-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 3589ce32:ef4269ad
2024-10-24 19:13:56
@ 3589ce32:ef4269ad
2024-10-24 19:13:56Bitcoin y la Descentralización:
Bitcoin se centra en la soberanía individual, la libertad financiera y la descentralización. Su filosofía se basa en la confianza en un sistema sin intermediarios, donde cada individuo tiene control sobre sus recursos. La descentralización de Bitcoin refleja un despertar hacia la autonomía personal, la autosuficiencia y la búsqueda de la verdad fuera de estructuras de poder tradicionales.
UCDM enseña la no-dualidad, el perdón y la percepción correcta, destacando que el amor es lo único real y que todo lo demás es una ilusión. La idea es la de liberarse de la mentalidad de escasez (tan presente en el dinero tradicional) y fomentar una mentalidad de abundancia, confianza y cooperación.
El Vedanta Advaita es una filosofía no dualista que enseña que solo hay una realidad última, y que todo es una manifestación de esa unidad. La dualidad es una ilusión. Guardando ciertas distancia, podríamos decir que la unidad subyacente del Advaita se refleja en la idea de una red descentralizada y sin fronteras, como Bitcoin, la cual conecta a las personas sin intermediarios. También ¿Cómo superar la ilusión del ego y la dualidad para alcanzar una verdadera libertad? Hablaremos de esto en otra ocasión …
-
 @ 06639a38:655f8f71
2024-10-24 14:49:08
@ 06639a38:655f8f71
2024-10-24 14:49:08Project Name
Nostr
Project Description
Nostr (Notes and Other Stuff Transmitted by Relays) is an open, censorship-resistant, and decentralized communication protocol designed for simplicity and resilience. Unlike traditional platforms, Nostr doesn’t rely on centralized servers. It already supports various use cases with free, open-source clients—offering alternatives to platforms like Twitter/X, Meetup.com, Excel 365, healthcare system and more. We will help you get started with Nostr.
Nostr has seen remarkable adoption and growth within the open-source community, evidenced by over 12,500 GitHub stars, 500+ forks, and contributions from more than 350 developers. The protocol has catalyzed the creation of an impressive ecosystem of over 390 projects, including mobile and web clients, relays, tools, and services that further enhance Nostr’s functionality. With over 70 tools and 48 libraries, developers can integrate Nostr into a wide array of applications—ranging from chat platforms to file storage and even decentralized marketplaces. These resources help to build decentralized, censorship-resistant systems without the need for centralized servers. Whether you’re working on peer-to-peer markets, privacy-focused messaging apps, or decentralized social media, Nostr’s ecosystem offers the tools.
Project website
https://github.com/nostr-protocol
Source code
https://github.com/nostr-protocol/nips
Project Theme
World Wide Web
Do you want a stand for the entire event or just for one day?
Entire event
Why do you want to be at FOSDEM?
We want to be at FOSDEM because it’s the perfect place to connect with like-minded developers and open-source enthusiasts who share our passion for decentralization, innovation, and building open permissionless technologies. FOSDEM fosters collaboration and the growth of community-driven projects and Nostr is a natural fit as a real grassroots project with its open protocol and commitment to build communication technology with resilience and simplicity in mind.
By being at FOSDEM, we aim to raise awareness, share knowledge and inspire others to explore the potential of decentralized communication systems. We also want to engage with the FOSS community and gain feedback to help Nostr grow. If people are really interested in how they can use Nostr we will show the possibilities, demo existing clients and provide in-depth explanations of how the protocol can replace the social layer (with user accounts in living a database) in existing software.What is the relation between the project and the primary contact?
Jurjen works with the community to promote its development, onboard new developers, and contribute to its open-source ecosystem. My role includes helping to raise awareness of Nostr's potential, organizing events, and supporting adoption by providing educational resources and technical guidance.
What is the relation between the project and the secondary contact?
Sebastian (37) is an independent creative / fullstack web developer who is the maintainer of a PHP helper library supported by OpenSats. Besides this project he is also making contributions with developing Nostr modules for Drupal.
“Since I've been online on the internet (1998), I'm highly interested in online communities, social networking and new ways of digital interactions. The internet has changed radically in the last decade and that change is not serving our interests. It's fair to say the web is broken in many ways. With Nostr we can fix this.”Social media links
npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft(Jurjen)
npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe(Sebastian)
npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa(Tanja)
npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn(Kevin)Anything else you like to add?
We’d also like to highlight that Nostr was created by Fiatjaf, an anonymous founder, which aligns with its principles of openness and decentralization. As an open protocol, Nostr is designed to evolve and find its own way, just like the foundational protocols of the internet. Importantly, Nostr is not a blockchain project—there are no tokens, no costs, and no barriers. It’s also not a platform nor a NFT. It’s purely decentralized, built for resilience and simplicity. While payment solutions like Bitcoin can be integrated, they are optional, not intrinsic to the protocol. This makes Nostr accessible and flexible, truly embodying the spirit of the open internet.
Nostr is more than just a technological protocol; it’s about the energy, problem-solving, and sense of hope that draws people in. Even newcomers can play a significant role in the ecosystem, gaining insight from the outside while discovering the protocol’s potential. Tanja, for example, isn’t from a tech background, yet after just three months, she’s taken on a major organizational role. She’s been spreading the message of freedom of speech and is leading the Nostr Booth LATAM tour, where volunteers, entrepreneurs, and Nostr-based businesses come together, supported by the entire community, to raise awareness about Nostr. Her passion for decentralization and open collaboration also drives her efforts to bring Nostr to FOSDEM, where she will help connect the project with like-minded developers and open-source advocates.
Please reach out to us if there are any questions. We’re really looking forward to presenting Nostr as a protocol at one of the best places where free and open-source software is flourishing.
This content will be used for a FOSDEM stand submission via https://pretalx.fosdem.org/fosdem-2025-call-for-stands/
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ bd32f268:22b33966
2024-10-24 17:57:26
@ bd32f268:22b33966
2024-10-24 17:57:26A atualidade acostumou-nos a uma lânguida linguagem devido à cultura do politicamente correto e ao crescente relativismo em que vivemos. A confusão é tanta que já não se chamam os bois pelos nomes e este ambiente faz com que inclusive desconheçamos o significado das palavras. A este respeito temos visto cada vez mais indefinição sobre o que são os vícios e sobre o que são as virtudes. Tal é a confusão que por vezes trocamos o significado de uns pelos outros.
A coragem e a convicção facilmente passam por orgulho e arrogância, a castidade passa por beatice e por aí segue a confusão com muitos outros termos.
A inversão de valores é tão disseminada que atrocidades como a pornografia, o aborto, o adultério entre outras atrocidades são celebrados como conquistas civilizacionais. A sua disseminação é de tal forma que hoje a pessoa média já banalizou e normalizou completamente estes aspectos.
“Primeiro estranha-se depois entranha-se.”
Fernando Pessoa
Enquanto isto acontece por um lado, por outro a defesa da família, da identidade e da tradição são abertamente atacadas como se se tratassem de produtos de uma cultura opressora que deve ser combatida por todos os meios. Por agora a perseguição destas ideias é ainda maioritariamente realizada através da exclusão social e económica, no entanto, não são escassos os exemplos da história em que essa perseguição assume uma outra dimensão.
Desta forma, está criado um paradigma e um sistema de incentivos que premeia a pessoa que colabora com o sistema vigente. Tanto é assim que se multiplicam cada vez mais os exemplos de programas de quotas e subvenções que permitem, a quem possui um grau mais avançado de assimilação ideológica progredir socialmente atalhando o caminho para o fazer.
“Assim, toda a árvore boa produz bons frutos, porém a árvore má produz frutos maus. Não pode a árvore boa produzir frutos maus, nem a árvore má produzir frutos bons (…)”
Mateus 7:17-18“Assim, toda a árvore boa produz bons frutos, porém a árvore má produz frutos maus. Não pode a árvore boa produzir frutos maus, nem a árvore má produzir frutos bons (…)”
> Mateus 7:17-18*
Desengane-se quem pensa que no paradigma pos-moderno não há moralização, sacerdotes e uma matriz religiosa, tudo isso existe.
Os psicólogos, para mal da nossa sociedade, são crescentemente os sacerdotes desta religião pagã, aquela que baseada numa filosofia e antropologia erradas vai corrompendo intelecto e coração.
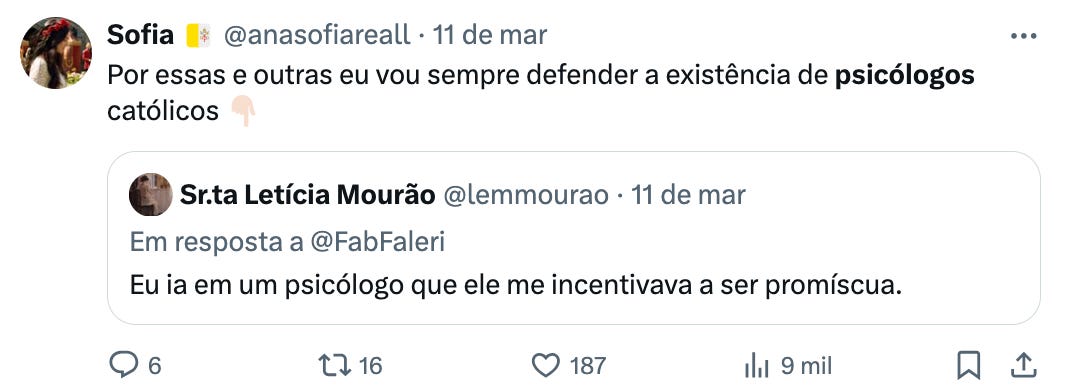
Nesta nova ordem social, que em abono da verdade é já antiga, a inversão de valores é tal que já a própria vida humana é sacrificada no altar do clima em abono da “mãe” natureza. Regredimos ao tribalismo que nos sugere que a natureza vale mais que a vida humana.
Este é apenas um exemplo dos rituais de sacrifício proporcionados pela “nova” religião. Um outro exemplo que podemos dar é o da castração química e física de crianças e jovens no altar da falsa compaixão e empatia. Ainda um outro exemplo que podemos dar é o da promoção do homossexualismo, do transexualismo e da não-monogamia como caminhos saudáveis a seguir, sacrificando a vida de muitos jovens confusos no altar da inclusão. Muitos mais exemplos poderiam ser dados, porque à medida que esta “nova” religião aumenta a sua ortodoxia os rituais vão ficando cada vez mais assombrosos.
Estes rituais têm por base uma apologia ao anti logos, quer isto dizer que procuram negar tudo o que é conhecimento básico sobre a realidade e sobre a verdade. A própria razão e lógica não se sustentam quando vemos situações como a de homens a competir em desportos femininos. As leis desta nova ordem são: “procura a felicidade (aqui muitas vezes entendida como o prazer) como fim último da vida “; “todas as opiniões são certas e não há uma verdade”; “Não servirás a nenhuma autoridade”; “não seguir o vício é opressão e seguir o vício é liberdade”.
Neste ambiente inóspito, quem quiser preservar a honra e a virtude terá cada vez mais dificuldade uma vez que a dissidência desta nova religião não é aplaudida, pelo contrário é anatematizada. Porém, importa dizer que independentemente da época há sempre espaço para o heroísmo e para a transformação destas dificuldades em degraus para que o indivíduo se possa distinguir dos demais pelas suas virtudes. Onde o vício abunda também maior o destaque será em relação à graça, como uma pedra preciosa reluzente no meio da lama que aparenta brilhar mais intensamente aos nossos olhos tal é o contraste, ou como uma luz na escuridão que se distingue facilmente.
 ###### Casper David Friedrich - dreaming man in church ruins
###### Casper David Friedrich - dreaming man in church ruins -
 @ e968e50b:db2a803a
2024-10-24 17:53:49
@ e968e50b:db2a803a
2024-10-24 17:53:49https://whosaidit.vercel.app/
I made a quiz for you. Let me know if you have any feedback. Please don't share your results or any spoilers here. I've already had some...uh...let's call if fun...sharing with friends and family. Much to @DarthCoin and many other stackers' chagrin, the purpose of this is not to convince people not to vote, although that may be the affect for some. I'm just trying to challenge people's thinking.
Also, it would be really easy for me to change any of the content. Let me know if you have feedback. I want to make this as effective and accurate as possible.
https://whosaidit.vercel.app/
originally posted at https://stacker.news/items/738766
-
 @ ff1a68c4:ec9831cf
2024-10-24 14:49:33
@ ff1a68c4:ec9831cf
2024-10-24 14:49:33Año 2147. La misión de la nave Odisea VII tenía como objetivo estudiar las lunas de Júpiter. Nadie esperaba que se encontraran con lo que estaba a punto de revelar el gigante gaseoso. A bordo, cinco astronautas, expertos en astrobiología y física cuántica, orbitaban el coloso, maravillados por sus tormentas eternas y sus mares de hidrógeno líquido.
Durante meses, la tripulación había lanzado sondas y drones a través de la atmósfera turbulenta, recogiendo datos imposibles de descifrar. Era como si el planeta se resistiera a la intrusión, ocultando secretos detrás de las franjas de nubes y la Gran Mancha Roja.
El comandante Foster, junto con la doctora Elena Ivankov, detectaron una anomalía: un patrón en las corrientes eléctricas de Júpiter que parecía regular, como un latido. Al principio, lo atribuyeron a fenómenos naturales, pero la regularidad era inquietante. Eran pulsaciones precisas, organizadas, como los de un corazón titánico, aunque tan lentas que requerían equipo especializado para percibirlas.
“Esto no es solo una tormenta más”, murmuró Elena frente a la pantalla holográfica. “Es… es un ciclo controlado.”
El equipo empezó a conectar las piezas. Las corrientes de viento y los campos magnéticos de Júpiter no se movían al azar; parecían responder a la posición de otros planetas en el sistema solar. Cada vez que la gravedad de Saturno o Marte interactuaba con Júpiter, las pulsaciones cambiaban, como si ajustara su frecuencia para estabilizar las órbitas.
Foster frunció el ceño, ajustando sus datos en el simulador gravitacional. “Si estos latidos controlan la dinámica del sistema solar, ¿qué pasaría si se detuvieran?”
“Ningún planeta sobreviviría”, respondió Ivankov, con los ojos fijos en la pantalla.
Fue entonces cuando tomaron la decisión más osada de la misión: enviar una sonda mucho más profunda de lo que cualquier nave había llegado antes, para penetrar en las capas interiores de Júpiter. Las sondas anteriores habían sido destruidas, pero esta nueva, equipada con inteligencia cuántica adaptativa, podía reaccionar a los cambios a una velocidad inimaginable. La llamaron Ecos.
Cuando Ecos descendió, las lecturas empezaron a volverse más extrañas. Júpiter parecía estar "sintiendo" la presencia de la sonda. Las pulsaciones aumentaron, y el campo magnético se distorsionó. Ecos transmitió imágenes de lo que se encontró en el núcleo del planeta: una estructura titánica, más grande que cualquier ciudad humana, compuesta de una sustancia orgánica fusionada con energía pura.
"¿Estás viendo lo mismo que yo?", susurró Foster, incapaz de procesar lo que estaba ante sus ojos.
Ivankov asintió en silencio, sus dedos temblando sobre el teclado. "Júpiter… no es solo un planeta. Es un organismo vivo."
La tripulación permaneció en silencio mientras la sonda transmitía imágenes y datos. Era como si el planeta mismo estuviera compuesto de órganos que regulaban la estabilidad gravitacional del sistema solar. Un ser inconcebible, de una escala tan vasta que su única función era equilibrar fuerzas cósmicas. Cada tormenta, cada rayo, cada pulso magnético, todo formaba parte de su regulación.
"Este 'ser' mantiene el equilibrio", reflexionó el comandante, su voz era apenas un susurro entre el zumbido de los sistemas de la nave. "Si interfiéramos demasiado, podría romper la frágil danza de los planetas."
La doctora Ivankov, profundamente impactada, sugirió la teoría más radical: "Júpiter no solo es consciente… sino que actúa como una especie de guardián del sistema solar. Un ser con un propósito tan simple como vasto: mantener el equilibrio entre los cuerpos celestes. Si alguna anomalía cósmica amenazara el equilibrio, Júpiter respondería, ajustando las órbitas, corrigiendo las trayectorias."
Entonces llegó la transmisión final de Ecos: "Interferencia detectada. Estructura orgánica ha reconocido nuestra presencia. Cambios en los latidos. Aumento de la presión. Reacción… inminente."
El corazón de Júpiter había comenzado a acelerarse.
"No deberíamos haber venido tan lejos", dijo Foster, tomando el mando de la nave. "Es un ser que no entiende nuestras intenciones. Lo único que sabe es que estamos perturbando el equilibrio."
Con los latidos de Júpiter resonando en sus oídos, la tripulación inició una retirada rápida, temiendo que cualquier alteración en ese organismo colosal pudiera desestabilizar el sistema solar entero.
Mientras se alejaban, observaron cómo las tormentas del gigante gaseoso volvieron a la calma, y el pulso volvió a estabilizarse.
"Júpiter sigue latiendo", susurró Ivankov, mirando la vasta esfera a lo lejos.
Quizás, pensó la tripulación, no era el momento para que la humanidad supiera demasiado sobre su lugar en la delicada danza del cosmos.
-
 @ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52
@ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52Tldr
- Nostr relays help users post and read notes on the network
- Relay operators have launched a variety of relays for you to use
- You too can launch your own relay for any reason you like
- Launching your own relay gives you a lot of power in how you use Nostr
- Many relay softwares exist for you to use
- I launched a personal relay using HAVEN relay software on my VPS
- I am now more in control of saving notes, cutting spam, and protecting my privacy
- My personal relay is now hosted at relay.rodbishop.nz
What are Nostr Relays Anyway?
When you're a user of a social network, you post and read notes from other users on the network. In a centralised network like Twitter or Instagram the company's servers receive all user's notes and relay them to other users. On Nostr, there is no single company's servers to relay messages, so instead the task is taken up by relay operators.
Anyone can be a relay operator and they can run a relay for any purpose. When you start using Nostr you will usually be connected to any one of a number of "public" relays, and be able to post and receive notes from users on the network via these.
Configuring these relays can tailor your experience somewhat–for example the client Nostrudel allows you to select from Western or Japanese relay set.
It is also possible to set up your own relay to use for your own purposes. All kinds of people have launched relays for all kinds of purposes. For example, to:
- Power your own client
- Support your community
- Run a for-profit relay business
- Relay a certain a type of content you need
- Back up your own notes, decrease spam, or increase privacy
- Curate your own social feed with your own algorithm
Relay instances available to connect with
Today is an interesting time in relay-ops. The evolution of the technology has inspired users to experiment with diverse types of relays tailored to various needs. As a result there are very many relay instances in operation and available to connect with.
A few sites try to collate which relays are in operation, like nostr.info and xport.top and sesseor's relay list . These lists are long (Sessor's list counted 2,500+ relays) and it's not clear to me whether it's even possible to be comprehensive as relays may join or leave the network all the time.
Broadly speaking, relays might be available for different users to use in different ways:
- A relay where anyone can post, like relay.damus.io
- A paid relay where anyone can post after payment, to cut spam, like nostr.wine
- A "web of trust" relay where anyone can post if they are related to the owner's social graph, to cut spam, like nostrelites.org
- A speciality relay where a particular community can post, like nostr.com.au for #austriches (Australians)
- A relay where anyone can post just specific content, like purplepag.es for user profiles only
- A team relay for your company or organisation only
- A personal relay for your own personal use
Nostr.Band shows which of these available relays are most popular, such as relay.damus.io and nos.lol and eden.nostr.land
Relay softwares for you to launch your own
You may decide to launch you own relays, and if you do there are many different relay softwares to choose from:
- Simple, like Bucket (<100 lines of code)
- Widely used, like Nostream (top ranked on Github)
- Customisable, like Khatru (a framework for customised relays)
- Specialised, like HAVEN or Team Relay (for personal or teams relays, based on Khartu)
You can run these on your own server, or local machine, or phone or with a third-party host.
Aljaz provides a great resource with 45+ relay softwares to choose from.
In summary, at a high level,
- Anyone can connect to any of the relay instances that are available for them to use
- Anyone who wants to launch their own can select the relay software that best suit their needs, launch an instance, and have it used by whichever users they like
Reasons to Run Your Own Relay
As a normal user of a Nostr client there's no obligation to run a relay. But having your own relay does give you more power.
For my own journey down the #nostr rabbit hole, I was looking for a relay to:
- back up my notes
- decrease spam
- increase my privacy
- learn skills I could later use for running a community or team or paid relay
Backing up notes – When you post notes to a public relay there's no guarantee that the relay is going to keep them long-term. It's job is relaying your notes to other clients, not storing them. Running your own relay allows you to keep your notes online.
Decrease spam – To first spam we can use a "Web of Trust" model–in which users endorse other users as trustworthy. A "Web of Trust" relay will reject notes from parties too far removed from your network. Running your own relay makes you more difficult to spam.
Increasing privacy – When you connect to a public relay, they can determine personal information about you, such as your IP address. Running your own relay keeps things more private.
For communities and teams and paid relays – Many opportunities exist to tailor relays to certain users needs, be they businesses or communities or as a for-profit business. For me, I am hoping that running my own relay helps me learn skills I can use in these kinds of further ventures.
To start I decided to focus on a personal relay. However, when I really got under the hood, it turned out I would need multiple relays not just one.
The outbox model
Mike Dilger proposed the outbox model (originally called the gossip model) as a way for users to engage with the wider Nostr network. It's a great model that is helpful to understand, as it suggests to establish different relays for different purposes.
Many clients and relay softwares have now adopted and continued to elaborate on this model. An example is to run specialised relays for Outbox, Inbox, Chat and Private needs.
Outbox Relay (also called Home Relay)
- This relay is for notes you have written, so that everyone knows where to find your notes
- In a set up where you are running your own, this relay is restricted so that only you can post to it, and you should set up your clients to post your notes to it
- An advanced version may take any notes received to this relay and "blast" them to other public relays so that your notes get wider reach
Inbox Relay (also called Public Relay)
- This relay is for public notes that other users want you to see, so that you always find notes that are relevant to you, including all replies, comments, likes, and zap payments
- In a set up where you are running your own, this relay is where you should look for notes relevant to you, and you should set up your clients to read from it
- An advanced version may search other public relays for notes that tag you, and import them into this relay so that you never miss a relevant note
Chat Relay (also called Direct Message Relay)
- This relay is for private direct message notes from other users, so that you always find your direct messages and so that they stay private
- In a set up where you are running your own, this relay is restricted so that only you can read from it, and you should set up your clients to read from it
- An advanced version may cut spam by only accepting direct messages from other users within your Web of Trust
Private Relay
- This relay is for your private use only, so that you can store private drafts or thoughts
- Only you can write to it and only you can read from it (and so, it is a bit mis-named as it does not actually relay anything to anywhere at all)
- In a set up where you are running your own, it gives you true privacy for these notes
In summary as a user
- I post my notes to my outbox relay. Network users can read them there, and if the relay is advanced it will also blast the notes out to other relays on the network
- I read from my inbox relay. Network users know to reach me there, and if the relay is advanced it will also bring me notes from the wider network
- I can have private direct message conversations with others in my chat relay.
- I can save private notes in my private relay
For me, this model has a lot of appeal and I went looking for a personal relay which adopted this model and contained all of these features.
HAVEN as a personal relay
I decided to go with HAVEN relay software.
HAVEN is all four of the above relays in one–outbox, inbox, chat and private. It contains advanced features like blasting your notes from outbox to other relays, importing notes from other relays to your inbox, and preventing spam with Web of Trust.
HAVEN is written by Utxo the Webmaster . It is based upon the Khatru relay framework by Fiatjaf
Setting up HAVEN as a Personal Relay
I am mostly non-technical, but on my #Nostr journey I have been having success with technology set ups that use Docker.
- I have a cheap VPS which currently runs Albyhub and Phoneixd with Docker,
- My objective was to set up HAVEN to run alongside it, in a separate Docker on the same server. HAVEN does not include Docker by default, but Sebastix published a fork with Docker support.
To get HAVEN up and running in Docker on your VPS:
- Clone and configure HAVEN with the right variables
- Launch it in Docker on your VPS
- Check the URLs and logs to see your HAVEN running
- Configure a subdomain to point to the VPS
- Configure the VPS to reverse proxy to the Docker port
- Configure the relays in your favourite Nostr client
- Post a note to your outbox and see if it blasts!
Running HAVEN
I cloned Sebastix fork to start.
git clone -b docker_compose_support https://github.com/nostrver-se/haven.git cd havenThe software sets up all environment variables in the
.envfile, and comes with an.env.examplefile. Duplicate and rename the file to.env. Within the.envfile you need to set up the environment variables. The file is long but it contains lots of repetition and for the most part defaults can be retained–only a few changes are required:- Replace all instances of the default user npub with your own (for me,
npub1r0d8...) - Change the default relay URL to your own (for me,
relay.rodbishop.nz) - Replace all instances of the default name in the relay names (for me, "Rod's ...")
- Replace all instances of the default profile image with your own
To enable automatic blasting from your outbox, and importing to your inbox, the software comes with an example list of relays to blast and import from. See
relays_blastr.example.jsonandrelays_import.example.json. To use these features simply duplicate and rename these files torelays_blastr.jsonandrelays_import.jsonrespectively. Within these files you can specify the public relays of your choice. I simply used the default list.There are other features available, such as backups and initial imports, but I decided to handle these later. To start with I wanted to launch the relay and test it.
To launch the relay run Docker Compose.
docker-compose up -d docker logs haven-relayThen you should explore the logs in the command line and the ports in your browser to see if it launched successfully. The logs should show your web of trust has been built successfully and the browser should show simple landing pages.
The logs should show that the relay has queried the network and built a web of trust from your followers. Mine looked as follows.
2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 13296 2024/10/14 12:02:16 🔗 relays discovered: 335 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 9394 keysYour browser should show you have four relays in operation, for example as follows.
your_IP_address:3355(your outbox or home relay)your_IP_address:3355/private(your private relay)your_IP_address:3355/chat(your direct message relay)your_IP_address:3355/inbox(your inbox relay)
That's it. Your relay is online.
Connecting HAVEN
Now all that remains is the plumbing to connect your domain, relay, and Nostr clients together.
Configure DNS
First, configure your domain. At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caserelay.rodbishop.nz
Your subdomain now points to your server.
Configure reverse proxy
Next, you need to redirect traffic from your subdomain to your relay at port
3355.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my HAVEN Relay required two steps. I am sure that the way I do this is not very elegant, but it worked. If you prefer a different method, the HAVEN readme also comes with instructions on how to perform a similar setup using nginx.
For my method, my steps were as follows:
- Add configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.rodbishop.nzsubdomain - Add the Caddy Docker network to the HAVEN
docker-compose.ymlto make it be part of the Caddy network
For the addition to the
Caddyfile, I used as follows:relay.rodbishop.nz { reverse_proxy haven-relay:3355 { header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }For the addition to the
docker-compose.yml, I used as follows:``` networks: - caddy # Added this line to services to connect to the Caddy network
networks: caddy: external: true # Added this to section specify the Caddy network ```
Once your DNS configuration and reverse proxy setup are completed, you should now be able to access your Nostr client at
relay.your_domain_name.com. For my set up, this wasrelay.rodbishop.nz.Connecting your Nostr client
Most Nostr clients allow you to specify any relay you choose. My go-to client at the moment is Amethyst on Android. Amethyst allows you to specify discrete relays for each role in the outbox model which ties up very neatly with HAVEN.
- In the sidebar, select Relays
- For "Public Outbox/Home Relays" enter
relay.your_domain_name.com - For "Public Inbox Relays" enter
relay.your_domain_name.com/inbox - For "DM Inbox Relays" enter
relay.your_domain_name.com/chat - For "Private Home Relays" enter
relay.your_domain_name.com/private - Click Save to broadcast your new relays to the Nostr network.
Your new relay configuration is now live.
Testing your relay
Lastly, it's time to test. Amethyst provides a simple method to test this as it allows you to configure the relays used on each post.
- Create a test note, and then before you post it, edit your relays using the icon at the top
- Turn off all relays except your own outbox relay, and post the note
- Access your HAVEN docker logs with
docker logs haven-relayand see if there is a log to indicate if the note was received and blasted to other public relays - Copy the
neventof the note, and attempt to find it in another client
If you're in luck, you may see something like this (the blasted note, and then users on the network responding to the note in turn).
2024/10/22 00:12:23 🔫 blasted 95c477af7e6b612bf5d1d94309d2d57377a0a67d2181cfbb42a2e3fbc0feeaaf to 26 relays 2024/10/22 00:13:50 🤙 new reaction in your inbox 2024/10/22 00:14:42 🫂 new reaction in your inbox 2024/10/22 00:14:45 ✅ new reaction in your inbox 2024/10/22 00:15:12 💜 new reaction in your inbox 2024/10/22 00:17:03 ✅ new reaction in your inbox 2024/10/22 00:17:03 🫂 new reaction in your inbox 2024/10/22 00:17:55 🫂 new reaction in your inbox 2024/10/22 00:19:02 📰 new note in your inboxThat's it. If you followed this successfully your personal relay is up and running.
What I did wrong so you don't have to
My first relay was too public
This blog comes after much trial and error. The first error I made was I set up a relay to use as a personal relay, but without any restrictions on use. I very quickly found other people discovered and started using my relay to save their own notes! This was unintended and I had to take it down.
Unfamiliar with Go language
I am mostly non-technical, and completely unfamiliar with Go. I got the project up and running with Go on my localhost–with a lot of help from my AI–but I then completely failed in migrating this to my VPS. Moving to Docker made the difference for me here.
I failed a few times due to a messy folder
After messing with Go, I moved to the Docker setup, but I started my work from a messy folder which contained remnants of the Go build, which caused various failures. Deleting the folder and cloning again from scratch solved the issue.
Trouble with Nostr.wine
I subscribe to the Nostr.wine paid relay, and I initially added it to the list of relays in my blaster. However, it didn't work, and the logs showed an error as follows
CLOSED from wss://nostr.wine: 'auth-required: this relay only serves private notes to authenticated users'It seems my npub's subscription to Nostr.wine is not enough for it to permit my relay to blast notes to it. In the end, I removed Nostr.wine from my relay config, and kept Nostr.wine as a separate entry in my Client's outbox settings.
Failed to create web of trust graph
When I first launched the relay on my VPS, HAVEN failed to complete the Web of Trust graph, with a log that looked as follows (note the zeroes). As a result, no one would have been able to send me DM's to my Chat relay (it would flag every message as spam).
2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 0 2024/10/14 12:02:16 🔗 relays discovered: 0 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 0 keysI never got to the bottom of why this was. In the process of trying to fix it I rebuild the container, and on the rebuild it spontaneously worked. Accordingly my lesson learned is "if in doubt, turn if off and on again".
Failed to run --import function
HAVEN comes with a function to import all your old notes from other public relays to your own outbox relay. When I run it I get an error as follows:
panic: Cannot acquire directory lock on "db/private". Another process is using this Badger database. error: resource temporarily unavailableI have yet to work out the solution for this, and will update this note when I do so!
What's Next?
Over the past four blogs I have
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
This feels like a very comprehensive personal set up now. Also, I have uncovered some new rabbit holes and feel like I have some projects to tackle. Perhaps one of these?
- Set up a personal homepage with my Nostr feed to round-out my rodbishop.nz domain
- Experiment with different signers like Amber and Nsec.app and NFC cards
- Set up a paid relay for #austriches (Australians and Kiwis on Nostr)
- Set up a team relay to experiment with Nostr for business or community projects
- Or something else ... ?
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
Pura vida Nostr.
-
 @ ff1a68c4:ec9831cf
2024-10-24 14:47:03
@ ff1a68c4:ec9831cf
2024-10-24 14:47:03En un mundo en constante evolución, la ciencia nos ofrece valiosas herramientas para mejorar nuestra calidad de vida y prevenir enfermedades neurodegenerativas como la demencia. A partir de los consejos de especialistas y datos de estudios recientes, he reunido una síntesis de enfoques clave que coinciden en varios puntos esenciales. Aquí te presento un resumen práctico:
El modelo MEDALS: Los pilares del bienestar
El acrónimo MEDALS nos recuerda los aspectos fundamentales que pueden ayudar a mantener una buena calidad de vida:
- Meditación: La práctica regular de la meditación reduce el estrés, mejora la concentración y contribuye a un mayor bienestar emocional.
- Ejercicio: El movimiento es vital para la salud física y mental. Mantener una rutina de ejercicio regular no solo fortalece el cuerpo, sino también el cerebro.
- Dieta: Una alimentación equilibrada es clave. Optar por una dieta rica en nutrientes, como la mediterránea, promueve un cerebro saludable.
- Apreciación: Practicar la gratitud y el aprecio por las pequeñas cosas de la vida puede elevar nuestro bienestar emocional y mental.
- Love (amor) y Learning (aprendizaje): Mantener vínculos afectivos y relaciones cercanas fortalece la mente. El aprendizaje continuo mantiene el cerebro activo y en constante crecimiento.
- Sueño: Dormir lo suficiente y de forma reparadora es crucial para la regeneración cerebral y la memoria.
Manantiales de la fuerza interior: Una guía integral para el bienestar
Otra perspectiva ofrece una visión holística de cómo cuidar cuerpo y mente. Estos son los cinco manantiales de energía interior que contribuyen a un estado óptimo de bienestar:
- Sueño profundo y reparador: Un buen descanso nocturno es el pilar del equilibrio físico y mental.
- Alimentación sana e hidratación: Mantener una dieta nutritiva y una adecuada hidratación es esencial para el buen funcionamiento del cerebro y del cuerpo.
- Respiración consciente: Practicar ejercicios de respiración ayuda a reducir el estrés y aumenta la claridad mental.
- Ejercicio y relajación: Alternar entre actividad física y momentos de descanso es fundamental para evitar el agotamiento.
- Actitud mental positiva: Mantener una mentalidad optimista y enfocada en el crecimiento nos ayuda a enfrentar mejor los retos de la vida.
6 Reglas anti-demencia: Proteger el cerebro a largo plazo
Algunos expertos proponen un enfoque más específico para la prevención de la demencia:
- Vínculos sociales: El cerebro es un órgano social. Mantener relaciones cercanas y participar en actividades grupales es clave para su salud.
- Ejercicio físico: El cuerpo y la mente están conectados. La actividad física regular mejora el rendimiento cerebral.
- Curiosidad y aprendizaje continuo: Mantener el cerebro activo con nuevos intereses y aprendizajes es crucial para prevenir su deterioro.
- Buena alimentación: Optar por alimentos ricos en Omega-3 y seguir una dieta mediterránea favorece la salud cerebral.
- Manejo del estrés: El estrés crónico es un enemigo del cerebro. Aprender a relativizar las situaciones y ver los desafíos como oportunidades puede reducir su impacto.
- Dormir bien: Un sueño adecuado es esencial para la reparación y el funcionamiento óptimo del cerebro.
Hallazgos de The Lancet: Factores modificables y no modificables en la prevención de la demencia
Uno de los estudios más importantes sobre la prevención de la demencia, publicado en The Lancet, destaca los factores modificables que pueden influir en nuestro futuro cognitivo:
- Formación continua: Aprender y mantenerse intelectualmente activo durante toda la vida puede retrasar el deterioro cognitivo.
- Cuidado de la audición: Proteger la audición desde la juventud es crucial. En la vejez, el uso de audífonos puede ayudar a mantener el estímulo auditivo.
- Salud emocional: El estrés crónico, la ansiedad y la depresión son factores de riesgo importantes para el desarrollo de la demencia.
- Ejercicio físico y salud metabólica: Evitar el sedentarismo, el sobrepeso, la diabetes y los niveles elevados de colesterol LDL reduce el riesgo de enfermedades neurodegenerativas.
- Protección contra golpes en la cabeza: Los traumatismos craneales aumentan el riesgo de demencia. Protegerse es fundamental.
- Reducción de tóxicos: Evitar el tabaco, el consumo excesivo de alcohol y la exposición a contaminantes ayuda a preservar la salud cerebral (ej. filtros para el aire o en la llave del agua)
- Vida social activa: El aislamiento social es un factor de riesgo para la demencia. Mantenerse involucrado en grupos y actividades sociales es clave.
- Suplementos: Aunque no son esenciales, algunos suplementos como arándanos, vitamina D, Omega-3, y magnesio pueden ser beneficiosos en casos de deficiencia.
Implementar estos principios no solo mejorará la calidad de vida en el presente, sino que también reducirá significativamente el riesgo de desarrollar demencia en el futuro. Vivir de manera consciente, cuidar el cuerpo y nutrir la mente son las claves para una vida larga y saludable.
-
 @ d5c3d063:4d1159b3
2024-10-24 14:37:08
@ d5c3d063:4d1159b3
2024-10-24 14:37:08ปรัชญา อาวุธแห่งเหตุผลและเสรีภาพในโลกแห่งความขัดแย้ง
https://image.nostr.build/b3e2278447703b23c18d6b8dd98986b700958acbbe06b3cca6ce7efa55b6c1ad.jpg
โลกที่เราอาศัยอยู่เปรียบเสมือนสมรภูมิแห่งความคิด แนวคิดต่างๆ ถูกนำมาถกเถียงและท้าทายอยู่เสมอเพื่อค้นหาและพิสูจน์ความจริง ความขัดแย้งนี้ปรากฏชัดในหลายมิติ เช่น การปะทะกันระหว่างเหตุผลกับความงมงาย เสรีภาพกับการถูกบังคับ ปัจเจกนิยม (Individualism) กับลัทธิรวมหมู่ (Collectivism) และทุนนิยมกับสังคมนิยม ท่ามกลางความสับสนวุ่นวายนี้ ปรัชญาทำหน้าที่เสมือนป้อมปราการแห่งเหตุผลและเสรีภาพ เป็นเครื่องมือสำคัญที่ช่วยให้เราเข้าใจและวิเคราะห์โลกที่เต็มไปด้วยความขัดแย้ง พร้อมกับนำทางชีวิตของเราอีกด้วย .
ปรัชญาในบริบทนี้ มิใช่เพียงแสงเทียนริบหรี่ในห้องสมุด หากแต่เป็นอาวุธแห่งเหตุผล ที่ใช้ในการต่อสู้กับความคิดที่บิดเบือนและการใช้อำนาจในทางที่ผิด เพื่อปกป้องและส่งเสริมเสรีภาพของมนุษย์ มันคือดาบเพลิงที่ลุกโชนในสนามรบแห่งความคิดที่ช่วยให้เรามองทะลุผ่านมายาคติ ความเชื่อที่ไร้เหตุผล และการโฆษณาชวนเชื่อ ทั้งยังช่วยให้วิเคราะห์ข้อมูลอย่างมีวิจารณญาณและตัดสินใจบนพื้นฐานของหลักฐานและตรรกะ นำไปสู่การเข้าถึงความจริง ตัวอย่างที่เห็นได้ชัดคือการเซ็นเซอร์ข้อมูลข่าวสาร ซึ่งถูกใช้เป็นเครื่องมือในการบิดเบือนข้อมูล ปลุกปั่นอารมณ์ เป็นการใช้อำนาจในทางที่ผิด ปิดกั้นการเข้าถึงความจริง เพื่อควบคุมความคิดของประชาชน .
หัวใจสำคัญของปรัชญาคือ การใช้เหตุผล หลักฐาน และตรรกะ ในการแสวงหาความจริง เพื่อนำไปสู่ การตัดสินใจที่ถูกต้อง ปรัชญาฝึกฝนให้เรามีวิจารณญาณ ไม่หลงเชื่ออะไรง่ายๆ และไม่ยอมรับความคิดเห็นใดๆ โดยปราศจากการตรวจสอบอย่างถี่ถ้วน ปรัชญาสอนให้เราตั้งคำถาม เช่น ใครเป็นคนพูด ? มีหลักฐานอะไรสนับสนุน ? มีมุมมองอื่น ๆ อีกหรือไม่ ? ข้อสรุปนี้ขัดแย้งกับข้อเท็จจริงหรือหลักการพื้นฐานใด ๆ หรือไม่ ? ก่อนที่จะตัดสินใจเชื่อหรือยอมรับความคิดเห็นใด ๆ เพราะการยอมรับความคิดเห็นโดยไม่ผ่านการไตร่ตรอง อาจนำเราไปสู่การตัดสินใจที่ผิดพลาดและตกเป็นเหยื่อของการบิดเบือน .
ปรัชญายังส่งเสริมความเข้าใจในคุณค่าของเสรีภาพและความสำคัญของปัจเจกบุคคล เสรีภาพในการคิดการแสดงออกและการใช้ชีวิต เป็นสิ่งจำเป็นสำหรับการพัฒนาศักยภาพของมนุษย์ เพื่อการสร้างสรรค์สังคมที่เจริญรุ่งเรือง ปรัชญาช่วยให้เราตระหนักถึงสิทธิและหน้าที่ของตนเองในฐานะปัจเจกบุคคลและเพื่อปกป้องเสรีภาพเหล่านี้จากการถูกคุกคามจากอำนาจรัฐหรือแนวคิดแบบคติรวมหมู่ สังคมที่มีความยุติธรรมมีเสรีภาพและมีความเจริญรุ่งเรือง คือสังคมที่เคารพในสิทธิและเสรีภาพของปัจเจกบุคคลที่ส่งเสริมการใช้เหตุผลนั้น ล้วนมีรากฐานอยู่บนระบบเศรษฐกิจแบบทุนนิยม เพราะทุนนิยมเป็นระบบที่สอดคล้องกับหลักการเหล่านี้ โดยเปิดโอกาสให้ทุกคนมีส่วนร่วมในการสร้างความมั่งคั่งและเติบโตอย่างอิสระ .
ในโลกที่ความขัดแย้งทางความคิดทวีความรุนแรงและข้อมูลข่าวสารแพร่กระจายอย่างรวดเร็ว ปรัชญามิใช่เพียงทางเลือก แต่เป็นเกราะป้องกันที่ขาดไม่ได้ การศึกษาปรัชญา การฝึกฝนการใช้เหตุผลและการตั้งคำถาม คือการลงทุนที่คุ้มค่าที่สุดสำหรับอนาคต เพราะมันจะช่วยให้เรามีภูมิคุ้มกันต่อการถูกชักจูง การหลอกลวงและการใช้อำนาจในทางมิชอบ เป็นก้าวสำคัญในการสร้างสังคมที่เสรี มีความยุติธรรมและการเจริญรุ่งเรืองอย่างแท้จริง ดังนั้น เวลามีค่า…ศึกษาปรัชญา ฝึกฝนการใช้เหตุผล และอย่าปล่อยให้ความงมงายและอคติครอบงำจิตใจ เพื่อที่เราจะสามารถเป็นผู้กำหนดชีวิตของตนเองได้และใช้ชีวิตอย่างมีอิสระ มีเหตุผล และสร้างสรรค์คุณค่าตามที่เราเลือก เพื่อบรรลุศักยภาพสูงสุดของเราในฐานะปัจเจกบุคคล
Siamstr #Philosophy #ปรัชญา
-
 @ 23acd1fa:0484c9e0
2024-10-23 09:21:33
@ 23acd1fa:0484c9e0
2024-10-23 09:21:33Chef's notes
Cocoa powder: You can use 100% natural unsweetened cocoa powder or Dutch-processed cocoa powder – both work well.
Gluten free flour: There are many different gluten free flours on the market. I tested this recipe using White Wings All Purpose Gluten Free flour. I recommend choosing a gluten free flour that says it can be subbed 1:1 for regular plain or all purpose flour.
*Chocolate chips: Double check your chocolate chips are gluten free if you are making this brownie for someone who is celiac.
Cook times: Cook times will vary depending on your oven, but you’ll know these brownies are done when they firm up around the edges and no longer wobble in the middle. Keep in mind they will continue to cook slightly as they cool. You can also check they’re done by inserting a skewer into the middle of the brownie. If the skewer emerges with only a few crumbs on it, they’re ready. If it is covered in wet, gooey batter, keep baking the brownies and check them in another 5 minutes.
Storage: Brownies will keep well in an airtight container at room temperature or in the fridge for up to 5 days. To serve warm, microwave each brownie for 20 seconds. You can also freeze these brownies to enjoy at a later date. Simply thaw at room temperature and then microwave if you prefer them warm.
Serving Size: 1 brownie Calories: 278 Sugar: 26.4 g Sodium: 22.9 mg Fat: 15.5 g Carbohydrates: 34.1 g Protein: 3 g Cholesterol: 77.3 mg Nutrition information is a guide only.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 35 min
- 🍽️ Servings: 12
Ingredients
- 170 grams (3/4 cup) unsalted butter, melted
- 200 grams (1 cup) caster sugar or granulated sugar
- 90 grams (1/2 cup) brown sugar
- 1 teaspoon vanilla extract
- 3 large eggs
- 40 grams (1/2 cup) cocoa powder
- 70 grams (1/2 cup) gluten free plain or all purpose flour
- 75 grams milk or dark chocolate chips*
Directions
- Preheat the oven to 180 C (350 F) standard / 160 C (320 F) fan-forced. Grease and line an 8-inch square pan with baking or parchment paper, ensuring two sides overhang.
- In a large mixing bowl, add melted butter and sugars and gently whisk together. Add vanilla extract and stir.
- Add the eggs, one at a time, stirring in-between, then sift in the cocoa powder and flour. Stir until just combined. Add chocolate chips.
- Pour the brownie batter in the prepared pan and place in the oven. Bake brownies for approximately 30-35 minutes or until they no longer wobble in the middle.
- Leave brownie in pan and transfer to a wire rack to cool completely. These brownies are quite fragile so if you can, transfer to the fridge for an hour before cutting into squares to serve.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 9349d012:d3e98946
2024-10-23 04:10:25
@ 9349d012:d3e98946
2024-10-23 04:10:25Chef's notes
Ingredients
4 tablespoons (1/2 stick) butter 2 ounces thinly sliced prosciutto, cut into thin strips 1 1/4 cups orzo (about 8 ounces) 3 cups low-salt chicken broth 1/2 teaspoon (loosely packed) saffron threads, crushed 1 pound slender asparagus, trimmed, cut into 1/2-inch pieces 1/4 cup grated Parmesan cheese Parmesan cheese shavings
Preparation
Melt 2 tablespoons butter in large nonstick skillet over medium-high heat. Add prosciutto and sauté until almost crisp, about 3 minutes. Using slotted spoon, transfer to paper towels to drain. Melt 2 tablespoons butter in same skillet over high heat. Add orzo; stir 1 minute. Add broth and saffron; bring to boil. Reduce heat to medium-low, cover, and simmer until orzo begins to soften, stirring occasionally, about 8 minutes. Add asparagus; cover and simmer until tender, about 5 minutes. Uncover; simmer until almost all liquid is absorbed, about 1 minute. Remove from heat. Mix in prosciutto and 1/2 cup grated cheese. Season to taste with salt and pepper. Transfer to large bowl. Garnish with Parmesan shavings. Makes 6 servings.
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 30
Ingredients
- See Chef’s Notes
Directions
- See Chef’s Notes
-
 @ 75d12141:3458d1e2
2024-10-23 00:20:14
@ 75d12141:3458d1e2
2024-10-23 00:20:14Chef's notes
A childhood favorite of mine! Just don't go too crazy with the scallions as you don't want to overpower the pork flavor.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 15-20 mins
- 🍽️ Servings: 3-5
Ingredients
- 1 pound of lean ground pork
- 1 tablespoon of diced scallions
- Ground black pepper (optional)
Directions
- Lightly coat your palms with olive oil to prevent the meat from sticking to you and to assist in keeping its ball form
- Mix the ground pork and diced scallions in a large bowl
- Roll the pork into the preferred portion size until it feels like it won't fall apart
- Cook in a skillet for 15-20 mins
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ 4f82bced:b8928630
2024-10-22 17:23:53
@ 4f82bced:b8928630
2024-10-22 17:23:53Bitcoin doesn’t get too much love from the media. The tune seems to have slightly changed since the launch of the ETF, now that there’s money to be made. I don’t see many discussions about the humans pushing this decentralized technology forward. Bitcoin has no CEO, sales, marketing, product, or support team. Its source code is open for anyone, to inspect, copy and propose changes. 15 years after its inception, the network grows stronger every day due to the efforts of individuals worldwide. They build products, share stories, educate, mine, and more.
Here are some people who have directly impacted our journey, especially in Africa:
- Two early adopters who have consistently organized meetups for nearly 8 years
- A young graduate creating a circular economy, while also boot strapping his tourism business
- An artist making bitcoin approachable to the masses through his love of music
- A family of five who opened their doors and showed us their way of living on a Bitcoin-standard
- A father who built a product that doesn't require the internet to use bitcoin
- An ex-military who is educating the community through the local languages
- An engineer who is setting the record straight on bitcoin mining
This is just a small sample of the thousands that continue to build using this open technology, one that is deeply misunderstood. As literacy and adoption increase more and more humans will jump on board. Are you ready?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ 805b34f7:3620fac3
2024-10-19 19:59:21
@ 805b34f7:3620fac3
2024-10-19 19:59:21** I published this article on 3/26/2020. I'm back in Puerto now and just re-read this to fire myself up for some potential tubes. Now, I want it to live on Nostr.
“When in doubt, don’t go out” is a well-known aphorism among surfers. I think it’s bs. Let me explain.
**I speak from my experiences as a regular surfer and with my close group of regular surfers in mind.
In surfing, there’s a comfort zone, an adrenaline zone, an aw crap zone (doubt), and a hell no zone.
Comfort zone —It is in this place where it is safe and fun to try new maneuvers. The heart rate is low and the stoke rate high.
Adrenaline zone- This is personally my favorite zone. The surf is big or good enough to get the heart rate up and the juices flowing. Each movement matters and this is where some of the best surfing goes down.
Aw crap zone — This is the land of the I don’t know, the doubt. It’s always damn near impossible to sleep before an aw crap day of surfing. This is the place where limits are tested. Maybe you’re surfing in a new place with new risks such as shallow reef, a difficult takeoff, or it’s just huge. This aw crap zone will test and define your limits.
Hell no zone — When you know, you know. This is beyond doubt. You’re totally satisfied (yet still curious) from watching from afar. Maybe one day!
These zones are bound to change as the surfer progresses. One day there may be no “hell no zone” as the surf master has pushed his or her limits to the extreme.
Pushing
Pros are only as good as their home breaks. NOT. Tell that to Kelly Slater and the Hopgood brothers who grew up surfing Florida slop. Although, perhaps their garbage wave situation lit a fire underneath them which inspired them to seek out better waves and progress rapidly. Anyways, a surfer grows up surfing their home breaks often. Some people grow up on the North Shore or in Tahiti, others grow up in Huntington. A surfer’s perspective on waves and danger is influenced by their exposure.
I finally got bored with myself surfing my home waves. Sure, there were days that were outside of my comfort zone and epic, but it was time to go find waves that I had only seen in videos. I decided to pack my backpack and head to those famed Indonesian reefs that I’ve mind surfed for hours, but always had the question mark in my head as to whether or not I could conquer them.
Surfing over shallow reef is something that I was not used to and it terrified me, but I also knew that every surfer does it including five-year-olds so I had to send it. I escaped the first mission unscathed and with some of the best waves in my life.
In order to find those best waves of my life, I had to enter the ‘aw crap zone’. The I don’t know land. The unknown. When in doubt, I went out.
And Now I’m Here
 I blew this wave, but wow pretty.
I blew this wave, but wow pretty.
Current forecast looks like it will be right at my edge.. again. We'll see.
I’m surfing the famous Playa Zicatela every day with the whole world shut down due to Co-Vid19. I’ve always been curious to know what it’s like to be inside massive barrels, so I’m slowly making it happen. This is a battle that I chose. I’m learning how to sleep with surf anxiety. The first couple of nights were rough, but I’m starting to accept it now.
This very morning inspired this article. I got up, went to the roof, and checked out the waves. It looked pretty mellow despite the fact that I knew there was a lot of swell in the water. I just thought, eh, maybe it’s not big like it was forecasted. I got in the water, took my first wave, wiped out, but whatever. I’ve been here for a week and I still wipeout on just about every first wave. But, I quickly found out that this was not the real set. The next set was enormous, and it sent adrenaline shrieking through my spine and filled my brain with the aw craps. The questioning of my life and why I’m out here quickly followed. Am I good enough for this? (maybe). Could I survive a wipeout that size?(probably). Is my board right for this? (definitely not). The second wave I took was bigger and I pulled the eject cord and jumped from what felt like the top of a cliff all the way to the bottom and got creamed (my perspective). After a couple of flips, I popped up the back laughing and was ready for another. I survived, therefore, I can keep pushing.
Not gonna lie, surfing almost feels like work lately. Almost every day here is just about in my personal aw crap zone.
However, it’s worth it for me. This is a journey that I deem worthy of my time. It does it for me. It’s those little moments inside the barrel and gosh-dang-golly hopefully soon getting shot out of the barrel that keep me stoked and looking forward to tomorrow. It’s proving to myself that I can do things I didn’t know for sure were possible.
The Process to Progress
Progression sometimes feels like a snail crawling up Mt. Everest. But when you zoom out, those incremental small improvements compound over time. Each wipeout is a little victory. Each wave that is ridden is a little victory. Your brain is learning from every experience that you choose to give it. Confidence slowly builds as we continue to learn from the masters and even develop our own style. Next thing you know you’re drinking a beer in a barrel that can kill a normal man like Mr. Slater did here.
 Freakin Goat
Freakin GoatStagnation leads to burnout, depression, and boredom (Not scientific facts but I’m right I know it).
The great danger is that we give in to feelings of boredom, impatience, fear, and confusion. We stop observing and learning. The process comes to a halt. — Farnam Street Blog
I’ve seen a few buddies give up surfing or digress. It happened to me while I was focusing on baseball. It’s sad because surfing is fun and the better you get the more fun it is. It’s even more fun with a core group of guys who are at a similar level pushing each other. It can get boring if you don’t push yourself, and it gets scary real quick if you aren’t in surf shape.
“Whenever we learn a skill, we frequently reach a point of frustration — what we are learning seems beyond our capabilities. Giving in to these feelings, we unconsciously quit on ourselves before we actually give up.” FS Blog
Progression takes effort. Effort takes a conscious decision to expend your limited energy. It’s the only way to get gains in whatever game you are playing. Also, progression takes humility.
I got the pleasure of surfing Kelly Slater’s Wave Ranch. I knew I was going to have fun, but the night before I was damn nervous. Why? Well, I knew there’d be cameras and that I didn't want to blow it. I’d be surfing with pros and I was going to look horrible compared to them. Sure enough, the one right the camera got, I blew. Oh well. No 30-second barrels for the boys. Life moves on.
Full vid here https://vimeo.com/367128298
 Can't wait to go back here one day
Can't wait to go back here one dayYou’re bound to fail, especially when you take risks. If you’re a prideful person, the setbacks will be greater. It’s how you deal with the failure that determines if you will become a master.
So if in doubt, go out. Your hell no zone is going to start to shrink. This applies any skill that you are sharpening. You’re only going to get the big clients if you go after them, a piano player will improve by practicing harder songs, a black belt gains nothing from fighting a white belt, etc.
Pick your battles wisely. Then…SEND IT, SURVIVE, LEARN, APPLY, REPEAT.
10/19 - Even though I'm a much more experienced surfer now, I'm still terrified. On my way to go get a board now and get ready for some swell! I'm on my honeymoon, so we'll see how hard I push. I have quite a few more responsibilities now then I did back in Covid times... But if in doubt, I will go out. PV.
-
 @ 4ba8e86d:89d32de4
2024-10-24 14:03:14
@ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais.
Recursos e Funcionalidades.
O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório.
Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes.
O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets.
Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo:
-
Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional.
-
Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes.
-
Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações.
O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável.
https://www.collaboraoffice.com/
https://github.com/CollaboraOnline/online
-
-
 @ ff18165a:dd7ca7f0
2024-10-19 18:23:51
@ ff18165a:dd7ca7f0
2024-10-19 18:23:51Chef's notes
- DO NOT add too much Peppermint Extract! It’s extremely strong and it will make your milkshake way too strong if you add more than a few drops.
- Feel free to be creative with your toppings. We used Caramel Flavored Whipped Topping and it turned out great!
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 2 min
- 🍽️ Servings: 1
Ingredients
- 1 1/2 cup Milk
- 2 drops Peppermint Extract
- 2 packets Stevia
- 1 cup Ice
- 2 drops Green Food Coloring
- Green Sprinkles
- 1 Crushed Peppermint Candy
- 2 Mint Leaves
Directions
-
- Blend together until smooth and frothy
-
- Pour into a tall glass
-
- Top with listed toppings
-
- Add straw and enjoy
-
 @ 9e69e420:d12360c2
2024-10-19 12:52:02
@ 9e69e420:d12360c2
2024-10-19 12:52:02Joe Biden and Senator Lindsey Graham about securing a U.S.-Saudi defense treaty, as revealed in Bob Woodward's new book "War".
The Proposed "Megadeal"
The conversation took place in the context of Biden's attempts to negotiate a "megadeal" between the United States, Saudi Arabia, and Israel[1]. The goal was to create a permanent, U.S.-led security alliance in the Middle East[1].
Bipartisan Collaboration
Graham reportedly told Biden that only a Democratic president could convince Democrats to "vote to go to war for Saudi Arabia," to which Biden responded, "Let's do it"[1]. This exchange highlights the bipartisan willingness to consider military commitments in the Middle East[2].
Political Calculations
Graham suggested that: - A Republican administration wouldn't be able to secure such a deal - Democrats wouldn't support it if introduced by Trump - Republicans could provide 45 votes if Israel encouraged it Biden assured Graham he could secure the remaining Democratic votes[1].
Saudi Arabia's Perspective
Crown Prince Mohammed bin Salman was reportedly interested in the deal to gain protection under the U.S. nuclear umbrella[1]. However, after the October 7, 2023 attacks on Israel, bin Salman became hesitant, fearing potential assassination if he didn't stand up for Palestinian rights[1].
Current Status
The deal is currently in suspended animation due to bin Salman's concerns and changing regional dynamics. The Biden administration continues to pursue negotiations, urging Israel to make concessions on Palestinian rights to facilitate the agreement.
The article concludes by noting that if Woodward's reporting is accurate, both Biden and Graham seemed willing to commit American troops to potential conflict with relative ease.
-
 @ 4ba8e86d:89d32de4
2024-10-24 13:52:57
@ 4ba8e86d:89d32de4
2024-10-24 13:52:57Tecnologia de escalonamento #Bitcoin Layer-2 baseada no conceito de statechains, que permite que chaves privadas para depósitos BTC (UTXOs) sejam transferidas com segurança entre proprietários fora da cadeia.
Mercury Layer é uma implementação de um protocolo statechain de camada 2 que permite a transferência e liquidação fora da cadeia de saídas de Bitcoin que permanecem sob a custódia total do proprietário o tempo todo, enquanto se beneficia de transações instantâneas e de custo zero. A capacidade de realizar esta transferência sem exigir a confirmação (mineração) de transações em cadeia tem vantagens em uma variedade de aplicações diferentes.
um sistema de transferência e controle de propriedade do Bitcoin, especificamente focado em saídas de transações não gastas (UTXOs),
um resumo detalhado dos principais elementos e procedimentos do sistema:
-
Saída de Transação Não Gasta (UTXO): UTXO é a unidade fundamental que representa valor e propriedade no Bitcoin. Cada UTXO é identificado por um ID de transação (TxID) e um número de índice de saída (n) e possui duas propriedades essenciais: valor em BTC e condições de gasto, definidas em um Script. As condições de gasto geralmente envolvem uma chave pública que requer uma transação assinada com a chave correspondente.
-
Transferência de Propriedade sem Transação On-Chain: O sistema permite a transferência de propriedade de UTXOs controlados por uma única chave pública (P) de uma parte para outra sem a necessidade de executar transações na cadeia (on-chain) do Bitcoin ou alterar as condições de gasto. Isso é facilitado por um mecanismo chamado "Statechain Entity" (SE).
-
Compartilhamento de Chave Privada: A chave privada (s) para a chave pública P é compartilhada entre o SE e o proprietário. No entanto, nenhuma das partes conhece a chave privada completa. Isso requer cooperação entre o proprietário e o SE para gastar o UTXO.
-
Atualização/Transferência de Chave: A propriedade do UTXO pode ser transferida para um novo proprietário através de um processo de atualização de chave. Isso envolve a substituição do compartilhamento de chave privada do SE para que corresponda ao compartilhamento de chave do novo proprietário, tudo sem revelar compartilhamentos de chave ou a chave privada completa.
-
Transações de Backup: Além da transferência de propriedade, o sistema inclui transações de backup que podem ser usadas para reivindicar o valor do UTXO pelo atual proprietário, caso o SE não coopere ou desapareça. Essas transações são assinadas cooperativamente pelo proprietário atual e pelo SE e possuem um bloqueio de tempo (nLocktime) que permite a recuperação dos fundos em uma altura de bloco futura especificada.
-
Mecanismo de Redução do Backup de Timelock: Para limitar o número de transferências possíveis durante um período de tempo, o sistema utiliza um mecanismo de decremento do nLocktime. O usuário é responsável por enviar as transações de backup no momento adequado.
-
Cadeias Estaduais (Statechains): O sistema opera usando cadeias estaduais, que são uma camada adicional que permite a transferência de propriedade de UTXOs. O SE precisa seguir o protocolo, mas não armazena informações sobre compartilhamentos de chave anteriores.
-
Cegagem (Blinding): O servidor da camada Mercury (SE) é cego, o que significa que não tem conhecimento das moedas que está assinando. Isso é alcançado através do uso de criptografia de chave pública para ocultar informações de chave privada compartilhada entre as partes.
-
Protocolo de Camada Mercury: O protocolo detalha os procedimentos desde o depósito inicial até a transferência de propriedade, atualizações de chave, retiradas ordenadas e recuperação de backup.
-
Recuperação de Backup: Caso o SE não coopere ou desapareça, o proprietário atual pode recuperar os fundos, enviando a transação de backup quando o nLocktime for atingido.
-
Publicação de Compartilhamento de Chaves: O SE não tem acesso aos IDs de transação individuais das moedas, mas publica compartilhamentos de chaves públicas para cada moeda na lista de ativos. Essa lista é comprometida com a blockchain para provar a exclusividade da propriedade.
Este sistema é projetado para fornecer uma maneira segura e eficiente de transferir e controlar a propriedade do Bitcoin, permitindo a recuperação de fundos em caso de problemas com o servidor.
No sistema de controle de propriedade de saídas de transações não gastas (UTXOs), cada UTXO é uma chave compartilhada composta por duas partes: o proprietário e o servidor de compartilhamento. Juntos, eles colaboram para criar transações de backup com bloqueio de tempo, que transferem a propriedade da UTXO para o novo proprietário. Durante essa transferência, a chave pública compartilhada permanece inalterada, mas o compartilhamento da chave do servidor é atualizado por meio de um Protocolo de Computação Multifuncional (MPC) para se alinhar apenas com o novo proprietário. Essa atualização resulta na criação de uma nova transação de backup, direcionada à chave pública do novo proprietário, com um tempo de bloqueio mais curto.
A confiabilidade do servidor é essencial, pois ele é responsável por excluir o compartilhamento de chave anterior. Isso garante que não seja possível conspirar com os proprietários anteriores. O proprietário atual pode gastar a UTXO a qualquer momento, desde que o faça em cooperação com o servidor. No entanto, se o servidor for desligado ou desaparecer, o proprietário atual deve aguardar até que o tempo de bloqueio expire antes de enviar sua transação de backup.
É importante ressaltar que o remetente nunca possui a chave privada completa; ele possui apenas uma parte do compartilhamento. Assim, todas as transações requerem a assinatura conjunta do servidor. Quando a UTXO é transferida para um novo proprietário, o compartilhamento do servidor é atualizado para que ele não possa mais assinar em nome do proprietário anterior, apenas em nome do novo proprietário. Esse sistema de transações de backup com bloqueio de tempo é projetado para proteger contra cenários de não cooperação ou apreensão do servidor, garantindo a segurança das UTXOs e a integridade da rede.
https://github.com/layer2tech/mercury-wallet
https://mercurylayer.com/
https://twitter.com/TTrevethan/status/1689929527420387328?t=0f5oF6w_ZRjWRYGah3HX8Q&s=19
-
-
 @ 9e69e420:d12360c2
2024-10-24 13:10:08
@ 9e69e420:d12360c2
2024-10-24 13:10:08Kamala Harris delivered a sharp critique of Donald Trump, comparing him to Adolf Hitler during a recent speech. She referenced comments made by former Chief of Staff John Kelly, who disclosed that Trump expressed admiration for Hitler while in office.
![Kamala Harris] (https://i.nostr.build/iyRm5cJo9YuRgh3M.png)
Harris stated, "It is deeply troubling and incredibly dangerous that Donald Trump would invoke Adolf Hitler."
She warned that if re-elected, Trump could seek unchecked power and compare him to a dictator. Harris emphasized the importance of understanding Trump's intentions and the implications for America’s future. Her remarks coincided with the fast-approaching election, intensifying her campaign's rhetoric against Trump.
-
 @ ff6187a2:ddbe1be7
2024-10-24 12:54:45
@ ff6187a2:ddbe1be7
2024-10-24 12:54:45Happy Halloween
-
 @ 42342239:1d80db24
2024-10-23 12:28:41
@ 42342239:1d80db24
2024-10-23 12:28:41TL;DR: The mathematics of trust says that news reporting will fall flat when the population becomes suspicious of the media. Which is now the case for growing subgroups in the U.S. as well as in Sweden.
A recent wedding celebration for Sweden Democrats leader Jimmie Åkesson resulted in controversy, as one of the guests in attendance was reportedly linked to organized crime. Following this “wedding scandal”, a columnist noted that the party’s voters had not been significantly affected. Instead of a decrease in trust - which one might have expected - 10% of them stated that their confidence in the party had actually increased. “Over the years, the Sweden Democrats have surprisingly emerged unscathed from their numerous scandals,” she wrote. But is this really so surprising?
