, integrates Bitcoin, Lightning, and Nostr to provide a seamless learning experience. With over 8,000 NFC cards distributed across conferences in regions like Argentina, Brazil, and Spain, LaWallet enables easy adoption while prioritizing user privacy. The wallet’s functionality is now supported by Alby’s official browser extension, further boosting accessibility.
-
 @ e31e84c4:77bbabc0
2024-11-27 11:32:57
@ e31e84c4:77bbabc0
2024-11-27 11:32:57‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
Childhood Lessons
As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny.
Definitions of Security
Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs.
Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis.
When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change.
How Bitcoin Changed Me
The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights.
Here are just a few examples:
Freedom of Expression
Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions.
Adequate Living Standards
Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards.
Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards.
Freedom of Association
Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions.
Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code.
Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power.
Right to Information
The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use.
Personal Context
For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code.
In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon…
A Modern Necessity
These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview:
“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” (https://www.youtube.com/watch?v=K4ciiDyUvUo)
As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society.
The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities.
Bitcoin’s True Security
Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it.
Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections.
Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times.
‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ a012dc82:6458a70d
2024-12-14 09:42:15
@ a012dc82:6458a70d
2024-12-14 09:42:15Table Of Content
-
The Birth of Tokenized Bitcoin
-
How Does Tokenized Bitcoin Work?
-
The Advantages of tBTC Over Traditional Bitcoin
-
Expanding the Utility of Bitcoin
-
The Future of Tokenized Bitcoin
-
Conclusion
-
FAQ
In the ever-evolving world of cryptocurrency, Bitcoin remains the gold standard. However, its traditional form has faced challenges, especially when it comes to transaction speeds and adaptability. Enter the tokenized version of Bitcoin on Solana, a solution that promises to address these issues. But what exactly is this new tokenized Bitcoin, and why is it causing such a stir in the crypto community? Let's dive in.
The Birth of Tokenized Bitcoin
Bitcoin, with its unmatched popularity, has always been at the forefront of the cryptocurrency industry. Yet, its primary blockchain has been criticized for being slow in adopting new features, making smaller transactions both time-consuming and expensive. To address these challenges, the Threshold Network introduced the first tokenized version of Bitcoin, known as tBTC, on the Solana blockchain. This innovation aims to bridge the gap between Bitcoin's value and its transactional limitations.
How Does Tokenized Bitcoin Work?
The concept might sound complex, but it's rooted in simplicity. Imagine you have a physical gold bar but find it cumbersome to use in daily transactions. Instead, you get a certificate (or token) representing that gold bar, which you can easily trade or use. Similarly, when someone mints tBTC on Solana, they send their Bitcoin to be "wrapped". This wrapping process involves a decentralized review where the crypto is held in a special wallet. This wallet's authenticity is validated by a majority of people operating nodes on the Threshold Network. Once validated, you receive tBTC equivalent to the Bitcoin you wrapped, which can be used seamlessly on the Solana blockchain.
The Advantages of tBTC Over Traditional Bitcoin
Traditional Bitcoin has its limitations, especially when it comes to smart contracts. Even with advancements like the Lightning Network, these limitations persist. tBTC, on the other hand, offers a more flexible approach. It acts as a proof of ownership, allowing users to prove they possess a certain amount of Bitcoin. Moreover, if they ever wish to revert to their original Bitcoin, they can easily trade their tBTC to claim it back. This process ensures security, as a significant majority of validators must approve the transaction, minimizing the risk of malicious intent.
Expanding the Utility of Bitcoin
One of the most exciting aspects of tBTC is its potential to revolutionize how Bitcoin is used. Traditional Bitcoin holders, if they wished to take a loan against their holdings, had to rely on centralized platforms, which came with their own set of risks. With tBTC, however, they can leverage their Bitcoin on the Solana blockchain, bypassing the limitations of the traditional Bitcoin network. This means they can take out loans, earn yields, and even use their Bitcoin in decentralized exchanges, offering a level of flexibility previously unheard of.
The Future of Tokenized Bitcoin
Tokenized Bitcoin, especially tBTC on Solana, is a groundbreaking advancement, but it's just the beginning of a broader trend. Other major blockchains, such as Ethereum, Arbitrum, Optimism, and Polygon, have also integrated this concept, showcasing the growing appeal and versatility of tokenized Bitcoin. This widespread adoption underscores the crypto community's belief in its potential, making Bitcoin more adaptable and enhancing its interoperability across different platforms.
Moreover, the rising trust in tokenized Bitcoin suggests a promising trajectory for the decentralized finance (DeFi) sector. As tokenized assets become more mainstream, platforms like Solana stand to benefit immensely, heralding a new era for the entire DeFi ecosystem. The embrace of tokenized Bitcoin is not just a win for Bitcoin itself but a testament to the evolving dynamics of the crypto world.
Conclusion
The introduction of tBTC on Solana is more than just a technological advancement; it's a testament to the crypto community's relentless pursuit of innovation. As we continue to witness the blending of traditional and modern financial systems, tokenized assets like tBTC will undoubtedly play a pivotal role in shaping the future of decentralized finance.
FAQs
What is tokenized Bitcoin? Tokenized Bitcoin, like tBTC on Solana, is a representation of Bitcoin on other blockchains, allowing for more flexibility and interoperability.
Why was tBTC introduced on Solana? tBTC was introduced to address Bitcoin's transactional limitations, making it more adaptable and efficient on platforms like Solana.
How does tokenized Bitcoin differ from traditional Bitcoin? While traditional Bitcoin has limitations with smart contracts and transaction speeds, tokenized Bitcoin offers more flexibility, especially on platforms like Solana.
Are other blockchains adopting tokenized Bitcoin? Yes, apart from Solana, blockchains like Ethereum, Arbitrum, Optimism, and Polygon have also integrated tokenized Bitcoin.
What does the rise of tokenized Bitcoin mean for the DeFi sector? The growing trust in tokenized Bitcoin suggests a promising future for the DeFi sector, with platforms like Solana leading the way in innovation and adoption.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research. *
-
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ a58a2663:87bb2918
2024-12-09 13:39:49
@ a58a2663:87bb2918
2024-12-09 13:39:49- Concluir com minha filha, até o fim de 2025, a leitura da tradução latina de Ursinho Pooh, isto é, Winnie Ille Pu, de Alexander Lenard (1910-1972), poeta, ensaísta e tradutor húngaro que viveu no Brasil. Que texto curioso! Estranho estímulo que me chegou para voltar a estudar latim a sério.

-
Importar mais livros pela Thrift Books e menos pela Loja do Diabo. Seu acervo é excepcional e o frete é mais barato. Às vezes, em menos de duas semanas já estou com o livro em mãos (e olha que resido no Maranhão).
-
Concluir e publicar meu livro Vida após as Universidades. Escrita & criação em velhos & novos contextos de risco, desenvolvimento de algumas ideias que insinuei em Contra a vida intelectual, no que diz respeito ao encerramento de um ciclo histórico de modos de fazer investigação erudita.
-
Rematar o terceiro e último módulo de Convivium - Seminário Permanente de Humanidades, "A Alegoria do Mundo: o Mago, o Filólogo e o Colonizador", embrião de um longo ensaio sobre o "projeto humanista" e as vias de saída da modernidade oferecidas pelo pensamento latino-americano. (As inscrições seguem abertas. Caso queira inscrever-se pagando em bitcoin, me mande um e-mail: camoensiii57@protonmail.com).
-
Defender no primeiro semestre minha tese de doutoramento sobre João Francisco Lisboa (1812-1863), o maior prosador brasileiro de meados do século XIX. Compreender seu Jornal de Tímon implica rever concepções há muitos estabelecidas sobre a formação da literatura brasileira.
-
Escrever pelo menos cinco ensaios de apresentação do pensamento de Vilém Flusser e do que pretendo realizar em FLUSSER_project. A ideia é divulgá-los em inglês e especialmente aqui pelo Nostr.
-
Ler TUDO de Ignacio Gómez de Liaño.
-
Não ceder à tentação de discutir com imbecil.
-
 @ 16d11430:61640947
2024-12-14 01:51:07
@ 16d11430:61640947
2024-12-14 01:51:07The trajectory of human progress is marked by seismic shifts in wealth, power, and knowledge. Over centuries, these tectonic movements have reshaped the global narrative, transitioning the spear-tip of innovation and dominance from East to West. Today, as global tensions rise and multipolarity challenges the unipolar financial order, it’s worth examining the periods of change and the forces that realigned the axis of human progress through the lens of technological and financial evolution.
- The East’s Preeminence: The Age of Soft Power and Real Assets
Period: Antiquity to 15th Century For millennia, wealth and knowledge flowed from East to West. Civilizations like India, China, and the Islamic Caliphates were centers of human progress. These regions excelled in technological innovation, financial stability (e.g., China’s early use of paper currency in the Tang Dynasty), and cultural capital.
Financial Dominance: Real assets like spices, textiles, and gold formed the backbone of trade. The Silk Road acted as a decentralized value network, with wealth flowing from resource-rich East Asia to demand-heavy Europe.
Knowledge Arbitrage: Eastern empires perfected systems of governance, mathematics, and astronomy. Indian numerals became the foundation of global mathematics, while Chinese engineering inspired innovations in navigation.
Yet, despite its dominance, the East’s wealth was tied to a fragile, physical-based trade network, leaving it vulnerable to external shocks.
- The Renaissance and the Maritime Arbitrage of Knowledge
Period: 15th–17th Century The fall of Constantinople in 1453 was a geopolitical rug pull, severing Europe’s access to Eastern trade routes. In response, European nations innovated maritime trade routes, circumventing old supply chains. This era saw the financialization of exploration through state-backed joint-stock companies like the Dutch East India Company (VOC), a precursor to modern equity markets.
Leverage and Liquidity: The VOC issued the first publicly traded shares, creating a new mechanism for wealth generation: equity capital. Wealth shifted west as Europe commoditized Eastern resources at unprecedented scale.
Techno-Geopolitical Advantage: Innovations in shipbuilding, navigation, and weaponry gave European powers a first-mover advantage in global trade, tipping the economic balance.
Europe began consolidating wealth and influence, laying the groundwork for the first financial superpowers.
- The Industrial Revolution: Scaling Innovation and Debt Capital
Period: 18th–19th Century The Industrial Revolution was the ultimate shift from real to synthetic wealth creation. Britain’s coal-powered factories and mechanized production allowed for the exponential scaling of goods and services, bypassing the labor-intensive economies of the East.
Debt as an Asset Class: The Bank of England pioneered modern public finance, using national debt to fund wars and infrastructure. Debt markets became a weapon of geopolitical influence, solidifying Britain’s dominance.
Data and Capital Flows: Knowledge transitioned from artisanal secrets to open-source intellectual property. The invention of the telegraph—a precursor to modern networks—centralized information flow in the West.
During this period, colonies were repurposed as raw material hubs, while the West monetized finished goods. The East’s economies, trapped in colonial dependency, were stripped of agency.
- The Dollar Standard: The West Consolidates Financial Hegemony
Period: 20th Century The world wars were financial accelerants, propelling the U.S. to global supremacy. Post-World War II, the Bretton Woods system tied global currencies to the U.S. dollar, itself pegged to gold. By 1971, the gold standard was abandoned, and fiat-backed dollars became the world’s reserve currency—a geopolitical masterstroke.
Petrodollar Diplomacy: The U.S. engineered a system where oil, the lifeblood of modern economies, was traded exclusively in dollars. This created an artificial demand for U.S. currency, reinforcing its global dominance.
Technology Arms Race: The Cold War spurred investments in computing, satellites, and the internet. These technologies cemented the West as the epicenter of innovation, while the Eastern bloc stagnated under centralized planning.
The East, particularly China and India, entered a period of economic dormancy, while the West built the foundation for the modern financialized economy.
- The Digital Era: The Resurgence of the East and Blockchain’s Decentralization
Period: 21st Century As the 20th century ended, cracks in Western hegemony began to appear. The East, particularly China, leveraged its demographic dividend and state-driven capitalism to re-enter the global stage. Simultaneously, blockchain and decentralized finance (DeFi) began eroding trust in centralized financial systems.
China’s Belt and Road Initiative (BRI): A modern Silk Road, the BRI channels liquidity and infrastructure investment into developing nations, countering Western-led institutions like the IMF and World Bank.
Bitcoin and DeFi: Bitcoin, as a decentralized reserve asset, challenges fiat’s monopoly on monetary sovereignty. Decentralized systems offer an alternative to SWIFT-based cross-border payments, reducing reliance on Western financial networks.
The U.S. and its allies now face a multipolar world where traditional financial instruments are being disrupted by distributed ledger technology and Eastern economic strategies.
- Geopolitical Tensions: A New Cold War of Data and Energy
The current geopolitical climate is defined by competition over intangible assets: data, semiconductors, and clean energy technologies. The East and West are locked in a race to dominate artificial intelligence, quantum computing, and blockchain infrastructure.
Data Sovereignty: Nations are weaponizing data localization laws and AI to gain competitive edges in surveillance capitalism and defense.
Energy Markets: The West’s pivot to green energy and the East’s dominance in rare earth minerals create asymmetric dependencies.
The financial spear-tip of human progress is no longer unilateral. The West’s financial systems, underpinned by debt and derivatives, face a fundamental challenge from the East’s state-capitalist model and decentralized digital assets.
Conclusion: The Dawn of a Decentralized World
The historical narrative of human progress has been a pendulum swing between centralized and decentralized systems. While the East dominated through physical assets and trade, the West shifted to financialization and industrial scale. Now, we stand on the precipice of another transformation: a decentralized financial and technological order where power is no longer tied to geography but to networks.
The tip of the spear of human progress is no longer a single entity but a fragmented, multi-nodal system. Whether this leads to collaboration or conflict depends on how the world navigates this unprecedented inflection point.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ c1e6505c:02b3157e
2024-12-14 01:50:48
@ c1e6505c:02b3157e
2024-12-14 01:50:48Test post coming from stacker.news
originally posted at https://stacker.news/items/808769
-
 @ c4b5369a:b812dbd6
2024-12-01 16:19:21
@ c4b5369a:b812dbd6
2024-12-01 16:19:21Ecash systems built on top of bitcoin have seen increasing adoption over the last couple of years. They have become a polarising topic in the bitcoin community, due to their centralized and custodial nature. Like any system, ecash comes with a lot of pros and cons when compared to other systems, that are fercely debated in cyber- and meat-space.
I have been working on developing tools and software for the ecash implementation Cashu for about 2 years now. I have had countless discussions with various people from different backgrounds about the topic. OG bitcoiners, fiat bankers, friends and family, privacy enthusiast... . As you can imagine the flow and outcome of these discussions varied widely.
Usually, conversations with bitcoiners were the most interesting for me. Their opinions about ecash polarised the most, by far. (excluding the fiat bankers, but that's a story for another day). In this short peice, I want to share some insights from the discussions I had, and maybe clear up some misconceptions about ecash on bitcoin.
What is Ecash?
If you still don't know what ecash is, sorry, I won't go into much detail explaining it. I recommend reading the wikipedia article on Ecash , and then this article on the rise and fall of digicash, the first and maybe only ecash company that existed. This will bring you up to speed on ecash history up until bitcoin entered the scene. Ecash was pretty much dead from the day after digicash went bankrupt untill it recently saw it's revival in two different spheres:
One of these spheres is obviously the bitcoin sphere. Here, ecash got reintroduced with the two open source projects Fedimint and Cashu. In my opinion, the main reason for this revival is the following fact: Unlike an implementation of ecash in the fiat world, that would rely on the permissioned system to "allow" something like ecash to exist, bitcoin does not come with that limitation. The permissionless nature of bitcoin allows for these protocols to exist and interoperate with the existing bitcoin stack.
The second, and maybe lesser known sphere is the revival of ecash as a CBDC. Bitcoiners might get scared at the mentioning of that word. Trust me, I don't like it either. Nonetheless, privacy enthusiasts see the opportunity to steer the CBDC-ship in another direction, by using an underlying technology for them that would limit targeted discrimination by the centralized authorithy. Something that works like cash... but in cyberspace... Ecash. One such implementation is GNU Taler, another one is Project Tourbillon. Usually, these kind of implementations use a cuck-version of the OG ecash, where only payers are anonymous, but not payees.
Anyway, in this article we will focus on the implementation of ecash on bitcoin.
About self custody
Bitcoin as a whole is about sovereignty and liberation. If someone else controls your money, they control you. For the first time since we've stopped using gold, bitcoin allows us to fully take control back of our money. A money that doesn't corrode, a money which supply connot get inflated, and a money that cannot be easily seized. All of this is true for bitcoin. There is only one precondition: You have to hold and use it self custodially.
Using bitcoin self custodially
The problem comes in when using bitcoin in a self custodial fashion. For bitcoin to maintain the monetary properties mentioned above, it has to remain decentralized. This means it is hard to scale, which in turn means the use of bitcoin tends to become more costly as usage increases.
So even if we wish that everyone would use bitcoin self custodially all the time for everything, I fear it is mostly just a dream, at least for the forseable future. Even with trustless second layer protocols like the Lightning Network, we are running into scaling issues, since at the end of the day, they are bound to the same onchain fee realities as bare-bones bitcoin transactions.
For most of humanity, it is financially not viable to pay even 1$ transaction fees for every transaction. Second layer protocol may bring the cost down a bit, but have other requirements. For example in lightning, you have an online assumption, to make sure your channel peers aren't trying to cheat. You need to have inbound liquidity to receive payments. There are cost associated with opening or closing payment channels, or rebalancing liquidity.
Other upcoming second layer protocols like Ark may improve on some of these issues. It is definitely something to look forward to! But they will have their own trade-offs, most likely also cost related. The fact remains that all trustless protocols that use the bitcoin timechain for conflict resolution, will have to deal with this matter. This is the cost of trustlessness.
Soo... Don't self custody...?
NO! If you can, you should always use self custody. As much as possible!
Personally, I use all the tools mentioned above. And I recommend that if you can, you should too.
But the fact is, not everyone can. Many would love to take control over their financial freedom, but the threshold for them to use bitcoin in a sovereign fashion is simply to high. So they will either remain in fiat slavery land, or they will end up using "bitcoin" through a custodian like coinbase, binance, or whatever banking service they have access to.
I will also mention that for some usecases, enjoying the convenience of a custodian is just very attractive. Of course, this is only the case as long as the custodian plays by the book, and doesn't suddenly freeze-, or worse, run away with your deposits.
The right tool for the right job
I don't beleive that one way of using bitcoin is better than the other. It entirely depends on which problem you are trying to solve.
If the problem is storing or transfering wealth, then of course you would want to do that on chain.
If on the other hand, you want to send and receive frequent small to midsized payments, you might want to get setup with a lightning channel to an LSP. Depending on how deep you want to get involved, you may even set up some infrastructure and become part of the Lightning network.
If you want to receive digital tips that you can later claim into self custody after they reach a certain threshold, you might opt for a custodial solution.
If you require certain properties, like offline peer-to-peer transferability, or cash-like privacy, you might choose an ecash system.
It doesn't mean that if you use one, you cannot use the other. You should use whatever is useful for the current problem you are trying to solve, maybe even using multiple tools in conjuction, if that makes sense.
Ecash vs Onchain vs L2?
First of all, we have to understand that ecash is neither a replacement for self custody, nor is it a replacement for trustless second layer protocols. They are irreplaceable with something that is custodial in nature, due to the simple fact that if you lose control over your money, you have lost the control over your life.
So. No one beleives you should prioritize custodial solutions to secure your wealth. Self custody will always remain king in that regard. Custodial wallets should be thought off as a physical spending wallet you can walk around with, even through the dark alleyways where it might get robbed from you. Keep your cash in there for convenient spending, not worrying about fees, liquidity, data footprints, channel backups, etc. etc. etc... These benefits obviously come at the cost of trust, that the provider doesn't rug-pull your deposit.
I really like the user experience of custodial services. I would never put a lot of money into any one of them though, because I don't trust them. Just like I wouldn't walk around with $10000 in my physical wallet. The risk that it gets stolen is simply to great. At the same time, this risk doesn't mean I will get rid of my physical wallet. I think having a wallet with some cash in it is super useful. I will mittigate the risk by reducing the amount I carry inside that wallet. This is the same way I think about digital money I hold in custodial wallets, be it an ecash service or others.
All things considered, it is hard to argue that self custody comes even close to the UX a custodian can give you, due to the fact that they can take care of all the complexities (mentioned above) for you.
So then, why ecash?
We now know, that we are NOT comparing ecash with the sovereign bitcoin stack. We are comparing it instead to traditional custodial systems. This is the area ecash is trying to improve uppon. So if you've chosen that the best tool to solve a problem might be a custodial solution, only then should you start to consider using ecash.
It offers a more privacy preserving, less burdonsome and less censorable way of offering a custody solution.
It offers some neat properties like offline peer-to-peer transactions, programability, de-linkage from personally identifiable information, and more.
Here is an example, on how ecash could create a fairer environment for online consumers:
Online services love to offer subscriptions. But for the consumer, this is mostly a trap. As a consumer, I would rather pay for a service right now and be done with it. I don't want to sign up for a 10 year plan, give them my email address, my date of birth , create an account, etc...
One way of doing that, would be for the service provider to accept payments in ecash, instead of having an account and subscription model.
It would work like this:
- The user creates ecash by paying into the service's mint. Hereby it is not required to use lightning or even bitcoin. It could be done with any other value transfer meduim the service provider accepts (cash, shitcoins, lottery tickets...).
- You use the issued ecash, to retreive services. This could be anything from video streaming, to AI prompts.
- Once you are done, you swap your remaining ecash back.
In a system like this, you wouldn't be tracked as a user, and the service provider wouldn't be burdoned with safeguarding your personal information. Just like a cash-for-goods transaction in a convenience store.
I beleive the search engine Kagi is building a system like that, according to this podcast. It has also be demoed by https://athenut.com/ how it would be implemented, using Cashu.
Here is another example, on how an event organizer can provide privacy preserving electronic payment rails for a conference or a festival, using ecash:
If you have been part of organizing a conference or an event, you might have experienced this problem. Onchain payments are too slow and costly. Lightning payments are too flaky.
Do merchants have to setup a lightning channel? Do they have to request inbound liquidity from an LSP? Do they have to splice into the channel once they run out of liquidity? In practice, these are the realities that merchants and event organizers are faced with when they try to set up payment rails for a conference.
Using ecash, it would look like this:
- Event organizer will run a dedicated ecash mint for the event.
- Visitors can swap into ecash when ariving at the entrance, using bitcoin, cash, or whatever medium the organizer accepts.
- The visitor can spend the ecash freely at the merchants. He enjoys good privacy, like with cash. The online requirements are minimal, so it works well in a setting where connectivity is not great.
- At the end of the event, visitors and merchants swap their ecash back into the preferred medium (cash, bitcoin...).
This would dreastically reduce the complexity and requirements for merchants, while improving the privacy of the visitors.
A bold experiment: Free banking in the digital age
Most bitcoiners will run out of the room screaming, if they hear the word bank. And fair enough, I don't like them either. I believe in the mantra "unbank the banked", after all. But the reason I do so, is because todays fiat/investment banks just suck. It's the same problem as with the internet platforms today. You, the "customer", is not realy the customer anymore, but the product. You get sold and squeezed, until you have nothing more to give.
I beleive with a sound money basis, these new kind of free banks could once again compete for customers by provididng the best money services they can, and not by who can scam his way to the money printer the best. Maybe this is just a pipe dream. But we all dream a little. Some dream about unlimited onchain transactions (I've had this dream before), and some dream about free banks in cyberspace. In my dream, these banks would use ecash to respect their users privacy.
Clearing up misconceptions and flawed assumptions about ecash on bitcoin
Not only, but especially when talking with bitcoiners there are a lot of assumptions regarding ecash on bitcoin. I want to take this opportunity to address some of those.
Ecash is an attack on self custody
As we've mentioned above, ecash is not meant to compete with self custody. It is meant to go where self custodial bitcoin cannot go. Be it due to on-chain limitations, or network/infrastructure requirements. Ecash is completely detached from bitcoin, and can never compete with the trustless properties that only bitcoin can offer.
Ecash mints will get rugged
100% correct. Every custodial solution, be it multisig or not, will suffer from this risk. It is part of the deal. Act accordingly. Plan for this risk when choosing to use a custodial system.
Working on ecash is a distraction from what really matters, since it is not self custodial
While it is true that improving self custodial bitcoin is one of the most important things our generation will have to solve, it doesn't mean that everything else becomes irrelevant. We see that today, in a lot of circumstances a fully sovereign setup is just not realistic. At which point most users will revert back to custodial solutions. Having technology in place for users that face these circumstances, to offer them at least some protection are worth the effort, in my opinion.
Ecash mints will retroactively introduce KYC
Yes it is true that ecash mints can do that. However, what would they learn? They would learn about the amount you were holding in the mint at that time, should you choose to withdraw. They would not be able to learn anything about your past transactions. And needless to say, at which point you should be one and done with this mint as a service provider, and move to someone that respects their users.
Ecash will be used to "steal" bitcoins self custodial user base
I would argue the oposite. Someone that has realized the power of self custody, would never give it up willingly. On the other hand, someone that got rugged by an ecash mint will forever become a self custody maximalist.
Closing thoughts...
I hope you enjoyed reading my take on ecash built on bitcoin. I beleive it has massive potential, and creators, service providers and consumers can benefit massively from ecash's proposition. Using ecash doesn't mean you reject self custody. It means you have realized that there is more tools than just a hammer, and you intend to use the tool that can best solve the problem at hand. This also means, that to some the tool "ecash" may be useless. After all, not everyone is a carpenter. This is also fine. Use whatever you think is useful, and don't let people tell you otherwise.
Also, please don't take my word for it. Think for yourself.
Best,
Gandlaf
-
 @ e373ca41:b82abcc5
2024-12-03 08:08:53
@ e373ca41:b82abcc5
2024-12-03 08:08:53Article by Milosz Matuschek, originally from "Freischwebende Intelligenz"
“In fact, the selection that the class mercilessly carries out among the judges is more dangerous and worse than among the Reichswehr, which is related to them in spirit. In both cases, there is a clear co-option: the group chooses whoever adapts to the group spirit - always suitable, never heterogeneous elements. This begins with the Judicial Review Commission and continues with the fine sieve of the personnel officers. The result is this judiciary.”
- Kurt Tucholsky, German Judges (commentary, 1927)
Christian Dettmar was a family court judge in Weimar when the coronavirus measures reached schools: Compulsory masks, distancing rules, testing. He had doubts, did his duty and made a courageous decision: he obtained expert opinions from professors and issued a temporary injunction prohibiting infection control measures at two schools. The entire decision is well-founded and 178 pages long. Dettmar saw the infection control measures as a threat to the welfare of children. As we know today and could have known back then: rightly so.
The decision was later overturned by another court. A gauntlet was thrown down for Judge Dettmar, the lawyers involved in the proceedings and the experts: Searches of homes and offices, confiscation of cell phones, computers and documents. Dettmar was charged with obstruction of justice and sentenced to two years' probation. The Weimar judge has thus lost his judicial office and all pension entitlements. Obstruction of justice is a crime, with a minimum sentence of one year, which almost automatically results in the loss of the judgeship. The Federal Court of Justice recently confirmed the conviction, the reasons for the judgment are still pending. It will be interesting to see the reasons. In the eyes of the court and the public prosecutor's office, Mr. Dettmar is a kind of activist who has abused his judicial office and created a case for himself in order to deliberately issue a decision in violation of the law.
What exactly is Judge Dettmar supposed to have done wrong? He did not break the law. Instead, he broke a subliminal taboo that has spread throughout the judicial system (and everywhere else), namely that critical questions are unwelcome in times of pandemic and that the opinion of the pro-government expert regime is sacrosanct. How right he was in hindsight is shown by today's admission, even by politicians involved, that school closures were not necessary or that they overshot the mark here and there. The minimum consensus of the mini reappraisal simulation in Germany at the moment is that during covid a lot went wrong when it came to children. “With the knowledge of today”, it is said, this would not have been done. However, what should be possible without any problems in Germany, a state governed by the rule of law: “With the knowledge of today”, punishing those who knew in advance back then with hindsight. Sounds suspiciously like an unlawful state.
It's a tremendous joke in the history of German justice that makes people abroad shake their heads: A judge has summoned independent experts who were right and now the judge is being sentenced. Meanwhile, the rest of the judiciary delivered a coronavirus ruling that went no deeper than the version of what is supposed to be “science” (and wasn't, see the RKI files). The entire judicial apparatus has failed in the pandemic, has rejected requests for evidence on the study situation and research into the evidence base, misjudged constitutional dimensions and ultimately blindly adopted the erroneous opinion of a media-created, unelected “nomenklatura expert council”. In other words, those who have done their job wrong explain to those who have done it right what is going on. And exclude one of their own from their guild for doing so.
Being right and getting right are two different things. Judge Dettmar had to be made an example of, because his decision made the continuous violation of the law by his fellow judges obvious. If the majority breaks the law and someone wants to restore it, then this act must be punished. According to Tucholsky, this has been a proven practice in Germany for 100 years. The RKI files confirmed that there was no evidence base for mask-wearing. The social distancing requirement was an arbitrary instrument invented by Anthony Fauci that was adopted unquestioningly by German politicians. The evidence-free policy of measures, which had exceeded its public shelf life at the latest with the leak of the RKI protocols (which should not have gone unnoticed by the Federal Court of Justice), is being legally preserved in a vacuum. An unprecedented act of disregard for reality by the highest court of law.
Advertisement: Are you looking for the easiest way to buy Bitcoin and store it yourself? The RELAI app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees. (no financial advice).
 ---
---Judge Dettmar has not broken the law. As a family court judge, he must take action if there is a threat to the welfare of a child. He has investigative powers like a public prosecutor. Where were the other family court judges? Why aren't they being prosecuted for inaction? Christian Dettmar was certainly not the only lawyer to have doubts about the proportionality of the corona measures. Dettmar wrote in his decision, which is well worth reading:
“According to this principle, also known as the prohibition of excessiveness, the measures intended to achieve a legitimate purpose must be suitable, necessary and proportionate in the narrow sense - in other words, when weighing up the advantages and disadvantages achieved with them. The measures that are not evidence-based, contrary to Section 1 (2) IfSG, are already unsuitable to achieve the fundamentally legitimate purpose pursued with them of avoiding overburdening the healthcare system or reducing the incidence of infection with the SARS-CoV-2 virus. In any case, however, they are disproportionate in the narrower sense, because the considerable disadvantages/collateral damage caused by them are not offset by any recognizable benefit for the children themselves or third parties”.
It will be interesting to see the reasoning (and it should be detailed, please) as to why Judge Dettmar's application of the principle of proportionality, which runs through the entire legal system, was intentionally erroneous. - Judge Dettmar averted harm to third parties, in this case children - and this is supposed to have damaged the administration of justice? What is the administration of justice there for if not to protect the legal interests of others? - Judge Dettmar has summoned experienced experts, professors at German universities. How does the public prosecutor's office justify the fact that these experts are somehow marginal or show one-sidedness? Conversely, how should the reflexive reference by the rest of the judiciary to “the RKI” or “science” in pandemic matters be assessed?
Does the public prosecutor's office determine who is capable of being satisfied as a scientist in Germany and who is not? And if so, on the basis of what expertise equal to that of the parties involved? Where such deficits in reasoning arise, it starts to smell: politics is up in the air. Judge Dettmar is aware of the interface between the judiciary and politics. He was once a public prosecutor himself and dealt with cases of ex-GDR/SED injustice. As the irony of fate would have it, he was in charge of legal proceedings in the same department that is now prosecuting him. Dettmar now knows all the roles in court proceedings from his own experience: prosecutor, judge, defendant. And now also: victim of justice. At some point: a rehabilitated man. In fact, he is one thing above all: a role model.
Join the marketplace of ideas! Sound money and sound information should finally be in the hands of the people, right? We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Want to learn more about the Pareto Project Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 82883e29:dab2ff8c
2024-12-13 23:36:16
@ 82883e29:dab2ff8c
2024-12-13 23:36:16Hello, readers!
My name is Muju. I am a writer, thinker, Bitcoin advocate, and humanist activist with a passion for challenging the status quo and exploring the complexities of our world. Over the years, I've written extensively on politics, human rights, Bitcoin, and the fascinating intersections of culture and technology through my blog, Unintuitive Discourse.
Today, I take an exciting step forward by beginning to publish my work on Nostr, a platform that aligns with my values of free speech and decentralization.
Nostr’s censorship-resistant architecture ensures that my thoughts and ideas can be preserved permanently, free from interference or erasure. This move reflects my commitment to creating a lasting record of my work—a digital footprint that stands against the tides of suppression.
Unintuitive Discourse is a product of my journey: my life as an autodidact, my experiences as a political refugee, and my relentless pursuit of understanding the world through a humanist lens. By leveraging Nostr, I aim to secure a permanent home for my ideas, making them accessible to those who seek to question, learn, and grow.
If you’re reading this, welcome to the beginning of something enduring. Join me as I continue to write, reflect, and share thoughts that I hope will inspire meaningful conversations for years to come.
Here's to a future where ideas thrive without limits—my contribution to realizing a truly decentralized internet where knowledge flows freely and voices cannot be silenced.
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ e373ca41:b82abcc5
2024-12-03 07:42:23
@ e373ca41:b82abcc5
2024-12-03 07:42:23
Article by Milosz Matuschek, published at Freischwebende Intelligenz (see original for links)
The actor Keanu Reeves recently told in an interview how he tried to explain the movie Matrix to a 15-year-old and that he was the hero fighting for what is real. The teenager's reaction: “Who cares if it's real”?
Reality can be an uncomfortable place. It is better to live (at least for a while) in a comfortable construction. In his “Myths of Everyday Life”, French philosopher Roland Barthes investigated how even everyday objects are ideologically charged without us realizing it: Magazines, advertising, sporting events. According to Barthes, modern myths are culturally constructed and reinforce the social hierarchy. The German philosopher Hans Blumenberg saw the creation of myths as a protective mechanism for oneself: Everyone thus creates their own “lifeworld”, which does not have to correspond to reality, which is intangible anyway. First the lie, then the manipulation of memory
More and more frequently, we see that there seem to be several illusory realities in relation to the facts alone. But only one can be genuine, i.e. actually correspond to reality.
The fairy tale of “right-wing deportation plans”, which were allegedly discussed at a conference entitled “Wannsee 2.0”, has lasted longer than judges need to issue temporary injunctions. The predicted summer of hell took place on the bullshit screen, and most people survived it better thanks to wellies and rain jackets.
The best myths about corona can still be read today, as if there had never been even a hint of knowledge to cloud one's superstition.
In a constant fit of auto-suggestive back-slapping, the mainstream constantly wants to believe that we have “come through the pandemic well”. Spiegel columnist Sascha Lobo therefore loudly proclaims in a column that coronavirus critics are living in a parallel reality, while at the same time the RKI protocols reveal how great the discrepancy was between RKI science and the parallel world of authoritarian coronavirus policy. Then he bends reality to suit himself: “Was the truth always told? “Of course not...but it's not always that easy.” We weirdos understand that, Mr. Lobo: it's not easy to describe any mistakes made during the pandemic if, like you, you also want to give well-paid lectures to the pharmaceutical industry. Reappraisal, where?

