-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8d34bd24:414be32b
2024-12-01 15:30:02
@ 8d34bd24:414be32b
2024-12-01 15:30:02As an American Christian who is no longer young, I have seen my nation go from wealth to debt, from promoting godliness to promoting evil, from a land of laws and blind justice to a land where people are judged more by their group affiliation than by their actions or disobedience of the law.
It is disheartening to see a nation that was founded on Biblical principles by people who left their nations in order to be able to serve God freely turn into a nation that mocks God and tramples His commandments. It doesn’t have to be this way.
Too often we try to fix America’s (or most nations) problems by changing the government leaders, but that isn’t how a nation is fixed. It is only when the people turn back to God that the nation is fixed. An ungodly nation will never be fixed even if a godly leader is put in place.
Heal Their Land
This particular passage is in reference to Israel in particular, but I do believe the principles are applicable for any nation, but especially for a nation that was founded on Biblical principles. The good news is that God blesses nations that honor Him. The bad news is that He punishes those nations more harshly when they leave Him than He does those nations that never served Him before.
Then the Lord appeared to Solomon at night and said to him, “I have heard your prayer and have chosen this place for Myself as a house of sacrifice. If I shut up the heavens so that there is no rain, or if I command the locust to devour the land, or if I send pestilence among My people, and My people who are called by My name humble themselves and pray and seek My face and turn from their wicked ways, then I will hear from heaven, will forgive their sin and will heal their land. Now My eyes will be open and My ears attentive to the prayer offered in this place. For now I have chosen and consecrated this house that My name may be there forever, and My eyes and My heart will be there perpetually. As for you, if you walk before Me as your father David walked, even to do according to all that I have commanded you, and will keep My statutes and My ordinances, then I will establish your royal throne as I covenanted with your father David, saying, ‘You shall not lack a man to be ruler in Israel.’ (2 Chronicles 7:12-18) {emphasis mine}
The key statement is, if “My people who are called by My name humble themselves and pray and seek My face and turn from their wicked ways, then I will hear from heaven, will forgive their sin and will heal their land.” It all starts with the people that are called by His name, whether Jew or Christian. We need to repent of our personal sins which include not standing up for God’s word and commands. We need to share the Gospel with those around us and live lives that are honoring to Him. We need to live Christ-like lives that draw people to our Savior.
When we are faithful servants, God will bless us and our nation. When we live Christ-like lives, people are drawn to God. As more people trust Jesus as Savior, we get a more godly nation and are more likely to get godly leaders. When we have more godly citizens and more godly leaders, many of our economic, cultural, and international woes are decreased.
The best way to heal our land is to repent and turn back to God. Defending righteousness through politics is good, but living a godly life and sharing the gospel with others is better.
Uproot From the Land
On the other hand, if we refuse to repent, live godly lives, and share the gospel with others, God promises us a curse and many woes.
“But if you turn away and forsake My statutes and My commandments which I have set before you, and go and serve other gods and worship them, then I will uproot you from My land which I have given you, and this house which I have consecrated for My name I will cast out of My sight and I will make it a proverb and a byword among all peoples. As for this house, which was exalted, everyone who passes by it will be astonished and say, ‘Why has the Lord done thus to this land and to this house?’ And they will say, ‘Because they forsook the Lord, the God of their fathers who brought them from the land of Egypt, and they adopted other gods and worshiped them and served them; therefore He has brought all this adversity on them.’ ” (2 Chronicles 7:19-22) {emphasis mine}
Is America losing its blessings and gaining a curse because they have turned away and forsaken God’s statues and His commandments? I believe this is true. Have Americans turned away from God to “serve other gods and worship them?” I believe they have even if this only means serving the god of self and worshipping pleasure. If America falls it will be because “they forsook the Lord, the God of their fathers.”
A Gentile Repentance
You may ask, “Can we really apply these blessings and curses to nations other than Israel?” I will use these passages from Jonah as an example of God’s blessings and curses based on the actions and repentance of a gentile nation.
Now the word of the Lord came to Jonah the second time, saying, “Arise, go to Nineveh the great city and proclaim to it the proclamation which I am going to tell you.” So Jonah arose and went to Nineveh according to the word of the Lord. Now Nineveh was an exceedingly great city, a three days’ walk. Then Jonah began to go through the city one day’s walk; and he cried out and said, “Yet forty days and Nineveh will be overthrown.” (Jonah 3:1-4)
Jonah was sent as a prophet to Nineveh, the capital of the Assyrian nation. This was a totally ungodly and evil nation that was known for its cruelty and lawlessness. Because of its evil, Jonah was sent to warn them of their imminent destruction. (Most of us know the story of Jonah’s misadventures, including being swallowed by a sea creature, while trying to not give this warning.)
What happened when these evil, ungodly people repented and turned to God in submission?
Then the people of Nineveh believed in God; and they called a fast and put on sackcloth from the greatest to the least of them. When the word reached the king of Nineveh, he arose from his throne, laid aside his robe from him, covered himself with sackcloth and sat on the ashes. He issued a proclamation and it said, “In Nineveh by the decree of the king and his nobles: Do not let man, beast, herd, or flock taste a thing. Do not let them eat or drink water. But both man and beast must be covered with sackcloth; and let men call on God earnestly that each may turn from his wicked way and from the violence which is in his hands. Who knows, God may turn and relent and withdraw His burning anger so that we will not perish.”
When God saw their deeds, that they turned from their wicked way, then God relented concerning the calamity which He had declared He would bring upon them. And He did not do it. (Jonah 3:5-10)
This nation, that had never served God and had never done good, was spared when the people and the king repented of their evil ways and honored God. How much more will a nation full of God’s children be healed, if they turn back to God and obey His commands?
The God of the Bible can raise the dead; he is definitely capable of healing a nation that repents. Join me in personal repentance, prayer for our nation, and faithful service to our awesome God.
Trust Jesus.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 8d34bd24:414be32b
2024-11-27 15:13:36
@ 8d34bd24:414be32b
2024-11-27 15:13:36There are so many evil and harmful things happening in the world today. Christians are being persecuted for their faith. Our health is falling apart and we are being given conflicting information. Nations are fighting against nations and it looks like a world war could be started in any of the numerous flashpoint locations. Nations are divided within and without. It is easy to be overwhelmed.
I’m going to use an Old Testament event as an example of how we should deal with all of these problems that are beyond what we can deal with ourselves.
Now in the fourteenth year of King Hezekiah, Sennacherib king of Assyria came up against all the fortified cities of Judah and seized them. (2 Kings 18:13)
At this time, Assyria was the most powerful nation on earth (or at least in the Middle East region). They were known for their violence and cruelty and now they had their sights set on conquering Judah. The people in Judah were truly terrified. They had seen what Assyria had done to other nations.
Then Rabshakeh stood and cried with a loud voice in Judean, saying, “Hear the word of the great king, the king of Assyria. Thus says the king, ‘Do not let Hezekiah deceive you, for he will not be able to deliver you from my hand; nor let Hezekiah make you trust in the Lord, saying, “The Lord will surely deliver us, and this city will not be given into the hand of the king of Assyria.” Do not listen to Hezekiah, for thus says the king of Assyria, “Make your peace with me and come out to me, and eat each of his vine and each of his fig tree and drink each of the waters of his own cistern, until I come and take you away to a land like your own land, a land of grain and new wine, a land of bread and vineyards, a land of olive trees and honey, that you may live and not die.” But do not listen to Hezekiah when he misleads you, saying, “The Lord will deliver us.” Has any one of the gods of the nations delivered his land from the hand of the king of Assyria? (2 Kings 18:28-33)
It was true that Assyria had conquered every nation they had attacked. It was true that neither the military, nor the religion, of any of those nations had saved them from Assyria, but these other nations did not serve the one true God and Creator of all. Judah was God’s chosen people. They were different.
Still, the people of Judah were terrified. They knew they could not withstand an attack by Assyria on their own. Fortunately Judah currently had one of its few faithful kings.
Then Hezekiah took the letter from the hand of the messengers and read it, and he went up to the house of the Lord and spread it out before the Lord. Hezekiah prayed before the Lord and said, “O Lord, the God of Israel, who are enthroned above the cherubim, You are the God, You alone, of all the kingdoms of the earth. You have made heaven and earth. Incline Your ear, O Lord, and hear; open Your eyes, O Lord, and see; and listen to the words of Sennacherib, which he has sent to reproach the living God. Truly, O Lord, the kings of Assyria have devastated the nations and their lands and have cast their gods into the fire, for they were not gods but the work of men’s hands, wood and stone. So they have destroyed them. Now, O Lord our God, I pray, deliver us from his hand that all the kingdoms of the earth may know that You alone, O Lord, are God.” (2 Kings 19:14-19) {emphasis mine}
How did King Hezekiah respond to the violent attack and the mocking of Judah, Hezekiah, and God? “He went up to the house of the Lord and spread it out before the Lord.” Hezekiah took his dreadful problem to God. He laid out the mocking letter before God. He prayed for deliverance, but he didn’t just pray for deliverance. He prayed for God to be glorified. He prayed for the destruction of those who mocked God. He laid his problems before God and trusted God to solve what Hezekiah could not. We need to do the same.
Are you or a family member suffering from a debilitating or deadly illness? Lay it before the Lord. Are you suffering persecution for your faith? Lay it before the Lord. Are you concerned with the evil that is seemingly overtaking the world? Lay it before the Lord. Are you worried by international disputes around the world that look like they could erupt into a world war or even a nuclear war? Lay it before the Lord.
There are many problems in the world that are far beyond what we can handle or fix, but there is no problem too big for our God and Savior. He’s got this.
Here is the same event described in Isaiah:
Then Hezekiah took the letter from the hand of the messengers and read it, and he went up to the house of the Lord and spread it out before the Lord. Hezekiah prayed to the Lord saying, “O Lord of hosts, the God of Israel, who is enthroned above the cherubim, You are the God, You alone, of all the kingdoms of the earth. You have made heaven and earth. Incline Your ear, O Lord, and hear; open Your eyes, O Lord, and see; and listen to all the words of Sennacherib, who sent them to reproach the living God. Truly, O Lord, the kings of Assyria have devastated all the countries and their lands, and have cast their gods into the fire, for they were not gods but the work of men’s hands, wood and stone. So they have destroyed them. Now, O Lord our God, deliver us from his hand that all the kingdoms of the earth may know that You alone, Lord, are God.” (Isaiah 37:14-20)
There is nothing God can’t handle. In our prayers, we also need to make sure our prayers are in line with glorifying God, upholding His word, standing for truth & righteousness, and following His eternal plan. We should put our problems before God, but we also need to glorify God and know that He has a perfect plan which may not include our momentary comfort. He will however always glorify Himself.
Then Isaiah the son of Amoz sent to Hezekiah saying, “Thus says the Lord, the God of Israel, ‘Because you have prayed to Me about Sennacherib king of Assyria, I have heard you.’ (2 Kings 19:20) {emphasis mine}
God hears our prayers and, when we pray according to His will, He answers them. Even when God says, “No” or “Wait,” He always “… causes all things to work together for good to those who love God, to those who are called according to His purpose.” (Romans 8:28)
Instead of trying to fix everything ourselves, we need to lay our problems before God. God knows all that ever was, all that is, and all that ever will be. His plans are perfect. We may want a particular solution, but God knows better than us. Sometimes the very thing we pray desperately to avoid is the very thing that we need most.
In case you have never read the story of Hezekiah, God saved Jerusalem miraculously and Judah didn’t have to lift a finger.
Then the angel of the Lord went out and struck 185,000 in the camp of the Assyrians; and when men arose early in the morning, behold, all of these were dead. So Sennacherib king of Assyria departed and returned home and lived at Nineveh. (Isaiah 37:36-37)
Trust Jesus.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 8d34bd24:414be32b
2024-11-24 15:41:30
@ 8d34bd24:414be32b
2024-11-24 15:41:30In America, there are a lot of people who call themselves Christians, but not nearly as many that live a life devoted to Christ. When I was a young Christian, one teacher or pastor made the comment, “If someone was accusing you of being a Christian, would there be enough evidence to convict you?” For so many “Christians,” I don’t think the answer would be, “Yes,” unless the only requirement was showing up for church most Sundays.
It amazes me how many Christians have never read their Bible cover to cover, from Genesis to Revelation. It amazes me how many Christians don’t pray daily. It amazes me how many Christians live lives like every other person except they attend church on Sunday (at least most of the time). Some people who call themselves Christians don’t even attend church. What makes these Christians any different than the unbelievers around the world?
If we truly have been saved from our sins by a merciful, all-powerful God, then we should be grateful. If we are actually a “new creation,” there should be signs of a changed life. If we know Jesus and know that everyone who rejects Him will be rejected by God and spend an eternity in Hell, then we should at least be sharing the Gospel with those we care about.
In my Bible study today, I read Isaiah 55. These verses really spoke to me about how our faith should affect our lives.
1“Ho! Every one who thirsts, come to the waters;\ And you who have no money come, buy and eat.\ Come, buy wine and milk\ Without money and without cost.
Jesus has called Jew and gentile to repent and has offered His forgiveness and salvation to all who trust in Him. It doesn’t cost anything. It just requires faith. Jesus paid the price, so we don’t have to.
2Why do you spend money for what is not bread,\ And your wages for what does not satisfy?\ Listen carefully to Me, and eat what is good,\ And delight yourself in abundance.
We are given the free gift of salvation and yet we are constantly seeking other things. We put all of our hard effort into seeking things that don’t satisfy. We seek fame or wealth or popularity or entertainment or pleasure. We don’t seek our Creator’s blessing. We don’t seek to serve and please our Savior. We complain about any and all hardships instead of being thankful for what we have. Why don’t we crave God’s word and His fellowship?
3Incline your ear and come to Me.\ Listen, that you may live;\ And I will make an everlasting covenant with you,\ According to the faithful mercies shown to David.
As believers we should “incline our ear,” “come to Him,” and “listen.” We should read the Bible, study the Scriptures, and pray with a listening spirit. God is faithful, but we won’t be blessed when we turn our backs on God.
4Behold, I have made him a witness to the peoples,\ A leader and commander for the peoples.
David was called “a man after God’s own heart,” and therefore God promised that a descendant of his would always be on the throne of Israel. This promise was fulfilled in Jesus — God’s son’s incarnation as a descendant of David, biologically through His mother Mary and legally through His step-father Joseph. David’s faith is an example to us of trusting fully in God and His promises.
5Behold, you will call a nation you do not know,\ And a nation which knows you not will run to you,\ Because of the Lord your God, even the Holy One of Israel;\ For He has glorified you.”
Most promises in the Old Testament are made to Israelites or descendants of Abraham, but there are a few promises made to the gentiles of the world, who will be blessed by the “Holy One of Israel,” Jesus Christ. We gentiles should be grateful that God’s promises have been shared with us and with those of every tongue, people, and nation. We have been reconciled to God through His holy life and the blood He shed for us. How can we possibly take this blessing for granted?
6Seek the Lord while He may be found;\ Call upon Him while He is near.
Right now we have the option to trust in Jesus1 and to receive His blessing, but this time will not last forever. In fact, I believe time is growing short. If you don’t know Jesus, don’t put off repenting and trusting in Him. If you do know Jesus, don’t put off getting your life right and following Him. Doing good deeds won’t get you into heaven, but it is pleasing to God and does lead to special blessings. We are to make the most of the time we have left.
7Let the wicked forsake his way\ And the unrighteous man his thoughts;\ And let him return to the Lord,\ And He will have compassion on him,\ And to our God,\ For He will abundantly pardon.
Technically there is nothing we can do to earn Salvation and forgiveness, but if we have been saved and forgiven, the Bible says “we are a new creation.” There will be signs of change if the salvation is real. God wants the wicked to forsake his way, the unrighteous to forsake his thoughts, and for everyone to return to Jesus as Lord. “If we confess our sins, He is faithful and righteous to forgive us our sins and to cleanse us from all unrighteousness.” (1 John 1:9)
8“For My thoughts are not your thoughts,\ Nor are your ways My ways,” declares the Lord.
If we are living according to our own wisdom and our own power, we are living to fail. It is only when we fully submit to God’s word and God’s plan, that we become what we were created to be. It is only then that we will feel complete and will honor our Creator.
We can’t obey God, if we don’t know His commands. We can’t trust Jesus, if we don’t know who He really is. We can’t serve God, if we haven’t submitted to the power and will of His Spirit. We can’t just drift down the river of life, but need to be driven and empowered by His power like the wind blowing a sailboat. The best way to know God’s commands, His character, and His plan is to know His word, the Bible. We can’t know this if we don’t read it and read all of it.
9“For as the heavens are higher than the earth,\ So are My ways higher than your ways\ And My thoughts than your thoughts.
There are so many times in the Bible that we are told that man’s wisdom is folly, yet so often we trust in what man tells us rather than what God tells us. We spend our efforts listening to human “experts” instead of listening to the words of the God who created everything “… and upholds all things by the word of His power. …” (Hebrews 1:3b) We can learn from wise and learned men, but we will never learn true wisdom except from God.
10For as the rain and the snow come down from heaven,\ And do not return there without watering the earth\ And making it bear and sprout,\ And furnishing seed to the sower and bread to the eater;
> 11*So will My word be which goes forth from My mouth;\
It will not return to Me empty,\ Without accomplishing what I desire,\ And without succeeding in the matter for which I sent it.
God’s word never returns empty. It always changes all it touches. We need to put in the effort to schedule time in God’s word every day. We should make sure we have read the whole Bible, so we can use Scripture to interpret Scripture instead of trusting solely on the wisdom of man. We need to take all of our concerns to God and follow His leading. We need to find fellow believers “and let us consider how to stimulate one another to love and good deeds, not forsaking our own assembling together, as is the habit of some, but encouraging one another; and all the more as you see the day drawing near.” (Hebrews 10:24-25)
I hope you all will live lives in such a way as to honor God and let all men know that you belong to Jesus.
Trust Jesus.
-
 @ c4b5369a:b812dbd6
2024-12-01 16:19:21
@ c4b5369a:b812dbd6
2024-12-01 16:19:21Ecash systems built on top of bitcoin have seen increasing adoption over the last couple of years. They have become a polarising topic in the bitcoin community, due to their centralized and custodial nature. Like any system, ecash comes with a lot of pros and cons when compared to other systems, that are fercely debated in cyber- and meat-space.
I have been working on developing tools and software for the ecash implementation Cashu for about 2 years now. I have had countless discussions with various people from different backgrounds about the topic. OG bitcoiners, fiat bankers, friends and family, privacy enthusiast... . As you can imagine the flow and outcome of these discussions varied widely.
Usually, conversations with bitcoiners were the most interesting for me. Their opinions about ecash polarised the most, by far. (excluding the fiat bankers, but that's a story for another day). In this short peice, I want to share some insights from the discussions I had, and maybe clear up some misconceptions about ecash on bitcoin.
What is Ecash?
If you still don't know what ecash is, sorry, I won't go into much detail explaining it. I recommend reading the wikipedia article on Ecash , and then this article on the rise and fall of digicash, the first and maybe only ecash company that existed. This will bring you up to speed on ecash history up until bitcoin entered the scene. Ecash was pretty much dead from the day after digicash went bankrupt untill it recently saw it's revival in two different spheres:
One of these spheres is obviously the bitcoin sphere. Here, ecash got reintroduced with the two open source projects Fedimint and Cashu. In my opinion, the main reason for this revival is the following fact: Unlike an implementation of ecash in the fiat world, that would rely on the permissioned system to "allow" something like ecash to exist, bitcoin does not come with that limitation. The permissionless nature of bitcoin allows for these protocols to exist and interoperate with the existing bitcoin stack.
The second, and maybe lesser known sphere is the revival of ecash as a CBDC. Bitcoiners might get scared at the mentioning of that word. Trust me, I don't like it either. Nonetheless, privacy enthusiasts see the opportunity to steer the CBDC-ship in another direction, by using an underlying technology for them that would limit targeted discrimination by the centralized authorithy. Something that works like cash... but in cyberspace... Ecash. One such implementation is GNU Taler, another one is Project Tourbillon. Usually, these kind of implementations use a cuck-version of the OG ecash, where only payers are anonymous, but not payees.
Anyway, in this article we will focus on the implementation of ecash on bitcoin.
About self custody
Bitcoin as a whole is about sovereignty and liberation. If someone else controls your money, they control you. For the first time since we've stopped using gold, bitcoin allows us to fully take control back of our money. A money that doesn't corrode, a money which supply connot get inflated, and a money that cannot be easily seized. All of this is true for bitcoin. There is only one precondition: You have to hold and use it self custodially.
Using bitcoin self custodially
The problem comes in when using bitcoin in a self custodial fashion. For bitcoin to maintain the monetary properties mentioned above, it has to remain decentralized. This means it is hard to scale, which in turn means the use of bitcoin tends to become more costly as usage increases.
So even if we wish that everyone would use bitcoin self custodially all the time for everything, I fear it is mostly just a dream, at least for the forseable future. Even with trustless second layer protocols like the Lightning Network, we are running into scaling issues, since at the end of the day, they are bound to the same onchain fee realities as bare-bones bitcoin transactions.
For most of humanity, it is financially not viable to pay even 1$ transaction fees for every transaction. Second layer protocol may bring the cost down a bit, but have other requirements. For example in lightning, you have an online assumption, to make sure your channel peers aren't trying to cheat. You need to have inbound liquidity to receive payments. There are cost associated with opening or closing payment channels, or rebalancing liquidity.
Other upcoming second layer protocols like Ark may improve on some of these issues. It is definitely something to look forward to! But they will have their own trade-offs, most likely also cost related. The fact remains that all trustless protocols that use the bitcoin timechain for conflict resolution, will have to deal with this matter. This is the cost of trustlessness.
Soo... Don't self custody...?
NO! If you can, you should always use self custody. As much as possible!
Personally, I use all the tools mentioned above. And I recommend that if you can, you should too.
But the fact is, not everyone can. Many would love to take control over their financial freedom, but the threshold for them to use bitcoin in a sovereign fashion is simply to high. So they will either remain in fiat slavery land, or they will end up using "bitcoin" through a custodian like coinbase, binance, or whatever banking service they have access to.
I will also mention that for some usecases, enjoying the convenience of a custodian is just very attractive. Of course, this is only the case as long as the custodian plays by the book, and doesn't suddenly freeze-, or worse, run away with your deposits.
The right tool for the right job
I don't beleive that one way of using bitcoin is better than the other. It entirely depends on which problem you are trying to solve.
If the problem is storing or transfering wealth, then of course you would want to do that on chain.
If on the other hand, you want to send and receive frequent small to midsized payments, you might want to get setup with a lightning channel to an LSP. Depending on how deep you want to get involved, you may even set up some infrastructure and become part of the Lightning network.
If you want to receive digital tips that you can later claim into self custody after they reach a certain threshold, you might opt for a custodial solution.
If you require certain properties, like offline peer-to-peer transferability, or cash-like privacy, you might choose an ecash system.
It doesn't mean that if you use one, you cannot use the other. You should use whatever is useful for the current problem you are trying to solve, maybe even using multiple tools in conjuction, if that makes sense.
Ecash vs Onchain vs L2?
First of all, we have to understand that ecash is neither a replacement for self custody, nor is it a replacement for trustless second layer protocols. They are irreplaceable with something that is custodial in nature, due to the simple fact that if you lose control over your money, you have lost the control over your life.
So. No one beleives you should prioritize custodial solutions to secure your wealth. Self custody will always remain king in that regard. Custodial wallets should be thought off as a physical spending wallet you can walk around with, even through the dark alleyways where it might get robbed from you. Keep your cash in there for convenient spending, not worrying about fees, liquidity, data footprints, channel backups, etc. etc. etc... These benefits obviously come at the cost of trust, that the provider doesn't rug-pull your deposit.
I really like the user experience of custodial services. I would never put a lot of money into any one of them though, because I don't trust them. Just like I wouldn't walk around with $10000 in my physical wallet. The risk that it gets stolen is simply to great. At the same time, this risk doesn't mean I will get rid of my physical wallet. I think having a wallet with some cash in it is super useful. I will mittigate the risk by reducing the amount I carry inside that wallet. This is the same way I think about digital money I hold in custodial wallets, be it an ecash service or others.
All things considered, it is hard to argue that self custody comes even close to the UX a custodian can give you, due to the fact that they can take care of all the complexities (mentioned above) for you.
So then, why ecash?
We now know, that we are NOT comparing ecash with the sovereign bitcoin stack. We are comparing it instead to traditional custodial systems. This is the area ecash is trying to improve uppon. So if you've chosen that the best tool to solve a problem might be a custodial solution, only then should you start to consider using ecash.
It offers a more privacy preserving, less burdonsome and less censorable way of offering a custody solution.
It offers some neat properties like offline peer-to-peer transactions, programability, de-linkage from personally identifiable information, and more.
Here is an example, on how ecash could create a fairer environment for online consumers:
Online services love to offer subscriptions. But for the consumer, this is mostly a trap. As a consumer, I would rather pay for a service right now and be done with it. I don't want to sign up for a 10 year plan, give them my email address, my date of birth , create an account, etc...
One way of doing that, would be for the service provider to accept payments in ecash, instead of having an account and subscription model.
It would work like this:
- The user creates ecash by paying into the service's mint. Hereby it is not required to use lightning or even bitcoin. It could be done with any other value transfer meduim the service provider accepts (cash, shitcoins, lottery tickets...).
- You use the issued ecash, to retreive services. This could be anything from video streaming, to AI prompts.
- Once you are done, you swap your remaining ecash back.
In a system like this, you wouldn't be tracked as a user, and the service provider wouldn't be burdoned with safeguarding your personal information. Just like a cash-for-goods transaction in a convenience store.
I beleive the search engine Kagi is building a system like that, according to this podcast. It has also be demoed by https://athenut.com/ how it would be implemented, using Cashu.
Here is another example, on how an event organizer can provide privacy preserving electronic payment rails for a conference or a festival, using ecash:
If you have been part of organizing a conference or an event, you might have experienced this problem. Onchain payments are too slow and costly. Lightning payments are too flaky.
Do merchants have to setup a lightning channel? Do they have to request inbound liquidity from an LSP? Do they have to splice into the channel once they run out of liquidity? In practice, these are the realities that merchants and event organizers are faced with when they try to set up payment rails for a conference.
Using ecash, it would look like this:
- Event organizer will run a dedicated ecash mint for the event.
- Visitors can swap into ecash when ariving at the entrance, using bitcoin, cash, or whatever medium the organizer accepts.
- The visitor can spend the ecash freely at the merchants. He enjoys good privacy, like with cash. The online requirements are minimal, so it works well in a setting where connectivity is not great.
- At the end of the event, visitors and merchants swap their ecash back into the preferred medium (cash, bitcoin...).
This would dreastically reduce the complexity and requirements for merchants, while improving the privacy of the visitors.
A bold experiment: Free banking in the digital age
Most bitcoiners will run out of the room screaming, if they hear the word bank. And fair enough, I don't like them either. I believe in the mantra "unbank the banked", after all. But the reason I do so, is because todays fiat/investment banks just suck. It's the same problem as with the internet platforms today. You, the "customer", is not realy the customer anymore, but the product. You get sold and squeezed, until you have nothing more to give.
I beleive with a sound money basis, these new kind of free banks could once again compete for customers by provididng the best money services they can, and not by who can scam his way to the money printer the best. Maybe this is just a pipe dream. But we all dream a little. Some dream about unlimited onchain transactions (I've had this dream before), and some dream about free banks in cyberspace. In my dream, these banks would use ecash to respect their users privacy.
Clearing up misconceptions and flawed assumptions about ecash on bitcoin
Not only, but especially when talking with bitcoiners there are a lot of assumptions regarding ecash on bitcoin. I want to take this opportunity to address some of those.
Ecash is an attack on self custody
As we've mentioned above, ecash is not meant to compete with self custody. It is meant to go where self custodial bitcoin cannot go. Be it due to on-chain limitations, or network/infrastructure requirements. Ecash is completely detached from bitcoin, and can never compete with the trustless properties that only bitcoin can offer.
Ecash mints will get rugged
100% correct. Every custodial solution, be it multisig or not, will suffer from this risk. It is part of the deal. Act accordingly. Plan for this risk when choosing to use a custodial system.
Working on ecash is a distraction from what really matters, since it is not self custodial
While it is true that improving self custodial bitcoin is one of the most important things our generation will have to solve, it doesn't mean that everything else becomes irrelevant. We see that today, in a lot of circumstances a fully sovereign setup is just not realistic. At which point most users will revert back to custodial solutions. Having technology in place for users that face these circumstances, to offer them at least some protection are worth the effort, in my opinion.
Ecash mints will retroactively introduce KYC
Yes it is true that ecash mints can do that. However, what would they learn? They would learn about the amount you were holding in the mint at that time, should you choose to withdraw. They would not be able to learn anything about your past transactions. And needless to say, at which point you should be one and done with this mint as a service provider, and move to someone that respects their users.
Ecash will be used to "steal" bitcoins self custodial user base
I would argue the oposite. Someone that has realized the power of self custody, would never give it up willingly. On the other hand, someone that got rugged by an ecash mint will forever become a self custody maximalist.
Closing thoughts...
I hope you enjoyed reading my take on ecash built on bitcoin. I beleive it has massive potential, and creators, service providers and consumers can benefit massively from ecash's proposition. Using ecash doesn't mean you reject self custody. It means you have realized that there is more tools than just a hammer, and you intend to use the tool that can best solve the problem at hand. This also means, that to some the tool "ecash" may be useless. After all, not everyone is a carpenter. This is also fine. Use whatever you think is useful, and don't let people tell you otherwise.
Also, please don't take my word for it. Think for yourself.
Best,
Gandlaf
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ 8d34bd24:414be32b
2024-11-20 16:16:25
@ 8d34bd24:414be32b
2024-11-20 16:16:25I’ve been studying a lot about end times prophecy because so much seems to be coming together and I believe our time left is short. I’m listening to a sermon series on Daniel and another on Revelation. I’m doing a Bible study on Revelation with the ladies at my church. In general I think our women’s Bible study curriculum is too focused on symbology and isn’t focused enough on what Revelation means for us and our future, but it has been good at pointing me at verses that have clarified my understanding of Revelation.
When trying to understand end times, I keep going back to “Who is Babylon the Great?” As I’ve been reading, I’ve been seeing things that may be clues. I’ll admit that I am not 100% certain in my interpretations, so I’m open to other interpretations and I don’t want anyone to take what I have to say as set in stone. That being said, when I consider what is happening in the world today and what Scripture predicts, the ideas I am about to present really seems to make sense. Hopefully this study will be useful to you even if you don’t agree with my conclusions. I do try to back all of my speculation with Scripture.
Revelation 17-18
I’ve always read Scripture and wondered, “Why is the US not mentioned?” I’ve usually assumed the US has to either be made unimportant on the world stage or be broken up into smaller countries (which is believable with how divided the nation has become). I’m now starting to wonder if the US is mentioned in end times prophecy, but I didn’t see it because it isn’t how I want to think of my country.
And he carried me away in the Spirit into a wilderness; and I saw a woman sitting on a scarlet beast, full of blasphemous names, having seven heads and ten horns. The woman was clothed in purple and scarlet, and adorned with gold and precious stones and pearls, having in her hand a gold cup full of abominations and of the unclean things of her immorality, and on her forehead a name was written, a mystery, “BABYLON THE GREAT, THE MOTHER OF HARLOTS AND OF THE ABOMINATIONS OF THE EARTH.” (Revelation 17: 3-5)
When reading this passage, the first thought is who or what is “Babylon the Great?” Is it a reincarnation of historical Babylon? Historical Babylon was situated in the center of what is modern Iraq. Does that make sense? It doesn’t to me. Is “Babylon the Great” just a figurative representation of evil? I don’t think so, because there are too many references to literal things for that to make sense. Is “Babylon the Great” a different city or nation? I believe this is the most probably interpretation.
And he said to me, “The waters which you saw where the harlot sits, are peoples and multitudes and nations and tongues. And the ten horns which you saw, and the beast, these will hate the harlot and will make her desolate and naked, and will eat her flesh and will burn her up with fire. For God has put it in their hearts to execute His purpose by having a common purpose, and by giving their kingdom to the beast, until the words of God will be fulfilled. The woman whom you saw is the great city, which reigns over the kings of the earth.” (Revelation 17:15-18) {emphasis mine}
Revelation talks of ten horns, being ten kings/kingdoms, that will then hand their authority over to the beast to rule the whole world. Do the ten kings, who give their kingdoms to the beast turn on Babylon because Babylon doesn’t want to submit to the Beast’s worldwide kingdom, but retain her own power? This passage sounds like the 10 horns and the beast will turn on “Babylon the Great” because Babylon will not join the beast’s system. Will it not join because it hates evil? Definitely not! Babylon is referred to as a harlot. The previous passage says, Babylon has “in her hand a gold cup full of abominations and of the unclean things of her immorality,” and that Babylon is “THE MOTHER OF HARLOTS AND OF THE ABOMINATIONS OF THE EARTH.” Why would Babylon the Great not join the rest of this evil cohort? Would it be that Babylon the Great was the world’s only super power and it doesn’t want to give up that power? Now that sounds very believable.
Now I put forth this premise that I don’t want to be true. What world super power currently exists that is resisting joining in a one world government? That sounds a lot like the US, but let us continue to see if this similarity becomes more obvious.
And he cried out with a mighty voice, saying, “Fallen, fallen is Babylon the great! She has become a dwelling place of demons and a prison of every unclean spirit, and a prison of every unclean and hateful bird. For all the nations have drunk of the wine of the passion of her immorality, and the kings of the earth have committed acts of immorality with her, and the merchants of the earth have become rich by the wealth of her sensuality.”
I heard another voice from heaven, saying, “Come out of her, my people, so that you will not participate in her sins and receive of her plagues; for her sins have piled up as high as heaven, and God has remembered her iniquities. Pay her back even as she has paid, and give back to her double according to her deeds; in the cup which she has mixed, mix twice as much for her. To the degree that she glorified herself and lived sensuously, to the same degree give her torment and mourning; for she says in her heart, ‘I sit as a queen and I am not a widow, and will never see mourning.’ For this reason in one day her plagues will come, pestilence and mourning and famine, and she will be burned up with fire; for the Lord God who judges her is strong. (Revelation 18:2-8) {emphasis mine}
Every time I read Revelation 18, I become more convinced that Babylon the Great is likely to be the US.
Let’s start with “For all the nations have drunk of the wine of the passion of her immorality, and the kings of the earth have committed acts of immorality with her.” The US has used its wealth and power to influence nearly every nation in the world. The US gives “aid,” but always with strings attached. They’ll give aid if the nation will support gay marriage. They’ll give aid if the nation will encourage gender transitions. They’ll give aid if the nation will join in a war against a nation that doesn’t do what the US tells it to do. This money for immorality is rampant, but not obvious to everyone because the media doesn’t advertise these actions.
“and the merchants of the earth have become rich by the wealth of her sensuality.” The US is known for her excesses. The government overspends. Her businesses overspend. Her citizens overspend and they believe they are in absolute poverty if they don’t have a car for every adult, a cell phone for everyone over 6, high speed internet, big screen TVs, etc. Even most of the poor in the US have no idea what real poverty looks like. The US buys tons of stuff from nations around the world and the “merchants of the earth have become rich by the wealth of her sensuality.” Has there ever been a nation throughout all of history that lived so extravagantly?
In the previous passage in Revelation 17, it states, “in her hand a gold cup full of abominations and of the unclean things of her immorality.” Could the golden cup be a reference to all of the blessings given to the US since her founding and how the US was founded on Biblical principles, but instead of using the spiritual, geographic, and economic blessings, the US turned to “abominations and of the unclean things,” all of the evils now pushed by the US government, US schools, and US media?
Sadly, “God has remembered her iniquities,” and “To the degree that she glorified herself and lived sensuously, to the same degree give her torment and mourning.” How much does this following verse sound like the US government and US citizens? “I sit as a queen and I am not a widow, and will never see mourning.” They can’t comprehend that the US will ever be anything other than the most powerful nation in the world — militarily, economically, and even morally.
When Babylon the Great is destroyed, Revelation 18 states:
“And the merchants of the earth weep and mourn over her, because no one buys their cargoes any more— cargoes of gold and silver and precious stones and pearls and fine linen and purple and silk and scarlet, and every kind of citron wood and every article of ivory and every article made from very costly wood and bronze and iron and marble, and cinnamon and spice and incense and perfume and frankincense and wine and olive oil and fine flour and wheat and cattle and sheep, and cargoes of horses and chariots and slaves and human lives. The fruit you long for has gone from you, and all things that were luxurious and splendid have passed away from you and men will no longer find them. The merchants of these things, who became rich from her, will stand at a distance because of the fear of her torment, weeping and mourning, saying, ‘Woe, woe, the great city, she who was clothed in fine linen and purple and scarlet, and adorned with gold and precious stones and pearls; for in one hour such great wealth has been laid waste!’ And every shipmaster and every passenger and sailor, and as many as make their living by the sea, stood at a distance, and were crying out as they saw the smoke of her burning, saying, ‘What city is like the great city?’ And they threw dust on their heads and were crying out, weeping and mourning, saying, ‘Woe, woe, the great city, in which all who had ships at sea became rich by her wealth, for in one hour she has been laid waste!’ (Revelation 18:11-19) {emphasis mine}
The saddest point is how Babylon the Great will be destroyed. What hints do we get? From Revelation 17, we read, “she will be burned up with fire.” From Revelation we read, “in one hour such great wealth has been laid waste!”, “they saw the smoke of her burning,” and again “in one hour she has been laid waste!” What could “lay waste” a great nation “in one hour” “with fire?” If all of the nuclear nations in the world (the ten horns and the beast) turned their nuclear weapons on the US and fired simultaneously, this is exactly what you would see.
We’re going to look at another passage and see what else we can find. This next passage I had not previously associated with Babylon the Great, but now think it does refer to both historical Babylon and Babylon the Great.
Jeremiah 50-51
The prophecies in Jeremiah chapters 50 & 51 seem to be predicting two events. One has already happened (Babylon being conquered by the Persians and Israel returning home after a 70 year exile) and one that has not happened (seems to parallel Revelation and what it says about Babylon the Great). Some of the prophecies against Babylon have clearly happened when Persia conquered Babylon. Some of the prophecies here do not seem to have been fulfilled. There are numerous examples of similar situations in predictions of the coming of the Messiah that predict both the first incarnation of Jesus and the 2nd coming at the end of the age. I believe these passages fit that pattern.
Jeremiah 50 & 51 talks about the mother of Babylon and the daughter of Babylon. My theory is that the mother of Babylon is the historical Babylon on the Euphrates River that conquered Israel and took away its people. My more speculative theory is that the daughter of Babylon is the same as Babylon the Great in Revelation. I also am speculating that the evil spirits that influenced historic Babylon will be influencing Babylon the Great in the end times.
Your mother will be greatly ashamed,\ She who gave you birth will be humiliated.\ Behold, she will be the least of the nations,\ A wilderness, a parched land and a desert.\ Because of the indignation of the Lord she will not be inhabited,\ But she will be completely desolate;\ Everyone who passes by Babylon will be horrified\ And will hiss because of all her wounds.\ Draw up your battle lines against Babylon on every side,\ All you who bend the bow;\ Shoot at her, do not be sparing with your arrows,\ For she has sinned against the Lord.\ Raise your battle cry against her on every side!\ She has given herself up, her pillars have fallen,\ Her walls have been torn down.\ For this is the vengeance of the Lord:\ Take vengeance on her;\ **As she has done to others, so do to her. (Jeremiah 50:12-15) {emphasis mine}
In Revelation 17-18 we read about Babylon the Great being destroyed in an hour with fire. This passage states, “All you who bend the bow; Shoot at her, do not be sparing with your arrows.” If you were writing a prophecy about a nuclear attack, to people back in the 600s B.C., how would you write it? Would you maybe mention arrows and bows because they are shot from a distance? Does “All you who bend the bow; Shoot” suggest all nations with nuclear weapons? Maybe.
“Summon many against Babylon,\ All those who bend the bow:\ Encamp against her on every side,\ Let there be no escape.\ Repay her according to her work;\ According to all that she has done, so do to her;\ For she has become arrogant against the Lord,\ Against the Holy One of Israel.\ Therefore her young men will fall in her streets,\ And all her men of war will be silenced in that day,” declares the Lord.\ “Behold, I am against you, O arrogant one,”\ Declares the Lord God of hosts,\ “For your day has come,\ The time when I will punish you.\ The arrogant one will stumble and fall\ With no one to raise him up;\ And I will set fire to his cities\ And it will devour all his environs.” (Jeremiah 50:29-32) {emphasis mine}
I’ve heard many Americans complain that the French are arrogant. They say this, because the French get upset at loud, self absorbed Americans traveling to France and expecting all of the French to speak English. Shouldn’t the people visiting a country at least make an attempt to speak the language of the nation they are visiting?
Americans are known for their arrogance. It is assumed that everyone will know what is happening in America. It is assumed that everyone will speak English to Americans. It is assumed that everyone will be best off if they have a government and culture exactly like ours. It is assumed that the US will always be the most powerful economically and militarily and that nothing we do will change that. Honestly, I don’t think it is possible for a nation to be more arrogant. As an American, I say all of this with sadness
A sword against their horses and against their chariots\ And against all the foreigners who are in the midst of her,\ And they will become women!\ A sword against her treasures, and they will be plundered!\ A drought on her waters, and they will be dried up!\ For it is a land of idols,\ And they are mad over fearsome idols. (Jeremiah 50:37-38) {emphasis mine}
Historical Babylon brought foreigners, who they conquered, back to Babylon and integrated them into their culture. The US has historically let in foreigners and integrated them into her culture. In the past, the US was referred to as a melting pot. Now the foreigners are coming in, but they frequently are not coming in legally and they are frequently not integrating into American society. Many are coming in for freebies or even to do harm to the US. Whatever the case, the division over what to do with all of the illegal aliens entering is dividing the US.
For most of my life, when I read “they will become women,” I assumed that meant the men would become weak and/or fearful, but could this refer to men actually trying to become women by chemical and surgical means? Maybe. God knew this craziness would occur. It may have surprised me, but it didn’t surprise God.
We don’t normally think of Americans as worshipping idols. They don’t normally worship a manmade statue, but they do worship idols, i.e. politicians, athletes, singers, influencers, media, and worldwide power & influence. Sadly, most Americans worship anything and everything except their creator God.
They seize their bow and javelin;\ They are cruel and have no mercy.\ Their voice roars like the sea;\ And they ride on horses,\ Marshalled like a man for the battle\ Against you, O daughter of Babylon. (Jeremiah 50:42) {emphasis mine}
This passage seems very similar to the Revelation 17:15-18. Many nations will attack from a distance, with “bow and javelin.” They will be “cruel and have no mercy … Against you, O daughter of Babylon.” By referring to “daughter of Babylon,” I believe this passage is not referring to historical Babylon, but a nation yet to come, that I am suggesting may be the US.
I will dispatch foreigners to Babylon that they may winnow her\ And may devastate her land;\ For on every side they will be opposed to her\ In the day of her calamity. (Jeremiah 51:2) {emphasis mine}
Could this passage mean the US will be attacked from within by the mass of foreigners in her land while her enemies from beyond her borders attack militarily and economically? Maybe. We do have illegal aliens, illegally entering the nation and being provided for with the hard earned money of American taxpayers to the point of bringing the economy to the breaking point.
Flee from the midst of Babylon,\ And each of you save his life!\ Do not be destroyed in her punishment,\ For this is the Lord’s time of vengeance;\ He is going to render recompense to her.\ *Babylon has been a golden cup in the hand of the Lord*,\ Intoxicating all the earth.\ The nations have drunk of her wine;\ Therefore the nations are going mad**. (Jeremiah 51:6-7) {emphasis mine}
When I read “The nations have drunk of her wine; Therefore the nations are going mad,” I think of how the nations submit to the insane requests made by the US if the nations want her money, loans, weapons, and friendship. So many of the ungodly evils in our nation are pushed on the nations of the globe through American aid and sanctions. Many nations have turned to promoting anti-God actions in order to receive US aid and protection.
I hate thinking this about my nation. I hate seeing what was started as a God fearing nation based on good principles become the largest purveyor of evil in the world. I don’t want the US to be Babylon the Great, but it at least has a lot in common with Babylon the Great.
One thing I’ve noticed in many of the passages in Revelation and in Jeremiah is the command, “Flee from the midst of Babylon, and each of you save his life!” If America is Babylon the Great, at what point would we be called to flee her? Is the call a call to Christians, or is it a call to Jewish people to return to Israel? There have been many Jews leaving the US (and other nations) to move to Israel because of severe antisemitism, but could this call be a call to all who believe in the one true God?
We applied healing to Babylon, but she was not healed;\ Forsake her and let us each go to his own country,\ For her judgment has reached to heaven\ And towers up to the very skies. (Jeremiah 51:9) {emphasis mine}
Now I will give my most speculative and least certain assumption. If the tribulation is near, if the US is Babylon the Great, and if this passage in Jeremiah is referring to the same Babylon discussed in Revelation, what is this “applied healing?” The US has been turning completely away from God. It has been promoting evil as good and calling good “evil.” We just had an election where the American people rejected this radical evil and claim to want to go back to healthier, more sane America. Could the “applied healing to Babylon” be the election of Donald Trump (I am not saying he is anything close to a savior)?
I was just listening to a sermon by R.C. Sproul entitled “Jesus Heals Many.” In it he commented that Jesus was healing many, then went off alone to pray, was reprimanded by His disciples for leaving when so many people were seeking healing, and then Jesus told them He was leaving for another town to preach His message. Jesus was there to share the Gospel, not to just play doctor. Most of the people following Jesus weren’t doing it because they believed He was God, nor were they doing it because they thought He taught the truth; they were following Him to get personal healing. Jesus was their magic genie. They only wanted Him as much as He gave them what they wanted. They didn’t care about what they actually needed or what Jesus demanded.
In the same way, Richard Dawkins, one of the most famous atheists in the world, recently lamented the loss of Christian culture. He enjoyed the loving attitudes, the Christmas spirit, the honesty, etc., but didn’t actually want anything to do with Jesus. Is God offering a moment of reprieve for us to turn back to Him? Do the people only want the Christian culture and Christian blessing without the repentance and without making Jesus Lord? Is this why we will not be healed?
No matter how much people want him to be, Trump is not a real savior and won’t be able to fix most of what ails America. Sadly most people want a return to God’s blessing, but they aren’t willing to repent and submit to the true Savior.
I don’t know if this was what God was trying to communicate to us from more than two millennia ago, but I do think it is something we need to consider. Are we longing for the Christian culture and the blessings that come with it, while being unwilling to accept and submit to the Jesus through whom all of these blessings come?
Sharpen the arrows, fill the quivers!\ The Lord has aroused the spirit of the kings of the Medes,\ Because His purpose is against Babylon to destroy it;\ For it is the vengeance of the Lord, vengeance for His temple. (Jeremiah 51:11) {emphasis mine}
Now this passage may only refer to historical Babylon and it being conquered by the Medes and Persians. I do find it interesting that the nation of the Medes1 were located in what is now Iran, East Turkey, and Afghanistan. There are many experts saying Iran has everything needed to make several nuclear weapons and they already have the missiles needed to launch them. Iran hates and wants to destroy Israel and the US and is now afraid due to the election of Trump and the people he is nominating for Secretary of Defense, Secretary of State, and Ambassador to Israel. Could this passage refer to Iran completing the creation of nuclear weapons in order to attack the US? Maybe.
Lift up a signal against the walls of Babylon;\ Post a strong guard,\ Station sentries,\ Place men in ambush!\ For the Lord has both purposed and performed\ What He spoke concerning the inhabitants of Babylon.\ O you who dwell by many waters,\ *Abundant in treasures*,\ Your end has come**,\ The measure of your end. (Jeremiah 51:12-13) {emphasis mine}
Although historical Babylon was rich and was located between the Euphrates and Tigris Rivers and had many canals for watering the land, this also sounds like the US. The US is between the Pacific and Atlantic Oceans with the Gulf of Mexico to the South. It is full of large, navigable rivers. There has never been a nation as rich and with as many treasures as the US. Once again, I’m not positive, but it would be a great description for the US.
The portion of Jacob is not like these;\ For the Maker of all is He,\ And of the tribe of His inheritance;\ The Lord of hosts is His name.\ He says, “You are My war-club, My weapon of war;\ And with you I shatter nations,\ And with you I destroy kingdoms. (Jeremiah 51:19-20) {emphasis mine}
This passage is less explicit, but still, I can very much see God saying of the US, “You are My war-club, My weapon of war; and with you I shatter nations.”
“But I will repay Babylon and all the inhabitants of Chaldea for all their evil that they have done in Zion before your eyes,” declares the Lord.\ “Behold, I am against you, O destroying mountain,\ Who destroys the whole earth,” declares the Lord,\ “And I will stretch out My hand against you,\ And roll you down from the crags,\ And I will make you a burnt out mountain.\ They will not take from you even a stone for a corner\ Nor a stone for foundations,\ But you will be desolate forever,” declares the Lord. (Jeremiah 51:24-26) {emphasis mine}
I am currently reading a book, “Eye to Eye,” that goes through the actions of Bush Sr, Clinton, and Bush Jr to divide Israel into a two state solution and the natural disasters in America that happened within days of each of the US’s major actions. Will the US help divide Israel leading to her destruction? Has there ever been a nation throughout history that you could really say, “O destroying mountain, who destroys the whole earth?” Before modern times, the empires didn’t affect the whole earth. Great Britain did have influence on the majority of it, but I don’t think you could call it a “destroying mountain” or say it “destroys the whole earth.” The US truly influences every nation on earth, through aid/sanctions and through threat of force.
Once again we see a reference to fire, “I will make you a burnt out mountain.” Will US hegemony be destroyed by a nuclear attack? What else could make it, or any other nation, into “a burnt out mountain.”
The mighty men of Babylon have ceased fighting,\ They stay in the strongholds;\ Their strength is exhausted,\ They are becoming like women;\ Their dwelling places are set on fire,\ The bars of her gates are broken. (Jeremiah 51:30) {emphasis mine}
Is the reason we don’t see the US in end times prophecy because it has “ceased fighting,” stays “in the strongholds,” “is exhausted,” (especially financially) is “becoming like women,” (literally?) and finally “Their dwelling places are set on fire?”(nuclear?)
It makes sense, but it is also possible I am reading too much into it. Even if the US isn’t THE Babylon the Great, just as there are antichrists and THE AntiChrist, I think the US is at least a form of Babylon.
Indeed Babylon is to fall for the slain of Israel,\ As also for Babylon the slain of all the earth have fallen.\ You who have escaped the sword,\ Depart! Do not stay!\ Remember the Lord from afar,\ And let Jerusalem come to your mind*. (Jeremiah 49-50) {emphasis mine}
Once again, I wonder, if this refers to all who trust God or if this call is specifically for the Jews. I don’t feel confident in the answer, but will continue to study Scripture and listen to the Holy Spirit.
Whether you agree or disagree with my conclusions and speculations, I hope this article has made you think and blessed you. I’d love feedback, especially if you have Scripture that either supports or denies my conclusions.
Because end times prophecy is not as clear as the historical parts of the Bible, I know my interpretations have changed as the world has changed and I see how God’s word may be fulfilled. I do believe my understanding is getting closer and closer to what God is trying to tell us as I see things that made zero sense suddenly seem immediately possible as new technologies are created, as national alliances change. and as culture changes. I am looking forward to going home to heaven to be with my God and creator soon. I hope to see you there.
Trust Jesus.\ \ your sister in Christ,
NOTE: Because of some uncertainty in this interpretation, after writing this article, I did a little research before posting. This websites has some interesting information on Babylon the Great.
This site furthers my argument that US is Babylon the Great and brings up some additional arguments that are very good and goes into when Babylon the Great is likely destroyed. I’d recommend reading it.
The only description of Babylon the Great that doesn’t fully seem to correspond to the US is “And in her was found the blood of prophets and of saints and of all who have been slain on the earth.” (Revelation 18:24) The rest of the arguments for why the US isn’t Babylon the Great were either arguments regarding America’s past godliness, not America’s current situation, or Americans that just seemed to not want the US to be Babylon the Great. Sometimes we all fail to see uncomfortable truths.
It is true that Christians are not “slain” in the US. It is also true that when the US has gone to war with many nations, such as Iraq, their actions have led to the end of the church in that nation. There had been a Christian church in Iraq for \~2,000 years, but after the US “liberated” Iraq, the Christian church was basically wiped out in a way that it had not been even under a tyrannical Muslim leader. Similar things have happened elsewhere. It is also true that persecution of Jews and Christians has been getting worse and worse in the US. Will this progression continue to the point of putting believers to death? I hope not, but it is possible.
I’m guessing most of us will eventually see who or what Babylon the Great is before too long, so we will see. Hopefully you will use this to get you thinking about end times and it will spur you on to live a life fully devoted to Jesus.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 8d34bd24:414be32b
2024-11-17 14:34:38
@ 8d34bd24:414be32b
2024-11-17 14:34:38In the Bible, there are many commands to obey or to submit to different authorities and to God. There is also much disagreement in the Church about when and how to obey and submit to authority. I’m making an attempt to look at verses on the subject to find the balance commanded by God in His word.
NOTE: This article was inspired by a sermon in his teaching series, Daniel Uncompromising, by Jace Cloud of Grace Bible Church Dallas. Several major ideas were taken from his sermon, but the context and purpose was different.
Commands to Obedience
What does the Bible say about obedience?
Children, obey your parents in the Lord, for this is right. (Ephesians 6:1)
Wives, be subject to your own husbands, as to the Lord. (Ephesians 5:22)
Remind them to be subject to rulers, to authorities, to be obedient, to be ready for every good deed, (Titus 3:1)
You shall therefore obey the Lord your God, and do His commandments and His statutes which I command you today. (Deuteronomy 27:10)
As we go through these commands we go from lower to greater and greater authority, but we are told to submit/obey in these ways:
-
Children must obey parents
-
Wives must submit to husbands
-
All are subject to and obedient to rulers and authorities
-
All must obey God and do His commandments
Most of us don’t really want to submit to or obey others. The original sin in the Garden of Eden came down to choosing to disobey God’s one command so they could be like God. Why did Adam and Eve want to be like God? They didn’t want to be under someone else’s authority.
Although we are supposed to submit/obey in each of these situations/relationships, what do we do when there is a contradiction between commands from various authorities? We must choose to obey the highest authority. What does this look like?
When Authority Commands to Do Wrong
We’ll start by looking at 4 young lads from Israel who were snatched from their homeland and families to a foreign land with foreign customs and foreign gods.
Then the king ordered Ashpenaz, the chief of his officials, to bring in some of the sons of Israel, including some of the royal family and of the nobles, youths in whom was no defect, who were good-looking, showing intelligence in every branch of wisdom, endowed with understanding and discerning knowledge, and who had ability for serving in the king’s court; and he ordered him to teach them the literature and language of the Chaldeans. The king appointed for them a daily ration from the king’s choice food and from the wine which he drank, and appointed that they should be educated three years, at the end of which they were to enter the king’s personal service. (Daniel 1:3-5)
These 4 young men were in a foreign land far away from anyone from their families, government, or religious leaders. They were “appointed for them a daily ration from the king’s choice food and from the wine which he drank.” There was something about this food and drink that made it not Kosher for them. They shouldn’t eat or drink this food and drink. It may have been offered to false gods. It may have included unclean foods like pork. The text doesn’t say exactly what the problem was, but these young men: Daniel (Belteshazzar), Hananiah (Shadrach), Mishael (Meshach), and Azariah (Abed-nego)1 decided that they would not defile themselves by eating the king’s food.
They did however give an example of the right way to deal with a refusal to disobey God’s commandments. Daniel made a very reasonable and submissive request.
But Daniel made up his mind that he would not defile himself with the king’s choice food or with the wine which he drank; so he sought permission from the commander of the officials that he might not defile himself. Now God granted Daniel favor and compassion in the sight of the commander of the officials, and the commander of the officials said to Daniel, “I am afraid of my lord the king, who has appointed your food and your drink; for why should he see your faces looking more haggard than the youths who are your own age? Then you would make me forfeit my head to the king.” But Daniel said to the overseer whom the commander of the officials had appointed over Daniel, Hananiah, Mishael and Azariah, “Please test your servants for ten days, and let us be given some vegetables to eat and water to drink. Then let our appearance be observed in your presence and the appearance of the youths who are eating the king’s choice food; and deal with your servants according to what you see.” (Daniel 1:8-13) {emphasis mine}
Daniel and his friends didn’t make a stink about the fact they didn’t want the food being provided. Daniel respectfully went to the person in authority over him, the commander of the officials, and made his request. The official was understanding, but afraid that he would get in trouble for disobeying the king’s command. Daniel trusted that God would take care of them if they were faithful and said, “Please test your servants for ten days, and let us be given some vegetables to eat and water to drink. Then let our appearance be observed in your presence and the appearance of the youths who are eating the king’s choice food; and deal with your servants according to what you see.” They made their request made known, considered the well-being of their commander, and trusted God to take care of them. God honored them and made them look better than all of the people receiving the king’s food.
This was just the first small step in them refusing to do what God said was wrong. Their next choice was even bigger and harder.
Nebuchadnezzar the king made an image of gold, the height of which was sixty cubits and its width six cubits; he set it up on the plain of Dura in the province of Babylon. Then Nebuchadnezzar the king sent word to assemble the satraps, the prefects and the governors, the counselors, the treasurers, the judges, the magistrates and all the rulers of the provinces to come to the dedication of the image that Nebuchadnezzar the king had set up. Then the satraps, the prefects and the governors, the counselors, the treasurers, the judges, the magistrates and all the rulers of the provinces were assembled for the dedication of the image that Nebuchadnezzar the king had set up; and they stood before the image that Nebuchadnezzar had set up. Then the herald loudly proclaimed: “To you the command is given, O peoples, nations and men of every language, that at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery, bagpipe and all kinds of music, you are to fall down and worship the golden image that Nebuchadnezzar the king has set up. But whoever does not fall down and worship shall immediately be cast into the midst of a furnace of blazing fire.” (Daniel 3:1-6) {emphasis mine}
Shadrach, Meshach, and Abed-nego knew the Ten Commandments well. They knew the second commandment, “You shall have no other gods before Me.” (Exodus 20:3) They decided to obey God no matter what it cost them. Their words to Nebuchadnezzar are some of the most inspiring and brave words in the Bible.
Nebuchadnezzar responded and said to them, “Is it true, Shadrach, Meshach and Abed-nego, that you do not serve my gods or worship the golden image that I have set up? Now if you are ready, at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery and bagpipe and all kinds of music, to fall down and worship the image that I have made, very well. But if you do not worship, you will immediately be cast into the midst of a furnace of blazing fire; and what god is there who can deliver you out of my hands?”
Shadrach, Meshach and Abed-nego replied to the king, “O Nebuchadnezzar, we do not need to give you an answer concerning this matter. If it be so, our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king. But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” (Daniel 3:14-16) {emphasis mine}
Being tossed into a fiery furnace would be a horrible way to die, but these young men stood firm in their faith for God and pronounced, “our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king.”
A statement like this, in light of the horrible punishment being promised, took amazing faith, but they didn’t stop there, but continued, “But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” These three young men, in a strange land far from home, stood up to the most powerful king in the world at that time in order to stay faithful to their God, the one true God. They fully believed that God was capable of protecting them from burning to death, but they were also willing to stay true even if God didn’t protect them. This is faith. This is refusing to do anything that disobeys God’s explicit commands, “Thall shalt not …”
When Authority Commands to Not Do Right
Sometimes authority may tell us to do something that God commands us not to do. On the other hand, sometimes authority tells us to not do something that God commands us to do. In the case of Daniel, the government command came because the other government officials didn’t like Daniel. They didn’t like his faithfulness to God. They didn’t like that he was more faithful to the king and more successful than they were. They were jealous that the king was about to make Daniel the 2nd in command.
Then these commissioners and satraps came by agreement to the king and spoke to him as follows: “King Darius, live forever! All the commissioners of the kingdom, the prefects and the satraps, the high officials and the governors have consulted together that the king should establish a statute and enforce an injunction that anyone who makes a petition to any god or man besides you, O king, for thirty days, shall be cast into the lions’ den. Now, O king, establish the injunction and sign the document so that it may not be changed, according to the law of the Medes and Persians, which may not be revoked.” Therefore King Darius signed the document, that is, the injunction. (Daniel 6:6-9)
Daniel was faithful in his prayers to God. He knew that God had promised that the Hebrews would be returned to the promise land after 70 years. He prayed three times a day, every day, but now the law of the Medes and Persians said that he was not allowed to pray to anyone other than the king for 30 days.
Daniel was no longer a young man. He was elderly. He knew God was faithful. Did he decide that God would understand if he didn’t pray for 30 days, but then he would go back to prayer when the command expired? No. Did he decide, instead of praying publicly by his window facing Jerusalem, that he would pray quietly and privately behind closed doors? No, not that either. What did Daniel do?
Now when Daniel knew that the document was signed, he entered his house (now in his roof chamber he had windows open toward Jerusalem); and he continued kneeling on his knees three times a day, praying and giving thanks before his God, as he had been doing previously. Then these men came by agreement and found Daniel making petition and supplication before his God. (Daniel 6:10-11)
Daniel knew the command and knew the consequences of disobedience. He also trusted God and knew that anything less than his consistent, open prayer would be dishonoring to God, so he prayed “as he had been doing previously.” Despite the consequences, he stayed true to God and kept his witness pure.
Most of us know the ending. Daniel was thrown in the lion’s den, but God sent an angel to shut their mouths and protect Daniel from even a scratch. Daniel was faithful to God and God was faithful to Daniel.
The king realized that his officials had tricked him into signing an irreversible law against his best official because of their jealousy. The next morning the king went running to the lion’s den to see if Daniel’s God was able to protect His faithful servant.
Then Daniel spoke to the king, “O king, live forever! My God sent His angel and shut the lions’ mouths and they have not harmed me, inasmuch as I was found innocent before Him; and also toward you, O king, I have committed no crime.” (Daniel 6:21-22)
When the king, who had made a foolish law due to ego, showed up, Daniel didn’t act with resentment. He honored the king “O king, live forever!” probably due to his position more than because of what he deserved. He said, “they have not harmed me, inasmuch as I was found innocent before Him; and also toward you, O king, I have committed no crime.”
Daniel declared his innocence before God and the king.
In these examples we see a law commanding ungodly actions where the believer must refuse to comply and we see a law commanding not to do a godly action we are commanded to do and continuing to obey and be a godly example. We will all face circumstances where we will have to make these choices. It helps if we have thought out our beliefs and plans ahead of time. Luckily for us, the consequences of disobedience aren’t usually as severe as being burnt up in a fiery furnace or being devoured by lions.
How to Honorably Disobey
I’m going to go back to the beginning of the story about Daniel and the lion’s den to see what kind of man Daniel was in his position and towards his king.
Then this Daniel began distinguishing himself among the commissioners and satraps because he possessed an extraordinary spirit, and the king planned to appoint him over the entire kingdom. Then the commissioners and satraps began trying to find a ground of accusation against Daniel in regard to government affairs; but they could find no ground of accusation or evidence of corruption, inasmuch as he was faithful, and no negligence or corruption was to be found in him. Then these men said, “We will not find any ground of accusation against this Daniel unless we find it against him with regard to the law of his God.” (Daniel 6:3-5) {emphasis mine}
Daniel worked hard. He did his job with excellence. He gave everything his best effort. Those trying to accuse him “they could find no ground of accusation or evidence of corruption, inasmuch as he was faithful.”
Believers, how many of you can say your coworkers would say the same about you? Are you known for your excellence and faithfulness? Are you known for having no negligence or corruption? God calls believers to be like Daniel in work and good deeds.
The most amazing thing said here is “We will not find any ground of accusation against this Daniel unless we find it against him with regard to the law of his God.” Every believer should live a life where no one around us can “ find any ground of accusation against” us “unless we find it against [us] with regard to the law of [our] God.”
Daniel was able to stand against the unjust law and still have the support of the king because he had been so faithful in the little things and over a long period of time. We also need to live and work in such a faithful way that we aren’t questioned when we do stand up to ungodly laws.
What Authority to Obey When
Although God commands us to obey authority, there is no higher authority than God Himself. Obedience to God always comes first. That being said, disobeying any authority needs to be done with caution and respect.
When Jesus’s disciples were told by the Jewish authorities to stop sharing the Gospel of Jesus Christ:
The high priest questioned them, saying, “We gave you strict orders not to continue teaching in this name, and yet, you have filled Jerusalem with your teaching and intend to bring this man’s blood upon us.” But Peter and the apostles answered, “We must obey God rather than men.” (Acts 5:27b-29) {emphasis mine}
Ultimately, the answer to the question, “Who do we obey when authorities give contradictory commands?” is “We must obey God rather than men.”
We do have to keep in mind that the apostles all suffered for their disobedience to authorities in obedience to God. Most died martyrs. John died in exile. All knew that they would choose to be faithful, knowing that God was capable of protecting them, but also willing to say, “But even if He does not… ."
I hope these examples were helpful to you and help you to honor God with your actions, your faithfulness, and your life.
Trust Jesus.\ \ your sister in Christ,
Christy
- Each man is named by his original Hebrew name followed by the Babylonian name given to them. Details come from Daniel 1:6-7.
-
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ fd208ee8:0fd927c1
2024-11-14 09:33:16
@ fd208ee8:0fd927c1
2024-11-14 09:33:16A discussion, today, reminded me of this excerpt, from G.K. Chesterton's, What's Wrong with the World:
This book must avoid religion, but there must (I say) be many, religious and irreligious, who will concede that this power of answering many purposes was a sort of strength which should not wholly die out of our lives. As a part of personal character, even the moderns will agree that many-sidedness is a merit and a merit that may easily be overlooked. This balance and universality has been the vision of many groups of men in many ages. It was the Liberal Education of Aristotle; the jack-of-all-trades artistry of Leonardo da Vinci and his friends; the august amateurishness of the Cavalier Person of Quality like Sir William Temple or the great Earl of Dorset. It has appeared in literature in our time in the most erratic and opposite shapes, set to almost inaudible music by Walter Pater and enunciated through a foghorn by Walt Whitman.
But the great mass of men have always been unable to achieve this literal universality, because of the nature of their work in the world. Not, let it be noted, because of the existence of their work. Leonardo da Vinci must have worked pretty hard; on the other hand, many a government office clerk, village constable or elusive plumber may do (to all human appearance) no work at all, and yet show no signs of the Aristotelian universalism. What makes it difficult for the average man to be a universalist is that the average man has to be a specialist; he has not only to learn one trade, but to learn it so well as to uphold him in a more or less ruthless society.
This is generally true of males from the first hunter to the last electrical engineer; each has not merely to act, but to excel. Nimrod has not only to be a mighty hunter before the Lord, but also a mighty hunter before the other hunters. The electrical engineer has to be a very electrical engineer, or he is outstripped by engineers yet more electrical. Those very miracles of the human mind on which the modern world prides itself, and rightly in the main, would be impossible without a certain concentration which disturbs the pure balance of reason more than does religious bigotry. No creed can be so limiting as that awful adjuration that the cobbler must not go beyond his last. So the largest and wildest shots of our world are but in one direction and with a defined trajectory: the gunner cannot go beyond his shot, and his shot so often falls short; the astronomer cannot go beyond his telescope and his telescope goes such a little way. All these are like men who have stood on the high peak of a mountain and seen the horizon like a single ring and who then descend down different paths towards different towns, traveling slow or fast. It is right; there must be people traveling to different towns; there must be specialists; but shall no one behold the horizon? Shall all mankind be specialist surgeons or peculiar plumbers; shall all humanity be monomaniac?

