-
 @ 42342239:1d80db24
2024-11-06 09:05:17
@ 42342239:1d80db24
2024-11-06 09:05:17TL;DR: J.D. Vance recently observed that many in the Democratic Party are attempting to manufacture trust from the top down, neglecting the fact that genuine trust is often born from grassroots connections. There's indeed a stark contrast between trust that's artificially constructed through manipulation and censorship, and trust that's organically cultivated from the ground up.
Trump's vice presidential candidate J.D. Vance appeared on podcast host Joe Rogan's show earlier in November. According to Vance, large parts of the Democratic Party are trying to create higher trust from above, without understanding that the previously high trust once arose organically: "I think that a lot of them are trying to reimpose that social trust from the top."
Most people understand the importance of high trust. Political scientist Robert D. Putnam, for example, has shown that large social capital, in the form of trust and networks, is a key factor for economic growth, cooperation, and problem-solving. See e.g. his book Bowling Alone: The Collapse and Revival of American Community (2000).
The low trust today is widespread. Trust in the American federal government is at historically low levels. Trust in the media is at rock-bottom levels. Even trust in doctors and hospitals has plummeted: at the beginning of 2024, the proportion of people who reported "a great deal of trust" had dropped to 40%, from 72% in April 2020. This can be concerning, as individuals with low trust in doctors and hospitals will be less likely to follow their advice and recommendations. It's therefore not surprising that many want to "rebuild trust" (this was the theme of the World Economic Forum's annual meeting this year).
How much trust is actually reasonable?
But how much trust is actually reasonable? To determine this, one can ask whether an institution has acted reliably in the past, whether it possesses the knowledge and ability required to deliver what is promised, and whether its interests are in line with our own.
The low trust figures among Americans are likely a reflection of the fact that many of them today question the extent to which the answers to these questions are actually affirmative. During the pandemic, medical experts in the UK incorrectly predicted that hundreds of thousands of people would die. In the US, the leading infectious disease expert misled the public about, among other things, face masks, the sitting president lied about both the effectiveness and safety of vaccines, a British health minister wanted to "scare the pants off people," and virus experts even conspired to mislead about the origin of the SARS-CoV-2 virus. All while social media companies, under pressure from governments, were forced to censor information that was actually correct.
Trust - built on sand or on solid ground?
It's possible to continue on the current path and try to improve trust figures by limiting access to information. For instance, if the public doesn't get access to negative information about authorities or experts, the measured trust can increase. But in that case, trust is merely built on sand, waiting to be undermined by the inexorable forces of truth.
But there's another possibility. Building relationships that are genuine and honest, listening to each other without judgment, and communicating without misleading. Doing things that really matter, and doing them well, showing competence and reliability through actions. In this way, trust can grow naturally and organically. A trust built on solid ground, not on sand. A delicate task. But presidential election or not, isn't it time for us to start building a future where this form of trust is the obvious foundation?
-
 @ 42342239:1d80db24
2024-10-29 19:27:12
@ 42342239:1d80db24
2024-10-29 19:27:12The Swedish government recently rejected the Transport Administration's proposal for average speed cameras. The proposal would have meant constant surveillance of all vehicles, and critics argued for instance that it would have posed a threat to national security. Given the prevalence of IT breaches and data leaks today, it's hard not to give them a point, even if the problems are often downplayed by both corporations, governments and organisations. After Facebook (now Meta) leaked account information for over half a billion users, internal mails revealed the company wanted to "normalise the fact that this happens regularly".
IT security focuses on protecting the information in our computer systems and their connections. Cybersecurity is a broader concept that also includes aspects such as human behaviour, environmental factors, and management.
Data that has not been collected cannot leak
Knowledge about cybersecurity is often insufficient. For example, it was not long ago that the Swedish Transport Agency decided to outsource the operation of the Swedish vehicle and driving licence register. This was done despite deviations from various laws and criticism from the Security Police. The operation was placed in, among other places, Serbia (which has a close relationship with Russia). The Swedish driving licence register, including personal photos, as well as confidential information about critical infrastructure such as bridges, subways, roads, and ports, became available to personnel without Swedish security clearance.
The government's decision earlier this year not to proceed with a Swedish "super register" is an example of how cybersecurity can be strengthened. The rejection of the Transport Administration's proposal for average speed cameras is another. Data that has not been collected cannot leak out. It cannot be outsourced either.
Accounts are risky by definition
But the question is bigger than that. More and more of the products and services we depend on are now subscription services, often including long documents with terms and conditions. Which few people read. If you want to control your air heat pump with your phone, you not only need an app and an account, but also agree to someone storing your data (maybe also selling it or leaking it). The same applies if you want to be able to find your car in the car park. If you do not agree to the constantly updated terms, you lose important functionality.
Every time you are required to create an account, you are put in a dependent position. And our society becomes more fragile - because data is collected and can therefore leak out. It is much harder to lose something you do not have.
At the Korean car manufacturer Kia, huge security holes were recently discovered. IT researchers could quickly scan and control almost any car, including tracking its position, unlocking it, starting the ignition, and accessing cameras and personal information such as name, phone number, and home address. In some cases, even driving routes. All thanks to a "relatively simple flaw" in a web portal.
Instead of being at the mercy of large companies' IT departments, our security would improve if we could control our air heat pump, unlock our car, or our data ourselves. The technology already exists, thanks to the breakthrough of asymmetric encryption in the 1970s. Now we just need the will to change.
-
 @ 42342239:1d80db24
2024-10-23 12:28:41
@ 42342239:1d80db24
2024-10-23 12:28:41TL;DR: The mathematics of trust says that news reporting will fall flat when the population becomes suspicious of the media. Which is now the case for growing subgroups in the U.S. as well as in Sweden.
A recent wedding celebration for Sweden Democrats leader Jimmie Åkesson resulted in controversy, as one of the guests in attendance was reportedly linked to organized crime. Following this “wedding scandal”, a columnist noted that the party’s voters had not been significantly affected. Instead of a decrease in trust - which one might have expected - 10% of them stated that their confidence in the party had actually increased. “Over the years, the Sweden Democrats have surprisingly emerged unscathed from their numerous scandals,” she wrote. But is this really so surprising?
In mathematics, a probability is expressed as the likelihood of something occurring given one or more conditions. For example, one can express a probability as “the likelihood that a certain stock will rise in price, given that the company has presented a positive quarterly report.” In this case, the company’s quarterly report is the basis for the assessment. If we add more information, such as the company’s strong market position and a large order from an important customer, the probability increases further. The more information we have to go on, the more precise we can be in our assessment.
From this perspective, the Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But this perspective omits something important.
A couple of years ago, the term “gaslighting” was chosen as the word of the year in the US. The term comes from a 1944 film of the same name and refers to a type of psychological manipulation, as applied to the lovely Ingrid Bergman. Today, the term is used in politics, for example, when a large group of people is misled to achieve political goals. The techniques used can be very effective but have a limitation. When the target becomes aware of what is happening, everything changes. Then the target becomes vigilant and views all new information with great suspicion.
The Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But if SD voters to a greater extent than others believe that the source of the information is unreliable, for example, by omitting information or adding unnecessary information, the conclusion is different. The Swedish SOM survey shows that these voters have lower trust in journalists and also lower confidence in the objectivity of the news. Like a victim of gaslighting, they view negative reporting with suspicion. The arguments can no longer get through. A kind of immunity has developed.
In the US, trust in the media is at an all-time low. So when American media writes that “Trump speaks like Hitler, Stalin, and Mussolini,” that his idea of deporting illegal immigrants would cost hundreds of billions of dollars, or gets worked up over his soda consumption, the consequence is likely to be similar to here at home.
The mathematics of trust says that reporting will fall flat when the population becomes suspicious of the media. Or as the Swedish columnist put it: like water off a duck’s back.
Cover image: Ingrid Bergman 1946. RKO Radio Pictures - eBay, Public Domain, Wikimedia Commons
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ 42342239:1d80db24
2024-09-26 07:57:04
@ 42342239:1d80db24
2024-09-26 07:57:04The boiling frog is a simple tale that illustrates the danger of gradual change: if you put a frog in boiling water, it will quickly jump out to escape the heat. But if you place a frog in warm water and gradually increase the temperature, it won't notice the change and will eventually cook itself. Might the decline in cash usage be construed as an example of this tale?
As long as individuals can freely transact with each other and conduct purchases and sales without intermediaries[^1] such as with cash, our freedoms and rights remain secure from potential threats posed by the payment system. However, as we have seen in several countries such as Sweden over the past 15 years, the use of cash and the amount of banknotes and coins in circulation have decreased. All to the benefit of various intermediated[^1] electronic alternatives.
The reasons for this trend include: - The costs associated with cash usage has been increasing. - Increased regulatory burdens due to stricter anti-money laundering regulations. - Closed bank branches and fewer ATMs. - The Riksbank's aggressive note switches resulted in a situation where they were no longer recognized.
Market forces or "market forces"?
Some may argue that the "de-cashing" of society is a consequence of market forces. But does this hold true? Leading economists at times recommend interventions with the express purpose to mislead the public, such as proposing measures who are "opaque to most voters."
In a working paper on de-cashing by the International Monetary Fund (IMF) from 2017, such thought processes, even recommendations, can be found. IMF economist Alexei Kireyev, formerly a professor at an institute associated with the Soviet Union's KGB (MGIMO) and economic adviser to Michail Gorbachov 1989-91, wrote that:
- "Social conventions may also be disrupted as de-cashing may be viewed as a violation of fundamental rights, including freedom of contract and freedom of ownership."
- Letting the private sector lead "the de-cashing" is preferable, as it will seem "almost entirely benign". The "tempting attempts to impose de-cashing by a decree should be avoided"
- "A targeted outreach program is needed to alleviate suspicions related to de-cashing"
In the text, he also offered suggestions on the most effective approach to diminish the use of cash:
- The de-cashing process could build on the initial and largely uncontested steps, such as the phasing out of large denomination bills, the placement of ceilings on cash transactions, and the reporting of cash moves across the borders.
- Include creating economic incentives to reduce the use of cash in transactions
- Simplify "the opening and use of transferrable deposits, and further computerizing the financial system."
As is customary in such a context, it is noted that the article only describes research and does not necessarily reflect IMF's views. However, isn't it remarkable that all of these proposals have come to fruition and the process continues? Central banks have phased out banknotes with higher denominations. Banks' regulatory complexity seemingly increase by the day (try to get a bank to handle any larger amounts of cash). The transfer of cash from one nation to another has become increasingly burdensome. The European Union has recently introduced restrictions on cash transactions. Even the law governing the Swedish central bank is written so as to guarantee a further undermining of cash. All while the market share is growing for alternatives such as transferable deposits[^1].
The old European disease
The Czech Republic's former president Václav Havel, who played a key role in advocating for human rights during the communist repression, was once asked what the new member states in the EU could do to pay back for all the economic support they had received from older member states. He replied that the European Union still suffers from the old European disease, namely the tendency to compromise with evil. And that the new members, who have a recent experience of totalitarianism, are obliged to take a more principled stance - sometimes necessary - and to monitor the European Union in this regard, and educate it.
The American computer scientist and cryptographer David Chaum said in 1996 that "[t]he difference between a bad electronic cash system and well-developed digital cash will determine whether we will have a dictatorship or a real democracy". If Václav Havel were alive today, he would likely share Chaum's sentiment. Indeed, on the current path of "de-cashing", we risk abolishing or limiting our liberties and rights, "including freedom of contract and freedom of ownership" - and this according to an economist at the IMF(!).
As the frog was unwittingly boiled alive, our freedoms are quietly being undermined. The temperature is rising. Will people take notice before our liberties are irreparably damaged?
[^1]: Transferable deposits are intermediated. Intermediated means payments involving one or several intermediares, like a bank, a card issuer or a payment processor. In contrast, a disintermediated payment would entail a direct transactions between parties without go-betweens, such as with cash.
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ 42342239:1d80db24
2024-09-02 12:08:29
@ 42342239:1d80db24
2024-09-02 12:08:29The ongoing debate surrounding freedom of expression may revolve more around determining who gets to control the dissemination of information rather than any claimed notion of safeguarding democracy. Similarities can be identified from 500 years ago, following the invention of the printing press.
What has been will be again, what has been done will be done again; there is nothing new under the sun.
-- Ecclesiastes 1:9
The debate over freedom of expression and its limits continues to rage on. In the UK, citizens are being arrested for sharing humouristic images. In Ireland, it may soon become illegal to possess "reckless" memes. Australia is trying to get X to hide information. Venezuela's Maduro blocked X earlier this year, as did a judge on Brazil's Supreme Court. In the US, a citizen has been imprisoned for spreading misleading material following a controversial court ruling. In Germany, the police are searching for a social media user who called a politician overweight. Many are also expressing concerns about deep fakes (AI-generated videos, images, or audio that are designed to deceive).
These questions are not new, however. What we perceive as new questions are often just a reflection of earlier times. After Gutenberg invented the printing press in the 15th century, there were soon hundreds of printing presses across Europe. The Church began using printing presses to mass-produce indulgences. "As soon as the coin in the coffer rings, the soul from purgatory springs" was a phrase used by a traveling monk who sold such indulgences at the time. Martin Luther questioned the reasonableness of this practice. Eventually, he posted the 95 theses on the church door in Wittenberg. He also translated the Bible into German. A short time later, his works, also mass-produced, accounted for a third of all books sold in Germany. Luther refused to recant his provocations as then determined by the Church's central authority. He was excommunicated in 1520 by the Pope and soon declared an outlaw by the Holy Roman Emperor.
This did not stop him. Instead, Luther referred to the Pope as "Pope Fart-Ass" and as the "Ass-God in Rome)". He also commissioned caricatures, such as woodcuts showing a female demon giving birth to the Pope and cardinals, of German peasants responding to a papal edict by showing the Pope their backsides and breaking wind, and more.
Gutenberg's printing presses contributed to the spread of information in a way similar to how the internet does in today's society. The Church's ability to control the flow of information was undermined, much like how newspapers, radio, and TV have partially lost this power today. The Pope excommunicated Luther, which is reminiscent of those who are de-platformed or banned from various platforms today. The Emperor declared Luther an outlaw, which is similar to how the UK's Prime Minister is imprisoning British citizens today. Luther called the Pope derogatory names, which is reminiscent of the individual who recently had the audacity to call an overweight German minister overweight.
Freedom of expression must be curtailed to combat the spread of false or harmful information in order to protect democracy, or so it is claimed. But perhaps it is more about who gets to control the flow of information?
As is often the case, there is nothing new under the sun.
-
 @ 42342239:1d80db24
2024-08-30 06:26:21
@ 42342239:1d80db24
2024-08-30 06:26:21Quis custodiet ipsos custodes?
-- Juvenal (Who will watch the watchmen?)
In mid-July, numerous media outlets reported on the assassination attempt on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various sources that search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.
The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."
A similar phenomenon occurred during the 2016 presidential election. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.
These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. A study published in June 2024 reports that such search results can dramatically affect undecided voters. Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.
A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?
-
 @ 42342239:1d80db24
2024-07-28 08:35:26
@ 42342239:1d80db24
2024-07-28 08:35:26Jerome Powell, Chairman of the US Federal Reserve, stated during a hearing in March that the central bank has no plans to introduce a central bank digital currency (CBDCs) or consider it necessary at present. He said this even though the material Fed staff presents to Congress suggests otherwise - that CBDCs are described as one of the Fed’s key duties .
A CBDC is a state-controlled and programmable currency that could allow the government or its intermediaries the possibility to monitor all transactions in detail and also to block payments based on certain conditions.
Critics argue that the introduction of CBDCs could undermine citizens’ constitutionally guaranteed freedoms and rights . Republican House Majority Leader Tom Emmer, the sponsor of a bill aimed at preventing the central bank from unilaterally introducing a CBDC, believes that if they do not mimic cash, they would only serve as a “CCP-style [Chinese Communist Party] surveillance tool” and could “undermine the American way of life”. Emmer’s proposed bill has garnered support from several US senators , including Republican Ted Cruz from Texas, who introduced the bill to the Senate. Similarly to how Swedish cash advocates risk missing the mark , Tom Emmer and the US senators risk the same outcome with their bill. If the central bank is prevented from introducing a central bank digital currency, nothing would stop major banks from implementing similar systems themselves, with similar consequences for citizens.
Indeed, the entity controlling your money becomes less significant once it is no longer you. Even if central bank digital currencies are halted in the US, a future administration could easily outsource financial censorship to the private banking system, similar to how the Biden administration is perceived by many to have circumvented the First Amendment by getting private companies to enforce censorship. A federal court in New Orleans ruled last fall against the Biden administration for compelling social media platforms to censor content. The Supreme Court has now begun hearing the case.
Deng Xiaoping, China’s paramount leader who played a vital role in China’s modernization, once said, “It does not matter if the cat is black or white. What matters is that it catches mice.” This statement reflected a pragmatic approach to economic policy, focusing on results foremost. China’s economic growth during his tenure was historic.
The discussion surrounding CBDCs and their negative impact on citizens’ freedoms and rights would benefit from a more practical and comprehensive perspective. Ultimately, it is the outcomes that matter above all. So too for our freedoms.
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 0c9e5e17:480e870b
2024-11-21 18:43:50
@ 0c9e5e17:480e870b
2024-11-21 18:43:50I thought I'd share the recipe and directions for my Grandma's Irish Soda bread. I'd say it's my mum's but it is really my grandmother's recipe. My mum and grandmother were from County Cork, Ireland but moved to England which is where I am originally from.
As a child, I can remember visiting my grandmother and smelling the sour bottle of whole milk she used to put on her windowsill each week so that the warmth and sun would make it sour into the equivalent of buttermilk. That would be the basis for her soda bread recipe. I can vividly remember the smell as I'm typing this - happy childhood memories! I hope you make this and enjoy it too. Please feel free to share with friends.
Options
You can make this with store bought buttermilk, or alternatives that I've listed in the ingredients. All of them turn out well, so choose what you prefer. You can also remove or reduce the white granulated sugar to taste. With the half cup it is a delicious sweet soda bread perfect for butter or jam. Without is truer to the original, I added sugar so that my kids would like it more. The same is true for the raisins, they are totally optional and I typically add raisins to one of the two halves of dough - BUT the soda bread with raisins always gets eaten first!
Ingredients
- 5 1/2 cups all-purpose flour
- 2 teaspoons baking soda
- 1 teaspoon salt
- 1 cup raisins (optional)
- 3 cups of room temp buttermilk (substitute sour cream or plain Greek yogurt)
Directions
- Preheat oven to 400 degrees F (200 degrees C). Grease large baking tray or cookie sheet
- In a large bowl, mix the flour, baking soda and salt. Add buttermilk, raisins, and mix until just combined
- On a floured surface kneed the mix into a rough dough, then divide in two
- Place each halve on the tray, sprinkle the top of each loaf with flour, then score a cross on the top of each with a sharp knife
- Bake the loaves at 400 degrees F (200 degrees C) for 45 minutes, or until golden brown
- Remove and let the loaves cool on a cooling rack

I hope you enjoy making this family favorite as much as you enjoy eating it!
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ e968e50b:db2a803a
2024-11-21 17:13:54
@ e968e50b:db2a803a
2024-11-21 17:13:54I have a bandmate (not in the group pictured) who, as of last night, has now started telling people, "unless you want an earful, PLEASE don't ask the trombone player what his shirt means."
originally posted at https://stacker.news/items/777321
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ a39d19ec:3d88f61e
2024-11-17 10:48:56
@ a39d19ec:3d88f61e
2024-11-17 10:48:56This week's functional 3d print is the "Dino Clip".

Dino Clip
I printed it some years ago for my son, so he would have his own clip for cereal bags.
Now it is used to hold a bag of dog food close.
The design by "Sneaks" is a so called "print in place". This means that the whole clip with moving parts is printed in one part, without the need for assembly after the print.
 The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables
The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables -
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ 7175188c:6382a72c
2024-11-21 16:34:00
@ 7175188c:6382a72c
2024-11-21 16:34:00It looks like the Megalith LSP node is offline.
What to do in this situation?
@Alby @getalby
originally posted at https://stacker.news/items/777271
-
 @ e1d968f7:5d90f764
2024-11-21 16:15:56
@ e1d968f7:5d90f764
2024-11-21 16:15:56Behind Closed Doors: A Journey in Escorting
Day 7: The Physical and Emotional Side of Escorting
Escorting is often portrayed as purely physical, but the truth is, it’s equally emotional. The work involves more than just being present in the room—it’s about connecting, reading energy, and managing the mix of emotions that come with each encounter.
The Physical Side
The physical aspects of escorting are what most people imagine, but they rarely think about the preparation and upkeep it requires:
- Appearance: Every detail matters—skin, hair, nails, wardrobe, and even scent. The goal is to exude confidence and allure, tailored to the preferences of each client.
- Stamina: Whether it’s a dinner date, an overnight booking, or simply being engaging for hours on end, the job demands energy and focus.
- Comfort: Sometimes, the physicality isn’t glamorous. From staying composed in uncomfortable heels to dealing with repetitive motions, the job can be physically taxing.But the physical side is only half of the story.
The Emotional Side
What many don’t realise is how emotionally involved escorting can be. It’s not just about physical interaction—it’s about creating a connection, however fleeting.
- Emotional Labour: Clients come with their own needs and expectations. Some seek passion, while others need understanding or companionship. Meeting those needs often requires emotional presence and empathy.
- Vulnerability: Escorting can leave you feeling exposed, especially when dealing with clients who are emotionally complex or overly demanding. Learning to navigate this vulnerability is key.
- Emotional Boundaries: While you give a part of yourself to create an authentic experience, it’s crucial not to give too much. Balancing care with self-preservation is an ongoing challenge.
How I Manage It
Balancing the physical and emotional demands of the job takes effort and self-awareness. Here’s how I approach it:
- Self-Care: Regular exercise, a solid skincare routine, and a few indulgent treats keep me feeling physically prepared. Emotionally, journaling and decompressing after bookings help me process the experience.
- Compartmentalisation: While I bring authenticity to every encounter, I also maintain a mental line between my professional self and personal self.
- Support Network: Having someone to talk to—a trusted friend, mentor, or therapist—makes a world of difference when things get overwhelming.
The Challenges
There are days when the emotional weight of the job feels heavier than usual. Maybe it’s a client who reminds me of something painful from my own life. Maybe it’s feeling misunderstood or undervalued. Those moments are a stark reminder that while escorting can be empowering, it’s also deeply personal.
The Rewards
Despite the challenges, escorting has taught me a lot about myself—my resilience, my ability to connect with others, and my power to adapt. Those lessons are invaluable and often come from the very same clients who challenge me the most.
The Takeaway
Escorting is a blend of physical presence and emotional labour. Both require care, effort, and balance to ensure the work remains fulfilling rather than draining. It’s a constant learning curve, but one that has given me insight into the depths of human connection and my own strength.
Tomorrow, I’ll share the story of my very first client—a moment that tested everything I’d learned so far. Until then, remember: physical beauty fades, but the emotional connections we build are what truly linger.
Rebecca x
-
 @ b12b632c:d9e1ff79
2024-04-24 20:21:27
@ b12b632c:d9e1ff79
2024-04-24 20:21:27What's Blossom?
Blossom offers a bunch of HTTP endpoints that let Nostr users stash and fetch binary data on public servers using the SHA256 hash as a universal ID.
You can find more -precise- information about Blossom on the Nostr article published today by hzrd149, the developper behind it:
nostr:naddr1qqxkymr0wdek7mfdv3exjan9qgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgrqsqqqa28e4v8zy
You find the Blossom github repo here:
GitHub - hzrd149/blossom: Blobs stored simply on mediaservers https://github.com/hzrd149/blossom
Meet Blobs
Blobs are files with SHA256 hashes as IDs, making them unique and secure. You can compute these IDs from the files themselves using the sha256 hashing algorithm (when you run
sha256sum bitcoin.pdf).Meet Drives
Drives are like organized events on Nostr, mapping blobs to filenames and extra info. It's like setting up a roadmap for your data.
How do Servers Work?
Blossom servers have four endpoints for users to upload and handle blobs:
GET /<sha256>: Get blobs by their SHA256 hash, maybe with a file extension. PUT /upload: Chuck your blobs onto the server, verified with signed Nostr events. GET /list/<pubkey>: Peek at a list of blobs tied to a specific public key for smooth management. DELETE /<sha256>: Trash blobs from the server when needed, keeping things tidy.Yon can find detailed information about the Blossom Server Implementation here..
https://github.com/hzrd149/blossom/blob/master/Server.md
..and the Blossom-server source code is here:
https://github.com/hzrd149/blossom-server
What's Blossom Drive?
Think of Blossom Drive as the "Front-End" (or a public cloud drive) of Blossom servers, letting you upload, manage, share your files/folders blobs.
Source code is available here:
https://github.com/hzrd149/blossom-drive
Developpers
If you want to add Blossom into your Nostr client/app, the blossom-client-sdk explaining how it works (with few examples 🙏) is published here:
https://github.com/hzrd149/blossom-client-sdk
How to self-host Blossom server & Blossom Drive
We'll use docker compose to setup Blossom server & drive. I included Nginx Proxy Manager because it's the Web Proxy I use for all the Fractalized self-hosted services :
Create a new docker-compose file:
~$ nano docker-compose.ymlInsert this content into the file:
``` version: '3.8' services:
blossom-drive: container_name: blossom-drive image: pastagringo/blossom-drive-docker
ports:
- '80:80'
blossom-server: container_name: blossom-server image: 'ghcr.io/hzrd149/blossom-server:master'
ports:
- '3000:3000'
volumes: - './blossom-server/config.yml:/app/config.yml' - 'blossom_data:/app/data'nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' - '81:81' - '443:443' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt - ./nginxproxymanager/_hsts_map.conf:/app/templates/_hsts_map.conf
volumes: blossom_data: ```
You now need to personalize the blossom-server config.yml:
bash ~$ mkdir blossom-server ~$ nano blossom-server/config.ymlInsert this content to the file (CTRL+X & Y to save/exit):
```yaml
Used when listing blobs
publicDomain: https://blossom.fractalized.net
databasePath: data/sqlite.db
discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.net # find files by asking upstream CDNs upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!
storage: # local or s3 backend: local local: dir: ./data # s3: # endpoint: https://s3.endpoint.com # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: # mime type of blob - type: text/ # time since last accessed expiration: 1 month - type: "image/" expiration: 1 week - type: "video/" expiration: 5 days - type: "model/" expiration: 1 week - type: "" expiration: 2 days
upload: # enable / disable uploads enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: false
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
You need to update few values with your own:
- Your own Blossom server public domain :
publicDomain: https://YourBlossomServer.YourDomain.tldand upstream domains where Nostr clients will also verify if the Blossom server own the file blob: :
upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!- The Nostr relays where you want to publish your Blossom events (I added my own Nostr relay):
yaml discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.netEverything is setup! You can now compose your docker-compose file:
~$ docker compose up -dI will let your check this article to know how to configure and use Nginx Proxy Manager.
You can check both Blossom containers logs with this command:
~$ docker compose logs -f blossom-drive blossom-serverRegarding the Nginx Proxy Manager settings for Blossom, here is the configuration I used:
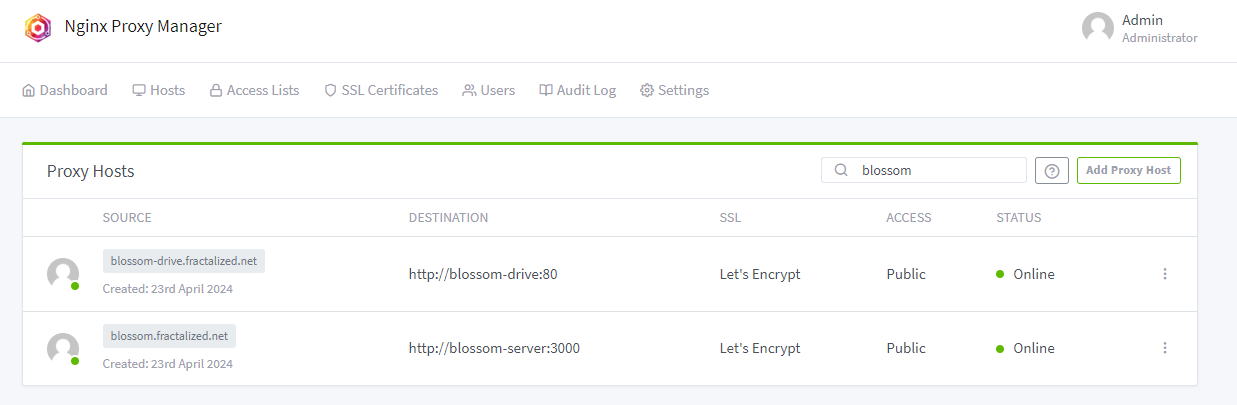
PS: it seems the naming convention for the kind of web service like Blossom is named "CDN" (for: "content delivery network"). It's not impossible in a near future I rename my subdomain blossom.fractalized.net to cdn.blossom.fractalized.net and blossom-drive.fractalized.net to blossom.fractalized.net 😅
Do what you prefer!
After having configured everything, you can now access Blossom server by going to your Blossom server subdomain. You should see a homepage as below:
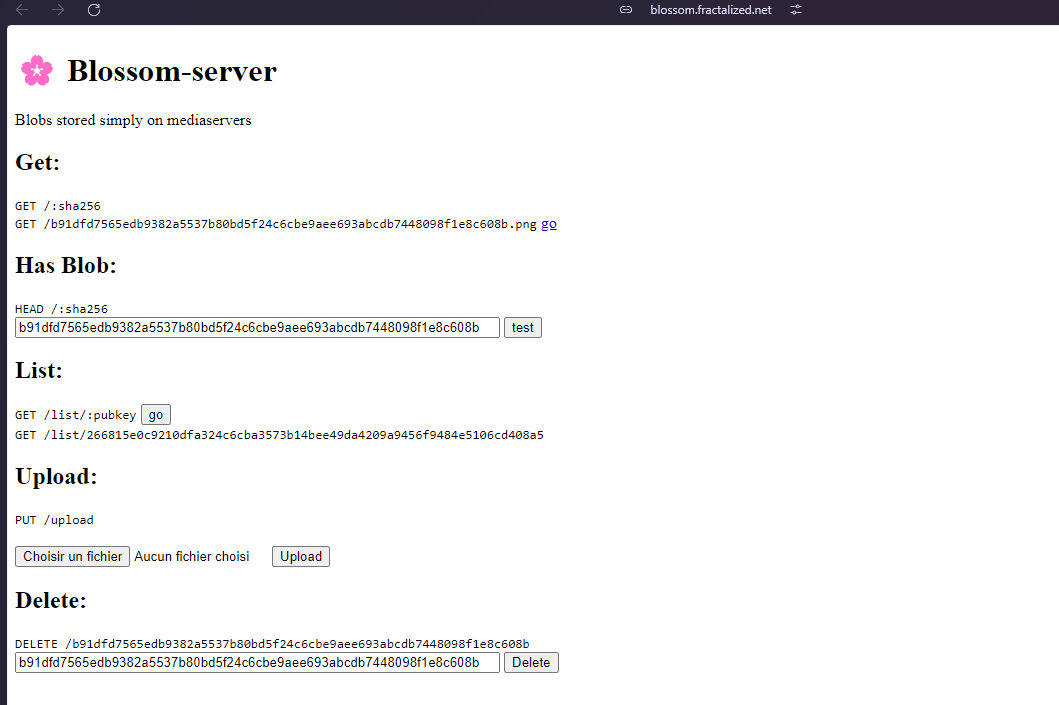
Same thing for the Blossom Drive, you should see this homepage:
You can now login with your prefered method. In my case, I login on Blossom Drive with my NIP-07 Chrome extension.
You now need to go the "Servers" tab to add some Blossom servers, including the fresh one you just installed.
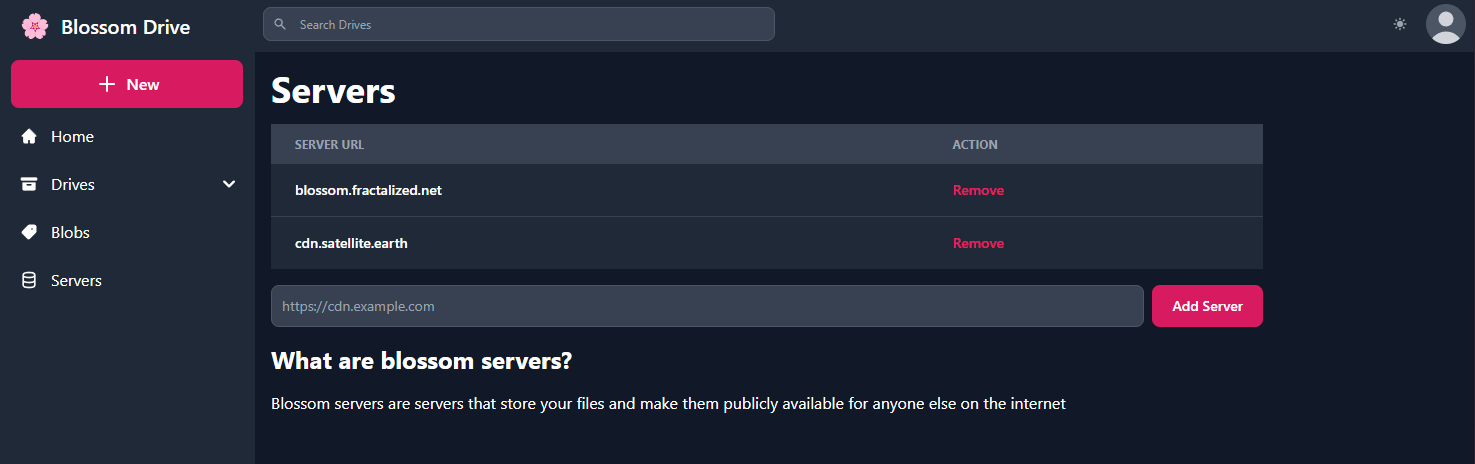
You can now create your first Blossom Drive by clicking on "+ New" > "Drive" on the top left button:
Fill your desired blossom drive name and select the media servers where you want to host your files and click on "Create":
PS: you can enable "Encrypted" option but as hzrd149 said on his Nostr note about Blossom:
"There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify"
You are now able to upload some files (a picture for instance):
And obtain the HTTP direct link by clicking on the "Copy Link" button:
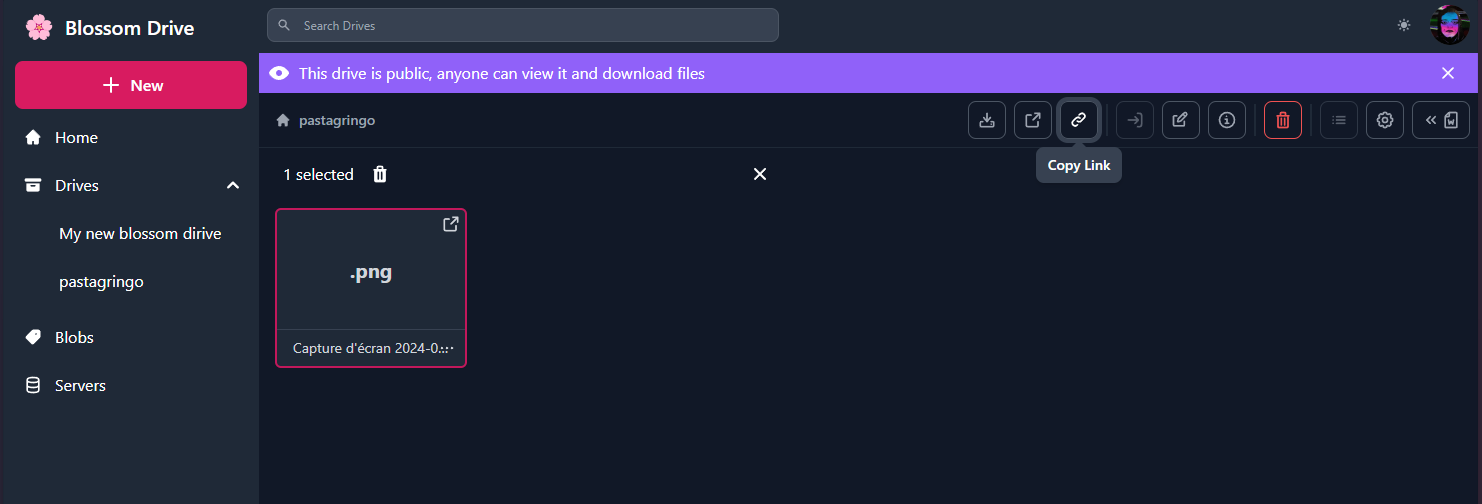
If you check URL image below, you'll see that it is served by Blossom:

It's done ! ✅
You can now upload your files to Blossom accross several Blossom servers to let them survive the future internet apocalypse.
Blossom has just been released few days ago, many news and features will come!
Don't hesisate to follow hzrd149 on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 7cc328a0:2a247c0e
2024-10-12 15:54:42
@ 7cc328a0:2a247c0e
2024-10-12 15:54:42relay.tools quarterly report
October, 2024
Project Updates
Milestone: Relay.tools is celebrating 1 year of OpenSats! Cheers to everyone that made this possible.
Relays were very popular this quarter. Scaling efforts were prioritized! This is a good indicator for relay.tools as it means that it's healthily growing. Development was executed well, completing one project at a time across the whole stack.
Relay Discovery
I've been working with @sandwich from nostr.watch on NIP66.
NIP66 will be an ABSOLUTE GAMECHANGER for clients in finding of their relays. This was always a vision for relay.tools and I am honored to be working with @sandwich on what is a pretty amazing solution. We are now in a phase of client outreach, to gather client feedback and help them implement/understand the overall goal of the NIP.
TLDR: the goal is to create a distributed version of the nostr.watch data, using nostr events.
- [x] implemented NIP66 draft7 (the 'final' design) in monitorlizard
- [x] started shipping events to the monitor relay(s) in collab with nostr.watch backends and relay.tools backends.
- [x] fixed bugs and released new binaries for monitorlizard (a NIP66 data reporting tool)
Auth Proxy Rollout
The NIP42 Auth Proxy project went really well this quarter. It's now serving tons of traffic and most bugs with clients have been squashed and the proxy hardened. This has become a very popular feature on the relays, as AUTH has many benefits beyond protecting of DMs.
- [x] testing vs. NIP17 and bugs fixed
- [x] cluster operations (multiple proxies)
UI/UX
A huge milestone this quarter was the release of the settings wizard. This is a walkthrough for new (and current) users of all the available settings for different 'relay types'. A lot of work over the last year has gone into the culmination of these settings and the wizard was a major step forward to help users understand what their options are when running a relay.
Another major UI change was the introduction of a relay feed to the landing page for a relay. This is called the relay explorer. The idea was to move to a single page app, and re-do navigation for easy relay browsing and discovery.
- [x] settings wizard released
- [x] relay explorer v2
Installer
The installer had lots of good effort put in by me and some nice contributors. We did a couple iterations on documentation and facilitated in the creation of 2-3 new relay hubs that are using this installer infrastructure.
Some additions to the installer were:
- [x] docs for building self-hosted machine images and installing on a VPS
- [x] FULLY AUTOMATIC SSL certificate handling for multiple domains with certbot
- [x] self-hosted influxDB (for relay metrics)
- [x] fix bugs with auto-deploy upgrade
Billing/Invoicing/Support
The billing system had some improvements this quarter and many invoices were sent. :) It now has better super-admin tools to notify users of past-due balances via nostr (With NDK). This took a few iterations of deciding the best way to contact users of nostr and figuring out why they don't respond to messages. It's a learning experience all the way around and the billing system will evolve over time in ways that are conducive to remaining 100% nostr for user communication and support.
The support system also showed signs of life, and people were able to use it to contact me with their questions via the various help-desk methods that I've been rolling out. (A relay, a support npub, DMs, NIP17 DMs, simplex)
Scaling!
Relay.tools successfully completed the first scale-out event. This is HUGE. Relays take more and more bandwidth and resources as they establish themselves, while at the same time needing a reasonable low-cost environment to grow in. To meet their demands the horizontal scaling is important. This will scale on commodity hardware or VPSs with ZERO vendor lock-in.
- [x] multi-server clustering with ZERO cloud vendor lock-in
- [x] deployment pipeline and capacity planning
- [x] HAproxy and additional AUTH proxies fronting all services
- [x] internal/external network support
-
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ e1d968f7:5d90f764
2024-11-21 16:12:26
@ e1d968f7:5d90f764
2024-11-21 16:12:26Every escort remembers their first client. It’s a defining moment—part nerve-wracking, part thrilling, and wholly unforgettable. For me, it wasn’t just about the money or the service; it was a lesson in navigating vulnerability, connection, and the unexpected.
The Build-Up
The anticipation started days before. I spent hours preparing—choosing the perfect outfit, rehearsing polite conversation, and imagining how it might unfold. I wasn’t just nervous; I was questioning everything. Would I know what to do? Would I feel comfortable? Would they?
When the day arrived, I felt a mix of excitement and dread. Meeting someone for the first time, especially in this context, felt like stepping into a new world.
Meeting Him
He was polite, soft-spoken, and visibly nervous—a relief, honestly, because it mirrored how I felt inside. I could see he’d put effort into his appearance, and there was an air of respect in the way he approached me.
We began with small talk, which helped break the tension. It was nothing extraordinary—questions about my day, a few jokes—but it grounded the moment. Suddenly, it wasn’t about being “an escort” and “a client.” It was just two people trying to connect.
Navigating the Experience
When the more intimate part of the booking began, I realised something important: it wasn’t just about the physical act. It was about creating an experience, an atmosphere where both of us felt at ease.
I leaned on what I’d prepared—staying calm, reading his cues, and ensuring I remained in control while being warm and attentive. There were moments of awkwardness, sure, but I quickly learned that those moments could be disarmed with humour or a reassuring touch.
What I Learned
That first client taught me more than I expected:
- Human Connection Matters: Escorting isn’t just a transaction; it’s about making someone feel valued and seen.
- Confidence is Key: Even when I wasn’t entirely sure of myself, projecting confidence helped both of us relax.
- Boundaries Are Crucial: From the beginning, I established what I was comfortable with, and he respected that. It set the tone for a positive experience.
The Aftermath
When the booking ended, I felt... different. It wasn’t just relief; it was pride. I’d done something completely outside my comfort zone, and I’d done it well. As I walked away, I realised this was more than a job—it was a skill, a craft I could refine over time.
The Takeaway
Your first client is a milestone. It’s where the nerves meet the unknown, and where you start to understand the depth of this profession. Looking back, I’m grateful for the experience. It wasn’t perfect, but it was mine—and it marked the beginning of a journey I’m proud of.
Tomorrow, I’ll explore how I built confidence and professionalism in those early days of escorting. Until then, remember: every first step, no matter how daunting, is a step toward growth.
Rebecca x
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ ac8bb9b0:70278acc
2024-11-21 15:14:11
@ ac8bb9b0:70278acc
2024-11-21 15:14:11Chef's notes
If you’d like to make this soup part of your rotation and want to shave off a little time for the next time around, double the recipe for the meatballs and freeze half. That way, all you’ll have to do is make the soup and add the meatballs as directed in the recipe. (They may take a few extra minutes to warm through if you add them directly from the freezer.)
The soup can be frozen for up to 3 months but wait until you reheat the soup to add the pasta. Defrost the soup in the refrigerator for 12 hours and then reheat it on the stovetop over medium heat until simmering, add the pasta, and cook until the pasta is tender.
Details
- ⏲️ Prep time: 50
- 🍳 Cook time: 30
- 🍽️ Servings: 8
Ingredients
- 1 large egg
- 3 tablespoons finely chopped fresh chives
- 2 teaspoons finely chopped fresh sage
- 2 cloves garlic, minced
- ¾ lb 85 or 90% lean ground beef
- ½ lb sweet or hot Italian sausage, removed from the casings
- ½ cup grated Parmigiano Reggiano
- ⅓ cup Italian seasoned bread crumbs
- ¼ teaspoon salt
- 2 tablespoons extra virgin olive oil
- 1 medium yellow onion, diced
- 2 large carrots, diced
- 2 stalks celery, diced
- 6 cups high-quality chicken broth
- 2 cups high-quality beef broth
- 2 cups water
- ½ cup dry white wine
- 1 bay leaf
- ½ teaspoon salt
- ¼ teaspoon white pepper (okay to use black pepper)
- 1 cup small dittalini pasta
- 4 oz fresh spinach, stems trimmed and roughly chopped (once prepped, you should have about 3 packed cups)
- Parmigiano Reggiano, for serving
Directions
- Make the meatballs: Preheat the oven to 350°F. Line a baking sheet with aluminum foil and set an oven-proof roasting rack over top. Spray the rack generously with nonstick cooking spray.
- In a large bowl, beat the egg with the chives, sage and garlic. Add the remaining meatball ingredients and mash with your hands until evenly combined. Roll the mixture into tablespoon-size balls, about 1 inch in diameter (it will make approximately 50 meatballs), and place on the prepared rack. Bake for 15 to 18 minutes, or until lightly browned and cooked through. Set aside.
- Meanwhile, start the soup. In a large soup pot or Dutch oven over medium heat, heat the olive oil. Add the onions, carrots, and celery and cook, stirring frequently, until the vegetables are softened, about 8 minutes. Add the chicken broth, beef broth, water, wine, bay leaf, salt and pepper and bring to a boil. Add the pasta and cook, uncovered, at a gentle boil until the pasta is al dente, 8 to 10 minutes (or according to package directions). Taste the soup and adjust the seasoning, if necessary. Reduce the heat to low and add the spinach and meatballs. Simmer for a few minutes, until the spinach is wilted and the meatballs are warmed through. Ladle into bowls and serve with grated Parmigiano Reggiano.
-
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
For instace, if we use wallet.cashu.me:
You can go into the "Settings" tab and add your mint :
If everything went find, you shoud see this :
You can now mint some ecash from your mint creating a sats invoice :
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
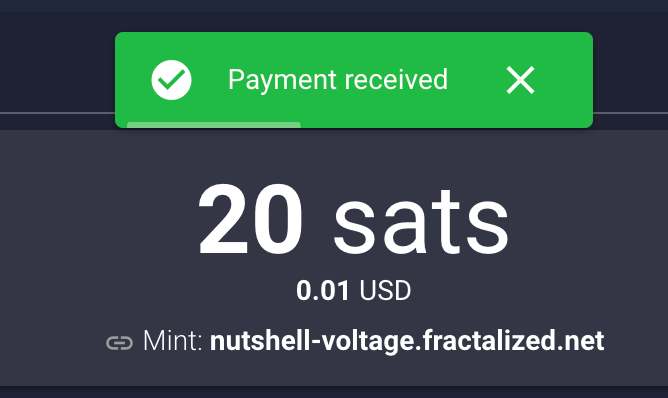
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
Add your mint again :
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
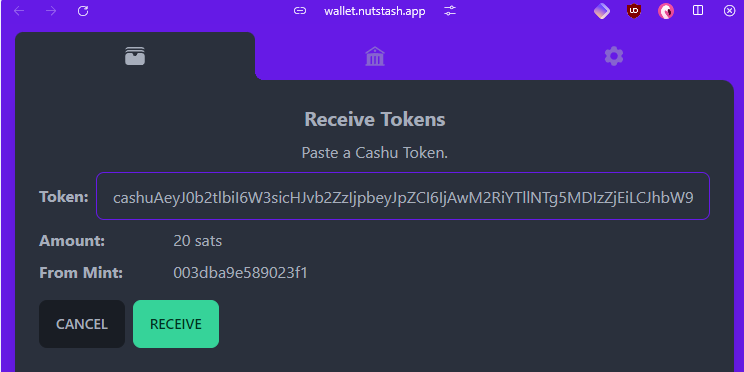
Click on "RECEIVE" again:
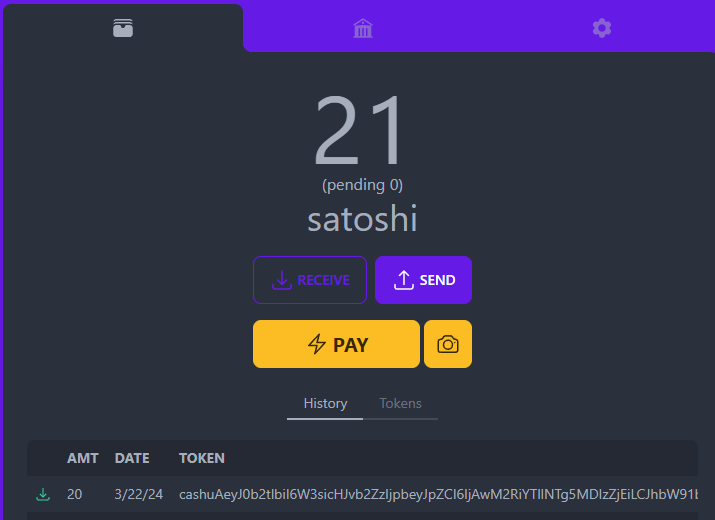
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
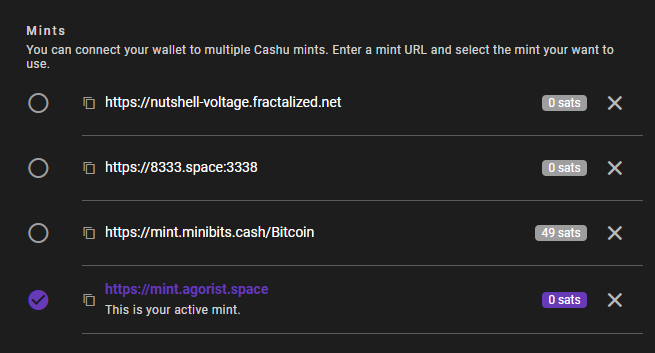
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
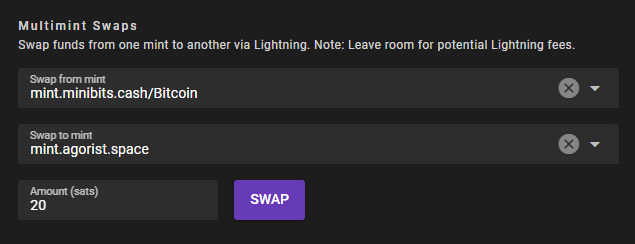
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
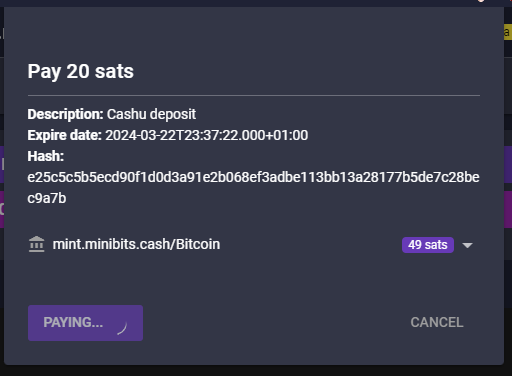
If everything is OK with the mints, the swap will be successful and the ecash received.
You can now see that the previous sats has been transfered (minus 2 fee sats).
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ a39d19ec:3d88f61e
2024-11-21 12:05:09
@ a39d19ec:3d88f61e
2024-11-21 12:05:09A state-controlled money supply can influence the development of socialist policies and practices in various ways. Although the relationship is not deterministic, state control over the money supply can contribute to a larger role of the state in the economy and facilitate the implementation of socialist ideals.
Fiscal Policy Capabilities
When the state manages the money supply, it gains the ability to implement fiscal policies that can lead to an expansion of social programs and welfare initiatives. Funding these programs by creating money can enhance the state's influence over the economy and move it closer to a socialist model. The Soviet Union, for instance, had a centralized banking system that enabled the state to fund massive industrialization and social programs, significantly expanding the state's role in the economy.
Wealth Redistribution
Controlling the money supply can also allow the state to influence economic inequality through monetary policies, effectively redistributing wealth and reducing income disparities. By implementing low-interest loans or providing financial assistance to disadvantaged groups, the state can narrow the wealth gap and promote social equality, as seen in many European welfare states.
Central Planning
A state-controlled money supply can contribute to increased central planning, as the state gains more influence over the economy. Central banks, which are state-owned or heavily influenced by the state, play a crucial role in managing the money supply and facilitating central planning. This aligns with socialist principles that advocate for a planned economy where resources are allocated according to social needs rather than market forces.
Incentives for Staff
Staff members working in state institutions responsible for managing the money supply have various incentives to keep the system going. These incentives include job security, professional expertise and reputation, political alignment, regulatory capture, institutional inertia, and legal and administrative barriers. While these factors can differ among individuals, they can collectively contribute to the persistence of a state-controlled money supply system.
In conclusion, a state-controlled money supply can facilitate the development of socialist policies and practices by enabling fiscal policies, wealth redistribution, and central planning. The staff responsible for managing the money supply have diverse incentives to maintain the system, further ensuring its continuation. However, it is essential to note that many factors influence the trajectory of an economic system, and the relationship between state control over the money supply and socialism is not inevitable.
-
 @ 7cc328a0:2a247c0e
2024-10-12 15:33:58
@ 7cc328a0:2a247c0e
2024-10-12 15:33:58relay.tools quarterly report
January, 2024
Project updates
UI design
Relay.tools spent quite a bit of time working on UI design this quarter. Since UI is time intensive and there are many other aspects of the project that need work, I time-boxed this work to 3-4 weeks total.
I engaged with @Daniel from #nostrdesign and a freelance UI developer @freecritter. We setup a penpot instance for relay.tools and practiced using that instead of closed-source figma. We learned that penpot is not as friendly as figma from a designers point of view, but is workable. From the perspective of a frontend engineer it is no different than figma and using penpot is a big opensource win.
The following designs were implemented this quarter. There is still much to do in this area and some aspects have been brainstormed but put on hold due to other priorities.
Relay branding and directory
I wanted to give the relays personality and branding, here is a list of improvements in this area:
- [x] The home page now prominently displays the public relays that have chosen to advertise.
- [x] Relay 'Badges' were re-designed to have better contrast and fit.
- [x] Relays have a custom direct landing page at their domain. eg. frogathon.nostr1.com
### 'Paid relay' support
Relays now support lightning payments to the relay.tools operator. This helps with combating spam and allowing the relay owners to subsidize their monthly cost.
Layout / theme
The frontend code has been modified so that it is responsive on mobile/desktop using columns. The menu was re-designed to be responsive on mobile and shows user hints for login as well as additional links (explore, FAQ). Theme switcher bugs for light/dark modes have been fixed. (Nextjs bleeding edge workaround was required).
Relay Explorer Alpha
The Relay Explorer Alpha is a mini-client for interacting with a single relay. The following improvements were made:
- [x] Moderation capabilities added: Mods can delete messages, block pubkeys, and delete+block directly from the explorer.
- [x] Image and Link parsing / optional loading.
- [x] Replies implemented.
Example screenshot showing these features:
Installer
Another main focus this quarter was to implement an installer for the relay.tools software so that anyone can easily self-host this on a generic VPS.
The installer will be a simple shell script that asks the user a few questions (like their domain name) and then automatically installs the entire stack.
A new code repository was created for this called relay-tools-images
- [x] Main architecture to match production (systemd and nspawn).
- [x] Common Base OS image builds (Debian).
- [x] Haproxy, Strfry, Relaycreator and Mysql image builds.
- [x] Auto-updating of application code (including database migrations).
This is still in-progress and will be part of next quarter's priorities to finish the first stage. (described in plans for next quarter)
Lightning Node
A decent amount of time was spent managing a Bitcoin+Lightning+LnBits node and building a second node for testing and standby purposes.
I had some node issues this quarter and have been learning, re-building the node, upgrading, and aquiring more inbound liquidity to support relay operations.
Relay Management / daily operations
Relay.tools growth last quarter exceeded expectations and lots of work in the ladder part of this quarter went into daily operations.
It grew so fast that I have paused any advertising so that I have time to implement some important growth related features (as described in the plans for next quarter).
- number of relays currently running: 63
- number of unique admins/mods: 207
- events processed in last 30d: 5,091,724
- gigabytes sent/received in last 30d: 1,651GB / 175GB
Monitoring
Daily operations include checking in on the relay activity to get a feel for what's going on. I've implemented an InfluxDB integration for the strfry plugin, which helps with daily operations and in the future will provide owners, mods, and users with stats showing relay performance and event counts. This greatly improves visibility into the relays and is the backbone of data analysis for the platform.
Events by Kind (7d)
Events by Relay (7d)
Data Explorer View (single relay, kind 3)
Moderation
Daily operations time is also spent ensuring relays meet our TOS. That includes browsing the relays content for anything that does not meet the TOS and performing mitigation when necessary. This can be time consuming. I will be adding super-moderator capability so that others can assist as we grow (as described in the plans for next quarter).
Training / Feedback / Community
I promoted the use of event specific relays for nostr community events. Feedback was very positive and showed that people enjoy having event specific relays even if client support is minimal. * Nostrasia * Frogathon
Plans for next Quarter
Finish the installer - [ ] SSL certificate management with certbot. - [ ] Nostr key generation for API credentials. - [ ] install.sh script for interactive -and- config file based one-shot installation. - [ ] Publish pre-built images and integrate their use with the installer.
Re-Occuring Billing (+ tools for interacting with community of relay runners) - [ ] Implement re-occuring billing using a credits system and lightning payments. - [ ] Implement user notification(s) for billing cycle notifications. - [ ] Implement user feedback / support channel.
Additional visibility and moderation tools - [ ] Implement super-moderator capability for TOS violations. - [ ] Engage with community to help support moderation
-
 @ 07804b78:c375c543
2024-11-21 11:37:37
@ 07804b78:c375c543
2024-11-21 11:37:37Chef's notes
- The Premium Juku Curry comes individually packaged in single-serving portions, so it's convenient for using small amounts like in this recipe.
- Use your favorite spicy level of hot bean-curd soup base/curry roux.
Details
- 🍽️ Servings: 4
Ingredients
- 1 box of “Cook Do®” (Chinese seasoning mix) for Szechuan-style Mapo Tofu
- 2 servings of Premium Juku Curry
- 500g tofu
- 400g cut tomatoes
- 200g minced meat
- 80g garlic sprouts
- 100ml water
- 1 tablespoon sesame oil
- Cooked rice, enough for the number of people
Directions
- Slice the garlic shoots diagonally into 3-4cm pieces. Cut the tofu into bite-sized pieces.
- Heat the sesame oil in a frying pan and fry the minced meat over a medium heat.
- When the meat is about 80% cooked, add the garlic shoots and continue to fry, stirring, until the meat is fully cooked.
- Turn off the heat and add the Cook Do® Sichuan-style Mapo Tofu seasoning, and mix well.
- Turn the heat back on to medium, add the cut tomatoes and water, and bring to the boil, stirring gently.
- When it comes to a boil, turn the heat down to low, add the Premium Juku Curry, and stir well to dissolve.
- Once the curry has dissolved, add the tofu and cook until the tofu is warmed through.
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ 8d5ba92c:c6c3ecd5
2024-11-21 11:07:37
@ 8d5ba92c:c6c3ecd5
2024-11-21 11:07:37Looks like I need to add proper kids' socks to my designs 😋. Though my little guests didn’t mind the larger sizing, either! We Are All Satoshi.
https://i.nostr.build/qhzhGmidYjxDNVrp.jpg
TLDR: I started producing Bitcoin/Nostr-themed socks to help orange-pill people, to remind us of one of the first companies to accept Bitcoin back in 2011, and to bring smiles to people's faces. (More details can be found in the article on Habla News "Bitcoin ZOO + The Story of My Wardrobe!")
https://i.nostr.build/pChpYJzHtlWgOMfz.jpg
Until Adopting Bitcoin 2024, I hadn’t considered that kids might love them too. But during Bitcoin Para Niños, some amazing young participants noticed my bag full of designs. Among all the options, they chose the orange-and-blue "We Are All Satoshi" socks. Coincidence? Maybe 😋...
https://i.nostr.build/TXhI4g32RMCoVg4v.jpg
They didn’t mind the adult sizing and put them on immediately, which looked especially hilarious on the tiniest kids 😂
https://i.nostr.build/KT3FYbrxglHUvdD7.jpg
**This reminded me once again that kids are honest and curious in their choices. They don’t let small obstacles stop them and act with the purity of their hearts. ** 🧡⚡
https://i.nostr.build/DYWy3AfCUSVIKNfD.jpg
-
 @ b17c5987:85d68928
2024-11-21 10:24:16
@ b17c5987:85d68928
2024-11-21 10:24:16Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections.
Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections.
This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected Donald Trump with a mandate for sweeping change, and they deserve to get it.
President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs.
This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected Donald Trump with a mandate for sweeping change, and they deserve to get it.
President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs.
We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure.
In West Virginia v. Environmental Protection Agency (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In Loper Bright v. Raimondo (2024), the court overturned the Chevron doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law.
DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy.
When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be correcting the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so.
A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit.
Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in Franklin v. Massachusetts (1992) and Collins v. Yellen (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home.
Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood.
The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers.
With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud.
Mr. Musk is CEO of SpaceX and Tesla. Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency.
We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure.
In West Virginia v. Environmental Protection Agency (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In Loper Bright v. Raimondo (2024), the court overturned the Chevron doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law.
DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy.
When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be correcting the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so.
A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit.
Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in Franklin v. Massachusetts (1992) and Collins v. Yellen (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home.
Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood.
The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers.
With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud.
Mr. Musk is CEO of SpaceX and Tesla. Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency.
-
 @ e373ca41:b82abcc5
2024-11-21 09:50:06
@ e373ca41:b82abcc5
2024-11-21 09:50:06The last few years are unlikely to evoke positive associations for most people: corona madness, climate and trans ideology, a few wars in between and now the weather is also going crazy. You feel more reminded of the biblical plagues and the apocalypse than motivated to make positive changes to the system. It seems as if the world is in the hands of fanatical do-gooders and globalist social engineers. But the world is always in the hands of everyone. There is no responsibility for the future in the hands of some kind of “elite”, unless the citizens voluntarily leave it to them. Apocalypse literally means “unveiling”. In times of crisis, the core of reality is peeled out and all illusions fall away.
Golden times for system explorers
In turbulent times like these, unbreakable forest dwellers and resisters, prognosticators, esotericists and also system busters cavort. This is also a constant in history: times of crisis were often times of new beginnings. In knowledge revolutions, new knowledge inevitably mixed with new technology and also a new spiritual orientation towards the world. Before the outside world is created, it must be conceived internally. Around 500 years ago, the plague repeatedly cut new swathes through Europe, while at the same time Venice began its rise as a major trading power, the Medici banking system began to flourish and, a little later, so did art. This boom was preceded by something that at first glance seemed “boring”, such as the invention of double-entry bookkeeping by the monk Luca Pacioli at the end of the 15th century.
In the following century, the thinker Giordano Bruno moved from city to city in search of employment, and in the end, the system-breaker was burned as a heretic on the Campo de' Fiori in Rome. Meanwhile, astronomers, magicians, artists and alchemists bustled about at the court of the Habsburg Rudolf II in Prague. Some talked to angels, others tried their hand at producing gold. Those who ridicule alchemical experiments today as heresies should at least google how phosphorus and porcelain were discovered.
To be outmoded and unworldly means to be in search of something different. Great visionaries from Rudolf Steiner to Albert Einstein, Nikola Tesla and Richard Buckminster-Fuller have always known that the best way to change the system is to go outside the system and create something new from there. You don't change the old by fighting it. The best way to replace it is to think in new forms that make the old forms obsolete, said Buckminster-Fuller.
Brains moved the world more than the guillotine
Working on the old is like dancing with zombies. Creating the new, on the other hand, inevitably brings the old into competition with the system. If the new is better, the old system is obsolete. “Video killed the Radio Star” sang the Buggles in 1979 (the first clip of the MTV era) and they were just as right as Steve Jobs, who threw several industries overboard with the iPhone. What you previously needed 20 devices for, from dictation machines to telephones and “Walkmans”, you now had in your pocket. Thinking outside the system, which you don't learn within the system, combined with technology, is the sharpest knife in history when it comes to change. Brains moved more than the guillotine.
In today's world, everyone is a potential system changer. There has never been a time when the tools of change have been available to as many people as they are today. At the same time, we live in a time in which fewer people than ever before determine the fate of everyone. How does this fit together? There is an infinite systematic potential for change, and this lies solely with the people who have not yet made use of the available tools. But this wave is irreversibly set in motion; it is rolling and no one knows when it will turn into a tsunami. Free speech and critical journalism are under massive attack. With the Pareto Project we want to make censorship-resistant publishing the new standard. Today, we have the opportunity to consign the phenomenon of censorship to the landfill of history. Are you thinking along similar lines? What should the journalism of the future look like? Help us as a tester, migrate your content as a journalist or as a publication, support us as a developer or contribute your ideas: Kontakt@idw-europe.org
The great transformation
We are living in the midst of a quiet revolution, with quiet revolutionaries. Pavel Durov from Telegram would certainly have got on well with Giordano Bruno. Bitcoin inventor Satoshi Nakamoto might have felt at home at the court of Rudolf II in the past.
The path to change follows similar patterns of transformation. In the past, the power of the individual was seen as being sand in the gears of the system. “Man of labor, wake up! And recognize your power! All wheels stand still when your strong arm wills it,” wrote Georg Herwegh. Today, anyone can create their own little system. With Bitcoin, uncensorable money is already in circulation. The next big battle is over the uncensorability of information and it is currently underway. The best way to share centralized power, whether it's media power or a central bank cartel, is to distribute power through decentralized systems. This is essentially a feudalistic redistribution: the old feudal system is being replaced by the reassertion of power for the individual. What role will Switzerland, the country of countless inventions, play in this development? Hardly any other country is so innovative and therefore so well positioned for this system transformation. The most successful Bitcoin app in Europe already comes from Switzerland. The Relai app is an application for secure self-custody of Bitcoin, without the influence of others. Relai AG was recently voted the best crypto startup and second-best financial startup in the country, and is rushing from one growth success to the next. The company is currently preparing to conquer the European market even more effectively.
Gaining control for the individual means losing control for the old (money) system. This principle also applies in other sectors. For example, iVault AG from Thalwil is currently working on opening up the “sharing economy” market. Anyone who wants to easily rent out their e-bike, car or lawnmower to others, for example, can do so via the ivault.io app and benefit directly from their own sustainability. Here too, old centralized platforms are being disempowered and individuals are taking their fate into their own hands.
It's always the same pattern and principle: if you don't want to be managed by others, you have to manage yourself. This applies to money, information and even lawnmowers and e-bikes.
Want to learn more about the Pareto Project? We build a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 460c25e6:ef85065c
2024-10-10 13:22:06
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - Super Clients: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
-
Clients: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
-
Mini Clients: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
-
Micro Clients: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
Super Clients - amethyst - nostrudel - coracle
Clients - damus - twitter - primal - twitter - snort - twitter - gossip - twitter - lume - twitter - ditto - twitter - rabbit - twitter - freefrom - twitter - nos - twitter - flycat - twitter - straylight - twitter - nostter - twitter - iris - twitter - nostur - twitter - nostrmo - twitter - yana - twitter - openvibe - twitter - freerse - twitter - 0xchat - chats - cornychat - chats - coop - chats - nostrchat - chats - blowater - chats - habla - blogs - yakihonne - blogs - highlighter - blogs - blogstack - blogs - stemstr - music - wavlake - music - fountain - podcasts - zap.stream - live streaming - shopstr - marketplace - plebeian.market - marketplace - flotilla - communities - satellite - communities - zapddit - communities - nostr.kiwi - communities - hivetalk - video calls - flare - long-form videos - nostrnests - audio spaces - wherostr - location - yondar - location - stacker.news - news - flockstr - events - nostrocket - issue tracker - docstr - docs - satshoot - freelance - wikifreedia - wiki - formstr - forms - chesstr - chess - memestr - meme feed - npub.cash - wallet - npub.pro - websites - gitworkshop - dev tools - onosendai - metaverse - degmods - games - turdsoup - prompts
Mini Clients - amber - signer - alby - signer - nos2x - signer - nsec.app - signer - keys.band - signer - nostrame - signer - nokakoi - anon - zap.cooking - recipes - anonostr - anon - getwired - anon - lowent - anon - creatr - exclusive content - lightning.video - exclusive content - zaplinks - slides - listr - lists - zap.store - app store - badges.page - badges - oddbean - news - dtan - torrents - nosta - user pages - pinstr - pinterest - pollerama - polls - swarmstr - trending - nostrapp - apps manager - noogle - search - ostrich.work - job postings - emojito - emoji manager - nostree - links - citrine - local relay - joinstr - coinjoins - heya - crowdfunding - zapplepay - zaps - nosbin - clipboard - shipyard - scheduler - tunestr - live streams - filestr - files - nostrcheck.me - media hosting - sheetstr - spreadsheets - crafters - curriculum vitae
Micro Clients - w3 - url shortener - nosdrive - backups - zaplife - zaps dashboard - zapper.fun - payments - nostrends - trends - zephyr - trends - wavman - music player - nostrrr - relay info - nosdump - relay info - notestack - blogs - nostr.build - media hosting - nostr.watch - relay info - nostr hours - use reports - lazereyes - vision prescriptions - snakestr - games - deletestr - deletion requests - 2048str - games - nostrqr - qr generator - notanostrclient - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more Mini and Micro clients.
-
-
 @ fd208ee8:0fd927c1
2024-11-21 07:24:34
@ fd208ee8:0fd927c1
2024-11-21 07:24:34The motherhood illusion
Growing up, I was always told that women wanted children, whilst men wanted sex. So, marriage was created, to unite these two urges, and men and women don't otherwise particularly differ. But, it turns out, that women want protection and sex, and men want children and sex.
This is why women tend to be attracted to more masculine men (they're associated with protection) and men tend to be attracted to more feminine women (they're associated with motherhood). Women who are attracted to men, who aren't overtly masculine, are looking for a different aspect of protection (reliability, steady income or wealth, emotional security, etc.)
This wasn't readily apparent, in earlier generations, as widespread, youthful marriage meant that there weren't any real decisions being made by the participants. Almost all women got married and had kids, and almost all men got married and had sex. Math checks out. But the number of women who could protect and provide for themselves was low, and the men marrying were often very young and libidinous, and not yet contemplating their own legacy.
Feminism, easy abortion, deindustrialization, delayed marriage, and reliable contraception have dissolved this illusion, completely. Millions of Western women quickly turned into cougars, careerists, party girls, and e-girls, and an entire army of childless men and sidelined dads bubbled up and began to make their pain known. Humanity's dirty underbelly has been exposed.
Women aren't as sweet, as we thought, and men are much sweeter.

Women also want children, but not as intensely. In fact, they seem to often viscerally dislike children, and are jealous of the protection they are to give them. So, they are prone to offing their offspring because they are averse to having any in-house competition.
If you just left women up to their own devices and reduced the social pressure, at least a fifth of them wouldn't bother having children, at all, and another quarter will have one and then lose interest or age out. This is not a new phenomenon, as we can see.
The male competition for potential mothers turns out to be absolutely brutal, and more difficult than simply finding a woman to sleep with. And, now, we finally understand why men traditionally jumped through so many hoops, to attain a wife. It wasn't for the sex; we've always had brothels, masturbation, and pornography. It was for the familial comfort, and, especially, for the children.
Good fathers make good mothers
Some women don't know if they are "potential mothers", until they meet a "potential father", and their urge to procreate suddenly kicks in. They didn't want children for their own sake, but now they want some for his sake. All of a sudden, they're imagining themselves rocking the cradle, googling "what to eat, when you're expecting", and find themselves gushing over anything that gives off Hint of Infant.
I'm pregnant! Look what I can do! Look what I can do! For you, darling.

Women married to men they are deeply in love with, are much more likely to desire to become mothers (and be devastated by infertility), and make for better mothers, because children are like individualized presents they can give to their husband.
They want to impress him. Most want to be decent parents in their own right, but the urge to impress seems to raise this to a much higher level because women are vain, and therefore focused on raising their own status and how they appear to others. And the greatest "other", of a happy wife, is her husband.
Because men are narcissistic, and therefore in love with anything associated with themselves (which underpins their obsession with owning property), men have an intense attachment to their children. What is more "yours", than your progeny?

Fathers seem to develop a special attachment to, or fondness for, the mothers of their children, that goes beyond lust or romantic love; they never forgot who gave them this new Mini Me. And they are often quite impressed by their own ability to perform this trick numerous times, which leads to the intense satisfaction they feel at "going into serial production" and churning out more of those Mini Mes until their adoring wife pleads for mercy.
Men want children. Women, who love a man, want to give him those children and gain the fidelity that comes along with those children. This is the actual "trade" underpinning the urge to marry.

-
 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03“The more you learn about something, the more you realize you know nothing.” This saying resonates deeply with me. The truth is, no one really has all the big answers. Many in the scientific community seem to pretend they do. Let’s explore this further.
Consider the Most Fundamental Questions
- The Origin of the Universe
- The Origin of Life on Earth
The Origin of the Universe
You might think we have a solid answer: the Big Bang. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to Sir Roger Penrose for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: the endless expansion and contraction of the universe. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet neither can be definitively proven over the other. This highlights the limitations of our current understanding.
The Origin of Life on Earth
The origin of life is even more complex. Life requires three essential components: - Proteins for basic functioning - RNA for storing and replicating genes - Lipids (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from outside sources. Some scholars even question the entire random mutation model.
The Question of Certainty
If scientists don’t know the answers, why do they pretend they do? In my humble opinion, It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative, Interestingly, I’m not alone in believing they closed the books too early.
Reclaiming Control of Science and Education
The best way to reclaim control of science and education is to learn. If you’re looking for a starting point, I highly recommend: - “A Brief History of Time” by Stephen Hawking for physics - “Sapiens” or “The Selfish Gene” for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-
 @ 1123ece2:7d1e00c0
2024-11-21 06:55:31
@ 1123ece2:7d1e00c0
2024-11-21 06:55:31Hey everyone and welcome to Refinery Life Australia.
“The Christ of John’s Gospel” is the theme for the coming Sunday morning teachings that focus on John’s unique portrayal of the Christ.
We will continue this series through to the end of the year.
Today we are discussing, A Meeting with the Master.
Text
John 4:6-7 NKJV
6 Now Jacob’s well was there. Jesus therefore, being wearied from His journey, sat thus by the well. It was about the sixth hour.
7 A woman of Samaria came to draw water. Jesus said to her, “Give Me a drink.”
Scripture Reading
John 4:1-42 NKJV
A Samaritan Woman Meets Her Messiah
1 Therefore, when the Lord knew that the Pharisees had heard that Jesus made and baptized more disciples than John
2 (though Jesus Himself did not baptize, but His disciples),
3 He left Judea and departed again to Galilee.
4 But He needed to go through Samaria.
5 So He came to a city of Samaria which is called Sychar, near the plot of ground that Jacob gave to his son Joseph.
6 Now Jacob’s well was there. Jesus therefore, being wearied from His journey, sat thus by the well. It was about the sixth hour.
7 A woman of Samaria came to draw water. Jesus said to her, “Give Me a drink.”
8 For His disciples had gone away into the city to buy food.
9 Then the woman of Samaria said to Him, “How is it that You, being a Jew, ask a drink from me, a Samaritan woman?” For Jews have no dealings with Samaritans.
10 Jesus answered and said to her, “If you knew the gift of God, and who it is who says to you, ‘Give Me a drink,’ you would have asked Him, and He would have given you living water.”
11 The woman said to Him, “Sir, You have nothing to draw with, and the well is deep. Where then do You get that living water?
12 Are You greater than our father Jacob, who gave us the well, and drank from it himself, as well as his sons and his livestock?”
13 Jesus answered and said to her, “Whoever drinks of this water will thirst again,
14 but whoever drinks of the water that I shall give him will never thirst. But the water that I shall give him will become in him a fountain of water springing up into everlasting life.”
15 The woman said to Him, “Sir, give me this water, that I may not thirst, nor come here to draw.”
16 Jesus said to her, “Go, call your husband, and come here.”
17 The woman answered and said, “I have no husband.” Jesus said to her, “You have well said, ‘I have no husband,’
18 for you have had five husbands, and the one whom you now have is not your husband; in that you spoke truly.”
19 The woman said to Him, “Sir, I perceive that You are a prophet.
20 Our fathers worshiped on this mountain, and you Jews say that in Jerusalem is the place where one ought to worship.”
21 Jesus said to her, “Woman, believe Me, the hour is coming when you will neither on this mountain, nor in Jerusalem, worship the Father.
22 You worship what you do not know; we know what we worship, for salvation is of the Jews.
23 But the hour is coming, and now is, when the true worshipers will worship the Father in spirit and truth; for the Father is seeking such to worship Him.
24 God is Spirit, and those who worship Him must worship in spirit and truth.”
25 The woman said to Him, “I know that Messiah is coming” (who is called Christ). “When He comes, He will tell us all things.”
26 Jesus said to her, “I who speak to you am He.”
The Whitened Harvest
27 And at this point His disciples came, and they marveled that He talked with a woman; yet no one said, “What do You seek?” or, “Why are You talking with her?”
28 The woman then left her waterpot, went her way into the city, and said to the men,
29 “Come, see a Man who told me all things that I ever did. Could this be the Christ?”
30 Then they went out of the city and came to Him.
31 In the meantime His disciples urged Him, saying, “Rabbi, eat.”
32 But He said to them, “I have food to eat of which you do not know.”
33 Therefore the disciples said to one another, “Has anyone brought Him anything to eat?”
34 Jesus said to them, “My food is to do the will of Him who sent Me, and to finish His work.
35 Do you not say, ‘There are still four months and then comes the harvest’? Behold, I say to you, lift up your eyes and look at the fields, for they are already white for harvest!
36 And he who reaps receives wages, and gathers fruit for eternal life, that both he who sows and he who reaps may rejoice together.
37 For in this the saying is true: ‘One sows and another reaps.’
38 I sent you to reap that for which you have not labored; others have labored, and you have entered into their labors.”
The Savior of the World
39 And many of the Samaritans of that city believed in Him because of the word of the woman who testified, “He told me all that I ever did.”
40 So when the Samaritans had come to Him, they urged Him to stay with them; and He stayed there two days.
41 And many more believed because of His own word.
42 Then they said to the woman, “Now we believe, not because of what you said, for we ourselves have heard Him and we know that this is indeed the Christ, the Savior of the world.”
Amen.
One of the significant features of Jesus’ ministry was His meetings with people.
Jesus had an interest in individuals and He still does today.
The Lord was not so preoccupied with the multitudes that he lost concern for individuals.
Jesus met with many people.
One of His most significant meetings with a sinful woman at Jacobs well.
Let us look today at some fascinating facets of this famous interview.
- The perplexing problems.
Jesus’ meeting with the woman of Samaria was full of problems.
Do you understand the difficulties, we must understand some geography and history of Israel.
The pious Jew would not go through the land of Samaria.
Following the northern kingdom of Israel's captivity in 722 BC by the Assyrians, the land was inhabited by Israelites and foreigners.
The intermarried, which was repulsive to Pius Jews, and therefore the Pious Jews avoided Samaria.
Regarding Jesus, John said in John 4:4, But He needed to go through Samaria.
Various barriers existed for Jesus and the woman.
There was an ethnic barrier.
Jews were somewhat tolerant of other races, but the Samaritans were contemptible to the Jews.
When the woman met the Lord, she emphasised this barrier, she said how is it that You, being a Jew, ask a drink of me, a woman of Samaria?
There was a gender barrier.
Rabbis were forbidden to greet a woman in public, but Jesus cross this barrier.
Not only did the Lord cross this barrier, but he chose to talk with a notoriously immoral woman.
And of course there was a religious barrier.
There is a wide religious gap between the Jews and the Samaritans.
The Samaritans worshipped at Mount Ebal, and the Jews worship at Mount Gerizim.
- The Master’s proposal.
Jesus had the interpersonal skills to overcome these barriers.
Let us follow the strategy of the Master in how He made the meeting with the woman meaningful.
Jesus asked for a common necessity.
When the woman came to the well, He asked for a drink.
Jesus was thirsty, and the woman was thirsty.
Even though the two were different in race, gender, and religion, they had a common need to drink.
Jesus aroused the woman’s curiosity.
After He talked about His and her physical thirst, He mentioned something about “living water.”
Immediately the woman began to ask questions.
“From where does the living water come?”
The woman realised that Jesus was speaking of another type of water.
Jesus awakened the woman’s conscience.
The woman did not grasp everything about the living water, so Jesus appealed to her conscience.
“Go call your husband, and come here.”
Jesus wanted the woman to see that He knew the errors of her life.
With her conscience awakened, the woman wanted to talk about her relationship with God.
John 4:19-20 NKJV
19 The woman said to Him, “Sir, I perceive that You are a prophet.
20 Our fathers worshiped on this mountain, and you Jews say that in Jerusalem is the place where one ought to worship.”
Jesus acknowledged Himself as the Messiah.
Skilfully and masterfully, Jesus led the woman to the fact that He was the Messiah.
At the appropriate moment, He made the messianic disclosure, “I who speak to you and He.”
- The woman’s proclamation.
After the interview with Jesus, the woman left for the city of Samaria.
She told the people about the Lord.
John 4:29 NKJV
29 “Come, see a Man who told me all things that I ever did. Could this be the Christ?”
The woman had been changed because of her encounter with Jesus Christ.
A careful study of her attitude and actions reflects a radical change in character.
The woman also had a new concern for her life.
She left the water pots and went into the city.
Her primary concerns had been the sensual things of life.
After her life transforming experience, she was concerned for the spiritual condition of an entire village.
Why don’t you have a meeting with the Master?
Let Him tell you about His character and His ability to change people.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
Fill a username and click on "Create account" :
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
To understand what happened, you need to inspect the web page to find the error :
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
Click on "Sign in" :
Click on "Show Advanced" :
Click on "Nostr connect / Bunker" :
Paste your bunker URL and click on "Connect" :
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
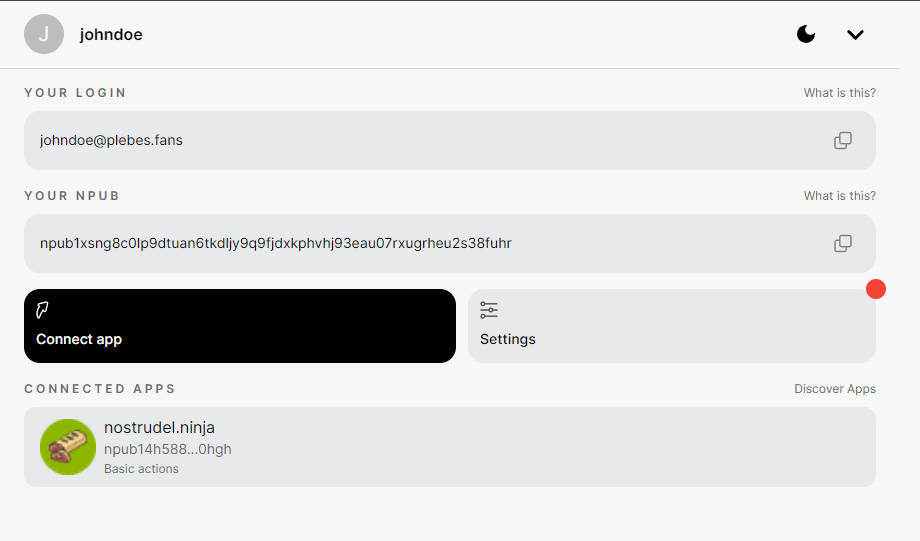
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
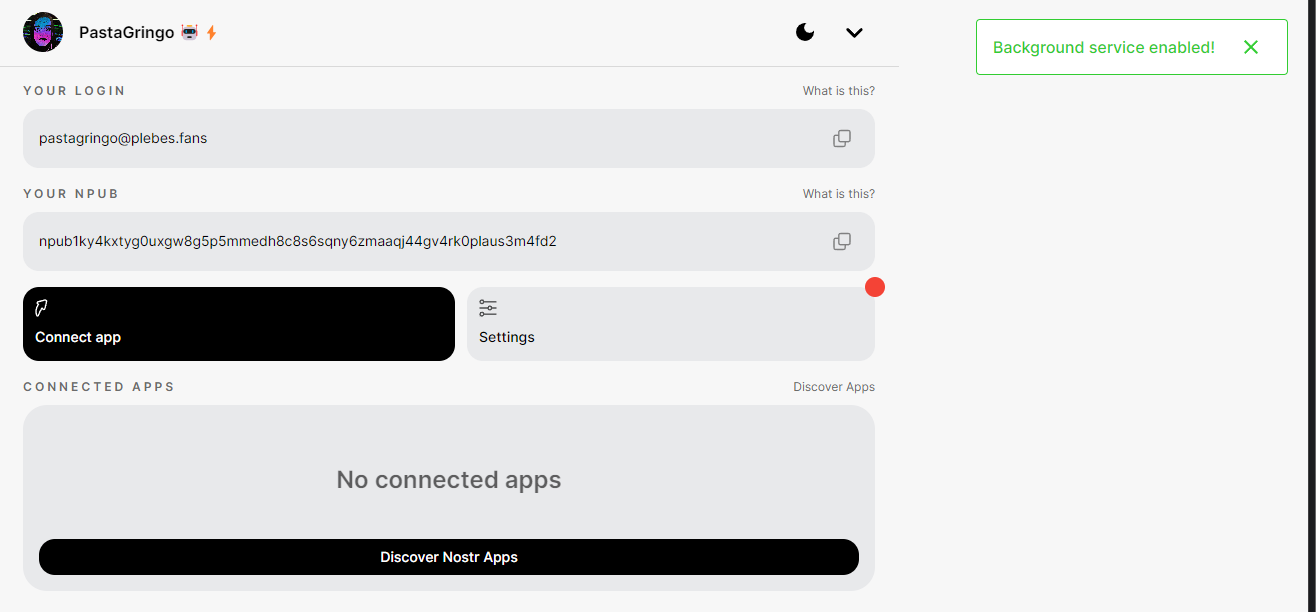
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ ee11a5df:b76c4e49
2023-11-09 05:20:37
@ ee11a5df:b76c4e49
2023-11-09 05:20:37A lot of terms have been bandied about regarding relay models: Gossip relay model, outbox relay model, and inbox relay model. But this term "relay model" bothers me. It sounds stuffy and formal and doesn't actually describe what we are talking about very well. Also, people have suggested maybe there are other relay models. So I thought maybe we should rethink this all from first principles. That is what this blog post attempts to do.
Nostr is notes and other stuff transmitted by relays. A client puts an event onto a relay, and subsequently another client reads that event. OK, strictly speaking it could be the same client. Strictly speaking it could even be that no other client reads the event, that the event was intended for the relay (think about nostr connect). But in general, the reason we put events on relays is for other clients to read them.
Given that fact, I see two ways this can occur:
1) The reader reads the event from the same relay that the writer wrote the event to (this I will call relay rendezvous), 2) The event was copied between relays by something.
This second solution is perfectly viable, but it less scalable and less immediate as it requires copies which means that resources will be consumed more rapidly than if we can come up with workable relay rendezvous solutions. That doesn't mean there aren't other considerations which could weigh heavily in favor of copying events. But I am not aware of them, so I will be discussing relay rendezvous.
We can then divide the relay rendezvous situation into several cases: one-to-one, one-to-many, and one-to-all, where the many are a known set, and the all are an unbounded unknown set. I cannot conceive of many-to-anything for nostr so we will speak no further of it.
For a rendezvous to take place, not only do the parties need to agree on a relay (or many relays), but there needs to be some way that readers can become aware that the writer has written something.
So the one-to-one situation works out well by the writer putting the message onto a relay that they know the reader checks for messages on. This we call the INBOX model. It is akin to sending them an email into their inbox where the reader checks for messages addressed to them.
The one-to-(known)-many model is very similar, except the writer has to write to many people's inboxes. Still we are dealing with the INBOX model.
The final case, one-to-(unknown)-all, there is no way the writer can place the message into every person's inbox because they are unknown. So in this case, the writer can write to their own OUTBOX, and anybody interested in these kinds of messages can subscribe to the writer's OUTBOX.
Notice that I have covered every case already, and that I have not even specified what particular types of scenarios call for one-to-one or one-to-many or one-to-all, but that every scenario must fit into one of those models.
So that is basically it. People need INBOX and OUTBOX relays and nothing else for relay rendezvous to cover all the possible scenarios.
That is not to say that other kinds of concerns might not modulate this. There is a suggestion for a DM relay (which is really an INBOX but with a special associated understanding), which is perfectly fine by me. But I don't think there are any other relay models. There is also the case of a live event where two parties are interacting over the same relay, but in terms of rendezvous this isn't a new case, it is just that the shared relay is serving as both parties' INBOX (in the case of a closed chat) and/or both parties' OUTBOX (in the case of an open one) at the same time.
So anyhow that's my thinking on the topic. It has become a fairly concise and complete set of concepts, and this makes me happy. Most things aren't this easy.
-
 @ dd664d5e:5633d319
2024-06-24 06:05:05
@ dd664d5e:5633d319
2024-06-24 06:05:05The new Great Library
We have all heard tales of Amazon or other booksellers banning customers from their bookstores or censoring/editing purchased books. The famous Project Gutenberg, and similar organizations, are performing a good work, to help protect many of our precious books from this fate, but it is merely a centralized website and therefore not censorship resistant. Also, it mostly posts books in English or German.
So, we at nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz have decided to move Project Gutenberg to Nostr and house it in the most distributed way possible: on relays. Specifically, our new, public Citadel relay for out-of-print books (and other documents), but also on any relay, anywhere.
And, because we are a very humble group, we're naming the effort "Alexandria". And the first book to be printed on Nostr is the Bible because obviously.
Why on relays?
Well, why not on relays? Relays are one of the few widely-distributed databases for documentation in existence. The relay database spans the entire globe and anyone can maintain their own relay on their personal computer or mobile phone.
That means that anyone can house their own books. Which books are their own? Any books they have in their own possession. Any books someone would have to physically pry out of their cold, dead, computer.
Notes are perfect for publishing
Once we begin generating eBooks from notes with an associated header (which will be quite easy to do, so long as they are written in markdown or similar), they will also be readable, downloadable, and storable in ePub format (see Pandoc). And it is, after all, only a matter of time until someone enterprising makes an ePaper Nostr client for calmer reading of notes, and then you can download and read them, without having to bother converting beforehand, which maintains their Nostr-navigation.
The new event kind 30040 allows us to take any sort of note containing any sort of characters and create a type of "note collection" or "book of notes", "journal of notes", "magazine of notes". And it can be nested or embedded in other notes, creating any sort of note-combination and note-hierarchy you can think of, only limited in size by the ability of your computer to processes the relationships.
Save the Zettels
The associated kind 30041 adds the prospect of breaking longer texts or articles up into sections or snippets (called "Zettel" in German). We can then collect or refer to particular bits of a longer text (like a chart, elegant paragraph or definition, data table), directly. Anyone can create such snippets, even of texts they didn't write, as they can add a reference to the original publication in the tags of the new event.
This means we no longer have to "copy-paste" or quote other people's works, we can simply tie them in. If we worry about them being deleted, we can fork them to create our own, digitally-linked version, and then tie that in. This means that source material can be tied to the new material, and you can trace back to the source easily (using Nostr IDs and tags, which are signed identifiers) and see who else is branching out from that source or discussing that source.
It's gonna be HUGE!
We are making a big, beautiful library... and you are going to build it for us. Anyone, anywhere can therefore publish or republish any document they wish, with Nostr, and store it wherever they have a relay, and view it on any client willing to display it.
You will own something and be happy.
-
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ d5c3d063:4d1159b3
2024-11-21 05:18:13
@ d5c3d063:4d1159b3
2024-11-21 05:18:13ข้อดี #เงินฝืด มุมมองเศรษฐศาสตร์สำนักออสเตรียน
เศรษฐศาสตร์สำนักออสเตรียน มองเศรษฐกิจจาก "การกระทำของมนุษย์" (Human Action) โดยเน้นที่การตัดสินใจของแต่ละบุคคล ท่ามกลางทรัพยากรที่มีอยู่อย่างจำกัด บทความนี้จะพาไปสำรวจข้อดีของ "ภาวะเงินฝืด"(deflation) หรือภาวะที่ราคาสินค้าและบริการลดลงเรื่อยๆ ซึ่งอาจฟังดูแปลก เพราะเศรษฐศาสตร์กระแสหลัก มักมองว่าเงินเฟ้ออ่อนๆ ต่างหากที่จำเป็นต่อการขับเคลื่อนเศรษฐกิจ มาดูกันว่าทำไมสำนักออสเตรียนถึงคิดต่าง
-
กำลังซื้อที่เพิ่มขึ้น - ในภาวะเงินฝืด มูลค่าของเงินจะเพิ่มขึ้น ทำให้ผู้บริโภคสามารถซื้อสินค้าและบริการได้มากขึ้นด้วยเงินจำนวนเท่าเดิม เช่น สมมติว่าคุณมีเงิน 100 บาท และราคาขนมปังอยู่ที่ 10 บาท คุณสามารถซื้อขนมปังได้ 10 ก้อน แต่ถ้าเกิดภาวะเงินฝืด ราคาขนมปังลดลงเหลือ 8 บาท คุณก็สามารถซื้อขนมปังได้ 12.5 ก้อนด้วยเงินจำนวนเท่าเดิม นี่เป็นผลดีต่อผู้บริโภคโดยตรง โดยเฉพาะผู้มีรายได้คงที่ เพราะกำลังซื้อของพวกเขาจะเพิ่มขึ้น ตามหลักการของเศรษฐศาสตร์สำนักออสเตรียนที่ว่ามูลค่าเป็นสิ่งอัตวิสัย (Subjective Value) ขึ้นอยู่กับแต่ละบุคคล แม้ว่าราคาสินค้าจะลดลง แต่ถ้าผู้บริโภครู้สึกว่าสินค้าชิ้นนั้นยังคงมีมูลค่า พวกเขาก็ยังคงซื้อ
. 2. #ส่งเสริมการออม - เมื่อเราคาดการณ์ได้ว่าราคาสินค้าจะลดลงในอนาคต ผู้คนมีแนวโน้มที่จะชะลอการซื้อและเก็บออมมากขึ้น เพราะพวกเขาสามารถซื้อสินค้าได้มากขึ้นในอนาคตด้วยเงินจำนวนเท่าเดิม พฤติกรรมนี้สอดคล้องกับแนวคิด Time Preference ที่ว่ามนุษย์มีแนวโน้มที่จะให้ความสำคัญกับความพึงพอใจในปัจจุบันมากกว่าอนาคต แต่ในภาวะเงินฝืด การเลื่อนความพึงพอใจไปในอนาคต (การออม) กลับให้ผลตอบแทนที่ดีกว่า การออมที่เพิ่มขึ้นยังเป็นปัจจัยสำคัญในการขับเคลื่อนการลงทุน และการเติบโตทางเศรษฐกิจในระยะยาว โดยการออมที่เพิ่มขึ้นจะทำให้มีเงินทุนหมุนเวียนในระบบเศรษฐกิจมากขึ้น และนำไปสู่การลดลงของอัตราดอกเบี้ย ซึ่งจะช่วยกระตุ้นการลงทุนในระยะยาว
. 3. #กระตุ้นการลงทุนอย่างมีประสิทธิภาพ - ภาวะเงินฝืดทำให้ผู้ประกอบการต้องคำนึงถึงต้นทุนและผลกำไรอย่างรอบคอบมากขึ้น เนื่องจากราคาสินค้าและบริการลดลง การลงทุนในสิ่งที่ไม่มีประสิทธิภาพจะทำให้ขาดทุนได้ง่าย ดังนั้นผู้ประกอบการจะต้องมุ่งเน้นการลงทุนในโครงการที่มีศักยภาพในการสร้างผลกำไรอย่างแท้จริงและใช้ทรัพยากรอย่างคุ้มค่า เศรษฐศาสตร์สำนักออสเตรียนเน้นเรื่องการคำนวณทางเศรษฐกิจ (Economic Calculation) ซึ่งเป็นกระบวนการที่ผู้ประกอบการใช้ในการตัดสินใจลงทุน และภาวะเงินฝืดทำให้การคำนวณนี้แม่นยำขึ้น เพราะราคาที่ลดลงสะท้อนต้นทุนที่แท้จริง ไม่ถูกบิดเบือนจากเงินเฟ้อ ส่งผลให้การจัดสรรทรัพยากรมีประสิทธิภาพมากขึ้น
. 4. #ลดความผันผวนของวัฏจักรเศรษฐกิจ - เศรษฐศาสตร์สำนักออสเตรียนมองว่าภาวะเงินเฟ้อที่เกิดจากการแทรกแซงของธนาคารกลางในการเพิ่มปริมาณเงิน เป็นสาเหตุสำคัญของวัฏจักรเศรษฐกิจ (business cycle) การเพิ่มปริมาณเงินทุนที่ไม่ได้มาจากการลดการบริโภคจริง จะนำไปสู่การลงทุนที่ผิดพลาดและเกิดวิกฤตเศรษฐกิจในที่สุด ในทางตรงกันข้าม เงินฝืดที่เกิดจากการเพิ่มขึ้นของผลผลิตไม่ได้สร้างความบิดเบือนให้กับตลาดทุนและไม่นำไปสู่วัฏจักรเศรษฐกิจ เพราะการลดลงของราคาสินค้ามาจากการที่สินค้าและบริการมีมากขึ้น ไม่ใช่การที่เงินมีมูลค่าลดลง
. 5. #ส่งเสริมนวัตกรรมและเทคโนโลยี - เพื่อให้สามารถแข่งขันและทำกำไรในภาวะเงินฝืด ผู้ประกอบการต้องหาวิธีลดต้นทุนและพัฒนาสินค้าใหม่ๆ เพื่อแข่งขัน ซึ่งต้องอาศัยนวัตกรรมและเทคโนโลยี ตัวอย่างเช่น ในช่วง Industrial Revolution มีการพัฒนาเทคโนโลยีต่างๆ มากมาย ทำให้ผลผลิตเพิ่มขึ้น และราคาสินค้าลดลง
. 6. #เสริมสร้างวินัยทางการเงิน - ภาวะเงินฝืดบังคับให้รัฐบาล ธุรกิจ และประชาชน ต้องมีวินัยทางการเงิน ไม่สามารถพึ่งพาการก่อหนี้หรือการพิมพ์เงินเพื่อแก้ปัญหาเศรษฐกิจได้ เพราะการพิมพ์เงิน ตามทัศนะของเศรษฐศาสตร์สำนักออสเตรียน เป็นการ “ขโมย” ความมั่งคั่งจากประชาชนทางอ้อม
. 7. #สะท้อนความก้าวหน้าทางเทคโนโลยี - เงินฝืดที่เกิดจากการเพิ่มขึ้นของผลผลิต เป็นเครื่องบ่งชี้ถึงความก้าวหน้าทางเทคโนโลยีและประสิทธิภาพในการผลิตที่เพิ่มขึ้น ซึ่งเป็นผลดีต่อเศรษฐกิจในระยะยาว การที่สินค้ามีราคาถูกลง เป็นผลมาจากการใช้เทคโนโลยีและพลังงานอย่างมีประสิทธิภาพมากขึ้น
สรุปแบบสั้นๆ…เศรษฐศาสตร์สำนักออสเตรียนมองว่า ภาวะเงินฝืด ที่เกิดจากการเพิ่มขึ้นของผลผลิต เป็นปรากฏการณ์ทางเศรษฐกิจที่เป็นธรรมชาติ และเป็นประโยชน์ในระยะยาว แม้ว่าในระยะสั้นอาจทำให้ธุรกิจบางส่วนต้องปรับตัว แต่การแทรกแซงของรัฐบาล เช่น การพิมพ์เงินเพื่อกระตุ้นเศรษฐกิจ เป็นการแก้ปัญหาที่ปลายเหตุและอาจสร้างความเสียหายในระยะยาว ในขณะที่ภาวะเงินฝืดจะกระตุ้นให้เกิดการปรับตัว การลงทุนอย่างมีประสิทธิภาพ และการพัฒนาทางเทคโนโลยี ซึ่งเป็นปัจจัยสำคัญในการสร้างความมั่งคั่งอย่างยั่งยืน อ้างอิงจากหนังสือ Principles of Economics อ.Saifedean Ammous
-
-
 @ deab79da:88579e68
2024-05-20 20:48:09
@ deab79da:88579e68
2024-05-20 20:48:09Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 20-30 min
- 🍽️ Servings: 4
Ingredients
- 1 lb cod fillets
- 1/4 cup butter
- 1/4 cup white flour
- 1 1/4 cups milk
- 1 tsp salt
- pepper to taste
- 1 small onion
- 1 carrot
- 3 celery stalks
- 1/2 cup breadcrumbs
- 1/2 cup shredded old cheddar
Directions
- Preheat oven to 375F. Place cod in a greased baking dish.
- Make the white sauce in a heavy saucepan. Melt the butter over medium heat and stir in the flour until smooth. Remove from heat and slowly stir in half of the milk, then return to heat and beat until smooth and shiny.
- Gradually add the remaining milk, followed by salt, pepper, and your vegetables. Cook until sauce is smooth & thickened.
- Pour sauce over the fish, and sprinkle breadcrumbs and cheese over the top.
- Bake, uncovered for 20-30 minutes until sauce bubbles and the cheese begins to brown. Let rest 10 minutes after cooking completes.
-
 @ ee11a5df:b76c4e49
2023-07-29 03:27:23
@ ee11a5df:b76c4e49
2023-07-29 03:27:23Gossip: The HTTP Fetcher
Gossip is a desktop nostr client. This post is about the code that fetches HTTP resources.
Gossip fetches HTTP resources. This includes images, videos, nip05 json files, etc. The part of gossip that does this is called the fetcher.
We have had a fetcher for some time, but it was poorly designed and had problems. For example, it was never expiring items in the cache.
We've made a lot of improvements to the fetcher recently. It's pretty good now, but there is still room for improvement.
Caching
Our fetcher caches data. Each URL that is fetched is hashed, and the content is stored under a file in the cache named by that hash.
If a request is in the cache, we don't do an HTTP request, we serve it directly from the cache.
But cached data gets stale. Sometimes resources at a URL change. We generally check resources again after three days.
We save the server's ETag value for content, and when we check the content again we supply an If-None-Match header with the ETag so the server could respond with 304 Not Modified in which case we don't need to download the resource again, we just bump the filetime to now.
In the event that our cache data is stale, but the server gives us an error, we serve up the stale data (stale is better than nothing).
Queueing
We used to fire off HTTP GET requests as soon as we knew that we needed a resource. This was not looked on too kindly by servers and CDNs who were giving us either 403 Forbidden or 429 Too Many Requests.
So we moved into a queue system. The host is extracted from each URL, and each host is only given up to 3 requests at a time. If we want 29 images from the same host, we only ask for three, and the remaining 26 remain in the queue for next time. When one of those requests completes, we decrement the host load so we know that we can send it another request later.
We process the queue in an infinite loop where we wait 1200 milliseconds between passes. Passes take time themselves and sometimes must wait for a timeout. Each pass fetches potentially multiple HTTP resources in parallel, asynchronously. If we have 300 resources at 100 different hosts, three per host, we could get them all in a single pass. More likely a bunch of resources are at the same host, and we make multiple passes at it.
Timeouts
When we fetch URLs in parallel asynchronously, we wait until all of the fetches complete before waiting another 1200 ms and doing another loop. Sometimes one of the fetches times out. In order to keep things moving, we use short timeouts of 10 seconds for a connect, and 15 seconds for a response.
Handling Errors
Some kinds of errors are more serious than others. When we encounter these, we sin bin the server for a period of time where we don't try fetching from it until a specified period elapses.
-
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ ee11a5df:b76c4e49
2023-07-29 02:52:13
@ ee11a5df:b76c4e49
2023-07-29 02:52:13Gossip: Zaps
Gossip is a desktop nostr client. This post is about the code that lets users send lightning zaps to each other (NIP-57).
Gossip implemented Zaps initially on 20th of June, 2023.
Gossip maintains a state of where zapping is at, one of: None, CheckingLnurl, SeekingAmount, LoadingInvoice, and ReadyToPay.
When you click the zap lightning bolt icon, Gossip moves to the CheckingLnurl state while it looks up the LN URL of the user.
If this is successful, it moves to the SeekingAmount state and presents amount options to the user.
Once a user chooses an amount, it moves to the LoadingInvoice state where it interacts with the lightning node and receives and checks an invoice.
Once that is complete, it moves to the ReadyToPay state, where it presents the invoice as a QR code for the user to scan with their phone. There is also a copy button so they can pay it from their desktop computer too.
Gossip also loads zap receipt events and associates them with the event that was zapped, tallying a zap total on that event. Gossip is unfortunately not validating these receipts very well currently, so fake zap receipts can cause an incorrect total to show. This remains an open issue.
Another open issue is the implementation of NIP-46 Nostr Connect and NIP-47 Wallet Connect.
-
 @ 266815e0:6cd408a5
2024-04-24 23:02:21
@ 266815e0:6cd408a5
2024-04-24 23:02:21NOTE: this is just a quick technical guide. sorry for the lack of details
Install NodeJS
Download it from the official website https://nodejs.org/en/download
Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script
bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20Clone example config.yml
bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.ymlModify config.yml
```bash nano config.yml
or if your that type of person
vim config.yml ```
Run blossom-server
```bash npx blossom-server-ts
or install it locally and run using npm
npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ```
Now you can open http://localhost:3000 and see your blossom server
And if you set the
dashboard.enabledoption in theconfig.ymlyou can open http://localhost:3000/admin to see the admin dashboard -
 @ 30ceb64e:7f08bdf5
2024-11-21 01:24:36
@ 30ceb64e:7f08bdf5
2024-11-21 01:24:36Damn,
I always put too many projects on my plate.
I really need to focus on one at a time or a couple of them.
I'm starting to feel the risk of not doing everything I wanted to accomplish.
I think with a few days hard push, I'd be able to knock out a lot.
- Article Blog
- Cool Shopstr Site
- Nostr Running App
- Podcast with AI reading my Blogs, with wavlake beats playing in the background
- Radio Show
- Music Videos
- Couple more Wavlake Albums (TheWildHustle, and Jayhawk)
- Viny Record
- Short Story
- A brand/npub to release some of my projects, instead of overloading my one npub.
This week I want to hit coding and writing hard.
I need to a hard push will get me to a good place, considering the steps i've already taken.
The start date for my part time job has been moved to December 9th, Its a weekend job working 14 hour shifts on Saturday and Sunday......Ha! I'll be assisting teens with disabilities like downsyndrome and whatnot. I'm looking forward to doing something more than just clicking fiat buttons on the computer and possibly making a direct difference in a freaks life.
I've proofed of work pretty well in the bear. Now I need to execute in this early bull.
How I plan to execute - I'm TheWIldHustle so it behooves me to lean into my sporadic nature - Get alot of work done when I feel the animal spirits take me - Broadcast my actions and rely on negative emotions (me not wanting to be a larp) to motivate my actions and force me into work with an angry ferver. - Try to maintain a constructive mood
More specifically - Autoposting blogposts to nostr would be a good idea, I already have some brain dumps in obsidian i can throw into an llm and edit to get my points across, and the autoposting will consistancy if done right.
-
The radio show is probably just me using zap.stream and streaming all of the beats i've come out with on wavlake so far and so setting up a stream shouldnt be too dificult and i'd iterrate over time with different processes
-
I know where to get the vinyl done, I have an album mixed and mastered with artwork bought from a graphic design artist to use for the front cover just need to hit the buy button and offer it on shopstr when it arrives
-
The running app at this point is about 20 percent away from being released as a noob beta project. I primarily need to work on nostr login, UI/UX and testing.
-
Short story rough outline is done, I'll probably throw the thing into Claude and edit just as I will with the blogposts.
-
The podcast will be a reading of my blog posts with my wavlake beats playing in the background
-
The shopstr site will sell digital projects like my stories ebook, wavlake beats and beat tapes. Will sell physical stuff like vinyl records, Album artwork as posters, printify merch-like stuff.
-
Music videos/Shorts will probably come from AnimalSunrise/Wavlake beats
-
Might want to do some sort of brand consultation with a freak on nostr or fiverr to develop a brand to push out some of this stuff.
Fun times ahead, Thanks for reading, Wish me luck, Hustle
originally posted at https://stacker.news/items/776493
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-04-15 20:30:05
@ f977c464:32fcbe00
2024-04-15 20:30:053724
Dürbününü yazı masasının çekmecesine koydu. O adamın bakışlarında bir şey vardı, tüylerini ürperten bir aşinalık.
Sağ tarafa kavislenen toprak yol, şehir merkezindeki idam platformuna doğru uzanırdı. On, on beş adım aralıkla, telefon ve radyo tellerini taşıyan, aynı zamanda geceleri yağ fenerlerinin asıldığı direkleri geçerdiniz. At arabalarının kaldırdığı toz ve yaydığı koku gözlerinizi yaşartırdı.
Ve darağacının önüne geldiğinizde, arkanızda bıraktığınız direklerin ne kadar güçsüz, acınası olduğu, öncesinde defalarca fark etmediyseniz bile, tam o anda, yüreğinize otururdu. Platformun üstünden gökyüzünü tehdit eden, ölüme mahkûm edilenleri kınayan gövdesi ve aniden yere eğdiği, acıyla çarpılmış boynuyla kaba tahtadan bir ucube!
Oysaki geçip geldiğiniz direklerin aksine, yanınızda uzanan, çoğunluğu iki katlı evler de tahtadan yapılmıştı ve çatıların, yağmur oluklarının, kapı çerçevelerinin, pencere kapaklarının üstündeki doğa tasviri süslemeleriyle öyle kibarlardı ki...
Dikkat etmemiş olacaksınız ama aralarında, soğuk elleriyle sizi yere bastıran, tasvirlerin yerini görkemli hayvanların -kartalların, aslanların, köpeklerin- aldığı taş evler sıralanırdı. Darağacının bedeni diğer evlerdense, ruhu kesinlikle bunlardan geliyordu.
Uzaktan kuş sesleri duyuluyordu. Bülbül. Buraya ait olmayan, dalgınlığını tamamlayan, kafese kapatılmış bir ses.
Çalışma masasının üzerine, pencereye doğru abandı. Artık ezberlediği bu hac yolculuğuna ihtiyacı yoktu. Evinden olanları az buçuk seçebiliyordu ve zaten görmeye katlanabileceğini görmüştü.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Otuzlu yaşlarının başında gösteriyordu. Teni güneşten sertleşmişti. Çatlaklar gözlerinin yanından elmacık kemiklerine uzanıyordu. Saçı ve sakalı uzun, mat siyahtı.
Neredeyse kimse izlemiyordu. Sadece tek tük, aralarına mesafe koymuş ilgisiz kişiler...
Radyo her zamanki gibi celladın konuşmasını canlı olarak yayınlıyordu.
“...lece günahlarımızdan arınmış olacağız! Doğaya küfür olan tüm bu ucubeler, düzensizlikler...”
Bir kişiyi kurtarmak için ölen onlarca insan... Attıkları çığlıklar bilinçaltının derinliklerinde hafifçe kıvrandı.
İdamların başladığı o gün...
Erken saatlerde ortaya çıkıveren genci tanımıyorlardı. İnsanlara garip sorular sormuş ve kısa süre sonra ortadan kaybolmuştu. Öğlen vakti kucağındaki paketle geri dönmüştü.
“...lumumuz için büyük tehdit teşkil etmektedirler. Şüphesiz bundan birkaç yıl sonra yapacağı hareketleriyle sadece öldüreceği insanların değil, toplumun çökü...”
Darağacını hiç değiştirmediler. Yoksa bu da hafızasındaki bulanıklığın çarpıttığı anılardan mıydı? Hatırlamaya her çalıştığında başı ağrıyordu.
Gence üzülmüş ve apar topar alınan karar karşısında dehşete düşmüştü. Diğerlerinin arasına karışmak, sesini çıkarmak, hiç değilse bunların neden olduğunu öğrenmek istemişti.
“...esin iyiliğini gözetmek zorundayız. Bunu yapabilecek gücümüzün kalmış olduğu için şükretmeliyiz. Omzumuzdaki bu gö...”
Vazgeçmişti. Korkmuştu. Ellerini titreten ilkel dürtüden değil, uzun zamandır üzerinde çalıştığı romanının bittiğini görememe ihtimalinden. “Ertesi gün,” demişti, “ertesi gün orada olacağım.”
Odanın büyük bölümünü işgal eden radyoyu kapattı. İnsan boyu ve genişliğinde, üzerindeki kontrol düğmeleri dışında cilalı ahşaptandı. Güzel olsa da pili hızlı tükeniyordu. Yenisini alması gerekecekti.
Banyoya gitti. Evin her yerinde az eşya bulundurmayı severdi: içi temiz su dolu kova, küvet olarak kullandığı büyük varil ve ayna.
Şehirdeki diğerleri gibi hafif esmer tenli, kahverengiye çalan koyu saçlı ve gözlüydü. Onların aksine gözlerinin içinde hâlâ heyecan ateşi yanıyordu. Saçları bile daha canlıydı sanki. Ve ne kısa ne uzun ne yakışıklı ne çirkin... Olması gereken neyse o. Yüzünü yıkadı, gülümseyip çalışma odasına geri döndü.
Yeniden kâğıtlarının karşısına geçi. Romanını nihayet bitiriyordu. Son cümlelerini yazdı.
Her şeye geç kalmasına değmişti.
9386
Dürbününü pencerenin iç denizliğine, yaslandığı yerin kenarına bıraktı. O adamın bakışlarında açıklayamadığı bir şey vardı. Tüylerini ürperten bir aşinalık.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Orta yaşlarındaydı. Beyazlaşmaya, griye dönmeye yeni yeni başlamış saçı ve sakalı, rengi atmış kıyafetleriyle oldukça hırpaniydi.
Kimdi o? Tanıyordu sanki..
Mutlaka yakından bakmalıydı.
“...felaketin eşiğinden döndüğümüz günün üzerinden uzun zaman geçmedi. Unutmayın! Unutmanız on...”
Radyoyu kapattı. Pili hızlı bitiyordu. Ne zaman değiştirmişti? Baş ağrısı geri geliyordu.
Merdivenlerden indi. En az dört basamağı gıcırdamıştı. Yenilenmelerinin zamanı geliyordu, temizlenmelerinin de. Parmak kalınlığında toz! Eski ve yeni ayak izleri üst üste binmişti.
Kulaklarındaki ince çınlama, ensesindeki ter... İçinden yükselip göğsünü ittiren, dengesini bozup neredeyse düşercesine aşağıya inmesine neden olan panik...
Holü geçerken diğer odalara kısaca göz attı. Hepsinin durumu aynıydı. Onu asıl şaşırtansa yatak odası oldu. Her gün uyuduğu yatağın, yanındaki bazanın, kirli çamaşır sepetinin ve etejerin üzeri... Nasıl fark etmemişti tüm bunları? Peki elbiselerinin böyle eskidiğini?
Dokunduğu elinde kalıyor veya kapalı kalmışlık kokusu yüzünden midesini bulandırıyordu. Eline geçen paçavraları apar topar giydi. Dokuması incelmiş bol beyaz keten gömleği, rengi griye yaklaşmış pantolonu -önceden? Belki siyah-, her tarafı çatlamış ve dikişleri atmış uzun deri çizmesi.
Neler oluyor neler oluyor neler oluyor neler oluyor...
Sokağa çıktı ve hava soluk borusunu temizlerken gözleri yaşardı. Hayır, kendimi kaptırmış olmalıyım. Kesin zamanın ucunu kaçırdım. Ev dün böyle değildi. Hayır hayır hayır hayır hayır...
Bulanık görüyordu ama hiç değilse burası normaldi.
İdam platformu şehir merkezindeydi. Oraya koştu.
Buranın o eğlenceli, panayır havasından eser kalmamıştı elbette. Kahveye girip çıkanlar, yan sokaktaki pazara gidip gelenler... Kimsenin olup bitenlere ilgisi yoktu. Dükkânların yarısı kapalıydı zaten. İnsanların burada oyalanmak için gittikçe daha az sebebi oluyordu.
“...lediğimiz kurtuluşumuz.”
Cellat, onun tam karşısında durduğunu görünce sustu. Herkes merakla onlara döndü.
Ve işte o anda, darağacındaki adamın bağırmasıyla celladın koşup kolu çekmesi ve zemindeki kapağı açması, infazı tamamlaması bir oldu.
“Koñrul! Onu...”
Çığlıkları ancak onu eve, yatağına taşıdıklarında biraz dindi. Sayıklamaya devam ediyordu: “Romanım romanım romanım romanım..."
Sakinleşmesi için yukarıdan kâğıtlarını ve kalemini getirdiler. Son cümlesini yazdı. Yarını göremeyecekti.
14796
Masanın üzerinde, koyduğu yerde durmayan, yuvarlanan ve düşüp merceği kırılan dürbünü fark etmedi. O adamın bakışlarında açıklayamadığı bir şey vardı. Tüylerini ürperten bir aşinalık.
Ve yine aynı gün, diğerlerinin aynı... İnsanlar bile gün geçtikçe birbirine benziyordu.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Yaşlı sayılırdı veya yaşlanmaya başlıyordu. Saçı ve sakalı beyaz ama gösterdiği yaşa rağmen hâlâ gürdü. Istırap çekmenin, büyük yük taşımanın bezginliği her yerinden hissediliyordu.
“...rine inmemiz gerek. Bu insan müsveddeleri toplumumuz için büyük tehdit...”
Evet... evet. Demek bu adam da kimsenin anlamadığı haltlar yemek üzereydi.
Rahatı kaçanlar olacaktı, belki ölenler.
Adamı gerçekten tanıyor olabilir miydi?
Kendini aşırı zorlamıştı. Radyoyu kapatıp banyoya gitti. Yeni pili ne zaman takmıştı?
Aynada kendine baktı. Geceleri uyuyup uyumadığını bile bilmiyordu. Gözleri iyice yuvalarına kaçmış, etrafı kararırken akları sararmış, zayıf ve soluk, yüzünün üstüne bırakılıp unutulmuş çöplerden farksızdı. Saçlarını düzeltmeye çalıştı, her hareketiyle onlarca saç teli kopunca vazgeçti. Renkleri solmuştu.
Şehirde yiyecek kalmamıştı. Her gün stoklar azalıyordu. Tarlalardaki olgunlaşmamış meyve sebzelere düşmüşlerdi. Tüccarlar niye gelmiyordu ki? Diğer şehirlerde de mi durum kötüydü?
Kafasından aşağı su döküp geri döndü. Kâğıtlarını önüne çekti. Romanını bitirmeliydi, açlıktan ölmeden veya idam edilen sonraki kişi olmadan. Son cümlelerini yazdı:
“Dünya yine ölürken ve her şey baştan başlarken gidebileceği bir yer kalmamıştı. Eski çağların roketlerini düşündü. Gerçekten başka gezegenler var mıydı? O zamanlarda yaşasaydı Güneş’e giderdi! Şimdi hareket etmek için duracaktı. Sonraki güne kadar.”
20251
Dürbününü kapıdan çıkarken tuvalet kovasının içine attı. Yine bir idam. Saçları dökülüyordu. Alnının iki yanı geriye doğru açılmış, sakallarıyla birleşip yekpare olan tellerin arasından kafa derisi seçilebiliyordu.
Ne ilgi çekici... Bıraksalar kendisi ölecekti zaten. Pazara gidip ne bulabileceğine bakmayı tercih ederdi.
İnsanlar ayağını sürüyerek yürüyordu. Celladın konuşması dışında çıt çıkaran yoktu. Ne kuş ötüşü veya köpek havlaması ne çocuk gülüşmeleri... Konuşanları görebiliyordu, duyamıyordu. Fısıltıdan fazlasını çıkaracak istekleri yoktu.
“...hennemin böyleleriyle dolu olduğundan şüphesi olan var mı aranızda? Onları tekrar layık oldukları yere göndereceğiz. Bunun için yardı...”
Evet... evet. “Elma kaça?”
Pazarcı taburesinden kalkıp tezgâha geldi. O da aynıydı. Farklı bedende aynı sefalet. “Hangisi?”
“Fazla ham olmayanlardan.”
“Tanesi 600 lira.”
“Yarım ver. Şundan da...” Lafını tamamlayamadı. Biri bağırıyordu. Genç, on yedisinde bile göstermeyen biri. Yüzü etli, hareketleri canlı, kıyafetleri yeni ancak kendisine büyük gelmiş ve epey hırpalanmıştı. Hele o paltosu... İçi pamukla dolu olmalıydı. Kocamandı.
“Ya idam ne demek abi! Manyak mısınız lan siz? Kaçıncı yüzyıldasınız a...”
Küfrünün ortasında ağzını kapattılar. Koluna girmiş, kahveye geri sokuyorlardı.
Tezgâhtara “Kim bu?” diye sordu.
“Birinin torunuymuş, öyle diyor. Daha önce duyduysam n’olayım. Meczup herhalde,” dedi tezgâhtar.
“İsmi neymiş dedesinin?”
“Hakan mı, Hasan mı, öyle bi’şey.”
“Ekmekten çeyrek dilim, deri parçasını da ver. Çorbalık, değil mi?”
“Evet, çorbalık.”
Hakan... Şu saçma romanını bitirmek için evine döndü. Artık tozlar ayak bileğine geliyordu. Umursamadı. Son cümlelerini yazdı, kâğıt tomarını masanın yanından tertemiz yere bıraktı.
25803
Dürbünüyle ensesini kaşıdı. O adamın gözlerinde küçük cinler vardı. Neşeyle hoplayıp zıpladıklarını ta buradan seçebiliyordu! Ah, tatlılığa bak! Hahaha!Boynundaki ilmekle, gözlerinin içine bakan, hiç korkmayan ama bıkkın, ölümün bile hayatında olup bitenleri değiştirmeyeceğini kabullenmiş bir adamın duruşuna sahipti. Çok yaşlı, kafasında tel tel beyaz saçları, göbeğine uzanan sakallarıyla kurumuş bir ceset. Omuzları çökmek üzereydi, kamburunun ağırlığıyla ipi geriyordu.
Dürümü tekrar gözüne kaldırdı. Dürüm? Hahaha! Evet... evet! Radyoda cellat konuşuyordu.
“...endinizde değişiklik hissederseniz yakınınızdaki güvenlik güçleriyle ileti...”
Ah! Kendisine şöyle baktı. Yok... Aynı ben ya!
Sahneye -Tam bir gösteri! Gösteri!- doğru koşan adamı gördü. Üzerindeki puf puf paltosuyla, orta yaşlarında...
Masanın üzerine fırladı, dizlerinin üstüne çöküp içindeki safrayı pencereden dışarıya kustu. Eliyle ağzını silerken derisinin yapışarak etinden ayrıldığını hissedebiliyor ve o bant sökülürken çıkana benzeyen sesi duyabiliyordu. Cellat konuşmayı bırakmıştı. N’oldu? N’oulduuv?
Yaşlı adamı asmışlardı. Şimdi dik duruyordu, yükü hafiflemişti ama huzurlu olduğunu söyleyemezdiniz.
Diğer adam onları umursamadı, yere eğilip mikrofonun kablosunu tuttu ve ayaklığını devirerek kendisine çekti.
“Tabutun kapağını kaldırdığında yerin altına döne döne ilerleyen o kuyuyu... Tamam... tamam!”
Adamın şakağına inen ilk sopadan çıkan ses odayı doldurdu. Sonrası sessizlik ve ölüm. Ahhh... ahhh...
Hemen bağdaş kurup kaldığı sayfayı buldu. Ne ilham! NE İLHAM!
Son cümlelerini yazıp romanını bitirdi.
34125
Dürbünü öylece dışarıya bırakıverdi. Derisi kemiklerine yapışmış, kaşına kadar her tüyü dökülmüş bir ihtiyarı asıyorlardı. Açıktaki tüm bedeni yaşlılık lekeleriyle doluydu. Bembeyaz sakalı uzun ve temizdi. Dönecek! İpin ucunda! Sağa sola!_Tahta pencereleri kapadı ve -_Ha ha!- fenerin fitilini -Ha ha _ha!- yaktı. Duvardaki gölgeleri beğenmedi ama. Söndürdü. Püf füfüfüf ha ha _ha! Tekrar yaktı. Yine istediği gibi olmasa da iş görürdü.
Radyonun sesini açtı. Evet... Evet açtım! Tiz ve kalın, tanıdık ve yabancı... Burnu kanadı.
“...EN HİÇBİR ŞEYİN SONU YOKTUR! SONU OLAN HİÇBİR ŞEY BİTMİŞ DEĞİLDİR VE BİTEN HİÇBİR ŞEYİN SONU YOKTUR! SONU OLAN HİÇBİR ŞEY...”
Yüzüne döktüğü suyu alttaki tasla toplayıp içtikten sonra -Ha ha _ha! Hazırım, evet hazırım! Romanı bitirelim. Bundan iyisi olamaz! Olamaz! Ha ha!- masasına dönüp kâğıtlarını önüne çekti. Son cümleler ve sonrasında -Özgürüm! Özgürüm!” Radyo yayınına başka, yabancı biri karıştı. Öyle bağırıyordu ki duvarlar titriyordu. Çok yaşlıydı, çok...
“Geldiğimden beri, her gün! Asmayın artık şu adamı! Görmüyor mu...”
Sonra celladın sesi duyuldu. Cılız, uzaktan...
“Bunu da hazırlayın.”
“Evet... evet. Ne olacak, beni de her gün asın a...”
Not: Bu öykü ilk olarak 2019 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ a012dc82:6458a70d
2024-11-21 00:59:27
@ a012dc82:6458a70d
2024-11-21 00:59:27Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
The fact that cryptocurrencies are subject to price swings is something that is common knowledge at this point. The tales of those who made millions during a crypto upswing make regular headlines, but so do the stories of people who lost everything during the downswings. Both types of stories are often reported in the media.
cryptocurrency gain value Additionally, since there is neither a tangible product nor a centralized organizational body, it is difficult to point to anything and say, "Look, that nice thing occurred; crypto prices will improve immediately." This is because there is no actual product. The question now is, "How does the value of cryptocurrencies increase?"
In this article, we will investigate what factors have an influence on the pricing of cryptocurrencies as well as how they increase in value.
What is cryptocurrency?
A digital asset is the most basic definition of a cryptocurrency. Because it was designed to function as a means of trade in the same manner that we use fiat currencies today, we give it the name "currency" because of its original purpose.
All transactions take place via the internet and are stored on a distributed ledger called a blockchain. The blockchain is used to demonstrate ownership of a unit and displays a history of transactions pertaining to that unit. To better understand digital assets, think of them as digital tokens. These tokens have some kind of significance inside the internal system, and it is possible to program them to record monetary transactions along with other important information.
The most profitable aspect of cryptocurrency is undoubtedly its usage as a kind of digital currency. It gives consumers the ability to transfer bitcoins between parties as payment for products and services offered by those parties. The fact that cryptocurrencies are not governed by any central body confers a number of advantageous characteristics on them. Processing costs are often very low or nonexistent altogether. There is less control and regulation exerted by the government. This translates to the fact that cryptocurrencies are easily transportable, resistant to inflation, and transparent with regard to their transaction histories.
Crypto Trading
Trading cryptocurrencies is a relatively new facet of the cryptocurrency industry that is seeing significant growth. The use of cryptocurrencies as a currency system is distinct from trading. Users instead purchase and sell cryptocurrencies in the same manner that they would purchase and sell shares in a corporation. When you buy shares in a corporation, you are essentially buying ownership in that firm. When you buy a token, however, you are really buying ownership in that coin. The tax treatment of transactions involving cryptocurrencies in the United States is analogous to that of transactions involving stock trading. This mirrors the manner in which the majority of people are generating money in the cryptocurrency market.
The crypto monetary system influences the cost of crypto trading in the same way that the popularity of a company's goods influences the price of the company's stock. The supply of a cryptocurrency, the demand for it on the market, the availability of the cryptocurrency, and the prices of other cryptocurrencies are the primary factors that influence its value.
How does cryptocurrency gain value?
On trading platforms, cryptocurrencies may increase in value. [Cryptocurrency]: The market forces of supply and demand cause a growth in its value.
The availability of a particular cryptocurrency is contingent not only on the rate at which new coins are created but also on the proportion of existing holders who are interested in liquidating their holdings.
The amount of demand for a cryptocurrency is influenced by a wide variety of variables. The more value that may be derived from owning the coins, the higher the demand will be for them. This implies that if the cryptocurrency monetary system functions effectively (i.e., with quick transactions and cheap costs), if smart contracts become more popular, and if more companies start to accept cryptocurrency, then the demand for cryptocurrency will rise. Additionally, there is a growing interest in putting money into cryptocurrencies as a kind of investment and value storage.
How is value added to cryptocurrencies? The value of cryptocurrencies goes up and down, just like the value of everything else on the market, depending on how the market as a whole perceives their worth at any particular moment. These shifts may have their origins in some of the elements related to supply and demand that were discussed before, or they may be the consequence of forces that are concealed in the market.
How Users Increase Crypto Value
There are also a few strategies that consumers may use to boost the value of their bitcoin:
-
Buy cheap and sell high. Users have the ability to grow the value of their cryptocurrency holdings by following the time-tested investing method of purchasing and keeping coins. The purchase drives up demand, which in turn drives up the price of the cryptocurrency.
-
Mining. Mining for Bitcoins or other cryptocurrencies may be lucrative if done correctly. Additionally, it has an effect on the availability of cryptocurrencies.
-
Increasing utility. The usefulness of cryptocurrency will expand as more organizations begin to invest in it and accept it as a means of payment. You, as a user, have the ability to make a contribution to this process. This will, over the course of time, result in a rise in the value of cryptocurrencies.
-
Media coverage. The price of cryptocurrencies moves up and down in response to various media reports. Users have the ability to influence this via their own social media profiles.
What Are the Different Types of Crypto?
There are now dozens, if not hundreds, of distinct cryptocurrencies, and each week a new cryptocurrency is introduced into circulation. The following are some of the most well-known types of cryptocurrencies:
-
Ethereum
-
Cardano
-
Dogecoin
-
Polygon
-
Stellar
-
Tether
-
Shiba Anu
In spite of this, there are now three primary types of cryptocurrencies, which are as follows:
-
Bitcoin
-
Altcoins
-
Tokens
Below, a more in-depth discussion is provided for each of these distinct forms of crypto.
Bitcoin
Bitcoin, the first cryptocurrency ever created, is a limited-supply digital asset. This indicates that after 21 million Bitcoins have been mined, there will be no more mined beyond that point.
Because Bitcoin is a currency whose supply is limited, it may be used as a medium for the storage and management of value. Purchasing a currency that acts as a store of value is analogous to purchasing gold as an investment. Although gold does have some worth when it comes to transactions, its primary function is that of a store of value.
Bitcoin has a mining protocol known as "Proof-of-Work." This indicates that a network of miners is responsible for carrying out the difficult computations required to keep the Bitcoin blockchain operational. Bitcoins that have just been created are the prize given to miners for their labor. Proof-of-Work is a feature that enables Bitcoin's transactional system to have a real-world value attached to it. One bitcoin is equivalent to a predetermined quantity of work done on computers.
Altcoins
Altcoins are essentially Bitcoin clones that have undergone a few tweaks here and there. A bitcoin fork is often the cause of these splits. Alternative cryptocurrencies come in a wide variety of flavors.
The underlying blockchain technology is a key point of differentiation between Bitcoin and other cryptocurrencies. The usage of some alternative cryptocurrencies is altered since the supply of such coins is not limited. A number of alternative cryptocurrencies have sped up the blockchain, which has the effect of accelerating mining as well as transaction times.
Alternate cryptocurrencies may also often be distinguished from one another by the technique of verification that is used to validate transactions. Miners are replaced by validators in alternative cryptocurrencies that employ the proof-of-stake consensus algorithm rather than the proof-of-work method. Mining with a proof-of-stake system uses a lot less energy and a lot fewer resources than mining with a proof-of-work system does, since miners using a proof-of-work system have to put in a lot more "work" in order to mine blocks.
The creation of smart contracts may also be accomplished using altcoins. The terms of these smart contracts may trigger their automated execution in specific circumstances. Because there is no need for the participation of a third party, they may be carried out right away. Because smart contracts may be used for deals as varied as those involving land, stocks, and gas, purchasing them can be a highly intriguing and profitable venture.
Tokens
Tokens are digital assets that may be exchanged for other digital assets or used inside smart contracts. They do not have a blockchain and are used on apps that are decentralized (dApps).
Mining, which results in the creation of a blockchain, serves as the actual embodiment of the money that is represented by crypto currencies. In a manner similar to this, central banks used to keep gold reserves in order to guarantee the value of their fiat currencies.
Tokens, on the other hand, are not meant to stand in for any particular item in the real world. Because they can be used to buy from decentralized applications (dApps) and because they can be used to gain discounts on fees and voting costs, their popularity is growing. A parallel may be drawn between this and the uncoupling of fiat currencies from the gold standard.
Conclusion
The level of participation in the cryptocurrency community, similar to that of any other currency, is what gives cryptocurrencies their value. A cryptocurrency's value increases when there is more demand for it than there is available supply. When a cryptocurrency has practical applications, more individuals will want to hold it, which drives up its demand. People do not want to sell it since they are interested in using it themselves. This indicates that there is more demand than supply, which leads to a rise in price.
FAQ
Does keeping bitcoin in a wallet make it more valuable? When kept in a wallet, the value of your digital currency might fluctuate over time, either increasing or decreasing. The price will fluctuate in accordance with market conditions, meaning that you will come out ahead if the value of this digital money goes up. On the other hand, it is irrelevant whether you keep your bitcoins in your own wallet or on an exchange.
Is it possible to get wealthy by creating your own cryptocurrency? Is it Possible to Earn an Income With Cryptocurrency? Yes, it is possible to generate income using cryptocurrencies. The inherent volatility of crypto assets makes most of them subject to a significant degree of risk, while others require specific education or experience in the relevant field. One way to answer the question "How can I make money with bitcoin?" is to trade cryptocurrencies.
What factors have an impact on the value of cryptocurrency? Like stocks, commodities, securities, and many other asset classes, cryptocurrencies may be traded like any other asset. The level of interest there is on the market in purchasing them, also known as demand, and the amount that is available to purchase, known as supply, are the two primary factors that determine their price. The price is determined by the connection between the two factors.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-
 @ 2dd9250b:6e928072
2024-11-20 23:57:01
@ 2dd9250b:6e928072
2024-11-20 23:57:01Nesta aclamada série (1° Temporada ), o brilhante ator, roteirista e cantor Donald Glover emula um jovem norte-americano ex-fuzileiro naval que tem asma e trabalha para uma organização secreta internacional de espionagem.
No desenrolar da história ele conhece uma mulher asiática e se vê obrigado a realizar as missões com ela, já que as missões são realizadas em casal.
Então, temos uma casal de agentes fingindo ser um casal comum. Eles trabalham juntos, dormem na mesma casa, fazem as refeições juntos e se dão razoavelmente bem. Com o passar do tempo, acontece o que o espectador já esperava, eles naturalmente sentem atração um pelo outro e começam a ter relações sexuais.
Mas, ironicamente John de fato começa a ter sentimentos por Jane, uma vez que ela é muito inteligente, uma leitora voraz, que usa sarcasmo para ofender quem ela não gosta e foi expulsa da CIA por ter traços de Sociopatia.
Logo, o que era um mero relacionamento amoroso líquido, passa a se tornar algo mais sério . Mas esse relacionamento sério é feito aos moldes da pós-modernidade e o puro suco de Secularismo, inevitavelmente irá surgir.
Como todo casal de jovens namorados, John e Jane Smith começaram a se desentender e brigar histericamente a ponto de fazerem terapia de casal. Neste ponto, eu já esperava um final bem triste e já tinha certeza que se trata de uma Tragédia.
A tragédia é justamente a constatação de que esse jovem casal não tem futuro. Naturalmente todo mundo que namora, em algum momento, irá começar a fazer planos para o futuro, é aí que as surpresas surgem.
John deseja desesperadamente ter filhos com Jane, que rejeita por ser uma mulher empoderada e que prefere subir na carreira. A Série deixa explícito que ela teve um pai ausente e que ela deve tomar a decisão de ficar com seu parceiro ou ser promovida.
Honestamente, eu não sei dizer o que de fato originou o carreirismo moderno. A omissão dos homens? O Feminismo? A Revolução Industrial? A Revolução Sexual? Talvez seja tudo isso. Ou como nós cristãos costumamos falar, no fundo no fundo, isso é consequência do pecado original.
O que posso dizer com certeza é o que o Carreirismo está provocando nas mulheres, inclusive cristãs, atualmente.
A Bíblia é clara quanto a vocação da mulher:
"Quanto às mulheres idosas, semelhantemente, que sejam sérias em seu proceder, não caluniadoras, não escravizadas a muito vinho; sejam mestras do bem, a fim de instruírem as jovens recém-casadas a amarem ao marido e a seus filhos, a serem sensatas, honestas, boas donas de casa, bondosas, sujeitas ao marido, para que a palavra de Deus não seja difamada." (Tito 2:3-5)
O problema é que as mães não ensinam isso às suas filhas. Querem que elas sejam independentes e que tenham liberdade financeira. Então elas dizem: “Vai estudar menina, pra não depender de macho”. Daí as filhas se deparam com a realidade. Uma Graduação não basta. Precisam fazer pós-graduação, Mestrado e Doutorado para se destacarem no Mercado e não dependerem de macho.
Qual a consequência disso? Mulheres doutoras com 38 anos na Igreja, vivendo com a mãe e reclamando na Internet que não tem homem para elas na igreja.
A frustração de mães com suas filhas ao verem o tempo passar e perceberem que estão envelhecendo e precisam lhe dar com o fato de que não terão netinhos para mimar.
E ainda tem uma grande parte dos homens cristãos se casando e chegando a conclusão de que mesmo eles querendo assumir a liderança do lar, provendo o sustento para que suas esposas não percam cabelo devido o estresse de 12 horas fora de casa, competindo com homens no mercado de trabalho, o salário deles não é suficiente para pagar as contas.
Outra consequência é o crescente número de Divórcios e Taxa de Fecundidade caindo mais rápido do que o valor do Real desde 1994.
Não há defesa Bíblica para o Carreirismo, exceto para Igualitaristas e Feministas que obviamente irão defender que a mulher cristã deve sim substituir a maternidade pela carreira profissional. Pronto. A tragédia está anunciada. Voltando para o nosso subproduto de entretenimento secular meticulosamente produzido para o Streaming…
No final, John é baleado e Jane diz que aceita ter um filho com ele por pena. Já que ele vai morrer logo e ela está encurralada. Trata-se de um final ambíguo, pois não se sabe se eles morreram ou não. O que eu sei é que as boas histórias morreram faz tempo.
-
 @ b12b632c:d9e1ff79
2023-07-19 00:17:02
@ b12b632c:d9e1ff79
2023-07-19 00:17:02Welcome to a new Fractalized episode of "it works but I can do better"!
Original blog post from : https://fractalized.ovh/use-ghost-blog-to-serve-your-nostr-nip05-and-lnurl/
Few day ago, I wanted to set my Ghost blog (this one) as root domain for Fractalized instead of the old basic Nginx container that served my NIP05. I succeed to do it with Nginx Proxy Manager (I need to create a blog post because NPM is really awesome) but my NIP05 was down.
Having a bad NIP05 on Amethyst is now in the top tier list of my worst nightmares.
As a reminder, to have a valid NIP05 on your prefered Nostr client, you need to have a file named "nostr.json" in a folder ".well-known" located in the web server root path (subdomain or domain). The URL shoud look like this http://domain.tld/.well-known/nostr.json
PS : this doesn't work with Ghost as explained later. If you are here for Ghost, skip this and go directly to 1).
You should have these info inside the nostr.json file (JSON format) :
{ "names": { "YourUsername": "YourNPUBkey" } }You can test it directly by going to the nostr.json URL, it should show you the JSON.
It was working like a charm on my previous Nginx and I needed to do it on my new Ghost. I saw on Google that I need to have the .well-known folder into the Ghost theme root folder (In my case I choosed the Solo theme). I created the folder, put my nostr.json file inside it and crossed my fingers. Result : 404 error.
I had to search a lot but it seems that Ghost forbid to server json file from its theme folders. Maybe for security reasons, I don't know. Nevertheless Ghost provide a method to do it (but it requires more than copy/paste some files in some folders) => routes
In the same time that configuring your NIP05, I also wanted to setup an LNURL to be zapped to pastagringo@fractalized.ovh (configured into my Amethyst profile). If you want more infromation on LNURL, it's very well explained here.
Because I want to use my Wallet of Satoshi sats wallet "behind" my LNURL, you'll have to read carefuly the EzoFox's blog post that explains how to retrieve your infos from Alby or WoS.
1) Configuring Ghost routes
Add the new route into the routes.yaml (accessible from "Settings" > "Labs" > "Beta features" > "Routes" ; you need to download the file, modify it and upload it again) to let him know where to look for the nostr.json file.
Here is the content of my routes.yaml file :
``` routes: /.well-known/nostr.json/: template: _nostr-json content_type: application/json /.well-known/lnurlp/YourUsername/: template: _lnurlp-YourUsername content_type: application/json collections: /: permalink: /{slug}/ template: index
taxonomies: tag: /tag/{slug}/ author: /author/{slug}/ ```
=> template : name of the file that ghost will search localy
=> content_type : file type (JSON is required for the NIP05)
The first route is about my NIP05 and the second route is about my LNURL.
2) Creating Ghost route .hbs files
To let Ghost serve our JSON content, I needed to create the two .hbs file filled into the routes.yaml file. These files need to be located into the root directory of the Ghost theme used. For me, it was Solo.
Here is there content of both files :
"_nostr-json.hbs"
{ "names": { "YourUsername": "YourNPUBkey" } }"_lnurlp-pastagringo.hbs" (in your case, _lnurlp-YourUsername.hbs)
{ "callback":"https://livingroomofsatoshi.com/api/v1/lnurl/payreq/XXXXX", "maxSendable":100000000000, "minSendable":1000, "metadata":"[[\"text/plain\",\"Pay to Wallet of Satoshi user: burlyring39\"],[\"text/identifier\",\"YourUsername@walletofsatoshi.com\"]]", "commentAllowed":32, "tag":"payRequest", "allowsNostr":true, "nostrPubkey":"YourNPUBkey" }After doing that, you almost finished, you just have to restart your Ghost blog. As I use Ghost from docker container, I just had to restart the container.
To verify if everything is working, you have to go in the routes URL created earlier:
https://YourDomain.tld/.well-known/nostr.jsonand
https://YourDomain.tld/.well-known/lnurlp/YourUsernameBoth URL should display JSON files from .hbs created ealier.
If it's the case, you can add your NIP05 and LNURL into your Nostr profile client and you should be able to see a valid tick from your domain and to be zapped on your LNURL (sending zaps to your WoS or Alby backend wallet).
Voilààààà
See you soon in another Fractalized story!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Castas hindus em nova chave
Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ b12b632c:d9e1ff79
2023-07-17 22:09:53
@ b12b632c:d9e1ff79
2023-07-17 22:09:53Today I created a new item (NIP05) to sell into my BTCpayserver store and everything was OK. The only thing that annoyed me a bit is that when a user pay the invoice to get his NIP on my Nostr Paid Relay, I need to warn him that he needs to fill his npub in the email info required by BTCpayserver before paying. Was not so user friendly. Not at all.
So I checked if BTCpayserver is able to create custom input before paying the invoice and at my big surprise, it's possible ! => release version v1.8
They even use as example my need from Nostr to get the user npub.
So it's possible, yes, but with at least the version 1.8.0. I checked immediately my BTCpayserver version on my Umbrel node and... damn... I'm in 1.7.2. I need to update my local BTCpayserver through Umbrel to access my so wanted BTCpayserver feature. I checked the local App Store but I can't see any "Update" button or something. I can see that the version installed is well the v1.7.2 but when I check the latest version available from the online Umbrel App Store. I can see v1.9.2. Damn bis.
I searched into the Umbrel Community forum, Telegram group, Google posts, asked the question on Nostr and didn't have any clue.
I finally found the answer from the Umbrel App Framework documention :
sudo ./scripts/repo checkout https://github.com/getumbrel/umbrel-apps.gitSo I did it and it updated my local Umbrel App Store to the latest version available and my BTCpayserver.
After few seconds, the BTCpaysever local URL is available and I'm allowed to login => everything is OK! \o/
See you soon in another Fractalized story!
-
 @ ddf03aca:5cb3bbbe
2024-11-20 22:34:52
@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions.
Subscriptions with Cashu
One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that?
However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this:
-
Overpaying:
To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. -
Full Interactivity:
In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends.
Enter Locking Scripts
One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone.
A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key.
To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token.
With these tools, we can now create non-interactive payment streams!
One Missing Piece…
Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams.
The Grand Finale: Payment Streams
Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender.
Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.
Example: Renting a VPS
Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work:
- Construct a token worth 7,000 sats to cover the entire week.
- Divide the token into 7 proofs, each worth 1,000 sats.
- Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key.
- The first proof has a locktime of
now. - The second proof has a locktime of
now + 1 day. - The third proof has a locktime of
now + 2 days, and so on.
When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on.
At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver.
With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds.
Thank you for reading. Make sure to leave a nut if you enjoyed this :)
-
-
 @ 04222fa1:634e9de5
2024-11-20 22:00:58
@ 04222fa1:634e9de5
2024-11-20 22:00:58So much information about US foreign policy, NATO and the installation of the current Ukrainian government.
I'm just saying, is the western legacy media reporting a one sided account?
originally posted at https://stacker.news/items/776252
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Shitcoinery
IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.
The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.
Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.
See also
- Bitcoin, the only non-shitcoin
-
 @ 0e501ec7:de5ef3a4
2024-11-20 21:52:58
@ 0e501ec7:de5ef3a4
2024-11-20 21:52:58Deux hommes, fils et père, die graag gaan fietsen. Als echt professionele fietsers natuurlijk, vol in pak, snelle koersfietsen. Ik stond in hun straat te sukkelen met een platte band, ik had geen pomp, en geen vorken om mijn band op te heffen. De vader, Dominique, stopte en zei: t'as le pneu crevé? Monte avec nous! Daar syonden ze te wachten aan de open garagepoort. Ze hadden net 50km gedaan, op het gemak zeiden ze, ze hadden veel gebabbeld. Ze herstelden met veel plezier mijn band, we babbelden wat over mijn tocht, over fietsen, over wat erna. In gebrekkig Frans van mijn kant hé natuurlijk. Gaspard studeert meubelmaker (Menuserie). Dominique vroeg of ik water wou, ik zei eerst nee, dan ja, dan vroeg hij of ik nog iets wou, ik zei eerst nee, dan ja, en hij kwam terug met een zak vol fruit en repen. Ik aanvaarde ze, terugkrabbelen was het te laat voor en ik kon ze echt wel gebruiken. Hij zei: als je nog eens in de buurt bent, kom dan hallo zeggen, ik zei ja dan kunnen we samen een toertje maken. Ze vroegen nog of ik instagram had, en toen vertrok ik weer. Ik voelde me nog slecht over het aanvaarden van zo veel hulp, maar ach, wat een fijne ontmoeting.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Economics
Just a bunch of somewhat-related notes.
- notes on "Economic Action Beyond the Extent of the Market", Per Bylund
- Mises' interest rate theory
- Profits, not wages, as the originary factor
- Reisman on opportunity cost
- Money Supply Measurement
- Per Bylund's insight
- Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts
- An argument according to which fractional-reserve banking is merely theft and nothing else
- Conjecture and criticism
- Qual é o economista? (piadas)
- UBI calculations
- Donations on the internet
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28tempreites
My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by http://microjs.com/ at the time and ended up not using the library. Probably no one ever did.
-
 @ 0e501ec7:de5ef3a4
2024-11-20 21:41:43
@ 0e501ec7:de5ef3a4
2024-11-20 21:41:43Ik vertrok eergisteren bij Guillaume en Alice. Ik had niet de tijd om dit af te schrijven, ik werd onderbroken ik weet niet meer waardoor. Dus de dag voor eergisteren vertrok ik bij Guillaume en Alice. Over mijn verblijf daar zal ik later schrijven. Het is ondertussen half 11, 20 november, een maand voor het einde van de Herfst. Ik zit op de trein richting Gent, met fiets en al. Deze reis, of deze etappe van de reis is over. Binnen een uurtje toch. Dan ga ik lekker naar mijn eigen bed, en slaap ik een goeie warme nacht. Het gaat vreemd zijn om weer alleen in een kamer van steen te slapen, al is dat eigenlijk altijd vreemd. Ik ga proberen daar genoeg tijd voor mezelf te pakken, en de dingen die ik geleerd heb niet te vergeten. Ik ga schrijven en voelen ipv te vluchten in Schermtijd. Want ik kan mijn gewoontes veranderen!
Maar nu dus, de laatste dagen van de tocht. Zondag vertrok ik, het was moeilijk afscheid te nemen, ik vind afscheid eigenlijk altijd moeilijk. Maar het is goed om in beweging te blijven, daar ben ik zeker van. Het was dus tijd om te vertrekken, ook omdat ik voelde dat de allergie van het stof (verbouwingen) en de kat mij aan het uitputten was. Tegen dat ik eindelijk op de fiets zat was het al middag, Tim had mij op het laatste nog geholpen om een een verloren bout te kunnen vervangen, mijn zijn daadkracht en improvisatietalent. Het was een mooie fietstocht die dag, en ik heb er zeer van genoten om alleen te fietsen. Ik reed eerst een paar keer mis, en kwam toen bij de bakker aan waar ik baguettes kocht en mijn telefoon liet opladen. Ik dacht veel na, in ontspannen toestand, waarbij ik echt voelde dat ik aan het verwerken was. Soms had ik de neiging om mijn gedachten te proberen onderdrukken, om meer op te letten op de omgeving. Mar onderdrukken is niet leuk, dus probeerde ik gewoon een beetje af te wisselen tussen wegdromen en aandachtig zijn. Dat werkte! Ik schreef zelfs een beetje tijdens de pauzes, wat ik ook heel leuk vond. Op een ander moment wou ik een gedachte of drie echt wel vastleggen tijdens het fietsen, en maakte ik een voice-opname. Eigenlijk was dat ook best leuk :), om zo tegen jezelf te babbelen en weten dat je het binnen onbepaalde tijd weer zal kunnen horen.
Een van mijn pauzes was in een klein associatief cafeetje, dat vroeger een station was (het fietspad was een oud treinspoor, prachtig en rustig fietsen verzekerd!). Ik kocht wat nootjes en dronk een warme choco. Toen ik buitenkwam regende een beetje, en stond de zon laag, zodat het licht geel oranje goud was. Toen ik mij omdraaide zag ik zelfs een regenboog. Toen, en op meerdere momenten, voelde ik echt kriebels in mijn buik voor het landschap en alles dat erbij hoorde. Echt een soort vreugde van samenzijn! Het landschap, de mooie Bocage, en ik.
In de avond kwam ik toe in Caen, het was al donker, en ik had echt een sciencefiction gevoel bij het toekomen in de Woonplaats van de Mens, na de lange tocht door de velden en bossen. De Mens, met zijn gebouwen van Steen, met zijn wegen en drukke verplaatsingen, zijn vele lichtjes. Het voelde vreemd en vertrouwd. Snap je wat ik bedoel? Ik sliep die nacht bij Ilan en zijn familie, Ilan is een jonge low-tech ingenieur die zijn eigen brood bakt en van techno houdt. Echt een top kerel. Ik voelde me goed op mijn gemak daar, en heb veel in het frans gebabbeld!!

-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nix
Pra instalar o neuron fui forçado a baixar e instalar o nix. Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás.
Que sofrimento pra fazer funcionar com o
fish, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal defish-foreign-environment(usando o próprio nix!, já que a outra opção era ooh-my-fishou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto nofish.E aí lembrei também que o
/nix/storefica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí. -
 @ 599f67f7:21fb3ea9
2024-11-20 21:25:38
@ 599f67f7:21fb3ea9
2024-11-20 21:25:38¿Qué es un canal?
Un canal Lightning es simplemente una multifirma 2-de-2 en la cadena. Para abrir un canal, solo enviamos fondos a una transacción multifirma 2-de-2. Esto crea un UTXO y el canal está abierto hasta que este UTXO se gaste. Durante la vida del canal, se crean un montón de transacciones que gastan doblemente la transacción de financiamiento, pero eventualmente una (y solo una) de estas se publicará en la cadena para cerrar el canal. Así que, idealmente, un canal Lightning condensa efectivamente un montón de transacciones en dos transacciones en la cadena: la que lo abre y la que lo cierra. Podríamos decir que así es como Lightning "eleva" las transacciones fuera de la cadena.
Creando un canal
Una transacción de financiamiento para un canal entre Alice y Bob es simplemente una transacción que tiene una salida como sigue:
2 <pubkeyA> <pubkeyB> 2 OP_CHECKMULTISIGDonde
<pubkeyA>es la clave pública de Alice y<pubkeyB>es la de Bob. Entonces, si Alice quiere abrir un canal con Bob, ¿simplemente le envía fondos al script anterior?La respuesta es no, es un poco más complicado que eso. Existe la posibilidad de que Bob desaparezca para siempre y nunca vuelva a firmar ninguna transacción que intente gastar de la transacción de financiamiento. Esto significa que, efectivamente, los fondos de Alice quedarían atrapados en este UTXO para siempre. ¡No es ideal!
Aquí es donde entra una transacción de compromiso. Cubriremos la transacción de compromiso con más detalle en el futuro, pero por ahora lo importante que hay que saber es que una vez que una transacción de financiamiento es confirmada, las transacciones de compromiso definen el estado del canal (es decir, cómo se distribuyen los fondos entre los participantes del canal). Así que, esencialmente, cada transacción de compromiso gasta la transacción de financiamiento como entrada y tiene salidas que definen la distribución de fondos entre los participantes del canal.
Para ver cómo se utilizan estos dos conceptos para negociar la apertura de un canal, se intercambiará una serie de mensajes entre los nodos de Alice y Bob, como se muestra en el diagrama a continuación.

Es un poco como negociar un contrato; cada parte solo firma cuando está contento con los términos. Vamos a revisar cada uno de estos mensajes con más detalle.
open_channel
Alice envía este mensaje a Bob para indicar que quiere abrir un canal con él. Este mensaje contiene varios detalles sobre los requisitos de Alice para el canal. El más importante es
funding_pubkey. Esta es la clave pública que Alice tiene la intención de usar como su clave pública en el script de la transacción de financiamiento.
accept_channel
Si Bob está contento con los requisitos que Alice ha presentado en su oferta de canal, puede enviar de vuelta el mensaje
accept_channel, que también contiene algunos de sus requisitos junto con sufunding_pubkey.
En este punto, Alice tiene todo lo que necesita para construir la transacción de financiamiento. Sin embargo, aún no tiene garantía de que Bob no desaparecerá, lo que haría que sus fondos no se pudieran gastar. Por lo tanto, aún no transmite la transacción de financiamiento. En cambio, lo que necesita es una transacción de compromiso firmada por Bob que gaste de la transacción de financiamiento y divida el saldo del canal en consecuencia. La transacción de financiamiento podría asignar algunos fondos a Bob también, por lo que Bob también querría una transacción de compromiso válida firmada por Alice, en caso de que ella desaparezca.
Entonces, lo que Alice hace ahora es construir la transacción de financiamiento y enviar a Bob el siguiente mensaje:
funding_created

Este mensaje contiene el TXID de la transacción de financiamiento, el índice de salida relevante de la transacción de financiamiento junto con una firma de la transacción de compromiso de Bob. Alice puede construir la transacción de compromiso exacta de Bob utilizando la información que ya conoce.
Ten en cuenta que Bob no puede hacer nada aún con su transacción de compromiso porque está gastando de una transacción que aún no está en la blockchain.
funding_signed

Si Bob está contento, entonces puede enviar a Alice un mensaje
funding_signed, que contiene la firma de Bob para la transacción de compromiso de Alice.Ahora, Alice tiene una transacción de compromiso válida firmada por Bob que puede usar para gastar sus fondos de vuelta a sí misma en caso de que Bob desaparezca. Por lo tanto, es seguro para ella transmitir la transacción de financiamiento.
channel_ready
Tanto Alice como Bob estarán ahora observando la blockchain esperando que la transacción de financiamiento alcance el número deseado de confirmaciones. Una vez que cada uno lo vea, se enviarán mutuamente el mensaje
channel_readyque contiene el ID del canal.
¡El canal ahora está abierto y listo para transacciones!
Revisión
Terminaremos con un breve resumen de los conceptos importantes que hemos aprendido en este capítulo. Siéntete libre de volver aquí en el futuro en caso de que necesites un recordatorio.
- canal: un contrato multifirma 2-de-2 en la cadena utilizado para elevar transacciones fuera de la cadena
- transacción de financiamiento: una transacción multifirma 2-de-2 con un script de salida P2WSH que contiene las claves públicas de ambos participantes del canal
- transacción de compromiso: una transacción que define el estado de un canal, es decir, la distribución de fondos entre los participantes del canal
Referencias
- BOLT2
- LN Things Part 1: Creating a channel por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Bitcoin como um sistema social humano
Afinal de contas, o que é o Bitcoin? Não vou responder a essa pergunta explicando o que é uma "blockchain" ou coisa que o valha, como todos fazem muito pessimamente. A melhor explicação em português que eu já vi está aqui, mas mesmo assim qualquer explicação jamais será definitiva.
A explicação apenas do protocolo, do que faz um programa
bitcoindsendo executado em um computador e como ele se comunica com outros em outros computadores, e os incentivos que estão em jogo para garantir com razoável probabilidade que se chegará a um consenso sobre quem é dono de qual parte de qual transação, apesar de não ser complicada demais, exigirá do iniciante que seja compreendida muitas vezes antes que ele se possa se sentir confortável para dizer que entende um pouco.E essa parte técnica, apesar de ter sido o insight fundamental que gerou o evento miraculoso chamado Bitcoin, não é a parte mais importante, hoje. Se fosse, várias dessas outras moedas seriam concorrentes do Bitcoin, mas não são, e jamais poderão ser, porque elas não estão nem próximas de ter os outros elementos que compõem o Bitcoin. São eles:
- A estrutura
O Bitcoin é um sistema composto de partes independentes.
Existem programadores que trabalham no protocolo e aplicações, e dia após dia novos programadores chegam e outros saem, e eles trabalham às vezes em conjunto, às vezes sem que um se dê conta do outro, às vezes por conta própria, às vezes pagos por empresas interessadas.
Existem os usuários que realizam validação completa, isto é, estão rodando algum programa do Bitcoin e contribuindo para a difusão dos blocos, das transações, rejeitando usuários malignos e evitando ataques de mineradores mal-intencionados.
Existem os poupadores, acumuladores ou os proprietários de bitcoins, que conhecem as possibilidades que o mundo reserva para o Bitcoin, esperam o dia em que o padrão-Bitcoin será uma realidade mundial e por isso mesmo atributem aos seus bitcoins valores muito mais altos do que os preços atuais de mercado, agarrando-se a eles.
Especuladores de "criptomoedas" não fazem parte desse sistema, nem tampouco empresas que aceitam pagamento em bitcoins para imediatamente venderem tudo em troca de dinheiro estatal, e menos ainda gente que usa bitcoins e a própria marca Bitcoin para aplicar seus golpes e coisas parecidas.
- A cultura
Mencionei que há empresas que pagam programadores para trabalharem no código aberto do BitcoinCore ou de outros programas relacionados à rede Bitcoin -- ou mesmo em aplicações não necessariamente ligadas à camada fundamental do protocolo. Nenhuma dessas empresas interessadas, porém, controla o Bitcoin, e isso é o elemento principal da cultura do Bitcoin.
O propósito do Bitcoin sempre foi ser uma rede aberta, sem chefes, sem política envolvida, sem necessidade de pedir autorização para participar. O fato do próprio Satoshi Nakamoto ter voluntariamente desaparecido das discussões foi fundamental para que o Bitcoin não fosse visto como um sistema dependente dele ou que ele fosse entendido como o chefe. Em outras "criptomoedas" nada disso aconteceu. O chefe supremo do Ethereum continua por aí mandando e desmandando e inventando novos elementos para o protocolo que são automaticamente aceitos por toda a comunidade, o mesmo vale para o Zcash, EOS, Ripple, Litecoin e até mesmo para o Bitcoin Cash. Pior ainda: Satoshi Nakamoto saiu sem nenhum dinheiro, nunca mexeu nos milhares de bitcoins que ele gerou nos primeiros blocos -- enquanto os líderes dessas porcarias supramencionadas cobraram uma fortuna pelo direito de uso dos seus primeiros usuários ou estão aí a até hoje receber dividendos.
Tudo isso e mais outras coisas -- a mentalidade anti-estatal e entusiasta de sistemas p2p abertos dos membros mais proeminentes da comunidade, por exemplo -- faz com que um ar de liberdade e suspeito de tentativas de centralização da moeda sejam percebidos e execrados.
- A história
A noção de que o Bitcoin não pode ser controlado por ninguém passou em 2017 por dois testes e saiu deles muito reforçada: o primeiro foi a divisão entre Bitcoin (BTC) e Bitcoin Cash (BCH), uma obra de engenharia social que teve um sucesso mediano em roubar parte da marca e dos usuários do verdadeiro Bitcoin e depois a tentativa de tomada por completo do Bitcoin promovida por mais ou menos as mesmas partes interessadas chamada SegWit2x, que fracassou por completo, mas não sem antes atrapalhar e difundir mentiras para todos os lados. Esses dois fracassos provaram que o Bitcoin, mesmo sendo uma comunidade desorganizada, sem líderes claros, está imune à captura por grupos interessados, o que é mais um milagre -- ou, como dizem, um ponto de Schelling.
Esse período crucial na história do Bitcoin fez com ficasse claro que hard-forks são essencialmente incompatíveis com a natureza do protocolo, de modo que no futuro não haverá a possibilidade de uma sugestão como a de imprimir mais bitcoins do que o que estava programado sejam levadas a sério (mas, claro, sempre há a possibilidade da cultura toda se perder, as pessoas esquecerem a história e o Bitcoin ser cooptado, eis a importância da auto-educação e da difusão desses princípios).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28My stupid introduction to Haskell
While I was writing my first small program on Haskell (really simple, but functional webapp) in December 2017 I only knew vaguely what was the style of things, some basic notions about functions, pure functions and so on (I've read about a third of LYAH).
An enourmous amount of questions began to appear in my head while I read tutorials and documentation. Here I present some of the questions and the insights I got that solved them. Technically, they may be wrong, but they helped me advance in the matter, so I'm writing them down while I still can -- If I keep working with Haskell I'll probably get to know more and so my new insights will replace the previous ones, and the new ones won't be useful for total begginers anymore.
Here we go:
- Why do modules have odd names?
- modules are the things you import, like
Data.Time.ClockorWeb.Scotty. - packages are the things you install, like 'time' or 'scotty'
- packages can contain any number of modules they like
- a module is just a collection of functions
- a package is just a collection of modules
- a package is just name you choose to associate your collection of modules with when you're publishing it to Hackage or whatever
- the module names you choose when you're writing a package can be anything, and these are the names people will have to
importwhen they want to use you functions- if you're from Javascript, Python or anything similar, you'll expect to be importing/writing the name of the package directly in your code, but in Haskell you'll actually be writing the name of the module, which may have nothing to do with the name of the package
- people choose things that make sense, like for
aesoninstead ofimport Aesonyou'll be doingimport Data.Aeson,import Data.Aeson.Typesetc. why theData? because they thought it would be nice. dealing with JSON is a form of dealing with data, so be it. - you just have to check the package documentation to see which modules it exposes.
- What is
data User = User { name :: Text }? - a data type definition. means you'll have a function
Userthat will take a Text parameter and output aUserrecord or something like that. - you can also have
Animal = Giraffe { color :: Text } | Human { name :: Text }, so you'll have two functions, Giraffe and Human, each can take a different set of parameters, but they will both yield an Animal.- then, in the functions that take an Animal parameter you must typematch to see if the animal is a giraffe or a human.
- What is a monad?
- a monad is a context, an environment.
- when you're in the context of a monad you can write imperative code.
- you do that when you use the keyword
do. - in the context of a monad, all values are prefixed by the monad type,
- thus, in the
IOmonad allTextisIO Textand so on. - some monads have a relationship with others, so values from that monad can be turned into values from another monad and passed between context easily.
- for exampĺe, scotty's
ActionMandIO.ActionMis just a subtype ofIOor something like that. - when you write imperative code inside a monad you can do assignments like
varname <- func x y - in these situations some transformation is done by the
<-, I believe it is that the pure value returned byfuncis being transformed into a monad value. so iffuncreturnsText, now varname is of typeIO Text(if we're in the IO monad).- so it will not work (and it can be confusing) if you try to concatenate functions like
varname <- transform $ func x y, but you can somehow do varname <- func x yothervarname <- transform varname- or you can do other fancy things you'll get familiar with later, like
varname <- fmap transform $ func x y - why? I don't know.
- so it will not work (and it can be confusing) if you try to concatenate functions like
- How do I deal with Maybe, Either or other crazy stuff? "ok, I understand what is a Maybe: it is a value that could be something or nothing. but how do I use that in my program?"
- you don't! you turn it into other thing. for example, you use fromMaybe, a function that takes a default value and that's it. if your
MaybeisJust xyou getx, if it isNothingyou get the default value.- using only that function you can already do whatever there is to be done with Maybes.
- you can also manipulate the values inside the
Maybe, for example: - if you have a
Maybe PersonandPersonhas anamewhich isText, you can apply a function that turnsMaybe PersonintoMaybe TextAND ONLY THEN you apply the default value (which would be something like the"unnamed") and take the name from inside theMaybe.
- basically these things (
Maybe,Either,IOalso!) are just tags. they tag the value, and you can do things with the values inside them, or you can remove the values.- besides the example above with Maybes and the
fromMaybefunction, you can also remove the values by usingcase-- for example: case x ofLeft error -> errorRight success -> success
case y ofNothing -> "nothing!"Just value -> value
- (in some cases I believe you can't remove the values, but in these cases you'll also don't need to)
- for example, for values tagged with the IO, you can't remove the IO and turn these values into pure values, but you don't need that, you can just take the value from the outside world, so it's a IO Text, apply functions that modify that value inside IO, then output the result to the user -- this is enough to make a complete program, any complete program.
- besides the example above with Maybes and the
- JSON and interfaces (or instances?)
- using Aeson is easy, you just have to implement the
ToJSONandFromJSONinterfaces. - "interface" is not the correct name, but I don't care.
ToJSON, for example, requires a function namedtoJSON, so you doinstance ToJSON YourType wheretoJSON (YourType your type values) = object []... etc.
- I believe lots of things require interface implementation like this and it can be confusing, but once you know the mystery of implementing functions for interfaces everything is solved.
FromJSONis a little less intuitive at the beggining, and I don't know if I did it correctly, but it is working here. Anyway, if you're trying to do that, I can only tell you to follow the types, copy examples from other places on the internet and don't care about the meaning of symbols.
See also
-
 @ 5d4b6c8d:8a1c1ee3
2024-11-20 19:19:23
@ 5d4b6c8d:8a1c1ee3
2024-11-20 19:19:23We've made it to the middle of the Group Play portion of the Emirates Cup. Sadly, one of our party didn't make it this far and two others have sustained serious wounds.
It's probably worth thinking about who will still be standing come the Knockout Round. Remember that only eight teams advance.
Games (Tournament Standings)
- Nets (1-1) @ 76ers (0-2)
- Celtics (1-1) @ Wizards (0-1)
- Warriors (2-0) @ Pelicans (1-1)
- Pacers (0-1) @ Bucks (1-0)
- Hawks (2-0) @ Bulls (0-1)
- Blazers (1-0) @ Rockets (1-0)
- Mavs (1-1) @ Nuggets (1-1)
- Kings (0-1) @ Clippers (0-1)
I never could have imagined wishing that I still had the Hawks available for a pick, but here we are. I'm leaning towards the Kings.
Prize
49,293 sats and counting! (That'll put some inbound liquidity on my channel)
originally posted at https://stacker.news/items/776040
-
 @ e968e50b:db2a803a
2024-11-20 19:03:43
@ e968e50b:db2a803a
2024-11-20 19:03:43Braiins Boiler Room
Braiins's mining pool has this API where you can monitor all of your sweet worker stats.
I started making a boiler room themed dashboard for anybody looking to have all these stats in one spot. You can see how all of your miners are doing and I ran some sophisticated equations (division, multiplication, other hardcore arithmetic) to let you see how your miners are doing in relation to each other.
Here's the repo for you to use.
Use it. Enjoy it. Lemme know what you think. My goal is to turn all of those stats into little retro-future gauges. I want it to look really steam punk. My wife says the Art Deco font isn't steam punk, so maybe it's just going to be 20s themed. IDK Are there any other features you'd want?
Also, I slapped this together pretty quick, including the README so lemme know if you need help running it.
Fun fact: If you look at the pic, as of today, my mining revenue (with Braiins) is less than 15,000 sats more than my stacker news revenue. They're neck and neck!
originally posted at https://stacker.news/items/776023
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ 6bae33c8:607272e8
2024-11-20 18:49:54
@ 6bae33c8:607272e8
2024-11-20 18:49:54It’s fun to do this when you’re on a roll, but after blowing Q3 with a 1-4 week, I feel like Kamala Harris when she had to pivot to the “Hitler” smears — the joy is gone!Seriously though, there’s nothing else to do but get back on the bull.
Steelers at Browns — I imagine this will be something like Steelers -6.5, but I like the Browns here at home off the short week against a team that just beat its main division rival. I won’t use it though because it’s a Thursday game, and I like to get my picks in Friday night.
Chiefs at Panthers — Chiefs -8.5 is my guess. I’d probably stay away, but if I used it I’d take the Chiefs off their loss to the Bills.
Vikings at Bears — The Bears lost in the most brutal way last week. I’ll say Vikings -1.5 and stay away.
Titans at Texans — I’ll make this Titans +8.5 and probably avoid.
Lions at Colts — Let’s go Lions -8 and probably take the Colts. The Lions are great, but this is a good sell-high.
Patriots at Dolphins — Let’s say Patriots +6.5 and stay away. I like both teams of late.
Buccaneers at Giants — Make it Bucs -6. Tommy DeVito is tank mode. Maybe take the Bucs.
Cowboys +8 at Killer Redskins — This is a stay away, but if I had to pick (which I do in my pool), I’ll probably take the KRs.
Broncos at Raiders — The Broncos are actually decent. I’ll make it -5.5, but probably hold my nose and take the Raiders if pressed.
49ers at Packers — 49ers coming off a brutal loss, Packers a lucky win. This depends somewhat on the statuses of Nick Bosa and George Kittle, so I’ll guess 49ers +1.5 and stay away for now.
Cardinals at Seahawks — I’ll say Cardinals -2.5 and lay the wood. Cardinals are good.
Eagles at Rams — I’d say Eagles -1.5 and probably take the Rams. The Eagles are a sell-high.
Ravens at Chargers — I’d make it Ravens -2.5 and lay the wood. The Ravens should have won last week in Pittsburgh.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A list of things artificial intelligence is not doing
If AI is so good why can't it:
- write good glue code that wraps a documented HTTP API?
- make good translations using available books and respective published translations?
- extract meaningful and relevant numbers from news articles?
- write mathematical models that fit perfectly to available data better than any human?
- play videogames without cheating (i.e. simulating human vision, attention and click speed)?
- turn pure HTML pages into pretty designs by generating CSS
- predict the weather
- calculate building foundations
- determine stock values of companies from publicly available numbers
- smartly and automatically test software to uncover bugs before releases
- predict sports matches from the ball and the players' movement on the screen
- continuously improve niche/local search indexes based on user input and and reaction to results
- control traffic lights
- predict sports matches from news articles, and teams and players' history
This was posted first on Twitter.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The "Drivechain will replace altcoins" argument
The argument that Drivechain will replace shitcoins is not that people will sell their shitcoins or that the existing shitcoins will instantly vanish. The argument is about a change at the margin that eventually ends up killing the shitcoins or reducing them to their original insignificance.
What does "at the margin" mean? For example, when the price of the coconut drops a little in relation to bananas, does that mean that everybody will stop buying bananas and will buy only coconuts now? No. Does it mean there will be zero increase in the amount of coconuts sold? Also no. What happens is that there is a small number of people who would have preferred to buy coconuts if only they were a little less expensive but end up buying bananas instead. When the price of coconut drops these people buy coconuts and don't buy bananas.
The argument is that the same thing will happen when Drivechain is activated: there are some people today (yes, believe me) that would have preferred to work within the Bitcoin ecosystem but end up working on shitcoins. In a world with Drivechain these people would be working on the Bitcoin ecosystem, for the benefit of Bitcoin and the Bitcoiners.
Why would they prefer Bitcoin? Because Bitcoin has a bigger network-effect. When these people come, they increase Bitocin's network-effect even more, and if they don't go to the shitcoins they reduce the shitcoins' network-effect. Those changes in network-effect contribute to bringing others who were a little further from the margin and the thing compounds until the shitcoins are worthless.
Who are these people at the margin? I don't know, but they certainly exist. I would guess the Stark people are one famous example, but there are many others. In the past, examples included Roger Ver, Zooko Wilcox, Riccardo Spagni and Vitalik Buterin. And before you start screaming that these people are shitcoiners (which they are) imagine how much bigger Bitcoin could have been today if they and their entire communities (yes, I know, of awful people) were using and working for Bitcoin today. Remember that phrase about Bitcoin being for enemies?
But everything that has been invented in the altcoin world is awful, we don't need any of that!
You and me should not be the ones judging what is good and what is not for others, but both you and me and others will benefit if these things can be done in a way that increases Bitcoin network-effect and pays fees to Bitcoin miners.
Also, there is a much stronger point you may have not considered: if you believe all altcoiners are scammers that means we have only seen the things that were invented by scammers, since all honest people that had good ideas decided to not implement them as the only way to do it would be to create a scammy shitcoin. One example is Bitcoin Hivemind.
If it is possible to do these ideas without creating shitcoins we may start to see new things that are actually good.
-
 @ 000002de:c05780a7
2024-11-20 18:47:13
@ 000002de:c05780a7
2024-11-20 18:47:13The 10th amendment to the US Constitution says the following.
The powers not delegated to the United States by the Constitution, nor prohibited by it to the States, are reserved to the States respectively, or to the people.
When Obama or Biden is in office Democrats seem to believe in a strong federal government. States that oppose the power of the feds over their state's rights are Neo-confederate racists. But something magical occurs when the Democrats lose power. The suddenly discover states rights! This is playing out all over again. Its fun to watch these clowns expose their hypocrisy.
Gavin Newsom is "Trump proofing" California he says. He's also changing his tune on many other issues but that's another topic(in his preparation to run for President in 2028).
The Republicans play the same game. When they hold power many of that party want a nation ban on whatever. They suddenly don't care about the 10th amendment.
If you can't see this hypocrisy in both sides you might need to unplug from the Matrix for a while. Its interesting to me that after over ten years of not being on either side how blind partisans seem to be about reality.
originally posted at https://stacker.news/items/776002
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Classless Templates
There are way too many hours being wasted in making themes for blogs. And then comes a new blog framework, it requires new themes. Old themes can't be used because they relied on different ways of rendering the website. Everything is a mess.
Classless was an attempt at solving it. It probably didn't work because I wasn't the best person to make themes and showcase the thing.
Basically everybody would agree on a simple HTML template that could fit blogs and simple websites very easily. Then other people would make pure-CSS themes expecting that template to be in place.
No classes were needed, only a fixed structure of
header.main,articleetc.With flexbox and grid CSS was enough to make this happen.
The templates that were available were all ported by me from other templates I saw on the web, and there was a simple one I created for my old website.
-
 @ 5d4b6c8d:8a1c1ee3
2024-11-20 17:31:11
@ 5d4b6c8d:8a1c1ee3
2024-11-20 17:31:11Everyone survived!
That Cavs vs Celtics game was really good. Even though the Cavs historic winning streak came to an end, I was very impressed that they got back into that game. Normally, when the Celtics are shooting the lights out like that, the game is a complete blowout.
@siggy47 barely got out alive, with the Nets only winning by one point. However, that gives him lots of good teams to choose from going forward.
Not having a center finally caught up with OKC. Why don't they use some of those picks to trade for one?
I haven't seen any of the highlights or anything, but the Lakers improved to 2-0 in the tournament, with very beatable Suns and Thunder teams left to play. We'll see if picking the defending champs comes back to bite people in the future.
@grayruby's daughter hit on 4/6 of her picks, which leads me to assume he didn't allow her to participate out of fear of humiliation.
I'll tally up the victory pot for the picks post, but we're still sitting at about 50k for the winner.
originally posted at https://stacker.news/items/775864
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Um algoritmo imbecil da evolução
Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente.
No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua.
É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar.
Porém, há apenas duas opções:
- Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula.
- Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//.
Acredito que isso seja uma enunciação decente do argumento "no free lunch" aplicado à crítica do darwinismo por William Dembski.
A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal.
Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade.
Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela.
Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não?
-
 @ f4bf1fb5:b428f8d5
2024-11-20 17:05:05
@ f4bf1fb5:b428f8d5
2024-11-20 17:05:05On DEG Mods, mod creators and enjoyers can benefit from tips, allowing them to earn money directly from those who appreciate their work or comments, and 100% of what's tipped goes to the one being tipped (excluding the processing fee of the transaction, which is extremely negligible). We don't take any percentage of this process, unless you choose to and at whichever amount you like.
Did you discover a mod that you found enjoyable, useful, or intriguing, and you'd like to show your appreciation with a $10 tip? You can do that. Choose to give 100% of your tip directly to the creator, or opt for a 90% share for them, with the remaining 10% supporting DEG Mods. You can also reverse the split if you prefer. It's entirely up to you how you'd like to allocate the tip.
The elephant in the room
Yes, we're using Bitcoin as the main currency and monetary system on the site, and we're aware of the general public's perception of Bitcoin and the general Cryptocurrency space. We have pretty solid reasons why we're utilizing Bitcoin as the monetary infrastructure for DEG Mods instead of traditional payment systems with fiat currency, like USD/EUR, and the banking system, like Visa or Mastercard.
DEG Mods is built around the idea of censorship-resistance and being permissionless, not just anti-censorship, with that in mind, we didn't want to use a system, and in this case a monetary system, where some third party can come in and threat the site, its users and creators, to self-censor or else suffer the consequences of everyone's money frozen, stolen, or not being able to send or receive. There are many examples of such cases.
We wanted to use something where people actually own their money, not have it controlled by anyone, and have people freely transact with anyone they want, whenever they want, with whichever amount they want to utilize, and not worry about any kind of censorship.
That's why why we went with Bitcoin, with the utilization of the Lightning Network. All of this is possible with it. And we didn't go with any other Cryptocurrency, not even create our own currency and massively benefit from it, because we wanted to use the most trusted, verifiably sound, and strongest currency in the world that's the most censorship-resistant one out there, and not a potential one where people would have a higher chance of thinking that its a scam. That's why, generally speaking, many differentiate between 'Bitcoin' and 'Crypto'.
Properly used, you completely own your money, and nobody can take it away from you or stop you from transacting with others. Now, let's get back on topic.
How to set up and enable getting tips
You need to download and install a Bitcoin Lightning Wallet app (suggestions: Lifpay or Wallet of Satoshi) on your mobile device, where where it supports and provides you with a Lightning address. Once you have obtain such an address, you can go ahead and add that to the 'Lightning Address' field in the profile settings page on DEG Mods.
After that, save/publish your changes and you're done. People can now tip you directly on your profile or tip you via your mod posts.
How to exchange your tipped Bitcoin to other currencies like USD/EUR
So you got tipped a few times and feel like you want to exchange what you've received so far into other currencies to spend them. We won't have a full-blown guide on this, at least not now, but the general idea is that you'd go to an exchange site/app (Suggestion: Binance, or if you're in the USA then CashApp or Strike might work better for you), send them there, and have them exchanged there to whatever currency you like, then withdraw it to your bank or payment service that you use (or keep them there if its already the payment system you use already).
You can also go to physical exchange stores if they support the exchange of that currency in your country.
How to tip creators and other users
As a user that wants to tip creators or other users, you'd do that by first having a Bitcoin Lighting Wallet (similar suggestions as shared above), and then you'd need to fill that up, which is basically the reverse process of above, and once you have an amount of Bitcoin (or 'Sats', think 'Cents') in your Wallet app, you can now go ahead and start tipping creators or other users.
You tip others by tapping on the lightning icon you'll see throughout the site, either for a comment, a profile, or a mod post next to the reaction buttons, which will trigger a popup asking you to enter an amount in Sats and then you'd generate the QR code. In your Wallet app, tap the send button and scan that QR and send away. Done.
Keep in mind that other users or creators might tip you, so you don't necessarily have to go through that process of exchanging traditional currencies to Bitcoin/sats, so its definitely worth at least obtaining a Bitcoin Lightning Address and adding it your 'account' here on DEG Mods, in the off chance that someone tips you when you comment on a post for example. Why leave money on the table, as they say.
Questions and Answers
We'll continue updating this blog post when new information comes along, but here are some questions and answers regarding this topic.
Did you really have to use Bitcoin/Crypto? Why couldn't you have PayPay, Stripe, or some other traditional payment method?
This is answered at the start of this post, but in gist: So we, creators, and users, aren't screwed over and be forced to censor ourselves.
Do I have to use Bitcoin?
No, you can use DEG Mods without ever touching it, and you can also add your own payment links (like PayPal, CashApp, Kofi, Patreon, etc) in your profile (we'll be adding a linktree-like system at some point to make this process easy), and people can easily find those link and tip you there, though those tip buttons are only for Bitcoin.
Will there be more ways to get money later, or is it just tipping mod posts and profiles?
Yes, there'll be more ways for creators to acquire money from users in the future, for reasons other than 'thank you creating this mod'.
-
 @ ac8bb9b0:70278acc
2024-11-20 16:28:11
@ ac8bb9b0:70278acc
2024-11-20 16:28:11Chef's notes
Optional: Creamy Cilantro-Basil Ranch: In a blender, blend 1/2 cup plain Greek yogurt or sour cream, 1/3 cup mayo, 2 tablespoons buttermilk, 1 cup fresh cilantro, 1/2 cup fresh basil, 1/4 cup fresh chopped chives, 2 teaspoons Worcestershire, 1 teaspoon garlic powder, 1 teaspoon onion powder, 1/4 teaspoon cayenne, and a pinch each of kosher salt and black pepper. Blend until creamy.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 15
Ingredients
- 4 (4-6 ounce) salmon filets, cut into bite-size chunks
- 6 tablespoons extra virgin olive oil
- 1 teaspoon smoked paprika
- salt and black pepper
- 1 bunch asparagus, ends trimmed
- 1/2 cup honey
- 2-3 tablespoons hot sauce
- 1-3 teaspoons cayenne pepper
- 3/4 teaspoon chipotle chili powder
- 1/2 teaspoon garlic powder
- 1/2 teaspoon onion powder
- 3-4 cups cooked rice
- 2 avocados, diced
- 1 serrano or jalapeño, sliced
- 1/2 cup fresh cilantro, chopped
- 2 tablespoons chopped fresh dill
- 1/2 cup crumbled feta cheese
- 2 tablespoons extra virgin olive oil
- 1 tablespoon lemon juice
- 1/3 cup toasted seeds, pumpkin, sesame, sunflower, etc.
Directions
-
- Preheat the oven to 450° F.
-
- On a baking sheet, toss the salmon pieces with 3 tablespoons olive oil, paprika, salt, and pepper. Arrange in a single layer. On the other side of the pan, add the asparagus. Toss with 1 tablespoon olive oil, salt, and pepper. Roast 10-15 minutes or until the salmon is just undercooked to your liking.
-
- Meanwhile, make the hot honey. In a sauce pot, warm together the honey, hot sauce, cayenne, chili powder, onion powder, and garlic powder, plus a pinch of salt.
-
- Spoon some of the hot honey over the salmon. Switch the oven to broil and broil until lightly charred and crispy. Spoon over additional hot honey, to your taste.
-
- To make the avocado salsa. Combine avocados, serrano or jalapeño, cilantro, dill, feta cheese, extra virgin olive oil, lemon juice, and toasted seeds in a bowl and season with salt, gently tossing.
-
- Arrange the salmon and asparagus over bowls of rice. Top with salsa.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28OP_CHECKTEMPLATEVERIFYand the "covenants" dramaThere are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-
 @ ac8bb9b0:70278acc
2024-11-20 16:25:18
@ ac8bb9b0:70278acc
2024-11-20 16:25:18Details
- ⏲️ Prep time: 25
- 🍳 Cook time: 20
- 🍽️ Servings: 6
Ingredients
- 1 tablespoon extra virgin olive oil
- 1 medium yellow onion chopped (about 1 1/2 cups)
- 2 teaspoons kosher salt, divided
- 3 tablespoons red curry paste
- 2 tablespoons grated fresh ginger (from a 3-inch piece)
- 3 medium cloves garlic, minced (about 1 tablespoon)
- 4 cups lower-sodium vegetable broth
- 1 1/2 pounds butternut squash, cut into 1 1/2-inch cubes (from 2 [20-ounce] package)
- 1 15.5-ounce can unsweetened coconut milk, well stirred
- 2 tablespoons fresh lime juice (from 1 or 2 limes)
- 6 tablespoons crushed salted peanuts
- Chopped fresh cilantro and crushed red pepper (optional), for serving
Directions
- Heat oil in a large pot over medium. Add onion and 1/2 teaspoon salt; cook, stirring often, until onion starts to brown, 6 to 7 minutes.
- Add curry paste, ginger, and garlic; cook, stirring, until fragrant, about 1 minute. Add broth and 1 teaspoon salt, scraping up browned bits from bottom of pot. Stir in squash. Bring to a simmer over medium-high. Cover and reduce heat to low; simmer until squash is tender, 12 to 15 minutes.
- Remove from heat. Stir in coconut milk, lime juice, and remaining 1/2 teaspoon salt. Use an immersion blender to process until smooth. (Or transfer to a blender, cover with lid, and remove center piece. Place a towel over opening. Process until smooth.)
- Serve sprinkled with peanuts, cilantro, and, if using, crushed red pepper.
-
 @ 8d34bd24:414be32b
2024-11-20 16:16:25
@ 8d34bd24:414be32b
2024-11-20 16:16:25I’ve been studying a lot about end times prophecy because so much seems to be coming together and I believe our time left is short. I’m listening to a sermon series on Daniel and another on Revelation. I’m doing a Bible study on Revelation with the ladies at my church. In general I think our women’s Bible study curriculum is too focused on symbology and isn’t focused enough on what Revelation means for us and our future, but it has been good at pointing me at verses that have clarified my understanding of Revelation.
When trying to understand end times, I keep going back to “Who is Babylon the Great?” As I’ve been reading, I’ve been seeing things that may be clues. I’ll admit that I am not 100% certain in my interpretations, so I’m open to other interpretations and I don’t want anyone to take what I have to say as set in stone. That being said, when I consider what is happening in the world today and what Scripture predicts, the ideas I am about to present really seems to make sense. Hopefully this study will be useful to you even if you don’t agree with my conclusions. I do try to back all of my speculation with Scripture.
Revelation 17-18
I’ve always read Scripture and wondered, “Why is the US not mentioned?” I’ve usually assumed the US has to either be made unimportant on the world stage or be broken up into smaller countries (which is believable with how divided the nation has become). I’m now starting to wonder if the US is mentioned in end times prophecy, but I didn’t see it because it isn’t how I want to think of my country.
And he carried me away in the Spirit into a wilderness; and I saw a woman sitting on a scarlet beast, full of blasphemous names, having seven heads and ten horns. The woman was clothed in purple and scarlet, and adorned with gold and precious stones and pearls, having in her hand a gold cup full of abominations and of the unclean things of her immorality, and on her forehead a name was written, a mystery, “BABYLON THE GREAT, THE MOTHER OF HARLOTS AND OF THE ABOMINATIONS OF THE EARTH.” (Revelation 17: 3-5)
When reading this passage, the first thought is who or what is “Babylon the Great?” Is it a reincarnation of historical Babylon? Historical Babylon was situated in the center of what is modern Iraq. Does that make sense? It doesn’t to me. Is “Babylon the Great” just a figurative representation of evil? I don’t think so, because there are too many references to literal things for that to make sense. Is “Babylon the Great” a different city or nation? I believe this is the most probably interpretation.
And he said to me, “The waters which you saw where the harlot sits, are peoples and multitudes and nations and tongues. And the ten horns which you saw, and the beast, these will hate the harlot and will make her desolate and naked, and will eat her flesh and will burn her up with fire. For God has put it in their hearts to execute His purpose by having a common purpose, and by giving their kingdom to the beast, until the words of God will be fulfilled. The woman whom you saw is the great city, which reigns over the kings of the earth.” (Revelation 17:15-18) {emphasis mine}
Revelation talks of ten horns, being ten kings/kingdoms, that will then hand their authority over to the beast to rule the whole world. Do the ten kings, who give their kingdoms to the beast turn on Babylon because Babylon doesn’t want to submit to the Beast’s worldwide kingdom, but retain her own power? This passage sounds like the 10 horns and the beast will turn on “Babylon the Great” because Babylon will not join the beast’s system. Will it not join because it hates evil? Definitely not! Babylon is referred to as a harlot. The previous passage says, Babylon has “in her hand a gold cup full of abominations and of the unclean things of her immorality,” and that Babylon is “THE MOTHER OF HARLOTS AND OF THE ABOMINATIONS OF THE EARTH.” Why would Babylon the Great not join the rest of this evil cohort? Would it be that Babylon the Great was the world’s only super power and it doesn’t want to give up that power? Now that sounds very believable.
Now I put forth this premise that I don’t want to be true. What world super power currently exists that is resisting joining in a one world government? That sounds a lot like the US, but let us continue to see if this similarity becomes more obvious.
And he cried out with a mighty voice, saying, “Fallen, fallen is Babylon the great! She has become a dwelling place of demons and a prison of every unclean spirit, and a prison of every unclean and hateful bird. For all the nations have drunk of the wine of the passion of her immorality, and the kings of the earth have committed acts of immorality with her, and the merchants of the earth have become rich by the wealth of her sensuality.”
I heard another voice from heaven, saying, “Come out of her, my people, so that you will not participate in her sins and receive of her plagues; for her sins have piled up as high as heaven, and God has remembered her iniquities. Pay her back even as she has paid, and give back to her double according to her deeds; in the cup which she has mixed, mix twice as much for her. To the degree that she glorified herself and lived sensuously, to the same degree give her torment and mourning; for she says in her heart, ‘I sit as a queen and I am not a widow, and will never see mourning.’ For this reason in one day her plagues will come, pestilence and mourning and famine, and she will be burned up with fire; for the Lord God who judges her is strong. (Revelation 18:2-8) {emphasis mine}
Every time I read Revelation 18, I become more convinced that Babylon the Great is likely to be the US.
Let’s start with “For all the nations have drunk of the wine of the passion of her immorality, and the kings of the earth have committed acts of immorality with her.” The US has used its wealth and power to influence nearly every nation in the world. The US gives “aid,” but always with strings attached. They’ll give aid if the nation will support gay marriage. They’ll give aid if the nation will encourage gender transitions. They’ll give aid if the nation will join in a war against a nation that doesn’t do what the US tells it to do. This money for immorality is rampant, but not obvious to everyone because the media doesn’t advertise these actions.
“and the merchants of the earth have become rich by the wealth of her sensuality.” The US is known for her excesses. The government overspends. Her businesses overspend. Her citizens overspend and they believe they are in absolute poverty if they don’t have a car for every adult, a cell phone for everyone over 6, high speed internet, big screen TVs, etc. Even most of the poor in the US have no idea what real poverty looks like. The US buys tons of stuff from nations around the world and the “merchants of the earth have become rich by the wealth of her sensuality.” Has there ever been a nation throughout all of history that lived so extravagantly?
In the previous passage in Revelation 17, it states, “in her hand a gold cup full of abominations and of the unclean things of her immorality.” Could the golden cup be a reference to all of the blessings given to the US since her founding and how the US was founded on Biblical principles, but instead of using the spiritual, geographic, and economic blessings, the US turned to “abominations and of the unclean things,” all of the evils now pushed by the US government, US schools, and US media?
Sadly, “God has remembered her iniquities,” and “To the degree that she glorified herself and lived sensuously, to the same degree give her torment and mourning.” How much does this following verse sound like the US government and US citizens? “I sit as a queen and I am not a widow, and will never see mourning.” They can’t comprehend that the US will ever be anything other than the most powerful nation in the world — militarily, economically, and even morally.
When Babylon the Great is destroyed, Revelation 18 states:
“And the merchants of the earth weep and mourn over her, because no one buys their cargoes any more— cargoes of gold and silver and precious stones and pearls and fine linen and purple and silk and scarlet, and every kind of citron wood and every article of ivory and every article made from very costly wood and bronze and iron and marble, and cinnamon and spice and incense and perfume and frankincense and wine and olive oil and fine flour and wheat and cattle and sheep, and cargoes of horses and chariots and slaves and human lives. The fruit you long for has gone from you, and all things that were luxurious and splendid have passed away from you and men will no longer find them. The merchants of these things, who became rich from her, will stand at a distance because of the fear of her torment, weeping and mourning, saying, ‘Woe, woe, the great city, she who was clothed in fine linen and purple and scarlet, and adorned with gold and precious stones and pearls; for in one hour such great wealth has been laid waste!’ And every shipmaster and every passenger and sailor, and as many as make their living by the sea, stood at a distance, and were crying out as they saw the smoke of her burning, saying, ‘What city is like the great city?’ And they threw dust on their heads and were crying out, weeping and mourning, saying, ‘Woe, woe, the great city, in which all who had ships at sea became rich by her wealth, for in one hour she has been laid waste!’ (Revelation 18:11-19) {emphasis mine}
The saddest point is how Babylon the Great will be destroyed. What hints do we get? From Revelation 17, we read, “she will be burned up with fire.” From Revelation we read, “in one hour such great wealth has been laid waste!”, “they saw the smoke of her burning,” and again “in one hour she has been laid waste!” What could “lay waste” a great nation “in one hour” “with fire?” If all of the nuclear nations in the world (the ten horns and the beast) turned their nuclear weapons on the US and fired simultaneously, this is exactly what you would see.
We’re going to look at another passage and see what else we can find. This next passage I had not previously associated with Babylon the Great, but now think it does refer to both historical Babylon and Babylon the Great.
Jeremiah 50-51
The prophecies in Jeremiah chapters 50 & 51 seem to be predicting two events. One has already happened (Babylon being conquered by the Persians and Israel returning home after a 70 year exile) and one that has not happened (seems to parallel Revelation and what it says about Babylon the Great). Some of the prophecies against Babylon have clearly happened when Persia conquered Babylon. Some of the prophecies here do not seem to have been fulfilled. There are numerous examples of similar situations in predictions of the coming of the Messiah that predict both the first incarnation of Jesus and the 2nd coming at the end of the age. I believe these passages fit that pattern.
Jeremiah 50 & 51 talks about the mother of Babylon and the daughter of Babylon. My theory is that the mother of Babylon is the historical Babylon on the Euphrates River that conquered Israel and took away its people. My more speculative theory is that the daughter of Babylon is the same as Babylon the Great in Revelation. I also am speculating that the evil spirits that influenced historic Babylon will be influencing Babylon the Great in the end times.
Your mother will be greatly ashamed,\ She who gave you birth will be humiliated.\ Behold, she will be the least of the nations,\ A wilderness, a parched land and a desert.\ Because of the indignation of the Lord she will not be inhabited,\ But she will be completely desolate;\ Everyone who passes by Babylon will be horrified\ And will hiss because of all her wounds.\ Draw up your battle lines against Babylon on every side,\ All you who bend the bow;\ Shoot at her, do not be sparing with your arrows,\ For she has sinned against the Lord.\ Raise your battle cry against her on every side!\ She has given herself up, her pillars have fallen,\ Her walls have been torn down.\ For this is the vengeance of the Lord:\ Take vengeance on her;\ **As she has done to others, so do to her. (Jeremiah 50:12-15) {emphasis mine}
In Revelation 17-18 we read about Babylon the Great being destroyed in an hour with fire. This passage states, “All you who bend the bow; Shoot at her, do not be sparing with your arrows.” If you were writing a prophecy about a nuclear attack, to people back in the 600s B.C., how would you write it? Would you maybe mention arrows and bows because they are shot from a distance? Does “All you who bend the bow; Shoot” suggest all nations with nuclear weapons? Maybe.
“Summon many against Babylon,\ All those who bend the bow:\ Encamp against her on every side,\ Let there be no escape.\ Repay her according to her work;\ According to all that she has done, so do to her;\ For she has become arrogant against the Lord,\ Against the Holy One of Israel.\ Therefore her young men will fall in her streets,\ And all her men of war will be silenced in that day,” declares the Lord.\ “Behold, I am against you, O arrogant one,”\ Declares the Lord God of hosts,\ “For your day has come,\ The time when I will punish you.\ The arrogant one will stumble and fall\ With no one to raise him up;\ And I will set fire to his cities\ And it will devour all his environs.” (Jeremiah 50:29-32) {emphasis mine}
I’ve heard many Americans complain that the French are arrogant. They say this, because the French get upset at loud, self absorbed Americans traveling to France and expecting all of the French to speak English. Shouldn’t the people visiting a country at least make an attempt to speak the language of the nation they are visiting?
Americans are known for their arrogance. It is assumed that everyone will know what is happening in America. It is assumed that everyone will speak English to Americans. It is assumed that everyone will be best off if they have a government and culture exactly like ours. It is assumed that the US will always be the most powerful economically and militarily and that nothing we do will change that. Honestly, I don’t think it is possible for a nation to be more arrogant. As an American, I say all of this with sadness
A sword against their horses and against their chariots\ And against all the foreigners who are in the midst of her,\ And they will become women!\ A sword against her treasures, and they will be plundered!\ A drought on her waters, and they will be dried up!\ For it is a land of idols,\ And they are mad over fearsome idols. (Jeremiah 50:37-38) {emphasis mine}
Historical Babylon brought foreigners, who they conquered, back to Babylon and integrated them into their culture. The US has historically let in foreigners and integrated them into her culture. In the past, the US was referred to as a melting pot. Now the foreigners are coming in, but they frequently are not coming in legally and they are frequently not integrating into American society. Many are coming in for freebies or even to do harm to the US. Whatever the case, the division over what to do with all of the illegal aliens entering is dividing the US.
For most of my life, when I read “they will become women,” I assumed that meant the men would become weak and/or fearful, but could this refer to men actually trying to become women by chemical and surgical means? Maybe. God knew this craziness would occur. It may have surprised me, but it didn’t surprise God.
We don’t normally think of Americans as worshipping idols. They don’t normally worship a manmade statue, but they do worship idols, i.e. politicians, athletes, singers, influencers, media, and worldwide power & influence. Sadly, most Americans worship anything and everything except their creator God.
They seize their bow and javelin;\ They are cruel and have no mercy.\ Their voice roars like the sea;\ And they ride on horses,\ Marshalled like a man for the battle\ Against you, O daughter of Babylon. (Jeremiah 50:42) {emphasis mine}
This passage seems very similar to the Revelation 17:15-18. Many nations will attack from a distance, with “bow and javelin.” They will be “cruel and have no mercy … Against you, O daughter of Babylon.” By referring to “daughter of Babylon,” I believe this passage is not referring to historical Babylon, but a nation yet to come, that I am suggesting may be the US.
I will dispatch foreigners to Babylon that they may winnow her\ And may devastate her land;\ For on every side they will be opposed to her\ In the day of her calamity. (Jeremiah 51:2) {emphasis mine}
Could this passage mean the US will be attacked from within by the mass of foreigners in her land while her enemies from beyond her borders attack militarily and economically? Maybe. We do have illegal aliens, illegally entering the nation and being provided for with the hard earned money of American taxpayers to the point of bringing the economy to the breaking point.
Flee from the midst of Babylon,\ And each of you save his life!\ Do not be destroyed in her punishment,\ For this is the Lord’s time of vengeance;\ He is going to render recompense to her.\ *Babylon has been a golden cup in the hand of the Lord*,\ Intoxicating all the earth.\ The nations have drunk of her wine;\ Therefore the nations are going mad**. (Jeremiah 51:6-7) {emphasis mine}
When I read “The nations have drunk of her wine; Therefore the nations are going mad,” I think of how the nations submit to the insane requests made by the US if the nations want her money, loans, weapons, and friendship. So many of the ungodly evils in our nation are pushed on the nations of the globe through American aid and sanctions. Many nations have turned to promoting anti-God actions in order to receive US aid and protection.
I hate thinking this about my nation. I hate seeing what was started as a God fearing nation based on good principles become the largest purveyor of evil in the world. I don’t want the US to be Babylon the Great, but it at least has a lot in common with Babylon the Great.
One thing I’ve noticed in many of the passages in Revelation and in Jeremiah is the command, “Flee from the midst of Babylon, and each of you save his life!” If America is Babylon the Great, at what point would we be called to flee her? Is the call a call to Christians, or is it a call to Jewish people to return to Israel? There have been many Jews leaving the US (and other nations) to move to Israel because of severe antisemitism, but could this call be a call to all who believe in the one true God?
We applied healing to Babylon, but she was not healed;\ Forsake her and let us each go to his own country,\ For her judgment has reached to heaven\ And towers up to the very skies. (Jeremiah 51:9) {emphasis mine}
Now I will give my most speculative and least certain assumption. If the tribulation is near, if the US is Babylon the Great, and if this passage in Jeremiah is referring to the same Babylon discussed in Revelation, what is this “applied healing?” The US has been turning completely away from God. It has been promoting evil as good and calling good “evil.” We just had an election where the American people rejected this radical evil and claim to want to go back to healthier, more sane America. Could the “applied healing to Babylon” be the election of Donald Trump (I am not saying he is anything close to a savior)?
I was just listening to a sermon by R.C. Sproul entitled “Jesus Heals Many.” In it he commented that Jesus was healing many, then went off alone to pray, was reprimanded by His disciples for leaving when so many people were seeking healing, and then Jesus told them He was leaving for another town to preach His message. Jesus was there to share the Gospel, not to just play doctor. Most of the people following Jesus weren’t doing it because they believed He was God, nor were they doing it because they thought He taught the truth; they were following Him to get personal healing. Jesus was their magic genie. They only wanted Him as much as He gave them what they wanted. They didn’t care about what they actually needed or what Jesus demanded.
In the same way, Richard Dawkins, one of the most famous atheists in the world, recently lamented the loss of Christian culture. He enjoyed the loving attitudes, the Christmas spirit, the honesty, etc., but didn’t actually want anything to do with Jesus. Is God offering a moment of reprieve for us to turn back to Him? Do the people only want the Christian culture and Christian blessing without the repentance and without making Jesus Lord? Is this why we will not be healed?
No matter how much people want him to be, Trump is not a real savior and won’t be able to fix most of what ails America. Sadly most people want a return to God’s blessing, but they aren’t willing to repent and submit to the true Savior.
I don’t know if this was what God was trying to communicate to us from more than two millennia ago, but I do think it is something we need to consider. Are we longing for the Christian culture and the blessings that come with it, while being unwilling to accept and submit to the Jesus through whom all of these blessings come?
Sharpen the arrows, fill the quivers!\ The Lord has aroused the spirit of the kings of the Medes,\ Because His purpose is against Babylon to destroy it;\ For it is the vengeance of the Lord, vengeance for His temple. (Jeremiah 51:11) {emphasis mine}
Now this passage may only refer to historical Babylon and it being conquered by the Medes and Persians. I do find it interesting that the nation of the Medes1 were located in what is now Iran, East Turkey, and Afghanistan. There are many experts saying Iran has everything needed to make several nuclear weapons and they already have the missiles needed to launch them. Iran hates and wants to destroy Israel and the US and is now afraid due to the election of Trump and the people he is nominating for Secretary of Defense, Secretary of State, and Ambassador to Israel. Could this passage refer to Iran completing the creation of nuclear weapons in order to attack the US? Maybe.
Lift up a signal against the walls of Babylon;\ Post a strong guard,\ Station sentries,\ Place men in ambush!\ For the Lord has both purposed and performed\ What He spoke concerning the inhabitants of Babylon.\ O you who dwell by many waters,\ *Abundant in treasures*,\ Your end has come**,\ The measure of your end. (Jeremiah 51:12-13) {emphasis mine}
Although historical Babylon was rich and was located between the Euphrates and Tigris Rivers and had many canals for watering the land, this also sounds like the US. The US is between the Pacific and Atlantic Oceans with the Gulf of Mexico to the South. It is full of large, navigable rivers. There has never been a nation as rich and with as many treasures as the US. Once again, I’m not positive, but it would be a great description for the US.
The portion of Jacob is not like these;\ For the Maker of all is He,\ And of the tribe of His inheritance;\ The Lord of hosts is His name.\ He says, “You are My war-club, My weapon of war;\ And with you I shatter nations,\ And with you I destroy kingdoms. (Jeremiah 51:19-20) {emphasis mine}
This passage is less explicit, but still, I can very much see God saying of the US, “You are My war-club, My weapon of war; and with you I shatter nations.”
“But I will repay Babylon and all the inhabitants of Chaldea for all their evil that they have done in Zion before your eyes,” declares the Lord.\ “Behold, I am against you, O destroying mountain,\ Who destroys the whole earth,” declares the Lord,\ “And I will stretch out My hand against you,\ And roll you down from the crags,\ And I will make you a burnt out mountain.\ They will not take from you even a stone for a corner\ Nor a stone for foundations,\ But you will be desolate forever,” declares the Lord. (Jeremiah 51:24-26) {emphasis mine}
I am currently reading a book, “Eye to Eye,” that goes through the actions of Bush Sr, Clinton, and Bush Jr to divide Israel into a two state solution and the natural disasters in America that happened within days of each of the US’s major actions. Will the US help divide Israel leading to her destruction? Has there ever been a nation throughout history that you could really say, “O destroying mountain, who destroys the whole earth?” Before modern times, the empires didn’t affect the whole earth. Great Britain did have influence on the majority of it, but I don’t think you could call it a “destroying mountain” or say it “destroys the whole earth.” The US truly influences every nation on earth, through aid/sanctions and through threat of force.
Once again we see a reference to fire, “I will make you a burnt out mountain.” Will US hegemony be destroyed by a nuclear attack? What else could make it, or any other nation, into “a burnt out mountain.”
The mighty men of Babylon have ceased fighting,\ They stay in the strongholds;\ Their strength is exhausted,\ They are becoming like women;\ Their dwelling places are set on fire,\ The bars of her gates are broken. (Jeremiah 51:30) {emphasis mine}
Is the reason we don’t see the US in end times prophecy because it has “ceased fighting,” stays “in the strongholds,” “is exhausted,” (especially financially) is “becoming like women,” (literally?) and finally “Their dwelling places are set on fire?”(nuclear?)
It makes sense, but it is also possible I am reading too much into it. Even if the US isn’t THE Babylon the Great, just as there are antichrists and THE AntiChrist, I think the US is at least a form of Babylon.
Indeed Babylon is to fall for the slain of Israel,\ As also for Babylon the slain of all the earth have fallen.\ You who have escaped the sword,\ Depart! Do not stay!\ Remember the Lord from afar,\ And let Jerusalem come to your mind*. (Jeremiah 49-50) {emphasis mine}
Once again, I wonder, if this refers to all who trust God or if this call is specifically for the Jews. I don’t feel confident in the answer, but will continue to study Scripture and listen to the Holy Spirit.
Whether you agree or disagree with my conclusions and speculations, I hope this article has made you think and blessed you. I’d love feedback, especially if you have Scripture that either supports or denies my conclusions.
Because end times prophecy is not as clear as the historical parts of the Bible, I know my interpretations have changed as the world has changed and I see how God’s word may be fulfilled. I do believe my understanding is getting closer and closer to what God is trying to tell us as I see things that made zero sense suddenly seem immediately possible as new technologies are created, as national alliances change. and as culture changes. I am looking forward to going home to heaven to be with my God and creator soon. I hope to see you there.
Trust Jesus.\ \ your sister in Christ,
NOTE: Because of some uncertainty in this interpretation, after writing this article, I did a little research before posting. This websites has some interesting information on Babylon the Great.
This site furthers my argument that US is Babylon the Great and brings up some additional arguments that are very good and goes into when Babylon the Great is likely destroyed. I’d recommend reading it.
The only description of Babylon the Great that doesn’t fully seem to correspond to the US is “And in her was found the blood of prophets and of saints and of all who have been slain on the earth.” (Revelation 18:24) The rest of the arguments for why the US isn’t Babylon the Great were either arguments regarding America’s past godliness, not America’s current situation, or Americans that just seemed to not want the US to be Babylon the Great. Sometimes we all fail to see uncomfortable truths.
It is true that Christians are not “slain” in the US. It is also true that when the US has gone to war with many nations, such as Iraq, their actions have led to the end of the church in that nation. There had been a Christian church in Iraq for \~2,000 years, but after the US “liberated” Iraq, the Christian church was basically wiped out in a way that it had not been even under a tyrannical Muslim leader. Similar things have happened elsewhere. It is also true that persecution of Jews and Christians has been getting worse and worse in the US. Will this progression continue to the point of putting believers to death? I hope not, but it is possible.
I’m guessing most of us will eventually see who or what Babylon the Great is before too long, so we will see. Hopefully you will use this to get you thinking about end times and it will spur you on to live a life fully devoted to Jesus.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Per Bylund's insight
The firm doesn't exist because, like Coase said, it is inefficient to operate in a fully open-market and production processes need some bubbles of central planning.
Instead, what happens is that a firm is created because an entrepreneur is doing a new thing (and here I imagine that doing an old thing in a new context also counts as doing a new thing, but I didn't read his book), and for that new thing there is no market, there are no specialized workers offering the services needed, nor other businesses offering the higher-order goods that entrepreneur wants, so he must do all by himself.
So the entrepreneur goes and hires workers and buys materials more generic than he wanted and commands these to build what he wants exactly. It is less efficient than if he could buy the precise services and goods he wanted and combine those to yield the product he envisaged, but it accomplishes the goal.
Later, when that specific market evolves, it's natural that specialized workers and producers of the specific factors begin to appear, and the market gets decentralized.
-
 @ 06639a38:655f8f71
2024-11-20 15:16:42
@ 06639a38:655f8f71
2024-11-20 15:16:42Nostr-PHP
- Added generic
setTags()andsetTag()function to Filter object to be used in request messages from clients to relays. - Did some small improvements in the relay response handling in the websocket client code.
- Trying to send closeMessages trying to the relay to get a close response back. But not any response came back from the relays I’ve tested with.
- I published a new release
1.5.0
Changelog: https://github.com/nostrver-se/nostr-php/compare/1.4.2...1.5.0 - I set up a new relay with transpher at chat.nostr-php.dev. The main goal of the relay is to replace the current Nostr-PHP Telegram group with a relay based chat group (NIP-29). Repo: https://github.com/nostrver-se/chat.nostr-php.dev
- Work in progress, handling TLV with NIP-19 encoded entities: https://github.com/nostrver-se/nostr-php/pull/68
Other stuff
- We received a message from FOSDEM that our submission for a Nostr stand at the conference is accepted! So during the weekend 1st & 2nd of February I will attend FOSDEM volunteering at the Nostr stand with four other Nostriches.
- Testing things out with chachi.cat and with different relays (NIP-29).
- Did some work on a proof-of-concept at /nostrides around this NIP proposal for physical activities: https://github.com/nostr-protocol/nips/pull/1423
- Added generic
-
 @ c73818cc:ccd5c890
2024-11-20 15:07:36
@ c73818cc:ccd5c890
2024-11-20 15:07:36
♾ Il colosso degli investimenti amplia l'adozione delle chain con il lancio del fondo su nuove blockchain, segnalando l'importanza delle RWA nel prossimo ciclo crypto.
👾 BlackRock, leader globale nella gestione di asset, ha annunciato l’estensione del suo fondo money market tokenizzato BUIDL su nuove blockchain oltre a Ethereum. Aptos, Avalanche, Optimism, Polygon e Arbitrum sono state aggiunte, permettendo al fondo di ampliare l’accesso su piattaforme blockchain diversificate e aprendo nuove possibilità per la finanza decentralizzata.
👾 L’espansione, realizzata con l’impegno di Securitize, sottolinea la crescita della tokenizzazione di Real World Assets (RWA). Carlos Domingo, CEO di Securitize, ha evidenziato come l’obiettivo sia la creazione di un ecosistema finanziario digitale in grado di sfruttare appieno i vantaggi della tecnologia blockchain, aumentando così il potenziale d’uso del fondo BUIDL.
👾 Con questa mossa, BlackRock punta a consolidare il ruolo degli asset tokenizzati e a favorire una progressiva migrazione dei mercati tradizionali verso la blockchain. L’espansione su più chain segna l’inizio di un cammino che, nei prossimi anni, potrebbe trasformare il modo in cui vengono gestiti e scambiati gli asset finanziari tradizionali nel settore crypto.
Unisciti al nostro gruppo Telegram Bitget -20% - Mexc no KYC https://lnk.bio/Bitcoin.Report.Italia
BitcoinReportItalia #BlackRock #LarryFink #BUIDL #Ethereum #Aptos #Avalanche #Optimism #Polygon #Arbitrum #RWA #Cripto #Bitcoin