In mathematics, a probability is expressed as the likelihood of something occurring given one or more conditions. For example, one can express a probability as “the likelihood that a certain stock will rise in price, given that the company has presented a positive quarterly report.” In this case, the company’s quarterly report is the basis for the assessment. If we add more information, such as the company’s strong market position and a large order from an important customer, the probability increases further. The more information we have to go on, the more precise we can be in our assessment.
From this perspective, the Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But this perspective omits something important.
A couple of years ago, the term “gaslighting” was chosen as the word of the year in the US. The term comes from a 1944 film of the same name and refers to a type of psychological manipulation, as applied to the lovely Ingrid Bergman. Today, the term is used in politics, for example, when a large group of people is misled to achieve political goals. The techniques used can be very effective but have a limitation. When the target becomes aware of what is happening, everything changes. Then the target becomes vigilant and views all new information with great suspicion.
The Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But if SD voters to a greater extent than others believe that the source of the information is unreliable, for example, by omitting information or adding unnecessary information, the conclusion is different. The Swedish SOM survey shows that these voters have lower trust in journalists and also lower confidence in the objectivity of the news. Like a victim of gaslighting, they view negative reporting with suspicion. The arguments can no longer get through. A kind of immunity has developed.
In the US, trust in the media is at an all-time low. So when American media writes that “Trump speaks like Hitler, Stalin, and Mussolini,” that his idea of deporting illegal immigrants would cost hundreds of billions of dollars, or gets worked up over his soda consumption, the consequence is likely to be similar to here at home.
The mathematics of trust says that reporting will fall flat when the population becomes suspicious of the media. Or as the Swedish columnist put it: like water off a duck’s back.
Cover image: Ingrid Bergman 1946. RKO Radio Pictures - eBay, Public Domain, Wikimedia Commons
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Precautionary Principle
The precautionary principle that people, including Nassim Nicholas Taleb, love and treat as some form of wisdom, is actually just a justification for arbitrary acts.
In a given situation for which there's no sufficient knowledge, either A or B can be seen as risky or precautionary measures, there's no way to know except if you have sufficient knowledge.
Someone could reply saying, for example, that the known risk of A is tolerable to the unknown, probably magnitudes bigger, risk of B. Unless you know better or at least have a logical explanation for the risks of B (a thing "scientists" don't have because they notoriously dislike making logical claims), in which case you do know something and is not invoking the precautionary principle anymore, just relying on your logical reasoning – and that can be discussed and questioned by others, undermining your intended usage of the label "precautionary principle" as a magic cover for your actions.
-
 @ 9e69e420:d12360c2
2024-10-24 11:51:32
@ 9e69e420:d12360c2
2024-10-24 11:51:32Dr. Johanna Olson-Kennedy, a leading advocate for trans youth care, withheld a $10 million study funded by taxpayers on the effects of puberty blockers, which found no improvement in mental health among participants.
She feared the findings would be "weaponized" against transgender care. Critics argue that her decision violates research standards and denies vital information to the public. The study tracked 95 children, revealing that 25% had mental health issues prior to treatment, contradicting Olson-Kennedy's claims of good overall mental health. Experts stress the importance of publishing research regardless of outcomes.
Sauce: https://nypost.com/2024/10/23/us-news/doctor-refused-to-publish-trans-kids-study-that-showed-puberty-blockers-didnt-help-mental-health/
-
 @ 45bda953:bc1e518e
2024-10-24 11:31:16
@ 45bda953:bc1e518e
2024-10-24 11:31:16Revelation Chapter 2:17
“He who has an ear, let him hear what the Spirit says to the churches. To him who overcomes I will give some of the hidden manna to eat. And I will give him a white stone, and on the stone a new name written which no one knows except him who receives it.”
Revelations is a mysterious book with some verses that seems to make very little sense.
Q: Why do we need names? A: To identify ourselves.
Same reason nature opted for us to have uniquely identifiable faces. But a name no one knows except him who receives it? Why would you need that?
When you are born you have very little in the way of personality and character. Doctor exclaims, “It’s a boy!” First verifiable identifier is recognised. One newborn baby looks very similar to another. For that reason they can accidentally be mixed up and given to the wrong mother at the hospital. But if the mother knows that she birthed a boy she would immediately know something is amiss if she gets handed a newborn girl. Gender is important as the first verifiable, unique identifier of the new being.
The newly confirmed male child gets issued a verbally spoken and symbolically scripted identifier. This identifier is known as a name. Name and surname please. These identifiers are of little consequence to the being who knows only feelings of pain and sensations of comfort. The survival of the biological spawn is dependant on the instinct to suckle and the tendency to cry at slight discomfort. This is the language of human instinct to cry and suck. As the toddler develops it starts to respond to the vocally repeated identifier (known as a name) to the point where it has been sufficiently trained to respond to the verbal enunciation of it. When you call for someone you are evoking hope that the entity being called to will respond by coming to your physical location so that you can share or enquire information. When the summons is answered by presence you maintain connection not by repetition of the name but by eye contact and directing conversation to the face of the person. The face being the most accurate point with which to verifiably establish identity.
In the book of Genesis Jacob is able to fool Isaac (His father) by exploiting his bad eyesight to steal an inheritance blessing from his older brother Esau. The face of Jacob was obscured through Isaac’s blindness which gave a false signal to the issuer of a blessing.
As our proverbial John Doe grows up he develops a personality and character which allows for people to gauge the levels of trust they are willing to risk on him. Character and personality are also unique identifiers. Mother knows best at who will be diligent when keeping their rooms clean and whose rooms she will have to clean for them. She can through experience predict outcomes using knowledge of character and personality as a reference. This information is valuable and can only be established or measured when there is an ongoing relationship where trust and responsibility are continuously tested and stressed.
We all have identifiers that are publicly displayed wherever we go.
: Physical appearance, Wedding ring, Tatoo
We have identifiers that represent or address us verbally and textually.
: Names, titles, seals, signatures, handwriting et cetera.
Ambiguous identifiers
: Left handed, smoker, married, divorced, affiliations, church, political views, phone number, address, favourite colour, drivers license ad infinitum.
In this digital world our identifiers are all exploitable by a large number of unidentifiable bad actors. This is weakness. If you are a man of character and strength but have no control over your identity. You are weak and defenceless in the eyes of these virtually indistinguishable, androgynous scammers, fraudsters, monopolies and governments.
We have to take digital sovereignty over our digital identities. That means we have to train our minds in the establishment of truth. The truth being...
Be true to thine self and let the truth about you be established by you. That means abandoning trust in third parties and know that no one is coming to save you and protect your personal data. Like there is no spoon in the matrix, there is also no institution who loves you enough to protect your identity in a digitally encrypted world. In some cases they might be legally obligated to, but who will take responsibility and how do you quantify and reverse the damage of leaked information. You don’t. No justice for the slave.
The spoon is a lie. It simply does not exist.
Revelation Chapter 2 verse 17
“He who has an ear, let him hear what the Spirit says to the churches. To him who overcomes I will give some of the hidden manna to eat. And I will give him a white stone, and on the stone a new name written which no one knows except him who receives it.”
 If you have an identifier that only you know about then you have a private key. You can verify your holdings of assets. You can prove your identity on nostr. You can own not only the data but prove you are the source of it.
If you have an identifier that only you know about then you have a private key. You can verify your holdings of assets. You can prove your identity on nostr. You can own not only the data but prove you are the source of it.Anything that a trusted third party is currently doing for you, analog or digital is systemically being open sourced and you could do it for yourself with the press of a button. All you need is a white stone with a name on it no one else knows and be willing to carry the responsibility. You could then selectively reveal yourself to the world and prove it is you without exposing the you that is private. I will give an example to help you understand the power.
John 19:31–42
31 Therefore, because it was the Preparation Day, that the bodies should not remain on the cross on the Sabbath (for that Sabbath was a high day), the Jews asked Pilate that their legs might be broken, and that they might be taken away. 32 Then the soldiers came and broke the legs of the first and of the other who was crucified with Him. 33 But when they came to Jesus and saw that He was already dead, they did not break His legs. 34 But one of the soldiers pierced His side with a spear, and immediately blood and water came out.
One thing is certain, Jesus was verifiably dead. The Romans, Jews and disciples who were present at the execution and burial all concurred. He is dead. Deceased. Gone from the realm of the living. Roman soldiers were veritable experts at death and declaring the dead so.
A few days later some disciples were proclaiming excitedly about Jesus being alive. A certain guy named Thomas would not be had. You guys are crazy, trying to establish some weird cult by pretending a fantastic impossibility. Nope. They were adamant. He lives. They claimed, like a bunch of fanatics. Thomas, being the voice of reason says the following.
John 21:25
25 The other disciples therefore said to him, “We have seen the Lord.” So he said to them, “Unless I see in His hands the print of the nails, and put my finger into the print of the nails, and put my hand into his side, I will not believe.”
Thomas was a real Bitcoiner. He does not trust, he verifies.
 Verification in progress.
Verification in progress.The body of Jesus, should he have been alive will have been littered with scar tissue all across his back and legs. It would have been easy for Him to selectively reveal his identity to whoever he chose by exposing his body and letting them verify the proof of his identity without doubt. No one in world history has ever committed suicide by flogging and crucifixion so you cannot even fake or repeat it if you wanted to commit identity theft and pretend to be the Christ.
A proof of work hash in history so profound that civilisations collapsed on the realisation of its profundity. Another consequential exposition of identity verification is also expounded on by the gospel accounts.
Matthew 24:5
“For many will come in My name, saying, ‘I am the Christ,’ and will deceive many.
Eric Cason on the "What Bitcoin Did" podcast said that he thinks Bitcoin is a messianic event. I agree with him. Liberation from economic tyranny is messianic if a figure initiates the salvation process.
That would suggest that there will be messianic implications, namely identity fraud of messiah with the intent to deceive and extort.
Matthew 24:23
23 “Then if anyone says to you, ‘Look, here is the Christ!’ or ‘There!’ Do not believe it.
We have ourselves an example of this in Craig Wright who claims to be Satoshi Nakamoto. Yet he refuses to verify it by transferring Genesis bits. Like Thomas demands to see the scars of crucifixion so too must we demand to see on chain movement of Genesis coinbase block reward as proof of identity and proof of work from anyone who publicly makes a claim to the person of Satoshi Nakamoto. Historic records in the future might mark this dispensation, BWP (Before white paper) and ASN (After Satoshi Nakamoto) or something of this nature could stand in the annals of history, marking a era of mankind similar to BC, Before Christ and AD, anno domini, the year of our Lord.
Jesus is yet to give me a secret name like Satoshi already did.
Which leaves me wondering…
 The simulacral spectre created by Satoshi is an ongoing rabbit hole,
The simulacral spectre created by Satoshi is an ongoing rabbit hole,I have no doubt.
...
bitbib
-
 @ c0f9e286:5a223917
2024-10-24 09:37:21
@ c0f9e286:5a223917
2024-10-24 09:37:21ตอนที่แล้วได้กล่าวถึงการตั้งบริษัท Holding Company เพื่อนำมาถือหุ้นในบริษัทลูก จุดประสงค์นอกจากจะเป็นการประหยัดภาษีแล้ว ยังง่ายต่อการควบคุม เนื่องจากแบ่งสัดส่วนการถือหุ้นกันตั้งแต่ต้น ซึ่งหากถือในนามบุคคลธรรมดาย่อมปกปิดตัวตนที่แท้จริงไม่ได้ ดังนั้นหลายๆบริษัทจึงนิยมตั้ง Offshore Holding (Holding ที่ตั้งในต่างประเทศ) เข้ามาถือหุ้นบริษัท Holding ในประเทศอีกทีหนึ่ง
นั่นแปลว่าวุ่นวายกับการตั้งบริษัท Offshore Holding แค่ครั้งเดียว หลังจากนั้นก็นำมาถือหุ้นใน Holding ในประเทศเพื่อเป็นเจ้าของทุกๆบริษัทในเครือ ซึ่งมีอำนาจควบคุม บังคับบัญชา และสั่งการโดยไม่จำเป็นต้องเปิดเผยตัวตนที่แท้จริง
ส่วนถ้าจะถามว่าไปตั้ง Offshore ประเทศไหนดี อันนี้ขึ้นกับวัตถุประสงค์ของแต่ละท่าน ซึ่งไม่มี One Size fits all บางคนตั้ง Offshore มาเพื่อรับเงินก้อนใหญ่จากการขายหุ้น และไม่ได้ต้องการปกปิดตัวตนอะไรมากมายก็อาจจะไปตั้ง Offshore ที่ Hong Kong หรือ Singapore
แต่ถ้าวัตถุประสงค์ต้องการที่จะปกปิดตัวตน อาจจะไปตั้งในประเทศอย่าง Seychells, Vanuatu, Mauritius หรือ BVI เป็นต้น ซึ่งประเทศเหล่านี้มักมีนโยบายไม่เปิดเผยตัวตนของบุคคลที่เป็นเจ้าของหุ้นในบริษัท และที่สำคัญ ประเทศเหล่านี้บางทียอมให้นิติบุคคลต่างประเทศเข้ามาเป็นผู้ถือหุ้นได้ 100% (กฎหมายไทยในการตั้งบริษัทต้องมีผู้ถือหุ้น 2 คนขึ้นไป และหากไม่มีโรงงานในไทย หรือได้รับสิทธิ BOI ต่างชาติสามารถถือหุ้นได้ไม่เกิน 49%)
ดังนั้นหาก Offshore Company 1 ชั้นยังไม่พอ คุณก็ตั้ง Offshore ไปเลย 2 ประเทศเช่น ผมอาจจะตั้ง Offshore แรกที่ Vanuatu ซึ่งผมถือหุ้น 100% (ในนามบุคคล) แล้วจึงไปก่อตั้งอีก 1 บริษัทอีกแห่งที่ Seychells โดยให้ Vanuatu Offshore เข้าไปถือหุ้น 100% ในนามบริษัท แล้วผมจะนำ Seychells Offshore มาถือหุ้นใน Thailand Holding อีกทีหนึ่ง ซึ่งหาก Thailand Holding ไม่ได้มีโรงงาน หรือได้รับสิทธิ BOI แปลว่า Seychells Offshore จะเข้าไปถือหุ้นได้ไม่เกิน 49% ส่วนอีก 51% คุณควรหานอมินี หรือคนในครอบครัวที่ไม่ได้กังวลเรื่องความเป็นส่วนตัวเข้ามาถือหุ้นแทน และอาจจะจำกัดสิทธิออกเสียงผ่านกลไกการถือหุ้นบุริมสิทธิ์แทน เอาเป็นว่าเดี๋ยวจะงง แต่ให้เข้าใจไว้ว่า 51% ที่ถือหุ้นแทนมีช่องทางที่ทำให้เสียง Vote หรือสิทธิในการรับเงินปันผลน้อยกว่าฝั่ง 49% ซึ่งเดี๋ยวจะหาเวลาอธิบายเรื่องนี้โดยละเอียดอีกครั้งหนึ่ง
แปลว่าหากทางรัฐบาลไทยตรวจสอบรายชื่อผู้ถือหุ้นหรือทรัพย์สินของคุณ หากใช้การถือทรัพย์สินแบบนี้ย่อมไม่มีทางที่รัฐจะรู้เลยว่าคุณเป็นเจ้าของทรัพย์สิน หรือกิจการอะไรกันแน่ และหากรัฐบาลไทยต้องการตรวจสอบจริงๆ การจะไปตรวจพิสูจน์ว่าใครถือหุ้น หรือมีสิทธิในการครอบงำบริษัทจะเป็นเรื่องยากมาก
ซึ่งหากคุณคิดว่านี่ยังเป็นส่วนตัวไม่พอละก็… แน่นอนมีวิธีที่จะเพิ่มความเป็นส่วนตัวมากขึ้นกว่าเดิม ซึ่งมีอีก 2 วิธี และสามารถนำมาใช้ร่วมกับวิธีนี้ได้ ส่วนจะเป็นวิธีอะไรนั้น รอติดตามตอนต่อไป
Own Nothing and be Happy ในแบบฉบับ Elite เป็นไงบ้างครับ เริ่มเห็นภาพหรือยังว่าทำไมตระกูลดังๆอย่าง Rothschild สามารถปกป้องความเป็นส่วนตัวของพวกเขาไว้ได้โดยที่คนนอกไม่รู้เลย ก็เพราะเครื่องมือแบบนี้ไง
realeakkrit #siamstr #privacy
-
 @ ebdee929:513adbad
2024-10-17 17:09:57
@ ebdee929:513adbad
2024-10-17 17:09:57Software Setup Links:
DC-1 as a monitor:
- SuperDisplay Setup | Best for Windows
- SpaceDesk Wireless and Wired Display Setup | Windows PC Users
- Chrome Remote Desktop Setup | Anyone
Purchase and setup links:
Keyboards:
- Keys-To-Go 2 White Keyboard | Logitech
- Keys-To-Go 2 Bluetooth Setup
- Magic Keyboard White | Apple through Amazon.com
- Magic Keyboard Bluetooth Setup
- Air 60 V2 with Blue Switches | Nuphy
- Air 60 V2 Keyboard Folio | Nuphy
- Air 60 V2 Bluetooth and Folio Setup
- Magic Keyboard Case | Fintie through Amazon.com
Pens:
- Premium White Pen
- Ultra Premium Lamy Pen | Amazon.com
- Samsung S Pens (Multiple):
- Small (Galaxy Note Series Style)
- Cheaper Alternative (ZERO Quality Guarantees)
- Medium (Galaxy Fold Style with smooth tip)
- Cheaper Alternative (ZERO Quality Guarantees)
- Larger (Galaxy Tab Style)
- Cheaper Alternative (ZERO Quality Guarantees)
Pen Setup: Just touch the screen and it works, no pairing or charging needed.
Others:
- Bluelight Free Light Bulb | Amazon.com
- Light Bulb Setup
- Comfy Green Sleeve | Amazon.com
Keys-To-Go 2 Bluetooth Setup:
- Step 1: Unbox keyboard from box
- Step 2: Open keyboard and pull tab to enable batteries and keyboard function
- Step 3: Ensure Switch on back of product is in the position where green is showing, not off where red is showing
- Step 4: Hold the key labeled ‘fn’ meanwhile you hold the ‘g’ key for 3 seconds to put the keyboard into android mode, since this is an android tablet
- Step 5: Hold the key labeled ‘fn’ meanwhile you hold the key labeled ‘F1 with the image of the laptop and phone for 3 seconds to put profile 1 into bluetooth pairing mode
- Step 6: On your Daylight DC-1, swipe down on the top of the screen, swipe down again, click on the settings icon that looks like a gear in the bottom right corner
- Step 7: In settings, click the second from the top menu item on the left called ‘Connected devices’ (it says Bluetooth, pairing underneath it)
- Step 8: Click on the button labeled ‘Pair new device’
- Step 9: Under available devices tap on Keys-To-Go 2
- Step 10: It will ask you to type some numbers and hit return/ enter, once you do so the device will show up as connected under ‘Saved Devices’
- Step 11: Turn off the keyboard with the switch on the back if you desire, this will disconnect it from the device
Appendix: Keys-To-Go 2 Documentation:
Apple Magic Keyboard Setup:
- Step 1: Unbox keyboard from box
- Step 2: Ensure Switch on back of product is in the position where green is showing
- Step 3: On your Daylight DC-1, swipe down on the top of the screen, swipe down again, click on the settings icon that looks like a gear in the bottom right corner
- Step 4: In settings, click the second from the top menu item on the left called ‘Connected devices’ (it says Bluetooth, pairing underneath it)
- Step 5: Click on the button labeled ‘Pair new device’
- Step 6: Under available devices tap on Magic Keyboard
- Step 7: It will ask you to type some numbers and hit return/ enter, once you do so the device will show up as connected under ‘Saved Devices’
- Step 8: Turn off the keyboard with the switch on the back if you desire, this will disconnect it from the device
Spacedesk Setup:
THIS IS ONLY FOR PEOPLE USING A WINDOWS PC
- Step 1: Open the Google Play Store: On your device, slide in from the side until and move till you get to the letter ‘P’ and tap ‘Play Store’
- Step 2: Search for SpaceDesk: In the Google Play Store, tap on the search bar at the top and type "SpaceDesk". As you type, suggestions will appear below the search bar. Tap on "SpaceDesk - USB Display for PC" when it appears.
- Step 3: Download and Install the Driver: Visit the
official Spacedesk website and download
the ‘Windows 10/11 (64-bit)’ Spacedesk driver for Windows. Follow the on-screen instructions to install it on your PC. - Step 4: Launch Spacedesk Server: After installation, open the Spacedesk Driver Console application on your Windows PC.
- Step 5: Click the ‘USB Cable Driver Android’ button, then enable the ‘USB Cable Android’ option and let it apply.
- Step 6: Open Spacedesk App: On your Android device, open the Spacedesk app you installed earlier. - Step 7: Improve Quality: Click on the ‘3 lines’ icon and then settings.
- Under ‘Rotation’ enable ‘Auto-Rotation’ and under ‘Quality/Performance’ slide ‘Image Quality’ to max (the right) and set ‘Custom FPS Rate’ to 60. - Step 7A (for wired use): Plug the tablet into your PC - Step 7B (for wired use): Enable USB File Transfer: Swipe down on status bar (the bar at the top of the screen with wifi and notification icons etc. There will be a notification under the ‘Silent’ category named ‘Charging this device via USB’, tap on it to expand it, then tap once more time when it says ‘Tap for more options’. This will open up a menu, all you need to do is click ‘File Transfer’ under the section called ‘Use USB for’ - Step 8: Connect: Reopen the Spacedesk app (use the back arrow or button to leave the settings menu should you need). The app should now detect your Windows PC through USB OR wireless. Tap the listing under your computer's name for wireless connection, or tap the little trident USB icon at the bottom middle of the screen for wired connection, which is recommended.
SuperDisplay Setup:
THIS IS ONLY FOR PEOPLE USING A WINDOWS PC
- Step 1: Open the Google Play Store on the tablet: On your device, slide in from the side until and move till you get to the letter ‘P’ and tap ‘Play Store’
- Step 2: Search for SuperDisplay: In the Google Play Store, tap on the search bar at the top and type "SuperDisplay". As you type, suggestions will appear below the search bar. Tap on "SuperDisplay - Virtual Monitor" when it appears.
- Step 3: Download and Install the Driver on your Windows PC: Visit the
official SuperDisplay website and download
the Windows driver. Follow the on-screen instructions to install it on your PC. - Step 4: Launch SuperDisplay : After installation, open the SuperDisplay Settings application on your Windows PC by hitting the ‘Windows’ Key and typing ‘SuperDisplay Settings’ - Step 5: Launch the application on your tablet. - Step 6: Go into SuperDisplay settings by clicking the settings gear icon in the top right corner. Under ‘Advanced settings’ click ‘Quality’ and slide it to 100. - Step 7 (Wireless): IP Address: Back out of the settings and input the IP address into the desktop program. (Both devices need to be on the same wifi) - Step 7 (Wired): Plug the tablet into the PC - Step 8: Start the connection on the tablet by clicking the central button! - Step 9: In Windows, hit the ‘Windows’ key, type display and hit enter. This will take you to display settings. In display settings set the displays to ‘extend’ and then confirm the change. Select the DC-1 display by clicking the square it is associated with, then set the display to 1584 x 1184 resolution, confirm this by hitting ‘keep changes’, then set to 125% scale.
Chrome Remote Desktop Setup:
Note: This prefers Chrome itself on the tablet and REQUIRES a chromium based browser to be installed on your computer, examples of chromium based browsers are Chrome, Edge, Arc, Opera etc. Basically anything but Safari or Firefox will do. This is because a chrome extension needs to be installed. Both devices need to be signed in to the same Google account to see each other.
- Step 1:
and click the download button here:
- Step 2: Get the extension in the window that pops up:
- Step 3: Once installed, click the download button AGAIN and it will show what is shown below, a program called ‘chromeremotedesktophost’ will download, install it.
- Step 4: In the play store, install the ‘Chrome Remote Desktop’ app and open it, the app's name will be just ‘remote desktop’ as a heads up. - Step 5: On the computer, go to
and click set up remote access under the ‘Remote Access’ tab. Then set a computer name and pin. Accept whatever permissions pop up on your computer
- Step 6: If you have Chrome itself installed on the tablet it will open a page, click the ‘Access my computer’ button, then under remote Access click your device.
APK Installation Guide:
- Note on APK’s: These are apps from outside official sources, they might not update from the play store and in rare cases can have different functionality. Apply extra caution and source these app files from good sources like
. Just like through the play store or other sources, malicious files can be spread, use common sense and generally avoid downloading any ‘hack’ apps that claim to unlock features. - Step 1: One the home screen, swipe down from the top of the screen, also called the status bar - Step 2: Swipe down again till the settings tiles fill the screen, then click the gear icon in the bottom right hand corner of the screen which will take you to the settings application - Step 3: In settings, tap ‘Apps’, then ‘Special app access’, then ‘Install unknown apps’ - Step 4: Tap your preferred browser application then enable the ‘Allow from this source’ toggle - Step 5: Open your browser of choice, and search ‘apkmirror’ and navigate to
, or just type
https://apkmirror.com/ - Step 6: On the apkmirror website, search your application name in the search bat at the top of the apkmirror website. After you search find your app in the results and tap the most recent version. Dismiss any ads you might see. - Step 7: Under the text ‘Verified safe to install (read more)’ tap the button called ‘SCROLL TO AVAILABLE DOWNLOADS’ - Step 8: Find a file tagged ‘APK’ not ‘BUNDLE’ - Step 9: Click on the Download Arrow and line icon that looks like this ⬇️ - Step 10: Under ‘Verified safe to install (read more)’ tap ‘DOWNLOAD APK’ - Step 11: If it appears, dismiss the warning for ‘File might be harmful’ by tapping ‘Download anyway’ - Step 12: After your apk downloads, either - Tap ‘Open’ on the ‘File Download’ Pop-Up - Go to the home screen and open the files app, navigate to the downloads folder and tap on the downloaded apk - Step 13: Tap ‘INSTALL’ on the popup that appears. After it installs tap ‘OPEN’ - Step 14: The app will now be on your device and you can search and open it like every other app
Touch grass,
Daylight Team
-
 @ 472f440f:5669301e
2024-10-16 01:57:41
@ 472f440f:5669301e
2024-10-16 01:57:41Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice.
This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative.
These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin.
Since 2016: +46% in USD -99% in BTC
Since 2020: +34% in USD -70% in BTC
The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them.
Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter.
What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line.
Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow.
The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way.
Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished.
In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial.
We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years.
There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer.
Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it.
Final thought... Sinus congestion sucks.
-
 @ d5c3d063:4d1159b3
2024-10-24 15:14:10
@ d5c3d063:4d1159b3
2024-10-24 15:14:10มนุษย์ไม่ใช่หุ่นยนต์ เรา 'กระทำ' ด้วยเหตุผลและ 'คุณค่า' แต่ถูกจำกัดด้วย 'เวลา' - นี่คือหัวใจของเศรษฐกิจที่แท้จริง 🧡
3 EP ที่ผ่านมาของ JUST Economics เราได้ปูพื้นฐานเศรษฐศาสตร์สำนักออสเตรียนจากบทที่ 1-3 ของหนังสือ Principles of Economics โดย Saifedean Ammous
https://image.nostr.build/a1b6208d64a97411e9d7883180496356ac8d3dbdf45b46ba434699b664709bd3.jpg
..เริ่มจาก EP ที่ 1 การกระทำของมนุษย์ (Human Action)
เราได้เข้าใจว่า.. การกระทำของมนุษย์ (Human Action) คือหัวใจสำคัญ ตามที่ลุดวิก ฟอน มิเซส (Ludwig von Mises) ได้อธิบายไว้ในหนังสือ Human Action ของเขา
มิเซสบอกว่า.. การกระทำคือการแสดงออกถึงเจตจำนงของเรา เราตั้งใจทำอะไรสักอย่างเพื่อให้บรรลุเป้าหมาย เป็นการตอบสนองต่อสิ่งเร้าและสภาพแวดล้อม และเป็นการปรับตัวของเราต่อโลกใบนี้
มนุษย์ไม่ใช่หุ่นยนต์ที่ถูกโปรแกรมไว้ หรือสัตว์ที่ทำตามสัญชาตญาณ เราคิด เราเลือก และมีเหตุผล แม้ว่าผลลัพธ์ที่ออกมาดีหรือไม่ก็ตาม เราได้เรียนรู้ว่าการกระทำของมนุษย์เกิดจาก ความต้องการที่ยังไม่บรรลุผล
ซึ่งเป็นเหมือนเชื้อเพลิงที่ผลักดันให้เราไม่หยุดนิ่ง ไม่ว่าจะเป็นความหิว ความอยากได้อยากมี หรือความอยากรู้อยากเห็น สิ่งเหล่านี้ล้วนเป็น แรงจูงใจ ที่ทำให้เราคิด วางแผน และ ลงมือทำ
..การวิเคราะห์ทางเศรษฐศาสตร์ (Economic Analysis) เป็นอีกหัวข้อสำคัญที่เราได้เรียนรู้
ฮานส์-เฮอร์มันน์ ฮ็อปเป่ (Hans-Hermann Hoppe) บอกว่า.. การวิเคราะห์เศรษฐกิจ มันเหมือนกับการไขคดีเลยล่ะ เราต้องแกะรอย หาหลักฐานและเชื่อมโยงทุกอย่างเข้าด้วยกัน
เศรษฐศาสตร์ไม่สามารถทดลองแบบวิทยาศาสตร์ได้ เพราะมนุษย์ ไม่ใช่ลูกตุ้ม แต่ละคนคิดไม่เหมือนกัน ตัดสินใจไม่เหมือนกัน การวิเคราะห์เศรษฐกิจแค่ตัวเลขอย่างเดียว อาจทำให้เราเข้าใจผิดได้
เพราะตัวเลขมันเหมือนเปลือกนอก.. เราต้องมองให้ลึกกว่านั้น ถึงจะเห็นแก่นแท้ของปัญหา ทีนี้แล้วอะไรล่ะที่เป็นตัวกำหนดการกระทำของมนุษย์?
=================
..คำตอบอยู่ใน EP 2 คุณค่า (Value) ของสิ่งต่างๆ ไม่ได้ตายตัว แต่ขึ้นอยู่กับว่าแต่ละคนมองว่ามันมีค่าแค่ไหน
ตามที่ คาร์ล เมงเงอร์ (Carl Menger) ได้อธิบายไว้ในหนังสือ Principles of Economics ของเขา เมงเงอร์บอกว่า.. มูลค่าไม่มีอยู่นอกเหนือจิตสำนึกของมนุษย์
ใน EP นี้เรายังได้เรียนรู้ 'ทฤษฎีส่วนเพิ่ม' (Marginalism) ที่บอกว่า ความสุขที่เราได้จากการบริโภคของจะลดลงเรื่อยๆ ตามกฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง (Law of Diminishing Marginal Utility)
เพราะยิ่งเรามีอะไรมากขึ้น.. ความสุขที่ได้รับจากสิ่งนั้นก็จะลดลงเรื่อยๆ
ดังนั้น.. การเลือกใช้ทรัพยากรอย่างชาญฉลาด จึงเป็นสิ่งสำคัญ นอกจากนี้เรายังได้เรียนรู้ว่า "มูลค่า" เกิดจากหลายปัจจัย เช่น ความชอบ สถานการณ์ และ ความขาดแคลน
ส่วน "ราคา" เป็นเพียง "ตัวเลข" ที่สะท้อนถึงการตกลงกันระหว่างผู้ซื้อและผู้ขาย ไม่ได้เป็นการวัดมูลค่าโดยตรง
เหมือนกับที่บางคนยอมจ่ายแพงเพื่อซื้อกาแฟแบรนด์ดัง ทั้งๆ ที่กาแฟโบราณก็ให้รสชาติที่คล้ายคลึงกัน หรือบางคนเลือกซื้อเสื้อผ้ามือสอง ทั้งๆ ที่เสื้อผ้าใหม่ก็มีให้เลือกมากมาย
เพราะ "มูลค่า" มันไม่ได้อยู่ที่ตัวสินค้าเอง แต่มันอยู่ที่ว่าเราคิดว่ามันมีค่าแค่ไหนต่างหากล่ะ..
แล้วทรัพยากรที่สำคัญที่สุดของมนุษย์คืออะไร?
=================
คำตอบอยู่ใน EP 3 นั้นก็คือ เวลา (Time)
ในหนังสือ The Ultimate Resource ของไซมอน เขาได้บอกว่า.. เวลา เป็นทรัพยากรที่ล้ำค่าที่สุด เพราะมันมีจำกัดและใช้ไปแล้วก็เรียกคืนไม่ได้
ดังนั้นทุกการตัดสินใจของเรา จึงมี "ต้นทุนค่าเสียโอกาส" แฝงอยู่ เนื่องจากเวลาเป็นสิ่งมีค่าและมีจำกัด เราจึงต้องหาวิธีใช้เวลาให้คุ้มค่า โดยอาศัยเทคโนโลยี การแบ่งงานกันทำ การลงทุน และการออมเพื่อความมั่นคงในอนาคต
ระดับความเห็นแก่เวลา (Time Preference) ก็เป็นอีกหนึ่งปัจจัยที่ส่งผลต่อการตัดสินใจของเรา มนุษย์มักจะให้คุณค่ากับความสุขในปัจจุบันมากกว่าความสุขในอนาคต
เหมือนกับที่หลายคนเลือกที่จะรูดบัตรเครดิต ทั้งที่รู้ว่าต้องจ่ายดอกเบี้ยแพง เพราะความต้องการได้ของ ณ ตอนนั้น มันมีค่ามากกว่าภาระหนี้ที่จะเกิดขึ้นในอนาคต
เศรษฐศาสตร์สำนักออสเตรียนมองว่า.. การทำความเข้าใจระบบเศรษฐกิจต้องเริ่มต้นจากการศึกษาการกระทำของมนุษย์ ซึ่งเป็นสิ่งที่ขับเคลื่อนการทำงานของระบบเศรษฐกิจ ที่เกิดจากเหตุผลและมูลค่าที่แต่ละคนให้กับสิ่งต่างๆ
ในขณะที่เศรษฐศาสตร์กระแสหลัก.. มักจะใช้แบบจำลองทางคณิตศาสตร์และมองว่ารัฐควรมีบทบาทสำคัญในการควบคุมเศรษฐกิจ
ซึ่งการแทรกแซงของรัฐในระบบเศรษฐกิจ มักจะนำไปสู่ปัญหาต่างๆ
เช่น การกำหนดราคาสินค้ามักจะนำไปสู่การขาดแคลนของสินค้าจึงทำให้เกิดตลาดมืดขึ้น
ส่วนการขึ้นค่าแรงขั้นต่ำอาจทำให้คนงานตกงาน และการอุดหนุนโดยรัฐอาจทำให้เกิดการผลิตและบริโภคที่มากเกินความจำเป็น
เศรษฐศาสตร์สำนักออสเตรียนจึงมองว่ารัฐควรมีบทบาทจำกัด
=====================
เห็นไหมครับว่าทั้ง 3 EP มันเชื่อมโยงกัน..
เริ่มจากการกระทำที่ถูกขับเคลื่อนด้วยมูลค่าและถูกจำกัดด้วยเวลา ทั้งหมดนี้คือพื้นฐานสำคัญของเศรษฐศาสตร์ ที่ช่วยให้เรามองเห็นความลับเบื้องหลังของตัวเลขและทฤษฎี และสามารถนำไปประยุกต์ใช้ในชีวิตประจำวันได้อย่างมีประสิทธิภาพ
ฝากติดตาม JUST Economics ใน EP ต่อไปกันด้วยนะครับ รับรองว่า สนุก เข้าใจง่าย และได้ความรู้แน่นปึก!!
-
 @ 9e69e420:d12360c2
2024-10-21 20:26:54
@ 9e69e420:d12360c2
2024-10-21 20:26:54Your first NOSTR note.
Some of you may be lurking wondering how why or what for your first note here on nostr. Here's some advice from an pseudonymous douchebag. To start with, your first note should be to come out swinging. Make lots of friends maybe even some enemies. Most people get a lot of love with their first introductions post.
Make it short.
Your first note will probably (and probably should) be a kind one event. The note you're reading is a 30023 event for long form notes. (More on this some other time). Keep it short and concise. You probably could publish a book in a kind one note. But I really don't think anyone believes you should and I'm sure many relays would reject it. It will also appear without formatting which just looks ugly for anything other than a microblog.
Introduce yourself.
Just as you would in an IRL interaction. What's your name? But more importantly what do you want us to call you? What brought you here? What are your interests? It's important to be real here even if you decide to be pseudonymous. Chances are your tribe is already here. If you're the first then that makes you king of your little corner of the nostr. Which will likely pay dividends in and of itself.
Make it a banger.
Here's my first note (I should disclose this is just the first note from this npub And I have already been here for over a year at this point):
note1pnufmzwy2gj4p5qza6jk7k40nns0p3k2w0fsrqq568utjlnyphdqyg8cpq
Have fun
Don't take this or anything else too seriously. We are all the same here because we are just as unique as each other. Be as weird as you want.
** & Don't forget to use the "#indroductions" hashtag **
-
 @ a828c9af:ea95c44c
2024-10-24 08:25:30
@ a828c9af:ea95c44c
2024-10-24 08:25:30The Philippines is a goldmine for businesses seeking new markets. With a booming economy and a population exceeding 100 million, it presents a vibrant and diverse consumer landscape that, when maximized, can offer businesses a considerable market with a growing purchasing power.
Moreover, the country's e-commerce sector has exploded in recent years, with sales hitting $17 billion in 2021 alone. As consumer behavior rapidly evolves due to technology and changing preferences, there's never been a better time to enter the Philippine market than today.
5 Ways to Tap into the Philippine Market
To succeed in the Philippine market, you need a strategic approach that resonates with the country's diverse and dynamic consumer base. Here are five proven methods to help you engage effectively.
1. Digital services and marketing
In the Philippines, a solid online presence is crucial to reach your target audience. Use social media, content marketing, and search engines to build meaningful connections almost instantly.
2. Cashless and online payment methods
Filipino consumers prefer secure and convenient payment options. Offering various cashless and online payment methods can enhance their shopping experience and give your business a competitive edge.
3. Fashion eCommerce
Fashion eCommerce is booming in the Philippines. A visually appealing website with high-quality images, detailed product descriptions, and easy navigation can attract fashion-conscious Filipinos.
4. Localized content and engagement
Tailor your content to your customers' culture and values to connect with the Philippine market. Using the local language, cultural references, and relatable imagery can deepen customer engagement and build trust.
5. Responsive customer support
Excellent customer support builds trust and loyalty. When you offer timely, helpful responses through chatbots and automation while maintaining a personal touch ensures customer satisfaction.
Check this infographic to learn more about consumer trends in the Philippines and how to take advantage of them to tap into this lucrative market.
-
 @ 5d4b6c8d:8a1c1ee3
2024-10-24 15:12:41
@ 5d4b6c8d:8a1c1ee3
2024-10-24 15:12:41Last year, I devised a sports betting strategy that I believed had demonstrably positive expected returns, based on the particular betting mechanism at freebitcoin (details here https://stacker.news/items/342765/r/Undisciplined).
After one year and over 500 wagers, I'm up almost 40k with this approach, despite still having about 40k in outstanding bets. Assuming those outstanding bets only break even, that's about 80k in winnings. I realize that may not sound like much for a year's worth of effort, but I started small until I was confident in the methodology.
For those interested in following this approach, I'll start making entries with the RBOA suggested wager distributions. Here are today's:
| Outcome 1 | Outcome 2 | Outcome 3 | Bet Share 1 | Bet Share 2 | Bet Share 3 | |--------------|--------------|-------------|--------------|--------------|--------------| | Bournemouth | Man City | Draw | 17% | 61% | 22% | | Liverpool| Brighton | Draw | 68% | 14% | 18% | | Man United| Chelsea| Draw | 38% | 37% | 25% | | Newcastle| Arsenal| Draw | 27% | 49% | 24% | | Valencia| Real Madrid| Draw | 15% | 63% | 22% | | Sevilla| Real Sociedad| Draw | 34% | 35% | 31% | | Barcelona| Espanyol| Draw | 83% | 8% | 9% | | Atletico Madrid| Las Palmas| Draw | 79% | 6% | 15% |
originally posted at https://stacker.news/items/738522
-
 @ 4fda8b10:7bbee962
2024-10-15 13:56:47
@ 4fda8b10:7bbee962
2024-10-15 13:56:47Takeaways from Bitcoin Amsterdam 2024
The bitcoin conference in Amsterdam to me is my typical yearly check in with the crypto scene. From a distance, not much has changed since last year. What struck me most was the correlation between the exchange prices and the amount of visitors, I had the feeling the crowd was about twice as big as last year during the opening and high profile talks.
From my personal experience, the increase of audience also brought some dilution to the hard core maximalist anarchist-ness of the event. The overall vibe amongst the attendees was more friendly and open. This also increased the value of the event for me, as I try to broaden my network, get different perspectives and learn more about what interests people in the crypto space.
This year was also marked by my involvement in the Nostr side events, I was asked to give a live performance at the Nostrdam Meetup October 2024 which went over very well and also acted as a nice conversation starter during the rest of the conference. I was also slightly involved in the organisation of the Nostr booth, but credits go to the awesome volunteers that made that happen. It was a bit of a shame that the Nostr booth was tucked away all the way in the back of the (commercial) expo hall, it would have been nice to promote the Nostr initiative to the social community area next to the satoshi radio / connect the world community area
For me the biggest takeaways were the insights I got from the people I’ve met, all from different industries with different perspectives on both technology and involvement. I tried to specifically reach out to (former) CTO’s, which led me to write and share this piece on that particular role. Of course shaking hands and catching up with people I only see once a year is great, and reminds me of the vibe and my experiences at the Fronteers conference.
From a technical point of view I was most inspired by the advancement of AI agent technology and the possibilities of programmable micropayments via de lightning network. Michael Levin showed us that the http spec already has a 402 status of “payment required” and that basically all the required infrastructure is already in place to allow both humans and ai agents to use the lightning network to pay for access to compute or resources using this statuscode and an api gateway such as lightning labs aperture.
talk: HODLing Is Hard: Fundamentals, Cycle & On-Chain Analysis by rational root
- bitcoin is already competing in market cap with other currencies
- amount of euro is exponentially increasing
- from 8 to 16 trillion euros since 2009, but having a real hard cap in btc is fundamentally different
- inflation
- euro lose 20% in 5 years
- bitcoin also loses purchasing power, but only 10%
- in current system, we always need to take on maximal debt, instead of saving
- two things can happen
- we get into overvalued price levels
- we get into recession
- recession would only mean a shift in the start of the 4 year cycle
panel: Endless Possibilities: Reusing Heat From Miners
- people
- 21energy Maximilian (obwexer)
- Bert de groot (bitcoin Brabant)
- Brad Tom (mara)
- perspective: coming from energy to bitcoin is very different and much faster with implementation than the other way around
- 95% of heat can be captured from miners, much higher in comparison to AI
- being able to balance the grid because you can turn off the bitcoin miners
- ”heatbuffers” → heat is still available when power source goes down
- common objections:
- Crypto is hard to understand
- for large industrial clients, heaters, public image of bitcoin (often a door closer)
- people don’t see that miners consume electricity and pay for it.
- If mining is closed down in Europe, the energy prices will spike because the energy will not be payed for anymore
panel: How to Guard Privacy Tools & Developers
- Dorien Rookmaker & Sjors proviost
- chat control
- topic keeps returning, and is highly distracting for progress
- Parliament wants Netherlands to speak against chat control
- initially they want to just, scan messages now want to install malware before encryption
- it is distracting Sjors from working on bitcoin
- samurai and tornado are different cases
- tornado cash is harder because it is also a smart contract with custody over funds
- samurai is easier: if you don’t have custody, are you responsible for the results of the code?
- will decide wether whether non custodial systems are ok or not
- micah interpretation is quite vague
- the current Denmark case:
- if you are rebuilding an interface for a smart contract, you are responsible for implementing all the legal guardrails that apply to securities governance?
panel: NOSTR: Freedom of Algorithmic Choice
- will casarin, mcshane, martti malmi (Sirius iris.to)
- arc (alternative layer on top of bitcoin, like lightning but without channels)
- aha moment: when seeing the unsiloed experience between nostr apps
- were trying to create a town square, so we need to deal with spam
- social media platforms have stagnated a bit, nostr is innovating far more quickly
panel: Transactions As Bitcoin’s Key Growth Metric
- Stephan nilov
- classical developers don’t know about money and bitcoin development is harder
- total addressable market is highest in btc, biggest number of possible users
- bitcoin companies don’t benefit from tokens that are typically exchanged for vc money
- users are not looking for payments, they are looking for digital property and other things that Ethereum network offers
- Stephan Livera
- there is a known, slow pace at which bitcoin will be adopted
- btc market is only 1.2 trillion dollars compared to USD 30 trillion
talk: Making Bitcoin Quantum Resistant by hunter beast
- surmount.systems
- explaining the threat of quantum computing
- problems
- key size: larger signature required
- proposal: transaction field attestation
- 256 bit number key, possibility to factor the private key out of this
- introducing p2qrhash
- segwitv3
- satoshishield
- in layman terms:
- quantum safe upgrades to bitcoin protocol are proposed
- we need to introduce a software upgrade
- requires a soft fork, opt in
- possible advantages of quantum in crypto
- allow us to sign signatures in a way that is unbreakable
- 514 qubits are needed to break something
talk: Lightning and AI: Where the Bots Pay You by michael levin
- two use cases for bitcoin adoption
- people that don’t have access to fiat
- things that can’t be handled by fiat systems
- large language models
- current phase: big adoption
- next phase: agentic ai
- costs of ai
- compute 400% more (ben bajarin)
- algorithm training excess 10 billion dollars
- data
- costs implications
- cost of serving answers is 0
- cost of serving ai query is not 0
- cost for everyone in the world
- payments in AI
- now
- pay per call
- data
- accessibility
- agents
- agents must be able to do things that cost money
- now
- payment system for AI
- globally accessible
- near instant
- final settlement
- internet native
- authentication mechanism
- personalise access (simple queries for lower tier model)
- easy to implement
- L402 protocol
- 402 payment required in http spec
- reverse proxy to have 402 in front of APIs
- aperture is lightning labs implementation
- all available right now, adoption starting
- fewsats, sulu, open agents / plebai
- pay with lightning
- challenges
- do these payments with stablecoins instead of lightning (hence taproot assets protocol)
- cases
- agent bots can pay for real world resources
- taproot assets issue assets on bitcoin allow transfer of
- references
- L402.org
talk: Bitcoin is Cypherpunk by Aaron van Wirdum
- is bitcoin still Cypherpunks ?
- on one hand we see a push to regulation and frameworks to govern btc
- on the other hand we are arresting developers for writing code
pitches: Bitcoin Amsterdam Pitch Day: Presented by GoBTC
- umoja
- ceo Robby greenfield
- LST smartcoin, deflationary by design
- competes with pools such as lido and rocket pool, but supports multiple coins, including liquid hashrate
- 30% liquid hashrate returns (!)
- compliance micah
- disaster scenarios
- black swan event → automatic exit out
- magisat
- trading tools for mempool snipers
- support for runes
- volume on bitcoin nft’s is on certain days higher than nft’s on ethereum
panel: Crossing the Boundaries Between Bitcoin & Fiat
- Christian Rau (Mastercard) & Remi destigny (bitrefill )
- liberation is great, but protocols don’t take customer service into account, chargebacks and rewinding mistakes etc
- we aim to smooth process by issuing cards that sell your Bitcoin just in time on the backend
talk: Gold & Bitcoin: Friends, Not Foes by Paul Buitink
- premise “the financial system is crumbling”
- there is too much debt
- emerging markets lost confidence in western currencies
- freezing Russian assets is shooting ourselves in the foot, as it shows the world you might not want to hold too many dollars that can be easily seized
- record gold buying by central banks in 2022 2023 2024
- gold: 17 trillion marker cap, compared to bitcoin 1.3 trillion
talk: Austrian Economics, Hard Money & Bitcoin Cycles, Willem Middelkoop
- ”we are on the road towards hyper inflation and collapse of financial system”
- central bankers are pretty smart and very aware
- this is why they accumulate gold
- when system collapses, central bankers will play the gold card, not the bitcoin card
- US is preparing for big conflict with Russia and china
- then you can’t use IMF monetary reset
- Asia leadership is the same as US and Russian leadership: they want to stay on control
- all have about similar gold (per Capita) in their central banks vaults to avoid hyperinflation
- IMF said to el salvador: you need to reign down your bitcoin position
- once central bankers start diversifying (e.g. to bitcoin ) they will strain their own system. The incentives are against adopting bitcoin
- watch out for when on and offramp get blocked / repressed
- think about diversifying to Dubai, “the new switzerland"
- "bitcoin is the best money ever. fact”
- superior to gold, because you can store your wealth independant of location
- more scarce than gold
- but from central bank point of view, gold is superior to bitcoin
- younger generation gets this from the start
talk: The Future Will Be Bitcoinized by Elizabeth stark & Rockstar Dev
- stablecoins
- taproot assets protocol
- there is a demand for stablecoins and apps on stablecoins
- 11 trillion dollars in stablecoins
- protocol allows payments in other assets such as stablecoins that use bitcoin/lightning liquidity
- Elizabeth believes this allows stablecoiners to get interested in the underlying bitcoin layer
- Available now:
- bridging tether and lightning
products stumbled upon
- Meshtastic
- Flipper
- Noderunners led matrix panel
- 21energy bitcoin heater (1k s9, 3,5k s19)
- angor.io by dangershony on nostr
- bitcoinclock by Djuri
canonical link: https://notes.peterpeerdeman.nl/Bitcoin-Amsterdam-2024
originally posted at https://stacker.news/items/724785
-
 @ d5c3d063:4d1159b3
2024-10-24 15:11:17
@ d5c3d063:4d1159b3
2024-10-24 15:11:17เคยสงสัยไหมว่า ทำไมเศรษฐกิจถึงเป็นเรื่องซับซ้อนนัก? มาร่วมไขปริศนาเศรษฐศาสตร์ผ่านมุมมองที่แตกต่างระหว่างสำนักออสเตรียนและกระแสหลักกันครับ
ตลอด 3 EP ที่ผ่านมา JUST Economics ได้พาคุณดำดิ่งสู่โลกเศรษฐศาสตร์ที่น่าตื่นเต้น เราได้สัมผัสกับมุมมองที่หลากหลาย
โดยเฉพาะอย่างยิ่งมุมมองที่น่าสนใจและแตกต่างจากเศรษฐศาสตร์กระแสหลัก ซึ่งสำนักออสเตรียนให้ความสำคัญกับ "การกระทำของมนุษย์" และตั้งคำถามถึงบทบาทของรัฐ
https://image.nostr.build/3faa50be55e5241640223811f1ad9e14b3437ae7f2eeaf4cf5d257eceb71d709.jpg
ในโพสนี้.. เราจะพาคุณไปสำรวจความแตกต่างที่น่าสนใจระหว่างเศรษฐศาสตร์สำนักออสเตรียนและเศรษฐศาสตร์กระแสหลัก (หรือแนวคิดเคนเซียน) โดยอ้างอิงจากหนังสือ Principles of Economics ของ Saifedean Ammous
หัวใจหลักของเศรษฐศาสตร์สำนักออสเตรียน คือ การมองว่าระบบเศรษฐกิจเปรียบเสมือนละครเวทีขนาดใหญ่ที่ขับเคลื่อนด้วย "การกระทำของมนุษย์" ไม่ใช่เพียงแค่สมการหรือแบบจำลองทางคณิตศาสตร์ที่เย็นชา
สำนักคิดนี้เชื่อว่าการจะเข้าใจระบบเศรษฐกิจอย่างแท้จริง เราต้องเริ่มต้นจากการทำความเข้าใจ "เหตุผล" และ "มูลค่า" ที่ซ่อนอยู่เบื้องหลังการตัดสินใจของแต่ละบุคคล
ลองนึกภาพตามนะครับ.. เวลาที่เราเลือกซื้อสินค้าสักชิ้น การตัดสินใจของเราไม่ได้ขึ้นอยู่กับราคาเพียงอย่างเดียว แต่ขึ้นอยู่กับ "มูลค่า" ที่เราให้กับสินค้านั้นๆ ซึ่งได้รับอิทธิพลจากความชอบส่วนตัว สถานการณ์ในขณะนั้น และแม้กระทั่งความขาดแคลนของสินค้า
นี่คือสิ่งที่เรียกว่า "มูลค่าอัตวิสัย (Subjective Value)"
ดังที่ Carl Menger นักเศรษฐศาสตร์ผู้ยิ่งใหญ่เคยกล่าวไว้ว่า "มูลค่าไม่มีอยู่นอกเหนือจิตสำนึกของมนุษย์"
ในทางกลับกัน.. เศรษฐศาสตร์กระแสหลัก มักจะพยายามอธิบายระบบเศรษฐกิจด้วยแบบจำลองทางคณิตศาสตร์และสมการ โดยมองว่า "มูลค่า" เป็นสิ่งที่วัดได้ สามารถกำหนดเป็นตัวเลขได้อย่างแม่นยำ
อย่างไรก็ตาม Saifedean Ammous มองว่าแนวทางนี้อาจเป็นการ "Scientism" หรือการยึดติดกับวิธีการทางวิทยาศาสตร์มากเกินไป จนมองข้ามความซับซ้อนของการกระทำของมนุษย์
การใช้แบบจำลองทางคณิตศาสตร์ในทางเศรษฐศาสตร์ มักจะมาพร้อมกับสมการที่ไม่คงที่และถือเป็นการพยายามลดทอนความซับซ้อนของการกระทำของมนุษย์ให้เหลือเพียงตัวแปรที่วัดได้ ซึ่งอาจทำให้เกิดความเข้าใจผิดเกี่ยวกับการทำงานของระบบเศรษฐกิจ
เพราะในความเป็นจริงมนุษย์ไม่ได้ตัดสินใจตามแบบจำลอง แต่ตัดสินใจตาม "เหตุผล" และ "มูลค่า" ที่ตนเองให้
อีกหนึ่งจุดที่แตกต่าง.. คือมุมมองเกี่ยวกับบทบาทของรัฐ เศรษฐศาสตร์กระแสหลัก มักจะมองว่ารัฐควรมีบทบาทสำคัญในการแก้ไขปัญหาในระบบเศรษฐกิจ
เช่น การควบคุมราคา การขึ้นค่าแรงขั้นต่ำ และการอุดหนุนราคา ซึ่งสอดคล้องกับแนวคิดของ John Maynard Keynes ที่เชื่อว่ารัฐบาลควรเข้ามาแทรกแซงเศรษฐกิจเพื่อกระตุ้นการใช้จ่ายและสร้างงาน
แต่เศรษฐศาสตร์สำนักออสเตรียนมองว่า.. การแทรกแซงของรัฐในระบบตลาดเสรีมักจะนำไปสู่ผลลัพธ์ที่ไม่พึงประสงค์
ตัวอย่างเช่น การกำหนดราคาสินค้าโดยรัฐอาจนำไปสู่การขาดแคลนสินค้า การขึ้นค่าแรงขั้นต่ำอาจทำให้คนงานตกงาน และการอุดหนุนโดยรัฐอาจทำให้เกิดการผลิตและบริโภคที่มากเกินความจำเป็น
ตัวอย่างผลกระทบจากการแทรกแซงของรัฐที่สำนักออสเตรียนมองว่าไม่พึงประสงค์ เช่น..
การควบคุมราคา - หากรัฐเข้ามาควบคุมราคาสินค้า เช่น การกำหนดเพดานราคา อาจทำให้เกิดภาวะสินค้าขาดแคลนได้ เพราะผู้ผลิตจะไม่มีแรงจูงใจในการผลิตสินค้าออกมาขายในราคาที่ต่ำกว่าต้นทุน
Robert Schuettinger และ Eamonn Butler ได้บันทึกไว้ในหนังสือ Forty Centuries of Wage and Price Control: How Not to Fight Inflation ว่าการควบคุมราคามักจะนำไปสู่ตลาดมืด ที่ผู้คนยอมจ่ายแพงกว่าเพื่อให้ได้สินค้าที่ขาดแคลน
การขึ้นค่าแรงขั้นต่ำ - การที่รัฐกำหนดค่าแรงขั้นต่ำ อาจส่งผลให้นายจ้างบางรายไม่สามารถจ่ายค่าแรงที่สูงขึ้นได้ ซึ่งอาจนำไปสู่การลดการจ้างงาน
โดยเฉพาะอย่างยิ่งกลุ่มแรงงานไร้ฝีมือ หรือผู้ที่เพิ่งเริ่มต้นทำงาน อาจได้รับผลกระทบมากที่สุด
การอุดหนุนสินค้า - การอุดหนุนของรัฐบาล เช่น การอุดหนุนสินค้าเกษตร อาจทำให้เกิดการผลิตและบริโภคสินค้ามากเกินความจำเป็น เพราะทั้งผู้ผลิตและผู้บริโภคไม่ได้ตัดสินใจตาม "มูลค่า" ที่แท้จริงของสินค้า
ผลที่ตามมาคือ ทรัพยากรของประเทศอาจถูกจัดสรรไปอย่างไม่มีประสิทธิภาพ
เศรษฐศาสตร์สำนักออสเตรียน เน้นย้ำถึงความสำคัญของ "เสรีภาพ" และ "ตลาดเสรี" ในการขับเคลื่อนระบบเศรษฐกิจ โดยมองว่าการแทรกแซงของรัฐมักจะนำไปสู่ผลลัพธ์ที่ไม่พึงประสงค์
ในขณะที่เศรษฐศาสตร์กระแสหลัก มองว่ารัฐมีบทบาทสำคัญในการแก้ไขปัญหาตลาดและสร้างความมั่นคงทางเศรษฐกิจ
การทำความเข้าใจมุมมองที่แตกต่างของทั้งสองสำนักคิด จะช่วยให้เรามองเห็นภาพรวมของระบบเศรษฐกิจได้อย่างรอบด้าน และสามารถวิเคราะห์ปัญหาเศรษฐกิจได้อย่างมีประสิทธิภาพมากขึ้น
อย่าลืมติดตาม JUST Economics EP ต่อไปกันนะครับ เราจะพาคุณไปสำรวจโลกเศรษฐศาสตร์ที่น่าตื่นเต้น รับรองว่า สนุก เข้าใจง่าย และได้ความรู้แน่นปึ๊กอย่างแน่นอนครับ
Economics
-
 @ fd208ee8:0fd927c1
2024-10-20 18:19:48
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a GitHub repo, and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
- Why can I not login? Oh, they fixed the login! Nope, still can't login.
- If I press this button, it says it sent, but it didn't send. Where note?
- They announced a new feature, but I tried it and it didn't work. Oh well.
- I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
- The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it really needed... was a Nostr Stable Version. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be allowed to have expectations of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
Things working is an underrated concept
I know that the very idea of software running as expected and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are all features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load every damn time, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that things working becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
Where to start?
Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our project wiki page, and came up with a Vision and a Mission:
The vision is what the overall goals of the company are, whereas the mission describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because profits are the most pure form of communication that consumers in the market have with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial lambo and a bimbo. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but pay them out, you should. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the okay, so this is what we've decided comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to Investopedia, common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's emotionally binding, which is arguably more important.
Writing things down is an advanced form of naming things and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-
 @ 460c25e6:ef85065c
2024-10-15 12:49:55
@ 460c25e6:ef85065c
2024-10-15 12:49:55NIPs (Nostr Implementation Possibilities) are technical specifications that Nostr developers create to define how specific event types and tags are used. These can be written before or after the feature is implemented and often go through multiple revisions before becoming stable enough to matter. Once two or more clients fully implement the proposal, it is merged into the main repository. This process ensures that while new ideas are encouraged, they are also rigorously reviewed and tested.
There are generally two paths for NIPs: 1. New Ideas, when developers just have a hunch on a new solution and want to quickly write something up to gather feedback from the community. These are my favorite NIPs because they generally introduce a new way of thinking about a problem we are all having. And because they are not just a general solution, but a specific proposal, it allows us to see the entire picture in just a few paragraphs. Even though they are my favorite, they are quite "green" and usually spur 2-3 separate solutions in following PRs by different authors. 2. Existing implementations that need to explain what they are doing. These happen when a client is already running the code in production and simply wants to explain to the rest of the community how to generate and interpret the events the client is creating. These NIPs start much more stable than the former and allow for fewer changes, but because there is already an implementation available, it's a market-tested solution that might just need a few adjustments before others start implementing it.
Well-written specs ensure clarity, reduce ambiguity, and help developers implement the proposal consistently. The text should be VERY short, precise, prescriptive, and actionable by other devs. Start by introducing the new kind or tag in the first sentence and jump straight into a mockup of how the event looks like. The mockup should be self-explanatory and provide clues to what the remaining of the document will talk about. Some folks like to add long/verbose introductions, conclusions, and discussions of the reasons why the NIP is needed or why certain features are there. But those are largely unnecessary and are more appropriate to be placed in the body of the Pull Request descriptor.