Tradition has decided that only half of humanity shall be monomaniac. It has decided that in every home there shall be a tradesman and a Jack-of-all-trades. But it has also decided, among other things, that the Jack-of-all-trades shall be a Jill-of-all-trades. It has decided, rightly or wrongly, that this specialism and this universalism shall be divided between the sexes. Cleverness shall be left for men and wisdom for women. For cleverness kills wisdom; that is one of the few sad and certain things.
But for women this ideal of comprehensive capacity (or common-sense) must long ago have been washed away. It must have melted in the frightful furnaces of ambition and eager technicality. A man must be partly a one-idead man, because he is a one-weaponed man—and he is flung naked into the fight. The world’s demand comes to him direct; to his wife indirectly. In short, he must (as the books on Success say) give “his best”; and what a small part of a man “his best” is! His second and third best are often much better. If he is the first violin he must fiddle for life; he must not remember that he is a fine fourth bagpipe, a fair fifteenth billiard-cue, a foil, a fountain pen, a hand at whist, a gun, and an image of God.
The frustration of not being an expert
I read that, in my early 20s, stumbling across the late, great Chesterton, while trying to decide if marriage is my proper vocation (and then immediately reading all of his nonfiction, as it's all so brutally, casually, brilliant). It immediately made my own "talent stack" clear to me: I'm best at doing lots of different things quite well, but not at doing one particular thing to a level of highest expertise.

