-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ b6424601:a11e4ff4
2024-10-26 12:12:56
@ b6424601:a11e4ff4
2024-10-26 12:12:56In 2007, my 10-year-old business had just signed a 5-year lease on Atlanta's Peachtree Road with enough space for my partner and our wives' separate companies to continue growing. We thought we were an overnight success 10 years in the making. 14K a month split between 3 companies, all in the housing and office design industry; what could go wrong?
As I look back on those early days, I realize that our business was fueled by the fiat jet fueled housing run-up. Two couples, three businesses, and all personally guaranteed. We thought we were an overnight success, but little did we know that the housing market was about to take a drastic turn.
In 2008, I joined a Vistage CEO group, where I was tasked with presenting to the group on my approach to designing buildings for individuals. I saw an opportunity to analyze the patterns that produced good projects for happy clients, and I teamed up with a contractor buddy to work on a joint presentation. Our efforts yielded ten principles that produced the highest ROI beyond providing a primary place to live.
These principles were the foundation of our approach to architecture, and they were based on our experiences working with individuals on their custom house projects. We focused on listening to our clients, designing buildings that stood out while fitting in, creating lifetime homes, and making projects sustainable and viable.
As I reflect on our journey, I realize that the principles we developed were an interesting reflection of what was happening to our clients in the housing market of that time and how we as architects help our clients get through the process. Over time, we had to adapt and evolve to respond to changing conditions.
In 2010, we made changes to respond to a client environment where projects happened without banks. Clients spent paper on their projects, and construction loans were not available. What the subsequent buyers wanted when the house was sold was off the table. Remember being thankful our clients had cash to spend on projects in our survival predicament.
In hindsight, our clients are probably grateful as well for being able to convert paper into a hard asset. The principles evolved slowly until the COVID came in 2020. I was ready to hunker down and go to business survival mode like back in the crash, converting staff to contractors again and only paying for billable work.
But "your" government made PPP rain from the sky on our small business with employees. In addition, clients working from home who needed change or from their vacation property added gasoline to the fire. By 2022, inflation raged, described as transitory, to change the build cost from 1.2 million to a new price of 2.2 million for the new Intown infill homes. That is 83% inflation over 2 years, no matter what the CPI said.
The principles pivoted to respond: going fast to respond to inflation, managing the stuff to deal with supply chain problems, providing a viability budget before starting work to help clients understand the cost, and guiding our clients through the choppy waters of inflation.
We added a new principle about stewardship, which has become a cornerstone of our approach. We want to become architects for life for our completed projects and owners. We want to maintain relationships, observe results, and be trusted advisors as our projects age and clients' needs evolve.
Today, we are proud to say that our principles have evolved into 10 guiding principles that organize our approach to producing architecture asset architecture for the individual. We leverage the team of clients, contractors, vendors, and our time through our principle based process to produce architecture worthy of being an asset for our clients and families.
These 10 principles are:
- Listen: Analyze and understand our client's goals, constraints, and opportunities to communicate our vision of what is possible.
- Establish Viability: Before starting our project process, we will engage our client in a pre-project viability phase to diagnose and prescribe our solutions with a timeline and budget for client approval.
- Be a Design Sherpa: Our process is the most important value we provide. Following our process milestones will lead new and experienced clients through the 1000’s of design decisions to evolve in the correct order at the proper time.
- Design in Context: We believe context is the caldron of good architecture fits into its location both from the outside and inside out. Designing in context allows a building to stand out while fitting into the adjacent network of spaces around it.
- Architecture is a team sport: We believe in custom teams for custom projects, collaborating with partners who care about our clients and believe in our process as much as we do.
- Design for the individual: We do our most fulfilling work with clients who will live in or operate architecture explicitly created for their needs.
- Investment iteration: We break down the design process into decision milestones, providing increasingly detailed pricing for initial ideas, building shell, and interior selections to empower clients to make informed decisions about the value they're willing to exchange for their desired architecture.
- Create Asset Architecture: Design and execute projects that hold long-term value and provide a return on investment beyond the currency used build the project.
- Be present: Designing and building stuff is an atypical and infrequent activity for our client. Help our clients enjoy the journey and results that could be life-changing (in a good way).
- Stewardship—We want to Become architects for life for our completed projects and owners. We want to maintain relationships, observe results, and be trusted advisors as our projects age and clients' needs evolve.
We're an architect tribe that has refined our principles to design buildings that truly matter for the people that use them. Aspire to create hard asset architecture worth exchanging for the hardest money there is.
HODL on.
-
 @ 599f67f7:21fb3ea9
2024-10-26 11:22:06
@ 599f67f7:21fb3ea9
2024-10-26 11:22:06Zer da Cashu?
Cashu Bitcoin-erako ecash protokolo ireki bat da, transakzio azkarrak eta komisio gabekoak eskaintzen dituena, pribatutasun ia perfektuarekin. Xehetasun gehiago nahi izanez gero, gure azalpena ikus dezakezu.
eNuts
eNuts Cashu-rako mugikorretarako zorro bikaina da, Android eta iOS (TestFlight) plataformetan eskuragarri dagoena. Mint anitzekin lan egitea ahalbidetzen du eta nostr bidez bidalketak egiteko aukera ere eskaintzen du.
⚠️ eNuts eta Cashu oraindik beta fasean daude. Funtsak galtzeko arriskua dago. Aplikazioa instalatzerakoan arriskuen inguruan irakurri. Galera ekonomikoei aurre egiteko gai zaren zenbateko txikiekin saiatu.
Probatu
Prozesu honetan zehar mint-ekin elkarreragin, ecash-a jaso eta bidali, segurtasun-kopiak egin, Lightning-era ateratzeak eta mint-en artean trukaketak egingo ditugu. Azkenik, nostr kontaktu funtzionalitatea probatuko dugu.
Instalatu
Sartu eNuts webgunera eta instalatu aplikazioa zure sistema eragilerako.
Mint bat gehitzea
Ecash-arekin elkarreragiteko, lehenik mint bat behar duzu. Mint honetan zure ecash token-ak sortzen eta itzultzen dira. Mint-a da zure Bitcoin-en zaindaria, baina ez daki nor zaren, norekin egiten duzun transakzioa, ezta zenbat diru duzun ere. Probetarako Txoko mint erabili dezakezu.
- Joan Txoko Mint-era. Kopiatu mint URL-a.
- eNuts-en, joan Aukerak > Mint kudeaketa eta sakatu + botoia. Itsatsi lehen urratsean kopiatu duzun mint URL-a.
💡 Mint gehigarriak ere gehitu ditzakezu. Mint publiko batzuk MintIndex-en aurki daitezke. Kontuan izan mint batzuek zenbateko jakin bat gordetzen dutela bideratze-gastuak ordaintzeko, eta, beraz, ezin dituzula zure sats guztiak atera.
Tokenak sortzea
Mint bat gehitu duzunean, eNuts-ek automatikoki galdetuko dizu mint horretatik Cashu token berriak sortu nahi dituzun.
- Erantzun Bai.
- Sortu faktura bat mintu nahi duzun zenbatekoarentzat. Zenbateko txiki batekin saiatu, adibidez, 100 sats.
- Ordaindu faktura Lightning zorro batetik. Faktura ordaindutakoan, ecash token-ak izango dituzu.
Prozesu honek aukera ematen dizu ecash token-ak sortzeko, eta horiek zure transakzioetarako erabiltzeko prest izango dituzu.
Ecash-ekin transakzioak egitea
Ecash-ekin transakzioak egitea, funtsean, datu multzoak bidaltzea eta jasotzea da. Funtzionalitate hauek zuk zeuk probatzeko, bidali eta jaso dezakezu zure buruari.
- Ecash bidaltzeko, sakatu Bidali > Ecash bidali.
- Mint bat baino gehiago erabiltzen baduzu, aukeratu bidali nahi duzun mint-a. Ondoren, aukeratu Kopiatu eta partekatu.
- Aukeratu zenbatekoa.
- Nahi izanez gero, gehitu ohar bat, eta sakatu Jarraitu.
- Berretsi ordainketa xehetasunak eta sortu token-a. Une honetan, coin selection funtzioa erabil dezakezu zein token erabili nahi dituzun hautatzeko.
Ohartu token-ak 1 sat, 2 sats, 4 sats, 8 sats, 16 sats eta antzeko zenbatekotan sailkatuta daudela. Horiek 10 euroko, 20 euroko edo 50 euroko billeteak bezala irudika ditzakezu. - Kopiatu token-a.
Une honetan, token-a beste norbaiti bidal diezaiokezu edo zure zorroan berreskuratu. Saiakera moduan, bigarren aukera hau egingo dugu.
- Ecash jasotzeko, sakatu Jaso > Itsatsi eta berreskuratu Ecash. eNuts-ek automatikoki irakurriko du zure arbeletik eta token-a berreskuratuko du.
💡 Zure transakzioen historian ecash token-a zain dagoen egiaztatu dezakezu, eta hartzaileak ez badu berreskuratu, itzuli dezakezu. Horretarako, sakatu zure historiako irteerako transakzioan eta aukeratu Egiaztatu token-a gastatu den. Token-a zain badago, Itzuli token-a sakatu dezakezu eta berriro zure zorroan izango duzu.
Multimint trukeak
Mint desberdinen artean bidalketak eta jasotzeak posibleak diren galdetu baduzu, erantzuna bai da, neurri batean. Hala ere, Cashu token-ak zuzenean mint batetik bestera bidaltzea ez da zuzenean egiten; horren ordez, transakzioak Lightning-era bideratzen dira, mint bat Lightning nodo bat ere badelako. Cashu token-ak ez dira bateragarriak nodo desberdinen artean.
Hau probatzeko, beste mint bat gehitu dezakezu oraindik egin ez baduzu, adibidez, cashme LNbits mint edo eNuts mint lehenetsia.
💡 Kontuan izan mint batzuek sats kopuru bat gordetzen dutela bideratze-gastuak ordaintzeko. Arazo hau konpontzeko, zure mint propioa sor dezakezu Bitcoin Txoko LNbits zorroarekin, Cashu luzapena aktibatuz.- Joan Aukerak > Mint kudeaketa atalera, eta aukeratu trukatu nahi duzun mint-a. Ondoren, joan Multimint trukeak atalean.
- Aukeratu trukatu nahi duzun mint-a.
- Aukeratu zenbatekoa eta sakatu Kuotak aurreikusi Lightning gastuen kalkulua egiteko.
- Sakatu Jarraitu.
- Egiaztatu xehetasunak, eta nahi izanez gero, coin selection funtzioa erabili. Ondoren, sakatu Orain trukatu.
Prozesu honetan, bidaltzen ari den mint-ak Lightning faktura bat ordaintzen du jasotzen ari den mint-aren bidez. Faktura osatu bezain laster, trukatuta dagoen token-a zure zorroaren saldoan agertu beharko litzateke jasotzen ari den mint-ean.
Ateratzea
Zure Cashu sats-ak berriro Lightning sats bihurtu nahi dituzunean, ateratzeko aukera duzu. Prozesua hauxe da:
- Sakatu Bidali > Lightning faktura ordaindu.
- Mint bat baino gehiago erabiltzen baduzu, aukeratu bidaliko duzun mint-a.
- LN faktura edo LNURL atalean, sartu faktura bat, LNURL edo Lightning helbide bat; edo, besterik gabe, QR kode bat eskaneatu.
- Aukeratu zenbatekoa eta sakatu Kuotak aurreikusi.
- Egiaztatu xehetasunak, eta dena zuzen dagoela ikusi ondoren, sakatu Ateratzea.
Prozesu hau amaitutakoan, mint-ak Cashu token-ak trukatzen ditu eta Lightning faktura ordaintzen du.
Segurtasun kopiak
Cashu token-ak babesteko prozesua, agian, ezberdina izango da Bitcoin eta Lightning zorroak babesteko ohiko prozesuekin alderatuta. Diru-funtsak datu blokeekin irudikatzen direnez, Cashu token-ak babesten dituzunean datu bloke horiek bakarrik babesten ari zara. Honek esan nahi du segurtasun-kopiak baliogabetzen direla transakzio berri bat egiten duzun bakoitzean.
eNuts aplikazioak Cashu token bat sortzen du zure funts guztiekin, eta token horiek zein mint-ekoak diren jasotzen du.
- Segurtasun-kopia bat sortzeko, joan Aukerak > Segurtasuna > Sortu babeskopia token. Kopiatu token-a eta gorde toki seguru batean.
Bestela, mint bakoitza banaka babestu dezakezu: - Horretarako, joan Aukerak > Mint kudeaketa atalera eta aukeratu babestu nahi duzun mint-a. Ondoren, sakatu Funtseak babestu, kopiatu token-a eta gorde toki seguru batean.
Berreskuratzea
Berreskuratzeko, kopiatu babeskopia token-a eta ireki eNuts aplikazioa. Aplikazioak automatikoki irakurriko du zure arbelean dagoena eta galdetuko dizu token-a berreskuratu nahi duzun.
Nostr
eNuts aplikazioak Nostr integrazioa eskaintzen du, horrela zure kontaktu zerrendara ecash bidali ahal izateko. Funtzio hau erabiltzeko, honako pauso hauek jarraitu behar dituzu:
- Joan Kontaktuak atalera eta itsatsi zure Nostr gako publikoa.
- eNuts-ek zure kontaktu zerrenda eskuratuko du relays-etatik. Tamalez, bilaketa funtzioa oraindik ez dago eskuragarri, eta horrek kontaktu zuzena aurkitzea zaildu dezake, kontaktu asko izanez gero.
Hartzaileak Nostr motako 4 mezu zuzena jasoko du, Cashu token-arekin. Hartzaileak mezu hau bere zorroan berreskuratu eta token-a erabili ahal izango du.
Ondorioa
Gida hau lagungarria iruditu zaizu? Saiatu Cashu token batzuk bidaltzen Nostr bidez!
-
 @ e97aaffa:2ebd765d
2024-10-26 10:10:21
@ e97aaffa:2ebd765d
2024-10-26 10:10:21Não é possível determinar o número exato de quantos bitcoins terá o Satoshi, já foram efectuados diversos estudos, apesar de discrepâncias nos resultados, estima-se entre os 900 mil a 1.1 milhões de moedas.
A Arkham identificou apenas 3 endereços (P2PKH) pertencentes ao Satoshi, não esquecendo que no início não existiam endereços, os bitcoins eram enviados diretamente para a pubkey (chave pública, P2PK).
Este gráfico apenas contabiliza os bitcoins em endereços. Mesmo após o desaparecimento de Satoshi, a comunidade continua a enviar moedas para os seus endereços.
O endereço principal recebe regularmente moedas, têm mais de 38 mil transações, entre elas, destaca-se as seguintes:
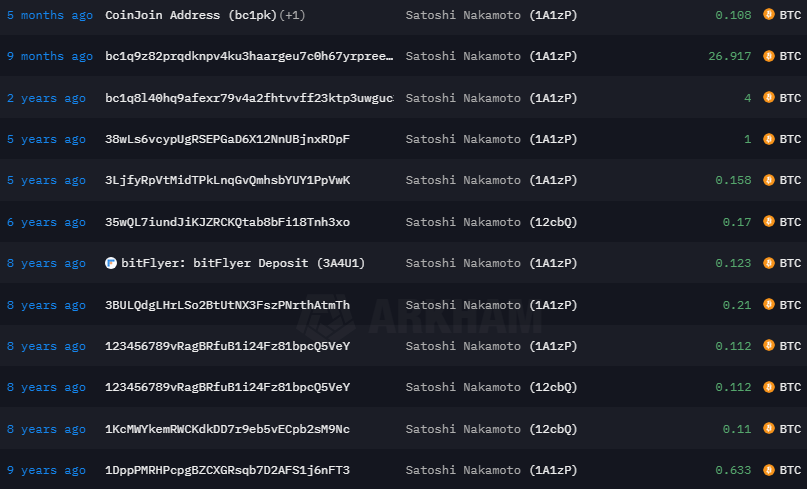
Este ano, um anônimo doou quase 27btc, incrível.
O problema
A muito longo prazo, com o desenvolvimento tecnológico, os computadores vão ficar cada vez mais poderosos. Conforme os computadores vão evoluindo, o desenvolvimento da computação quântica, o bitcoin vai acompanhar essa evolução tecnológica, para se manter seguro. Os utilizadores terão que migrar de endereços mais antigos para endereços mais resilientes. É uma evolução natural.
O problema está nas moedas que estão em tecnologias/endereços mais antigos, sobretudo nos que têm a pubkey exposta, estes serão os primeiros alvos. Vai demorar muitos anos, mas um dia será possível ter acesso a esses UTXOs. O pagamento para P2PK foi utilizado entre 2009 e 2010, hoje em dia é quase inexistente.
Não é necessário entrar em pânico, os endereços SegWit são muito mais seguros e resilientes, porque oculta a pubkey. A pubkey só é revelada no momento em que efetua a primeira transação(enviar), assim para garantir uma melhor segurança é essencial não reutilizar endereços.
Só que existem 45370 UTXOs que não realizaram a migração para tecnologias mais seguras, isto representa mais de 1.7 milhões de Bitcoins, ou seja, 8.73% do supply.
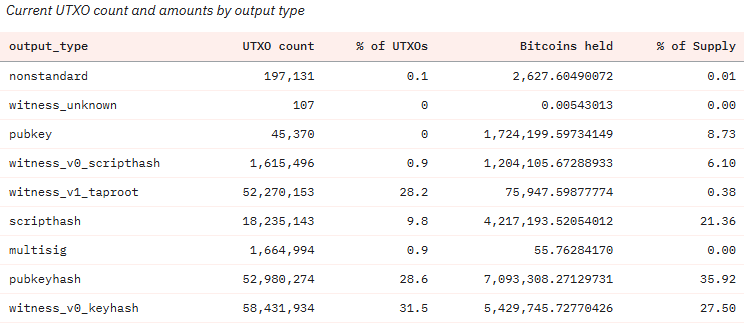
Apenas uma minoria dessas moedas pertence a bitcoiners no “ativos”, a grande maioria pertence ao Satoshi e as pessoas que perderam as chaves. Apesar de tudo, esporadicamente algumas dessas moedas são movidas, este ano já foram 172 UTXOs, equivalente a 7707 BTC.
Além dos P2PK ainda existem os endereços que foram reutilizados, que tem a chave pública exposta, assim o número aumenta para 4 milhões de moedas, apesar de ser um número elevado, não é preocupante, porque parte destas moedas ainda tem donos ativos, quando for necessário, vão se mover para endereços mais seguros.
O dilema
«Moedas perdidas apenas fazem com que as moedas de todos os outros valham um pouco mais. Pense nisso como uma doação para todos.» – Satoshi
O problema é que essas moedas não estão perdidas para sempre, talvez daqui a 5 ou 20 anos, não sei, mas uma coisa é certa, um dia vão ser recuperadas e não serão pelos legítimos donos.
Assim, nos próximos anos a comunidade de bitcoiners terá um dilema para resolver, o que fazer com os Bitcoins do Satoshi/P2PK?
Existem duas possibilidades: não fazer nada e essas moedas voltam a circular ou então, mudar o código para bloquear as moedas para sempre.
Qualquer uma das soluções será algo extremamente polémica, certamente vai dividir a comunidade, vai ser uma discussão acirrada, dificilmente haverá um consenso, por isso é mais provável ficar tudo como está.
Vendo bem, o bitcoin vai passar por uma situação similar ao ouro, periodicamente são descobertas moedas de ouro, que foram escondidas durante décadas ou séculos pelos nossos antepassados. O ouro que estava “perdido”, volta à circulação.
Será uma nova corrida ao “ouro”, o resgate das moedas do Satoshi. Se esse resgate for lento e gradual, não terá grande impacto, mas se for num curto espaço de tempo será um enorme problema, são mais de 8% de supply que entram no mercado.
O preço poderá ser um problema, mas a meu ver, o grande problema é a busca em si, porque será mais lucrativo gastar energia na procura das moedas do Satoshi do que minerar novos bitcoins.
Será que a hashrate não cairá drasticamente? Colocando em causa a segurança da rede.
Esta é a minha principal dúvida e receio.
A minha opinião
Hoje eu penso que deveríamos optar por algo intermédio, nem com a proibição total, nem sem restrições. Apenas nos blocos com o número múltiplo de 144, ou seja, um bloco por dia, seria possível incluir transações P2PK. Além disso, o número de transações por bloco seria limitado: 1 UTXO maior que 10 btc ou vários UTXOs com uma soma inferior a 10 btcs.
Este limite de “espaço” é suficiente para os legítimos donos das moedas efetuarem as transações no período pré quântica. No período pós quântica, se a quebra da criptografia for muito rápida, o limite de bloco vai criar uma gargalo, vai obrigar o aumento drástico do fee, reduzindo o lucro do “ladrão”, além de financiar os mineradores.
Conclusão
A minha ideia é muito complexa, mas o bitcoin é um protocolo simples, a comunidade é muito conservadora, dificilmente aceitaria algo assim tão complexo. Por isso eu digo, só existem dois caminhos plausíveis, ou não fazer nada ou a proibição total dos P2PK.
Mas vamos ter muitos anos para pensar sobre o assunto.
-
 @ 07e188a1:24d232f3
2024-10-26 09:16:44
@ 07e188a1:24d232f3
2024-10-26 09:16:44Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
A sub heading goes a long way
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
-
 @ 599f67f7:21fb3ea9
2024-10-26 11:54:10
@ 599f67f7:21fb3ea9
2024-10-26 11:54:10Zer da Cashu?
Cashu Bitcoinentzako Ecash protokolo irekia da, transakzio azkarrak eta doakoak eskaintzen dituena. Protokolo honen ezaugarri nabarmenetako bat pribatutasun ia perfektua eskaintzea da. Nostr nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg erabiltzaileak sortu zuen.
Hona hemen Cashu eta on-chain Bitcoin alderatzen dituen taula, Bangkok 2023ko Bitcoin Konferentzian nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6-k aurkeztutako Nuts and Bolts hitzaldian oinarrituta:
| Cashu | Bitcoin (on-chain) | |-----------------------|----------------------------| | Libururik gabe | Liburu banatua | | Titulartasun tokena | UTXO (Ustiaketa Ezberdinen Irteera) | | Transakzio itsutuak | Transakzio publikoak | | Zentralizatua | Deszentralizatua | | Konfiantzazkoa | Konfiantzarik gabe | | Aldi baterako transakzioak | Betiko transakzioak |
Ikusten dugunez, Cashuk pribatutasuna hobetzeko konfiantza gabeko izaera eta deszentralizazioa sakrifikatzen ditu. Konpentsazio hauek zentzuzkoak dira zaintza-zerbitzuetan, erabiltzailea dagoeneko zerbitzu zentralizatu eta fidagarri bat erabiltzen ari baita. Zaintza tradizionaleko irtenbideek pribatutasun eskasa dute, zaintzaileak erabiltzailearen funtsak zenbat diren eta norekin ari den transakzioak egiten jakin dezakeelako. Horrek esan nahi du norbanakoak erraz helburu eta zentsura daitezkeela. Gainera, datu-erregistroek "honeypot" bihurtzeko arriskua dute, hau da, erasotzaileentzat erakargarri.
Alderantziz, Cashu-ren mint-ek zaintzaile gisa jardun dezakete, baina erabiltzaileen nortasuna, duten funtsen kopurua edo norekin ari diren transakzioak egiten ezagutzeko aukerarik gabe. Mint-ek duten datu-erregistro bakarra gastatutako sekretuen zerrenda da, berriro erabili ezin direnak, baina erabiltzaileekin lotzeko modurik gabe. Horrela, Cashu-k pribatutasuna bermatzen du, zaintzaileak ez duelako inolako informaziorik erabiltzaileen jarduerei buruz, ohiko zaintza-soluzioekin gertatzen denaren kontrara.

Cashu-ren erabilera kasu batzuk
Cashu-ren erabilera kasu batzuk honako hauek dira: bonuak, dagoeneko zentralizatuak eta zaintza-zerbitzuak dituztenak; baliabide bakoitzeko ordainketa (pay-per-resource) APIak, nostr bideratzaileak eta mixnet-ak bezalako zerbitzuetarako; sistema integratuak, kontu eta saldo eredu tradizionala ordezkatzen dutenak; eta truke/mixinge zerbitzuak, gordailuak eta ateratzeak deslotzeko, pribatutasuna hobetzeko.
Historia
Ecash David Chaum-ek 1982an asmatu zuen, sinadura itsuak erabiliz balio elektronikoaren transmisiorako protokolo gisa. Cashu Ecash-en inplementazio bat da, David Wagner-en 1996ko Chaum-en itsutze-aldaketan oinarrituta dagoena, eta nostr sortu zuen.
Terminologia
Cashu nola funtzionatzen duen ulertzen laguntzeko, lehenik eta behin funtsezko terminologia batzuk azalduko ditugu.
Mint
Cashu-ren mint-a erabiltzaileen funtsen zaintzailea da. Bere zeregina tokenak jaulkitzea eta erretzea da, baita bikoiztutako gastuak saihestea ere. Cashu-ren mint-a Lightning nodo baten gainean dago, beraz, Lightning ordainketak bidali eta jaso ditzake, beste mint batzuekin trukeak barne. Hala ere, Lightning nodoa lineaz kanpo badago ere, ecash tokenekin transakzioak egin daitezke. Lightning-ekin ez bezala, jasotzailea linean egon beharrik ez du tokenak jasotzeko.
Mint-ak ez daki nor den erabiltzailea, zenbat funts dituzten edo norekin ari diren transakzioak egiten. Hala ere, mint-a erabiltzaileen funtsen zaintzailea denez, fidagarria den mint bat aukeratu behar duzu, eta eragilea nor den jakin. Erabil ezazu funts txikiekin edo tokenak berehala trukatu.
Token
Cashu token-a mint-ak sinatutako datu-puska bat da, eta erabiltzaileak token horiek bere zorroan gordetzen ditu. Ecash tokenak testu-kate hutsak direnez, edozein testu bidezko protokoloaren bidez bidal daitezke, adibidez, nostr, posta elektronikoa, SMS, etab. Cashu-k txanpon-sistema bat erabiltzen du, zenbateko finkatuak dituena. Analogia bat eginez, hau moneta fiduziarioen billeteen zenbatekoei dagokie. Adibidez, eurotan 5, 10, 20, 50, 100 euroko billeteak daude. Cashu-n, tokenak 2ren indarren arabera sailkatzen dira. Adibidez, 1, 2, 4, 8, 16, 32, 64, 128 satoshi, eta horrela aurrera.
Zenbatekoak erabiltzea erabiltzaileen artean anonimotasuna areagotzeko egiten da, eta mint-ek transakzioak erabiltzaileen nortasunekin lotzea zailagoa bihurtzeko.
Nola funtzionatzen duen, 5 urteko bati bezala azaldua

Erabiltzaile Alice-k Cashu token berriak sortu nahi ditu. Horregatik, Bob mint-aren arduradunarengana joaten da eta esaten dio: "Kaixo! Cashu token berriak sortu nahi ditut."

Bob-ek erantzuten dio: "Ados, ordaindu iezadazu eta bidali iezadazu sekretu itsu bat." Sekretu itsua esan nahi du Alice-k sekretua ezagutzen duela, baina Bob-ek ezin duela sekretu hori ikusi.

Alice-k sekretu bat sortzen du, eta ondoren itsutzen du, horrela Bob-ek ez dezan jakin zein den sekretu hori.

Alice-k Bob-i ordainketa egiten dio eta ordainketaren egiaztagiria eta sekretu itsua bidaltzen dizkio. Bob ordainketa jaso duela ziur dagoenean, Alice-ren sekretu itsua sinatzen du eta sinatutako sekretu itsua itzultzen dio. Bob-ek sinatu duelako, etorkizunean ziur egon daiteke tokena baliozkoa dela.


Alice-k Carol-i ordaindu nahi dio. Horretarako, sekretua eta sinatutako sekretu itsua desitsutzeko gakoa bidaltzen dizkio Carol-i.


Carol-ek bere tokena trukatu nahi du. Beraz, Bob-engana (mint-aren arduradunera) joaten da eta Alice-k eman dion sekretua eta desitsututako gakoa erakusten dizkio.
Nola jakiten du mint-ak Carol-i zenbat satoshi eman behar dizkion?
Lehenago aipatu genuen bezala, Cashu tokenak 2ren indarren araberako zenbatekoetan banatuta daude (1, 2, 4, 8, 16, 32...), paperezko diru billeteen antzera. Bob mint-ak zenbateko bakoitza sinatzeko gako pribatu berezi bat du. Adibidez, 1 satoshi zenbatekoaren tokenak sinatzeko gako pribatu bat du, 2 satoshi zenbatekoaren beste bat, 8 satoshi zenbatekoaren beste bat, eta abar. Horrela, Carol tokenak trukatzera datorrenean, Bob-ek badaki zein gako pribaturekin sinatu zuen token hori, eta horren arabera, tokenak zein zenbatekotakoak diren ezagutzen du. Horrela, Bob-ek Carol-i dagokion satoshi kopurua itzuli diezaioke, sinatutako tokenaren zenbatekoa kontuan hartuta.
Zer gertatzen da itzulkinekin?
Cashu-n ez dago itzulkinik diru fisikoan bezala. Horren ordez, mint-ari (Bob-i) eskatu behar diozu token zaharrak suntsitzeko eta berriak sortzeko, zenbateko berarekin. Adibide batekin azalduz: Demagun Alice-k bi token dituela, guztira 10 satoshi balio dutenak. Bata 8 satoshi da eta bestea 2 satoshi. Alice-k 9 satoshi bidali nahi dizkio Carol-i. Horretarako, mint-ari (Bob-i) eskatzen dio bere 2 satoshi tokena bi 1 satoshi token bihurtzeko. Horrela, Alice-k 9 satoshi bidal diezazkioke Carol-i: 8 satoshi token bat eta 1 satoshi token bat erabiliz. Gainera, beste 1 satoshi tokena berarentzat gordetzen du.
Lightning sarearen papera konektatzeko elementu gisa
Zer gertatzen da Alice-k David-i ordaindu nahi dionean, baina David-ek Bob-en mint-a ez du fidatzen, eta, aldiz, Erin ezagutzen du eta bere mint-a erabiltzen du? Alice-k bere tokenak Bob-en mint-ean trukatzen ditu, eta Bob-i eskatzen dio token horiek "urtzeko" edo Lightning satoshietara bihurtzeko. Ondoren, Bob-en mint-ak Lightning transakzio bat bidaltzen dio Erin-en mint-ari. Erin-en mint-ak transakzio hori jasotzen du, eta David-entzat token berriak sortzen ditu Lightning sarearen bidez Bob-en mint-etik jasotako satoshiekin. Horrela, Lightning sareak mint ezberdinak konektatzen ditu, erabiltzaileak (Alice eta David) mint ezberdinak fidatu arren, transakzioak segurtasunez egiteko.

Zer dator hurrengoa Cashu-rentzat?
Programagarri den ecash
Cashu-ri gastatzeko baldintzak gehitu ahal izango zaizkio, mint-ak baldintza horiek betearaziko dituelarik. Horrek ahalbidetu dezake kontratu adimendun sendoak sortzea, oinarrizko katean (Bitcoin blockchain) edo Lightning sarean sartu gabe. Horrela, ordainketa publikoak, lineaz kanpokoak eta maiztasun handikoak posible izango dira.
Zorren froga eskema (Proof of Liabilities Scheme)
Zorren Froga (PoL) Eskema Cashu-rentzat zaintzailea den mint-ak erabiltzaileak iruzurrez erabiltzea zailtzen du, epoka kontzeptua aurkeztuz. Eskema honetan, zaintzaile den mint-ak epoka bakoitzean gako pribatuak aldian-aldian biratzen ditu, eta azken epokan jaulkitako eta erretako tokenen zerrenda publikoak argitaratzen ditu. Hau Erreserben Froga (Proof of Reserves) eskemarekin uztartzen da, non erreserbak katean bertan multisig batean gordetzen diren. Horrela, mint-ak ezingo du bere erantzukizunak murriztu, erabiltzaileek iruzurra detektatzeko arriskua handitu gabe. Xehetasun gehiagorako, eskema honen azalpen osoa kontsultatu dezakezu.
Saiatu Cashu
Cashu probatzeko, [Nutstash] eta [eNuts] gidak erabil ditzakezu. Horretarako Lightning zorro bat eta telefono edo ordenagailu bat besterik ez duzu behar.
-
 @ 599f67f7:21fb3ea9
2024-10-26 11:20:48
@ 599f67f7:21fb3ea9
2024-10-26 11:20:48Zer da lightning address bat?
Lightning address bat irakurgarria den helbide elektroniko baten antza duen helbidea da, adibidez username@domein.com, baina bitcoinetan ordainketak berehala eta merke jasotzeko aukera ematen du. Ez duzu zure gailuan nodo bat linean izatea behar, eta ez duzu eskuz faktura bat sortu behar norbaitek ordainketa egin nahi dizunean.
Oso interesgarria, ezta?Nola funtzionatzen du, orduan?
Lightning Address-ek LNURL pay protokoloa erabiltzen du, Lightning Network-aren gainean dagoen geruza bat da.

Prozesua hurrengo urratsetan laburbil daiteke:
- Erabiltzaile batek zure Lightning Address erabiliz ordainketa egin nahi duenean, haien zorroak helbide hori LNURL payRequest batean bihurtzen du.
- LNURL payRequest arrakastatsu baten bidez, zorroak BOLT11 faktura bat eskuratzen du, eta faktura hori ordainketa burutzeko erabiltzen da.
Hau da, prozesuaren oinarrizko pausoak hurrengoak dira:
💡 Lightning Address > LNURLp > BOLT11 faktura.
Lightning Network-ekin integratuta dagoen sistema honi esker, ordainketak erraz, azkar eta modu automatizatuan burutu daitezke.Oso ondo dirudi, baina zein da tranpa?
Lightning Address-en inplementazio askok kustodia dute (nahiz eta ez den beti horrela), izan ere, domeinu bat eta beti linean dagoen nodo bat behar dira Lightning Address-ak funtzionatzeko. Kustodia sistema bat denez, zure fondoak kudeatzen dituenak edozein momentutan kontrolatu edo kendu ahal dizkizu eta zure transakzioak monitorizatu ditzake.
Domeinuaren jabearengan fidatu behar duzu, zure Lightning Address-aren erregistroa aldatu ez dezan. Eta, gainera, LNURL zerbitzaria linean ez badago, sistema ez da funtzionatzen.
Bitcoin Txoko-k LNbits-en oinarritutako Lightning Address irtenbide sinplea eskaintzen du. Hau ere kustodia sistemakoa da, beraz, gomendagarria da Bitcoin Txoko zorroan kopuru txiki bat bakarrik gordetzea eta gero auto-kustodia zorro batera ateratzea, satoshi gehiago jasotzen dituzun heinean.Hasteko prest bazaude, hona hemen behar duzuna:
-
Zure zorroa sortzea
Lehenik eta behin, ez baduzu oraindik egin, joan bitcointxoko.com webgunera eta zorro bat sortu. Zorroari nahi duzun izena jar diezaiokezu. -
Luzapenak aktibatzea
Lightning Address-ak funtzionatzeko Pay Links luzapena behar da. Horretarako: -
Joan tresna-barrako Extensions (Luzapenak) atalera eta Pay Links luzapena aktibatu.
-
Ordainketa esteka bat sortzea
- Ireki Pay Links luzapena eta egin klik New Pay Link (Ordainketa Esteka Berria) aukeran.
- Aukeratu sortu duzun zorroa.
- "Item Description" atalean, nahi duzun testua sar dezakezu.
- Aukeratu zure Lightning Address-erako erabiltzaile izena. Zure Lightning Address hau bezalakoa izango da: erabiltzailea@bitcointxoko.com.
-
Fixed Amount aukera desmarkatu eta jarri gutxieneko balioa 1 eta gehienekoa 500000.

⚠️ Gehienezko balioa handiagoa jar dezakezu, baina ordainketa handiek huts egiteko probabilitate handiagoa dute, Bitcoin Txoko Lightning nodoaren kanalaren sarrera-gaitasun mugatua dela eta. Gomendagarria da 500000 satoshitan mantentzea. - Orain, ireki Advanced Options (Aukera Aurreratuak) eta aldatu Comment maximum characters (Komentarioaren gehieneko karaktere kopurua) 799-ra. Ez da beharrezkoa, baina aurrerantzean funtzionalitate gehiago emango dizu. - Azkenik, markatu Enable nostr zaps aukera behealdean, Lightning Address bidez zaps jasotzeko aukera izateko.
Aukera aurreratuak beste parametro batzuk konfiguratzea ahalbidetzen dute, baina nahi baduzu hutsik utz ditzakezu.
Azkenik, dena zuzen dagoela egiaztatu ondoren, egin klik Create Pay Link (Sortu Ordainketa Esteka) botoian.Horrela, zure Lightning Address sortuta izango duzu eta ordainketak jaso ahal izango dituzu!
Proba egitea
Zure Lightning Address ondo funtzionatzen duen probatu nahi baduzu, beste zorro batera joan, Bidali (Send) aukera hautatu eta helmuga gisa zure Lightning Address idatzi. Ondoren, bidali zeure buruari satoshi batzuk.
Ondoren, itzuli Bitcoin Txoko zorrora eta egiaztatu ordainketa jaso duzun. Litekeena da orria freskatu behar izatea ordainketa agertzeko.
Dena ondo atera bada, zorionak! 🥳
Bestela, jakinarazi iezaguzu. Beti prest gaude laguntzeko.Hurrengo urratsak
Nostr zaps
Zure Bitcoin Txoko Lightning Address nostr profilean gehitu dezakezu eta horrela zaps jasotzeko erabil dezakezu. Normalean, hau hurrengo pausuekin egiten da: - Joan Profile (Profila) atalera. - Hautatu Edit (Editatu) eta Lightning Address aldatu.
LNDhub
Zure LNbits zorroa telefonoan inporta dezakezu LNDhub bezala, Zeus edo BlueWallet bezalako aplikazioak erabiliz. Horrela, ez duzu nabigatzailean zorroa ireki beharko aldian-aldian saldoa egiaztatu edo ordainketak egiteko.
Nola egin jakiteko, ikus ezazu nostr:naddr1qqxnzdej8y6ryvejxc6nvwpnqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65w4hhl8s.QR kodea
Zure LNURLp QR kodea parteka edo inprima dezakezu, jendeak mugikorrarekin eskaneatu dezan. Oso erabilgarria da zure denda lokaleko jabeak Lightning ordainketak jasotzeko sistema ezartzea nahi baduzu! - Parteka ezazu Sharable Page (Parteka daitekeen Orrialdea) esteka. - Edo, QR kodea PDF formatuan inprima dezakezu: joan View Link (Esteka Ikusi) atalera eta hautatu Print (Inprimatu).
Horrela, zure Lightning Address erabilera praktikoa handitu eta errazago kudeatu dezakezu! Hasi zaitez !
-
 @ d625c21c:dfa2ef0f
2024-10-26 08:26:23
@ d625c21c:dfa2ef0f
2024-10-26 08:26:23Join the best SSC coaching for top-notch faculty, comprehensive materials, and proven success. Start your journey today! Securing a position in the Staff Selection Commission (SSC) exams requires dedicated preparation, strategic guidance, and comprehensive resources. Our coaching center offers the best SSC coaching with high-quality, free study materials to streamline your journey towards success.
SSC Coaching Overview SSC exams cover multiple levels, including CGL (Combined Graduate Level), CHSL (Combined Higher Secondary Level), CPO (Central Police Organization), and JE (Junior Engineer). Each level tests different skills, but all require strong analytical abilities, time management, and a grasp of essential concepts. Scholars Academy SSC coaching program focuses on: Conceptual Clarity: Breaking down complex topics for an in-depth understanding. Practice-Centric Approach: Emphasis on solving a variety of questions to tackle different exam scenarios. Customized Plans: Adaptive study plans tailored to your strengths and weaknesses.
Why Choose SSC Coaching? Expert Guidance: Learning from experienced professionals with years of SSC coaching expertise helps streamline preparation. Time Efficiency: Structured coaching saves time, allowing candidates to cover the syllabus thoroughly and systematically. Updated Content: Our free study materials are regularly updated, following the latest SSC exam patterns and question trends. Motivational Environment: Being part of a focused, competitive setting helps maintain discipline and motivation.
The benefits of Scholars Academy SSC Coaching with free study material are as follows: Cost Efficiency: Free study material reduces the financial burden, providing students with access to top resources without additional costs. Comprehensive Coverage: From previous year question papers and e-books to mock tests, our free material includes everything essential for SSC preparation. Flexibility and Accessibility: Materials are provided in digital formats, allowing students to study anytime, anywhere. Focused Practice: Our free materials include topic-wise exercises and full-length tests to reinforce concepts and improve time management. Performance Analytics: With self-evaluation features, students can track their progress, identify areas for improvement, and receive targeted feedback.
Success Stories and Testimonials Over the years, many of our students have achieved top ranks in SSC exams, showcasing the effectiveness of our coaching methodology and materials. Here’s what some of them have to say: Anita Sharma (SSC CGL Topper): “The structured coaching, combined with regular tests and free materials, helped me focus on key areas and strengthen my weaknesses. The faculty’s insights were invaluable in my journey.” Rohit Mehta (SSC CHSL Qualifier): “The study materials were comprehensive, with questions modeled on actual exams. The coaching team’s support made a big difference in boosting my confidence.” Megha Verma (SSC JE Selection): “Getting quality materials for free and continuous guidance from experienced mentors was instrumental in my success.”
Our Coaching Methodology Personalized Learning Plans: We create individualized study schedules, focusing on each student’s specific needs and exam goals. Intensive Practice Sessions: Our program includes regular mock tests, speed drills, and concept quizzes to build both speed and accuracy. Doubt Clearing Sessions: Dedicated sessions with mentors allow students to resolve doubts, clarify complex topics, and strengthen their conceptual understanding. Real-Time Feedback: Each student receives actionable feedback on their performance, focusing on areas for improvement and boosting overall confidence. Motivational Support: We foster a positive, motivating environment to keep students engaged and confident throughout their preparation journey.
Enroll Today By joining our SSC coaching program, you’re not only investing in expert guidance but also gaining access to a wealth of resources, including free study materials, that bring you closer to your SSC aspirations. Free Study Material for SSC Exams Our SSC coaching center offers a range of free study materials designed to equip students with essential tools for effective preparation. From foundational concepts to advanced practice, we cover everything needed to excel in SSC exams.
Comprehensive Study Material for SSC Exams We provide detailed, well-organized study materials covering all SSC exam sections, including Quantitative Aptitude, Reasoning Ability, English Language, and General Awareness. Each module is crafted to ensure in-depth learning and thorough practice: Concept Notes: Detailed explanations of fundamental concepts and problem-solving techniques. Topic-Wise Exercises: Practice questions for each topic, allowing students to focus on individual sections. Revision Guides: Concise notes summarizing key concepts and formulas for quick revisions.
Free SSC Study Material Download Students can access and download our SSC study materials at no cost. These downloadable resources include: PDF Notes: Covers all topics comprehensively with examples and practice questions. Formula Sheets: Essential for quick reference, especially useful in Quantitative Aptitude. E-Books: Covering General Awareness and English, these books provide an extensive base of knowledge. How to Download: Visit our website, sign up for a free account, and access the downloadable materials instantly.
Practice Tests and Mock Exams Our practice tests and mock exams are designed to simulate real SSC exams, providing students with essential test-taking experience: Topic-Based Tests: Focus on specific areas, ideal for targeted practice. Full-Length Mock Exams: Simulate the actual SSC exam experience, helping students gauge their readiness and time management skills. Instant Feedback: After each test, students receive a detailed performance analysis with actionable insights.
Previous Year Question Papers Accessing and practicing with previous years' question papers is crucial for SSC preparation. We offer a collection of past papers, enabling students to understand the question patterns and difficulty levels: Detailed Solutions: Each question is accompanied by a step-by-step solution. Topic Distribution Analysis: Learn which topics frequently appear, allowing for focused study. Time-Based Practice: Helps students build speed and accuracy under exam conditions.
Study Material FAQs 1. What materials are included in the free downloads? We provide PDF notes, topic-specific exercises, formula sheets, mock tests, and previous year question papers. 2. Are the materials updated to match the latest SSC exam pattern? Yes, all materials are regularly updated to reflect the latest SSC exam trends and patterns. 3. Can I access the study material offline? Once downloaded, all materials can be accessed offline, allowing you to study anytime. 4. Do I need to pay for additional study resources? Our free materials cover all major topics required for SSC exams. However, for advanced guidance, premium resources are available. 5. Are there solutions provided for practice questions and mock tests? Yes, all practice questions and mock tests come with detailed solutions for effective learning. SSC Exam Preparation Guide Preparing for SSC exams demands dedication, structured study plans, and access to quality resources. Here’s a comprehensive guide to our offerings for SSC CGL, CHSL, and MTS exams, covering everything from coaching and study materials to syllabus details and preparation tips.
SSC CGL (Combined Graduate Level) Coaching Our SSC CGL coaching is designed to help students excel in one of the most competitive government exams. We offer: In-Depth Coverage of All Topics: From Quantitative Aptitude to General Awareness, every topic is thoroughly covered. Experienced Faculty: Trainers with a proven track record in SSC exams provide guidance and mentorship. Doubt Clearing Sessions: Personalized sessions to address individual queries and doubts.
SSC CGL Syllabus and Exam Pattern The SSC CGL exam consists of multiple tiers, each with a specific syllabus: Tier I: General Intelligence & Reasoning, General Awareness, Quantitative Aptitude, English Comprehension. Tier II: Quantitative Abilities, English Language & Comprehension, Statistics, and General Studies (Finance and Economics). Tier III: Descriptive Paper (Essay/Letter Writing). Tier IV: Computer Proficiency Test/Skill Test. Exam Pattern: Each section has multiple-choice questions with negative marking in Tiers I and II.
SSC CGL Free Study Material To aid students in preparation, we offer free downloadable materials: Notes and eBooks: Covers each section with explanations and examples. Formula Sheets and Tips: Key formulas and shortcuts for Quantitative Aptitude. Previous Year Papers: Solved papers for familiarity with exam patterns.
SSC CGL Preparation Tips Understand the Exam Pattern: Familiarize yourself with the tier system and focus on scoring sections. Time Management: Allocate specific hours daily for each subject to ensure balanced preparation. Daily Practice: Attempt questions regularly to build speed and accuracy. Revision: Revisit important concepts and formulas frequently.
SSC CGL Practice Tests Our mock tests include: Full-Length Mock Tests: Real exam simulation to assess your preparedness. Sectional Tests: Focus on specific sections for targeted practice. Performance Analysis: Get detailed feedback on your performance.
SSC CHSL (Combined Higher Secondary Level) Coaching Our SSC CHSL coaching program is structured to help students aiming for higher secondary level positions: Special Focus on Core Areas: Reasoning, Quantitative Aptitude, English, and General Awareness. Conceptual Learning: Breaking down complex concepts for easy understanding. Regular Mock Tests: To help students practice under timed conditions.
SSC CHSL Syllabus and Exam Pattern Tier I: General Intelligence, Quantitative Aptitude, English Language, General Awareness. Tier II: Descriptive Paper (Essay and Letter Writing). Tier III: Skill Test/Typing Test. Exam Pattern: Tier I is objective type, while Tier II is descriptive. There is negative marking in Tier I.
SSC CHSL Free Study Material We provide free resources including: PDF Study Notes: Detailed notes covering all important topics. Solved Previous Year Papers: Provides insight into commonly asked questions. Mock Papers: Realistic practice papers with varying difficulty levels.
SSC CHSL Preparation Tips Focus on Basics: Strengthen foundational knowledge in all subjects. Practice Writing: Essential for the descriptive section in Tier II. Review Past Papers: Familiarize yourself with the question types and difficulty. Stay Updated: For General Awareness, read current affairs regularly.
SSC CHSL Practice Tests Our practice tests help students gain confidence and improve time management: Sectional and Full-Length Tests: Practice in both focused and exam-like settings. Instant Feedback: Detailed analysis of each test for targeted improvement.
SSC MTS (Multi-Tasking Staff) Coaching SSC MTS coaching is designed for candidates aiming for Group C positions. Our coaching covers all essentials for this entry-level exam: Focused Coaching: Covering all required topics in Quantitative Aptitude, Reasoning, and General Awareness. Basic to Advanced Training: Sessions tailored for beginners as well as advanced learners. Mock Tests: Practice in an exam-like environment.
SSC MTS Syllabus and Exam Pattern Paper I: General Intelligence, English Language, Numerical Aptitude, General Awareness. Paper II: Descriptive Test (Essay/Letter Writing). Exam Pattern: Paper I is objective with negative marking, and Paper II is descriptive to assess writing skills.
SSC MTS Free Study Material Our free study materials include: Topic-Wise Notes: Clear explanations with practice questions. Previous Year Question Papers: Helps understand the exam pattern. Study Guides: Focus on key concepts and frequently asked questions.
SSC MTS Preparation Tips Regular Revision: Particularly for Numerical Aptitude and General Awareness. Practice Writing: Essential for the descriptive paper. Mock Tests: Practice regularly to improve speed and accuracy.
SSC MTS Practice Tests To ensure readiness, we offer: Timed Mock Tests: To simulate real exam conditions. Sectional Practice: For focused improvement in weaker areas. Performance Insights: Detailed feedback after each test. Courses Offered Our SSC coaching center provides various courses tailored to meet the unique needs of SSC aspirants. From classroom and online coaching to personalized programs, we offer a range of options with comprehensive study resources for effective SSC preparation.
-
SSC Classroom Coaching Our classroom coaching program is ideal for students who thrive in a traditional, interactive learning environment. It includes: In-Person Lectures: Delivered by expert faculty with years of experience in SSC coaching. Daily Practice and Doubt Sessions: Regular practice sessions and personalized doubt-clearing. Mock Tests and Performance Tracking: Assess your progress with regular tests and track your improvement.
-
SSC Online Coaching Our online coaching program offers flexibility for students who prefer remote learning or have time constraints: Live Online Classes: Real-time, interactive classes covering the entire syllabus. Recorded Lectures: Access recorded sessions for self-paced study and revision. 24/7 Doubt Resolution: Online discussion boards and chat support for resolving doubts.
-
Personalized Coaching Programs Our personalized coaching programs are tailored to the individual strengths and needs of each student, focusing on: Customized Study Plans: Adaptive schedules based on your strengths and areas for improvement. One-on-One Sessions: Individual mentoring sessions for focused attention. Goal Setting and Tracking: Personalized targets and regular progress reviews.
-
Study Resources Our coaching includes a variety of study resources designed for comprehensive SSC preparation, accessible across platforms.
Online Video Lectures Topic-Wise Video Lectures: Covering each subject thoroughly. Concept-Focused Videos: Explaining complex concepts in an easy-to-understand manner. Downloadable Content: Download videos for offline access and revision.
Important SSC Exam Topics and Guides Exam Guides: Complete topic breakdowns for SSC exams, focusing on high-scoring areas. Tips and Strategies: Subject-specific strategies to tackle each section efficiently. Frequently Asked Questions: Insights into commonly asked questions across all SSC exam tiers.
SSC Exam Preparation Apps and Tools We recommend and provide access to apps and tools to assist with SSC preparation: Daily Practice Apps: Mobile-friendly apps offering quizzes and daily practice questions. Performance Analytics Tools: Track your performance, identify weak areas, and customize your study plan. SSC Prep Games: Engaging apps with educational games and flashcards for easy learning.
Downloadable E-Books for SSC Exams Access a library of downloadable e-books covering key SSC topics: Quantitative Aptitude and Reasoning: Books with solved examples, formulas, and practice questions. General Awareness and English Language: Comprehensive guides with theory, practice, and revision notes. Mock Test Collections: E-books with mock tests and detailed solutions for exam practice.
Blog Our blog keeps students updated with the latest insights and tips for SSC exam preparation. SSC Exam Updates and News: Stay informed about exam dates, syllabus changes, and other key updates. SSC Exam Preparation Tips: Practical tips from experts to help students maximize their potential. Time Management for SSC Exams: Guides on managing time effectively for each section. Common Mistakes to Avoid in SSC Exams: Learn about common pitfalls and how to avoid them.
-
-
 @ 2df170ea:90d2b157
2024-10-26 06:43:03
@ 2df170ea:90d2b157
2024-10-26 06:43:03If you're experiencing the issue of Orbi not connected to the internet, start by accessing the Orbi Login page through your web browser. Once logged in, check the status of your internet connection and ensure all cables are securely connected. Look for any error notices on the dashboard. If the problem persists, reset your Orbi router and modem. Additionally, check for firmware upgrades in the settings. Following these instructions will help you restore your internet connection fast and efficiently.
-
 @ a012dc82:6458a70d
2024-10-26 02:54:27
@ a012dc82:6458a70d
2024-10-26 02:54:27Table Of Content
-
Understanding MicroStrategy's Bitcoin Holdings
-
A Strategic Hedge Against Inflation
-
Embracing Digital Transformation
-
Maximizing Long-Term Returns
-
Enhancing Shareholder Value
-
Creating Synergies with Business Operations
-
Leveraging Bitcoin's Network Effect
-
Conclusion
-
FAQ
In the world of finance, few moves have been as bold and controversial as MicroStrategy's decision to invest heavily in Bitcoin. As uncertainty looms over traditional investment avenues, this technology-focused company has chosen to embrace the decentralized digital currency. With a commitment of billions of dollars, MicroStrategy's Bitcoin holdings have attracted attention from investors, analysts, and enthusiasts alike. This article delves into the motivations and implications of MicroStrategy's Bitcoin holdings, examining the potential risks and rewards in these uncertain times.
Bitcoin Holdings
Understanding MicroStrategy's Bitcoin Holdings To comprehend the significance of MicroStrategy's Bitcoin holdings, it is crucial to grasp their approach and strategy. Here are the key aspects to consider:
A Strategic Hedge Against Inflation
In an era of economic uncertainty, many investors seek alternative assets to protect against inflation. Bitcoin's limited supply and decentralized nature make it an appealing option for wealth preservation.
MicroStrategy recognized the potential value of Bitcoin as a hedge against inflation and made a bold move by investing a substantial portion of its treasury reserves in the cryptocurrency.
Embracing Digital Transformation
MicroStrategy, a renowned technology-focused company, believes in the power of digital transformation. By incorporating Bitcoin into its treasury strategy, the company demonstrates its confidence in the future of digital currencies and the underlying blockchain technology.
This move positions MicroStrategy as a pioneer in the corporate adoption of Bitcoin, potentially encouraging other companies to explore similar avenues.
Maximizing Long-Term Returns
MicroStrategy's CEO, Michael Saylor, has been a vocal advocate for Bitcoin, emphasizing its potential as a long-term investment. By converting a significant portion of their reserves into Bitcoin, the company aims to maximize returns over time, capitalizing on the cryptocurrency's potential growth.
Enhancing Shareholder Value
MicroStrategy's decision to invest in Bitcoin is not only driven by financial considerations but also by a commitment to enhancing shareholder value. By diversifying their assets and potentially generating substantial returns, the company aims to provide long-term benefits to its shareholders.
Creating Synergies with Business Operations
MicroStrategy's business revolves around data analytics and intelligence. By investing in Bitcoin, the company can leverage its expertise to analyze blockchain data and gain insights into market trends, potentially opening up new business opportunities and revenue streams.
Leveraging Bitcoin's Network Effect
Bitcoin's status as the largest and most recognized cryptocurrency grants it a significant network effect. MicroStrategy's investment in Bitcoin allows them to participate in this thriving ecosystem, potentially reaping benefits from increased adoption and acceptance.
Conclusion
MicroStrategy's Bitcoin holdings represent a bold move in uncertain times. By embracing Bitcoin as a strategic asset, the company positions itself at the forefront of the digital currency revolution. While risks accompany this venture, the potential rewards could reshape the corporate investment landscape. MicroStrategy's decision sets a precedent for other companies to explore the merits of Bitcoin and highlights the growing importance of cryptocurrencies in the financial world.
FAQ
Why did MicroStrategy choose Bitcoin over other cryptocurrencies? MicroStrategy's decision to focus on Bitcoin stems from its established market presence, robust infrastructure, and reputation as a store of value. Additionally, Bitcoin's limited supply and extensive adoption make it a favorable choice for long-term investment.
How does MicroStrategy's Bitcoin investment impact its financial position? MicroStrategy's investment in Bitcoin adds a new dimension to its financial position. While it introduces volatility due to Bitcoin's price fluctuations, the potential upside can significantly impact the company's overall balance sheet and shareholder value.
What are the risks associated with MicroStrategy's Bitcoin holdings? Investing in Bitcoin involves inherent risks, such as market volatility, regulatory uncertainty, and potential security breaches. MicroStrategy's substantial exposure to Bitcoin amplifies these risks, making the company vulnerable to significant losses in the event of a market downturn.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 4ba8e86d:89d32de4
2024-10-26 02:51:21
@ 4ba8e86d:89d32de4
2024-10-26 02:51:21Inicialmente criado como uma evolução do projeto CopperheadOS, o GrapheneOS é uma versão modificada do Android que concentra seus esforços na proteção da privacidade e segurança dos usuários. Foi iniciado por Daniel Micay, também conhecido como thestinger, após um desentendimento com os cofundadores do CopperheadOS em 2018. O foco principal do GrapheneOS é fornecer um sistema operacional móvel altamente seguro e com ênfase na privacidade para dispositivos Google Pixel.
Uma das principais características do GrapheneOS é sua rápida atualização de segurança, juntamente com recursos avançados de privacidade. O sistema operacional adota tecnologias que mitigam diferentes tipos de vulnerabilidades, dificultando a exploração das principais fontes de risco. Ele também aprimora a segurança dos aplicativos em execução no sistema operacional, reforçando a sandbox do aplicativo e outros limites de segurança.
O GrapheneOS se esforça para garantir que os recursos de privacidade e segurança não afetem negativamente a experiência do usuário. Idealmente, esses recursos são projetados para estar sempre ativados, sem adicionar complexidade adicional ou opções de configuração que possam sobrecarregar o usuário. No entanto, em certos casos, são adicionados interruptores para recursos como permissões de rede, permissões de sensores e restrições quando o dispositivo está bloqueado (por exemplo, periféricos USB, câmera, ladrilhos rápidos).
O GrapheneOS tem ganhado popularidade como uma escolha confiável para usuários que valorizam a privacidade e a segurança em seus dispositivos móveis. É reconhecido como uma das opções mais seguras e privadas disponíveis para o sistema Android.
Recomenda-se a compra dos seguintes dispositivos para usar o GrapheneOS devido à sua melhor segurança e garantia mínima de 5 anos para atualizações completas de segurança:
- Pixel 7a
- Pixel 7 Pro
- Pixel 7
- Pixel 6a
- Pixel 6 Pro
- Pixel 6
Os dispositivos mais recentes possuem uma garantia mínima de 5 anos, mas o suporte real pode ser ainda maior. O Pixel 7 e o Pixel 7 Pro apresentam melhorias em relação aos modelos anteriores, como GPU e rádio celular aprimorados, além de uma atualização incremental da CPU. O Pixel 7a oferece um bom custo-benefício com recursos semelhantes ao Pixel 7, exceto pelo carregamento sem fio lento e proteção contra poeira/água mais fraca.
O Pixel 6, Pixel 6 Pro e Pixel 6a ainda podem ser uma opção válida se encontrados a um preço atrativo, pois possuem de 3,5 a 4 anos de garantia mínima de suporte restante.
Dispositivo
Google Pixel 7a , maio de 2028 , 5 anos.
Google Pixel 7 Pro , outubro de 2027 , 5 anos.
Google Pixel 7 , outubro de 2027 , 5 anos.
Google Pixel 6a, julho de 2027 ,5 anos.
Google Pixel 6 Pro , outubro de 2026 ,5 anos.
Google Pixel 6 ,outubro de 2026 ,5 anos.
Google Pixel 5a , agosto de 2024 ,3 anos.
Google Pixel 5 , outubro de 2023 , 3 anos.
Google Pixel 4a 5G , novembro de 2023 ,3 anos.
Google Pixel 4a, agosto de 2023 ,3 anos.
Google Pixel 4 , Outubro 2022 , 3 anos.
Google Pixel 4 XL ,Outubro 2022 ,3 anos.
No que diz respeito à segurança e privacidade, o GrapheneOS utiliza uma versão aprimorada da criptografia de disco baseada no sistema de arquivos do Android OpenSource Project. Os dispositivos suportados possuem suporte substancial baseado em hardware para aumentar a segurança da criptografia. A autenticidade e integridade das partições de firmware e do sistema operacional são verificadas em cada inicialização. O GrapheneOS implementa criptografia de disco completo por meio de criptografia baseada em sistema de arquivos, garantindo que todos os dados, nomes de arquivos e metadados sejam armazenados criptografados.
O sistema utiliza chaves de criptografia de disco geradas aleatoriamente e armazenadas criptografadas. Dados confidenciais são armazenados em perfis de usuário com suas próprias chaves de criptografia. O GrapheneOS permite o suporte para encerrar sessões de perfil de usuário secundário após o login, o que limpa totalmente as chaves de criptografia e coloca os perfis em repouso. Além disso, o GrapheneOS suporta o uso de armazenamento de chaves de hardware e implementações de criptografia em aplicativos para adicionar camadas adicionais de proteção. Detalhes adicionais sobre essas funcionalidades estão além do escopo desta resposta.
Um dos Recurso GrapheneOS tem é Duress PIN! Que você pode definir um PIN especial de “coação” para que, em vez de desbloquear o telefone, ele limpe imediatamente as chaves de criptografia no elemento seguro, tornando os dados de armazenamento irrecuperáveis. vídeo - Tuxsudo🐧 https://video.nostr.build/ec077345a2109811ef83afc38c33f5ee06aa687ec2bfdf8685ebc8af90293d48.mp4
Os aplicativos podem espionar a área de transferência em segundo plano ou injetar conteúdo nela? A partir do Android 10, apenas o teclado de entrada padrão configurado (o teclado de sua escolha) e o aplicativo atualmente em foco têm acesso à área de transferência. Aplicativos em segundo plano não podem acessar a área de transferência. Essa restrição é mais rigorosa do que simplesmente impedir que aplicativos em segundo plano a acessem, pois nem mesmo um aplicativo ou serviço em primeiro plano pode acessá-la, apenas o aplicativo em primeiro plano que está em foco no momento. Os gerenciadores de área de transferência precisam ser implementados pelo teclado definido como padrão pelo usuário. Anteriormente, o GrapheneOS restringia o acesso à área de transferência em segundo plano, mas essa abordagem foi substituída por uma restrição mais rigorosa implementada pelo Android 10. Assim, a funcionalidade de permitir que os gerenciadores de área de transferência estejam na lista de permissões não é mais necessária, pois os teclados devem implementar essa funcionalidade.
A partir do Android 12, o usuário recebe uma notificação quando um aplicativo lê o conteúdo da área de transferência definido por outro aplicativo. Essa notificação está ativada por padrão e pode ser alterada em Configurações -> Privacidade -> Mostrar acesso à área de transferência.
Os aplicativos podem monitorar conexões de rede ou estatísticas? Os aplicativos não podem monitorar conexões de rede, a menos que sejam realizadas por meio de um serviço de VPN ativo definido pelo usuário. Normalmente, os aplicativos não têm acesso às estatísticas de rede e não podem solicitar acesso direto a elas. No entanto, os usuários podem conceder explicitamente permissões de estatísticas de uso do aplicativo, que fornecem estatísticas específicas do aplicativo. Isso foi introduzido como parte das melhorias de privacidade do Android 10.
O GrapheneOS fornece um firewall? Sim, o GrapheneOS herda o firewall profundamente integrado do Android Open Source Project, que é usado para implementar partes do modelo de segurança e vários outros recursos. Historicamente, o projeto GrapheneOS fez várias melhorias no firewall, mas ao longo do tempo a maioria dessas mudanças foi integrada à versão principal do sistema operacional ou se tornaram irrelevantes.
O GrapheneOS adiciona uma opção de permissão de rede voltada para o usuário, oferecendo uma maneira robusta de negar o acesso direto e indireto à rede para os aplicativos. Essa opção baseia-se na permissão padrão de INTERNET, que não é voltada para o usuário, mas já é amplamente adotada pelo ecossistema de aplicativos. Ao revogar a permissão de INTERNET, o acesso indireto por meio de componentes do sistema operacional e aplicativos que exigem a permissão de INTERNET, como o DownloadManager, é negado. O acesso direto é bloqueado, impedindo o acesso a soquetes de rede de baixo nível.
O GrapheneOS incluirá suporte para serviços do Google? Assim como o Android Open Source Project, o GrapheneOS não inclui aplicativos e serviços do Google. Eles nunca serão empacotados com o sistema operacional. No entanto, o GrapheneOS possui uma camada de compatibilidade para os Serviços do Google Play, que permite que os aplicativos que dependem desses serviços sejam instalados e executados em um ambiente sandbox sem privilégios.
Essa camada de compatibilidade garante que os aplicativos do Google Play possam funcionar, mas sem comprometer a segurança e a privacidade do sistema operacional.
O GrapheneOS é um sistema operacional móvel baseado no Android Open Source Project que prioriza a segurança e a privacidade dos usuários. Ele oferece atualizações rápidas de segurança, recursos avançados de privacidade e um firewall integrado para proteger os dispositivos. O sistema operacional é projetado para garantir que recursos de segurança e privacidade não afetem negativamente a experiência do usuário. O GrapheneOS não inclui aplicativos e serviços do Google, É uma escolha confiável para aqueles que valorizam a privacidade e a segurança em seus dispositivos móveis.
Este é o instalador baseado em WebUSB para GrapheneOS e é a abordagem recomendada para a maioria dos usuários. https://grapheneos.org/install/web
O guia de instalação da linha de comando é a abordagem mais tradicional para instalar o GrapheneOS.
https://grapheneos.org/install/cli
https://grapheneos.org/
https://github.com/GrapheneOS
Pixel tem chip Titan M2 que leva o pixel outro nivel de segurança. https://www.androidauthority.com/titan-m2-google-3261547/
-
 @ 4ba8e86d:89d32de4
2024-10-25 15:26:47
@ 4ba8e86d:89d32de4
2024-10-25 15:26:47Ele foi criado por Mark Harman e lançado sob a licença GNU General Public License (GPL), o que significa que qualquer pessoa pode acessar, modificar e distribuir o código-fonte do aplicativo.
Recursos e Funcionalidades: O Open Camera oferece uma ampla gama de recursos e funcionalidades que permitem aos usuários aproveitar ao máximo suas câmeras em dispositivos Android. Alguns dos recursos notáveis incluem:
-
Controles Manuais: O aplicativo permite ajustar manualmente as configurações da câmera, como exposição, foco, balanço de branco, ISO e muito mais. Isso oferece maior flexibilidade e controle sobre a qualidade e o estilo das fotos tiradas.
-
Suporte a Formatos de Arquivo Avançados: O Open Camera suporta uma variedade de formatos de arquivo, incluindo RAW, que é uma opção preferida por fotógrafos profissionais devido à maior quantidade de informações capturadas e à flexibilidade durante a pós-produção.
-
Modo de Gravação de Vídeo Avançado: Além da fotografia, o Open Camera também oferece recursos avançados de gravação de vídeo, como gravação em câmera lenta, gravação de lapso de tempo e suporte a taxas de quadros personalizadas.
-
Marcação de Geolocalização: O aplicativo permite que os usuários adicione informações de localização às fotos tiradas, o que pode ser útil para organizar e recordar onde cada imagem foi capturada.
-
Interface Personalizável: O Open Camera oferece opções para personalizar a interface do usuário de acordo com as preferências individuais, incluindo a escolha de cores e layouts.
O código-fonte aberto permite que os usuários examinem e verifiquem como o aplicativo funciona. Isso aumenta a transparência e a confiança na segurança e privacidade dos dados. Os desenvolvedores podem modificar o aplicativo para atender às suas necessidades específicas ou adicionar novos recursos. Isso cria um ecossistema de desenvolvimento vibrante e incentiva a inovação. O Open Camera possui uma comunidade ativa de desenvolvedores e usuários que contribuem com melhorias, correções de bugs e compartilham conhecimentos. Isso garante que o aplicativo seja continuamente atualizado e aprimorado.
O Open Camera é uma opção poderosa e personalizável para aqueles que desejam aproveitar ao máximo a câmera de seus dispositivos Android. Com recursos avançados e a flexibilidade proporcionada pelo código aberto, o aplicativo oferece uma experiência fotográfica aprimorada para entusiastas e profissionais da fotografia. Se você está procurando um aplicativo de câmera versátil e repleto de recursos, o Open Camera é definitivamente uma escolha que vale a pena considerar.
https://sourceforge.net/p/opencamera/code/ci/master/tree/
https://opencamera.org.uk/
https://f-droid.org/packages/net.sourceforge.opencamera/
-
-
 @ 4ba8e86d:89d32de4
2024-10-25 12:12:40
@ 4ba8e86d:89d32de4
2024-10-25 12:12:40Projetado para atender tanto a usuários iniciantes quanto avançados, o K-9 Mail apresenta uma ampla gama de recursos e funcionalidades.
Desenvolvido inicialmente por Jesse Vincent em 2008, o K-9 Mail foi concebido como uma opção de código aberto para superar as limitações do aplicativo de e-mail padrão do Android. O nome "K-9" é uma referência ao robô cão da série de televisão "Doctor Who". Desde então, o projeto tem crescido com a colaboração de uma comunidade de desenvolvedores ativos.
O K-9 Mail integra-se aos protocolos de e-mail IMAP e POP3, permitindo aos usuários configurar suas contas de e-mail e sincronizar mensagens diretamente no aplicativo. Além disso, o K-9 Mail oferece suporte a recursos avançados de segurança, como criptografia de e-mail por meio de métodos como S/MIME e OpenPGP, garantindo a proteção das comunicações por e-mail.
O aplicativo K-9 Mail oferece recursos diversos para aprimorar a experiência de e-mail no Android. Entre eles, destacam-se: - Suporte a múltiplas contas de e-mail: Os usuários podem configurar e gerenciar várias contas de e-mail em um único aplicativo. - Criptografia e segurança: O K-9 Mail suporta métodos de criptografia, como S/MIME e OpenPGP, para garantir a segurança das mensagens de e-mail. - Personalização: O aplicativo disponibiliza opções de personalização para ajustar as preferências do usuário, incluindo notificações, sincronização e aparência. - Pesquisa avançada: O K-9 Mail oferece recursos poderosos de pesquisa para facilitar a localização rápida de e-mails específicos. - Gerenciamento de pastas: Os usuários podem organizar suas mensagens em pastas personalizadas, simplificando a localização e organização das mensagens.
O K-9 Mail é uma opção confiável de cliente de e-mail de código aberto para dispositivos Android, oferecendo recursos avançados de gerenciamento, segurança e personalização. Sua comunidade ativa de desenvolvedores continua aprimorando e atualizando o aplicativo, garantindo uma experiência de e-mail eficiente e adaptada às necessidades dos usuários.
https://k9mail.app/
https://github.com/k9mail/k9mail.app
-
 @ 4ba8e86d:89d32de4
2024-10-25 11:40:05
@ 4ba8e86d:89d32de4
2024-10-25 11:40:05A loja Aurora vem com um excelente design, interface de usuário amigável para iniciantes e muitos recursos.
A loja Aurora foi originalmente baseada na loja Yalp de Sergei Yeriomin, mas a versão 3.0 passou do zero para a conclusão seguindo o Material Design reescrito para rodar em todos os dispositivos Android 5.0.
Dentre as diversas características oferecidas pela Aurora Store, destacam-se:
- Login Anônimo: Para garantir sua privacidade, você pode fazer login anonimamente, assegurando que suas atividades permaneçam confidenciais.
- Login do Google: Além do anonimato, a opção de login do Google permite acessar aplicativos pagos e instalar versões beta.
- Falsificação de Dispositivo: Caso um aplicativo não esteja disponível para o seu dispositivo, você pode recorrer à funcionalidade de falsificação de dispositivo, permitindo a instalação.
- Filtragem de Aplicativos F-Droid: A possibilidade de filtrar aplicativos do F-Droid evita que eles apareçam em sua lista de atualizações.
- Aplicativos na Lista Negra: Ao adicionar aplicativos à lista negra, você mantém o Google no escuro quanto aos aplicativos instalados.
A loja de aplicativos se apresenta com um design clássico, apresentando uma capa de apps e jogos em destaque, proporcionando um visual convidativo. A aba de aplicativos instalados permite uma gestão mais eficiente, possibilitando atualizações automáticas para a versão mais recente disponível.
A busca por aplicativos é facilitada por categorias que abrangem diversos interesses, como fotografia, música e áudio, compras, personalização, livros e quadrinhos, entre outras. A eficaz função de busca permite localizar aplicativos específicos de maneira rápida e fácil.
A Aurora Store se diferencia pela tecnologia de pesquisa única, agilizando a descoberta de aplicativos em questão de segundos. Além disso, a loja vem com a licença GPLv3, reforçando seu compromisso com o software livre.
Privacidade é um foco central da Aurora Store, sendo considerada uma excelente alternativa para quem preza por manter suas informações pessoais protegidas. O aplicativo suporta contas pessoais e permite downloads com contas anônimas, assegurando que suas atividades não estejam vinculadas a você.
Com a integração do Exodus, a Aurora Store verifica rastreadores presentes nos códigos dos aplicativos, proporcionando uma visão mais transparente das informações coletadas.
O aplicativo se destaca por ser livre de anúncios e pop-ups, proporcionando uma experiência de uso mais limpa. O suporte ao modo escuro oferece conforto visual em ambientes com pouca luz ou durante a noite.
A Aurora Store é uma alternativa valiosa à Google Play Store, oferecendo um ambiente mais privado, recursos robustos e um design elegante que visa aprimorar a experiência do usuário em busca e gerenciamento de aplicativos.
https://github.com/whyorean/AuroraStore
https://f-droid.org/packages/com.aurora.store/
https://gitlab.com/AuroraOSS/AuroraStore/-/releases
-
 @ 4ba8e86d:89d32de4
2024-10-25 11:06:58
@ 4ba8e86d:89d32de4
2024-10-25 11:06:58Ele se concentra em fornecer uma experiência de usuário aprimorada, mantendo a liberdade e o controle do usuário sobre seu dispositivo.
O projeto LineageOS foi iniciado em 2016, quando o desenvolvimento do CyanogenMod, uma ROM personalizada popular, foi interrompido. Uma comunidade dedicada de desenvolvedores e entusiastas do Android se uniu para criar o LineageOS como uma continuação do CyanogenMod.
Uma das principais características do LineageOS é a capacidade de personalizar e ajustar o sistema operacional de acordo com as preferências do usuário. Ele oferece uma ampla gama de opções de personalização, permitindo que os usuários alterem a aparência, o comportamento e os recursos do sistema de acordo com suas necessidades.
Além da personalização, o LineageOS também se concentra na segurança e privacidade dos usuários. Ele fornece atualizações regulares de segurança para corrigir vulnerabilidades e proteger os dispositivos contra ameaças. Além disso, o LineageOS oferece controle granular sobre as permissões de aplicativos, permitindo que os usuários decidam quais permissões um aplicativo pode acessar.
O LineageOS também é conhecido por estender o ciclo de vida de dispositivos mais antigos, fornecendo suporte para modelos mais antigos que não recebem mais atualizações oficiais do fabricante. Isso permite que os usuários continuem usando seus dispositivos com um sistema operacional atualizado e seguro.
O projeto LineageOS é impulsionado pela comunidade e mantido por uma equipe de desenvolvedores voluntários. A comunidade é ativa e colaborativa, fornecendo suporte, solução de problemas e contribuições para melhorar o sistema operacional.
O LineageOS oferece aos usuários de dispositivos Android uma opção alternativa, personalizável e segura em relação ao sistema operacional padrão. Com sua ênfase na personalização, segurança e suporte a dispositivos mais antigos, o LineageOS atrai uma base de usuários dedicada que valoriza a liberdade e o controle sobre seus dispositivos.
Obtenha o LineageOS agora! LineageOS, uma distribuição Android de código aberto, está disponível para vários dispositivos, com mais sendo continuamente adicionados graças à maior e crescente comunidade de código aberto Android. Junte-se a nós e dê nova vida ao seu dispositivo, seja ele antigo ou novo.
https://wiki.lineageos.org/devices/
Lista disponivel
Google Pixel Samsung Xiaomi Motorola LG ASUS Lenovo OnePlus Sony Nokia ZUK Banana Pi BQ Dynalink Essential F(x)tec Fairphone HardKernel LeEco 10.or Nextbit Nothing Nubia NVIDIA Radxa Razer SHIFT
Xiaomi: - Xiaomi 11 Lite 5G NE (AKAXiaomi 11 Lite NE 5GMi 11 LE) - Mi 10T (AKAMi 10T ProRedmi K30S Ultra) - Mi 10T Lite (AKAMi 10iRedmi Note 9 Pro 5G) - Mi 11 Lite 5G (renoir) - Mi 11 Pro (mars) - Mi 11i (AKARedmi K40 ProRedmi K40 Pro+Mi 11X Pro) - Mi 5 (gemini) - Mi 5s Plus (natrium) - Mi 6 (sagit) - Mi 8 (dipper) - Mi 8 Explorer Edition (ursa) - Mi 8 Pro (equuleus) - Mi 8 SE (xmsirius) - Mi 9 SE (grus) - Mi 9T (AKARedmi K20 (China)Redmi K20 (India)) - Mi A1 (tissot) - Mi CC 9 (AKAMi 9 Lite) - Mi CC9 Meitu Edition (vela) - Mi MIX 2 (chiron) - Mi MIX 2S (polaris) - Poco F1 (beryllium) - POCO F2 Pro (AKARedmi K30 ProRedmi K30 Pro Zoom Edition) - POCO F3 (AKARedmi K40Mi 11X alioth) - POCO M2 Pro (AKARedmi Note 9SRedmi Note 9 Pro (Global)Redmi Note 9 Pro (India)Redmi Note 9 Pro MaxRedmi Note 10 Lite miatoll) - POCO X3 NFC (surya) - POCO X3 Pro (vayu) - Redmi 3S (AKARedmi 3XRedmi 4 (India)Redmi 4XRedmi Note 5A PrimeRedmi Y1 Prime Mi8937) - Redmi 4A (AKARedmi 5ARedmi Note 5A LiteRedmi Y1 Lite Mi8917) - Redmi 7 (AKARedmi Y3 onclite) - Redmi 7A (AKARedmi 8Redmi 8ARedmi 8A Dual Mi439)
- Redmi 9 (lancelot)
- Redmi Note 10 Pro (AKARedmi Note 10 Pro (India)Redmi Note 10 Pro Max (India) sweet)
- Redmi Note 10S (AKARedmi Note 10S NFCRedmi Note 10S Latin America rosemary)
- Redmi Note 7 Pro (violet)
- Redmi Note 8 (AKARedmi Note 8T ginkgo)
- Redmi Note 9 (merlinx)
LG: - G5 (International) (h850) - G5 (T-Mobile) (h830) - G5 (US Unlocked) (rs988) - G6 (EU Unlocked) (h870) - G6 (T-Mobile) (h872) - G6 (US Unlocked) (us997) - V20 (AT&T) (h910) - V20 (Global) (h990) - V20 (GSM Unlocked - DirtySanta) (us996d) - V20 (GSM Unlocked) (us996) - V20 (Sprint) (ls997) - V20 (T-Mobile) (h918) - V20 (Verizon) (vs995) - V30 (T-Mobile) (h932) - V30 (Unlocked) (joan)
Motorola: - edge (racer) - edge 20 (berlin) - edge 20 pro (pstar) - edge 2021 (berlna) - edge 30 (dubai) - edge s (AKAmoto g100 nio) - moto e5 plus (XT1924-1/2/4/5) (rhannah) - moto e5 plus (XT1924-3/9) (ahannah) - moto e5 plus (XT1924-6/7/8) (hannah) - moto g 5G (AKAmoto one 5G ace kiev) - moto g 5G plus (AKAmoto one 5G nairo) - moto g200 5G (AKAEdge S30 xpeng) - moto g32 (devon) - moto g42 (hawao) - moto g5 (cedric) - moto g52 (rhode) - moto g5s (montana) - moto g6 plus (evert) - moto g7 (river) - moto g7 play (channel) - moto g7 plus (lake) - moto g7 power (ocean) - moto x (2014) (victara) - moto x4 (payton) - moto z (griffin) - moto z play (addison) - moto z2 force (nash) - moto z2 play (albus) - moto z3 (messi) - moto z3 play (beckham) - one action (troika) - one fusion+ (liber) - one power (chef) - one vision (AKAp50 kane) - one zoom (parker)
Google: - ADT-3 (deadpool) - Nexus 6 (shamu) - Nexus 7 2013 (LTE, Repartitioned) (debx) - Nexus 7 2013 (Wi-Fi, Repartitioned) (flox) - Pixel (sailfish) - Pixel 2 (walleye) - Pixel 2 XL (taimen) - Pixel 3 (blueline) - Pixel 3 XL (crosshatch) - Pixel 3a (sargo) - Pixel 3a XL (bonito) - Pixel 4 (flame) - Pixel 4 XL (coral) - Pixel 4a (sunfish) - Pixel 4a 5G (bramble) - Pixel 5 (redfin) - Pixel 5a (barbet) - Pixel 6 (oriole) - Pixel 6 Pro (raven) - Pixel 6a (bluejay) - Pixel 7 (panther) - Pixel 7 Pro (cheetah) - Pixel 7a (lynx) - Pixel tablet - Pixel XL
Samsung: - Galaxy S4 (SCH-R970, SPH-L720) - jfltespr - Galaxy S4 (SGH-I337) - jflteatt - Galaxy S4 Active - jactivelte - Galaxy S4 Value Edition (GT-I9515/L) - jfvelte - Galaxy S5 Active (G870F) - klteactivexx - Galaxy S5 LTE (G9006V/8V) - kltechn - Galaxy S5 LTE (G900AZ/S902L) - klteaio - Galaxy S5 LTE (G900F/M/R4/R7/T/V/W8) - klte - Galaxy S5 LTE (G900I/P) - kltedv - Galaxy S5 LTE (G900K/L/S) - kltekor
- Galaxy S5 LTE (SC-04F/SCL23) - kltekdi
- Galaxy S5 LTE Duos (G9006W/8W) - kltechnduo
- Galaxy S5 LTE Duos (G900FD/MD) - klteduos
- Galaxy S9 - starlte
- Galaxy S9+ - star2lte
- Galaxy Tab A 8.0 (2019) - gtowifi
- Galaxy Tab S5e (LTE) - gts4lv
- Galaxy Tab S5e (Wi-Fi) - gts4lvwifi
- Galaxy Tab S6 Lite (LTE) - gta4xl
- Galaxy Tab S6 Lite (Wi-Fi) - gta4xlwifi
https://lineageos.org/
https://github.com/lineageos
-
 @ bec0c9d3:c4e9cd29
2024-10-26 01:55:04
@ bec0c9d3:c4e9cd29
2024-10-26 01:55:04The Bitcoin Culture Festival is just around the corner, and we're excited to present our artists with physical artworks at the Cyphermunk House. In addition, we will be showcasing these pieces on our 2140 Auction Portal.
The "Culture of Code" gallery will be held at:
CypherMunk House 9 John Street Bloomsbury, London, UK WC1N 2ES
Before the festival, you can read our latest article about this one-of-a-kind house here on Yakihonne.
Online auctions will be available on 2140.wtf starting from October 29th to November 2nd 2024.
During the Bitcoin Culture Festival ART Gallery, you will have the opportunity to see the works of many talented Bitcoin artists. The sale will take place through our auction.
ART Gallery opening hours:
October 29 - Private viewing: 6:30 pm - 8:30 pm October 30 - November 2 - 10:00 am - 5:00 pm November 1 and 2 - 5:00 pm - 10:00 pm during NostrLDN and ART Panels
Entry to the gallery is FREE

This event is only possible due to the passion and dedication of our crew, partners , and sponsors . All made by People for the People. Cypherpunk vibe, pure from the bottom. We look forward to seeing you there!
Follow us also on all socials NOSTREE.me - NOSTR LinkTree INSTAGRAM TWETTER - X YOUTUBE
LINKS
OUR PARNERS / SPONSORS

STAY TUNED !!
2140 Crew
Hashtags:
ArtGallery
ArtPanel
2140wtf
2140army
CyhermunkHouse
art
artstr
nostrart
craft
culture
music
bitcoin
nostr
TootingMarket
NostrLDN
NostrLondon
yakihonne
-
 @ 1e286f5c:cc2c5009
2024-10-25 21:23:22
@ 1e286f5c:cc2c5009
2024-10-25 21:23:22Running a test, publishing a note in Obsidian to Nostr with 2 photos attached to ensure all works as planned.
Photo 1: L.A.B + Spirulina

Photo 2: A peek into the scope

D.
-
 @ 4e4fc3e3:e935140a
2024-10-25 20:29:27
@ 4e4fc3e3:e935140a
2024-10-25 20:29:27This is a test using frost bunker from Highlighter 🤞
chances of working = \~0.1
-
 @ 09fbf8f3:fa3d60f0
2024-10-25 18:43:59
@ 09fbf8f3:fa3d60f0
2024-10-25 18:43:59在线直播:
央视体育版CCTV5:
央视体育版CCTV16 :
翡翠台:
-
 @ 185e9a1b:f608e37b
2024-10-25 18:31:05
@ 185e9a1b:f608e37b
2024-10-25 18:31:05 -
 @ 42342239:1d80db24
2024-10-23 12:28:41
@ 42342239:1d80db24
2024-10-23 12:28:41TL;DR: The mathematics of trust says that news reporting will fall flat when the population becomes suspicious of the media. Which is now the case for growing subgroups in the U.S. as well as in Sweden.
A recent wedding celebration for Sweden Democrats leader Jimmie Åkesson resulted in controversy, as one of the guests in attendance was reportedly linked to organized crime. Following this “wedding scandal”, a columnist noted that the party’s voters had not been significantly affected. Instead of a decrease in trust - which one might have expected - 10% of them stated that their confidence in the party had actually increased. “Over the years, the Sweden Democrats have surprisingly emerged unscathed from their numerous scandals,” she wrote. But is this really so surprising?
In mathematics, a probability is expressed as the likelihood of something occurring given one or more conditions. For example, one can express a probability as “the likelihood that a certain stock will rise in price, given that the company has presented a positive quarterly report.” In this case, the company’s quarterly report is the basis for the assessment. If we add more information, such as the company’s strong market position and a large order from an important customer, the probability increases further. The more information we have to go on, the more precise we can be in our assessment.
From this perspective, the Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But this perspective omits something important.
A couple of years ago, the term “gaslighting” was chosen as the word of the year in the US. The term comes from a 1944 film of the same name and refers to a type of psychological manipulation, as applied to the lovely Ingrid Bergman. Today, the term is used in politics, for example, when a large group of people is misled to achieve political goals. The techniques used can be very effective but have a limitation. When the target becomes aware of what is happening, everything changes. Then the target becomes vigilant and views all new information with great suspicion.
The Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But if SD voters to a greater extent than others believe that the source of the information is unreliable, for example, by omitting information or adding unnecessary information, the conclusion is different. The Swedish SOM survey shows that these voters have lower trust in journalists and also lower confidence in the objectivity of the news. Like a victim of gaslighting, they view negative reporting with suspicion. The arguments can no longer get through. A kind of immunity has developed.
In the US, trust in the media is at an all-time low. So when American media writes that “Trump speaks like Hitler, Stalin, and Mussolini,” that his idea of deporting illegal immigrants would cost hundreds of billions of dollars, or gets worked up over his soda consumption, the consequence is likely to be similar to here at home.
The mathematics of trust says that reporting will fall flat when the population becomes suspicious of the media. Or as the Swedish columnist put it: like water off a duck’s back.
Cover image: Ingrid Bergman 1946. RKO Radio Pictures - eBay, Public Domain, Wikimedia Commons
-
 @ 3cd2ea88:bafdaceb
2024-10-25 18:30:47
@ 3cd2ea88:bafdaceb
2024-10-25 18:30:47Metti in staking i tuoi SOL facilmente e approfitta di molteplici vantaggi :
1️⃣ Ricevi BGSOL : La versione tokenizzata dei tuoi SOL in staking. 2️⃣ Guadagna rendimenti sostanziali : Ottieni fino al 30.15% APR stimato e sblocca guadagni di liquidità con BGSOL. 3️⃣ Sblocca SOL con flessibilità : Nessun periodo di blocco! Puoi convertire BGSOL in SOL in qualsiasi momento.
💡Cos'è BGSOL? BGSOL è una soluzione di liquidity staking sviluppata da Bitget. Ti permette di mantenere la liquidità dei tuoi asset mentre guadagni con lo staking e partecipi ad altre attività DeFi. Approfitta ora!
🔗 Unisciti alla community BGSOL su Telegram 👉 https://t.me/BitgetBGSOL 🔗 Partecipa alla promo qui 👉 https://www.bitget.com/it/events/bitget-sol-staking?utmTerm=KOC
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ 8f2fe968:0fbf4901
2024-10-25 17:34:06
@ 8f2fe968:0fbf4901
2024-10-25 17:34:06 -
 @ 9e69e420:d12360c2
2024-10-21 20:26:54
@ 9e69e420:d12360c2
2024-10-21 20:26:54Your first NOSTR note.
Some of you may be lurking wondering how why or what for your first note here on nostr. Here's some advice from an pseudonymous douchebag. To start with, your first note should be to come out swinging. Make lots of friends maybe even some enemies. Most people get a lot of love with their first introductions post.
Make it short.
Your first note will probably (and probably should) be a kind one event. The note you're reading is a 30023 event for long form notes. (More on this some other time). Keep it short and concise. You probably could publish a book in a kind one note. But I really don't think anyone believes you should and I'm sure many relays would reject it. It will also appear without formatting which just looks ugly for anything other than a microblog.
Introduce yourself.
Just as you would in an IRL interaction. What's your name? But more importantly what do you want us to call you? What brought you here? What are your interests? It's important to be real here even if you decide to be pseudonymous. Chances are your tribe is already here. If you're the first then that makes you king of your little corner of the nostr. Which will likely pay dividends in and of itself.
Make it a banger.
Here's my first note (I should disclose this is just the first note from this npub And I have already been here for over a year at this point):
note1pnufmzwy2gj4p5qza6jk7k40nns0p3k2w0fsrqq568utjlnyphdqyg8cpq
Have fun
Don't take this or anything else too seriously. We are all the same here because we are just as unique as each other. Be as weird as you want.
** & Don't forget to use the "#indroductions" hashtag **
-
 @ 4ba8e86d:89d32de4
2024-10-25 15:20:13
@ 4ba8e86d:89d32de4
2024-10-25 15:20:13Imagine um mundo onde 99 pessoas estão verificando a ação de uma única pessoa para garantir a integridade das transações. Isso é exatamente o que o sidechain bitVM propõe. Aqui está uma explicação detalhada do processo:
- Prova e Verificação:
- Uma pessoa atua como uma comprovadora, enquanto 99 pessoas são verificadoras.
- Antes de depositar na sidechain, a comprovadora faz um contrato com os verificadores. Ela coloca 100 BTC como garantia.
-
Se um verificador alegar que alguém fez uma solicitação de saque válida na sidechain, a comprovadora deve provar que processou essa solicitação em X blocos. Caso contrário, qualquer verificador pode penalizá-la, resultando na perda da garantia.
-
Mecanismo de Penalidade e Rotação:
- Se a comprovadora for penalizada, o próximo verificador na fila assume como a nova comprovadora.
- Cada verificador também tem 100 BTC como garantia.
-
A nova comprovadora (ex-verificadora) deve provar que processou a solicitação de saque dentro de X blocos ou será penalizada.
-
Segurança em Camadas:
- A garantia impede comportamentos inadequados, garantindo que todos os participantes tenham algo em jogo.
-
O modelo de pegada dupla oferece camadas adicionais de segurança. Qualquer tentativa de fraude pode ser detectada e punida.
-
Contratos Laterais e Confiança Mínima:
- Um usuário pode fazer um "contrato lateral" com qualquer verificador. Se uma solicitação de saque válida for apresentada, o verificador deve provar o processamento dentro de X blocos.
-
Não é necessário confiar apenas em uma pessoa; se a comprovadora falhar, ela pode ser penalizada.
-
Prova de Ocorrência em Sidechain:
- O bitVM requer a capacidade de "provar" que algo aconteceu em uma sidechain.
-
Um cliente leve SPV no bitVM, compreendendo as regras de consenso da sidechain, é essencial.
-
Depósito e Saque:
- Para depositar, a comprovadora fornece garantia e prova que processará futuras solicitações de saque.
-
Ao sacar, o bitVM valida a solicitação. Se a comprovadora não processar, ela é penalizada, e o usuário recebe 100 BTC de um verificador.
-
Garantia como Parâmetro Variável:
- Tanto comprovadoras quanto verificadoras devem postar garantias.
- A quantidade de garantia é um parâmetro variável; mais garantia significa uma sidechain mais segura.
O sidechain bitVM propõe uma abordagem descentralizada e segura, onde a confiança é distribuída e a segurança é reforçada por penalidades significativas. Este modelo inovador tem o potencial de oferecer eficiência e confiança aprimoradas nas transações de sidechain.
Ótima explicação sobre bitVM. Supertest , Robin .
https://open.spotify.com/episode/6rcOVwcxkzcZRXnVcwKlTq?si=s5E31_HWQEqOoRbzoAzpZQ
-
 @ b83e6f82:73c27758
2024-10-25 14:19:14
@ b83e6f82:73c27758
2024-10-25 14:19:14Citrine 0.5.4
- Fix notification icon size
- Fix loading screen
- Update dependencies
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v0.5.4.txtandmanifest-v0.5.4.txt.sigare in the current directory) with:bash gpg --verify manifest-v0.5.4.txt.sig manifest-v0.5.4.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v0.5.4.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 4ba8e86d:89d32de4
2024-10-25 13:17:33
@ 4ba8e86d:89d32de4
2024-10-25 13:17:33Foi criado com o objetivo de fornecer aos usuários uma experiência de navegação mais privada e segura na internet. O LibreWolf é uma excelente alternativa ao Firefox, com algumas diferenças significativas em relação ao navegador da Mozilla.
O LibreWolf foi desenvolvido com foco na privacidade e segurança do usuário. Ele bloqueia rastreadores de terceiros, impede o envio de dados de telemetria e desabilita recursos de rastreamento de usuário que vêm ativados por padrão no Firefox. Além disso, ele vem pré-configurado com diversas extensões de privacidade, como uBlock Origin, Privacy Badger e HTTPS Everywhere, que ajudam a bloquear anúncios, scripts maliciosos e outras ameaças de segurança enquanto você navega na web.
Outra característica notável do LibreWolf é que ele usa o mecanismo de pesquisa Searx como padrão, em vez do Google. O Searx é conhecido por fornecer resultados de pesquisa mais privados e anônimos, sem rastrear as suas atividades online. O LibreWolf também possui suporte nativo ao Tor, que permite aos usuários acessar a internet anonimamente.
Além dos recursos de privacidade e segurança, o LibreWolf é muito semelhante ao Firefox em termos de usabilidade e funcionalidades. Ele é fácil de instalar e configurar, e possui um grande número de extensões disponíveis na sua loja de extensões.
O LibreWolf é uma excelente opção para usuários que buscam um navegador mais privado e seguro. Se você se preocupa com a sua privacidade online, vale a pena experimentar o LibreWolf. Ele é gratuito e de código aberto, o que significa que você pode baixá-lo e personalizá-lo de acordo com suas necessidades específicas.
https://librewolf.net/
https://github.com/librewolf-community
-
 @ 6bae33c8:607272e8
2024-10-25 12:50:49
@ 6bae33c8:607272e8
2024-10-25 12:50:49I went 4-1 last week which brings my two-week run to 8-2, though it’s not enough to salvage Q2 because I was 2-3 in Week 5. Even if I go 5-0 this week, that’s only 15-5, and that won’t cut it to get a share of the prize. But I’d like to keep it going if only to confirm that after a slow start I’m finally getting in sync.
My Picks
Lions -11.5 vs Titans — I rarely take double-digit favorites, but 11.5 seems low to me. In a normal year this would be 14 in Detroit.
Browns +8.5 vs Ravens — This is a big line on the road, and the Browns have to feel good putting the Deshaun Watson fiasco behind them. (Almost like a relaxing massage.) Might also be a look-ahead game after quality wins for the Ravens.
Jets -7 at Patriots — This line is too big, and Drake Maye might turn out to be a player. But this feels like a get-well spot for the Jets after some tough losses.
Bengals -2.5 vs Eagles — The Eagles are a good sell high off a big win against a weak Giants team. The Bengals are slow starters, but they’re starting to get going.
Raiders +8.5 vs Chiefs — This line is up to 9.5 in places, I knew that, but took the Raiders anyway. Just seems like a divisional game where the beaten-down dog shows up.
-
 @ 4ba8e86d:89d32de4
2024-10-25 12:45:38
@ 4ba8e86d:89d32de4
2024-10-25 12:45:38A privacidade é uma preocupação crescente para muitos usuários da internet, especialmente quando se trata de pesquisar na web. É aqui que entra o Searx, um buscador de código aberto que se destaca por seu compromisso com a privacidade do usuário.
Searx é um mecanismo de metabusca descentralizado na forma de software livre, sob a licença GNU AGPLv3, desenvolvido pelo programador Húngaro, Adam Tauber, que agrega resultados por volta de 70 serviços de busca. O mecanismo não salva consultas de pesquisa e não repassa ou mesmo vende dados privados a terceiros. Os usuários não são rastreados e além disso, pode ser usado na rede Tor para o anonimato online.
O Searx foi criado em 2011 como um projeto de código aberto, o que significa que seu código-fonte está disponível para todos os usuários e desenvolvedores examinarem e contribuírem para seu desenvolvimento. Como um buscador de código aberto, o Searx não coleta ou armazena dados pessoais de seus usuários, o que o diferencia de grandes buscadores como o Google.
Uma das principais vantagens do Searx é sua capacidade de preservar a privacidade do usuário. Ele não rastreia suas pesquisas e não compartilha dados com terceiros. Ao contrário do Google e outros buscadores que exibem anúncios personalizados com base no histórico de navegação do usuário, o Searx não exibe anúncios.
O Searx é altamente personalizável, o que significa que os usuários podem escolher quais fontes de dados usar para suas pesquisas. O Searx é capaz de buscar resultados em mais de 70 fontes de dados, incluindo Google, Bing, Yahoo, Wikipedia, Reddit, entre outros. Os usuários podem personalizar suas pesquisas para excluir determinadas fontes ou incluir outras, conforme necessário.
Outra vantagem do Searx é a capacidade de utilizar motores de busca especializados. O Searx pode ser configurado para buscar em motores de busca especializados em áreas específicas, como tecnologia, ciência, artes, entre outros. Isso significa que os usuários podem encontrar resultados mais precisos e relevantes para suas pesquisas.
O Searx oferece uma experiência de busca semelhante à do Google, com uma barra de pesquisa simples e fácil de usar. No entanto, ele se destaca pela sua capacidade de preservar a privacidade do usuário e oferecer resultados personalizados e precisos. Como um projeto de código aberto, o Searx está em constante desenvolvimento e melhoria, e os usuários podem contribuir para seu desenvolvimento, sugerindo melhorias e correções.
O Searx é uma excelente opção para aqueles que se preocupam com a privacidade e segurança de seus dados pessoais na internet. Como um buscador de código aberto, ele se destaca por sua transparência e compromisso com a privacidade do usuário, além de oferecer uma experiência de busca personalizada e altamente personalizável. Se você valoriza a privacidade online, experimente o Searx.
https://searx.thegpm.org/
https://github.com/searx/searx
-
 @ 6bae33c8:607272e8
2024-10-25 12:14:12
@ 6bae33c8:607272e8
2024-10-25 12:14:12I had the Rams in my picking pool and Sam Darnold in the Steak League which worked out fine, but the Vikings defense got me just two points for one of my good NFFC teams, so that did not.
-
Sam Darnold can make all the throws, and he moves decently in the pocket. It just seems like he’s missing a “read” gene, and that limits his upside and makes him more likely to be a backup than a long-term answer.
-
Justin Jefferson had like six catches in the first quarter, but finished with only eight. The Rams adjusted well defensively in the second half.
-
Kyren Williams scored again, this time as a receiver. One of the elite fantasy players over the last two years and passes the eye test every time.
-
Puka Nacua dropped his first target, then caught seven out the next eight. He looks all the way back. Cooper Kupp also looked healthy and is unlikely to be traded now that the Rams are back in the thick of it in their divison.
-
I loved seeing Demarcus Robinson catch two TDs because no one used him.
-
Matthew Stafford played a great game, even with the pick. He evaded the rush and threw aggresively down the field against a good defense. With his top receivers back he’ll be startable even in one-QB leagues.
-
-
 @ 4ba8e86d:89d32de4
2024-10-25 11:19:28
@ 4ba8e86d:89d32de4
2024-10-25 11:19:28Uma carteira Samourai em um dispositivo Android com airgap em combinação com o Sentinel é suficiente. Sua seed nunca chega à internet, você cria transações offline com o Sentinel, assinar com sua carteira Samourai offline e as transmite com o Sentinel.
Esse guia foi baseado na postagem da Samourai Wallet , Basicamente vamos seguir o que está escrito abaixo.
https://nostrcheck.me/media/public/nostrcheck.me_9551356128214364941706187762.webp
Vamos Precisa de dois aplicativos pra verificação do aplicativo samourai Wallet.
OpenKeychain HashEasily
Primeiramente baixe a carteira samourai Wallet no Site oficial : https://samouraiwallet.com/download
-Importar a chave pública PGP do desenvolvedor.
-Verifique se a impressão digital hash foi assinada pela chave PGP do desenvolvedor.
-Execute o hash sha256 no arquivo baixado.
-Compare visualmente as duas impressões digitais hash.
-antes de instalação da Samourai wallet desligue rede , Wi-Fi, Bluetooth é coloque em modo avião.
-Instale a Samourai Wallet.
Vídeo com a explicação pra fazer a verificação da carteira Samourai wallet em 1:40 e bem curto vídeo.
https://link.storjshare.io/raw/juf373xj3cmu2ezvjn3lcdm2jygq/production/7beed1e67a931522ad7d5bcba61f764fff154f64eb847f856611d75542b33fbb.MP4
Você Pode baixar e verificar no celular online e passa pro celular offline via cabo OTG ou Bluetooth.
https://nostrcheck.me/media/public/nostrcheck.me_6506239047168614881706190998.webp - Por padrão, a MAINNET está habilitada. Toque em "Ok".
https://nostrcheck.me/media/public/nostrcheck.me_4665959278675525031706191125.webp
-
Começar e avance nas configurações.
-
Vai aparecer esse mensagem pra escolher o local pra guarda o arquivo criptografado com sua passphase e PIN escolha um local ou criar uma pasta nova. No caso não vamos salva , se for utilizar o celular com hardwallet salve o backup.
https://nostrcheck.me/media/public/nostrcheck.me_3282756078392669321706191370.webp
https://nostrcheck.me/media/public/nostrcheck.me_1775948496649077751706191388.webp
Toque em "criar uma nova"
Atenção agora vamos pro próximo passo muito IMPORTANTE e que demanda muita atenção e cuidado. Você vai criar uma passphase pra sua carteira , é padrão tem que ter a passphase.
Atenção! A passphase deve ser algo fácil de lembrar, mas que ao mesmo tempo , não seja tão óbvio.
Use sua imaginação , guarde na sua mente a passphase, não vai no óbvio. Igual a passphase que usei " testesamourai "
https://nostrcheck.me/media/public/nostrcheck.me_3673278837059709561706195580.webp
Toque em “ próximo ”
Agora próximo passo é Definir o Código PIN. PIN pode ter de 5 a 8 números. Novamente escolha um PIN fácil de lembrar mas não tão óbvio.
https://nostrcheck.me/media/public/nostrcheck.me_7682063920335318611706195737.webp
Após escolher o PIN digitar duas vezes vai pra próxima tela só toque em Avança. https://nostrcheck.me/media/public/nostrcheck.me_2169630565955263891706195863.webp
Atenção agora vamos pro próximo passo muito IMPORTANTE e que demanda muita atenção e cuidado. O aplicativo te impede de tira print da tela. Pra você não deixa essa informação importante exporta em nenhum local , não guarde online essa informação.
ESCREVA AS 12 PALAVRAS NO PAPEL.
escreva com calma é atenção de uma forma legível de preferência letra de Forma , Após escreve todas as palavras revise se escreveu corretamente.Você pode escrever em vários papéis pra guarda locais diferentes.
Se voce perde essa palavras , você numca mais terá acesso aos Seus Bitcoin guarde bem as palavras..
https://nostrcheck.me/media/public/nostrcheck.me_6115428046070793411706220149.webp
Apos anotar as palavras no papel só dá toque em “ avança”
Vai aparece a sua passphrase pra você certificar que é exatamente o que você digitou verifique e guarde bem na sua mente de preferencia. https://nostrcheck.me/media/public/nostrcheck.me_9156075966432894981706220507.webp
Ter um toque em “ SKIP” e pronto carteira feita totalmente off-line. https://nostrcheck.me/media/public/nostrcheck.me_5297928365552180711706220777.webp
Depois pra testa se anotou corretamente as Seed pode apagar a carteira e testa backup Seed novamente.
Lado esquerdo superior toque no símbolo do robô depois em "configurações" https://nostrcheck.me/media/public/nostrcheck.me_6061690846490213311706222509.webp
Toque na opção “carteira” https://nostrcheck.me/media/public/nostrcheck.me_9171400908043570781706222485.webp
Na última opção "apagar a carteira de forma segura" https://nostrcheck.me/media/public/nostrcheck.me_1243247222498822271706222578.webp https://nostrcheck.me/media/public/nostrcheck.me_2087393619387830581706222599.webp https://nostrcheck.me/media/public/nostrcheck.me_8707025408907536041706222610.webp
Pronto foi apagado só fazer o procedimento de recuperação da Seed.
Toque na Opção " Restore uma carteira existente"
https://nostrcheck.me/media/public/nostrcheck.me_4898356114912667061706223121.webp
Toque na opção de recuperação da sua carteira de bitcoin com seed e passphase.
https://nostrcheck.me/media/public/nostrcheck.me_6380354635899069741706223161.webp
Após fazer a verificação que deu certo o backup da Seed ,Agora vamos pro próximo passo.
https://nostrcheck.me/media/public/nostrcheck.me_7307761562752931011706223812.webp Prepare-se para configurar sua carteira Sentinel, uma aplicação móvel exclusivamente voltada para visualização que permite monitorar saldos e transações em suas carteiras Bitcoin. Essa carteira é projetada de forma a nunca ter acesso às suas chaves privadas, assegurando a proteção dos seus fundos.
O Sentinel é capaz de rastrear diversos tipos de endereços Bitcoin e chaves públicas estendidas. Além disso, oferece funcionalidades como a criação de PSBTs (transações de bitcoin parcialmente assinadas), permitindo que sejam assinadas offline pela sua carteira Samourai ou carteira de hardware.
Ao utilizar o Sentinel, você pode gerar facilmente endereços de recebimento de bitcoin a partir de qualquer uma das suas chaves públicas rastreadas. Além disso, o aplicativo oferece integração nativa com o Tor, proporcionando roteamento seguro no Sentinel.
Para começar, faça o download da carteira Sentinel no site oficial: https://samouraiwallet.com/download
Realize a mesma verificação feita na primeira etapa com a Samourai Wallet.
Em seguida, toque na opção "Configuração".
https://nostrcheck.me/media/public/nostrcheck.me_8214493108314323431706231322.webp
Toque na opção "configuração"
https://nostrcheck.me/media/public/nostrcheck.me_6272143319509445531706231344.webp
Toque na opção "exibir SegWit ZPUB" Quando você quiser adicionar endereços de sua carteira Samourai ao Sentinel, basta inserir a chave pública estendida (geralmente zpub para endereços SegWit bech32 nativos).
https://nostrcheck.me/media/public/nostrcheck.me_9303936705478476931706231362.webp
Com esse código ou qrcode só basta baixa a carteira de visualização da Samourai a Sentinel e pronto adicionar Zpub pra visualização do saldo. Pronto agora é só apagar a carteira samourai Wallet e desinstalar o app ou ficar com a carteira samourai airgap você cria transações offline com o Sentinel, assinar com sua carteira Samourai offline e as transmite com o Sentinel. Parabéns, você acabou de economizar mais de R$500 em uma "carteira de hardware" para a qual você precisa anotar as 12 palavras de qualquer maneira. Este guia é especialmente dedicado aos iniciantes que estão no início de sua jornada no universo do Bitcoin, buscando opções acessíveis para começar. Ao seguir os passos abaixo, mesmo com recursos limitados, é possível criar uma carteira segura e iniciar sua trajetória no mundo do Bitcoin.
https://medium.com/@alexemidio/samourai-wallet-um-carteira-de-bitcoin-pra-ruas-3003ebb79e57
https://blog.ronindojo.io/discover-version-5-0-0-of-sentinel/
-
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 8f69ac99:4f92f5fd
2024-10-25 09:49:56
@ 8f69ac99:4f92f5fd
2024-10-25 09:49:56O recente relatório do Banco Central Europeu, As Consequências Distribucionais do Bitcoin, recicla a velha narrativa de que o Bitcoin é um activo especulactivo que causa desigualdade de riqueza sem oferecer benefícios económicos tangíveis. Os autores, Ulrich Bindseil e Jürgen Schaaf, desfilam as críticas de sempre, afirmando que o Bitcoin falhou como sistema de pagamento global e que se transformou numa bolha, enriquecendo os primeiros utilizadores à custa da sociedade. Também lançam uma pitada de alarmismo ambiental e argumentam que o Bitcoin ameaça a democracia.
Como era de esperar, o BCE continua apegado às mesmas concepções erradas que já foram desmentidas inúmeras vezes. O que este relatório não percebe, de forma espectacular, é que o Bitcoin não é apenas mais um activo; é uma tábua de salvação para aqueles desiludidos com os sistemas fiduciários inflacionários e governos corruptos. Ao longo desta análise, vamos desmontar os argumentos do BCE, expondo não só o seu profundo desconhecimento sobre o Bitcoin, mas também a ignorância gritante em relação ao seu potencial de conceder soberania financeira a milhões de pessoas em todo o mundo. O BCE retrata o Bitcoin como uma ferramenta elitista, mas ignora como as suas próprias políticas têm sistematicamente enriquecido alguns poucos à custa da maioria. Vamos então entrar no assunto.
1. Deturpam o Papel do Bitcoin como Sistema de Pagamentos
"O Bitcoin nunca foi usado em grande escala para transacções legais no mundo real."
Que originalidade. Os autores descartam a utilidade de pagamento do Bitcoin com um gesto, mostrando que não compreendem a Lightning Network, que facilita transacções rápidas, baratas e escaláveis a nível global. Certamente, talvez os europeus ainda não estejam a comprar os seus cafés com Bitcoin, mas isso é irrelevante. O Bitcoin é uma tábua de salvação financeira em locais como El Salvador e em inúmeras outras regiões que sofrem com sistemas fiduciários em colapso.
Esta visão eurocêntrica, como se todo o mundo partilhasse das mesmas condições económicas, reflecte uma total falta de perspectiva. Os autores seleccionam dados a dedo para encaixar na sua narrativa anti-Bitcoin, enquanto convenientemente ignoram os milhões que utilizam o Bitcoin para escapar à hiperinflação e a regimes autoritários. A afirmação de que o Bitcoin não é usado para transacções "legais" é não só enganosa, como revela a sua ignorância sobre as necessidades reais de quem vive fora da sua bolha privilegiada.
2. Deturpam o Bitcoin como activo Especulactivo
"O Bitcoin não gera qualquer fluxo de caixa (como o imobiliário), juros (como as obrigações) ou dividendos (como as ações)."
Parabéns, BCE, acabaram de perder o ponto fulcral do Bitcoin. Esta afirmação mostra uma falta de entendimento fundamental do que torna o Bitcoin único. Ao contrário de imóveis ou obrigações, o Bitcoin é uma forma alternativa de dinheiro—não algum esquema de rendimento passivo.
O valor do Bitcoin não depende de gerar dividendos ou juros, mas advém da sua escassez, descentralização e resistência à censura. Ao reduzir o Bitcoin a modelos de activos tradicionais, o BCE ignora o paradigma económico revolucionário que este oferece: uma escapatória aos sistemas fiduciários inflacionários, particularmente para os milhares de milhões de pessoas presas em sistemas financeiros corruptos.
Ao tentar enquadrar o Bitcoin em modelos convencionais, os autores revelam a sua preguiça intelectual. A utilidade do Bitcoin reside no seu potencial como dinheiro sólido, e não como um veículo de investimento para especuladores atrás de rendimento.
3. Deturpam os Custos Ambientais e Sociais da Mineração
"A mineração de Bitcoin consome muita energia e causa danos ecológicos e sociais."
Ah sim, o argumento gasto sobre o consumo energético. Enquanto a mineração de Bitcoin realmente requer energia, os autores omitem convenientemente os enormes avanços que a indústria fez em direcção à sustentabilidade. Cada vez mais, os mineradores de Bitcoin recorrem a fontes de energia renovável e, em alguns casos, estão até a ajudar a financiar infraestruturas de energia verde.
A ironia aqui é que o BCE, uma instituição que fomenta políticas que inflam bolhas imobiliárias e de acções, de repente está preocupado com os custos sociais e ambientais. E mais, ignoram como a procura de energia barata por parte do Bitcoin incentiva realmente o desenvolvimento de soluções energéticas sustentáveis. Num mundo onde os sistemas fiduciários alimentam a ganância corporativa e a degradação ambiental, o Bitcoin está posicionado para impulsionar uma verdadeira inovação na energia verde.
4. Visão Deturpada da Redistribuição de Riqueza
"Os efeitos de riqueza do Bitcoin beneficiam os primeiros utilizadores à custa dos que chegam mais tarde e dos que não o possuem."
Isto é pura comédia. Aparentemente, o BCE acabou de descobrir que os primeiros investidores em qualquer activo beneficiam mais do que os que chegam depois. Não é assim que os mercados funcionam? Os primeiros investidores em acções, imóveis e ouro beneficiam de forma desproporcional—mas, curiosamente, isto só se torna um problema quando se trata de Bitcoin.
O que o BCE realmente teme é que o Bitcoin democratize a riqueza de uma maneira que eles não conseguem controlar. Com o Bitcoin, não precisas de acesso privilegiado para participar. Não precisas de um corretor XPTO ou de permissão dos guardiões financeiros. Ao contrário das próprias políticas do BCE—concebidas para inflacionar a riqueza dos já ricos através de bolhas imobiliárias e do mercado de acções—Bitcoin oferece um campo de jogo nivelado para qualquer pessoa com uma ligação à internet.
5. Sensacionalismo: a Ameaça à Democracia
"O aumento perpétuo do preço do Bitcoin empobrece o resto da sociedade e põe em risco a democracia."
Aqui, os autores entram no melodrama, avisando que o aumento do preço do Bitcoin põe em risco a democracia. É fascinante como ignoram a verdadeira ameaça à democracia: as suas próprias políticas inflacionárias.
Na realidade, os sistemas fiduciários, através da inflação incessante e do quantitative easing, erodem sistematicamente a riqueza dos mais pobres e da classe média. Os ricos, com as suas carteiras de acções e imóveis, conseguem resistir à tempestade. Mas o trabalhador comum, cujo salário compra cada vez menos a cada ano, é esmagado. Se há algo que ameaça a democracia, é o poder descontrolado do BCE de desvalorizar a moeda que as pessoas usam para viver. Bitcoin, por outro lado, dá às pessoas uma reserva de valor incorruptível e descentralizada, imune aos caprichos dos banqueiros centrais.
6. Percepção "Equivocada" da Escalabilidade do Bitcoin
"As transações em Bitcoin na blockchain são lentas e caras."
Esta crítica ignora a realidade do progresso tecnológico. As transacções on-chain de Bitcoin nunca foram pensadas para compras diárias—para isso é que serve a Lightning Network. Os autores agarram-se a esta crítica desactualizada, como se o Bitcoin fosse uma entidade estática que não evoluiu na última década.
Soluções de segunda camada como a Lightning Network permitem transacções quase instantâneas e de baixo custo, tornando o Bitcoin escalável de maneiras que o BCE se recusa a reconhecer. Mas porque deixar que os factos estraguem uma boa história de medo?
7. Ignoram o Impacto Económico Global do Bitcoin
"O Bitcoin não tem casos de uso benéficos para a sociedade."
Esta afirmação é tão limitada que é quase impressionante. A utilidade do Bitcoin não se trata de conveniência para os ocidentais comprarem café; trata-se de sobrevivência para as pessoas em países como a Venezuela, o Líbano ou a Nigéria.
Quando as moedas locais colapsam e as pessoas não podem confiar nos seus bancos, o Bitcoin oferece uma saída. Ao descartar o impacto real de Bitcoin sobre os milhares de milhões (mais de metade da população mundial) de pessoas que vivem sob regimes opressivos e em hiperinflação, o BCE revela um embaraçoso viés ocidental e falta de empatia. O Bitcoin é mais do que apenas um activo alternativo, é uma tábua de salvação para pessoas em todo o mundo que sofrem com sistemas fiduciários falhados.
Conclusão
O relatório do BCE recicla críticas desactualizadas e já desmentidas, não conseguindo ver o panorama geral. Aplica modelos financeiros antigos a uma nova forma de dinheiro, ignorando o potencial de Bitcoin para democratizar o acesso a um sistema financeiro justo, descentralizado e incorruptível. Enquanto os bancos centrais, como o BCE, continuam a desvalorizar moedas e a inflacionar bolhas de activos (e parece que vem ai mais...), Bitcoin oferece às pessoas um caminho para a soberania financeira.
O verdadeiro valor de Bitcoin não se encontra nas críticas superficiais e eurocêntricas do BCE. O seu valor reside na capacidade de fornecer liberdade financeira a indivíduos em todo o mundo, libertos da má gestão de governantes e banqueiros centrais. Se há algo que ameaça a democracia, é o historial do BCE de enriquecer alguns poucos à custa de muitos. Bitcoin, por outro lado, oferece um futuro mais justo—um onde são os indivíduos, e não as instituições, que têm o poder.
Alguma literatura: - Universidade de Cornell - Bitcoin pode impulsionar o desenvolvimento de energias renovaveis - Aldeias em Africa com electricidade atraves de Bitcoin - Relatorio de 2023 sobre a Lightning Network da River - Adopcao de Bitcoin por Pais
Photo by Taras Chernus on Unsplash
Bitcoin #BCE
-
 @ ee7d2dbe:4a5410b0
2024-10-25 07:25:41
@ ee7d2dbe:4a5410b0
2024-10-25 07:25:41Today, outsourcing and offshoring are integral parts of almost every business strategy, as they help in efficiency and innovation, by continually evolving in response to economic, technological, and geopolitical shifts.
In short, these models not only help to shape your corporate strategies but also influence global labor markets and economies. So, if you are not using them in your business, you are behind the curve.
That’s why in this post, we start with…
A basic understanding of them, Then go over the top 10 differences between outsourcing and offshoring, And lastly, discuss the key factors to keep in mind while choosing between them.
Understanding of Outsourcing & Offshoring
Outsourcing, at its core, means you are hiring third-party services to complete a piece of work or a whole project, which involves delegating specific tasks or services to external companies, often to harness specialized expertise or reduce costs.
For example, Google outsources IT management to firms in India, and Nike outsources manufacturing to factories in Vietnam and China.
Offshoring means you are relocating your business operations to other countries frequently where labor costs are lower like India and China to emphasize geographical cost advantages and talent pools.
For instance, Apple offshores its manufacturing to China, and Wells Fargo offshores customer service to India and the Philippines.
Evolution of Outsourcing
Outsourcing began during the Industrial Revolution in the 18th century when businesses started contracting out non-core activities to outside experts with a view of improving efficiency.
First, it was limited to simple clerical work such as accounting, but, in the late 20th century, outsourcing expanded with the emergence of Business Process Outsourcing (BPO), which also includes more complex service activities such as call center and IT support.
Evolution of Offshoring
Offshoring started to gain momentum in the 1980s and the 1990s due to enhanced telecommunications and the Internet. From then, most developed Western firms started relocating manufacturing and IT services to developing countries like India and China. So, you can mark this era as the start of a new global economy, where geographic boundaries became less relevant to scale businesses.
Outsourcing v/s Offshoring: An In-depth Analysis
As the title suggests, this will be an in-depth analysis of outsourcing vs. offshoring. However, if you are in a hurry and just want to know the differences, please refer to the chart below.
But our recommendation is to go through all the points and understand them thoroughly so you can make the right decision for your company’s future.
Types of Outsourcing and Offshoring
Actually, the types of outsourcing depend on individual perspectives. For instance, HubSpot covers 7 types, PearlTalent covers 9, and Digital Minds BPO covers 11 types of outsourcing in their articles.
Here, we list 4 categories that encompass almost all types:
IT Outsourcing: Hiring top companies, like Agicent, to facilitate IT functions like software development, maintenance, and support.
Business Process Outsourcing (BPO): It is about delegating non-core business processes such as payroll, HR, and customer service.
Source: https://www.agicent.com/blog/outsourcing-vs-offshoring/
-
 @ fd208ee8:0fd927c1
2024-10-20 18:19:48
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a GitHub repo, and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
- Why can I not login? Oh, they fixed the login! Nope, still can't login.
- If I press this button, it says it sent, but it didn't send. Where note?
- They announced a new feature, but I tried it and it didn't work. Oh well.
- I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
- The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it really needed... was a Nostr Stable Version. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be allowed to have expectations of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
Things working is an underrated concept
I know that the very idea of software running as expected and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are all features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load every damn time, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that things working becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
Where to start?
Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our project wiki page, and came up with a Vision and a Mission:
The vision is what the overall goals of the company are, whereas the mission describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because profits are the most pure form of communication that consumers in the market have with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial lambo and a bimbo. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but pay them out, you should. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the okay, so this is what we've decided comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to Investopedia, common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's emotionally binding, which is arguably more important.
Writing things down is an advanced form of naming things and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-
 @ a10260a2:caa23e3e
2024-10-25 03:41:11
@ a10260a2:caa23e3e
2024-10-25 03:41:11It seems like blogstack is meant to replace Substack if not already apparent by the name. If that's the case, it's already better in a few ways.
1. Hit the ground running
I'm already getting started out of the gate with more readers than I would have if I just started a Substack. This, of course, is due to the fact that I'm creating on top of a protocol where I'm able to have the same audience across all clients of that protocol. This is in stark contrast to the legacy apps from centralized entities where you have to corral your audience from one platform to the next.
2. Readers need not subscribe
Technically, if you're following me, you're subscribed. But you don't have to subscribe for a set price and amount of time (e.g. $5/month or $50/year). I believe this is a win for both of us as I can write my best notes and you can choose to reward me as you see fit. Value 4 value.
3. More conducive to conversation
Writing on Substack felt like writing into a void, with little to no feedback. A post shows up in my readers' inbox and I'll see some stats on whether it was opened or not. That's it. Based on what I've seen so far, blog posts created on Nostr appear in the client apps (e.g Damus, Primal, and Plebstr) as just another note, but with nice formatting and such. From there, I can receive zaps, shakas, comments, and even be reposted.
This is just the beginning. Right now, I'm using blogstack. But what's to stop me from using another tool down the line? I'll have the ability to do so by simply connecting my private key. Can't wait to see what new tools are created in the future.
Bullish on #Nostr
-
 @ bcea2b98:7ccef3c9
2024-10-20 17:33:12
@ bcea2b98:7ccef3c9
2024-10-20 17:33:12originally posted at https://stacker.news/items/732719
-
 @ a012dc82:6458a70d
2024-10-25 02:23:55
@ a012dc82:6458a70d
2024-10-25 02:23:55Table Of Content
-
Stay Abreast of Market Trends
-
Technical Analysis: Chart the Course
-
Fundamental Analysis: Digging Deeper
-
Follow Expert Insights and Predictions
-
Diversify Your Portfolio
-
Conclusion
-
FAQ
Investing in Bitcoin has become a hot topic in recent years, attracting both seasoned investors and newcomers alike. The potential for significant returns and the excitement surrounding this digital currency make it an attractive choice for those seeking to expand their investment portfolio. However, with great potential comes great risk. The volatile nature of Bitcoin requires investors to stay informed and employ smart strategies to maximize their investments. In this article, we'll explore five proven prediction hacks that can help you navigate the unpredictable world of Bitcoin and enhance your chances of success.
1. Stay Abreast of Market Trends
Keeping up with the latest market trends is essential for any successful investor. In the realm of Bitcoin, this holds even more significance due to its highly volatile nature. By staying informed about market trends, you can identify patterns, understand market sentiment, and make more informed decisions. Regularly monitoring reliable sources of information such as cryptocurrency news websites, influential social media accounts, and industry reports can provide valuable insights that help you stay ahead of the game.
2. Technical Analysis: Chart the Course
Technical analysis is a powerful tool used by seasoned investors to predict price movements based on historical data. By analyzing price charts, identifying patterns, and utilizing indicators, you can gain a deeper understanding of market trends and potential price movements. Whether you're examining candlestick patterns, moving averages, or relative strength index (RSI), technical analysis equips you with valuable information to make well-informed investment decisions.
3. Fundamental Analysis: Digging Deeper
In addition to technical analysis, fundamental analysis helps investors evaluate the intrinsic value of an asset. When it comes to Bitcoin, understanding the underlying technology, adoption rates, regulatory developments, and major partnerships can provide crucial insights into its future prospects. By conducting thorough research and considering these fundamental factors, you can make informed investment decisions based on a comprehensive understanding of Bitcoin's potential.
4. Follow Expert Insights and Predictions
In the world of Bitcoin investments, expert opinions can be invaluable. Keeping an eye on reputable cryptocurrency analysts and influential figures in the industry can provide you with valuable insights and predictions. These experts often share their views through blogs, podcasts, interviews, and social media channels. While it's important to do your own research and not rely solely on others' opinions, expert insights can help you validate your own predictions and make more informed investment choices.
5. Diversify Your Portfolio
Diversification is a key principle in any investment strategy, and Bitcoin is no exception. Spreading your investments across different cryptocurrencies, as well as other asset classes, can help mitigate risks and maximize your chances of profiting. Consider allocating a portion of your investment portfolio to Bitcoin, while also diversifying into other cryptocurrencies or traditional assets like stocks or real estate. By diversifying, you ensure that your financial well-being is not solely reliant on the performance of one asset, reducing potential losses and increasing overall stability.
Conclusion
Investing in Bitcoin can be a thrilling and potentially rewarding endeavor. By employing these five proven prediction hacks, you can navigate the ever-changing landscape of cryptocurrencies with increased confidence and maximize your chances of success. Remember to stay informed, conduct thorough research, and exercise caution when making investment decisions. With the right strategies and a solid understanding of the market, you can unlock the full potential of Bitcoin and optimize your investments.
FAQ
Should I invest in Bitcoin for the long term? While Bitcoin has shown incredible growth over the years, it's important to remember that past performance is not indicative of future results. Investing in Bitcoin for the long term can be rewarding, but it also carries risks. It's crucial to conduct thorough research, consider your financial goals, and seek professional advice before making any investment decisions.
Can I use these prediction hacks for other cryptocurrencies? Absolutely! While this article focuses on Bitcoin, the prediction hacks discussed can be applied to other cryptocurrencies as well. The key is to stay informed, conduct analysis, and consider both technical and fundamental factors when making investment decisions.
Is it possible to predict Bitcoin's price with 100% accuracy? Unfortunately, no prediction method can guarantee 100% accuracy when it comes to Bitcoin's price. The cryptocurrency market is highly volatile and influenced by various factors, making it challenging to predict with absolute certainty.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ a10260a2:caa23e3e
2024-10-25 01:51:45
@ a10260a2:caa23e3e
2024-10-25 01:51:45A zero-dependency, zero-framework QR code web component for Bitcoin on-chain, Lightning, and unified BIP-21 payments.
Just discovered this tool by nostr:npub18agram6s6kulwwhc638d8q8y5vysutrrvvdll2wdjxd75wp4dfjqshytrf and found it to be very useful. Also, did I mention easy-to-use?
You can find the GitHub here and a demo I made (complete with a function to check for payment) on the Bullish Prototype. 👨💻
originally posted at https://stacker.news/items/737255
-
 @ bcea2b98:7ccef3c9
2024-10-20 15:50:27
@ bcea2b98:7ccef3c9
2024-10-20 15:50:27The Bitcoin space is constantly evolving with new ideas, technologies, and innovations. From Lightning Network advancements to privacy improvements, there’s always something happening that could change the future of Bitcoin.
What do you think is the most exciting or innovative development in Bitcoin right now? I've been following a lot of privacy related advancement in Bitcoin and LN and look forward to learning about more solutions.
originally posted at https://stacker.news/items/732534
-
 @ 599f67f7:21fb3ea9
2024-10-20 11:32:36
@ 599f67f7:21fb3ea9
2024-10-20 11:32:36LNDhub-ek zure zorroa erraz inportatzea ahalbidetzen du bateragarriak diren aplikazioetan. Bitcoin Txoko LNbits zorroa progresiboko web aplikazio (PWA) modura gorde dezakezun arren zure telefonoan, Zeus edo BlueWallet bezalako aplikazio natibo batek erabiltzaile-esperientzia hobea eta segurtasun handiagoa eskaintzen du.
Alby erabiliz, zorroa zure nabigatzailearen luzapenean ere inporta dezakezu, webgunean Lightning ordainketak egiteko eta Nostr zap-ak egiteko erraztasun handiagoz. Zorionez, zorro hauek guztiek hizkuntza komun bat ulertzen dute, LNDhub izenekoa.
Gida honetan, zorroa zure nabigatzailera eta telefonora nola inportatu azalduko dugu. Zorroa nabigatzailean eta telefonoan erabili nahi baduzu, hasi Alby konfigurazioarekin, pausoetako batek zorroa Zeus-era erraz inportatzeko aukera emango baitizu. Baina zorroa soilik zure telefonoan erabili nahi baduzu, zuzenean Zeus atalera jo dezakezu.
Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 nabigatzailearen luzapena da, Lightning eta Nostr nabigatzailera ekartzen dituena. WebLN protokoloa erabiliz, luzapenak webguneetan fakturak automatikoki detekta eta ordaintzen ditu, eta Lightning bidez webguneetan saioa hasteko aukera ematen du. Gainera, Lightning gune gogokoenetan aurrekontuak ezar ditzakezu. Luzapen honek NIP-07 protokoloa erabiliz Nostr sinadura gisa ere funtziona dezake, zure giltza pribatua web bezeroetan sartzea baino askoz seguruagoa dena.
Zer behar dut?
- Chrome edo Firefox luzapenak onartzen dituen web nabigatzailea.
- LNbits zorroa. Oraindik zorro bat ez baduzu, joan gure zorroen orrira eta sortu bat.
- (Aukerazkoa) Zeus konfiguratzeko mugikor bat.
1. LNDhub luzapena gaitzea zure LNbits zorroan
Nabigatzailean, joan zure zorroaren estekara. Egin klik Extensions atalean eta gaitzazu
LNDhubluzapena. Gaitu ondoren, joan LNDhub luzapenaren orrira.2. Alby luzapena instalatu
Joan getalby.com-era eta egin klik
Add Browser Extensionbotoian. Instalatu luzapena zure nabigatzailearen luzapen dendetik. Ezarri desblokeatzeko pasahitza eta gorde toki seguruan.3. Inportatu Alby-ra

Hurrengo pantailan, aukeratu
Connect, eta ondoren aukeratuLNDhub. Itzuli zure LNDhub luzapenera eta kopiatu konexioaren URL-a. Itsatsi hori LNDhub esportazioaren URI eremuan. SakatuContinue. Orain LNbits zorroa LNDhub bidez konektatuta eduki beharko zenuke!💡 Aukeratu dezakezu Invoice URL eta Admin URL artean. Bi hauek Alby-ri zure LNbits zorroarekin elkarreragiteko baimen desberdinak ematen dizkiote: - Invoice URL-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - Admin URL-ak ordainketak bidaltzeko aukera ere ematen du.
4. (Aukerazkoa) Zeus konfiguratu Alby-rekin

Orain LNbits zorroa Alby-rekin konektatu duzunez, Zeus-en ere erraz inportatu dezakezu. Ireki luzapena, egin klik zure zorroaren izenean, eta joan
Account Settingsatalean.Accountazpian aurkituko duzuConnect your mobile walletaukera. SakatuConnect, eta Zeus-ekin eskaneatzeko QR kode bat erakutsiko dizu.Zeus aurretik instalatu ez baduzu, joan zeusln.app-era eta deskargatu Zeus zure mugikorreko sistema eragilerako. Zeus deskargatu ondoren, joan
Settings>Add a new nodeatalera. Hemen, Alby-k erakusten dizun QR kodea eskaneatu eta zorroa inportatu dezakezu.Listo! Orain Lightning-aren indarra zure eskuetan duzu. Jainko baten moduan sentitzen al zara jada?
Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf kode irekiko aplikazio bikaina da, zure nodo propioa mugikorrean konektatzeko aukera ematen duena. Lightning nodo nagusi guztiak onartzen ditu, hala nola LND, CLN eta Eclair, bai eta Tor bidezko zein clearnet bidezko konexioak ere. Azkenaldian, beren LSP (Lightning Service Provider) propioa iragarri dute.
Zer behar dut?
- Android edo iOS telefono bat.
- LNbits zorroa ikusi ahal izateko beste gailu bat (QR kodea eskaneatzeko).
- LNbits zorroa eskuragarri izatea. Zorro bat oraindik ez baduzu, joan gure zorroen orrira eta sortu bat.
1. Zeus deskargatu
Deskargatu Zeus aplikazioa zure sistema eragilerako hemen.
2. LNDhub luzapena gaitzea zure LNbits zorroan
Zure LNbits zorroaren orrian, egin klik
Extensionsatalean eta gaitzazuLNDhubluzapena. Gaitu ondoren, ireki LNDhub luzapenaren orria.3. Inportatu Zeus-en
Joan
Settings>Add a new nodeatalera Zeus-en. Eskaneatu nahi duzun zorroa inportatzeko.💡 Aukeratu dezakezu Invoice URL eta Admin URL artean: - Invoice URL-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - Admin URL-ak ordainketak bidaltzeko aukera ere ematen du.
QR kodea eskaneatu ondoren, Zeus-en eremu guztiak automatikoki beteko dira. Zorroarentzat ezizena ere gehitu dezakezu.

Orain,
Save Node Configsakatu eta zorroa zure mugikorretik kontrolatu dezakezu!Bonus
Zeus-ek ezaugarri interesgarriak ere eskaintzen ditu, hala nola gai pertsonalizatuak, prezioen bihurketak, lurker modua eta biometria bidezko egiaztapena. Gida honen esparrutik haratago doazen ezaugarriak dira hauek, baina aplikazioa erabili eta zuk zeuk aurkitu ditzakezu!
-
 @ dd32f3e0:498f1df9
2024-10-25 01:42:06
@ dd32f3e0:498f1df9
2024-10-25 01:42:06eyJfaWQiOiJkMmVkZDBkMy0yZmM3LTQxNWYtYTA5MC1iY2Q2ZDE2YTc2YjYiLCJwdWJsaWNLZXkiOiJkZDMyZjNlMDgzNDdlYTYzM2U2MzZkODlhMjMzOWQ0N2IyOTM2MWZkZTQ3MTZjZjNhZTBhMzhhYTQ5OGYxZGY5IiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6IkZJWEVEIiwibWFyZ2luIjowLCJtYXJrZXRQcmljZSI6bnVsbCwiZml4ZWRQcmljZSI6MTUwLCJtaW5BbW91bnQiOjAsIm1heEFtb3VudCI6NTAwLCJsaW1pdFRvRmlhdEFtb3VudHMiOiIiLCJwYXltZW50TWV0aG9kRGV0YWlsIjoibmljZSB0cmFkZXIiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsInBheW1lbnRXaW5kb3dNaW51dGVzIjo2MCwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMC0yNVQwMTo0MjowNi4yNzBaIn0=
-
 @ 599f67f7:21fb3ea9
2024-10-20 11:28:08
@ 599f67f7:21fb3ea9
2024-10-20 11:28:08LNDhub te permite importar fácilmente una billetera en aplicaciones compatibles. Si bien puedes guardar tu billetera Bitcoin Txoko LNbits en tu teléfono como una aplicación web progresiva (PWA), una aplicación nativa como Zeus o BlueWallet ofrece una mejor experiencia de usuario así como un mayor nivel de seguridad. Con Alby, también puedes importar la billetera a la extensión de tu navegador para facilitar los pagos Lightning en la web y para los zaps de Nostr. Por suerte para nosotros, todas estas billeteras hablan un lenguaje común llamado LNDhub.
En esta guía cubriremos cómo importar la billetera a tu navegador y a tu móvil. Si quieres usar tu billetera tanto en el navegador como en tu móvil, empieza con la configuración de Alby, ya que uno de los pasos te permitirá importar fácilmente tu billetera también a Zeus. Pero si sólo te interesa utilizar la billetera en tu móvil, puedes pasar directamente a la sección de Zeus.
Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 es una extensión de navegador que lleva Lightning y Nostr a tu navegador. Utilizando el protocolo WebLN, esta extensión puede detectar facturas LN en paginas web y pagarlas, así como posibilita iniciar sesión en sitios web con Lightning. También puedes fijar presupuestos para tus sitios favoritos de Lightning. Por otro lado también puedes utilizarla para firmar en Nostr utilizando NIP-07, lo cual es mucho más seguro que ingresar tu clave privada en clientes web.
¿Qué necesito?
- Un navegador web que soporte extensiones Chrome o Firefox
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
- (Opcional) Un dispositivo móvil para configurar Zeus
1. Habilita la extensión LNDhub en tu LNbits wallet
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez se haya habilitado, dirígete a la página de extensión de LNDhub.2. Instala la extensión Alby
Dirígete a getalby.com y instala la extensión desde el store de extensiones del navegador. Configura tu contraseña de desbloqueo y guárdala en un lugar seguro.
3. Importar a Alby
 (Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)
(Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)En la siguiente pantalla, elige
Conectary luego eligeLNDhub. Vuelve a tu extensión LNDhub y copia la URL de conexión. Pégala en el campoURI de exportación de LNDhub. Pulsa continuar. ¡Ahora deberías haber estado conectado a tu billetera de LNbits con LNDhub!💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). Le dan a Alby diferentes permisos para interactuar con tu cartera de LNbits.
- La URL de factura te permite crear facturas y recibir pagos
- La URL de administración también te permite enviar pagos
4. Configurar Zeus con Alby (opcional)

Ahora que ya has conectado tu LNbits con Alby, también puedes importarlo de una manera sencilla a Zeus con Alby. Abre la extensión, haz cilc en el nombre de tu billetera y navega a la configuración de la cuenta. En
Wallet Settings>Generalse encuentra la opción de conectar tu billetera móvil. Al pulsar conectar, se mostrará un código QR para escanear desde Zeus.Si no tienes instalada Zeus con anterioridad, dirígete a zeusln.app y descarga la aplicación de Zeus para tu sistema operativo móvil.
Una vez tengas descargado Zeus, entra en
Configuración>Añadir un nuevo nodo. Aquí puedes escanear el código QR que te muestra Alby para importar la billetera.Voilà! Ahora tienes el poder de Lightning al alcance de la mano ¿Ya te sientes como un dios?
Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf es una formidable aplicación de código abierto que permite conectar tu propio nodo a tu dispositivo movil. Es compatible con todas las principales implementaciones de nodos Lightning, como LND, CLN y Eclair, así como conexiones a través de Tor y clearnet. Recientemente también han anunciado su propio LSP (Lightning Service Provider).
¿Qué necesito?
- Teléfono Android o iOS
- Otro dispositivo en el que puede acceder a tu billetera LNbits (para mostrar el código QR para escanear)
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
1. Descarga Zeus
Puedes descargar la aplicación Zeus para tu sistema operativo aquí.
2. Habilita la extensión LNDhub en tu billetera LNbits
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez habilitada, abre la pagina de la extensión LNDhub.3. Importar a Zeus
Ve a
Configuración>Añadir un nuevo nodo en Zeus.Escanea la cartera que quieras instalar.
💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). - La URL de la factura te da permiso para generar facturas y recibir pagos. - La URL de administración también te permite enviar pagos.
Una vez que hayas escaneado el código QR, todos los campos en Zeus deberían rellenarse automáticamente. También puedes añadir un apodo para tu billetera.

¡Ahora puedes guardar la configuración del nodo y controlar la billetera desde tu teléfono!
Extra
Zeus también ofrece funciones interesantes como temas personalizados, conversiones de precios, modo acechador y verificación biométrica. Estos temas están más allá del alcance de esta guía, ¡juega en la aplicación y descubre todas esas características por ti mismo!
-
 @ 599f67f7:21fb3ea9
2024-10-19 15:20:46
@ 599f67f7:21fb3ea9
2024-10-19 15:20:46Merkatari bat zara eta zure negozioan Bitcoin onartzen hasteko prest zaude? Edo agian Bitcoin zale sutsua zara, tokiko negozioak Bitcoinen mundura erakartzeko gogoz? Beharbada, ez zaizu Bitcoin interesatzen, baina ordainketa-prozesadore azkar eta merke bat erabili nahi duzu edo web-denda sinple bat sortu nahi duzu? Galdera hauetakoren bati baiezkoa erantzun badiozu, gida hau zuretzat da. Bitcoin Txoko-k ostatatutako BTCPay Server-en denda bat konfiguratu dezakezu eta zure produktuak eta zerbitzuak Bitcoinen truke saltzen hasi hamar minuturen buruan, doan.
Zer behar dut?
Mugikor edo ordenadore bat baduzu eta posta elektronikoko kontu bat ere bai, orduan prest zaude!
Kontu bat sortu
Bitcoin Txoko-n BTCPay Server-en kontu bat sortzea doakoa da. Joan btcpay.bitcointxoko.com helbidera kontu bat erregistratzeko. Egiaztatu zure posta elektronikoa, bertan bitcointxoko@gmail.com helbidetik bidalitako mezu bat aurkituko duzu, baieztapen-esteka bat izango duena.
Zure lehen denda sortu
Baieztapen-estekan klik egitean, dendaren sorrera orrialdera eramango zaitu. Eman zure dendari izen bat eta hautatu moneta lehenetsia eta prezio iturri hobetsia. Adibidez, EUR eta Kraken aukeratu ditzakezu, azken hau gomendatutako prezio iturria baita. BTCPay Server-ek zure produktuen edo zerbitzuen prezioa EUR-tik Bitcoin-era bihurtuko du, erosketa unean aukeratutako prezio iturriaren arabera.
Zorro bat konfiguratu
Ordainketak onartzen hasteko, lehenik eta behin zure denda zorro batera lotu behar duzu. Transakzio handiak (500 EUR baino gehiago) maiz espero ez badituzu, Lightning zorro bat konfiguratzeko gomendioa egiten dizugu, eta une honetan (on-chain) Bitcoin zorroa ez erabiltzea gomendatzen da. Lightning zorroa erabiliz, transakzioak azkarragoak eta merkeagoak izango dira.
💡 Lightning sarea Bitcoin ordainketak jasotzeko sare ezin hobea da, transakzio berehalakoak eta komisiorik baxuenak eskaintzen baititu on-chain transakzioekin alderatuta. Horrela, zure negozioak eraginkortasunez eta kostu txikiarekin jaso ditzake ordainketak.
Lightning zorro bat konektatzeko modurik errazena LNDhub erabiltzea da, zure Lightning nodo propioa exekutatu beharrik ez baituzu izango. LNDhub zorro bat ez baduzu oraindik, ez kezkatu; Bitcoin Txoko-k doako LNDhub zorroak eskaintzen ditu, eta bost minutu baino gutxiago behar dira konfiguratzeko. Begiratu nostr:naddr1qqxnzd3exuerqdfkxccnyv3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28nkyu7t zure LNDhub zorroa nola lortu jakiteko, eta prest zaudenean itzuli konfigurazioa jarraitzeko.

Zure LNDhub zorroa prest dagoenean, jarraitu urrats hauek BTCPay kontuan konfiguratzen: 1. Joan zure BTCPay kontura eta
Walletsaukera bilatu alboko barran, ondorenLightningaukeratu. 2. HautatuUse custom node. 3. Kopiatu zure LNDhub administrazio URL-a eta itsatsi konexioaren konfigurazioan. 4. Proba ezazu zure zorroaren konexioa. 5. Ondo joan bada, honako mezua agertu beharko litzateke: Connection to the Lightning node successful, but no public address has been configured. Ez kezkatu "no public address has been configured" atalaz, horrek zure nodo propioa exekutatzen ari bazara bakarrik du garrantzia. 6. Zorroaren konexioa arrakastaz probatu ondoren, sakatuSavebotoia. 7.Savesakatu ondoren,LNURLatalean, desaktibatuEnable LNURLaukera. Egin aldaketak eta ez ahaztu berriroSavebotoian klik egitea. 8. (Hautazkoa) Une honetan, gomendagarria daDisplay Lightning payment amounts in Satoshisaukera markatzea, Satoshitan zenbatutako ordainketa kopuruak irakurtzeko errazagoak baitira. Satoshi Bitcoin-en zatirik txikiena da; Bitcoin bat 100 milioi satoshik osatzen dute.Jarraitu urrats hauek zure zorroa arrakastaz konfiguratuta izateko eta Lightning bidezko ordainketak onartzeko.

💡 Zure Lightning nodo propioa erabiltzen ari bazara, konfigurazio prozesua antzekoa da. Ziurtatu zure nodo inplementaziorako konexio kate egokia ematen duzula.
Saltoki puntua (PoS) sortu
Urrats honetara iritsi bazara, zorionak! Zati aspergarriena amaitu da, eta orain zure Saltoki puntua (Point of Sale, PoS) sortzeko unea iritsi da, BTCPay bidez zure lehen Bitcoin ordainketa onartzen hasteko!
Saltoki puntu bat sortzeko: 1. Joan
Plugins>Point of Saleatalera. 2. Eman izen bat zure Saltoki puntuari eta sakatuCreatebotoia.Jarraian, zure PoS aplikazioarekin egin ditzakezun gauza erraz batzuk azalduko ditugu. BTCPay-k ezaugarri asko ditu, baina gida honetan oinarrizkoak soilik azalduko ditugu, hasiera emateko.
💡 Gogoratu BTCPay Server-en saltoki puntu bat baino gehiago sor ditzakezula, bakoitza erabilera jakin baterako. Horrela, negozio desberdinetarako edo produktu eta zerbitzu berezietarako konfigurazio bereiziak izatea posible da.
Teklatua (Keypad)

Demostrazio erraz baterako, PoS estilo gisa teklatuaren eredua erabiliko dugu.
- Eman zure PoS-ari izen bat eta erakusteko titulua.
- Hautatu
KeypadestiloaPoint of Sale styleaukeraren azpian. - Sakatu
Saveeskuineko goiko izkinan, eta ondorenViewsakatu zure PoS begiratzeko.
Ordainketak lehenago konfiguratutako LNDhub zorroan jasoko dira. Jolas ezazu fakturak sortzen eta deskontu eta tip (aholkularitza) aukerak aktibatuz. Gainera, telefono bat baduzu (adibidez, iPhone ez den bat) NFC teknologia onartzen duena, bezeroek NFC txartelak erabiliz ere ordain dezakete, hala nola BoltCard erabiliz (ikusi nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28qjzxr4). Ez al da zoragarria?
💡 PoS estilo honen erraztasuna maximizatzeko, Keypad PoS zure telefonoan Progressive Web App (PWA) gisa gorde dezakezu sarbide azkarrerako. Mugikor gehienetako nabigatzaileetan aukera hau
Install AppedoGehitu orri nagusianizenarekin agertzen da.Horrela, zure negozioan Bitcoin ordainketak erraz onar ditzakezu, eta erabiltzaileek ere modu intuitibo batean ordaindu ahal izango dute.
Product list (with cart)

Posible da saltoki puntu bat sortzea produktu zehatzekin, bakoitza bere prezioarekin. Ezaugarri hau erabil dezakezu kutxa sinple bat, bezeroen auto-ordainketa sistema edo web denda bat konfiguratzeko.
Nola sortu produktu-zerrendadun Saltoki Puntua: 1. Joan berriro alboko barrara eta aukeratu
Point of Sale. 2. Oraingoan,Point of Sale Styleazpian, hautatuProduct list with cart. "With cart" aukerak bezeroari produktu bat baino gehiago aldi berean erosteko aukera ematen dio. 3. Zure produktuak sortu, edo zuzenean sakatuSaveetaViewproduktu laginak probatzeko.Ondorioa
Gida honetan, zure negozioan Bitcoin onartzen hasteko BTCPay Server erabiliz jarraitu beharreko oinarrizko urratsak azaldu ditugu. BTCPay Server proiektu irekia da eta etengabe garatzen ari da. Askoz ere ezaugarri eta funtzionalitate gehiago eskaintzen ditu, hala nola Shopify integrazioa, crowdfunding eta ordainketen banaketa automatikoa. Gainera, zure denda pertsonaliza dezakezu gaikako diseinuekin, ordainketa-gune pertsonalizatuarekin, erabiltzaileen kudeaketarekin, posta elektronikoko jakinarazpenekin eta askoz gehiago.
BTCPay Server-en ahalmen guztiak aprobetxatu nahi badituzu, zure Lightning nodoa konfiguratu eta zure BTCPay zerbitzaria ostatatzea gomendatzen dizugu. Informazio gehiago lortzeko, haien dokumentazioa eta bideoak ikustea komeni da.
Zalantzarik edo galderarik baduzu, jakinarazi iezaguzu! Zure iritziak entzutea gustatuko litzaiguke eta galderak argitzen lagundu nahi dizugu.
Bitcoin Txoko komunitate ireki bat da. Gure zerbitzu guztiak dohaintzekin finantzatzen dira. Gida hau erabilgarria iruditu bazaizu, kontuan hartu gure zerbitzariak martxan mantentzen laguntzeko dohaintza bat egitea. Eskerrik asko aldez aurretik!
-
 @ 6f0ba1ef:58eb4351
2024-10-25 01:16:41
@ 6f0ba1ef:58eb4351
2024-10-25 01:16:41eyJfaWQiOiIzMjFkMjkyNi0xOGUyLTRjYTgtOWIwYy0xNGMwNWExZDc4ZTAiLCJwdWJsaWNLZXkiOiI2ZjBiYTFlZjc4YjE3ZTVkMjNkMmVjZDlkYWNlNmJhMzBlODI1NzUxMGY0NmYxNjA0NGUyZjY5ZjU4ZWI0MzUxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6Ik1BUktFVCIsIm1hcmdpbiI6MywibWFya2V0UHJpY2UiOjE1Ny40NiwiZml4ZWRQcmljZSI6MCwibWluQW1vdW50IjoxMCwibWF4QW1vdW50IjoyMDAsImxpbWl0VG9GaWF0QW1vdW50cyI6IiIsInBheW1lbnRNZXRob2REZXRhaWwiOiJ2ZXJ5IGZhc3QgYW5kIGVhc3kiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsInBheW1lbnRXaW5kb3dNaW51dGVzIjo2MCwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMC0yNVQwMToxNjo0MS41MDBaIn0=
-
 @ bcea2b98:7ccef3c9
2024-10-18 17:29:00
@ bcea2b98:7ccef3c9
2024-10-18 17:29:00originally posted at https://stacker.news/items/729964
-
 @ bcea2b98:7ccef3c9
2024-10-17 17:02:57
@ bcea2b98:7ccef3c9
2024-10-17 17:02:57originally posted at https://stacker.news/items/728382
-
 @ 4ba8e86d:89d32de4
2024-10-24 23:42:27
@ 4ba8e86d:89d32de4
2024-10-24 23:42:27Um canal Lightning pode ser pensado como uma sequência de contas esticadas entre duas pessoas. Consultando a Fig. 1, Alice pode pagar Bob empurrando uma de suas contas para o lado dele. Se Bob também tiver um canal Lightning com Carol, Alice pode pagar Carol por meio de Bob: ela empurra uma conta para Bob, que então empurra uma conta para Carol. A regra fundamental — e a razão por trás dos problemas de liquidez da Lightning Network — é que as contas podem se mover de um lado para o outro, mas não podem sair do cordão em que estão.
https://nostrcheck.me/media/public/nostrcheck.me_7999139148267863241703513103.webp Fig. 1. Alice pode enviar um pagamento para Carol roteando-o por Bob. Como as contas não podem sair do cordão em que estão, Bob acaba com uma conta a mais em seu cordão com Alice e uma conta a menos em seu cordão com Carol.
Isso é tudo que você precisa saber para entender como o dinheiro pode fluir na Lightning Network. No entanto, esse modelo não nos diz nada sobre por que os pagamentos na Lightning são seguros. Por exemplo, o que impede Bob de simplesmente manter a conta que Alice empurrou para ele e nunca enviar uma para Carol? O objetivo deste artigo é responder à pergunta "o que torna os pagamentos na Lightning 'sem confiança'?"
Ao final do artigo, revelaremos o sujo segredinho da Lightning Network: que os pagamentos pequenos não são realmente "sem confiança" — nós nós de roteamento podem perder fundos dos clientes.
Contratos Hash-Time-Lock (HTLCs) Para explicar o que impede Bob de manter a conta de Alice sem enviá-la para Carol, precisamos introduzir "travas" em nossa analogia física para os canais Lightning. Travas podem ser colocadas nos cordões para restringir o movimento das contas e só são abertas se condições específicas forem atendidas. Os contratos hash-time-lock (HTLCs) usados nos pagamentos Lightning envolvem dois tipos de travas (cf. Fig. 2): a primeira é uma trava que se abre se apresentada com a senha correta (vamos chamá-la de "hash-lock"), e a segunda é uma trava que se abre automaticamente após um atraso de tempo (vamos chamá-la de "time-lock").
https://nostrcheck.me/media/public/nostrcheck.me_9607840347208938921703514339.webp Fig. 2. O hash-lock se abre quando uma senha é inserida e gera o valor especificado (45f8 neste caso). O time-lock se abre após o tempo especificado ter decorrido (48 horas neste caso).
Agora, voltemos ao pagamento de uma conta de Alice para Carol por meio de Bob. Para tornar o pagamento "sem confiança", Alice, Bob e Carol precisam estar online ao mesmo tempo e participar de um elaborado ritual.
Primeiro, Alice pede a Carol que pense em uma senha secreta e diga a ela o hash da senha. Vamos fingir que a senha que Carol inventou foi "boondoggle" e seu hash foi "45f8". Em seguida, Alice coloca um hash-lock entre ela e Bob, configurado para abrir quando apresentado com uma senha que gera o hash "45f8". Neste ponto, nem Alice nem Bob podem abrir a trava, pois nenhum deles conhece a senha. Alice então empurra uma conta contra o hash-lock. Por fim, ela coloca um time-lock no lado esquerdo da conta, configurado para abrir automaticamente após 48 horas (Fig. 3).
https://nostrcheck.me/media/public/nostrcheck.me_3127046972622599461703514704.webp Fig. 3. Com o conhecimento do hash da senha secreta de Carol, Alice pode configurar um hash-lock para proteger a conta que ela transfere para Bob (para depois encaminhar para Carol). Ela trava a conta com um time-lock para que ela possa recuperá-la caso Bob não conclua o pagamento dentro de 48 horas.
Bob percebe que a conta é dele se conseguir descobrir a senha antes de 48 horas se passarem. Ele também sabe (porque Alice disse a ele) que Carol revelará a senha em troca de uma de suas contas. Para incentivar Carol a agir, Bob coloca o mesmo hash-lock entre ele e Carol, empurra uma de suas contas e então a trava com outro time-lock (Fig. 4). Ele sabe que, para Carol abrir o hash-lock e pegar a conta, ela precisará inserir a senha — à vista de todos — que é a mesma senha que Bob precisa para abrir o hash-lock com Alice.
https://nostrcheck.me/media/public/nostrcheck.me_4635793414256087711703515032.webp Fig. 4. Bob percebe que a conta de Alice é dele se Carol revelar sua senha antes de 48 horas. Ele configura o mesmo hash-lock, empurra uma conta em direção a Carol e a trava com um time-lock. A única maneira de Carol pegar a conta de Bob é revelar a senha que Bob precisa para reivindicar a conta de Alice.
Carol, ao ver que a conta está lá para ser pega, insere "boondoggle" na trava (lembre-se de que está à vista de Bob). A CPU da trava confirma que hash("boondoggle") = 45f8, e então se abre. Carol move a conta para o lado dela do cordão (Fig. 5).
https://nostrcheck.me/media/public/nostrcheck.me_6790828350788856531703516541.webp Fig. 5. Carol revela sua senha para abrir a trava e pegar a conta.
Com o conhecimento da senha de Carol, Bob desbloqueia sua conta de Alice da mesma forma (Fig. 6). O pagamento está completo.
https://nostrcheck.me/media/public/nostrcheck.me_8432131267156524571703517282.webp Fig. 6. Com o conhecimento da senha secreta de Carol, Bob pode agora pegar a conta de Alice, completando assim o pagamento.
Você pode se perguntar por que Bob se incomodaria em participar desse ritual em primeiro lugar. Se Carol não tivesse sido cooperativa, sua conta poderia ter sido congelada até que o time-lock expirasse. Na prática, Alice enviaria a Bob um pouco mais do que ela pede a Bob para enviar a Carol, como uma taxa para compensar por esse risco e pelo esforço de Bob. Quando o pagamento estiver completo, Bob terá um pouco mais do que começou, motivando-o assim a concluir o pagamento.
Você também pode se perguntar qual é o propósito dos time-locks. Os time-locks permitem que os participantes recuperem seus fundos se o pagamento falhar. Por exemplo, imagine que Bob se torna não cooperativo depois que Alice transfere sua conta e adiciona os dois locks. O time-lock é o que permite a Alice recuperar seus fundos. Ela só precisa esperar o time-lock expirar. Não há como Bob roubar a conta nesse ínterim, porque ele precisa da senha de Carol, o que ele não pode obter sem dar a Carol uma de suas contas e, assim, completar o pagamento.
Leitores interessados podem explorar o que acontece se uma das partes se tornar não cooperativa em diferentes etapas do processo de pagamento do Lightning para se convencer de que nem Alice, Bob, nem Carol estão em risco de perder dinheiro devido às ações de suas contrapartes.
O Sujo Pequeno Segredo da Lightning Network A Lightning Network tem um sujo pequeno segredo que poucas pessoas conhecem. Para entender qual é o segredo — e suas ramificações para os pagamentos do Lightning — precisamos cavar um pouco mais.
Lembre-se de que quando Alice enviou o pagamento para Carol através de Bob, o estado intermediário mostrado na Fig. 7 existia. Quando expresso como uma transação de bitcoin, o estado do canal contém três saídas: as moedas de Alice, as moedas de Bob e a moeda "em voo".
https://nostrcheck.me/media/public/nostrcheck.me_9561697518547468611703528026.webp Fig. 7. A transação de estado do canal Lightning neste ponto do tempo contém três saídas: as moedas de Alice, as moedas de Bob e as moedas em trânsito.
Aqui está o problema: se o valor em trânsito estiver abaixo do limite de poeira do BTC, então não pode ser representado como uma terceira saída na transação de estado do canal! Portanto, não é possível usar hash- e time-locks para proteger o pagamento se o pagamento for muito pequeno.
Para explicar como o LN lida com esse problema, devo primeiro fazer uma confissão. Não é exatamente verdade que o número de contas em uma string seja constante. Na verdade, há um balde ao lado de cada string rotulado como "Taxa do Minerador" que contém pequenas frações de contas. O valor neste balde é reivindicado pelo minerador que confirma a transação de estado do canal, caso o estado do canal seja empurrado para o blockchain. Frações de contas podem se mover da string para o balde, ou do balde de volta para a string, mas apenas se as pessoas em ambos os lados do canal concordarem.
Em vez de travar o valor em trânsito com hash- e time-locks, para pagamentos pequenos, Alice e Bob simplesmente movem o valor em trânsito para o balde de taxas (Fig. 8). Bob confia que Alice cooperará com ele para retirar o valor em trânsito do balde de taxas quando ele revelar a senha secreta de Carol.
https://nostrcheck.me/media/public/nostrcheck.me_3836418249379116631703528340.webp Fig. 8. Se as moedas em trânsito estiverem abaixo do limite de poeira, o mecanismo HTLC não pode ser usado porque a transação de estado do canal não seria minerada se fosse transmitida. Em vez de usar o mecanismo HTLC, as moedas em trânsito são despejadas no balde de "Taxa do Minerador".
https://nostrcheck.me/media/public/nostrcheck.me_3836418249379116631703528340.webp Fig. 8. Se as moedas em trânsito estiverem abaixo do limite mínimo ("dust threshold"), o mecanismo HTLC não pode ser usado, pois a transação do estado do canal não seria minerada se transmitida. Em vez de utilizar o mecanismo HTLC, as moedas em trânsito são depositadas no "Miner's Fee" (Taxa do Minerador).
Neste esquema alternativo, Bob transfere o valor em trânsito para um segundo compartimento de taxas que ele compartilha com Carol, prometendo entregá-lo a ela se contar a Bob a senha secreta. Carol revela o segredo a Bob, e juntos movem o pagamento do compartimento de taxas para o lado de Carol. Bob então volta para Alice, conta a ela o segredo de Carol e, se tudo correr bem, Alice coopera com ele para retirar o valor em trânsito do compartimento de taxas e colocá-lo no lado de Bob da sequência.
Ao contrário do esquema HTLC descrito anteriormente, este esquema depende da confiança. Por exemplo, Carol poderia revelar a senha a Bob, que poderia deixar o pagamento no compartimento de taxas e ainda assim ir a Alice e entregar a senha em troca de seu pagamento.
As opções de Carol nesse cenário são limitadas: ou ela não faz nada e aceita a perda, ou ela encerra o canal com Bob. No entanto, encerrar o canal com Bob não a deixa totalmente compensada, pois o valor que ela deveria ter recebido é enviado para um minerador!
Apesar de parecer quebrado, esse esquema realmente funciona razoavelmente bem na prática. Bob não tem um incentivo real para não dar o dinheiro a Carol. Se ele não devolver, ele não ficará em uma situação melhor (o minerador ficará com os fundos extras, não ele) e provavelmente em uma situação pior (Carol provavelmente fechará o canal, já que Bob se mostrou não confiável). O dano que Bob pode causar parece limitado ao valor do pagamento mais o custo de estabelecer um novo canal relâmpago.
Por que isso é significativo O segredo sujo do Lightning é significativo porque revela como a fricção da Camada 1 (L1) vaza para a L2, forçando soluções complexas e mal compreendidas¹ para o protocolo L2. A solução alternativa neste caso alterou a natureza "sem confiança" dos pagamentos do Lightning: para pagamentos acima do limite de poeira, nem Alice, Bob, nem Carol podem perder dinheiro devido às ações de suas contrapartes. Para pagamentos abaixo do limite de poeira, Alice, Bob e Carol podem perder dinheiro sem culpa própria. É um modelo de segurança fundamentalmente diferente do que as pessoas entendiam.
Alguém poderia argumentar: "estamos falando apenas de pagamentos pequenos, então quem se importa?" Eu não concordo com esse argumento por duas razões:
-
O plano de escalonamento do Core, usando o blockchain como uma camada de liquidação com taxas elevadas, aumentará o limite para o que constitui "poeira". Poeira são saídas que não podem ser gastas economicamente porque a taxa on-chain para gastá-las é maior do que seu valor. Com taxas de $100, a maior parte do salário mensal de todo o mundo é "poeira".
-
Perder vários pagamentos pequenos em rápida sucessão (por exemplo, devido a um ataque de roteamento no LN) poderia resultar em uma perda significativa.
Imagine um futuro em que a maioria dos pagamentos ocorra na Lightning Network, e as taxas de transação na L1 sejam consistentemente superiores a $100. As saídas de poeira abaixo de $100 na mainchain não têm valor porque custa mais gastá-las do que valem.
Agora a Lightning Network enfrenta o problema de que até mesmo pagamentos de $50 não são "sem confiança". No caso em que $50 estão abaixo do limite de poeira (o que seria uma política razoável considerando que $50 seria economicamente impossível de gastar na L1), então os HTLCs não podem ser usados para proteger o pagamento de $50. Os clientes podem perder pagamentos de $50 sem culpa própria.
No caso em que os desenvolvedores tentam contornar alguma "brecha legal" definindo o limite de poeira como $1 para que os HTLCs ainda possam ser usados, o efeito ainda é uma perda de $50 para o cliente, pois a saída não será economicamente gasta! Os clientes ainda podem perder pagamentos de $50 sem culpa própria.
Alguém poderia argumentar "bem, os nós de roteamento podem perder fundos dos clientes e esses fundos podem ser significativos em um futuro com taxas altas, mas os nós de roteamento são pares, não empresas." Eu também não concordo com isso porque o objetivo principal do roteamento de pagamentos do Lightning é ganhar dinheiro em taxas de transação em troca de empréstimo de liquidez. Já hoje, os desenvolvedores do Lightning abandonaram a ideia de que todos os usuários roteariam pagamentos; agora é incentivado que usuários normais usem canais não divulgados e nunca roteiem.
Em um futuro com altas taxas, um hub tem controle custodial efetivo sobre o dinheiro de seus usuários. Um usuário não pode liquidar no blockchain para recuperar fundos de pagamentos não protegidos por HTLCs. Além disso, se o saldo do usuário estiver na mesma ordem de grandeza das taxas on-chain, o usuário também está preso ao hub. Não vale a pena escapar de um canal "ruim", pois isso custaria ao usuário todo o seu saldo. Hubs também podem bloquear os fundos do cliente indefinidamente, recusando-se a rotear pagamentos a menos que certas condições sejam atendidas (por exemplo, desembrulhar as informações de roteamento de cebola para fins de AML/KYC). A única escolha do usuário é liquidar no blockchain e perder todo o seu dinheiro — o que não é uma escolha real! Hubs também podem roubar seus usuários na forma de taxas exorbitantes. Novamente, o usuário está preso e não tem escolha a não ser pagar se quiser acessar seu dinheiro.
Hubs significativamente conectados na Lightning Network, em um futuro com taxas elevadas na camada base, deveriam ser regulamentados devido ao controle efetivo que possuem sobre os fundos de seus clientes.
Gostaria de propor a hipótese de que o seguinte princípio existe:
Pagamentos na Camada 2, para quantias abaixo do que é economicamente viável na Camada 1, não podem alcançar uma natureza "sem confiança".
A eficácia do Lightning depende da liberdade da blockchain subjacente, alinhando-se com as expectativas dos usuários.
Isso é apenas uma das muitas razões pelas quais um futuro em que a maioria das transações ocorre na Lightning Network e a blockchain possui taxas elevadas será muito diferente do que as pessoas esperam. Outras razões incluem:
-
O Lightning dimensiona transações, não usuários. O custo de operar um nó completo de validação ainda será alto.
-
A fricção na Camada 1 afeta a fungibilidade na Camada 2; as moedas têm um valor dependente da posição.
-
Liquidez: a maioria dos "estados de riqueza" não é alcançável por meio de transações na Lightning. Falhas em pagamentos são inevitáveis.
-
Roteamento é difícil se o grafo de rede for extenso: os hubs da Lightning tenderão a se centralizar para reduzir problemas de roteamento e liquidez.
-
A experiência típica do usuário ao executar uma carteira não custodial sempre será complicada: os usuários precisam estar online para receber dinheiro, contratar torres de vigilância para monitorar fraudes em canais, assinar serviços de roteamento de origem para enviar pagamentos e fazer backup dinâmico de seus estados de canal contra corrupção de dados.
-
Risco sistêmico: uma quantidade muito grande de moedas precisa ser bloqueada em canais da Lightning (carteiras quentes) para fornecer a liquidez necessária.
-
As taxas agregadas dos mineradores na Camada 1 não serão suficientes para garantir a segurança da blockchain quando a recompensa por bloco se esgotar.
Esse texto apontar que LN não é “sem confiança” para pequenos pagamentos e que os fundos dos clientes poderiam ser redirecionados para o mineradores sem culpa do cliente. A crença amplamente difundida, mas falsa, dentro da comunidade BTC era que todos os pagamentos Lightning eram “sem confiança” por design .
-
-
 @ 599f67f7:21fb3ea9
2024-10-17 15:35:19
@ 599f67f7:21fb3ea9
2024-10-17 15:35:19Nostr proxy baten erabilera modu oso eraginkorra da internet banda-zabaleraren eta mugikorretan bateriaren kontsumoa optimizatzeko.
Proxy batek hainbat errelei-konexio konexio bakarrean biltzen dituenez, baliabideen erabilera nabarmen murrizten du, eta erabiltzailearen IP helbidea ezkutatuz pribatutasun-geruza bat gehitzen du.
Hona hemen nola funtzionatzen duen eta nola konfigura daitekeen:
Nola funtzionatzen du?
Nostr proxy batek hainbat erreleirekin konektatzen du. Errele horietara gertaerak eskuratu eta argitaratzen ditu. Bezeroaren aplikazioak WebSocket konexio bakarra ireki behar du proxy-ra, eta horren bidez proxy-ak konektatuta dituen errele guztiak eskuragarri izango ditu.

Irudiaren egiletza: Yonle 2023
Bezeroak konexio bakarra irekitzen duenez, datuak eta bateria aurrezten ditu.
Proxy-ak bezeroaren izenean erreleekin konektatzen denez, erreleek proxy-aren IP helbidea ikusten dute, eta ez bezeroarena. (Hala ere, proxy hornitzailearengan konfiantza izan behar duzu).
Erabiltzeko Modua
Nostr proxy bat erraz auto-ostata daiteke. Auto-ostatatzeko jarraibideak lortzeko, begiratu nostr:npub1x3azxuysp5vmfer4vgs4jn5tmfcx4ew8sh0qnev7gczljxsr7jwqa3g4el erabiltzailearen biltegi hau.
Auto-ostatzeko baliabiderik ez dutenentzat, Bitcoin Txoko-k komunitate-instantzia bat ostalaratzen du.
Erabiltzeko, gehitu besterik ez duzu:
wss://bostr.bitcointxoko.comzure errele zerrendara.
Orain ez duzunez zuzeneko konexioak behar, errele bikoiztuak ezabatu ditzakezu.
Ikusiko dugu elkar Nostr-en!
-
 @ bcea2b98:7ccef3c9
2024-10-17 14:47:01
@ bcea2b98:7ccef3c9
2024-10-17 14:47:01Sometimes you have to take risks to grow. What's the biggest risk you've ever taken that ended up paying off.
My biggest risk that paid off was moving to another country and starting a new life 10 years ago due to corruption and torture in my home country.
originally posted at https://stacker.news/items/728159
-
 @ 7ab1ed7a:f8e15275
2024-10-17 14:06:46
@ 7ab1ed7a:f8e15275
2024-10-17 14:06:46I'm proud and thankful to announce that funding has been granted by OpenSats to fund the development of the Nostr library for Arduino.
The fund will help with work on the development of the Arduino Nostr library as well as fund work on IoT related NIPs.
-
 @ 4ba8e86d:89d32de4
2024-10-24 23:36:47
@ 4ba8e86d:89d32de4
2024-10-24 23:36:47OP_CAT é um opcode simples, mas poderoso, que combina dois valores de entrada em uma saída. Originalmente, ele foi desativado devido a preocupações com problemas de memória, mas as condições mudaram. OP_CAT é um opcode que lida com a concatenação de valores de entrada, unindo dois valores em um. Embora possa parecer simples à primeira vista, suas possibilidades são amplas e intrigantes.
Especificação
O opcode OP_CAT opera abrindo dois elementos da pilha, concatenando-os na ordem em que estão empilhados e empurrando o elemento resultante de volta para a pilha. Dada a pilha [x1, x2], onde x2 está no topo da pilha, o OP_CAT colocará x1 x2 na pilha, onde '' denota concatenação.
Implementação
cpp if (stack.size() < 2) return set_error(serror, SCRIPT_ERR_INVALID_STACK_OPERATION); valtype vch1 = stacktop(-2); valtype vch2 = stacktop(-1);
if (vch1.size() + vch2.size() > MAX_SCRIPT_ELEMENT_SIZE) return set_error(serror, SCRIPT_ERR_INVALID_STACK_OPERATION);
valtype vch3; vch3.reserve(vch1.size() + vch2.size()); vch3.insert(vch3.end(), vch1.begin(), vch1.end()); vch3.insert(vch3.end(), vch2.begin(), vch2.end());
stack.pop(); stack.pop(); stack.push_back(vch3);
Essa implementação é baseada na implementação do OP_CAT em elementos.
O valor de MAX_SCRIPT_ELEMENT_SIZE é 520 bytes.
Notas
O OP_CAT existia na base de código Bitcoin antes do commit "alterações diversas" 4bd188c que o desativou. A implementação original funcionava da seguinte forma:
cpp // (x1 x2 -- fora) if (stack.size() < 2) return false; valtype& vch1 = stacktop(-2); valtype& vch2 = stacktop(-1); vch1.insert(vch1.end(), vch2.begin(), vch2.end()); stack.pop_back(); if (stacktop(-1).size() > 5000) return false;
Essas informações detalhadas sobre a especificação e a implementação do OP_CAT esclarecem como ele funciona e como as operações são executadas.
OP_CAT não é uma novidade, sendo parte das instruções do Bitcoin Script em versões antigas. Foi desativado devido a preocupações de aumento exponencial de memória na pilha de elementos. No entanto, desde que foi desativado, um tamanho máximo de 512 bytes foi fornecido para elementos de pilha, e isso também é aplicado ativamente hoje no Tapscript, que é o Bitcoin Script na atualização Taproot. O problema daquela época realmente não se aplica aqui, pois um script que desejasse criar elementos acima desse limite seria simplesmente inválido.
OP_CAT possibilita novas opções de assinatura, assinaturas Lamport com segurança quântica, cofres Bitcoin e convênios/CTV que determinam as condições de saída. Isso abre portas para métodos de escalonamento , Confirmação instantânea de transações on-chain , Livre mercado de sidechains, como Ark, e simplifica a implementação de BitVM para contratos inteligentes.
Várias aplicações possíveis para o OP_CAT, como covenants, verificação de provas SPV, proteção contra gastos duplos em transações não confirmadas, tornar o BitVM mais eficiente, realizar aritmética com números grandes, criar vaults e assinaturas resistentes a computadores quânticos.
Para reintroduzir o OP_CAT, seria necessária uma atualização (soft fork) nas regras de consenso do Bitcoin, o que exige planejamento cuidadoso. No entanto, a proposta atual é gerenciável e não apresenta as preocupações anteriores devido às limitações estabelecidas.
O OP_CAT promete ser uma adição valiosa à linguagem de script do Bitcoin, proporcionando um leque de possibilidades interessantes para desenvolvedores e usuários. A reintrodução desse opcode parece promissora, oferecendo um equilíbrio entre esforço e casos de uso potenciais, e ainda há espaço para discussões sobre suas vantagens e desvantagens.
https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2023-October/022049.html
https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2023-October/022049.html
https://github.com/EthanHeilman/op_cat_draft/blob/main/cat.mediawiki
https://medium.com/blockstream/cat-and-schnorr-tricks-i-faf1b59bd298
https://gist.github.com/RobinLinus/9a69f5552be94d13170ec79bf34d5e85
-
 @ 8947a945:9bfcf626
2024-10-17 08:06:55
@ 8947a945:9bfcf626
2024-10-17 08:06:55สวัสดีทุกคนบน Nostr ครับ รวมไปถึง watchersและ ผู้ติดตามของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
เมื่อวันที่ 16 กย.2024 มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ
นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint 0.15 - 0.2 ETH … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

-
Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
-
ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
- ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
- ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
- ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT 0.2 ETH
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH "code is law" smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-
 @ 4ba8e86d:89d32de4
2024-10-24 23:30:46
@ 4ba8e86d:89d32de4
2024-10-24 23:30:46Com o Boltz, os usuários podem trocar perfeitamente seus bitcoins entre camadas, por exemplo. usar produtos financeiros avançados ou gerenciar a liquidez de seus canais relâmpago. Os Boltz Swaps não têm custódia, o que significa que os usuários podem sempre ter a certeza de ter controle total de seu bitcoin durante todo o fluxo de um swap.
Swap da Lightning Network (LN) para Bitcoin Onchain utilizando a plataforma Boltz.
Basta acessar o site Onion da Boltz:
http://boltzzzbnus4m7mta3cxmflnps4fp7dueu2tgurstbvrbt6xswzcocyd.onion/
Também é possível visitar o site oficial em:
https://boltz.exchange/
https://nostrcheck.me/media/public/nostrcheck.me_4413004608613998691706870605.webp
https://nostrcheck.me/media/public/nostrcheck.me_6400873373279640511706870649.webp
Primeiro, selecione qual tipo de Swap deseja realizar, por exemplo, você pode escolher LN para Bitcoin Onchain. Em seguida, insira o endereço Onchain de sua carteira. Após isso, basta efetuar o pagamento da fatura LN com o valor necessário e o Swap será concluído com sucesso!
Criar Atomic Swap. O pagamento inclui taxas de serviço de rede e boltz Enviar Mín .: 50.000 , Máx .: 1.000.0000
Para melhorar a resistência à censura e a privacidade, o Boltz não está disponível nas lojas de aplicativos, mas pode ser instalado como Progressive Web App (PWA) em todos os dispositivos Android e iOS, bem como em computadores desktop.
Como instalar o Boltz como App PWA.
Android.
-
Abra https://boltz.exchange/ em um navegador móvel como chorme ou Vanadium abra o menu do navegador e toque em "Instalar aplicativo": https://nostrcheck.me/media/public/nostrcheck.me_6529645890412951071706872223.webp
-
Confirme em "Install": https://nostrcheck.me/media/public/nostrcheck.me_1285765778020048231706872279.webp
-
Agora você encontra o Boltz como ícone do aplicativo na tela inicial, que pode ser usado como qualquer outro aplicativo.
iOS
-
Abra https://boltz.exchange/ em seu navegador móvel Safari e toque no botão de compartilhamento https://nostrcheck.me/media/public/nostrcheck.me_6654634165994432521706871151.webp
-
Toque em "Adicionar á tela incial ": https://nostrcheck.me/media/public/nostrcheck.me_4387192956979181391706871163.webp
-
Confirme tocando em "adicionar ": https://nostrcheck.me/media/public/nostrcheck.me_1403675023106875721706871174.webp
-
Agora você encontra o Boltz como ícone do aplicativo na tela inicial, que pode ser usado como qualquer outro aplicativo.
Desktop
- Aqui está um exemplo de como instalar o Boltz como aplicativo em um computador desktop Ubuntu usando Chromium: Abra https://boltz.exchange/ e clique no ícone de instalação que aparece automaticamente:
https://nostrcheck.me/media/public/nostrcheck.me_3169379622874819051706871546.webp
-
Confirme clicando em "Install": https://nostrcheck.me/media/public/nostrcheck.me_3547123478071766331706871554.webp
-
Agora você encontra o Boltz como ícone do aplicativo em sua coleção de aplicativos: https://nostrcheck.me/media/public/nostrcheck.me_3356870245715316401706871564.webp
Também pode executá-lo localmente:
Incentivamos nossos usuários técnicos a verificar o código e executar o aplicativo da web localmente a partir da fonte, seguindo as instruções abaixo.
Dependências.
Certifique-se de ter o Node.js LTS e NPM mais recente instalado. Recomendamos usar o nvm para gerenciar instalações do npm: nvm install --lts
Execução.
Clone o repositório, mude para a pasta do projeto e execute " npm install " para instalar todas as dependências. Em seguida, execute " npm run mainnet " e " npx serve dist " para iniciá-lo.
Abra: http://localhost:3000
no seu navegador e comece a trocar!
https://github.com/BoltzExchange/boltz-web-app#run
https://docs.boltz.exchange/
-
-
 @ 8947a945:9bfcf626
2024-10-17 07:33:00
@ 8947a945:9bfcf626
2024-10-17 07:33:00Hello everyone on Nostr and all my watchersand followersfrom DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
On September 16, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.
Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from 0.15 to 0.2 ETH

-
The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
-
I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
- I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
- I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
- I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of 0.2 ETH. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
This raised a red flag, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you.
My Perspective why I Believe This is a Scam and What the Scammers Gain
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time Take care
Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen
-
 @ bcea2b98:7ccef3c9
2024-10-16 21:33:15
@ bcea2b98:7ccef3c9
2024-10-16 21:33:15When people talk about financial freedom, they often focus on investing, saving, or building wealth. But sometimes, the most valuable skills or habits are the ones that aren’t talked about enough. Maybe it’s discipline, emotional resilience, or even something unexpected like negotiation or patience.
What do you think is the most underrated skill or habit for achieving real financial independence?
For me, the most underrated skill is delayed gratification. It’s not just about resisting the urge to spend money now, it’s about thinking long-term in everything you do. When I first started learning about Bitcoin and freedom, I realized that the biggest hurdle wasn’t just making money, but knowing when to hold off on spending it for the right opportunities.
originally posted at https://stacker.news/items/727313
-
 @ 4ba8e86d:89d32de4
2024-10-24 23:20:51
@ 4ba8e86d:89d32de4
2024-10-24 23:20:51VeraCrupt foi lançado em 2013 como um fork do projeto TrueCrypt descontinuado. Desde então, o VeraCrypt tem passado por diversas atualizações e melhorias de segurança, incluindo a correção de problemas identificados por auditorias de código do TrueCrypt. O VeraCrypt inclui implementações otimizadas de funções criptográficas de hash e cifras, o que aumenta o desempenho em CPUs modernas. O software permite criar e gerenciar volumes criptografados em computadores ou dispositivos de armazenamento externo, com suporte para vários algoritmos de criptografia e recursos adicionais, como proteção contra ataques de keylogger e ocultação de volumes , tem opção de segurança robusta para proteger seus dados.
Quando você cria um volume criptografado no VeraCrypt, o software cria um arquivo virtual que funciona como um disco rígido criptografado. Esse arquivo é montado como uma unidade lógica no seu sistema operacional e pode ser acessado como qualquer outro disco rígido.
Antes que você possa acessar o volume criptografado, você precisa fornecer a senha correta. A senha é usada para desbloquear o arquivo virtual criptografado e permitir que o sistema operacional acesse o conteúdo. O VeraCrypt suporta vários algoritmos de criptografia, incluindo AES, Serpent e Twofish, que podem ser selecionados pelo usuário ao criar o volume criptografado.
O VeraCrypt também oferece recursos adicionais de segurança, como proteção contra keyloggers, que podem registrar as teclas digitadas no teclado para capturar senhas. Ele faz isso fornecendo uma interface virtual para digitar senhas, o que impede que os keyloggers capturem a senha real. O VeraCrypt também permite ocultar volumes criptografados dentro de outros volumes criptografados, o que fornece uma camada adicional de segurança.
O veracrypt proteger informações confidenciais armazenadas em dispositivos de armazenamento, como discos rígidos, unidades flash USB e cartões de memória, contra acesso não autorizado. Se um usuário estiver executando o Tails a partir de uma unidade flash USB, e o disco rígido estiver criptografado com o VeraCrypt, o Tails não terá acesso ao conteúdo do disco rígido, a menos que o usuário monte o volume criptografado do VeraCrypt e forneça a senha correta.
No entanto, é importante lembrar que a criptografia do disco rígido por si só não garante a segurança completa do sistema. Os usuários também devem tomar outras medidas de segurança, como manter o sistema operacional e o software atualizados, usar senhas fortes e não compartilhá-las com ninguém, e tomar cuidado com o acesso físico ao computador ou dispositivo de armazenamento externo.
https://veracrypt.fr
https://github.com/veracrypt/VeraCrypt/
-
 @ bb0174ae:75f7239a
2024-10-24 21:23:55
@ bb0174ae:75f7239a
2024-10-24 21:23:55What is Cyphermunk House? It is everything that is unprovided. It is the education that is never taught. It is the culture that is never commissioned. It is the space for the community that was never allowed to flourish because an equitable economy was never allowed to grow. It is a space to BE YOUR OWN BANK and a space to STAY HUMBLE.
Cyphermunk House is London’s Bitcoin beacon. Providing sanctuary from the mainstream; from the politics of division, the brainwashing of legacy media, the predictive programming of film, the ‘three-quarter reptiles’ of music, the ‘shock value, indignation and existential angst’ of modern art and the centuries long corruption and exploitation of central banking. It is counter culture in extremis. A hotspot of no fear. A 21st space where fiat pastimes are secondary and pleb living is primary.
What is bitcoin? Cross the threshold. How do you obtain it? Take a seat. Want to stack? Let’s begin. Dive into the mathematics of hope, the code of change and the magic of self-sovereignty. In here we educate, providing knowledge to match the student whether you are a stone-cold newb or a humble stacktivist. In return we learn that there are still so many who are yet to realise that money is broken, issuance matters and a bitcoin can be divided into things called sats. In other words, there is work to be done.
Work that is evolving like that which inspires us. Can we educate? Can we provide space for people from all walks of life? Can we provide the seeds for discussion, the platform for ideas and the spectacle that confronts the issues in our society? Can we get a former Minister of State to laser eye his image?
So far, we are meeting these challenges, with more newbs through our doors than we could ever imagine, lured in by the rabbit of an upended banknote and their own curiosity. What the hell is that? And what's going on inside this rabbit warren of a building a mile’s crow flight from the life supported heart of British financial might.
The ‘what’ is huge. Education. Culture. Freedom. And community. That same orange cocktail that bitcoin is pouring all over the world. Standing in direct opposition to the trends of indoctrination, centralisation and isolation that have pushed the group to the fringe and questioned the very idea that humans are social beings. In our world, meetups, conferences and real-world spaces are thriving. Education is pleb-led and free. And our culture is king.

I have witnessed the artistic offerings of this capital a lifetime over; dance on rooftops, songs beneath the river and Shakespeare performed by a man and a cast of sheep. In three short decades I have worked across music, theatre, film and art, and now find myself at the helm of Cyphermunk House. What is being created within these walls is more inspiring and exciting than anything the Tate has ever shown me, or the West End, or the Dome. This is the edge of the cultural moment. Lightning sharp and electric.
Because our culture does more than entertain. It informs. And transforms. And it is happening everywhere, simultaneously. And in this tiny postcode of West Central London, it is happening hard. We are 'Privacy Defenders'. We will expose 'The Ugly Reality of War Crimes' and we will declare that 'Coin Mixing is My Right' and yours too as we work towards a 'Humanity in Consensus'. Inspired? Come along and chuck it on the walls in the paradise paint of a world being built from the ground up. For this is the culture of code and it will not be put back in the box.

And yes the space is temporary, six more months perhaps, but its temporality is tangible forever, nostr makes it so. Our records permanent, our doors always open. Always sharing knowledge, wisdom and advice. While in these moments of tangibility, these blocks of time in meters of space, we will fire up the beacons and summon the zaps, for bitcoiners, artists, outcasts and dreamers to the temporal dance of rebellion that burns behind these doors.
“In the same way El Salvador felt way ahead of its time – a nation state adopting bitcoin as legal tender. This feels like it’s a cycle too early too. Surely, we shouldn’t have something this good till the 6th epoch." - Si, Bitcoin Events UK
And when we close our doors and move to pastures new, we will not forget the power we are finding - the power to redefine the rules. For this is how to use bitcoin and release the burden on the current system. It stands as a testament to the power of code that you can run an entity, without barriers, without red tape, without announcing your names or identity, where you create the rules.
And so we invite you to the Bitcoin Culture Festival at Tooting Market, The Dockside Vaults and Cyphermunk House, and an explosion of culture from the We Are 2140 collective. Together we will host a brand-new exhibition; the Culture of Code and stamp a sequence of blocks with so much creativity that no Londoner will miss it.
These are the signals of hope found in a civilisation mathematically backed by a money that extracts nothing from you. Embrace them. Support them - your fellow plebs and meetups. Network, connect and build. There is so much more to do and so much more to learn, but for now I've learnt this much - align your passions with bitcoin and every moment is a pill.
Onward plebs.
FIND OUT MORE
OUR PARTNERS / SPONSORS
-
 @ 472f440f:5669301e
2024-10-16 01:57:41
@ 472f440f:5669301e
2024-10-16 01:57:41Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice.
This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative.
These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin.
Since 2016: +46% in USD -99% in BTC
Since 2020: +34% in USD -70% in BTC
The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them.
Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter.
What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line.
Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow.
The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way.
Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished.
In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial.
We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years.
There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer.
Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it.
Final thought... Sinus congestion sucks.
-
 @ 95a69326:6ac402e2
2024-10-24 20:09:01
@ 95a69326:6ac402e2
2024-10-24 20:09:01That is true for the rate of growth of addresses, of hashrate, and even of price.
None follow an exponential curve.
And that is fantastic news, because it’s a reality check on where we are today with Bitcoin adoption, and how to actually make it happen faster. Let us collectively break the culture that has formed around the S curve. The very idea that adoption is exponential.
It’s the hopium that keeps some going, waiting on the #OmegaCandle chanting NGU and hodling onto their Bitcoin like it’s their “precious”.
So much of Bitcoin’s narrative is centered around an imminent inflection point, a face-melting exponential curve. We will wake up one day (soon!), Bitcoin will be over 1m per coin, the Federal Reserve will be blown into pieces, and all Bitcoiners around the world will come together to sing Kumbaya.
Then one more year passes, then one more year passes, then one… Just one more! It’s around the corner guys! Just hold on to your Bitcoin, and everyone else can have fun staying poor.
Don’t get me wrong, Bitcoin is a marvellous savings technology. Once you see it, you understand it’s the best way to safeguard your financial future.
But this is not a game measured in weeks, or months. It’s a game measured in years, decades. And I am starting to believe that the reason so many Bitcoiners still have an unrealistic expectation of the short term adoption rate of Bitcoin, is exactly because so many still believe Bitcoin growth follows an exponential.
But that mentality is actually harming Bitcoin adoption. When you ground your belief system into an exponential, it also becomes very easy to believe the path is set. That you can sit back, and wait. That it’s “any day now”.
And you’re wrong! The path is not set, the path is still being written, and at the moment it’s being increasingly written by some suits at BlackRock. So extend your time horizon.
Stop believing hyper-Bitcoinisation is around the corner, and start asking yourself: what can I do to make Bitcoin adoption happen?
The truth is, if you want Bitcoin adoption, hodling Bitcoin won’t get you there. Spending it, and getting more people to use it will.
No, I’m not trying to psy-op you into selling your Bitcoin. And the idea that spreading Bitcoin promotes adoption is not just theory.
Let’s go over some data.
If you’re allergic to charts and data, maybe stop reading here, and ponder on the above question for a little while.
But if you’re not, take a look at this chart:
This is what it looks like when you chart the ratio of Bitcoin’s hashrate, price and number of addresses. Bitcoin is a beautiful combination of power laws.
We’re not making any predictions here. This is what is, and what has been since Bitcoin’s Genesis Block. It’s Bitcoin’s DNA. And what it tells us is that there is a known, quantifiable, symbiotic relationship between Bitcoin’s number of participants (\~addresses), Bitcoin’s security (hashrate) and Bitcoin’s price.
What else do we know?
Bitcoin’s address count (\~ participants) grows at a rate of x³, where x is time. That’s the growth rate of viruses, it’s the growth rate of social networks. Metcalfe’s Law says that the value of a network is approximatly equal to the square of its participants. And with Bitcoin that checks out. Bitcoin’s price grows at a rate of x⁶, which is x³ (participants) squared (again refer to Giovanni’s work for the in-depth data analysis).
That’s pretty solid data to say that:
Bitcoin’s price is not exponential The number of participants in the network has a quantifiable impact on its price So, Bitcoin growth follows a power law. And that’s fast! But compared to an exponential, that’s slooooow.
“But ETFs are here! NgU!! Scarcity!! Bitcoin will break all your models to the upside!!!”
It get’s tiring, and you know it.
Before you get all excited about ETFs buying up all the Bitcoin, leading to the mother of all supply squeezes and sending Bitcoin to the moon, realise this: the number of people owning Bitcoin has a bigger impact on price than supply and scarcity.
Sorry Stock2Flow fanatics, I’ll say that again. The number of people owning Bitcoin has a bigger impact on price than supply and scarcity.
And, to be fair, ETFs are bringing a lot of new network participants. But HODLING isn’t. And a lot of the Bitcoin that is going into the ETFs, is on a one way street to be hodled forever.
So going back to the big question: What can I do to accelerate Bitcoin adoption?
The answer is simple: get more people using Bitcoin.
Ok, that sounds obvious, and you already knew that. So this post was pointless.
But what is the pre-dominant narrative for getting more people to use Bitcoin today? It’s NgU, it’s scarcity, in other words, it’s all the wrong things. You won’t bring more network participants by buying up as much Bitcoin as you can to stash it away for the next 20 years.
Oh, and you won’t retire in 2 years for hodling that 0.1BTC either.
You’ll beat inflation, by a healthy margin, and you will get more purchasing power over time.
But the truth is, from Bitcoin’s adoption perspective, you’re a rent seeker.
You’re living off the work of those that are actually doing something to push Bitcoin’s adoption, ultimately having a real impact on its demand, and thus its price.
Who are they?
The educators teaching Bitcoin to new people. The meetup organisers bringing people together to talk about Bitcoin. * Those building circular economies. The protocol devs working on improvements to scale Bitcoin. The app devs working on making Bitcoin usable in every day life. The people spending Bitcoin on their everyday expenses. Those are the people pushing forward Bitcoin adoption.
Heck, even the wall street guy that orange pilled Larry Funk has done more for adoption than the perpetual holder waiting on the day he’ll be a citadel king.
I’ll end this rant here, and if there’s only one thing you remember from it let it be this:
Stop hodling Bitcoin to your death. Spend it, spread it, replace it. Support circular economies and Bitcoin educators, find local stores that accept it, get more people actually using the thing and you might just get to enjoy hyper-Bitcoinisation in your lifetime.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
Bitcoin Power Law refs:
[Modelling Bitcoin Growth with Network Theory] https://bitposeidon.com/f/modeling-bitcoin-growth-with-network-theory…
[Intro to the Power Law] https://bitposeidon.com/f/simple-introduction-to-the-power-law-theory
-
 @ 83794dfe:e46c6636
2024-10-24 20:08:28
@ 83794dfe:e46c6636
2024-10-24 20:08:28i can post a note from my desktop to Nostr using Comet @captv
iuihuhjhjhjk
-
 @ eac63075:b4988b48
2024-10-15 20:18:52
@ eac63075:b4988b48
2024-10-15 20:18:52Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy.
https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD
Centralization and the Exclusivity of Nostr
Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche.
Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation.
Individual Freedom and Data Protection
A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom.
The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this.
Hyperbitcoinization and the Illusion of Store of Value
Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth.
However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value.
The Role of the Community in Bitcoin's Development
Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all.
It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence.
Sidechains, Second Layers, and the Lightning Network
Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets.
The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional.
The Fight Against Centralization on the Internet
Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters.
Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control.
The Future of Bitcoin and the Need for Action
The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility.
Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority.
Conclusion
Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom.
The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy.
-
 @ 0e501ec7:de5ef3a4
2024-10-24 20:03:28
@ 0e501ec7:de5ef3a4
2024-10-24 20:03:28Ik maak even een kleine sprong in de tijd, stichting Elzeard bespreek ik later nog ;)
Vandaag (24/10) vertrokken we bij Patsy en Els. Patsy is de meter van Tim, en hij heeft een kleine traditie om altijd bij hun langs te gaan als hij in de Ardennen fietst. Ze kochten ongeveer tien jaar geleden een wei in Marcourt, en besloten op een gegeven moment om daar te gaan wonen en een huis te bouwen. Ze hebben een bijna-passief woning, een leuke moestuin en veel fruitbomen, en op de wei staan er schapen van een zekere Eddy. Ze spreken aardig wat frans, en zijn zeer betrokken bij het sociale leven in het dorp! Niet zoals de tweede-verblijf-vlamingen die in grote getallen rust opzoeken in de Ardennen dus. We hielpen bij hun in de tuin, brandhout zagen en kappen, hooi leggen in de moestuin (ze doen geen bodembewerking! Voeren enkel hooi aan om de structuur te verbeteren en kruid tegen te werken). Daarnaast hielpen we ook met wat bomen en struiken te verplanten, en deed Tim zijn job als fietsenmaker. We aten verrukkelijk in de avond, van de heerlijke kookkunsten van Els. Een van de avonden (triggerwarning: vlees eten) was het een gerecht met vlees van een Lam, een van de diertjes die op de wei zelf geboren was en gegroeid. Tot het dus geslacht werd, en Patsy en Els er hun deeltje van kregen/kochten. Ik vond het wel een heftige ervaring om dat te eten, maar het voelde niet persé slecht. Denk ik. Al zag ik wel af en toe een Lammetje door een veld huppelen als ik met mijn ogen knipperde.
Het waren fijne dagen bij hun, maar het deed ook deugd om weer verder te gaan: gewoon op de fiets, en niet meer te hoeven socialiseren. In het begin van de dag moest ik nog even op gang komen, had wat pijn aan mijn rug van een forse beklimming zonder opgewarmd te zijn (het was ook een koude ochtend). Ook was Tim een paar keer een beetje fors (ms was het ook voor hem ochtend, kan zijn :) )waardoor ik mij even niet heel top voelde, moe en wat verdrietig, niet zo geborgen en energiek. Ik begon te twijfelen of ik wel sterk genoeg was voor deze reis, om met Tim mee te kunnen, om zonder veilige haven te zijn. Na een tijdje chieken en tobben, probeerde ik naar het landschap te kijken, en dat als veilige haven te zien. Niet zo heel makkelijk, geen vanzelfsprekende veilige haven, je moet eerst voorbij het landschap als decor, en het landschap als vluchtige voorbijgaandheid. Maar het hielp wel. De glooiingen van de Aarde, hun heuvels, de Bomen in de wind, de zachte Wolken met hun zwevende texturen, de verbaasde Koeien, het is ook wel thuis. Ik ben ook hier thuis. (Deze avond toen we begonnen te koken kwam een Reetje op bezoek, keek even heel doordringend en stoof rond ons weg. Dag Reetje; tot ziens.) Daarna overwon ik mijn obsakels en begon ik erover tegen Tim, niet gemakkelijk, maar was wel heel fijn, hij begreep het wel, luisterde wel. Zei ook dat hij zich al afvroeg of er iets was (zie je wel). Daarna voelte ik mij dus helemaal beter, en hadden we nog een zalige fietstocht. De zon kwam erdoor, het was warm, de heuvels gingen omhoog en omlaag, zoeffff. Ergens verloor ik mijn handschoenen, die had ik los op mijn bagage gelegd en was dan vertrokken. Dus: terug! Gelukkig lagen ze niet al te ver weg, ze waren pas bij een grote boebel van mijn bagage gekieperd. We fietsten uiteindelijk 67km, en stegen bijna 1000m. Echt wel de zwaarste tocht tot nu, maar fysiek voelde het al een pak minder lastig als in de eerste weken. Mischief ben ik dan toch (fysiek) sterk genoeg? We passeerden onderweg nog het meest cute (cuteste?) Bio-winkeltje ooit, een klein kamertje vol met verse groenten, waar we waterkers en eitjes en nog een brood voor morgenvroeg kochten. Nu liggen we hier in een bos naast Sovet, en gaan we morgen weer verder. Slaapwel!
-
 @ bcea2b98:7ccef3c9
2024-10-15 16:37:10
@ bcea2b98:7ccef3c9
2024-10-15 16:37:10I've always been interested in Eastern philosophies and Stoicism. When I first heard about Bitcoin, it seemed to align well with the beliefs, ideas, and lifestyle I was already living. I try my best to be self-sovereign, practice a low-time preference, and delayed gratification. I've also learned so much about Linux, servers, etc...
I'm curious to hear what skills you have gained from Bitcoin, or how it has changed or aligns with your lifestyle.
originally posted at https://stacker.news/items/724982
-
 @ 83794dfe:e46c6636
2024-10-24 20:01:44
@ 83794dfe:e46c6636
2024-10-24 20:01:44i can post a note from my desktop to Nostr using Comet @captv
-
 @ 4fda8b10:7bbee962
2024-10-15 13:56:47
@ 4fda8b10:7bbee962
2024-10-15 13:56:47Takeaways from Bitcoin Amsterdam 2024
The bitcoin conference in Amsterdam to me is my typical yearly check in with the crypto scene. From a distance, not much has changed since last year. What struck me most was the correlation between the exchange prices and the amount of visitors, I had the feeling the crowd was about twice as big as last year during the opening and high profile talks.
From my personal experience, the increase of audience also brought some dilution to the hard core maximalist anarchist-ness of the event. The overall vibe amongst the attendees was more friendly and open. This also increased the value of the event for me, as I try to broaden my network, get different perspectives and learn more about what interests people in the crypto space.
This year was also marked by my involvement in the Nostr side events, I was asked to give a live performance at the Nostrdam Meetup October 2024 which went over very well and also acted as a nice conversation starter during the rest of the conference. I was also slightly involved in the organisation of the Nostr booth, but credits go to the awesome volunteers that made that happen. It was a bit of a shame that the Nostr booth was tucked away all the way in the back of the (commercial) expo hall, it would have been nice to promote the Nostr initiative to the social community area next to the satoshi radio / connect the world community area
For me the biggest takeaways were the insights I got from the people I’ve met, all from different industries with different perspectives on both technology and involvement. I tried to specifically reach out to (former) CTO’s, which led me to write and share this piece on that particular role. Of course shaking hands and catching up with people I only see once a year is great, and reminds me of the vibe and my experiences at the Fronteers conference.
From a technical point of view I was most inspired by the advancement of AI agent technology and the possibilities of programmable micropayments via de lightning network. Michael Levin showed us that the http spec already has a 402 status of “payment required” and that basically all the required infrastructure is already in place to allow both humans and ai agents to use the lightning network to pay for access to compute or resources using this statuscode and an api gateway such as lightning labs aperture.
talk: HODLing Is Hard: Fundamentals, Cycle & On-Chain Analysis by rational root
- bitcoin is already competing in market cap with other currencies
- amount of euro is exponentially increasing
- from 8 to 16 trillion euros since 2009, but having a real hard cap in btc is fundamentally different
- inflation
- euro lose 20% in 5 years
- bitcoin also loses purchasing power, but only 10%
- in current system, we always need to take on maximal debt, instead of saving
- two things can happen
- we get into overvalued price levels
- we get into recession
- recession would only mean a shift in the start of the 4 year cycle
panel: Endless Possibilities: Reusing Heat From Miners
- people
- 21energy Maximilian (obwexer)
- Bert de groot (bitcoin Brabant)
- Brad Tom (mara)
- perspective: coming from energy to bitcoin is very different and much faster with implementation than the other way around
- 95% of heat can be captured from miners, much higher in comparison to AI
- being able to balance the grid because you can turn off the bitcoin miners
- ”heatbuffers” → heat is still available when power source goes down
- common objections:
- Crypto is hard to understand
- for large industrial clients, heaters, public image of bitcoin (often a door closer)
- people don’t see that miners consume electricity and pay for it.
- If mining is closed down in Europe, the energy prices will spike because the energy will not be payed for anymore
panel: How to Guard Privacy Tools & Developers
- Dorien Rookmaker & Sjors proviost
- chat control
- topic keeps returning, and is highly distracting for progress
- Parliament wants Netherlands to speak against chat control
- initially they want to just, scan messages now want to install malware before encryption
- it is distracting Sjors from working on bitcoin
- samurai and tornado are different cases
- tornado cash is harder because it is also a smart contract with custody over funds
- samurai is easier: if you don’t have custody, are you responsible for the results of the code?
- will decide wether whether non custodial systems are ok or not
- micah interpretation is quite vague
- the current Denmark case:
- if you are rebuilding an interface for a smart contract, you are responsible for implementing all the legal guardrails that apply to securities governance?
panel: NOSTR: Freedom of Algorithmic Choice
- will casarin, mcshane, martti malmi (Sirius iris.to)
- arc (alternative layer on top of bitcoin, like lightning but without channels)
- aha moment: when seeing the unsiloed experience between nostr apps
- were trying to create a town square, so we need to deal with spam
- social media platforms have stagnated a bit, nostr is innovating far more quickly
panel: Transactions As Bitcoin’s Key Growth Metric
- Stephan nilov
- classical developers don’t know about money and bitcoin development is harder
- total addressable market is highest in btc, biggest number of possible users
- bitcoin companies don’t benefit from tokens that are typically exchanged for vc money
- users are not looking for payments, they are looking for digital property and other things that Ethereum network offers
- Stephan Livera
- there is a known, slow pace at which bitcoin will be adopted
- btc market is only 1.2 trillion dollars compared to USD 30 trillion
talk: Making Bitcoin Quantum Resistant by hunter beast
- surmount.systems
- explaining the threat of quantum computing
- problems
- key size: larger signature required
- proposal: transaction field attestation
- 256 bit number key, possibility to factor the private key out of this
- introducing p2qrhash
- segwitv3
- satoshishield
- in layman terms:
- quantum safe upgrades to bitcoin protocol are proposed
- we need to introduce a software upgrade
- requires a soft fork, opt in
- possible advantages of quantum in crypto
- allow us to sign signatures in a way that is unbreakable
- 514 qubits are needed to break something
talk: Lightning and AI: Where the Bots Pay You by michael levin
- two use cases for bitcoin adoption
- people that don’t have access to fiat
- things that can’t be handled by fiat systems
- large language models
- current phase: big adoption
- next phase: agentic ai
- costs of ai
- compute 400% more (ben bajarin)
- algorithm training excess 10 billion dollars
- data
- costs implications
- cost of serving answers is 0
- cost of serving ai query is not 0
- cost for everyone in the world
- payments in AI
- now
- pay per call
- data
- accessibility
- agents
- agents must be able to do things that cost money
- now
- payment system for AI
- globally accessible
- near instant
- final settlement
- internet native
- authentication mechanism
- personalise access (simple queries for lower tier model)
- easy to implement
- L402 protocol
- 402 payment required in http spec
- reverse proxy to have 402 in front of APIs
- aperture is lightning labs implementation
- all available right now, adoption starting
- fewsats, sulu, open agents / plebai
- pay with lightning
- challenges
- do these payments with stablecoins instead of lightning (hence taproot assets protocol)
- cases
- agent bots can pay for real world resources
- taproot assets issue assets on bitcoin allow transfer of
- references
- L402.org
talk: Bitcoin is Cypherpunk by Aaron van Wirdum
- is bitcoin still Cypherpunks ?
- on one hand we see a push to regulation and frameworks to govern btc
- on the other hand we are arresting developers for writing code
pitches: Bitcoin Amsterdam Pitch Day: Presented by GoBTC
- umoja
- ceo Robby greenfield
- LST smartcoin, deflationary by design
- competes with pools such as lido and rocket pool, but supports multiple coins, including liquid hashrate
- 30% liquid hashrate returns (!)
- compliance micah
- disaster scenarios
- black swan event → automatic exit out
- magisat
- trading tools for mempool snipers
- support for runes
- volume on bitcoin nft’s is on certain days higher than nft’s on ethereum
panel: Crossing the Boundaries Between Bitcoin & Fiat
- Christian Rau (Mastercard) & Remi destigny (bitrefill )
- liberation is great, but protocols don’t take customer service into account, chargebacks and rewinding mistakes etc
- we aim to smooth process by issuing cards that sell your Bitcoin just in time on the backend
talk: Gold & Bitcoin: Friends, Not Foes by Paul Buitink
- premise “the financial system is crumbling”
- there is too much debt
- emerging markets lost confidence in western currencies
- freezing Russian assets is shooting ourselves in the foot, as it shows the world you might not want to hold too many dollars that can be easily seized
- record gold buying by central banks in 2022 2023 2024
- gold: 17 trillion marker cap, compared to bitcoin 1.3 trillion
talk: Austrian Economics, Hard Money & Bitcoin Cycles, Willem Middelkoop
- ”we are on the road towards hyper inflation and collapse of financial system”
- central bankers are pretty smart and very aware
- this is why they accumulate gold
- when system collapses, central bankers will play the gold card, not the bitcoin card
- US is preparing for big conflict with Russia and china
- then you can’t use IMF monetary reset
- Asia leadership is the same as US and Russian leadership: they want to stay on control
- all have about similar gold (per Capita) in their central banks vaults to avoid hyperinflation
- IMF said to el salvador: you need to reign down your bitcoin position
- once central bankers start diversifying (e.g. to bitcoin ) they will strain their own system. The incentives are against adopting bitcoin
- watch out for when on and offramp get blocked / repressed
- think about diversifying to Dubai, “the new switzerland"
- "bitcoin is the best money ever. fact”
- superior to gold, because you can store your wealth independant of location
- more scarce than gold
- but from central bank point of view, gold is superior to bitcoin
- younger generation gets this from the start
talk: The Future Will Be Bitcoinized by Elizabeth stark & Rockstar Dev
- stablecoins
- taproot assets protocol
- there is a demand for stablecoins and apps on stablecoins
- 11 trillion dollars in stablecoins
- protocol allows payments in other assets such as stablecoins that use bitcoin/lightning liquidity
- Elizabeth believes this allows stablecoiners to get interested in the underlying bitcoin layer
- Available now:
- bridging tether and lightning
products stumbled upon
- Meshtastic
- Flipper
- Noderunners led matrix panel
- 21energy bitcoin heater (1k s9, 3,5k s19)
- angor.io by dangershony on nostr
- bitcoinclock by Djuri
canonical link: https://notes.peterpeerdeman.nl/Bitcoin-Amsterdam-2024
originally posted at https://stacker.news/items/724785
-
 @ a367f9eb:0633efea
2024-10-24 19:46:10
@ a367f9eb:0633efea
2024-10-24 19:46:10In the corridors of power in board rooms, lecture halls, and legislative chambers, Bitcoin is no longer an enigma resigned to just technology or economics enthusiasts.
After a decade of gradual adoption, Bitcoin is an innovation invoked in political debates, presidential speeches, quarterly earnings reports, and is now the most recognized “crypto” by anyone with an Internet connection.
And as adoption has grown, the ecosystem has grown with it, sprouting all kinds of various exchanges, hardware signing devices, applications, and much more. Even betting on political outcomes is now enabled by Bitcoin.
With more liquidity pouring into the protocol and people using Bitcoin as an investment or as a currency to buy and sell things, it is inevitable that rules and regulations will be introduced to set the rules of the game and to try to protect consumers.
The rules of the game
From the federal government down to state and sometimes municipal jurisdictions, there are now plenty of laws on the books that give direction to citizens on how their bitcoin is taxed, what rules exchanges must follow, and whether you can mine it in a certain area.
Think money transmission licenses, capital gains taxes, environmental permits, accounting standards, and regulatory guidance to institutions. With more yet to come, it is prudent for those of us in policy and business to advocate for the best policies that will empower bitcoin holders and entrepreneurs while ensuring a base layer of protection. We should also make the case for why Bitcoin is different and shouldn’t be pigeon-holed to just yet another financial product.
While many new legislative efforts are gaining steam in the House of Representatives in Washington or in state capitals, both positive and negative, we should never lose sight of one of the most unique qualities of Bitcoin that sets it apart from any other technology or money in the world: self-custody.
With Bitcoin, individuals have the ability to sovereignly hold their money without counterparties and censorship risk. By holding one’s own keys, simplified in 12 or 24-word seed phrases, people can claim ownership over their small unlocked portion of the Bitcoin blockchain at the total exclusion of anyone else. This is one of Satoshi’s most brilliant gifts in the code.
As digital cash, bitcoin cannot be unilaterally usurped or confiscated from a bank account. Its value is the representation of a true free market set by buyers and sellers, and those who own the keys are the only ones who can move the units from one address to another.
There is always the risk of physical theft, either by so-called 5 dollar wrench attacks or seed phrase compromise, but the point remains that the ownership model of Bitcoin makes it unique. As long as a holder is using their own keys to move or safeguard their bitcoin, we should also be clear that any legislative proposal that aims to restrict the movement or possession of bitcoin is beyond the pale.
Self-custody as the prime directive
As policy advocates who seek to influence smart, defensive rules on Bitcoin, that means that our prime directive must be protecting, defending, and demarcating self-custody from other custodial solutions that may exist in the market. Self-custody, as a practice, an innovation, or a method of possession, is nonnegotiable.
We know there will be stringent regulations on institutions holding bitcoin on behalf of their customers or products that custody bitcoin, and that is fine and likely necessary. There are well-founded concerns that jurisdictions should protect users from risk if their assets are stored outside of their control.
We can submit that there will be reasonable rules on the various interactions between fiat money from the traditional system and Bitcoin. The on and off ramps will always be the places for regulatory scrutiny, as will concerns about sanctions lists and illicit activities. So will ensuring that no one is committing fraud or deception, or as in the case of FTX and other exchanges, discretely re-allocating customer assets for risky bets.
But once these rules begin to restrict the activities of users with bitcoin in self-custody, who send funds to other wallets and users who also maintain self-custody, there must be an effective line in the sand. This also applies to protocols and software that allow users to perform collaborative transactions, or to privately send between addresses, as in the case of the developers of Samourai Wallet and similar services (be sure to check out P2P Rights).
Previous attempts at flagging or IDing “self-hosted” wallets that receive amounts over a certain threshold were initially found in the European Union’s cryptocurrency regulations, but those were thankfully scuttled. But we must remain vigilant that no similar proposal aims to do the same in our own country.
Regardless of how Bitcoin grows, we must articulate the case for self-custody to be clear and distinctly separate from custodial solutions, as my colleague and BPI Legal Fellow Zack Shapiro has eloquently covered. Shoehorning noncustodial products into legislation or rules meant for custody relationships would be overburdensome, unnecessary, and essentially erase the entire point of Bitcoin in the first place.
The right to self-custody shall not be infringed.
Originally published at the Bitcoin Policy Institute.
-
 @ 599f67f7:21fb3ea9
2024-10-14 19:36:50
@ 599f67f7:21fb3ea9
2024-10-14 19:36:50Inoiz pentsatu al duzu norbaiti satoshiak modu originalean oparitzea, Bitcoin mundura hurbiltzeko? LNbits zorro batekin NFC opari txartel bat erraz sor dezakezu. Honek LNURLw esteka bat NFC txartelean idatziz funtzionatzen du, eta jasotzaileak bere satoshiak erabili ditzake LNURL gaitutako zorro batekin.
Zer behar dut?
- LNbits zorroa
- Android telefono bat
- NTAG2* gaitasunak dituen NFC txartela, adibidez NTAG216.
💡 NTAG2 txartelek esteka bat* idazteko aukera ematen dute. Adibidez, enpresaren webgunerako URLa duen bisita-txartel gisa joka dezakete. NTAG424 txartelek ez dute memoria handiagoa bakarrik, baizik eta SUN parametro deitzen den zerbait ere badute, zerbitzariaren autentifikazioa ahalbidetzen duena, eta horrek segurtasun gehiago ematen die zure ordainketei. Azkenean txartel mota hau BoltCard bat bihur daiteke.
1. Hedapena aktibatu
Ireki zure LNbits zorroa. Tresna-barran, aktibatu
Withdraw Linkshedapena eta ondoren joan hedapenera.2. Erretiratzeko esteka sortu
Withdraw Linkshedapen orrian, aukeratuAdvanced Withdraw Link(s)aukera.Ondoren, aukeratu satoshiak ateratzeko erabiliko duzun zorroa. Ziurrenik, hori zure LNbits zorro nagusitik bereizi nahi izango duzu. Horretarako, LNbits zorro berri bat sor dezakezu tresna-barratik,
+ Add a new walletaukera hautatuz. Behin zorro berria sortuta, sartu satoshi batzuk bertan.
Eman izenburu bat erretiratzeko estekari.
Ezarri erreskatatu daitezkeen gutxieneko eta gehienezko zenbatekoak.
Ezarri esteka zenbat aldiz erabil daitekeen eta erretiratze saiakeren arteko denbora.
Aukeran, argazki pertsonalizatu bat gehi dezakezu
Use a custom voucher designlaukitxoa markatuz, eta .png irudi baten URL-a sartuz.Gogoan izan “assmilking” laukitxoa ez markatzea.
Konfigurazioa amaitu ondoren, jarraitu erretiratzeko esteka sortzera.
3. Idatzi esteka NFC txartelean
Zure erretiratzeko esteka berrian, klikatu
View LNURLestekan. Ondoren, sakatuWrite to NFCbotoia eta eutsi NFC txartela telefonoaren aurrean idazketa-prozesua burutzeko.
✔️ EGINDA
💡 Esan txartelaren jasotzaileari satoshi saldoari buruz, denbora ez dezan galdu azkeneko satoshia lortzen saiatzeko.
💡 Jasotzaileak txartelaren satoshiak atera ondoren, bere zorroan berridatzi dezake eta berrerabili. Gainera, eman diozun txartela NTAG424 bada, aurreko gidako (nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65whwqrr5) bezala Lightning "zor txartela" bihur dezake. Baina txartela NTAG2* bakarrik bada, beste opari txartel bat bihur dezake soilik.
-
 @ 3589ce32:ef4269ad
2024-10-24 19:13:56
@ 3589ce32:ef4269ad
2024-10-24 19:13:56Bitcoin y la Descentralización:
Bitcoin se centra en la soberanía individual, la libertad financiera y la descentralización. Su filosofía se basa en la confianza en un sistema sin intermediarios, donde cada individuo tiene control sobre sus recursos. La descentralización de Bitcoin refleja un despertar hacia la autonomía personal, la autosuficiencia y la búsqueda de la verdad fuera de estructuras de poder tradicionales.
UCDM enseña la no-dualidad, el perdón y la percepción correcta, destacando que el amor es lo único real y que todo lo demás es una ilusión. La idea es la de liberarse de la mentalidad de escasez (tan presente en el dinero tradicional) y fomentar una mentalidad de abundancia, confianza y cooperación.
El Vedanta Advaita es una filosofía no dualista que enseña que solo hay una realidad última, y que todo es una manifestación de esa unidad. La dualidad es una ilusión. Guardando ciertas distancia, podríamos decir que la unidad subyacente del Advaita se refleja en la idea de una red descentralizada y sin fronteras, como Bitcoin, la cual conecta a las personas sin intermediarios. También ¿Cómo superar la ilusión del ego y la dualidad para alcanzar una verdadera libertad? Hablaremos de esto en otra ocasión …
-
 @ bd32f268:22b33966
2024-10-24 17:57:26
@ bd32f268:22b33966
2024-10-24 17:57:26A atualidade acostumou-nos a uma lânguida linguagem devido à cultura do politicamente correto e ao crescente relativismo em que vivemos. A confusão é tanta que já não se chamam os bois pelos nomes e este ambiente faz com que inclusive desconheçamos o significado das palavras. A este respeito temos visto cada vez mais indefinição sobre o que são os vícios e sobre o que são as virtudes. Tal é a confusão que por vezes trocamos o significado de uns pelos outros.
A coragem e a convicção facilmente passam por orgulho e arrogância, a castidade passa por beatice e por aí segue a confusão com muitos outros termos.
A inversão de valores é tão disseminada que atrocidades como a pornografia, o aborto, o adultério entre outras atrocidades são celebrados como conquistas civilizacionais. A sua disseminação é de tal forma que hoje a pessoa média já banalizou e normalizou completamente estes aspectos.
“Primeiro estranha-se depois entranha-se.”
Fernando Pessoa
Enquanto isto acontece por um lado, por outro a defesa da família, da identidade e da tradição são abertamente atacadas como se se tratassem de produtos de uma cultura opressora que deve ser combatida por todos os meios. Por agora a perseguição destas ideias é ainda maioritariamente realizada através da exclusão social e económica, no entanto, não são escassos os exemplos da história em que essa perseguição assume uma outra dimensão.
Desta forma, está criado um paradigma e um sistema de incentivos que premeia a pessoa que colabora com o sistema vigente. Tanto é assim que se multiplicam cada vez mais os exemplos de programas de quotas e subvenções que permitem, a quem possui um grau mais avançado de assimilação ideológica progredir socialmente atalhando o caminho para o fazer.
“Assim, toda a árvore boa produz bons frutos, porém a árvore má produz frutos maus. Não pode a árvore boa produzir frutos maus, nem a árvore má produzir frutos bons (…)”
Mateus 7:17-18“Assim, toda a árvore boa produz bons frutos, porém a árvore má produz frutos maus. Não pode a árvore boa produzir frutos maus, nem a árvore má produzir frutos bons (…)”
> Mateus 7:17-18*
Desengane-se quem pensa que no paradigma pos-moderno não há moralização, sacerdotes e uma matriz religiosa, tudo isso existe.
Os psicólogos, para mal da nossa sociedade, são crescentemente os sacerdotes desta religião pagã, aquela que baseada numa filosofia e antropologia erradas vai corrompendo intelecto e coração.
Nesta nova ordem social, que em abono da verdade é já antiga, a inversão de valores é tal que já a própria vida humana é sacrificada no altar do clima em abono da “mãe” natureza. Regredimos ao tribalismo que nos sugere que a natureza vale mais que a vida humana.
Este é apenas um exemplo dos rituais de sacrifício proporcionados pela “nova” religião. Um outro exemplo que podemos dar é o da castração química e física de crianças e jovens no altar da falsa compaixão e empatia. Ainda um outro exemplo que podemos dar é o da promoção do homossexualismo, do transexualismo e da não-monogamia como caminhos saudáveis a seguir, sacrificando a vida de muitos jovens confusos no altar da inclusão. Muitos mais exemplos poderiam ser dados, porque à medida que esta “nova” religião aumenta a sua ortodoxia os rituais vão ficando cada vez mais assombrosos.
Estes rituais têm por base uma apologia ao anti logos, quer isto dizer que procuram negar tudo o que é conhecimento básico sobre a realidade e sobre a verdade. A própria razão e lógica não se sustentam quando vemos situações como a de homens a competir em desportos femininos. As leis desta nova ordem são: “procura a felicidade (aqui muitas vezes entendida como o prazer) como fim último da vida “; “todas as opiniões são certas e não há uma verdade”; “Não servirás a nenhuma autoridade”; “não seguir o vício é opressão e seguir o vício é liberdade”.
Neste ambiente inóspito, quem quiser preservar a honra e a virtude terá cada vez mais dificuldade uma vez que a dissidência desta nova religião não é aplaudida, pelo contrário é anatematizada. Porém, importa dizer que independentemente da época há sempre espaço para o heroísmo e para a transformação destas dificuldades em degraus para que o indivíduo se possa distinguir dos demais pelas suas virtudes. Onde o vício abunda também maior o destaque será em relação à graça, como uma pedra preciosa reluzente no meio da lama que aparenta brilhar mais intensamente aos nossos olhos tal é o contraste, ou como uma luz na escuridão que se distingue facilmente.
 ###### Casper David Friedrich - dreaming man in church ruins
###### Casper David Friedrich - dreaming man in church ruins -
 @ e968e50b:db2a803a
2024-10-24 17:53:49
@ e968e50b:db2a803a
2024-10-24 17:53:49https://whosaidit.vercel.app/
I made a quiz for you. Let me know if you have any feedback. Please don't share your results or any spoilers here. I've already had some...uh...let's call if fun...sharing with friends and family. Much to @DarthCoin and many other stackers' chagrin, the purpose of this is not to convince people not to vote, although that may be the affect for some. I'm just trying to challenge people's thinking.
Also, it would be really easy for me to change any of the content. Let me know if you have feedback. I want to make this as effective and accurate as possible.
https://whosaidit.vercel.app/
originally posted at https://stacker.news/items/738766
-
 @ c80b5248:6b30d720
2024-10-12 22:46:35
@ c80b5248:6b30d720
2024-10-12 22:46:35Using tools like Continue in your vault
As the capabilities of artificial intelligence continue to expand, integrating AI into our workflows has become an increasingly attractive option. One of the most exciting applications of AI is its potential to enhance the way we manage and organize information. Obsidian, a powerful knowledge management tool, provides a robust platform for building a personal knowledge base. By layering AI tools like Continue over your Obsidian vault, you can unlock new levels of efficiency, creativity, and insight. This article will start to explore how to effectively use AI tools within Obsidian to enhance your note-taking, information management, and productivity.
An Explosion of AI Tools
Over the past few years, I have tinkered with ChatGPT and other chat interfaces, but I only recently stumbled upon the rapidly growing space of AI tools for coding. In such a short time, some amazing tools have emerged, most notably:
- Aider: A command line interface tool to iteratively generate, edit, and refactor code.
- Cursor: A fork of Visual Studio Code (VS Code) with integrated AI functionality.
- Cline: A plug-in to for command line and code editor built to work with Antropic's Claude 3.5.
- Continue: A customizable VS Code plug-in with chat and code editing abilities.
These tools are designed to assist developers in writing, debugging, and even generating code from natural language prompts. They are powered by large language models (LLMs) like GPT-4 and Llama 3, which are trained on vast amounts of text data and can produce human-like responses to a wide range of prompts.
In this article, I will focus on Continue, a VS Code that offers multiple ways to interact with AI. It features autocomplete powered by an LLM of your choice, as well as the ability to generate new code blocks directly in the editor. It can also incorporate context from external sources or the local codebase. Additionally, it includes a standard chat window for interacting with the LLM.
The new twist is that I won't be using Continue to write code, but rather to write notes in Obsidian. I will be using the chat window to generate notes, and the autocomplete feature to assist me in writing them. By leveraging the context feature, I can bring in information from my Obsidian vault, allowing me to create more complete, accurate, and better-organized notes. I can also use the vault as context to ask for summaries or retrieve information from my notes, even as the vault continues to grow.
It's worth mentioning that while I am focusing on Continue, there are likely other tools that can be used in a similar way or provide better features. One example is the text-generator plug-in for Obsidian. This plug-in allows you to generate text using an LLM of your choice, and it can be used to generate notes, summaries, or even entire documents. It can also generate code, but I was unable to get the plug-in working with my LLM provider. Using Continue is a bit of a hack, as it requires working through an IDE like VS Code, but it's a good way to get started with AI tools in Obsidian. I will assume that you already have an Obsidian vault set up. If you don't, you can ask your assistant to help you organize it once you have it up and running.
The system I am going to describe here relies on two primary components: 1. Continue (installed in an IDE like VS Code) 2. An LLM provider to power Continue
Let's start by talking about LLM Providers. If you already know how these work, feel free to skip to the next section.
LLM Providers
LLM providers are services that offer access to large language models (LLMs) like GPT-4 or Llama 3.1, typically via an API (application programming interface). These providers usually charge by the token, which is the number of words processed by the model. You can go directly to a provider like OpenAI or Anthropic, or you can use an aggregation site like OpenRouter that provides a single API to access multiple models. Each provider has its own data privacy policies, so it's important to review them carefully. For this reason, I have been using DeepInfra. They run their own models and offer a clear privacy policy - even better, they tend to have the lowest costs.
h/t nostr:npub17vhnjkt04m6thytr8dna67v2pa4tjk7uh3ut40eq9wy8d28u0kvq7qnhkq nostr:note1qfckzxm687peaddwjpmms92kj3v59wrrx0cs2fcxlkm6pm9lyu3squscxa
Another option is to use Ollama to run some of these models locally. However, the hardware requirements for achieving good results quickly are quite demanding. For example, the smaller chat model I use in my configuration, which has 72 billion parameters, requires a 48 GB GPU to run efficiently—something that is not within my budget. This is why I am using DeepInfra.
Note: If you are setting this up for the first time, consider adding a small amount (less than $5) to a provider like DeepInfra and testing it out before you invest time in setting up a local Ollama instance. I have also had some issues with shutting down Ollama on Windows, so your mileage may vary.
If you choose to use a provider like DeepInfra, you are ready to move to the next section. If you prefer to set up Ollama, you can refer to their documentation for installation instructions. I prefer to run it in Docker, which can be done in Linux by running
bash docker run -d -v ollama:/root/.ollama -p 11434:11434 --name ollama ollama/ollamaor if you want to have an interface like ChatGPT, you can even run Open WebUI in the same command with
bash docker run -d -p 3000:8080 --add-host=host.docker.internal:host-gateway -v open-webui:/app/backend/data --name open-webui --restart always ghcr.io/open-webui/open-webui:mainGetting Started with Continue
Continue is installed as a plug-in for VS Code or JetBrains. I personally use it with VS Code, so my instructions will be based on that. If you are using a JetBrains IDE, you should refer to the Continue documentation for installation instructions.
After installing the plug-in, continue will prompt you to set up your LLM provider. In my experience, once this initial GUI goes away, you can't get it back. Instead, you will do most of the configuration within the
config.jsonfile for Continue, which you can access by clicking in the lower right corner of the Chat box. In VS Code, if you ever can't find anything,F1is your friend and will launch a searchable menu.Continue provides recommended settings from each provider, which you can find here. For my coding and writing, I chose the very new Qwen2.5 72B Instruct due to its high benchmark scores and relatively low costs. This model costs $0.35-0.40 USD per million tokens, compared to the best available on DeepInfra, the Llama3.1 405B Instruct, which costs $1.78 per million tokens. The results may be slightly worse, but I prefer cheaper and faster for my purposes. For autocomplete, I am using a faster and code-specific model, Qwen2.5-Coder-7B. I have not yet tried changing the autocomplete model for usage with Obsidian, but that is on my to-do list. Lastly, by the time you read this article, these models may be out of date. One nice thing about having a provider API is that you can easily switch and test different models to see how they work. Aider has one of many model leaderboards that will show you some benchmarks.
After working through the configuration, your
config.jsonfile will have a list of chat models and a tab for the autocomplete model. It will look something like this:```json "models": [ { "title": "DeepInfra Qwen2.5 72B Instruct", "provider": "deepinfra", "model": "Qwen/Qwen2.5-72B-Instruct", "apiKey": "your-api-key" }, { "title": "DeepInfra Llama3.1 405B Instruct", "provider": "deepinfra", "model": "meta-llama/Meta-Llama-3.1-405B-Instruct", "apiKey": "your-api-key" }, ],
"tabAutocompleteModel": { "title": "DeepInfra Qwen/Qwen2.5-Coder-7B", "provider": "deepinfra", "model": "Qwen/Qwen2.5-Coder-7B", "apiKey": "your-api-key" } ```
Trying it Out
The Chat UI
Once you have Continue configured, you can open your Obsidian Vault in VS Code. You will want to add a
.continueignorefile in your folder that lists.obsidianand any other files or folders you want Continue to ignore for context purposes.
Click the three dots in the bottom of the chat bar and check that your vault (@codebase) index is complete. You can now chat with the LLM and ask it questions using your vault as a reference.
@codebase what are some common themes from this vault?Continue provides a docs page that lists some types of questions that an LLM will be able to help with. Naturally, I asked the LLM to put these in the context of an Obsidian Vault and here is what it told me:
```md
Useful Questions
- High-Level Questions About Your Notes:
- "What are the main themes in my notes on personal development?"
-
"How do I incorporate agile methodologies into my project management?"
-
Specific Information:
- "What are the key points in my notes about productivity hacks?"
-
"Can you find any references to neuropsychology in my notes on cognitive science?"
-
Generating Content:
- "Write a new note on the benefits of meditation, using the same structure as my other wellness notes."
-
"Draft a summary of my recent project retrospective, following the format of my previous summaries."
-
Contextual Questions About a Specific Folder:
- "What is the main purpose of the 'Research' folder?"
-
"How do we use the concept of 'flow' in the 'Psychology' folder?"
-
Relationships and Connections:
- "What are the connections between my notes on 'Time Management' and 'Goal Setting'?"
-
"How do my notes on 'Digital Marketing' relate to 'SEO'?"
-
Task and Project Management:
- "What are the next steps I should take based on my notes for the 'Personal Finance' project?"
-
"Can you list the tasks I need to complete for my 'Career Development' plan?"
-
Deep Dives and Analysis:
- "Can you provide a detailed explanation of the concept of 'reflective practice' found in my notes?"
-
"What insights can you derive from my notes on 'Project Management'?"
-
Insight and Reflection:
- "What have I learned from my notes on 'Mindfulness'?"
- "Can you help me reflect on my progress based on my notes for the 'Health and Wellness' topic?"
Not Useful Questions
- Literal Review of All Files:
- "Find everywhere where the term 'mindfulness' is mentioned in my entire vault."
-
"Review all my notes and find any spelling mistakes."
-
Comprehensive Tasks that Require Literal Access:
- "Add a new section to all notes that discuss 'productivity' and summarize the main points."
-
"Rewrite all my notes on 'Digital Marketing' to include the latest industry trends."
-
Refactoring and Detailed Edits:
- "Update all references to 'Scrum' to 'Kanban' in my 'Agile' folder."
- "Add a new parameter to the function
calculate_scoreand update all usages in my 'Programming' notes."
Summary
- Useful Questions: Focus on high-level insights, specific information, generating new content, contextual questions about specific folders, and reflecting on your notes.
- Not Useful Questions: Require the LLM to see and edit every file, perform comprehensive reviews, or make detailed edits across multiple notes. ```
Text Generation
Continue also offers in-editor code generation with the hotkey
Ctrl+Iand an entered prompt. I have only tried a few things with this, but it was able to successfully review a set of meeting notes I had written and summarize all of the outstanding questions. I expect you could also use this to autogenerate backlinks on a note where a follow-up note might be helpful, or quickly generate templates to be used in Obsidian. I ended up editing this entire article by selecting sections and prompting the AI with the following: "You are a proficient writer. Please edit this text for style, typos, spelling, and grammar."Autocomplete
Continue will also attempt to autocomplete unless you turn it off in the bottom right bar in VS Code. While writing this article, the autocomplete feature was somewhat helpful even though it is not code. Further configuration may optimize this even more. Keep in mind that autocomplete triggers frequently and will burn through a lot of tokens, so you will want to keep an eye on your usage. With the cheaper models I am using, I have only spent 10 cents over the past four days of moderate usage at work and at home. A bulk of that cost is due to autocomplete, and I sometimes turn it off to keep costs down. You may be able to limit these costs effectively by configuring the number of input tokens that can be sent to the API, but I am not sure how that will impact the results.
Conclusion - Brought to You by Qwen 72B
In conclusion, integrating AI tools like Continue into your Obsidian vault opens up a multitude of possibilities for enhancing your note-taking, information management, and productivity. By leveraging the chat window, text generation, and autocomplete features, you can create more comprehensive and accurate notes, generate summaries, and automate routine tasks. The integration of LLMs into your workflow not only streamlines your processes but also provides deeper insights and connections within your knowledge base. While there are initial setup steps and some considerations around cost and configuration, the benefits of AI-assisted note-taking in Obsidian are well worth the effort. As AI tools continue to evolve, the potential for further enhancements and optimizations is immense, making this an exciting and valuable addition to any knowledge management system.
-
 @ ff1a68c4:ec9831cf
2024-10-24 14:49:33
@ ff1a68c4:ec9831cf
2024-10-24 14:49:33Año 2147. La misión de la nave Odisea VII tenía como objetivo estudiar las lunas de Júpiter. Nadie esperaba que se encontraran con lo que estaba a punto de revelar el gigante gaseoso. A bordo, cinco astronautas, expertos en astrobiología y física cuántica, orbitaban el coloso, maravillados por sus tormentas eternas y sus mares de hidrógeno líquido.
Durante meses, la tripulación había lanzado sondas y drones a través de la atmósfera turbulenta, recogiendo datos imposibles de descifrar. Era como si el planeta se resistiera a la intrusión, ocultando secretos detrás de las franjas de nubes y la Gran Mancha Roja.
El comandante Foster, junto con la doctora Elena Ivankov, detectaron una anomalía: un patrón en las corrientes eléctricas de Júpiter que parecía regular, como un latido. Al principio, lo atribuyeron a fenómenos naturales, pero la regularidad era inquietante. Eran pulsaciones precisas, organizadas, como los de un corazón titánico, aunque tan lentas que requerían equipo especializado para percibirlas.
“Esto no es solo una tormenta más”, murmuró Elena frente a la pantalla holográfica. “Es… es un ciclo controlado.”
El equipo empezó a conectar las piezas. Las corrientes de viento y los campos magnéticos de Júpiter no se movían al azar; parecían responder a la posición de otros planetas en el sistema solar. Cada vez que la gravedad de Saturno o Marte interactuaba con Júpiter, las pulsaciones cambiaban, como si ajustara su frecuencia para estabilizar las órbitas.
Foster frunció el ceño, ajustando sus datos en el simulador gravitacional. “Si estos latidos controlan la dinámica del sistema solar, ¿qué pasaría si se detuvieran?”
“Ningún planeta sobreviviría”, respondió Ivankov, con los ojos fijos en la pantalla.
Fue entonces cuando tomaron la decisión más osada de la misión: enviar una sonda mucho más profunda de lo que cualquier nave había llegado antes, para penetrar en las capas interiores de Júpiter. Las sondas anteriores habían sido destruidas, pero esta nueva, equipada con inteligencia cuántica adaptativa, podía reaccionar a los cambios a una velocidad inimaginable. La llamaron Ecos.
Cuando Ecos descendió, las lecturas empezaron a volverse más extrañas. Júpiter parecía estar "sintiendo" la presencia de la sonda. Las pulsaciones aumentaron, y el campo magnético se distorsionó. Ecos transmitió imágenes de lo que se encontró en el núcleo del planeta: una estructura titánica, más grande que cualquier ciudad humana, compuesta de una sustancia orgánica fusionada con energía pura.
"¿Estás viendo lo mismo que yo?", susurró Foster, incapaz de procesar lo que estaba ante sus ojos.
Ivankov asintió en silencio, sus dedos temblando sobre el teclado. "Júpiter… no es solo un planeta. Es un organismo vivo."
La tripulación permaneció en silencio mientras la sonda transmitía imágenes y datos. Era como si el planeta mismo estuviera compuesto de órganos que regulaban la estabilidad gravitacional del sistema solar. Un ser inconcebible, de una escala tan vasta que su única función era equilibrar fuerzas cósmicas. Cada tormenta, cada rayo, cada pulso magnético, todo formaba parte de su regulación.
"Este 'ser' mantiene el equilibrio", reflexionó el comandante, su voz era apenas un susurro entre el zumbido de los sistemas de la nave. "Si interfiéramos demasiado, podría romper la frágil danza de los planetas."
La doctora Ivankov, profundamente impactada, sugirió la teoría más radical: "Júpiter no solo es consciente… sino que actúa como una especie de guardián del sistema solar. Un ser con un propósito tan simple como vasto: mantener el equilibrio entre los cuerpos celestes. Si alguna anomalía cósmica amenazara el equilibrio, Júpiter respondería, ajustando las órbitas, corrigiendo las trayectorias."
Entonces llegó la transmisión final de Ecos: "Interferencia detectada. Estructura orgánica ha reconocido nuestra presencia. Cambios en los latidos. Aumento de la presión. Reacción… inminente."
El corazón de Júpiter había comenzado a acelerarse.
"No deberíamos haber venido tan lejos", dijo Foster, tomando el mando de la nave. "Es un ser que no entiende nuestras intenciones. Lo único que sabe es que estamos perturbando el equilibrio."
Con los latidos de Júpiter resonando en sus oídos, la tripulación inició una retirada rápida, temiendo que cualquier alteración en ese organismo colosal pudiera desestabilizar el sistema solar entero.
Mientras se alejaban, observaron cómo las tormentas del gigante gaseoso volvieron a la calma, y el pulso volvió a estabilizarse.
"Júpiter sigue latiendo", susurró Ivankov, mirando la vasta esfera a lo lejos.
Quizás, pensó la tripulación, no era el momento para que la humanidad supiera demasiado sobre su lugar en la delicada danza del cosmos.
-
 @ 0f4795bf:a8365abe
2024-10-12 20:25:34
@ 0f4795bf:a8365abe
2024-10-12 20:25:34Die Redefreiheit wird überall auf der Welt angegriffen. Wir sind als Urheber von Inhalten heute nicht frei, sondern Sklaven im Silo der Tech-Giganten.
Es ist an der Zeit, uns zu befreien und unseren Worten in einer Ära grassierender Zensur, verengter Debatten, Deplatforming und dysfunktionaler öffentlicher Diskurse Geltung zu verschaffen.
Das Pareto-Projekt ist ein privat finanziertes Open-Source-Projekt mit Sitz in der Schweiz, das Publikationslösungen entwickelt, die von allen genutzt, weiterentwickelt und ausgebaut werden können.
-
 @ 1b5ee74d:bb1aae6e
2024-10-12 19:49:12
@ 1b5ee74d:bb1aae6e
2024-10-12 19:49:12On October 8th, the American production company HBO—owned by Warner Bros. Discovery—released Money Electric: The Bitcoin Mystery. The documentary, directed by Cullen Hoback and currently available only to the U.S. audience, was immediately shared via P2P file-sharing platforms and can thus be easily found online.
Considering all the elements presented in the hour-and-a-half-long documentary, my personal judgment swings between two feelings:
- Satisfaction for having witnessed a thorough explanation of Bitcoin’s origins, its cultural roots, the reasons behind its creation, and the intrinsic problems of the traditional financial system.
- Frustration over a conspiracy theory—claiming that Bitcoin was sabotaged by U.S. government agents infiltrating the Bitcoin community to prevent it from functioning as a medium of exchange—and a baseless hunt for Satoshi Nakamoto, which is especially dangerous for the man identified: Peter Todd.
The Negative Aspects
The Surreal Conspiracy Around Replace-By-Fee (RBF)
One of the documentary's central issues is the inclusion of conspiracy theories aimed at explaining Bitcoin's evolution through external interventions, mainly by government actors, who allegedly tried to manipulate the technology to prevent it from scaling in terms of processed transactions. The goal, it is claimed, was to keep Bitcoin as a store of value and technically render it impossible for it to function as a medium of exchange.
The ultimate reason for this, according to the theory, is that everyday transactions could only occur through intermediaries and, as a result, would be easily controllable by authorities. The U.S. government's goal, therefore, would have been to negatively influence Bitcoin’s development. This idea is not unrealistic in itself, but this is where things get absurd.
Hoback, spurred on by Roger Ver, resurrects a story about an email allegedly sent to Peter Todd in 2013 by someone named John Dillon. Dillon, claiming to hold a “high-level” role in intelligence, supposedly requested the development of Replace-By-Fee (RBF) for the paltry sum of $500.
RBF is a function that allows an unconfirmed transaction to be replaced with a different version of the transaction that pays a higher fee, with the goal of achieving quicker confirmation. And here, Roger Ver provides the narrative hook: RBF would have driven transaction fees through the roof, making it uneconomical to use Bitcoin for everyday transactions, thereby fulfilling the U.S. government's objective.
History has shown that this theory was baseless—fees didn’t skyrocket with RBF—but the fact that Todd actually contributed to developing RBF convinced the documentary’s author that this was a credible hypothesis. The theory that Todd collaborated with the government is presented with alarming carelessness, despite a lack of concrete evidence, and Todd, understandably, denies everything. This conspiracy also contains a fundamental inconsistency: why would Satoshi Nakamoto have wanted to collaborate with the government to prevent Bitcoin from becoming digital cash?
The Blocksize War: Misunderstood and Poorly Told
The documentary presents a distorted view of the so-called Blocksize War. The thesis reflects the exact opposite of what actually happened. Again misled by Roger Ver's words, Hoback hypothesizes that the failed attempt to increase Bitcoin's block size led to a centralization of the network around the Blockstream team. The truth is the opposite: had the blockspace been increased, the network would have faced inevitable centralization, as the unfortunate fate of Bitcoin Cash demonstrated.
According to the documentary, the outcome of the war even allowed everyday Bitcoin transactions to occur “only through tools provided by Blockstream.” No names are mentioned, although it’s suspected that the reference is to Liquid. What reveals the documentary’s evident bad faith is that there isn’t a single mention of the Lightning Network, which allows low-cost transactions, doesn’t necessarily require intermediaries, and is certainly not controlled by Blockstream.
In general, Hoback gives too much screen time to controversial figures like Roger Ver and Gavin Andresen, whose opinions, while representative of a certain point in Bitcoin’s history, are distorted by the context in which they are presented.
The Baseless Manhunt
The hunt for Peter Todd is perhaps the most problematic aspect of the documentary. The narrative focuses on seemingly irrelevant details, weaving a sensationalist plot to make viewers believe that Todd might be Satoshi Nakamoto. This attempt poses a serious risk to Todd’s personal safety, which should not be underestimated. The narrative, while effective in capturing the attention of an uninformed audience, is highly dangerous.
The “evidence” provided is completely inconsistent. Consider that the most damning proof is a 2010 BitcoinTalk post in response to Satoshi Nakamoto, which Hoback claims was accidentally posted using Todd’s profile. That is, according to the author, Satoshi himself completed his post through a response but mistakenly logged in with his personal profile: Todd's.
This is a groundless hypothesis and, moreover, not a new revelation. It's also important to note that Peter Todd's nickname at the time was “retep,” and no one knew who he was. If it had been Satoshi Nakamoto, he could have easily deleted the post without leaving any unwanted traces.
The Myth of Satoshi’s One Million Bitcoins
The documentary repeatedly claims that Satoshi Nakamoto accumulated one million bitcoins and that a massive sale of these coins could “break the system.” This, too, is a misleading statement, as there is no certainty regarding the exact number of bitcoins Nakamoto possesses, and the idea that the sale of this alleged fortune could destroy Bitcoin is completely unfounded. In fact, it is never explained.
The Positive Aspects
The Roots of Bitcoin
Money Electric does have some merits, particularly in the first part, where it focuses on an accurate explanation of Bitcoin’s origins and the historical context in which it emerged. The documentary effectively recounts how earlier attempts to create digital currencies, like E-Gold, failed and how E-Gold’s founder, Douglas Jackson, was arrested for his activities. The author understands and communicates a key concept: if you build a product that can compete with the U.S. dollar, the government will come after you. Therefore, the decision to remain anonymous makes perfect sense. One is left to wonder: why did you try to reveal Satoshi’s identity?
The description of Bitcoin’s founding values, linked to the cypherpunk movement, is one of the most successful parts. The crypto wars of the 1990s and the battle for the use of cryptography, portrayed as a sort of weapon by the U.S. government, are explained in an accessible way, even to those unfamiliar with the topic, offering valuable historical context for understanding Bitcoin’s birth.
Mining and Energy
Mining is described as a lottery, finally breaking away from the common narrative that portrays it as an activity based on “complex calculations” or “advanced algorithms.” The simplified approach is well-executed and makes one of Bitcoin’s most misunderstood aspects comprehensible to the general public.
Another positive aspect is the documentary’s exploration of the relationship between Bitcoin and energy consumption. Rather than demonizing the energy link, it smartly compares it to the relationship between the dollar and oil, presenting this connection as inevitable for any form of money with intrinsic value. Money, it is specified, must evidently be tied to something that people consider valuable, like an energy source.
Traditional Financial System and CBDCs
The portrayal of the 2008 financial crisis and the parallel with the current fragility of the global monetary system is well done, showing how Bitcoin emerged in response to a failing system. In this sense, the documentary raises a warning about the future use of Central Bank Digital Currencies (CBDCs), which are described as dystopian tools of control, with a particular focus on the Chinese e-yuan, which is literally called a “government-backed shitcoin.”
The author casts doubt on the stability of the U.S. dollar itself, suggesting that even the American currency could face collapses similar to those of hyperinflated currencies. While not a definitive claim, this perspective introduces an important question about the future of the global financial system, undermining the steadfast beliefs of a large portion of the market that sees the dollar as an indestructible fortress.
Cold Judgment
Money Electric is a documentary that, perhaps for the first time, effectively explains several aspects of Bitcoin in a way that is both compelling and easily understandable. The fact that such a product comes from a major production house should be considered a success.
On the other hand, the misleading portrayal of events like the Blocksize War and the relentless search for a conspiracy to destroy Bitcoin—both tainted by the biased opinions of individuals defeated by history, like Roger Ver and Gavin Andresen—undermines the solid foundations initially laid with the description of the technology.
Lastly, such a blatant ad hominem accusation, supported by such flimsy evidence, is unacceptable. Identifying someone as Satoshi Nakamoto is, for the same reasons acknowledged by the author at the beginning of the documentary, extremely dangerous for that individual’s personal safety. How many people, swayed by HBO's gripping editing, could now believe that Peter Todd is truly Satoshi? And how many of these could be willing to physically attack him for the fortune Bitcoin’s creator supposedly accumulated? Too many hypotheticals to draw a plausible conclusion and to place such a risk on a person.
Money Electric: The Bitcoin Mystery is a decent product, fatally marred by bad faith.
-
 @ 06639a38:655f8f71
2024-10-24 14:49:08
@ 06639a38:655f8f71
2024-10-24 14:49:08Project Name
Nostr
Project Description
Nostr (Notes and Other Stuff Transmitted by Relays) is an open, censorship-resistant, and decentralized communication protocol designed for simplicity and resilience. Unlike traditional platforms, Nostr doesn’t rely on centralized servers. It already supports various use cases with free, open-source clients—offering alternatives to platforms like Twitter/X, Meetup.com, Excel 365, healthcare system and more. We will help you get started with Nostr.
Nostr has seen remarkable adoption and growth within the open-source community, evidenced by over 12,500 GitHub stars, 500+ forks, and contributions from more than 350 developers. The protocol has catalyzed the creation of an impressive ecosystem of over 390 projects, including mobile and web clients, relays, tools, and services that further enhance Nostr’s functionality. With over 70 tools and 48 libraries, developers can integrate Nostr into a wide array of applications—ranging from chat platforms to file storage and even decentralized marketplaces. These resources help to build decentralized, censorship-resistant systems without the need for centralized servers. Whether you’re working on peer-to-peer markets, privacy-focused messaging apps, or decentralized social media, Nostr’s ecosystem offers the tools.
Project website
https://github.com/nostr-protocol
Source code
https://github.com/nostr-protocol/nips
Project Theme
World Wide Web
Do you want a stand for the entire event or just for one day?
Entire event
Why do you want to be at FOSDEM?
We want to be at FOSDEM because it’s the perfect place to connect with like-minded developers and open-source enthusiasts who share our passion for decentralization, innovation, and building open permissionless technologies. FOSDEM fosters collaboration and the growth of community-driven projects and Nostr is a natural fit as a real grassroots project with its open protocol and commitment to build communication technology with resilience and simplicity in mind.
By being at FOSDEM, we aim to raise awareness, share knowledge and inspire others to explore the potential of decentralized communication systems. We also want to engage with the FOSS community and gain feedback to help Nostr grow. If people are really interested in how they can use Nostr we will show the possibilities, demo existing clients and provide in-depth explanations of how the protocol can replace the social layer (with user accounts in living a database) in existing software.What is the relation between the project and the primary contact?
Jurjen works with the community to promote its development, onboard new developers, and contribute to its open-source ecosystem. My role includes helping to raise awareness of Nostr's potential, organizing events, and supporting adoption by providing educational resources and technical guidance.
What is the relation between the project and the secondary contact?
Sebastian (37) is an independent creative / fullstack web developer who is the maintainer of a PHP helper library supported by OpenSats. Besides this project he is also making contributions with developing Nostr modules for Drupal.
“Since I've been online on the internet (1998), I'm highly interested in online communities, social networking and new ways of digital interactions. The internet has changed radically in the last decade and that change is not serving our interests. It's fair to say the web is broken in many ways. With Nostr we can fix this.”Social media links
npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft(Jurjen)
npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe(Sebastian)
npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa(Tanja)
npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn(Kevin)Anything else you like to add?
We’d also like to highlight that Nostr was created by Fiatjaf, an anonymous founder, which aligns with its principles of openness and decentralization. As an open protocol, Nostr is designed to evolve and find its own way, just like the foundational protocols of the internet. Importantly, Nostr is not a blockchain project—there are no tokens, no costs, and no barriers. It’s also not a platform nor a NFT. It’s purely decentralized, built for resilience and simplicity. While payment solutions like Bitcoin can be integrated, they are optional, not intrinsic to the protocol. This makes Nostr accessible and flexible, truly embodying the spirit of the open internet.
Nostr is more than just a technological protocol; it’s about the energy, problem-solving, and sense of hope that draws people in. Even newcomers can play a significant role in the ecosystem, gaining insight from the outside while discovering the protocol’s potential. Tanja, for example, isn’t from a tech background, yet after just three months, she’s taken on a major organizational role. She’s been spreading the message of freedom of speech and is leading the Nostr Booth LATAM tour, where volunteers, entrepreneurs, and Nostr-based businesses come together, supported by the entire community, to raise awareness about Nostr. Her passion for decentralization and open collaboration also drives her efforts to bring Nostr to FOSDEM, where she will help connect the project with like-minded developers and open-source advocates.
Please reach out to us if there are any questions. We’re really looking forward to presenting Nostr as a protocol at one of the best places where free and open-source software is flourishing.
This content will be used for a FOSDEM stand submission via https://pretalx.fosdem.org/fosdem-2025-call-for-stands/
-
 @ ff1a68c4:ec9831cf
2024-10-24 14:47:03
@ ff1a68c4:ec9831cf
2024-10-24 14:47:03En un mundo en constante evolución, la ciencia nos ofrece valiosas herramientas para mejorar nuestra calidad de vida y prevenir enfermedades neurodegenerativas como la demencia. A partir de los consejos de especialistas y datos de estudios recientes, he reunido una síntesis de enfoques clave que coinciden en varios puntos esenciales. Aquí te presento un resumen práctico:
El modelo MEDALS: Los pilares del bienestar
El acrónimo MEDALS nos recuerda los aspectos fundamentales que pueden ayudar a mantener una buena calidad de vida:
- Meditación: La práctica regular de la meditación reduce el estrés, mejora la concentración y contribuye a un mayor bienestar emocional.
- Ejercicio: El movimiento es vital para la salud física y mental. Mantener una rutina de ejercicio regular no solo fortalece el cuerpo, sino también el cerebro.
- Dieta: Una alimentación equilibrada es clave. Optar por una dieta rica en nutrientes, como la mediterránea, promueve un cerebro saludable.
- Apreciación: Practicar la gratitud y el aprecio por las pequeñas cosas de la vida puede elevar nuestro bienestar emocional y mental.
- Love (amor) y Learning (aprendizaje): Mantener vínculos afectivos y relaciones cercanas fortalece la mente. El aprendizaje continuo mantiene el cerebro activo y en constante crecimiento.
- Sueño: Dormir lo suficiente y de forma reparadora es crucial para la regeneración cerebral y la memoria.
Manantiales de la fuerza interior: Una guía integral para el bienestar
Otra perspectiva ofrece una visión holística de cómo cuidar cuerpo y mente. Estos son los cinco manantiales de energía interior que contribuyen a un estado óptimo de bienestar:
- Sueño profundo y reparador: Un buen descanso nocturno es el pilar del equilibrio físico y mental.
- Alimentación sana e hidratación: Mantener una dieta nutritiva y una adecuada hidratación es esencial para el buen funcionamiento del cerebro y del cuerpo.
- Respiración consciente: Practicar ejercicios de respiración ayuda a reducir el estrés y aumenta la claridad mental.
- Ejercicio y relajación: Alternar entre actividad física y momentos de descanso es fundamental para evitar el agotamiento.
- Actitud mental positiva: Mantener una mentalidad optimista y enfocada en el crecimiento nos ayuda a enfrentar mejor los retos de la vida.
6 Reglas anti-demencia: Proteger el cerebro a largo plazo
Algunos expertos proponen un enfoque más específico para la prevención de la demencia:
- Vínculos sociales: El cerebro es un órgano social. Mantener relaciones cercanas y participar en actividades grupales es clave para su salud.
- Ejercicio físico: El cuerpo y la mente están conectados. La actividad física regular mejora el rendimiento cerebral.
- Curiosidad y aprendizaje continuo: Mantener el cerebro activo con nuevos intereses y aprendizajes es crucial para prevenir su deterioro.
- Buena alimentación: Optar por alimentos ricos en Omega-3 y seguir una dieta mediterránea favorece la salud cerebral.
- Manejo del estrés: El estrés crónico es un enemigo del cerebro. Aprender a relativizar las situaciones y ver los desafíos como oportunidades puede reducir su impacto.
- Dormir bien: Un sueño adecuado es esencial para la reparación y el funcionamiento óptimo del cerebro.
Hallazgos de The Lancet: Factores modificables y no modificables en la prevención de la demencia
Uno de los estudios más importantes sobre la prevención de la demencia, publicado en The Lancet, destaca los factores modificables que pueden influir en nuestro futuro cognitivo:
- Formación continua: Aprender y mantenerse intelectualmente activo durante toda la vida puede retrasar el deterioro cognitivo.
- Cuidado de la audición: Proteger la audición desde la juventud es crucial. En la vejez, el uso de audífonos puede ayudar a mantener el estímulo auditivo.
- Salud emocional: El estrés crónico, la ansiedad y la depresión son factores de riesgo importantes para el desarrollo de la demencia.
- Ejercicio físico y salud metabólica: Evitar el sedentarismo, el sobrepeso, la diabetes y los niveles elevados de colesterol LDL reduce el riesgo de enfermedades neurodegenerativas.
- Protección contra golpes en la cabeza: Los traumatismos craneales aumentan el riesgo de demencia. Protegerse es fundamental.
- Reducción de tóxicos: Evitar el tabaco, el consumo excesivo de alcohol y la exposición a contaminantes ayuda a preservar la salud cerebral (ej. filtros para el aire o en la llave del agua)
- Vida social activa: El aislamiento social es un factor de riesgo para la demencia. Mantenerse involucrado en grupos y actividades sociales es clave.
- Suplementos: Aunque no son esenciales, algunos suplementos como arándanos, vitamina D, Omega-3, y magnesio pueden ser beneficiosos en casos de deficiencia.
Implementar estos principios no solo mejorará la calidad de vida en el presente, sino que también reducirá significativamente el riesgo de desarrollar demencia en el futuro. Vivir de manera consciente, cuidar el cuerpo y nutrir la mente son las claves para una vida larga y saludable.
-
 @ 5e5fc143:393d5a2c
2024-10-11 22:26:08
@ 5e5fc143:393d5a2c
2024-10-11 22:26:08Just revisiting some quick tips for #newbies #pow #public #blockchain users only.
if you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.
Hot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process
Cold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts Paper wallets are best n cheapest form of cold wallet that can used once n thrown away.
Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/

Any thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.
Beginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet
Almost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value
You can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !
Always delete hot wallet to test practice restoration before sending any large refunds to it to be safe.
Large funds are always best to keep in self custody node wallets rare n occasional use
Final word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲
Use wallet which u learn or understand best only
That’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️
Some Cold wallet nostr posts nostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2 nostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw nostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q
some nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option nostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8 related blog post nostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87
-
 @ 472f440f:5669301e
2024-10-11 14:20:54
@ 472f440f:5669301e
2024-10-11 14:20:54As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward.
Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years.
It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering.
Speaking of the job market, the numbers that came in yesterday were worse than expected: The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now.
All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential.
There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries.
The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority. The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare. I'll leave you with some thoughts from Porter Stansberry:
"We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked.
-
Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet.
-
Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow.
-
Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror.
Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it.
Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money.
And that day is here."
Final thought... I hope my tux still fits for this wedding. Enjoy your weekend, freaks.Use the code "TFTC" for 15% off
-
-
 @ e88a691e:27850411
2024-10-11 13:17:16
@ e88a691e:27850411
2024-10-11 13:17:16An opinionated guide to Sauna.
Introduction
Updated from the Sauna, October 7th 2024
After years of experimenting with different sauna types, I’ve developed strong opinions on the subject. The purpose of this article is to share these opinions with anyone who is interested in them and, hopefully, help others get more out of their sauna experience.
I’m certain my opinions will offend some, including all the people who (in my view) are doing it wrong. I know that saunas are important to many cultures around the world and that my strongly held opinions may offend some of those cultures.
Mind you, although I grew up in South America, I do have a fair amount of slavic blood in me. When I was a child, my grandfather regularly took me with him to the shvitz. One of my fondest memories from this time was the “Scottish Bath”, which involves standing against the sauna wall, execution-style, so that someone can spray you with freezing water from a high pressure hose. I’ve never heard of this outside of South American and can’t attest to whether it has any real Scottish origins.
The various health claims about using a sauna are beyond the scope of this article. All I have to say is that, like many things in my life, like Bitcoin, the meat/keto diet, and fasting, I find sauna to be yet another cheat code to life: it’s a simple thing that just makes life a lot better. If you want a good primer on scientific health benefits of sauna, I recommend starting with this article by Rhonda Patric. She goes in depth.
To be clear, it should go without saying that I am not a medical expert or professional. None of the opinions below are, or should be interpreted as, medical advice. There are many people for whom sauna use is not recommended. It would be prudent for any sauna user to consult with his or her doctor before entering a sauna.
Thanks to S. for taking the time to do a very helpful first review of this article. And thanks to The Wife for helping make my words legible and helping me make time to sauna–I don’t know which sacrifice was bigger.
Banya or Nothing
When I talk about saunas, I’m talking about a sauna with a stove, either wood or electric, that allows for steam. I call this “Banya style”. To be clear, I’m distinguishing between saunas and steam baths. Steam baths have their own place, but they aren’t my thing and I don’t consider them saunas.
A breakdown of the main types of saunas may be helpful, so you know which to avoid:
- Wet saunas, which are typically cedar rooms with wood burning or electric stoves onto which you throw liquid to create steam (I call this “Banya style”);
- Dry saunas, which are typically cedar rooms with wood burning or electric stoves without added steam (like Korean style saunas); and
- Infrared saunas, which, unlike traditional saunas, don’t heat the surrounding air. Instead, they use infrared panels to warm your body directly.
In my opinion, it’s Banya style or nothing. I’m not a huge fan of dry saunas, and I don’t even bother with infrared saunas. Infrared is a fiat-shitcoin. I want steam!
How to Sauna
Sauna Etiquette
If you read no other part of this already-too-long-article, read this.
Saunas are social places. There are proper ways of being in a sauna with others, and there are ways to do it wrong. You don’t want to be the person who ruins it for everyone. Here are some important etiquette tips:
Silence vs. Chatting: It’s not a question of whether you have to stay silent in a sauna or if it’s ok to talk. It depends on the circumstances and who else is around. If you’re using a sauna that isn’t your own, ask the staff about the preferred custom. The noise level in a sauna differs depending on the group in the sauna at a particular time. If you do want to chat with others, there’s nothing wrong with that. But, pay attention to whether there are others in the sauna who'd prefer it quiet. And definitely do NOT be obnoxiously loud – yes, I’m looking at you bachelor(ette) group who just discovered the Russian Banya.
Coming and Going: People rotate in and out of the sauna at different paces, so there will be people coming and going during your shvitz. But there are ways to come and go that are considerate and proper.
Keep the f-ing door closed (which was the working title of this article). Once you leave, don’t come back inside moments later. Doing so disturbs your fellow sauna users, lets out the all-important steam, and prevents the sauna from reaching an appropriate temperature.
If you’re in the sauna with a group of friends, try to coordinate your comings and goings so you’re all on the same cycle.
If you can only last 5 min at a sauna, don’t go in too often at the risk of ruining it for others (assuming it’s not your own private sauna).
Be fast when closing the sauna door when you come or leave. Otherwise, you will get dirty looks from others and may even hear mumbles of “quick quick, fast fast” from a Gray Beard. And you will deserve it.
Never open the door right after someone puts water on the stove to make steam. It’s all about the steam. Don’t waste it.
Controlling the heat: if you can’t handle the heat in the sauna, don’t just turn the heat down, because it ruins it for others. Instead, go to a lower bench or get out and take your break. Saunas are meant to be hot. That’s the whole point.
Personal Hygiene: Shower before you go into the sauna. Don’t wear perfume, smelly deodorant, or fragrant lotions. Smells get amplified in a sauna. Have a towel under you, don't leave your drippings behind. Best yet, make a Z with your towel, this covers your butt and down under your feet.
Clothing: sauna is not a place for wearing clothing. It is a place to get back to nature. If you are shy, just wrap a towel around yourself. People ask if I don't feel awkward, the answer is no. Who cares, humans naked is not novel. In many countries, it is strictly forbidden to wear clothing or bring anything but a towel into the sauna. It's understandable that may not be possible in North American public saunas on mix gender "family" days. If you have to wear something, then wear something 100% cotton or marino wool. You don't want plastic being backed into your genitals. One more thing, leave the watch out as it gets hot and will burn you. Also, flip-flops/sandals, stay outside.
Some saunas sell body scrubs and masks for you to apply before or in the sauna. Note that once in the heat, these can get goopy and drippy and may melt into your eyes and mouth. So (in this opinionated guides’ wife’s opinion), they are better in theory than reality.
Adding Oils and scents: As discussed below, it can be nice to add certain oils and other scents to the steam. But if there are others in the sauna, ask first before you do.
Where and how to sit: Hot air rises. So, the higher benches are hotter and the lower benches are cooler. If you are a newbie, pick a lower bench so you don’t have to leave as quickly and open the door unnecessarily.
It’s great to lay down in the sauna, but if it gets crowded, sit up to make room for others.
When moving around to find your seat, don’t walk on the benches in your sandals. Leave your sandals outside the sauna or on the sauna floor.
Sauna Temperature
In most proper Russian style Banyas you will find temperatures of 80-95 degrees celsius, which, in my opinion, is the best range. Thats near your body. "Offical" on the dial will he 100-120C. But sometimes you want to take it a little easier or last a little longer in the sauna. In these cases, 65-85 at body, dial at 80-100. degrees celsius will do.
However, if your sauna is below 85 degrees celsius on the dial, you might as well just go hide under your bed sheets and not waste your time.
At some saunas in hotels, gyms, or spas, you may not be allowed to set the sauna as high as you’d like (see below). There are many tricks to circumvent these frustrating restrictions, but my legal counsel has advised me not to go into any details here.
Sauna Duration
The amount of time you spend in the sauna is a matter of personal preference and depends on the number of cycles you do (more on cycles, below).
For your first round, my opinion is that most people should try to last 15 minutes in the sauna. If a sauna is at the proper temperature, most people will struggle to stay inside any longer. If you can stay inside for 20-30 minutes, your sauna is probably too cold and/or there is not enough steam. Many saunas have hourglasses inside to keep time, and I’ve never seen a sauna hourglass with more than 15 minutes, which should be a good hint.
My preferred is;
Cold Plunge => Sauna 15 min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest
if you can rest in the sun even better (no sunscreen poison please). You can add alcohol drinks to the hydration if you feel comfortable with that. But only add food after the last cycle.
For subsequent rounds, hydration starts to play a bigger role in how long you stay inside. Most people seem to last longer on their first round than on their second or third. If you can do 15 minutes on your second round, great. But 5-10 minutes is also fine.
Sauna Cycles
The traditional Russian Banya method (and in this writer’s opinion, the best method) is to do sauna cycles. Go into the sauna and just stay as long as you can take it (up to 15 minutes or so). Then take a cold shower and/or cold plunge (see below). Then robe-up and go relax with water, tea or beer. Once you start feeling “normal” again, repeat. For me, three cycles is the sweet spot. I’ll do more cycles if I’m spending the day at the Banya facility. If I’m at home, where I often sauna every other day, I find just one or two cycles does the trick. Sometimes I add a cycle or two on the weekend.
Occasionally, I like to go into the sauna as it’s warming up and before it reaches optimum heat (i.e. at around 60 degree celsius). This way, I can stay longer in the sauna for my first round (about 30-40 minutes). If I take this approach, I generally only do one more short round after my cold plunge.
Cold showers and plunges
In my experience, you want to take a cold shower or a cold plunge (or both, plunge is better) after the sauna cycle.After you come out of the sauna, immediately jump into cold plunge for a bit, i don't like to stay too long. Some Banya facilities will have a bucket filled with cold water that you can pull with a string to let the water pour over you, pull a couple times. The banyas may also have a cold pool of water into which you can plunge for a bit.

If I’m at my country place, after I get out of the sauna I jump into the cold lake. If it’s winter, I like to roll in the snow, which is satisfying. Some cultures would say that it’s not a real sauna experience unless you roll in at least one foot of snow.
After your cold shower or plunge, put on a warm robe and go relax before going back into the sauna. I like to relax for 5-20 minutes, depending on how much time I have. This allows the body’s temperature to decrease slowly. I do not recommend going directly back into the sauna after your cold plunge. If you don’t give yourself enough time after the cold plunge, you will overheat and won’t last very long when you return to the sauna.
Position
There really are no rules here. The way you position yourself in the sauna depends on your mood and preference, and there are many options. For example, you can sauna seated with your legs hanging down or with your knees up. You can lie down if there’s room. My favorite position is to lie down on my back with my legs up against the wall and, assuming the ceiling is low enough, with my feet stretched against the ceiling. This is a great way to stretch the hamstrings (check out stretching under “Sauna Activities”, below).
Choosing whether to sit on a higher bencher or lower bench is the best way to control the temperature you experience without adjusting the room temperature itself. You will notice the heat in the sauna increases exponentially every inch you go up. If you are struggling to stay in the sauna but don’t want to get out just yet, try moving down to a lower bench to last a little longer. Lying on the floor is the coolest spot and a great place for kids to start getting exposed to saunas.
There is no shame in going to lower benches or even the floor, there is only shame in opening the door before 15min
Getting Steamy
Without steam, the sauna would just be a sad, hot oven (I’m looking at you, infrared sauna).
The steam in the sauna has many benefits but most importantly it increases the thermal coupling of your body to the air and it feels great.
The amount of steam in the sauna is a matter of personal taste. You don’t want to make it into a steam room (remember, steam rooms are NOT saunas). But, you do want the sauna to be very moist. I find that two to four ladles of water in a mid-size sauna every five to seven minutes does the trick. Keep it between 50-60% humidity.
I keep a bucket of water in the sauna at all times so that I can continue to ladle water as I shvitz. Make sure to get a wood bucket and a metal ladle with a wooden handle. Wood ladles will crack, and if the handle is metal, it’ll burn you when you grab it.
If, when you enter the sauna, it’s already been on for a while, the wood is likely to already be wet and the sauna full of steam, so you may not need to add too much water. However, if you’ve just turned on the sauna and the wood walls are dry, you will need to ladle more water to make the air moist enough. If the sauna is too moist for comfort, open the door and let it dry out a bit (obviously, only do this in a private sauna).
Essential oils and even beer can all be added to the water to create scented steam. I recommend starting your sauna with just water, and add the scent as you get going.
You can try all sorts of different essential oils. I’ve tried everything from oak and cedar to tangerine and cinnamon (gag) essential oil. In the end, there are really only two oils that are worth it, in my opinion. The first is eucalyptus. I’ve experimented with different types of eucalyptus oil, and the variety you use makes a difference. My favorite is eucalyptus globulus. I also like diluted pine tar oil.
When you settle on your essential oil, add a healthy dose of the oil to the ladle filled with water. Never put the oil onto the oven directly. It’ll just burn.
In a few Russian facilities, I’ve seen Gray Beards pour Russian beer onto the oven and it was actually quite nice. It’s almost like being in a cozy bakery while you sweat
Some people like to place a salt brick or compressed solid blocks in their sauna from time to time. Put the salt block on the stove and pour water over it. The steam takes on a saltiness that feels nice. If a salt block is not available, you can get a cast iron teapot, fill it up with salt water, and place it on top of the stove.
And for my most important steam tip, I recommend using the “towel spin”. This is an effective and underrated technique to help circulate steam in the sauna. After creating steam, take your towel above your head and spin it around hard, like a ceiling fan. This movement works like a convection oven and spreads and equalizes the heat and steam throughout the room. It might make the folks sitting lower down in the sauna a little hotter, but that's what they’re there for, isn’t it?
Hydration
Being hydrated is important to having a positive sauna experience. You will lose a lot of your body’s water in the sauna. Ideally, start to hydrate well up to an hour before your sauna. I like to add a pinch of salt to my water to encourage water retention.
Do not bring any drinks into the sauna (the exception being a dedicated steam-beer, see above). Have your water or beverage when you’re outside the sauna, resting. If you find you need to drink water inside the sauna in order to cool yourself down, then it’s time for you to get out and allow your body a cool-down.
When you’re outside the sauna, don’t immediately down a glass of super cold water because you will cool down your internal body too fast. Personally, I like to drink warm tea after my first two cycles. After my second cycle, I enjoy a beer (pre-keto days), soup, or vodka drink. When non-keto, I do enjoy adult drinks in the cycles.
If you are doing a sauna while on a multi-day fast, you need to have water and salt, at a minimum. Otherwise, you will deplete your natural reserve of electrolytes and not be able to think straight.
Sauna Frequency
When it comes to frequency, if you are not in the equatorial heat do it every day. I now do mornings and end of day if I can. so 2x 2-3x cycles. In the summer, living in a hot & humid location, I sauna a lot less frequently. My desire to sauna is greatly diminished because I spend a lot of time in the sun and heat.
What to wear
Sauna Hat: I highly recommend wearing a Russian/Finish style wool hat when you’re inside the sauna. It may seem counterintuitive, but wearing a hat keeps your head cooler. An overheated head is not good for your brain. Wearing the hat stops you from overheating and lets you stay longer in the sauna. The temperature in a sauna is significantly hotter the higher in the room you are, and one’s head is at the top of the body (for most people). So protect your brain in style with a felt sauna hat. If you don’t have a felt sauna hat, buy one. They are easily found online. But in the meantime, you can wrap a dry towel around your head. Don’t forget to take your sauna hat off as you relax between cycles so your head can cool down.

Clothing: These days, many public saunas will have family days, men-only days, and women-only days. For obvious reasons, you’re only allowed to sauna naked if you’re attending one of the single-sex days.
If you’re at home, there’s no good reason to wear shorts or a bathing suit. Sauna naked. It's a lot more pleasant.
If you do wear clothing in the sauna, be careful with items with materials like metal or plastic attached. Things like pins, buttons, or string-ends will get very hot and probably burn you. Remember to take off any heat-conductive jewelry and leave your smart watch outside, as the heat will ruin its battery.
Don’t wear your robe inside the sauna. A robe is what you wear outside when relaxing or eating. If you wear it inside, you’ll overheat (and look like an idiot). Go ahead and sweat out that body shame robe-free. You can bring a towel into the sauna to sit on, if you want.
Shoes or sandals are highly recommended in public facilities. I mean, there are many people walking around wet. Ew. But keep your sandals outside the sauna itself, or on the sauna floor.
Sauna activities.
Don’t overthink it. Sitting in a sauna is activity enough, in my opinion. But there are some sauna activities you can do:
Veniks/Viht beating: these are bundles of leaves (commonly birch, oak, or eucalyptus) that are pre-soaked in hot water. Someone with both strength and capacity to exert themselves in the heat will beat your whole body with the leaves. This exfoliates your skin and also gets the plant oils to permeate your skin. And it’s very relaxing. If you’re at a sauna facility, don’t just grab any bundle you see lying around - that belongs to someone else and veniks aren’t shared. You have to bring your own or buy them at the front desk.
Stretching: this is a great activity to do in the sauna, but make sure to go very easy. Your muscles will be super warm and you don’t want to overdo it and hurt yourself.
Exercise or Sex: your heart better be in good shape if you try out these high intensity activities in the sauna. If you engage in the latter, you better be in your own home sauna. With respect to the former, I think doing some leg-ups can be very satisfying.
Phone use: If you’re at home, it’s nice to use your sauna time to shit-post on Twitter or read an article, if you feel like it. Just keep your phone close to the colder, lower parts near the floor or it’ll overheat and shut down. You can also place the phone outside of the air vent and play a podcast! The Bitcoin.review is great ;)
Napping: I don’t recommend this. If you fall asleep or pass out, you will probably die due to overheating or dehydration.
Chatting: Saunas are great places for conversations (subject to the caveats I address above). Note that nowadays, microphone modules are both very tiny and can withstand high temperatures, so it’s no longer recommended to reenact mafia movie sauna scenes.
Eating and Drinking: As discussed above, never have food or drink inside the sauna. But when you finish your sauna, take advantage of whatever snacks the facility offers. For Russian joints, the soups, fish roe and dry salty fish snacks are great. Again, don’t eat before your sauna; wait until you’re done. Some places will have bottled salty-ish lake water, and beer seems to be a good source of salts and re-hydration. Vodka drinks are nice sometimes, too. My favorites are vodka with beet juice and horseradish, vodka with pickle juice, or just a chilled shot of Zubrowka (vodka infused with bison grass). Teas are also very enjoyable post-sauna. I prefer non-caffeinated berry teas. Some Banyas even offer free tea to patrons.

Ready to Sweat It Out?
Thanks to this fantastic guide to sauna, you’re now feeling confident and excited to seek out a solid sauna. So where do you go?
Where to Find a Sauna
Spas: Spas are not the best place to have an optimal sauna experience. Saunas at spas are typically not hot enough and spas have annoying staff whose job it is to enforce idiotic rules and practices that prevent you from having a real sauna experience.
Gyms & Hotels: These are some of the worst places to sauna. For liability reasons, these saunas tend to be too cold and there are often mechanisms that prevent you from raising the temperature. Here, you’ll often see saunas with glass doors, which may look chic, but are inefficient and stupid because they don’t seal properly and leak steam. Gyms and hotels are high traffic areas, so people who don’t know what they are doing are constantly coming and going from the sauna, which, as we discussed, is a sauna no-no. If you still want to try the sauna at your gym or hotel, I recommend going in naked. It’ll deter people from joining you and ruining the little steam you managed to get going.
Traditional bath houses (Banyas): These usually offer a great experience because they deliver a super hot sauna, good cold baths and plunges, delicious food and drinks, and knowledgeable staff.
Home: Yes, you can build a great sauna in your own home! You can create a small space in your basement, turn a closet or cold room into a sauna, or just add an outdoor hut or barrel sauna in your backyard. This is the best way for you to control the whole experience and do it often. As with anything, the easier it is to access, the more you will do it.
Build it. They will Come
Many people have asked me for details about sauna building. If you’re ready to build your own personal home sauna, here are some important considerations.
Materials
Saunas are insulated rooms, most commonly finished with cedar tung and groove slats. Cedar is used because it doesn’t rot with moisture. You don’t want treated wood as it will release all the bad stuff that keeps the wood from rotting into the air when heated. Cedar interior is often placed over a vapor barrier, followed by insulation and then the outer wall. Many outdoor saunas are not insulated. They simply have a single layer of cedar 2x6 planks functioning as both the interior and exterior. Non-insulated saunas need much more heating power in the winter.
Structure
For indoor saunas, you may want to find a bricklayer to build something for you. Traditional facilities often have brick-lined rooms and very large wood-burning stoves.
You can buy prefab outdoor saunas, which are often sheds or barrels. After experimenting with both, I’ve concluded that barrel saunas are inferior, even though that’s what I have at my country property. This is because barrels have concave ceilings and inner walls. This means the benches are lower and the curve makes the topmost part of the ceiling (and the hottest part) the furthest from you, or inaccessible. The spinning towel trick really helps in the barrel.
When it comes to buying a sauna, go with the most traditional structure possible. They are based on thousands of years of evolution and knowledge.
Portable tent saunas are fun, but impractical because you have to set them up before each use.
Bench height inside the sauna is important. I think the top-most bench should be very near the ceiling. This way, when you’re lying down, you can use the ceiling to stretch the hamstrings. As a rule of thumb, bench length should allow you to lie down completely. It is also nice to have at least one lower bench for visitors or less intense sauna days.

Sauna Ovens
There are two main types of sauna ovens: wood burning and electrical (with gas heating being available, but not common). If the location you are building allows for it, go with electrical. It’s practical and easy to get going quickly. This means you will use it more often. Wood burning saunas are romantic and smell great, but it is a lot more work to get a fire going, especially in the winter.
Opt for oven sizes that are recommended or above recommended for the size of the sauna. A larger oven means more thermic inertia, more rocks for steam, and therefore less time to warm up the room. Bigger is better. The Scandinavians make the best quality ovens.
Oven controllers
There are two types of temperature control devices: the analog cooking-style or the digital type. I think, due to liability and safety, all ovens have a timer that max out at one hour.
The digital oven controllers are fantastic and I have one in the city in my basement sauna.
However, you have to consider your environment. For me, temperatures in the winter can reach below -30C and in the summer, over 40C. This massive range can take a toll on outdoor equipment and materials. For this reason, I opted for an analog controller for my outdoor sauna in the country, since the weather will likely ruin the electronics of the digital controller.
I would avoid ovens with analog pre-heat timers. They are great in theory, but the implementation is utter garbage. The timer won’t be precise and it’ll just lead to frustration, for example, when you thought you set the oven to start in three hours, but it actually started in two hours and already turned off.
Important Sauna Gear
Windows are nice to have, especially if you have a view to enjoy. Opt for at least a cedar door with a little window. Do not go with modern glass door styles. They are crap. They have gaps, no insulation, and let in too much light.
Saunas need thermometers and hygrometers (to measure humidity). The thermometers should be rated for saunas and be visible inside. This is both for safety and bragging rights.
I think having an hourglass inside your sauna is a must. Being able to know for sure how long you’ve been inside is important, since your sense of timing inside the sauna may be off depending on the state of your mind and body on a given day. You shouldn’t wear a watch inside the sauna, since it’ll overheat or break. Having a clock visible from the inside is also a good idea, especially if you sauna often and have a wife and kids who you don’t want to leave you.
Air circulation is an often-overlooked but important part of a sauna design. Saunas should not have stale air. The best sauna design creates natural “real convection” by placing an air intake under the oven wall and another at the top opposite wall. This allows fresh air to enter the sauna while in use. Be sure to add regulators, since you don’t want to cool the sauna or expel all steam. Without regulators you may get too much or too little air in. With too much air, you may cool the sauna down too much and/or lose too much steam.
Nice Things to Have
Lights are optional but welcome additions. It can be unpleasant to have no lighting at all, especially in an outdoor sauna on a cold, dark night. Lights should be warm-temperature and low power. I recommend an oven light, since they don’t sweat the heat (get it?) and are often low power.
Put a baking tray under your oven–thank me later.
Wood “pillows” for your head are nice and don’t get sweat-stained and stinky, like a fabric pillow.
Keep some extra felt hats near your sauna so when you or your guests forget their hat, you still have easy access to one.
I like to keep a couple of essential oils on the floor of the sauna, for easy access. If you keep the oils too high in the sauna, they’ll get too hot and spoil.
I place some duck boards over floor tiles in the sauna to prevent cold feet.
I also like to keep a small, natural broom inside the sauna to sweep up any dirt or leaves that come into the sauna on people’s feet.
Final words
As you can tell, I have some strong opinions when it comes to the proper way to enjoy a sauna. My hope is that my musings will help you to maximize your own sauna experience.. If you follow this guide, I’m certain you will benefit from and enjoy the sauna as much as I do and, just maybe, you too will develop your own strongly held opinions that will most definitely offend me.
Thanks for reading, please close the F-ing door.
ps, you can get a Bitcoin Honey Badger Sauna Hat here
- EOF
-
 @ d5c3d063:4d1159b3
2024-10-24 14:37:08
@ d5c3d063:4d1159b3
2024-10-24 14:37:08ปรัชญา อาวุธแห่งเหตุผลและเสรีภาพในโลกแห่งความขัดแย้ง
https://image.nostr.build/b3e2278447703b23c18d6b8dd98986b700958acbbe06b3cca6ce7efa55b6c1ad.jpg
โลกที่เราอาศัยอยู่เปรียบเสมือนสมรภูมิแห่งความคิด แนวคิดต่างๆ ถูกนำมาถกเถียงและท้าทายอยู่เสมอเพื่อค้นหาและพิสูจน์ความจริง ความขัดแย้งนี้ปรากฏชัดในหลายมิติ เช่น การปะทะกันระหว่างเหตุผลกับความงมงาย เสรีภาพกับการถูกบังคับ ปัจเจกนิยม (Individualism) กับลัทธิรวมหมู่ (Collectivism) และทุนนิยมกับสังคมนิยม ท่ามกลางความสับสนวุ่นวายนี้ ปรัชญาทำหน้าที่เสมือนป้อมปราการแห่งเหตุผลและเสรีภาพ เป็นเครื่องมือสำคัญที่ช่วยให้เราเข้าใจและวิเคราะห์โลกที่เต็มไปด้วยความขัดแย้ง พร้อมกับนำทางชีวิตของเราอีกด้วย .
ปรัชญาในบริบทนี้ มิใช่เพียงแสงเทียนริบหรี่ในห้องสมุด หากแต่เป็นอาวุธแห่งเหตุผล ที่ใช้ในการต่อสู้กับความคิดที่บิดเบือนและการใช้อำนาจในทางที่ผิด เพื่อปกป้องและส่งเสริมเสรีภาพของมนุษย์ มันคือดาบเพลิงที่ลุกโชนในสนามรบแห่งความคิดที่ช่วยให้เรามองทะลุผ่านมายาคติ ความเชื่อที่ไร้เหตุผล และการโฆษณาชวนเชื่อ ทั้งยังช่วยให้วิเคราะห์ข้อมูลอย่างมีวิจารณญาณและตัดสินใจบนพื้นฐานของหลักฐานและตรรกะ นำไปสู่การเข้าถึงความจริง ตัวอย่างที่เห็นได้ชัดคือการเซ็นเซอร์ข้อมูลข่าวสาร ซึ่งถูกใช้เป็นเครื่องมือในการบิดเบือนข้อมูล ปลุกปั่นอารมณ์ เป็นการใช้อำนาจในทางที่ผิด ปิดกั้นการเข้าถึงความจริง เพื่อควบคุมความคิดของประชาชน .
หัวใจสำคัญของปรัชญาคือ การใช้เหตุผล หลักฐาน และตรรกะ ในการแสวงหาความจริง เพื่อนำไปสู่ การตัดสินใจที่ถูกต้อง ปรัชญาฝึกฝนให้เรามีวิจารณญาณ ไม่หลงเชื่ออะไรง่ายๆ และไม่ยอมรับความคิดเห็นใดๆ โดยปราศจากการตรวจสอบอย่างถี่ถ้วน ปรัชญาสอนให้เราตั้งคำถาม เช่น ใครเป็นคนพูด ? มีหลักฐานอะไรสนับสนุน ? มีมุมมองอื่น ๆ อีกหรือไม่ ? ข้อสรุปนี้ขัดแย้งกับข้อเท็จจริงหรือหลักการพื้นฐานใด ๆ หรือไม่ ? ก่อนที่จะตัดสินใจเชื่อหรือยอมรับความคิดเห็นใด ๆ เพราะการยอมรับความคิดเห็นโดยไม่ผ่านการไตร่ตรอง อาจนำเราไปสู่การตัดสินใจที่ผิดพลาดและตกเป็นเหยื่อของการบิดเบือน .
ปรัชญายังส่งเสริมความเข้าใจในคุณค่าของเสรีภาพและความสำคัญของปัจเจกบุคคล เสรีภาพในการคิดการแสดงออกและการใช้ชีวิต เป็นสิ่งจำเป็นสำหรับการพัฒนาศักยภาพของมนุษย์ เพื่อการสร้างสรรค์สังคมที่เจริญรุ่งเรือง ปรัชญาช่วยให้เราตระหนักถึงสิทธิและหน้าที่ของตนเองในฐานะปัจเจกบุคคลและเพื่อปกป้องเสรีภาพเหล่านี้จากการถูกคุกคามจากอำนาจรัฐหรือแนวคิดแบบคติรวมหมู่ สังคมที่มีความยุติธรรมมีเสรีภาพและมีความเจริญรุ่งเรือง คือสังคมที่เคารพในสิทธิและเสรีภาพของปัจเจกบุคคลที่ส่งเสริมการใช้เหตุผลนั้น ล้วนมีรากฐานอยู่บนระบบเศรษฐกิจแบบทุนนิยม เพราะทุนนิยมเป็นระบบที่สอดคล้องกับหลักการเหล่านี้ โดยเปิดโอกาสให้ทุกคนมีส่วนร่วมในการสร้างความมั่งคั่งและเติบโตอย่างอิสระ .
ในโลกที่ความขัดแย้งทางความคิดทวีความรุนแรงและข้อมูลข่าวสารแพร่กระจายอย่างรวดเร็ว ปรัชญามิใช่เพียงทางเลือก แต่เป็นเกราะป้องกันที่ขาดไม่ได้ การศึกษาปรัชญา การฝึกฝนการใช้เหตุผลและการตั้งคำถาม คือการลงทุนที่คุ้มค่าที่สุดสำหรับอนาคต เพราะมันจะช่วยให้เรามีภูมิคุ้มกันต่อการถูกชักจูง การหลอกลวงและการใช้อำนาจในทางมิชอบ เป็นก้าวสำคัญในการสร้างสังคมที่เสรี มีความยุติธรรมและการเจริญรุ่งเรืองอย่างแท้จริง ดังนั้น เวลามีค่า…ศึกษาปรัชญา ฝึกฝนการใช้เหตุผล และอย่าปล่อยให้ความงมงายและอคติครอบงำจิตใจ เพื่อที่เราจะสามารถเป็นผู้กำหนดชีวิตของตนเองได้และใช้ชีวิตอย่างมีอิสระ มีเหตุผล และสร้างสรรค์คุณค่าตามที่เราเลือก เพื่อบรรลุศักยภาพสูงสุดของเราในฐานะปัจเจกบุคคล
Siamstr #Philosophy #ปรัชญา
-
 @ ec965405:63996966
2024-10-11 11:53:23
@ ec965405:63996966
2024-10-11 11:53:23Gratitude
In light of all the doom, gloom, and meaningless state sponsored violence in the world these days, I want to practice shedding light on some dope things I have going on lately that I am grateful for. To start, I'm always grateful for my dog's health and companionship. Kaido is a 4 year old 15 lb Chiweeny with an under bite and a big attitude who never lets anybody sneak up behind me.

I'm grateful for the community I've plugged into since I made my Nostr keys and won a creator account with nostr.build in a blog contest last year. I'm coming out of the Creator Residency at nos.social this month with a new group of internet friends and was even just awarded a grant from Yakihonne to spin up a relay for a youth organization I am involved with.
My grant proposal writing skills are sharpening thanks to my participation in a cohort of young "World Builders" who meet weekly via video chat to learn the ins and outs of fundraising and building ethical social impact organizations. A friend of mine I recently reconnected with introduced me to the facilitator of this group, a professional in the development space on a mission to "hack" the non profit sector by training the next generation of youth leaders. It's exactly what I needed to evolve my writing skills and apply for funding to build the better world I want to see for the next generation.
The friend who connected me and I met as foster youth members of a California-based social impact organization dedicated to transforming policy and practice in the foster care and juvenile justice systems. We fell out of touch after high school before crossing paths again a few years ago while I was a staff member at the organization. He's now a professional software developer who runs a learning community dedicated to helping folks learn programming and get into tech roles. My participation in the community has rekindled a passion for computers and the internet that started back in middle school when I first flashed a custom firmware on my Playstation Portable but paused in high school as I became increasingly sick of the internet and more interested in politics and media production. These days, I find myself increasingly sick of the corporate politics and media that define our shared realities and more interested in fixing the internet.
Crisis
In today's perpetual state of polycrisis, systems-involved youth (which include unhoused, foster, and incarcerated youth or orphans) are among the most vulnerable in our society. Higher rates of trauma-induced mental illness culminate into poor life outcomes for this population, including higher rates of unemployment and incarceration. Compounding this is the fact that they use social media at higher rates than other demographics due to a lack of robust social support networks, making them prime targets for bullies and human traffickers on the web. The Center for Humane Technology reports on their website that "more screen time is associated with mental health and behavioral problems, poor academic performance, and worse sleep" for youth.
We had a situation at the California-based organization I mentioned where a frustrated youth member created a "finsta" (fake Instagram account) to drag the Executive Director (one of the founding youth members of the organization in the 80's) and some staff (including me) through the digital mud. The youth tagged the organization's account and spread hurtful memes and rumors throughout our network. It even sparked a staff rebellion in which a disgruntled coordinator sent out a letter to our network detailing their personal beef with management and announcing their departure. A petition of no confidence in the Executive Director was circulated, resulting in their resignation from the organization they helped start decades ago. Needless to say, the whole thing left the community pretty traumatized and we lost a few great staff members.
I can't help but imagine how the situation would have played out if our organization had something like a white-listed Nostr relay to organize our community around instead of an Instagram account. The burner account would not have been able to post anything to the relay, so the memes and rumors probably wouldn't have spread as far or as quickly as they did. The white-listed youth members of the communications committee I ran could have posted content to the relay to ensure verified information was spread throughout the membership. Maybe this kind of setup would have created an environment for the frustrated member to feel more connected to the organization and it's mission and prevented such a mess from ever taking place. In the moment, I felt powerless to stop it.
Digital Neighborhoods
When I catch myself feeling down about the state of the world and how powerless I've felt to change it over the last year, I try to remember Rabble's metaphor about building digital neighborhoods in the recent presentation he gave at Nostriga. Before long, I'm reaching for my digital construction hat on my way to my computer to jot some ideas down. I've heard a lot of lip service at different non profits I've worked for over the years be given to the idea of safe physical spaces for youth (like playgrounds and soccer fields), but I never heard this idea extended to the digital spaces where the majority of young people spend an increasing amount of their time. These days, I serve on the board of directors for a different organization that I intend to build a digital neighborhood for with the Yakihonne Relay Grant I was awarded recently. I've been building transnational support networks for youth involved in state care with the International Foster Care Alliance since 2016 when I first trained a delegation of Japanese foster youth on community organizing strategies. There are a few reasons why I think Nostr is a natural fit for systems-involved youth.

-
Confidentiality laws surrounding minors in state care make it hard for organizations like ours to engage them in storytelling on social media because of the personal identifying information required to participate on corporate platforms. A Nostr key pair empowers a youth with a layer of anonymity in line with one of the tips in the Child Welfare Gateway's Social Media Factsheet about limiting the sharing of personal information. This anonymity grows their capacity to share painful pasts intentionally and with purpose. Since Nostr profiles can't be traced to a personal identity, youth advocates are empowered to use their voice to make a difference.
-
For foster youth who are disempowered in all other areas of their lives, ownership of their identity and data gives them control over how they present themselves and engage with others online. This gives way for an increased sense of connectedness, personal capacity, and resilience in storytelling without fear of being tokenized. Our organization's web presence will evolve into a powerful tool for narrative change and foster deeper connections among youth members globally, strengthening their cultural identities while contributing to a broader conversation on child welfare reform.
-
Next generation features and a vast app ecosystem will transcend geographical boundaries and time zones, significantly enhancing communication and collaboration between organizations in the alliance. In particular, in app translations provided by many Nostr clients will allow youth to socialize with their counterparts in other countries across language barriers and facilitate smoother communication.
What's not to look forward to? I'm grateful to be part of this movement and for the opportunities the community has provided for me up until now. We've come a long way since GeoCities and Myspace but, in the words of Tim Berner's Lee, "The future is still so much bigger than the past."
-
-
 @ 4ba8e86d:89d32de4
2024-10-24 14:03:14
@ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais.
Recursos e Funcionalidades.
O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório.
Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes.
O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets.
Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo:
-
Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional.
-
Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes.
-
Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações.
O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável.
https://www.collaboraoffice.com/
https://github.com/CollaboraOnline/online
-
-
 @ 4ba8e86d:89d32de4
2024-10-24 13:52:57
@ 4ba8e86d:89d32de4
2024-10-24 13:52:57Tecnologia de escalonamento #Bitcoin Layer-2 baseada no conceito de statechains, que permite que chaves privadas para depósitos BTC (UTXOs) sejam transferidas com segurança entre proprietários fora da cadeia.
Mercury Layer é uma implementação de um protocolo statechain de camada 2 que permite a transferência e liquidação fora da cadeia de saídas de Bitcoin que permanecem sob a custódia total do proprietário o tempo todo, enquanto se beneficia de transações instantâneas e de custo zero. A capacidade de realizar esta transferência sem exigir a confirmação (mineração) de transações em cadeia tem vantagens em uma variedade de aplicações diferentes.
um sistema de transferência e controle de propriedade do Bitcoin, especificamente focado em saídas de transações não gastas (UTXOs),
um resumo detalhado dos principais elementos e procedimentos do sistema:
-
Saída de Transação Não Gasta (UTXO): UTXO é a unidade fundamental que representa valor e propriedade no Bitcoin. Cada UTXO é identificado por um ID de transação (TxID) e um número de índice de saída (n) e possui duas propriedades essenciais: valor em BTC e condições de gasto, definidas em um Script. As condições de gasto geralmente envolvem uma chave pública que requer uma transação assinada com a chave correspondente.
-
Transferência de Propriedade sem Transação On-Chain: O sistema permite a transferência de propriedade de UTXOs controlados por uma única chave pública (P) de uma parte para outra sem a necessidade de executar transações na cadeia (on-chain) do Bitcoin ou alterar as condições de gasto. Isso é facilitado por um mecanismo chamado "Statechain Entity" (SE).
-
Compartilhamento de Chave Privada: A chave privada (s) para a chave pública P é compartilhada entre o SE e o proprietário. No entanto, nenhuma das partes conhece a chave privada completa. Isso requer cooperação entre o proprietário e o SE para gastar o UTXO.
-
Atualização/Transferência de Chave: A propriedade do UTXO pode ser transferida para um novo proprietário através de um processo de atualização de chave. Isso envolve a substituição do compartilhamento de chave privada do SE para que corresponda ao compartilhamento de chave do novo proprietário, tudo sem revelar compartilhamentos de chave ou a chave privada completa.
-
Transações de Backup: Além da transferência de propriedade, o sistema inclui transações de backup que podem ser usadas para reivindicar o valor do UTXO pelo atual proprietário, caso o SE não coopere ou desapareça. Essas transações são assinadas cooperativamente pelo proprietário atual e pelo SE e possuem um bloqueio de tempo (nLocktime) que permite a recuperação dos fundos em uma altura de bloco futura especificada.
-
Mecanismo de Redução do Backup de Timelock: Para limitar o número de transferências possíveis durante um período de tempo, o sistema utiliza um mecanismo de decremento do nLocktime. O usuário é responsável por enviar as transações de backup no momento adequado.
-
Cadeias Estaduais (Statechains): O sistema opera usando cadeias estaduais, que são uma camada adicional que permite a transferência de propriedade de UTXOs. O SE precisa seguir o protocolo, mas não armazena informações sobre compartilhamentos de chave anteriores.
-
Cegagem (Blinding): O servidor da camada Mercury (SE) é cego, o que significa que não tem conhecimento das moedas que está assinando. Isso é alcançado através do uso de criptografia de chave pública para ocultar informações de chave privada compartilhada entre as partes.
-
Protocolo de Camada Mercury: O protocolo detalha os procedimentos desde o depósito inicial até a transferência de propriedade, atualizações de chave, retiradas ordenadas e recuperação de backup.
-
Recuperação de Backup: Caso o SE não coopere ou desapareça, o proprietário atual pode recuperar os fundos, enviando a transação de backup quando o nLocktime for atingido.
-
Publicação de Compartilhamento de Chaves: O SE não tem acesso aos IDs de transação individuais das moedas, mas publica compartilhamentos de chaves públicas para cada moeda na lista de ativos. Essa lista é comprometida com a blockchain para provar a exclusividade da propriedade.
Este sistema é projetado para fornecer uma maneira segura e eficiente de transferir e controlar a propriedade do Bitcoin, permitindo a recuperação de fundos em caso de problemas com o servidor.
No sistema de controle de propriedade de saídas de transações não gastas (UTXOs), cada UTXO é uma chave compartilhada composta por duas partes: o proprietário e o servidor de compartilhamento. Juntos, eles colaboram para criar transações de backup com bloqueio de tempo, que transferem a propriedade da UTXO para o novo proprietário. Durante essa transferência, a chave pública compartilhada permanece inalterada, mas o compartilhamento da chave do servidor é atualizado por meio de um Protocolo de Computação Multifuncional (MPC) para se alinhar apenas com o novo proprietário. Essa atualização resulta na criação de uma nova transação de backup, direcionada à chave pública do novo proprietário, com um tempo de bloqueio mais curto.
A confiabilidade do servidor é essencial, pois ele é responsável por excluir o compartilhamento de chave anterior. Isso garante que não seja possível conspirar com os proprietários anteriores. O proprietário atual pode gastar a UTXO a qualquer momento, desde que o faça em cooperação com o servidor. No entanto, se o servidor for desligado ou desaparecer, o proprietário atual deve aguardar até que o tempo de bloqueio expire antes de enviar sua transação de backup.
É importante ressaltar que o remetente nunca possui a chave privada completa; ele possui apenas uma parte do compartilhamento. Assim, todas as transações requerem a assinatura conjunta do servidor. Quando a UTXO é transferida para um novo proprietário, o compartilhamento do servidor é atualizado para que ele não possa mais assinar em nome do proprietário anterior, apenas em nome do novo proprietário. Esse sistema de transações de backup com bloqueio de tempo é projetado para proteger contra cenários de não cooperação ou apreensão do servidor, garantindo a segurança das UTXOs e a integridade da rede.
https://github.com/layer2tech/mercury-wallet
https://mercurylayer.com/
https://twitter.com/TTrevethan/status/1689929527420387328?t=0f5oF6w_ZRjWRYGah3HX8Q&s=19
-
-
 @ 9e69e420:d12360c2
2024-10-24 13:10:08
@ 9e69e420:d12360c2
2024-10-24 13:10:08Kamala Harris delivered a sharp critique of Donald Trump, comparing him to Adolf Hitler during a recent speech. She referenced comments made by former Chief of Staff John Kelly, who disclosed that Trump expressed admiration for Hitler while in office.
![Kamala Harris] (https://i.nostr.build/iyRm5cJo9YuRgh3M.png)
Harris stated, "It is deeply troubling and incredibly dangerous that Donald Trump would invoke Adolf Hitler."
She warned that if re-elected, Trump could seek unchecked power and compare him to a dictator. Harris emphasized the importance of understanding Trump's intentions and the implications for America’s future. Her remarks coincided with the fast-approaching election, intensifying her campaign's rhetoric against Trump.
-
 @ 460c25e6:ef85065c
2024-10-10 13:22:06
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - Super Clients: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
-
Clients: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
-
Mini Clients: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
-
Micro Clients: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
Super Clients - amethyst - nostrudel - coracle
Clients - damus - twitter - primal - twitter - snort - twitter - gossip - twitter - lume - twitter - ditto - twitter - rabbit - twitter - freefrom - twitter - nos - twitter - flycat - twitter - straylight - twitter - nostter - twitter - iris - twitter - nostur - twitter - nostrmo - twitter - yana - twitter - openvibe - twitter - freerse - twitter - 0xchat - chats - cornychat - chats - coop - chats - nostrchat - chats - blowater - chats - habla - blogs - yakihonne - blogs - highlighter - blogs - blogstack - blogs - stemstr - music - wavlake - music - fountain - podcasts - zap.stream - live streaming - shopstr - marketplace - plebeian.market - marketplace - flotilla - communities - satellite - communities - zapddit - communities - nostr.kiwi - communities - hivetalk - video calls - flare - long-form videos - nostrnests - audio spaces - wherostr - location - yondar - location - stacker.news - news - flockstr - events - nostrocket - issue tracker - docstr - docs - satshoot - freelance - wikifreedia - wiki - formstr - forms - chesstr - chess - memestr - meme feed - npub.cash - wallet - npub.pro - websites - gitworkshop - dev tools - onosendai - metaverse - degmods - games - turdsoup - prompts
Mini Clients - amber - signer - alby - signer - nos2x - signer - nsec.app - signer - keys.band - signer - nostrame - signer - nokakoi - anon - zap.cooking - recipes - anonostr - anon - getwired - anon - lowent - anon - creatr - exclusive content - lightning.video - exclusive content - zaplinks - slides - listr - lists - zap.store - app store - badges.page - badges - oddbean - news - dtan - torrents - nosta - user pages - pinstr - pinterest - pollerama - polls - swarmstr - trending - nostrapp - apps manager - noogle - search - ostrich.work - job postings - emojito - emoji manager - nostree - links - citrine - local relay - joinstr - coinjoins - heya - crowdfunding - zapplepay - zaps - nosbin - clipboard - shipyard - scheduler - tunestr - live streams - filestr - files - nostrcheck.me - media hosting - sheetstr - spreadsheets - crafters - curriculum vitae
Micro Clients - w3 - url shortener - nosdrive - backups - zaplife - zaps dashboard - zapper.fun - payments - nostrends - trends - zephyr - trends - wavman - music player - nostrrr - relay info - nosdump - relay info - notestack - blogs - nostr.build - media hosting - nostr.watch - relay info - nostr hours - use reports - lazereyes - vision prescriptions - snakestr - games - deletestr - deletion requests - 2048str - games - nostrqr - qr generator - notanostrclient - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more Mini and Micro clients.
-
-
 @ ff6187a2:ddbe1be7
2024-10-24 12:54:45
@ ff6187a2:ddbe1be7
2024-10-24 12:54:45Happy Halloween
-
 @ 1bda7e1f:bb97c4d9
2024-10-10 03:05:10
@ 1bda7e1f:bb97c4d9
2024-10-10 03:05:10Tldr
- Nostr identities can be linked to a third-party service
- You can set up that verification at your own domain, and
- You can also set up your own Lightning Address at your own domain
- These both require files in the .well-known directory on your domain
- You can set these up together, quickly and for free, with Sveltekit and Vercel
- Now I am identified and can receive payments with my username "rb" at my own domain "rodbishop.nz"
Getting .Well-Known
For your npub
The first step in setting up a Nostr profile is to get your keys. I wrote about it in this article, Mining Your Vanity Pubkey.
These keys represent your identity and are issued by you, not a third-party issuer. This is good for personal ownership, but creates an issue around identification.
If you have an ID issued by an issuer, I can ask the issuer to confirm that you are who you say you are. But with a Nostr npub, which has no issuer, how do I confirm that an npub which claims to be yours, is in fact yours?
Nostr allows you to link your npub to a username and to a third-party service of your choice to help in confirming that your npub is really yours (It is documented in NIP-05).
Normal users can use a service like nostrplebs.com and to set up a username very quickly and easily. However, it is also possible to set up your own identification that relates your username to your npub using any domain you own.
In my view having your username tied to your own domain is better branding, and more self-ownership, and so that's what I'll set up using my domain rodbishop.nz.
For your lightning address
Nostr has integrated payments which allow people to send you Bitcoin over the Lightning network the same way they would send you an email. I wrote about it in Setting up Payments on Nostr.
The path I took in setting up my lightning address was to use Alby, and with an Alby Account you automatically get a Lightning Address at getalby.com.
Normal users can use that Lightning Address just fine. However, it is also possible to set up your own Lightning Address which will forward payments to your Lightning Wallet using any domain you own.
Similar to with NIP-05, my view is having your Lightning Address tied to your own domain is better branding, and so again that's what I'll set up.
Both of these tasks use the .well-known folder on your web server.
Preparing .Well-Known with Sveltekit
There are many ways to do this. NVK published a very simple method using Github pages which is free and which you can read about on his blog.
For me, I will set up .well-known using Sveltekit and Vercel. I have been learning Sveltekit and Nostr together, thanks to fantastic tutorials by Jeff G on his Youtube.
Using Sveltekit and Vercel to set up Nostr NIP-05 and Lightning URLs on your own domain is easy and free.
Create a new project
To start, create a new Sveltekit project with NodeJS and Node Package Manager using the code documented on the Sveltekit website.
npm create svelte@latest my-app cd my-app npm install npm run dev -- --openSveltekit contains many convenient short-cuts for web hosting, and one of them is the file structure. The structure contains an
/srcfolder to contain javascript files to build complex applications, and a/staticfolder to contain other simple static files which need to be hosted at the domain. It is this/staticfolder you'll be using for now.NIP-05 identification with nostr.json
For your NIP-05 identification, you need to create the folder and file for /.well-known/nostr.json as follows–
static └── .well-known └── nostr.jsonIn that file, you will use some JSON to link a username to a hex-format public key, which will enable Nostr apps to confirm that the username relates to the key. In my case, I create a link between the username "rb" and the public key formatted in hex format "1bda7e1..."–
{ "names": { "rb": "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" } }That's it!
Lightning Address forwarding with lnurlp
For your Lightning Address, you need to create the folder and file for /.well-known/lnurlp/your-username as follows, replacing the "your-username" text with your username (in my case, "rb") –
static └── .well-known └── lnurlp └── your-usernameIn that file, you create a link between the username on your domain, and the provider of your Lightning service (in my case, Alby). Alby provides a helpful guide on how to do this, which you can read on the Alby site.
- Visit the Alby page for your Lightning Address which Alby hosts
- Copy that text across to the new file you have created
That's it! These files are now ready and can be hosted anywhere.
Hosting .well-known with Vercel
I chose Vercel to host with because it was very easy to use, and provides all the hosting I need for free. To deploy, you first create a Github repository for my Sveltekit project, and then you set up Vercel to deploy every push by default.
At a high level –
- Set up a Github repository
- Push your project to Github
- Sign up for Vercel
- Link your Vercel to your Github, and Vercel will then show all your Git repositories
- Import your project from Github, and Vercel will deploy it to a Vercel.com domain
Once your project has deployed to Vercel, you will be given a deployment URL, and you can test to see that your static .well-known files are successfully online.
- E.g. I was given https://rodbishop-mw64m8ylx-rods-projects-c9b67f57.vercel.app
- I can add /.well-known/nostr.json or /.well-known/lnurlp/rb to the domain and view my files
Now that the files are deployed, you need to link them to your domain. At a high level –
- Get your domain (buy one if you need to)
- In Vercel, navigate to your project’s settings and add your domain. Vercel will provide DNS records for you to add to your domain registrar
- In your domain's DNS settings add those records as an A record to your root domain
Your .well-known files are now hosted in Vercel and pointed at your domain.
Setting up CORS in Vercel
You need to tell Vercel to allow third-party applications to access those files, by enabling CORS ("Cross-Origin Resource Sharing"). Vercel has good CORS documentation on their website.
To set this up, return to your project, and in the root folder create a new file named vercel.json. This file will tell Vercel to allow third-party applications to access your nostr.json file. Add the following to it
{ "headers": [ { "source": "/.well-known/nostr.json", "headers": [ { "key": "Access-Control-Allow-Origin", "value": "*" }, { "key": "Access-Control-Allow-Methods", "value": "GET, OPTIONS" }, { "key": "Access-Control-Allow-Headers", "value": "Content-Type" } ] } ] }Then– - Push to Github - Vercel will deploy the push automatically by default
That's it. Your .well-known files are able to be reached by every Nostr app.
Testing it with your Nostr profile
Now that this is hosted at your domain, you can connect your Nostr profile. In any Nostr client, visit your profile page and edit, then update your NIP-05 and Lightning Address fields.
Once your client has refreshed, give it a test
- Your NIP-05 identity should show a "success" type icon, rather than a "fail" type icon (what icons depends on the client you're using, but think "green tick" rather than "red cross")
- Your Lightning Address should simply work–get someone to send you a payment to your new Address and it should go through successfully and appear in your wallet.
Things I Did Wrong
Initially, my NIP-05 verification didn't work. I had done two things wrong.
Wrong form of pubkey
The first mistake I made was in the NIP-05 nostr.json file I used the wrong format of public key. The public key that you mostly use in clients is your "npub" which starts with "npub1..." However, the public key this file needs is formatted in hex and starts with "1...".
If you don't have your hex formatted pubkey, you can use a site like https://nostrtool.com/ –enter your pubkey in npub format, and it will return it in hex format.
Redirects caused CORS issues
The second mistake was caused by a URL redirect. Your .well known files need to be served at the root of your domain, not at a www prefix (e.g. for me https://rodbishop.nz, not https://www.rodishop.nz). For this to work, you need to ensure that requests to your root domain aren’t redirected to www.
In Vercel domain configuration, you can configure your redirects. By default, it will redirect traffic to www, and this is wrong for our purposes. To correct it, visit your domain settings, click "Edit" and look for "Redirect to". The correct setting is "No Redirect".
The issue is caused because when applications go looking for your nostr.json, they need to receive a clean "Success" (200) response from your server prior to accessing the file. If you are redirecting to www, then the server gives a "Redirect" (300) response instead.
In case you think your CORS is failing, take a look at the server http response code to see if there is a redirect. I used as follows–
curl -X OPTIONS -i [https://rodbishop.nz/.well-known/nostr.json](https://rodbishop.nz/.well-known/nostr.json) \ -H "Origin: [https://anotherdomain.com](https://anotherdomain.com/)" \ -H "Access-Control-Request-Method: GET"- Initially the response was "HTTP/2 308" which means a redirect was in place (and so the process was failing)
- Once I resolved the redirect issue at Vercel, the response was "HTTP/2 204" which means success, and from that point, Nostr apps recognised the NIP-05 successfully
What's Next
Over the last three blogs I have - Mined a Nostr pubkey and backed up the mnemonic - Set up Nostr payments with a Lightning wallet plus all the bells and whistles - Set up NIP-05 and Lighting Address at my own domain
At this point I am up and running with a great Nostr profile and able to fully engage with the network.
But there are still many rabbit holes to explore. The next place I will explore deeply is running my own relay, and if I have some success I will be back to blog about it soon.
I'm looking forward to sharing what I learn as I explore what’s possible on Nostr.
-
 @ 319ad3e7:cc01d50a
2024-10-08 18:05:44
@ 319ad3e7:cc01d50a
2024-10-08 18:05:44LETTER FROM THE FOUNDER
Welcome to the inaugural edition of the Zap.Cooking newsletter!
What began as a simple idea and a collaborative effort has grown into a vibrant community. Food, in its unique way, transcends culture and connects us all. It’s at the dinner table where we break bread and share our lives. Here, we’ve created a space where people come together to exchange ideas and celebrate a shared passion for cooking and culinary excellence.
This is the Nostr way—a community built on shared ideas and a constructive culture. We are excited to embark on this new journey of sharing a newsletter with friends of Nostr and Zap.Cooking. We hope you enjoy this fresh approach and look forward to many shared recipes and conversations.
Bon appétit!
Seth, Founder of Zap.Cooking
\ __________________
Food Clubs For Life Outside The System
Jack Spirko is the founder and host of The Survival Podcast. In episode 3552, titled "Food Clubs for Life Outside The System," Jack engages in a fascinating two-hour conversation with Joshua Longbrook, who established a food club and hub in Chattanooga, TN, as a means of building a parallel society that respects food freedom and self-sovereignty. Agora Food Club is a private association of members who value natural, organic food and regenerative farming practices, creating and sustaining a locally based alternative food system. In this episode, they discuss the blueprint and what it takes to start a food club in your neighborhood.

Links to YT video and Food Club:
https://www.youtube.com/watch?v=5uPcAfG-9AU

The Six-Ingredient Grandma Betty's Chicken Dijon Family Recipe
https://image.nostr.build/55d3f300fdc4563265f49f729476724f98ff0a062ce7f8d769bf136f0de05cf5.jpg
“Growing up there are a few staple foods that stick with you. For me, it was my Grandma Betty's Chicken Dijon. It was my birthday request every year and every time we cook it up it touches my heart. Grandma Betty passed away 7 years ago. This dish is dedicated to her, directly from her recipe book.” - Quiet Warrior
Grandma Betty's Chicken Dijon on zap.cooking
Glowing Rolls: Raw Vegan Sushi for a Healthy Boost!
https://image.nostr.build/b11da1b878fe48ee74cb1c6c1cc66692ce12827f26c256ecd7a184f99d9c7649.png
“All you need are your favorite vegetables, nori sheets, a bamboo mat, a cutting board, and a knife. For the dip, you can simply use soy sauce, or try this recipe for a delicious creamy dip. I make my own cream cheese with soaked cashews, nutritional yeast, salt, lime juice, and vinegar. You can also find vegan cream cheese or cashew cheese at a health food store. Feel free to add other veggies like bell pepper, chili, cucumber, fresh onion or anything you like! In the image I also used red bell pepper and shiitake.” - Essencial
Glowing Rolls: Raw Vegan Sushi for a Healthy Boost! on zap.cooking
Slow Cookin’ Tender Sweet-and-Sour Brisket
https://image.nostr.build/97a8a78e39fbe4d19f913ea3c7cac9b94ee20d155596a83e241f0fa71a51517a.jpg
“In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.” - Lizsweig
Sweet-and-Sour Brisket on zap.cooking
2024 Nostriga Photo Album
\ Community Photos by AZA_to_₿_myself, Jeroen, elsat, Derek Ross, realjode, and SimplySarah
To share your Nostr community photos, please DM @ZapCooking on Nostr
https://image.nostr.build/388b3bb338672728337ef1c04c90f65655cc29c716f168d35dd4c7343d5802b0.jpg
https://image.nostr.build/011edabbe3f427c60506fddab024bfeb46c72cf5e0a808b562d7c3ace9f239a0.jpg
https://image.nostr.build/5fcb47e3a21bbbedafe245f311b6d43f1f610ad96eec26aa85cdcbd0958fdabf.jpg
https://image.nostr.build/c2eac240326a7e4ab176776c5d140d0017ccdfef89ef733eaf85efda8e0d39f5.jpg
https://image.nostr.build/078682ee987734911886592f377a356245b5a5ea2a15c44ba80e3101ae523b52.jpg
https://image.nostr.build/c28418d851f3ad7f61435813d8aee82d87af3de4472b4d718a1d2573ae7d38c8.jpg
https://image.nostr.build/d3a55e11d7927c7cae106491d00a0cfda8323b976aa29123a0fd4e4e3fe78505.jpg
https://image.nostr.build/bdd055b0b37a9ebcdc91411796ae6cf785338679e7f44aebf1dc721cc09b076c.jpg
https://image.nostr.build/e7bf6c58de70510e96ec3b10630f4a4cfb770026532e2d307b4f95346a4d9ea4.jpg
https://image.nostr.build/b8eb934f8f15aae87ed0db66e898062ec723a8f16d9e93229cd2783d2b158e9d.jpg
https://image.nostr.build/f999d2389c363be56543444f301e443ddc126f1caebb9462b74b800d54ed2c28.jpg
https://image.nostr.build/0ca2d868703298d222f9cabc3e10a73dcd2d1f82f1b22f8526d9360e9bec8cc7.jpg
https://image.nostr.build/94460309bf933bcd89887f16ea6c384fa5bc5e3eb74500de099a3a1405da8edc.jpg
UPCOMING NOSTR HAPPENINGS
To submit your Nostr event, please DM @ZapCooking on Nostr
Nostr Valley @ Happy Valley Brewing Company - October 12, 2024 - 12pm to 4pm (est)
https://image.nostr.build/6c830618389046460ad41e3704864adb338b2a980cc765de51106a2f65adba67.jpg
Nostrville 2.0 No Panels, All Party! @ Bitcoin Park - November 6, 2024 - 4:30pm to 7:30pm (cst)
Nostrville 2.0 - No panels, all party!, Wed, Nov 6, 2024, 4:30 PM | Meetup
ZAP.COOKING PRESENTS: LACE
https://image.nostr.build/fb37dfaa7efe8add086d75af2dfd193181de728e108bd2c8e095a60f7e64bc4f.jpg
\ SimplySarah: Let’s start by learning a little background on Lace. What is your food story?
\ Lace: Food for me runs in my veins. My family is from Jamaica and my grandmother began cooking as a girl. She brought her recipes with her to the UK in the 1950s and cooks the most delicious dishes. My mother has been a professional chef for over 40 years. Family meals at Christmas were always a big deal. However, it wasn't until 18, I began cooking at university where I vowed my children would know how to cook a healthy meal and not end up like the people around me living on take out and micro meals. As a student, I just recreated things I ate at home and when I was unsure, I'd call my mum or my grandmother for help. When I had kids, I put them in the kitchen at age 2 and my eldest, now 15, is an incredible chef. We are also well traveled and always enjoying local cuisine which also inspires our cooking.
SimplySarah: That is a lovely background. It seems it was a natural progression to want to get into writing cookbooks. I understand you are working on your second currently, but let's backtrack and talk about how the first one came to life.
Lace: It would seem so. I always wanted to write a book but a cookbook wasn't what I thought I would write first 😅 And yes, the second is coming next year, a co-authored book. The first, came about because of Facebook, actually. Admittedly, I am one of those people who posts food pictures. And my Facebook followers began asking me for my recipes all the time. And I would write them out... and then decided it made more sense to write them once inside a book and sell it. Hence Lace's Bad Ass Yard Food was born.
https://image.nostr.build/563b2d4299d824ef4fbb8b85749ba1bb24b0fb4025bf6b10fa2ddaed7217240a.jpg
SimplySarah: That's an awesome title! What IS Bad Ass Yard Food?
Lace: Hahaha, thank you! Yard food is what we (as Jamaicans in my family) call our cuisine. Yard food. Yard means home. So it's basically great homemade food. Typically, this is things like Curry Chicken, Fry Fish, Jerk Chicken, Rice and Peas, Hard Food (yam, dumplings and green bananas) and many other things.
SimplySarah: All those dishes sound phenomenal. If you had a go-to dish from the first cookbook what would you select? Maybe something that is always served on a weekly or regular basis at your home?
Lace: Oh they are! My favorite is curry goat. Curry Chicken has got to be the go to, I still cook it weekly now! And no matter where I've lived in the world, I can always prepare it.
https://image.nostr.build/da216e149bee8676a806f010ddde5a29eb4ffa0adeaf5f68265e0e2cc3f11649.jpg
SimplySarah: Funny, I believe you just posted on Nostr that you were in the process of making curry chicken if I recall correctly. Is the next cookbook following the same roots? Or are you and your partner exploring different cuisines?
Lace: That's right! I did just post that curry on Nostr. The next book is going to feature 8 of my favorite recipes. Some will be Jamaican but I also happen to love Asian inspired dishes and have some European favorites too which will be featured. This will be the first time I'm sharing non Caribbean dishes. As for me and my boyfriend, he is Colombian and an ex-military Chef. He has been sharing his food with us and has been enjoying eating food from different regions for the first time as a result of meeting me. It's great fun to bond through food.
Lace’s Curry Chicken with Purple Cabbage, Plantains, and White Rice:\ https://image.nostr.build/fb37dfaa7efe8add086d75af2dfd193181de728e108bd2c8e095a60f7e64bc4f.jpg
SimplySarah: Is he the co-author you are speaking about?
\ Lace: Nope. The other Authors of the book are all entrepreneurs who love food. The first edition will be available in november, it's called Made with Love. I will be featured in the second coming 2025.
SimplySarah: Oh, nice! How did you get tapped into this project?
Lace: Again, my facebook network. I was chatting with a lady who is a self made millionaire about money. She checked out my fb profile and said.. ohh I love your cooking videos, what a fun way to market (my tech business) and then invited me to check out the cookbook project and be part of it. And just like that I was in.
SimplySarah: Facebook definitely brings a lot of people together based on their favorite topics. Now that you are exploring Nostr and have such an incredible background with culinary arts, what do you hope to achieve here on this social protocol?
Lace: Yes, socials are great for that! Honestly, I just want to connect with folks who love great food and are into self development, natural living, love travel and sovereignty. On my second day on Nostr, I met you, a fellow foodie, so it's certainly working out well so far. :) And without all the ads and other crap fb force on it's users
SimplySarah: Personally, I am super thrilled you have joined Nostr. We need more foodies, and I love nerding out about anything food related, especially the food travel stories. I would absolutely love to follow your food journey, and I think all the Nostr foodies should too. Where can everyone find you, follow you, and maybe buy a cookbook?
Lace: Yay! Thank you. I love talking about food, cooking, sharing food, buying ingredients and trying food. You can find me on Facebook - the loved and hated, Nostr, and my personal website. There's no fancy sales page for the cookbook yet! 11 of my Jamaican recipes in one cute ebook :) I'm coming over to Zap Cooking too.
SimplySarah: One day you will be Nostr Only and forget all about Facebook. Haha! We look forward to having you on Zap.Cooking. We have a lot of ideas in the works and would love for you to be involved! I have one final question. First, I want to thank you for taking your time to spend your Saturday morning with me. This was fun. You mentioned you put your children in the kitchen at an early age. I'm a big fan of teaching kids life skills when they are young. Do you have any tips for parents to help them in the kitchen with their children?
Lace: I'm sure that will happen. My fb network has been instrumental in my success and surviving the rough time in my travel. Do tell me all about your ideas for Zap, I'd love to see how I can be involved!
Yes, tips for parents, When kids are eating solids, feed them home cooked meals, no jars, no processed stuff, healthy, varied, adventurous meals you eat. If you're eating octopus, let ‘em try. If you're eating veg, let them try. If you're eating chicken liver pate, let them try. Encourage a varied diet and pallet. Then at 2, get them in the kitchen. Let them peel garlic cloves, add herbs to meat, make meatballs, mix and taste things. Invite them to cook everyday. And have fun with it!
It's been my pleasure to spend time with you this Saturday morning Sarah. Thank YOU.
You can find the talented Lace at:
https://www.facebook.com/iamlaceflowers
https://primal.net/p/npub1ruhmx2wy663u9k2sams6qrlvgq86t3p4q3ygwgp5wqzcrgd6fh7sr20ys2
https://www.iamlaceflowers.com/workwithme
Follow Zap.Cooking Content Coordinator SimplySarah at:
https://image.nostr.build/c208bb8d562421beb00cc26fcf38417a0d52660659f4ac9d40365f3761a486b8.png
-
 @ 9e69e420:d12360c2
2024-10-24 11:51:32
@ 9e69e420:d12360c2
2024-10-24 11:51:32Dr. Johanna Olson-Kennedy, a leading advocate for trans youth care, withheld a $10 million study funded by taxpayers on the effects of puberty blockers, which found no improvement in mental health among participants.
She feared the findings would be "weaponized" against transgender care. Critics argue that her decision violates research standards and denies vital information to the public. The study tracked 95 children, revealing that 25% had mental health issues prior to treatment, contradicting Olson-Kennedy's claims of good overall mental health. Experts stress the importance of publishing research regardless of outcomes.
Sauce: https://nypost.com/2024/10/23/us-news/doctor-refused-to-publish-trans-kids-study-that-showed-puberty-blockers-didnt-help-mental-health/
-
 @ 6ad3e2a3:c90b7740
2024-10-08 09:11:10
@ 6ad3e2a3:c90b7740
2024-10-08 09:11:10I wanted to post a quote from Jiddu Krishnamurti who if I remember correctly once said something to the effect of:
An artist should be like Beethoven. The music just flowed out of him, and he could neither stop it nor control it.
But I can’t find the source, I’m just going by memory, and it was from a long time ago. It doesn’t matter though if he really said it, because it’s the quote I wanted to post.
. . .
When I was 21, my friend Andrew and I made a four hour drive one Saturday morning from New York to Germantown, Maryland to see a Korean Buddhist monk. I heard about the monk from my Korean college roommate whose mom knew him. Andrew and I had been reading books about Buddhism for the preceding year and thought it would be worthwhile to see the real thing. We also had various anxieties about our lives and figured maybe he could offer some guidance.
When we arrived at the farm where he lived, we parked and stepped out of the car. I don’t want to exaggerate, but even in the lot which had to be 40 yards from the main building was this strong feeling like you could just fall to the ground and start weeping for the sorrows of your life.
We walked to the door of the monastery and knocked. A few seconds later, a bald, 50-something Korean man opened it, looked out at us with a blank face. We awkwardly told him we had come to see him. In a thick Korean accent he said today was the wrong day for us, come back tomorrow and shut the door. We stood there dumbfounded. We had woken up at 6 am and driven four hours. He was an enlightened monk. He couldn’t just turn us away.
Nervously, I knocked again. He came back out, same blank look. I told him we had driven all the way from New York. He motioned for us to come in, and we followed.
Inside were maybe 25 Koreans all waiting to see the monk whose name it turned out was Dr. Shin. The Koreans had filled a large wooden table with a massive buffet of Korean food, and Andrew and I were invited to help ourselves which we did. People were individually or in couples going into a small meditation room where Dr. Shin sat and attended to them. After at least an hour, someone motioned to us it was our turn.
We were there for probably 5-10 minutes. I don’t remember who spoke first, or the entirety of the conversation, only a few snippets which have stayed with me. I told him I didn’t really know what I wanted to do with my life. I thought maybe I wanted to be a writer. He laughed out loud. “You want to be artist?” he said with his thick accent. “You pumping gas. Hahahahahah!” Then he looked at me seriously, and said, “Business and law. You study business and law.”
. . .
I’m 53 years old as I type this in October of 2024, and my “job” now is to write and talk about things as I see fit. I started my Substack in 2020, and while my first post was about large numbers, my second one was more from the heart. I create for a “living”, and I suppose that makes me an artist of sorts. But when I think back to the words of Dr. Shin, he was 100 percent right.
. . .
Most people should not try to be artists. You can’t easily make a living at it. It’s the wrong way to go about achieving status or security in society. There are some people who simply have no choice. They live for what they do, and even if they die broke and alone, they could not have done otherwise. Those are artists.
So what the hell am I doing?
I belong to a relatively small minority, those with something to say. I was always like this, even during the visit with Dr. Shin. But in my 20s and 30s I could not have done it. I needed to contribute something, get the reward part out of the way. I lacked the confidence and conviction to create whether or not anyone were interested in my work or wanted to compensate me for it. And unlike real artists, I had a choice. I don’t know if I could have dealt with a real job, but helping run a small fantasy sports business, something I loved, was possible for me, and I was lucky enough to find it.
. . .
Now I’m beyond that phase. I have enough money, a partner, a daughter and a dog. I like recognition and paychecks as much as the next person, but I’m not thirsty. I’ll say what I think (mostly) without regard for how it’ll affect my readership or reputation. I can open my mind and let the ideas out. Maybe it’s not quite like Beethoven, but more along the lines of Jorge Luis Borges who said:
I do not write for a select minority, which means nothing to me, nor for that adulated platonic entity known as ‘The Masses’. Both abstractions, so dear to the demagogue, I disbelieve in. I write for myself and for my friends, and I write to ease the passing of time.
-
 @ 4ec341e6:6dc2fdaf
2024-10-08 01:25:08
@ 4ec341e6:6dc2fdaf
2024-10-08 01:25:08There is a reference to chapter 12 - Relating design patterns to the model and also to chapter 4 - Layered Architecture.
An interesting part here in chapter 1 was about making business rules more explicit, an example is given where the rule is implicit within an application method:
java public int makeBooking(Cargo cargo, Voyage voyage) { double maxBooking = voyage.capacity() * 1.1; if ((voyage.bookedCargoSize() + cargo.size()) > maxBooking) return –1; int confirmation = orderConfirmationSequence.next(); voyage.addCargo(cargo, confirmation); return confirmation; }So the code is refactored to something like this:
```java public int makeBooking(Cargo cargo, Voyage voyage) { if (!overbookingPolicy.isAllowed(cargo, voyage)) return –1; int confirmation = orderConfirmationSequence.next(); voyage.addCargo(cargo, confirmation); return confirmation; }
public boolean isAllowed(Cargo cargo, Voyage voyage) { return (cargo.size() + voyage.bookedCargoSize()) <= (voyage.capacity() * 1.1); } ```
The advantage here is that the overbooking business rule is more explicit and accessible, which makes it easier for everyone involved in the project to understand. In addition, of course, to making the rule clearer (explicit).
In my opinion, this also brings another series of advantages, it makes maintenance easier and helps functions do only one thing.
The chapter also talks about the importance of deepening the understanding of the domain (that is, the company's business rules) to create more useful and representative models.
-
 @ 45bda953:bc1e518e
2024-10-24 11:31:16
@ 45bda953:bc1e518e
2024-10-24 11:31:16Revelation Chapter 2:17
“He who has an ear, let him hear what the Spirit says to the churches. To him who overcomes I will give some of the hidden manna to eat. And I will give him a white stone, and on the stone a new name written which no one knows except him who receives it.”
Revelations is a mysterious book with some verses that seems to make very little sense.
Q: Why do we need names? A: To identify ourselves.
Same reason nature opted for us to have uniquely identifiable faces. But a name no one knows except him who receives it? Why would you need that?
When you are born you have very little in the way of personality and character. Doctor exclaims, “It’s a boy!” First verifiable identifier is recognised. One newborn baby looks very similar to another. For that reason they can accidentally be mixed up and given to the wrong mother at the hospital. But if the mother knows that she birthed a boy she would immediately know something is amiss if she gets handed a newborn girl. Gender is important as the first verifiable, unique identifier of the new being.
The newly confirmed male child gets issued a verbally spoken and symbolically scripted identifier. This identifier is known as a name. Name and surname please. These identifiers are of little consequence to the being who knows only feelings of pain and sensations of comfort. The survival of the biological spawn is dependant on the instinct to suckle and the tendency to cry at slight discomfort. This is the language of human instinct to cry and suck. As the toddler develops it starts to respond to the vocally repeated identifier (known as a name) to the point where it has been sufficiently trained to respond to the verbal enunciation of it. When you call for someone you are evoking hope that the entity being called to will respond by coming to your physical location so that you can share or enquire information. When the summons is answered by presence you maintain connection not by repetition of the name but by eye contact and directing conversation to the face of the person. The face being the most accurate point with which to verifiably establish identity.
In the book of Genesis Jacob is able to fool Isaac (His father) by exploiting his bad eyesight to steal an inheritance blessing from his older brother Esau. The face of Jacob was obscured through Isaac’s blindness which gave a false signal to the issuer of a blessing.
As our proverbial John Doe grows up he develops a personality and character which allows for people to gauge the levels of trust they are willing to risk on him. Character and personality are also unique identifiers. Mother knows best at who will be diligent when keeping their rooms clean and whose rooms she will have to clean for them. She can through experience predict outcomes using knowledge of character and personality as a reference. This information is valuable and can only be established or measured when there is an ongoing relationship where trust and responsibility are continuously tested and stressed.
We all have identifiers that are publicly displayed wherever we go.
: Physical appearance, Wedding ring, Tatoo
We have identifiers that represent or address us verbally and textually.
: Names, titles, seals, signatures, handwriting et cetera.
Ambiguous identifiers
: Left handed, smoker, married, divorced, affiliations, church, political views, phone number, address, favourite colour, drivers license ad infinitum.
In this digital world our identifiers are all exploitable by a large number of unidentifiable bad actors. This is weakness. If you are a man of character and strength but have no control over your identity. You are weak and defenceless in the eyes of these virtually indistinguishable, androgynous scammers, fraudsters, monopolies and governments.
We have to take digital sovereignty over our digital identities. That means we have to train our minds in the establishment of truth. The truth being...
Be true to thine self and let the truth about you be established by you. That means abandoning trust in third parties and know that no one is coming to save you and protect your personal data. Like there is no spoon in the matrix, there is also no institution who loves you enough to protect your identity in a digitally encrypted world. In some cases they might be legally obligated to, but who will take responsibility and how do you quantify and reverse the damage of leaked information. You don’t. No justice for the slave.
The spoon is a lie. It simply does not exist.
Revelation Chapter 2 verse 17
“He who has an ear, let him hear what the Spirit says to the churches. To him who overcomes I will give some of the hidden manna to eat. And I will give him a white stone, and on the stone a new name written which no one knows except him who receives it.”
 If you have an identifier that only you know about then you have a private key. You can verify your holdings of assets. You can prove your identity on nostr. You can own not only the data but prove you are the source of it.
If you have an identifier that only you know about then you have a private key. You can verify your holdings of assets. You can prove your identity on nostr. You can own not only the data but prove you are the source of it.Anything that a trusted third party is currently doing for you, analog or digital is systemically being open sourced and you could do it for yourself with the press of a button. All you need is a white stone with a name on it no one else knows and be willing to carry the responsibility. You could then selectively reveal yourself to the world and prove it is you without exposing the you that is private. I will give an example to help you understand the power.
John 19:31–42
31 Therefore, because it was the Preparation Day, that the bodies should not remain on the cross on the Sabbath (for that Sabbath was a high day), the Jews asked Pilate that their legs might be broken, and that they might be taken away. 32 Then the soldiers came and broke the legs of the first and of the other who was crucified with Him. 33 But when they came to Jesus and saw that He was already dead, they did not break His legs. 34 But one of the soldiers pierced His side with a spear, and immediately blood and water came out.
One thing is certain, Jesus was verifiably dead. The Romans, Jews and disciples who were present at the execution and burial all concurred. He is dead. Deceased. Gone from the realm of the living. Roman soldiers were veritable experts at death and declaring the dead so.
A few days later some disciples were proclaiming excitedly about Jesus being alive. A certain guy named Thomas would not be had. You guys are crazy, trying to establish some weird cult by pretending a fantastic impossibility. Nope. They were adamant. He lives. They claimed, like a bunch of fanatics. Thomas, being the voice of reason says the following.
John 21:25
25 The other disciples therefore said to him, “We have seen the Lord.” So he said to them, “Unless I see in His hands the print of the nails, and put my finger into the print of the nails, and put my hand into his side, I will not believe.”
Thomas was a real Bitcoiner. He does not trust, he verifies.
 Verification in progress.
Verification in progress.The body of Jesus, should he have been alive will have been littered with scar tissue all across his back and legs. It would have been easy for Him to selectively reveal his identity to whoever he chose by exposing his body and letting them verify the proof of his identity without doubt. No one in world history has ever committed suicide by flogging and crucifixion so you cannot even fake or repeat it if you wanted to commit identity theft and pretend to be the Christ.
A proof of work hash in history so profound that civilisations collapsed on the realisation of its profundity. Another consequential exposition of identity verification is also expounded on by the gospel accounts.
Matthew 24:5
“For many will come in My name, saying, ‘I am the Christ,’ and will deceive many.
Eric Cason on the "What Bitcoin Did" podcast said that he thinks Bitcoin is a messianic event. I agree with him. Liberation from economic tyranny is messianic if a figure initiates the salvation process.
That would suggest that there will be messianic implications, namely identity fraud of messiah with the intent to deceive and extort.
Matthew 24:23
23 “Then if anyone says to you, ‘Look, here is the Christ!’ or ‘There!’ Do not believe it.
We have ourselves an example of this in Craig Wright who claims to be Satoshi Nakamoto. Yet he refuses to verify it by transferring Genesis bits. Like Thomas demands to see the scars of crucifixion so too must we demand to see on chain movement of Genesis coinbase block reward as proof of identity and proof of work from anyone who publicly makes a claim to the person of Satoshi Nakamoto. Historic records in the future might mark this dispensation, BWP (Before white paper) and ASN (After Satoshi Nakamoto) or something of this nature could stand in the annals of history, marking a era of mankind similar to BC, Before Christ and AD, anno domini, the year of our Lord.
Jesus is yet to give me a secret name like Satoshi already did.
Which leaves me wondering…
 The simulacral spectre created by Satoshi is an ongoing rabbit hole,
The simulacral spectre created by Satoshi is an ongoing rabbit hole,I have no doubt.
...
bitbib
-
 @ e6817453:b0ac3c39
2024-10-06 11:21:27
@ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias.
1. Privacy and Ownership: Foundations of Personal AI
At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations.
In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI.
2. Bias and Fairness: The Ethical Dilemma of LLMs
Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values.
This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks.
Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge.
3. Explainability: The Need for Transparency
One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions.
Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm.
This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks.
Addressing the Ethical Landscape of Personal AI
As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development.
Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources.
There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom.
The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development.
Conclusion
In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values.
If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
-
 @ c0f9e286:5a223917
2024-10-24 09:37:21
@ c0f9e286:5a223917
2024-10-24 09:37:21ตอนที่แล้วได้กล่าวถึงการตั้งบริษัท Holding Company เพื่อนำมาถือหุ้นในบริษัทลูก จุดประสงค์นอกจากจะเป็นการประหยัดภาษีแล้ว ยังง่ายต่อการควบคุม เนื่องจากแบ่งสัดส่วนการถือหุ้นกันตั้งแต่ต้น ซึ่งหากถือในนามบุคคลธรรมดาย่อมปกปิดตัวตนที่แท้จริงไม่ได้ ดังนั้นหลายๆบริษัทจึงนิยมตั้ง Offshore Holding (Holding ที่ตั้งในต่างประเทศ) เข้ามาถือหุ้นบริษัท Holding ในประเทศอีกทีหนึ่ง
นั่นแปลว่าวุ่นวายกับการตั้งบริษัท Offshore Holding แค่ครั้งเดียว หลังจากนั้นก็นำมาถือหุ้นใน Holding ในประเทศเพื่อเป็นเจ้าของทุกๆบริษัทในเครือ ซึ่งมีอำนาจควบคุม บังคับบัญชา และสั่งการโดยไม่จำเป็นต้องเปิดเผยตัวตนที่แท้จริง
ส่วนถ้าจะถามว่าไปตั้ง Offshore ประเทศไหนดี อันนี้ขึ้นกับวัตถุประสงค์ของแต่ละท่าน ซึ่งไม่มี One Size fits all บางคนตั้ง Offshore มาเพื่อรับเงินก้อนใหญ่จากการขายหุ้น และไม่ได้ต้องการปกปิดตัวตนอะไรมากมายก็อาจจะไปตั้ง Offshore ที่ Hong Kong หรือ Singapore
แต่ถ้าวัตถุประสงค์ต้องการที่จะปกปิดตัวตน อาจจะไปตั้งในประเทศอย่าง Seychells, Vanuatu, Mauritius หรือ BVI เป็นต้น ซึ่งประเทศเหล่านี้มักมีนโยบายไม่เปิดเผยตัวตนของบุคคลที่เป็นเจ้าของหุ้นในบริษัท และที่สำคัญ ประเทศเหล่านี้บางทียอมให้นิติบุคคลต่างประเทศเข้ามาเป็นผู้ถือหุ้นได้ 100% (กฎหมายไทยในการตั้งบริษัทต้องมีผู้ถือหุ้น 2 คนขึ้นไป และหากไม่มีโรงงานในไทย หรือได้รับสิทธิ BOI ต่างชาติสามารถถือหุ้นได้ไม่เกิน 49%)
ดังนั้นหาก Offshore Company 1 ชั้นยังไม่พอ คุณก็ตั้ง Offshore ไปเลย 2 ประเทศเช่น ผมอาจจะตั้ง Offshore แรกที่ Vanuatu ซึ่งผมถือหุ้น 100% (ในนามบุคคล) แล้วจึงไปก่อตั้งอีก 1 บริษัทอีกแห่งที่ Seychells โดยให้ Vanuatu Offshore เข้าไปถือหุ้น 100% ในนามบริษัท แล้วผมจะนำ Seychells Offshore มาถือหุ้นใน Thailand Holding อีกทีหนึ่ง ซึ่งหาก Thailand Holding ไม่ได้มีโรงงาน หรือได้รับสิทธิ BOI แปลว่า Seychells Offshore จะเข้าไปถือหุ้นได้ไม่เกิน 49% ส่วนอีก 51% คุณควรหานอมินี หรือคนในครอบครัวที่ไม่ได้กังวลเรื่องความเป็นส่วนตัวเข้ามาถือหุ้นแทน และอาจจะจำกัดสิทธิออกเสียงผ่านกลไกการถือหุ้นบุริมสิทธิ์แทน เอาเป็นว่าเดี๋ยวจะงง แต่ให้เข้าใจไว้ว่า 51% ที่ถือหุ้นแทนมีช่องทางที่ทำให้เสียง Vote หรือสิทธิในการรับเงินปันผลน้อยกว่าฝั่ง 49% ซึ่งเดี๋ยวจะหาเวลาอธิบายเรื่องนี้โดยละเอียดอีกครั้งหนึ่ง
แปลว่าหากทางรัฐบาลไทยตรวจสอบรายชื่อผู้ถือหุ้นหรือทรัพย์สินของคุณ หากใช้การถือทรัพย์สินแบบนี้ย่อมไม่มีทางที่รัฐจะรู้เลยว่าคุณเป็นเจ้าของทรัพย์สิน หรือกิจการอะไรกันแน่ และหากรัฐบาลไทยต้องการตรวจสอบจริงๆ การจะไปตรวจพิสูจน์ว่าใครถือหุ้น หรือมีสิทธิในการครอบงำบริษัทจะเป็นเรื่องยากมาก
ซึ่งหากคุณคิดว่านี่ยังเป็นส่วนตัวไม่พอละก็… แน่นอนมีวิธีที่จะเพิ่มความเป็นส่วนตัวมากขึ้นกว่าเดิม ซึ่งมีอีก 2 วิธี และสามารถนำมาใช้ร่วมกับวิธีนี้ได้ ส่วนจะเป็นวิธีอะไรนั้น รอติดตามตอนต่อไป
Own Nothing and be Happy ในแบบฉบับ Elite เป็นไงบ้างครับ เริ่มเห็นภาพหรือยังว่าทำไมตระกูลดังๆอย่าง Rothschild สามารถปกป้องความเป็นส่วนตัวของพวกเขาไว้ได้โดยที่คนนอกไม่รู้เลย ก็เพราะเครื่องมือแบบนี้ไง
realeakkrit #siamstr #privacy
-
 @ a828c9af:ea95c44c
2024-10-24 08:25:30
@ a828c9af:ea95c44c
2024-10-24 08:25:30The Philippines is a goldmine for businesses seeking new markets. With a booming economy and a population exceeding 100 million, it presents a vibrant and diverse consumer landscape that, when maximized, can offer businesses a considerable market with a growing purchasing power.
Moreover, the country's e-commerce sector has exploded in recent years, with sales hitting $17 billion in 2021 alone. As consumer behavior rapidly evolves due to technology and changing preferences, there's never been a better time to enter the Philippine market than today.
5 Ways to Tap into the Philippine Market
To succeed in the Philippine market, you need a strategic approach that resonates with the country's diverse and dynamic consumer base. Here are five proven methods to help you engage effectively.
1. Digital services and marketing
In the Philippines, a solid online presence is crucial to reach your target audience. Use social media, content marketing, and search engines to build meaningful connections almost instantly.
2. Cashless and online payment methods
Filipino consumers prefer secure and convenient payment options. Offering various cashless and online payment methods can enhance their shopping experience and give your business a competitive edge.
3. Fashion eCommerce
Fashion eCommerce is booming in the Philippines. A visually appealing website with high-quality images, detailed product descriptions, and easy navigation can attract fashion-conscious Filipinos.
4. Localized content and engagement
Tailor your content to your customers' culture and values to connect with the Philippine market. Using the local language, cultural references, and relatable imagery can deepen customer engagement and build trust.
5. Responsive customer support
Excellent customer support builds trust and loyalty. When you offer timely, helpful responses through chatbots and automation while maintaining a personal touch ensures customer satisfaction.
Check this infographic to learn more about consumer trends in the Philippines and how to take advantage of them to tap into this lucrative market.
-
 @ 97fc03df:8bf891df
2024-10-24 07:53:50
@ 97fc03df:8bf891df
2024-10-24 07:53:50A Value Internet Sharing Bitcoin’s Consensus Security
Author: BEVM, October 2024
Abstract
Super Bitcoin is a value-based internet centered on BTC, and share Bitcoin's consensus security. This value internet not only inherits the security of the existing Bitcoin network but also transcends BTC's current limitations of being solely used for transfer, providing the Bitcoin network infinite potential for scalability and flexibility.
While the Lightning Network [2] inherits Bitcoin's network security and offers partial scalability solutions, it still falls short in supporting smart contracts and further enhancing scalability. We propose a five-layer architecture for Super Bitcoin using the Bitcoin network as the kernel layer, maintaining system security and transaction irreversibility through the proof-of-work (PoW) consensus mechanism; we build an efficient communication layer based on the Lightning Network, facilitating rapid transmission of asset information while preserving Bitcoin's decentralized nature; we introduce the Taproot Consensus as the extension layer, abstracting Lightning Network communication and asset information to provide a standardized interface for the upper virtual machine layer; we set up a multi-chain layer, also known as the fusion layer, which consists of multiple lightning chains secured by BTC consensus, integrating any mainstream virtual machine (VM) to achieve a "Multi-chain interconnection“ and ”multi-chain interoperability” unified by BTC consensus; finally, we support the application layer, providing developers with rich tools and interfaces to build a decentralized application (DApp) ecosystem, all sharing the security of BTC consensus.
1. Introduction
As the pioneer of cryptocurrencies, Bitcoin (BTC), through its proof-of-work (PoW) consensus mechanism and decentralized network structure, has garnered an immense level of consensus, becoming a supranational currency. This security stems from the perfect combination of its vast network hash power and economic incentives. The birth of Bitcoin not only ushered in a new era of decentralized digital currency but also pointed the way for the subsequent development of blockchain technology. However, the limitations of Bitcoin’s scripting language soon became apparent, as it only supports simple value transfers and limited contract logic, unable to meet the demands of more complex decentralized applications.
The evolution of blockchain technology is essentially all about expanding and enhancing Bitcoin's capabilities. Vitalik Buterin, the founder of Ethereum, initially envisioned adding smart contract functionality to Bitcoin. However, due to the technological constraints of the time and the limitations of the Bitcoin network, Ethereum had to establish its own independent consensus system. While this approach allowed for the creation of Turing-complete smart contracts, it also introduced new security risks and scalability challenges. Many projects followed suit, building independent blockchain ecosystems, gradually diverging from and even forgetting the original intention of extending Bitcoin’s capabilities.
However, two key factors remind us of the need to reconsider this direction. First, the continued rise in Bitcoin’s value relative to other cryptocurrencies like Ethereum has validated the trust people place in its security and stability. Second, the collapse of Luna/UST, which wiped out nearly $100 billion in market value, highlighted the severe security vulnerabilities present in independent consensus chains, especially when faced with complex economic models and rapidly growing network value.
In this context, we introduce Super Bitcoin to create a true value internet sharing Bitcoin's consensus security. It fundamentally differs from the existing Bitcoin Layer 2 solutions: traditional Bitcoin Layer 2 solutions (such as the Lightning Network) mainly achieve fast payments through off-chain state channels and limited scripts, while sharing Bitcoin's consensus security but lacking flexibility. Meanwhile, sidechains like Stacks or Layer 2 solutions, although they support smart contracts, still rely on independent multi-signature mechanisms for security, thus not fully inheriting the security of the Bitcoin mainnet.
2. Technical Background
To fully understand the proposed solution, it is necessary to first review the background and development of several key technologies. This chapter briefly introduces the Lightning Network, the Substrate framework [3], BEVM's Taproot Consensus, and the multi-chain interoperability system to provide a foundation for understanding our solution.
2.1 Lightning Network
The Lightning Network is a Layer2 scaling solution for Bitcoin, with its core design principles detailed in the BOLT (Basis of Lightning Technology) specifications. These specifications not only ensure the efficient operation of the Lightning Network but also ingeniously achieve deep integration with the consensus security of the Bitcoin mainnet. Several parts of the BOLT specifications play a key role in sharing Bitcoin’s consensus security.
BOLT #2 and BOLT #3 provide detailed guidelines on the lifecycle management of payment channels and the structure of transactions. The opening of a channel involves creating a multi-signature output on the Bitcoin blockchain, while closing the channel requires broadcasting the final state to the mainnet. BOLT #3 specifically defines commitment transactions, which are the core mechanism by which the Lightning Network shares Bitcoin's consensus security. Each time the channel state is updated, a new commitment transaction is generated, which can be broadcast to the Bitcoin mainnet if needed. The design of commitment transactions ensures that even if one party in the channel becomes uncooperative, the other party can still close the channel by broadcasting the most recent commitment transaction and receive their due funds. This mechanism directly relies on Bitcoin’s consensus rules and security, meaning the Lightning Network’s security is essentially guaranteed by the Bitcoin network.
BOLT #5 defines the penalty mechanism for channel closures. This mechanism introduces the concept of "revocating private keys," effectively preventing participants from broadcasting outdated channel states. If dishonest behavior is detected, the honest party can use these keys to punish the other party on the Bitcoin main chain, thereby ensuring the accuracy of the channel state and enforcing honest behavior among participants through Bitcoin's consensus mechanism.
Additionally, the commitment transaction format specified in BOLT #3 connects Lightning Network transactions to Bitcoin's fee market through "anchor outputs." This not only enhances the security of transactions but also ensures that Lightning Network transactions can still be confirmed promptly during periods of network congestion.
These meticulously designed specifications collectively ensure that the Lightning Network, while providing fast and low-cost transactions, can still fully leverage Bitcoin's robust consensus security.
2.2 Substrate Framework
The Substrate framework is a highly modular blockchain development toolkit written in Rust, providing a powerful and flexible technical foundation for the implementation of Super Bitcoin. Its core strength lies in its pluggable Pallet system, where these pre-built functional modules serve as "blockchain Legos," enabling us to quickly and efficiently assemble and customize the desired features.
For Super Bitcoin, Substrate's modular design is crucial. It allows us to flexibly build and integrate various functional components on top of the shared Bitcoin consensus security. By leveraging Substrate's Pallet, we can easily support and integrate different virtual machine environments, thereby increasing the system's flexibility and adaptability. This design not only accelerates the development process but also provides Super Bitcoin with powerful scalability, allowing it to better meet the evolving needs of the blockchain ecosystem.
Super Bitcoin utilizes these features of Substrate to customize the BEVM-stack framework, which enables one-click deployment of lightning chains.
2.3 Taproot Consensus
BEVM’s Taproot Consensus integrates Bitcoin’s Taproot upgrade [4] technology. This technology combines several key elements: Schnorr signatures [5] provide signature aggregation capabilities, Merkelized Abstract Syntax Tree (MAST) support complex conditional scripts, and Musig2 enables two-round communication in multi-signature schemes. Through the combination of these technologies, BEVM successfully implements a decentralized threshold signature network with (t, n) support.
Additionally, BEVM leverages Bitcoin SPV (Simplified Payment Verification) technology to achieve lightweight decentralized block header synchronization. This allows transaction verification without downloading the full blockchain data, enabling BEVM to synchronize with the BTC mainnet in a decentralized manner. In Super Bitcoin architecture, Taproot Consensus plays a key role as the extension layer: it interfaces with the Lightning Network below, abstracting and integrating asset information, and provides standardized interfaces for different virtual machine execution environments above, realizing the transmission and utilization of asset information.
Such design makes Taproot Consensus a core component of the Super Bitcoin architecture. It not only inherits the security and privacy-preserving characteristics of the Bitcoin network but also provides rich functional support for upper-layer applications.
2.4 Multi-Chain Interoperability System
The concept of a multi-chain interoperability system was first introduced by Polkadot. Polkadot [6] is a multi-chain interoperability system based on the Substrate framework, sharing the security of DOT consensus, and using parachains for application chain expansion. Correspondingly, Super Bitcoin is a multi-chain interoperability system built on Bitcoin and the Lightning Network, sharing BTC consensus security, and using Lightning Chains for application chain expansion.
The differences between the two are as follows:
-
Shared Consensus Security: Both Polkadot and Super Bitcoin’s multi-chain networks achieve shared consensus security, but Polkadot shares DOT consensus, while Super Bitcoin shares Bitcoin consensus. The strength of BTC’s consensus is far greater than that of DOT. Theoretically, the security of the Super Bitcoin architecture is 200 times higher than that of the Polkadot network. This "200 times" represents the current ratio of BTC’s $1.3 trillion market cap to DOT’s $6.5 billion market cap. Therefore, the Lightning Chains on Super Bitcoin offer approximately 200 times the security of Polkadot's parachains.
-
Application Chain Architecture: Super Bitcoin’s lightning chain is deployed with one click based on BEVM-stack, whereas on Polkadot, parachains are deployed via Substrate with one-click.
-
Cross-Chain Communication Protocol: Super Bitcoin uses lightning channels as the communication protocol between Lightning Chains, while Polkadot uses XCMP as the communication protocol between parachains.
3. System Architecture

3.1 System Architecture Overview
Super Bitcoin is a five-layer architecture protocol built by BEVM guided by the three problems of blockchain - decentralization, security and scalability.. This protocol is based on the Bitcoin protocol and utilizes the Lightning Network for efficient peer-to-peer communication. To extend the functionality of Lightning Network nodes, Super Bitcoin integrates Taproot Consensus and combines Bitcoin SPV, Schnorr signatures, MAST contracts, and a BFT PoS consensus mechanism to achieve scalable state management and transaction processing.
On this foundation, Super Bitcoin further integrates multiple virtual machines, including WASM, EVM, SVM, MoveVM, and CairoVM, creating a multi-chain system based on lightning chains that offers a diverse range of smart contract execution environments. This modular framework significantly enhances the system's scalability and flexibility while maintaining the decentralized nature of the Bitcoin network. Importantly, all lightning chains share the Bitcoin network's consensus security, ensuring that the system remains highly secure as it scales.
3.2 Kernel Layer
The Bitcoin network serves as the kernel layer of Super Bitcoin, maintaining the security and irreversibility of the entire system through the Proof-of-Work (PoW) consensus mechanism. This decentralized peer-to-peer electronic cash system primarily supports BTC transfers and basic opcode execution, managing state using the UTXO model. The Bitcoin network’s block structure and transaction data serve as the input for the Lightning Network, providing reliable foundational data for the upper layers. Although Bitcoin’s scripting system is not Turing-complete, it can support the most basic smart contract functionality through stack-based operations, conditional checks, and cryptographic functions. The network maintains a block time of approximately 10 minutes using a difficulty adjustment algorithm and uses Merkle tree structures to optimize transaction verification efficiency. The security and decentralization of this foundational layer provide a robust consensus security foundation for the entire Super Bitcoin architecture, while its simple design and limited scripting capabilities offer a stable and predictable environment for upper-layer expansion.
3.3 Communication Layer
The Lightning Network serves as the communication layer of Super Bitcoin, achieving efficient asset information transmission while sharing the BTC consensus security. It acts as a bridge between users and the Super Bitcoin ecosystem, enabling bidirectional payment channels through a Hashed Time Lock Contract (HTLC), supporting multi-hop routing and atomic swaps. Users can establish state channels with Super Bitcoin nodes to deposit funds and conduct instant off-chain transactions.
Super Bitcoin nodes, as specialized Lightning Network nodes, not only maintain direct channels with users but also remain compatible with the existing Lightning Network by implementing the BOLT (Basis of Lightning Technology) specifications. This design allows users to leverage the existing Lightning Network infrastructure for cross-node, cross-chain payments and value transfers, providing a secure communication foundation for the lightning chains.
3.4 Extension Layer
Taproot Consensus serves as the extension layer in Super Bitcoin, playing a critical role in connecting the Lightning Network with the upper-layer lightning chains. It abstracts the asset information transmitted through the Lightning Network and converts it into blockchain data that can be processed by the upper layers, balancing the payment efficiency of the Lightning Network with the logical needs of upper-layer applications.
This expansion layer integrates Bitcoin SPV, Schnorr signatures, MAST (Merkelized Abstract Syntax Tree) structures, and a BFT (Byzantine Fault Tolerance) PoS consensus mechanism to achieve multiple functions:
1. Connecting the Lower Layer :Bitcoin SPV enables lightweight block header verification, allowing nodes to synchronize with the Bitcoin network in a decentralized manner, providing reliable on-chain data input for the Lightning Network.
2. Information Processing and Storage: The PoS-based blockchain network provides distributed storage of Lightning Network channel states. It also processes information for BTC and Taproot Assets, supplying necessary data for upper-layer applications. This mechanism ensures data redundancy and resistance to censorship.
3. Security Assurance : Decentralized threshold signatures replace the local key management system of Lightning Network nodes, enhancing key security and flexibility. The aggregation feature of Schnorr Signatures is used to construct a (t, n) threshold signature network, replacing the traditional single-key management model of the Lightning Network.
4. Privacy and Complexity : The MAST structure allows complex conditional scripts to be represented on-chain as a single hash, improving both privacy and script complexity. Through these mechanisms, the Taproot Consensus extension layer effectively converts verified Lightning Network data into standardized blockchain states. While ensuring security and privacy, it enhances the overall system's performance and scalability. It not only connects the underlying Bitcoin and Lightning Networks but also provides the upper-layer applications with rich and reliable data and functional support.
#### 3.5 Fusion Layer The Fusion Layer reflects the scalability of Super Bitcoin. It builds on top of Taproot Consensus and utilizes the extensibility of the Substrate framework to achieve a multi-chain interconnected system. Its key features include:
1. Scalable Multi-Chain Architecture: Supports the deployment and interconnection of an unlimited number of lightning chains, with BEVM serving as a special lightning chain responsible for managing cross-chain interactions and resource scheduling.
2. Heterogeneous Compatibility and Standardized Protocols: Compatible with multiple virtual machines (such as MoveVM, CairoVM, SVM, EVM) and achieves atomic asset exchange and state synchronization through a standardized cross-chain protocol based on the Lightning Network.
3. Shared Security and Flexible Consensus: All lightning chains inherit the security of the Bitcoin network, while adopting a pluggable consensus design, with the default being a Taproot-compatible BFT variant.
4. Ecosystem Expansion: Facilitates the rapid migration of existing blockchain technologies, extending the decentralized BTC ecosystem to various Turing-complete blockchain applications.
With these features, the Fusion Layer enables Super Bitcoin to evolve into a highly scalable, secure, and interoperable multi-chain ecosystem, providing robust infrastructure support for blockchain innovation.
3.6 Application Layer
The Application Layer is built on top of Super Bitcoin's multi-chain architecture, offering developers a diverse decentralized application (DApp) ecosystem. Leveraging the security, scalability, and interoperability of the underlying layers, it supports the deployment of applications on any Turing-complete virtual machine. Developers can choose to quickly deploy proprietary application chains within the lightning chain framework, or they can deploy various applications directly on the lightning chains. All these applications and chains automatically inherit the consensus and security guarantees of the Bitcoin network.
The Application Layer integrates multiple smart contract execution environments, supporting programming languages such as Solidity (EVM), Move, Cairo, and Rust. The Application Layer lowers the entry barrier for developers and accelerates the innovation cycle. Through standardized API interfaces, developers can utilize Lightning Network channels to achieve decentralized cross-chain asset transfers and information exchanges. Additionally, it incorporates protocols like Taproot Assets, which are compatible with the Lightning Network, further enhancing cross-chain functionality.
Although the services provided by the Application Layer are similar to other VM-based public blockchains, it has two distinctive features: first, it allows the use of decentralized native BTC as the base currency for applications; second, the entire application layer shares the security of the Bitcoin network. Such design not only offers a rich development environment but also ensures that applications are built on solid security and native cryptocurrency support.
4. Shared Consensus Security
Shared BTC consensus security is the security core of our five-layer architecture. This concept is derived from Polkadot's shared security model, which Polkadot defines as Shared Security, also known as Pooled Security, is one of Polkadot's unique value propositions. In essence, it means that all parachains connected to Polkadot's relay chain benefit from the full security of the entire Polkadot network.
Our five-layer protocol architecture further extends this concept by leveraging the Bitcoin (BTC) network—currently recognized as the most secure blockchain consensus system—to ensure the security of the entire ecosystem. Compared to Polkadot's parachains, which share Polkadot's consensus security, our architecture is directly built on top of the Bitcoin network, sharing Bitcoin’s consensus security.
Existing BTC Layer2 solutions typically ensure security through cross-chain mechanisms or BTC staking, which only utilize part of Bitcoin’s consensus security. In contrast, our five-layer protocol is built on the Lightning Network, using HTLC (Hashed Timelockd Contract) and commitment transactions, with security fully dependent on BTC consensus. This design allows our system to fully inherit the consensus security of the Bitcoin network.
Specifically, our architecture achieves shared BTC consensus security through the following methods:
-
Leveraging the peer-to-peer channels of the Lightning Network to ensure that all transactions are ultimately settled on the Bitcoin mainnet.
-
Using HTLC commitment transactions, where each state update is protected by the consensus of the Bitcoin network.
-
Through the Taproot Consensus extension layer, extending Bitcoin's security features to more complex smart contract environments.
-
In the multi-chain system, all lightning chains share Bitcoin’s network consensus security, ensuring consistency and reliability across the entire ecosystem.
5. Lightning Chain
Based on the shared BTC consensus security, we utilize the lightning chain to create a Value Internet. To achieve this, the architecture of the lightning chain network is inspired by Polkadot's relay chain and parachain design:
-
Relay Chain: It serves as the central nervous system of the entire network, responsible for the overall security, cross-chain communication, and consensus mechanism. The relay chain does not execute specific application logic but focuses on coordinating the operations of the entire ecosystem.
-
Parachains: These are independent blockchains that run in parallel with the relay chain. Each parachain can have its own token economy and governance mechanism, achieving interoperability through the relay chain and sharing the security guarantees provided by the relay chain. Drawing from Polkadot’s design, Super Bitcoin proposes a multi-chain interoperability system based on Bitcoin and the Lightning Network. In this system, the Lightning Chain functions similarly to Polkadot's parachains, with the following unique characteristics:
Shared BTC Consensus Security: Unlike Polkadot’s independent consensus model based on PoS staking, Lightning Chain directly inherits the consensus security of the Bitcoin network, providing unprecedented security for the entire ecosystem.
-
Lightning Network Integration: Lightning Chain deeply integrates Lightning Network technology, enabling high-speed, low-cost transaction processing, significantly enhancing the throughput and efficiency of the entire system.
-
Scalability: Theoretically, an unlimited number of Lightning Chains can be deployed, with each Lightning Chain optimized for specific application scenarios or industry needs, offering a high degree of flexibility and scalability.
-
BEVM as the Core Coordinator: In this ecosystem, BEVM (Bitcoin-Enhanced Virtual Machine) acts as a special Lightning Chain, playing a role similar to that of Polkadot’s relay chain. It is responsible for the governance and resource allocation of the entire network, ensuring efficient collaboration between different Lightning Chains.
-
Shared Lightning Network Liquidity: All Lightning Chains share the same Lightning Network, which means they can access a common liquidity pool, improving capital efficiency.
These features not only highlight the innovative design of Lightning Chain but also underscore its fundamental differences from existing BTC Layer 2 solutions. By directly sharing Bitcoin network consensus security and Lightning Network liquidity, Lightning Chain achieves a qualitative leap in both security and interoperability.
5.1 Lightning Chain
The Lightning Chain is the core component of Super Bitcoin that directly interacts with users. Its main responsibilities include handling user transactions, managing asset mapping, and executing smart contracts.
5.1.1 BTC Asset Mapping

Lightning Chain functions as both a node in the Lightning Network and a PoS (Proof of Stake) network. In this system, BTC is locked within the Lightning Network, while L-BTC represents the user's BTC balance in their Lightning Chain account. The mapping process between these two ensures the consistency and security of the assets. The specific BTC-to-L-BTC mapping process is as follows: - The user establishes a channel with the Lightning Chain via the standard Lightning Network protocol. - The user deposits A BTC into the Lightning Network channel. - As the Lightning Chain operates as a PoS network, the validators within the network observe this new BTC deposit. - Once more than two-thirds of the validators reach consensus and confirm the BTC deposit event, the Lightning Chain will issue A L-BTC accordingly.
This process ensures that the issuance of L-BTC always maintains a 1:1 ratio with the BTC locked in the Lightning Network channel. It's important to note that L-BTC is self-custodied by the user, so there is no need to worry about asset security. Additionally, PoS consensus here is not used to secure L-BTC assets but acts as a distributed ledger for the state of the Lightning Network channel, solving the potential issue of data loss in local storage by Lightning Network nodes.
5.1.2 Smart Contract Interaction on the Lightning Chain

Interaction with smart contracts on the Lightning Chain follows a "authorize first, execute later" paradigm. In this process, users need to convert L-BTC into M-BTC, where M-BTC represents the asset that can interact with smart contracts on the Lightning Chain. The specific interaction process is as follows:
- Asset Preparation: The user holds A BTC in the Lightning Network state channel and decides to interact with a smart contract using 1 BTC.
- Authorization Operation: The user authorizes the Lightning Chain network to convert 1 L-BTC into 1 M-BTC. This step does not immediately execute the conversion but provides the necessary permissions for subsequent interactions.
- Smart Contract Invocation: The user initiates a smart contract call, specifying the use of 1 M-BTC. The Lightning Chain network checks the authorization and, upon confirming its validity, performs the following actions: destroys 1 L-BTC from the user’s balance, mints 1 M-BTC, and uses it directly for interaction with the smart contract.
- Transaction Execution: The smart contract executes the specified operation using the minted M-BTC.
This process enables the seamless application of Bitcoin assets within a smart contract environment while maintaining a clear separation between L-BTC, which functions as channel liquidity, and M-BTC, which serves as a medium for contract interaction.
5.2 System Chain

System Chain is the core coordination component of Super Bitcoin implemented through the upgraded BEVM (Bitcoin-Enhanced Virtual Machine). As a special Lightning Chain, it establishes direct connections with all regular Lightning Chains in the network, forming an efficient star topology structure. This design makes the System Chain the central hub of Super Bitcoin.
The System Chain is primarily responsible for incentivizing Lightning Network nodes and coordinating cross-chain interoperability, effectively managing the entire network to ensure its efficient operation. In terms of node incentives, the System Chain implements a complex and sophisticated mechanism. It uses a dynamic reward algorithm that adjusts reward distribution based on the activity level, liquidity provided, and overall contribution to the network. During this process, the System Chain considers multi-dimensional evaluation metrics, such as the node’s uptime, transaction throughput, and routing efficiency.
In terms of cross-chain interoperability, the System Chain plays a key coordination role, facilitating seamless interactions between different Lightning Chains. It implements a secure cross-chain communication protocol based on Hashed Time Lock Contract (HTLC), ensuring the security and reliability of message transmission. Additionally, the System Chain introduces an atomic swap mechanism, which effectively prevents potential loss of funds during cross-chain asset transfers. Furthermore, by defining a unified cross-chain asset standard, the System Chain simplifies the asset mapping process between different Lightning Chains, further improving the efficiency and convenience of cross-chain operations.
6. Economic Model
The economic model of BEVM (Bitcoin-Enhanced Virtual Machine) combines Bitcoin’s issuance mechanism with the functional characteristics of the Lightning Network. It aims to address the sustainable competitiveness of Super Bitcoin and provide a long-term incentive system for the Lightning Network.
At the core of this model is the combination of Lightning Network node incentives and a staking-mining mechanism. Lightning Network nodes that establish state channels with the BEVM network can participate in staking mining. Staking mining uses a Verifiable Random Function (VRF) to determine mining probabilities, rather than distributing rewards proportionally based on the staked amount.
During the staking mining process, participants stake BTC in state channels, and the system calculates the mining probability based on the VRF. For example, if three nodes stake 100 BTC, 10 BTC, and 1 BTC, their respective mining probabilities would be 90.09%, 9.01%, and 0.90%. This mechanism ensures that smaller stakers also have a substantial opportunity to earn rewards. A dedicated whitepaper on the economic model will be released for this section, so this document will not go into further details.
7. Future Development
7.1 Short-Term Goals
The short-term goals of Super Bitcoin focus on implementing core functionalities and building the necessary infrastructure. By realizing the proposed five-layer protocol, we will introduce smart contract functionality based on the Lightning Network while sharing BTC consensus security. For users, participating in Super Bitcoin ensures that the BTC they hold remains fully under their control. At the same time, they will be able to use BTC, Taproot Assets, and other native assets within smart contracts.
7.2 Long-Term Vision
The long-term vision of Super Bitcoin is to build a global Value Internet that shares BTC consensus security. We aim to design an incentive mechanism through an innovative economic model, promoting widespread use of Lightning Network nodes. Furthermore, we are committed to deeply integrating existing blockchain ecosystems with Super Bitcoin, enabling the free flow and interaction of BTC assets. By doing so, we aim to create a secure, efficient, and interoperable blockchain ecosystem where BTC becomes the core, and all blockchain consensus models share the security of the Bitcoin network. Ultimately, our goal is to enable the Bitcoin network to scale infinitely while maintaining decentralization.
7.3 Potential Challenges and Solutions
Super Bitcoin faces several potential challenges in achieving its goals. Transforming Lightning Network nodes into a full-fledged network involves complex technical challenges that require extensive testing. Another challenge is designing a better economic incentive model to attract enough Lightning Network node operators to adopt Super Bitcoin. Ensuring seamless communication and atomic swaps between different node networks is also crucial, and the team will focus on developing standardized protocols and interfaces to enhance network interoperability. As the system’s complexity increases, maintaining network security will become more challenging. Super Bitcoin will adopt rigorous security audit processes and consider introducing advanced cryptographic technologies to strengthen system security. As the number of lightning chains grows, managing the state and interaction between networks may pose scalability challenges. By actively addressing these challenges, Super Bitcoin aims to bring revolutionary changes to the Bitcoin and Lightning Network ecosystems, creating a more flexible, efficient, and scalable infrastructure.
8. Conclusion
The five-layer architecture introduced by Super Bitcoin not only solves the problem of existing BTC Layer 2 solutions not being able to share Bitcoin's consensus security but also addresses the limitation of the Lightning Network being restricted to payment scenarios. It perfectly combines the shared BTC consensus security with smart contract functionality. Our protocol uses the Bitcoin network as the core, ensuring the highest level of security. It leverages the Lightning Network to construct an efficient communication layer, significantly improving scalability and flexibility while preserving the security of the native BTC consensus. By introducing Taproot Consensus as the extension layer, it abstracts Bitcoin and Lightning Network data to provide actionable data for the upper layers. Through the multi-chain fusion layer formed by lightning chains, we achieve a "multi-chain interconnection" supporting the free flow of cross-chain assets. The application layer offers developers a rich set of tools, fostering the development of a diverse DApp ecosystem. Combined with the innovative VRF-based staking mining mechanism, Super Bitcoin adds an incentive layer to the Lightning Network and allows the decentralized Bitcoin network to have unlimited flexibility and scalability.
9. References
[1] Nakamoto, S. (2008). "Bitcoin: A Peer-to-Peer Electronic Cash System." https://bitcoin.org/bitcoin.pdf
[2] Poon, J., & Dryja, T. (2016). "The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments." https://lightning.network/lightning-network-paper.pdf
[3]Habermeier, S., et al. (2020). "Substrate: A modular framework for building blockchains." https://www.parity.io/substrate/
[4]Wuille, P., Nick, J., & Towns, A. (2019). "Taproot: SegWit version 1 spending rules." https://github.com/bitcoin/bips/blob/master/bip-0341.mediawiki
[5] Nick, J., Seurin, Y., & Wuille, P. (2020). "Schnorr Signatures for secp256k1." https://github.com/bitcoin/bips/blob/master/bip-0340.mediawiki
[6]Wood, G. (2016). "Polkadot: Vision for a heterogeneous multi-chain framework." https://polkadot.network/PolkaDotPaper.pdf
-
-
 @ 599f67f7:21fb3ea9
2024-10-06 05:10:31
@ 599f67f7:21fb3ea9
2024-10-06 05:10:31¿Alguna vez has querido regalarle sats a alguien en forma física? Con una billetera LNbits, puedes crear fácilmente una tarjeta de regalo NFC. Esto funciona escribiendo un enlace LNURLw en la tarjeta NFC, desde el cual el destinatario puede retirar sus sats con una billetera compatible con LNURL.
¿Qué necesitas?
- Billetera LNbits
- Teléfono Android
- Tarjeta NFC con capacidades de al menos NTAG2*, por ejemplo, NTAG216. Consulta la nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65whwqrr5 para saber dónde comprar las tarjetas.
💡 Las tarjetas NTAG2 te permiten escribir un* enlace en ellas. Por ejemplo, pueden funcionar como una tarjeta de presentación que contiene la URL del sitio web de la empresa. Las tarjetas NTAG424 no solo tienen más memoria, sino que también cuentan con un parámetro SUN que permite la autenticación del servidor web, lo cual añade más seguridad a tus pagos. Este último tipo de tarjetas también se pueden convertir en BoltCards.
1. Activa la extensión
Abre tu billetera LNbits. Activa la extensión LNURLw desde la barra de herramientas y entra en la extensión.
2. Crea un enlace de retiro
-
En la página de la extensión LNURLw, elige
Advanced Withdraw Link(s)("Enlace(s) de retiro avanzado"). -
Selecciona la billetera desde la cual se retirarán los sats. Probablemente quieras separar esto de tu billetera principal de LNbits. Para hacerlo, puedes crear primero una nueva billetera LNbits yendo a la barra de herramientas y seleccionando
+ Agregar nueva billetera, luego depositando algunos sats en la billetera recién creada.

-
Asigna un título al enlace de retiro.
-
Establece los montos mínimo y máximo que se pueden canjear.
-
Establece el número de veces que se puede utilizar el enlace y el tiempo entre intentos de retiro.
-
Opcionalmente, puedes añadir una imagen personalizada marcando la casilla
Use a custom voucher design("Usar un diseño de cupón personalizado") e ingresando la URL de una imagen en formato .png. -
No marques la casilla de usar un codigo QR único.
Cuando estés satisfecho con la configuración, procede a crear el enlace de retiro.
3. Escribe el enlace en la tarjeta NFC
En tu enlace de retiro recién creado, haz clic en
view LNURL("ver LNURL"). Haz clic en el botónWrite to NFC("Escribir en NFC") y acerca tu tarjeta NFC a tu teléfono para que se pueda escribir en ella.
✔️ HECHO
💡 Informa al destinatario de la tarjeta sobre el saldo de sats que tiene para que no pierda tiempo intentando obtener hasta el último satoshi.
💡 Una vez que el destinatario haya retirado sus sats de la tarjeta de regalo, puede volver a escribir en ella su propia billetera y reutilizarla. ¡Dos pájaros de un tiro! Si la tarjeta que le diste es NTAG424, puede convertirla en una "tarjeta de débito" de Lightning como describimos en la nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65whwqrr5. Si la tarjeta es solo NTAG2*, entonces solo puede convertirla en otra tarjeta de regalo.