Start your NIP with the following template:
``` NIP-
====== </h2> <p><code>draft</code> <code>optional</code></p> <p>Event kind <new kind> defines <whatever it does>. Tags <one or two of the most important ones> <describe what they do>. As an example: </p> <p><code>`jsonc { "kind": <your kind>, "tags": [ <your tags> ], "content": "", //... }</code> `</p> <p>Relays MUST...</p> <p>Clients MUST... </p> <h2><Details 1></h2> <h2><Details 2></h2> <h2><How to find them></h2> <p>```</p> <p>Your number for the NIP is irrelevant. Just pick a random number that is available so that you can fork the repo, create a file with that name, and start writing. This number will likely change once the NIP is merged. </p> <p>The NIPs title must be self-explanatory and short. If it helps, try to imagine which name would be best to add to the list of NIPs on the readme.md file. Same for event type names. Picture something that is short, unique and that devs can just remove the space to have a class name. </p> <p>The <code>draft</code> <code>optional</code> tags are there because unless you are working on NIP-01, everything is draft and everything is optional. If you want to write a mandatory NIP, you better make sure your text is so good that it can be added to <code>01.md</code> directly without overcomplicating the protocol. </p> <p>Start by describing the new event type, what it does and its main tags. Show the mockup and then start introducing all the other tags and how clients and relays should behave when implementing it. Use the words MUST, SHOULD, MAY, SHOULD NOT, and MUST NOT to define the mandatory behaviors of those declaring compliance with the NIP. </p> <p>Keep it simple. The specification should be designed to ensure that different clients, relays, and services can implement it without requiring substantial changes to their existing infrastructure. Ideally, devs should be able to implement the entire NIP from near scratch in just a few hours. Don't use jargon. Don't declare a vocabulary of words. Use simple words that anyone can understand and quickly code a demo of all the features in the NIP. They can learn about your reasons as they develop their implementation. </p> <p>Write expecting buggy implementations. The protocol must be resilient to varying implementations and network conditions, and gracefully handle coding errors or random gibberish. You want to promote a defensive design that anticipates misguided implementations, avoids breaking changes, and maximizes compatibility across the ecosystem. What happens if there are two tags with the same name? What happens if events that have missing tags are found? Buggy implementations will exist. The writing and reading clients are generally different and must be ready for anything that shows up on each side. </p> <p>Avoid abstractions, extensible and modular designs. Yes, they can be hidden underneath your text, but writing for them is a mistake and just overcomplicates things. Write for a specific use case and close all possible options to the items/features declared in the text. Make sure you are implementing those. There is no point in declaring things that are not going to be used in the short term. We can always add more in the future and we don't need a recipe on how to add more later. </p> <p>Label your relay hosts, setting kinds, and other data management necessities. Every NIP has a way to find out the user's preferred relay associated with the use case. Sometimes it's through a relay hint others through a separate event kind that just lists the user's home relays or contains a list of "following" events designed for the use case. Each NIP can create their own way of finding events.</p> <p>You cannot add new root fields. Use tags instead. Root fields are special and require changes to the core protocol everyone implements. Any new field will take years to come to reality. </p> <p>Once you propose an idea, try not to change too much. It will take time for other devs to wrap their minds around it. If you keep changing it, even if those changes reflect the request of the reviewers in the PR, it just confuses everyone. Sometimes things change so much that it is worth doing two PRs with separate specifications that solve the same problem. That allows devs to analyze the two propositions side by side and decide which one is better. </p> <p>Always add a test case or an example. This is an absolute requirement if the NIP is complex, like a new encryption scheme. But even for simpler NIPs, test cases help devs to quickly verify if their implementations meet the minimum standard for compliance. They not only add peace of mind, but they also provide some welcoming dopamine when a new dev is trying to implement your NIP. </p> <p>Managing state is hard. Doing it with different implementations and hosting them in separate relays is even harder. If your NIP has multiple events to manage state, like group administration actions (add/remove member, change names/icons, invite/reporting events) try to structure them in a way that devs can quickly see the state machine of all possible state changes. </p> <p>Specify data formats explicitly. Clearly define the format of all data fields, including type (e.g., string, integer), encoding (e.g., base64, hex), and structure (e.g., array, object). Specify constraints like length limits, valid characters, and optional/required fields. Tags are case-sensitive. Avoid having to specify new encodings, but if you do, make sure to include test cases that encompass all potential cases. </p> <p>It's ok to not propose the most efficient way of solving the problem. A simple but slightly less efficient design is preferred over a complex but more efficient one. We already use hex and base64 codes to represent binary bytes in JSON, which wastes 25-50% of space. That level of waste is ok if the solution becomes simpler to code. </p> <p>It's not about you. You may think you must convince everyone that your particular way of solving the problem is the best and get some ego points with yourself. While some of that is beneficial to the debate, be open-minded to the other possible solutions. Once merged, the NIP is not yours anymore. Anyone can change in any way they see fit. If your work is great, people will remember your name. If it just got the conversation started to become something completely different from what you proposed, they will also remember you. </p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4f82bced:b8928630 <div class="time" style="margin-left: auto;">2024-10-15 12:06:04</div> </div> <div> <p>Lusaka was a short stop as we headed towards Victoria Falls. Its infrastructure caught us off guard. Good roads, accessible amenities, and many malls. A stark contrast to Malawi, a neighboring country we had just visited. Entering one such mall in Lusaksa felt like we were back in Toronto. Driven by government, private, and foreign investment, Lusaka seemed to be miles ahead of other landlocked countries we had visited.</p> <p>During our time in the city, we visited a restaurant that accepts bitcoin and hosts local bitcoin meet-ups. While interacting with the owner it was clear he viewed bitcoin as a competitive differentiator and an efficient easier form of payment acceptance. Since our meeting, he has increased his marketing efforts to raise awareness and inform his customers about bitcoin. </p> <p>Victoria Falls (Mosi-oa-Tunya) is a major tourist attraction in Zambia, stretching nearly 1.7km! Due to recent droughts, the falls were no longer a blanket of water. Only certain sections had a steady flow, exposing the rock formations behind the water, an uncommon sight for visitors. </p> <p>The waterfalls aside, we were invited to speak at the Bitcoin community meetup, Bitcoin Victoria Falls. The founder of this community is American, who decided to kickstart the project during a recent visit to the area. It was the first time we had encountered a community founded by a foreigner who didn't live in the region. It shows that anyone can bring forth change regardless of where they live! Can't forget his co-founder and running mate, Humprey, a local who has helped progress their mission!</p> <p>Our presentation topic? Bitcoin for Businesses. We discussed the basics of bitcoin, how it works, how to earn it, and most importantly, how to onboard merchants. It's great interacting with the local community to understand their challenges. Fortunately, this community has decent bitcoin penetration. The lodge where the meetup was held accepts bitcoin, including a taxi service, a tour operator, and a stationary provider. During our stay, we onboarded the bar and its servers within the lodge premises. The owners appreciated the speed at which they could settle payments and easily accept money from foreigners who may not have cash.</p> <p>Did you know, that the Zambezi River which runs below Victoria Falls is world renowned for its white water rafting? We had the chance to experience it ourselves and pay with bitcoin! </p> <p>Botswana here we come.</p> <p>Sources: Victoria Falls. Britannia. https://www.britannica.com/place/Victoria-Falls-waterfall-Zambia-Zimbabwe</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsy50scgvdj5fwygmnwu6pwwsyj6vsmztwjpt2uj704qxse2xz5wdqzyp8c908dgfvy56k0emf2v4a44j4uf7gdwk54a5ll3z8nkp9cj2rrqrhfw3l" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsy50scgvdj5fwygmnwu6pwwsyj6vsmztwjpt2uj704qxse2xz5wdqzyp8c908dgfvy56k0emf2v4a44j4uf7gdwk54a5ll3z8nkp9cj2rrqrhfw3l" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsy50scgvdj5fwygmnwu6pwwsyj6vsmztwjpt2uj704qxse2xz5wdqzyp8c908dgfvy56k0emf2v4a44j4uf7gdwk54a5ll3z8nkp9cj2rrqrhfw3l" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsy50scgvdj5fwygmnwu6pwwsyj6vsmztwjpt2uj704qxse2xz5wdqzyp8c908dgfvy56k0emf2v4a44j4uf7gdwk54a5ll3z8nkp9cj2rrqrhfw3l" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ eac63075:b4988b48 <div class="time" style="margin-left: auto;">2024-10-21 08:11:11</div> </div> <div> <p>Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.</p> <p>https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV</p> <p>https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de</p> <h3><strong>Sections:</strong></h3> <ul> <li><strong>Introduction</strong></li> <li><strong>What Is Chat Control?</strong></li> <li><strong>Why Is the EU Pushing for Chat Control?</strong></li> <li><strong>The Privacy Concerns and Risks</strong></li> <li><strong>The Technical Debate: Encryption and Backdoors</strong></li> <li><strong>Global Reactions and the Debate in Europe</strong></li> <li><strong>Possible Consequences for Messaging Services</strong></li> <li><strong>What Happens Next? The Future of Chat Control</strong></li> <li><strong>Conclusion</strong></li> </ul> <hr /> <h3><strong>What Is Chat Control?</strong></h3> <p>"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.</p> <p>At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.</p> <h4><strong>Origins of the Proposal</strong></h4> <p>The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.</p> <h4><strong>How Messaging Services Work</strong></h4> <p>Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.</p> <p><img src="https://blossom.primal.net/31ace3b729fb9f6b4de286686f31a71db6dd7e3a363f868e1255a6f287eb0b94.png"></p> <h4><strong>Key Elements of Chat Control</strong></h4> <ul> <li><strong>Automated Content Scanning</strong>: Service providers would use algorithms to scan messages for illegal content.</li> <li><strong>Circumvention of Encryption</strong>: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.</li> <li><strong>Mandatory Reporting</strong>: If illegal content is detected, providers would be required to report it to authorities.</li> <li><strong>Broad Applicability</strong>: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.</li> </ul> <h4><strong>Why It Matters</strong></h4> <p>Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.</p> <hr /> <h3><strong>Why Is the EU Pushing for Chat Control?</strong></h3> <p>The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.</p> <h4><strong>Protecting Children and Preventing Crime</strong></h4> <p>One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.</p> <p>Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.</p> <h4><strong>Legal Context and Legislative Drivers</strong></h4> <p>The push for Chat Control is rooted in several legislative initiatives:</p> <ul> <li> <p><strong>ePrivacy Directive</strong>: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.</p> </li> <li> <p><strong>Temporary Derogation</strong>: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.</p> </li> <li> <p><strong>Regulation Proposals</strong>: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.</p> </li> </ul> <h4><strong>Balancing Security and Privacy</strong></h4> <p>EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.</p> <p>However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:</p> <ul> <li> <p><strong>Targeted Scanning</strong>: Focusing on specific threats rather than broad, indiscriminate monitoring.</p> </li> <li> <p><strong>Judicial Oversight</strong>: Requiring court orders or oversight for accessing private communications.</p> </li> <li> <p><strong>Data Protection Safeguards</strong>: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.</p> </li> </ul> <p><img src="https://blossom.primal.net/9533aedc9f83564d53633eac1a6d431d1e311028a478dd4b7f3a59b2c449e95a.png"></p> <h4><strong>The Urgency Behind the Push</strong></h4> <p>High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.</p> <h4><strong>Criticism and Controversy</strong></h4> <p>Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.</p> <hr /> <h3><strong>The Privacy Concerns and Risks</strong></h3> <p>While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.</p> <h4><strong>Infringement on Privacy Rights</strong></h4> <p>At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.</p> <h4><strong>Erosion of End-to-End Encryption</strong></h4> <p>End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.</p> <h4><strong>Concerns from Privacy Advocates</strong></h4> <p>Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:</p> <ul> <li><strong>Security Risks</strong>: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.</li> <li><strong>Global Implications</strong>: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.</li> <li><strong>Ineffectiveness Against Crime</strong>: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.</li> </ul> <p><img src="https://blossom.primal.net/51722887ebf55c827cc20bcfade3ea9b3628265b7fa3547504b2fff45f34f175.png"></p> <h4><strong>Potential for Government Overreach</strong></h4> <p>There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.</p> <h4><strong>Real-World Implications for Users</strong></h4> <ul> <li><strong>False Positives</strong>: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.</li> <li><strong>Chilling Effect</strong>: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.</li> <li><strong>Data Misuse</strong>: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.</li> </ul> <h4><strong>Legal and Ethical Concerns</strong></h4> <p>Privacy advocates also highlight potential conflicts with existing laws and ethical standards:</p> <ul> <li><strong>Violation of Fundamental Rights</strong>: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.</li> <li><strong>Questionable Effectiveness</strong>: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.</li> </ul> <h4><strong>Opposition from Member States and Organizations</strong></h4> <p>Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.</p> <hr /> <h3><strong>The Technical Debate: Encryption and Backdoors</strong></h3> <p>The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.</p> <h4><strong>What Is End-to-End Encryption (E2EE)?</strong></h4> <p>End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.</p> <ul> <li><strong>Security Assurance</strong>: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.</li> <li><strong>Widespread Use</strong>: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.</li> </ul> <h4><strong>How Chat Control Affects Encryption</strong></h4> <p>Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:</p> <ul> <li><strong>Introduce Backdoors</strong>: Create a means for third parties (including the service provider or authorities) to access encrypted messages.</li> <li><strong>Client-Side Scanning</strong>: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.</li> </ul> <h4><strong>The Risks of Weakening Encryption</strong></h4> <p><strong>1. Compromised Security for All Users</strong></p> <p>Introducing backdoors or client-side scanning tools can create vulnerabilities:</p> <ul> <li><strong>Exploitable Gaps</strong>: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.</li> <li><strong>Universal Impact</strong>: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.</li> </ul> <p><strong>2. Undermining Trust in Digital Services</strong></p> <ul> <li><strong>User Confidence</strong>: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.</li> <li><strong>Business Implications</strong>: Companies relying on secure communications might face increased risks, affecting economic activities.</li> </ul> <p><strong>3. Ineffectiveness Against Skilled Adversaries</strong></p> <ul> <li><strong>Alternative Methods</strong>: Criminals might shift to other encrypted channels or develop new ways to avoid detection.</li> <li><strong>False Sense of Security</strong>: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.</li> </ul> <h4><strong>Signal’s Response and Stance</strong></h4> <p>Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:</p> <ul> <li><strong>Refusal to Weaken Encryption</strong>: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.</li> <li><strong>Advocacy for Privacy</strong>: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.</li> </ul> <h4><strong>Understanding Backdoors</strong></h4> <p>A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:</p> <ul> <li><strong>Security Vulnerabilities</strong>: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.</li> <li><strong>Ethical Concerns</strong>: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.</li> </ul> <p><img src="https://blossom.primal.net/67f45fd79ccdb7e2e2ecdc56297207dc0d1d073acb216857b6165b3bf9906997.png"></p> <h4><strong>The Slippery Slope Argument</strong></h4> <p>Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:</p> <ul> <li><strong>Expanded Surveillance</strong>: Once in place, these measures could be extended to monitor other types of content beyond the original scope.</li> <li><strong>Erosion of Rights</strong>: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.</li> </ul> <h4><strong>Potential Technological Alternatives</strong></h4> <p>Some suggest that it's possible to fight illegal content without undermining encryption:</p> <ul> <li><strong>Metadata Analysis</strong>: Focusing on patterns of communication rather than content.</li> <li><strong>Enhanced Reporting Mechanisms</strong>: Encouraging users to report illegal content voluntarily.</li> <li><strong>Investing in Law Enforcement Capabilities</strong>: Strengthening traditional investigative methods without compromising digital security.</li> </ul> <h4></h4> <p>The technical community largely agrees that weakening encryption is not the solution:</p> <ul> <li><strong>Consensus on Security</strong>: Strong encryption is essential for the safety and privacy of all internet users.</li> <li><strong>Call for Dialogue</strong>: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.</li> </ul> <hr /> <h3><strong>Global Reactions and the Debate in Europe</strong></h3> <p>The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.</p> <h4><strong>Support for Chat Control</strong></h4> <p>Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:</p> <ul> <li><strong>Enhanced Security</strong>: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.</li> <li><strong>Responsibility of Service Providers</strong>: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.</li> <li><strong>Public Safety Priorities</strong>: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.</li> </ul> <h4><strong>Opposition within the EU</strong></h4> <p>Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.</p> <p><strong>Germany</strong></p> <ul> <li><strong>Stance</strong>: Germany has been one of the most vocal opponents of the proposed measures.</li> <li><strong>Reasons</strong>:</li> <li><strong>Constitutional Concerns</strong>: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.</li> <li><strong>Security Risks</strong>: Weakening encryption is seen as a threat to cybersecurity.</li> <li><strong>Legal Challenges</strong>: Potential conflicts with national laws protecting personal data and communication secrecy.</li> </ul> <p><strong>Netherlands</strong></p> <ul> <li><strong>Recent Developments</strong>: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.</li> <li><strong>Arguments</strong>:</li> <li><strong>Effectiveness Doubts</strong>: Skepticism about the actual effectiveness of the measures in combating crime.</li> <li><strong>Negative Impact on Privacy</strong>: Concerns about mass surveillance and the infringement of citizens' rights.</li> </ul> <p><img alt="" src="https://blossom.primal.net/fe2c7229d0f6320cbd5c3c8d43713c8ebc4e698e1db91829b7b1f03850162f7c.png" />Table reference: Patrick Breyer - Chat Control in 23 September 2024</p> <h4><strong>Privacy Advocacy Groups</strong></h4> <p><strong>European Digital Rights (EDRi)</strong></p> <ul> <li><strong>Role</strong>: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.</li> <li><strong>Position</strong>:</li> <li><strong>Strong Opposition</strong>: EDRi argues that Chat Control is incompatible with fundamental rights.</li> <li><strong>Awareness Campaigns</strong>: Engaging in public campaigns to inform citizens about the potential risks.</li> <li><strong>Policy Engagement</strong>: Lobbying policymakers to consider alternative approaches that respect privacy.</li> </ul> <p><strong>Politicians and Activists</strong></p> <p><strong>Patrick Breyer</strong></p> <ul> <li><strong>Background</strong>: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.</li> <li><strong>Actions</strong>:</li> <li><strong>Advocacy</strong>: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.</li> <li><strong>Public Outreach</strong>: Using social media and public events to raise awareness.</li> <li><strong>Legal Expertise</strong>: Highlighting the legal inconsistencies and potential violations of EU law.</li> </ul> <h4><strong>Global Reactions</strong></h4> <p><strong>International Organizations</strong></p> <ul> <li><strong>Human Rights Watch and Amnesty International</strong>: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.</li> </ul> <p><strong>Technology Companies</strong></p> <ul> <li><strong>Global Tech Firms</strong>: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.</li> <li><strong>Industry Associations</strong>: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.</li> </ul> <p><img src="https://blossom.primal.net/e761aa2dd240a1a2e7d943565ccbda427b5a8054bf4e6e17c946711ab6370d5d.png"></p> <h4><strong>The Broader Debate</strong></h4> <p>The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:</p> <ul> <li><strong>Legal Precedents</strong>: How the EU's decision might influence laws and regulations in other countries.</li> <li><strong>Digital Sovereignty</strong>: The desire of nations to control digital spaces within their borders.</li> <li><strong>Civil Liberties</strong>: The importance of protecting freedoms in the face of technological advancements.</li> </ul> <h4><strong>Public Opinion</strong></h4> <ul> <li><strong>Diverse Views</strong>: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.</li> <li><strong>Awareness Levels</strong>: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.</li> </ul> <h4></h4> <p>The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.</p> <hr /> <h3><strong>Possible Consequences for Messaging Services</strong></h3> <p>The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.</p> <h4><strong>Impact on Encrypted Messaging Services</strong></h4> <p><strong>Signal and Similar Platforms</strong></p> <ul> <li> <p><strong>Compliance Challenges</strong>: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.</p> </li> <li> <p><strong>Operational Decisions</strong>: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.</p> </li> </ul> <h4><strong>Potential Blocking or Limiting of Services</strong></h4> <ul> <li> <p><strong>Regulatory Enforcement</strong>: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.</p> </li> <li> <p><strong>Access Restrictions</strong>: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.</p> </li> </ul> <h4><strong>Effects on Smaller Providers</strong></h4> <ul> <li> <p><strong>Resource Constraints</strong>: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.</p> </li> <li> <p><strong>Innovation Stifling</strong>: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.</p> </li> </ul> <p><img src="https://blossom.primal.net/60a9cad69b45cc3ded1d1759312e49a57b3aa997db62e36016f40642943be5e9.png"></p> <h4><strong>User Experience and Trust</strong></h4> <ul> <li> <p><strong>Privacy Concerns</strong>: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.</p> </li> <li> <p><strong>Migration to Unregulated Platforms</strong>: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.</p> </li> </ul> <h4><strong>Technical and Security Implications</strong></h4> <ul> <li> <p><strong>Increased Vulnerabilities</strong>: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.</p> </li> <li> <p><strong>Global Security Risks</strong>: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.</p> </li> </ul> <h4><strong>Impact on Businesses and Professional Communications</strong></h4> <ul> <li> <p><strong>Confidentiality Issues</strong>: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.</p> </li> <li> <p><strong>Compliance Complexity</strong>: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.</p> </li> </ul> <h4><strong>Economic Consequences</strong></h4> <ul> <li> <p><strong>Market Fragmentation</strong>: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.</p> </li> <li> <p><strong>Loss of Revenue</strong>: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.</p> </li> </ul> <h4><strong>Responses from Service Providers</strong></h4> <ul> <li> <p><strong>Legal Challenges</strong>: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.</p> </li> <li> <p><strong>Policy Advocacy</strong>: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.</p> </li> </ul> <h4><strong>Possible Adaptations</strong></h4> <ul> <li> <p><strong>Technological Innovation</strong>: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.</p> </li> <li> <p><strong>Transparency Measures</strong>: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.</p> </li> </ul> <h4></h4> <p>The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.</p> <hr /> <h3><strong>What Happens Next? The Future of Chat Control</strong></h3> <p>The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.</p> <h4><strong>Current Status of Legislation</strong></h4> <ul> <li> <p><strong>Ongoing Negotiations</strong>: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.</p> </li> <li> <p><strong>Timeline</strong>: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.</p> </li> </ul> <h4><strong>Key Influencing Factors</strong></h4> <p><strong>1. Legal Challenges and Compliance with EU Law</strong></p> <ul> <li> <p><strong>Fundamental Rights Assessment</strong>: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.</p> </li> <li> <p><strong>Court Scrutiny</strong>: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.</p> </li> </ul> <p><strong>2. Technological Feasibility</strong></p> <ul> <li> <p><strong>Development of Privacy-Preserving Technologies</strong>: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.</p> </li> <li> <p><strong>Implementation Challenges</strong>: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.</p> </li> </ul> <p><strong>3. Political Dynamics</strong></p> <ul> <li> <p><strong>Member State Positions</strong>: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.</p> </li> <li> <p><strong>Public Opinion and Advocacy</strong>: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.</p> </li> </ul> <p><strong>4. Industry Responses</strong></p> <ul> <li> <p><strong>Negotiations with Service Providers</strong>: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.</p> </li> <li> <p><strong>Potential for Self-Regulation</strong>: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.</p> </li> </ul> <h4><strong>Possible Scenarios</strong></h4> <p><strong>Optimistic Outcome:</strong></p> <ul> <li><strong>Balanced Regulation</strong>: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.</li> </ul> <p><strong>Pessimistic Outcome:</strong></p> <ul> <li><strong>Adoption of Strict Measures</strong>: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.</li> </ul> <p><strong>Middle Ground:</strong></p> <ul> <li><strong>Incremental Implementation</strong>: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.</li> </ul> <h4><strong>How to Stay Informed and Protect Your Privacy</strong></h4> <ul> <li> <p><strong>Follow Reputable Sources</strong>: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.</p> </li> <li> <p><strong>Engage in the Dialogue</strong>: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.</p> </li> <li> <p><strong>Utilize Secure Practices</strong>: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.</p> </li> </ul> <p><img src="https://blossom.primal.net/1e2c0cd70d88629c54ac84f928ab107f08f698d2c7f0df511277fb44c1480f0a.png"></p> <h4><strong>The Global Perspective</strong></h4> <ul> <li> <p><strong>International Implications</strong>: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.</p> </li> <li> <p><strong>Collaboration Opportunities</strong>: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.</p> </li> </ul> <h4><strong>Looking Ahead</strong></h4> <p>The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.</p> <p>As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.</p> <hr /> <h3><strong>Conclusion</strong></h3> <p>The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.</p> <p>Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.</p> <p>The potential consequences of implementing Chat Control are far-reaching:</p> <ul> <li><strong>Erosion of Trust</strong>: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.</li> <li><strong>Security Vulnerabilities</strong>: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.</li> <li><strong>Stifling Innovation</strong>: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.</li> <li><strong>Global Implications</strong>: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.</li> </ul> <p>As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.</p> <p>The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.</p> <p>In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.</p> <p><img src="https://blossom.primal.net/d3f07d8bc7a49ac291f14eb449879462c76ae407abbe728ddc6f93e11fabe11d.png"></p> <hr /> <p>Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.</p> <h2>Read more:</h2> <ul> <li>https://www.patrick-breyer.de/en/posts/chat-control/</li> <li>https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/</li> <li>https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/</li> <li>https://signal.org/blog/pdfs/ndss-keynote.pdf</li> <li>https://tuta.com/blog/germany-stop-chat-control</li> <li>https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal</li> <li>https://mullvad.net/en/why-privacy-matters</li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs8cp4vxk90vj4la2a9l8fs3wsuwmdl8fs9ms7u4pq6tlk6pmyrdegzyr4vvvr4nccnsvky6qgnh8sssgnelv80565uaqwd4852xe45nz95s6pwt22" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs8cp4vxk90vj4la2a9l8fs3wsuwmdl8fs9ms7u4pq6tlk6pmyrdegzyr4vvvr4nccnsvky6qgnh8sssgnelv80565uaqwd4852xe45nz95s6pwt22" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs8cp4vxk90vj4la2a9l8fs3wsuwmdl8fs9ms7u4pq6tlk6pmyrdegzyr4vvvr4nccnsvky6qgnh8sssgnelv80565uaqwd4852xe45nz95s6pwt22" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs8cp4vxk90vj4la2a9l8fs3wsuwmdl8fs9ms7u4pq6tlk6pmyrdegzyr4vvvr4nccnsvky6qgnh8sssgnelv80565uaqwd4852xe45nz95s6pwt22" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d5c3d063:4d1159b3 <div class="time" style="margin-left: auto;">2024-10-24 15:05:42</div> </div> <div> <h1>เมื่อ WEF วาดฝัน (ร้าย) โลกที่ไร้ทรัพย์สิน ไร้ตัวตน แต่ทุกคนแฮปปี้ในปี 2030</h1> <h2>World Economic Forum หรือ WEF องค์กรระดับโลกที่รวมตัวผู้นำทางธุรกิจและการเมือง ได้ออกมาทำนายอนาคตของโลกในปี 2030 ไว้แบบชวนขนหัวลุก</h2> <p>https://image.nostr.build/9244fa84d941e2548d6a189c93bd40346d5c55145292325614737638a6106949.jpg</p> <p>โดยเฉพาะอย่างยิ่งกับคนที่รักอิสรภาพและความเป็นส่วนตัว เพราะ WEF บอกไว้ว่าเราจะไม่มีกรรมสิทธิ์ในทรัพย์สินส่วนตัวอีกต่อไป แถมชีวิตทุกด้านยังจะถูกควบคุมโดยรัฐบาลอีกด้วย ฟังดูเหมือนหลุดออกมาจากหนังไซไฟดิสโทเปียเลยทีเดียว</p> <p>มีการคาดการณ์ว่าโลกในปี 2030 จะเปลี่ยนไปแบบหน้ามือเป็นหลังมือ โดยเฉพาะวิถีชีวิตและการทำงานของเรา</p> <p>ต่อไปนี้คือ 8 คำทำนายหลักๆ ที่ฟังแล้วชวนให้เราเสียวสันหลัง</p> <ol> <li> <p>ทรัพย์สินส่วนตัวอาจกลายเป็นอดีต สิ่งของต่างๆ จะถูกควบคุมโดยรัฐ และเราจะต้องเช่าหรือยืมใช้แทน ซึ่งอาจส่งผลกระทบต่อวิถีชีวิตและเสรีภาพส่วนบุคคล</p> </li> <li> <p>สหรัฐอาจสูญเสียสถานะผู้นำโลก ขณะที่กลุ่มประเทศอื่นๆ กำลังก้าวขึ้นมามีบทบาทสำคัญแทน ภูมิทัศน์ทางการเมืองและเศรษฐกิจโลกจะเปลี่ยนแปลงไป</p> </li> <li> <p>การพิมพ์อวัยวะทดแทนอาจกลายเป็นเรื่องปกติ ช่วยแก้ปัญหาการขาดแคลนอวัยวะและยกระดับคุณภาพชีวิต วงการแพทย์จะก้าวหน้าอย่างก้าวกระโดด</p> </li> <li> <p>แนวโน้มการบริโภคเนื้อสัตว์จะลดลง และอาหารจากพืชจะได้รับความนิยมมากขึ้น เพื่อแก้ปัญหาสิ่งแวดล้อมและสุขภาพ อุตสาหกรรมอาหารและการเกษตรต้องเตรียมพร้อมปรับตัว</p> </li> <li> <p>การอพยพย้ายถิ่นฐานขนาดใหญ่อาจส่งผลกระทบต่อสังคมและเศรษฐกิจทั่วโลก ท้าทายระบบการจัดการและความมั่นคง ที่รัฐบาลต่างๆ ต้องเตรียมรับมือ</p> </li> <li> <p>ราคาคาร์บอนจะถูกกำหนดให้สูงขึ้น เพื่อกระตุ้นให้ทุกภาคส่วนลดการปล่อยก๊าซเรือนกระจก ซึ่งอาจส่งผลต่อต้นทุนสินค้าและบริการ ธุรกิจและผู้บริโภคต้องเตรียมรับมือกับภาระค่าใช้จ่ายที่เพิ่มขึ้น</p> </li> <li> <p>มนุษย์อาจเริ่มตั้งรกรากบนดาวอังคาร และเดินหน้าสำรวจอวกาศเพื่อค้นหาสิ่งมีชีวิตนอกโลก เปิดศักราชใหม่ของการเดินทางระหว่างดวงดาว เทคโนโลยีอวกาศจะพัฒนาไปอย่างรวดเร็ว</p> </li> <li> <p>ค่านิยมแบบตะวันตก เช่น เสรีภาพ ประชาธิปไตย อาจถูกตั้งคำถาม นำไปสู่การเปลี่ยนแปลงทางสังคมและวัฒนธรรมครั้งใหญ่ เราต้องเตรียมพร้อมรับมือกับความเปลี่ยนแปลงนี้</p> </li> </ol> <p>Ida Auken นักเคลื่อนไหวด้านสิ่งแวดล้อมชาวเดนมาร์ก ได้เขียนบทความชื่อ “Welcome to 2030” วาดภาพโลกอนาคตอันสวยหรู (สำหรับบางคน) ที่ “ฉันไม่มีอะไรเป็นของตัวเอง ไม่มีสิทธิความเป็นส่วนตัว แต่ชีวิตฉันดีขึ้นกว่าเดิม”</p> <p>ในโลกใบนี้ การซื้อหาสินค้าและการเป็นเจ้าของกลายเป็นเรื่องเชย เพราะทุกอย่างจะเปลี่ยนเป็นบริการหมด อยากได้อะไรก็แค่ใช้บริการเอา ไม่ว่าจะเป็นที่อยู่อาศัย อาหาร การเดินทาง หรือสิ่งของจำเป็นอื่นๆ Auken อ้างว่าปัญหาต่างๆ ในโลกปัจจุบัน เช่น โรคภัยไข้เจ็บ ภาวะโลกร้อน วิกฤตผู้ลี้ภัย มลพิษ และการว่างงาน จะหมดไป ผู้คนจะมีความสุขกับชีวิตที่ดีกว่าเดิม…แต่ชีวิตแบบนี้ มันคือชีวิตที่เราต้องการจริงๆ หรือ?</p> <p>คำถามคือ แล้วจะโน้มน้าวให้คนยอมรับระบบแบบนี้ได้ยังไง คำตอบง่ายๆ ก็คือ ต้องมีของล่อใจ WEF เลยโฆษณาว่าโลกใหม่นี้จะมีระบบสาธารณสุขที่ครอบคลุม แถมยังแจก “รายได้พื้นฐานถ้วนหน้า” ให้ทุกคนอีกด้วย ใครบ้างที่ไม่อยากได้เงินใช้ฟรีๆ โดยไม่ต้องทำงาน</p> <p>นอกจากนี้ยังมีการขายฝันเรื่องเทคโนโลยีชีวภาพที่จะช่วยยืดอายุขัย แถมอาจทำให้เราเป็นอมตะได้อีกต่างหาก ใครๆ ก็อยากมีชีวิตยืนยาวเป็นอมตะจริงไหม แต่ใครล่ะ ที่จะเป็นผู้ควบคุมเทคโนโลยีเหล่านี้ และมีจุดประสงค์แอบแฝงอะไรหรือไม่?</p> <p>สิ่งที่เขาไม่ได้บอกก็คือ แล้วใครจะเป็นคนปกครองโลกใบนี้ แล้วเราจะแน่ใจได้ยังไงว่าคนพวกนี้จะเป็นคนดี และอำนาจที่มากขึ้นจะยิ่งลดทอนความเป็นคนดีของมนุษย์เสมอ</p> <p>ต่อให้เป็นคนดีจริงๆ ทำไมคนกลุ่มเล็กๆ ถึงอยากแบ่งปันความมั่งคั่งและเทคโนโลยีสุดล้ำให้กับคนทั่วไป? ทำไมไม่เก็บไว้ใช้เองล่ะ หรือมันคือการ คัดเลือกสายพันธุ์มนุษย์ ในรูปแบบใหม่ โดยใช้ พันธุวิศวกรรม และ ปรัชญาเหนือมนุษย์ เป็นเครื่องมือ ซึ่งสุดท้ายแล้ว คนธรรมดาอย่างเราก็คงไม่มีที่ยืนในโลกใบนี้</p> <p>โลกอนาคตที่ไร้ทรัพย์สินส่วนตัวและความเป็นส่วนตัว โดยใช้เทคโนโลยีควบคุมภายใต้หน้ากากของความเท่าเทียมและความยั่งยืน แต่บทความนี้ตั้งคำถามถึงความเป็นไปได้ ผลกระทบ และวาระซ่อนเร้นของ WEF โดยเฉพาะอย่างยิ่งการสูญเสียกรรมสิทธิ์ในทรัพย์สิน การควบคุมจากรัฐบาล และการเปลี่ยนแปลงทางสังคม ซึ่งอาจนำไปสู่สังคมนิยมแบบสุดโต่งและการสูญเสียอิสรภาพ You own nothing and be happy.</p> <p>Mueller, Antony P. “No Privacy, No Property: The World in 2030 According to the WEF.” Mises Wire, 12 Aug. 2020</p> <h1>Siamstr #WEF</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9sjw7met4nkfnnpxrrdxumlpadhzsrx998e39yv8dh8acn9nxfwczyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxl9upqc" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9sjw7met4nkfnnpxrrdxumlpadhzsrx998e39yv8dh8acn9nxfwczyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxl9upqc" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9sjw7met4nkfnnpxrrdxumlpadhzsrx998e39yv8dh8acn9nxfwczyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxl9upqc" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9sjw7met4nkfnnpxrrdxumlpadhzsrx998e39yv8dh8acn9nxfwczyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxl9upqc" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ be7bf5de:09420d0a <div class="time" style="margin-left: auto;">2024-10-14 22:21:23</div> </div> <div> <p>We're excited to launch our new company, <a href="https://nosfabrica.com/">NosFabrica</a>! Our mission is to empower sovereign healthcare by building tools for peer-to-peer healthcare interactions, giving individuals and providers the keys to their own health data. We are building a healthcare application factory, shipping health clients built on Nostr and Bitcoin and bootstrapping a decentralized ecosystem of health tools. We want to onboard thousands of people to Nostr and Bitcoin and enable people to live healthy lives. By utilizing Nostr for identity resolution and bitcoin for payments, we're paving the way for interoperable healthcare applications to exchange health information, and individuals to track and own data that matters to them, connecting to healthcare providers on their health journey.</p> <p><strong>The Problem:</strong></p> <p>The fiat healthcare system has led to a dangerous centralization of healthcare records in the US and globally, where companies ultimately own health data, not individuals. Current protocols of oAuths and APIs have led to bloated and expensive walled gardens (eg, Epic, Cerner) and a honeypot for healthcare hackers, most notably the recent <a href="https://medriva.com/news/healthcare-policy/cyberattack-on-change-healthcare-exposes-fragility-in-us-health-system-infrastructure">Change Healthcare hack</a>, owned by United Healthcare - affecting Avi's work. In 2023, <a href="https://www.medtechdive.com/news/patient-records-exposed-healthcare-data-breaches-double-fortified-health-security/705149/">more than 115 million health records were compromised across 655 data breaches</a>. </p> <p>High cost and poor outcomes are the current product of fiat healthcare. Of the <a href="https://www.kff.org/from-drew-altman/the-two-health-care-cost-crises/">$4.5 trillion annual US healthcare spend</a>, <a href="https://www.pgpf.org/blog/2023/04/almost-25-percent-of-healthcare-spending-is-considered-wasteful-heres-why#:~:text=Approximately%2025%20percent%20of%20healthcare,interventions%20that%20address%20such%20waste.">25% is administrative cost</a>, and half of that is waste. <a href="https://www.businessnewsdaily.com/8693-medical-billing-services.html">6-10% </a>of every healthcare transaction goes to a medical billing middleman. Meanwhile, <a href="https://www.cdc.gov/chronic-disease/about/index.html">6 in 10 Americans</a> has a chronic health condition. </p> <p>A decentralized healthcare application ecosystem would give the healthy sovereign individual the opportunity to take back ownership of their healthcare data, and their health, too. </p> <p><strong>The Solution:</strong></p> <p>NosFabrica means "our factory" in Latin, with of course the nod to Nostr. We aim to build a new, parallel health system on top of open source protocols Nostr and bitcoin. This decentralized healthcare ecosystem will be driven by peer-to-peer interactions between patients and providers. We will move healthcare onto a bitcoin and Nostr standard, giving independent healthcare providers the tools to integrate bitcoin deeper into their practice while maintaining practice sovereignty. </p> <p>By establishing an open-source protocol for the private exchange of health data on Nostr, NosFabrica will set a foundation for a decentralized healthcare system and enable bitcoin-native electronic medical record (EMR) software clients to be built on top of Nostr. </p> <p>We will cut out middlemen in healthcare and build tools that put the individual at the center of the solution. The benefits to patients include owning their own medical data, care discovery at competitive prices, portability of health data, and ultimately improve health outcomes. Doctors will also have the ability to reach a much broader population, reduce their administrative cost, and own their key demographic data such as licenses, credentials, and board certifications. Ultimately, we envision a more robust ecosystem of independent providers, combatting the trend of <a href="https://www.finalis.com/blog/healthcare-m-a-2024-recent-deals-and-trends">M&A and centralization</a> we see under the current fiat healthcare regime.</p> <p>There are several impacts for the broader free and open-source community, as it gives tools for individuals with different healthcare use cases to bring solutions to sorely needed applications such as medical consent, data sharing, clinical trials, and public health.</p> <p><strong>Nostr enables the NosFabrica future in three primary ways.</strong></p> <p><strong>Identity and Access:</strong></p> <ul> <li>User identity exists at the protocol layer via your npub/nsec, instead of the application layer.</li> <li>Users can sign into any application connected to the protocol</li> <li>Users can sign and certify events with their key pair, verifiably demonstrating ownership</li> </ul> <p><strong>Data Standardization</strong></p> <ul> <li>We can develop specific Nostr event "kinds" created for medical data. Vitor has already started by building <a href="https://github.com/nostr-protocol/nips/pull/357">NIP-82 for medical data.</a></li> <li>Existing international data standards and formats such as <a href="https://fhir.org/">FHIR/HL7</a> can be "wrapped" within Nostr events"</li> <li>This structure provides seamless data portability and interoperability across applications.</li> </ul> <p><strong>Persistence and Availability:</strong></p> <ul> <li>HIPAA compliant, encrypted healthcare data is stored on relays</li> <li>Only the owner of the data and those authorized by the owner can decrypt or view the data - in other words, selective disclosure, which is a cornerstone of privacy.</li> </ul> <p>Boosting the Nostr network effect and flywheel will continue, as there are already <a href="https://nostr.band/">40,000 weekly active users</a>. By building healthcare applications on Nostr, we can onboard more people to the ecosystem, who may not be interested in social media.</p> <p><strong>Call to Action:</strong></p> <p>Of course, Nostr and Bitcoin are global protocols and networks that anyone can opt into. While the US gets a lot of the focus due to its expensive and complex healthcare system, there are many challenges globally including healthcare access, affordability, and timely care that we can address with open source tools and permissionless, sound money. We'd love to hear from you if you're interested in joining our mission.</p> <p><strong>About the team:</strong></p> <p>Avi Burra is an experienced healthcare veteran, working as senior director of product management at Optum. He is also the host of <a href="https://fountain.fm/show/0N6GGdZuYNNG7ysagCg9">PlebChain Radio</a>, a leading bitcoin and nostr podcast. With masters in electrical engineering and financial engineering, Avi brings a wealth of healthcare software product experience to NosFabrica.</p> <p>Jon Gordon has worked across the healthcare industry, including in provider strategy, payers and suppliers. Jon has been helping healthcare providers integrate a bitcoin strategy with his consulting business, <a href="https://www.satoshihealth.com/">Satoshi Health Advisors</a>. He also has a double masters in health economics and policy.</p> <p>Vitor Pamplona is the creator of <a href="https://github.com/vitorpamplona/amethyst">Amethyst</a>, the top Android client for Nostr. Vitor previously led a company spun out of the MIT lab utilizing VR for eye exams at EyeNetra. Vitor has a PhD in computer science from MIT.</p> <p><strong>Go to <a href="https://nosfabrica.com/">nosfabrica.com</a> to learn more and follow us along on Nostr!</strong></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvrmrylzdzstcdcdqfjuhu8fpweryz2s8qnadr5dc8plfzngphgkszyzl8haw7q6xpmppw6d98cfc9qlkfgr6755t8rn7sv254a8gfggxs5zxzt34" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvrmrylzdzstcdcdqfjuhu8fpweryz2s8qnadr5dc8plfzngphgkszyzl8haw7q6xpmppw6d98cfc9qlkfgr6755t8rn7sv254a8gfggxs5zxzt34" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvrmrylzdzstcdcdqfjuhu8fpweryz2s8qnadr5dc8plfzngphgkszyzl8haw7q6xpmppw6d98cfc9qlkfgr6755t8rn7sv254a8gfggxs5zxzt34" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvrmrylzdzstcdcdqfjuhu8fpweryz2s8qnadr5dc8plfzngphgkszyzl8haw7q6xpmppw6d98cfc9qlkfgr6755t8rn7sv254a8gfggxs5zxzt34" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d5c3d063:4d1159b3 <div class="time" style="margin-left: auto;">2024-10-24 14:58:48</div> </div> <div> <h1>“การลงทุน เป็นบาปหรือไม่” ประเด็นที่น่าสงสัย ในโลกการเงินที่ขับเคลื่อนด้วยกิเลส</h1> <h2>CDC Talk EP3 นำเสนอมุมมองที่น่าสนใจ โดยอาจารย์พิริยะและลุงโฉลกที่ได้ผสานหลักธรรมะเข้ากับโลกการเงินอย่างลึกซึ้ง</h2> <p>https://image.nostr.build/2e6fbf0fe27536acfc4e02b351572b6b4a2493b7980b65c8e4d4fcef60b3ea46.jpg .</p> <p>ลุงโฉลกอธิบายด้วยหลัก “มรรคมีองค์ 8” การตัดสินว่าการกระทำใดดีหรือชั่ว ต้องดูที่เจตนาและองค์ประกอบอื่นๆ เหมือนกับมรรค 8 ไม่ใช่แค่หลักปฏิบัติ 8 ข้อที่แยกจากกัน แต่เป็นองค์ประกอบ 8 ประการที่สัมพันธ์กัน ตั้งแต่สัมมาทิฐิถึงสัมมาสมาธิ ดังนั้นการจะบอกว่าอาชีพใดเป็นสัมมาอาชีพหรือมิจฉาอาชีพ จึงต้องพิจารณาองค์ประกอบทั้งหมด โดยเฉพาะ “เจตนา” ในขณะนั้น แม้แต่คำว่า “ศรัทธา” หากปราศจาก “ปัญญา” ก็เป็นเพียงความงมงาย เช่นเดียวกับการลงทุน หากมีแต่ความเชื่อแต่ขาดความรู้ความเข้าใจ ก็อาจนำไปสู่การตัดสินใจที่ผิดพลาดได้ ทางชมรมโฉลกจึงมีธรรมเนียมในการทำบุญด้วยเงิน 108 บาท เพื่อย้ำเตือนให้สมาชิกชมรมลงทุนโดยไม่ยึดติดกับความร่ำรวย เพราะหากมุ่งหวังแต่ความมั่งคั่ง ก็จะเป็นการลงทุนที่ตั้งอยู่บนโลภะ ซึ่งเป็นอกุศลมูลจิต .</p> <p>ลุงโฉลกอธิบายเรื่องเจตนาด้วยตัวอย่างของการอธิษฐาน ท่านชี้ว่าการอธิษฐานให้เกิดผลต้องมี "สัจจะ" เป็นพื้นฐาน เช่นเดียวกับ "สัมมาอาชีวะ" ที่ต้องมีสัมมาทิฐิและสัมมาสังกัปปะนำทาง แล้ววาจา การกระทำ และอาชีพจึงจะเป็นสัมมาได้อย่างแท้จริง ตัวอย่างเรื่องของการกวาดลานวัด หากทำด้วยจิตใจที่เบิกบานก็เป็นสัมมาอาชีพ แต่หากทำด้วยจิตใจเศร้าหมองก็อาจเป็นมิจฉาอาชีพ เช่นเดียวกับการลงทุน หากทำด้วยความโลภก็อาจเป็นมิจฉาอาชีพ แต่หากลงทุนด้วยความเข้าใจมีสติและเจตนาที่ดี เช่น การลงทุนเพื่อสร้างคุณค่าให้สังคม ก็เป็นสัมมาอาชีพได้ .</p> <p>อาจารย์พิริยะเสริมว่า หลายคนมองตลาดหุ้นเป็น Zero-Sum Game คือคิดว่ากำไรของคนหนึ่งจะต้องมาจากการขาดทุนของอีกคนหนึ่งเสมอ ไม่ต่างอะไรกับการขโมยมาเลย....อาจารย์พิริยะบอกว่า เป็นความเข้าใจที่คลาดเคลื่อน เพราะตลาดหุ้นมีบทบาทสำคัญในการขับเคลื่อนเศรษฐกิจ โดยทำหน้าที่เป็นตัวกลางระดมทุนให้ธุรกิจ นำไปสู่การสร้างผลิตภัณฑ์และบริการ สร้างงานสร้างรายได้และสร้างคุณค่าให้สังคม นอกจากนี้ตลาดยังเป็นพื้นที่สำหรับการแลกเปลี่ยนและบริหารความเสี่ยง ที่สำคัญคือตลาดเป็นกลไกสำคัญในการค้นหาราคาที่เหมาะสม ซึ่งเกิดจากปฏิสัมพันธ์ระหว่างผู้ซื้อและผู้ขาย โดยการตัดสินใจซื้อขายในตลาดนั้นเกิดขึ้นโดยสมัครใจ กลไกราคานี้เองที่ช่วยให้เศรษฐกิจหมุนเวียนได้อย่างมีประสิทธิภาพและทำให้ทุกคนรับรู้ถึงความต้องการของตลาด เพื่อนำไปสู่การปรับตัวและพัฒนาอย่างต่อเนื่อง</p> <p>. ลุงโฉลกเน้นย้ำว่า การลงทุนที่ดีต้องมี “สัมมาทิฐิ” มองเห็นคุณค่าที่แท้จริง ไม่ใช่แค่แสวงหากำไร แล้วต้องรู้จัก “พอ” ตามหลัก “สันโดษ” ซึ่งไม่ได้หมายถึงการมักน้อย แต่หมายถึงการ “พอใจในสิ่งที่ตนมีอยู่” ที่ไม่ปล่อยให้ “ตัณหา” ครอบงำ ดังพุทธสุภาษิต “นตฺถิ ตณฺหาสมา นที” ไม่มีแม่น้ำใดกว้างใหญ่เท่าตัณหา เพราะหากปล่อยให้ความโลภครอบงำ ก็ยากที่จะประสบความสำเร็จอย่างยั่งยืน ท่านยังได้อธิบายหลักอริยสัจ 4 เพื่อให้เห็นว่าความทุกข์ในการลงทุนนั้นเกิดจากความอยาก และการเข้าใจความจริงของชีวิตตามหลักอริยสัจ 4 นี้เอง จะเป็นหนทางสู่การลงทุนอย่างมีสติ</p> <p>สรุปแล้ว การลงทุนไม่ใช่บาปหรือบุญในตัวมันเอง แต่ขึ้นอยู่กับเจตนาของนักลงทุนเป็นสำคัญ ลงทุนด้วยใจที่บริสุทธิ์ การลงทุนไม่ใช่เรื่องของผลกำไรเพียงอย่างเดียว แต่เป็นเรื่องของการพัฒนาจิตใจ รู้จักประมาณและการมีสติ ซึ่งเป็นพื้นฐานสำคัญสู่ความสำเร็จและความสุขที่ยั่งยืน ไม่ว่าจะในโลกการลงทุนหรือการใช้ในชีวิตประจำวันก็ตาม </p> <h1>CDCTalk #Siamstr</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0yy9ke05nq2js6tdlyxdrclhzw73x5qj2hxlps08fwtwqhautspszyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxtsl3xt" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0yy9ke05nq2js6tdlyxdrclhzw73x5qj2hxlps08fwtwqhautspszyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxtsl3xt" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0yy9ke05nq2js6tdlyxdrclhzw73x5qj2hxlps08fwtwqhautspszyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxtsl3xt" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0yy9ke05nq2js6tdlyxdrclhzw73x5qj2hxlps08fwtwqhautspszyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxtsl3xt" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d5c3d063:4d1159b3 <div class="time" style="margin-left: auto;">2024-10-24 14:55:55</div> </div> <div> <h1>"ขาดทุนทนได้ กำไรสองสลึงทนไม่ได้" ประโยคที่ฟังดูเหมือนจะขำ แต่ลุงโฉลกกลับบอกว่า มันขำไม่ออก!</h1> <p>เพราะสะท้อนความจริงอันน่าเศร้าของนักลงทุน ที่มักพ่ายแพ้ต่อกิเลสในใจตัวเอง ไม่ต่างจากการติดกับดัก ที่มอง "สิงโตเป็นหมา" ซึ่ง CDC Talk EP 2 จะพาเราไปเรียนรู้เรื่องราวเหล่านี้ด้วยการนำหลักธรรมะมาประยุกต์ใช้กับการลงทุนในบิตคอยน์ เพื่อค้นหาเส้นทางสู่ความสำเร็จที่ยั่งยืนทั้งในการลงทุนและการใช้ชีวิต</p> <p>https://image.nostr.build/180f5864057351d0e2a725d0ab021ae58f30942d2b87ad1697030d7d51f6bae0.jpg</p> <p>. อาจารย์พิริยะยกตัวอย่างพฤติกรรมของนักลงทุนบิตคอยน์ บางคนทนขาดทุนมาได้ถึง 3 ปี พอราคากลับมาเท่าทุน ก็รีบขายทิ้งทันที ในขณะที่บางคนติดดอยแล้วตัดสินใจขายขาดทุนอย่างเจ็บปวด จนเกิดความโกรธเกลียดบิตคอยน์ สาปส่งว่าเป็นสิ่งหลอกลวงและไม่เหลียวแลมันอีกเลย แต่เมื่อราคาบิตคอยน์พุ่งขึ้น ก็กลับมาสนใจมันอีกครั้ง พฤติกรรมที่เหล่านี้ลุงโฉลกอธิบายว่า เป็นเพราะนักลงทุนขาดสติ ไม่รู้เท่าทันสภาวะที่แท้จริงของสิ่งต่างๆ จึงตัดสินใจโดยใช้อารมณ์เป็นที่ตั้ง กลัวที่จะยอมรับความผิดพลาด กลัวว่ากำไรจะหายไปทำให้พลาดโอกาสทำกำไรและตกเป็นทาสของราคาที่ผันผวน . ลุงโฉลกเปรียบเทียบพฤติกรรมเหล่านี้กับคนที่ "เห็นสิงโตเป็นหมา" สะท้อนถึงความไม่รู้ ความประมาท ที่ทำให้มองไม่เห็นอันตรายไม่รู้จักป้องกันตัวเอง เช่นเดียวกับนักลงทุนที่มีความไม่รู้นี้ทำให้มองไม่เห็นความเสี่ยง ตัดสินใจลงทุนโดยใช้อารมณ์ สุดท้ายก็เจ็บตัว ลุงโฉลกเน้นย้ำว่าต้องเข้าใจ psychology รู้เท่าทันความโลภและความกลัว . ต้นตอของความไม่รู้นั้น ลุงโฉลกอธิบายว่า คือ "โมหะ" ที่บดบังปัญญา ทำให้เกิดความโลภ ความกลัว ความโกรธ และ "เจตนา" ที่ผิดพลาด ซึ่งล้วนเกิดจากการรับรู้ผ่าน ตา หู จมูก ลิ้น กาย ใจ หรือที่เรียกว่า บริวารทั้ง 6 โดย "ทิฐิ" หรือความยึดมั่นในความคิดเห็นของตัวเอง ก็เป็นหนึ่งในบริวารเหล่านั้น ที่ทำให้เราไม่เปิดใจเรียนรู้สิ่งใหม่ๆ ไม่ยอมรับความจริง วิธีแก้คือต้องฝึกสติ รู้เท่าทันความคิดและอารมณ์ของตัวเอง ใช้ โยนิโสมนสิการ คือคิดพิจารณาอย่างรอบคอบถี่ถ้วน ไตร่ตรองให้ถ่องแท้ก่อนตัดสินใจ ไม่ว่าจะเรื่องการเงิน การงาน หรือแม้แต่การใช้ชีวิต . ลุงโฉลกอธิบายหลัก อริยสัจ 4 โดยเริ่มจาก ทุกข์ ความจริงที่ว่าชีวิตย่อมมีทุกข์ ทั้งความทุกข์ทางกายและทางใจ เช่น ความผิดหวัง ความไม่สมหวัง จากการลงทุน ความโกรธ ความกลัว ที่เกิดจากความผันผวนของตลาดบิตคอยน์ ต้นเหตุของทุกข์เหล่านี้ หรือ สมุทัย ก็คือ ความอยาก ความยึดมั่นถือมั่น ความไม่รู้ เช่น ความอยากรวยเร็ว ความเชื่อมั่นในระบบเทรดที่ไม่มั่นคง หรือความไม่รู้เท่าทันกลไกตลาด ลุงโฉลกเปรียบเทียบการแสวงหาความสุข เหมือนการเดินไปหากล่อง คิดว่าข้างในกล่องคือความสุข แต่สุดท้ายเมื่อไปถึง ก็พบว่าว่างเปล่า นี่สะท้อนให้เห็นถึง นิโรธ หรือการดับทุกข์ ที่เกิดจากการรู้เท่าทันความไม่เที่ยง (อนิจจัง) และการไม่มีตัวตนที่แท้จริง (อนัตตา) และ มรรค หรือหนทางดับทุกข์ ที่ลุงโฉลกสื่อถึง คือ การฝึกฝนสติปัญญา การวางแผนอย่างรอบคอบ และการรู้เท่าทันอารมณ์ของตัวเอง . ทั้งลุงโฉลกและอาจารย์พิริยะเชื่อว่าราคาบิตคอยน์และทองคำมีแนวโน้มพุ่งสูงขึ้นเมื่อเทียบกับเงินดอลลาร์ที่กำลังเผชิญภาวะเงินเฟ้ออย่างต่อเนื่อง อาจารย์พิริยะอธิบายว่า ในมาตรฐานของเงินที่แข็งแกร่ง สินค้าและบริการต่างๆ ควรจะมีราคาถูกลงเมื่อเวลาผ่านไป ทำให้คนเราใช้จ่ายและซื้อของได้มากขึ้น แต่ถ้ายังใช้เงินดอลลาร์เป็นมาตรฐานในการวัดมูลค่า เช่น การมองราคาทองคำและบิตคอยน์เป็นเงินดอลลาร์ ทุกอย่างก็จะแพงขึ้น หากบิตคอยน์กลายเป็น "เงินของโลก" ได้จริง มูลค่าของมันควรจะสะท้อน GDP ของโลก หารด้วยจำนวนบิตคอยน์ที่มีอยู่ ซึ่งปัจจุบันอยู่ที่ราว 27 billion dollars ต่อ 1 บิตคอยน์ และมีแนวโน้มเพิ่มขึ้นอีกมาก สะท้อนความหมายของ "1 BTC = 1 BTC" ที่ไม่ได้ผูกติดกับมูลค่าเงินดอลลาร์ การทำความเข้าใจธรรมชาติของเงินตราที่เปลี่ยนแปลงได้ตลอดเวลาเป็นสิ่งสำคัญ เพราะทุกอย่างเป็นไปได้ การมองเห็นสภาพความเป็นจริงจะช่วยให้เรารับมือกับความเปลี่ยนแปลงได้อย่างมีสติ . เช่นเดียวกับระบบเงินตรา ลุงโฉลกเล่าว่าสมัยท่านเด็กๆ เงิน 1 สตางค์ยังมีรู มีหน่วย อัด เฟื้อง ไพ ซึ่งคนรุ่นใหม่ไม่รู้จักแล้ว เพราะระบบเงินตราหน่วยเงินมีการเปลี่ยนแปลงไปตามกาลเวลา เช่นเดียวกับดอลลาร์ ที่แม้จะเป็นสกุลเงินหลักของโลกในปัจจุบัน แต่อนาคตก็ไม่มีอะไรแน่นอน อาจจะถูกแทนที่ด้วย บิตคอยน์ ลุงย้ำว่า "ต้องเรียน เพื่อเข้าใจ" ถึงจะสามารถปรับตัวและรับมือกับการเปลี่ยนแปลงได้ . สุดท้าย อาจารย์พิริยะทิ้งท้ายไว้ว่าการลงทุนไม่ใช่การเล่น ต้องศึกษาหาความรู้วางแผนให้ดีและที่สำคัญคือ ต้องมีสติรู้เท่าทันอารมณ์ของตัวเอง เพื่อไม่ให้ตกเป็นทาสของความโลภและความกลัว ซึ่งเป็นกุญแจสู่ความสำเร็จในการลงทุนระยะยาว</p> <h1>CDCTalk #Siamstr</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9k2v2sez3acewdkwlahcns7wdv9tlem7yguk0974s43j035eud5czyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxdsmd9g" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9k2v2sez3acewdkwlahcns7wdv9tlem7yguk0974s43j035eud5czyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxdsmd9g" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9k2v2sez3acewdkwlahcns7wdv9tlem7yguk0974s43j035eud5czyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxdsmd9g" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9k2v2sez3acewdkwlahcns7wdv9tlem7yguk0974s43j035eud5czyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxdsmd9g" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 97fc03df:8bf891df <div class="time" style="margin-left: auto;">2024-10-24 07:53:50</div> </div> <div> <h2><strong>A Value Internet Sharing Bitcoin’s Consensus Security</strong></h2> <h6>Author: BEVM, October 2024</h6> <h3>Abstract</h3> <p>Super Bitcoin is a value-based internet centered on BTC, and share Bitcoin's consensus security. This value internet not only inherits the security of the existing Bitcoin network but also transcends BTC's current limitations of being solely used for transfer, providing the Bitcoin network infinite potential for scalability and flexibility.</p> <p>While the Lightning Network [2] inherits Bitcoin's network security and offers partial scalability solutions, it still falls short in supporting smart contracts and further enhancing scalability. We propose a five-layer architecture for Super Bitcoin using the Bitcoin network as the kernel layer, maintaining system security and transaction irreversibility through the proof-of-work (PoW) consensus mechanism; we build an efficient communication layer based on the Lightning Network, facilitating rapid transmission of asset information while preserving Bitcoin's decentralized nature; we introduce the Taproot Consensus as the extension layer, abstracting Lightning Network communication and asset information to provide a standardized interface for the upper virtual machine layer; we set up a multi-chain layer, also known as the fusion layer, which consists of multiple lightning chains secured by BTC consensus, integrating any mainstream virtual machine (VM) to achieve a "Multi-chain interconnection“ and ”multi-chain interoperability” unified by BTC consensus; finally, we support the application layer, providing developers with rich tools and interfaces to build a decentralized application (DApp) ecosystem, all sharing the security of BTC consensus.</p> <h3>1. Introduction</h3> <p>As the pioneer of cryptocurrencies, Bitcoin (BTC), through its proof-of-work (PoW) consensus mechanism and decentralized network structure, has garnered an immense level of consensus, becoming a supranational currency. This security stems from the perfect combination of its vast network hash power and economic incentives. The birth of Bitcoin not only ushered in a new era of decentralized digital currency but also pointed the way for the subsequent development of blockchain technology. However, the limitations of Bitcoin’s scripting language soon became apparent, as it only supports simple value transfers and limited contract logic, unable to meet the demands of more complex decentralized applications.</p> <p>The evolution of blockchain technology is essentially all about expanding and enhancing Bitcoin's capabilities. Vitalik Buterin, the founder of Ethereum, initially envisioned adding smart contract functionality to Bitcoin. However, due to the technological constraints of the time and the limitations of the Bitcoin network, Ethereum had to establish its own independent consensus system. While this approach allowed for the creation of Turing-complete smart contracts, it also introduced new security risks and scalability challenges. Many projects followed suit, building independent blockchain ecosystems, gradually diverging from and even forgetting the original intention of extending Bitcoin’s capabilities.</p> <p>However, two key factors remind us of the need to reconsider this direction. First, the continued rise in Bitcoin’s value relative to other cryptocurrencies like Ethereum has validated the trust people place in its security and stability. Second, the collapse of Luna/UST, which wiped out nearly $100 billion in market value, highlighted the severe security vulnerabilities present in independent consensus chains, especially when faced with complex economic models and rapidly growing network value.</p> <p>In this context, we introduce Super Bitcoin to create a true value internet sharing Bitcoin's consensus security. It fundamentally differs from the existing Bitcoin Layer 2 solutions: traditional Bitcoin Layer 2 solutions (such as the Lightning Network) mainly achieve fast payments through off-chain state channels and limited scripts, while sharing Bitcoin's consensus security but lacking flexibility. Meanwhile, sidechains like Stacks or Layer 2 solutions, although they support smart contracts, still rely on independent multi-signature mechanisms for security, thus not fully inheriting the security of the Bitcoin mainnet.</p> <h3>2. Technical Background</h3> <p>To fully understand the proposed solution, it is necessary to first review the background and development of several key technologies. This chapter briefly introduces the Lightning Network, the Substrate framework [3], BEVM's Taproot Consensus, and the multi-chain interoperability system to provide a foundation for understanding our solution.</p> <h4>2.1 Lightning Network</h4> <p>The Lightning Network is a Layer2 scaling solution for Bitcoin, with its core design principles detailed in the BOLT (Basis of Lightning Technology) specifications. These specifications not only ensure the efficient operation of the Lightning Network but also ingeniously achieve deep integration with the consensus security of the Bitcoin mainnet. Several parts of the BOLT specifications play a key role in sharing Bitcoin’s consensus security.</p> <p>BOLT #2 and BOLT #3 provide detailed guidelines on the lifecycle management of payment channels and the structure of transactions. The opening of a channel involves creating a multi-signature output on the Bitcoin blockchain, while closing the channel requires broadcasting the final state to the mainnet. BOLT #3 specifically defines commitment transactions, which are the core mechanism by which the Lightning Network shares Bitcoin's consensus security. Each time the channel state is updated, a new commitment transaction is generated, which can be broadcast to the Bitcoin mainnet if needed. The design of commitment transactions ensures that even if one party in the channel becomes uncooperative, the other party can still close the channel by broadcasting the most recent commitment transaction and receive their due funds. This mechanism directly relies on Bitcoin’s consensus rules and security, meaning the Lightning Network’s security is essentially guaranteed by the Bitcoin network.</p> <p>BOLT #5 defines the penalty mechanism for channel closures. This mechanism introduces the concept of "revocating private keys," effectively preventing participants from broadcasting outdated channel states. If dishonest behavior is detected, the honest party can use these keys to punish the other party on the Bitcoin main chain, thereby ensuring the accuracy of the channel state and enforcing honest behavior among participants through Bitcoin's consensus mechanism.</p> <p>Additionally, the commitment transaction format specified in BOLT #3 connects Lightning Network transactions to Bitcoin's fee market through "anchor outputs." This not only enhances the security of transactions but also ensures that Lightning Network transactions can still be confirmed promptly during periods of network congestion.</p> <p>These meticulously designed specifications collectively ensure that the Lightning Network, while providing fast and low-cost transactions, can still fully leverage Bitcoin's robust consensus security.</p> <h4>2.2 Substrate Framework</h4> <p>The Substrate framework is a highly modular blockchain development toolkit written in Rust, providing a powerful and flexible technical foundation for the implementation of Super Bitcoin. Its core strength lies in its pluggable Pallet system, where these pre-built functional modules serve as "blockchain Legos," enabling us to quickly and efficiently assemble and customize the desired features.</p> <p>For Super Bitcoin, Substrate's modular design is crucial. It allows us to flexibly build and integrate various functional components on top of the shared Bitcoin consensus security. By leveraging Substrate's Pallet, we can easily support and integrate different virtual machine environments, thereby increasing the system's flexibility and adaptability. This design not only accelerates the development process but also provides Super Bitcoin with powerful scalability, allowing it to better meet the evolving needs of the blockchain ecosystem.</p> <p>Super Bitcoin utilizes these features of Substrate to customize the <strong>BEVM-stack framework</strong>, which enables one-click deployment of lightning chains.</p> <h4>2.3 Taproot Consensus</h4> <p>BEVM’s Taproot Consensus integrates Bitcoin’s Taproot upgrade [4] technology. This technology combines several key elements: Schnorr signatures [5] provide signature aggregation capabilities, Merkelized Abstract Syntax Tree (MAST) support complex conditional scripts, and Musig2 enables two-round communication in multi-signature schemes. Through the combination of these technologies, BEVM successfully implements a decentralized threshold signature network with (t, n) support.</p> <p>Additionally, BEVM leverages Bitcoin SPV (Simplified Payment Verification) technology to achieve lightweight decentralized block header synchronization. This allows transaction verification without downloading the full blockchain data, enabling BEVM to synchronize with the BTC mainnet in a decentralized manner. In Super Bitcoin architecture, Taproot Consensus plays a key role as the extension layer: it interfaces with the Lightning Network below, abstracting and integrating asset information, and provides standardized interfaces for different virtual machine execution environments above, realizing the transmission and utilization of asset information.</p> <p>Such design makes Taproot Consensus a core component of the Super Bitcoin architecture. It not only inherits the security and privacy-preserving characteristics of the Bitcoin network but also provides rich functional support for upper-layer applications.</p> <h4>2.4 Multi-Chain Interoperability System</h4> <p>The concept of a multi-chain interoperability system was first introduced by Polkadot. Polkadot [6] is a multi-chain interoperability system based on the Substrate framework, sharing the security of DOT consensus, and using parachains for application chain expansion. Correspondingly, Super Bitcoin is a multi-chain interoperability system built on Bitcoin and the Lightning Network, sharing BTC consensus security, and using Lightning Chains for application chain expansion.</p> <p>The differences between the two are as follows:</p> <ul> <li> <p>Shared Consensus Security: Both Polkadot and Super Bitcoin’s multi-chain networks achieve shared consensus security, but Polkadot shares DOT consensus, while Super Bitcoin shares Bitcoin consensus. The strength of BTC’s consensus is far greater than that of DOT. Theoretically, the security of the Super Bitcoin architecture is 200 times higher than that of the Polkadot network. This "200 times" represents the current ratio of BTC’s $1.3 trillion market cap to DOT’s $6.5 billion market cap. Therefore, the Lightning Chains on Super Bitcoin offer approximately 200 times the security of Polkadot's parachains.</p> </li> <li> <p>Application Chain Architecture: Super Bitcoin’s lightning chain is deployed with one click based on BEVM-stack, whereas on Polkadot, parachains are deployed via Substrate with one-click.</p> </li> <li> <p>Cross-Chain Communication Protocol: Super Bitcoin uses lightning channels as the communication protocol between Lightning Chains, while Polkadot uses XCMP as the communication protocol between parachains.</p> </li> </ul> <h3>3. System Architecture</h3> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/97fc03df5774bf35f439a31629b7cc753f7992be62535d6d9addcb068bf891df/files/1729754845208-YAKIHONNES3.jpg" /></p> <h4>3.1 System Architecture Overview</h4> <p>Super Bitcoin is a five-layer architecture protocol built by BEVM guided by the three problems of blockchain - decentralization, security and scalability.. This protocol is based on the Bitcoin protocol and utilizes the Lightning Network for efficient peer-to-peer communication. To extend the functionality of Lightning Network nodes, Super Bitcoin integrates Taproot Consensus and combines Bitcoin SPV, Schnorr signatures, MAST contracts, and a BFT PoS consensus mechanism to achieve scalable state management and transaction processing.</p> <p>On this foundation, Super Bitcoin further integrates multiple virtual machines, including WASM, EVM, SVM, MoveVM, and CairoVM, creating a multi-chain system based on lightning chains that offers a diverse range of smart contract execution environments. This modular framework significantly enhances the system's scalability and flexibility while maintaining the decentralized nature of the Bitcoin network. Importantly, all lightning chains share the Bitcoin network's consensus security, ensuring that the system remains highly secure as it scales.</p> <h4>3.2 Kernel Layer</h4> <p>The Bitcoin network serves as the kernel layer of Super Bitcoin, maintaining the security and irreversibility of the entire system through the Proof-of-Work (PoW) consensus mechanism. This decentralized peer-to-peer electronic cash system primarily supports BTC transfers and basic opcode execution, managing state using the UTXO model. The Bitcoin network’s block structure and transaction data serve as the input for the Lightning Network, providing reliable foundational data for the upper layers. Although Bitcoin’s scripting system is not Turing-complete, it can support the most basic smart contract functionality through stack-based operations, conditional checks, and cryptographic functions. The network maintains a block time of approximately 10 minutes using a difficulty adjustment algorithm and uses Merkle tree structures to optimize transaction verification efficiency. The security and decentralization of this foundational layer provide a robust consensus security foundation for the entire Super Bitcoin architecture, while its simple design and limited scripting capabilities offer a stable and predictable environment for upper-layer expansion.</p> <h4>3.3 Communication Layer</h4> <p>The Lightning Network serves as the communication layer of Super Bitcoin, achieving efficient asset information transmission while sharing the BTC consensus security. It acts as a bridge between users and the Super Bitcoin ecosystem, enabling bidirectional payment channels through a Hashed Time Lock Contract (HTLC), supporting multi-hop routing and atomic swaps. Users can establish state channels with Super Bitcoin nodes to deposit funds and conduct instant off-chain transactions.</p> <p>Super Bitcoin nodes, as specialized Lightning Network nodes, not only maintain direct channels with users but also remain compatible with the existing Lightning Network by implementing the BOLT (Basis of Lightning Technology) specifications. This design allows users to leverage the existing Lightning Network infrastructure for cross-node, cross-chain payments and value transfers, providing a secure communication foundation for the lightning chains.</p> <h4>3.4 Extension Layer</h4> <p>Taproot Consensus serves as the extension layer in Super Bitcoin, playing a critical role in connecting the Lightning Network with the upper-layer lightning chains. It abstracts the asset information transmitted through the Lightning Network and converts it into blockchain data that can be processed by the upper layers, balancing the payment efficiency of the Lightning Network with the logical needs of upper-layer applications.</p> <p>This expansion layer integrates Bitcoin SPV, Schnorr signatures, MAST (Merkelized Abstract Syntax Tree) structures, and a BFT (Byzantine Fault Tolerance) PoS consensus mechanism to achieve multiple functions:</p> <p><strong>1. Connecting the Lower Layer</strong> :Bitcoin SPV enables lightweight block header verification, allowing nodes to synchronize with the Bitcoin network in a decentralized manner, providing reliable on-chain data input for the Lightning Network.</p> <p><strong>2. Information Processing and Storage</strong>: The PoS-based blockchain network provides distributed storage of Lightning Network channel states. It also processes information for BTC and Taproot Assets, supplying necessary data for upper-layer applications. This mechanism ensures data redundancy and resistance to censorship.</p> <p><strong>3. Security Assurance</strong> : Decentralized threshold signatures replace the local key management system of Lightning Network nodes, enhancing key security and flexibility. The aggregation feature of Schnorr Signatures is used to construct a (t, n) threshold signature network, replacing the traditional single-key management model of the Lightning Network.</p> <p><strong>4. Privacy and Complexity</strong> : The MAST structure allows complex conditional scripts to be represented on-chain as a single hash, improving both privacy and script complexity. Through these mechanisms, the Taproot Consensus extension layer effectively converts verified Lightning Network data into standardized blockchain states. While ensuring security and privacy, it enhances the overall system's performance and scalability. It not only connects the underlying Bitcoin and Lightning Networks but also provides the upper-layer applications with rich and reliable data and functional support.</p> <p>#### 3.5 Fusion Layer The Fusion Layer reflects the scalability of Super Bitcoin. It builds on top of Taproot Consensus and utilizes the extensibility of the Substrate framework to achieve a multi-chain interconnected system. Its key features include:</p> <p><strong>1. Scalable Multi-Chain Architecture</strong>: Supports the deployment and interconnection of an unlimited number of lightning chains, with BEVM serving as a special lightning chain responsible for managing cross-chain interactions and resource scheduling.</p> <p><strong>2. Heterogeneous Compatibility and Standardized Protocols</strong>: Compatible with multiple virtual machines (such as MoveVM, CairoVM, SVM, EVM) and achieves atomic asset exchange and state synchronization through a standardized cross-chain protocol based on the Lightning Network.</p> <p><strong>3. Shared Security and Flexible Consensus</strong>: All lightning chains inherit the security of the Bitcoin network, while adopting a pluggable consensus design, with the default being a Taproot-compatible BFT variant.</p> <p><strong>4. Ecosystem Expansion</strong>: Facilitates the rapid migration of existing blockchain technologies, extending the decentralized BTC ecosystem to various Turing-complete blockchain applications.</p> <p>With these features, the Fusion Layer enables Super Bitcoin to evolve into a highly scalable, secure, and interoperable multi-chain ecosystem, providing robust infrastructure support for blockchain innovation.</p> <h4>3.6 Application Layer</h4> <p>The Application Layer is built on top of Super Bitcoin's multi-chain architecture, offering developers a diverse decentralized application (DApp) ecosystem. Leveraging the security, scalability, and interoperability of the underlying layers, it supports the deployment of applications on any Turing-complete virtual machine. Developers can choose to quickly deploy proprietary application chains within the lightning chain framework, or they can deploy various applications directly on the lightning chains. All these applications and chains automatically inherit the consensus and security guarantees of the Bitcoin network.</p> <p>The Application Layer integrates multiple smart contract execution environments, supporting programming languages such as Solidity (EVM), Move, Cairo, and Rust. The Application Layer lowers the entry barrier for developers and accelerates the innovation cycle. Through standardized API interfaces, developers can utilize Lightning Network channels to achieve decentralized cross-chain asset transfers and information exchanges. Additionally, it incorporates protocols like Taproot Assets, which are compatible with the Lightning Network, further enhancing cross-chain functionality.</p> <p>Although the services provided by the Application Layer are similar to other VM-based public blockchains, it has two distinctive features: first, it allows the use of decentralized native BTC as the base currency for applications; second, the entire application layer shares the security of the Bitcoin network. Such design not only offers a rich development environment but also ensures that applications are built on solid security and native cryptocurrency support.</p> <h3>4. Shared Consensus Security</h3> <p>Shared BTC consensus security is the security core of our five-layer architecture. This concept is derived from Polkadot's shared security model, which Polkadot defines as Shared Security, also known as Pooled Security, is one of Polkadot's unique value propositions. In essence, it means that all parachains connected to Polkadot's relay chain benefit from the full security of the entire Polkadot network.</p> <p>Our five-layer protocol architecture further extends this concept by leveraging the Bitcoin (BTC) network—currently recognized as the most secure blockchain consensus system—to ensure the security of the entire ecosystem. Compared to Polkadot's parachains, which share Polkadot's consensus security, our architecture is directly built on top of the Bitcoin network, sharing Bitcoin’s consensus security.</p> <p>Existing BTC Layer2 solutions typically ensure security through cross-chain mechanisms or BTC staking, which only utilize part of Bitcoin’s consensus security. In contrast, our five-layer protocol is built on the Lightning Network, using HTLC (Hashed Timelockd Contract) and commitment transactions, with security fully dependent on BTC consensus. This design allows our system to fully inherit the consensus security of the Bitcoin network.</p> <p>Specifically, our architecture achieves shared BTC consensus security through the following methods:</p> <ul> <li> <p>Leveraging the peer-to-peer channels of the Lightning Network to ensure that all transactions are ultimately settled on the Bitcoin mainnet.</p> </li> <li> <p>Using HTLC commitment transactions, where each state update is protected by the consensus of the Bitcoin network.</p> </li> <li> <p>Through the Taproot Consensus extension layer, extending Bitcoin's security features to more complex smart contract environments.</p> </li> <li> <p>In the multi-chain system, all lightning chains share Bitcoin’s network consensus security, ensuring consistency and reliability across the entire ecosystem.</p> </li> </ul> <h3>5. Lightning Chain</h3> <p>Based on the shared BTC consensus security, we utilize the lightning chain to create a Value Internet. To achieve this, the architecture of the lightning chain network is inspired by Polkadot's relay chain and parachain design:</p> <ul> <li> <p><strong>Relay Chain</strong>: It serves as the central nervous system of the entire network, responsible for the overall security, cross-chain communication, and consensus mechanism. The relay chain does not execute specific application logic but focuses on coordinating the operations of the entire ecosystem.</p> </li> <li> <p><strong>Parachains</strong>: These are independent blockchains that run in parallel with the relay chain. Each parachain can have its own token economy and governance mechanism, achieving interoperability through the relay chain and sharing the security guarantees provided by the relay chain. Drawing from Polkadot’s design, Super Bitcoin proposes a multi-chain interoperability system based on Bitcoin and the Lightning Network. In this system, the Lightning Chain functions similarly to Polkadot's parachains, with the following unique characteristics:</p> </li> </ul> <p>Shared BTC Consensus Security: Unlike Polkadot’s independent consensus model based on PoS staking, Lightning Chain directly inherits the consensus security of the Bitcoin network, providing unprecedented security for the entire ecosystem.</p> <ul> <li> <p><strong>Lightning Network Integration</strong>: Lightning Chain deeply integrates Lightning Network technology, enabling high-speed, low-cost transaction processing, significantly enhancing the throughput and efficiency of the entire system.</p> </li> <li> <p><strong>Scalability</strong>: Theoretically, an unlimited number of Lightning Chains can be deployed, with each Lightning Chain optimized for specific application scenarios or industry needs, offering a high degree of flexibility and scalability.</p> </li> <li> <p><strong>BEVM as the Core Coordinator</strong>: In this ecosystem, BEVM (Bitcoin-Enhanced Virtual Machine) acts as a special Lightning Chain, playing a role similar to that of Polkadot’s relay chain. It is responsible for the governance and resource allocation of the entire network, ensuring efficient collaboration between different Lightning Chains.</p> </li> <li> <p><strong>Shared Lightning Network Liquidity</strong>: All Lightning Chains share the same Lightning Network, which means they can access a common liquidity pool, improving capital efficiency.</p> </li> </ul> <p>These features not only highlight the innovative design of Lightning Chain but also underscore its fundamental differences from existing BTC Layer 2 solutions. By directly sharing Bitcoin network consensus security and Lightning Network liquidity, Lightning Chain achieves a qualitative leap in both security and interoperability.</p> <h3>5.1 Lightning Chain</h3> <p>The Lightning Chain is the core component of Super Bitcoin that directly interacts with users. Its main responsibilities include handling user transactions, managing asset mapping, and executing smart contracts.</p> <h4>5.1.1 BTC Asset Mapping</h4> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/97fc03df5774bf35f439a31629b7cc753f7992be62535d6d9addcb068bf891df/files/1729755460719-YAKIHONNES3.jpg" /></p> <p><strong>Lightning Chain</strong> functions as both a node in the Lightning Network and a PoS (Proof of Stake) network. In this system, BTC is locked within the Lightning Network, while <strong>L-BTC</strong> represents the user's BTC balance in their Lightning Chain account. The mapping process between these two ensures the consistency and security of the assets. The specific BTC-to-L-BTC mapping process is as follows: - The user establishes a channel with the Lightning Chain via the standard Lightning Network protocol. - The user deposits <strong>A</strong> BTC into the Lightning Network channel. - As the Lightning Chain operates as a PoS network, the validators within the network observe this new BTC deposit. - Once more than two-thirds of the validators reach consensus and confirm the BTC deposit event, the Lightning Chain will issue <strong>A</strong> L-BTC accordingly.</p> <p>This process ensures that the issuance of L-BTC always maintains a 1:1 ratio with the BTC locked in the Lightning Network channel. It's important to note that L-BTC is self-custodied by the user, so there is no need to worry about asset security. Additionally, PoS consensus here is not used to secure L-BTC assets but acts as a distributed ledger for the state of the Lightning Network channel, solving the potential issue of data loss in local storage by Lightning Network nodes.</p> <h4>5.1.2 Smart Contract Interaction on the Lightning Chain</h4> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/97fc03df5774bf35f439a31629b7cc753f7992be62535d6d9addcb068bf891df/files/1729755652361-YAKIHONNES3.jpg" /></p> <p>Interaction with smart contracts on the <strong>Lightning Chain</strong> follows a "authorize first, execute later" paradigm. In this process, users need to convert <strong>L-BTC</strong> into <strong>M-BTC</strong>, where M-BTC represents the asset that can interact with smart contracts on the Lightning Chain. The specific interaction process is as follows:</p> <ul> <li><strong>Asset Preparation</strong>: The user holds A BTC in the Lightning Network state channel and decides to interact with a smart contract using 1 BTC.</li> <li><strong>Authorization Operation</strong>: The user authorizes the Lightning Chain network to convert 1 L-BTC into 1 M-BTC. This step does not immediately execute the conversion but provides the necessary permissions for subsequent interactions.</li> <li><strong>Smart Contract Invocation</strong>: The user initiates a smart contract call, specifying the use of 1 M-BTC. The Lightning Chain network checks the authorization and, upon confirming its validity, performs the following actions: destroys 1 L-BTC from the user’s balance, mints 1 M-BTC, and uses it directly for interaction with the smart contract.</li> <li><strong>Transaction Execution</strong>: The smart contract executes the specified operation using the minted M-BTC.</li> </ul> <p>This process enables the seamless application of Bitcoin assets within a smart contract environment while maintaining a clear separation between L-BTC, which functions as channel liquidity, and M-BTC, which serves as a medium for contract interaction.</p> <h3>5.2 System Chain</h3> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/97fc03df5774bf35f439a31629b7cc753f7992be62535d6d9addcb068bf891df/files/1729755765902-YAKIHONNES3.jpg" /></p> <p><strong>System Chain</strong> is the core coordination component of Super Bitcoin implemented through the upgraded BEVM (Bitcoin-Enhanced Virtual Machine). As a special Lightning Chain, it establishes direct connections with all regular Lightning Chains in the network, forming an efficient star topology structure. This design makes the System Chain the central hub of Super Bitcoin.</p> <p>The System Chain is primarily responsible for incentivizing Lightning Network nodes and coordinating cross-chain interoperability, effectively managing the entire network to ensure its efficient operation. In terms of node incentives, the System Chain implements a complex and sophisticated mechanism. It uses a dynamic reward algorithm that adjusts reward distribution based on the activity level, liquidity provided, and overall contribution to the network. During this process, the System Chain considers multi-dimensional evaluation metrics, such as the node’s uptime, transaction throughput, and routing efficiency.</p> <p>In terms of cross-chain interoperability, the System Chain plays a key coordination role, facilitating seamless interactions between different Lightning Chains. It implements a secure cross-chain communication protocol based on Hashed Time Lock Contract (HTLC), ensuring the security and reliability of message transmission. Additionally, the System Chain introduces an atomic swap mechanism, which effectively prevents potential loss of funds during cross-chain asset transfers. Furthermore, by defining a unified cross-chain asset standard, the System Chain simplifies the asset mapping process between different Lightning Chains, further improving the efficiency and convenience of cross-chain operations.</p> <h3>6. Economic Model</h3> <p>The economic model of BEVM (Bitcoin-Enhanced Virtual Machine) combines Bitcoin’s issuance mechanism with the functional characteristics of the Lightning Network. It aims to address the sustainable competitiveness of Super Bitcoin and provide a long-term incentive system for the Lightning Network.</p> <p>At the core of this model is the combination of Lightning Network node incentives and a staking-mining mechanism. Lightning Network nodes that establish state channels with the BEVM network can participate in staking mining. Staking mining uses a Verifiable Random Function (VRF) to determine mining probabilities, rather than distributing rewards proportionally based on the staked amount.</p> <p>During the staking mining process, participants stake BTC in state channels, and the system calculates the mining probability based on the VRF. For example, if three nodes stake 100 BTC, 10 BTC, and 1 BTC, their respective mining probabilities would be 90.09%, 9.01%, and 0.90%. This mechanism ensures that smaller stakers also have a substantial opportunity to earn rewards. A dedicated whitepaper on the economic model will be released for this section, so this document will not go into further details.</p> <h3>7. Future Development</h3> <h4>7.1 Short-Term Goals</h4> <p>The short-term goals of Super Bitcoin focus on implementing core functionalities and building the necessary infrastructure. By realizing the proposed five-layer protocol, we will introduce smart contract functionality based on the Lightning Network while sharing BTC consensus security. For users, participating in Super Bitcoin ensures that the BTC they hold remains fully under their control. At the same time, they will be able to use BTC, Taproot Assets, and other native assets within smart contracts.</p> <h4>7.2 Long-Term Vision</h4> <p>The long-term vision of Super Bitcoin is to build a global Value Internet that shares BTC consensus security. We aim to design an incentive mechanism through an innovative economic model, promoting widespread use of Lightning Network nodes. Furthermore, we are committed to deeply integrating existing blockchain ecosystems with Super Bitcoin, enabling the free flow and interaction of BTC assets. By doing so, we aim to create a secure, efficient, and interoperable blockchain ecosystem where BTC becomes the core, and all blockchain consensus models share the security of the Bitcoin network. Ultimately, our goal is to enable the Bitcoin network to scale infinitely while maintaining decentralization.</p> <h4>7.3 Potential Challenges and Solutions</h4> <p>Super Bitcoin faces several potential challenges in achieving its goals. Transforming Lightning Network nodes into a full-fledged network involves complex technical challenges that require extensive testing. Another challenge is designing a better economic incentive model to attract enough Lightning Network node operators to adopt Super Bitcoin. Ensuring seamless communication and atomic swaps between different node networks is also crucial, and the team will focus on developing standardized protocols and interfaces to enhance network interoperability. As the system’s complexity increases, maintaining network security will become more challenging. Super Bitcoin will adopt rigorous security audit processes and consider introducing advanced cryptographic technologies to strengthen system security. As the number of lightning chains grows, managing the state and interaction between networks may pose scalability challenges. By actively addressing these challenges, Super Bitcoin aims to bring revolutionary changes to the Bitcoin and Lightning Network ecosystems, creating a more flexible, efficient, and scalable infrastructure.</p> <h3>8. Conclusion</h3> <p>The five-layer architecture introduced by Super Bitcoin not only solves the problem of existing BTC Layer 2 solutions not being able to share Bitcoin's consensus security but also addresses the limitation of the Lightning Network being restricted to payment scenarios. It perfectly combines the shared BTC consensus security with smart contract functionality. Our protocol uses the Bitcoin network as the core, ensuring the highest level of security. It leverages the Lightning Network to construct an efficient communication layer, significantly improving scalability and flexibility while preserving the security of the native BTC consensus. By introducing Taproot Consensus as the extension layer, it abstracts Bitcoin and Lightning Network data to provide actionable data for the upper layers. Through the multi-chain fusion layer formed by lightning chains, we achieve a "multi-chain interconnection" supporting the free flow of cross-chain assets. The application layer offers developers a rich set of tools, fostering the development of a diverse DApp ecosystem. Combined with the innovative VRF-based staking mining mechanism, Super Bitcoin adds an incentive layer to the Lightning Network and allows the decentralized Bitcoin network to have unlimited flexibility and scalability.</p> <h3>9. References</h3> <p>[1] Nakamoto, S. (2008). "Bitcoin: A Peer-to-Peer Electronic Cash System." https://bitcoin.org/bitcoin.pdf</p> <p>[2] Poon, J., & Dryja, T. (2016). "The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments." https://lightning.network/lightning-network-paper.pdf</p> <p>[3]Habermeier, S., et al. (2020). "Substrate: A modular framework for building blockchains." https://www.parity.io/substrate/</p> <p>[4]Wuille, P., Nick, J., & Towns, A. (2019). "Taproot: SegWit version 1 spending rules." https://github.com/bitcoin/bips/blob/master/bip-0341.mediawiki</p> <p>[5] Nick, J., Seurin, Y., & Wuille, P. (2020). "Schnorr Signatures for secp256k1." https://github.com/bitcoin/bips/blob/master/bip-0340.mediawiki</p> <p>[6]Wood, G. (2016). "Polkadot: Vision for a heterogeneous multi-chain framework." https://polkadot.network/PolkaDotPaper.pdf</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs99twtuy543ajurzc94e5578tnpmflcct344c6lecktllm49nq2eqzyztlcq7l2a6t7d058x33v2dhe36n77vjhe39xhtdntwukp5tlzga7x2sytw" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs99twtuy543ajurzc94e5578tnpmflcct344c6lecktllm49nq2eqzyztlcq7l2a6t7d058x33v2dhe36n77vjhe39xhtdntwukp5tlzga7x2sytw" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs99twtuy543ajurzc94e5578tnpmflcct344c6lecktllm49nq2eqzyztlcq7l2a6t7d058x33v2dhe36n77vjhe39xhtdntwukp5tlzga7x2sytw" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs99twtuy543ajurzc94e5578tnpmflcct344c6lecktllm49nq2eqzyztlcq7l2a6t7d058x33v2dhe36n77vjhe39xhtdntwukp5tlzga7x2sytw" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d42dac70:ed6cd749 <div class="time" style="margin-left: auto;">2024-10-14 07:55:34</div> </div> <div> <h2>NOSTR</h2> <p>NOSTR, heard of it yet? I have a feeling we are all going to hear about it alot more.</p> <p><strong>N</strong>otes and <strong>O</strong>ther <strong>S</strong>tuff <strong>T</strong>ransmitted by <strong>R</strong>elays, is a client-relay model with privacy, user control and censorship resistance at the heart of this social network protocol.</p> <h4>Why?</h4> <p>It’s a step shift in centralised social media platforms such as Twitter, Instagram that suffer from corporate and/or state influence, control and censorship. See the <a href="https://en.m.wikipedia.org/wiki/Twitter_Files">Twitter files</a> to find out more about that. NOSTR addresses these with an open, private, decentralised and permission-less approach.</p> <h3>Public Key Encryption.</h3> <p>Rather than having an ‘account’ with email/username and password, and more often than not, some personal details such as telephone, and whatever personal data you wish to hand over. The protocol this on it's head and uses <a href="https://www.cloudflare.com/en-gb/learning/ssl/how-does-public-key-encryption-work/">public key encryption</a>. Thus all you need is the private key (which you keep safe), and you share your public key on the network. The use of public key encryption is a real strength, you own your identity, no authority has it.</p> <h3>Free for development:</h3> <p>NOSTR is open to extension and development. There is an array of clients, such as <a href="https://nostrapps.com/amethyst">Amethyst</a>, and <a href="https://damus.io/">Damus</a>, amongst other, https://nostr.com/clients Anyone can build on the protocol, apps, clients, relays and tools. Only imagination will limit it.</p> <h3>User control:</h3> <p>The user has control of their audience, having the ability to choose their preferred relays. Customise your feed to what you prefer. No central algorithm deciding what you are going to get. As mentioned with the public key encryption, It allows anonymity. It’s freedom to express, without bans, shadow bans, account locks or censorship.</p> <h3>Simple:</h3> <p>In a now fragmented world of social media, the most secure, user-centric, decentralised, simple, reliable platform will have a head start to other centralised or server controlled platforms. NOSTR gives freedom and control.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsgruvf7ev6xcqkyvk27zmwuexnmkh3dskqkgvlr7c3eqsv3lhjy4szyr2zmtrsjhyml3nnwugagryt3hrzj8wmpg6s9nk5c7k40uhddnt5jnueml6" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsgruvf7ev6xcqkyvk27zmwuexnmkh3dskqkgvlr7c3eqsv3lhjy4szyr2zmtrsjhyml3nnwugagryt3hrzj8wmpg6s9nk5c7k40uhddnt5jnueml6" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsgruvf7ev6xcqkyvk27zmwuexnmkh3dskqkgvlr7c3eqsv3lhjy4szyr2zmtrsjhyml3nnwugagryt3hrzj8wmpg6s9nk5c7k40uhddnt5jnueml6" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsgruvf7ev6xcqkyvk27zmwuexnmkh3dskqkgvlr7c3eqsv3lhjy4szyr2zmtrsjhyml3nnwugagryt3hrzj8wmpg6s9nk5c7k40uhddnt5jnueml6" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 45bda953:bc1e518e <div class="time" style="margin-left: auto;">2024-10-12 08:37:38</div> </div> <div> <p>This post will be edited and refined over time.</p> <p>Eschatology is the study of Biblical prophecy pertaining to what is commonly referred to as the end times. Bitcoin is the transformation of Austrian school economics theory into an efficient and applicable method driven by incentives and free market consensus mechanisms.</p> <p>What happens when eschatology is viewed through a Bitcoin world view?</p> <p>In this thesis I contend that it is possible and very probable that the consequences of what Satoshi Nakamoto created in Bitcoin and the prophecies surrounding Jesus Christ with regards to the second coming and a thousand year kingdom of peace and prosperity convalesce into a very compelling argument for Biblical prophecy fulfilment.</p> <p>...</p> <p>No one would argue that modern major banks are today more powerful than kings of old and governments are mere puppets to the sway that the banking empires hold over them.</p> <p>In Biblical prophecy when kings and powers are mentioned people rarely think of banking but nothing is comparable to the immense scale of the wealth, power and territory controlled directly or indirectly by banks.</p> <p>IMF, BIS, the FED and Blackrock are where the levers of power are pulled in the current dispensation. Governments restructure more frequently than these institutions whom endure and exercise unmerited influence over governments and the public they claim to represent.</p> <p>An excerpt from the King James Bible, Daniel chapter 2 describes prophetically the ages of man and its rotations of power.</p> <p>Interesting to note that it is symbolically portrayed in monetary/industrial metals. All used as tokens for trade, symbols of wealth and manufacture.</p> <p>Gold, silver, bronze, iron and clay. Gold has been a dominant symbol of power and wealth through millennia. Silver, brass and iron ores are mainly industrial metals although they both had prominent turns as coinage. Due to the debasement and concentration of gold specifically</p> <p>Clay on the other hand is only a symbol of power in construction and iron has never been used in construction to the extent it is in the 20th and 21st century. Skyscrapers are the symbols of money and power today, i.e. Big Banks and government buildings.</p> <p>Daniel Chapter 2:24–45</p> <p><strong>24Therefore Daniel went to Arioch, whom the king had appointed to destroy the wise <em>men</em> of Babylon. He went and said thus to him: “Do not destroy the wise <em>men</em> of Babylon; take me before the king, and I will tell the king the interpretation.”</strong></p> <p>25Then Arioch quickly brought Daniel before the king, and said thus to him, “I have found a man of the captives of Judah, who will make known to the king the interpretation.”</p> <p>26The king answered and said to Daniel, whose name <em>was</em> Belteshazzar, “Are you able to make known to me the dream which I have seen, and its interpretation?”</p> <p>27Daniel answered in the presence of the king, and said, “The secret which the king has demanded, the wise <em>men,</em> the astrologers, the magicians, and the soothsayers cannot declare to the king. 28But there is a God in heaven who reveals secrets, and He has made known to King Nebuchadnezzar what will be in the latter days. Your dream, and the visions of your head upon your bed, were these: 29As for you, O king, thoughts came <em>to</em> your <em>mind while</em> on your bed, <em>about</em> what would come to pass after this; and He who reveals secrets has made known to you what will be. 30But as for me, this secret has not been revealed to me because I have more wisdom than anyone living, but for <em>our</em> sakes who make known the interpretation to the king, and that you may know the thoughts of your heart.</p> <p>31“You, O king, were watching; and behold, a great image! This great image, whose splendor <em>was</em> excellent, stood before you; and its form <em>was</em> awesome. 32This image’s head <em>was</em> of fine gold, its chest and arms of silver, its belly and thighs of bronze, 33its legs of iron, its feet partly of iron and partly of clay. 34You watched while a stone was cut out without hands, which struck the image on its feet of iron and clay, and broke them in pieces. 35Then the iron, the clay, the bronze, the silver, and the gold were crushed together, and became like chaff from the summer threshing floors; the wind carried them away so that no trace of them was found. And the stone that struck the image became a great mountain and filled the whole earth.</p> <p>36“This <em>is</em> the dream. Now we will tell the interpretation of it before the king. 37You, O king, <em>are</em> a king of kings. For the God of heaven has given you a kingdom, power, strength, and glory; 38and wherever the children of men dwell, or the beasts of the field and the birds of the heaven, He has given <em>them</em> into your hand, and has made you ruler over them all — you <em>are</em> this head of gold. 39But after you shall arise another kingdom inferior to yours; then another, a third kingdom of bronze, which shall rule over all the earth. 40And the fourth kingdom shall be as strong as iron, inasmuch as iron breaks in pieces and shatters everything; and like iron that crushes, <em>that kingdom</em> will break in pieces and crush all the others. 41Whereas you saw the feet and toes, partly of potter’s clay and partly of iron, the kingdom shall be divided; yet the strength of the iron shall be in it, just as you saw the iron mixed with ceramic clay. 42And <em>as</em> the toes of the feet <em>were</em> partly of iron and partly of clay, <em>so</em> the kingdom shall be partly strong and partly fragile. 43As you saw iron mixed with ceramic clay, they will mingle with the seed of men; but they will not adhere to one another, just as iron does not mix with clay. 44And in the days of these kings the God of heaven will set up a kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. 45Inasmuch as you saw that the stone was cut out of the mountain without hands, and that it broke in pieces the iron, the bronze, the clay, the silver, and the gold — the great God has made known to the king what will come to pass after this. The dream is certain, and its interpretation is sure.”</p> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:700/1*4I01kq4ybEruX9dD0tZs4w.png" /></p> <p>I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time resources and energy.</p> <p>Skyscrapers and large construction are the modern symbols of money and power. Not so much kings, palaces and temples. The stone breaking the power of the statue has to break something contemporary other than kings and palaces if it is to be eschatological prophecy fulfilled in our time.</p> <p><a href="https://www.britannica.com/technology/cement-building-material/History-of-cement"><strong>https://www.britannica.com/technology/cement-building-material/History-of-cement</strong></a></p> <p>The invention of <a href="https://www.britannica.com/technology/portland-cement">portland cement </a>usually is attributed to <a href="https://www.britannica.com/biography/Joseph-Aspdin">Joseph Aspdin </a>of <a href="https://www.britannica.com/place/Leeds-England">Leeds</a>, <a href="https://www.britannica.com/place/Yorkshire-former-county-England">Yorkshire</a>, England, who in <strong>1824</strong> took out a patent for a material that was produced from a <a href="https://www.merriam-webster.com/dictionary/synthetic">synthetic </a>mixture of <a href="https://www.britannica.com/science/limestone">limestone </a>and <a href="https://www.britannica.com/science/clay-mineral">clay</a>.</p> <p><a href="https://www.thoughtco.com/how-skyscrapers-became-possible-1991649"><strong>https://www.thoughtco.com/how-skyscrapers-became-possible-1991649</strong></a></p> <p>Later, taller and taller buildings were made possible through a series of architectural and engineering innovations, including the invention of the first process to mass-produce steel.</p> <p>Construction of skyscrapers was made possible thanks to Englishman <a href="https://www.thoughtco.com/henry-bessemer-the-steel-man-4075538">Henry Bessemer</a>, (<strong>1856 to 1950</strong>) who invented the first process to mass-produce steel inexpensively.</p> <p><strong>You watched while a stone was cut out without hands,</strong></p> <p>No hands needed when the stone is an idea.</p> <p>As a thought experiment, imagine there was a base metal as scarce as gold but with the following properties:\ — boring grey in colour\ — not a good conductor of electricity\ — not particularly strong, but not ductile or easily malleable either\ — not useful for any practical or ornamental purpose\ \ and one special, magical property:\ — can be transported over a communications channel</p> <p><strong>Greshams Law illustrated in slow motion picture.</strong></p> <p><strong>1: The banks collapse. Being fundamentally weak because of zero reserve lending, any student of Austrian economics has been correctly predicting banking collapse, and have incorrectly been advocating gold as the solution to this collapse. Many of the big economies are valued through their housing market. Housing will be demonetised (Iron and clay economy) meaning shelter and property will become affordable to the average wage earner again. The large cement and iron structures become redundant. Everyone will work from home and a value to value economy will make banks seem like relics from an age of stupidity and evil.</strong></p> <p><strong>2: Industrial metal iron will not be for mega structures that house speculators and bookkeepers who have fiat jobs slaving for fiat money. Iron will be used to improve the lives of individuals. Iron as coinage is already demonetised.</strong> </p> <p><strong>3: Brass is demonetised as coinage only valuable in industry. Ammunition, music, plumbing etcetera</strong></p> <p><strong>4: Silver has been a terrible money throughout history and when the silver investors wake up to the fact that they are holding onto a redundant asset with zero monetary properties compared to the alternative they will dump crashing silver and reducing the prices of producing</strong></p> <p>Solder and brazing alloys, Batteries, Dentistry, TV screens, Smart Phones Microwave ovens, ad infinitum. To quote Jeff Booth. Prices always fall to the marginal cost of production.</p> <p><strong>5: Finally, the big boss Gold, people get excited about the Bitcoin exchange traded funds but it is nothing compared to the value proposition when gold pundits, large investment funds, governments and reserve banks finally realise that gold is worthless as money in this new dispensation.</strong></p> <p><strong>To illustrate the point more vividly.</strong></p> <p><strong>Ezekiel 7:19</strong></p> <p><strong>They shall cast their silver in the streets, and their gold shall be removed: their silver and their gold shall not be able to deliver them in the day of the wrath of the LORD: they shall not satisfy their souls, neither fill their bowels: because it is the stumblingblock of their iniquity.</strong></p> <p><strong>That will be the biggest rug pull the world have ever seen. In this future metals will be exclusively used for industrial use cases after being stripped of their monetary premium.</strong></p> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:700/1*a-S251iw1_D6onntqxRLug.png" /></p> <p>This collapse is something that happens slowly over a long period of time. More or less one hour.</p> <p>Revelation 18 verse 11–19 (The fall of Babylon)</p> <p><a href="https://biblehub.com/revelation/18-11.htm"><strong>11</strong></a> And the merchants of the earth shall weep and mourn over her; for no man buyeth their merchandise any more: <a href="https://biblehub.com/revelation/18-12.htm"><strong>12</strong></a> The merchandise of gold, and silver, and precious stones, and of pearls, and fine linen, and purple, and silk, and scarlet, and all thyine wood, and all manner vessels of ivory, and all manner vessels of most precious wood, and of brass, and iron, and marble, <a href="https://biblehub.com/revelation/18-13.htm"><strong>13</strong></a> And cinnamon, and odours, and ointments, and frankincense, and wine, and oil, and fine flour, and wheat, and beasts, and sheep, and horses, and chariots, and slaves, and souls of men. <a href="https://biblehub.com/revelation/18-14.htm"><strong>14</strong></a> And the fruits that thy soul lusted after are departed from thee, and all things which were dainty and goodly are departed from thee, and thou shalt find them no more at all. <a href="https://biblehub.com/revelation/18-15.htm"><strong>15</strong></a> The merchants of these things, which were made rich by her, shall stand afar off for the fear of her torment, weeping and wailing, <a href="https://biblehub.com/revelation/18-16.htm"><strong>16</strong></a> And saying, Alas, alas, that great city, that was clothed in fine linen, and purple, and scarlet, and decked with gold, and precious stones, and pearls! <a href="https://biblehub.com/revelation/18-17.htm"><strong>17</strong></a> For in one hour so great riches is come to nought. And every shipmaster, and all the company in ships, and sailors, and as many as trade by sea, stood afar off, <a href="https://biblehub.com/revelation/18-18.htm"><strong>18</strong></a> And cried when they saw the smoke of her burning, saying, What <em>city is</em> like unto this great city! <a href="https://biblehub.com/revelation/18-19.htm"><strong>19</strong></a> And they cast dust on their heads, and cried, weeping and wailing, saying, Alas, alas, that great city, wherein were made rich all that had ships in the sea by reason of her costliness! for in <strong>one hour</strong> is she made desolate.</p> <p>TLDR - No more money printer go BRRR. means death to the bourgeoisie cantillionaire class.** </p> <p><strong>Is it realistic to assume that all the worlds monetised industries collapse to fair value?</strong></p> <p>Coming back to eschatology, 2 Peter 3:8</p> <p>But, beloved, be not ignorant of this one thing, that one day <em>is</em> with the Lord as a thousand years, and a thousand years as one day.</p> <p>Eschatology students use this verse to speculatively project the fulfilment of Biblical prophecies with regards to their time occurrence. Now let’s apply this to Babylon falling in one hour.</p> <p>1000 (one day) divided by 24 (hours) equals 41,6 years (one hour)</p> <p>Since the first block was mined in January 2009 you add 41,6 years you get 2050 a.d</p> <p>But contemporary sources must reflect this probability if it is a good theory.</p> <p><a href="https://web.archive.org/web/20221025093858/https://www.newsbtc.com/news/50-of-population-to-use-bitcoin-by-2043-if-crypto-follows-internet-adoption/">https://web.archive.org/web/20221025093858/https://www.newsbtc.com/news/50-of-population-to-use-bitcoin-by-2043-if-crypto-follows-internet-adoption/</a></p> <p>If the banking system is first to collapse or show cracks we can give it +- 10 years and we are already 14 years in since (<strong>Genesis Block</strong>) the stone struck the feet. People are slow to see the reality of the world they are living in. If all this is accurate then the world banking system is doomed.</p> <p><a href="https://www.youtube.com/watch?v=exK5yFEuBsk">https://www.youtube.com/watch?v=exK5yFEuBsk</a></p> <p>Regards</p> <p>Echo Delta</p> <h1>bitbib</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsf8r9rlfkhfz58y9srvsyhhwur5ykqjfpyt5gthdw85c4emvc3pngzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcuerrrxt" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsf8r9rlfkhfz58y9srvsyhhwur5ykqjfpyt5gthdw85c4emvc3pngzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcuerrrxt" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsf8r9rlfkhfz58y9srvsyhhwur5ykqjfpyt5gthdw85c4emvc3pngzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcuerrrxt" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsf8r9rlfkhfz58y9srvsyhhwur5ykqjfpyt5gthdw85c4emvc3pngzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcuerrrxt" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ df8f0a64:057d87a5 <div class="time" style="margin-left: auto;">2024-10-10 15:18:39</div> </div> <div> <h2>書き散らす動機</h2> <p>残暑続きからの急な気温低下で鼻炎がひどくなる今日この頃、皆様お元気でしょうか</p> <p>株主への抗議のために退職してから2ヶ月半、流石に暇を持て余してきました 時間がある上に能動的に働く気も起きず、ひたすらボーッとしたりうねうね考え事をする日々です 幸いにして人生も折り返しにさしかかる頃になり、時折「今、人生が終わって構わないのでは?」というようなことも考えたりします (鬱病既往歴ありますが私は元気です)</p> <p>子どものお迎えを終えて、いつもどおり夕食をとり、またうねうねしているうちに ふと、6年前の年末に急死された、仕事でお世話になったTさんのことを思い出しました</p> <p>子を寝かしつけてもまだ頭の中をぐるぐるしていたので、ここに吐き出してすっきりしようという魂胆です</p> <h2>Tさんとの出会い</h2> <p>私のキャリアの(ほぼ)スタートはVC(ベンチャーキャピタル)でした 誰のせいでもないとある経緯もあり、周囲からは警戒され避けられ、わずか6年ではありますが、 インナーサークルに入り込めない時期を過ごし、当時の上司と二人、とにかくやれることをやり続ける毎日でした</p> <p>いつものようにピッチイベントに参加しているとき、近くの席にいたスーツ姿の3人組と目が一瞬合います</p> <p>「事業会社の人だ」</p> <p>協調投資やファンド出資のきっかけを掴むべく、その3人に話かけます</p> <p>「よろしければ弊社投資先のご紹介や御社の...」</p> <p>ひととおりの挨拶を済ませ、この人たちにも避けられるんだろうと思いながらも要件を切り出します</p> <p>「是非やりましょう」</p> <p>いつもとは違う嬉しい返事をくれたのがTさんでした</p> <h2>面倒見の良い他社の先輩</h2> <p>そのときの3人組であるMさん・Iさん・Tさんには、私の仕事人生の中で最もお世話になったと言っても過言ではありません</p> <p>ファンドの営業を受けていただき、協調投資を行い、VCからの転職後にも協業相手として他部署のキーマンをご紹介いただき...</p> <p>社会人になったばかりの私の、今思い返せば恥ずかしい(部下がこんな提案したら卒倒する)レベルの提案を、 誰もが知る一流企業の多忙な役職持ちであるにも関わらず、毎回一時間も割いて丁寧に対応してくださる心の広い方でした</p> <p>当時、VCと接点をもつような事業会社の対スタートアップ部隊は、本業でご活躍されている方が兼任で取り組むパターンが多く、Mさん・Iさん・Tさんももちろんそう</p> <p>その後も昇進され、最後には本社の取締役に。今年遂に退任され、所謂「あがり」でしょうか、子会社の取締役に異動 長い社会人人生をほぼ走りきり、有終の美を飾ろうとする時期にさしかかっています</p> <p>でもTさんはそこにはいません</p> <h2>残される側</h2> <p>冒頭触れたとおり、Tさんは6年前のこの時期に急死されました 死因については、Tさんのご友人がFBに投稿していた文章を読んでも、Iさんに聞いてもわからない</p> <p>悲しいかな、四十年近く生きていると、死因が明かされない理由がわかるようになる機会が一度や二度はあります Tさんもおそらくそうだったのでしょう</p> <p>直前まで、Iさんと一緒にベイエリアに出張され、楽しそうなコメントと共に写真を投稿されていたのに 晩婚なのか再婚なのか、とにかくご結婚されて一年ちょっと。お子様も生まれたばかりだったのに Tさんは近い人間に心中を隠して、静かにこの世を去りました</p> <p>あなたの快い返事に、どれほど私が救われたのか 転職後の提案のとき、受付で顔を出してすぐ「元気?」と声をかけてくださったことがどれほど私を安心させてくれたか あなたが声をかけてくれる度、私の社会人としての成果が生まれたことに、私は十分に感謝を伝えられていません</p> <h2>まだしばらく残る理由</h2> <p>振り返って、Tさんのように誰かの人生をenhanceできたのか?と自分に問うと、まだできたとは思えません。残念ですが</p> <p>今ここで死んでも私は構わないけど、まだもうちょっと頑張るべきかな、老いてから誰かに感謝をしてもらうまで生きてみてもいいかな</p> <p>そうふと思い直しているうちに日付が変わりました</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9utd4lcvqzt9amh687un7a75fr0jev7xctskgtqgd3d6f5aq0srgzyr0c7znypsll6z0zjwve4narn8g9wny9q87d408v55rjacs90kr620q8zjv" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9utd4lcvqzt9amh687un7a75fr0jev7xctskgtqgd3d6f5aq0srgzyr0c7znypsll6z0zjwve4narn8g9wny9q87d408v55rjacs90kr620q8zjv" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9utd4lcvqzt9amh687un7a75fr0jev7xctskgtqgd3d6f5aq0srgzyr0c7znypsll6z0zjwve4narn8g9wny9q87d408v55rjacs90kr620q8zjv" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9utd4lcvqzt9amh687un7a75fr0jev7xctskgtqgd3d6f5aq0srgzyr0c7znypsll6z0zjwve4narn8g9wny9q87d408v55rjacs90kr620q8zjv" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ a012dc82:6458a70d <div class="time" style="margin-left: auto;">2024-10-24 02:48:43</div> </div> <div> <p><strong>Table Of Content</strong></p> <ul> <li> <p>Project A: Solar-Powered Mining Farms</p> </li> <li> <p>Project B: Hydroelectricity-Powered Mining</p> </li> <li> <p>Project C: Waste Heat Recovery</p> </li> <li> <p>Project D: Energy-Efficient Mining Hardware</p> </li> <li> <p>Project E: Proof of Stake (PoS) Consensus</p> </li> <li> <p>Project F: Carbon Offset Initiatives</p> </li> <li> <p>Conclusion</p> </li> <li> <p>FAQ</p> </li> </ul> <p>The rising popularity of Bitcoin has raised concerns about its environmental impact. Traditional Bitcoin mining processes consume vast amounts of energy, contributing to carbon emissions and environmental degradation. However, there is a growing movement towards sustainable mining practices that aim to minimize the ecological footprint of cryptocurrency production. In this article, we will delve into the world of green Bitcoin mining and highlight six exciting projects that are leading the charge towards sustainable practices.</p> <p><strong>1. Project A: Solar-Powered Mining Farms</strong></p> <p>With solar energy being one of the cleanest and renewable sources available, Project A aims to harness its power for Bitcoin mining. By setting up solar-powered mining farms, this project significantly reduces reliance on fossil fuels and minimizes carbon emissions. Additionally, excess solar energy can be stored for later use, making mining operations more resilient and sustainable.</p> <p><strong>2. Project B: Hydroelectricity-Powered Mining</strong></p> <p>Project B taps into the potential of hydroelectricity, utilizing the power of flowing water to generate electricity for Bitcoin mining. Hydroelectric power is not only renewable but also provides a consistent and reliable energy source. By harnessing this form of energy, Project B aims to achieve sustainable mining operations while reducing the carbon footprint associated with traditional mining methods.</p> <p><strong>3. Project C: Waste Heat Recovery</strong></p> <p>Project C focuses on utilizing waste heat generated from industrial processes for Bitcoin mining. By capturing and repurposing this excess heat, mining operations become more energy-efficient and environmentally friendly. This approach not only reduces carbon emissions but also maximizes the use of resources that would otherwise go to waste, promoting a circular economy.</p> <p><strong>4. Project D: Energy-Efficient Mining Hardware</strong></p> <p>Project D tackles the sustainability challenge by developing energy-efficient mining hardware. By optimizing the design and performance of mining equipment, this project aims to reduce energy consumption without compromising mining capabilities. The use of advanced technologies and materials enables miners to achieve higher processing power with lower energy requirements, leading to more sustainable mining operations.</p> <p><strong>5. Project E: Proof of Stake (PoS) Consensus</strong></p> <p>Project E explores an alternative consensus mechanism called Proof of Stake (PoS), which requires significantly less energy compared to the traditional Proof of Work (PoW) algorithm. Instead of relying on computational power, PoS validates transactions based on the amount of cryptocurrency held by a participant. This shift in consensus mechanism can drastically reduce energy consumption and make Bitcoin mining more environmentally friendly.</p> <p><strong>6. Project F: Carbon Offset Initiatives</strong></p> <p>Project F recognizes that some carbon emissions may still be unavoidable in the mining process. To mitigate this impact, they focus on supporting carbon offset initiatives. By investing in projects that reduce or remove carbon dioxide from the atmosphere, such as reforestation or renewable energy projects, Project F aims to offset the environmental impact of Bitcoin mining, making it more sustainable in the long run.</p> <p><strong>Conclusion</strong></p> <p>As the demand for Bitcoin continues to rise, so does the need for sustainable mining practices. The projects mentioned above represent just a glimpse of the innovative solutions being developed to make crypto mining more environmentally friendly. By harnessing renewable energy sources, optimizing mining equipment, and exploring alternative consensus mechanisms, these projects are leading the race for sustainable mining. Through their efforts, they are shaping a future where Bitcoin and other cryptocurrencies can coexist harmoniously with a greener planet.</p> <p><strong>FAQ</strong></p> <p><strong>What is sustainable mining?</strong> Sustainable mining refers to the practice of conducting mining operations while minimizing the negative environmental impact. It involves adopting strategies and technologies that reduce energy consumption, carbon emissions, and other ecological footprints associated with mining activities.</p> <p><strong>How does solar-powered mining work?</strong> Solar-powered mining harnesses the energy from the sun using solar panels to generate electricity. This clean and renewable energy source powers the mining equipment, reducing reliance on fossil fuels and minimizing carbon emissions.</p> <p><strong>What is the difference between Proof of Stake (PoS) and Proof of Work (PoW)?</strong> Proof of Stake (PoS) and Proof of Work (PoW) are two different consensus mechanisms used in blockchain networks. PoW relies on computational power to validate transactions, while PoS validates transactions based on the amount of cryptocurrency held by participants. PoS requires significantly less energy compared to PoW, making it more environmentally friendly.</p> <p><strong>How can waste heat recovery be used for mining?</strong> Waste heat recovery involves capturing and repurposing excess heat generated from industrial processes. This heat is used to power mining equipment, making the mining operations more energy-efficient and sustainable. It reduces the need for additional energy sources and minimizes waste.</p> <p><strong>That's all for today</strong></p> <p><strong>If you want more, be sure to follow us on:</strong></p> <p><strong>NOSTR: croxroad@getalby.com ** </strong>X: <a href="https://x.com/croxroadnewsco">@croxroadnews</a>**</p> <p><strong>Instagram: <a href="https://www.instagram.com/croxroadnews.co/">@croxroadnews.co</a></strong></p> <p><strong>Youtube: <a href="https://www.youtube.com/@croxroadnews">@croxroadnews</a></strong></p> <p><strong>Store: https://croxroad.store</strong></p> <p><strong>Subscribe to CROX ROAD Bitcoin Only Daily Newsletter</strong></p> <p><strong>https://www.croxroad.co/subscribe</strong></p> <p><em>DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.</em></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9hv6weduzlywcctln8awkgfr5vr58uk3fmc5ffkp974xnlsjvflczyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns6ut432k" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9hv6weduzlywcctln8awkgfr5vr58uk3fmc5ffkp974xnlsjvflczyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns6ut432k" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9hv6weduzlywcctln8awkgfr5vr58uk3fmc5ffkp974xnlsjvflczyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns6ut432k" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9hv6weduzlywcctln8awkgfr5vr58uk3fmc5ffkp974xnlsjvflczyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns6ut432k" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ bcea2b98:7ccef3c9 <div class="time" style="margin-left: auto;">2024-10-20 17:33:12</div> </div> <div> <p><img alt="" src="https://m.stacker.news/58647" /></p> <p>originally posted at https://stacker.news/items/732719</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0kc2en665pmx2ckyel6rxeyg9nfj9at56w40y0jrgsm226lpltnszyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfxxq0l" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0kc2en665pmx2ckyel6rxeyg9nfj9at56w40y0jrgsm226lpltnszyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfxxq0l" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0kc2en665pmx2ckyel6rxeyg9nfj9at56w40y0jrgsm226lpltnszyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfxxq0l" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0kc2en665pmx2ckyel6rxeyg9nfj9at56w40y0jrgsm226lpltnszyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfxxq0l" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ bcea2b98:7ccef3c9 <div class="time" style="margin-left: auto;">2024-10-20 15:50:27</div> </div> <div> <p>The Bitcoin space is constantly evolving with new ideas, technologies, and innovations. From Lightning Network advancements to privacy improvements, there’s always something happening that could change the future of Bitcoin.</p> <p>What do you think is the most exciting or innovative development in Bitcoin right now? I've been following a lot of privacy related advancement in Bitcoin and LN and look forward to learning about more solutions.</p> <p>originally posted at https://stacker.news/items/732534</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsrak0g8kx2y974a0algec89dxrfadyahtzl70msjthu0jwc2andfqzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujeukf6m" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsrak0g8kx2y974a0algec89dxrfadyahtzl70msjthu0jwc2andfqzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujeukf6m" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsrak0g8kx2y974a0algec89dxrfadyahtzl70msjthu0jwc2andfqzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujeukf6m" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsrak0g8kx2y974a0algec89dxrfadyahtzl70msjthu0jwc2andfqzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujeukf6m" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 2ec0583a:63f20df5 <div class="time" style="margin-left: auto;">2024-10-11 13:19:29</div> </div> <div> <p><em>I liked Twitter.</em> News, politics, artists, memes, controversial thoughts that people discuss longer than it deserves. That Twitter wasn't what X is now. Verification doesn't mean anything, it's just an algorithm boost everybody can buy. Crowds of bots leave random overcompressed jpegs in replies to get more attention to get more money for its owner. Somehow it's normal there to want entire nation dead.</p> <p>I wish it was easy to leave, but it still has hundreds of millions active users. It still has all the memes we like, the controversial thoughts people discuss too much, all the big companies and politicians have to have an account.</p> <p>I checked out the biggest alternatives to decide where to go. No complicated tech terms ahead, I looked at them as a regular user who just wants to have fun.</p> <p><strong>TL;DR</strong>: Twitter/X is still the most effective and active platform, but if you really want to change it you should take part in transition to another platform and not wait for more people to be there.</p> <h2>Nostr</h2> <p>Decentralized, censorship resistant due to its nature. Of course, it's not perfect and <a href="https://habla.news/fiatjaf/87a208d9">is quite far from reaching its true potential</a>. Out of all the alternatives, Nostr might have the most complicated registration. Do regular users really need to think about public and private keys? Yes, yes, I get it — users <em>have</em> to keep in mind their privacy if they want to have it. But you have to read at least something to understand what you're doing, which is automatically more difficult than simply press "Sign up". And then you have to choose between web clients... And then Android/iOS clients... And some of them might be buggy on your device, so you switch to another client... The flow could be better, but Nostr is a new social network, it keeps improving every day.</p> <p>After all this, you open an app and see... <em>Bitcoins, AI images, jokes about Elon Musk.</em> And some anarchists. 90% of what you see is people praising Bitcoin. The universal social network protocol turns out to has a pretty narrow view. I guess, the feature of attaching your cryptocurrency wallet made it extremely popular amongst Bitcoiners, but why is it the biggest — and probably the only — community there?</p> <p>How does one find another community? Hashtags don't seem to work, perhaps because of tiny size of non-Bitcoin communities. Trending is all Bitcoin. I didn't even know it's possible to discuss something that long.</p> <p>It's close to being decentralized and censorship resistant; you can write and read Twitter-like notes or long posts — whatever you like! But I don't feel comfortable because I'm an alien without a Bitcoin wallet here. It could be a great place for everybody, but now it lacks diversity. It may not even want to be universal. Maybe it's the Bitcoin network and that's fine.</p> <h2>Mastodon</h2> <p>Decentralized, not so censorship resistant but way better than having everything on one company's servers. 500 symbols per post is more than Twitter, but less than long format, it's somewhere in-between. It literally has no feed algorithm, so you have to find people and hashtags you want to follow, and Mastodon won't help. You don't know what it has in the first place? Bad for you.</p> <p>Sooner or later your feed start to look like one you're actually want to read. And that's when I started to like Mastodon. The UI is neat, everything is in its place and works as expected — you can tell the social network has been here for a while. <a href="https://www.itworldcanada.com/article/mastodon-passes-the-10-million-account-milestone/533720">There are more than 10 million users as of 2023</a>, and it still grows slowly. Mastodon is mature but fresh, and it does scare you away at first glance. Every discussion is serious for some reason, and I'm yet to discover meme accounts to follow. Mastodon is probably the only decentralized social network on this list which has at least some officials registered here.</p> <h2>Bluesky</h2> <p>If you want to move back in time to see the old Twitter again — take a look at Bluesky. Everything is <em>literally</em> the same as Twitter, and it actually might be both a blessing and a curse. It seems to lack its identity and feels not like something new, but like uninhabited, decentralized Twitter.</p> <p>There is a feed algorithm that shows you a mix of viral and recent posts, so you don't have a desert feeling (which sometimes occurs in Mastodon). Bluesky was launched in open access to the public in February 2024 and has <a href="https://bsky.app/profile/bsky.app/post/3l4cilpvtr22w">reached 10 millions</a> already. There is nothing serious about it — memes, shitposts, random thoughts put in 300 symbols. People barely use hashtags here, one would probably find something interesting or funny just scrolling the feed.</p> <h2>Threads</h2> <p>It's weird and soulless. You can't create a Threads account without an Instagram one, so you <em>have</em> to use both while <a href="https://www.facebook.com/privacy/policy/">Meta collects a huge amount of data about you</a>. It just doesn't feel great.</p> <p>You can't ignore the power of a big corporation — the experience is smooth, the UI is nice, and I personally like the little curl every thread has. And what do you see scrolling the feed? AI images and ridiculously serious inspirational quotes with a beach at the background. They're all different, but none of them makes sense. Do people actually discuss something? Not really. You just post pretty images just like you did on Instagram. And those are beautiful, you can't take that from Instagram userbase, so your feed looks absolutely incredible. And empty. There is nothing wild — no hot takes, no fresh jokes, everything is sterile and correct. It feels dead despite having <a href="https://www.threads.net/@zuck/post/C89oeSORn81">over 175 million monthly active users</a>.</p> <p>UPD: <a href="https://techcrunch.com/2024/02/09/instagram-and-threads-will-no-longer-proactively-recommend-political-content/">Threads decided you don't want to read any politics</a> and then <a href="https://www.theverge.com/2024/10/9/24266096/instagram-threads-moderation-account-post-deleted-limited">disabled a lot of accounts because their AI moderation went insane, apparently</a>.</p> <p>UPD2: <a href="https://www.theverge.com/2024/10/7/24264382/threads-engagement-bait-problem-mosseri-meta">Threads now has an engagement bait problem.</a></p> <h2>Tumblr</h2> <p>Yeah, yeah, I know, but hear me out. Tumblr looks interesting for creative communities where people have fun. It goes from the cringiest actor gifs to a detailed book subplot analysis. Your posts don't disappear in the void thanks to hashtag search. There is also a feed algorithm to spend time. If you're really into discussing weirdest story and fanfiction ideas, that's the default social network for you.</p> <p><em>But.</em></p> <p>It's also owned by a company that can do everything it wants. <a href="https://www.theverge.com/2018/12/3/18123752/tumblr-adult-content-porn-ban-date-explicit-changes-why-safe-mode">And it actually did</a>.</p> <p>UPD: I'd been using Tumblr for a week, wrote two posts, liked and reposted a few times, and then my account got terminated for seemingly no reason. Maybe they found something wrong in those two posts, I don't know. I'm not that type of person who would publish anything even remotely aggressive, both posts were about SFW writing tropes.</p> <h2>Conclusion</h2> <p>There is no perfect platform to move to. If one of them had a clear advantage and/or a big userbase, many people would move there with no hesitation. But the situation is different, there is no obvious preferable social network to stick with. The vast majority stays on X trying to ignore the weird stuff. If we really want to have better and safer social networks, we should encourage competition and migration. All the X alternatives lack communities people would like to join, whereas it should be friendly and welcoming to all. <em>Not the criminals, obviously.</em></p> <p>My personal favorite is Nostr, but right now Bluesky seems the most convenient option.</p> <p>P.S. Sorry for mistakes, English is not my native language. This post is not supposed to be some serious analysis, it's just another internet rant.