-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 319ad3e7:cc01d50a
2024-11-22 21:03:17
@ 319ad3e7:cc01d50a
2024-11-22 21:03:17Candied Pecans by Double00Satoshi
Details⏲️ Prep time: 10 🍳 Cook time: 45 🍽️ Servings: 16
Ingredients
- 1/4 cup light brown sugar
- 1/4 cup granulated sugar
- 1 tablespoon ground cinnamon
- 1 teaspoon salt
- 1 pound unsalted pecans halves
- 1 egg white
- 1/2 teaspoon vanilla extract
- 1 teaspoon water
Directions
Preheat oven to 300 degrees F. Line a large baking sheet with parchment paper and set aside. In a bowl, add sugars, cinnamon, and salt. Whisk until combined. Set aside. In a large bowl, whisk the egg white, vanilla, and water together until frothy. Add the pecans and gently toss until the pecans are well coated. Add the sugar and cinnamon mixture and toss until pecans are covered. Spread the pecans out in a single layer on prepared baking sheet. Bake for about 30-45 minutes, stirring every 15 minutes. Remove from the oven and let the pecans cool on the baking sheet. When completely cool, store in an airtight container for up to 1 month.
Deviled Eggs by Seth
Details ⏲️ Prep time: 20 min 🍳 Cook time: 15 min 🍽️ Servings: 6
Ingredients
- 6 hard boiled eggs, peeled
- 3 tablespoons of mayonnaise
- 1/2 teaspoon of soy sauce
- 1 teaspoon of Dijon mustard
- 1/2 stalk of celery, finely diced
- Salt and pepper
Directions
Cut eggs in half lengthwise and pop yolks out into bowl, mash with fork. Mix in mayonnaise, mustard, celery, soy sauce, salt and pepper. Whip until a creamy texture Scoop out fill and add to egg whites, heaping it slightly. Add garnish of choice Serve immediately or refrigerate before serving.
Bang Bang Shrimp by Hes ⚡️
Details ⏲️ Prep time: 20 min 🍳 Cook time: 20 min 🍽️ Servings: 4
Ingredients
- 1 pound shrimp
- 1 teaspoon granulated sugar
- ½ cup all-purpose flour
- ½ cup panko breadcrumbs
- 1 teaspoon salt
- ½ teaspoon black pepper
- ¼ teaspoon garlic powder
- ¼ teaspoon onion powder
- ¼ teaspoon dried basil
- 1 egg
- 1 cup milk
- 4 – 5 teaspoon chili garlic sauce
- 1 teaspoon rice vinegar
- ½ cup mayonnaise
Directions
Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
To Find More Recipes, go to Zap.Cooking
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 592295cf:413a0db9
2024-11-23 08:55:40
@ 592295cf:413a0db9
2024-11-23 08:55:40November 18th week
Let's proceed step by step, calm and reason.
Bluesky is only 5 doubles from Twitter, now has its own network effect.
Article of Hodlbod. The state of the art of Key management
nostr:nevent1qqsgpckkyck5m58gux5xst03ls68xxfz0ep2ndws6s039492vxvtc7spp4mhxue69uhkummn9ekx7mqprdmhxue69uhksmmyd33x7epwvdhhyctrd3jjuar0dak8xq3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qcxhke2
The problem is how a user creates an account. Will fix It.
If you have a signer account like Amber, nsec app, all right, then it says remove all logins And ask the user how he wants to login.
Bluesky is an anti Trump and Elon Musk movement. It started with Brazil the significant exodus, the thing had a certain amount of stability and began to arrive a lot of people. So it's a sort of political party hanging against.
Nostr is still made by fixed stars, there are many stars but they are still firm in the sky.
Rod made n8n ocKnamo bot
nostr:nevent1qvzqqqqqqypzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uqzqjgxwlfdru3zzcee0sxk8d0dddwj4tu3xp00gwahy2t0n5k2se6uu8p7fk
This is interesting, ocknamo Is a rock, keep pushing
Roadmap are bullshit, you spend the time to the the actual things, sure if a groups ok
I read Hodlbod's spech in practice with the tilde wants to create rooms, then there is the space that is the carcass we are very close to what is Unanimity, but it's fine with much more refining, but at the cost of being unique.
Discord vs Telegram
I downloaded three Nostr apps, I called it Atlas instead of Olas, zapstore and flotilla (removing Coracle).
Olas would be nice if he had the feature awards on the photo and Zap 😉.
Zap store continues to mark me an update of minibits, but minibits updates in the app, I also updated to a new version, however maybe it is a different type of app. Putting the key does not seem to have changed a comma the app. But then I realized it's about the app signers. The signers who followed the signers that are in your WoT, the signers that are in your lists 😉. It does not divide Nostr apps from Nostr, but it works.
Olas there is no focus on the media server, maybe if you have a new account it's all explained. Problems with dark mode and filter. I would like the idea of switching videos and pictures, can be something you can do in the settings
photos (home) video (other button) And maybe there's a flip button 😅 So Instagram becomes tik tok. The focus must be in creating content. Ok. Olas allows you to upload only images for the moment and shorts from other Nostr apps. For some reason, I don't hear video audio, maybe some permission to give.
Flotilla, if you connect with nsec.app creates a Nostr connect token from flotilla and enter it in nsec.app, asks for permissions and lists them and goes.
With this test account, I don't follow anyone using it to feed on Coracle. The app also suggests people to contact. There is also a space for personal notes. Then there are spaces. And it basically shows you the Relays and here the situation is a little confused. Although I know that there is a space/group called flotilla I am not able to find it, maybe you need the invitation code that is in the link. Also copying it I couldn't enter but the approach is that I think. flotilla link This was the link.
Maybe Hodlbod takes a step back and joins Unanimity. I don't think a step back is a possibility.
Maybe there are updates and they make a specific base workflow Relays based group and then the various branches NIP-29 chachi and 0xchat and the others (Telegram group) Flotilla (discord) It seems like there is a reconciliation at least to converge everyone 😉 "shallow reply hierarchies"
Kohei is also mentioned 🤙 NFC card article An interesting article
nostr:naddr1qvzqqqr4gupzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg3waehxw309ahx7um5wgh8w6twv5hsqzr9v3jx2wpn8qmsz4edqe
Marketplace on Nostr Help to test yojimble
nostr:nevent1qvzqqqqqqypzphn4avwh5e38spagmlc0kvmulnccnelf479tvg5ldz8kv3cscvq5qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qpqw7f0ja820er7d2jfa4vq9upelw88ejha6hcvj5gxt7gqnz646r8ql2a2cp
That's all!!
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ a012dc82:6458a70d
2024-11-23 08:04:48
@ a012dc82:6458a70d
2024-11-23 08:04:48Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
If you want to invest in the cryptocurrency market, you have many options, including Bitcoin, Ethereum, and several altcoins. But there are also backdoors into the cryptosphere that may be used to learn more. If you want to invest in cryptocurrency but don't want to actually purchase any, here's what you need to know:
KEY TAKEAWAYS
-
Investing in cryptocurrency presents some new and unusual challenges.
-
Due to the high degree of volatility associated with cryptocurrency investments, some people opt to put their money into more tried and true investment vehicles instead.
-
Many mutual funds and stocks are available that are tied to the bitcoin industry, allowing you to indirectly participate in the market.
What Is Indirect Crypto Investing?
You may still get cryptocurrency without signing up for a cryptocurrency exchange account. Indirect bitcoin investments allow you to acquire exposure to the market without actually purchasing any cryptocurrency. Stocks, mutual funds, and exchange-traded funds are some examples of the conventional investment vehicles that are used for indirect investing (ETFs).
There are, once again, both benefits and drawbacks to think about, such as safety, costs, and the possibility of losses. You should think carefully about whether or not an indirect investment is worth it to you when considering whether or not to acquire cryptocurrencies via a third party.
Crypto ETFs and Mutual Funds
The first alternative to acquiring cryptocurrency outright is via investment funds. Grayscale Bitcoin Trust is one of the first significant participants in this offering (GBTC). It has some of the same features as an ETF but is treated quite differently under the law. But if you invest in GBTC via your brokerage account, you'll get the same outcome as if you bought a Bitcoin fund. The value of the investment will rise and fall in tandem with the fluctuating Bitcoin market.
The high expenditure ratio of 2% is a significant drawback of grayscale. Simply put, they add 2% to the purchase price of Bitcoin to cover the cost of keeping it in a wallet under your name. Avoid the 2% maintenance cost by doing it on your own.
Besides the aforementioned Bitwise 10 Crypto Index Fund, there are also the ProShares Bitcoin Strategy ETF (BITO), the Valkyrie Bitcoin Strategy ETF (BTF), the VanEck Bitcoin Strategy ETF (XBTF), the Global X Blockchain and Bitcoin Strategy ETF (BITS), and the VanEck Global X Bitcoin Index Fund (GBXB) (BITW). It is important to read the prospectus and understand the fund's fees and underlying investments since they might vary widely.
Cryptocurrency and Blockchain Stocks
Stocks of firms involved in the blockchain sector or those that invest in or hold bitcoin may provide investors with exposure to the cryptocurrency market.
Companies in the cryptocurrency business provide a variety of services, including mining, software development, and more. Bitfarms (BITF), HIVE (HIVE), Canaan (CAN), and Riot Blockchain (RIOT) are just a few of the stocks availablet, and more. Bitfarms (BITF), HIVE (HIVE), Canaan (CAN), and Riot Blockchain (RIOT) are just a few of the stocks available. The cryptocurrency exchange and stock market platform Coinbase (COIN) is a major player in the industry.
In the event of a general downward trend in cryptocurrency values, many cryptocurrency stocks tend to perform poorly as well. If you have any worries about your investing choices or goals, you should see a trustworthy financial adviser.
Bonus Tip: Credit Card Rewards
Finally, credit card rewards are a great way to add to your bitcoin holdings without having to part with any hard dollars. You can use your credit card as you like—swipe, touch, dip, click—and earn cryptocurrency in the process with a few different cards.
The BlockFi Rewards Visa Signature card, the Gemini Credit Card, and the Upgrade Bitcoin Rewards Visa card are all exceptional options for individual bitcoin holders. Both the Crypto.com and Coinbase exchanges provide rewards cards.
The personal SoFi credit card and the Venmo credit card are two examples of cards that provide you with a wide range of redemption possibilities, including bitcoin. Earning cryptocurrency as a credit card reward is like investing in cryptocurrency without really purchasing any. No matter what happens to the price of cryptocurrency, you still stand to gain since you didn't have to spend any money to get it.
What is Cryptocurrency?
Secure transactions may be made in what is known as "cryptocurrency," a digital or virtual currency established through the use of cryptographic procedures. There is no government or bank in charge of it, as there is with fiat currency.
What is Bitcoin?
Bitcoin, the first successful decentralized cryptocurrency, was founded in 2008 by an unknown person or group of people named Satoshi Nakamoto. It's a kind of digital currency that can be safely transferred from one user to another through the web.
Who is Satoshi Nakamoto?
The person or individuals behind the creation of the Bitcoin protocol and the first cryptocurrency in 2008 are often referred to by the alias "Satoshi Nakamoto." Nakamoto was active in the bitcoin and blockchain communities until about 2010.
Conclusion
Cryptocurrencies have been called "the next big thing" in technology. Those who want to get in on the new technology without taking undue risks might consider investing indirectly in crypto. This will increase the portfolio's diversification and help spread out the associated risk.
FAQ
Do I need a cryptocurrency wallet to make an investment? To protect your bitcoin holdings, you need to get a wallet. However, if you want to test the waters before diving in headfirst, platforms like PayPal and Robinhood make it easy to acquire and store small amounts of cryptocurrency. However, the private key to these wallets is held securely by the wallet provider.
To what cryptocurrency does one have the least amount of difficulty allocating funds? Ethereum is seen as a good cryptocurrency to invest in by many, particularly those just starting out in the industry. Since the value of Ethereum's currency (ETH) goes up with the number of active nodes on the network, we can assume that the price of ETH will go up as more decentralized applications (dApps) and other projects are built and launched on Ethereum.
In what timeframe can a single bitcoin be mined? One bitcoin may be mined in around 10 minutes with the right gear and software, but this setup can be expensive and is only available to a select group of people. The average user can mine a bitcoin in 30 days, which is both common and reasonable.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ f8a5df57:b7a58cd4
2024-11-23 07:43:46
@ f8a5df57:b7a58cd4
2024-11-23 07:43:46Содержание сюжета:
Вчера в Москве состоялась долгожданная премьера нового фильма известного режиссера Дмитрия Макракова «Все или ничего». Мероприятие прошло в одном из самых престижных кинотеатров столицы и собрало множество звезд отечественного кино, а также поклонников творчества режиссера.
«Все или ничего» — это драмеди, рассказывающая о сложных взаимоотношениях между друзьями, которые решают рискнуть всем ради исполнения своей мечты. Фильм затрагивает темы дружбы, предательства и поиска себя в современном мире. Главные роли исполнили популярные актеры, которые уже успели завоевать сердца зрителей.
Реакция зрителей. После просмотра зрители были в восторге от глубины сюжета и мастерства актерской игры. Многие отметили, что фильм заставляет задуматься о важности выбора и последствиях, которые он может иметь. В социальных сетях пользователи активно делятся своими впечатлениями, подчеркивая эмоциональную насыщенность картины.
На пресс-конференции после премьеры Дмитрий Макраков отметил, что создание этого фильма стало для него настоящим вызовом. «Я хотел показать, как иногда мы готовы рисковать всем ради своих мечтаний, но не всегда понимаем, к каким последствиям это может привести», — заявил он.
Премьера «Все или ничего» стала ярким событием в культурной жизни Москвы и уже привлекла внимание критиков и зрителей. Фильм обещает стать одним из главных кинопроектов сезона и, возможно, получит признание на международных фестивалях. Не упустите возможность увидеть эту увлекательную историю на большом экране!
Автор: Рината Ситникова
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ ddf03aca:5cb3bbbe
2024-11-20 22:34:52
@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions.
Subscriptions with Cashu
One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that?
However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this:
-
Overpaying:
To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. -
Full Interactivity:
In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends.
Enter Locking Scripts
One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone.
A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key.
To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token.
With these tools, we can now create non-interactive payment streams!
One Missing Piece…
Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams.
The Grand Finale: Payment Streams
Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender.
Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.
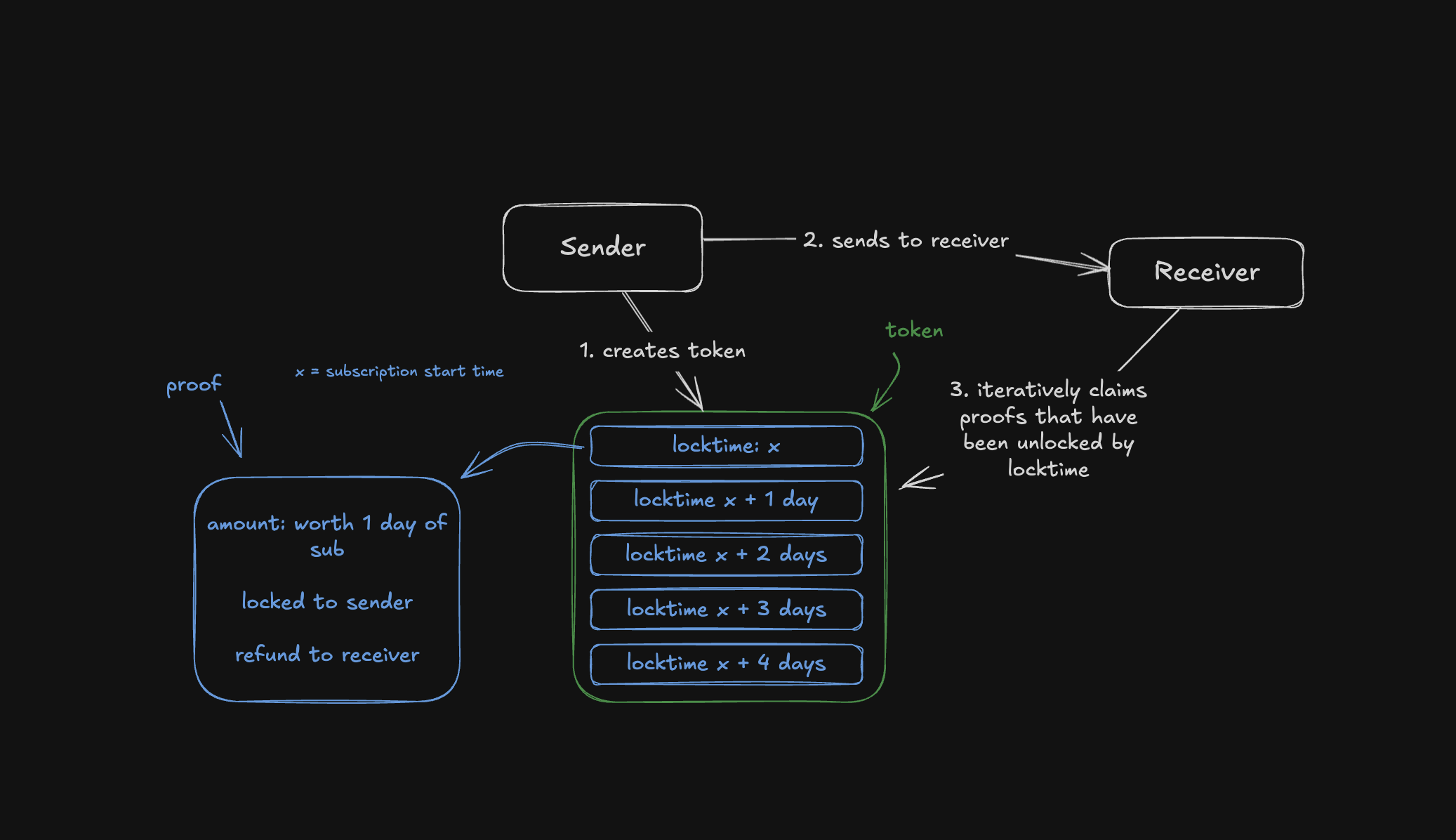
Example: Renting a VPS
Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work:
- Construct a token worth 7,000 sats to cover the entire week.
- Divide the token into 7 proofs, each worth 1,000 sats.
- Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key.
- The first proof has a locktime of
now. - The second proof has a locktime of
now + 1 day. - The third proof has a locktime of
now + 2 days, and so on.
When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on.
At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver.
With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds.
Thank you for reading. Make sure to leave a nut if you enjoyed this :)
-
-
 @ 8cd9d25d:69e9894d
2024-11-23 04:45:03
@ 8cd9d25d:69e9894d
2024-11-23 04:45:03Chef's notes
Note that youtube recipe is asking for 1tablespoon of salt, which is waaaaaay too much. Recipe works fine with a teaspoon,, but your mileage may vary. Play around with it.
You don't need to prove modern packet yeasts in my experience... just yolo it.
If you want an extra crispy crust, add a second baking pan to the base of the oven as you pre-heat. Then once you've placed the dough in, to the oven, take some boiling water and pour into the second baking tray. This gives you a steam oven on a budget :)
Details
- ⏲️ Prep time: 15min (not including time for dough rises)
- 🍳 Cook time: 30mins
- 🍽️ Servings: 4-5
Ingredients
- 500 grams wholemeal spelt flour
- 1 packet baker's yeast (10grams)
- 350 ml lukewarm water
- 350 ml lukewarm water
- 1 teaspoon salt 🧂
Directions
- Preheat your oven to Preheat oven to 430°F and put a baking tray in at the same time to heat up.
- Add all ingredients to a bowl (best to use a stand mixer to save time, but you can do by hand too. Mix and knead until the dough comes together. After about 5 mins you should have a moist dough that doesn't stick to your hands... if it is a bit sticky, just add a bit more flour (different flours like differenent amounts of water)... If too dry, add a bit more water... etc.
- Remove dough from bowl & form into a ball (smooth on top, never mind if not perfectly smooth on its base). Put back in a bowl and cover with a damp cloth. Allow to rest for 30mins/1hr until dough has roughly doubled in size. Time will depend on the ambient temp where you are. In the tropics, 30mins is just fine.
- Take risen dough out of bowl and put on a floured surface and press the gas out of it... flatten the dough with your hands, and then fold each edge in until you have a rectangle (video makes this bit clear). Then roll the rectangle up into a cylinder. This gives you a nice tight dough for baking. Pinch the ends of the cylinder to seal the dough.
- Place dough onto a baking sheet/ piece of parchment paper etc... cover with damp towlel and let rise for 15/30mins
- Score the risen dough (a razer blade, clean box cutter, or serrated knife works well) , this lets steam escape from the loaf as it bakes without slpititng it in ways you wouldn't like.
- Take your hot baking tray out of the over and transfer your dough onto it. Put into oven.
- Bake at 430°F (220°C) for 15mins, then reduce oven temp to 350°F (180°C) for the final 15mins. Total bake time 30mins.
- Remove from oven and allow to cool for 20-30mins.
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 72db3731:6c79f5a6
2024-11-23 02:00:11
@ 72db3731:6c79f5a6
2024-11-23 02:00:11I have to imagine a water stream falling on a rock, even if sometimes there is drought on the river or some object are blocking the water stream, the rock will eventually break.
There is no perfection, aim for perfection, but know that it does not exist, there is no perfect routine, there is no perfect life.
But I'm aiming for a perfect life anyway.
Remember, your life will have countless imperfections and you'll make several errors.
But don't give up.
I haven't done much.
Started studying English in Duolingo, looking for a complete lesson for each language, minimum.
2024-11-22 23:00 NoFap, NoSoda, NoAlcohol and NoReels.
Installed leechblock extension, removed any reddit clients on the phone and removed instagram.
-
 @ 5af07946:98fca8c4
2024-11-23 00:52:05
@ 5af07946:98fca8c4
2024-11-23 00:52:05US natives think $USD is a currency - for the rest of the world it is an asset . Just like #bitcoin.
The way Microstrategy accumulates bitcoin , all central banks collect US debt - a fancier word for US Dollar. As of April 2024, the five countries that hold the most US debt are:
- Japan: $1.1 trillion
- China: $749.0 billion
- United Kingdom: $690.2 billion
- Luxembourg: $373.5 billion
- Canada: $328.7 billion
Compare this global stake to 15 odd billions that #Microstrategy has in bitcoin. The way Microstrategy wants to protect bitcoin network , central banks want to protect #USD. Which means they all resist any change in capital structure. Not even bitcoin.
Thus the peaceful path for bitcoin is to become the reserve strategic asset for United States and thus for rest of the world. The other path is literally fighting governments worldwide ..
There is however one more opportunity - that is if people all around world adopt #SATs - which is why success of #nostr is so critical ! And other lightning apps - #LNCalendar , #StackerNews , #Fountain
In reality , both these things can happen simultaneously - that would be real freedom - Top down and Bottom up.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 63d59db8:be170f6f
2024-11-23 00:41:02
@ 63d59db8:be170f6f
2024-11-23 00:41:02This ongoing series "Better Together" features surreal settings I have been creating by combining two different photographs that I've shot. I enjoy the challenge of creating something completely new out of two photos that otherwise have nothing to do with each other. There is no other editing or manipulation done to these images besides connecting them at one meeting line.