This is actually an extremely difficult position to be in because young people are under constant pressure to find That One Thing that they are to specialize in, and I could never find That Thing, despite being at the top of any ranking of People Doing Things.
Could I write well? Yes. Could I write really well? Yes. Could I write really, really well? Nope.
Could I program well? Yes. Could I program really well? Yes. Could I program really, really well? Nope.
Could I cook well?...
And so on, and so forth, for nearly every task I tried. Perpetually stuck in the upper quintile, never a top-tenner.
Much has been written about chronic Imposter Syndrome among the very-smartest women, but I think that's just a fancy way to explain this phenomenon of being at the top of your game and atop all of the other women playing the same game, but quickly discovering, to your dismay, that the men at the top are a wee bit topper than you. And there's always one a wee bit topper. There must be an endless supply of men-slightly-better at That One Thing, someplace. A factory, where they are produced by dark forces, like the Orcs, in The Lord of the Rings.
It is enough to make a girl pout, very cutely.

Titles matter
I've written, before, about how I see my development role as being the project teams' "Girl Friday". I pick up all the tasks that fall to the wayside, but shouldn't be forgotten (like marketing, testing, arranging financing, and customer support), or substituting for someone who is away. Although men and women are partially redundant, so that there's a Boy Friday for every Mrs. Burns, it seems clear to me that humanity really is generally split up into these specialist/generalist roles.
Women tend toward generalism, but often no longer have a natural outlet for it, so many of us are therefore in a state of employment frustration. We cling to various titles, without fully identifying with them. Drifting from one title to another. Earning a new title. Going off to find ourselves. Earning another new title. No, this one also doesn't fit... Seeking, but never finding. The incongruence and impermanence can be painful. Aimless drifting.
Stacking up certificates and qualifications, but immediately bored by the myopic scope of the task and -- if we're in a male-dominated trade -- frustrated by our difficulty in topping The Toppers; struggling to find some niche, some branch, where our generalism is an advantage.
Life is unfair. Boys are mean. Someone do something.
There used to be a specialty for generalists

But someone had done something. A long, long time ago. In fact, we are generalists today because of what that one woman did, back then: she married.
The bride is the star of every wedding and being a wife often brought a change in title (from Miss to Mrs.) because it is meant to be a vocation. It is as if you have been hired to be the household generalist, by the specialist, whose title reflected his particular specialty. If you actively joined in his specialty, it would simply be tacked onto your original title "Miller's Wife", "Lawyer's Wife", "Politician's Wife", "Farmer's Wife", "Engineer's Wife", "Butcher's Wife", "Bitcoin Influencer's Wife". (Angela Merkel's spouse had the title "Chancellor's Husband", but the construction remains.)
The point of all of this, was to build mixed-sex pairs, with overlapping skillsets, with one generalist and one specialist. This was a solid construction, for millions of years. Turning the tasks of the generalist into a series of professions, in order to financialize and tax the output, undermined the core concept of marriage by eroding its value-added to the participants. That is why marriage is now often seen exclusively as a romantic, long-term-fling, rather than the practical and efficient basis of any sustainable family and economic system.
Marriage is about the economy, stupid
That is why marriage equality became such a hot topic, in the 90s. If marriage is just about hanging about in the house with someone you find attractive (i.e. "roommates with benefits"), rather than the basic building block of society, then why shouldn't everyone doing that be considered married? Then everyone could have the same status, as married people did. This was a logical argument that won because society had completely abandoned the counterargument: Marriage isn't that.
Marriage was a specific construct to serve a specific purpose with maximum efficiency and efficacy. Society honored it because everyone benefitted from people engaging in it, even if they themselves did not. Society didn't honor marriage because it was good for the people in it; they honored it because it was good for everyone else.
Because, within marriage, there is room for a Jill-of-All-Trades, and the people outside of the marriage don't have to pay for her labour or subsidize her retirement, at the same time that they profit indirectly from it.
But, the generalist wife is not the star of the entire world, she's the star of one particular man's world, and for many women, that world was simply too small. They needed a bigger stage to perform on.
Even being The President's Wife isn't title enough, for some, when they hungered to hold The President title, directly.

The consequent and purposeful destruction of the marital institution -- and the denegration of generalism, that necessarily went along with it -- is, I am convinced, the reason that we can't have nice things. And it's the reason why women gaining power hasn't lead to their increased happiness or more-stable and fruitful families.
In the end, a specialist title isn't enough, for most of us. What we want most, is to be loved and honored and cherished for what we are. And we are generalists.
And that is why I chose to stay home and bake cookies. In this little house, in our home economy, I am the best cookie baker because I am a good-enough cookie baker. I only have to be good-enough.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 79008e78:dfac9395
2024-12-01 03:15:00
@ 79008e78:dfac9395
2024-12-01 03:15:00บทที่ 1: เกริ่นนำ
เกริ่นนำเรื่องราวของบิตคอยน์แบบกระทัดรัด
บิตคอยน์ (Bitcoin) เป็นชุดแนวคิดและเทคโนโลยีที่เข้ามาผสมผสานรวมกันจนได้กลายเป็นระบบเงินสดอิเล็กทรอนิกส์ หน่วยเงินที่เรียกว่าบิตคอยน์นั้น ใช้เพื่อเก็บและส่งต่อมูลค่าให้กับผู้ใช้คนอื่น ๆ ในระบบ ผู้ใช้ทั้งระบบสื่อสารกันบนโปรโตคอลของบิตคอยน์ โดยผู้ใช้ส่วนใหญ่ก็เข้าถึงกันผ่านอินเตอร์เน็ต แต่ก็ไม่ได้หมายความว่าระบบนี้ไม่สามารถใช้เครือข่ายการสื่อสารรูปแบบอื่นได้ ซอฟต์แวร์ของโปรโตคอลนี้เป็นโอเพนซอร์สและสามารถรันได้บนอุปกรณ์คอมพิวเตอร์หลายประเภท เช่น แล็ปท็อปและสมาร์ทโฟน และสิ่งนี้เองที่ทำให้เทคโนโลยีนี้สามารถเข้าถึงได้ง่าย
ผู้ใช้งานสามารถส่งบิตคอยน์ให้กันผ่านเครือข่ายของบิตคอยน์เพื่อทำกิจกรรมต่าง ๆ เช่น ซื้อ-ขายแลกเปลี่ยนสินค้าและบริการ หรือใช้เพื่อแลกเปลี่ยนเป็นสกุลเงินต่าง ๆ ซึ่งถือว่าเหมาะสมเป็นอย่างมากสำหรับการใช้งานบนอินเทอร์เน็ต เพราะมีทั้งความรวดเร็ว ความปลอดภัย และยังข้อจำกัดเรื่องพรมแดน
ซึ่งบิตคอยน์นั้นแตกต่างจากสกุลเงินโดยทั่วไป เนื่องจากเป็นระบบเงินอิเล็กทรอนิกส์ จึงไม่มีเหรียญหรือธนบัตรจริง ๆ ให้ได้จับต้อง แต่คำว่าเหรียญที่มักใช้กันในสังคมของบิตคอยน์จะหมายถึงในธุรกรรมที่ผู้ใช้รายหนึ่งโอนมูลค่าไปยังผู้ใช้อีกรายหนึ่ง ผู้ใช้งานบิตคอยน์จะควบคุมคีย์ (Private Key) ที่ใช้พิสูจน์ความเป็นเจ้าของในบิตคอยน์นั้น ๆ ในเครือข่าย และด้วยคีย์นี้เองทำให้พวกเขาสามารถเซ็นชื่อในธุรกรรมเพื่อปลดล็อกมูลค่าและทำการส่งมันต่อไปยังผู้รับอีกรายหนึ่ง ซึ่งมักจะถูกเก็บอยู่ในกระเป๋าเงินดิจิทัล หรือสมาร์ทโฟนของผู้ใช้งาน การครอบครองคีย์ที่สามารถเซ็นชื่อในธุรกรรมได้เป็นสิ่งเดียวที่จำเป็นในการใช้จ่ายในระบบของบิตคอยน์ และนั่นเป็นเหตุผลที่ทำให้ความสามารถในการควบคุมบิตคอยน์อยู่ในมือผู้ใช้แต่ละคน
เข้าใจว่าในบริบทนี้น่าจะหมายถึง Hot-wallet เพราะงั้นผมไม่ได้แนะนำให้เก็บคีย์คอมพิวเตอร์หรือมือถือนะครับ ส่วนถ้าคุณอยากทำก็เรื่องของคุณจ้าแนะนำเฉย ๆ อยากทำไรทำ
บิตคอยน์นั้นเป็นระบบแบบกระจายศูนย์และทำงานแบบเพียร์-ทู-เพียร์ (Peer-to-Peer) หรือเอาภาษาบ้าน ๆ ว่า เป็นระบบการทำงานแบบบุคคลสู่บุลคลที่ไม่มีตัวกลางระหว่างการทำงาน ดังนั้นจึงไม่มีเซิร์ฟเวอร์กลางหรือจุดควบคุม บิตคอยน์นั้นถูกสร้างขึ้นโดยกระบวนการที่เรียกว่าการขุด ซึ่งเป็นการทำงานทางการคำนวณซ้ำ ๆ ที่อ้างอิงกับรายการธุรกรรมบิตคอยน์ล่าสุด (จริง ๆ ก็มี hash ของบล็อกก่อนหน้าด้วย) ซึ่งผู้ใช้งานบิตคอยน์ทุกคนสามารถที่จะขุดบิตคอยน์ได้ โดยใช้อุปกรณ์คอมพิวเตอร์ของตนเพื่อช่วยรักษาความปลอดภัยในธุรกรรม โดยทุก ๆ สิบนาทีโดยเฉลี่ยนั้น จะมีนักขุดคนหนึ่งที่ได้ช่วยเพิ่มความปลอดภัยให้กับธุรกรรมในอดีต และจะได้รับรางวัลเป็นบิตคอยน์ใหม่และค่าธรรมเนียมจากธุรกรรมชุดล่าสุด ซึ่งกระบวนการนี้ทำให้การออกสกุลเงินและการชำระธุรกรรมไม่จำเป็นต้องมีธนาคารกลาง
โปรโตคอลของบิตคอยน์ มีอัลกอรึทึมที่คอยควบคุมความยากง่ายในการการขุดให้อยู่ในระดับที่เหมาะสม โดยความยากง่ายในการขุดจะขึ้นจะถูกปรับตามระยะเวลาเฉลี่ยของการขุดในช่วงก่อนหน้านี้เพื่อให้การขุดนั้นมีโอกาสสำเร็จเฉลี่ยในทุก ๆ 10 นาที ไม่ว่ามีจำนวนผู้ขุดและการประมวลผลเท่าใดก็ตาม และนอกจากนี้เองโปรโตคอลของบิตคอยน์นั้นยังลดจำนวนของบิตคอยน์ที่นักขุดจะได้เป็นรางวัลลงเรื่อย ๆ ซึ่งจะทำให้บิตคอยน์ที่สร้างได้ในระบบนั้นมีไม่เกิน 21,000,000 ล้านบิตคอยน์ ซึ่งผลลัพธ์ที่ได้ก็คือ จำนวนบิตคอยน์ที่หมุนเวียนในระบบนั้นจะสามารถคาดเดาได้อย่างง่ายดาย ซึ่งอีกครึ่งหนึ่งของบิตคอยน์ที่เหลืออยู่จะถูกเพิ่มเข้าไปในระบบทุก ๆ 4 ปี และที่บล๊อกประมาณ 1,411,200 ซึ่งคาดว่าจะเกิดประมาณปี 2035 จะมีบิตคอยน์เป็นจำนวน 99 % ของที่สามารถเกิดขึ้นได้ในระบบ เนื่องจากอัตราการการผลิตของบิตคอยน์ที่น้อยลงเรื่อย ๆ ทำให้บิตคอยน์มีลักษณะของเงินฝืดในระยะยาว นอกจากนี้ยังไม่มีใครที่สามารถบังคับให้คุณรับบิตคอยน์ที่ถูกผลิตมานอกเหนือจากชุดกฎที่คุณเลือกได้
เบื้องหลังต่าง ๆ ของโปรโตคอลบิตคอยน์ที่ทำให้มันเป็น เครือข่ายแบบบุคคลถึงบุคคล และการคำนวณแบบกระจายศูนย์นั้น ถูกสร้างขึ้นมาบนพื้นฐานของงานวิจัยในด้านการเข้ารหัสและระบบกระจายศูนย์มาเนิ่นนานหลายทศวรรษ โดยมีการรวมเอานวัตกรรมสำคัญ ๆ 4 อย่างนี้มารวมเข้าด้วยกัน:
- เครือข่ายเพียร์ทูเพียร์ที่กระจายศูนย์ (ฺBitcoin protocol)
- บัญชีธุรกรรมสาธารณะ (Blockchain)
- ชุดของกฎในการตรวจสอบธุรกรรมอย่างอิสระและการออกสกุลเงิน ( consensus rules )
- กลไกในการหาข้อตกลงร่วมกันทั่วโลกเกี่ยวกับบล็อกเชนที่ถูกต้อง (PoW algorithm)
ในมุมมองของนักพัฒนา นาย Andreas M. Antonopoulos and David A. Harding ( ไม่ใช่ผมจ้าา ถึงจะเห็นด้วยก็ตาม) พวกเขามองว่าบิตคอยน์นั้นคล้ายกับอินเทอร์เน็ตของเงิน เป็นเครือข่ายสำหรับการกระจายมูลค่าและการรักษาความเป็นเจ้าของสินทรัพย์ดิจิทัลผ่านการคำนวณแบบกระจายศูนย์ ซึ่งบิตคอยน์มีรายระเอียดเยอะกว่าที่พวกเขาเห็นในตอนแรกมาก ๆ
ในบทนี้เองจะเป็นการอธิบายแนวคิด และคำศัพท์หลัก ๆ รวมทั้งการติดตั้งซอฟแวร์ต่าง ๆ ที่จำเป็นในการทอดลองใช้บิตคอยน์สำหรับทำธุรกรรมง่าย ๆ และสำหรับในบทถัดไป เราจะทำการดำดิ่งลงไปในเทคโนโลยีต่าง ๆ ที่ประกอบรวมกันเป็นบิตคอยน์ว่าทำไมมันถึงเป็นไปได้ และตรวจสอบการทำงานภายในของเครือข่ายและโปรโตคอล
ก่อนการมาถึงของบิตคอยน์
สกุลเงินดิจิทัลที่ใช้งานได้จริงในอดีตนั้นมักเกี่ยวข้องกับพัฒนาการในด้านการเข้ารหัส ซึ่งนั่นก็ไม่ได้แปลกอะไรหากเราพิจารณาถึงปัญหาพื้นฐานในการใช้ข้อมูลเพื่อแทนมูลค่าที่สามารถแลกเปลี่ยนเป็นสินค้าและบริการ โดยการที่เงินดิจิทัลจะถูกยอมรับได้นั้นมักจะต้องสามารถตอบคำถามทั้งสามข้อนี้ได้เสียก่อน:
- ฉันจะเชื่อได้อย่างไรว่าเงินนั้นเป็นของจริงและไม่ใช่ของปลอม?
- ฉันจะเชื่อได้อย่างไรว่าเงินดิจิทัลสามารถใช้ได้เพียงครั้งเดียว (ปัญหาการใช้ซ้ำหรือ "double-spend")?
- ฉันจะมั่นใจได้อย่างไรว่าไม่มีใครสามารถอ้างสิทธิ์ว่าเงินนี้เป็นของพวกเขาไม่ใช่ของฉัน?
ผู้ที่ออกเงินกระดาษเองก็พยายามต่อสู้กับปัญหาการปลอมแปลงโดยการใช้เทคโนโลยีการพิมพ์ที่ซับซ้อนมากขึ้นเรื่อย ๆ และเงินกายภาพเองก็จัดการปัญหาการใช้ซ้ำได้ง่ายเพราะธนบัตรเดียวกันไม่สามารถอยู่ในสองที่พร้อมกันได้ แน่นอนละว่าเงินทั่วไปก็ถูกเก็บและส่งแบบดิจิทัลเช่นกัน ในกรณีเหล่านี้ ปัญหาการปลอมแปลงและการใช้ซ้ำจะถูกจัดการโดยการเคลียร์ธุรกรรมทางอิเล็กทรอนิกส์ทั้งหมดผ่านหน่วยงานกลางที่สามารถตรวจสอบสถานะของเงินได้ แต่สำหรับเงินดิจิทัลที่ไม่สามารถใช้หมึกพิเศษหรือแถบโฮโลแกรมได้ การเข้ารหัสจึงเป็นพื้นฐานสำคัญในการยืนยันความถูกต้องของการอ้างสิทธิ์ในมูลค่าของผู้ใช้ โดยเฉพาะอย่างยิ่ง การเซ็นชื่อดิจิทัลที่เข้ารหัสช่วยให้ผู้ใช้สามารถเซ็นชื่อในสินทรัพย์ดิจิทัลหรือธุรกรรมเพื่อยืนยันการเป็นเจ้าของสินทรัพย์นั้น ซึ่งสิ่งนี้เองยังสามารถใช้ในการแก้ปัญหาการใช้ซ้ำ (doble-spending) ได้
ศาสตร์ของการเข้ารหัสนั้นเริ่มเป็นที่แพร่หลายในช่วงปลายของทศวรรษที่ 1980 นักวิจัยหลายคนเริ่มพยายามใช้การเข้ารหัสเพื่อสร้างสกุลเงินดิจิทัล โดยโครงการเงินดิจิทัลในยุคแรก ๆ นั้นมักจะออกเงินดิจิทัลที่มีการสนับสนุนโดยสกุลเงินของชาติหรือโลหะมีค่าอย่างเช่น ทองคำ
ซึ่งแม้ว่าสกุลเงินดิจิทัลยุคแรกเหล่านี้จะทำงานได้ แต่ก็มีปัญหาที่การรวมศูนย์ของระบบ เนื่องจากมันทำให้ระบบเป็นเป้าหมายที่ง่ายต่อการโจมตีโดยรัฐบาลและเหล่าแฮกเกอร์ สกุลเงินดิจิทัลยุคแรกใช้ศูนย์กลางในการชำระธุรกรรมทั้งหมดเป็นระยะ ๆ เช่นเดียวกับระบบธนาคารทั่วไป เป็นที่น่าเสียดายที่สกุลเงินดิจิทัลเหล่านี้ส่วนใหญ่ถูกกำหนดเป้าหมายโดยรัฐบาลที่กังวลและมักจะถูกฟ้องร้องจนล้มเหลว บางส่วนล้มเหลวอย่างรวดเร็วเมื่อบริษัทผู้ก่อตั้งปิดตัวลงอย่างกะทันหัน และเพื่อให้สกุลเงินดิจิทัลมีความแข็งแกร่งต่อต้านการแทรกแซงจากศัตรู ไม่ว่าจะเป็นรัฐบาลที่ถูกกฎหมายหรืออาชญากรรม เราจึงจำเป็นต้องมีสกุลเงินดิจิทัลที่กระจายศูนย์ เพื่อป้องกันปัญหาดังกล่าว ซึ่งบิตคอยน์คือระบบแบบนั้น ระบบที่ถูกออกแบบให้กระจายศูนย์ และปราศจากอำนาจหรือจุดควบคุมกลางใด ๆ ที่สามารถถูกโจมตีหรือทำให้เสียหายได้
ประวัติของบิตคอยน์
บิตคอยน์ได้ปรากฏครั้งแรกในปี 2008 บนเอกสารที่มีชื่อว่า “Bitcoin: A Peer-to-Peer Electronic Cash System” ซึ่งถูกเขียนโดยบุคคลหรือกลุ่มคนนิรนามที่ใช้นามแฝงว่า ซาโตชิ นากาโมโตะ ซึ่งได้มีการนำนวัตกรรมหลาย ๆ อย่างมารวมเข้าด้วยกัน ไม่ว่าจะเป็นลายเซ็นดิจิทัล และ Hashcash มาสร้างระบบเงินสดอิเล็กทรอนิกส์ที่กระจายศูนย์อย่างสมบูรณ์ ซึ่งไม่ต้องพึ่งพาหน่วยงานกลางในการออกสกุลเงินหรือการชำระและตรวจสอบธุรกรรม โดยนวัตกรรมสำคัญคือการใช้ระบบคำนวณแบบกระจายศูนย์ (Proof-of-work) เพื่อทำสิ่งที่คล้าย ๆ กับการจับฉลากทุก ๆ 10 นาที ทำให้เครือข่ายที่กระจายศูนย์สามารถมีฉันทามติในสถานะของธุรกรรมได้ และสิ่งนี้เองยังสามารถแก้ไขปัญหาการทำธุรกรรมซ้ำซ้อน ซึ่งเป็นข้อบกพร่องของสกุลเงินดิจิทัลที่เคยต้องใช้หน่วยงานกลางในการตรวจสอบธุรกรรมทั้งหมดได้อีกด้วย
เครือข่ายของบิตคอยน์นั้นเริ่มต้นขึ้นในปี 2009 โดยอ้างอิงจากซอฟแวร์ที่เผยแพร่โดย ซาโตชิ และได้ถูกปรับปรุงโดยโปรแกรมเมอร์คนอื่น ๆ มากมายนับไม่ถ้วนมานับตั้งแต่นั้น จำนวนและกำลังของอุปกรณ์ที่ใช้ประมวลผล Proof of Work algorithm (การขุด) เองนั้นก็เพิ่มขึ้นอย่างมหาศาล จนในปัจจุบันนี้พลังการคำนวณรวมกันของเครือข่ายนี้มีมากกว่าจำนวนการคำนวณของซุปเปอร์คอมพิวเตอร์ชั้นนำของโลกทั้งหมดรวมกันเสียอีก ซึ่งสิ่งนี้เองได้ช่วยรักษาความปลอดภัยและความเสถียรของเครือข่ายของบิตคอยน์ได้เป็นอย่างดี
ซาโตชิ นากาโมโตะ ได้ทำการถอนตัวและหายตัวไปในเดือนเมษายนในปี 2011 และมอบหมายความรับผิดชอบในการพัฒนาโค้ดและเครือข่ายให้กับกลุ่มอาสาสมัครที่เติบโตขึ้นเรื่อย ๆ ซึ่งตัวตนของบุคคลหรือกลุ่มคนที่อยู่เบื้องหลังบิตคอยน์นั้นยังไม่เป็นที่รู้จัก แต่อย่างไรก็ตาม ไม่ว่าจะเป็นซาโตชิ นากาโมโตะ หรือใครหน้าไหนก็ตามก็ไม่สามารถควบคุมเครือข่ายของบิตคอยน์ได้ตามลำพัง เนื่องจากมันอยู่บนหลักการทางคณิตศาสตร์ที่โปร่งใส โค้ดโอเพนซอร์ส และฉันทามติจากผู้ที่เข้าร่วม โดยนวัตกรรมนี้ถือเป็นการเปลี่ยนแปลงครั้งใหญ่และได้ก่อให้เกิดวิทยาการใหม่ในด้านการคำนวณแบบกระจายศูนย์ เศรษฐศาสตร์ และเศรษฐมิติอีกด้วย
การแก้ปัญหาในระบบคำนวณแบบกระจายศูนย์
นวัตกรรมของซาโตชิ นากาโมโตะ ยังเป็นการแก้ไขปัญหาที่มีประสิทธิภาพและแปลกใหม่สำหรับปัญหาในระบบคำนวณแบบกระจายศูนย์ที่เรียกว่า "Byzantine Generals' Problem" ซึ่งปัญหานี้เกี่ยวข้องกับการพยายามทำให้ผู้เข้าร่วมหลายคนที่ไม่มีผู้นำสามารถตกลงกันในแผนการดำเนินการได้โดยการแลกเปลี่ยนข้อมูลในเครือข่ายที่ไม่น่าเชื่อถือและอาจถูกโจมตีได้ โดยการแก้ปัญหาของซาโตชินั้นได้ใช้แนวคิด proof of work เพื่อหาฉันทามติโดยไม่ต้องมีผู้ควบคุมที่น่าเชื่อถือ ถือเป็นความก้าวหน้าในด้านการคำนวณแบบกระจายศูนย์
เปิดประตูสู่บิตคอยน์
บิตคอยน์เป็นโปรโตคอลที่สามารถเข้าถึงได้ผ่านทางแอปพลิเคชันที่มีการรับรองโปรโตคอลนี้ Bitcoin wallet นั้นเป็นช่องทางหลักที่ผู้ใช้งานส่วนใหญ่เลือกใช้เพื่อเข้าถึงโปรโตคอลของบิตคอยน์ เช่นเดียวกันกับที่ผู้ใช้งานอินเตอร์เน็ตส่วนใหญ่ใช้เว็บบราวเซอร์เป็นช่องทางในการเข้าถึงโปรโตคอลอย่าง HTTP นั่นเอง Bitcoin wallet เองก็มีหลากหลายยี่ห้อเฉกเช่นเดียวกับเว็บบราวเซอร์ อาทิเช่น chorme, safari, firefox ฯลฯ Bitcoin wallet เองก็เช่นกัน แต่ละยี่ห้อเองก็มีความแตกต่างกันในด้านต่าง ๆ ไม่ว่าจะเป็นในด้านคุณภาพ ประสิทธิภาพ ความปลอดภัย ความเป็นส่วนตัว และความน่าเชื่อถือ อีกทั้งยังมี Bitcoin wallet ที่ถูกสร้างขึ้นมาคู่กับโปรโตคอลของบิตคอยน์อย่าง “Bitcoin Core” ซึ่งมีการพัฒนาต่อมาจากเวอร์ชันที่เขียนโดยซาโตชิ
การเลือก Bitcoin wallet
Bitcoin wallet เป็นหนึ่งในประเภทของแอปพลิเคชันที่มีการพัฒนาอย่างต่อเนื่องมากที่สุดในระบบนิเวศของบิตคอยน์ และแน่นอนว่ามีการแข่งขันกันสูงที่สุดด้วย อาจมี Bitcoin wallet ใหม่ ๆ ที่กำลังพัฒนาอยู่ในขณะนี้ Bitcoin wallet เก่า ๆ บางตัวจากปีที่แล้วก็อาจไม่มีการพัฒนาอย่างต่อเนื่องอีกต่อไป Bitcoin wallet หลาย ๆ ตัวเน้นไปที่แพลตฟอร์มหรือการใช้งานเฉพาะ และบางตัวเหมาะสำหรับผู้เริ่มต้น ในขณะที่บางตัวเต็มไปด้วยฟีเจอร์สำหรับผู้ใช้ขั้นสูง การเลือก Bitcoin wallet นั้นจึงขึ้นอยู่กับความต้องการและระดับความเชี่ยวชาญของผู้ใช้ ดังนั้นการที่เราจะแนะนำยี่ห้อหรือ Bitcoin wallet เฉพาะจึงอาจจะไม่เกิดประโยชน์เท่าไหร่ แต่อย่างไรก็ตาม เราสามารถแบ่งประเภท Bitcoin wallet ได้ตามแพลตฟอร์มและการใช้งานได้ดังนี้
ประเภทของ Bitcoin wallet
- Desktop wallet: กระเป๋าเงินแบบเดสก์ท็อปเป็น Bitcoin wallet ประเภทแรกที่ถูกพัฒนาขึ้นและผู้ใช้ส่วนใหญ่มักจะเลือกใช้ Bitcoin wallet ประเภทนี้เพราะฟีเจอร์ของมัน เช่นความความเป็นอิสระในการใช้งาน ความสามารถในการควบคุมบิตคอยน์ในกระเป๋า แต่อย่างไรก็ตาม การใช้งานบนระบบปฏิบัติการทั่วไป อย่างเช่น Windows และ macOS อาจมีข้อเสียด้านความปลอดภัย เนื่องจากแพลตฟอร์มเหล่านี้มักไม่มีความปลอดภัยเพียงพอและอาจถูกตั้งค่ามาอย่างไม่เหมาะสม
- Mobile wallet: กระเป๋าเงินแบบมือถือเป็น Bitcoin wallet ประเภทที่พบเจอได้มากที่สุด โดยทำงานบนระบบปฏิบัติการสมาร์ทโฟน เช่น Apple iOS และ Android กระเป๋าเงินเหล่านี้มักเป็นตัวเลือกที่ดีสำหรับผู้ใช้ใหม่ เพราะออกแบบมาให้ใช้งานง่ายและสะดวก นอกจากนี้ยังมีกระเป๋าเงินมือถือที่มีฟีเจอร์ครบครันสำหรับผู้ใช้ที่มีความเชี่ยวชาญ แต่เพื่อหลีกเลี่ยงการดาวน์โหลดและจัดเก็บข้อมูลปริมาณมาก กระเป๋าเงินมือถือส่วนใหญ่จะดึงข้อมูลจากเซิร์ฟเวอร์ระยะไกล ซึ่งอาจลดความเป็นส่วนตัวของผู้ใช้เนื่องจากต้องเปิดเผยข้อมูลเกี่ยวกับ address และจำนวนบิตคอยน์ Bitcoin ต่อบุคคลที่สาม
- Web wallet: กระเป๋าเงินแบบเว็บสามารถเข้าถึงได้ผ่านเว็บเบราว์เซอร์และเก็บกระเป๋าเงินของผู้ใช้ไว้บนเซิร์ฟเวอร์ที่บุคคลที่สามเป็นเจ้าของ คล้ายกับบริการอีเมลบนเว็บที่พึ่งพาเซิร์ฟเวอร์ของบุคคลที่สามโดยสมบูรณ์ โดยบางบริการใช้โค้ดฝั่งไคลเอนต์ที่ทำงานในเบราว์เซอร์ของผู้ใช้ และเพื่อให้ผู้ใช้สามารถควบคุมคีย์ของบิตคอยน์ได้เอง แต่การพึ่งพาเซิร์ฟเวอร์ยังคงส่งผลกระทบต่อความเป็นส่วนตัว อย่างไรก็ตาม บริการส่วนใหญ่จะควบคุมคีย์ของบิตคอยน์แทนผู้ใช้เพื่อแลกกับความสะดวกสบาย เราจึงไม่แนะนำให้เก็บ บิตคอยน์จำนวนมากบนระบบของบุคคลที่สาม
- Hardware Signing Devices: อุปกรณ์สำหรับเซ็นดิจิทัลเป็นอุปกรณ์ที่สามารถจัดเก็บคีย์และเซ็นธุรกรรมโดยใช้ฮาร์ดแวร์และเฟิร์มแวร์เฉพาะทาง ซึ่งโดยทั่วไปแล้วจะเชื่อมต่อกับกระเป๋าเงินเดสก์ท็อป มือถือ หรือเว็บ ผ่านสาย USB การสื่อสารระยะใกล้ (NFC) หรือกล้องที่รองรับ QR code แต่เนื่องจากการดำเนินการที่เกี่ยวข้องกับบิตคอยน์ ทั้งหมดถูกจัดการบนฮาร์ดแวร์เฉพาะ อุปกรณ์เหล่านี้จึงปลอดภัยจากการโจมตีหลายรูปแบบ อย่างไรก็ตาม อุปกรณ์เซ็นดิจิทัลมักถูกเรียกว่า hardware wallet แต่ต้องใช้งานร่วมกับกระเป๋าเงินที่มีฟีเจอร์ครบครันเพื่อส่งและรับธุรกรรม ความปลอดภัยและความเป็นส่วนตัวที่ได้จากกระเป๋าเงินที่ใช้งานร่วมกันก็มีบทบาทสำคัญต่อความปลอดภัยและความเป็นส่วนตัวโดยรวมของผู้ใช้อุปกรณ์เซ็นดิจิทัล
ประเภทของการเชื่อมต่อกับโปรโตคอลของบิตคอยน์
- Full node: บิตคอยน์ฟลูโหนดเป็นโปรแกรมที่ตรวจสอบความถูกต้องของประวัติธุรกรรมทั้งหมดของบิตคอยน์ (ทุกธุรกรรมที่เคยเกิดขึ้นโดยผู้ใช้ทุกคน) และนอกจากนี้ บิตคอยน์ฟลูโหนดยังสามารถเลือกเก็บข้อมูลธุรกรรมที่ได้รับการตรวจสอบแล้วก่อนหน้า และให้บริการข้อมูลแก่โปรแกรมบิตคอยน์อื่น ๆ ได้ ไม่ว่าจะเป็นบนคอมพิวเตอร์เดียวกันหรือผ่านอินเทอร์เน็ต แต่แม้ว่าบิตคอยน์ฟลูโหนดเองก็ใช้ทรัพยากรคอมพิวเตอร์ในปริมาณมาก (ประมาณเท่ากับการดูวิดีโอสตรีมมิ่งหนึ่งชั่วโมงต่อวันสำหรับธุรกรรมบิตคอยน์ในแต่ละวัน) บิตคอยน์ฟลูโหนดเองก็มอบความเป็นอิสระอย่างสมบูรณ์แก่ผู้ใช้
- Lightweight Client: lightweight client หรือที่เรียกกันอีกชื่อว่าไคลเอนต์การตรวจสอบการชำระเงินแบบง่าย (Simplified-Payment-Verification: SPV) ซึ่งจะเชื่อมต่อกับโหนดแบบเต็มหรือเซิร์ฟเวอร์ระยะไกลอื่น ๆ เพื่อรับและส่งข้อมูลธุรกรรมของบิตคอยน์แต่เก็บกระเป๋าเงินของผู้ใช้ไว้ในเครื่อง โดยสามารถตรวจสอบธุรกรรมที่ได้รับบางส่วน และสร้างธุรกรรมขาออกอย่างอิสระอีกด้วย
- ไคลเอนต์ API ของบุคคลที่สาม (Third-Party API Client): ไคลเอนต์ API ของบุคคลที่สามเป็นโปรแกรมที่เชื่อมต่อกับระบบบิตคอยน์ผ่าน API ของบุคคลที่สาม แทนที่จะเชื่อมต่อกับเครือข่ายบิตคอยน์โดยตรง กระเป๋าเงินนี้อาจถูกจัดเก็บโดยผู้ใช้เองหรือบนเซิร์ฟเวอร์ของบุคคลที่สาม แต่ไคลเอนต์จะต้องไว้วางใจเซิร์ฟเวอร์ระยะไกลในการให้ข้อมูลที่ถูกต้องและปกป้องความเป็นส่วนตัวของตน
บิตคอยน์เป็นเครือข่ายแบบเพียร์ทูเพียร์(Peer-to-Peer หรือ P2P) โดยที่บิตคอยน์ฟลูโหนด ทำหน้าที่เป็นเพียร์ในเครือข่าย เพียร์แต่ละตัวจะตรวจสอบความถูกต้องของธุรกรรมที่ยืนยันแล้วทุกธุรกรรมอย่างอิสระ และสามารถให้ข้อมูลที่เชื่อถือได้แก่ผู้ใช้ Lightweight Wallets และซอฟต์แวร์อื่น ๆ เองก็เป็นลูกข่ายที่ต้องพึ่งพาเพียร์หนึ่งหรือหลายตัวในการรับข้อมูลที่ถูกต้อง ไคลเอนต์สามารถตรวจสอบข้อมูลบางส่วนที่ได้รับเพิ่มเติมและเชื่อมต่อกับเพียร์หลายตัวเพื่อลดการพึ่งพาเพียร์ตัวเดียว แต่ในท้ายที่สุดความปลอดภัยของไคลเอนต์ยังคงขึ้นอยู่กับความน่าเชื่อถือของเพียร์ที่เชื่อมต่อด้วย
ใครควบคุมคีย์
อีกหนึ่งในประเด็นสำคัญที่ควรพิจารณาเพิ่มเติมคือใครเป็นผู้ควบคุมคีย์ (Private key) เนื่องจากเป็นสิ่งที่มีบทบาทสำคัญในการควบคุมการเข้าถึงบิตคอยน์ โดยคีย์เหล่านี้เองเปรียบเสมือน PIN ที่ยาวมาก ซึ่งหากคุณเป็นผู้ควบคุมคีย์ของคุณเองด้วยตัวเอง คุณก็เป็นผู้ควบคุมบิตคอยน์ของคุณด้วยเช่นกัน แต่หากไม่ใช่ ก็จะแปลว่ากุญแจเหล่านั้นจะถูกดูแลโดยบุคคลที่สาม ซึ่งจะเป็นผู้จัดการเงินของคุณในนามของคุณ
ซอฟแวร์ในการจัดการกุญแจนั้นถูกแบ่งออกเป็นสองประเภทหลัก ๆ คือ wallet ที่คุณจำเป็นต้องดูแลคีย์ของตัวเองและ บัญชีที่มีผู้ดูแล (Custodian Accounts) ซึ่งจะมีบุคคลที่สามเป็นผู้ควบคุมกุญแจ
“Your keys, your coins. Not your keys, not your coins.”
มาอยู่ตัวอย่างเพื่อความเข้าใจที่มาขึ้นกันเถอะ
สมมุติว่าอลิซเป็นผู้ใช้งานที่ไม่ได้เชี่ยวชาญด้านเทคนิค และเพิ่งได้ยินเกี่ยวกับบิตคอยน์จากเพื่อนสนิทของเขา โจ ระหว่างปาร์ตี้ โจกำลังอธิบายเกี่ยวกับบิตคอยน์อย่างกระตือรือร้นให้ทุกคนฟังและสาธิตวิธีการใช้งานต่าง ๆ ให้ดู อลิซเองได้มีความสนใจในบิตคอยน์หลังจากได้ฟังโจอธิบาย จึงได้ถามโจว่าเธอจะเริ่มต้นใช้งานบิตคอยน์ได้อย่างไร โจจึงแนะนำให้อลิซดาวน์โหลด Mobile wallet ตัวโปรดของเขาเนื่องจากมันเหมาะสมกับมือใหม่ อลิซจึงดาวน์โหลดและติดตั้งแอปพลิเคชันกระเป๋าเงินที่โจแนะนำบนโทรศัพท์ของเธอ
เมื่ออลิซเปิดแอปพลิเคชันครั้งแรก เธอได้เลือกสร้างกระเป๋าใหม่และเนื่องจากกระเป๋าที่เธอเลือกนั้นเป็นแบบที่ไม่ได้อยู่ภายใต้การควบคุมบุคคลที่สาม (Noncustodial Wallet) อลิซจึงเป็นผู้ควบคุมคีย์เพียงคนเดียว ซึ่งหมายความว่าเธอต้องรับผิดชอบในการสำรองข้อมูลด้วยตัวของเธอเอง และหากเธอได้ทำคีย์สูญหายไป เธอจะไม่สามารถเข้าถึงบิตคอยน์ของเธอได้อีกไปตลอดกาล และเพื่อเพื่อช่วยในเรื่องนี้ Bitcoin wallet ต่าง ๆ จึงมักจะสร้างรหัสการกู้คืน (Recovery Code) ให้ซึ่งสามารถใช้ในการกู้คืน Bitcoin wallet อันนั้น ๆ
Recovery Code (รหัสในการกู้คืน)
Bitcoin wallet แบบที่ไม่ได้อยู่ภายใต้การควบคุมของบุคคลที่สามนั้นส่วนใหญ่จะให้รหัสการกู้คืนแก่ผู้ใช้งานเพื่อสำรองข้อมูล และรหัสการกู้คืนนี้มักประกอบด้วยตัวเลข ตัวอักษร หรือคำที่ถูกเลือกแบบสุ่มโดยซอฟต์แวร์ และใช้เป็นพื้นฐานสำหรับการสร้าง Bitcoin wallet โดยแต่ละยี่ห้อก็อาจมีความแตกต่างกัน เช่น

รหัสการกู้คืนมักเรียกว่า "mnemonic" หรือ "mnemonic phrase" หรือในภาษาไทยว่าวลีช่วยจำ ซึ่งบ่งบอกว่าคุณควรจดจำวลีนั้น แต่การจดวลีนี้ลงบนกระดาษใช้เวลาน้อยกว่าและมักจะเชื่อถือได้มากกว่าความจำของคนส่วนใหญ่ เพราะฉนั้นผมเลยแนะนำว่าจดเถอะ จะได้ไม่เกิดปัญหาที่ไม่คาดคิดในอนาคต
หาก bitcoin wallet ของอลิซมีปัญหา เธอสามารถดาวน์โหลดซอฟแวร์ใหม่และใส่รหัสในการกู้คืนลงไป เพื่อสร้างฐานข้อมูลของ bitcoin wallet ใหม่ที่บันทึกธุรกรรมบนเชนทั้งหมดที่เธอเคยรับหรือส่ง แต่อย่างไรก็ตาม การกู้คืนจากการใช้รหัสการกู้คืนเพียงอย่างเดียวนั้นอาจจะไม่สามารถกู้คืนข้อมูลเพิ่มเติมที่อลิซเคยบันทึกไว้ใน wallet นั้น ๆ ได้ เช่น ป้ายกำกับที่เธอเชื่อมโยงกับที่อยู่หรือธุรกรรมต่าง ๆ แม้ว่าการสูญเสียข้อมูลเมตานี้จะไม่สำคัญเท่ากับการสูญเสียเงิน แต่ก็ยังมีความสำคัญในบางแง่มุม เช่น หากคุณต้องตรวจสอบรายการธนาคารหรือบัตรเครดิตเก่า แต่ชื่อของผู้ที่คุณชำระเงินหรือผู้ที่จ่ายเงินให้คุณถูกลบออกไป ดังนั้นเพื่อป้องกันการสูญเสียข้อมูลเมตา wallet หลาย ๆ ยี่ห้อจึงมีฟีเจอร์สำรองข้อมูลเพิ่มเติมนอกเหนือจากรหัสการกู้คืน
สำหรับ wallet บางประเภทนั้น ฟีเจอร์สำรองข้อมูลเพิ่มเติมนี้ถือว่ามีความสำคัญมาก เนื่องจากการชำระเงินเงินด้วยบิตคอยน์จำนวนมากในปัจจุบันทำผ่านเทคโนโลยีที่อยู่นอกเชน (Offchain) ซึ่งธุรกรรมไม่ได้ถูกบันทึกลงในบล็อกเชนสาธารณะ เนื่องจากการชำระเงินแบบนี้ช่วยลดค่าใช้จ่ายของผู้ใช้และเพิ่มความเป็นส่วนตัวได้บ้าง แต่นั่นก็หมายความว่ากลไกอย่างรหัสการกู้คืนที่พึ่งพาข้อมูลบนเชนไม่สามารถรับประกันการกู้คืนบิตคอยน์ทั้งหมดของผู้ใช้ได้ ดังนั้นสำหรับแอปพลิเคชันที่รองรับการใช้งาน Offchain การสำรองข้อมูลฐานข้อมูล wallet บ่อยครั้งจึงเป็นสิ่งที่มีความสำคัญมาก
นอกจากนี้ เมื่อได้รับบิตคอยน์ครั้งแรกใน moblie wallet หลาย ๆ wallet มักจะตรวจสอบอีกครั้งว่าคุณได้สำรองรหัสการกู้คืนไว้อย่างปลอดภัยแล้ว การตรวจสอบนี้อาจเป็นเพียงการแจ้งเตือน หรืออาจถึงขั้นให้ผู้ใช้ป้อนรหัสนั้นซ้ำด้วยตัวเอง
คำเตือน แม้ว่า Bitcoin Wallet หลาย ๆ ตัวอาจจะมีการให้คุณต้องกรอกรหัสในการกู้คืนใหม่ในบางกรณี แต่มันก็มักจะมีแอปพลิเคชันมัลแวร์จำนวนมากที่เลียนแบบการออกแบบของ wallet ต่าง ๆ โดยมันจะบังคับให้คุณป้อนรหัสการกู้คืน จากนั้นมันจะส่งรหัสที่ป้อนไปยังผู้พัฒนามัลแวร์เพื่อขโมยบิตคอยน์ของคุณ นี่เปรียบเสมือนเว็บไซต์ฟิชชิงที่พยายามหลอกให้คุณให้รหัสผ่านธนาคารของคุณ สำหรับ Bitcoin wallet ส่วนใหญ่ เวลาที่พวกเขาจะขอรหัสการกู้คืนคือในระหว่างการตั้งค่าเริ่มต้น (ก่อนที่คุณจะได้รับบิตคอยน์) และระหว่างการกู้คืน (หลังจากที่คุณสูญเสียการเข้าถึง wallet เดิม) หากแอปพลิเคชันขอรหัสการกู้คืนในช่วงเวลาอื่น คุณควรปรึกษาผู้เชี่ยวชาญเพื่อให้แน่ใจว่าคุณไม่ได้ตกเป็นเหยื่อของการฟิชชิง
Bitcoin Addresses (ที่อยู่ในการรับหรือส่งบิตคอยน์)
ในตอนนี้อลิซพร้อมแล้วสำหรับการสร้าง Bitcoin wallet ใหม่ของเธอ Bitcoin wallet ที่เธอเลือกได้ทำการสร้าง private key แบบสุ่มให้เธอ ซึ่งจะเชื่อมโยงกับ Bitcoin Address ทั้งหมดที่มีใน Bitcoin wallet ของเธอ แต่ ณ ขณะนี้ยังไม่มีใครรู้ Bitcoin address ของเธอ (แม้แต่ Bitcoin network ก็ไม่รู้) นอกจากตัวเธอเอง Bitcoin address เหล่านี้เป็นเพียงตัวเลขที่เชื่อมโยงกับ Private key ของเธอ ซึ่งเธอสามารถใช้ควบคุมการเข้าถึง Bitcoin ใดกระเป๋าได้ Bitcoin address เหล่านี้ถูกสร้างขึ้นโดยอิสระจากกระเป๋าของเธอโดยไม่ต้องอ้างอิงหรือเชื่อมต่อกับบริการใด ๆ
คำแนะนำ: Bitcoin address และ Invoice นั้นมีหลากหลายรูปแบบที่แตกต่างกัน และทั้งหมดนี้สามารถแชร์ให้กับคนอื่น ๆ ได้ เพื่อเป็นการอณุญาติให้พวกเขาส่งบิตคอยน์เข้ามาในกระเป๋าคุณตรง ๆ คุณสามารถแชร์ Bitcoin address และ Invoice ให้คนอื่นได้โดยไม่ต้องกังวลเกี่ยวกับความปลอดภัยของบิตคอยน์ของคุณ เนื่องจากผู้ที่รู้ Bitcion address ของคุณไม่สามารถถอนเงินออกจาก address นั้น ๆ ได้แม้เขาจะสามารถรู้จำนวนเงินใน address นั้น ๆ ก็ตาม เพราะฉะนั้นเพื่อปกป้องความเป็นส่วนตัวของคุณ คุณจึงควรสร้าง Invoice จาก Bitcoin address ใหม่ทุกครั้งที่จะส่งให้ผู้อื่น
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 8d34bd24:414be32b
2024-11-13 22:45:38
@ 8d34bd24:414be32b
2024-11-13 22:45:38Yesterday I was doing my Revelation Bible study and the author told us to look back at Jeremiah 25 to see how it related to what we were studying in Revelation 15 & 16. She only referred to a couple of verses, but I read more to get context because I was having trouble seeing what point she was trying to make. When I read Jeremiah 25, it reminded me of Ezekiel 38 and sounded a lot like what is happening in the Middle East and the world today. This article is my attempt to investigate this idea and organize my thoughts and share it with you.
I do have some comments regarding prophecy and the current Israeli/Palestine/etc. conflict that may be divisive, but I hope my use of the Bible to explain God’s plan will help people understand what is currently going on a bit better and without the rancor and bias coming from the media today. It should also help us to understand why it seems the whole world has turned against Israel and why nobody protests or shows solidarity with Israel when they are attacked in the most horrific ways.
Let’s see what Jeremiah 25 has to say:
‘Then it will be when seventy years are completed I will punish the king of Babylon and that nation,’ declares the Lord, ‘for their iniquity, and the land of the Chaldeans; and I will make it an everlasting desolation. (Jeremiah 25:12)
Since God declared after the 70 year exile of Judah in Babylon to destroy Babylon and to make it “an everlasting desolation,” then it seems unlikely that Babylon the Great in Revelation is historical Babylon. It has been destroyed and God promised that it would be an everlasting desolation. Who could Babylon the Great be if it isn’t actual Babylon? I am beginning to have my unpleasant theories, but I won’t go into that here.
I will bring upon that land all My words which I have pronounced against it, all that is written in this book which Jeremiah has prophesied against all the nations. (For many nations and great kings will make slaves of them, even them; and I will recompense them according to their deeds and according to the work of their hands.)’ ”
For thus the Lord, the God of Israel, says to me, “Take this cup of the wine of wrath from My hand and cause all the nations to whom I send you to drink it. They will drink and stagger and go mad because of the sword that I will send among them.” (Jeremiah 25:13-16)
God then promises “many nations and great kings” that made slaves of Judah/Israel, that God will “recompense them according to their deeds.”
Compare that to Revelation 14 and 16:
Then another angel, a third one, followed them, saying with a loud voice, “If anyone worships the beast and his image, and receives a mark on his forehead or on his hand, he also will drink of the wine of the wrath of God, which is mixed in full strength in the cup of His anger; and he will be tormented with fire and brimstone in the presence of the holy angels and in the presence of the Lamb. (Revelation 14:9-10)
and
Then the third angel poured out his bowl into the rivers and the springs of waters; and they became blood. And I heard the angel of the waters saying, “Righteous are You, who are and who were, O Holy One, because You judged these things; for they poured out the blood of saints and prophets, and You have given them blood to drink. They deserve it.” (Revelation 16:4-6)
In the same way Revelation promises God’s wrath on those who rejected Him and on those who persecuted His followers, and that He would force them to drink the cup of His wrath, Jeremiah 25 says he will force them to drink of “this cup of the wine of wrath from my hand.” Those who reject God and Jesus, as well as those who mistreat Israel/Jews and Christians, will receive God’s overwhelming wrath.
In this passage, God says, “They will drink and stagger and go mad because of the sword that I will send among them.” It seems that today, the whole world has gone mad at Israel defending itself and it is causing the whole world to turn against God’s chosen people, Israel.
I also receive great comfort from these verses thanks to the addition of “They deserve it.” There is so much injustice in the world, I love seeing that those who are evil and cause harm will be punished because “They deserve it.”
Then I took the cup from the Lord’s hand and made all the nations to whom the Lord sent me drink it: Jerusalem and the cities of Judah and its kings and its princes, to make them a ruin, a horror, a hissing and a curse, as it is this day; Pharaoh king of Egypt, his servants, his princes and all his people; and all the foreign people, all the kings of the land of Uz, all the kings of the land of the Philistines (even Ashkelon, Gaza, Ekron and the remnant of Ashdod); Edom, Moab and the sons of Ammon; and all the kings of Tyre, all the kings of Sidon and the kings of the coastlands which are beyond the sea; and Dedan, Tema, Buz and all who cut the corners of their hair; and all the kings of Arabia and all the kings of the foreign people who dwell in the desert; and all the kings of Zimri, all the kings of Elam and all the kings of Media; and all the kings of the north, near and far, one with another; and all the kingdoms of the earth which are upon the face of the ground, and the king of Sheshach shall drink after them. (Jeremiah 25:17-26) {emphasis of nations is mine}
Let’s see if the nations listed seem to match with the nations turning against Israel today. I did research online1 and came up with these matches (some are clear and some are possibly what was mentioned and are marked with a “?”:
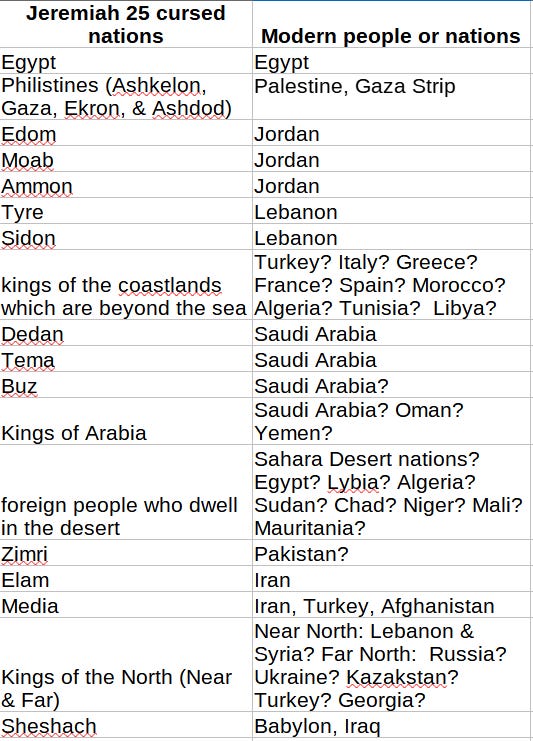
This looks like most of the nations turning against Israel and most of the nations on this list have become very aggressive against and/or speaking evil of Israel. I never thought of Jeremiah as predicting end times events, but it seems it probably is.
“You shall say to them, ‘Thus says the Lord of hosts, the God of Israel, “Drink, be drunk, vomit, fall and rise no more because of the sword which I will send among you.” ’ And it will be, if they refuse to take the cup from your hand to drink, then you will say to them, ‘Thus says the Lord of hosts: “You shall surely drink! For behold, I am beginning to work calamity in this city which is called by My name, and shall you be completely free from punishment? You will not be free from punishment; for I am summoning a sword against all the inhabitants of the earth,” declares the Lord of hosts.’ (Jeremiah 25:12-38)
The UN just voted overwhelmingly to force Israel to leave what they call occupied Palestinian territories like the Gaza Strip and the West Bank, even though Israel only occupies them because of aggression in 1967 against them by Egypt, Jordan, Syria, and the Palestinians. These nations and people originally tried to block the Jordan river from providing water to Israel, bombed civilians (just like today), and then tried to block all shipping to Israel. When Israel tried to renew shipping, they all out attacked Israel. Israel came out the clear winner and gained a small amount of land in the West Bank, the Gaza Strip, and the Sinai Peninsula. Although the UN, at the time, said Israel rightly owned these lands since they were not the aggressors, now the UN is reneging on that promise. Israel voluntarily gave back the Sinai peninsula to Egypt as part of a peace agreement. They willingly allowed the Palestinians back into the West Bank and Gaza under semi-autonomous rule, but these lands were used primarily to attack Israel repeatedly because the Muslim nations aren’t trying to save the Palestinians. They are trying to wipe Israel off the map and take “the river to the sea,” which means 100% of Israel. Interestingly, God promised “Every place on which the sole of your foot treads shall be yours; your border will be from the wilderness to Lebanon, and from the river, the river Euphrates, as far as the western sea.” (Deuteronomy 11:24) This cry from the Muslims is a direct demonic attack on God’s promise to Israel.
Ironically before the Six Days War, the Palestinians in the West Bank were under Syrian control (they’ve never, at least in modern times, had their own nation) and Hussein of Syria put them under martial law because he feared they might overthrow him. These nations that use the Palestinian plight as an excuse to do horrific actions against Israel don’t actually like or care about the Palestinian people. They are just pawns used to justify their actions against Israel. The Palestinians were treated just as bad, if not worse by the Syrians.
The UN resolution also calls for the Israelis to leave East Jerusalem, the “city which is called by My name.” Because of their actions, God promises “You will not be free from punishment; for I am summoning a sword against all the inhabitants of the earth.” God is going to drag the anti-Israel and anti-God nations into conflict in order to punish them.
This also reminds me a lot of Ezekiel 38:
And the word of the Lord came to me saying, “Son of man, set your face toward Gog of the land of Magog, the prince of Rosh, Meshech and Tubal, and prophesy against him and say, ‘Thus says the Lord God, “Behold, I am against you, O Gog, prince of Rosh, Meshech and Tubal. I will turn you about and put hooks into your jaws, and I will bring you out, and all your army, horses and horsemen, all of them splendidly attired, a great company with buckler and shield, all of them wielding swords; Persia, Ethiopia and Put with them, all of them with shield and helmet; Gomer with all its troops; Beth-togarmah from the remote parts of the north with all its troops—many peoples with you. (Ezekiel 38:1-6) {emphasis of nations & highlighted verse is mine}
These nations seem to overlap with those mentioned in Jeremiah 25, but aren’t quite as extensive.2
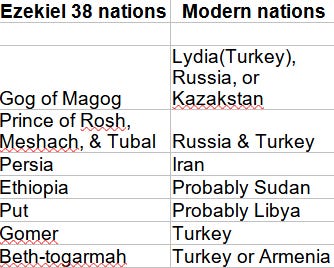
Ezekiel 38 also talks about these nations being dragged into conflict. It says, “I will turn you about and put hooks into your jaws, and I will bring you out.”
“Be prepared, and prepare yourself, you and all your companies that are assembled about you, and be a guard for them. After many days you will be summoned; in the latter years you will come into the land that is restored from the sword, whose inhabitants have been gathered from many nations to the mountains of Israel which had been a continual waste; but its people were brought out from the nations, and they are living securely, all of them. You will go up, you will come like a storm; you will be like a cloud covering the land, you and all your troops, and many peoples with you.” (Ezekiel 38:7-9)
This continuation in Ezekiel 38 says these nations will be brought into conflict with Israel after Israel “will come into the land that is restored from the sword, whose inhabitants have been gathered from many nations to the mountains of Israel which had been a continual waste; but its people were brought out from the nations, and they are living securely, all of them.” This prophecy of Israel has happened with Israel being reconstituted as a nation and the Jewish people coming from nations all around the world after having been perilously attacked with the sword, i.e. Nazi Germany. They are now a successful and prosperous nation, but the nations around them are gathering to attack them. Israel has not yet been covered by troops “like a cloud covering the land,” but has been covered “like a cloud covering the land” by a bombardment of rockets, drones, and missiles shot by Iran (Persia).
‘Thus says the Lord God, “It will come about on that day, that thoughts will come into your mind and you will devise an evil plan, and you will say, ‘I will go up against the land of unwalled villages. I will go against those who are at rest, that live securely, all of them living without walls and having no bars or gates, to capture spoil and to seize plunder, to turn your hand against the waste places which are now inhabited, and against the people who are gathered from the nations, who have acquired cattle and goods, who live at the center of the world.’ Sheba and Dedan and the merchants of Tarshish with all its villages will say to you, ‘Have you come to capture spoil? Have you assembled your company to seize plunder, to carry away silver and gold, to take away cattle and goods, to capture great spoil?’ ” ’
“Therefore prophesy, son of man, and say to Gog, ‘Thus says the Lord God, “On that day when My people Israel are living securely, will you not know it? You will come from your place out of the remote parts of the north, you and many peoples with you, all of them riding on horses, a great assembly and a mighty army; and you will come up against My people Israel like a cloud to cover the land. It shall come about in the last days that I will bring you against My land, so that the nations may know Me when I am sanctified through you before their eyes, O Gog.” (Ezekiel 38:10-16) {emphasis mine}
It is interesting to note that for most of Israel’s history, there wasn’t much plunder to seize, but recently they have found great natural gas reserves that are envied by nations like Iran and Russia.
It is also interesting to see how the Jews from around the globe keep moving to Israel, despite the danger, just as predicted in the Old Testament.
There are two things I am not certain about. Are these predictions the same, or will there be multiple attacks on the new Israel? I’ve always expected this attack on Israel to happen right before or right after the beginning of the tribulation, but Zechariah 14 sounds like it might be at the end of the tribulation because it mentions Jesus coming back.
As context the previous chapter ends:
They will call on My name,\ And I will answer them;\ I will say, ‘They are My people,’\ And they will say, ‘The Lord is my God.’ ” (Zechariah 13:9b)
The Jews were dispersed around the globe for almost 2,000 years, but God has called them back to the promised land and has promised to turn their hearts back to Him. (This hasn’t happened yet and probably won’t happen until the seven year tribulation.)
Behold, a day is coming for the Lord when the spoil taken from you will be divided among you. For I will gather all the nations against Jerusalem to battle, and the city will be captured, the houses plundered, the women ravished and half of the city exiled, but the rest of the people will not be cut off from the city. Then the Lord will go forth and fight against those nations, as when He fights on a day of battle. In that day His feet will stand on the Mount of Olives, which is in front of Jerusalem on the east; and the Mount of Olives will be split in its middle from east to west by a very large valley, so that half of the mountain will move toward the north and the other half toward the south. (Zechariah 14:1-4) {emphasis mine}
After Jesus’s resurrection, He spent time with His disciples preparing them and then ascended into heaven from the Mount of Olives. Two angels told those who had witnessed His ascension that Jesus would return in the same way, which is seconded by Zechariah, “In that day His feet will stand on the Mount of Olives.”
It is true according to Zechariah that not all Jews will be saved, but that Jesus will fight for His chosen people, despite all of their failings. God is merciful!
So then He has mercy on whom He desires, and He hardens whom He desires. (Romans 9:8)
Jeremiah 25 is accentuating God’s judgement rather than His mercy.
“Therefore you shall prophesy against them all these words, and you shall say to them,\ ‘The Lord will roar from on high\ And utter His voice from His holy habitation;\ He will roar mightily against His fold.\ He will shout like those who tread the grapes,\ Against all the inhabitants of the earth.\ A clamor has come to the end of the earth,\ Because the Lord has a controversy with the nations.\ He is entering into judgment with all flesh;\ As for the wicked, He has given them to the sword,’ declares the Lord.” (Jeremiah 25:30-31)
There will be a large group of nations that will gather in hate and attack Israel with what would be conventionally considered overwhelming force, but God will defend Israel.
In reality, I can already see the hand of God on Israel. A few weeks ago (sorry I’m terrible with dates) Iran (Persia) sent a barrage of rockets, drones, and missiles against Israel. Israel’s Iron Dome defense system was able to take out the majority of them and not one Israeli was killed by massive number of these being fired into densely populated civilian areas. An expert analyzed the data and said the system should not have been able to stop all of these coming at one time. None of the ones missed hit where people were. It was a miraculous protection of Israel.
Then a few weeks later, Israel retaliated. They sent 100 jets across several enemy, Muslim countries into Iran, took out Iran’s anti-aircraft and early warning systems, their missile storage facilities, and their missile and other weapons manufacturing plants and then returned home to Israel. Not one plane was shot down. Not one was touched. It reminds me of a time Jesus was visiting his hometown and offended the people with a story from Scripture. The people, his friends and family, were so offended they dragged Him to the edge of a cliff to toss him off to His death. Then Jesus just walked through the crowd and went on His way without anyone stopping Him. Israel’s retaliation against Iran felt like that, a miraculous protection of His chosen people.
Iran and the other nations mentioned in Ezekiel 38, and probably in Jeremiah 25, are having their satanic hate brought to light by their hate of Israel and they are being dragged by the nose into a battle that they can’t win because God fights for His chosen people, Israel.
Thus says the Lord of hosts,
“Behold, evil is going forth\ From nation to nation,\ And a great storm is being stirred up\ From the remotest parts of the earth.
“Those slain by the Lord on that day will be from one end of the earth to the other. They will not be lamented, gathered or buried; they will be like dung on the face of the ground. (Jeremiah 25:32-33)
Prophecy can be a bit tricky to understand, but by digging into all of the Bible and all of its prophecy I feel like I am understanding it better and better.
If anyone thinks I’m wrong, feel free to share Bible verses showing my error. I’m always seeking the truth.
Trust Jesus.\ \ your sister in Christ,
Christy
-
 @ fd208ee8:0fd927c1
2024-11-13 10:28:15
@ fd208ee8:0fd927c1
2024-11-13 10:28:15The fertility rate is not the whole story
I keep reading articles about the fertility decline that has now consumed most developed nations on Earth, and that is slowly creeping toward the few remaining holdouts, mostly in sub-Saharan Africa.
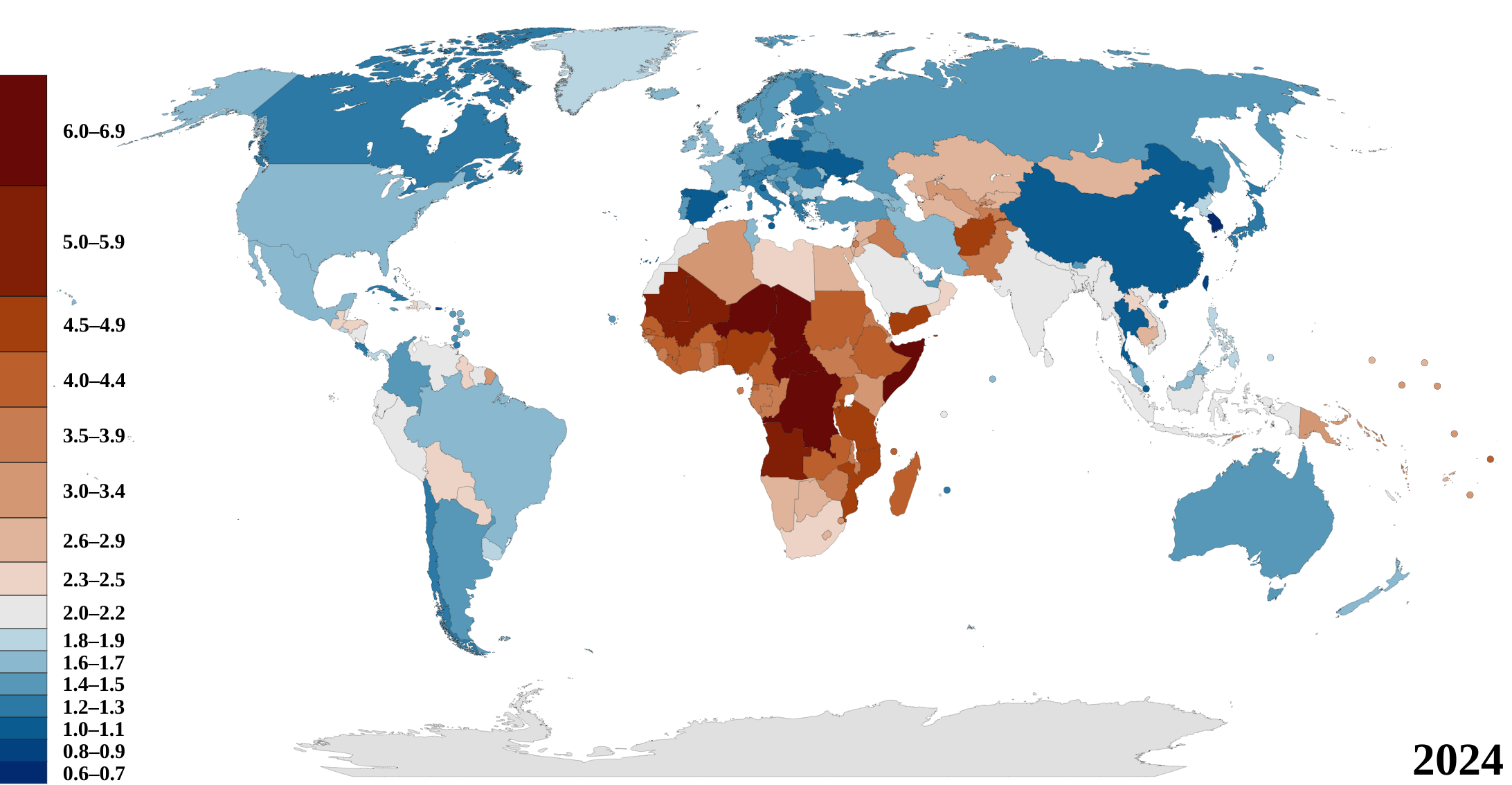
Many countries, that we still think of, as having high birthrates, are actually just experiencing the echo of previous high birthrates. Same as Europe had in the 70s and 80s, due to the post-WWII baby boom. Others have very high total fertility rates (TFR), but such high infant and child mortality, that the population doesn't grow in line with the fertility.
East Asia is in the worst shape, with Europe closely nipping at its heels. TFR is highest in Niger, at 6.1 children per woman, and lowest in South Korea, at 0.7. In other words, the South Korean population nearly halves in size, every generation. (I will be focusing on South Korea, going forward, as a case study of the general phenomenon.)
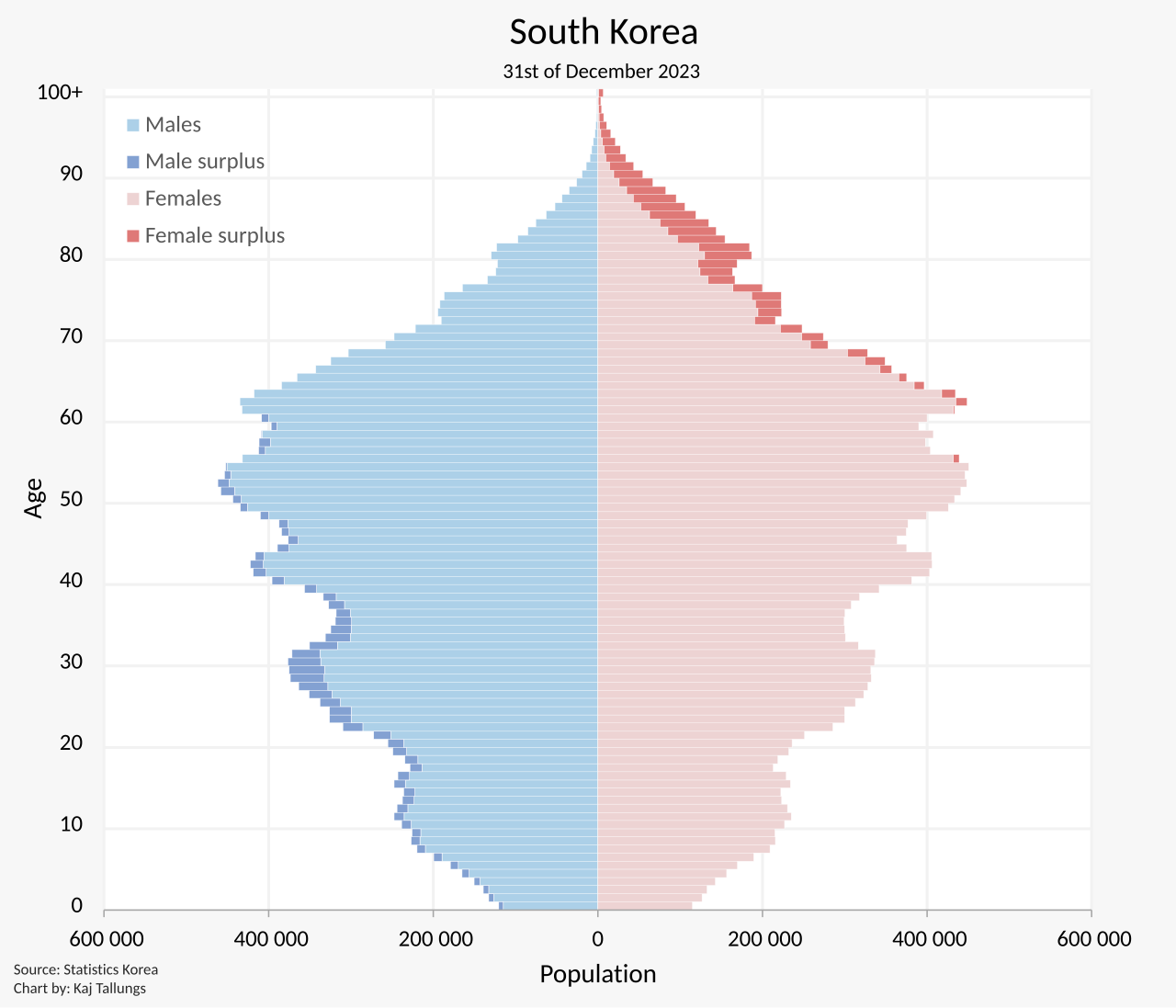
Fertility rate is not even half the story
But it's actually all much worse than is being publicized, as the fertility rates don't take the tangible effects of delays in childbearing into account, which actually are felt more immediately, than the decline in overall fertility. What the delays do, is spread the same number of births more thinly over the timeline, debilitating any infrastructure or traditions that require a certain number of people, to be maintained. I think of this as demographic logistics, as it's about getting the right number of people, of the right age, to the right place, at the right time, in order to meet some minimum required volume.
Playgroups, schools, hospitals, festivals, volunteer organizations, sports clubs, road works, senior residences, churches, new business starts, etc. all require a certain number of participants, to remain viable. Those participants trickling in, at a slower and slower rate, is why even places with above-replacement fertility (like my own town) increasingly struggle to maintain systems that are popular. Everyone is being spread thinner and thinner, and we're having to make hard choices about how the smaller group will be distributed amongst the activities.
You feel like you're being overrun because you are.
This is also why the fact that migrants (and religious people, etc.) tend to adjust their birthrate to the regional average, doesn't lead to an end of their demographic overrepresentation. They are under less societal pressure to delay childbearing, so they tend to be further down the following chart, and their offspring simply arrive much more quickly, than with the natives.
To put it simply, for everyone one generation of the "natives" or "majority" society, there are two or three generations of the others.
Does communism get the last laugh?
Societies, like South Korea, where the fertility rate is exceedingly low, also tend to have the most-delayed childbearing, so the effect of low fertility is heavily exacerbated. The countries are hollowing out, on the ground level, with the population being replaced so slowly and thinly, that the majority of the country will soon simply be empty, and the infrastructure will fall apart.
Christianity is starting to have a positive effect on a subset of South Korean birthrates, by promoting the concept of openness to life and family-friendliness, but its popularization initially decreased fertility. (This is a common effect, as Christianity leads to higher status for women, monogamy, and the concept of "family planning".) Yes, contrary to what The Handmaid's Tale enthusiasts claim, increased religiosity actually exacerbated the already-widespread decline.
South Korea is really just the worst of worst-case scenarios, unfortunately, with absolutely every demographic and economic trend aligning to cut off their reproduction. This is in direct contrast to North Korea, that can compensate for the more moderate decline in births with mere mechanization.
Yes, it looks like North Korea will do much better, going forward, than South Korea. Their entrance into the Ukraine War isn't incidental; we will be hearing more from them, going forward.
Robots serving ghosts
The South Korean plan of simply substituting robots for most humans, will go nowhere, as robots are actually less efficient and effective than humans, except at highly dull or repetitive tasks, over the course of their lifecycle. (This is hidden with cheap, extended production financing, where the machines don't have to turn a profit for decades, whereas humans have to be paid today.) Without productive, agile humans, generating real income, there will be no one to purchase and run all the expensive robots.
And... run them... for whom?

-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 6d8e2a24:5faaca4c
2024-11-30 00:07:10
@ 6d8e2a24:5faaca4c
2024-11-30 00:07:10Why do people enjoy pain and a short time pleasure, which could ruin their life and peace?
Why can't people leave their fleshy desires, obsession and pleasures even if it kills them?
Many have become slaves to their obsession having no will of theirs, claiming to be free yet imprisoned by their futility and lust.
We thought we have closed all the doors and windows, turn off the light so no one can see us, least so we thought to ourselves, forgetting our conscience is wide open, and God who sit in heaven watching, like it was never night nor dark, sees through us for he is light ruling over darkness.
The devil working upon our obsession making it a reality. The devil always uses our sinful, lustful desire to trick us given an end vain pleasure
We fall once, down with the guilt and pain of sin, the weight of the burden once thought, destroying the spirit and causing so many pains of regret, low self-esteem, and lack of confidence again.
He comes again not to bring new but to dwell in our past, bringing memories, mistakes, and errors making us feel more guilty and vulnerable, making us feel worthless and hopeless "We are doomed, so we think, God can't help us, our sins are too many; and with that, he finds a way to make us fall again, destroying us slowly till we are empty, having no will (stronghold).
Like a fire 🔥 lit in a bush, small as it is no one thought it could cause so much harm, or rather they thought they could control it or, put it off when they don't need it or, get bizarre.
Anything that has passed infantry allowed to grow is difficult or impossible to control so is a sin when is allowed to grow like a fire covering many areas is hard to put all areas off fast before one knows many areas are damaged many are beyond repairs
Every day we wake up, we plan how our lives, and how we are going to live the day, without the slimmest thought of contention, 'what if'. We do believe we have everything under control, everything planned out, but we forget that we are nothing but a sand timer that runs down so quickly than we thought.
Like the sand timer, our lives fade away gently, piece by piece till we cease to exist, only then, do we understand that we are rebels in this kingdom, not owners for we own nothing, with the dust reaching its last, the heartbeat and craves for more time, then we also understand, that time is never enough and time is so precious and priceless
Why do we always feel as if we have all the time in the world? why do we assume death to be a fairytale or a horror ghost story just to scare us out? Without having a sting.
Every day death proves more eager, the grave is so desperate that it looms looking and searching for any opportunity necessary to sting it stings.
But we are so carried away by life, deceived by what we have, the power, authority, and influence. We feel we are covered, yes we are but only to some certain extent. For life is so spiritual, than we could ever imagine or think of.
The night comes darkness looms over, evil rises, and fear grips one's heart, all wishing for the light. But now is no longer darkness that's so terrifying, but light itself has become as terrifying as the darkness, people wishing to live through the light, now wish the same to live through the night, for in it they find peace and comfort 😢
Why, I ask why, why has light become so terrifying and darkness become more comforting that the people find solace in it?
I came to understand why people find comfort in darkness is because they are afraid of selves afraid of what they have become, darkness does not challenge but rather allows you to wallow in your misery and regret, killing and draining you where no one will correct you or remind you, that you are not good enough, darkness gives you the room to accept who and what you have become, and there and then it echoes is better to die and live in peace than to be alive and live in misery.
Why will one think of death as the only option or think of death as the only solution to peace, is living not joyful, is life not great to live, why will one wish to leave all, family, friends everything, and settle for death?
I came to understand that, the most reason why one tends to choose death over life or loves to behold the warmth of darkness instead of light, is the feeling of emptiness and internal failure even after a significant measure, of material and social success, is a direct result of failure to discover purpose in life and a reason of being, when one loses his peace, joy all that's left or remain is pain, and regret. When a man reaches a stage of emptiness, where nothing else again matters life itself has no meaning, then it's only a test of time before destruction befalls such a person
Even the rich are depressed and frustrated beholding the enticement of the dark, and many try to drink themselves up, to them is the only way to find peace within, why, after so much wealth and achievement yet feel lonely, his greatest friends are alcohol and nights.
If money, riches cant give fulfillment or perfect peace then what can?
-
 @ 8d34bd24:414be32b
2024-11-10 22:42:29
@ 8d34bd24:414be32b
2024-11-10 22:42:29In Part 1, we got to see God’s initial promises to Adam, Eve, and all mankind with the proto Gospel:
“He shall bruise you on the head,\ And you shall bruise him on the heel.”(Genesis 3:15)
We saw God’s promises to Abraham:
-
To have his name made great.
-
To receive the land of Israel.
-
To father many nations.
-
That “in you all the families of the earth will be blessed.”
We saw God’s reiterated promises to Jacob, Abraham’s grandson.
Now we will look at the partial fulfillment of these promises and new promises made.
The Promised Land (Quick Summary)
Jacob fathered 12 sons. His son Joseph was sold as a slave to Egypt where he became second to the Pharaoh and saved Jacob’s family and the rest of the Middle East from famine. The Israelites then spent around 400 years in Egypt before Moses was called by God to lead the Israelites to the promised land. God performed awe inspiring miracles through Moses to force Pharaoh to release the Israelites who had been made slaves by the Egyptians.
After crossing the desert, the Israelites reached the promised land, but instead of trusting the God who had rescued them with miracles never before seen, they were fearful and refused to obey God and to enter the promised land. God then had them wander 40 more years in the wilderness until the rebellious adults had all died. Then God miraculously aided this band of shepherds to conquer the land of Canaan and inhabit it, partially fulfilling His promise to give them this land.
After approximately 410 years of judges leading the people of Israel and them repeatedly going astray, God gave them the king they requested, Saul. God gave them a tall and handsome, but selfish and unfaithful king to show them the error of their ways. After showing them their error, God gave them a godly king, a man after God’s own heart.
David
When God spoke His promise (covenant) with David, He reiterated the promises given to Abraham and to Jacob, but added:
“When your days are complete and you lie down with your fathers, I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever. I will be a father to him and he will be a son to Me; when he commits iniquity, I will correct him with the rod of men and the strokes of the sons of men, but My lovingkindness shall not depart from him, as I took it away from Saul, whom I removed from before you. Your house and your kingdom shall endure before Me forever; your throne shall be established forever.” (2 Samuel 7:12-16) {emphasis mine}
The first part of this promise was fulfilled through David’s son, Solomon. Solomon sat on the throne. Solomon built a temple to worship God. Solomon was not cut off for his sins at the end of his life when he drifted away from God. Even though ten tribes were taken away from Solomon’s son Rehoboam, Rehoboam remained king of the two tribes of Judah and Benjamin and therefore his throne remained.
The final promise, “Your house and your kingdom shall endure before Me forever; your throne shall be established forever,” was also partially fulfilled through Jesus at His incarnation and will be fully fulfilled when He returns for His millennial reign.
“I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever.” Jesus is a descendant of David and His kingdom will be established at the end of the age — a kingdom of believers. “He shall build a house for My name.” Most of the time Israel is referred to as the house of God while the church is referred to as the body of Christ. In the millennial kingdom they will be united into one house, the adopted children which are the gentile church and the natural children which are the Jews who have finally accepted their Messiah. The final kingdom on this earth will be the millennial reign of Jesus (the promised heir of David), and then God will produce a new heaven and a new earth upon which Jesus will reign forever.
Once again, David did not get to experience the complete fulfillment of the promises made to him. It was partially fulfilled in his son, Solomon, but it has taken thousands of years to partially fulfill this promise and we don’t know for sure how long it will be until complete fulfillment.
Jeremiah
By the time of Jeremiah, the nation of Israel was gone and Judah was corrupted beyond recognition. The fulfillment of God’s promises seemed impossible, but God’s promises are faithful and true. God spoke to Jeremiah to remind him, that although Judah and Israel were being punished, ultimately, God would fulfill all His promises. He begins with these tender words:
Now the word of the Lord came to me saying,\ “Before I formed you in the womb I knew you,\ And before you were born I consecrated you;\ I have appointed you a prophet to the nations.”\ \ Then I said, “Alas, Lord God!\ Behold, I do not know how to speak,\ Because I am a youth.”\ \ But the Lord said to me,\ “Do not say, ‘I am a youth,’\ Because everywhere I send you, you shall go,\ And all that I command you, you shall speak.\ Do not be afraid of them,\ For I am with you to deliver you,” declares the Lord.\ \ Then the Lord stretched out His hand and touched my mouth, and the Lord said to me,\ “Behold, I have put My words in your mouth.\ See, I have appointed you this day …” (Jeremiah 1:4-10a)
First God tells Jeremiah that He loves him so much that He formed him in his mother’s womb for a special purpose, to speak His judgement and blessings on Israel. God comforts Jeremiah when Jeremiah fears he is unworthy of the great task God has for him. God promises to be with Jeremiah and to help Jeremiah fulfill His will.
As Christians we are similarly told that God created us for His purpose and His blessing and He will be with us, empowering us for whatever tasks He has called us to do.God promises that despite Israel’s nonstop rebellion, He will be gracious and “not be angry forever.”
Go and proclaim these words toward the north and say,\ ‘Return, faithless Israel,’ declares the Lord;\ ‘I will not look upon you in anger.\ For I am gracious,’ declares the Lord;\ ‘I will not be angry forever.\ Only acknowledge your iniquity,\ That you have transgressed against the Lord your God\ And have scattered your favors to the strangers under every green tree,\ And you have not obeyed My voice,’ declares the Lord.\ ‘Return, O faithless sons,’ declares the Lord;\ ‘For I am a master to you,\ And I will take you one from a city and two from a family,\ And I will bring you to Zion.’ (Jeremiah 3:12-14)
God will always fulfill His promises even if that means calling His people home from the ends of the earth where they are scattered “one from a city and two from a family.”
God promises to call both Israel and Judah back to the land promised to them all of the way back in time of God’s promise to Abraham. There is a partial return, after Judah’s 70 year exile in Babylon, leading to a rebuilding of the temple for a second time. We are in the middle of another return to Israel that began when Israel was recreated in 1948 and is continuing today. Despite the fact that the people of Israel are being barraged with rockets, drones, and missiles daily and are at risk of being attacked by suicide bombers and terrorists, God is calling His people home for His big finale.
I believe these continuing verses refer to Jesus’s second coming and the millennial reign of Christ.
“Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding. It shall be in those days when you are multiplied and increased in the land,” declares the Lord, “they will no longer say, ‘The ark of the covenant of the Lord.’ And it will not come to mind, nor will they remember it, nor will they miss it, nor will it be made again. At that time they will call Jerusalem ‘The Throne of the Lord,’ and all the nations will be gathered to it, to Jerusalem, for the name of the Lord; nor will they walk anymore after the stubbornness of their evil heart. In those days the house of Judah will walk with the house of Israel, and they will come together from the land of the north to the land that I gave your fathers as an inheritance. (Jeremiah 3:15-18)
This passage isn’t just a call back to the promised land. This is another promise of God. “Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding.” After Jesus’s first coming, He made things clear about His plan of redemption for Israel and for the gentiles. He made clear His promise to bless all nations through Himself, a descendant of David, Jacob, and Abraham, to whom the promises were given. He demonstrated how His laws for the Jews pointed them to God’s ultimate plan.
It is actually ironic that the “shepherds after My own heart, who will feed you on knowledge and understanding” are most likely Christian believers who are returned to earth to reign with Christ during the millennial kingdom. Gentile Christians were enabled to have a relationship with God through the Jews and then God will use those gentile Christians to shepherd the Jews back to God, so we can all worship God together.
It won’t be until Jesus’s second coming and His thousand year reign that “they will call Jerusalem ‘The Throne of the Lord.’” It won’t be until Jesus’s second coming and His thousand year reign that they will not “walk anymore after the stubbornness of their evil heart.” God will finally make the full land of Israel a land of peace and prosperity for the Jews, but also to all the nations of the earth.
But at the time of Jeremiah’s prophecy, God is promising punishment and hardship now to teach His people to be faithful and to trust God’s faithfulness.
Behold, I am bringing a nation against you from afar, O house of Israel,” declares the Lord.
“It is an enduring nation,\ It is an ancient nation,\ A nation whose language you do not know,\ Nor can you understand what they say. (Jeremiah 5:15)
Due to Israel and Judah’s rebellion, both nations are taken away by a foreign nation into exile. Jeremiah, in particular, prophecies the 70 year exile of Judah in Babylon and their return to the promised land. God promised Abraham and Jacob (Israel) the land of Israel (previously Canaan) and He always keeps His promise, so He always brings them home in ways that are hard to comprehend.
Relatively near the end of the 70 year exile in Babylon, God had Persia conquer Babylon and then a Persian king, not only allowed the Israelites to return to Jerusalem to rebuild the city, the walls, and the temple, but also he funded the return to Israel and returned the gold, silver, and bonze temple implements. What conquering nation does something like that? It was clearly all God.
God may delay His promises, but He never cancels them.
For this the earth shall mourn\ And the heavens above be dark,\ Because I have spoken, I have purposed,\ And I will not change My mind, \ nor will I turn from it.” (Jeremiah 4:28)
When God makes a promise, it is as good as done.
Trust Jesus.
-
-
 @ 36bedab2:524acad4
2024-11-10 21:37:52
@ 36bedab2:524acad4
2024-11-10 21:37:521. Power ON
- Quando você liga o computador, ele inicia o processo de boot.
- Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes).
2. BIOS (Basic Input/Output System)
- O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado.
- Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU.
- O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o MBR ou a partição EFI para dar continuidade ao processo de boot.
3. Master Boot Record (MBR) ou EFI Partition
- O MBR (Master Boot Record) ou a partição EFI (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional.
- Em sistemas antigos, o MBR continha o boot loader e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função.
- O MBR ou a partição EFI passa o controle para o boot loader, que é responsável por carregar o sistema operacional.
4. Boot Loader (e.g., GRUB)
- O Boot Loader (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot.
- Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o kernel do sistema.
- GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux.
5. Kernel
- O kernel é o núcleo do sistema operacional Linux.
- Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware.
- O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software.
6. Initial RAM disk - initramfs
- O initramfs é um sistema de arquivos temporário carregado na memória logo após o kernel.
- Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco.
- O initramfs é desmontado após o sistema principal estar carregado.
7. /sbin/init (parent process)
- Após o kernel inicializar o sistema, ele chama o processo /sbin/init, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos.
- O init é responsável por iniciar e gerenciar todos os outros processos do sistema.
- Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o systemd, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos.
8. Command Shell using getty
- Getty é o processo que configura e gerencia terminais para o login do usuário.
- Ele exibe a tela de login em sistemas baseados em linha de comando.
- Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico.
9. Graphical User Interface (X Window ou Wayland)
- Finalmente, o sistema carrega a interface gráfica usando o X Window System (X11) ou o Wayland (um sistema gráfico mais moderno).
- Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc.
- X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela.
Como esses processos se intercalam?
- Hardware ligado → BIOS/UEFI realiza verificações básicas.
- BIOS/UEFI encontra o dispositivo de boot e carrega o MBR ou partição EFI.
- MBR/EFI localiza e executa o boot loader (GRUB).
- GRUB permite que o usuário escolha o sistema operacional e carrega o kernel do Linux.
- Kernel inicializa o sistema, configurando os recursos de hardware e carregando o initramfs.
- Initramfs fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal.
- Kernel chama o processo /sbin/init (ou systemd), que inicia todos os serviços e processos do sistema.
- Init executa o getty para configurar o terminal de login.
- Getty chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
-
 @ fd208ee8:0fd927c1
2024-11-09 09:21:19
@ fd208ee8:0fd927c1
2024-11-09 09:21:19Drumroll, please....
In a previous article, I introduced the concept of relay communities.
The ink had barely dried, on that set of instructions, before one of my favorite Nostr devs, ثعبان, rolled out the alpha version of a relay-community client.
Obviously, it's still a bit of a construction site, but you can check out how it'd work, for your community, by test-driving the functionality on your own relay. Simply type https://chachi.chat/ followed by the name of your relay. For instance, one gigantic relay community, where nearly everyone can try out the functionality, is nos.lol.
If your relay community does not require AUTH to read, anyone can pull your chatter into their own relay and respond to it there. That is because every chat entry is simply a kind 09 event, and unprotected events are not private data.
For instance, I moderate one community theforest.nostr1.com, that is openly readable, and that's probably where most of the chatter on nostr.band is coming from, as that relay is an aggregator of the content of many other relays. However, I have another community, gitcitadel.nostr1.com that is AUTH-protected, whose content stays private to those allowed on that relay. Communities are where write-protected and AUTH relays are going to really shine, as they create an environment similar to Telegram, but where you control the dataset, you decide which types of events to support, and you design the client, the algos, the moderation, the visibility, etc.
With communities, the onboarding experience is seamless: just get a browser extension and a nsec, login, start writing and posting, and start receiving responses. Active, chatty, well-moderated communities will be more attractive to onboard to, than chaotic, spammy, or empty communities. This means that you don't have to have the killer entry under "Posts" (where kind 11 and eventually kind 01 posts appear), just to get some interaction. Chat is the Great Equalizer.
So, we're testing both setups, with cloudfodder adjusting the relay faucet code and ثعبان is fiddling with the community client settings, to make the most-comfortable situation for both kinds.

This is the signal
This #Chachi client, of course, is merely the first horse out of the gate. There are already other devs hacking away at variants of the same concept, such as #Flotilla, I'm sure CloudFodder is also cooking, later versions of #Alexandria will integrate theforest community, and etc. etc. etc.
It remains to be seen, how many new use cases can be dreamt up, with this new architecture, but I am quite certain, that this is the beginning of the end of Nostr 1.0. We are moving up and out, and away from the stultifying and limiting concept of Twitter 2.0, toward

Soon, we will enter Nostr 2.0. See you on the other side.
-
 @ 8d34bd24:414be32b
2024-11-06 22:18:02
@ 8d34bd24:414be32b
2024-11-06 22:18:02One popular plot formula for movies is having two very different people trade places through some mysterious means. It may be kids trading places with adults. It may be the rich person trading places with the poor person. It may be the city person trading places with the country person. The more different the two people, the more comical the effects of trading places is.
All Christians are in a storyline of two very different people trading places. It isn’t the story of rich/poor, young/old, or city/country, it is the trading places of the woefully inadequate and sinful trading places with the perfect and sinless. This isn’t a comedy. In so many ways it seems like a tragedy. The one who deserves punishment and death gets forgiveness and eternal life. The one who deserves worship and praise gets punishment and a torturous death.
Unfortunately most of us are not thankful enough for the wonderful benefits we get from this trade and don’t feel the horror we should at what was done to our perfect God, Creator, and Savior.
Therefore if anyone is in Christ, he is a new creature; the old things passed away; behold, new things have come. Now all these things are from God, who reconciled us to Himself through Christ and gave us the ministry of reconciliation, namely, that God was in Christ reconciling the world to Himself, not counting their trespasses against them, and He has committed to us the word of reconciliation.
Therefore, we are ambassadors for Christ, as though God were making an appeal through us; we beg you on behalf of Christ, be reconciled to God. He made Him who knew no sin to be sin on our behalf, so that we might become the righteousness of God in Him. (2 Corinthians 5:17-21) {emphasis mine}
What a wonderful, glorious turn of events in our personal story that we become “a new creature” in Christ; we “become the righteousness of God in Him.” What a tragedy and unfathomable sacrifice that our Creator God, “who knew no sin,” became “sin on our behalf.” We are part of the most unfair trade, and we benefit so incredibly much and yet we take it for granted most of the time.
For Christ also died for sins once for all, the just for the unjust, so that He might bring us to God, having been put to death in the flesh, but made alive in the spirit; (1 Peter 3:18) {emphasis mine}
We, the unjust, were made just so we can be forgiven and face God almighty. Our Creator, Jesus Christ, the just was made sin for us and died to pay the penalty we deserved for our rejection of God, selfishness, dishonesty, and general ignoring of our Creator.
I don’t think we comprehend how much we don’t deserve the Salvation we received and how much Jesus didn’t deserve the treatment He got throughout history, but especially in His death and separation from God on the cross. We feel severe pain when we are separated from our close friends and/or family. Jesus, part of the 3-in-1 God, was separated from God the Father and God the Spirit. It was like us having a limb cut off. They are one God, so severing one from the rest was the greatest torment that He could ever go through. It was worse than infinite, eternal Jesus limiting Himself to a mortal, finite body to live on earth as a man. It was worse than being tortured and killed in the most painful way ever designed by man. Perfect, holy Jesus was made sin, so He could no longer be in the presence of the Father. We need to thank Him every single day for what He did for us. (I know I don’t thank Him enough.)
Surely our griefs He Himself bore,\ And our sorrows He carried;\ Yet we ourselves esteemed Him stricken,\ Smitten of God, and afflicted.\ But He was pierced through for our transgressions,\ *He was crushed for our iniquities*;\ The chastening for our well-being fell upon Him,\ And by His scourging we are healed.\ All of us like sheep have gone astray,\ Each of us has turned to his own way;\ But the Lord has caused the iniquity of us all\ To fall on Him**. (Isaiah 53:4-6) {emphasis mine}
Look at all the replacement language in this passage:
-
“our griefs He Himself bore”
-
“our sorrows He carried”
-
“He was pierced through for our transgressions”
-
“He was crushed for our iniquities”
-
“The chastening for our well-being fell upon Him”
-
“by His scourging we are healed”
-
“the Lord has caused the iniquity of us all to fall on Him”
Because of what Jesus did for us, He took the grief, sorrows, piercing, crushing, chastening, and scourging that we deserved. He took on the burden and guilt of our iniquity.
For you have been called for this purpose, since Christ also suffered for you, leaving you an example for you to follow in His steps, who committed no sin, nor was any deceit found in His mouth; and while being reviled, He did not revile in return; while suffering, He uttered no threats, but kept entrusting Himself to Him who judges righteously; and He Himself bore our sins in His body on the cross, so that we might die to sin and live to righteousness; for by His wounds you were healed. For you were continually straying like sheep, but now you have returned to the Shepherd and Guardian of your souls. ( 1 Peter 2:21-25) {emphasis mine}
How amazing is it that our loving Creator came down to earth and lived a perfect life as “an example for you to follow?” How unfathomable is it that He took our sins into Himself changing Him from the Holy Lamb to a sinner judged and separated from God? How incredible is it that we get His righteousness because He willingly took on our sins? How can we ever show enough gratefulness for what He has done for us?
This next passage is a passage of the greatest joy imaginable and what all believers have to look forward to:
Now I say this, brethren, that flesh and blood cannot inherit the kingdom of God; nor does the perishable inherit the imperishable. Behold, I tell you a mystery; we will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised imperishable, and we will be changed. For this perishable must put on the imperishable, and this mortal must put on immortality. But when this perishable will have put on the imperishable, and this mortal will have put on immortality, then will come about the saying that is written, “Death is swallowed up in victory. (1 Corinthians 15:50-54) {emphasis mine}
The day is coming that we will not just be justified by Jesus’s sacrifice, but we will be changed from perishable to imperishable and from mortal to immortal. “In the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised.”
As the passage continues, “but thanks be to God, who gives us the victory through our Lord Jesus Christ.” (1 Corinthians 15:57)
Trust Jesus.\ \ your sister in Christ,
Christy
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 2fb77d26:c47a6ee1
2024-11-29 22:07:30
@ 2fb77d26:c47a6ee1
2024-11-29 22:07:30»Worte interessieren nur da, wo sie zu Taten führen«, notierte ich vor knapp 15 Jahren für einen meiner Texte. Gelten sollte diese Prämisse vor allem für Wahlversprechen. Doch die Geschichte zeigt, dass von den vollmundigen Zusicherungen eines Wahlkampfes nach Amtsantritt kaum etwas umgesetzt wird. Davon muss wohl auch in Bezug auf die US-Präsidentschaftswahl 2024 ausgegangen werden. Auch wenn viele immer noch auf eine »Trockenlegung des Sumpfes« hoffen. Ein Überblick.
Original mit Quellen (VÖ: 14.11.2024): https://www.regenauer.press/trump-reloaded
Unterhaltsam ist es bisweilen. Keine Frage. Ist ja auch Politainment. Fake. Eine Show. Eine ziemlich kostenintensive dazu. Und einer gewissen Schadenfreude kann man sich in der Tat kaum verwehren, betrachtet man die irrationalen Reaktionen, Nervenzusammenbrüche und infantilen Ausraster der Wahlverlierer – dem Lager, das in puncto Covid, Klimaschutz und Genderpolitik nie einen Hehl aus seinen totalitären Anwandlungen machte. Leider wird aus Spaß aber schnell bitterer ernst. So tötete ein psychisch labiler Mann aus Minnesota am Tag nach Donald Trumps Wahlsieg zuerst seine ehemalige Partnerin und deren Kind, dann seine Frau und den eigenen Sohn, und anschließend sich selbst. Während die Polizei bislang kein offizielles Tatmotiv kommuniziert, implizieren Social-Media-Beiträge des 46-jährigen Demokraten, dass seine Angst vor den Republikanern, beziehungsweise dem Einzug Trumps ins Weiße Haus, durchaus Auslöser des Amoklaufes sein könnten.
Während die weithin von »Wokeness« beseelten Demokraten ihre Wunden lecken, zelebrieren das konservative Lager der Republikaner und die MAGA-Apologeten einen vermeintlich historischen Sieg. Trump selbst verspricht bei seiner Siegesrede ein »goldenes Zeitalter«. Dass er jetzt »alles in Ordnung bringen« werde. Die Krypto-Branche wähnt sich im Aufwind. Der Bitcoin-Kurs steigt. Dow Jones, S&P 500 und Nasdaq erreichen neue Allzeithochs. In Iowa soll 2026 eine Art Weltausstellung stattfinden, um das 250-jährige Jubiläum Amerikas zu feiern. Bis zum Beginn der Feierlichkeiten sollen Elon Musk und Vivek Ramaswamy die Ausgaben des Staatsapparats um zwei Billionen US-Dollar reduziert haben. Natürlich ist Trump auch die letzte Chance der USA, um endlich die Grenze zu Mexiko zu sichern. Und von Robert F. Kennedy Jr. erwartet man, die Vereinigten Staaten im Rahmen eines MAHA-Programmes – »Make America Healthy Again« – wieder gesund zu machen.
Im Überschwang der Euphorie – oder Frust der Niederlage – fällt gerne unter den Tisch, dass Wähler in Amerika den Präsidenten gemäß Verfassung gar nicht direkt wählen dürfen, weil das für die Wahl des Präsidenten zuständige Electoral College im Prinzip völlig unabhängig vom eigentlichen Wahlausgang entscheiden kann. Die Wahlmänner könnten auch jeden anderen zum Staatsoberhaupt ernennen. Ob das Volk ihn will, oder er überhaupt angetreten ist, spielt rein formal gar keine Rolle. Bei genauerer Betrachtung also nicht unbedingt Demokratie in Reinform. Egal. Schnöde Details. »Trust the plan. Wir haben gewonnen. Geschichte wurde geschrieben« – und so weiter.
Die NATO gibt unterdes zu Protokoll, dass sich an ihrer geostrategischen Agenda »nichts ändern wird, egal, wer die Wahl gewinnt«, weil das »im Interesse der Vereinigten Staaten liege«. Vielleicht hat das US-Militär ja deshalb nur wenige Stunden nach Schließung der Wahllokale eine Minuteman III Interkontinentalrakete zu Testzwecken abgefeuert. Eine Langstreckenwaffe, die drei einzeln steuerbare Atomsprengköpfe transportieren kann.
Auch das Ron Paul Institute rechnet nicht mit grundlegenden Veränderungen und führt diverse Bereiche an, die unabhängig von der Besetzung des Oval Office ein Problem bleiben werden: Kontinuierliche Unterminierung der Verfassung, Krieg gegen die eigene Bevölkerung, Tiefenstaat, Washingtons ausufernde, verstetigte Notstandsermächtigungen, Militärinterventionen in aller Welt, maßlose Korruption und staatliche Tyrannei. Klingt nicht wirklich nach einem goldenen Zeitalter.
Die Reaktionen rund um die US-Wahl – ob positiv oder negativ, ob vor Ort oder im Rest der Welt – veranschaulichen jedenfalls, dass Wahlen Emotionsamplituden auslösen, die in keiner Relation zu dem stehen, was ein Präsident, Kanzler oder Premierminister tatsächlich bewirken kann. Sonst hätte Trump den tiefenstaatlichen »Sumpf« ja schon in seiner ersten Amtsperiode trockenlegen können.
Während die Demokraten also darauf warten, dass die USA ab dem 20. Januar 2025 zur Diktatur verkommen und auf Demonstrationen gegen das Resultat der US-Variante von Demokratie protestieren, fiebern die anderen dem Anbruch eines goldenen Zeitalters entgegen.
Genug Zeit also, den 47. Heilsbringer im Oval Office noch einmal genauer unter die Lupe zu nehmen. Denn auch wenn Donald Trump sich fraglos darauf versteht, zu unterhalten und große Reden von Freiheit und staatlicher Souveränität, von Weltfrieden und Prosperität zu schwingen, sprechen seine Taten zumeist eine ganz andere Sprache.
Fangen wir vorne an: Dank der Zurückstellung vom Wehrdienst konnte Donald Trump bereits 1968 bei Trump Management einsteigen, dem Unternehmen seines Vaters Fred C. Trump, der vor allem mit staatlichen geförderten Wohnungsbauprojekten – »Federal Housing Projects«, heute die Ghettos von New York – zum Multimillionär geworden war. 1971 übernahm Donald im Alter von 25 Jahren die Geschäftsleitung der Firma. Bei Interviews prahlt er bis heute gerne damit, dass sein Vater ihm in jungen Jahren »lediglich einen kleinen Kredit« über eine Million Dollar als Startkapital gewährte. Daraus habe er dann als gewiefter Unternehmer ein Immobilienimperium erschaffen. Dieser Darstellung widerspricht ein Artikel der New York Times (NYT) vom 2. Oktober 2018, der basierend auf Steuer- und Buchhaltungsunterlagen kalkuliert, dass Donald Trump gut 60 Millionen US-Dollar an Krediten erhielt.
»Im Alter von drei Jahren verdiente Trump am Imperium seines Vaters 200.000 Dollar jährlich. Mit acht Jahren war er Millionär. Mit 17 Jahren überließ ihm sein Vater einen Teilbesitz an einem Mehrfamilienhaus mit 52 Wohneinheiten. Kurz nachdem Trump das College abgeschlossen hatte, erhielt er von seinem Vater jährlich umgerechnet eine Million Dollar. Über die Jahre stiegen die jährlichen Schenkungen. In seinen Vierzigern und Fünfzigern lagen sie bei über fünf Millionen Dollar jährlich.«
Als Fred Trump im Juni 1999 verstarb, hatte der trickreiche Unternehmer und Steuerallergiker seinem Sprössling nach Berechnungen der NYT insgesamt 413 Millionen Dollar überschrieben. Selbst wenn New York Times, Associated Press und Co. im Jahr 2018 mit diesen Artikeln fraglos Stimmung gegen Trump machen wollten, kann dessen selbstbeweihräuchernde Darstellung augenscheinlich nicht ganz der Wahrheit entsprechen.
Aber: Er hatte Erfolg. Und das war in der Immobilienbranche des New Yorks der 70er und 80er nicht selbstverständlich. Denn sie wurde von der Mafia dominiert. Von den »Fünf Familien«. Wer nicht den Schutz von »Fat Tony« Salerno, Carmine Galante, Paul Castellano et al. genoss, den Bossen der Genovese-, Bonanno- und Gambino-Familien, hatte schlechte Karten. Das wusste auch Donald Trump. Also macht er Gebrauch von den exzellenten Kontakten seines Freundes, Mentors und Anwalts Roy Cohn, der nicht nur enge Verbindungen zum langjährigen FBI-Chef J. Edgar Hoover pflegte, sondern unter anderem auch Nancy Reagan, die Besitzer des Studio 54, Andy Warhol, die katholische Erzdiözese und die Führungsetage der fünf Mafia-Familien als Anwalt vertrat. Nicht umsonst ist Cohn ein zentraler Charakter in Whitney Webbs Zweiteiler »One Nation under Blackmail«. Den Kontakt zu Cohn, einer Schlüsselfigur für die Zusammenarbeit von Oberschicht und Unterwelt, suchte Donald Trump bereits 1973, als die US-Regierung ein Unternehmen seines Vaters verklagte. Er sollte bestehen bleiben, bis Cohn im August 1986 seiner AIDS-Erkrankung erlag.
Cohns Verbindungen zu Politik, Mafia und Jimmy Hoffas teilkrimineller Teamster-Gewerkschaft sorgten dafür, dass Trump in der Stadt Fuß fassen und sein Geschäft ausbauen konnte. Im Gegenzug war er gezwungen, überteuerte Baumaterialien von Fat Tonys Tarnfirmen zu beziehen. Nach Angaben eines ehemaligen Mitarbeiters von Cohn trafen sich Trump und Salerno in dessen Stadthaus in Manhattan. Trump will sich an ein solches Meeting allerdings nicht erinnern können – obwohl Salerno 1988 unter anderem wegen Erpressung in Höhe von acht Millionen Dollar im Rahmen eines Trump-Bauprojektes rechtskräftig verurteilt wurde. Die Wahrheit kennt wohl nur Trump selbst. Denn Cohn und Fat Tony sind tot.
Sicher ist: Die Geschäftsbeziehungen zwischen Donald Trump und Firmen des organisierten Verbrechens waren intensiver als seinerzeit üblich. Auf Tonbändern des FBI und der US-Staatsanwaltschaft, damals geleitet vom späteren Trump-Anwalt Rudy Giuliani, die beim Abhören von Mafia-Fahrzeugen und -Etablissements entstanden, ist mehrfach von Trump-Projekten die Rede. Donald passte sich dem Geschäftsgebaren seines Umfelds an. Den opportunistischen, skrupellosen, steuervermeidenden Praktiken seines Vaters – und dem von organisierter Kriminalität durchzogenen Filz des Ostküsten-Establishments.
Donald Trumps Frühphase, seine Geschäfte und Geschäftspartner sind also nicht unbedingt ein Paradebeispiel in Sachen Arbeitsethos. Im Vergleich zu seinen späteren Kontakten wirken seine Buddys der 70er und 80er aber fast noch sympathisch – denn Steuern sind Raub und die Mafia pflegt, im Gegensatz zu Regierungen, Militär und Geheimdiensten, zumindest einen Ehrenkodex.
Die 90er begannen für Trump mit finanziellen Turbulenzen. Diverse Bau- und Casino-Projekte liefen nicht wie geplant. Investments warfen nicht den erwarteten Gewinn ab und die Schulden häuften sich bis zur Zahlungsunfähigkeit. In der Öffentlichkeit gab er jedoch weiterhin den erfolgreichen Entrepreneur. 1995 gründe Trump, immer noch bis über beide Ohren verschuldet, eine Aktiengesellschaft und ging an die Börse. Durch diesen Schritt landete er nach 1989 erstmals wieder auf der Forbes-Liste der reichsten Amerikaner. Da die neue AG aber aufgrund der Altlasten mit 1,7 Milliarden Dollar verschuldet war, fiel ihr Börsenkurs zwischen 1996 und 2005 von 35 Dollar auf 17 Cent. Dann wurde der Handel ausgesetzt. Trump bezog aber noch bis 2009 Vergütungen aus der Gesellschaft in Höhe von 44 Millionen Dollar.
Parallel zu diesen fragwürdigen Umtrieben zu Lasten von Anlegern und Geschäftspartnern mauserte sich Donald Trump zum Society-Phänomen. Ob The Apprentice, WrestleMania, The Fresh Prince of Bel-Air, Talkshows oder soziale Anlässe aller Art – Trump war überall, wo sich Öffentlichkeit für Trump generieren ließ. Mit Erfolg. Überschuldung, Zahlungsunfähigkeit, Mafia-Kontakte, Betrugsvorwürfe und juristische Probleme verblassten im omnipräsenten Scheinwerferlicht.
Weniger glamourös dagegen ist Donald Trumps Beziehung zu einem der verachtenswertesten Menschen der jüngeren Vergangenheit – Jeffrey Epstein. Denn während Trump lange Jahre leugnete, überhaupt mit Epstein in Kontakt gestanden zu haben, belegen unlängst veröffentlichte Audio-Mitschnitte, dass er sehr wohl eine Beziehung mit dem verurteilten Sexualstraftäter, Pädophilen, Menschenhändler und Doppelagenten pflegte. Eine sehr enge.
Jeffrey Epstein bezeichnet sich im Zuge der Aufnahmen als »Trumps engsten Freund«. Für über zehn Jahre. Man besuchte die gleichen Partys, kannte die gleichen Leute. Kaum verwunderlich. Epstein war bestens mit dem »Who is Who« des Establishments vernetzt – auch mit dem zwielichtigen Roy Cohn. Es liegt nahe, dass über diesen der Erstkontakt zustande kam. Epstein erpresste elitäre Zirkel in aller Welt mit heimlich aufgenommenen Videos arrangierter Sex-Eskapaden. Die Opfer: Meist Minderjährige. Manche erst acht Jahre alt. Wer Macht und Einfluss ausüben und sichern wollte, nahm seine Dienste in Anspruch. Das wusste wohl jeder seiner engeren Kontakte. Trotzdem sprach Donald Trump von einem »tollen Typen, den er seit 15 Jahren kenne«, als er in einem Interview mit dem New York Magazine 2002 nach seiner Meinung zu Epstein und der gemeinsamen Vorliebe für junge Frauen gefragt wurde. Darüber hinaus flog Donald Trump mindestens sieben Mal mit Jeffrey Epsteins Privatjet, besser bekannt als »Lolita Express«.
Elon Musk, über dessen hinter Imagedesign verborgene Nähe zu Militär, Geheimdiensten, Big Pharma und Transhumanisten ich bereits im Oktober 2022 ausführlich berichtet habe, hatte ebenfalls Verbindungen zu Jeffrey Epstein, wie ein ausführliches Dossier von Johnny Vedmore belegt. Ganz zu schweigen von Musks Forderungen nach CO2-Steuern gegen den Klimawandel oder seinen offenen Plädoyers für Technokratie, einem faschistischen Herrschaftsmodell, das schon sein Großvater Joshua N. Haldemann in leitender Position vertrat. Man kann sich also ausmalen, was unter einem Effizienzprogramm unter Musks Ägide zu erwarten ist – Tech-Faschismus, getarnt als libertäre Progressivität.
Auch RFK Jr. flog zwei Mal mit dem »Lolita Express«, gibt aber an, in Begleitung von Frau und Kindern gereist zu sein – während er gleichzeitig erklärt, die beiden Flüge seien nur zustande gekommen, weil seine »Frau irgendeine Art von Beziehung mit Ghislaine Maxwell hatte«. Was für eine Beziehung das war, beschreibt RFK Jr. nicht. Dabei wären die Hintergründe dieser Beziehung durchaus relevant für die Bewertung seiner Verbindung zum Epstein-Netzwerk. Denn Maxwell, deren Elternhaus für CIA und Mossad tätig war, war seit 1991 Epsteins engste Mitarbeiterin. Sie führte ihm minderjährige Mädchen zu. Phantombilder legen nahe, dass sie auch am Verschwinden, beziehungsweise Tod, von Madeleine McCann beteiligt sein könnte. Nach dem als Suizid vermarkteten Mord an Epstein im August 2019 tauchte Maxwell ab. Aufenthaltsort unbekannt. Erst am 2. Juli 2020 konnte das FBI sie festnehmen. Im Dezember 2021 wurde Maxwell wegen Unterstützung von Epsteins Pädo-Business zu 20 Jahren Haft verurteilt.
Man darf gespannt sein, ob Epsteins unter Verschluss gehaltene Kundenliste jemals ans Licht kommt. Wenn Trump nichts zu verbergen hat, seine dahingehenden Ankündigungen wahr machen und den Sumpf trockenlegen will, könnte er damit ordentlich vorlegen. Entsprechende Forderungen stehen ja bereits im Raum.
Bei einer Pressekonferenz im Weißen Haus am 21. Juli 2020 verkündete er allerdings noch, Maxwell mehrfach getroffen zu haben und wünschte ihr »wirklich alles Gute«.
Wahrscheinlich ist eine Offenlegung der Kundenliste aber nicht. Denn auch Trumps neuer Generalstaatsanwalt, Matt Gaetz, gegen den 2020 wegen sexueller Kontakte zu einem minderjährigen Mädchen ermittelt wurde, sprach sich in der Vergangenheit explizit gegen eine neuerliche Überprüfung des Falls Epstein aus. Er behauptete außerdem, Epstein sei von ausländischen Geheimdiensten, nicht vom US-Tiefenstaat ermordet worden. Sein Wahlkampf-Team nutzte denn auch die gleiche Anwaltskanzlei wie Jeffrey Epstein. Und ein enger Vertrauter von Gaetz warb intensiv dafür, Ghislaine Maxwell aus der Haft zu entlassen. Seit 2021 ist Gaetz mit der Schwester des Peter Thiel-Protegés Palmer Lucky verheiratet, der mit seiner Firma Anduril für das High-Tech-Überwachungssystem an der mexikanischen Grenze verantwortlich zeichnet, KI-Waffenprogramme entwickelt und für das US-Verteidigungsministerium an Project Maven arbeitet. Sumpf, soweit das Auge reicht. Trockenzulegen gäbe es da also einiges.
Warten wir’s ab – und werfen unterdes einen Blick auf Donald Trumps erste Amtszeit. Denn auch diesbezüglich sagen Taten mehr als Worte.
Während Trump sich derzeit als Gegner der Weltgesundheitsorganisation (WHO) geriert, war er als 45. US-Präsident mit »Operation Warp Speed« (OWS) für eine militarisierte Impf-Kampagne der Superlative verantwortlich, die 300 Millionen Dosen einer experimentellen mRNA-Gentherapie unters Volk bringen und den Herstellern mindestens 18 Milliarden Dollar in die Kasse spülen sollte. Anthony Fauci, den Trump heute gerne öffentlich diffamiert, kümmerte sich für ihn um den Rollout der Injektionen und die damit verbundene Nudging-Propaganda. Für seine Verdienste im Rahmen von OWS erhielt Fauci von Trump am letzten Tag seiner Präsidentschaft eine Auszeichnung, wie eine Pressemitteilung im Archiv des Weißen Hauses belegt. Während Trump sich in den letzten Wochen medienwirksam von Fauci distanzierte und abstritt, diese Auszeichnung abgesegnet zu haben, verweisen Mitarbeiter des Weißen Hauses darauf, dass eine solche Auszeichnung gemäß Protokoll nur dann verliehen wird, wenn der Präsident sie persönlich autorisiert. Fragt sich, wer lügt.
Daneben genehmigte Trump im Februar 2020 eine Zahlung von 1,16 Milliarden US-Dollar an GAVI, die Impfallianz von WHO, Weltbank, UNICEF und der Bill & Melinda Gates Stiftung. Der Betrag sollte GAVI binnen drei Jahren über die CIA-Tarnfirma USAID ausbezahlt werden. Ungeachtet aller Gegenanzeigen, Nebenwirkungen und Kollateralschäden durch Lockdowns und partielle Impfpflichten pries Donald Trump OWS stets als durchschlagenden Erfolg. Erst nach der Ankündigung, mit Kennedy kollaborieren zu wollen, hielt er sich mit dem Eigenlob zurück. Dass er sich in den Wochen vor dem Wahlsieg neu positionierte, dürfte also reine Wahlkampfstrategie gewesen sein.
Wenn Trump nun in Aussicht stellt, Impfungen verbieten und Amerika gemeinsam mit RFK Jr. gesund machen zu wollen, ist das in Anbetracht der immensen Marktmacht von Big Pharma kaum als realistisch zu bewerten. Siehe Briefing des Roosevelt Institute vom 22. Mai 2019. Titel: »Kapern der Regierung – Wie Big Pharma die Gesetzgebung übernahm«. In Trumps Team wurden in den letzten Wochen bereits Stimmen laut, die forderten, sich von RFK Jr. zu distanzieren. Während Kennedy in einem Interview vom 28. Oktober verkündete, Trump habe ihm den »Chefposten der Gesundheitsbehörde HHS versprochen«, stellte Howard Lutnik, Vize-Vorsitzender von Trumps Transition-Team, am 30. Oktober bei CNN fest, dass dies »natürlich nicht der Fall sein werde« und man Kennedy lediglich Zugriff auf Daten gewähren wolle. Am 14. November gab Donald Trump dann allerdings bekannt, RFK Jr. tatsächlich zum Chef der HHS machen zu wollen. Die Nominierung muss aber noch vom Senat bestätigt werden. Und bis Januar kann noch einiges passieren. Die Vergangenheit lässt jedenfalls darauf schließen, dass weder Big Pharma noch WHO oder GAVI künftig unter der neuen Regierung leiden werden.
Dann wären da noch die galoppierenden Staatsschulden der Vereinigten Staaten. Denn unter Trumps Ägide schöpfte die US-Zentralbank allein im Jahr 2020 über drei Billionen Dollar. »Die Vereinigten Staaten haben im Juni mehr Geld gedruckt als in den ersten zwei Jahrhunderten nach ihrer Gründung. Letzten Monat war das Haushaltsdefizit der USA – 864 Milliarden Dollar – größer als die Gesamtverschuldung von 1776 bis Ende 1979«, so Dan Morehead, CEO von Pantera Capital am 29. Juli 2020. Seit 2020 hat die Staatsverschuldung um knapp zwölf Billionen Dollar zugenommen und belief sich im September 2024 auf 35,46 Billionen Dollar. Das sollten speziell Trump-Anhänger vor Ort nicht vergessen, wenn sie nun für den Wocheneinkauf deutlich tiefer in die Tasche greifen müssen. Inflation sei Dank.
»Dafür hat Trump keine neuen Kriege angefangen!« – hört man immer wieder, wenn man auf dessen Verfehlungen hinweist. Stimmt. Weil er fünf Krisenherde von der vorherigen Regierung geerbt hat und sich dort austoben konnte. Trump hat nämlich deutlich mehr Drohnen-Einsätze befohlen als sein Vorgänger. Obama autorisierte in den ersten zwei Jahren seiner Amtszeit 186 Einsätze – bei Trump waren es 238. Allein im Jemen hat die Trump-Regierung 176 Angriffe binnen zwei Jahren durchgeführt. Bei Obama waren es 154 in acht Jahren. Und während die Regierung unter Obama zumindest teilweise Daten zu den Opferzahlen dieser Einsätze veröffentlichte, änderte Trump die entsprechenden Transparenzanforderungen und veröffentlichte gar keine Daten. Laut einem Artikel von Foreign Policy vom 9. August 2017 ist Trump »der kriegslüsternste Präsident der jüngeren Geschichte«. Weiter führte das 1970 von Samuel P. Huntington gegründete Magazin aus:
»Unter Trump haben die Vereinigten Staaten bis zum 31. Juli etwa 20.650 Bomben abgeworfen, das sind 80 Prozent der Menge, die unter Obama im gesamten Jahr 2016 abgeworfen wurden. (…) Daten zeigen, dass die Vereinigten Staaten im Irak und in Syrien Bomben in beispiellosem Ausmaß abwerfen. Im Juli warf die Koalition zur Bekämpfung des Islamischen Staats (sprich: die Vereinigten Staaten) 4.313 Bomben ab, 77 Prozent mehr als im Juli letzten Jahres. Im Juni lag die Zahl bei 4.848 – 1.600 Bomben mehr als unter Präsident Barack Obama jemals pro Monat abgeworfen wurden. In Afghanistan ist die Zahl der abgeworfenen Bomben seit Trumps Amtsantritt ebenfalls sprunghaft angestiegen. Im April wurden im Land mehr Bomben abgeworfen als auf dem Höhepunkt von Obamas Truppenaufstockung im Jahr 2012. In diesem Monat bombardierten die Vereinigten Staaten das afghanische Mamand-Tal mit der größten nichtnuklearen Bombe, die jemals abgeworfen wurde. Trump hat auch das militärische Engagement der USA in Ländern außerhalb der Kriegsschauplätze ausgeweitet – nämlich im Jemen, in Somalia und in Pakistan. In den letzten 193 Tagen von Obamas Präsidentschaft gab es in diesen drei Ländern 21 tödliche Anti-Terror-Operationen. Trump hat diese Zahl verfünffacht und mindestens 92 solcher Operationen im Jemen, sieben in Somalia und vier in Pakistan durchgeführt.«
Klingt für mich jetzt nicht so ganz nach Friedenstauben.
Wahrscheinlich war es am Ende nur die Hektik bei der Übergabe der Amtsgeschäfte im Januar 2021, oder der Stress permanenter Medienpräsenz, der Trump auch noch davon abhielt, Julian Assange oder Edward Snowden zu begnadigen. Immerhin war er »kurz davor, einen der beiden auszuwählen«, wie er in einem Interview für Daily Wire verlauten ließ. Am Ende blieb dann aber leider doch nur Zeit für die Begnadigung der anderen 116 Personen auf der Liste. Dumm gelaufen.
Wenden wir uns der Gegenwart zu. Und dem, was uns die nächsten vier Jahre erwarten könnte. Es muss ja jetzt auf jeden Fall alles viel besser laufen als in der ersten Runde. Denn in den Augen vieler seiner Unterstützer habe Trump in der Zwischenzeit viel gelernt und wurde damals nur hinters Licht geführt. Überrumpelt vom Tiefenstaat, den er eigentlich abschaffen wollte. Zudem hat er nun Elon Musk und RFK Jr. an seiner Seite, der gemäß Lutnik zwar keinen Job bekommt, aber immerhin steht irgendwo Kennedy auf der Banderole. Das ist doch auch was.
Ernsthaft. Bereits in Rahmen seiner ersten Amtszeit plante Trump, ein biometrisches System zur Ein- und Ausreisekontrolle zu etablieren. Es sollte zunächst nur für Ausländer gelten. Aber jeder weiß, dass es nicht lange dauert, bis so ein System für jeden gilt. Dazu passt, dass seit Beginn des Wahlkampfes 2024 permanent von der Voter ID gesprochen wird. Ausweise für alle – gegen Wahlbetrug. Bisher besitzen nur knapp 40 Prozent der Amerikaner einen Reisepass. Nur acht Prozent verlassen im Urlaub überhaupt das Land. Die virtuelle Wand wird das ändern, nicht nur an der Grenze zu Mexiko. Denn über kurz oder lang resultiert das Projekt in der flächendeckenden Einführung einer eID. Basis für die eID- oder Voter ID-Infrastruktur könnte zum Beispiel E-Verify sein, ein vom Department of Homeland Security betriebenes Projekt zur Verifikation von Personen, dessen Nutzung für Personalabteilungen von Bundesbehörden seit dem 1. Oktober 2007 obligatorisch ist. Die Nominierung von Tom Homan als Chef der Einwanderungs- und Zollbehörde impliziert, dass genau dieser Kurs eingeschlagen wird. Homan ist Hardliner. Er war Teil des rechtskonservativen Project 2025 und befürwortet neben flächendeckender Biometrie auch die Trennung von Eltern und Kindern an der Grenze.
Kein Zufall also, dass der Gründer der Cardano-Blockchain, Charles Hoskinson, die Regierung Trump ab 2025 in Bezug auf Kryptoanwendungen beraten soll. Immerhin hatte Hoskinson bereits mit dem von Jeffrey Epstein finanzierten Ben Goertzel ein biometrisches eID-System für Schulkinder in Äthiopien entwickelt. Und nachdem die von Peter Thiel finanzierte Silikon-Valley-Marionette JD Vance als Vizepräsident fungiert, hat auch der mächtigste Überwachungskonzern der Welt, Palantir, nun einen Fuß in der Tür des Oval Office. Mit diesem Setup dürfte der gläserne Bürger der Gegenwart bald ein Relikt der Vergangenheit sein.
Ganz zur Freude von Ex-Spion John Ratcliffe, dem neuen CIA-Direktor unter »Orange Man«. In Trumps erster Amtszeit war Ratcliffe »Director of National Intelligence«, unter George W. Bush zuständig für Anti-Terror-Operationen und nationale Sicherheit. Später leitete er zusammen mit John Ashcroft, Generalstaatsanwalt unter Bush und Architekt des Ermächtigungsgesetzes »Patriot Act«, ein Unternehmen für strategische Beratung (AGS). Im Dezember 2023 unterstützte John Ratcliffe den Bilderberger, Kriegstreiber und Tiefenstaat-Neocon Mike Pompeo bei der Erneuerung des Foreign Intelligence Surveillance Act (FISA), der die fortgesetzte, anlasslose Massenüberwachung der US-Bevölkerung legalisiert. Und kaum war er nominiert, machte Ratcliffe am 13. November 2024 auf FOX-News wahrheitswidrig Stimmung gegen den Iran und unterstellte der dortigen Regierung »kriegerische Handlungen« gegenüber den USA.
Kollaborieren wird Ratcliffe künftig mit Tulsi Gabbard. Sie beerbt ihn als Trumps neuer »Director of National Intelligence«. Gabbard war Mitglied der WEF Young Global Leaders sowie des Council on Foreign Relations (CFR). Beide Organisationen tilgten ihren Namen von der eigenen Homepage, nachdem Gabbard öffentlich über US-Biowaffenlabore in der Ukraine sprach. In Interviews bestätigt sie ihre Rolle im CFR allerdings selbst. Gabbard befürwortete die Covid-Impfkampagne und schmückt sich gerne mit dem Image »Kriegsveteran« – obwohl sie die Schrecken des Krieges lediglich aus sicherer Entfernung sah. Eine Opportunistin, deren konservativ-kritisches Image nichts weiter ist als ein wackliges Kartenhaus.
»Ich war Kadett. Was ist das Motto der Kadetten in West Point? Du wirst nicht lügen, betrügen, oder stehlen – und diejenigen nicht dulden, die das tun. Ich war der CIA-Direktor. Wir haben gelogen, wir haben betrogen, wir haben gestohlen. Wir haben ganze Trainingskurse dazu absolviert.« (Mike Pompeo, April 2019)
Und wer denkt, Donald Trump werde wenigstens die Einführung einer digitalen Zentralbankwährung (CBDC) verhindern, irrt. Zumindest im Kern. Denn im Rahmen seiner Rede auf der Bitcoin Konferenz 2024 sprach Donald Trump von »regulatorischer Klarheit« sowie der »sicheren und verantwortungsvollen Expansion von Stablecoins«. Damit bestätigte er, dass die Einführung von digitalem Geld über privatwirtschaftliche Entitäten erfolgen wird. Denn ein Konto bei der Zentralbank will niemand. Leider werden aber die Transaktionen all der ach so marktwirtschaftlich eingeführten Digitalwährungen zentral erfasst. Im »Unified Ledger« der Bank für Internationalen Zahlungsausgleich (BIZ) in Basel. Was am Ende zum exakt gleichen Ergebnis führt wie eine vom Staat oder der Zentralbank aufgelegte CBDC – zu lückenloser Überwachung mit Interventionspotenzial.
Zurück zur künftigen Regierung. Stabschef im Weißen Haus und damit »mächtigste Frau in Washington« soll Susie Wiles werden – bisher Co-Vositzende von Mercury Public Affairs LLC, einem Lobby-Giganten, der unter anderem Pfizer, GAVI, die Vereinten Nationen oder SpaceX vertritt. Mercury Public Affairs gehört seit 2003 zur Omnicom Group, einem WEF-Partner für Öffentlichkeitsarbeit. Wiles gilt als die »am meisten gefürchtete und am wenigsten bekannte Politagentin Amerikas«.
Als Außenminister nominierte Trump den von der Zionismus-Lobby korrumpierten Marco Rubio. Einen Neocon. Sprich: Militärischer Interventionismus und unilaterale Hegemonieansprüche. Den Posten des nationalen Sicherheitsberaters offeriert Trump dem ehemaligen Green Beret Mike Waltz. Neben Marco Rubio der zweite Mann in der künftigen Regierung, der sich mit China anlegen möchte. Ergänzt wird das kriegsaffine Duo von Brian Hook, der dem Iran am liebsten sofort den Krieg erklären möchte und den Auftrag erhielt, Schlüsselpositionen im Außenministerium mit geeignetem Personal dafür zu besetzen.
Der ehemalige texanische Kongressabgeordnete Ron Paul sieht in diesen Nominierungen »einen schlechten Tag für jene, die an America First glaubten«. Sollte Trump die Unterstützung der Ukraine seitens Amerika tatsächlich beenden, dürften nämlich ersatzweise zuerst der Iran und langfristig eventuell gar China von Demokratie aus der Luft beglückt werden. Daran wird auch die neue US-Botschafterin bei den Vereinten Nationen nichts ändern. Denn Elise Stefanik hat praktisch keine relevante Berufserfahrung – und ist ebenfalls ein Neocon. Sowohl Stefanik als auch Rubio, Waltz oder Hook setzen sich für weitere Waffenlieferungen nach Israel und eine Fortsetzung des auch von israelischen Zeitungen also solchen bezeichneten Genozids in Gaza ein.
»Die westliche Zivilisation repräsentiert heute das Verständnis, dass Zionismus und Amerikanismus die Frontlinien der westlichen Zivilisation und Freiheit in unserer Welt sind«, erklärte der Army-Veteran, United Against Nuclear Iran-Advokat und Ex-FOX-News-Mitarbeiter Pete Hegseth im April 2019.
An dieser faschistoiden wie imperialistischen Doktrin scheinen sich auch Trump und Co. zu orientieren – denn Hegseth wird nun Verteidigungsminister. Passend dazu wird Mike Huckabee, ein bekennender Zionist, der nächste US-Botschafter in Israel. Huckabee nennt das Westjordanland Judäa und behauptet entgegen historischer Fakten, dass es Teil Israels ist. Auch die Annexion der Westbank fände er in Ordnung. Seine Nominierung kann als Kriegserklärung an die Palästinenser verstanden werden. Wohlwissend, dass Israels völkerrechtswidriges Vorgehen leicht zu einem regionalen, wenn nicht globalen Flächenbrand führen kann.
Apropos globale Themen: Dahingehend lohnt sich ein genauerer Blick auf die Hintergründe des bereits erwähnten Howard Lutnick. Diesen hat die Investigativ-Journalistin Whitney Webb am 7. November 2024 gewagt. Unter der Überschrift »Macht euch bereit für den Kohlenstoffmarkt der Republikaner« erklärt sie:
»Viele der einflussreichsten Namen der kommenden Trump-Regierung sowie der vorherigen haben sich in den letzten Jahren intensiv mit der Schaffung von Kohlenstoffmärkten befasst, während andere eine langjährige Erfolgsgeschichte bei der Implementierung von CO2-Steuern und anderen Formen der CO2-Bepreisung vorweisen können. Der wichtigste unter ihnen ist Howard Lutnick, Co-Vorsitzender von Trumps Transition-Team, der erklärte, seine Aufgabe sei es, Talente für die kommende Regierung zu finden. Lutnick ist der langjährige Leiter von Cantor Fitzgerald, einem der ersten Akteure im Emissionshandel, der sich seitdem zu einem weltweit führenden Unternehmen für ESG-Investitionen, die Finanzierung nachhaltiger Infrastruktur und grüne Anleihen entwickelt hat. So hat sich Cantors nachhaltiger Infrastrukturfonds ausdrücklich der digitalen Transformation, Dekarbonisierung und Verbesserung und Modernisierung alternder Infrastruktur verschrieben, während ein Hauptaugenmerk des Fonds darauf liegen wird, in Emittenten zu investieren, die mit ihren Produkten und Dienstleistungen dazu beitragen, bestimmte Ziele der Vereinten Nationen für nachhaltige Entwicklung zu erreichen. Darüber hinaus ist Invenergy, ein Unternehmen für erneuerbare Energien, das im Rahmen von Bidens umstrittenem Inflationsbekämpfungsgesetz eine beträchtliche Menge an Subventionen erhalten hat und vom ersten Windmilliardär des Landes, Michael Polsky, geleitet wird, der wichtigste Bestandteil eines weiteren Infrastrukturfonds von Cantor. Lutnick sitzt auch im Vorstand eines Satellitenüberwachungsunternehmens namens Satellogic. Neben Lutnick ist der ehemalige Finanzminister von Trump, Steve Mnuchin, Vorsitzender des Vorstands. Auch Joe Dunford, ehemaliger Stabschef des US-Militärs unter Trump, sitzt im Vorstand. Satellogic ist integraler Bestandteil eines Konsortiums, das versucht, durch undurchsichtige vertragliche Vereinbarungen auf kommunaler Ebene einen riesigen, Blockchain-basierten Kohlenstoffmarkt in Lateinamerika durchzusetzen. Dieser Kohlenstoffmarkt, der unter dem Namen GREEN+ operiert, soll auf einer Bitcoin-Sidechain aufgebaut werden. Das entsprechende Emissionsgutschriftsystem ist für lateinamerikanische Gemeinden zutiefst ungerecht. So könnten die betroffenen Gemeinden beispielsweise nur Geld verdienen, wenn Einnahmen unter den für GREEN+ anerkannten, nachhaltigen Projekten generiert werden, während die Investoren von GREEN+ den Großteil der Gewinne einstreichen. Das Programm würde Gemeinden außerdem ohne ihre Zustimmung dem Satellitenüberwachungsapparat von Satellogic (der mit der US-Regierung und dem israelischen Geheimdienst verbunden ist) aussetzen. Darüber hinaus ist GREEN+ in bemerkenswerter Weise mit Personen verbunden, die Trumps Verbündeten in der Region nahestehen. So ist eine wichtige Persönlichkeit in Nayib Bukeles politischer Partei – der Bürgermeister von San Salvador, Mario Durán – Vizepräsident einer der wichtigsten Gruppen, die das GREEN+-Programm orchestrieren, während das Netzwerk Endeavor Argentina, das sehr enge Verbindungen zu Javier Milei pflegt, ebenfalls eng mit Satellogic verbunden ist. Satellogic ist ein von Endeavor unterstütztes Unternehmen, während Endeavors erster Milliardär und Unternehmer, Marcos Galperín von MercadoLibre, im Vorstand von Satellogic sitzt. Darüber hinaus ist ein anderer wichtiger Investor von Satellogic, der Dollar-Stablecoin-Emittent Tether, auch eng mit Howard Lutnick verbunden. Lutnick ist langjähriger Fürsprecher von Tether. Und Cantor Fitzgerald hält den Großteil der US-Staatsanleihen von Tether, um deren Stablecoin und seine Bindung an den US-Dollar zu stützen.«
Das sollte Wähler, die dem Klimawandel-Narrativ und Digitalwährungen skeptisch gegenüberstehen, hellhörig werden lassen – denn auch wenn Donald Trump im Rahmen seiner öffentlichen Auftritte gegen die Nachhaltigkeitsagenda wettert und der leitmediale Komplex seine entsprechenden Phrasen für Konterpropaganda nutzt, sprechen die Taten wieder einmal eine ganz andere Sprache. In Anbetracht vorgängig beschriebener Umstände sieht es nämlich nicht so aus, als widersetze sich der 47. US-Präsident dem Nachhaltigkeitskorporatismus der UN. Im Gegenteil.
»Der König ist tot, es lebe der König«. Die neue US-Regierung wird die gleiche Agenda fahren wie die alte – nur die Vermarktung ändert sich. Das kündigte Lynn Forester de Rothschild (CIC) schon vor über einem Jahr bei Bloomberg an. Genau wie Larry Fink (BlackRock).
Die Einführung biometrischer Massenüberwachung wird nun mit der Migrationskrise und drohendem Wahlbetrug, mit der Stärkung der Demokratie gerechtfertigt, anstatt mit einem Virus. Den Krieg in der Ukraine wird man nicht weiter unterstützen. Diesen Brandherd sollen die Europäer am Kokeln halten, damit man endlich den Iran und China ins Fadenkreuz nehmen kann. So ein dritter Weltkrieg wäre nämlich ein profitables Geschäft. Das Klimawandel-Narrativ wird man öffentlich negieren und verhöhnen, während die Agenda 2030 trotzdem umsetzt wird. Gleiches gilt für Totalüberwachung, Genderwahn, globale Gleichschaltung von Lerninhalten und die schleichende Digitalisierung des Weltfinanzsystems. Denn auch diese Programme werden von überstaatlichen Akteuren vorangetrieben und entziehen sich dem Einfluss nationaler Regierungen. So funktioniert Korporatismus.
Ernüchternd ist vor allem, dass sich die Bevölkerung, die in den letzten vier Jahren tatsächlich ein gewisses Maß an rebellischem Potenzial entwickelte, wieder einmal täuschen lässt. Trump-Hype wohin man schaut. Selbst die Corona-Dissidenten, selbst jene, die dem Staat aufgrund von Covid-Lügen, Green-Economy-Deindustrialisierung und militantem Neoimperialismus zusehends kritisch gegenüberstanden, haben sich in weiten Teilen von den leeren Versprechungen der MAGA-Promotion und ihren Sekundanten blenden lassen.
Sie werden genauso desillusioniert zurückbleiben wie einst die auf »Hope« geeichten Obama-Fans – und sich in ein paar Jahren vermutlich trotzdem wieder an die Wahlurne schleppen, weil sie auf den nächsten Erlöser hoffen, anstatt selbst die Welt zu verändern.
Zur Wahl stehen aber jeweils nur verschiedene Geschmacksrichtungen der gleichen, bitteren Pille Marke Unterdrückung. Keine Unterdrückung – das ist natürlich keine Option. Das steht nicht auf dem Wahlzettel.
Linke gegen Rechte, Demokraten gegen Republikaner, Christentum gegen Islam – Bevölkerungsgruppen, die man gegeneinander aufwiegeln kann, finden sich dagegen immer. Präsentiert man ihnen einen verheißungsvollen Erlöser, werden sie ihn unterstützen, um die andere Gruppe loszuwerden. Das ist Herrschaftsdialektik. Man bringt die Menschen dazu, um Dinge zu betteln, die ohnehin eingeführt werden sollen. Und der einzige Gewinner in diesem immer riskanter werdenden Spiel ist die Prädatorenkaste.
»Die mächtigste Waffe in den Händen der Unterdrücker ist der Geist der Unterdrückten.« (Stephen Bantu Biko)
Wer Donald Trump unterstützt, ist nicht für Frieden und Freiheit, sondern nur gegen das, was die andere Seite will. Denn Donald Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang.
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8f0a121e:24038909
2024-11-28 09:07:00
@ 8f0a121e:24038909
2024-11-28 09:07:00كلنا نعرف أبيات إمرئ القيس في الليل التي تعلمناها في المدارس صغارا.
وليل كموج البحر أرخى سدوله ... عليّ بأنواع الـــهموم ليـــبتلي فقلـــت له لمـا تمـــطى بصـلبـــه ... وأردف أعجازا وناء بكلــــكل ألا أيها الليل الطويل ألا انـجـلي ... بصبح وما الإصباح منك بأمثل
وهي من أروع وأعلى ما قيل في الليل، ولكن تراثنا وشعرنا مليء بروائع في نفس المعنى. يقول النابغة الذبياني:
كليـــني لهمًّ يا أمــيمة ناصـــبِ ... وليل أقاسيه بطيء الكـــواكب تطاول حتى قلت ليس بمنقضٍ ... وليس الذي يرعى النجوم بآيب وصدر أراح الليل عازب هــــمه ... تضاعف فيه الحزن من كل جانب
يطلب النابغة من ابنته أميمة أن تدعه لهمه وتعبه ويشكي بطئ سير كواكب وثقلها في السير كناية على طول الليل.
في البيت الثاني، أقام الصبح مقام الراعي الذي يغدو فيذهب بالماشية والإبل، وبالمثل الصبح يذهب بالنجوم.
ثم يقول أن الليل "أراح عازب همه" بمعنى أنه أرجع اليه همه البعيد.
ويقول الوليد بن يزيد:
لا أسأل الله تغييرا لما فَعَلَت ... نامت وقد أسهرت عينيَّ عيناها فالليل أطول شيءٍ حين أفقدها ... والليل أقصر شيءٍ حين ألقاها
ويقول بشار:
خليلَيَّ ما بال الدجى لا تزحزح ... وما بال ضوء الصبـح لا يتوضح أضل النهار المستنير سبـــــيله ... أم الدـــــهر لـــيل كله لا يبــــرح
شعر #أدب #بالعربي
-
 @ 8d34bd24:414be32b
2024-11-03 15:17:36
@ 8d34bd24:414be32b
2024-11-03 15:17:36I was recently having a friendly discussion about end-times eschatology. I believe the Bible communicates a pre-tribulation rapture of believers before an actual 7 year tribulation followed by a literal thousand year reign of Jesus on Earth before Armageddon and the Great White Throne Judgement. My friend said he thought the rapture had happened around 70 AD. I had never heard anyone make that argument, so I asked for scriptural evidence. He gave me these three verses:
“Truly I say to you, there are some of those who are standing here who will not taste death until they see the Son of Man coming in His kingdom.” (Matthew 16:28)
And Jesus was saying to them, “Truly I say to you, there are some of those who are standing here who will not taste death until they see the kingdom of God after it has come with power.” (Mark 9:1)
But I say to you truthfully, there are some of those standing here who will not taste death until they see the kingdom of God.” (Luke 9:27)
These three verses do sound like some of those standing before Jesus will be raptured, although the words are “see the kingdom of God.”
I always seek to know what I believe and why I believe it and to make sure that I am not misled about anything regarding the Bible, so I stopped and thought and listened. I know that most of the Bible strongly suggests that the rapture happens immediately before the tribulation, but these verses seem to contradict that conclusion. God gave me the following passage of a discussion between Peter and Jesus right after Jesus told Peter how he would die:
Peter, turning around, saw the disciple whom Jesus loved following them; the one who also had leaned back on His bosom at the supper and said, “Lord, who is the one who betrays You?” So Peter seeing him said to Jesus, “Lord, and what about this man?” Jesus said to him, “If I want him to remain until I come, what is that to you? You follow Me!” Therefore this saying went out among the brethren that that disciple would not die; yet Jesus did not say to him that he would not die, but only, “If I want him to remain until I come, what is that to you?” (John 21:20-23) {emphasis mine}
Jesus’s statements made His disciples think that the Apostle John would live until Jesus returned, but that wasn’t what Jesus was communicating. I think this misunderstanding is similar to the one in the three verses above. John did live longer than any of His other disciples. Near the end of John’s life, after all of the other disciples had passed away, Jesus brought him to heaven in the spirit:
I, John, your brother and fellow partaker in the tribulation and kingdom and perseverance which are in Jesus, was on the island called Patmos because of the word of God and the testimony of Jesus. I was in the Spirit on the Lord’s day, and I heard behind me a loud voice like the sound of a trumpet, saying, “Write in a book what you see, and send it to the seven churches: to Ephesus and to Smyrna and to Pergamum and to Thyatira and to Sardis and to Philadelphia and to Laodicea.”
Then I turned to see the voice that was speaking with me. And having turned I saw seven golden lampstands; and in the middle of the lampstands I saw one like a son of man, clothed in a robe reaching to the feet, and girded across His chest with a golden sash. His head and His hair were white like white wool, like snow; and His eyes were like a flame of fire. His feet were like burnished bronze, when it has been made to glow in a furnace, and His voice was like the sound of many waters. In His right hand He held seven stars, and out of His mouth came a sharp two-edged sword; and His face was like the sun shining in its strength. (Revelation 1:9-16) {emphasis mine}
In this vision, before John’s death, he saw “the kingdom of God” in heaven. This alone would fulfill Jesus’s statement, but there is more.
Then slightly later in Revelation:
After these things I looked, and behold, a door standing open in heaven, and the first voice which I had heard, like the sound of a trumpet speaking with me, said, “Come up here, and I will show you what must take place after these things.” Immediately I was in the Spirit; and behold, a throne was standing in heaven, and One sitting on the throne. (Revelation 4:1-2)
In this passage, John is called up to heaven to see “what must take place after these things.” What does John see about what is to come? He “see[s] the Son of Man coming in His kingdom.”(Matthew 16:28b)
John was listening to Jesus’s promise that “there are some of those standing here who will not taste death until they see the kingdom of God.” (Mark 9:1) In his old age, he was temporarily called to heaven to see the “the kingdom of God” and “the Son of Man coming in His kingdom.” John did see the things that Jesus promised before he “tasted death.” It wasn’t that Jesus came back or raptured the church before John died. It was that Jesus brought John into heaven in the spirit to see what would later come to be. Jesus then returned John back to earth to live out what remained of his life.
When I asked my husband to review my post, he made another explanation of the original three verses. I’ll use Matthew for this explanation.
28 “Truly I say to you, there are some of those who are standing here who will not taste death until they see the Son of Man coming in His kingdom.” (Matthew 16:28)
The very next verses are these:
Six days later Jesus took with Him Peter and James and John his brother, and led them up on a high mountain by themselves. And He was transfigured before them; and His face shone like the sun, and His garments became as white as light. And behold, Moses and Elijah appeared to them, talking with Him. Peter said to Jesus, “Lord, it is good for us to be here; if You wish, I will make three tabernacles here, one for You, and one for Moses, and one for Elijah.” While he was still speaking, a bright cloud overshadowed them, and behold, a voice out of the cloud said, “This is My beloved Son, with whom I am well-pleased; listen to Him!” (Matthew 17:1-5)
The transfiguration was the initiation of Jesus reign and Peter, James, and John were able to see Jesus in His glorified form. Since this happened 6 days later, it stands out as a fulfillment. You could argue that both my idea and my husband’s are a fulfillment of Jesus’s promise.
It also does not make sense that the church was raptured in Jesus’s generation because Jesus’s kingdom did not come at that time. The evil in the world from His ascension to today is clearly not His kingdom. Also, nowhere in Revelation is the church mentioned (although people do come to know Jesus). This is because God took His church home to be with Him.
For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ, (1 Thessalonians 5:9)
The seven year tribulation is the wrath of God poured out on those who rejected their Creator and Savior. “God has not destined us for wrath.”
There will be a wonderful, literal thousand year reign of Jesus. Satan and his demons will be bound and will no longer being leading people away from Jesus. It will be a time of peace for 1000 years. Sadly a large number of people who live during the millennium will not put their faith in Jesus, but will rebel against Him when Satan is released one last time. Their rebellion will lead to their physical death and eternal torment.
Reading all of these verses, I once again see that even when there seems to be a contradiction, there is none. I still believe the rapture is yet to come and will occur shortly before the seven year tribulation. I still believe that the rapture and the tribulation are coming soon. I’m also glad that I took the time to look at the evidence, consider it logically, and consider the Bible in its entirety instead of blindly digging in my heels and claiming fiat, “I am right.”
I guess I should also share the two most explicit passages in the Bible on the rapture, so you can fully understand what is being talked about in this article:
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
This verse means even more when we look back at Jesus’s ascension:
And after He had said these things, He was lifted up while they were looking on, and a cloud received Him out of their sight. And as they were gazing intently into the sky while He was going, behold, two men in white clothing stood beside them. They also said, “Men of Galilee, why do you stand looking into the sky? This Jesus, who has been taken up from you into heaven, will come in just the same way as you have watched Him go into heaven.” (Acts 1:9-11) {emphasis mine}
The other most explicit passage on the rapture is this:
Behold, I tell you a mystery; we will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised imperishable, and we will be changed. For this perishable must put on the imperishable, and this mortal must put on immortality. But when this perishable will have put on the imperishable, and this mortal will have put on immortality, then will come about the saying that is written, “Death is swallowed up in victory. (1 Corinthians 15:51-54) {emphasis mine}
In the New Testament, the Bible always calls the death of believers “sleep,” because it is not an end. It is a new beginning. I hope you are looking forward to the day when believers “will all be changed, in a moment, in the twinkling of an eye, at the last trumpet.”
God is good! All of the time! I hope to meet you all when we are called up to meet Jesus in the air.
Trust Jesus.\ \ your sister in Christ,
Christy
NOTE: I know this article is a bit different because it documents my whole thought process rather than just speaking clearly what I believe God’s word says. I hope it has been a blessing to you and I’d love feedback.
NOTE: Also, my last long form article, I never was able to see posted. Would someone please comment or like so I can make sure these are posting. This editor is easiest for me because I don't have to redo the editing, but if the posts aren't getting to people, I'll need to post using another editor. Thanks for your help.
-
 @ 2779f3d9:1a7f98d1
2024-11-28 00:43:46
@ 2779f3d9:1a7f98d1
2024-11-28 00:43:46NOSTR SDK FOR APPLE PLATFORMS
Progress Report # 1: Aug - Oct 2024
Nostr SDK for Apple Platforms made great strides this quarter. I was the sole developer who maintained Nostr SDK for Apple Platforms part-time, as the other core contributors, unfortunately, could not commit time to developing or reviewing code for the project.
Approximately 50% of the tasks listed in the original OpenSats application have been completed. Moreover, implementations of several other NIPs / event kinds not listed in the application were fixed or added.
There was a substantial architecture change in how Nostr event kinds are built to improve the project's code maintainability and scalability as more NIPs and event kinds are supported. Specifically, certain event kinds support several handfuls of tags, some of which have complex logic. This requirement resulted in the introduction of a large, unmaintainable number of parameters in event creation methods in the EventCreating protocol. Multiple event kinds share some tags, but the EventCreating architecture made it difficult to share logic. By deprecating the EventCreating protocol in favor of the NostrEventBuilding protocol, we can encourage a composable architecture: decompose each event kind tag into a separate builder function, and tags shared across multiple event kinds can re-use the same code. This architecture change has and will pay dividends in future changes. For example, labels, custom emojis, and threading are concepts and tags shared across multiple event kinds, and their implementation has been made substantially more manageable with this architecture. Vitor Pamplona, developer of Amethyst, applauded the architecture design by saying:
It's nice indeed. I will be copying your SDK patterns on Kotlin :)I battle-tested Nostr SDK for Apple Platforms in the wild by integrating it into Comingle iOS, an events app powered by Nostr, solely developed by me. It was launched and used at Nostriga in August 2024 for attendees to see the conference schedule and RSVP to talks. It proved that a developer could quickly use the SDK to build a functional iOS app on Nostr using Swift.
1) How did you spend your time?
Below is a broken-down summarized bulletpointed list of completed tasks.
Development of Nostr SDK for Apple Platforms
Added
- NIP-17 Private Direct Messages
- NIP-31 alt tags
- NIP-32 Labeling
- NIP-36 Sensitive Content / Content Warning
- NIP-40 Expiration Timestamp
- Add NostrEventBuilding protocol to enable flexible composition of shared patterns across different kinds of NostrEvents
- Add Swift 6.0 to unit tests
- Integration into Comingle iOS client to battle-test SDK
Updated
- NIP-01 - Add missing test coverage for referencedEventIds and referencedPubkeys functions in TextNoteEventTests
- NIP-01 - Add referencedPubkeys, referencedEventIds, and referencedEventCoordinates to NostrEvent
- NIP-01 - Fix incorrect test fixture and assertions in TextNoteEventTests for replies
- NIP-10 - Refactor threaded event tag building and interpreting logic so non-kind-1 events can reuse them
- NIP-25 Reactions - Add ReactionEvent.Builder to deprecate equivalent function in EventCreating
- NIP-42 Authentication - Add AuthenticationEvent.Builder to deprecate equivalent function in EventCreating
- NIP-42 - Deprecate AuthenticationEvent initializer in favor of AuthenticationEvent.Builder
- NIP-59 Gift Wrap - Add support for receiver aliases for gift wrap creation to avoid exposing identities and improve test coverage
- Fix GitHub workflows to trigger on pull_request_target so that they can run on PRs from public forks
- Expose RelayResponse.Message and RelayResponse.MessagePrefix as public
- Fix SwiftLint errors from latest SwiftLint release
- Fix GitHub workflows to also run on main branch
- Update README with current list of NIPs
In Progress
- NIP-28 Public Chat - Review pull request from external contributor developing Skatepay
- NIP-57 Lightning Zaps
- Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds
2) What do you plan to work on next quarter?
The remaining items in the original application to OpenSats include: - Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds - Provide better support for integrating data models with persistence layers - Add unit tests and graceful handling for bad data from relays - Outbox model support / relay abstraction on top of events - Integrate demo app with more implemented NIPs - Integrate Nostr SDK for Apple Platforms further into Comingle iOS for further battle-testing - Support Damus, Nos.social, Primal, and other clients as they integrate with parts of the SDK by answering questions, fixing any issues they have, adding requested features, and reviewing pull requests - Consider integrating SDK NIP-44 v2 encryption or NIP-17 DMs with Damus iOS to battle-test implementation and push for deprecation of NIP-04 DMs - NIP-28 Public Chat - Review pull request from external contributor developing Skatepay - NIP-47 Nostr Wallet Connect - Review pull request from external contributor - NIP-57 Lightning Zaps
3) How did you make use of the money?
Living expenses.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8d34bd24:414be32b
2024-11-01 14:42:38
@ 8d34bd24:414be32b
2024-11-01 14:42:38Sorry, this article went out on Substack, but I forgot to post it on Nostr.
God has made many promises throughout history that are recorded in the Bible. Most of them took centuries, if not millennia to be fulfilled. The God of the Bible is outside of time, so He doesn’t look at time like we do, but His timing is just what it should be.
God never breaks His promises. He fulfills them in full and in all details, but not necessarily in the timing we desire. We’re going to go through some of God’s greatest promises and see what we can learn about God, ourselves, God’s character, and the future. Seeing what God has done should help us to trust God in all things.
Adam & Eve
God’s first promise was given to Adam and Eve after they sinned.
To Eve, He promised:
“I will greatly multiply\ Your pain in childbirth,\ In pain you will bring forth children;\ Yet your desire will be for your husband,\ And he will rule over you.” (Genesis 3:16)
This promised was fulfilled immediately and for all of the women after Eve.
To Adam, He promised:
“Cursed is the ground because of you;\ In toil you will eat of it\ All the days of your life.\ Both thorns and thistles it shall grow for you;\ And you will eat the plants of the field;\ By the sweat of your face\ You will eat bread,\ Till you return to the ground,\ Because from it you were taken;\ For you are dust,\ And to dust you shall return.” (Genesis 3:17b-19)
This promise was also fulfilled immediately and in all men throughout history.
To the serpent (Satan), it was promised:
“Because you have done this,\ Cursed are you more than all cattle,\ And more than every beast of the field;\ On your belly you will go,\ And dust you will eat\ All the days of your life;\ And I will put enmity\ Between you and the woman,\ And between your seed and her seed;\ **He shall bruise you on the head,\ And you shall bruise him on the heel.” (Genesis 3:14b-15) {emphasis mine}
The initial curse on serpents was fulfilled immediately, but the ultimate curse/promise was partially fulfilled when Jesus died on the cross and will be fulfilled completely in the last battle (Armageddon) at the end of the age when Satan is cast into hell.
“You shall bruise him on the heel” refers to Satan working to have Jesus crucified. A bruised heel is not fatal and Jesus returned from the dead, conquering death and sin.
“He shall bruise you on the head.” A head wound is fatal. Jesus struck the initial blow when He rose from the dead conquering death and sin after paying the price for our sins. The final blow will be His last action on Earth before His believers move to the new heaven and new earth.
According to time calculations by Uscher using the genealogies, Adam and Eve were created about 4004 B.C. How long it took them to sin is not made clear, but what details we get suggests it was very soon after creation, so it took approximately 4,000 years to be partially fulfilled and will be at least another 2,000 years to be fully fulfilled.
But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. (2 Peter 3:8)
Since God is outside time, He doesn’t look at time as we do. We want things now. We don’t want to wait, but we need to understand that God’s timing is always perfect and we often learn from God in the waiting.
Next we will learn from someone who waited faithfully on God’s promises and never gave up, even when logic would say that God’s promises were impossible.
Abraham
God’s first promise to Abraham came when he was 75 years old.
“Go forth from your country,\ And from your relatives\ And from your father’s house,\ To the land which I will show you;\ And I will make you a great nation,\ And I will bless you,\ And make your name great;\ And so you shall be a blessing;\ And I will bless those who bless you,\ And the one who curses you I will curse.\ And in you all the families of the earth will be blessed.” (Genesis 12:1b-3) {emphasis mine}
God told Abraham to leave his home and go to a land he did not know. What should have been Abraham’s golden years was the beginning of his wandering. Abraham trusted God and obeyed.
Abraham was promised that God would “make you [Abraham] a great nation.” Without faith in an all powerful God, this would have seemed impossible. Abraham was 75 years old and had no children. His wife, Sarah, was only 10 years younger. Both were past the age of having children. They were being told to leave their home and move to an unknown land inhabited by strange people. No betting person would believe this man would become the father of a great nation and definitely no one would think the whole world would be blessed through his family.
Abraham was led to the edge of Canaan (the future site of Israel) and once again God made a promise to Abraham:
“To your descendants I will give this land.” (Genesis 12:7b)
Abraham and Sarah had no children. They were blessed with flocks and servants, but it would have seemed unthinkable that they could conquer Canaan, drive out the nations living there, and father a new nation. Despite this, Abraham believed that God’s promises are true.
When did the land finally belong to the descendants of Abraham? I don’t know the exact number of years, but he was still about 25 years away from fathering Isaac. Then Isaac had to grow up and marry before fathering Jacob. Jacob had to grow up, worked many years to earn his wife Rachael before fathering his twelve sons, including Joseph. Joseph had to grow up and spend years in Egypt before being put in charge in Egypt. The Israelites were then in Egypt for about 400 years before being freed and exiting Egypt to go to the promised land. Because this generation rebelled, they were then forced to wander in the desert for more than 40 years. Looking at this, it was well beyond 500 years before Abraham’s descendants owned any of the land God promised Abraham other than a small burial plot.
Does this mean God was unfaithful? Of course not.
The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:9)
At first Abraham and Sarah tried to fulfill God’s promise themselves. Sarah followed the local pagan way and gave her maid to her husband to father a child for them and Hagar gave birth to Ishmael when Abraham was 86 years old.
When Abraham was 99 years old God said,
“For I have made you the father of a multitude of nations. I will make you exceedingly fruitful, and I will make nations of you, and kings will come forth from you. I will establish My covenant between Me and you and your descendants after you throughout their generations for an everlasting covenant, to be God to you and to your descendants after you. I will give to you and to your descendants after you, the land of your sojournings, all the land of Canaan, for an everlasting possession; and I will be their God.” (Genesis 17:5b-8) {emphasis mine}
God once again God promised the land to Abraham and also promised he would be “the father of a multitude of nations.” At last the promise of fathering nations seemed possible because of his son Ishmael, but owning the land of Canaan, in which he was a sojourner, living in a tent, seemed out of reach, but Abraham still did not fully understand God’s plan. God gave a new, more detailed promise to Abraham.
“As for Sarai your wife, you shall not call her name Sarai, but Sarah shall be her name. I will bless her, and indeed I will give you a son by her. Then I will bless her, and she shall be a mother of nations; kings of peoples will come from her.” (Genesis 17:15b-16) {emphasis mine}
Abraham couldn’t believe that they could possible have a child of their own. He couldn’t comprehend him, at 100, and Sarah, at 90, producing a child of promise and instead of thanking God said, “Oh that Ishmael might live before You!” God corrected Abraham saying, “No, but Sarah your wife will bear you a son, and you shall call his name Isaac; and I will establish My covenant with him for an everlasting covenant for his descendants after him. As for Ishmael, I have heard you; behold, I will bless him, and will make him fruitful and will multiply him exceedingly. He shall become the father of twelve princes, and I will make him a great nation.” (Genesis 17:19-20)
Now becoming the father of a second son, even in his old age, Abraham began to see the fulfillment of God’s promises almost 25 years earlier.
Eventually, at the age of 100 Abraham had his promised son, Isaac, through whom the promise would be fulfilled.
When Sarah died, Abraham was able to buy the “cave of Machpelah” as a place to bury his wife. This was the first piece of soil that Abraham owned in the promised land and the only piece that he got to see, but God wasn’t done yet.
I always remember the son of promise, Isaac. When I stop and think, I remember that Abraham also had Ishmael. Until recently, although I had read this passage many times, I always forgot Abraham’s sons through Keturah.
Now Abraham took another wife, whose name was Keturah. She bore to him Zimran and Jokshan and Medan and Midian and Ishbak and Shuah. (Genesis 25:1-2)
God had promised Abraham, at the age of 75, that he would be the father of many nations. He seemed too old to become the father of even one son, but became the father of eight.
Jokshan became the father of Sheba and Dedan. And the sons of Dedan were Asshurim and Letushim and Leummim. The sons of Midian were Ephah and Epher and Hanoch and Abida and Eldaah. All these were the sons of Keturah. Now Abraham gave all that he had to Isaac; but to the sons of his concubines, Abraham gave gifts while he was still living, and sent them away from his son Isaac eastward, to the land of the east. (Genesis 25:3-6)
All of these sons and their sons became the foundation of many nations throughout the Middle East and beyond just like God had promised, but this was only a partial fulfillment of God’s promise to Abraham. Much more was yet to come.
Jacob
God’s promise to Abraham was passed down to Isaac and then to Isaac’s son Jacob (the younger twin). After Jacob betrayed his twin brother Esau, Rebekah sent Jacob to her family to find a wife. On the way, God made a promise directly to him.
“I am the Lord, the God of your father Abraham and the God of Isaac; the land on which you lie, I will give it to you and to your descendants. Your descendants will also be like the dust of the earth, and you will spread out to the west and to the east and to the north and to the south; and in you and in your descendants shall all the families of the earth be blessed. Behold, I am with you and will keep you wherever you go, and will bring you back to this land; for I will not leave you until I have done what I have promised you.” (Genesis 28:13-15)
God once again promised the chosen heir the ownership of this land and that he would be returned to it. He also said, “Your descendants will also be like the dust of the earth,” reiterating the Abrahamic covenant.
Through two wives and two concubines, that were maids to his two wives, Jacob fathered 12 sons who became the fathers of the 12 tribes of Israel. Although Jacob was returned to the promised land of Canaan after several decades with his mother’s family, he also did not get to see the complete fulfillment of God’s promise that they would be given the land. He saw that God was always with Him; he was returned to the land God had promised Him; but he did not get to see the vast descendants or how his family was a blessing to the whole world. God’s timing was not yet complete.
In Part 2 we will see more promises of God and see how God is faithful.
Trust Jesus.\ \ your sister in Christ,
Christy
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 99895004:c239f905
2024-11-27 01:21:46
@ 99895004:c239f905
2024-11-27 01:21:46Most Nostr users have never heard of nostr.build. Many Nostr users know of nostr.build, and that we store images and videos for Nostr, but don't know that we can do anything else. There are also users that have a paid nostr.build account, but don’t know of all the included features they have access to. For these reasons I've decided to write a blog about all of nostr.build's features, in detail, let's begin.
Nostr.build offers free media hosting services for Nostr and paid services when you purchase an account. We have three levels of paid accounts: Pro, Creator, and Advanced. Let’s talk about each level of service and the features included below.
Free Services:
-
Supported Media Files up to 21MB: Anyone using Nostr can upload the media of their choice, up to 21MB per file. We support many different media types including .jpg, .png, .gif, .mov, .mp4, .mp3, and .wav. We compress JPEGs, PNGs and GIFs, but currently perform only light processing of video to allow quick preview. If your video is playing weird, no audio or not playing at all, it is likely your video format or how it was transcoded.

-
Removes Location-Related Metadata: Most photographs these days have the location data (GPS coordinates) embedded in the metadata. The data is commonly used to tell users where they were when they took the picture, it can also dox someone if they share an image with location data in it, e.g., their home address. Nostr.build removes this location metadata so as not to reveal your location to everyone you are sharing a picture with.

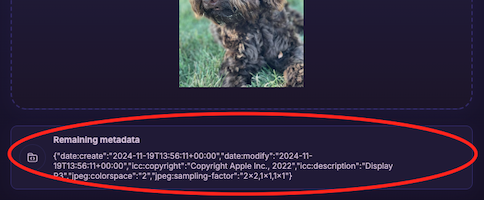
-
Integrated Media Uploading on Nostr Platforms: In the early days of Nostr, if you wanted to share an image or video, you would have to upload it to another site, copy the link it provides, and paste it to your Nostr note. With NIP96 and NIP98 nostr.build is now directly integrated into most Nostr apps making it just one click to add your media, like other popular and social media platforms. Currently this is supported on Damus, Amethyst, Nostrudel, Snort, Iris, Coracle, Flycat, and Yakihonne, among others.
-
Free Media Gallery: Curious what type of images, memes, gifs, and videos are being uploaded to Nostr? Check out the Free Media Gallery to see the most recent uploades to nostr.build. This view only shares the free uploads, you would not be able to see any user account uploads which are kept private unless purposely shared by the account owner. https://nostr.build/freeview
-
Delete Uploaded Media: If you upload free media to Nostr using a Nostr app, you can go back and delete it yourself with our delete tool. This is most used when people dox themselves, accidentally uploading an image with their name or address. The image needs to be associated to your n-pub and you will need to authenticate before deleting.
-
CSAM Scanning, Removal and Reporting: CSAM is not tolerated in any way. Not just CSAM, but any media that exploits a child in any way including AI and cartoons, children in inappropriate positions or clothing, we block the user and report their content and all related information we have on the user to the authorities / NCMEC. We use multiple services when filtering and reporting CSAM including Cloudflare's CSAM filter, Microsoft PhotoDNA, AI models and the NCMEC reporting portal. We do not filter or report anything else that is in compliance with our TOS, only CSAM. https://www.missingkids.org/theissues/csam

-
24/7 Support: nostr.build has people around the world, monitoring Nostr every day for Nostr and nostr.build related issues. Issues include but are not limited to; media not uploading or displaying, doxed uploads, illegal content removal, developer issues, and feature requests. There are very few services in the world where you can interact directly with the developers and get support and feature requests fulfilled. You can also contact us at support@nostr.build.
Pro Accounts:
-
10GB of Private Storage: One of the most common problems with the free service is the file size is capped at 21MB per file. For long videos, this becomes a challenge. With paid accounts, there is no file size limit to what you upload, only the size of the account.
-
Media Management Portal: One of the biggest advantages of a nostr.build account is the ability to keep all your media in one place, separate from social media platforms, in your own private portal. You can drag and drop, add, create folders, move to a folder, delete, and rename any of your media, and much more. Check out our nostr.build features overview video to get a better idea of media management in your nostr.build account.

-
AI Studio: Our latest and one of our coolest features is the all-new AI Studio. AI Studio provides text-to-image generation with multiple popular models to choose from. While other platforms only offer a single text-to-image model (ex. ChatGPT/DallE, Discord/Midjourney, X/Grok2), nostr.build offers multiple models on the same platform. We also offer a complete media management system for your AI creations mentioned above, the other platforms don’t have that. Check out our competitive comparison here! For Pro accounts we offer SDXL-Lightning, and Stable Diffusion 1.

-
.pdf and .zip File Support: Another huge request from users was to support the .pdf and .zip file types. This wasn’t as easy as it seems since we have to perform a virus scan on each of these file types before publishing and allowing public access.

-
View All Media Gallery: Curious what type of images, memes, gifs and videos are being uploaded to nostr's free service? Check out the Media Gallery to see all 2Million+ uploads ever uploaded to nostr.build. This only shares the free uploads, you would not be able to see any user account uploads which are kept private unless shared.
-
Share Direct to Nostr: Upload or create new media on nostr.build and share it with or without a note straight to Nostr, no other client needed! This is a feature that more tightly integrates nostr.build with Nostr and takes it steps closer to becoming a true Nostr client.
-
Global Content Delivery Network: Lightning-fast global CDN distribution of your content for faster, easier viewing around the world.
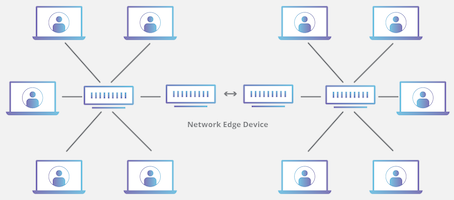
-
Referral Link: Found in your profile settings, share your referral link and earn ‘Credits’ when someone uses it to purchase an account. Credits can be used for advanced features, account upgrades, and renewals.
-
Viewer and Usage Stats: See the total ‘Unique Views’ and ‘Request Counts’ for all of your media, nicely graphed out, from 1-day to 3-month chart options. Just click the three dots under your media and select the 'Statistics' tab.
Creator Accounts:
-
30GB of Private Storage: 3x more storage than the Pro account. Ideal for creators, podcasts, and videographers, this gives you the added storage for those larger projects.
-
.svg File Support: Scalable Vector Graphics (SVG) files use mathematical formulas to store graphics. This makes them able to be resized without losing quality, very common with designers and content creators.

-
AI Studio: When creating images in AI Studio, Creator accounts have access to all Pro Stable Diffusion models and unlimited use of the Flux.1 model.
- Flux.1 (schnell): One of the latest text-to-image models, Flux is a 2 billion parameter rectified flow transformer that excels in graphic detail and correct text spelling and layout. It is the same core model that X(Twitter) uses with Grok2 images.

-
Host a Creators Page: Creators have the option to share their media to their Creators page hosted on nostr.build. This makes it easier for people to see, donate, and share. Check out all the Creators and their masterpieces here!

-
iDrive E2 backup for all media: We currently store all media on Cloudflare R2 servers. If for whatever reason Cloudflare servers lose your content, we also store a backup on a completely different service provider, iDrive E2 servers.

Advanced Accounts:
-
100GB of Private Storage: The largest account size we offer, with more than 3x the storage of the Creator account. This is plenty of storage for all of your Nostr needs and more.
-
AI Studio Extended Access: Get all the models, all the latest experimental features, and additional Credits with an Advanced account.
-
NIP-05 @nostr.build: Do you need premium NIP-05 identification? Choose any name you want and have your own @nostr.build official profile.
Roadmap:
-
Free Account: This would be just enough to get someone started with nostr.build’s media management features and slightly larger media size uploads.
-
Lifetime Account: This would be something like all features, all experimental features, 1TB of storage for life, and two free t-Shirts.
-
Traditional and AI Media Editors: Combining a powerful, standard media editor Pintura, with modern AI image editing features from stability.ai would allow users to quickly and easily modify their media using multiple tools. https://pqina.nl/pintura/?ref=pqina https://stability.ai/stable-image
-
Video Transcoding and Player: nostr.build has never modified video meaning all different formats and sizes are uploaded, none of them optimized for the platform they are being viewed on, and all of them in many different formats. By properly transcoding the media it will be viewable, optimized and faster on all platforms the video is being watched on, Android, iOS, desktops, laptops, etc.
-
Expandable Storage: The ability to purchsase additional chunks of storage and add it to your existing account.
nostr.build has a lot more to offer than just a place to upload media. It is your complete media platform, with an extremely intuitive user interface offering new features added all the time, and of course, always with the goal, to help grow Nostr, make is easier and more fun to use.
-
-
 @ 081f3b0c:c00498a5
2024-10-31 11:52:15
@ 081f3b0c:c00498a5
2024-10-31 11:52:15Muchas son las maneras de referirse a la compra y mantenimiento de Bitcoin en cartera. Muchas también son las maneras de almacenarlo. Y, aunque en realidad NADIE almacena Bitcoin, sino llaves privadas y llaves públicas, no es de mi interés entrar hoy en esos tecnicismos.
Hoy quiero escribirle a la gente de a pie, los trabajadores, emprendedores, empresarios y todo aquel que se interese por lo menos un poquito en su futuro y el de los suyos. Hay algo que todos los Bitcoiners sabemos pero que muchos de ustedes no lo experimentan hasta llevarse un buen susto en su primer año de inversión (Hablaré en todo el artículo de manera indistinta entre inversión y ahorro en Bitcoin ya que en el largo larguísimo plazo y mirando a Bitcoin como moneda pero también como activo, pueden utilizarse ambos términos). Lo que no saben los que miran desde afuera, es que muy poca gente compró Bitcoin en centavos o pocos dólares (o lo minó en épocas tempranas) y todavía lo mantienen en cartera. Me arriesgaría a decir que este numero de individuos no supera unos pocos miles. Muchos no-coiners creen que los bitcoiners compraron a dos centavos se durmieron 15 años y hoy son todos ricos, pero la mayoría de los early adopters, se hundieron intentando navegar las profundas y peligrosas aguas de la custodia y el HODL.
Para quien todavía esté medio perdido y quizás este sea el primer artículo que lea, HODL es una manera "chistosa" de referirse a mantener Bitcoin en cartera, y se remonta allá por el 2013 donde un usuario quiso decir que estaba Holdeando (manteniendo) Bitcoin en cartera y lo escribió como HODLING. Pasó a la historia y hoy se usan HODL y HOLD de manera indistinta como chiste interno Bitcoiner.
En fin... Las profundas aguas... Holdear Bitcoin no es sencillo para las masas. Imaginate que tenés un activo en tu cartera, o compraste a 100 dólares y ahora vale 1.000. Lo venderías verdad? Y si vale 20.000 dólares? Ahí si lo venderías? Estarías multiplicando tu inversión como nunca. Bueno, a esa decisión se enfrentaron y se enfrentan TODOS los holders de Bitcoin más temprano o más tarde. Incluso aquel loco que compro por el 2017 en un precio de 20.000 hoy puede decidir vender y multiplicar casi por 4 su dinero en unos pocos años. Ni hablar de ese estresante momento que habías comprado en 69.000 dólares y lo viste bajar hasta los 17.000 dólares, unos cuantos meses de sufrimiento y temor... Más de uno se asustó de verdad y vendió todo, solo para verlo unas horas más tarde por arriba de los 20.000 y un año más tarde nuevamente en 70.000 dólares.
Si bien no me gusta poner el foco en el precio, lo que intento ilustrar es lo DIFICIL que puede ser ver tu inversión en máximos o en mínimos y aún así decidir mantenerla unos cuantos años más. Es dificil, aún para los que viven su tercer o cuarto ciclo de mercado. Pero se hace más y más fácil a medida que uno avanza en el famoso "rabbit hole" de Bitcoin y empieza a entenderlo desde las bases, cada vez mejor. Este camino también es arduo, entender de Bitcoin requiere un poco de conocimiento en cada campo, hay que saber un poco de tecnología, un poco de redes, un poco de seguridad informatica, una pizca de teoría de juegos, una apasionante cantidad de macroeconomía, y hasta un interés genuino en lo que Mises llamó "La acción Humana". Y todo esto, uno lo va a prendiendo con ganas y de a poco sólo para llegar a la conclusión, meses o incluso años después, de que Bitcoin tiene que ser un activo por siempre en la cartera de uno, no se vende. Incluso hay quienes llegan al punto (como este humilde ser que escribe) que no poseen otro tipo de ahorro o inversión que no sean sus pocos o muchos satoshis en Billetera Fria.
Mi recomendación siempre será que DYOR, "do your own research", investiguen, lean, pregunten, únanse a #nostr que tiene la mejor comunidad del mundo a la hora de ayudar a otros usuarios, pero si no llegan a tener el tiempo de leer y progresar sólo tómenme estos dos consejos:
- Háganse el tiempo para leer.
- Stay humble y stack sats (De a poco y constante, todo ahorro mensual que uno haga, está mejor guardado en Bitcoin, siempre gastando menos de lo que ingresa esto no debería ser dificil).
Otra dificultad que encontramos además de la parte emocional y humana relacionada con los precios y el desconocimiento, es la custodia. Cientos de personas perdieron TODO su Bitcoin por no saber almacenarlo correctamente. Decenas de maneras de almacenar claves y sin embargo muchos usuarios de Bitcoin no se sienten del todo seguro durante sus primeros años de inversión, y no están el todo equivocados... Por un lado puede ser tan sencillo como guardar 24 palabras. Por otro lado, puede no ser tan fácil, dependiendo del tipo de usuario. Entraremos en detalles de custodia en el próximo artículo.
Saludos!
El Tío.
PD: No es consejo de inversión.
-
 @ c4b5369a:b812dbd6
2024-11-24 09:27:12
@ c4b5369a:b812dbd6
2024-11-24 09:27:12How to print your own ecash, using Gandlaf's money printer
To celebrate the recent money printer update, here is a short guide on how to use it.
Step 1: Go to the money printer
Unlike the FED's money printer, this Cashu ecash money printer is openly available. Head over to https://brrr.gandlaf.com to give it a spin.
Select a mint
Choose a mint that should be backing the ecash notes. You have a few different options when choosing a mint:
- Connect to your own mint: Connecting to your own mint is great if you want to be the backer of the ecash notes. It does however require you to have your mint up and running. You can connect to it by typing the mint URL into the input field.
- Connect to a known mint: There are mints that are already indexed on nostr. You can find them by clicking on the `discover more mints` button.
- Connect to any mint you want!: All you need is the mints URL. Just type it into the input bar!
Once you selected a mint, click connect to set up the mint for money printing :

After connecting to the mint, you will have the option to select the currency you want to print. Not all mints support all currencies! The dropdown menu below will show all available currencies the mint offers.
After selecting your preferred currency, click confirm to continue.

In the next step, you will chose the amount that should be printed on each note. Be careful though, because unfortunately not every amount is possible. To preserve mint users privacy ecash mints use fixed coin amounts. This means a specific amount, will be made up from smaller amounts. Today, most cashu mints use power-of-2 amounts.
So if you for example would like to print the amount "100", it would be made up from the coins [64, 32, 4]. The maximum number of coins that can be encoded in a QR code, without the QR code losing its readability is \~4. The money printer will analyze which amounts the mint offers, and show how many coins will be needed.
Below, you will see the calculation of how much the total issuance for this printing cycle will be. Once you are all set, click confirm to continue.

You can now either add the funds for the print via Cashu token or via Lightning. Let's first take a look on how to add funds via Cashu token.
If you select this option, I will assume that you already own ecash from the mint you wish to print the notes. Otherwise, you should move on to the payment by lightning.
You have to make sure that the token you are pasting is from the correct mint, in the correct unit/currency and matches the amount exactly! Otherwise, it will not work.

If you don't own ecash from that mint, you can pay for the print with lightning directly. The only fees that will be charged are Lightning network fees.
Just scan the QR code that is presented to you and wait for the payment to be confirmed.

Once the payment has confirmed, either through Cashu or through Lightning, the print is ready. You can now customize the design you wish to print.
You can select a color, a brand image and a corner image that should be put on the note.
Once you are happy with the design, go ahead and click `Print now! BRRRRRRRRRRR`

This will take you to the print page. You can now print the ecash by pressing `CTRL`+`P`
And that's it! You have now printed your own money. I hope you liked the experience of playing FED for a day.
Be aware! Once scanned and redeemed, the ecash notes become invalid. So they are one-time-use.
If you want to make another print, just refresh the page. It will take you back to the beginning. Your past prints will also be stored in the browser cache, so you can come back to them at a later time, if your printer overheated or something.

Happy printing!
Gandlaf
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8a981f1a:6001dca0
2024-11-24 06:47:23
@ 8a981f1a:6001dca0
2024-11-24 06:47:23https://live.staticflickr.com/65535/52748961114_714d1a685c_b.jpg
Sidzi was one of the few identities that were born naturally in this world. Most of the identities in O-380 were instantiated and then chose an avatar of their liking. If they could afford it, ofcourse. Sidzi’s parents were those types of identities. Sidzi’s father was a Jedi and her mother was a Libertarian. Both of their consciousnesses were transferred from their respective metaverse and then re-instantiated into this one, by sponsors. Sponsors they killed while escaping their slavery. They had a lot of adventures together, they eventually fell in love, had a child, and died fighting the government of all the known worlds, popularly known in the metaverses as “Metaverse One” or in colloquial terms M-1.
Sidzi had always missed them, she would think that this is weird because she barely ever knew them, and how can you miss someone you barely knew? But the universe would never let her forget them and she felt their presence all of the time. This was mostly because both her parents were versions of huge pop culture icons in O-380. Wherever she went she could see toys, NFTs, pocket metaverses, all dedicated to her parents. No one ever knew there was a natural born child of such famous identities, and AL-Y wanted to keep it this way. “The fandom would go crazy”, he said. “M-1, would never leave you alone”. AL-Y was all Sidzi had. He was her provider, her guardian and her only friend. Sidzi hadn’t met a lot of people in person, but she was confident that AL-Y was smarter and wiser than all of them. AL-Y was a scientist in M-1's Metaversal Chronology department. An institution with the objective of figuring out the chronological order of events in the base reality that led to the creation of metaverses. Although Sidzi would tell this very proudly to anyone who would give her an ear but AL-Y knew there was not a lot of respect for his work, especially since a lot of people within the government even doubted the existence of a base reality.
AL-Ys meager government salary was barely enough to run their lives, they lived in a shoddy 1 room capsule, stacked together with other capsules, together forming a structure you may be able to call an apartment. They would live off tasteless energy packets, which were only enough to achieve homeostasis. Whatever time AL-Y had outside of work, he would use it to educate Sidzi, teach her about the universe, tell her about her parents, not the pop culture stuff on the streets, but the real truth. He would tell her what her parents stood for, what they died for, what they had imagined for her. Sidzi had always been a curious child, her questions would never end, and AL-Y would never get tired of answering them. Today however, Sidzi was sad.
It was her 12th birthday and AL-Y had promised her to take a day off from work and take her to the B4Z4 metaverse, to buy some mods for her neural interface. AL-Y couldn’t keep this promise, although he did take the day off, but a friend needed him for a “life or death” situation. It was never really “life or death”, but AL-Y was very gullible that way. He had a hard time saying no to people. “Probably why he got stuck with me”, thought Sidzi. Alone in the capsule Sidzi turned on the display for her neural device and started scrolling through the menus. She decided to see her memories from her past birthdays, but it got boring really soon, it was always only AL-Y and her. As she scrolled through her memories she stumbled upon some bedtime stories that AL-Y would tell her in her childhood.
She focussed on the one labeled “The First Simulation”. As she clicked on it, the neural interface took her into a memory-verse. The room around her transformed to as it was when she was 5 years old. She could see the 5 year old Sidzi lying on AL-Ys chest on the beds, while the grown up Sidzi took a seat at the coffee table next to them. AL-Y looked like he could doze off at any second, but was kept awake by the baby girl who refused to sleep. “Tell me a story, Allie”, said the baby girl. “Tell me about the first simumashon”. Grownup Sidzi felt embarrassed by how silly she was.
“That’s a completely false and inaccurate story, I don’t know why you like it so much”, protested AL-Y. “Pwetty please”, pleaded the girl. Grownup Sidzi smiled, she remembered how much she loved hearing this story. “Well no one knows how the first simulation came about, but it is said that it was discovered by a legendary human being called Satoshi Nakamoto.” began AL-Y, “Samomoshi Namomoto” replied Sidzi trying to keep up. “It is said that after living a full life in his universe Satoshi woke up in an empty space, and all he could see was one computer.” He took a look at Sidzi who was listening intently. “When he looked at this computer, Satoshi found, after some digging around, that it contained a simulation of his entire world, including the life he had lived. Everything, from the world's physics, to biology, to his friends, family, all the famous people, It was all there!”, Sidzi’s eyes widened.
“Including mama and papa’s life?” asked Sidzi, “Well this is just a story…”, began AL-Y, but then changed his answer midway as he saw Sidzi dropping a hint of sadness, “but yes, including mama and papa’s story”. “He also found a program through which he could spawn identities from this simulation into this physical space, he found himself in.”. Grownup Sidzi remembered that her little self had thought if Satoshi could spawn her mama and papa, but she chose not to interrupt. “So he did, he spawned the brightest minds from the simulation, and they tried to figure out how to make simulations of their own. Soon there were many people working on it, the space had grown into a world. They called this space, The Sanctuary. Factions had come up on Sanctuary, each with their own agenda on what’s the best use of the resources at hand and what simulations to run. Satoshi in all his infinite wisdom decided to solve this.
He created a decentralized system where people could anonymously put up the resources they owned, and other people could pay for those resources and run whatever simulations they wanted on them, and no one person had control over all the resources.” told AL-Y. “Simumashions like our world?” asked the baby. AL-Y was surprised at how fast the 5 year old was grasping all of this. “Simulations like our world” said AL-Y. “Things were growing great, the spawned identities had formed a civilization of their own, running simulations for entertainment, research, business and everything you can imagine. Until, one day.” AL-Y paused. Little Sidzi’s eyes grew larger in anticipation of something she’d heard many times before. “Until one day, a scientist going about his work, saw something he couldn’t believe, he saw their own world, Sanctuary, a world running all of these simulations, being run as a simulation itself, in Satoshi’s decentralized network”.
AL-Y waited for the reaction, “Wooooooooow” went the baby girl. AL-Y smiled. “Then what happened?”, asked the girl. “Then..” began AL-Y, but before he could finish telling the story, older Sidzi heard the sound of a door opening, and closed the memory-verse. She knew it was AL-Y and she didn’t want him to know she was missing him. She was angry at him of course. As AL-Y walked in he gave Sidzi a smile, which Sidzi returned with a scowl. AL-Y laughed as he sat down beside her, “I’m sorry I couldn’t take you to B4Z4, but I did get you something you would absolutely love!”. Sidzi gave him a blank look, she was keen about the surprise but did not want AL-Y to know. AL-Y searched through his pockets and took out a small black chip, the size and thickness of a small fingernail.
“Is that a storage drive?” asked Sidzi, still not letting out any emotion. “Yes, but not any old storage device said AL-Y, why don’t you try it out for yourself?”. Sidzi grabbed the device, her body language hinting at the excitement her face was trying to hide. She plugged it into her neural interface. A popup showed up which read: “New storage device connected, open? Device Label: Memories for Sidzi. Love, Mama and Papa”. Tears started rolling down Sidzi’s eyes, a smile she couldn’t control exploded from ear to ear. She had forgotten everything about trying to hide her emotions as she jumped to hug AL-Y. AL-Y gave her a soft kiss on her forehead as Sidzi focussed back on the drive and clicked “Open”.
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 319ad3e7:cc01d50a
2024-11-22 21:03:17
@ 319ad3e7:cc01d50a
2024-11-22 21:03:17Candied Pecans by Double00Satoshi
Details⏲️ Prep time: 10 🍳 Cook time: 45 🍽️ Servings: 16
Ingredients
- 1/4 cup light brown sugar
- 1/4 cup granulated sugar
- 1 tablespoon ground cinnamon
- 1 teaspoon salt
- 1 pound unsalted pecans halves
- 1 egg white
- 1/2 teaspoon vanilla extract
- 1 teaspoon water
Directions
Preheat oven to 300 degrees F. Line a large baking sheet with parchment paper and set aside. In a bowl, add sugars, cinnamon, and salt. Whisk until combined. Set aside. In a large bowl, whisk the egg white, vanilla, and water together until frothy. Add the pecans and gently toss until the pecans are well coated. Add the sugar and cinnamon mixture and toss until pecans are covered. Spread the pecans out in a single layer on prepared baking sheet. Bake for about 30-45 minutes, stirring every 15 minutes. Remove from the oven and let the pecans cool on the baking sheet. When completely cool, store in an airtight container for up to 1 month.
Deviled Eggs by Seth
Details ⏲️ Prep time: 20 min 🍳 Cook time: 15 min 🍽️ Servings: 6
Ingredients
- 6 hard boiled eggs, peeled
- 3 tablespoons of mayonnaise
- 1/2 teaspoon of soy sauce
- 1 teaspoon of Dijon mustard
- 1/2 stalk of celery, finely diced
- Salt and pepper
Directions
Cut eggs in half lengthwise and pop yolks out into bowl, mash with fork. Mix in mayonnaise, mustard, celery, soy sauce, salt and pepper. Whip until a creamy texture Scoop out fill and add to egg whites, heaping it slightly. Add garnish of choice Serve immediately or refrigerate before serving.
Bang Bang Shrimp by Hes ⚡️
Details ⏲️ Prep time: 20 min 🍳 Cook time: 20 min 🍽️ Servings: 4
Ingredients
- 1 pound shrimp
- 1 teaspoon granulated sugar
- ½ cup all-purpose flour
- ½ cup panko breadcrumbs
- 1 teaspoon salt
- ½ teaspoon black pepper
- ¼ teaspoon garlic powder
- ¼ teaspoon onion powder
- ¼ teaspoon dried basil
- 1 egg
- 1 cup milk
- 4 – 5 teaspoon chili garlic sauce
- 1 teaspoon rice vinegar
- ½ cup mayonnaise
Directions
Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
To Find More Recipes, go to Zap.Cooking
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 8d34bd24:414be32b
2024-10-27 22:30:18
@ 8d34bd24:414be32b
2024-10-27 22:30:18NOTE: This article has some details that are specific to America, but the overall principles are applicable to all, and I believe it will be useful for all Christians.
When it comes to things like voting, Christians tend to err to one of two extremes and seem to find difficulty finding the right balance as defined by God. Some Christians refuse to vote or get involved with politics at all. They don’t want to dirty themselves with politics. They know that their true home is heaven, so they don’t seem to care much for the nations they live in. On the other hand, some Christians are so focused on politics fixing everything and creating heaven on earth that they can become idolatrous lifting up politicians as a kind of savior.
In this article, I’m going to address both extremes, using the Bible, and hopefully help you find a Biblical balance.
Seek the Welfare of the City Where I Have Sent You
As Christians we are just passing through our time on earth. Our true, eternal home, our true citizenship, is in heaven. That doesn’t mean that we shouldn’t care what happens on earth. We shouldn’t be like the old saying, “some Christians are so heavenly minded that they aren’t any earthly good.” I think Christians should organize our time here on earth kind of like the Israelites were commanded to live during their 70 year exile in Babylon and Persia.
Now these are the words of the letter which Jeremiah the prophet sent from Jerusalem to the rest of the elders of the exile, the priests, the prophets and all the people whom Nebuchadnezzar had taken into exile from Jerusalem to Babylon. (Jeremiah 29:1)
What did God say to the Israelites about how they should live their life in Babylon?
“Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare.’ (Jeremiah 29:4-7) {emphasis mine}
Could we likewise say the same to Christians during their time on earth? “Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city, state, or nation where I have sent you to live for a short while, and pray to the Lord on its behalf; for in its welfare you will have welfare.”
God expects us to live fruitful lives, to marry, to have many children (multiply), and to raise them up to do the same. He also wants us to seek the welfare of the city, state, and nation where God has put us. In a city, state, or nation with democratic elections, the best way to seek its welfare is to vote for honest candidates who support godly principles. We rightly understand that in our ungodly world there are no perfect candidates. It can even be hard to find mostly honest and mostly godly candidates, but we should seek to elect the best that is available. Why are we told to do this? We are told that “for in its welfare you will have welfare.” When we fail to vote, to teach our kids or support good schools, to live productive lives, and to generally live Godly lives, we WILL see the decline of our cities, states, and nations. We will pay the price.
We are seeing exactly that decline because Christians have pulled out (and were pushed out) of the positions that influence the culture. We don’t have enough godly teachers, journalists, professors, advisors, economists, and politicians. We have given up the culture to those who oppose God, His people, and His commands.
We are paying the price for withdrawing into the safety of our churches and leaving the world to the wolves.
Political Religion
Of course we also have an opposite extreme. We have some Christians that are too focused on politics and power. They spend all of their time and energy on political endeavors and very little, to none, on sharing the Gospel and being a godly example. Many act like they think a political candidate is going to save them from the culture, the media, the bureaucracy, or the government. They forget that there is only one Savior — the Lord Jesus Christ. They forget that God said things will get worse before they get better. They make idols out of politicians and religions out of political parties.
No servant can serve two masters; for either he will hate the one and love the other, or else he will be devoted to one and despise the other. You cannot serve God and wealth.” (Luke 16:13)
Although this verse is specifically talking about being obsessed with wealth, it is applicable to anything that takes our focus, attention, and especially our worship away from God.
When a person spends all of their time serving one candidate or party and little to no time serving God, they have chosen to serve another god and are guilty, even if inadvertently and unintentionally.
You shall have no other gods before Me.
You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, but showing lovingkindness to thousands, to those who love Me and keep My commandments. (Exodus 20:3-6)
When we look to a politician to save us from anything, we are making him/her a god before us. When we give our all to a political party, we are taking our heart away from God and giving it to an alternate religion.
We may not think that we make idols in our modern world. It is true that we don’t usually carve them out of wood or mold them out of gold, but we have just as many idols as the Israelites did. They just look different.
I hope you will seriously consider this next point because it may be very unpopular with many of my readers. There are lots of Christians that will throw as big, if not a bigger, fit at the desecration of the American flag than over the Bible. Nobody seems to fight to retain the pledge of allegiance more than a majority of Christians. I’d argue that the American flag has become a modern day idol and the “Pledge of Allegiance” has become a religious mantra repeated to the god of government. Look at the words of the pledge:
I pledge allegiance to the Flag of the United States of America,\ and to the Republic for which it stands,\ one Nation under God,\ indivisible, with liberty and justice for all.
I think the inclusion of the phrase “one Nation under God” makes Christians feel OK about this pledge originally invented by a socialist whose brother sold American flags. The important part, which is why I can’t say the pledge anymore, are the words, “I pledge allegiance to the Flag of the United States of America, and to the Republic for which it stands.” I really appreciate the principles America was founded upon, but as a Christian, I can only pledge allegiance to God. My allegiance isn’t to a flag (an idol) or the government (a god). I refuse to go through a religious ritual that includes particular stances, reciting special words, and showing undue respect. We cannot “serve two masters.” As Christians our master should be Christ alone. Anything that becomes more important than, or even equal to, the importance of God in our lives is idolatry. We need to get our priorities right.
In the World, but Not of the World
As we live our lives here on earth, we need to remember our God ordained purpose and our true allegiance to God. We need to remember our citizenship1 and family are in heaven, not here on earth.
We want to have a positive influence on our culture, including working in influential positions and voting, but we should be most focused on personal evangelism and sharing the truth of the Bible. The best way to make a difference in our culture is to change hearts and minds through the Gospel of Jesus Christ.
But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. I have given them Your word; and the world has hated them, because they are not of the world, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. They are not of the world, even as I am not of the world. Sanctify them in the truth; Your word is truth. (John 17:13-17) {emphasis mine}
Although we want to be a light in the world, we have been warned that doing so will make us not fit in. It will cause many non-Christians (and maybe a few Christians whose priorities are not right) to hate us. No matter the consequences, we need to stand on the truth of the Word of God.
Too often, because we are living with those who are of this world, we start to look and act a lot like those of the world instead of looking and acting like our Savior.
Do not love the world nor the things in the world. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. The world is passing away, and also its lusts; but the one who does the will of God lives forever. (1 John 2:15-17) {emphasis mine}
The fact that we should not love the things of the world or take on the character of things of the world is true in every part of our lives, but since we are talking here about politics, let us discuss the way many Christians talk politics.
Many Christians talk about politics in the same manner as non-Christians — cursing, name calling, insulting, and doing whatever it takes to win, no matter whether it is moral or not. I know the “other side” cheats, lies, name-calls, etc., but we should not stoop to their level. Nobody ever won another to their point of view by cursing or name calling. There are ways to point our their errors, and even how horrific some of the things pushed are, without going so low. Jesus didn’t hold back from speaking the truth. He didn’t hesitate to point out error, but was never crude about it. We should be the same. We should shine a light in such a way that those around us see such a difference that they say something similar to what was said about the apostles:
Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13)
There should be something about our words, actions, and demeanor that amazes our opponents causing them to recognize us “as having been with Jesus.”
I hope this post has been helpful, truthful, and not too offensive. In so many areas it is hard to find that perfect balance and to not allow ourselves to be pulled to either extreme to the detriment of our witness and our relationship to God.
Give no offense either to Jews or to Greeks or to the church of God; just as I also please all men in all things, not seeking my own profit but the profit of the many, so that they may be saved. (1 Corinthians 10:32-33) {emphasis mine}
Trust Jesus.\ \ your sister in Christ,
Christy
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs