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsgv4uthpxhnuhs6v9mfk24a8x3zx39s4adyvlx52u0wtfmyjt2txszyqhvqkp60k4k6llwxths65japjj622jnt7exajyzwfvja7mr7gxl20d4dxp" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsgv4uthpxhnuhs6v9mfk24a8x3zx39s4adyvlx52u0wtfmyjt2txszyqhvqkp60k4k6llwxths65japjj622jnt7exajyzwfvja7mr7gxl20d4dxp" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsgv4uthpxhnuhs6v9mfk24a8x3zx39s4adyvlx52u0wtfmyjt2txszyqhvqkp60k4k6llwxths65japjj622jnt7exajyzwfvja7mr7gxl20d4dxp" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsgv4uthpxhnuhs6v9mfk24a8x3zx39s4adyvlx52u0wtfmyjt2txszyqhvqkp60k4k6llwxths65japjj622jnt7exajyzwfvja7mr7gxl20d4dxp" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ c69b71dc:426ba763 <div class="time" style="margin-left: auto;">2024-10-10 09:05:29</div> </div> <div> <h2>Chef's notes</h2> <p>This cashew blue cheese is a true plant-based delight, delivering the rich, tangy flavours you’d expect from traditional blue cheeses like Roquefort or Gorgonzola. The fermentation process, with the help of «Penicillium Roqueforti», creates a beautifully marbled, creamy cheese that’s both bold and complex. It’s a labor of love that rewards your patience with an unforgettable vegan cheese experience! Whether enjoyed on crackers, in salads, or simply on its own, this cheese will elevate any dish with its unique flavour profile.</p> <p>Note 1: For this recipe you need parchment paper, a potent blender, glass jars with lid and two cheesecloths.</p> <p>Note 2: Always use very clean tools, and avoid touching with your fingers or tasting with them while working on the cheese!</p> <h2>Details</h2> <ul> <li>⏲️ Prep time: 4-5 weeks</li> <li>🍳 Cook time: 0</li> <li>🍽️ Servings: Two small cheese loaves (2x 10-12 cm diameter)</li> </ul> <h2>Ingredients</h2> <ul> <li>300g raw cashews </li> <li>3 tbsp water </li> <li>3 tbsp kefir, kombucha or rejuvelac </li> <li>2 tbsp coconut oil (raw, unrefined) </li> <li>1-4 capsules vegan probiotics </li> <li>1/2 tsp Himalayan salt (iodine-free, no additives) </li> <li>1/16 tsp «Penicillium Roqueforti» (blue cheese mold culture) </li> </ul> <h2>Directions</h2> <ol> <li>Day 1: Soak 300g of cashews overnight in water.</li> <li>Day 2: Rinse the soaked cashews thoroughly and let them drain well. </li> <li>In a high-speed blender, combine the cashews, 3 tbsp of water, 3 tbsp kefir or rejuvelac, and 2 tbsp coconut oil. Blend until the mixture is smooth and creamy.</li> <li>Add 1-4 capsules of vegan probiotics, 1/2 tsp Himalayan salt (free of iodine and additives), and blend again briefly. </li> <li>Add a pinch (about 1/16 tsp) of «Penicillium Roqueforti» powder (blue cheese culture) and give it another quick mix. </li> <li>Transfer the cashew mixture to a glass container, leaving the lid lightly on top (do not seal it completely) and store in a warm place, ideally in your kitchen, for 24 hours to ferment.</li> <li>Day 3: Divide the fermented cashew mixture into two smaller glass containers lined with cheesecloth. Press the mixture down firmly to eliminate air pockets.</li> <li>Store in a cool place (12-14°C / 53-57°F), ideally in a wine fridge.</li> <li>Day 4: Remove the cheese from the containers, take off the cheesecloth, and turn the cheese onto parchment paper.</li> <li>Sprinkle salt all over the cheese, ensuring it is evenly coated.</li> <li>Cover the cheese with larger glass bowls, ensuring that air can flow from underneath, and return to the wine fridge or the cool storage area.</li> <li>Days 4-7: Turn the cheese daily onto fresh parchment paper to maintain its texture.</li> <li>Day 7 or 8: Pierce the cheese with a thicker wooden skewer to create holes, allowing oxygen to reach the center, encouraging the blue mold to grow throughout the cheese, not just on the surface.</li> <li>Alternatively, crumble the cheese completely and then press it back into shape to ensure oxygen distribution.</li> <li>Days 8 toaround 12 or 15: Once the blue mold has fully developed around and inside the cheese, wrap the cheese in parchment paper, place it in a wooden cheese box, and then wrap it in a cloth bag.</li> <li>Transfer to a regular fridge to age for another 2-3 weeks or even several months, depending on your desired strength of flavour.</li> </ol> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvjpr42t7rnmvr45u06qm7fn47uqxyg9aqjtg7fu3a5fgysfn3t7qzyrrfkuwu2e8acdg2eh0lj20jt4eq9tq5wry8fzrq30tdnrjzdwnkxalkvee" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvjpr42t7rnmvr45u06qm7fn47uqxyg9aqjtg7fu3a5fgysfn3t7qzyrrfkuwu2e8acdg2eh0lj20jt4eq9tq5wry8fzrq30tdnrjzdwnkxalkvee" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvjpr42t7rnmvr45u06qm7fn47uqxyg9aqjtg7fu3a5fgysfn3t7qzyrrfkuwu2e8acdg2eh0lj20jt4eq9tq5wry8fzrq30tdnrjzdwnkxalkvee" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvjpr42t7rnmvr45u06qm7fn47uqxyg9aqjtg7fu3a5fgysfn3t7qzyrrfkuwu2e8acdg2eh0lj20jt4eq9tq5wry8fzrq30tdnrjzdwnkxalkvee" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 1bda7e1f:bb97c4d9 <div class="time" style="margin-left: auto;">2024-10-10 03:05:10</div> </div> <div> <h3>Tldr</h3> <ul> <li>Nostr identities can be linked to a third-party service</li> <li>You can set up that verification at your own domain, and</li> <li>You can also set up your own Lightning Address at your own domain</li> <li>These both require files in the .well-known directory on your domain</li> <li>You can set these up together, quickly and for free, with Sveltekit and Vercel</li> <li>Now I am identified and can receive payments with my username "rb" at my own domain "rodbishop.nz"</li> </ul> <h3>Getting .Well-Known</h3> <h5>For your npub</h5> <p>The first step in setting up a Nostr profile is to get your keys. I wrote about it in this article, <a href="nostr:naddr1qvzqqqr4gupzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyesvp3njy">Mining Your Vanity Pubkey</a>. </p> <p>These keys represent your identity and are issued by you, not a third-party issuer. This is good for personal ownership, but creates an issue around identification. </p> <p>If you have an ID issued by an issuer, I can ask the issuer to confirm that you are who you say you are. But with a Nostr npub, which has no issuer, how do I confirm that an npub which claims to be yours, is in fact yours?</p> <p>Nostr allows you to link your npub to a username and to a third-party service of your choice to help in confirming that your npub is really yours (It is <a href="https://github.com/nostr-protocol/nips/blob/master/05.md">documented in NIP-05</a>).</p> <p>Normal users can use a service like nostrplebs.com and to set up a username very quickly and easily. However, it is also possible to set up your own identification that relates your username to your npub using any domain you own. </p> <p>In my view having your username tied to your own domain is better branding, and more self-ownership, and so that's what I'll set up using my domain rodbishop.nz.</p> <h5>For your lightning address</h5> <p>Nostr has integrated payments which allow people to send you Bitcoin over the Lightning network the same way they would send you an email. I wrote about it in <a href="nostr:naddr1qvzqqqr4gupzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmscnxk5d">Setting up Payments on Nostr</a>.</p> <p>The path I took in setting up my lightning address was to use Alby, and with an Alby Account you automatically get a Lightning Address at getalby.com.</p> <p>Normal users can use that Lightning Address just fine. However, it is also possible to set up your own Lightning Address which will forward payments to your Lightning Wallet using any domain you own.</p> <p>Similar to with NIP-05, my view is having your Lightning Address tied to your own domain is better branding, and so again that's what I'll set up.</p> <p>Both of these tasks use the .well-known folder on your web server.</p> <h3>Preparing .Well-Known with Sveltekit</h3> <p>There are many ways to do this. NVK published a very simple method using Github pages which is free and which you can <a href="https://nvk.org/n00b-nip5">read about on his blog</a>.</p> <p>For me, I will set up .well-known using Sveltekit and Vercel. I have been learning Sveltekit and Nostr together, thanks to fantastic tutorials by <a href="https://www.youtube.com/channel/UCwjWOu_QJCjusHKlOo9_52w">Jeff G on his Youtube</a>.</p> <p>Using Sveltekit and Vercel to set up Nostr NIP-05 and Lightning URLs on your own domain is easy and free.</p> <h5>Create a new project</h5> <p>To start, create a new Sveltekit project with NodeJS and Node Package Manager using the code documented on the <a href="https://kit.svelte.dev/">Sveltekit website</a>.</p> <p><code>npm create svelte@latest my-app cd my-app npm install npm run dev -- --open</code></p> <p>Sveltekit contains many convenient short-cuts for web hosting, and one of them is the file structure. The structure contains an <code>/src</code> folder to contain javascript files to build complex applications, and a <code>/static</code> folder to contain other simple static files which need to be hosted at the domain. It is this <code>/static</code> folder you'll be using for now.</p> <h5>NIP-05 identification with nostr.json</h5> <p>For your NIP-05 identification, you need to create the folder and file for /.well-known/nostr.json as follows–</p> <p><code>static └── .well-known └── nostr.json</code></p> <p>In that file, you will use some JSON to link a username to a hex-format public key, which will enable Nostr apps to confirm that the username relates to the key. In my case, I create a link between the username "rb" and the public key formatted in hex format "1bda7e1..."–</p> <p><code>{ "names": { "rb": "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" } }</code></p> <p>That's it!</p> <h5>Lightning Address forwarding with lnurlp</h5> <p>For your Lightning Address, you need to create the folder and file for /.well-known/lnurlp/your-username as follows, replacing the "your-username" text with your username (in my case, "rb") –</p> <p><code>static └── .well-known └── lnurlp └── your-username</code></p> <p>In that file, you create a link between the username on your domain, and the provider of your Lightning service (in my case, Alby). Alby provides a helpful guide on how to do this, which you can <a href="https://guides.getalby.com/user-guide/alby-account-and-browser-extension/alby-account/use-your-lightning-address/own-domain">read on the Alby site</a>.</p> <ul> <li>Visit the Alby page for your Lightning Address which Alby hosts</li> <li>Copy that text across to the new file you have created</li> </ul> <p>That's it! These files are now ready and can be hosted anywhere.</p> <h3>Hosting .well-known with Vercel</h3> <p>I chose Vercel to host with because it was very easy to use, and provides all the hosting I need for free. To deploy, you first create a Github repository for my Sveltekit project, and then you set up Vercel to deploy every push by default.</p> <p>At a high level – </p> <ol> <li>Set up a Github repository</li> <li>Push your project to Github</li> <li>Sign up for Vercel </li> <li>Link your Vercel to your Github, and Vercel will then show all your Git repositories</li> <li>Import your project from Github, and Vercel will deploy it to a Vercel.com domain</li> </ol> <p>Once your project has deployed to Vercel, you will be given a deployment URL, and you can test to see that your static .well-known files are successfully online.</p> <ul> <li>E.g. I was given https://rodbishop-mw64m8ylx-rods-projects-c9b67f57.vercel.app</li> <li>I can add /.well-known/nostr.json or /.well-known/lnurlp/rb to the domain and view my files</li> </ul> <p>Now that the files are deployed, you need to link them to your domain. At a high level –</p> <ol> <li>Get your domain (buy one if you need to)</li> <li>In Vercel, navigate to your project’s settings and add your domain. Vercel will provide DNS records for you to add to your domain registrar</li> <li>In your domain's DNS settings add those records as an A record to your root domain</li> </ol> <p>Your .well-known files are now hosted in Vercel and pointed at your domain. </p> <h5>Setting up CORS in Vercel</h5> <p>You need to tell Vercel to allow third-party applications to access those files, by enabling CORS ("Cross-Origin Resource Sharing"). Vercel has good <a href="https://vercel.com/guides/how-to-enable-cors">CORS documentation on their website</a>. </p> <p>To set this up, return to your project, and in the root folder create a new file named vercel.json. This file will tell Vercel to allow third-party applications to access your nostr.json file. Add the following to it</p> <p><code>{ "headers": [ { "source": "/.well-known/nostr.json", "headers": [ { "key": "Access-Control-Allow-Origin", "value": "*" }, { "key": "Access-Control-Allow-Methods", "value": "GET, OPTIONS" }, { "key": "Access-Control-Allow-Headers", "value": "Content-Type" } ] } ] }</code></p> <p>Then– - Push to Github - Vercel will deploy the push automatically by default</p> <p>That's it. Your .well-known files are able to be reached by every Nostr app.</p> <h5>Testing it with your Nostr profile</h5> <p>Now that this is hosted at your domain, you can connect your Nostr profile. In any Nostr client, visit your profile page and edit, then update your NIP-05 and Lightning Address fields.</p> <p>Once your client has refreshed, give it a test</p> <ul> <li>Your NIP-05 identity should show a "success" type icon, rather than a "fail" type icon (what icons depends on the client you're using, but think "green tick" rather than "red cross")</li> <li>Your Lightning Address should simply work–get someone to send you a payment to your new Address and it should go through successfully and appear in your wallet.</li> </ul> <h3>Things I Did Wrong</h3> <p>Initially, my NIP-05 verification didn't work. I had done two things wrong.</p> <h5>Wrong form of pubkey</h5> <p>The first mistake I made was in the NIP-05 nostr.json file I used the wrong format of public key. The public key that you mostly use in clients is your "npub" which starts with "npub1..." However, the public key this file needs is formatted in hex and starts with "1...".</p> <p>If you don't have your hex formatted pubkey, you can use a site like https://nostrtool.com/ –enter your pubkey in npub format, and it will return it in hex format.</p> <h5>Redirects caused CORS issues</h5> <p>The second mistake was caused by a URL redirect. Your .well known files need to be served at the root of your domain, not at a www prefix (e.g. for me https://rodbishop.nz, not https://www.rodishop.nz). For this to work, you need to ensure that requests to your root domain aren’t redirected to www.</p> <p>In Vercel domain configuration, you can configure your redirects. By default, it will redirect traffic to www, and this is wrong for our purposes. To correct it, visit your domain settings, click "Edit" and look for "Redirect to". The correct setting is "No Redirect".</p> <p>The issue is caused because when applications go looking for your nostr.json, they need to receive a clean "Success" (200) response from your server prior to accessing the file. If you are redirecting to www, then the server gives a "Redirect" (300) response instead.</p> <p>In case you think your CORS is failing, take a look at the server http response code to see if there is a redirect. I used as follows–</p> <p><code>curl -X OPTIONS -i [https://rodbishop.nz/.well-known/nostr.json](https://rodbishop.nz/.well-known/nostr.json) \ -H "Origin: [https://anotherdomain.com](https://anotherdomain.com/)" \ -H "Access-Control-Request-Method: GET"</code></p> <ul> <li>Initially the response was "HTTP/2 308" which means a redirect was in place (and so the process was failing)</li> <li>Once I resolved the redirect issue at Vercel, the response was "HTTP/2 204" which means success, and from that point, Nostr apps recognised the NIP-05 successfully</li> </ul> <h3>What's Next</h3> <p>Over the last three blogs I have - Mined a Nostr pubkey and backed up the mnemonic - Set up Nostr payments with a Lightning wallet plus all the bells and whistles - Set up NIP-05 and Lighting Address at my own domain</p> <p>At this point I am up and running with a great Nostr profile and able to fully engage with the network. </p> <p>But there are still many rabbit holes to explore. The next place I will explore deeply is running my own relay, and if I have some success I will be back to blog about it soon.</p> <p>I'm looking forward to sharing what I learn as I explore what’s possible on Nostr.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqspfq4rgj3h0dyye0hr9tw7v505dph2sp98v6v9z6tc4gy4tf2eukszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjrpr2dy" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqspfq4rgj3h0dyye0hr9tw7v505dph2sp98v6v9z6tc4gy4tf2eukszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjrpr2dy" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqspfq4rgj3h0dyye0hr9tw7v505dph2sp98v6v9z6tc4gy4tf2eukszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjrpr2dy" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqspfq4rgj3h0dyye0hr9tw7v505dph2sp98v6v9z6tc4gy4tf2eukszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjrpr2dy" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 13e63e99:25525c6a <div class="time" style="margin-left: auto;">2024-10-24 02:44:17</div> </div> <div> <p><img src="https://blossom.primal.net/ad17ea8453218ae5d0890c551183a92712a59e4792855213d5ce6c9547f6efdc.webp"></p> <p>Bitcoin has experienced a notable 129.2% price increase this year, with a solid 8.9% gain this month alone. This rise has been driven by an improving risk-on sentiment in the market, spurred by better-than-expected earnings from major Wall Street firms. The strong earnings reports have helped bolster investor confidence, contributing to a broader appetite for riskier assets like Bitcoin, which has been increasingly seen as a hedge against traditional financial uncertainties.</p> <p>Additionally, growing speculation around a potential Federal Reserve rate cut in November has further fueled Bitcoin's momentum. Investors are factoring in the possibility that the Fed may pivot from its current monetary tightening, which could lead to a more favorable macroeconomic environment for assets like Bitcoin that thrive in low-interest-rate scenarios.</p> <p><img src="https://blossom.primal.net/c4b501d5007f923dafc850d7c3c9ac1b4ef079dce58e60ea7a1e32cf60aff4a6.webp"></p> <p>Moreover, the political landscape is playing a significant role in driving Bitcoin's price action. The increasing odds of pro-Bitcoin candidate Donald Trump winning the 2024 presidential election are adding to market optimism. Trump's favorable stance on cryptocurrency and his potential return to office are viewed by many investors as a catalyst for more crypto-friendly regulations and policies, further boosting Bitcoin's appeal.</p> <p>In combination, these factors—improving market sentiment, potential Fed rate cuts, and political developments—are creating a bullish outlook for Bitcoin as we move toward the end of 2024. Investors are increasingly viewing Bitcoin as both a hedge and a speculative asset, positioning it well in the current economic and political climate.</p> <blockquote> <p>Reference: <a href="https://www.google.com/finance/quote/BTC-USD?sa=X&ved=2ahUKEwi-742ph5-JAxWLIkQIHQ8XHZYQ-fUHegQILBAf&window=1Y">Yahoo Finance</a></p> </blockquote> <p><img src="https://blossom.primal.net/e6157097d276a7b569850fc05d8e5ecb68fc2146abe05c7e6066e82a9b7751f5.webp"></p> <p>Tesla transfers $765 million to self-custody wallets, highlighting the importance of Bitcoin self-custody. Bitcoin self-custody refers to the practice of directly controlling and managing your own Bitcoin holdings, rather than relying on a third-party custodian such as a cryptocurrency exchange or wallet service. When you hold Bitcoin in self-custody, you are responsible for securely storing your private keys—unique cryptographic codes that grant access to your Bitcoin and allow you to send or spend it. This approach gives individuals full control over their assets and eliminates the need to trust a centralized institution with their funds.</p> <p>Self-custody is a critical component of Bitcoin’s ethos, which emphasizes decentralization, financial sovereignty, and the ability to own and transfer wealth without reliance on intermediaries. By opting for self-custody, individuals are empowered to truly "own" their Bitcoin, free from the risks associated with third-party custodians, such as hacks, mismanagement, or insolvency. The mantra "Not your keys, not your coins" reflects the idea that if someone else holds your private keys, they effectively control your Bitcoin, and you are at risk of losing access.</p> <p><strong>The Importance of Multisignature in Bitcoin Self-Custody</strong></p> <p>While self-custody offers enhanced control and security, it also comes with the responsibility of safeguarding your private keys. Losing access to these keys means losing access to your Bitcoin permanently, which can be a daunting prospect. This is where multisignature (multisig) technology plays a crucial role in bolstering the security of Bitcoin self-custody.</p> <p>Multisignature refers to a security feature that requires multiple private keys to authorize a Bitcoin transaction, rather than relying on a single key. For example, a 2-of-3 multisig setup might require two out of three designated keys to approve any movement of funds. This adds an extra layer of protection in several ways:</p> <p><img src="https://blossom.primal.net/af513ce7c40b195bfb17081d97845771e366d4f0c82ab2bea02e8da8a997510a.webp"></p> <ul> <li> <p><strong>Enhanced Security:</strong> Multisig helps mitigate the risk of a single point of failure. If one key is lost, stolen, or compromised, the funds are still safe because the attacker would need access to multiple keys. This protects against theft, hacking, and loss of keys.</p> </li> <li> <p><strong>Redundancy and Backup:</strong> With a multisig setup, you can distribute your keys across different locations or devices, ensuring that even if one key is lost or damaged, you can still recover your funds using the remaining keys. For example, you might store one key on a hardware wallet, another in a safe, and give a trusted family member or service provider control of the third.</p> </li> <li> <p><strong>Shared Control:</strong> Multisig is particularly useful in shared ownership scenarios, such as for businesses, trusts, or family members who want joint control over Bitcoin holdings. It ensures that no single individual can act alone in transferring or spending the Bitcoin, which provides a governance structure and reduces the risk of rogue actors.</p> </li> <li> <p><strong>Mitigating Human Error:</strong> Managing private keys can be intimidating, especially for individuals new to Bitcoin. Multisig setups can reduce the risk of human error by allowing for the recovery of funds even if a single key is lost or forgotten. It provides a balance between the autonomy of self-custody and the security measures of traditional custodianship.</p> </li> </ul> <p>Multisignature solutions offer a powerful tool to enhance security, reduce risks, and provide flexibility in managing Bitcoin holdings. By combining self-custody with multisig, users can significantly reduce the likelihood of loss or theft while maintaining full control over their assets.Some prominent Multisig platforms: <a href="https://unchained.com/">Unchained Capital</a>, <a href="https://luminbitcoin.com/">Lumin</a>, <a href="https://casa.io/">Casa</a></p> <blockquote> <p>Reference:<a href="https://atadndr.medium.com/multisig-wallets-in-bitcoin-2ca91c383d6a">Multis.co</a>, <a href="https://unchained.com/">Unchained Capital</a>, <a href="https://luminbitcoin.com/">Lumin</a>, <a href="https://casa.io/">Casa</a></p> </blockquote> <p><img src="https://blossom.primal.net/48eec84de8c16b491ebead4aec96a31c5e817fa59bb006b8e706fa2e9f486939.webp"></p> <h2>Bitcoin Hashrate Hits All-Time High, Signaling Stronger Network Security and Potential Miner Consolidation</h2> <p>The Bitcoin hashrate has reached a new all-time high of 791.6 exahashes per second (EH/s) on Oct. 21, reflecting the increasing security of the network. This rise, driven by advancements in mining hardware like ASICs, has been on a steady upward trend since 2021.</p> <p>While a higher hashrate boosts the security of the Bitcoin network, it also increases the cost to mine 1 BTC, potentially leading to miner consolidation, especially for smaller firms with less efficient rigs. With the 2024 Bitcoin halving reducing block rewards, energy-efficient mining equipment will be essential for profitability.</p> <p>Despite the rising mining costs, Bitcoin miners have not significantly increased their selling, minimal miner transfers to centralized exchanges during this period.</p> <p><img src="https://blossom.primal.net/914cc9e1f497de842364f413fa2f87d0d7b1bf17cdf8c6cb1612e71a90e9ee2a.webp"></p> <blockquote> <p>Reference: <a href="https://ycharts.com/indicators/bitcoin_network_hash_rate">Ycharts</a>, <a href="https://cointelegraph.com/news/bitcoin-hashrate-hits-all-time-high">Cointelegraph</a></p> </blockquote> <h2>Nearly Half of Traditional Hedge Funds Now Invest in Digital Assets Amid Regulatory Clarity and ETF Launches</h2> <p>Nearly half of hedge funds focused on traditional assets now have exposure to cryptocurrencies, driven by clearer regulations and the launch of ETFs in the U.S. and Asia, according to the Global Crypto Hedge Fund Report by AIMA and PwC.</p> <p>The report revealed 47% of traditional hedge funds now invest in digital assets, up from 29% in 2023. Of those, 67% plan to maintain their digital assets investments, while the rest intend to increase by year-end.</p> <p>Hedge funds, once focused on spot trading, are now deploying more sophisticated strategies. In 2024, 58% traded crypto derivatives, up from 38% in 2023, while spot trading dropped to 25% from 69%.</p> <p><img src="https://blossom.primal.net/0cb862fdfdd4c565cf054b3f7ae3a65f48de437ebd292ce5440319c78a7962a6.webp"></p> <blockquote> <p>Reference: <a href="https://www.pwc.com/gx/en/industries/financial-services/assets/6th-annual-global-crypto-hedge-fund-report.pdf">Pwc</a></p> </blockquote> <h2>UAE Exempts Digital Assets Transactions from VAT, Aligning with Traditional Financial Services</h2> <p><img src="https://blossom.primal.net/7e5ffa84c49a87c00ffdc0d9a3e18c1b45eef86791acb71d7064b564fd7305f5.webp"></p> <p>The United Arab Emirates (UAE) has exempted cryptocurrency transactions from value-added tax (VAT), aligning the industry with several traditional financial services. Effective Nov. 15, this change retroactively applies to transactions dating back to Jan. 1, 2018. The Arabic version of the Federal Tax Authority’s update was released on Oct. 2, 2024, with the English translation following on Oct. 4.</p> <p>This exemption clarifies that digital assets are not subject to the 5% VAT. It covers the exchange and transfer of ownership of cryptocurrencies, meaning all digital assets transfers and conversions are now VAT-exempt.</p> <p>"The UAE has essentially classified virtual assets in the same category as traditional financial services, many of which are already VAT-exempt. This move legitimizes virtual assets," said Ankita Dhawan, a senior associate at the Métis Institute, a dispute resolution think tank.</p> <blockquote> <p>Reference: <a href="https://www.coindesk.com/policy/2024/10/07/uae-exempts-crypto-transactions-from-value-added-tax/?utm_source=substack&utm_medium=email">CoinDesk</a>, <a href="https://www.cryptopolitan.com/uae-removes-taxes-for-crypto-transactions/">Cryptopolitan</a></p> </blockquote> <p><img src="https://blossom.primal.net/e31ef1bb7df4f0d7e83b4cc60739290b28eea53c599f92a8b3afa3c9725a6bbf.webp"></p> <h2>We are going to El Salvador!</h2> <p>Our managing partner will be speaking at Adopting Bitcoin 2024! If you're a founder, entrepreneur, or Bitcoin enthusiast, feel free to reach out. We look forward to hearing from you!</p> <p><img src="https://blossom.primal.net/6a873ee06e73ae49052016298948c40db861bd29eef9980b7c7a2fcf5133e2c5.webp"></p> <blockquote> <p>Reference: <a href="https://x.com/AdoptingBTC/status/1829367809794560489">X.com</a></p> </blockquote> <p><img src="https://blossom.primal.net/4de7ea518aa994d18813489a6ea14297ea8cc51fecc4ce60a1b8bcf46b8022f8.webp"></p> <h2>LifPay NFC Card Manufacturing Program has officially launched!</h2> <p><img src="https://blossom.primal.net/1e9631d1277190904f0bfb683c05ce991ccde7527f5c33453ec7b0a9105da80e.webp"></p> <blockquote> <p>Reference: <a href="https://x.com/LifPay/status/1844628018255495668">X.com</a></p> </blockquote> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsrudeck74fxtjeu683glzgdwyat8tln95h2jdj0r44q60lmx4vlqszyqf7v05e0jjwnpslr306y7egrqqv3vwug9anr7yul4a2gjp92fwx5fwu4qj" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsrudeck74fxtjeu683glzgdwyat8tln95h2jdj0r44q60lmx4vlqszyqf7v05e0jjwnpslr306y7egrqqv3vwug9anr7yul4a2gjp92fwx5fwu4qj" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsrudeck74fxtjeu683glzgdwyat8tln95h2jdj0r44q60lmx4vlqszyqf7v05e0jjwnpslr306y7egrqqv3vwug9anr7yul4a2gjp92fwx5fwu4qj" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsrudeck74fxtjeu683glzgdwyat8tln95h2jdj0r44q60lmx4vlqszyqf7v05e0jjwnpslr306y7egrqqv3vwug9anr7yul4a2gjp92fwx5fwu4qj" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d5c3d063:4d1159b3 <div class="time" style="margin-left: auto;">2024-10-24 14:48:43</div> </div> <div> <h1>เวลามีค่า...บทเรียนจากลุงโฉลก CDC Talk EP1</h1> <p>https://image.nostr.build/bf870a0818bdefec9c992efcfa6db05c1ff7c897576159a89b7f6800a4ca9991.jpg</p> <h3>โลกการลงทุนที่เต็มไปด้วยความผันผวน นักลงทุนหลายคนมักจมอยู่กับการไล่ล่ากำไร จ้องกราฟตาแทบไม่กระพริบ วิ่งตามข่าวสารจนหัวหมุน เคยรู้สึกแบบนี้ไหมครับ? ผมเองก็เคยเป็นครับ</h3> <p>นอกจากอาจารย์พิริยะที่ทำให้ผมสนใจศึกษาบิตคอยน์ ก็มีลุงโฉลกที่ทำให้ผมเปลี่ยนมุมมองการลงทุนไปอย่างสิ้นเชิง สิ่งที่ลุงโฉลกให้ความสำคัญยิ่งกว่าผลกำไรคือ “เวลา” ที่ใช้ในการเรียนรู้และพัฒนาตนเอง ท่านบอกว่า “เวลา” สำคัญยิ่งกว่าการหาเงิน ไม่ใช่การหาจังหวะซื้อๆ ขายๆ แต่เป็นเวลาแห่งการเรียนรู้ การเติบโตทางความคิด และการมองภาพรวมของตลาดอย่างแท้จริง</p> <p>ประโยคนี้สะท้อนมุมมองที่แตกต่าง การลงทุนไม่ใช่แค่การเก็งกำไรระยะสั้น แต่คือการลงทุนในความรู้ สติปัญญาและวิสัยทัศน์ของเรา ลุงโฉลกเชื่อว่าการลงทุนที่แท้จริงต้องอาศัยปัญญา ท่านยกพุทธสุภาษิตที่ว่า "นตฺถิ ปญฺญาสมา อาภา" ความหมายคือ แสงสว่างเสมอด้วยปัญญาไม่มี พูดง่ายๆ ก็คือ ไม่มีแสงสว่างใด จะยิ่งใหญ่ไปกว่าแสงสว่างแห่งปัญญา เพราะปัญญานั้นไม่ได้เกิดขึ้นชั่วข้ามคืน แต่มันสั่งสมมาจากการศึกษา การฝึกฝนและที่ขาดไม่ได้เลยก็คือ “เวลา”</p> <p>ในตลาดทุนที่โหดร้าย ไม่มีใครใหญ่เกินกว่าตลาด การมุ่งแต่จะรวยโดยไม่พัฒนาตัวเอง มีแต่จะทำให้การลงทุนนั้นพังไม่เป็นท่า ดังที่ลุงโฉลกบอกว่า "ความโลภของจิตใจ…ทำลายทุกสิ่งทุกอย่าง" แล้วเราจะหาเวลาพัฒนาตัวเองได้อย่างไร ? ลุงโฉลกแนะนำให้ "ควบคุมความโลภ" และ "มักน้อย"</p> <p>ลุงโฉลกเตือนนักลงทุนด้วยพุทธสุภาษิต "นตฺถิ ตณฺหาสมา นที" ความหมายคือ แม่น้ำเสมอด้วยตัณหาไม่มี เปรียบความโลภเหมือนแม่น้ำที่ไหลไปไม่รู้จบ หากปล่อยให้ความโลภครอบงำ ย่อมนำไปสู่การตัดสินใจที่ผิดพลาด การควบคุมความโลภไม่ใช่แค่การตั้ง Stop Loss แต่คุณลุงบอกว่าต้อง "กำราบความโลภ…ในใจเรา" ด้วยการฝึกฝนจิตใจให้รู้จักพอ เมื่อเรามีจิตใจที่สงบแล้ว ย่อมวิเคราะห์และตัดสินใจได้ดีขึ้น และตระหนักถึงคุณค่าของเวลา เหมือนที่ลุงโฉลกบอกไว้ว่า "พอเริ่มเข้าใจปั๊บ…เวลาสำคัญนี่หว่า"</p> <p>ผมเคยเจอนักลงทุนหลายคนที่ขาดทุนย่อยยับเพราะความโลภ เห็นกำไรนิดหน่อยก็อยากได้เพิ่มและสุดท้ายก็ไปยืนอยู่บนดอย ส่วนคนที่ประสบความสำเร็จ มักเป็นคนที่ควบคุมความโลภได้ ใจเย็นและใช้เวลาไปกับการศึกษาหาความรู้</p> <p>"มักน้อย" เป็นสิ่งที่ลุงโฉลกให้ความสำคัญ ท่านมองว่าไม่จำเป็นต้องเทรดทุก Wave การจับจังหวะทำกำไรใน Wave 3 ซึ่งมักจะเป็นช่วงที่ราคาขึ้นแรงที่สุดก็เพียงพอแล้ว ส่วนเวลาที่เหลือ ท่านแนะนำให้ "พิจารณาอย่างอื่น…มีเรื่องน่าสนใจกว่าเกิดขึ้นเยอะแยะเลย" เช่น การศึกษาบิตคอยน์ หรือแม้แต่การใช้เวลากับครอบครัว</p> <p>ลุงโฉลกเปรียบเปรยนักลงทุนกับนักมวย "ขยับแขนซ้ายลงนิดนึง…ก็รู้แล้วว่าจะต่อยหมัดขวา" เป็นนักมวยก็ต้องฝึกฝนจนเชี่ยวชาญ นักลงทุนก็ต้องสั่งสมประสบการณ์ ศึกษาและฝึกฝน เพื่อที่จะเรียนรู้ตลาด มองเห็นโอกาสและตัดสินใจลงทุนได้อย่างมีประสิทธิภาพ ซึ่งจะนำไปสู่ความสำเร็จในระยะยาว</p> <p>เพราะฉะนั้น คุณค่าของเวลาในการลงทุน ไม่ใช่แค่การบริหารเวลาให้มีประสิทธิภาพ แต่คือการสร้างเวลา ด้วยการฝึกฝนจิตใจ ควบคุมความโลภและมักน้อย เพื่อให้เรามีเวลา มองเห็นโอกาส และบรรลุเป้าหมายการลงทุนอย่างยั่งยืน แล้วคุณคิดว่า...อะไรคืออุปสรรคที่สำคัญที่สุดของคุณในการควบคุมความโลภ ? ลองแลกเปลี่ยนแบ่งปันประสบการณ์กันดูได้นะครับ</p> <h1>CDCTalk #Siamstr</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsxfxdd3rnm5l5cnngc8fgcpkn7sxlqxf7ydf57lu06lkju4karclqzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxthx08p" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsxfxdd3rnm5l5cnngc8fgcpkn7sxlqxf7ydf57lu06lkju4karclqzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxthx08p" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsxfxdd3rnm5l5cnngc8fgcpkn7sxlqxf7ydf57lu06lkju4karclqzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxthx08p" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsxfxdd3rnm5l5cnngc8fgcpkn7sxlqxf7ydf57lu06lkju4karclqzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxthx08p" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 1bda7e1f:bb97c4d9 <div class="time" style="margin-left: auto;">2024-10-10 01:40:25</div> </div> <div> <p><strong>Tldr</strong></p> <ul> <li>Your Nostr identity may be the first ID you every own</li> <li>You can create one that easier to backup using a 12-word mnemonic, and</li> <li>You can create one that has a bit of branding to it, called a “vanity npub”</li> <li>Many tools exist which you can use</li> <li>I tried a few and settled on Rana by Negrunch</li> <li>Now I am npub1<strong>r0d8</strong>...</li> </ul> <p><strong>The first ID you’ll ever own</strong></p> <p>The first step in setting up a Nostr profile is to get your keys. These keys are your identity. For almost everyone, this is the first ID you’ll have that you truly own. That is, this ID is yours because <em>you</em> say it is. That’s different from almost every other ID, which was issued to you by someone else, and is yours because <em>they</em> say it is.</p> <p>Not only is it yours. It’s portable. You can use this ID to be yourself in any app that supports Nostr.</p> <p>Consider the legacy internet—every app requires a separate account. That’s a separate login and password to remember. And worse than that, it’s a separate set of content you have to generate, and a separate following you have to create. Every time a new platform launches, you need to encourage your followers to join you on the new platform. At any time, any platform can deplatform you. If they do, you lose your content and your following, with no recourse.</p> <p>On Nostr, it’s different. All your content and all your following is linked to your identity, and you take it with you everywhere. You build your content once, and it appears with you everywhere. You build one following once, and they follow you everywhere. If a platform deplatforms you, you don’t lose your following or content, you just take it all to another platform.</p> <p>This may be the first ID you ever own, and if Nostr keeps on growing, it may be the last ID you’ll ever need.</p> <p><strong>Getting branded with a “vanity” npub</strong></p> <p>Every nostr user has an identity like this, and every user can be found and known by their public key, their “npub” or “pubkey”. By default, most people go by a pubkey that is completely random, like npub1asdfgh….</p> <p>My view is, if you’re going to create your first-ever ID that is truly yours, you might as well make it special. It’s possible to create a pubkey that has a bit of branding to it.</p> <p>The technical name for these is a “vanity npub”. You could call it a branded npub.</p> <p>There are some good examples:</p> <ul> <li>Snowden at npub1<strong>sn0wden...</strong></li> <li>Negrunch at npub1<strong>qqqqqqq</strong>...</li> </ul> <p>These pubkeys have specific characters at the start (or at the end). It is better branding. It’s also helpful for defeating spammers who might choose to imitate you, as only you have the vanity npub.</p> <p>Keys are generated at random. To get one with your specific branding on it, you need to set up your computer to generate keys at random until it finds one that suits your needs. Once set up your computer will generate keys by the millions–checking and discarding each one until it creates the one with your characters.</p> <p>The more characters you want, the longer this process will take.</p> <p>Nostrogen provides a helpful table for that:</p> <ul> <li>1 character = usually less than a 0.1 seconds</li> <li>2 characters = usually less than a 1 second</li> <li>3 characters = usually less than a 30 seconds</li> <li>4 characters = usually less than a 10 minutes</li> <li>5 characters = usually less than a 1 hour</li> <li>6+ characters = keep fire extinguisher handy</li> </ul> <p>The good news is, for your npub to have nice branding, you don’t need a lot of characters.</p> <p>For myself I only needed four “<strong>r0d8</strong>”.</p> <p><strong>Getting a mnemonic, for backup, and for lightning</strong></p> <p>Once you have your ID, you will want to use it different places and back it up securely. The problem with writing down your ID as an nsec is that it’s long and complicated to write, and too easy to misread and enter the wrong characters when you type it back into your device.</p> <p>A better alternative exists. You can generate a 12-word mnemonic, and then use that to derive your nsec (documented in <a href="https://github.com/nostr-protocol/nips/blob/master/06.md">NIP-06</a>). The mnemonic is much easier to read, easier to type into new apps, and easier to backup correctly.</p> <p>If you generate your keys directly as npub and nsec you can never go “backward” to generate a mnemonic. But if you generate a mnemonic first, you can always generate an npub and nsec from it. Furthermore if you generate a mnemonic, you can (optionally) use that same mnemonic to generate your lightning wallet for making payments with.</p> <p>For these reasons, my view is that using an identity with a mnemonic is best.</p> <p>Once we have our 12-word mnemonic, we generate our keys (npub and nsec), and we’re ready to use anything in the Nostr ecosystem.</p> <ul> <li>Where the app supports mnemonics you can use that</li> <li>For everywhere else you can use your nsec</li> <li>In either case you’ll be recognised everywhere you go by your vanity npub</li> </ul> <p><strong>How to mine a 12-word mnemonic with a branded vanity npub</strong></p> <p>You’ll need an application for mining. There are very many to choose from, which you can see on this <a href="https://github.com/aljazceru/awesome-nostr?tab=readme-ov-file">awesome Nostr list</a> by <a href="nostr:npub1aljazgxlpnpfp7n5sunlk3dvfp72456x6nezjw4sd850q879rxqsthg9jp">Aljaz</a></p> <p>Some work in your web browser, like <a href="http://nostr.rest">nostr.rest</a>. Many others you can find on github and install. I tried many including nostr-pubminer, and nostr_vanity_npub, before settling on <a href="https://github.com/grunch/rana">Rana</a>.</p> <p>To run these requires basic command line knowledge. I didn’t have that, so I fed the GitHub readme page to ChatGPT, and it walked me through getting everything set up.</p> <p><strong>Failing many times</strong></p> <p>Here’s what I did wrong so you don’t have to make the same mistakes.</p> <ul> <li>You can only use bech32 characters in your npub, and may not be every character you want! The allowed character set is only 023456789acdefghjklmnpqrstuvwxyz. Importantly for me there is no “o” “b” or “i” which makes it impossible to generate “rod” or “bishop”! Only “r0d” and “8lsh0p” are possible.</li> <li>Not every vanity npub miner tell you if you’re using valid characters. <a href="http://Nostr.rest">Nostr.rest</a> and nostr-pubminer happily sat for hours using my CPU to look for a key that started with “rod” and failed to find one, as they must, because “rod” is not possible (only ”r0d” is possible).</li> <li>Some miners will ask you “how many threads” would you like to use. It’s a question that relates to how much processor power you want to spend on the task. I didn't know the "correct" answer but found it didn’t matter at all what number I entered.</li> <li>Some miners will generate npubs just fine, but can not generate the mnemonic. For my needs I needed one that could do both.</li> </ul> <p><strong>Success with Rana</strong></p> <p>In the end I succeed using Rana by <a href="nostr:npub1qqqqqqqx2tj99mng5qgc07cgezv5jm95dj636x4qsq7svwkwmwnse3rfkq">Negrunch</a></p> <p>You can find <a href="https://github.com/grunch/rana">Rana here on Github</a> with a very helpful readme.</p> <p>In short the process is:</p> <ul> <li>Install Rust (the programming language) and install Rana (the mining application)</li> <li>Run a command to generate your npub.</li> <li>For me that command was: “cargo run —release — -n=r0d8 -g 12”</li> </ul> <p>That command breaks down as:</p> <ul> <li>“cargo run” telling Rust to run the application</li> <li>“-n=r0d8” look for an npub with a prefix of “r0d8”, and</li> <li>“-g 12” including a 12 word mnemonic</li> </ul> <p>And the outcome is:</p> <ul> <li>A 12 word mnemonic</li> <li>Private and public keys derived from that mnemonic</li> <li>My branded vanity npub starting with npub1<strong>r0d8</strong>...</li> </ul> <p><strong>In summary</strong></p> <p>The first step in setting up a Nostr profile is to get your identity.</p> <p>While it’s easy to get an identity made with random keys, if we think our Nostr IDs are going to mean something important in the future, then we may as well set ourselves up with keys that are easy to use, and branded.</p> <p><em>That means</em></p> <ul> <li>12-word mnemonic backups (feature NIP-06)</li> <li>Branded vanity npub</li> </ul> <p>The mnemonic is easier to backup and also can be used to create a lightning wallet. The branding helps people know your npub is really you</p> <p><em>To do this</em></p> <ul> <li>You need an application for mining a vanity npub</li> <li>There are many, and I had success with Rana which provided both the mnemonic and the vanity prefix, in one command line instruction.</li> </ul> <p><strong>Next</strong></p> <ul> <li>Please let me know if this kind of post is helpful or anything you’d like me to improve or expand upon!</li> <li>For my next post I’ll show how to set up a self-custody lightning wallet to make payments on Nostr with Phoenixd and Albyhub</li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsdamm0e8z8jdy90tf8wa6yl0qelg32vgw7f53cxy9gn4saztxet4czyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjm9vzt8" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsdamm0e8z8jdy90tf8wa6yl0qelg32vgw7f53cxy9gn4saztxet4czyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjm9vzt8" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsdamm0e8z8jdy90tf8wa6yl0qelg32vgw7f53cxy9gn4saztxet4czyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjm9vzt8" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsdamm0e8z8jdy90tf8wa6yl0qelg32vgw7f53cxy9gn4saztxet4czyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjm9vzt8" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 599f67f7:21fb3ea9 <div class="time" style="margin-left: auto;">2024-10-20 11:32:36</div> </div> <div> <p>LNDhub-ek zure zorroa erraz inportatzea ahalbidetzen du bateragarriak diren aplikazioetan. Bitcoin Txoko LNbits zorroa progresiboko web aplikazio (PWA) modura gorde dezakezun arren zure telefonoan, <a href="https://zeusln.app/">Zeus</a> edo <a href="https://bluewallet.io/">BlueWallet</a> bezalako aplikazio natibo batek erabiltzaile-esperientzia hobea eta segurtasun handiagoa eskaintzen du. </p> <p><a href="https://getalby.com/">Alby</a> erabiliz, zorroa zure nabigatzailearen luzapenean ere inporta dezakezu, webgunean Lightning ordainketak egiteko eta Nostr zap-ak egiteko erraztasun handiagoz. Zorionez, zorro hauek guztiek hizkuntza komun bat ulertzen dute, <a href="https://github.com/BlueWallet/LndHub/tree/master">LNDhub</a> izenekoa.</p> <p>Gida honetan, zorroa zure nabigatzailera eta telefonora nola inportatu azalduko dugu. Zorroa nabigatzailean eta telefonoan erabili nahi baduzu, hasi <a href="#Alby">Alby konfigurazioarekin</a>, pausoetako batek zorroa Zeus-era erraz inportatzeko aukera emango baitizu. Baina zorroa soilik zure telefonoan erabili nahi baduzu, zuzenean <a href="#Zeus">Zeus atalera</a> jo dezakezu.</p> <h2>Alby</h2> <p>nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 nabigatzailearen luzapena da, Lightning eta Nostr nabigatzailera ekartzen dituena. <a href="https://www.webln.dev/">WebLN</a> protokoloa erabiliz, luzapenak webguneetan fakturak automatikoki detekta eta ordaintzen ditu, eta Lightning bidez webguneetan saioa hasteko aukera ematen du. Gainera, Lightning gune gogokoenetan aurrekontuak ezar ditzakezu. Luzapen honek <a href="https://github.com/nostr-protocol/nips/blob/master/07.md">NIP-07</a> protokoloa erabiliz Nostr sinadura gisa ere funtziona dezake, zure giltza pribatua web bezeroetan sartzea baino askoz seguruagoa dena.</p> <h3>Zer behar dut?</h3> <ul> <li>Chrome edo Firefox luzapenak onartzen dituen web nabigatzailea.</li> <li>LNbits zorroa. Oraindik zorro bat ez baduzu, joan <a href="https://bitcointxoko.com">gure zorroen orrira</a> eta sortu bat.</li> <li>(Aukerazkoa) Zeus konfiguratzeko mugikor bat.</li> </ul> <h3>1. LNDhub luzapena gaitzea zure LNbits zorroan</h3> <p>Nabigatzailean, joan zure zorroaren estekara. Egin klik Extensions atalean eta gaitzazu <code>LNDhub</code> luzapena. Gaitu ondoren, joan LNDhub luzapenaren orrira.</p> <h3>2. Alby luzapena instalatu</h3> <p>Joan <a href="https://getalby.com/">getalby.com</a>-era eta egin klik <code>Add Browser Extension</code> botoian. Instalatu luzapena zure nabigatzailearen luzapen dendetik. Ezarri desblokeatzeko pasahitza eta gorde toki seguruan.</p> <h3>3. Inportatu Alby-ra</h3> <p><img alt="alby-config" src="https://cdn.satellite.earth/2074a44ea548ce28368d0aba2d54eafdc698159c5ee0956afa87fa155e3b511d.webp" /></p> <p>Hurrengo pantailan, aukeratu <code>Connect</code>, eta ondoren aukeratu <code>LNDhub</code>. Itzuli zure LNDhub luzapenera eta kopiatu konexioaren URL-a. Itsatsi hori LNDhub esportazioaren URI eremuan. Sakatu <code>Continue</code>. Orain LNbits zorroa LNDhub bidez konektatuta eduki beharko zenuke!</p> <p>💡 Aukeratu dezakezu Invoice URL eta Admin URL artean. Bi hauek Alby-ri zure LNbits zorroarekin elkarreragiteko baimen desberdinak ematen dizkiote: - <em>Invoice URL</em>-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - <em>Admin URL</em>-ak ordainketak bidaltzeko aukera ere ematen du.</p> <h3>4. (Aukerazkoa) Zeus konfiguratu Alby-rekin</h3> <p><img alt="alby-export" src="https://cdn.satellite.earth/8807b296bb8bd6086a795616cc49068a17d93df450d0a65ce3818e5539eb6a09.webp" /></p> <p>Orain LNbits zorroa Alby-rekin konektatu duzunez, Zeus-en ere erraz inportatu dezakezu. Ireki luzapena, egin klik zure zorroaren izenean, eta joan <code>Account Settings</code> atalean. <code>Account</code> azpian aurkituko duzu <code>Connect your mobile wallet</code> aukera. Sakatu <code>Connect</code>, eta Zeus-ekin eskaneatzeko QR kode bat erakutsiko dizu.</p> <p>Zeus aurretik instalatu ez baduzu, joan <a href="https://zeusln.app/">zeusln.app</a>-era eta deskargatu Zeus zure mugikorreko sistema eragilerako. Zeus deskargatu ondoren, joan <code>Settings</code> > <code>Add a new node</code> atalera. Hemen, Alby-k erakusten dizun QR kodea eskaneatu eta zorroa inportatu dezakezu.</p> <p>Listo! Orain Lightning-aren indarra zure eskuetan duzu. Jainko baten moduan sentitzen al zara jada?</p> <h2>Zeus</h2> <p>nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf kode irekiko aplikazio bikaina da, zure nodo propioa mugikorrean konektatzeko aukera ematen duena. Lightning nodo nagusi guztiak onartzen ditu, hala nola LND, CLN eta Eclair, bai eta Tor bidezko zein clearnet bidezko konexioak ere. Azkenaldian, beren LSP (Lightning Service Provider) propioa iragarri dute.</p> <h3>Zer behar dut?</h3> <ul> <li>Android edo iOS telefono bat.</li> <li>LNbits zorroa ikusi ahal izateko beste gailu bat (QR kodea eskaneatzeko).</li> <li>LNbits zorroa eskuragarri izatea. Zorro bat oraindik ez baduzu, joan <a href="https://bitcointxoko.com">gure zorroen orrira</a> eta sortu bat.</li> </ul> <h3>1. Zeus deskargatu</h3> <p>Deskargatu Zeus aplikazioa zure sistema eragilerako <a href="https://zeusln.app">hemen</a>. </p> <h3>2. LNDhub luzapena gaitzea zure LNbits zorroan</h3> <p>Zure LNbits zorroaren orrian, egin klik <code>Extensions</code> atalean eta gaitzazu <code>LNDhub</code> luzapena. Gaitu ondoren, ireki LNDhub luzapenaren orria.</p> <h3>3. Inportatu Zeus-en</h3> <p>Joan <code>Settings</code> > <code>Add a new node</code> atalera Zeus-en. Eskaneatu nahi duzun zorroa inportatzeko.</p> <p>💡 Aukeratu dezakezu Invoice URL eta Admin URL artean: - <em>Invoice URL</em>-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - <em>Admin URL</em>-ak ordainketak bidaltzeko aukera ere ematen du.</p> <p>QR kodea eskaneatu ondoren, Zeus-en eremu guztiak automatikoki beteko dira. Zorroarentzat ezizena ere gehitu dezakezu.</p> <p><img alt="zeus-config" src="https://cdn.satellite.earth/3be62f55d32460b7aa33d58fd9c25f3260e379ddde60fa1fe2c99016915da8b3.webp" /></p> <p>Orain, <code>Save Node Config</code> sakatu eta zorroa zure mugikorretik kontrolatu dezakezu!</p> <h3>Bonus</h3> <p>Zeus-ek ezaugarri interesgarriak ere eskaintzen ditu, hala nola gai pertsonalizatuak, prezioen bihurketak, lurker modua eta biometria bidezko egiaztapena. Gida honen esparrutik haratago doazen ezaugarriak dira hauek, baina aplikazioa erabili eta zuk zeuk aurkitu ditzakezu!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsth7plqyldqeswfpv20k3spm639ypgfrqt7vurkn4vlwsz0eqckpqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j9a0h90" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsth7plqyldqeswfpv20k3spm639ypgfrqt7vurkn4vlwsz0eqckpqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j9a0h90" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsth7plqyldqeswfpv20k3spm639ypgfrqt7vurkn4vlwsz0eqckpqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j9a0h90" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsth7plqyldqeswfpv20k3spm639ypgfrqt7vurkn4vlwsz0eqckpqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j9a0h90" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 7362636d:eec5ab4c <div class="time" style="margin-left: auto;">2024-10-23 21:31:29</div> </div> <div> <p>/start</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqspvvl2swdz3h73uhz0ladt9ed932ulc4trrma3w8nnl3s57umyrxszypekycmdllr9l0ureq0uhel5tgxsctecyr7jq90lzd299g0wck45ct7gx7x" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqspvvl2swdz3h73uhz0ladt9ed932ulc4trrma3w8nnl3s57umyrxszypekycmdllr9l0ureq0uhel5tgxsctecyr7jq90lzd299g0wck45ct7gx7x" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqspvvl2swdz3h73uhz0ladt9ed932ulc4trrma3w8nnl3s57umyrxszypekycmdllr9l0ureq0uhel5tgxsctecyr7jq90lzd299g0wck45ct7gx7x" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqspvvl2swdz3h73uhz0ladt9ed932ulc4trrma3w8nnl3s57umyrxszypekycmdllr9l0ureq0uhel5tgxsctecyr7jq90lzd299g0wck45ct7gx7x" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 599f67f7:21fb3ea9 <div class="time" style="margin-left: auto;">2024-10-20 11:28:08</div> </div> <div> <p>LNDhub te permite importar fácilmente una billetera en aplicaciones compatibles. Si bien puedes guardar tu billetera Bitcoin Txoko LNbits en tu teléfono como una aplicación web progresiva (PWA), una aplicación nativa como <a href="https://zeusln.app/">Zeus</a> o <a href="https://bluewallet.io/">BlueWallet</a> ofrece una mejor experiencia de usuario así como un mayor nivel de seguridad. Con <a href="https://getalby.com/">Alby</a>, también puedes importar la billetera a la extensión de tu navegador para facilitar los pagos Lightning en la web y para los zaps de Nostr. Por suerte para nosotros, todas estas billeteras hablan un lenguaje común llamado <a href="https://github.com/BlueWallet/LndHub/tree/master">LNDhub</a>. </p> <p>En esta guía cubriremos cómo importar la billetera a tu navegador y a tu móvil. Si quieres usar tu billetera tanto en el navegador como en tu móvil, empieza con <a href="#Alby">la configuración de Alby</a>, ya que uno de los pasos te permitirá importar fácilmente tu billetera también a Zeus. Pero si sólo te interesa utilizar la billetera en tu móvil, puedes pasar directamente a <a href="#Zeus">la sección de Zeus</a>.</p> <h3>Alby</h3> <p>nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 es una extensión de navegador que lleva Lightning y Nostr a tu navegador. Utilizando el protocolo <a href="https://www.webln.dev/">WebLN</a>, esta extensión puede detectar facturas LN en paginas web y pagarlas, así como posibilita iniciar sesión en sitios web con Lightning. También puedes fijar presupuestos para tus sitios favoritos de Lightning. Por otro lado también puedes utilizarla para firmar en Nostr utilizando <a href="https://github.com/nostr-protocol/nips/blob/master/07.md">NIP-07</a>, lo cual es mucho más seguro que ingresar tu clave privada en clientes web.</p> <h4>¿Qué necesito?</h4> <ul> <li>Un navegador web que soporte extensiones Chrome o Firefox</li> <li>Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a <a href="https://bitcointxoko.com">nuestra página de billeteras</a> y crea una</li> <li>(Opcional) Un dispositivo móvil para configurar Zeus</li> </ul> <h4>1. Habilita la extensión LNDhub en tu LNbits wallet</h4> <p>Dirígete a tu billetera LNbits. Haz clic en <code>Extensiones</code> y habilita la extensión <code>LNDhub</code>. Una vez se haya habilitado, dirígete a la página de extensión de LNDhub.</p> <h4>2. Instala la extensión Alby</h4> <p>Dirígete a <a href="https://getalby.com/">getalby.com</a> y instala la extensión desde el store de extensiones del navegador. Configura tu contraseña de desbloqueo y guárdala en un lugar seguro.</p> <h4>3. Importar a Alby</h4> <p><img alt="alby-config" src="https://cdn.satellite.earth/2074a44ea548ce28368d0aba2d54eafdc698159c5ee0956afa87fa155e3b511d.webp" /> (Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)</p> <p>En la siguiente pantalla, elige <code>Conectar</code> y luego elige <code>LNDhub</code>. Vuelve a tu extensión LNDhub y copia la URL de conexión. Pégala en el campo <code>URI de exportación de LNDhub</code>. Pulsa continuar. ¡Ahora deberías haber estado conectado a tu billetera de LNbits con LNDhub!</p> <p>💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). Le dan a Alby diferentes permisos para interactuar con tu cartera de LNbits.</p> <ul> <li>La URL de factura te permite crear facturas y recibir pagos</li> <li>La URL de administración también te permite enviar pagos</li> </ul> <h4>4. Configurar Zeus con Alby (opcional)</h4> <p><img alt="alby-export" src="https://cdn.satellite.earth/8807b296bb8bd6086a795616cc49068a17d93df450d0a65ce3818e5539eb6a09.webp" /></p> <p>Ahora que ya has conectado tu LNbits con Alby, también puedes importarlo de una manera sencilla a Zeus con Alby. Abre la extensión, haz cilc en el nombre de tu billetera y navega a la configuración de la cuenta. En <code>Wallet Settings</code> > <code>General</code> se encuentra la opción de conectar tu billetera móvil. Al pulsar conectar, se mostrará un código QR para escanear desde Zeus.</p> <p>Si no tienes instalada Zeus con anterioridad, dirígete a <a href="https://zeusln.app/">zeusln.app</a> y descarga la aplicación de Zeus para tu sistema operativo móvil.</p> <p>Una vez tengas descargado Zeus, entra en <code>Configuración</code> > <code>Añadir un nuevo nodo</code>. Aquí puedes escanear el código QR que te muestra Alby para importar la billetera.</p> <p>Voilà! Ahora tienes el poder de Lightning al alcance de la mano ¿Ya te sientes como un dios?</p> <h3>Zeus</h3> <p>nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf es una formidable aplicación de código abierto que permite conectar tu propio nodo a tu dispositivo movil. Es compatible con todas las principales implementaciones de nodos Lightning, como LND, CLN y Eclair, así como conexiones a través de Tor y clearnet. Recientemente también han anunciado su propio LSP (Lightning Service Provider). </p> <h3>¿Qué necesito?</h3> <ul> <li>Teléfono Android o iOS</li> <li>Otro dispositivo en el que puede acceder a tu billetera LNbits (para mostrar el código QR para escanear)</li> <li>Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a <a href="https://bitcointxoko.com">nuestra página de billeteras</a> y crea una</li> </ul> <h4>1. Descarga Zeus</h4> <p>Puedes descargar la aplicación Zeus para tu sistema operativo <a href="https://zeusln.app/">aquí</a>.</p> <h4>2. Habilita la extensión LNDhub en tu billetera LNbits</h4> <p>Dirígete a tu billetera LNbits. Haz clic en <code>Extensiones</code> y habilita la extensión <code>LNDhub</code>. Una vez habilitada, abre la pagina de la extensión LNDhub.</p> <h4>3. Importar a Zeus</h4> <p>Ve a <code>Configuración</code> > <code>Añadir un nuevo nodo en Zeus</code>.</p> <p>Escanea la cartera que quieras instalar.</p> <p>💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). - La URL de la factura te da permiso para generar facturas y recibir pagos. - La URL de administración también te permite enviar pagos.</p> <p>Una vez que hayas escaneado el código QR, todos los campos en Zeus deberían rellenarse automáticamente. También puedes añadir un apodo para tu billetera.</p> <p><img alt="zeus-config" src="https://cdn.satellite.earth/3be62f55d32460b7aa33d58fd9c25f3260e379ddde60fa1fe2c99016915da8b3.webp" /></p> <p>¡Ahora puedes guardar la configuración del nodo y controlar la billetera desde tu teléfono!</p> <h4>Extra</h4> <p>Zeus también ofrece funciones interesantes como temas personalizados, conversiones de precios, modo acechador y verificación biométrica. Estos temas están más allá del alcance de esta guía, ¡juega en la aplicación y descubre todas esas características por ti mismo!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsqccrdeqpqe98tsrw4m63ynp4n3p0mzz09m6tlt37yl9hcd9zq76szypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jaty3mw" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsqccrdeqpqe98tsrw4m63ynp4n3p0mzz09m6tlt37yl9hcd9zq76szypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jaty3mw" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsqccrdeqpqe98tsrw4m63ynp4n3p0mzz09m6tlt37yl9hcd9zq76szypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jaty3mw" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsqccrdeqpqe98tsrw4m63ynp4n3p0mzz09m6tlt37yl9hcd9zq76szypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jaty3mw" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ fd208ee8:0fd927c1 <div class="time" style="margin-left: auto;">2024-10-09 12:27:53</div> </div> <div> <h2>Why waste time, looking at other people's stuff?</h2> <p>I get this question a lot, on Nostr, and it feeds immediately back to the next question: <em>Why don't you just build your own client, if you're so smart?</em></p> <p>This was a completely new question for me, as I'm used to collaborating with at least one other person, even when doing FOSS stuff. (No, this isn't my first such project; we just used to call it "volunteering" and "sharing the code", which sounds way less glamorous.) It never occurred to me, that a habit of collaboration and interaction was some sign of my ignorance and incompetence, or somehow proof that I can't vomit up "Hello World!" in 5 different programming languages.</p> <p>I also made the deadly political mistake, when I entered the Nostrsphere, of refusing to call myself a "dev". For me, "dev" is a special title, given to someone doing a specific type of programming (fiddling with GUIs, mostly, which I've only done occasionally, as a sub), whereas the types I've done are "test automation", "development operations", "database management and data curation", "requirements engineering", and "application administration". Because it's so much easier to find someone interested in building a GUI, rather than building AnythingElse, I tend to slide into AnythingElse and it eventually became my professional specialty to be the Girl Friday of every project.</p> <p><img alt="The Girl for AnythingElse" src="https://s3.amazonaws.com/criterion-production/images/7918-c2ea72b6fb210e7123bd9b83dd221a30/Current_27903id_104_medium.jpg" /></p> <p>But, in Nostr, there is no AnythingElse category. There are only (GUI) client devs and AllOfTheIdiotsWhoMustBowDownToTheDevs. Which merely doubled my instinct to distance myself from the term. I do not want to join some cargo cult and be pedestalized and regarded as some sort of superhuman everyone owes fealty to, in return for raining GUI presents down on my loyal subjects.</p> <p>Software engineers are simply people who are skilled craftsman, not gods, and it is fair to point out that some are more skilled than others. It is also completely fair to criticize their products, report bugs, and wonder aloud at endemic low-quality.</p> <p>Which brings me back to the initial question:</p> <h2>What does the inquisitive dev know, that the others don't?</h2> <p>1) You learn an awful lot about an awful lot, by looking at specs, reviewing code, and trying out various implementations of concepts you are already familiar with. There are, in fact, n number of use cases for every event type, and I've seen so many of them, that I can conjure them up, or invent new ones, on the fly, rather than wasting time inventing similar events. 2) They don't have to explain their concept to you, later, when you interact. Each interaction brings you closer to parallel-levels of knowledge, which raises the signal-strength of the interaction, and widens your own knowledge base, for interacting with third parties. 3) You are increasingly-likely to contribute code or perform some other more-advanced task, for other people, as you don't face the hurdle of adjusting to a new repo or unfamiliar language, while being less-likely to merely fork-and-ignore because you have a standing business relationship with the other developer. 4) If the other dev stops maintaining the repo, you'll be inclined to continue on your own. You may even eventually receive administrative access, rather than needing to fork, as they trust you with their stuff. This means that the risk of the repo becoming abandoned falls, with each active dev snooping around it, even if that is not their primary project. 5) It helps you determine who to focus your energy on interacting with, further. Is this person new to software development, perhaps, but has some interesting transfer-knowledge from some other branch, that has resulted in a surprisingly novel concept? Is this person able to write very clean code, so that merely reading their code feels like mental training for your own craftsman's toolbox?</p> <p>...and many more reasons, but this is getting too long, so, let's just cut to the chase.</p> <h2>What does a craftswoman want?</h2> <p>But, this still doesn't answer the question of my private motivation. Why do I want to gather all of this knowledge, from those further ahead, than I?</p> <p>I think Nostr has long moved past the initial stage, where mere speed was of the essence, so that one npub could <em>finally</em> post a note and have it appear on the other npubs' client. That must have felt like a miracle, but it increasingly feels like a disaster, as the steadily-rising complexity of the Nostr ecosystem causes haphazardly-structured and largely-unexamined code bases to begin to atrophy, or result in developers running around at an exhausting speed, with their bug-extinguishers, to put out fire after fire.</p> <p>I think the time has arrived, for a different kind of development. Maybe even for a different kind of developer. Not replacing the experimentalism that made Nostr fun, but adding the realm of production-quality software engineering. The sort of software development that requires relay administration, testing, support... collaboration, interaction, maybe even someone who does AnythingElse.</p> <p>I want to build useful, elegant products people enjoy using and feel comfortable relying on. I want them to use them, naturally and happily, to accomplish tasks they consider worthwhile. I don't want them thinking about me, while they use it. The craftswoman should never be greater than her work.</p> <p>I want them to feel free -- nay, be eager! -- to give me both positive and negative feedback. My assumption is <em>always</em> that our production is imperfect because we are imperfect, so you do us a favor, by pointing out where we can improve. That's why we wish to integrate a feedback form that produces ngit issue events, putting your questions and comments straight on our board.</p> <p>And there will be an AnythingElse person, reading that board, and responding promptly, rest assured.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs2s8ufk7u4vcpx4x9zytlxq3l0kjrtxs5xcr5qujskp5lgvzaetpgzyr7jprhgeregx7q2j4fgjmjgy0xfm34l63pqvwyf2acsd9q0mynuzn3k5av" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs2s8ufk7u4vcpx4x9zytlxq3l0kjrtxs5xcr5qujskp5lgvzaetpgzyr7jprhgeregx7q2j4fgjmjgy0xfm34l63pqvwyf2acsd9q0mynuzn3k5av" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs2s8ufk7u4vcpx4x9zytlxq3l0kjrtxs5xcr5qujskp5lgvzaetpgzyr7jprhgeregx7q2j4fgjmjgy0xfm34l63pqvwyf2acsd9q0mynuzn3k5av" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs2s8ufk7u4vcpx4x9zytlxq3l0kjrtxs5xcr5qujskp5lgvzaetpgzyr7jprhgeregx7q2j4fgjmjgy0xfm34l63pqvwyf2acsd9q0mynuzn3k5av" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 599f67f7:21fb3ea9 <div class="time" style="margin-left: auto;">2024-10-19 15:20:46</div> </div> <div> <p>Merkatari bat zara eta zure negozioan Bitcoin onartzen hasteko prest zaude? Edo agian Bitcoin zale sutsua zara, tokiko negozioak Bitcoinen mundura erakartzeko gogoz? Beharbada, ez zaizu Bitcoin interesatzen, baina ordainketa-prozesadore azkar eta merke bat erabili nahi duzu edo web-denda sinple bat sortu nahi duzu? Galdera hauetakoren bati baiezkoa erantzun badiozu, gida hau zuretzat da. Bitcoin Txoko-k ostatatutako <a href="https://btcpayserver.org">BTCPay Server</a>-en denda bat konfiguratu dezakezu eta zure produktuak eta zerbitzuak Bitcoinen truke saltzen hasi hamar minuturen buruan, doan.</p> <h2>Zer behar dut?</h2> <p>Mugikor edo ordenadore bat baduzu eta posta elektronikoko kontu bat ere bai, orduan prest zaude!</p> <h2>Kontu bat sortu</h2> <p>Bitcoin Txoko-n BTCPay Server-en kontu bat sortzea doakoa da. Joan <a href="https://btcpay.bitcointxoko.com">btcpay.bitcointxoko.com</a> helbidera kontu bat erregistratzeko. Egiaztatu zure posta elektronikoa, bertan bitcointxoko@gmail.com helbidetik bidalitako mezu bat aurkituko duzu, baieztapen-esteka bat izango duena.</p> <h2>Zure lehen denda sortu</h2> <p>Baieztapen-estekan klik egitean, dendaren sorrera orrialdera eramango zaitu. Eman zure dendari izen bat eta hautatu moneta lehenetsia eta prezio iturri hobetsia. Adibidez, <em>EUR</em> eta <em>Kraken</em> aukeratu ditzakezu, azken hau gomendatutako prezio iturria baita. BTCPay Server-ek zure produktuen edo zerbitzuen prezioa <em>EUR</em>-tik <em>Bitcoin</em>-era bihurtuko du, erosketa unean aukeratutako prezio iturriaren arabera.</p> <h2>Zorro bat konfiguratu</h2> <p>Ordainketak onartzen hasteko, lehenik eta behin zure denda zorro batera lotu behar duzu. Transakzio handiak (500 EUR baino gehiago) maiz espero ez badituzu, Lightning zorro bat konfiguratzeko gomendioa egiten dizugu, eta une honetan (on-chain) Bitcoin zorroa ez erabiltzea gomendatzen da. Lightning zorroa erabiliz, transakzioak azkarragoak eta merkeagoak izango dira.</p> <p>💡 <strong>Lightning</strong> sarea Bitcoin ordainketak jasotzeko sare ezin hobea da, transakzio berehalakoak eta komisiorik baxuenak eskaintzen baititu <strong>on-chain</strong> transakzioekin alderatuta. Horrela, zure negozioak eraginkortasunez eta kostu txikiarekin jaso ditzake ordainketak.</p> <p>Lightning zorro bat konektatzeko modurik errazena LNDhub erabiltzea da, zure Lightning nodo propioa exekutatu beharrik ez baituzu izango. LNDhub zorro bat ez baduzu oraindik, ez kezkatu; Bitcoin Txoko-k doako LNDhub zorroak eskaintzen ditu, eta bost minutu baino gutxiago behar dira konfiguratzeko. Begiratu nostr:naddr1qqxnzd3exuerqdfkxccnyv3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28nkyu7t zure LNDhub zorroa nola lortu jakiteko, eta prest zaudenean itzuli konfigurazioa jarraitzeko.</p> <p><img alt="connect" src="https://cdn.satellite.earth/038642b9f6e77623b7affb20adfce5af46a64d9cecb53c1cb651043a88a72597.webp" /></p> <p>Zure LNDhub zorroa prest dagoenean, jarraitu urrats hauek BTCPay kontuan konfiguratzen: 1. Joan zure BTCPay kontura eta <code>Wallets</code> aukera bilatu alboko barran, ondoren <code>Lightning</code> aukeratu. 2. Hautatu <code>Use custom node</code>. 3. Kopiatu zure LNDhub administrazio URL-a eta itsatsi konexioaren konfigurazioan. 4. Proba ezazu zure zorroaren konexioa. 5. Ondo joan bada, honako mezua agertu beharko litzateke: <em>Connection to the Lightning node successful, but no public address has been configured</em>. Ez kezkatu <em>"no public address has been configured"</em> atalaz, horrek zure nodo propioa exekutatzen ari bazara bakarrik du garrantzia. 6. Zorroaren konexioa arrakastaz probatu ondoren, sakatu <code>Save</code> botoia. 7. <code>Save</code> sakatu ondoren, <code>LNURL</code> atalean, desaktibatu <code>Enable LNURL</code> aukera. Egin aldaketak eta ez ahaztu berriro <code>Save</code> botoian klik egitea. 8. (Hautazkoa) Une honetan, gomendagarria da <code>Display Lightning payment amounts in Satoshis</code> aukera markatzea, Satoshitan zenbatutako ordainketa kopuruak irakurtzeko errazagoak baitira. Satoshi Bitcoin-en zatirik txikiena da; Bitcoin bat 100 milioi satoshik osatzen dute.</p> <p>Jarraitu urrats hauek zure zorroa arrakastaz konfiguratuta izateko eta Lightning bidezko ordainketak onartzeko.</p> <p><img alt="config" src="https://cdn.satellite.earth/d0f30a95573894f674dd7e21646e583bcc69f1a5179556b8cc7853de1cf1bb02.webp" /></p> <p>💡 Zure Lightning nodo propioa erabiltzen ari bazara, konfigurazio prozesua antzekoa da. Ziurtatu zure nodo inplementaziorako konexio kate egokia ematen duzula.</p> <h2>Saltoki puntua (PoS) sortu</h2> <p>Urrats honetara iritsi bazara, zorionak! Zati aspergarriena amaitu da, eta orain zure Saltoki puntua (Point of Sale, PoS) sortzeko unea iritsi da, BTCPay bidez zure lehen Bitcoin ordainketa onartzen hasteko!</p> <p>Saltoki puntu bat sortzeko: 1. Joan <code>Plugins</code> > <code>Point of Sale</code> atalera. 2. Eman izen bat zure Saltoki puntuari eta sakatu <code>Create</code> botoia.</p> <p>Jarraian, zure PoS aplikazioarekin egin ditzakezun gauza erraz batzuk azalduko ditugu. BTCPay-k ezaugarri asko ditu, baina gida honetan oinarrizkoak soilik azalduko ditugu, hasiera emateko.</p> <p>💡 <strong>Gogoratu</strong> BTCPay Server-en saltoki puntu bat baino gehiago sor ditzakezula, bakoitza erabilera jakin baterako. Horrela, negozio desberdinetarako edo produktu eta zerbitzu berezietarako konfigurazio bereiziak izatea posible da.</p> <h3>Teklatua (Keypad)</h3> <p><img alt="keypad" src="https://cdn.satellite.earth/019bd809f089c02d44a10d1824a9226b89d0199f4eeef06d09f859fce1b97310.webp" /></p> <p>Demostrazio erraz baterako, PoS estilo gisa teklatuaren eredua erabiliko dugu.</p> <ol> <li>Eman zure PoS-ari izen bat eta erakusteko titulua.</li> <li>Hautatu <code>Keypad</code> estiloa <code>Point of Sale style</code> aukeraren azpian.</li> <li>Sakatu <code>Save</code> eskuineko goiko izkinan, eta ondoren <code>View</code> sakatu zure PoS begiratzeko.</li> </ol> <p>Ordainketak lehenago konfiguratutako LNDhub zorroan jasoko dira. Jolas ezazu fakturak sortzen eta deskontu eta tip (aholkularitza) aukerak aktibatuz. Gainera, telefono bat baduzu (adibidez, iPhone ez den bat) NFC teknologia onartzen duena, bezeroek NFC txartelak erabiliz ere ordain dezakete, hala nola BoltCard erabiliz (ikusi nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28qjzxr4). Ez al da zoragarria?</p> <p>💡 PoS estilo honen erraztasuna maximizatzeko, Keypad PoS zure telefonoan Progressive Web App (PWA) gisa gorde dezakezu sarbide azkarrerako. Mugikor gehienetako nabigatzaileetan aukera hau <code>Install App</code> edo <code>Gehitu orri nagusian</code> izenarekin agertzen da.</p> <p>Horrela, zure negozioan Bitcoin ordainketak erraz onar ditzakezu, eta erabiltzaileek ere modu intuitibo batean ordaindu ahal izango dute.</p> <h3>Product list (with cart)</h3> <p><img alt="product-list-with-cart" src="https://cdn.satellite.earth/3f7572de5585455096375bf05ead665f2172f6c0dd3b2caa8f67e79f30b13b4e.webp" /></p> <p>Posible da saltoki puntu bat sortzea produktu zehatzekin, bakoitza bere prezioarekin. Ezaugarri hau erabil dezakezu kutxa sinple bat, bezeroen auto-ordainketa sistema edo web denda bat konfiguratzeko.</p> <p>Nola sortu produktu-zerrendadun Saltoki Puntua: 1. Joan berriro alboko barrara eta aukeratu <code>Point of Sale</code>. 2. Oraingoan, <code>Point of Sale Style</code> azpian, hautatu <code>Product list with cart</code>. "With cart" aukerak bezeroari produktu bat baino gehiago aldi berean erosteko aukera ematen dio. 3. Zure produktuak sortu, edo zuzenean sakatu <code>Save</code> eta <code>View</code> produktu laginak probatzeko.</p> <h2>Ondorioa</h2> <p>Gida honetan, zure negozioan Bitcoin onartzen hasteko BTCPay Server erabiliz jarraitu beharreko oinarrizko urratsak azaldu ditugu. BTCPay Server <a href="https://github.com/btcpayserver/btcpayserver">proiektu irekia</a> da eta etengabe garatzen ari da. Askoz ere ezaugarri eta funtzionalitate gehiago eskaintzen ditu, hala nola Shopify integrazioa, crowdfunding eta ordainketen banaketa automatikoa. Gainera, zure denda pertsonaliza dezakezu gaikako diseinuekin, ordainketa-gune pertsonalizatuarekin, erabiltzaileen kudeaketarekin, posta elektronikoko jakinarazpenekin eta askoz gehiago.</p> <p>BTCPay Server-en ahalmen guztiak aprobetxatu nahi badituzu, zure <a href="https://v2.minibolt.info/home/readme">Lightning nodoa konfiguratu</a> eta zure <a href="https://docs.btcpayserver.org/Deployment/">BTCPay zerbitzaria ostatatzea</a> gomendatzen dizugu. Informazio gehiago lortzeko, haien <a href="https://github.com/btcpayserver/btcpayserver">dokumentazioa</a> eta <a href="https://www.youtube.com/@BTCPayServer">bideoak</a> ikustea komeni da.</p> <p>Zalantzarik edo galderarik baduzu, jakinarazi iezaguzu! Zure iritziak entzutea gustatuko litzaiguke eta galderak argitzen lagundu nahi dizugu.</p> <p>Bitcoin Txoko komunitate ireki bat da. Gure zerbitzu guztiak dohaintzekin finantzatzen dira. Gida hau erabilgarria iruditu bazaizu, kontuan hartu gure zerbitzariak martxan mantentzen laguntzeko <a href="https://fund.bitcointxoko.com">dohaintza</a> bat egitea. Eskerrik asko aldez aurretik!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs8hgu30xnwe4qscde8mup84kh3wz8x938k8fa8k8h28g6w6hla0nqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j3yrx62" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs8hgu30xnwe4qscde8mup84kh3wz8x938k8fa8k8h28g6w6hla0nqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j3yrx62" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs8hgu30xnwe4qscde8mup84kh3wz8x938k8fa8k8h28g6w6hla0nqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j3yrx62" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs8hgu30xnwe4qscde8mup84kh3wz8x938k8fa8k8h28g6w6hla0nqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j3yrx62" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3ad01248:962d8a07 <div class="time" style="margin-left: auto;">2024-10-23 18:59:53</div> </div> <div> <p>Well I casted my vote early and I didn't vote for Donald Trump or Kamala Harris. I ended up voting for Chase Oliver, the Libertarian candidate for president. Even though I know he has snowball's chance in hell of winning, I simply couldn't bring myself to vote for the two candidates that are pro-war and pro-genocide. </p> <p>I needed to be able to sleep at night knowing that I did not lend my consent to the mass killing of people in Gaza and around the world using American military equipment to do it. My vote was in protest to the two parties twisted sense of entitlement and delusions of grandeur. The policies that are put in place by these candidates do have an impact on the rest of the world. As much as we would like it not to be the case, it simply is. </p> <p>So if you are voting for Donald Trump or Kamala Harris you know full well that they represent and what their policies are in regards to foreign policy. When it comes to foreign policy both parties are indistinguishable from each other. </p> <p>Democrats and Republicans are strong supporters of Israel and will not do anything to stop the genocide occurring there at the moment. The question you have to ask yourself as you step into that voting booth is are you Ok with being complicit in a genocide. Your vote makes you a supporter of this policy. It may sound mean but that's how strongly I feel about this topic. </p> <p>As Bitcoiners we should want to make the world a better place anyway that we can even if its voting for a candidate that isn't likely going to win. In the long run yes Bitcoin will make situations like this less prevalent but this is a long term goal that isn't going to be achieved today. We must also focus on what we can accomplish in the short term. </p> <p>Voting for a presidential candidate that believes in free markets and disentangling us from all of these wars and awkward alliances, is in line with the Bitcoin ethos and a step in the right direction. At the end of the day do you want to be able to rest your head at night knowing that you didn't vote for more wars, more killing and more destruction? Is your Bitcoin bag really worth more than your soul and your humanity? </p> <p>We are here for more than NGU, right? This wasn't an easy decision for me because I understand that Kamala Harris is probably going to be worse for Bitcoin than Donald Trump but at the end of the day I just didn't feel comfortable voting for Trump knowing that he will keep supplying weapons that enable women and children to be wiped off the map. </p> <p>I urge every Bitcoiner who reads this to look inside yourself and ask what do I stand for and are you willing to sacrifice material wealth to do the right thing? You can't take your Bitcoin with you when you die. Bitcoin will be here long after we are all dead and gone. Tick Toc next block. Life will go on without you being here. </p> <p>My goal is to be a positive force for good during the little time we have on Earth. I want to believe that most Bitcoiners feels the same way to and will act according to their values. </p> <h1>Bitcoin #Nostr #Politics</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs84tazudwmggu4sqdwwmt5wre86fxx30njr74s3xhyf3aze6d0ytszyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwg8ssxj" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs84tazudwmggu4sqdwwmt5wre86fxx30njr74s3xhyf3aze6d0ytszyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwg8ssxj" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs84tazudwmggu4sqdwwmt5wre86fxx30njr74s3xhyf3aze6d0ytszyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwg8ssxj" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs84tazudwmggu4sqdwwmt5wre86fxx30njr74s3xhyf3aze6d0ytszyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwg8ssxj" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 6bae33c8:607272e8 <div class="time" style="margin-left: auto;">2024-10-23 18:57:42</div> </div> <div> <p>I’ve been on a decent run of late — 8-2 the last two weeks. It’s not enough to salvage the quarter or the year, but I’ve got one more “bye” week, so to speak, then have to put together a good Q3.</p> <p><strong>Vikings at Rams</strong> — I’ll say Vikings -4.5 and probably stay away on the short week.</p> <p><strong>Ravens at Browns</strong> — Alan Seslowsky told me it was nine. I would have made it around 7.5, but not sure that’s enough to take the Browns. Might be a dead cat bounce off the Deshaun Watson injury.</p> <p><strong>Titans at Lions</strong> — I’d have made this 13, but Seslowsky told me it was 11.5. Could be a look-ahead game, but otherwise Lions win by 20-plus.</p> <p><strong>Colts at Texans</strong> — I’ll say this is six. Anthony Richardson drags down Indy, but the Texans can’t pass block, and the offense is sluggish.</p> <p><strong>Packers at Jaguars</strong> — Maybe Packers -4.5. I’ll stay away.</p> <p><strong>Cardinals at Dolphins</strong> — If Tua is back, maybe Cardinals +4.5. Stay away.</p> <p><strong>Jets at Patriots</strong> — Seslowsky told me it was Jets -6.5. I kind of like the Jets here in a get well spot. Drake Maye might be a player though.</p> <p><strong>Falcons at Buccaneers</strong> — The Bucs are missing both star wideouts. The Falcons offense is out of sync. I’ll say Falcons +1.5 and consider taking them.</p> <p><strong>Eagles at Bengals</strong> — I’ll say Eagles +2.5 and probably take Cincy.</p> <p><strong>Saints at Chargers</strong> — If no Derek Carr, then Saints +6.5. The Chargers offense is pretty bad, though.</p> <p><strong>Bills at Seahawks</strong> — I’ll go Bills -2.5 and probably sell the Seahawks off last week’s win over the Falcons.</p> <p><strong>Bears at Indigenous Peoples</strong> — If Jayden Daniels is playing then Bears +2.5. If not, then Bears -2.5. Stay away probably.</p> <p><strong>Panthers at Broncos</strong> — I think Seslowsky said this was nine. I’d hold my nose and take the Panthers, but probably a stay away.</p> <p><strong>Chiefs at Raiders</strong> — I’d say Chiefs -7 and consider the Raiders in a division game.</p> <p><strong>Cowboys at 49ers</strong> — Maybe Cowboys +4.5. I have to think about this one.</p> <p><strong>Giants at Steelers</strong> — Giants +7.5 with the offensive line problems. I’d probably lay the wood, to be honest, but their defense is decent.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvzcgwyuvvawj4s9dnuffwus96rcjuuydzmxa7ygkledc23mmzngqzyp46uv7ghsn2t3tnjy40fwttdmmfqfvw5de4h2gv5pwek7nqwfewsfkhfkk" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvzcgwyuvvawj4s9dnuffwus96rcjuuydzmxa7ygkledc23mmzngqzyp46uv7ghsn2t3tnjy40fwttdmmfqfvw5de4h2gv5pwek7nqwfewsfkhfkk" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvzcgwyuvvawj4s9dnuffwus96rcjuuydzmxa7ygkledc23mmzngqzyp46uv7ghsn2t3tnjy40fwttdmmfqfvw5de4h2gv5pwek7nqwfewsfkhfkk" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvzcgwyuvvawj4s9dnuffwus96rcjuuydzmxa7ygkledc23mmzngqzyp46uv7ghsn2t3tnjy40fwttdmmfqfvw5de4h2gv5pwek7nqwfewsfkhfkk" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ aa8de34f:a6ffe696 <div class="time" style="margin-left: auto;">2024-10-09 21:56:39</div> </div> <div> <p>```</p> <p>Technion - Israel Institute of Technology\ Foundations of Quantum Mechanics\ Date: 2024-08-25 Submitted by: Max Peter</p> <p>```</p> <p># Quantum Mechanics and Consciousness: Strange Bedfellows </p> <p><em>"Does consciousness play a special role in quantum mechanics?"</em></p> <h2>Abstract</h2> <p>Could there be a connection between quantum mechanics and consciousness? This Question has fascinated scholars for years. Some believe that consciousness plays a role in how we interpret quantum theory. This essay explores whether consciousness is a fundamental component of quantum mechanics, addressing both the "hard problem" of consciousness and the various interpretations of quantum theory. By critically analyzing arguments from prominent figures like David Chalmers and Barry Loewer, the essay argues that while consciousness presents a significant challenge in understanding reality, current quantum theories may not provide the final answers. Instead, the <em>"hard problem"</em> of consciousness could be the unresolved issue that quantum mechanics needs to address, making it the <em>"elephant in the room"</em> that scientists often avoid.</p> <h2>1. Introduction</h2> <p>The relationship between quantum mechanics and consciousness is one of the most intriguing and contentious debates in modern science and philosophy. Quantum mechanics, the physics of the very small, has upended our classical understanding of the universe, introducing phenomena such as superposition, entanglement, and wavefunction collapse that defy intuition. Simultaneously, consciousness - the subjective experience of being aware - remains one of the most profound mysteries in science, famously described by David Chalmers (1995) as the "hard problem." The intersection of these two enigmatic fields has led to the proposal that consciousness may play a special role in quantum mechanics, particularly in the process of wavefunction collapse, where observation seems to determine physical reality. This essay explores the question: Does consciousness play a special role in quantum mechanics?</p> <p>Advocates of this idea, such as Wigner and Stapp, have argued that consciousness is not merely an observer in quantum mechanics but an active participant that influences quantum events. However, this view is not without its critics. Many physicists and philosophers, including Barry Loewer, argue that connecting consciousness to quantum mechanics is speculative and unsupported by empirical evidence. Despite these criticisms, the possibility that consciousness could be the "elephant in the room" that quantum mechanics needs to address remains an open question. This essay will explore the various interpretations of quantum mechanics that engage with or avoid the issue of consciousness and will argue that the hard problem of consciousness is maybe a vital, yet often ignored, aspect of a better understanding of quantum physics.</p> <h2>2. The Basics of Quantum Mechanics</h2> <p>Quantum mechanics is the branch of physics that deals with the behavior of particles at the smallest scale - atoms and subatomic particles. It is governed by principles that are vastly different from the deterministic laws of classical physics. One of the foundational concepts of quantum mechanics is the wavefunction, a mathematical function that describes the probabilities of a particle's properties, such as position and momentum. Unlike in classical mechanics, where a particle has a definite position and momentum, in quantum mechanics, these properties are described by a probability distribution.</p> <p>One of the most famous principles of quantum mechanics is superposition, which states that a particle can exist in multiple states simultaneously until it is observed. This is famously illustrated by Schrödinger's cat thought experiment, where a cat in a box is simultaneously alive and dead until the box is opened, and an observation is made. Another critical concept is entanglement, where particles become linked, so the state of one particle instantaneously affects the state of another, regardless of the distance between them.</p> <p>The wavefunction collapse is perhaps the most perplexing aspect of quantum mechanics. When a quantum system is observed, the wavefunction collapses, and the system settles into a definite state. This raises the question: What causes the wavefunction to collapse? Is it the act of measurement itself, or does consciousness play a role in this process? The measurement problem in quantum mechanics has led some to propose that consciousness is necessary for wavefunction collapse, thus connecting the two fields in a profound way.</p> <h2>3. The Hard Problem of Consciousness</h2> <p>David Chalmers (1995) famously distinguished between the "easy" and "hard" problems of consciousness. The easy problems involve explaining the cognitive functions and processes that underlie perception, memory, and behavior. These problems, while challenging, are considered solvable through the standard methods of cognitive science and neuroscience. The hard problem, on the other hand, is the problem of subjective experience - why and how physical processes in the brain give rise to the rich inner life of sensation, emotion, and awareness. This subjective aspect of consciousness, also known as qualia (Latin “of what sort”), remains resistant to reductive explanation.</p> <p>Chalmers (1995) argues that the hard problem of consciousness cannot be solved by merely explaining the functions of the brain. There is a gap between physical processes and the experience of those processes - a gap that traditional science struggles to bridge. This has led some theorists to propose that consciousness might be fundamental to the universe, rather than a byproduct of physical processes. This idea has significant implications for quantum mechanics, particularly in the context of the measurement problem. If consciousness is indeed fundamental, it may play a direct role in the collapse of the wavefunction, linking the hard problem of consciousness with the mysteries of quantum mechanics.</p> <h2>4. Consciousness and Quantum Mechanics</h2> <p>The idea that consciousness plays a special role in quantum mechanics is most closely associated with the Consciousness Collapse Proposal (CCP). This theory suggests that the act of observation by a conscious being is what causes the wavefunction to collapse into a definite state. This view was championed by physicists like Eugene Wigner and Henry Stapp, who argued that consciousness must be integrated into our understanding of quantum mechanics. According to Wigner, consciousness is the ultimate cause of the wavefunction collapse, implying that the physical world does not exist in a definite state until it is observed by a conscious mind (Wigner, 1967).</p> <p>However, the CCP is not without its critics. Barry Loewer (2003) argues that the connection between consciousness and quantum mechanics is speculative and lacks empirical support. He contends that while quantum mechanics may involve strange and counterintuitive phenomena, there is no evidence that consciousness plays a direct role in these processes. Loewer suggests that alternative interpretations of quantum mechanics, such as the Ghirardi-Rimini-Weber (GRW) theory and Bohmian mechanics, offer explanations for wavefunction collapse that do not require the involvement of consciousness (Loewer, 2003).</p> <p>Despite these criticisms, the idea that consciousness could be fundamental to quantum mechanics remains a compelling possibility. The CCP aligns with the notion that consciousness is not just an epiphenomenon of brain activity but a fundamental aspect of reality. This perspective challenges the materialist view that physical processes alone are sufficient to explain all phenomena, including consciousness. Instead, it suggests that consciousness might be the key to resolving the mysteries of quantum mechanics.</p> <h2>5. The Elephant in the Room: The Hard Problem of Consciousness in Quantum Mechanics</h2> <p>The central thesis of this section is that the hard problem of consciousness, as articulated by David Chalmers (1995), represents an unresolved issue in the interpretation of quantum mechanics, and may be the "elephant in the room" that most scientific theories attempt to avoid. While many physicists adopt materialist interpretations of quantum mechanics that sidestep the issue of consciousness, it is increasingly difficult to ignore the possibility that consciousness might play a fundamental role in the behaviour of quantum systems. This section will argue that the hard problem of consciousness is not just a philosophical curiosity but a crucial component in understanding the true nature of quantum mechanics.</p> <h3>Consciousness as a Fundamental Aspect of Reality</h3> <p>The hard problem of consciousness refers to the challenge of explaining how and why physical processes in the brain give rise to subjective experience—what it feels like to perceive, think, and be aware. Chalmers (1995) argues that the hard problem is distinct from the "easy" problems of explaining cognitive functions and behaviours because it involves the subjective nature of experience, which cannot be fully captured by a purely physical explanation. This problem is central to the question of whether consciousness plays a role in quantum mechanics because it challenges the materialist assumption that everything can be explained in terms of physical processes.</p> <p>One argument in favour of consciousness playing a fundamental role in quantum mechanics is that it may help solve the measurement problem—the question of why and how the wavefunction collapses when a measurement is made. According to the Consciousness Collapse Proposal (CCP), the collapse of the wavefunction occurs when a conscious observer interacts with the system, suggesting that consciousness is a necessary component of reality. This idea challenges the traditional view of quantum mechanics as a purely objective, observer-independent theory and implies that consciousness is more than just a byproduct of physical processes (Stapp, 1993).</p> <p>In this view, consciousness is not simply an epiphenomenon of the brain but a fundamental aspect of reality that interacts with the physical world in a way that science has yet to fully understand. This perspective aligns with certain interpretations of quantum mechanics, such as the von Neumann-Wigner interpretation, which posits that consciousness plays an active role in the collapse of the wavefunction. While this interpretation remains controversial, it highlights the possibility that consciousness could be integral to the functioning of the universe at a fundamental level.</p> <h3>Avoidance of the Hard Problem in Mainstream Science</h3> <p>Despite the compelling nature of the hard problem, mainstream scientific interpretations of quantum mechanics often avoid addressing consciousness directly. For example, the Many Worlds Interpretation (MWI) of quantum mechanics sidesteps the issue of wavefunction collapse altogether by proposing that all possible outcomes of a quantum measurement exist simultaneously in parallel worlds. In this framework, there is no need to invoke consciousness as a factor in determining the outcome of a quantum event, as every possible outcome is realized in some branch of the multiverse (Everett, 1957). While MWI elegantly avoids the problem of collapse, it does so at the cost of ignoring the role of consciousness, which remains unexplained.</p> <p>Similarly, the Ghirardi-Rimini-Weber (GRW) theory offers an objective collapse model that introduces spontaneous collapses of the wavefunction, independent of observation or consciousness. This theory attempts to solve the measurement problem without invoking consciousness by suggesting that wavefunctions collapse randomly after a certain threshold is reached (Ghirardi, Rimini, & Weber, 1986). Although GRW provides a mathematically consistent solution to the measurement problem, it does not address the hard problem of consciousness, leaving the nature of subjective experience untouched.</p> <p>These interpretations reflect a broader tendency in science to focus on solving the technical aspects of quantum mechanics while avoiding the deeper philosophical questions about consciousness. This approach is understandable, given that the hard problem of consciousness is notoriously difficult to address within the framework of materialist science. However, by sidestepping the issue, these interpretations may be missing a crucial piece of the puzzle. If consciousness is indeed fundamental to the collapse of the wavefunction, as proponents of the CCP suggest, then any interpretation that ignores consciousness is inherently incomplete.</p> <h3>The Case for Addressing Consciousness in Quantum Mechanics</h3> <p>Given the limitations of current interpretations of quantum mechanics, there is a strong case to be made for addressing the hard problem of consciousness directly. One of the key challenges in integrating consciousness into quantum mechanics is the lack of empirical evidence linking consciousness to wavefunction collapse. Critics like Barry Loewer (2003) argue that the CCP is speculative and lacks the rigorous experimental support needed to be taken seriously as a scientific theory. This criticism is valid, as science requires empirical validation to support theoretical claims.</p> <p>However, the absence of empirical evidence does not necessarily invalidate the idea that consciousness could play a role in quantum mechanics. The lack of direct evidence may simply reflect the limitations of current experimental methods, which are not yet sophisticated enough to test the relationship between consciousness and quantum phenomena. Furthermore, the hard problem of consciousness remains unresolved by conventional science, suggesting that new approaches may be needed to explore the connection between consciousness and the physical world.</p> <p>In response to critics, proponents of the CCP could argue that quantum mechanics itself has a long history of challenging conventional notions of reality. The very existence of phenomena like entanglement and superposition defies classical logic and suggests that our understanding of the universe is incomplete. If consciousness is indeed fundamental to the fabric of reality, then it is possible that it plays a role in these quantum phenomena in ways that we do not yet fully understand. Rather than dismissing the CCP as speculative, it may be more productive to consider it as a potential avenue for further research, one that could ultimately lead to a deeper understanding of both consciousness and quantum mechanics.</p> <h2>6. Personal Viewpoint: Consciousness as a Vital Component in Quantum Mechanics</h2> <p>In my view, the hard problem of consciousness is not just an interesting philosophical challenge but a vital issue that must be addressed if we are to fully understand quantum mechanics. The reluctance of many scientists to engage with the hard problem is understandable, given the difficulty of the question and the lack of empirical evidence. However, this avoidance may be preventing us from making significant progress in understanding the true nature of reality.</p> <p>I believe that the hard problem of consciousness represents a fundamental gap in our understanding of the universe - one that cannot be ignored if we are to develop a complete theory of quantum mechanics. While alternative interpretations like the GRW theory and the Many Worlds Interpretation offer solutions to the technical problems of quantum mechanics, they do so by avoiding the deeper question of consciousness. This approach, while pragmatic, may ultimately prove to be a dead end if consciousness is indeed integral to the behaviour of quantum systems.</p> <p>Addressing the hard problem of consciousness in the context of quantum mechanics requires a willingness to think beyond the current boundaries of science and to explore new theoretical frameworks that integrate consciousness into our understanding of the physical world. This may involve revisiting ideas like the Consciousness Collapse Proposal or developing entirely new theories that link consciousness with quantum phenomena in ways that we have not yet imagined.</p> <p>At the same time, it is important to approach this question with a critical and balanced perspective. While the idea that consciousness plays a role in quantum mechanics is intriguing, it is essential to remain open to alternative explanations and to demand rigorous empirical evidence to support any claims. The history of science is filled with theories that seemed promising but ultimately proved to be incorrect, and we must be careful not to fall into the trap of speculation without evidence.</p> <h2>Conclusion</h2> <p>In Summary, I believe that the hard problem of consciousness is the <em>"elephant in the room"</em> that quantum mechanics needs to address. While traditional interpretations of quantum theory have tried to solve the measurement problem without involving consciousness it might be ignoring a part of reality. </p> <p>By blending the matter of consciousness into quantum mechanics we could potentially gain a comprehensive view of the universe - one that appreciates both the enigmatic nature of subjective experiences and the elegant mathematics of some quantum mechanics theories. Even though this viewpoint is speculative and needs investigation it presents a glimpse into a future where consciousness and quantum mechanics are seen as interconnected elements of existence.</p> <h3>References</h3> <p>- CHALMERS, D. J. (1995). FACING UP TO THE PROBLEM OF CONSCIOUSNESS. JOURNAL OF CONSCIOUSNESS STUDIES, 2(3), 200-219.</p> <p>- EVERETT, H. (1957). “RELATIVE STATE” FORMULATION OF QUANTUM MECHANICS. REVIEWS OF MODERN PHYSICS, 29(3), 454-462.</p> <p>- GHIRARDI, G. C., RIMINI, A., & WEBER, T. (1986). UNIFIED DYNAMICS FOR MICROSCOPIC AND MACROSCOPIC SYSTEMS. PHYSICAL REVIEW D, 34(2), 470-491.</p> <p>- LOEWER, B. (2003). CONSCIOUSNESS AND QUANTUM THEORY: STRANGE BEDFELLOWS.</p> <p>- STAPP, H. P. (1993). MIND, MATTER, AND QUANTUM MECHANICS. SPRINGER.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsqel4at3rg6rxfgtkg4e3n8kp8g9dadnrm9madpw5vxjp9nju90uszyz4gmc60lzcc4s7v2m0vmljk79lvxqrnskvneq6vnwvuswdxllnfvdgqq2f" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsqel4at3rg6rxfgtkg4e3n8kp8g9dadnrm9madpw5vxjp9nju90uszyz4gmc60lzcc4s7v2m0vmljk79lvxqrnskvneq6vnwvuswdxllnfvdgqq2f" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsqel4at3rg6rxfgtkg4e3n8kp8g9dadnrm9madpw5vxjp9nju90uszyz4gmc60lzcc4s7v2m0vmljk79lvxqrnskvneq6vnwvuswdxllnfvdgqq2f" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsqel4at3rg6rxfgtkg4e3n8kp8g9dadnrm9madpw5vxjp9nju90uszyz4gmc60lzcc4s7v2m0vmljk79lvxqrnskvneq6vnwvuswdxllnfvdgqq2f" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3ad01248:962d8a07 <div class="time" style="margin-left: auto;">2024-10-23 18:55:25</div> </div> <div> <p>Well I casted my vote early and I didn't vote for Donald Trump or Kamala Harris. I ended up voting for Chase Oliver, the Libertarian candidate for president. Even though I know he has snowball's chance in hell of winning, I simply couldn't bring myself to vote for the two candidates that are pro-war and pro-genocide. </p> <p>I needed to be able to sleep at night knowing that I did not lend my consent to the mass killing of people in Gaza and around the world using American military equipment to do it. My vote was in protest to the two parties twisted sense of entitlement and delusions of grandeur. The policies that are put in place by these candidates do have an impact on the rest of the world. As much as we would like it not to be the case, it simply is. </p> <p>So if you are voting for Donald Trump or Kamala Harris you know full well that they represent and what their policies are in regards to foreign policy. When it comes to foreign policy both parties are indistinguishable from each other. </p> <p>Democrats and Republicans are strong supporters of Israel and will not do anything to stop the genocide occurring there at the moment. The question you have to ask yourself as you step into that voting booth is are you Ok with being complicit in a genocide. Your vote makes you a supporter of this policy. It may sound mean but that's how strongly I feel about this topic. </p> <p>As Bitcoiners we should want to make the world a better place anyway that we can even if its voting for a candidate that isn't likely going to win. In the long run yes Bitcoin will make situations like this less prevalent but this is a long term goal that isn't going to be achieved today. We must also focus on what we can accomplish in the short term. </p> <p>Voting for a presidential candidate that believes in free markets and disentangling us from all of these wars and awkward alliances, is in line with the Bitcoin ethos and a step in the right direction. At the end of the day do you want to be able to rest your head at night knowing that you didn't vote for more wars, more killing and more destruction? Is your Bitcoin bag really worth more than your soul and your humanity? </p> <p>We are here for more than NGU, right? This wasn't an easy decision for me because I understand that Kamala Harris is probably going to be worse for Bitcoin than Donald Trump but at the end of the day I just didn't feel comfortable voting for Trump knowing that he will keep supplying weapons that enable women and children to be wiped off the map. </p> <p>I urge every Bitcoiner who reads this to look inside yourself and ask what do I stand for and are you willing to sacrifice material wealth to do the right thing? You can't take your Bitcoin with you when you die. Bitcoin will be here long after we are all dead and gone. Tick Toc next block. Life will go on without you being here. </p> <p>My goal is to be a positive force for good during the little time we have on Earth. I want to believe that most Bitcoiners feels the same way to and will act according to their values. </p> <h1>Bitcoin #Nostr #Politics</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsqgyyykmdewj8pfq5fmmv53eqsr3d2c5d6cw5x3yn409my2z9ygmgzyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwlknaqz" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsqgyyykmdewj8pfq5fmmv53eqsr3d2c5d6cw5x3yn409my2z9ygmgzyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwlknaqz" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsqgyyykmdewj8pfq5fmmv53eqsr3d2c5d6cw5x3yn409my2z9ygmgzyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwlknaqz" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsqgyyykmdewj8pfq5fmmv53eqsr3d2c5d6cw5x3yn409my2z9ygmgzyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwlknaqz" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ b83e6f82:73c27758 <div class="time" style="margin-left: auto;">2024-10-09 14:25:01</div> </div> <div> <h2>Citrine 0.5.2</h2> <p>- If you are coming from version 0.4.4 or lower you will need to first export the database, uninstall the app and install the new version</p> <p>- Check if port is in use</p> <p>- Support for tor proxy when restoring contact list</p> <p>- Support for auto backup every 24 hours</p> <p>Download it with [<a href="http://zap.store">zap.store</a>](<a href="https://zap.store/download">https://zap.store/download</a>), [Obtainium](<a href="https://github.com/ImranR98/Obtainium">https://github.com/ImranR98/Obtainium</a>), [f-droid](<a href="https://f-droid.org/packages/com.greenart7c3.citrine">https://f-droid.org/packages/com.greenart7c3.citrine</a>) or download it directly in the [releases page </p> <p>](<a href="https://github.com/greenart7c3/Citrine/releases/tag/v0.5.2">https://github.com/greenart7c3/Citrine/releases/tag/v0.5.2</a>)</p> <p>If you like my work consider making a [donation](<a href="https://greenart7c3.com">https://greenart7c3.com</a>)</p> <h2>Verifying the release</h2> <p>In order to verify the release, you'll need to have <code>gpg</code> or <code>gpg2</code> installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:</p> <p>``` bash</p> <p>gpg --keyserver hkps://<a href="http://keys.openpgp.org">keys.openpgp.org</a> --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6D</p> <p>```</p> <p>Once you have his PGP key you can verify the release (assuming <code>manifest-v0.5.2.txt</code> and <code>manifest-v0.5.2.txt.sig</code> are in the current directory) with:</p> <p>``` bash</p> <p>gpg --verify manifest-v0.5.2.txt.sig manifest-v0.5.2.txt</p> <p>```</p> <p>You should see the following if the verification was successful:</p> <p>``` bash</p> <p>gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03</p> <p>gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D</p> <p>gpg: Good signature from "greenart7c3 <<a href="mailto:greenart7c3@proton.me">greenart7c3@proton.me</a>>"</p> <p>```</p> <p>That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:</p> <p>``` bash</p> <p>cat manifest-v0.5.2.txt</p> <p>```</p> <p>One can use the <code>shasum -a 256 <file name here></code> tool in order to re-compute the <code>sha256</code> hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsxe6graauruysahwlt0zny9kzvzp75e467crx86pxaft0hddm0skszyzurumuzn6dnurel3rwr0s5jnlvnzjet773mcs7jte4zqwnncfm4s2chpnj" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsxe6graauruysahwlt0zny9kzvzp75e467crx86pxaft0hddm0skszyzurumuzn6dnurel3rwr0s5jnlvnzjet773mcs7jte4zqwnncfm4s2chpnj" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsxe6graauruysahwlt0zny9kzvzp75e467crx86pxaft0hddm0skszyzurumuzn6dnurel3rwr0s5jnlvnzjet773mcs7jte4zqwnncfm4s2chpnj" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsxe6graauruysahwlt0zny9kzvzp75e467crx86pxaft0hddm0skszyzurumuzn6dnurel3rwr0s5jnlvnzjet773mcs7jte4zqwnncfm4s2chpnj" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ c3f12a9a:06c21301 <div class="time" style="margin-left: auto;">2024-10-23 17:59:45</div> </div> <div> <h1><strong>Destination: Medieval Venice, 1100 AD</strong></h1> <p><em>How did Venice build its trade empire through collaboration, innovation, and trust in decentralized networks?</em></p> <hr /> <h2><strong>Venice: A City of Merchants and Innovators</strong></h2> <p>In medieval times, Venice was a symbol of freedom and prosperity. Unlike the monarchies that dominated Europe, Venice was a republic – a city-state where important decisions were made by the Council of Nobles, and (the Doge, the elected chief magistrate of Venice who served as a ceremonial head of state with limited power), not an absolute ruler. Venice became synonymous with innovative approaches to governance, banking, and trade networks, which led to its rise as one of the most powerful trading centers of its time.</p> <hr /> <h3><strong>Decentralized Trade Networks</strong></h3> <p>The success of Venice lay in its trust in decentralized trade networks. Every merchant, known as a <strong>patrician</strong>, could freely develop their trade activities and connect with others. While elsewhere trade was often controlled by kings and local lords, Venetians believed that prosperity would come from a free market and collaboration between people.</p> <p>Unlike feudal models based on hierarchy and absolute power, Venetian trade networks were <strong>open</strong> and based on <strong>mutual trust</strong>. Every merchant could own ships and trade with the Middle East, and this decentralized ownership of trade routes led to unprecedented prosperity.</p> <hr /> <h3><strong>Story: The Secret Venetian Alliance</strong></h3> <p>A young merchant named <strong>Marco</strong>, who inherited a shipyard from his father, was trying to make a name for himself in the bustling Venetian spice market. In Venice, there were many competitors, and competition was fierce. Marco, however, learned that an opportunity lay outside the traditional trade networks – among <strong>small merchants</strong> who were trying to maintain their independence from the larger Venetian patricians.</p> <p>Marco decided to form an alliance with several other small merchants. Together, they began to share ships, crew costs, and information about trade routes. By creating this informal network, they were able to compete with the larger patricians who controlled the major trade routes. Through <strong>collaboration</strong> and shared resources, they began to achieve profits they would never have achieved alone.</p> <p>In the end, Marco and his fellow merchants succeeded, not because they had the most wealth or influence, but because they trusted each other and worked together. They proved that small players could thrive, even in a market dominated by powerful patricians.</p> <p>Satoshi ends his journey here, enlightened by the lesson that even in a world where big players exist, trust and collaboration can ensure that the market remains free and open for everyone.</p> <hr /> <h2><strong>Venice and Trust in Decentralized Systems</strong></h2> <p>Venice was a symbol of how <strong>decentralization</strong> could lead to prosperity. There was no need for kings or powerful rulers, but instead, trust and collaboration among merchants led to the creation of a wealthy city-state.</p> <p>Venice demonstrated that when people collaborate and share resources, they can achieve greater success than in a hierarchical system with a single central ruler.</p> <hr /> <h2><strong>A Lesson from Venice for Today's World</strong></h2> <p>Today, as we think about the world of Bitcoin and decentralized finance (DeFi), Venice reminds us that trust among individuals and collaboration are key to maintaining independence and freedom. Just as in Venice, where smaller merchants found strength in collaboration, we can also find ways to keep the crypto world decentralized, open, and fair.</p> <hr /> <h2><strong>Key</strong></h2> <p>| Term | Explanation | |------|-------------| | Doge | The elected chief magistrate of Venice who served as a ceremonial head of state with limited power. | | Patrician | A member of the noble class in Venice, typically involved in trade and governance. | | Decentralized Finance (DeFi) | A financial system that does not rely on central financial intermediaries, instead using blockchain technology and smart contracts. |</p> <p>originally posted at https://stacker.news/items/737232</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs8fv6ek09f2mm6rp4ytl2amwm5yfmzmspje2hw32dm8y0znyxuq0czyrplz256sklw53h2vvwf2ef2zlsz6w7tu3mm69cfx58jzlsxcgfszxshwwx" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs8fv6ek09f2mm6rp4ytl2amwm5yfmzmspje2hw32dm8y0znyxuq0czyrplz256sklw53h2vvwf2ef2zlsz6w7tu3mm69cfx58jzlsxcgfszxshwwx" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs8fv6ek09f2mm6rp4ytl2amwm5yfmzmspje2hw32dm8y0znyxuq0czyrplz256sklw53h2vvwf2ef2zlsz6w7tu3mm69cfx58jzlsxcgfszxshwwx" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs8fv6ek09f2mm6rp4ytl2amwm5yfmzmspje2hw32dm8y0znyxuq0czyrplz256sklw53h2vvwf2ef2zlsz6w7tu3mm69cfx58jzlsxcgfszxshwwx" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ bcea2b98:7ccef3c9 <div class="time" style="margin-left: auto;">2024-10-18 17:29:00</div> </div> <div> <p><img alt="" src="https://m.stacker.news/58340" /></p> <p>originally posted at https://stacker.news/items/729964</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsgdymz75acue7rwa33dqdt8648ragwkl5ryhse7zml7t4n88rzaygzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfuaxhh" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsgdymz75acue7rwa33dqdt8648ragwkl5ryhse7zml7t4n88rzaygzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfuaxhh" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsgdymz75acue7rwa33dqdt8648ragwkl5ryhse7zml7t4n88rzaygzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfuaxhh" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsgdymz75acue7rwa33dqdt8648ragwkl5ryhse7zml7t4n88rzaygzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfuaxhh" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ bcea2b98:7ccef3c9 <div class="time" style="margin-left: auto;">2024-10-17 17:02:57</div> </div> <div> <p><img alt="" src="https://m.stacker.news/58097" /></p> <p>originally posted at https://stacker.news/items/728382</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsg233xzz8lg3mvh0ek727rjyuc0hqsfk4nxmrzvydkxwu9fj2m8wczyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujjjzxk2" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsg233xzz8lg3mvh0ek727rjyuc0hqsfk4nxmrzvydkxwu9fj2m8wczyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujjjzxk2" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsg233xzz8lg3mvh0ek727rjyuc0hqsfk4nxmrzvydkxwu9fj2m8wczyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujjjzxk2" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsg233xzz8lg3mvh0ek727rjyuc0hqsfk4nxmrzvydkxwu9fj2m8wczyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujjjzxk2" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 319ad3e7:cc01d50a <div class="time" style="margin-left: auto;">2024-10-08 18:05:44</div> </div> <div> <p>LETTER FROM THE FOUNDER</p> <p>Welcome to the inaugural edition of the <a href="http://Zap.Cooking">Zap.Cooking</a> newsletter!</p> <p>What began as a simple idea and a collaborative effort has grown into a vibrant community. Food, in its unique way, transcends culture and connects us all. It’s at the dinner table where we break bread and share our lives. Here, we’ve created a space where people come together to exchange ideas and celebrate a shared passion for cooking and culinary excellence.</p> <p>This is the Nostr way—a community built on shared ideas and a constructive culture. We are excited to embark on this new journey of sharing a newsletter with friends of Nostr and <a href="http://Zap.Cooking">Zap.Cooking</a>. We hope you enjoy this fresh approach and look forward to many shared recipes and conversations. </p> <p>Bon appétit!</p> <p>Seth, Founder of <a href="http://Zap.Cooking">Zap.Cooking</a></p> <p>\ _<strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong><strong><em>_</em></strong>___</p> <h1><strong>Food Clubs For Life Outside The System</strong></h1> <p>Jack Spirko is the founder and host of The Survival Podcast. In episode 3552, titled "Food Clubs for Life Outside The System," Jack engages in a fascinating two-hour conversation with Joshua Longbrook, who established a food club and hub in Chattanooga, TN, as a means of building a parallel society that respects food freedom and self-sovereignty. Agora Food Club is a private association of members who value natural, organic food and regenerative farming practices, creating and sustaining a locally based alternative food system. In this episode, they discuss the blueprint and what it takes to start a food club in your neighborhood.</p> <p><img src="https://blossom.primal.net/2f812b12db413cd1a8a0b8a9487d66e2ad41f3b5f000fc89d2aaac83c986b623.jpg"></p> <p>Links to YT video and Food Club:</p> <p><a href="https://www.youtube.com/watch?v=5uPcAfG-9AU">https://www.youtube.com/watch?v=5uPcAfG-9AU</a></p> <p><a href="https://theagorafoodclub.com">https://theagorafoodclub.com</a></p> <p><img src="https://blossom.primal.net/02a572d592445b1abe54221099423847bcc35876d7ce5e7f37e79959745f0214.jpg"></p> <p><strong>The Six-Ingredient Grandma Betty's Chicken Dijon Family Recipe</strong></p> <p><a href="https://image.nostr.build/55d3f300fdc4563265f49f729476724f98ff0a062ce7f8d769bf136f0de05cf5.jpg">https://image.nostr.build/55d3f300fdc4563265f49f729476724f98ff0a062ce7f8d769bf136f0de05cf5.jpg</a></p> <p>“Growing up there are a few staple foods that stick with you. For me, it was my Grandma Betty's Chicken Dijon. It was my birthday request every year and every time we cook it up it touches my heart. Grandma Betty passed away 7 years ago. This dish is dedicated to her, directly from her recipe book.” - Quiet Warrior</p> <p><a href="https://zap.cooking/recipe/naddr1qqwkwunpdejx6cfdvfjhgareyaej6cmgd93kketw94jxj6n0dcpzqkcpsw4kc03j906dg8rt8thes432z3yy0d6fj4phylz48xs3g437qvzqqqr4guem0q4t">Grandma Betty's Chicken Dijon on </a><a href="http://zap.cooking">zap.cooking</a></p> <p><strong>Glowing Rolls: Raw Vegan Sushi for a Healthy Boost!</strong></p> <p><a href="https://image.nostr.build/b11da1b878fe48ee74cb1c6c1cc66692ce12827f26c256ecd7a184f99d9c7649.png">https://image.nostr.build/b11da1b878fe48ee74cb1c6c1cc66692ce12827f26c256ecd7a184f99d9c7649.png</a></p> <p>“All you need are your favorite vegetables, nori sheets, a bamboo mat, a cutting board, and a knife. For the dip, you can simply use soy sauce, or try this recipe for a delicious creamy dip. I make my own cream cheese with soaked cashews, nutritional yeast, salt, lime juice, and vinegar. You can also find vegan cream cheese or cashew cheese at a health food store. Feel free to add other veggies like bell pepper, chili, cucumber, fresh onion or anything you like! In the image I also used red bell pepper and shiitake.” - Essencial</p> <p><a href="https://zap.cooking/recipe/naddr1qqekwmr0wa5kueedwfhkcmrn8gkhycth94mx2empdckhxatndp5j6en0wgkkzttgv4skcarg0ykkymm0wd6zzq3qc6dhrhzkflwr2zkdmlujnujawgp2c9rsep6gscyt6mvcusnt5a3sxpqqqp65wenuyur">Glowing Rolls: Raw Vegan Sushi for a Healthy Boost! on </a><a href="http://zap.cooking">zap.cooking</a></p> <p><strong>Slow Cookin’ Tender Sweet-and-Sour Brisket</strong> </p> <p><a href="https://image.nostr.build/97a8a78e39fbe4d19f913ea3c7cac9b94ee20d155596a83e241f0fa71a51517a.jpg">https://image.nostr.build/97a8a78e39fbe4d19f913ea3c7cac9b94ee20d155596a83e241f0fa71a51517a.jpg</a></p> <p>“In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.” - Lizsweig</p> <p><a href="https://zap.cooking/recipe/naddr1qqt8xam9v46z6ctwvskhxmm4wgkkyunfwd4k2aqzyq8dct68gjz8dx7fhak5w8gcpe8zszcte4cekmd8jyqph6mnpnl3kqcyqqq823cvgeugf">Sweet-and-Sour Brisket on </a><a href="http://zap.cooking">zap.cooking</a></p> <h1><strong>2024 Nostriga Photo Album</strong></h1> <p>\ Community Photos by AZA_to_₿_myself, Jeroen, elsat, Derek Ross, realjode, and SimplySarah</p> <p><em>To share your Nostr community photos, please DM @ZapCooking on Nostr</em></p> <p><a href="https://image.nostr.build/388b3bb338672728337ef1c04c90f65655cc29c716f168d35dd4c7343d5802b0.jpg">https://image.nostr.build/388b3bb338672728337ef1c04c90f65655cc29c716f168d35dd4c7343d5802b0.jpg</a></p> <p><a href="https://image.nostr.build/011edabbe3f427c60506fddab024bfeb46c72cf5e0a808b562d7c3ace9f239a0.jpg">https://image.nostr.build/011edabbe3f427c60506fddab024bfeb46c72cf5e0a808b562d7c3ace9f239a0.jpg</a></p> <p><a href="https://image.nostr.build/5fcb47e3a21bbbedafe245f311b6d43f1f610ad96eec26aa85cdcbd0958fdabf.jpg">https://image.nostr.build/5fcb47e3a21bbbedafe245f311b6d43f1f610ad96eec26aa85cdcbd0958fdabf.jpg</a></p> <p><a href="https://image.nostr.build/c2eac240326a7e4ab176776c5d140d0017ccdfef89ef733eaf85efda8e0d39f5.jpg">https://image.nostr.build/c2eac240326a7e4ab176776c5d140d0017ccdfef89ef733eaf85efda8e0d39f5.jpg</a></p> <p><a href="https://image.nostr.build/078682ee987734911886592f377a356245b5a5ea2a15c44ba80e3101ae523b52.jpg">https://image.nostr.build/078682ee987734911886592f377a356245b5a5ea2a15c44ba80e3101ae523b52.jpg</a></p> <p><a href="https://image.nostr.build/c28418d851f3ad7f61435813d8aee82d87af3de4472b4d718a1d2573ae7d38c8.jpg">https://image.nostr.build/c28418d851f3ad7f61435813d8aee82d87af3de4472b4d718a1d2573ae7d38c8.jpg</a></p> <p><a href="https://image.nostr.build/d3a55e11d7927c7cae106491d00a0cfda8323b976aa29123a0fd4e4e3fe78505.jpg">https://image.nostr.build/d3a55e11d7927c7cae106491d00a0cfda8323b976aa29123a0fd4e4e3fe78505.jpg</a></p> <p><a href="https://image.nostr.build/bdd055b0b37a9ebcdc91411796ae6cf785338679e7f44aebf1dc721cc09b076c.jpg">https://image.nostr.build/bdd055b0b37a9ebcdc91411796ae6cf785338679e7f44aebf1dc721cc09b076c.jpg</a></p> <p><a href="https://image.nostr.build/e7bf6c58de70510e96ec3b10630f4a4cfb770026532e2d307b4f95346a4d9ea4.jpg">https://image.nostr.build/e7bf6c58de70510e96ec3b10630f4a4cfb770026532e2d307b4f95346a4d9ea4.jpg</a></p> <p><a href="https://image.nostr.build/b8eb934f8f15aae87ed0db66e898062ec723a8f16d9e93229cd2783d2b158e9d.jpg">https://image.nostr.build/b8eb934f8f15aae87ed0db66e898062ec723a8f16d9e93229cd2783d2b158e9d.jpg</a></p> <p><a href="https://image.nostr.build/f999d2389c363be56543444f301e443ddc126f1caebb9462b74b800d54ed2c28.jpg">https://image.nostr.build/f999d2389c363be56543444f301e443ddc126f1caebb9462b74b800d54ed2c28.jpg</a></p> <p><a href="https://image.nostr.build/0ca2d868703298d222f9cabc3e10a73dcd2d1f82f1b22f8526d9360e9bec8cc7.jpg">https://image.nostr.build/0ca2d868703298d222f9cabc3e10a73dcd2d1f82f1b22f8526d9360e9bec8cc7.jpg</a></p> <p><a href="https://image.nostr.build/94460309bf933bcd89887f16ea6c384fa5bc5e3eb74500de099a3a1405da8edc.jpg">https://image.nostr.build/94460309bf933bcd89887f16ea6c384fa5bc5e3eb74500de099a3a1405da8edc.jpg</a></p> <p>UPCOMING NOSTR HAPPENINGS</p> <p><em>To submit your Nostr event, please DM @ZapCooking on Nostr</em></p> <p>Nostr Valley @ Happy Valley Brewing Company - October 12, 2024 - 12pm to 4pm (est)</p> <p><a href="https://signal.group/#CjQKIPpjU0ei5H_gZyVeVnH82APL7xlDQxQExa9LzTn_TL8KEhA9hy2YPENMD1JWr9ICTasw">Signal Group</a></p> <p><a href="https://image.nostr.build/6c830618389046460ad41e3704864adb338b2a980cc765de51106a2f65adba67.jpg">https://image.nostr.build/6c830618389046460ad41e3704864adb338b2a980cc765de51106a2f65adba67.jpg</a></p> <p>Nostrville 2.0 No Panels, All Party! @ Bitcoin Park - November 6, 2024 - 4:30pm to 7:30pm (cst)</p> <p><a href="https://www.meetup.com/bitcoinpark/events/303283108/">Nostrville 2.0 - No panels, all party!, Wed, Nov 6, 2024, 4:30 PM | Meetup</a></p> <h1><a href="http://ZAP.COOKING"><strong>ZAP.COOKING</strong></a> <strong>PRESENTS: LACE</strong></h1> <p><a href="https://image.nostr.build/fb37dfaa7efe8add086d75af2dfd193181de728e108bd2c8e095a60f7e64bc4f.jpg">https://image.nostr.build/fb37dfaa7efe8add086d75af2dfd193181de728e108bd2c8e095a60f7e64bc4f.jpg</a></p> <p>\ <strong>SimplySarah</strong>: Let’s start by learning a little background on Lace. What is your food story?</p> <p>\ <strong>Lace</strong>: Food for me runs in my veins. My family is from Jamaica and my grandmother began cooking as a girl. She brought her recipes with her to the UK in the 1950s and cooks the most delicious dishes. My mother has been a professional chef for over 40 years. Family meals at Christmas were always a big deal. However, it wasn't until 18, I began cooking at university where I vowed my children would know how to cook a healthy meal and not end up like the people around me living on take out and micro meals. As a student, I just recreated things I ate at home and when I was unsure, I'd call my mum or my grandmother for help. When I had kids, I put them in the kitchen at age 2 and my eldest, now 15, is an incredible chef. We are also well traveled and always enjoying local cuisine which also inspires our cooking.</p> <p><strong>SimplySarah</strong>: That is a lovely background. It seems it was a natural progression to want to get into writing cookbooks. I understand you are working on your second currently, but let's backtrack and talk about how the first one came to life. </p> <p><strong>Lace</strong>: It would seem so. I always wanted to write a book but a cookbook wasn't what I thought I would write first 😅 And yes, the second is coming next year, a co-authored book. The first, came about because of Facebook, actually. Admittedly, I am one of those people who posts food pictures. And my Facebook followers began asking me for my recipes all the time. And I would write them out... and then decided it made more sense to write them once inside a book and sell it. Hence <em>Lace's Bad Ass Yard Food</em> was born.</p> <p><a href="https://image.nostr.build/563b2d4299d824ef4fbb8b85749ba1bb24b0fb4025bf6b10fa2ddaed7217240a.jpg">https://image.nostr.build/563b2d4299d824ef4fbb8b85749ba1bb24b0fb4025bf6b10fa2ddaed7217240a.jpg</a></p> <p><strong>SimplySarah</strong>: That's an awesome title! What IS Bad Ass Yard Food? </p> <p><strong>Lace</strong>: Hahaha, thank you! Yard food is what we (as Jamaicans in my family) call our cuisine. Yard food. Yard means home. So it's basically great homemade food. Typically, this is things like Curry Chicken, Fry Fish, Jerk Chicken, Rice and Peas, Hard Food (yam, dumplings and green bananas) and many other things.</p> <p><strong>SimplySarah</strong>: All those dishes sound phenomenal. If you had a go-to dish from the first cookbook what would you select? Maybe something that is always served on a weekly or regular basis at your home? </p> <p><strong>Lace</strong>: Oh they are! My favorite is curry goat. Curry Chicken has got to be the go to, I still cook it weekly now! And no matter where I've lived in the world, I can always prepare it.</p> <p><a href="https://image.nostr.build/da216e149bee8676a806f010ddde5a29eb4ffa0adeaf5f68265e0e2cc3f11649.jpg">https://image.nostr.build/da216e149bee8676a806f010ddde5a29eb4ffa0adeaf5f68265e0e2cc3f11649.jpg</a></p> <p><strong>SimplySarah</strong>: Funny, I believe you just posted on Nostr that you were in the process of making curry chicken if I recall correctly. Is the next cookbook following the same roots? Or are you and your partner exploring different cuisines? </p> <p><strong>Lace</strong>: That's right! I did just post that curry on Nostr. The next book is going to feature 8 of my favorite recipes. Some will be Jamaican but I also happen to love Asian inspired dishes and have some European favorites too which will be featured. This will be the first time I'm sharing non Caribbean dishes. As for me and my boyfriend, he is Colombian and an ex-military Chef. He has been sharing his food with us and has been enjoying eating food from different regions for the first time as a result of meeting me. It's great fun to bond through food.</p> <p><em>Lace’s Curry Chicken with Purple Cabbage, Plantains, and White Rice:</em>\ <a href="https://image.nostr.build/fb37dfaa7efe8add086d75af2dfd193181de728e108bd2c8e095a60f7e64bc4f.jpg">https://image.nostr.build/fb37dfaa7efe8add086d75af2dfd193181de728e108bd2c8e095a60f7e64bc4f.jpg</a></p> <p><strong>SimplySarah</strong>: Is he the co-author you are speaking about? </p> <p>\ <strong>Lace</strong>: Nope. The other Authors of the book are all entrepreneurs who love food. The first edition will be available in november, it's called Made with Love. I will be featured in the second coming 2025.</p> <p><strong>SimplySarah</strong>: Oh, nice! How did you get tapped into this project? </p> <p><strong>Lace</strong>: Again, my facebook network. I was chatting with a lady who is a self made millionaire about money. She checked out my fb profile and said.. ohh I love your cooking videos, what a fun way to market (my tech business) and then invited me to check out the cookbook project and be part of it. And just like that I was in.</p> <p><strong>SimplySarah</strong>: Facebook definitely brings a lot of people together based on their favorite topics. Now that you are exploring Nostr and have such an incredible background with culinary arts, what do you hope to achieve here on this social protocol? </p> <p><strong>Lace</strong>: Yes, socials are great for that! Honestly, I just want to connect with folks who love great food and are into self development, natural living, love travel and sovereignty. On my second day on Nostr, I met you, a fellow foodie, so it's certainly working out well so far. :) And without all the ads and other crap fb force on it's users</p> <p><strong>SimplySarah</strong>: Personally, I am super thrilled you have joined Nostr. We need more foodies, and I love nerding out about anything food related, especially the food travel stories. I would absolutely love to follow your food journey, and I think all the Nostr foodies should too. Where can everyone find you, follow you, and maybe buy a cookbook? </p> <p><strong>Lace</strong>: Yay! Thank you. I love talking about food, cooking, sharing food, buying ingredients and trying food. You can find me on Facebook - the loved and hated, Nostr, and my personal website. There's no fancy sales page for the cookbook yet! 11 of my Jamaican recipes in one cute ebook :) I'm coming over to Zap Cooking too.</p> <p><strong>SimplySarah</strong>: One day you will be Nostr Only and forget all about Facebook. Haha! We look forward to having you on <a href="http://Zap.Cooking">Zap.Cooking</a>. We have a lot of ideas in the works and would love for you to be involved! I have one final question. First, I want to thank you for taking your time to spend your Saturday morning with me. This was fun. You mentioned you put your children in the kitchen at an early age. I'm a big fan of teaching kids life skills when they are young. Do you have any tips for parents to help them in the kitchen with their children? </p> <p><strong>Lace</strong>: I'm sure that will happen. My fb network has been instrumental in my success and surviving the rough time in my travel. Do tell me all about your ideas for Zap, I'd love to see how I can be involved!</p> <p>Yes, tips for parents, When kids are eating solids, feed them home cooked meals, no jars, no processed stuff, healthy, varied, adventurous meals you eat. If you're eating octopus, let ‘em try. If you're eating veg, let them try. If you're eating chicken liver pate, let them try. Encourage a varied diet and pallet. Then at 2, get them in the kitchen. Let them peel garlic cloves, add herbs to meat, make meatballs, mix and taste things. Invite them to cook everyday. And have fun with it! </p> <p>It's been my pleasure to spend time with you this Saturday morning Sarah. Thank YOU.</p> <p>You can find the talented Lace at:</p> <p><a href="https://www.facebook.com/iamlaceflowers">https://www.facebook.com/iamlaceflowers</a></p> <p><a href="https://primal.net/p/npub1ruhmx2wy663u9k2sams6qrlvgq86t3p4q3ygwgp5wqzcrgd6fh7sr20ys2">https://primal.net/p/npub1ruhmx2wy663u9k2sams6qrlvgq86t3p4q3ygwgp5wqzcrgd6fh7sr20ys2</a></p> <p><a href="https://www.iamlaceflowers.com/workwithme">https://www.iamlaceflowers.com/workwithme</a></p> <p>Follow Zap.Cooking Content Coordinator SimplySarah at:</p> <p><a href="https://image.nostr.build/c208bb8d562421beb00cc26fcf38417a0d52660659f4ac9d40365f3761a486b8.png">https://image.nostr.build/c208bb8d562421beb00cc26fcf38417a0d52660659f4ac9d40365f3761a486b8.png</a></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqstj8zxxyrd9yej292f0nzxmjgu3ca3zue9q34fhz930vessd27x5czyqce45l8jp35m05x79xmns5etvnwu0rz9zl9t7yuf3l74xkvq82s5r7kp5e" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqstj8zxxyrd9yej292f0nzxmjgu3ca3zue9q34fhz930vessd27x5czyqce45l8jp35m05x79xmns5etvnwu0rz9zl9t7yuf3l74xkvq82s5r7kp5e" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqstj8zxxyrd9yej292f0nzxmjgu3ca3zue9q34fhz930vessd27x5czyqce45l8jp35m05x79xmns5etvnwu0rz9zl9t7yuf3l74xkvq82s5r7kp5e" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqstj8zxxyrd9yej292f0nzxmjgu3ca3zue9q34fhz930vessd27x5czyqce45l8jp35m05x79xmns5etvnwu0rz9zl9t7yuf3l74xkvq82s5r7kp5e" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ fa0165a0:03397073 <div class="time" style="margin-left: auto;">2024-10-23 17:19:41</div> </div> <div> <h2>Chef's notes</h2> <p>This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.</p> <p>The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven</p> <p>When done: Enjoy during Fika!</p> <p>PS;</p> <ul> <li> <p>Can be frozen and thawed in microwave for later enjoyment as well.</p> </li> <li> <p>If you need unit conversion, this site may be of help: https://www.unitconverters.net/</p> </li> <li> <p>Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker</p> </li> </ul> <h2>Ingredients</h2> <ul> <li>150 g butter</li> <li>5 dl milk</li> <li>50 g baking yeast (normal or for sweet dough)</li> <li>1/2 teaspoon salt</li> <li>1-1 1/2 dl sugar</li> <li>(Optional) 2 teaspoons of crushed or grounded cardamom seeds.</li> <li>1.4 liters of wheat flour</li> <li>Filling: 50-75 g butter, room temperature</li> <li>Filling: 1/2 - 1 dl sugar</li> <li>Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)</li> <li>Garnish: 1 egg, sugar or Almond Shavings</li> </ul> <h2>Directions</h2> <ol> <li>Melt the butter/margarine in a saucepan.</li> <li>Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).</li> <li>Dissolve the yeast in a dough bowl with the help of the salt.</li> <li>Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.</li> <li>Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.</li> <li>Add if necessary. additional flour but save at least 1 dl for baking.</li> <li>Let the dough rise covered (by a kitchen towel), about 30 minutes.</li> <li>Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.</li> <li>Stir together the ingredients for the filling and spread it.</li> <li>Roll up and cut each roll into 24 pieces.</li> <li>Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.</li> <li>Brush the buns with beaten egg and sprinkle your chosen topping.</li> <li>Bake in the middle of the oven at 250 ° C, 5-8 minutes.</li> <li>Allow to cool on a wire rack under a baking sheet.</li> </ol> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9zqjl0peyw8zalel8yw8f6sj0hphgv93m0l3nge789nntvv6cgxszyraqzedq7xf0kr53clv8zrjh2u9dy7ehzh99yxqld3funvsr89c8x6l8gww" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9zqjl0peyw8zalel8yw8f6sj0hphgv93m0l3nge789nntvv6cgxszyraqzedq7xf0kr53clv8zrjh2u9dy7ehzh99yxqld3funvsr89c8x6l8gww" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9zqjl0peyw8zalel8yw8f6sj0hphgv93m0l3nge789nntvv6cgxszyraqzedq7xf0kr53clv8zrjh2u9dy7ehzh99yxqld3funvsr89c8x6l8gww" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9zqjl0peyw8zalel8yw8f6sj0hphgv93m0l3nge789nntvv6cgxszyraqzedq7xf0kr53clv8zrjh2u9dy7ehzh99yxqld3funvsr89c8x6l8gww" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 57d1a264:69f1fee1 <div class="time" style="margin-left: auto;">2024-10-23 16:11:26</div> </div> <div> <h5><em>Welcome back to our weekly <code>JABBB</code>, <strong>Just Another Bitcoin Bubble Boom</strong>, a comics and meme contest crafted for you, creative stackers!</em></h5> <p>If you'd like to learn more, check our welcome post <a href="https://stacker.news/items/480740/r/Design_r">here</a>.</p> <hr /> <h3>This week sticker: <code>Bitcoin Students Network</code></h3> <p>You can download the source file directly from the <a href="https://www.herecomesbitcoin.org/">HereComesBitcoin</a> website in <a href="https://www.herecomesbitcoin.org/assets/Flower-god.svg">SVG</a> and <a href="https://www.herecomesbitcoin.org/assets/Flower-god.png">PNG</a>. <img alt="" src="https://m.stacker.news/59164" /></p> <h3>The task</h3> <blockquote> <p>Starting from this sticker, design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious take on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.</p> <p>Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the <a href="https://www.herecomesbitcoin.org/">Gif Station</a> section and craft your best meme... Let's Jabbb!</p> </blockquote> <hr /> <p>If you enjoy designing and memeing, feel free to check our <a href="https://stacker.news/Design_r#jabbbs--just-another-bitcoin-bubble-boom--comic--meme-contests">JABBB archive</a> and create more to spread Bitcoin awareness to the moon.</p> <p>Submit each proposal on the relative thread, bounties will be distributed next week together with the release of next JABBB contest. </p> <p>₿ creative and have fun!</p> <hr /> <p>originally posted at https://stacker.news/items/736536</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs83mc2ejdfarfctv3l2a92twvkxe9sztmhcn867znmdwas0ehnnxgzyptargnyexaazzclhs9jnqw3xw2hta7certu8gvfufm2ecmf78lwzl9h0j4" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs83mc2ejdfarfctv3l2a92twvkxe9sztmhcn867znmdwas0ehnnxgzyptargnyexaazzclhs9jnqw3xw2hta7certu8gvfufm2ecmf78lwzl9h0j4" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs83mc2ejdfarfctv3l2a92twvkxe9sztmhcn867znmdwas0ehnnxgzyptargnyexaazzclhs9jnqw3xw2hta7certu8gvfufm2ecmf78lwzl9h0j4" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs83mc2ejdfarfctv3l2a92twvkxe9sztmhcn867znmdwas0ehnnxgzyptargnyexaazzclhs9jnqw3xw2hta7certu8gvfufm2ecmf78lwzl9h0j4" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 319ad3e7:cc01d50a <div class="time" style="margin-left: auto;">2024-10-08 14:33:14</div> </div> <div> <p>https://image.nostr.build/4824c65d9a07c577bee8591b18ee147e7a457849fbaee53244667ec062914751.jpg</p> <p><strong>OCT 2024 | ISSUE 2</strong> | LETTER FROM THE FOUNDER | LIFE EXPERIENCE | FEATURED RECIPES | REVIEWED RECIPES | ECONOMICS | MICROFICTION | FAMILY FOODLOVE | FOOD SWOON | NOTE SYNCING | SOUNDS | QUOTE OF THE MONTH | UPCOMING EVENTS | ANNOUNCEMENTS | LANGUAGE | #NOSTRASIA2024 ALBUM | FINAL THOUGHTS</p> <hr /> <h2>LETTER FROM THE FOUNDER 📝</h2> <hr /> <p>Hey Everyone!</p> <p>Exciting things are cooking at Zap Cooking! We’re thrilled to announce that we’ll be in Happy Valley, State College, PA, on October 12th as proud sponsors of Nostr Valley. It’s shaping up to be an incredible weekend, and we can’t wait to share it with you! We’ll be hosting a dynamic panel that dives deep into the intersection of food, culture, and, of course, the unique world of Nostr. This event promises a great mix of good times and engagement, and we’d love to have you join us! If you're interested, sign up now at <a href="">nostrvalley.com</a>.</p> <p>We’re also excited to have you reading our second monthly newsletter. At Zap Cooking, our focus goes beyond development - we're committed to creating content that inspires. Follow our npub on Nostr to catch flavorful food ideas and captivating creative content. We’re working on fresh perspectives and new projects that celebrate cultural diversity, all while keeping the quirky, authentic spirit of Nostr alive. Thanks for being part of this journey with us. Let’s keep Nostr weird and delicious!</p> <p><em>Seth</em></p> <p>https://i.nostr.build/nQqsPGmJ8hjvxROK.png</p> <blockquote> <p>Artwork by Bread and Toast | https://breadandtoast.com/</p> </blockquote> <hr /> <h2>LIFE EXPERIENCE 😮💨</h2> <hr /> <p>In August 2024, Nostriga held the afterparties at the Basement, an underground Bitcoin bar in Riga, Latvia. The crowd spent the nights enchanted in conversations, dancing, drinking, and smoking cigars to celebrate freedom and life.</p> <p>It was a fascinating experience smoking cigars with the Nostr men on those cobblestone streets, reminding me of my younger years working in a private social club, where the cocktail lounge would fill with a thick layer of cigar smoke as I crafted and served Bourbon or Rye Manhattans, Old Fashioned cocktails (one with Sweet 'n Low!), and neat single malt Scotch whiskies.</p> <p>Recently one of the voices of Nostr - The Beave - tagged me in a note, introducing me to Duchess and their love of coffee & cigars. In less than twenty minutes, Duchess and I were collaborating for the next Zap.Cooking newsletter. The following review is going to take us out of the nightlife and into a morning zen session. - SimplySarah</p> <h4>CIGAR & COFFEE | Duchess</h4> <p>https://image.nostr.build/eff42693d5d4c9f086c25a11e57563b5163dad2f3da600de5e835ba2e1a1a842.jpg</p> <p>There’s nothing quite like starting your day with a good cigar and a cup of coffee. The rich, earthy flavors of a cigar paired with the bold aroma of coffee create a perfect harmony that awakens all the senses. The Coffee will give you that little morning boost, while the cigar will ease you into a calm, zen-like state. Together, it’s a ‘boosted zen’ that really sets the tone for a productive yet relaxed day.</p> <h4>CIGAR | PDR 1878 DARK ROAST CAFE</h4> <p>A cigar known for its rich, coffee-infused flavor. This particular one is designed to complement a dark roast coffee experience.</p> <p>https://image.nostr.build/0ab1bb066281c4d6ed2cf0f65548076255535552c27b7a723953bd1ba5713cbe.png</p> <p>The PDR 1878 Dark Roast Cafe cigar has a unique, slightly spicy profile that pairs beautifully with a cup of dark roast coffee. The coffee I paired with my cigar this morning was one of my favorite dark roasts: Jamaican Blue Mountain Roast, from Jamaica. Another dark roast that I love but didn’t have on hand is Black Ivory Coffee from Thailand.</p> <h4>COFFEE | JAMAICAN BLUE MOUNTAIN COFFEE</h4> <p>Known for its exceptional smoothness, mild flavor, and low acidity, Jamaican Blue Mountain Coffee is one of the world’s most luxurious and sought-after coffees. Grown at high elevations in Jamaica’s Blue Mountains, this coffee is loved for its balanced and refined taste.</p> <p>https://image.nostr.build/57700f4defe71f9f01c9406ca7c1d6cbf4ccdc621a9b48db31065834079b0b17.png</p> <p>Most purists drink Jamaican Blue Mountain Coffee without milk or cream to fully appreciate its unique and subtle flavors. However, I like to add fresh cream from the farm if you have access to a local farmer. I feel that adding cream creates a richer, smoother cup, no matter what coffee I’m drinking.</p> <p>Coffee and cigars are both fascinating rabbit holes, much like wine, if you're interested in going down them.</p> <p><strong>ENJOYABLE PART OF SMOKING A CIGAR</strong> | Cigars are enjoyed primarily for their flavor. The rich taste of a cigar comes from the blend of different tobaccos, which is best experienced by holding the smoke in your mouth, where your taste buds can fully appreciate it. Inhaling isn't necessary and actually makes the experience less enjoyable because cigar smoke is much stronger and can be harsh on your lungs.</p> <p><strong>HEALTH BENEFITS OF SMOKING A CIGAR</strong> | Nicotine, in small doses, can have some positive effects, like improving focus and mental sharpness. It also stimulates certain receptors in the brain that can support heart health. Cigars are the healthiest vehicle to deliver nicotine into your body, as they offer a slower, more natural release of nicotine compared to cigarettes or other forms of tobacco.</p> <p><strong>ENJOYABLE PART OF DRINKING COFFEE</strong> | Coffee is widely enjoyed for its flavor and aroma. The rich, complex taste of coffee comes from carefully roasted beans, which can range from bold and dark to mild and fruity, depending on the origin and roast. Sipping coffee slowly allows the palate to savor the intricate layers of flavor, from chocolaty and nutty to floral and fruity notes. Whether black or with milk, coffee offers a comforting and energizing experience.</p> <p><strong>HEALTH BENEFITS OF DRINKING COFFEE</strong> | In moderate amounts, coffee offers several health benefits. It is rich in antioxidants, which are known to support heart health, brain function, and help combat inflammation. The caffeine in coffee can boost focus, mental sharpness, and physical endurance by stimulating the central nervous system. Some studies have also suggested that coffee may support heart health, improve metabolic rate, and reduce the risk of certain diseases, such as Parkinson’s and Alzheimer's. Organic coffee—free from pesticides and chemicals—provides a cleaner, more natural source of these benefits.</p> <p>Find Duchess on Nostr: duchess@orangepiller.org</p> <hr /> <h2>FEATURED RECIPES 🥪</h2> <hr /> <h2>https://image.nostr.build/8ec8e09bc081e7f70de446fda8fc85d485c01ed4579b13f511753568b21f3c8b.jpg</h2> <p>https://image.nostr.build/e902abea3014325e848f7cbc8f1bd00f8899880fedcd2490361d12ec595c451a.png zap.cooking/recipe/naddr1qqsxxmrpwdekjcedwp3zv63dwa5hg6pdvykkx6r9v4ehjtt5wa5hxaqzyzmjwnfgu05c80mjpk6tfgf2x86u0mexyvsdqhp9ajgy3xkfjc5vkqcyqqq823cfuzkwc</p> <hr /> <p>https://image.nostr.build/b2a84afc5ea7948c3f8087b555ce9a43a5f543402b1ecb283cc884b93f1f8a2b.png</p> <p>zap.cooking/recipe/naddr1qqvxyet9vckkzmny94sh2cn9wfnkjmn9943h2unj0ypzq3xurskmnslm67lwjft7e66jhc7033qt4aak8arw266c5ycuwnctqvzqqqr4guhg7y8e</p> <hr /> <p>https://image.nostr.build/ec7ef7667e252d63164682ed420ae94dc15758798cd80d62e8491ec35cef0f69.png</p> <p>zap.cooking/recipe/naddr1qqfkvetjd4jkuar9vskksmm5945x7mn90ypzqqwsh0u4xlh3l5xalq2lg8qcjeec7636pasq75w8s2ma3zg3xr2vqvzqqqr4guvhlwd6</p> <hr /> <p>https://image.nostr.build/13b8af46a09dcf0ab04a37aae7f22c16fe31740ef4bc0984e8cf7b582e45332f.png zap.cooking/recipe/naddr1qq8xyetpdeej6mmw946x7ctnwspzp89qh469qapddgsrr8qw84xx08y7q34fm3cw3m64c2g9ufq9ydqtqvzqqqr4gug3lkp4</p> <hr /> <h2>RECIPE REVIEWS ✏️</h2> <hr /> <p>https://image.nostr.build/5ef1e884bde50d01215de6c3ed63e2d9a78bac0bd8eade1df6bf91c1b63ad3c1.png zap.cooking/recipe/naddr1qqtkwctjd35kxumpw43k2ttxdaez6ctw0ykkycn3qgswat02dja4qx9pjrcpz7zhmegnesn36fxfgl2kekpv2jntvjhy0fqrqsqqqa28m4rxcx</p> <hr /> <p>https://image.nostr.build/96299dcb152c513360f171038d032de102c29497634e1ba7b60abc1b215a4a42.png zap.cooking/recipe/naddr1qqjkket5dukksctd9skk2em895nz6cmgv4jhxefdvfex2cttveshxapdvd6hquczyzdu956dmk5rm9p2rlwndf6g07d2a36qmvjw57tn9kgw8q73n555sqcyqqq823c8r4tsp</p> <hr /> <h2>ECONOMICS 🍞</h2> <hr /> <h4>AN ARTICLE ABOUT BAKERS | Silberengel (4 minute read)</h4> <p>https://image.nostr.build/4f11eea6d6a5f7476c0bbe0504f57e7111454c9b30ee0816ee0f85816d240e3b.jpg</p> <h4>Let's Talk About Baking Bread</h4> <p>I've mentioned a few times, how large-scale central planning inevitably leads to artificial scarcity and rising prices. Allow me to illustrate -- using a completely invented allegory about bread -- that has absolutely no parallels to any economy you may already be familiar with…</p> <p>Read More | habla.news/a/naddr1qvzqqqr4gupzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqqxnzdejxucnwvfnxvmnsd3cgqxylq</p> <hr /> <h2>MICROFICTION 📖</h2> <hr /> <h4>GOOD DEEDS | Rustypuppy</h4> <p>Being a trail guide at the UCP (Unique Creatures Preserve) meant I saw a lot of weird things. Some I show to the tourists; some I don’t. </p> <p>The starved, green-skinned toddler with the turtle shell back, beak, and dish of water on his head was one of the latter. As he ignored the bologna sandwich and devoured the cucumber salad from my lunch, I flipped through my identification guide. Finally found him in the Japanese yokai section; a kappa - known for drowning animals and people, loves cucumbers and sumo wrestling, can be friendly and helpful, empty the dish on its head to severely weaken.</p> <p>I filled up his dish from my water bottle, and he followed me down the mountain trail. As soon as he saw the glimmer of water, he ran ahead and dove in. I assumed from the lack of frothing water and the fact he didn’t end up punted onto the bank meant the lake god had accepted him. </p> <p>Later that week, two teens stumbled into our office. One guy, obviously stoned, wanted us to give him the official wizard certificate since he had just walked on water. The other guy, obviously drunk, said his friend needed the druid certificate because he had summoned a turtle to appear under his feet, which is how he had spent the past half hour walking across the lake. I told the intern to take their contact info and arrange a taxi.</p> <p>The next day, I left a large container of cucumber salad at the edge of the lake. </p> <p><em>RECIPE REFERENCE | Grandma’s cucumber recipe</em> zap.cooking/recipe/naddr1qq0kwunpdejx6cf8wvkkxun9v9khjttrw43h2mtzv4ez6umpd3skgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxpqqqp65wss0rqd</p> <p>Follow Rustypuppy | https://rustypuppy.npub.pro/</p> <hr /> <h2>FAMILY FOODLOVE 🐤</h2> <hr /> <p>https://image.nostr.build/c5b498d176a03742a864de6ae1c833107089e798e4a9c3c111b5be8850df2397.png</p> <p>https://image.nostr.build/55a8948263766f0f4360d9bddb30ada915cae51a93b3d7be1b4a7a9e6cc21b71.png</p> <p>https://image.nostr.build/f17a5dd1cf93ae0d20b7904e0e0274d4dda3a6dd4c90c506b512232af08bec83.png</p> <p>https://image.nostr.build/ef81f242c481e60cff9dd4a66ac74326a8e27ff0f87ae1f51a915046eecb8258.png</p> <hr /> <h2>FOOD SWOON 💌</h2> <hr /> <p>https://image.nostr.build/a0eeb835a8eee1221f4e6aeeb884b5897eea7335680f2e5b35bee35b517db432.png https://image.nostr.build/f2a8a21cd1587a39d0ce5fe09ef5176b773416d0419a6b5fb404c02fa6616730.png https://image.nostr.build/c4f54698566500ace19d12bef5168b0a6e7047a0c8c1daa3faa207253177b104.png https://image.nostr.build/22a0aaacbf37e88db702db655a4f9e7b0692d586304e9ecfffa694f379a88fd9.jpg https://image.nostr.build/f3918b3c68dc04bc3aae4e5202702875ebd4668676abe64fbc1e8cb001dde3c2.png</p> <hr /> <h2>NOTE SYNCING 🗒️</h2> <hr /> <p>“..everyone needs to eat pizza. Each individual country can choose what toppings they want on their pizza, so whether that’s pepperoni or mushrooms or anchovies if you are weird…” | OpnState on https://fountain.fm/episode/dg7rlmtOICVDGwtr7Jnc</p> <p>"I eat sardines out of the tin with chopsticks." | @the_beave </p> <p>“Chef has renamed Sardines to ‘Salt Daddies’. Please inform the staff.” | @enki </p> <p>“My segue into sardines #FoodPorn” | @Deva Pyne (talking about HowToFoodPrep’s Sardine Dish) https://image.nostr.build/0f979d1bb7c0ba3c600694b83c5bc8e84ce4ff039839fb9f9af7ea727accef8b.jpg</p> <hr /> <h2>SOUNDS 🔊</h2> <hr /> <h4>MUSIC</h4> <h3>MAN LIKE KWEKS x BILLIV</h3> <p>Shoutout to <strong>Man Like Kweks x Billiv</strong> for making songs about PB & J cool! | <em>singing</em> Go together like peanut butter and jelly... | <strong>NOSTR CITY | KWEKS x BILLIV • Man Like Kweks (wavlake.com)</strong> | https://wavlake.com/track/f46d82f2-7f26-4357-9258-32da68324f74 | Man Like Kweks made a special appearance on <strong>Detox Radio</strong> | https://fountain.fm/episode/hGH0AgRj6hvrZEnSlX6n/ | https://image.nostr.build/baf111d653e75e88fc818529ba7872563e72be9540b21d0dea70b712d565dadd.png </p> <h4>PODCASTS</h4> <h3>PLEBCHAIN RADIO</h3> <p>https://image.nostr.build/748c4c9f104582f583c3e3e30603be3964d0ddd3c8041a72680d5b8d48bc7108.png <strong>Zap.Cooking's</strong> very own <strong>Seth</strong> joins <strong>former Nostr CEO Derek Ross</strong> on <strong>Plebchain Radio</strong> hosted by the infamous duo: <strong>QW & Avi</strong> | <strong>CLIP - Super Rare Nostr.Cooking Magnet</strong> | "That's one of those physical NFTs" | https://fountain.fm/clip/dTzOg3VXOtLaXdR28oKE</p> <h3>ON THE FLY WITH STU</h3> <p>https://image.nostr.build/56ac7daf7d8158cde5f31ac2555f03ba26fe9de1afb5eeb26f4ba54f350bb7b8.jpg Recommended listening from our new fly fishing aficionado, onthefly@iris.to with Stu aka <strong>ON THE FLY WITH STU</strong> | https://fountain.fm/clip/9KjsUBPwmnmpR11UscKP</p> <h3>THE BITCOIN PODCAST</h3> <p>https://image.nostr.build/53fcc6f8468f3f18d0920fa0dcf386c01b7f02833101984bb26fff31916da498.jpg <strong>A VERY special thanks</strong> to <strong>Walker</strong>, the host of <strong>The Bitcoin Podcast</strong>, for giving Zap.Cooking a shoutout on his platform | "Okay this is pretty neat. Recipes on Nostr. Like the recipe? #zap it. Check out https://zap.cooking #grownostr" | Please check out one of the best voices that Nostr has to offer at bitcoinpodcast.net/podcast</p> <hr /> <h2>QUOTE OF THE MONTH 📣</h2> <hr /> <h6>"Nostr and Bitcoin will change the world because they're like peanut butter and jelly - decentralized freedom meets unstoppable money, making sure no middleman gets a slice of your sandwich!" | Uncle Rockstar✊</h6> <hr /> <h2>UPCOMING EVENTS 🥳</h2> <hr /> <p><em>Submit your Nostr event with @ZapCooking on Nostr</em></p> <p><strong>Nostr Valley @ Happy Valley Brewing Company</strong> | October 12, 2024 - 12pm to 4pm (est) Sign Up @ www.nostrvalley.com </p> <p><strong>Nostrville 2.0 No Panels, All Party! @ Bitcoin Park</strong> | November 6, 2024 - 4:30pm to 7:30pm (cst) https://www.meetup.com/bitcoinpark/events/303283108/</p> <p>https://image.nostr.build/d484fb5058f39d7f15dfe048dc91b1b697c45c117612ec0202d8a5bb681af02a.jpg</p> <hr /> <h2>ANNOUNCEMENT 📰</h2> <hr /> <h4>RABBIT HOLE RECAP REBRANDING</h4> <p>https://image.nostr.build/dacfbb06c6b76582814ad035ff44d9a66a885cdb97783e56b491d6b2e4b6d1f5.png https://video.nostr.build/a6b670ea0839d2d5d35ee4d38d9a082a0ce4b93aeb6ffaad18c89de829ccbc95.mp4</p> <h6><em>https://rhr.tv/ | Please send them a warm congratulations!</em> 🤠</h6> <p>https://image.nostr.build/497029805a46bbb4942bcb13a0e8f0238e3c7956282d4d2866ca342d19f54bad.jpg</p> <hr /> <h2>LANGUAGE 🏫</h2> <hr /> <h4>SCHOOL'S IN SESSION</h4> <p><em>Write "egg" in 50 of the Most Popular Languages</em></p> <p>English: egg | Spanish: huevo | French: œuf | German: Ei | Italian: uovo | Portuguese: ovo | Russian: яйцо (yaytso) | Chinese (Simplified): 蛋 (dàn) | Japanese: 卵 (tamago) | Korean: 계란 (gyeran) | Arabic: بيضة (bayda) | Hindi: अंडा (anda) | Bengali: ডিম (dim) | Turkish: yumurta | Vietnamese: trứng | Thai: ไข่ (khai) | Persian (Farsi): تخممرغ (tokhm morgh) | Swedish: ägg | Danish: æg | Norwegian: egg | Finnish: muna | Hungarian: tojás | Czech: vejce | Slovak: vajce | Romanian: ou | Bulgarian: яйце (yaytse) | Ukrainian: яйце (yaytse) | Malay: telur | Indonesian: telur | Filipino: itlog | Swahili: yai | Serbian: јаје (jaje) | Croatian: jaje | Bosnian: jaje | Lithuanian: kiaušinis | Latvian: ola | Estonian: muna | Icelandic: egg | Maltese: bajda | Welsh: wy | Irish: ubh | Scottish Gaelic: ugh | Basque: arrautza | Catalan: ou | Galician: ovo | Armenian: ձու (dzu) | Georgian: კვერცხი (k'verts'khi) | Tatar: йомырка (yomyrka) | Kazakh: жұмыртқа (jumyrtqa) | Tamil: முட்டை (muttai)</p> <hr /> <h2>#NOSTRASIA2024 ALBUM 📷</h2> <hr /> <p>https://image.nostr.build/9243af94d1ae162bcf9ea14baad39286c4162dc838dd3d82f988e7a032f50328.png</p> <p><em>Community Photos & Videos by A.k.A. radish on fire🎤 @hakkadaikon, @HonokaShisha, @Kojira, @Jeroen and the contributors of the hashtag #NostrAsia2024 | Share your Nostr community photos or videos with @ZapCooking</em></p> <h4>MESSAGE from A.k.A. radish on fire🎤 @hakkadaikon</h4> <p><em>Hello!</em> </p> <p>Thank you very much for coming to Nostrasia 2024 on the 23rd of September!</p> <p>Now, you can see the live-streamed videos of the speaker events and the afterparty from the YouTube archive. Please check them out especially if you could not join the talking events. You can jump into a session you like from the chapter lists in the video descriptions.</p> <p><em>Thank you!</em></p> <p><strong>Nostrasia 2024 Part 1</strong> https://www.youtube.com/live/i-oHjdYWo1E</p> <p><strong>Nostrasia 2024 Part 2</strong> https://www.youtube.com/live/tGeHKrqTA4A</p> <p><strong>Nostrasia 2024 Part 3 - Afterparty (Tuna cutting show)</strong> https://www.youtube.com/live/ery0aWATjWk</p> <h4>GIKOGIKO KAIJI TUNA | KOJIRA</h4> <p>https://i.nostr.build/Y2jTdGxblC98KeWI.jpg https://v.nostr.build/dKSZbmNOZ9JbM8wv.mp4</p> <h4>SHISHA CAFE, BAR & COMMUNITY SPACE</h4> <p>https://i.nostr.build/UdNbeXdB628wW2dK.jpg</p> <h4>JEROEN'S TOKYO VISIT</h4> <p>https://image.nostr.build/8e384c2620088f3fe5001f797576625649e0c0f53f3415193d2f51a92d16ba3b.jpg https://image.nostr.build/b43988efa086653155b7c9109ca5f4d2903adb5e0879a302a9ef743c05263523.jpg https://image.nostr.build/f2b584e728f95b747a5795741451df63c36c5eafef5886ecd3635c381bcd40e2.jpg https://image.nostr.build/d9e6c2ccd290a558202747e471ec5df025e0c37720f0563a7f5928ed56429a9b.jpg https://image.nostr.build/c9f5ec9f7ec03cd2f4d9c12f151e7548879b022590d063dc2226f5deb00c40f1.jpg https://image.nostr.build/cd58ed78004f46a65b84ea279fee5a07e4ca6762b4964b1b95149dde2303bc6a.jpg https://image.nostr.build/674ef0111ee987967bf1f98bb880bc3d7c4667033d5f067668881fd3d8bf1918.jpg https://image.nostr.build/5df690358d06cc62fe9260311d606c812a67a0d4b4b6779a3c48f4986446799e.jpg https://image.nostr.build/837696634b1e546ee1f6e2ec8cd1aa4f813df017010c4434c9b93291fa4a6d1c.jpg https://image.nostr.build/771c0b2f8e15aa901f4ef1da34be8843eeac716a1f792be714745283be71eecd.jpg https://image.nostr.build/48555bd4db7bb7f707dd78882dafd669cb1f860d851389d18ab0b1f2e3423da6.jpg https://image.nostr.build/76d3c990cb337d9f8a413032a0c4b7ab60c7b3faffc52baed6c7bcda9ddec8ee.jpg https://image.nostr.build/4c532360c28aaceb7fadbcc0ff0e9737be27d41a8213c79cbd0621f2b367a15b.jpg</p> <hr /> <h2>FINAL THOUGHTS 🤔</h2> <hr /> <h4>What are your thoughts on the instant translation of food videos to enhance global accessibility?</h4> <p>https://video.nostr.build/4dba5f5e87d2f9bfda5f04dae82c3ce8d7cee41f19033906c6d59a60dd42a9a5.mp4</p> <h4>What is your opinion regarding Trump’s visit to PUBKEY and purchasing food & beverages with Bitcoin?</h4> <blockquote> <p><strong>PUBKEY:</strong> * Smash Burger: $12.50 x 50 = $625.00 * Diet Coke: $3.00 x 50 = $150.00 * Subtotal: $775.00 * Tax: $68.77 * 20% gratuity: $155.00 * <strong>Total: $998.77</strong> A former president spending #bitcoin at your bar: PRICELESS.</p> </blockquote> <p>https://image.nostr.build/70c72f924b9cd8d429e0f1c030ce35c52604485e553f1c24af0b1d1737f3adc9.jpg https://image.nostr.build/f1bd17df540bceb7f8f4f2ed7979cc20c86e7d38ddc35d1d8988321c08cc1ee4.jpg https://media.primal.net/uploads/2/ed/89/2ed896f3be4eaec166230e582e4228a53d82652e38a90620aef09cb5da5b1c7d.png https://v.nostr.build/sbPbqOIvSpCffo4I.mp4</p> <hr /> <p>fin💐</p> <p><em>September Issue 1</em> | https://habla.news/u/zap.cooking/ZAP-COOKING-NEWSLETTER-4yxs6s</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsv0l28staznr5qu8jds2vglc95ctteq292jwu2uc8nhk5jmnmucdszyqce45l8jp35m05x79xmns5etvnwu0rz9zl9t7yuf3l74xkvq82s5dux4mm" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsv0l28staznr5qu8jds2vglc95ctteq292jwu2uc8nhk5jmnmucdszyqce45l8jp35m05x79xmns5etvnwu0rz9zl9t7yuf3l74xkvq82s5dux4mm" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsv0l28staznr5qu8jds2vglc95ctteq292jwu2uc8nhk5jmnmucdszyqce45l8jp35m05x79xmns5etvnwu0rz9zl9t7yuf3l74xkvq82s5dux4mm" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsv0l28staznr5qu8jds2vglc95ctteq292jwu2uc8nhk5jmnmucdszyqce45l8jp35m05x79xmns5etvnwu0rz9zl9t7yuf3l74xkvq82s5dux4mm" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 8d34bd24:414be32b <div class="time" style="margin-left: auto;">2024-10-23 15:30:53</div> </div> <div> <p>Check out earlier posts in <em>God Makes Himself Known</em> series:</p> <ul> <li> <p><a href="https://trustjesus.substack.com/p/god-demonstrates-his-power">God Demonstrates His Power: </a>Part 1 (Egypt)</p> </li> <li> <p><a href="https://trustjesus.substack.com/p/god-defends-his-honor">God Defends His Honor</a>: Part 2 (Phillistines)</p> </li> <li> <p><a href="https://trustjesus.substack.com/p/the-one-true-god">The One True God:</a> Part 3 (Who deserves worship)</p> </li> <li> <p><a href="https://trustjesus.substack.com/p/jesus-is-god">Jesus is God</a>: Part 4 (Jews & Gentiles)</p> </li> </ul> <p>Throughout history, God has shown His power and glory at different times and different places and to different people, but never shown it to everyone at once. The time is coming when God will show His power, glory, and judgement to all mankind.</p> <blockquote> <p>But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. <strong>For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air</strong>, and so we shall always be with the Lord. (1 Thessalonians 4:13-17) {emphasis mine}</p> </blockquote> <p>God’s first end times miracle will be the rapture of the church. All true believers (dead & alive) will be taken out of this world, given new, perfect, eternal bodies, and join Jesus in paradise. The world will see these Christians disappear. They will be there one moment and gone the next.</p> <p>I always thought it strange, that after the Bible’s prophecies of the church being raptured, that most people would not believe God had removed His followers. I think something (maybe fallen angels pretending to be aliens who have rescued mankind) will make people not get panicked about millions of Christians all disappearing in an instant. Maybe it will be solely based on people’s hard hearts and their unwillingness to consider an unpleasant thought (that they were left behind), but life will go on.</p> <p>The Bible makes it sound like there will be a short time of disarray, but then a man will come who make peace for a time (the Anti-Christ). After 3.5 years, things will get worse than they have ever been in the history of mankind.</p> <h2>The 7 Seals</h2> <p>In the end times, the world will experience unfathomably hard times. At first everything that happens will be things that have happened before, just worse. In Revelation 6, we see each of the 7 seals opened:</p> <ol> <li> <p>White Horse = Conquering</p> </li> <li> <p>Red Horse = Takes away peace so men slay one another</p> </li> <li> <p>Black Horse = Famine</p> </li> <li> <p>Pale (Ashen) Horse = A quarter of the earth killed by war, famine, pestilence, and animals.</p> </li> <li> <p>Those who trust in Jesus are martyred.</p> </li> <li> <p>Awesome, terrifying natural disasters:\ — A great earthquake,\ — the sun becomes black,</p> </li> </ol> <p>— the moon becomes like blood,\ — the stars fall to earth,\ — the sky is split like a scroll,\ — every mountain & island moved out of its place,\ — everyone from kings to slaves hide in fear due to the wrath of the Lord.</p> <h2>The 7 Trumpets</h2> <p>The opening of the 7th Seal leads to the 7 trumpets which are more terrifying than the first 6 seals and in faster succession. These miraculous signs of God’s wrath are beyond anything mankind has ever experienced and to a degree never experienced. First there is a half hour of silence and reprieve before the sounding of the trumpets in Revelation 8 & 9:</p> <ol> <li> <p>Hail & fire, mixed with blood, fall to earth and “<em>a third of the earth was burned up, and a third of the trees were burned up, and all the green grass was burned up</em>.” This burning will likely destroy crops and kill livestock causing famine.</p> </li> <li> <p>“<em>something like a great mountain burning with fire</em> [asteroid?] <em>was thrown into the sea; and a third of the sea became blood, and a third of the creatures which were in the sea and had life, died; and a third of the ships were destroyed</em>.” A mountain sized asteroid would cause terrible tsunamis. The death of a third of the sea creatures will cause worse famine. The destruction of a third of the ships will cause a disruption in international trade leading to shortages and prices skyrocketing.</p> </li> <li> <p>“<em>a great star</em> [comet?] <em>fell from heaven, burning like a torch, and it fell on a third of the rivers and on the springs of waters.</em>” A third of the waters of earth are poisoned. If you don’t have clean water, you die. People will be dying of thirst and of drinking the poisoned waters out of desperation.</p> </li> <li> <p>“<em>a third of the sun and a third of the moon and a third of the stars were struck, so that a third of them would be darkened.</em>” The world will experience fearful darkness. Sinful man hid their evil deeds under the cover of darkness and will now experience darkness that they don’t want.</p> </li> <li> <p>A “<em>star from heaven</em>” (most likely a fallen angel) falls to earth with the key to the bottomless pit and “<em>smoke went up out of the pit, like the smoke of a great furnace; and the sun and the air were darkened by the smoke of the pit. Then out of the smoke came locusts</em> [fallen angels that procreated with women: see Genesis 6] <em>upon the earth</em>.” These “locusts” will torment those who reject God and are forbidden from harming the remaining plants. The torment will last 5 months and will be so bad that people will desperately want to die.</p> </li> <li> <p>Four angels will “<em>kill a third of mankind</em>.” Death comes through an army of 200 million that kills with “<em>fire and smoke and brimstone</em>” that comes out of their mouths. The fourth seal resulted in the death of a quarter of mankind. The sixth trumpet will then lead to an additional third of mankind dying.</p> </li> </ol> <h2>The 2 Witnesses</h2> <p>God’s wrath will be unimaginably bad, but God still cares and he sends two witnesses to witness to the world to make sure that every person on earth has the opportunity to repent and turn to God. Many will, but many more will reject God despite His miraculous judgements upon them.</p> <blockquote> <p>And I will grant authority to my two witnesses, and they will <strong>prophesy</strong> for twelve hundred and sixty days, clothed in sackcloth.” These are the two olive trees and the two lampstands that stand before the Lord of the earth. And if anyone wants to harm them, <strong>fire flows out of their mouth</strong> and devours their enemies; so if anyone wants to harm them, he must be killed in this way. These have the power to <strong>shut up the sky, so that rain will not fall</strong> during the days of their prophesying; and they <strong>have power over the waters to turn them into blood</strong>, and to <strong>strike the earth with every plague</strong>, as often as they desire. (Revelation 11:3-6) {emphasis mine}</p> </blockquote> <p>God’s two witnesses will:</p> <ul> <li> <p>Prophecy</p> </li> <li> <p>Shoot flames out of their mouths to devour those who want to harm them</p> </li> <li> <p>Stop the rain as judgement</p> </li> <li> <p>Turn water into blood</p> </li> <li> <p>Strike the earth with every plague</p> </li> </ul> <p>After 1260 days, God will allow:</p> <ul> <li> <p>The beast to kill them</p> </li> <li> <p>Their bodies lie in the streets watched by the world as the world celebrates</p> </li> </ul> <p>But after 3.5 days, the witnesses will be raised from the dead in the view of every person on earth and be raised in the air up to heaven. God’s unmistakable power will be demonstrated in a way that there will not be any excuse for any person to reject Him as God and Creator.</p> <blockquote> <p>And in that hour there was a great earthquake, and a tenth of the city fell; seven thousand people were killed in the earthquake, and the rest were terrified and gave glory to the God of heaven. (Revelation 11:13)</p> </blockquote> <p>At this point the unholy trinity (Satan always copies God because he can’t create anything himself) will rule the world and will begin to seriously persecute all those who have believed in Jesus and trusted Him as savior.</p> <p>Amazingly, after all that God has demonstrated, the majority of people will worship the Anti-Christ rather than their creator who is the one, true God.</p> <h2>Additional Witnesses</h2> <p>As if the two witnesses that are seen by every person on earth is not enough, God sends other witnesses. He makes sure that every person truly knows who He is, what everyone is expected to do, and the consequences of refusing.</p> <p>First God marks 144,000 Jews, 12,000 from every tribe, to be witnesses throughout the world. Then God sends an angel up in the sky to witness:</p> <blockquote> <p>And I saw another angel flying in midheaven, having an eternal gospel to preach to those who live on the earth, and to every nation and tribe and tongue and people; and he said with a loud voice, “Fear God, and give Him glory, because the hour of His judgment has come; worship Him who made the heaven and the earth and sea and springs of waters.” (Revelation 14:6-7)</p> </blockquote> <p>He sends a second angel to warn that Babylon the Great has fallen. He then sends a third angel to give warning to people against following the Beast (Anti-Christ) or receiving his mark.</p> <blockquote> <p>“<strong>If anyone worships the beast and his image, and receives a mark on his forehead or on his hand</strong>, he also <strong>will drink of the wine of the wrath of God</strong>, which is mixed in full strength in the cup of His anger; and he will be tormented with fire and brimstone in the presence of the holy angels and in the presence of the Lamb. And the smoke of their torment goes up forever and ever; they have no rest day and night, those who worship the beast and his image, and whoever receives the mark of his name.” (Revelation 14:9b-11) {emphasis mine}</p> </blockquote> <p>Most of those who believe and are saved during the seven year tribulation will be martyred, but they are promised “<em>rest from their labors</em>” and that “<em>their deeds follow with them</em>”:</p> <blockquote> <p>… “Blessed are the dead who die in the Lord from now on!’ ” “Yes,” says the Spirit, “so that they may rest from their labors, for their deeds follow with them.” (Revelation 14:13b)</p> </blockquote> <h2>The 7 Bowls</h2> <p>The final miracles that show the wrath of God against those who refuse to trust in Him come in the 7 bowls (or vials). These are poured out in very rapid succession, probably hours or a few days.</p> <ol> <li> <p>“… <em>a loathsome and malignant sore on the people who had the mark of the beast and who worshiped his image</em>.” (Revelation 16:2b)</p> </li> <li> <p>“<em>the sea … became blood like that of a dead man; and every living thing in the sea died</em>.” (Revelation 16:3b) Notice that this blood isn’t like the other instances where it is like fresh blood. This blood is “<em>like that of a dead man</em>.” Every creature in the sea died, and I’m sure caused a rotting, putrid mess that smelled of death.</p> </li> <li> <p>“… rivers and the springs of waters … became blood.” (Revelation 16:4b) God gave those who had murdered the prophets blood as the only thing they could drink, as a just punishment.</p> </li> <li> <p>“… <em>the sun … was given to it to scorch men with fire.</em>” (Revelation 16:8b)</p> </li> <li> <p>“… <em>his *[the beast’s*] kingdom became darkened; and they gnawed their tongues because of pain</em>.” (Revelation 16:10b) [clarification mine]</p> </li> <li> <p>“… <em>the Euphrates … water was dried up, so that the way would be prepared for the kings from the east</em>.” (Revelation 16:12b)</p> </li> <li> <p>“… <em>a loud voice came out of the temple from the throne, saying, “It is done</em>.” (Revelation 16:17b) and “… <em>there was a great earthquake, such as there had not been since man came to be upon the earth</em> …” (Revelation 16:18b) “<em>And every island fled away, and the mountains were not found. And huge hailstones, about one hundred pounds each, came down from heaven upon men.</em> …” (Revelation 16:20-21a)</p> </li> </ol> <p>More than half of the population of earth will be killed during the tribulation. Some will repent and turn to God, but then pay with their lives. Others will willfully disobey and reject God and refuse to submit to Him despite knowing who He is and why He should be worshipped. God will have shared His mercy and then His wrath in order to turn people back to Him, but too many will be hard hearted and reject Him. They will be guilty and every punishment they receive will be well deserved. Justice will ultimately be served.</p> <h2>The 4 Hallelujahs</h2> <p>Right before the end the whole earth will hear the voice of a great multitude in heaven saying:</p> <blockquote> <p>“<strong>Hallelujah!</strong> Salvation and glory and power belong to our God; because His judgments are true and righteous; for He has judged the great harlot who was corrupting the earth with her immorality, and He has avenged the blood of His bond-servants on her.” And a second time they said, “<strong>Hallelujah!</strong> Her smoke rises up forever and ever.” And the twenty-four elders and the four living creatures fell down and worshiped God who sits on the throne saying, “Amen. <strong>Hallelujah!</strong>” And a voice came from the throne, saying, “Give praise to our God, all you His bond-servants, you who fear Him, the small and the great.” Then I heard something like the voice of a great multitude and like the sound of many waters and like the sound of mighty peals of thunder, saying, “<strong>Hallelujah!</strong> For the Lord our God, the Almighty, reigns. (Revelation 19:4-6) {emphasis mine}</p> </blockquote> <h2>The 2nd Coming of Jesus</h2> <p>Last of all is the greatest moment in all of history when Jesus returns to earth as Lord and King to claim His own and to judge those who rejected Him and lived evil lives.</p> <blockquote> <p>And I saw heaven opened, and behold, a white horse, and He who sat on it is called Faithful and True, and in righteousness He judges and wages war. His eyes are a flame of fire, and on His head are many diadems; and He has a name written on Him which no one knows except Himself. He is clothed with a robe dipped in blood, and His name is called The Word of God. (Revelation19:11-13)</p> </blockquote> <p>The most magnificent man who ever lived, the eternal, creator God comes down from heaven in the sight of all with all of His followers behind Him dressed in white, but all those, both man and angel, who refused to worship Him and submit to Him decide to line up for battle against Him. They somehow think they have a chance against the very one who upholds their life with the power of His mind. All of the men who took the mark of the beast will line up for battle against their creator.</p> <h2>The Millennium</h2> <p>Of course these rebels have no chance. The beast and false prophet are thrown into the lake of fire. The rest are destroyed by the sword in the mouth of Jesus while His followers watch, never having to lift a hand or dirty their white attire. Satan is bound for a thousand years and Jesus reigns over all of the earth for a thousand years on earth fulfilling the promises to Abraham, Isaac, Jacob, Moses, Joshua, David, and everyone else in the Bible. There will be a thousand years without the evil influences of Satan and his fallen angels. What a wonderful time that will be, but sadly, not all will fully submit to the perfect, sinless, creator God and one more moment of glory will be shown before the earth is burned with fire.</p> <h2>Judgement Throne of God</h2> <p>At the end of 1,000 years, there will be one more rebellion when Satan is released.</p> <p>I used to think it strange that God would allow Satan to be released again to mislead, but I think it is a test to expose those who are not really trusting in Jesus. During the millennial reign, there will not be much outright sin, but not all will follow with all their heart, mind, soul, and strength. Many will be going through the motions. They will be going along to stay out of trouble, but not because their hearts are following Jesus. When temptation comes along, many will turn away from God again into judgment. Satan will gather people from all the nations to surround the saints, but God will send fire down from heaven to devour all of the rebels</p> <blockquote> <p>And the devil who deceived them was thrown into the lake of fire and brimstone, where the beast and the false prophet are also; and they will be tormented day and night forever and ever. (Revelation 20:10)</p> </blockquote> <h2>Great White Throne Judgement</h2> <p>In the end, everyone that rejected Jesus will have their lives judged at the Great White Throne.</p> <blockquote> <p>And I saw the dead, the great and the small, standing before the throne, and books were opened; and another book was opened, which is the book of life; and the dead were judged from the things which were written in the books, according to their deeds. (Revelation 20:12)</p> </blockquote> <p>We are all sinners and do not want to be given what we deserve. We want God’s grace. Those who had trusted Jesus before the tribulation were judged by Jesus to determine their rewards. Those who rejected Jesus will be judged at the Great White Throne Judgement and will experience the just wrath of our holy, creator God. I hope you will be one of those who trust Jesus, otherwise you will receive your just punishment:</p> <blockquote> <p>And if anyone’s name was not found written in the book of life, he was thrown into the lake of fire. (Revelation 20:15)</p> </blockquote> <p>By the end every person who has ever lived on earth will know who God is and will understand how much they have failed Him. Every knee will bow — whether in awe or in terror.</p> <p>God made Himself known through His creation. God made Himself known through His blessings. God made Himself known by coming to earth to die for mankind to take away our sins. God made Himself known through His written word. God made Himself known through His wrath. Nobody can reject Him and claim they did not know.</p> <p>Trust Jesus.\ \ your sister in Christ,</p> <p>Christy</p> <p>Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs86z8l23a4t2v06ltvmetpdcs7uuj8yqrajhacwy2287l6ewmq33gzyzxnf0fyxgjqc43hza9rmvv3s79658qn8tk88xmy5fjzt86pf03jkpde8px" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs86z8l23a4t2v06ltvmetpdcs7uuj8yqrajhacwy2287l6ewmq33gzyzxnf0fyxgjqc43hza9rmvv3s79658qn8tk88xmy5fjzt86pf03jkpde8px" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs86z8l23a4t2v06ltvmetpdcs7uuj8yqrajhacwy2287l6ewmq33gzyzxnf0fyxgjqc43hza9rmvv3s79658qn8tk88xmy5fjzt86pf03jkpde8px" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs86z8l23a4t2v06ltvmetpdcs7uuj8yqrajhacwy2287l6ewmq33gzyzxnf0fyxgjqc43hza9rmvv3s79658qn8tk88xmy5fjzt86pf03jkpde8px" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d5c3d063:4d1159b3 <div class="time" style="margin-left: auto;">2024-10-24 14:31:36</div> </div> <div> <h1>แว่นตา...เข็มทิศ...ชีวิต...ทางเลือก</h1> <h2>เคยรู้สึกมั้ยครับว่า เรากำลังมองโลกต่างจากคนอื่น เหมือนใส่แว่นตาคนละแบบ เห็นภาพคนละมุม บางคนมองโลกสวยงาม บางคนมองโลกโหดร้าย บางคนมองโลกแสนสับสน...นั่นแหละครับ "ปรัชญา"</h2> <p>https://image.nostr.build/13ec632e4bb720d8b6729ddc07428be7f3fd89d02b117a9eff89ecb80540a1fd.jpg</p> <p>หลายคนอาจมองว่า ปรัชญาเป็นเรื่องไกลตัว เป็นเรื่องของนักคิด นักปราชญ์ อยู่ในตำราเล่มหนา แต่จริงๆ แล้ว ปรัชญาอยู่รอบตัวเราและใกล้ตัวเรามากกว่าที่คิด เพราะมันคือเข็มทิศที่นำทางชีวิต มันคือระบบความคิด ชุดความเชื่อ และค่านิยมหรือคุณค่าที่เรายึดถือ ซึ่งส่งผลต่อทุกการตัดสินใจ ทุกการกระทำ และสุดท้ายก็คือชีวิตของเราเอง</p> <p>นั่นหมายความว่า ทุกวันนี้ เรากำลังเลือกว่าจะเป็นมนุษย์ที่ใช้ชีวิตอย่างมีสติ มีเหตุผล และมีความรับผิดชอบต่อการกระทำของเราหรือไม่ หรือจะเป็นแค่ทาสของอารมณ์ ของความเชื่อและความงมงาย...?</p> <p>ลองนึกภาพดูนะครับ ถ้าเข็มทิศของเราชี้ผิดทิศ มันจะพาเราไปถึงจุดหมายได้ยังไง การเลือกปรัชญาที่ผิดพลาด ก็เหมือนการใช้เข็มทิศที่ผุพัง และในที่สุดปลายทางนั้นก็คือความล้มเหลวหรือความทุกข์ยาก</p> <p>ปรัชญาที่มีเหตุผล ใช้การคิดวิเคราะห์กับความรับผิดชอบ คือเข็มทิศที่แม่นยำที่สุดที่จะนำทางเราไปสู่ชีวิตที่ดีงาม ชีวิตที่มีอิสระมีความหมายและมีคุณค่า</p> <p>เหตุผล คือแสงสว่าง นำทางเราไปสู่ความจริง ช่วยให้เรามองเห็นโลกในอย่างที่มันเป็น โดยไม่ถูกบิดเบือนด้วยอคติ อารมณ์ หรือความเชื่อแบบผิดๆ ในขณะเดียวกันความเชื่อที่ผ่านการไตร่ตรองด้วยเหตุผลบนพื้นฐานของความจริง ก็สามารถเป็นรากฐานที่มั่นคงให้กับชีวิตและเป็นแรงผลักดันให้เราก้าวไปข้างหน้าได้ การคิดวิเคราะห์คือเครื่องมือที่ทรงพลัง ช่วยให้เราเข้าใจปัญหาอย่างลึกซึ้ง มองเห็นเหตุและผลเพื่อหาทางแก้ไขได้อย่างมีประสิทธิภาพ ส่วนความรับผิดชอบคือการยืนหยัดในความเป็นมนุษย์ คือการยอมรับผลของการกระทำของเราทั้งดีและไม่ดีนั้น ที่จะส่งผลต่อตัวเราและคนรอบข้าง ซึ่งเป็นหนทางสู่ "อิสรภาพ" ที่แท้จริง</p> <p>ในทางกลับกัน ปรัชญาที่ปฏิเสธเหตุผล ปล่อยให้อารมณ์ความเชื่อที่งมงายหรืออำนาจภายนอกครอบงำ ก็เหมือนเข็มทิศที่มันพัง มันก็จะพาเราไปสู่ความหายนะ ชีวิตที่ไร้สติไร้จุดหมายและการตกเป็นทาสของผู้อื่น</p> <p>ชีวิตเรา เราเลือกได้ เลือกที่จะใช้ชีวิตแบบมนุษย์ที่คิดเป็น ใช้เหตุผลเป็นหลักในการตัดสินใจ หรือจะใช้ชีวิตแบบไร้สติ ปล่อยให้อารมณ์ ความเชื่อความงมงายมาควบคุม แต่อย่าลืมว่าอารมณ์เป็นส่วนหนึ่งของเรา การทำความเข้าใจและจัดการกับอารมณ์ จึงมีความสำคัญอย่างยิ่งในการนำทางชีวิตเราให้ไปในทิศทางที่ดีงาม</p> <p>เลือกปรัชญาของคุณอย่างชาญฉลาด เพราะนั่นหมายถึงคุณกำลังเลือกเส้นทางชีวิตของคุณเอง</p> <h1>Siamstr #Philosophy #ปรัชญา</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9jc8mpqm4569uj6dvmye7kaj7cwr2uzrt9ml6tp5y7mye4lvqt5gzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxrrgjj3" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9jc8mpqm4569uj6dvmye7kaj7cwr2uzrt9ml6tp5y7mye4lvqt5gzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxrrgjj3" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9jc8mpqm4569uj6dvmye7kaj7cwr2uzrt9ml6tp5y7mye4lvqt5gzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxrrgjj3" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9jc8mpqm4569uj6dvmye7kaj7cwr2uzrt9ml6tp5y7mye4lvqt5gzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxrrgjj3" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 599f67f7:21fb3ea9 <div class="time" style="margin-left: auto;">2024-10-17 15:35:19</div> </div> <div> <p>Nostr proxy baten erabilera modu oso eraginkorra da internet banda-zabaleraren eta mugikorretan bateriaren kontsumoa optimizatzeko.</p> <p>Proxy batek hainbat errelei-konexio konexio bakarrean biltzen dituenez, baliabideen erabilera nabarmen murrizten du, eta erabiltzailearen IP helbidea ezkutatuz pribatutasun-geruza bat gehitzen du.</p> <p>Hona hemen nola funtzionatzen duen eta nola konfigura daitekeen:</p> <h3>Nola funtzionatzen du?</h3> <p>Nostr proxy batek hainbat erreleirekin konektatzen du. Errele horietara gertaerak eskuratu eta argitaratzen ditu. Bezeroaren aplikazioak WebSocket konexio bakarra ireki behar du proxy-ra, eta horren bidez proxy-ak konektatuta dituen errele guztiak eskuragarri izango ditu.</p> <p><img alt="bostr" src="https://github.com/Yonle/bostr/blob/master/img/how_it_works.png?raw=true" /></p> <p><em>Irudiaren egiletza: Yonle 2023</em></p> <p>Bezeroak konexio bakarra irekitzen duenez, datuak eta bateria aurrezten ditu.</p> <p>Proxy-ak bezeroaren izenean erreleekin konektatzen denez, erreleek proxy-aren IP helbidea ikusten dute, eta ez bezeroarena. (Hala ere, proxy hornitzailearengan konfiantza izan behar duzu).</p> <h3>Erabiltzeko Modua</h3> <p>Nostr proxy bat erraz auto-ostata daiteke. Auto-ostatatzeko jarraibideak lortzeko, begiratu nostr:npub1x3azxuysp5vmfer4vgs4jn5tmfcx4ew8sh0qnev7gczljxsr7jwqa3g4el erabiltzailearen <a href="https://github.com/Yonle/bostr/">biltegi</a> hau.</p> <p>Auto-ostatzeko baliabiderik ez dutenentzat, <a href="https://bostr.bitcointxoko.com">Bitcoin Txoko-k komunitate-instantzia</a> bat ostalaratzen du.</p> <p>Erabiltzeko, gehitu besterik ez duzu:</p> <p><code>wss://bostr.bitcointxoko.com</code></p> <p>zure errele zerrendara. </p> <p>Orain ez duzunez zuzeneko konexioak behar, errele bikoiztuak ezabatu ditzakezu.</p> <p>Ikusiko dugu elkar Nostr-en!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsg9z5hkdhf6edjn822339pj8wctftjz9vz0m0qazgwjx7qtmhy5pgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j52zq2d" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsg9z5hkdhf6edjn822339pj8wctftjz9vz0m0qazgwjx7qtmhy5pgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j52zq2d" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsg9z5hkdhf6edjn822339pj8wctftjz9vz0m0qazgwjx7qtmhy5pgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j52zq2d" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsg9z5hkdhf6edjn822339pj8wctftjz9vz0m0qazgwjx7qtmhy5pgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2j52zq2d" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4f82bced:b8928630 <div class="time" style="margin-left: auto;">2024-10-24 14:19:51</div> </div> <div> <p>I was invited to tag along with a film crew heading to a <a href="https://gridlesscompute.com/">Gridless</a> facility in Kenya earlier this year. An exciting opportunity to see how Bitcoin mining leverages renewable energy and supports rural communities.</p> <p>Two hours from Nairobi is a town with a mini-grid powered by hydroelectric energy. The river flowing downstream is captured by generators, converted into electricity, and powers the community. The community only utilizes a portion of the energy produced, resulting in a large surplus wasted. Additionally, the demand is constantly fluctuating: factories ramp up demand during the day, households require more in the evenings, and demand plummets at night.</p> <p>This leaves the producer wasting energy that could be monetized otherwise. Enter Gridless! They use bitcoin miners to stabilize the mini-grid and smooth out energy demand. How? Any surplus energy at any given moment is directed to the bitcoin miners. If no surplus energy exists, the miners receive no power. The energy needs of the community come first!</p> <p>If you don’t know what bitcoin miners are, a quick TLDR: they are machines that guess a combination of numbers to find a hash below a certain target value. Sound confusing? In simpler terms, the machines are rolling multiple dice, hoping for the right outcome. This results in a new block being added to the blockchain, and the miner is rewarded with bitcoin for their efforts.</p> <p>Walking into the container filled with miners, you hear a loud buzzing noise similar to a large hornet’s nest. If you pay close attention, you’ll hear a symphony of miners turning on and off based on the energy available. Unlike traditional industrial systems that may require time to ramp up or down, bitcoin miners can be flipped on and off instantly. That means if only some energy is available, only some miners run. If more energy becomes available, more miners turn on.</p> <p>A common misconception is that bitcoin uses too much energy. It consumes <a href="https://bitcoinminingcouncil.com/wp-content/uploads/2023/08/BMC-H1-2023-Presentation.pdf">0.21% of the world's energy</a> production and 60% of it comes from <a href="https://bitcoinminingcouncil.com/wp-content/uploads/2023/08/BMC-H1-2023-Presentation.pdf">renewable sources</a>. This consumption increases the resilience and security of the network (an article for another day). </p> <p>Gridless continues similar work around Africa to capture excess energy produced by renewable means and stabilize local grids with an extremely flexible solution. It ensures that the energy produced for local communities will never go to waste and can be monetized through bitcoin mining.</p> <p>https://youtu.be/YB2q0J65VDg</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsd3r76rn3dw7rfpk6hhy9q8h2fdxr3xd4u53zzpqlkcdw6q7kld8szyp8c908dgfvy56k0emf2v4a44j4uf7gdwk54a5ll3z8nkp9cj2rrq78zsx9" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsd3r76rn3dw7rfpk6hhy9q8h2fdxr3xd4u53zzpqlkcdw6q7kld8szyp8c908dgfvy56k0emf2v4a44j4uf7gdwk54a5ll3z8nkp9cj2rrq78zsx9" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsd3r76rn3dw7rfpk6hhy9q8h2fdxr3xd4u53zzpqlkcdw6q7kld8szyp8c908dgfvy56k0emf2v4a44j4uf7gdwk54a5ll3z8nkp9cj2rrq78zsx9" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsd3r76rn3dw7rfpk6hhy9q8h2fdxr3xd4u53zzpqlkcdw6q7kld8szyp8c908dgfvy56k0emf2v4a44j4uf7gdwk54a5ll3z8nkp9cj2rrq78zsx9" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ a012dc82:6458a70d <div class="time" style="margin-left: auto;">2024-10-23 15:23:26</div> </div> <div> <p><strong>Table Of Content</strong></p> <ul> <li> <p>The Origins of the Debate</p> </li> <li> <p>The Rise of Bitcoin</p> </li> <li> <p>HODLing: A Strategy to Weather the Storm</p> </li> <li> <p>The Skepticism of Peter Schiff</p> </li> <li> <p>The Bitcoin Community's Response</p> </li> <li> <p>Conclusion</p> </li> <li> <p>FAQ</p> </li> </ul> <p>In the world of finance, few debates have garnered as much attention as the showdown between Peter Schiff and Bitcoin. As an outspoken critic of the cryptocurrency, Peter Schiff, a well-known economist, has long been skeptical of its value and viability. However, as the Bitcoin market experienced unprecedented growth and adoption, the concept of "HODLing" emerged victorious. This article delves into the clash between Schiff and Bitcoin, exploring the reasons behind their differing views and ultimately highlighting how the strategy of HODLing prevailed.</p> <p><strong>The Origins of the Debate</strong></p> <p>It all began when Bitcoin, the first decentralized cryptocurrency, was introduced to the world in 2009. While many were intrigued by the concept of digital currency, Schiff expressed skepticism and voiced his concerns regarding its lack of intrinsic value. Schiff, a proponent of traditional investments like gold, believed that Bitcoin's meteoric rise was nothing more than a speculative bubble waiting to burst. This clash of ideologies set the stage for an ongoing battle between Schiff and Bitcoin enthusiasts.</p> <p><strong>The Rise of Bitcoin</strong></p> <p>Despite Schiff's reservations, Bitcoin steadily gained traction and captured the imagination of investors worldwide. Its decentralized nature, limited supply, and potential as a store of value attracted a growing number of individuals looking to diversify their portfolios. Bitcoin's disruptive technology and its ability to facilitate fast and secure transactions also played a significant role in its ascent.</p> <p><strong>HODLing: A Strategy to Weather the Storm</strong></p> <p>As Bitcoin's price exhibited volatility, a strategy emerged among its proponents: HODLing. This term, originating from a misspelling of "hold" in a Bitcoin forum post, refers to the practice of holding onto Bitcoin for the long term, irrespective of short-term market fluctuations. HODLers believed that Bitcoin's underlying technology and its potential to revolutionize the financial industry made it a worthwhile investment, regardless of temporary setbacks.</p> <p><strong>The Skepticism of Peter Schiff</strong></p> <p>While Bitcoin continued to surge in popularity, Peter Schiff remained steadfast in his skepticism. He argued that Bitcoin's lack of intrinsic value made it a speculative asset rather than a legitimate currency or store of wealth. Schiff often compared Bitcoin to gold, highlighting the tangible and historical significance of the precious metal. He warned investors of the potential risks associated with Bitcoin, emphasizing the possibility of a catastrophic collapse.</p> <p><strong>The Bitcoin Community's Response</strong></p> <p>Bitcoin enthusiasts fervently defended their chosen asset against Schiff's criticism. They pointed out that while Bitcoin may not possess intrinsic value like gold, its value is derived from its decentralized network, scarcity, and the trust placed in its underlying technology. They highlighted the benefits of Bitcoin's borderless transactions, low fees, and the potential for financial inclusion. The community also stressed that Bitcoin's volatility was merely a temporary characteristic during its early stages of adoption.</p> <p><strong>Conclusion</strong></p> <p>In the ultimate showdown between Peter Schiff and Bitcoin, the concept of HODLing emerged victorious. Despite Schiff's skepticism, Bitcoin's decentralized nature, technological innovation, and growing adoption propelled it forward. The strategy of HODLing, fueled by the belief in Bitcoin's long-term potential, allowed investors to weather the storm of market volatility. As the world continues to embrace digital currencies and explore the possibilities they offer, the clash between traditionalists and innovators will persist. The story of Peter Schiff vs Bitcoin serves as a testament to the ever-evolving landscape of finance.</p> <p><strong>FAQ</strong></p> <p><strong>Is Bitcoin a reliable investment in the long term?</strong> Bitcoin's reliability as an investment depends on one's risk tolerance and long-term perspective. While it has exhibited significant growth, its volatility and regulatory uncertainties make it a speculative asset that carries inherent risks.</p> <p><strong>Can Bitcoin replace traditional forms of currency?</strong> Bitcoin's potential to replace traditional forms of currency is still highly debated. While it offers certain advantages, such as faster and cheaper cross-border transactions, widespread adoption and regulatory clarity would be necessary for it to become a mainstream currency.</p> <p><strong>How does HODLing differ from traditional investing?</strong> HODLing differs from traditional investing as it involves holding onto an asset for the long term, regardless of short-term market fluctuations. Traditional investing often involves active management, buying and selling based on market trends and analysis.</p> <p><strong>That's all for today</strong></p> <p><strong>If you want more, be sure to follow us on:</strong></p> <p><strong>NOSTR: croxroad@getalby.com</strong></p> <p><strong>X: <a href="https://x.com/croxroadnewsco">@croxroadnews</a></strong></p> <p><strong>Instagram: <a href="https://www.instagram.com/croxroadnews.co/">@croxroadnews.co</a></strong></p> <p><strong>Youtube: <a href="https://www.youtube.com/@croxroadnews">@croxroadnews</a></strong></p> <p><strong>Store: https://croxroad.store</strong></p> <p><strong>Subscribe to CROX ROAD Bitcoin Only Daily Newsletter</strong></p> <p><strong>https://www.croxroad.co/subscribe</strong></p> <p><em>DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.</em></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsd2w0ulv84v48uqtnlcd5zmxhtwhsmrypl6kfy3sp0fct0uv6mgmszyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns67m6xnr" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsd2w0ulv84v48uqtnlcd5zmxhtwhsmrypl6kfy3sp0fct0uv6mgmszyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns67m6xnr" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsd2w0ulv84v48uqtnlcd5zmxhtwhsmrypl6kfy3sp0fct0uv6mgmszyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns67m6xnr" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsd2w0ulv84v48uqtnlcd5zmxhtwhsmrypl6kfy3sp0fct0uv6mgmszyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns67m6xnr" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ bcea2b98:7ccef3c9 <div class="time" style="margin-left: auto;">2024-10-17 14:47:01</div> </div> <div> <p>Sometimes you have to take risks to grow. What's the biggest risk you've ever taken that ended up paying off.</p> <p>My biggest risk that paid off was moving to another country and starting a new life 10 years ago due to corruption and torture in my home country.</p> <p>originally posted at https://stacker.news/items/728159</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsp60d8t3dvega7as86agtfg9j44y9zut6k2a3l9hxxqfgxxjqhxhgzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujhtsa36" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsp60d8t3dvega7as86agtfg9j44y9zut6k2a3l9hxxqfgxxjqhxhgzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujhtsa36" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsp60d8t3dvega7as86agtfg9j44y9zut6k2a3l9hxxqfgxxjqhxhgzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujhtsa36" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsp60d8t3dvega7as86agtfg9j44y9zut6k2a3l9hxxqfgxxjqhxhgzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujhtsa36" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 1bda7e1f:bb97c4d9 <div class="time" style="margin-left: auto;">2024-10-08 09:46:01</div> </div> <div> <p><strong>Tldr</strong></p> <ul> <li>Nostr comes with integrated Bitcoin payments called zaps</li> <li>It’s possible to set up a self-custodial wallet that you host yourself, plus</li> <li>Add all kinds of bells and whistles, like phone app and browser plugin</li> <li>The software I’m using is Albyhub and Phoenixd, deployed with Docker to a cheap VPS</li> <li>I can now receive payments to my Lightning Address rodbishop@getalby.com</li> </ul> <p><strong>Payments on Nostr</strong></p> <p>One of the great features of Nostr is integrated payments. This feature integrates financial transactions directly into the social network, as a seamless part of using the network.</p> <p>You can get paid by and pay anyone on the network, to or from anywhere in the world, and for any reason, in a way that is instant and nearly free.</p> <p>The payments get to be instant and global and free because they are made in Bitcoin, using the Bitcoin payments network called The Lightning Network.</p> <p>Per Bitcoin, payments are denominated in satoshis (sats). A sat is a one-hundred-millionth of a Bitcoin– US$1 is about 1,700 sats at the time of writing. Making a payment like this on Nostr is called a “zap” and usually indicated with a lightning bolt symbol (you are getting “zapped by lightning”). You might say to your friend ”I'll zap you 1,700 sats”.</p> <p>This unlocks all kinds of interesting things that are not possible with other social networks, like</p> <ul> <li>“value for value”–A publisher publishes something of value and you can tip them if you like it</li> <li>Payments between friends–Nostr can do everything that Cash App and Venmo can do, right down to splitting payments to multiple recipients</li> <li>Payments for creators–you can sell or pay to access premium content similar to any kind of paywall site like Patreon or Substack</li> <li>Payments to AIs–you can pay for automated AI-based services including for translation, image generation, or creating custom curated social media feeds</li> <li>All other kinds of ecommerce–you can sell or buy anything you want similar to Gumtree or Facebook marketplace</li> </ul> <p>Every Nostr user can have this set up. It's free or nearly free to set up, nearly free to make payments, and some apps like Primal will even set it up for you by default.</p> <p>Moreover it's useful and it's fun.</p> <ul> <li>When you help someone out to receive a little tip for doing so, or</li> <li>When you get some great advice to show your appreciation in a more meaningful way than a like</li> </ul> <p><strong>Ways to set up lightning for zaps on Nostr</strong></p> <p>You can get paid in Bitcoin to a lightning address. This looks exactly like an email address except you can make a payment to it from a lightning wallet.</p> <p>Anyone can publish their lightning address on Nostr so that you can pay them. And you can also get your own lightning address on your own Nostr profile so that people can pay you.</p> <p>The lightning address links to a server that’s always active and ready to credit your balance whenever you receive payments.</p> <p>To make that happen at a high level there are two options, either:</p> <ul> <li>Open an account with a custodial lightning provider who will keep an always on server with your wallet on it, live and ready to receive payments for you. Primal does this automatically for you in their Nostr client, or you can use any one of the other popular custodial wallets like Wallet of Satoshi, Zeus, Coinos, or many others</li> <li>Set up your own self-custodial lightning server that runs on an always-on computer or server, which you can administer yourself</li> </ul> <p>Generally using a custodial service will be easier, but comes with the need to trust that third party custodian, and may limit you to pay within their app.</p> <p>For myself I'm going to self host using Albyhub by npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, and Phoenixd by Acinq.</p> <p><strong>Hosting your own lightning server with Albyhub and Phoenixd</strong></p> <p>Anyone who's experimented with self-sovereign setups for Bitcoin know that historically there's been quite a bit of heavy lifting.</p> <p>My number one favourite feature of what Albyhub and Phoenixd have done together is to create a nearly instant set up with no heavy lifting. I was stunned. For anyone who's used to jumping through hoops with this, it was like magic.</p> <p>You can use Albyhub with any lightning wallet backend, but in my view none are as automatic, and magic, as Phoenixd.</p> <p>Compare the traditional set up with the Albyhub and Phoenixd setup.</p> <p>Traditional–</p> <ul> <li>Set up a Bitcoin core node</li> <li>Download the entire Bitcoin blockchain (wait several days for it to download)</li> <li>Set up a Bitcoin lightning node</li> <li>Purchase payment liquidity to enable payments to the network</li> <li>On an ongoing basis continue to keep your blockchain in sync with the network</li> <li>On an ongoing basis manage your inbound and outbound liquidity to your network peers</li> </ul> <p>Vs Albyhub and Phoenixd–</p> <ul> <li>No Bitcoin core</li> <li>No initial block download</li> <li>Phoenixd provides liquidity for you automatically and by default</li> <li>Nothing to keep in sync with the network</li> <li>No liquidity to manage</li> </ul> <p>For any normal non-technical user, self-hosting your own lightning node just went from being too hard, to very achievable.</p> <p><strong>Unpacking the parts</strong></p> <p>There are a few parts to this set up and there’s a bit of assumed knowledge here, so let’s quickly unpack it</p> <ul> <li>Bitcoin–money for the internet, which enables payments to and from anywhere</li> <li>Lightning–the main payments network that sits on top of Bitcoin, which makes transactions instantly and with very low fees</li> <li>Phoenixd–a lightning wallet back-end with special methods for managing liquidity that makes it almost no-touch to set up and manage</li> <li>Albyhub–a lightning front-end with an easy to-use wallet, and a feature called “Nostr Wallet Connect” (NWC) which connects the wallet to Nostr</li> <li>AlbyGo–a phone app so you can make payments on your phone</li> <li>Alby Plugin–a web browser plugin so you can make payments on your browser, and also log into Nostr from your browser (using NIP-07)</li> <li>NWC–a method for connecting your wallet directly to Nostr apps so that you can spend from your wallet balance without even leaving the app</li> <li>Lightning Address–an address like an email address where you can receive payments (using LNURLp; Lightning Network URL)</li> </ul> <p>I'm going to plug it all together, so that I can pay for anything in any way I like (from NWC, Alby Plugin or Alby Go), and receive payment from anyone (to our Lightning Address), with all funds managed on my own server (hosting Albyhub and Phoenixd).</p> <p><strong>How to set up Albyhub and Phoenixd</strong></p> <p>To set this up requires basic command line knowledge, and some experience with Docker. I didn’t have that experience, so I gave ChatGPT the docs on each of Albyhub and Phoenixd and it walked me through the setup.</p> <p>To start with, I got myself a cheap VPS, and installed Docker. Docker then allowed me to deploy Albyhub and Phoenixd as a container.</p> <p>The Albyhub Github contains very helpful readme, here <a href="https://github.com/getAlby/hub">https://github.com/getAlby/hub</a></p> <p>And Phoenixds own docs here <a href="https://phoenix.acinq.co/server">https://phoenix.acinq.co/server</a> and here <a href="https://github.com/ACINQ/phoenixd">https://github.com/ACINQ/phoenixd</a></p> <p>Alby also has a dedicated section to working with Albyhub with Phoenixd backend, here <a href="https://github.com/getAlby/hub/blob/master/scripts/linux-x86_64/phoenixd/README.md">https://github.com/getAlby/hub/blob/master/scripts/linux-x86_64/phoenixd/README.md</a></p> <p>First, install Docker and make sure it is running.</p> <p>Then working with the code on the Albyhub with Phoenixd page–</p> <ul> <li>Get the docker-compose.yml file which will instruct Docker to create the relevant containers,</li> <li>Create the directories for the files to be stored in</li> <li>Launch the containers</li> </ul> <p>That’s it. Docker will proceed to create the application for you running on port 8080</p> <p>You can then log in in a web browser and start the setup–</p> <ul> <li>There’s a helpful step-by-step guide to walk you through the set up including to set up a password for your hub</li> <li>It will ask you to connect your Alby account. I skipped that step as I didn’t have one at the time, I only created one later</li> <li>If you used the default lightning back-end, Alby will then ask you to buy your first liquidity to enable you to make payments. Or, if you are using Phoenixd, then the step is automatic and you can go right ahead to transfer in some initial funds</li> </ul> <p><strong>Setting up the bells and whistles</strong></p> <p>That's the hard part done. The next step is add all the little extra pieces that make for a great Nostr experience.</p> <p>Alby Browser Plugin–</p> <ul> <li>Download the Alby Browser Plugin to your web browser and create an account</li> <li>It will give you a new Nostr and Lightning account by default, and you can replace it</li> <li>For me I had my own keys already saved with a mnemonic backup, and I wanted to use these. I went to Settings and clicked “Remove Master Key”, then entered the mnemonic backup of my own keys. I also went to Nostr Settings and clicked “Derive from Master Key” to replace the one it generated by default.</li> <li>Visit Albyhub, and connect the Alby Account</li> <li>This completes the set up to login and zap with Nostr on any Nostr site</li> </ul> <p>Alby Go App</p> <ul> <li>Download the Alby Go App to your phone from your phone’s app store</li> <li>Vist Albyhub, go to the Alby App Store, and click Alby Go</li> <li>It will help you to create a connection between your Albyhub and Alby Go</li> </ul> <p>Nostr Wallet Connect</p> <ul> <li>You can use the Alby App Store to connect any Nostr app in the same way</li> <li>Vist Albyhub, go to the Alby App Store, and click on any Nostr App</li> <li>I used Amethyst, and I was able to create a connection between Amethyst Nostr app and Albyhub, so that when I click the “zap” icon in Amethyst it can automatically spend from my Albyhub wallet without any further clicks</li> </ul> <p>Your own Lightning Address</p> <ul> <li>Your Alby Account in your Alby Browser Plugin gives you a Lightning Address by default. It is generated randomly to start with, and you can replace it.</li> <li>Open the Alby Browser Plugin and visit Settings</li> <li>Click “Change on <a href="http://getalby.com">getalby.com</a>” and change it to something that suits you</li> <li>I changed mine to rodbishop@getalby.com </li> </ul> <p>That completes the set up.</p> <p><strong>Backups</strong></p> <p>Now that everything is set up, it’s time to make a backup.</p> <p>I already had my Nostr keys as a mnemonic backup from my last article, and I’m using these keys for my Alby Account, so there is nothing new to back up there.</p> <p>But we still need backups for the Albyhub login credentials, and the Phoenixd wallet.</p> <p>When started for the first time, Phoenixd will generate a 12-word mnemonic of its own, which it will use to restore your wallet balance in case of any issue. This recovery phrase is stored in the phoenix folder you created, at \~/.phoenixd/seed.dat.</p> <p>In total, your backups will contain:</p> <ul> <li>Your 12 word mnemonic backup of your Nostr keys, that is also the same master 12 word mnemonic for your Alby account</li> <li>Your 12 word mnemonic backup for your Phoenixd wallet, that is created by the daemon when it first runs at \~/.phoenixd/seed.dat</li> <li>Three passwords: 1) Your password for your Alby account, 2) Your password for your Alby Hub, 3) Your password for your Phoenixd (that is hardcoded into the docker-compose.yml)</li> </ul> <p>Once these are backed up somewhere safely, you can fully recover your set up if ever anything goes wrong.</p> <p><strong>Things I did wrong in set up so that you don’t have to</strong></p> <p>Initially I had some trouble with user permissions. I was able to resolve it by changing the user configuration in the docker-compose.yml.</p> <p>I also had some trouble with the initial funds transfer. In order to test everything without risking significant funds, I made an initial transfer to the hub of 10 satoshis.</p> <ul> <li>The transfer was received immediately, but</li> <li>The available balance stayed at zero, and</li> <li>I couldn’t make any payments (insufficient funds)</li> </ul> <p>I thought this was a bug in my set up, but it turns out this is a feature of Phoenixd auto-liquidity, that it keeps some initial sats as a payment credit to buy the required lightning channel liquidity. The total cost amounts to on average 1% charge, but it is also front-loaded, and because my payment was so very tiny (10 satoshis worth a fraction of a cent) the payment was entirely front-loaded.</p> <p>I diagnosed this by accessing Phoenixd directly in the cli, and by doing so, I was able to see the balance present, as a fee credit.</p> <p>To check, run–</p> <ul> <li>docker-compose exec albyhub-phoenixd /phoenix/bin/phoenix-cli --http-password=<your-password-here> getbalance</li> </ul> <p>And receive a response like this, which shows the credit on the account –</p> <ul> <li>{ "balanceSat": 0, "feeCreditSat": 10 }</li> </ul> <p>The above command–</p> <ul> <li>accesses the albyhub-phoenixd container “docker-compose exec albyhub-phoenixd”,</li> <li>then accesses the phoenix-cli application at “/phoenix/bin/phoenix-cli”</li> <li>and asks the application to “getbalance”</li> </ul> <p>Helpful docs–</p> <ul> <li>Phoenixd talks about that fee credit behaviour quite clearly at their own site, here <a href="https://phoenix.acinq.co/server">https://phoenix.acinq.co/server</a></li> <li>They also provide docs on their cli to interact directly with their daemon (rather than using Alby), which you can read here <a href="https://phoenix.acinq.co/server/get-started">https://phoenix.acinq.co/server/get-started</a></li> </ul> <p>I wondered what the total initial amount would be that would be captured as fee credit. Your mileage might vary, but for me:</p> <ul> <li>I transferred in 2,100 sats (about $1.20)</li> <li>I received a working balance of 775 sats, so I paid 1,325 sats in fees</li> <li>I then transferred in another 2,100 sats</li> <li>I received all 2,100 sats (paid no fees at all on the second transaction)</li> </ul> <p>All up only a few cents to get started with initial liquidity.</p> <p><strong>In summary</strong></p> <p>Nostr has integrated payments that are instant and nearly free, using Satoshis on the Lightning Network. Some Nostr clients come with a wallet set up automatically, and it is quite easy to set up your own self-custody wallet, with all the bells and whistles.</p> <p>I wanted to set up my own self-custody wallet so that I could test and learn the full set up of the system. For this I used Albyhub and Phoenixd, and I deployed it to a cheap VPS using Docker.</p> <p>Once set up, I added all the extra bits so that now–</p> <ul> <li>I can login to Nostr from my web browser with the Alby Browser Plugin</li> <li>I can make payments from there too, or from the AlbyGo App, or from any Nostr app I like</li> <li>I can receive payments to my Lightning Address <a href="mailto:rodbishop@getalby.com">rodbishop@getalby.com</a></li> </ul> <p>And in doing this–</p> <ul> <li>I don’t rely on any third-party custodian to take care of my funds</li> <li>I had no hard work to install this setup, and expect no ongoing admin to keep it running</li> <li>With everything set up, the system simply works (so far!)</li> </ul> <p>For anyone interested in Nostr or Bitcoin software or technologies, I recommend to go through a set up like this as it really covers the full gamut or the Nostr–Lightning–Bitcoin stack. It’s clear how far this technology has come and how powerful it can get from here.</p> <p><strong>Up next</strong></p> <ul> <li>Please let me know if this kind of post is helpful or anything you’d like me to improve or expand upon</li> <li>For my next post I’ll show how I set up Nostr and lightning addresses at your own domain with Sveltekit and Vercel</li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsp34n7rknutkk438pwqwrrr23f67xulscclm59q6e8mxj6qvnv78czyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqtces4" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsp34n7rknutkk438pwqwrrr23f67xulscclm59q6e8mxj6qvnv78czyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqtces4" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsp34n7rknutkk438pwqwrrr23f67xulscclm59q6e8mxj6qvnv78czyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqtces4" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsp34n7rknutkk438pwqwrrr23f67xulscclm59q6e8mxj6qvnv78czyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqtces4" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 6ad3e2a3:c90b7740 <div class="time" style="margin-left: auto;">2024-10-08 09:11:10</div> </div> <div> <p>I wanted to post a quote from Jiddu Krishnamurti who if I remember correctly once said something to the effect of:</p> <p><em>An artist should be like Beethoven. The music just flowed out of him, and he could neither stop it nor control it.</em></p> <p>But I can’t find the source, I’m just going by memory, and it was from a long time ago. It doesn’t matter though if he really said it, because it’s the quote I wanted to post.</p> <p>. . .</p> <p>When I was 21, my friend Andrew and I made a four hour drive one Saturday morning from New York to Germantown, Maryland to see a Korean Buddhist monk. I heard about the monk from my Korean college roommate whose mom knew him. Andrew and I had been reading books about Buddhism for the preceding year and thought it would be worthwhile to see the real thing. We also had various anxieties about our lives and figured maybe he could offer some guidance.</p> <p>When we arrived at the farm where he lived, we parked and stepped out of the car. I don’t want to exaggerate, but even in the lot which had to be 40 yards from the main building was this strong feeling like you could just fall to the ground and start weeping for the sorrows of your life.</p> <p>We walked to the door of the monastery and knocked. A few seconds later, a bald, 50-something Korean man opened it, looked out at us with a blank face. We awkwardly told him we had come to see him. In a thick Korean accent he said today was the wrong day for us, come back tomorrow and shut the door. We stood there dumbfounded. We had woken up at 6 am and driven four hours. He was an enlightened monk. He couldn’t just turn us away.</p> <p>Nervously, I knocked again. He came back out, same blank look. I told him we had driven all the way from New York. He motioned for us to come in, and we followed.</p> <p>Inside were maybe 25 Koreans all waiting to see the monk whose name it turned out was Dr. Shin. The Koreans had filled a large wooden table with a massive buffet of Korean food, and Andrew and I were invited to help ourselves which we did. People were individually or in couples going into a small meditation room where Dr. Shin sat and attended to them. After at least an hour, someone motioned to us it was our turn.</p> <p>We were there for probably 5-10 minutes. I don’t remember who spoke first, or the entirety of the conversation, only a few snippets which have stayed with me. I told him I didn’t really know what I wanted to do with my life. I thought maybe I wanted to be a writer. He laughed out loud. “You want to be artist?” he said with his thick accent. “You pumping gas. Hahahahahah!” Then he looked at me seriously, and said, “Business and law. You study business and law.”</p> <p>. . .</p> <p>I’m 53 years old as I type this in October of 2024, and my “job” now is to write and talk about things as I see fit. I started my Substack in 2020, and while my <a href="https://www.chrisliss.com/p/zero-and-infinity">first post</a> was about large numbers, my <a href="https://www.chrisliss.com/p/brainwashing-your-kids">second one</a> was more from the heart. I create for a “living”, and I suppose that makes me an artist of sorts. But when I think back to the words of Dr. Shin, he was 100 percent right.</p> <p>. . .</p> <p>Most people should not try to be artists. You can’t easily make a living at it. It’s the wrong way to go about achieving status or security in society. There are some people who simply have no choice. They live for what they do, and even if they die broke and alone, they could not have done otherwise. Those are artists.</p> <p>So what the hell am I doing?</p> <p>I belong to a relatively small minority, those with something to say. I was always like this, even during the visit with Dr. Shin. But in my 20s and 30s I could not have done it. I needed to contribute something, get the reward part out of the way. I lacked the confidence and conviction to create whether or not anyone were interested in my work or wanted to compensate me for it. And unlike real artists, I had a choice. I don’t know if I could have dealt with a real job, but helping run a small fantasy sports business, something I loved, was possible for me, and I was lucky enough to find it.</p> <p>. . .</p> <p>Now I’m beyond that phase. I have enough money, a partner, a daughter and a dog. I like recognition and paychecks as much as the next person, but I’m not thirsty. I’ll say what I think (mostly) without regard for how it’ll affect my readership or reputation. I can open my mind and let the ideas out. Maybe it’s not quite like Beethoven, but more along the lines of Jorge Luis Borges who said:</p> <p><em>I do not write for a select minority, which means nothing to me, nor for that adulated platonic entity known as ‘The Masses’. Both abstractions, so dear to the demagogue, I disbelieve in. I write for myself and for my friends, and I write to ease the passing of time.</em></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsdgaxm8nftkw74zeqmnewcclj2w9l6hcyzqfpuxqkn4hmsj0tnungzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5ql5qqwv" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsdgaxm8nftkw74zeqmnewcclj2w9l6hcyzqfpuxqkn4hmsj0tnungzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5ql5qqwv" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsdgaxm8nftkw74zeqmnewcclj2w9l6hcyzqfpuxqkn4hmsj0tnungzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5ql5qqwv" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsdgaxm8nftkw74zeqmnewcclj2w9l6hcyzqfpuxqkn4hmsj0tnungzyp4d8c4rfqvtz57grayvtr6yu5veu760erd7x7qs5qqdec7fpdm5ql5qqwv" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 7ab1ed7a:f8e15275 <div class="time" style="margin-left: auto;">2024-10-17 14:06:46</div> </div> <div> <p>I'm proud and thankful to announce that funding has been granted by OpenSats to <a href="https://opensats.org/blog/7th-wave-of-nostr-grants#nostr-arduino">fund the development of the Nostr library for Arduino</a>.</p> <p>The fund will help with work on the development of the Arduino Nostr library as well as fund work on IoT related NIPs.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsqskn7zdvcqxhfrqumdetaqexjwylallzxvry7y57u2d9ac3ue4lczypatrmt6kh063cn0qemsp243ufd29kr0yy5c3rka4qlff80cu9f8286ezsk" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsqskn7zdvcqxhfrqumdetaqexjwylallzxvry7y57u2d9ac3ue4lczypatrmt6kh063cn0qemsp243ufd29kr0yy5c3rka4qlff80cu9f8286ezsk" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsqskn7zdvcqxhfrqumdetaqexjwylallzxvry7y57u2d9ac3ue4lczypatrmt6kh063cn0qemsp243ufd29kr0yy5c3rka4qlff80cu9f8286ezsk" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsqskn7zdvcqxhfrqumdetaqexjwylallzxvry7y57u2d9ac3ue4lczypatrmt6kh063cn0qemsp243ufd29kr0yy5c3rka4qlff80cu9f8286ezsk" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 8947a945:9bfcf626 <div class="time" style="margin-left: auto;">2024-10-17 08:06:55</div> </div> <div> <p><a href="https://stock.adobe.com/stock-photo/id/1010191703"><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/8947a94537bdcd2e62d0b40db57636ece30345a0f63c806b530a5f1f9bfcf626/files/1729148821549-YAKIHONNES3.jpeg" /></a></p> <p><strong>สวัสดีทุกคนบน Nostr ครับ</strong> รวมไปถึง <strong>watchers</strong>และ <strong>ผู้ติดตาม</strong>ของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ</p> <p>ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ</p> <p>ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย</p> <p><strong>เมื่อวันที่ 16 กย.2024</strong> มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ</p> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/8947a94537bdcd2e62d0b40db57636ece30345a0f63c806b530a5f1f9bfcf626/files/1729148088676-YAKIHONNES3.PNG" /></p> <h3>นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ</h3> <p>(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)</p> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/8947a94537bdcd2e62d0b40db57636ece30345a0f63c806b530a5f1f9bfcf626/files/1729148348755-YAKIHONNES3.jpg" /></p> <ul> <li>Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint <strong>0.15 - 0.2 ETH</strong> … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ</li> </ul> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/8947a94537bdcd2e62d0b40db57636ece30345a0f63c806b530a5f1f9bfcf626/files/1729148387032-YAKIHONNES3.jpg" /></p> <ul> <li> <p>Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :</p> </li> <li> <p>ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา</p> </li> <li>ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา</li> <li>ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา</li> <li>ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok</li> </ul> <p>สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT <strong>0.2 ETH</strong></p> <p>ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้</p> <p><strong>Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก</strong> เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)</p> <p>ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย</p> <p>โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า </p> <p>mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม</p> <p>เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ</p> <p>เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง</p> <p>ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม</p> <hr /> <h3>ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร</h3> <p><a href="https://stock.adobe.com/stock-photo/id/1010196295"><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/8947a94537bdcd2e62d0b40db57636ece30345a0f63c806b530a5f1f9bfcf626/files/1729148837871-YAKIHONNES3.jpeg" /></a></p> <p>อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม</p> <p>ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)</p> <p>บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน</p> <p>บบโลกของ ETH <strong>"code is law"</strong> smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล</p> <p>ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก</p> <p>อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน</p> <h2>Note</h2> <ul> <li>ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock</li> <li>อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน</li> </ul> <p>ผลงานของผมครับ - Anime girl fanarts : <a href="https://linktr.ee/hikariharmonypatreon">HikariHarmony</a> - <a href="https://shorturl.at/I8Nu4">HikariHarmony on Nostr</a> - General art : <a href="https://linktr.ee/keshikirakuen">KeshikiRakuen</a> - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsq3kd0relghyunph00ulwmh6kpx3vhr0enkkgtpaejfx2nuy2wsyczyzy50229x77u6tnz6z6qmdtkxmkwxq695rmreqrt2v9978umlnmzvf94y80" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsq3kd0relghyunph00ulwmh6kpx3vhr0enkkgtpaejfx2nuy2wsyczyzy50229x77u6tnz6z6qmdtkxmkwxq695rmreqrt2v9978umlnmzvf94y80" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsq3kd0relghyunph00ulwmh6kpx3vhr0enkkgtpaejfx2nuy2wsyczyzy50229x77u6tnz6z6qmdtkxmkwxq695rmreqrt2v9978umlnmzvf94y80" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsq3kd0relghyunph00ulwmh6kpx3vhr0enkkgtpaejfx2nuy2wsyczyzy50229x77u6tnz6z6qmdtkxmkwxq695rmreqrt2v9978umlnmzvf94y80" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-23 15:19:11</div> </div> <div> <p>Para ajudar a contornar a censura da Internet em locais onde o acesso ao Tor é bloqueado. Ele é uma espécie de ponte do Tor que permite que os usuários se conectem à rede Tor por meio de um sistema distribuído de voluntários.</p> <p>A história do Snowflake começou em 2019, quando o Tor Project percebeu que muitas pessoas em locais com restrições de acesso à Internet estavam recorrendo a soluções de VPN e proxies para contornar a censura. No entanto, muitas dessas soluções eram bloqueadas pelas autoridades governamentais, o que criou a necessidade de encontrar novas maneiras de contornar a censura. Foi aí que surgiu a ideia do Snowflake, que foi lançado como uma solução para ajudar a aumentar a capacidade do Tor de contornar a censura da Internet em todo o mundo.</p> <p>O Snowflake funciona por meio de um sistema distribuído de voluntários que oferecem seus proxies para ajudar a contornar a censura. Quando um usuário se conecta ao Snowflake, seu tráfego é roteado por meio de um conjunto de proxies voluntários que se oferecem para ajudar a contornar a censura. Esses proxies são distribuídos em todo o mundo, o que ajuda a garantir que haja sempre uma opção disponível para os usuários que desejam acessar a Internet livremente.</p> <p>O Snowflake resolve o problema de acesso à Internet em locais onde o acesso ao Tor é bloqueado. Ele permite que os usuários contornem a censura e a vigilância da Internet, acessando sites e aplicativos que seriam bloqueados em suas regiões. Com o Snowflake, os usuários podem navegar na Internet com mais privacidade e segurança, evitando serem detectados pelos censores da Internet.</p> <p>"A privacidade é necessária para uma sociedade aberta na era eletrônica. Privacidade não é sigilo. Uma sociedade livre requer privacidade na comunicação, bem como privacidade na busca e na associação." - Eric Hughes</p> <p>https://snowflake.torproject.org/</p> <p>https://youtu.be/ZC6GXRJOWmo</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqstqyqvv8nfj99etnxs7tjluzn5q58fwu266mfsujsr933dl0c0s7qzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gp0r5u0" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqstqyqvv8nfj99etnxs7tjluzn5q58fwu266mfsujsr933dl0c0s7qzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gp0r5u0" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqstqyqvv8nfj99etnxs7tjluzn5q58fwu266mfsujsr933dl0c0s7qzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gp0r5u0" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqstqyqvv8nfj99etnxs7tjluzn5q58fwu266mfsujsr933dl0c0s7qzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gp0r5u0" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-06 19:03:02</div> </div> <div> <p>Com o RiMusic, os usuários podem pesquisar e reproduzir facilmente músicas, álbuns e artistas de seu interesse, além de aproveitar recursos adicionais, como download de músicas e playlists para audição offline e marcação de favoritos para fácil acesso posterior. O RiMusic oferece uma experiência musical completa e envolvente, reunindo os recursos do YouTube Music em um aplicativo fácil de usar e altamente personalizável.</p> <p>Principais Funcionalidades</p> <ul> <li>Busca por Músicas, Álbuns, Artistas e Playlists: Encontre facilmente suas músicas, álbuns, artistas e playlists favoritas.</li> <li>Marcação de Artistas e Álbuns: Marque seus artistas e álbuns favoritos para acesso rápido.</li> <li>Importação de Playlists Online: Importe playlists de outras plataformas de streaming.</li> <li>Gerenciamento de Playlists Local: Crie, edite e organize suas playlists diretamente no aplicativo.</li> <li>Reordenação de Músicas: Altere a ordem das músicas na playlist ou fila.</li> <li>Fila Persistente e Limpeza de Fila: Mantenha ou limpe a fila de reprodução conforme sua preferência.</li> <li>Letras de Músicas: Busque, edite e traduza letras de músicas, sincronizadas ou não.</li> <li>Temas Diversos: Escolha entre temas Claro, Escuro, Dinâmico, PureBlack e ModernBack.</li> <li>Temporizador: Configure um temporizador personalizável para a reprodução de música.</li> <li>Normalização de Áudio e Salto de Silêncio: Melhore a qualidade da reprodução de áudio.</li> </ul> <p>Opções de Personalização</p> <ul> <li>Download de Músicas ou Playlists Inteiras para Reprodução Offline: Baixe suas músicas favoritas ou playlists completas para ouvir offline, sem depender de uma conexão com a internet.</li> <li>Reprodução em Segundo Plano: Continue ouvindo música mesmo quando o aplicativo estiver fechado, com interrupção automática ao sair do gerenciador de tarefas.</li> <li>Otimizações do Reprodutor Minimizado: Oferece otimizações para o modo de reprodução minimizada, garantindo uma experiência suave e eficiente mesmo ao usar outros aplicativos.</li> <li>Visualizador de Áudio: Crie uma experiência visual cativante com diferentes tipos de efeitos de visualização, ativados nas configurações.</li> </ul> <p>Suporte e Compatibilidade</p> <ul> <li>Suporte ao Android Auto: Acesse sua música favorita enquanto está no carro.</li> <li>Suporte ao Android TV: Desfrute de sua música favorita na tela grande, transformando sua sala de estar em um ambiente de entretenimento musical.</li> <li>Compatibilidade Multilíngue: Suporte para vários idiomas, incluindo inglês, italiano, alemão, russo, francês, espanhol, tcheco, turco, romeno e muitos outros.</li> </ul> <p>Permissões Necessárias</p> <p>Para oferecer todos esses recursos, o RiMusic requer várias permissões:</p> <ul> <li>INTERNET: Conexão à internet.</li> <li>ACCESS_NETWORK_STATE: Verificação do estado da conexão.</li> <li>POST_NOTIFICATIONS: Funcionamento como serviço.</li> <li>RECEIVE_BOOT_COMPLETED: Inicialização após reinicialização do dispositivo.</li> <li>WAKE_LOCK: Impedir suspensão do dispositivo durante reprodução (se configurado).</li> <li>REQUEST_IGNORE_BATTERY_OPTIMIZATIONS: Evitar restrições de uso da bateria.</li> <li>FOREGROUND_SERVICE: Reprodução de música em segundo plano.</li> <li>FOREGROUND_SERVICE_MEDIA_PLAYBACK e DATA_SYNC: Reprodução e download de músicas.</li> <li>READ_MEDIA_AUDIO: Leitura de músicas locais.</li> <li>RECORD_AUDIO: Necessário apenas para usar o efeito do visualizador (desativado por padrão).</li> <li>MODIFY_AUDIO_SETTINGS: Mostrar configurações de áudio.</li> <li>READ_EXTERNAL_STORAGE e WRITE_EXTERNAL_STORAGE: Leitura e escrita de músicas até Android 12/11.</li> <li>READ_MEDIA_VISUAL_USER_SELECTED: Seleção de arquivos de playlist até Android 13.</li> </ul> <p>Existe Uma Maneira de Transferir Playlists e Favoritos do Vimusic? Sim, crie um backup do ViMusic e depois importe-o para o App RiMusic usando a função de restauração. Ambas as funções de backup e restauração são encontradas nas configurações do Banco de Dados.</p> <p>O RiMusic é uma solução completa para quem busca uma experiência musical rica e personalizável. Com sua integração com o YouTube Music, variadas opções de personalização, suporte a múltiplos idiomas e compatibilidade com diversos dispositivos, o RiMusic se destaca como um dos melhores aplicativos de streaming de música disponíveis. Aproveite todas as funcionalidades do RiMusic e eleve sua experiência musical a um novo patamar.</p> <p>https://github.com/fast4x/RiMusic</p> <p>F-Droid https://f-droid.org › it.fast4x.rimusic RiMusic | F-Droid - Free and Open Source Android App Repository</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsyeu0jla9j4rgq9ghnw5pmv6ug2gageer3u8arvf62925lezsr9lszyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gwzndqx" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsyeu0jla9j4rgq9ghnw5pmv6ug2gageer3u8arvf62925lezsr9lszyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gwzndqx" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsyeu0jla9j4rgq9ghnw5pmv6ug2gageer3u8arvf62925lezsr9lszyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gwzndqx" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsyeu0jla9j4rgq9ghnw5pmv6ug2gageer3u8arvf62925lezsr9lszyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gwzndqx" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d5c3d063:4d1159b3 <div class="time" style="margin-left: auto;">2024-10-24 13:47:14</div> </div> <div> <h2>เราได้ยินคำว่า "สิทธิ" กันจนชินหูไปแล้ว นักการเมืองก็พูดกันจังเลยว่าให้สิทธินั่นสิทธินี่ แต่เคยสงสัยกันบ้างไหมว่าสิทธิพวกนี้มันมาจากไหนกันแน่ จริงๆ แล้วรัฐเป็นคนหยิบยื่นสิทธิให้เราเหรอ หรือจริงๆ แล้วเรามีสิทธิเหล่านี้อยู่แล้วโดยกฎธรรมชาติ</h2> <p>. https://image.nostr.build/d03cc1428b49045550ef7203db1de9f36c8c1f923bfdc96a4953254be5fdb6c2.png</p> <p>เริ่มจากเรื่อง "กฎธรรมชาติ" (Natural Law) ย้อนเวลาหน่อยแล้วกัน ตั้งแต่สมัยกรีกโบราณโน่นเลย นักปัชญาสมัยนั้นเค้าเชื่อว่า ทั้งจักรวาลและสังคมของเรามันมีกฎเกณฑ์บางอย่างที่เป็นความจริงสากล ไม่ว่าจะอยู่ที่ไหนบนโลกก็หนีไม่พ้น เหมือนกับเวลาโยนน้ำขึ้นฟ้า ยังไงน้ำก็ต้องตกลงมาอยู่ดีถูกไหม นั่นแหละเค้าเรียกว่า "กฎธรรมชาติ" หรือยกตัวอย่างง่ายๆ เช่น "กฎอุปสงค์-อุปทาน" ที่เราเรียนกันในวิชาเศรษฐศาสตร์นั่นแหละ ลองคิดดูนะ ถ้าสินค้ามันมีน้อยแต่คนอยากได้เยอะ ราคามันก็ต้องพุ่งสูงขึ้นเป็นธรรมดา เป็นกลไกของตลาด เป็นความจริงที่เกิดขึ้นเองโดยธรรมชาติ ไม่ต้องมีใครไปบังคับเลย .</p> <p>ทีนี้มาถึง Aristotle "อริสโตเติล" เขาเชื่อว่าสิ่งที่ทำให้มนุษย์เราพิเศษกว่าสัตว์อื่นๆ ก็คือ "เหตุผล" นี่แหละ เพราะเรามีเหตุผล เราถึงรู้จักผิดชอบชั่วดี รู้จักใช้ชีวิตอย่างมีคุณธรรม ต่อมานักปรัชญาสโตอิกส์ (Stoics) ก็เอาไอเดียเรื่องกฎธรรมชาติมาขยายความต่อ พวกเขาเน้นว่า เมื่อมนุษย์ทุกคนเกิดมาพร้อมกับการมี "เหตุผล" เหมือนๆ กัน เพราะฉะนั้น "กฎธรรมชาติ" จึงเปรียบเสมือน "กฎศีลธรรม" (Moral Law) ที่เป็นสากล ใช้ได้กับทุกคนบนโลกใบนี้ ไม่ว่าคุณจะเป็นใคร มาจากไหน รวยหรือจน ก็ต้องอยู่ภายใต้กฎเดียวกันหมด ไม่ใช่แค่สโตอิกส์นะ นักคิดดังๆ อีกหลายคนในโลกตะวันตก ไม่ว่าจะเป็น Cicero, Aquinas หรือ Grotius พวกเขาก็เห็นด้วยกับเรื่องกฎธรรมชาติเหมือนกัน .</p> <p>ทีนี้มาถึงศตวรรษที่ 17 ก็มีนักปรัชญาคนสำคัญชื่อ John Locke (จอห์น ล็อค) เขาเอาไอเดียเรื่อง "กฎธรรมชาติ" มาเชื่อมโยงกับ "สิทธิธรรมชาติ" (Natural Rights) มาอธิบายได้อย่างเป็นระบบ โดย Locke เชื่อว่ามนุษย์ทุกคนเกิดมาพร้อมกับสิทธิพื้นฐาน 3 อย่าง นั่นก็คือ สิทธิที่จะมีชีวิต มีเสรีภาพในการเลือก และสิทธิในการเป็นเจ้าของทรัพย์สิน ซึ่งสิทธิเหล่านี้มีติดตัวเรามาตั้งแต่เกิด มีอยู่ก่อนที่จะมีรัฐชาติด้วยซ้ำ มนุษย์เราสามารถใช้ "เหตุผล" ที่เรามีอยู่ในการทำความเข้าใจสิทธิธรรมชาติเหล่านี้ได้ .</p> <p>สมัยก่อนที่ยังไม่มีรัฐบาล Locke เรียกช่วงเวลานั้นว่า "สภาวะธรรมชาติ" (State of Nature) ที่จริงๆ แล้วมนุษย์เราสามารถใช้ "เหตุผล" ในการอยู่ร่วมกันได้นะ ถึงจะไม่มีรัฐบาลก็ตาม แต่! ประเด็นคือ ในสภาวะธรรมชาติ มันอาจจะไม่มีศาลหรือตำรวจแบบที่เราคุ้นเคยไง (แต่ก็อาจจะมีวิธีจัดการความยุติธรรมแบบอื่นๆ อยู่) Locke บอกว่า คนบางกลุ่มอาจจะตกลงกันว่า เรามาตั้งรัฐบาลกันดีกว่า (ซึ่งการตั้งรัฐบาลก็อาจจะไม่ได้รับความเห็นชอบจากทุกคนก็ได้นะ) เพื่อที่จะได้มีระบบยุติธรรม มีคนดูแลความสงบเรียบร้อยอย่างเป็นทางการ แต่ที่สำคัญที่สุดคือรัฐบาลต้องปกป้องสิทธิธรรมชาติที่มีก่อนที่การตั้งรัฐ</p> <p>คือ Locke เขาก็รู้นะว่า "อำนาจรัฐ" มันเหมือนดาบสองคม ถ้ารัฐบาลไม่ดี เอาอำนาจไปใช้ในทางที่ผิด ก็จะกลายเป็นการละเมิดสิทธิของประชาชนซะเอง เพราะงั้น Locke ถึงเน้นย้ำมากๆ ว่า รัฐบาลต้องมี "อำนาจที่จำกัด" (Limited Government) และต้องให้ความเคารพสิทธิธรรมชาติของประชาชนเป็นอันดับแรก ซึ่งอำนาจของรัฐบาลต้องมาจากความยินยอมของประชาชน ประชาชนมีสิทธิ์ตั้งคำถาม วิพากษ์วิจารณ์ หรือแม้แต่ต่อต้านรัฐบาลที่ใช้อำนาจในทางที่ผิด .</p> <p>น่าเสียดายที่ทุกวันนี้ คำว่า "สิทธิ" มันถูกนักการเมืองเอาไปใช้หาเสียงกันจัง เช่น สิทธิเรียนฟรี สิทธิรักษาฟรี สิทธิความเท่าเทียมทางเศรษฐกิจ ฟังดูดี๊ดีเนอะ แต่จริงๆ แล้วมันก็แค่นโยบายหาเสียง ไม่ใช่ "สิทธิขั้นพื้นฐาน" จริงๆ สักหน่อย</p> <p>สิทธิขั้นพื้นฐานที่แท้จริงมันต้องเป็นอะไรที่ติดตัวเรามาตั้งแต่เกิด อย่างเช่น สิทธิที่จะมีชีวิตอยู่ สิทธิในการเป็นเจ้าของทรัพย์สิน สิทธิในการพูดหรือแสดงความคิดเห็น</p> <p>ส่วนนโยบายเรียนฟรี รักษาฟรี แจกเงิน พวกนี้มันเป็นแค่นโยบายของรัฐ ที่รัฐจะยกเลิกเมื่อไหร่ก็ได้ ที่สำคัญคือนโยบายพวกนี้มันมักจะไปละเมิดสิทธิของคนอื่นโดยไม่รู้ตัว เช่น รัฐบาลจะเก็บภาษีเราเพิ่มขึ้น เพื่อเอาเงินไปทำโครงการต่างๆ โดยที่เราไม่เห็นด้วยหรือเต็มใจ นี่มันก็คือการละเมิดสิทธิในทรัพย์สินของเรานะ หรือบางทีรัฐบาลก็เข้าไปแทรกแซงเศรษฐกิจ เช่น บังคับให้เราต้องทำนู่นทำนี่ ซึ่งมันก็ละเมิดเสรีภาพในการเลือกของเราเหมือนกัน อีกตัวอย่างที่เห็นชัดๆ คือ รัฐบาลสร้างเงินเฟ้อ ทำให้เงินในกระเป๋าเรามันมีค่าน้อยลง นี่มันปล้นกันชัดๆ แต่เขาทำได้อย่างถูกกฎหมายนะ ซึ่งจริงๆ แล้ว รัฐบาลไม่มีสิทธิ์ทำแบบนี้ เพราะมันเป็นการละเมิดสิทธิของประชาชนอย่างชัดเจน การที่รัฐบาลก็ชอบเอา "กฎหมาย" มาอ้างก็เพื่อให้ตัวเองดูชอบธรรม .</p> <p>สรุปง่ายๆ เลยนะ "สิทธิ" ที่แท้จริงมันไม่ได้เกิดจากการใช้อำนาจหรือความรุนแรง แต่มันมีรากฐานมาจาก "กฎธรรมชาติ" และสิทธิก็ต้องมาพร้อมกับ "ความรับผิดชอบ" ด้วย เราต้องไม่เอาสิทธิของเราไปละเมิดสิทธิของคนอื่น</p> <p>"กฎหมาย" มีไว้เพื่อปกป้องสิทธิของทุกคนอย่างเท่าเทียม ไม่ใช่เพื่อสร้างสิทธิหรือเอาไปใช้เป็นเครื่องมือในการละเมิดสิทธิของประชาชน กฎหมายต้องเป็นเหมือนเกราะป้องกันสิทธิของเรา ไม่ใช่โซ่ตรวนที่พันธนาการเสรีภาพของเรา</p> <p>เพราะฉะนั้น "สิทธิ" กับ "ความรับผิดชอบ" มันเป็นของคู่กัน เวลาเราใช้สิทธิอะไรก็ตาม ต้องคิดถึงใจเขาใจเราด้วย อย่าเผลอไปละเมิดสิทธิของคนอื่นเข้าล่ะ .</p> <p>ก่อนที่จะเชื่อนักการเมืองที่ชอบโฆษณาว่าให้สิทธินั่นนี่ เราต้องตั้งคำถามกับตัวเองก่อนว่าสิทธินั้น มันมาจากการใช้อำนาจหรือการบังคับใช้โดยกฎหมายด้วยความรุนแรงหรือเปล่า และที่สำคัญคือมันไปละเมิดสิทธิของคนอื่นรึเปล่า .</p> <p>การตั้งคำถามกับสิ่งเหล่านี้ มันคือจุดเริ่มต้นของการเข้าใจ "สิทธิ" ที่แท้จริง และเป็นก้าวแรกของการลุกขึ้นมาปกป้องสิทธิของเราเอง เพื่อไม่ให้กลายเป็นเหยื่อของอำนาจรัฐ เพราะท้ายที่สุดแล้ว สิ่งที่มนุษย์ต้องการก็คือการมีชีวิตที่มีอิสระ อยู่ในสังคมที่มีความยุติธรรม และมีศักดิ์ศรีของความเป็นมนุษย์</p> <h1>Siamstr #NaturalLaw #NaturalRights</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs8wm0q7sr0dn4wlhhv5c09txs4q8k0wc22xltjxfyh4ugryfwn3egzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxd6kcgn" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs8wm0q7sr0dn4wlhhv5c09txs4q8k0wc22xltjxfyh4ugryfwn3egzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxd6kcgn" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs8wm0q7sr0dn4wlhhv5c09txs4q8k0wc22xltjxfyh4ugryfwn3egzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxd6kcgn" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs8wm0q7sr0dn4wlhhv5c09txs4q8k0wc22xltjxfyh4ugryfwn3egzyr2u85rrvu2lr2w4hc403tdwpykh24ukyw4jy0m7juz3vxzdz9vmxd6kcgn" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-23 13:28:09</div> </div> <div> <p>Ele possibilita o compartilhamento seguro de arquivos e mensagens entre dispositivos próximos em uma rede Wi-Fi local, sem a necessidade de uma conexão com a Internet.</p> <p>O LocalSend é um aplicativo de plataforma cruzada que utiliza uma API REST e criptografia HTTPS para garantir a segurança da comunicação. Diferentemente de outros aplicativos de mensagens que dependem de servidores externos, o LocalSend não requer acesso à Internet ou servidores de terceiros.</p> <p>Para assegurar a máxima segurança, o LocalSend utiliza um protocolo de comunicação seguro em que todos os dados são enviados por HTTPS, e um certificado TLS/SSL é gerado instantaneamente em cada dispositivo durante a comunicação.</p> <p>https://f-droid.org/pt_BR/packages/org.localsend.localsend_app/</p> <p>https://github.com/localsend/localsend</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsqvhhmpf7v7ysd3e48zvpxkc5vz5vglfkanlcgywhhpjmd6k2n3aqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gjdp6gm" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsqvhhmpf7v7ysd3e48zvpxkc5vz5vglfkanlcgywhhpjmd6k2n3aqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gjdp6gm" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsqvhhmpf7v7ysd3e48zvpxkc5vz5vglfkanlcgywhhpjmd6k2n3aqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gjdp6gm" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsqvhhmpf7v7ysd3e48zvpxkc5vz5vglfkanlcgywhhpjmd6k2n3aqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gjdp6gm" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 47750177:8969e41a <div class="time" style="margin-left: auto;">2024-10-05 17:40:25</div> </div> <div> <h1>28.0 Release Notes</h1> <p>Bitcoin Core version 28.0 is now available from:</p> <ul> <li>🌐 <a href="https://bitcoincore.org/bin/bitcoin-core-28.0/">https://bitcoincore.org/bin/bitcoin-core-28.0/</a></li> <li>🧲 <magnet:?xt=urn:btih:e18e92024fc9d4026cf8cdef174f03c24080fd1f&dn=bitcoin-core-28.0&tr=udp%3A%2F%2Ftracker.coppersurfer.tk%3A6969%2Fannounce&tr=udp%3A%2F%2Ftracker.openbittorrent.com%3A80&tr=udp%3A%2F%2Ftracker.opentrackr.org%3A1337%2Fannounce&tr=udp%3A%2F%2Ftracker.torrent.eu.org%3A451%2Fannounce&tr=udp%3A%2F%2Ftracker.leechers-paradise.org%3A6969%2Fannounce&tr=udp%3A%2F%2Fexplodie.org%3A6969%2Fannounce&tr=udp%3A%2F%2Ftracker.bitcoin.sprovoost.nl%3A6969&ws=http://bitcoincore.org/bin/></li> </ul> <p>This release includes new features, various bug fixes and performance improvements, as well as updated translations.</p> <p>Please report bugs using the issue tracker at GitHub:</p> <p><a href="https://github.com/bitcoin/bitcoin/issues">https://github.com/bitcoin/bitcoin/issues</a></p> <p>To receive security and update notifications, please subscribe to:</p> <p><a href="https://bitcoincore.org/en/list/announcements/join/">https://bitcoincore.org/en/list/announcements/join/</a></p> <h1>How to Upgrade</h1> <p>If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over <code>/Applications/Bitcoin-Qt</code> (on macOS) or <code>bitcoind</code>/<code>bitcoin-qt</code> (on Linux).</p> <p>Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.</p> <p>Running Bitcoin Core binaries on macOS requires self signing. <code>cd /path/to/bitcoin-28.0/bin xattr -d com.apple.quarantine bitcoin-cli bitcoin-qt bitcoin-tx bitcoin-util bitcoin-wallet bitcoind test_bitcoin codesign -s - bitcoin-cli bitcoin-qt bitcoin-tx bitcoin-util bitcoin-wallet bitcoind test_bitcoin</code></p> <h1>Compatibility</h1> <p>Bitcoin Core is supported and extensively tested on operating systems using the Linux Kernel 3.17+, macOS 11.0+, and Windows 7 and newer. Bitcoin Core should also work on most other UNIX-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.</p> <h1>Notable changes</h1> <h2>Testnet4/BIP94 support</h2> <p>Support for Testnet4 as specified in <a href="https://github.com/bitcoin/bips/blob/master/bip-0094.mediawiki">BIP94</a> has been added. The network can be selected with the <code>-testnet4</code> option and the section header is also named <code>[testnet4]</code>.</p> <p>While the intention is to phase out support for Testnet3 in an upcoming version, support for it is still available via the known options in this release. (#29775)</p> <h2>Windows Data Directory</h2> <p>The default data directory on Windows has been moved from <code>C:\Users\Username\AppData\Roaming\Bitcoin</code> to <code>C:\Users\Username\AppData\Local\Bitcoin</code>. Bitcoin Core will check the existence of the old directory first and continue to use that directory for backwards compatibility if it is present. (#27064)</p> <h2>JSON-RPC 2.0 Support</h2> <p>The JSON-RPC server now recognizes JSON-RPC 2.0 requests and responds with strict adherence to the <a href="https://www.jsonrpc.org/specification">specification</a>. See <a href="https://github.com/bitcoin/bitcoin/blob/master/doc/JSON-RPC-interface.md#json-rpc-11-vs-20">JSON-RPC-interface.md</a> for details. (#27101)</p> <p>JSON-RPC clients may need to be updated to be compatible with the JSON-RPC server. Please open an issue on GitHub if any compatibility issues are found.</p> <h2>libbitcoinconsensus Removal</h2> <p>The libbitcoin-consensus library was deprecated in 27.0 and is now completely removed. (#29648)</p> <h2>P2P and Network Changes</h2> <ul> <li>Previously if Bitcoin Core was listening for P2P connections, either using default settings or via <code>bind=addr:port</code> it would always also bind to <code>127.0.0.1:8334</code> to listen for Tor connections. It was not possible to switch this off, even if the node didn't use Tor. This has been changed and now <code>bind=addr:port</code> results in binding on <code>addr:port</code> only. The default behavior of binding to <code>0.0.0.0:8333</code> and <code>127.0.0.1:8334</code> has not been changed.</li> </ul> <p>If you are using a <code>bind=...</code> configuration without <code>bind=...=onion</code> and rely on the previous implied behavior to accept incoming Tor connections at <code>127.0.0.1:8334</code>, you need to now make this explicit by using <code>bind=... bind=127.0.0.1:8334=onion</code>. (#22729)</p> <ul> <li> <p>Bitcoin Core will now fail to start up if any of its P2P binds fail, rather than the previous behaviour where it would only abort startup if all P2P binds had failed. (#22729)</p> </li> <li> <p>UNIX domain sockets can now be used for proxy connections. Set <code>-onion</code> or <code>-proxy</code> to the local socket path with the prefix <code>unix:</code> (e.g. <code>-onion=unix:/home/me/torsocket</code>). (#27375)</p> </li> <li> <p>UNIX socket paths are now accepted for <code>-zmqpubrawblock</code> and <code>-zmqpubrawtx</code> with the format <code>-zmqpubrawtx=unix:/path/to/file</code> (#27679)</p> </li> <li> <p>Additional "in" and "out" flags have been added to <code>-whitelist</code> to control whether permissions apply to inbound connections and/or manual ones (default: inbound only). (#27114)</p> </li> <li> <p>Transactions having a feerate that is too low will be opportunistically paired with their child transactions and submitted as a package, thus enabling the node to download 1-parent-1-child packages using the existing transaction relay protocol. Combined with other mempool policies, this change allows limited "package relay" when a parent transaction is below the mempool minimum feerate. Topologically Restricted Until Confirmation (TRUC) parents are additionally allowed to be below the minimum relay feerate (i.e., pay 0 fees). Use the <code>submitpackage</code> RPC to submit packages directly to the node. Warning: this P2P feature is limited (unlike the <code>submitpackage</code> interface, a child with multiple unconfirmed parents is not supported) and not yet reliable under adversarial conditions. (#28970)</p> </li> </ul> <h2>Mempool Policy Changes</h2> <ul> <li> <p>Transactions with version number set to 3 are now treated as standard on all networks (#29496), subject to opt-in Topologically Restricted Until Confirmation (TRUC) transaction policy as described in <a href="https://github.com/bitcoin/bips/blob/master/bip-0431.mediawiki">BIP 431</a>. The policy includes limits on spending unconfirmed outputs (#28948), eviction of a previous descendant if a more incentive-compatible one is submitted (#29306), and a maximum transaction size of 10,000vB (#29873). These restrictions simplify the assessment of incentive compatibility of accepting or replacing TRUC transactions, thus ensuring any replacements are more profitable for the node and making fee-bumping more reliable.</p> </li> <li> <p>Pay To Anchor (P2A) is a new standard witness output type for spending, a newly recognised output template. This allows for key-less anchor outputs, with compact spending conditions for additional efficiencies on top of an equivalent <code>sh(OP_TRUE)</code> output, in addition to the txid stability of the spending transaction. N.B. propagation of this output spending on the network will be limited until a sufficient number of nodes on the network adopt this upgrade. (#30352)</p> </li> <li> <p>Limited package RBF is now enabled, where the proposed conflicting package would result in a connected component, aka cluster, of size 2 in the mempool. All clusters being conflicted against must be of size 2 or lower. (#28984)</p> </li> <li> <p>The default value of the <code>-mempoolfullrbf</code> configuration option has been changed from 0 to 1, i.e. <code>mempoolfullrbf=1</code>. (#30493)</p> </li> </ul> <h2>Updated RPCs</h2> <ul> <li> <p>The <code>dumptxoutset</code> RPC now returns the UTXO set dump in a new and improved format. Correspondingly, the <code>loadtxoutset</code> RPC now expects this new format in the dumps it tries to load. Dumps with the old format are no longer supported and need to be recreated using the new format to be usable. (#29612)</p> </li> <li> <p>AssumeUTXO mainnet parameters have been added for height 840,000. This means the <code>loadtxoutset</code> RPC can now be used on mainnet with the matching UTXO set from that height. (#28553)</p> </li> <li> <p>The <code>warnings</code> field in <code>getblockchaininfo</code>, <code>getmininginfo</code> and <code>getnetworkinfo</code> now returns all the active node warnings as an array of strings, instead of a single warning. The current behaviour can be temporarily restored by running Bitcoin Core with the configuration option <code>-deprecatedrpc=warnings</code>. (#29845)</p> </li> <li> <p>Previously when using the <code>sendrawtransaction</code> RPC and specifying outputs that are already in the UTXO set, an RPC error code of <code>-27</code> with the message "Transaction already in block chain" was returned in response. The error message has been changed to "Transaction outputs already in utxo set" to more accurately describe the source of the issue. (#30212)</p> </li> <li> <p>The default mode for the <code>estimatesmartfee</code> RPC has been updated from <code>conservative</code> to <code>economical</code>, which is expected to reduce over-estimation for many users, particularly if Replace-by-Fee is an option. For users that require high confidence in their fee estimates at the cost of potentially over-estimating, the <code>conservative</code> mode remains available. (#30275)</p> </li> <li> <p>RPC <code>scantxoutset</code> now returns 2 new fields in the "unspents" JSON array: <code>blockhash</code> and <code>confirmations</code>. See the scantxoutset help for details. (#30515)</p> </li> <li> <p>RPC <code>submitpackage</code> now allows 2 new arguments to be passed: <code>maxfeerate</code> and <code>maxburnamount</code>. See the subtmitpackage help for details. (#28950)</p> </li> </ul> <p>Changes to wallet-related RPCs can be found in the Wallet section below.</p> <h2>Updated REST APIs</h2> <ul> <li>Parameter validation for <code>/rest/getutxos</code> has been improved by rejecting truncated or overly large txids and malformed outpoint indices via raising an HTTP_BAD_REQUEST "Parse error". These requests were previously handled silently. (#30482, #30444)</li> </ul> <h2>Build System</h2> <ul> <li> <p>GCC 11.1 or later, or Clang 16.0 or later, are now required to compile Bitcoin Core. (#29091, #30263)</p> </li> <li> <p>The minimum required glibc to run Bitcoin Core is now 2.31. This means that RHEL 8 and Ubuntu 18.04 (Bionic) are no-longer supported. (#29987)</p> </li> <li> <p><code>--enable-lcov-branch-coverage</code> has been removed, given incompatibilities between lcov version 1 & 2. <code>LCOV_OPTS</code> should be used to set any options instead. (#30192)</p> </li> </ul> <h2>Updated Settings</h2> <ul> <li>When running with <code>-alertnotify</code>, an alert can now be raised multiple times instead of just once. Previously, it was only raised when unknown new consensus rules were activated. Its scope has now been increased to include all kernel warnings. Specifically, alerts will now also be raised when an invalid chain with a large amount of work has been detected. Additional warnings may be added in the future. (#30058)</li> </ul> <p>Changes to GUI or wallet related settings can be found in the GUI or Wallet section below.</p> <h2>Wallet</h2> <ul> <li> <p>The wallet now detects when wallet transactions conflict with the mempool. Mempool-conflicting transactions can be seen in the <code>"mempoolconflicts"</code> field of <code>gettransaction</code>. The inputs of mempool-conflicted transactions can now be respent without manually abandoning the transactions when the parent transaction is dropped from the mempool, which can cause wallet balances to appear higher. (#27307)</p> </li> <li> <p>A new <code>max_tx_weight</code> option has been added to the RPCs <code>fundrawtransaction</code>, <code>walletcreatefundedpsbt</code>, and <code>send</code>. It specifies the maximum transaction weight. If the limit is exceeded during funding, the transaction will not be built. The default value is 4,000,000 WU. (#29523)</p> </li> <li> <p>A new <code>createwalletdescriptor</code> RPC allows users to add new automatically generated descriptors to their wallet. This can be used to upgrade wallets created prior to the introduction of a new standard descriptor, such as taproot. (#29130)</p> </li> <li> <p>A new RPC <code>gethdkeys</code> lists all of the BIP32 HD keys in use by all of the descriptors in the wallet. These keys can be used in conjunction with <code>createwalletdescriptor</code> to create and add single key descriptors to the wallet for a particular key that the wallet already knows. (#29130)</p> </li> <li> <p>The <code>sendall</code> RPC can now spend unconfirmed change and will include additional fees as necessary for the resulting transaction to bump the unconfirmed transactions' feerates to the specified feerate. (#28979)</p> </li> <li> <p>In RPC <code>bumpfee</code>, if a <code>fee_rate</code> is specified, the feerate is no longer restricted to following the wallet's incremental feerate of 5 sat/vb. The feerate must still be at least the sum of the original fee and the mempool's incremental feerate. (#27969)</p> </li> </ul> <h2>GUI Changes</h2> <ul> <li> <p>The "Migrate Wallet" menu allows users to migrate any legacy wallet in their wallet directory, regardless of the wallets loaded. (gui#824)</p> </li> <li> <p>The "Information" window now displays the maximum mempool size along with the mempool usage. (gui#825)</p> </li> </ul> <h1>Low-level Changes</h1> <h2>Tests</h2> <ul> <li> <p>The BIP94 timewarp attack mitigation is now active on the <code>regtest</code> network. (#30681)</p> </li> <li> <p>A new <code>-testdatadir</code> option has been added to <code>test_bitcoin</code> to allow specifying the location of unit test data directories. (#26564)</p> </li> </ul> <h2>Blockstorage</h2> <ul> <li>Block files are now XOR'd by default with a key stored in the blocksdir. Previous releases of Bitcoin Core or previous external software will not be able to read the blocksdir with a non-zero XOR-key. Refer to the <code>-blocksxor</code> help for more details. (#28052)</li> </ul> <h2>Chainstate</h2> <ul> <li>The chainstate database flushes that occur when blocks are pruned will no longer empty the database cache. The cache will remain populated longer, which significantly reduces the time for initial block download to complete. (#28280)</li> </ul> <h2>Dependencies</h2> <ul> <li>The dependency on Boost.Process has been replaced with cpp-subprocess, which is contained in source. Builders will no longer need Boost.Process to build with external signer support. (#28981)</li> </ul> <h1>Credits</h1> <p>Thanks to everyone who directly contributed to this release: - 0xb10c - Alfonso Roman Zubeldia - Andrew Toth - AngusP - Anthony Towns - Antoine Poinsot - Anton A - Ava Chow - Ayush Singh - Ben Westgate - Brandon Odiwuor - brunoerg - bstin - Charlie - Christopher Bergqvist - Cory Fields - crazeteam - Daniela Brozzoni - David Gumberg - dergoegge - Edil Medeiros - Epic Curious - Fabian Jahr - fanquake - furszy - glozow - Greg Sanders - hanmz - Hennadii Stepanov - Hernan Marino - Hodlinator - ishaanam - ismaelsadeeq - Jadi - Jon Atack - josibake - jrakibi - kevkevin - kevkevinpal - Konstantin Akimov - laanwj - Larry Ruane - Lőrinc - Luis Schwab - Luke Dashjr - MarcoFalke - marcofleon - Marnix - Martin Saposnic - Martin Zumsande - Matt Corallo - Matthew Zipkin - Matt Whitlock - Max Edwards - Michael Dietz - Murch - nanlour - pablomartin4btc - Peter Todd - Pieter Wuille - @RandyMcMillan - RoboSchmied - Roman Zeyde - Ryan Ofsky - Sebastian Falbesoner - Sergi Delgado Segura - Sjors Provoost - spicyzboss - StevenMia - stickies-v - stratospher - Suhas Daftuar - sunerok - tdb3 - TheCharlatan - umiumi - Vasil Dimov - virtu - willcl-ark</p> <p>As well as to everyone that helped with translations on <a href="https://www.transifex.com/bitcoin/bitcoin/">Transifex</a>.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0fn0768k9ezueyxgezd5kxcq6rn3kjvxt4sautmdk4pk7l5kxe4czyprh2qthhd4mzymcfeyh8a4ju0wj0mc7lu386m3c6qzx6cvfd8jp5gp50q2" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0fn0768k9ezueyxgezd5kxcq6rn3kjvxt4sautmdk4pk7l5kxe4czyprh2qthhd4mzymcfeyh8a4ju0wj0mc7lu386m3c6qzx6cvfd8jp5gp50q2" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0fn0768k9ezueyxgezd5kxcq6rn3kjvxt4sautmdk4pk7l5kxe4czyprh2qthhd4mzymcfeyh8a4ju0wj0mc7lu386m3c6qzx6cvfd8jp5gp50q2" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0fn0768k9ezueyxgezd5kxcq6rn3kjvxt4sautmdk4pk7l5kxe4czyprh2qthhd4mzymcfeyh8a4ju0wj0mc7lu386m3c6qzx6cvfd8jp5gp50q2" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ c73818cc:ccd5c890 <div class="time" style="margin-left: auto;">2024-10-24 13:18:26</div> </div> <div> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/c73818cc95d6adf098fbff289cda4c3cf50d5f370d25f0b6f3677231ccd5c890/files/1729775834258-YAKIHONNES3.jpeg" /></p> <p>🖕 Saylor delega la custodia dei suoi Bitcoin a istituzioni bancarie</p> <p>🤮 Un cambio di rotta inaspettato </p> <p>🖕 Michael Saylor, figura centrale nel panorama Bitcoin, ha sorpreso molti con la sua recente affermazione. Nonostante sia sempre stato un sostenitore della custodia personale di BTC, oggi invita i detentori a fare affidamento sulle grandi banche, considerandole più sicure. Una mossa che ha sollevato diverse critiche tra i più ferventi Bitcoiner.</p> <p>🤮 Il potere delle istituzioni: pericolo o opportunità? </p> <p>🖕 Secondo Saylor, la paura di un sequestro statale di Bitcoin è eccessiva. Preferisce ora affidare la custodia di BTC a banche "troppo grandi per fallire", contraddicendo la sua precedente posizione. Molti critici vedono in questo un tentativo di normalizzare Bitcoin come semplice asset speculativo, allontanandolo dal suo ruolo di strumento di libertà finanziaria.</p> <p>🤮 La comunità Bitcoin è divisa </p> <p>🖕 Personalità di spicco come Simon Dixon e John Carvalho hanno espresso forti perplessità. Dixon teme che MicroStrategy possa trasformarsi in una sorta di banca Bitcoin, mentre Carvalho sottolinea come questo discorso rischi di minare la visione originale di Bitcoin come "speranza per tutti", marginalizzando i veri sostenitori della decentralizzazione.</p> <p>🤮 Un messaggio per le grandi aziende? </p> <p>🖕 Alcuni analisti ritengono che il messaggio di Saylor sia destinato principalmente a grandi imprese e fondi di investimento. Per queste entità, la custodia personale non è praticabile, e le banche rappresentano una soluzione più adatta. Tuttavia, questo potrebbe spingere ulteriormente Bitcoin nelle mani di pochi potenti, riducendo la libertà individuale di chi lo detiene.</p> <p>🤮 Un futuro incerto per Bitcoin</p> <p>🖕 Mentre Saylor continua a prevedere un futuro da trilione di dollari per Bitcoin, resta da vedere se riuscirà a mantenere l'equilibrio tra le sue ambizioni finanziarie e i principi cardine delle criptovalute. Il rischio di una Bitcoin centralizzata nelle mani di istituzioni bancarie e fondi resta un'ombra incombente, soprattutto sapendo che MicroStrategy è controllata per il 30% da Vanguard.</p> <p>Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia</p> <p>Referral Bitget -20% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK</p> <h1>BitcoinReportItalia #MichaelSaylor #MicroStrategy #BlackRock #ETF #Hodl #Hold #Vanguard #Banche #Cripto #Bitcoin</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9yyuk0ee55v8v3m3uv4l80cdmt289zhxxf2hvn37mxw8s2r2u53gzyrrnsxxvjht2muycl0lj38x6fs702r2lxuxjtu9k7dnhyvwv6hyfq6hhp7l" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9yyuk0ee55v8v3m3uv4l80cdmt289zhxxf2hvn37mxw8s2r2u53gzyrrnsxxvjht2muycl0lj38x6fs702r2lxuxjtu9k7dnhyvwv6hyfq6hhp7l" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9yyuk0ee55v8v3m3uv4l80cdmt289zhxxf2hvn37mxw8s2r2u53gzyrrnsxxvjht2muycl0lj38x6fs702r2lxuxjtu9k7dnhyvwv6hyfq6hhp7l" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9yyuk0ee55v8v3m3uv4l80cdmt289zhxxf2hvn37mxw8s2r2u53gzyrrnsxxvjht2muycl0lj38x6fs702r2lxuxjtu9k7dnhyvwv6hyfq6hhp7l" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 9e69e420:d12360c2 <div class="time" style="margin-left: auto;">2024-10-23 13:05:29</div> </div> <div> <p>Former Democratic Representative Tulsi Gabbard has officially joined the Republican Party, announcing her decision at a Donald Trump rally in North Carolina. As one of the few voices of reason within the Democratic Party, Gabbard's departure marks the end of her journey from Democratic presidential candidate to Republican Party member[1]. Her transition began with her exit from the Democratic Party in 2022, when she accurately called it an "elitist cabal of warmongers"[3].</p> <p>Throughout her congressional career, Gabbard demonstrated a consistent anti-interventionist stance and a strong defense of civil liberties. She was an original member of the bi-partisan 4th Amendment Caucus, fighting against warrantless searches and championing privacy rights in the digital age[4]. Her principled opposition to the surveillance state and bulk data collection set her apart from the establishment of both major parties.</p> <p>While some may view her political evolution as opportunistic, Gabbard's core positions on foreign policy have remained remarkably consistent. She has maintained her opposition to unnecessary foreign interventions and has been vocal about the risks of nuclear war[2]. Her criticism of the military-industrial complex and her calls for the Democratic party to renounce the influence of military contractors and corporate lobbyists demonstrate a commitment to principles over party loyalty[4]. Though her recent alignment with Trump may raise eyebrows, her consistent advocacy for peace and opposition to the warfare state make her a unique figure in American politics[1].</p> <p>Sauce: [1] Tulsi Gabbard's Political Evolution | TIME https://time.com/7096376/tulsi-gabbard-democrat-republican-political-evolution-history-trump/ [2] Tulsi Gabbard wants to serve under Trump, but do their policies align? https://www.usatoday.com/story/news/politics/elections/2024/06/19/tulsi-gabbard-trump-vp-secretary-policy/73968445007/ [3] Tulsi Gabbard announces she is leaving Democratic Party https://abcnews.go.com/Politics/tulsi-gabbard-announces-leaving-democratic-party/story?id=91326164%2F [4] Political positions of Tulsi Gabbard - Wikipedia https://en.wikipedia.org/wiki/Political_positions_of_Tulsi_Gabbard [5] Tulsi Gabbard Turning Republican Is 'Surprise' to Donald Trump https://www.newsweek.com/tulsi-gabbard-donald-trump-republican-party-1973340</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqswaw5yyl2q0kvahfpjl6cakqscrl6cz3d3z05f5f3xm8zq5jfxlrqzyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyt5qede" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqswaw5yyl2q0kvahfpjl6cakqscrl6cz3d3z05f5f3xm8zq5jfxlrqzyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyt5qede" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqswaw5yyl2q0kvahfpjl6cakqscrl6cz3d3z05f5f3xm8zq5jfxlrqzyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyt5qede" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqswaw5yyl2q0kvahfpjl6cakqscrl6cz3d3z05f5f3xm8zq5jfxlrqzyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyt5qede" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> </ul> </div> </div> <script> // 处理回车键 function handleKeyDown(event) { if (event.key === 'Enter') { handleSearch(); } } // 处理搜索 function handleSearch() { const keyword = document.getElementById('searchInput').value.trim(); if (keyword) { window.location.href = `/search?q=${encodeURIComponent(keyword)}`; } else { alert('请输入搜索关键词!'); } } </script> </body> </html>