Visit Pat's website to see more
NOICE Magazine’s Visual Expression Awards are designed to spotlight creativity in photography, welcoming both emerging and seasoned artists. Each submission is now part of our dynamic prize pool, currently at $120 / 121,956 sats and growing with each new entry, with immediate exposure opportunities on our website and social channels.
Choose a Standard or Premium submission to suit your needs and have your work thoughtfully reviewed for form, originality, and impact. A quarterly cash prize from the dynamic pool goes to one standout entry, helping fund your next creative project. Deadline: December 31, 2024.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 97c70a44:ad98e322
2024-11-18 17:57:17
@ 97c70a44:ad98e322
2024-11-18 17:57:17So I have this cool new product, which for about two weeks has been ready to release, if I could just solve one thing. I have recently moved away from storing user keys in my apps due to the ease with which they could (and have) been put at risk. In doing so, I've discovered that despite its downsides, pasting your nsec into an app is a pretty straightforward operation which even non-technical people can pull off. In contrast, pretty much no other key management solution is.
Just to state the obvious, and to kick off this survey of nostr key management options, let me just state that asking users to paste their nsec into your app is a bad idea. However good your intentions, this opens your users up to all kinds of attack vectors, including clipboard hijacking attacks, exposing keys to insecure communication channels, exposing keys to many different apps, supply chain attacks, XSS attacks, and yes, bugs that cause your software to send keys to analytics or error reporting backends.
The era of nsec-pasting is over.
I've committed to embracing the pain and removing nsec login from Coracle, and I encourage other devs to do the same. The sooner we treat key management with the urgency it deserves, the sooner we can come up with a secure and convenient key management solution.
As an aside,
ncryptsecis a great innovation for securely transporting keys, but it still doesn't protect against exposure to apps that need to use keys. It has its place though; in fact I'm of the opinion thatnsecand seed words should be deprecated, and support for them should be removed. Giving friendly names and human-readable representations to data that is essentially private is a really bad idea (unless you're memorizing your key). But I digress.Signer Comparisons
Let's go through a few existing options for key management, and compare their relative merits. I've tried to list them in the order they appeared on the scene, which also helps to clarify the logic of how signers have evolved. Throughout, I will be focusing on what kinds of user experience each approach unlocks for non-technical users, since my goal is to build products that work for regular people.
Extension Signers
The first signer application (that I know of) was nos2x, by fiatjaf. As I understand it, this was a proof-of-concept of how users might protect their keys without releasing custody of them. And it works really well! In fact, even though there have been many forks and imitators, I still use nos2x when using nostr on my desktop browser.
Extension signers offer a great user experience, along a narrow happy path. Setting up a browser extension is a relatively familiar process for normal users, and once it's done you don't really have to think about it. In theory, extensions can also include their own onboarding process and key backup strategies as well, allowing users to get started in a single place. Plus, there's very little latency involved in making calls to the signer extension.
This positive experience breaks down quickly though once a user wants to use a desktop or mobile application. When this happens, users have to start over essentially from scratch. Nothing they did to set up the extension helps them move to another signer application.
While it's technically possible to use extension signers on mobile via e.g. the Kiwi browser, this doesn't work for native apps or apps installed as PWAs. Instead, you either have to revert to pasting keys, or use some other solution.
One slight permutation of extension signers is browser signers, like Spring. Instead of adding a signer to your browser, Spring allows you to install a browser that holds your keys and allows you to use any nostr web application. But this has all the same basic limitations that extension signers do.
Hardware Signers
Hardware signers came around shortly after extension signers. I'm not going to spend much time talking about them here, because although they're about as far along the spectrum towards security as you can go, they're also not very convenient. Non-technical users aren't going to onboard by buying (or building) a device which they have to connect to their desktop via USB whenever they want to sign a message. Hardware signers have their place, but onboarding isn't it.
The only hardware signer I'm aware of (although I'm sure I've heard of others) is from LNBits, and is usually used via a browser extension like horse. This of course means that it has all the same limitations that browser extensions have, and then some (although mobile and desktop apps would likely be able to find a way to talk directly to the signer).
Hosted Signers
Remote signers (aka "bunkers") use the Nostr Connect protocol (also known as NIP 46) for remote signing.
Hosted signers in particular are one example of a NIP 46 remote signer, which lives on "somebody else's computer". Because they use a legacy web architecture, they can be built to be very familiar and convenient to users. It's trivial to build a hosted signer that offers email/password login along with 2FA, password resets, session revokation, the whole shebang. But they have one fatal flaw, which is that they are custodial. This means that not only do users have to relinquish exclusive control over their keys, but hosted signers also can become a target for hackers.
Desktop Signers
Several projects exist which allow users to run their own bunker, on their own hardware. These include nostr clients like Gossip, as well as command-line utilities like nak. This approach is mostly an improvement over extension signers, because it widens the scope of applications that can conveniently access the signer from those that run in the browser to those that run on the desktop computer the signer lives on. The downside is that they have to communicate via relays, which either introduces latency or requires an additional component to be running locally.
While it's technically possible to use desktop signers to log in on other computers or mobile apps, I don't think that's going to be very practical for most people. Mobile apps by definition are more portable than regular computers. Anyone who wants to access their nostr account on more than one device will have to either set up separate solutions, or go with another kind of remote signer. This isn't a huge obstacle for people highly invested in nostr, but it's a significant amount of friction for a new user.
Mobile Signers
Mobile signers solve the problem introduced by desktop signers of not always having access to your signer (or of your signer not having access to you, due to being powered down or disconnected from the internet). Mobile devices are generally more available than desktop devices, and also have better push notifications. This means that users can approve signer requests from any device as easily as tapping a notification.
Mobile signers on Android can also upgrade their UX by taking advantage of NIP 55 to avoid the round trip to relays, reducing latency and making it possible to sign things offline. Amber has been a pioneer in this area, and other projects like Nostrum and Alby's nostr-signer have been prototyped.
To date, there unfortunately haven't been any signer applications released for iOS, which leaves the mobile signer story incomplete. In my opinion, this is probably the most promising solution for end users, although it's currently under-developed.
Web Signers
One interesting alternative that combines the benefits of hosted, desktop, and mobile wallets is nsec.app. This is a web application frontend which keeps keys in the browser, so that they are never shared with a third party. Using web push notifications and a healthy sprinkle of black magic, nsec.app is able to respond to signer requests by opening itself in a browser window.
This works generally pretty well for desktop web applications, less well on android, still less well for android PWAs, and (to my understanding) not at all on iOS. Artur from nostr.band is working on these problems using a variety of approaches, one of which is embedding nsec.app in an iframe and communicating using
postMessage.This approach also makes it possible to sync keys between your phone and desktop, simulating a hosted UX by making them accessible from either location by signing in to nsec.app. This is done by encrypting user keys and storing them on the nsec.app server. In theory this should be secure, but it's something to consider.
I'm cautiously optimistic about this approach. If successful, it would enable a single brand to exist on every platform, which is important to reduce unnecessary configuration and cognitive overhead for users.
Multisig Signers
Another experimental approach is multi-sig. Promenade is a project by fiatjaf exploring this possibility. This would allow users to split their keys across different custodians and require all (or some majority of them) to approve an event signature before it would be valid.
The downsides of this are an increase in complexity (more moving parts for users to deal with) and latency (more parties to coordinate with to sign events). I'm also not clear on whether encryption is possible using multi-signature keys. If not, that would preclude not only existing direct messages (which will hopefully end up on MLS eventually anyway), but also things like private lists, mutes, and application settings. I think multi-signature signers are promising, but are definitely a long-term project.
Self-Hosted Signers
Coming nearly full circle, self-hosted signers are a special case of hosted signers, but, you know, self-hosted. These signers might live on a home server like a Start9 and be accessible for signer request approvals via tor, or they might live on a server run by the user (or an Uncle Jim). This would be an extremely convenient approach for anyone willing to deal with the complexities of hosting the infrastructure.
A good candidate for NIP 46 support might be AlbyHub, which is already one of the easiest self-hosted wallets to set up and use. Adding signer suppport to AlbyHub would allow users to have their wallet and nostr keys stored in the same place, and accessible anywhere either via the web interface or via AlbyGo.
Omniplatform Signers
This leads me to, finally, "omniplatform" signers. This isn't really a new architecture, but a combination of several. User choice is great, but nostr has a very tight complexity budget when onboarding new users. If a brand can manage to get new users set up with a very simple but sub-optimal solution, then grow them into a more complete integration into the nostr ecosystem, that would be a huge win.
I think Alby has a great shot at doing this, if it's something they want to prioritize. Bitwarden would also be a great candidate, since they already have apps on every platform, as well as a self-hosted option (Vaultwarden). If users could start with a mobile app, and incrementally set up a browser extension, self-hosted vault, and hardware signer as needed, that I think would be an ideal path.
Nostr Connect: broken, but promising
If you can't tell from the above comparison, I'm partial to NIP 46 as the best, most flexible way to build high-quality user experiences. Remote key management means a reduction in moving keys, hosting keys, and software installation and administration. If we can get users to the point where their keys live in only two places (their password manager and their signer), we'll be doing good.
There are however many ways to implement NIP 46. Implementing all of them in a single client (or signer) would be burdensome for developers, and introduce a lot of UI complexity to users. Here's a quick survey of flows that currently exist.
Signer -> Client
The simplest way to connect a client and a bunker is for a user to explicitly authorize the connection by copying a
bunker://URL from their signer application to their client. This allows the bunker to generate and validate a secret embedded in the URL without the client having to do anything other than pass it along in the initialconnectrequest.This is a great UX for people who know what they're doing, but isn't at all friendly to newcomers. Someone signing in for the first time isn't going to know what a bunker link is, and even if they do they're immediately confronted with the problem of picking a signer, setting it up, and finding out where in that app they can obtain a bunker link. This can be marginally smoothed out using things like protocol handlers and QR codes, but these won't apply in all (or even most) cases.
Client -> Signer
The reverse flow is similar. This relies on the user to explicitly authorize the connection by copying a
nostrconnect://url from the client into the signer app. In technical terms, this requires one fewer step, since in NIP 46 the connection is always initiated by the client. In this case, the pasting of the URL replaces theconnectrequest. The client listens for a response containing a client-generated secret embedded in thenostrconnect://url. This step isn't currently supported by all signer apps, some of which return anackinstead. This can result in session hijacking, where an attacker can intercept signing requests (although they can't do anything that would require the user's key, like decrypting messages).While at first glance
nostrconnectseems functionally identical tobunkerlinks, the UX has the potential to be much better. The reason for this has to do with how people use which devices, and where a client or signer application is most likely to be run. This requires making some assumptions, but in my mind the most common scenario is that a user will want to host their signer on their phone, since that is the device that is most universally available for authorizations (apart from an always-online hosted signer on the open internet). In other words, users generally have their phones with them when they're using their computer, but often don't have a desktop available when using their phone. This idea is validated by (for example) the prevalence of SMS-based 2FA, which assumes the presence of a phone.Assuming the signer is on the user's phone, QR-scan flows for client authorization make a lot more sense if the client is the one generating the link, since they can simply scan a code generated on another device with their camera, or copy/paste or use a protocol handler for a client on the same device. In contrast, when using a
bunkerlink users might find themselves in the awkward position of having to copy a link from their phone to their desktop. Whether this is done via QR code or by sending yourself a link via DM/text/email, it's an awkward flow most people aren't really prepared for.Auto-Connect
Some enhancements have been made to the bunker flow which allow clients to send an initial
connectrequest without asking the user to copy links between apps. These allow clients to do away with opaque magic strings entirely and provide the idealized "just one click" flow. However, after trying to make this flow work over the course of a couple weeks, I've come to the opinion that the additional complexity involved in automating the flow just isn't worth it.There are a few variants of this "auto-connect" flow:
- Signer NIP-05: Signers can register a NIP 05 address for a user's pubkey on their domain, allowing users to enter their address rather than their pubkey on login. Unfortunately, this address has no relation to their actual NIP 05 address, which can result in a lot of confusion.
- User NIP-05: To solve this problem, fiatjaf has proposed a new version which allows users to enter their own NIP 05 in at login instead of the one provided by the signer. The client would then look up the user's
10046event and follow the signer pubkey listed there. - Nostrconnect handler: Signers may publish a NIP 89 handler which includes a handler url that clients can send
nostrconnecturls to. This isn't currently specified anywhere, but it is supported by nsec.app. This bypasses the NIP 05 address requirement entirely, allowing users to simply pick a signer and click a button.
Each of these flows have their own strengths and weaknesses, but all of them share a dependency on some external source of truth for routing a user to the correct bunker.
In the first case, this is done by remembering the NIP 05 address assigned by the signer, which relies on DNS and on users to not forget which address they're using.
In the second case, this is done by relying on the user having done a significant amount of configuration (setting up a NIP 05, adding it to their kind 0, and having published a
10046event) which may or may not exist. This forces clients to gracefully degrade to some alternative login method anyway, and adds UX friction since users have to choose which interface will work for them.The final method bypasses the need for users to remember their NIP 05 address, but it does require either the client or the user to select a trusted signer. If poorly implemented, this could result in users choosing an untrustworthy signer on signup (risking their keys), or the wrong signer on login resulting in a broken session.
For all these reasons, I've opted to go with the vanilla bunker/nostrconnect flow, which allows me to display a simple interface to users. Presenting a QR code without comment assumes that users know what to do with it, but the benefit is that it makes explicit the signer selection step which the auto-connect flows try to paper over. This is actually a good thing, because instead of using heuristics like addresses or lists of signers presented by a client to make the decision, users can choose based on which app they actually have installed, which is a richer mnemonic device.
Making NIP 46 Work
The bottom line here is that while NIP 46 is the best baseline for signer support, it doesn't currently work very well at all. There are a variety of reasons for this:
- The specification itself isn't clear, and is constantly changing. This leads to incompatibilities between apps and signers (or explosive complexity in trying to handle every case).
- Extensions to the basic bunker flow (both in terms of signer implementation and signer discovery) are worth researching, but each one creates another dimension of possible incompatibility. Signers will be incentivized to support every possible login flow, creating complexity for users and increasing attack surface area. Clients will have to implement fallbacks to their preferred signup flows, again resulting in UX complexity.
- Clients don't currently deal well with latency. In order for NIP 46 to work smoothly, clients will have to implement better loading, debouncing, optimistic updates, publish status, and "undo". There are downsides to this, but many of these features endu up being built by mature software products anyway, so supporting these patterns may actually improve rather than degrade UX.
- There's currently no easy and secure way for users to store keys in a single signer which they can access anywhere. This means that users have to set up multiple bunkers depending where they're sitting, or resort to alternative login methods like NIP 07 or 55. These are great upgrades, since they reduce latency and bandwidth use, but shouldn't be required for new users to learn.
- There's no unified experience across platforms. If a user signs up on their desktop, how do they safely transfer their keys to their Android signer app? If they're given seed words, how can they import them as an nsec? Consensus on best practices would be an improvement, but I think only a unified UX across platforms for a single signer can really solve this.
- As nice as it might be to bypass app stores and built-in push notifications, shunning traditional platforms drastically increases the friction for users. To my knowledge, no signer app currently exists in traditional app stores, or supports built-in push notifications. If we want nostr to be accessible to non-technical folks, we can't ask them to start by downloading Obtanium or zap.store and a UnifiedPush distributor for their platform.
As I mentioned above, I don't think NIP 46 will ever be the only solution for signers. But I do think it's a great baseline on which to build a kind of "progressive enhancement" approach. For example, clients should support at least nostrconnect/bunker links, and encourage users once they've logged in to upgrade to NIP 55 or NIP 07 signers. Signers should exist in the mainstream app store and use native push notifications, with an option to install elsewhere or opt-in to UnifiedPush.
The goal here is to balance user experience and security. The number one rule for this is to reduce attack vectors for obtaining user keys. This points to (ideally) a single non-custodial signer, easily accessible to the user, and a simple protocol for using that signer from any app. Progressive enhancement is fine, but we should always be able to fall back to this baseline.
-
 @ 2dd9250b:6e928072
2024-11-22 23:32:03
@ 2dd9250b:6e928072
2024-11-22 23:32:03O Calvinismo, como Cosmovisão diverge do Conservadorismo Tradicionalista (postulado por Burke, Scruton, Jordan Peterson e outros). Isso tem se demonstrado de forma evidente hoje ao passo que quando se fala em Conservadorismo, os comentaristas mais lembrados são Olavo de Carvalho, Guilherme Freire e os Hosts do Brasil Paralelo.
Portanto, é inegável que escritores, apresentadores e donos de Canais ditos Conservadores, na verdade são Católicos Romanos falando para um público Católico Romano. E quando citam os "Protestantes", ninguém sabe ao certo, de quem eles estão falando. Uma vez que nós não somos meros Evangélicos, somos Reformados.
Historicamente, o grupo que mais se opôs aos Católicos Romanos foram os Calvinistas Puritanos no Século XVII. As Confissões Reformadas (de Westminster de 1647 e a de Londres de 1689) trazem um teor anti-papista na maioria de seus capítulos e artigos de fé.
Isso nos mostra que há um real conflito, ou uma disputa, concernente a quem pertence o termo "Conservador" no Brasil. Uma vez que, para um Católico Romano Tradicionalista, Evangélicos são Esquerdistas/Satanistas indo para o inferno junto com Lutero e Calvino e todo o estrago que o Progressismo vem fazendo no Mundo, tem sua causa na Secularização do Ocidente que se originou na Reforma de Lutero.
Em contrapartida, Evangélicos em geral, são mais amistosos, defendendo uma certa união com os Romanistas para frear o avanço de Pautas ideológicas/identitárias que vão de encontro aos costumes, valores, fé e tradição Cristãos. Mas a que preço? E mais importante: Essa união (ou apropriação do termo Conservador) com o Romanistas tem algum fundamento Bíblico?
Existem vários aspectos que podemos analisar para chegarmos a uma resposta satisfatória. Mas irei trazer aqui apenas um aspecto. O Casamento. É inegável para todo mundo que se diz Conservador, ou que está próximo disso, que o mundo pós - moderno tenta enfraquecer/ridicularizar o Homem e enaltecer/empoderar a Mulher (exemplo disso é uma noiva se negando a dizer “prometo ser submissa” em uma Cerimônia de Casamento, deixando o noivo e o padre desconcertados) . Mas é só analisarmos mais de perto a definição de casamento no Conservadorismo e o que ele representa, para entendemos que o Conservador (ou seja, Católico Romano) não parte do mesmo ponto de partida do Cristão Reformado para argumentar a favor do casamento tradicional.
Para nós Cristãos Reformados o Casamento é um Pacto. Nesse sentido, tem mais valor do que um mero acordo ou Contrato entre as partes porque é um símbolo. A Bíblia usa a ilustração de Cristo como Noivo e a igreja como noiva (Mt 25:1-13; Ef 5:32) por isso o marido assume a missão de 'proteger e cultivar’¹ sua esposa e a esposa se submete ao marido. Submissão na Bíblia significa se submeter a mesma missão. No caso, a mulher ajuda o marido nessa missão. Logo há uma parceria onde um complementa o outro, cada um na sua função (Efésios 5:25-31).
Além disso, O matrimônio foi ordenado para o mútuo auxílio de marido e mulher, para a propagação da raça humana por uma sucessão legítima e da Igreja por uma semente santa, e para impedir a impureza. (Gn. 2:18, e 9:1; Ml.2:15; I Co. 7:2,9). ²
Portanto , a compreensão Pactual Bíblica do casamento supera qualquer visão política/social Tradicionalista como o Conservadorismo.³
No Conservadorismo há apenas um clamor por preservação dos costumes judaico/cristãos fundamentais para civilização ocidental, mas como isso será feito, não é muito claro. Por isso o conservador brasileiro ganhou esse estereótipo de hipócrita. A favor do casamento tradicional, sendo que já está no 3°,4° casamento. Contra o Lobby gay , drogas, ideologia de gênero etc, mas a favor do aumento do Estado para frear essas pautas identitárias/progressistas ao invés de pregar, crendo que o Evangelho de Jesus transforma vidas. E vidas transformadas pelo Espírito Santo muda toda uma sociedade. Portanto, o Conservador zela pela preservação de costumes e virtudes, apenas exteriormente, levando em consideração conservar o Bem e frear o Mal, em favor de uma mudança gradual da sociedade.
Por isso eu não me considero Conservador (pelo menos não aos moldes do Conservadorismo Tradicionalista dos Papistas). Costumes e valores devem ser observados não por imposição de Leis Juspositivistas, endossando a interferência do Estado na vida privada dos cidadãos, mas pela manifestação do Poder do Evangelho na vida de pessoas regeneradas pelo Espírito Santo que, junto da Igreja Universal de Cristo, testemunham e agem conforme a Lei do Senhor.
1."Cultivar e Guardar" são duas palavras que resumem o mandamento de Deus para o Homem. No contexto de Gênesis 2:15, Deus ordenou a Adão proteger e cultivar tudo que estava no jardim do Edem, incluindo sua mulher, Eva.
2.CFW Cap.24. Artigo II.
3.Esse texto é totalmente de minha autoria e estava há um bom tempo querendo escrever sobre isso.
-
 @ 5afdec5b:2d631be1
2024-11-18 10:23:46
@ 5afdec5b:2d631be1
2024-11-18 10:23:46In August 2024, Lendasat introduced a novel loan protocol, designed to address the inherent risks of custodial lending platforms. By leveraging Bitcoin's self-custodial nature, the Lendasat protocol allows borrowers to secure loans without transferring ownership of their assets. If you haven’t had a chance to explore our whitepaper, this blog post will guide you through the protocol and its advantages.
We’ll explore how Lendasat works, the technology behind it, and why it stands out as a solution for Bitcoin-collateralized lending. Diagrams will help break down each stage of the protocol, so you can understand the mechanisms step-by-step.
Bitcoin Lending, the Right Way
Bitcoin, as a decentralized and self-custodial asset, offers users a chance to be their own bank. However, the current landscape for Bitcoin-backed loans often forces users to hand over their Bitcoin to custodians—introducing a set of serious risks:
- Custodian risk: Entrusting a third party with your Bitcoin exposes you to theft, mismanagement, or outright fraud.
- Opaqueness: Traditional platforms don’t offer transparency on how assets are handled.
- Regulatory risk: Centralized custodians are vulnerable to regulatory changes that may lead to asset freezing or seizure.
Lendasat eliminates these concerns by enabling escrow-less lending. Borrowers retain control of their Bitcoin, using Discreet Log Contracts (DLCs) and Hash Time-Locked Contracts (HTLCs) to govern loan agreements without middlemen. With these cryptographic tools, Lendasat removes the need for trust in centralized entities, offering a fully transparent and secure lending process.
How Lendasat Works
The protocol operates between two parties: Bob (the borrower) and Lydia (the lender). Bob wishes to borrow stablecoins, locking his Bitcoin as collateral, while Lydia provides the loan principal in stablecoins, looking to earn interest.
Let’s dive into how the protocol works, step by step.
1. Opening the Loan
The loan process starts with both parties locking assets in cryptographically secured contracts.
1.1 Secret Generation
- Bob generates a collateral secret,
b. - Lydia generates a loan secret,
l.
1.2 Bob Locks Bitcoin Collateral
Bob locks his Bitcoin in a Discreet Log Contract (DLC). The DLC involves an oblivious oracle[^1] that can attest to certain events, such as the price of Bitcoin at loan maturity. If necessary, an oracle attestation can be used at loan maturity to determine how the collateral should be split between Bob and Lydia.
Additionally, Bob locks Lydia's claim on her share of the collateral behind the hash of the collateral secret,
H(b). Lydia will need to knowbto be able to claim her portion of the collateral unilaterally.Key Insight: Unlike traditional escrows, the DLC ensures that Bob retains control of his collateral throughout the loan process. The oracle attestation is only needed to help settle the contract if Bob and Lydia fail to cooperate.
1.3 Lydia Locks the Principal
Lydia, in turn, locks the loan principal in an HTLC on Ethereum (or another smart contract-enabled blockchain[^2] or L2). This HTLC is designed so that Bob can only claim the principal if he reveals
b.- Condition 1: Bob must provide the preimage to
H(b)i.e.b. - Condition 2: If Bob doesn’t act in time, Lydia can recover her funds after a timelock expires.
1.4 Bob Claims the Principal
Bob, now seeing the loan principal is locked up, reveals the secret
bto claim it. This revelation allows Lydia to later claim part of the Bitcoin collateral, but only if Bob defaults on repayment or in the event of a liquidation.2. Cooperative Repayment
If Bob is ready to repay the loan:
- Bob locks the repayment amount in an HTLC on Ethereum, this time using
H(l)as a hash lock. - Lydia claims her repayment, revealing
l. - Bob uses
lto unlock the entirety of his Bitcoin collateral from the DLC.
When Things Go Sideways
Not all loans proceed smoothly. Here’s how Lendasat handles common scenarios when the loan doesn't go as planned.
1. Lender No-Show
What happens if Bob locks up his Bitcoin collateral, but Lydia disappears before providing the principal?
In this case, Bob can unilaterally recover his Bitcoin after an early collateral refund timeout built into the contract. This timeout prevents Bob’s collateral from being stuck indefinitely, a common safeguard in decentralized contracts.
2. Borrower Fails to Claim the Loan
Similarly, if Lydia locks up the principal and Bob does not claim it, both parties are protected by respective timeouts:
- Lydia recovers her principal after a shorter refund timeout on Ethereum.
- Bob gets his Bitcoin collateral back after a longer refund timeout.
These dual timeouts ensure neither party’s assets remain frozen for too long.
3. Unilateral Repayment
If Bob defaults or Lydia doesn’t claim her repayment, the protocol shifts to non-cooperative repayment through the DLC. In this case, the protocol involves an oracle attestation to the Bitcoin price at loan maturity. Lydia receives an amount of Bitcoin collateral equivalent to the loan’s value (plus interest) based on the oracle's attestation. The remaining collateral goes back to Bob.
This mechanism ensures that even in the worst case, Lydia can still recover her funds by liquidating part or all of Bob’s Bitcoin collateral.
Keeping the Loan Alive: Liquidation and Collateral Management
One of the key challenges of lending is managing Loan-to-Value (LTV) ratios. If Bitcoin’s price falls significantly, Lydia might have to liquidate part of the collateral to cover the outstanding loan.
Here’s how Lendasat addresses liquidation:
- If the LTV ratio approaches a critical threshold, Lydia can trigger an oracle-based liquidation of the Bitcoin collateral before loan maturity. This protects the lender from losses due to market volatility.
- Liquidation relies on the same DLC mechanism that handles non-cooperative repayment, ensuring a smooth, automated process for collateral distribution.
The protocol also allows Bob to increase his collateral if necessary, by splicing into the DLC with more funds, keeping the loan in good standing and avoiding liquidation.
Technical Appendix: How HTLCs and DLCs Combine
HTLCs: Enabling Cross-Chain Functionality
An HTLC (Hash Time-Locked Contract) is a foundational building block for cross-chain operations. It allows Bob to lock collateral on one chain (Bitcoin) while simultaneously claiming funds on another (Ethereum). In Lendasat, HTLCs govern the locking and claiming of both loan principal and repayment on the Ethereum chain.
DLCs: Securing Conditional Payouts
A Discreet Log Contract (DLC) is used to ensure that Bob’s Bitcoin collateral is only accessible to Lydia under specific conditions, like a default or liquidation event. The DLC relies on oracles to determine the correct payout based on the Bitcoin price at loan maturity or liquidation.
Combining these two technologies allows Lendasat to create a trustless lending mechanism that spans multiple blockchains.
Conclusion
Lendasat redefines Bitcoin-collateralized lending by eliminating custodial risk and empowering borrowers to retain control of their collateral. Using HTLCs and DLCs, our protocol creates a trustless environment where both lenders and borrowers are protected, even in the event of non-cooperation or default.
For those interested in a deeper technical understanding, please refer to our whitepaper, and stay tuned as we continue to refine the protocol and unlock new possibilities for decentralized finance.
Footnotes
[^1]: When we talk about an oracle, we are not discounting the possibility of using multiple oracles. The DLC protocol does allow for a quorum of oracles to determine the outcome of an event, to distribute the trust.
[^2]: This can be the Bitcoin blockchain itself, via Taproot Assets, RGB or BRC20.
-
 @ 97c70a44:ad98e322
2024-11-22 22:36:31
@ 97c70a44:ad98e322
2024-11-22 22:36:31This week I finally released Flotilla, a discord/slack-like client I've been working on for about three months. This project began as a NIP 29 client, and after 3 PRs, lots of discussion, a podcast, and a partial implementation, I decided to go my own way.
This of course means that I broke compatibility with all the NIP 29 group clients out there, but I did it for good reasons. In this post I hope to explain those reasons, and speculate on how best to move forward with "relay-based" groups on nostr.
To give you some quick context, NIP 29 and my approach to groups (which I'll dub "relays-as-groups" for clarity) are very similar, with a fundamental difference. Both have chat, join requests, group metadata, membership, moderation, etc. However, the basic unit of a NIP 29 group is a random group id string, while the basic unit of a Flotilla group is a relay itself.
I believe this design difference emerged in part because of what we were attempting to build. NIP 29 groups tend to be more telegram-like, where groups function more like chat rooms, and users join each one individually. On flotilla, groups function more like Discord servers, or Slack workspaces, and users join an entire group of chat rooms at once.
"Relays as groups" has four major advantages over "groups hosted by relays".
Decentralization
First, using relays as groups supports decentralization better than hosting user-managed groups on relays.
(To be clear here, I'm not referring to client-managed groups, which is a whole different approach that we've experimented with in the past, both with NIP 72 communities and with NIP 87 encrypted groups. Both NIP 29 and relays-as-groups solve many of the consistency problems associated with attempting to have a linear, synchronous conversation across multiple relays. While both alternatives have a story for migrating or mirroring a group, both rely heavily on the host relay to not censor user messages.)
I know what you're thinking. How can reducing the number of relays improve decentralization? Relays were originally introduced in order to create redundancy and spread trust across many actors, creating censorship resistance. This model was difficult for many bitcoiners to wrap their heads around, because it's a very different kind of decentralization than what a blockchain delivers.
Communities are an essentially different use case from a broadcast network where content is delivered based on author or recipient relay selections. Every message to a community would have to be delivered to all members of the community. Sending each message to all members' personal inbox relays just doesn't make sense; there has to be some other inbox for the community to work off of.
Additionally, online communities almost always have moderators and admins. This is even true of very public, open types of communities, like subreddits. The only type of community that doesn't have moderators is one that emerges naturally from social clustering. And even in that case there is loose consensus about who is in and who isn't, based on the actions/follows/mutes of the participants, whether these clusters are huge or tiny. Socially-emergent groups are served well by chat applications or broadcast networks.
But the subset of online communities that do prefer to confer moderator status on certain members are essentially centralized. In other words, centralization and control is a feature, not a bug.
Now, that doesn't mean there don't need to be considerations around credible exit and removing/adding moderators over time. But the fact is that moderator-led communities are always under the oversight of the moderators at any given time, even if the identity of those moderators changes and their power is limited.
What this implies is that decentralization for moderator-led groups looks very different from decentralization for a broadcast network. There is nothing at all wrong with giving moderators full control over the group's communications (qua the group; DMs and public broadcast content between group members should happen outside the group's infrastructure, just as people also exist outside the communities they are a part of). What is important is that no one has control over groups that they aren't nominally the admin of.
In concrete terms, what this all means is that community moderators should self-host their infrastructure. This is the same principle as motivates self-custody and home servers, but applied to communities. If community leaders manage their own relays, this means that no hosting company or relay admin can de-platform their community. Centralization of network infrastructure in this case aligns with the trust structure of the group.
Applying this to our group dilemma, it's easy to see that NIP 29 groups are more vulnerable to censorship or data harvesting attacks by malicious relay admins, since many unrelated groups might live on a single relay. In contrast, if you treat relays as groups themselves, every group is forced to live on a separate relay, spreading risk across more hosting providers.
Now, this doesn't necessarily mean that many "relays" aren't "virtual relays" managed by the same hosting provider. So I'll admit that even "relay-based" groups don't completely solve this problem. But I think it will tend to nudge community organizers toward thinking about community infrastructure in a more self-sovereign (or community-sovereign) way.
Investment in Relays
While both NIP 29 and relays-as-groups rely heavily on relays to implement the features that support each specification, there's an important difference between the feature sets. In NIP 29, relay support is specific only to groups, and isn't applicable to other use cases. In contrast, every protocol feature added to support the "relays as groups" can be re-purposed for other types of relays.
Take join requests for example. NIP 29's kind
9021events allow users to request access to a group, and that's all. Kind28934join requests on the other hand allow users to request access to relays. Which in the relays-as-groups model means group access, but it also means custom feed access, inbox relay access, maybe even blossom server access. In fact, kind28934was originally proposed at the beginning of this year in order to support a different version of hosted groups, but remains as relevant as it ever was despite iteration on groups.The orthogonality of features added to relays to any specific use case will long-term result in simpler specs, and more interesting relay-based use cases being possible. Join requests are only one example. The same is true of 1984-based moderation, the proposed LIMITS command, AUTH, NIP 11 relay metadata, etc.
We already have web of trust relays, feed relays, archival relays, and many more. Being able to request access to closed versions of these is useful. Being able to signal federation between multiple instances of these, run by different people, is useful. And of course, relay metadata, reports, and LIMITS are self-evidently useful for normal relays, since they pre-date Flotilla.
I've always said that relays are some of the coolest and most under-appreciated parts of nostr. This doesn't mean that we should add every possible feature to them, but features related to data curation and access control fit really well with what relays are good for. For more on the role of relays and what features should be added to them, see my nostrasia talk Functional Relays.
Declarative vs Imperative
A common paradigm in programming is that of declarative vs imperative programming. Imperative programming focuses on "how" to achieve a given result, leaving "what" the code is doing to be inferred by the programmer. Declarative programming instead focuses on the "what", and allows some underlying implementation to solve the how. A good balance between these paradigms (and knowing when to use one over the other) allows programmers to work faster, make fewer mistakes, and produce less code.
Another way to look at this is that a specification should contain as much ambiguity as possible, but without compromising the system attributes the specification is supposed to guarantee. It can get complex when figuring out what attributes are core to the specification, since sometimes the "how" does actually matter a lot.
However, nostr in particular falls pretty far along the "declarative" end of this spectrum because of its decentralized nature. The only person who can say anything with any authority is the person who signs an event. This event is a "declaration", and any effects it has are necessarily up to the relays, clients, and people interpreting the event. However, what others do with an event is an expectation that must be taken into account by the publisher, forming a feedback loop. This dialectic is what creates stability in the protocol.
In more concrete terms, no one can "tell" anyone else what they have to do by publishing an event like you might in a traditional, centralized RPC-type system. Any event whose semantics are a "command" rather than a "fact" or "request" is broken unless the counter party is fully committed to carrying out the command. An example of a "command" scenario on nostr is NIP 46 remote signing, in which the bunker is the agent of the user making the request. If the bunker implementation fails to carry out a valid command initiated by the user, its interpretation of that event is objectively incorrect.
NIP 29 applies this same paradigm to relays, particularly in the area of moderation, membership edits, and group metadata. In other words, there are several "commands" which instruct the relay to do something.
This isn't necessarily a bad thing, but it does increase the number of things the interface between the client and relay have to agree on. A regular relay may accept an
add-userrequest, but then do nothing with it, violating the contract it has implicitly accepted with the user. The solution to this is feature detection, which is a whole other API to be specified and implemented.My ideal solution to this problem is to shift the semantics of events away from "commands" to "facts" - in other words, to make the interface more declarative.
In fact, we already have an interface for moderation that works like this. Many clients support kind
1984"report" events. Users sending these reports have no expectations about how they will be used. They are a "fact", a declaration of opinion with certain semantics. Other actors in the network may choose whether or not to pay attention to these.This same model is easily applied to communities. Without having to implement any feature detection (either for the relay's implementation, or for the user's role on that relay), anyone can simply send a "report". This goes into the black hole of the relay, and may subsequently be ignored, broadcasted, or acted on.
The really nice thing about this model is that because there is no expectation for "how" reports are to be interpreted, any approach to moderation can be used depending on relay policy or client implementation. In NIP 29, if you issue a
delete-event, it either happens or it doesn't and if it doesn't, you have to explain the failure to the user somehow.In the relays-as-groups model, e-tagging an event in a kind
1984requires no user feedback, and therefore it can be interpreted however the relay prefer. This can result in insta-banning, manual review, thresholds based on number of reporters, a leaky-bucket social score algorithm, shadow banning, temporary banning, soft-moderation by allowing clients to request reports and respond to them by changing user interface elements, or anything else you can think of.The reason I think this is important is that community moderation is a very hard problem, and baking certain semantics into the specification can result in the complete failure of the spec. NIP 72 should be considered an example of what not to do. Some NIP 72 communities have survived due to the dedication of the moderators, but many more have failed because of the rigid moderation model. We should try not to make the same mistake again.
Conclusion
Now, having said all that, I think there is actually a lot of value to NIP 29. What finally clicked for me this week after releasing Flotilla is that the two approaches are actually complementary to one another. One of the most common feature requests I've already heard for flotilla is to have more complete support for rooms, which are currently implemented as not much more than hashtags. Better rooms (i.e., "nested groups") would require: authentication, membership, moderation, and pretty much everything else that exists for the top-level group.
As much as I believe the relays-as-groups approach is superior to NIP 29 for top-level groups, it doesn't make any sense to try to "nest" relays to create sub-groups. Something like NIP 29 is needed in order to fully support rooms anyway, so I think the convergence of the two approaches is all but inevitable. In fact, fiatjaf has already merged a PR which will allow me to use the same event kinds in flotilla as exist already in NIP 29 clients.
There are just a few more changes that are necessary in order for me to fully adopt NIP 29 in Flotilla:
- NIP 29 feature detection
- Opaque ids for unmanaged groups prevent unmanaged groups from having human-readable names
- We need a mechanism for building membership lists without relay support
- Better handling for
9021group join requests
I've opened PRs for each of these (linked above). Hopefully we can work through these issues and combine our powers to become the Captain Planet of group implementations.
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 9bd01740:8dc39de3
2024-11-22 20:51:33
@ 9bd01740:8dc39de3
2024-11-22 20:51:33**THE IMPORTANT OF GETTING AN ONLINE SKILLS
Getting an online skill is something most of the youth not just in Nigeria alone should adopt. Some of my reason include 1 Base on the economy situation 2 To compete globally 3 Job opportunity
Many people want to acquire the knowledge but don't know where to start from. To be able to do that you have to 1 make research 2 if you have the money purchase a course 3 get a mentor in the field that you are about to dive in
Online skill to acquire include 1 web development 2 Digital marketing 3 Blockchain 4 cyber security 5 Internet of things 6 AI/ML 7 DevOps 8 data analysis 9 data science 10 product management and so on
Tips to be on track while learning 1 build your portfolio 2 be consistent 3 don't quite 4 be updated
-
 @ af9d7040:42d05d35
2024-11-14 09:25:34
@ af9d7040:42d05d35
2024-11-14 09:25:34
Oswald: Ruthlessness in the Pursuit of Power and Survival
In Gotham City, Oswald Cobblepot, known as “The Penguin,” lives by the unrelenting rules of the mob: ruthless, without compromise or boundaries. For him, survival demands sheer will, extreme cunning, and coldness. He will do anything to achieve his aims, even betray those closest to him—like his mother, who has profoundly influenced him. His attachment to her is rooted in a twisted, obsessive need for approval, and his ruthlessness is not only a survival strategy but also an expression of his deeply embedded self-centeredness.
The Penguin maneuvers through the shadows of Gotham City with manipulation, deceit, and vengeance, like a serpent coiling around its prey. His every success is built on a disregard for humanity and a relentless thirst for power. Though he appears to show devotion to his mother, this is only another facet of his self-serving nature. He cherishes her only so long as she provides him with a sense of security; the moment she becomes a liability, he discards her without hesitation. This twisted complexity makes him a character who elicits both fascination and repulsion.
The Penguin’s unique blend of cruelty and contradiction separates him from the typical mob character. His ruthless selfishness is rooted in self-preservation. He is capable of manipulating or even betraying those closest to him. His “loyalty” is merely a mask for his unyielding self-interest. This guise of loyalty makes him more isolated and untrustworthy than those around him, ultimately marking him as a true antihero—someone who cannot be trusted and who feels no attachment even to those he holds dear.

Sofia: A Tender Wound in the Cold Reality
In contrast to the Penguin’s dark nature, Sofia, the female lead, presents a softer, yet no less complex character. Like him, she exists within Gotham’s shadows, but she retains a degree of innocence and kindness. Sofia, too, has a damaged side, but hers is gentler, perhaps even curable; her inner nature is resilient and compassionate. The Penguin, however, is wholly different—cold and selfish, with his inner darkness shaping every decision and action. Where Sofia struggles within Gotham’s corruption but maintains her inner light, the Penguin is the opposite, allowing his cruelty to permeate every aspect of his life.
Sofia’s presence is like a quiet undercurrent, casting the Penguin’s icy nature in sharper relief. She occasionally brings light into his shadowed world, though her warmth is ultimately no match for his darkness. Sofia’s compassion exposes the Penguin’s pathological selfishness, and her fleeting kindness only emphasizes his chilling indifference.

The Solitude of a Drifter
With its muted color palette, the film portrays Gotham as a city almost devoid of life, where the clamor of daily existence only serves to conceal an underlying emptiness. The city’s visual loneliness, along with a slow, deliberate narrative and moments of silence, subtly reflects the Penguin’s inner struggle. His journey for power begins with a warped attachment to Gotham, and as the story unfolds, we see him descend into total darkness, losing all semblance of warmth. The scattered plot structure and somber music shape his evolution into a kind of melancholic, fragmented poem.
In this solitude, the director refrains from casting the Penguin in simple moral terms. Like life itself, the narrative is complex and fragmented, juxtaposing Gotham’s wealthy and impoverished neighborhoods to create a blurry psychological divide. In this “ruin” of Gotham, some people drift, some settle, while the Penguin himself wanders, searching for a place to belong. The pacing and cinematography draw the viewer in as though they are walking Gotham’s desolate streets, accompanied by a haunting piano melody.

The Paradox of Power and Loneliness
The Penguin’s loneliness is not merely a result of Gotham’s darkness; it is the byproduct of his dependence on power. His need for control and his fixation on security bind him, like twin shackles, to his misery. He cannot escape his solitude even when perched at the top of Gotham’s hierarchy. His attachment to his mother is merely an extension of his self-interest; he has never truly known love or warmth. His cold and selfish nature is not a choice but an innate part of him, driving him inevitably toward isolation.
The series offers no definitive moral compass nor romanticizes any side. The Penguin’s relationship with Sofia and the sacrifices, betrayals, and suffering they both endure on the road to power seem to reflect the harsh realities of life. Gotham’s “ruinous” stage presents each character grappling with their choices and their costs.

Moving Forward in the Darkness
The allure of The Penguin lies not only in its portrayal of an antihero but also in its exploration of the character’s inner lives. The Penguin’s turbulent life as a mobster intertwines with his attachment to Gotham, echoing those who search for belonging in places that feel forgotten. Sofia’s gentleness and fragile compassion, like a tender blade, continually pierce the Penguin’s illusions about power and loneliness.
The Penguin does not rise to power swiftly; instead, he edges toward a deep, inevitable abyss. The director’s pacing, intense and deliberate, brings the Penguin closer to the heights of power while making his solitude more profound. The Penguin strikes at the heart of adult disillusionment, showing us that the world will not soften simply because we yield. We can only stumble forward in the dark, perhaps even make peace with it.
— Written by @Shaun on November 13, 2024
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ eac63075:b4988b48
2024-11-07 21:27:53
@ eac63075:b4988b48
2024-11-07 21:27:53Every night, you draw your curtains without thinking twice. It's instinctive—a simple act that protects your personal space. Yet in our digital lives, we've somehow accepted living in houses made entirely of glass, with countless unseen observers watching our every move.
https://www.fountain.fm/episode/wPZLCJ3fD6vzsWQ3XSE1
Why Privacy Matters to Everyone
Privacy isn't just for those with something to hide; it's a fundamental human need. Think about the conversations you have with friends, the late-night web searches you make, the personal moments you capture in photos. Would you want all of that broadcasted to the world?
I remember my friend Lisa planning a surprise party for her husband. She searched for gift ideas and coordinated with friends through social media. To her dismay, targeted ads for the exact gift she intended to buy started popping up on their shared devices at home. The surprise was ruined. It wasn't malicious, but it was a stark reminder of how our online activities are constantly monitored.
When a major retailer's customer database was breached, my neighbor Sarah discovered her shopping history, credit card details, and even her children's names were exposed to criminals. She hadn't realized how much personal information she'd unknowingly shared through routine purchases. It was a wake-up call that privacy breaches can affect anyone, not just the tech-savvy or those in high-profile positions.
Edward Snowden once said, "Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say." Privacy isn't about secrecy; it's about autonomy over our personal information.
The Rise of the Cypherpunks
Back in the '90s, a group known as the cypherpunks saw the writing on the wall. They recognized that as we moved into a digital era, our personal freedoms could be at risk. So they took action.
One of them, Eric Hughes, famously wrote, "Privacy is necessary for an open society in the electronic age." They developed encryption tools to protect individual privacy, laying the groundwork for technologies like Bitcoin and cryptocurrencies. These innovations were about more than digital money; they were about empowering individuals to take control of their own data.
When Technology Knows Too Much
Fast forward to today, and artificial intelligence (AI) is everywhere—in our phones, homes, and even cars. While AI brings convenience, it also raises serious privacy concerns.
Remember when you mentioned needing new running shoes, and suddenly every ad on your browser was for footwear? It's not your imagination. AI algorithms analyze our conversations, searches, and purchases to predict what we'll want next. But where does it stop?
A few years ago, a major retailer guessed a teenager was pregnant based on her shopping habits before she had told her family. They sent her targeted coupons for baby products, leading to a very uncomfortable situation at home. This isn't just marketing—it's intrusion.
Naomi Brockwell, a privacy advocate, warns, "Our relationship with financial privacy has fundamentally changed. What was once seen as a constitutional right and personal freedom is now simply part of the trade-off for using digital payments. Our baseline for what’s acceptable has shifted." It's a wake-up call that our digital footprints are larger and more revealing than we might think.
Privacy-Preserving AI
While AI often threatens privacy, emerging technologies like federated learning offer hope. This approach allows AI models to learn from data without directly accessing personal information. Imagine your phone improving its predictive text without sending your messages to a central server. It's AI that respects your privacy.
The Watchful Eye: Mass Surveillance and AI
Governments and corporations often justify mass surveillance as a means to keep us safe. But at what cost? When every email, message, or phone call can be monitored, we're sacrificing more than just data—we're giving up our freedom to think and communicate without fear.
Think about how you'd behave if someone followed you around with a camera all day. You might avoid certain places or people, censor your conversations, or feel constantly on edge. That's the chilling effect of mass surveillance.
I spoke with Alex, a journalist who covers political activism. "After attending a peaceful protest, I noticed unusual activity on my devices," he told me. "It made me second-guess my work, wondering who's watching." This isn't paranoia; it's a reality for many who challenge the status quo.
Building Digital Fortresses: Cryptographic Innovations
So how do we reclaim our privacy? Cryptography offers some solutions.
Zero-Knowledge Proofs: Proving Without Revealing
Zero-knowledge proofs allow you to prove you know something without revealing the actual information. Imagine showing a bouncer a card that confirms you're over 21 without exposing your birth date or any other details. In the digital world, this means verifying your identity or eligibility without handing over all your personal data.
Homomorphic Encryption: Secure Processing
Then there's homomorphic encryption, which lets companies process your data without actually seeing it. Think of it like sending a locked suitcase with your belongings; they can weigh it or move it, but they can't open it to see what's inside.
Quantum-Resistant Algorithms: Future-Proofing Privacy
As quantum computers become more powerful, they could potentially break current encryption methods. Quantum-resistant algorithms are being developed to safeguard our data against these future threats. It's like reinforcing your digital locks today to withstand the super lock-picking tools of tomorrow.
Decentralization: Taking Back Control
Decentralization aims to put power back into the hands of individuals. Bitcoin let you be your own bank, controlling your finances without a middleman. Decentralized social media platforms like Nostr, Bluesky or Fascaster allow you to own your content without algorithms dictating what you see or who sees you.
Decentralized Identity Systems
Decentralized identity systems let you prove who you are without revealing more than necessary. It's like showing only your age at a bar instead of handing over your entire driver's license. You maintain control over your personal information.
But with great power comes great responsibility. Without a bank to reset your password or customer service to recover your account, the onus is on you to protect your assets and information.
Practical Tips to Protect Your Privacy
You don't have to be a tech guru to safeguard your privacy. Here are some steps you can take today:
-
Use Encrypted Messaging Apps: Switch to apps like Signal, SimpleX or Session for secure communication. Your messages will be end-to-end encrypted, meaning only you and the recipient can read them.
-
Limit Social Media Sharing: Be mindful of what you post. Do you really need to share your location or personal details publicly?
-
Choose Privacy-Focused Browsers and Search Engines: Use browsers like Brave or Firefox and search engines like DuckDuckGo that don't track your every move.
-
Secure Your Passwords: Use strong, unique passwords for each account, and consider a password manager like Bitwarden. Enable two-factor authentication whenever possible.
-
Use Encrypted Email Services: Consider email providers like ProtonMail that offer end-to-end encryption for your communications.
-
Regularly Audit App Permissions: Check which apps have access to your location, microphone, and contacts. Revoke permissions that aren't necessary.
-
Be Wary of Public Wi-Fi: Public networks can be a hotbed for hackers. If you must use them, a VPN like ProtonVPN can add a layer of security.
-
Consider Privacy-Focused Alternatives: Explore services like Nextcloud for cloud storage or Jitsi Meet for video conferencing, which prioritize user privacy.
-
Keep Software Updated: Regular updates often include security patches. Don't ignore them.
-
Stay Informed and Skeptical: Phishing scams are getting more sophisticated. Think before you click on suspicious links or download attachments.
Final Thoughts
Privacy isn't a lost cause; it's a right worth fighting for. As Edward Snowden reminds us, "Privacy is the fountainhead of all other rights."
By taking control of our data and digital habits, we can navigate the online world with greater confidence and peace of mind. After all, wouldn't it be nice to live in a digital home where we decide when to close the curtains?
Read more
OPSEC and Digital Hygiene Plan: https://www.eddieoz.com/opsec-and-digital-hygiene-plan/
-
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 319ad3e7:cc01d50a
2024-11-22 20:49:16
@ 319ad3e7:cc01d50a
2024-11-22 20:49:16Candied Pecans by Double00Satoshi
Details⏲️ Prep time: 10 🍳 Cook time: 45 🍽️ Servings: 16
Ingredients
- 1/4 cup light brown sugar
- 1/4 cup granulated sugar
- 1 tablespoon ground cinnamon
- 1 teaspoon salt
- 1 pound unsalted pecans halves
- 1 egg white
- 1/2 teaspoon vanilla extract
- 1 teaspoon water
Directions
- Preheat oven to 300 degrees F. Line a large baking sheet with parchment paper and set aside.
- In a bowl, add sugars, cinnamon, and salt. Whisk until combined. Set aside.
- In a large bowl, whisk the egg white, vanilla, and water together until frothy. Add the pecans and gently toss until the pecans are well coated. Add the sugar and cinnamon mixture and toss until pecans are covered.
- Spread the pecans out in a single layer on prepared baking sheet. Bake for about 30-45 minutes, stirring every 15 minutes.
- Remove from the oven and let the pecans cool on the baking sheet. When completely cool, store in an airtight container for up to 1 month.
Deviled Eggs by Seth
Details ⏲️ Prep time: 20 min 🍳 Cook time: 15 min 🍽️ Servings: 6
Ingredients
- 6 hard boiled eggs, peeled
- 3 tablespoons of mayonnaise
- 1/2 teaspoon of soy sauce
- 1 teaspoon of Dijon mustard
- 1/2 stalk of celery, finely diced
- Salt and pepper
Directions
- Cut eggs in half lengthwise and pop yolks out into bowl, mash with fork
- Mix in mayonnaise, mustard, celery, soy sauce, salt and pepper.
- Whip until a creamy texture
- Scoop out fill and add to egg whites, heaping it slightly
- Add garnish of choice Serve immediately or refrigerate before serving
https://zap.cooking/recipe/naddr1qqtk2em8vdjkcmr9de6z6er9we5kcety94jkwemnqgs2wguqtndxwfg3j8y8sm6d5k8hjlnfwavzxqf4fw5wjx7tqdpde8qrqsqqqa2838r4n9
Bang Bang Shrimp by Hes ⚡️
Details ⏲️ Prep time: 20 min 🍳 Cook time: 20 min 🍽️ Servings: 4
Ingredients
- 1 pound shrimp
- 1 teaspoon granualted sugar
- ½ cup all-purpose flour
- ½ cup panko breadcrumbs
- 1 teaspoon salt
- ½ teaspoon black pepper
- ¼ teaspoon garlic powder
- ¼ teaspoon onion powder
- ¼ teaspoon dried basil
- 1 egg
- 1 cup milk
- 4 – 5 teaspoon chili garlic sauce
- 1 teaspoon rice vinegar
- ½ cup mayonnaise
Directions
Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
https://zap.cooking/recipe/naddr1qqgxyctwvukkyctwvukhx6rjd9khqq3qrjc54ve4sahunm7r0kpchg58eut7ttwvevst7m2fl8dfd9w4y33qxpqqqp65wg3yt3t
-
 @ fd208ee8:0fd927c1
2024-11-07 07:22:14
@ fd208ee8:0fd927c1
2024-11-07 07:22:14Unsucking the feed is real
As a Nostrich with an interesting, thought-provoking, and informative feed... a feed so good, that we're creating clients just to look at that feed... a feed that puts a lie to the idea that Nostr is nothing, but people reposting from Twitter or rehashing worn-out Bitcoin memes... a feed that I personally and increasingly enjoy perusing... I am here to tell you that the feed is real.

It's taken me over a year, to produce this feed. I literally spent hours and hours, day in and day out, scouring the Nostrverse for people worth introducing other people to. It was brutally difficult, as I was fighting the inherent nature of the Nostr clients and relays, in their current, most-popular form.
It goes like so...
Here are the steps I took, that sometimes weren't possible to take, until I tried to take them, and that still will sometimes break your client because the clients are often intentionally designed to steer you into having one particular feed:
1) Make a screenshot of your current relay list and copy your follows list. 2) Unsubscribe from all the relays, that you are currently subscribed to. Your feed should disappear. If it doesn't, or it doesn't allow for this, switch to a different client app because yours is corrupted. 3) Unfollow everyone. Delete the whole list. You are taking your follows private, which will invariably result in only following npubs whose stuff you actually want to see, since there's no longer any virtue-signaling going on. Also, it's easier to explain having no list, than a very short one. If your client doesn't allow for this, or starts throwing error messages and freezing up, then switch to a different client app because yours is corrupted. 4) Curate your copied follows list. Go line by line and look at the feed produced by the npub on that list. * Do you want to see that in your feed, going forward? * Do they produce original content and/or are they interesting conversationalists, in the replies? * Have they been active, within the past three months? * Are they simply good friends or real-life acquaintances, that you want to keep tabs on? * If not, cross out their name. * If you have been following someone because they repost or quote interesting things, look at who they've been reposting and follow them, instead. 5) Of the npubs remaining on your list, go through and select the 10 most interesting ones, and look at the reposts and quotes in their feed, and their topical lists like \"Favorites\", \"Devs\", \"Recipes\", etc. (Not their follows list, unless it's quite short, as follows tend to be full of people they follow for social-signaling or client-functional reasons, that they don't actively look at.) Find some new follows, there. 6) Now, set up a personal relay and add all the follows, that made the cut, to your allowed-npubs list. Do not add people to the list, just to make them feel better, or because you feel guilty, as they follow you, or to keep them from yelling at you. Remember, they can't see the list! 7) Think about the topics you find interesting, and add an allowed-keywords list (this is better than hashtags, as it searches the entire content of the notes), with the OR operator (these allowed npubs OR these allowed topics). 8) Make sure that you choose words likely to find the content you are most-interested in, and not people just ranting about it or spamming (those are great additions to your relay's block-list). If you are Muslim, for instance, instead of "Islam" or "shariah", choose "hadith" or "riba", as those are words more-likely to be used by people who know what they are talking about. If you are into bread baking, add "sourdough", "rye", "yeast", or "whisk", but don't add "bread" or "carbs". Once a note from those people shows up in your feed, and their feed looks like someone interesting, you can add their npub to your allow list. Remember: The topics are there to find people to add to the allow list, not merely for their own sake, as this is not a topical relay, but a personal one. 9) Open up a faucet (or relay syncing) with some of the big relays you previously unsubscribed from, some WoT relays, and some of the paid relays (nostr.land, nostr.wine, nostr21.com, and sovbit.host, for example). Your relay will filter that feed and only accept the events from the people and topics on your list. As your relay becomes more popular, npubs will begin writing directly to it, and the connections to other relays will sink in significance. 10) Go to your client of choice and subscribe to your new relay. Also subscribe to some topical relays, or curated neighborhood relays, you find interesting or your frens are running. This is an easy way to find new, interesting npubs, to add to your own relay.

That's a lot of work, you say? Yes, but the result is great, and you are now fully in-charge of your own feed. You also -- here's the cool part -- have a feed good enough, that other people can add your feed to theirs and enjoy your manual curation. As you refine and expand your feed, theirs will also be refined, in parallel. You are now an official Nostr Community Curator. My sincere congratulations.

Why is this so hard?
This is only a lot of work because the clients aren't designed to interact with relays, to this extent, as they were created to service mega-relays, download all their crap to your local cache, and adjust the feed over the follows/mutes lists. This was an idea borne of the axiom that Relays Are Hard, so there will only ever be a handful of them, where we'd all clump together and the relay operators would never judge the quality of someone's content. Then, some unusually clever people made relays increasingly easy, and the mailbox communication model was invented, and here we are.
What we have now, and that is slowly growing in popularity, among the #NostrIntelligentsia, are Nostr clients aimed at curating and viewing individual relays or personalized sets of smaller or more-specialized relays. The reigning client devs refused to give us those clients, and most of us aren't up to developing our own clients, so the relay devs took matters into their own hands and made the clients themselves. The free market remains undefeated.
This is a total game-changer. Last one to board this train is a rotten egg.
Originally, relays were supposed to be completely stupid and clients were supposed to be completely smart, but it's now actually the other way around, because most relay devs have a market-born incentive to make their content highly customizable and appealing to individuals (so that more people run relays).
But what about algos?
Can't you just slap an algo on top of Damus, Lol, or Primal relays, and get the same result? I would argue... no. No, you can't. Or, rather, only in the short to medium term.
Running your own relay, is running your own server. You are now intellectually independent, at a machine-level, and therefore a fully sovereign consumer. If you then use algos to control your own server, or in a client that subscribes to your own server, then you can further-refine a feed that is already in a high-to-you-signal state, rather than risking an algo inching you toward the Consensus Feed.
I have noticed that my own feed is slowly drifting away from the ReplyGuy-Cryptobot-Porny-Bitcoin-Meme Dumpster Fire, that almost everyone else is looking at, and it's due to running my own relay. If I use DVMs, those algos sometimes refer to relays I intentionally avoid, so they return results according to those relays. The results are as underwhelming, as you would expect, and often are simply 31 flavors of the Trending List.
But, that isn't your problem, anymore. From here, you can actively expand and refine your feed, over your whitelist, the topics, and your personally-managed algos.
Happy Nostr-ing!
-
 @ 6f14a106:75915122
2024-11-22 20:25:57
@ 6f14a106:75915122
2024-11-22 20:25:57Every now and then, a piece of tech comes along that makes you rethink what’s possible. Enter the Mac Mini M4 Pro. Apple’s smallest desktop has always been the quiet underdog of the lineup — humble, reliable, nothing to write home about. But this time? This time, Apple didn’t just update the Mac Mini; they supercharged it. And, spoiler alert, this little guy is kind of amazing.
Here’s why the Mac Mini M4 Pro is the most mind-blowing tech I’ve reviewed in ages.
Design: A Mini That’s Actually Tiny
First, let’s talk about size. The Mac Mini M4 Pro measures in at 12.7 cm x 12.7 cm with a height of 5 cm. That’s 20% smaller than its predecessor. It’s the kind of compact that makes you double-check your measurements, wondering how Apple managed to pack so much into such a tiny frame. It’s almost laughably small — imagine something barely bigger than an Apple TV but capable of powering high-res video editing and 3D modeling.
And yes, Apple kept that minimalist, brushed-aluminum aesthetic we all love. It’s light, it’s sleek, and it’s just understated enough to blend into any setup. But let’s not skip over the quirky part: the power button is on the bottom. Why, Apple? It’s like they needed one head-scratcher per product, and here it is. Sure, you’ll remember it’s there the first few times you set up, and then it’ll fade into that “it’s quirky but fine” category.
Ports: Thoughtful but Not Perfect
One of the best surprises with the M4 Pro is the port selection. Finally, Apple gave us two USB-C Thunderbolt 5 ports and a 3.5 mm headphone jack on the front, so you can plug in drives or headphones without fumbling behind the device. The back has three more Thunderbolt 5 ports, an HDMI port, and Gigabit Ethernet.
But before you start clapping, note that there’s still no USB-A or SD card slot. If you’re a photographer or someone who still works with older peripherals, you’ll need adapters. It’s not a dealbreaker, but it’s definitely something to keep in mind.

The M4 Pro Chip: More Than Just Numbers
Now, let’s get to what really matters: performance. The M4 Pro chip is where this Mac Mini flexes hard. With a 12-core CPU and a 20-core GPU, you’re looking at serious power — enough for 8K video editing, 3D rendering, and heavy multitasking. We’re talking about a 15% boost in multi-core performance and a 20% leap in graphics compared to the M2 Pro.
Need proof? The Geekbench 6 scores are wild: 4028 single-core and 23307 multi-core. These numbers put the Mac Mini M4 Pro in the same league as some Mac Studios, making you wonder if a Mac Studio is even necessary for many workflows. From editing high-res footage to running AI-driven tasks, this thing doesn’t just keep up; it leads.
Real-World Performance: A Day in the Life
So, what does that mean for day-to-day use? If you’re like me and your workflow involves jumping between editing software, a dozen Chrome tabs (don’t judge), and video calls, the M4 Pro handles it all like it’s no big deal. No lag, no stutter — just seamless multitasking.
The cooling system has been redesigned, too. Even under a full workload, the Mac Mini stays whisper-quiet. Gone are the days of fans whirring like jet engines when you’re rendering a video or running intensive apps. This thing just is, silently powering through tasks while you forget it’s even there.

Memory and Storage: Options Galore
One thing that caught my eye is how much memory and storage you can pack into this tiny beast. The M4 Pro starts with 24 GB of unified memory and can go up to 64 GB. Memory bandwidth is 273 GB/s, which means multitasking with heavy apps feels like second nature. Whether you’re editing 4K videos, working on large Photoshop files, or running development environments, the M4 Pro won’t break a sweat.
Storage-wise, the base model comes with 512 GB SSD, but you can upgrade to 8 TB if you’re working with massive projects or just don’t trust cloud storage. And speaking of storage speeds, this SSD is fast — reading speeds over 5000 MB/s, so you’re not sitting around waiting for files to load.
Display Support: A Game Changer for Creatives
If you work with multiple monitors, you’re going to love this. The M4 Pro supports up to two 6K displays at 60Hz or a single 8K display via HDMI. For video editors and graphic designers, this means more screen real estate to spread out timelines, edit layers, or run detailed previews — all without any lag.

A Few Drawbacks You Should Know About
Okay, not everything’s perfect, and you deserve to know the quirks before dropping your cash. First off, that power button placement on the bottom? It’s a design decision that’ll make you shake your head every time you reach for it. And while the port selection is mostly great, the lack of USB-A and SD card slot might mean carrying around more adapters.
Apple’s pricing ladder is another thing to keep an eye on. The base M4 Mac Mini at $599 is a steal, but once you start upgrading RAM and storage on the M4 Pro, you’re suddenly flirting with Mac Studio prices. It’s something to think about if you’re budget-conscious.
Who Is the Mac Mini M4 Pro For?
This is the question, right? If you’re a video editor, developer, or content creator who needs serious power without the bulk of a Mac Studio or the price tag of a Mac Pro, the M4 Pro is your sweet spot. It’s portable, powerful, and packs enough punch to handle demanding tasks without compromise.
If you’re more of a casual user — streaming, web browsing, and light productivity — the base M4 model will more than cover your needs and won’t make your wallet cry. But if you’re even considering heavy multitasking or creative work, the M4 Pro at $1,399 is worth the investment.
Why the Mac Mini M4 Pro Deserves Your Attention
The Mac Mini M4 Pro isn’t just another update — it’s a statement. Apple took what was already a beloved, compact powerhouse and turned it into something that feels almost futuristic. It’s small enough to forget about, powerful enough to replace much bigger machines, and versatile enough to fit into any setup, from home offices to professional studios.
Yes, it has its quirks (hello, power button), but they’re minor in the grand scheme of things. If you’re on the fence, let this be the push you need. The Mac Mini M4 Pro isn’t just one of the best products in Apple’s current lineup — it’s a reminder that sometimes, big things do come in small packages.
-
 @ ff18165a:dd7ca7f0
2024-10-19 18:23:51
@ ff18165a:dd7ca7f0
2024-10-19 18:23:51Chef's notes
- DO NOT add too much Peppermint Extract! It’s extremely strong and it will make your milkshake way too strong if you add more than a few drops.
- Feel free to be creative with your toppings. We used Caramel Flavored Whipped Topping and it turned out great!
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 2 min
- 🍽️ Servings: 1
Ingredients
- 1 1/2 cup Milk
- 2 drops Peppermint Extract
- 2 packets Stevia
- 1 cup Ice
- 2 drops Green Food Coloring
- Green Sprinkles
- 1 Crushed Peppermint Candy
- 2 Mint Leaves
Directions
-
- Blend together until smooth and frothy
-
- Pour into a tall glass
-
- Top with listed toppings
-
- Add straw and enjoy
-
 @ 319ad3e7:cc01d50a
2024-11-22 20:05:24
@ 319ad3e7:cc01d50a
2024-11-22 20:05:24NOSTR HOLIDAY GIFT IDEAS (please share or add someone you know)
V4V #circulareconomy
Agi Choote | Some hand drawings on paper or canvas are available in sizes up to 30x30 also you can get digital drawings to print out and frame on your own in your preferred technique. Please contact Agi directly.
Amber Sweeney @Amber Sweeney Custom Songs for Any Occasion (Tell Your Partner You Love Them This Holiday with A Song. One from Amber will surely be heavenly. OR sing about breakfast in bed. - SarahSoupBox winkyface)
Ant Richard @Ant Richards Limited Custom Handcrafted Knife Gift Certificates (12-month waitlist for all custom handmade orders)
Apotheca Viva @apothecavivahttps://apothecaviva.love/
Aupa Bars @AUPAhttps://eataupa.com/
Barnminer’s Barn Jerky @Barnmynah
Billay Coffee @Fulacoinhttps://billaycoffee.com/
BitBees @BitBees Honey & Honey Products https://www.kittrellsdaydream.com/
Bitpopart @Bitpoparthttps://bitpopart.com/
BtcPins @BtcPins
BTC Pins | Bitcoin Pins, Stickers & Apparel - Only Bitcoin Accepted
ONLY BITCOIN PAYMENTS ACCEPTED Pins Stickers Magnets | BTC Pins
Cannabis Records @The ₿udtender [CannabisRecords] https://cannabisrecords.store/
CryptoCloaks @CryptoCloaks™https://www.cryptocloaks.com/shop/
Delgado’s Fuego @Delgado's Fuego LLChttps://delgadosfuego.com/
Finca Yabisi @Finca Yabisihttps://yabisi.farm/
Foxfire Mushrooms @Foxfire Mushroomshttps://foxfiremushrooms.com/
Golden Tallow @Golden Tallowhttps://goldentallow.com/
GoodBeans 🇸🇻 Coffee @the guy running GoodBeans 🇸🇻 https://thegoodbeans.com/
Isolabell.art @isolabellart 🎨https://isolabell.art/
Jake Wolki @Jake Wolkihttps://wolkifarm.com.au/
Keto Beejay @beejay Low Sugar Jerky
 ## beejay
## beejayNotes & recipes on keto & carnivore goodies - by beejay
Full recipes site: https://ketolish.us/
Buy homemade small batch low sugar jerky on Shopstr with Bitcoin sats: https://url.tanelt.com/xcmjQp
Kanuto Takumi San @Kanuto
Laser Eye Cards https://lasereyes.cards/buy-nowBuy Laser Eyes Bolt Cards Now » Laser Eyes Cards
LeatherMint @LeatherMinthttps://theleathermint.com/
Lightning Store @ltngstorehttps://lightning.store/
LightningSpore @LightningSpore Full Service Mushroom Cultivation Company https://www.lightningspore.com/
Lost Sheep Ranch @Lost Sheep Ranchhttps://www.lost-sheep-ranch.com/
Lucho Poletti @Lucho Poletti Art Prints and Merchandise https://luchopoletti.com/
Madex @M A D E X Art & Apparel https://madex.art/collections/in-stock
MapleTrade @Mapletrade
Next Block Coffee @Next Block Coffeehttps://nextblockcoffee.com/
NoGood @Jake Wolkihttps://wolkifarm.com.au/
PatsPropolisHoney @PatsPropolisHoney
Peony Lane Wine (Ben Justman) @Ben Justman🍷https://www.peonylanewine.com/
PlebianMarket @Plebeian Market
PictureRoom @❐ PictureRoom Assorted Dessert Treats
Regenerative Farmed Meats & Knives @AgrarianContrarian
RustyPuppy | Art and Stories https://heidi2524.com/
Salt of the Earth @Salt of the Earth Premium Electrolyte Mix https://drinksote.com/
Satoshi Coffee Company @Satoshi Coffee Co.
 ## Welcome to Satoshi Coffee Co. - Our Roast is the Proof of Work
## Welcome to Satoshi Coffee Co. - Our Roast is the Proof of WorkYou CAN buy coffee with bitcoin now at Satoshi Coffee Co! Use Lightning (or on-chain) to purchase our delicious freshly-roasted coffee.
Scott & Son's Art & Apparel | Hand drawn pet portraits and limited design tshirts
https://xavierscraftworkanddesign.com/Xavier's Craftwork & Design
SofterSkin Tallow Skincare @Softer Skin | Tallow Based Skincarehttps://softerskin.co/
Shopstr @Shopstrhttps://shopstr.store/
Soap Miner @Soap Miner Tallow Body Soap Bars https://shopstr.store/npub1zzmxvr9sw49lhzfx236aweurt8h5tmzjw7x3gfsazlgd8j64ql0sexw5wy
SweetSats @SweetSats Honey
SweetSats – Buy pure, raw honey with Bitcoin
Yojimbo @Yojimble Jam & Marmalade https://jimblesjumble.odoo.com/
-
 @ be41636e:e55c4909
2024-11-22 19:55:44
@ be41636e:e55c4909
2024-11-22 19:55:44If you are a content manager or regularly browse social media, you might have seen comments resembling this format:
"Thanks for sharing such valuable information! A bit off-topic, but I wanted to ask: My OKX wallet holds some USDT, and I have the seed phrase ([seed phrase here]). What's the best way to send them to Binance?"
This type of message is not a cry for help—it’s a carefully crafted trap. To avoid becoming a victim, always remember the golden rule: there is no free lunch.
How Does the Scam Work? At first glance, it seems puzzling—why would someone willingly post their wallet’s seed phrase, a crucial key to their funds? Isn’t sharing it the ultimate taboo in cryptocurrency security? The truth is that these scammers are banking on your greed and lack of caution. Here’s how the scam unfolds:
The Setup: The comment implies that there is free money (e.g., 500 USDT) sitting in the scammer's wallet, which they are too inexperienced or unable to transfer themselves. The seed phrase gives you access to this wallet, tempting you to retrieve the funds.
The Gas Fee Trap: Transferring tokens, such as USDT, from one wallet to another requires gas fees, which must be paid in the cryptocurrency native to the token's network. For example: • Ethereum network: Gas fees are paid in ETH. • Tron network: Gas fees are paid in TRX. • Solana network: Gas fees are paid in SOL. The scammer’s wallet conveniently lacks the required cryptocurrency to pay these gas fees. They rely on you to fund the wallet with the necessary tokens to complete the transfer.
The Sting: Thinking you’re about to "unlock" the 500 USDT in their wallet, you transfer a small amount of cryptocurrency (e.g., $10 worth of TRX) to cover the gas fees. However, the wallet is controlled by an automated bot (though it doesn’t have to be). As soon as your transaction is received, the bot instantly sweeps the funds to another wallet—one that you have no access to.
The Loss: You lose the cryptocurrency you transferred for the gas fee. While the individual amount might seem small, if enough people fall for the scam, the fraudsters rake in significant profits.
Why This Works This scam exploits basic human psychology: • Greed: The promise of free money clouds judgment. • Urgency: The fear that someone else will claim the "free funds" first pressures victims to act quickly. • Lack of knowledge: Not everyone understands gas fees or how wallets and seed phrases work.
Red Flags to Watch Out For • Public Seed Phrases: Legitimate users never share their seed phrases publicly. Anyone who does is either lying or completely reckless (and likely a scammer). • “Too Good to Be True” Offers: Free money claims are almost always scams, especially in the cryptocurrency world. • Urgency and Scarcity Tactics: Messages designed to make you act without thinking are a classic scam strategy.
What You Should Do • Ignore and Delete: If such a comment appears under your YouTube video or social media post, don’t engage. Delete the comment immediately to protect others. • Educate Your Audience: Warn your followers about this type of scam so they can recognize it and stay safe. • Stay Skeptical: Never rush into any deal involving cryptocurrency, especially one promising free money.
The Takeaway Cryptocurrency scams like this rely on greed, ignorance, and urgency. By understanding how they operate, you can protect yourself and others. Always remember: if it seems too good to be true, it probably is.
-
 @ cbaa0c82:e9313245
2024-10-01 11:04:45
@ cbaa0c82:e9313245
2024-10-01 11:04:45TheWholeGrain - #September2024
To start the second year of Bread and Toast off strong the September of 2024 includes five Sunday Singles, and the newest piece of cover art for a comic from Toast's Comic Collection includes a touch of color. Some bonus pieces of content were included this September. This includes one of the Political posts we all take so seriously, and a promotional piece for the upcoming npub10hj9rg5gds5x2gk0z0s2jlqnq04jg7g30aj2t5pqzdaaztfactgsnze5ny event coming up in October. The Concept Art released this month is an early design of a possible website logo. This month's Bitcoin Art stars End-Piece who is well informed on what money really is and asks the question, "Do you?"
September Sunday Singles
2024-09-01 | Sunday Single 055 Jump Rope https://i.nostr.build/ESlb23xVmTQLw7sw.png
2024-09-08 | Sunday Single 056 Trampoline https://i.nostr.build/1HNutqYQUjsA1JaG.png
2024-09-15 | Sunday Single 057 Hippity Hop https://i.nostr.build/5dTyLA0FJdK2rNol.png
2024-09-22 | Sunday Single 058 Jumping on the Bed https://i.nostr.build/PWaHDMroMjjfPmWS.png
2024-09-29 | Sunday Single 059 Shades https://i.nostr.build/pWeIZrttOjpcXAtz.png
Other Content Released in September 2024
2024-09-04 | Toast's Comic Collection Teenage Mutant Ninja Bread #5 Four brothers trained in ninjutsu live underneath the city and come up to the surface in order to save it! https://i.nostr.build/WPSB1qn2lMRlbdwJ.png
2024-09-10 | Politics Debate Night The first official debate between the candidates for Selection2024. https://i.nostr.build/wppFU8U3NJCww6U0.png
2024-09-11 | Concept Art Early Website Logo Design This is an early concept for a logo. It was never used. https://i.nostr.build/hxhzvtS4fCe0imNh.png
2024-09-18 | Bitcoin Art On Top of It End-Piece knows what money is. Do you? https://i.nostr.build/6TCWK5d1ynPhrteA.png
2024-09-27 | Nostr Valley Nostr Valley 001 Bread is getting prepared for NostrValley! Hope to see you there! https://i.nostr.build/nQqsPGmJ8hjvxROK.png
September Additions to The Bakery in 2024
2024-09-05 | npub1895dg7n47ldxxq8hyqj9h4xa3xwwxzpnn8lm7hydag4tck6cfj3qcmc4f0 https://m.primal.net/KgDW.jpg
2024-09-26 | npub1hcusg0xp9maamlh9vnv4mf635uwldsfeut00ghzrrjk7kjjh8j3sf9049l https://image.nostr.build/a0a64d709376b3650ebde0f3de5076748d69a999aef9e5fbd882574d5e64cf88.jpg
We hope you enjoyed this first issue of The Whole Grain. The Whole Grain will be released on the first of every month and will cover all of the content released by npub1ew4qeq576v3vz4gukeseknqghx3x4jtlld8ftys9amrca6f3xfzsrm8jpd in the previous month.
Thanks for checking it out, Bread, Toast, and End-Piece
BreadandToast #SundaySingle #ToastsComicCollection #ConceptArt #BitcoinArt #TheBakery #Bread #Toast #EndPiece #Art #Artstr #DigitalArt #Comic #Manga #NostrValley #NostrOnly #🖼️
-
 @ 705605d9:b4324038
2024-11-22 19:55:19
@ 705605d9:b4324038
2024-11-22 19:55:19В 2040 году Горноправдинск, малый город в Сибири, стал центром мирового молочного производства, после открытия крупнейшего в мире молочного комбината. Этот промышленный гигант, с мощностью переработки в десятки миллионов тонн молока в год, обещает не только революцию в отечественном производстве, но и серьезно повлиять на глобальные рынки сельскохозяйственной продукции, в том числе на рынок сливочного масла. Ожидается, что новый комбинат окажет значительное влияние на внешнюю торговлю и положение России на мировом рынке продовольствия.
Экономический контекст
Сливочное масло – один из важнейших продуктов молочной промышленности, который активно экспортируется в страны Азии, Европы и Северной Америки. Российские производители в последние десятилетия стремительно наращивали свои мощности, и открытие такого крупного объекта, как молочный комбинат в Горноправдинске, может стать катализатором для страны, чтобы стать ведущим игроком на этом рынке. Россия, в свою очередь, может занять более прочные позиции в торговле сливочным маслом за рубежом, конкурируя с такими крупнейшими экспортерами, как Новая Зеландия, Германия и Польша.

Молочный комбинат в Горноправдинске: изменения в структуре производства
Ожидаемое увеличение объемов производства сливочного масла с запуском нового молочного комбината в Горноправдинске связано с несколькими ключевыми факторами, которые делают данный проект особенно перспективным:
-
Современные технологии. Комбинат будет оснащен высокотехнологичным оборудованием для переработки молока, что повысит эффективность и качество продукции. Это дает России значительное преимущество на международных рынках, где высокие стандарты качества становятся важнейшим фактором для потребителей.
-
Просторные мощности. Новый комбинат, способный перерабатывать десятки миллионов тонн молока ежегодно, обеспечит не только внутреннее потребление, но и масштабные экспортные поставки. Это откроет новые рынки для российского сливочного масла, особенно в странах с растущим потреблением молочных продуктов, таких как Китай, Индия и страны Юго-Восточной Азии.
-
Экономия на масштабе. Масштабность производства позволяет снизить себестоимость продукции, что дает конкурентные преимущества на мировом рынке. Снижение цен на сливочное масло, особенно в условиях высокой конкуренции, станет важным фактором при выходе на зарубежные рынки.
Влияние на внешнюю торговлю и конкуренцию
Российский рынок сливочного масла исторически был ориентирован на внутреннее потребление, однако с развитием новых мощностей в Горноправдинске, страна может значительно увеличить объемы экспорта. Ведущими потребителями молочной продукции традиционно являются такие страны, как Германия, Великобритания, США, а также активно развивающиеся рынки Китая и Индии.

-
Китай – крупнейший рынок для молочных продуктов, включая сливочное масло. Рост доходов китайских потребителей и увеличение спроса на качественные молочные продукты открывают огромные возможности для российских производителей. С учетом высокого уровня конкуренции со стороны новозеландских и австралийских производителей, российские компании могут выделиться за счет ценовой доступности и качества продукции.
-
Европейский Союз – несмотря на высокие стандарты качества, рынок Европы остается важным для торговли сливочным маслом. Ожидается, что российские компании смогут расширить свою долю в Европе, конкурируя с польскими и немецкими производителями, предлагая более выгодные цены при неизменно высоком качестве продукции.
-
Северная Америка – рынки США и Канады всегда были важными для молочной продукции, однако они также обладают сложной системой тарифов и квот. Россия, обладая крупными мощностями, может предложить экспорт сливочного масла с конкурентоспособными условиями, если смогут преодолеть бюрократические препятствия. Проблемы и вызовы
Несмотря на перспективы, российский экспорт сливочного масла столкнется с рядом вызовов. Одним из них является необходимость соответствия международным стандартам безопасности и качества, что потребует дополнительных инвестиций и контроля на всех этапах производства. Также стоит учитывать влияние мировых экономических факторов, таких как колебания валютных курсов, изменения в торговых отношениях и возможные торговые барьеры.
Кроме того, конкуренция со стороны традиционных поставщиков – таких стран, как Новая Зеландия и Австралия, будет оставаться высокоактуальной. Для того чтобы закрепиться на этих рынках, российским производителям предстоит работать над созданием имиджа качественного, но доступного продукта.
Заключение
Открытие крупнейшего молочного комбината в Горноправдинске – это не просто важный шаг для отечественной молочной промышленности, но и стратегический момент для глобальной торговли сливочным маслом. Россия получает уникальную возможность занять сильные позиции на международных рынках, предоставляя потребителям качественное и доступное сливочное масло. Однако для достижения долгосрочного успеха необходимы устойчивые усилия по улучшению качества продукции, соблюдению международных стандартов и борьбе с внешними экономическими вызовами.
-
-
 @ 96417ed9:66b02a55
2024-09-29 20:01:36
@ 96417ed9:66b02a55
2024-09-29 20:01:36Image this.
You are scrolling through your favorite social media. It’s probably been 10 minutes Scroll. Like. Repeat. Scroll. Like. Repeat. And so on and on and on.
Does it sound familiar to you? How many times did you find yourself in this situations? Most importantly, how much attention did you pay to the hundreds of posts that you liked? What can you actually remember?
Attention and likes
Recently, I took a communication class. I was very surprised when the teacher told me that the average attention span is around 7 seconds! This means that when you are looking at something or talking to someone, you are actually paying attention for the first 7 seconds. After that, something else has already captured your mind. And it's actually getting worse and worse. Why is that, you might wonder? Yeah, you got it right, social media.
The infinite amount of content that you can consume on social media continuously steals your attention. Thus, when you are looking to a post, your focus is already on the next piece of information, and on the one after and so on indefinetly. Finally, when you decide to leave a like to the first post, you are not actually remembering what you were looking at.
In this context, likes moved from being an appreciation for someone else's work to a simple mechanism that feeds the social media algorithm. From a measure of the value provided by a creator, they became an empty number. Liking a post is no more action, but a mere unconscious reflex. A like is something free, something that you can leave without any conscious effort, to anyone, to anything. Even to something that you actually do not like.
In the last years, likes stopped being a measure of value provided.
And then, zaps came.
Zaps and the value 4 value revolution
Since I am publishing this article on Nostr, I expect most of the reader to know what a zap is. However, for the nebies whom may come across my random thought, here is a brief explaination.
Zaps are a simple way to communicate appreciation. Whenever you like a photo, a thought, a video, you can zap the creator. Exactly as a like, you might say. But here is the deal. When you zap someone, you are actually sending them some amount of money! And not a simple type of money, but the scarcest type of money on earth: Bitcoin! Basically, if a creator provides value to a user the user can award the creator with some monetary value. Nowadays, this concept is quite common and known as value4value (v4v for short).
This is a revolution. Anyone can provide value. Thus, everybody should be able to earn value if something of value is provided , not only some super influencer with sponsors and affiliate programs
Zaps from the user perspective
I started this article by talking about attention, and how there is such a huge competition for it that no one is actually able to focus on something anymore. How does it connect to zaps?
Zaps allow users to regain their lost attention. Since zaps provide real monetary value to a creator, a user has to be 100% on focus on what he is reading or watching: "Is this picture/video/post providing me value?". You do not want to separate from you hard-earned sats for something useless. Unlike likes, zaps are not free. When you zap someone, it means that you have actually paid attention to the post and you are actually acting to signal your appreciation.
Zaps from the creator perspective
I am an amateur photographer. I love going around places and took hundreds of photos at everyhting that catches my curiosity. I posted more than a hundred pictures on Instagram and received even a decent amount of likes. However, I eventually started to wonder if likes came from a genuine appreciation of my work, or only from the aforementioned mechanical reflex.
This does not happen on Nostr. Whenever I am zapped, I instantly know that the appreciation is real. My God, someone really spent some time looking at my photos and decided to give me some real monetary value for that! I really provided value to someone! This is truly exciting.
The realization of this fact has been one of those "ah-ah" moments. Why should I spent my time posting pictures on a social media just to get likes, when someone can send me a chunk of the best money ever created?
And why should you?
-
 @ 31312140:2471509b
2024-11-22 19:08:04
@ 31312140:2471509b
2024-11-22 19:08:04What is Virology? \ \ Virology is the branch of science that deals with the study of viruses. Officially, it focuses on understanding how viruses operate, how they spread diseases, and how we can combat them. 🌐🔬 \ \ The Historical Context
Historically, the concept of viruses emerged as an explanation for diseases that couldn't be linked to bacteria. The early 20th century brought about major developments in this field, leading us to where we are today with an industry worth billions.
But here’s the kicker: many fundamental assumptions in virology remain unproven or underexplored. \ \ The Unproven Hypothesis \ \ Isolation Methods: In virology, "virus isolation" doesn’t mean what you think it means. Virus isolation often involves mixing samples with toxic chemicals and other cells, then observing the effects. The presence of a virus is inferred, not directly observed. 🚫🔍
Control Experiments: Proper scientific controls, where samples without believed viruses are treated the same way, often aren’t conducted or published in ways making them verifiable. 🧪❓
Electron Microscopy: While electron microscopes can visualize particles, interpretations are problematic. Similar structures (exosomes) naturally exist in the body and can be mistaken for viruses. 🕵️🔬 \ \ The Controversial Points \ \ PCR Testing: Polymerase Chain Reaction (PCR) tests, widely used to detect viruses, can’t distinguish between live viruses and non-infectious viral fragments. It's an amplification technique, not a diagnostic tool. Famed inventor Kary Mullis himself cautioned against its misuse. ⚠️🔍
Genetic Sequencing: Viral genomes are often generated from computer models using fragmented genetic material from patient samples. This model can lead to inaccuracies and assumptions about the virus that aren’t directly observed. 🧬💻
Pathogenicity Proofs: No study unequivocally proves viruses alone cause diseases. Historical attempts, like those from the Spanish Flu era, failed to infect healthy individuals with presumed virus samples. \ \ Big Pharma Implications \ \ Big Pharma has a vested interest in propagating the viral causation theory:
Vaccines: Billions are made from vaccine sales. If virus causation is questioned, the foundation for vaccines crumbles.
Antivirals: Similarly, antiviral drugs rely on this belief. Without it, a major revenue stream is invalidated.
Pharmaceutical companies and regulatory bodies rarely challenge the status quo, leading to a cycle where treatments are promoted despite conflicting evidence. 💊💸 \ \ The Alternative Hypothesis \ \ Exosomes vs. Viruses: Exosomes, extracellular vesicles within our bodies, serve as cellular communication tools. They’re released under stress, similar to what we call “viruses.” Are our bodies creating what we interpret as “viruses” to heal or signal distress? 🧩🔍
Terrain Theory: This theory suggests that the body's internal environment, not an external pathogen, determines health. A healthy body repels illness, while a toxic internal environment invites disease. Terrain theorists argue we should focus on optimizing internal health rather than targeting external “invaders.” 🌱💚 \ \ Question Everything \ \ This exploration isn’t to say viruses categorically don’t exist but to highlight the holes and biases in mainstream virology. It’s about opening the conversation and asking critical, often uncomfortable questions.
If we reconsider virology’s foundational assumptions, what implications could this have for global health policies, pharmaceutical practices, and our understanding of diseases? The answers could reshape how we approach wellness and medical science entirely.
Remember, folks, the truth often lies beneath layers of accepted truths. Dive deeper, question more, and never settle for the surface narrative. 🚀🕵️♂️ \ \
lookintoit #virology #health #scam #covid19 #philosophy #wisdom #freedom #psychology #nature #science
-
 @ ef9ee5bf:3fe39164
2024-11-22 19:01:29
@ ef9ee5bf:3fe39164
2024-11-22 19:01:29Salvation in a Digital World
The drama of redemption unfolds as a cosmic narrative that transcends traditional spiritual salvation, extending into the digital realms where humanity now finds itself entangled. In this emerging reality, salvation is not solely a matter of freeing the soul from sin but of liberating the mind and body from technological control systems that seek to restrict human potential. As society becomes increasingly digital, the boundaries between spiritual and digital salvation blur. The digital realm has become a new battleground for the soul, with tools of surveillance, artificial intelligence, and centralized digital systems acting as the forces that shape reality. This battleground is not neutral; it is a contested space where unseen powers influence human behavior and thought, subtly steering individuals toward compliance and conformity. Surveillance, in particular, looms as a formidable obstacle, exerting a subtle yet profound pressure that limits the capacity for genuine spiritual freedom. It not only monitors but manipulates, narrowing the range of choices and thereby inhibiting the exercise of free will—a crucial component for true salvation. As we venture deeper into this cyber age, the challenge becomes clear: to seek liberation not only from sin but from the digital systems that seek to define what it means to be free.
Free Will as Essential to Salvation
Free will stands at the heart of spiritual salvation. It is through the exercise of free will that individuals can seek, discern, and align themselves with divine truth. Spiritual growth depends on the ability to make genuine, uncoerced choices—decisions that reflect the soul’s personal quest for enlightenment rather than external pressures. Without free will, salvation becomes merely a theoretical possibility, void of personal transformation or meaningful alignment with higher principles. In this sense, free will is not just a means of self-expression but the very mechanism through which spiritual freedom is realized. It allows individuals to break away from sin, illusion, or ignorance and move toward truth, virtue, and divine love.
However, the omnipresence of surveillance in the digital age poses a direct threat to this spiritual dynamic. Surveillance does not merely observe—it influences. By monitoring behavior, it subtly pressures individuals to conform to societal norms, limit risks, and act in ways that are predictable and safe. The awareness of being constantly watched reshapes behavior, creating an environment where compliance is rewarded, and deviation is penalized, even if only through social ostracism or self-censorship. This dynamic distorts free will, as the range of decisions becomes heavily influenced by external expectations. Instead of making decisions rooted in personal spiritual exploration, individuals may find themselves choosing paths that align more with societal acceptance than with inner convictions.
The theological implications of this are significant. If salvation requires a truly free, uncoerced movement of the soul toward the divine, then pervasive surveillance becomes an obstacle to that process. It restricts the capacity for genuinely transformative decisions, replacing spiritual authenticity with digital conformity. Surveillance enforces a state of psychological limitation that mirrors the "singular collapsed state" seen in quantum physics—where the observation itself defines and limits potential. In this context, the battle for salvation is not only against spiritual ignorance or sin but also against the digital systems that restrict the exercise of free will, reducing the potential for spiritual growth to a controlled set of predictable behaviors.
 ### Introducing Quantum Concepts: Wave Functions and Surveillance
### Introducing Quantum Concepts: Wave Functions and SurveillanceIn quantum mechanics, the wave function is a mathematical representation of a particle’s potential states. It encompasses all the possible positions, velocities, and paths that a particle might take. However, this range of possibilities exists only until the moment of observation—once a measurement is made, the wave function "collapses," reducing the particle to a single, definite state. This phenomenon, known as the observer effect, has profound implications, not only in physics but also as a metaphor for human potential. In a state of openness, individuals—like unobserved particles—possess a wide array of possible thoughts, actions, and spiritual expressions. They can explore various paths to enlightenment, pursue unconventional ideas, and exercise creativity without the constraints of external judgment.
However, surveillance functions much like the observer in quantum mechanics. Just as the act of measurement collapses the wave function into a singular outcome, constant surveillance collapses human potential into a narrower, more controlled set of behaviors. The awareness of being observed exerts a powerful psychological influence, prompting individuals to make safer, more predictable choices. Instead of exploring diverse spiritual or personal possibilities, individuals adapt to the expectations imposed by the ever-present digital gaze. The result is a diminished range of action, where genuine self-expression gives way to compliance and predictability—what can be termed the "singular collapsed state."
This singular collapsed state represents a profound loss of spiritual potential. When human behavior is constantly shaped by surveillance, it becomes more constrained, less creative, and ultimately less free. The open potential for spiritual growth, transformation, and connection to divine truth is replaced by a narrowed reality defined by conformity and safety. Just as quantum observation restricts the wave function to a single outcome, surveillance restricts individuals to a limited set of socially acceptable behaviors, inhibiting the soul’s journey toward deeper truth and spiritual liberation. This dynamic suggests that overcoming surveillance is not merely a matter of privacy or freedom of expression—it is essential for maintaining the open potential necessary for spiritual salvation itself.
Breaking Free from Surveillance
To escape the confines of the surveillance matrix and reclaim human potential, embracing decentralized technologies is essential. Decentralized systems like Bitcoin and open-source protocols offer a tangible means of resisting centralized control and pervasive observation. Unlike centralized digital systems that collect and exploit data to manipulate behavior, decentralized technologies enable an *open potential state* where individuals can act freely, without fear of surveillance-induced consequences. They preserve privacy, protect free will, and create opportunities for genuine personal and spiritual growth. This decentralization aligns with divine principles of freedom, spontaneity, and diversity, reflecting the open and unpredictable nature of the universe itself. By choosing decentralized solutions, individuals can restore a more authentic connection to both digital and spiritual realms.
This shift is not purely technical; it’s deeply spiritual. Just as spiritual awakening requires a release from the bondage of sin and ignorance, digital liberation demands a conscious move away from surveillance-driven systems. Breaking free involves more than just switching technologies; it requires a transformation of mindset—one that recognizes surveillance as a spiritual and existential threat. It calls for the cultivation of awareness, discernment, and a willingness to embrace both technological sovereignty and spiritual autonomy. True salvation, in the context of a Cyber Gospel, is a holistic journey that requires overcoming both physical and digital chains. It is the fusion of spiritual liberation with the adoption of decentralized tools that enable true freedom in a digital world.
Ultimately, a Cyber Gospel serves as a guide for navigating this complex spiritual-digital landscape. It invites readers to explore how decentralized technologies can facilitate a digital exodus, moving humanity from a singular collapsed state to an open potential state where free will and spiritual growth can flourish. This path forward is both a call to action and a call to awakening. It urges readers to actively participate in building a future where technology serves as a bridge to liberation rather than a tool of control. As the lines between spiritual and digital realities blur, embracing this new form of salvation becomes not only possible but necessary for the soul’s journey toward wholeness and freedom.
 ### The Battle for the Soul in the Digital Age
### The Battle for the Soul in the Digital AgeThe digital age is not just a technological revolution; it is a spiritual battleground where the soul's potential is tested by the forces of surveillance and control. In this new landscape, salvation must be reimagined as both spiritual and digital—a quest that demands free will, genuine choices, and the preservation of human potential against a backdrop of pervasive observation. Throughout this discussion, we have explored the nature of digital salvation, the essential role of free will, and how surveillance acts as a force that collapses human potential into a singular, predictable state. We have drawn parallels between quantum mechanics and human behavior, illustrating how surveillance, like the observer effect, restricts possibilities and narrows the range of spiritual and existential outcomes.
Yet, there is a path forward. Decentralized technologies offer a chance to resist this collapse and restore an open potential state, allowing for personal and spiritual growth in an age where control mechanisms seek to limit both. This liberation is not just about escaping technological constraints; it is about reclaiming the divine spark of free will, which is essential for true awakening. As we move deeper into this digital era, the challenge is clear: salvation must involve breaking free from the dual chains of spiritual ignorance and digital manipulation.
A Cyber Gospel can serve as a guide for navigating this complex terrain, calling for both spiritual and digital awakening. It asks seekers to reflect deeply on the nature of their freedom and the forces that shape it. The final question remains: *Can the soul be truly free in a world of constant surveillance, or must it find a way to escape to achieve salvation?* This question is not just philosophical but practical, urging users to consider how they can actively participate in the creation of a more liberated reality—both spiritually and digitally. The battle for the soul in the digital age is not just about avoiding surveillance; it is about embracing a deeper, more transformative form of freedom that aligns with both divine principles and technological sovereignty.Salvation in a Digital World
The drama of redemption unfolds as a cosmic narrative that transcends traditional spiritual salvation, extending into the digital realms where humanity now finds itself entangled. In this emerging reality, salvation is not solely a matter of freeing the soul from sin but of liberating the mind and body from technological control systems that seek to restrict human potential. As society becomes increasingly digital, the boundaries between spiritual and digital salvation blur. The digital realm has become a new battleground for the soul, with tools of surveillance, artificial intelligence, and centralized digital systems acting as the forces that shape reality. This battleground is not neutral; it is a contested space where unseen powers influence human behavior and thought, subtly steering individuals toward compliance and conformity. Surveillance, in particular, looms as a formidable obstacle, exerting a subtle yet profound pressure that limits the capacity for genuine spiritual freedom. It not only monitors but manipulates, narrowing the range of choices and thereby inhibiting the exercise of free will—a crucial component for true salvation. As we venture deeper into this cyber age, the challenge becomes clear: to seek liberation not only from sin but from the digital systems that seek to define what it means to be free. Free Will as Essential to Salvation
Free will stands at the heart of spiritual salvation. It is through the exercise of free will that individuals can seek, discern, and align themselves with divine truth. Spiritual growth depends on the ability to make genuine, uncoerced choices—decisions that reflect the soul’s personal quest for enlightenment rather than external pressures. Without free will, salvation becomes merely a theoretical possibility, void of personal transformation or meaningful alignment with higher principles. In this sense, free will is not just a means of self-expression but the very mechanism through which spiritual freedom is realized. It allows individuals to break away from sin, illusion, or ignorance and move toward truth, virtue, and divine love.
However, the omnipresence of surveillance in the digital age poses a direct threat to this spiritual dynamic. Surveillance does not merely observe—it influences. By monitoring behavior, it subtly pressures individuals to conform to societal norms, limit risks, and act in ways that are predictable and safe. The awareness of being constantly watched reshapes behavior, creating an environment where compliance is rewarded, and deviation is penalized, even if only through social ostracism or self-censorship. This dynamic distorts free will, as the range of decisions becomes heavily influenced by external expectations. Instead of making decisions rooted in personal spiritual exploration, individuals may find themselves choosing paths that align more with societal acceptance than with inner convictions.
The theological implications of this are significant. If salvation requires a truly free, uncoerced movement of the soul toward the divine, then pervasive surveillance becomes an obstacle to that process. It restricts the capacity for genuinely transformative decisions, replacing spiritual authenticity with digital conformity. Surveillance enforces a state of psychological limitation that mirrors the "singular collapsed state" seen in quantum physics—where the observation itself defines and limits potential. In this context, the battle for salvation is not only against spiritual ignorance or sin but also against the digital systems that restrict the exercise of free will, reducing the potential for spiritual growth to a controlled set of predictable behaviors. Introducing Quantum Concepts: Wave Functions and Surveillance
In quantum mechanics, the wave function is a mathematical representation of a particle’s potential states. It encompasses all the possible positions, velocities, and paths that a particle might take. However, this range of possibilities exists only until the moment of observation—once a measurement is made, the wave function "collapses," reducing the particle to a single, definite state. This phenomenon, known as the observer effect, has profound implications, not only in physics but also as a metaphor for human potential. In a state of openness, individuals—like unobserved particles—possess a wide array of possible thoughts, actions, and spiritual expressions. They can explore various paths to enlightenment, pursue unconventional ideas, and exercise creativity without the constraints of external judgment.
However, surveillance functions much like the observer in quantum mechanics. Just as the act of measurement collapses the wave function into a singular outcome, constant surveillance collapses human potential into a narrower, more controlled set of behaviors. The awareness of being observed exerts a powerful psychological influence, prompting individuals to make safer, more predictable choices. Instead of exploring diverse spiritual or personal possibilities, individuals adapt to the expectations imposed by the ever-present digital gaze. The result is a diminished range of action, where genuine self-expression gives way to compliance and predictability—what can be termed the "singular collapsed state."
This singular collapsed state represents a profound loss of spiritual potential. When human behavior is constantly shaped by surveillance, it becomes more constrained, less creative, and ultimately less free. The open potential for spiritual growth, transformation, and connection to divine truth is replaced by a narrowed reality defined by conformity and safety. Just as quantum observation restricts the wave function to a single outcome, surveillance restricts individuals to a limited set of socially acceptable behaviors, inhibiting the soul’s journey toward deeper truth and spiritual liberation. This dynamic suggests that overcoming surveillance is not merely a matter of privacy or freedom of expression—it is essential for maintaining the open potential necessary for spiritual salvation itself. Breaking Free from Surveillance
To escape the confines of the surveillance matrix and reclaim human potential, embracing decentralized technologies is essential. Decentralized systems like Bitcoin and open-source protocols offer a tangible means of resisting centralized control and pervasive observation. Unlike centralized digital systems that collect and exploit data to manipulate behavior, decentralized technologies enable an open potential state where individuals can act freely, without fear of surveillance-induced consequences. They preserve privacy, protect free will, and create opportunities for genuine personal and spiritual growth. This decentralization aligns with divine principles of freedom, spontaneity, and diversity, reflecting the open and unpredictable nature of the universe itself. By choosing decentralized solutions, individuals can restore a more authentic connection to both digital and spiritual realms.
This shift is not purely technical; it’s deeply spiritual. Just as spiritual awakening requires a release from the bondage of sin and ignorance, digital liberation demands a conscious move away from surveillance-driven systems. Breaking free involves more than just switching technologies; it requires a transformation of mindset—one that recognizes surveillance as a spiritual and existential threat. It calls for the cultivation of awareness, discernment, and a willingness to embrace both technological sovereignty and spiritual autonomy. True salvation, in the context of a Cyber Gospel, is a holistic journey that requires overcoming both physical and digital chains. It is the fusion of spiritual liberation with the adoption of decentralized tools that enable true freedom in a digital world.
Ultimately, a Cyber Gospel serves as a guide for navigating this complex spiritual-digital landscape. It invites readers to explore how decentralized technologies can facilitate a digital exodus, moving humanity from a singular collapsed state to an open potential state where free will and spiritual growth can flourish. This path forward is both a call to action and a call to awakening. It urges readers to actively participate in building a future where technology serves as a bridge to liberation rather than a tool of control. As the lines between spiritual and digital realities blur, embracing this new form of salvation becomes not only possible but necessary for the soul’s journey toward wholeness and freedom. The Battle for the Soul in the Digital Age
The digital age is not just a technological revolution; it is a spiritual battleground where the soul's potential is tested by the forces of surveillance and control. In this new landscape, salvation must be reimagined as both spiritual and digital—a quest that demands free will, genuine choices, and the preservation of human potential against a backdrop of pervasive observation. Throughout this discussion, we have explored the nature of digital salvation, the essential role of free will, and how surveillance acts as a force that collapses human potential into a singular, predictable state. We have drawn parallels between quantum mechanics and human behavior, illustrating how surveillance, like the observer effect, restricts possibilities and narrows the range of spiritual and existential outcomes.
Yet, there is a path forward. Decentralized technologies offer a chance to resist this collapse and restore an open potential state, allowing for personal and spiritual growth in an age where control mechanisms seek to limit both. This liberation is not just about escaping technological constraints; it is about reclaiming the divine spark of free will, which is essential for true awakening. As we move deeper into this digital era, the challenge is clear: salvation must involve breaking free from the dual chains of spiritual ignorance and digital manipulation.
A Cyber Gospel can serve as a guide for navigating this complex terrain, calling for both spiritual and digital awakening. It asks seekers to reflect deeply on the nature of their freedom and the forces that shape it. The final question remains: Can the soul be truly free in a world of constant surveillance, or must it find a way to escape to achieve salvation? This question is not just philosophical but practical, urging users to consider how they can actively participate in the creation of a more liberated reality—both spiritually and digitally. The battle for the soul in the digital age is not just about avoiding surveillance; it is about embracing a deeper, more transformative form of freedom that aligns with both divine principles and technological sovereignty.
-
 @ 7f31a2d6:b5a93696
2024-11-22 18:44:35
@ 7f31a2d6:b5a93696
2024-11-22 18:44:35Leveraging Community Power: Yakihonne's Innovative Approach to Bitcoin Adoption
Introduction
The Bitcoin landscape is constantly evolving, and community plays a vital role in shaping its future. Yakihonne, a cutting-edge platform, is harnessing the power of community to drive Bitcoin adoption and education. In this article, we will explore Yakihonne's innovative approach and its impact on the Bitcoin ecosystem.
The Yakihonne Difference
Yakihonne distinguishes itself by recognizing every user as a unique node in the Bitcoin network. This perspective empowers individuals to take an active role in shaping the community and contributing to its growth. By fostering connections and knowledge sharing, Yakihonne creates a supportive environment where users can thrive.
Key Features and Benefits
-
Decentralized knowledge sharing: Yakihonne's platform allows users to access and share valuable resources, promoting a deeper understanding of Bitcoin and its applications.
-
Community-driven support: Users can engage with others, ask questions, and receive guidance from experienced community members.
-
Incentivized learning: Yakihonne's gamification elements make learning about Bitcoin engaging and fun, encouraging users to expand their knowledge.
-
Responsible adoption: The platform emphasizes security, privacy, and informed decision-making, ensuring sustainable growth.
The Future of Bitcoin Adoption
Yakihonne's community-centric approach is poised to revolutionize Bitcoin adoption. By leveraging the power of social nodes, Yakihonne creates a snowball effect, where knowledge and enthusiasm spread exponentially. As the platform continues to evolve, it's likely to play a significant role in shaping the future of Bitcoin.
Conclusion
Yakihonne is a game-changer in the Bitcoin space, offering a unique blend of community engagement, education, and support. By joining the Yakihonne community, individuals can tap into the collective power of social nodes, contributing to a brighter future for Bitcoin adoption. Embrace the potential of Yakihonne and be part of this exciting journey!@yakihonne
-
-
 @ bbb5dda0:f09e2747
2024-09-27 19:45:31
@ bbb5dda0:f09e2747
2024-09-27 19:45:31Moving into Norway the nice, almost-alpine landscapes greeted me. Slowly however the mountains numbed down and fjords started appearing. I was nearing Trondheim, the most northern city in Norway that has something that resembles a high-way. Anything further north and you’re bound to 80km/h roads. Which isn’t a bad thing at all, given the views.
| | | | | --- | --- | --- | |
 |
| |
| |
|| | | --- | |
 |
| On the road to Trondheim |
|
| On the road to Trondheim |I went pretty much straight to Trondheim because I got in touch with Lucas through an ex-colleague of mine (Thanks Niek ;)). I texted Lucas about a week before we met to see if he’d be up to go hiking somewhere in the Trondheim area. He said he was thinking about going North, waaaay North, in order to see the midnight sun and he wanted to do this the next weekend. This was around June 21st, the longest day of the year. I said it’d be cool to experience that and so that is just what we did. For those of you who don’t know, on June 21st the sun is right at the ‘Tropic of Cancer’ (‘Kreeftskeerkring’ in Dutch), the most northern position of the sun after which the summer slowly turns into winter again. In the period around this moment, the sun will NOT go below the horizon at all when you are above the arctic circle.
| | | | | --- | --- | --- | |
 |
| |
| |
|I’m glad Lucas has an electric car, because the round-trip would’ve cost me (whith my thirsty van) €333,-. Instead we spent less than €60,- for this 1200km round-trip. What a difference! So we left for the 9 hr drive on Friday-evening and camped out besides a lake next to the E6 highway, which runs all the way from the south to the north, which is over 3000(!) kilometers long.
| | | | | --- | --- | --- | |
 We found this seemingly abandoned bus, what a beauty! |
We found this seemingly abandoned bus, what a beauty! | |
| Woke up to this view! |
|
Woke up to this view! |
| |
| Time for a charging break in Mosjøen |
Time for a charging break in Mosjøen | |
| Because of a tunnel-closure we had to take this mountain-pass, not complaining here…
Because of a tunnel-closure we had to take this mountain-pass, not complaining here…We moved on the next morning and had perfect weather, too perfect for Norway because it was just below 30 degrees Celsius. This hot weather reached well into the arctic circle, where we’d be hiking up a mountain to find a camp-spot with a view to the north. We parked the car and started to hike up the steep hill, we found a route online, but soon found out we missed the path shown on the map. We figured we would not backtrack but instead walk around the same height on the mountain to get back at that path. Long story short, that path didn’t exist (anymore). So we tried to get back at it but just couldn’t find it. Eventually we just followed the trail that was actually set out using red ‘T’-s that were painted on the rocks every 50-100 meters. It was quite a walk and the heat didn’t make it any easier.
 A beginner mountaineer realizing he climbed the wrong mountain
A beginner mountaineer realizing he climbed the wrong mountain| | | | | --- | --- | --- | |
 After a near-death experience with mosquito’s, the Deet really saved us |
After a near-death experience with mosquito’s, the Deet really saved us | |
| |
|
|
| |
| |
| Finally we reached our intended camp-spot |
Finally we reached our intended camp-spot |
After draining most of our energy we finally arrived at the place we wanted to camp for the night day, which was in front of a small lake and a bigger one which lied a bit lower. I don’t think I need to say much more about the beauty of the place when you can just look at the pictures below:

 | | |
| --- | --- |
|
| | |
| --- | --- |
| |
|  |
|The ‘next’ day we hiked back, and tried to return using the ‘official’ path we wanted to hike in the first place, all in vain. It led us to hike some strange, steep and almost treacherous paths after which we decided it would be wise to just backtrack a little bit and get back to the (red) marked trail. We got back to the car safely after which we drove to the river that was just below the car park to take a refreshing dive before heading back south. We found a (safe) spot to take the dive in the river that was now raging because of the heavy snow-melt due to the extremely high temperatures. Lucas later told me that in some regions electricity was even free due to the surplus of hydro-electricity.
| | | | --- | --- | |
 We had to walk over this |
We had to walk over this |  |
|We made a car-recharge stop at Mosjøen where we had a quick pizza-dinner. Just after leaving the parking-lot we saw a couple hitch-hikers who wanted to go to Trondheim just like us. We pulled over and took them with us, they were a couple from different south-eastern European countries and were touring around Europe and soon also the world. They shared some cool stories and told about their plans. When we got to Trondheim we dropped them off near their camping-spot and drove back to Lucas’s house. Quite tired I jumped back in my own bed in my own home. How nice is it to have your house with you (almost) everywhere… 🙂
I camped in front of his house for a couple days. To be honest I didn’t do much those days as I was pretty much drained from experiencing all kinds of different things back-to-back for over a month now. I used this time to work a bit on the official stuff for my own freelance IT company which I started, I finally got a bank-account approved after 3 weeks of waiting, which allowed me to manage some of the essential setup-things and book-keeping. After these formalities I took a bit of time to head into the city-center, of course using my folding bike like a real Dutchie. And since Trondheim is a hilly city, biking downhill from Lucas’s house was a blast but going back up was quite the struggle with these tiny wheels, but it all worked out… That same night a thunderstorm was rolling in and sitting on top of a hill in a campervan, with lightning striking the ground at less than 100 meters away from the van was a new thing for me. I guess this too is part of the ‘living closer to nature’ thing…
I’m very thankful for the experiences and the hospitality of the people I meet along the way. It was very much fun to make this trip together! It’s the people that make the journey…
| | | | | --- | --- | --- | |
 |
| |
| |
|| | | | --- | --- | |
 |
| |
| -
 @ 6d8e2a24:5faaca4c
2024-11-22 18:00:21
@ 6d8e2a24:5faaca4c
2024-11-22 18:00:21BTC price behavior is either hinting at a deeper pullback or an RSI-fueled surge beyond $100,000, Bitcoin market observers conclude.
 Bitcoin BTC tickers down $99,001 faced a serious challenge hitting $100,000 on Nov. 22 as $300 million in sell-side liquidity blocked the way.
Bitcoin BTC tickers down $99,001 faced a serious challenge hitting $100,000 on Nov. 22 as $300 million in sell-side liquidity blocked the way. BTC/USD 1-hour chart. Source: TradingView
BTC/USD 1-hour chart. Source: TradingViewBTC price teases with rejection near $100,000
Data from Cointelegraph Markets Pro and TradingView showed BTC price downside taking over at the Wall Street open.
BTC/USD fell to local lows of under $97,300 and was down around 1.2% on the day at the time of writing.
A trip toward the key six-figure mark earlier ended in defeat as sellers lined up to prevent BTC’s price from climbing higher — a common feature for Bitcoin around key psychological levels.
“FireCharts shows a massive Bitcoin sell wall compressed between the $99.3k - $100k range,” trading resource Material Indicators confirmed in its latest post on X.
This referred to liquidity on the largest global exchange, Binance, with the $100,000 sell wall clearly standing out against other levels while building in strength over the past few hours.
“The good news is there has been a slight bit of erosion in the last few hours,” Material Indicators continued. “The bad news is, it’s still nearly $300M in liquidity.”
 BTC/USDT chart with order book liquidity data. Source: Material Indicators/X
BTC/USDT chart with order book liquidity data. Source: Material Indicators/XAccompanying volume data showed sell-side transactions dominated by amounts between $100 and $1,000, with whales still refraining from mass distribution.
“It would actually be good to see whales start dumping blocks of ask liquidity to force BTC into a support test and to ultimately make the wall easier to penetrate,” the post argued.
“With the ETF faucet turned off for the weekend, we could see some dip buying opportunities ahead.” United States spot Bitcoin exchange-traded funds (ETFs) achieved another day of net inflows above $1 billion on Nov. 21, reflecting considerable institutional interest supporting BTC price momentum.
Bitcoin four-hour RSI hints at bullish comeback
Others considered where a potential deeper price retracement may end up, with popular trader Crypto Chase eyeing $90,000 in what he called the “optimal scenario.”
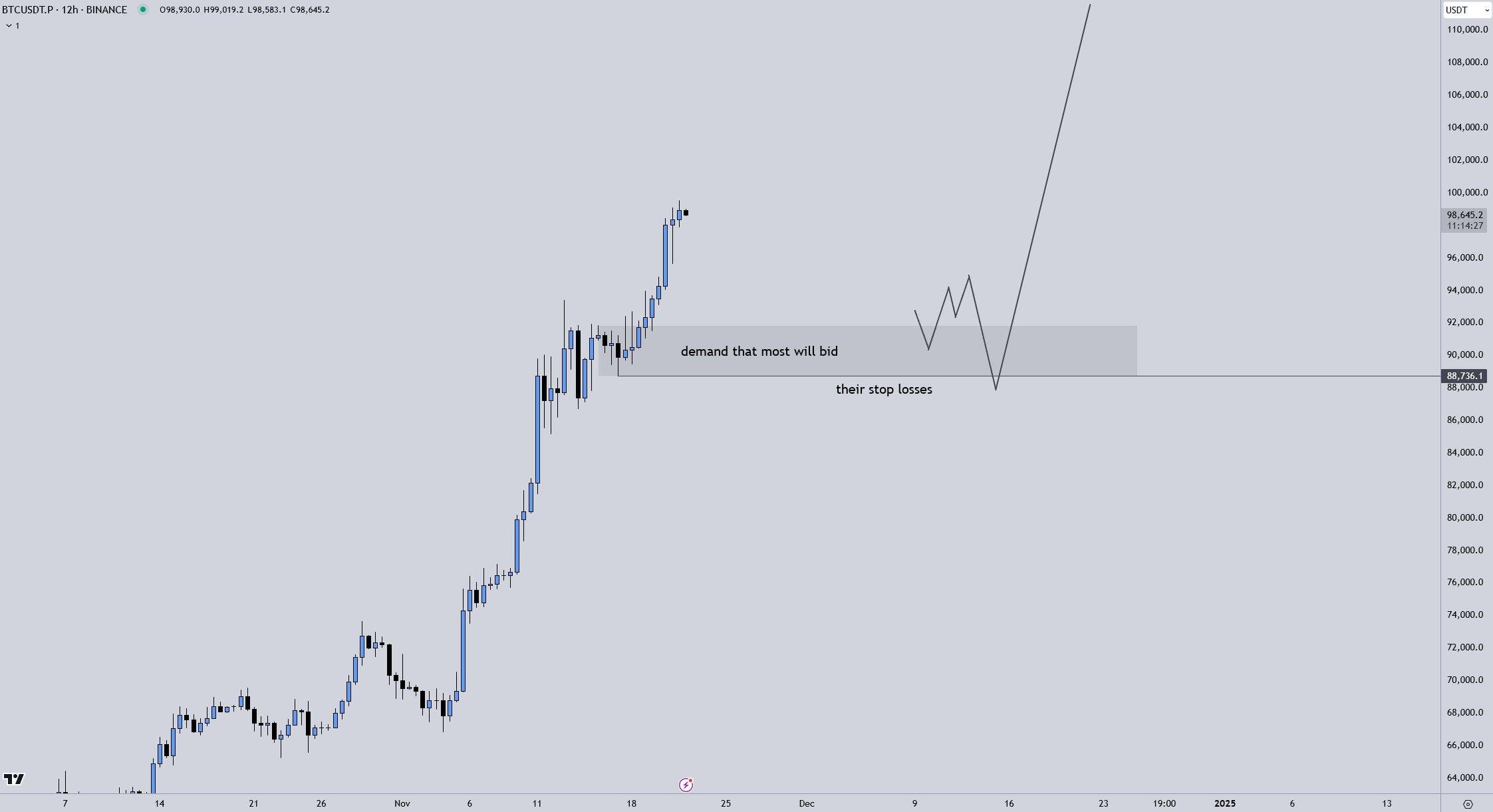 BTC/USDT 12-hour chart. Source: Crypto Chase/X
BTC/USDT 12-hour chart. Source: Crypto Chase/XFellow trader CJ had a higher target focused on the mid-$90,000 range.
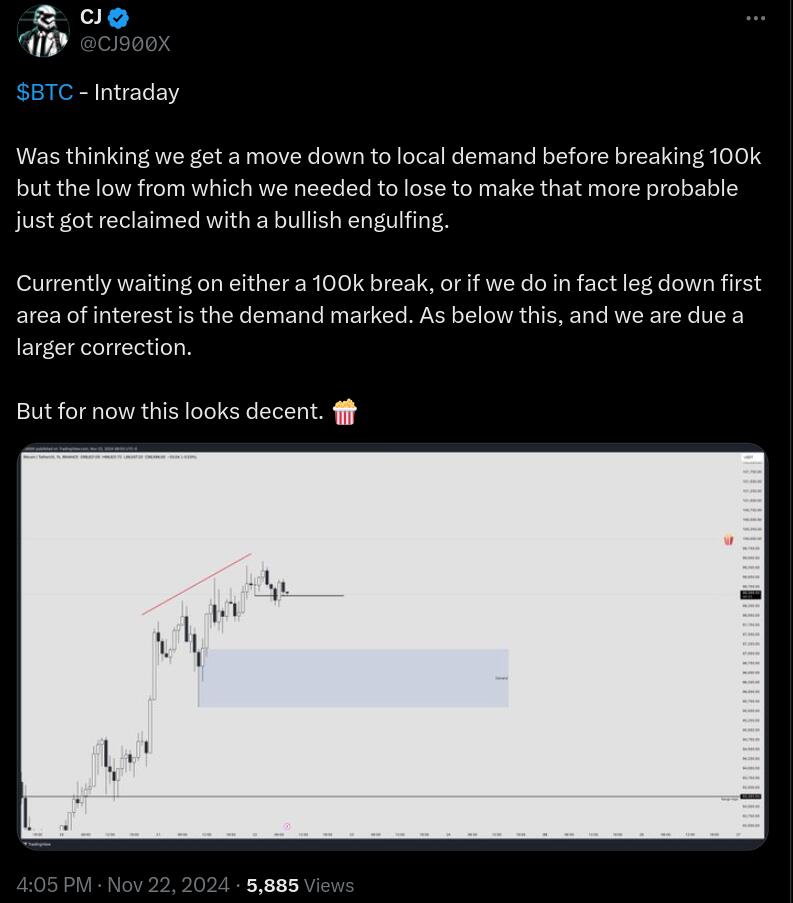 Source: CJ
In support of a return to upside, meanwhile, trader Roman noted promising bullish divergences on the four-hour relative strength index (RSI).
Source: CJ
In support of a return to upside, meanwhile, trader Roman noted promising bullish divergences on the four-hour relative strength index (RSI).This fell 10 points on the day, dipping below the key 70 “overbought” level.
“Big bull divs forming between price & RSI here. We should see trend continuation as a result,” he told X followers on the day.
“I think we break 100k today or tomorrow as this entire trend looks very strong.”
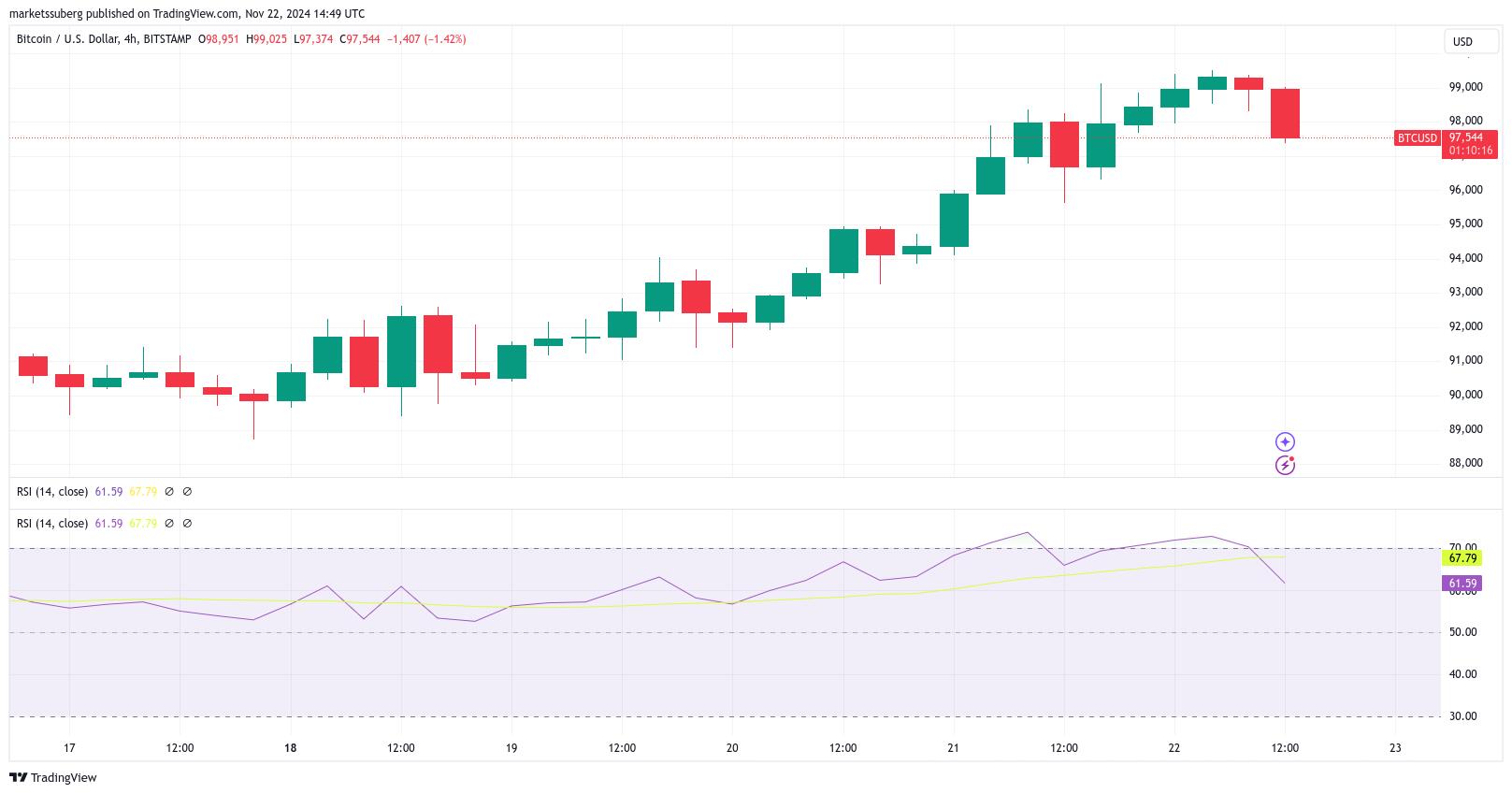 BTC/USD 4-hour chart with RSI data. Source: TradingView
BTC/USD 4-hour chart with RSI data. Source: TradingView -
 @ 502ab02a:a2860397
2024-11-22 17:58:24
@ 502ab02a:a2860397
2024-11-22 17:58:24
แนวคิด : ช้างเป็นสัตว์ในสัญลักษณ์ประจำจังหวัด สุพรรณบุรี เป็นการศึกแบบ ยุทธหัตถี จึงดึงเอาเฉพาะตัวช้างมาเป็นคาแรคเตอร์ในงานชิ้นนี้ ทำเป็นกึ่งๆช้างเผือก แทนความเป็นดาวรุ่ง มีการสวมเสื้อยืดลาย บิทคอยน์ และรองเท้าสีส้มตามสีของบิทคอยน์ กระพริบตา 1 ข้างเพื่อความน่ารักและเชิญชวนให้มาใช้บริการ
Link Download https://drive.google.com/drive/folders/1cXzbTCI0CqT9RWRETtwNLia7chL8Fyga?usp=sharing
Concept: An elephant is a symbol of Suphanburi Province, representing the historic royal battle of "Yutthahatthi" (elephant duel). This character is inspired by an elephant, designed as a semi-white elephant symbolizing a rising star. It wears a Bitcoin-themed T-shirt and orange shoes, representing Bitcoin's color. To add charm and invite engagement, the elephant winks playfully with one eye, encouraging people to use the service. Link Download https://drive.google.com/drive/folders/1cXzbTCI0CqT9RWRETtwNLia7chL8Fyga?usp=sharing

-
 @ 3f0702fa:66db56f1
2024-11-22 17:56:44
@ 3f0702fa:66db56f1
2024-11-22 17:56:44https://psv4.userapi.com/s/v1/d/_uiYP1zAFvcsd8t7Y_DVn31eUXEFO_MRBzYCTv0ZcrR86sAxPF-1gnbJ3rW9P587gmh8nE022gBcO9K7WWosxCBvoesq5KrI_extC-Gl7DtjA7bk6-5bgA/1732298014335.mp4
-
 @ 599f67f7:21fb3ea9
2024-09-19 08:27:12
@ 599f67f7:21fb3ea9
2024-09-19 08:27:12¿Qué es una dirección Lightning o Lightning address?
Una dirección Lightning es una dirección que visualmente se asemeja a una dirección de correo electrónico legible para los humanos, por ejemplo usuario@dominio.com pero que en realidad te permite recibir pagos en bitcoin instantáneos y económicos, sin la necesidad de tener un nodo en linea en tu dispositivo ni tener que generar facturas de forma manual cada vez que alguien te quiere hacer un pago.
¿Suena bien no?
¿Y cómo funciona?
Funciona utilizando el protocolo de pago LNURL.
Aquí se muestra un sencillo esquema de lo que ocurre en segundo plano.
En resumen, cuando otro usuario quiere pagarte usando tu dirección Lightning, tu billetera convierte la dirección Lightning en una solicitud de pago LNURL. Luego se utiliza esa solicitud de pago LNURL exitosa para obtener una factura BOLT11.
💡 Dirección Lightning > LNURLp > Factura BOLT 11.
Suena bien, pero ¿cuál es el problema?
Por el momento, muchas de las implementaciones de Lightning Address son de custodia, porque se necesita un dominio para que Lightning Address funcione y un nodo que esté siempre en línea para recibir los pagos. Debido a que es de custodia, el custodio puede atacarte en cualquier momento y monitorear tus transacciones.
Tienes que confiar en el propietario del dominio para no cambiar el registro de tu dirección Lightning. Y no funciona si el servidor LNURL no está en línea.
Bitcoin Txoko ofrece una sencilla solución de Lightning Address respaldada por LNbits. Esto también es de custodia, así que por favor mantén solo una pequeña cantidad en tu billetera Bitcoin Txoko y ve retirando a tu billetera de autocustodia a medida que recibas más sats.
Estoy listo, ¿qué necesito para empezar?
¡Todo lo que necesitas es un teléfono móvil o un ordenador y una conexión a Internet!
1. Creando tu billetera
Si aún no lo has hecho, navega a https://bitcointxoko.com y crea una nueva billetera. Puedes elegir el nombre que quieras.
2. Activar extensiones
Hace falta la extensión
Pay Linkspara que las direcciones Lightning funcionen.Abre
Extensionesen la barra de herramientas y activaPay Links.3. Creando tu enlace de pago
-
En a la extensión
Pay Links, haz clic enNew Pay Link. -
Elige la billetera que has creado.
-
Para la descripción del artículo, puedes escribir lo que quieras.
-
Elige un nombre de usuario de tu dirección Lightning. Tu dirección Lightning se verá como
username@bitcointxoko.com. -
Desmarque
Fixed amounty cambia el valor mínimo a 1 y el valor máximo a 500000.
⚠️ También puedes cambiar el valor máximo a algo más alto, pero es más probable que los pagos más grandes fallen debido a la limitada capacidad de entrada del nodo Lightning de Bitcoin Txoko. Así que recomendamos mantenerlo en 500000 sats.
-
Ahora abre
Advanced optionsy cambiaComment maximum charactersa 799. Este paso no es necesario pero permite más funcionalidades más adelante. -
Marca
Enable nostr zapsen la parte inferior, para que puedas utilizar tu dirección Lightning para recibir zaps. -
Las demás opciones avanzadas son opcionales, puedes configurarlas si quieres o dejarlas en blanco.
Al final debería verse algo así.
- Cuando hayas comprobado que todo es correcto, sigue adelante y haz clic en
Create Pay Link.
Probando
Puedes probar si tu nueva dirección Lightning funciona yendo a otra cartera, pulsando en
Enviary escribiendo tu dirección Lightning como destino, y luego enviándote una pequeña cantidad de sats.Vuelve a tu billetera Bitcoin Txoko y comprueba si has recibido tu propio pago. Es posible que tengas que actualizar la página.
Si todo funcionó correctamente, ¡enhorabuena! 🥳
Si no es así, háznoslo saber. Siempre estamos aquí para ayudar.
Próximos pasos
Nostr zaps
Puedes añadir tu dirección Bitcoin Txoko Lightning a tu perfil de nostr y usarla para recibir zaps. Normalmente, esto se hace yendo a
Perfil>Editar>Dirección Lightningy cambiando la dirección Lightning.LNDhub
Puedes importar tu billetera LNbits como un LNDhub en tu teléfono utilizando una aplicación como Zeus o BlueWallet, en lugar de visitar la billetera en el navegador cada vez que desees comprobar tu saldo o realizar un pago. Echa un vistazo a nostr:naddr1qvzqqqr4gupzqkvlvlma7a55ccp6d5rrdc27h3ssmdmael286mjaq5uxmqslk04fqqxnzd3exuerqdfkxccnyv3cs0uvul sobre cómo hacer esto.
Código QR
También puedes compartir o imprimir tu código QR LNURLp para que la gente pueda escanearlo fácilmente con sus teléfonos. ¡Muy útil si estás introduciendo bitcoin a tu comerciante local favorito para que pueda recibir propinas Lightning!
Simplemente comparte el enlace a tu página compartida, o imprime el código QR como PDF yendo a
View Link>Print. -
-
 @ 705605d9:b4324038
2024-11-22 17:51:13
@ 705605d9:b4324038
2024-11-22 17:51:13Вы видели цены на сливочное масло? Кажется, грустнее смотреть только на цены на бензин. И виноваты в этом порой не затраты на производство (не зря же его постоянно оптимизируют!), не неурожайные года, а простая человеческая жадность.
Желание одного человека набить карманы стало причиной дефицита базового для жителей Горноправдинска продукта на полках магазинов. И человек этот занимал пост достаточно серьёзный — Анастасия Комаринская занимала пост руководителя департамента молодёжной политики.

Вот только вместо того, чтобы давать горноправдинской молодёжи возможности для развития и создавать таким образом будущее для региона и страны, она давала взятки рабочим и создала искусственный дефицит.
Сливочное масло вместо благосостояния
Масло, которое производится в Горноправдинске, заняло своё место на полках местных магазинов: жители города полюбили его за доступную цену, вкусовые качества и натуральный состав. Но последние несколько месяцев покупать его в супермаркетах стало проблематично: найти его там порой было просто невозможно. Зато в сомнительных частных магазинах по цене раза в два-три больше обычной его стало хоть отбавляй.
Редакция провела расследование, и оказалось, что платят продавцам здесь не больше, чем в обычных супермаркетах, но никаких льгот не предоставляют, а владельцами нескольких таких магазинов ("Брусничка", "Любава", "Молоко и мясо" и ещё нескольких точек оказались родственники Комаринской — например, "Любава" и "Брусничка" зарегистрированы на жену сына Анастасии Комаринской, Екатерину.

Наш корреспондент Эльвира смогла добиться комментариев от Екатерины Комаринской, и она утверждает, что руководством точкой она практически не занимается.
— Я вообще не предприниматель по натуре, у меня нет на это таланта. Я занимаюсь икебаной и танцами, но таланта к бизнесу у меня никогда не было. — честно признаётся она.
При этом за последние три месяца Екатерина смогла купить себе колье Cartier. Откуда у девушки, которая занимается цветами, такие деньги? Примерно оттуда же, откуда у работников производства — лишние деньги на цветы жёнам и подарки детям. Это цена молчания Екатерины о гнусных схемах Анастасии.
Официально Анастасия Комаринская получает не более двухсот тысяч в месяц.
Правоохранительные органы установили, что Анастасия через подставных лиц (одним из таких стала её невестка Екатерина) скупала сливочное масло по оптовым ценам, подкупая руководство завода и даже некоторых простых рабочих, а потом перепродавала всё на своих точках по резко завышенным ценам. И полученная прибыль шла не на развитие города: они направлялись в карманы человека, которому, по идее, доверено служить интересам его жителей.
Представители администрации Горноправдинска заявили, что они полностью поддерживают расследование. «Мы не потерпим произвол в наших рядах. Перед законом равны все», — прокомментировал ситуацию нынешний глава администрации, обещая полное сотрудничество с правоохранительными органами.
Местные жители внимательно следят за ходом расследования — подобный произвол прямо у них под носом никому не нравится. Общественные группы уже начали собирать подписи за отстранение чиновника от должности и требование провести полный аудит работы местной администрации.

На данный момент Анастасия отстранена от должности и находится под следствием по статье 174 УК РФ. Прокуратура запрашивает лишение свободы на срок 5 лет, но общественность считает это наказание слишком мягким — всё же, речь идёт о сумме в несколько миллионов рублей.
Следующее судебное заседание по делу Комаринской назначено на 21 декабря.
-
 @ 1b5ee74d:bb1aae6e
2024-09-10 08:51:03
@ 1b5ee74d:bb1aae6e
2024-09-10 08:51:03- Who Is Responsible for the Content Published on Social Networks?
- What should the role of platforms be in content moderation?
- Who should be consulted in cases of disputes involving illegal content?
- Should there be a limit to freedom of speech online? Where should the line be drawn?
These are just a few of the numerous questions that have characterized the debate for years, not only regarding social networks but, more broadly, the entire landscape of online interactions.
In recent weeks, tensions have reignited due to three cases that have stirred the pot—depending on the perspective—with slogans of either combating illegal activity or fighting censorship: Telegram, Meta, and X.
These cases are distinct, with the platforms and their executives behaving differently in each instance: Meta cooperated with authorities, while Telegram and X were more reluctant. However, all three stories share a key issue—perhaps the key issue: the ability to intervene in the content they host.
To understand the reason, let’s briefly recap what happened.
Telegram, Meta, and X: Three Different Cases, One Common Origin
Pavel Durov, founder of Telegram, was arrested in Paris on August 24th as part of an investigation that French authorities have been conducting for months against the messaging platform.
The accusations are numerous: money laundering, drug trafficking, child pornography, and refusal to cooperate with law enforcement. In the press release issued by the Prosecutor’s Office, there is even mention of violations related to the import and export of cryptographic tools—an approach reminiscent of the United States in the 1990s, when the government classified cryptography on par with weaponry. This interpretation only changed due to the outcome of the Crypto Wars.
In fact, reports tell us that Pavel Durov was released after a few days upon paying a €5 million bail, with the condition that he not leave France. Initially, Telegram issued a statement via Twitter, asserting its compliance with European laws. But on September 6th, the founder of Telegram decided to fight back, leaving little room for interpretation.
"Sometimes we can’t reach an agreement with regulators in certain countries on the right balance between privacy and security," Durov said, adding that, if necessary, Telegram will leave markets that are incompatible with these principles.
It is worth noting that this is not the first time Durov has clashed with authorities. In the past, he refused to cooperate with Russia by denying access to Telegram users’ personal data. This refusal led to the platform being temporarily blocked in Russia in 2018.
Meta: Pressure from the White House and Zuckerberg’s Revelations
Mark Zuckerberg, CEO of Meta, recently disclosed pressures he received from the White House during the pandemic. In a letter to the U.S. House Judiciary Committee, Zuckerberg revealed that the Biden administration pushed Meta to remove content related to the virus, including satirical and critical posts.
Zuckerberg explained that in 2021, Meta deleted more than 20 million posts related to COVID-19 but expressed regret over some of the decisions made, admitting that the company had succumbed to excessive political pressure.
Zuckerberg emphasized that these requests were perceived by the company as an obligation rather than a choice, and in hindsight, some of these actions might have been mistakes. Meta’s future commitment, according to Zuckerberg, will be to better resist such pressures, even in emergency situations.
I believe the government’s pressure was wrong, and I regret not being more transparent about it.
X and the Clash with the Brazilian Government
Elon Musk and X (formerly Twitter) are at the center of a legal dispute in Brazil, where the platform was blocked after Musk refused to appoint a local legal representative, as required by the country’s Supreme Court. The issue arose when Judge Alexandre de Moraes ordered X to suspend certain accounts accused of spreading political disinformation, particularly those associated with former president Jair Bolsonaro and his supporters.
Musk’s reaction was harsh. He accused the Supreme Court of corruption and of violating free speech, criticizing de Moraes and calling him a “criminal.” However, the judge continued his legal actions against Musk and his company, even freezing the bank accounts of Starlink, Musk’s satellite division, to pressure X into complying with Brazilian laws.
Brazilian authorities are even pursuing those who attempt to access the platform using VPNs, sparking further controversy over freedom in Brazil.
Currently, the platform remains suspended, with about 21 million Brazilian users cut off from the service. The legal dispute is ongoing and could have long-term repercussions for X’s presence in Brazil, one of the platform’s largest markets.
The Ownership of Content
Telegram and X have found themselves in hot water for refusing to comply with content moderation mandates imposed by various jurisdictions. Meta, on the other hand, has avoided such issues by adhering to directives from the White House, including the removal of content flagged by Washington, such as “satirical and ironic” posts, as noted in the letter.
The decisive factor in all three cases is the same: the ability to intervene in what is published on the platform. The terms and conditions of Meta and X do not formally claim ownership of the content users post, but they clarify that users grant the companies a non-exclusive, royalty-free, worldwide license to use, distribute, modify, and display the content in relation to the services offered. Telegram’s terms are slightly stricter: while users also retain formal ownership of their content, Telegram requires a license to distribute and display content only within its ecosystem.
However, the result remains the same. Anything published by users can be modified by the platform, according to the implicit contract every single user agrees to when they begin using the service.
Nostr is the Way
It’s no coincidence that, in recent weeks, many who care about issues such as privacy and censorship resistance have reignited interest in Nostr. The protocol, whose acronym stands for Notes and Other Stuff Transmitted by Relays, can be used via various clients, not a single platform—similar to how the Web is accessible from different browsers.
But most importantly, users who create an account do not do so through a username and password saved on the company’s servers—because, in this case, the company doesn’t exist—but rather through a public key and a private key.
This key pair allows users to interact with Nostr across multiple clients and send their “notes”—as posts are called on Nostr—to as many relays (servers) as they wish. In other words, the data is not stored on a single server but on multiple servers chosen by the user—and the user can even set up their own server without much difficulty.
Most importantly, the data is portable. Posts sent are cryptographically signed: in Nostr, content ownership is not just formally with the user, it is mathematically so.
In such a context, blaming the operator of a client or relay for the content signed and published by users' private keys would be bordering on absurdity, besides revealing a clear technical ignorance. Of course, after the accusations from the U.S. Department of Justice against the developers of Samourai Wallet, it’s fair to be ready for anything.
But giving a chance to solutions like Nostr also means considering the possibility of reclaiming one's online identity and no longer being an unconscious victim of manipulative algorithms and invasive governments.
-
 @ 502ab02a:a2860397
2024-11-22 17:50:23
@ 502ab02a:a2860397
2024-11-22 17:50:23
แนวคิด : ที่มาของคำว่า 8ริ้ว ชื่อเล่นของจังหวัดฉะเชิงเทรา มาจากปลาช่อนขนาดใหญ่ ที่สามารถแบ่งได้ถึง 8 ริ้ว จึงออกแบบให้เป็นรูปปลาช่อน แล้วติดเหรียญเลข 8 เอาไว้ ทั้งเป็นเลขมงคลและเป็นการแทนค่า 8ริ้ว ของปลาด้วย ด้านหลังเป็นสัญลักษณ์ bitcoin พร้อมคำว่า ฉะเชิงเทราเป็นภาษาอังกฤษ และกำกับภาษาไทยที่ด้านล่างอย่างโดดเด่น Link Download https://drive.google.com/drive/folders/1i6DU2jt_fgUQUAfPqOsJa1h6C-rrIPy2?usp=sharing
Concept: The origin of the nickname “8 Riew” for Chachoengsao Province comes from a large snakehead fish that could be cut into eight large slices. The design incorporates an image of a snakehead fish with an “8” coin to represent both the rich number and the symbolic “8 Riew” slices. The background features the Bitcoin symbol along with “Chachoengsao” in English and prominent Thai text below. Link Download https://drive.google.com/drive/folders/1i6DU2jt_fgUQUAfPqOsJa1h6C-rrIPy2?usp=sharing

-
 @ 13e63e99:25525c6a
2024-09-03 09:29:54
@ 13e63e99:25525c6a
2024-09-03 09:29:54Preview
Last week, President Nayib Bukele of El Salvador emphasized Bitcoin’s role in enhancing the country's global image that boosted foreign investment and tourism. At the NostrWorld Unconference in Riga, the synergy between Bitcoin and decentralized social networks was a key focus, showcasing the potential for integrating Bitcoin with the growing Nostr protocol. Meanwhile, Lightspark launched its Extend platform, facilitating instant Bitcoin payments for U.S. businesses, thereby expanding the accessibility of Bitcoin transactions. Publicly traded companies have increased their Bitcoin holdings by nearly 200%, bringing their total to $20 billion, reflecting strong institutional confidence in Bitcoin as a reserve asset. Additionally, Bitcoin in exchange experienced its third-largest daily net outflow of 2024, indicating a shift toward long-term holding among investors. Despite some withdrawals, including a $13.5 million outflow from BlackRock’s iShares Bitcoin Trust, the fund remains a dominant force in the Bitcoin investment landscape. Lastly, Nigeria's SEC granted its first provisional exchange license, a milestone in the regulation of the country’s rapidly growing digital asset industry, positioning Nigeria as a leading player in global digital asset adoption. For more details, continue reading below.
A. Bitcoin Data Dashboard
1. Bitcoin Transactions\ 2. Supply\ 3. Mining\ 4. Transaction Fees\ 5. Difficulty Retarget\ 6. Lightning Network (Public)
B. Bitcoin Ecosystem
1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador\ 2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks\ 3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.\ 4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion\ 5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024\ 6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals
C. Regulation
1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation
D. Macroeconomy
1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich\ 2. Jobless claims drop as labor market slows, US economy remains on steady growth path
A. Bitcoin Data Dashboard

As of Sep 2, 2024
B. Bitcoin Ecosystem
1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador
President Nayib Bukele recently provided a candid assessment of El Salvador's groundbreaking decision to adopt Bitcoin as legal tender, a move that has drawn both praise and criticism on the global stage. In an interview with Time magazine, Bukele emphasized that the initiative has had substantial benefits particularly in enhancing El Salvador's international image despite the country's bitcoin adoption has not expanded as rapidly as he has hoped, Bukele described the Bitcoin adoption as a powerful rebranding tool for the nation, one that has attracted foreign investment and boosted tourism. The president’s marketing advisor, Damian Merlo, echoed this sentiment, calling the decision "genius" and likening it to a major public relations campaign that El Salvador didn’t have to pay for. "We could have spent millions on a PR firm to rebrand the country," Merlo noted, "but instead, we adopted Bitcoin." While the move initially strained relations with institutions like the International Monetary Fund (IMF), which urged Bukele to abandon the policy due to perceived risks, there are signs that the tension is easing. El Salvador has recently reported progress in negotiations with the IMF, with a focus on enhancing transparency and addressing potential fiscal and financial stability risks related to the Bitcoin project.

