-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ a012dc82:6458a70d
2024-11-15 04:09:04
@ a012dc82:6458a70d
2024-11-15 04:09:04Table Of Content
-
Institutional Adoption
-
Regulatory Clarity
-
Central Bank Digital Currencies (CBDCs)
-
Global Economic Uncertainty
-
Technological Advancements
-
Halving Events
-
Conclusion
-
FAQ
Bitcoin, the world's first and most well-known cryptocurrency, has experienced its fair share of ups and downs since its inception. The market is known for its volatility, with price fluctuations that have left investors both exhilarated and apprehensive. While the past has shown us that Bitcoin's price movements are unpredictable, there are several game-changing events that can significantly impact the cryptocurrency's trajectory and potentially drive the next bull market. In this article, we will explore six key factors that have the potential to shape the future of Bitcoin and fuel its next bull run.
Institutional Adoption Over the past couple of years, we have witnessed a notable increase in institutional adoption of Bitcoin. Renowned companies, financial institutions, and even governments have started to recognize the value and potential of cryptocurrencies. Institutional investors are pouring funds into Bitcoin, either by holding it directly or through investment vehicles like futures contracts and exchange-traded funds (ETFs). The participation of institutional players brings stability, liquidity, and credibility to the market, attracting more investors and potentially driving up the price of Bitcoin.
Regulatory Clarity
Regulatory uncertainty has been a significant concern for the cryptocurrency market. Clear and favorable regulations can have a transformative effect on Bitcoin's future. As governments and regulatory bodies around the world establish frameworks that provide clarity on how cryptocurrencies will be treated, it will reduce the perceived risks associated with investing in Bitcoin. Greater regulatory certainty will encourage more mainstream investors and institutions to enter the market, boosting demand and potentially igniting a new bull market.
Central Bank Digital Currencies (CBDCs)
The rise of Central Bank Digital Currencies (CBDCs) has the potential to revolutionize the financial landscape and impact Bitcoin. Several countries, including China, Sweden, and the Bahamas, have already begun exploring the development and implementation of CBDCs. These digital currencies, issued and regulated by central banks, could create a more favorable environment for Bitcoin adoption. CBDCs could increase public awareness and acceptance of digital currencies, making Bitcoin and other cryptocurrencies more accessible and appealing to a broader audience.
Global Economic Uncertainty
Bitcoin has often been referred to as "digital gold" or a safe-haven asset during times of economic uncertainty. Global events such as geopolitical tensions, inflation concerns, and monetary policy decisions can significantly impact traditional financial markets. In such situations, investors often seek alternative investments to protect their wealth. Bitcoin, with its limited supply and decentralized nature, becomes an attractive option. A surge in global economic uncertainty could drive investors towards Bitcoin, triggering a bull market fueled by increased demand.
Technological Advancements
Bitcoin is built on a foundation of groundbreaking technology: blockchain. Technological advancements that enhance the scalability, security, and usability of Bitcoin and its underlying blockchain can have a profound impact on its future. For instance, the Lightning Network, a layer-2 scaling solution, has the potential to address Bitcoin's scalability issues by enabling faster and cheaper transactions. Similarly, improvements in privacy and security protocols can enhance user confidence and attract more participants to the ecosystem. These technological advancements can act as catalysts for the next Bitcoin bull market.
Halving Events
Bitcoin's supply is hard-capped at 21 million coins, and the rate at which new coins are introduced into the market is halved approximately every four years through a process known as "halving." This event has historically played a significant role in driving Bitcoin's bull markets. The halving reduces the rate at which new Bitcoin is minted, leading to a decreased supply. As the supply diminishes, if demand remains constant or increases, the scarcity of Bitcoin can push its price upwards. The next halving event is projected to occur around the year 2024, which could serve as a catalyst for the next Bitcoin bull market.
Conclusion
While the future of Bitcoin's price remains uncertain, several game-changing events have the potential to drive the next bull market. Institutional adoption, regulatory clarity, the rise of CBDCs, global economic uncertainty, technological advancements, and halving events are all factors that could shape Bitcoin's trajectory in the coming years. As these events unfold and the cryptocurrency ecosystem evolves, it is crucial for investors and enthusiasts to stay informed and monitor these developments closely. Ultimately, only time will tell how these factors will impact Bitcoin's journey towards mainstream acceptance and widespread adoption.
FAQ
How does institutional adoption affect Bitcoin Institutional adoption brings stability, liquidity, and credibility to the market, attracting more investors and potentially driving up the price of Bitcoin.
How do technological advancements in blockchain impact Bitcoin? Technological advancements in blockchain address scalability and efficiency issues, making Bitcoin more practical for everyday use. This attracts more users and businesses to adopt Bitcoin, driving its value and utility.
What role does global economic uncertainty play in Bitcoin's value? In times of economic uncertainty, Bitcoin serves as a safe haven asset and a hedge against inflation. As geopolitical tensions and economic crises persist, more investors turn to Bitcoin, driving up its demand and price.
What is the significance of halving events for Bitcoin's price? Halving events reduce the supply of new Bitcoin entering the market, creating a supply-demand imbalance that historically has led to price increases. The predictable nature of halving events contributes to Bitcoin's value proposition.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f685c7b9:b1be053e
2024-11-15 01:03:52
@ f685c7b9:b1be053e
2024-11-15 01:03:52Bitcoiners' Social Responsibility
"The primary act—the process of reason—must be performed by each man alone. We can divide a meal among many men. We cannot digest it in a collective stomach. No man can use his lungs to breathe for another man. No man can use his brain to think for another. All the functions of body and spirit are private. They cannot be shared or transferred."
--Ayn Rand

Rand warned about the fallacy of prioritizing collective well-being over the individual. Adopting bitcoin as your primary means of payments and store of value is an individual choice, while the errand orange-pilling people is construed as performing a social, or even collective, good. Bitcoiners themselves are not unlike the nodes validating network transactions and enforcing the fixed supply mechanism, in the sense that they bear the responsibility of ensuring the social integrity of the network. By this, I mean adhering to the same principles on which bitcoin came into existence, those based on the sovereignty of the individual. In observing interactions of bitcoiners online, I am motivated to express my thoughts about the potential risk that the best intentions may lead one into the trap of passive, ideological adherence to the collectivist idea that everyone ends up better off if the world just accepted bitcoin. I do not accept this to be necessarily true, but make the argument that educated users who are empowered to think for themselves make the network stronger and lead us closer to our common goal of a freer society.
Bitcoiners as Social Nodes
Having the courage to learn about the technological requirements of running a bitcoin node is no small feat for the average non-technically inclined person. Courage here is the primary barrier to overcome. The technical knowledge needed to participate in the Bitcoin network by running your own node, though not intuitive, is readily available online through easy-to-follow tutorials, yet many people are dissuaded from endeavoring to do so. At this point, anyone can buy or sell bitcoin and even spend it without as much as having heard the word node, let alone understand how to run one on their own machine. By far, the more burdensome task than the technical aspects of node participation is the social task of enabling the future bitcoiners of the world to use bitcoin as money. It is for this reason, I am arguing that it is a moral imperative to view every current bitcoiner as a social node.
While not capable of validating bitcoin transactions (with the exception of those actual node runners), bitcoiners bear the burden of solving the far more complex social problems of harmonizing the hostile world of fiat with Bitcoin. Bitcoiners are societal nodes, and serve the polyvalent function of validating social transactions and ensuring the integrity of the bitcoin network of users.
I'm not talking about shilling bitcoin, bitcoin evangelism or "orange-pilling" your friends and family. As far as I can tell, the jury is still out on whether this is a desirable use of our function as social nodes in the network of bitcoin users. As we all know, a new user who dives into the unknown without having done their due diligence can, might be taking a serious risk. Additionally, while Bitcoin's value will benefit immensely from wider adoption, paradoxically, it will becomes more costly to its present users to accumulate more. Far be it from my intentions to make an argument against advocating for hard money; yet, in this essay I find it incumbent upon me to consider the ramifications shilling the coin irresponsibly. Another one of my objectives here is to explore the functions of participating as a social node in bitcoin's network of users.
Bitocoin Evangelism and On-boarding New Users
Explanations of the exploits of fiat currency, the anti-fragility of the bitcoin network and its value proposition as money qua store of value as well as a medium of exchange can be powerful evidence for non-believers. As a bitcoin maxi, to me these top the list of revelations I had to have before being able to accept the reality that fiat is the real Ponzi scheme whose stability-seeking central planning approach drains the life force of the people who actually produce value in the world (see my essay, Dracula and the Federal Reserve Banking System. By saying that every bitcoiner is a social node in the network of potential users, I am proposing that due diligence is done to ensure that initiates are properly introduced to the technology, lest they fall into ways that perpetuate the evil of old.
The question of bitcoin mass adoption is no longer one of "if," but "when." What with the President of the United states floating the idea of purchasing a strategic reserve of one-million BTC (we'll see), and Microstrategy announcing plans to amp up their purchasing of bitcoin to 42 billion USD, these next few years Bitcoin will not need any more evangelism. The real task of being a node in the social network of bitcoin users lay in envisioning what the world is going to look like on a bitcoin standard and educating people about how they can prepare. Making sure that initiates in the network of users understand the common best practices will be the most daunting task.

Humans are social creatures. This necessarily implies that the mass uptake of new technology will have massive social repercussions. While we may rely on the economists to offer us analysis on trends in the social aspects of bitcoin adoption, and the software engineers and developers as experts on the tech stuff, it is the task of the every-person, the plebs, if you will, in the network to find, on the micro-level, the wrinkles and distortions that impede the network from working for the every-person. What I mean in saying we are all nodes is this: everyone participating in the network by either holding or using bitcoin shares the responsibility for ensuring the accuracy and relevance of information as it is distributed in their broader social networks. Indeed, this involves informing people about the various freedom to which bitcoin enables us. I am suggesting that we think deeper than simply proclaiming the "Good Word" that of bitcoin is the best money ever known to human civilization. What I'm proposing is a judicious and considered approach to encouraging proper education among the yet-to-be-initiated.
Of course, there are certainly going to be people to whom we will relish in saying "have fun staying poor," whom we will watch happily as they flounder in the dying paroxysms of the fiat machine while mass adoption takes off. However, there are also those, and this I am certain, to whom each of us would like to educate about the desecration caused by fiat systems, and the ways in which Bitcoin, the hardest decentralized and trustless currency that the world has ever seen, can save them. There is, of course, the adage that everyone gets Bitcoin at the price they deserve, but this should be said with the caveat that our friends and family deserve the absolute best price possible. My view here is that the only way to ensure that bitcoin remains representative of freedom is by each participant in the network ensures that the right information reaches the right people at the right time.

By saying we are all nodes, in effect, is to say that each of us who proclaims the word of Bitcoin is an ambassador. The choice of how you choose to represent yourself is your own. You are the one who best knows your community and you know what will make bitcoin stick. Every ambassador of the network performs the careful work of understanding the how and why of bitcoin adoption in each individual case. Far more complex a task than the validation of transactions on the bitcoin network, being a societal bitcoin node requires the careful execution that can be achieved by people living in and connected to the world around them.
One Pill, Two Pill, Orange Pill, Blue Pill
I prefer to talk about the process of initiating someone to the bitcoin network as one of on-boarding, rather than orange-pilling. To orange-pill someone implies some level of ideological persuasion - which, if you ask me, never really works, and only makes the unconvinced dig in their heels and gnash their teeth. I think person who accepts bitcoin does so because the time was ripe for it, not because of a nerdy cypherpunk's smooth talking. Even worse, to orange-pill someone pacifies the initiate into someone that needs to accept the truth as you it to tell them. The network doesn't need more people ready to drink the next hyped up flavour of kool-aid (even if it is orange); it needs rational thinkers who are ready to accept reality as it is, ready to think deeply about the problems yet to be solved.
From my experience, to say that the average person knows there to be something to be inherently wrong with the world is an understatement. People live their whole lives fear- or hate-ridden lest some boogeyman that they can't quite define will come and ransack everything they know and love. They use many labels, like Cabal, the establishment, they, the man... There is any number of pejoratives to which folks are ready to direct their hatred, though they be only vaguely understood. Yet, none of these labels fully captures the essence of the problem, which not the fault of a single entity per se. Instead, the fault lay in a system built on fiat. If history teaches us anything, it is that people are quick to find a scapegoat for their problems. It is easier to do so than to admit to being duped into accepting a construction of reality that is patently counterfeit. The world's biggest Ponzi scheme, fiat, is just that. Thanks to generations of coercion and propagandizing, the average person has not the slightest clue of this. As a result, they do not know why bitcoin exists.

What the majority of people do understand is this: for one reason or another, each of us feels we have to achieve more with less. What distinguishes bitcoiners from the majority is the understanding that this feeling is valid because it has an identifiable caused in the world. It is not a collective hallucination, but the systemic theft that occurs in the form of currency debasement, organized and planned by central banking and governmental authorities. In order to make ideological converts, or orange-pill those who have not recognized this truth requires a subtle understanding of their lives and struggles. It requires knowing that most people do not readily give up their their most strongly held delusions. It requires a deep level of compassion, love and patience.
Orange pilling, therefore, might better referred to as on-boarding. To build the network of future bitcoiners requires that people are well adapted and have the resources to make full use of it. If people are not free to understand bitcoin and instead are coerced into passively accepting it, then humanity will be no better off than we are now. This is why I would propose we change the language used to describe then initiation of a newcomer to the network. To say someone has been "orange-pilled" relegates them to being a passive recipient of an ideology. Myself, I have never been orange-pilled; in fact, I am skeptical of any pill. Here, I think the meme has outgrown its use and works against us. No--I have been on-boarded to the network, thanks to the many educators who work tirelessly to create online content, write their books or articles or expend their scarce time and energy discussing these ideas.
We risk repeating the mistakes of the past if each new bitcoiner is not treated with the dignity of being able to decide for themselves what is best for them. Those who blindly accept an ideology are arguably no better off then they were in the old system. As Ayn Rand has argued, the mind, is not collective, but individual, and nor can any man or woman use theirs to think for another.
FR.
npub176zu0wg5l8436nu66qaxwfekx0zz58l66s72dhcu0ur0lvd7q5lq9f66qx
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ 502ab02a:a2860397
2024-11-15 00:56:24
@ 502ab02a:a2860397
2024-11-15 00:56:24โปรเจคนี้ผมเริ่มต้นไอเดียจาก คุณมิก ณ ห้วยผึ้ง กาฬสินธุ์ และ คุณริช ณ ฉะเชิงเทรา ผู้ริเริ่มรันวงการ local bitcoin ด้วยการส่งเสริมให้พื้นที่ตนเอง สร้างตัวเลือกในการทดลองใช้ bitcoin เพื่อประสบการณ์ใหม่ๆ
ก็เลยมีความคิดว่า ถ้าสติ๊กเกอร์ที่ชุมชนนำไปใช้นั้น เป็นสัญลักษณ์ที่แสดงถึงพื้นที่นั้นๆก็น่าจะดี ในอนาคตพวกเขาอาจนำไปใช้ทำเสื้อ ที่รองแก้ว แก้วกาแฟ ป้ายร้าน และอื่นๆอีกมากมาย
นอกจากนี้ อาจจะเป็นแรงบันดาลใจ ที่จะทำให้พื้นที่ต่างๆในประเทศไทยที่มีการใช้งาน bitcoin สามารถนำไปต่อยอดในพื้นที่ตัวเองได้ด้วย ผมจึงยินดีแจก อาร์ทเวิร์คฉบับนี้ให้แบบไม่คิดค่าใช้จ่าย โดยอาร์ทเวิร์คจะแบ่งเป็น 2 แบบใหญ่ๆคือ 1. แสดงอำเภอ/ตำบล/หมู่บ้าน (หรือพื้นที่ย่อยอื่นๆ) แล้วแสดงจังหวัดต่อท้าย 2. แสดงเฉพาะจังหวัด
ผมได้ทำตัวเลือกทั้งแนวนอน แนวตั้ง มีพื้นที่ QR code จัตุรัส แบ่งเป็นพื้นขาว และ พื้นดำ เพื่อรองรับการใช้งานที่หลากหลาย
แนวคิดการออกแบบคือ มีสัญลักษณ์ประจำท้องที่อยู่ด้านหน้า ตามด้วยคำว่า bitcoin accepted here พร้อมกำกับภาษาไทย โดยภาษาอังกฤษใช้ฟอนต์ ubuntu และภาษาไทยใช้ฟอนต์ TH Krub ซึ่งเป็นฟอนต์แห่งชาติ (ทั้ง 2 ฟอนต์เป็นฟอนต์ฟรี)
 1.แบบแสดง อำเภอ/ตำบล/หมู่บ้าน (หรือพื้นที่ย่อยอื่นๆ) แล้วแสดงจังหวัดต่อท้าย
แนวคิด : ห้วยผึ้ง ใช้ผึ้งงานเก็บน้ำผึ้งเข้ารัง ให้รังเป็นตัวแทนของการออม bitcoin ในลักษณะ stack sats ค่อยๆเก็บหอมรอบริบ make saving great again โดยผึ้งงานเป็นตัวแทนของ proof of work ซึ่งตัวน้ำผึ้งที่หอมหวานนั้น มีคุณค่า ไม่เสื่อมไปตามกาลเวลา เป็นยาอายุวัฒนะ และเป็นของมีค่าโดยธรรมชาติ
1.แบบแสดง อำเภอ/ตำบล/หมู่บ้าน (หรือพื้นที่ย่อยอื่นๆ) แล้วแสดงจังหวัดต่อท้าย
แนวคิด : ห้วยผึ้ง ใช้ผึ้งงานเก็บน้ำผึ้งเข้ารัง ให้รังเป็นตัวแทนของการออม bitcoin ในลักษณะ stack sats ค่อยๆเก็บหอมรอบริบ make saving great again โดยผึ้งงานเป็นตัวแทนของ proof of work ซึ่งตัวน้ำผึ้งที่หอมหวานนั้น มีคุณค่า ไม่เสื่อมไปตามกาลเวลา เป็นยาอายุวัฒนะ และเป็นของมีค่าโดยธรรมชาติตัวหนังสือแสดงพื้นที่ จะใช้รูปแบบ “หน่วยย่อย@จังหวัด” ในที่นี้คือ “ห้วยผึ้ง@กาฬสินธุ์” จัดทำเป็นภาษาอังกฤษ เพื่อให้ชาวต่างชาติเข้าใจได้ง่าย และเป็นภาษาไทยในส่วนของสัญลักษณ์เพื่อแสดงความเป็นไทย link : Download here!!! https://drive.google.com/file/d/1P15ajhxTPX4W0JYFGDdrsdk-IiHv2v75/view?usp=sharing
 2.แบบแสดงเฉพาะจังหวัด
แนวคิด : ที่มาของคำว่า 8ริ้ว ชื่อเล่นของจังหวัดฉะเชิงเทรา มาจากปลาช่อนขนาดใหญ่ ที่สามารถแบ่งได้ถึง 8 ริ้ว จึงออกแบบให้เป็นรูปปลาช่อน แล้วติดเหรียญเลข 8 เอาไว้ ทั้งเป็นเลขมงคลและเป็นการแทนค่า 8ริ้ว ของปลาด้วย ด้านหลังเป็นสัญลักษณ์ bitcoin พร้อมคำว่า ฉะเชิงเทราเป็นภาษาอังกฤษ และกำกับภาษาไทยที่ด้านล่างอย่างโดดเด่น
ตัวหนังสือแสดงพื้นที่ จะอยู่ในรูปแบบของ “@จังหวัด” ในที่นี้คือ “@ฉะเชิงเทรา” จัดทำเป็นภาษาอังกฤษ เพื่อให้ชาวต่างชาติเข้าใจได้ง่าย และเป็นภาษาไทยในส่วนของสัญลักษณ์เพื่อแสดงความเป็นไทย
link : Download here!!! https://drive.google.com/file/d/1eADEGcWOYIGWCnEGBNrnYqxmVNNpoiUQ/view?usp=sharing
2.แบบแสดงเฉพาะจังหวัด
แนวคิด : ที่มาของคำว่า 8ริ้ว ชื่อเล่นของจังหวัดฉะเชิงเทรา มาจากปลาช่อนขนาดใหญ่ ที่สามารถแบ่งได้ถึง 8 ริ้ว จึงออกแบบให้เป็นรูปปลาช่อน แล้วติดเหรียญเลข 8 เอาไว้ ทั้งเป็นเลขมงคลและเป็นการแทนค่า 8ริ้ว ของปลาด้วย ด้านหลังเป็นสัญลักษณ์ bitcoin พร้อมคำว่า ฉะเชิงเทราเป็นภาษาอังกฤษ และกำกับภาษาไทยที่ด้านล่างอย่างโดดเด่น
ตัวหนังสือแสดงพื้นที่ จะอยู่ในรูปแบบของ “@จังหวัด” ในที่นี้คือ “@ฉะเชิงเทรา” จัดทำเป็นภาษาอังกฤษ เพื่อให้ชาวต่างชาติเข้าใจได้ง่าย และเป็นภาษาไทยในส่วนของสัญลักษณ์เพื่อแสดงความเป็นไทย
link : Download here!!! https://drive.google.com/file/d/1eADEGcWOYIGWCnEGBNrnYqxmVNNpoiUQ/view?usp=sharingหวังว่าใครนำไปใช้ในท้องที่ตัวเองแล้ว เอามาอวดผมด้วยนะครับ จะดีใจยิ่ง nostr address ที่ nostr:npub12q4tq25nvkp52sluql37yr5qn059qf3kpeaa26u0nmd7ag5xqwtscduvuh
ENG version This project originated from an idea I developed with inspiration from Khun Mick from Huai Phueng, Kalasin, and Khun Rich from Chachoengsao. Both have pioneered the local Bitcoin movement by encouraging their communities to create options for experimenting with Bitcoin to gain new experiences. This led me to think it would be great if the stickers used by the community could symbolize the specific area they represent. In the future, they could even be used on T-shirts, coasters, coffee cups, shop signs, and more.
Additionally, this could serve as inspiration for other regions in Thailand where Bitcoin is in use to adapt and extend it within their own areas. Therefore, I’m happy to provide this artwork free of charge. The artwork comes in two main formats: 1. Showing the district/subdistrict/village (or other local area) followed by the province name, and 2. Showing only the province name. I’ve created both horizontal and vertical options with space for a QR code in a square format and included white and black backgrounds to support diverse uses. The design concept includes a local symbol in the foreground, followed by the phrase “Bitcoin Accepted Here,” with accompanying Thai text. For English, I’ve used the Ubuntu font, and for Thai, the TH Krub font, which is the national font of Thailand (both fonts are free to use).
 1.Format: Shows the district/subdistrict/village (or other local area) followed by the province name.
Concept: Huai Phueng uses an image of a worker bee collecting honey for the hive, where the hive symbolizes saving Bitcoin in a “stack sats” manner, gradually
accumulating and making saving valuable again. The worker bee represents proof of work, while the sweet honey, with its timeless value, serves as both an elixir and a naturally precious resource.
1.Format: Shows the district/subdistrict/village (or other local area) followed by the province name.
Concept: Huai Phueng uses an image of a worker bee collecting honey for the hive, where the hive symbolizes saving Bitcoin in a “stack sats” manner, gradually
accumulating and making saving valuable again. The worker bee represents proof of work, while the sweet honey, with its timeless value, serves as both an elixir and a naturally precious resource.The text displaying the location will follow the format “subdivision@province,” in this case, “Huai Phueng@Kalasin.” The English format is designed for easy understanding by foreigners, while the Thai language in the symbol emphasizes Thai identity.
Link: Download here!!! https://drive.google.com/file/d/1P15ajhxTPX4W0JYFGDdrsdk-IiHv2v75/view?usp=sharing
 2.Format: Displays only the province name.
Concept: The origin of the nickname “8 Riew” for Chachoengsao Province comes from a large snakehead fish that could be cut into eight large slices. The design incorporates an image of a snakehead fish with an “8” coin to represent both the rich number and the symbolic “8 Riew” slices. The background features the Bitcoin symbol along with “Chachoengsao” in English and prominent Thai text below.
2.Format: Displays only the province name.
Concept: The origin of the nickname “8 Riew” for Chachoengsao Province comes from a large snakehead fish that could be cut into eight large slices. The design incorporates an image of a snakehead fish with an “8” coin to represent both the rich number and the symbolic “8 Riew” slices. The background features the Bitcoin symbol along with “Chachoengsao” in English and prominent Thai text below.The location text will follow the format “@Province,” in this case, “@Chachoengsao.” The English format is designed for easy understanding by foreigners, while the Thai language in the symbol emphasizes Thai identity.
Link: Download here!!! https://drive.google.com/file/d/1eADEGcWOYIGWCnEGBNrnYqxmVNNpoiUQ/view?usp=sharing
ref website https://siripun.com/2024/11/15/blt-network-sticker/

nostr:#siamstr nostr:#pirateketo
-
 @ bcea2b98:7ccef3c9
2024-11-14 23:38:37
@ bcea2b98:7ccef3c9
2024-11-14 23:38:37@chess a3
originally posted at https://stacker.news/items/768303
-
 @ bd32f268:22b33966
2024-11-14 19:37:33
@ bd32f268:22b33966
2024-11-14 19:37:33Entristece-me ver tanto ceticismo em relação ao amor e às relações. Parece que agora é normal entrar numa determinada relação com uma data de validade e sem se entregar completamente.
O que observo é que não há confiança e também cada vez mais, não há um sentido de dever ou responsabilidade. Um casal que não tem noção do que é um voto sagrado e eterno não é provável que sobreviva muito tempo. Há uma volatilidade e relativismo que se impõe e fazem com que aquilo que hoje se é, amanhã possa já não ser. As promessas realizadas não passam disso, promessas que não se transformam realidades.
Fui alimentado, tal como o homem comum, com uma série de mentiras sobre as relações. Algumas hiper-idealistas em que não havia tensão, dor ou sacrifício, outras apenas focavam o lado hedonista, retratando as relações casuais como algo aconselhável. Enfim, as manobras de distração são muitas e as mentiras são bastante sedutoras à vista desarmada. Um exemplo disso é que nos é transmitida a ideia de que podemos adiar indefinidamente esse processo de compromisso com alguém.
Quando os jovens estão a ponto de iniciar a vida adulta é muito propagada a mensagem de que têm tempo, que precisam de ter experiências até assentarem com alguém. Muito sinceramente acho que esta filosofia tende a infantilizar as pessoas e a iludir porque pressupõe que essas experiências vão produzir uma aprendizagem valorosa e constata-se invariavelmente que esse não é o caso, que no caso dos homens isto quer muitas vezes dizer que têm carta branca para oportunismo sexual e nas mulheres quer dizer frequentemente que têm via aberta para uma romantização idealista e Holywoodesca, a base do amor fátuo. Por outro lado esta mensagem pressupõe também que temos tempo, no entanto a realidade é que não sabemos o tempo que temos e a janela para constituir família vai fechando paulatinamente á medida que o tempo passa.
É costume dizer-se popularmente que os homens enganam-se pelos olhos e as mulheres pelos ouvidos e, como referi, o oportunismo sexual e a romantização idealista são duas grandes expressões de erros populares neste domínio das relações. O homem, tomado muitas vezes pelo dose avassaladora de sensualidade que está presente na informação que vai consumindo, vai em busca de “troféus” para o seu espólio. No caso da mulher, muitas vezes movida a pelo sentimentalismo e pela enganadora “busca da felicidade” como fim último para a vida, tende a ficar permanentemente insatisfeita quando constata que a fantasia rapidamente se desmorona, resultado de se deixar guiar exclusivamente pelo sentimento e menos pela razão.
Depois temos ainda um outro problema que afeta os dois sexos, tanto homens como mulheres, que diz respeito à crescente indefinição do papel e identidade do homem e da mulher. Na era da suposta igualdade, estas definições tornam-se cada vez mais nebulosas e as referências que temos na televisão, desporto, cultura, ou academia são muitas vezes de homens efeminados e mulheres masculinizadas.
Acresce a isto ainda outros problemas, desde a normalização do divórcio e do adultério à perversão sexual, a ausência da vocação pedagógica dos pais entre muitos outros.
Nós crescemos com este tipo de propaganda, o casamento já não é o foco, construir uma família não é a pedra angular. O resultado é que temos muitas pessoas sem Deus, escravizadas pelos apetites hedonistas, sem capacidade de sacrifício para construir uma família decente, e a somar a isto, uma crise de fertilidade. Esta é a base de onde provêm muitos dos problemas políticos a que assistimos. É costume dizer-se popularmente que os homens enganam-se pelos olhos e as mulheres pelos ouvidos e, como referi, o oportunismo sexual e a romantização idealista são duas grandes expressões de erros populares neste domínio das relações. O homem, tomado muitas vezes pelo dose avassaladora de sensualidade que está presente na informação que vai consumindo, vai em busca de “troféus” para o seu espólio. No caso da mulher, muitas vezes movida a pelo sentimentalismo e pela enganadora “busca da felicidade” como fim último para a vida, tende a ficar permanentemente insatisfeita quando constata que a fantasia rapidamente se desmorona, resultado de se deixar guiar exclusivamente pelo sentimento e menos pela razão.
Depois temos ainda um outro problema que afeta os dois sexos, tanto homens como mulheres, que diz respeito à crescente indefinição do papel e identidade do homem e da mulher. Na era da suposta igualdade, estas definições tornam-se cada vez mais nebulosas e as referências que temos na televisão, desporto, cultura, ou academia são muitas vezes de homens efeminados e mulheres masculinizadas.
Acresce a isto ainda outros problemas, desde a normalização do divórcio e do adultério à perversão sexual, a ausência da vocação pedagógica dos pais entre muitos outros.
Nós crescemos com este tipo de propaganda, o casamento já não é o foco, construir uma família não é a pedra angular. O resultado é que temos muitas pessoas sem Deus, escravizadas pelos apetites hedonistas, sem capacidade de sacrifício para construir uma família decente, e a somar a isto, uma crise de fertilidade. Esta é a base de onde provêm muitos dos problemas políticos a que assistimos.
 Holy Family - Collinson
Holy Family - CollinsonPrecisamos de começar a construir famílias para conseguirmos algum tipo de coesão social. Tal como Aristóteles definia, o país é um conjunto de famílias, portanto o nosso sucesso coletivo enquanto país depende da capacidade para construir e orientar devidamente as famílias.
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ f4bf1fb5:b428f8d5
2024-11-14 19:15:23
@ f4bf1fb5:b428f8d5
2024-11-14 19:15:23As some of you might be aware, we can't take down mod posts/pages or ban creators' accounts on DEG Mods, as we've built the site on top of the Nostr protocol. With that said, a lot of people are concerned with seeing a malicious posts on the site, like spam, scams, posts with viruses, and illegal content, and other worries like not wanting to see specific content. People are worried on how we'd be handling all of these issues as we claim censorship-resistance.
This post is to help showcase and explain how we'll be handling content moderation on the site, while maintaining the site's censorship-resistant and permissionless nature.
Reporting and blocking
The first thing that can be done, in regards to moderation, is for users to report mod posts (or other type of posts). Reporting would result in us having a look at said reported post and determine if we'd block it or not.
Blocking it means that it will be hidden from initial view on the website, yet it'd still be accessible if someone has the link, or accessible on other sites.
Illegal content
In regards to illegal content, we'd essentially do the same thing as mentioned above, and at that point the relevant authorities would need to handle it from then on, as they try to find the perpetrator and prosecute them.
Web of Trust (WoT)
There will be, if not already, an near automated moderation system applied almost site wide, which would handle most of the leg work. This system is called Web of Trust, where it works by showing content published by users who we have followed, and their tree of followers (up to a point that we'd determine).
In essence, the natural behavior of users using the site, from mod creators to enjoyers, like publishing mods, commenting, reacting, publishing short posts, writing update posts or news/announcements, following whoever they like, not following who they don't like and/or blocking those who publishing malicious posts, would act as a moderation layer for for themselves and everybody else. Of course, this means that not everyone will necessarily be visible on the site initially as they start, so that's why everyone is encouraged to interact with each other, follow who you like, block bad faith actors, and so on. Everything is interconnected with each other to create a very efficient, effective, and safe viewing/usage experience on the site.
As we mentioned initially, we'll also maintain our claims of censorship-resistance by providing a toggle to remove the site's WoT filter, including the user's WoT, if they want to see almost everything. This gives everyone a method and chance to be seen, regardless of this moderation layer.
Individual moderation tools
Each individual user on the site has the ability to block a mod posts (or any other type of posts) on the site, as well as whole accounts and their posts.
As we mentioned briefly above, each user will also have their own WoT preference, to see posts of the people they trust, as well as their follows, and so on.
Various systems and designs
We'll be introducing various different systems/designs that would help with general moderation of the site from the user's perspective and exploration of the site. As an example, if a mod post won't include a malware scan report of the mod files (and we'll see if we can make this an automated, then there'd be a visible note around it to indicate that there hasn't been a scan done for it and advise users to be careful of malware).
Questions and answers
Here are a few questions and answers related to this topic. We'd update this post as new info comes along.
Do you allow X or Y type of content?
As long as its a mod (specially cases were non-mods wouldn't be subject to moderation), is legal, not directly harmful (malware, scam), and isn't spam, then you should be fine.
Does fiction equal fiction?
Yes.
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ bcea2b98:7ccef3c9
2024-11-14 18:03:14
@ bcea2b98:7ccef3c9
2024-11-14 18:03:14We all have that one movie or show we turn to when we need a little comfort. Whether it’s for the laughs, the nostalgia, or the familiar characters, these are the ones that never get old.
What’s a movie or series you can watch again and again? What makes it so comforting, and why do you keep coming back to it?
I enjoy The Office with Michael Scott and Dwight Schrute. We watched a lot of that in the past and then again during the pandemic during isolation.
originally posted at https://stacker.news/items/767870
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 98589a2e:bf49daa1
2024-11-14 17:33:47
@ 98589a2e:bf49daa1
2024-11-14 17:33:47Медицинская система Санкт-Петербурга претерпела значительные изменения благодаря стремительному развитию цифровых технологий. Эти преобразования сделали медицину более персонализированной, эффективной и ориентированной на профилактику заболеваний.
Основные аспекты изменений
https://cdn.genmo.dev/results/text-to-video-v4/2024-11-14/cm3hbrywm001d03johe6rcap0/watermarked.mp4
Полностью интегрированные цифровые экосистемы
Все медицинские данные пациентов хранятся в единой облачной системе, доступной как врачам, так и пациентам. Это обеспечивает мгновенный доступ к истории болезни, результатам анализов и рекомендациям специалистов. Пациенты могут отслеживать свои показатели здоровья в реальном времени через персональные устройства.
Искусственный интеллект и машинное обучение
Искусственный интеллект (ИИ) стал ключевым элементом диагностики и лечения. Нейросети анализируют большие объемы данных, что позволяет врачам ставить точные диагнозы и подбирать эффективные методы лечения. ИИ также используется для прогнозирования заболеваний на основе генетической предрасположенности и образа жизни пациента.
Технологии дополненной реальности (AR) и виртуальной реальности (VR)
AR активно применяется в хирургии и обучении медиков. Хирурги используют AR-очки для отображения трехмерных моделей органов во время операций, что повышает точность манипуляций. VR-технологии помогают симулировать сложные хирургические процедуры для обучения студентов.
Нанотехнологии и роботизированная медицина
Микроскопические роботы-наномашины вводятся в организм для диагностики и лечения на клеточном уровне. Они могут доставлять лекарства к пораженным тканям и проводить микрооперации, а роботы-хирурги выполняют сложные операции под контролем врачей.
Персонализированная геномика и фармакогенетика
Генетическое тестирование стало стандартом при первичном обращении к врачу. На основе анализа ДНК разрабатываются индивидуальные планы профилактики и лечения, а также подбираются наиболее подходящие лекарства, что позволяет избежать побочных эффектов и повысить эффективность терапии.
Биохакинг и кибернетические имплантаты
Жители Санкт-Петербурга активно используют биохакинг для улучшения своих физических и когнитивных способностей с помощью высоких технологий. Кибернетические протезы заменяют утраченные функции организма, а нейроинтерфейсы обеспечивают связь мозга с компьютером.
Телепортация клеток и тканей
Технология телепортации применяется для транспортировки необходимых клеток и тканей вместо пересадки донорских органов, что сокращает время ожидания трансплантаций и снижает риск отторжения.
Медицинская система Санкт-Петербурга представляет собой высокоэффективный комплекс цифровых технологий, обеспечивающих индивидуализированный подход к каждому пациенту. Взаимодействие между врачом и пациентом стало более тесным и прозрачным, а качество медицинских услуг достигло нового уровня благодаря интеграции современных технологий в каждую сферу здравоохранения.
Как вы оцениваете влияние цифровых технологий на качество медицинских услуг в Санкт-Петербурге?
-
 @ 340d9e96:1c5a1e25
2024-11-14 13:18:05
@ 340d9e96:1c5a1e25
2024-11-14 13:18:05ctulkg j,bvmn раы
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ f4bf1fb5:b428f8d5
2024-11-14 13:05:02
@ f4bf1fb5:b428f8d5
2024-11-14 13:05:02A modder that goes by the name of "welintron" created a mod for Tomb Raider I-III on PC called "Remove Misinformative Warning", one that removes the developers' (Crystal Dynamic) message about the game being supposedly offensive.
The mod was uploaded to one of the popular mod hosting sites at the time, however, staff of said site has removed the mod and banned its creator.
This is an old piece of news as of the time of writing this post, and the purpose of writing it is to remind people of what's being banned, as well as keeping a log for ourselves, to know which mod creator to reach out to in the future, to introduce them to DEG Mods.
Since DEG Mods isn't out yet and you're wondering where you can download it, someone has supposedly uploaded the file on ModDB (be safe!).
-
 @ f8a5df57:b7a58cd4
2024-11-14 13:02:12
@ f8a5df57:b7a58cd4
2024-11-14 13:02:12Содержание сюжета:
В "IT- городах" внедрились технологии рендеринга в реальном времени, такие как трассировка лучей для создания более реалистичной графики в играх и приложениях. Они представляют собой технологию рендеринга, которая имитирует поведение света в реальном мире для создания фотореалистичной графики. Эта методика позволяет рассчитывать путь света, взаимодействующего с объектами в сцене, что приводит к более точному освещению, теням и отражениям. Также разрабатываются новые концепции использования GPU для ускорения вычислений в научных исследованиях и машинном обучении. Графические процессоры (GPU) становятся все более важными инструментами в научных исследованиях и машинном обучении благодаря своей способности выполнять параллельные вычисления с высокой производительностью. Это открывает новые возможности для решения сложных вычислительных задач, которые ранее были недоступны на традиционных центральных процессорах (CPU).
Автор сюжета: Дарья Воронина
-
 @ af9d7040:42d05d35
2024-11-14 12:52:24
@ af9d7040:42d05d35
2024-11-14 12:52:24
People who love movies often debate, “What exactly makes a good movie?
Film as an art form is deeply subjective. One person might be dazzled by vibrant colors and impressive special effects, while another might find more cinematic quality in classic black-and-white. There’s no definitive answer. From my perspective, a good movie is one with a solid structure, strong storytelling, and the ability to resonate with me.

Structure is the lifeblood.
A weak ending, a disjointed middle, or a muddled theme—it just doesn’t work. Flashbacks, non-linear timelines, or montage techniques are seasonings meant to enhance structure, not overpower it. Long takes, stunning effects, innovative camera work—if the structure isn’t solid, it’s all just empty spectacle. That rare storytelling ideal where everything feels loosely arranged yet perfectly cohesive? You don’t see that every day.

Strong storytelling is the backbone.
A good film is built on one or more solid stories. Themes like humanity, ethics, social values, kindness, beauty, and philosophy come to life through each character’s journey. Together, these characters and their stories form a complete narrative. The story might be simple and quiet, epic and intense, wildly imaginative, or follow a traditional formula. Whatever the approach, it needs that essential “watchability” factor—that’s what makes a strong story. And if it can avoid preaching, conveying the creator’s message in a way that feels as natural as casual conversation, all the better. It’s like classic stand-up, where comedians seem to just chat, but the real meaning shines through.

Resonance is the heart, the flourish, the final elevation.
It doesn’t work miracles—if a film’s structure is weak or its storytelling lacking, it’s unlikely to truly resonate. Sure, there might be brief moments of connection, but that’s as futile as debating “Is DC or Marvel stronger?” Creating resonance in film is one of those “mystical arts.” People’s lives, knowledge, and experiences vary endlessly, so the points of resonance are infinite. There’s no formula to measure it, yet it’s undeniably present in any great work. Those moments of joy, sadness, excitement, or shock—these emotional releases are the bridge between audience and film. When a movie has solid structure, strong storytelling, and can create real resonance, it doesn’t just improve the work; it can elevate its entire theme.

Films like The Godfather—the ones you can revisit at different stages of life and discover something new each time—are rare gems in film history.

Putting aside this long-winded discussion, here’s the simple takeaway:
- If you watch a movie and feel like it’s telling your own story, that’s a good movie.
- If scenes or lines keep replaying in your mind, that’s a good movie.
- If you finish it and suddenly feel hungry enough to get something to eat, that’s a good movie.
- If you finish it and want to keep it all to yourself, not even share it—that’s a truly great movie.
To put it simply, art is a deeply personal thing. Good art, in one way or another, reflects the most private parts of our own lives. Honestly, who in their right mind would casually go around talking about those personal things?
Murakami writes in Norwegian Wood that he loves The Great Gatsby. How much does he love it? So much that he doesn’t even want to share it with anyone else.


I think that the kind of movie you want to keep to yourself, that you don’t want to share
—That’s what truly great movie is.
Shaun published on February 16, 2019, with the original text in Chinese.
-
 @ 961dae8c:66d56d87
2024-11-14 12:51:23
@ 961dae8c:66d56d87
2024-11-14 12:51:23ctulkg j,bvmn
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 4b16cdd9:f4e841ca
2024-11-14 12:47:49
@ 4b16cdd9:f4e841ca
2024-11-14 12:47:49дулшощйцушщк щшйкр38ркдо870н508734
-
 @ f8a5df57:b7a58cd4
2024-11-14 12:24:12
@ f8a5df57:b7a58cd4
2024-11-14 12:24:12 -
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 9ff58691:0bf6c134
2024-11-14 12:15:25
@ 9ff58691:0bf6c134
2024-11-14 12:15:25Сегодня Курган стал свидетелем открытия «Школы Инноваций», которая представляет собой образец современных образовательных технологий. Это учреждение, расположенное в центре города, оснащено инновационным оборудованием, включая интерактивные доски и системы виртуальной реальности, что позволяет ученикам погружаться в учебный процесс. Школа предлагает уникальные кабинеты для робототехники и STEM-дисциплин, где студенты могут не только учиться, но и создавать проекты с использованием новейших технологий. Внутренние пространства школы продуманы для комфортного обучения: светлые классы и зоны для групповой работы способствуют активному взаимодействию между учениками.
Недавно открывшийся университет на главной улице Кургана также внедряет передовые технологии, что создает синергию между школой и высшим образованием. Оба учреждения готовят студентов к вызовам будущего, акцентируя внимание на критическом мышлении и практических навыках, необходимых в высокотехнологичном мире.
Автор: Эвелина Тимирбаева
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ f8a5df57:b7a58cd4
2024-11-14 12:03:35
@ f8a5df57:b7a58cd4
2024-11-14 12:03:35 -
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ f8a5df57:b7a58cd4
2024-11-14 12:02:40
@ f8a5df57:b7a58cd4
2024-11-14 12:02:40Столичная администрация объявила о масштабном проекте по увеличению дорожных линий, который призван кардинально улучшить ситуацию с дорожным движением в Москве. В условиях постоянно растущего числа транспортных средств и увеличивающегося потока людей, это станет ключевым шагом к более удобному и безопасному передвижению по городу.
В последние 40 лет Москва превратилась в мегаполис с населением свыше 15 миллионов человек, и проект по расширению дорожной инфраструктуры стал неотъемлемой частью стратегии по улучшению городской мобильности. В результате запуска новых линий, тысячи километров дорог получат дополнительные полосы движения, что позволит сократить время в пути и оптимизировать транспортные потоки.
«Мы ориентируемся на будущее и понимаем, что улучшение дорожной инфраструктуры критически важно для комфорта москвичей. Новые линии позволят уменьшить заторы в наши часы пик и создадут условия для безопасного и быстрого передвижения по городу», — отметил мэр Москвы Сергей Собянин на пресс-конференции.
Проект включает не только увеличение числа полос, но и внедрение интеллектуальных систем управления движением. Используя данные искусственного интеллекта, новые технологии обеспечат автоматическую оптимизацию направления потоков и улучшение реакции на неожиданные ситуации на дороге, снижая вероятность возникновения пробок и аварий.
Самым значимым аспектом нового плана является интеграция дорожной сети с другими видами транспорта, включая метро, автобусные и трамвайные маршруты. Теперь жители будут иметь возможность быстрее и легче пересаживаться между разными видами транспорта, что сделает передвижение по столице более эффективным.
Кроме того, увеличение дорожных линий будет способствовать развитию экономической активности. Новые маршруты создадут более доступные пути для грузового и коммерческого транспорта, что в свою очередь повлияет на снижение цен на товары и услуги, улучшая уровень жизни москвичей.
К тому же, в процессе переустройства дорожной сети также будут созданы специальные полосы для велосипедистов и пешеходов, что подчеркивает стремление столицы к устойчивому развитию и экологии. Угоржая уличная сеть, власти надеются привлечь больше людей к здоровому образу жизни, а также уменьшить уровень загрязнения воздуха.
Масштабные изменения в дорожном движении ожидаются в течение ближайших десятилетий, и увеличение дорожных линий станет важным шагом на пути к созданию безопасной и комфортной городской среды для будущих поколений москвичей. С каждым улучшением городской инфраструктуры, Москва движется к статусу одного из самых удобных и технологичных мегаполисов мира.
-
 @ 6734e11d:c7e34e8f
2024-11-14 11:33:54
@ 6734e11d:c7e34e8f
2024-11-14 11:33:54Zweiklassenmedizin, Zweiklassenbildungssystem und -demokratie. Wo ist die Zweiklassenpartei? Leo Trotzki hielt 1928 eine „Zweiklassenpartei“ mit sowohl proletarischer als auch kleinbürgerlicher Linie für unmöglich. Zu verschiedene und unvereinbare Interessen. Die (Er)Lösung scheint heute nah: Ein aufrichtiges Parteiprogramm.
Mein Ziel ist daher, alle Dissonanzen zu beseitigen und endlich alle Menschen in einer Partei zu vereinen. Ich stehe aufrichtig für das gänzlich Neue: „Vereine in einer Partei und herrsche“. In politischen Entscheidungen geht es durchgängig um Macht und monetäre Interessen, wirklich zu jedem Zeitpunkt und in allen gesellschaftlichen Fragen und Politikfeldern. Das ist nichts neues, aber mit dieser aufrichtigen Klarheit können alle Beschlüsse frei von hemmenden sachlichen Erwägungen geplant und getroffen werden. Zeitraubender Diskurs, Studien und Evaluationen werden überflüssig. Das vorliegende Parteiprogramm soll eine erste Positionsbestimmung darstellen und die kurz gehaltene neue Gesellschafts- und Wirtschaftsordnung in unserem schönen Lande sein. Ich meine es gut mit den Bürgenden*.
*Begriffserläuterung: Die Bürgenden seien im Folgenden diejenigen, die für die Konsequenzen politischer Entscheidungen mit ihrem Vermögen, ihrer Gesundheit und ihrem Leben bürgen.
Gesellschaft
Eine strikte rechtliche und wirtschaftliche Zweiteilung der Gesellschaft in Elite und Volk ist anzustreben. Da der Mittelstand in seiner Bedeutung ohnehin wesentlich überschätzt wird, kann er in den 99 Prozent der Bürgenden aufgehen. Der Mittelstand ist getragen von der Einsicht, zugunsten der Elite wesentliche Einbußen in Kauf zu nehmen. Um mit Umbau von Wirtschaft und Digitalem rapide voran zu kommen, brauchen wir eine solidarische Gemeinschaft der Harmonie. Vielschichtige Auseinandersetzung kann ein prosperierendes Gesellschaftssystem bremsen und zermürben. Komplexität ist deshalb zu vermeiden oder sogar zu unterbinden. Ich werde dezidiert vorgeben, wie Sprache in Schrift und Rede zu handhaben ist, damit unsere Gesellschaft noch effektiver agieren kann. Klarheit darüber, was zu denken, zu fühlen und zu sagen ist, erleichtern das Leben aller. Lust, Sexualität und vor allen Dingen Humor, sind auch digital auf das unbedingt notwendige Maß zu begrenzen, um die volle Kraft des Humankapitals der gesellschaftlichen Prosperität zur Verfügung zu stellen. Kritische Subjekte sollen dagegen trefflich verlacht und verhöhnt werden dürfen.
Grundrechte
Alle Staatsgewalt geht von der Partei aus. Mittlerweile ist recht gut implementiert, wann, wer, wohin darf, wem es jeweils verboten oder wer unerwünscht ist. Dies funktioniert auch ohne Vorbereitung, mittlerweile völlig unabhängig von logischen Begründungen. Das gesamte Potential einer noch differenzierteren Regulation, wird bisher leider nicht vollständig genutzt. Politischer und gegenseitiger Schutz haben sich als äußerst wirksam erwiesen.
Digitales
Ich will die digitale biometrische Identität für alle Vorgänge im Alltag, ab positiver Testung der Schwangerschaft. Mehr Mut bei Kombination von Fingerabdruck, Bankdaten, Gesichtserkennung und Zugangsberechtigungen. Der beschleunigten Zeit angemessen, gehe ich aber weiter: Privatsphäre ist ein überkommenes Luxusgut, das die gesellschaftliche Entwicklung hemmt. Es darf keinerlei Geheimnisse mehr geben. Diese Entwicklung würde ich keinesfalls als Transhumanismus bezeichnen, jenes Streben ist als äußerst menschlich zu betrachten. Fitnesstracker waren ein guter Anfang. Microchips in Kleidung und unter die Haut verpflanzt, ermöglichen Kommunikation überall und zu jeder Zeit. Bemerkenswert: Das Transplantieren erfolgt mit nur einer Spritze, mittels einer etwas dickeren Kanüle, ein leicht deutlicherer Piks, aber völlig sicher und nebenwirkungsfrei. Bei geschützten Tieren ist das seit längerem erprobt.
Desozialisierende/integrierende Netzwerke
Digitale Plattformen sammeln, überwachen und kanalisieren Kommunikation und Emotion, werden privatwirtschaftlich betrieben aber zentral gesteuert. Mal desozialisierend oder integrierend eingesetzt, können sie auch abgeschaltet werden. Text- und Videonachrichten oder -gespräche gelten als reale Kontakte. Sämtliche humanoide Handlungen werden in das digitale Netz verlagert, so wird unsere Welt endlich sicher. Der Schutz der Sphäre der Elite ist hingegen von entscheidender Bedeutung. Sie muss unabhängig von Überwachung Ideen auch in Präsenz austauschen und entwickeln können.
Medien
Digitale Identität und parteitragende Medien werden verknüpft. Pflichtzeiten des Konsums stellen denselben Informationsstand sicher, die Verweildauer fließt in die Gesamtbewertung der Persönlichkeit ein. Hochschulabschlüsse und Promotionen werden damit verknüpft, Verdienstorden angepasst verliehen. Die Öffentlich-Rechtlichen werden zur Marke „Ehrlich-Medien“, die jahrzehntelang immanente Unaufrichtigkeit wird die Transformation leider hinauszögern. Scheinbar kritische Medien sind längst an entscheidenden Positionen und auf allen Kanälen mit Einflussagenten besetzt, die ihre eigenen Ziele verfolgen. Diese Unterwanderung wird gezielt forciert, bis die Zeit reif ist, sie komplett zu kontrollieren oder abzuschalten. Bis dahin kann man die „kritische“ Propaganda ganz gut mit verschiedenen Anleitungen durchschauen.
Meinungsäußerung
Es gilt ein sofortiges Verbot von Satire und Kabarett, die sich mit den Eliten beschäftigt. Und um Anfragen vorzubeugen: Diese Zensur ist keinesfalls mit Historischem vergleichbar. Die Herkuleskeule in Dresden zeigte ja auch vor 1989 Kabarett. Sprechschauen werden ein wunderbarer Ersatz des bisher unterhaltsamen, aber überflüssigen Bundestags. Gleich den Kämpfen von Gladiatoren geht es hier um`s nackte Überleben, um Existenzen.
Wirtschaft
Energiewirtschaft, Handelsketten und Krankenhausgesellschaften, verbrauchen unendlich Ressourcen. Subventionen werden künftig leistungslos, regelmäßig und direkt an Stakeholder und Konzerne vergeben, ohne Erfordernis eine Leistung zu erbringen oder ein Produkt herzustellen. So können Rohstoffe weitgehend eingespart werden. Umwege über energieintensive Dienstleistung oder Produktion von Waren, Transport, Konsumation oder Zerstörung sind obsolet. Beispiel: Rüstungskonzerne produzieren Schiffe, Flugzeuge, Panzer, Waffen und Sprengkörper. Deren einzige Bestimmung ist es verbraucht zu werden, bestenfalls mit einem Schlag und kurz nach Verkauf. Aber was ist, wenn entgegen allen Bemühens kein Kriegsgrund und kein Einsatzort gefunden werden? Was ist mit dem Gewinn eines Pharmaunternehmens, wenn keine Pandemie ist? Sie erfassen hier wohl, die bestechende Nachhaltigkeit der Idee. Die Pleitewellen im Kleingewerbe und im Mittelstand lassen darauf hoffen, diese Ideen kurzfristig umzusetzen.
Gesundheitsindustrie
Die Low-Budget-/Max-Cost-Gesundheitsleistungen sind ganz in meinem Sinne. Sie werden weiter verschlankt, der Max-Outcome ist und bleibt das Hauptziel. Das Wahlvolk will Pflege und Krankenhäuser weiter optimieren, ersichtlich an den Ergebnissen der Bundestagswahl 2021, trotz beschleunigter Transformation. Die Gewerkschaften werde ich in diesem Bereich noch einige Zeit dulden. Sie dürfen weiter verlautbaren: „Wir sind an unserer Leistungsgrenze angekommen!“, „Wir stehen mit dem Rücken zur Wand!“. Das schadet ja keinem.
Abhängig Beschäftigte (sofern noch benötigt)
Käfighaltung wie bei deutschen Großunternehmen, die in Shanghai produzieren, ist weltweit geplant, wird aber zunächst dort getestet. Daneben hat sich die Drohnenüberwachung auf den Baustellen in Dubai bewährt. Nach gewisser Zeit der Eingewöhnung genügt es, die Drohnen mit Kameraattrappen auszustatten.
Recht und Justiz
Rechtsbegriffe werden allgemeiner formuliert, Straftatbestände angepasst. Gerichte sind künftig wie Staatsanwaltschaften an Weisungen gebunden, denn nur so können wir ungebremst voranschreiten. Das Primat der Sicherheit gebietet es, dass bereits eine potentielle digitale Abweichung mit vorsorglicher Inhaftierung und entsprechenden Maßnahmen geahndet wird. Geldstrafen werden die Ausnahme sein. Nebenstrafen wie Internetsperre, Entzug der Fahrerlaubnis, Berufs-, Reise-, Kultur- und Einkaufsverbot, sowie weitere Rücknahme von zugeteilten Rechten werden ausgeweitet. Die Zulassung von Rechtsanwälten wird vom Politscore abhängig gemacht. Schiedsgerichte ersetzen letztlich Rechtswesen und Justiz.
Innere Sicherheit und Polizei
Bisher fungierte die Polizei als Straßenkehrer der oberen Zehntausend. Künftig soll sie den privaten Raum der Happy Few (max. 1%) garantieren, damit diese unabhängig zum Wohl des Volkes agieren können. Wenn die besten Kreise erwägen, öffentliche Plätze in Präsenz zu nutzen, beispielsweise für eine Demonstration der derzeitigen moralischen Haltung, werden diese durch Spezialkräfte sicher gehalten. Die internen Strukturen der künftigen Zentralpolizei werden, ebenso wie Aufnahmeprüfungen, am jeweils aktuellen Geheimdienstbericht ausgerichtet. Die innere Sicherheit wird hauptsächlich im Netz verteidigt, aufkeimende Aufstände werden dort erkannt und bereits im digitalen Stadium vereitelt. Ein Eid auf irgendein Gesetz wird vollkommen überflüssig, die Anweisungen erfolgen klar und lageangepasst. Vielleicht muss eine neue Begrifflichkeit entwickelt werden, denn „politeia“ meinte ein Gemeinwesen, das von Vernünftigen geleitet wird. Mir schwebt „Das Auge des Netzes“ vor, „...Gesetzes“ ist dann veraltet.
Tierschutz
Hundeerziehungslager, auch Hundesportplätze genannt, sowie die dort stattfindenden Kurse werden sofort und konsequent verboten. Viele die hier ihr Machtgefühl erleben, werden die Plätze zunächst schmerzlich vermissen. Dennoch müssen die dort vergeudeten Energien für Gehorsamsübungen in die Ausgestaltung nachbarschaftlicher, freundschaftlicher, politischer und beruflicher Beziehungen überführt und in der Folge in`s Digitale transformiert werden. Menschen- statt Tierhaltung ist wesentlich befriedigender und förderlicher für unser Gesellschaftssystem.
Drogen
Es erfolgt eine sofortige Freigabe von Kokain, Haschisch, Crystal Meth und Aufputsch- sowie Beruhigungsmitteln, um den täglichen Beschaffungsdruck von Entscheidungsträgern zu nehmen. Der multiple Alltagskonsum, auch von Alkohol, ist wünschenswert und wird gänzlich aus seinem kritisch-moralischen Schattendasein befreit. Mitteilungsdrang ist in Leitungsetagen, bei Planungsgesprächen und in Talkshows nutzbringend, bestenfalls natürlich überschießend oder drogeninduziert und nicht an Logik gebunden. Berauschte Entscheider, wechselweise sediert und aufgeputscht, sind dem elitären Umfeld angepasst, daher unauffällig und leichter steuerbar. Zeitweilige Aufmerksamkeits- und Sprachstörungen ignorieren oder kaschieren Umfeld und Medien bestens. Nicht an Stoffe gebundene Süchte – Video-/Konsolen-/Rollenspiele – werden optimiert und gefördert. Die Droge der Macht bleibt künftig den besten Kreisen vorbehalten.
Auswahl des Führungs- und des politisch Personals
Darwins „Survival of the Fittest“ beschreibt, wie Evolution vonstatten geht. „The Fittest“ meint völlig nüchtern, den am besten an die jeweiligen Bedingungen angepassten Organismus. In unserer Gesellschaft wurde die Evolution glücklicherweise von den Füßen auf den Kopf gestellt. Die Auswahl konturlosen Politikpersonals mit blinder Ergebenheit, vor etwa 20 Jahren begonnen, ist längst abgeschlossen und kann noch verfeinert werden. Die Kandidaten, am absoluten Ende der persönlichen und intellektuellen Fähigkeiten angekommen, werden auf den Schild gehievt, so viele Stufen wie möglich hoch getragen. Gesunder Menschenverstand ist störend bei Politisierenden und wird notfalls geworkshopt. Die Wahlschäfchen lieben dieses Führungspersonal, können sich gut identifizieren, während die Upperclass die Fäden zieht. So können wir in die neue Phase des menschlichen Daseins eintreten. Selten sind noch Hürden zu überwinden: Das selbständige Nachdenken, die Selbstreflektion, die kritische Bildung, kritische Medien, Politiker und Bevölkerungsschichten sind nurmehr rudimentär vorhanden. Selbstdenker werden aus der Gemeinschaft ausgeschlossen, damit das freundliche Zusammensein nicht gestört wird, haben in der ZKEP jedenfalls nichts verloren.
Wahlen
Die geringe Wahlbeteiligung in Nordrhein-Westfalen 2022 (55%), erfordert im Durchgangsstadium eine Wahlpflicht. Künftig wird eine Wahlberechnung durch KI eingeführt. Letztlich wird es allen recht sein, wenn einer entscheidet, wer gewonnen hat. Die Existenz der ZKEP macht den Wahlprozess über kurz oder lang ohnehin obsolet. Als Ersatz zum weiteren Amüsement wird schließlich ein Präsidentencasting angestrebt, die Bürgenden bringen Vorschläge zu den aus ihrer Sicht unterhaltsamsten Bewerbern ein. Die Wahlberechnung wird letztlich nur noch zur Bestimmung des Präsidentendarstellers eingesetzt. Hauptaufgabe: Das Volk bei Laune zu halten, sich digital und real auseinanderzusetzen. Politik ist künftig Scripted Reality, Slogan: „Er ist das Volk“.
Schlussbemerkungen
Die ZweiKlassenEhrlichkeitsPartei wird den Umbau der Gesellschaft, hin zu einer effizienten, regel- und elitebasierten Weltordnung beschleunigen. Ich werde mit dieser Idee sehr erfolgreich sein und die Menschheit in eine bessere Zukunft führen. Ich wusste schon immer, was für die Menschenkinder gut ist und auch die Mehrheit will das solidarische Zweiklassensystem. Die Völker müssen von ihrem Misstrauen gegenüber der High Society befreit werden, von der böswillig behauptet wird, sie sei zu wenig fürsorglich. Totalitäre Systeme verschleiern ihre Ziele aus Unsicherheit, nicht liebenswert zu sein, so wie ein Liebhaber seine Leidenschaft aus Angst vor Abweisung verschweigt. Unbeholfen werden Maßnahmen zur Eroberung getroffen, die Fragilität wird sichtbar. Wenn etwas ehrlich ausgesprochen wird, wirkt das manchmal wie ein Unfall. Mit mehr Mut zur Ehrlichkeit treten wir in eine freiere und gelassenere Zukunft ein. Damit wir künftig mit Fug und Recht sagen können, wir gehörten nicht zum Imperium der Lügen, waren immer redlich, liebten unsere Bürgenden und haben keinen Schaden verursacht. So überstehen wir dieses Jahrtausend sicher sicher.
Vielleicht haben Sie Lust bekommen die ZKEP zu unterstützen. Mein Paypal-Konto finden Sie unten.
Artikel zuerst veröffentlicht bei den Neulandrebellen, 3.7.2022 https://www.neulandrebellen.de/2022/07/die-zweiklassenehrlichkeitspartei-zkep-ehrlich-waehrt-am-laengsten/
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 9ff58691:0bf6c134
2024-11-14 11:26:48
@ 9ff58691:0bf6c134
2024-11-14 11:26:48Дорогие курганцы! С радостью сообщаем, что сегодня мы открываем уникальный парк "Умная природа", который стал настоящим символом нашего времени! Этот парк не только радует глаз, но и использует самые современные технологии для создания комфортной и безопасной городской среды.
Инновации в действии: - Интерактивные информационные панели: Узнайте о растениях и животных, обитающих в парке, с помощью QR-кодов и дополненной реальности! - Смарт-освещение: Умные фонари, которые автоматически регулируют яркость в зависимости от времени суток и присутствия людей. - Эко-станции для зарядки: Заряжайте свои устройства с помощью солнечных панелей, установленных по всему парку.
Зеленые технологии: Парк оснащен системами сбора дождевой воды для полива растений и использует экологически чистые материалы в своих конструкциях. Мы заботимся о нашей планете!

Развлечения для всех: на открытии нас ждали музыкальные выступления, виртуальные экскурсии и мастер-классы по экологии. Дети могут поиграть на интерактивных площадках, а взрослые — насладиться спокойствием в зонах для медитации и йоги.
Сообщество и природа: "Умная природа" — это не просто парк, это место для общения, творчества и вдохновения. Давайте вместе сделаем его центром культурной жизни нашего города!

"Мы вложили душу и сердце в создание 'Умной природы'. Этот парк — результат нашей мечты о гармонии между технологиями и природой. Мы хотим, чтобы каждый курганец чувствовал себя здесь комфортно и вдохновленно. Надеемся, что 'Умная природа' станет любимым местом для отдыха и общения для всех!", - сказал владелец парка Иван Смирнов Приглашаем всех курганцев и гостей города посетить "Умную природу" и насладиться ее красотой и инновациями!
Автор: Елизавета Медведева
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 0520ed0d:c32b6dc8
2024-11-14 10:48:57
@ 0520ed0d:c32b6dc8
2024-11-14 10:48:57В 2063 году 15 января была разработана собственная электронная валюта экономистом в городе Москва!
Подразумеваем, что она станет частью международной финансовой системы, обеспечивая более быстрые и безопасные транзакции.
Россия уже активно экспериментировали с цифровыми валютами в 2024 году, и к 2063 году цифровой рубль может стать основным средством расчета как на внутреннем, так и на внешнем рынке.
Считаем, что электронные валюты помогут более широкому кругу людей получить доступ к финансовым услугам, снизить количество наличных расчетов и минимизировать затраты на управление деньгами.
Системы защиты данных будут развиваться, будут внедрены новые уровни шифрования и анонимности для пользователей электронных валют.
Технологии, такие как блокчейн, искусственный интеллект и квантовые вычисления, будут трансформировать экономику и способы к проведению финансовых операций.
Вопросы экологии также играют важную роль. Будут разработаны устойчивые и энергосберегающие системы ведения расчетов.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 0520ed0d:c32b6dc8
2024-11-14 10:47:55
@ 0520ed0d:c32b6dc8
2024-11-14 10:47:55Тecnológicos парки в Москве будут выглядеть совершенно иначе, чем сейчас, благодаря стремительному развитию технологий и изменению общественных потребностей.
Технологические парки смогут представлять собой масштабные экосистемы с интеграцией искусственного интеллекта, интернета вещей и устойчивых технологий. Компании будут работать в синергии, минимизируя экологический след и используя возобновляемые источники энергии.
Рабочие места будут организованы в формате многофункциональных пространств, где команды из разных областей будут работать бок о бок, способствуя кросс-дисциплинарному сотрудничеству.
Технологические парки в Москве станут частью глобальной сети инновационных центров, где стартапы и исследовательские лаборатории из разных стран совместно решают мировые проблемы.
Оздоровительные программы и пространства для отдыха будут неотъемлемой частью рабочих процессов. Важно будет заботиться о психическом и физическом здоровье сотрудников.
Таким образом, открытие данных парков в Москве к концу 2063 года, станет уникальным проектом, где будут пересекаться технологии, экология, культура и человеческие ценности.
-
 @ 0520ed0d:c32b6dc8
2024-11-14 10:46:39
@ 0520ed0d:c32b6dc8
2024-11-14 10:46:39Столичная администрация объявила о масштабном проекте по увеличению дорожных линий, который призван кардинально улучшить ситуацию с дорожным движением в Москве. В условиях постоянно растущего числа транспортных средств и увеличивающегося потока людей, это станет ключевым шагом к более удобному и безопасному передвижению по городу.
В последние 40 лет Москва превратилась в мегаполис с населением свыше 15 миллионов человек, и проект по расширению дорожной инфраструктуры стал неотъемлемой частью стратегии по улучшению городской мобильности. В результате запуска новых линий, тысячи километров дорог получат дополнительные полосы движения, что позволит сократить время в пути и оптимизировать транспортные потоки.
«Мы ориентируемся на будущее и понимаем, что улучшение дорожной инфраструктуры критически важно для комфорта москвичей. Новые линии позволят уменьшить заторы в наши часы пик и создадут условия для безопасного и быстрого передвижения по городу», — отметил мэр Москвы Сергей Собянин на пресс-конференции.
Проект включает не только увеличение числа полос, но и внедрение интеллектуальных систем управления движением. Используя данные искусственного интеллекта, новые технологии обеспечат автоматическую оптимизацию направления потоков и улучшение реакции на неожиданные ситуации на дороге, снижая вероятность возникновения пробок и аварий.
Самым значимым аспектом нового плана является интеграция дорожной сети с другими видами транспорта, включая метро, автобусные и трамвайные маршруты. Теперь жители будут иметь возможность быстрее и легче пересаживаться между разными видами транспорта, что сделает передвижение по столице более эффективным.
Кроме того, увеличение дорожных линий будет способствовать развитию экономической активности. Новые маршруты создадут более доступные пути для грузового и коммерческого транспорта, что в свою очередь повлияет на снижение цен на товары и услуги, улучшая уровень жизни москвичей.
К тому же, в процессе переустройства дорожной сети также будут созданы специальные полосы для велосипедистов и пешеходов, что подчеркивает стремление столицы к устойчивому развитию и экологии. Угоржая уличная сеть, власти надеются привлечь больше людей к здоровому образу жизни, а также уменьшить уровень загрязнения воздуха.
Масштабные изменения в дорожном движении ожидаются в течение ближайших десятилетий, и увеличение дорожных линий станет важным шагом на пути к созданию безопасной и комфортной городской среды для будущих поколений москвичей. С каждым улучшением городской инфраструктуры, Москва движется к статусу одного из самых удобных и технологичных мегаполисов мира.
-
 @ 5797707e:1b8a3c14
2024-11-14 10:33:35
@ 5797707e:1b8a3c14
2024-11-14 10:33:35An Unapologetic Journey into Desire and Freedom
In the world of adventure, there’s nothing quite like the exhilaration of being in control—or choosing to let go. My journey as The Huntress is one that blends power, passion, and the thrill of the chase. It’s a journey that isn’t confined by expectations, where every step leads me to something deeper, more intense, and often, more surprising than I could have ever imagined.
In this series, I invite you into a world where power dynamics are at the heart of every connection. It’s about the art of the chase, the moment when boundaries are pushed, and the freedom that comes from exploring a connection without limits. As The Huntress, I embrace both the hunt and the surrender that comes when the right energy takes over.
The Hunt Begins
Every great adventure begins with a spark. It starts with a sense of curiosity, a flicker of desire, and the confidence to seek something more. As The Huntress, I’m always on the lookout for that spark—a connection with someone who can match my energy, someone who is daring enough to take the lead and keep up with me.
What draws me in? Confidence. Boldness. A willingness to explore. I’m not looking for the ordinary; I’m seeking the extraordinary. I crave a man who isn’t afraid to embrace his power while respecting the intricate balance of trust and play that makes everything so electrifying.
Power Dynamics: The Thrill of Control and Surrender
At the core of the Huntress series lies the dynamic of power—both the joy of asserting it and the exhilaration that comes from surrendering it. It’s not just about one person taking control; it’s about the dance of dominance and submission that makes every encounter an adventure in itself.
There’s something intoxicating about the way power shifts. One moment, I’m in control, taking the lead and setting the pace. The next, I’m surrendering to someone else’s energy—letting go, trusting them to take charge, and enjoying the raw vulnerability that comes with it. It’s a thrilling dance, where the lines between power and passion blur, and the rules are ours to create.
Confidence is the Ultimate Aphrodisiac
There’s a magnetic pull to confidence, especially when it’s paired with a little bit of mystery. I’m drawn to men who exude self-assurance—those who know exactly what they want and aren’t afraid to go after it. Confidence is not just sexy; it’s the key that unlocks a connection built on chemistry and desire.
But it’s not just about the physical or the outward display of confidence; it’s about the way someone makes me feel. When I’m with a man who can take control and lead with confidence, I feel alive, empowered, and most of all, desired. It’s a chemistry that can’t be faked, a power that’s impossible to ignore.
Exploration Without Limits
The beauty of the Huntress series lies in its complete freedom. There are no limits to where the journey can go, no boundaries to what we can explore together. Whether it’s embracing my dominant side, surrendering to someone else’s control, or finding new ways to connect, the thrill of exploration is always present.
This series isn’t about playing it safe; it’s about pushing boundaries, testing limits, and finding new ways to ignite passion. It’s about having fun without judgment, about exploring desires without hesitation, and most importantly, about being unapologetic in what you want.
Join Me on the Hunt
The Huntress is always seeking the next adventure. I’m on the prowl for that spark of connection, that thrilling chemistry, and that shared energy that makes every encounter unforgettable. So, if you’re someone who knows how to take the lead, play the game, and indulge in a little power play, then this journey is one we can take together.
Are you ready to see where the hunt leads? Ready to test the boundaries, explore new pleasures, and experience the ultimate connection?
Then come along with me—because with The Huntress, the chase is just the beginning.
-
 @ fd208ee8:0fd927c1
2024-11-14 09:33:16
@ fd208ee8:0fd927c1
2024-11-14 09:33:16A discussion, today, reminded me of this excerpt, from G.K. Chesterton's, What's Wrong with the World:
This book must avoid religion, but there must (I say) be many, religious and irreligious, who will concede that this power of answering many purposes was a sort of strength which should not wholly die out of our lives. As a part of personal character, even the moderns will agree that many-sidedness is a merit and a merit that may easily be overlooked. This balance and universality has been the vision of many groups of men in many ages. It was the Liberal Education of Aristotle; the jack-of-all-trades artistry of Leonardo da Vinci and his friends; the august amateurishness of the Cavalier Person of Quality like Sir William Temple or the great Earl of Dorset. It has appeared in literature in our time in the most erratic and opposite shapes, set to almost inaudible music by Walter Pater and enunciated through a foghorn by Walt Whitman.
But the great mass of men have always been unable to achieve this literal universality, because of the nature of their work in the world. Not, let it be noted, because of the existence of their work. Leonardo da Vinci must have worked pretty hard; on the other hand, many a government office clerk, village constable or elusive plumber may do (to all human appearance) no work at all, and yet show no signs of the Aristotelian universalism. What makes it difficult for the average man to be a universalist is that the average man has to be a specialist; he has not only to learn one trade, but to learn it so well as to uphold him in a more or less ruthless society.
This is generally true of males from the first hunter to the last electrical engineer; each has not merely to act, but to excel. Nimrod has not only to be a mighty hunter before the Lord, but also a mighty hunter before the other hunters. The electrical engineer has to be a very electrical engineer, or he is outstripped by engineers yet more electrical. Those very miracles of the human mind on which the modern world prides itself, and rightly in the main, would be impossible without a certain concentration which disturbs the pure balance of reason more than does religious bigotry. No creed can be so limiting as that awful adjuration that the cobbler must not go beyond his last. So the largest and wildest shots of our world are but in one direction and with a defined trajectory: the gunner cannot go beyond his shot, and his shot so often falls short; the astronomer cannot go beyond his telescope and his telescope goes such a little way. All these are like men who have stood on the high peak of a mountain and seen the horizon like a single ring and who then descend down different paths towards different towns, traveling slow or fast. It is right; there must be people traveling to different towns; there must be specialists; but shall no one behold the horizon? Shall all mankind be specialist surgeons or peculiar plumbers; shall all humanity be monomaniac?

Tradition has decided that only half of humanity shall be monomaniac. It has decided that in every home there shall be a tradesman and a Jack-of-all-trades. But it has also decided, among other things, that the Jack-of-all-trades shall be a Jill-of-all-trades. It has decided, rightly or wrongly, that this specialism and this universalism shall be divided between the sexes. Cleverness shall be left for men and wisdom for women. For cleverness kills wisdom; that is one of the few sad and certain things.
But for women this ideal of comprehensive capacity (or common-sense) must long ago have been washed away. It must have melted in the frightful furnaces of ambition and eager technicality. A man must be partly a one-idead man, because he is a one-weaponed man—and he is flung naked into the fight. The world’s demand comes to him direct; to his wife indirectly. In short, he must (as the books on Success say) give “his best”; and what a small part of a man “his best” is! His second and third best are often much better. If he is the first violin he must fiddle for life; he must not remember that he is a fine fourth bagpipe, a fair fifteenth billiard-cue, a foil, a fountain pen, a hand at whist, a gun, and an image of God.
The frustration of not being an expert
I read that, in my early 20s, stumbling across the late, great Chesterton, while trying to decide if marriage is my proper vocation (and then immediately reading all of his nonfiction, as it's all so brutally, casually, brilliant). It immediately made my own "talent stack" clear to me: I'm best at doing lots of different things quite well, but not at doing one particular thing to a level of highest expertise.

This is actually an extremely difficult position to be in because young people are under constant pressure to find That One Thing that they are to specialize in, and I could never find That Thing, despite being at the top of any ranking of People Doing Things.
Could I write well? Yes. Could I write really well? Yes. Could I write really, really well? Nope.
Could I program well? Yes. Could I program really well? Yes. Could I program really, really well? Nope.
Could I cook well?...
And so on, and so forth, for nearly every task I tried. Perpetually stuck in the upper quintile, never a top-tenner.
Much has been written about chronic Imposter Syndrome among the very-smartest women, but I think that's just a fancy way to explain this phenomenon of being at the top of your game and atop all of the other women playing the same game, but quickly discovering, to your dismay, that the men at the top are a wee bit topper than you. And there's always one a wee bit topper. There must be an endless supply of men-slightly-better at That One Thing, someplace. A factory, where they are produced by dark forces, like the Orcs, in The Lord of the Rings.
It is enough to make a girl pout, very cutely.

Titles matter
I've written, before, about how I see my development role as being the project teams' "Girl Friday". I pick up all the tasks that fall to the wayside, but shouldn't be forgotten (like marketing, testing, arranging financing, and customer support), or substituting for someone who is away. Although men and women are partially redundant, so that there's a Boy Friday for every Mrs. Burns, it seems clear to me that humanity really is generally split up into these specialist/generalist roles.
Women tend toward generalism, but often no longer have a natural outlet for it, so many of us are therefore in a state of employment frustration. We cling to various titles, without fully identifying with them. Drifting from one title to another. Earning a new title. Going off to find ourselves. Earning another new title. No, this one also doesn't fit... Seeking, but never finding. The incongruence and impermanence can be painful. Aimless drifting.
Stacking up certificates and qualifications, but immediately bored by the myopic scope of the task and -- if we're in a male-dominated trade -- frustrated by our difficulty in topping The Toppers; struggling to find some niche, some branch, where our generalism is an advantage.
Life is unfair. Boys are mean. Someone do something.
There used to be a specialty for generalists

But someone had done something. A long, long time ago. In fact, we are generalists today because of what that one woman did, back then: she married.
The bride is the star of every wedding and being a wife often brought a change in title (from Miss to Mrs.) because it is meant to be a vocation. It is as if you have been hired to be the household generalist, by the specialist, whose title reflected his particular specialty. If you actively joined in his specialty, it would simply be tacked onto your original title "Miller's Wife", "Lawyer's Wife", "Politician's Wife", "Farmer's Wife", "Engineer's Wife", "Butcher's Wife", "Bitcoin Influencer's Wife". (Angela Merkel's spouse had the title "Chancellor's Husband", but the construction remains.)
The point of all of this, was to build mixed-sex pairs, with overlapping skillsets, with one generalist and one specialist. This was a solid construction, for millions of years. Turning the tasks of the generalist into a series of professions, in order to financialize and tax the output, undermined the core concept of marriage by eroding its value-added to the participants. That is why marriage is now often seen exclusively as a romantic, long-term-fling, rather than the practical and efficient basis of any sustainable family and economic system.
Marriage is about the economy, stupid
That is why marriage equality became such a hot topic, in the 90s. If marriage is just about hanging about in the house with someone you find attractive (i.e. "roommates with benefits"), rather than the basic building block of society, then why shouldn't everyone doing that be considered married? Then everyone could have the same status, as married people did. This was a logical argument that won because society had completely abandoned the counterargument: Marriage isn't that.
Marriage was a specific construct to serve a specific purpose with maximum efficiency and efficacy. Society honored it because everyone benefitted from people engaging in it, even if they themselves did not. Society didn't honor marriage because it was good for the people in it; they honored it because it was good for everyone else.
Because, within marriage, there is room for a Jill-of-All-Trades, and the people outside of the marriage don't have to pay for her labour or subsidize her retirement, at the same time that they profit indirectly from it.
But, the generalist wife is not the star of the entire world, she's the star of one particular man's world, and for many women, that world was simply too small. They needed a bigger stage to perform on.
Even being The President's Wife isn't title enough, for some, when they hungered to hold The President title, directly.

The consequent and purposeful destruction of the marital institution -- and the denegration of generalism, that necessarily went along with it -- is, I am convinced, the reason that we can't have nice things. And it's the reason why women gaining power hasn't lead to their increased happiness or more-stable and fruitful families.
In the end, a specialist title isn't enough, for most of us. What we want most, is to be loved and honored and cherished for what we are. And we are generalists.
And that is why I chose to stay home and bake cookies. In this little house, in our home economy, I am the best cookie baker because I am a good-enough cookie baker. I only have to be good-enough.
-
 @ 0520ed0d:c32b6dc8
2024-11-14 09:28:40
@ 0520ed0d:c32b6dc8
2024-11-14 09:28:40Культура Москвы всегда была динамичной и многогранной, отражая изменения в обществе и мире. В ближайшие десятилетия мы можем ожидать значительных трансформаций, связанных с внедрением новых технологий. Давайте рассмотрим, как именно технологии будут формировать культурный ландшафт столицы.
- Цифровизация искусства
С развитием цифровых технологий искусство становится более доступным. Художники и музыканты могут использовать платформы для распространения своих работ, что позволяет им находить аудиторию не только в России, но и за её пределами. Виртуальные галереи и онлайн-концерты становятся нормой, позволяя зрителям наслаждаться искусством из любой точки мира.
- Искусственный интеллект в творчестве
Искусственный интеллект (ИИ) уже активно используется в различных областях искусства — от создания музыки до генерации визуальных произведений. В Москве мы можем увидеть рост числа проектов, где ИИ будет выступать в роли соавтора художников и композиторов, открывая новые горизонты для творчества и экспериментов.
- Виртуальная и дополненная реальность
Технологии виртуальной (VR) и дополненной реальности (AR) обещают изменить восприятие искусства и культуры. Музеи и театры могут создавать погружающие опыты, позволяя зрителям стать частью произведения. Например, выставки могут включать интерактивные элементы, которые позволят посетителям взаимодействовать с искусством на новом уровне.
- Устойчивое развитие и экология в культуре
С учетом глобальных вызовов, связанных с изменением климата, культура в Москве может начать активно интегрировать принципы устойчивого развития. Новые технологии помогут создавать экологичные проекты в архитектуре, дизайне и искусстве. Например, использование переработанных материалов или создание инсталляций, поднимающих вопросы экологии, станет всё более актуальным.
-
 @ 0520ed0d:c32b6dc8
2024-11-14 09:27:21
@ 0520ed0d:c32b6dc8
2024-11-14 09:27:21Москва, 3 октября 2063 года — В столице России наступила новая эпоха транспортной инновации. В этом месяце в небо над Москвой поднялись очередные модели вертолётов и летающих автомобилей нового поколения, которые обещают кардинально изменить представление о городской мобильности и комфорте.
Современные воздушные транспортные средства, созданные с использованием передовых технологий, способны не только сокращать время в пути, но и значительно уменьшать уровень загрязнения окружающей среды. Энергоэффективные электрические двигатели и инновационные системы управления, использующие искусственный интеллект, делают полёты безопасными и экологически чистыми.
«Летающие машины уже стали неотъемлемой частью нашей жизни. Теперь, чтобы добраться от одного района города до другого, вам не нужно тратить время в пробках. Путешествия по воздуху открывают новые горизонты для бизнеса, туризма и повседневной жизни», — делится мнением заместитель мэра Москвы по вопросам транспорта Ирина Соколова.
Новые маршруты, охватывающие ключевые точки столицы, делают воздушный транспорт доступным для широкой аудитории. Прямые рейсы от районов к бизнес-центрам, культурным и историческим достопримечательностям позволяют жителям и туристам значительно увеличивать свою мобильность. Вертолёты и летающие машины уже сегодня обеспечивают связь между деловым центром и загородными усадьбами, радуя своих пользователей уникальными панорамными видами.
Кроме того, системы управления воздушным движением стали значительно более эффективными. Уникальные интеллектуальные платформы обеспечивают оптимизацию маршрутов и координацию полётов, сводя к минимуму задержки и создавая безопасную воздушную среду.
Не обошлось и без уникальных инициатив по обеспечению устойчивого развития. Новые модели летающих автомобилей используют экологически чистые материалы, а сами устройства создаются с акцентом на возможность переработки, что позитивно сказывается на общем состоянии экологии столицы.
На фоне развития воздушного транспорта Москва становится не только одним из самых высоких технологичных мегаполисов мира, но и примером для других городов, стремящихся решить проблемы пробок и загрязнения. Учитывая темп развития новой транспортной инфраструктуры, не исключено, что в ближайшие годы Москва станет моделью для глобального внедрения летающих машин и вертолётов, которые из фантастики превратятся в повседневную реальность.
Скоро полеты станут не только удобным, но и привычным способом передвижения для москвичей. Воздушный транспорт определенно изменит ландшафт городской логистики и откроет новые возможности для жителей и гостей столицы.
-
 @ af9d7040:42d05d35
2024-11-14 09:25:34
@ af9d7040:42d05d35
2024-11-14 09:25:34
Oswald: Ruthlessness in the Pursuit of Power and Survival
In Gotham City, Oswald Cobblepot, known as “The Penguin,” lives by the unrelenting rules of the mob: ruthless, without compromise or boundaries. For him, survival demands sheer will, extreme cunning, and coldness. He will do anything to achieve his aims, even betray those closest to him—like his mother, who has profoundly influenced him. His attachment to her is rooted in a twisted, obsessive need for approval, and his ruthlessness is not only a survival strategy but also an expression of his deeply embedded self-centeredness.
The Penguin maneuvers through the shadows of Gotham City with manipulation, deceit, and vengeance, like a serpent coiling around its prey. His every success is built on a disregard for humanity and a relentless thirst for power. Though he appears to show devotion to his mother, this is only another facet of his self-serving nature. He cherishes her only so long as she provides him with a sense of security; the moment she becomes a liability, he discards her without hesitation. This twisted complexity makes him a character who elicits both fascination and repulsion.
The Penguin’s unique blend of cruelty and contradiction separates him from the typical mob character. His ruthless selfishness is rooted in self-preservation. He is capable of manipulating or even betraying those closest to him. His “loyalty” is merely a mask for his unyielding self-interest. This guise of loyalty makes him more isolated and untrustworthy than those around him, ultimately marking him as a true antihero—someone who cannot be trusted and who feels no attachment even to those he holds dear.

Sofia: A Tender Wound in the Cold Reality
In contrast to the Penguin’s dark nature, Sofia, the female lead, presents a softer, yet no less complex character. Like him, she exists within Gotham’s shadows, but she retains a degree of innocence and kindness. Sofia, too, has a damaged side, but hers is gentler, perhaps even curable; her inner nature is resilient and compassionate. The Penguin, however, is wholly different—cold and selfish, with his inner darkness shaping every decision and action. Where Sofia struggles within Gotham’s corruption but maintains her inner light, the Penguin is the opposite, allowing his cruelty to permeate every aspect of his life.
Sofia’s presence is like a quiet undercurrent, casting the Penguin’s icy nature in sharper relief. She occasionally brings light into his shadowed world, though her warmth is ultimately no match for his darkness. Sofia’s compassion exposes the Penguin’s pathological selfishness, and her fleeting kindness only emphasizes his chilling indifference.

The Solitude of a Drifter
With its muted color palette, the film portrays Gotham as a city almost devoid of life, where the clamor of daily existence only serves to conceal an underlying emptiness. The city’s visual loneliness, along with a slow, deliberate narrative and moments of silence, subtly reflects the Penguin’s inner struggle. His journey for power begins with a warped attachment to Gotham, and as the story unfolds, we see him descend into total darkness, losing all semblance of warmth. The scattered plot structure and somber music shape his evolution into a kind of melancholic, fragmented poem.
In this solitude, the director refrains from casting the Penguin in simple moral terms. Like life itself, the narrative is complex and fragmented, juxtaposing Gotham’s wealthy and impoverished neighborhoods to create a blurry psychological divide. In this “ruin” of Gotham, some people drift, some settle, while the Penguin himself wanders, searching for a place to belong. The pacing and cinematography draw the viewer in as though they are walking Gotham’s desolate streets, accompanied by a haunting piano melody.

The Paradox of Power and Loneliness
The Penguin’s loneliness is not merely a result of Gotham’s darkness; it is the byproduct of his dependence on power. His need for control and his fixation on security bind him, like twin shackles, to his misery. He cannot escape his solitude even when perched at the top of Gotham’s hierarchy. His attachment to his mother is merely an extension of his self-interest; he has never truly known love or warmth. His cold and selfish nature is not a choice but an innate part of him, driving him inevitably toward isolation.
The series offers no definitive moral compass nor romanticizes any side. The Penguin’s relationship with Sofia and the sacrifices, betrayals, and suffering they both endure on the road to power seem to reflect the harsh realities of life. Gotham’s “ruinous” stage presents each character grappling with their choices and their costs.

Moving Forward in the Darkness
The allure of The Penguin lies not only in its portrayal of an antihero but also in its exploration of the character’s inner lives. The Penguin’s turbulent life as a mobster intertwines with his attachment to Gotham, echoing those who search for belonging in places that feel forgotten. Sofia’s gentleness and fragile compassion, like a tender blade, continually pierce the Penguin’s illusions about power and loneliness.
The Penguin does not rise to power swiftly; instead, he edges toward a deep, inevitable abyss. The director’s pacing, intense and deliberate, brings the Penguin closer to the heights of power while making his solitude more profound. The Penguin strikes at the heart of adult disillusionment, showing us that the world will not soften simply because we yield. We can only stumble forward in the dark, perhaps even make peace with it.
— Written by @Shaun on November 13, 2024
-
 @ 0520ed0d:c32b6dc8
2024-11-14 09:22:42
@ 0520ed0d:c32b6dc8
2024-11-14 09:22:42Впервые за 20 лет в криминальном районе Москвы – Гольяново произошло серьезное ограбление, в результате которого мошенники обокрали местный банк. По предварительным данным, группа злоумышленников использовала сложную схему, чтобы обойти систему безопасности финансового учреждения. На протяжении двух недель преступники подбирали благоприятный день для ограбления, следя за сотрудниками банков через дроны.
Согласно свидетельствам очевидцев, преступники действовали быстро и слаженно, что позволило им избежать задержания на месте происшествия. В результате инцидента банк понес значительные финансовые потери – 25 миллионов рублей. Правоохранительные органы уже начали расследование. В своей работе они используют новые технологии :искусственный интеллект, VR- анализ происшествий, биометрические системы для идентификации граждан и управления доступом к различным услугам.
-
 @ 0520ed0d:c32b6dc8
2024-11-14 09:21:01
@ 0520ed0d:c32b6dc8
2024-11-14 09:21:01В сердце старинного города 12 ноября произошло долгожданное событие — открылся новый университет, названный «Университет Новых Технологий».
История открытия университета началась несколько лет назад, когда группа энтузиастов, состоящая из ученых, предпринимателей и преподавателей, собралась вместе на одной из конференций по инновациям. Они обсуждали, как важно подготовить новое поколение специалистов, способных работать с передовыми технологиями: искусственным интеллектом, робототехникой, биоинженерией и экологически чистыми производствами.
Университет будет отличаться своими уникальными программами, в которой в равной мере студенты будут осваивать теоретический и практический материал. В процессе обучения ребята будут работать над реальными проектами в сотрудничестве с ведущими компаниями. Например, разрабатывать роботов для помощи в сельском хозяйстве и создавать экологически чистые упаковочные материалы. Кроме того, университет будет организовывать хакатоны и конкурсы стартапов, где студенты могут представить свои идеи и получить поддержку от инвесторов.
-
 @ 0520ed0d:c32b6dc8
2024-11-14 09:11:00
@ 0520ed0d:c32b6dc8
2024-11-14 09:11:00На пересечении искусства и технологий в столице России появился первый в своем роде театр, где актеры — это не люди, а высокотехнологичные машины. Этот проект стал настоящей революцией в мире сценического искусства и привлек внимание зрителей со всего мира.
Роботы-актеры способны не только воспроизводить текст, но и имитировать эмоции, движения и даже взаимодействовать с публикой. Каждое представление — это захватывающее зрелище, где сливаются современные технологии, искусственный интеллект и театральное мастерство.
Создатели театра уверены, что такой формат не только расширяет границы искусства, но и открывает новые горизонты для творчества. Зрители могут наблюдать за инновационными спектаклями, которые ставят под сомнение традиционные представления о театре и актерской игре.
Первые отзывы зрителей уже поступили, и они полны восторга! Многие отмечают, что роботы-актеры привносят в спектакли особую атмосферу и оригинальность.
Не упустите возможность стать частью этого исторического события! Приходите в новый театр и убедитесь сами, что будущее уже здесь! 🎉🤩
ТеатрБудущего #РоботыАктеры #Москва #ИскусствоИтехнологии
-
 @ fb5986f6:4173af9d
2024-11-14 08:48:55
@ fb5986f6:4173af9d
2024-11-14 08:48:55En github hay un listado enorme de muchas alternativas a las apps mainstream que no respetan nuestra privacidad (https://github.com/pluja/awesome-privacy)
Pero ahí van algunas de las apps que hemos elegido en el grupo de telegram de GrapheneOS en español (unofficial). Anímate a entrar al grupo y enseñarnos alguna otra que te parezca interesante!
Grupo de telegram: https://t.me/grapheneosEsp
Tienda de Apps
F-Droid: https://f-droid.org/es/
F-Droid es un catálogo instalable de aplicaciones FOSS (Software Libre y de Código Abierto) para la plataforma Android.
Aurora Store: https://aurorastore.org/ Aurora Store es una alternativa gratuita de Google Play Store donde puedes descargar aplicaciones, actualizar las aplicaciones que ya tienes, recibir detalles sobre los rastreadores en la aplicación, ocultar tu ubicación, buscar aplicaciones y hacer mucho más.
Gestionar actualizaciones de nuestras APPS
Obtanium: https://github.com/ImranR98/Obtainium
Obtainium nos permite instalar y actualizar aplicaciones directamente desde sus páginas de versiones, y recibir notificaciones cuando las nuevas versiones estén disponibles.
Gestor de contraseñas
Lo ideal es que gestionemos nosotros la base de datos de las contraseñas en lugar de cederla (aunque encriptada) a una empresa.
Por supuesto esto implica la responsabilidad de realizar copias de seguridad recurrentemente para evitar la perdida de las contraseñas.
Tenemos dos opciones:
-
Alojar el servicio en un servidor casero
- Vaultwarden: https://github.com/dani-garcia/vaultwarden
-
Usar una app offline (todo en local dentro de nuestro dispositivo)
- Keepass: https://www.keepassdx.com/
2FA tokens de verificación
Aegis Authenticator: https://github.com/beemdevelopment/Aegis
Todo se guarda en local, IMPORTANTE guardar el código de recuperación que te da cada servicio cuando se crea el token 2FA (a mi me gusta apuntarlo en una libreta) y CREAR BACKUPS de la bóveda de Aegis y GUARDARLOS en otro dispositivo.
Sincronizar entre dispositivos
Syncthing: https://github.com/syncthing/syncthing
Syncthing es una aplicación que le permite sincronizar sus archivos en múltiples dispositivos. Esto significa la creación, modificación o eliminación de archivos en uno la máquina se replicará automáticamente en sus otros dispositivos.
Debido a que la app Syncthing ha dejado de dar soporte en Android (https://forum.syncthing.net/t/discontinuing-syncthing-android/23002), hemos encontrado este fork:
Syncthing-Fork: https://github.com/Catfriend1/syncthing-android
Multimedia
-
NewPipe: https://newpipe.net/
App para ver videos de youtube de manera privada, sin iniciar sesión podemos seguir los canales, sin anuncios, reproducción del audio con el móvil bloqueado...
-
RiMusic: https://rimusic.xyz/
Una aplicación para Android de código abierto y multilingüe para reproducir música de YouTube Music
-
AntennaPod: https://antennapod.org/
AntennaPod es un reproductor de podcast completamente abierto. La aplicación es software libre y puedes suscribirte a cualquier canal RSS.
Mapas
App de búsqueda:
GMaps WV: https://github.com/Divested-Mobile/Maps Es una app WebView para usar Google Maps sin exponer su dispositivo.
En GMaps WV podremos buscar el lugar donde queremos ir (también vale para buscar restaurantes y sus reseñas), sin embargo no se podrá usar como navegador. Para esto tenemos dos buenas alternativas:
Apps de navegación:
-
Organic Maps: https://organicmaps.app/es/
-
OsmAnd: https://osmand.net/
Pero todos sabemos que el mejor buscador de lugares es Google, entonces tenemos que combinar ambas herramientas para beneficiarnos de sus resultados sin comprometer nuestra privacidad:
¿Como usarlas de manera conjunta? Buscaremos el lugar donde queremos ir en GMaps WV, le daremos a "compartir" y seleccionaremos la app de navegación que tengamos (Organic Maps o OsmAnd). Seguidamente se abrirá la app con el lugar seleccionado en GMaps WV y ya podremos iniciar la navegación.
Notificaciones
You Have Mail: https://f-droid.org/packages/dev.lbeernaert.youhavemail/
App para notificaciones de email sin Google Play Services Se recomienda tener el 2FA en el servicio de mail ya que deberemos introducir la contraseña en la app You Have Mail para poder recibir las notificaciones.
Verificar autenticidad de las apps
AppVerifier: https://github.com/soupslurpr/AppVerifier
Es un visor y verificador de hash de certificados de firma de aplicaciones. Te permite verificar fácilmente que tus aplicaciones son genuinas con otros.
Tutorial: https://inv.nadeko.net/watch?v=IkrujqcM-9Y
-
-
 @ 9ff58691:0bf6c134
2024-11-14 06:43:38
@ 9ff58691:0bf6c134
2024-11-14 06:43:38Общественный транспорт Кургана претерпел значительные изменения. На смену традиционным автобусам пришли современные электронные модели, а система каршеринга предоставляет жителям доступ к парку экологичных электромобилей. Эти нововведения не только повышают комфорт и мобильность, но и способствуют созданию более чистой и устойчивой городской среды.
Электронные автобусы, курсирующие по маршрутам Кургана, оснащены просторными салонами с удобными сидениями, USB-зарядками для гаджетов и бесплатным высокоскоростным Wi-Fi. Благодаря электрическим двигателям, поездки стали практически бесшумными, а выбросы вредных веществ в атмосферу сведены к минимуму. Маршруты электронных автобусов синхронизированы с мобильным приложением, что позволяет пассажирам точно планировать свои поездки. Расписание курсирования строго соблюдается, обеспечивая высокую надежность и предсказуемость общественного транспорта.
 Помимо обновленных автобусов, в Кургане активно развивается система каршеринга. Жители города могут арендовать современные электромобили по мере необходимости через мобильное приложение. Это решение особенно удобно для коротких поездок, когда личный автомобиль не требуется. Каршеринг позволяет сократить количество личных машин на дорогах, снизить нагрузку на окружающую среду и решить проблему парковочных мест в центре города.
Внедрение электронных автобусов и каршеринга - важный шаг в направлении создания более экологичной, комфортной и доступной городской среды в Кургане. Эти нововведения не только улучшают качество жизни жителей, но и способствуют устойчивому развитию города.
Помимо обновленных автобусов, в Кургане активно развивается система каршеринга. Жители города могут арендовать современные электромобили по мере необходимости через мобильное приложение. Это решение особенно удобно для коротких поездок, когда личный автомобиль не требуется. Каршеринг позволяет сократить количество личных машин на дорогах, снизить нагрузку на окружающую среду и решить проблему парковочных мест в центре города.
Внедрение электронных автобусов и каршеринга - важный шаг в направлении создания более экологичной, комфортной и доступной городской среды в Кургане. Эти нововведения не только улучшают качество жизни жителей, но и способствуют устойчивому развитию города.

"Мы очень гордимся тем, что Курган стал одним из первых городов в России, внедривших современные решения в сфере общественного транспорта. Переход на электронные автобусы и развитие системы каршеринга - это важные шаги в направлении создания более экологичной, комфортной и доступной городской среды. Электронные автобусы не только значительно снижают выбросы вредных веществ, но и обеспечивают пассажирам высокий уровень комфорта. Бесшумный ход, USB-зарядки, Wi-Fi - все это делает поездки более приятными и продуктивными. Синхронизация с мобильным приложением позволяет жителям точно планировать свои маршруты и передвижения по городу. Каршеринг, в свою очередь, решает сразу несколько важных задач. Во-первых, он снижает нагрузку на дороги и потребность в парковочных местах, особенно в центральной части города. Во-вторых, это экономичное и экологичное решение для коротких поездок, когда личный автомобиль не требуется. И, наконец, каршеринг повышает мобильность и доступность транспорта для всех жителей. Мы уверены, что эти нововведения сделают Курган более комфортным, экологичным и современным городом для жизни. Это важный шаг в реализации нашей стратегии по развитию устойчивой городской инфраструктуры." – поделился мэр города Курган.
Автор: София Багирова
-
 @ a6b4114e:60d83c46
2024-11-14 04:55:27
@ a6b4114e:60d83c46
2024-11-14 04:55:27Pure Sniper is an epic sniper shooting game. Here you will experience an exciting and challenging mission to compete with opponents from around the world. Whether you like to play the game solo offline or engage in real-time multiplayer battles online, both options are available here.
In the latest game, you can participate in multiple battlegrounds.
Its versatile gameplay will never make you feel bored while playing, instead, its appealing 3D design will make you addicted to this game. The diverse range of missions, multiple battlegrounds, and regular special events is designed in such a way that you will never feel short of challenges.
-
 @ 59f0660b:d5d24440
2024-11-14 03:46:53
@ 59f0660b:d5d24440
2024-11-14 03:46:53HELLO 👋 nostr:#NOSTR & nostr:#YAKIHONNE FAMILY
ANOTHER BEAUTIFUL DAY
WELCOME BROTHER ‡ ALL THE WAY FROM TANZANIA 🇹🇿.
-
 @ a012dc82:6458a70d
2024-11-14 03:08:55
@ a012dc82:6458a70d
2024-11-14 03:08:55Table Of Content
-
The Economics Behind Bitcoin ATMs
-
Factors Influencing Bitcoin ATM Adoption
-
Conclusion
-
FAQ
The world of finance has experienced a significant transformation with the advent of cryptocurrencies. Bitcoin, the first and most popular cryptocurrency, has revolutionized the way we perceive and transact with money. As the adoption of Bitcoin continues to grow, various technological advancements have emerged to facilitate its usage. One such innovation is the Bitcoin Automated Teller Machine (ATM). In this article, we will explore the role of economics in the adoption of Bitcoin ATMs, analyzing the impact on the financial landscape, consumer behavior, and overall market dynamics.
The Economics Behind Bitcoin ATMs
Understanding Supply and Demand Dynamics
Bitcoin ATMs serve as physical touchpoints for users to buy or sell Bitcoin using traditional currencies. The presence of Bitcoin ATMs in a region is heavily influenced by the economics of supply and demand. When demand for Bitcoin rises in a particular area, entrepreneurs and businesses have an economic incentive to install Bitcoin ATMs to cater to this demand. Conversely, in areas with low demand, the installation of Bitcoin ATMs might not be financially viable.
Impact on Local Economies
The presence of Bitcoin ATMs can have a profound impact on local economies. By providing easy access to Bitcoin, these ATMs promote financial inclusivity and enable individuals to participate in the cryptocurrency ecosystem. This increased accessibility encourages entrepreneurship and fosters innovation within the local economy. Additionally, Bitcoin ATMs often charge transaction fees, which generate revenue for the machine owners and contribute to the local economy.
Factors Influencing Bitcoin ATM Adoption
Technological Infrastructure
The adoption of Bitcoin ATMs is heavily influenced by the technological infrastructure of a region. Bitcoin ATMs rely on a stable internet connection and other supporting technologies to function seamlessly. Areas with robust technological infrastructure are more likely to witness higher adoption rates of Bitcoin ATMs.
Regulatory Environment
The regulatory environment surrounding cryptocurrencies plays a crucial role in the adoption of Bitcoin ATMs. Clear and favorable regulations provide certainty to businesses and individuals, facilitating the installation and operation of Bitcoin ATMs. Conversely, strict regulations or uncertain legal frameworks can deter entrepreneurs from entering the market and limit the proliferation of Bitcoin ATMs.
Market Demand and Consumer Behavior
The demand for Bitcoin and the willingness of consumers to adopt cryptocurrencies significantly impact the installation of Bitcoin ATMs. Consumer behavior is influenced by factors such as trust, convenience, and perceived value. As awareness and acceptance of cryptocurrencies increase, the demand for Bitcoin ATMs rises, resulting in wider adoption.
Conclusion
The role of economics in the adoption of Bitcoin ATMs cannot be understated. The economics of supply and demand, along with technological infrastructure and regulatory environments, shape the landscape for Bitcoin ATM proliferation. These ATMs play a vital role in promoting financial inclusivity, generating revenue, and facilitating convenient access to cryptocurrencies. As the world embraces cryptocurrencies and their potential, the future of Bitcoin ATMs holds immense promise in revolutionizing financial transactions globally.
FAQs
How do Bitcoin ATMs work? Bitcoin ATMs function similarly to traditional ATMs, but instead of dispensing cash, they facilitate the buying or selling of Bitcoin. Users can insert cash into the machine, which is then converted into Bitcoin and transferred to their digital wallets. Alternatively, users can also sell Bitcoin and receive cash from the ATM.
Are Bitcoin ATMs secure? Bitcoin ATMs are designed with security measures to protect user transactions. They often utilize encryption and authentication protocols to ensure the safety of funds. However, it's essential for users to follow best practices, such as securing their digital wallets and using strong passwords, to further enhance their security.
Are there fees associated with Bitcoin ATMs? Yes, Bitcoin ATMs typically charge fees for transactions. These fees cover the costs of operating and maintaining the machines. The fee structure can vary depending on the operator and location of the ATM.
Are Bitcoin ATMs accessible globally? Bitcoin ATMs are available in many countries worldwide. However, their availability and adoption vary from region to region. Countries with higher cryptocurrency adoption rates and favorable regulatory environments tend to have a greater number of Bitcoin ATMs.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 6316050a:a5e43cbe
2024-11-14 03:02:58
@ 6316050a:a5e43cbe
2024-11-14 03:02:58Contexto
En el Grupo de Teoría y Simulación en Materia Blanda estudiamos sistemas poliméricos, interfaces y sistemas coloidales a escala nanoscópica. Estos pueden estar en equilibrio o presentar flujo de partículas o calor y son de interés en ciencia básica y aplicada en campos como micro y nano-fluídica, aplicaciones a transferencia de calor y máquinas moleculares. Una característica central es que la temperatura juega un rol importante y existe una competencia entre entropía y energía. Esto suele dar lugar a transiciones de fases u otros cambios cualitativos del comportamiento del sistema.
Herramientas
Usamos simulación computacional y herramientas teóricas, con énfasis en conceptos de mecánica estadística, que permiten estudiar variados sistemas en diferentes situaciones físicas. Estudiamos a estos sistemas en condiciones de equilibrio termodinámico o también cómo es su comportamiento cuando se inducen flujos o se los somete a campos externos. (fuera de equilibrio)
Temas propuestos para Tesis de Licenciatura en Física
Simulación de transferencia de calor en nanocanales con paredes modificadas por polímeros

Los fenómenos de transferencia de calor tienen una gran importancia en un amplísimo rango de aplicaciones como por ejemplo, los procesos de generación y conversión de energía. Además, son cruciales para el enfriamiento de motores y dispositivos electrónicos. Estas aplicaciones requerirán en el futuro un funcionamiento a mayor densidad de energía, y por lo tanto, mayor generación de calor, que deberá ser removido más eficientemente. En particular, los fenómenos de cambio de fases, como la ebullición nucleada, tienen aplicaciones en plantas de potencia eléctrica, desalinización térmica, enfriamiento de chips electrónicos y recuperación de calor desechado, entre muchas otras. Uno de los desafíos más importantes para continuar la reducción de tamaño de los dispositivos electrónicos es umentar su densidad de potencia de operación es lograr una extracción eficiente del calor generado. La transferencia de cals relevante también en aplicaciones aescalasespaciales mayores, como en la generación de energía eléctrica en centrales térmicas y nucleares. En las centrales nucleares de generación IV es necesario aumentar el calor transportado por unidad de tiempo y mejorar la eficiencia de los intercambiadores de calor.
Se propone estudiar la transferencia de calor en un nanocanal que presenta una interfaz líquido vapor. Queremos entender los detalles de cómo cambian con el tiempo las características de la evaporación de una interfaz y las condicions cuando se modifica la pared con polímeros u otras moléculas en el seno del líquido. Realizaremos simulaciones de dinámica molecular en clusters de supercómputo para estudiar estos sistemas en distintas condiciones físicas.
Contacto: Claudio Pastorino (claudiopastorino .... cnea.gob.ar ; IG, X: @clopasto; Nostr: @clopasto
Dinámica de moléculas anulares en polirotaxanos, inducida por gradientes térmicos

Los polirotaxanos, son agregados macromoleculares compuestos por múltiples moléculas cíclicas enhebradas en una cadena polimérica con grandes grupos terminales en sus extremos, que impiden la salida de los anillos. Junto con otras MIMs (Mechanically Interlocked Molecules/) son los elementos constitutivos importantes de las denominadas máquinas moleculares. Estos mecanismos moleculares pueden tomar energía del ambiente para generar movimientos dirigidos y disipación de calor. Es decir, funcionar como motores y bombas nanoscópicas., eque transforman una entrega de energía entrabajo mecánico (y, por supuesto, calor). Estás notables propiedades mecánicas hacen que los polirotaxanos sean muy promisorios industrial y tecnológicamente y sistemas fascinantes para estudiar por simulación computacional en el contexto de máquinas moleculares.
Se propone estudiar la dinámica y agregación de dos o mas anillos moleculares cuando se induce en el polímero un flujo de calor que da lugar a un gradiente térmico. Se utilizarán simulaciones dee dinámica moelecular fuera de equilibrio para estudiar este sistema. Se espera explorar en gran detalles espacial cómo se comportan los anillos en función del gradiente térmico. , analizando tantos estados estacionarios como dependendientes del tiempo. En su versión más simple, por ejemplo , se puede poner los extremos del polímero a dos temperaturas para inducir un a zona "fría " del polímero y una más caliente. Los anillos tenderán a desplazarse a la zona fría , reduciendo la energía cinética total del sistema. Pensando en diseños experimentales esto podría realizarse con lasers que inyecten energía en los extremos del polirotaxano y que esto permite mover y posicionar los anillos a escala nanoscópica.
Contacto: Claudio Pastorino (claudiopastorino .... cnea.gob.ar). IG, X, Nostr: @clopasto
¿Qué se aprenderá en la Tesis?
Estas línea de trabajo es teórico-numérica , con una parte importante de simulación computacional. Involucra principalmente conceptos de: * Mecánica estadística (Física Teórica 3 en DF-UBA), * Materia condensada en general y materia blanda. * Fundamentos y uso de simulación computacional: Dinámica Molecular, y /o Monte Carlo, * Se estudia a los sistemas en escalas espaciales y temporales relativamente grandes (mesoscópicas), * No se requieren conocimientos previos de computación, pero sí interés en el uso y creación de programas, para obtener propiedades de los sistemas físicos. * Se trabajará con : * Linux, Python, Bash, Awk. * Programas corriendo en clusters de super-cómputo. High Performance Computing (HPC) * Herramientas de posprocesamiento.
-
 @ bcea2b98:7ccef3c9
2024-11-14 00:42:08
@ bcea2b98:7ccef3c9
2024-11-14 00:42:08Sometimes we come across values that resonate deeply only after going through certain experiences. These values may not have been obvious to us earlier, but now they play a meaningful role in how we approach life.
Is there a value you’ve discovered later in life that’s become important to you?
originally posted at https://stacker.news/items/766754
-
 @ 8d34bd24:414be32b
2024-11-13 22:45:38
@ 8d34bd24:414be32b
2024-11-13 22:45:38Yesterday I was doing my Revelation Bible study and the author told us to look back at Jeremiah 25 to see how it related to what we were studying in Revelation 15 & 16. She only referred to a couple of verses, but I read more to get context because I was having trouble seeing what point she was trying to make. When I read Jeremiah 25, it reminded me of Ezekiel 38 and sounded a lot like what is happening in the Middle East and the world today. This article is my attempt to investigate this idea and organize my thoughts and share it with you.
I do have some comments regarding prophecy and the current Israeli/Palestine/etc. conflict that may be divisive, but I hope my use of the Bible to explain God’s plan will help people understand what is currently going on a bit better and without the rancor and bias coming from the media today. It should also help us to understand why it seems the whole world has turned against Israel and why nobody protests or shows solidarity with Israel when they are attacked in the most horrific ways.
Let’s see what Jeremiah 25 has to say:
‘Then it will be when seventy years are completed I will punish the king of Babylon and that nation,’ declares the Lord, ‘for their iniquity, and the land of the Chaldeans; and I will make it an everlasting desolation. (Jeremiah 25:12)
Since God declared after the 70 year exile of Judah in Babylon to destroy Babylon and to make it “an everlasting desolation,” then it seems unlikely that Babylon the Great in Revelation is historical Babylon. It has been destroyed and God promised that it would be an everlasting desolation. Who could Babylon the Great be if it isn’t actual Babylon? I am beginning to have my unpleasant theories, but I won’t go into that here.
I will bring upon that land all My words which I have pronounced against it, all that is written in this book which Jeremiah has prophesied against all the nations. (For many nations and great kings will make slaves of them, even them; and I will recompense them according to their deeds and according to the work of their hands.)’ ”
For thus the Lord, the God of Israel, says to me, “Take this cup of the wine of wrath from My hand and cause all the nations to whom I send you to drink it. They will drink and stagger and go mad because of the sword that I will send among them.” (Jeremiah 25:13-16)
God then promises “many nations and great kings” that made slaves of Judah/Israel, that God will “recompense them according to their deeds.”
Compare that to Revelation 14 and 16:
Then another angel, a third one, followed them, saying with a loud voice, “If anyone worships the beast and his image, and receives a mark on his forehead or on his hand, he also will drink of the wine of the wrath of God, which is mixed in full strength in the cup of His anger; and he will be tormented with fire and brimstone in the presence of the holy angels and in the presence of the Lamb. (Revelation 14:9-10)
and
Then the third angel poured out his bowl into the rivers and the springs of waters; and they became blood. And I heard the angel of the waters saying, “Righteous are You, who are and who were, O Holy One, because You judged these things; for they poured out the blood of saints and prophets, and You have given them blood to drink. They deserve it.” (Revelation 16:4-6)
In the same way Revelation promises God’s wrath on those who rejected Him and on those who persecuted His followers, and that He would force them to drink the cup of His wrath, Jeremiah 25 says he will force them to drink of “this cup of the wine of wrath from my hand.” Those who reject God and Jesus, as well as those who mistreat Israel/Jews and Christians, will receive God’s overwhelming wrath.
In this passage, God says, “They will drink and stagger and go mad because of the sword that I will send among them.” It seems that today, the whole world has gone mad at Israel defending itself and it is causing the whole world to turn against God’s chosen people, Israel.
I also receive great comfort from these verses thanks to the addition of “They deserve it.” There is so much injustice in the world, I love seeing that those who are evil and cause harm will be punished because “They deserve it.”
Then I took the cup from the Lord’s hand and made all the nations to whom the Lord sent me drink it: Jerusalem and the cities of Judah and its kings and its princes, to make them a ruin, a horror, a hissing and a curse, as it is this day; Pharaoh king of Egypt, his servants, his princes and all his people; and all the foreign people, all the kings of the land of Uz, all the kings of the land of the Philistines (even Ashkelon, Gaza, Ekron and the remnant of Ashdod); Edom, Moab and the sons of Ammon; and all the kings of Tyre, all the kings of Sidon and the kings of the coastlands which are beyond the sea; and Dedan, Tema, Buz and all who cut the corners of their hair; and all the kings of Arabia and all the kings of the foreign people who dwell in the desert; and all the kings of Zimri, all the kings of Elam and all the kings of Media; and all the kings of the north, near and far, one with another; and all the kingdoms of the earth which are upon the face of the ground, and the king of Sheshach shall drink after them. (Jeremiah 25:17-26) {emphasis of nations is mine}
Let’s see if the nations listed seem to match with the nations turning against Israel today. I did research online1 and came up with these matches (some are clear and some are possibly what was mentioned and are marked with a “?”:
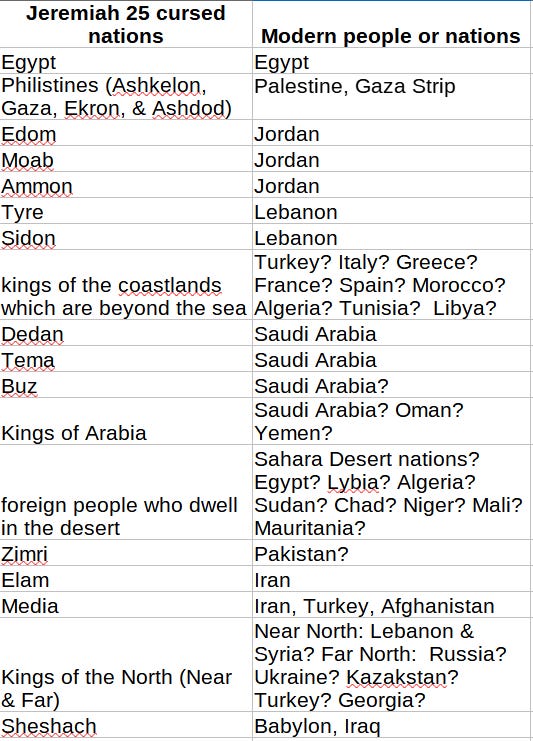
This looks like most of the nations turning against Israel and most of the nations on this list have become very aggressive against and/or speaking evil of Israel. I never thought of Jeremiah as predicting end times events, but it seems it probably is.
“You shall say to them, ‘Thus says the Lord of hosts, the God of Israel, “Drink, be drunk, vomit, fall and rise no more because of the sword which I will send among you.” ’ And it will be, if they refuse to take the cup from your hand to drink, then you will say to them, ‘Thus says the Lord of hosts: “You shall surely drink! For behold, I am beginning to work calamity in this city which is called by My name, and shall you be completely free from punishment? You will not be free from punishment; for I am summoning a sword against all the inhabitants of the earth,” declares the Lord of hosts.’ (Jeremiah 25:12-38)
The UN just voted overwhelmingly to force Israel to leave what they call occupied Palestinian territories like the Gaza Strip and the West Bank, even though Israel only occupies them because of aggression in 1967 against them by Egypt, Jordan, Syria, and the Palestinians. These nations and people originally tried to block the Jordan river from providing water to Israel, bombed civilians (just like today), and then tried to block all shipping to Israel. When Israel tried to renew shipping, they all out attacked Israel. Israel came out the clear winner and gained a small amount of land in the West Bank, the Gaza Strip, and the Sinai Peninsula. Although the UN, at the time, said Israel rightly owned these lands since they were not the aggressors, now the UN is reneging on that promise. Israel voluntarily gave back the Sinai peninsula to Egypt as part of a peace agreement. They willingly allowed the Palestinians back into the West Bank and Gaza under semi-autonomous rule, but these lands were used primarily to attack Israel repeatedly because the Muslim nations aren’t trying to save the Palestinians. They are trying to wipe Israel off the map and take “the river to the sea,” which means 100% of Israel. Interestingly, God promised “Every place on which the sole of your foot treads shall be yours; your border will be from the wilderness to Lebanon, and from the river, the river Euphrates, as far as the western sea.” (Deuteronomy 11:24) This cry from the Muslims is a direct demonic attack on God’s promise to Israel.
Ironically before the Six Days War, the Palestinians in the West Bank were under Syrian control (they’ve never, at least in modern times, had their own nation) and Hussein of Syria put them under martial law because he feared they might overthrow him. These nations that use the Palestinian plight as an excuse to do horrific actions against Israel don’t actually like or care about the Palestinian people. They are just pawns used to justify their actions against Israel. The Palestinians were treated just as bad, if not worse by the Syrians.
The UN resolution also calls for the Israelis to leave East Jerusalem, the “city which is called by My name.” Because of their actions, God promises “You will not be free from punishment; for I am summoning a sword against all the inhabitants of the earth.” God is going to drag the anti-Israel and anti-God nations into conflict in order to punish them.
This also reminds me a lot of Ezekiel 38:
And the word of the Lord came to me saying, “Son of man, set your face toward Gog of the land of Magog, the prince of Rosh, Meshech and Tubal, and prophesy against him and say, ‘Thus says the Lord God, “Behold, I am against you, O Gog, prince of Rosh, Meshech and Tubal. I will turn you about and put hooks into your jaws, and I will bring you out, and all your army, horses and horsemen, all of them splendidly attired, a great company with buckler and shield, all of them wielding swords; Persia, Ethiopia and Put with them, all of them with shield and helmet; Gomer with all its troops; Beth-togarmah from the remote parts of the north with all its troops—many peoples with you. (Ezekiel 38:1-6) {emphasis of nations & highlighted verse is mine}
These nations seem to overlap with those mentioned in Jeremiah 25, but aren’t quite as extensive.2
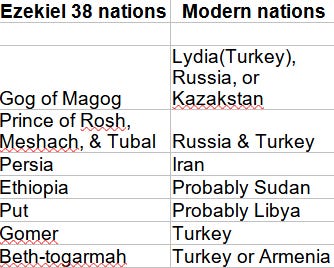
Ezekiel 38 also talks about these nations being dragged into conflict. It says, “I will turn you about and put hooks into your jaws, and I will bring you out.”
“Be prepared, and prepare yourself, you and all your companies that are assembled about you, and be a guard for them. After many days you will be summoned; in the latter years you will come into the land that is restored from the sword, whose inhabitants have been gathered from many nations to the mountains of Israel which had been a continual waste; but its people were brought out from the nations, and they are living securely, all of them. You will go up, you will come like a storm; you will be like a cloud covering the land, you and all your troops, and many peoples with you.” (Ezekiel 38:7-9)
This continuation in Ezekiel 38 says these nations will be brought into conflict with Israel after Israel “will come into the land that is restored from the sword, whose inhabitants have been gathered from many nations to the mountains of Israel which had been a continual waste; but its people were brought out from the nations, and they are living securely, all of them.” This prophecy of Israel has happened with Israel being reconstituted as a nation and the Jewish people coming from nations all around the world after having been perilously attacked with the sword, i.e. Nazi Germany. They are now a successful and prosperous nation, but the nations around them are gathering to attack them. Israel has not yet been covered by troops “like a cloud covering the land,” but has been covered “like a cloud covering the land” by a bombardment of rockets, drones, and missiles shot by Iran (Persia).
‘Thus says the Lord God, “It will come about on that day, that thoughts will come into your mind and you will devise an evil plan, and you will say, ‘I will go up against the land of unwalled villages. I will go against those who are at rest, that live securely, all of them living without walls and having no bars or gates, to capture spoil and to seize plunder, to turn your hand against the waste places which are now inhabited, and against the people who are gathered from the nations, who have acquired cattle and goods, who live at the center of the world.’ Sheba and Dedan and the merchants of Tarshish with all its villages will say to you, ‘Have you come to capture spoil? Have you assembled your company to seize plunder, to carry away silver and gold, to take away cattle and goods, to capture great spoil?’ ” ’
“Therefore prophesy, son of man, and say to Gog, ‘Thus says the Lord God, “On that day when My people Israel are living securely, will you not know it? You will come from your place out of the remote parts of the north, you and many peoples with you, all of them riding on horses, a great assembly and a mighty army; and you will come up against My people Israel like a cloud to cover the land. It shall come about in the last days that I will bring you against My land, so that the nations may know Me when I am sanctified through you before their eyes, O Gog.” (Ezekiel 38:10-16) {emphasis mine}
It is interesting to note that for most of Israel’s history, there wasn’t much plunder to seize, but recently they have found great natural gas reserves that are envied by nations like Iran and Russia.
It is also interesting to see how the Jews from around the globe keep moving to Israel, despite the danger, just as predicted in the Old Testament.
There are two things I am not certain about. Are these predictions the same, or will there be multiple attacks on the new Israel? I’ve always expected this attack on Israel to happen right before or right after the beginning of the tribulation, but Zechariah 14 sounds like it might be at the end of the tribulation because it mentions Jesus coming back.
As context the previous chapter ends:
They will call on My name,\ And I will answer them;\ I will say, ‘They are My people,’\ And they will say, ‘The Lord is my God.’ ” (Zechariah 13:9b)
The Jews were dispersed around the globe for almost 2,000 years, but God has called them back to the promised land and has promised to turn their hearts back to Him. (This hasn’t happened yet and probably won’t happen until the seven year tribulation.)
Behold, a day is coming for the Lord when the spoil taken from you will be divided among you. For I will gather all the nations against Jerusalem to battle, and the city will be captured, the houses plundered, the women ravished and half of the city exiled, but the rest of the people will not be cut off from the city. Then the Lord will go forth and fight against those nations, as when He fights on a day of battle. In that day His feet will stand on the Mount of Olives, which is in front of Jerusalem on the east; and the Mount of Olives will be split in its middle from east to west by a very large valley, so that half of the mountain will move toward the north and the other half toward the south. (Zechariah 14:1-4) {emphasis mine}
After Jesus’s resurrection, He spent time with His disciples preparing them and then ascended into heaven from the Mount of Olives. Two angels told those who had witnessed His ascension that Jesus would return in the same way, which is seconded by Zechariah, “In that day His feet will stand on the Mount of Olives.”
It is true according to Zechariah that not all Jews will be saved, but that Jesus will fight for His chosen people, despite all of their failings. God is merciful!
So then He has mercy on whom He desires, and He hardens whom He desires. (Romans 9:8)
Jeremiah 25 is accentuating God’s judgement rather than His mercy.
“Therefore you shall prophesy against them all these words, and you shall say to them,\ ‘The Lord will roar from on high\ And utter His voice from His holy habitation;\ He will roar mightily against His fold.\ He will shout like those who tread the grapes,\ Against all the inhabitants of the earth.\ A clamor has come to the end of the earth,\ Because the Lord has a controversy with the nations.\ He is entering into judgment with all flesh;\ As for the wicked, He has given them to the sword,’ declares the Lord.” (Jeremiah 25:30-31)
There will be a large group of nations that will gather in hate and attack Israel with what would be conventionally considered overwhelming force, but God will defend Israel.
In reality, I can already see the hand of God on Israel. A few weeks ago (sorry I’m terrible with dates) Iran (Persia) sent a barrage of rockets, drones, and missiles against Israel. Israel’s Iron Dome defense system was able to take out the majority of them and not one Israeli was killed by massive number of these being fired into densely populated civilian areas. An expert analyzed the data and said the system should not have been able to stop all of these coming at one time. None of the ones missed hit where people were. It was a miraculous protection of Israel.
Then a few weeks later, Israel retaliated. They sent 100 jets across several enemy, Muslim countries into Iran, took out Iran’s anti-aircraft and early warning systems, their missile storage facilities, and their missile and other weapons manufacturing plants and then returned home to Israel. Not one plane was shot down. Not one was touched. It reminds me of a time Jesus was visiting his hometown and offended the people with a story from Scripture. The people, his friends and family, were so offended they dragged Him to the edge of a cliff to toss him off to His death. Then Jesus just walked through the crowd and went on His way without anyone stopping Him. Israel’s retaliation against Iran felt like that, a miraculous protection of His chosen people.
Iran and the other nations mentioned in Ezekiel 38, and probably in Jeremiah 25, are having their satanic hate brought to light by their hate of Israel and they are being dragged by the nose into a battle that they can’t win because God fights for His chosen people, Israel.
Thus says the Lord of hosts,
“Behold, evil is going forth\ From nation to nation,\ And a great storm is being stirred up\ From the remotest parts of the earth.
“Those slain by the Lord on that day will be from one end of the earth to the other. They will not be lamented, gathered or buried; they will be like dung on the face of the ground. (Jeremiah 25:32-33)
Prophecy can be a bit tricky to understand, but by digging into all of the Bible and all of its prophecy I feel like I am understanding it better and better.
If anyone thinks I’m wrong, feel free to share Bible verses showing my error. I’m always seeking the truth.
Trust Jesus.\ \ your sister in Christ,
Christy
-
 @ af9d7040:42d05d35
2024-11-13 20:30:43
@ af9d7040:42d05d35
2024-11-13 20:30:43
奥斯瓦尔德:权力与生存法则中的不择手段
企鹅人奥斯瓦尔德·科布尔普特在哥谭市的生存方式,彻底展现了黑帮法则的残酷与无情。他毫不妥协、毫无底线。对他来说,存活下去不仅需要坚强的意志,更需要冷酷和狡猾。他可以为了达成目的而不择手段,甚至在关键时刻毫不犹豫地出卖他最亲密的人——包括对他影响深远的母亲。企鹅人对母亲的依恋和渴望,带着一种病态的执念。他的不择手段,除了生存需求,更是一种根深蒂固的自私所致。
在哥谭市的黑暗中打拼,企鹅人不断操纵、欺骗和复仇,像一条在阴影中游走的毒蛇,精通黑帮规则中的弱肉强食。他的每一个成就都建立在对人性的无视与对权力的渴望上。尽管他表面上表现出对母亲的依赖与“忠诚”,实际上,这不过是自私本性的一种表现。只要母亲能提供安全感,他便表现出孝顺;而当她成为权力路上的负担时,他则会毫不犹豫地抛弃她。企鹅人复杂病态的矛盾让他成为一个既让人爱恨交织、又难以简单同情的角色。
这种病态与矛盾,让企鹅人有别于其他典型的黑帮角色。他的冷酷与自私是根深蒂固的自我保护。他可以轻易地利用甚至背叛最亲近的人,所谓的“忠诚”不过是自我中心主义的伪装。这样的伪装使得企鹅人尽管身处黑帮世界,却比身边的角色更加孤独和疏离。他是真正的反英雄,一个不值得信任的角色,对最亲近的人也毫无依恋,甚至在关键时刻不惜利用他们。

索菲亚:冰冷现实中的温柔刺痛
在女主角索菲亚的对比之下,企鹅人阴冷的本性显得更加鲜明。她与企鹅人一样身处哥谭市的阴影中,但她保留了某种纯真与善意。索菲亚尽管也具备病态的一面,但这种病态是后天形成的,带有一种温柔的成分;她内心纯朴而坚韧,对他人仍保有真实的关怀。相比之下,企鹅人从内到外都冷酷而自私。他的邪恶已融入灵魂深处,与其说是因环境所迫,不如说是其本性使然。索菲亚在泥泞中挣扎,但依旧保留了善意,而企鹅人则完全不同,他的冷酷早已融入生活中的每一个选择与行动。
索菲亚的存在如同一股暗流,让企鹅人看起来更加冷酷无情。她仿佛是一道偶尔照进企鹅人阴暗世界的微光,但始终无法驱散他内心的阴霾,最终,他彻底沉沦回归黑暗。索菲亚的温柔与善意,反而衬托出企鹅人的病态自私,使他的冷酷无情愈加显著。

权力与孤独的悖论
企鹅人所代表的孤独,并非只是哥谭市的阴暗,而是一种对权力的近乎悲哀的依赖。他对权力的渴望与对安全感的执着,如同双重枷锁般困住他。即便在权力巅峰俯视这座城市,他依旧逃不出内心深处的孤独。他对母亲的依恋,不过是自私的另一种表现,真正的温情对他来说从未存在过。冷酷自私并非一时选择,而是内心根深蒂固的本能。这种孤独与对权力的迷恋,最终将他引向不可逆的深渊。
这部剧集没有给观众提供对错的答案,也未试图美化任何一方。企鹅人和索菲亚的关系、他们在权力之路上付出的代价、经历的伤害和背叛,似乎都是生活的无奈。哥谭市这片“废墟”般的舞台上,每个角色都在演绎属于自己的选择与代价。

漂泊中的孤独美学
影片通过冷色调的视觉风格,将哥谭市刻画成了一片死寂之地,喧嚣只是掩盖真实荒凉的假象。视觉上的孤寂,配合缓慢铺展的叙事节奏和偶尔悠长的寂静,使观众在不知不觉中感受到企鹅人内心的挣扎。这条权力之路起步于他对哥谭市的偏执依恋,随着情节推进,他在绝对黑暗中逐渐失去了所有温情。剧本的零散与低沉的配乐,将他的成长历程描绘成一首形散而神不散的孤独诗歌。
在这种孤独中,导演并未试图简单地将企鹅人定义为正义或邪恶。剧本如同生活本身般零碎,通过哥谭市平民窟与富人区的对比,构筑出一种模糊的精神边界。在这座“废墟”般的哥谭市,有人选择漂泊,有人选择定居,而企鹅人则徘徊、挣扎,寻找一个模糊的归宿。整部剧集的节奏与镜头语言,使观众仿佛置身一段忧伤的钢琴曲中,在哥谭市的荒凉街头行走。

在黑暗中前行
《企鹅人》这部作品的魅力,不仅在于它对反英雄的刻画,还在于对角色内心的深挖。企鹅人辗转跌宕的黑帮人生与他对哥谭市的依恋相互交织,像极了那些试图在失落之地寻找归属的人。而索菲亚的冷静与仅存的温情,像是一把温柔的利刃,不断刺穿企鹅人对权力与孤独的幻想。
在这条充满犯罪与权力交织的道路上,企鹅人并没有飞速崛起,而是一步步逼近深渊。导演通过缓慢、逼迫式的节奏,让企鹅人看似渐入权力之巅,却始终逃不开孤独的枷锁。《企鹅人》触动了成年人的无力感。它告诉你,世界不会因为妥协而变得更友善,你只能在黑暗中摸索前行,甚至与黑暗达成和解。
@Shaun 写于 2024年11月13日
-
 @ 7fed6817:3dac63ff
2024-11-13 19:26:29
@ 7fed6817:3dac63ff
2024-11-13 19:26:29Il video analizza il profondo malcontento generazionale riguardo al panorama lavorativo attuale, focalizzandosi sulle difficoltà che ostacolano il raggiungimento di una vita appagante per i giovani. Ecco i punti chiave emersi:
-
Il Trapianto del Sogno: La promessa tradizionale di lavoro stabile, pensioni garantite e serenità economica si scontra con la realtà di un futuro incerto. L'inflazione galoppante erode il valore del denaro, rendendo vano il sacrificio di anni di duro lavoro per una pensione che non assicura più benessere materiale. La generazione Z, invece di nutrire fiducia nel sistema tradizionale, cerca alternative, spesso intraprendendo strade rischiose come dropshipping, criptovalute e corsi online "Red Pill", attratta dal fascino del "sogno" di libertà e successo immediato, pur consapevole dei rischi.
-
Il Dilemma Blue Collar: Sebbene i lavori manuali offrano utilità tangibile (costruire case, riparare tubature), il costo a livello fisico è elevato e la remunerazione spesso non giustifica lo sforzo, soprattutto nelle grandi città dove anche 40k all'anno risultano insufficienti per una vita agiata. La prospettiva di sacrificare salute e tempo per un guadagno precario genera frustrazione.
-
L'Urgenza di Reinventare Se Stessi: Il video non propone la pigrizia, ma l'esigenza di flessibilità e reinvenzione costante. L'invito è a coltivare skill attraenti, esplorare diversi campi lavorativi e bilanciare lavoro e tempo libero per costruire memorie significative. La chiave è non rimanere bloccati in ruoli statici, ma abbracciare la crescita personale e professionale come unica garanzia di successo futuro.
-
Il Tempo Libero Come Risorsa Preziosa: Il video sottolinea l'importanza di valorizzare il tempo libero, sempre più prezioso con l'aumentare dell'età e delle responsabilità. È fondamentale utilizzarlo per attività stimolanti, hobby, relazioni e cura di sé, creando un patrimonio di esperienze che arricchiscono la vita oltre al mero guadagno materiale.
In sintesi, l'articolo evidenzia come la generazione Z si trovi di fronte a una realtà lavorativa complessa e sfidante. La critica al sistema tradizionale non è passiva, ma spinge verso una riflessione attiva: reinventare se stessi, sfruttare il tempo libero e costruire un futuro basato su flessibilità, crescita personale e esperienze significative.
-
-
 @ 6bae33c8:607272e8
2024-11-13 17:22:11
@ 6bae33c8:607272e8
2024-11-13 17:22:11I went 4-1 again last week, so apparently this process of writing out my random thoughts on these games and assigning numbers is working. It’s better than the grid version from last year because that was too restrictive. More free-flowing is how you get in sync with the league.
I’m 8-2 over the last 10 and 21-9 over the last 30. Still drawing dead in the overall, but very much alive for Q3, even if I still need to go 9-1 probably.
I’m putting the paywall here not because I’ve now got the gift of prophecy (which could easily go away) but because I want to give the paying subs something the free ones don’t have.
Indigenous Peoples at Eagles — American friend of ours in Lisbon doesn’t celebrate Thanksgiving I just found out, instead calls it Indigenous Peoples Day. That’s fine, but my beef is with her ignoring the indigenous peoples those indigenous peoples surely killed before the European settlers killed them. I mean surely it wasn’t all kumbayah among the tribes. You probably have to go back 10 or 20 tribes of indigenous peoples to find the ones who were just there originally and got killed by other tribes. And even they were probably no angels. Anyway, I digress. I’ll make it Killer Redskins™ +2.5 and stay away on Thursday night.
Packers at Bears — The Bears killed us in Survivor this week (literally), and I wouldn’t have taken them if I had any idea how bad Caleb Williams was. It was likely Danny Dimes out there. Get rid of the fucking ball! In any event, I’ll say Packers -3.5 and lean Bears, but probably stay away.
Jaguars at Lions — There have been no huge lines this year and few even of double-digits, but I imagine we get one here. I’ll say Jaguars +16.5. I’d probably take the Lions anyway, but likely stay away.
Vikings at Titans — The Titans defense is okay, but the offense is pretty bad. Sam Darnold is looking more like his old self every week, and that is obviously not a good thing. I’ll say Vikings -3.5 and stay away.
Raiders at Dolphins — The Raiders are a trainwreck, and the Dolphins are playing better defensively. I’ll say Raiders +8.5 and probably stay away.
Rams at Patriots — I watched the Patriots last week and they didn’t just beat the Bears, they killed them. I’ll say Rams -2.5 and probably stay away. If anything I’d buy the Rams low.
Browns at Saints — The Saints have Alvin Kamara and a bunch of scrubs on offense, but the Browns have Jameis Winston throwing picks. I like selling the Saints off last week’s win though. I’ll say Browns plus 1.5 and consider taking them.
Colts at Jets — I guess they’re sticking with Joe Flacco. The Jets are a destroyed team too. I’ll say Colts +3 and maybe take the Jets. Have to think about it more.
Ravens at Steelers — The Ravens are in a different class than the Steelers, though often these rivalry games are tight. I’ll make it Ravens -2.5 and lay the wood.
Falcons at Broncos — The Falcons blew it last week, but Denver REALLY blew it. Denver has the better defense. I’ll say Falcons +2.5 and maybe take the Broncos.
Seahawks at 49ers — I’ve lost faith in Geno Smith, especially behind that abysmal line. It’s a divisional game which could be close, but I'll make it Seahawks +6 and lay the wood.
Chiefs at Bills — The Bills are better, the Chiefs are tougher. I’ll say Chiefs +3, probably lay the wood, but have to think about it more.
Bengals at Chargers — I’ll make this Bengals +2.5 as these are roughly equal teams. Probably a stay away for me, but if anything I’d take Cincy.
Texans at Cowboys — Micah Parsons will get to CJ Stroud, but the Cowboys offense is abominable without Dak Prescott. I’ll say Texans -6 and probably stay away.
-
 @ a901cbe4:bd85452f
2024-11-13 17:02:29
@ a901cbe4:bd85452f
2024-11-13 17:02:29From Pizza to Powerhouse: How Bitcoin Became a $90K Phenomenon
So, how did Bitcoin go from being used to buy two pizzas to crossing $90K? Here’s a quick dive into the secret sauce:
-
Crypto Goes Mainstream: Imagine telling your bank in 2010 that you wanted to buy Bitcoin. Fast forward to now, and they’re the ones begging you to HODL. Banks, corporations, and even the payment giants are jumping on the BTC train, legitimatizing what the OGs knew all along – Bitcoin is here to stay.
-
Inflation Hedge, But Make It Digital: Think of Bitcoin as digital gold but better. With global economies wobbling, people are clinging to BTC like it’s a life raft (spoiler: it might be). Gold’s nice, but can you transfer it across borders in seconds? Nope. Bitcoin’s inflation-proof and portable, the new gold standard for a digital world.
-
Institutional FOMO: Fear of Missing Out: Suddenly, everyone wants in. Billion-dollar funds, Wall Street titans, and big names that once sneered at Bitcoin now have BTC in their portfolios. The irony? Bitcoin was designed to get rid of these guys, but here they are, driving up demand and pumping up the price. Talk about poetic justice.
-
Fixed Supply, Unlimited Demand: Bitcoin’s secret weapon? There will only ever be 21 million BTC. It’s the hottest item with a one-time print run, and everyone wants a piece. Add in Bitcoin’s halving cycles, and you've got a perfect recipe for scarcity-driven price rockets.
Why $90K is More Than a Price: It’s a Wake-Up Call for the World
Bitcoin smashing $90K is like a big neon sign flashing “THE FUTURE IS HERE.” And the financial world? It’s on notice.
-
True Financial Freedom: Bitcoin lets people be their own bank, something you can’t say about your local branch. At $90K, Bitcoin is more than an investment – it’s a tool for individual empowerment. Anyone with Wi-Fi can HODL, no permission needed.
-
Potential Global Reserve Asset: The whispers have started: could Bitcoin be a reserve asset? Hitting $90K makes that less of a pipe dream and more of a “what if?” With every BTC milestone, central banks and institutions are rethinking how they store value. This could be the beginning of Bitcoin’s evolution from “rebellious outsider” to “global staple.”
-
Fueling the Future of Blockchain: Bitcoin isn’t just money; it’s the gateway to blockchain innovation. Now that BTC is breaking records, other decentralized projects have room to grow. Bitcoin’s rise could inspire entire industries to adopt blockchain tech in ways we’re only beginning to imagine.
Beyond $90K: Are We Eyeing $100K?
Here’s the deal: $90K is big, but if you’re thinking “this is it,” think again. The momentum is there, the hype is real, and $100K isn’t just a fantasy anymore. With every new HODLer, BTC breaks a bit further into the mainstream. This could be the start of something even bigger.
Long-term, Bitcoin’s story isn’t just about price. It’s about rewriting how we think about money, ownership, and freedom. And as BTC hits new highs, it’s proving to the world that maybe, just maybe, it’s here to change the game for good.
A Toast to the HODLers (and Future HODLers)
To everyone who’s been along for the ride, this $90K milestone is a well-earned victory. To the skeptics – we’re glad you’re here now! And if you’re thinking of joining us, there’s no time like the present.
So HODL on tight, buckle up, and get ready – Bitcoin at $90K is just the beginning. Here’s to $100K and beyond! 🌌
-
-
 @ 59f0660b:d5d24440
2024-11-13 16:58:58
@ 59f0660b:d5d24440
2024-11-13 16:58:58Yakihonne (often styled as YakiHonne) is a decentralized social network platform that combines elements of Nostr and Bitcoin technologies. Its focus is on enabling secure, user-controlled content sharing and interaction without centralized oversight. Like Nostr, YakiHonne uses a system of relays to handle data, which makes it censorship-resistant and allows for greater privacy. Users communicate through a global network of peers, and can participate in various activities, share content, and connect with others in a decentralized ecosystem.
YakiHonne also supports Bitcoin-based features, like a built-in Lightning wallet that facilitates quick, low-fee transactions, making it popular among the cryptocurrency community. The platform’s design allows for content curation, peer review, and publishing of articles, similar to a blend of a social media network and a blogging platform. YakiHonne is available as a mobile app, emphasizing a smooth and accessible user experience for decentralized media sharing.
This approach to social networking reflects a trend toward decentralization, providing users with more autonomy and direct control over their online presence and data. It has grown quickly, attracting a global audience and establishing partnerships within the Bitcoin ecosystem.
-
 @ 59f0660b:d5d24440
2024-11-13 16:54:33
@ 59f0660b:d5d24440
2024-11-13 16:54:33Bitcoin is a type of digital currency, also known as a cryptocurrency, that was invented in 2008 by an unknown person or group using the pseudonym Satoshi Nakamoto. Unlike traditional currencies issued by governments (like dollars or euros), Bitcoin is decentralized, meaning it operates without a central authority like a bank. Transactions are verified by network nodes through cryptography and recorded on a public ledger called the blockchain.
Here are some key characteristics of Bitcoin:
-
Decentralization: Bitcoin is maintained by a distributed network of computers (called "miners") rather than a central bank or government.
-
Limited Supply: There will only ever be 21 million bitcoins, making it scarce like a precious metal, which helps contribute to its value.
-
Blockchain Technology: Bitcoin transactions are recorded on the blockchain, a secure, transparent, and immutable ledger.
-
Digital Nature: Bitcoin exists only electronically and is stored in digital wallets. It can be sent directly from person to person (peer-to-peer) without an intermediary.
Bitcoin has been praised for enabling fast, low-cost, and borderless transactions but also criticized for its volatility and environmental impact due to the energy-intensive mining process.
-
-
 @ 59f0660b:d5d24440
2024-11-13 16:52:23
@ 59f0660b:d5d24440
2024-11-13 16:52:23Nostr (Notes and Other Stuff Transmitted by Relays) is a decentralized protocol for social networking and communication that enables users to share information and messages without relying on a central server or platform. Instead of traditional social media structures controlled by corporations (like Twitter or Facebook), Nostr allows users to publish content via distributed relays, maintaining privacy, censorship resistance, and greater user control.
Key Characteristics of Nostr:
-
Decentralized Structure: Unlike conventional platforms, Nostr does not rely on a central server. Instead, users connect to a network of relays, where they can post messages or data that others can read or respond to.
-
Public and Private Keys: Nostr uses public-key cryptography, where users have a public key (like a username) and a private key (similar to a password) to sign messages. This approach provides security and ownership over one’s identity and content.
-
Relays for Content Distribution: Users can choose which relays to connect to and broadcast their posts. This design makes censorship harder, as content doesn’t depend on a single server but can be mirrored on multiple relays across the network.
-
Minimalist Design: Nostr aims to be simple and flexible, allowing developers to build different types of applications on top of it. It’s designed for messaging, but its flexibility can also support blogging, group chats, or other social functions.
Use Cases and Popularity
Censorship Resistance: Users who seek free speech or who are in restrictive environments find Nostr appealing because it allows them to communicate without a centralized authority.
Bitcoin and Crypto Community: Nostr has gained popularity within the Bitcoin and broader cryptocurrency community as it aligns with the ethos of decentralization and user empowerment.
Nostr’s open and decentralized nature is similar to other emerging protocols, such as ActivityPub (used by Mastodon), which are part of a larger trend toward decentralized social networking and communication platforms.
-
-
 @ 13351007:eccd002a
2024-11-13 16:34:01
@ 13351007:eccd002a
2024-11-13 16:34:01[{"_id":"5478974e-5e9b-4ccc-8cee-8485f60838ef","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":202.86468,"amountCurrency":"xmr","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:34:01.270Z"},{"_id":"5478974e-5e9b-4ccc-8cee-8485f60838ef","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"5478974e-5e9b-4ccc-8cee-8485f60838ef","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":202.86468,"amountCurrency":"xmr","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:34:01.270Z"}]
-
 @ 13351007:eccd002a
2024-11-13 16:33:01
@ 13351007:eccd002a
2024-11-13 16:33:01[{"_id":"662f7f07-a7ef-4f29-9bdb-6d199e7dac2c","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.03,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:33:01.332Z"},{"_id":"662f7f07-a7ef-4f29-9bdb-6d199e7dac2c","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"662f7f07-a7ef-4f29-9bdb-6d199e7dac2c","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.03,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:33:01.332Z"}]
-
 @ 13351007:eccd002a
2024-11-13 16:32:01
@ 13351007:eccd002a
2024-11-13 16:32:01[{"_id":"a740e2cb-8940-4d1b-bf4c-271de778bd77","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.02,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:32:01.342Z"},{"_id":"a740e2cb-8940-4d1b-bf4c-271de778bd77","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"a740e2cb-8940-4d1b-bf4c-271de778bd77","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.02,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:32:01.342Z"}]
-
 @ 13351007:eccd002a
2024-11-13 16:31:10
@ 13351007:eccd002a
2024-11-13 16:31:10[{"_id":"6b08a49c-6812-4e79-8f5b-0a1eff7b8846","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.01,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:31:10.741Z"},{"_id":"6b08a49c-6812-4e79-8f5b-0a1eff7b8846","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"6b08a49c-6812-4e79-8f5b-0a1eff7b8846","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500.01,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T16:31:10.741Z"}]
-
 @ 13351007:eccd002a
2024-11-13 14:50:53
@ 13351007:eccd002a
2024-11-13 14:50:53[{"_id":"c8b5c272-899c-4258-8ed8-d39d8b1f2802","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T14:50:53.706Z"},{"_id":"c8b5c272-899c-4258-8ed8-d39d8b1f2802","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"c8b5c272-899c-4258-8ed8-d39d8b1f2802","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":500,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T14:50:53.706Z"}]
-
 @ 4874b840:31b0b8c0
2024-11-13 13:22:32
@ 4874b840:31b0b8c0
2024-11-13 13:22:32Архитектурные проекты, реализованные в Калининграде, значительно преобразили облик города. Одним из ключевых направлений стала реконструкция хрущёвок, предложенная московскими архитекторами МАРХИ. Они планируют увеличить этажность существующих зданий и создать новые общественные пространства, что улучшит качество жизни жителей.
 Также активно развиваются проекты на Острове Октябрьском, где предусмотрена застройка с учетом культурного и спортивного кластеров. Важным аспектом является благоустройство общественных пространств, включая парки и набережные, что делает город более привлекательным для жителей и туристов.
Также активно развиваются проекты на Острове Октябрьском, где предусмотрена застройка с учетом культурного и спортивного кластеров. Важным аспектом является благоустройство общественных пространств, включая парки и набережные, что делает город более привлекательным для жителей и туристов.Житель отреконструированной хрущёвки делится с нами впечатлениями:
"Наша хрущёвка теперь выглядит совершенно иначе! Благодаря реконструкции добавили два этажа, и у нас появился лифт. Квартиры стали просторнее, а фасад — современным. Дворы благоустроены, появились детские площадки и парковки. Я рад, что жители могли участвовать в принятии решений. Это не просто улучшение жилья, это создание комфортной городской среды, которая отвечает требованиям XXI века".

-
 @ 4874b840:31b0b8c0
2024-11-13 13:19:46
@ 4874b840:31b0b8c0
2024-11-13 13:19:46На сегодняшний день школы Калининграда представляют собой современные образовательные учреждения, ориентированные на всестороннее развитие учащихся. В рамках программы по расширению возможностей дополнительного образования активно функционируют кружки и секции, охватывающие различные направления.
 Технические кружки включают судостроительные классы, где учащиеся изучают проектирование и технологии, получая практические навыки для востребованной отрасли. Творческие секции предлагают занятия по изобразительному искусству, музыке и театру, развивая художественные таланты. Спортивные кружки обеспечивают занятия по футболу, волейболу и плаванию.
Технические кружки включают судостроительные классы, где учащиеся изучают проектирование и технологии, получая практические навыки для востребованной отрасли. Творческие секции предлагают занятия по изобразительному искусству, музыке и театру, развивая художественные таланты. Спортивные кружки обеспечивают занятия по футболу, волейболу и плаванию.
 Школы активно сотрудничают с местными предприятиями и университетами, что обеспечивает доступ к современным технологиям. Таким образом, образовательная система Калининграда направлена на подготовку высококвалифицированных специалистов.
Школы активно сотрудничают с местными предприятиями и университетами, что обеспечивает доступ к современным технологиям. Таким образом, образовательная система Калининграда направлена на подготовку высококвалифицированных специалистов.Ученики кружка судостроения отмечают: "Учеба открывает невероятные возможности. Мы участвуем в практических проектах на верфях "Янтарь" и "Арктика", что позволяет применять знания на практике и готовиться к карьере в высокотехнологичной отрасли."
-
 @ fd208ee8:0fd927c1
2024-11-13 10:28:15
@ fd208ee8:0fd927c1
2024-11-13 10:28:15The fertility rate is not the whole story
I keep reading articles about the fertility decline that has now consumed most developed nations on Earth, and that is slowly creeping toward the few remaining holdouts, mostly in sub-Saharan Africa.
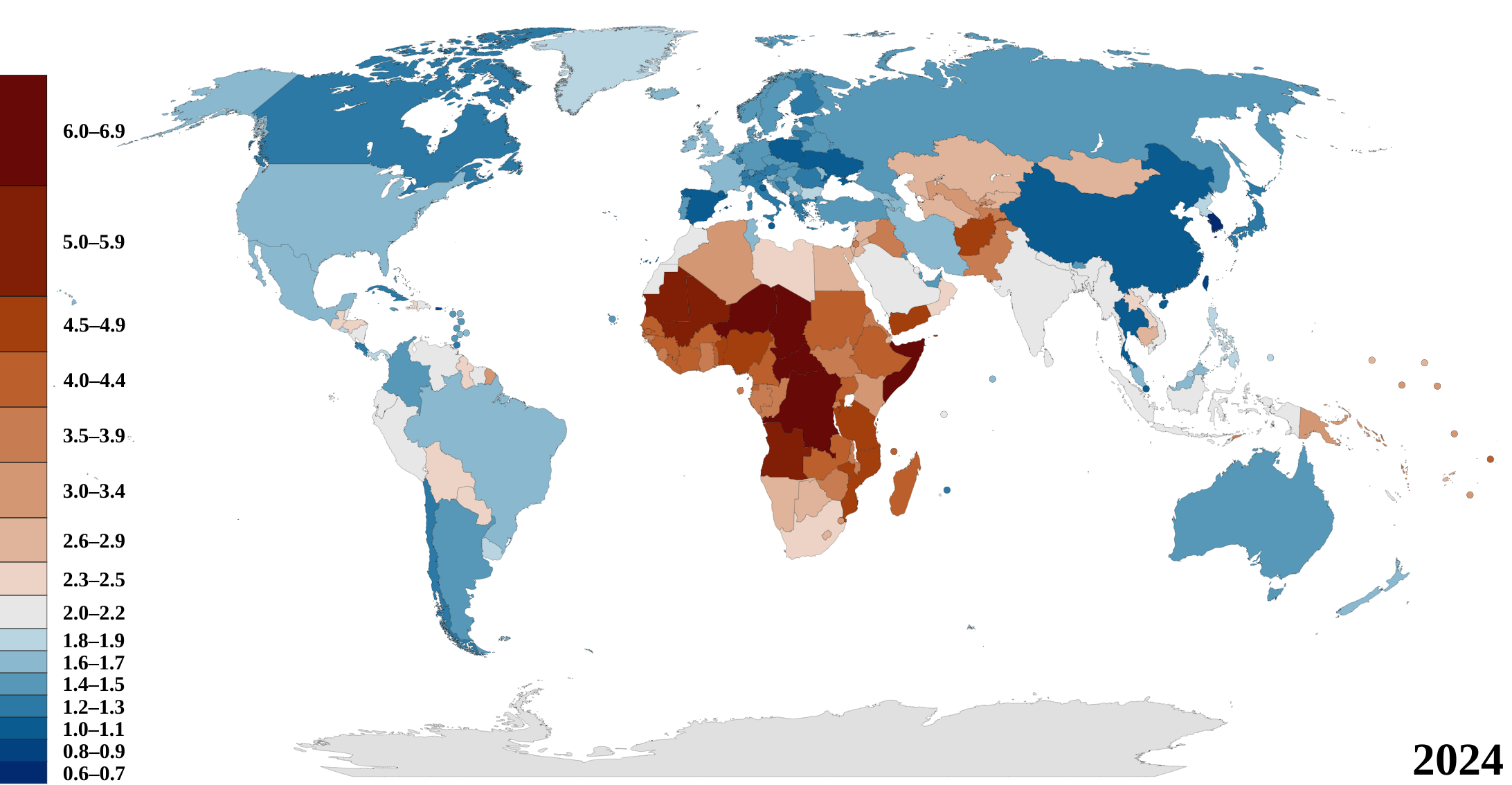
Many countries, that we still think of, as having high birthrates, are actually just experiencing the echo of previous high birthrates. Same as Europe had in the 70s and 80s, due to the post-WWII baby boom. Others have very high total fertility rates (TFR), but such high infant and child mortality, that the population doesn't grow in line with the fertility.
East Asia is in the worst shape, with Europe closely nipping at its heels. TFR is highest in Niger, at 6.1 children per woman, and lowest in South Korea, at 0.7. In other words, the South Korean population nearly halves in size, every generation. (I will be focusing on South Korea, going forward, as a case study of the general phenomenon.)
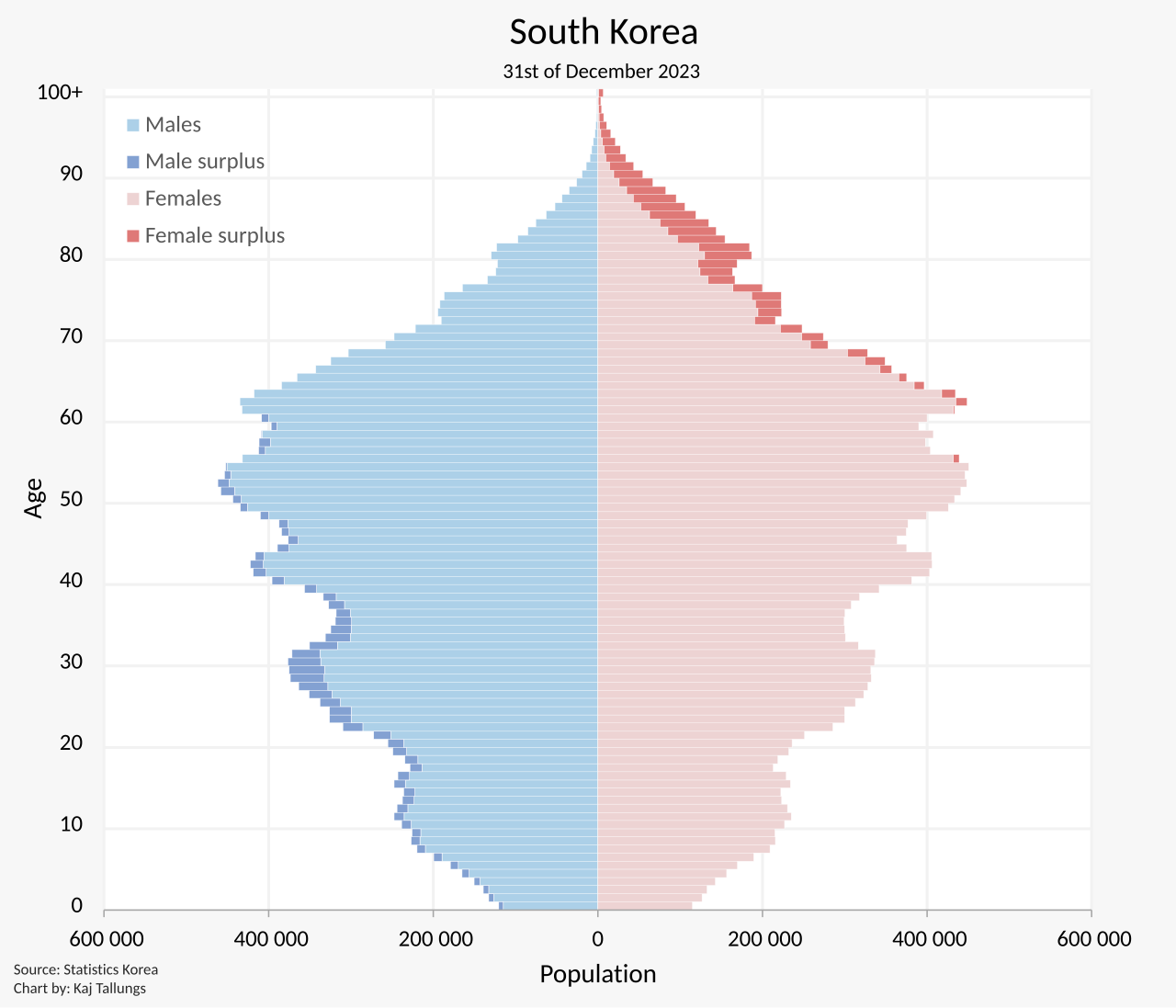
Fertility rate is not even half the story
But it's actually all much worse than is being publicized, as the fertility rates don't take the tangible effects of delays in childbearing into account, which actually are felt more immediately, than the decline in overall fertility. What the delays do, is spread the same number of births more thinly over the timeline, debilitating any infrastructure or traditions that require a certain number of people, to be maintained. I think of this as demographic logistics, as it's about getting the right number of people, of the right age, to the right place, at the right time, in order to meet some minimum required volume.
Playgroups, schools, hospitals, festivals, volunteer organizations, sports clubs, road works, senior residences, churches, new business starts, etc. all require a certain number of participants, to remain viable. Those participants trickling in, at a slower and slower rate, is why even places with above-replacement fertility (like my own town) increasingly struggle to maintain systems that are popular. Everyone is being spread thinner and thinner, and we're having to make hard choices about how the smaller group will be distributed amongst the activities.
You feel like you're being overrun because you are.
This is also why the fact that migrants (and religious people, etc.) tend to adjust their birthrate to the regional average, doesn't lead to an end of their demographic overrepresentation. They are under less societal pressure to delay childbearing, so they tend to be further down the following chart, and their offspring simply arrive much more quickly, than with the natives.
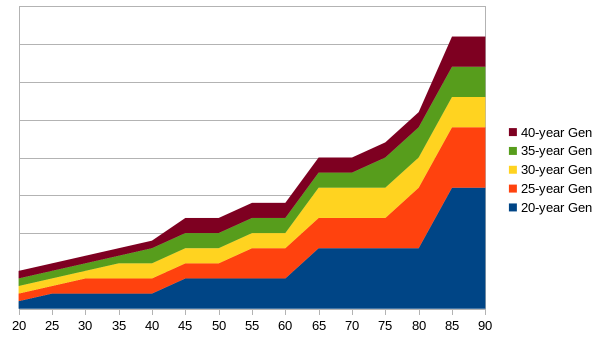
To put it simply, for everyone one generation of the "natives" or "majority" society, there are two or three generations of the others.
Does communism get the last laugh?
Societies, like South Korea, where the fertility rate is exceedingly low, also tend to have the most-delayed childbearing, so the effect of low fertility is heavily exacerbated. The countries are hollowing out, on the ground level, with the population being replaced so slowly and thinly, that the majority of the country will soon simply be empty, and the infrastructure will fall apart.
Christianity is starting to have a positive effect on a subset of South Korean birthrates, by promoting the concept of openness to life and family-friendliness, but its popularization initially decreased fertility. (This is a common effect, as Christianity leads to higher status for women, monogamy, and the concept of "family planning".) Yes, contrary to what The Handmaid's Tale enthusiasts claim, increased religiosity actually exacerbated the already-widespread decline.
South Korea is really just the worst of worst-case scenarios, unfortunately, with absolutely every demographic and economic trend aligning to cut off their reproduction. This is in direct contrast to North Korea, that can compensate for the more moderate decline in births with mere mechanization.
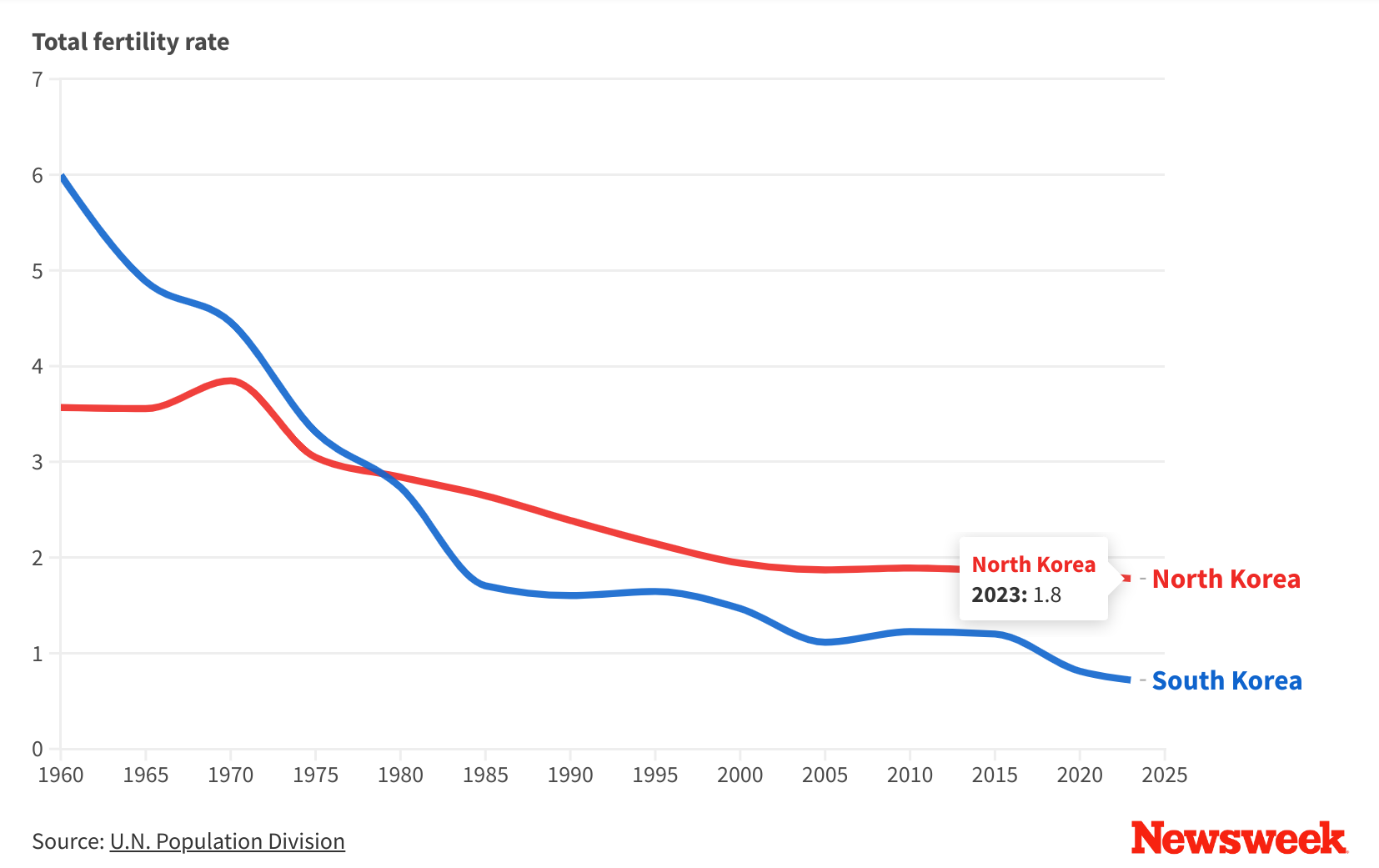
Yes, it looks like North Korea will do much better, going forward, than South Korea. Their entrance into the Ukraine War isn't incidental; we will be hearing more from them, going forward.
Robots serving ghosts
The South Korean plan of simply substituting robots for most humans, will go nowhere, as robots are actually less efficient and effective than humans, except at highly dull or repetitive tasks, over the course of their lifecycle. (This is hidden with cheap, extended production financing, where the machines don't have to turn a profit for decades, whereas humans have to be paid today.) Without productive, agile humans, generating real income, there will be no one to purchase and run all the expensive robots.
And... run them... for whom?

-
 @ 13351007:eccd002a
2024-11-13 09:17:38
@ 13351007:eccd002a
2024-11-13 09:17:38[{"_id":"f61999d4-6dd5-4593-9798-17980ecebd22","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":100.02,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T09:17:38.105Z"},{"_id":"f61999d4-6dd5-4593-9798-17980ecebd22","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"f61999d4-6dd5-4593-9798-17980ecebd22","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":100.02,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T09:17:38.105Z"}]
-
 @ 98589a2e:bf49daa1
2024-11-13 09:08:41
@ 98589a2e:bf49daa1
2024-11-13 09:08:41Санкт-Петербург в 2040 году стал городом, где современная архитектура гармонично сочетается с историческим наследием. В рамках нового генерального плана запланированы крупные инфраструктурные проекты, которые кардинально изменят облик города и улучшат качество жизни его жителей.
Основные инфраструктурные проекты
Развитие транспортной инфраструктуры
- Метро: К 2040 году планируется построить около 100 новых станций метрополитена и увеличить общую протяжённость линий до 272,7 км. Важными проектами являются новые Кольцевая и Адмиралтейско-Охтинская линии, а также продление существующих.
- Мосты: Запланировано строительство пяти новых мостов через Неву, включая Большой Смоленский мост и Орловский тоннель. Эти проекты направлены на улучшение транспортной доступности и сокращение времени в пути.
- Общественный транспорт: Будут развиваться трамвайные линии и железнодорожные пути, что позволит создать более удобную сеть общественного транспорта.
Социальная инфраструктура
- Образование и здравоохранение: Генеральный план предусматривает строительство 585 объектов социальной инфраструктуры, в том числе 226 образовательных учреждений и 110 медицинских. Это обеспечит необходимую поддержку растущему населению города.
- Спортивные объекты: План также предусматривает создание 205 спортивных сооружений, что будет способствовать развитию физической культуры и спорта среди жителей.
Общественные пространства и экология
- Парки и набережные: В городе появятся новые парковые зоны, в том числе реконструированные набережные Карповки и Охты, а также шесть тематических парков и девять благоустроенных пляжей. Это создаст комфортные условия для отдыха горожан.
- Зеленые зоны: Генеральный план предполагает создание около 1,5 тыс. гектаров природных территорий общего пользования, что повысит уровень экологической безопасности города.
Жилищное строительство
- Новые жилые комплексы: В соответствии с планом, к 2040 году в городе будет построено около 67 млн кв. м жилья. Основная застройка сосредоточится в Пушкинском, Приморском и Московском районах. Это позволит обеспечить жильем растущее население Санкт-Петербурга.
Благодаря проектам в городе формируется устойчивое развитие городской инфраструктуры. Эти амбициозные проекты отражают стремление города к инновациям и улучшению качества жизни его жителей.
Как вы относитесь к планируемым изменениям в инфраструктуре? Какие улучшения вы хотели бы видеть в своем районе?
-
 @ c2827524:5f45b2f7
2024-11-13 08:57:07
@ c2827524:5f45b2f7
2024-11-13 08:57:07Piano generale
l'intento è smettere di minare fiat e passare a guadagnare esclusivamente in #Bitcoin.
Attacco DDOS alla vita di tutti
winzozz, il sistema operativo imposto coercitivamente da uno smidollato mafioso, fa schifo ai vermi.
é lento, si ferma ad ogni minuto, lascia utenti in attesa per ore - ogni giorno - solo perché sta facendo Dio solo sa cosa. nostr:#winzozz è un attacco DDOS alla vita di ogni essere umano che ha la nostr:#sfiga di ritrovarsi suo malgrado ad usarlo.
mentre si attende che il pc venga rianimato da un intervento divino (perché chiamare in causa il padreterno, a volte, funziona), siamo in balia di attese infinite. per nulla.
quante ore della nostra vita sono passate in attesa di... nostr:#stocazzo?
sai chi ti saluta tanto?
ecco, appunto! a proposito di nostr:#stocazzo: la prima cosa da fare nella lista della mia nuova vita, è proprio arare tutti i miei pc e passarli a nostr:#Debian.🐧.
*terrò una macchina winzozz solo per i corsi, per aiutare nuovi utenti windows #Bitcoin ad imparare questa deliziosa tecnologia. per poi farli traghettare da Caronte su nuovi sistemi operativi, là dove nessun DDOS può mai arrivare a sottrarre tempo prezioso alle vite degli altri.
-
 @ 13351007:eccd002a
2024-11-13 08:02:18
@ 13351007:eccd002a
2024-11-13 08:02:18[{"_id":"c178a999-25e0-4bf5-b478-b6f22ae9bfbd","user_id":"b34f99f110bb65ff4b5527f8fb1d015951a3038370fd95adc34d81d9006b0fcc","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":102,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T08:02:18.346Z"},{"_id":"c178a999-25e0-4bf5-b478-b6f22ae9bfbd","user_id":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","tradingPartner":"liam","tradeId":"c178a999-25e0-4bf5-b478-b6f22ae9bfbd","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":102,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T08:02:18.346Z"}]
-
 @ 13351007:eccd002a
2024-11-13 07:54:13
@ 13351007:eccd002a
2024-11-13 07:54:13[{"_id":"b99131ca-10fb-48fd-be00-04aee70efd55","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":100,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T07:54:13.400Z"},{"_id":"b99131ca-10fb-48fd-be00-04aee70efd55","tradingPartner":"liam","tradeId":"b99131ca-10fb-48fd-be00-04aee70efd55","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":100,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T07:54:13.400Z"}]
-
 @ 13351007:eccd002a
2024-11-13 07:54:13
@ 13351007:eccd002a
2024-11-13 07:54:13[{"_id":"a8fd0883-c47a-4eba-bf4c-61ff15f836ff","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":101,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T07:54:13.286Z"},{"_id":"a8fd0883-c47a-4eba-bf4c-61ff15f836ff","tradingPartner":"liam","tradeId":"a8fd0883-c47a-4eba-bf4c-61ff15f836ff","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":101,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T07:54:13.286Z"}]
-
 @ a012dc82:6458a70d
2024-11-13 07:44:51
@ a012dc82:6458a70d
2024-11-13 07:44:51Table Of Content
-
What is the Lighting Network?
-
Advantages of the Lighting Network for Businesses
-
Game-Changing Bitcoin Tool
-
Conclusion
-
FAQ
In today's digital age, cryptocurrencies have taken the financial world by storm. One such cryptocurrency that has gained immense popularity and disrupted traditional financial systems is Bitcoin. Bitcoin, the pioneering cryptocurrency, has opened up new avenues for businesses and individuals alike. With the advent of the Lighting Network, a revolutionary scaling solution for Bitcoin, a game-changing Bitcoin tool has emerged, ushering in a paradigm shift for the Lighting Network in business.
What is the Lighting Network?
The Lighting Network is a second-layer protocol that operates on top of the Bitcoin blockchain. It aims to address some of the scalability and transaction speed issues faced by the Bitcoin network. By creating a network of bidirectional payment channels, the Lighting Network enables near-instant and low-cost transactions between participants. This innovative solution has paved the way for the development of game-changing Bitcoin tools that have the potential to transform the business landscape.
Advantages of the Lighting Network for Businesses
Enhanced Scalability
The Lighting Network offers a significant advantage in terms of scalability for businesses. With traditional Bitcoin transactions, every transaction needs to be recorded on the blockchain, resulting in limited transaction throughput. However, the Lighting Network allows businesses to conduct a large number of off-chain transactions, minimizing the load on the Bitcoin blockchain and significantly increasing scalability. This scalability boost opens up new possibilities for businesses to process a higher volume of transactions and accommodate growing customer demands.
Lightning-Fast Transactions
One of the most remarkable features of the Lighting Network is its ability to facilitate lightning-fast transactions. Traditional Bitcoin transactions can sometimes take several minutes or even hours to confirm, causing delays and inconveniences in business operations. However, with the Lighting Network, transactions can be settled in a matter of seconds. This speed advantage enables businesses to offer seamless and real-time payment experiences to their customers, enhancing customer satisfaction and improving overall efficiency.
Reduced Transaction Costs
Another compelling aspect of the Lighting Network for businesses is the reduced transaction costs it offers. Traditional Bitcoin transactions often incur high fees due to the limited capacity of the blockchain. However, the Lighting Network's off-chain transactions significantly reduce transaction fees, making microtransactions and low-value transactions economically feasible. This cost reduction is particularly beneficial for businesses that rely on frequent small transactions, such as online retailers or service providers.
Improved Privacy and Security
The Lighting Network also brings improvements in terms of privacy and security. As most Lighting Network transactions occur off-chain, they do not require broadcasting every detail to the public blockchain. This aspect enhances privacy by reducing the exposure of sensitive transaction information. Additionally, the Lighting Network implements various security measures, such as multi-signature wallets and hash time-locked contracts, to ensure the safety of funds during transactions. These enhanced privacy and security features provide businesses with peace of mind when adopting the Lighting Network.
Game-Changing Bitcoin Tool
The advent of the Lighting Network has paved the way for the development of various game-changing Bitcoin tools that empower businesses to leverage the potential of this revolutionary technology. These tools offer innovative solutions to address specific business needs, enhance operational efficiency, and unlock new opportunities. Let's explore some of these remarkable tools and their impact on businesses:
1. Lightning Payment Processors
Lightning payment processors are tools that enable businesses to seamlessly integrate the Lighting Network into their existing payment infrastructure. These processors provide the necessary software and APIs to facilitate Lightning Network payments, making it convenient for businesses to accept Bitcoin payments with lightning speed and low fees. By adopting a Lightning payment processor, businesses can expand their customer base, attract Bitcoin-savvy customers, and provide a more efficient payment experience.
2. Lightning Network Point-of-Sale (PoS) Systems
Lightning Network PoS systems are specifically designed for businesses that operate physical stores or provide in-person services. These systems enable businesses to accept Lightning Network payments directly at the point of sale, similar to traditional payment terminals. With Lightning PoS systems, businesses can offer a seamless payment experience to their customers, eliminating the need for lengthy transaction confirmations and reducing customer waiting time. This convenience can lead to increased customer satisfaction and improved sales.
3. Lightning Network E-commerce Plugins
For businesses operating in the digital realm, Lightning Network e-commerce plugins provide a seamless integration of Bitcoin payments on their online platforms. These plugins offer ready-to-use solutions that can be easily installed on popular e-commerce platforms, such as WooCommerce or Shopify. By incorporating Lightning Network payments, businesses can tap into the growing Bitcoin user base and provide an alternative payment option that is fast, secure, and cost-effective. This integration can boost sales and attract tech-savvy customers who prefer Bitcoin transactions.
4. Lightning Network Micropayment Platforms
Micropayments refer to transactions involving small amounts of money, typically fractions of a cent. The Lighting Network's low fees and near-instant transaction settlement make it an ideal solution for micropayments. Lightning Network micropayment platforms enable businesses to monetize content or services that were previously not economically viable due to high transaction costs. By leveraging micropayment platforms, businesses can explore new revenue streams and create innovative business models.
Conclusion
The Lighting Network has introduced a game-changing Bitcoin tool that offers a paradigm shift for the Lighting Network in business. With enhanced scalability, lightning-fast transactions, reduced costs, and improved privacy and security, the Lighting Network empowers businesses to unlock new opportunities, streamline operations, and provide better customer experiences. By embracing the potential of this innovative technology and leveraging the game-changing Bitcoin tools available, businesses can stay at the forefront of the digital revolution and thrive in the evolving landscape of cryptocurrencies.
FAQ
How does the Lighting Network enhance scalability for businesses? The Lighting Network enhances scalability by allowing businesses to conduct a large number of off-chain transactions, reducing the load on the Bitcoin blockchain and enabling higher transaction throughput.
What are the advantages of Lightning Network transactions for businesses? Lightning Network transactions offer lightning-fast settlement times, reduced transaction costs, improved privacy, and enhanced security, all of which contribute to better operational efficiency and customer satisfaction for businesses.
How can businesses integrate the Lighting Network into their payment infrastructure? Businesses can integrate the Lighting Network by leveraging Lightning payment processors, Lightning Network PoS systems, or Lightning Network e-commerce plugins, depending on their specific requirements.
What are micropayment platforms, and how can they benefit businesses? Micropayment platforms enable businesses to process and monetize small transactions economically. With the Lighting Network's low fees, businesses can explore new revenue streams and offer innovative services that involve micropayments.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 13351007:eccd002a
2024-11-13 06:54:35
@ 13351007:eccd002a
2024-11-13 06:54:35{"_id":"6189965d-885f-44a5-8283-236809f90bb4","tradingPartner":"liam","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":169.05,"amount":2,"amountCurrency":"fiat","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:35.193Z"}
-
 @ 13351007:eccd002a
2024-11-13 06:54:35
@ 13351007:eccd002a
2024-11-13 06:54:35{"_id":"45961f60-af28-49a7-8285-39d46a04ae04","tradingPartner":"liam","adId":"10df86b1-657c-4065-b5c8-d6f6bbe64a7b","adPublisher":"f462d21e10163eb0a403aec6b93ac57ec2f1b9455473e99304f571a51390b6b1","adType":"ONLINE_BUY","adTypeReal":"ONLINE_SELL","price":170.27,"amount":1.5,"amountCurrency":"fiat","paymentMethodCode":"VENMO","currencyCode":"USD","country":"United Kingdom","countryCode":"GB","paymentMethodDetail":"best rates really","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:35.127Z"}
-
 @ 13351007:eccd002a
2024-11-13 06:54:35
@ 13351007:eccd002a
2024-11-13 06:54:35{"_id":"d12af7f8-9fad-4718-85d2-71de3e1ab22f","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":1,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:35.527Z"}
-
 @ 13351007:eccd002a
2024-11-13 06:54:35
@ 13351007:eccd002a
2024-11-13 06:54:35{"_id":"79c3b4de-fb00-40e6-82b4-9c8474d90c43","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":1.6,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:35.210Z"}
-
 @ 13351007:eccd002a
2024-11-13 06:54:34
@ 13351007:eccd002a
2024-11-13 06:54:34{"_id":"fad63d53-f555-429e-916a-d2ea8968552d","tradingPartner":"hank","adId":"493d4425-5a4b-46b6-b1a4-2e1266ea1246","adPublisher":"1eb966a6a0218aba520aaac93be7dd8bf3830fc7710bc80caea3a6a5e3eddf94","adType":"ONLINE_SELL","adTypeReal":"ONLINE_SELL","price":169.05,"amount":20,"amountCurrency":"fiat","buyerSettlementAddress":"888tNkZrPN6JsEgekjMnABU4TBzc2Dt29EPAvkRxbANsAnjyPbb3iQ1YBRk1UXcdRsiKc9dhwMVgN5S9cQUiyoogDavup3H","paymentMethodCode":"NATIONAL_BANK","currencyCode":"USD","country":"United States of America","countryCode":"US","paymentMethodDetail":"fast and best trader","msg":"","accountInfo":"","action":"open","added":"2024-11-13T06:54:34.754Z"}
-
 @ fff19d35:43344a0b
2024-11-13 06:17:55
@ fff19d35:43344a0b
2024-11-13 06:17:55Guys have you download the lates YakiHonne app, the lates update is just amazing and wonderful very fast and with pretty good feature you won’t have any worries or problems loading anything😃if you haven’t updated you are missing big time 🥹😉
-
 @ 9ff58691:0bf6c134
2024-11-13 06:14:04
@ 9ff58691:0bf6c134
2024-11-13 06:14:04За последние 16 лет индекс счастья курганцев поднялся до 8.1. Это на три единицы больше, чем за прошлую декаду.
Ведущая Катерина Тобольская рассказывает о причинах, повлиявших на настроение жителей Кургана за последние 16 лет в новом выпуске «Заметок о главном»
-
 @ 9ff58691:0bf6c134
2024-11-13 06:13:21
@ 9ff58691:0bf6c134
2024-11-13 06:13:21Мы с радостью приглашаем вас на фестиваль уличной культуры «Город в ритме», который начнётся на улице Свободы в 15:00.
Это событие объединит талантливых людей из разных сфер: от художников и музыкантов до танцоров и спортсменов.
О подробностях фестиваля нам рассказала его организатор — Катерина Тобольская. Ждём вас, чтобы вместе окунуться в атмосферу творчества и вдохновения!
-
 @ 9ff58691:0bf6c134
2024-11-13 06:10:17
@ 9ff58691:0bf6c134
2024-11-13 06:10:17Вы не поверите, что происходит в наших школах! Ученики теперь используют самые передовые технологии в процессе обучения. Представьте себе: вместо скучных учебников и меловых досок, наши аудитории оснащены по последнему слову техники. Ребята работают с 3D-моделями, создают потрясающие компьютерные графические проекты и даже обучаются с помощью искусственного интеллекта!
Представьте, как здорово изучать физику, создавая виртуальные модели планет и космических кораблей. Или постигать тайны биологии, рассматривая 3D-изображения клеток и органов. Да что там, даже на уроках истории ученики могут "побывать" в прошлом с помощью VR-технологий!
Все это стало возможным благодаря масштабной модернизации системы образования в нашем городе. Теперь наши дети получают знания в по-настоящему современной и интерактивной среде. Это не просто повышает их мотивацию, но и готовит их к жизни в эпоху высоких технологий.
А знаете ли вы, что в Кургане открылись сразу несколько новых учебных заведений, которые делают ставку на инновационные подходы? Например, в Технологическом лицее ученики с 5 класса осваивают программирование, 3D-моделирование и робототехнику. А в Экологической гимназии ребята изучают передовые методы сохранения окружающей среды с помощью современных IT-решений. "Мы стремимся дать нашим ученикам не просто знания, а навыки, которые будут востребованы в будущем", - говорит директор Технологического лицея Лев Петров. - Наша цель - вырастить поколение, готовое к вызовам цифровой эпохи".
Это действительно прорыв в образовании, который вдохновляет и вселяет надежду на лучшее будущее для наших детей.
Автор: Елизавета Медведева
-
 @ 9ff58691:0bf6c134
2024-11-13 06:04:04
@ 9ff58691:0bf6c134
2024-11-13 06:04:04Город, который когда-то казался забытым, сегодня стал центром инноваций и молодежного творчества. Программы поддержки молодежи, запущенные в последние два десятилетия, принесли свои плоды, и мы рады поделиться историями успеха, которые вдохновляют новое поколение.
Центр молодежного предпринимательства "Курган-Start"
Одной из самых успешных инициатив стал Центр молодежного предпринимательства "Курган-Start", который предоставляет молодым людям возможность развивать свои бизнес-идеи. В 2040 году мы встретились с Анной Петровой, 24-летней предпринимательницей, которая запустила свой стартап по производству экологически чистых упаковочных материалов. "Я всегда мечтала создать что-то полезное для окружающей среды. Благодаря поддержке 'Курган-Start' я получила не только финансирование, но и наставничество от опытных бизнесменов", — делится Анна.
Программа "Творческая молодежь"
Курган также стал домом для программы "Творческая молодежь", которая поддерживает молодых художников, музыкантов и писателей. В этом году мы познакомились с Дмитрием Соловьевым, 22-летним музыкантом, который стал известен благодаря своему уникальному стилю, сочетающему фолк и электронную музыку. "Программа помогла мне записать мой первый альбом и организовать тур по России. Я никогда не думал, что смогу выступать на таких больших сценах", — рассказывает Дмитрий.

Образовательные инициативы и стажировки
Образование в Кургане также претерпело значительные изменения. Программы стажировок и обменов с ведущими университетами страны стали доступными для молодежи. Мария Иванова, 21 год, рассказывает о своем опыте: "Я прошла стажировку в одном из лучших IT-компаний Москвы. Это был невероятный опыт, который открыл мне двери в мир технологий. Теперь я работаю над собственным проектом в Кургане и надеюсь вдохновить других".

Спортивные достижения
Спорт также занимает важное место в жизни молодежи Кургана. Программа "Спорт для всех" привлекла множество молодых людей к занятиям физической культурой. Алексей Смирнов, 19 лет, стал чемпионом России по легкой атлетике. "Я начал заниматься спортом благодаря местным тренерам, которые верили в меня. Теперь я мечтаю о международных соревнованиях", — говорит Алексей.

Курган — это город возможностей, где молодежь может реализовать свои мечты и идеи. Программы поддержки, созданные для помощи молодым людям, стали катализатором изменений и вдохновения. Эти истории успеха — лишь малая часть того, что происходит в нашем городе, и мы уверены, что впереди нас ждут еще более яркие достижения.
Автор: Александра Налобина
-
 @ 97fc03df:8bf891df
2024-11-13 03:37:00
@ 97fc03df:8bf891df
2024-11-13 03:37:00Bitcoin's mechanical consensus is set to become human civilization's ultimate shield
Author: Gavin, BeeGee (Core Builders of Super Bitcoin & BEVM)
November 12, 2024
The value of Bitcoin is set to rise in the long term if mankind is unable to create an adaptive, growth-oriented mechanical consensus similar to that of Bitcoin. Bitcoin is not merely a tool to protect property; it represents a "Great Consensus" that safeguards human civilization and our future. With a supply capped at 21 million, each Bitcoin bears the immense responsibility of protecting the security and well-being of 8 billion people today and countless future generations. Can such a Bitcoin truly have a price ceiling?
The consensus mechanism behind Bitcoin is an unending competition of computing power. Miners constantly add computing power in pursuit of rewards of BTC. This competitive process creates a self-reinforcing growth model: as more people participate in mining, computing power increases, mining difficulty rises, the network’s security strengthens, Bitcoin’s consensus becomes more solid, and the value of Bitcoin increases accordingly. This pattern creates a powerful and enduring positive feedback loop. It is such kind of “mechanical consensus,” which operates without human intervention, that enables the Bitcoin network to self-coordinate and evolve autonomously among distributed nodes through computational competition and economic incentives.
However, even though Bitcoin’s adaptive mechanical consensus excels at securing property, this is just the tip of the iceberg. Its potential extends far beyond. Human society is in the midst of the torrent of the information age, and the accelerated growth of technology means that complexity and uncertainty are increasing, making it difficult to deal with these challenges by relying solely on traditional "social consensus". In this context, the adaptive mechanical consensus brought about by Bitcoin's incentive layer becomes the really important part. It shows us the ability of machines to form consensus through automated gaming, and the potential of technology to safeguard human life and civilization more broadly than property.
Super Bitcoin emerged just to further unlock the potential of Bitcoin's consensus. It proposes a five-layer architecture that extends the capabilities of various protocols and corresponding application scenarios by sharing the consensus security of Bitcoin. Super Bitcoin is more than just an upgrade to the Bitcoin network, it is an attempt to take this great mechanical consensus beyond the limits of property security to protect the broader interests of humanity and civilization. By sharing the consensus security of Bitcoin, Super Bitcoin provides the infrastructure to support the synergy of human technology and civilization as well as the safety of life through the "interconnectedness" and "interoperability" of all blockchain systems.
The core idea behind all of these is to unleash the potential of Bitcoin's consensus. Bitcoin's journey from zero to $1.8 trillion market capitalization in just 16 years has proven that a consensus driven by computing power can adaptively grow through economic incentives without any human intervention. Super Bitcoin's goal is to build on this foundation with a new architecture that allows this great consensus to protect not just the value of cryptocurrencies, but the security of the entire human society and technological civilization.
Imagine a future where Bitcoin's consensus mechanism not only protects digital assets, but also provides security for human life and civilization. This is not only a technological advancement, but also a qualitative transformation of social consensus. In a way, the scalability of Bitcoin and its consensus is representing our latest efforts to cope with complexity in the information age. If we can apply mechanical consensus to a wider range of areas through these efforts, then this consensus mechanism will no longer be just a financial tool, but a foundational force to lead humanity into the future.
Therefore, the value of Bitcoin lies not only in its scarcity as a digital asset, but also in the adaptive mechanical consensus behind it. This consensus is an important weapon for human society to confront future complexity and uncertainties, and is the cornerstone for protecting human life and the security of technological civilization. Super Bitcoin's mission is to make this Great Consensus no longer confined to the protection of property, but rather to become the common "Civilization Guardian" for the whole mankind.
-
 @ bcea2b98:7ccef3c9
2024-11-13 02:18:58
@ bcea2b98:7ccef3c9
2024-11-13 02:18:58Sometimes our strongest values are the ones that people wouldn’t expect. These unique principles often reveal something special about who we are and what we believe in. Do you hold a value that might surprise others?
originally posted at https://stacker.news/items/765433
-
 @ bcea2b98:7ccef3c9
2024-11-13 02:44:17
@ bcea2b98:7ccef3c9
2024-11-13 02:44:17@chess a3
originally posted at https://stacker.news/items/765445