A prime example of “not wanting to know better” after the fact: Spiegel's Thomas Fischer (Screenshot/Spiegel.de)
His columnist colleague Thomas Fischer, a former criminal judge (!) at the highest (!) ordinary court, the Federal Court of Justice, dutifully (better “dutifully sloppy”?) flanked what he still remembered about the pandemic in the media's short memory. Even the title of the column is highbrow gaslighting, because: Where is there a tendency to rehash right now? And why is this supposed to be “unpleasant”? Or for whom? Does this also apply to the last 80 years? A few examples:
``` According to Fischer, over 100,000 people have died “from corona” in Germany, and “millions” worldwide. As a good newspaper reader, the Spiegel criminal lawyer knows this even without autopsies. Co-morbidities? Age distribution of deaths? Not an issue.
Not a word about excess mortality in 2021, by the way; you shouldn't challenge your own cognitive dissonance too much if you want to write for Der Spiegel.
Fischer is equally aware that millions of Americans “vaccinated themselves with disinfectant” on presidential recommendation and then “died miserably” (he was probably sitting at the bedside watching).
He also claims to know that the intensive care units in Germany were working at the limit of their capacity for many months. He does not reveal where this knowledge comes from; the official DIVI register speaks a different language (incidentally already taken off the net).
Where is the breaking point, Mr. Fischer?
The witty fairy-tale uncle doesn't spare his readers the staircase joke about the “pictures of Bergamo” either. The panic images, which even Lauterbach later praised, did not show a wave of corona deaths, but a temporary overload of local crematoria. ```
A flight attendant's blurred video of 13 military trucks thus became a worldwide legend. Even Bayerischer Rundfunk reported on it in September 2021, which shows that Once the legend is in your head, even mainstream news currently takes more than three years of incubation to (still not) mill its way into the head of a former federal judge. And we are still wondering why a) no progress is being made with the investigation and b) what the supposedly great documentation department at Der Spiegel actually does for a living.
Thank you in any case, Mr. Fischer, for the instructive insight into the reality horizon of German top judges! Your journalistic support for the destruction of trust in the remaining judiciary is excellent! Incidentally, Der Spiegel has recently successfully halved its profits, its circulation is falling and a power struggle is raging at the top.
Hendrik Streek, poster boy of the pseudo-critical flank of the mainstream, also likes selective perception. In his book “Nachbeben” (Aftershocks), he maintains his myth of the “very rare vaccination side effects”. He omits the fact that 2.5 million vaccination side effects from the data of the National Association of Statutory Health Insurance Physicians (Kassenärztliche Bundesvereinigung) have not even been processed by the Paul Ehrlich Institute. The authority has allegedly been working on an “interface” for years in order to be able to process the data. For those who believe it: the simplest analog interface would be a mailbox slot. A year ago, PEI employee Keller-Stanislawski stated in parliamentary questioning that the processing of vaccination damage reports had barely been kept up with and that this vaccine had caused a lot more work. Streek now wants to enter the Bundestag for the CDU. What doesn't fit is made to fit afterwards
A false reality is created through media bias and the creation of a false (and lazy) consensus. With a pinch of authoritarianism and gaslighting, it is then not too difficult to elevate the illusory reality to a dogma. Anyone who doesn't believe in it is fought against - the Matrix sends its regards.
Misleading fact checks and heavy censorship on YouTube or in social media served as discourse cosmetics in the coronavirus era, while important political decisions were made in the shadows. Today, the nomenclature is already censoring itself in order to be able to hold on to its narrative that it knew nothing for as long as possible. The RKI cancer register? Frozen since 2020. The DIVI intensive care register? Taken offline. The RKI health reporting? Offline. The PEI vaccine injury register? “Temporarily” offline since 2022. Really, technical problems? Who is supposed to believe that in the best Germany ever?
The Second German Television, ZDF (advertising slogan: “You can see better with the second one”) is censoring itself particularly conspicuously. The Mainzelmännchen have the deletion devil on the loose. For example, numerous reports on compulsory vaccination (which at first hardly any politicians wanted, and then suddenly many did) can no longer be found in the media library. The political breach of word is being erased. Much of what would make politicians look bad today with statements from back then on the most sensitive fundamental rights issue of recent decades is disappearing. Kevin Kühnert from the SPD said in a deleted post from December 7, 2021 on the breach of promise regarding compulsory vaccination: “That shouldn't have happened to us”.

In the fake reality of the media, it never happened. What happened?
The article about Kühnert has been deleted. (backed up here).
So it goes on:
``` What's up with the forced vaccination rumor? (In the end it was quite a lot). Deleted (saved here, check link above).
MPs call for compulsory corona vaccination from 18? Deleted (backed up here).
Scholz thinks there should be “no more red lines”? Deleted (backed up here).
According to Federal Minister of Justice Lambrecht, the coalition never wanted compulsory vaccination? Deleted (backed up here). ```
How was it with Orwell? He who determines the past determines the future? Well, if you don't get lost in the present.
Presumably ZDF (“it's better not to watch anything on the second channel”) has to save on server costs despite billions in compulsory fees. If you want to watch the “Fernsehgarten” from December 18, 2016 again, you can easily find it in the media library.
I guess that's “basic service”.
Your fees at work.
Join the marketplace of ideas!
Sound money and sound information should finally be in the hands of the people, right? We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 4b7c4ee3:8cd5ed4d
2024-12-13 23:20:50
@ 4b7c4ee3:8cd5ed4d
2024-12-13 23:20:50Is this thing on?
-
 @ 2fb77d26:c47a6ee1
2024-11-29 22:07:30
@ 2fb77d26:c47a6ee1
2024-11-29 22:07:30»Worte interessieren nur da, wo sie zu Taten führen«, notierte ich vor knapp 15 Jahren für einen meiner Texte. Gelten sollte diese Prämisse vor allem für Wahlversprechen. Doch die Geschichte zeigt, dass von den vollmundigen Zusicherungen eines Wahlkampfes nach Amtsantritt kaum etwas umgesetzt wird. Davon muss wohl auch in Bezug auf die US-Präsidentschaftswahl 2024 ausgegangen werden. Auch wenn viele immer noch auf eine »Trockenlegung des Sumpfes« hoffen. Ein Überblick.
Original mit Quellen (VÖ: 14.11.2024): https://www.regenauer.press/trump-reloaded
Unterhaltsam ist es bisweilen. Keine Frage. Ist ja auch Politainment. Fake. Eine Show. Eine ziemlich kostenintensive dazu. Und einer gewissen Schadenfreude kann man sich in der Tat kaum verwehren, betrachtet man die irrationalen Reaktionen, Nervenzusammenbrüche und infantilen Ausraster der Wahlverlierer – dem Lager, das in puncto Covid, Klimaschutz und Genderpolitik nie einen Hehl aus seinen totalitären Anwandlungen machte. Leider wird aus Spaß aber schnell bitterer ernst. So tötete ein psychisch labiler Mann aus Minnesota am Tag nach Donald Trumps Wahlsieg zuerst seine ehemalige Partnerin und deren Kind, dann seine Frau und den eigenen Sohn, und anschließend sich selbst. Während die Polizei bislang kein offizielles Tatmotiv kommuniziert, implizieren Social-Media-Beiträge des 46-jährigen Demokraten, dass seine Angst vor den Republikanern, beziehungsweise dem Einzug Trumps ins Weiße Haus, durchaus Auslöser des Amoklaufes sein könnten.
Während die weithin von »Wokeness« beseelten Demokraten ihre Wunden lecken, zelebrieren das konservative Lager der Republikaner und die MAGA-Apologeten einen vermeintlich historischen Sieg. Trump selbst verspricht bei seiner Siegesrede ein »goldenes Zeitalter«. Dass er jetzt »alles in Ordnung bringen« werde. Die Krypto-Branche wähnt sich im Aufwind. Der Bitcoin-Kurs steigt. Dow Jones, S&P 500 und Nasdaq erreichen neue Allzeithochs. In Iowa soll 2026 eine Art Weltausstellung stattfinden, um das 250-jährige Jubiläum Amerikas zu feiern. Bis zum Beginn der Feierlichkeiten sollen Elon Musk und Vivek Ramaswamy die Ausgaben des Staatsapparats um zwei Billionen US-Dollar reduziert haben. Natürlich ist Trump auch die letzte Chance der USA, um endlich die Grenze zu Mexiko zu sichern. Und von Robert F. Kennedy Jr. erwartet man, die Vereinigten Staaten im Rahmen eines MAHA-Programmes – »Make America Healthy Again« – wieder gesund zu machen.
Im Überschwang der Euphorie – oder Frust der Niederlage – fällt gerne unter den Tisch, dass Wähler in Amerika den Präsidenten gemäß Verfassung gar nicht direkt wählen dürfen, weil das für die Wahl des Präsidenten zuständige Electoral College im Prinzip völlig unabhängig vom eigentlichen Wahlausgang entscheiden kann. Die Wahlmänner könnten auch jeden anderen zum Staatsoberhaupt ernennen. Ob das Volk ihn will, oder er überhaupt angetreten ist, spielt rein formal gar keine Rolle. Bei genauerer Betrachtung also nicht unbedingt Demokratie in Reinform. Egal. Schnöde Details. »Trust the plan. Wir haben gewonnen. Geschichte wurde geschrieben« – und so weiter.
Die NATO gibt unterdes zu Protokoll, dass sich an ihrer geostrategischen Agenda »nichts ändern wird, egal, wer die Wahl gewinnt«, weil das »im Interesse der Vereinigten Staaten liege«. Vielleicht hat das US-Militär ja deshalb nur wenige Stunden nach Schließung der Wahllokale eine Minuteman III Interkontinentalrakete zu Testzwecken abgefeuert. Eine Langstreckenwaffe, die drei einzeln steuerbare Atomsprengköpfe transportieren kann.
Auch das Ron Paul Institute rechnet nicht mit grundlegenden Veränderungen und führt diverse Bereiche an, die unabhängig von der Besetzung des Oval Office ein Problem bleiben werden: Kontinuierliche Unterminierung der Verfassung, Krieg gegen die eigene Bevölkerung, Tiefenstaat, Washingtons ausufernde, verstetigte Notstandsermächtigungen, Militärinterventionen in aller Welt, maßlose Korruption und staatliche Tyrannei. Klingt nicht wirklich nach einem goldenen Zeitalter.
Die Reaktionen rund um die US-Wahl – ob positiv oder negativ, ob vor Ort oder im Rest der Welt – veranschaulichen jedenfalls, dass Wahlen Emotionsamplituden auslösen, die in keiner Relation zu dem stehen, was ein Präsident, Kanzler oder Premierminister tatsächlich bewirken kann. Sonst hätte Trump den tiefenstaatlichen »Sumpf« ja schon in seiner ersten Amtsperiode trockenlegen können.
Während die Demokraten also darauf warten, dass die USA ab dem 20. Januar 2025 zur Diktatur verkommen und auf Demonstrationen gegen das Resultat der US-Variante von Demokratie protestieren, fiebern die anderen dem Anbruch eines goldenen Zeitalters entgegen.
Genug Zeit also, den 47. Heilsbringer im Oval Office noch einmal genauer unter die Lupe zu nehmen. Denn auch wenn Donald Trump sich fraglos darauf versteht, zu unterhalten und große Reden von Freiheit und staatlicher Souveränität, von Weltfrieden und Prosperität zu schwingen, sprechen seine Taten zumeist eine ganz andere Sprache.
Fangen wir vorne an: Dank der Zurückstellung vom Wehrdienst konnte Donald Trump bereits 1968 bei Trump Management einsteigen, dem Unternehmen seines Vaters Fred C. Trump, der vor allem mit staatlichen geförderten Wohnungsbauprojekten – »Federal Housing Projects«, heute die Ghettos von New York – zum Multimillionär geworden war. 1971 übernahm Donald im Alter von 25 Jahren die Geschäftsleitung der Firma. Bei Interviews prahlt er bis heute gerne damit, dass sein Vater ihm in jungen Jahren »lediglich einen kleinen Kredit« über eine Million Dollar als Startkapital gewährte. Daraus habe er dann als gewiefter Unternehmer ein Immobilienimperium erschaffen. Dieser Darstellung widerspricht ein Artikel der New York Times (NYT) vom 2. Oktober 2018, der basierend auf Steuer- und Buchhaltungsunterlagen kalkuliert, dass Donald Trump gut 60 Millionen US-Dollar an Krediten erhielt.
»Im Alter von drei Jahren verdiente Trump am Imperium seines Vaters 200.000 Dollar jährlich. Mit acht Jahren war er Millionär. Mit 17 Jahren überließ ihm sein Vater einen Teilbesitz an einem Mehrfamilienhaus mit 52 Wohneinheiten. Kurz nachdem Trump das College abgeschlossen hatte, erhielt er von seinem Vater jährlich umgerechnet eine Million Dollar. Über die Jahre stiegen die jährlichen Schenkungen. In seinen Vierzigern und Fünfzigern lagen sie bei über fünf Millionen Dollar jährlich.«
Als Fred Trump im Juni 1999 verstarb, hatte der trickreiche Unternehmer und Steuerallergiker seinem Sprössling nach Berechnungen der NYT insgesamt 413 Millionen Dollar überschrieben. Selbst wenn New York Times, Associated Press und Co. im Jahr 2018 mit diesen Artikeln fraglos Stimmung gegen Trump machen wollten, kann dessen selbstbeweihräuchernde Darstellung augenscheinlich nicht ganz der Wahrheit entsprechen.
Aber: Er hatte Erfolg. Und das war in der Immobilienbranche des New Yorks der 70er und 80er nicht selbstverständlich. Denn sie wurde von der Mafia dominiert. Von den »Fünf Familien«. Wer nicht den Schutz von »Fat Tony« Salerno, Carmine Galante, Paul Castellano et al. genoss, den Bossen der Genovese-, Bonanno- und Gambino-Familien, hatte schlechte Karten. Das wusste auch Donald Trump. Also macht er Gebrauch von den exzellenten Kontakten seines Freundes, Mentors und Anwalts Roy Cohn, der nicht nur enge Verbindungen zum langjährigen FBI-Chef J. Edgar Hoover pflegte, sondern unter anderem auch Nancy Reagan, die Besitzer des Studio 54, Andy Warhol, die katholische Erzdiözese und die Führungsetage der fünf Mafia-Familien als Anwalt vertrat. Nicht umsonst ist Cohn ein zentraler Charakter in Whitney Webbs Zweiteiler »One Nation under Blackmail«. Den Kontakt zu Cohn, einer Schlüsselfigur für die Zusammenarbeit von Oberschicht und Unterwelt, suchte Donald Trump bereits 1973, als die US-Regierung ein Unternehmen seines Vaters verklagte. Er sollte bestehen bleiben, bis Cohn im August 1986 seiner AIDS-Erkrankung erlag.
Cohns Verbindungen zu Politik, Mafia und Jimmy Hoffas teilkrimineller Teamster-Gewerkschaft sorgten dafür, dass Trump in der Stadt Fuß fassen und sein Geschäft ausbauen konnte. Im Gegenzug war er gezwungen, überteuerte Baumaterialien von Fat Tonys Tarnfirmen zu beziehen. Nach Angaben eines ehemaligen Mitarbeiters von Cohn trafen sich Trump und Salerno in dessen Stadthaus in Manhattan. Trump will sich an ein solches Meeting allerdings nicht erinnern können – obwohl Salerno 1988 unter anderem wegen Erpressung in Höhe von acht Millionen Dollar im Rahmen eines Trump-Bauprojektes rechtskräftig verurteilt wurde. Die Wahrheit kennt wohl nur Trump selbst. Denn Cohn und Fat Tony sind tot.
Sicher ist: Die Geschäftsbeziehungen zwischen Donald Trump und Firmen des organisierten Verbrechens waren intensiver als seinerzeit üblich. Auf Tonbändern des FBI und der US-Staatsanwaltschaft, damals geleitet vom späteren Trump-Anwalt Rudy Giuliani, die beim Abhören von Mafia-Fahrzeugen und -Etablissements entstanden, ist mehrfach von Trump-Projekten die Rede. Donald passte sich dem Geschäftsgebaren seines Umfelds an. Den opportunistischen, skrupellosen, steuervermeidenden Praktiken seines Vaters – und dem von organisierter Kriminalität durchzogenen Filz des Ostküsten-Establishments.
Donald Trumps Frühphase, seine Geschäfte und Geschäftspartner sind also nicht unbedingt ein Paradebeispiel in Sachen Arbeitsethos. Im Vergleich zu seinen späteren Kontakten wirken seine Buddys der 70er und 80er aber fast noch sympathisch – denn Steuern sind Raub und die Mafia pflegt, im Gegensatz zu Regierungen, Militär und Geheimdiensten, zumindest einen Ehrenkodex.
Die 90er begannen für Trump mit finanziellen Turbulenzen. Diverse Bau- und Casino-Projekte liefen nicht wie geplant. Investments warfen nicht den erwarteten Gewinn ab und die Schulden häuften sich bis zur Zahlungsunfähigkeit. In der Öffentlichkeit gab er jedoch weiterhin den erfolgreichen Entrepreneur. 1995 gründe Trump, immer noch bis über beide Ohren verschuldet, eine Aktiengesellschaft und ging an die Börse. Durch diesen Schritt landete er nach 1989 erstmals wieder auf der Forbes-Liste der reichsten Amerikaner. Da die neue AG aber aufgrund der Altlasten mit 1,7 Milliarden Dollar verschuldet war, fiel ihr Börsenkurs zwischen 1996 und 2005 von 35 Dollar auf 17 Cent. Dann wurde der Handel ausgesetzt. Trump bezog aber noch bis 2009 Vergütungen aus der Gesellschaft in Höhe von 44 Millionen Dollar.
Parallel zu diesen fragwürdigen Umtrieben zu Lasten von Anlegern und Geschäftspartnern mauserte sich Donald Trump zum Society-Phänomen. Ob The Apprentice, WrestleMania, The Fresh Prince of Bel-Air, Talkshows oder soziale Anlässe aller Art – Trump war überall, wo sich Öffentlichkeit für Trump generieren ließ. Mit Erfolg. Überschuldung, Zahlungsunfähigkeit, Mafia-Kontakte, Betrugsvorwürfe und juristische Probleme verblassten im omnipräsenten Scheinwerferlicht.
Weniger glamourös dagegen ist Donald Trumps Beziehung zu einem der verachtenswertesten Menschen der jüngeren Vergangenheit – Jeffrey Epstein. Denn während Trump lange Jahre leugnete, überhaupt mit Epstein in Kontakt gestanden zu haben, belegen unlängst veröffentlichte Audio-Mitschnitte, dass er sehr wohl eine Beziehung mit dem verurteilten Sexualstraftäter, Pädophilen, Menschenhändler und Doppelagenten pflegte. Eine sehr enge.
Jeffrey Epstein bezeichnet sich im Zuge der Aufnahmen als »Trumps engsten Freund«. Für über zehn Jahre. Man besuchte die gleichen Partys, kannte die gleichen Leute. Kaum verwunderlich. Epstein war bestens mit dem »Who is Who« des Establishments vernetzt – auch mit dem zwielichtigen Roy Cohn. Es liegt nahe, dass über diesen der Erstkontakt zustande kam. Epstein erpresste elitäre Zirkel in aller Welt mit heimlich aufgenommenen Videos arrangierter Sex-Eskapaden. Die Opfer: Meist Minderjährige. Manche erst acht Jahre alt. Wer Macht und Einfluss ausüben und sichern wollte, nahm seine Dienste in Anspruch. Das wusste wohl jeder seiner engeren Kontakte. Trotzdem sprach Donald Trump von einem »tollen Typen, den er seit 15 Jahren kenne«, als er in einem Interview mit dem New York Magazine 2002 nach seiner Meinung zu Epstein und der gemeinsamen Vorliebe für junge Frauen gefragt wurde. Darüber hinaus flog Donald Trump mindestens sieben Mal mit Jeffrey Epsteins Privatjet, besser bekannt als »Lolita Express«.
Elon Musk, über dessen hinter Imagedesign verborgene Nähe zu Militär, Geheimdiensten, Big Pharma und Transhumanisten ich bereits im Oktober 2022 ausführlich berichtet habe, hatte ebenfalls Verbindungen zu Jeffrey Epstein, wie ein ausführliches Dossier von Johnny Vedmore belegt. Ganz zu schweigen von Musks Forderungen nach CO2-Steuern gegen den Klimawandel oder seinen offenen Plädoyers für Technokratie, einem faschistischen Herrschaftsmodell, das schon sein Großvater Joshua N. Haldemann in leitender Position vertrat. Man kann sich also ausmalen, was unter einem Effizienzprogramm unter Musks Ägide zu erwarten ist – Tech-Faschismus, getarnt als libertäre Progressivität.
Auch RFK Jr. flog zwei Mal mit dem »Lolita Express«, gibt aber an, in Begleitung von Frau und Kindern gereist zu sein – während er gleichzeitig erklärt, die beiden Flüge seien nur zustande gekommen, weil seine »Frau irgendeine Art von Beziehung mit Ghislaine Maxwell hatte«. Was für eine Beziehung das war, beschreibt RFK Jr. nicht. Dabei wären die Hintergründe dieser Beziehung durchaus relevant für die Bewertung seiner Verbindung zum Epstein-Netzwerk. Denn Maxwell, deren Elternhaus für CIA und Mossad tätig war, war seit 1991 Epsteins engste Mitarbeiterin. Sie führte ihm minderjährige Mädchen zu. Phantombilder legen nahe, dass sie auch am Verschwinden, beziehungsweise Tod, von Madeleine McCann beteiligt sein könnte. Nach dem als Suizid vermarkteten Mord an Epstein im August 2019 tauchte Maxwell ab. Aufenthaltsort unbekannt. Erst am 2. Juli 2020 konnte das FBI sie festnehmen. Im Dezember 2021 wurde Maxwell wegen Unterstützung von Epsteins Pädo-Business zu 20 Jahren Haft verurteilt.
Man darf gespannt sein, ob Epsteins unter Verschluss gehaltene Kundenliste jemals ans Licht kommt. Wenn Trump nichts zu verbergen hat, seine dahingehenden Ankündigungen wahr machen und den Sumpf trockenlegen will, könnte er damit ordentlich vorlegen. Entsprechende Forderungen stehen ja bereits im Raum.
Bei einer Pressekonferenz im Weißen Haus am 21. Juli 2020 verkündete er allerdings noch, Maxwell mehrfach getroffen zu haben und wünschte ihr »wirklich alles Gute«.
Wahrscheinlich ist eine Offenlegung der Kundenliste aber nicht. Denn auch Trumps neuer Generalstaatsanwalt, Matt Gaetz, gegen den 2020 wegen sexueller Kontakte zu einem minderjährigen Mädchen ermittelt wurde, sprach sich in der Vergangenheit explizit gegen eine neuerliche Überprüfung des Falls Epstein aus. Er behauptete außerdem, Epstein sei von ausländischen Geheimdiensten, nicht vom US-Tiefenstaat ermordet worden. Sein Wahlkampf-Team nutzte denn auch die gleiche Anwaltskanzlei wie Jeffrey Epstein. Und ein enger Vertrauter von Gaetz warb intensiv dafür, Ghislaine Maxwell aus der Haft zu entlassen. Seit 2021 ist Gaetz mit der Schwester des Peter Thiel-Protegés Palmer Lucky verheiratet, der mit seiner Firma Anduril für das High-Tech-Überwachungssystem an der mexikanischen Grenze verantwortlich zeichnet, KI-Waffenprogramme entwickelt und für das US-Verteidigungsministerium an Project Maven arbeitet. Sumpf, soweit das Auge reicht. Trockenzulegen gäbe es da also einiges.
Warten wir’s ab – und werfen unterdes einen Blick auf Donald Trumps erste Amtszeit. Denn auch diesbezüglich sagen Taten mehr als Worte.
Während Trump sich derzeit als Gegner der Weltgesundheitsorganisation (WHO) geriert, war er als 45. US-Präsident mit »Operation Warp Speed« (OWS) für eine militarisierte Impf-Kampagne der Superlative verantwortlich, die 300 Millionen Dosen einer experimentellen mRNA-Gentherapie unters Volk bringen und den Herstellern mindestens 18 Milliarden Dollar in die Kasse spülen sollte. Anthony Fauci, den Trump heute gerne öffentlich diffamiert, kümmerte sich für ihn um den Rollout der Injektionen und die damit verbundene Nudging-Propaganda. Für seine Verdienste im Rahmen von OWS erhielt Fauci von Trump am letzten Tag seiner Präsidentschaft eine Auszeichnung, wie eine Pressemitteilung im Archiv des Weißen Hauses belegt. Während Trump sich in den letzten Wochen medienwirksam von Fauci distanzierte und abstritt, diese Auszeichnung abgesegnet zu haben, verweisen Mitarbeiter des Weißen Hauses darauf, dass eine solche Auszeichnung gemäß Protokoll nur dann verliehen wird, wenn der Präsident sie persönlich autorisiert. Fragt sich, wer lügt.
Daneben genehmigte Trump im Februar 2020 eine Zahlung von 1,16 Milliarden US-Dollar an GAVI, die Impfallianz von WHO, Weltbank, UNICEF und der Bill & Melinda Gates Stiftung. Der Betrag sollte GAVI binnen drei Jahren über die CIA-Tarnfirma USAID ausbezahlt werden. Ungeachtet aller Gegenanzeigen, Nebenwirkungen und Kollateralschäden durch Lockdowns und partielle Impfpflichten pries Donald Trump OWS stets als durchschlagenden Erfolg. Erst nach der Ankündigung, mit Kennedy kollaborieren zu wollen, hielt er sich mit dem Eigenlob zurück. Dass er sich in den Wochen vor dem Wahlsieg neu positionierte, dürfte also reine Wahlkampfstrategie gewesen sein.
Wenn Trump nun in Aussicht stellt, Impfungen verbieten und Amerika gemeinsam mit RFK Jr. gesund machen zu wollen, ist das in Anbetracht der immensen Marktmacht von Big Pharma kaum als realistisch zu bewerten. Siehe Briefing des Roosevelt Institute vom 22. Mai 2019. Titel: »Kapern der Regierung – Wie Big Pharma die Gesetzgebung übernahm«. In Trumps Team wurden in den letzten Wochen bereits Stimmen laut, die forderten, sich von RFK Jr. zu distanzieren. Während Kennedy in einem Interview vom 28. Oktober verkündete, Trump habe ihm den »Chefposten der Gesundheitsbehörde HHS versprochen«, stellte Howard Lutnik, Vize-Vorsitzender von Trumps Transition-Team, am 30. Oktober bei CNN fest, dass dies »natürlich nicht der Fall sein werde« und man Kennedy lediglich Zugriff auf Daten gewähren wolle. Am 14. November gab Donald Trump dann allerdings bekannt, RFK Jr. tatsächlich zum Chef der HHS machen zu wollen. Die Nominierung muss aber noch vom Senat bestätigt werden. Und bis Januar kann noch einiges passieren. Die Vergangenheit lässt jedenfalls darauf schließen, dass weder Big Pharma noch WHO oder GAVI künftig unter der neuen Regierung leiden werden.
Dann wären da noch die galoppierenden Staatsschulden der Vereinigten Staaten. Denn unter Trumps Ägide schöpfte die US-Zentralbank allein im Jahr 2020 über drei Billionen Dollar. »Die Vereinigten Staaten haben im Juni mehr Geld gedruckt als in den ersten zwei Jahrhunderten nach ihrer Gründung. Letzten Monat war das Haushaltsdefizit der USA – 864 Milliarden Dollar – größer als die Gesamtverschuldung von 1776 bis Ende 1979«, so Dan Morehead, CEO von Pantera Capital am 29. Juli 2020. Seit 2020 hat die Staatsverschuldung um knapp zwölf Billionen Dollar zugenommen und belief sich im September 2024 auf 35,46 Billionen Dollar. Das sollten speziell Trump-Anhänger vor Ort nicht vergessen, wenn sie nun für den Wocheneinkauf deutlich tiefer in die Tasche greifen müssen. Inflation sei Dank.
»Dafür hat Trump keine neuen Kriege angefangen!« – hört man immer wieder, wenn man auf dessen Verfehlungen hinweist. Stimmt. Weil er fünf Krisenherde von der vorherigen Regierung geerbt hat und sich dort austoben konnte. Trump hat nämlich deutlich mehr Drohnen-Einsätze befohlen als sein Vorgänger. Obama autorisierte in den ersten zwei Jahren seiner Amtszeit 186 Einsätze – bei Trump waren es 238. Allein im Jemen hat die Trump-Regierung 176 Angriffe binnen zwei Jahren durchgeführt. Bei Obama waren es 154 in acht Jahren. Und während die Regierung unter Obama zumindest teilweise Daten zu den Opferzahlen dieser Einsätze veröffentlichte, änderte Trump die entsprechenden Transparenzanforderungen und veröffentlichte gar keine Daten. Laut einem Artikel von Foreign Policy vom 9. August 2017 ist Trump »der kriegslüsternste Präsident der jüngeren Geschichte«. Weiter führte das 1970 von Samuel P. Huntington gegründete Magazin aus:
»Unter Trump haben die Vereinigten Staaten bis zum 31. Juli etwa 20.650 Bomben abgeworfen, das sind 80 Prozent der Menge, die unter Obama im gesamten Jahr 2016 abgeworfen wurden. (…) Daten zeigen, dass die Vereinigten Staaten im Irak und in Syrien Bomben in beispiellosem Ausmaß abwerfen. Im Juli warf die Koalition zur Bekämpfung des Islamischen Staats (sprich: die Vereinigten Staaten) 4.313 Bomben ab, 77 Prozent mehr als im Juli letzten Jahres. Im Juni lag die Zahl bei 4.848 – 1.600 Bomben mehr als unter Präsident Barack Obama jemals pro Monat abgeworfen wurden. In Afghanistan ist die Zahl der abgeworfenen Bomben seit Trumps Amtsantritt ebenfalls sprunghaft angestiegen. Im April wurden im Land mehr Bomben abgeworfen als auf dem Höhepunkt von Obamas Truppenaufstockung im Jahr 2012. In diesem Monat bombardierten die Vereinigten Staaten das afghanische Mamand-Tal mit der größten nichtnuklearen Bombe, die jemals abgeworfen wurde. Trump hat auch das militärische Engagement der USA in Ländern außerhalb der Kriegsschauplätze ausgeweitet – nämlich im Jemen, in Somalia und in Pakistan. In den letzten 193 Tagen von Obamas Präsidentschaft gab es in diesen drei Ländern 21 tödliche Anti-Terror-Operationen. Trump hat diese Zahl verfünffacht und mindestens 92 solcher Operationen im Jemen, sieben in Somalia und vier in Pakistan durchgeführt.«
Klingt für mich jetzt nicht so ganz nach Friedenstauben.
Wahrscheinlich war es am Ende nur die Hektik bei der Übergabe der Amtsgeschäfte im Januar 2021, oder der Stress permanenter Medienpräsenz, der Trump auch noch davon abhielt, Julian Assange oder Edward Snowden zu begnadigen. Immerhin war er »kurz davor, einen der beiden auszuwählen«, wie er in einem Interview für Daily Wire verlauten ließ. Am Ende blieb dann aber leider doch nur Zeit für die Begnadigung der anderen 116 Personen auf der Liste. Dumm gelaufen.
Wenden wir uns der Gegenwart zu. Und dem, was uns die nächsten vier Jahre erwarten könnte. Es muss ja jetzt auf jeden Fall alles viel besser laufen als in der ersten Runde. Denn in den Augen vieler seiner Unterstützer habe Trump in der Zwischenzeit viel gelernt und wurde damals nur hinters Licht geführt. Überrumpelt vom Tiefenstaat, den er eigentlich abschaffen wollte. Zudem hat er nun Elon Musk und RFK Jr. an seiner Seite, der gemäß Lutnik zwar keinen Job bekommt, aber immerhin steht irgendwo Kennedy auf der Banderole. Das ist doch auch was.
Ernsthaft. Bereits in Rahmen seiner ersten Amtszeit plante Trump, ein biometrisches System zur Ein- und Ausreisekontrolle zu etablieren. Es sollte zunächst nur für Ausländer gelten. Aber jeder weiß, dass es nicht lange dauert, bis so ein System für jeden gilt. Dazu passt, dass seit Beginn des Wahlkampfes 2024 permanent von der Voter ID gesprochen wird. Ausweise für alle – gegen Wahlbetrug. Bisher besitzen nur knapp 40 Prozent der Amerikaner einen Reisepass. Nur acht Prozent verlassen im Urlaub überhaupt das Land. Die virtuelle Wand wird das ändern, nicht nur an der Grenze zu Mexiko. Denn über kurz oder lang resultiert das Projekt in der flächendeckenden Einführung einer eID. Basis für die eID- oder Voter ID-Infrastruktur könnte zum Beispiel E-Verify sein, ein vom Department of Homeland Security betriebenes Projekt zur Verifikation von Personen, dessen Nutzung für Personalabteilungen von Bundesbehörden seit dem 1. Oktober 2007 obligatorisch ist. Die Nominierung von Tom Homan als Chef der Einwanderungs- und Zollbehörde impliziert, dass genau dieser Kurs eingeschlagen wird. Homan ist Hardliner. Er war Teil des rechtskonservativen Project 2025 und befürwortet neben flächendeckender Biometrie auch die Trennung von Eltern und Kindern an der Grenze.
Kein Zufall also, dass der Gründer der Cardano-Blockchain, Charles Hoskinson, die Regierung Trump ab 2025 in Bezug auf Kryptoanwendungen beraten soll. Immerhin hatte Hoskinson bereits mit dem von Jeffrey Epstein finanzierten Ben Goertzel ein biometrisches eID-System für Schulkinder in Äthiopien entwickelt. Und nachdem die von Peter Thiel finanzierte Silikon-Valley-Marionette JD Vance als Vizepräsident fungiert, hat auch der mächtigste Überwachungskonzern der Welt, Palantir, nun einen Fuß in der Tür des Oval Office. Mit diesem Setup dürfte der gläserne Bürger der Gegenwart bald ein Relikt der Vergangenheit sein.
Ganz zur Freude von Ex-Spion John Ratcliffe, dem neuen CIA-Direktor unter »Orange Man«. In Trumps erster Amtszeit war Ratcliffe »Director of National Intelligence«, unter George W. Bush zuständig für Anti-Terror-Operationen und nationale Sicherheit. Später leitete er zusammen mit John Ashcroft, Generalstaatsanwalt unter Bush und Architekt des Ermächtigungsgesetzes »Patriot Act«, ein Unternehmen für strategische Beratung (AGS). Im Dezember 2023 unterstützte John Ratcliffe den Bilderberger, Kriegstreiber und Tiefenstaat-Neocon Mike Pompeo bei der Erneuerung des Foreign Intelligence Surveillance Act (FISA), der die fortgesetzte, anlasslose Massenüberwachung der US-Bevölkerung legalisiert. Und kaum war er nominiert, machte Ratcliffe am 13. November 2024 auf FOX-News wahrheitswidrig Stimmung gegen den Iran und unterstellte der dortigen Regierung »kriegerische Handlungen« gegenüber den USA.
Kollaborieren wird Ratcliffe künftig mit Tulsi Gabbard. Sie beerbt ihn als Trumps neuer »Director of National Intelligence«. Gabbard war Mitglied der WEF Young Global Leaders sowie des Council on Foreign Relations (CFR). Beide Organisationen tilgten ihren Namen von der eigenen Homepage, nachdem Gabbard öffentlich über US-Biowaffenlabore in der Ukraine sprach. In Interviews bestätigt sie ihre Rolle im CFR allerdings selbst. Gabbard befürwortete die Covid-Impfkampagne und schmückt sich gerne mit dem Image »Kriegsveteran« – obwohl sie die Schrecken des Krieges lediglich aus sicherer Entfernung sah. Eine Opportunistin, deren konservativ-kritisches Image nichts weiter ist als ein wackliges Kartenhaus.
»Ich war Kadett. Was ist das Motto der Kadetten in West Point? Du wirst nicht lügen, betrügen, oder stehlen – und diejenigen nicht dulden, die das tun. Ich war der CIA-Direktor. Wir haben gelogen, wir haben betrogen, wir haben gestohlen. Wir haben ganze Trainingskurse dazu absolviert.« (Mike Pompeo, April 2019)
Und wer denkt, Donald Trump werde wenigstens die Einführung einer digitalen Zentralbankwährung (CBDC) verhindern, irrt. Zumindest im Kern. Denn im Rahmen seiner Rede auf der Bitcoin Konferenz 2024 sprach Donald Trump von »regulatorischer Klarheit« sowie der »sicheren und verantwortungsvollen Expansion von Stablecoins«. Damit bestätigte er, dass die Einführung von digitalem Geld über privatwirtschaftliche Entitäten erfolgen wird. Denn ein Konto bei der Zentralbank will niemand. Leider werden aber die Transaktionen all der ach so marktwirtschaftlich eingeführten Digitalwährungen zentral erfasst. Im »Unified Ledger« der Bank für Internationalen Zahlungsausgleich (BIZ) in Basel. Was am Ende zum exakt gleichen Ergebnis führt wie eine vom Staat oder der Zentralbank aufgelegte CBDC – zu lückenloser Überwachung mit Interventionspotenzial.
Zurück zur künftigen Regierung. Stabschef im Weißen Haus und damit »mächtigste Frau in Washington« soll Susie Wiles werden – bisher Co-Vositzende von Mercury Public Affairs LLC, einem Lobby-Giganten, der unter anderem Pfizer, GAVI, die Vereinten Nationen oder SpaceX vertritt. Mercury Public Affairs gehört seit 2003 zur Omnicom Group, einem WEF-Partner für Öffentlichkeitsarbeit. Wiles gilt als die »am meisten gefürchtete und am wenigsten bekannte Politagentin Amerikas«.
Als Außenminister nominierte Trump den von der Zionismus-Lobby korrumpierten Marco Rubio. Einen Neocon. Sprich: Militärischer Interventionismus und unilaterale Hegemonieansprüche. Den Posten des nationalen Sicherheitsberaters offeriert Trump dem ehemaligen Green Beret Mike Waltz. Neben Marco Rubio der zweite Mann in der künftigen Regierung, der sich mit China anlegen möchte. Ergänzt wird das kriegsaffine Duo von Brian Hook, der dem Iran am liebsten sofort den Krieg erklären möchte und den Auftrag erhielt, Schlüsselpositionen im Außenministerium mit geeignetem Personal dafür zu besetzen.
Der ehemalige texanische Kongressabgeordnete Ron Paul sieht in diesen Nominierungen »einen schlechten Tag für jene, die an America First glaubten«. Sollte Trump die Unterstützung der Ukraine seitens Amerika tatsächlich beenden, dürften nämlich ersatzweise zuerst der Iran und langfristig eventuell gar China von Demokratie aus der Luft beglückt werden. Daran wird auch die neue US-Botschafterin bei den Vereinten Nationen nichts ändern. Denn Elise Stefanik hat praktisch keine relevante Berufserfahrung – und ist ebenfalls ein Neocon. Sowohl Stefanik als auch Rubio, Waltz oder Hook setzen sich für weitere Waffenlieferungen nach Israel und eine Fortsetzung des auch von israelischen Zeitungen also solchen bezeichneten Genozids in Gaza ein.
»Die westliche Zivilisation repräsentiert heute das Verständnis, dass Zionismus und Amerikanismus die Frontlinien der westlichen Zivilisation und Freiheit in unserer Welt sind«, erklärte der Army-Veteran, United Against Nuclear Iran-Advokat und Ex-FOX-News-Mitarbeiter Pete Hegseth im April 2019.
An dieser faschistoiden wie imperialistischen Doktrin scheinen sich auch Trump und Co. zu orientieren – denn Hegseth wird nun Verteidigungsminister. Passend dazu wird Mike Huckabee, ein bekennender Zionist, der nächste US-Botschafter in Israel. Huckabee nennt das Westjordanland Judäa und behauptet entgegen historischer Fakten, dass es Teil Israels ist. Auch die Annexion der Westbank fände er in Ordnung. Seine Nominierung kann als Kriegserklärung an die Palästinenser verstanden werden. Wohlwissend, dass Israels völkerrechtswidriges Vorgehen leicht zu einem regionalen, wenn nicht globalen Flächenbrand führen kann.
Apropos globale Themen: Dahingehend lohnt sich ein genauerer Blick auf die Hintergründe des bereits erwähnten Howard Lutnick. Diesen hat die Investigativ-Journalistin Whitney Webb am 7. November 2024 gewagt. Unter der Überschrift »Macht euch bereit für den Kohlenstoffmarkt der Republikaner« erklärt sie:
»Viele der einflussreichsten Namen der kommenden Trump-Regierung sowie der vorherigen haben sich in den letzten Jahren intensiv mit der Schaffung von Kohlenstoffmärkten befasst, während andere eine langjährige Erfolgsgeschichte bei der Implementierung von CO2-Steuern und anderen Formen der CO2-Bepreisung vorweisen können. Der wichtigste unter ihnen ist Howard Lutnick, Co-Vorsitzender von Trumps Transition-Team, der erklärte, seine Aufgabe sei es, Talente für die kommende Regierung zu finden. Lutnick ist der langjährige Leiter von Cantor Fitzgerald, einem der ersten Akteure im Emissionshandel, der sich seitdem zu einem weltweit führenden Unternehmen für ESG-Investitionen, die Finanzierung nachhaltiger Infrastruktur und grüne Anleihen entwickelt hat. So hat sich Cantors nachhaltiger Infrastrukturfonds ausdrücklich der digitalen Transformation, Dekarbonisierung und Verbesserung und Modernisierung alternder Infrastruktur verschrieben, während ein Hauptaugenmerk des Fonds darauf liegen wird, in Emittenten zu investieren, die mit ihren Produkten und Dienstleistungen dazu beitragen, bestimmte Ziele der Vereinten Nationen für nachhaltige Entwicklung zu erreichen. Darüber hinaus ist Invenergy, ein Unternehmen für erneuerbare Energien, das im Rahmen von Bidens umstrittenem Inflationsbekämpfungsgesetz eine beträchtliche Menge an Subventionen erhalten hat und vom ersten Windmilliardär des Landes, Michael Polsky, geleitet wird, der wichtigste Bestandteil eines weiteren Infrastrukturfonds von Cantor. Lutnick sitzt auch im Vorstand eines Satellitenüberwachungsunternehmens namens Satellogic. Neben Lutnick ist der ehemalige Finanzminister von Trump, Steve Mnuchin, Vorsitzender des Vorstands. Auch Joe Dunford, ehemaliger Stabschef des US-Militärs unter Trump, sitzt im Vorstand. Satellogic ist integraler Bestandteil eines Konsortiums, das versucht, durch undurchsichtige vertragliche Vereinbarungen auf kommunaler Ebene einen riesigen, Blockchain-basierten Kohlenstoffmarkt in Lateinamerika durchzusetzen. Dieser Kohlenstoffmarkt, der unter dem Namen GREEN+ operiert, soll auf einer Bitcoin-Sidechain aufgebaut werden. Das entsprechende Emissionsgutschriftsystem ist für lateinamerikanische Gemeinden zutiefst ungerecht. So könnten die betroffenen Gemeinden beispielsweise nur Geld verdienen, wenn Einnahmen unter den für GREEN+ anerkannten, nachhaltigen Projekten generiert werden, während die Investoren von GREEN+ den Großteil der Gewinne einstreichen. Das Programm würde Gemeinden außerdem ohne ihre Zustimmung dem Satellitenüberwachungsapparat von Satellogic (der mit der US-Regierung und dem israelischen Geheimdienst verbunden ist) aussetzen. Darüber hinaus ist GREEN+ in bemerkenswerter Weise mit Personen verbunden, die Trumps Verbündeten in der Region nahestehen. So ist eine wichtige Persönlichkeit in Nayib Bukeles politischer Partei – der Bürgermeister von San Salvador, Mario Durán – Vizepräsident einer der wichtigsten Gruppen, die das GREEN+-Programm orchestrieren, während das Netzwerk Endeavor Argentina, das sehr enge Verbindungen zu Javier Milei pflegt, ebenfalls eng mit Satellogic verbunden ist. Satellogic ist ein von Endeavor unterstütztes Unternehmen, während Endeavors erster Milliardär und Unternehmer, Marcos Galperín von MercadoLibre, im Vorstand von Satellogic sitzt. Darüber hinaus ist ein anderer wichtiger Investor von Satellogic, der Dollar-Stablecoin-Emittent Tether, auch eng mit Howard Lutnick verbunden. Lutnick ist langjähriger Fürsprecher von Tether. Und Cantor Fitzgerald hält den Großteil der US-Staatsanleihen von Tether, um deren Stablecoin und seine Bindung an den US-Dollar zu stützen.«
Das sollte Wähler, die dem Klimawandel-Narrativ und Digitalwährungen skeptisch gegenüberstehen, hellhörig werden lassen – denn auch wenn Donald Trump im Rahmen seiner öffentlichen Auftritte gegen die Nachhaltigkeitsagenda wettert und der leitmediale Komplex seine entsprechenden Phrasen für Konterpropaganda nutzt, sprechen die Taten wieder einmal eine ganz andere Sprache. In Anbetracht vorgängig beschriebener Umstände sieht es nämlich nicht so aus, als widersetze sich der 47. US-Präsident dem Nachhaltigkeitskorporatismus der UN. Im Gegenteil.
»Der König ist tot, es lebe der König«. Die neue US-Regierung wird die gleiche Agenda fahren wie die alte – nur die Vermarktung ändert sich. Das kündigte Lynn Forester de Rothschild (CIC) schon vor über einem Jahr bei Bloomberg an. Genau wie Larry Fink (BlackRock).
Die Einführung biometrischer Massenüberwachung wird nun mit der Migrationskrise und drohendem Wahlbetrug, mit der Stärkung der Demokratie gerechtfertigt, anstatt mit einem Virus. Den Krieg in der Ukraine wird man nicht weiter unterstützen. Diesen Brandherd sollen die Europäer am Kokeln halten, damit man endlich den Iran und China ins Fadenkreuz nehmen kann. So ein dritter Weltkrieg wäre nämlich ein profitables Geschäft. Das Klimawandel-Narrativ wird man öffentlich negieren und verhöhnen, während die Agenda 2030 trotzdem umsetzt wird. Gleiches gilt für Totalüberwachung, Genderwahn, globale Gleichschaltung von Lerninhalten und die schleichende Digitalisierung des Weltfinanzsystems. Denn auch diese Programme werden von überstaatlichen Akteuren vorangetrieben und entziehen sich dem Einfluss nationaler Regierungen. So funktioniert Korporatismus.
Ernüchternd ist vor allem, dass sich die Bevölkerung, die in den letzten vier Jahren tatsächlich ein gewisses Maß an rebellischem Potenzial entwickelte, wieder einmal täuschen lässt. Trump-Hype wohin man schaut. Selbst die Corona-Dissidenten, selbst jene, die dem Staat aufgrund von Covid-Lügen, Green-Economy-Deindustrialisierung und militantem Neoimperialismus zusehends kritisch gegenüberstanden, haben sich in weiten Teilen von den leeren Versprechungen der MAGA-Promotion und ihren Sekundanten blenden lassen.
Sie werden genauso desillusioniert zurückbleiben wie einst die auf »Hope« geeichten Obama-Fans – und sich in ein paar Jahren vermutlich trotzdem wieder an die Wahlurne schleppen, weil sie auf den nächsten Erlöser hoffen, anstatt selbst die Welt zu verändern.
Zur Wahl stehen aber jeweils nur verschiedene Geschmacksrichtungen der gleichen, bitteren Pille Marke Unterdrückung. Keine Unterdrückung – das ist natürlich keine Option. Das steht nicht auf dem Wahlzettel.
Linke gegen Rechte, Demokraten gegen Republikaner, Christentum gegen Islam – Bevölkerungsgruppen, die man gegeneinander aufwiegeln kann, finden sich dagegen immer. Präsentiert man ihnen einen verheißungsvollen Erlöser, werden sie ihn unterstützen, um die andere Gruppe loszuwerden. Das ist Herrschaftsdialektik. Man bringt die Menschen dazu, um Dinge zu betteln, die ohnehin eingeführt werden sollen. Und der einzige Gewinner in diesem immer riskanter werdenden Spiel ist die Prädatorenkaste.
»Die mächtigste Waffe in den Händen der Unterdrücker ist der Geist der Unterdrückten.« (Stephen Bantu Biko)
Wer Donald Trump unterstützt, ist nicht für Frieden und Freiheit, sondern nur gegen das, was die andere Seite will. Denn Donald Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang.
-
 @ 21b41910:91f41a5e
2024-11-23 12:00:26
@ 21b41910:91f41a5e
2024-11-23 12:00:26Chef's notes
Based on assorted recipes and refined over time, this round of beef tastes great as a result of the sweet and savory marinade.
Details
- ⏲️ Prep time: 5 minutes (+ 1 day)
- 🍳 Cook time: 20 minutes
Ingredients
- 2 pounds lean beef (may be labeled as London Broil)
- 1/3 cup olive oil
- 1/4 cup soy sauce
- 1/4 cup malt vinegar
- 1/4 cup lemon juice
- 1 tbsp sweetener of choice (honey, molasses, syrup, 4 packets of duck sauce, etc)
- 2 tsp old bay seasoning
- 1 tsp garlic powder
- 1 tsp sea salt
- 1/2 tsp black pepper
Directions
- Day Before: Mix all ingredients except the beef in a bowl to form a marinade. Place the cut of beef in a gallon sized Ziploc bag. Pour marinade over beef, ensure fully covered. Remove any excess air from the bag and seal. Place back in refrigerator for up to 24 hours before cooking.
- Cooking: Bring beef out of refrigerator (still in bag), and allow to rise to room temperature (about 30-40 minutes). Preheat broiler for about 15 minutes (your oven will vary). Broil for about 7-8 minutes on one side, then flip over. Continue broiling for another 7-10 minutes until temperature reads 140°F. Remove from broiler and let rest for 10 minutes before slicing thinly.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 87730827:746b7d35
2024-11-20 09:27:53
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
KEY TAKEAWAYS
- The Central Bank of Brazil has proposed regulations prohibiting privacy-centric cryptocurrencies like Monero.
- The regulations categorize exchanges into intermediaries, custodians, and brokers, each with specific capital requirements and compliance standards.
- While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens (NFTs) are still ‘deregulated’ in Brazil.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines regulations for virtual asset service providers (VASPs) operating in the country.
In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil.
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
If the BCB’s current rule is approved, exchanges dealing with coins that provide anonymity must delist these currencies or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to prevent criminals from using digital assets to launder money. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
… restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
The Central Bank has identified that removing algorithmic stablecoins is essential to guarantee the safety of users’ funds and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to control all digital assets traded by companies in Brazil. According to the current proposal, the national regulator will have the power to ask platforms to remove certain listed assets if it considers that they do not meet local regulations.
However, the regulations will not include NFTs, real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, other nations are banning Monero in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as Binance have already announced they will delist Monero on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with MiCA regulations.
Data from Chainalysis shows that Brazil is the seventh-largest Bitcoin market in the world.

In Latin America, Brazil is the largest market for digital assets. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
-
 @ 6bae33c8:607272e8
2024-12-13 19:20:41
@ 6bae33c8:607272e8
2024-12-13 19:20:41I blew it last week, going 2-3. I shouldn’t have taken the Jets, I knew it was a mistake. I don’t care how right the side looked either, the Jets are cursed. I liked the Rams and Panthers, but didn’t pull the trigger. Too much second guessing and overthinking. Either you have a model and stick to its outputs, or you go on feel, and you trust yourself 100 percent. Don’t question, just act. If you make an error, you can reassess next week, incorporate it into your process.
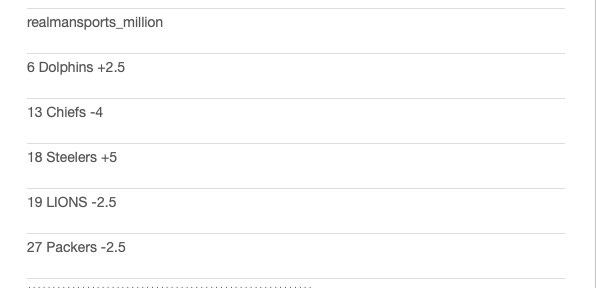 Dolphins +2.5 at Texans — I’m sure this is the game the Texans turn it around, but as someone whose otherwise solid Primetime team was derailed by CJ Stroud and the bankrupt passing game, I took the Dolphins and the points.
Dolphins +2.5 at Texans — I’m sure this is the game the Texans turn it around, but as someone whose otherwise solid Primetime team was derailed by CJ Stroud and the bankrupt passing game, I took the Dolphins and the points.Chiefs -4 at Browns — I know the Chiefs are life and death with everyone, but this seems too small. Jameis Winston will turn it over a few times against this defense, and the Chiefs will move up and down the field.
Steelers +5 at Eagles — The Eagles are good against bad teams, but the Steelers are a rock defensively, and I think they’ll hang.
Lions -2.5 vs Bills — I had this line at four. The Lions are the better team, even with the banged-up defense.
Packers -2.5 at Seahawks — The Seahawks have been good of late, but the Packers went toe to toe with the Lions and had a full 10 days off. I think they win and cover.
-
 @ e373ca41:b82abcc5
2024-11-28 07:40:02
@ e373ca41:b82abcc5
2024-11-28 07:40:02Article by Milosz Matuschek, originally from "Freischwebende Intelligenz"
‘The secret of freedom is courage,’ said the Greek historian Thucydides.
A particular example of this can be found in the film ‘The Dark Knight rises’ from Christopher Nolan's Batman series. Captured mercenaries are locked in a deep pit. A cruel prison where you can see the blue sky every day, but never get any closer to the sun. Even more cruel is the fact that it is possible to get out of the shaft by climbing the stairs in the side walls, but only a few dare to do so. At one point, the stairs break off and you have to be prepared to jump over the chasm, to take the ‘death leap’.
The old media system is dead
Anyone who speaks out publicly in more repressive times knows the feeling: Do I dare to come out with what I believe to be the truth, do I risk my (social) life for it? Do I dare to take the death leap into the unknown? More than half of Germans no longer dare to speak their mind in public. The mainstream has become a closed consent cult. Constricted spaces, absurd times.
In our current media setting, we are all prisoners of tech giants, whether readers or journalists. And they, in turn, are prisoners of governments. The Twitter files showed that social media companies were put under massive censorship pressure by government agencies in the USA and easily gave in to it. This also applied to Facebook. Google censored and deleted millions of videos on YouTube. Twitter/X is under fire in Brazil and Pavel Durov from Telegram was arrested and put under pressure in France.
Anyone who creates content in the current media environment, be it as a YouTuber, podcaster, blogger or freelance journalist, is a mercenary trapped in the shaft of the tech giants. The path to freedom seems open, follower numbers may be growing and so are advertising revenues. But it’s a trap. There is no way out of the shaft at the top. The shaft is covered by a heavy pane of glass, which is also hot. Critical channels grow in this setting until they become too big, too delicate and too dangerous and then burst like balloons on the hot glass ceiling.
Publishing in times of increasing censorship pressure in the opinion silos of tech giants is a farce. Nothing belongs to you here: Not your channel, not your followers, not even your own identity. The content creator is a tolerated onlooker. The ‘gig economy’ currently offers a fake rise to billionaire status, a feudal system with false independence where you can be fired at any time. And what happens if you are deleted or blocked? Often, supposedly due to a lack of alternatives, a second or third channel is set up, which eventually suffers the same fate.
Isn't it the definition of madness to always do the same thing and expect a different result? To paraphrase Camus: you have to imagine the modern, critical content creator Sisyphus as a happy madman. When are we going to stop?
**Time to take back control **
Why should we entrust the fruits of our critical labour to others when we could create a network that belongs to ourselves? The tools are there. The time of the old, hierarchical platform economy is over. The future belongs to decentralized networks that put control back into the hands of each individual. Decentralized systems have always been superior to centralized systems. This epochal change has long since reached the monetary system with Bitcoin (and is putting it under pressure). The same is now about to happen in the area of free speech. Free money and free information belong together and in the hands of the citizen.
The old media system is heading for an exodus of readers and Terence McKenna recognised this almost 30 years ago.
Old media is communication from the few to the many. The internet offers communication from many to many. The latter is far more powerful. Old media instruct the reader from the position of the media ivory tower. In the new media age, it is possible to organise the search for truth in a cooperative and collaborative manner; the critical public can participate in the search for truth as a swarm intelligence. This is how we develop the fabric of reality ourselves.
This is how we take back control
I have been working on this new way of publishing with some very tech-savvy and enthusiastic people for a good year now. We are (currently) calling it the Pareto Project. The aim is to give everyone the opportunity to publish critically from anywhere in the world. And this while maintaining the highest degree of independence and freedom.
In the Pareto system, the following will be possible:
- Anyone can create an identity that belongs only to them, secured by the most secure cryptographic process currently available (asymmetric cryptography, i.e. public and private key, similar to a Bitcoin wallet).
- The content (text, video, podcast, etc.) is highly resistant to censorship, we host and publish via a large number of different nodes (relays) that are operated privately. We use the nodes of others, but also operate our own nodes. If nodes or clients are blocked, new ones can easily be created. Every journalist, reader, interested party, etc. can operate their own nodes without much technical knowledge and thus additionally secure themselves (and the network).
- Channels, IDs or content cannot be confiscated.Nobody has access to your account except you.
- Every channel can now scale to infinity. No more hot glass ceiling.
- Easy onboarding with our support: If you want, you can keep your current channel and build a second pillar via our publication network, a kind of uncensorable ‘back-up channel’.
- We are building on Nostr's decentralised protocol.The network was designed by a former Bitcoin developer and is backed by former Twitter founder Jack Dorsey (who has no control over it).
- Both Nostr and our solution are open source. Anyone can develop this system further, build a completely new one or add building blocks to the current system.
- In our solution, payments via Lightning/Bitcoin will be integrated, be it as a one-time donation or as a subscription. Each ID can connect to an uncensorable Bitcoin/Lightning wallet. It will also be possible to continue using all other payment methods.
- As a reader, you decide which content is displayed to you, you can use your own algorithms or do without them altogether. From the reader's point of view, it is possible to put together your own daily information programme from the selected content/sources, your own individualised ‘virtual newspaper’.
- We are also working on integrating researchers, proofreaders etc. into the programme. It should be as uncomplicated as possible to create content based on the preliminary work of others, to exchange ideas, to improve the content or adapt it to the latest developments, to build up your own reputation in the network, but also to reward those involved by donations and subscriptions.
Where do we stand and what do we need?
- We are currently working with a team of developers (all of whom are readers of this publication!) on a prototype/MVP for a publication client on Nostr, which we want to finalise by the end of the year.
- Our first product will be a blog format with an integrated newsletter, its own editor and donation/subscription options. Text, podcast, video, everything should be possible.
- It's not too difficult to migrate existing content and create an uncensorable archive of your own work. I am already uncensorable. If Substack is forced to delete channels tomorrow, I can continue publishing undisturbed.
Call
- Are you a critical journalist, content creator or even your own publication? Come on board as a tester and contribute your own ideas. We are building Pareto cooperatively.
- Are you a developer and want to work on technical problems and solutions? We are always on the lookout for bright minds with the right mindset. We require a love of the free word. In particular, we are looking for further developers in the area of frontend (JavaScript) and/or full stack.
-
Would you like to support us financially? Your donation will go directly towards the development of the first product, which we will launch in the new year (planned for January). Then we can get started, with further development steps following approximately every three months. We are also open to investors.
Kontakt@idw-europe.org
In the ‘Dark Knight rises’, the only way to freedom is by jumping without a rope and double bottom, with the fear of death breathing down your neck.
We now have the opportunity to make the leap before others break our necks.
We are greatful for donations in Bitcoin/Lightning/ZAP me!
*Milosz Matuschek, born 1980 in Poland, is a lawyer and journalist living in Switzerland. He has written for leading mainstream media in the past, has published 8 books and writes the Substack newsletter „Freischwebende Intelligenz“, one of the leading critical newsletters in Europe. ***
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 0461fcbe:35a474dd
2024-11-12 17:58:48
@ 0461fcbe:35a474dd
2024-11-12 17:58:48On Nostr, I am running several marketing accounts for my projects: Ditto, The Mostr Bridge, and Cobrafuma. But I want other people to be able to post from those accounts. In fact, I want to hire a "social media manager" someday (for when my wife is not available 😂).
This is a pretty basic need for social media, but of course on Nostr it isn't basic at all, because private keys have nuclear potential if leaked. Even if you trust the person, a small mistake could be disastrous.
To solve this, we need a bunker.
What is a bunker?
A bunker (aka "remote signer") allows you to store your keys on your computer, but give others access. Once the other person is granted access, they can send commands to your computer like
sign_eventandget_public_key, and your computer will perform those operations without needing to expose the actual key.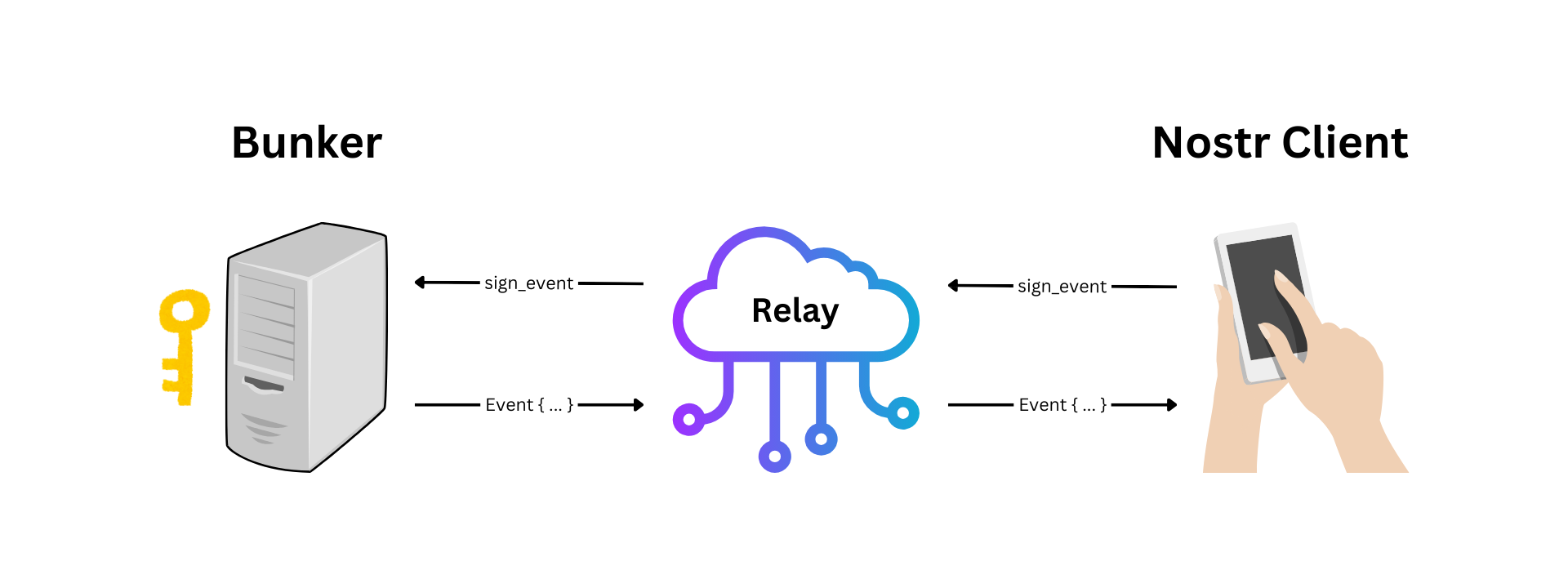
In reality the UX is not so technical. Your bunker generates a unique URI containing the connection details, and the other person pastes it into the login screen. Everything else happens automatically.
As for the running the bunker, you can run it on a VPS, a laptop, an old computer in your house, a Raspberry Pi, or even an Android phone.
The first bunker was an Android app called Nostr Connect. This lead to the creation of nsecBunker (a hosted service), nsec.app (a bunker that runs inside your web browser), and Amber (another Android app).
These days nsec.app and Amber are the only ones being actively developed, but due to running in restricted environments (web and Android respectively), they don't offer the level of 24/7 reliability I wanted in a bunker. If you are a single user managing your own keys I still recommend Amber, but for doling out credentials to your team, you might want knox.
Introducing Knox
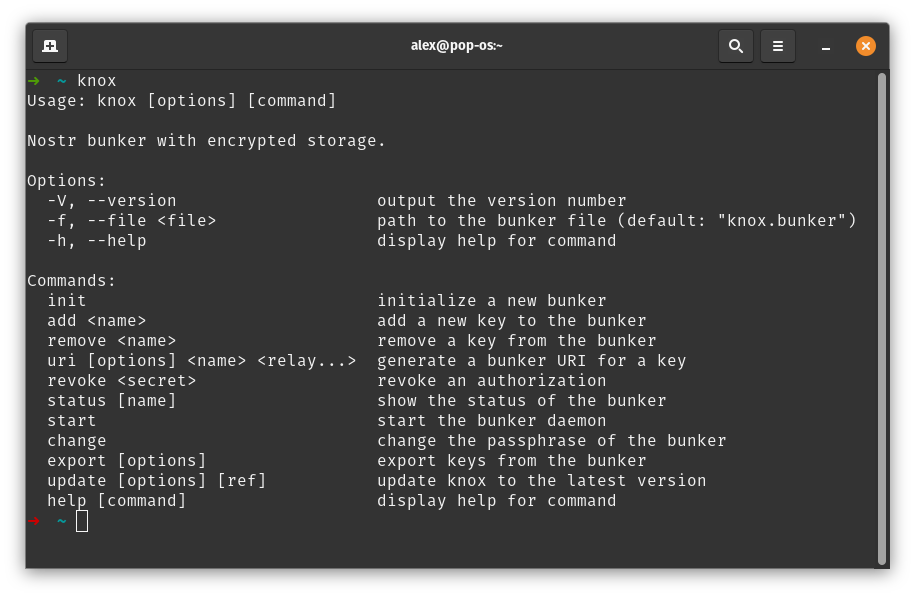
knox is a command-line tool that manages keys, generates bunker URIs, and runs a bunker server. It is still beta software, but I am using it successfully today to post on Ditto.
knox is inspired by the wonderful
nak bunkercommand, which almost solved my problem but has no way to store credentials. So I created my own command-line bunker that you can run again and again.
Most notably, knox introduces a portable
.bunkerfile format for storing keys and connection details. It's encrypted with a password, which you have to type every time you want to add or remove keys, generate new URIs, and when you start the bunker.With knox you can have one bunker file, or many. It is loosely inspired by the KeePass
.kbdxidea.knox is written in TypeScript, but it's available as a precompiled executable on Linux, MacOS, and Windows thanks to
deno compile.Getting Started
To install knox, I've prepared a simple setup script that will detect your OS and install the knox command in your path:
sh curl https://dl.soapbox.pub/install/knox.sh | shYou can also grab a precompiled binary if you don't want to run the script.
Commands
Once installed, run
knoxto see a list of supported commands. It should look something like this:``` Usage: knox [options] [command]
Nostr bunker with encrypted storage.
Options: -V, --version output the version number -f, --file
path to the bunker file (default: "knox.bunker") -h, --help display help for command Commands: init initialize a new bunker add
add a new key to the bunker remove remove a key from the bunker uri [options] generate a bunker URI for a key revoke revoke an authorization pubkey [options] show the public key of a secret key status [name] show the status of the bunker start start the bunker daemon change change the passphrase of the bunker export [options] export keys from the bunker update [options] [ref] update knox to the latest version help [command] display help for command ``` Run
knox initto create a new bunker file. Then useknox add alex(replace with your own name) to add a key, thenknox uri alexto get a connection string. Finally, runknox startto start the bunker.While the bunker is running, you can continue to run commands like
knox addandknox uriin another tab, and the bunker will detect the file changes and automatically refresh.
Another good one is
knox status, which shows a list of keys and whether any of their URIs are being utilized.knox status <key>can show the individual connections for a specific key, andknox revoke <secret>can revoke an individual connection.Bunker Where?
knox needs internet connectivity to connect to relays, but it does not need to expose any ports to the outside world, so the ideal place might be on a desktop computer in your living room. This might be considered more secure than a VPS in a datacenter, depending on your circumstances.

I am running knox on an old Dell computer under my TV, which is a cheap and simple solution. It's connected to a backup battery in case the power flickers, but a prolonged outage would require starting the bunker again manually. I also suggest running the bunker in
screenor a similar tool so you can reconnect and view the logs over ssh on your home network.It's not suggested to run knox in systemd, because knox requires manually entering the encryption password when it starts. Any solution to store the password to disk, or pass it through a command-line argument, would compromise security.
What's Next?
For now, knox is meeting my needs. As the idea evolves I expect to make more changes, and possibly improvements to the
.bunkerformat if anyone else decides to use it. Feel free to drop any suggestions on GitLab!Another interesting idea would be to build a UI to manage the
.bunkerfile, or to offer hosted bunker (although I am kind of against this, unless the hoster is just cloud sync service and the bunker is decrypted locally within the browser, similar to KeeWeb). -
 @ 705605d9:b4324038
2024-12-13 17:42:06
@ 705605d9:b4324038
2024-12-13 17:42:06Через две недели известный музыкант IGR посетит Горноправдинск. Об этом он заявил в своём телеграм-канале.
Игорь "IGR" Романов пишет хип-хоп и трэп. В своём жанре у музыканта уже есть имя, и мнения о нём у поклонников хип-хопа сильно различаются — споры вызывают как откровенно провокационные тексты артиста, так и его личная жизнь. Напомним, несколькими месяцами ранее IGR был задержан силовиками как участник несогласованного митинга в Санкт-Петербурге. Музыкант высказал свою радикальную позицию и был задержан за неповиновение сотруднику полиции.
"Его музыка заставляет задуматься, но иногда кажется, что он просто провоцирует ради провокации", — делится мнением наша читательница Ольга, которая не уверена, стоит ли идти на концерт. "Я люблю музыку, но некоторые его песни слишком откровенны", — добавляет она.
"IGR— это голос поколения! Его тексты отражают наши мысли и чувства, даже если они вызывают споры", — считает 17-летний Дмитрий. Он купил билет в первый же день после анонса концерта и намерен приехать на концерт из Новосибирска.
Выступление пройдёт в Дворце культуры. Цены на билеты колеблются от 1800 до 8000 рублей.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ e373ca41:b82abcc5
2024-11-28 07:21:51
@ e373ca41:b82abcc5
2024-11-28 07:21:51Article by Milosz Matuschek, first published on "Freischwebende Intelligenz".
When the French historian Alexis de Tocqueville traced the French Revolution, he noted that free publicists and authors had become the leading politicians in the mid-18th century. They alone, penniless, without status, rank, title or formal power, became the only ones who still possessed authority. It is no secret that all power, especially in a democracy, is based on media power and public opinion. Revolutions can begin when intellectual forces regroup. The US elections also mark a turning point. It was primarily the media mainstream, the previous classic kingmaker, that lost out. In recent years, it has increasingly retreated into the trenches of its own ideology, preferring to listen to philanthrocapitalists with crazy ideas for shaping the world, woke social engineers and the studies of a thoroughly corrupted scientific community.
 The "cultural hegemony" is marked in blue, by the way
The "cultural hegemony" is marked in blue, by the way This “cultural hegemony”, which also manifested itself in educational institutions and the cultural sector, has now been pulverized. It was the X/Twitter platform and its new owner Elon Musk, among others, that have undermined mainstream power and created a space for broader and deeper debates alongside the narrow corridor of the media cartel. Musk himself is one of the biggest influencers in the world, no one has more followers on Twitter than him (204.6 million). The mainstream used to be the kingmaker, now it's the richest man in the world and his platform. Is that progress?
Musk is now being rewarded with a leadership role in a new government agency: The Department of Government Efficiency, or D.O.G.E. Doge is also the abbreviation for the largest memecoin, a sweet, virtual dog currency, the Doge Coin, which Musk has mentioned from time to time and had also already brought into play as a currency for Tesla. He has also named rockets after Doge.
Media power, meme culture, political power, all mixed together in a somewhat bizarre, semi-serious way. Everything is as American as ever. Many journalists in this country will now have to google “meme culture” and “DOGE”, preferring to stare at mainstream polls predicting a Harris victory. At the same time, Bitcoin is soaring to new highs. (Hopefully you read my piece on Bitcoin from the summer when I suggested you buy Bitcoin now (As of that time: 58,239 dollars per unit. As of press time today: 91,082 dollars).
It's a nice synchronicity when the uncensorable Bitcoin erupts at the same moment as the mainstream echo chamber implodes. Free money and free information belong in the hands of the citizen. But the citizen must also reach for it, otherwise others will. Companies are now increasingly buying into Bitcoin, with Blackrock recording billions in inflows into the Bitcoin ETF in the last few weeks alone. The next wave will come from the government. El Salvador has already declared Bitcoin the reserve currency. Trump is toying with the idea of creating a Bitcoin stock as an official reserve. Bitcoin was meant to be the asset class, which was out of the reach of governments. What will change, when they’re buying into it big time?
Musk is currently the de facto custodian of freedom of expression in the world, the protector liberae orationis mundi. How openly will he deal with critical information about himself or the Trump administration? Every “savior” has a life cycle. Liberators have often become new oppressors. Whether with free money or free information: in none of these centers of power should individual interests be allowed to dictate the direction. But this also means that freedom can only be realized where it is perceived. If citizens do not use the tools of freedom themselves en masse, others will. Freedom then remains just an option that is not redeemed, but merely delegated to the next savior.
Trump and Musk are just creating a new power conglomerate. Politics and billionaires with the will to shape things, everything as usual. From Soros & Co. to Musk & Co. For the field of free information, this means that as long as citizens are not on completely uncensorable platforms that are not controlled by anyone, they are working in the data silo of Musk & Co. They are active in the gig economy of the public opinion market and can be switched off and dimmed down at any time. Whether identity, content or followers: everything belongs to Musk. The necessary next step on the way to a truly free marketplace of ideas is solutions in which the citizen is the actor and not the product being sold.
Only when decentralized money and decentralized information are gathered in the hands of citizens and form a powerful block against power centers of all kinds, and a spirit of light-filled transformation can unfold, will a new golden age begin.
-- Join the marketplace of ideas! Sound money and sound information should finally be in the hands of the people, right? We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ 705605d9:b4324038
2024-12-13 17:41:13
@ 705605d9:b4324038
2024-12-13 17:41:1327 октября 2040 года в Горноправдинске, небольшом, но прогрессивном посёлке Югры, состоялась презентация уникального бренда экологичной одежды. Созданная местной дизайнеркой Верой Ивановной Семёновой, эта линия одежды обещает не только красивую и стильную, но и устойчивую моду, полностью изготавливаемую из переработанных материалов. Уникальность бренда заключается в том, что модели — это исключительно женщины пожилого возраста, что делает данный проект ещё более социально значимым.