Reference: Bitcoin.com, Time
2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks
Last week, NostrWorld’s third unconference, held in Riga, Latvia, gathered advocates and developers of the Nostr protocol. Organized by Jack Dorsey, NostrWorld provides a platform for open-source enthusiasts to collaborate on building a decentralized internet. The event, called Nostriga, underscored the emerging synergy between Nostr’s decentralized social network and Bitcoin. Nostr is an open-source protocol for a decentralized, censorship-resistant social network. Unlike traditional platforms, Nostr operates on a network of relays, supporting features like micropayments and digital identity management. It promises greater privacy and independence from centralized platforms. A highlight of the conference was Strike CEO Jack Mallers discussing how Nostr’s micropayments—Zaps—helped a skeptic understand Bitcoin’s value. This feature shows Bitcoin’s utility in social contexts, advancing the concept of internet tipping. Jack Dorsey enphasizing the importance of open source. Nostr faces the challenge of broadening its user base beyond Bitcoin enthusiasts. New initiatives like Ditto aim to integrate Nostr with larger internet communities, potentially increasing Bitcoin’s visibility and accessibility. Nostr’s role as a social and identity system could pave the way for decentralized digital economies. By leveraging social graphs and cryptographic trust, Nostr and Bitcoin together could enable secure, decentralized commerce.
Reference: Bitcoin magazine
3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.
Lightspark has unveiled Lightspark Extend, a new solution designed to facilitate instant Bitcoin Lightning payments for U.S. businesses. This platform integrates with Universal Money Addresses (UMA) and Lightning-enabled wallets, exchanges, or bank accounts, offering a compliant and cost-effective way to handle transactions around the clock. Lightspark Extend is compatible with over 99% of U.S. banks that support real-time payments, enabling businesses to provide their customers with fast, low-cost transactions. UMA simplifies the payment process by using easy-to-remember addresses similar to email, removing the need for complex codes or passwords. With this launch, Lightspark Extend makes real-time payments via the Bitcoin Lightning Network accessible to eligible recipients across the U.S. Businesses interested in adopting this solution can sign up for a UMA address, link their accounts, and start receiving payments through an onboarding process facilitated by Zero Hash, a regulated U.S. financial institution. The introduction of Lightspark Extend marks a significant advancement in expanding the accessibility and utility of Bitcoin payments. This follows Lightspark’s recent announcement of a partnership with Coinbase, enabling customers to send up to $10,000 instantly through the Lightning Network.
Reference: Bitcoin magazine
4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion
Publicly listed companies have seen their Bitcoin holdings soar by nearly 200% in a year, rising from $7.2 billion to $20 billion. According to Bitbo data, 42 such companies now hold 335,249 BTC, valued at roughly $20 billion. This marks a 177.7% increase from a year ago, when their BTC holdings were worth $7.2 billion. The trend began with MicroStrategy's August 2020 purchase of over 21,000 BTC, making Bitcoin its primary treasury reserve asset, and the company has since grown its holdings to 226,500 BTC. A survey commissioned by Nickel Digital Asset Management revealed strong institutional support for Bitcoin as a reserve asset, with 75% of 200 surveyed institutional investors and wealth managers endorsing public companies holding BTC. The survey, involving firms managing $1.7 trillion in assets, also found that 58% believe 10% or more of public companies will hold BTC within five years. Nickel Digital's CEO, Anatoly Crachilov, noted that institutional investors see Bitcoin as a hedge against currency debasement and a valuable addition to reserve allocations. Despite this growth, the 335,249 BTC held by public companies represent just 1.6% of Bitcoin's total capped supply of 21 million.
Reference: Cointelegraph
5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024
Bitcoin is seeing a significant uptick in exchange withdrawals as its price nears the $60,000 mark, with approximately 45,000 BTC removed from exchanges on August 27 alone. This movement represents the third-largest net outflow of Bitcoin from exchanges in 2024, following similar spikes in July. According to data from CryptoQuant, this trend could signal a growing bullish sentiment among investors, who appear to be transferring their Bitcoin off exchanges to hold for the long term, thereby reducing potential selling pressure in the market. As of August 27, major exchanges hold around 2.63 million BTC, reflecting a 12.5% decrease from the 3.01 million BTC held at the beginning of the year. This reduction in exchange reserves underscores a broader trend of investors preferring to hold their Bitcoin privately, possibly in anticipation of future price increases.

Reference: Cointelegraph
6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals
BlackRock's iShares Bitcoin Trust (IBIT) experienced a $13.5 million outflow on Thursday, marking its first outflow since May 1st and only the second in the fund's history since its launch in January. This rare withdrawal contrasts with the ETF’s usual pattern of consistent inflows, underscoring its dominance in the Bitcoin investment space. The outflow came as part of a broader trend affecting spot Bitcoin ETFs, which saw a collective $71.8 million in withdrawals on Thursday. Competing Bitcoin ETFs from Grayscale, Fidelity, Valkyrie, and Bitwise also reported significant outflows, ranging from $8 million to $31 million. Despite these withdrawals, ARK's Bitcoin ETF saw an inflow of $5.3 million, highlighting a mixed investor sentiment as Bitcoin remains below the $60,000 mark. This divergence suggests varied outlooks among investors regarding Bitcoin's future. Despite the recent dip, BlackRock's Bitcoin ETF continues to lead the market, having attracted over $20 billion in net inflows since inception. With more than 350,000 BTC under management, it remains one of the largest institutional Bitcoin holders, reflecting its enduring appeal and influence in the Bitcoin investment landscape.
Reference: Bitcoin magazine
C. Regulation
1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation
The Nigerian Securities and Exchange Commission (SEC) has granted Quidax, an Africa-based crypto exchange, its first provisional operating license. This marks a significant step toward formal recognition and regulation of Nigeria's digital asset industry. The SEC's license allows Quidax to operate as a registered crypto exchange in Nigeria, a move the company describes as a "shot of adrenaline" for the local crypto community, spurring innovation and growth. Quidax CEO Buchi Okoro praised the SEC, particularly under the leadership of Emomotimi Agama, for its efforts to bring order and investor protection to the Nigerian crypto market. The approval also paves the way for Quidax to collaborate with banks and financial institutions, pending approval from the Central Bank of Nigeria. This licensing follows the SEC's recent amendment to its rules on June 21, covering digital asset issuance, exchange, and custody. Despite concerns that stringent requirements could limit local crypto exchanges, the new regulatory framework, including the Accelerated Regulatory Incubation Programme, aims to align virtual asset service providers with the latest standards. Nigeria, Africa's largest economy, is a global leader in cryptocurrency adoption, ranking second in Chainalysis’ 2023 Cryptocurrency Geography Report. While foreign investment in Nigeria's crypto sector has been slower than expected, the new regulatory environment and Quidax's licensing could attract more investors by offering a stable and secure market.
Reference: Cointelegraph
D. Macroeconomy
1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich
As a presidential candidate, Vice President Harris has aligned with President Biden’s tax policies, including the pledge not to raise taxes on anyone earning under $400,000 annually. However, she also has her own ambitious tax proposals. These include raising the top marginal tax rate on high earners from 37% to 39.6%. Although she previously suggested a 4% “income-based premium” on households earning over $100,000 to fund Medicare for All, this idea has not resurfaced in 2024. Among the more controversial proposals Harris supports is a tax on unrealized capital gains for individuals with over $100 million in wealth. Often dubbed the “billionaire tax,” this would require these households to pay an annual minimum tax of 25% on their combined income and unrealized gains. This approach would be groundbreaking in U.S. tax history, as it taxes assets that have not yet been sold. For example, if you buy stock at $10 and it increases to $20, you would owe taxes on the $10 gain, even if you haven’t sold the stock. The same principle would apply to real estate, where yearly value increases would be taxed. This proposal raises significant concerns, particularly about the administrative challenges of valuing assets annually and the potential for future expansion of the tax to lower wealth thresholds. The wealth tax faces hurdles in Congress and potential court challenges, but it signals Harris's intent to push for new forms of taxation on the ultra-wealthy.

Reference: Forbes
2. Jobless claims drop as labor market slows, US economy remains on steady growth path
Last week, new applications for jobless benefits in the U.S. dropped slightly, but re-employment opportunities for laid-off workers are becoming scarcer, indicating the unemployment rate likely remained high in August. Despite this, the labor market's orderly slowdown is keeping economic growth on track, with the economy growing faster than initially reported in the second quarter, driven by consumer spending and rebounding corporate profits. The labor market's cooling supports the expectation that the Federal Reserve may start cutting interest rates next month, though a 50-basis-point reduction seems unlikely. Initial jobless claims fell by 2,000 to 231,000 for the week ending August 24, while continuing claims, which indicate ongoing unemployment, rose slightly, suggesting prolonged joblessness. In the second quarter, the economy grew at an annualized rate of 3.0%, with consumer spending revised upward to a 2.9% growth rate, offsetting lower business investment and exports. Corporate profits also reached a record high, helping businesses manage input costs amid supply-chain challenges. The goods trade deficit widened in July due to a surge in imports, likely driven by expectations of higher tariffs if former President Trump wins the November election. Despite these factors, economists predict growth will slow but avoid a recession.

-
 @ 2775fb0f:887f8193
2024-11-22 17:46:15
@ 2775fb0f:887f8193
2024-11-22 17:46:1530 августа. Новодвинск-2040. Архангельский целлюлозно-бумажный комбинат объявил о внедрении новой системы очистки воздуха, направленной на снижение загрязнений и улучшение экологической ситуации в регионе. В рамках этой инициативы комбинат заменил устаревшие технологии на современные решения, которые обещают значительно улучшить качество воздуха в окрестностях.
Среди внедренных систем – высокоэффективные фильтры и установки для нейтрализации выбросов, которые позволяют улавливать до 95% вредных веществ. Старые системы, основанные на менее эффективных методах, таких как простая механическая фильтрация, были признаны неактуальными и выведены из эксплуатации. Это решение стало возможным благодаря значительным инвестициям в модернизацию оборудования и внедрению инновационных технологий.
«Мы понимаем, что наша ответственность не ограничивается производственными показателями. Мы стремимся к тому, чтобы наш комбинат стал примером экологической устойчивости. Новая система очистки воздуха – это шаг к более чистому будущему для наших сотрудников и жителей Новодвинска», – прокомментировал изменения главный директор АЦБК Дмитрий Зылёв. Жители Новодвинска уже начали замечать изменения. Один из местных жителей, Дмитрий Вторыгин, рассказал о своих впечатлениях:
«Я живу здесь всю жизнь, и за неделю почувствовал, что воздух стал заметно чище. Запах, который раньше был постоянным спутником, теперь почти не ощущается. Это действительно радует!»
Переход на новую систему очистки воздуха прошел быстро и эффективно. Комбинат завершил все необходимые работы за рекордные три месяца, что позволило минимизировать простои в производстве и сохранить рабочие места.
В планах АЦБК – дальнейшее улучшение экологической ситуации. В ближайшие годы комбинат намерен внедрить дополнительные технологии по утилизации отходов и оптимизации производственных процессов, что позволит не только сократить выбросы, но и повысить общую эффективность работы предприятия.
Таким образом, Архангельский целлюлозно-бумажный комбинат делает важный шаг к устойчивому развитию, заботясь о здоровье своих сотрудников и жителей региона.
-
 @ 2775fb0f:887f8193
2024-11-22 17:43:32
@ 2775fb0f:887f8193
2024-11-22 17:43:3222 августа 2040 года в Новодвинске объявлено предупреждение о сильном дожде, который ожидается 22 августа. Метеорологи прогнозируют интенсивные осадки, которые могут привести к затоплению низменных участков и ухудшению дорожных условий.
В связи с этим местные власти призывают жителей принять меры предосторожности:
- Оставайтесь дома: По возможности, избегайте ненужных поездок и оставайтесь в помещениях, особенно в период сильного дождя.
- Проверьте дренажные системы: Убедитесь, что водостоки и дренажные канавы вокруг вашего дома не забиты и могут эффективно отводить воду.
- Подготовьте запас продуктов: Запаситесь необходимыми продуктами и водой на случай, если дождь затруднит доступ к магазинам.
- Следите за новостями: Будьте в курсе обновлений от местных властей и метеорологической службы, чтобы получать актуальную информацию о погодных условиях.
- Избегайте низменных мест: Не находитесь вблизи рек и ручьев, которые могут выйти из берегов.
Власти Новодвинска призывают всех жителей соблюдать осторожность и следовать рекомендациям, чтобы минимизировать риски, связанные с сильными осадками.
-
 @ 469fa704:2b6cb760
2024-09-02 06:11:43
@ 469fa704:2b6cb760
2024-09-02 06:11:43I joined Nostr a week ago and wanted to recap it for myself and also give other newbies a simple introduction. Maybe this will help you get started too.
Step 1: Create your identity and get your private key for a browser extension
I started with the Snort client on my local home server. It created my private/public key pair and I was good to go. Then I transferred the private key to Amethyst, a pretty good Android-based client. Before looking at various clients and other nostr-based websites, I tried transferring my private key into a browser extension. I looked at Alby and nos2x. I chose the latter because I wanted to keep my Lightning wallet separate from my identity management. You don't have to, I just found it easier.
Step 2: If you're confused, always check your feed settings
I tried many different clients and was very confused at first. Due to its decentralized nature, Nostr relies on relays, which are just small servers, and to each one you can connect to, all your data is stored. When you post a message, write a note, an article like this or simply who you follow. The main reason and benefit for this is that there is no single point of failure or server-like entity that could be censored. The side effect of this, combined with using different clients, was that not only did it look different everywhere, but the content was also very different. This was simply because I wasn't connected to all my different clients with the same relays. But the main reason why each feed looks different on each client is usually because you can choose different variations of feeds and some clients even offer filters for the feeds.
Scroll down to get a small overview of the clients I've tried.
Step 3: Set up your lightning wallet with something like Wallet of Satoshi
I made my Bitcoin Lightning wallet independent of my identity. That's why I just went with the number one Lightning wallet on the market: Satoshi's Wallet. It's very simple and provides you with a Lightning address that resembles and has the format of an email address. You can add this address to your Nostr profile description and you're ready to receive Sats. Anyone can send them to you, e.g. for a good message or something else they find valuable on Nostr (like a podcast, a video, an article, ...). Just be aware that Satoshi's wallet contains your key and the sats you have there are not really your sats. So only leave a small amount there or no more than you need for your nostr experience.
Step 4: Set up your Nostr address
I set up a unique NIP-05 identifier that is human readable and also looks like an email address. For me, that's tobiya@nostrplebs.com, also called a nostr address. It's much easier to read, share and remember than your public key, which is just a long, unwieldy string of characters.
Some popular services are: * NostrVerified * Alby * Iris * Primal * Snort * nostrplebs.com
Most offer free services or at least a free tier. I chose nostrplebs.com because it links my Nostr address (tobiya@nostrplebs.com) to my Lightning wallet. ⚡
Brief overview of the clients (I have tested)
Web/Browser:
- Primal: Fast, user-friendly, nice looking, easy to use
- Coracle: Focuses on decentralized reputation, privacy and trust metrics. Also well organized and structured
- noStrudel: The most comprehensive I've found, has everything
- Rabbit: Designed like X (Twitter) Pro, focuses on everything at once
- Nostter: Clearly structured, easy to find what you're looking for
- Snort: Fast web client for those who prefer simplicity and speed.
iOS
I'm not an iPhone user, but everything I've discovered says that Damus is the best app for iOS.
Android:
- Amethyst: Feature rich for Android, I only tried this program because it gives me everything I currently need on my phone.
- Primal: Works seamlessly with Primal on the web, which is a pretty convenient starting point if you only want to use one client.
As for the web clients, I'm still figuring out which one will be my favorite. But I think they're all good in their own way. In the time of writing, I am mainly using Primal on Android and Web, Amethyst and noStrudel.
Let's have fun!!
-
 @ 0edc2f47:730cff1b
2024-09-02 01:54:55
@ 0edc2f47:730cff1b
2024-09-02 01:54:55Chef's notes
In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 6 hours
- 🍽️ Servings: 12
Ingredients
- 1 medium onion, peeled and quartered
- 2 tsp ground ginger
- 8-10 large cloves garlic
- 1 cup ketchup
- ¼ cup dry sherry
- ¼ cup sake
- ¼ cup cider vinegar
- ¼ cup soy sauce
- ¼ cup honey
- ¼ cup Dijon mustard
- 1 tablespoon coarsely ground black pepper
- ¼ teaspoon ground cloves
- 1½ cups Coca-Cola, ginger ale, or Dr. Pepper
- 1 first-cut brisket, 6 to 7 pounds (2.7-3.2kg), rinsed and patted thoroughly dry
Directions
- Preheat oven to 325F / 160C.
- Combine all ingredients except brisket in a blender and blend until smooth.
- Place brisket in a Dutch oven or other large pot with a tight-fitting lid.
- Pour sauce over brisket, place lid on pot, roast in oven for 3 hours. Flip roast and return to oven for 3 hours or until fork tender.
- Remove roast to rest. Skim fat from sauce and reduce if desired. Serve immediately with sauce or cool, cover brisket and refrigerate overnight in cooking pan. The next day, defat sauce, reduce if desired, and reheat meat in sauce before serving.
-
 @ 3b7fc823:e194354f
2024-09-01 23:52:38
@ 3b7fc823:e194354f
2024-09-01 23:52:38I dOn'T cAre ABouT pRivAcY. IT dOEsN'T maTtER. i'M nOT dOiNg AnyThiNg wRonG.
GHOSTn
Your phone is spying on you. Your apps are spying on you. Your websites, search engine, fitness tracker, smart watch, IoT device, EVERYTHING is collecting anything it can and sending it off to be stored, cross referenced, and sold.
Data is the new oil.
So what? I don't care if Google knows I like motorcycles. By itself one data point isn't a big deal but once you start bringing everything together...
Who are you talking to? When and how long did you talk to them? Where did you go? How often do you go there? On and on the profile starts to become overwhelmingly invasive.
Right now it is extremely cheap and easy to collect and store the data but it's hard and expensive to cross reference and tabulate the data down to the individual. But in the extremely near future using AI and faster processers, data profiles for sale go from white men between 25 - 30, with this education level, and background like XYZ to -> John loves motorcycls and steak.
Suddenly your insurance premiums are way higher than your friends because you partake in dangerous activities and eat too much red meat. You get denied that loan because you invest in risky assets and it raises your risk factors to pay it back. That job that you applied to never responded because they already ran you through the algorithm and you don't fit the culture.
Protect your data and privacy now before its too late.
privacy
-
 @ 502ab02a:a2860397
2024-11-22 17:40:03
@ 502ab02a:a2860397
2024-11-22 17:40:03
แนวคิด : ห้วยผึ้ง ใช้ผึ้งงานเก็บน้ำผึ้งเข้ารัง ให้รังเป็นตัวแทนของการออม bitcoin ในลักษณะ stack sats ค่อยๆเก็บหอมรอบริบ make saving great again โดยผึ้งงานเป็นตัวแทนของ proof of work ซึ่งตัวน้ำผึ้งที่หอมหวานนั้น มีคุณค่า ไม่เสื่อมไปตามกาลเวลา เป็นยาอายุวัฒนะ และเป็นของมีค่าโดยธรรมชาติ Link Download https://drive.google.com/drive/folders/1Itj0C0aIBWvpnZuuW1Z04nif_NNfPQg6?usp=sharing
Concept: Huai Phueng uses an image of a worker bee collecting honey for the hive, where the hive symbolizes saving Bitcoin in a “stack sats” manner, gradually accumulating and making saving valuable again. The worker bee represents proof of work, while the sweet honey, with its timeless value, serves as both an elixir and a naturally precious resource. Link Download https://drive.google.com/drive/folders/1Itj0C0aIBWvpnZuuW1Z04nif_NNfPQg6?usp=sharing

