-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ ec42c765:328c0600
2024-10-16 08:08:40
@ ec42c765:328c0600
2024-10-16 08:08:40カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ c73818cc:ccd5c890
2024-11-07 14:22:58
@ c73818cc:ccd5c890
2024-11-07 14:22:58
💰 Con una vittoria decisiva, Trump torna alla presidenza con un chiaro messaggio di supporto alla finanza decentralizzata e all’indipendenza economica americana.
💸 Trump ha riconquistato la Casa Bianca con una vittoria cruciale in Pennsylvania e Wisconsin, superando i 270 voti elettorali necessari. Nonostante i forti risultati di Kamala Harris in California e New York, la strategia di Trump di rivolgersi al Midwest ha prevalso, assicurandogli un secondo mandato. Con oltre il 51% dei voti popolari, la vittoria rappresenta una chiara volontà popolare di tornare a politiche economiche orientate alla deregolamentazione.
💸 La sua elezione è storica per il mondo delle criptovalute: Trump è il primo presidente dichiaratamente pro-Bitcoin. Tra le sue promesse per la comunità crypto ci sono il sostegno all'industria del mining e l'idea di una riserva strategica in Bitcoin, che potrebbe rappresentare una svolta nella politica economica americana, rafforzando il ruolo di Bitcoin come riserva di valore alternativa e contro l’inflazione.
💸 Oltre a opporsi fermamente alle valute digitali delle banche centrali (CBDC), viste come una minaccia per la libertà finanziaria, Trump si è impegnato a considerare la grazia per Ross Ulbricht, una figura simbolica per la comunità Bitcoin. Questa postura antistatalista e pro-crypto ha consolidato il sostegno dei Bitcoiner e pone la sua amministrazione in netto contrasto con le precedenti rispetto alla regolamentazione delle criptovalute.
Unisciti al nostro gruppo Telegram Bitget -20% - Mexc no KYC https://lnk.bio/Bitcoin.Report.Italia
BitcoinReportItalia #USA #Democrazia #Elezioni #StatiUniti #America #Harris #Trump #Musk #CasaBianca #Presidente #Cripto #Bitcoin
-
 @ 361d3e1e:50bc10a8
2024-11-07 16:18:55
@ 361d3e1e:50bc10a8
2024-11-07 16:18:55https://forex-strategy.com/2024/11/07/the-water-crisis-and-the-future-of-humanity/ When Heaven Warns: The Water Crisis and the Future of Humanity What is the connection between the strange clouds in the sky and the future of man in new conditions. What is the best investment now?
haarp #clouds #strange #mystery #truth #crisis #water #flood
-
 @ fd208ee8:0fd927c1
2024-11-07 07:22:14
@ fd208ee8:0fd927c1
2024-11-07 07:22:14Unsucking the feed is real
As a Nostrich with an interesting, thought-provoking, and informative feed... a feed so good, that we're creating clients just to look at that feed... a feed that puts a lie to the idea that Nostr is nothing, but people reposting from Twitter or rehashing worn-out Bitcoin memes... a feed that I personally and increasingly enjoy perusing... I am here to tell you that the feed is real.

It's taken me over a year, to produce this feed. I literally spent hours and hours, day in and day out, scouring the Nostrverse for people worth introducing other people to. It was brutally difficult, as I was fighting the inherent nature of the Nostr clients and relays, in their current, most-popular form.
It goes like so...
Here are the steps I took, that sometimes weren't possible to take, until I tried to take them, and that still will sometimes break your client because the clients are often intentionally designed to steer you into having one particular feed:
1) Make a screenshot of your current relay list and copy your follows list. 2) Unsubscribe from all the relays, that you are currently subscribed to. Your feed should disappear. If it doesn't, or it doesn't allow for this, switch to a different client app because yours is corrupted. 3) Unfollow everyone. Delete the whole list. You are taking your follows private, which will invariably result in only following npubs whose stuff you actually want to see, since there's no longer any virtue-signaling going on. Also, it's easier to explain having no list, than a very short one. If your client doesn't allow for this, or starts throwing error messages and freezing up, then switch to a different client app because yours is corrupted. 4) Curate your copied follows list. Go line by line and look at the feed produced by the npub on that list. * Do you want to see that in your feed, going forward? * Do they produce original content and/or are they interesting conversationalists, in the replies? * Have they been active, within the past three months? * Are they simply good friends or real-life acquaintances, that you want to keep tabs on? * If not, cross out their name. * If you have been following someone because they repost or quote interesting things, look at who they've been reposting and follow them, instead. 5) Of the npubs remaining on your list, go through and select the 10 most interesting ones, and look at the reposts and quotes in their feed, and their topical lists like \"Favorites\", \"Devs\", \"Recipes\", etc. (Not their follows list, unless it's quite short, as follows tend to be full of people they follow for social-signaling or client-functional reasons, that they don't actively look at.) Find some new follows, there. 6) Now, set up a personal relay and add all the follows, that made the cut, to your allowed-npubs list. Do not add people to the list, just to make them feel better, or because you feel guilty, as they follow you, or to keep them from yelling at you. Remember, they can't see the list! 7) Think about the topics you find interesting, and add an allowed-keywords list (this is better than hashtags, as it searches the entire content of the notes), with the OR operator (these allowed npubs OR these allowed topics). 8) Make sure that you choose words likely to find the content you are most-interested in, and not people just ranting about it or spamming (those are great additions to your relay's block-list). If you are Muslim, for instance, instead of "Islam" or "shariah", choose "hadith" or "riba", as those are words more-likely to be used by people who know what they are talking about. If you are into bread baking, add "sourdough", "rye", "yeast", or "whisk", but don't add "bread" or "carbs". Once a note from those people shows up in your feed, and their feed looks like someone interesting, you can add their npub to your allow list. Remember: The topics are there to find people to add to the allow list, not merely for their own sake, as this is not a topical relay, but a personal one. 9) Open up a faucet (or relay syncing) with some of the big relays you previously unsubscribed from, some WoT relays, and some of the paid relays (nostr.land, nostr.wine, nostr21.com, and sovbit.host, for example). Your relay will filter that feed and only accept the events from the people and topics on your list. As your relay becomes more popular, npubs will begin writing directly to it, and the connections to other relays will sink in significance. 10) Go to your client of choice and subscribe to your new relay. Also subscribe to some topical relays, or curated neighborhood relays, you find interesting or your frens are running. This is an easy way to find new, interesting npubs, to add to your own relay.

That's a lot of work, you say? Yes, but the result is great, and you are now fully in-charge of your own feed. You also -- here's the cool part -- have a feed good enough, that other people can add your feed to theirs and enjoy your manual curation. As you refine and expand your feed, theirs will also be refined, in parallel. You are now an official Nostr Community Curator. My sincere congratulations.

Why is this so hard?
This is only a lot of work because the clients aren't designed to interact with relays, to this extent, as they were created to service mega-relays, download all their crap to your local cache, and adjust the feed over the follows/mutes lists. This was an idea borne of the axiom that Relays Are Hard, so there will only ever be a handful of them, where we'd all clump together and the relay operators would never judge the quality of someone's content. Then, some unusually clever people made relays increasingly easy, and the mailbox communication model was invented, and here we are.
What we have now, and that is slowly growing in popularity, among the #NostrIntelligentsia, are Nostr clients aimed at curating and viewing individual relays or personalized sets of smaller or more-specialized relays. The reigning client devs refused to give us those clients, and most of us aren't up to developing our own clients, so the relay devs took matters into their own hands and made the clients themselves. The free market remains undefeated.
This is a total game-changer. Last one to board this train is a rotten egg.
Originally, relays were supposed to be completely stupid and clients were supposed to be completely smart, but it's now actually the other way around, because most relay devs have a market-born incentive to make their content highly customizable and appealing to individuals (so that more people run relays).
But what about algos?
Can't you just slap an algo on top of Damus, Lol, or Primal relays, and get the same result? I would argue... no. No, you can't. Or, rather, only in the short to medium term.
Running your own relay, is running your own server. You are now intellectually independent, at a machine-level, and therefore a fully sovereign consumer. If you then use algos to control your own server, or in a client that subscribes to your own server, then you can further-refine a feed that is already in a high-to-you-signal state, rather than risking an algo inching you toward the Consensus Feed.
I have noticed that my own feed is slowly drifting away from the ReplyGuy-Cryptobot-Porny-Bitcoin-Meme Dumpster Fire, that almost everyone else is looking at, and it's due to running my own relay. If I use DVMs, those algos sometimes refer to relays I intentionally avoid, so they return results according to those relays. The results are as underwhelming, as you would expect, and often are simply 31 flavors of the Trending List.
But, that isn't your problem, anymore. From here, you can actively expand and refine your feed, over your whitelist, the topics, and your personally-managed algos.
Happy Nostr-ing!
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 42342239:1d80db24
2024-11-06 09:05:17
@ 42342239:1d80db24
2024-11-06 09:05:17TL;DR: J.D. Vance recently observed that many in the Democratic Party are attempting to manufacture trust from the top down, neglecting the fact that genuine trust is often born from grassroots connections. There's indeed a stark contrast between trust that's artificially constructed through manipulation and censorship, and trust that's organically cultivated from the ground up.
Trump's vice presidential candidate J.D. Vance appeared on podcast host Joe Rogan's show earlier in November. According to Vance, large parts of the Democratic Party are trying to create higher trust from above, without understanding that the previously high trust once arose organically: "I think that a lot of them are trying to reimpose that social trust from the top."
Most people understand the importance of high trust. Political scientist Robert D. Putnam, for example, has shown that large social capital, in the form of trust and networks, is a key factor for economic growth, cooperation, and problem-solving. See e.g. his book Bowling Alone: The Collapse and Revival of American Community (2000).
The low trust today is widespread. Trust in the American federal government is at historically low levels. Trust in the media is at rock-bottom levels. Even trust in doctors and hospitals has plummeted: at the beginning of 2024, the proportion of people who reported "a great deal of trust" had dropped to 40%, from 72% in April 2020. This can be concerning, as individuals with low trust in doctors and hospitals will be less likely to follow their advice and recommendations. It's therefore not surprising that many want to "rebuild trust" (this was the theme of the World Economic Forum's annual meeting this year).
How much trust is actually reasonable?
But how much trust is actually reasonable? To determine this, one can ask whether an institution has acted reliably in the past, whether it possesses the knowledge and ability required to deliver what is promised, and whether its interests are in line with our own.
The low trust figures among Americans are likely a reflection of the fact that many of them today question the extent to which the answers to these questions are actually affirmative. During the pandemic, medical experts in the UK incorrectly predicted that hundreds of thousands of people would die. In the US, the leading infectious disease expert misled the public about, among other things, face masks, the sitting president lied about both the effectiveness and safety of vaccines, a British health minister wanted to "scare the pants off people," and virus experts even conspired to mislead about the origin of the SARS-CoV-2 virus. All while social media companies, under pressure from governments, were forced to censor information that was actually correct.
Trust - built on sand or on solid ground?
It's possible to continue on the current path and try to improve trust figures by limiting access to information. For instance, if the public doesn't get access to negative information about authorities or experts, the measured trust can increase. But in that case, trust is merely built on sand, waiting to be undermined by the inexorable forces of truth.
But there's another possibility. Building relationships that are genuine and honest, listening to each other without judgment, and communicating without misleading. Doing things that really matter, and doing them well, showing competence and reliability through actions. In this way, trust can grow naturally and organically. A trust built on solid ground, not on sand. A delicate task. But presidential election or not, isn't it time for us to start building a future where this form of trust is the obvious foundation?
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 361d3e1e:50bc10a8
2024-11-07 15:04:11
@ 361d3e1e:50bc10a8
2024-11-07 15:04:11https://forex-strategy.com/2024/11/07/everything-is-repeated-strange-clouds-scared-people-again/ What's next, downpours or earthquakes?: Everything is repeated strange clouds scared people again
mystery #sky #clouds #haarp #truth #crisis
-
 @ b8a9df82:6ab5cbbd
2024-11-05 17:45:14
@ b8a9df82:6ab5cbbd
2024-11-05 17:45:14Last week, I got to experience the energy of Buenos Aires—a city as lively as it is massive. My journey began with a painfully long flight (easily my worst yet), but my excitement to meet everyone face-to-face kept me going. Despite being exhausted, I couldn’t wait to explore the city, take in the sights, and feel its unique vibe.
Buenos Aires was even bigger than I’d anticipated. I’d heard it was large, but I was still surprised by the sheer size of the avenues and the steady stream of traffic. It has a European feel—somewhat like Madrid—but with a laid-back attitude that’s far different from Berlin’s intensity. One thing I didn’t expect, though, was the cost; I thought it would be more affordable, but it was closer to European prices. Still, I quickly found myself adapting to its rhythms and taking in all the city had to offer.
Then came the Airbnb situation. Our first place was a disaster—mouldy, noisy, and with a broken bathroom. After some frustrating back-and-forth with the host, we decided to find somewhere else. We ended up switching apartments and moved from a place with issues to another one with even more issues... but we made it work. This was by far the worst experience, yet somehow it became part of the adventure.
Once I settled in, I was thrilled to finally meet the local community I’d been working with remotely for weeks. There’s nothing quite like getting to hug the people you’ve only seen on a screen. The Nostr community here, known as La Crypta, was incredibly welcoming, and working from their community center made me feel like I belonged. I’ll be writing more about this wonderful group soon!
In the days leading up to the conference, my schedule was packed with last-minute prep for both the conference itself and Nostr Day. One of the biggest lessons I learned was to let go of control. In Buenos Aires, things run on a different kind of timing—schedules are flexible, and punctuality isn’t a priority. I came with a detailed plan, but I soon realised I’d need to adjust and go with the flow. Once I did, I could really enjoy each moment as it came.
The language barrier was another challenge. I don’t speak Spanish (turns out Duolingo didn’t quite prepare me!), so I often needed others to help translate, which meant that sometimes details got a little lost. Still, we made it work, and the Nostr booth turned out to be a hit. People stopped by to chat, learn, and hang out, which was exactly what we’d hoped for. We wanted to make Nostr accessible to everyone—from content creators to developers—and seeing people’s enthusiasm to join the protocol was rewarding.

One of the highlights of the week was moderating the Nostr panel on the main stage, as well as speaking on another one. I was nervous leading up to it, especially with the sound issues that made it hard to hear other panelists. But despite those hiccups, the experience turned out great. The panelists were awesome and engaging, and I left feeling inspired and grateful.


After two intense conference days spent in dark, noisy spaces, we wrapped things up with Nostr Day at La Crypta. Conferences can be draining, and I found myself missing my regular routines—morning workouts, sunlight, and a bit of peace and quiet. Originally, we had a packed agenda for Nostr Day, but after a late Halloween celebration the night before, everyone was ready for a slower pace. We adjusted and turned it into a relaxed networking day, sitting outside, sharing Mate, and soaking up the fresh air. It was the perfect way to connect at a comfortable pace.
This week in Buenos Aires showed me just how open and curious people are about Nostr. From exploring the ecosystem together to helping new users get their first taste of it, it was a week of shared learning and connection. Thank you to everyone who poured their heart and energy into making this experience unforgettable. And a special thanks to Buenos Aires for feeding me endless amounts of incredible meat! After over 20 years as a vegetarian, I recently started eating meat again, and I have to say—it felt amazing.
Next stop: SatsConf!
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 1b5ee74d:bb1aae6e
2024-11-02 17:01:36
@ 1b5ee74d:bb1aae6e
2024-11-02 17:01:36A paper bordering on parody but, unfortunately, all too real. Titled “The Distributive Effects of Bitcoin,” it’s authored by Ulrich Bindseil and Jürgen Schaaf: the former manages the ECB’s Market Infrastructure and Payments division, while the latter serves as his advisor. Hosting this paper on its own servers, the Frankfurt institution safeguards itself with a disclaimer: “The views expressed are those of the authors and do not necessarily reflect the views of the ECB.” The disclaimer is understandable, as the positions of the two authors are so blatantly biased and devoid of any logical foundation that they seem too much even for Bitcoin’s number one enemy: the central bank itself.
The underlying assumption of the entire document is simple: Bitcoin does not increase the productive potential of the economy. Based on this shortsighted foundation, the authors construct an entire narrative that ignores some of the fundamental changes introduced by Bitcoin.
“Bitcoin does not increase the productive potential of the economy”
Since Bitcoin doesn’t increase the productive potential of the economy, the alleged increase in value is essentially redistributive. This means that the enrichment of the early bitcoin holders can only come at the expense of the rest of society.
Right from the abstract, the authors assert that Bitcoin in no way contributes to increasing the productive potential of the economy. Their thesis is that Bitcoin, lacking any connection to the creation of tangible goods or services, represents an asset with no intrinsic productive value. According to the document, while investments in sectors like technology or industry improve the efficiency and productive capacity of the economic system, Bitcoin provides no such benefit, as it does not directly contribute to production growth or innovation.
For the authors, much of Bitcoin’s attributed value derives solely from financial speculation and the perception of those who purchase it, without any tangible increase in “economic capacity.”
The redistributive potential: penalizing latecomers
Bindseil and Schaaf then explore what they call Bitcoin’s “redistributive structure,” claiming that its mechanism rewards early investors at the expense of latecomers. Their shocking revelation is that Bitcoin’s value increases for early purchasers as demand rises, generating higher returns for those who entered the market first.
In other words, Bindseil and Schaaf have discovered the wonderful world of supply and demand dynamics within that mysterious entity called “the market”—perhaps too complex to grasp for those dreaming of a Soviet-style economy. Not coincidentally, they describe this process as inherently unjust, arguing that people who decide to invest later don’t receive the same advantages and are forced to buy at higher prices.
If the rational part of your mind is screaming in desperation, I ask for one last effort.
The document describes this effect as a negative feature of Bitcoin, comparing it to a “speculative bubble” destined to collapse when new investors can no longer sustain the asset’s high price.
A point-by-point rebuttal
I confess, I would never have found the strength to sit down at my keyboard to debunk, once again, arguments so erroneous that they’d make anyone with a basic understanding of economics cringe. Fortunately, Murray Rudd and Dennis Porter of Satoshi Action Education, along with Allen Farrington of Axiom and Freddie New of Bitcoin Policy UK, have taken on this task.
Bitcoin’s productive potential: a central misunderstanding
The main assumption—that Bitcoin does not contribute to the productive potential of the economy—is challenged by highlighting how Bitcoin is fueling an ecosystem of technological and financial innovation. Tools like the Lightning Network reduce transaction costs and increase system efficiency, bringing tangible benefits to the economy. “Considering Bitcoin as a mere speculative tool,” the analysis states, “means ignoring the immense infrastructural and social value of payment networks and decentralized technologies deriving from its adoption.”
Bindseil and Schaaf also overlook how Bitcoin is already used to reduce the cost of international remittances, a vital function in parts of the world where transaction costs via traditional banking systems are often exorbitant, reaching up to 20% in some regions. This application provides both direct and indirect productive benefits in contexts with low financial inclusion.
Further, the response notes:
“Bitcoin is promoting innovation beyond payments. It has catalyzed advances in cryptography and energy efficiency, particularly through mining. Bitcoin mining using waste gas can mitigate methane emissions and improve renewable energy generation, contributing to grid flexibility thanks to the unique features of mining.”
Beyond technological advances, the arguments against Bitcoin reflect a fundamental misunderstanding of the role of money in capital accumulation and, consequently, economic prosperity. Productivity is driven by capital accumulation, and economic growth is the result of increased productivity through effective capital use. Arguing that capital growth does not contribute to productivity reveals a deep ignorance of basic market dynamics.
Bitcoin’s redistributive potential: a market dynamic
The final criticism from the two ECB-affiliated individuals concerns the accusation that Bitcoin only benefits early investors at the expense of newcomers. The authors of the rebuttal paper observe that this phenomenon exists in any asset—from real estate to gold—where early investors benefit from an increase in value. Furthermore, Bitcoin lacks privileged distributions, as seen in other cryptocurrencies issued with pre-mines or venture capital models. Bitcoin’s distribution model, which began with open and transparent mining, is considered by the authors “one of the fairest in the history of digital assets.” I would even go so far as to say the fairest.
The authors also point out that the fiat system, widely supported by the ECB, favors inequality through monetary devaluation—a form of reverse redistribution that penalizes small savers in favor of those with greater access to financial resources. Bitcoin, with its maximum issuance cap, offers an alternative to this erosion of purchasing power caused by inflation. In short, such an accusation from those representing the primary cause of the Cantillon effect is almost laughable.
The Federal Reserve’s direct attack
A few days after the publication of Bindseil and Schaaf’s paper, their American counterparts also decided to attack Bitcoin. The Federal Reserve of Minneapolis published a study titled “Unique Implementation of Permanent Primary Deficits?”
I won’t drag this out: in nearly forty pages of formulas and calculations, Fed experts managed to rediscover the obvious—if Bitcoin were to become widespread, the government would no longer be able to run deficits!
“Good morning, princess,” as Roberto Benigni would say in La Vita è Bella. In this newsletter, we’ve been discussing this topic for about three years, yet I haven’t received a job offer from Washington. Perhaps it’s because my views are slightly at odds with those of the employees of the monetary monopolist. The Fed, in fact, sees a very simple solution: ban Bitcoin! They state it plainly:
“The government could simply make Bitcoin illegal.”
Here, we encounter a fundamental disagreement. Believing that Bitcoin can be banned by a few lines in a law reflects a profound misunderstanding of the technology. If you’d like a consultation on the subject, dear friends at the Fed, I’ll be here.
Or rather, I’ll be enjoying your decline.
Sincerely,
Federico.
-
 @ 3f770d65:7a745b24
2024-10-29 17:38:20
@ 3f770d65:7a745b24
2024-10-29 17:38:20Amber
Amber is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications.

Amber is supported by a growing list of apps, including Amethyst, 0xChat, Voyage, Fountain, and Pokey, as well as any web application that supports NIP-46 NSEC bunkers, such as Nostr Nests, Coracle, Nostrudel, and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms.

Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's GitHub page, via Obtainium or Zap.store.
To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com.

Citrine
Citrine is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control.

With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality.
Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration.

Pokey
Pokey for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device.

Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem.
Zap.store
Zap.store is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency.

Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing Zap.store on your favorite Android device, and install all of the applications mentioned above.
Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems.
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:17:56
@ 4ba8e86d:89d32de4
2024-11-07 13:17:56O aplicativo permite que os usuários se comuniquem com outras pessoas sem ter que fornecer identificadores de usuário, como números de telefone ou endereços de e-mail. é 100% privado e seguro, Por design, garantindo que suas mensagens nunca sejam rastreadas ou armazenadas. O SimpleXChat possui recursos como bate-papo em grupo, envio de arquivos e uma interface amigável para dispositivos móveis, desktop, CLI. O SimpleXChat é um dos aplicativos construídos sobre a plataforma SimpleX, que também serve como um exemplo e aplicativo de referência. O SimpleX Messaging Protocol (SMP) é um protocolo que permite enviar mensagens em uma direção para um destinatário, usando um servidor intermediário. As mensagens são entregues por meio de filas unidirecionais criadas pelos destinatários.
O SMP é executado em um protocolo de transporte (TLS), que fornece integridade, autenticação do servidor, confidencialidade e vinculação do canal de transporte. A Rede SimpleX é o coletivo de servidores SimpleX que facilitam o SMP. As bibliotecas SimpleX Client falam SMP para SimpleX Servers e fornecem uma API de baixo nível, geralmente não destinada a ser usada por aplicativos.
O aplicativo permite que os usuários se comuniquem com outras pessoas sem ter que fornecer identificadores de usuário, como números de telefone ou endereços de e-mail. O SimpleXChat possui recursos como bate-papo em grupo, envio de arquivos e uma interface amigável para dispositivos móveis.
O SimpleX tem como objetivo fornecer uma infraestrutura de mensagens distribuídas que seja segura, privada, confiável, com entrega assíncrona e baixa latência. Ele visa oferecer melhor privacidade de metadados e segurança contra invasores de rede ativos e servidores mal-intencionados em comparação com soluções alternativas de mensagens instantâneas, ao mesmo tempo em que prioriza a experiência do usuário, especialmente em dispositivos móveis.
Por que o SimpleX é único
- Privacidade total de sua identidade, perfil, contatos e metadados
Ao contrário de outras plataformas de mensagens, o SimpleX não possui identificadores atribuídos aos usuários . Ele não depende de números de telefone, endereços baseados em domínio (como e-mail ou XMPP), nomes de usuário, chaves públicas ou mesmo números aleatórios para identificar seus usuários - não sabemos quantas pessoas usam nossos servidores SimpleX
Para entregar mensagens, o SimpleX usa endereços anônimos emparelhados de filas de mensagens unidirecionais, separadas para mensagens recebidas e enviadas, geralmente por meio de servidores diferentes. Usar o SimpleX é como ter um e-mail ou telefone “gravador” diferente para cada contato e sem problemas para gerenciá-los.
Esse design protege a privacidade de quem você está se comunicando, ocultando-a dos servidores da plataforma SimpleX e de quaisquer observadores. Para ocultar seu endereço IP dos servidores, você pode se conectar aos servidores SimpleX via Tor .
-
A melhor proteção contra spam e abuso Como você não possui um identificador na plataforma SimpleX, ninguém pode entrar em contato com você, a menos que você compartilhe um endereço de usuário único ou temporário, como um código QR ou um link. Mesmo com o endereço de usuário opcional, embora possa ser usado para enviar solicitações de contato de spam, você pode alterá-lo ou excluí-lo completamente sem perder nenhuma de suas conexões.
-
Propriedade, controle e segurança de seus dados
O SimpleX Chat armazena todos os dados do usuário apenas em dispositivos clientes usando um formato de banco de dados criptografado portátil que pode ser exportado e transferido para qualquer dispositivo compatível.
As mensagens criptografadas de ponta a ponta são mantidas temporariamente em servidores de retransmissão SimpleX até serem recebidas e, em seguida, são excluídas permanentemente.
Ao contrário dos servidores de redes federadas (e-mail, XMPP ou Matrix), os servidores SimpleX não armazenam contas de usuários, apenas retransmitem mensagens, protegendo a privacidade de ambas as partes.
Ao contrário dos servidores de redes federadas (e-mail, XMPP ou Matrix), os servidores SimpleX não armazenam contas de usuários, apenas retransmitem mensagens, protegendo a privacidade de ambas as partes.
Não há identificadores ou texto cifrado em comum entre o tráfego do servidor enviado e recebido - se alguém estiver observando, não poderá determinar facilmente quem se comunica com quem, mesmo que o TLS esteja comprometido.
- Totalmente descentralizado — os usuários são proprietários da rede SimpleX
Você pode usar o SimpleX com seus próprios servidores e ainda se comunicar com pessoas que usam os servidores pré-configurados fornecidos por nós.
A plataforma SimpleX usa um protocolo aberto e fornece SDK para criar bots de bate-papo , permitindo a implementação de serviços com os quais os usuários podem interagir por meio de aplicativos de bate-papo SimpleX. A rede SimpleX é totalmente descentralizada e independente de qualquer criptomoeda ou qualquer outra plataforma, exceto a Internet.
Você pode usar o SimpleX com seus próprios servidores ou com os servidores fornecidos por nós.
Características SimpleXchat • Mensagens criptografadas por E2E com remarcação e edição
• Imagens e arquivos criptografados por E2E
• Grupos secretos descentralizados apenas os usuários sabem que eles existem
• Mensagens de voz criptografadas por E2E
• Mensagens desaparecidas
• Chamadas de áudio e vídeo criptografadas com E2E
• Banco de dados criptografado portátil — mova seu perfil para outro dispositivo
• Modo de navegação anônima exclusivo do SimpleX Chat
O que torna o SimpleX privado
https://nostr.build/i/nostr.build_4e6fa7bc41d22d7a9672fa23b04b7aa6d69938d7013ac1ea31212a854e6d1e97.jpg Identificadores par a par anônimos temporários O SimpleX usa endereços emparelhados anônimos temporários e credenciais para cada contato do usuário ou membro do grupo. Ele permite entregar mensagens sem identificadores de perfil de usuário, fornecendo melhor privacidade de metadados do que alternativas.
Troca de chaves fora de banda Muitas plataformas de comunicação são vulneráveis a ataques MITM por servidores ou provedores de rede. Para evitar que os aplicativos SimpleX passem chaves únicas fora de banda, quando você compartilha um endereço como um link ou um código QR. https://nostr.build/i/nostr.build_9065e2600cf42d0bcf7bb89deb674eb0630c590bd043b1f8c92272011ec7a2ec.jpg
2 camadas de criptografia de ponta a ponta Protocolo de catraca dupla — mensagens OTR com sigilo de encaminhamento perfeito e recuperação de invasão. Criptobox NaCL em cada fila para evitar a correlação de tráfego entre as filas de mensagens se o TLS estiver comprometido. https://nostr.build/i/nostr.build_defe978ea10526b657bf35e6809f4385c82c7eca58b91ae3a0e81447dbf0bda3.jpg
Verificação da integridade da mensagem Para garantir a integridade as mensagens são numeradas sequencialmente e incluem o hash da mensagem anterior. Se alguma mensagem for adicionada, removida ou alterada, o destinatário será alertado. https://nostr.build/i/nostr.build_debf9317b88a015af37f8c610d4e1671bc495d1a80c2b6ea090d202fb332ba84.jpg Camada adicional de criptografia do servidor
Camada adicional de criptografia do servidor para entrega ao destinatário, para evitar a correlação entre o tráfego do servidor recebido e enviado se o TLS estiver comprometido. https://nostr.build/i/nostr.build_13793f89276380e221bd15f6173fe1221f550993a0902a249b5ba86e5fe1d237.jpg
Mistura de mensagens para reduzir a correlação Os servidores SimpleX atuam como nós de mistura de baixa latência — as mensagens recebidas e enviadas têm ordem diferente. https://nostr.build/i/nostr.build_1c7146ca7b3871ff1de184be78785e9e0c45cf2567f6147b260009d9c74925ed.jpg
Transporte TLS autenticado seguro Somente o TLS 1.2/1.3 com algoritmos fortes é usado para conexões cliente-servidor. A impressão digital do servidor e a ligação do canal evitam ataques MITM e de repetição. A retomada da conexão é desativada para evitar ataques de sessão. https://nostr.build/i/nostr.build_515af3c35a729f3dd47619965f76e3a8499ad1fe7694f2bbab14404cf5a77f6a.jpg
Acesso opcional via Tor Para proteger seu endereço IP, você pode acessar os servidores via Tor ou alguma outra rede de sobreposição de transporte. Para usar o SimpleX via Tor, instale o aplicativo Orbot e habilite o proxy SOCKS5 (ou VPN no iOS ). https://nostr.build/i/nostr.build_0c8f651db74c9ae2ab4d4424972b21d64af8dab2aa5364d4b140898bebfc42b0.jpg
Filas de mensagens unidirecionais Cada fila de mensagens passa mensagens em uma direção, com diferentes endereços de envio e recebimento. Ele reduz os vetores de ataque, em comparação com os corretores de mensagens tradicionais e os metadados disponíveis. https://nostr.build/i/nostr.build_a7b6103be59dbffb242e6b5d371767f6df3219a1cad2a0f05a278cfb7596ad3d.jpg
Várias camadas de preenchimento de conteúdo SimpleX usa preenchimento de conteúdo para cada camada de criptografia para frustrar ataques de tamanho de mensagem. Faz mensagens de tamanhos diferentes parecerem iguais para os servidores e observadores de rede. https://nostr.build/i/nostr.build_6ac8491d3e0236460bb914ea5dc1a23fea03e6c598cef6643949eea38e5fad44.jpg
A rede SimpleX diferente de outras redes P2P ao ser composta por clientes e servidores sem depender de um componente centralizado. Ele usa filas de mensagens unidirecionais redundantes (simplex) para comunicação, eliminando a necessidade de endereços exclusivos globalmente. As solicitações de conexão são protegidas contra ataques man-in-the-middle e as filas de mensagens simples são usadas pelos clientes para criar cenários de comunicação mais complexos. Os servidores não armazenam nenhuma informação do usuário e os usuários podem mudar de servidor com interrupção mínima.
Rede SimpleX
Simplex Chat fornece a melhor privacidade combinando as vantagens de redes P2P e federadas. https://nostr.build/i/nostr.build_062b212b3c43e9cab9e7290e6a052012c54acabadfeb962190ffe9783647f356.jpg
Ao contrário das redes P2P
Todas as mensagens são enviadas pelos servidores, proporcionando melhor privacidade de metadados e entrega de mensagens assíncronas confiáveis, evitando muitos problemas de redes P2P .
-
As redes P2P dependem de alguma variante do DHT para rotear mensagens. Os projetos DHT precisam equilibrar a garantia de entrega e a latência. O SimpleX tem melhor garantia de entrega e menor latência do que o P2P, pois a mensagem pode ser passada de forma redundante por vários servidores em paralelo, utilizando os servidores escolhidos pelo destinatário. Em redes P2P a mensagem é passada por nós O(log N) sequencialmente, usando nós escolhidos pelo algoritmo.
-
O design SimpleX, ao contrário da maioria das redes P2P, não possui identificadores globais de usuário de qualquer tipo, mesmo temporários, e usa apenas identificadores temporários emparelhados, fornecendo melhor anonimato e proteção de metadados.
-
O P2P não resolve o problema do ataque MITM e a maioria das implementações existentes não usa mensagens fora de banda para a troca inicial de chaves. O SimpleX usa mensagens fora de banda ou, em alguns casos, conexões seguras e confiáveis pré-existentes para a troca inicial de chaves.
-
As implementações P2P podem ser bloqueadas por alguns provedores de Internet (como BitTorrent ). O SimpleX é agnóstico de transporte - ele pode funcionar sobre protocolos da Web padrão, por exemplo, WebSockets.
-
Todas as redes P2P conhecidas podem ser vulneráveis ao ataque Sybil , porque cada nó é detectável e a rede opera como um todo. As medidas conhecidas para mitigá-lo exigem um componente centralizado ou uma prova de trabalho cara . A rede SimpleX não tem capacidade de descoberta de servidor, é fragmentada e opera como várias sub-redes isoladas, impossibilitando ataques em toda a rede.
-
As redes P2P podem ser vulneráveis a ataques DRDoS , quando os clientes podem retransmitir e amplificar o tráfego, resultando em negação de serviço em toda a rede. Os clientes SimpleX apenas retransmitem o tráfego de conexão conhecida e não podem ser usados por um invasor para amplificar o tráfego em toda a rede.
Ao contrário das redes federadas
Os servidores de retransmissão SimpleX NÃO armazenam perfis de usuário, contatos e mensagens entregues, NÃO se conectam entre si e NÃO há diretório de servidores. https://nostr.build/i/nostr.build_abadeb8361026101dc2e5888217cd7620d7cf01233a7961071bb07c49f7f9f0e.jpg
os servidores fornecem filas unidirecionais para conectar os usuários, mas não têm visibilidade do grafo de conexão de rede — somente os usuários têm. https://nostr.build/i/nostr.build_0f281d6b89e96efcc9334384ae9f251c529feb136748dd0846e249a715e2a5e3.jpg
Simplex explicado
- O que os usuários experimentam https://nostr.build/i/nostr.build_157aa796dd3953b830e5643a5e98bb07b09d1ab8737a4f8b39d26e3637902ae8.jpg Você pode criar contatos e grupos e ter conversas bidirecionais, como em qualquer outro messenger.
Como trabalhar com filas unidirecionais e sem identificadores de perfil de usuário?
- Como funciona https://nostr.build/i/nostr.build_fda66ead74bed1a72139cf9ce9cbe96eea7a09b9007151a576124f8cab39952d.jpg
Para cada conexão, você usa duas filas de mensagens separadas para enviar e receber mensagens por meio de servidores diferentes.
Os servidores passam mensagens apenas de uma maneira, sem ter uma imagem completa da conversa ou das conexões do usuário.
- O que os servidores veem https://nostr.build/i/nostr.build_e95db233e71ef8ff53590e740095429338c8aba8fba846431d81112ffba01932.jpg
Os servidores possuem credenciais anônimas distintas para cada fila e não têm conhecimento da identidade dos usuários.
A implementação Roteamento de Mensagens Privadas na Rede SimpleX é um marco significativo na evolução do Protocolo de Mensagens SimpleX, elevando a privacidade dos usuários a outro patamar! https://image.nostr.build/f77c4336cb335cb87dab6645bbac7a8f6a99d8b8e7a787511918c740558b5be7.jpg
Qual é o problema? https://image.nostr.build/4ad92ca6d702155c97849fce854f6c3101ac979b21781620500edd357ab6d7a3.jpg
Design da rede Simplex sempre se concentrou na proteção da identidade do usuário no nível do protocolo de mensagens - não há identificadores de perfil de usuário de qualquer tipo no design do protocolo, nem mesmo números aleatórios ou chaves criptográficas. Porém, até este lançamento, a rede SimpleX não tinha proteção integrada de identidades de transporte de usuários - endereços IP. Como anteriormente os usuários só podiam escolher quais retransmissores de mensagens usar para receber mensagens, esses retransmissores poderiam observar os endereços IP dos remetentes e, se esses retransmissores fossem controlados pelos destinatários, os próprios destinatários também poderiam observá-los - seja modificando o código do servidor ou simplesmente rastreando todos os endereços IP conectados.
Para contornar essa limitação, muitos usuários se conectaram a retransmissores de rede SimpleX via Tor ou VPN – para que os retransmissores dos destinatários não pudessem observar os endereços IP dos usuários quando eles enviassem mensagens. Ainda assim, foi a limitação mais importante e mais criticada da rede SimpleX pelos usuários.
O que é roteamento de mensagens privadas e como funciona?
O roteamento de mensagens privadas é um marco importante para a evolução da rede SimpleX. É um novo protocolo de roteamento de mensagens que protege os endereços IP dos usuários e as sessões de transporte dos retransmissores de mensagens escolhidos por
Seus contatos. O roteamento de mensagens privadas é, efetivamente, um protocolo de roteamento cebola de 2 saltos inspirado no design do Tor, mas com uma diferença importante - o primeiro retransmissor (encaminhamento) é sempre escolhido pelo remetente da mensagem e o segundo (destino) - pelo destinatário da mensagem. Desta forma, nenhum lado da conversa pode observar o endereço IP ou a sessão de transporte do outro.
Ao mesmo tempo, os retransmissores escolhidos pelos clientes remetentes para encaminhar as mensagens não conseguem observar para quais conexões (filas de mensagens) as mensagens são enviadas, devido à camada adicional de criptografia ponta a ponta entre o remetente e o retransmissor de destino, semelhante ao funcionamento do roteamento cebola na rede Tor, e também graças ao design do protocolo que evita quaisquer identificadores repetidos ou não aleatórios associados às mensagens, que de outra forma permitiriam correlacionar as mensagens enviadas para diferentes conexões como enviadas pelo mesmo usuário. Cada mensagem encaminhada para o retransmissor de destino é adicionalmente criptografada com uma chave efêmera única, para ser independente das mensagens enviadas para diferentes conexões.
O protocolo de roteamento também evita a possibilidade de ataque MITM pelo retransmissor de encaminhamento, que fornece ao certificado as chaves de sessão do servidor de destino para o cliente remetente que são assinadas criptograficamente pelo mesmo certificado que está incluído no endereço do servidor de destino, para que o cliente possa verifique se as mensagens são enviadas para o destino pretendido e não interceptadas.
O diagrama abaixo mostra todas as camadas de criptografia usadas no roteamento de mensagens privadas: https://image.nostr.build/c238546e47b00dfea742ab1fc008ff51811240025a603dfbcc94b5bc14b5aa88.jpg
e2e - duas camadas de criptografia ponta a ponta entre clientes remetentes e receptores, uma das quais usa algoritmo de catraca dupla E2EE Post-quantum. Essas camadas de criptografia também estão presentes na versão anterior do protocolo de roteamento de mensagens.
s2d - criptografia entre o cliente remetente e o retransmissor de destino do destinatário . Essa nova camada de criptografia oculta os metadados da mensagem (endereço de conexão de destino e sinalizador de notificação de mensagem) da retransmissão de encaminhamento.
f2d - nova camada de criptografia adicional entre retransmissores de encaminhamento e destino , protegendo contra correlação de tráfego caso o TLS seja comprometido - não há identificadores ou texto cifrado em comum entre o tráfego de entrada e saída de ambos os retransmissores dentro da conexão TLS.
d2r - camada de criptografia adicional entre o retransmissor de destino e o destinatário, protegendo também da correlação de tráfego caso o TLS seja comprometido.
TLS - criptografia de transporte TLS 1.3. Para que o roteamento privado funcione, tanto a retransmissão de encaminhamento quanto a de destino devem suportar o protocolo de mensagens atualizado - ele é compatível com a versão 5.8 das retransmissões de mensagens.
https://image.nostr.build/2edbb7721c3ccf8a21274e96e25ee076c3522323870d92b73dbd1f6bda66fce8.jpg
Passo a passo do aplicativo nostr:nprofile1qqsvnx99ww0sfall7gpv2jtz4ftc9v6wevgdd7g4hh7awkpfvwlezugpzdmhxue69uhhqatjwpkx2urpvuhx2ue0chkv5c
Backup e Recuperação de Dados:
-
instalação do aplicativo.
-
Exportação do banco de dados Backup.
-
Importação do Backup do banco de dados.
-
Baixe e Instale o Aplicativo:
-
baixar o SimpleXchat no F-droid ou Obtainium.
F-droid
https://simplex.chat/fdroid/
https://f-droid.org/packages/chat.simplex.app/
Obtainium.
https://github.com/simplex-chat/simplex-chat
- Faça o download e instale o aplicativo em seu dispositivo móvel.
Criando seu perfil:
-
Criar perfil:
-
Clique em “CRIE SEU PERFIL”, contatos e mensagens são armazenados localmente em seu dispositivo.
https://image.nostr.build/e109c9fd5ea327640f0af2d6396aaa7e7d85594c6b20fd6ed426a558195a0021.jpg
-
Nome de Exibição exemplo: Alex teste :-)
-
Toque em "Criar" para configurar seu perfil e começar a usar o SimpleXchat.
https://image.nostr.build/96a1c59d370d554ada31e91301857825af7975b29eb82fe8fcb5cbba9d40bf23.jpg
-
Endereço SimpleX:
-
Clique no nome “Criar endereço SimpleX “
-
clicar em " continuar "
Ou Clicar em " Não criar endereço " pode criá-lo mais tarde.
https://image.nostr.build/cb91c0c1d43ce6c1a310cf2547cc88510529db3c2a5ce17ca79ec5d9269cb58e.jpg
https://image.nostr.build/47595ab6c17183c267fab2892a8d188b2e9fe29f067c8d96afec2ddbb9feda95.jpg
-
Notificação privadas
-
Escolha o tipo de notificação que prefere 3 opções.
Escolha a opção aberta em “ USAR BATE- PAPO “
https://image.nostr.build/96027dc0c47bdcb8a9c5017592bd6828f8e2d752883c826c08105aec340f1d81.jpg
• Backup e Recuperação de Dados:
- Cópia de segurança. “Clicar no canto superior lado esquerdo na foto de perfil“
Selecione a opção “Senha e Exportação de Banco de Dados“
https://image.nostr.build/7918c90aec373af57ccdcb1194e9277ab85aabadf83ac1d35065ec2a9f2b0aef.jpg
Desabilite a opção “O bate-papo está em execução ”
Clique em “parar”
https://image.nostr.build/8473fac2cef41d35451abcf8b40101630caf92b30f01e51767df1cc428dd8a70.jpg
https://image.nostr.build/bdd691b738712f98107c7da404d693d9cccce58c2afb89a2d6f649190e13a3e2.jpg
Seu banco de dados de bate-papo tem 4 opções.
-
Senha do banco de dados
-
Exportar banco de dados
-
Importar banco de dados
-
Excluir banco de dados
Clique na primeira opção " Senha do banco de dados "
- O Banco de Dados tem seus contatos e grupos e é protegido por sua senha que criptografa o banco de dados. Recomenda-se trocar essa senha padrão.
https://image.nostr.build/91859f269fbca9d02009652f2f9b3f76abcaa9de8647b48b5d20bee291e32ba3.jpg
Clicar na primeira opção " Senha de banco de dados "
Lembre-se de usar uma senha forte.
Após adicionar senha clique em “Atualizar senha do banco de dados”
https://image.nostr.build/3d84eb9954080589ea79050420300baa7e095f1dfc37c925ec4abf7abb047675.jpg
Vai aparecer um aviso.
Alterar senha do banco de dados? A senha de criptografia do banco de dados será atualizada e armazenada no keystore. Guarde a senha em um local seguro, você NÃO poderá alterá-la se a perder.
https://image.nostr.build/61dcdfdb82764df8855ef9e15c453b42d9c87fd23ea9e797ea066ad31f94fd61.jpg
Só clique em “Atualizar” demora 1 minuto aparece a mensagem “banco de dados criptografado!” Só clique em “ok”
https://image.nostr.build/8c303857ae63b803792f71273b4891f7adcfdbc3d0a428ecde2abbfef168781d.jpg
• Clique na opção 2.
Exportar banco de dados.
https://image.nostr.build/91859f269fbca9d02009652f2f9b3f76abcaa9de8647b48b5d20bee291e32ba3.jpg
Tem duas poções para salvar na memória do Celular, Pendrive, componentes externos de sua preferência.
-
Por padrão Vai abrir a memória do celular para salvar o arquivo backup criptografado na pasta de sua escolha.
-
Pra guardei no pendrive é necessário um cabo OTG para salvar o backup criptografado. Conecte um cabo OTG no celular, alguns celulares já confirmam automaticamente e entram diretamente na pasta do seu pendrive outros aparece um aviso pra aceitar pendrive. Depois basta selecionar o pendrive e salvar o backup.
https://image.nostr.build/c3bd4ca72270d651f4ea7125ac697cd11cb47316e4f0d18e8dfef732579ae77b.jpg
• Clique na opção
- Importar banco de dados.
https://image.nostr.build/91859f269fbca9d02009652f2f9b3f76abcaa9de8647b48b5d20bee291e32ba3.jpg
-
Caso você perca seu celular, você não tem acesso ao backup. Mas se você tiver salvo no pendrive ou componentes externos, basta seguir as etapas a seguir.
-
Faça a instalação do aplicativo e crie uma nova conta, selecione a opção "Senha e Exportação de Banco de Dados" e desabilite a opção "Chat em Execução". Isso permitirá que você faça a importação do backup.
Clique na opção Importar banco de dados.
Selecione o artigo do backup no pendrive ou na pasta dentro do novo celular só basta clicar no arquivo.
https://image.nostr.build/47cac70f4ba0520c060da98b4b3559f621757d98b4f963b1b1fd2cc522eafa45.jpg
Vai aparecer um aviso.
Importa banco de dados de Chat?
Seu banco de dados do Chat atual será EXCLUÍDO ou SUBSTITUÍDO pelo importado.
Essa ação não pode ser desfeita - Seu perfil, contatos, mensagens e arquivos serão perdidos de forma irreversível.
Só clique em "importar"
https://image.nostr.build/fdfa5e4ba2b6cd1a2b9116633da3f8a7cf91f41dd6d5739582f4e112ae384f7a.jpg
Vai aparecer um aviso.
Banco de dados de chat Importado.
Reinicie o aplicativo para usar o banco de dados do chat Importado.
Só clique em "ok"
Depois Habilite a opção "o bate-papo está parado"
https://image.nostr.build/1f261f36262d5a6cf593b5cb09abdb63ace7bf63f0e66bee7b949850972b3f92.jpg
A senha do banco de dados é necessária para abrir o Chat.
Digite a senha do seu banco de dados.
Depois é só clicar em "salvar senha e abrir Chat"
Pronto foi feita a recuperação de todos os meus dados, incluindo contatos, mensagens e grupos✅️
https://image.nostr.build/28f13ac654c68c890495cbf9689d09946b7af1ecc00a796b9ffd6d64059f4516.jpg
https://image.nostr.build/aae866f7577995bda6735e0a5e4683770bac2af845ae8b552da6526c4f589f08.jpg
Protegendo sua Privacidade no SimpleX Chat.
https://image.nostr.build/88fe0bf337105a3be94754c64bedfbe17d35c586714aa225d0179a379f9a1f71.jpg
Recentemente, tive uma experiência interessante ao explorar as opções de privacidade e segurança no SimpleX Chat. Uma funcionalidade que me chamou a atenção foi a opção de senha de auto destruição, que oferece uma camada adicional de proteção aos dados sensíveis.
Ao configurar o SimpleX Chat para usar senha de auto destruição, percebi o quão poderosa essa ferramenta pode ser para proteger minha privacidade. Após ativar essa opção, qualquer tentativa de acessar meu perfil precisa da senha escolhida por mim. E, se alguém tentasse forçar a abertura do aplicativo, eu posso simplesmente digitar a senha de auto destruição seria apresentado um perfil vazio, sem histórico de conversas. Essa função e bem útil em situações extremas.
A configuração da senha de auto destruição é simples mas poderosa.
Basta acessar as configurações de privacidade e segurança.
https://image.nostr.build/4fb6166656b544c645f316dfc4dad3b9e787b280745992dab30786b0bd0c2ee5.jpg
Aberta na opção de bloqueio SimpleX.
https://image.nostr.build/b866d08644b64884101aae6d011248a3557ac80bcc6e442ae8f62bdb3ee69776.jpg
mudar para a opção de senha. Em seguida, é possível escolher se deseja ativar a senha de auto destruição e inserir a senha desejada.
https://image.nostr.build/867d375825640721ee888e524455fb539df50be87df901dcf0ccfa19f2267576.jpg
Só basta adicionar a senha.
https://image.nostr.build/5bfb500816f814eab189283a64086ad47f32671d8e42558f3f911676ff4df741.jpg
https://image.nostr.build/59323fa6900d4f3b27b39b032f7c2cffdbf379a77c53ed9180c0ace0ca903950.jpg
Pronto. Está Ativado a senha de auto destruição.
https://image.nostr.build/511f82832d1e72d0363cfc5b7b201aaba56f65cfa00360d1c1f4d8d188bb3cdf.jpg
Uma vez configurada, a senha de auto destruição garante que todos os dados, incluindo backups, sejam eliminados permanentemente se a senha de auto destruição for inserida ao desbloquear o aplicativo.
Tenha um backup no pendrive ou em outro local guardado.
https://image.nostr.build/dfbbc5ef805194cc00a09fb690fc76896ada9a9d3f98e8b141f52c72342e2625.jpg
https://image.nostr.build/32a771a0ba2bae47f45f900fc765ffbeae0374724a1a0140c0f2cef83a2e5c2f.jpg
Essa funcionalidade oferece uma tranquilidade adicional ao utilizar o SimpleX Chat, pois sei que meus dados estão protegidos contra acesso não autorizado. Além disso, a capacidade de criar um perfil vazio para ocultar a identidade real é uma ferramenta valiosa em situações críticas , proteger meus dados sensíveis e manter minha privacidade intacta.
https://medium.com/@alexemidio/o-simplexchat-%C3%A9-uma-plataforma-de-mensagens-revolucion%C3%A1rias-que-redefinem-a-privacidade-sendo-o-4690f2a1b2d4
Podcast muito bom no @optoutpod com o criador @epoberezkin https://youtu.be/LrLsS7-woN0
Site : https://simplex.chat/
Protocolo de bate-papo: https://github.com/simplex-chat/simplex-chat/blob/stable/docs/protocol/simplex-chat.md
Whitepaper, incluindo modelagem de ameaças: https://github.com/simplex-chat/simplexmq/blob/stable/protocol/overview-tjr.md
Execute seu próprio servidor SimpleX SMP: https://github.com/simplex-chat/simplexmq
https://play.google.com/store/apps/details?id=chat.simplex.app
Como auto-hospedar servidor Simplexchat
https://youtu.be/p1NF68KIt7M?si=Nhwa8ZajmAvke6lW
https://youtu.be/p1NF68KIt7M?si=uZqOtVu0sLWLXBJX
https://simplex.chat/docs/server.html
https://github.com/simplex-chat/simplexmq
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 13b9f773:4f4efe54
2024-11-07 13:54:18
@ 13b9f773:4f4efe54
2024-11-07 13:54:18«Es una tontería pensar que tienes que leer todos los libros que compras, ya que es una tontería criticar a aquellos que compran más libros de lo que nunca podrán leer. Sería como decir que hay que usar todos los cubiertos o gafas o destornilladores o puntas de taladro que hayas comprado antes de comprar nuevos. Hay cosas en la vida que necesitamos tener siempre un montón de suministros, incluso si solo usaremos una pequeña porción. Si, por ejemplo, consideramos los libros como medicina, entendemos que es bueno tener muchos en casa en lugar de pocos: cuando quieres sentirte mejor, entonces vas al 'armario de medicina' y eliges un libro. No uno al azar, sino el libro correcto para ese momento. ¡Es por eso que siempre debes tener una elección de nutrición!. Los que compran un solo libro, leen sólo ese y luego se deshacen de él. Simplemente aplican la mentalidad de consumidor a los libros, es decir, los consideran un producto de consumo, un bien. Los que aman los libros saben que un libro es cualquier cosa menos una mercancía».
Umberto Eco ↗️
-
 @ 3bf0c63f:aefa459d
2024-10-26 14:18:23
@ 3bf0c63f:aefa459d
2024-10-26 14:18:23kind:1maximalism and the future of other stuff and Nostr decentralizationThese two problems exist on Nostr today, and they look unrelated at first:
- People adding more stuff to
kind:1notes, such as making them editable, or adding special corky syntax thas has to be parsed and rendered in complicated UIs; - The discovery of "other stuff" content (i.e. long-form articles, podcasts, calendar events, livestreams etc) is hard due to the fact that most people only use microblogging clients and they often don't appear there for them.
Point 2 above has 3 different solutions:
- a. Just publish everything as
kind:1notes; - b. Publish different things as different kinds, but make microblogging clients fetch all the event kinds from people you follow, then render them natively or use NIP-31, or NIP-89 to point users to other clients that would render them better;
- c. Publish different things as different kinds, and reference them in
kind:1notes that would act as announcements to these other events, also relying on NIP-31 and NIP-89 for displaying references and recommending other clients.
Solution a is obviously very bad, so I won't address it.
For a while I have believed solution b was the correct one, and many others seem to tacitly agree with it, given that some clients have been fetching more and more event kinds and going out of their way to render them in the same feed where only
kind:1notes were originally expected to be.I don't think clients doing that is necessarily bad, but I do think this have some centralizing effects on the protocol, as it pushes clients to become bigger and bigger, raising the barrier to entry into the
kind:1realm. And also in the past I have talked about the fact that I disliked that some clients would display my long-form articles as if they were normalkind:1notes and just dump them into the feeds of whoever was following me: nostr:nevent1qqsdk90k9k30vtzwpj6grxys9mvsegu5kkwd4jmpyhlmtjnxet2rvggprpmhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmdqy8hwumn8ghj7mn0wd68ytnddaksygpm7rrrljungc6q0tuh5hj7ue863q73qlheu4vywtzwhx42a7j9n5hae35cThese and other reasons have made me switch my preference to solution c, as it gives the most flexibility to the publisher: whoever wants to announce stuff so it can be discovered can, whoever doesn't don't have to. And it allows microblogging clients the freedom to render just render tweets and having a straightforward barrier between what they can render and what is just a link to an external app or webapp (of course they can always opt to render the referenced content in-app if they want).
It also makes the case for microapps more evident. If all microblogging clients become superapps that can render recipe events perfectly why would anyone want to use a dedicated recipes app? I guess there are still reasons, but blurring the line between content kinds in superapps would definitely remove some of the reasons and eventually kill all the microapps.
That brings us back to point 1 above (the overcomplication of
kind:1events): if solution c is what we're going to, that makeskind:1events very special in Nostr, and not just another kind among others. Microblogging clients become the central plaza of Nostr, thus protecting their neutrality and decentralization much more important. Having a lot of clients with different userbases, doing things in slightly different ways, is essential for that decentralization.It's ok if Nostr ends up having just 2 recipe-sharing clients, but it must have dozens of microblogging clients -- and maybe not even full-blown microblogging clients, but other apps that somehow deal with
kind:1events in multiple ways. It's ok if implementing a client for public audio-rooms is very hard and complicated, but at the same time it should be very simple to write a client that can render akind:1note referencing an audio-room and linking to that dedicated client.I hope you got my point and agreed because this article is ended.
- People adding more stuff to
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 13b9f773:4f4efe54
2024-11-07 12:19:18
@ 13b9f773:4f4efe54
2024-11-07 12:19:18Keep things interesting with number one – you! By Rae Witte on May 24, 2024

Credit: Ian Moore / Mashable

May is National Masturbation Month, and we're celebrating with Feeling Yourself, a series exploring the finer points of self-pleasure.
While there is this unspoken notion that humility is regarded and desirable, life is better lived when you’re feeling yourself – figuratively and literally. For that reason, it’s time to take masturbation more seriously.
Although self-gratification is historically stigmatized, it’s also heralded as a healthy sexual behavior and there are loads of physiological, psychological, and sexual benefits. Self-pleasure promotes the release of "happiness" hormones like serotonin, dopamine, endorphins and oxytocin. These have a fundamental role in boosting your mood and pleasure and decreasing stress, anxiety and depression. Ultimately, rubbing one out can put a little pep in your step.
Dr. Jessica O’Reilly, the sex and relationships expert at vibrator brand Womanizer said, "It can aid in pelvic floor health, potentially reducing the risk of erectile dysfunction or urinary incontinence."
It’s like "exercise" for the pelvic floor according to Shelby Sells, a relationship coach with ICF and AASECT certifications. She also noted, "For penis-having individuals, it can help you last longer in bed, which is great – that is a big one. For people with vaginas, it helps with period cramps."
The literal act of feeling yourself can also metaphorically help how you feel yourself. In a recent Rolling Stone interview with Billie Eilish, the singer talks at length about how masturbation positively impacted her relationship with her body and herself in general, particularly when doing so in the mirror. "I have learned that looking at myself and watching myself feel pleasure has been an extreme help in loving myself and accepting myself, and feeling empowered and comfortable," Eilish told the magazine.
"If you're maintaining your physical relationship with yourself, the better it is for your sex life overall."
Allowing yourself to indulge in yourself and watching can build comfort in your pleasure and subsequently evolve your self-confidence. "Not only is it good for you and your relationship with yourself, but it's also really good for your physical relationships with other people," Sells said. "If you're maintaining your physical relationship with yourself, the better it is for your sex life overall."
Like any relationship, one with yourself, your pleasure and specifically masturbation takes an intentional investment, so keeping things spicy is a must. Sells said shame often deters people from exploring their sexuality and desires on their own. For that reason, if they are masturbating, she says, "They'll get in and they'll get out."
The easiest way to deviate from your typical masturbation routine and explore solo is to simply switch it up. Different positions shouldn’t be reserved only for sex with another. "Depending on what you're working with, try standing, leaning over something, on your hands and knees, sitting up instead of laying down, or if you're laying down, putting a cushion underneath your butt to elevate you," Sells suggests. "It’s really just playing around with your body in various positions, and seeing what works best for you because everyone's body is inherently different."
You can also change locations. With respect to anyone you may live with, this move can be from your room to the couch or even the shower. Your bedroom has other options too. "If it's not in your bed, then try the chair that usually holds all your clothes," Sells jokes.
Another low maintenance and small adjustment – trade what you’re masturbating with. "If you're always using one toy, specifically, try a different toy or try going back to your hand. Mix it up! If you have a penis, you're used to using one hand, maybe try the other hand, or try different techniques," Sells said.
There are a variety of sex toys to choose from as well. Vibrators have continuous or patterned buzz to stimulate genitals and can be used on the outside or inside of the body. In the same vein, there are "clit-sucking" options too. Dildos and anal plugs are for penetration and can vary vastly in size, which allows for a range of switching it up in this category alone. And, for penisis, there’s sleeves and cock-rings.
As for different techniques, for vaginas this can include clitoral stimulation, vaginal penetration or both. For penises, try different strokes, grips or speed. And, a pro-tip Sells recommends: breathwork. Slowing down your breathing to take in deeper breaths brings more oxygen to the body helping with arousal and orgasming. "If you’re incorporating breathwork into masturbating, it’s really going to elevate it!" Sells said.
-
 @ 4ba8e86d:89d32de4
2024-11-07 12:05:00
@ 4ba8e86d:89d32de4
2024-11-07 12:05:00SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : nostr:nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : nostr:nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : nostr:nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : nostr:nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : nostr:nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : nostr:nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : nostr:nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : nostr:nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : nostr:nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : nostr:nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : nostr:nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : nostr:nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
nostr:nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : nostr:nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : nostr:nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: nostr:nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : nostr:nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : nostr:nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : nostr:nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : nostr:nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : nostr:nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: nostr:nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Bitwaden: nostr:nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: nostr:nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : nostr:nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : nostr:nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : nostr:nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : nostr:nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: nostr:nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : nostr:nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : nostr:nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : nostr:nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : nostr:nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : nostr:nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : nostr:nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : nostr:nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : nostr:nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : nostr:nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : nostr:nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : nostr:nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : nostr:nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : nostr:nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : nostr:nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : nostr:nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : nostr:nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : nostr:nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : nostr:nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : nostr:nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : nostr:nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : nostr:nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : nostr:nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : nostr:nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: nostr:nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : nostr:nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : nostr:nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : nostr:nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : nostr:nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : nostr:nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : nostr:nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : nostr:nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : nostr:nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : nostr:nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : nostr:nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : nostr:nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : nostr:nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : nostr:nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : nostr:nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : nostr:nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : nostr:nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : nostr:nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : nostr:nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : nostr:nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : nostr:nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : nostr:nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : nostr:nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : nostr:nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : nostr:nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : nostr:nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : nostr:nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : nostr:nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : nostr:nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : nostr:nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ bec0c9d3:c4e9cd29
2024-10-26 01:55:04
@ bec0c9d3:c4e9cd29
2024-10-26 01:55:04The Bitcoin Culture Festival is just around the corner, and we're excited to present our artists with physical artworks at the Cyphermunk House. In addition, we will be showcasing these pieces on our 2140 Auction Portal.
The "Culture of Code" gallery will be held at:
CypherMunk House 9 John Street Bloomsbury, London, UK WC1N 2ES
Before the festival, you can read our latest article about this one-of-a-kind house here on Yakihonne.
Online auctions will be available on 2140.wtf starting from October 29th to November 2nd 2024.
During the Bitcoin Culture Festival ART Gallery, you will have the opportunity to see the works of many talented Bitcoin artists. The sale will take place through our auction.
ART Gallery opening hours:
October 29 - Private viewing: 6:30 pm - 8:30 pm October 30 - November 2 - 10:00 am - 5:00 pm November 1 and 2 - 5:00 pm - 10:00 pm during NostrLDN and ART Panels
Entry to the gallery is FREE

This event is only possible due to the passion and dedication of our crew, partners , and sponsors . All made by People for the People. Cypherpunk vibe, pure from the bottom. We look forward to seeing you there!
Follow us also on all socials NOSTREE.me - NOSTR LinkTree INSTAGRAM TWETTER - X YOUTUBE
LINKS
OUR PARNERS / SPONSORS

STAY TUNED !!
2140 Crew
Hashtags:
ArtGallery
ArtPanel
2140wtf
2140army
CyhermunkHouse
art
artstr
nostrart
craft
culture
music
bitcoin
nostr
TootingMarket
NostrLDN
NostrLondon
yakihonne
-
 @ bb0174ae:75f7239a
2024-10-24 21:23:55
@ bb0174ae:75f7239a
2024-10-24 21:23:55What is Cyphermunk House? It is everything that is unprovided. It is the education that is never taught. It is the culture that is never commissioned. It is the space for the community that was never allowed to flourish because an equitable economy was never allowed to grow. It is a space to BE YOUR OWN BANK and a space to STAY HUMBLE.
Cyphermunk House is London’s Bitcoin beacon. Providing sanctuary from the mainstream; from the politics of division, the brainwashing of legacy media, the predictive programming of film, the ‘three-quarter reptiles’ of music, the ‘shock value, indignation and existential angst’ of modern art and the centuries long corruption and exploitation of central banking. It is counter culture in extremis. A hotspot of no fear. A 21st space where fiat pastimes are secondary and pleb living is primary.
What is bitcoin? Cross the threshold. How do you obtain it? Take a seat. Want to stack? Let’s begin. Dive into the mathematics of hope, the code of change and the magic of self-sovereignty. In here we educate, providing knowledge to match the student whether you are a stone-cold newb or a humble stacktivist. In return we learn that there are still so many who are yet to realise that money is broken, issuance matters and a bitcoin can be divided into things called sats. In other words, there is work to be done.
Work that is evolving like that which inspires us. Can we educate? Can we provide space for people from all walks of life? Can we provide the seeds for discussion, the platform for ideas and the spectacle that confronts the issues in our society? Can we get a former Minister of State to laser eye his image?
So far, we are meeting these challenges, with more newbs through our doors than we could ever imagine, lured in by the rabbit of an upended banknote and their own curiosity. What the hell is that? And what's going on inside this rabbit warren of a building a mile’s crow flight from the life supported heart of British financial might.
The ‘what’ is huge. Education. Culture. Freedom. And community. That same orange cocktail that bitcoin is pouring all over the world. Standing in direct opposition to the trends of indoctrination, centralisation and isolation that have pushed the group to the fringe and questioned the very idea that humans are social beings. In our world, meetups, conferences and real-world spaces are thriving. Education is pleb-led and free. And our culture is king.

I have witnessed the artistic offerings of this capital a lifetime over; dance on rooftops, songs beneath the river and Shakespeare performed by a man and a cast of sheep. In three short decades I have worked across music, theatre, film and art, and now find myself at the helm of Cyphermunk House. What is being created within these walls is more inspiring and exciting than anything the Tate has ever shown me, or the West End, or the Dome. This is the edge of the cultural moment. Lightning sharp and electric.
Because our culture does more than entertain. It informs. And transforms. And it is happening everywhere, simultaneously. And in this tiny postcode of West Central London, it is happening hard. We are 'Privacy Defenders'. We will expose 'The Ugly Reality of War Crimes' and we will declare that 'Coin Mixing is My Right' and yours too as we work towards a 'Humanity in Consensus'. Inspired? Come along and chuck it on the walls in the paradise paint of a world being built from the ground up. For this is the culture of code and it will not be put back in the box.

And yes the space is temporary, six more months perhaps, but its temporality is tangible forever, nostr makes it so. Our records permanent, our doors always open. Always sharing knowledge, wisdom and advice. While in these moments of tangibility, these blocks of time in meters of space, we will fire up the beacons and summon the zaps, for bitcoiners, artists, outcasts and dreamers to the temporal dance of rebellion that burns behind these doors.
“In the same way El Salvador felt way ahead of its time – a nation state adopting bitcoin as legal tender. This feels like it’s a cycle too early too. Surely, we shouldn’t have something this good till the 6th epoch." - Si, Bitcoin Events UK
And when we close our doors and move to pastures new, we will not forget the power we are finding - the power to redefine the rules. For this is how to use bitcoin and release the burden on the current system. It stands as a testament to the power of code that you can run an entity, without barriers, without red tape, without announcing your names or identity, where you create the rules.
And so we invite you to the Bitcoin Culture Festival at Tooting Market, The Dockside Vaults and Cyphermunk House, and an explosion of culture from the We Are 2140 collective. Together we will host a brand-new exhibition; the Culture of Code and stamp a sequence of blocks with so much creativity that no Londoner will miss it.
These are the signals of hope found in a civilisation mathematically backed by a money that extracts nothing from you. Embrace them. Support them - your fellow plebs and meetups. Network, connect and build. There is so much more to do and so much more to learn, but for now I've learnt this much - align your passions with bitcoin and every moment is a pill.
Onward plebs.
FIND OUT MORE
OUR PARTNERS / SPONSORS
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 9ca8f9b2:70031a71
2024-11-07 09:43:51
@ 9ca8f9b2:70031a71
2024-11-07 09:43:51Opinion about Phoenix Wallet (iphone)
Personally, I love this App! The developers of this app have worked so hard over the years to make the UI of this app as simple and smoothe as it can possibly be as a non custodial wallet.
WalletScrutiny #nostrOpinion
-
 @ a012dc82:6458a70d
2024-11-07 08:55:21
@ a012dc82:6458a70d
2024-11-07 08:55:21Table Of Content
-
Unveiling Bitcoin's Legacy Amid Debt Ceiling Debates
-
Bitcoin's Decentralized Nature
-
Bitcoin as a Store of Value
-
Bitcoin's Role in International Remittances
-
Regulatory Challenges and Opportunities
-
Bitcoin and Financial Inclusion
-
Conclusion
-
FAQ
In today's fast-paced digital age, cryptocurrencies have taken the world by storm. Among them, Bitcoin stands tall as the pioneer and most prominent cryptocurrency. As financial systems evolve and debt ceiling debates continue to shape economic policies, it is crucial to examine the legacy of Bitcoin and its impact on the financial landscape. This article aims to delve into the intricacies of Bitcoin's legacy and how it intertwines with the ongoing discussions surrounding debt ceilings. By exploring the factors contributing to the money in motion phenomenon and understanding the role of Bitcoin, we can gain valuable insights into the future of finance.
Unveiling Bitcoin's Legacy Amid Debt Ceiling Debates
The concept of money in motion refers to the dynamic nature of funds circulating within an economy. It encompasses various financial transactions, investments, and movements that shape economic activities. When exploring the legacy of Bitcoin amid debt ceiling debates, it is essential to recognize the unique characteristics that set it apart from traditional currencies.
Bitcoin's Decentralized Nature
One of the key aspects that define Bitcoin's legacy is its decentralized nature. Unlike traditional currencies that are controlled by central banks and governments, Bitcoin operates on a decentralized network known as blockchain. This decentralized structure provides several advantages, including enhanced security, transparency, and the ability to bypass traditional financial intermediaries. As debt ceiling debates raise concerns about the stability of traditional financial systems, Bitcoin's decentralized nature offers a potential solution to mitigate these risks.
Bitcoin as a Store of Value
Bitcoin's emergence as a store of value has been instrumental in shaping its legacy. With a limited supply capped at 21 million coins, Bitcoin exhibits scarcity, making it an attractive option for individuals seeking to preserve their wealth. Amid debt ceiling debates, where economic uncertainties prevail, Bitcoin's status as a decentralized store of value becomes even more appealing. Investors can hedge against inflation and potential economic downturns by allocating a portion of their portfolio to Bitcoin.
Bitcoin's Role in International Remittances
Remittances, the act of sending money across borders, play a significant role in global economies. Traditional remittance channels often involve hefty fees and slow transaction times. Bitcoin has emerged as a viable alternative, offering faster, more cost-effective international transfers. By utilizing Bitcoin's decentralized network, individuals can send and receive funds with reduced friction, bypassing intermediaries and lowering transaction costs. In the context of debt ceiling debates, Bitcoin's role in facilitating seamless cross-border transactions becomes increasingly relevant.
Regulatory Challenges and Opportunities
Bitcoin's legacy also includes its interaction with regulatory frameworks worldwide. As cryptocurrencies gained popularity, governments and regulatory bodies have been grappling with how to incorporate them into existing financial systems. Debt ceiling debates often shed light on the need for effective regulations to address economic challenges. While regulations can provide stability and protect consumers, they should also foster innovation and maintain the core principles of decentralization that define cryptocurrencies like Bitcoin. Striking the right balance is crucial to harnessing the potential benefits of cryptocurrencies while mitigating risks.
Bitcoin and Financial Inclusion
Financial inclusion, the accessibility and availability of financial services to individuals and businesses, remains a pressing global challenge. Bitcoin's legacy intertwines with the pursuit of financial inclusion by providing an alternative financial system that is accessible to anyone with an internet connection. This opens up opportunities for the unbanked and underbanked populations to participate in economic activities and access financial services. Amid debt ceiling debates, where financial systems' stability is under scrutiny, Bitcoin's potential to foster financial inclusion gains even greater significance.
Conclusion
The legacy of Bitcoin amid debt ceiling debates encompasses its decentralized nature, role as a store of value, facilitation of international remittances, interaction with regulatory frameworks, and potential for financial inclusion. As the world grapples with economic uncertainties, Bitcoin's unique characteristics offer solutions and opportunities for individuals and the financial system as a whole. By embracing the potential of cryptocurrencies like Bitcoin, we can pave the way for a more inclusive, efficient, and resilient financial future.
FAQ
What is Bitcoin's role in the legacy of money in motion amid debt ceiling debates? Bitcoin plays a significant role in the legacy of money in motion amid debt ceiling debates. Its decentralized nature, ability to serve as a store of value, facilitation of international remittances, and interaction with regulatory frameworks all contribute to shaping the future of finance in the midst of these discussions.
How does Bitcoin's decentralized nature impact its legacy amid debt ceiling debates? Bitcoin's decentralized nature ensures that it is not subject to the control of central banks or governments. This characteristic provides a potential solution to the risks associated with debt ceiling debates and offers enhanced security, transparency, and the ability to bypass traditional financial intermediaries.
Why is Bitcoin considered a store of value amid debt ceiling debates? Bitcoin's limited supply and scarcity make it an attractive option for individuals seeking to preserve their wealth amid debt ceiling debates. As economic uncertainties prevail, Bitcoin's status as a decentralized store of value provides a hedge against inflation and potential economic downturns.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ fd208ee8:0fd927c1
2024-11-07 07:28:06
@ fd208ee8:0fd927c1
2024-11-07 07:28:06The newspaper barons are all into crypto, now
Watching the outsized-impact we crypto enthusiasts (I'm including Bitcoin in that category), had on the 2024 USA presidential election, was a sobering affair. At the moment, our impact is primarily over the voting box, but, already, indirectly, (over Elon Musik, Donald Trump, and Jack Dorsey, etc.) through our sheer wealth (and the ingenuity that brought us that wealth) being able to influence the voting population, by changing/shifting the communications channels and influencing what is written there.
Elon even reached deep into his foreign-learned bag of political tricks and started handing out money, directly, to petition signers.

Survival of the fittest, ongoing
Now, you all know that I have full respect for an expert player, when I see one, so no hating the hustle, from my side. We all play the hand we are dealt, and the political game is now such a pigsty, that you have to get a bit dirty, to have a chance at winning. Trying to stay neat and above the fray cost Republicans the last election.

It was the most dramatic display of the greatest power following the best money, that has been seen, since the Medici family began minting gold coins. The entire world is in shock. Change is upon us.
He who has the best money, makes the rules.
On a smaller, but not insignificant scale, private wealth and access to Bitcoin funding, have allowed quite a few of us Nostriches, to dedicate time and energy toward promoting and developing the New Internet. Whereas, other people's hobby is increasingly the night shift at the gas station, or doing something mind-numbing, to escape the realities of their current economic misery.
You don't need money to be here, but you can spend more time here, if you have money. And we are here, writing the rules. We call them NIPs.

Same ole, same ole
But back to us Bitcoiners...
I increasingly don't see us morally any different than the clever people crowding into any safe asset, during any financial crisis. Like the people who bought agricultural land, gold, and Swiss Francs, before the Reichsmark melted down. The people who had that stuff, mostly managed to keep it, and their children and grandchildren have inherited it. Or they managed to marry back into families, that have done so, by remaining in the same social class, through beauty or talent.

We Bitcoiners have a good narrative to go along with our flight to economic safety, but everyone has that narrative. Humans have a conscience and need to justify their own actions, to themselves. I'm also a goldbug, you see, and a stockholder, and all three assets are rife with the same virtuous narrative.
How do we save our financial behinds, without being evil?
Some people are simply more situationally aware and have more agency, by nature and circumstances, and they adapt faster. It's not mere intelligence, rather, it also requires a willingness to act and take risks. There's an element of chance to it, but it's still always the same types of people ending up with the assets, with the winners slightly shifting with each round, due to evolution and changes in the environment.
Charity was invented, to get such people to willingly share their assets, or the fruits of their assets, for the common good. So, rather than fret over the morality of the asset, itself, the better response is to consider stepping up your charity (effort or payments), to balance out the inevitable negative impact of the coming Age of Bitcoin Inequality.

Coming down from the ATH
Even now, Bitcoin isn't the only safe asset; it's just the most-fungible and partitionable one, so that it's the one most akin to money. And lines are being blurred, as corporations, funds, governments, and insurers discharge dollars and stock up on harder reserve assets, including Bitcoin.
They can hear the money printers rolling out, already, because nobody can print-n-spend, like Trump can. Let's not forget that the money for the last big bump came from the infamous Trump stimmy checks, that lots of us stacked on crypto.

As Bitcoin flows into such markets, the power will rest with both groups (the direct-hodlers and the title-holders), although the hodlers will initially have the upper hand. I say, initially because many hodlers will need to discharge or invest Bitcoin, to live off of it, but the others don't need to, so it should eventually even out. It could take dozens or even hundreds of years to rebalance. By then, the world will be a very different place, and we don't know if Bitcoin will even still be a part of it.
Assets come, assets go, and I'm just glad I didn't let down my forefathers, by leaving them with the first generation, who failed to adapt. Even if I'm a bit late, to the Bitcoin game, the ball is still in play.
May the best money win. And may it be mine. And may I do good with it.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 06639a38:655f8f71
2024-10-24 14:49:08
@ 06639a38:655f8f71
2024-10-24 14:49:08Project Name
Nostr
Project Description
Nostr (Notes and Other Stuff Transmitted by Relays) is an open, censorship-resistant, and decentralized communication protocol designed for simplicity and resilience. Unlike traditional platforms, Nostr doesn’t rely on centralized servers. It already supports various use cases with free, open-source clients—offering alternatives to platforms like Twitter/X, Meetup.com, Excel 365, healthcare system and more. We will help you get started with Nostr.
Nostr has seen remarkable adoption and growth within the open-source community, evidenced by over 12,500 GitHub stars, 500+ forks, and contributions from more than 350 developers. The protocol has catalyzed the creation of an impressive ecosystem of over 390 projects, including mobile and web clients, relays, tools, and services that further enhance Nostr’s functionality. With over 70 tools and 48 libraries, developers can integrate Nostr into a wide array of applications—ranging from chat platforms to file storage and even decentralized marketplaces. These resources help to build decentralized, censorship-resistant systems without the need for centralized servers. Whether you’re working on peer-to-peer markets, privacy-focused messaging apps, or decentralized social media, Nostr’s ecosystem offers the tools.
Project website
https://github.com/nostr-protocol
Source code
https://github.com/nostr-protocol/nips
Project Theme
World Wide Web
Do you want a stand for the entire event or just for one day?
Entire event
Why do you want to be at FOSDEM?
We want to be at FOSDEM because it’s the perfect place to connect with like-minded developers and open-source enthusiasts who share our passion for decentralization, innovation, and building open permissionless technologies. FOSDEM fosters collaboration and the growth of community-driven projects and Nostr is a natural fit as a real grassroots project with its open protocol and commitment to build communication technology with resilience and simplicity in mind.
By being at FOSDEM, we aim to raise awareness, share knowledge and inspire others to explore the potential of decentralized communication systems. We also want to engage with the FOSS community and gain feedback to help Nostr grow. If people are really interested in how they can use Nostr we will show the possibilities, demo existing clients and provide in-depth explanations of how the protocol can replace the social layer (with user accounts in living a database) in existing software.What is the relation between the project and the primary contact?
Jurjen works with the community to promote its development, onboard new developers, and contribute to its open-source ecosystem. My role includes helping to raise awareness of Nostr's potential, organizing events, and supporting adoption by providing educational resources and technical guidance.
What is the relation between the project and the secondary contact?
Sebastian (37) is an independent creative / fullstack web developer who is the maintainer of a PHP helper library supported by OpenSats. Besides this project he is also making contributions with developing Nostr modules for Drupal.
“Since I've been online on the internet (1998), I'm highly interested in online communities, social networking and new ways of digital interactions. The internet has changed radically in the last decade and that change is not serving our interests. It's fair to say the web is broken in many ways. With Nostr we can fix this.”Social media links
npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft(Jurjen)
npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe(Sebastian)
npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa(Tanja)
npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn(Kevin)Anything else you like to add?
We’d also like to highlight that Nostr was created by Fiatjaf, an anonymous founder, which aligns with its principles of openness and decentralization. As an open protocol, Nostr is designed to evolve and find its own way, just like the foundational protocols of the internet. Importantly, Nostr is not a blockchain project—there are no tokens, no costs, and no barriers. It’s also not a platform nor a NFT. It’s purely decentralized, built for resilience and simplicity. While payment solutions like Bitcoin can be integrated, they are optional, not intrinsic to the protocol. This makes Nostr accessible and flexible, truly embodying the spirit of the open internet.
Nostr is more than just a technological protocol; it’s about the energy, problem-solving, and sense of hope that draws people in. Even newcomers can play a significant role in the ecosystem, gaining insight from the outside while discovering the protocol’s potential. Tanja, for example, isn’t from a tech background, yet after just three months, she’s taken on a major organizational role. She’s been spreading the message of freedom of speech and is leading the Nostr Booth LATAM tour, where volunteers, entrepreneurs, and Nostr-based businesses come together, supported by the entire community, to raise awareness about Nostr. Her passion for decentralization and open collaboration also drives her efforts to bring Nostr to FOSDEM, where she will help connect the project with like-minded developers and open-source advocates.
Please reach out to us if there are any questions. We’re really looking forward to presenting Nostr as a protocol at one of the best places where free and open-source software is flourishing.
This content will be used for a FOSDEM stand submission via https://pretalx.fosdem.org/fosdem-2025-call-for-stands/
-
 @ 9930618d:d802e299
2024-11-07 07:18:53
@ 9930618d:d802e299
2024-11-07 07:18:53Shawshank
-
 @ cf6b9d54:11ef2370
2024-11-07 01:42:11
@ cf6b9d54:11ef2370
2024-11-07 01:42:11As interest in Hamster Kombat declines, PAWS surges, outperforming the once-top Telegram Mini App. Once a leading tap-to-earn game on Telegram, Hamster Kombat has seen a steep decline in its user base and engagement due to political backlash, bans and new competition.
Hamster Kombat boasted 300 million users in August, but as of Nov. 5, the game has only 41 million active monthly players — an 86% decrease.
Meanwhile, Paws, a newly launched Mini App on Telegram, has surged in popularity, reaching 20.5 million users in its first eight days, surpassing Hamster Kombat’s growth trajectory.
According to IntoTheBlock (ITB) data, on Sept. 27, active Hamster Kombat addresses peaked at around 772,330. Since then, user activity and token interest have waned, falling more than 36% in the past week.
Token price and activity plummet Hamster Kombat’s challenges are reflected in its HMSTR token price, which has fallen nearly 70% from an all-time high of $0.01 on Sept. 26 to about $0.0022 as of Nov. 4, according to CoinGecko data. This decline correlates with lower network engagement and fewer daily active users.
This downward trend is reinforced by ITB’s active addresses ratio (AAR) chart — which calculates the ratio of active addresses to addresses holding HMSTR — revealing a 30-day low of just 0.34% active users.
Still, according to ITB data, the total addresses holding HMSTR have continued to increase, establishing a 30-day high of 3.5 million holders on Nov. 4.
Compared to the performance of other popular Telegram games, a pattern emerges, as seen with the Dogs (DOGS) token airdrop, which dropped from $0.0014 to $0.0004 between August and Nov. 4.
The DOGS AAR chart also shows a steady drop in activity alongside the token’s falling value, hitting a 30-day low of 0.27% active users on Nov. 3.
Scrutiny and volatility response Hamster Kombat has faced criticism from Iranian government officials and has been hit with rumors of bans in Uzbekistan, which have since been proven inaccurate.
The Hamster Kombat team previously told Cointelegraph that its future plans include payment system integration, launching new games and including non-fungible tokens (NFTs) as in-game assets.
One falls, one rises In stark contrast to the fall of Hamster Kombat’s network activity and token price, the Paws Mini App saw over 11 million users join in the first two days alone.
A Nov. 4 announcement on the Paws Telegram channel said that 10 million wallets had connected to the app and it had one million followers on the project’s X account.
-
 @ fc792576:bab046e9
2024-11-06 20:13:55
@ fc792576:bab046e9
2024-11-06 20:13:55Russian Presidential Press Secretary Dmitry Peskov said he does not know whether Vladimir Putin plans to congratulate Donald Trump on his election victory, but he recalled that the United States is an unfriendly country involved in a war against Russia.
"As for congratulations, I am not aware of the president's plans to congratulate Trump," Peskov told reporters in response to a question on the matter.
At the same time, he noted: “Let’s not forget that we are talking about an unfriendly country that is directly and indirectly involved in a war against our state.”
Peskov was asked whether he thought Trump might be offended if Putin did not congratulate him on his victory, and whether this would worsen relations between Russia and the US even more.
"It is practically impossible to worsen things further; relations are at their historical lowest point. And what happens next will depend on the next US leadership. President Putin has repeatedly said that he is open to constructive dialogue based on justice, equality and a willingness to take each other's concerns into account. And President Putin maintains this attitude. He has repeatedly confirmed it. At the moment, the US administration is diametrically opposed. We will see what happens in January," Peskov said.
In general, the elections, he noted, are an internal matter for the United States. "We, of course, are closely monitoring all the information flows that are coming from overseas on this matter, we are analyzing the words that are being said, and of course, we will mainly draw conclusions based on the statements, on the topics that are on our agenda, when they come in," the Kremlin representative said.
In addition, conclusions will be drawn based on the first concrete steps, Peskov added.
At the same time, the press secretary reminded that this will have to wait, since the current US president will continue to perform his duties for at least another month and a half.
At the same time, responding to a clarification about what would happen if Trump made friendly statements, Peskov said: “As our diplomats say, eventual discussions are inappropriate here.”
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ 13b9f773:4f4efe54
2024-11-06 18:21:50
@ 13b9f773:4f4efe54
2024-11-06 18:21:50No podemos forzar que las cosas sucedan en nuestra línea de tiempo ideal. A veces simplemente tenemos que aceptar la incertidumbre, tener paciencia y confiar en que, si seguimos avanzando, eventualmente encontraremos lo que es correcto para nosotros.

-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52
@ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52Tldr
- Nostr relays help users post and read notes on the network
- Relay operators have launched a variety of relays for you to use
- You too can launch your own relay for any reason you like
- Launching your own relay gives you a lot of power in how you use Nostr
- Many relay softwares exist for you to use
- I launched a personal relay using HAVEN relay software on my VPS
- I am now more in control of saving notes, cutting spam, and protecting my privacy
- My personal relay is now hosted at relay.rodbishop.nz
What are Nostr Relays Anyway?
When you're a user of a social network, you post and read notes from other users on the network. In a centralised network like Twitter or Instagram the company's servers receive all user's notes and relay them to other users. On Nostr, there is no single company's servers to relay messages, so instead the task is taken up by relay operators.
Anyone can be a relay operator and they can run a relay for any purpose. When you start using Nostr you will usually be connected to any one of a number of "public" relays, and be able to post and receive notes from users on the network via these.
Configuring these relays can tailor your experience somewhat–for example the client Nostrudel allows you to select from Western or Japanese relay set.
It is also possible to set up your own relay to use for your own purposes. All kinds of people have launched relays for all kinds of purposes. For example, to:
- Power your own client
- Support your community
- Run a for-profit relay business
- Relay a certain a type of content you need
- Back up your own notes, decrease spam, or increase privacy
- Curate your own social feed with your own algorithm
Relay instances available to connect with
Today is an interesting time in relay-ops. The evolution of the technology has inspired users to experiment with diverse types of relays tailored to various needs. As a result there are very many relay instances in operation and available to connect with.
A few sites try to collate which relays are in operation, like nostr.info and xport.top and sesseor's relay list . These lists are long (Sessor's list counted 2,500+ relays) and it's not clear to me whether it's even possible to be comprehensive as relays may join or leave the network all the time.
Broadly speaking, relays might be available for different users to use in different ways:
- A relay where anyone can post, like relay.damus.io
- A paid relay where anyone can post after payment, to cut spam, like nostr.wine
- A "web of trust" relay where anyone can post if they are related to the owner's social graph, to cut spam, like nostrelites.org
- A speciality relay where a particular community can post, like nostr.com.au for #austriches (Australians)
- A relay where anyone can post just specific content, like purplepag.es for user profiles only
- A team relay for your company or organisation only
- A personal relay for your own personal use
Nostr.Band shows which of these available relays are most popular, such as relay.damus.io and nos.lol and eden.nostr.land
Relay softwares for you to launch your own
You may decide to launch you own relays, and if you do there are many different relay softwares to choose from:
- Simple, like Bucket (<100 lines of code)
- Widely used, like Nostream (top ranked on Github)
- Customisable, like Khatru (a framework for customised relays)
- Specialised, like HAVEN or Team Relay (for personal or teams relays, based on Khartu)
You can run these on your own server, or local machine, or phone or with a third-party host.
Aljaz provides a great resource with 45+ relay softwares to choose from.
In summary, at a high level,
- Anyone can connect to any of the relay instances that are available for them to use
- Anyone who wants to launch their own can select the relay software that best suit their needs, launch an instance, and have it used by whichever users they like
Reasons to Run Your Own Relay
As a normal user of a Nostr client there's no obligation to run a relay. But having your own relay does give you more power.
For my own journey down the #nostr rabbit hole, I was looking for a relay to:
- back up my notes
- decrease spam
- increase my privacy
- learn skills I could later use for running a community or team or paid relay
Backing up notes – When you post notes to a public relay there's no guarantee that the relay is going to keep them long-term. It's job is relaying your notes to other clients, not storing them. Running your own relay allows you to keep your notes online.
Decrease spam – To first spam we can use a "Web of Trust" model–in which users endorse other users as trustworthy. A "Web of Trust" relay will reject notes from parties too far removed from your network. Running your own relay makes you more difficult to spam.
Increasing privacy – When you connect to a public relay, they can determine personal information about you, such as your IP address. Running your own relay keeps things more private.
For communities and teams and paid relays – Many opportunities exist to tailor relays to certain users needs, be they businesses or communities or as a for-profit business. For me, I am hoping that running my own relay helps me learn skills I can use in these kinds of further ventures.
To start I decided to focus on a personal relay. However, when I really got under the hood, it turned out I would need multiple relays not just one.
The outbox model
Mike Dilger proposed the outbox model (originally called the gossip model) as a way for users to engage with the wider Nostr network. It's a great model that is helpful to understand, as it suggests to establish different relays for different purposes.
Many clients and relay softwares have now adopted and continued to elaborate on this model. An example is to run specialised relays for Outbox, Inbox, Chat and Private needs.
Outbox Relay (also called Home Relay)
- This relay is for notes you have written, so that everyone knows where to find your notes
- In a set up where you are running your own, this relay is restricted so that only you can post to it, and you should set up your clients to post your notes to it
- An advanced version may take any notes received to this relay and "blast" them to other public relays so that your notes get wider reach
Inbox Relay (also called Public Relay)
- This relay is for public notes that other users want you to see, so that you always find notes that are relevant to you, including all replies, comments, likes, and zap payments
- In a set up where you are running your own, this relay is where you should look for notes relevant to you, and you should set up your clients to read from it
- An advanced version may search other public relays for notes that tag you, and import them into this relay so that you never miss a relevant note
Chat Relay (also called Direct Message Relay)
- This relay is for private direct message notes from other users, so that you always find your direct messages and so that they stay private
- In a set up where you are running your own, this relay is restricted so that only you can read from it, and you should set up your clients to read from it
- An advanced version may cut spam by only accepting direct messages from other users within your Web of Trust
Private Relay
- This relay is for your private use only, so that you can store private drafts or thoughts
- Only you can write to it and only you can read from it (and so, it is a bit mis-named as it does not actually relay anything to anywhere at all)
- In a set up where you are running your own, it gives you true privacy for these notes
In summary as a user
- I post my notes to my outbox relay. Network users can read them there, and if the relay is advanced it will also blast the notes out to other relays on the network
- I read from my inbox relay. Network users know to reach me there, and if the relay is advanced it will also bring me notes from the wider network
- I can have private direct message conversations with others in my chat relay.
- I can save private notes in my private relay
For me, this model has a lot of appeal and I went looking for a personal relay which adopted this model and contained all of these features.
HAVEN as a personal relay
I decided to go with HAVEN relay software.
HAVEN is all four of the above relays in one–outbox, inbox, chat and private. It contains advanced features like blasting your notes from outbox to other relays, importing notes from other relays to your inbox, and preventing spam with Web of Trust.
HAVEN is written by Utxo the Webmaster . It is based upon the Khatru relay framework by Fiatjaf
Setting up HAVEN as a Personal Relay
I am mostly non-technical, but on my #Nostr journey I have been having success with technology set ups that use Docker.
- I have a cheap VPS which currently runs Albyhub and Phoneixd with Docker,
- My objective was to set up HAVEN to run alongside it, in a separate Docker on the same server. HAVEN does not include Docker by default, but Sebastix published a fork with Docker support.
To get HAVEN up and running in Docker on your VPS:
- Clone and configure HAVEN with the right variables
- Launch it in Docker on your VPS
- Check the URLs and logs to see your HAVEN running
- Configure a subdomain to point to the VPS
- Configure the VPS to reverse proxy to the Docker port
- Configure the relays in your favourite Nostr client
- Post a note to your outbox and see if it blasts!
Running HAVEN
I cloned Sebastix fork to start.
git clone -b docker_compose_support https://github.com/nostrver-se/haven.git cd havenThe software sets up all environment variables in the
.envfile, and comes with an.env.examplefile. Duplicate and rename the file to.env. Within the.envfile you need to set up the environment variables. The file is long but it contains lots of repetition and for the most part defaults can be retained–only a few changes are required:- Replace all instances of the default user npub with your own (for me,
npub1r0d8...) - Change the default relay URL to your own (for me,
relay.rodbishop.nz) - Replace all instances of the default name in the relay names (for me, "Rod's ...")
- Replace all instances of the default profile image with your own
To enable automatic blasting from your outbox, and importing to your inbox, the software comes with an example list of relays to blast and import from. See
relays_blastr.example.jsonandrelays_import.example.json. To use these features simply duplicate and rename these files torelays_blastr.jsonandrelays_import.jsonrespectively. Within these files you can specify the public relays of your choice. I simply used the default list.There are other features available, such as backups and initial imports, but I decided to handle these later. To start with I wanted to launch the relay and test it.
To launch the relay run Docker Compose.
docker-compose up -d docker logs haven-relayThen you should explore the logs in the command line and the ports in your browser to see if it launched successfully. The logs should show your web of trust has been built successfully and the browser should show simple landing pages.
The logs should show that the relay has queried the network and built a web of trust from your followers. Mine looked as follows.
2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 13296 2024/10/14 12:02:16 🔗 relays discovered: 335 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 9394 keysYour browser should show you have four relays in operation, for example as follows.
your_IP_address:3355(your outbox or home relay)your_IP_address:3355/private(your private relay)your_IP_address:3355/chat(your direct message relay)your_IP_address:3355/inbox(your inbox relay)
That's it. Your relay is online.
Connecting HAVEN
Now all that remains is the plumbing to connect your domain, relay, and Nostr clients together.
Configure DNS
First, configure your domain. At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caserelay.rodbishop.nz
Your subdomain now points to your server.
Configure reverse proxy
Next, you need to redirect traffic from your subdomain to your relay at port
3355.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my HAVEN Relay required two steps. I am sure that the way I do this is not very elegant, but it worked. If you prefer a different method, the HAVEN readme also comes with instructions on how to perform a similar setup using nginx.
For my method, my steps were as follows:
- Add configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.rodbishop.nzsubdomain - Add the Caddy Docker network to the HAVEN
docker-compose.ymlto make it be part of the Caddy network
For the addition to the
Caddyfile, I used as follows:relay.rodbishop.nz { reverse_proxy haven-relay:3355 { header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }For the addition to the
docker-compose.yml, I used as follows:``` networks: - caddy # Added this line to services to connect to the Caddy network
networks: caddy: external: true # Added this to section specify the Caddy network ```
Once your DNS configuration and reverse proxy setup are completed, you should now be able to access your Nostr client at
relay.your_domain_name.com. For my set up, this wasrelay.rodbishop.nz.Connecting your Nostr client
Most Nostr clients allow you to specify any relay you choose. My go-to client at the moment is Amethyst on Android. Amethyst allows you to specify discrete relays for each role in the outbox model which ties up very neatly with HAVEN.
- In the sidebar, select Relays
- For "Public Outbox/Home Relays" enter
relay.your_domain_name.com - For "Public Inbox Relays" enter
relay.your_domain_name.com/inbox - For "DM Inbox Relays" enter
relay.your_domain_name.com/chat - For "Private Home Relays" enter
relay.your_domain_name.com/private - Click Save to broadcast your new relays to the Nostr network.
Your new relay configuration is now live.
Testing your relay
Lastly, it's time to test. Amethyst provides a simple method to test this as it allows you to configure the relays used on each post.
- Create a test note, and then before you post it, edit your relays using the icon at the top
- Turn off all relays except your own outbox relay, and post the note
- Access your HAVEN docker logs with
docker logs haven-relayand see if there is a log to indicate if the note was received and blasted to other public relays - Copy the
neventof the note, and attempt to find it in another client
If you're in luck, you may see something like this (the blasted note, and then users on the network responding to the note in turn).
2024/10/22 00:12:23 🔫 blasted 95c477af7e6b612bf5d1d94309d2d57377a0a67d2181cfbb42a2e3fbc0feeaaf to 26 relays 2024/10/22 00:13:50 🤙 new reaction in your inbox 2024/10/22 00:14:42 🫂 new reaction in your inbox 2024/10/22 00:14:45 ✅ new reaction in your inbox 2024/10/22 00:15:12 💜 new reaction in your inbox 2024/10/22 00:17:03 ✅ new reaction in your inbox 2024/10/22 00:17:03 🫂 new reaction in your inbox 2024/10/22 00:17:55 🫂 new reaction in your inbox 2024/10/22 00:19:02 📰 new note in your inboxThat's it. If you followed this successfully your personal relay is up and running.
What I did wrong so you don't have to
My first relay was too public
This blog comes after much trial and error. The first error I made was I set up a relay to use as a personal relay, but without any restrictions on use. I very quickly found other people discovered and started using my relay to save their own notes! This was unintended and I had to take it down.
Unfamiliar with Go language
I am mostly non-technical, and completely unfamiliar with Go. I got the project up and running with Go on my localhost–with a lot of help from my AI–but I then completely failed in migrating this to my VPS. Moving to Docker made the difference for me here.
I failed a few times due to a messy folder
After messing with Go, I moved to the Docker setup, but I started my work from a messy folder which contained remnants of the Go build, which caused various failures. Deleting the folder and cloning again from scratch solved the issue.
Trouble with Nostr.wine
I subscribe to the Nostr.wine paid relay, and I initially added it to the list of relays in my blaster. However, it didn't work, and the logs showed an error as follows
CLOSED from wss://nostr.wine: 'auth-required: this relay only serves private notes to authenticated users'It seems my npub's subscription to Nostr.wine is not enough for it to permit my relay to blast notes to it. In the end, I removed Nostr.wine from my relay config, and kept Nostr.wine as a separate entry in my Client's outbox settings.
Failed to create web of trust graph
When I first launched the relay on my VPS, HAVEN failed to complete the Web of Trust graph, with a log that looked as follows (note the zeroes). As a result, no one would have been able to send me DM's to my Chat relay (it would flag every message as spam).
2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 0 2024/10/14 12:02:16 🔗 relays discovered: 0 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 0 keysI never got to the bottom of why this was. In the process of trying to fix it I rebuild the container, and on the rebuild it spontaneously worked. Accordingly my lesson learned is "if in doubt, turn if off and on again".
Failed to run --import function
HAVEN comes with a function to import all your old notes from other public relays to your own outbox relay. When I run it I get an error as follows:
panic: Cannot acquire directory lock on "db/private". Another process is using this Badger database. error: resource temporarily unavailableI have yet to work out the solution for this, and will update this note when I do so!
What's Next?
Over the past four blogs I have
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
This feels like a very comprehensive personal set up now. Also, I have uncovered some new rabbit holes and feel like I have some projects to tackle. Perhaps one of these?
- Set up a personal homepage with my Nostr feed to round-out my rodbishop.nz domain
- Experiment with different signers like Amber and Nsec.app and NFC cards
- Set up a paid relay for #austriches (Australians and Kiwis on Nostr)
- Set up a team relay to experiment with Nostr for business or community projects
- Or something else ... ?
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
Pura vida Nostr.
-
 @ 13b9f773:4f4efe54
2024-11-06 15:04:32
@ 13b9f773:4f4efe54
2024-11-06 15:04:32"No seas juez de la gente; No hagas suposiciones sobre los demás".
• Buda

-
 @ 23acd1fa:0484c9e0
2024-10-23 09:21:33
@ 23acd1fa:0484c9e0
2024-10-23 09:21:33Chef's notes
Cocoa powder: You can use 100% natural unsweetened cocoa powder or Dutch-processed cocoa powder – both work well.
Gluten free flour: There are many different gluten free flours on the market. I tested this recipe using White Wings All Purpose Gluten Free flour. I recommend choosing a gluten free flour that says it can be subbed 1:1 for regular plain or all purpose flour.
*Chocolate chips: Double check your chocolate chips are gluten free if you are making this brownie for someone who is celiac.
Cook times: Cook times will vary depending on your oven, but you’ll know these brownies are done when they firm up around the edges and no longer wobble in the middle. Keep in mind they will continue to cook slightly as they cool. You can also check they’re done by inserting a skewer into the middle of the brownie. If the skewer emerges with only a few crumbs on it, they’re ready. If it is covered in wet, gooey batter, keep baking the brownies and check them in another 5 minutes.
Storage: Brownies will keep well in an airtight container at room temperature or in the fridge for up to 5 days. To serve warm, microwave each brownie for 20 seconds. You can also freeze these brownies to enjoy at a later date. Simply thaw at room temperature and then microwave if you prefer them warm.
Serving Size: 1 brownie Calories: 278 Sugar: 26.4 g Sodium: 22.9 mg Fat: 15.5 g Carbohydrates: 34.1 g Protein: 3 g Cholesterol: 77.3 mg Nutrition information is a guide only.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 35 min
- 🍽️ Servings: 12
Ingredients
- 170 grams (3/4 cup) unsalted butter, melted
- 200 grams (1 cup) caster sugar or granulated sugar
- 90 grams (1/2 cup) brown sugar
- 1 teaspoon vanilla extract
- 3 large eggs
- 40 grams (1/2 cup) cocoa powder
- 70 grams (1/2 cup) gluten free plain or all purpose flour
- 75 grams milk or dark chocolate chips*
Directions
- Preheat the oven to 180 C (350 F) standard / 160 C (320 F) fan-forced. Grease and line an 8-inch square pan with baking or parchment paper, ensuring two sides overhang.
- In a large mixing bowl, add melted butter and sugars and gently whisk together. Add vanilla extract and stir.
- Add the eggs, one at a time, stirring in-between, then sift in the cocoa powder and flour. Stir until just combined. Add chocolate chips.
- Pour the brownie batter in the prepared pan and place in the oven. Bake brownies for approximately 30-35 minutes or until they no longer wobble in the middle.
- Leave brownie in pan and transfer to a wire rack to cool completely. These brownies are quite fragile so if you can, transfer to the fridge for an hour before cutting into squares to serve.
-
 @ 13b9f773:4f4efe54
2024-11-06 12:32:47
@ 13b9f773:4f4efe54
2024-11-06 12:32:47Gaza-Krieg
02.11.2024 | 00:02
Israel hat im Süden des Gazastreifens einen weiteren Hamas-Anführer gezielt mit einer Rakete getötet. Eine Freilassung der Geiseln könnte das eher komplizierter machen.

Is al-Din Kassab soll bei einem Luftangriff in Chan Junis getötet worden sein.
Quelle: AFP
Die israelische Armee hat nach eigenen Angaben einen der letzten hochrangigen Hamas-Vertreter im Gazastreifen getötet. Das Mitglied des Politbüros der islamistischen Terrororganisation, Is al-Din Kassab, sei für die Beziehungen zu anderen extremistischen Gruppen in dem Küstenstreifen zuständig gewesen.
Die Armee veröffentlichte ein aus der Luft aufgenommenes Video, das den Raketenangriff auf das Fahrzeug des Hamas-Funktionärs zeigen soll. Auch ein Mitarbeiter Kassabs sei getötet worden. Die Hamas bestätigte den Tod der beiden.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 13b9f773:4f4efe54
2024-11-06 12:06:17
@ 13b9f773:4f4efe54
2024-11-06 12:06:17"En la vida, cada final es solo el principio de otra historia".
- Julian Barnes

-
 @ 35f3a26c:92ddf231
2024-11-06 00:07:28
@ 35f3a26c:92ddf231
2024-11-06 00:07:28Who is the Cult of the Dead Cow (cDc)?
A known USA based hacktivist group. According to the record in Wikipedia, it was started in 1984 at the Farm Pac slaughterhouse by Grandmaster Ratte' (aka Swamp Ratte'), Franken Gibe, Sid Vicious, and three BBS SysOps
You can check their member list in their web site
Thinks of the cDc group that I have found quite interesting
- Group member Drunkfux (Jesse Dryden) is the grand nephew of Charlie Chaplin
- In 1991, the group began distributing music in the form of cassette tape albums
- In November 1994, the group claimed responsibility for giving President Ronald Reagan Alzheimer's disease, claiming to have done so in 1986 with a blowgun
- In 1995, the group declared war on the Church of Scientology stating "We believe that El Ron Hubbard [sic] is actually none other than Heinrich Himmler of the SS, who fled to Argentina and is now responsible for the stealing of babies from hospitals and raising them as 'super-soldiers' for the purpose of overthrowing the U.S. Fed. Govt. in a bloody revolution. We fear plans for a 'Fourth Reich' to be established on our home soil under the vise-like grip of oppression known as Scientology!"
- On January 7, 1999, the group joined with an international coalition of hackers to denounce a call to cyber-war against the governments of China and Iraq
- In February 2000, the group was the subject of an 11 minute documentary short titled "Disinformation".
- In February 2000, a member of the group by the code-name Mudge briefed President Bill Clinton on "Internet security".
- In 2003 the tool created by the group by the name of Six/Four System became the first product of a hacker group to receive approval from the United States Department of Commerce for export of strong encryption
- Member by the name of "Psychedelic Warlord" is congressman Beto O'Rourke, an American politician who served as the U.S. representative for Texas's 16th congressional district from 2013 to 2019. A member of the Democratic Party, party's nominee for the U.S. Senate in 2018, candidate for the presidential nomination in 2020, and the party's nominee for the 2022 Texas gubernatorial election.
Do they have a political affiliation?
From the previous section we could at least assume that they sympathize with the USA Democratic party, they supported President Bill Clinton and claimed responsibility for doing serious harm to President Ronald Reagan, I could not find any information if the government opened an investigation about this allegation or not.
Their latest contribution?
Recently, they have developed an application framework by the name of Veilid, described as "like TOR" but for apps.
This application framework, if adopted by many developers will improve privacy by default for applications developed under that framework. The web site claim that it is open source
You can review the information and project at the web site: VEILID
In the Web site the group describe it as follows:
"Veilid allows anyone to build a distributed, private app. Veilid gives users the privacy to opt out of data collection and online tracking. Veilid is being built with user experience, privacy, and safety as our top priorities. It is open source and available to everyone to use and build upon."
"Veilid goes above and beyond existing privacy technologies and has the potential to completely change the way people use the Internet. Veilid has no profit motive, which puts us in a unique position to promote ideals without the compromise of capitalism."
Summary
Veilid seems to be exactly what is needed at the moment to bring privacy to the masses, even though TOR is doing a very good job and with the improved throughput its usage experience has improved, having a native privacy oriented FOSS application framework is paramount.
Most people is not technically savvy and therefore, not skilled in cyber security, they are constantly victims of cyber crime in many forms and shapes. eliminating one vector of attack by making the applications to opt out of data collection and online tracking from the get go is a step in the right direction, the question is, Would developers in general use the framework? Considering the ads will not be a possible source of income if the framework is used, well... Time will say...
-
 @ 9349d012:d3e98946
2024-10-23 04:10:25
@ 9349d012:d3e98946
2024-10-23 04:10:25Chef's notes
Ingredients
4 tablespoons (1/2 stick) butter 2 ounces thinly sliced prosciutto, cut into thin strips 1 1/4 cups orzo (about 8 ounces) 3 cups low-salt chicken broth 1/2 teaspoon (loosely packed) saffron threads, crushed 1 pound slender asparagus, trimmed, cut into 1/2-inch pieces 1/4 cup grated Parmesan cheese Parmesan cheese shavings
Preparation
Melt 2 tablespoons butter in large nonstick skillet over medium-high heat. Add prosciutto and sauté until almost crisp, about 3 minutes. Using slotted spoon, transfer to paper towels to drain. Melt 2 tablespoons butter in same skillet over high heat. Add orzo; stir 1 minute. Add broth and saffron; bring to boil. Reduce heat to medium-low, cover, and simmer until orzo begins to soften, stirring occasionally, about 8 minutes. Add asparagus; cover and simmer until tender, about 5 minutes. Uncover; simmer until almost all liquid is absorbed, about 1 minute. Remove from heat. Mix in prosciutto and 1/2 cup grated cheese. Season to taste with salt and pepper. Transfer to large bowl. Garnish with Parmesan shavings. Makes 6 servings.
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 30
Ingredients
- See Chef’s Notes
Directions
- See Chef’s Notes
-
 @ 45bda953:bc1e518e
2024-11-07 06:56:26
@ 45bda953:bc1e518e
2024-11-07 06:56:26PREFACE
This is a controversial rambling, just thoughts on some interesting phenomena with regards to the evolution of societal norms, comparisons and oddities with regards to the distinct differences of understanding and mentality of people a couple millennia ago. I touch on cultural fundamentals, feminism, masculinity, information warfare and the protection of what makes society function, the protection of women from harm. It has some comic relief elements worked in to just soften the dark and morbid reality of recorded human history.
...
The Streisand Effect
In 2002 or 2003, I am not certain, a dude named Kenneth was being flown along the coast taking pictures from a helicopter. Flying past Barbara Streisand's luxury coastal home in Malibu California he took another pretty picture. This picture among hundreds was posted on a website where they were documenting and measuring coastal erosion with the intent to help make informed policy decisions. He was being flown by, out at sea and not directly over her property. It caused her much emotional distress. He was sued $50 million for violating her privacy. She believed it to be an invasion of her privacy, like Nancy Pelosi believed the January 6 invasion of Capitol was a violent insurrection. Imagine that. The lawsuit was chucked out by the courts and she was ordered to pay Kenneth $177,000 to cover his legal expenses. Before the lawsuit the image had been downloaded six times. Obviously it had gone viral after the lawsuit. Since the lawsuit, well... man, wow, certain scummy 4chan meme drenched websites were on fire. Everyone was talking about Barbara Streisand and sharing pictures and jokes of her house for weeks. It was ironic and hilarious. The purpose of the lawsuit was to remove the picture from the internet and the result was everyone was poking fun at her expensive mansion. The memes, I can't even...
Imagine the precedent set and lawsuits against google for satellite maps and street view had her case won.
In this situation there were a few weird coincidences. I will label it, the cause, the desire and the outcome. None of them were predictable because the collective social internet was so fresh it changed how everything worked.
The cause: Guy flies and takes pictures for research, probably does not even know it's her house.
The desire: She wants the picture removed and receive compensation for her emotional distress. Nothing less than $50 million will be sufficient.
The outcome: A new type of cause and affect is discovered with regards to a world where everyone has equal access to the masses. No longer are celebrities talking at us through small or large square windows in our theatres and homes. We get to talk back at them and about them and explore their weaknesses and failures. We get to embarrass and humiliate them if they do not behave like decent normal people should. We don't mind their ivory towers. Just don't pick on the average Joe anymore, the average Joe collectively has a voice more powerful than yours now. Like Leonardo DiCaprio preaching about global warming from his private jet. We don't care about you flier miles, just don't be a hypocrite.
Which got me thinking. As a peasant, proletariat, a plebeian, how do you make your voice heard in a time where there is no media? I am not talking about no social media, I mean ancient times, no media. No local newspaper where you can post a missing cat picture. No radio with which to advertise your business. Nothing. A time where the king has a dude who shouts decrees from a paper on a hill. Those type of times.
It bothered me, thankfully I have an extensive library of history available to study and find an answer to this interesting question. I found it in the book of Judges in a wild west of ancient savagery where kings would cut off the heads of men just to bed the latters wives. A time where woman were property. Yes, crazy wild times.
Let us set a precedent for this cultural phenomenon and work our way back to media, the virality of said media and the subsequent outrage generated by the news spread by the channels/mediums of media. An ancient example of problem, reaction, solution.
First let's discover an ancient outrage on a smaller more localised platform and then scale it up to something more spectacular.
Genesis Chapter 34
1: Now Dinah the daughter of Leah, whom she had borne to Jacob, went out to see the daughters of the land. ---She wanted to make friends with other girls and was allowed to leave her families protection unescorted.--- 2: And when in Shechem the son of Hamor the Hivite, prince of that country, saw her, he took her and lay with her, and violated her. ---In those days, princes were literally just the son of the chief in the settlement, they were nothing special and they were common and illiterate agrarian goat herders, just like Jacob. You could find a prince every 30 kilometres in those regions at the time. A dime a dozen.--- 5: And Jacob heard that he defiled Dinah his daughter. Now his sons were with his livestock in the field; so Jacob held his peace until they came. 7: And the sons of Jacob came in from the field when they heard it; and the men were grieved and very angry, because he had done a disgraceful thing in Israel by lying with Jacob's daughter, a thing which ought not be done. ---The modern definition of non consensual laying is rape. It is still a thing that ought not be done to this very day.--- 8: But Hamor spoke with them, saying, "The soul of my son Shechem longs for your daughter. Please give her to him as a wife."--- Now I see this guy as trying to appease the group of angry men, appealing to taking the responsibility of caring for the violated girl off her families hands as she is now become a liability. Her worth has been "degraded" by loss of virginity. Her brothers felt this violation was disrespectful, not only to their sister but also to their entire family. Imagine a guy rapes your sister and then pops in the next day and is like "Bro, she resisted, but I love her more than she could possibly understand. WTF."--- 9: And make marriages with us; give your daughters to us, and take our daughters to yourselves. 10: So you shall dwell with us, and the land shall be before you. Dwell and trade in it, and acquire possessions for yourselves in it.” 11: Then Shechem said to her (Dinah's) father and her brothers, “Let me find favor in your eyes, and whatever you say to me I will give. 12: Ask me ever so much dowry and gift, and I will give according to what you say to me; but give me the young woman as a wife.” 13: But the sons of Jacob answered Shechem and Hamor his father, and spoke deceitfully, because he had defiled Dinah their sister. ---The Israelite brothers must have read Sun Tzu, because they were at a huge numerical disadvantage. This might be why these Hivite gents were so confident in confronting them directly. They probably had a whole entourage of armed men with them during these negotiations. It's just the way men meet in barbaric times. With more and bigger spears.--- 14: And they said to them, “We cannot do this thing, to give our sister to one who is uncircumcised, for that would be a reproach to us. ---They opted to have a literal dick measuring contest. The first in recorded history.--- 15: But on this condition we will consent to you: If you will become as we are, if every male of you is circumcised, 16: then we will give our daughters to you, and we will take your daughters to us; and we will dwell with you, and we will become one people. 17: But if you will not heed us and be circumcised, then we will take our daughter and be gone.” ---Now Abraham had himself circumcised as an adult being the first dude to undertake the procedure. He made it obligatory that his male descendants should all be circumcised a few days after birth. To the modern observer this "command" from god to slice off a piece of your dick seems stupid. But is it? Thought experiment. Let's say Bob lives in dangerous times with dangerous men in a desert where there are no modern ablution facilities. John rocks up at a Bob's tent and claims he is family of Bob travelling far and asks for hospitality and to be hosted for the night. Bob is like hmm, "He speaks my language, he has a similar complexion to me, but his bandit buddies might be hiding behind a hill waiting for his signal when me and my family are fast asleep." So Bob gives him lots of nice wine to drink and they break bread together. Later John needs to take a piss, Bob tells him that he also wants to take a leak, Bob walks with John behind a bush. John pulls up his robe whips out his dick and Bob can then decide how he is going to handle the situation from there. Seeing John's uncircumcised appendage Bob is safe to assume that him and his family are in danger. Also think of how vulnerable John is with his pants down draining the main vein, it might be Bob's opportune and only moment to strike first and unexpectedly. Bet you never heard an explanation like that in favour of having a cut foreskin. A secret sign of sign of familiarity. As a pragmatist I have interpreted all God's commandments following common sense and useful logic to explain them.--- 18: And their words pleased Hamor and Shechem, Hamor’s son. 19: So the young man did not delay to do the thing, because he delighted in Jacob’s daughter. ---He was like LFG bring that knife I'm ready. I can imagine Shia LaBeouf playing this part in the NETFLIX original series.
 --- He was more honourable than all the household of his father. ---I think this simply means the bravest. Being circumcised as a little kid is easier when you have no say in the matter. You require more mental fortitude as a grown man to voluntarily submit to this procedure. Like playing Russian roulette with a fully loaded revolver.---
--- He was more honourable than all the household of his father. ---I think this simply means the bravest. Being circumcised as a little kid is easier when you have no say in the matter. You require more mental fortitude as a grown man to voluntarily submit to this procedure. Like playing Russian roulette with a fully loaded revolver.---20: And Hamor and Shechem his son came to the gate of their city, and spoke with the men of their city, saying: 21: “These men are at peace with us. Therefore let them dwell in the land and trade in it. For indeed the land is large enough for them. Let us take their daughters to us as wives, and let us give them our daughters. 22: Only on this condition will the men consent to dwell with us, to be one people: if every male among us is circumcised as they are circumcised. 23: Will not their livestock, their property, and every animal of theirs be ours? Only let us consent to them, and they will dwell with us.” --- They really had to make it sound like a good deal.
 24: And all who went out of the gate of his city heeded Hamor and Shechem his son; every male was circumcised, all who went out of the gate of his city.
24: And all who went out of the gate of his city heeded Hamor and Shechem his son; every male was circumcised, all who went out of the gate of his city.25: Now it came to pass on the third day, when they were in pain, that two of the sons of Jacob, Simeon and Levi, Dinah’s brothers, each took his sword and came boldly upon the city and killed all the males. 26: And they killed Hamor and Shechem his son with the edge of the sword, and took Dinah from Shechem’s house, and went out. ---I must admit that this is as awesome as 300 or some Herculean feat. These okes were Alpha Chads.--- 27: The sons of Jacob came upon the slain, and plundered the city, because their sister had been defiled. ---So they sent their sister as a gift to show good faith albeit deceitfully I doubt she was wise to their plan. They knew that the guy cannot have sex with her because time has to pass for his wound to heal.--- 28: They took their sheep, their oxen, and their donkeys, what was in the city and what was in the field, 29: and all their wealth. All their little ones and their wives they took captive; and they plundered even all that was in the houses. ---The small tribe of Israelites probably had a baby boom as a people because of the influx of women gained through this specific conquest.---
30: Then Jacob said to Simeon and Levi, “You have troubled me by making me obnoxious among the inhabitants of the land, among the Canaanites and the Perizzites; and since I am few in number, they will gather themselves together against me and kill me. I shall be destroyed, my household and I.”
31: But they said, “Should he treat our sister like a harlot?” --- To all the feminists who say "How dare you deny a girl the freedom to go where she wants a chase her dreams. Girls can do anything! Girl power!" No, they just end up in some sleazeball's harem. Girls can only do "anything" in Western Civilisation because men have agreed on a very specific set of moral principles which are Christian in nature. Biblical record teaches us why we have freedom, how to facilitate and maintain these freedoms. If you are a feminist you should find a good man and thank him for disciplining his base desires and holds you up with esteem and respect. Feminists are destroying the pedestal men built to support them. But I digress once again.
So now we know why ancient women were under men's protection as their most valuable possession. Women could not acquire and retain agency by themselves for themselves by reason of their physical vulnerability in a wilderness of savages. Not rocket science, just common sense. When cows are money women are not entrepreneurs. There are technological and societal advances required before womens gain of agency and independence is possible.
We have just witnessed how a small group of men conspired and through cunning devised a strategy wherewith they managed to avenge a wrong committed against them. Tooth for teeth and eye for eyes. Violence begets escalation of violence. It might be the first time a nation went to war over a woman's honour. It's not the last time nations went to war over a woman either.
About 600 hundred years later, circa 1100 BC.
Judges 19
1: And it came to pass in those days, when there was no king in Israel, that there was a certain Levite staying in the remote mountains of Ephraim. He took for himself a concubine from Bethlehem in Judah. ---A concubine is a woman under the legal protection of a man who performs the same duties as a wife but does not receive the same status and social recognition as a wife. She cohabits and even bears children. Sounds rough and unpleasant. Almost like a type of slave. A concubine is rarely given in marriage and more frequently exchanged like a good. I believe that the man was legally obligated to support and protect her but anyone can imagine that this is not the ideal outcome for a woman of any culture born in any age. It must have sucked.--- 2: But his concubine played the harlot against him, and went away from him to her father’s house at Bethlehem in Judah, and was there four whole months. ---Here it helps to have some perspective on where the Overton window was lying when this episode of history was recorded and happened. To a lesser extent it was similar just a century or two ago. Have you watched Roland Emmerich's movie The Patriot starring Mel Gibson and Heath Ledger. Do you remember the scene where they had to tie Gabriel Martin (Heath) up when he spent the night over at his sweethearts house. This was because her father had to be able to guarantee the chastity of his daughter on the day of her wedding. No unmarried girl could freely travel alone about the countryside without being under supervision and when she was permitted to court a suitor, a chaperone was required to escort the couple. This was to ensure that no accusation of unseemly behaviour could be made without angering the man who is responsible for her protection. If a girl was raped there were massacres. Some cultures even had intrusive forms of testing the bride to be for proof of virginity, sometimes before and sometimes after the marriage bed. If a woman was a product in a transaction or given as a bride she was required to be a virgin unless she was sold as a whore, meaning for a cheap price. The father, brothers and later the husband carried responsibility for her chaste and loyal behaviour. This does not mean that men behaved with honour. Most were self righteous pigs. But many were good husbands and fathers.--- 3: Then her husband arose and went after her, to speak kindly to her and bring her back, having his servant and a couple of donkeys with him. So she brought him into her father’s house; and when the father of the young woman saw him, he was glad to meet him. 4: Now his father-in-law, the young woman’s father, detained him; and he stayed with him three days. So they ate and drank and lodged there. ---She was not having indiscriminate affairs with random men. She just missed her family and ran away. She would not have been labelled a harlot if she was travelling with her husbands blessing and an escort for protection, she ran away and he could not protect her or be witness to her behaviour. Almost like being guilty by association but more like being guilty for lack of evidence. She becomes Schrodinger's cat. Faithful? Unfaithful? You could not know even with the box open.--- 5: Then it came to pass on the fourth day that they arose early in the morning, and he stood to depart; but the young woman’s father said to his son-in-law, “Refresh your heart with a morsel of bread, and afterward go your way.” 6: So they sat down, and the two of them ate and drank together. Then the young woman’s father said to the man, “Please be content to stay all night, and let your heart be merry.” 7: And when the man stood to depart, his father-in-law urged him; so he lodged there again. 8: Then he arose early in the morning on the fifth day to depart, but the young woman’s father said, “Please refresh your heart.” So they delayed until afternoon; and both of them ate. 9: And when the man stood to depart—he and his concubine and his servant—his father-in-law, the young woman’s father, said to him, “Look, the day is now drawing toward evening; please spend the night. See, the day is coming to an end; lodge here, that your heart may be merry. Tomorrow go your way early, so that you may get home.” 10: However, the man was not willing to spend that night; so he rose and departed, and came opposite Jebus (that is, Jerusalem). With him were the two saddled donkeys; his concubine was also with him. 11: They were near Jebus, and the day was far spent; and the servant said to his master, “Come, please, and let us turn aside into this city of the Jebusites and lodge in it.” 12: But his master said to him, “We will not turn aside here into a city of foreigners, who are not of the children of Israel; we will go on to Gibeah.”---The city of Jerusalem would would not be conquered by king David for another 100 years. This guy did not want to trust foreigners who did not respect his culture and customs with the security of his party. It seems wise. He opted to stay with people who were kin.--- 13: So he said to his servant, “Come, let us draw near to one of these places, and spend the night in Gibeah or in Ramah.” 14: And they passed by and went their way; and the sun went down on them near Gibeah, which belongs to Benjamin. 15: They turned aside there to go in to lodge in Gibeah. And when he went in, he sat down in the open square of the city, for no one would take them into his house to spend the night. ---He arrived late during the day as well making it difficult to arrange lodging at the last minute.--- 16: Just then an old man came in from his work in the field at evening, who also was from the mountains of Ephraim; he was staying in Gibeah, whereas the men of the place were Benjamites. 17: And when he raised his eyes, he saw the traveller in the open square of the city; and the old man said, “Where are you going, and where do you come from?” 18: So he said to him, “We are passing from Bethlehem in Judah toward the remote mountains of Ephraim; I am from there. I went to Bethlehem in Judah; now I am going to the house of the Lord. But there is no one who will take me into his house, 19: although we have both straw and fodder for our donkeys, and bread and wine for myself, for your female servant, and for the young man who is with your servant; there is no lack of anything.”
20: And the old man said, “Peace be with you! However, let all your needs be my responsibility; only do not spend the night in the open square.” ---The old man knew how lawless his city was and did not want to leave the Levite vulnerable in the town square, unfortunately the strangers presence in the city was already noted.--- 21: So he brought him into his house, and gave fodder to the donkeys. And they washed their feet, and ate and drank. 22: As they were enjoying themselves, suddenly certain men of the city, perverted men, surrounded the house and beat on the door. They spoke to the master of the house, the old man, saying, “Bring out the man who came to your house, that we may know him carnally!” 23: But the man, the master of the house, went out to them and said to them, “No, my brethren! I beg you, do not act so wickedly! Seeing this man has come into my house, do not commit this outrage. ---He is asking them nicely without physical authority to respect his private property.--- 24: Look, here is my virgin daughter and the man’s concubine; let me bring them out now. Humble them, and do with them as you please; but to this man do not do such a vile thing!” ---How sad that a woman's honour is traded for a mans personal safety. This history is definitely not a heroes epic.--- 25: But the men would not heed him. So the man took his concubine and brought her out to them. And they knew her and abused her all night until morning; and when the day began to break, they let her go. ---Many modern day scholars of the humanist persuasion pull up their noses at Biblical texts precisely because of these types of occurrences recorded in it. When a historian is willing to record for posterity their failures as well as their victories it only garners trust that the history is true and unmolested by those who would wish to hide and twist the truth to suit their narrative or motives. The aftershock of this event was and is still significant and warrants explanation to the descendants of these people to help them understand their current reality at the time of learning it 2800-2000 years ago. The Bible is not a toy, it is also not a fairy tale. It is the most comprehensive exposition of the human condition currently available for study.--- 26: Then the woman came as the day was dawning, and fell down at the door of the man’s house where her master was, till it was light. 27: When her master arose in the morning, and opened the doors of the house and went out to go his way, there was his concubine, fallen at the door of the house with her hands on the threshold. 28: And he said to her, “Get up and let us be going.” But there was no answer. So the man lifted her onto the donkey; and the man got up and went to his place. ---The modern reader of this might feel a crime of murder and rape was committed. I assure you that this is not the crime. The crime here is that private property was vandalised and destroyed. I pity the woman with my modern Western mind. But as a student of history I have to face the fact that the man was the victim in his day and age. The emotions and pain of this event is not described and could not be described in it's full detail. We do not know if a distraught and scared man was lying inside the house crying, being shushed and detained by his host? I doubt that this was the case, I can only speculate. We only have the information which was deemed sufficient and necessary to be carved onto a slab of stone or scribed onto papyrus. Historians of ages past were not as privileged as I to be able to write and babble thousands of words without the laborious cost which written or carved words claimed from the ancient and even more recent thinkers. Modern critics of ancient texts are not sufficiently recognising these costs. We learn more important lessons from histories scandals than we do from it's triumph's.--- 29: When he entered his house he took a knife, laid hold of his concubine, and divided her into twelve pieces, limb by limb, and sent her throughout all the territory of Israel. 30: And so it was that all who saw it said, “No such deed has been done or seen from the day that the children of Israel came up from the land of Egypt until this day. Consider it, confer, and speak up!” --- Wait what? This guy gone did what? He chopped his wife into 12 pieces? If there was a king which there was not he could have made a plea for justice. If there was a court he could have made a claim. If he had a gun he could have shot them all in a righteous fury. He wanted justice but justice did not have a door for him to knock on. His own people whom he chose to trust above the foreigner abused his trust. It is here where I solemnly confer that it's better to not have expectations of valour from people you don't know, don't trust if you can help it. No one is coming to save you. I'm sorry? I forgot to explain why he couriered his concubines corpse all across the country you say. He did it because he did not have a mobile phone, facebook, twitter, newspapers, radio, or cable TV from where he could broadcast the injustice and pain he and his deceased concubine was subjected to. He knew to get his situation trending on the network of human conversation he had to create sensation. A Streisand effect but intentionally. A rallying cry, like Peanut the squirrel, just a bit more gruesome.---
 Judges 21
Judges 211: So all the children of Israel came out, from Dan to Beersheba, as well as from the land of Gilead, and the congregation gathered together as one man before the Lord at Mizpah. 2: And the leaders of all the people, all the tribes of Israel, presented themselves in the assembly of the people of God, four hundred thousand foot soldiers who drew the sword. 3 (Now the children of Benjamin heard that the children of Israel had gone up to Mizpah.) Then the children of Israel said, “Tell us, how did this wicked deed happen?” 4: So the Levite, the husband of the woman who was murdered, answered and said, “My concubine and I went into Gibeah, which belongs to Benjamin, to spend the night. 5: And the men of Gibeah rose against me, and surrounded the house at night because of me. They intended to kill me, but instead they ravished my concubine so that she died. 6: So I took hold of my concubine, cut her in pieces, and sent her throughout all the territory of the inheritance of Israel, because they committed lewdness and outrage in Israel. 7: Look! All of you are children of Israel; give your advice and counsel here and now!”
8: So all the people arose as one man, saying, “None of us will go to his tent, nor will any turn back to his house; 9: but now this is the thing which we will do to Gibeah: We will go up against it by lot. 10: We will take ten men out of every hundred throughout all the tribes of Israel, a hundred out of every thousand, and a thousand out of every ten thousand, to make provisions for the people, that when they come to Gibeah in Benjamin, they may repay all the vileness that they have done in Israel.” 11: So all the men of Israel were gathered against the city, united together as one man.
12: Then the tribes of Israel sent men through all the tribe of Benjamin, saying, “What is this wickedness that has occurred among you? 13: Now therefore, deliver up the men, the perverted men who are in Gibeah, that we may put them to death and remove the evil from Israel!” But the children of Benjamin would not listen to the voice of their brethren, the children of Israel. 14: Instead, the children of Benjamin gathered together from their cities to Gibeah, to go to battle against the children of Israel. 15: And from their cities at that time the children of Benjamin numbered twenty-six thousand men who drew the sword, besides the inhabitants of Gibeah, who numbered seven hundred select men. 16: Among all this people were seven hundred select men who were left-handed; every one could sling a stone at a hair’s breadth and not miss. 17: Now besides Benjamin, the men of Israel numbered four hundred thousand men who drew the sword; all of these were men of war. ---A civil war in which 65100 men were slain broke out among distantly related brethren. The idea I am trying to convey is that if a man has no speech he cannot campaign for his desired cause. Sensation and virality propels speech into the public arena of popular discourse and is discussed until the prevailing message is precise and clear. If there is no shock factor your speech falls on the ground before your feet. If your speech aligns with the general narrative everyone agrees and nods but the impact of your speech is marginal.
I am glad that we are in a new age where human beings are not so atrociously violated by men with power as it was in ancient times. No wait, it's still a problem. Women are still abused and brothers are still violating each others property and different groups with different interests are still bombing the shit out of each other.
What gives me hope is this.
The internet has dropped the barriers of audible speech and enabled everyone equal access to generate Streisand effects of their own making. Purposely and accidentally.
We are the new mainstream media. Podcasters, influencers, youtubers, and bloggers. We get to decide and form narratives and we get to put our ideas in the arena to battle for acceptance and prominence. The world is now our oyster just as much as it was Barbara Streisand's in the golden age of Hollywood before the internet was there to humble her. Time will tell if we are collectively better custodians of this responsibility than celebrities, corporations and governments. The responsibility of forming the narrative. Not centrally, but decentralised. Let good ideas form and old ideas rest.
Can we be a voice of reason and bring peace and order to a chaotic clown world through the power of speech and ideas? I can only hope.
Echdel
bitbib
-
 @ 13b9f773:4f4efe54
2024-11-06 09:58:17
@ 13b9f773:4f4efe54
2024-11-06 09:58:17"Hay que sentir el pensamiento y pensar el sentimiento".
- Miguelde Unamuno

-
 @ 35f3a26c:92ddf231
2024-11-05 22:14:02
@ 35f3a26c:92ddf231
2024-11-05 22:14:02What is Bitaxe?
Bitaxe is an open source ASIC (Application-Specific Integrated Circuit) Bitcoin miner that has been making waves in the cryptocurrency community. This innovative project aims to empower miners at every level with powerful, efficient, and low-cost mining solutions.
It is a fully open source ASIC Bitcoin miner developed by Skot9000, an advocate for open-source innovation in the Bitcoin space.
With all software and hardware specs available on GitHub, this project aims to provide miners with a transparent and accessible platform for Bitcoin mining.
https://image.nostr.build/db35c2a028e9f740181daabe2deef4e707653fa2d82f1602086e0ac4b5ee84fd.png
Pros
-
Open Source: The Bitaxe is fully open source, allowing users to access and modify its source code, hardware designs, and build gerbers for PCB ordering.
-
Low Cost: Bitaxe offers low-cost solutions for miners, making it an attractive option for those looking to enter the world of Bitcoin mining without breaking the bank.
-
Efficient: The Bitaxe series is designed to be power-efficient, utilizing either the Bitmain BM1387 or BM1397 ASICs for SHA256 hashing.
Cons
-
Technical Complexity: Being an open-source project, users are required to be technically savvy to set up and maintain the miner, which could pose challenges for those without experience.
-
Bricking Potential: Like any complex technology, there is a risk of bricking (rendering the device unusable) the Bitaxe if not handled properly.
Summary
The Bitaxe represents an exciting development in the world of Bitcoin mining, offering a low cost, efficient, and open-source solution for miners. While it may present some challenges for users who are new to the technology or lack technical expertise, the potential benefits far outweigh these drawbacks. As the project continues to evolve and gain traction, we can expect to see further improvements in performance, accessibility, and innovation within the Bitcoin mining landscape.
Where can I get more information
Go to their Github page: https://github.com/skot/bitaxe
originally posted at https://stacker.news/items/659572
-
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ f462d21e:1390b6b1
2024-11-07 03:52:04
@ f462d21e:1390b6b1
2024-11-07 03:52:04eyJfaWQiOiI2Njk1ZmZjZDUyYTMzYTg2YTMxOGUxYzAiLCJ1c2VybmFtZSI6ImtoYWxlZCIsImZlZWRiYWNrU2NvcmUiOjAsImNyZWF0ZWRfb24iOiIyMDI0LTA3LTE2VDA1OjA2OjIxLjA0OFoiLCJ0cmFkZXMiOjEsInRyYWRpbmdQYXJ0bmVycyI6MSwicHVibGljS2V5IjoiZGI0MzViZjAzYzU4Zjk4NTEwMzZiODZkYjI4OGIxMTJkYWRkYzAzMjc5ZTQ0MzkzOTY2MzkzYzE0MDQ3OWEwYyIsImZlZWRiYWNrIjp7ImZlZWRiYWNrIjowLCJwYWdlciI6eyJ0b3RhbEl0ZW1zIjowfSwibWVzc2FnZSI6Im5vIHJlc3VsdHMgZm91bmQifX0=
-
 @ df478568:2a951e67
2024-11-07 03:25:45
@ df478568:2a951e67
2024-11-07 03:25:45I'm writing a long form post from the Yakihonne app I downloaded from the Aurora store. I signed in using Amber. This means I never needed to enter my private key into the app. I also didn't provide an email, nor password.
This is a link to Clark Moody's Dashboard I made by clicking a button and pasting the link.
This post won't be too long as I'm testing the software out, but it's not so bad for being so new. It even let's you save drafts.
https://nostree.me/marc26z@nostrplebs.com/ 869,210
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ 13b9f773:4f4efe54
2024-11-06 08:22:47
@ 13b9f773:4f4efe54
2024-11-06 08:22:47Hewlêr (Rûdaw) - Hevseroka Şaredariya Êlihê Gulistan Sonukê got, “Heta qeyûm hebin diyalog û gotûbêj nabin.”
Wezareta Karên Navxwe ya Tirkiyeyê 4ê Çiriya Paşîn bi daxuyaniyeke nivîskî da zanîn ku wan qeyûm daniye ser şaredariyên parêzgehên Mêrdîn û Êlihê û navçeya Xelfetiyê ya Rihayê.
Gelê Bakurê Kurdistanê li gelek bajar û navçeyan protestoyan li dar dixe û vê biryarê şermezar dike.
Polîs jî li gelek deveran êrişî xelkê dikin û gelek kesan bi lêdanê desteser dikin.
Bi taybetî ji Êlihê gelek dîmen hatibûn ku şkence li xelkê tê kirin.
Di protestoyên li Êlih, Mêrdîn û Xelfetiyê de heta niha zêdeyî 100 kesî hatine desteserkirin.
Li Êlihê û gelek deverên din xwenîşandan û protesto di roja sêyem de jî berdewam dikin.
“Kurd qeyûman qebûl nakin”
Hevseroka Şaredariya Êlihê Gulistan Sonukê amaje pê kir ku berxwedan berdewam dike û li pey çû:
“Em dê li kolan û qadan li dijî qeyûm li ber xwe bidin.
Me ev şaredarî li kolanan bi gel re standin û em dê dîsa li kolanan bi ciwan, jin û gelê Batmanê re û li bajarên din jî bi gelê Mêrdîn û Xelfetiyê û li Esenyurtê jî bi gelan re biparêzin.
Kurd qeyûman qebûl nakin.”
“Heta qeyûm hebin gotûbêj û diyalog nabin”
Gulistan Sonukê diyar kir, “Ji aliyekî ve behsa çareseriyê dikin û ji aliyê din ve dest dirêjî ser îradeya gel dikin” û got:
“Em ji gotinan zêdetir li pratîkê dinêrin. Radibin ji ser kursiyan behsa aştî û çareseriyê dikin û li rêveberiyên cihî qeyûman datînin.
Ev durûtî ye û ne ji dil e. Wan bi danîna qeyûman hinekî xwest ku hêvîya aştî û çareseriyê ya ku bi gelan re çêbûbû, tune bikin.
Piştî axaftinên çareseriyê li cem xelkê hêvî çêbû, ji ber ku ew dijminê xelkê ne, ji bo nehiştina hêviyê qeyûm danîn.
Ji aliyekî ve dibêjin min dest dirêj kir û ji aliyê din ve dest dirêjî îradeya te dike, ev durûtî ye û ne ji dil e.
Li cem me ti qîmetê wê nîne, gelê Kurd û jin vê yekê dibêjin. Heta qeyûm hebin gotûbêj û diyalog nabin.”
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ a10260a2:caa23e3e
2024-11-05 06:21:10
@ a10260a2:caa23e3e
2024-11-05 06:21:10TIL Google Authenticator can potentially collect a lot of data, more than some of the other popular 2FA apps^1.
Whether it does or it doesn’t, if you’re like me, you don’t turn down an opportunity to remove some Google from your life and add in some open-source.
Here’s a quick overview of the migration process.
Step 1: Download 2FAS
Step 2: Export accounts from Authenticator
This can be done via “Transfer accounts” in the sidebar. If you’re transferring on the same phone, take a screenshot of the QR code.
Step 3: Import accounts into 2FAS
During the setup process for 2FAS, you’ll be given the option to import existing tokens from Google. This is where you’ll tap “Choose QR Code” and select the screenshot you took in step 2.
Note that when you tap continue after importing the tokens, you’ll be taken back to the same screen as above. I think it should take you to your list of accounts after. Either way, don’t think the import failed. Just tap cancel, and you’ll be taken there.
If you’re on Android, check out Aegis. 🫡
originally posted at https://stacker.news/items/753472
-
 @ a012dc82:6458a70d
2024-11-06 03:21:36
@ a012dc82:6458a70d
2024-11-06 03:21:36Table Of Content
-
Understanding the Bitcoin Sale
-
Potential Reasons for the Sale
-
Impact on the Market
-
Market Response and Investor Sentiment
-
Conclusion
-
FAQ
The cryptocurrency market is known for its volatility and the constant fluctuations in asset prices. In 2023, a significant Bitcoin sale took place, capturing the attention of investors and enthusiasts alike. Long-term investors made a decision to sell off nearly 50,000 BTC, leading to discussions about the implications of this sale and the factors that might have influenced it.
Understanding the Bitcoin Sale
The sale of nearly 50,000 BTC by long-term investors suggests a shift in market dynamics. These investors, who had held their Bitcoin for an extended period, decided to realize their profits and exit their positions. Such large-scale sales can have a considerable impact on the market, affecting Bitcoin's price and overall market sentiment.
Potential Reasons for the Sale
Several factors might have influenced long-term investors to sell off their Bitcoin holdings:
Profit-taking
Long-term investors often accumulate Bitcoin with the intention of selling it at a higher price in the future. If they believed that the current price levels provided a satisfactory return on their investment, they may have chosen to take profits.
Market Conditions
Cryptocurrency markets are highly volatile, and investors closely monitor market trends. If they perceived a potential downturn or correction in Bitcoin's price, they may have decided to sell to protect their gains or minimize potential losses.
Portfolio Diversification
Investors may have decided to rebalance their investment portfolios by reducing their exposure to Bitcoin. Diversifying their holdings across various asset classes can help manage risk and potentially enhance long-term returns.
Personal Circumstances
Individual investors may have had specific personal or financial reasons for selling their Bitcoin. These could include the need for liquidity, funding other investment opportunities, or addressing personal financial obligations.
Impact on the Market
A significant sale of Bitcoin by long-term investors can have a short-term impact on the market. Depending on the volume of the sale and the prevailing market conditions, it may lead to a temporary decline in Bitcoin's price due to increased selling pressure. However, market dynamics are complex, and the impact of such sales can vary depending on the overall market sentiment and the response of other market participants.
Market Response and Investor Sentiment
The response to this significant Bitcoin sale largely depends on investor sentiment and market perception. Some investors may interpret it as a sign of decreasing confidence in Bitcoin's long-term prospects. Others may see it as a natural occurrence in a market characterized by profit-taking and portfolio adjustments. The market's response to such events can offer insights into the overall sentiment and provide valuable information for future investment decisions.
Conclusion
The significant Bitcoin sale by long-term investors in 2023 highlights the dynamic nature of the cryptocurrency market. Investors' decisions to sell off nearly 50,000 BTC can be influenced by various factors, including profit-taking, market conditions, portfolio diversification, and personal circumstances. While such sales can impact the market in the short term, it is essential to consider them within the broader context of market dynamics and individual investment strategies.
FAQ
What is the significance of the significant Bitcoin sale by long-term investors? The significant Bitcoin sale by long-term investors indicates a shift in market dynamics and can impact Bitcoin's price and overall market sentiment.
Why did long-term investors decide to sell off nearly 50,000 BTC? There can be several reasons behind the decision to sell, including profit-taking, market conditions, portfolio diversification, and personal circumstances.
How does such a sale affect the market? A significant sale of Bitcoin can lead to a temporary decline in its price due to increased selling pressure. However, the impact on the market depends on various factors and the response of other market participants.
What does this sale suggest about investor sentiment towards Bitcoin? The response to the sale can vary among investors. Some may view it as a lack of confidence in Bitcoin's long-term prospects, while others may see it as a natural occurrence in a volatile market.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 75d12141:3458d1e2
2024-10-23 00:20:14
@ 75d12141:3458d1e2
2024-10-23 00:20:14Chef's notes
A childhood favorite of mine! Just don't go too crazy with the scallions as you don't want to overpower the pork flavor.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 15-20 mins
- 🍽️ Servings: 3-5
Ingredients
- 1 pound of lean ground pork
- 1 tablespoon of diced scallions
- Ground black pepper (optional)
Directions
- Lightly coat your palms with olive oil to prevent the meat from sticking to you and to assist in keeping its ball form
- Mix the ground pork and diced scallions in a large bowl
- Roll the pork into the preferred portion size until it feels like it won't fall apart
- Cook in a skillet for 15-20 mins
-
 @ 4f82bced:b8928630
2024-10-22 17:23:53
@ 4f82bced:b8928630
2024-10-22 17:23:53Bitcoin doesn’t get too much love from the media. The tune seems to have slightly changed since the launch of the ETF, now that there’s money to be made. I don’t see many discussions about the humans pushing this decentralized technology forward. Bitcoin has no CEO, sales, marketing, product, or support team. Its source code is open for anyone, to inspect, copy and propose changes. 15 years after its inception, the network grows stronger every day due to the efforts of individuals worldwide. They build products, share stories, educate, mine, and more.
Here are some people who have directly impacted our journey, especially in Africa:
- Two early adopters who have consistently organized meetups for nearly 8 years
- A young graduate creating a circular economy, while also boot strapping his tourism business
- An artist making bitcoin approachable to the masses through his love of music
- A family of five who opened their doors and showed us their way of living on a Bitcoin-standard
- A father who built a product that doesn't require the internet to use bitcoin
- An ex-military who is educating the community through the local languages
- An engineer who is setting the record straight on bitcoin mining
This is just a small sample of the thousands that continue to build using this open technology, one that is deeply misunderstood. As literacy and adoption increase more and more humans will jump on board. Are you ready?
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 015c8941:3ea77b51
2024-11-05 18:52:23
@ 015c8941:3ea77b51
2024-11-05 18:52:23the US could gain a strategic advantage over other countries that are contemplating starting a bitcoin reserve and can reinforce the US’ influence over global financial standards
-
 @ b184e3ed:27924b0d
2024-11-07 03:06:37
@ b184e3ed:27924b0d
2024-11-07 03:06:37When I joined AA, this question started to haunt my thoughts during those frequent nighttime anxiety attacks. Among all the chaos in my life, there were a few things I was certain of. And one of those things was the certainty of never having felt God, I didn't even know that God was something you could feel. For me, when I started the 12-step program, God was a social construct, something humans had invented to control a society thirsty for basic survival instincts. And perhaps I wasn't so wrong, but like everything in life, this was only half the truth. Despite my deep cognitive analysis that my anxiety forced me to do almost every night for hours, often until the first ray of sun pierced my bedroom window, my spiritual bias didn't allow me to see the whole picture, or a complete reality. On that side, there had always been a void Later, I realized that this emptiness was the main cause of all my problems. From there came that feeling of always being incomplete, that anxiety of always feeling like something was missing, that need to always want to fill voids that weren't mine, without realizing that it was only creating more emptiness within me Once, in those heart-to-heart talks that we in AA call sponsorship, my soul expressed the painful doubt, 'What does it mean to feel God?' My sponsor simply replied, 'I assure you that when you feel God, you won't doubt that what you feel is God. There is no doubt in matters of God. And so I left, with that answer that left me right where I started. And with more doubts. Why is there no doubt in matters of God?
After thinking about it for so long, I paused for a few seconds. I closed my eyes and decided, for the first time, to talk to this so-called God. I let go of all my feelings, all my disbelief, and I prepared myself to accept anything different from what I already had, because what I had wasn't working for me at all. With all sincerity and feeling a pressure in my chest, closer to my heart than usual, I asked in a low voice God, what does it feel like to feel you? What should I do to feel you? What's the manual for feeling you? I've tried everything, I don't know what else to do, what else to plan. I accept that I need to feel you. Everyone tells me that when I feel you, everything will make sense and only then will I start to let go of this violent need to consume my drug of choice. But nobody tells me how. What am I not seeing? Please, give me something. I can't take it anymore, I'm running out of strength, I'm wasting my life stuck in the same cycle. I can't do this anymore, help me feel you. Then a pain began to flow, but a particular one that every addict knows, that soul-deep pain that comes from emptiness, that pain that turns on the faucet of tears that began to flow non-stop. I allowed myself to feel that pain, everything turned dark and negative, suicidal thoughts returned, hate, resentment, selfishness, depression, all together, all that is lived in darkness, all that is felt in solitude, all that came from emptiness. And only by feeling it, could I see where that deep pain came from, I could visualize the path it left behind. For the first time, I recognized my spiritual emptiness. And it was only then that I began to see the whole picture of my life. Doubt has no place in the things of God because God is not logic, God is not reason, much less a manual. Doubt comes from logic, therefore where there is doubt, there is also an absence of God, emptiness. And right at the moment of recognizing that, very specific images came to my mind. My sponsor hugging me for the first time when I arrived and interviewed me. With that hug came the words, 'You're not alone, you're already in a safe harbor, we'll be with you from start to finish. One day at a massive AA event, right in the middle of a workshop dynamic, that deep and sincere hug my fellow sufferer and I shared, in the midst of deep crying with our eyes closed, someone guided our arms to each other. To end up keeping each other company in that darkness we had always gone through alone. That trip to a Group Anniversary outside the city, where a fellow member of my group and I were simply enjoying the scenery, the wind on our faces, and laughing at the craziness of our daily lives, this on my motorcycle on the highway. That hug it took me years to find in the arms of my younger sister, right after arriving after a writing session. That hug of forgiveness to my mother and father that I had never been able to give before because I didn't want to go through the pain that came with feeling. Those few seconds in the rain that we spent lost on our way to the new location of our Group that I experienced in the company of a fellow member. Seeing a new person arrive with a desire to start their process. Connecting in the same feeling and emotion that comes with the death of a best friend. Serving a cup of coffee to that fellow member who returns after months of absence. Arriving at the group with hope of seeing that fellow member who hasn't been coming for weeks and little is known about what happened, but they no longer come to meetings. Day after day, their chair remains empty. And then start letting go of their defenses and their craziness. Standing in front of several strangers, with my head held high, my gaze firm, saying my name and then, 'I am a drug addict. To say, 'I feel like shit, but I'm here for whatever I can contribute. To feel like I'm that support for those who were my support when I was at rock bottom. And not just feel it, but also be able to be it. And that, to mention just a few of the scenes that came to my mind, then I understood 'I had already felt God.' I wasn't lacking spirituality, I wasn't lacking God, I just needed to stay still for a moment to feel it. And to feel that he has always been there. And that he will never leave my side. So today I can answer my own question, 'That's what it feels like to feel God' but not just any God. But a very special one, the God of the 4th and 5th step addicts and alcoholics...
originally posted at https://stacker.news/items/756957
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ 472f440f:5669301e
2024-11-05 04:24:47
@ 472f440f:5669301e
2024-11-05 04:24:47All eyes are, unsurprisingly, on the US Presidential election. Tomorrow is the big day. I don't want to come off as preachy, however it is pretty clear to me that if you are an American citizen who cares about bitcoin and would like to live under an administration that is eager to embrace the industry as opposed to an administration that is actively hostile toward bitcoin there is only one candidate who deserves your vote; Donald J. Trump. I think he's a better candidate for other reasons, but if you've read this rag for long enough you probably already know what those are. Instead of writing a screed about why I am voting for Trump, let's highlight some things outside of the election that you should be paying attention to this week.
First up, there are two Treasury auctions; $42B of 10-Year notes tomorrow and $25B 30-Year bonds on Wednesday.
It will be interesting to see what the demand for these auctions is and how they affect rates. The long end of the yield curve has been pumping since the Fed's rate cut in the middle of September, which is the market signaling that it does not believe inflation has been appropriately tamed. Yields came down today, but as you can see from the charts things are trending in the wrong direction.
As the Treasury issues new debt at higher rates, the interest expense on that debt, naturally, drifts higher. If the long end of the yield curve doesn't come down aggressively over the course of the next year this is going to be a big problem. There are trillions of dollars worth of Treasury debt that needs the be rolled over in the next few years and it would be advantageous for the Treasury if that debt wasn't being rolled over with yields as high as they are. With the amount of debt the country has accrued in recent decades, every incremental dollar of debt that gets issued and/or rolled over at higher interest rates exacerbates the problem. We are approaching the territory of runaway exponentials, as evidenced by this chart. The growth slope gets steeper and steeper
This debt problem is the elephant in the room that needs to be addressed as quickly as possible. The national debt hit $1.2T in early 1983. It then took 26 years to 10x from $1.2T to $12T in late 2009 and has only taken another 15 years to triple from there to $36T or 30x from the arbitrary base I picked out (Q1 1983).
With this in mind, keep an eye out for these auctions tomorrow and Wednesday, where rates end at the end of trading on Wednesday, and whether or not we officially push over $36T. Regardless of who wins the election tomorrow, this is a problem that needs to be confronted. Whether or not it can be solved at all is up for debate. I don't see how what can be done to reel in this runaway train at this point. However, at the very least, we should acknowledge that we're in the realm of exponentials and have people prepare accordingly by accumulating hard assets that cannot be debased (bitcoin).
The other thing to pay attention to is the FOMC meeting on Wednesday and the announcement of the results of the meeting on Thursday. Will Jerome and the other Fed board members to keep rates where they are, cut, or raise rates? Raising rates seems to be out of the question despite the fact that many believe it would be the most prudent move considering how the long end of the yield curve reacted to the 50bps cut in September. If they decide to cut rates, by how much will they cut them? Will they slow the pace with a 25bps cut or continue at the 50bps clip established in September?
We'll find toward the end of this week. Don't lose sight of these events while the world is enthralled with the elections in the US.
I don't know about you freaks, but I couldn't feel more fortunate that bitcoin exists at a time like this. Having access to a distributed peer-to-peer digital cash system with a fixed supply during a time of incredible political divisiveness and out-of-control runaway sovereign debt feels like a Godsend.
Stay sane out there.
Final thought...
We're going to win.
-
 @ 805b34f7:3620fac3
2024-10-19 19:59:21
@ 805b34f7:3620fac3
2024-10-19 19:59:21** I published this article on 3/26/2020. I'm back in Puerto now and just re-read this to fire myself up for some potential tubes. Now, I want it to live on Nostr.
“When in doubt, don’t go out” is a well-known aphorism among surfers. I think it’s bs. Let me explain.
**I speak from my experiences as a regular surfer and with my close group of regular surfers in mind.
In surfing, there’s a comfort zone, an adrenaline zone, an aw crap zone (doubt), and a hell no zone.
Comfort zone —It is in this place where it is safe and fun to try new maneuvers. The heart rate is low and the stoke rate high.
Adrenaline zone- This is personally my favorite zone. The surf is big or good enough to get the heart rate up and the juices flowing. Each movement matters and this is where some of the best surfing goes down.
Aw crap zone — This is the land of the I don’t know, the doubt. It’s always damn near impossible to sleep before an aw crap day of surfing. This is the place where limits are tested. Maybe you’re surfing in a new place with new risks such as shallow reef, a difficult takeoff, or it’s just huge. This aw crap zone will test and define your limits.
Hell no zone — When you know, you know. This is beyond doubt. You’re totally satisfied (yet still curious) from watching from afar. Maybe one day!
These zones are bound to change as the surfer progresses. One day there may be no “hell no zone” as the surf master has pushed his or her limits to the extreme.
Pushing
Pros are only as good as their home breaks. NOT. Tell that to Kelly Slater and the Hopgood brothers who grew up surfing Florida slop. Although, perhaps their garbage wave situation lit a fire underneath them which inspired them to seek out better waves and progress rapidly. Anyways, a surfer grows up surfing their home breaks often. Some people grow up on the North Shore or in Tahiti, others grow up in Huntington. A surfer’s perspective on waves and danger is influenced by their exposure.
I finally got bored with myself surfing my home waves. Sure, there were days that were outside of my comfort zone and epic, but it was time to go find waves that I had only seen in videos. I decided to pack my backpack and head to those famed Indonesian reefs that I’ve mind surfed for hours, but always had the question mark in my head as to whether or not I could conquer them.
Surfing over shallow reef is something that I was not used to and it terrified me, but I also knew that every surfer does it including five-year-olds so I had to send it. I escaped the first mission unscathed and with some of the best waves in my life.
In order to find those best waves of my life, I had to enter the ‘aw crap zone’. The I don’t know land. The unknown. When in doubt, I went out.
And Now I’m Here
 I blew this wave, but wow pretty.
I blew this wave, but wow pretty.
Current forecast looks like it will be right at my edge.. again. We'll see.
I’m surfing the famous Playa Zicatela every day with the whole world shut down due to Co-Vid19. I’ve always been curious to know what it’s like to be inside massive barrels, so I’m slowly making it happen. This is a battle that I chose. I’m learning how to sleep with surf anxiety. The first couple of nights were rough, but I’m starting to accept it now.
This very morning inspired this article. I got up, went to the roof, and checked out the waves. It looked pretty mellow despite the fact that I knew there was a lot of swell in the water. I just thought, eh, maybe it’s not big like it was forecasted. I got in the water, took my first wave, wiped out, but whatever. I’ve been here for a week and I still wipeout on just about every first wave. But, I quickly found out that this was not the real set. The next set was enormous, and it sent adrenaline shrieking through my spine and filled my brain with the aw craps. The questioning of my life and why I’m out here quickly followed. Am I good enough for this? (maybe). Could I survive a wipeout that size?(probably). Is my board right for this? (definitely not). The second wave I took was bigger and I pulled the eject cord and jumped from what felt like the top of a cliff all the way to the bottom and got creamed (my perspective). After a couple of flips, I popped up the back laughing and was ready for another. I survived, therefore, I can keep pushing.
Not gonna lie, surfing almost feels like work lately. Almost every day here is just about in my personal aw crap zone.
However, it’s worth it for me. This is a journey that I deem worthy of my time. It does it for me. It’s those little moments inside the barrel and gosh-dang-golly hopefully soon getting shot out of the barrel that keep me stoked and looking forward to tomorrow. It’s proving to myself that I can do things I didn’t know for sure were possible.
The Process to Progress
Progression sometimes feels like a snail crawling up Mt. Everest. But when you zoom out, those incremental small improvements compound over time. Each wipeout is a little victory. Each wave that is ridden is a little victory. Your brain is learning from every experience that you choose to give it. Confidence slowly builds as we continue to learn from the masters and even develop our own style. Next thing you know you’re drinking a beer in a barrel that can kill a normal man like Mr. Slater did here.
 Freakin Goat
Freakin GoatStagnation leads to burnout, depression, and boredom (Not scientific facts but I’m right I know it).
The great danger is that we give in to feelings of boredom, impatience, fear, and confusion. We stop observing and learning. The process comes to a halt. — Farnam Street Blog
I’ve seen a few buddies give up surfing or digress. It happened to me while I was focusing on baseball. It’s sad because surfing is fun and the better you get the more fun it is. It’s even more fun with a core group of guys who are at a similar level pushing each other. It can get boring if you don’t push yourself, and it gets scary real quick if you aren’t in surf shape.
“Whenever we learn a skill, we frequently reach a point of frustration — what we are learning seems beyond our capabilities. Giving in to these feelings, we unconsciously quit on ourselves before we actually give up.” FS Blog
Progression takes effort. Effort takes a conscious decision to expend your limited energy. It’s the only way to get gains in whatever game you are playing. Also, progression takes humility.
I got the pleasure of surfing Kelly Slater’s Wave Ranch. I knew I was going to have fun, but the night before I was damn nervous. Why? Well, I knew there’d be cameras and that I didn't want to blow it. I’d be surfing with pros and I was going to look horrible compared to them. Sure enough, the one right the camera got, I blew. Oh well. No 30-second barrels for the boys. Life moves on.
Full vid here https://vimeo.com/367128298
 Can't wait to go back here one day
Can't wait to go back here one dayYou’re bound to fail, especially when you take risks. If you’re a prideful person, the setbacks will be greater. It’s how you deal with the failure that determines if you will become a master.
So if in doubt, go out. Your hell no zone is going to start to shrink. This applies any skill that you are sharpening. You’re only going to get the big clients if you go after them, a piano player will improve by practicing harder songs, a black belt gains nothing from fighting a white belt, etc.
Pick your battles wisely. Then…SEND IT, SURVIVE, LEARN, APPLY, REPEAT.
10/19 - Even though I'm a much more experienced surfer now, I'm still terrified. On my way to go get a board now and get ready for some swell! I'm on my honeymoon, so we'll see how hard I push. I have quite a few more responsibilities now then I did back in Covid times... But if in doubt, I will go out. PV.
-
 @ 3584cea4:0951bbef
2024-11-05 17:58:45
@ 3584cea4:0951bbef
2024-11-05 17:58:45The understanding of a caregiver and healthcare advocate for my mom.
I have been involved in one way or another in the insurance business for a long time. I run a small insurance brokerage which primarily caters to my family and friends of friends. In that role, we perform a needs assessment with prospective clients' & family members to understand what keeps them up at night to help them build a tailor fitted protection plan for their families.
As part of that process I get a good sense of one’s financial obligations, specific cultural and family values that need to be factored and a general indication of their health status.
However, in the most recent year, I have been unexpectedly thrust into (and gladly accepted) the role of caregiver and health care advocate for my mom. As her dementia is quite severe and had been getting worse until recently. That combined with a series of strokes she experienced earlier this year, has left her unable to retain her independence and live by herself.
As such, I’ve had to understand the inner workings of aspects of the insurance industry that apply to older people that I was quite unfamiliar with.
One of the most poignant observations while on this journey for my mom’s complete recovery became clear to me about two weeks ago when we met with mom’s neurologist where we both met her for the first time after 7 months of trying to get a visit. There is a 4 month lead time to get an appointment and we missed one in June (work emergencies back home in PA). Hence, the rescheduled appointment 4 months later which was about 2 weeks ago.
Before I describe that visit, I need to explain what my experience has been working with the 6+ different medical specialists and mom’s PCP has been like for me.
The healthcare professionals I've encountered have been a mixed bag, of mostly kind, genuinely caring, overworked and underappreciated professionals. This accounts for >95% of my encounters with healthcare workers most recently.
Many of these healthcare institutions still use fax machines and mostly operate on 1990s tech. Healthcare workers are graded regularly not so much on the quality of the healthcare they provide to their patients, but how well they follow the rules that have been established by whichever governance body regulates the important incentives. If you know anyone that works in the healthcare industry and are able to follow the incentives, it doesn’t take much clicking and googling to see that it’s usually big pharma at the tail end of their incentive structure.
It’s my subjective opinion most (>95%) of the people in healthcare want to and believe they are doing the right thing. However, they are so overwhelmed, they sometimes don’t see the irony in their recommendations (a topic for another essay) or behavior that often leaves me baffled and wondering (out loud sometimes) “did they just say that”. With that said, it is of this 95% I speak of in this essay, the genuinely caring but overworked and under appreciated healthcare providers. From the physician’s assistants, to the doctors, specialists, nurses and so on.
How the visits typically play out.
We’re waiting for an hour or more to be seen (even with an appointment on the books).
Eventually, someone will come out to the waiting area to call my mom’s name and from there we are escorted to a private observation room. In the observation room we’ll sit and wait some more, sometimes just a few minutes other times longer.
After a few minutes, if we are lucky, someone else (presumably a nurse or PA) comes in to ask a few questions, checks mom’s vitals and make a few notes in her chart/records.
Sometimes moments “lay - tor” [spoken in a thick french accent] the actual doctor comes in. Other times we may be waiting an additional 30 minutes or more in the observation room.
The actual time spent with the doctor once they meet us in the observation room is usually 5-10 minutes depending on the office, then we are off to scheduling and referrals to get future appointments scheduled and on the books. The whole event from the time we walk into the office to departure is usually less than 2 hours. But, it’s OK if it ends up being a little longer as I always budget these appointments for 4 hours. Otherwise, the day’s schedule begins to fall apart, I miss meetings, calls and other demands on my time and stress ensues and I don’t like this type of stress.
Getting back to the point of this essay, mom’s neurologist.
We were waiting in the observation room by ourselves for what seemed to be a good 20 minutes, so I decided to quickly run out to the car and check on Wiggles. She had been out in the car making sure the AC was working for about an hour and a half at that point.
Sure enough the neurologist showed up while I was away. She entered the observation room to find my mom, by herself (and nonverbal). The doctor was somewhat confused and was looking around for someone to ask about my mom and get a sense of what she was supposed to be doing to/with her.
Arriving in time to see the neuro with a crayon and scratch pad in hand attempting to hand it over to my mom in hopes she would be able to say/explain herself in writing. It was more funny than anything. You have to know my mom to understand her attitude about a lot of what is going on around her. As my mom watched the neuro with crayon and paper in hand, she was likely thinking “I am old, retired, I only have to do things I want to do, and pen and paper sounds an awful lot like work. So, you can keep it and I’ll wait for my son.
Some additional context about this doctor's office. I would consider it one of the larger ones in the area, highly recommended, this is a very busy office with many employees hurriedly bustling about the hallways and bouncing from one observation room to another.
Back to the observation room. The neuro was likely alone with mom for just a moment before I returned from the doggy in the car check.
I expected this doctor visit to be like the rest and that I was going to get maybe 2 minutes with this doctor and she would be off seconds later to the next patient and observation room.
But that was not all the case. The neurologist engaged with my mom for a period, probably a good 15-20 minutes, without and prior to barely acknowledging I was even in the room. This is likely procedural, their way of making sure my mom is not a victim or being abused in some form. This was unusual, but oddly appreciated. But, most importantly my mom’s neurologist educated me on a few things regarding my mom’s health and spent almost an hour with us altogether. My mom’s neuro got more context around my mom and her lifestyle leading to this delicate state in her health. More than any other doctor my mom had been seeing. I can tell the neuro was slightly impressed or entertained (hard to tell the difference sometimes) that I understood what my mom was saying. Observing my mom and I interact as an outsider does look weird to people when in public and add to that visual a cane corso usually in a sit position right beside us. Self-admittedly, even funnier when she is scolding me about something I am doing or asking her to do.
I digress!
At the end of mom’s neuro visit, the doctor gave us her office and personal information so that I may contact her day/night/weekend for anything “you don’t have to wait for business hours if you have any questions or if any health concerns should arise.” While I have not tested those numbers to confirm their validity, I do believe she was being genuine in her gesture.
In conclusion, and all that to say, It was overall the best doctor visit I’ve had with respect to this situation I find myself in with my mom.
Don’t get me wrong, all the other doctors mean well. But the bandwidth simply isn’t there. As such, this is not a judgment on all the beautiful and caring people that have cared for my mom and countless others in the past and into the future. These are just the facts from these boots on the ground as I see it.
As for the brain damage to my mom’s left frontal lobe, it has diminished slightly and continues to shrink. It’s not all permanently damaged. But, there is no knowing at her age (86) how much repair we can expect or whether her speech will ever return. But my family and I are optimistic. As for mom’s speech or lack there of, a little peace and quiet never killed anyone. In many ways, mom is lucky because I sometimes wish I didn’t have to speak. I miss those days often. But being in Florida, especially now, is more important, so we are good with what needs to be done.
As for mom’s neurologist, I will do something nice for her. The next appointment is in February, let’s hope I don’t have to use that private number before then.
Mom’s neuro might have the initials of KBMD, but that’s just a guess.
BrainThings #LivingWithLala #caregiver #doctors #neurologist
-
 @ 9349d012:d3e98946
2024-11-05 00:42:37
@ 9349d012:d3e98946
2024-11-05 00:42:37Chef's notes
2 cups pureed pumpkin 2 cups white sugar 3 eggs, beaten 1/2 cup olive oil 1 tablespoon cinnamon 1 1/2 teaspoon baking powder 1 teaspoon baking soda 1/2 teaspoon salt 2 1/4 cups flour 1/4 cup chopped pecans
Preheat oven to 350 degrees Fahrenheit. Coat a bread pan with olive oil. Mix all ingredients minus nuts, leaving the flour for last, and adding it in 2 parts. Stir until combined. Pour the batter into the bread pan and sprinkle chopped nuts down the middle of the batter, lenghtwise. Bake for an hour and ten minutes or until a knife insert in the middle of the pan comes out clean. Allow bread to cool in the pan for five mintes, then use knife to loosen the edges of the loaf and pop out of the pan. Rest on a rack or plate until cool enough to slice. Spread bread slices with Plugra butter and serve.
https://cookeatloveshare.com/pumpkin-bread/
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 1 hour and ten minutes
- 🍽️ Servings: 6
Ingredients
- See Chef's Notes
Directions
- See Chef's Notes
-
 @ 18bdb66e:82eb5e5d
2024-11-04 23:38:03
@ 18bdb66e:82eb5e5d
2024-11-04 23:38:03Chef's notes
This recipe needs to sit in the refrigerator at least one hour, or overnight prior to baking. Link sausage may be used but casing must be removed prior to frying.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4-6
Ingredients
- 1 lb breakfast sausage
- 1 large onion, chopped
- 1 green bell pepper
- Cooking spray
- 4 cups dehydrated/dried bread cubes
- 6 large eggs
- 1 1/2 cups milk
- 1/4 tsp salt (optional)
- 1/4 tsp black pepper
- 1 cup shredded Cheddar cheese
Directions
- Spray 13x9 baking dish with cooking spray, like PAM.
- Crumble sausage into a skillet, fry breaking up pieces
- Add onion to the sausage
- Chop bell pepper, add to sausage and onion, fry until tender
- Remove from heat, drain if needed, set aside.
- Spread bread cubes on bottom of baking dish
- Spoon sausage mixture over bread
- Blend eggs, milk, salt, and pepper in a bowl or large measuring cup.
- Pour egg mixture over sausage and bread.
- Cover and place in refrigerator.
- Refrigerate at least one hour or overnight.
- Preheat oven to 375F.
- Place casserole in oven, bake 55 minutes
- Top with cheese and bake 5 minutes longer.
- Let rest 10 minutes before cutting.
-
 @ 8d34bd24:414be32b
2024-11-06 22:18:02
@ 8d34bd24:414be32b
2024-11-06 22:18:02One popular plot formula for movies is having two very different people trade places through some mysterious means. It may be kids trading places with adults. It may be the rich person trading places with the poor person. It may be the city person trading places with the country person. The more different the two people, the more comical the effects of trading places is.
All Christians are in a storyline of two very different people trading places. It isn’t the story of rich/poor, young/old, or city/country, it is the trading places of the woefully inadequate and sinful trading places with the perfect and sinless. This isn’t a comedy. In so many ways it seems like a tragedy. The one who deserves punishment and death gets forgiveness and eternal life. The one who deserves worship and praise gets punishment and a torturous death.
Unfortunately most of us are not thankful enough for the wonderful benefits we get from this trade and don’t feel the horror we should at what was done to our perfect God, Creator, and Savior.
Therefore if anyone is in Christ, he is a new creature; the old things passed away; behold, new things have come. Now all these things are from God, who reconciled us to Himself through Christ and gave us the ministry of reconciliation, namely, that God was in Christ reconciling the world to Himself, not counting their trespasses against them, and He has committed to us the word of reconciliation.
Therefore, we are ambassadors for Christ, as though God were making an appeal through us; we beg you on behalf of Christ, be reconciled to God. He made Him who knew no sin to be sin on our behalf, so that we might become the righteousness of God in Him. (2 Corinthians 5:17-21) {emphasis mine}
What a wonderful, glorious turn of events in our personal story that we become “a new creature” in Christ; we “become the righteousness of God in Him.” What a tragedy and unfathomable sacrifice that our Creator God, “who knew no sin,” became “sin on our behalf.” We are part of the most unfair trade, and we benefit so incredibly much and yet we take it for granted most of the time.
For Christ also died for sins once for all, the just for the unjust, so that He might bring us to God, having been put to death in the flesh, but made alive in the spirit; (1 Peter 3:18) {emphasis mine}
We, the unjust, were made just so we can be forgiven and face God almighty. Our Creator, Jesus Christ, the just was made sin for us and died to pay the penalty we deserved for our rejection of God, selfishness, dishonesty, and general ignoring of our Creator.
I don’t think we comprehend how much we don’t deserve the Salvation we received and how much Jesus didn’t deserve the treatment He got throughout history, but especially in His death and separation from God on the cross. We feel severe pain when we are separated from our close friends and/or family. Jesus, part of the 3-in-1 God, was separated from God the Father and God the Spirit. It was like us having a limb cut off. They are one God, so severing one from the rest was the greatest torment that He could ever go through. It was worse than infinite, eternal Jesus limiting Himself to a mortal, finite body to live on earth as a man. It was worse than being tortured and killed in the most painful way ever designed by man. Perfect, holy Jesus was made sin, so He could no longer be in the presence of the Father. We need to thank Him every single day for what He did for us. (I know I don’t thank Him enough.)
Surely our griefs He Himself bore,\ And our sorrows He carried;\ Yet we ourselves esteemed Him stricken,\ Smitten of God, and afflicted.\ But He was pierced through for our transgressions,\ *He was crushed for our iniquities*;\ The chastening for our well-being fell upon Him,\ And by His scourging we are healed.\ All of us like sheep have gone astray,\ Each of us has turned to his own way;\ But the Lord has caused the iniquity of us all\ To fall on Him**. (Isaiah 53:4-6) {emphasis mine}
Look at all the replacement language in this passage:
-
“our griefs He Himself bore”
-
“our sorrows He carried”
-
“He was pierced through for our transgressions”
-
“He was crushed for our iniquities”
-
“The chastening for our well-being fell upon Him”
-
“by His scourging we are healed”
-
“the Lord has caused the iniquity of us all to fall on Him”
Because of what Jesus did for us, He took the grief, sorrows, piercing, crushing, chastening, and scourging that we deserved. He took on the burden and guilt of our iniquity.
For you have been called for this purpose, since Christ also suffered for you, leaving you an example for you to follow in His steps, who committed no sin, nor was any deceit found in His mouth; and while being reviled, He did not revile in return; while suffering, He uttered no threats, but kept entrusting Himself to Him who judges righteously; and He Himself bore our sins in His body on the cross, so that we might die to sin and live to righteousness; for by His wounds you were healed. For you were continually straying like sheep, but now you have returned to the Shepherd and Guardian of your souls. ( 1 Peter 2:21-25) {emphasis mine}
How amazing is it that our loving Creator came down to earth and lived a perfect life as “an example for you to follow?” How unfathomable is it that He took our sins into Himself changing Him from the Holy Lamb to a sinner judged and separated from God? How incredible is it that we get His righteousness because He willingly took on our sins? How can we ever show enough gratefulness for what He has done for us?
This next passage is a passage of the greatest joy imaginable and what all believers have to look forward to:
Now I say this, brethren, that flesh and blood cannot inherit the kingdom of God; nor does the perishable inherit the imperishable. Behold, I tell you a mystery; we will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised imperishable, and we will be changed. For this perishable must put on the imperishable, and this mortal must put on immortality. But when this perishable will have put on the imperishable, and this mortal will have put on immortality, then will come about the saying that is written, “Death is swallowed up in victory. (1 Corinthians 15:50-54) {emphasis mine}
The day is coming that we will not just be justified by Jesus’s sacrifice, but we will be changed from perishable to imperishable and from mortal to immortal. “In the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised.”
As the passage continues, “but thanks be to God, who gives us the victory through our Lord Jesus Christ.” (1 Corinthians 15:57)
Trust Jesus.\ \ your sister in Christ,
Christy
-
-
 @ 6871d8df:4a9396c1
2024-11-05 14:26:45
@ 6871d8df:4a9396c1
2024-11-05 14:26:45Today is Election Day here in the US, and it's a big deal.
As of now, this is my bet on the vote:
For myself, as I did in 2020, I will be voting for Donald Trump.
My biggest reasons for this are as follows: 1. Dismantling the bureaucracy. 2. Financial Freedom 3. Food Freedom
There are others, but those are my top three.
For me, the fact that unelected bureaucrats essentially run our government (Joe Biden is still our President right now, though no one has seen or heard from him in months) is our largest red flag. I think it is our biggest priority to return to a place where the people we elect to run our government actually run our government.
Trump swung and missed on this in his first term, but with his commitment to RFK and having people on his side like Vivek, I do not think he will sing and miss this time.
Next is financial freedom. The Biden-Harris administration has been incredibly hostile to what I am calling financial freedom. They mostly got their policies from the Warren camp, which hates digital currencies.
Being a part of Bitcoin startups for most of the Biden admin, I have seen this first hand. Operation Chokepoint 2.0 was a real thing and it was scary living through it. Actively seeing the government try to de-bank you was something I never would have thought was possible in the 'Land of the Free.'
The fact that the gov could de-bank you at all was an even bigger catalyst of how necessary a neutral, open, digital, and global money was critical for not only freedom itself, but our future.
Trump clearly is the better candidate regarding this. Yes, he may have launched a grifting shitcoin, but he doesn't want my industry — and financial freedom itself — dead. This is a no-brainer.
Andreessen Horowitz had a great podcast summarizing this that is worth the listen. It sums up where I sit as opposed to the current administration.
Trump has also promised to free Ross, which is absolutely necessary.
Last is food freedom.
I think the US is going the absolute wrong direction when it comes to health and food. In the name of saving animals and climate, food guidelines have been captured by this horrible, anti-human ideology.
I personally think it's not only necessary but good for humans to eat lots of beef and just meat in general. So much of what we've been told about nutrition and cholesterol is blatantly wrong.
Only one side of the aisle is trying to mandate this in the name of 'science.' I think they are wrong.
There is also only one side of the aisle that is anti-seed oils. I haven't eaten seed oils for almost four years, and bringing that mainstream, I think, is incredibly important. RFK is leading the way here. Trump putting him in a position of power to 'Make America Healthy Again,' I believe, is a fantastic initiative and one that is at the forefront for me for this election.
-
 @ ff18165a:dd7ca7f0
2024-10-19 18:23:51
@ ff18165a:dd7ca7f0
2024-10-19 18:23:51Chef's notes
- DO NOT add too much Peppermint Extract! It’s extremely strong and it will make your milkshake way too strong if you add more than a few drops.
- Feel free to be creative with your toppings. We used Caramel Flavored Whipped Topping and it turned out great!
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 2 min
- 🍽️ Servings: 1
Ingredients
- 1 1/2 cup Milk
- 2 drops Peppermint Extract
- 2 packets Stevia
- 1 cup Ice
- 2 drops Green Food Coloring
- Green Sprinkles
- 1 Crushed Peppermint Candy
- 2 Mint Leaves
Directions
-
- Blend together until smooth and frothy
-
- Pour into a tall glass
-
- Top with listed toppings
-
- Add straw and enjoy
-
 @ fd208ee8:0fd927c1
2024-11-03 21:51:39
@ fd208ee8:0fd927c1
2024-11-03 21:51:39All memed out
It finally happened. I think it was October 25th, at circa 18:45 in the evening. I was doomscrolling my Nostr feed, and kept seeing the same Bitcoin memes repeated over and over, by different people. They weren't even reposts, they were copy-pasted versions of the same image. A very funny image. Well, it was very funny last year... and the year before that... and probably the year before that, when it appeared on a different network.
Because it's all just reposts, copy-pastes and rehashes of the Best of Bitcoin Twitter, just like the tiresome influencers, with their groupies and their Episode 498 of Let's all eat a large chunk of lightly-burnt dead animal and count our stacks before jetting off to talk about how to save the poors by getting them to buy individual satoshis with money they don't have.

I'm the poors your looking for
It's all so tiresome. It has little bearing on the real world I see around me, where most people are thinking all day about 99 problems and Bitcoin ain't one.

Which is, of course, what the Bitcoin influencers would have you believe, is the reason that they're poor. What in the world could be more important, than thinking about Bitcoin? Why do these people not get with the program? Don't they know, that we are trying to save them?

Why are they worrying about OtherProblems? Don't they know that all OtherProblems can be fixed with Bitcoin? Really, if you just go back far enough, in any current, situational problem, you will discover that there was some slight, negative shift to the history record that involved soft money. It's the financial version of the Butterfly Effect.

That's why #BitcoinFixesThis. Bitcoin fixes everything, if you just think about it, for long enough.
The same way that we all actually come out of Africa, supposedly, if you go back enough generations. So, coming out of Africa, now, as a Real Life Person in The Present is supposed to have no significance. What does someone from Cameroon know about Africa, that someone from Alaska doesn't? Both people come out of Africa, if you just think about it, for long enough.

And maybe that really is true. Maybe Bitcoin will eventually end all vice and crimes, save the planet, and we will all just hold hands and sing kumbaya all day, while waiting for the Singularity to upload us to Satoshi.
Bitcoin envelope budgeting
Or maybe it's not. Maybe it's just a really hard, digital money that incentivizes savings, functions as a reliable measure, and makes micropayments possible on a global scale. Those really are things that will help the poors, including myself. I can see it, already, when trying to organize pre-paid meetups or figure out what to do with our household's meager savings, when the stock market is looking particularly bubblicious.

But this is what I would consider Boring Bitcoin. Bitcoin home economics. Penny-pinching Bitcoin. Bitcoin for homemakers. How to use the Bitcoin envelope budgeting system to beat inflation by a margin of 13%.
The actual use of Bitcoin as money, rather than as a mere investment gamble or hype machine. That's the part of Bitcoin that nobody seems to really talk about because it's incredibly practical, dull, and useful, and it can only be tested by -- Oh, the horror! -- actually spending Bitcoin.
But... perhaps I will begin talking about it. Perhaps those of us, Bitcoiners, who are having fun staying poor, while stacking sats, should speak up a bit more. Perhaps the boring stuff is actually the interesting stuff. Perhaps there is more to say about Bitcoin, than can fit into a meme.
-
 @ 5a69e82d:aa41c382
2024-11-05 11:50:02
@ 5a69e82d:aa41c382
2024-11-05 11:50:02Dhruv Bansal, CSO dan Co-Founder Unchained mengeksplorasi prinsip-prinsip dan sejarah yang mengarah pada penciptaan Bitcoin dan mengajukan pertanyaan: "Apa yang telah dilakukan Satoshi"?
Bitcoin sering dibandingkan dengan internet pada tahun 1990an, namun saya yakin analogi yang lebih baik adalah dengan telegraf pada tahun 1840an.[^1]
Telegraf adalah teknologi pertama yang mengirimkan data yang dikodekan dengan kecepatan mendekati cahaya dalam jarak jauh. Ini menandai lahirnya industri telekomunikasi. Internet, meskipun skalanya lebih besar, kontennya lebih kaya, dan many-to-many, bukan one-to-one, pada dasarnya masih merupakan teknologi telekomunikasi.
Baik telegraf maupun internet bergantung pada model bisnis di mana perusahaan mengerahkan modal untuk membangun jaringan fisik dan kemudian membebankan biaya kepada pengguna untuk mengirim pesan melalui jaringan ini. Jaringan AT&T secara historis mengirimkan telegram, panggilan telepon, paket TCP/IP, pesan teks, dan sekarang TikTok.
Transformasi masyarakat melalui telekomunikasi telah menghasilkan kebebasan yang lebih besar namun juga sentralisasi yang lebih besar. Internet telah meningkatkan jangkauan jutaan pembuat konten dan usaha kecil, namun juga memperkuat jangkauan perusahaan, otoritas pusat, dan lembaga lain yang memiliki posisi yang cukup baik untuk memantau dan memanipulasi aktivitas online.
Namun Bitcoin bukanlah akhir dari transformasi apa pun—ini adalah awal dari sebuah transformasi. Seperti halnya telekomunikasi, Bitcoin akan mengubah kebiasaan umat manusia dan kehidupan sehari-harinya. Memprediksi seluruh cakupan perubahan saat ini sama dengan membayangkan internet saat hidup di era telegraf.
Seri ini mencoba membayangkan masa depan dengan memulai dari masa lalu. Artikel awal ini menelusuri sejarah mata uang digital sebelum Bitcoin. Hanya dengan memahami kegagalan proyek-proyek sebelumnya, kita dapat memahami apa yang membuat Bitcoin berhasil—dan bagaimana hal itu menyarankan metodologi untuk membangun sistem desentralisasi di masa depan.
Daftar isi
- Sistem yang Terdesentralisasi Adalah Pasar
- Pasar yang Terdesentralisasi Membutuhkan Barang yang Terdesentralisasi
- Bagaimana Sistem Desentralisasi dapat Menentukan Harga Komputasi?
- Tujuan Kebijakan Moneter Satoshi Menghasilkan Bitcoin
- Kesimpulan
Klaim utama dari artikel ini adalah bahwa Bitcoin dapat dianggap sebagai adaptasi dari proyek B-money Dai yang menghilangkan kebebasan untuk menciptakan uang. Hanya beberapa minggu setelah artikel ini pertama kali diterbitkan, email baru muncul di mana Satoshi mengaku tidak terbiasa dengan B-money, namun mengakui bahwa Bitcoin dimulai “tepat dari titik itu.” Mengingat bukti baru ini, kami yakin klaim utama ini, meskipun tidak akurat secara historis, masih merupakan cara yang bermakna dan bermanfaat untuk memikirkan asal usul Bitcoin.
Bagaimana Satoshi Nakamoto Memikirkan Bitcoin?
Satoshi memang cerdas, tetapi Bitcoin tidak muncul begitu saja.
Bitcoin mengulangi pekerjaan yang ada di bidang kriptografi, sistem terdistribusi, ekonomi, dan filsafat politik. Konsep proof-of-work sudah ada jauh sebelum digunakan dalam uang dan cypherpunk sebelumnya seperti Nick Szabo, Wei Dai, & Hal Finney mengantisipasi dan memengaruhi desain Bitcoin dengan proyek-proyek seperti bit gold, B-money, dan RPoW. Pertimbangkan bahwa, pada tahun 2008, ketika Satoshi menulis white paper Bitcoin[^2], banyak ide penting Bitcoin telah diusulkan dan/atau diimplementasikan:
- Mata uang digital harus berupa jaringan P2P
- Proof-of-work adalah dasar penciptaan uang
- Uang diciptakan melalui lelang
- Kunci publik kriptografi digunakan untuk menentukan kepemilikan dan transfer koin
- Transaksi dikelompokkan menjadi beberapa blok
- Blok dirangkai bersama melalui proof-of-work
- Semua blok disimpan oleh semua peserta
Bitcoin memanfaatkan semua konsep ini, tetapi Satoshi tidak menciptakan satu pun konsep tersebut. Untuk lebih memahami kontribusi Satoshi, kita harus menentukan prinsip Bitcoin mana yang tidak ada dalam daftar.
Beberapa kandidat yang jelas adalah persediaan Bitcoin yang terbatas, konsensus Nakamoto, dan algoritma penyesuaian kesulitan. Tapi apa yang mendorong Satoshi pada ide ini?
Artikel ini mengeksplorasi sejarah mata uang digital dan menyatakan bahwa fokus Satoshi pada kebijakan moneter yang sehat adalah hal yang menyebabkan Bitcoin mengatasi tantangan yang mengalahkan proyek-proyek sebelumnya seperti bit gold dan B-money.
Sistem yang Terdesentralisasi Adalah Pasar
Bitcoin sering digambarkan sebagai sistem terdesentralisasi atau terdistribusi. Sayangnya, kata “desentralisasi” dan “terdistribusi” sering kali membingungkan. Ketika diterapkan pada sistem digital, kedua istilah tersebut mengacu pada cara aplikasi monolitik dapat didekomposisi menjadi jaringan bagian-bagian yang berkomunikasi.

Untuk tujuan kita, perbedaan utama antara sistem terdesentralisasi dan terdistribusi bukanlah topologi diagram jaringannya, namun cara mereka menegakkan aturan. Kami meluangkan waktu di bagian berikut untuk membandingkan sistem terdistribusi dan desentralisasi dan memotivasi gagasan bahwa sistem desentralisasi yang kuat adalah pasar.
Sistem Terdistribusikan Bergantung pada Otoritas Pusat
Dalam hal ini, kami mengartikan “terdistribusi” sebagai sistem apa pun yang telah dipecah menjadi beberapa bagian (sering disebut sebagai "node") yang harus berkomunikasi, biasanya melalui jaringan.
Insinyur perangkat lunak semakin mahir dalam membangun sistem yang terdistribusi secara global. Internet terdiri dari sistem terdistribusi yang secara kolektif berisi miliaran node. Kita masing-masing memiliki simpul di saku kita yang berpartisipasi dan bergantung pada sistem ini.
Namun hampir semua sistem terdistribusi yang kita gunakan saat ini diatur oleh beberapa otoritas pusat, biasanya administrator sistem, perusahaan, atau pemerintah yang saling dipercaya oleh semua node dalam sistem.
Otoritas pusat memastikan semua node mematuhi aturan sistem dan menghapus, memperbaiki, atau menghukum node yang gagal mematuhinya. Mereka dipercaya untuk melakukan koordinasi, menyelesaikan konflik, dan mengalokasikan sumber daya bersama. Seiring waktu, otoritas pusat mengelola perubahan pada sistem, memperbarui atau menambahkan fitur, dan memastikan bahwa node yang berpartisipasi mematuhi perubahan tersebut.
Manfaat yang diperoleh sistem terdistribusi karena mengandalkan otoritas pusat juga disertai dengan biaya. Meskipun sistem ini kuat terhadap kegagalan node-nodenya, kegagalan otoritas pusat dapat menyebabkan sistem berhenti berfungsi secara keseluruhan. Kemampuan otoritas pusat untuk mengambil keputusan secara sepihak berarti menumbangkan atau menghilangkan otoritas pusat sudah cukup untuk mengendalikan atau menghancurkan keseluruhan sistem.
Terlepas dari adanya trade-off ini, jika ada persyaratan bahwa satu partai atau koalisi harus mempertahankan otoritas pusat, atau jika peserta dalam sistem tersebut puas dengan mengandalkan otoritas pusat, maka sistem terdistribusi tradisional adalah solusi terbaik. Tidak diperlukan blockchain, token, atau sistem desentralisasi serupa.
Secara khusus, kasus VC atau mata uang kripto yang didukung oleh pemerintah, dengan persyaratan bahwa satu pihak dapat memantau atau membatasi pembayaran dan membekukan akun, adalah kasus penggunaan yang sempurna untuk sistem terdistribusi tradisional.
Sistem Desentralisasi Tidak Memiliki Otoritas Pusat
Kami menganggap “desentralisasi” memiliki arti yang lebih kuat daripada “terdistribusi”: sistem desentralisasi adalah bagian dari sistem terdistribusi yang tidak memiliki otoritas pusat. Sinonim yang mirip dengan “desentralisasi” adalah “peer-to-peer” (P2P).
Menghapus otoritas pusat memberikan beberapa keuntungan. Sistem terdesentralisasi:
- Tumbuh dengan cepat karena tidak ada hambatan untuk masuk—siapa pun dapat mengembangkan sistem hanya dengan menjalankan node baru, dan tidak ada persyaratan untuk registrasi atau persetujuan dari otoritas pusat.
- Kuat karena tidak ada otoritas pusat yang kegagalannya dapat membahayakan berfungsinya sistem. Semua node adalah sama, jadi kegagalan bersifat lokal dan jaringan merutekan sekitar kerusakan.
- Sulit untuk ditangkap, diatur, dikenakan pajak, atau diawasi karena tidak adanya titik kendali terpusat yang dapat ditumbangkan oleh pemerintah.
Kekuatan inilah yang menjadi alasan Satoshi memilih desain Bitcoin yang terdesentralisasi dan peer-to-peer:
“Pemerintah pandai memotong… jaringan yang dikendalikan secara terpusat seperti Napster, namun jaringan P2P murni seperti Gnutella dan Tor tampaknya masih mampu bertahan.” - Satoshi Nakamoto, 2008
Namun kekuatan ini juga disertai dengan kelemahan. Sistem yang terdesentralisasi bisa menjadi kurang efisien karena setiap titik harus memikul tanggung jawab tambahan untuk koordinasi yang sebelumnya diambil alih oleh otoritas pusat.
Sistem yang terdesentralisasi juga sering dilanda perilaku yang bersifat penipuan dan bertentangan. Terlepas dari persetujuan Satoshi terhadap Gnutella, siapa pun yang menggunakan program berbagi file P2P untuk mengunduh file yang ternyata kotor atau berbahaya memahami alasan mengapa berbagi file P2P tidak pernah menjadi model utama untuk transfer data online.
Satoshi tidak menyebutkannya secara eksplisit, namun email adalah sistem terdesentralisasi lainnya yang menghindari kendali pemerintah. Dan email juga terkenal sebagai spam.
Sistem Desentralisasi diatur Melalui Insentif
Akar masalahnya, dalam semua kasus ini adalah, bahwa perilaku kejahatan (menyebarkan file buruk, mengirim email spam) tidak dihukum, dan perilaku kooperatif (menyebarkan file bagus, hanya mengirim email berguna) tidak dihargai. Sistem desentralisasi yang mengandalkan partisipannya untuk menjadi aktor yang baik gagal untuk berkembang karena sistem tersebut tidak dapat mencegah aktor jahat untuk ikut berpartisipasi.
Tanpa memaksakan otoritas pusat, satu-satunya cara untuk menyelesaikan masalah ini adalah dengan menggunakan insentif ekonomi. Aktor yang baik, menurut definisinya, bermain sesuai aturan karena mereka secara inheren termotivasi untuk melakukannya. Pelaku kejahatan, menurut definisinya, adalah orang yang egois dan licik, namun insentif ekonomi yang tepat dapat mengarahkan perilaku buruk mereka ke arah kebaikan bersama. Sistem yang terdesentralisasi melakukan hal ini dengan memastikan bahwa perilaku kooperatif menguntungkan dan perilaku kejahatan merugikan.
Cara terbaik untuk menerapkan layanan terdesentralisasi yang kuat adalah dengan menciptakan pasar di mana semua pelaku, baik dan buruk, dibayar untuk menyediakan layanan tersebut. Kurangnya hambatan masuk bagi pembeli dan penjual di pasar yang terdesentralisasi mendorong skala dan efisiensi. Jika protokol pasar dapat melindungi partisipan dari penipuan, pencurian, dan penyalahgunaan, maka pelaku kejahatan akan merasa lebih menguntungkan untuk mengikuti aturan atau menyerang sistem lain.
Pasar yang Terdesentralisasi Membutuhkan Barang yang Terdesentralisasi
Namun pasar itu rumit. Mereka harus memberi pembeli dan penjual kemampuan untuk mengirimkan penawaran dan permintaan serta menemukan, mencocokkan, dan menyelesaikan pesanan. Kebijakan tersebut harus adil, memberikan konsistensi yang kuat, dan menjaga ketersediaan meskipun terjadi masa-masa yang tidak menentu.
Pasar global saat ini sangat mumpuni dan canggih, namun menggunakan barang-barang tradisional dan jaringan pembayaran untuk menerapkan insentif di pasar yang terdesentralisasi bukanlah hal yang baru. Setiap penggabungan antara sistem desentralisasi dan uang fiat, aset tradisional, atau komoditas fisik akan menimbulkan kembali ketergantungan pada otoritas pusat yang mengontrol pemroses pembayaran, bank, dan bursa.

Sistem terdesentralisasi tidak dapat mentransfer uang tunai, mencari saldo rekening perantara, atau menentukan kepemilikan properti. Barang-barang tradisional sama sekali tidak terbaca dalam sistem desentralisasi. Hal sebaliknya tidak benar—sistem tradisional dapat berinteraksi dengan Bitcoin semudah aktor lainnya (begitu mereka memutuskan ingin melakukannya). Batasan antara sistem tradisional dan desentralisasi bukanlah sebuah tembok yang tidak dapat dilewati, melainkan sebuah membran semi-permeabel.
Ini berarti bahwa sistem yang terdesentralisasi tidak dapat melaksanakan pembayaran dalam mata uang barang tradisional apa pun. Mereka bahkan tidak dapat menentukan saldo rekening yang didominasi fiat atau kepemilikan real estat atau barang fisik. Seluruh perekonomian tradisional sama sekali tidak terbaca dalam sistem desentralisasi.
Menciptakan pasar yang terdesentralisasi membutuhkan perdagangan barang-barang baru yang terdesentralisasi yang dapat dibaca dan ditransfer dalam sistem yang terdesentralisasi.
Komputasi Adalah Barang Terdesentralisasi yang Pertama
Contoh pertama dari “barang terdesentralisasi” adalah kelas komputasi khusus yang pertama kali diusulkan pada tahun 1993 oleh Cynthia Dwork dan Moni Naor.[^3]
Karena adanya hubungan mendalam antara matematika, fisika, dan ilmu komputer, komputasi ini memerlukan energi dan sumber daya perangkat keras di dunia nyata—hal ini tidak dapat dipalsukan. Karena sumber daya di dunia nyata langka, komputasi ini juga langka.
input untuk komputasi ini dapat berupa data apa pun. Keluaran yang dihasilkan adalah “bukti” digital bahwa pengkomputasian telah dilakukan pada data input yang diberikan. Pembuktian mengandung “kesulitan” tertentu yang merupakan bukti (statistik) dari sejumlah pekerjaan komputasi tertentu. Yang terpenting, hubungan antara data input, pembuktian, dan pekerjaan komputasi asli yang dilakukan dapat diverifikasi secara independen tanpa perlu mengajukan banding ke otoritas pusat mana pun.
Gagasan untuk menyebarkan beberapa data input bersama dengan bukti digital sebagai bukti kerja komputasi dunia nyata yang dilakukan pada input tersebut sekarang disebut “proof-of-work”.[^4] Proof-of-work adalah, jika menggunakan ungkapan Nick Szabo, “biaya yang tidak dapat ditiru”. Karena proof-of-work dapat diverifikasi oleh siapa pun, maka proof-of-work merupakan sumber daya ekonomi yang dapat dibaca oleh semua peserta dalam sistem desentralisasi. Proof-of-work mengubah penghitungan data menjadi barang yang terdesentralisasi. Dwork & Naor mengusulkan penggunaan komputasi untuk membatasi penyalahgunaan sumber daya bersama dengan memaksa peserta untuk memberikan proof-of-work dengan tingkat kesulitan minimum tertentu sebelum mereka dapat mengakses sumber daya:
“Dalam makalah ini kami menyarankan pendekatan komputasi untuk memerangi penyebaran surat elektronik. Secara umum, kami telah merancang mekanisme kontrol akses yang dapat digunakan kapan pun diinginkan untuk membatasi, namun tidak melarang, akses ke sumber daya.” - Dwoak & Naor, 1993
Dalam proposal Dwork & Naor, administrator sistem email akan menetapkan tingkat kesulitan bukti kerja minimum untuk mengirimkan email. Pengguna yang ingin mengirim email perlu melakukan sejumlah komputasi yang sesuai dengan email tersebut sebagai data input. Bukti yang dihasilkan akan dikirimkan ke server bersamaan dengan permintaan pengiriman email.
Dwork & Naor menyebut kesulitan proof-of-work sebagai “fungsi penetapan harga” karena, dengan menyesuaikan kesulitan tersebut, “otoritas penetapan harga” dapat memastikan bahwa sumber daya bersama tetap murah untuk digunakan bagi pengguna yang jujur dan rata-rata, namun mahal bagi pengguna yang mencari untuk mengeksploitasinya. Di pasar pengiriman email, administrator server adalah otoritas penetapan harga; mereka harus memilih “harga” untuk pengiriman email yang cukup rendah untuk penggunaan normal namun terlalu tinggi untuk spam.
Meskipun Dwork & Naor membingkai proof-of-work sebagai disinsentif ekonomi untuk memerangi penyalahgunaan sumber daya, nomenklatur “fungsi penetapan harga” dan “otoritas penetapan harga” mendukung interpretasi yang berbeda dan berbasis pasar: pengguna membeli akses ke sumber daya dengan imbalan komputasi pada tingkat yang sama. harga yang ditetapkan oleh pengontrol sumber daya.
Dalam interpretasi ini, jaringan pengiriman email sebenarnya adalah pengiriman email perdagangan pasar yang terdesentralisasi untuk komputasi. Kesulitan minimum dari proof-of-work adalah harga yang diminta untuk pengiriman email dalam mata uang komputasi.
Mata Uang Adalah Barang Terdesentralisasi yang kedua
Namun komputasi bukanlah mata uang yang baik.
Bukti yang digunakan untuk “memperdagangkan” komputasi hanya valid untuk input yang digunakan dalam komputasi tersebut. Hubungan yang tidak dapat dipecahkan antara bukti spesifik dan input tertentu berarti bahwa proof-of-work untuk satu input tidak dapat digunakan kembali untuk input yang berbeda.

Proof-of-work awalnya diusulkan sebagai mekanisme kontrol akses untuk membatasi email spam. Pengguna diharapkan memberikan bukti kerja bersama email apa pun yang ingin mereka kirim. Mekanisme ini juga dapat dianggap sebagai pasar di mana pengguna membeli pengiriman email dengan komputasi pada harga yang dipilih oleh penyedia layanan email.
Batasan ini berguna – dapat digunakan untuk mencegah pekerjaan yang dilakukan oleh satu pembeli di pasar kemudian dibelanjakan kembali oleh pembeli lain. Misalnya, HashCash, implementasi nyata pertama dari pasar pengiriman email, menyertakan metadata seperti stempel waktu saat ini dan alamat email pengirim dalam data masukan untuk penghitungan bukti kerja. Bukti yang dihasilkan oleh pengguna tertentu untuk email tertentu, tidak dapat digunakan untuk email yang berbeda.
Namun ini juga berarti bahwa komputasi bukti kerja adalah barang yang dipesan lebih dahulu. Dana tersebut tidak dapat dipertukarkan, tidak dapat dibelanjakan kembali,[^5] dan tidak memecahkan masalah kebutuhan yang terjadi secara kebetulan. Properti moneter yang hilang ini mencegah komputasi menjadi mata uang. Terlepas dari namanya, tidak ada insentif bagi penyedia pengiriman email untuk ingin mengakumulasikan HashCash, karena akan ada uang tunai sebenarnya.
Adam Back, penemu HashCash, memahami masalah berikut:
"Hashcash tidak dapat ditransfer secara langsung karena untuk membuatnya didistribusikan, setiap penyedia layanan hanya menerima pembayaran dalam bentuk tunai yang dibuat untuk mereka. Anda mungkin dapat menyiapkan pencetakan gaya digicash (dengan chaumian ecash) dan meminta bank hanya mencetak uang tunai pada penerimaan tabrakan hash yang ditangani. Namun ini berarti Anda harus mempercayai bank untuk tidak mencetak uang dalam jumlah tak terbatas untuk digunakan sendiri." - Adam Back, 1997
Kita tidak ingin menukar komputasi yang dibuat khusus untuk setiap barang atau jasa yang dijual dalam perekonomian yang terdesentralisasi. Kita menginginkan mata uang digital serba guna yang dapat langsung digunakan untuk mengoordinasikan pertukaran nilai di pasar mana pun.
Membangun mata uang digital yang berfungsi namun tetap terdesentralisasi merupakan tantangan yang signifikan. Mata uang membutuhkan unit yang dapat dipertukarkan dengan nilai yang sama yang dapat ditransfer antar pengguna. Hal ini memerlukan model penerbitan, definisi kriptografi kepemilikan dan transfer, proses penemuan dan penyelesaian transaksi, dan buku besar historis. Infrastruktur ini tidak diperlukan ketika bukti kerja hanya dianggap sebagai “mekanisme kontrol akses”.
Terlebih lagi, sistem desentralisasi adalah pasar, jadi semua fungsi dasar mata uang ini harus disediakan melalui penyedia layanan berbayar… dalam satuan mata uang yang sedang dibuat!
Seperti mengkompilasi compiler pertama, permulaan jaringan listrik yang gelap, atau evolusi kehidupan itu sendiri, pencipta mata uang digital dihadapkan pada masalah bootstrapping: bagaimana mendefinisikan insentif ekonomi yang mendasari mata uang yang berfungsi tanpa memiliki mata uang yang berfungsi di dalamnya yang akan mendenominasikan atau membayar insentif tersebut.

Komputasi dan mata uang adalah barang pertama dan kedua di pasar yang terdesentralisasi. Proof-of-work sendiri memungkinkan pertukaran komputasi tetapi mata uang yang berfungsi memerlukan lebih banyak infrastruktur. Butuh waktu 15 tahun bagi komunitas cypherpunk untuk mengembangkan infrastruktur tersebut.
Pasar Terdesentralisasi Pertama harus Memperdagangkan Komputasi untuk Mata Uang
Kemajuan dalam masalah bootstrapping ini berasal dari penyusunan batasan yang tepat.
Sistem yang terdesentralisasi harus menjadi pasar. Pasar terdiri dari pembeli dan penjual yang saling bertukar barang. Pasar terdesentralisasi untuk mata uang digital hanya memiliki dua barang yang dapat dibaca di dalamnya:
- Komputasi melalui proof-of-work
- Unit mata uang yang kita coba bangun
Oleh karena itu, satu-satunya perdagangan pasar yang memungkinkan adalah antara kedua barang tersebut. Komputasi harus dijual untuk satuan mata uang atau setara dengan satuan mata uang harus dijual untuk komputasi. Menyatakan hal ini sangatlah mudah—bagian tersulitnya adalah menata pasar ini sehingga sekadar menukar mata uang untuk komputasi akan mem-bootstrap semua kemampuan mata uang itu sendiri!
Seluruh sejarah mata uang digital yang berpuncak pada white paper Satoshi tahun 2008 adalah serangkaian upaya yang semakin canggih dalam menata pasar ini. Bagian berikut mengulas proyek-proyek seperti bit gold milik Nick Szabo dan B-money milik Wei Dai. Memahami bagaimana proyek-proyek ini menyusun pasar mereka dan mengapa mereka gagal akan membantu kita memahami mengapa Satoshi dan Bitcoin berhasil.

Bagaimana Sistem Desentralisasi Dapat Menentukan Harga Komputasi?
Fungsi utama pasar adalah penemuan harga. Oleh karena itu, komputasi perdagangan pasar untuk mata uang harus menemukan harga komputasi itu sendiri, dalam satuan mata uang tersebut.
Kita biasanya tidak memberikan nilai moneter pada komputasi. Kita biasanya menghargai kapasitas untuk melakukan komputasi karena kita menghargai output dari komputasi, bukan komputasi itu sendiri. Jika keluaran yang sama dapat dilakukan dengan lebih efisien, dengan komputasi yang lebih sedikit, hal ini biasanya disebut “kemajuan”.
Proof-of-work mewakili komputasi spesifik yang keluarannya hanya berupa bukti bahwa komputasi tersebut telah dilakukan. Menghasilkan bukti yang sama dengan melakukan lebih sedikit komputasi dan lebih sedikit pekerjaan tidak akan menghasilkan kemajuan—hal ini akan menjadi bug. Oleh karena itu, komputasi yang terkait dengan Proof-of-work merupakan hal yang aneh dan baru untuk dicoba dihargai.
Ketika bukti kerja dianggap sebagai disinsentif terhadap penyalahgunaan sumber daya, maka bukti kerja tidak perlu dinilai secara tepat dan konsisten. Yang terpenting adalah penyedia layanan email menetapkan tingkat kesulitan yang cukup rendah sehingga tidak terlihat oleh pengguna yang sah, namun cukup tinggi sehingga menjadi penghalang bagi pelaku spam. Oleh karena itu, terdapat beragam “harga” yang dapat diterima dan setiap peserta bertindak sebagai otoritas penetapan harga mereka sendiri, dengan menerapkan fungsi penetapan harga lokal.
Namun satuan mata uang dimaksudkan agar dapat dipertukarkan, masing-masing memiliki nilai yang sama. Karena perubahan teknologi dari waktu ke waktu, dua unit mata uang yang dibuat dengan tingkat kesulitan proof-of-work yang sama—yang diukur dengan jumlah komputasi yang sesuai—mungkin memiliki biaya produksi yang sangat berbeda di dunia nyata, yang diukur dengan waktu, energi, dan/atau modal untuk melakukan komputasi tersebut. Ketika komputasi dijual dengan menggunakan mata uang, dan biaya produksi yang mendasarinya bervariasi, bagaimana pasar dapat memastikan harga yang konsisten?
Nick Szabo dengan jelas mengidentifikasi masalah harga ini ketika menjelaskan bit gold:
"Masalah utamanya...adalah bahwa skema pembuktian kerja bergantung pada arsitektur komputer, bukan hanya matematika abstrak yang didasarkan pada "siklus komputasi" abstrak. ...Jadi, ada kemungkinan untuk menjadi produsen berbiaya sangat rendah (dengan beberapa kali lipat besarnya) dan membanjiri pasar dengan bit gold." - Szabo, 2005

Mata uang terdesentralisasi yang diciptakan melalui proof-of-work akan mengalami kelebihan pasokan dan penurunan pasokan seiring dengan perubahan pasokan komputasi seiring waktu. Untuk mengakomodasi volatilitas ini, jaringan harus belajar menghitung harga secara dinamis.
Mata uang digital awal mencoba memberi harga pada komputasi dengan mencoba mengukur “biaya komputasi” secara kolektif. Wei Dai, misalnya, mengusulkan solusi praktis berikut dalam B-money:
"Jumlah unit moneter yang diciptakan sama dengan biaya upaya komputasi dalam sekeranjang komoditas standar. Sebagai contoh, jika sebuah masalah memerlukan waktu 100 jam untuk diselesaikan pada komputer yang dapat menyelesaikannya dengan cara yang paling ekonomis, dan diperlukan 3 keranjang standar untuk membeli 100 jam waktu komputasi pada komputer tersebut di pasar terbuka, maka setelah solusi terhadap masalah tersebut disiarkan, setiap orang mengkredit rekening penyiar sebanyak 3 unit." - Dai, 1998
Sayangnya, Dai tidak menjelaskan bagaimana pengguna dalam sistem yang seharusnya terdesentralisasi seharusnya menyetujui definisi “keranjang standar”, komputer mana yang memecahkan masalah tertentu “paling ekonomis”, atau biaya komputasi di “pasar terbuka”. Mencapai konsensus di antara semua pengguna mengenai kumpulan data bersama yang berubah-ubah terhadap waktu adalah masalah penting dalam sistem desentralisasi!
Agar adil bagi Dai, dia menyadari hal ini:
“Salah satu bagian yang lebih bermasalah dalam protokol B-money adalah penciptaan uang. Bagian dari protokol ini mengharuskan semua [pengguna] memutuskan dan menyetujui biaya perhitungan tertentu. Sayangnya karena teknologi komputasi cenderung berkembang pesat dan tidak selalu bersifat publik, informasi ini mungkin tidak tersedia, tidak akurat, atau ketinggalan jaman, yang semuanya akan menyebabkan masalah serius pada protokol." - Dai, 1998
Dai kemudian mengusulkan mekanisme penetapan harga berbasis lelang yang lebih canggih yang kemudian dikatakan Satoshi sebagai titik awal idenya. Kita akan kembali ke skema lelang di bawah ini, tapi pertama-tama mari kita beralih ke bit gold, dan pertimbangkan wawasan Szabo tentang masalahnya.
Gunakan Pasar Eksternal
Szabo mengklaim bahwa proof-of-work harus “diberi stempel waktu dengan aman”:
"Bukti kerja diberi stempel waktu yang aman. Ini harus bekerja secara terdistribusi, dengan beberapa layanan stempel waktu berbeda sehingga tidak ada layanan stempel waktu tertentu yang perlu diandalkan secara substansial." - Szabo, 2005
Szabo tertaut ke halaman sumber daya tentang protokol penandaan waktu yang aman tetapi tidak menjelaskan algoritme spesifik apa pun untuk penandaan waktu yang aman. Ungkapan “aman” dan “fesyen terdistribusi” mempunyai pengaruh yang besar di sini, sehingga dapat mengatasi kerumitan dalam mengandalkan satu (atau banyak) layanan “di luar sistem” untuk penandaan waktu.[^6]

Waktu pembuatan unit mata uang digital penting karena menghubungkan komputasi yang dilakukan dengan biaya produksi di dunia nyata.
Terlepas dari ketidakjelasan implementasi, Szabo benar—waktu pembuatan proof-of-work merupakan faktor penting dalam menentukan harga karena terkait dengan biaya komputasi:
"…Namun, karena bit gold diberi stempel waktu, waktu yang dibuat serta tingkat kesulitan matematis dari pekerjaan tersebut dapat dibuktikan secara otomatis. Dari sini, biasanya dapat disimpulkan berapa biaya produksi selama periode waktu tersebut..." - Szabo, 2005
"Menyimpulkan" biaya produksi adalah hal yang penting karena bit gold tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat bit gold dengan melakukan perhitungan yang sesuai. Tanpa kemampuan untuk mengatur penerbitan, bit gold sama dengan barang koleksi:
"…Tidak seperti atom emas yang dapat dipertukarkan, tetapi seperti halnya barang-barang kolektor, pasokan dalam jumlah besar selama jangka waktu tertentu akan menurunkan nilai barang-barang tersebut. Dalam hal ini, emas kecil bertindak lebih seperti barang-barang kolektor daripada seperti emas..." - Szabo, 2005
Bit gold memerlukan proses eksternal tambahan untuk menciptakan unit mata uang yang sepadan:
“…[B]it Gold tidak dapat dipertukarkan berdasarkan fungsi sederhana, misalnya, panjang tali. Sebaliknya, untuk membuat unit yang dapat dipertukarkan, dealer harus menggabungkan potongan-potongan bit gold dengan nilai berbeda ke dalam satuan yang lebih besar kira-kira dengan nilai yang sama. Hal ini serupa dengan apa yang dilakukan banyak pedagang komoditas saat ini untuk memungkinkan pasar komoditas bekerja. Kepercayaan masih terdistribusi karena perkiraan nilai dari kumpulan tersebut dapat diverifikasi secara independen oleh banyak pihak lain dengan cara yang sebagian besar atau seluruhnya otomatis." - Szabo, 2005
Mengutip Szabo, “untuk menguji nilai… bit gold, dealer memeriksa dan memverifikasi tingkat kesulitan, masukan, dan stempel waktu”. Dealer yang mendefinisikan “unit yang lebih besar dengan nilai yang kira-kira sama” menyediakan fungsi penetapan harga yang serupa dengan “keranjang komoditas standar” Dai. Unit yang dapat dipertukarkan tidak dibuat dalam bentuk bit gold ketika bukti kerja diproduksi, hanya kemudian ketika bukti tersebut digabungkan menjadi “unit yang kira-kira bernilai sama” oleh dealer di pasar di luar jaringan.

Yang patut disyukuri, Szabo mengakui kelemahan ini:
"…Potensi kelebihan pasokan yang awalnya tersembunyi karena inovasi tersembunyi dalam arsitektur mesin adalah potensi kelemahan dalam bit gold, atau setidaknya ketidaksempurnaan yang harus diatasi oleh lelang awal dan pertukaran ex post bit gold." - Szabo, 2005
Sekali lagi, meskipun belum sampai pada (yang sekarang kita kenal sebagai) solusinya, Szabo menunjukkan solusinya: karena biaya komputasi berubah seiring waktu, jaringan harus merespons perubahan pasokan komputasi dengan menyesuaikan harga uang.
Gunakan Pasar Internal
Dealer Szabo akan menjadi pasar eksternal yang menentukan harga (bundel dari) bit gold setelah penciptaannya. Apakah mungkin menerapkan pasar ini di dalam sistem dan bukan di luar sistem?
Mari kita kembali ke Wei Dai dan B-money. Seperti disebutkan sebelumnya, Dai mengusulkan model alternatif berbasis lelang untuk pembuatan B-money. Desain Satoshi untuk Bitcoin meningkat secara langsung pada model lelang B-money[^7]:
“Jadi saya mengusulkan subprotokol penciptaan uang alternatif, di mana [pengguna]… memutuskan dan menyetujui jumlah B-money yang akan dibuat setiap periode, dengan biaya pembuatan uang tersebut ditentukan melalui lelang. Setiap periode pembuatan uang adalah dibagi menjadi empat tahap, sebagai berikut:
Planning. Para [pengguna] menghitung dan bernegosiasi satu sama lain untuk menentukan peningkatan jumlah uang beredar yang optimal untuk periode berikutnya. Apakah [jaringan] dapat mencapai konsensus atau tidak, mereka masing-masing menyiarkan kuota penciptaan uang mereka dan komputasi makroekonomi apa pun yang dilakukan untuk mendukung angka tersebut.
Bidding. Siapapun yang ingin membuat B-money menyiarkan tawaran dalam bentuk dimana x adalah banyaknya B-money yang ingin dibuatnya, dan y adalah soal yang belum terselesaikan dari kelas soal yang telah ditentukan. Setiap masalah di kelas ini harus memiliki biaya nominal (katakanlah dalam MIPS-years) yang disetujui secara publik.
Computation. Setelah melihat penawaran, pihak yang mengajukan penawaran pada tahap penawaran sekarang dapat menyelesaikan masalah dalam penawarannya dan menyiarkan solusinya. Penciptaan uang.
Money creation. Setiap [pengguna] menerima tawaran tertinggi (di antara mereka yang benar-benar menyiarkan solusi) dalam hal biaya nominal per unit B-money yang dibuat dan memberikan kredit kepada akun penawar sesuai dengan itu."
- Dai, 1998B-money membuat kemajuan signifikan menuju struktur pasar yang tepat untuk mata uang digital. Ini berupaya untuk menghilangkan dealer eksternal Szabo dan memungkinkan pengguna untuk terlibat dalam penemuan harga dengan menawar satu sama lain secara langsung.
Namun menerapkan proposal Dai seperti yang tertulis akan menjadi sebuah tantangan:
- Dalam fase "Planning”, pengguna menanggung beban menegosiasikan “peningkatan optimal jumlah uang beredar untuk periode berikutnya”. Bagaimana “optimal” harus didefinisikan, bagaimana pengguna harus bernegosiasi satu sama lain, dan bagaimana hasil negosiasi tersebut dibagikan tidak dijelaskan.
- Terlepas dari apa yang direncanakan, fase “Bidding” memungkinkan siapa saja untuk mengajukan “tawaran” untuk membuat B-money. Tawaran mencakup jumlah B-money yang akan dibuat serta jumlah bukti kerja yang sesuai sehingga setiap penawaran adalah harga, jumlah perhitungan yang bersedia dilakukan oleh penawar tertentu untuk membeli sejumlah tertentu. dari B-money.
- Setelah penawaran diserahkan, fase “Computation” terdiri dari peserta lelang yang melakukan proof-of-work yang mereka tawarkan dan menyiarkan solusi. Tidak ada mekanisme untuk mencocokkan penawar dengan solusi yang disediakan. Yang lebih problematis adalah tidak jelasnya bagaimana pengguna dapat mengetahui bahwa semua penawaran telah diajukan – kapan fase “Bidding” berakhir dan fase “Computation” dimulai?
- Masalah-masalah ini berulang dalam fase “Money creation”. Karena sifat proof-of-work, pengguna dapat memverifikasi bahwa bukti yang mereka terima dalam solusi adalah asli. Namun bagaimana pengguna dapat secara kolektif menyepakati serangkaian “tawaran tertinggi”? Bagaimana jika pengguna yang berbeda memilih set yang berbeda, baik karena preferensi atau latensi jaringan?
Sistem yang terdesentralisasi kesulitan dalam melacak data dan membuat pilihan secara konsisten, namun B-money memerlukan pelacakan tawaran dari banyak pengguna dan membuat pilihan konsensus di antara mereka. Kompleksitas ini menghalangi penerapan B-money.
Akar dari kompleksitas ini adalah keyakinan Dai bahwa tingkat “optimal” penciptaan B-money harus berfluktuasi seiring waktu berdasarkan “perhitungan makroekonomi” penggunanya. Seperti bit gold, B-money tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat unit B-money dengan menyiarkan tawaran dan kemudian melakukan proof-of-work yang sesuai.
Baik Szabo maupun Dai mengusulkan penggunaan pasar pertukaran mata uang digital untuk komputasi, namun baik bit gold maupun B-money tidak menentukan kebijakan moneter untuk mengatur pasokan mata uang di pasar ini.
Tujuan Kebijakan Moneter Satoshi Menghasilkan Bitcoin
Sebaliknya, kebijakan moneter yang sehat adalah salah satu tujuan utama Satoshi dalam proyek Bitcoin. Dalam postingan milis pertama tempat Bitcoin diumumkan, Satoshi menulis:
“Akar permasalahan mata uang konvensional adalah kepercayaan yang diperlukan agar mata uang tersebut dapat berfungsi. Bank sentral harus dipercaya untuk tidak merendahkan mata uang tersebut, namun sejarah mata uang fiat penuh dengan pelanggaran terhadap kepercayaan tersebut.” - Satoshi, 2009
Satoshi selanjutnya menjelaskan masalah lain dengan mata uang fiat seperti perbankan cadangan fraksional yang berisiko, kurangnya privasi, pencurian & penipuan yang merajalela, dan ketidakmampuan melakukan pembayaran mikro. Namun Satoshi memulai dengan isu penurunan nilai oleh bank sentral—dengan kekhawatiran mengenai kebijakan moneter.
Satoshi ingin Bitcoin pada akhirnya mencapai pasokan sirkulasi terbatas yang tidak dapat terdilusi seiring waktu. Tingkat penciptaan Bitcoin yang “optimal”, bagi Satoshi, pada akhirnya akan menjadi nol.
Tujuan kebijakan moneter ini, lebih dari karakteristik lain yang mereka miliki secara pribadi (atau kolektif!), adalah alasan Satoshi “menemukan” Bitcoin, blockchain, konsensus Nakamoto, dll. —dan bukan orang lain. Ini adalah jawaban singkat atas pertanyaan yang diajukan dalam judul artikel ini: Satoshi memikirkan Bitcoin karena mereka fokus pada penciptaan mata uang digital dengan persediaan terbatas.
Pasokan Bitcoin yang terbatas bukan hanya tujuan kebijakan moneter atau meme bagi para Bitcoiner untuk berkumpul. Penyederhanaan teknis penting inilah yang memungkinkan Satoshi membangun mata uang digital yang berfungsi sementara B-money Dai tetap menjadi postingan web yang menarik.
Bitcoin adalah B-money dengan persyaratan tambahan berupa kebijakan moneter yang telah ditentukan. Seperti banyak penyederhanaan teknis lainnya, pembatasan kebijakan moneter memungkinkan kemajuan dengan mengurangi ruang lingkup. Mari kita lihat bagaimana masing-masing fase pembuatan B-money disederhanakan dengan menerapkan batasan ini.
Semua Pasokan 21 Juta Bitcoin Sudah Ada
Dalam b-money, setiap “periode penciptaan uang” mencakup fase “Perencanaan”, di mana pengguna diharapkan untuk membagikan “perhitungan makroekonomi” mereka yang membenarkan jumlah b-money yang ingin mereka ciptakan pada saat itu. Tujuan kebijakan moneter Satoshi yaitu pasokan terbatas dan emisi nol tidak sesuai dengan kebebasan yang diberikan b-money kepada pengguna individu untuk menghasilkan uang. Oleh karena itu, langkah pertama dalam perjalanan dari bmoney ke bitcoin adalah menghilangkan kebebasan ini. Pengguna bitcoin perorangan tidak dapat membuat bitcoin. Hanya jaringan bitcoin yang dapat membuat bitcoin, dan hal ini terjadi tepat sekali, pada tahun 2009 ketika Satoshi meluncurkan proyek bitcoin.
Satoshi mampu menggantikan fase “Perencanaan” b-money yang berulang menjadi satu jadwal yang telah ditentukan sebelumnya di mana 21 juta bitcoin yang dibuat pada tahun 2009 akan dilepaskan ke peredaran. Pengguna secara sukarela mendukung kebijakan moneter Satoshi dengan mengunduh dan menjalankan perangkat lunak Bitcoin Core yang kebijakan moneternya dikodekan secara keras.
Hal ini mengubah semantik pasar bitcoin untuk komputasi. Bitcoin yang dibayarkan kepada penambang bukanlah hal baru yang diterbitkan; itu melainkan baru dirilis ke peredaran dari persediaan yang ada.
Pandangan ini sangat berbeda dari klaim naif bahwa “penambang bitcoin menciptakan bitcoin”. Penambang Bitcoin tidak menciptakan bitcoin, mereka membelinya. Bitcoin tidak berharga karena “bitcoin terbuat dari energi”—tetapi nilai bitcoin didemonstrasikan dengan dijual untuk mendapatkan energi.
Mari kita ulangi sekali lagi: bitcoin tidak dibuat melalui proof-of-work, bitcoin dibuat melalui konsensus.

Desain Satoshi menghilangkan persyaratan untuk fase “Perencanaan” yang berkelanjutan dari b-money dengan melakukan semua perencanaan terlebih dahulu. Hal ini memungkinkan Satoshi untuk membuat kebijakan moneter yang sehat namun juga menyederhanakan penerapan bitcoin.
Bitcoin dihargai Melalui Konsensus
Kebebasan yang diberikan kepada pengguna untuk menghasilkan uang menimbulkan beban yang sesuai bagi jaringan bmoney. Selama fase “Penawaran” jaringan b-money harus mengumpulkan dan membagikan “tawaran” pembuatan uang dari banyak pengguna yang berbeda.
Menghilangkan kebebasan untuk menghasilkan uang akan meringankan beban jaringan bitcoin. Karena seluruh 21 juta bitcoin sudah ada, jaringan tidak perlu mengumpulkan tawaran dari pengguna untuk menghasilkan uang, jaringan hanya perlu menjual bitcoin sesuai jadwal Satoshi yang telah ditentukan.
Jaringan bitcoin dengan demikian menawarkan konsensus harga permintaan untuk bitcoin yang dijualnya di setiap blok. Harga tunggal ini dihitung oleh setiap node secara independen menggunakan salinan blockchainnya. Jika node memiliki konsensus pada blockchain yang sama (poin yang akan kita bahas nanti) mereka semua akan menawarkan harga permintaan yang sama di setiap blok.[^8]
Bagian pertama kalkulasi harga konsensus menentukan berapa banyak bitcoin yang akan dijual. Hal ini diperbaiki oleh jadwal rilis Satoshi yang telah ditentukan sebelumnya. Semua node bitcoin di jaringan menghitung jumlah yang sama untuk blok tertentu:
$ bitcoin-cli getblockstats <block\_height> {... "subsidy": 6250000000, ... } # 6.25 BTCBagian kedua dari harga yang diminta secara konsensus adalah jumlah komputasi yang akan menjual subsidi saat ini. Sekali lagi, semua node bitcoin di jaringan menghitung nilai yang sama (kita akan meninjau kembali kalkulasi tingkat kesulitan ini di bagian berikutnya):
$ bitcoin-cli getdifficulty {... "result": 55621444139429.57, ... }Bersama-sama, subsidi dan kesulitan jaringan menentukan permintaan bitcoin saat ini sebagai mata uang komputasi. Karena blockchain berada dalam konsensus, harga ini adalah harga konsensus.
Pengguna b-money juga dianggap memiliki konsensus “blockchain” yang berisi riwayat semua transaksi. Namun Dai tidak pernah memikirkan solusi sederhana berupa konsensus tunggal yang meminta harga untuk pembuatan b-money baru, yang hanya ditentukan oleh data di blockchain tersebut.
Sebaliknya, Dai berasumsi bahwa penciptaan uang harus berlangsung selamanya. Oleh karena itu, pengguna individu perlu diberdayakan untuk mempengaruhi kebijakan moneter – seperti halnya mata uang fiat. Persyaratan yang dirasakan ini membuat Dai merancang sistem penawaran yang mencegah penerapan b-money.
Kompleksitas tambahan ini dihilangkan dengan persyaratan Satoshi mengenai kebijakan moneter yang telah ditentukan sebelumnya.
Waktu Menutup Semua Penyebaran
Dalam fase “Komputasi” b-money, pengguna individu akan melakukan komputasi yang telah mereka lakukan dalam penawaran sebelumnya. Dalam bitcoin, seluruh jaringan adalah penjual – tetapi siapa pembelinya?
Di pasar pengiriman email, pembelinya adalah individu yang ingin mengirim email. Otoritas penetapan harga, penyedia layanan email, akan menetapkan harga yang dianggap murah bagi individu namun mahal bagi pelaku spam. Namun jika jumlah pengguna yang sah bertambah, harganya masih bisa tetap sama karena kekuatan komputasi masing-masing pengguna akan tetap sama.
Di b-money, setiap pengguna yang menyumbangkan tawaran untuk pembuatan uang selanjutnya harus melakukan sendiri jumlah komputasi yang sesuai. Setiap pengguna bertindak sebagai otoritas penetapan harga berdasarkan pengetahuan mereka tentang kemampuan komputasi mereka sendiri.
Jaringan bitcoin menawarkan satu harga yang diminta dalam komputasi subsidi bitcoin saat ini. Namun tidak ada penambang individu yang menemukan blok yang melakukan komputasi sebanyak ini.[^9] Blok pemenang penambang individu adalah bukti bahwa semua penambang secara kolektif melakukan jumlah komputasi yang diperlukan. Pembeli bitcoin dengan demikian adalah industri penambangan bitcoin global.
Setelah mencapai konsensus harga yang diminta, jaringan bitcoin tidak akan mengubah harga tersebut sampai lebih banyak blok diproduksi. Blok-blok ini harus berisi proof-of-work dengan harga yang diminta saat ini. Oleh karena itu, industri pertambangan tidak punya pilihan jika ingin “melakukan perdagangan” selain membayar harga yang diminta saat ini dalam komputasi.
Satu-satunya variabel yang dapat dikontrol oleh industri pertambangan adalah berapa lama waktu yang dibutuhkan untuk memproduksi blok berikutnya. Sama seperti jaringan bitcoin yang menawarkan satu harga yang diminta, industri pertambangan juga menawarkan satu penawaran—waktu yang diperlukan untuk menghasilkan blok berikutnya yang memenuhi harga yang diminta jaringan saat ini.
Untuk mengimbangi peningkatan kecepatan perangkat keras dan minat yang berbeda-beda dalam menjalankan node dari waktu ke waktu, kesulitan proof-of-work ditentukan oleh rata-rata bergerak yang menargetkan jumlah rata-rata blok per jam. Jika dihasilkan terlalu cepat, kesulitannya akan meningkat. - Nakamoto, 2008
Satoshi dengan sederhana menjelaskan algoritma penyesuaian kesulitan, yang sering disebut sebagai salah satu ide paling orisinal dalam implementasi bitcoin. Hal ini benar, namun alih-alih berfokus pada daya cipta solusi, mari kita fokus pada mengapa penyelesaian masalah sangat penting bagi Satoshi.
Proyek-proyek seperti bit gold dan b-money tidak perlu membatasi nilai tukar pada saat penciptaan uang karena mereka tidak memiliki pasokan tetap atau kebijakan moneter yang telah ditentukan sebelumnya. Periode penciptaan uang yang lebih cepat atau lebih lambat dapat dikompensasikan melalui cara lain, misalnya melalui pajak. Dealer eksternal memasukkan token bit gold ke dalam bundler yang lebih besar atau lebih kecil atau pengguna b-money mengubah tawaran mereka.
Namun tujuan kebijakan moneter Satoshi mengharuskan bitcoin memiliki tingkat pelepasan bitcoin yang telah ditentukan untuk diedarkan. Membatasi laju (statistik) produksi blok dari waktu ke waktu adalah hal yang wajar dalam bitcoin karena laju produksi blok adalah laju penjualan pasokan awal bitcoin. Menjual 21 juta bitcoin selama 140 tahun adalah proposisi yang berbeda dibandingkan membiarkannya dijual dalam 3 bulan.
Selain itu, bitcoin sebenarnya dapat menerapkan batasan ini karena blockchain adalah “protokol cap waktu aman” milik Szabo. Satoshi menggambarkan bitcoin sebagai yang pertama dan terutama sebagai “server stempel waktu terdistribusi secara peer-to-peer,” dan implementasi awal kode sumber bitcoin menggunakan “rantai waktu” dunia, bukan “blockchain” untuk menggambarkan struktur data bersama yang mengimplementasikan pasar proof-of-work bitcoin.[^10]

Tidak seperti bit gold atau b-money, token dalam bitcoin tidak mengalami kelebihan pasokan. Jaringan bitcoin menggunakan penyesuaian kesulitan untuk mengubah harga uang sebagai respons terhadap perubahan pasokan komputasi.
Algoritme penyesuaian ulang kesulitan Bitcoin memanfaatkan kemampuan ini. Blockchain konsensus digunakan oleh peserta untuk menghitung penawaran historis yang dibuat oleh industri pertambangan dan menyesuaikan kembali kesulitan agar bisa mendekati waktu blok target.
Pesanan Terunggul Menciptakan Konsensus
Rantai penyederhanaan yang disebabkan oleh tuntutan kebijakan moneter yang kuat meluas ke fase “penciptaan uang” dari b-money.
Tawaran yang diajukan pengguna di b-money mengalami masalah “tidak ada yang dipertaruhkan”. Tidak ada mekanisme untuk mencegah pengguna mengajukan tawaran dengan sejumlah besar b-money untuk pekerjaan yang sangat sedikit. Hal ini mengharuskan jaringan untuk melacak tawaran mana yang telah diselesaikan dan hanya menerima “tawaran tertinggi…dalam hal biaya nominal per unit b-money yang dibuat” untuk menghindari tawaran yang mengganggu tersebut. Setiap peserta b-money harus melacak seluruh tawaran senilai buku pesanan, mencocokkan tawaran dengan perhitungan selanjutnya, dan hanya menyelesaikan pesanan yang telah selesai dengan harga tertinggi.
Masalah ini merupakan contoh dari masalah konsensus yang lebih umum dalam sistem desentralisasi, yang juga dikenal sebagai “Byzantine generals” atau terkadang masalah “pembelanjaan ganda” dalam konteks mata uang digital. Berbagi urutan data yang identik di antara semua peserta merupakan suatu tantangan dalam jaringan yang saling bermusuhan dan terdesentralisasi. Solusi yang ada untuk masalah ini – yang disebut “algoritma konsensus Byzantine-fault tolerant (BFT)” – memerlukan koordinasi sebelumnya di antara peserta atau mayoritas (>67%) peserta agar tidak berperilaku bermusuhan.
Bitcoin tidak harus mengelola buku pesanan dalam jumlah besar karena jaringan bitcoin menawarkan harga permintaan konsensus tunggal. Ini berarti node bitcoin dapat menerima blok pertama (valid) yang mereka lihat yang memenuhi harga yang diminta jaringan saat ini—tawaran gangguan dapat dengan mudah diabaikan dan merupakan pemborosan sumber daya penambang.
Komputasi harga berdasarkan konsensus memungkinkan pencocokan pesanan beli/jual dalam bitcoin dilakukan secara antusias, dengan sistem siapa cepat dia dapat. Berbeda dengan b-money, pencocokan pesanan yang cepat ini berarti bahwa pasar bitcoin tidak memiliki fase—pasar ini beroperasi terus-menerus, dengan harga konsensus baru dihitung setelah setiap pesanan dicocokkan (blok ditemukan). Untuk menghindari percabangan yang disebabkan oleh latensi jaringan atau perilaku bertentangan, node juga harus mengikuti aturan rantai terberat. Aturan penyelesaian pesanan yang serakah ini memastikan bahwa hanya tawaran tertinggi yang diterima oleh jaringan.
Kombinasi algoritma yang antusias dan serakah ini, dimana node menerima blok valid pertama yang mereka lihat dan juga mengikuti rantai terberat, adalah algoritma BFT baru yang dengan cepat menyatu pada konsensus tentang urutan blok. Satoshi menghabiskan 25% dari white paper bitcoin untuk mendemonstrasikan klaim ini.[^11]
Kita telah menetapkan di bagian sebelumnya bahwa harga permintaan konsensus bitcoin itu sendiri bergantung pada konsensus blockchain. Namun ternyata keberadaan harga permintaan konsensus tunggal inilah yang memungkinkan perhitungan pasar untuk mencocokkan pesanan dengan penuh semangat, dan itulah yang pertama-tama mengarah pada konsensus!
Terlebih lagi, “konsensus Nakamoto” yang baru ini hanya mengharuskan 50% peserta untuk tidak bertentangan, sebuah kemajuan yang signifikan dibandingkan dengan kondisi sebelumnya. Seorang cypherpunk seperti Satoshi membuat terobosan ilmu komputer teoretis ini, dibandingkan dengan akademisi tradisional atau peneliti industri, karena fokus mereka yang sempit pada penerapan uang yang sehat, dibandingkan algoritma konsensus umum untuk komputasi terdistribusi.
Kesimpulan
B-money adalah kerangka kerja yang kuat untuk membangun mata uang digital tetapi tidak lengkap karena tidak memiliki kebijakan moneter. Membatasi b-money dengan jadwal rilis yang telah ditentukan untuk bitcoin mengurangi cakupan dan menyederhanakan implementasi dengan menghilangkan persyaratan untuk melacak dan memilih di antara tawaran pembuatan uang yang diajukan pengguna. Mempertahankan kecepatan sementara dari jadwal rilis Satoshi menghasilkan algoritma penyesuaian kesulitan dan memungkinkan konsensus Nakamoto, yang secara luas diakui sebagai salah satu aspek paling inovatif dalam implementasi bitcoin.
Ada lebih banyak hal dalam desain bitcoin daripada aspek yang dibahas sejauh ini. Kita memfokuskan artikel ini pada pasar “utama” dalam bitcoin, pasar yang mendistribusikan pasokan awal bitcoin ke dalam sirkulasi.
Artikel berikutnya dalam seri ini akan mengeksplorasi pasar penyelesaian transaksi bitcoin dan kaitannya dengan pasar pendistribusian pasokan bitcoin. Hubungan ini akan menyarankan metodologi bagaimana membangun pasar masa depan untuk layanan terdesentralisasi selain bitcoin.
Sumber artikel: HOW DID SATOSHI THINK OF BITCOIN? https://bitcoinmagazine.com/technical/how-did-satoshi-think-of-bitcoin
Diterjemahkan oleh: Abengkris
[^1]: Judul seri ini diambil dari pesan telegraf pertama dalam sejarah, yang dikirimkan oleh Samuel Morse pada tahun 1844: “What hath God wrought?”.
[^2]: Bitcoin: Sistem Uang Elektronik Peer-to-Peer, tersedia di: https://bitcoin.org/bitcoin.pdf
[^3]: Pricing via Processing or Combatting Junk Mail oleh Dwork dan Naor. tersedia di:
https://www.wisdom.weizmann.ac.il/../../pvp.pdf[^4]: Meskipun merupakan pencetus ide tersebut, Dwork & Naor tidak menciptakan “proof-of-work”—julukan tersebut kemudian diberikan pada tahun 1999 oleh Markus Jakobsson dan Ari Juels.
[^5]: Proyek RPoW Hal Finney adalah upaya untuk menciptakan proof-of-work yang dapat ditransfer, tetapi bitcoin tidak menggunakan konsep ini karena tidak memperlakukan komputasi sebagai mata uang. Seperti yang akan kita lihat nanti ketika kita memeriksa bit gold dan b-money, komputasi tidak dapat berupa mata uang karena nilai komputasi berubah seiring waktu sementara unit mata uang harus memiliki nilai yang sama. Bitcoin bukanlah komputasi, bitcoin adalah mata uang yang dijual untuk komputasi.
[^6]: Pada saat ini, beberapa pembaca mungkin percaya bahwa saya meremehkan kontribusi Dai atau Szabo karena kontribusi mereka tidak jelas atau tidak jelas dalam beberapa hal. Perasaan saya justru sebaliknya: Dai dan Szabo pada dasarnya benar dan fakta bahwa mereka tidak mengartikulasikan setiap detail seperti yang dilakukan Satoshi tidak mengurangi kontribusi mereka. Sebaliknya, hal ini seharusnya meningkatkan apresiasi kita terhadap hal tersebut, karena hal ini menunjukkan betapa menantangnya munculnya mata uang digital, bahkan bagi para praktisi terbaiknya.
[^7]: Postingan b-money Dai adalah referensi pertama dalam white paper Satoshi, tersedia di: http://www.weidai.com/bmoney.txt
[^8]: Ada dua penyederhanaan yang dilakukan di sini: 1. Jumlah bitcoin yang dijual di setiap blok juga dipengaruhi oleh biaya transaksi pasar, yang berada di luar cakupan artikel ini, namun tetap menunggu pekerjaan selanjutnya. 2. Kesulitan yang dilaporkan oleh bitcoin bukanlah jumlah perhitungan yang diharapkan; seseorang harus mengalikannya dengan faktor proporsionalitas.
[^9]: Setidaknya sejak masa lalu yang buruk ketika Satoshi adalah satu-satunya penambang di jaringan.
[^10]: Bitcoin is Time klasik dari Gigi adalah pengenalan yang bagus tentang hubungan mendalam antara bitcoin dan waktu, tersedia di: https://dergigi.com/2021/01/14/bitcoin-is-time/
[^11]: Satoshi melakukan kesalahan baik dalam analisis mereka di buku putih maupun implementasi awal bitcoin berikutnya dengan menggunakan aturan “rantai terpanjang” dan bukan aturan “rantai terberat”.
-
 @ fd208ee8:0fd927c1
2024-11-03 12:01:43
@ fd208ee8:0fd927c1
2024-11-03 12:01:43It arrived!
I was feeling impatient, waiting for my snazzy, brand-spanking new mobile phone to arrive, but when it got here, I just stared at the box, in trepidation. Everyone kept walking by, asking how it is, but I just shook my head. After nearly four years, with my (originally Android 10), Moto G8 Power, which I loved to death, I wasn't yet ready to move on. I needed a moment, to grieve.
RIP, my trusty fren.

Anyways...
Around 10 pm, I managed to emotionally recover enough to begin the Big Transition, and I was up until 2 am, and still didn't finish.
My SimpleX database is sort of large, and slow to migrate. Also, took me a while to figure out how to do it, and the whole thing made me terribly nervous, that I'd accidentally get locked out. But it worked, after eight failed attempts, so yay.
Telegram was back online, almost immediately, since it's tied to the SIM card. Which was convenient, but sorta creeped me out.
Our family-internal favorite, Threema, was a snap. Took 5 minutes.
I had four failed starts with Slack, as it kept sending a login code to my Proton Mail, but I didn't have Proton app installed on my new phone, yet, and I was really sleepy, so I kept confirming on the old phone and then Slack would freeze up, and I had to kill the process and restart.
My key manager is cloud-based, so that went really fast, and I had the nos2x browser extension going in Firefox within 10 minutes, or so. Logged into Habla.News, Nostr.Build, Zap.Cooking, and Nostrudel.Ninja, immediately, so that I can get my Nostr fix.
Then I took a deep breath and mass-installed F-Droid, Minibits, Amethyst, Citrine, Orbot, and Amber. And breathed out, again, because MIRACLES NEVER CEASE: it seems to be actually working.

Everyone knows that this is the unbeatable Android Nostr setup, but it's also a resource-gobbling monster, that should only be tried at home, kids. Make sure you don't use Amethyst when out-and-about, unless you have a gigantic battery and an unlimited, high-speed, mobile plan. So, basically, everyone in the First World, who isn't me, can do it.
Oh, well. At least, I can now indulge over WiFi.
The phone itself is just like the old one, but thinner, faster, and doesn't freeze up or take a long time to start. The Motorola is dead. Long live the Motorola.
-
 @ fd208ee8:0fd927c1
2024-11-03 09:20:33
@ fd208ee8:0fd927c1
2024-11-03 09:20:33It's that season, again
I've been growing my hair out (too lazy to cut it) and it has -- once again -- quickly reached a length at which it draws unnecessary attention and sheds everywhere. I suppose it always sheds everywhere, but shedding short hairs is just generally less-gross than finding a 12-inch strand lying on the toast, you were about to consume.
So, I'm back to the 50 Shades of Updo stage, where I struggle to figure out how to best wear my head, usually defaulting to the Messy Bun look, because it's still too short to do anything more elaborate and looks silly, as a ponytail.


It's really not that great of a look for me, I know, especially, now that my chin is finally succumbing to gravity, but doing something more-elegant is usually more time-consuming and doesn't have that wonderful "swept up" feeling to it. You know that feeling, when you tie all of that heavy hair to a higher point on your skull and the roots just sigh with relief.
Another look, I tend to gravitate toward, at the moment, is head scarves, like this one:

...or a Bavarian-style bandana, for gardening or hiking (don't have a selfie handy, so here is some random chick, who also suffers from poofy, dark hair).

Hiking bare-headed, with flowing tresses, is not recommended, due to all of the Nature, that you have to comb back out of it.
Generally, just bored of my inbetween length and looking forward to braiding it, in a few months. Or giving up, in frustration, and cutting it all off.
-
 @ 47750177:8969e41a
2024-11-04 12:00:00
@ 47750177:8969e41a
2024-11-04 12:00:0027.2 Release Notes
Bitcoin Core version 27.2 is now available from:
This release includes various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Compatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux Kernel 3.17+, macOS 11.0+, and Windows 7 and newer. Bitcoin Core should also work on most other Unix-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
P2P
-
30394 net: fix race condition in self-connect detection
Init
-
30435 init: change shutdown order of load block thread and scheduler
RPC
-
30357 Fix cases of calls to FillPSBT errantly returning complete=true
PSBT
-
29855 psbt: Check non witness utxo outpoint early
Test
-
30552 test: fix constructor of msg_tx
Doc
-
30504 doc: use proper doxygen formatting for CTxMemPool::cs
Build
-
30283 upnp: fix build with miniupnpc 2.2.8
-
30633 Fixes for GCC 15 compatibility
CI
-
30193 ci: move ASan job to GitHub Actions from Cirrus CI
-
30299 ci: remove unused bcc variable from workflow
Credits
Thanks to everyone who directly contributed to this release:
- Ava Chow
- Cory Fields
- Martin Zumsande
- Matt Whitlock
- Max Edwards
- Sebastian Falbesoner
- Vasil Dimov
- willcl-ark
As well as to everyone that helped with translations on Transifex.
-
-
 @ fb5986f6:4173af9d
2024-11-06 20:55:08
@ fb5986f6:4173af9d
2024-11-06 20:55:08Instalación de proxmox: https://www.youtube.com/watch?v=iUXX1dKAGxA
No Solo Hacking - Virtualización con Proxmox https://www.youtube.com/watch?v=qaWpaNX_rL8&list=PLznRNLIWBPwH5Li7Co2i57rUVhve7m_ZQ
-
 @ 9e69e420:d12360c2
2024-10-19 12:52:02
@ 9e69e420:d12360c2
2024-10-19 12:52:02Joe Biden and Senator Lindsey Graham about securing a U.S.-Saudi defense treaty, as revealed in Bob Woodward's new book "War".
The Proposed "Megadeal"
The conversation took place in the context of Biden's attempts to negotiate a "megadeal" between the United States, Saudi Arabia, and Israel[1]. The goal was to create a permanent, U.S.-led security alliance in the Middle East[1].
Bipartisan Collaboration
Graham reportedly told Biden that only a Democratic president could convince Democrats to "vote to go to war for Saudi Arabia," to which Biden responded, "Let's do it"[1]. This exchange highlights the bipartisan willingness to consider military commitments in the Middle East[2].
Political Calculations
Graham suggested that: - A Republican administration wouldn't be able to secure such a deal - Democrats wouldn't support it if introduced by Trump - Republicans could provide 45 votes if Israel encouraged it Biden assured Graham he could secure the remaining Democratic votes[1].
Saudi Arabia's Perspective
Crown Prince Mohammed bin Salman was reportedly interested in the deal to gain protection under the U.S. nuclear umbrella[1]. However, after the October 7, 2023 attacks on Israel, bin Salman became hesitant, fearing potential assassination if he didn't stand up for Palestinian rights[1].
Current Status
The deal is currently in suspended animation due to bin Salman's concerns and changing regional dynamics. The Biden administration continues to pursue negotiations, urging Israel to make concessions on Palestinian rights to facilitate the agreement.
The article concludes by noting that if Woodward's reporting is accurate, both Biden and Graham seemed willing to commit American troops to potential conflict with relative ease.
-
 @ 526e9d4c:2ecfb055
2024-11-04 04:22:33
@ 526e9d4c:2ecfb055
2024-11-04 04:22:33Chef's notes
最好的是用慢炖锅炖一个晚上. Best if cooked in a slow cooker overnight.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 8 hours
Ingredients
- 金耳一块 // 1 piece of golden tremella
- 银耳2片 // 2 pieces of silver ear fungus
- 红枣10颗 // 10 red dates
- 枸杞7-8粒 // 7-8 goji berries
- 桃胶20颗 // 20 peach gum pieces
- 黄冰糖3块 // 3 blocks of yellow rock sugar
Directions
- 把银耳和桃胶用水清洗并用水泡发20分钟。 Wash the silver ear fungus and peach gum with water and soak them for 20 minutes.
- 水煮沸放入3块冰糖,溶解后把银耳和红枣倒入沸水中。 Bring the water to a boil and add 3 blocks of rock sugar. After it dissolves, add the silver ear fungus and red dates to the boiling water.
- 5分钟后加入金耳和桃胶煮30-40分钟(中途可加水稀释。 After 5 minutes, add the golden tremella and peach gum, and cook for 30-40 minutes (you can add water to dilute if needed)
- 煮开后,放5分钟即可使用,如果觉得不是很甜,可以再放一点冰糖(根绝个人口味) After boiling, let it sit for 5 minutes before serving. If you find it's not sweet enough, you can add a bit more rock sugar (according to personal taste)
-
 @ 5a69e82d:aa41c382
2024-11-05 11:38:19
@ 5a69e82d:aa41c382
2024-11-05 11:38:19Dhruv Bansal, CSO dan Co-Founder Unchained mengeksplorasi prinsip-prinsip dan sejarah yang mengarah pada penciptaan Bitcoin dan mengajukan pertanyaan: "Apa yang telah dilakukan Satoshi"?
Bitcoin sering dibandingkan dengan internet pada tahun 1990an, namun saya yakin analogi yang lebih baik adalah dengan telegraf pada tahun 1840an.[^1]
Telegraf adalah teknologi pertama yang mengirimkan data yang dikodekan dengan kecepatan mendekati cahaya dalam jarak jauh. Ini menandai lahirnya industri telekomunikasi. Internet, meskipun skalanya lebih besar, kontennya lebih kaya, dan many-to-many, bukan one-to-one, pada dasarnya masih merupakan teknologi telekomunikasi.
Baik telegraf maupun internet bergantung pada model bisnis di mana perusahaan mengerahkan modal untuk membangun jaringan fisik dan kemudian membebankan biaya kepada pengguna untuk mengirim pesan melalui jaringan ini. Jaringan AT&T secara historis mengirimkan telegram, panggilan telepon, paket TCP/IP, pesan teks, dan sekarang TikTok.
Transformasi masyarakat melalui telekomunikasi telah menghasilkan kebebasan yang lebih besar namun juga sentralisasi yang lebih besar. Internet telah meningkatkan jangkauan jutaan pembuat konten dan usaha kecil, namun juga memperkuat jangkauan perusahaan, otoritas pusat, dan lembaga lain yang memiliki posisi yang cukup baik untuk memantau dan memanipulasi aktivitas online.
Namun Bitcoin bukanlah akhir dari transformasi apa pun—ini adalah awal dari sebuah transformasi. Seperti halnya telekomunikasi, Bitcoin akan mengubah kebiasaan umat manusia dan kehidupan sehari-harinya. Memprediksi seluruh cakupan perubahan saat ini sama dengan membayangkan internet saat hidup di era telegraf.
Seri ini mencoba membayangkan masa depan dengan memulai dari masa lalu. Artikel awal ini menelusuri sejarah mata uang digital sebelum Bitcoin. Hanya dengan memahami kegagalan proyek-proyek sebelumnya, kita dapat memahami apa yang membuat Bitcoin berhasil—dan bagaimana hal itu menyarankan metodologi untuk membangun sistem desentralisasi di masa depan.
Daftar isi
- Sistem yang Terdesentralisasi Adalah Pasar
- Pasar yang Terdesentralisasi Membutuhkan Barang yang Terdesentralisasi
- Bagaimana Sistem Desentralisasi dapat Menentukan Harga Komputasi?
- Tujuan Kebijakan Moneter Satoshi Menghasilkan Bitcoin
- Kesimpulan
Klaim utama dari artikel ini adalah bahwa Bitcoin dapat dianggap sebagai adaptasi dari proyek B-money Dai yang menghilangkan kebebasan untuk menciptakan uang. Hanya beberapa minggu setelah artikel ini pertama kali diterbitkan, email baru muncul di mana Satoshi mengaku tidak terbiasa dengan B-money, namun mengakui bahwa Bitcoin dimulai “tepat dari titik itu.” Mengingat bukti baru ini, kami yakin klaim utama ini, meskipun tidak akurat secara historis, masih merupakan cara yang bermakna dan bermanfaat untuk memikirkan asal usul Bitcoin.
Bagaimana Satoshi Nakamoto Memikirkan Bitcoin?
Satoshi memang cerdas, tetapi Bitcoin tidak muncul begitu saja.
Bitcoin mengulangi pekerjaan yang ada di bidang kriptografi, sistem terdistribusi, ekonomi, dan filsafat politik. Konsep proof-of-work sudah ada jauh sebelum digunakan dalam uang dan cypherpunk sebelumnya seperti Nick Szabo, Wei Dai, & Hal Finney mengantisipasi dan memengaruhi desain Bitcoin dengan proyek-proyek seperti bit gold, B-money, dan RPoW. Pertimbangkan bahwa, pada tahun 2008, ketika Satoshi menulis white paper Bitcoin[^2], banyak ide penting Bitcoin telah diusulkan dan/atau diimplementasikan:
- Mata uang digital harus berupa jaringan P2P
- Proof-of-work adalah dasar penciptaan uang
- Uang diciptakan melalui lelang
- Kunci publik kriptografi digunakan untuk menentukan kepemilikan dan transfer koin
- Transaksi dikelompokkan menjadi beberapa blok
- Blok dirangkai bersama melalui proof-of-work
- Semua blok disimpan oleh semua peserta
Bitcoin memanfaatkan semua konsep ini, tetapi Satoshi tidak menciptakan satu pun konsep tersebut. Untuk lebih memahami kontribusi Satoshi, kita harus menentukan prinsip Bitcoin mana yang tidak ada dalam daftar.
Beberapa kandidat yang jelas adalah persediaan Bitcoin yang terbatas, konsensus Nakamoto, dan algoritma penyesuaian kesulitan. Tapi apa yang mendorong Satoshi pada ide ini?
Artikel ini mengeksplorasi sejarah mata uang digital dan menyatakan bahwa fokus Satoshi pada kebijakan moneter yang sehat adalah hal yang menyebabkan Bitcoin mengatasi tantangan yang mengalahkan proyek-proyek sebelumnya seperti bit gold dan B-money.
Sistem yang Terdesentralisasi Adalah Pasar
Bitcoin sering digambarkan sebagai sistem terdesentralisasi atau terdistribusi. Sayangnya, kata “desentralisasi” dan “terdistribusi” sering kali membingungkan. Ketika diterapkan pada sistem digital, kedua istilah tersebut mengacu pada cara aplikasi monolitik dapat didekomposisi menjadi jaringan bagian-bagian yang berkomunikasi.

Untuk tujuan kita, perbedaan utama antara sistem terdesentralisasi dan terdistribusi bukanlah topologi diagram jaringannya, namun cara mereka menegakkan aturan. Kami meluangkan waktu di bagian berikut untuk membandingkan sistem terdistribusi dan desentralisasi dan memotivasi gagasan bahwa sistem desentralisasi yang kuat adalah pasar.
Sistem Terdistribusikan Bergantung pada Otoritas Pusat
Dalam hal ini, kami mengartikan “terdistribusi” sebagai sistem apa pun yang telah dipecah menjadi beberapa bagian (sering disebut sebagai "node") yang harus berkomunikasi, biasanya melalui jaringan.
Insinyur perangkat lunak semakin mahir dalam membangun sistem yang terdistribusi secara global. Internet terdiri dari sistem terdistribusi yang secara kolektif berisi miliaran node. Kita masing-masing memiliki simpul di saku kita yang berpartisipasi dan bergantung pada sistem ini.
Namun hampir semua sistem terdistribusi yang kita gunakan saat ini diatur oleh beberapa otoritas pusat, biasanya administrator sistem, perusahaan, atau pemerintah yang saling dipercaya oleh semua node dalam sistem.
Otoritas pusat memastikan semua node mematuhi aturan sistem dan menghapus, memperbaiki, atau menghukum node yang gagal mematuhinya. Mereka dipercaya untuk melakukan koordinasi, menyelesaikan konflik, dan mengalokasikan sumber daya bersama. Seiring waktu, otoritas pusat mengelola perubahan pada sistem, memperbarui atau menambahkan fitur, dan memastikan bahwa node yang berpartisipasi mematuhi perubahan tersebut.
Manfaat yang diperoleh sistem terdistribusi karena mengandalkan otoritas pusat juga disertai dengan biaya. Meskipun sistem ini kuat terhadap kegagalan node-nodenya, kegagalan otoritas pusat dapat menyebabkan sistem berhenti berfungsi secara keseluruhan. Kemampuan otoritas pusat untuk mengambil keputusan secara sepihak berarti menumbangkan atau menghilangkan otoritas pusat sudah cukup untuk mengendalikan atau menghancurkan keseluruhan sistem.
Terlepas dari adanya trade-off ini, jika ada persyaratan bahwa satu partai atau koalisi harus mempertahankan otoritas pusat, atau jika peserta dalam sistem tersebut puas dengan mengandalkan otoritas pusat, maka sistem terdistribusi tradisional adalah solusi terbaik. Tidak diperlukan blockchain, token, atau sistem desentralisasi serupa.
Secara khusus, kasus VC atau mata uang kripto yang didukung oleh pemerintah, dengan persyaratan bahwa satu pihak dapat memantau atau membatasi pembayaran dan membekukan akun, adalah kasus penggunaan yang sempurna untuk sistem terdistribusi tradisional.
Sistem Desentralisasi Tidak Memiliki Otoritas Pusat
Kami menganggap “desentralisasi” memiliki arti yang lebih kuat daripada “terdistribusi”: sistem desentralisasi adalah bagian dari sistem terdistribusi yang tidak memiliki otoritas pusat. Sinonim yang mirip dengan “desentralisasi” adalah “peer-to-peer” (P2P).
Menghapus otoritas pusat memberikan beberapa keuntungan. Sistem terdesentralisasi:
- Tumbuh dengan cepat karena tidak ada hambatan untuk masuk—siapa pun dapat mengembangkan sistem hanya dengan menjalankan node baru, dan tidak ada persyaratan untuk registrasi atau persetujuan dari otoritas pusat.
- Kuat karena tidak ada otoritas pusat yang kegagalannya dapat membahayakan berfungsinya sistem. Semua node adalah sama, jadi kegagalan bersifat lokal dan jaringan merutekan sekitar kerusakan.
- Sulit untuk ditangkap, diatur, dikenakan pajak, atau diawasi karena tidak adanya titik kendali terpusat yang dapat ditumbangkan oleh pemerintah.
Kekuatan inilah yang menjadi alasan Satoshi memilih desain Bitcoin yang terdesentralisasi dan peer-to-peer:
“Pemerintah pandai memotong… jaringan yang dikendalikan secara terpusat seperti Napster, namun jaringan P2P murni seperti Gnutella dan Tor tampaknya masih mampu bertahan.” - Satoshi Nakamoto, 2008
Namun kekuatan ini juga disertai dengan kelemahan. Sistem yang terdesentralisasi bisa menjadi kurang efisien karena setiap titik harus memikul tanggung jawab tambahan untuk koordinasi yang sebelumnya diambil alih oleh otoritas pusat.
Sistem yang terdesentralisasi juga sering dilanda perilaku yang bersifat penipuan dan bertentangan. Terlepas dari persetujuan Satoshi terhadap Gnutella, siapa pun yang menggunakan program berbagi file P2P untuk mengunduh file yang ternyata kotor atau berbahaya memahami alasan mengapa berbagi file P2P tidak pernah menjadi model utama untuk transfer data online.
Satoshi tidak menyebutkannya secara eksplisit, namun email adalah sistem terdesentralisasi lainnya yang menghindari kendali pemerintah. Dan email juga terkenal sebagai spam.
Sistem Desentralisasi diatur Melalui Insentif
Akar masalahnya, dalam semua kasus ini adalah, bahwa perilaku kejahatan (menyebarkan file buruk, mengirim email spam) tidak dihukum, dan perilaku kooperatif (menyebarkan file bagus, hanya mengirim email berguna) tidak dihargai. Sistem desentralisasi yang mengandalkan partisipannya untuk menjadi aktor yang baik gagal untuk berkembang karena sistem tersebut tidak dapat mencegah aktor jahat untuk ikut berpartisipasi.
Tanpa memaksakan otoritas pusat, satu-satunya cara untuk menyelesaikan masalah ini adalah dengan menggunakan insentif ekonomi. Aktor yang baik, menurut definisinya, bermain sesuai aturan karena mereka secara inheren termotivasi untuk melakukannya. Pelaku kejahatan, menurut definisinya, adalah orang yang egois dan licik, namun insentif ekonomi yang tepat dapat mengarahkan perilaku buruk mereka ke arah kebaikan bersama. Sistem yang terdesentralisasi melakukan hal ini dengan memastikan bahwa perilaku kooperatif menguntungkan dan perilaku kejahatan merugikan.
Cara terbaik untuk menerapkan layanan terdesentralisasi yang kuat adalah dengan menciptakan pasar di mana semua pelaku, baik dan buruk, dibayar untuk menyediakan layanan tersebut. Kurangnya hambatan masuk bagi pembeli dan penjual di pasar yang terdesentralisasi mendorong skala dan efisiensi. Jika protokol pasar dapat melindungi partisipan dari penipuan, pencurian, dan penyalahgunaan, maka pelaku kejahatan akan merasa lebih menguntungkan untuk mengikuti aturan atau menyerang sistem lain.
Pasar yang Terdesentralisasi Membutuhkan Barang yang Terdesentralisasi
Namun pasar itu rumit. Mereka harus memberi pembeli dan penjual kemampuan untuk mengirimkan penawaran dan permintaan serta menemukan, mencocokkan, dan menyelesaikan pesanan. Kebijakan tersebut harus adil, memberikan konsistensi yang kuat, dan menjaga ketersediaan meskipun terjadi masa-masa yang tidak menentu.
Pasar global saat ini sangat mumpuni dan canggih, namun menggunakan barang-barang tradisional dan jaringan pembayaran untuk menerapkan insentif di pasar yang terdesentralisasi bukanlah hal yang baru. Setiap penggabungan antara sistem desentralisasi dan uang fiat, aset tradisional, atau komoditas fisik akan menimbulkan kembali ketergantungan pada otoritas pusat yang mengontrol pemroses pembayaran, bank, dan bursa.

Sistem terdesentralisasi tidak dapat mentransfer uang tunai, mencari saldo rekening perantara, atau menentukan kepemilikan properti. Barang-barang tradisional sama sekali tidak terbaca dalam sistem desentralisasi. Hal sebaliknya tidak benar—sistem tradisional dapat berinteraksi dengan Bitcoin semudah aktor lainnya (begitu mereka memutuskan ingin melakukannya). Batasan antara sistem tradisional dan desentralisasi bukanlah sebuah tembok yang tidak dapat dilewati, melainkan sebuah membran semi-permeabel.
Ini berarti bahwa sistem yang terdesentralisasi tidak dapat melaksanakan pembayaran dalam mata uang barang tradisional apa pun. Mereka bahkan tidak dapat menentukan saldo rekening yang didominasi fiat atau kepemilikan real estat atau barang fisik. Seluruh perekonomian tradisional sama sekali tidak terbaca dalam sistem desentralisasi.
Menciptakan pasar yang terdesentralisasi membutuhkan perdagangan barang-barang baru yang terdesentralisasi yang dapat dibaca dan ditransfer dalam sistem yang terdesentralisasi.
Komputasi Adalah Barang Terdesentralisasi yang Pertama
Contoh pertama dari “barang terdesentralisasi” adalah kelas komputasi khusus yang pertama kali diusulkan pada tahun 1993 oleh Cynthia Dwork dan Moni Naor.[^3]
Karena adanya hubungan mendalam antara matematika, fisika, dan ilmu komputer, komputasi ini memerlukan energi dan sumber daya perangkat keras di dunia nyata—hal ini tidak dapat dipalsukan. Karena sumber daya di dunia nyata langka, komputasi ini juga langka.
input untuk komputasi ini dapat berupa data apa pun. Keluaran yang dihasilkan adalah “bukti” digital bahwa pengkomputasian telah dilakukan pada data input yang diberikan. Pembuktian mengandung “kesulitan” tertentu yang merupakan bukti (statistik) dari sejumlah pekerjaan komputasi tertentu. Yang terpenting, hubungan antara data input, pembuktian, dan pekerjaan komputasi asli yang dilakukan dapat diverifikasi secara independen tanpa perlu mengajukan banding ke otoritas pusat mana pun.
Gagasan untuk menyebarkan beberapa data input bersama dengan bukti digital sebagai bukti kerja komputasi dunia nyata yang dilakukan pada input tersebut sekarang disebut “proof-of-work”.[^4] Proof-of-work adalah, jika menggunakan ungkapan Nick Szabo, “biaya yang tidak dapat ditiru”. Karena proof-of-work dapat diverifikasi oleh siapa pun, maka proof-of-work merupakan sumber daya ekonomi yang dapat dibaca oleh semua peserta dalam sistem desentralisasi. Proof-of-work mengubah penghitungan data menjadi barang yang terdesentralisasi. Dwork & Naor mengusulkan penggunaan komputasi untuk membatasi penyalahgunaan sumber daya bersama dengan memaksa peserta untuk memberikan proof-of-work dengan tingkat kesulitan minimum tertentu sebelum mereka dapat mengakses sumber daya:
“Dalam makalah ini kami menyarankan pendekatan komputasi untuk memerangi penyebaran surat elektronik. Secara umum, kami telah merancang mekanisme kontrol akses yang dapat digunakan kapan pun diinginkan untuk membatasi, namun tidak melarang, akses ke sumber daya.” - Dwoak & Naor, 1993
Dalam proposal Dwork & Naor, administrator sistem email akan menetapkan tingkat kesulitan bukti kerja minimum untuk mengirimkan email. Pengguna yang ingin mengirim email perlu melakukan sejumlah komputasi yang sesuai dengan email tersebut sebagai data input. Bukti yang dihasilkan akan dikirimkan ke server bersamaan dengan permintaan pengiriman email.
Dwork & Naor menyebut kesulitan proof-of-work sebagai “fungsi penetapan harga” karena, dengan menyesuaikan kesulitan tersebut, “otoritas penetapan harga” dapat memastikan bahwa sumber daya bersama tetap murah untuk digunakan bagi pengguna yang jujur dan rata-rata, namun mahal bagi pengguna yang mencari untuk mengeksploitasinya. Di pasar pengiriman email, administrator server adalah otoritas penetapan harga; mereka harus memilih “harga” untuk pengiriman email yang cukup rendah untuk penggunaan normal namun terlalu tinggi untuk spam.
Meskipun Dwork & Naor membingkai proof-of-work sebagai disinsentif ekonomi untuk memerangi penyalahgunaan sumber daya, nomenklatur “fungsi penetapan harga” dan “otoritas penetapan harga” mendukung interpretasi yang berbeda dan berbasis pasar: pengguna membeli akses ke sumber daya dengan imbalan komputasi pada tingkat yang sama. harga yang ditetapkan oleh pengontrol sumber daya.
Dalam interpretasi ini, jaringan pengiriman email sebenarnya adalah pengiriman email perdagangan pasar yang terdesentralisasi untuk komputasi. Kesulitan minimum dari proof-of-work adalah harga yang diminta untuk pengiriman email dalam mata uang komputasi.
Mata Uang Adalah Barang Terdesentralisasi yang kedua
Namun komputasi bukanlah mata uang yang baik.
Bukti yang digunakan untuk “memperdagangkan” komputasi hanya valid untuk input yang digunakan dalam komputasi tersebut. Hubungan yang tidak dapat dipecahkan antara bukti spesifik dan input tertentu berarti bahwa proof-of-work untuk satu input tidak dapat digunakan kembali untuk input yang berbeda.

Proof-of-work awalnya diusulkan sebagai mekanisme kontrol akses untuk membatasi email spam. Pengguna diharapkan memberikan bukti kerja bersama email apa pun yang ingin mereka kirim. Mekanisme ini juga dapat dianggap sebagai pasar di mana pengguna membeli pengiriman email dengan komputasi pada harga yang dipilih oleh penyedia layanan email.
Batasan ini berguna – dapat digunakan untuk mencegah pekerjaan yang dilakukan oleh satu pembeli di pasar kemudian dibelanjakan kembali oleh pembeli lain. Misalnya, HashCash, implementasi nyata pertama dari pasar pengiriman email, menyertakan metadata seperti stempel waktu saat ini dan alamat email pengirim dalam data masukan untuk penghitungan bukti kerja. Bukti yang dihasilkan oleh pengguna tertentu untuk email tertentu, tidak dapat digunakan untuk email yang berbeda.
Namun ini juga berarti bahwa komputasi bukti kerja adalah barang yang dipesan lebih dahulu. Dana tersebut tidak dapat dipertukarkan, tidak dapat dibelanjakan kembali,[^5] dan tidak memecahkan masalah kebutuhan yang terjadi secara kebetulan. Properti moneter yang hilang ini mencegah komputasi menjadi mata uang. Terlepas dari namanya, tidak ada insentif bagi penyedia pengiriman email untuk ingin mengakumulasikan HashCash, karena akan ada uang tunai sebenarnya.
Adam Back, penemu HashCash, memahami masalah berikut:
"Hashcash tidak dapat ditransfer secara langsung karena untuk membuatnya didistribusikan, setiap penyedia layanan hanya menerima pembayaran dalam bentuk tunai yang dibuat untuk mereka. Anda mungkin dapat menyiapkan pencetakan gaya digicash (dengan chaumian ecash) dan meminta bank hanya mencetak uang tunai pada penerimaan tabrakan hash yang ditangani. Namun ini berarti Anda harus mempercayai bank untuk tidak mencetak uang dalam jumlah tak terbatas untuk digunakan sendiri." - Adam Back, 1997
Kita tidak ingin menukar komputasi yang dibuat khusus untuk setiap barang atau jasa yang dijual dalam perekonomian yang terdesentralisasi. Kita menginginkan mata uang digital serba guna yang dapat langsung digunakan untuk mengoordinasikan pertukaran nilai di pasar mana pun.
Membangun mata uang digital yang berfungsi namun tetap terdesentralisasi merupakan tantangan yang signifikan. Mata uang membutuhkan unit yang dapat dipertukarkan dengan nilai yang sama yang dapat ditransfer antar pengguna. Hal ini memerlukan model penerbitan, definisi kriptografi kepemilikan dan transfer, proses penemuan dan penyelesaian transaksi, dan buku besar historis. Infrastruktur ini tidak diperlukan ketika bukti kerja hanya dianggap sebagai “mekanisme kontrol akses”.
Terlebih lagi, sistem desentralisasi adalah pasar, jadi semua fungsi dasar mata uang ini harus disediakan melalui penyedia layanan berbayar… dalam satuan mata uang yang sedang dibuat!
Seperti mengkompilasi compiler pertama, permulaan jaringan listrik yang gelap, atau evolusi kehidupan itu sendiri, pencipta mata uang digital dihadapkan pada masalah bootstrapping: bagaimana mendefinisikan insentif ekonomi yang mendasari mata uang yang berfungsi tanpa memiliki mata uang yang berfungsi di dalamnya yang akan mendenominasikan atau membayar insentif tersebut.

Komputasi dan mata uang adalah barang pertama dan kedua di pasar yang terdesentralisasi. Proof-of-work sendiri memungkinkan pertukaran komputasi tetapi mata uang yang berfungsi memerlukan lebih banyak infrastruktur. Butuh waktu 15 tahun bagi komunitas cypherpunk untuk mengembangkan infrastruktur tersebut.
Pasar Terdesentralisasi Pertama harus Memperdagangkan Komputasi untuk Mata Uang
Kemajuan dalam masalah bootstrapping ini berasal dari penyusunan batasan yang tepat.
Sistem yang terdesentralisasi harus menjadi pasar. Pasar terdiri dari pembeli dan penjual yang saling bertukar barang. Pasar terdesentralisasi untuk mata uang digital hanya memiliki dua barang yang dapat dibaca di dalamnya:
- Komputasi melalui proof-of-work
- Unit mata uang yang kita coba bangun
Oleh karena itu, satu-satunya perdagangan pasar yang memungkinkan adalah antara kedua barang tersebut. Komputasi harus dijual untuk satuan mata uang atau setara dengan satuan mata uang harus dijual untuk komputasi. Menyatakan hal ini sangatlah mudah—bagian tersulitnya adalah menata pasar ini sehingga sekadar menukar mata uang untuk komputasi akan mem-bootstrap semua kemampuan mata uang itu sendiri!
Seluruh sejarah mata uang digital yang berpuncak pada white paper Satoshi tahun 2008 adalah serangkaian upaya yang semakin canggih dalam menata pasar ini. Bagian berikut mengulas proyek-proyek seperti bit gold milik Nick Szabo dan B-money milik Wei Dai. Memahami bagaimana proyek-proyek ini menyusun pasar mereka dan mengapa mereka gagal akan membantu kita memahami mengapa Satoshi dan Bitcoin berhasil.

Bagaimana Sistem Desentralisasi Dapat Menentukan Harga Komputasi?
Fungsi utama pasar adalah penemuan harga. Oleh karena itu, komputasi perdagangan pasar untuk mata uang harus menemukan harga komputasi itu sendiri, dalam satuan mata uang tersebut.
Kita biasanya tidak memberikan nilai moneter pada komputasi. Kita biasanya menghargai kapasitas untuk melakukan komputasi karena kita menghargai output dari komputasi, bukan komputasi itu sendiri. Jika keluaran yang sama dapat dilakukan dengan lebih efisien, dengan komputasi yang lebih sedikit, hal ini biasanya disebut “kemajuan”.
Proof-of-work mewakili komputasi spesifik yang keluarannya hanya berupa bukti bahwa komputasi tersebut telah dilakukan. Menghasilkan bukti yang sama dengan melakukan lebih sedikit komputasi dan lebih sedikit pekerjaan tidak akan menghasilkan kemajuan—hal ini akan menjadi bug. Oleh karena itu, komputasi yang terkait dengan Proof-of-work merupakan hal yang aneh dan baru untuk dicoba dihargai.
Ketika bukti kerja dianggap sebagai disinsentif terhadap penyalahgunaan sumber daya, maka bukti kerja tidak perlu dinilai secara tepat dan konsisten. Yang terpenting adalah penyedia layanan email menetapkan tingkat kesulitan yang cukup rendah sehingga tidak terlihat oleh pengguna yang sah, namun cukup tinggi sehingga menjadi penghalang bagi pelaku spam. Oleh karena itu, terdapat beragam “harga” yang dapat diterima dan setiap peserta bertindak sebagai otoritas penetapan harga mereka sendiri, dengan menerapkan fungsi penetapan harga lokal.
Namun satuan mata uang dimaksudkan agar dapat dipertukarkan, masing-masing memiliki nilai yang sama. Karena perubahan teknologi dari waktu ke waktu, dua unit mata uang yang dibuat dengan tingkat kesulitan proof-of-work yang sama—yang diukur dengan jumlah komputasi yang sesuai—mungkin memiliki biaya produksi yang sangat berbeda di dunia nyata, yang diukur dengan waktu, energi, dan/atau modal untuk melakukan komputasi tersebut. Ketika komputasi dijual dengan menggunakan mata uang, dan biaya produksi yang mendasarinya bervariasi, bagaimana pasar dapat memastikan harga yang konsisten?
Nick Szabo dengan jelas mengidentifikasi masalah harga ini ketika menjelaskan bit gold:
"Masalah utamanya...adalah bahwa skema pembuktian kerja bergantung pada arsitektur komputer, bukan hanya matematika abstrak yang didasarkan pada "siklus komputasi" abstrak. ...Jadi, ada kemungkinan untuk menjadi produsen berbiaya sangat rendah (dengan beberapa kali lipat besarnya) dan membanjiri pasar dengan bit gold." - Szabo, 2005

Mata uang terdesentralisasi yang diciptakan melalui proof-of-work akan mengalami kelebihan pasokan dan penurunan pasokan seiring dengan perubahan pasokan komputasi seiring waktu. Untuk mengakomodasi volatilitas ini, jaringan harus belajar menghitung harga secara dinamis.
Mata uang digital awal mencoba memberi harga pada komputasi dengan mencoba mengukur “biaya komputasi” secara kolektif. Wei Dai, misalnya, mengusulkan solusi praktis berikut dalam B-money:
"Jumlah unit moneter yang diciptakan sama dengan biaya upaya komputasi dalam sekeranjang komoditas standar. Sebagai contoh, jika sebuah masalah memerlukan waktu 100 jam untuk diselesaikan pada komputer yang dapat menyelesaikannya dengan cara yang paling ekonomis, dan diperlukan 3 keranjang standar untuk membeli 100 jam waktu komputasi pada komputer tersebut di pasar terbuka, maka setelah solusi terhadap masalah tersebut disiarkan, setiap orang mengkredit rekening penyiar sebanyak 3 unit." - Dai, 1998
Sayangnya, Dai tidak menjelaskan bagaimana pengguna dalam sistem yang seharusnya terdesentralisasi seharusnya menyetujui definisi “keranjang standar”, komputer mana yang memecahkan masalah tertentu “paling ekonomis”, atau biaya komputasi di “pasar terbuka”. Mencapai konsensus di antara semua pengguna mengenai kumpulan data bersama yang berubah-ubah terhadap waktu adalah masalah penting dalam sistem desentralisasi!
Agar adil bagi Dai, dia menyadari hal ini:
“Salah satu bagian yang lebih bermasalah dalam protokol B-money adalah penciptaan uang. Bagian dari protokol ini mengharuskan semua [pengguna] memutuskan dan menyetujui biaya perhitungan tertentu. Sayangnya karena teknologi komputasi cenderung berkembang pesat dan tidak selalu bersifat publik, informasi ini mungkin tidak tersedia, tidak akurat, atau ketinggalan jaman, yang semuanya akan menyebabkan masalah serius pada protokol." - Dai, 1998
Dai kemudian mengusulkan mekanisme penetapan harga berbasis lelang yang lebih canggih yang kemudian dikatakan Satoshi sebagai titik awal idenya. Kita akan kembali ke skema lelang di bawah ini, tapi pertama-tama mari kita beralih ke bit gold, dan pertimbangkan wawasan Szabo tentang masalahnya.
Gunakan Pasar Eksternal
Szabo mengklaim bahwa proof-of-work harus “diberi stempel waktu dengan aman”:
"Bukti kerja diberi stempel waktu yang aman. Ini harus bekerja secara terdistribusi, dengan beberapa layanan stempel waktu berbeda sehingga tidak ada layanan stempel waktu tertentu yang perlu diandalkan secara substansial." - Szabo, 2005
Szabo tertaut ke halaman sumber daya tentang protokol penandaan waktu yang aman tetapi tidak menjelaskan algoritme spesifik apa pun untuk penandaan waktu yang aman. Ungkapan “aman” dan “fesyen terdistribusi” mempunyai pengaruh yang besar di sini, sehingga dapat mengatasi kerumitan dalam mengandalkan satu (atau banyak) layanan “di luar sistem” untuk penandaan waktu.[^6]

Waktu pembuatan unit mata uang digital penting karena menghubungkan komputasi yang dilakukan dengan biaya produksi di dunia nyata.
Terlepas dari ketidakjelasan implementasi, Szabo benar—waktu pembuatan proof-of-work merupakan faktor penting dalam menentukan harga karena terkait dengan biaya komputasi:
"…Namun, karena bit gold diberi stempel waktu, waktu yang dibuat serta tingkat kesulitan matematis dari pekerjaan tersebut dapat dibuktikan secara otomatis. Dari sini, biasanya dapat disimpulkan berapa biaya produksi selama periode waktu tersebut..." - Szabo, 2005
"Menyimpulkan" biaya produksi adalah hal yang penting karena bit gold tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat bit gold dengan melakukan perhitungan yang sesuai. Tanpa kemampuan untuk mengatur penerbitan, bit gold sama dengan barang koleksi:
"…Tidak seperti atom emas yang dapat dipertukarkan, tetapi seperti halnya barang-barang kolektor, pasokan dalam jumlah besar selama jangka waktu tertentu akan menurunkan nilai barang-barang tersebut. Dalam hal ini, emas kecil bertindak lebih seperti barang-barang kolektor daripada seperti emas..." - Szabo, 2005
Bit gold memerlukan proses eksternal tambahan untuk menciptakan unit mata uang yang sepadan:
“…[B]it Gold tidak dapat dipertukarkan berdasarkan fungsi sederhana, misalnya, panjang tali. Sebaliknya, untuk membuat unit yang dapat dipertukarkan, dealer harus menggabungkan potongan-potongan bit gold dengan nilai berbeda ke dalam satuan yang lebih besar kira-kira dengan nilai yang sama. Hal ini serupa dengan apa yang dilakukan banyak pedagang komoditas saat ini untuk memungkinkan pasar komoditas bekerja. Kepercayaan masih terdistribusi karena perkiraan nilai dari kumpulan tersebut dapat diverifikasi secara independen oleh banyak pihak lain dengan cara yang sebagian besar atau seluruhnya otomatis." - Szabo, 2005
Mengutip Szabo, “untuk menguji nilai… bit gold, dealer memeriksa dan memverifikasi tingkat kesulitan, masukan, dan stempel waktu”. Dealer yang mendefinisikan “unit yang lebih besar dengan nilai yang kira-kira sama” menyediakan fungsi penetapan harga yang serupa dengan “keranjang komoditas standar” Dai. Unit yang dapat dipertukarkan tidak dibuat dalam bentuk bit gold ketika bukti kerja diproduksi, hanya kemudian ketika bukti tersebut digabungkan menjadi “unit yang kira-kira bernilai sama” oleh dealer di pasar di luar jaringan.

Yang patut disyukuri, Szabo mengakui kelemahan ini:
"…Potensi kelebihan pasokan yang awalnya tersembunyi karena inovasi tersembunyi dalam arsitektur mesin adalah potensi kelemahan dalam bit gold, atau setidaknya ketidaksempurnaan yang harus diatasi oleh lelang awal dan pertukaran ex post bit gold." - Szabo, 2005
Sekali lagi, meskipun belum sampai pada (yang sekarang kita kenal sebagai) solusinya, Szabo menunjukkan solusinya: karena biaya komputasi berubah seiring waktu, jaringan harus merespons perubahan pasokan komputasi dengan menyesuaikan harga uang.
Gunakan Pasar Internal
Dealer Szabo akan menjadi pasar eksternal yang menentukan harga (bundel dari) bit gold setelah penciptaannya. Apakah mungkin menerapkan pasar ini di dalam sistem dan bukan di luar sistem?
Mari kita kembali ke Wei Dai dan B-money. Seperti disebutkan sebelumnya, Dai mengusulkan model alternatif berbasis lelang untuk pembuatan B-money. Desain Satoshi untuk Bitcoin meningkat secara langsung pada model lelang B-money[^7]:
“Jadi saya mengusulkan subprotokol penciptaan uang alternatif, di mana [pengguna]… memutuskan dan menyetujui jumlah B-money yang akan dibuat setiap periode, dengan biaya pembuatan uang tersebut ditentukan melalui lelang. Setiap periode pembuatan uang adalah dibagi menjadi empat tahap, sebagai berikut:
Planning. Para [pengguna] menghitung dan bernegosiasi satu sama lain untuk menentukan peningkatan jumlah uang beredar yang optimal untuk periode berikutnya. Apakah [jaringan] dapat mencapai konsensus atau tidak, mereka masing-masing menyiarkan kuota penciptaan uang mereka dan komputasi makroekonomi apa pun yang dilakukan untuk mendukung angka tersebut.
Bidding. Siapapun yang ingin membuat B-money menyiarkan tawaran dalam bentuk dimana x adalah banyaknya B-money yang ingin dibuatnya, dan y adalah soal yang belum terselesaikan dari kelas soal yang telah ditentukan. Setiap masalah di kelas ini harus memiliki biaya nominal (katakanlah dalam MIPS-years) yang disetujui secara publik.
Computation. Setelah melihat penawaran, pihak yang mengajukan penawaran pada tahap penawaran sekarang dapat menyelesaikan masalah dalam penawarannya dan menyiarkan solusinya. Penciptaan uang.
Money creation. Setiap [pengguna] menerima tawaran tertinggi (di antara mereka yang benar-benar menyiarkan solusi) dalam hal biaya nominal per unit B-money yang dibuat dan memberikan kredit kepada akun penawar sesuai dengan itu."
- Dai, 1998B-money membuat kemajuan signifikan menuju struktur pasar yang tepat untuk mata uang digital. Ini berupaya untuk menghilangkan dealer eksternal Szabo dan memungkinkan pengguna untuk terlibat dalam penemuan harga dengan menawar satu sama lain secara langsung.
Namun menerapkan proposal Dai seperti yang tertulis akan menjadi sebuah tantangan:
- Dalam fase "Planning”, pengguna menanggung beban menegosiasikan “peningkatan optimal jumlah uang beredar untuk periode berikutnya”. Bagaimana “optimal” harus didefinisikan, bagaimana pengguna harus bernegosiasi satu sama lain, dan bagaimana hasil negosiasi tersebut dibagikan tidak dijelaskan.
- Terlepas dari apa yang direncanakan, fase “Bidding” memungkinkan siapa saja untuk mengajukan “tawaran” untuk membuat B-money. Tawaran mencakup jumlah B-money yang akan dibuat serta jumlah bukti kerja yang sesuai sehingga setiap penawaran adalah harga, jumlah perhitungan yang bersedia dilakukan oleh penawar tertentu untuk membeli sejumlah tertentu. dari B-money.
- Setelah penawaran diserahkan, fase “Computation” terdiri dari peserta lelang yang melakukan proof-of-work yang mereka tawarkan dan menyiarkan solusi. Tidak ada mekanisme untuk mencocokkan penawar dengan solusi yang disediakan. Yang lebih problematis adalah tidak jelasnya bagaimana pengguna dapat mengetahui bahwa semua penawaran telah diajukan – kapan fase “Bidding” berakhir dan fase “Computation” dimulai?
- Masalah-masalah ini berulang dalam fase “Money creation”. Karena sifat proof-of-work, pengguna dapat memverifikasi bahwa bukti yang mereka terima dalam solusi adalah asli. Namun bagaimana pengguna dapat secara kolektif menyepakati serangkaian “tawaran tertinggi”? Bagaimana jika pengguna yang berbeda memilih set yang berbeda, baik karena preferensi atau latensi jaringan?
Sistem yang terdesentralisasi kesulitan dalam melacak data dan membuat pilihan secara konsisten, namun B-money memerlukan pelacakan tawaran dari banyak pengguna dan membuat pilihan konsensus di antara mereka. Kompleksitas ini menghalangi penerapan B-money.
Akar dari kompleksitas ini adalah keyakinan Dai bahwa tingkat “optimal” penciptaan B-money harus berfluktuasi seiring waktu berdasarkan “perhitungan makroekonomi” penggunanya. Seperti bit gold, B-money tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat unit B-money dengan menyiarkan tawaran dan kemudian melakukan proof-of-work yang sesuai.
Baik Szabo maupun Dai mengusulkan penggunaan pasar pertukaran mata uang digital untuk komputasi, namun baik bit gold maupun B-money tidak menentukan kebijakan moneter untuk mengatur pasokan mata uang di pasar ini.
Tujuan Kebijakan Moneter Satoshi Menghasilkan Bitcoin
Sebaliknya, kebijakan moneter yang sehat adalah salah satu tujuan utama Satoshi dalam proyek Bitcoin. Dalam postingan milis pertama tempat Bitcoin diumumkan, Satoshi menulis:
“Akar permasalahan mata uang konvensional adalah kepercayaan yang diperlukan agar mata uang tersebut dapat berfungsi. Bank sentral harus dipercaya untuk tidak merendahkan mata uang tersebut, namun sejarah mata uang fiat penuh dengan pelanggaran terhadap kepercayaan tersebut.” - Satoshi, 2009
Satoshi selanjutnya menjelaskan masalah lain dengan mata uang fiat seperti perbankan cadangan fraksional yang berisiko, kurangnya privasi, pencurian & penipuan yang merajalela, dan ketidakmampuan melakukan pembayaran mikro. Namun Satoshi memulai dengan isu penurunan nilai oleh bank sentral—dengan kekhawatiran mengenai kebijakan moneter.
Satoshi ingin Bitcoin pada akhirnya mencapai pasokan sirkulasi terbatas yang tidak dapat terdilusi seiring waktu. Tingkat penciptaan Bitcoin yang “optimal”, bagi Satoshi, pada akhirnya akan menjadi nol.
Tujuan kebijakan moneter ini, lebih dari karakteristik lain yang mereka miliki secara pribadi (atau kolektif!), adalah alasan Satoshi “menemukan” Bitcoin, blockchain, konsensus Nakamoto, dll. —dan bukan orang lain. Ini adalah jawaban singkat atas pertanyaan yang diajukan dalam judul artikel ini: Satoshi memikirkan Bitcoin karena mereka fokus pada penciptaan mata uang digital dengan persediaan terbatas.
Pasokan Bitcoin yang terbatas bukan hanya tujuan kebijakan moneter atau meme bagi para Bitcoiner untuk berkumpul. Penyederhanaan teknis penting inilah yang memungkinkan Satoshi membangun mata uang digital yang berfungsi sementara B-money Dai tetap menjadi postingan web yang menarik.
Bitcoin adalah B-money dengan persyaratan tambahan berupa kebijakan moneter yang telah ditentukan. Seperti banyak penyederhanaan teknis lainnya, pembatasan kebijakan moneter memungkinkan kemajuan dengan mengurangi ruang lingkup. Mari kita lihat bagaimana masing-masing fase pembuatan B-money disederhanakan dengan menerapkan batasan ini.
Semua Pasokan 21 Juta Bitcoin Sudah Ada
Dalam b-money, setiap “periode penciptaan uang” mencakup fase “Perencanaan”, di mana pengguna diharapkan untuk membagikan “perhitungan makroekonomi” mereka yang membenarkan jumlah b-money yang ingin mereka ciptakan pada saat itu. Tujuan kebijakan moneter Satoshi yaitu pasokan terbatas dan emisi nol tidak sesuai dengan kebebasan yang diberikan b-money kepada pengguna individu untuk menghasilkan uang. Oleh karena itu, langkah pertama dalam perjalanan dari bmoney ke bitcoin adalah menghilangkan kebebasan ini. Pengguna bitcoin perorangan tidak dapat membuat bitcoin. Hanya jaringan bitcoin yang dapat membuat bitcoin, dan hal ini terjadi tepat sekali, pada tahun 2009 ketika Satoshi meluncurkan proyek bitcoin.
Satoshi mampu menggantikan fase “Perencanaan” b-money yang berulang menjadi satu jadwal yang telah ditentukan sebelumnya di mana 21 juta bitcoin yang dibuat pada tahun 2009 akan dilepaskan ke peredaran. Pengguna secara sukarela mendukung kebijakan moneter Satoshi dengan mengunduh dan menjalankan perangkat lunak Bitcoin Core yang kebijakan moneternya dikodekan secara keras.
Hal ini mengubah semantik pasar bitcoin untuk komputasi. Bitcoin yang dibayarkan kepada penambang bukanlah hal baru yang diterbitkan; itu melainkan baru dirilis ke peredaran dari persediaan yang ada.
Pandangan ini sangat berbeda dari klaim naif bahwa “penambang bitcoin menciptakan bitcoin”. Penambang Bitcoin tidak menciptakan bitcoin, mereka membelinya. Bitcoin tidak berharga karena “bitcoin terbuat dari energi”—tetapi nilai bitcoin didemonstrasikan dengan dijual untuk mendapatkan energi.
Mari kita ulangi sekali lagi: bitcoin tidak dibuat melalui proof-of-work, bitcoin dibuat melalui konsensus.

Desain Satoshi menghilangkan persyaratan untuk fase “Perencanaan” yang berkelanjutan dari b-money dengan melakukan semua perencanaan terlebih dahulu. Hal ini memungkinkan Satoshi untuk membuat kebijakan moneter yang sehat namun juga menyederhanakan penerapan bitcoin.
Bitcoin dihargai Melalui Konsensus
Kebebasan yang diberikan kepada pengguna untuk menghasilkan uang menimbulkan beban yang sesuai bagi jaringan bmoney. Selama fase “Penawaran” jaringan b-money harus mengumpulkan dan membagikan “tawaran” pembuatan uang dari banyak pengguna yang berbeda.
Menghilangkan kebebasan untuk menghasilkan uang akan meringankan beban jaringan bitcoin. Karena seluruh 21 juta bitcoin sudah ada, jaringan tidak perlu mengumpulkan tawaran dari pengguna untuk menghasilkan uang, jaringan hanya perlu menjual bitcoin sesuai jadwal Satoshi yang telah ditentukan.
Jaringan bitcoin dengan demikian menawarkan konsensus harga permintaan untuk bitcoin yang dijualnya di setiap blok. Harga tunggal ini dihitung oleh setiap node secara independen menggunakan salinan blockchainnya. Jika node memiliki konsensus pada blockchain yang sama (poin yang akan kita bahas nanti) mereka semua akan menawarkan harga permintaan yang sama di setiap blok.[^8]
Bagian pertama kalkulasi harga konsensus menentukan berapa banyak bitcoin yang akan dijual. Hal ini diperbaiki oleh jadwal rilis Satoshi yang telah ditentukan sebelumnya. Semua node bitcoin di jaringan menghitung jumlah yang sama untuk blok tertentu:
$ bitcoin-cli getblockstats <block\_height> {... "subsidy": 6250000000, ... } # 6.25 BTCBagian kedua dari harga yang diminta secara konsensus adalah jumlah komputasi yang akan menjual subsidi saat ini. Sekali lagi, semua node bitcoin di jaringan menghitung nilai yang sama (kita akan meninjau kembali kalkulasi tingkat kesulitan ini di bagian berikutnya):
$ bitcoin-cli getdifficulty {... "result": 55621444139429.57, ... }Bersama-sama, subsidi dan kesulitan jaringan menentukan permintaan bitcoin saat ini sebagai mata uang komputasi. Karena blockchain berada dalam konsensus, harga ini adalah harga konsensus.
Pengguna b-money juga dianggap memiliki konsensus “blockchain” yang berisi riwayat semua transaksi. Namun Dai tidak pernah memikirkan solusi sederhana berupa konsensus tunggal yang meminta harga untuk pembuatan b-money baru, yang hanya ditentukan oleh data di blockchain tersebut.
Sebaliknya, Dai berasumsi bahwa penciptaan uang harus berlangsung selamanya. Oleh karena itu, pengguna individu perlu diberdayakan untuk mempengaruhi kebijakan moneter – seperti halnya mata uang fiat. Persyaratan yang dirasakan ini membuat Dai merancang sistem penawaran yang mencegah penerapan b-money.
Kompleksitas tambahan ini dihilangkan dengan persyaratan Satoshi mengenai kebijakan moneter yang telah ditentukan sebelumnya.
Waktu Menutup Semua Penyebaran
Dalam fase “Komputasi” b-money, pengguna individu akan melakukan komputasi yang telah mereka lakukan dalam penawaran sebelumnya. Dalam bitcoin, seluruh jaringan adalah penjual – tetapi siapa pembelinya?
Di pasar pengiriman email, pembelinya adalah individu yang ingin mengirim email. Otoritas penetapan harga, penyedia layanan email, akan menetapkan harga yang dianggap murah bagi individu namun mahal bagi pelaku spam. Namun jika jumlah pengguna yang sah bertambah, harganya masih bisa tetap sama karena kekuatan komputasi masing-masing pengguna akan tetap sama.
Di b-money, setiap pengguna yang menyumbangkan tawaran untuk pembuatan uang selanjutnya harus melakukan sendiri jumlah komputasi yang sesuai. Setiap pengguna bertindak sebagai otoritas penetapan harga berdasarkan pengetahuan mereka tentang kemampuan komputasi mereka sendiri.
Jaringan bitcoin menawarkan satu harga yang diminta dalam komputasi subsidi bitcoin saat ini. Namun tidak ada penambang individu yang menemukan blok yang melakukan komputasi sebanyak ini.[^9] Blok pemenang penambang individu adalah bukti bahwa semua penambang secara kolektif melakukan jumlah komputasi yang diperlukan. Pembeli bitcoin dengan demikian adalah industri penambangan bitcoin global.
Setelah mencapai konsensus harga yang diminta, jaringan bitcoin tidak akan mengubah harga tersebut sampai lebih banyak blok diproduksi. Blok-blok ini harus berisi proof-of-work dengan harga yang diminta saat ini. Oleh karena itu, industri pertambangan tidak punya pilihan jika ingin “melakukan perdagangan” selain membayar harga yang diminta saat ini dalam komputasi.
Satu-satunya variabel yang dapat dikontrol oleh industri pertambangan adalah berapa lama waktu yang dibutuhkan untuk memproduksi blok berikutnya. Sama seperti jaringan bitcoin yang menawarkan satu harga yang diminta, industri pertambangan juga menawarkan satu penawaran—waktu yang diperlukan untuk menghasilkan blok berikutnya yang memenuhi harga yang diminta jaringan saat ini.
Untuk mengimbangi peningkatan kecepatan perangkat keras dan minat yang berbeda-beda dalam menjalankan node dari waktu ke waktu, kesulitan proof-of-work ditentukan oleh rata-rata bergerak yang menargetkan jumlah rata-rata blok per jam. Jika dihasilkan terlalu cepat, kesulitannya akan meningkat. - Nakamoto, 2008
Satoshi dengan sederhana menjelaskan algoritma penyesuaian kesulitan, yang sering disebut sebagai salah satu ide paling orisinal dalam implementasi bitcoin. Hal ini benar, namun alih-alih berfokus pada daya cipta solusi, mari kita fokus pada mengapa penyelesaian masalah sangat penting bagi Satoshi.
Proyek-proyek seperti bit gold dan b-money tidak perlu membatasi nilai tukar pada saat penciptaan uang karena mereka tidak memiliki pasokan tetap atau kebijakan moneter yang telah ditentukan sebelumnya. Periode penciptaan uang yang lebih cepat atau lebih lambat dapat dikompensasikan melalui cara lain, misalnya melalui pajak. Dealer eksternal memasukkan token bit gold ke dalam bundler yang lebih besar atau lebih kecil atau pengguna b-money mengubah tawaran mereka.
Namun tujuan kebijakan moneter Satoshi mengharuskan bitcoin memiliki tingkat pelepasan bitcoin yang telah ditentukan untuk diedarkan. Membatasi laju (statistik) produksi blok dari waktu ke waktu adalah hal yang wajar dalam bitcoin karena laju produksi blok adalah laju penjualan pasokan awal bitcoin. Menjual 21 juta bitcoin selama 140 tahun adalah proposisi yang berbeda dibandingkan membiarkannya dijual dalam 3 bulan.
Selain itu, bitcoin sebenarnya dapat menerapkan batasan ini karena blockchain adalah “protokol cap waktu aman” milik Szabo. Satoshi menggambarkan bitcoin sebagai yang pertama dan terutama sebagai “server stempel waktu terdistribusi secara peer-to-peer,” dan implementasi awal kode sumber bitcoin menggunakan “rantai waktu” dunia, bukan “blockchain” untuk menggambarkan struktur data bersama yang mengimplementasikan pasar proof-of-work bitcoin.[^10]

Tidak seperti bit gold atau b-money, token dalam bitcoin tidak mengalami kelebihan pasokan. Jaringan bitcoin menggunakan penyesuaian kesulitan untuk mengubah harga uang sebagai respons terhadap perubahan pasokan komputasi.
Algoritme penyesuaian ulang kesulitan Bitcoin memanfaatkan kemampuan ini. Blockchain konsensus digunakan oleh peserta untuk menghitung penawaran historis yang dibuat oleh industri pertambangan dan menyesuaikan kembali kesulitan agar bisa mendekati waktu blok target.
Pesanan Terunggul Menciptakan Konsensus
Rantai penyederhanaan yang disebabkan oleh tuntutan kebijakan moneter yang kuat meluas ke fase “penciptaan uang” dari b-money.
Tawaran yang diajukan pengguna di b-money mengalami masalah “tidak ada yang dipertaruhkan”. Tidak ada mekanisme untuk mencegah pengguna mengajukan tawaran dengan sejumlah besar b-money untuk pekerjaan yang sangat sedikit. Hal ini mengharuskan jaringan untuk melacak tawaran mana yang telah diselesaikan dan hanya menerima “tawaran tertinggi…dalam hal biaya nominal per unit b-money yang dibuat” untuk menghindari tawaran yang mengganggu tersebut. Setiap peserta b-money harus melacak seluruh tawaran senilai buku pesanan, mencocokkan tawaran dengan perhitungan selanjutnya, dan hanya menyelesaikan pesanan yang telah selesai dengan harga tertinggi.
Masalah ini merupakan contoh dari masalah konsensus yang lebih umum dalam sistem desentralisasi, yang juga dikenal sebagai “Byzantine generals” atau terkadang masalah “pembelanjaan ganda” dalam konteks mata uang digital. Berbagi urutan data yang identik di antara semua peserta merupakan suatu tantangan dalam jaringan yang saling bermusuhan dan terdesentralisasi. Solusi yang ada untuk masalah ini – yang disebut “algoritma konsensus Byzantine-fault tolerant (BFT)” – memerlukan koordinasi sebelumnya di antara peserta atau mayoritas (>67%) peserta agar tidak berperilaku bermusuhan.
Bitcoin tidak harus mengelola buku pesanan dalam jumlah besar karena jaringan bitcoin menawarkan harga permintaan konsensus tunggal. Ini berarti node bitcoin dapat menerima blok pertama (valid) yang mereka lihat yang memenuhi harga yang diminta jaringan saat ini—tawaran gangguan dapat dengan mudah diabaikan dan merupakan pemborosan sumber daya penambang.
Komputasi harga berdasarkan konsensus memungkinkan pencocokan pesanan beli/jual dalam bitcoin dilakukan secara antusias, dengan sistem siapa cepat dia dapat. Berbeda dengan b-money, pencocokan pesanan yang cepat ini berarti bahwa pasar bitcoin tidak memiliki fase—pasar ini beroperasi terus-menerus, dengan harga konsensus baru dihitung setelah setiap pesanan dicocokkan (blok ditemukan). Untuk menghindari percabangan yang disebabkan oleh latensi jaringan atau perilaku bertentangan, node juga harus mengikuti aturan rantai terberat. Aturan penyelesaian pesanan yang serakah ini memastikan bahwa hanya tawaran tertinggi yang diterima oleh jaringan.
Kombinasi algoritma yang antusias dan serakah ini, dimana node menerima blok valid pertama yang mereka lihat dan juga mengikuti rantai terberat, adalah algoritma BFT baru yang dengan cepat menyatu pada konsensus tentang urutan blok. Satoshi menghabiskan 25% dari white paper bitcoin untuk mendemonstrasikan klaim ini.[^11]
Kita telah menetapkan di bagian sebelumnya bahwa harga permintaan konsensus bitcoin itu sendiri bergantung pada konsensus blockchain. Namun ternyata keberadaan harga permintaan konsensus tunggal inilah yang memungkinkan perhitungan pasar untuk mencocokkan pesanan dengan penuh semangat, dan itulah yang pertama-tama mengarah pada konsensus!
Terlebih lagi, “konsensus Nakamoto” yang baru ini hanya mengharuskan 50% peserta untuk tidak bertentangan, sebuah kemajuan yang signifikan dibandingkan dengan kondisi sebelumnya. Seorang cypherpunk seperti Satoshi membuat terobosan ilmu komputer teoretis ini, dibandingkan dengan akademisi tradisional atau peneliti industri, karena fokus mereka yang sempit pada penerapan uang yang sehat, dibandingkan algoritma konsensus umum untuk komputasi terdistribusi.
Kesimpulan
B-money adalah kerangka kerja yang kuat untuk membangun mata uang digital tetapi tidak lengkap karena tidak memiliki kebijakan moneter. Membatasi b-money dengan jadwal rilis yang telah ditentukan untuk bitcoin mengurangi cakupan dan menyederhanakan implementasi dengan menghilangkan persyaratan untuk melacak dan memilih di antara tawaran pembuatan uang yang diajukan pengguna. Mempertahankan kecepatan sementara dari jadwal rilis Satoshi menghasilkan algoritma penyesuaian kesulitan dan memungkinkan konsensus Nakamoto, yang secara luas diakui sebagai salah satu aspek paling inovatif dalam implementasi bitcoin.
Ada lebih banyak hal dalam desain bitcoin daripada aspek yang dibahas sejauh ini. Kita memfokuskan artikel ini pada pasar “utama” dalam bitcoin, pasar yang mendistribusikan pasokan awal bitcoin ke dalam sirkulasi.
Artikel berikutnya dalam seri ini akan mengeksplorasi pasar penyelesaian transaksi bitcoin dan kaitannya dengan pasar pendistribusian pasokan bitcoin. Hubungan ini akan menyarankan metodologi bagaimana membangun pasar masa depan untuk layanan terdesentralisasi selain bitcoin.
Sumber artikel: HOW DID SATOSHI THINK OF BITCOIN? https://bitcoinmagazine.com/technical/how-did-satoshi-think-of-bitcoin
Diterjemahkan oleh: Abengkris
[^1]: Judul seri ini diambil dari pesan telegraf pertama dalam sejarah, yang dikirimkan oleh Samuel Morse pada tahun 1844: “What hath God wrought?”.
[^2]: Bitcoin: Sistem Uang Elektronik Peer-to-Peer, tersedia di: https://bitcoin.org/bitcoin.pdf
[^3]: Pricing via Processing or Combatting Junk Mail oleh Dwork dan Naor. tersedia di:
https://www.wisdom.weizmann.ac.il/../../pvp.pdf[^4]: Meskipun merupakan pencetus ide tersebut, Dwork & Naor tidak menciptakan “proof-of-work”—julukan tersebut kemudian diberikan pada tahun 1999 oleh Markus Jakobsson dan Ari Juels.
[^5]: Proyek RPoW Hal Finney adalah upaya untuk menciptakan proof-of-work yang dapat ditransfer, tetapi bitcoin tidak menggunakan konsep ini karena tidak memperlakukan komputasi sebagai mata uang. Seperti yang akan kita lihat nanti ketika kita memeriksa bit gold dan b-money, komputasi tidak dapat berupa mata uang karena nilai komputasi berubah seiring waktu sementara unit mata uang harus memiliki nilai yang sama. Bitcoin bukanlah komputasi, bitcoin adalah mata uang yang dijual untuk komputasi.
[^6]: Pada saat ini, beberapa pembaca mungkin percaya bahwa saya meremehkan kontribusi Dai atau Szabo karena kontribusi mereka tidak jelas atau tidak jelas dalam beberapa hal. Perasaan saya justru sebaliknya: Dai dan Szabo pada dasarnya benar dan fakta bahwa mereka tidak mengartikulasikan setiap detail seperti yang dilakukan Satoshi tidak mengurangi kontribusi mereka. Sebaliknya, hal ini seharusnya meningkatkan apresiasi kita terhadap hal tersebut, karena hal ini menunjukkan betapa menantangnya munculnya mata uang digital, bahkan bagi para praktisi terbaiknya.
[^7]: Postingan b-money Dai adalah referensi pertama dalam white paper Satoshi, tersedia di: http://www.weidai.com/bmoney.txt
[^8]: Ada dua penyederhanaan yang dilakukan di sini: 1. Jumlah bitcoin yang dijual di setiap blok juga dipengaruhi oleh biaya transaksi pasar, yang berada di luar cakupan artikel ini, namun tetap menunggu pekerjaan selanjutnya. 2. Kesulitan yang dilaporkan oleh bitcoin bukanlah jumlah perhitungan yang diharapkan; seseorang harus mengalikannya dengan faktor proporsionalitas.
[^9]: Setidaknya sejak masa lalu yang buruk ketika Satoshi adalah satu-satunya penambang di jaringan.
[^10]: Bitcoin is Time klasik dari Gigi adalah pengenalan yang bagus tentang hubungan mendalam antara bitcoin dan waktu, tersedia di: https://dergigi.com/2021/01/14/bitcoin-is-time/
[^11]: Satoshi melakukan kesalahan baik dalam analisis mereka di buku putih maupun implementasi awal bitcoin berikutnya dengan menggunakan aturan “rantai terpanjang” dan bukan aturan “rantai terberat”.
-
 @ a039ecde:18bc0b8c
2024-11-06 20:49:18
@ a039ecde:18bc0b8c
2024-11-06 20:49:18Ensure top-notch food safety standards with Telsen’s food hygiene app, designed to simplify daily tasks and streamline hygiene management. This user-friendly app supports businesses in maintaining compliance by digitising checklists, tracking cleaning schedules, and providing timely reminders. Ideal for restaurants, catering services, and food manufacturers, Telsen’s app improves operational efficiency and helps meet stringent hygiene regulations. With real-time updates and easy-to-use features, our app is a vital tool for enhancing food safety practices. Choose Telsen’s food hygiene app for comprehensive, reliable hygiene management at your fingertips.
-
 @ 526e9d4c:2ecfb055
2024-11-04 04:13:46
@ 526e9d4c:2ecfb055
2024-11-04 04:13:46Ingredients
- 金耳一块 // 1 piece of golden tremella
- 银耳2片 // 2 pieces of silver ear fungus
- 红枣10颗 // 10 red dates
- 枸杞7-8粒 // 7-8 goji berries
- 桃胶20颗 // 20 peach gum pieces
- 黄冰糖3块 // 3 blocks of yellow rock sugar
Directions
- 煮开后,放5分钟即可使用,如果觉得不是很甜,可以再放一点冰糖(根绝个人口味)
-
 @ ebdee929:513adbad
2024-10-17 17:09:57
@ ebdee929:513adbad
2024-10-17 17:09:57Software Setup Links:
DC-1 as a monitor:
- SuperDisplay Setup | Best for Windows
- SpaceDesk Wireless and Wired Display Setup | Windows PC Users
- Chrome Remote Desktop Setup | Anyone
Purchase and setup links:
Keyboards:
- Keys-To-Go 2 White Keyboard | Logitech
- Keys-To-Go 2 Bluetooth Setup
- Magic Keyboard White | Apple through Amazon.com
- Magic Keyboard Bluetooth Setup
- Air 60 V2 with Blue Switches | Nuphy
- Air 60 V2 Keyboard Folio | Nuphy
- Air 60 V2 Bluetooth and Folio Setup
- Magic Keyboard Case | Fintie through Amazon.com
Pens:
- Premium White Pen
- Ultra Premium Lamy Pen | Amazon.com
- Samsung S Pens (Multiple):
- Small (Galaxy Note Series Style)
- Cheaper Alternative (ZERO Quality Guarantees)
- Medium (Galaxy Fold Style with smooth tip)
- Cheaper Alternative (ZERO Quality Guarantees)
- Larger (Galaxy Tab Style)
- Cheaper Alternative (ZERO Quality Guarantees)
Pen Setup: Just touch the screen and it works, no pairing or charging needed.
Others:
- Bluelight Free Light Bulb | Amazon.com
- Light Bulb Setup
- Comfy Green Sleeve | Amazon.com
Keys-To-Go 2 Bluetooth Setup:
- Step 1: Unbox keyboard from box
- Step 2: Open keyboard and pull tab to enable batteries and keyboard function
- Step 3: Ensure Switch on back of product is in the position where green is showing, not off where red is showing
- Step 4: Hold the key labeled ‘fn’ meanwhile you hold the ‘g’ key for 3 seconds to put the keyboard into android mode, since this is an android tablet
- Step 5: Hold the key labeled ‘fn’ meanwhile you hold the key labeled ‘F1 with the image of the laptop and phone for 3 seconds to put profile 1 into bluetooth pairing mode
- Step 6: On your Daylight DC-1, swipe down on the top of the screen, swipe down again, click on the settings icon that looks like a gear in the bottom right corner
- Step 7: In settings, click the second from the top menu item on the left called ‘Connected devices’ (it says Bluetooth, pairing underneath it)
- Step 8: Click on the button labeled ‘Pair new device’
- Step 9: Under available devices tap on Keys-To-Go 2
- Step 10: It will ask you to type some numbers and hit return/ enter, once you do so the device will show up as connected under ‘Saved Devices’
- Step 11: Turn off the keyboard with the switch on the back if you desire, this will disconnect it from the device
Appendix: Keys-To-Go 2 Documentation:
Apple Magic Keyboard Setup:
- Step 1: Unbox keyboard from box
- Step 2: Ensure Switch on back of product is in the position where green is showing
- Step 3: On your Daylight DC-1, swipe down on the top of the screen, swipe down again, click on the settings icon that looks like a gear in the bottom right corner
- Step 4: In settings, click the second from the top menu item on the left called ‘Connected devices’ (it says Bluetooth, pairing underneath it)
- Step 5: Click on the button labeled ‘Pair new device’
- Step 6: Under available devices tap on Magic Keyboard
- Step 7: It will ask you to type some numbers and hit return/ enter, once you do so the device will show up as connected under ‘Saved Devices’
- Step 8: Turn off the keyboard with the switch on the back if you desire, this will disconnect it from the device
Spacedesk Setup:
THIS IS ONLY FOR PEOPLE USING A WINDOWS PC
- Step 1: Open the Google Play Store: On your device, slide in from the side until and move till you get to the letter ‘P’ and tap ‘Play Store’
- Step 2: Search for SpaceDesk: In the Google Play Store, tap on the search bar at the top and type "SpaceDesk". As you type, suggestions will appear below the search bar. Tap on "SpaceDesk - USB Display for PC" when it appears.
- Step 3: Download and Install the Driver: Visit the
official Spacedesk website and download
the ‘Windows 10/11 (64-bit)’ Spacedesk driver for Windows. Follow the on-screen instructions to install it on your PC. - Step 4: Launch Spacedesk Server: After installation, open the Spacedesk Driver Console application on your Windows PC.
- Step 5: Click the ‘USB Cable Driver Android’ button, then enable the ‘USB Cable Android’ option and let it apply.
- Step 6: Open Spacedesk App: On your Android device, open the Spacedesk app you installed earlier. - Step 7: Improve Quality: Click on the ‘3 lines’ icon and then settings.
- Under ‘Rotation’ enable ‘Auto-Rotation’ and under ‘Quality/Performance’ slide ‘Image Quality’ to max (the right) and set ‘Custom FPS Rate’ to 60. - Step 7A (for wired use): Plug the tablet into your PC - Step 7B (for wired use): Enable USB File Transfer: Swipe down on status bar (the bar at the top of the screen with wifi and notification icons etc. There will be a notification under the ‘Silent’ category named ‘Charging this device via USB’, tap on it to expand it, then tap once more time when it says ‘Tap for more options’. This will open up a menu, all you need to do is click ‘File Transfer’ under the section called ‘Use USB for’ - Step 8: Connect: Reopen the Spacedesk app (use the back arrow or button to leave the settings menu should you need). The app should now detect your Windows PC through USB OR wireless. Tap the listing under your computer's name for wireless connection, or tap the little trident USB icon at the bottom middle of the screen for wired connection, which is recommended.
SuperDisplay Setup:
THIS IS ONLY FOR PEOPLE USING A WINDOWS PC
- Step 1: Open the Google Play Store on the tablet: On your device, slide in from the side until and move till you get to the letter ‘P’ and tap ‘Play Store’
- Step 2: Search for SuperDisplay: In the Google Play Store, tap on the search bar at the top and type "SuperDisplay". As you type, suggestions will appear below the search bar. Tap on "SuperDisplay - Virtual Monitor" when it appears.
- Step 3: Download and Install the Driver on your Windows PC: Visit the
official SuperDisplay website and download
the Windows driver. Follow the on-screen instructions to install it on your PC. - Step 4: Launch SuperDisplay : After installation, open the SuperDisplay Settings application on your Windows PC by hitting the ‘Windows’ Key and typing ‘SuperDisplay Settings’ - Step 5: Launch the application on your tablet. - Step 6: Go into SuperDisplay settings by clicking the settings gear icon in the top right corner. Under ‘Advanced settings’ click ‘Quality’ and slide it to 100. - Step 7 (Wireless): IP Address: Back out of the settings and input the IP address into the desktop program. (Both devices need to be on the same wifi) - Step 7 (Wired): Plug the tablet into the PC - Step 8: Start the connection on the tablet by clicking the central button! - Step 9: In Windows, hit the ‘Windows’ key, type display and hit enter. This will take you to display settings. In display settings set the displays to ‘extend’ and then confirm the change. Select the DC-1 display by clicking the square it is associated with, then set the display to 1584 x 1184 resolution, confirm this by hitting ‘keep changes’, then set to 125% scale.
Chrome Remote Desktop Setup:
Note: This prefers Chrome itself on the tablet and REQUIRES a chromium based browser to be installed on your computer, examples of chromium based browsers are Chrome, Edge, Arc, Opera etc. Basically anything but Safari or Firefox will do. This is because a chrome extension needs to be installed. Both devices need to be signed in to the same Google account to see each other.
- Step 1:
and click the download button here:
- Step 2: Get the extension in the window that pops up:
- Step 3: Once installed, click the download button AGAIN and it will show what is shown below, a program called ‘chromeremotedesktophost’ will download, install it.
- Step 4: In the play store, install the ‘Chrome Remote Desktop’ app and open it, the app's name will be just ‘remote desktop’ as a heads up. - Step 5: On the computer, go to
and click set up remote access under the ‘Remote Access’ tab. Then set a computer name and pin. Accept whatever permissions pop up on your computer
- Step 6: If you have Chrome itself installed on the tablet it will open a page, click the ‘Access my computer’ button, then under remote Access click your device.
APK Installation Guide:
- Note on APK’s: These are apps from outside official sources, they might not update from the play store and in rare cases can have different functionality. Apply extra caution and source these app files from good sources like
. Just like through the play store or other sources, malicious files can be spread, use common sense and generally avoid downloading any ‘hack’ apps that claim to unlock features. - Step 1: One the home screen, swipe down from the top of the screen, also called the status bar - Step 2: Swipe down again till the settings tiles fill the screen, then click the gear icon in the bottom right hand corner of the screen which will take you to the settings application - Step 3: In settings, tap ‘Apps’, then ‘Special app access’, then ‘Install unknown apps’ - Step 4: Tap your preferred browser application then enable the ‘Allow from this source’ toggle - Step 5: Open your browser of choice, and search ‘apkmirror’ and navigate to
, or just type
https://apkmirror.com/ - Step 6: On the apkmirror website, search your application name in the search bat at the top of the apkmirror website. After you search find your app in the results and tap the most recent version. Dismiss any ads you might see. - Step 7: Under the text ‘Verified safe to install (read more)’ tap the button called ‘SCROLL TO AVAILABLE DOWNLOADS’ - Step 8: Find a file tagged ‘APK’ not ‘BUNDLE’ - Step 9: Click on the Download Arrow and line icon that looks like this ⬇️ - Step 10: Under ‘Verified safe to install (read more)’ tap ‘DOWNLOAD APK’ - Step 11: If it appears, dismiss the warning for ‘File might be harmful’ by tapping ‘Download anyway’ - Step 12: After your apk downloads, either - Tap ‘Open’ on the ‘File Download’ Pop-Up - Go to the home screen and open the files app, navigate to the downloads folder and tap on the downloaded apk - Step 13: Tap ‘INSTALL’ on the popup that appears. After it installs tap ‘OPEN’ - Step 14: The app will now be on your device and you can search and open it like every other app
Touch grass,
Daylight Team
-
 @ 472f440f:5669301e
2024-10-16 01:57:41
@ 472f440f:5669301e
2024-10-16 01:57:41Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice.
This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative.
These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin.
Since 2016: +46% in USD -99% in BTC
Since 2020: +34% in USD -70% in BTC
The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them.
Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter.
What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line.
Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow.
The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way.
Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished.
In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial.
We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years.
There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer.
Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it.
Final thought... Sinus congestion sucks.
-
 @ 5469030c:61ca3e1e
2024-11-03 22:03:47
@ 5469030c:61ca3e1e
2024-11-03 22:03:47Chef's notes
Make sure to prep your ingredients, before boiling the pasta.
A little Tajín seasoning per serving is also great for some extra flavor. 🌶
Details
- ⏲️ Prep time: 21
- 🍳 Cook time: 21
- 🍽️ Servings: 5
Ingredients
- • 12oz Tricolor Penne Pasta ❤️💛💚
- • 3 cups rotisserie chicken, shredded🍗
- • 4 cups chopped celery🥬
- • 1/2 cup chopped red bell pepper 🌶
- • 1/2 cup chopped green bell pepper 🫑
- • 6 slices turkey bacon, cooked and crumbled. 🦃
- • 4 tbsp avocado mayo 🥑
- • 3 tablespoons olive oil 🫒
- Sea salt & Black Pepper to taste. 🧂
Directions
- • Add 9 cups of water to a medium to large pot to boil for 15 mins over medium high heat
- Preheat oven to 375°F (190°C) then add turkey bacon on lightly coated baking sheet with a little olive oil to prevent the bacon from sticking. Bake for 15 mins.
- • In a large bowl, combine the pasta shredded chicken, chopped celery, red and green peppers, crumbled turkey bacon, and avocado mayo.
- • Drizzle 3 table spoons olive oil and stir.
- • Chill in the refrigerator for at least 30 minutes before serving
-
 @ fd208ee8:0fd927c1
2024-10-31 11:03:08
@ fd208ee8:0fd927c1
2024-10-31 11:03:08Chef's notes
I got the recipe from the byanjushka website. She includes a lot more information on there, and lots of pictures and instructions. But it's all in German, so here's my quickie, English version. I've doubled the amounts, as I first baked this for the #PurpleKonnektiv meetup, and I knew I'd have some hungry guests.
The cookies are vegan, but they're mostly just peanut, so it's sort of irrelevant. Just make sure you get the really high-quality peanut butter that is 100% peanut. You can usually identify it by the fact that the oil separates from the base, a bit. Everything else is probably with hardened palm oil, or something.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 10 min
- 🍽️ Servings: 30 cookies
Ingredients
- 500 g peanut butter, normal or crunchy
- 300 g brown (or raw) sugar
- 160 ml plant-based milk (or cows' milk, if you don't care about vegan)
- 1 pkg vanilla sugar (bourbon is nice) or 1 tsp vanilla
- 250 g flour
- 2 tsp baking powder
- 2/3 tsp salt
Directions
- Preheat oven to 180 °C (350 °F).
- Beat together the peanut butter and the sugars, with an electric mixer.
- Mix in milk and vanilla.
- In a separate bowl, stir together flour, salt, and baking powder.
- Stir the dry ingredients into the wet ingredients, and then knead the dough a bit.
- (At this point, I put the dough in the fridge overnight, and baked it the next day.)
- Line your baking sheet with baking paper.
- Form tbsp-spoon-sized balls of dough.
- Press each one flat, with a fork, dipping the fork in water, before each press (to keep the dough from sticking to the fork).
-
 @ 569d3ee7:6120020e
2024-11-06 20:05:35
@ 569d3ee7:6120020e
2024-11-06 20:05:35Enhance user experience with Responsive Website Design Orange County by Urban Geko. Our team creates mobile-first designs that adapt perfectly to any device, ensuring seamless usability and higher engagement. With responsive design, your website will load fast, look stunning, and function flawlessly across smartphones, tablets, and desktops. Urban Geko specializes in blending creativity with technology to deliver dynamic, interactive websites that leave lasting impressions. Whether you’re a local business or a global enterprise, our Orange County experts ensure your website is future-ready. Partner with Urban Geko for innovative web solutions that elevate your brand.
-
 @ fd208ee8:0fd927c1
2024-10-31 07:35:50
@ fd208ee8:0fd927c1
2024-10-31 07:35:50You don't choose software. You choose software developers.
I've done lots of internal and external software project audits. The clue to a good audit, is that you are judging the building and the builder, because the former determines the present state of the code and the latter determines how things will be built going forward.
Here's what to look for in a good developer:
- curious : eager to learn from others
- humble : seems slightly embarrassed, when you report an issue, and tries to reproduce and fix the problem
- responsive : they try to get back to you within 24 hours, or they arrange a sub or post a notice, when they'll be away for a while. They feel bad, if they leave someone waiting, so they'll send updates, even if it's just to ask them to be patient.
- diligent : they don't leave websites rotting, abandoned. They either maintain it or pull it down. They check their repos regularly and actively manage the PRs and issues.
- egalitarian : they care about all of their users, whether they are rich or poor, famous or unknown, premium or freewarers
- agile : they don't let the system go stale, for months, and then dump a gigantic commit
- honest : they don't lie, ever. Never ever. They're not sneaky or evasive. If something they promised won't work out, they announce it. They readily admit to things that make them look bad.
- calm : they are not histrionic, hyperventilatory or prone to needing a Wellness Break, to recover from the stress of dealing with humans and code
- centered : they have a plan, for their software, that they regularly refine, but they don't flit from one Next Big Thing, to another. They resist hype and examine concepts soberly and analytically.
- concerned : they test their software before giving it to other people because they want them to have a positive experience, while using it. If something is just a prototype, they make that clear, when announcing it.
-
 @ 5469030c:61ca3e1e
2024-11-03 21:59:54
@ 5469030c:61ca3e1e
2024-11-03 21:59:54Chef's notes
Make sure to prep your ingredients, before boiling the pasta.
A little Tajín seasoning per serving is also great for some extra flavor. 🌶
Details
- ⏲️ Prep time: 21
- 🍳 Cook time: 21
- 🍽️ Servings: 5
Ingredients
- • 12oz Tricolor Penne Pasta ❤️💛💚
- • 3 cups rotisserie chicken, shredded🍗
- • 4 cups chopped celery🥬
- • 1/2 cup chopped red bell pepper 🌶
- • 1/2 cup chopped green bell pepper 🫑
- • 6 slices turkey bacon, cooked and crumbled. 🦃
- • 4 tbsp avocado mayo 🥑
- • 3 tablespoons olive oil 🫒
- Sea salt & Black Pepper to taste. 🧂
Directions
- • Add 9 cups of water to a medium to large pot to boil for 15 mins over medium high heat
- Preheat oven to 375°F (190°C) then add turkey bacon on lightly coated baking sheet with a little olive oil to prevent the bacon from sticking. Bake for 15 mins.
- • In a large bowl, combine the pasta shredded chicken, chopped celery, red and green peppers, crumbled turkey bacon, and avocado mayo.
- • Drizzle 3 table spoons olive oil and stir.
- • Chill in the refrigerator for at least 30 minutes before serving
-
 @ 5a69e82d:aa41c382
2024-11-05 11:22:51
@ 5a69e82d:aa41c382
2024-11-05 11:22:51Dhruv Bansal, CSO dan Co-Founder Unchained mengeksplorasi prinsip-prinsip dan sejarah yang mengarah pada penciptaan Bitcoin dan mengajukan pertanyaan: "Apa yang telah dilakukan Satoshi"?
Bitcoin sering dibandingkan dengan internet pada tahun 1990an, namun saya yakin analogi yang lebih baik adalah dengan telegraf pada tahun 1840an.[^1]
Telegraf adalah teknologi pertama yang mengirimkan data yang dikodekan dengan kecepatan mendekati cahaya dalam jarak jauh. Ini menandai lahirnya industri telekomunikasi. Internet, meskipun skalanya lebih besar, kontennya lebih kaya, dan many-to-many, bukan one-to-one, pada dasarnya masih merupakan teknologi telekomunikasi.
Baik telegraf maupun internet bergantung pada model bisnis di mana perusahaan mengerahkan modal untuk membangun jaringan fisik dan kemudian membebankan biaya kepada pengguna untuk mengirim pesan melalui jaringan ini. Jaringan AT&T secara historis mengirimkan telegram, panggilan telepon, paket TCP/IP, pesan teks, dan sekarang TikTok.
Transformasi masyarakat melalui telekomunikasi telah menghasilkan kebebasan yang lebih besar namun juga sentralisasi yang lebih besar. Internet telah meningkatkan jangkauan jutaan pembuat konten dan usaha kecil, namun juga memperkuat jangkauan perusahaan, otoritas pusat, dan lembaga lain yang memiliki posisi yang cukup baik untuk memantau dan memanipulasi aktivitas online.
Namun Bitcoin bukanlah akhir dari transformasi apa pun—ini adalah awal dari sebuah transformasi. Seperti halnya telekomunikasi, Bitcoin akan mengubah kebiasaan umat manusia dan kehidupan sehari-harinya. Memprediksi seluruh cakupan perubahan saat ini sama dengan membayangkan internet saat hidup di era telegraf.
Seri ini mencoba membayangkan masa depan dengan memulai dari masa lalu. Artikel awal ini menelusuri sejarah mata uang digital sebelum Bitcoin. Hanya dengan memahami kegagalan proyek-proyek sebelumnya, kita dapat memahami apa yang membuat Bitcoin berhasil—dan bagaimana hal itu menyarankan metodologi untuk membangun sistem desentralisasi di masa depan.
Daftar isi
- Sistem yang Terdesentralisasi Adalah Pasar
- Pasar yang Terdesentralisasi Membutuhkan Barang yang Terdesentralisasi
- Bagaimana Sistem Desentralisasi dapat Menentukan Harga Komputasi?
- Tujuan Kebijakan Moneter Satoshi Menghasilkan Bitcoin
- Kesimpulan
Klaim utama dari artikel ini adalah bahwa Bitcoin dapat dianggap sebagai adaptasi dari proyek B-money Dai yang menghilangkan kebebasan untuk menciptakan uang. Hanya beberapa minggu setelah artikel ini pertama kali diterbitkan, email baru muncul di mana Satoshi mengaku tidak terbiasa dengan B-money, namun mengakui bahwa Bitcoin dimulai “tepat dari titik itu.” Mengingat bukti baru ini, kami yakin klaim utama ini, meskipun tidak akurat secara historis, masih merupakan cara yang bermakna dan bermanfaat untuk memikirkan asal usul Bitcoin.
Bagaimana Satoshi Nakamoto Memikirkan Bitcoin?
Satoshi memang cerdas, tetapi Bitcoin tidak muncul begitu saja.
Bitcoin mengulangi pekerjaan yang ada di bidang kriptografi, sistem terdistribusi, ekonomi, dan filsafat politik. Konsep proof-of-work sudah ada jauh sebelum digunakan dalam uang dan cypherpunk sebelumnya seperti Nick Szabo, Wei Dai, & Hal Finney mengantisipasi dan memengaruhi desain Bitcoin dengan proyek-proyek seperti bit gold, B-money, dan RPoW. Pertimbangkan bahwa, pada tahun 2008, ketika Satoshi menulis white paper Bitcoin[^2], banyak ide penting Bitcoin telah diusulkan dan/atau diimplementasikan:
- Mata uang digital harus berupa jaringan P2P
- Proof-of-work adalah dasar penciptaan uang
- Uang diciptakan melalui lelang
- Kunci publik kriptografi digunakan untuk menentukan kepemilikan dan transfer koin
- Transaksi dikelompokkan menjadi beberapa blok
- Blok dirangkai bersama melalui proof-of-work
- Semua blok disimpan oleh semua peserta
Bitcoin memanfaatkan semua konsep ini, tetapi Satoshi tidak menciptakan satu pun konsep tersebut. Untuk lebih memahami kontribusi Satoshi, kita harus menentukan prinsip Bitcoin mana yang tidak ada dalam daftar.
Beberapa kandidat yang jelas adalah persediaan Bitcoin yang terbatas, konsensus Nakamoto, dan algoritma penyesuaian kesulitan. Tapi apa yang mendorong Satoshi pada ide ini?
Artikel ini mengeksplorasi sejarah mata uang digital dan menyatakan bahwa fokus Satoshi pada kebijakan moneter yang sehat adalah hal yang menyebabkan Bitcoin mengatasi tantangan yang mengalahkan proyek-proyek sebelumnya seperti bit gold dan B-money.
Sistem yang Terdesentralisasi Adalah Pasar
Bitcoin sering digambarkan sebagai sistem terdesentralisasi atau terdistribusi. Sayangnya, kata “desentralisasi” dan “terdistribusi” sering kali membingungkan. Ketika diterapkan pada sistem digital, kedua istilah tersebut mengacu pada cara aplikasi monolitik dapat didekomposisi menjadi jaringan bagian-bagian yang berkomunikasi.

Untuk tujuan kita, perbedaan utama antara sistem terdesentralisasi dan terdistribusi bukanlah topologi diagram jaringannya, namun cara mereka menegakkan aturan. Kami meluangkan waktu di bagian berikut untuk membandingkan sistem terdistribusi dan desentralisasi dan memotivasi gagasan bahwa sistem desentralisasi yang kuat adalah pasar.
Sistem Terdistribusikan Bergantung pada Otoritas Pusat
Dalam hal ini, kami mengartikan “terdistribusi” sebagai sistem apa pun yang telah dipecah menjadi beberapa bagian (sering disebut sebagai "node") yang harus berkomunikasi, biasanya melalui jaringan.
Insinyur perangkat lunak semakin mahir dalam membangun sistem yang terdistribusi secara global. Internet terdiri dari sistem terdistribusi yang secara kolektif berisi miliaran node. Kita masing-masing memiliki simpul di saku kita yang berpartisipasi dan bergantung pada sistem ini.
Namun hampir semua sistem terdistribusi yang kita gunakan saat ini diatur oleh beberapa otoritas pusat, biasanya administrator sistem, perusahaan, atau pemerintah yang saling dipercaya oleh semua node dalam sistem.
Otoritas pusat memastikan semua node mematuhi aturan sistem dan menghapus, memperbaiki, atau menghukum node yang gagal mematuhinya. Mereka dipercaya untuk melakukan koordinasi, menyelesaikan konflik, dan mengalokasikan sumber daya bersama. Seiring waktu, otoritas pusat mengelola perubahan pada sistem, memperbarui atau menambahkan fitur, dan memastikan bahwa node yang berpartisipasi mematuhi perubahan tersebut.
Manfaat yang diperoleh sistem terdistribusi karena mengandalkan otoritas pusat juga disertai dengan biaya. Meskipun sistem ini kuat terhadap kegagalan node-nodenya, kegagalan otoritas pusat dapat menyebabkan sistem berhenti berfungsi secara keseluruhan. Kemampuan otoritas pusat untuk mengambil keputusan secara sepihak berarti menumbangkan atau menghilangkan otoritas pusat sudah cukup untuk mengendalikan atau menghancurkan keseluruhan sistem.
Terlepas dari adanya trade-off ini, jika ada persyaratan bahwa satu partai atau koalisi harus mempertahankan otoritas pusat, atau jika peserta dalam sistem tersebut puas dengan mengandalkan otoritas pusat, maka sistem terdistribusi tradisional adalah solusi terbaik. Tidak diperlukan blockchain, token, atau sistem desentralisasi serupa.
Secara khusus, kasus VC atau mata uang kripto yang didukung oleh pemerintah, dengan persyaratan bahwa satu pihak dapat memantau atau membatasi pembayaran dan membekukan akun, adalah kasus penggunaan yang sempurna untuk sistem terdistribusi tradisional.
Sistem Desentralisasi Tidak Memiliki Otoritas Pusat
Kami menganggap “desentralisasi” memiliki arti yang lebih kuat daripada “terdistribusi”: sistem desentralisasi adalah bagian dari sistem terdistribusi yang tidak memiliki otoritas pusat. Sinonim yang mirip dengan “desentralisasi” adalah “peer-to-peer” (P2P).
Menghapus otoritas pusat memberikan beberapa keuntungan. Sistem terdesentralisasi:
- Tumbuh dengan cepat karena tidak ada hambatan untuk masuk—siapa pun dapat mengembangkan sistem hanya dengan menjalankan node baru, dan tidak ada persyaratan untuk registrasi atau persetujuan dari otoritas pusat.
- Kuat karena tidak ada otoritas pusat yang kegagalannya dapat membahayakan berfungsinya sistem. Semua node adalah sama, jadi kegagalan bersifat lokal dan jaringan merutekan sekitar kerusakan.
- Sulit untuk ditangkap, diatur, dikenakan pajak, atau diawasi karena tidak adanya titik kendali terpusat yang dapat ditumbangkan oleh pemerintah.
Kekuatan inilah yang menjadi alasan Satoshi memilih desain Bitcoin yang terdesentralisasi dan peer-to-peer:
“Pemerintah pandai memotong… jaringan yang dikendalikan secara terpusat seperti Napster, namun jaringan P2P murni seperti Gnutella dan Tor tampaknya masih mampu bertahan.” - Satoshi Nakamoto, 2008
Namun kekuatan ini juga disertai dengan kelemahan. Sistem yang terdesentralisasi bisa menjadi kurang efisien karena setiap titik harus memikul tanggung jawab tambahan untuk koordinasi yang sebelumnya diambil alih oleh otoritas pusat.
Sistem yang terdesentralisasi juga sering dilanda perilaku yang bersifat penipuan dan bertentangan. Terlepas dari persetujuan Satoshi terhadap Gnutella, siapa pun yang menggunakan program berbagi file P2P untuk mengunduh file yang ternyata kotor atau berbahaya memahami alasan mengapa berbagi file P2P tidak pernah menjadi model utama untuk transfer data online.
Satoshi tidak menyebutkannya secara eksplisit, namun email adalah sistem terdesentralisasi lainnya yang menghindari kendali pemerintah. Dan email juga terkenal sebagai spam.
Sistem Desentralisasi diatur Melalui Insentif
Akar masalahnya, dalam semua kasus ini adalah, bahwa perilaku kejahatan (menyebarkan file buruk, mengirim email spam) tidak dihukum, dan perilaku kooperatif (menyebarkan file bagus, hanya mengirim email berguna) tidak dihargai. Sistem desentralisasi yang mengandalkan partisipannya untuk menjadi aktor yang baik gagal untuk berkembang karena sistem tersebut tidak dapat mencegah aktor jahat untuk ikut berpartisipasi.
Tanpa memaksakan otoritas pusat, satu-satunya cara untuk menyelesaikan masalah ini adalah dengan menggunakan insentif ekonomi. Aktor yang baik, menurut definisinya, bermain sesuai aturan karena mereka secara inheren termotivasi untuk melakukannya. Pelaku kejahatan, menurut definisinya, adalah orang yang egois dan licik, namun insentif ekonomi yang tepat dapat mengarahkan perilaku buruk mereka ke arah kebaikan bersama. Sistem yang terdesentralisasi melakukan hal ini dengan memastikan bahwa perilaku kooperatif menguntungkan dan perilaku kejahatan merugikan.
Cara terbaik untuk menerapkan layanan terdesentralisasi yang kuat adalah dengan menciptakan pasar di mana semua pelaku, baik dan buruk, dibayar untuk menyediakan layanan tersebut. Kurangnya hambatan masuk bagi pembeli dan penjual di pasar yang terdesentralisasi mendorong skala dan efisiensi. Jika protokol pasar dapat melindungi partisipan dari penipuan, pencurian, dan penyalahgunaan, maka pelaku kejahatan akan merasa lebih menguntungkan untuk mengikuti aturan atau menyerang sistem lain.
Pasar yang Terdesentralisasi Membutuhkan Barang yang Terdesentralisasi
Namun pasar itu rumit. Mereka harus memberi pembeli dan penjual kemampuan untuk mengirimkan penawaran dan permintaan serta menemukan, mencocokkan, dan menyelesaikan pesanan. Kebijakan tersebut harus adil, memberikan konsistensi yang kuat, dan menjaga ketersediaan meskipun terjadi masa-masa yang tidak menentu.
Pasar global saat ini sangat mumpuni dan canggih, namun menggunakan barang-barang tradisional dan jaringan pembayaran untuk menerapkan insentif di pasar yang terdesentralisasi bukanlah hal yang baru. Setiap penggabungan antara sistem desentralisasi dan uang fiat, aset tradisional, atau komoditas fisik akan menimbulkan kembali ketergantungan pada otoritas pusat yang mengontrol pemroses pembayaran, bank, dan bursa.

Sistem terdesentralisasi tidak dapat mentransfer uang tunai, mencari saldo rekening perantara, atau menentukan kepemilikan properti. Barang-barang tradisional sama sekali tidak terbaca dalam sistem desentralisasi. Hal sebaliknya tidak benar—sistem tradisional dapat berinteraksi dengan Bitcoin semudah aktor lainnya (begitu mereka memutuskan ingin melakukannya). Batasan antara sistem tradisional dan desentralisasi bukanlah sebuah tembok yang tidak dapat dilewati, melainkan sebuah membran semi-permeabel.
Ini berarti bahwa sistem yang terdesentralisasi tidak dapat melaksanakan pembayaran dalam mata uang barang tradisional apa pun. Mereka bahkan tidak dapat menentukan saldo rekening yang didominasi fiat atau kepemilikan real estat atau barang fisik. Seluruh perekonomian tradisional sama sekali tidak terbaca dalam sistem desentralisasi.
Menciptakan pasar yang terdesentralisasi membutuhkan perdagangan barang-barang baru yang terdesentralisasi yang dapat dibaca dan ditransfer dalam sistem yang terdesentralisasi.
Komputasi Adalah Barang Terdesentralisasi yang Pertama
Contoh pertama dari “barang terdesentralisasi” adalah kelas komputasi khusus yang pertama kali diusulkan pada tahun 1993 oleh Cynthia Dwork dan Moni Naor.[^3]
Karena adanya hubungan mendalam antara matematika, fisika, dan ilmu komputer, komputasi ini memerlukan energi dan sumber daya perangkat keras di dunia nyata—hal ini tidak dapat dipalsukan. Karena sumber daya di dunia nyata langka, komputasi ini juga langka.
input untuk komputasi ini dapat berupa data apa pun. Keluaran yang dihasilkan adalah “bukti” digital bahwa pengkomputasian telah dilakukan pada data input yang diberikan. Pembuktian mengandung “kesulitan” tertentu yang merupakan bukti (statistik) dari sejumlah pekerjaan komputasi tertentu. Yang terpenting, hubungan antara data input, pembuktian, dan pekerjaan komputasi asli yang dilakukan dapat diverifikasi secara independen tanpa perlu mengajukan banding ke otoritas pusat mana pun.
Gagasan untuk menyebarkan beberapa data input bersama dengan bukti digital sebagai bukti kerja komputasi dunia nyata yang dilakukan pada input tersebut sekarang disebut “proof-of-work”.[^4] Proof-of-work adalah, jika menggunakan ungkapan Nick Szabo, “biaya yang tidak dapat ditiru”. Karena proof-of-work dapat diverifikasi oleh siapa pun, maka proof-of-work merupakan sumber daya ekonomi yang dapat dibaca oleh semua peserta dalam sistem desentralisasi. Proof-of-work mengubah penghitungan data menjadi barang yang terdesentralisasi. Dwork & Naor mengusulkan penggunaan komputasi untuk membatasi penyalahgunaan sumber daya bersama dengan memaksa peserta untuk memberikan proof-of-work dengan tingkat kesulitan minimum tertentu sebelum mereka dapat mengakses sumber daya:
“Dalam makalah ini kami menyarankan pendekatan komputasi untuk memerangi penyebaran surat elektronik. Secara umum, kami telah merancang mekanisme kontrol akses yang dapat digunakan kapan pun diinginkan untuk membatasi, namun tidak melarang, akses ke sumber daya.” - Dwoak & Naor, 1993
Dalam proposal Dwork & Naor, administrator sistem email akan menetapkan tingkat kesulitan bukti kerja minimum untuk mengirimkan email. Pengguna yang ingin mengirim email perlu melakukan sejumlah komputasi yang sesuai dengan email tersebut sebagai data input. Bukti yang dihasilkan akan dikirimkan ke server bersamaan dengan permintaan pengiriman email.
Dwork & Naor menyebut kesulitan proof-of-work sebagai “fungsi penetapan harga” karena, dengan menyesuaikan kesulitan tersebut, “otoritas penetapan harga” dapat memastikan bahwa sumber daya bersama tetap murah untuk digunakan bagi pengguna yang jujur dan rata-rata, namun mahal bagi pengguna yang mencari untuk mengeksploitasinya. Di pasar pengiriman email, administrator server adalah otoritas penetapan harga; mereka harus memilih “harga” untuk pengiriman email yang cukup rendah untuk penggunaan normal namun terlalu tinggi untuk spam.
Meskipun Dwork & Naor membingkai proof-of-work sebagai disinsentif ekonomi untuk memerangi penyalahgunaan sumber daya, nomenklatur “fungsi penetapan harga” dan “otoritas penetapan harga” mendukung interpretasi yang berbeda dan berbasis pasar: pengguna membeli akses ke sumber daya dengan imbalan komputasi pada tingkat yang sama. harga yang ditetapkan oleh pengontrol sumber daya.
Dalam interpretasi ini, jaringan pengiriman email sebenarnya adalah pengiriman email perdagangan pasar yang terdesentralisasi untuk komputasi. Kesulitan minimum dari proof-of-work adalah harga yang diminta untuk pengiriman email dalam mata uang komputasi.
Mata Uang Adalah Barang Terdesentralisasi yang kedua
Namun komputasi bukanlah mata uang yang baik.
Bukti yang digunakan untuk “memperdagangkan” komputasi hanya valid untuk input yang digunakan dalam komputasi tersebut. Hubungan yang tidak dapat dipecahkan antara bukti spesifik dan input tertentu berarti bahwa proof-of-work untuk satu input tidak dapat digunakan kembali untuk input yang berbeda.

Proof-of-work awalnya diusulkan sebagai mekanisme kontrol akses untuk membatasi email spam. Pengguna diharapkan memberikan bukti kerja bersama email apa pun yang ingin mereka kirim. Mekanisme ini juga dapat dianggap sebagai pasar di mana pengguna membeli pengiriman email dengan komputasi pada harga yang dipilih oleh penyedia layanan email.
Batasan ini berguna – dapat digunakan untuk mencegah pekerjaan yang dilakukan oleh satu pembeli di pasar kemudian dibelanjakan kembali oleh pembeli lain. Misalnya, HashCash, implementasi nyata pertama dari pasar pengiriman email, menyertakan metadata seperti stempel waktu saat ini dan alamat email pengirim dalam data masukan untuk penghitungan bukti kerja. Bukti yang dihasilkan oleh pengguna tertentu untuk email tertentu, tidak dapat digunakan untuk email yang berbeda.
Namun ini juga berarti bahwa komputasi bukti kerja adalah barang yang dipesan lebih dahulu. Dana tersebut tidak dapat dipertukarkan, tidak dapat dibelanjakan kembali,[^5] dan tidak memecahkan masalah kebutuhan yang terjadi secara kebetulan. Properti moneter yang hilang ini mencegah komputasi menjadi mata uang. Terlepas dari namanya, tidak ada insentif bagi penyedia pengiriman email untuk ingin mengakumulasikan HashCash, karena akan ada uang tunai sebenarnya.
Adam Back, penemu HashCash, memahami masalah berikut:
"Hashcash tidak dapat ditransfer secara langsung karena untuk membuatnya didistribusikan, setiap penyedia layanan hanya menerima pembayaran dalam bentuk tunai yang dibuat untuk mereka. Anda mungkin dapat menyiapkan pencetakan gaya digicash (dengan chaumian ecash) dan meminta bank hanya mencetak uang tunai pada penerimaan tabrakan hash yang ditangani. Namun ini berarti Anda harus mempercayai bank untuk tidak mencetak uang dalam jumlah tak terbatas untuk digunakan sendiri." - Adam Back, 1997
Kita tidak ingin menukar komputasi yang dibuat khusus untuk setiap barang atau jasa yang dijual dalam perekonomian yang terdesentralisasi. Kita menginginkan mata uang digital serba guna yang dapat langsung digunakan untuk mengoordinasikan pertukaran nilai di pasar mana pun.
Membangun mata uang digital yang berfungsi namun tetap terdesentralisasi merupakan tantangan yang signifikan. Mata uang membutuhkan unit yang dapat dipertukarkan dengan nilai yang sama yang dapat ditransfer antar pengguna. Hal ini memerlukan model penerbitan, definisi kriptografi kepemilikan dan transfer, proses penemuan dan penyelesaian transaksi, dan buku besar historis. Infrastruktur ini tidak diperlukan ketika bukti kerja hanya dianggap sebagai “mekanisme kontrol akses”.
Terlebih lagi, sistem desentralisasi adalah pasar, jadi semua fungsi dasar mata uang ini harus disediakan melalui penyedia layanan berbayar… dalam satuan mata uang yang sedang dibuat!
Seperti mengkompilasi compiler pertama, permulaan jaringan listrik yang gelap, atau evolusi kehidupan itu sendiri, pencipta mata uang digital dihadapkan pada masalah bootstrapping: bagaimana mendefinisikan insentif ekonomi yang mendasari mata uang yang berfungsi tanpa memiliki mata uang yang berfungsi di dalamnya yang akan mendenominasikan atau membayar insentif tersebut.

Komputasi dan mata uang adalah barang pertama dan kedua di pasar yang terdesentralisasi. Proof-of-work sendiri memungkinkan pertukaran komputasi tetapi mata uang yang berfungsi memerlukan lebih banyak infrastruktur. Butuh waktu 15 tahun bagi komunitas cypherpunk untuk mengembangkan infrastruktur tersebut.
Pasar Terdesentralisasi Pertama harus Memperdagangkan Komputasi untuk Mata Uang
Kemajuan dalam masalah bootstrapping ini berasal dari penyusunan batasan yang tepat.
Sistem yang terdesentralisasi harus menjadi pasar. Pasar terdiri dari pembeli dan penjual yang saling bertukar barang. Pasar terdesentralisasi untuk mata uang digital hanya memiliki dua barang yang dapat dibaca di dalamnya:
- Komputasi melalui proof-of-work
- Unit mata uang yang kita coba bangun
Oleh karena itu, satu-satunya perdagangan pasar yang memungkinkan adalah antara kedua barang tersebut. Komputasi harus dijual untuk satuan mata uang atau setara dengan satuan mata uang harus dijual untuk komputasi. Menyatakan hal ini sangatlah mudah—bagian tersulitnya adalah menata pasar ini sehingga sekadar menukar mata uang untuk komputasi akan mem-bootstrap semua kemampuan mata uang itu sendiri!
Seluruh sejarah mata uang digital yang berpuncak pada white paper Satoshi tahun 2008 adalah serangkaian upaya yang semakin canggih dalam menata pasar ini. Bagian berikut mengulas proyek-proyek seperti bit gold milik Nick Szabo dan B-money milik Wei Dai. Memahami bagaimana proyek-proyek ini menyusun pasar mereka dan mengapa mereka gagal akan membantu kita memahami mengapa Satoshi dan Bitcoin berhasil.

Bagaimana Sistem Desentralisasi Dapat Menentukan Harga Komputasi?
Fungsi utama pasar adalah penemuan harga. Oleh karena itu, komputasi perdagangan pasar untuk mata uang harus menemukan harga komputasi itu sendiri, dalam satuan mata uang tersebut.
Kita biasanya tidak memberikan nilai moneter pada komputasi. Kita biasanya menghargai kapasitas untuk melakukan komputasi karena kita menghargai output dari komputasi, bukan komputasi itu sendiri. Jika keluaran yang sama dapat dilakukan dengan lebih efisien, dengan komputasi yang lebih sedikit, hal ini biasanya disebut “kemajuan”.
Proof-of-work mewakili komputasi spesifik yang keluarannya hanya berupa bukti bahwa komputasi tersebut telah dilakukan. Menghasilkan bukti yang sama dengan melakukan lebih sedikit komputasi dan lebih sedikit pekerjaan tidak akan menghasilkan kemajuan—hal ini akan menjadi bug. Oleh karena itu, komputasi yang terkait dengan Proof-of-work merupakan hal yang aneh dan baru untuk dicoba dihargai.
Ketika bukti kerja dianggap sebagai disinsentif terhadap penyalahgunaan sumber daya, maka bukti kerja tidak perlu dinilai secara tepat dan konsisten. Yang terpenting adalah penyedia layanan email menetapkan tingkat kesulitan yang cukup rendah sehingga tidak terlihat oleh pengguna yang sah, namun cukup tinggi sehingga menjadi penghalang bagi pelaku spam. Oleh karena itu, terdapat beragam “harga” yang dapat diterima dan setiap peserta bertindak sebagai otoritas penetapan harga mereka sendiri, dengan menerapkan fungsi penetapan harga lokal.
Namun satuan mata uang dimaksudkan agar dapat dipertukarkan, masing-masing memiliki nilai yang sama. Karena perubahan teknologi dari waktu ke waktu, dua unit mata uang yang dibuat dengan tingkat kesulitan proof-of-work yang sama—yang diukur dengan jumlah komputasi yang sesuai—mungkin memiliki biaya produksi yang sangat berbeda di dunia nyata, yang diukur dengan waktu, energi, dan/atau modal untuk melakukan komputasi tersebut. Ketika komputasi dijual dengan menggunakan mata uang, dan biaya produksi yang mendasarinya bervariasi, bagaimana pasar dapat memastikan harga yang konsisten?
Nick Szabo dengan jelas mengidentifikasi masalah harga ini ketika menjelaskan bit gold:
"Masalah utamanya...adalah bahwa skema pembuktian kerja bergantung pada arsitektur komputer, bukan hanya matematika abstrak yang didasarkan pada "siklus komputasi" abstrak. ...Jadi, ada kemungkinan untuk menjadi produsen berbiaya sangat rendah (dengan beberapa kali lipat besarnya) dan membanjiri pasar dengan bit gold." - Szabo, 2005

Mata uang terdesentralisasi yang diciptakan melalui proof-of-work akan mengalami kelebihan pasokan dan penurunan pasokan seiring dengan perubahan pasokan komputasi seiring waktu. Untuk mengakomodasi volatilitas ini, jaringan harus belajar menghitung harga secara dinamis.
Mata uang digital awal mencoba memberi harga pada komputasi dengan mencoba mengukur “biaya komputasi” secara kolektif. Wei Dai, misalnya, mengusulkan solusi praktis berikut dalam B-money:
"Jumlah unit moneter yang diciptakan sama dengan biaya upaya komputasi dalam sekeranjang komoditas standar. Sebagai contoh, jika sebuah masalah memerlukan waktu 100 jam untuk diselesaikan pada komputer yang dapat menyelesaikannya dengan cara yang paling ekonomis, dan diperlukan 3 keranjang standar untuk membeli 100 jam waktu komputasi pada komputer tersebut di pasar terbuka, maka setelah solusi terhadap masalah tersebut disiarkan, setiap orang mengkredit rekening penyiar sebanyak 3 unit." - Dai, 1998
Sayangnya, Dai tidak menjelaskan bagaimana pengguna dalam sistem yang seharusnya terdesentralisasi seharusnya menyetujui definisi “keranjang standar”, komputer mana yang memecahkan masalah tertentu “paling ekonomis”, atau biaya komputasi di “pasar terbuka”. Mencapai konsensus di antara semua pengguna mengenai kumpulan data bersama yang berubah-ubah terhadap waktu adalah masalah penting dalam sistem desentralisasi!
Agar adil bagi Dai, dia menyadari hal ini:
“Salah satu bagian yang lebih bermasalah dalam protokol B-money adalah penciptaan uang. Bagian dari protokol ini mengharuskan semua [pengguna] memutuskan dan menyetujui biaya perhitungan tertentu. Sayangnya karena teknologi komputasi cenderung berkembang pesat dan tidak selalu bersifat publik, informasi ini mungkin tidak tersedia, tidak akurat, atau ketinggalan jaman, yang semuanya akan menyebabkan masalah serius pada protokol." - Dai, 1998
Dai kemudian mengusulkan mekanisme penetapan harga berbasis lelang yang lebih canggih yang kemudian dikatakan Satoshi sebagai titik awal idenya. Kita akan kembali ke skema lelang di bawah ini, tapi pertama-tama mari kita beralih ke bit gold, dan pertimbangkan wawasan Szabo tentang masalahnya.
Gunakan Pasar Eksternal
Szabo mengklaim bahwa proof-of-work harus “diberi stempel waktu dengan aman”:
"Bukti kerja diberi stempel waktu yang aman. Ini harus bekerja secara terdistribusi, dengan beberapa layanan stempel waktu berbeda sehingga tidak ada layanan stempel waktu tertentu yang perlu diandalkan secara substansial." - Szabo, 2005
Szabo tertaut ke halaman sumber daya tentang protokol penandaan waktu yang aman tetapi tidak menjelaskan algoritme spesifik apa pun untuk penandaan waktu yang aman. Ungkapan “aman” dan “fesyen terdistribusi” mempunyai pengaruh yang besar di sini, sehingga dapat mengatasi kerumitan dalam mengandalkan satu (atau banyak) layanan “di luar sistem” untuk penandaan waktu.[^6]

Waktu pembuatan unit mata uang digital penting karena menghubungkan komputasi yang dilakukan dengan biaya produksi di dunia nyata.
Terlepas dari ketidakjelasan implementasi, Szabo benar—waktu pembuatan proof-of-work merupakan faktor penting dalam menentukan harga karena terkait dengan biaya komputasi:
"…Namun, karena bit gold diberi stempel waktu, waktu yang dibuat serta tingkat kesulitan matematis dari pekerjaan tersebut dapat dibuktikan secara otomatis. Dari sini, biasanya dapat disimpulkan berapa biaya produksi selama periode waktu tersebut..." - Szabo, 2005
"Menyimpulkan" biaya produksi adalah hal yang penting karena bit gold tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat bit gold dengan melakukan perhitungan yang sesuai. Tanpa kemampuan untuk mengatur penerbitan, bit gold sama dengan barang koleksi:
"…Tidak seperti atom emas yang dapat dipertukarkan, tetapi seperti halnya barang-barang kolektor, pasokan dalam jumlah besar selama jangka waktu tertentu akan menurunkan nilai barang-barang tersebut. Dalam hal ini, emas kecil bertindak lebih seperti barang-barang kolektor daripada seperti emas..." - Szabo, 2005
Bit gold memerlukan proses eksternal tambahan untuk menciptakan unit mata uang yang sepadan:
“…[B]it Gold tidak dapat dipertukarkan berdasarkan fungsi sederhana, misalnya, panjang tali. Sebaliknya, untuk membuat unit yang dapat dipertukarkan, dealer harus menggabungkan potongan-potongan bit gold dengan nilai berbeda ke dalam satuan yang lebih besar kira-kira dengan nilai yang sama. Hal ini serupa dengan apa yang dilakukan banyak pedagang komoditas saat ini untuk memungkinkan pasar komoditas bekerja. Kepercayaan masih terdistribusi karena perkiraan nilai dari kumpulan tersebut dapat diverifikasi secara independen oleh banyak pihak lain dengan cara yang sebagian besar atau seluruhnya otomatis." - Szabo, 2005
Mengutip Szabo, “untuk menguji nilai… bit gold, dealer memeriksa dan memverifikasi tingkat kesulitan, masukan, dan stempel waktu”. Dealer yang mendefinisikan “unit yang lebih besar dengan nilai yang kira-kira sama” menyediakan fungsi penetapan harga yang serupa dengan “keranjang komoditas standar” Dai. Unit yang dapat dipertukarkan tidak dibuat dalam bentuk bit gold ketika bukti kerja diproduksi, hanya kemudian ketika bukti tersebut digabungkan menjadi “unit yang kira-kira bernilai sama” oleh dealer di pasar di luar jaringan.

Yang patut disyukuri, Szabo mengakui kelemahan ini:
"…Potensi kelebihan pasokan yang awalnya tersembunyi karena inovasi tersembunyi dalam arsitektur mesin adalah potensi kelemahan dalam bit gold, atau setidaknya ketidaksempurnaan yang harus diatasi oleh lelang awal dan pertukaran ex post bit gold." - Szabo, 2005
Sekali lagi, meskipun belum sampai pada (yang sekarang kita kenal sebagai) solusinya, Szabo menunjukkan solusinya: karena biaya komputasi berubah seiring waktu, jaringan harus merespons perubahan pasokan komputasi dengan menyesuaikan harga uang.
Gunakan Pasar Internal
Dealer Szabo akan menjadi pasar eksternal yang menentukan harga (bundel dari) bit gold setelah penciptaannya. Apakah mungkin menerapkan pasar ini di dalam sistem dan bukan di luar sistem?
Mari kita kembali ke Wei Dai dan B-money. Seperti disebutkan sebelumnya, Dai mengusulkan model alternatif berbasis lelang untuk pembuatan B-money. Desain Satoshi untuk Bitcoin meningkat secara langsung pada model lelang B-money[^7]:
“Jadi saya mengusulkan subprotokol penciptaan uang alternatif, di mana [pengguna]… memutuskan dan menyetujui jumlah B-money yang akan dibuat setiap periode, dengan biaya pembuatan uang tersebut ditentukan melalui lelang. Setiap periode pembuatan uang adalah dibagi menjadi empat tahap, sebagai berikut:
Planning. Para [pengguna] menghitung dan bernegosiasi satu sama lain untuk menentukan peningkatan jumlah uang beredar yang optimal untuk periode berikutnya. Apakah [jaringan] dapat mencapai konsensus atau tidak, mereka masing-masing menyiarkan kuota penciptaan uang mereka dan komputasi makroekonomi apa pun yang dilakukan untuk mendukung angka tersebut.
Bidding. Siapapun yang ingin membuat B-money menyiarkan tawaran dalam bentuk dimana x adalah banyaknya B-money yang ingin dibuatnya, dan y adalah soal yang belum terselesaikan dari kelas soal yang telah ditentukan. Setiap masalah di kelas ini harus memiliki biaya nominal (katakanlah dalam MIPS-years) yang disetujui secara publik.
Computation. Setelah melihat penawaran, pihak yang mengajukan penawaran pada tahap penawaran sekarang dapat menyelesaikan masalah dalam penawarannya dan menyiarkan solusinya. Penciptaan uang.
Money creation. Setiap [pengguna] menerima tawaran tertinggi (di antara mereka yang benar-benar menyiarkan solusi) dalam hal biaya nominal per unit B-money yang dibuat dan memberikan kredit kepada akun penawar sesuai dengan itu."
- Dai, 1998B-money membuat kemajuan signifikan menuju struktur pasar yang tepat untuk mata uang digital. Ini berupaya untuk menghilangkan dealer eksternal Szabo dan memungkinkan pengguna untuk terlibat dalam penemuan harga dengan menawar satu sama lain secara langsung.
Namun menerapkan proposal Dai seperti yang tertulis akan menjadi sebuah tantangan:
- Dalam fase "Planning”, pengguna menanggung beban menegosiasikan “peningkatan optimal jumlah uang beredar untuk periode berikutnya”. Bagaimana “optimal” harus didefinisikan, bagaimana pengguna harus bernegosiasi satu sama lain, dan bagaimana hasil negosiasi tersebut dibagikan tidak dijelaskan.
- Terlepas dari apa yang direncanakan, fase “Bidding” memungkinkan siapa saja untuk mengajukan “tawaran” untuk membuat B-money. Tawaran mencakup jumlah B-money yang akan dibuat serta jumlah bukti kerja yang sesuai sehingga setiap penawaran adalah harga, jumlah perhitungan yang bersedia dilakukan oleh penawar tertentu untuk membeli sejumlah tertentu. dari B-money.
- Setelah penawaran diserahkan, fase “Computation” terdiri dari peserta lelang yang melakukan proof-of-work yang mereka tawarkan dan menyiarkan solusi. Tidak ada mekanisme untuk mencocokkan penawar dengan solusi yang disediakan. Yang lebih problematis adalah tidak jelasnya bagaimana pengguna dapat mengetahui bahwa semua penawaran telah diajukan – kapan fase “Bidding” berakhir dan fase “Computation” dimulai?
- Masalah-masalah ini berulang dalam fase “Money creation”. Karena sifat proof-of-work, pengguna dapat memverifikasi bahwa bukti yang mereka terima dalam solusi adalah asli. Namun bagaimana pengguna dapat secara kolektif menyepakati serangkaian “tawaran tertinggi”? Bagaimana jika pengguna yang berbeda memilih set yang berbeda, baik karena preferensi atau latensi jaringan?
Sistem yang terdesentralisasi kesulitan dalam melacak data dan membuat pilihan secara konsisten, namun B-money memerlukan pelacakan tawaran dari banyak pengguna dan membuat pilihan konsensus di antara mereka. Kompleksitas ini menghalangi penerapan B-money.
Akar dari kompleksitas ini adalah keyakinan Dai bahwa tingkat “optimal” penciptaan B-money harus berfluktuasi seiring waktu berdasarkan “perhitungan makroekonomi” penggunanya. Seperti bit gold, B-money tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat unit B-money dengan menyiarkan tawaran dan kemudian melakukan proof-of-work yang sesuai.
Baik Szabo maupun Dai mengusulkan penggunaan pasar pertukaran mata uang digital untuk komputasi, namun baik bit gold maupun B-money tidak menentukan kebijakan moneter untuk mengatur pasokan mata uang di pasar ini.
Tujuan Kebijakan Moneter Satoshi Menghasilkan Bitcoin
Sebaliknya, kebijakan moneter yang sehat adalah salah satu tujuan utama Satoshi dalam proyek Bitcoin. Dalam postingan milis pertama tempat Bitcoin diumumkan, Satoshi menulis:
“Akar permasalahan mata uang konvensional adalah kepercayaan yang diperlukan agar mata uang tersebut dapat berfungsi. Bank sentral harus dipercaya untuk tidak merendahkan mata uang tersebut, namun sejarah mata uang fiat penuh dengan pelanggaran terhadap kepercayaan tersebut.” - Satoshi, 2009
Satoshi selanjutnya menjelaskan masalah lain dengan mata uang fiat seperti perbankan cadangan fraksional yang berisiko, kurangnya privasi, pencurian & penipuan yang merajalela, dan ketidakmampuan melakukan pembayaran mikro. Namun Satoshi memulai dengan isu penurunan nilai oleh bank sentral—dengan kekhawatiran mengenai kebijakan moneter.
Satoshi ingin Bitcoin pada akhirnya mencapai pasokan sirkulasi terbatas yang tidak dapat terdilusi seiring waktu. Tingkat penciptaan Bitcoin yang “optimal”, bagi Satoshi, pada akhirnya akan menjadi nol.
Tujuan kebijakan moneter ini, lebih dari karakteristik lain yang mereka miliki secara pribadi (atau kolektif!), adalah alasan Satoshi “menemukan” Bitcoin, blockchain, konsensus Nakamoto, dll. —dan bukan orang lain. Ini adalah jawaban singkat atas pertanyaan yang diajukan dalam judul artikel ini: Satoshi memikirkan Bitcoin karena mereka fokus pada penciptaan mata uang digital dengan persediaan terbatas.
Pasokan Bitcoin yang terbatas bukan hanya tujuan kebijakan moneter atau meme bagi para Bitcoiner untuk berkumpul. Penyederhanaan teknis penting inilah yang memungkinkan Satoshi membangun mata uang digital yang berfungsi sementara B-money Dai tetap menjadi postingan web yang menarik.
Bitcoin adalah B-money dengan persyaratan tambahan berupa kebijakan moneter yang telah ditentukan. Seperti banyak penyederhanaan teknis lainnya, pembatasan kebijakan moneter memungkinkan kemajuan dengan mengurangi ruang lingkup. Mari kita lihat bagaimana masing-masing fase pembuatan B-money disederhanakan dengan menerapkan batasan ini.
Semua Pasokan 21 Juta Bitcoin Sudah Ada
Dalam b-money, setiap “periode penciptaan uang” mencakup fase “Perencanaan”, di mana pengguna diharapkan untuk membagikan “perhitungan makroekonomi” mereka yang membenarkan jumlah b-money yang ingin mereka ciptakan pada saat itu. Tujuan kebijakan moneter Satoshi yaitu pasokan terbatas dan emisi nol tidak sesuai dengan kebebasan yang diberikan b-money kepada pengguna individu untuk menghasilkan uang. Oleh karena itu, langkah pertama dalam perjalanan dari bmoney ke bitcoin adalah menghilangkan kebebasan ini. Pengguna bitcoin perorangan tidak dapat membuat bitcoin. Hanya jaringan bitcoin yang dapat membuat bitcoin, dan hal ini terjadi tepat sekali, pada tahun 2009 ketika Satoshi meluncurkan proyek bitcoin.
Satoshi mampu menggantikan fase “Perencanaan” b-money yang berulang menjadi satu jadwal yang telah ditentukan sebelumnya di mana 21 juta bitcoin yang dibuat pada tahun 2009 akan dilepaskan ke peredaran. Pengguna secara sukarela mendukung kebijakan moneter Satoshi dengan mengunduh dan menjalankan perangkat lunak Bitcoin Core yang kebijakan moneternya dikodekan secara keras.
Hal ini mengubah semantik pasar bitcoin untuk komputasi. Bitcoin yang dibayarkan kepada penambang bukanlah hal baru yang diterbitkan; itu melainkan baru dirilis ke peredaran dari persediaan yang ada.
Pandangan ini sangat berbeda dari klaim naif bahwa “penambang bitcoin menciptakan bitcoin”. Penambang Bitcoin tidak menciptakan bitcoin, mereka membelinya. Bitcoin tidak berharga karena “bitcoin terbuat dari energi”—tetapi nilai bitcoin didemonstrasikan dengan dijual untuk mendapatkan energi.
Mari kita ulangi sekali lagi: bitcoin tidak dibuat melalui proof-of-work, bitcoin dibuat melalui konsensus.

Desain Satoshi menghilangkan persyaratan untuk fase “Perencanaan” yang berkelanjutan dari b-money dengan melakukan semua perencanaan terlebih dahulu. Hal ini memungkinkan Satoshi untuk membuat kebijakan moneter yang sehat namun juga menyederhanakan penerapan bitcoin.
Bitcoin dihargai Melalui Konsensus
Kebebasan yang diberikan kepada pengguna untuk menghasilkan uang menimbulkan beban yang sesuai bagi jaringan bmoney. Selama fase “Penawaran” jaringan b-money harus mengumpulkan dan membagikan “tawaran” pembuatan uang dari banyak pengguna yang berbeda.
Menghilangkan kebebasan untuk menghasilkan uang akan meringankan beban jaringan bitcoin. Karena seluruh 21 juta bitcoin sudah ada, jaringan tidak perlu mengumpulkan tawaran dari pengguna untuk menghasilkan uang, jaringan hanya perlu menjual bitcoin sesuai jadwal Satoshi yang telah ditentukan.
Jaringan bitcoin dengan demikian menawarkan konsensus harga permintaan untuk bitcoin yang dijualnya di setiap blok. Harga tunggal ini dihitung oleh setiap node secara independen menggunakan salinan blockchainnya. Jika node memiliki konsensus pada blockchain yang sama (poin yang akan kita bahas nanti) mereka semua akan menawarkan harga permintaan yang sama di setiap blok.[^8]
Bagian pertama kalkulasi harga konsensus menentukan berapa banyak bitcoin yang akan dijual. Hal ini diperbaiki oleh jadwal rilis Satoshi yang telah ditentukan sebelumnya. Semua node bitcoin di jaringan menghitung jumlah yang sama untuk blok tertentu:
$ bitcoin-cli getblockstats <block\_height> {... "subsidy": 6250000000, ... } # 6.25 BTCBagian kedua dari harga yang diminta secara konsensus adalah jumlah komputasi yang akan menjual subsidi saat ini. Sekali lagi, semua node bitcoin di jaringan menghitung nilai yang sama (kita akan meninjau kembali kalkulasi tingkat kesulitan ini di bagian berikutnya):
$ bitcoin-cli getdifficulty {... "result": 55621444139429.57, ... }Bersama-sama, subsidi dan kesulitan jaringan menentukan permintaan bitcoin saat ini sebagai mata uang komputasi. Karena blockchain berada dalam konsensus, harga ini adalah harga konsensus.
Pengguna b-money juga dianggap memiliki konsensus “blockchain” yang berisi riwayat semua transaksi. Namun Dai tidak pernah memikirkan solusi sederhana berupa konsensus tunggal yang meminta harga untuk pembuatan b-money baru, yang hanya ditentukan oleh data di blockchain tersebut.
Sebaliknya, Dai berasumsi bahwa penciptaan uang harus berlangsung selamanya. Oleh karena itu, pengguna individu perlu diberdayakan untuk mempengaruhi kebijakan moneter – seperti halnya mata uang fiat. Persyaratan yang dirasakan ini membuat Dai merancang sistem penawaran yang mencegah penerapan b-money.
Kompleksitas tambahan ini dihilangkan dengan persyaratan Satoshi mengenai kebijakan moneter yang telah ditentukan sebelumnya.
Waktu Menutup Semua Penyebaran
Dalam fase “Komputasi” b-money, pengguna individu akan melakukan komputasi yang telah mereka lakukan dalam penawaran sebelumnya. Dalam bitcoin, seluruh jaringan adalah penjual – tetapi siapa pembelinya?
Di pasar pengiriman email, pembelinya adalah individu yang ingin mengirim email. Otoritas penetapan harga, penyedia layanan email, akan menetapkan harga yang dianggap murah bagi individu namun mahal bagi pelaku spam. Namun jika jumlah pengguna yang sah bertambah, harganya masih bisa tetap sama karena kekuatan komputasi masing-masing pengguna akan tetap sama.
Di b-money, setiap pengguna yang menyumbangkan tawaran untuk pembuatan uang selanjutnya harus melakukan sendiri jumlah komputasi yang sesuai. Setiap pengguna bertindak sebagai otoritas penetapan harga berdasarkan pengetahuan mereka tentang kemampuan komputasi mereka sendiri.
Jaringan bitcoin menawarkan satu harga yang diminta dalam komputasi subsidi bitcoin saat ini. Namun tidak ada penambang individu yang menemukan blok yang melakukan komputasi sebanyak ini.[9] Blok pemenang penambang individu adalah bukti bahwa semua penambang secara kolektif melakukan jumlah komputasi yang diperlukan. Pembeli bitcoin dengan demikian adalah industri penambangan bitcoin global.
Setelah mencapai konsensus harga yang diminta, jaringan bitcoin tidak akan mengubah harga tersebut sampai lebih banyak blok diproduksi. Blok-blok ini harus berisi proof-of-work dengan harga yang diminta saat ini. Oleh karena itu, industri pertambangan tidak punya pilihan jika ingin “melakukan perdagangan” selain membayar harga yang diminta saat ini dalam komputasi.
Satu-satunya variabel yang dapat dikontrol oleh industri pertambangan adalah berapa lama waktu yang dibutuhkan untuk memproduksi blok berikutnya. Sama seperti jaringan bitcoin yang menawarkan satu harga yang diminta, industri pertambangan juga menawarkan satu penawaran—waktu yang diperlukan untuk menghasilkan blok berikutnya yang memenuhi harga yang diminta jaringan saat ini.
Untuk mengimbangi peningkatan kecepatan perangkat keras dan minat yang berbeda-beda dalam menjalankan node dari waktu ke waktu, kesulitan proof-of-work ditentukan oleh rata-rata bergerak yang menargetkan jumlah rata-rata blok per jam. Jika dihasilkan terlalu cepat, kesulitannya akan meningkat. - Nakamoto, 2008
Satoshi dengan sederhana menjelaskan algoritma penyesuaian kesulitan, yang sering disebut sebagai salah satu ide paling orisinal dalam implementasi bitcoin. Hal ini benar, namun alih-alih berfokus pada daya cipta solusi, mari kita fokus pada mengapa penyelesaian masalah sangat penting bagi Satoshi.
Proyek-proyek seperti bit gold dan b-money tidak perlu membatasi nilai tukar pada saat penciptaan uang karena mereka tidak memiliki pasokan tetap atau kebijakan moneter yang telah ditentukan sebelumnya. Periode penciptaan uang yang lebih cepat atau lebih lambat dapat dikompensasikan melalui cara lain, misalnya melalui pajak. Dealer eksternal memasukkan token bit gold ke dalam bundler yang lebih besar atau lebih kecil atau pengguna b-money mengubah tawaran mereka.
Namun tujuan kebijakan moneter Satoshi mengharuskan bitcoin memiliki tingkat pelepasan bitcoin yang telah ditentukan untuk diedarkan. Membatasi laju (statistik) produksi blok dari waktu ke waktu adalah hal yang wajar dalam bitcoin karena laju produksi blok adalah laju penjualan pasokan awal bitcoin. Menjual 21 juta bitcoin selama 140 tahun adalah proposisi yang berbeda dibandingkan membiarkannya dijual dalam 3 bulan.
Selain itu, bitcoin sebenarnya dapat menerapkan batasan ini karena blockchain adalah “protokol cap waktu aman” milik Szabo. Satoshi menggambarkan bitcoin sebagai yang pertama dan terutama sebagai “server stempel waktu terdistribusi secara peer-to-peer,” dan implementasi awal kode sumber bitcoin menggunakan “rantai waktu” dunia, bukan “blockchain” untuk menggambarkan struktur data bersama yang mengimplementasikan pasar proof-of-work bitcoin.[^10]

Tidak seperti bit gold atau b-money, token dalam bitcoin tidak mengalami kelebihan pasokan. Jaringan bitcoin menggunakan penyesuaian kesulitan untuk mengubah harga uang sebagai respons terhadap perubahan pasokan komputasi.
Algoritme penyesuaian ulang kesulitan Bitcoin memanfaatkan kemampuan ini. Blockchain konsensus digunakan oleh peserta untuk menghitung penawaran historis yang dibuat oleh industri pertambangan dan menyesuaikan kembali kesulitan agar bisa mendekati waktu blok target.
Pesanan Terunggul Menciptakan Konsensus
Rantai penyederhanaan yang disebabkan oleh tuntutan kebijakan moneter yang kuat meluas ke fase “penciptaan uang” dari b-money.
Tawaran yang diajukan pengguna di b-money mengalami masalah “tidak ada yang dipertaruhkan”. Tidak ada mekanisme untuk mencegah pengguna mengajukan tawaran dengan sejumlah besar b-money untuk pekerjaan yang sangat sedikit. Hal ini mengharuskan jaringan untuk melacak tawaran mana yang telah diselesaikan dan hanya menerima “tawaran tertinggi…dalam hal biaya nominal per unit b-money yang dibuat” untuk menghindari tawaran yang mengganggu tersebut. Setiap peserta b-money harus melacak seluruh tawaran senilai buku pesanan, mencocokkan tawaran dengan perhitungan selanjutnya, dan hanya menyelesaikan pesanan yang telah selesai dengan harga tertinggi.
Masalah ini merupakan contoh dari masalah konsensus yang lebih umum dalam sistem desentralisasi, yang juga dikenal sebagai “Byzantine generals” atau terkadang masalah “pembelanjaan ganda” dalam konteks mata uang digital. Berbagi urutan data yang identik di antara semua peserta merupakan suatu tantangan dalam jaringan yang saling bermusuhan dan terdesentralisasi. Solusi yang ada untuk masalah ini – yang disebut “algoritma konsensus Byzantine-fault tolerant (BFT)” – memerlukan koordinasi sebelumnya di antara peserta atau mayoritas (>67%) peserta agar tidak berperilaku bermusuhan.
Bitcoin tidak harus mengelola buku pesanan dalam jumlah besar karena jaringan bitcoin menawarkan harga permintaan konsensus tunggal. Ini berarti node bitcoin dapat menerima blok pertama (valid) yang mereka lihat yang memenuhi harga yang diminta jaringan saat ini—tawaran gangguan dapat dengan mudah diabaikan dan merupakan pemborosan sumber daya penambang.
Komputasi harga berdasarkan konsensus memungkinkan pencocokan pesanan beli/jual dalam bitcoin dilakukan secara antusias, dengan sistem siapa cepat dia dapat. Berbeda dengan b-money, pencocokan pesanan yang cepat ini berarti bahwa pasar bitcoin tidak memiliki fase—pasar ini beroperasi terus-menerus, dengan harga konsensus baru dihitung setelah setiap pesanan dicocokkan (blok ditemukan). Untuk menghindari percabangan yang disebabkan oleh latensi jaringan atau perilaku bertentangan, node juga harus mengikuti aturan rantai terberat. Aturan penyelesaian pesanan yang serakah ini memastikan bahwa hanya tawaran tertinggi yang diterima oleh jaringan.
Kombinasi algoritma yang antusias dan serakah ini, dimana node menerima blok valid pertama yang mereka lihat dan juga mengikuti rantai terberat, adalah algoritma BFT baru yang dengan cepat menyatu pada konsensus tentang urutan blok. Satoshi menghabiskan 25% dari white paper bitcoin untuk mendemonstrasikan klaim ini.[^11]
Kita telah menetapkan di bagian sebelumnya bahwa harga permintaan konsensus bitcoin itu sendiri bergantung pada konsensus blockchain. Namun ternyata keberadaan harga permintaan konsensus tunggal inilah yang memungkinkan perhitungan pasar untuk mencocokkan pesanan dengan penuh semangat, dan itulah yang pertama-tama mengarah pada konsensus!
Terlebih lagi, “konsensus Nakamoto” yang baru ini hanya mengharuskan 50% peserta untuk tidak bertentangan, sebuah kemajuan yang signifikan dibandingkan dengan kondisi sebelumnya. Seorang cypherpunk seperti Satoshi membuat terobosan ilmu komputer teoretis ini, dibandingkan dengan akademisi tradisional atau peneliti industri, karena fokus mereka yang sempit pada penerapan uang yang sehat, dibandingkan algoritma konsensus umum untuk komputasi terdistribusi.
Kesimpulan
B-money adalah kerangka kerja yang kuat untuk membangun mata uang digital tetapi tidak lengkap karena tidak memiliki kebijakan moneter. Membatasi b-money dengan jadwal rilis yang telah ditentukan untuk bitcoin mengurangi cakupan dan menyederhanakan implementasi dengan menghilangkan persyaratan untuk melacak dan memilih di antara tawaran pembuatan uang yang diajukan pengguna. Mempertahankan kecepatan sementara dari jadwal rilis Satoshi menghasilkan algoritma penyesuaian kesulitan dan memungkinkan konsensus Nakamoto, yang secara luas diakui sebagai salah satu aspek paling inovatif dalam implementasi bitcoin.
Ada lebih banyak hal dalam desain bitcoin daripada aspek yang dibahas sejauh ini. Kita memfokuskan artikel ini pada pasar “utama” dalam bitcoin, pasar yang mendistribusikan pasokan awal bitcoin ke dalam sirkulasi.
Artikel berikutnya dalam seri ini akan mengeksplorasi pasar penyelesaian transaksi bitcoin dan kaitannya dengan pasar pendistribusian pasokan bitcoin. Hubungan ini akan menyarankan metodologi bagaimana membangun pasar masa depan untuk layanan terdesentralisasi selain bitcoin.
Catatan kaki
[^1]: Judul seri ini diambil dari pesan telegraf pertama dalam sejarah, yang dikirimkan oleh Samuel Morse pada tahun 1844: “What hath God wrought?”.
[^2]: Bitcoin: Sistem Uang Elektronik Peer-to-Peer, tersedia di: https://bitcoin.org/bitcoin.pdf
[^3]: Pricing via Processing or Combatting Junk Mail oleh Dwork dan Naor. tersedia di:
https://www.wisdom.weizmann.ac.il/../../pvp.pdf[^4]: Meskipun merupakan pencetus ide tersebut, Dwork & Naor tidak menciptakan “proof-of-work”—julukan tersebut kemudian diberikan pada tahun 1999 oleh Markus Jakobsson dan Ari Juels.
[^5]: Proyek RPoW Hal Finney adalah upaya untuk menciptakan proof-of-work yang dapat ditransfer, tetapi bitcoin tidak menggunakan konsep ini karena tidak memperlakukan komputasi sebagai mata uang. Seperti yang akan kita lihat nanti ketika kita memeriksa bit gold dan b-money, komputasi tidak dapat berupa mata uang karena nilai komputasi berubah seiring waktu sementara unit mata uang harus memiliki nilai yang sama. Bitcoin bukanlah komputasi, bitcoin adalah mata uang yang dijual untuk komputasi.
[^6]: Pada saat ini, beberapa pembaca mungkin percaya bahwa saya meremehkan kontribusi Dai atau Szabo karena kontribusi mereka tidak jelas atau tidak jelas dalam beberapa hal. Perasaan saya justru sebaliknya: Dai dan Szabo pada dasarnya benar dan fakta bahwa mereka tidak mengartikulasikan setiap detail seperti yang dilakukan Satoshi tidak mengurangi kontribusi mereka. Sebaliknya, hal ini seharusnya meningkatkan apresiasi kita terhadap hal tersebut, karena hal ini menunjukkan betapa menantangnya munculnya mata uang digital, bahkan bagi para praktisi terbaiknya.
[^7]: Postingan b-money Dai adalah referensi pertama dalam white paper Satoshi, tersedia di: http://www.weidai.com/bmoney.txt
[^8]: Ada dua penyederhanaan yang dilakukan di sini:
- Jumlah bitcoin yang dijual di setiap blok juga dipengaruhi oleh biaya transaksi pasar, yang berada di luar cakupan artikel ini, namun tetap menunggu pekerjaan selanjutnya.
- Kesulitan yang dilaporkan oleh bitcoin bukanlah jumlah perhitungan yang diharapkan; seseorang harus mengalikannya dengan faktor proporsionalitas.
[^9]: Setidaknya sejak masa lalu yang buruk ketika Satoshi adalah satu-satunya penambang di jaringan.
[^10]: Bitcoin is Time klasik dari Gigi adalah pengenalan yang bagus tentang hubungan mendalam antara bitcoin dan waktu, tersedia di: https://dergigi.com/2021/01/14/bitcoin-is-time/
[^11]: Satoshi melakukan kesalahan baik dalam analisis mereka di buku putih maupun implementasi awal bitcoin berikutnya dengan menggunakan aturan “rantai terpanjang” dan bukan aturan “rantai terberat”.
Sumber artikel: HOW DID SATOSHI THINK OF BITCOIN? https://bitcoinmagazine.com/technical/how-did-satoshi-think-of-bitcoin
Diterjemahkan oleh: Abengkris
-
 @ 4fda8b10:7bbee962
2024-10-15 13:56:47
@ 4fda8b10:7bbee962
2024-10-15 13:56:47Takeaways from Bitcoin Amsterdam 2024
The bitcoin conference in Amsterdam to me is my typical yearly check in with the crypto scene. From a distance, not much has changed since last year. What struck me most was the correlation between the exchange prices and the amount of visitors, I had the feeling the crowd was about twice as big as last year during the opening and high profile talks.
From my personal experience, the increase of audience also brought some dilution to the hard core maximalist anarchist-ness of the event. The overall vibe amongst the attendees was more friendly and open. This also increased the value of the event for me, as I try to broaden my network, get different perspectives and learn more about what interests people in the crypto space.
This year was also marked by my involvement in the Nostr side events, I was asked to give a live performance at the Nostrdam Meetup October 2024 which went over very well and also acted as a nice conversation starter during the rest of the conference. I was also slightly involved in the organisation of the Nostr booth, but credits go to the awesome volunteers that made that happen. It was a bit of a shame that the Nostr booth was tucked away all the way in the back of the (commercial) expo hall, it would have been nice to promote the Nostr initiative to the social community area next to the satoshi radio / connect the world community area
For me the biggest takeaways were the insights I got from the people I’ve met, all from different industries with different perspectives on both technology and involvement. I tried to specifically reach out to (former) CTO’s, which led me to write and share this piece on that particular role. Of course shaking hands and catching up with people I only see once a year is great, and reminds me of the vibe and my experiences at the Fronteers conference.
From a technical point of view I was most inspired by the advancement of AI agent technology and the possibilities of programmable micropayments via de lightning network. Michael Levin showed us that the http spec already has a 402 status of “payment required” and that basically all the required infrastructure is already in place to allow both humans and ai agents to use the lightning network to pay for access to compute or resources using this statuscode and an api gateway such as lightning labs aperture.
talk: HODLing Is Hard: Fundamentals, Cycle & On-Chain Analysis by rational root
- bitcoin is already competing in market cap with other currencies
- amount of euro is exponentially increasing
- from 8 to 16 trillion euros since 2009, but having a real hard cap in btc is fundamentally different
- inflation
- euro lose 20% in 5 years
- bitcoin also loses purchasing power, but only 10%
- in current system, we always need to take on maximal debt, instead of saving
- two things can happen
- we get into overvalued price levels
- we get into recession
- recession would only mean a shift in the start of the 4 year cycle
panel: Endless Possibilities: Reusing Heat From Miners
- people
- 21energy Maximilian (obwexer)
- Bert de groot (bitcoin Brabant)
- Brad Tom (mara)
- perspective: coming from energy to bitcoin is very different and much faster with implementation than the other way around
- 95% of heat can be captured from miners, much higher in comparison to AI
- being able to balance the grid because you can turn off the bitcoin miners
- ”heatbuffers” → heat is still available when power source goes down
- common objections:
- Crypto is hard to understand
- for large industrial clients, heaters, public image of bitcoin (often a door closer)
- people don’t see that miners consume electricity and pay for it.
- If mining is closed down in Europe, the energy prices will spike because the energy will not be payed for anymore
panel: How to Guard Privacy Tools & Developers
- Dorien Rookmaker & Sjors proviost
- chat control
- topic keeps returning, and is highly distracting for progress
- Parliament wants Netherlands to speak against chat control
- initially they want to just, scan messages now want to install malware before encryption
- it is distracting Sjors from working on bitcoin
- samurai and tornado are different cases
- tornado cash is harder because it is also a smart contract with custody over funds
- samurai is easier: if you don’t have custody, are you responsible for the results of the code?
- will decide wether whether non custodial systems are ok or not
- micah interpretation is quite vague
- the current Denmark case:
- if you are rebuilding an interface for a smart contract, you are responsible for implementing all the legal guardrails that apply to securities governance?
panel: NOSTR: Freedom of Algorithmic Choice
- will casarin, mcshane, martti malmi (Sirius iris.to)
- arc (alternative layer on top of bitcoin, like lightning but without channels)
- aha moment: when seeing the unsiloed experience between nostr apps
- were trying to create a town square, so we need to deal with spam
- social media platforms have stagnated a bit, nostr is innovating far more quickly
panel: Transactions As Bitcoin’s Key Growth Metric
- Stephan nilov
- classical developers don’t know about money and bitcoin development is harder
- total addressable market is highest in btc, biggest number of possible users
- bitcoin companies don’t benefit from tokens that are typically exchanged for vc money
- users are not looking for payments, they are looking for digital property and other things that Ethereum network offers
- Stephan Livera
- there is a known, slow pace at which bitcoin will be adopted
- btc market is only 1.2 trillion dollars compared to USD 30 trillion
talk: Making Bitcoin Quantum Resistant by hunter beast
- surmount.systems
- explaining the threat of quantum computing
- problems
- key size: larger signature required
- proposal: transaction field attestation
- 256 bit number key, possibility to factor the private key out of this
- introducing p2qrhash
- segwitv3
- satoshishield
- in layman terms:
- quantum safe upgrades to bitcoin protocol are proposed
- we need to introduce a software upgrade
- requires a soft fork, opt in
- possible advantages of quantum in crypto
- allow us to sign signatures in a way that is unbreakable
- 514 qubits are needed to break something
talk: Lightning and AI: Where the Bots Pay You by michael levin
- two use cases for bitcoin adoption
- people that don’t have access to fiat
- things that can’t be handled by fiat systems
- large language models
- current phase: big adoption
- next phase: agentic ai
- costs of ai
- compute 400% more (ben bajarin)
- algorithm training excess 10 billion dollars
- data
- costs implications
- cost of serving answers is 0
- cost of serving ai query is not 0
- cost for everyone in the world
- payments in AI
- now
- pay per call
- data
- accessibility
- agents
- agents must be able to do things that cost money
- now
- payment system for AI
- globally accessible
- near instant
- final settlement
- internet native
- authentication mechanism
- personalise access (simple queries for lower tier model)
- easy to implement
- L402 protocol
- 402 payment required in http spec
- reverse proxy to have 402 in front of APIs
- aperture is lightning labs implementation
- all available right now, adoption starting
- fewsats, sulu, open agents / plebai
- pay with lightning
- challenges
- do these payments with stablecoins instead of lightning (hence taproot assets protocol)
- cases
- agent bots can pay for real world resources
- taproot assets issue assets on bitcoin allow transfer of
- references
- L402.org
talk: Bitcoin is Cypherpunk by Aaron van Wirdum
- is bitcoin still Cypherpunks ?
- on one hand we see a push to regulation and frameworks to govern btc
- on the other hand we are arresting developers for writing code
pitches: Bitcoin Amsterdam Pitch Day: Presented by GoBTC
- umoja
- ceo Robby greenfield
- LST smartcoin, deflationary by design
- competes with pools such as lido and rocket pool, but supports multiple coins, including liquid hashrate
- 30% liquid hashrate returns (!)
- compliance micah
- disaster scenarios
- black swan event → automatic exit out
- magisat
- trading tools for mempool snipers
- support for runes
- volume on bitcoin nft’s is on certain days higher than nft’s on ethereum
panel: Crossing the Boundaries Between Bitcoin & Fiat
- Christian Rau (Mastercard) & Remi destigny (bitrefill )
- liberation is great, but protocols don’t take customer service into account, chargebacks and rewinding mistakes etc
- we aim to smooth process by issuing cards that sell your Bitcoin just in time on the backend
talk: Gold & Bitcoin: Friends, Not Foes by Paul Buitink
- premise “the financial system is crumbling”
- there is too much debt
- emerging markets lost confidence in western currencies
- freezing Russian assets is shooting ourselves in the foot, as it shows the world you might not want to hold too many dollars that can be easily seized
- record gold buying by central banks in 2022 2023 2024
- gold: 17 trillion marker cap, compared to bitcoin 1.3 trillion
talk: Austrian Economics, Hard Money & Bitcoin Cycles, Willem Middelkoop
- ”we are on the road towards hyper inflation and collapse of financial system”
- central bankers are pretty smart and very aware
- this is why they accumulate gold
- when system collapses, central bankers will play the gold card, not the bitcoin card
- US is preparing for big conflict with Russia and china
- then you can’t use IMF monetary reset
- Asia leadership is the same as US and Russian leadership: they want to stay on control
- all have about similar gold (per Capita) in their central banks vaults to avoid hyperinflation
- IMF said to el salvador: you need to reign down your bitcoin position
- once central bankers start diversifying (e.g. to bitcoin ) they will strain their own system. The incentives are against adopting bitcoin
- watch out for when on and offramp get blocked / repressed
- think about diversifying to Dubai, “the new switzerland"
- "bitcoin is the best money ever. fact”
- superior to gold, because you can store your wealth independant of location
- more scarce than gold
- but from central bank point of view, gold is superior to bitcoin
- younger generation gets this from the start
talk: The Future Will Be Bitcoinized by Elizabeth stark & Rockstar Dev
- stablecoins
- taproot assets protocol
- there is a demand for stablecoins and apps on stablecoins
- 11 trillion dollars in stablecoins
- protocol allows payments in other assets such as stablecoins that use bitcoin/lightning liquidity
- Elizabeth believes this allows stablecoiners to get interested in the underlying bitcoin layer
- Available now:
- bridging tether and lightning
products stumbled upon
- Meshtastic
- Flipper
- Noderunners led matrix panel
- 21energy bitcoin heater (1k s9, 3,5k s19)
- angor.io by dangershony on nostr
- bitcoinclock by Djuri
canonical link: https://notes.peterpeerdeman.nl/Bitcoin-Amsterdam-2024
originally posted at https://stacker.news/items/724785
-
 @ fd208ee8:0fd927c1
2024-10-29 08:52:42
@ fd208ee8:0fd927c1
2024-10-29 08:52:42Yesterday was also a day
I'm still quite bullish about using Nostr to publish, and generally for OtherStuff, but I was feeling a bit pessimistic about the microblogging (kind 01) feeds on Nostr, yesterday. And, rightly so. Mine has been grinding slowly to a halt, and not for lack of effort, on my part. I regularly hear reports, from other npubs, that they sense the same phenomenon.
Most of the people I have whitelisted on the wss://theforest.nostr1.com relay (currently 302, in number) are beginning to give up on Kind 01 clients, except for occasionally making an announcement, and are increasingly moving their chatting off-Nostr. (I'm still privy to those conversations, but most of you no longer are.)
So, my feed has been getting quieter and quieter. Even adding new people doesn't help much, as they don't tend to stick around, for long, so it's a Sisyphean task.

Some others are still bothering to show up, regularly, but they increasingly see it as a chore, or something they do to "keep up appearances". Add me to this group of wearied, diligent noters, holding down the microblogging feeds, with our exhausting attempt at #KeepingNostrWeird, while the influencers surround the gates and the Kind 01 feeds dissolve into nothing but warmed-over Bitcoin memes, GM notes, notifications from the OtherStuff, and Things Copied from X.

The problem of barren, intellectually-emptying Kind 01 feeds is further exacerbated by the fact that new entrants to the Nostrverse find it increasingly easy to "find good follows", but they're all only finding the same follows: whoever is on the trending list.
The See-Nothings
I keep complaining about this, but the responses I get are generally unhelpful. They are:
- mockery -- Oh, Miss Hoity-Toity wants more attention!
- insults -- Nobody is talking to you because you are boring and stupid, and nobody likes you.
- clueless -- You should try replying to other people, then they might reply to you.
- or they tell me to just stop looking at the list, if it upsets me.

What people are missing, by telling me to just not look at the trending lists, is that the lists are a statistic of what real humans are looking at, on Nostr. The bizarrely-high concentration of npubs, on the list, so that their entries show up multiple times, suggests that what people are primarily looking at... is the trending list.
Either directly, because they use a client that has that built in, or indirectly, as they have been onboarded with the lists or told to "just follow the people I follow", which leads to a steadily-rising concentration of follows. This concentrating effect is accelerating.
The newly-popular WoT (web of trust) relays further exacerbate this effect, as they put a premium on the npubs that have the highest WoT score, which -- surprise, surprise! -- are the same people as on the trending list.
And this is why everyone on the trending list insists Nostr is a fun, happening place, full of human interaction. A place where replying reverently to Jack and posting GM religiously will make you a sought-after conversant. It is that place. For them.
In fact, they've reached that glorious state of #PeakSocialMedia, where they have become famous for being famous, and no longer have to even pretend to be trying to appeal to anyone with their content. They can post literal garbage, and their ~~fans~~ ~~groupies~~ ~~sycophants~~ commentariat will cheer them on, and flood their replies with ardent encouragement. Less because those other npubs actually cared about what they posted, than because they are hoping to pick up new followers in those threads, since they know that everyone is looking at those threads, because those threads are trending.
It's a pyramid scheme of following.
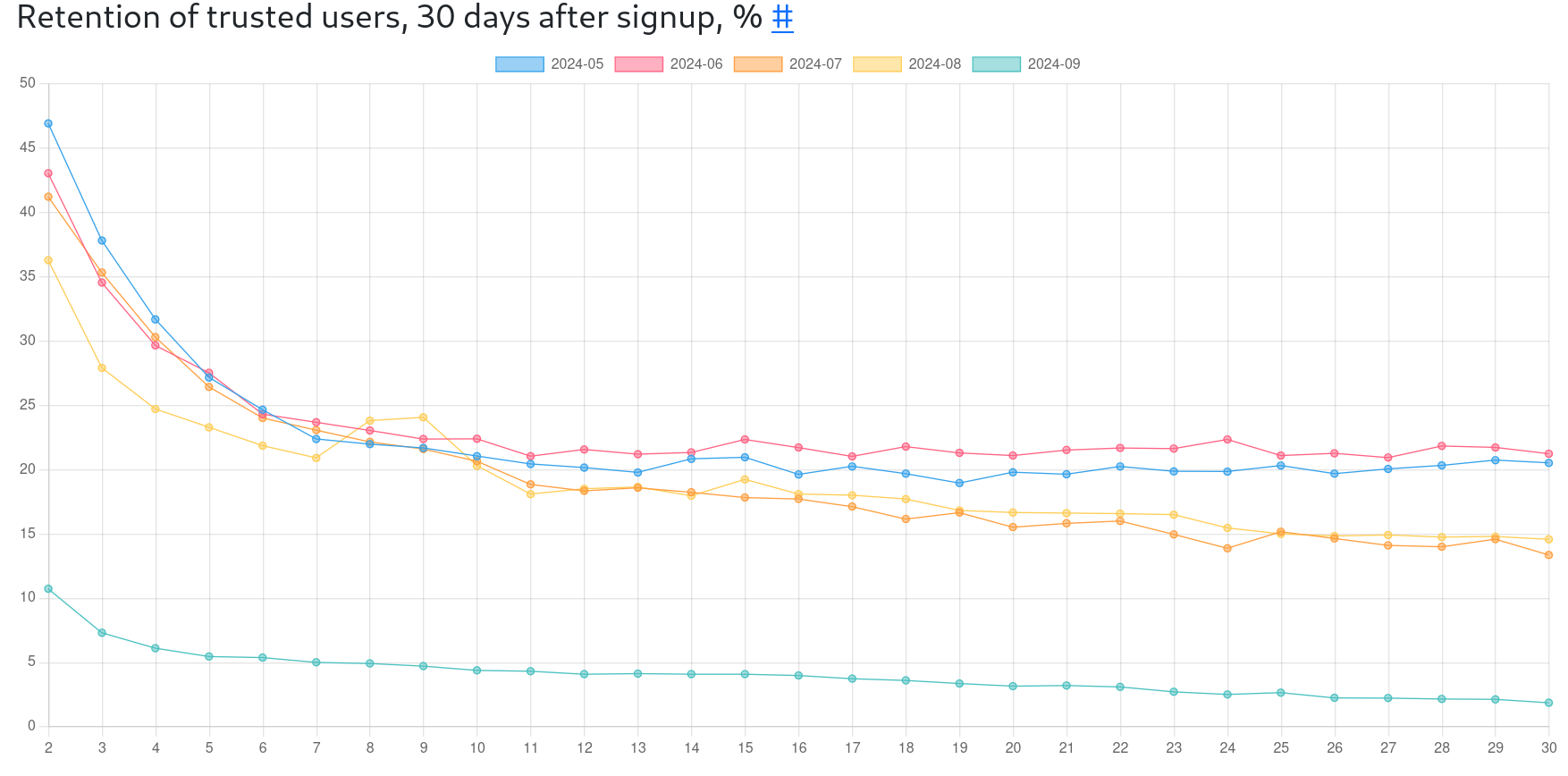
For the rest of us... the vast majority of us... that blue line at the bottom is mostly how it feels.
The trend is to trending.
What we no longer have, is people looking directly at relay feeds, to find new people, or even their own follow list feeds, to see npubs they've already subscribed to. Even when people follow me, they usually don't respond until I'm trending, which suggests that they're also seeing me on the trending list because that is what they're primarily looking at. This is why, as soon as you get on the trending list, your replies explode. And your replies will be concentrated in a hardcore few, otherwise.
Those few are the reason I keep coming back, but as they're also often chatting with me off-Nostr, I am facing the question of: Why bother with Nostr microblogging?
This is the question I am struggling with. If kind 01 isn't for plebs chatting, anymore, (and it increasingly isn't) then it's mostly a sort of bulletin board, where we post notifications of items we've added in OtherStuff clients, or make announcements of meetups, software releases, or conferences. This, however, is compounding the dullness of the feeds and turning it into a sort of "info flyer", except for a lucky few. But, perhaps, I am simply a #NostrBoomer, who is failing to move with the times and get with the program.

I'm slowly reaching the conclusion that Kind 01 in an open, centralized market of notes, will always coalesce around a small subset of #NostrElite and turn into a largely passive form of entertainment, or a frustratingly lonely place, for everyone else. There can only be so many people talking, at once, in a public square.
The only movement I currently see, that might end the slow slide of Kind 01 into irrelevance and tedium, is to create lots of smaller, public squares, through single-relay communities. This has been such a long time, in coming, and has been resisted by client devs so ferociously, that I worry that it's merely an attempt to close the barn door after the npubs have escaped.
I sincerely hope to be proven wrong, though. Perhaps the relay devs, who have valiantly taken up the fight, will #SaveKind01. We shall see.
-
 @ 460c25e6:ef85065c
2024-10-15 12:49:55
@ 460c25e6:ef85065c
2024-10-15 12:49:55NIPs (Nostr Implementation Possibilities) are technical specifications that Nostr developers create to define how specific event types and tags are used. These can be written before or after the feature is implemented and often go through multiple revisions before becoming stable enough to matter. Once two or more clients fully implement the proposal, it is merged into the main repository. This process ensures that while new ideas are encouraged, they are also rigorously reviewed and tested.
There are generally two paths for NIPs: 1. New Ideas, when developers just have a hunch on a new solution and want to quickly write something up to gather feedback from the community. These are my favorite NIPs because they generally introduce a new way of thinking about a problem we are all having. And because they are not just a general solution, but a specific proposal, it allows us to see the entire picture in just a few paragraphs. Even though they are my favorite, they are quite "green" and usually spur 2-3 separate solutions in following PRs by different authors. 2. Existing implementations that need to explain what they are doing. These happen when a client is already running the code in production and simply wants to explain to the rest of the community how to generate and interpret the events the client is creating. These NIPs start much more stable than the former and allow for fewer changes, but because there is already an implementation available, it's a market-tested solution that might just need a few adjustments before others start implementing it.
Well-written specs ensure clarity, reduce ambiguity, and help developers implement the proposal consistently. The text should be VERY short, precise, prescriptive, and actionable by other devs. Start by introducing the new kind or tag in the first sentence and jump straight into a mockup of how the event looks like. The mockup should be self-explanatory and provide clues to what the remaining of the document will talk about. Some folks like to add long/verbose introductions, conclusions, and discussions of the reasons why the NIP is needed or why certain features are there. But those are largely unnecessary and are more appropriate to be placed in the body of the Pull Request descriptor.
Start your NIP with the following template:
``` NIP-
====== </h2> <p><code>draft</code> <code>optional</code></p> <p>Event kind <new kind> defines <whatever it does>. Tags <one or two of the most important ones> <describe what they do>. As an example: </p> <p><code>`jsonc { "kind": <your kind>, "tags": [ <your tags> ], "content": "", //... }</code> `</p> <p>Relays MUST...</p> <p>Clients MUST... </p> <h2><Details 1></h2> <h2><Details 2></h2> <h2><How to find them></h2> <p>```</p> <p>Your number for the NIP is irrelevant. Just pick a random number that is available so that you can fork the repo, create a file with that name, and start writing. This number will likely change once the NIP is merged. </p> <p>The NIPs title must be self-explanatory and short. If it helps, try to imagine which name would be best to add to the list of NIPs on the readme.md file. Same for event type names. Picture something that is short, unique and that devs can just remove the space to have a class name. </p> <p>The <code>draft</code> <code>optional</code> tags are there because unless you are working on NIP-01, everything is draft and everything is optional. If you want to write a mandatory NIP, you better make sure your text is so good that it can be added to <code>01.md</code> directly without overcomplicating the protocol. </p> <p>Start by describing the new event type, what it does and its main tags. Show the mockup and then start introducing all the other tags and how clients and relays should behave when implementing it. Use the words MUST, SHOULD, MAY, SHOULD NOT, and MUST NOT to define the mandatory behaviors of those declaring compliance with the NIP. </p> <p>Keep it simple. The specification should be designed to ensure that different clients, relays, and services can implement it without requiring substantial changes to their existing infrastructure. Ideally, devs should be able to implement the entire NIP from near scratch in just a few hours. Don't use jargon. Don't declare a vocabulary of words. Use simple words that anyone can understand and quickly code a demo of all the features in the NIP. They can learn about your reasons as they develop their implementation. </p> <p>Write expecting buggy implementations. The protocol must be resilient to varying implementations and network conditions, and gracefully handle coding errors or random gibberish. You want to promote a defensive design that anticipates misguided implementations, avoids breaking changes, and maximizes compatibility across the ecosystem. What happens if there are two tags with the same name? What happens if events that have missing tags are found? Buggy implementations will exist. The writing and reading clients are generally different and must be ready for anything that shows up on each side. </p> <p>Avoid abstractions, extensible and modular designs. Yes, they can be hidden underneath your text, but writing for them is a mistake and just overcomplicates things. Write for a specific use case and close all possible options to the items/features declared in the text. Make sure you are implementing those. There is no point in declaring things that are not going to be used in the short term. We can always add more in the future and we don't need a recipe on how to add more later. </p> <p>Label your relay hosts, setting kinds, and other data management necessities. Every NIP has a way to find out the user's preferred relay associated with the use case. Sometimes it's through a relay hint others through a separate event kind that just lists the user's home relays or contains a list of "following" events designed for the use case. Each NIP can create their own way of finding events.</p> <p>You cannot add new root fields. Use tags instead. Root fields are special and require changes to the core protocol everyone implements. Any new field will take years to come to reality. </p> <p>Once you propose an idea, try not to change too much. It will take time for other devs to wrap their minds around it. If you keep changing it, even if those changes reflect the request of the reviewers in the PR, it just confuses everyone. Sometimes things change so much that it is worth doing two PRs with separate specifications that solve the same problem. That allows devs to analyze the two propositions side by side and decide which one is better. </p> <p>Always add a test case or an example. This is an absolute requirement if the NIP is complex, like a new encryption scheme. But even for simpler NIPs, test cases help devs to quickly verify if their implementations meet the minimum standard for compliance. They not only add peace of mind, but they also provide some welcoming dopamine when a new dev is trying to implement your NIP. </p> <p>Managing state is hard. Doing it with different implementations and hosting them in separate relays is even harder. If your NIP has multiple events to manage state, like group administration actions (add/remove member, change names/icons, invite/reporting events) try to structure them in a way that devs can quickly see the state machine of all possible state changes. </p> <p>Specify data formats explicitly. Clearly define the format of all data fields, including type (e.g., string, integer), encoding (e.g., base64, hex), and structure (e.g., array, object). Specify constraints like length limits, valid characters, and optional/required fields. Tags are case-sensitive. Avoid having to specify new encodings, but if you do, make sure to include test cases that encompass all potential cases. </p> <p>It's ok to not propose the most efficient way of solving the problem. A simple but slightly less efficient design is preferred over a complex but more efficient one. We already use hex and base64 codes to represent binary bytes in JSON, which wastes 25-50% of space. That level of waste is ok if the solution becomes simpler to code. </p> <p>It's not about you. You may think you must convince everyone that your particular way of solving the problem is the best and get some ego points with yourself. While some of that is beneficial to the debate, be open-minded to the other possible solutions. Once merged, the NIP is not yours anymore. Anyone can change in any way they see fit. If your work is great, people will remember your name. If it just got the conversation started to become something completely different from what you proposed, they will also remember you. </p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> </ul> </div> </div> <script> // 处理回车键 function handleKeyDown(event) { if (event.key === 'Enter') { handleSearch(); } } // 处理搜索 function handleSearch() { const keyword = document.getElementById('searchInput').value.trim(); if (keyword) { window.location.href = `/search?q=${encodeURIComponent(keyword)}`; } else { alert('请输入搜索关键词!'); } } </script> </body> </html>