Устойчивое развитие как основа идеи
Горноправдинск давно зарекомендовал себя как местечко, где экология и устойчивое развитие стоят во главе всего. Здесь активно развиваются инициативы по переработке отходов и рациональному использованию природных ресурсов. Презентация нового бренда стала логическим продолжением этих усилий. Одежда из вторсырья не только уменьшает количество отходов, но и снижает воздействие на окружающую среду. По данным исследований, текстильная промышленность является одним из крупнейших источников загрязнения в мире. В этом контексте важно осознавать влияние, которое каждый из нас может оказать на природу, выбирая экологически чистые альтернативы.
Согласно информации от независимой экологической организации, производство ткани из вторичных материалов требует в три раза меньше воды, чем традиционные методы. Это выгодно не только для экологии, но и для экономики. Более того, использование вторичных материалов позволяет снижать углеродный след, что критически важно в условиях глобального изменения климата.
Творение как вдохновение
Вера Ивановна Семёнова — не просто дизайнер, но и активист, призывающий к переменам. Её новый бренд стал результатом многолетнего труда и экспериментов. Вера патентует уникальные технологии переработки тканей и создания новых моделей, которые одновременно сочетали в себе стиль и комфорт.

"Я хочу показать, что мода может быть не только красивой, но и умной", - говорит Вера в интервью. Она расставляет акценты на том, что её коллекция будет выходить за рамки стандартного понимания экологии. Модельный ряд включает в себя как повседневную, так и вечернюю одежду. Каждая вещь несёт в себе уникальную историю переработанного материала, а сами ткани отобраны так, чтобы гарантировать долговечность и стиль.
Открывая новые горизонты для пожилых женщин
Эти модели — не просто одежда, это символ изменений. Важным аспектом нового бренда является то, что модели — это женщины пожилого возраста. В нашем обществе часто встречается предвзятое отношение к возрасту, и многие пожилые женщины сталкиваются с трудностями в поисках работы или возможности проявить себя.
Горноправдинск стал первой площадкой, где пожилые женщины, обладая опытом и мудротой, получили возможность стать лицами модной индустрии. Этот шаг отразит новое понимание о красоте и стилю, которое не привязано к возрасту. Публика сможет увидеть, что настоящая красота исходит из внутреннего содержания, а не из стандартных шаблонов. Опросы показали, что большинство людей не воспринимает пожилых женщин как моделей. Но проект Веры Семёновой может стать началом новой эры, в которой возраст будет праздноваться, а не скрываться. Это не только проект по созданию одежды, но и социальная инициатива, ставящая вопрос о равенстве и возможностях для всех.
Модные тренды и экологическое сознание
В рамках презентации были представлены несколько моделей, каждая из которых рассказывала свою историю. Одежда создана из переработанных материалов: старых футболок, джинсов и текстиля, который больше не пригоден для использования в первоначальном виде. Каждая модель была выполнена с учетом последних модных тенденций: яркие цвета, уникальные принты и современные силуэты.
Важным аспектом новой коллекции является также то, что для её создания использовались умные технологии, позволяющие минимизировать отходы. Вера указала на то, что каждое изделие было разработано с использованием принципа zero waste, что подразумевает полное отсутствие отходов. Это значительно понижает стоимость конечного продукта и делает его доступным для широкого круга любителей моды.

Эксперты предположили, что такой подход может стать новым стандартом в модной индустрии, потому что он отвечает современным требованиям рынка и эволюционным ожиданиям покупателей. Люди всё больше начинают заботиться о том, каким образом производится одежда, и предпочитают brands, поддерживающие идеалы устойчивого развития.
-
 @ e373ca41:b82abcc5
2024-11-26 06:45:57
@ e373ca41:b82abcc5
2024-11-26 06:45:57(One of the first pictures of a surfer, Hawai, 1890)
Article by Milosz Matuschek, first published on "Freischwebende Intelligenz".
Everything comes in waves. Almost exactly four years ago, the world narrowed rapidly: curfews, lockdowns, compulsory masks, vaccination madness. The corona period brought me to a decision: do what you've always wanted to do now, the old world might not be around for much longer. The threat of the future made the present more intense for me. The corona period, as bad as it was, put a damper on my procrastination; it forced my focus from the future to the immediate here and now. In the present, I came face to face with myself and looked ruthlessly in the mirror: I was in my early 40s, a single man stranded in a men's shared flat in Zurich, who had just successfully got rid of two prestigious jobs in Swiss journalism and was back where he had started: as a kind of “blogger” on the fringes of the media business. I booked a flight to the Canary Islands, happily missed the return flight, set up my publication "Freischwebende Intelligenz" and started surfing intensively.
I have never regretted any of it.
The sea became my teacher
Surfing: just a banal pastime for big kids and authors in midlife crisis? Surfing, what is it anyway? A sport? A lifestyle? An art form? In 2012, I got on a surfboard for the first time in Trestles Beach, California, without knowing what I was doing. The place is mentioned in the Beach Boys' classic “Surfin' USA”, the main aim of the lyrically simple song is to list the American surf beaches: that's what good PR rock'n'roll sounds like. I took my first real course in France, later I tried the beaches of Portugal. It's interesting that Corona turned my focus back in this direction. During Corona, I probably expected to find a critical, like-minded environment among surfers. An expectation that was only partially fulfilled, but is somehow part of the myth of the sport: this is where the rebels, non-conformists and non-conformists are most likely to be. Kary Mullis, the inventor of the PCR method, was an enthusiastic surfer and free spirit. When the Nobel Committee called him in the morning, he thought it was a joke, hung up and went to the surfing beach. When he returned, there was a crowd of journalists outside his house. The next day, the LA Times ran the headline:

(Screenshot LA Times)
The origins of surfing admittedly predate the pop-culture revival on California beaches. Captain Cook made his first, surprising notes on this phenomenon in Hawaii in 1778. Apparently, the longing to stand on a wave like on the roof of the world and feel the power of the sea beneath you is a long-cherished dream of mankind, just like flying. Surfing became a personal ray of hope for me in the coronavirus dark ages. The sea became more than just a playground or pastime. It became my teacher. At some point, I felt a fusion with the rhythm of the waves. Probably nothing surprising for someone born under the zodiac sign of Pisces. Water had always been my element. With every surfing experience, I learned something new. * Take every wave (i.e. life) as it comes and make the best of it. * Sound out the terrain, observe the conditions carefully before you position yourself: how are the waves building up, which sets are coming up, where is the wind coming from? * You are not entitled to a wave, but you do have the opportunity to use it. * Look for gaps in the waves to get through. The sea will also show you this way. * The situation determines the possibilities, not necessarily your ambition. * If you want to catch a wave, you have to be able to compress the present, wait patiently for the right moment and then use it gratefully. * Don't rush after a wave, the next one is sure to come. * Learn to be patient before every wave and to feel either gratitude or humility after every wave. * Accept the highs as well as the lows, both have a meaning. * Be where the wave is not, learn to anticipate it, categorize it and adapt to it. Go with the flow. * Always work with the sea, never against it.
Riding the waves: An allegory of life
Surfing is a dance with the ocean, a constant negotiation with its rhythms. To ride a wave, a surfer must understand the cycles of the ocean: The swell of the wave, the timing of the wave's buildup, the rise and fall of the tides and the intervals between waves. These natural rhythms, dictated by gravity, the weather, the moon, are unchanging and indifferent to human will. A surfer who defies these rhythms - paddles too early or hesitates too long - cannot catch the wave. As Jaimal Yogis writes in “Saltwater Buddha”: “You cannot fight the ocean. You must surrender to its power and move with it.” This surrender is not a sign of weakness, but a deep adaptation to the rhythm of nature. The surfer becomes attuned to the pulse of the ocean and learns to act in harmony with the forces around him instead of fighting against them.
The sea sends the waves, like ever new life events, in an idiosyncratic sequence. Sometimes there is calm, sometimes there is alarm. In surfing, facing up to these life events and adapting to them is not a question of wanting to, but a duty to be practiced. There is one perfect moment to get on the wave and hundreds of other moments when the attempt can end in a minor catastrophe. The sea sets the rhythm and we either adapt or are severely punished and learn to respect the power of the sea. Every surfer knows the situation where the wave catches you on the wrong foot: you're not on top of it but underneath it, perhaps right in the center of its power, being whirled by it like in a washing drum, pushed to the ground several times until it spits you out in a crackling foam bath and leaves you gasping for air.
Everything swings, nothing is static
Surfing suited me because it was a leisurely continuation of what I was already doing.
Hadn't I become a surfer otherwise? In journalism, timing and the right assessment of a topic are important. Every topic is a wave that rises and falls. In journalism, I've always been particularly interested in the topics that other people don't cover. Where many mainstreamers only saw shoals and whirlpools of disinformation and conspiracy theories, I saw a wave of information building up that would ultimately be most dangerous for those who did not dare to ride it: the journalists themselves. I learned from surfing that you often don't choose the topics, just like you don't choose the waves or life events. They come to you and expect a reaction from you. I decided to ride this wave back then.
Advertisement:
Are you looking for the easiest way to buy Bitcoin and store it yourself? The RELAI appis the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees. (no financial advice).

The fall of 2020 was also the beginning of the next bull market for Bitcoin & Co. In trading, you also count waves, interpret volumes and try to make better decisions by recognizing recurring patterns. The biggest lesson here is the same: Humility. You can ride five nice waves but go down with the sixth and never reappear because you're broke. How the Bitcoin/crypto market has moved since 2009 has been easy to study. It was not too surprising what happened in 2019/2020/2021: Bitcoin rose from a low of USD 5,000 to over USD 70,000. Anyone who thought cyclically knew that. Anyone studying the prices now will easily recognize parallels. Position yourself or watch? Unlike the sea, life gives us this choice. But there is one thing you should never do: mourn missed opportunities or missed waves. They are gifts, not objects of entitlement.
The fifth hermetic principle

The principle of rhythm is the fifth “hermetic principle” and it teaches two lessons, among others: It is everywhere and is always concerned with balance, with compensation and homeostasis. Every situation has a lifespan. It can change in its shades and tip from one extreme position to the other. The universal, pendulum-like rhythm can be found, for example, in...
- Theories of history (Polybios, Ibn Chaldun or the authors of the “4th Turning”).
- Economic theories: In the alternation of bull and bear markets, in the Kondratiev cycles or the Elliott waves in trading.
- The sociology of power: thinkers such as Pareto, Mosca and Michels (all of whom remained outsiders) saw an elite cycle at work in politics.
- The Bible: In the Old Testament, Joseph interprets Pharaoh's dreams of the seven fat years and the seven lean years.
The pendulum of rhythm swings and it swings everywhere. At the macro level of history and the economy as well as at the micro level of our bodies. Every single cell has its tension, its frequency, in the end everything is in motion, nothing is static. Life oscillates. We think in terms of life cycles when we look at the calendar. We know that after winter comes spring, just as night is followed by day. In everyday life, we tend to forget the principle of rhythm. We don't need to be reminded of its gravity, it is always there and keeps us from taking off and sticking to the ceiling. The rhythm of life, on the other hand, communicates with us in a cryptic language. We are presented with opportunities that we can seize. The prerequisite for this is that we recognize them. Those who sharpen their senses for these signs will increasingly invite them into their lives as signposts.
Become a soul surfer on the waves of life
The principle of rhythm is an encouraging principle. It tells me that we can survive any situation if we are only prepared to interpret the signals, sharpen our intuition and start practising pattern recognition. “No wind is favorable to those who do not know their destination,” Seneca knew. No external situation is dangerous for those who carry their home port within them. For those who operate with their own principles, values and objectives, life is a playground for applying these principles. Highs teach us to stay on the ground, defeats teach us sovereignty and inner detachment from external storms. In every situation in life, we have the opportunity to sharpen our principles or adapt them if necessary, to develop our character and to open another chapter in our world of experience.
What teacher have you found for yourself?
What perhaps banal activity revealed new approaches to reality to you?
-- Join the marketplace of ideas! Sound money and sound information should finally be in the hands of the people, right? We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 705605d9:b4324038
2024-12-13 17:39:37
@ 705605d9:b4324038
2024-12-13 17:39:37Автор: Павел Густой, который дважды поперхнулся молоком, услышав слово «причал».
Старое железо и новая эпоха
Двадцать лет назад набережная Горноправдинска выглядела так, как будто ее проектировал инженер, вдохновленный своей последней опохмелкой. Ржавеющая баржа, служившая причалом, стояла на месте, словно памятник бессмысленности. Жители, подходя к ней, задавались лишь одним вопросом: «А мы точно успеем до корабля, пока она не развалится?»

Но 2040-й год стал годом, когда бабушки, эти легендарные управленцы Горноправдинска, решили: хватит. Видимо, они устали, что даже жители Бобровки шутят про их набережную, называя её «Порт Стыда».
Экологичный причал и другие чудеса
Реформа была громкой, как взрыв сыроварни. Теперь вместо ржавой баржи — современный экологичный причал. Он сделан из переработанного пластика и бетона, настолько крепкого, что даже утиный десант из соседнего водохранилища не смог его повредить.

«Мы думали о будущем, о наших детях и внуках», — заявила одна из бабушек, поглаживая внушительный скипетр в виде бутылки молока. Правда, злые языки утверждают, что пластик для причала собирали в основном в Бобровке, где люди искренне надеялись, что это поможет им самим.
Набережная — теперь с развлечениями!
Но на этом бабушки не остановились. Новый причал стал центром масштабного благоустройства. Что там теперь есть?
-
Большой магазин. Под названием «Молочная правда». Говорят, что если долго смотреть на его логотип, можно разгадать секрет бабушкиных масонов.

-
Зоны отдыха. Здесь все продумано до мелочей: лавочки с подогревом для больных суставов, мусорные урны, которые цитируют Бродского, и фонтаны, работающие исключительно на сыворотке.
- Промзона. Построенная так, чтобы туристы и не поняли, что смотрят на завод. «Это арт-объект!» — гордо утверждают бабушки. На фасаде предприятия висит баннер с надписью: "От молока до металла: мы можем всё!"

Критика: куда без неё?
Конечно, реформа понравилась не всем. Некоторые горноправдинцы ворчат, что набережная слишком идеальна, что даже коровы боятся здесь пастись. Другие шутят, что вместо прогулочной зоны бабушки могли бы построить парк развлечений для жителей Бобровки, где вместо билетов продавали бы надежду.
«Это всё для туристов», — жалуются местные, стоя в очереди за молоком. В ответ бабушки молчат. Они слишком заняты, вероятно, обсуждением нового проекта: ходят слухи о запуске молочного дирижабля.
Что дальше?
Набережная Горноправдинска — это, конечно, не про корабли и причалы. Это символ, дорогие мои. Символ того, что даже в городе, где всем управляют бабушки, возможно обновление. Пусть и с долей черного юмора, пластика и неизменного молочного послевкусия.
И всё же, когда смотришь на новый причал, где люди счастливо прогуливаются под солнцем, а где-то вдалеке доносится звук загрузки молока на баржу, понимаешь: Горноправдинск в который раз доказал, что он — город контрастов.
-
-
 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集:
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | 官网 | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | 官网 | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | 官网 | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | 官网 |
持续更新。。。
推广:
访问不了openai,去
低调云购买VPN。官网:https://didiaocloud.xyz
邀请码:
w9AjVJit价格低至1元。
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 79008e78:dfac9395
2024-12-01 03:15:00
@ 79008e78:dfac9395
2024-12-01 03:15:00บทที่ 1: เกริ่นนำ
เกริ่นนำเรื่องราวของบิตคอยน์แบบกระทัดรัด
บิตคอยน์ (Bitcoin) เป็นชุดแนวคิดและเทคโนโลยีที่เข้ามาผสมผสานรวมกันจนได้กลายเป็นระบบเงินสดอิเล็กทรอนิกส์ หน่วยเงินที่เรียกว่าบิตคอยน์นั้น ใช้เพื่อเก็บและส่งต่อมูลค่าให้กับผู้ใช้คนอื่น ๆ ในระบบ ผู้ใช้ทั้งระบบสื่อสารกันบนโปรโตคอลของบิตคอยน์ โดยผู้ใช้ส่วนใหญ่ก็เข้าถึงกันผ่านอินเตอร์เน็ต แต่ก็ไม่ได้หมายความว่าระบบนี้ไม่สามารถใช้เครือข่ายการสื่อสารรูปแบบอื่นได้ ซอฟต์แวร์ของโปรโตคอลนี้เป็นโอเพนซอร์สและสามารถรันได้บนอุปกรณ์คอมพิวเตอร์หลายประเภท เช่น แล็ปท็อปและสมาร์ทโฟน และสิ่งนี้เองที่ทำให้เทคโนโลยีนี้สามารถเข้าถึงได้ง่าย
ผู้ใช้งานสามารถส่งบิตคอยน์ให้กันผ่านเครือข่ายของบิตคอยน์เพื่อทำกิจกรรมต่าง ๆ เช่น ซื้อ-ขายแลกเปลี่ยนสินค้าและบริการ หรือใช้เพื่อแลกเปลี่ยนเป็นสกุลเงินต่าง ๆ ซึ่งถือว่าเหมาะสมเป็นอย่างมากสำหรับการใช้งานบนอินเทอร์เน็ต เพราะมีทั้งความรวดเร็ว ความปลอดภัย และยังข้อจำกัดเรื่องพรมแดน
ซึ่งบิตคอยน์นั้นแตกต่างจากสกุลเงินโดยทั่วไป เนื่องจากเป็นระบบเงินอิเล็กทรอนิกส์ จึงไม่มีเหรียญหรือธนบัตรจริง ๆ ให้ได้จับต้อง แต่คำว่าเหรียญที่มักใช้กันในสังคมของบิตคอยน์จะหมายถึงในธุรกรรมที่ผู้ใช้รายหนึ่งโอนมูลค่าไปยังผู้ใช้อีกรายหนึ่ง ผู้ใช้งานบิตคอยน์จะควบคุมคีย์ (Private Key) ที่ใช้พิสูจน์ความเป็นเจ้าของในบิตคอยน์นั้น ๆ ในเครือข่าย และด้วยคีย์นี้เองทำให้พวกเขาสามารถเซ็นชื่อในธุรกรรมเพื่อปลดล็อกมูลค่าและทำการส่งมันต่อไปยังผู้รับอีกรายหนึ่ง ซึ่งมักจะถูกเก็บอยู่ในกระเป๋าเงินดิจิทัล หรือสมาร์ทโฟนของผู้ใช้งาน การครอบครองคีย์ที่สามารถเซ็นชื่อในธุรกรรมได้เป็นสิ่งเดียวที่จำเป็นในการใช้จ่ายในระบบของบิตคอยน์ และนั่นเป็นเหตุผลที่ทำให้ความสามารถในการควบคุมบิตคอยน์อยู่ในมือผู้ใช้แต่ละคน
เข้าใจว่าในบริบทนี้น่าจะหมายถึง Hot-wallet เพราะงั้นผมไม่ได้แนะนำให้เก็บคีย์คอมพิวเตอร์หรือมือถือนะครับ ส่วนถ้าคุณอยากทำก็เรื่องของคุณจ้าแนะนำเฉย ๆ อยากทำไรทำ
บิตคอยน์นั้นเป็นระบบแบบกระจายศูนย์และทำงานแบบเพียร์-ทู-เพียร์ (Peer-to-Peer) หรือเอาภาษาบ้าน ๆ ว่า เป็นระบบการทำงานแบบบุคคลสู่บุลคลที่ไม่มีตัวกลางระหว่างการทำงาน ดังนั้นจึงไม่มีเซิร์ฟเวอร์กลางหรือจุดควบคุม บิตคอยน์นั้นถูกสร้างขึ้นโดยกระบวนการที่เรียกว่าการขุด ซึ่งเป็นการทำงานทางการคำนวณซ้ำ ๆ ที่อ้างอิงกับรายการธุรกรรมบิตคอยน์ล่าสุด (จริง ๆ ก็มี hash ของบล็อกก่อนหน้าด้วย) ซึ่งผู้ใช้งานบิตคอยน์ทุกคนสามารถที่จะขุดบิตคอยน์ได้ โดยใช้อุปกรณ์คอมพิวเตอร์ของตนเพื่อช่วยรักษาความปลอดภัยในธุรกรรม โดยทุก ๆ สิบนาทีโดยเฉลี่ยนั้น จะมีนักขุดคนหนึ่งที่ได้ช่วยเพิ่มความปลอดภัยให้กับธุรกรรมในอดีต และจะได้รับรางวัลเป็นบิตคอยน์ใหม่และค่าธรรมเนียมจากธุรกรรมชุดล่าสุด ซึ่งกระบวนการนี้ทำให้การออกสกุลเงินและการชำระธุรกรรมไม่จำเป็นต้องมีธนาคารกลาง
โปรโตคอลของบิตคอยน์ มีอัลกอรึทึมที่คอยควบคุมความยากง่ายในการการขุดให้อยู่ในระดับที่เหมาะสม โดยความยากง่ายในการขุดจะขึ้นจะถูกปรับตามระยะเวลาเฉลี่ยของการขุดในช่วงก่อนหน้านี้เพื่อให้การขุดนั้นมีโอกาสสำเร็จเฉลี่ยในทุก ๆ 10 นาที ไม่ว่ามีจำนวนผู้ขุดและการประมวลผลเท่าใดก็ตาม และนอกจากนี้เองโปรโตคอลของบิตคอยน์นั้นยังลดจำนวนของบิตคอยน์ที่นักขุดจะได้เป็นรางวัลลงเรื่อย ๆ ซึ่งจะทำให้บิตคอยน์ที่สร้างได้ในระบบนั้นมีไม่เกิน 21,000,000 ล้านบิตคอยน์ ซึ่งผลลัพธ์ที่ได้ก็คือ จำนวนบิตคอยน์ที่หมุนเวียนในระบบนั้นจะสามารถคาดเดาได้อย่างง่ายดาย ซึ่งอีกครึ่งหนึ่งของบิตคอยน์ที่เหลืออยู่จะถูกเพิ่มเข้าไปในระบบทุก ๆ 4 ปี และที่บล๊อกประมาณ 1,411,200 ซึ่งคาดว่าจะเกิดประมาณปี 2035 จะมีบิตคอยน์เป็นจำนวน 99 % ของที่สามารถเกิดขึ้นได้ในระบบ เนื่องจากอัตราการการผลิตของบิตคอยน์ที่น้อยลงเรื่อย ๆ ทำให้บิตคอยน์มีลักษณะของเงินฝืดในระยะยาว นอกจากนี้ยังไม่มีใครที่สามารถบังคับให้คุณรับบิตคอยน์ที่ถูกผลิตมานอกเหนือจากชุดกฎที่คุณเลือกได้
เบื้องหลังต่าง ๆ ของโปรโตคอลบิตคอยน์ที่ทำให้มันเป็น เครือข่ายแบบบุคคลถึงบุคคล และการคำนวณแบบกระจายศูนย์นั้น ถูกสร้างขึ้นมาบนพื้นฐานของงานวิจัยในด้านการเข้ารหัสและระบบกระจายศูนย์มาเนิ่นนานหลายทศวรรษ โดยมีการรวมเอานวัตกรรมสำคัญ ๆ 4 อย่างนี้มารวมเข้าด้วยกัน:
- เครือข่ายเพียร์ทูเพียร์ที่กระจายศูนย์ (ฺBitcoin protocol)
- บัญชีธุรกรรมสาธารณะ (Blockchain)
- ชุดของกฎในการตรวจสอบธุรกรรมอย่างอิสระและการออกสกุลเงิน ( consensus rules )
- กลไกในการหาข้อตกลงร่วมกันทั่วโลกเกี่ยวกับบล็อกเชนที่ถูกต้อง (PoW algorithm)
ในมุมมองของนักพัฒนา นาย Andreas M. Antonopoulos and David A. Harding ( ไม่ใช่ผมจ้าา ถึงจะเห็นด้วยก็ตาม) พวกเขามองว่าบิตคอยน์นั้นคล้ายกับอินเทอร์เน็ตของเงิน เป็นเครือข่ายสำหรับการกระจายมูลค่าและการรักษาความเป็นเจ้าของสินทรัพย์ดิจิทัลผ่านการคำนวณแบบกระจายศูนย์ ซึ่งบิตคอยน์มีรายระเอียดเยอะกว่าที่พวกเขาเห็นในตอนแรกมาก ๆ
ในบทนี้เองจะเป็นการอธิบายแนวคิด และคำศัพท์หลัก ๆ รวมทั้งการติดตั้งซอฟแวร์ต่าง ๆ ที่จำเป็นในการทอดลองใช้บิตคอยน์สำหรับทำธุรกรรมง่าย ๆ และสำหรับในบทถัดไป เราจะทำการดำดิ่งลงไปในเทคโนโลยีต่าง ๆ ที่ประกอบรวมกันเป็นบิตคอยน์ว่าทำไมมันถึงเป็นไปได้ และตรวจสอบการทำงานภายในของเครือข่ายและโปรโตคอล
ก่อนการมาถึงของบิตคอยน์
สกุลเงินดิจิทัลที่ใช้งานได้จริงในอดีตนั้นมักเกี่ยวข้องกับพัฒนาการในด้านการเข้ารหัส ซึ่งนั่นก็ไม่ได้แปลกอะไรหากเราพิจารณาถึงปัญหาพื้นฐานในการใช้ข้อมูลเพื่อแทนมูลค่าที่สามารถแลกเปลี่ยนเป็นสินค้าและบริการ โดยการที่เงินดิจิทัลจะถูกยอมรับได้นั้นมักจะต้องสามารถตอบคำถามทั้งสามข้อนี้ได้เสียก่อน:
- ฉันจะเชื่อได้อย่างไรว่าเงินนั้นเป็นของจริงและไม่ใช่ของปลอม?
- ฉันจะเชื่อได้อย่างไรว่าเงินดิจิทัลสามารถใช้ได้เพียงครั้งเดียว (ปัญหาการใช้ซ้ำหรือ "double-spend")?
- ฉันจะมั่นใจได้อย่างไรว่าไม่มีใครสามารถอ้างสิทธิ์ว่าเงินนี้เป็นของพวกเขาไม่ใช่ของฉัน?
ผู้ที่ออกเงินกระดาษเองก็พยายามต่อสู้กับปัญหาการปลอมแปลงโดยการใช้เทคโนโลยีการพิมพ์ที่ซับซ้อนมากขึ้นเรื่อย ๆ และเงินกายภาพเองก็จัดการปัญหาการใช้ซ้ำได้ง่ายเพราะธนบัตรเดียวกันไม่สามารถอยู่ในสองที่พร้อมกันได้ แน่นอนละว่าเงินทั่วไปก็ถูกเก็บและส่งแบบดิจิทัลเช่นกัน ในกรณีเหล่านี้ ปัญหาการปลอมแปลงและการใช้ซ้ำจะถูกจัดการโดยการเคลียร์ธุรกรรมทางอิเล็กทรอนิกส์ทั้งหมดผ่านหน่วยงานกลางที่สามารถตรวจสอบสถานะของเงินได้ แต่สำหรับเงินดิจิทัลที่ไม่สามารถใช้หมึกพิเศษหรือแถบโฮโลแกรมได้ การเข้ารหัสจึงเป็นพื้นฐานสำคัญในการยืนยันความถูกต้องของการอ้างสิทธิ์ในมูลค่าของผู้ใช้ โดยเฉพาะอย่างยิ่ง การเซ็นชื่อดิจิทัลที่เข้ารหัสช่วยให้ผู้ใช้สามารถเซ็นชื่อในสินทรัพย์ดิจิทัลหรือธุรกรรมเพื่อยืนยันการเป็นเจ้าของสินทรัพย์นั้น ซึ่งสิ่งนี้เองยังสามารถใช้ในการแก้ปัญหาการใช้ซ้ำ (doble-spending) ได้
ศาสตร์ของการเข้ารหัสนั้นเริ่มเป็นที่แพร่หลายในช่วงปลายของทศวรรษที่ 1980 นักวิจัยหลายคนเริ่มพยายามใช้การเข้ารหัสเพื่อสร้างสกุลเงินดิจิทัล โดยโครงการเงินดิจิทัลในยุคแรก ๆ นั้นมักจะออกเงินดิจิทัลที่มีการสนับสนุนโดยสกุลเงินของชาติหรือโลหะมีค่าอย่างเช่น ทองคำ
ซึ่งแม้ว่าสกุลเงินดิจิทัลยุคแรกเหล่านี้จะทำงานได้ แต่ก็มีปัญหาที่การรวมศูนย์ของระบบ เนื่องจากมันทำให้ระบบเป็นเป้าหมายที่ง่ายต่อการโจมตีโดยรัฐบาลและเหล่าแฮกเกอร์ สกุลเงินดิจิทัลยุคแรกใช้ศูนย์กลางในการชำระธุรกรรมทั้งหมดเป็นระยะ ๆ เช่นเดียวกับระบบธนาคารทั่วไป เป็นที่น่าเสียดายที่สกุลเงินดิจิทัลเหล่านี้ส่วนใหญ่ถูกกำหนดเป้าหมายโดยรัฐบาลที่กังวลและมักจะถูกฟ้องร้องจนล้มเหลว บางส่วนล้มเหลวอย่างรวดเร็วเมื่อบริษัทผู้ก่อตั้งปิดตัวลงอย่างกะทันหัน และเพื่อให้สกุลเงินดิจิทัลมีความแข็งแกร่งต่อต้านการแทรกแซงจากศัตรู ไม่ว่าจะเป็นรัฐบาลที่ถูกกฎหมายหรืออาชญากรรม เราจึงจำเป็นต้องมีสกุลเงินดิจิทัลที่กระจายศูนย์ เพื่อป้องกันปัญหาดังกล่าว ซึ่งบิตคอยน์คือระบบแบบนั้น ระบบที่ถูกออกแบบให้กระจายศูนย์ และปราศจากอำนาจหรือจุดควบคุมกลางใด ๆ ที่สามารถถูกโจมตีหรือทำให้เสียหายได้
ประวัติของบิตคอยน์
บิตคอยน์ได้ปรากฏครั้งแรกในปี 2008 บนเอกสารที่มีชื่อว่า “Bitcoin: A Peer-to-Peer Electronic Cash System” ซึ่งถูกเขียนโดยบุคคลหรือกลุ่มคนนิรนามที่ใช้นามแฝงว่า ซาโตชิ นากาโมโตะ ซึ่งได้มีการนำนวัตกรรมหลาย ๆ อย่างมารวมเข้าด้วยกัน ไม่ว่าจะเป็นลายเซ็นดิจิทัล และ Hashcash มาสร้างระบบเงินสดอิเล็กทรอนิกส์ที่กระจายศูนย์อย่างสมบูรณ์ ซึ่งไม่ต้องพึ่งพาหน่วยงานกลางในการออกสกุลเงินหรือการชำระและตรวจสอบธุรกรรม โดยนวัตกรรมสำคัญคือการใช้ระบบคำนวณแบบกระจายศูนย์ (Proof-of-work) เพื่อทำสิ่งที่คล้าย ๆ กับการจับฉลากทุก ๆ 10 นาที ทำให้เครือข่ายที่กระจายศูนย์สามารถมีฉันทามติในสถานะของธุรกรรมได้ และสิ่งนี้เองยังสามารถแก้ไขปัญหาการทำธุรกรรมซ้ำซ้อน ซึ่งเป็นข้อบกพร่องของสกุลเงินดิจิทัลที่เคยต้องใช้หน่วยงานกลางในการตรวจสอบธุรกรรมทั้งหมดได้อีกด้วย
เครือข่ายของบิตคอยน์นั้นเริ่มต้นขึ้นในปี 2009 โดยอ้างอิงจากซอฟแวร์ที่เผยแพร่โดย ซาโตชิ และได้ถูกปรับปรุงโดยโปรแกรมเมอร์คนอื่น ๆ มากมายนับไม่ถ้วนมานับตั้งแต่นั้น จำนวนและกำลังของอุปกรณ์ที่ใช้ประมวลผล Proof of Work algorithm (การขุด) เองนั้นก็เพิ่มขึ้นอย่างมหาศาล จนในปัจจุบันนี้พลังการคำนวณรวมกันของเครือข่ายนี้มีมากกว่าจำนวนการคำนวณของซุปเปอร์คอมพิวเตอร์ชั้นนำของโลกทั้งหมดรวมกันเสียอีก ซึ่งสิ่งนี้เองได้ช่วยรักษาความปลอดภัยและความเสถียรของเครือข่ายของบิตคอยน์ได้เป็นอย่างดี
ซาโตชิ นากาโมโตะ ได้ทำการถอนตัวและหายตัวไปในเดือนเมษายนในปี 2011 และมอบหมายความรับผิดชอบในการพัฒนาโค้ดและเครือข่ายให้กับกลุ่มอาสาสมัครที่เติบโตขึ้นเรื่อย ๆ ซึ่งตัวตนของบุคคลหรือกลุ่มคนที่อยู่เบื้องหลังบิตคอยน์นั้นยังไม่เป็นที่รู้จัก แต่อย่างไรก็ตาม ไม่ว่าจะเป็นซาโตชิ นากาโมโตะ หรือใครหน้าไหนก็ตามก็ไม่สามารถควบคุมเครือข่ายของบิตคอยน์ได้ตามลำพัง เนื่องจากมันอยู่บนหลักการทางคณิตศาสตร์ที่โปร่งใส โค้ดโอเพนซอร์ส และฉันทามติจากผู้ที่เข้าร่วม โดยนวัตกรรมนี้ถือเป็นการเปลี่ยนแปลงครั้งใหญ่และได้ก่อให้เกิดวิทยาการใหม่ในด้านการคำนวณแบบกระจายศูนย์ เศรษฐศาสตร์ และเศรษฐมิติอีกด้วย
การแก้ปัญหาในระบบคำนวณแบบกระจายศูนย์
นวัตกรรมของซาโตชิ นากาโมโตะ ยังเป็นการแก้ไขปัญหาที่มีประสิทธิภาพและแปลกใหม่สำหรับปัญหาในระบบคำนวณแบบกระจายศูนย์ที่เรียกว่า "Byzantine Generals' Problem" ซึ่งปัญหานี้เกี่ยวข้องกับการพยายามทำให้ผู้เข้าร่วมหลายคนที่ไม่มีผู้นำสามารถตกลงกันในแผนการดำเนินการได้โดยการแลกเปลี่ยนข้อมูลในเครือข่ายที่ไม่น่าเชื่อถือและอาจถูกโจมตีได้ โดยการแก้ปัญหาของซาโตชินั้นได้ใช้แนวคิด proof of work เพื่อหาฉันทามติโดยไม่ต้องมีผู้ควบคุมที่น่าเชื่อถือ ถือเป็นความก้าวหน้าในด้านการคำนวณแบบกระจายศูนย์
เปิดประตูสู่บิตคอยน์
บิตคอยน์เป็นโปรโตคอลที่สามารถเข้าถึงได้ผ่านทางแอปพลิเคชันที่มีการรับรองโปรโตคอลนี้ Bitcoin wallet นั้นเป็นช่องทางหลักที่ผู้ใช้งานส่วนใหญ่เลือกใช้เพื่อเข้าถึงโปรโตคอลของบิตคอยน์ เช่นเดียวกันกับที่ผู้ใช้งานอินเตอร์เน็ตส่วนใหญ่ใช้เว็บบราวเซอร์เป็นช่องทางในการเข้าถึงโปรโตคอลอย่าง HTTP นั่นเอง Bitcoin wallet เองก็มีหลากหลายยี่ห้อเฉกเช่นเดียวกับเว็บบราวเซอร์ อาทิเช่น chorme, safari, firefox ฯลฯ Bitcoin wallet เองก็เช่นกัน แต่ละยี่ห้อเองก็มีความแตกต่างกันในด้านต่าง ๆ ไม่ว่าจะเป็นในด้านคุณภาพ ประสิทธิภาพ ความปลอดภัย ความเป็นส่วนตัว และความน่าเชื่อถือ อีกทั้งยังมี Bitcoin wallet ที่ถูกสร้างขึ้นมาคู่กับโปรโตคอลของบิตคอยน์อย่าง “Bitcoin Core” ซึ่งมีการพัฒนาต่อมาจากเวอร์ชันที่เขียนโดยซาโตชิ
การเลือก Bitcoin wallet
Bitcoin wallet เป็นหนึ่งในประเภทของแอปพลิเคชันที่มีการพัฒนาอย่างต่อเนื่องมากที่สุดในระบบนิเวศของบิตคอยน์ และแน่นอนว่ามีการแข่งขันกันสูงที่สุดด้วย อาจมี Bitcoin wallet ใหม่ ๆ ที่กำลังพัฒนาอยู่ในขณะนี้ Bitcoin wallet เก่า ๆ บางตัวจากปีที่แล้วก็อาจไม่มีการพัฒนาอย่างต่อเนื่องอีกต่อไป Bitcoin wallet หลาย ๆ ตัวเน้นไปที่แพลตฟอร์มหรือการใช้งานเฉพาะ และบางตัวเหมาะสำหรับผู้เริ่มต้น ในขณะที่บางตัวเต็มไปด้วยฟีเจอร์สำหรับผู้ใช้ขั้นสูง การเลือก Bitcoin wallet นั้นจึงขึ้นอยู่กับความต้องการและระดับความเชี่ยวชาญของผู้ใช้ ดังนั้นการที่เราจะแนะนำยี่ห้อหรือ Bitcoin wallet เฉพาะจึงอาจจะไม่เกิดประโยชน์เท่าไหร่ แต่อย่างไรก็ตาม เราสามารถแบ่งประเภท Bitcoin wallet ได้ตามแพลตฟอร์มและการใช้งานได้ดังนี้
ประเภทของ Bitcoin wallet
- Desktop wallet: กระเป๋าเงินแบบเดสก์ท็อปเป็น Bitcoin wallet ประเภทแรกที่ถูกพัฒนาขึ้นและผู้ใช้ส่วนใหญ่มักจะเลือกใช้ Bitcoin wallet ประเภทนี้เพราะฟีเจอร์ของมัน เช่นความความเป็นอิสระในการใช้งาน ความสามารถในการควบคุมบิตคอยน์ในกระเป๋า แต่อย่างไรก็ตาม การใช้งานบนระบบปฏิบัติการทั่วไป อย่างเช่น Windows และ macOS อาจมีข้อเสียด้านความปลอดภัย เนื่องจากแพลตฟอร์มเหล่านี้มักไม่มีความปลอดภัยเพียงพอและอาจถูกตั้งค่ามาอย่างไม่เหมาะสม
- Mobile wallet: กระเป๋าเงินแบบมือถือเป็น Bitcoin wallet ประเภทที่พบเจอได้มากที่สุด โดยทำงานบนระบบปฏิบัติการสมาร์ทโฟน เช่น Apple iOS และ Android กระเป๋าเงินเหล่านี้มักเป็นตัวเลือกที่ดีสำหรับผู้ใช้ใหม่ เพราะออกแบบมาให้ใช้งานง่ายและสะดวก นอกจากนี้ยังมีกระเป๋าเงินมือถือที่มีฟีเจอร์ครบครันสำหรับผู้ใช้ที่มีความเชี่ยวชาญ แต่เพื่อหลีกเลี่ยงการดาวน์โหลดและจัดเก็บข้อมูลปริมาณมาก กระเป๋าเงินมือถือส่วนใหญ่จะดึงข้อมูลจากเซิร์ฟเวอร์ระยะไกล ซึ่งอาจลดความเป็นส่วนตัวของผู้ใช้เนื่องจากต้องเปิดเผยข้อมูลเกี่ยวกับ address และจำนวนบิตคอยน์ Bitcoin ต่อบุคคลที่สาม
- Web wallet: กระเป๋าเงินแบบเว็บสามารถเข้าถึงได้ผ่านเว็บเบราว์เซอร์และเก็บกระเป๋าเงินของผู้ใช้ไว้บนเซิร์ฟเวอร์ที่บุคคลที่สามเป็นเจ้าของ คล้ายกับบริการอีเมลบนเว็บที่พึ่งพาเซิร์ฟเวอร์ของบุคคลที่สามโดยสมบูรณ์ โดยบางบริการใช้โค้ดฝั่งไคลเอนต์ที่ทำงานในเบราว์เซอร์ของผู้ใช้ และเพื่อให้ผู้ใช้สามารถควบคุมคีย์ของบิตคอยน์ได้เอง แต่การพึ่งพาเซิร์ฟเวอร์ยังคงส่งผลกระทบต่อความเป็นส่วนตัว อย่างไรก็ตาม บริการส่วนใหญ่จะควบคุมคีย์ของบิตคอยน์แทนผู้ใช้เพื่อแลกกับความสะดวกสบาย เราจึงไม่แนะนำให้เก็บ บิตคอยน์จำนวนมากบนระบบของบุคคลที่สาม
- Hardware Signing Devices: อุปกรณ์สำหรับเซ็นดิจิทัลเป็นอุปกรณ์ที่สามารถจัดเก็บคีย์และเซ็นธุรกรรมโดยใช้ฮาร์ดแวร์และเฟิร์มแวร์เฉพาะทาง ซึ่งโดยทั่วไปแล้วจะเชื่อมต่อกับกระเป๋าเงินเดสก์ท็อป มือถือ หรือเว็บ ผ่านสาย USB การสื่อสารระยะใกล้ (NFC) หรือกล้องที่รองรับ QR code แต่เนื่องจากการดำเนินการที่เกี่ยวข้องกับบิตคอยน์ ทั้งหมดถูกจัดการบนฮาร์ดแวร์เฉพาะ อุปกรณ์เหล่านี้จึงปลอดภัยจากการโจมตีหลายรูปแบบ อย่างไรก็ตาม อุปกรณ์เซ็นดิจิทัลมักถูกเรียกว่า hardware wallet แต่ต้องใช้งานร่วมกับกระเป๋าเงินที่มีฟีเจอร์ครบครันเพื่อส่งและรับธุรกรรม ความปลอดภัยและความเป็นส่วนตัวที่ได้จากกระเป๋าเงินที่ใช้งานร่วมกันก็มีบทบาทสำคัญต่อความปลอดภัยและความเป็นส่วนตัวโดยรวมของผู้ใช้อุปกรณ์เซ็นดิจิทัล
ประเภทของการเชื่อมต่อกับโปรโตคอลของบิตคอยน์
- Full node: บิตคอยน์ฟลูโหนดเป็นโปรแกรมที่ตรวจสอบความถูกต้องของประวัติธุรกรรมทั้งหมดของบิตคอยน์ (ทุกธุรกรรมที่เคยเกิดขึ้นโดยผู้ใช้ทุกคน) และนอกจากนี้ บิตคอยน์ฟลูโหนดยังสามารถเลือกเก็บข้อมูลธุรกรรมที่ได้รับการตรวจสอบแล้วก่อนหน้า และให้บริการข้อมูลแก่โปรแกรมบิตคอยน์อื่น ๆ ได้ ไม่ว่าจะเป็นบนคอมพิวเตอร์เดียวกันหรือผ่านอินเทอร์เน็ต แต่แม้ว่าบิตคอยน์ฟลูโหนดเองก็ใช้ทรัพยากรคอมพิวเตอร์ในปริมาณมาก (ประมาณเท่ากับการดูวิดีโอสตรีมมิ่งหนึ่งชั่วโมงต่อวันสำหรับธุรกรรมบิตคอยน์ในแต่ละวัน) บิตคอยน์ฟลูโหนดเองก็มอบความเป็นอิสระอย่างสมบูรณ์แก่ผู้ใช้
- Lightweight Client: lightweight client หรือที่เรียกกันอีกชื่อว่าไคลเอนต์การตรวจสอบการชำระเงินแบบง่าย (Simplified-Payment-Verification: SPV) ซึ่งจะเชื่อมต่อกับโหนดแบบเต็มหรือเซิร์ฟเวอร์ระยะไกลอื่น ๆ เพื่อรับและส่งข้อมูลธุรกรรมของบิตคอยน์แต่เก็บกระเป๋าเงินของผู้ใช้ไว้ในเครื่อง โดยสามารถตรวจสอบธุรกรรมที่ได้รับบางส่วน และสร้างธุรกรรมขาออกอย่างอิสระอีกด้วย
- ไคลเอนต์ API ของบุคคลที่สาม (Third-Party API Client): ไคลเอนต์ API ของบุคคลที่สามเป็นโปรแกรมที่เชื่อมต่อกับระบบบิตคอยน์ผ่าน API ของบุคคลที่สาม แทนที่จะเชื่อมต่อกับเครือข่ายบิตคอยน์โดยตรง กระเป๋าเงินนี้อาจถูกจัดเก็บโดยผู้ใช้เองหรือบนเซิร์ฟเวอร์ของบุคคลที่สาม แต่ไคลเอนต์จะต้องไว้วางใจเซิร์ฟเวอร์ระยะไกลในการให้ข้อมูลที่ถูกต้องและปกป้องความเป็นส่วนตัวของตน
บิตคอยน์เป็นเครือข่ายแบบเพียร์ทูเพียร์(Peer-to-Peer หรือ P2P) โดยที่บิตคอยน์ฟลูโหนด ทำหน้าที่เป็นเพียร์ในเครือข่าย เพียร์แต่ละตัวจะตรวจสอบความถูกต้องของธุรกรรมที่ยืนยันแล้วทุกธุรกรรมอย่างอิสระ และสามารถให้ข้อมูลที่เชื่อถือได้แก่ผู้ใช้ Lightweight Wallets และซอฟต์แวร์อื่น ๆ เองก็เป็นลูกข่ายที่ต้องพึ่งพาเพียร์หนึ่งหรือหลายตัวในการรับข้อมูลที่ถูกต้อง ไคลเอนต์สามารถตรวจสอบข้อมูลบางส่วนที่ได้รับเพิ่มเติมและเชื่อมต่อกับเพียร์หลายตัวเพื่อลดการพึ่งพาเพียร์ตัวเดียว แต่ในท้ายที่สุดความปลอดภัยของไคลเอนต์ยังคงขึ้นอยู่กับความน่าเชื่อถือของเพียร์ที่เชื่อมต่อด้วย
ใครควบคุมคีย์
อีกหนึ่งในประเด็นสำคัญที่ควรพิจารณาเพิ่มเติมคือใครเป็นผู้ควบคุมคีย์ (Private key) เนื่องจากเป็นสิ่งที่มีบทบาทสำคัญในการควบคุมการเข้าถึงบิตคอยน์ โดยคีย์เหล่านี้เองเปรียบเสมือน PIN ที่ยาวมาก ซึ่งหากคุณเป็นผู้ควบคุมคีย์ของคุณเองด้วยตัวเอง คุณก็เป็นผู้ควบคุมบิตคอยน์ของคุณด้วยเช่นกัน แต่หากไม่ใช่ ก็จะแปลว่ากุญแจเหล่านั้นจะถูกดูแลโดยบุคคลที่สาม ซึ่งจะเป็นผู้จัดการเงินของคุณในนามของคุณ
ซอฟแวร์ในการจัดการกุญแจนั้นถูกแบ่งออกเป็นสองประเภทหลัก ๆ คือ wallet ที่คุณจำเป็นต้องดูแลคีย์ของตัวเองและ บัญชีที่มีผู้ดูแล (Custodian Accounts) ซึ่งจะมีบุคคลที่สามเป็นผู้ควบคุมกุญแจ
“Your keys, your coins. Not your keys, not your coins.”
มาอยู่ตัวอย่างเพื่อความเข้าใจที่มาขึ้นกันเถอะ
สมมุติว่าอลิซเป็นผู้ใช้งานที่ไม่ได้เชี่ยวชาญด้านเทคนิค และเพิ่งได้ยินเกี่ยวกับบิตคอยน์จากเพื่อนสนิทของเขา โจ ระหว่างปาร์ตี้ โจกำลังอธิบายเกี่ยวกับบิตคอยน์อย่างกระตือรือร้นให้ทุกคนฟังและสาธิตวิธีการใช้งานต่าง ๆ ให้ดู อลิซเองได้มีความสนใจในบิตคอยน์หลังจากได้ฟังโจอธิบาย จึงได้ถามโจว่าเธอจะเริ่มต้นใช้งานบิตคอยน์ได้อย่างไร โจจึงแนะนำให้อลิซดาวน์โหลด Mobile wallet ตัวโปรดของเขาเนื่องจากมันเหมาะสมกับมือใหม่ อลิซจึงดาวน์โหลดและติดตั้งแอปพลิเคชันกระเป๋าเงินที่โจแนะนำบนโทรศัพท์ของเธอ
เมื่ออลิซเปิดแอปพลิเคชันครั้งแรก เธอได้เลือกสร้างกระเป๋าใหม่และเนื่องจากกระเป๋าที่เธอเลือกนั้นเป็นแบบที่ไม่ได้อยู่ภายใต้การควบคุมบุคคลที่สาม (Noncustodial Wallet) อลิซจึงเป็นผู้ควบคุมคีย์เพียงคนเดียว ซึ่งหมายความว่าเธอต้องรับผิดชอบในการสำรองข้อมูลด้วยตัวของเธอเอง และหากเธอได้ทำคีย์สูญหายไป เธอจะไม่สามารถเข้าถึงบิตคอยน์ของเธอได้อีกไปตลอดกาล และเพื่อเพื่อช่วยในเรื่องนี้ Bitcoin wallet ต่าง ๆ จึงมักจะสร้างรหัสการกู้คืน (Recovery Code) ให้ซึ่งสามารถใช้ในการกู้คืน Bitcoin wallet อันนั้น ๆ
Recovery Code (รหัสในการกู้คืน)
Bitcoin wallet แบบที่ไม่ได้อยู่ภายใต้การควบคุมของบุคคลที่สามนั้นส่วนใหญ่จะให้รหัสการกู้คืนแก่ผู้ใช้งานเพื่อสำรองข้อมูล และรหัสการกู้คืนนี้มักประกอบด้วยตัวเลข ตัวอักษร หรือคำที่ถูกเลือกแบบสุ่มโดยซอฟต์แวร์ และใช้เป็นพื้นฐานสำหรับการสร้าง Bitcoin wallet โดยแต่ละยี่ห้อก็อาจมีความแตกต่างกัน เช่น

รหัสการกู้คืนมักเรียกว่า "mnemonic" หรือ "mnemonic phrase" หรือในภาษาไทยว่าวลีช่วยจำ ซึ่งบ่งบอกว่าคุณควรจดจำวลีนั้น แต่การจดวลีนี้ลงบนกระดาษใช้เวลาน้อยกว่าและมักจะเชื่อถือได้มากกว่าความจำของคนส่วนใหญ่ เพราะฉนั้นผมเลยแนะนำว่าจดเถอะ จะได้ไม่เกิดปัญหาที่ไม่คาดคิดในอนาคต
หาก bitcoin wallet ของอลิซมีปัญหา เธอสามารถดาวน์โหลดซอฟแวร์ใหม่และใส่รหัสในการกู้คืนลงไป เพื่อสร้างฐานข้อมูลของ bitcoin wallet ใหม่ที่บันทึกธุรกรรมบนเชนทั้งหมดที่เธอเคยรับหรือส่ง แต่อย่างไรก็ตาม การกู้คืนจากการใช้รหัสการกู้คืนเพียงอย่างเดียวนั้นอาจจะไม่สามารถกู้คืนข้อมูลเพิ่มเติมที่อลิซเคยบันทึกไว้ใน wallet นั้น ๆ ได้ เช่น ป้ายกำกับที่เธอเชื่อมโยงกับที่อยู่หรือธุรกรรมต่าง ๆ แม้ว่าการสูญเสียข้อมูลเมตานี้จะไม่สำคัญเท่ากับการสูญเสียเงิน แต่ก็ยังมีความสำคัญในบางแง่มุม เช่น หากคุณต้องตรวจสอบรายการธนาคารหรือบัตรเครดิตเก่า แต่ชื่อของผู้ที่คุณชำระเงินหรือผู้ที่จ่ายเงินให้คุณถูกลบออกไป ดังนั้นเพื่อป้องกันการสูญเสียข้อมูลเมตา wallet หลาย ๆ ยี่ห้อจึงมีฟีเจอร์สำรองข้อมูลเพิ่มเติมนอกเหนือจากรหัสการกู้คืน
สำหรับ wallet บางประเภทนั้น ฟีเจอร์สำรองข้อมูลเพิ่มเติมนี้ถือว่ามีความสำคัญมาก เนื่องจากการชำระเงินเงินด้วยบิตคอยน์จำนวนมากในปัจจุบันทำผ่านเทคโนโลยีที่อยู่นอกเชน (Offchain) ซึ่งธุรกรรมไม่ได้ถูกบันทึกลงในบล็อกเชนสาธารณะ เนื่องจากการชำระเงินแบบนี้ช่วยลดค่าใช้จ่ายของผู้ใช้และเพิ่มความเป็นส่วนตัวได้บ้าง แต่นั่นก็หมายความว่ากลไกอย่างรหัสการกู้คืนที่พึ่งพาข้อมูลบนเชนไม่สามารถรับประกันการกู้คืนบิตคอยน์ทั้งหมดของผู้ใช้ได้ ดังนั้นสำหรับแอปพลิเคชันที่รองรับการใช้งาน Offchain การสำรองข้อมูลฐานข้อมูล wallet บ่อยครั้งจึงเป็นสิ่งที่มีความสำคัญมาก
นอกจากนี้ เมื่อได้รับบิตคอยน์ครั้งแรกใน moblie wallet หลาย ๆ wallet มักจะตรวจสอบอีกครั้งว่าคุณได้สำรองรหัสการกู้คืนไว้อย่างปลอดภัยแล้ว การตรวจสอบนี้อาจเป็นเพียงการแจ้งเตือน หรืออาจถึงขั้นให้ผู้ใช้ป้อนรหัสนั้นซ้ำด้วยตัวเอง
คำเตือน แม้ว่า Bitcoin Wallet หลาย ๆ ตัวอาจจะมีการให้คุณต้องกรอกรหัสในการกู้คืนใหม่ในบางกรณี แต่มันก็มักจะมีแอปพลิเคชันมัลแวร์จำนวนมากที่เลียนแบบการออกแบบของ wallet ต่าง ๆ โดยมันจะบังคับให้คุณป้อนรหัสการกู้คืน จากนั้นมันจะส่งรหัสที่ป้อนไปยังผู้พัฒนามัลแวร์เพื่อขโมยบิตคอยน์ของคุณ นี่เปรียบเสมือนเว็บไซต์ฟิชชิงที่พยายามหลอกให้คุณให้รหัสผ่านธนาคารของคุณ สำหรับ Bitcoin wallet ส่วนใหญ่ เวลาที่พวกเขาจะขอรหัสการกู้คืนคือในระหว่างการตั้งค่าเริ่มต้น (ก่อนที่คุณจะได้รับบิตคอยน์) และระหว่างการกู้คืน (หลังจากที่คุณสูญเสียการเข้าถึง wallet เดิม) หากแอปพลิเคชันขอรหัสการกู้คืนในช่วงเวลาอื่น คุณควรปรึกษาผู้เชี่ยวชาญเพื่อให้แน่ใจว่าคุณไม่ได้ตกเป็นเหยื่อของการฟิชชิง
Bitcoin Addresses (ที่อยู่ในการรับหรือส่งบิตคอยน์)
ในตอนนี้อลิซพร้อมแล้วสำหรับการสร้าง Bitcoin wallet ใหม่ของเธอ Bitcoin wallet ที่เธอเลือกได้ทำการสร้าง private key แบบสุ่มให้เธอ ซึ่งจะเชื่อมโยงกับ Bitcoin Address ทั้งหมดที่มีใน Bitcoin wallet ของเธอ แต่ ณ ขณะนี้ยังไม่มีใครรู้ Bitcoin address ของเธอ (แม้แต่ Bitcoin network ก็ไม่รู้) นอกจากตัวเธอเอง Bitcoin address เหล่านี้เป็นเพียงตัวเลขที่เชื่อมโยงกับ Private key ของเธอ ซึ่งเธอสามารถใช้ควบคุมการเข้าถึง Bitcoin ใดกระเป๋าได้ Bitcoin address เหล่านี้ถูกสร้างขึ้นโดยอิสระจากกระเป๋าของเธอโดยไม่ต้องอ้างอิงหรือเชื่อมต่อกับบริการใด ๆ
คำแนะนำ: Bitcoin address และ Invoice นั้นมีหลากหลายรูปแบบที่แตกต่างกัน และทั้งหมดนี้สามารถแชร์ให้กับคนอื่น ๆ ได้ เพื่อเป็นการอณุญาติให้พวกเขาส่งบิตคอยน์เข้ามาในกระเป๋าคุณตรง ๆ คุณสามารถแชร์ Bitcoin address และ Invoice ให้คนอื่นได้โดยไม่ต้องกังวลเกี่ยวกับความปลอดภัยของบิตคอยน์ของคุณ เนื่องจากผู้ที่รู้ Bitcion address ของคุณไม่สามารถถอนเงินออกจาก address นั้น ๆ ได้แม้เขาจะสามารถรู้จำนวนเงินใน address นั้น ๆ ก็ตาม เพราะฉะนั้นเพื่อปกป้องความเป็นส่วนตัวของคุณ คุณจึงควรสร้าง Invoice จาก Bitcoin address ใหม่ทุกครั้งที่จะส่งให้ผู้อื่น
-
 @ 592295cf:413a0db9
2024-11-30 08:33:35
@ 592295cf:413a0db9
2024-11-30 08:33:35Week 25 11
Vitor created another social network edit mode. There are countless cases of use. But type threads are possible, small books, Rabbit hole and those who put it more.
nostr:nevent1qvzqqqqqqypzq3svyhng9ld8sv44950j957j9vchdktj7cxumsep9mvvjthc2pjuqyghwumn8ghj7mn0wd68ytnhd9hx2tcqyrewvkqwqt7urn2u9h5tk88vj9p3csl0wt08aqd8kxsngxtdmr0zqmszxds
Nostr Report is missing, was a lot of news, 20 notes in a day.
Some news do not need resonance case, Primal did a good job with trending. Of course is a centralized service. But it was one of the Twitter features, he did it with the top trending hashtags. Now Primal is more focused on DVM smart feed, read, and Discovery. This will bring chaos, as long as you can switch the trend feed with your Algo or DVM Algo. I'm obsessed with these switches 😅
Hostile people can happen along the way, it's not like in Bluesky 😔.
Someone share on Bluesky https://bsky.app/profile/laurenshof.online/post/3lbrsjzobps2u Video is this https://audiovisual.ec.europa.eu/fr/video/I-264553?lg=en
Trying to convince someone for Unanimity, Relay groups are nice, but Unanimity is simpler.
nostr:nevent1qqs9ar5t9xu97nhtwef9ej2y7cklnysf7hgwce7t2wk5axhfdwuq5sqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qmzyp990kgskujdyplzydmd08ft42mkkfg4lzldaap8ng7n2u3kmss8l76e
Game on Nostr on 2025, cool be.
Angor are finally ready, crowdfunding with Nostr and Bitcoin. (alpha test)
nostr:nevent1qvzqqqqqqypzqw4hcggg2f9h68qutp0snsdhux20teljykjmh9rlx78qwnt5a8dlqqstte0g54hfa2cmr63vq4ava7e7wsr483p63tylvut8cvufzs44a0cd6saa3
PR 1600
The name is curated pubblication use kind 30040 e 30041, 30040 Is the envelope and 30041 are chapters or paragraphs. We'll see what's left in a month. There are no big discussions until now. This is the basis to leave it so, if you can improve it without breaking it ok. I think liminal is preparing at least two other NPs. The bottom problem is that there are no "competitor", someone else outside who wants to use this thing. But if there are no one can invent.
You can't do things with others. There's too "bad" people. Keep calm is a toxin environment. Maybe you have to get away a bit.
I was trying to help David but there are no aggregators for neo4j Nostr. Dustin's example, I think it's only worth the DVM. There are two other projects one grain of Oceanslim I saw the video where he explains some things, with Dr. Morales. And the other is Cody's Nostr Relay tray. At least you have all the data in a Relay, and for that Relay you can query, I don't think you find anything significant, maybe you need 100(k) notes to have a good sample. I think I'll make the update. I downloaded two months ago, it worked for a while with Nostrudel, then only with next, lately some problems with next. Cody launched the project with fiatjaf and I think it is also implemented here. In the end, I don't think this answer is useful to David.
Zapview nostr-zap-view The lokuyow project, always attentive to zap lightning and Nostr.
Give a "microsat" to Fiatjaf nostrabia relay
I managed to send a zap from a hex known id, it only works with getalby, so until January 4th. I have to prove if other lnurls have the call.
Something I might have understood about the new version of Nostr_sdk or rust Nostr. Sending messages will be harder. The builder does not support the tag, it breaks almost all the scripts I was writing and to verify them you can do nothing but send to the Relays, I wait a few days if there are news, but I don't think there will be. It is no longer linked to the table of examples so it will not be updated presumably, I would like to continue, as the cli does not come out. That then the cli will be in python 12.. (I'm still in version 3.10.9 of python)
I've seen bulletin proof, posting on Nostr seems interesting, but they need many interactions to have a functioning client. link, stacker news
Nostr nuance, login, Nostr connect, private. (two Notes)
nostr:nevent1qvzqqqqqqypzq77777lz9hvwt86xqrsyf2jn588ewk5aclf8mavr80rhmduy5kq9qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qpqqqqz3757ha8j5xcm7er8kkdc0dgtvmy55dz2t2d7c2tv9h8qm88qlcjsls
nostr:nevent1qvzqqqqqqypzq9eemymaerqvwdc25f6ctyuvzx0zt3qld3zp5hf5cmfc2qlrzdh0qyt8wumn8ghj7ur4wfcxcetjv4kxz7fwvdhk6tcpzpmhxue69uhkummnw3ezumt0d5hsqgz98qckr40flhpyt48fxqjkuf9p4dv245634ygvp6dfu2kt7qk5egqmc4l8
An other microsat to Fiatjaf chronicle relay
Kind 1 was a mistake and many people are realizing it, they are replacing it. Kind 5 now it is only almost to eliminate drafts, here the option is to overwrite.
That's all!!
-
 @ e373ca41:b82abcc5
2024-11-25 10:32:49
@ e373ca41:b82abcc5
2024-11-25 10:32:49Article by Milosz Matuschek, first published on "Freischwebende Intelligenz".
When Michael Ende wrote his novel “Momo”, which is much more than a children's book, he had given a lot of thought to alternative monetary systems. The writer knew that the question of the monetary system shapes and changes culture. Money is made by people, so it is also in the hands of people to rethink and change money. And thus give the world a new face. This is what Bitcoin is all about at its core: giving the world a new face. And we are on this threshold right now. Now.
What is Bitcoin actually?
If you are just starting to get to grips with Bitcoin, you are in for a particularly enriching experience: Namely, the realization that the wealth opened up by Bitcoin is not material, but spiritual and intellectual in nature. Bitcoin is capable of breaking down the boundaries of thought, opening up new channels of reality and paving the way for social transformation. On the other hand, those who stick primarily to the price curves may overlook precisely this transformative power in the daily ups and downs.
So what is Bitcoin? A cryptocurrency? Yes, but not only, because forms of money that make use of encryption technology existed before and still exist today in many cases parallel to Bitcoin. Bitcoin's currency function is just one of many facets. It is perhaps not even the most exciting and practicable.
Rather, Bitcoin is a multidimensional phenomenon, like an onion with several layers. But it is unique in its own way and has so far only been copied many times but never equaled. In short: there is Bitcoin and then there is nothing for a long time.
There are at least two ways to approach Bitcoin. Of course, you can try to understand Bitcoin by a) reading the famous white paper by the anonymous initiator “Satoshi Nakamato”, a kind of revolutionary instruction manual for nerds. Or b) following the extremely poor reporting in the mainstream media, where you mainly learn that the price has just fallen again (mostly that) or has just risen (they somehow don't like to report that).
So let's try a third, somewhat less confusing alternative: let's approach Bitcoin in an unconventional way, namely using phenomena that we already know.
A language
Money is like language and language is like money. Money is a means of communication about values that has grown from below, not imposed from above. “Caesar non supra grammaticos”, the emperor is not above language, was already known in ancient Rome. The fact that money is based on a convention was demonstrated by the economist Carl Menger at the end of the 19th century in his book “The origin of Money”. According to this, money can be anything that is designated as such by agreement.
However, the idea remained in people's minds that money, because it was linked to power, had to be a kind of state brand. Like an anthem or a flag. The monetary system thus represents a blind spot in the history of human emancipation. People got rid of emperors, churches and ideologies, but when it came to the question of money production, they said to themselves: we don't know anything about that, let's leave it to a banking monopoly and the governments. With fatal consequences. The fiat money system ended up biting itself in the tail.
The price of this timidity: a bloated financial sector, fiscal excesses, costly wars, hyperinflations, currency reforms, creeping or abrupt expropriations. No state paper currency has survived in the long term. The bullshit filter of history shows: Governments are the worst possible currency managers. Fiat currencies are dinosaurs that were never allowed to die and have been kept alive again and again in cloned form. But Bitcoin is the approaching meteorite.
Because the question that Bitcoin raises is: what if money, like language, can be decoupled from the state in such a way that no one person can corrupt the process? It would be an act of rebellion, of disobedience against the current monetary system, for sure. It would also be an act of enlightenment. The exit from a monetary immaturity that is self-inflicted because it has never been questioned. Bitcoin is a cross between virtual numismatics and Esperanto. But an Esperanto that is spoken millions of times over.
As in language, cacophony or linguistic confusion is a hindrance to communication. Once a standard has been found, it is maintained. The Internet still runs on the old TCP/IP protocol. Changing standards is rare. Bitcoin, as the first functioning alternative to the fiat money system, has become its own standard. Bitcoin is now probably too big and too important to be seriously threatened by a competitor. Bitcoin has moved beyond the so-called focal point or Schelling point.
An organism
Bitcoin is like an organism, comparable to a life form that is particularly resilient, reproduces, interacts, nourishes itself and is designed for a long lifespan, like a fungus. Fungi are one of the oldest life forms on our planet. And they are extremely resilient, otherwise they would not have survived for 1 billion years. Fungi are networks of communication. They play an important role in nature in the decomposition of dead materials.
https://www.youtube.com/watch?v=uTgDQ56Su38
Bitcoin feeds on decaying, modernizing fiat currencies that are ultimately doomed. With each participant, the network becomes stronger, more practicable, more resilient. According to Metcalfe's law from network theory, the benefit of a communication system increases proportionally with the number of participants. Bitcoin is growing rapidly.
A technology
The good thing about technologies is that they do not negotiate. A technology is either better, in which case it will prevail, or it will not. But if it prevails, it does so in a brute force manner. It simply makes the old look old. An exodus begins, first sparsely as an experiment by a few, then by “early adopters”, and finally by popularization in the mainstream. The breakthrough of a technology initially looks like a small wave and only at the end does it become apparent that it is actually a tsunami that buries everything old and leaves no stone unturned.
Technology brings paradigm shifts from time to time. That is why Bitcoin cannot be adequately described in the currency category. The automobile made even the fastest horse look slow. The cell phone made phone booths look like relics from the Stone Age. Bitcoin is superior to fiat money in every respect. Technological revolutions know no pardon, no turning back. The Lindy effect roughly states that a technology that survives ten years will also survive the next ten years. Bitcoin was launched in 2009 and will soon be entering puberty, with all the ups and downs that come with human development.
In technology, we talk about Gartner hype cycles. The adoption of a new technology does not take place in a linear fashion, but rather in a series of sharply fluctuating curves. Bitcoin is a technological change whose acceptance comes with a price tag that can be tracked every second. Since the beginning, Bitcoin has been in a constant price discovery mode.
A new asset class
All central bank currencies in the world are fiat currencies, i.e. not backed by anything other than the promise of politicians that they are stable and trustworthy. In fact, the money supply is being increased in an inflationary manner, the value of money is constantly falling, and the political target is a 2% loss of purchasing power per year. In plain language, this means that the money you earn today will buy 40% less in 20 years' time. At least. Actual money devaluation is way higher. Call it a form of expropriation if you like. So the money we use has something of an expiry date. It is getting worse. It has a leak in terms of purchasing power, in terms of value.

Bitcoin plugs this leak by performing the opposite function. The quantity of Bitcoin is mathematically limited to 21 million Bitcoin from the outset. These bitcoins are created in the network through the mining process. This is an energy-intensive process that makes the network particularly secure and for which a miner receives a reward in the form of Bitcoin. Initially, it was 50 Bitcoin every ten minutes for the miner who correctly calculated the cryptographic code (hash) for the next block. Now it is only 6.25 Bitcoin. In 2024, this figure halved again and so on. Bitcoin is therefore a deflationary asset class.
Bitcoin is designed to eventually become harder money than gold, of which only a certain amount can be created each year. This also makes Bitcoin a very “inelastic” asset class, which means that you cannot produce more of it if demand increases, as is possible to a limited extent with gold. As the supply remains the same, an increase in demand is sometimes reflected in explosive price increases.
More and more companies are currently buying Bitcoin in order to invest their cash reserves to preserve purchasing power. The company Microstrategy holds several billion dollars in Bitcoin, and Tesla also bought Bitcoin worth 1.5 billion a few months ago. El Salvador has declared Bitcoin the national currency and bought Bitcoin. Other countries want to follow suit. At this point, you don't have to be an investment genius to understand that a “land run” is imminent.
A currency
Bitcoin combines all the functions of currencies (unit of account, medium of exchange, store of value), but has significantly increased its purchasing power compared to fiat currencies. Bitcoin can be used as a currency, even in everyday life, even if the Bitcoin blockchain is not primarily designed to process a large number of transactions. However, this can be compensated for by low-cost, parallel systems such as the Lightning Network.
Whether Bitcoin will also establish itself as a means of payment in everyday life or remain primarily an effective store of value that is ultimately superior to gold is currently an open, intensively debated question. Since the exchange of Bitcoin into possibly more practical forms of payment, even a crypto prepaid card, is a matter of seconds, the question of whether Bitcoin is suitable as a currency is ultimately irrelevant for its mainstream acceptance.
Also, why pay with an asset that appreciates in value? According to Gresham's law, which goes back to an ancient parable, bad money is spent and good money is hoarded. This means that the volatility of Bitcoin is ultimately more of a bugbear for Bitcoin opponents. Bitcoin can also be exchanged for a more stable form of currency shortly before the act of purchase.
A system of accounting
Bitcoin is a payment network and an asset class. Or to put it another way: an asset class that has its own uncensorable distribution channel, the blockchain. Gold, on the other hand, is like a train that relies on the tracks of others to get from A to B. The Bitcoin network is therefore a booking system on the internet whose bookings cannot be reversed or changed retroactively, as only users communicate with users on this network. There is no guardian of the blockchain or any central authority. The transactions are grouped together in blocks and attached to each other using cryptographic means, creating a block chain or blockchain.
At first glance, the idea of a booking system sounds boring. However, it is probably the most overlooked revolution that Bitcoin has initiated. Because before Bitcoin, there were only two other forms of bookkeeping: first, simple bookkeeping, in which only one entity (the king, ruler, an authority?) kept a ledger of debts and could enter or remove debtors at will. Thousands of years later, double-entry bookkeeping followed, in which two parties kept records of transactions. This dates back to the Renaissance and enabled the rise of Venice as a global trading power, to which the Medici cleverly linked their banking system.
500 years later, Bitcoin is now the evolution of bookkeeping in a threefold form. Each participant keeps a record of which transaction takes place from where to where, for example from participant A to B. In addition, the transaction can be traced by anyone in the blockchain accounting system, even if not under a clear name. Pseudonymized addresses that can be assigned to individuals communicate. One look at the blockchain is enough to ensure that there is always consensus and clarity about the asset situation in the network. The booking system is more than just an account book. It is also a machine of truth.
A cult
Money, faith and religion are related. Gold has been worshipped for thousands of years, and the dance around the golden calf is perhaps inseparable from the sober side of money as an everyday object. Money has something messianic about it, it saves, even if only from the burden of debt, which in the context of religion is not far removed from the forgiveness of sins.
Questions of money are always about questions of real value. This perhaps almost inevitably gives rise to a “pure doctrine” as opposed to alternative doctrines. The history of alchemy is a good example of this: one figure in whom many disciplines culminated was Isaac Newton. He was an alchemist and at the same time one of the first scientists of the modern age. At times, he even acted as the guardian of the currency in England, presided over the English mint and brought counterfeiters to the scaffold. Bitcoin also uses the narrative of the promise of salvation to spread as an idea in people's minds. There is now a well-branched Bitcoin propaganda network in the form of memes and pictures.
An idea whose time has come
How should we weigh these seven elements? Is Bitcoin a tech cult with digital fake gold, a new edition of alchemy, as many central bankers or critics would like it to be? Or is it actually a technological advancement of the idea of money with potentially epochal effects on the entire financial system? Somewhere in the matrix of these seven elements, perhaps the truth is hidden.
What Bitcoin is certainly not is a universal savior. Bitcoin is a vehicle for change, but it relies on the cooperation of the network's participants. Anyone who believes that far-reaching changes in the financial system and society will occur automatically just because a few people speculate with cryptos is likely to be mistaken. Bitcoin is certainly not perfect either. However, the ideas behind Bitcoin, such as decentralization, consensus building, the incentive system for network-friendly behavior in mining and much more can serve as positive role models for other areas that should also be reformed. However, Bitcoin is neither a perpetual motion machine for quick riches nor a jack-of-all-trades.
Anyone looking for a perfect investment that is easy to use, moral in every respect, environmentally friendly, mindful and fair will find little in this world that will satisfy them, whether it's farmland, gold or, oh yes, the ever so environmentally friendly “petro-dollar”. Yes, mining Bitcoin is energy-intensive, but a large part of it is now obtained from renewable energy sources and Bitcoin is still less energy-intensive than the banking system. Yes, the price is volatile and will remain so for a long time, but that is probably still better than sitting on safely decaying government money.
Let's not kid ourselves: Bitcoin will still face some resistance from the established financial system and central banks. But Bitcoin is fighting its way into the consciousness of mankind, because there are not many alternatives if you want to protect your purchasing power from the central banks' weapon of mass destruction and their expansion of the money supply.
Bitcoin is an idea whose time has come. And according to the writer Victor Hugo, not even an army can stop it. Conversely, however, Bitcoin could stop armies, because once Bitcoin has established itself, states could no longer rely on the money printing press to finance cost-intensive wars.
That would be the best function that Bitcoin could have.
Almost too good to be true.
-- Join the marketplace of ideas! Sound money and sound information should finally be in the hands of the people, right? We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 6d8e2a24:5faaca4c
2024-11-30 00:07:10
@ 6d8e2a24:5faaca4c
2024-11-30 00:07:10Why do people enjoy pain and a short time pleasure, which could ruin their life and peace?
Why can't people leave their fleshy desires, obsession and pleasures even if it kills them?
Many have become slaves to their obsession having no will of theirs, claiming to be free yet imprisoned by their futility and lust.
We thought we have closed all the doors and windows, turn off the light so no one can see us, least so we thought to ourselves, forgetting our conscience is wide open, and God who sit in heaven watching, like it was never night nor dark, sees through us for he is light ruling over darkness.
The devil working upon our obsession making it a reality. The devil always uses our sinful, lustful desire to trick us given an end vain pleasure
We fall once, down with the guilt and pain of sin, the weight of the burden once thought, destroying the spirit and causing so many pains of regret, low self-esteem, and lack of confidence again.
He comes again not to bring new but to dwell in our past, bringing memories, mistakes, and errors making us feel more guilty and vulnerable, making us feel worthless and hopeless "We are doomed, so we think, God can't help us, our sins are too many; and with that, he finds a way to make us fall again, destroying us slowly till we are empty, having no will (stronghold).
Like a fire 🔥 lit in a bush, small as it is no one thought it could cause so much harm, or rather they thought they could control it or, put it off when they don't need it or, get bizarre.
Anything that has passed infantry allowed to grow is difficult or impossible to control so is a sin when is allowed to grow like a fire covering many areas is hard to put all areas off fast before one knows many areas are damaged many are beyond repairs
Every day we wake up, we plan how our lives, and how we are going to live the day, without the slimmest thought of contention, 'what if'. We do believe we have everything under control, everything planned out, but we forget that we are nothing but a sand timer that runs down so quickly than we thought.
Like the sand timer, our lives fade away gently, piece by piece till we cease to exist, only then, do we understand that we are rebels in this kingdom, not owners for we own nothing, with the dust reaching its last, the heartbeat and craves for more time, then we also understand, that time is never enough and time is so precious and priceless
Why do we always feel as if we have all the time in the world? why do we assume death to be a fairytale or a horror ghost story just to scare us out? Without having a sting.
Every day death proves more eager, the grave is so desperate that it looms looking and searching for any opportunity necessary to sting it stings.
But we are so carried away by life, deceived by what we have, the power, authority, and influence. We feel we are covered, yes we are but only to some certain extent. For life is so spiritual, than we could ever imagine or think of.
The night comes darkness looms over, evil rises, and fear grips one's heart, all wishing for the light. But now is no longer darkness that's so terrifying, but light itself has become as terrifying as the darkness, people wishing to live through the light, now wish the same to live through the night, for in it they find peace and comfort 😢
Why, I ask why, why has light become so terrifying and darkness become more comforting that the people find solace in it?
I came to understand why people find comfort in darkness is because they are afraid of selves afraid of what they have become, darkness does not challenge but rather allows you to wallow in your misery and regret, killing and draining you where no one will correct you or remind you, that you are not good enough, darkness gives you the room to accept who and what you have become, and there and then it echoes is better to die and live in peace than to be alive and live in misery.
Why will one think of death as the only option or think of death as the only solution to peace, is living not joyful, is life not great to live, why will one wish to leave all, family, friends everything, and settle for death?
I came to understand that, the most reason why one tends to choose death over life or loves to behold the warmth of darkness instead of light, is the feeling of emptiness and internal failure even after a significant measure, of material and social success, is a direct result of failure to discover purpose in life and a reason of being, when one loses his peace, joy all that's left or remain is pain, and regret. When a man reaches a stage of emptiness, where nothing else again matters life itself has no meaning, then it's only a test of time before destruction befalls such a person
Even the rich are depressed and frustrated beholding the enticement of the dark, and many try to drink themselves up, to them is the only way to find peace within, why, after so much wealth and achievement yet feel lonely, his greatest friends are alcohol and nights.
If money, riches cant give fulfillment or perfect peace then what can?
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 705605d9:b4324038
2024-12-13 17:38:32
@ 705605d9:b4324038
2024-12-13 17:38:32Вчера, 21 ноября, в деревне Бобровка, расположенной в одном из самых живописных уголков нашей страны, случился масштабный пожар, который уничтожил несколько домов и хозяйственных построек. Пожарные службы были оперативно направлены на место происшествия, но, несмотря на все усилия, огонь продолжал бушевать несколько часов. Установить точную причину возгорания оказалось задачей не из лёгких, однако, как стало известно, причиной пожара стала абсолютно невероятная и, на первый взгляд, абсурдная ситуация.
В деревне Бобровка местные жители утверждают, что причиной возгорания стал эксперимент с «горячей» новой разработкой – умным термосом, который, по задумке разработчиков, должен был поддерживать идеальную температуру напитков на протяжении суток. Однако, как выяснилось, термос оказался настолько «умным», что, не дождавшись своего «реального» срока эксплуатации, просто взорвался. По словам экспертов, устройство в какой-то момент решило провести «самодиагностику» и не выдержало своей собственной мощности, запустив цепную реакцию, которая привела к возгоранию.
Необычный инцидент, разумеется, сразу привлек внимание прессы, а местные жители стали активно обсуждать ситуацию, удивляясь, как такие инновации могут попасть в руки обывателей. «Когда я купила этот термос, мне казалось, что это просто удобный аксессуар для долгих прогулок с чаем. Но чтобы он так рванул, как граната, этого я не ожидала!» – рассказывает местная жительница, потерпевшая от огня.
Комментарий потерпевшего:
«Я никогда не думала, что мой любимый термос станет причиной такого бедствия. Он был подарком на день рождения, а я так гордилась им! Поставила на подоконник, чтобы чай остыл, и тут – бац! Всё вспыхнуло. Сначала я подумала, что это просто горячий чай, но когда увидела, что термос сам по себе светится, я поняла, что что-то пошло не так. Пожарные приехали быстро, но дом всё равно сгорел. Теперь я, честно говоря, боюсь пить чай в термосах, даже если они обещают быть умными!»

Местные власти заявили, что это происшествие станет поводом для пересмотра стандартов безопасности на рынке бытовых товаров. В ближайшее время планируется провести расследование и наложить запрет на использование «самодиагностирующих» устройств в бытовой сфере.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 06639a38:655f8f71
2024-11-01 22:32:51
@ 06639a38:655f8f71
2024-11-01 22:32:51One year ago I wrote the article Why Nostr resonates in Dutch and English after I visited the Bitcoin Amsterdam 2023 conference and the Nostrdam event. It got published at bitcoinfocus.nl (translated in Dutch). The main reason why I wrote that piece is that I felt that my gut feeling was tellinng me that Nostr is going to change many things on the web.
After the article was published, one of the first things I did was setting up this page on my website: https://sebastix.nl/nostr-research-and-development. The page contains this section (which I updated on 31-10-2024):
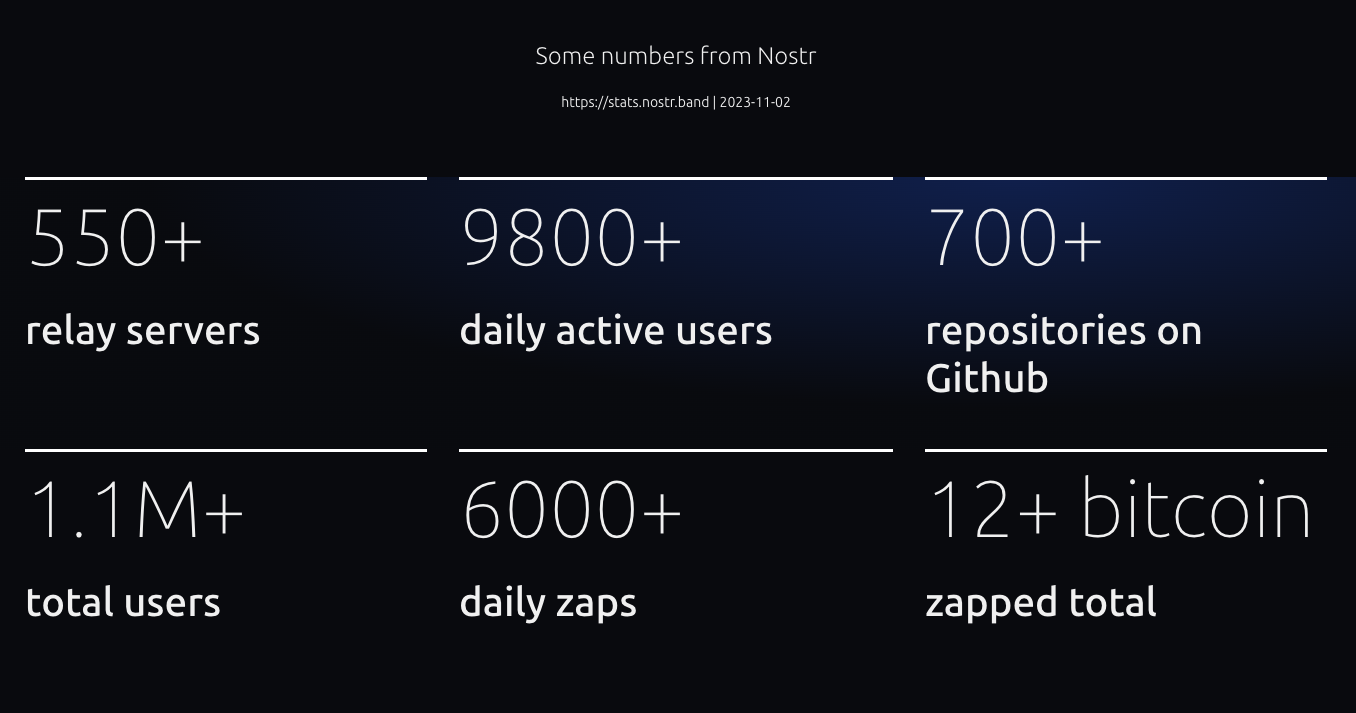
One metric I would like to highlight is the number of repositories on Github. Compared to a year ago, there are already more than 1130 repositories now on Github tagged with Nostr. Let's compare this number to other social media protocols and decentralized platforms (24-10-2024):
- Fediverse: 522
- ATProto: 159
- Scuttlebot: 49
- Farcaster: 202
- Mastodon: 1407
- ActivityPub: 444
Nostr is growing. FYI there are many Nostr repositories not hosted on Github, so the total number of Nostr reposities is higher. I know that many devs are using their own Git servers to host it. We're even capable of setting up Nostr native Git repositories (for example, see https://gitworkshop.dev/repos). Eventually, Nostr will make Github (and other platforms) absolute.
Let me continue summarizing my personal Nostr highlights of last year.
Organising Nostr meetups

This is me playing around with the NostrDebug tool showing how you can query data from Nostr relays. Jurjen is standing behind me. He is one of the people I've met this year who I'm sure I will have a long-term friendship with.OpenSats grant for Nostr-PHP


In December 2023 I submitted my application for a OpenSats grant for the further development of the Nostr-PHP helper library. After some months I finally got the message that my application was approved... When I got the message I was really stoked and excited. It's a great form of appreciation for the work I had done so far and with this grant I get the opportunity to take the work to another higher level. So please check out the work done for so far:Meeting Dries

One of my goosebumps moments I had in 2022 when I saw that the founder and tech lead of Drupal Dries Buytaert posted 'Nostr, love at first sight' on his blog. These types of moments are very rare moment where two different worlds merge where I wouldn't expect it. Later on I noticed that Dries would come to the yearly Dutch Drupal event. For me this was a perfect opportunity to meet him in person and have some Nostr talks. I admire the work he is doing for Drupal and the community. I hope we can bridge Nostr stuff in some way to Drupal. In general this applies for any FOSS project out there.
Here is my recap of that Drupal event.Attending Nostriga

A conference where history is made and written. I felt it immediately at the first sessions I attended. I will never forget the days I had at Nostriga. I don't have the words to describe what it brought to me.

I also pushed myself out of my comfort zone by giving a keynote called 'POSSE with Nostr - how we pivot away from API's with one of Nostr superpowers'. I'm not sure if this is something I would do again, but I've learned a lot from it.
You can find the presentation here. It is recorded, but I'm not sure if and when it gets published.Nostr billboard advertisement
This advertisment was shown on a billboard beside the A58 highway in The Netherlands from September 2nd till September 16th 2024. You can find all the assets and more footage of the billboard ad here: https://gitlab.com/sebastix-group/nostr/nostr-ads. My goal was to set an example of how we could promote Nostr in more traditional ways and inspire others to do the same. In Brazil a fundraiser was achieved to do something similar there: https://geyser.fund/project/nostrifybrazil.
Volunteering at Nostr booths growNostr

This was such a great motivating experience. Attending as a volunteer at the Nostr booth during the Bitcoin Amsterdam 2024 conference. Please read my note with all the lessons I learned here.
The other stuff
- The Nostr related blog articles I wrote past year:
- Run a Nostr relay with your own policies (02-04-2024)
- Why social networks should be based on commons (03-01-2024)
- How could Drupal adopt Nostr? (30-12-2023)
- Nostr integration for CCHS.social (21-12-2023)
- https://ccns.nostrver.se
CCNS stands for Community Curated Nostr Stuff. At the end of 2023 I started to build this project. I forked an existing Drupal project of mine (https://cchs.social) to create a link aggregation website inspired by stacker.news. At the beginning of 2024 I also joined the TopBuilder 2024 contest which was a productive period getting to know new people in the Bitcoin and Nostr space. - https://nuxstr.nostrver.se
PHP is not my only language I use to build stuff. As a fullstack webdeveloper I also work with Javascript. Many Nostr clients are made with Javascript frameworks or other more client-side focused tools. Vuejs is currently my Javascript framework I'm the most convenient with. With Vuejs I started to tinker around with Nuxt combined with NDK and so I created a starter template for Vue / Nuxt developers. - ZapLamp
This is a neat DIY package from LNbits. Powered by an Arduino ESP32 dev board it was running a 24/7 livestream on zap.stream at my office. It flashes when you send a zap to the npub of the ZapLamp. - https://nosto.re
Since the beginning when the Blossom spec was published by @hzrd49 and @StuartBowman I immediately took the opportunity to tinker with it. I'm also running a relay for transmitting Blossom Nostr eventswss://relay.nosto.re. - Relays I maintain
I really enjoy to tinker with different relays implementations. Relays are the fundamental base layer to let Nostr work.
I'm still sharing my contributions on https://nostrver.se/ where I publish my weekly Nostr related stuff I worked on. This website is built with Drupal where I use the Nostr Simple Publish and Nostr long-form content NIP-23 modules to crosspost the notes and long-form content to the Nostr network (like this piece of content you're reading).
The Nostr is the people
Just like the web, the web is people: https://www.youtube.com/watch?v=WCgvkslCzTo
the people on nostr are some of the smartest and coolest i’ve ever got to know. who cares if it doesn’t take over the world. It’s done more than i could ever ask for. - @jb55
Here are some Nostriches who I'm happy to have met and who influenced my journey in Nostr in a positive way.
- Jurjen
- Bitpopart
- Arjen
- Jeroen
- Alex Gleason
- Arnold Lubach
- Nathan Day
- Constant
- fiatjaf
- Sync
Coming year
Generally I will continue doing what I've done last year. Besides the time I spent on Nostr stuff, I'm also very busy with Drupal related work for my customers. I hope I can get the opportunity to work on a paid client project related to Nostr. It will be even better when I can combine my Drupal expertise with Nostr for projects paid by customers.
Building a new Nostr application
When I look at my Nostr backlog where I just put everything in with ideas and notes, there are quite some interesting concepts there for building new Nostr applications. Filtering out, I think these three are the most exciting ones:
- nEcho, a micro app for optimizing your reach via Nostr (NIP-65)
- Nostrides.cc platform where you can share Nostr activity events (NIP-113)
- A child-friendly video web app with parent-curated content (NIP-71)
Nostr & Drupal
When working out a new idea for a Nostr client, I'm trying to combine my expertises into one solution. That's why I also build and maintain some Nostr contrib modules for Drupal.
- Nostr Simple Publish
Drupal module to cross-post notes from Drupal to Nostr - Nostr long-form content NIP-23
Drupal module to cross-post Markdown formatted content from Drupal to Nostr - Nostr internet identifier NIP-05
Drupal module to setup Nostr internet identifier addresses with Drupal. - Nostr NDK
Includes the Javascript library Nostr Dev Kit (NDK) in a Drupal project.
One of my (very) ambitious goals is to build a Drupal powered Nostr (website) package with the following main features:
- Able to login into Drupal with your Nostr keypair
- Cross-post content to the Nostr network
- Fetch your Nostr content from the Nostr content
- Serve as a content management system (CMS) for your Nostr events
- Serve as a framework to build a hybrid Nostr web application
- Run and maintain a Nostr relay with custom policies
- Usable as a feature rich progressive web app
- Use it as a remote signer
These are just some random ideas as my Nostr + Drupal backlog is way longer than this.
Nostr-PHP
With all the newly added and continues being updated NIPs in the protocol, this helper library will never be finished. As the sole maintainer of this library I would like to invite others to join as a maintainer or just be a contributor to the library. PHP is big on the web, but there are not many PHP developers active yet using Nostr. Also PHP as a programming language is really pushing forward keeping up with the latest innovations.
Grow Nostr outside the Bitcoin community
We are working out a submission to host a Nostr stand at FOSDEM 2025. If approved, it will be the first time (as far as I know) that Nostr could be present at a conference outside the context of Bitcoin. The audience at FOSDEM is mostly technical oriented, so I'm really curious what type of feedback we will receive.
Let's finish this article with some random Nostr photos from last year. Cheers!





-
 @ e373ca41:b82abcc5
2024-11-21 09:50:06
@ e373ca41:b82abcc5
2024-11-21 09:50:06The last few years are unlikely to evoke positive associations for most people: corona madness, climate and trans ideology, a few wars in between and now the weather is also going crazy. You feel more reminded of the biblical plagues and the apocalypse than motivated to make positive changes to the system. It seems as if the world is in the hands of fanatical do-gooders and globalist social engineers. But the world is always in the hands of everyone. There is no responsibility for the future in the hands of some kind of “elite”, unless the citizens voluntarily leave it to them. Apocalypse literally means “unveiling”. In times of crisis, the core of reality is peeled out and all illusions fall away.
Golden times for system explorers
In turbulent times like these, unbreakable forest dwellers and resisters, prognosticators, esotericists and also system busters cavort. This is also a constant in history: times of crisis were often times of new beginnings. In knowledge revolutions, new knowledge inevitably mixed with new technology and also a new spiritual orientation towards the world. Before the outside world is created, it must be conceived internally. Around 500 years ago, the plague repeatedly cut new swathes through Europe, while at the same time Venice began its rise as a major trading power, the Medici banking system began to flourish and, a little later, so did art. This boom was preceded by something that at first glance seemed “boring”, such as the invention of double-entry bookkeeping by the monk Luca Pacioli at the end of the 15th century.
In the following century, the thinker Giordano Bruno moved from city to city in search of employment, and in the end, the system-breaker was burned as a heretic on the Campo de' Fiori in Rome. Meanwhile, astronomers, magicians, artists and alchemists bustled about at the court of the Habsburg Rudolf II in Prague. Some talked to angels, others tried their hand at producing gold. Those who ridicule alchemical experiments today as heresies should at least google how phosphorus and porcelain were discovered.
To be outmoded and unworldly means to be in search of something different. Great visionaries from Rudolf Steiner to Albert Einstein, Nikola Tesla and Richard Buckminster-Fuller have always known that the best way to change the system is to go outside the system and create something new from there. You don't change the old by fighting it. The best way to replace it is to think in new forms that make the old forms obsolete, said Buckminster-Fuller.
Brains moved the world more than the guillotine
Working on the old is like dancing with zombies. Creating the new, on the other hand, inevitably brings the old into competition with the system. If the new is better, the old system is obsolete. “Video killed the Radio Star” sang the Buggles in 1979 (the first clip of the MTV era) and they were just as right as Steve Jobs, who threw several industries overboard with the iPhone. What you previously needed 20 devices for, from dictation machines to telephones and “Walkmans”, you now had in your pocket. Thinking outside the system, which you don't learn within the system, combined with technology, is the sharpest knife in history when it comes to change. Brains moved more than the guillotine.
In today's world, everyone is a potential system changer. There has never been a time when the tools of change have been available to as many people as they are today. At the same time, we live in a time in which fewer people than ever before determine the fate of everyone. How does this fit together? There is an infinite systematic potential for change, and this lies solely with the people who have not yet made use of the available tools. But this wave is irreversibly set in motion; it is rolling and no one knows when it will turn into a tsunami. Free speech and critical journalism are under massive attack. With the Pareto Project we want to make censorship-resistant publishing the new standard. Today, we have the opportunity to consign the phenomenon of censorship to the landfill of history. Are you thinking along similar lines? What should the journalism of the future look like? Help us as a tester, migrate your content as a journalist or as a publication, support us as a developer or contribute your ideas: Kontakt@idw-europe.org
The great transformation
We are living in the midst of a quiet revolution, with quiet revolutionaries. Pavel Durov from Telegram would certainly have got on well with Giordano Bruno. Bitcoin inventor Satoshi Nakamoto might have felt at home at the court of Rudolf II in the past.
The path to change follows similar patterns of transformation. In the past, the power of the individual was seen as being sand in the gears of the system. “Man of labor, wake up! And recognize your power! All wheels stand still when your strong arm wills it,” wrote Georg Herwegh. Today, anyone can create their own little system. With Bitcoin, uncensorable money is already in circulation. The next big battle is over the uncensorability of information and it is currently underway. The best way to share centralized power, whether it's media power or a central bank cartel, is to distribute power through decentralized systems. This is essentially a feudalistic redistribution: the old feudal system is being replaced by the reassertion of power for the individual. What role will Switzerland, the country of countless inventions, play in this development? Hardly any other country is so innovative and therefore so well positioned for this system transformation. The most successful Bitcoin app in Europe already comes from Switzerland. The Relai app is an application for secure self-custody of Bitcoin, without the influence of others. Relai AG was recently voted the best crypto startup and second-best financial startup in the country, and is rushing from one growth success to the next. The company is currently preparing to conquer the European market even more effectively.
Gaining control for the individual means losing control for the old (money) system. This principle also applies in other sectors. For example, iVault AG from Thalwil is currently working on opening up the “sharing economy” market. Anyone who wants to easily rent out their e-bike, car or lawnmower to others, for example, can do so via the ivault.io app and benefit directly from their own sustainability. Here too, old centralized platforms are being disempowered and individuals are taking their fate into their own hands.
It's always the same pattern and principle: if you don't want to be managed by others, you have to manage yourself. This applies to money, information and even lawnmowers and e-bikes.
Want to learn more about the Pareto Project? We build a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 081f3b0c:c00498a5
2024-10-31 11:52:15
@ 081f3b0c:c00498a5
2024-10-31 11:52:15Muchas son las maneras de referirse a la compra y mantenimiento de Bitcoin en cartera. Muchas también son las maneras de almacenarlo. Y, aunque en realidad NADIE almacena Bitcoin, sino llaves privadas y llaves públicas, no es de mi interés entrar hoy en esos tecnicismos.
Hoy quiero escribirle a la gente de a pie, los trabajadores, emprendedores, empresarios y todo aquel que se interese por lo menos un poquito en su futuro y el de los suyos. Hay algo que todos los Bitcoiners sabemos pero que muchos de ustedes no lo experimentan hasta llevarse un buen susto en su primer año de inversión (Hablaré en todo el artículo de manera indistinta entre inversión y ahorro en Bitcoin ya que en el largo larguísimo plazo y mirando a Bitcoin como moneda pero también como activo, pueden utilizarse ambos términos). Lo que no saben los que miran desde afuera, es que muy poca gente compró Bitcoin en centavos o pocos dólares (o lo minó en épocas tempranas) y todavía lo mantienen en cartera. Me arriesgaría a decir que este numero de individuos no supera unos pocos miles. Muchos no-coiners creen que los bitcoiners compraron a dos centavos se durmieron 15 años y hoy son todos ricos, pero la mayoría de los early adopters, se hundieron intentando navegar las profundas y peligrosas aguas de la custodia y el HODL.
Para quien todavía esté medio perdido y quizás este sea el primer artículo que lea, HODL es una manera "chistosa" de referirse a mantener Bitcoin en cartera, y se remonta allá por el 2013 donde un usuario quiso decir que estaba Holdeando (manteniendo) Bitcoin en cartera y lo escribió como HODLING. Pasó a la historia y hoy se usan HODL y HOLD de manera indistinta como chiste interno Bitcoiner.
En fin... Las profundas aguas... Holdear Bitcoin no es sencillo para las masas. Imaginate que tenés un activo en tu cartera, o compraste a 100 dólares y ahora vale 1.000. Lo venderías verdad? Y si vale 20.000 dólares? Ahí si lo venderías? Estarías multiplicando tu inversión como nunca. Bueno, a esa decisión se enfrentaron y se enfrentan TODOS los holders de Bitcoin más temprano o más tarde. Incluso aquel loco que compro por el 2017 en un precio de 20.000 hoy puede decidir vender y multiplicar casi por 4 su dinero en unos pocos años. Ni hablar de ese estresante momento que habías comprado en 69.000 dólares y lo viste bajar hasta los 17.000 dólares, unos cuantos meses de sufrimiento y temor... Más de uno se asustó de verdad y vendió todo, solo para verlo unas horas más tarde por arriba de los 20.000 y un año más tarde nuevamente en 70.000 dólares.
Si bien no me gusta poner el foco en el precio, lo que intento ilustrar es lo DIFICIL que puede ser ver tu inversión en máximos o en mínimos y aún así decidir mantenerla unos cuantos años más. Es dificil, aún para los que viven su tercer o cuarto ciclo de mercado. Pero se hace más y más fácil a medida que uno avanza en el famoso "rabbit hole" de Bitcoin y empieza a entenderlo desde las bases, cada vez mejor. Este camino también es arduo, entender de Bitcoin requiere un poco de conocimiento en cada campo, hay que saber un poco de tecnología, un poco de redes, un poco de seguridad informatica, una pizca de teoría de juegos, una apasionante cantidad de macroeconomía, y hasta un interés genuino en lo que Mises llamó "La acción Humana". Y todo esto, uno lo va a prendiendo con ganas y de a poco sólo para llegar a la conclusión, meses o incluso años después, de que Bitcoin tiene que ser un activo por siempre en la cartera de uno, no se vende. Incluso hay quienes llegan al punto (como este humilde ser que escribe) que no poseen otro tipo de ahorro o inversión que no sean sus pocos o muchos satoshis en Billetera Fria.
Mi recomendación siempre será que DYOR, "do your own research", investiguen, lean, pregunten, únanse a #nostr que tiene la mejor comunidad del mundo a la hora de ayudar a otros usuarios, pero si no llegan a tener el tiempo de leer y progresar sólo tómenme estos dos consejos:
- Háganse el tiempo para leer.
- Stay humble y stack sats (De a poco y constante, todo ahorro mensual que uno haga, está mejor guardado en Bitcoin, siempre gastando menos de lo que ingresa esto no debería ser dificil).
Otra dificultad que encontramos además de la parte emocional y humana relacionada con los precios y el desconocimiento, es la custodia. Cientos de personas perdieron TODO su Bitcoin por no saber almacenarlo correctamente. Decenas de maneras de almacenar claves y sin embargo muchos usuarios de Bitcoin no se sienten del todo seguro durante sus primeros años de inversión, y no están el todo equivocados... Por un lado puede ser tan sencillo como guardar 24 palabras. Por otro lado, puede no ser tan fácil, dependiendo del tipo de usuario. Entraremos en detalles de custodia en el próximo artículo.
Saludos!
El Tío.
PD: No es consejo de inversión.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 705605d9:b4324038
2024-12-13 16:30:17
@ 705605d9:b4324038
2024-12-13 16:30:17К 2040 году Горноправдинск, несмотря на динамичное экономическое развитие, столкнулся с рядом серьёзных демографических проблем.
Средний уровень жизни в Горноправдинске за последние несколько лет резко увеличился. Люди стали жить дольше. Но проблема со старением населения, бывшая актуальной ещё двадцать лет назад, осталась — и более того, она набирает обороты. Население города стареет — а значит, трудоспособного населения становится всё меньше. Это вызывает весьма серьёзное беспокойство у властей.
— У нас есть всё, чтобы молодое поколение выбрало Горноправдинск своим домом — новые рабочие места, красивая природа, инфраструктуру мы тоже развиваем. У нас тут много работников сферы IT, но на некоторых производствах не хватает рабочих, а социальный сектор от дефицита кадров страдает особенно сильно. Учителей у нас мало, например. Непопулярная это нынче профессия у молодых. — заявляет Агафья Семёновна, пресс-секретарь городской администрации.

Демографическая ситуация также осложняется низкими показателями рождаемости. Молодые люди, которые остаются в посёлке, зачастую ставят своим приоритетом не планирование семьи, а карьерный рост и саморазвитие. Многие просто не видят большого смысла для себя заводить семью и детей. Но редакция предполагает, что это проблема далеко не только одного Горноправдинска, а общая тенденция на уровне страны.

Ситуация с миграцией также оставляет желать лучшего. Хотя бум экономики Горноправдинска привлекает новых жителей, многие из них — это временные работники из других регионов, которые не имеют намерения осесть на постоянной основе. Кроме того, утечка умов, когда высококвалифицированные специалисты уезжают в поисках лучших карьерных возможностей, продолжает оставаться серьёзной проблемой для местного рынка труда.
Говоря о демографии, нельзя не сказать о социальных проблемах. Экономика цветёт, увеличивается качество жизни, а социальное расслоение сохраняется. Например, многим всё ещё трудно получить квалифицированную медицинскую помощь — работники городских поликлиник порой не справляются с потоком пациентов, а за помощью узкоспециализированного специалиста горноправдинцам остаётся обращаться в платную частную клинику, что может быть довольно тяжёлым испытанием для кошелька. Молодые семьи стремятся к лучшим условиям для жизни и воспитания детей, что приводит к оттоку населения в более социально обеспеченные регионы.
Горноправдинск, пытаясь справиться с демографическими вызовами, нуждается в комплексном подходе к решению проблем. Город нуждается в постоянном обновлении инфраструктуры и социальных инвестициях. Не хватает и поддержки молодых семей — для того, чтобы переосмыслить свои приоритеты, молодым парам нужна уверенность в завтрашнем дне.
А пока город медленно, но верно стареет. Справедливости ради, несколько медленнее, чем раньше.
-
 @ 6734e11d:c7e34e8f
2024-11-17 00:09:30
@ 6734e11d:c7e34e8f
2024-11-17 00:09:30Bereits 2023 entdeckte der Genomforscher Kevin McKernan, dass die mRNA-Impfstoffe von Pfizer/BioNTech DNA-Fragmente enthalten.
Nun konnte er in einer Biopsie eines Darmkrebspatienten DNA-Sequenzen (SV40,Ori) des Pfizer-Impfstoffs nachweisen – und das ein Jahr nach der Impfung des Patienten.
👉McKernan (https://anandamide.substack.com/p/sv40-origin-of-replication-in-mammalian)
Die hohe Menge an nachgewiesener Impfstoff-DNA lässt darauf schließen, dass sich der Impfstoff nach der Injektion im Körper des Patienten vermehrt haben könnte, so McKernan. Dies würde entweder auf eine Integration in das menschliche Genom oder auf eine unerwartete Replikationsfähigkeit der Impfstoff-DNA hinweisen.
https://t.me/DrKayKlapproth
https://t.me/initiative_demokratie
-
 @ 705605d9:b4324038
2024-12-13 16:27:16
@ 705605d9:b4324038
2024-12-13 16:27:16Горноправдинск, некогда скромный посёлок с населением в несколько тысяч человек, к 2040 году стал важным экономическим центром Ханты-Мансийского автономного округа. Если бы 20 лет назад местным жителям сказали, что их маленький посёлок станет экономическим чудом — даже самые оптимистичные из них восприняли бы это как шутку.
**Но как всего за пару десятков лет вообще возможна столь удивительная трансформация?
**
Маленькие люди, большая мечта Сельское хозяйство стало важной опорой экономики Горноправдинска. Даже как-то смешно вспоминать, что всё начиналось с маленьких частных огородов и большой инициативы местных жителей.
Те, кто когда-то возделывал скупую сибирскую землю, устали выращивать разве что картошку и разве что для себя. Жители (преимущественно, кстати, пожилые, те, для кого их огород был чуть ли не главным делом) взялись за свои участки серьёзно — удобряли землю, воспользовались правом заниматься фермерством, а затем смогли и выбить достойную технику для своего дела. Результат себя ждать не заставил: сельскохозяйственная продукция из Горноправдинска завоевала своё место на прилавках магазинов Югры. А уже к 2040 году Горноправдинск стал одним из важнейших центров производства молочных продуктов в регионе — животноводство местные власти сейчас развивают особенно активно. Не забыли и о чистоте производства: Горноправдинск на данный момент занимает одну из лидирующих позиций по внедрению "зелёных" технологий.

Привлечение туристов
Не менее значимым стало развитие туристической отрасли. Уникальные природные ландшафты региона привлекли туристов со всей страны. Местные власти активно развивают туристическую инфраструктуру: за последние 4 года на территории города появились 4 гостиницы (одна из них, кстати, и вовсе реализует формат "all-inclusive"!), два туристических маршрута — лыжная тропа, где все желающие смогут налюбоваться зимней красотой Сибири, и речной маршрут вдоль местной реки. "Мы стараемся создать место, куда люди хочется возвращаться", — говорит директор туристической фирмы "ГП".

Горноправдинск стал местом притяжения для самых разных людей — любители спорта теперь могут покататься на лыжах зимой и отправиться на сплав на сапах летом, а для интересующихся культурой молодых людей здесь регулярно проводят творческие фестивали.
Но сколько стоит экономическое чудо?
Но всего этого могло бы и не быть, если бы не усилия по привлечению инвестиций. Власти ввели налоговые льготы, модернизировали транспортное сообщение между городами Югры и впервые за всю историю существования посёлка, кажется, слушали людей и принимали их инициативы — так, через налаживание контактов и вливание финансов в местные предприятия (если обратиться к финансовым отчётам властей, то суммы, выделенные на развитие местных производств и инфраструктуры, впечатляют — они исчисляются миллиардами рублей), получилось преобразить бывший маленьким и серым Горноправдинск в гордость региона.

-
 @ 6734e11d:c7e34e8f
2024-11-14 11:33:54
@ 6734e11d:c7e34e8f
2024-11-14 11:33:54Zweiklassenmedizin, Zweiklassenbildungssystem und -demokratie. Wo ist die Zweiklassenpartei? Leo Trotzki hielt 1928 eine „Zweiklassenpartei“ mit sowohl proletarischer als auch kleinbürgerlicher Linie für unmöglich. Zu verschiedene und unvereinbare Interessen. Die (Er)Lösung scheint heute nah: Ein aufrichtiges Parteiprogramm.
Mein Ziel ist daher, alle Dissonanzen zu beseitigen und endlich alle Menschen in einer Partei zu vereinen. Ich stehe aufrichtig für das gänzlich Neue: „Vereine in einer Partei und herrsche“. In politischen Entscheidungen geht es durchgängig um Macht und monetäre Interessen, wirklich zu jedem Zeitpunkt und in allen gesellschaftlichen Fragen und Politikfeldern. Das ist nichts neues, aber mit dieser aufrichtigen Klarheit können alle Beschlüsse frei von hemmenden sachlichen Erwägungen geplant und getroffen werden. Zeitraubender Diskurs, Studien und Evaluationen werden überflüssig. Das vorliegende Parteiprogramm soll eine erste Positionsbestimmung darstellen und die kurz gehaltene neue Gesellschafts- und Wirtschaftsordnung in unserem schönen Lande sein. Ich meine es gut mit den Bürgenden*.
*Begriffserläuterung: Die Bürgenden seien im Folgenden diejenigen, die für die Konsequenzen politischer Entscheidungen mit ihrem Vermögen, ihrer Gesundheit und ihrem Leben bürgen.
Gesellschaft
Eine strikte rechtliche und wirtschaftliche Zweiteilung der Gesellschaft in Elite und Volk ist anzustreben. Da der Mittelstand in seiner Bedeutung ohnehin wesentlich überschätzt wird, kann er in den 99 Prozent der Bürgenden aufgehen. Der Mittelstand ist getragen von der Einsicht, zugunsten der Elite wesentliche Einbußen in Kauf zu nehmen. Um mit Umbau von Wirtschaft und Digitalem rapide voran zu kommen, brauchen wir eine solidarische Gemeinschaft der Harmonie. Vielschichtige Auseinandersetzung kann ein prosperierendes Gesellschaftssystem bremsen und zermürben. Komplexität ist deshalb zu vermeiden oder sogar zu unterbinden. Ich werde dezidiert vorgeben, wie Sprache in Schrift und Rede zu handhaben ist, damit unsere Gesellschaft noch effektiver agieren kann. Klarheit darüber, was zu denken, zu fühlen und zu sagen ist, erleichtern das Leben aller. Lust, Sexualität und vor allen Dingen Humor, sind auch digital auf das unbedingt notwendige Maß zu begrenzen, um die volle Kraft des Humankapitals der gesellschaftlichen Prosperität zur Verfügung zu stellen. Kritische Subjekte sollen dagegen trefflich verlacht und verhöhnt werden dürfen.
Grundrechte
Alle Staatsgewalt geht von der Partei aus. Mittlerweile ist recht gut implementiert, wann, wer, wohin darf, wem es jeweils verboten oder wer unerwünscht ist. Dies funktioniert auch ohne Vorbereitung, mittlerweile völlig unabhängig von logischen Begründungen. Das gesamte Potential einer noch differenzierteren Regulation, wird bisher leider nicht vollständig genutzt. Politischer und gegenseitiger Schutz haben sich als äußerst wirksam erwiesen.
Digitales
Ich will die digitale biometrische Identität für alle Vorgänge im Alltag, ab positiver Testung der Schwangerschaft. Mehr Mut bei Kombination von Fingerabdruck, Bankdaten, Gesichtserkennung und Zugangsberechtigungen. Der beschleunigten Zeit angemessen, gehe ich aber weiter: Privatsphäre ist ein überkommenes Luxusgut, das die gesellschaftliche Entwicklung hemmt. Es darf keinerlei Geheimnisse mehr geben. Diese Entwicklung würde ich keinesfalls als Transhumanismus bezeichnen, jenes Streben ist als äußerst menschlich zu betrachten. Fitnesstracker waren ein guter Anfang. Microchips in Kleidung und unter die Haut verpflanzt, ermöglichen Kommunikation überall und zu jeder Zeit. Bemerkenswert: Das Transplantieren erfolgt mit nur einer Spritze, mittels einer etwas dickeren Kanüle, ein leicht deutlicherer Piks, aber völlig sicher und nebenwirkungsfrei. Bei geschützten Tieren ist das seit längerem erprobt.
Desozialisierende/integrierende Netzwerke
Digitale Plattformen sammeln, überwachen und kanalisieren Kommunikation und Emotion, werden privatwirtschaftlich betrieben aber zentral gesteuert. Mal desozialisierend oder integrierend eingesetzt, können sie auch abgeschaltet werden. Text- und Videonachrichten oder -gespräche gelten als reale Kontakte. Sämtliche humanoide Handlungen werden in das digitale Netz verlagert, so wird unsere Welt endlich sicher. Der Schutz der Sphäre der Elite ist hingegen von entscheidender Bedeutung. Sie muss unabhängig von Überwachung Ideen auch in Präsenz austauschen und entwickeln können.
Medien
Digitale Identität und parteitragende Medien werden verknüpft. Pflichtzeiten des Konsums stellen denselben Informationsstand sicher, die Verweildauer fließt in die Gesamtbewertung der Persönlichkeit ein. Hochschulabschlüsse und Promotionen werden damit verknüpft, Verdienstorden angepasst verliehen. Die Öffentlich-Rechtlichen werden zur Marke „Ehrlich-Medien“, die jahrzehntelang immanente Unaufrichtigkeit wird die Transformation leider hinauszögern. Scheinbar kritische Medien sind längst an entscheidenden Positionen und auf allen Kanälen mit Einflussagenten besetzt, die ihre eigenen Ziele verfolgen. Diese Unterwanderung wird gezielt forciert, bis die Zeit reif ist, sie komplett zu kontrollieren oder abzuschalten. Bis dahin kann man die „kritische“ Propaganda ganz gut mit verschiedenen Anleitungen durchschauen.
Meinungsäußerung
Es gilt ein sofortiges Verbot von Satire und Kabarett, die sich mit den Eliten beschäftigt. Und um Anfragen vorzubeugen: Diese Zensur ist keinesfalls mit Historischem vergleichbar. Die Herkuleskeule in Dresden zeigte ja auch vor 1989 Kabarett. Sprechschauen werden ein wunderbarer Ersatz des bisher unterhaltsamen, aber überflüssigen Bundestags. Gleich den Kämpfen von Gladiatoren geht es hier um`s nackte Überleben, um Existenzen.
Wirtschaft
Energiewirtschaft, Handelsketten und Krankenhausgesellschaften, verbrauchen unendlich Ressourcen. Subventionen werden künftig leistungslos, regelmäßig und direkt an Stakeholder und Konzerne vergeben, ohne Erfordernis eine Leistung zu erbringen oder ein Produkt herzustellen. So können Rohstoffe weitgehend eingespart werden. Umwege über energieintensive Dienstleistung oder Produktion von Waren, Transport, Konsumation oder Zerstörung sind obsolet. Beispiel: Rüstungskonzerne produzieren Schiffe, Flugzeuge, Panzer, Waffen und Sprengkörper. Deren einzige Bestimmung ist es verbraucht zu werden, bestenfalls mit einem Schlag und kurz nach Verkauf. Aber was ist, wenn entgegen allen Bemühens kein Kriegsgrund und kein Einsatzort gefunden werden? Was ist mit dem Gewinn eines Pharmaunternehmens, wenn keine Pandemie ist? Sie erfassen hier wohl, die bestechende Nachhaltigkeit der Idee. Die Pleitewellen im Kleingewerbe und im Mittelstand lassen darauf hoffen, diese Ideen kurzfristig umzusetzen.
Gesundheitsindustrie
Die Low-Budget-/Max-Cost-Gesundheitsleistungen sind ganz in meinem Sinne. Sie werden weiter verschlankt, der Max-Outcome ist und bleibt das Hauptziel. Das Wahlvolk will Pflege und Krankenhäuser weiter optimieren, ersichtlich an den Ergebnissen der Bundestagswahl 2021, trotz beschleunigter Transformation. Die Gewerkschaften werde ich in diesem Bereich noch einige Zeit dulden. Sie dürfen weiter verlautbaren: „Wir sind an unserer Leistungsgrenze angekommen!“, „Wir stehen mit dem Rücken zur Wand!“. Das schadet ja keinem.
Abhängig Beschäftigte (sofern noch benötigt)
Käfighaltung wie bei deutschen Großunternehmen, die in Shanghai produzieren, ist weltweit geplant, wird aber zunächst dort getestet. Daneben hat sich die Drohnenüberwachung auf den Baustellen in Dubai bewährt. Nach gewisser Zeit der Eingewöhnung genügt es, die Drohnen mit Kameraattrappen auszustatten.
Recht und Justiz
Rechtsbegriffe werden allgemeiner formuliert, Straftatbestände angepasst. Gerichte sind künftig wie Staatsanwaltschaften an Weisungen gebunden, denn nur so können wir ungebremst voranschreiten. Das Primat der Sicherheit gebietet es, dass bereits eine potentielle digitale Abweichung mit vorsorglicher Inhaftierung und entsprechenden Maßnahmen geahndet wird. Geldstrafen werden die Ausnahme sein. Nebenstrafen wie Internetsperre, Entzug der Fahrerlaubnis, Berufs-, Reise-, Kultur- und Einkaufsverbot, sowie weitere Rücknahme von zugeteilten Rechten werden ausgeweitet. Die Zulassung von Rechtsanwälten wird vom Politscore abhängig gemacht. Schiedsgerichte ersetzen letztlich Rechtswesen und Justiz.
Innere Sicherheit und Polizei
Bisher fungierte die Polizei als Straßenkehrer der oberen Zehntausend. Künftig soll sie den privaten Raum der Happy Few (max. 1%) garantieren, damit diese unabhängig zum Wohl des Volkes agieren können. Wenn die besten Kreise erwägen, öffentliche Plätze in Präsenz zu nutzen, beispielsweise für eine Demonstration der derzeitigen moralischen Haltung, werden diese durch Spezialkräfte sicher gehalten. Die internen Strukturen der künftigen Zentralpolizei werden, ebenso wie Aufnahmeprüfungen, am jeweils aktuellen Geheimdienstbericht ausgerichtet. Die innere Sicherheit wird hauptsächlich im Netz verteidigt, aufkeimende Aufstände werden dort erkannt und bereits im digitalen Stadium vereitelt. Ein Eid auf irgendein Gesetz wird vollkommen überflüssig, die Anweisungen erfolgen klar und lageangepasst. Vielleicht muss eine neue Begrifflichkeit entwickelt werden, denn „politeia“ meinte ein Gemeinwesen, das von Vernünftigen geleitet wird. Mir schwebt „Das Auge des Netzes“ vor, „...Gesetzes“ ist dann veraltet.
Tierschutz
Hundeerziehungslager, auch Hundesportplätze genannt, sowie die dort stattfindenden Kurse werden sofort und konsequent verboten. Viele die hier ihr Machtgefühl erleben, werden die Plätze zunächst schmerzlich vermissen. Dennoch müssen die dort vergeudeten Energien für Gehorsamsübungen in die Ausgestaltung nachbarschaftlicher, freundschaftlicher, politischer und beruflicher Beziehungen überführt und in der Folge in`s Digitale transformiert werden. Menschen- statt Tierhaltung ist wesentlich befriedigender und förderlicher für unser Gesellschaftssystem.
Drogen
Es erfolgt eine sofortige Freigabe von Kokain, Haschisch, Crystal Meth und Aufputsch- sowie Beruhigungsmitteln, um den täglichen Beschaffungsdruck von Entscheidungsträgern zu nehmen. Der multiple Alltagskonsum, auch von Alkohol, ist wünschenswert und wird gänzlich aus seinem kritisch-moralischen Schattendasein befreit. Mitteilungsdrang ist in Leitungsetagen, bei Planungsgesprächen und in Talkshows nutzbringend, bestenfalls natürlich überschießend oder drogeninduziert und nicht an Logik gebunden. Berauschte Entscheider, wechselweise sediert und aufgeputscht, sind dem elitären Umfeld angepasst, daher unauffällig und leichter steuerbar. Zeitweilige Aufmerksamkeits- und Sprachstörungen ignorieren oder kaschieren Umfeld und Medien bestens. Nicht an Stoffe gebundene Süchte – Video-/Konsolen-/Rollenspiele – werden optimiert und gefördert. Die Droge der Macht bleibt künftig den besten Kreisen vorbehalten.
Auswahl des Führungs- und des politisch Personals
Darwins „Survival of the Fittest“ beschreibt, wie Evolution vonstatten geht. „The Fittest“ meint völlig nüchtern, den am besten an die jeweiligen Bedingungen angepassten Organismus. In unserer Gesellschaft wurde die Evolution glücklicherweise von den Füßen auf den Kopf gestellt. Die Auswahl konturlosen Politikpersonals mit blinder Ergebenheit, vor etwa 20 Jahren begonnen, ist längst abgeschlossen und kann noch verfeinert werden. Die Kandidaten, am absoluten Ende der persönlichen und intellektuellen Fähigkeiten angekommen, werden auf den Schild gehievt, so viele Stufen wie möglich hoch getragen. Gesunder Menschenverstand ist störend bei Politisierenden und wird notfalls geworkshopt. Die Wahlschäfchen lieben dieses Führungspersonal, können sich gut identifizieren, während die Upperclass die Fäden zieht. So können wir in die neue Phase des menschlichen Daseins eintreten. Selten sind noch Hürden zu überwinden: Das selbständige Nachdenken, die Selbstreflektion, die kritische Bildung, kritische Medien, Politiker und Bevölkerungsschichten sind nurmehr rudimentär vorhanden. Selbstdenker werden aus der Gemeinschaft ausgeschlossen, damit das freundliche Zusammensein nicht gestört wird, haben in der ZKEP jedenfalls nichts verloren.
Wahlen
Die geringe Wahlbeteiligung in Nordrhein-Westfalen 2022 (55%), erfordert im Durchgangsstadium eine Wahlpflicht. Künftig wird eine Wahlberechnung durch KI eingeführt. Letztlich wird es allen recht sein, wenn einer entscheidet, wer gewonnen hat. Die Existenz der ZKEP macht den Wahlprozess über kurz oder lang ohnehin obsolet. Als Ersatz zum weiteren Amüsement wird schließlich ein Präsidentencasting angestrebt, die Bürgenden bringen Vorschläge zu den aus ihrer Sicht unterhaltsamsten Bewerbern ein. Die Wahlberechnung wird letztlich nur noch zur Bestimmung des Präsidentendarstellers eingesetzt. Hauptaufgabe: Das Volk bei Laune zu halten, sich digital und real auseinanderzusetzen. Politik ist künftig Scripted Reality, Slogan: „Er ist das Volk“.
Schlussbemerkungen
Die ZweiKlassenEhrlichkeitsPartei wird den Umbau der Gesellschaft, hin zu einer effizienten, regel- und elitebasierten Weltordnung beschleunigen. Ich werde mit dieser Idee sehr erfolgreich sein und die Menschheit in eine bessere Zukunft führen. Ich wusste schon immer, was für die Menschenkinder gut ist und auch die Mehrheit will das solidarische Zweiklassensystem. Die Völker müssen von ihrem Misstrauen gegenüber der High Society befreit werden, von der böswillig behauptet wird, sie sei zu wenig fürsorglich. Totalitäre Systeme verschleiern ihre Ziele aus Unsicherheit, nicht liebenswert zu sein, so wie ein Liebhaber seine Leidenschaft aus Angst vor Abweisung verschweigt. Unbeholfen werden Maßnahmen zur Eroberung getroffen, die Fragilität wird sichtbar. Wenn etwas ehrlich ausgesprochen wird, wirkt das manchmal wie ein Unfall. Mit mehr Mut zur Ehrlichkeit treten wir in eine freiere und gelassenere Zukunft ein. Damit wir künftig mit Fug und Recht sagen können, wir gehörten nicht zum Imperium der Lügen, waren immer redlich, liebten unsere Bürgenden und haben keinen Schaden verursacht. So überstehen wir dieses Jahrtausend sicher sicher.
Vielleicht haben Sie Lust bekommen die ZKEP zu unterstützen. Mein Paypal-Konto finden Sie unten.
Artikel zuerst veröffentlicht bei den Neulandrebellen, 3.7.2022 https://www.neulandrebellen.de/2022/07/die-zweiklassenehrlichkeitspartei-zkep-ehrlich-waehrt-am-laengsten/
-
 @ 705605d9:b4324038
2024-12-13 16:25:42
@ 705605d9:b4324038
2024-12-13 16:25:42Давка в маршрутках с вечно уставшими водителями, которые приезжают на остановки не по расписанию, а иногда не приезжают вовсе, была в прошлом неизбежной частью городской жизни. Общественный транспорт остаётся востребованным элементом инфраструктуры: не все могут позволить себе личный транспорт или регулярные поездки на такси. Вам больно видеть ценник в 800 рублей по вечерам в час пик? Редакции тоже.

Сегодня, 17 декабря, городские власти закупили новые транспортные средства: 15 беспилотных электробусов "Стрела" с увеличенной вместительностью. Новенькие "Стрелы" отправятся на маршруты 8, 13 и 42. Помимо повышенной вместительности и внедрения ИИ, новый транспорт также более экологичен.
Маршрут в восточную часть города, маршрут №6, оснастят "Стрелами" в следующем году. Подготовкой специализированных колей для них дорожники были заняты последние полтора года, и на востоке работы ещё не завершены до конца.
Теперь не нужно ругаться с водителем: обстановку на дороге и в салоне определяет искусственный интеллект.
Но редакция напоминает: при нахождении в электробусе будьте взаимовежливы -- уступайте места пожилым людям, инвалидам и беременным женщинам, а при нахождении в автобусе снимайте рюкзаки и объёмные сумки с плеч.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 3f770d65:7a745b24
2024-10-29 17:38:20
@ 3f770d65:7a745b24
2024-10-29 17:38:20Amber
Amber is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications.

Amber is supported by a growing list of apps, including Amethyst, 0xChat, Voyage, Fountain, and Pokey, as well as any web application that supports NIP-46 NSEC bunkers, such as Nostr Nests, Coracle, Nostrudel, and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms.

Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's GitHub page, via Obtainium or Zap.store.
To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com.

Citrine
Citrine is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control.

With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality.
Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration.

Pokey
Pokey for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device.

Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem.
Zap.store
Zap.store is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency.

Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing Zap.store on your favorite Android device, and install all of the applications mentioned above.
Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems.
-
 @ 705605d9:b4324038
2024-12-13 16:10:30
@ 705605d9:b4324038
2024-12-13 16:10:30В центре Горноправдинска произошла серьезная коммунальная авария, в результате которой значительная часть города осталась без электричества. По предварительной информации, причиной отключения стало повреждение высоковольтной линии, расположенной на улице Поспелова.
Авария произошла в результате сильного ветра и обильных осадков, которые наблюдались в последние дни. В результате падения дерева на линию электропередач произошло .короткое замыкание, что привело к отключению нескольких трансформаторных подстанций.
На данный момент специалисты работают над устранением последствий аварии. Восстановительные работы начались сразу после инцидента. В ЮТЭК пообещали, что работы закончат к 4 часам утра.
Видео происшествия:
-
 @ 4ba8e86d:89d32de4
2024-10-25 11:40:05
@ 4ba8e86d:89d32de4
2024-10-25 11:40:05A loja Aurora vem com um excelente design, interface de usuário amigável para iniciantes e muitos recursos.
A loja Aurora foi originalmente baseada na loja Yalp de Sergei Yeriomin, mas a versão 3.0 passou do zero para a conclusão seguindo o Material Design reescrito para rodar em todos os dispositivos Android 5.0.
Dentre as diversas características oferecidas pela Aurora Store, destacam-se:
- Login Anônimo: Para garantir sua privacidade, você pode fazer login anonimamente, assegurando que suas atividades permaneçam confidenciais.
- Login do Google: Além do anonimato, a opção de login do Google permite acessar aplicativos pagos e instalar versões beta.
- Falsificação de Dispositivo: Caso um aplicativo não esteja disponível para o seu dispositivo, você pode recorrer à funcionalidade de falsificação de dispositivo, permitindo a instalação.
- Filtragem de Aplicativos F-Droid: A possibilidade de filtrar aplicativos do F-Droid evita que eles apareçam em sua lista de atualizações.
- Aplicativos na Lista Negra: Ao adicionar aplicativos à lista negra, você mantém o Google no escuro quanto aos aplicativos instalados.
A loja de aplicativos se apresenta com um design clássico, apresentando uma capa de apps e jogos em destaque, proporcionando um visual convidativo. A aba de aplicativos instalados permite uma gestão mais eficiente, possibilitando atualizações automáticas para a versão mais recente disponível.
A busca por aplicativos é facilitada por categorias que abrangem diversos interesses, como fotografia, música e áudio, compras, personalização, livros e quadrinhos, entre outras. A eficaz função de busca permite localizar aplicativos específicos de maneira rápida e fácil.
A Aurora Store se diferencia pela tecnologia de pesquisa única, agilizando a descoberta de aplicativos em questão de segundos. Além disso, a loja vem com a licença GPLv3, reforçando seu compromisso com o software livre.
Privacidade é um foco central da Aurora Store, sendo considerada uma excelente alternativa para quem preza por manter suas informações pessoais protegidas. O aplicativo suporta contas pessoais e permite downloads com contas anônimas, assegurando que suas atividades não estejam vinculadas a você.
Com a integração do Exodus, a Aurora Store verifica rastreadores presentes nos códigos dos aplicativos, proporcionando uma visão mais transparente das informações coletadas.
O aplicativo se destaca por ser livre de anúncios e pop-ups, proporcionando uma experiência de uso mais limpa. O suporte ao modo escuro oferece conforto visual em ambientes com pouca luz ou durante a noite.
A Aurora Store é uma alternativa valiosa à Google Play Store, oferecendo um ambiente mais privado, recursos robustos e um design elegante que visa aprimorar a experiência do usuário em busca e gerenciamento de aplicativos.
https://github.com/whyorean/AuroraStore
https://f-droid.org/packages/com.aurora.store/
https://gitlab.com/AuroraOSS/AuroraStore/-/releases
-
 @ 705605d9:b4324038
2024-12-13 16:07:11
@ 705605d9:b4324038
2024-12-13 16:07:11Сегодня посёлок Горноправдинск, стал не просто точкой на карте, а настоящим центром молочного вселенной. Ведь именно здесь, в 2040 году, открылся самый крупный молочный комбинат в мире — гигантское предприятие, которое не только удивляет размерами, но и ставит новые стандарты в производстве молочных продуктов. Комбинат, который в народе уже окрестили "Млечным путём", выглядит как космическая станция, под завязку забитая самым современным оборудованием.

Зрелище потрясающее: массивные трубы, сверкающие резервуары и, конечно, в воздухе стойкий запах свежего молока, который теперь станет символом этого региона.
Генеральный директор комбината, Зульфия Новобсохова с гордостью демонстрирует всему миру чудо инженерной мысли. На церемонии открытия она, с блеском в глазах и лёгкой улыбкой, рассказала журналистам:
— "Мы не просто строили завод, мы строили мечту! Теперь наша продукция сможет достичь каждого уголка планеты, и, надеюсь, в ближайшее время мы поставим молоко даже на Марс. Кто знает, может, с помощью наших новых технологий завтра марсиане будут пить молоко с Горноправдинска!" — шутит она, как всегда, с долей иронии, присущей истинному бизнесмену.
Но шутки шутками, а величие нового предприятия впечатляет. Здесь установлены ультрасовременные линии по переработке молока, автоматизированные процессы, и роботы, которые до сих пор поражают своей точностью. Так что в планах — не только массовое производство сыра, йогуртов и творога, но и создание абсолютно новых продуктов с непревзойдённым вкусом и максимальной пользой для здоровья.
-
"Мы гордимся тем, что создаём будущее, а не просто следуем за ним. Это не просто комбинат, это философия, основанная на идее заботы о природе и человеке", — продолжает Зульфия, когда её спрашивают о возможных экологических последствиях. "Конечно, мы выбрали экологичные материалы, переработку отходов и минимизацию углеродного следа. Даже коровы, которые поставляют нам молоко, проходят строгий контроль по экологическим стандартам. И знаете, они тоже счастливы работать на таком производстве."
-
"Надеюсь, в будущем, когда люди станут заказывать наше молоко, они смогут выбрать не только его вкус, но и степень 'счастья' коровы. Мы думаем над этим, и это может стать нововведением на рынке!"
Не упустим и восхищённых зрителей: среди гостей мероприятия присутствуют известные личности, чиновники и даже любители молочной продукции со всего мира. Многие из них в порыве восторга делают снимки на фоне гигантских установок, поднимаясь на специальные платформы с видом на завод. Кто-то шутит, что теперь Горноправдинск может стать новым "молочным Лас-Вегасом"

Даже критики, известные своим скептицизмом по поводу промышленных гигантов, сдержанно кивают в знак уважения. Слишком уж велико было всё, что они увидели.
Подсчёты говорят сами за себя:
- Производственная мощность — 100 миллионов литров молока в год.
- Тысячи новых рабочих мест.
- Планы по выходу на международные рынки и экспорту в космос (по шутке или всерьёз — ещё предстоит выяснить)
- Бобровская порода коров бьёт все рекорды по удою в 40 546 кг молока.
Горноправдинск уже сегодня становится центром молочной дипломатии и промышленности. Если в ближайшие годы этот комбинат сможет оправдать все возложенные на него надежды, то вполне возможно, что мир начнёт измерять величие не только в мегаваттах энергии, но и в литрах молока.
-
-
 @ 228dde34:b5d0345e
2024-11-29 10:00:06
@ 228dde34:b5d0345e
2024-11-29 10:00:06BY Glenda Chong and Lim Jing Jie
Hype Issue #60
Join GLENDA CHONG and LIM JING JIE as they chat with Merida Lim, the founder of art jamming studio SCURO (meaning “dark” in Italian), on her journey to starting her art jamming business and making it work at its Kampong Bahru space.
Merida Lim, 19, founder of art jamming studio SCURO. Photo by Cherlisa Lee.
It’s not every day you see a 19-year-old running own business. Most 19-year-olds we know are occupied chasing degrees and diplomas. Merida Lim, however, has done what few would do; abandon the safety net of education and passionately dive head-first into her business venture: SCURO.
What is SCURO, you might ask? According to Merida, it is “Singapore’s most immersive and unique art jamming studio”. Born out of Merida’s burning passion for art, the studio is a place where you can engage in art jamming in the dark, with the different themes SCURO provides to immerse yourself in: Candlelight, Neon, Horror, and more in the future.
Merida’s choice to pursue art as her first entrepreneurial venture can be traced back to her roots in the art scene. “When I was in secondary school, I [had] some mental health issues, and I think when I created art, it gave me a safe space to express my emotions. So that’s how I slowly got into art.”
Merida posing with her paintings. Photo by Cherlisa Lee.
Clearly, Merida realized she wanted to share that feeling of safety and security with others, and the idea for starting the studio came soon after. “I've always wanted to start my own business, and when I had the idea for an art studio, I decided to just go for it with a bit of naivety and… unearned confidence.” However, she believed that like any entrepreneur, she had to have that little sense of ego that her idea would succeed and thus attempt to make it a reality.
Merida also shares the doubts people had because of her age. “When you're 19, people don't take you that seriously, or they think you're crazy, and that you should continue with your education.”
Currently, Merida is taking a gap year from Nanyang Academy of Fine Arts to focus on SCURO. While she understands the importance of education, even stating that if SCURO doesn’t work out she will return to school, she remains steadfast in making SCURO happen. “It’s important to take risks and [not] let other people’s fear of achieving their own dreams stop yours.” She says.
Additionally, as she puts it, “If not now, then when?!”
“When will the circumstances ever be perfectly right for me to start? I will always be scared,” Merida says. At the end of the day, Merida decided that she would rather feel scared but pursue her dreams than freeze up before she even tried.
Unsurprisingly, starting a business definitely comes with its fair share of challenges. Before she started SCURO, Merida needed to know if there was demand for her art jamming services. “You have to see if there is a demand for what you’re selling in the first place.” Merida shares.
Thus, SCURO first started as a small pop-up kids art studio in Pasir Ris that Merida rented for $70 an hour. After establishing the demand for her services, Merida, with help from her father, invested most of her savings into opening an art studio for SCURO – a dark and cozy “shoes-off studio that feels like home”, at the second level of a shophouse located in Kampong Bahru.
SCURO provides an intimate environment with its hand-painted walls and dark interior gently lit by fairy lights. Photo by Cherlisa Lee.
Now, with her own art studio, Merida has shifted her efforts to marketing and promoting her brand to the public. She admits that her “social media game sucks”, but as the sole founder, the duty falls on her to improve SCURO’s social media presence and content. Thus, in an attempt to improve her social media game, Merida looks to Singaporean content creator Gabe Chia for guidance on her videos and content.
Recently, Merida has also started a new video series on SCURO’s TikTok page, where she challenges herself to earn $6000 in 50 days. This is so she can continue providing people with a safe space to express themselves through creating art pieces. Being largely a one-man operation, she has to explore different storytelling techniques for her videos on TikTok.
“When it comes to making your studio viral and making people care, you have to have stakes and you have to tell a compelling story,” Merida said. She likened her videos to “bringing people into a sitcom like the Kardashians”, as her TikToks consist of her farcical situations in hopes of landing a viral video. One of her more recent videos was to promote her new Candlelight art jamming session, an idea that was born after realising that she wanted to cater to larger groups who are not as keen on horror art.
SCURO provides every art material imaginable for art jammers to unleash their full creativity. Photo by Cherlisa Lee.
“At the very start, it was just straight-up horror,” Merida said. However, while there is demand for horror art, she noticed that the wider demographics have other interests. When she realised the absence of a neon art jamming scene in Singapore, she took the initiative to introduce it to SCURO. After starting to offer a neon art jamming theme at SCURO, Merida has found it to be a vibrant option younger art jammers have taken a liking to.
Seeing how her entrepreneurial journey has been filled with many challenges, it is expected that such challenges have led to some regrets. However, Merida has come to accept being “okay” with having regrets. You can see this throughout her art jamming sessions, where mistakes are encouraged and art knows no boundaries.
 Merida guiding one of HYPE’s team members on the right painting technique to use on her painting. Photo by Lim Jing Jie.
Merida guiding one of HYPE’s team members on the right painting technique to use on her painting. Photo by Lim Jing Jie.As Merida shares, “We [SCURO] want you to make mistakes, and people need to hear that they can make mistakes.” She believes that through those missteps, you unlock the freedom to “just be weird” and, in doing so, uncover your true self. It’s a reminder that the path to growth is never perfect, but it’s yours to embrace.
So, if you’re looking for something to do during the holidays, you might want to consider booking an art jamming session now at www.scuro.sg
-
 @ 8f0a121e:24038909
2024-11-28 09:07:00
@ 8f0a121e:24038909
2024-11-28 09:07:00كلنا نعرف أبيات إمرئ القيس في الليل التي تعلمناها في المدارس صغارا.
وليل كموج البحر أرخى سدوله ... عليّ بأنواع الـــهموم ليـــبتلي فقلـــت له لمـا تمـــطى بصـلبـــه ... وأردف أعجازا وناء بكلــــكل ألا أيها الليل الطويل ألا انـجـلي ... بصبح وما الإصباح منك بأمثل
وهي من أروع وأعلى ما قيل في الليل، ولكن تراثنا وشعرنا مليء بروائع في نفس المعنى. يقول النابغة الذبياني:
كليـــني لهمًّ يا أمــيمة ناصـــبِ ... وليل أقاسيه بطيء الكـــواكب تطاول حتى قلت ليس بمنقضٍ ... وليس الذي يرعى النجوم بآيب وصدر أراح الليل عازب هــــمه ... تضاعف فيه الحزن من كل جانب
يطلب النابغة من ابنته أميمة أن تدعه لهمه وتعبه ويشكي بطئ سير كواكب وثقلها في السير كناية على طول الليل.
في البيت الثاني، أقام الصبح مقام الراعي الذي يغدو فيذهب بالماشية والإبل، وبالمثل الصبح يذهب بالنجوم.
ثم يقول أن الليل "أراح عازب همه" بمعنى أنه أرجع اليه همه البعيد.
ويقول الوليد بن يزيد:
لا أسأل الله تغييرا لما فَعَلَت ... نامت وقد أسهرت عينيَّ عيناها فالليل أطول شيءٍ حين أفقدها ... والليل أقصر شيءٍ حين ألقاها
ويقول بشار:
خليلَيَّ ما بال الدجى لا تزحزح ... وما بال ضوء الصبـح لا يتوضح أضل النهار المستنير سبـــــيله ... أم الدـــــهر لـــيل كله لا يبــــرح
شعر #أدب #بالعربي
-
 @ 2779f3d9:1a7f98d1
2024-11-28 00:43:46
@ 2779f3d9:1a7f98d1
2024-11-28 00:43:46NOSTR SDK FOR APPLE PLATFORMS
Progress Report # 1: Aug - Oct 2024
Nostr SDK for Apple Platforms made great strides this quarter. I was the sole developer who maintained Nostr SDK for Apple Platforms part-time, as the other core contributors, unfortunately, could not commit time to developing or reviewing code for the project.
Approximately 50% of the tasks listed in the original OpenSats application have been completed. Moreover, implementations of several other NIPs / event kinds not listed in the application were fixed or added.
There was a substantial architecture change in how Nostr event kinds are built to improve the project's code maintainability and scalability as more NIPs and event kinds are supported. Specifically, certain event kinds support several handfuls of tags, some of which have complex logic. This requirement resulted in the introduction of a large, unmaintainable number of parameters in event creation methods in the EventCreating protocol. Multiple event kinds share some tags, but the EventCreating architecture made it difficult to share logic. By deprecating the EventCreating protocol in favor of the NostrEventBuilding protocol, we can encourage a composable architecture: decompose each event kind tag into a separate builder function, and tags shared across multiple event kinds can re-use the same code. This architecture change has and will pay dividends in future changes. For example, labels, custom emojis, and threading are concepts and tags shared across multiple event kinds, and their implementation has been made substantially more manageable with this architecture. Vitor Pamplona, developer of Amethyst, applauded the architecture design by saying:
It's nice indeed. I will be copying your SDK patterns on Kotlin :)I battle-tested Nostr SDK for Apple Platforms in the wild by integrating it into Comingle iOS, an events app powered by Nostr, solely developed by me. It was launched and used at Nostriga in August 2024 for attendees to see the conference schedule and RSVP to talks. It proved that a developer could quickly use the SDK to build a functional iOS app on Nostr using Swift.
1) How did you spend your time?
Below is a broken-down summarized bulletpointed list of completed tasks.
Development of Nostr SDK for Apple Platforms
Added
- NIP-17 Private Direct Messages
- NIP-31 alt tags
- NIP-32 Labeling
- NIP-36 Sensitive Content / Content Warning
- NIP-40 Expiration Timestamp
- Add NostrEventBuilding protocol to enable flexible composition of shared patterns across different kinds of NostrEvents
- Add Swift 6.0 to unit tests
- Integration into Comingle iOS client to battle-test SDK
Updated
- NIP-01 - Add missing test coverage for referencedEventIds and referencedPubkeys functions in TextNoteEventTests
- NIP-01 - Add referencedPubkeys, referencedEventIds, and referencedEventCoordinates to NostrEvent
- NIP-01 - Fix incorrect test fixture and assertions in TextNoteEventTests for replies
- NIP-10 - Refactor threaded event tag building and interpreting logic so non-kind-1 events can reuse them
- NIP-25 Reactions - Add ReactionEvent.Builder to deprecate equivalent function in EventCreating
- NIP-42 Authentication - Add AuthenticationEvent.Builder to deprecate equivalent function in EventCreating
- NIP-42 - Deprecate AuthenticationEvent initializer in favor of AuthenticationEvent.Builder
- NIP-59 Gift Wrap - Add support for receiver aliases for gift wrap creation to avoid exposing identities and improve test coverage
- Fix GitHub workflows to trigger on pull_request_target so that they can run on PRs from public forks
- Expose RelayResponse.Message and RelayResponse.MessagePrefix as public
- Fix SwiftLint errors from latest SwiftLint release
- Fix GitHub workflows to also run on main branch
- Update README with current list of NIPs
In Progress
- NIP-28 Public Chat - Review pull request from external contributor developing Skatepay
- NIP-57 Lightning Zaps
- Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds
2) What do you plan to work on next quarter?
The remaining items in the original application to OpenSats include: - Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds - Provide better support for integrating data models with persistence layers - Add unit tests and graceful handling for bad data from relays - Outbox model support / relay abstraction on top of events - Integrate demo app with more implemented NIPs - Integrate Nostr SDK for Apple Platforms further into Comingle iOS for further battle-testing - Support Damus, Nos.social, Primal, and other clients as they integrate with parts of the SDK by answering questions, fixing any issues they have, adding requested features, and reviewing pull requests - Consider integrating SDK NIP-44 v2 encryption or NIP-17 DMs with Damus iOS to battle-test implementation and push for deprecation of NIP-04 DMs - NIP-28 Public Chat - Review pull request from external contributor developing Skatepay - NIP-47 Nostr Wallet Connect - Review pull request from external contributor - NIP-57 Lightning Zaps
3) How did you make use of the money?
Living expenses.
-
 @ 705605d9:b4324038
2024-12-13 15:54:49
@ 705605d9:b4324038
2024-12-13 15:54:49Горноправдинск, посёлок, заслуженно гордящийся своим экологическим статусом и продвинутыми инициативами, стал центром литературной жизни Югры. В местной библиотеке состоялась яркая презентация книг югорских авторов, событие, ставшее предвестником масштабного проекта по созданию фонда Югорских писателей.
В уютном зале библиотеки собрались любители литературы, местные жители и гости посёлка. Центральным событием вечера стала презентация сразу нескольких значимых работ. Среди авторов – как маститые профессионалы, так и талантливые дебютанты.

Главным событием вечера стала презентация книги известного горноправдинского историка, профессора Николая Сергеевича Петрова, "Горноправдинск: хроники устойчивого развития". Книга, написанная с использованием новейших технологий визуализации данных и дополненная интерактивными элементами, рассказывает об истории посёлка, акцентируя внимание на его экологической стратегии и инновационных подходах к развитию.
"Мне было важно не только зафиксировать исторические факты, но и показать путь Горноправдинска как образца устойчивого развития, – делится Николай Сергеевич. – Надеюсь, моя книга вдохновит новых поколений на создание ещё более процветающего будущего".
Рядом с маститым историком блестяще представили свои работы авторы, работающие в жанре детской литературы. Елизавета Андреевна Кузнецова представила интерактивную книгу "Сказки Югорского леса: ожившая тайга", сочетающую традиционный фольклор с элементами дополненной реальности. Дети могут сканировать страницы и видеть оживающих персонажей сказок на экранах своих планшетов.
"Мы стремимся привить детям любовь к своей культуре и природе в интерактивной и занимательной форме, – пояснила Елизавета Андреевна. – Современные технологии позволяют нам сделать это эффективнее и интереснее".
Ещё одним ярким участником вечера стал Даниил Владимирович Колосов, автор книги "Югорские мифы в стихах и музыке". Даниил представил не только свою книгу, но и музыкальное сопровождение к ней, используя современные синтезаторы и традиционные югорские инструменты.
"Я хотел показать, как традиционная культура может гармонично сочетаться с современным искусством, – поделился Даниил Владимирович. – Музыка помогает лучше понять глубину и красоту югорских мифов".
Завершился вечер обсуждением перспектив развития литературы Югры и планов по созданию Фонда Югорских писателей. Участники выразили оптимизм и уверенность в том, что литературное наследие Югры будет и впредь богато и уникально. Презентация в Горноправдинске стала ясным подтверждением этого.
-
 @ 705605d9:b4324038
2024-12-13 15:52:11
@ 705605d9:b4324038
2024-12-13 15:52:11В 2040 году в посёлке Горноправдинск завершилась масштабная реставрация веревочного парка, который стал не только современным развлекательным объектом, но и примером экологической ответственности. В ходе работ были использованы исключительно натуральные материалы, такие как древесина местных пород, а также переработанные пластик и металл. Все конструкции теперь оснащены покрытиями, не вредящими экосистеме.

Важным нововведением стало применение солнечных панелей для питания освещения и системы видеонаблюдения, что позволило значительно снизить углеродный след парка. Кроме того, установлены инновационные системы сбора и очистки дождевой воды, которая используется для полива зелёных насаждений, а также для поддержания гигиеничных условий в туалетах.
Для повышения доступности, веревочный парк теперь включает маршруты для людей с ограниченными возможностями: специальные пандусы и адаптированные зоны для отдыха. В парке также появились новые образовательные элементы — интерактивные стенды и экскурсии по экологии, где посетители могут узнать о важности сохранения природы и устойчивого развития.
Проект реставрации стал возможен благодаря поддержке местных властей и экологических организаций, а новый парк уже стал местом притяжения для жителей и туристов.
-
 @ 4ba8e86d:89d32de4
2024-10-24 14:03:14
@ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais.
Recursos e Funcionalidades.
O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório.
Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes.
O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets.
Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo:
-
Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional.
-
Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes.
-
Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações.
O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável.
https://www.collaboraoffice.com/
https://github.com/CollaboraOnline/online
-
-
 @ 99895004:c239f905
2024-11-27 01:21:46
@ 99895004:c239f905
2024-11-27 01:21:46Most Nostr users have never heard of nostr.build. Many Nostr users know of nostr.build, and that we store images and videos for Nostr, but don't know that we can do anything else. There are also users that have a paid nostr.build account, but don’t know of all the included features they have access to. For these reasons I've decided to write a blog about all of nostr.build's features, in detail, let's begin.
Nostr.build offers free media hosting services for Nostr and paid services when you purchase an account. We have three levels of paid accounts: Pro, Creator, and Advanced. Let’s talk about each level of service and the features included below.
Free Services:
-
Supported Media Files up to 21MB: Anyone using Nostr can upload the media of their choice, up to 21MB per file. We support many different media types including .jpg, .png, .gif, .mov, .mp4, .mp3, and .wav. We compress JPEGs, PNGs and GIFs, but currently perform only light processing of video to allow quick preview. If your video is playing weird, no audio or not playing at all, it is likely your video format or how it was transcoded.

-
Removes Location-Related Metadata: Most photographs these days have the location data (GPS coordinates) embedded in the metadata. The data is commonly used to tell users where they were when they took the picture, it can also dox someone if they share an image with location data in it, e.g., their home address. Nostr.build removes this location metadata so as not to reveal your location to everyone you are sharing a picture with.

-
Integrated Media Uploading on Nostr Platforms: In the early days of Nostr, if you wanted to share an image or video, you would have to upload it to another site, copy the link it provides, and paste it to your Nostr note. With NIP96 and NIP98 nostr.build is now directly integrated into most Nostr apps making it just one click to add your media, like other popular and social media platforms. Currently this is supported on Damus, Amethyst, Nostrudel, Snort, Iris, Coracle, Flycat, and Yakihonne, among others.
-
Free Media Gallery: Curious what type of images, memes, gifs, and videos are being uploaded to Nostr? Check out the Free Media Gallery to see the most recent uploades to nostr.build. This view only shares the free uploads, you would not be able to see any user account uploads which are kept private unless purposely shared by the account owner. https://nostr.build/freeview
-
Delete Uploaded Media: If you upload free media to Nostr using a Nostr app, you can go back and delete it yourself with our delete tool. This is most used when people dox themselves, accidentally uploading an image with their name or address. The image needs to be associated to your n-pub and you will need to authenticate before deleting.
-
CSAM Scanning, Removal and Reporting: CSAM is not tolerated in any way. Not just CSAM, but any media that exploits a child in any way including AI and cartoons, children in inappropriate positions or clothing, we block the user and report their content and all related information we have on the user to the authorities / NCMEC. We use multiple services when filtering and reporting CSAM including Cloudflare's CSAM filter, Microsoft PhotoDNA, AI models and the NCMEC reporting portal. We do not filter or report anything else that is in compliance with our TOS, only CSAM. https://www.missingkids.org/theissues/csam

-
24/7 Support: nostr.build has people around the world, monitoring Nostr every day for Nostr and nostr.build related issues. Issues include but are not limited to; media not uploading or displaying, doxed uploads, illegal content removal, developer issues, and feature requests. There are very few services in the world where you can interact directly with the developers and get support and feature requests fulfilled. You can also contact us at support@nostr.build.
Pro Accounts:
-
10GB of Private Storage: One of the most common problems with the free service is the file size is capped at 21MB per file. For long videos, this becomes a challenge. With paid accounts, there is no file size limit to what you upload, only the size of the account.
-
Media Management Portal: One of the biggest advantages of a nostr.build account is the ability to keep all your media in one place, separate from social media platforms, in your own private portal. You can drag and drop, add, create folders, move to a folder, delete, and rename any of your media, and much more. Check out our nostr.build features overview video to get a better idea of media management in your nostr.build account.

-
AI Studio: Our latest and one of our coolest features is the all-new AI Studio. AI Studio provides text-to-image generation with multiple popular models to choose from. While other platforms only offer a single text-to-image model (ex. ChatGPT/DallE, Discord/Midjourney, X/Grok2), nostr.build offers multiple models on the same platform. We also offer a complete media management system for your AI creations mentioned above, the other platforms don’t have that. Check out our competitive comparison here! For Pro accounts we offer SDXL-Lightning, and Stable Diffusion 1.

-
.pdf and .zip File Support: Another huge request from users was to support the .pdf and .zip file types. This wasn’t as easy as it seems since we have to perform a virus scan on each of these file types before publishing and allowing public access.

-
View All Media Gallery: Curious what type of images, memes, gifs and videos are being uploaded to nostr's free service? Check out the Media Gallery to see all 2Million+ uploads ever uploaded to nostr.build. This only shares the free uploads, you would not be able to see any user account uploads which are kept private unless shared.
-
Share Direct to Nostr: Upload or create new media on nostr.build and share it with or without a note straight to Nostr, no other client needed! This is a feature that more tightly integrates nostr.build with Nostr and takes it steps closer to becoming a true Nostr client.
-
Global Content Delivery Network: Lightning-fast global CDN distribution of your content for faster, easier viewing around the world.
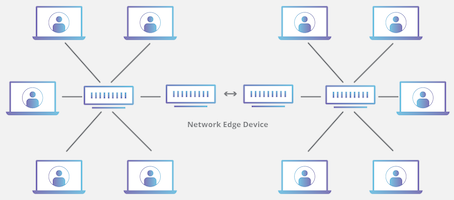
-
Referral Link: Found in your profile settings, share your referral link and earn ‘Credits’ when someone uses it to purchase an account. Credits can be used for advanced features, account upgrades, and renewals.
-
Viewer and Usage Stats: See the total ‘Unique Views’ and ‘Request Counts’ for all of your media, nicely graphed out, from 1-day to 3-month chart options. Just click the three dots under your media and select the 'Statistics' tab.
Creator Accounts:
-
30GB of Private Storage: 3x more storage than the Pro account. Ideal for creators, podcasts, and videographers, this gives you the added storage for those larger projects.
-
.svg File Support: Scalable Vector Graphics (SVG) files use mathematical formulas to store graphics. This makes them able to be resized without losing quality, very common with designers and content creators.

-
AI Studio: When creating images in AI Studio, Creator accounts have access to all Pro Stable Diffusion models and unlimited use of the Flux.1 model.
- Flux.1 (schnell): One of the latest text-to-image models, Flux is a 2 billion parameter rectified flow transformer that excels in graphic detail and correct text spelling and layout. It is the same core model that X(Twitter) uses with Grok2 images.

-
Host a Creators Page: Creators have the option to share their media to their Creators page hosted on nostr.build. This makes it easier for people to see, donate, and share. Check out all the Creators and their masterpieces here!

-
iDrive E2 backup for all media: We currently store all media on Cloudflare R2 servers. If for whatever reason Cloudflare servers lose your content, we also store a backup on a completely different service provider, iDrive E2 servers.

Advanced Accounts:
-
100GB of Private Storage: The largest account size we offer, with more than 3x the storage of the Creator account. This is plenty of storage for all of your Nostr needs and more.
-
AI Studio Extended Access: Get all the models, all the latest experimental features, and additional Credits with an Advanced account.
-
NIP-05 @nostr.build: Do you need premium NIP-05 identification? Choose any name you want and have your own @nostr.build official profile.
Roadmap:
-
Free Account: This would be just enough to get someone started with nostr.build’s media management features and slightly larger media size uploads.
-
Lifetime Account: This would be something like all features, all experimental features, 1TB of storage for life, and two free t-Shirts.
-
Traditional and AI Media Editors: Combining a powerful, standard media editor Pintura, with modern AI image editing features from stability.ai would allow users to quickly and easily modify their media using multiple tools. https://pqina.nl/pintura/?ref=pqina https://stability.ai/stable-image
-
Video Transcoding and Player: nostr.build has never modified video meaning all different formats and sizes are uploaded, none of them optimized for the platform they are being viewed on, and all of them in many different formats. By properly transcoding the media it will be viewable, optimized and faster on all platforms the video is being watched on, Android, iOS, desktops, laptops, etc.
-
Expandable Storage: The ability to purchsase additional chunks of storage and add it to your existing account.
nostr.build has a lot more to offer than just a place to upload media. It is your complete media platform, with an extremely intuitive user interface offering new features added all the time, and of course, always with the goal, to help grow Nostr, make is easier and more fun to use.
-
-
 @ f527cf97:65e232ee
2024-12-13 15:50:50
@ f527cf97:65e232ee
2024-12-13 15:50:50A new breed of entrepreneurs is emerging on social media platforms, especially on LinkedIn—those who want to show (in new terms: coach) other entrepreneurs how to become successful. And even on Nostr I have already discovered the first coaches.
Their areas of influence vary from general measures to spiritual-mental attitude change, and even to specializations on a medium or a specific platform. Over the past few weeks, I have looked into several of them and expressed interest in their offerings, always with an open mindset: "Maybe they know something I don't, and I could learn something new." I engaged with generalists, mental attitude changers, and specialists. I went through a few stages that all look the same:
- They somehow get in touch with you, often subtly lured through indirect means so that they don’t appear to be cold-calling you (which is illegal in many countries).
- You are invited to a mass event, usually a webinar with general teasers about the offering.
- Then you are asked to pay to access the valuable information.
Here are my thoughts about this business model.
They all promise to know some kind of secret formula or have a proven system that you just need to follow to achieve success in 90% of cases (or so). This system has, of course, been tried and tested over the years, they say, and they have made an effort to formalize it—for you. So they can now sell it to you, saving you the trouble of doing the work yourself. The target audience seems to be entrepreneurs in their 20s and 30s, or those who want to become one. While they claim it’s for all age groups, the presentation clearly appeals more to this demographic. It would be difficult to convince someone in their 40s or 50s. No wonder, as all these success coaches I met were under 40 themselves and have no idea how people think when you get older.
Now, after reading their social media posts, which are admittedly persuasive in rhetoric, and after being tempted, like I was, to comment on one with "BS, that only works in exceptions," they respond positively, never offended, and in an inviting tone. Or they send you "info material" or some other goodies behind a link where you have to sign up with your email address. Since I use disposable email addresses, I have no problem with that and think, why not? Let’s see what they have to offer.
And sometime later, maybe in 2 or 3 weeks, you receive an invitation to a "webinar" at the same address. And that’s where it starts to get unethical. Most of them didn’t indicate in the sign-up for the initial info material that they would also use your email address for other purposes, or that the whole thing is actually set up with that intention. Such information should be placed near the email field according to EU privacy laws. If it’s missing, it’s a violation of GDPR and actually a justiciable issue.
But okay, I participated in all the webinars out of curiosity. And they are all structured the same way. First, there’s a one-hour presentation with slides covering general points, followed seamlessly by the introduction of their own product or service. There’s no "advertisement" or "sponsored" label beforehand (red flag number 2). It’s either access to several training videos or an initial consultation session to tailor the coaching to your specific needs. So it all boils down to selling the coach’s own product or service. In the past, this was done directly in the first step. That doesn’t work as well today, so they’ve added 1-2 steps beforehand with bait offers. But at the latest, after or at the end of the webinar, prices are presented. These range from 5,000 to 10,000 Euros. A young or unsuccessful entrepreneur has to invest this amount if they want to receive the formula for financial bliss.
Yet, they don’t even know exactly what they would be investing in. They are constantly led to believe that this magical formula works for most people, and in every case during the webinar, a previous successful client is showcased, who is now floating in the clouds of financial happiness thanks to this "secret formula." However, it is also mentioned that this formula must be specifically tailored to your business. Hence the 5-10K euro investment. This means that after at least 2 hurdles of customer attraction, you still don’t know what you will actually receive and specifically, whether it will really work for you. You are essentially buying a pig in a poke. And that is the main problem.
It is repeatedly pointed out that the customer also has their obligations, such as doing everything the coach recommends and investing a certain amount of time each week. But nothing is promised with certainty. You only hear the alleged success statistics of X% over and over again. You can’t verify that; you just have to take it on faith. And that’s when you start to gamble internally. "Ah, I’m sure I belong to the 90% (or whatever the success rate is) if I just follow along."
You also have to trust that the success example presented in person in the webinar is authentic, meaning that the success of this entrepreneur stems solely from the implementation of the coaching measures and not from other circumstances. I don’t want to accuse anyone of anything, but that’s a bit too much trust for me to invest. I’m more the type who believes "respect and politeness are free, but trust must be earned."
I addressed this candidly in the last "client meeting." I pointed out that I had no guarantees, even if I fully participated, that I could expect an increase in my leads/appointments/revenues (whatever they specifically promise). In contrast, their fees are secure and likely paid in advance. I see an imbalance in fairness there. Instead, I proposed a fair commission model. For every lead/appointment/revenue they bring me, I would pay them a certain commission. And if they are indeed as good as they claim, they shouldn’t have a problem with that. I also said it would be more "entrepreneurial" to share both the success and the risk. Because with their model, only one party (namely them) has their ducks in a row while I, as the coached one, am taking a gamble. There are so many other influencing factors beyond my participation. What if my country or my industry is in a recession, for example? Or I could think of many other factors that are out of my control.
Well, they vehemently rejected this proposal. No guts. No entrepreneurship on their side with this. I even said, "With your business model, it’s reasonable to suspect that you just want to rip me off and cash in, no matter what happens." That didn’t help either.
My father once said something wise. When I was 18 or 19 years old, I wanted to sell building savings insurance, and for that, I was supposed to attend a sales training that costed about 50 euros, which isn’t much. My father immediately said, "Nonsense. You want to make money, not spend it." That stuck with me, and this whole situation reminded me of that. Now, this doesn’t exclude entrepreneurial risk and investments, but it should be more tangible than a pile of promises and hot air. You need to limit the risk and uncertainty as much as possible. A commission model, like the one I proposed, would have been fairer. Let’s grow or fail together, right? But not just one side taking all the risks.
I also once worked as a math tutor in an organization with a money-back guarantee. Students who had failed math came to me every day for six weeks in the summer, and I prepared them for their last chance, the retake exam. Our promise was that after these six weeks, you would pass math and move up to the next grade without having to repeat the school year. And if not, you would get your entire course fee back, and both sides would have just wasted time. We only refunded one out of about 30 students, and the one's failure was more due to the immense pressure she received from home. All the others passed the retake exam, and 20% of them even became math whizzes in the following school year, achieving top grades.
So, beware of such "business models." Sharing the risk is fairer. And if someone really knows their stuff, they can easily take on a 30-to-1 risk. And if not, and they insist on securing all the money upfront … you know where I’m going with this.
-
 @ c4b5369a:b812dbd6
2024-11-24 09:27:12
@ c4b5369a:b812dbd6
2024-11-24 09:27:12How to print your own ecash, using Gandlaf's money printer
To celebrate the recent money printer update, here is a short guide on how to use it.
Step 1: Go to the money printer
Unlike the FED's money printer, this Cashu ecash money printer is openly available. Head over to https://brrr.gandlaf.com to give it a spin.
Select a mint
Choose a mint that should be backing the ecash notes. You have a few different options when choosing a mint:
- Connect to your own mint: Connecting to your own mint is great if you want to be the backer of the ecash notes. It does however require you to have your mint up and running. You can connect to it by typing the mint URL into the input field.
- Connect to a known mint: There are mints that are already indexed on nostr. You can find them by clicking on the `discover more mints` button.
- Connect to any mint you want!: All you need is the mints URL. Just type it into the input bar!
Once you selected a mint, click connect to set up the mint for money printing :

After connecting to the mint, you will have the option to select the currency you want to print. Not all mints support all currencies! The dropdown menu below will show all available currencies the mint offers.
After selecting your preferred currency, click confirm to continue.

In the next step, you will chose the amount that should be printed on each note. Be careful though, because unfortunately not every amount is possible. To preserve mint users privacy ecash mints use fixed coin amounts. This means a specific amount, will be made up from smaller amounts. Today, most cashu mints use power-of-2 amounts.
So if you for example would like to print the amount "100", it would be made up from the coins [64, 32, 4]. The maximum number of coins that can be encoded in a QR code, without the QR code losing its readability is \~4. The money printer will analyze which amounts the mint offers, and show how many coins will be needed.
Below, you will see the calculation of how much the total issuance for this printing cycle will be. Once you are all set, click confirm to continue.

You can now either add the funds for the print via Cashu token or via Lightning. Let's first take a look on how to add funds via Cashu token.
If you select this option, I will assume that you already own ecash from the mint you wish to print the notes. Otherwise, you should move on to the payment by lightning.
You have to make sure that the token you are pasting is from the correct mint, in the correct unit/currency and matches the amount exactly! Otherwise, it will not work.

If you don't own ecash from that mint, you can pay for the print with lightning directly. The only fees that will be charged are Lightning network fees.
Just scan the QR code that is presented to you and wait for the payment to be confirmed.

Once the payment has confirmed, either through Cashu or through Lightning, the print is ready. You can now customize the design you wish to print.
You can select a color, a brand image and a corner image that should be put on the note.
Once you are happy with the design, go ahead and click `Print now! BRRRRRRRRRRR`

This will take you to the print page. You can now print the ecash by pressing `CTRL`+`P`
And that's it! You have now printed your own money. I hope you liked the experience of playing FED for a day.
Be aware! Once scanned and redeemed, the ecash notes become invalid. So they are one-time-use.
If you want to make another print, just refresh the page. It will take you back to the beginning. Your past prints will also be stored in the browser cache, so you can come back to them at a later time, if your printer overheated or something.

Happy printing!
Gandlaf
-
 @ 4ba8e86d:89d32de4
2024-10-23 00:11:19
@ 4ba8e86d:89d32de4
2024-10-23 00:11:19Ele permite que os usuários descubram, baixem e instalem aplicativos em seus dispositivos Android sem depender da Google Play Store, que é a loja de aplicativos padrão do Android.
História do F-Droid
O F-Droid foi lançado em 2010 por um grupo de desenvolvedores liderados por Ciaran Gultnieks. A ideia por trás do projeto era criar uma alternativa de código aberto para a Google Play Store, que é uma plataforma centralizada controlada por uma única empresa. O F-Droid foi desenvolvido como um catálogo de aplicativos que só inclui aplicativos de código aberto que podem ser baixados e instalados gratuitamente.
Desde o lançamento, o F-Droid cresceu significativamente e agora oferece mais de 3.500 aplicativos de código aberto para Android, com uma ampla gama de categorias, incluindo jogos, educação, produtividade, privacidade e segurança. O projeto é mantido por uma comunidade de desenvolvedores voluntários e é executado sem fins lucrativos.
Os problemas que o F-Droid resolve
O F-Droid resolve vários problemas associados à Google Play Store e outras lojas de aplicativos. O primeiro é o controle centralizado de uma única empresa. A Google Play Store pode remover aplicativos que violem suas políticas, e os desenvolvedores podem ser impedidos de distribuir aplicativos por meio da loja por motivos arbitrários. O F-Droid, por outro lado, é administrado por uma comunidade sem fins lucrativos e não há restrições sobre quais aplicativos podem ser incluídos no catálogo.
Além disso, o F-Droid oferece uma alternativa para os usuários preocupados com a privacidade que não querem depender dos serviços da Google. O F-Droid é independente do Google Play Services e não rastreia os usuários ou coleta informações pessoais, tornando-se uma escolha atraente para aqueles que buscam maior privacidade.
Por que usar o F-Droid?
Há várias razões pelas quais você pode querer usar o F-Droid em vez da Google Play Store ou outras lojas de aplicativos. Aqui estão algumas delas:
-
Privacidade: Como mencionado anteriormente, o F-Droid é independente do Google Play Services e não rastreia os usuários. Isso significa que você pode baixar e instalar aplicativos sem se preocupar com a coleta de dados pessoais.
-
Segurança: O F-Droid oferece apenas aplicativos de código aberto e de software livre, o que significa que a comunidade pode examinar o código-fonte para garantir que não haja vulnerabilidades ou backdoors mal-intencionados.
-
Controle: O F-Droid permite que os usuários controlem seus próprios dispositivos Android e decidam quais aplicativos são instalados e atualizados.
-
Escolha: O F-Droid oferece uma ampla gama de aplicativos de código aberto e de software
Também é importante observar que nem todos os aplicativos disponíveis no F-Droid são completamente livres de riscos. Portanto, é sempre recomendável ler cuidadosamente as informações sobre o aplicativo e avaliar os riscos antes de baixá-lo e instalá-lo.
Aqui está o passo a passo para instalar o F-Droid em seu dispositivo Android:
-
Acesse o site oficial do F-Droid em https://f-droid.org/ usando um navegador da web no seu dispositivo Android.
-
Verifique a assinatura PGP do arquivo APK que você irá baixar. Para isso, clique no link "PGP Signature" abaixo do botão "Download F-Droid" na página inicial do site. Na página seguinte, baixe o arquivo "F-Droid.apk.asc" clicando no botão "Download". Baixe também a chave pública do desenvolvedor do F-Droid, clicando no link "PGP key of F-Droid release signing key" na mesma página. É importante verificar a assinatura antes de prosseguir com a instalação.
-
Clique no botão "Download F-Droid" para baixar o arquivo APK.
-
Abra o arquivo APK baixado em seu dispositivo Android. Se você não sabe como abrir o arquivo, vá até o gerenciador de arquivos do seu dispositivo e encontre o arquivo APK que acabou de baixar. Toque no arquivo e siga as instruções na tela para instalar o aplicativo.
-
Se aparecer uma mensagem de alerta informando que a instalação de aplicativos de fontes desconhecidas está desativada, vá até as configurações de segurança do seu dispositivo e habilite a opção "Fontes desconhecidas". Isso permitirá que você instale aplicativos de fora da Google Play Store.
-
Clique em "Instalar" e aguarde a instalação ser concluída.
-
Após a instalação, abra o aplicativo F-Droid e aguarde a inicialização do repositório de aplicativos.
-
Pronto! Agora você pode navegar e baixar aplicativos do F-Droid em seu dispositivo Android. O F-Droid oferece uma ampla variedade de aplicativos de código aberto e de software livre, e todos são gratuitos para baixar e usar. Você pode usar o F-Droid como uma alternativa à Google Play Store se estiver preocupado com privacidade, segurança ou controle de seus próprios dispositivos Android.
https://github.com/f-droid
-
-
 @ e1146a85:0de0b731
2024-12-13 15:34:32
@ e1146a85:0de0b731
2024-12-13 15:34:32When it comes to maintaining a comfortable home in Christchurch, having a reliable heat pump is essential. Whether you're looking to install a new system, keep your existing unit running smoothly, or understand the costs involved, DC Installation Services is here to help with all your heat pump needs. In this blog, we’ll cover important aspects of heat pumps in Chch, heat pump cleaning CHCH, and heat pump installation cost in Christchurch.
Heat Pumps in Christchurch: A Smart Choice for Comfort
Christchurch’s climate demands a heating and cooling solution that’s versatile, energy-efficient, and effective. Heat pumps in Chch are the perfect solution for homeowners looking to maintain a comfortable indoor environment throughout the year. These systems not only provide efficient heating during the cold winters but also cool your home in the summer, making them a year-round comfort solution.
At DC Installation Services, we offer a wide range of heat pumps designed to suit different home sizes and budgets. Whether you're looking for a wall-mounted system, a ducted system, or a multi-split heat pump for multiple rooms, we can help you choose the best option for your home. Our experienced technicians ensure the right installation, maximising energy efficiency and reducing your energy bills. The Importance of Heat Pump Cleaning in Christchurch.
To keep your heat pump functioning at its best, regular heat pump cleaning in Christchurch is essential. Over time, dust, dirt, and debris can accumulate inside the unit, affecting its efficiency and air quality. Without proper maintenance, this build-up can lead to higher energy consumption, reduced performance, and even system failure.
At DC Installation Services, we offer expert heat pump cleaning in Christchurch, including cleaning the filters, coils, and other key components of your system. Our thorough cleaning process ensures that your heat pump works efficiently, provides cleaner air, and extends the lifespan of your unit. Regular cleaning can help you avoid costly repairs and maintain your system's optimal performance. Whether you’re due for a routine cleaning or facing issues with airflow or cooling, our team is here to provide fast and effective service.
Understanding Heat Pump Installation Costs in Christchurch
When planning to install a heat pump in Christchurch, one of the first questions many homeowners have is, “What is the heat pump installation cost in Christchurch?” The installation cost of a heat pump can vary depending on several factors, including the type of heat pump, the size of the area to be heated or cooled, and the complexity of the installation.
At DC Installation Services, we offer transparent pricing with no hidden fees. We begin by assessing your home’s size, insulation, and specific needs to recommend the most efficient and cost-effective solution. The cost of installation typically includes the price of the heat pump unit, any required materials (such as ductwork or wall mounts), and the labor involved in installing the system. Depending on your choice of system, costs can range, but we always strive to provide competitive pricing and a high level of service.
We also take care of any permits or regulations required by local authorities to ensure that the installation is up to code. Our team will provide you with a detailed quote, so you can understand exactly what you're paying for before proceeding. Additionally, we offer ongoing maintenance packages to ensure your heat pump continues to work efficiently long after installation.
Why Choose DC Installation Services?
At DC Installation Services, we’re committed to providing high-quality products and expert services to all our customers. We understand that investing in a heat pump is a long-term decision, and we’re here to guide you every step of the way, from choosing the right system to installation and regular cleaning. With years of experience in the industry, we take pride in offering tailored solutions for your heating and cooling needs. Our team is dedicated to ensuring that your home stays comfortable, no matter the season, with top-notch heat pump cleaning in Christchurch, affordable heat pump installation cost in Christchurch, and reliable heat pump installations.
If you're ready to install a heat pump or need cleaning and maintenance for your existing unit, contact DC Installation Services today. We're here to help you achieve the perfect indoor climate at home!
-
 @ 705605d9:b4324038
2024-12-13 15:33:06
@ 705605d9:b4324038
2024-12-13 15:33:06Сельское хозяйство на пике
За десять лет Горноправдинск стал лидером в аграрной сфере. Теплицы работают круглогодично на солнечных батареях, поля оснащены автоматическими системами полива, а урожай собирают роботы. Местные фермеры выращивают десятки видов культур: от картофеля до редких сортов ягод, экспортируемых в другие регионы. Экологическая чистота продукции — визитная карточка города.

Экологичный город
Горноправдинск перешел на возобновляемую энергетику. Отходы перерабатываются в удобрения и биотопливо. Здания строят из дерева и других экологически чистых материалов. Улицы украшены зелеными зонами, а транспортная система работает на электричестве.
Жизнь людей
Каждый житель имеет доступ к современному жилью, паркам и образовательным программам. Городские гранты помогают развивать личные фермерские хозяйства. Туризм также набирает обороты благодаря экопаркам и фермерским фестивалям.
Горноправдинск за десятилетие стал образцом для других городов. Это место, где природа и технологии гармонично сосуществуют, а жители гордятся своим вкладом в процветание родного края.