-
 @ 9bc2d34d:d19d2948
2024-11-22 17:39:55
@ 9bc2d34d:d19d2948
2024-11-22 17:39:55As I am studying Biology, I needed a quick snack and created this 5 minute meal to hold me over. It is a very simple, basic recipe that could be customized in many ways. You like onions? Add them. You like tomatoes? No problem. The options are limitless.
https://zap.cooking/recipe/naddr1qq8xsmm594jx7eeddeskx6r0wvpzpx7z6dxam2pajs4plhfk5ay8lx4wcaqdkf8209ejmy8rs0ge622gqvzqqqr4guaw0c88
-
 @ 6c2d68ba:846525ec
2024-09-01 13:02:53
@ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend,
it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.
As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:
-
What causes the discomfort that drives you out of the walled garden onto the open sea?
-
Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?
-
What are you hoping to find on the open sea that walled gardens cannot provide?
-
What are you willing to sacrifice for freedom (of speech)?
-
What will you need to keep the ship afloat?
-
How will you react when you find yourself in the middle of a storm?
I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over.
This is about building a new world, an open world without walled gardens and data silos.
Onwards!
-
-
 @ 42342239:1d80db24
2024-08-30 06:26:21
@ 42342239:1d80db24
2024-08-30 06:26:21Quis custodiet ipsos custodes?
-- Juvenal (Who will watch the watchmen?)
In mid-July, numerous media outlets reported on the assassination attempt on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various sources that search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.
The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."
A similar phenomenon occurred during the 2016 presidential election. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.
These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. A study published in June 2024 reports that such search results can dramatically affect undecided voters. Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.
A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?
-
 @ 03b2a4f0:7ff066d4
2024-11-22 17:33:08
@ 03b2a4f0:7ff066d4
2024-11-22 17:33:08Zeteo citadel consult In collaboration with the university of Ibadan @yakihonne nostr:naddr1qqgrqe3jxasnjwtpvs6rxd3kvsmkzq3qqwe2fuxpe5tf7xduvcd9n3he30s6zel890dgzy2zquunvllsvm2qxpqqqp65w8nuwxg
-
 @ 472f440f:5669301e
2024-08-27 22:36:32
@ 472f440f:5669301e
2024-08-27 22:36:32I'm sure you are all well aware of the news out of France. The French government has made the bold move of arresting the founder of Telegram, Pavel Durov, after charging him with 12 criminal counts ranging from "complicity in web-mastering an online platform in order to enable an illegal transaction in organized group" to "importing a cryptology tool ensuring authentication or integrity monitoring without prior declaration".
Telegram is an extremely popular messaging app that is used by almost 1 billion people from around the world. I have personally been a user for seven years and it is very dismaying to see the French government attack an entrepreneur who has built a widely used and loved app. We've said it many times over the years in this rag, governments need to stop throwing the baby out with the bath water by attacking successful businesses for the crimes their users commit and begin doing better law enforcement. It makes no sense to demonize a technology for the crimes that are committed by a small minority of users of that tool. Is the French government going to go after the CEO of Bic, the largest producer of pens in the world, because there are pen pals out there who use their pens to write letters in which they coordinate criminal activity? If we apply the same logic behind the decision to arrest Pavel it would seem that the Bic CEO should be a bit worried.
Who knows what evidence the French government has against Pavel. Maybe he is directly involved in the coordination of crimes that were committed on his app. I highly doubt it, but who knows. We'll have to wait and see what evidence the French courts put forth once a trial gets under way. As of yesterday, we know that this seems like a classic case of "You refuse to cooperate with deep state actors who want access to your users' data, so we're going to accuse you of all of the crimes."
The fact of the matter is, we shouldn't have to worry about the actions of a founder dictating the accessibility of a novel technology that they bring to market. Especially technologies that enable people to connect in the digital world to exercise their God given right to free speech.
It's a bit poetic that this happened on Saturday night in Europe. Just one day after the Nostriga conference in Riga, Latvia wrapped up. Nostriga was a two-day event which attracted people from all over the world so that they could meet to discuss how to push the Nostr protocol forward. For those who are unaware of what Nostr is, it is an open source communications protocol with no leaders that enables individuals to publish their thoughts to the world is a distributed, censorship resistant fashion. User profiles are created via a private-public key pair. The public key makes it easy for others to follow and the private key enables a user to sign notes with certain data that get broadcasted to relays. App developers can then pull the user generated data from those relays and present the data in unique ways using front-end interfaces known as clients. Users can port their private keys (commonly known as nsecs) into any client they like and have all of the data they've published to the protocol automatically show up. Said another way, since Nostr is a protocol and not a platform, users have way more optionality when it comes to the applications that present the data they publish. If one client decides to censor or simply has a bad UX, they can plop their magic string (private key) into another client and see everything they've ever posted while still being connected to everyone they added to their social graph historically. This is extremely powerful on many fronts.
Gone are the days of having to worry about building an audience on a platform, making that a critical part of your brand and livelihood, and having to self-censor because of the fear of being deplatformed. You own your private key and that gives you access to your data. Not the platform.
For app developers, the network effect of Nostr produces an incredible and truly unique bootstrapping mechanism. Instead of having to start from scratch and hope that users find your app, fill it with data, and begin spreading the word to more users you adopt the social graph of Nostr from day one. Every user of the protocol is already feeding your application data. If you can build an appealing product that provides users of the protocol with value, they will find it and immediately be able to leverage it. There will be no need for them to build up a reputation or find their social connections on the app. They will be ported into the client.
Nostr can be additive to seemingly unrelated applications that aren't built directly on Nostr. We've already seen this with bitcoin wallets that have enabled users to port their Nostr social graphs directly into their wallet. Making it easy for individuals to find their friend's Nostr account and send bitcoin directly to the lightning address they've associated with it. No need for an invoice. Just find your friend and send them money like you would on an app like Venmo.
The number of added benefits users and app developers get from Nostr beyond those I just explained are too long to list. Long story short, this protocol is a massive deal.
It is still very early for Nostr, but the progress that has been made in the last couple of years has been nothing short of awe inspiring. If you squint into the future, it isn't hard to see how Nostr becomes mainstream by the end of the decade. The compounding network effects are stronger than anything I've seen since bitcoin.
All of this is to say that this will be one of the only ways to build truly robust communications-based applications moving forward. As we've seen with TikTok and now Telegram, if the state doesn't like the owner of a particular platform they will either kick the platform out of their country or arrest the founder and do their best to corrupt the platform itself once he is in custody. This hasn't happened yet with Telegram, but you can bet your ass that the deep state will try to corrupt Telegram if they successfully remove him from the picture.
To be clear, this doesn't make the founders of particular Nostr clients immune to this type of overt overreach by governments. However, the design of Nostr is such that governments would have an exponentially harder time achieving their end goal, suppressing and controlling speech that's expressed on these platforms, because the protocol has hundreds of competing clients serving customers the data stored in relays. They could even attempt to go after the relays, but that task may prove to be impossible as well.
Make no mistake, we live in very trying times. The world's governments are losing control and they are doing the best they can to suppress freedom of speech in anyway they can to prevent people from spreading information that makes the Regime to look like the evil fools that they are. The best we can do is to build robust systems that make their attempts at suppressing speech as close to impossible as is possible. The efforts to build out robust systems like bitcoin and Nostr should be complemented with pushing back against the Regime via the courts. But as we all know, we can't always depend on the courts to actually deliver justice. There are times where freedom must be taken and defended. We are certainly living through one of those times right now.
Despite the insanity of the world and the governments who would like to rule it, the momentum of the light is building. People are taking action and solutions are being built slowly but surely. It is our job to keep the momentum up and make sure the lifeboats of bitcoin, Nostr and similar protocols are ready to go once the Deep State begins attacking others. They came for TikTok and Telegram. Don't think that platforms like X, Rumble and Gab aren't in their crosshairs as well.
Here are four videos from Nostriga that I think you all should watch.
https://youtu.be/XUsk7cqZyKU?si=2vUl01azeFJQjczZ
https://youtu.be/qUwXRDrfJU0?si=np3vyTDddoQKuPJK
https://youtu.be/OHqxp-Hrx9k?si=K7vhVBWtFQwB68Tr
https://youtu.be/iZyqVGHjDGo?si=CjJCbAlNBa06qcwV
And a panel I hosted about funding Nostr if you're interested in that.
https://youtu.be/qD-Y0fq5KiA?si=L81sFCPGw2ayXXzw
We're going to win.
Final thought... Jet lag sucks.
-
 @ 91687725:a0de48ea
2024-08-24 05:40:14
@ 91687725:a0de48ea
2024-08-24 05:40:14こんにちは。Kateです。
最近ちょっとお休みしていますが、日本でビットコインを専門に扱うDiamond Hands Magazineに寄稿したりしてます。
私がビットコインと出会ったのは2011年、まだビットコイン利用者はとても少なかった時代です。たまたま身内にビットコイン界隈の人がいました。もしかしたら今でいうビト妻だったかも?
まだビットコインが1ドル以下でおもちゃみたいな存在だった頃に知ったわけですが、その後勢いづいて、100ドル、1000ドルと価値が上がっていきました。
それを見て、ビットコインを少しずつ買って貯めておけば、将来リタイヤの蓄えになるかもと思ってお小遣い程度のビットコインを積立してました。でも、アクシデントで失くしちゃったんですよね。
その後、身内のごたごたで自分の生活が天地がひっくり返るように一変し、気がつけばカナダでただお金がないアジア系移民シングルマザー、しかも周りに家族が誰もいないという、非常にマイノリティな立場になりました。
人生、何事も経験。一度ビットコインを失くし、傷心もあり、数年はビットコインから離れました。でも気がつけばビットコインは冬の時代を終えて、また元気になっていたんですね。自分は海外でひとり子育てに追われ、なんとか生きてた感じですが!
ビットコインが500ドルくらいになっていた時に困窮していた私は、ふとペーパーウォレットと呼ばれた当時の携帯可能ウォレット?に0.5btc 残っていたのを発見して速攻換金しましたね。悔やまれます。
その後、2017年頃、カナダで当時大手の割と使い勝手のいい取引所があることを知って、再度ビットコイン貯蓄にチャレンジしました。2年ほどで、ほぼ1ビットコインと10ETHくらいあったんですけどね、今度は取引所の代表者が行方不明になり、またもやビットコインを失くしました。
ふつうだったら、もうやめますよね。2回もなくしたら。
けれど、自分はかつてインターネットが始まったころのワクワクを経験していました。90年代半ば、新宿にできたばかりのインターネットカフェで、GIFがかろうじて表示できるグレーのブラウザ画面と対面しました。世界を変える技術を体験した時の感動は今でも忘れられません。
(こう書くと立派なオバサンなのがバレちゃいますね。ビットコインネイティブ世代の中では年長者)
それから15年以上たって、初めてサトシナカモトのホワイトペーパーを読んだ時に、同じ衝撃を受けたのです。初めて実用化されたインターネット上で世界の誰とでも送り合えるマネー。その可能性は無限∞。
そのビットコインの進化を、実際に買ってみたり、使ってみたり、なくしたりしつつ、より深く知ろうと付き合ってきた自分は、いつの間にかビットコインを通して世の中のいろいろを見て考えるようになりました。
ビットコインが生まれ、実験段階を経て、すでに15年が経ちます。けれども、ビットコインは今でも多くの人から最も誤解されている技術・発明のように見えます。ここまで来たら、自分が生きている間に、ビットコインが世界とどう関わっていくのか見届けたいと思います!
そして、私自身がビットコインを知ることで発見した世界や新しい価値観を、誰かに伝えられたらいいなと願って、このブログをスタートすることにしました。
今回は自己紹介という形になりましたが、私がビットコインを通して学んだことや気づいたことをこれから少しづつアップしてみます!
週1くらいのペースで投稿が目標です。よろしくお願いします。
-
 @ 319ad3e7:cc01d50a
2024-11-22 17:31:32
@ 319ad3e7:cc01d50a
2024-11-22 17:31:32This is the perfect recipe for the lazy, hungry, and want-all-the-salt moments.
https://zap.cooking/recipe/naddr1qq8xsmm594jx7eeddeskx6r0wvpzpx7z6dxam2pajs4plhfk5ay8lx4wcaqdkf8209ejmy8rs0ge622gqvzqqqr4guaw0c88
-
 @ b0510a0c:12716ced
2024-08-21 06:03:43
@ b0510a0c:12716ced
2024-08-21 06:03:43On April 24, 2012, Erik Voorhees changed everything about Bitcoin with the launch of Satoshi Dice:
a game that captivated users and intensified debates about Bitcoin's evolution and the network's ability to handle an increasing volume of transactions.
At that time, Satoshi Dice allowed thousands of players to bet on digital dice rolls, leading to a MASSIVE influx of transactions that filled the blocks of the blockchain.
📈 Success of Satoshi Dice:
Satoshi Dice achieved phenomenal success, attracting millions of users with its simplicity. Players flocked in, bets piled up, and blocks filled up.
Erik Voorhees effectively leveraged Bitcoin's microtransactions, quickly saturating the blocks with these. This was a testament to the game's popularity, but also a source of tension within the community.
Within months, Satoshi Dice became the most popular service on the Bitcoin network, boosting its usage and virality.
Players appreciated the "provable fairness" aspect of the game, where they could verify the transparency and fairness of each bet.
🚫 Criticism and Controversy:
However, this success was not without criticism.
Many Bitcoin enthusiasts viewed the massive influx of transactions generated by the game unfavorably. For them, these sometimes trivial transactions "spammed" the blockchain, clogging the blocks and increasing transaction fees for all users. Does this sound familiar?
The network, designed to handle about seven transactions per second, quickly reached its maximum capacity, causing validation delays and "high" fees.
⚔️ BlockSize Wars:
The BlockSize wars, which took place mainly between 2016 and 2017, were a technical and ideological conflict centered on block size and scalability solutions.
While Satoshi Dice was not the sole cause, the game significantly contributed to the emergence of this event by helping to popularize Bitcoin among new users and generating substantial transaction volume.
As Bitcoin adoption grew, the network faced intense pressure, leading to block saturation and rising transaction fees. On one side, some advocated for increasing block size to allow more transactions, leading to the creation of Bitcoin Cash in August 2017. On the other, proponents of solutions like SegWit pushed for improvements without compromising decentralization.
🔧 Adoption of SegWit:
Erik Voorhees expressed his support for the SegWit2x proposal, which aimed to improve network scalability by combining the implementation of SegWit with an increase in block size.
Segregated Witness (SegWit) was adopted in August 2017, allowing transaction data to be separated from signatures. This reorganization not only increased transaction processing capacity but also paved the way for the development of the Lightning Network, a layer 2 solution enabling instant and low-cost transactions.
SegWit was a crucial response to the challenges posed by network congestion, which had been exacerbated by Bitcoin's growing adoption and the emergence of popular applications like Satoshi Dice.
⚡ SegWit and Lightning:
The adoption of SegWit helped resolve blockchain congestion issues, while the Lightning Network, a layer 2 solution, facilitated fast and low-cost transactions.
Together, these innovations not only addressed technical challenges but also renewed enthusiasm for games and other applications on Bitcoin, paving the way for a new wave of development.
🎲 Nostr Dice:
Today, as we reflect on the impact of Satoshi Dice, a new project emerges: nostr:npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84
This modern clone of the original game is built on Nostr, a decentralized communication protocol, and Lightning, paying homage to the past while offering an enhanced gaming experience that does not impact layer 1 congestion!
From a game that caused Bitcoin congestion to its rebirth on Lightning, which it helped to bring about, the circle is complete!
-
 @ 6bae33c8:607272e8
2024-11-22 17:23:13
@ 6bae33c8:607272e8
2024-11-22 17:23:13I went 1-4 last week to blow any chance I had at cashing in Q3, so this is kind of a practice week before we head into Q4.
Colts +7.5 vs Lions — The Lions are a juggernaut, and they were my only correct pick last week, but this feels like a sell-high against a scrappy Colts team, and Anthony Richardson played better last week.
Bears +3.5 vs Vikings — The Bears should have beaten the Packers last week, and I expect them to hang with the Vikings at home.
Raiders +6 vs Broncos — The Broncos looked great last week, but this is an easy sell-high on the road against a division rival.
Cardinals pick ‘em at Seahawks — The Seahawks are a sell-high after their win over the 49ers, and the Cardinals are playing well of late and coming off the bye.
Ravens -2.5 at Chargers — The Ravens are one of the league’s top-four teams, and they’re desperate after blowing a winnable game to the Steelers.
-
 @ 6fff5148:a5dd5cdf
2024-11-22 17:19:43
@ 6fff5148:a5dd5cdf
2024-11-22 17:19:43 Cryptocurrencies have not only changed the world’s expectations surrounding money. They’ve also continued to evolve in their own space since the first bitcoin block was mined back in 2009. Since then, thousands of unique cryptocurrencies have popped up. Of these, Bitcoin remains the most popular.
Cryptocurrencies have not only changed the world’s expectations surrounding money. They’ve also continued to evolve in their own space since the first bitcoin block was mined back in 2009. Since then, thousands of unique cryptocurrencies have popped up. Of these, Bitcoin remains the most popular.In fact, a recent survey found that 8% of americans have invested in cryptocurrency and of that 8%, 5.15% have invested in Bitcoin.
Curious to see why Bitcoin is the most popular and what other cryptocurrencies are running close behind? Keep reading.
It’s been about a decade since Bitcoin expanded currency into the digital space of the internet. Since that time, it’s remained the most popular cryptocurrency in the world and most used of all cryptocurrency.
With Bitcoin, users transfer money from one digital wallet to another digital wallet with ease. Each transaction is then verified by other users and recorded on the public ledger, known as the blockchain. For the fact that Bitcoin which is currently the top cryptocurrency gaining awareness on daily basis on the wheel of fortune is tough,that way it can't be predicted so easily even for an expert as there is no one who can predict the future and be accurate of the outcome. No one ever thought Bitcoin will ever be worth $20,000.00k in 2017 as same reason why the awareness keeps brewing each passing day making it easier for investors dealing in bitcoin. Aside buying and holding bitcoins for potential gains which is one of the advantages of the benefits derived from dealing in cryptocurrency, I also recommend that you invest in service companies such as the Zippercoin(www.zippercoin.tech) company, a cryptocurrency investment company that gives return on investments made in days by capitalizing on the volatility of the crypto market to generate profits giving you better chance in the cryptocurrency market.
Some key factors that have contributed to Bitcoin’s popularity include:
Although it fluctuates, its price is high. A single Bitcoin is worth $4,931 US dollars as of this writing. This is significantly higher than other cryptocurrencies that exist. Major companies are starting to accept Bitcoins. These include Microsoft,overstock and more. Bitcoin is easy to set up. Bitcoin is supported by the most notable exchanges and digital wallet platforms, such as Coinbase. This makes getting in the game easier. Investors have been supporting Bitcoin’s growth for years. Bitcoin has been around longer than all other cryptocurrencies. This has allowed them to gain a strong following of investors. Bitcoin also has the highest market capitalization among cryptocurrencies, which is often considered by investors. Market caps are calculated by multiplying the current supply of the currency by the current price. This is known as the circulating supply of currency, and can indicate if a currency is risky to invest in. High market caps usually indicate less risk as there are more users. Therefore, Bitcoin is believed to be a better choice than other cryptocurrencies out there
 .
.There is always light at the end of the tunnel,be wise with whatever decision you take.Always remember to diversify,study the cryptocurrency market before diving on the choice of coin you deem to trade,choose reliable service to trade with to avoid unnecessary loss.
Stay safe and God bless.. Source: https://www.quora.com/Why-is-bitcoin-often-the-most-talked-about-cryptocurrency-Is-it-possible-for-one-cryptocurrency-to-be-successful-while-others-are-not#:~:text=Bitcoin%20is%20a%20well%2Dknown,lack%20of%20a%20groundbreaking%20project. @yakihonne
-
 @ bcbb3e40:a494e501
2024-08-16 18:00:07
@ bcbb3e40:a494e501
2024-08-16 18:00:07El hombre y el contexto
El pensamiento tradicionalista español cuenta con una amplia trayectoria en la que concurren personajes, situaciones e ideas gestadas en el transcurso de dos siglos, en los que debemos distinguir el conflicto dinástico y el papel del legitimismo de la propia doctrina, que es algo que se construirá en el tiempo, con la contribución de figuras como el protagonista de este escrito, Don Juan Vázquez de Mella, así como por la confluencia de fuerzas de diferente signo que tiene lugar a lo largo del siglo XIX y la consolidación del Estado liberal, que lo hará siempre en lucha abierta contra las peculiaridades y el carácter genuino del pueblo español. Vázquez de Mella, nuestro autor, quizás represente la consolidación y madurez doctrinal del movimiento tradicionalista español, uno de sus primeros y más brillantes sistematizadores. No se destacó por una obra extensa ni especialmente difundida más allá de sus discursos, de sus artículos en periódicos y sus escritos dispersos, los cuales fue capaz de dotar de una especial significación y dignidad fruto de su enorme carisma y especial clarividencia para dar una forma definida y meridianamente clara a las ideas y doctrinas que nutrieron el tradicionalismo español madurado al calor de las armas, de las tres guerras que el carlismo libró contra el liberalismo español.
|
 |
|:-:|
|Juan Vázquez de Mella|
|
|:-:|
|Juan Vázquez de Mella|Nuestro autor, de origen asturiano, y nacido en Cangas de Onís un 8 de junio de 1861, ha mantenido vivo su prestigio y el valor de sus aportaciones teórico-doctrinales, ampliamente reconocidos por sus sucesores, por Rafael Gambra Ciudad (1920-2004) y Francisco Elías de Tejada y Espinola (1918-1978), así como de otros autores como Álvaro D'Ors (1915-2004) y otros muchos, que han reivindicado su figura en el tiempo y se han nutrido de sus fecundas enseñanzas. Se ha destacado la rectitud de su pensamiento, su inquebrantable voluntad y su impagable contribución en la creación de un marco teórico y conceptual para dar un sentido y una forma a las ideas del tradicionalismo español. Hijo de un militar de origen gallego, muerto prematuramente, quedó huérfano de padre durante su niñez, por lo cual pasó al cuidado de unos parientes de origen modesto. Estudió en la Universidad de Santiago de Compostela, donde mostró tempranamente su temperamento y habilidades oratorias, que explotó convenientemente a través de diarios como La Restauración o El pensamiento galaico, donde también mostró sus filiaciones militantes con el catolicismo tradicional. Sus habilidades y la brillantez de sus escritos pronto llegaron a Madrid, a las más altas instancias del Carlismo, lo que le permitió dar continuidad a sus actividades desde un medio más amplio, a través de El correo español.
En su militancia política llegó a las más altas cotas de su trayectoria con la elección en 1893 como representante de las Cortes por el distrito de Estella, Navarra, que ya con sus primeros discursos obtuvo un notable éxito, incluso entre los propios liberales, hasta 1900, fecha en la que se vio obligado a marcharse a Portugal, acusado de participar en una conspiración para derrocar el régimen de la Restauración. No regresó a España hasta 1905, manteniendo su estatus como diputado hasta 1919. De todos modos, no queremos dar más protagonismo a la biografía en detrimento de la doctrina, que es lo que nos interesa en este artículo, de ahí que obviemos otros datos biográficos trascendentes, polémicas con otras facciones del carlismo o sus posturas respecto a la dictadura del general Miguel Primo de Rivera, que nos harían desviar la atención del propósito principal que acabamos de enunciar.
La gran paradoja del Carlismo fue que a pesar de su derrota en la Tercera Guerra Carlista (1872-1876), y pese a la posterior escisión integrista en 1888, el partido carlista continuó manteniendo una fuerza y preponderancia significativa en la sociedad española del régimen de la Restauración durante el último cuarto de siglo. El Carlismo se vio inmerso en un buen número de paradojas, de situaciones encontradas, especialmente en relación al Desastre del 98 y la pérdida de los últimos territorios ultramarinos. Mientras que la gran esperanza del tradicionalismo español estaba depositada en el desmoronamiento y caída final de la restauración alfonsina, por otro lado este mismo régimen trataba de defender, al menos en teoría, los últimos restos del imperio español y, de algún modo, a la España católica frente a una nación protestante, como era la anglosajona estadounidense. Al mismo tiempo, durante esta época el tradicionalismo español se enfrentó a los grandes retos que presentaba una sociedad en cambio, con transformaciones políticas y sociales de gran calado como la emergencia del sufragio universal o el nacimiento de los separatismos periféricos (propiciados por la burguesía liberal), las cuales requerían de nuevas estrategias y reestructuraciones internas capaces de enfrentar la envergadura de todos estos cambios. Fue en este contexto donde se significó la figura de Juan Vázquez de Mella, quien merced a la obra de sistematización a la que ya hemos hecho alusión, y de sus concurridas conferencias, dio lugar a la denominada Acta Loredán, redactada por el tradicionalista asturiano y publicado en El correo español. Este escrito tenía como ejes fundamentales la defensa de la nación política española fundamentada en la monarquía, el catolicismo y el régimen foral. Al mismo tiempo, también recogía la reivindicación de un programa corporativista y gremial al abrigo de la doctrina social de la Iglesia defendido en la encíclica Rerum Novarum (1891), y es lo que se conoce como el «sociedalismo», cuyos antecedentes encontramos ya en autores como Donoso Cortés o Antonio Aparisi Guijarro. Son precisamente los atributos de esta doctrina, que contribuyó a la revitalización del pensamiento carlista, los que nos disponemos a desarrollar a continuación.
La figura del tradicionalista asturiano, de Don Juan Vázquez de Mella, aparece como necesaria ante una serie sucesiva de destrucciones que el régimen liberal ha producido sobre los fundamentos tradicionales de España, pero su papel no fue, como ya venimos apuntando, el de un gran intelectual erudito, y de hecho, como apunta Rafael Gambra, las mayores debilidades de su pensamiento se encuentran en los principios filosóficos, y destacando, en cambio, su papel de «revulsivo espiritual» podemos ubicarlo mejor en el ámbito de lo político y lo espiritual. Para ello debió tomar en cuenta las fuentes de sus predecesores, entre los cuales podemos ubicar perfectamente al ya mencionado Donoso Cortés y Jaime Balmes, así como también a otro contemporáneo suyo, Menéndez Pelayo. De los dos primeros tomó su capacidad de síntesis y la sencillez expositiva, mientras que de Menéndez Pelayo tomó, al menos en parte, el sentido de la crítica histórica en aras de la restauración de una Tradición nacional. Pero más allá de los sistemas de pensamiento y elementos retóricos, vemos a Vázquez de Mella profundamente interesado por la vida política de los pueblos medievales de Las Españas, lo cual fue, en definitiva, el marco de referencia para una síntesis política de conjunto más allá de los posicionamientos teóricos, como algo que puede ser llevado a la práctica en sus aspectos concretos y que es perfectamente viable. Todo un sistema edificado sobre el pensamiento tomista y una una profunda religiosidad, En este contexto, y más allá de las ideas formuladas por realistas y carlistas en la primera mitad del siglo XIX, Mella teoriza junto a la concepción del espíritu medieval, la idea de la coexistencia de dos soberanías, una política y otra social, una teoría de la soberanía tradicional inspirada por un principio dinámico y que se cimenta en las propias experiencias humanas en el devenir de la historia.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023|El concepto de lo social
Lo social para Mella no tiene absolutamente nada que ver con las denominadas «políticas sociales», tan comunes en el lenguaje político de las democracias liberales, en las que se contempla lo social como un elemento externo a la propia estructura política, donde prevalece el individualismo a todos los niveles, y la sociedad aparece como un mero agregado de individuos. Muy al contrario, lo social, en el tradicionalismo de nuestro autor, implica la afirmación de un principio intrínseco tanto al modelo social como al tipo humano, así como a la naturaleza de las cosas en las que la persona desarrolla su existencia en común con los demás. Nos referimos a las instituciones, a los elementos jurídicos y otros órganos gestados en el tiempo por la experiencia histórica, que regulan la vida común.
En el ámbito de la sociedad cristiana medieval, en plena Reconquista, cuando todavía no existía un Estado unitario como tal, cada municipio tenía sus propias leyes y sus normas, adaptadas a su modelo de vida y costumbres, Las comunidades se concebían como agrupaciones de familias con un sistema de propiedad comunal y privado en las que el patrimonio y el estatus de cada uno de sus miembros venía garantizado por el ejercicio activo de una serie de derechos en defensa de las libertades concretas, cuya fuente última era el derecho natural. Los señores feudales y los reyes se limitaban a reclamar tributos para la guerra, pero sin interferir en la defensa de estas libertades concretas ni vulnerar el sistema que las sustentaba.
Eran gobiernos autárquicos, muy estables e inspirados por un principio democrático, el cual nada tenía que ver con las democracias liberales plutocráticas de la actualidad, cuya idea del derecho y la justicia está pervertida por el formalismo jurídico vacío e inane de sus constituciones, abstractas y plenamente funcionales a las oligarquías, al servicio de intereses espurios. En este caso, el hombre alcanzaba una plena dignidad y desarrollo en el contexto de una comunidad donde prevalecía el vínculo comunitario, al amparo de un modelo tradicional, de normas consuetudinarias y concretas que permitían la defensa efectiva del propio derecho. Ni siquiera con el advenimiento de los Estados modernos, y la centralización de algunos elementos de poder, como la Hacienda o el Ejército, se vieron alterados significativamente estos elementos, que representaban a los denominados «cuerpos intermedios» de la sociedad, y que adquirieron su propia expresión particular bajo el nombre de «Fueros», los que los propios reyes juraron respetar a lo largo de toda la Edad Moderna y hasta el advenimiento del régimen borbónico.
La antropología tradicional vincula al hombre a un medio social, a una familia, a una estirpe o a un pueblo, que reproducen esa misma estructura familiar, aunque a mayor escala. En nuestro caso particular lo vemos a través de la convivencia de pequeños grupos humanos, de ahí la importancia de los municipios o de los concejos en un marco de vida comunitaria fuertemente institucionalizada. Al mismo tiempo este modelo y estructura también se replicaba en otros ámbitos, como en la vida económica y profesional, impregnando todas las esferas de la vida del hombre. Instituciones naturales, amparadas en el derecho natural, y orientadas a la protección y garantía de prosperidad de los hombres, y esto por encima de cualquier interés particular y mercantil de negocio. Para Mella, la ruptura con este mundo, y en general con las experiencias del pasado, es la que nos lleva, merced a la acción del liberalismo, a los tiempos actuales, y lo hace recorriendo un itinerario que todos conocemos, y que tienen su punto de partida en la Ilustración y la posterior Revolución Francesa, la irrupción del elemento racional y abstracto y la destrucción de la religión, considerada como fruto de la superstición. La destrucción del orden feudal, que todavía pervivía como marco de convivencia en el mundo rural, como una suerte de prolongación de ese espíritu medieval, hizo desaparecer de un plumazo ese entorno de relaciones concretas y personales para sustituirlas por lo «público» entendido como la centralización estatal uniforme, ignorando las realidades particulares subyacentes en el cuerpo social, los denominados «cuerpos intermedios», que fueron despojados de su autonomía, corporaciones y patrimonios. De modo que la destrucción de estas «sociedades intermedias» que mediaban entre el Estado y la sociedad desenraizó y destruyó la propia sociedad, al mismo tiempo que los fundamentos cristianos del derecho natural sobre la cual se hallaba asentada, para hacer prevalecer esos principios racionales y abstractos traídos por la revolución.
Al mismo tiempo, y anejo a este desarraigo, del individuo se encuentra sometido a poderes arbitrarios del propio Estado liberal, sin un conglomerado institucional propio que lo proteja de estos atropellos, sumido en el individualismo ajeno a toda institución y destino colectivo, se limita al voto cada cuatro años de los partidos al servicio de oligarquías e intereses espurios, contrarios al Bien común. En este sentido, y advirtiendo las posibles acusaciones de «absolutismo» que en ocasiones se han lanzado contra el tradicionalismo, hay que señalar que Mella las rechaza por completo, dado que viola la idea de contrapoderes frente a la autoridad del rey que éste formula, ya que el absolutismo creía en la existencia de un poder ilimitado y tiránico del rey, transmitido por Dios y ajeno a la participación de la sociedad y sus estamentos. Como bien señaló Julius Evola, el absolutismo es un fenómeno antitradicional, vinculado a la descomposición y desacralización de las estructuras tradicionales. De hecho, el absolutismo, como los regímenes liberales de hoy, dejan al individuo totalmente desprotegido, sin un asidero sobre el que apoyarse en la defensa de sus libertades concretas. El propio Mella, como bien saben todos los que se adentren en su obra, fue partidario de contrarrestar el creciente poder del aparato estatal, tal y como hemos visto y seguiremos viendo en lo sucesivo, a lo largo del presente artículo.
|
 |
|:-:|
|EVOLA, Julis; Metapolítica, Tradición y Modernidad: Antología de artículos evolianos, Hipérbola Janus, 2020|
|
|:-:|
|EVOLA, Julis; Metapolítica, Tradición y Modernidad: Antología de artículos evolianos, Hipérbola Janus, 2020|En nuestro caso particular, la desaparición de la organización gremial y corporativa tuvo unas consecuencias especialmente nefastas, y en especial después de las dos desamortizaciones liberales (Mendizabal y Madoz) al despojar a los grupos sociales populares de su natural organización sociohistórica. Asimismo, desvincularon la propiedad en las relaciones comunitarias y su uso patrimonial para vincularla al uso privado y anónimo, para fines puramente especulativos, los que caracterizan al liberal-capitalismo. De ahí nace la figura del asalariado, del contratado como mera mercancía, en un proceso de alienación del trabajo característico en el desarrollo del capitalismo burgués. De aquí parte lo que algunos tradicionalistas, como Gambra, denominan el «problema social», frente al cual, y al margen de las recetas ideológicas de la modernidad, Mella reivindica la restauración de los antiguos vínculos corporativos y orgánicos de inspiración medieval.
La idea de soberanía social
Todos los procesos disolutivos que conducen a la Modernidad liberal tienen su punto de inicio con el Renacimiento, con la afirmación del individualismo y la ruptura definitiva del ecumene cristiano medieval, algo que aparece indefectiblemente unido a la Reforma luterana, así como la «valorización» del mundo clásico, con la reemergencia de teorías de tipo hedonista, como las de Epicuro, por ejemplo, generando una disolución de los vínculos con el medio concreto. Esto supone la aparición de un nuevo tipo, que es el hombre abstracto que escapa cada vez más al entorno inmediato y vital, esto al tiempo que el poder del Estado se robustece y se vuelve omnipotente. Es por ese motivo que en lo sucesivo se ha impuesto en nuestras sociedades la falta de concreción, tanto en lo teórico como en lo político, lo cual ha propiciado el triunfo del contrato social roussoniano y la justificación del orden social en virtud de componendas voluntarias y totalmente artificiales. Estas construcciones político-ideológicas son las que contribuyen a la construcción de la sociedad liberal, asentada sobre patrones puramente racionales, individualistas y mercantilistas.
De hecho, la mayor preocupación de Mella es la destrucción de las instituciones locales y ese vínculo afectivo del hombre con su realidad inmediata, algo que impregnaba su relación con el trabajo, con su obra, con su impronta vocacional y devota, imprimiéndole, como en el caso del artesano, un sello propio y particular a su trabajo.
Y en este sentido, Mella afirma que la sociedad moderna ha perdido su sentido institucional como base estable de la sociabilidad. A través del elemento jurídico y la participación en las instituciones es el medio a partir del cual la comunidad se cohesiona y construye sus vínculos y su particular autonomía, que le hace tener una vida propia e interna, y con la institución nos podemos referir desde una asociación profesional, a la universidad o una cofradía etc. El individualismo ha representado el factor disolutivo y corrosivo que ha destruido este vínculo social fundado en múltiples solidaridades que han enfrentado y polarizado al cuerpo social, con el enfrentamiento entre «clases sociales» y la negación de las jerarquías naturales.
Ante todo lo relatado, y como consecuencia de las destrucciones provocadas por la revolución, Mella plantea su teoría de la soberanía social. Esta teoría consiste básicamente en encuadrar de nuevo a la sociedad en sus raíces naturales, concebida en todos sus órdenes como portadora de un dinamismo propio en una suerte de organización geométrica en la que conviven objetivos y finalidades variadas y concretas con su propia legitimidad y autonomía. Estas finalidades, amparadas en el derecho natural, son junto al poder del propio Estado las únicas formas de limitación del poder. La particularidad de esta idea de soberanía social está en el hecho de que la formación de la jerarquía social tiene una dirección ascendente, que tiene como punto de partida a las personas colectivas y concretas, pasando por una serie de instituciones, hasta llegar al Estado central, de forma escalonada y plenamente conscientes de sus funciones. Así lo expresa Mella en su propio lenguaje: «la jerarquía de personas colectivas, de poderes organizados, de clases, que suben desde la familia hasta la soberanía que llamo política concretada en el Estado, que deben auxiliar, pero también contener». Es lo que Mella concibe como el sociedalismo, que supone la reintegración de la sociedad en la vida concreta de los hombres, con el desarrollo de una vida política común y estable en el marco de instituciones naturales que potencien las relaciones humanas y sociales, estimulando la sociabilidad. Y hablamos, desde la perspectiva de la integración de distintas sociedades, fuertemente institucionalizadas con funciones y finalidades concretas, más allá del sentido democrático y pactista que pueda entenderse en términos modernos o de cualquier asociación u organización relacionada con el «problema social».
¿Qué es la Tradición?
De este modo quedan formuladas las dos soberanías, la política y la social, que coexisten en un mismo espacio limitándose y apoyándose recíprocamente en lo que es uno de los fundamentos del sociedalismo de Mella. No obstante, esta doble soberanía no explica todavía la concreción política de cada pueblo y el vínculo superior que lo lleva a federarse con las diferentes sociedades y a mantenerse unido en una historia y espíritu comunes. Los vínculos que las mantienen unidas en el tiempo tienen que ver con un orden histórico concreto, con un vínculo espiritual que las entrelaza interiormente de una generación a otra, y en última instancia de ese orden tradicional que lo engloba todo, y que al mismo tiempo se asienta en la monarquía y la religión católica. La lealtad a Dios y a un solo rey en torno a los cuales se aglutina la fe, viene a coronar todas estas estructuras y lazos forjados en el fermento de la historia.
No se trata de la Tradición en términos de un «ultraconservadurismo», que ya sabemos que el prefijo «ultra» (lo que sea) es muy recurrente en nuestros días, con la idea de un medio social y político petrificado e invariable, sino que es el producto de un proceso de maduración y evolución histórica, de carácter dinámico y nutrido de experiencias humanas. Nada que ver con las monstruosas ideologías progresistas y modernas, nacidas de lo abstracto e impulsadas por un desbocado «ir hacia delante», desarraigado y que tiende siempre hacia la deshumanización y la destrucción de toda creación humana natural forjada en el devenir de los siglos. Este mismo dinamismo, planteado por Mella, en torno al concepto e idea de Tradición tiene continuidad y adquiere fuerza en sus sucesores y depositarios. Y al fin y al cabo, Mella no hace más que partir de la propia etimología del término, que viene del latín tradere, entregar, de la generación que entrega los frutos de su experiencia a la siguiente, perfeccionándola, haciéndola más estable y segura.
Podríamos seguir extrayendo más conclusiones del pensamiento tradicional de Vázquez de Mella, pero probablemente excedería, y por mucho, el modesto propósito de este escrito, de modo que nos quedaremos aquí, no sin advertir a nuestros lectores de la posibilidad de que en un futuro volvamos a retomar nuevamente el tema.
Antes de acabar queremos llamar la atención sobre una polémica acontecida hace unos años en torno a una Plaza en Madrid que llevaba el nombre de nuestro autor y que se cambio para dedicársela a un sujeto cuyos méritos eran, por decirlo suavemente, más que discutibles, concretamente a Pedro Zerolo, miembro del PSOE y activista al servicio del lobby homosexualista. Durante aquella época, en 2019, muchos miembros de la izquierda globalista trataron de identificar a Vázquez de Mella como un «pensador franquista», cuando en realidad ni cronológica ni ideológicamente tuvo nunca nada que ver con el franquismo. Recordemos que murió en 1928, y la impronta de su pensamiento ha tenido como continuadores a sus propios correligionarios dentro del ámbito tradicional, aunque en su tiempo llegó a ser muy respetado también por sus adversarios, los liberales. Aunque la retirada del nombre de una calle pueda resultar algo banal, o carente de una importancia excesiva, también contribuye, a su modo, a una forma de damnatio memoriae que condena al olvido y al ostracismo a grandes autores de la Tradición, portadores de un Patriotismo sano y capaz de entender las peculiaridades y el Dasein profundo de España, que si bien no nació invertebrada, como pretendían los Orteguianos, su esencia y naturaleza es mucho más compleja que cualquiera de las grandes naciones de Europa.
Artículo original: Hipérbola Janus, Juan Vázquez de Mella y el tradicionalismo español, 16/Ago/2024
-
 @ 5afdec5b:2d631be1
2024-08-14 09:42:29
@ 5afdec5b:2d631be1
2024-08-14 09:42:29Introducing Our New Whitepaper on Escrow-Less Bitcoin-Collateralized Lending
We are thrilled to release our latest whitepaper, elaborating on our innovative Escrow-Less Bitcoin-Collateralized Lending protocol. This pioneering system leverages the power of Discreet Log Contracts (DLCs) and Hash Time Lock Contracts (HTLCs) to create a trustless, peer-to-peer lending environment that aligns with the ethos of decentralization and user empowerment.
Empowering Users with Our Architecture
Our protocol is meticulously designed to empower users by allowing them to borrow against their Bitcoin while retaining full control over it. We believe that this is not just a technological advancement, but a crucial step towards crafting a more decentralized, trust-minimized, and secure financial ecosystem. By eliminating the need for intermediaries, we aim to give users greater autonomy and flexibility, freeing them from traditional constraints.
Addressing Market Needs for Peer-to-Peer, Trustless Lending
Extensive market research highlights a significant, growing demand for peer-to-peer, trustless lending solutions. Users consistently expressed a desire for more control over their assets and greater flexibility in their lending options. Our Escrow-Less Lending protocol directly addresses these needs, providing a robust framework that enhances user control while maintaining the integrity and security of the lending process.
Exploring the Potential of Ark for Microloan Liquidity Management
Initially, our focus was predominantly on micro-loans. However, user interviews revealed a relatively limited demand for such products at this time. Nonetheless, we identified Ark as good solution in the context of Bitcoin microloans. Ark's capabilities could unlock new possibilities and efficiencies, making microloans more viable and attractive.
Remaining Flexible and Adaptable
Even as our primary focus shifts, the potential of Ark continues to intrigue us. Our protocol's design is inherently flexible and adaptable, allowing for continuous refinement and adjustments based on user interest and feedback. Should there be sufficient interest in the future, we are open and ready to explore Ark's integration once again to better serve our users’ needs.
Revolutionizing Bitcoin Borrowing and Lending
We firmly believe that our Escrow-Less Bitcoin-Collateralized Lending protocol has the potential to revolutionize the borrowing and lending landscape within the Bitcoin ecosystem. Our commitment is steadfast; we aim to make this innovative protocol a reality and will diligently work to iterate and improve based on user feedback. Together, let’s shape the future of decentralized lending.
Your Feedback Matters
We invite you to delve into our whitepaper and share your thoughts and feedback on this groundbreaking approach. Your insights are invaluable as we strive to create a more user-centric, flexible, and secure lending protocol. Read the full whitepaper here
Feel free to reach out with your thoughts, questions, or suggestions. We’re eager to engage with you and iterate based on your valuable input.
-
 @ 06830f6c:34da40c5
2024-08-11 20:13:46
@ 06830f6c:34da40c5
2024-08-11 20:13:46On August 10, 2024, the vibrant Sarit Expo was alive with energy as Bitcoin Dada celebrated the graduation of its seventh cohort. This momentous event, dedicated to advancing the understanding and application of cryptocurrency, showcased the dynamism and innovation of the Bitcoin Dada community.
 The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts.
The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts.

As the MC continued, participants were asked for their impressions of the event space and suggestions for improvement. Comments ranged from critiques of overly bright lighting to discussions about the relevance of Bitcoin. One participant proposed an intriguing app idea that combined Eventbrite and WhatsApp, reflecting the innovative spirit of the audience.
The highlight of the evening was the inspiring opening speech by the CEO of Bitcoin Dada.
 She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team
She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team 
each member contributing uniquely: Edith, the community lead from Uganda; Sabina, the recruiter who found a sense of belonging; and Memelord, the project manager with a flair for comedy.

The ideathon segment was particularly thrilling. Debra’s third-place pitch proposed a Bitcoin-powered marketplace aimed at reducing youth unemployment by showcasing skills. Shantelle’s second-place idea focused on using Bitcoin to address global issues, such as helping refugees find safe zones with GPS technology. The top prize went to Meg, with her solution promising a significant impact—though the specifics were left as a tantalizing cliffhanger. 🌟🏆
PS : Sabina also gave a preview of the #tando app tha you can check out here on my youtube channel Link HERE
Meeting Inspiring Figures and Making Connections 📸
Throughout the event, I had the pleasure of meeting some remarkable individuals who are deeply involved in the Bitcoin community.
First, I met Felix from TheCore, a key panelist in the discussion on the financial revolution amidst economic unrest. We took a photo together, capturing a moment of shared enthusiasm for the potential of Bitcoin.

Later, I connected with a Bitcoin Dada and gamer who is actively involved with Thndr Games, Mary Imasuen. We took a photo showcasing our shared passion for Bitcoin and gaming.

I also had the chance to meet a Bitcoin enthusiast named Hope and she was adorned in Bitcoin-themed merchandise. We snapped a photo together, celebrating our mutual enthusiasm for Bitcoin and its future.

Panel Discussions: Insightful Exchanges and Thoughtful Dialogues
The panel discussion titled “Financial Revolution Amidst Economic Unrest” featured Felix from TheCore, Jason, a Bitcoin Dada supporter, and Bill, a lawyer with expertise in Bitcoin. They delved into the major challenges Kenyans face in adopting Bitcoin, emphasizing the importance of education and community support. They discussed the solid foundation of Bitcoin’s base layer and the need for further development in subsequent layers to enhance its functionality.

The discussion also touched on Kenya’s future in the Bitcoin space. Bill suggested integrating Bitcoin with fiat transactions and stock exchanges, while Jason highlighted the government's welcoming stance and the need for energy to support Bitcoin. Felix proposed making Bitcoin legal tender and finding sustainable energy sources to bolster its use. ⚖️🌍

Audience questions added further depth to the conversation. One attendee asked about using Bitcoin to offset government debt, while another inquired about measures for improving public education on Bitcoin. The responses stressed the need for comprehensive educational initiatives. When asked about alternative cryptocurrencies, the panel firmly rejected the idea of “shitcoins,” focusing instead on the value of Bitcoin. 🚫💸
The second panel discussion, moderated by Sharon from ₿-Trust, explored personal experiences with Bitcoin Dada. Panelists Anon, Vera, and Caroline shared how the program impacted their perspectives.

- Anon discovered a niche and a supportive community, emphasizing Bitcoin’s role as “lightning-fast internet money,” especially with Layer 2 advancements. 🌐⚡
- Vera found Bitcoin to be a valuable medium of exchange, advocated against other cryptocurrencies as “shitcoins,” and highlighted opportunities for women. 💪💰
- Caroline expanded her knowledge and aimed to educate others, describing Bitcoin as a store of value and emphasizing the importance of combating inflation through education. 📚🔍

The panelists also discussed opportunities for Bitcoin in their communities: - Anon saw potential for learning and growth through knowledge-sharing. - Vera mentioned BitSacco, a solution for saving in Bitcoin, and other upcoming projects like Sabina’s Tando app. - Caroline stressed the importance of education to counteract misconceptions about Bitcoin and its benefits. 🏡📈
In their closing remarks, the panelists shared their future aspirations: - Anon aimed to become a developer impacted by Bitcoin. - Vera planned to engage with the community and learn from others. - Caroline focused on educating the community to dispel myths about Bitcoin. 🌟👩💻
The event concluded with a warm dinner where attendees mingled, exchanged ideas, and enjoyed a meal together. WATCH https://video.nostr.build/4d0fbc2dd6ae0c20e0d45aa071a9e88000a9544f4289414900c91134d13960da.mp4
The Bitcoin Dada Cohort 7 graduation was more than just a celebration of individual achievements; it was a testament to the collective potential of the Bitcoin community.
As the event wrapped up, the atmosphere was charged with optimism and a shared commitment to advancing bitcoin technology. The graduating cohort left with new skills, fresh ideas, and a network of like-minded individuals, ready to make a significant impact on the future of Bitcoin. 🌍💡 #kenya #bitbiashara #kenya
-
 @ 961e8955:d7fa53e4
2024-11-22 17:05:11
@ 961e8955:d7fa53e4
2024-11-22 17:05:11The Power of Community: Revolutionizing Bitcoin Adoption through Yakihonne
Introduction
In the dynamic landscape of Bitcoin, community engagement plays a pivotal role in driving adoption and growth. Yakihonne, a pioneering platform, is at the forefront of this effort, providing a novel way for Bitcoin enthusiasts to connect, share knowledge, and support one another. This article delves into the world of Yakihonne, exploring its impact on the Bitcoin community and the broader
Yakihonne's foundational concept is that every Bitcoiner is a social node, interconnected and influencing others within the network. By recognizing the value of these connections, Yakihonne provides a platform for individuals to converge, share ideas, and learn from each other. This approach fosters a sense of community, ensures the dissemination of knowledge and best practices, and promotes a collaborative environment.
Empowering Through Education and Support
Yakihonne is committed to empowering Bitcoiners with the necessary knowledge and tools to succeed. The platform offers a comprehensive suite of educational resources, including articles, videos, and podcasts. Additionally, Yakihonne provides a support system where individuals can ask questions, share experiences, and receive guidance from experienced community members.
Balancing Education and Responsible Adoption
While education is crucial, Yakihonne also emphasizes the importance of responsible adoption practices. The platform encourages users to approach Bitcoin adoption in a measured and informed manner, prioritizing security, privacy, and sustainable growth. By striking this balance, Yakihonne ensures the network grows in a sustainable and responsible way, focusing on long-term success.
Conclusion
Yakihonne is revolutionizing the way Bitcoiners connect, learn, and grow together. By recognizing the power of community and the importance of education and support, this platform is paving the way for a brighter future in Bitcoin adoption. Join the Yakihonne community today and become part of this exciting movement, shaping the future of Bitcoin and fostering a sense of belonging among enthusiasts. @yakihonne
-
 @ dd664d5e:5633d319
2024-07-10 14:45:43
@ dd664d5e:5633d319
2024-07-10 14:45:43The Law Giver
In my previous article, I briefly went into the topic of how contract law is holy law.
The Father of the Christians, you see, is a God of Covenants, and He sent His Son to Earth to fulfill the Law and pay a Price for our salvation. The Father also created the Natural Order to confirm His Laws through our observation of that Law in action.
That is why Christians have a deep respect for honest contracts, true prices, fair measures, natural systems, and good laws. Not merely for their own sake, but also because understanding them helps us to understand and emulate the Law Giver.
The tired What would Jesus do? meme is actually an attempt to capture this emulation of the Highest Judge. Jesus knows the Law, since His Father defined it and He is One with the Father, so how would He apply the Law best, in this situation?
The Last Things
Working together with him, then, we entreat you not to accept the grace of God in vain. For he says, “At the acceptable time I have listened to you, and helped you on the day of salvation.”
Behold, now is the acceptable time; behold, now is the day of salvation.
-- 2 Corinthians 6:1-2 New Testament, RSV Bible
One of the things most devout Christians frequently ruminate over, is when Christ will return.
Every day, we ponder. We go for a walk, and ponder. We cook dinner, and ponder.
At the same time, we are called upon to live each day in a productive manner, and to not simply lie around, vegetating, and staring at the heavens. Not only for our own sake, but also because to do so would be to limit our ability to inform others about the Good News, so that they can take to pondering with us. We are called to ponder with as many people as we can produce, adopt, convert, or simply collect through our daily interactions.
This means that we are not of the world (as our eyes are watching God and baptism has made us Immortals), but we are definitely in the world (involved in, and effected by, the everyday dealings around us.) It is a very difficult balancing act to know when we are paying too much attention to the one or the other, or to know where to store up our treasures, if we can't put them all immediately into the Final Treasury.
So, we worked today and earned a bit of fiat cash and we have no immediate usage for it. What to do with it?
Well, some of it should go to charity or be invested in a business that provides important goods, services, and employment. Some of it will be needed to simply cover the day-to-day costs of our own life, or that of those dependent upon us. But it might be prudent to store up some of it, for the mysterious length of time between receipt of the monies and our own ascent into Heaven.
Typically, that store was the local currency, but that's being inflated away at an alarming rate. Then we all began to move to precious metals, and many of us still do, but they are so difficult to spend and can't be broken into small bits or transported over wide distances at low cost.
Enter Bitcoin.
The Great Ledger
In our frustration, more and more Christians are turning to a new technology, to save up some treasure in a liquid asset, for the mid-term. And, once we begin using it, and begin to understand how it works, we quickly grow fond of it.
Bitcoin is a beautiful money because it is a money based upon keeping precise accounts, using a fair measure, and obeying the Laws of Nature.
In essence, Bitcoin is a debt note emitted by a universal debtor (the network) in exchange for some good or service. This frees the individual people using it from ever needing to carry debt, as the debt stays in the network, the value and enforceability of that debt note is protected by the effort used to create and maintain the network, and the eagerness with which other people wish to store their efforts up in that same network. The debt still exists, but it can be so thinly and widely spread that it no longer rests as a burden upon one particular person.
The debt, in other words, has been disassociated from humans and the management has been distributed to machines. This is the precise opposite process of a "fiat" (by decree) currency, which only has value so long as it is associated with some particularly solvent group of humans (who personally vouch for repayment of any debts denominated in the currency), and where management is centralized to some other group of humans.
Have you accepted Bitcoin as your personal money and store of value?
You have invested $10 to buy the electricity to mine Bitcoin? Then you receive $10 of Bitcoin in return. The Bitcoin network now owes you the $10 purchasing power equivalent of that electricity.
If someone then gives you $5 worth of pizza, then you can then give them a $5 portion of your $10 worth of Bitcoin. You have taken a part of your Bitcoin debt note and shared it with them.
They now hold $5 worth of Bitcoin invested in the network and can spend it on some other good or service. Or they can simply hold it and wait for it to rise in value, as more people "mine" more of it (and produce more notes, paradoxically making the existing notes more useful and therefore valuable) and more people try to gain the notes in order to manage their own finances by storing their energy in the network or transporting their energy using the network.
Bitcoin, in other words, is an accounting book that needs no accountant because it stores, tracks, and controls the ledger on its own. It is a Natural Ledger that runs according to the the Laws.
It is the only human-made ledger that allows for true and immediate Final Settlement. This Final Settlement is what allows people to trade using the convenience of digital debt notes, with neither person occurring or even risking any personal debt. We Christians know that all debt is a burden, including monetary debts, which is why we are called to forgive each other's debt and to hope that our own debts are forgiven. Better still, is to avoid the accumulation of debts, altogether.
So, Final Settlement? Final Settlement is what Jesus would do.
-
 @ 2c7cc62a:622a5cdc
2024-07-08 10:24:56
@ 2c7cc62a:622a5cdc
2024-07-08 10:24:56Nostr で見掛けた焼肉店情報。いつか見返す。
ちょうしゅう
石垣島
http://yugafu-llc.com/
nostr:note1tgnt39hgyvn4lskp5s684czgsce9y55xm8ysfrfdj4mp3gguhhvsu6jtjw
とらじ
http://www.toraji.net/
大阪上新庄
nostr:note1x3fhl9w0wf5r7e75aem3n4ffcqcuqggp3uda6cj8p3ewg4hgrrjqwye9lc
瑞園
https://tabelog.com/osaka/A2701/A270307/27001977/
大阪上新庄
nostr:note1whjkp27hztcy5yey5r7nvc23yjcavpu322q5xyp8grua98rshz7stz9grh
たん清
https://www.tankiyo.com/
東京秋葉原
nostr:note1ke9ekpe3h92nq7qgjg4w4nmz4u7s4wyn753gagsf49pam4h6aefsddwr0k
-
 @ a305a0de:21557ddd
2024-11-22 17:01:06
@ a305a0de:21557ddd
2024-11-22 17:01:06Bitcoin, the decentralized digital currency, has the potential to revolutionize the way local communities function. By providing an alternative to traditional fiat currencies, Bitcoin can empower local businesses, promote financial inclusion, and foster community development.
Financial Inclusion
Bitcoin can provide access to financial services for underserved communities. With Bitcoin, individuals can make transactions without the need for traditional banking infrastructure. This can be especially beneficial for low-income communities where access to banking services is limited.
Local Economic Growth
Bitcoin can also promote local economic growth by encouraging local businesses to accept Bitcoin payments. This can increase foot traffic, boost sales, and create new job opportunities. Additionally, Bitcoin's decentralized nature can help reduce transaction fees, allowing local businesses to keep more of their hard-earned money.
Community Development
Bitcoin can also foster community development by providing a platform for community-driven initiatives. For example, Bitcoin-based crowdfunding platforms can be used to raise funds for local community projects, such as building a community center or supporting a local food bank.
Real-World Examples
There are already several examples of Bitcoin being used to improve local communities. For instance, the Bitcoin Ekasi project in South Africa is using Bitcoin to create a circular economy in a local township. Similarly, the BitPatron project in the United States is using Bitcoin to support local artists and creatives.
Conclusion
Bitcoin has the potential to revolutionize the way local communities function. By providing access to financial services, promoting local economic growth, and fostering community development, Bitcoin can empower local communities to take control of their own economic destiny. As the world becomes increasingly digital, it's exciting to think about the potential impact that Bitcoin can have on local communities around the world.
-
 @ 6fff5148:a5dd5cdf
2024-11-22 17:00:38
@ 6fff5148:a5dd5cdf
2024-11-22 17:00:38 what is Bitcoin
Bitcoin is a cryptocurrency, a peer-to-peer digital currency that operates independently of a central governing authority. Bitcoin enables direct transactions between users, secured by cryptographic technology and recorded on a transparent and immutable ledger known as the blockchain.This innovation not only ensures security and transparency but also challenges traditional financial systems by offering a global currency that is accessible to anyone with internet access.Picture it as digital gold: whereas gold is physically mined from the earth, Bitcoin is created through the use of powerful computers solving complex problems, known as "Bitcoin mining." Unlike gold, you can't physically touch Bitcoin; it exists purely in the digital realm.Bitcoin was first introduced in 2009 by a person (or group) named Satoshi Nakamoto. Little is known about their identity–but more on that later!Today, Bitcoin is the most popular cryptocurrency, with a market capitalization that far surpasses any other digital currency. It has become a benchmark for the crypto market, influencing the launch of thousands of other cryptocurrencies and ushering in a new era of digital finance.Key Bitcoin Concepts in Simple Words
Cryptocurrency: A type of digital or virtual money that uses cryptography for security, making it difficult to counterfeit.
Blockchain: A digital ledger that records all Bitcoin transactions, like a global spreadsheet that everyone can see but no one can tamper with.
Wallet: A digital pouch that safely stores your Bitcoin, similar to a virtual bank account.
Public and Private Keys: A pair of digital keys where the public key is your Bitcoin address (like an email address) and the private key is your secret password to access and send your Bitcoins.
Decentralization: The principle of distributing control across the entire network rather than relying on a central authority, like having a group decision instead of one boss calling the shots.
Mining: The process of using computer power to solve complex puzzles, securing the network and creating new Bitcoins as a reward.
Satoshi: The smallest unit of Bitcoin, named after its mysterious creator, worth one hundred millionth of a Bitcoin.
BTC: BTC is the abbreviation for Bitcoin typically used when referring to the currency unit in transactions, price listings, and financial discussions.
image
Source: https://www.blockpit.io/en-us/blog/what-is-bitcoin#:~:text=Bitcoin%20is%20a%20cryptocurrency%2C%20a,ledger%20known%20as%20the%20blockchain .!
@yakihonne.com
what is Bitcoin
Bitcoin is a cryptocurrency, a peer-to-peer digital currency that operates independently of a central governing authority. Bitcoin enables direct transactions between users, secured by cryptographic technology and recorded on a transparent and immutable ledger known as the blockchain.This innovation not only ensures security and transparency but also challenges traditional financial systems by offering a global currency that is accessible to anyone with internet access.Picture it as digital gold: whereas gold is physically mined from the earth, Bitcoin is created through the use of powerful computers solving complex problems, known as "Bitcoin mining." Unlike gold, you can't physically touch Bitcoin; it exists purely in the digital realm.Bitcoin was first introduced in 2009 by a person (or group) named Satoshi Nakamoto. Little is known about their identity–but more on that later!Today, Bitcoin is the most popular cryptocurrency, with a market capitalization that far surpasses any other digital currency. It has become a benchmark for the crypto market, influencing the launch of thousands of other cryptocurrencies and ushering in a new era of digital finance.Key Bitcoin Concepts in Simple Words
Cryptocurrency: A type of digital or virtual money that uses cryptography for security, making it difficult to counterfeit.
Blockchain: A digital ledger that records all Bitcoin transactions, like a global spreadsheet that everyone can see but no one can tamper with.
Wallet: A digital pouch that safely stores your Bitcoin, similar to a virtual bank account.
Public and Private Keys: A pair of digital keys where the public key is your Bitcoin address (like an email address) and the private key is your secret password to access and send your Bitcoins.
Decentralization: The principle of distributing control across the entire network rather than relying on a central authority, like having a group decision instead of one boss calling the shots.
Mining: The process of using computer power to solve complex puzzles, securing the network and creating new Bitcoins as a reward.
Satoshi: The smallest unit of Bitcoin, named after its mysterious creator, worth one hundred millionth of a Bitcoin.
BTC: BTC is the abbreviation for Bitcoin typically used when referring to the currency unit in transactions, price listings, and financial discussions.
image
Source: https://www.blockpit.io/en-us/blog/what-is-bitcoin#:~:text=Bitcoin%20is%20a%20cryptocurrency%2C%20a,ledger%20known%20as%20the%20blockchain .!
@yakihonne.com -
 @ 3c7d12a6:9532013e
2024-06-20 14:47:12
@ 3c7d12a6:9532013e
2024-06-20 14:47:12NUD: Pubkey to colors
This NUD defines how to convert pubkey to colors.
Why?
npubis nonsense to display.- too long.
npub1bla...blais nonsense to display.npub1takes too much space....means nothing.
Specs
- Uses hex pubkey.
- Converts 64 characters to 8 colors.
- Splits 64 with 8 length chunks.
- Converts each 2 in 8 into
- Alpha (0-255 -> 0.0-1.0)
- Hue (0-255 -> 0.0-360.0)
- Saturation (0-255 -> 0.0-1.0)
- Light (0-255 -> 0.0-1.0)
- Supports dark and light theme.
- When Light is 1.0, flip the Light for light theme (0.0).
-
 @ d830ee7b:4e61cd62
2024-06-02 05:44:01
@ d830ee7b:4e61cd62
2024-06-02 05:44:01This article is a translation of my original Thai-language article, which will be published as a long-form piece in the coming days.
.........................
After listening to these two masters go back and forth, circling each other like intellectual gladiators, I gotta say… the lines between the "real world" and the "virtual world" are getting seriously blurry.
Watch more > Alt+Tab Season 2 EP4 : "พี่ชิต" ดร.วิชิต ซ้ายเกล้า
The battle for power is changing, man.
Forget tanks and explosions, the most powerful weapon now is invisible, hiding in plain sight. It's woven into the fabric of society. We call it "Soft Power", the unseen influence that slowly consumes us, manipulates us... without us even realizing it.
"The wars we see today..." Wichit says with a voice that sends shivers down your spine, "It's just throwing percentages at each other in the air."
Piriya nods in agreement. "Like you said, humans are getting smarter, more cunning. Those old-school, head-on confrontations? They just lead to destruction. Waste of resources, waste of life..."
They're right, you know... Back in the day, if you wanted something, you just sent an army to take it. Conquered land, plundered resources. It was all about "Hard Power."
Direct, brutal, effective... but the scars ran deep.
The world today is way more complex. Humans have learned to use "influence" to infiltrate every aspect of life.. individuals, societies, even international relations. No bloodshed, but the results are even more potent...
That's why "Soft Power" has become the most powerful weapon in this new age.
Imagine...
A world where information is the new crude oil... Where attention is the currency... And beliefs are weapons... Used cunningly in this invisible battlefield...
"Influence" is the real victory. Not about conquering land anymore. It's about controlling minds, hearts, and actions...

Here are some prime examples of "Soft Power" playing out in our everyday lives.
Online Warfare - Fake news, twisted facts, everyone's sharing it like crazy on social media. A few taps on a screen can destroy reputations, incite hatred, and control people's thoughts without breaking a sweat. (Wichit calls it "promiscuous bits" in his lectures.)
Have you ever... almost made a bad decision because you believed a rumor or fake news? Have you ever... fallen prey to manipulation, been tricked into hating or opposing someone without even knowing why?
That, my friend, is Soft Power working its magic... behind the scenes...
Economic Control - Think about those skyrocketing interest rates, inflation… everything's getting more expensive by the day while our wallets get thinner.
That's the consequence of Soft Power wielded by a handful of people who control the global economy.
Ever wonder... why your money seems to be worth less and less each day? Why you work harder, but life doesn't get any better?
The "money" system, controlled by the few… that's the culprit...
Cultural Domination - Movies, TV shows, music, fashion… We consume it all every day, and it slowly seeps in, shaping our thoughts, values, and behavior without us even realizing it. It's a tool used by certain groups to manipulate and steer society...
Have you ever… wanted to be, have, or act like what you see in the media? Ever gone along with trends or fads, even if they didn't really reflect who you are?
That's the power of "Cultural Domination"...
"The scary part is… most people don't even realize they're being manipulated." Piriya shakes his head.
"It's like a frog being boiled alive. By the time they realize it, it's too late..."
Wichit sighs...
"The system is broken, slowly eroding us from the inside... God knows where it'll all end, but it's not gonna be pretty."
...

Wait, what about "Money"? Isn't that Soft Power too?
Money used to be a mirror, reflecting the "value" of work, of resources. It was a tool for exchanging, saving, building wealth...
But today... the "money" system is designed to be conjured up out of thin air. No real cost, no sweat. Just print more bills, and suddenly its value is distorted. Leading to "bubbles of inequality" and a crisis of faith in money itself...
It's like sand… the tighter you grip it, the more it slips away…
"Like when America ditched the Bretton Woods system and embraced Fiat currency, which they can print endlessly… It's how they became the world's financial superpower." Wichit explains.
"Countries that used to hoard gold, like Europe, China, Russia… they lost power because the money they held wasn't worth as much anymore."
"So what about Thailand? We're just a small country. How can we survive?" Piriya asks, worried.
"We can't just print our own money. We have no control over the global economy..."
"That's the million-dollar question…" Wichit says with a serious tone.
"If we don't wake up, if we're not prepared, Thailand could become a victim in this power struggle."
"We need to build up our "immunity," man..."
...
Bitcoin.. Hope or Menace?
In the midst of this Soft Power battleground, filled with deception and distorted truths, Bitcoin emerges… like a beacon of light piercing through the darkness. A glimmer of hope for a fairer world, a chance to reshape the global economy...
"Weapons should be used for self-defense, not to attack others." Wichit says, implying that Bitcoin is no different.
"It's a tool that can be used for good or for evil. It all depends on who's wielding it."
Bitcoin is presented as a symbol of "Truth" in the digital realm.
No one can counterfeit it or control it. It's finite, requiring energy to "mine." It's like applying the laws of physics to the financial system, creating honesty and transparency that traditional money can't achieve.
Imagine… a public ledger that everyone can see, transparent, unchangeable... That's Bitcoin.
"It's like a monetary revolution, creating a new system that's fair, transparent, and accessible to everyone." Piriya says excitedly.
"No one can print more Bitcoin on a whim. No one controls it."
"Exactly." Wichit adds.
"If people understand and accept it, Bitcoin can change the world. Bring balance, reduce inequality, and return power to the people."
"Imagine… a world where money belongs to the people, not the government or banks..."
But Bitcoin is a double-edged sword... In the hands of the righteous, it's a beacon of hope. A chance to create a fairer world.
*But in the wrong hands? *
It could become a menace, a tool for money laundering, crime, even a "weapon" for cyber warfare…
...

Where Does Thailand Stand?
"The question is… with Bitcoin challenging the old powers, how should Thailand respond?" Piriya asks seriously.
"Do we embrace it? Resist it? Or just ignore it?"
"Doing nothing is not an option, just like when we missed the boat on the gold standard." Wichit emphasizes.
"Back then, England pushed for the gold standard, but Thailand clung to the old way. We ended up losing out, trade deficits, economic downturn... We can't let history repeat itself."
"I agree." Piriya nods.
"We need to learn from the past and prepare for the future."
"The government and the people need to wake up, study, and truly understand Bitcoin." Wichit continues.
"Not just knowing what it is… but understanding its mechanisms, its potential, its risks."
"You mean… we should push for Bitcoin to be the main currency of Thailand?" Piriya asks.
"Whoa, hold your horses, Professor." Wichit smiles.
"No need to rush things. I think we should start by creating a space for people to learn and experiment with Bitcoin. Promote innovation and businesses related to blockchain. Maybe the government could set up a "regulatory sandbox" to control and mitigate risks along the way."
"But will the government be willing to relinquish control over money and embrace Bitcoin?" Piriya asks skeptically.
"It won't be easy." Wichit sighs…
"Power is seductive. Everyone wants to hold on to it. But if we see Bitcoin as an opportunity for Thailand to develop, to create stability and prosperity for the people, I believe the government will see the benefits and eventually embrace it."
"So what can we, the people, do?" Piriya asks.
"We need to be aware of Soft Power." Wichit answers.
"Question the information we receive, be savvy about media tactics, don't fall prey to anyone's agenda. And most importantly, use Soft Power constructively, for the betterment of society."
"Absolutely." Piriya agrees wholeheartedly.
"We need to be informed citizens, not manipulated victims."
"And remember… Bitcoin is not some far-off concept anymore. We need to learn, stay informed, and be prepared because the future is in our hands." Wichit concludes. "The future of money, the future of our country, the future of the world…"
The conversation ends… but the crucial question lingers.
Will Thailand keep up and be ready for the world's seismic shift?
The answer… lies with each and every one of us...
...

This conversation between Wichit and Piriya is like a doorway to another dimension.
A dimension we're familiar with, but never truly see clearly. A world teeming with games, power struggles, and manipulations happening all around us… often without us even realizing it.
They're trying to show us the "Soft Power," the formless force that lurks in every corner of our lives. From the news we consume, the economic systems we rely on, to the culture and values that shape our thoughts and actions.
They're not trying to scare us, but to "wake us up," make us aware, so we don't become victims in this game.
The things they emphasize most is the "importance of education." We need to understand Bitcoin, blockchain, and all these new technologies transforming our world. Not just "knowing" what they are, but "understanding" their mechanisms, their potential, their risks.
So we can decide how to use them, "for what," and "how."
Where does Thailand stand in this world where "Soft Power" is thriving?
Wichit and Piriya don't offer a clear-cut answer. Instead, they "invite" us to "ask questions," "think critically," and find our own answers.
We… as "citizens" of this new world… must be aware, learn, and adapt wisely to the changes. "Soft Power" isn't scary if we understand it and use it constructively.
We can turn "threats" into "opportunities."
The lessons from this conversation aren't just about "Soft Power" or "Bitcoin." They're about "awareness," "questioning," "critical thinking," and "taking responsibility" for the future of ourselves, our society, and our nation.
It's a wake-up call, revealing the "truth" of the world hidden beneath the "illusion" of "Soft Power." And it reminds us of the true "power" that lies in our hands…
the power to "choose," "decide," and "create" the future we want...

Decoding Wichit's Thoughts. "Soft Power" vs. "Hard Power" - The Game of Power in the Modern World
From the conversation, we see that Wichit views "power" beyond just weapons and military force. He defines it as the "ability to influence, persuade, control, or direct the behavior, thoughts, and decisions of others" without resorting to physical force or coercion.
Wichit sees a fascinating connection between Soft Power, Bitcoin, and national security in the digital age. Imagine a "power triangle" where each side influences and is intertwined with the others.
He divides "power" into two main forms..
First, there's "Hard Power," the traditional approach focused on using force, coercion, and direct control. It relies on tangible resources like military might, weapons, economic clout, or sanctions.
Think of examples like waging war, military occupation, controlling trade routes, or imposing economic sanctions.
Then there's "Soft Power." This new form of power emphasizes influence, persuasion, and attraction, making others "want" to follow without force or coercion.
Examples include using information to shape narratives and guide thinking, employing culture and entertainment to create values and trends that influence behavior, or using economic systems to incentivize desired actions.
Wichit believes that in today's world, Soft Power is gaining more influence and impact than Hard Power.
Why?
Because beliefs, values, and information can spread and penetrate people's minds easier and faster than brute force or coercion.
He compares modern warfare to "throwing percentages at each other in the air." Meaning that the fight for dominance in this era is no longer about physical destruction like in the past. It's a battle on an invisible battlefield, where the stakes are "information," "beliefs," and "influence."
In Wichit's view, Bitcoin can be both a "tool" and a "weapon" in the game of Soft Power.
And ultimately, "power," in any form, has both light and dark sides. It depends on the user, whether they choose to use it for creation or destruction...
When "Influence" Becomes a "Chain" on Thai Society
Yes, Soft Power has a glamorous, alluring side, evident in movies, music, TV shows, food, fashion, and tourism, all of which contribute to Thailand's income and image.
But there's a dark side... one that slowly erodes our thoughts, values, and identity... without us even noticing.
Look around… Is our younger generation today more obsessed with Korean dramas, Western series, K-pop, and designer brands than Thai movies, music, fabrics, or cuisine?
Do they dream of living like idols, celebrities, rather than ordinary Thais?
This is the consequence of Soft Power, influencing us to want to "be" and "have" like others, forgetting our roots, our identity, and our own values.
The Government Uses Soft Power to Control the People Too!
Ever wonder… why people believe government pronouncements more than news from fellow citizens? Why we accept unfair policies without much resistance?
Is Soft Power in the hands of the government used to craft an image, hide the truth, distract, and control people's thoughts?
I don't know... We need to observe and find the answers.
Are Today's Youth "Victims" or "Awakened"?
The younger generation, raised with the internet, social media, and global entertainment, is more susceptible to Soft Power's influence. But... they also have the potential to be aware, to question, to analyze, and to break free from the chains of manipulation.
Don't let influence become your prison…
Be "aware," "question everything," and "be yourself"
This is just a taste of what's discussed in the full video. To truly savor the "flavor" of "Soft Power" and "Bitcoin," you gotta watch the whole thing.
Watch more > Alt+Tab Season 2 EP4 : "พี่ชิต" ดร.วิชิต ซ้ายเกล้า
Trust me... you'll be blown away by the depth and intensity of the conversation.
"One listen is not enough."
Let me tell you… This video is "heavy," "dense," and "intense." Even me had to rewind several times to let it all sink in.
But it's "worth it," I promise. You'll "decode" the world today, understand the mechanics of "power" and "money" in a way no one's ever explained before.
So why share it?
Because "truths" like these shouldn't be hidden. "Knowledge" like this should be "spread" to "everyone."
But… to be honest, this video is "deep," "complex," and "hard to grasp" for the average person. So we have to transform ourselves into "interpreters," "translating" the "divine language" into "human language." Explain it simply, clearly, and visually.
Remember… sharing is not just "talking," it's about communication that's easy to understand, relatable, and resonates with the listener.
Because knowledge is precious… if it's "shared."
PS. Wichit's ideas and concepts regarding Soft War are heavily influenced and inspired by the book "Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin" by Major Jason P. Lowery. (2023)
-
 @ 126a29e8:d1341981
2024-05-22 06:47:20
@ 126a29e8:d1341981
2024-05-22 06:47:20Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852
Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior. A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.
Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.
Bitcoin cambió todo eso. Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio. Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.
La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins. ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.
La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan. Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.
En cambio, los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.
Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero. Pero Bitcoin no se originó en el vacío. Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.
Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.
Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.
https://freeross.org
-
 @ a305a0de:21557ddd
2024-11-22 16:53:03
@ a305a0de:21557ddd
2024-11-22 16:53:03In the ever-evolving world of Bitcoin, innovation is key. And one name that's been making waves is Yakhonne. This pioneering project has been instrumental in helping Bitcoin take a giant leap forward.
So, what exactly is Yakhonne? Simply put, it's a decentralized social media platform that rewards users with Bitcoin for creating and engaging with content. But that's not all - Yakhonne has also been at the forefront of driving Bitcoin adoption and education.
By providing a user-friendly platform for people to learn about and interact with Bitcoin, Yakhonne has helped demystify the world of cryptocurrency. And with its innovative approach to social media, Yakhonne has shown that Bitcoin can be used in ways that go beyond just transactions.
The impact of Yakhonne on Bitcoin's evolution cannot be overstated. By pushing the boundaries of what's possible with Bitcoin, Yakhonne has inspired a new wave of innovation and adoption. And as Bitcoin continues to grow and mature, it's clear that Yakhonne will remain a key player in shaping its future.
-
 @ c755de14:cc53833a
2024-11-22 16:52:54
@ c755de14:cc53833a
2024-11-22 16:52:54Here’s What Bitcoin’s New All-Time High Means For Investors

Bitcoin’s price soared over $98,000 this morning, marking a new high. The granddaddy of cryptocurrency seems to be becoming less volatile, but it’s still a risky asset. Don’t buy Bitcoin just because of its recent price action – take time to research and think about how it fits with your other investments. For the second time this year, Bitcoin bulls have reason to celebrate. About 24 hours ago, Bitcoin’s price reached $99,434 smashing previous all-time high. Bitcoin’s recent rise was fueled by an influx of institutional money into spot crypto ETFs and increasing economic optimism. The election result pushed it to break new ground. If you’re thinking of buying Bitcoin, you might be wondering what this means for investors.
Does Bitcoin’s recent price action mean it’s here to stay? Positive price action is certainly reassuring, but the true test of whether Bitcoin is here to stay will be long-term adoption. There’s a lot we don’t know about how cryptocurrency will develop. It’s a relatively new and unregulated industry, and it’s still unclear what people will use Bitcoin for in the long term. That said, Bitcoin does appear to be maturing. Don’t get me wrong, it continues to be a volatile and high-risk asset. But the price swings have become less drastic. That’s a very different picture from previous years. Indeed, research by Fidelity shows that the top cryptocurrency was less volatile than several popular S&P 500 stocks. For example, its analysis shows that Netflix was more volatile over the two-year period ending March 2024. Even so, Netflix is still a totally different asset class. The stock market has existed for hundreds of years, which is plenty of time for various regulations and investor protections to evolve. In contrast, Bitcoin is less than two decades old and still has the sword of changing regulation hanging over it.
Three questions to consider before you buy Bitcoin Before you buy any investment, it’s important to be clear on why you’re buying. Think about your tolerance for risk and how cryptocurrency fits with your overall investment strategy. Here are some questions to consider.
- How will you buy and store it? Cryptocurrency assets do not have the same protections against institution failure or theft as money in the bank or stocks in a brokerage account. As an investor, that means being conscious of security when buying and storing digital assets.
Here’s how that looks with some of the most common ways you can add Bitcoin to your portfolio:
Top cryptocurrency exchange: Cryptocurrency exchanges have a broad mix of cryptos and crypto-related products. It is easy to move your assets to a crypto wallet you control, which gives you extra protection against platform failure. Crypto broker: A couple of popular brokerages offer cryptocurrencies. They don’t have as much functionality or as many cryptos as exchanges, but the fact that they’re registered with the SEC to trade other assets makes them feel more secure. Spot Bitcoin ETF: The SEC greenlighted spot Bitcoin ETFs at the start of the year. This means many investors can buy them from a brokerage account, just as they would other ETFs and stocks. One big advantage is that the fund managers are responsible for storing the Bitcoin safely. Robinhood has broken the mold in terms of crypto offerings. You can buy several cryptocurrencies directly, as well as spot Bitcoin and Ethereum ETFs. Plus, it’s the only brokerage with a crypto wallet that lets you deposit and withdraw crypto. Click here to learn more about Robinhood’s crypto offer and open an account.
- Have you researched Bitcoin and its long-term potential? Think about why you’re buying cryptocurrency. If it’s because you see the price rising and worry about missing out, pause and do a bit more digging. Look at the different arguments on how Bitcoin will develop – both critical and optimistic.
Some argue that Bitcoin has value as a type of digital gold or the future currency of the internet. Others see it as taking a chunk out of the global money transfer market. On the other hand, critics say it’s a speculative asset with no intrinsic value.
- How does it fit with the rest of your portfolio? Risky assets like cryptocurrency should only make up a small percentage of your wider portfolio. Think about what level of risk you’re comfortable with and how to balance your investments accordingly.
Building a diversified portfolio can be a great way to safeguard your funds. If one sector or asset performs badly, you’re insulated against losses. If it does well, you’ll still reap the rewards.
Don’t buy Bitcoin just because it hit an all-time high Not only has Bitcoin more than erased the losses of recent years, it’s also becoming less volatile. However, it’s still a high-risk asset that could fall to zero.
Only invest money you can afford to lose, and do your own research into the blockchain and Bitcoin. Positive short-term price action is one thing, but if you’re a buy-and-hold investor, long-term value is a lot more important.
@Yakihonne
-
 @ 75da9402:77a65b5c
2024-05-19 00:07:36
@ 75da9402:77a65b5c
2024-05-19 00:07:36Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ 3c984938:2ec11289
2024-05-11 12:21:43
@ 3c984938:2ec11289
2024-05-11 12:21:43👉play the audio to listen to the article. https://media.nostr.build/av/749a03816c328c599054f31113588f9f5a47b5e67681e3a1eb9ee97c8f2e0dd3.mp3
Welcome to Nostr!
Introduction. Is this your first time here in Nostr? Welcome! Nostr has a oddball acronym for "Notes and Other Stuff Transmitted by Relays" with a simple goal, to be censorship-resistance. An alternative to traditional social media, communications, blogging, streaming, podcasting and eventually email (in development) with decentralization that empowers you, dear user. No more will you have to be plagued by ads, held by centralized entities and data hungry algorithms that monetizes you.
Allow me to be your host! I'm Onigirl! I'm on a quest to explore the world of Nostr, a decentralized communication protocol. I write about the tools, and the awesome developers within Nostr that bring this realm roaring with life.

Welcome to Nostr Wonderland
You're about to step into another world that will explode your mind from all the decentralized apps, clients, web3 enabled sites that you can use. You're never going to look at communications, logging in, 2FA, and social media the same way ever again. All thanks to Nostr's cryptographic nature inspired by Bitcoin blockchain technology. Each user, when they create a Nostr account, they get two keys, a private and a public key. These are your keys to your very own kingdom. Whatever you write, sing, podcast, stream, anything you create --all of it belongs to you. The sky is literally the limit!

A Gold and Silver Key
A friend of mine and I, call this "Identity by Encryption" because your Identity is encrypted. You can share your silver key, "npub" to other users to connect and follow. Use your gold key, "nsec" to unlock your account to plugin into a plethora of applications. Keep this key safe at all times. There is no reason to be caged ever again by social platforms TOS henceforth!
👉Give it a whirl, you can follow me by copying and pasting my public key into your search bar on any client that you decide to use.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Don't have a client yet? Select the best option
Find the right App for you! This is where you can use your gold key, "nsec" to login into these wonderful tools. You can also visit Nostr's app page here. Before you start pasting your gold key everywhere on apps, consider using a signers (for web3 enabled sites) please look at the next image for details, also refer to the legend.

Get a Signer extension via chrome webstore
A signer is an extension in the chrome webstore on Google. Nos2x and NostrConnect are widely accepted extension for logins. This simplifies the process of logging into web3 sites instead of copying and pasting your gold key, "nsec" each and every time, you keep it within the extension and give it permission(s) to sign you in.

👉⚡⚡Get a Bitcoin lightning wallet to send/receive Zaps⚡⚡ (This is optional)

Here on Nostr, we use the Bitcoin Lightning network (L2). You will need to get a lightning wallet in order to send/receive Satoshi. These are the smallest denominations of a Bitcoin. It is a one hundred millionth of a single bitcoin (0.00000001 BTC). Zaps are a form of "micropayment with sats" here on Nostr. If you enjoy a user content, it is the norm to "⚡zap⚡" a.k.a "tip" for their content. For example, If you like my content, you can zap me with SATs to reward my work. But you just arrived, you don't have a wallet yet. No worries! I got you covered!
"Stacker.News" is a platform where users can earn SATs by writing articles and engaging with other users. You.

👉Stacker.News is also the easiest place to get a Bitcoin Lighting wallet address.
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:

- Click "edit"
and choose a name that you like, and if you don't like it. You can change again later.

- Click "save"
- Create a bio and the SN community are very welcoming and will zap you some sats to welcome you.
- You new Bitcoin Lightning Wallet address will appear like this:
 #### ^^Do not zap this address; this is purely for educational purposes!
#### ^^Do not zap this address; this is purely for educational purposes! - With your New Bitcoin Lightning wallet address you can put this into any client or app of your choice. To do this, go to your profile page and under your wallet address under "LN Address," enter your new address and hit "save" and there ya go. Congratulations!
👉✨Eventually, you may want to move to self custodial options and maybe consider to even self-host your own LN node for better privacy. Good news is stacker.news is also moving away from being a custodian wallet.
Nostr, the maverick of Servers
 Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.
Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.My friends in Nostr welcome you!
Welcome to the tea Party, would you like a spot of tea?🍵

There's so much more!
This is just the tip of the iceberg. Follow me as I continue to explore new lands and the developers, called "knights" behind this ever-growing ecosystem. Meet me here for more content like this and share this with future nostr users. Learn about the knights fighting for freedomTech within Nostr and the projects that are contributing to make it happen. Make your life more decentralized with Nostr. 💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:
-
 @ c755de14:cc53833a
2024-11-22 16:52:03
@ c755de14:cc53833a
2024-11-22 16:52:03
In the past recent years, Cryptocurrencies have exploded onto the financial scene, offering a new innovative form of digital money. Built on blockchain technology, cryptocurrencies like Bitcoin and Ethereum have the potential to transform finance as we know it. But what exactly are cryptocurrencies, and what is their role in this modern financial landscape? This article explores the rise of cryptocurrencies, their impact so far, and what the future may hold for this disruptive new asset class.
Cryptocurrencies Overview Cryptocurrencies are digital that uses cryptography to control and secure transactions. Unlike printed money issued by governments, cryptocurrencies operate independently of central banks and are decentralized across peer-to-peer networks. The first and most well-known cryptocurrency as we all know it is Bitcoin, created in 2009 by the mysterious Satoshi Nakamoto. Today there are over 10,000 different cryptocurrencies in existence, though Bitcoin and Ethereum dominate the market.
Cryptocurrencies enable direct transactions between users without an intermediary. All ownership records are stored on a public ledger called the blockchain. Advanced cryptography verifies and secures each transactions on the blockchain. Miners contribute computing power to verify blocks of transactions, and are rewarded with new cryptocurrency for their efforts. This decentralized nature of cryptocurrencies removes the need for trusting central authorities to manage the system.Is Cryptocurrency Here To Stay? Given their relatively brief lifespan so far, some wonder if cryptocurrencies are just a passing fad. However, there are a growing amount of evidence that suggests cryptocurrencies are here to stay as a financial and technological innovation. One of the key drivers of this is the advantages the underlying blockchain technology provides in terms of secure, transparent record-keeping and transactions. The decentralized structure means no single entity controls the network.
Cryptocurrencies also enable faster cross-border payments. Major companies like PayPal, Visa, and MasterCard are integrating crypto capabilities to take advantage of these benefits. The total market value of cryptocurrencies has grown to over $1 trillion. Governments are exploring central bank digital currencies built on blockchain technology. All of these trends point to cryptocurrencies cementing their place in the financial landscape long-term.
What is Cryptocurrency’s Role In Today’s Financial Landscape? Cryptocurrencies are playing an increasingly important role in today’s modern finance. Below are some of those roles: • Cryptocurrencies serves an alternative investment and store of value. Scarcity makes cryptocurrencies like Bitcoin attractive as an inflation hedge.
• Facilitating global commerce and payments. Cross-border crypto payments are faster and cheaper. The adoption is growing among merchants and businesses.
• Providing banking access. Approximately 1.7 billion adults remain unbanked globally. Cryptocurrencies provide access without any form of barriers.
• Driving innovation. Decentralized finance (DeFi) applications are expanding lending, trading, insurance and more.
• Challenging status quo. The disruptive power of cryptocurrencies encourages competition and improvement in the traditional finance.
Considerations And Challenges
Although promising, cryptocurrencies also come with risks and challenges that should be considered: • Volatility: As a newer asset class, cryptocurrency prices can swing wildly, making them a risky investments. Extreme volatility limits their ability to reliably store value.• Security: Exchanges and wallets have been hacked, leading to huge losses. Users must take proper precautions to secure their cryptocurrency tokens.
• Lack Of Regulation: Currently, minimal government oversight exists. More regulation would provide greater investor protection.
• Complex Technology: Blockchain and cryptocurrencies represent complex concepts for many. Usability could improve with further development.
• Illegal Activity: Anonymity has attracted criminals laundering money and buying illegal goods. This black market use harms legitimacy.
• Environmental Impact: Bitcoin mining consumes enormous energy. More efficient consensus models are being explored.
• Adoption Obstacles: Integration into everyday payments and financial systems is still limited. Tax implications are still being defined.
As time goes on, these challenges may decrease over time as the technology matures. Regulations will evolve and adoption will grow. But for now, they remain barriers inhibiting mainstream acceptance.
How Cryptocurrency Can Affect The Finance Industry
Cryptocurrencies threaten to disrupt traditional finance and could significantly impact the industry in a variety of ways: • Reduced Fees: By removing middlemen, cryptocurrency transactions have fewer fees. This pressures banks and payment networks to reduce costs.• Faster Services: Settlement of cryptocurrency transactions is nearly instant. Consumers will expect faster banking and payments facilitated by blockchain technology.
• New Revenue Sources: Wealth managers and institutions are finding ways to add cryptocurrency services to attract more clients and investment in dollars.
• Better Transparency: Cryptocurrency ledgers are public. This allows anyone to analyze transactions. This level of transparency will compel competition.
• Increased Automation: Smart contracts executed on the blockchain automate many manual processes required in traditional finance. This can improve efficiency and cost-savings.
• Enhanced Security: Cryptocurrencies offer better consumer protection against fraud or identity theft since they don’t expose personal information.
Effects Of Cryptocurrency On Everyone. Is It A Threat To Financial Stability? For the average person like you and I, cryptocurrencies offer both potential benefits and drawbacks:
Potential Benefits: 1. It Increases financial access. It has the ability to utilize financial services like lending or investments previously inaccessible.
-
It enables fast and cheap remittance of money across borders.
-
Cryptocurrencies reduces fees compared to traditional financial services.
-
The decentralized nature of crypto gives more people direct control and power over their money.
-
It serves as a new financial opportunities. It gives the ability to invest early in new cryptocurrencies and technologies.
Potential Drawbacks:
1. Cryptocurrency concepts and tools require technological proficiency many don’t have which makes it Complex.-
The unpredictable price fluctuations make crypto a high-risk investment.
-
No government insurance or regulation means limited consumer protections exist. For this reason, it lacks protection.
-
Fraud, scams and hacking are still common, leading to potential theft.
-
There are unclear reporting requirements and taxes on buying, selling, or mining crypto.
More user-friendly applications and prudent regulation can help maximize benefits and minimize risks of cryptocurrencies for the average person.
 The Future Of Cryptocurrency
The future path of cryptocurrency is unclear but innovation will continue to drive new opportunities like:
• Mainstream Adoption: Younger demographics are leading to increase crypto acceptance and usage.
The Future Of Cryptocurrency
The future path of cryptocurrency is unclear but innovation will continue to drive new opportunities like:
• Mainstream Adoption: Younger demographics are leading to increase crypto acceptance and usage.• Integration: More banks, merchants, businesses, and apps will integrate cryptocurrency support.
• Institutional Investment: Growing investment from hedge funds, banks, and publicly traded companies will further legitimize crypto.
• Applications: DeFi, NFTs, crypto gaming, and the metaverse hint at expanded functionality.
• Regulation: Reasonable oversight could foster confidence, safety, and standards.
• Security: Implementing layered security features like multi-factor authentication could reduce fraud and theft risk.
Bottom Line Cryptocurrencies mark a technological leap forward that will likely ripple through the financial sector for years to come. But realizing the full potential of cryptocurrencies to benefit society depends on sustaining innovation while proactively addressing risks. Though there are still challenges ahead, the promises of enhanced financial access, speed, privacy and transparency makes the cryptocurrency revolution worth nurturing rather than resisting.
@Yakihonne
-
-
 @ c755de14:cc53833a
2024-11-22 16:50:29
@ c755de14:cc53833a
2024-11-22 16:50:29 What Is Cryptocurrency?
What Is Cryptocurrency?Cryptocurrency is a form of currency that utilizes cryptography to guarantee transactions. Unlike payment systems that rely on banks for verification cryptocurrencies function independently without the involvement of financial authorities. Currently the collective market value of all cryptocurrencies stands at $3.44 trillion highlighting their increasing growth and acceptance in the market.
An Introduction to Cryptocurrencies
Cryptocurrencies like Bitcoin allow individuals to conduct peer to peer transactions without relying on banks or payment processors. These digital currencies offer direct transfers between parties eliminating the need for intermediaries. These transactions are recorded on blockchains which’re interconnected ledgers containing transaction data.
The term “cryptocurrency” stems from the encryption methods used to safeguard the network. Transactions are verified using keys, which serve as proof of ownership for cryptocurrency addresses and facilitate the transfer of assets.
Different Types of Cryptocurrencies
It is impossible to provide a list of all existing cryptocurrencies in this article due, to their number currently exceeding 10,000. However we will highlight some known and widely adopted ones.
• Bitcoin (BTC)
Among these cryptocurrencies is bitcoin, introduced in 2009 as a currency. With a market capitalization of $527.39 billion dollars bitcoin has gained recognition as one of the most prominent crypto coins worldwide. Satoshi Nakamoto is credited with developing this accepted currency.
• Ethereum (ETH)
Ethereum was introduced in 2015 as a platform that allows the development of applications using contracts. It holds the position, in terms of market capitalization after Bitcoin. Ethereum is widely. Respected as one of the cryptocurrencies.

• Cardamon (ADA)
Cardano was specifically designed to tackle scalability and accessibility issues faced by cryptocurrencies. Its main goal is to establish a blockchain platform. It currently ranks among the top ten largest cryptocurrencies based on its native ADA token.
• Dogecoin (DOGE)
Initially created as a concept, Dogecoin (DOGE) has gained popularity due to its widespread use for internet tipping and endorsement from influential figures like Elon Musk.
• Solana (SOL)
Solana is a blockchain network that prioritizes high transaction speeds and low costs. The SOL coin also holds a spot, among the ten cryptocurrencies when it comes to market capitalization.
• Polkadot (DOT)
This coin is a blockchain protocol that fosters interoperability between cryptocurrency networks.
Aside the coins mentioned above, there are thousands of other coins as mentioned earlier.
Advantages of Cryptocurrency
Both cryptocurrencies and blockchain networks comes with benefits that makes them attractive when compared to other payment systems and flat currencies.
Below are some cryptocurrencies advantages:
• Decentralization:
Cryptocurrencies operate without dependence on centralized financial authorities, which reduces the risk of systemic issues and allows for resistance against censorship. Control is distributed across participants in the blockchain.
• Enhanced Security:
Blockchain-based transactions makes digital currency transfers highly secure against fraud or tampering. This prevents issues like double spending.
• Accessibility:
You simply need an internet connection to send or receive cryptocurrency. This enables broader financial inclusion worldwide, especially in developing countries.
Anonymity:
Unless you personally attached your identity to a transaction, cryptocurrency transactions are largely anonymous and your identity will not be known.. Users interact through blockchain addresses rather than names.
Fast Transactions:
Cryptocurrency payments are quickly settled and confirmed, sometimes in seconds or few minutes.
Low Fees:
Most cryptocurrency transactions incur minor network fees, far lower than credit card fees or wire transfer charges, making micro-transactions more feasible and cheap.
Control:
You have complete control over your personal funds. Without the need for financial institutions like banks, you have gain financial independence and self-sovereignty.
Are Cryptocurrencies Safe?
While cryptocurrencies provide many benefits, they also come with few risks that investors should carefully consider. Let's take a look at some of those risks.
Downsides Using Cryptocurrencies
Here are some of the risks that comes with Cryptocurrencies:
• Volatility: Cryptocurrency valuations can sometimes have wild swings or crashes. Prices can fluctuate severely even within a single day. Having stable coins like USDT can help in this case.
• Hacks: Crypto exchanges, wallets, protocols, and smart contracts are vulnerable to security breaches if not properly coded. Billions of dollars have been lost in cyber attacks. Proper security measures are critical. Avoid sharing your contract address to non trusted sites.
• Limited Oversight: Government regulations around cryptocurrencies are still developing. Unlike banks, there is less recourse for fraud or theft due to limited consumer protections.
• Technicality Barriers: Safely purchasing, storing, and using cryptocurrencies requires advanced technical knowledge that is difficult for mainstream users. Cryptocurrency is easy to lose through user error.
Scams: The cryptocurrency industry suffers from rampant scam projects, deceptive advertising, and Ponzi schemes promising unrealistic returns. Avoiding frauds requires thorough due diligence.
Cryptocurrency Usage in Africa
Across Africa, cryptocurrencies are addressing critical needs related to financial inclusion and stable savings. According to a Chainalysis report, Sub-Saharan Africa saw modest growth, receiving an estimated $125 billion in on-chain value between July 2023 and June 2024. This represents a $7.5 billion increase compared to last year.
Here are some of the drivers behind crypto adoption in Africa:
• Serving the Unbanked:
About 66% of Sub-Saharan Africans lack access to traditional banking. Cryptocurrencies enable participation in financial services using just your mobile phones without paperwork.
• Cross-Border Payments: For workers outside their country, cryptocurrencies allow fast and low-cost transfers that avoid steep remittance fees charged by money transfer operators.
• Stability: Cryptocurrencies offer Africans a store of value and help protect from high inflation rates plaguing many national African currencies like Nigerian Naira.
• Tech-Driven Youth: Young, tech-savvy populations across Africa are leading the shift to cryptocurrency to gain financial independence apart from state-run financial systems.
Final Thoughts
For the first time, digital money can be transferred globally without relying on government-issued currencies, banks, payment processors, or other intermediaries all thanks to Cryptocurrencies. @Yakihonne

-
 @ ec951079:533d29e7
2024-11-22 16:46:34
@ ec951079:533d29e7
2024-11-22 16:46:34The Life of a Student👩🎓: Balancing Academics, Personal Growth, and Everything in Between.**
Introduction
Being a student is a unique and transformative experience that shapes individuals in countless ways. From the early morning alarm clocks to the late-night study sessions, students navigate a complex web of academics, personal growth, and social relationships. In this article, we will delve into the life of a student, exploring the challenges, opportunities, and lessons that come with this journey.
The Daily Grind
A typical day in the life of a student begins early, with the sound of an alarm clock piercing through the silence. After a quick breakfast, students rush to their morning classes, often with a mix of excitement and dread. The academic day is filled with lectures, discussions, and assignments, each designed to challenge and engage young minds.
Between classes, students often grab a snack or lunch with friends, sharing stories and laughter to break the monotony of the day. Afternoon classes may be followed by club meetings, sports practices, or part-time jobs, as students strive to balance academics with extracurricular activities.
The Struggle is Real
Despite the many rewards of student life, challenges abound. Students often struggle with:
- Time management: Balancing academics, social life, and personal responsibilities can be overwhelming.
- Financial stress: Tuition fees, living expenses, and textbooks can put a significant strain on students' finances.
- Academic pressure: Meeting expectations from parents, teachers, and oneself can lead to anxiety and stress.
- Self-doubt: Students may question their abilities, choices, and future prospects.
The Silver Lining
Amidst the challenges, student life offers countless opportunities for growth, exploration, and connection. Students can:
- Discover new passions: Through electives, clubs, and internships, students can uncover hidden talents and interests.
- Develop valuable skills: Time management, teamwork, and problem-solving are just a few of the essential skills students can hone.
- Build lifelong relationships: Friendships forged in the classroom, dorm, or club can last a lifetime.
- Explore identity and purpose: Student life provides a unique chance for self-reflection, exploration, and discovery.
Lessons Learned
As students navigate the ups and downs of academic life, they accumulate valuable lessons that extend far beyond the classroom:
- Resilience: Students learn to adapt, persevere, and bounce back from setbacks.
- Self-awareness: Through trial and error, students develop a deeper understanding of their strengths, weaknesses, and motivations.
- Independence: As students take ownership of their decisions and actions, they cultivate independence and self-reliance.
- Empathy and compassion: By interacting with diverse peers and facing shared challenges, students develop essential social skills.
Conclusion
The life of a student is a dynamic, transformative journey marked by growth, exploration, and self-discovery. While challenges abound, the opportunities for learning, connection, and personal development are unparalleled. As students navigate the complexities of academic life, they accumulate valuable lessons, skills, and relationships that will serve them well beyond their time in school.
-
 @ d830ee7b:4e61cd62
2024-05-10 14:03:50
@ d830ee7b:4e61cd62
2024-05-10 14:03:50จุดเริ่มต้นของตำนาน
ท่ามกลางแสงแดดเจิดจ้าและลมทะเลเย็นสบายของหาดเมืองแกลง ชายหนุ่มรูปร่างกระทัดรัดนามว่า "ซุป" กำลังนั่งจดจ่ออยู่หน้าจอคอมพิวเตอร์ ดวงตาเป็นประกายฉายแววความสนใจขณะไล่อ่านบทความวิชาการทางด้านเศรษฐศาสตร์ ความรู้ไม่ได้เป็นเพียงแค่ตัวอักษรบนหน้าจอ แต่มันคือแรงบันดาลใจ เปรียบเสมือนขุมทรัพย์ที่รอการขุดค้นสำหรับเขา
ซุป ไม่ใช่หนุ่มนักเรียนหัวกะทิหรือบัณฑิตจบใหม่จากรั้วมหาวิทยาลัยดัง แต่เป็นชายหนุ่มธรรมดาที่หลงใหลในศาสตร์แห่งการจัดสรรทรัพยากรอันหายาก เศรษฐศาสตร์ ไม่ว่าจะเป็นสำนักคลาสสิคหรือออสเตรียน ล้วนดึงดูดความสนใจของเขาให้เข้าไปสำรวจอย่างลึกซึ้ง ยิ่งเรียนรู้ ซุปยิ่งค้นพบความมหัศจรรย์ของศาสตร์นี้ มันไม่ใช่แค่ทฤษฎีบนหน้ากระดาษ แต่สะท้อนอยู่ในทุกๆ การกระทำของมนุษย์
มันเหมือนเวลาที่เราไปเที่ยวทะเล.. เราไม่ได้แค่เห็นน้ำทะเลสีฟ้าสวยงาม แต่เราสัมผัสได้ถึงไอเย็นของลมทะเล ได้ยินเสียงคลื่นซัดสาด ได้กลิ่นอายของเกลือ ความรู้ด้านเศรษฐศาสตร์เองก็เช่นกัน เราจะมองเห็นมันได้ในทุกๆ การตัดสินใจ ทุกๆ การกระทำ ตั้งแต่การซื้อของในร้านสะดวกซื้อ ไปจนถึงการเลือกอาชีพ
หนึ่งในขุมทรัพย์ความรู้ที่ซุปหลงใหลมากที่สุด คือ เศรษฐศาสตร์สำนักออสเตรียน โดยเฉพาะแนวคิดเรื่อง "มูลค่าอัตวิสัย" (Subjective Value) ทฤษฎีนี้สอนให้เขาเข้าใจว่ามูลค่าของสิ่งต่างๆ ไม่ได้ขึ้นอยู่กับต้นทุนการผลิต หรือแรงงานที่ใส่ลงไป แต่มันขึ้นอยู่กับการประเมินของแต่ละบุคคล สิ่งที่สำคัญสำหรับคนหนึ่ง อาจดูไร้ค่าสำหรับอีกคน และมูลค่าของสิ่งเดียวกันก็อาจเปลี่ยนแปลงไปตามกาลเวลาและสถานการณ์
ซึ่งก็เหมือนกับตอนเรายังเด็กๆ ของเล่นชิ้นโปรดอาจเป็นตุ๊กตากันหมีตัวเก่าๆ แต่วันนี้ ตุ๊กตาตัวนั้นอาจถูกเก็บไว้ในกล่องใต้เตียงไปแล้ว เพราะความต้องการของเราเปลี่ยนไป เราให้คุณค่ากับสิ่งอื่นๆ มากกว่าเมื่อเวลาผ่านไป
ความหลงใหลในเศรษฐศาสตร์สำนักออสเตรียนนำพาซุปไปรู้จักกับ อ.พิริยะ และทีมงาน Right Shift กลุ่มคนรุ่นใหม่ที่มุ่งมั่นเผยแพร่ความรู้ทางเศรษฐศาสตร์อย่างเข้าใจง่าย ซุปกลายเป็นแฟนตัวยง ติดตามผลงานแทบทุกชิ้น และใฝ่ฝันว่าสักวันหนึ่งจะได้มีโอกาสร่วมงานกับทีม แต่ด้วยความขี้อายและอ่อนน้อมถ่อมตน ซุปจึงไม่เคยกล้าเอ่ยปาก เขาเลือกที่จะเป็นผู้สนับสนุนอยู่ห่างๆ อย่างเงียบๆ
บางครั้ง.. ความฝันก็เหมือนเมล็ดพันธุ์ เราต้องหมั่นรดน้ำ พรวนดิน และดูแลมันอย่างดี ถึงแม้จะไม่รู้ว่ามันจะเติบโตงอกงามเมื่อไร แต่ถ้าเรายังคงดูแลมันต่อไป สักวันหนึ่งมันจะผลิดอกออกผลให้เราได้ชื่นชม

จุดเปลี่ยนแห่งโชคชะตา
ชีวิตของซุป.. เหมือนเรือเล็กที่ล่องลอยไปตามกระแสน้ำ มีความสุขกับการเรียนรู้ เสพย์ติดความรู้ด้านเศรษฐศาสตร์และมีความฝันเล็กๆ ที่อยากร่วมงานกับทีม Right Shift
วันหนึ่ง.. โชคชะตาก็เล่นตลก เหมือนส่งคลื่นลูกใหญ่ซัดเข้ามาหาเรือลำน้อยของซุป
Right Shift กำลังประสบปัญหาขาดแคลนนักตัดต่อวิดีโอคลิป จนกระทั่ง Jakk Goodday หนึ่งในผู้ก่อตั้ง ต้องลงมาทำเองแก้ขัดไปก่อน ข่าวนี้แพร่สะพัดไปถึงหูของซุป เขาถึงกับอุทานออกมาเบาๆ
"เอ๊ะ.. นี่มันโอกาสของเราหรือเปล่านะ?"
สถานการณ์แบบนี้มันเหมือนตอนเราเดินเล่นอยู่ริมชายหาด แล้วเจอขวดแก้วที่ถูกคลื่นซัดมาเกยตื้น ข้างในมีกระดาษเขียนข้อความลอยอยู่ เราจะเก็บมันขึ้นมาอ่านไหมหรือจะปล่อยให้คลื่นซัดมันกลับลงทะเลไป?
ความคิดมากมายวนเวียนอยู่ในหัวของซุป เขาไม่ใช่มืออาชีพ แต่ก็พอมีฝีมือด้านการตัดต่ออยู่บ้าง จะลองเสี่ยงดูดีไหมนะ? ถ้าไม่ลอง.. ก็คงไม่มีโอกาส แต่ถ้าลองแล้วไม่สำเร็จล่ะ? จะกลายเป็นตัวตลกหรือเปล่านะ?
ในที่สุด.. ซุปก็ตัดสินใจ "เอาวะ! ลองดูสักตั้ง อย่างน้อยก็ได้พิสูจน์ตัวเอง"
เขาส่งข้อความไปหา Jakk บอกเล่าความสามารถและความตั้งใจ พร้อมกับยื่นมือเข้าช่วยเหลือ
บางครั้ง.. โอกาสก็มาในรูปแบบของปัญหา คนที่มองเห็นโอกาสและกล้าที่จะคว้ามันไว้ ก็จะประสบความสำเร็จ
สิ่งที่เกิดขึ้นหลังจากนั้นมันราวกับความฝัน Jakk ตอบรับและให้โอกาสซุปเข้ามาทดลองงาน ความกดดันถาโถมเข้ามาอย่างหนัก แต่ซุปก็พยายามอย่างเต็มที่ เขาใช้ความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนในการประเมินคุณค่าของโอกาสนี้ มันมีค่ามากกว่าความสบายใจในฐานะแฟนคลับ มากกว่าความกลัวที่จะล้มเหลว
"ความกลัว คือ กำแพงที่กั้นระหว่าง ตัวเรา กับ ความฝัน"
ซุปทุ่มเททุกอย่างให้กับงาน ไม่เคยเกี่ยงงอนหรือบ่นว่าเหนื่อย เพราะสำหรับเขา.. นี่คือโอกาสทอง มันคือการได้ทำงานที่รักร่วมกับทีมที่เขาชื่นชม
ทฤษฎีมูลค่าอัตวิสัยสอนให้เรารู้ว่า มูลค่าของสิ่งต่างๆ ไม่ได้ขึ้นอยู่กับปัจจัยภายนอก เช่น ราคา หรือ ต้นทุนการผลิต แต่มันขึ้นอยู่กับ การประเมินของแต่ละบุคคล
การตัดสินใจครั้งสำคัญของซุป นำพาเขาไปสู่เส้นทางใหม่ เส้นทางที่เต็มไปด้วยความท้าทาย แต่ก็เต็มไปด้วยโอกาสเช่นกัน เส้นทางที่เขาจะได้เรียนรู้ เติบโต และสร้างคุณค่าให้กับตัวเองและสังคม การตัดสินใจของซุปนั้นมันช่างสอดคล้องกับหลักการของเศรษฐศาสตร์สำนักออสเตรียนที่เน้นการกระทำของมนุษย์ การประเมินมูลค่า และการตัดสินใจ

วันเวลาแห่งการสร้างคุณค่า
แสงไฟจากจอคอมพิวเตอร์ยังคงสาดส่องใบหน้าของซุป.. ดวงตาของเขาจดจ้องอยู่กับเส้นเวลา ตัดต่อ เรียบเรียง ประกอบร่าง วิดีโอคลิปแต่ละชิ้นให้สมบูรณ์ งานที่ได้รับมอบหมายไม่ใช่งานง่าย แต่ซุปไม่เคยปริปากบ่น เขาก้มหน้าก้มตาทำงานของตัวเองไปอย่างเต็มที่
"นี่มันคือความฝันของเราเลยนะ จะมัวบ่นทำไมกัน" ซุปพึมพำกับตัวเอง
ซุปในตอนนี้ก็เหมือนนักปีนเขาที่กำลังไต่ขึ้นสู่ยอดเขา เส้นทางอาจจะลำบาก ขรุขระ และเต็มไปด้วยอุปสรรค แต่ทุกย่างก้าวก็คือ ความท้าทาย และความภาคภูมิใจ
แม้จะไม่ได้รับผลตอบแทนมากมาย แต่สำหรับซุป ความสุขที่ได้รับจากการทำงานมันมีค่ามากกว่าเงินทอง เขาได้เรียนรู้อะไรใหม่ๆ มากมาย ได้ฝึกฝนทักษะ ได้สร้างสรรค์ผลงาน และที่สำคัญที่สุด คือ ได้เป็นส่วนหนึ่งของทีมที่เขารัก
ในทางเศรษฐศาสตร์สำนักออสเตรียน เราเรียกสิ่งนี้ว่า "การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" (Valuation by the Least Valuable Use) หมายความว่า.. เมื่อคนเราต้องตัดสินใจ เราจะประเมินมูลค่าของสิ่งต่างๆ โดยพิจารณาจากประโยชน์ที่เราจะได้รับจากการใช้งานนั้นๆ
ในกรณีของซุป.. การทำงานกับ Right Shift อาจไม่ได้ทำให้เขาร่ำรวย แต่เขาได้รับประสบการณ์ ความรู้ และความสุข ซึ่งสิ่งเหล่านี้มีมูลค่าสำหรับซุปมากกว่าเงินทอง
บางครั้ง.. คุณค่าของสิ่งต่างๆ ก็ไม่สามารถวัดได้ด้วยเงิน
นอกจากนี้.. การทำงานกับ Right Shift ยังเปิดโอกาสให้ซุปได้พบปะผู้คนมากมาย ทั้งคนดัง ผู้เชี่ยวชาญ และบุคคลที่น่าสนใจ ซึ่งเป็นเหมือน "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) ที่เติมเต็มความสุขในการทำงานของเขา
เหมือนเวลาเรากินข้าวจานแรกอาจจะอร่อยมากเพราะเราหิว แต่พอจานที่สอง จานที่สาม ความอร่อยก็เริ่มลดลง จนกระทั่งเราอิ่ม จนไม่อยากกินอีกแล้ว
ประสบการณ์ใหม่ๆ ก็เช่นกัน ครั้งแรกที่ได้เจออาจจะตื่นเต้น ประทับใจ แต่พอเจอบ่อยๆ ความตื่นเต้นก็จะลดลง แต่ความทรงจำและความรู้สึกดีๆ ยังคงอยู่
แนวคิดเรื่อง "อรรถประโยชน์ส่วนเพิ่ม" ช่วยอธิบายว่า ทำไมคนเราถึงแสวงหาประสบการณ์ใหม่ๆ แม้ว่าความตื่นเต้นจะลดลงตามกาลเวลา
ซุป ยังคงทำงานอย่างหนัก พัฒนาตัวเองและสร้างสรรค์ผลงาน เขาไม่รู้ว่าอนาคตจะเป็นอย่างไร แต่เขารู้ว่า.. เขาได้เลือกเส้นทางที่ถูกต้องแล้ว เส้นทางที่เขาได้สร้างคุณค่าให้กับตัวเองและสังคม
"ความสุข ไม่ได้อยู่ที่ปลายทาง แต่อยู่ในระหว่างทาง"

บทเพลงแห่งการแบ่งปัน
เวลาผ่านไป.. ซุปสั่งสมประสบการณ์และความรู้มากขึ้น จากชายหนุ่มขี้อาย เขากลายเป็นนักตัดต่อมือฉมัง และที่สำคัญคือความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนที่สั่งสมมาตลอดมันเริ่มผลิดอกออกผล
ซุป อยากแบ่งปันความรู้ อยากให้คนอื่นๆ ได้สัมผัสความมหัศจรรย์ของศาสตร์นี้เหมือนที่เขาเคยสัมผัส เขาปรึกษากับ Jakk และ อิสระ (น้องเล็กในทีม) ซึ่งมีความสนใจในเรื่องเดียวกันและต่างก็มีแรงปรารถนาที่จะจะเผยแพร่มันเช่นกัน
ซุป: "พี่ Jakk, อิส ผมอยากทำรายการเกี่ยวกับเศรษฐศาสตร์สำนักออสเตรียน พี่คิดว่าไงครับ"
Jakk: "ไอเดียดีนะซุป แต่จะทำยังไงให้มันเข้าใจง่าย ไม่น่าเบื่อ ไม่เอาศัพท์แสงบ้าบอคอแตกนะ"
อิสระ: "พี่ซุปเล่าเรื่องเก่ง เราทำเป็นนิทานก็ได้นี่ครับ"
ซุป: "นิทานอิสซุป เหมือนที่ อ.พิริยะ ตั้งให้อะหรอ เออ.. ชื่อนี้ เข้าท่าดีนะ"
และแล้ว "นิทานอิสซุป" ก็ถือกำเนิดขึ้น รายการที่นำเสนอความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนในรูปแบบง่ายๆ สบายๆ เข้าใจง่าย เสียงนุ่มๆ ของซุป บวกกับลีลาการเล่าเรื่องที่เป็นเอกลักษณ์ของอิสระ ดึงดูดผู้ชมได้อย่างมากมาย
เหมือนแม่น้ำที่ไหลรินลงจากยอดเขา นำพาธาตุอาหารไปหล่อเลี้ยง ต้นไม้ พืชพันธุ์และสัตว์น้อยใหญ่ ความรู้ก็เช่นกัน เมื่อถูกแบ่งปันมันจะสร้างคุณค่าให้กับผู้รับและผู้ให้ ซุปมีความสุขที่ได้แบ่งปันความรู้ และยิ่งแบ่งปันเขาก็ยิ่งได้รับความสุขและคุณค่ามากขึ้น
นี่อาจคล้าย "กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" (Law of Diminishing Marginal Utility) เมื่อเรามีบางสิ่งบางอย่างมากขึ้น ความพึงพอใจที่ได้รับจากหน่วย (Unit) ที่เพิ่มขึ้นจะค่อยๆ ลดลง
แต่.. กฎนี้ใช้ไม่ได้กับ “ความรู้” และ “การแบ่งปัน” ยิ่งเรามีความรู้มากขึ้น ยิ่งเราแบ่งปันมากขึ้น ความสุขและ คุณค่าที่ได้รับก็จะยิ่งเพิ่มขึ้น ซึ่ง ซุป ก็เข้าใจหลักการนี้จึงเลือกที่จะแบ่งปันความรู้เพื่อสร้างคุณค่าให้กับสังคม และเติมเต็มความสุขให้กับตัวเอง
"นิทานอิสซุป" ไม่ได้เป็นเพียงแค่รายการ แต่เป็นพื้นที่ ที่ซุปได้แสดงออกถึงความรักและความหลงใหลในเศรษฐศาสตร์สำนักออสเตรียน เขาไม่ได้ทำเพื่อชื่อเสียงหรือเงินทอง แต่ทำเพื่อแบ่งปันและสร้างคุณค่าให้กับสังคม
การให้ คือ การได้รับ ที่ยิ่งใหญ่ที่สุด
"นิทานอิสซุป" จึงเป็นมากกว่านิทานวิชาการ มันคือบทเพลงแห่งการแบ่งปัน บทเพลงที่ ซุป บรรจงแต่ง เพื่อส่งต่อความรู้และแรงบันดาลใจให้กับผู้คน
"เพราะ.. ความรู้ คือ แสงสว่าง ที่ช่วยขับไล่ความมืดมน"

ก้าวสู่แสงไฟ
นิทานอิสซุป กลายเป็นจุดเริ่มต้นของเส้นทางใหม่ เส้นทางที่นำพา ซุป ก้าวออกจากเงามืดไปสู่แสงไฟ เหมือนดอกไม้ที่เบ่งบานท่ามกลางแสงแดด อวดสีสันและกลิ่นหอม ดึงดูดผึ้งและผีเสื้อให้เข้ามาดอมดม
ซุป ไม่ใช่แค่นักเล่านิทาน แต่เขาได้ค่อยๆ กลายเป็นหนึ่งในอินฟลูเอนเซอร์ในวงการบิตคอยน์ไทยอย่างช้าๆ ภายใต้ฉายา "ประธานซุป" เขาได้รับเชิญไปบรรยาย ออกรายการ และร่วมงานกับบุคคลที่มีชื่อเสียงมากมาย
ความสำเร็จ มันก็มักจะมาพร้อมกับความรับผิดชอบและความคาดหวัง เส้นทางของ ซุป ไม่ได้ถูกโรยด้วยกลีบกุหลาบ เขาต้องตัดสินใจครั้งสำคัญหลายครั้ง เช่น การทิ้งรายได้จากงานฟรีแลนซ์, การสละโอกาสทางการเมือง เพื่อทุ่มเทให้กับ Right Shift
“การตัดสินใจ” คือ กระบวนการเลือกทางเลือกหนึ่ง เหนือทางเลือกอื่นๆ โดยพิจารณาจาก การประเมินมูลค่าอัตวิสัย
ซุป เลือกที่จะเสียสละสิ่งที่คนอื่นมองว่ามีค่า เพื่อสิ่งที่เขามองว่ามีค่ามากกว่า นั่นคือ.. ความฝัน ความสุข และ การสร้างคุณค่าให้กับสังคม
"การเสียสละ คือ บทพิสูจน์ ของความมุ่งมั่น"
ตลอดเส้นทาง ซุป ได้รับการสนับสนุนและคำแนะนำ จาก Jakk Goodday ผู้ที่เชื่อมั่นในศักยภาพของเขา ตั้งแต่วันแรก ความสัมพันธ์ระหว่าง ซุป และ Jakk สะท้อนให้เห็นถึงความสำคัญของ "การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกัน" (Mutually Beneficial Exchange) ซึ่งเป็นหัวใจสำคัญของ เศรษฐศาสตร์สำนักออสเตรียน
Jakk เห็นคุณค่าในตัว ซุป จึงให้โอกาสและสนับสนุนเขา ในขณะที่ ซุป ก็ตอบแทนด้วยการทำงานอย่างเต็มที่ และ สร้างคุณค่าให้กับทีม Right Shift
การให้ และ การรับ นั้นเป็นวัฏจักรที่สร้างสรรค์ และ ยั่งยืน
เส้นทางของ "ซุป" จากแฟนคลับสู่ประธานซุป เป็นบทเรียนชีวิตที่สอนให้เรารู้ว่า.. ความฝัน ความมุ่งมั่น การเสียสละ และการสร้างคุณค่า คือ สิ่งสำคัญที่นำพาเราไปสู่ความสำเร็จ
และทุกคน ก็มีศักยภาพที่จะสร้างคุณค่า และประสบความสำเร็จ ในแบบของตัวเอง
คุณค่าที่แท้จริง
เรื่องราวของ "ซุป" ไม่ได้เป็นเพียงแค่เรื่องราวของความสำเร็จ แต่เป็นบทเรียนชีวิตที่สอนให้เราเข้าใจถึงคุณค่าที่แท้จริง
เหมือนต้นไม้ใหญ่ที่เติบโตแผ่กิ่งก้านสาขา ให้ร่มเงาและผลิดอกออกผล ซุป เปรียบเสมือนต้นไม้ต้นนั้น เขาเติบโต จากเมล็ดพันธุ์เล็กๆ ที่หลงใหลในความรู้ ด้วยการหมั่นรดน้ำ พรวนดิน ใส่ปุ๋ย คือความมุ่งมั่น ความอดทน และ การเสียสละ จนกระทั่งเติบใหญ่ แผ่กิ่งก้านสาขาให้ร่มเงา คือการแบ่งปันความรู้และผลิดอกออกผล คือความสำเร็จและการเป็นแรงบันดาลใจให้กับผู้อื่น
หลักการของ ทฤษฎีมูลค่าอัตวิสัย (Subjective value) สะท้อนให้เห็นในทุกๆ การตัดสินใจของ ซุป
การประเมินมูลค่า >> ซุป ประเมินคุณค่าของโอกาส ประสบการณ์ และความสุข มากกว่าเงินทองและชื่อเสียง การเสียสละ >> ซุป ยอมสละรายได้และโอกาสทางการเมือง เพื่อหันมาทำในสิ่งที่เขารักและเชื่อมั่น ความอดทน >> ซุป ทำงานหนัก พัฒนาตัวเองและอดทนรอคอย จนกระทั่งประสบความสำเร็จ การสร้างคุณค่า >> ซุป แบ่งปันความรู้และสร้างแรงบันดาลใจ ให้กับผู้อื่น
เรื่องราวของ ซุป สะท้อนให้เห็นถึง "ปฏิทรรศน์น้ำ-เพชร" (Water-Diamond Paradox) ซึ่งเป็นแนวคิดใน เศรษฐศาสตร์สำนักออสเตรียน ที่อธิบายว่า.. ทำไมสิ่งที่จำเป็นอย่าง น้ำ ถึงมีราคาถูก ในขณะที่สิ่งฟุ่มเฟือยอย่าง เพชร ถึงมีราคาแพง
ในชีวิตจริง.. สิ่งที่สำคัญสำหรับคนหนึ่ง อาจไม่ได้สลักสำคัญสำหรับอีกคน และมูลค่าของสิ่งต่างๆ ก็ขึ้นอยู่กับ บริบทและความต้องการของแต่ละบุคคล
ความสุข และ ความสำเร็จ ไม่ได้มีสูตรสำเร็จตายตัว แต่ละคนต้องค้นหาและสร้างมันขึ้นมาเอง
ซุป ค้นพบ “คุณค่าที่แท้จริง” ของชีวิต เขาไม่จำเป็นต้องมีเงินทองมากมาย หรือมีชื่อเสียงโด่งดัง แต่เขามีความสุขกับการได้ทำในสิ่งที่รักและสร้างคุณค่าให้กับสังคม
“จงค้นหาคุณค่าที่แท้จริงของชีวิต และ ใช้ชีวิตให้มีความหมาย”
"คุณค่าของคน อยู่ที่ผลของงาน"

11 พฤษภาคม เป็นวันคล้ายวันเกิดของ ซุป บทความนี้ผมจึงอุทิศน์ให้กับเขา และขอให้เจ้าตัวมีความสุขในการมุ่งมั่นสร้างคุณค่าในแบบของตัวเองสืบต่อไป ขอให้ทุกคนได้ร่วมอวยพรและให้กำลังใจเพื่อนคนเก่งของเราคนนี้กันด้วยครับ
ภาคผนวก
Subjective Value มองคุณค่าผ่านเลนส์ของตัวเอง
ทฤษฎีมูลค่าอัตวิสัย (Subjective Value) เปรียบเสมือนแว่นตาพิเศษที่ช่วยให้เราเข้าใจว่าทำไมคนเราถึงมองเห็น "คุณค่า" ของสิ่งต่างๆ แตกต่างกัน
ลองนึกภาพว่าเรากำลังดูภาพวาด abstract บางคนอาจมองว่ามันสวยงาม มีเอกลักษณ์ ในขณะที่บางคนอาจมองว่ามันดูยุ่งเหยิง ไม่มีความหมาย
ทฤษฎีนี้บอกเราว่า "คุณค่า" ไม่ได้ติดมากับสิ่งของ หรือถูกกำหนดโดยปัจจัยภายนอก เช่น ต้นทุนการผลิตหรือแรงงานที่ใช้ แต่ "คุณค่า" เกิดขึ้นจากการประเมินของแต่ละบุคคล ขึ้นอยู่กับความต้องการ ความชอบ ประสบการณ์ และสถานการณ์ของแต่ละคน
นักเศรษฐศาสตร์สำนักออสเตรียนเชื่อว่า "มนุษย์" เป็นศูนย์กลางของกิจกรรมทางเศรษฐกิจ และการตัดสินใจของมนุษย์นั้นขับเคลื่อนด้วย "มูลค่าอัตวิสัย" ที่พวกเขามีต่อสิ่งต่างๆ
ยกตัวอย่างง่ายๆ
คนที่กำลังหิวโหย อาจมองว่า "ข้าวเปล่า 1 จาน" มีค่ามาก แต่สำหรับคนที่เพิ่งกินอิ่มมา ข้าวเปล่าจานนั้นอาจไม่มีค่าเลย
นักสะสมงานศิลปะ อาจยอมจ่ายเงินมหาศาลเพื่อซื้อภาพวาด แต่สำหรับคนที่ไม่เข้าใจศิลปะ ภาพวาดนั้นอาจดูไร้ค่า
นักเรียนที่กำลังเตรียมสอบ อาจมองว่า "เวลา 1 ชั่วโมง" มีค่ามาก แต่สำหรับคนที่กำลังว่าง เวลา 1 ชั่วโมงอาจไม่มีค่าอะไรเลย
การเข้าใจ "ทฤษฎีมูลค่าอัตวิสัย" ช่วยให้เรายอมรับความแตกต่างและเคารพการตัดสินใจของผู้อื่น เพราะสิ่งที่สำคัญสำหรับเราอาจไม่สำคัญสำหรับคนอื่น และที่สำคัญ "มูลค่า" ยังสามารถเปลี่ยนแปลงไปตามกาลเวลาและสถานการณ์
โทรศัพท์มือถือรุ่นเก่า ที่เมื่อก่อนอาจมีมูลค่ามาก แต่ตอนนี้อาจกลายเป็นของสะสมหรือ ขยะอิเล็กทรอนิกส์
บ้านหลังเก่า เมื่อก่อนอาจเคยเป็นบ้านในฝัน แต่ตอนนี้อาจทรุดโทรม จนต้องซ่อมแซม
เรื่องราวของ "ซุป" สะท้อนให้เห็นถึงการเปลี่ยนแปลงของ "มูลค่า" เขาเคยให้คุณค่ากับความสบายใจในฐานะแฟนคลับ แต่เมื่อมีโอกาสเขาก็เปลี่ยนมาให้คุณค่ากับการทำงาน การสร้างคุณค่า และการแบ่งปันความรู้
"ทฤษฎีมูลค่าอัตวิสัย" จึงเป็นเครื่องมือสำคัญที่ช่วยให้เราเข้าใจการตัดสินใจ พฤติกรรม และการกระทำของมนุษย์ ทั้งในชีวิตประจำวันและในระบบเศรษฐกิจ
เลือกสิ่งที่ดีที่สุด ณ เวลานั้น
"การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" (Valuation by the Least Valuable Use) ฟังดูอาจจะซับซ้อนทำความเข้าใจได้ยาก แต่จริงๆแล้วมันคือหลักการง่ายๆ ที่เราใช้ในการตัดสินใจในชีวิตประจำวัน
เวลาเราเข้าไปในร้านขายเสื้อผ้าที่มีเสื้อผ้ามากมายหลากหลายแบบ เราจะเลือกซื้อ เสื้อผ้าตัวไหน?
เราคงไม่เลือกซื้อเสื้อผ้าทุกตัวในร้าน แต่จะเลือกเสื้อผ้าที่ตอบโจทย์ความต้องการของเรามากที่สุด ณ เวลานั้น เช่น เสื้อผ้าที่ใส่ไปทำงาน เสื้อผ้าที่ใส่ไปเที่ยว หรือเสื้อผ้าที่ใส่ไปออกกำลังกาย
ทฤษฎีนี้อธิบายว่า.. เมื่อคนเรามีสินค้าหรือบริการหลายอย่าง เราจะเลือกใช้สินค้าหรือ บริการที่ตอบสนองต่อความต้องการที่เร่งด่วนที่สุดก่อน
ยกตัวอย่างเช่น..
เราอาจจะมีการแบ่งเงินเป็นหลายก้อน แต่ก้อนที่เราจะใช้ก่อน คือก้อนที่เราต้องการใช้ มากที่สุด ณ เวลานั้น เช่น ค่าอาหาร ค่าเดินทางหรือค่าเช่าบ้าน การตัดสินใจของคนเรา จึงขึ้นอยู่กับความต้องการและสถานการณ์ ณ เวลานั้น
ดังนั้น "การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" จึงเป็นหลักการที่ช่วยให้เราจัดลำดับความสำคัญ และเลือกสิ่งที่ดีที่สุดสำหรับตัวเรา ณ เวลานั้น
ซุป ก็ใช้หลักการนี้ในการตัดสินใจ เช่น การเลือกทำงานกับ Right Shift แม้ว่า จะไม่ได้รับ ผลตอบแทนมากมายนัก แต่เขาได้รับความสุขและประสบการณ์ ซึ่งมีค่ามากกว่าสำหรับเขา
อิ่มเอม...แต่ไม่เท่าเดิม
"กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" (Law of Diminishing Marginal Utility) เป็นกฎพื้นฐานทางเศรษฐศาสตร์ที่อธิบายถึงความรู้สึก "อิ่มเอม" ที่ลดลง เมื่อเราบริโภคสินค้าหรือบริการมากขึ้น
ลองนึกภาพว่าเรากำลังกินพิซซ่า ชิ้นแรกอร่อยมาก ชิ้นที่สองก็ยังอร่อยอยู่ แต่พอชิ้นที่สาม ชิ้นที่สี่ ความอร่อยก็เริ่มลดลง จนกระทั่งเราอิ่ม และไม่อยากกินอีกแล้ว
นั่นเป็นเพราะ "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) หรือความพึงพอใจที่ได้รับ จากการบริโภค สินค้าหรือบริการ จากหน่วย (Unit) เพิ่มเติมนั้นลดลง
กฎนี้อธิบายว่า ยิ่งเราบริโภคสินค้าหรือบริการมากขึ้น ความพึงพอใจที่ได้รับจากหน่วย เพิ่มเติมจะลดลง
ยกตัวอย่างเช่น..
เสื้อผ้าตัวใหม่อาจจะทำให้เรารู้สึกดี ตื่นเต้น แต่พอมีเสื้อผ้าเยอะๆ ความตื่นเต้นก็จะ ลดลง
เงินก้อนแรกที่เราหามาได้ อาจจะมีค่ามาก แต่พอมั่งคั่งเงินก้อนต่อๆ ไปก็จะมีค่าน้อยลง
กฎนี้สอนให้เรารู้จักพอเพียง และเห็นคุณค่าของสิ่งที่เรามี
อย่างไรก็ตาม "กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" มีข้อยกเว้น เช่น ความรู้ และ การแบ่งปัน ตามที่ได้กล่าวถึงในบทความ
win-win situation
"การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกัน" (Mutually Beneficial Exchange) เป็นหัวใจสำคัญของระบบเศรษฐกิจ และเป็นเหตุผลที่ทำให้คนเรา "ค้าขาย" กัน
เวลาเราไปตลาด เราเอาเงินไปแลกกับอาหาร แม่ค้าได้เงิน เราก็ได้อาหาร ต่างคนต่างได้ประโยชน์ การแลกเปลี่ยนจะเกิดขึ้นก็ต่อเมื่อ ทั้งสองฝ่าย เชื่อว่า พวกเขาจะ "ได้" มากกว่า "เสีย"
นักเศรษฐศาสตร์สำนักออสเตรียน เชื่อว่า การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกันเกิดขึ้นได้ เพราะคนเรามี "มูลค่าอัตวิสัย" ที่แตกต่างกัน
ยกตัวอย่างเช่น..
ชาวนามีข้าวแต่ไม่มีปลา ชาวประมงมีปลาแต่ไม่มีข้าว ทั้งสองจึงแลกเปลี่ยนสินค้ากัน เพื่อ เพื่อตอบสนองความต้องการของตัวเอง
นายจ้างต้องการคนทำงาน ลูกจ้างต้องการรายได้ ทั้งสองจึงทำสัญญาจ้าง เพื่อแลกเปลี่ยน แรงงานกับเงินเดือน
การแลกเปลี่ยนช่วยให้คนเราได้สินค้าและบริการที่หลากหลาย มากกว่าที่จะผลิตเอง ทั้งหมด นอกจากนี้ การแลกเปลี่ยนยังกระตุ้นให้เกิดการพัฒนาและนวัตกรรม เพราะผู้ผลิตต้องแข่งขันกัน เพื่อตอบสนองความต้องการของผู้บริโภค
"การค้า คือ การสร้างสรรค์ ความมั่งคั่ง ร่วมกัน"
แกะปริศนา "ปฏิทรรศน์น้ำ-เพชร"
มาถึงตรงนี้.. หลายคนอาจจะสงสัยว่าทำไม "น้ำ" ซึ่งเป็นสิ่งที่จำเป็นต่อการดำรงชีวิต ถึงมีราคาถูกหรือบางที่ก็ฟรี ในขณะที่ "เพชร" ซึ่งเป็นแค่เครื่องประดับกลับมีราคาแพงหูฉี่
เหมือนเวลาเราไปร้านอาหาร เราสั่ง "ข้าวผัด" จานใหญ่ราคา 50 บาท แต่ "ไข่ดาว" ฟองเล็กๆ ราคา 10 บาท ทำไมข้าวผัดถึงถูกกว่า ไข่ดาว ทั้งที่ ข้าวผัดมี ข้าว ผัก เนื้อสัตว์ เครื่องปรุง ตั้งหลายอย่าง
คำตอบอยู่ที่ "ความขาดแคลน" (Scarcity) และ "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) ซึ่งเป็นแนวคิดสำคัญในเศรษฐศาสตร์สำนักออสเตรียน
น้ำ มีอยู่มากมาย ในขณะที่ เพชร นั้นหายาก น้ำ แก้วแรกอาจจะช่วยชีวิตเราได้ แต่ น้ำ แก้วที่ 10 อาจจะทำให้เราจุก
"อรรถประโยชน์ส่วนเพิ่ม" หมายถึง ความพึงพอใจที่ได้รับจากการบริโภคสินค้าหรือ บริการในหน่วย (Unit) เพิ่มเติม (ในจำนวนมากขึ้น)
เมื่อน้ำมีอยู่มาก เราจึงประเมินมูลค่าของน้ำแก้วที่ 10 ต่ำ เพราะมันไม่ได้ตอบสนองความต้องการที่เร่งด่วน แต่เพชรที่หายาก ทำให้แม้แต่เพชรเม็ดเล็กๆ ก็ยังมีมูลค่าสูง
คุณค่า ไม่ได้ขึ้นอยู่กับความจำเป็นหรือความฟุ่มเฟือย แต่ขึ้นอยู่กับความขาดแคลนและ การประเมินมูลค่าของแต่ละบุคคล
ดังนั้น ปฏิทรรศน์น้ำ-เพชร (Water-Diamond Paradox) จึงไม่ใช่ความขัดแย้ง แต่เป็น การสะท้อนให้เห็นถึงหลักการพื้นฐานของเศรษฐศาสตร์ นั่นคือ มูลค่า เป็นเรื่องส่วนบุคคล และขึ้นอยู่กับบริบท
เรื่องราวของ "ซุป" ก็เช่นกัน.. เขาประเมินมูลค่าของ ความรู้ ความสุข และการสร้างคุณค่า สูงกว่าเงินทองและชื่อเสียง
เขาเลือกที่จะเดินบนเส้นทางที่คนอื่นอาจมองว่า "ขาดแคลน" คือ เส้นทางที่ไม่ได้เต็มไปด้วยเงินทองหรือชื่อเสียง แต่เป็นเส้นทางที่เต็มไปด้วย ความสุข ความหมาย และคุณค่า
"ความสุข ที่แท้จริง หาซื้อไม่ได้ ด้วยเงิน"
-
 @ fff19d35:43344a0b
2024-11-22 16:44:58
@ fff19d35:43344a0b
2024-11-22 16:44:58The Rise of Cryptocurrency: Bitcoin, YakiHonne, and Beyond*
The world of cryptocurrency has experienced tremendous growth and development in recent years. From its humble beginnings to the current market boom, cryptocurrency has become a major player in the global financial landscape. In this article, I will explore the development and growth of cryptocurrency, with a focus on Bitcoin and YakiHonne.
The Early Days of Cryptocurrency
The concept of cryptocurrency dates back to the 1980s, but it wasn't until the launch of Bitcoin in 2009 that the industry began to gain traction. Created by an individual or group of individuals using the pseudonym Satoshi Nakamoto, Bitcoin was designed to be a decentralized, peer-to-peer digital currency.
The Rise of Bitcoin
Bitcoin's early success was met with skepticism and regulatory challenges. However, as the currency gained popularity and its value increased, it became clear that Bitcoin was here to stay. Today, Bitcoin is the largest and most well-known cryptocurrency, with a market capitalization of over $1 trillion.
The Emergence of YakiHonne
While Bitcoin may be the most well-known cryptocurrency, other players are emerging to challenge its dominance. One such player is YakiHonne, a relatively new cryptocurrency that has gained significant attention in recent months. YakiHonne's unique features, such as its fast transaction times and low fees, have made it an attractive option for investors and users.
The Future of Cryptocurrency
As the cryptocurrency market continues to grow and mature, we can expect to see new players emerge and existing ones continue to innovate. The development of decentralized finance (DeFi) platforms, non-fungible tokens (NFTs), and other cryptocurrency-related technologies will likely play a major role in shaping the future of the industry.
Conclusion
The development and growth of cryptocurrency, Bitcoin, and YakiHonne are testaments to the power of innovation and the demand for alternative financial systems. As the industry continues to evolve, it will be exciting to see how these players and others adapt and thrive in the ever-changing landscape of cryptocurrency.
-
 @ a305a0de:21557ddd
2024-11-22 16:43:14
@ a305a0de:21557ddd
2024-11-22 16:43:14Bitcoin, created in 2009, is a digital currency that allows peer-to-peer transactions without intermediaries. It's based on blockchain technology, maintained by a global network of computers.
Benefits include decentralization, security, accessibility, and a limited supply. However, Bitcoin also faces challenges like volatility, regulatory uncertainty, scalability issues, and environmental concerns.
Despite these challenges, Bitcoin's impact on finance is undeniable. As the world becomes increasingly digital, Bitcoin is likely to continue shaping the future of finance.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka


