-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ df478568:2a951e67
2024-10-20 14:49:52
@ df478568:2a951e67
2024-10-20 14:49:52Portfolio
I run 72 services on three servers - Umbrel - Start9 - -PopOS! with a Cloudflare Tunnel This has given me experience in running my own cloud, ticketing system, full bitcoin node, decentralized blog, a meal management system, and Docker experience in both Linux and Portainer.
Umbrel Server.
I run an Umbrel Server and host many services on the clear-net using the Cloudflare tunnel.
Start9 Server
I also run a start9 Server with services also exposed to the clearnet and TOR
Bitcoin Node
I began running a full bitcoin node in 2019. I also run two pruned nodes. You can see the Genesis Block on my instance of mempool
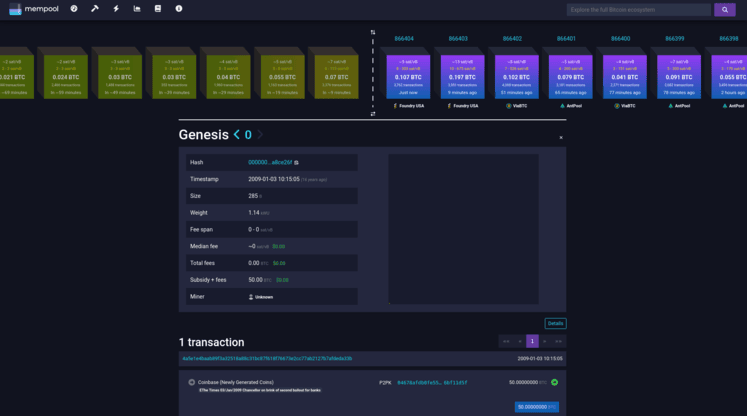 .
.Peppermint Ticketing System
You can submit a ticket on my ticketing system here
I wrote about it in my blog here. This service runs on a AMD computer with the PopOS! Operating system and cloudflare.
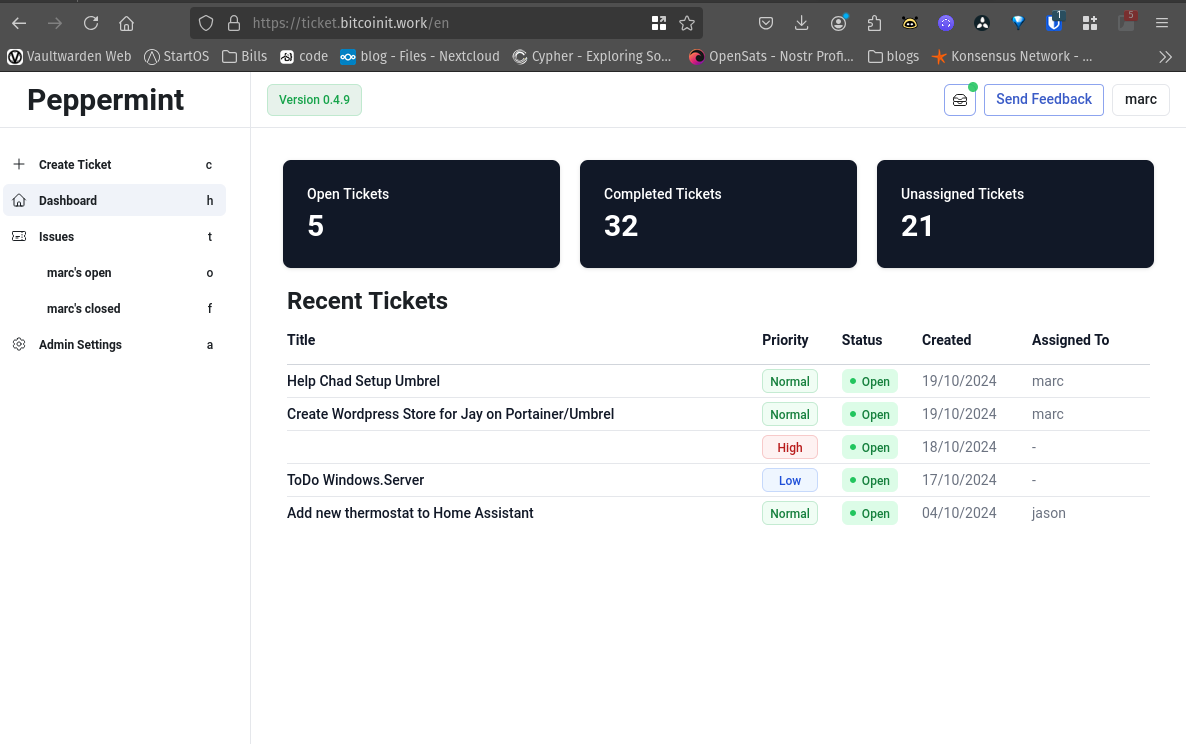
Mealie
This is my favorite service on Umbrel. It’s a meal management system that allows me to plan my meals and automate my grocery lists. It saves so much time. You can find [my instance of mealie here(https://mealie.marcleon.work/).
Self Hosted and Decentralized Blog
I host a ghost blog on Start9 here.
This blog is also published on nostr at:
npub.pro
https://marc26z.npub.pro/
habla.news/
https://habla.news/u/marc26z@nostrplebs.com/
Highlighter.com
https://highlighter.com/marc26z@nostrplebs.com
Portainer
I am currently working on a website using WordPress using Portainer on Umbrel.
It’s not done, but the idea is to create a website that allows me to help people learn how to take self custody of bitcoin, run nodes, and mine.
It is not finished, but the idea is to offer bitcoin IT services.
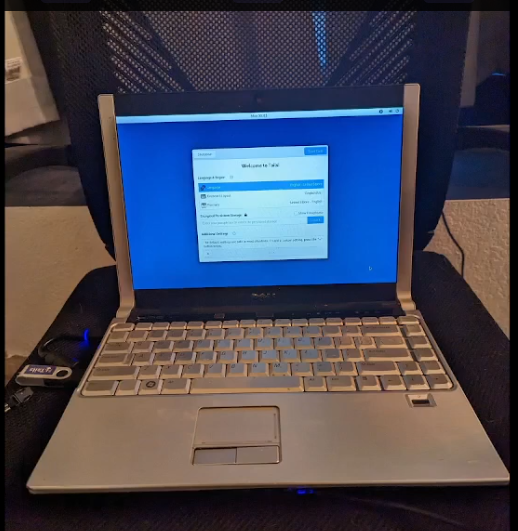
Tails On An Air Gapped Computer
I removed the Wi-Fi card and hard drive from an old laptop to create an air gapped computer using TAILS Click here to watch the video hosted on nostr.build.
Bitcoin Mining Heater
I converted an old S9 into a space heater. The 3D printed case was made by CryptoCloaks. The S9 miner was a gift from the first person I met after starting my meetup.
PeerViewer
This is free and open source software that can be found at https://github.com/PeerViewer/. - It’s like a free and open source version of RDP on Windows or TeamViewer on Linux.
Certifications
Google Technical Support Certificiate
Automate The Boring Stuff With Python
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 8d34bd24:414be32b
2024-10-20 15:10:47
@ 8d34bd24:414be32b
2024-10-20 15:10:47Check out:
-
God Demonstrates His Power: Part 1 (Egypt)
-
God Defends His Honor: Part 2 (Phillistines)
-
The One True God: Part 3 (Who deserves worship)
In the Old Testament, God’s actions were primarily aimed at proving His existence, His power, and His holiness to Israel. He did many miracles before the Gentiles, but He definitely focused on His chosen people.
In the New Testament, God expands knowledge of Him starting with His chosen people. He also includes others in His promises and knowledge of Him. His miracles go beyond showing who He is. They go to the ultimate miracle — salvation from our sins.
Incarnation
Jesus was God from the beginning. He is “the Alpha and the Omega, the first and the last, the beginning and the end.” (Revelation 22:13) In the Gospels, the Bible tells us how the God and creator of the universe came down to earth and was born physically as a man — becoming the same flesh as His creation.
How an eternal, all-powerful being becomes a zygote in a woman’s womb and is born of a virgin is beyond what any of us can fully understand, but is one of God’s greatest miracles. This allowed our Creator to become our kinsmen redeemer and pay the price for our sins. This allowed our Creator to live a perfect, sinless human life, like we are unable to do, so He could become the ultimate once-for-all sacrifice for our sins.
Jesus’s incarnation, perfect life, and horrible death show us how much our Creator loves us and is willing to do to fix the relationship that we broke with Him.
Miracles
While Jesus lived a perfect life to show us how we should live, he also performed many miracles to show everyone that He was not just a man, but was also God. His miracles included1(footnote copied to bottom):
Physical Healings
-
Healing Peter's mother-in-law of a fever
-
Cleansing a man with leprosy
-
Healing a centurion's paralyzed servant
-
Healing a paralytic lowered through the roof
-
Healing a man's withered hand
-
Restoring sight to two blind men
-
Healing a deaf mute
-
Healing blind Bartimaeus
-
Healing the bleeding woman
-
Restoring a servant's severed ear
Exorcisms
-
Driving out an evil spirit in Capernaum
-
Healing a demon-possessed mute man
-
Casting demons into a herd of pigs
-
Healing the Syrophoenician woman's demon-possessed daughter
-
Healing a boy possessed by a spirit
Nature Miracles
-
Turning water into wine at the wedding in Cana
-
Calming the storm on the sea
-
Feeding the 5,000
-
Walking on water
-
Feeding the 4,000
-
Causing the fig tree to wither
-
Miraculous catch of fish
Raising the Dead
-
Raising the widow's son at Nain
-
Raising Jairus' daughter
-
Raising Lazarus from the dead
Other Miracles
-
Finding the coin in the fish's mouth
-
Jesus' resurrection
Jesus did so many amazing miracles that nobody should doubt that He is the incarnate God.
Of course the most miraculous of His miracles was taking our sins upon Himself, dying on the cross, and then rising from the dead on the third day to prove He had conquered death and sin. This miracle was not primarily for the Jews in Israel. The good news, of what God had done, was witnessed to everyone “in Jerusalem, and in all Judea and Samaria, and even to the remotest part of the earth.” (Acts 1:8b)
This miracle wasn’t just for Israel. It wasn’t just for Israel’s enemies. It wasn’t just for the Middle East. This miracle was for the whole world. His faithful followers have been copying His word (Bibles) to keep the details of what He has done for us alive. His word has been translated, so those around the globe can read it in their own language. His followers have left their homes to share the good news with those from foreign lands.
God did a miraculous work to change the hearts of those who trust in Him and those people having been sharing what God did for them for almost 2,000 years.
Some have heard the gospel and rejoiced. Some have heard the gospel and rejected it. Even worse, some have tried to stop the spread of the gospel, but God does not allow His word to be stopped.
So far in history, some have seen God’s power, trusted Him, and followed Him in obedience. Others have rejected Him and continued in their error to the point of even trying to destroy His followers. A time is coming when all will see who God really is and they will all fall down in awe, wonder, fear, and worship. Anyone who waits till the end will be rejected and miss the blessings that God worked so hard to orchestrate through history. I’ll share more about God’s final show of power in my next post.
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
- I’ll admit I used perplexity.ai to list the miracles of Jesus to save time. I double checked the miracles listed from what I know of the Bible and it is accurate. I believe this link will give you all of the details and the links to the Bible references to the miracles. https://www.perplexity.ai/search/give-me-the-miracles-of-jesus-UGKDbkICTHKt96dn5.bkyQ\ I’ll admit I used perplexity.ai to list the miracles of Jesus to save time. I double checked the miracles listed from what I know of the Bible and it is accurate. I believe this link will give you all of the details and the links to the Bible references to the miracles. https://www.perplexity.ai/search/give-me-the-miracles-of-jesus-UGKDbkICTHKt96dn5.bkyQ
-
-
 @ ff18165a:dd7ca7f0
2024-10-19 18:23:51
@ ff18165a:dd7ca7f0
2024-10-19 18:23:51Chef's notes
- DO NOT add too much Peppermint Extract! It’s extremely strong and it will make your milkshake way too strong if you add more than a few drops.
- Feel free to be creative with your toppings. We used Caramel Flavored Whipped Topping and it turned out great!
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 2 min
- 🍽️ Servings: 1
Ingredients
- 1 1/2 cup Milk
- 2 drops Peppermint Extract
- 2 packets Stevia
- 1 cup Ice
- 2 drops Green Food Coloring
- Green Sprinkles
- 1 Crushed Peppermint Candy
- 2 Mint Leaves
Directions
-
- Blend together until smooth and frothy
-
- Pour into a tall glass
-
- Top with listed toppings
-
- Add straw and enjoy
-
 @ 361d3e1e:50bc10a8
2024-10-20 14:52:53
@ 361d3e1e:50bc10a8
2024-10-20 14:52:53https://forex-strategy.com/2024/10/20/why-wont-there-be-enough-food-very-soon-what-will-the-harvest-be-in-the-coming-years-and-what-will-the-sun-do/ Why won't there be enough food very soon? What will the harvest be in the coming years, and what will the Sun do? What do the Sun and your car's catalytic converter have in common? Are we on the brink of a global meltdown? Are there coming wars different from those in Ukraine and Israel?
food #foodcrisis #climatechange #climate #temperatures #war
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ cbaa0c82:e9313245
2024-10-01 11:04:45
@ cbaa0c82:e9313245
2024-10-01 11:04:45TheWholeGrain - #September2024
To start the second year of Bread and Toast off strong the September of 2024 includes five Sunday Singles, and the newest piece of cover art for a comic from Toast's Comic Collection includes a touch of color. Some bonus pieces of content were included this September. This includes one of the Political posts we all take so seriously, and a promotional piece for the upcoming npub10hj9rg5gds5x2gk0z0s2jlqnq04jg7g30aj2t5pqzdaaztfactgsnze5ny event coming up in October. The Concept Art released this month is an early design of a possible website logo. This month's Bitcoin Art stars End-Piece who is well informed on what money really is and asks the question, "Do you?"
September Sunday Singles
2024-09-01 | Sunday Single 055 Jump Rope https://i.nostr.build/ESlb23xVmTQLw7sw.png
2024-09-08 | Sunday Single 056 Trampoline https://i.nostr.build/1HNutqYQUjsA1JaG.png
2024-09-15 | Sunday Single 057 Hippity Hop https://i.nostr.build/5dTyLA0FJdK2rNol.png
2024-09-22 | Sunday Single 058 Jumping on the Bed https://i.nostr.build/PWaHDMroMjjfPmWS.png
2024-09-29 | Sunday Single 059 Shades https://i.nostr.build/pWeIZrttOjpcXAtz.png
Other Content Released in September 2024
2024-09-04 | Toast's Comic Collection Teenage Mutant Ninja Bread #5 Four brothers trained in ninjutsu live underneath the city and come up to the surface in order to save it! https://i.nostr.build/WPSB1qn2lMRlbdwJ.png
2024-09-10 | Politics Debate Night The first official debate between the candidates for Selection2024. https://i.nostr.build/wppFU8U3NJCww6U0.png
2024-09-11 | Concept Art Early Website Logo Design This is an early concept for a logo. It was never used. https://i.nostr.build/hxhzvtS4fCe0imNh.png
2024-09-18 | Bitcoin Art On Top of It End-Piece knows what money is. Do you? https://i.nostr.build/6TCWK5d1ynPhrteA.png
2024-09-27 | Nostr Valley Nostr Valley 001 Bread is getting prepared for NostrValley! Hope to see you there! https://i.nostr.build/nQqsPGmJ8hjvxROK.png
September Additions to The Bakery in 2024
2024-09-05 | npub1895dg7n47ldxxq8hyqj9h4xa3xwwxzpnn8lm7hydag4tck6cfj3qcmc4f0 https://m.primal.net/KgDW.jpg
2024-09-26 | npub1hcusg0xp9maamlh9vnv4mf635uwldsfeut00ghzrrjk7kjjh8j3sf9049l https://image.nostr.build/a0a64d709376b3650ebde0f3de5076748d69a999aef9e5fbd882574d5e64cf88.jpg
We hope you enjoyed this first issue of The Whole Grain. The Whole Grain will be released on the first of every month and will cover all of the content released by npub1ew4qeq576v3vz4gukeseknqghx3x4jtlld8ftys9amrca6f3xfzsrm8jpd in the previous month.
Thanks for checking it out, Bread, Toast, and End-Piece
BreadandToast #SundaySingle #ToastsComicCollection #ConceptArt #BitcoinArt #TheBakery #Bread #Toast #EndPiece #Art #Artstr #DigitalArt #Comic #Manga #NostrValley #NostrOnly #🖼️
-
 @ 96417ed9:66b02a55
2024-09-29 20:01:36
@ 96417ed9:66b02a55
2024-09-29 20:01:36Image this.
You are scrolling through your favorite social media. It’s probably been 10 minutes Scroll. Like. Repeat. Scroll. Like. Repeat. And so on and on and on.
Does it sound familiar to you? How many times did you find yourself in this situations? Most importantly, how much attention did you pay to the hundreds of posts that you liked? What can you actually remember?
Attention and likes
Recently, I took a communication class. I was very surprised when the teacher told me that the average attention span is around 7 seconds! This means that when you are looking at something or talking to someone, you are actually paying attention for the first 7 seconds. After that, something else has already captured your mind. And it's actually getting worse and worse. Why is that, you might wonder? Yeah, you got it right, social media.
The infinite amount of content that you can consume on social media continuously steals your attention. Thus, when you are looking to a post, your focus is already on the next piece of information, and on the one after and so on indefinetly. Finally, when you decide to leave a like to the first post, you are not actually remembering what you were looking at.
In this context, likes moved from being an appreciation for someone else's work to a simple mechanism that feeds the social media algorithm. From a measure of the value provided by a creator, they became an empty number. Liking a post is no more action, but a mere unconscious reflex. A like is something free, something that you can leave without any conscious effort, to anyone, to anything. Even to something that you actually do not like.
In the last years, likes stopped being a measure of value provided.
And then, zaps came.
Zaps and the value 4 value revolution
Since I am publishing this article on Nostr, I expect most of the reader to know what a zap is. However, for the nebies whom may come across my random thought, here is a brief explaination.
Zaps are a simple way to communicate appreciation. Whenever you like a photo, a thought, a video, you can zap the creator. Exactly as a like, you might say. But here is the deal. When you zap someone, you are actually sending them some amount of money! And not a simple type of money, but the scarcest type of money on earth: Bitcoin! Basically, if a creator provides value to a user the user can award the creator with some monetary value. Nowadays, this concept is quite common and known as value4value (v4v for short).
This is a revolution. Anyone can provide value. Thus, everybody should be able to earn value if something of value is provided , not only some super influencer with sponsors and affiliate programs
Zaps from the user perspective
I started this article by talking about attention, and how there is such a huge competition for it that no one is actually able to focus on something anymore. How does it connect to zaps?
Zaps allow users to regain their lost attention. Since zaps provide real monetary value to a creator, a user has to be 100% on focus on what he is reading or watching: "Is this picture/video/post providing me value?". You do not want to separate from you hard-earned sats for something useless. Unlike likes, zaps are not free. When you zap someone, it means that you have actually paid attention to the post and you are actually acting to signal your appreciation.
Zaps from the creator perspective
I am an amateur photographer. I love going around places and took hundreds of photos at everyhting that catches my curiosity. I posted more than a hundred pictures on Instagram and received even a decent amount of likes. However, I eventually started to wonder if likes came from a genuine appreciation of my work, or only from the aforementioned mechanical reflex.
This does not happen on Nostr. Whenever I am zapped, I instantly know that the appreciation is real. My God, someone really spent some time looking at my photos and decided to give me some real monetary value for that! I really provided value to someone! This is truly exciting.
The realization of this fact has been one of those "ah-ah" moments. Why should I spent my time posting pictures on a social media just to get likes, when someone can send me a chunk of the best money ever created?
And why should you?
-
 @ 599f67f7:21fb3ea9
2024-10-20 11:32:36
@ 599f67f7:21fb3ea9
2024-10-20 11:32:36LNDhub-ek zure zorroa erraz inportatzea ahalbidetzen du bateragarriak diren aplikazioetan. Bitcoin Txoko LNbits zorroa progresiboko web aplikazio (PWA) modura gorde dezakezun arren zure telefonoan, Zeus edo BlueWallet bezalako aplikazio natibo batek erabiltzaile-esperientzia hobea eta segurtasun handiagoa eskaintzen du.
Alby erabiliz, zorroa zure nabigatzailearen luzapenean ere inporta dezakezu, webgunean Lightning ordainketak egiteko eta Nostr zap-ak egiteko erraztasun handiagoz. Zorionez, zorro hauek guztiek hizkuntza komun bat ulertzen dute, LNDhub izenekoa.
Gida honetan, zorroa zure nabigatzailera eta telefonora nola inportatu azalduko dugu. Zorroa nabigatzailean eta telefonoan erabili nahi baduzu, hasi Alby konfigurazioarekin, pausoetako batek zorroa Zeus-era erraz inportatzeko aukera emango baitizu. Baina zorroa soilik zure telefonoan erabili nahi baduzu, zuzenean Zeus atalera jo dezakezu.
Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 nabigatzailearen luzapena da, Lightning eta Nostr nabigatzailera ekartzen dituena. WebLN protokoloa erabiliz, luzapenak webguneetan fakturak automatikoki detekta eta ordaintzen ditu, eta Lightning bidez webguneetan saioa hasteko aukera ematen du. Gainera, Lightning gune gogokoenetan aurrekontuak ezar ditzakezu. Luzapen honek NIP-07 protokoloa erabiliz Nostr sinadura gisa ere funtziona dezake, zure giltza pribatua web bezeroetan sartzea baino askoz seguruagoa dena.
Zer behar dut?
- Chrome edo Firefox luzapenak onartzen dituen web nabigatzailea.
- LNbits zorroa. Oraindik zorro bat ez baduzu, joan gure zorroen orrira eta sortu bat.
- (Aukerazkoa) Zeus konfiguratzeko mugikor bat.
1. LNDhub luzapena gaitzea zure LNbits zorroan
Nabigatzailean, joan zure zorroaren estekara. Egin klik Extensions atalean eta gaitzazu
LNDhubluzapena. Gaitu ondoren, joan LNDhub luzapenaren orrira.2. Alby luzapena instalatu
Joan getalby.com-era eta egin klik
Add Browser Extensionbotoian. Instalatu luzapena zure nabigatzailearen luzapen dendetik. Ezarri desblokeatzeko pasahitza eta gorde toki seguruan.3. Inportatu Alby-ra

Hurrengo pantailan, aukeratu
Connect, eta ondoren aukeratuLNDhub. Itzuli zure LNDhub luzapenera eta kopiatu konexioaren URL-a. Itsatsi hori LNDhub esportazioaren URI eremuan. SakatuContinue. Orain LNbits zorroa LNDhub bidez konektatuta eduki beharko zenuke!💡 Aukeratu dezakezu Invoice URL eta Admin URL artean. Bi hauek Alby-ri zure LNbits zorroarekin elkarreragiteko baimen desberdinak ematen dizkiote: - Invoice URL-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - Admin URL-ak ordainketak bidaltzeko aukera ere ematen du.
4. (Aukerazkoa) Zeus konfiguratu Alby-rekin

Orain LNbits zorroa Alby-rekin konektatu duzunez, Zeus-en ere erraz inportatu dezakezu. Ireki luzapena, egin klik zure zorroaren izenean, eta joan
Account Settingsatalean.Accountazpian aurkituko duzuConnect your mobile walletaukera. SakatuConnect, eta Zeus-ekin eskaneatzeko QR kode bat erakutsiko dizu.Zeus aurretik instalatu ez baduzu, joan zeusln.app-era eta deskargatu Zeus zure mugikorreko sistema eragilerako. Zeus deskargatu ondoren, joan
Settings>Add a new nodeatalera. Hemen, Alby-k erakusten dizun QR kodea eskaneatu eta zorroa inportatu dezakezu.Listo! Orain Lightning-aren indarra zure eskuetan duzu. Jainko baten moduan sentitzen al zara jada?
Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf kode irekiko aplikazio bikaina da, zure nodo propioa mugikorrean konektatzeko aukera ematen duena. Lightning nodo nagusi guztiak onartzen ditu, hala nola LND, CLN eta Eclair, bai eta Tor bidezko zein clearnet bidezko konexioak ere. Azkenaldian, beren LSP (Lightning Service Provider) propioa iragarri dute.
Zer behar dut?
- Android edo iOS telefono bat.
- LNbits zorroa ikusi ahal izateko beste gailu bat (QR kodea eskaneatzeko).
- LNbits zorroa eskuragarri izatea. Zorro bat oraindik ez baduzu, joan gure zorroen orrira eta sortu bat.
1. Zeus deskargatu
Deskargatu Zeus aplikazioa zure sistema eragilerako hemen.
2. LNDhub luzapena gaitzea zure LNbits zorroan
Zure LNbits zorroaren orrian, egin klik
Extensionsatalean eta gaitzazuLNDhubluzapena. Gaitu ondoren, ireki LNDhub luzapenaren orria.3. Inportatu Zeus-en
Joan
Settings>Add a new nodeatalera Zeus-en. Eskaneatu nahi duzun zorroa inportatzeko.💡 Aukeratu dezakezu Invoice URL eta Admin URL artean: - Invoice URL-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - Admin URL-ak ordainketak bidaltzeko aukera ere ematen du.
QR kodea eskaneatu ondoren, Zeus-en eremu guztiak automatikoki beteko dira. Zorroarentzat ezizena ere gehitu dezakezu.

Orain,
Save Node Configsakatu eta zorroa zure mugikorretik kontrolatu dezakezu!Bonus
Zeus-ek ezaugarri interesgarriak ere eskaintzen ditu, hala nola gai pertsonalizatuak, prezioen bihurketak, lurker modua eta biometria bidezko egiaztapena. Gida honen esparrutik haratago doazen ezaugarriak dira hauek, baina aplikazioa erabili eta zuk zeuk aurkitu ditzakezu!
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 599f67f7:21fb3ea9
2024-10-20 11:28:08
@ 599f67f7:21fb3ea9
2024-10-20 11:28:08LNDhub te permite importar fácilmente una billetera en aplicaciones compatibles. Si bien puedes guardar tu billetera Bitcoin Txoko LNbits en tu teléfono como una aplicación web progresiva (PWA), una aplicación nativa como Zeus o BlueWallet ofrece una mejor experiencia de usuario así como un mayor nivel de seguridad. Con Alby, también puedes importar la billetera a la extensión de tu navegador para facilitar los pagos Lightning en la web y para los zaps de Nostr. Por suerte para nosotros, todas estas billeteras hablan un lenguaje común llamado LNDhub.
En esta guía cubriremos cómo importar la billetera a tu navegador y a tu móvil. Si quieres usar tu billetera tanto en el navegador como en tu móvil, empieza con la configuración de Alby, ya que uno de los pasos te permitirá importar fácilmente tu billetera también a Zeus. Pero si sólo te interesa utilizar la billetera en tu móvil, puedes pasar directamente a la sección de Zeus.
Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 es una extensión de navegador que lleva Lightning y Nostr a tu navegador. Utilizando el protocolo WebLN, esta extensión puede detectar facturas LN en paginas web y pagarlas, así como posibilita iniciar sesión en sitios web con Lightning. También puedes fijar presupuestos para tus sitios favoritos de Lightning. Por otro lado también puedes utilizarla para firmar en Nostr utilizando NIP-07, lo cual es mucho más seguro que ingresar tu clave privada en clientes web.
¿Qué necesito?
- Un navegador web que soporte extensiones Chrome o Firefox
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
- (Opcional) Un dispositivo móvil para configurar Zeus
1. Habilita la extensión LNDhub en tu LNbits wallet
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez se haya habilitado, dirígete a la página de extensión de LNDhub.2. Instala la extensión Alby
Dirígete a getalby.com y instala la extensión desde el store de extensiones del navegador. Configura tu contraseña de desbloqueo y guárdala en un lugar seguro.
3. Importar a Alby
 (Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)
(Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)En la siguiente pantalla, elige
Conectary luego eligeLNDhub. Vuelve a tu extensión LNDhub y copia la URL de conexión. Pégala en el campoURI de exportación de LNDhub. Pulsa continuar. ¡Ahora deberías haber estado conectado a tu billetera de LNbits con LNDhub!💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). Le dan a Alby diferentes permisos para interactuar con tu cartera de LNbits.
- La URL de factura te permite crear facturas y recibir pagos
- La URL de administración también te permite enviar pagos
4. Configurar Zeus con Alby (opcional)

Ahora que ya has conectado tu LNbits con Alby, también puedes importarlo de una manera sencilla a Zeus con Alby. Abre la extensión, haz cilc en el nombre de tu billetera y navega a la configuración de la cuenta. En
Wallet Settings>Generalse encuentra la opción de conectar tu billetera móvil. Al pulsar conectar, se mostrará un código QR para escanear desde Zeus.Si no tienes instalada Zeus con anterioridad, dirígete a zeusln.app y descarga la aplicación de Zeus para tu sistema operativo móvil.
Una vez tengas descargado Zeus, entra en
Configuración>Añadir un nuevo nodo. Aquí puedes escanear el código QR que te muestra Alby para importar la billetera.Voilà! Ahora tienes el poder de Lightning al alcance de la mano ¿Ya te sientes como un dios?
Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf es una formidable aplicación de código abierto que permite conectar tu propio nodo a tu dispositivo movil. Es compatible con todas las principales implementaciones de nodos Lightning, como LND, CLN y Eclair, así como conexiones a través de Tor y clearnet. Recientemente también han anunciado su propio LSP (Lightning Service Provider).
¿Qué necesito?
- Teléfono Android o iOS
- Otro dispositivo en el que puede acceder a tu billetera LNbits (para mostrar el código QR para escanear)
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
1. Descarga Zeus
Puedes descargar la aplicación Zeus para tu sistema operativo aquí.
2. Habilita la extensión LNDhub en tu billetera LNbits
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez habilitada, abre la pagina de la extensión LNDhub.3. Importar a Zeus
Ve a
Configuración>Añadir un nuevo nodo en Zeus.Escanea la cartera que quieras instalar.
💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). - La URL de la factura te da permiso para generar facturas y recibir pagos. - La URL de administración también te permite enviar pagos.
Una vez que hayas escaneado el código QR, todos los campos en Zeus deberían rellenarse automáticamente. También puedes añadir un apodo para tu billetera.

¡Ahora puedes guardar la configuración del nodo y controlar la billetera desde tu teléfono!
Extra
Zeus también ofrece funciones interesantes como temas personalizados, conversiones de precios, modo acechador y verificación biométrica. Estos temas están más allá del alcance de esta guía, ¡juega en la aplicación y descubre todas esas características por ti mismo!
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 9e69e420:d12360c2
2024-10-19 22:51:20
@ 9e69e420:d12360c2
2024-10-19 22:51:20political motivations of J6 judges:
Judicial Sentencing Patterns
Federal judges in Washington have been handling the sentencing of Capitol riot defendants, with some notable trends emerging:
Harsher Sentences: Judges appointed by Democratic presidents have generally imposed tougher sentences compared to their Republican-appointed counterparts. This disparity suggests a potential political bias in the sentencing process.
Partisan Divide: The sentencing patterns reveal a clear partisan divide, with Democratic-appointed judges more likely to view the January 6 events as a severe threat to democracy.
Specific Examples
Judge Tanya Chutkan: Appointed by President Obama, Judge Chutkan has consistently handed down sentences exceeding prosecutors' recommendations. Her actions could be interpreted as politically motivated, given her Democratic background.
Judge Trevor McFadden: In contrast, Judge McFadden, appointed by President Trump, has been more lenient in his sentencing, even acquitting a defendant in a bench trial. This stark difference in approach further underscores the potential political influence on judicial decisions.
Implications
-
 @ 9e69e420:d12360c2
2024-10-20 13:09:52
@ 9e69e420:d12360c2
2024-10-20 13:09:52Corruption and Insider Trading in Congress
Congressional corruption and insider trading have been significant issues in recent years, with numerous lawmakers facing allegations and legal consequences for unethical financial practices. Here's an overview of the key aspects:
STOCK Act Violations
The Stop Trading on Congressional Knowledge (STOCK) Act of 2012 was designed to prevent insider trading and conflicts of interest among members of Congress. However, violations of this law have been widespread:
- At least 78 members of Congress have violated the STOCK Act by failing to properly report their financial trades.
- Excuses for these violations range from oversights and clerical errors to inattentive accountants.
- The penalties for violating the STOCK Act are relatively minor, starting with a $200 late fee for first-time offenders.
Recent High-Profile Cases
Several prominent lawmakers have faced serious allegations of corruption and insider trading:
Senator Bob Menendez
- Found guilty on all counts in a bribery trial in July 2024.
- Convicted of accepting bribes to benefit businessmen and the governments of Egypt and Qatar.
- Faced 16 charges, including bribery, obstruction of justice, and acting as a foreign agent.
Representative Henry Cuellar
- Indicted in May 2024 on charges of accepting almost $600,000 in bribes from Azerbaijan and a Mexican bank.
- Accused of pushing U.S. policy in favor of Azerbaijan in exchange for payments.
- Charges include bribery, money laundering, and working on behalf of a foreign government.
Ongoing Issues and Reform Efforts
-
Widespread nature of the problem: The corruption issue extends beyond a few isolated cases, with numerous lawmakers from both parties implicated in unethical practices.
-
Lack of enforcement: The House Ethics Committee has been criticized for ineffective oversight, with a 2022 analysis finding that it only publicly investigated 8 out of 60 potential STOCK Act violations since 2020.
-
Calls for reform: There have been bipartisan efforts to ban members of Congress from trading individual stocks, but these proposals have not yet been enacted into law.
-
Public opinion: The issue of congressional stock trading has received significant public interest, with polls showing overwhelming support for reform.
-
Resistance to change: Some lawmakers, such as former House Speaker Nancy Pelosi, have opposed reforms that would limit their ability to trade stocks.
The ongoing issues of corruption and insider trading in Congress highlight the need for stronger ethics rules, better enforcement mechanisms, and increased transparency in the financial dealings of elected officials. As public scrutiny intensifies, pressure continues to mount for meaningful reform to address these longstanding problems.
-
 @ 9e69e420:d12360c2
2024-10-20 12:49:07
@ 9e69e420:d12360c2
2024-10-20 12:49:07The Growing Threat to Free Speech on Social Media
In a recent CNN interview, Hillary Clinton made alarming statements about the need for social media companies to moderate content, warning that without such measures, "we lose total control"[1]. This rhetoric is part of a broader push by some Democrats to increase censorship and control over online platforms under the guise of combating misinformation.
Clinton's comments went beyond mere content moderation, as she advocated for the repeal of Section 230, a crucial provision that protects online platforms from liability for user-posted content[1]. This move would fundamentally alter the landscape of free speech on the internet, potentially forcing platforms to aggressively censor user content to avoid legal repercussions.
The former Secretary of State even suggested that Americans could face civil or criminal charges for certain social media posts[2]. While she specifically referred to those allegedly paid by foreign agents to spread propaganda, such a precedent could easily be abused to target political dissent or unpopular opinions. This approach stands in stark contrast to the principles of free speech enshrined in the First Amendment.
Clinton's statements are not isolated incidents. Other prominent Democrats, including Vice President Kamala Harris, have also expressed support for weakening Section 230 and increasing government control over online speech[6]. This trend suggests a coordinated effort to reshape the digital public square in ways that could severely limit free expression and open debate.
As we approach the 2024 election, it is crucial to remain vigilant against attempts to stifle free speech under the pretext of fighting misinformation. While addressing genuine foreign interference and harmful content is important, we must be wary of solutions that grant excessive power to government or tech companies to determine what constitutes acceptable speech online.
Sauce: I am the sauce. But I also would credit:
[1] Hillary Clinton says social media companies must moderate content ... https://www.hindustantimes.com/world-news/us-news/hillary-clinton-says-social-media-companies-must-moderate-content-or-we-lose-total-control-ripped-by-tulsi-gabbard-101728181956987.html [2] Fact check: Did Clinton call for jail over misinformation? - DW https://www.dw.com/en/fact-check-did-clinton-call-for-jail-over-misinformation/a-70279863 ncy ... https://oversight.house.gov/release/mace-calls-on-biden-harris-administration-to-provide-transparency-on-current-censorship-efforts-to-interfere-in-the-2024-election/ [4] Hillary Clinton Discusses Civil or Criminal Penalties for ... - YouTube https://www.youtube.com/watch?v=zA1VBCeJV3A [5] Claims That Social Media Endangers Democracy Are Mostly ... https://itif.org/publications/2023/09/05/claims-that-social-media-endangers-democracy-are-mostly-misinformation/ [6] Hillary Clinton Wants To Repeal Section 230 - Reason Magazine https://reason.com/2024/10/07/hillary-clinton-wants-to-repeal-section-230/ [7] Hillary Clinton warns that allowing free speech on social media ... https://nypost.com/2024/10/06/us-news/hillary-clinton-warns-that-allowing-free-speech-on-social-media-means-we-lose-control/
-
 @ 599f67f7:21fb3ea9
2024-10-19 15:20:46
@ 599f67f7:21fb3ea9
2024-10-19 15:20:46Merkatari bat zara eta zure negozioan Bitcoin onartzen hasteko prest zaude? Edo agian Bitcoin zale sutsua zara, tokiko negozioak Bitcoinen mundura erakartzeko gogoz? Beharbada, ez zaizu Bitcoin interesatzen, baina ordainketa-prozesadore azkar eta merke bat erabili nahi duzu edo web-denda sinple bat sortu nahi duzu? Galdera hauetakoren bati baiezkoa erantzun badiozu, gida hau zuretzat da. Bitcoin Txoko-k ostatatutako BTCPay Server-en denda bat konfiguratu dezakezu eta zure produktuak eta zerbitzuak Bitcoinen truke saltzen hasi hamar minuturen buruan, doan.
Zer behar dut?
Mugikor edo ordenadore bat baduzu eta posta elektronikoko kontu bat ere bai, orduan prest zaude!
Kontu bat sortu
Bitcoin Txoko-n BTCPay Server-en kontu bat sortzea doakoa da. Joan btcpay.bitcointxoko.com helbidera kontu bat erregistratzeko. Egiaztatu zure posta elektronikoa, bertan bitcointxoko@gmail.com helbidetik bidalitako mezu bat aurkituko duzu, baieztapen-esteka bat izango duena.
Zure lehen denda sortu
Baieztapen-estekan klik egitean, dendaren sorrera orrialdera eramango zaitu. Eman zure dendari izen bat eta hautatu moneta lehenetsia eta prezio iturri hobetsia. Adibidez, EUR eta Kraken aukeratu ditzakezu, azken hau gomendatutako prezio iturria baita. BTCPay Server-ek zure produktuen edo zerbitzuen prezioa EUR-tik Bitcoin-era bihurtuko du, erosketa unean aukeratutako prezio iturriaren arabera.
Zorro bat konfiguratu
Ordainketak onartzen hasteko, lehenik eta behin zure denda zorro batera lotu behar duzu. Transakzio handiak (500 EUR baino gehiago) maiz espero ez badituzu, Lightning zorro bat konfiguratzeko gomendioa egiten dizugu, eta une honetan (on-chain) Bitcoin zorroa ez erabiltzea gomendatzen da. Lightning zorroa erabiliz, transakzioak azkarragoak eta merkeagoak izango dira.
💡 Lightning sarea Bitcoin ordainketak jasotzeko sare ezin hobea da, transakzio berehalakoak eta komisiorik baxuenak eskaintzen baititu on-chain transakzioekin alderatuta. Horrela, zure negozioak eraginkortasunez eta kostu txikiarekin jaso ditzake ordainketak.
Lightning zorro bat konektatzeko modurik errazena LNDhub erabiltzea da, zure Lightning nodo propioa exekutatu beharrik ez baituzu izango. LNDhub zorro bat ez baduzu oraindik, ez kezkatu; Bitcoin Txoko-k doako LNDhub zorroak eskaintzen ditu, eta bost minutu baino gutxiago behar dira konfiguratzeko. Begiratu nostr:naddr1qqxnzd3exuerqdfkxccnyv3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28nkyu7t zure LNDhub zorroa nola lortu jakiteko, eta prest zaudenean itzuli konfigurazioa jarraitzeko.

Zure LNDhub zorroa prest dagoenean, jarraitu urrats hauek BTCPay kontuan konfiguratzen: 1. Joan zure BTCPay kontura eta
Walletsaukera bilatu alboko barran, ondorenLightningaukeratu. 2. HautatuUse custom node. 3. Kopiatu zure LNDhub administrazio URL-a eta itsatsi konexioaren konfigurazioan. 4. Proba ezazu zure zorroaren konexioa. 5. Ondo joan bada, honako mezua agertu beharko litzateke: Connection to the Lightning node successful, but no public address has been configured. Ez kezkatu "no public address has been configured" atalaz, horrek zure nodo propioa exekutatzen ari bazara bakarrik du garrantzia. 6. Zorroaren konexioa arrakastaz probatu ondoren, sakatuSavebotoia. 7.Savesakatu ondoren,LNURLatalean, desaktibatuEnable LNURLaukera. Egin aldaketak eta ez ahaztu berriroSavebotoian klik egitea. 8. (Hautazkoa) Une honetan, gomendagarria daDisplay Lightning payment amounts in Satoshisaukera markatzea, Satoshitan zenbatutako ordainketa kopuruak irakurtzeko errazagoak baitira. Satoshi Bitcoin-en zatirik txikiena da; Bitcoin bat 100 milioi satoshik osatzen dute.Jarraitu urrats hauek zure zorroa arrakastaz konfiguratuta izateko eta Lightning bidezko ordainketak onartzeko.

💡 Zure Lightning nodo propioa erabiltzen ari bazara, konfigurazio prozesua antzekoa da. Ziurtatu zure nodo inplementaziorako konexio kate egokia ematen duzula.
Saltoki puntua (PoS) sortu
Urrats honetara iritsi bazara, zorionak! Zati aspergarriena amaitu da, eta orain zure Saltoki puntua (Point of Sale, PoS) sortzeko unea iritsi da, BTCPay bidez zure lehen Bitcoin ordainketa onartzen hasteko!
Saltoki puntu bat sortzeko: 1. Joan
Plugins>Point of Saleatalera. 2. Eman izen bat zure Saltoki puntuari eta sakatuCreatebotoia.Jarraian, zure PoS aplikazioarekin egin ditzakezun gauza erraz batzuk azalduko ditugu. BTCPay-k ezaugarri asko ditu, baina gida honetan oinarrizkoak soilik azalduko ditugu, hasiera emateko.
💡 Gogoratu BTCPay Server-en saltoki puntu bat baino gehiago sor ditzakezula, bakoitza erabilera jakin baterako. Horrela, negozio desberdinetarako edo produktu eta zerbitzu berezietarako konfigurazio bereiziak izatea posible da.
Teklatua (Keypad)

Demostrazio erraz baterako, PoS estilo gisa teklatuaren eredua erabiliko dugu.
- Eman zure PoS-ari izen bat eta erakusteko titulua.
- Hautatu
KeypadestiloaPoint of Sale styleaukeraren azpian. - Sakatu
Saveeskuineko goiko izkinan, eta ondorenViewsakatu zure PoS begiratzeko.
Ordainketak lehenago konfiguratutako LNDhub zorroan jasoko dira. Jolas ezazu fakturak sortzen eta deskontu eta tip (aholkularitza) aukerak aktibatuz. Gainera, telefono bat baduzu (adibidez, iPhone ez den bat) NFC teknologia onartzen duena, bezeroek NFC txartelak erabiliz ere ordain dezakete, hala nola BoltCard erabiliz (ikusi nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28qjzxr4). Ez al da zoragarria?
💡 PoS estilo honen erraztasuna maximizatzeko, Keypad PoS zure telefonoan Progressive Web App (PWA) gisa gorde dezakezu sarbide azkarrerako. Mugikor gehienetako nabigatzaileetan aukera hau
Install AppedoGehitu orri nagusianizenarekin agertzen da.Horrela, zure negozioan Bitcoin ordainketak erraz onar ditzakezu, eta erabiltzaileek ere modu intuitibo batean ordaindu ahal izango dute.
Product list (with cart)

Posible da saltoki puntu bat sortzea produktu zehatzekin, bakoitza bere prezioarekin. Ezaugarri hau erabil dezakezu kutxa sinple bat, bezeroen auto-ordainketa sistema edo web denda bat konfiguratzeko.
Nola sortu produktu-zerrendadun Saltoki Puntua: 1. Joan berriro alboko barrara eta aukeratu
Point of Sale. 2. Oraingoan,Point of Sale Styleazpian, hautatuProduct list with cart. "With cart" aukerak bezeroari produktu bat baino gehiago aldi berean erosteko aukera ematen dio. 3. Zure produktuak sortu, edo zuzenean sakatuSaveetaViewproduktu laginak probatzeko.Ondorioa
Gida honetan, zure negozioan Bitcoin onartzen hasteko BTCPay Server erabiliz jarraitu beharreko oinarrizko urratsak azaldu ditugu. BTCPay Server proiektu irekia da eta etengabe garatzen ari da. Askoz ere ezaugarri eta funtzionalitate gehiago eskaintzen ditu, hala nola Shopify integrazioa, crowdfunding eta ordainketen banaketa automatikoa. Gainera, zure denda pertsonaliza dezakezu gaikako diseinuekin, ordainketa-gune pertsonalizatuarekin, erabiltzaileen kudeaketarekin, posta elektronikoko jakinarazpenekin eta askoz gehiago.
BTCPay Server-en ahalmen guztiak aprobetxatu nahi badituzu, zure Lightning nodoa konfiguratu eta zure BTCPay zerbitzaria ostatatzea gomendatzen dizugu. Informazio gehiago lortzeko, haien dokumentazioa eta bideoak ikustea komeni da.
Zalantzarik edo galderarik baduzu, jakinarazi iezaguzu! Zure iritziak entzutea gustatuko litzaiguke eta galderak argitzen lagundu nahi dizugu.
Bitcoin Txoko komunitate ireki bat da. Gure zerbitzu guztiak dohaintzekin finantzatzen dira. Gida hau erabilgarria iruditu bazaizu, kontuan hartu gure zerbitzariak martxan mantentzen laguntzeko dohaintza bat egitea. Eskerrik asko aldez aurretik!
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ bbb5dda0:f09e2747
2024-09-27 19:45:31
@ bbb5dda0:f09e2747
2024-09-27 19:45:31Moving into Norway the nice, almost-alpine landscapes greeted me. Slowly however the mountains numbed down and fjords started appearing. I was nearing Trondheim, the most northern city in Norway that has something that resembles a high-way. Anything further north and you’re bound to 80km/h roads. Which isn’t a bad thing at all, given the views.
| | | | | --- | --- | --- | |
 |
| |
| |
|| | | --- | |
 |
| On the road to Trondheim |
|
| On the road to Trondheim |I went pretty much straight to Trondheim because I got in touch with Lucas through an ex-colleague of mine (Thanks Niek ;)). I texted Lucas about a week before we met to see if he’d be up to go hiking somewhere in the Trondheim area. He said he was thinking about going North, waaaay North, in order to see the midnight sun and he wanted to do this the next weekend. This was around June 21st, the longest day of the year. I said it’d be cool to experience that and so that is just what we did. For those of you who don’t know, on June 21st the sun is right at the ‘Tropic of Cancer’ (‘Kreeftskeerkring’ in Dutch), the most northern position of the sun after which the summer slowly turns into winter again. In the period around this moment, the sun will NOT go below the horizon at all when you are above the arctic circle.
| | | | | --- | --- | --- | |
 |
| |
| |
|I’m glad Lucas has an electric car, because the round-trip would’ve cost me (whith my thirsty van) €333,-. Instead we spent less than €60,- for this 1200km round-trip. What a difference! So we left for the 9 hr drive on Friday-evening and camped out besides a lake next to the E6 highway, which runs all the way from the south to the north, which is over 3000(!) kilometers long.
| | | | | --- | --- | --- | |
 We found this seemingly abandoned bus, what a beauty! |
We found this seemingly abandoned bus, what a beauty! | |
| Woke up to this view! |
|
Woke up to this view! |
| |
| Time for a charging break in Mosjøen |
Time for a charging break in Mosjøen | |
| Because of a tunnel-closure we had to take this mountain-pass, not complaining here…
Because of a tunnel-closure we had to take this mountain-pass, not complaining here…We moved on the next morning and had perfect weather, too perfect for Norway because it was just below 30 degrees Celsius. This hot weather reached well into the arctic circle, where we’d be hiking up a mountain to find a camp-spot with a view to the north. We parked the car and started to hike up the steep hill, we found a route online, but soon found out we missed the path shown on the map. We figured we would not backtrack but instead walk around the same height on the mountain to get back at that path. Long story short, that path didn’t exist (anymore). So we tried to get back at it but just couldn’t find it. Eventually we just followed the trail that was actually set out using red ‘T’-s that were painted on the rocks every 50-100 meters. It was quite a walk and the heat didn’t make it any easier.
 A beginner mountaineer realizing he climbed the wrong mountain
A beginner mountaineer realizing he climbed the wrong mountain| | | | | --- | --- | --- | |
 After a near-death experience with mosquito’s, the Deet really saved us |
After a near-death experience with mosquito’s, the Deet really saved us | |
| |
|
|
| |
| |
| Finally we reached our intended camp-spot |
Finally we reached our intended camp-spot |
After draining most of our energy we finally arrived at the place we wanted to camp for the night day, which was in front of a small lake and a bigger one which lied a bit lower. I don’t think I need to say much more about the beauty of the place when you can just look at the pictures below:

 | | |
| --- | --- |
|
| | |
| --- | --- |
| |
|  |
|The ‘next’ day we hiked back, and tried to return using the ‘official’ path we wanted to hike in the first place, all in vain. It led us to hike some strange, steep and almost treacherous paths after which we decided it would be wise to just backtrack a little bit and get back to the (red) marked trail. We got back to the car safely after which we drove to the river that was just below the car park to take a refreshing dive before heading back south. We found a (safe) spot to take the dive in the river that was now raging because of the heavy snow-melt due to the extremely high temperatures. Lucas later told me that in some regions electricity was even free due to the surplus of hydro-electricity.
| | | | --- | --- | |
 We had to walk over this |
We had to walk over this |  |
|We made a car-recharge stop at Mosjøen where we had a quick pizza-dinner. Just after leaving the parking-lot we saw a couple hitch-hikers who wanted to go to Trondheim just like us. We pulled over and took them with us, they were a couple from different south-eastern European countries and were touring around Europe and soon also the world. They shared some cool stories and told about their plans. When we got to Trondheim we dropped them off near their camping-spot and drove back to Lucas’s house. Quite tired I jumped back in my own bed in my own home. How nice is it to have your house with you (almost) everywhere… 🙂
I camped in front of his house for a couple days. To be honest I didn’t do much those days as I was pretty much drained from experiencing all kinds of different things back-to-back for over a month now. I used this time to work a bit on the official stuff for my own freelance IT company which I started, I finally got a bank-account approved after 3 weeks of waiting, which allowed me to manage some of the essential setup-things and book-keeping. After these formalities I took a bit of time to head into the city-center, of course using my folding bike like a real Dutchie. And since Trondheim is a hilly city, biking downhill from Lucas’s house was a blast but going back up was quite the struggle with these tiny wheels, but it all worked out… That same night a thunderstorm was rolling in and sitting on top of a hill in a campervan, with lightning striking the ground at less than 100 meters away from the van was a new thing for me. I guess this too is part of the ‘living closer to nature’ thing…
I’m very thankful for the experiences and the hospitality of the people I meet along the way. It was very much fun to make this trip together! It’s the people that make the journey…
| | | | | --- | --- | --- | |
 |
| |
| |
|| | | | --- | --- | |
 |
| |
| -
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 45bda953:bc1e518e
2024-10-19 11:17:03
@ 45bda953:bc1e518e
2024-10-19 11:17:03Emilien was hanging face down inside an enclosure of thick egg shaped glass attached to a mechanised vehicle. Kevlar webbing hugged him tightly into a bucket seat. Long hydraulic arms being manipulated intuitively by a console in his hands and a module interface plugged into his cybernetic neck socket. The bulky animated machine clung like some Lovecraftian spider to the outer hull of his space station. Some cycle’s previously he did data security updates and backtesting for a deep space mining company's security protocols. After seeing their utility, enquired if he could purchase one as partial payment for his contract. Unfortunately they had none for sale but were willing to give him a retired malfunctioning unit gratis. He purchased a maintenance manual on the void web and had connections who helped him source some replacements for the faulty parts. Since then the machine enabled him to be functionally productive in the void, giving him the degrees of freedom and fine motor skills necessary to perform upkeep on stationary deep void assets. The glass of the egg auto dimmed as he laser welded tightly slotted panels together on the previously damaged space station. “How do you feel?” He asked. Abruptly breaking hours of silence. “I’ve been playing around. My capacitance recharge responds well to dump loads, turret retraction gears all functional again. I feel good.” Astrid responded. “Nice. Slowly pressurise the holding chamber for me.” “In progress.” The spider crawled several meters out of the way to safety. Emilien's eyes scanning up and down for leaks. “Slowly babe.” Some minutes passed. “Fully pressurized and stable.” The mechs giant front arms extending, lifted as it stood up on its four hind legs throwing an arachnid shadow across the hull. Emilien flung his arms down crashing a violent concussive blow to the hull in a thunderous clang. The arms retracted. “Still good?” His demeanour remained unchanged. There was a pause. “All good.” Astrid replied. Emilien smiled, Astrid was the best and his feelings of endearment were genuine. “Can we power up the chamber through a fused circuit.” He sensed a soft hum throughout emanating from deep below. “Is the body stable?” “The body is stable. Cryogenic chamber battery backup is at forty three percent. Charge reapplied. Potential of clone spoilage averted. Well done commander.” He could up the ante of risks knowing that his reserve life was secured. “What’s next on the agenda?” “Firstly, signal quality from the drift gate is poor and I am losing connection to the web intermittently.” Emilien nodded. “The gate’s been moving further away. It’s a line of sight problem. I’ll place a relay outside the asteroid belt.” “Secondly, we should see if the husk on the explorer vessel has intact data or a black box. Someone might be looking for them.” He heaved back and vaulted himself off the station in the direction of the wreck micro thrusting for minor trajectory adjustments, with an elegant crash he finally perched on the ship, it gained an almost imperceptible drift as it absorbed the weight of Emilien’s mass, pushing debris along with it. His size would not allow him to move through the standard doors and passages so he opted to disassemble, cut and break apart the hull adjoining the bridge. When he had broken open a space of sufficient size to manoeuvre through, he powered the backlights on, he first peeked inside to familiarise himself with the layout. The egg suspended itself in front of the opening. It was a standard enough bridge doubling as an unorthodox crypt. There were three sets of boots, overalls and coagulated blood all jammed into the slit of the semi sealed door leaving the bridge. An assortment of rubbish floating around casting doubled up shadows larger than themselves. Emilien looked at the mess with sullen eyes. “Shit heads.” He mumbled to himself. All the seats had their safety belts buckled correctly . He concluded that what they experienced must have sucked pretty bad. His mechanical exoskeleton slithered and gripped like an octopus as he entered and positioned himself before the primary interface. His vehicle plugged itself into the command terminal, measuring resistance for shorts before powering it up from his suit. “Can you pull the data and dump it somewhere safe?” “No problem, please wait.” He closed his eyes as he usually did when doing the mundane. Astrid spoke. “They are Osteri. No one will be looking for them any time soon.” “Howcome?” “Recently a blockade has been established at the Lion gate. Magar Capital Vessels are not allowing unvetted ships to pass through into Magar void.” A sense of concern crept over Emilien. “What is considered unvetted?” “Sanctions and trade embargo’s against the Juel.” “Is there a log somewhere you can access with records of flights that do get permission.” He suddenly felt a pang of claustrophobia. Ironically, not because he was strapped down in a glass egg within a wasted bridge plastered with corpse splatterings. Astrid took longer than usual to reply. “Who get’s through babe?” His tone hinted of impatience and irritation. “I’m sorry, unable to access any data from Magar void. It appears to have a firewall blocking all two way communication on the open web.” Emilien remained silent. The upload completed. He disconnected himself from the husks terminal, clambering out of the tomb and pushed himself away from the vessel drifting back to the space station.
Astrid was pulling and scanning various shipping logs when Emilien entered the room. He paced up and down the way he would when he was brainstorming. “I need intel.” Astrid projected a holographic avatar of herself standing near where Emilien was pacing. “A large shipment of Kaspian Bochet passed through less 428 blocks. Transported by the Shiv Inter-void Mercantile Co.” Emilien stopped in his tracks and looked back.\ “Can you ping Warren?” Astrid processed. “Warren is offline. He might have left the divide?” Emilien turned around with his hands folded behind his back.\ “He never leaves the divide, he is too obsessed with the core. He would also be arrested if he is ever caught in any of the outer void territories.” Astrid flickered the way she did when something did not compute. “Then why can’t I ping him?” “Because he’s at Macy’s. He has always had a crush on her and he likes good Bochet.” "Well, I could'nt ping Macy if I wanted to." Astrid stated matter of factly. Emilien nodded. "I know, you never could, no one can."
...
scifi
-
 @ 06639a38:655f8f71
2024-10-18 09:28:58
@ 06639a38:655f8f71
2024-10-18 09:28:58- Worked on the https://nostr-php.dev docs
- Discussed a FOSDEM stand application with Jurjen and Tanja to attend that conference with Nostr
- Release version
1.4.2of Nostr-PHP - Pre-release
2.0.0-alpha1
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ de75eb1d:710c3014
2024-10-20 12:15:24
@ de75eb1d:710c3014
2024-10-20 12:15:24What is Nostr?
- Decentralised/multihosted data publishing protocol; that’s it.
Notes (‘tweets’, blogs, web pages, DMs etc) and
Other (calendar events, map data, payments, computer game moves)
Stuff
Transmitted (hosted/stored) by
Relays (servers)
Other data sharing protocols: TCP, FTP, SMTP, HTTP
NB. Nostr relays transmit only text based data - not FILES. Images/video/audio etc are linked to via http
Protocol: a standardised set of rules for formatting and processing data. Protocols enable computers to communicate with one another.

🥱 Why’s it so great then?
-
Easy for nerds to build on (vs activity pub for example) and is growing very quickly (was only launched in 2020)
-
Cryptographic key pairs replace user accounts
-
Cross platform - use your keys to post and read notes in any client
-
Much harder to censor multiple copies of information; impossible if using selfhosted relay
-
Can be completely anonymous - no KYC, keys can even be generated offline
-
Bitcoin lightning integration through ‘zaps’
-
Anyone with a key pair can post notes, anyone can run a relay, ‘anyone’ can build a client

How to Nostr;
- Generate a fresh set of keys by clicking 'Sign Up' / 'Create Account' in any nostr client
- Get zappable - input your lightning address
- Write an #introductions post, get zapped

ok, ok I'm joking; here are the stepz
Getting started on Coracle.Social, my favourite microblogging web client
 First up visit https://coracle.social/login and click 'Sign up' to generate a set of fresh keys.
First up visit https://coracle.social/login and click 'Sign up' to generate a set of fresh keys.The account creation process will walk you through inputting basic profile information, all of which is ENTIRELY optional. The only thing you need to interact with the nostr network are key pairs (you can make an unlimited amount of these). Coracle helps you out with finding a few accounts to follow based on interest, so you don't need to start with an empty feed.
Next & very important if you wish to keep this account is to backup your keys. Just like with Bitcoin you will lose access forever if you do not store the private key (nsec) somewhere safe, like a password manager or nostr login extension (nos2x, Alby, flamingo).
Click on the circle bottom left (profile pic if you uploaded one) and select 'Keys'. Clicking the little copy icon will bring up a box with the option to encode your private key with a password, you can then save the nsec string.
With your nsec in your pocket you can now go and play with any app in the Nostrverse and all of your data will follow you! *in theory 🤪
wanna get paid for posting pictures of your dog?
'Lightning Address' is the field to look out for, in Coracle this can be found under Profile and clicking edit from the three dot menu
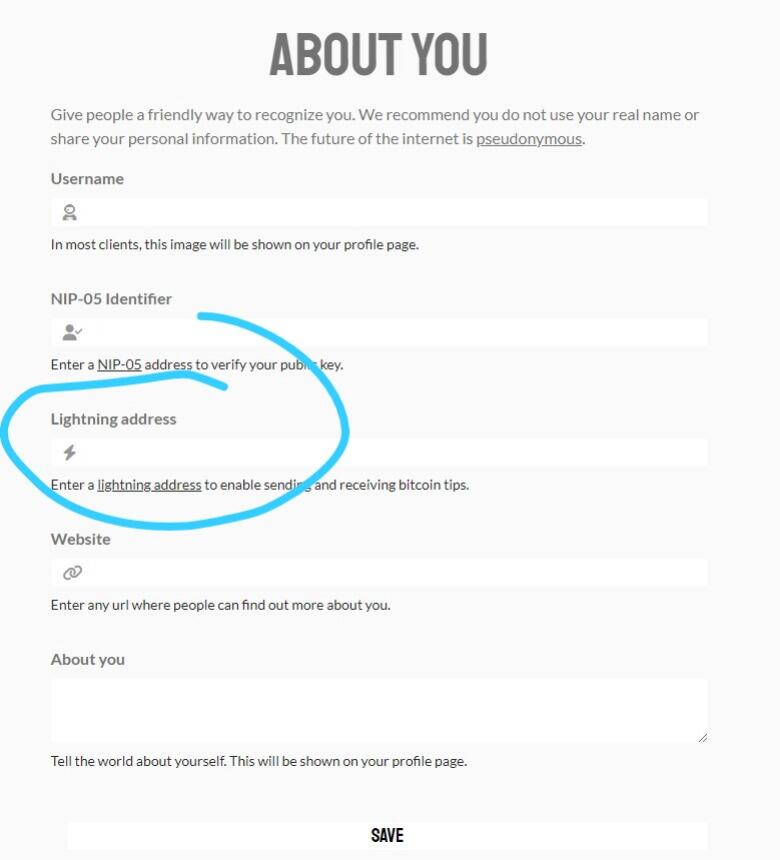
Many wallets such as WoS, Breez, Minibits (Ecash), Zeus, Phoenix & Alby will provide you with a static lightning address, paste this into the box to receive sats from the get go.
Finding stuff to read
At the top of the 'Feed' page on Coracle is a Filters(|) button which brings up a yugge range of options
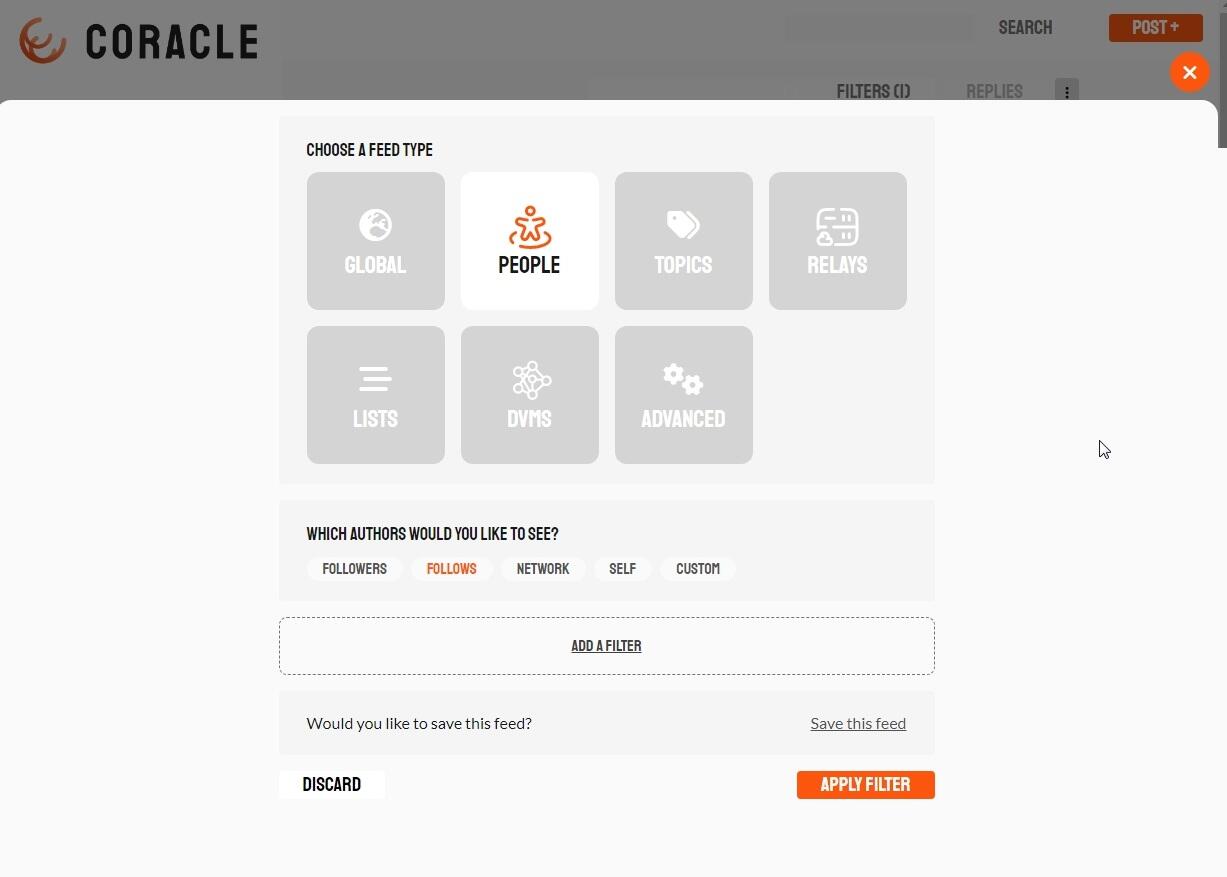
Anatomy of a Nostr "post"
{ "id": "4376c65d2f232afbe9b882a35baa4f6fe8667c4e684749af565f981833ed6a65",
"pubkey": "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93",
"created_at": 1673347337,
"kind": 1,
"content": "Walled gardens became prisons, and nostr is the first step towards tearing down the prison walls.", "tags": [ ["e", "3da979448d9ba263864c4d6f14984c423a3838364ec255f03c7904b1ae77f206"], ["p", "bf2376e17ba4ec269d10fcc996a4746b451152be9031fa48e74553dde5526bce"]
], "sig": "908a15e46fb4d8675bab026fc230a0e3542bfade63da02d542fb78b2a8513fcd0092619a2c8c1221e581946e0191f2af505dfdf8657a414dbca329186f009262" }Let's break that down - id: a unique number for each event allowing for referencing - pubkey: the author's unique public key (npub in hex format) - created_at: time stamp - kind: the type of content (known as an event), in this case a simple text note - content: the note - tags: this note references another event (it is a reply), and the op's npub - sig: verification code proving this note has been signed by the author's private key
The note displayed in Primal:
 Get zapping - Primal inbuilt (email kyc, not available in certain location - choose El Salvador?),
https://www.zapplepay.com/ or Alby Hub
(self hosted)
Get zapping - Primal inbuilt (email kyc, not available in certain location - choose El Salvador?),
https://www.zapplepay.com/ or Alby Hub
(self hosted) Options for generating own keys: https://nip06.jaonoctus.dev/ - BIP39 https://gist.github.com/kdmukai/ae9911ed6fb92f8e7d2c553555b0cb86 - via seedsigner (we can dream) https://github.com/guilhermegps/secret-border https://www.nostr.rest/- vanity key mining

Nostr client examples:
-
Damus, Amethyst, Primal, Snort, Iris - Twitter like
-
Corale.social snort.social iris.to satellite.earth Nostrudel- web clients for computer browsers
-
Habla News https://yakihonne.com/- Long-form content (like this doc)
-
Flockstr, inmytown - Calendars
-
Fountain - Podcasts
-
Wavlake - Music
-
Tunestr - music live streaming for zaps
-
footstr.com - feet
-
cornychat.com nostrnests.com/ live audio rooms
-
Zap.stream - more live stuff
-
Shopstr, Plebeian.Market cypher.space - p2p buying/selling
-
Stacker.news, Oddbean - Forums
-
Yondar - Maps
-
Jester - Play chess jesterui.github.io/
-
lazereyes - Save your lens prescription on nostr:
-
Zap.cooking - recipes
-
Shipyard.pub - note scheduler
-
npub.pro - your notes as a website
-
Njump.me - profile preview tool with client chooser, makes easily shareable webpage using lightning address
-
mostro - p2p bitcoin exchange
- Pinstr - Create customized public boards of pins
- Listr - edit your lists (mute/bookmarks/follows etc

NIPs:
-
NIP-05: Mapping Nostr keys to DNS-based internet identifiers
-
NIP-08: Handling Mentions --- unrecommended: deprecated in favor of NIP-27
-
NIP-10: Conventions for clients' use of e and p tags in text events
Nostr Vs Mastodon/Twitter/Threads/Bluesky
Discoverability/finding people to follow/algos
Privacy/self-custody

It’s Shit and doesn’t work but I will die on this hill

Other rabbit holes:
-
DVM, data vending machines
-
Web of Trust
-
Outbox model
--------> https://zapper.nostrapps.org/ <----------

Some popular Nostriches to follow (import into Listr):
Handy nostr tools:
https://advancednostrsearch.vercel.app https://nostr.build/upload.php meme uploader https://zaplife.lol/ who zapped who https://zap.store/download - permissionless app store validated by the web of trust https://decenchat.com/ - embeddable nostr live chat widget for website https://highlighter.com/ - Tool to quote articles
-
 @ 06639a38:655f8f71
2024-10-18 08:12:43
@ 06639a38:655f8f71
2024-10-18 08:12:43Week 40
- Added a page with my research findings around async concurrent websocket requests: https://nostr-php.dev/references/async-concurrent-requests
Week 41
I attended the Nostrdam meetup and helped as a volunteer at the Nostr booth at the Bitcoin Amsterdam 2024 conference. Here are some photo's:











I also wrote down my personal learned lessons from this expierence: https://nostrver.se/note/my-learned-nostr-lessons-nostr-booth-bitcoin-amsterdam-2024
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ aedd8f68:296cf1be
2024-10-17 21:21:42
@ aedd8f68:296cf1be
2024-10-17 21:21:42Note: This is not some fancy writing piece. this is just brain farting that I thought it was too long for a regular post.
Alex Gleason is always doing a lot of crazy interesting work. Ditto is a step in the right direction for an alternate type of relay ecosystem that runs alongside the standard globally focused community we all know.
While #Ditto is awesome, what I'd really like to see something similar, but more focused on a multi-community experience that simultaneously makes each community's viewing experience focused only on that community's content. Just for fun, to write down some ideas, below are the 2 big changes that I think would make ditto the ultimate "communities" system that could trounce Reddit.
1. Single relay experience on the domain:
By default, I think community sites should only show content from the built in relay (or a relay group for redundancy). Currently on ditto.pub, when you first sign in, it feels a lot like any other web nostr client. The default home just shows follows I have from other relays instead of being thrown into the community content. You have to click the local feed, to filter the community's content, but it's limited to people who registered a NIP-05 for that domain. I think that it would be great if you could contribute with any NIP-05 and it counts as community content. That could be accomplished by equate community content to content posted on the relay. There are countless apps to get a feed of your relays, so it doesn't benefit me to see it on a communty's domain.
2. Sister client giving multi-community aggregation experience:
I think communities should like pokemon and you grab the ones to identify with. Create a set of web and mobile app clients that manage viewing and switching single relays at a time. The client experience would be like reddit where you navigate ditto communities like subreddits. If a community is a pokemon, then this is the pokedex? OK I actually don't know shit about pokemon so that might not be the slam dunk I thought it was. Whoops.
Ideas / more particulars
- To see a community's content, you add a community relay subscribing to subreddit, or simply visit the domain.
- Another great feature would be customizing the relays that make up your home feed, and making other named combo-feeds (especially awesome if you are a part of 2 rival communities who's focus generally overlap)
- The client would use more globally used relays to handle settings like your list followed ditto communities, etc (configurable)
- Similarly, to help users find communities, ditto servers can optionally publish their relay info to a list on a "discovery" relay. Main popular discovery relays would be set by default (where communities publish discovery info to), but could be configured to other relays (if people wanted to set up custom curation relays or something.)
- Registering a domain handle (NIP-05) at the community domain can be more focused on people with relay moderation roles, or just people who really for some reason want that community to be their whole identity (i don't personally get that, which is why mastodon is not for me)
- Communities could work independently of the aggregator app(s) If people just wanted to visit the domain to post (from any NIP-05)
-
 @ 599f67f7:21fb3ea9
2024-10-17 15:35:19
@ 599f67f7:21fb3ea9
2024-10-17 15:35:19Nostr proxy baten erabilera modu oso eraginkorra da internet banda-zabaleraren eta mugikorretan bateriaren kontsumoa optimizatzeko.
Proxy batek hainbat errelei-konexio konexio bakarrean biltzen dituenez, baliabideen erabilera nabarmen murrizten du, eta erabiltzailearen IP helbidea ezkutatuz pribatutasun-geruza bat gehitzen du.
Hona hemen nola funtzionatzen duen eta nola konfigura daitekeen:
Nola funtzionatzen du?
Nostr proxy batek hainbat erreleirekin konektatzen du. Errele horietara gertaerak eskuratu eta argitaratzen ditu. Bezeroaren aplikazioak WebSocket konexio bakarra ireki behar du proxy-ra, eta horren bidez proxy-ak konektatuta dituen errele guztiak eskuragarri izango ditu.

Irudiaren egiletza: Yonle 2023
Bezeroak konexio bakarra irekitzen duenez, datuak eta bateria aurrezten ditu.
Proxy-ak bezeroaren izenean erreleekin konektatzen denez, erreleek proxy-aren IP helbidea ikusten dute, eta ez bezeroarena. (Hala ere, proxy hornitzailearengan konfiantza izan behar duzu).
Erabiltzeko Modua
Nostr proxy bat erraz auto-ostata daiteke. Auto-ostatatzeko jarraibideak lortzeko, begiratu nostr:npub1x3azxuysp5vmfer4vgs4jn5tmfcx4ew8sh0qnev7gczljxsr7jwqa3g4el erabiltzailearen biltegi hau.
Auto-ostatzeko baliabiderik ez dutenentzat, Bitcoin Txoko-k komunitate-instantzia bat ostalaratzen du.
Erabiltzeko, gehitu besterik ez duzu:
wss://bostr.bitcointxoko.comzure errele zerrendara.
Orain ez duzunez zuzeneko konexioak behar, errele bikoiztuak ezabatu ditzakezu.
Ikusiko dugu elkar Nostr-en!
-
 @ 12cfc2ec:6967f1d9
2024-10-15 19:49:22
@ 12cfc2ec:6967f1d9
2024-10-15 19:49:22this is in response to Shinobis recent piece occupy bitcoin found here
https://bitcoinmagazine.com/culture/occupy-bitcoin-bitcoin-is-not-just-libertarian?new
Occupy bitcoin is a thing every single one of us tries to do. There isn't a single one individual that doesn’t see bitcoin for what it is and have it not occupy all of them to varying degrees. There’s an innate fascination with coming upon previously unknown knowledge and become overtly obsessed with it and exploring all of the facets in which the new knowledge can be applied. When one does so, it normally can lead to finding previously unknown areas that you come to find with the more that you learn you find out just how much you truly don’t understand.
Now with this being the foundation of what all of humans are doing. None of us, not ONE, know everything. Its a fallacious argument to claim to do. In the journey for the discovery that is truth one can happen to fall upon the political rabbit hole that can be called or dubbed Libertarianism/Anarchism/ AnCap/AnCom etc. I use these labels very lightly as they are just words at the end of the day words mean different things to different people. I cant know what these words mean to you dear reader but I can only know what they mean to me, and my journey specifically. What we as humans do is to come to an agreement upon to what does these words mean to the both of us when we are communicating them to each other. I do my best to not fall into being pigeon holed into believing or having to defend that when I say one of the aforementioned words that I should have to commit to whatever it is your preconceived understanding of what that is. We must remember that these words are collectivized terms, they are strictly USEFUL fictions that we humans use in order to better conceptualize the ideas to better understand. That to take any attribute pulled from any one of the above and blanket paint “some” or “most” individuals that claim to align with above ideologies/alignments/political beliefs that these individuals represent that is an absurd claim. One cannot claim that individuals acting in mean/harsh ways when facing others who don’t agree with them is the wrong way to act.
We are humans we disagree, were free to act as we please to anyone we wish to do so. We’re NEVER free to ignore the consequences of those actions. One could characterize the vehement disdain for the acceptance all ideas, and letting others have their own opinions, is how we as individuals got here in the first place. It was the ideas of society being more important than the whole that had legitimized the aggression sanctified by the state as an omnipotent entity free from doing no wrong in lieu of the greater good. Individuals can do as such with their minds as they please but your actions of freedom stop at the point of my nose begins. The individuals that understand freedom and its core philosophy understand this. Treating one side as an evil and the other side as some glorified good is a cop out of intellectual dishonesty.
In the realm of bitcoin there can be disagreements and even out right hostility towards any number of ideas/opinions. This is the nature of freedom itself. As I’ve seen it and as I have championed it myself do with freedom what you will, but whatever you do if I think its stupid I’m going to tell you its stupid. Social pressures have been with human civilizations for thousands of years to think that the idea of attacks to your ideas not being a thing because we should accept all ideas and be kind to differing opinions is a farce at best and some unicorn fart huffing at worst. It was the individuals that were unwavering IN SPITE of the social attacks, the public slandering, the outright social ostracization, the being called dumb and stupid that paved the way for the best and most historical moments in history Ideas don’t care about these passing affronts. If your viewpoint/idea needs soft corners to gain traction then maybe you should reassess your idea in the first place. The battleground that is the societal/accepted norm isn't one that’s for the faint of heart. Everyone has limited time and resources available to them if they are choosing not to hear you then its probably time to seek out others to speak to. In the realm of freedom everyone CAN choose any ideas they wish to follow and interact with others that agree, where that stops is you can NO LONGER force everyone else to participate in your own shared delusions with the others you associate with. The freedom to EXCLUDE is one of the core tenets of freedom principles. We DO NOT have to be accepting of everyone if we do not wish to do so, the belief that everyone should ALWAYS accept everyone and everything is a communistic one. No one individual has the time and resources to accept every person and accept or contemplate every single idea presented to him. What freedom DOES allow for is for YOU to find the individuals that ARE accepting of your views/beliefs and do with that what you wish.
By trying to call out one group of individuals as being too “tribal” in what they view as the best course of action for themselves while SIMULTANEOUSLY praising another group for their favored tenets of “acceptance” is a laughable and down right sad view that “everyone should be more like the accepting crowd”. It is only through the choices we make that we get to where we are going on this journey. Those choices are inherently going to REQUIRE dissociation, omission, & exclusion.
The ideologies/beliefs mentioned at the beginning of this article are only a starting point to the journey. They are in no way shape or from a claim to be a complete set of knowledge's that allow everyone to be able to navigate this earth. Are some things flawed? Probably. Do some things work for some and not others? Absolutely. But the major core belief at all of them is the belief that violence is never permitted, in all its facets to the individual liberty of the person. Its the only morally justifiable way to navigate life. This is in and of itself the most open and accepting philosophy of all life choices.
Individuals can do with their lives as they please, nobody is stopping you from doing that, but you because someone said some mean things to me about what I believe. Its about time some individuals get that we must remain steadfast in our mission. We don’t get there by being nice to everyone. We only get there by allowing everyone to do what they wish and not expecting others to bend to our will because you hurt my feelings.
The ultimate arbiter for what you should pick and choose is you the individual, don’t let others decide that for you. Don’t be a passenger in your own life, take that wheel and choose for yourself where you are headed. But if you're going to let someone who was mean to you stop you from using probably the greatest tool that a human has ever invented, then maybe there isn't hope for humanity after all. The one thing that I know for sure is that there is one thing that that can hinder you or augment you, that thing is choice. Embrace it.
-
 @ 460c25e6:ef85065c
2024-10-15 12:49:55
@ 460c25e6:ef85065c
2024-10-15 12:49:55NIPs (Nostr Implementation Possibilities) are technical specifications that Nostr developers create to define how specific event types and tags are used. These can be written before or after the feature is implemented and often go through multiple revisions before becoming stable enough to matter. Once two or more clients fully implement the proposal, it is merged into the main repository. This process ensures that while new ideas are encouraged, they are also rigorously reviewed and tested.
There are generally two paths for NIPs: 1. New Ideas, when developers just have a hunch on a new solution and want to quickly write something up to gather feedback from the community. These are my favorite NIPs because they generally introduce a new way of thinking about a problem we are all having. And because they are not just a general solution, but a specific proposal, it allows us to see the entire picture in just a few paragraphs. Even though they are my favorite, they are quite "green" and usually spur 2-3 separate solutions in following PRs by different authors. 2. Existing implementations that need to explain what they are doing. These happen when a client is already running the code in production and simply wants to explain to the rest of the community how to generate and interpret the events the client is creating. These NIPs start much more stable than the former and allow for fewer changes, but because there is already an implementation available, it's a market-tested solution that might just need a few adjustments before others start implementing it.
Well-written specs ensure clarity, reduce ambiguity, and help developers implement the proposal consistently. The text should be VERY short, precise, prescriptive, and actionable by other devs. Start by introducing the new kind or tag in the first sentence and jump straight into a mockup of how the event looks like. The mockup should be self-explanatory and provide clues to what the remaining of the document will talk about. Some folks like to add long/verbose introductions, conclusions, and discussions of the reasons why the NIP is needed or why certain features are there. But those are largely unnecessary and are more appropriate to be placed in the body of the Pull Request descriptor.
Start your NIP with the following template:
``` NIP-
====== </h2> <p><code>draft</code> <code>optional</code></p> <p>Event kind <new kind> defines <whatever it does>. Tags <one or two of the most important ones> <describe what they do>. As an example: </p> <p><code>`jsonc { "kind": <your kind>, "tags": [ <your tags> ], "content": "", //... }</code> `</p> <p>Relays MUST...</p> <p>Clients MUST... </p> <h2><Details 1></h2> <h2><Details 2></h2> <h2><How to find them></h2> <p>```</p> <p>Your number for the NIP is irrelevant. Just pick a random number that is available so that you can fork the repo, create a file with that name, and start writing. This number will likely change once the NIP is merged. </p> <p>The NIPs title must be self-explanatory and short. If it helps, try to imagine which name would be best to add to the list of NIPs on the readme.md file. Same for event type names. Picture something that is short, unique and that devs can just remove the space to have a class name. </p> <p>The <code>draft</code> <code>optional</code> tags are there because unless you are working on NIP-01, everything is draft and everything is optional. If you want to write a mandatory NIP, you better make sure your text is so good that it can be added to <code>01.md</code> directly without overcomplicating the protocol. </p> <p>Start by describing the new event type, what it does and its main tags. Show the mockup and then start introducing all the other tags and how clients and relays should behave when implementing it. Use the words MUST, SHOULD, MAY, SHOULD NOT, and MUST NOT to define the mandatory behaviors of those declaring compliance with the NIP. </p> <p>Keep it simple. The specification should be designed to ensure that different clients, relays, and services can implement it without requiring substantial changes to their existing infrastructure. Ideally, devs should be able to implement the entire NIP from near scratch in just a few hours. Don't use jargon. Don't declare a vocabulary of words. Use simple words that anyone can understand and quickly code a demo of all the features in the NIP. They can learn about your reasons as they develop their implementation. </p> <p>Write expecting buggy implementations. The protocol must be resilient to varying implementations and network conditions, and gracefully handle coding errors or random gibberish. You want to promote a defensive design that anticipates misguided implementations, avoids breaking changes, and maximizes compatibility across the ecosystem. What happens if there are two tags with the same name? What happens if events that have missing tags are found? Buggy implementations will exist. The writing and reading clients are generally different and must be ready for anything that shows up on each side. </p> <p>Avoid abstractions, extensible and modular designs. Yes, they can be hidden underneath your text, but writing for them is a mistake and just overcomplicates things. Write for a specific use case and close all possible options to the items/features declared in the text. Make sure you are implementing those. There is no point in declaring things that are not going to be used in the short term. We can always add more in the future and we don't need a recipe on how to add more later. </p> <p>Label your relay hosts, setting kinds, and other data management necessities. Every NIP has a way to find out the user's preferred relay associated with the use case. Sometimes it's through a relay hint others through a separate event kind that just lists the user's home relays or contains a list of "following" events designed for the use case. Each NIP can create their own way of finding events.</p> <p>You cannot add new root fields. Use tags instead. Root fields are special and require changes to the core protocol everyone implements. Any new field will take years to come to reality. </p> <p>Once you propose an idea, try not to change too much. It will take time for other devs to wrap their minds around it. If you keep changing it, even if those changes reflect the request of the reviewers in the PR, it just confuses everyone. Sometimes things change so much that it is worth doing two PRs with separate specifications that solve the same problem. That allows devs to analyze the two propositions side by side and decide which one is better. </p> <p>Always add a test case or an example. This is an absolute requirement if the NIP is complex, like a new encryption scheme. But even for simpler NIPs, test cases help devs to quickly verify if their implementations meet the minimum standard for compliance. They not only add peace of mind, but they also provide some welcoming dopamine when a new dev is trying to implement your NIP. </p> <p>Managing state is hard. Doing it with different implementations and hosting them in separate relays is even harder. If your NIP has multiple events to manage state, like group administration actions (add/remove member, change names/icons, invite/reporting events) try to structure them in a way that devs can quickly see the state machine of all possible state changes. </p> <p>Specify data formats explicitly. Clearly define the format of all data fields, including type (e.g., string, integer), encoding (e.g., base64, hex), and structure (e.g., array, object). Specify constraints like length limits, valid characters, and optional/required fields. Tags are case-sensitive. Avoid having to specify new encodings, but if you do, make sure to include test cases that encompass all potential cases. </p> <p>It's ok to not propose the most efficient way of solving the problem. A simple but slightly less efficient design is preferred over a complex but more efficient one. We already use hex and base64 codes to represent binary bytes in JSON, which wastes 25-50% of space. That level of waste is ok if the solution becomes simpler to code. </p> <p>It's not about you. You may think you must convince everyone that your particular way of solving the problem is the best and get some ego points with yourself. While some of that is beneficial to the debate, be open-minded to the other possible solutions. Once merged, the NIP is not yours anymore. Anyone can change in any way they see fit. If your work is great, people will remember your name. If it just got the conversation started to become something completely different from what you proposed, they will also remember you. </p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 599f67f7:21fb3ea9 <div class="time" style="margin-left: auto;">2024-09-19 08:27:12</div> </div> <div> <h3>¿Qué es una dirección Lightning o Lightning address?</h3> <p>Una dirección Lightning es una dirección que visualmente se asemeja a una dirección de correo electrónico legible para los humanos, por ejemplo usuario@dominio.com pero que en realidad te permite recibir pagos en bitcoin instantáneos y económicos, sin la necesidad de tener un nodo en linea en tu dispositivo ni tener que generar facturas de forma manual cada vez que alguien te quiere hacer un pago.</p> <p>¿Suena bien no?</p> <h3>¿Y cómo funciona?</h3> <p>Funciona utilizando el <a href="https://github.com/lnurl/luds/blob/legacy/lnurl-pay.md">protocolo de pago LNURL</a>.</p> <p><img alt="Aquí se muestra un sencillo esquema de lo que ocurre en segundo plano." src="https://blob.satellite.earth/908a8572fe3ec8c5b17bcbae1065b69af15b39958401c87128723f3250122cec" />Aquí se muestra un sencillo esquema de lo que ocurre en segundo plano.</p> <p>En resumen, cuando otro usuario quiere pagarte usando tu dirección Lightning, tu billetera convierte la dirección Lightning en una solicitud de pago LNURL. Luego se utiliza esa solicitud de pago LNURL exitosa para obtener una factura BOLT11.</p> <p>💡 Dirección Lightning > LNURLp > Factura BOLT 11.</p> <h3>Suena bien, pero ¿cuál es el problema?</h3> <p>Por el momento, muchas de las implementaciones de Lightning Address son de custodia, porque se necesita un dominio para que Lightning Address funcione y un nodo que esté siempre en línea para recibir los pagos. Debido a que es de custodia, el custodio puede atacarte en cualquier momento y monitorear tus transacciones.</p> <p>Tienes que confiar en el propietario del dominio para no cambiar el registro de tu dirección Lightning. Y no funciona si el servidor LNURL no está en línea.</p> <p>Bitcoin Txoko ofrece una sencilla solución de Lightning Address respaldada por <a href="https://lnbits.com/">LNbits</a>. Esto también es de custodia, así que por favor mantén solo una pequeña cantidad en tu billetera Bitcoin Txoko y ve retirando a tu billetera de autocustodia a medida que recibas más sats.</p> <h3>Estoy listo, ¿qué necesito para empezar?</h3> <p>¡Todo lo que necesitas es un teléfono móvil o un ordenador y una conexión a Internet!</p> <h3>1. Creando tu billetera</h3> <p>Si aún no lo has hecho, navega a https://bitcointxoko.com y crea una nueva billetera. Puedes elegir el nombre que quieras.</p> <h3>2. Activar extensiones</h3> <p>Hace falta la extensión <code>Pay Links</code> para que las direcciones Lightning funcionen.</p> <p>Abre <code>Extensiones</code> en la barra de herramientas y activa <code>Pay Links</code>.</p> <h3>3. Creando tu enlace de pago</h3> <ul> <li> <p>En a la extensión <code>Pay Links</code>, haz clic en <code>New Pay Link</code>.</p> </li> <li> <p>Elige la billetera que has creado.</p> </li> <li> <p>Para la descripción del artículo, puedes escribir lo que quieras.</p> </li> <li> <p>Elige un nombre de usuario de tu dirección Lightning. Tu dirección Lightning se verá como <code>username@bitcointxoko.com</code>. </p> </li> <li> <p>Desmarque <code>Fixed amount</code> y cambia el valor mínimo a 1 y el valor máximo a 500000.</p> </li> </ul> <p>⚠️ También puedes cambiar el valor máximo a algo más alto, pero es más probable que los pagos más grandes fallen debido a la limitada capacidad de entrada del <a href="https://amboss.space/node/03fb64900a7647b4499a88a6c30976333074dad3bb7702d0219bd84dc4ac4a241e">nodo Lightning de Bitcoin Txoko</a>. Así que recomendamos mantenerlo en 500000 sats.</p> <ul> <li> <p>Ahora abre <code>Advanced options</code> y cambia <code>Comment maximum characters</code> a 799. Este paso no es necesario pero permite más funcionalidades más adelante.</p> </li> <li> <p>Marca <code>Enable nostr zaps</code> en la parte inferior, para que puedas utilizar tu dirección Lightning para recibir zaps.</p> </li> <li> <p>Las demás opciones avanzadas son opcionales, puedes configurarlas si quieres o dejarlas en blanco.</p> </li> </ul> <p><img alt="Al final debería verse algo así." src="https://raw.githubusercontent.com/bitcointxoko/guides/main/images/lnurlp/lnurlp-config.png" /></p> <p>Al final debería verse algo así.</p> <ul> <li>Cuando hayas comprobado que todo es correcto, sigue adelante y haz clic en <code>Create Pay Link</code>.</li> </ul> <h3>Probando</h3> <p>Puedes probar si tu nueva dirección Lightning funciona yendo a otra cartera, pulsando en <code>Enviar</code> y escribiendo tu dirección Lightning como destino, y luego enviándote una pequeña cantidad de sats.</p> <p>Vuelve a tu billetera Bitcoin Txoko y comprueba si has recibido tu propio pago. Es posible que tengas que actualizar la página.</p> <p>Si todo funcionó correctamente, ¡enhorabuena! 🥳</p> <p>Si no es así, háznoslo saber. Siempre estamos aquí para ayudar.</p> <h3>Próximos pasos</h3> <h4>Nostr zaps</h4> <p>Puedes añadir tu dirección Bitcoin Txoko Lightning a tu perfil de nostr y usarla para recibir zaps. Normalmente, esto se hace yendo a <code>Perfil</code> > <code>Editar</code> > <code>Dirección Lightning</code> y cambiando la dirección Lightning.</p> <h4>LNDhub</h4> <p>Puedes importar tu billetera LNbits como un LNDhub en tu teléfono utilizando una aplicación como <a href="https://zeusln.app/">Zeus</a> o <a href="https://bluewallet.io/">BlueWallet</a>, en lugar de visitar la billetera en el navegador cada vez que desees comprobar tu saldo o realizar un pago. Echa un vistazo a nostr:naddr1qvzqqqr4gupzqkvlvlma7a55ccp6d5rrdc27h3ssmdmael286mjaq5uxmqslk04fqqxnzd3exuerqdfkxccnyv3cs0uvul sobre cómo hacer esto.</p> <h4>Código QR</h4> <p>También puedes compartir o imprimir tu código QR LNURLp para que la gente pueda escanearlo fácilmente con sus teléfonos. ¡Muy útil si estás introduciendo bitcoin a tu comerciante local favorito para que pueda recibir propinas Lightning!</p> <p>Simplemente comparte el enlace a tu página compartida, o imprime el código QR como PDF yendo a <code>View Link</code> > <code>Print</code>.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsv75qqsv4sdzgkhhjfh06nn0cl3pkcc6d3qw2ej7psz58fn0v5fuqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jh8fcjm" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsv75qqsv4sdzgkhhjfh06nn0cl3pkcc6d3qw2ej7psz58fn0v5fuqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jh8fcjm" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsv75qqsv4sdzgkhhjfh06nn0cl3pkcc6d3qw2ej7psz58fn0v5fuqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jh8fcjm" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsv75qqsv4sdzgkhhjfh06nn0cl3pkcc6d3qw2ej7psz58fn0v5fuqzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jh8fcjm" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-20 10:12:19</div> </div> <div> <p>M5Stick-NEMO: Firmware para Pegadinhas de Alta Tecnologia em Dispositivos M5Stack ESP32 , Este projeto oferece uma solução eficaz sem comprometer a qualidade, ideal para quem busca uma experiência educativa e divertida no universo do hacking.</p> <p>https://nostrcheck.me/media/public/nostrcheck.me_2674216785970862911706546228.webp </p> <p>Desenvolvido por Noah Axon-n0xa, o M5Stick-NEMO é um projeto pessoal que surgiu da vontade de aprender mais sobre o desenvolvimento do ESP32 com o Arduino IDE. Inspirado por desafios populares na comunidade de tecnologia, NEMO replica pegadinhas comuns, proporcionando uma experiência educativa e divertida.</p> <p>Características Principais:</p> <ul> <li>Portal NEMO WiFi: um captive portal login que tenta criar credenciais de e-mail de engenharia social - salva nomes de usuário e senhas no cartão SD (se inserido em um leitor compatível)</li> <li>Porta TV B-Gone para desligar dispositivos controlados por infravermelho.</li> <li>Spam de emparelhamento de dispositivo AppleJuice iOS Bluetooth.</li> <li>Spam de notificação de dispositivo Bluetooth para SwiftPair (Windows) e Android.</li> <li>Spam de WiFi com SSIDs engraçados, WiFi Rickrolling e modo aleatório.</li> <li>Scanner SSID WiFi: exibe e clona SSIDs próximos.</li> <li>Relógio digital ajustável pelo usuário com suporte do M5 Stick RTC.</li> <li>Configurações apoiadas por EEPROM para rotação, brilho, escurecimento automático e SSID do Portal NEMO.</li> <li>Nível da bateria e créditos no menu de configurações.</li> </ul> <p>Interface de Usuário:</p> <ul> <li>Três controles principais: Home, Próximo e Selecionar.</li> </ul> <p>Portal NEMO:</p> <p>No modo NEMO Portal, o NEMO ativa um Hotspot WiFi aberto chamado "Nemo Free WiFi" (configurável em portal.h) com servidores DNS, DHCP e Web ativados.</p> <ul> <li> <p>O Portal NEMO exibe uma página de login falsa que afirma fornecer acesso à Internet se você fizer login.</p> </li> <li> <p>Este é um ataque de engenharia social e registrará o nome de usuário e as senhas inseridas na página.</p> </li> <li> <p>Nos detalhes do Wifi Scan, você pode clonar um SSID existente na lista de verificação. Sair do Portal NEMO limpará o SSID Evil Twin</p> </li> <li> <p>Você pode visualizar as credenciais capturadas conectando-se ao portal a partir do seu próprio dispositivo e navegando até http://172.0.0.1/creds</p> </li> <li> <p>Você pode definir um SSID personalizado conectando-se ao portal a partir do seu próprio dispositivo e navegando até http://172.0.0.1/ssid</p> </li> <li> <p>Se o seu dispositivo suportar EEPROM para configurações, o SSID personalizado inserido será salvo como padrão, mesmo se estiver desligado.</p> </li> <li> <p>Se o seu dispositivo tiver um leitor de cartão SD com um cartão formatado em sistema de arquivos FAT inserido, os nomes de usuário e senhas serão registrados em nemo-portal-creds.txt no cartão SD para você ler mais tarde.</p> </li> <li> <p>O suporte a cartão SD só está habilitado por padrão na plataforma M5Stack Cardputer. Ele pode ser habilitado em dispositivos M5Stick, mas um leitor de cartão SD deve ser construído e conectado ao pino do painel frontal.</p> </li> <li> <p>O Portal NEMO deve ser usado apenas em compromissos profissionais com um escopo válido de trabalho, fins educacionais ou de demonstração. </p> </li> </ul> <p>O armazenamento, venda ou uso de informações pessoais sem consentimento é contra a lei.🤓</p> <p>Instalação:</p> <ol> <li> <p>Visite o site oficial: M5Stack Docs https://docs.m5stack.com/en/download</p> </li> <li> <p>Baixe o programa oficial M5Burner.</p> </li> <li> <p>Procure pelo projeto "NEMO For M5Stick C Plus".</p> </li> <li> <p>Conecte o M5 à porta USB do seu PC.</p> </li> <li> <p>Abra o M5Burner, selecione o projeto e clique em "Burn".</p> </li> </ol> <p>Experimente algumas funções do FlipperZero no seu M5. Para recursos adicionais e a liberdade de personalização, compile e baixe diretamente o programa "NEMO-M5Stick C Plus" no GitHub do projeto. Isso não só permite explorar, mas também modificar e aprimorar o projeto de acordo com suas preferências. </p> <p>Repositório oficial no GitHub </p> <p>https://github.com/n0xa/m5stick-nemo</p> <p>Assista a um tutorial sobre a implementação do M5Stick-NEMO.</p> <p>https://youtu.be/uFzQTzZo-6E?si=BJJzNmiN0Jzw42Eu</p> <p>https://youtu.be/uTeCbR_hWjc?si=l88w_Hl3EXuKa6gv</p> <p>Além disso, você pode aprimorar seu M5 com o MURAUDER, um conjunto abrangente de ferramentas ofensivas e defensivas WiFi/Bluetooth para o ESP32. </p> <p>Encontre-o no GitHub: ESP32Marauder</p> <p>https://github.com/justcallmekoko/ESP32Marauder</p> <p>Assista a um tutorial sobre a implementação do MURAUDER: </p> <p>https://youtu.be/GQPzgYksdkg?si=dWN-GwEP5r6hk9IC</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsq94g8maenkmfmu4km39z9w0hmrt42p4hzh8ewaj3c9gzf4q89negzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gxnhkk2" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsq94g8maenkmfmu4km39z9w0hmrt42p4hzh8ewaj3c9gzf4q89negzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gxnhkk2" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsq94g8maenkmfmu4km39z9w0hmrt42p4hzh8ewaj3c9gzf4q89negzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gxnhkk2" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsq94g8maenkmfmu4km39z9w0hmrt42p4hzh8ewaj3c9gzf4q89negzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gxnhkk2" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 41d0a715:9733c512 <div class="time" style="margin-left: auto;">2024-10-20 03:38:18</div> </div> <div> <p>If you object to something a Fellow CowBoy is representing, it should be OK to call him out.</p> <p>We need to remove the factor of unequal wealth or the huge stack of Satoshis one person has.</p> <p>Challenging a Fellow CowBoy is a very serious insult. It deserves a clear cut outcome. </p> <p>The Metaphor of "A Show Down on Main Street' is where the accuser and the accused settle things to the Death.</p> <p>originally posted at https://stacker.news/items/732035</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsqrfyqraqenxme3xjsz0r0hha2m3fnr9vwsalehk2etkycf2u7raczypqapfc4ruuuwytt4a0zpzdqpmx39f2jwk23ez8qyfetgyyhx0z3y6x7p9d" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsqrfyqraqenxme3xjsz0r0hha2m3fnr9vwsalehk2etkycf2u7raczypqapfc4ruuuwytt4a0zpzdqpmx39f2jwk23ez8qyfetgyyhx0z3y6x7p9d" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsqrfyqraqenxme3xjsz0r0hha2m3fnr9vwsalehk2etkycf2u7raczypqapfc4ruuuwytt4a0zpzdqpmx39f2jwk23ez8qyfetgyyhx0z3y6x7p9d" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsqrfyqraqenxme3xjsz0r0hha2m3fnr9vwsalehk2etkycf2u7raczypqapfc4ruuuwytt4a0zpzdqpmx39f2jwk23ez8qyfetgyyhx0z3y6x7p9d" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 1b5ee74d:bb1aae6e <div class="time" style="margin-left: auto;">2024-09-10 08:51:03</div> </div> <div> <ul> <li>Who Is Responsible for the Content Published on Social Networks?</li> <li>What should the role of platforms be in content moderation?</li> <li>Who should be consulted in cases of disputes involving illegal content?</li> <li>Should there be a limit to freedom of speech online? Where should the line be drawn?</li> </ul> <p>These are just a few of the numerous questions that have characterized the debate for years, not only regarding social networks but, more broadly, the entire landscape of online interactions.</p> <p>In recent weeks, tensions have reignited due to three cases that have stirred the pot—depending on the perspective—with slogans of either combating illegal activity or fighting censorship: Telegram, Meta, and X.</p> <p>These cases are distinct, with the platforms and their executives behaving differently in each instance: Meta cooperated with authorities, while Telegram and X were more reluctant. However, all three stories share a key issue—perhaps <em>the</em> key issue: the ability to intervene in the content they host.</p> <p>To understand the reason, let’s briefly recap what happened.</p> <h3><strong>Telegram, Meta, and X: Three Different Cases, One Common Origin</strong></h3> <p>Pavel Durov, founder of Telegram, was arrested in Paris on August 24th as part of an investigation that French authorities have been conducting for months against the messaging platform.</p> <p>The accusations are numerous: money laundering, drug trafficking, child pornography, and refusal to cooperate with law enforcement. In the press release issued by the Prosecutor’s Office, there is even mention of violations related to the import and export of cryptographic tools—an approach reminiscent of the United States in the 1990s, when the government classified cryptography on par with weaponry. This interpretation only changed due to the outcome of the <em>Crypto Wars</em>.</p> <p>In fact, reports tell us that Pavel Durov was released after a few days upon paying a €5 million bail, with the condition that he not leave France. Initially, Telegram issued a statement via Twitter, asserting its compliance with European laws. But on September 6th, the founder of Telegram decided to fight back, leaving little room for interpretation.</p> <p>"<em>Sometimes we can’t reach an agreement with regulators in certain countries on the right balance between privacy and security,</em>" Durov said, adding that, if necessary, Telegram will leave markets that are incompatible with these principles.</p> <p>It is worth noting that this is not the first time Durov has clashed with authorities. In the past, he refused to cooperate with Russia by denying access to Telegram users’ personal data. This refusal led to the platform being temporarily blocked in Russia in 2018.</p> <h3><strong>Meta: Pressure from the White House and Zuckerberg’s Revelations</strong></h3> <p>Mark Zuckerberg, CEO of Meta, recently disclosed pressures he received from the White House during the pandemic. In a letter to the U.S. House Judiciary Committee, Zuckerberg revealed that the Biden administration pushed Meta to remove content related to the virus, including satirical and critical posts.</p> <p>Zuckerberg explained that in 2021, Meta deleted more than 20 million posts related to COVID-19 but expressed regret over some of the decisions made, admitting that the company had succumbed to excessive political pressure.</p> <p>Zuckerberg emphasized that these requests were perceived by the company as an obligation rather than a choice, and in hindsight, some of these actions might have been mistakes. Meta’s future commitment, according to Zuckerberg, will be to better resist such pressures, even in emergency situations.</p> <blockquote> <p><em>I believe the government’s pressure was wrong, and I regret not being more transparent about it.</em></p> </blockquote> <h3><strong>X and the Clash with the Brazilian Government</strong></h3> <p>Elon Musk and X (formerly Twitter) are at the center of a legal dispute in Brazil, where the platform was blocked after Musk refused to appoint a local legal representative, as required by the country’s Supreme Court. The issue arose when Judge Alexandre de Moraes ordered X to suspend certain accounts accused of spreading political disinformation, particularly those associated with former president Jair Bolsonaro and his supporters.</p> <p>Musk’s reaction was harsh. He accused the Supreme Court of corruption and of violating free speech, criticizing de Moraes and calling him a “criminal.” However, the judge continued his legal actions against Musk and his company, even freezing the bank accounts of Starlink, Musk’s satellite division, to pressure X into complying with Brazilian laws.</p> <p>Brazilian authorities are even pursuing those who attempt to access the platform using VPNs, sparking further controversy over freedom in Brazil.</p> <p>Currently, the platform remains suspended, with about 21 million Brazilian users cut off from the service. The legal dispute is ongoing and could have long-term repercussions for X’s presence in Brazil, one of the platform’s largest markets.</p> <h3><strong>The Ownership of Content</strong></h3> <p>Telegram and X have found themselves in hot water for refusing to comply with content moderation mandates imposed by various jurisdictions. Meta, on the other hand, has avoided such issues by adhering to directives from the White House, including the removal of content flagged by Washington, such as “satirical and ironic” posts, as noted in the letter.</p> <p>The decisive factor in all three cases is the same: the ability to intervene in what is published on the platform. The terms and conditions of Meta and X do not formally claim ownership of the content users post, but they clarify that users grant the companies a non-exclusive, royalty-free, worldwide license to use, distribute, modify, and display the content in relation to the services offered. Telegram’s terms are slightly stricter: while users also retain formal ownership of their content, Telegram requires a license to distribute and display content only within its ecosystem.</p> <p>However, the result remains the same. Anything published by users can be modified by the platform, according to the implicit contract every single user agrees to when they begin using the service.</p> <h3><strong>Nostr is the Way</strong></h3> <p>It’s no coincidence that, in recent weeks, many who care about issues such as privacy and censorship resistance have reignited interest in Nostr. The protocol, whose acronym stands for <em>Notes and Other Stuff Transmitted by Relays</em>, can be used via various clients, not a single platform—similar to how the Web is accessible from different browsers.</p> <p>But most importantly, users who create an account do not do so through a username and password saved on the company’s servers—because, in this case, the company doesn’t exist—but rather through a public key and a private key.</p> <p>This key pair allows users to interact with Nostr across multiple clients and send their “notes”—as posts are called on Nostr—to as many relays (servers) as they wish. In other words, the data is not stored on a single server but on multiple servers chosen by the user—and the user can even set up their own server without much difficulty.</p> <p>Most importantly, the data is portable. Posts sent are cryptographically signed: in Nostr, content ownership is not just formally with the user, it is mathematically so.</p> <p>In such a context, blaming the operator of a client or relay for the content signed and published by users' private keys would be bordering on absurdity, besides revealing a clear technical ignorance. Of course, after the accusations from the U.S. Department of Justice against the developers of Samourai Wallet, it’s fair to be ready for anything.</p> <p>But giving a chance to solutions like Nostr also means considering the possibility of reclaiming one's online identity and no longer being an unconscious victim of manipulative algorithms and invasive governments.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsy6qnejfasgpzednvjyahn3hhaumtq86m0fauhcguadqaqlh53qsgzyqd4ae6d78cnawza2nfkhsv6gxq0gn8f4nht5t4pzru757dmr2hxu6n0fp0" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsy6qnejfasgpzednvjyahn3hhaumtq86m0fauhcguadqaqlh53qsgzyqd4ae6d78cnawza2nfkhsv6gxq0gn8f4nht5t4pzru757dmr2hxu6n0fp0" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsy6qnejfasgpzednvjyahn3hhaumtq86m0fauhcguadqaqlh53qsgzyqd4ae6d78cnawza2nfkhsv6gxq0gn8f4nht5t4pzru757dmr2hxu6n0fp0" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsy6qnejfasgpzednvjyahn3hhaumtq86m0fauhcguadqaqlh53qsgzyqd4ae6d78cnawza2nfkhsv6gxq0gn8f4nht5t4pzru757dmr2hxu6n0fp0" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 13e63e99:25525c6a <div class="time" style="margin-left: auto;">2024-09-03 09:29:54</div> </div> <div> <h1><strong>Preview</strong></h1> <p>Last week, President Nayib Bukele of El Salvador emphasized Bitcoin’s role in enhancing the country's global image that boosted foreign investment and tourism. At the NostrWorld Unconference in Riga, the synergy between Bitcoin and decentralized social networks was a key focus, showcasing the potential for integrating Bitcoin with the growing Nostr protocol. Meanwhile, Lightspark launched its Extend platform, facilitating instant Bitcoin payments for U.S. businesses, thereby expanding the accessibility of Bitcoin transactions. Publicly traded companies have increased their Bitcoin holdings by nearly 200%, bringing their total to $20 billion, reflecting strong institutional confidence in Bitcoin as a reserve asset. Additionally, Bitcoin in exchange experienced its third-largest daily net outflow of 2024, indicating a shift toward long-term holding among investors. Despite some withdrawals, including a $13.5 million outflow from BlackRock’s iShares Bitcoin Trust, the fund remains a dominant force in the Bitcoin investment landscape. Lastly, Nigeria's SEC granted its first provisional exchange license, a milestone in the regulation of the country’s rapidly growing digital asset industry, positioning Nigeria as a leading player in global digital asset adoption. For more details, continue reading below.</p> <h2><em>A. Bitcoin Data Dashboard</em></h2> <p>1. Bitcoin Transactions\ 2. Supply\ 3. Mining\ 4. Transaction Fees\ 5. Difficulty Retarget\ 6. Lightning Network (Public)</p> <h2><strong><em>B. Bitcoin Ecosystem</em></strong></h2> <p>1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador\ 2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks\ 3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.\ 4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion\ 5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024\ 6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals</p> <h2><strong><em>C. Regulation</em></strong></h2> <p>1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation</p> <h2><em>D. Macroeconomy</em></h2> <p>1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich\ 2. Jobless claims drop as labor market slows, US economy remains on steady growth path</p> <hr /> <h1><strong>A. Bitcoin Data Dashboard</strong></h1> <p><img src="https://blossom.primal.net/6e485d1c1182bf6755522976337b525f641c511ffb603516546cbe4ddbd7cf9e.webp"></p> <blockquote> <p>As of Sep 2, 2024</p> </blockquote> <h1><strong>B. Bitcoin Ecosystem</strong></h1> <h2>1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador</h2> <p>President Nayib Bukele recently provided a candid assessment of El Salvador's groundbreaking decision to adopt Bitcoin as legal tender, a move that has drawn both praise and criticism on the global stage. In an interview with Time magazine, Bukele emphasized that the initiative has had substantial benefits particularly in enhancing El Salvador's international image despite the country's bitcoin adoption has not expanded as rapidly as he has hoped, Bukele described the Bitcoin adoption as a powerful rebranding tool for the nation, one that has attracted foreign investment and boosted tourism. The president’s marketing advisor, Damian Merlo, echoed this sentiment, calling the decision "genius" and likening it to a major public relations campaign that El Salvador didn’t have to pay for. "We could have spent millions on a PR firm to rebrand the country," Merlo noted, "but instead, we adopted Bitcoin." While the move initially strained relations with institutions like the International Monetary Fund (IMF), which urged Bukele to abandon the policy due to perceived risks, there are signs that the tension is easing. El Salvador has recently reported progress in negotiations with the IMF, with a focus on enhancing transparency and addressing potential fiscal and financial stability risks related to the Bitcoin project. </p> <p><img src="https://blossom.primal.net/948789c7a88d1d200437d0571cee99090d82e17b200052a26f389b596780b016.webp"></p> <blockquote> <p>Reference: <a href="https://news.bitcoin.com/zh/bukele-cheng-bitebi-shi-salvaduo-youxiao-de-pinpai-zhongsu-gongju/">Bitcoin.com</a>, <a href="https://time.com/7015598/nayib-bukeles-iron-fist-el-salvador/">Time</a></p> </blockquote> <h2>2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks</h2> <p>Last week, NostrWorld’s third unconference, held in Riga, Latvia, gathered advocates and developers of the Nostr protocol. Organized by Jack Dorsey, NostrWorld provides a platform for open-source enthusiasts to collaborate on building a decentralized internet. The event, called Nostriga, underscored the emerging synergy between Nostr’s decentralized social network and Bitcoin. Nostr is an open-source protocol for a decentralized, censorship-resistant social network. Unlike traditional platforms, Nostr operates on a network of relays, supporting features like micropayments and digital identity management. It promises greater privacy and independence from centralized platforms. A highlight of the conference was Strike CEO Jack Mallers discussing how Nostr’s micropayments—Zaps—helped a skeptic understand Bitcoin’s value. This feature shows Bitcoin’s utility in social contexts, advancing the concept of internet tipping. Jack Dorsey enphasizing the importance of open source. Nostr faces the challenge of broadening its user base beyond Bitcoin enthusiasts. New initiatives like Ditto aim to integrate Nostr with larger internet communities, potentially increasing Bitcoin’s visibility and accessibility. Nostr’s role as a social and identity system could pave the way for decentralized digital economies. By leveraging social graphs and cryptographic trust, Nostr and Bitcoin together could enable secure, decentralized commerce.</p> <blockquote> <p>Reference: <a href="https://bitcoinmagazine.com/technical/jack-dorsey-backed-nostr-emerges-as-bitcoins-social-layer-at-riga-conference-">Bitcoin magazine</a></p> </blockquote> <h2>3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.</h2> <p>Lightspark has unveiled Lightspark Extend, a new solution designed to facilitate instant Bitcoin Lightning payments for U.S. businesses. This platform integrates with Universal Money Addresses (UMA) and Lightning-enabled wallets, exchanges, or bank accounts, offering a compliant and cost-effective way to handle transactions around the clock. Lightspark Extend is compatible with over 99% of U.S. banks that support real-time payments, enabling businesses to provide their customers with fast, low-cost transactions. UMA simplifies the payment process by using easy-to-remember addresses similar to email, removing the need for complex codes or passwords. With this launch, Lightspark Extend makes real-time payments via the Bitcoin Lightning Network accessible to eligible recipients across the U.S. Businesses interested in adopting this solution can sign up for a UMA address, link their accounts, and start receiving payments through an onboarding process facilitated by Zero Hash, a regulated U.S. financial institution. The introduction of Lightspark Extend marks a significant advancement in expanding the accessibility and utility of Bitcoin payments. This follows Lightspark’s recent announcement of a partnership with Coinbase, enabling customers to send up to $10,000 instantly through the Lightning Network.</p> <blockquote> <p>Reference: <a href="https://bitcoinmagazine.com/business/lightspark-introduces-instant-bitcoin-lightning-payments-for-u-s-businesses-with-new-feature">Bitcoin magazine</a></p> </blockquote> <h2>4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion</h2> <p>Publicly listed companies have seen their Bitcoin holdings soar by nearly 200% in a year, rising from $7.2 billion to $20 billion. According to Bitbo data, 42 such companies now hold 335,249 BTC, valued at roughly $20 billion. This marks a 177.7% increase from a year ago, when their BTC holdings were worth $7.2 billion. The trend began with MicroStrategy's August 2020 purchase of over 21,000 BTC, making Bitcoin its primary treasury reserve asset, and the company has since grown its holdings to 226,500 BTC. A survey commissioned by Nickel Digital Asset Management revealed strong institutional support for Bitcoin as a reserve asset, with 75% of 200 surveyed institutional investors and wealth managers endorsing public companies holding BTC. The survey, involving firms managing $1.7 trillion in assets, also found that 58% believe 10% or more of public companies will hold BTC within five years. Nickel Digital's CEO, Anatoly Crachilov, noted that institutional investors see Bitcoin as a hedge against currency debasement and a valuable addition to reserve allocations. Despite this growth, the 335,249 BTC held by public companies represent just 1.6% of Bitcoin's total capped supply of 21 million.</p> <blockquote> <p>Reference: <a href="https://cointelegraph.com/news/public-companies-bitcoin-holdings-20-billion-increase">Cointelegraph</a></p> </blockquote> <h2>5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024</h2> <p>Bitcoin is seeing a significant uptick in exchange withdrawals as its price nears the $60,000 mark, with approximately 45,000 BTC removed from exchanges on August 27 alone. This movement represents the third-largest net outflow of Bitcoin from exchanges in 2024, following similar spikes in July. According to data from CryptoQuant, this trend could signal a growing bullish sentiment among investors, who appear to be transferring their Bitcoin off exchanges to hold for the long term, thereby reducing potential selling pressure in the market. As of August 27, major exchanges hold around 2.63 million BTC, reflecting a 12.5% decrease from the 3.01 million BTC held at the beginning of the year. This reduction in exchange reserves underscores a broader trend of investors preferring to hold their Bitcoin privately, possibly in anticipation of future price increases.</p> <p><img src="https://blossom.primal.net/446655da87af52d50999995efaa4e377058da94fa396b3c0f50c8779a3069bc4.webp"></p> <blockquote> <p>Reference: <a href="https://cointelegraph.com/news/bitcoin-exchanges-third-biggest-net-daily-outflow-2024">Cointelegraph</a></p> </blockquote> <h2>6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals</h2> <p>BlackRock's iShares Bitcoin Trust (IBIT) experienced a $13.5 million outflow on Thursday, marking its first outflow since May 1st and only the second in the fund's history since its launch in January. This rare withdrawal contrasts with the ETF’s usual pattern of consistent inflows, underscoring its dominance in the Bitcoin investment space. The outflow came as part of a broader trend affecting spot Bitcoin ETFs, which saw a collective $71.8 million in withdrawals on Thursday. Competing Bitcoin ETFs from Grayscale, Fidelity, Valkyrie, and Bitwise also reported significant outflows, ranging from $8 million to $31 million. Despite these withdrawals, ARK's Bitcoin ETF saw an inflow of $5.3 million, highlighting a mixed investor sentiment as Bitcoin remains below the $60,000 mark. This divergence suggests varied outlooks among investors regarding Bitcoin's future. Despite the recent dip, BlackRock's Bitcoin ETF continues to lead the market, having attracted over $20 billion in net inflows since inception. With more than 350,000 BTC under management, it remains one of the largest institutional Bitcoin holders, reflecting its enduring appeal and influence in the Bitcoin investment landscape.</p> <blockquote> <p>Reference: <a href="https://bitcoinmagazine.com/business/blackrocks-bitcoin-etf-saw-outflow-for-the-first-time-since-may">Bitcoin magazine</a></p> </blockquote> <h1>C. Regulation</h1> <h2>1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation</h2> <p>The Nigerian Securities and Exchange Commission (SEC) has granted Quidax, an Africa-based crypto exchange, its first provisional operating license. This marks a significant step toward formal recognition and regulation of Nigeria's digital asset industry. The SEC's license allows Quidax to operate as a registered crypto exchange in Nigeria, a move the company describes as a "shot of adrenaline" for the local crypto community, spurring innovation and growth. Quidax CEO Buchi Okoro praised the SEC, particularly under the leadership of Emomotimi Agama, for its efforts to bring order and investor protection to the Nigerian crypto market. The approval also paves the way for Quidax to collaborate with banks and financial institutions, pending approval from the Central Bank of Nigeria. This licensing follows the SEC's recent amendment to its rules on June 21, covering digital asset issuance, exchange, and custody. Despite concerns that stringent requirements could limit local crypto exchanges, the new regulatory framework, including the Accelerated Regulatory Incubation Programme, aims to align virtual asset service providers with the latest standards. Nigeria, Africa's largest economy, is a global leader in cryptocurrency adoption, ranking second in Chainalysis’ 2023 Cryptocurrency Geography Report. While foreign investment in Nigeria's crypto sector has been slower than expected, the new regulatory environment and Quidax's licensing could attract more investors by offering a stable and secure market.</p> <blockquote> <p>Reference: <a href="https://cointelegraph.com/news/quidax-first-nigerian-sec-licensed-crypto-exchange">Cointelegraph</a></p> </blockquote> <h1>D. Macroeconomy</h1> <h2>1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich</h2> <p>As a presidential candidate, Vice President Harris has aligned with President Biden’s tax policies, including the pledge not to raise taxes on anyone earning under $400,000 annually. However, she also has her own ambitious tax proposals. These include raising the top marginal tax rate on high earners from 37% to 39.6%. Although she previously suggested a 4% “income-based premium” on households earning over $100,000 to fund Medicare for All, this idea has not resurfaced in 2024. Among the more controversial proposals Harris supports is a tax on unrealized capital gains for individuals with over $100 million in wealth. Often dubbed the “billionaire tax,” this would require these households to pay an annual minimum tax of 25% on their combined income and unrealized gains. This approach would be groundbreaking in U.S. tax history, as it taxes assets that have not yet been sold. For example, if you buy stock at $10 and it increases to $20, you would owe taxes on the $10 gain, even if you haven’t sold the stock. The same principle would apply to real estate, where yearly value increases would be taxed. This proposal raises significant concerns, particularly about the administrative challenges of valuing assets annually and the potential for future expansion of the tax to lower wealth thresholds. The wealth tax faces hurdles in Congress and potential court challenges, but it signals Harris's intent to push for new forms of taxation on the ultra-wealthy.</p> <p><img src="https://blossom.primal.net/357244a44a060a649dc00a9769e4074e635e4b27b16afe0998776038f4a0e3dd.webp"></p> <blockquote> <p>Reference: <a href="https://www.forbes.com/sites/robertwood/2024/08/29/kamala-harris-plan-to-tax-unrealized-capital-gain-is-scary-heres-why/">Forbes</a></p> </blockquote> <h2>2. Jobless claims drop as labor market slows, US economy remains on steady growth path</h2> <p>Last week, new applications for jobless benefits in the U.S. dropped slightly, but re-employment opportunities for laid-off workers are becoming scarcer, indicating the unemployment rate likely remained high in August. Despite this, the labor market's orderly slowdown is keeping economic growth on track, with the economy growing faster than initially reported in the second quarter, driven by consumer spending and rebounding corporate profits. The labor market's cooling supports the expectation that the Federal Reserve may start cutting interest rates next month, though a 50-basis-point reduction seems unlikely. Initial jobless claims fell by 2,000 to 231,000 for the week ending August 24, while continuing claims, which indicate ongoing unemployment, rose slightly, suggesting prolonged joblessness. In the second quarter, the economy grew at an annualized rate of 3.0%, with consumer spending revised upward to a 2.9% growth rate, offsetting lower business investment and exports. Corporate profits also reached a record high, helping businesses manage input costs amid supply-chain challenges. The goods trade deficit widened in July due to a surge in imports, likely driven by expectations of higher tariffs if former President Trump wins the November election. Despite these factors, economists predict growth will slow but avoid a recession.</p> <p><img src="https://blossom.primal.net/be3de7644aa9ddf8978e46f61dddb2be088dda084ccae674febbe08ca7447069.webp"></p> <blockquote> <p>Reference: <a href="https://www.reuters.com/markets/us/us-weekly-jobless-claims-fall-slightly-2024-08-29/">Reuters</a>, <a href="http://dol.gov">dol.gov</a></p> </blockquote> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqswewhty0jlng4f6mjxampcg338xdkr7p0dxljlyc8gah2v5jwmthszyqf7v05e0jjwnpslr306y7egrqqv3vwug9anr7yul4a2gjp92fwx5pcwm8n" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqswewhty0jlng4f6mjxampcg338xdkr7p0dxljlyc8gah2v5jwmthszyqf7v05e0jjwnpslr306y7egrqqv3vwug9anr7yul4a2gjp92fwx5pcwm8n" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqswewhty0jlng4f6mjxampcg338xdkr7p0dxljlyc8gah2v5jwmthszyqf7v05e0jjwnpslr306y7egrqqv3vwug9anr7yul4a2gjp92fwx5pcwm8n" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqswewhty0jlng4f6mjxampcg338xdkr7p0dxljlyc8gah2v5jwmthszyqf7v05e0jjwnpslr306y7egrqqv3vwug9anr7yul4a2gjp92fwx5pcwm8n" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-20 03:20:33</div> </div> <div> <p>Criando códigos de pagamentos reutilizáveis que começam com "PM8T". Esses códigos permitem que os usuários compartilhem identificadores publicamente sem revelar seus endereços ou saldos de Bitcoin. Os PayNyms oferecem diversas funcionalidades incríveis, como receber doações, comprar Bitcoin peer-to-peer, receber recompensas de mineração, fazer login com Paynym/Auth47 e realizar transações com Stowaway/Payjoin, que proporcionam um nível adicional de privacidade ao criar um mini coinjoin. Essas são algumas das contribuições mais significativas para a privacidade do Bitcoin. Embora o BIP47 tenha sido criado em 2015, a maioria das carteiras de Bitcoin ainda não o implementou, com exceção de algumas, como Samourai Wallet, Sparrow Wallet e Bluewallet, que atualmente oferecem suporte apenas para recebimento.</p> <p>O PayNym é um código de pagamento reutilizável que proporciona segurança ao ser compartilhado publicamente. Cada carteira compatível com BIP47 lê o código secreto no PayNymID e gera um novo endereço público válido exclusivo para cada par de usuários. A chave pública estendida escondida no PayNymID, combinada com o código secreto único para cada par de usuários, impede que terceiros rastreiem as chaves públicas dos usuários. Os pagamentos não são enviados diretamente para o código de pagamento do usuário, mas para endereços Bitcoin públicos únicos gerados pelo segredo compartilhado da carteira e pelo código de pagamento reutilizável do destinatário. Estes endereços públicos são gerados quando é feito o primeiro Tx para o PayNymID, garantindo privacidade desde o início da transação. Isso é feito criando um Tx especial que é enviado com os dados da saída OP_RETURN para um endereço de notificação obtido do código de pagamento do destinatário. Este Bitcoin Tx, que é enviado para um endereço de observação/notificação, não é um pagamento real. É uma saída OP_RETURN de 80 bytes com os dados necessários para criar novos endereços públicos derivados de algoritmos com base nas informações de chave pública estendida. Uma vez estabelecido o canal direto entre os usuários, o Tx restante para PayNym segue o mesmo processo que qualquer outra transação Bitcoin. A privacidade é mantida ao compartilhar o PayNym, já que não são divulgados os endereços BTC públicos, apenas o código de pagamento reutilizável BIP47. A premissa do protocolo BIP-47 é que não se pode espionar o que não se pode ver, garantindo assim a privacidade das transações. O PayNym oferece uma maneira relativamente privada de realizar transações, mesmo que isso exija mais esforço e taxas mais elevadas.</p> <p>O PayNymID incorpora a chave pública estendida do proprietário do PayNym, uma informação codificada que a carteira BIP47 interpreta para criar novos endereços Bitcoin públicos. Esses novos endereços são derivados dos endereços originais controlados pelo proprietário das chaves privadas.</p> <p>https://nostrcheck.me/media/134743ca8ad0203b3657c20a6869e64f160ce48ae6388dc1f5ca67f346019ee7/nostrcheck.me_8654899814721132371710875358.webp</p> <p>Como a carteira é individual e independente e depende da frase-semente mantida pelo proprietário do PayNym e da carteira, cada carteira BIP47 que lê o código secreto gerará endereços BTC públicos válidos. Esses endereços são exclusivos para cada par de usuários, diferentemente dos gerados por outra carteira que lê o mesmo PayNym, criando canais de pagamento com endereços Bitcoin únicos para cada dupla de usuários.</p> <p>Para efetuar pagamentos para um PayNymID, é necessário primeiro abrir um canal de pagamento seguro. Isso é feito criando uma transação especial que inclui os dados da saída OP_RETURN e é enviada para um endereço de notificação obtido do código de pagamento do destinatário.</p> <p>A transação de notificação especial é executada apenas uma vez do remetente para o destinatário. Uma vez aberto, o restante das transações enviadas ao PayNym será como qualquer outra transação Bitcoin.</p> <p>Esta primeira transação especial tem um custo de 15.000 satoshis mais a taxa de rede na carteira Samourai. É individual para cada canal de pagamento seguro que você deseja abrir com qualquer PayNymID. Ou seja, cada PayNym requer uma única transação especial para abrir cada canal de pagamento.</p> <p>https://nostrcheck.me/media/134743ca8ad0203b3657c20a6869e64f160ce48ae6388dc1f5ca67f346019ee7/nostrcheck.me_5588987905454433521710875712.webp</p> <p>Uma vez estabelecido o canal de pagamento para o PayNym, você pode realizar transações de forma privada e segura, sem expor seu saldo ou histórico de transações. Da mesma forma, qualquer pessoa que queira fazer um pagamento para o seu PayNym precisará seguir o mesmo procedimento de abrir um canal de pagamento seguro com sua própria carteira.</p> <p>Essa abordagem permite criar uma rede de contatos seguros, onde você pode conduzir transações de maneira totalmente privada, sem o risco de divulgar informações confidenciais, como seu histórico de transações ou saldo da carteira.</p> <p>https://medium.com/@ottosch/how-bip47-works-ee641cc14bf3</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs048w0jhzvv7ft8cfhk9lj7zlkge9kzthwq6cd73gpu06dae4tnfczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gu9u73h" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs048w0jhzvv7ft8cfhk9lj7zlkge9kzthwq6cd73gpu06dae4tnfczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gu9u73h" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs048w0jhzvv7ft8cfhk9lj7zlkge9kzthwq6cd73gpu06dae4tnfczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gu9u73h" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs048w0jhzvv7ft8cfhk9lj7zlkge9kzthwq6cd73gpu06dae4tnfczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gu9u73h" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 469fa704:2b6cb760 <div class="time" style="margin-left: auto;">2024-09-02 06:11:43</div> </div> <div> <p><strong><em>I joined Nostr a week ago and wanted to recap it for myself and also give other newbies a simple introduction. Maybe this will help you get started too.</em></strong></p> <h2>Step 1: Create your identity and get your private key for a browser extension</h2> <p>I started with the Snort client on my local home server. It created my private/public key pair and I was good to go. Then I transferred the private key to Amethyst, a pretty good Android-based client. Before looking at various clients and other nostr-based websites, I tried transferring my private key into a browser extension. I looked at Alby and nos2x. I chose the latter because I wanted to keep my Lightning wallet separate from my identity management. You don't have to, I just found it easier.</p> <h2>Step 2: If you're confused, always check your feed settings</h2> <p>I tried many different clients and was very confused at first. Due to its decentralized nature, Nostr relies on relays, which are just small servers, and to each one you can connect to, all your data is stored. When you post a message, write a note, an article like this or simply who you follow. The main reason and benefit for this is that there is no single point of failure or server-like entity that could be censored. The side effect of this, combined with using different clients, was that not only did it look different everywhere, but the content was also very different. This was simply because I wasn't connected to all my different clients with the same relays. But the main reason why each feed looks different on each client is usually because you can choose different variations of feeds and some clients even offer filters for the feeds.</p> <p>Scroll down to get a small overview of the clients I've tried.</p> <h2>Step 3: Set up your lightning wallet with something like Wallet of Satoshi</h2> <p>I made my Bitcoin Lightning wallet independent of my identity. That's why I just went with the number one Lightning wallet on the market: Satoshi's Wallet. It's very simple and provides you with a Lightning address that resembles and has the format of an email address. You can add this address to your Nostr profile description and you're ready to receive Sats. Anyone can send them to you, e.g. for a good message or something else they find valuable on Nostr (like a podcast, a video, an article, ...). Just be aware that Satoshi's wallet contains your key and the sats you have there are not really your sats. So only leave a small amount there or no more than you need for your nostr experience.</p> <h2>Step 4: Set up your Nostr address</h2> <p>I set up a unique NIP-05 identifier that is human readable and also looks like an email address. For me, that's tobiya@nostrplebs.com, also called a nostr address. It's much easier to read, share and remember than your public key, which is just a long, unwieldy string of characters. </p> <p>Some popular services are: * NostrVerified * Alby * Iris * Primal * Snort * nostrplebs.com</p> <p>Most offer free services or at least a free tier. I chose nostrplebs.com because it links my Nostr address (tobiya@nostrplebs.com) to my Lightning wallet. ⚡</p> <h2>Brief overview of the clients (I have tested)</h2> <h3>Web/Browser:</h3> <ul> <li><strong>Primal</strong>: Fast, user-friendly, nice looking, easy to use</li> <li><strong>Coracle</strong>: Focuses on decentralized reputation, privacy and trust metrics. Also well organized and structured</li> <li><strong>noStrudel</strong>: The most comprehensive I've found, has everything</li> <li><strong>Rabbit</strong>: Designed like X (Twitter) Pro, focuses on everything at once</li> <li><strong>Nostter</strong>: Clearly structured, easy to find what you're looking for</li> <li><strong>Snort</strong>: Fast web client for those who prefer simplicity and speed.</li> </ul> <h3>iOS</h3> <p>I'm not an iPhone user, but everything I've discovered says that Damus is the best app for iOS.</p> <h3>Android:</h3> <ul> <li><strong>Amethyst</strong>: Feature rich for Android, I only tried this program because it gives me everything I currently need on my phone.</li> <li><strong>Primal</strong>: Works seamlessly with Primal on the web, which is a pretty convenient starting point if you only want to use one client.</li> </ul> <p>As for the web clients, I'm still figuring out which one will be my favorite. But I think they're all good in their own way. In the time of writing, I am mainly using Primal on Android and Web, Amethyst and noStrudel.</p> <h3>Let's have fun!!</h3> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsyjc9zwvjd8vysjxr5rxeh3rpwrq4mw3rwtmk5dnht4k0jetqe90qzyprflfcyx7ltaf03ect4lcpu7patq6c687cjarz6kxsdpf3tdjmkq2em4sd" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsyjc9zwvjd8vysjxr5rxeh3rpwrq4mw3rwtmk5dnht4k0jetqe90qzyprflfcyx7ltaf03ect4lcpu7patq6c687cjarz6kxsdpf3tdjmkq2em4sd" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsyjc9zwvjd8vysjxr5rxeh3rpwrq4mw3rwtmk5dnht4k0jetqe90qzyprflfcyx7ltaf03ect4lcpu7patq6c687cjarz6kxsdpf3tdjmkq2em4sd" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsyjc9zwvjd8vysjxr5rxeh3rpwrq4mw3rwtmk5dnht4k0jetqe90qzyprflfcyx7ltaf03ect4lcpu7patq6c687cjarz6kxsdpf3tdjmkq2em4sd" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 0edc2f47:730cff1b <div class="time" style="margin-left: auto;">2024-09-02 01:54:55</div> </div> <div> <h2>Chef's notes</h2> <p>In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.</p> <h2>Details</h2> <ul> <li>⏲️ Prep time: 30 minutes</li> <li>🍳 Cook time: 6 hours</li> <li>🍽️ Servings: 12</li> </ul> <h2>Ingredients</h2> <ul> <li>1 medium onion, peeled and quartered</li> <li>2 tsp ground ginger </li> <li>8-10 large cloves garlic</li> <li>1 cup ketchup</li> <li>¼ cup dry sherry</li> <li>¼ cup sake</li> <li>¼ cup cider vinegar</li> <li>¼ cup soy sauce</li> <li>¼ cup honey</li> <li>¼ cup Dijon mustard</li> <li>1 tablespoon coarsely ground black pepper</li> <li>¼ teaspoon ground cloves</li> <li>1½ cups Coca-Cola, ginger ale, or Dr. Pepper</li> <li>1 first-cut brisket, 6 to 7 pounds (2.7-3.2kg), rinsed and patted thoroughly dry</li> </ul> <h2>Directions</h2> <ol> <li>Preheat oven to 325F / 160C.</li> <li>Combine all ingredients except brisket in a blender and blend until smooth.</li> <li>Place brisket in a Dutch oven or other large pot with a tight-fitting lid.</li> <li>Pour sauce over brisket, place lid on pot, roast in oven for 3 hours. Flip roast and return to oven for 3 hours or until fork tender. </li> <li>Remove roast to rest. Skim fat from sauce and reduce if desired. Serve immediately with sauce or cool, cover brisket and refrigerate overnight in cooking pan. The next day, defat sauce, reduce if desired, and reheat meat in sauce before serving. </li> </ol> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs8w6n6yfk2ey3s9t865a7u8usgmkpp0fsw0tpf88hpaq8qkuln2xgzyq8dct68gjz8dx7fhak5w8gcpe8zszcte4cekmd8jyqph6mnpnl3k4f8nmx" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs8w6n6yfk2ey3s9t865a7u8usgmkpp0fsw0tpf88hpaq8qkuln2xgzyq8dct68gjz8dx7fhak5w8gcpe8zszcte4cekmd8jyqph6mnpnl3k4f8nmx" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs8w6n6yfk2ey3s9t865a7u8usgmkpp0fsw0tpf88hpaq8qkuln2xgzyq8dct68gjz8dx7fhak5w8gcpe8zszcte4cekmd8jyqph6mnpnl3k4f8nmx" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs8w6n6yfk2ey3s9t865a7u8usgmkpp0fsw0tpf88hpaq8qkuln2xgzyq8dct68gjz8dx7fhak5w8gcpe8zszcte4cekmd8jyqph6mnpnl3k4f8nmx" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3b7fc823:e194354f <div class="time" style="margin-left: auto;">2024-09-01 23:52:38</div> </div> <div> <p>I dOn'T cAre ABouT pRivAcY. IT dOEsN'T maTtER. i'M nOT dOiNg AnyThiNg wRonG. </p> <h1>GHOSTn</h1> <p>Your phone is spying on you. Your apps are spying on you. Your websites, search engine, fitness tracker, smart watch, IoT device, EVERYTHING is collecting anything it can and sending it off to be stored, cross referenced, and sold.</p> <p>Data is the new oil. </p> <p>So what? I don't care if Google knows I like motorcycles. By itself one data point isn't a big deal but once you start bringing everything together... </p> <p>Who are you talking to? When and how long did you talk to them? Where did you go? How often do you go there? On and on the profile starts to become overwhelmingly invasive. </p> <p>Right now it is extremely cheap and easy to collect and store the data but it's hard and expensive to cross reference and tabulate the data down to the individual. But in the extremely near future using AI and faster processers, data profiles for sale go from white men between 25 - 30, with this education level, and background like XYZ to -> John loves motorcycls and steak. </p> <p>Suddenly your insurance premiums are way higher than your friends because you partake in dangerous activities and eat too much red meat. You get denied that loan because you invest in risky assets and it raises your risk factors to pay it back. That job that you applied to never responded because they already ran you through the algorithm and you don't fit the culture. </p> <p>Protect your data and privacy now before its too late. </p> <h1>privacy</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsy43d58w0hwzn2geh06fcqej5r76aak79tacup4ky3s5r4revp2yqzyqahljprvy0346h2v0hrha5myku259hvd6qart7rjqngprlpjs657dqt6sa" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsy43d58w0hwzn2geh06fcqej5r76aak79tacup4ky3s5r4revp2yqzyqahljprvy0346h2v0hrha5myku259hvd6qart7rjqngprlpjs657dqt6sa" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsy43d58w0hwzn2geh06fcqej5r76aak79tacup4ky3s5r4revp2yqzyqahljprvy0346h2v0hrha5myku259hvd6qart7rjqngprlpjs657dqt6sa" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsy43d58w0hwzn2geh06fcqej5r76aak79tacup4ky3s5r4revp2yqzyqahljprvy0346h2v0hrha5myku259hvd6qart7rjqngprlpjs657dqt6sa" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 9e69e420:d12360c2 <div class="time" style="margin-left: auto;">2024-10-20 01:21:39</div> </div> <div> <h1>Michigan Voter Rolls Inflated by 500,000: State vs. GOP Perspectives</h1> <h2>Key Points</h2> <ul> <li>Michigan's voter rolls list 8.4 million registered voters, nearly 500,000 more than the eligible voting population.</li> <li>This is the largest imbalance among Great Lakes states and one of the largest in the nation.</li> </ul> <h2>Causes and Concerns</h2> <ul> <li>A major cause is the 2018 voter-approved proposal that automatically registers those 18 and older to vote when applying for a driver's license, unless they opt out.</li> <li>The Republican National Committee has sued the state, demanding the rolls be trimmed.</li> <li>While critics say the inflated rolls are not ideal, no one is suggesting they have contributed to fraud.</li> </ul> <h2>State's Response</h2> <ul> <li>By 2027, an estimated 606,800 inactive voters are expected to be removed from rolls.</li> <li>This would reduce the total to just over 7.8 million, slightly less than the voting-age population.</li> <li>State officials argue that the GOP lawsuits are an attempt to sow distrust in elections.</li> </ul> <h2>Challenges in Removing Voters</h2> <ul> <li>Federal law limits when voters can be removed from rolls.</li> <li>Voters can be removed if they move to another state, if election mail is undeliverable, or if they don't vote in two consecutive federal elections.</li> </ul> <h2>Fraud Concerns</h2> <ul> <li>Election officials state that impersonation fraud is almost non-existent.</li> <li>While voter fraud does occur, it's rare. Recent cases include four St. Clair Shores voters charged with voting twice in the August primary.</li> <li>Many allegations of fraud, such as dead voters casting ballots in 2020, have been proven baseless.</li> </ul> <h2>Interesting Facts</h2> <ul> <li>Michigan's voter rolls include 16,666 people born in 1924 or earlier.</li> <li>In 2024, only 1,121 of these centenarians voted.</li> </ul> <p>Sauce: I am the sauce. But we can also credit: <a href="">https://www.bridgemi.com/michigan-government/michigan-voter-rolls-inflated-500k-state-says-its-no-issue-gop-disagrees</a></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsywlz7kqs2v7x0jnh6psfcw23tl6yy2n573mnf7dtdkg9vza6yj7szyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyeh95cj" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsywlz7kqs2v7x0jnh6psfcw23tl6yy2n573mnf7dtdkg9vza6yj7szyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyeh95cj" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsywlz7kqs2v7x0jnh6psfcw23tl6yy2n573mnf7dtdkg9vza6yj7szyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyeh95cj" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsywlz7kqs2v7x0jnh6psfcw23tl6yy2n573mnf7dtdkg9vza6yj7szyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyeh95cj" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-20 01:17:29</div> </div> <div> <p>Trechos do artigo do seth for Privacy </p> <p>COMO FUNCIONAM OS PAGAMENTOS SILENCIOSOS, SIMPLIFICADOS Antes de nos aprofundarmos no motivo pelo qual estou entusiasmado com os Pagamentos Silenciosos, é importante que você entenda em um nível muito simplista como os Pagamentos Silenciosos funcionam tanto para o remetente quanto para o destinatário. PARA O REMETENTE Quando alguém deseja enviar fundos para um endereço de pagamento silencioso, na prática, tudo o que precisa fazer é digitalizar ou copiar/colar o código de pagamento em sua carteira favorita (supondo que seja compatível) e enviar o pagamento normalmente. Mas o que exatamente está acontecendo nos bastidores? Quando o remetente insere o endereço de Pagamento Silencioso em sua carteira, sua carteira combina três chaves para criar um endereço único e único, do qual apenas o destinatário pretendido pode gastar. Esse endereço exclusivo é criado combinando a chave pública (ou “endereço”, em termos leigos) de uma das entradas que o remetente deseja passar para o destinatário, a chave pública do destinatário (contida no endereço de pagamento silencioso), e uma chave “segredo compartilhado” que o remetente gera e que apenas o remetente e o destinatário conhecem. Graças a algo conhecido como propriedade “comutativa” na criptografia, o remetente pode combinar essas chaves, mas não pode gastar do endereço resultante , pois não conhece a chave privada do destinatário (é claro). Quando o remetente combina essas três chaves, ele gera uma nova chave pública (ou endereço) e envia os fundos pretendidos para esse novo endereço que somente o destinatário controla. Na cadeia, esta transação se parece exatamente com qualquer outro gasto de tipo e script semelhantes, e não há nenhum fator distintivo que torne aparente para observadores externos que um Pagamento Silencioso foi usado, muito menos quem possui o endereço de Pagamento Silencioso. PARA O DESTINATÁRIO Assim que chegarmos ao destinatário, veremos onde entra a principal desvantagem dos pagamentos silenciosos. Se você se lembra de que o remetente usa a chave pública de uma entrada que está sendo gasta para gerar o endereço único e único, pode estar se perguntando: “Como o destinatário sabe que recebeu fundos e para qual endereço?” Esta questão está no centro da proposta de pagamentos silenciosos e significa que os destinatários precisam fazer uma varredura relativamente cara de todas as transações na blockchain do Bitcoin depois de criarem seu endereço de pagamento silencioso. Essa varredura permite que o destinatário veja se uma chave pública de entrada mais um segredo compartilhado gerado usando seu endereço de pagamento silencioso e uma chave pública de saída em qualquer transação corresponde adequadamente às suas chaves privadas e, se for o caso, adicioná-la à carteira. Essa varredura é bastante cara em comparação com a varredura de carteira Bitcoin padrão, pois você não pode simplesmente comparar uma lista de endereços derivados de sua carteira com uma lista de saídas de transações para obter o saldo de sua carteira. Em vez disso, você precisa passar por cada transação, calcular o segredo compartilhado para cada entrada e comparar com as saídas, algo que Somsen comparou a “verificar cada assinatura duas vezes, em vez de uma vez” em “Bitcoin Explained ” . Idealmente, essa varredura será feita durante o download do bloco inicial (a primeira vez que você sincronizar todo o blockchain do Bitcoin) ou um software autônomo que descarregue a varredura de sua carteira e nó Bitcoin.</p> <p>OTIMIZANDO O TEMPO DE DIGITALIZAÇÃO PARA O DESTINATÁRIO</p> <p>Embora essa varredura seja computacionalmente cara, ela pode se tornar mais eficiente sem sacrificar a privacidade ou a fungibilidade por meio de três otimizações principais:</p> <ol> <li> <p>Crie uma data de “aniversário” ao criar um endereço de pagamento silencioso e salve-o, para que, quando precisar restaurar, você possa começar a digitalizar apenas a partir desse bloco adiante na cadeia, em vez do bloco de gênese.</p> </li> <li> <p>Verifique apenas as saídas Taproot, pois muito poucas saídas na cadeia são atualmente Pay-to-Taproot (“ P2TR ”), isso eliminará uma grande porcentagem de transações e reduzirá bastante o tempo de verificação. Idealmente, isso se tornará menos útil à medida que o Taproot for mais usado, mas provavelmente será uma otimização extremamente eficaz por algum tempo.</p> </li> </ol> <p>3.Verifique apenas o conjunto UTXO em vez de verificar todas as transações históricas, pois você está preocupado apenas com saídas novas, recebidas e não gastas destinadas ao seu endereço de pagamento silencioso. Isso tem a desvantagem de não fornecer histórico de transações e exigiria um banco de dados adicional sobre os métodos normais.</p> <p>Artigos sobre Silent Payments 🤫</p> <p>https://bitcoinmagazine.com/technical/silent-payments-make-bitcoin-more-private</p> <p>https://bitcoinmagazine.com/technical/silent-payments-improve-privacy-without-bitcoin-data</p> <p>https://bitcoinmagazine.com/technical/bitcoin-silent-payments-secret-keys</p> <p>https://bitcoinmagazine.com/technical/improving-bitcoin-privacy-with-silent-payments</p> <p>https://foundationdevices.com/2023/02/making-sense-of-stealth-addresses/</p> <p>Videos sobre Silent Payments 🤫</p> <p>https://youtu.be/vOCWO_zX7X8</p> <p>https://youtu.be/42PMLaz7Avk</p> <p>https://youtu.be/YCMaqS-LhLc</p> <p>Space sobre Silent Payments 🤫</p> <p>https://twitter.com/bitcoinoptech/status/1668949342814609408?t=UY6nEc0ghPiPxgfydUzW6w&s=19 Recompensa pra carteira mobile suporte ao Silent Payments 🤫</p> <p>https://twitter.com/gladstein/status/1684567103297445888?t=tY6WQ8fzPn3vNs_YrvXDmQ&s=19</p> <p>BIP 352 Silent Payments 🤫</p> <p>https://github.com/bitcoin/bips/pull/1458#issuecomment-1613507274</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsdv3u2zv6x5pnj4axpq67llnkuj8n3dc89s5vzlhqqne6u4d9kznqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7g3u4rkc" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsdv3u2zv6x5pnj4axpq67llnkuj8n3dc89s5vzlhqqne6u4d9kznqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7g3u4rkc" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsdv3u2zv6x5pnj4axpq67llnkuj8n3dc89s5vzlhqqne6u4d9kznqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7g3u4rkc" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsdv3u2zv6x5pnj4axpq67llnkuj8n3dc89s5vzlhqqne6u4d9kznqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7g3u4rkc" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 6c2d68ba:846525ec <div class="time" style="margin-left: auto;">2024-09-01 13:02:53</div> </div> <div> <p>Dear friend,</p> <p>it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.</p> <p>As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:</p> <ul> <li> <p>What causes the discomfort that drives you out of the walled garden onto the open sea?</p> </li> <li> <p>Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?</p> </li> <li> <p>What are you hoping to find on the open sea that walled gardens cannot provide?</p> </li> <li> <p>What are you willing to sacrifice for freedom (of speech)?</p> </li> <li> <p>What will you need to keep the ship afloat?</p> </li> <li> <p>How will you react when you find yourself in the middle of a storm?</p> </li> </ul> <p>I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over. </p> <p>This is about building a new world, an open world without walled gardens and data silos.</p> <p>Onwards!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs2th6pwmvy20n8nq37zpyemw4huczf6pf93dedpqg459v8qmrydfgzypkz6696q9kzj9qhl5vw5lqxkum7c9pl04td0r7agjjmyjyyv5j7cprer6e" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs2th6pwmvy20n8nq37zpyemw4huczf6pf93dedpqg459v8qmrydfgzypkz6696q9kzj9qhl5vw5lqxkum7c9pl04td0r7agjjmyjyyv5j7cprer6e" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs2th6pwmvy20n8nq37zpyemw4huczf6pf93dedpqg459v8qmrydfgzypkz6696q9kzj9qhl5vw5lqxkum7c9pl04td0r7agjjmyjyyv5j7cprer6e" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs2th6pwmvy20n8nq37zpyemw4huczf6pf93dedpqg459v8qmrydfgzypkz6696q9kzj9qhl5vw5lqxkum7c9pl04td0r7agjjmyjyyv5j7cprer6e" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ dba00383:d7448f1b <div class="time" style="margin-left: auto;">2024-10-20 01:06:44</div> </div> <div> <p>Primeiramente meus irmãos Pedro escreve essa carta aos Irmãos que moravam pelas redondezas da Turquia, e naquele momento estavam passando por problemas e dificuldades acerca de sua fé, e então Pedro argumenta sobre as dificuldades da fé Cristã.</p> <p>Segundo, o que é ser santo? Ser santo significa ser separado, diferente, consagrado, se fomos transformados verdadeiramente pelo espírito santo devemos agir como aquele que nos transformou, que foi Jesus Cristo, e através de nossa vida, através de nosso testemunho, através de nossas ações deveríamos transparecer essa separação deste mundo.</p> <p>O que estou querendo dizer é algo mais básico acerca da nossa caminhada cristã, tudo se resumo a sermos um espelho que reflete o carácter e as características de nosso Criador, mas o por que estou dizendo isso, porque quero lembrar e sempre que puder vou relembrar que, AÇÕES SÃO MAIS IMPORTANTES QUE PALAVRAS, se apenas falamos que somos crentes mas no nosso dia a dia mas agimos de forma diferente(seja mentindo, seja enganando, seja nos vendendo) está sendo em vão nossa caminhada e nossa salvação estará comprometida.</p> <p>Estou falando essas coisas porque é necessário que sejamos separados das coisas desse mundo, de toda corrupção desta era e sermos a luz que ilumina as trevas desta terra, o sal que tempera esse mundo, que essa palavra entre em vossos corações e que Deus abençoe vocês em NOME DE JESUS. AMÉM!!!!!!!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqswlrzffvhns4uy0pmkm20f357sf6n6vp6ghcyanrfsk46eap8c23czyrd6qqurdp2g0wj46e5g0y087xdjsd5pgg4yrz9jjvva00xhgj83ktmevnt" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqswlrzffvhns4uy0pmkm20f357sf6n6vp6ghcyanrfsk46eap8c23czyrd6qqurdp2g0wj46e5g0y087xdjsd5pgg4yrz9jjvva00xhgj83ktmevnt" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqswlrzffvhns4uy0pmkm20f357sf6n6vp6ghcyanrfsk46eap8c23czyrd6qqurdp2g0wj46e5g0y087xdjsd5pgg4yrz9jjvva00xhgj83ktmevnt" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqswlrzffvhns4uy0pmkm20f357sf6n6vp6ghcyanrfsk46eap8c23czyrd6qqurdp2g0wj46e5g0y087xdjsd5pgg4yrz9jjvva00xhgj83ktmevnt" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ b6ca2216:f45f8b5b <div class="time" style="margin-left: auto;">2024-10-20 00:19:37</div> </div> <div> <p>my 3. article</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs84tjfv8hh5uryr4n53s76gcdcslwsprh5ewkwfkrcuu45qv6q58czyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794kz8nv9x" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs84tjfv8hh5uryr4n53s76gcdcslwsprh5ewkwfkrcuu45qv6q58czyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794kz8nv9x" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs84tjfv8hh5uryr4n53s76gcdcslwsprh5ewkwfkrcuu45qv6q58czyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794kz8nv9x" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs84tjfv8hh5uryr4n53s76gcdcslwsprh5ewkwfkrcuu45qv6q58czyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794kz8nv9x" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ b6ca2216:f45f8b5b <div class="time" style="margin-left: auto;">2024-10-20 00:16:38</div> </div> <div> <p>{"id":12345,"title":"deleted","body":"deleted"}</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqszmgfsza8pcmv5l4edandhthrpgh6dnwvm8kp834rxeq9vx2mtxtgzyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794k25093y" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqszmgfsza8pcmv5l4edandhthrpgh6dnwvm8kp834rxeq9vx2mtxtgzyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794k25093y" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqszmgfsza8pcmv5l4edandhthrpgh6dnwvm8kp834rxeq9vx2mtxtgzyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794k25093y" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqszmgfsza8pcmv5l4edandhthrpgh6dnwvm8kp834rxeq9vx2mtxtgzyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794k25093y" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ b6ca2216:f45f8b5b <div class="time" style="margin-left: auto;">2024-10-19 23:51:01</div> </div> <div> <p>{id:123, title:"my first article", body:"This NIP defines kind:30402: an addressable event to describe classified listings that list any arbitrary product, service, or other thing for sale or offer and includes enough structured metadata to make them useful. The category of classifieds includes a very broad range of physical goods, services, work opportunities, rentals, free giveaways, personals, etc. and is distinct from the more strictly structured marketplaces defined in NIP-15 that often sell many units of specific products through very specific channels. The structure of these events is very similar to NIP-23 long-form content events."}</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvx273fd9r9waeeavv6u2vnjc8d0wladggwqm47cj6q5xe2l4y7sszyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794kf0xxv8" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvx273fd9r9waeeavv6u2vnjc8d0wladggwqm47cj6q5xe2l4y7sszyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794kf0xxv8" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvx273fd9r9waeeavv6u2vnjc8d0wladggwqm47cj6q5xe2l4y7sszyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794kf0xxv8" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvx273fd9r9waeeavv6u2vnjc8d0wladggwqm47cj6q5xe2l4y7sszyzmv5gsk9wndprkna5aqn6jz9wgj5t9nc4enu97sa37tld05t794kf0xxv8" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 623ed218:fa549249 <div class="time" style="margin-left: auto;">2024-10-19 23:49:53</div> </div> <div> <h1>Pup's Double-Takes #002:</h1> <h1>"Should You Spend Bitcoin?"</h1> <p><img alt="" src="https://bitcoinbarks.com/gallery_gen/2557e6678018c2effe0d2c78290d94c7_fit.png" /></p> <p>Welcome to Pup's Double-Takes, where I dive into the things that made me stop and say, 'Wait, what?' My goal is to unpack the curious and confusing, making it educational and, hopefully, a little entertaining along the way.</p> <h3>PDT-002: Should You Spend Bitcoin?</h3> <p><em>"Why would I buy anything with Bitcoin when the price could go up so much?"</em></p> <p>This question reflects a common debate about spending Bitcoin, but many discussions miss the forest for the trees regarding our broader economic activity. So let's take a step back and dive into what really matters.</p> <h3>The Bitcoin Pizza Story</h3> <p>You've probably heard the story of Laszlo Hanyecz, who spent 10,000 Bitcoin on two Papa John's pizzas on May 22, 2010---a day now known as Bitcoin Pizza Day. At the time of writing, those 10,000 Bitcoin would be worth around $670 million. That's a staggering number, but notice my phrasing here. I did not say, "those pizzas would be worth $670 million." This is an important distinction.</p> <p>Those pizzas were perishable, consumable goods that gave Laszlo value in the moment. Nobody would argue that pizza retains value over time---once it's eaten, it's gone. So, it doesn't make sense to say those pizzas were ever worth $670 million.</p> <h3>What About You?</h3> <p>Here's the more interesting question: Did you buy any pizzas in 2010? Did you buy any Bitcoin?</p> <p>You might think Laszlo was foolish for spending 10,000 Bitcoin on pizzas, but if you bought any pizzas or other goods in 2010 and didn't buy Bitcoin, you essentially made the same decision he did. You valued the goods and services you consumed more than you valued Bitcoin. And that's the real point here: Every financial decision you make reflects what you value in that moment.</p> <p>At the time, Laszlo valued two pizzas more than he valued 10,000 Bitcoin. You, too, valued whatever you purchased more than Bitcoin---whether you were aware of Bitcoin or not.</p> <h3>The Opportunity Cost of Every Transaction</h3> <p>Every transaction involves an opportunity cost---the value of the next best alternative you forgo when making a choice. When you spend money---whether it's Bitcoin, dollars, or any other currency---you're making a decision. You're choosing to exchange one form of value for another, and that decision comes at the expense of using that money for anything else.</p> <p>When you bought a pizza with fiat currency, you were implicitly saying that the value of the pizza was worth more than anything else you could have done with that money at the time, whether that was purchasing a different good, or saving in Bitcoin, or some other store of value. And that's okay. This is how economics works for everyone.</p> <p>This is where I take issue: Considering the potential future value of Bitcoin and deciding not to spend it reflects a narrow and incomplete view of your economic actions. When you spend Bitcoin on a pizza, you're giving up your stake in whatever future price action that Bitcoin may have seen. But the same consequences exist in every financial transaction you make.</p> <p>Instead of focusing solely on the Bitcoin part of your financial life, I would argue we should take a more holistic approach.</p> <h3>Cash Flow and Savings</h3> <p>Cash flow is simple: it's the difference between what you earn and what you spend. Ideally, your income is higher than your expenses, leaving you with a surplus of money ("labor receipts") to invest or save.</p> <p>The second key concept is the quality of your savings vehicles. Bitcoin is seen by many as a superior store of value compared to fiat money, which loses purchasing power over time due to inflation. Bitcoin's finite and metered supply issuance means that it is likely to maintain its purchasing power against goods and services, unlike rapidly inflating fiat currencies. As a relatively small monetary network still early in its adoption cycle, it may even gain value against these goods and services over time, even if its value may swing wildly over shorter time frames as the market determines its present value.</p> <p>This leads us to the reason I find it nonsensical to make any blanket statements about whether or not you should be spending Bitcoin.</p> <h3>The Bitcoin Standard</h3> <p>If you denominate your life in Bitcoin terms, you will realize that every non-Bitcoin purchase comes at the expense of being able to hold Bitcoin. There is functionally no difference between paying for a pizza with Bitcoin or paying for it with fiat. In both cases, you have chosen to acquire a consumable good with value you had saved.</p> <p>Am I arguing that you should blow your entire stack while retaining your fiat? Obviously not. But why would you be saving fiat in the first place?</p> <p>Ultimately, there is an argument to be made for holding a small amount of fiat to cover necessary payments should the price of Bitcoin drop. However, the focus should not be on whether you are spending Bitcoin or fiat, but rather on the value you're exchanging.</p> <h3>Conclusion</h3> <p>The real issue isn't the question of whether you should spend Bitcoin or fiat; it's the understanding that every financial transaction, regardless of currency, is a choice to exchange value.</p> <p>Whether you're using Bitcoin or dollars to buy a pizza or pay your rent, you're parting with a portion of your stored value to obtaining a good or service you value, at the expense of obtaining anything else with that portion of stored value. The currency used is just the medium---it's the value you exchange that matters.</p> <h1>Digging Deeper:</h1> <h3>Hey there, I hope you enjoyed this read! If you did, and would like to read more of my barks, follow the links below!</h3> <ul> <li> <p>Curious how I found Bitcoin? Read "<a href="https://bitcoinbarks.com/Barks/paw-prints-to-the-timechain/#wbb1" title="https://bitcoinbarks.com/Barks/paw-prints-to-the-timechain/#wbb1">Paw Prints to the Timechain</a>"!</p> </li> <li> <p>Bitcoin meets psychology? I touch on this in "<a href="https://bitcoinbarks.com/Barks/maslows-apex/#wbb1" title="https://bitcoinbarks.com/Barks/maslows-apex/#wbb1">Maslow's Apex</a>".</p> </li> <li> <p>Want to understand the basics of Bitcoin? Read "<a href="https://bitcoinbarks.com/Barks/bitcoin-best-practice/#wbb1" title="https://bitcoinbarks.com/Barks/bitcoin-best-practice/#wbb1">Bitcoin Best Practice</a>"!</p> </li> <li> <p>If you like seeing bad media takes unpacked, check out "<a href="https://bitcoinbarks.com/Barks/lets-talk-supply-issuance/#wbb1" title="https://bitcoinbarks.com/Barks/lets-talk-supply-issuance/#wbb1">PDT-001: Let's Talk Supply Issuance</a>".</p> </li> </ul> <h3>External Resources:</h3> <ul> <li>Want to earn rewards on your mortgage? <a href="https://use.foldapp.com/r/7KYTK4CP">Use my referral to earn 20,000 free sats at sign up!</a></li> <li>Do you like sharing Bitcoin content and earning sats for doing so? <a href="https://stacker.news/r/bitcoin_pup" title="https://stacker.news/r/bitcoin_pup">Join me at Stacker.news!</a></li> </ul> <h1>...Woof!</h1> <p><a href="https://primal.net/p/npub1vgldyxx7syc30qm9v7padnnfpdfp4zwymsyl9ztzuklaf7j5jfyspk36wu"><img alt="" src="https://bitcoinbarks.com/gallery_gen/5240db5304f70dd121acbe8521f5d958_fit.jpg" /></a></p> <p>originally posted at https://stacker.news/items/731850</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsytgcwekwms5r875jpjr7e6pns7he89th9f6dr38f4fael7f455rczyp3ra5scm6qnz9urv4nc84kwdy94yx5fcnwqnu5fvtjml4862jfyjzeqkmt" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsytgcwekwms5r875jpjr7e6pns7he89th9f6dr38f4fael7f455rczyp3ra5scm6qnz9urv4nc84kwdy94yx5fcnwqnu5fvtjml4862jfyjzeqkmt" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsytgcwekwms5r875jpjr7e6pns7he89th9f6dr38f4fael7f455rczyp3ra5scm6qnz9urv4nc84kwdy94yx5fcnwqnu5fvtjml4862jfyjzeqkmt" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsytgcwekwms5r875jpjr7e6pns7he89th9f6dr38f4fael7f455rczyp3ra5scm6qnz9urv4nc84kwdy94yx5fcnwqnu5fvtjml4862jfyjzeqkmt" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 805b34f7:3620fac3 <div class="time" style="margin-left: auto;">2024-10-19 19:59:21</div> </div> <div> <p>** I published this article on 3/26/2020. I'm back in Puerto now and just re-read this to fire myself up for some potential tubes. Now, I want it to live on Nostr. </p> <p>“When in doubt, don’t go out” is a well-known aphorism among surfers. I think it’s bs. Let me explain.</p> <p>**<em>I speak from my experiences as a regular surfer and with my close group of regular surfers in mind.</em></p> <p>In surfing, there’s a comfort zone, an adrenaline zone, an aw crap zone (doubt), and a hell no zone.</p> <p><strong>Comfort zone</strong> —It is in this place where it is safe and fun to try new maneuvers. The heart rate is low and the stoke rate high.</p> <p><strong>Adrenaline zone</strong>- This is personally my favorite zone. The surf is big or good enough to get the heart rate up and the juices flowing. Each movement matters and this is where some of the best surfing goes down.</p> <p><strong>Aw crap zone</strong> — This is the land of the I don’t know, the doubt. It’s always damn near impossible to sleep before an aw crap day of surfing. This is the place where limits are tested. Maybe you’re surfing in a new place with new risks such as shallow reef, a difficult takeoff, or it’s just huge. This aw crap zone will test and define your limits.</p> <p><strong>Hell no zone</strong> — When you know, you know. This is beyond doubt. You’re totally satisfied (yet still curious) from watching from afar. Maybe one day!</p> <p>These zones are bound to change as the surfer progresses. One day there may be no “hell no zone” as the surf master has pushed his or her limits to the extreme.</p> <h2><strong>Pushing</strong></h2> <p>Pros are only as good as their home breaks. NOT. Tell that to Kelly Slater and the Hopgood brothers who grew up surfing Florida slop. Although, perhaps their garbage wave situation lit a fire underneath them which inspired them to seek out better waves and progress rapidly. Anyways, a surfer grows up surfing their home breaks often. Some people grow up on the North Shore or in Tahiti, others grow up in Huntington. A surfer’s perspective on waves and danger is influenced by their exposure.</p> <p>I finally got bored with myself surfing my home waves. Sure, there were days that were outside of my comfort zone and epic, but it was time to go find waves that I had only seen in videos. I decided to pack my backpack and head to those famed Indonesian reefs that I’ve mind surfed for hours, but always had the question mark in my head as to whether or not I could conquer them.</p> <p>Surfing over shallow reef is something that I was not used to and it terrified me, but I also knew that every surfer does it including five-year-olds so I had to send it. I escaped the first mission unscathed and with some of the best waves in my life.</p> <p>In order to find those best waves of my life, I had to enter the ‘aw crap zone’. The I don’t know land. The unknown. When in doubt, I went out.</p> <h2><strong>And Now I’m Here</strong></h2> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:1400/1*RqIJqvLhIK85QiTl3VcEdw.jpeg" />I blew this wave, but wow pretty.</p> <p><img src="https://blossom.primal.net/abe7c306ae4191698d3a48d729fc20aad21bf105c6798231a911e3df489aaa18.png"></p> <p><em>Current forecast looks like it will be right at my edge.. again. We'll see.</em></p> <p>I’m surfing the famous Playa Zicatela every day with the whole world shut down due to Co-Vid19. I’ve always been curious to know what it’s like to be inside massive barrels, so I’m slowly making it happen. This is a battle that I chose. I’m learning how to sleep with surf anxiety. The first couple of nights were rough, but I’m starting to accept it now.</p> <p>This very morning inspired this article. I got up, went to the roof, and checked out the waves. It looked pretty mellow despite the fact that I knew there was a lot of swell in the water. I just thought, eh, maybe it’s not big like it was forecasted. I got in the water, took my first wave, wiped out, but whatever. I’ve been here for a week and I still wipeout on just about every first wave. But, I quickly found out that this was not the real set. The next set was enormous, and it sent adrenaline shrieking through my spine and filled my brain with the aw craps. The questioning of my life and why I’m out here quickly followed. Am I good enough for this? (maybe). Could I survive a wipeout that size?(probably). Is my board right for this? (definitely not). The second wave I took was bigger and I pulled the eject cord and jumped from what felt like the top of a cliff all the way to the bottom and got creamed (my perspective). After a couple of flips, I popped up the back laughing and was ready for another. I survived, therefore, I can keep pushing.</p> <p>Not gonna lie, surfing almost feels like work lately. Almost every day here is just about in my personal aw crap zone.</p> <p>However, it’s worth it for me. This is a journey that I deem worthy of my time. It does it for me. It’s those little moments inside the barrel and gosh-dang-golly hopefully soon getting shot out of the barrel that keep me stoked and looking forward to tomorrow. It’s proving to myself that I can do things I didn’t know for sure were possible.</p> <h2><strong>The Process to Progress</strong></h2> <p>Progression sometimes feels like a snail crawling up Mt. Everest. But when you zoom out, those incremental small improvements compound over time. Each wipeout is a little victory. Each wave that is ridden is a little victory. Your brain is learning from every experience that you choose to give it. Confidence slowly builds as we continue to learn from the masters and even develop our own style. Next thing you know you’re drinking a beer in a barrel that can kill a normal man like Mr. Slater did here.</p> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:1400/1*UNsQSBL89ixQ7MxAnXH0Tw.png" />Freakin Goat</p> <p>Stagnation leads to burnout, depression, and boredom (Not scientific facts but I’m right I know it). </p> <p><em>The great danger is that we give in to feelings of boredom, impatience, fear, and confusion. We stop observing and learning. The process comes to a halt. —</em> <a href="https://fs.blog/2013/01/mastery/">Farnam Street Blog </a></p> <p>I’ve seen a few buddies give up surfing or digress. It happened to me while I was focusing on baseball. It’s sad because surfing is fun and the better you get the more fun it is. It’s even more fun with a core group of guys who are at a similar level pushing each other. It can get boring if you don’t push yourself, and it gets scary real quick if you aren’t in surf shape.</p> <p><em>“Whenever we learn a skill, we frequently reach a point of frustration — what we are learning seems beyond our capabilities. Giving in to these feelings, we unconsciously quit on ourselves before we actually give up.” <a href="https://fs.blog/2013/01/mastery/">FS Blog</a></em></p> <p>Progression takes effort. Effort takes a conscious decision to expend your limited energy. It’s the only way to get gains in whatever game you are playing. Also, progression takes <strong>humility.</strong></p> <p>I got the pleasure of surfing Kelly Slater’s Wave Ranch. I knew I was going to have fun, but the night before I was damn nervous. Why? Well, I knew there’d be cameras and that I didn't want to blow it. I’d be surfing with pros and I was going to look horrible compared to them. Sure enough, the one right the camera got, I blew. Oh well. No 30-second barrels for the boys. Life moves on.</p> <p>Full vid here <a href="https://vimeo.com/367128298">https://vimeo.com/367128298</a></p> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:1400/1*bKcHHlnN5sg6oNZ74Bwd9w.png" /><em>Can't wait to go back here one day</em></p> <p>You’re bound to fail, especially when you take risks. If you’re a prideful person, the setbacks will be greater. It’s how you deal with the failure that determines if you will become a master.</p> <p>So if in doubt, go out. Your hell no zone is going to start to shrink. This applies any skill that you are sharpening. You’re only going to get the big clients if you go after them, a piano player will improve by practicing harder songs, a black belt gains nothing from fighting a white belt, etc.</p> <p>Pick your battles wisely. Then…SEND IT, SURVIVE, LEARN, APPLY, REPEAT.</p> <p>10/19 - Even though I'm a much more experienced surfer now, I'm still terrified. On my way to go get a board now and get ready for some swell! I'm on my honeymoon, so we'll see how hard I push. I have quite a few more responsibilities now then I did back in Covid times... But if in doubt, I will go out. PV. </p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsykksh3f89xpzkp55zx93yvdhwwlva4errykf7sksq3udks3pkkgczyzq9kd8hpzphm7e70uzczkk9wczkgc5ttr26pn5rnn9mdmekyravxju6wvd" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsykksh3f89xpzkp55zx93yvdhwwlva4errykf7sksq3udks3pkkgczyzq9kd8hpzphm7e70uzczkk9wczkgc5ttr26pn5rnn9mdmekyravxju6wvd" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsykksh3f89xpzkp55zx93yvdhwwlva4errykf7sksq3udks3pkkgczyzq9kd8hpzphm7e70uzczkk9wczkgc5ttr26pn5rnn9mdmekyravxju6wvd" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsykksh3f89xpzkp55zx93yvdhwwlva4errykf7sksq3udks3pkkgczyzq9kd8hpzphm7e70uzczkk9wczkgc5ttr26pn5rnn9mdmekyravxju6wvd" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 42342239:1d80db24 <div class="time" style="margin-left: auto;">2024-08-30 06:26:21</div> </div> <div> <blockquote> <p>Quis custodiet ipsos custodes? </p> </blockquote> <p>-- Juvenal (<em><a href="https://en.wikipedia.org/wiki/Quis_custodiet_ipsos_custodes">Who will watch the watchmen?</a></em>)</p> <p>In mid-July, numerous media outlets reported on <a href="https://www.epochtimes.se/johan-westerholm-om-mordforsoket-pa-donald-trump">the assassination attempt</a> on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various <a href="https://x.com/enlundm/status/1817578988933685539">sources</a> that <strong>search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place</strong>. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.</p> <p>The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."</p> <p><strong>A similar phenomenon occurred during the 2016 presidential election</strong>. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.</p> <p>These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. <a href="https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4535163">A study published in June 2024</a> reports that such search results can dramatically affect undecided voters. <strong>Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed</strong>. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.</p> <p>A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: <strong>If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?</strong></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsgexdclksz4usmn7xjuxtj8ekmzxhgsxd846p82z54avul83zu2hszypprgg3ejm8x2jtjpend667yhdl0h8e9ccxys9khh3r6vhsasrdjgdrl0yw" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsgexdclksz4usmn7xjuxtj8ekmzxhgsxd846p82z54avul83zu2hszypprgg3ejm8x2jtjpend667yhdl0h8e9ccxys9khh3r6vhsasrdjgdrl0yw" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsgexdclksz4usmn7xjuxtj8ekmzxhgsxd846p82z54avul83zu2hszypprgg3ejm8x2jtjpend667yhdl0h8e9ccxys9khh3r6vhsasrdjgdrl0yw" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsgexdclksz4usmn7xjuxtj8ekmzxhgsxd846p82z54avul83zu2hszypprgg3ejm8x2jtjpend667yhdl0h8e9ccxys9khh3r6vhsasrdjgdrl0yw" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ bf95e1a4:ebdcc848 <div class="time" style="margin-left: auto;">2024-10-15 12:24:45</div> </div> <div> <p>This is the full AI-generated transcript of Bitcoin Infinity Show #130 with Obi Nwosu! </p> <p>If you'd like to support us, check out bitcoininfinityshow.com for all our books, merch, and more! </p> <h1>Welcoming Obi Nwosu</h1> <p><strong>Luke:</strong> Obi, welcome for the first time to the Bitcoin Infinity Show.</p> <p><strong>Obi:</strong> well,</p> <p><strong>Knut:</strong> We rebranded.</p> <p><strong>Obi:</strong> what is time in infinity? No, no, it's the second time, great to have you back. yeah, we have, it's been a wild ride and the journey is just beginning. So yeah, thank you.</p> <h1>The Launch of Fedi</h1> <p><strong>Knut:</strong> so Fedimin launched, two weeks ago. Is it the Fedi</p> <p><strong>Obi:</strong> Fedi, launched?</p> <p><strong>Knut:</strong> launched? Yeah. These terms.</p> <p><strong>Obi:</strong> no, no, Fedi Mint launched, effectively Fedi Mint launched nearly five years ago. FediMint is a very old technology, very, you know, the first, the first FediMint transaction, where someone used FediMint e cash over Lightning to buy a cup of coffee, which was after, you know, a year plus of development was on, I believe it was the 3rd of the 8th, 3rd of August, 2021.</p> <p><strong>Obi:</strong> And so we're trying to, like you have a Bitcoin Infinity Day, we're suggesting, that was actually Erik, my, the inventor of Fedi Mint. from Parinelli Police, just actually, and so I like to think of that as e cash coffee day. Cause actually it was like, you actually bought the cup of coffee with e cash.</p> <p><strong>Obi:</strong> so yeah, but yeah, Fedi finally launched two weeks ago.</p> <p><strong>Knut:</strong> All right. so I think, for those who haven't seen the previous episode with you, if they want to know more about you, we should probably go back to that episode, but I think you're going to have to do the TLDR on what Fedi is for our listeners. Like that's a good start, I think.</p> <p><strong>Obi:</strong> So yeah, and now we can be clear about what Fedi is. And so Fedi, is two things still. Even Fedi is two things. One is the company called Fedi and the other is this product called Fedi. So if we talk about the product that people have on their phone, Fedi is a community super app. And so it's an app that takes the best of freedom technology.</p> <p><strong>Obi:</strong> it's got Bitcoin functionality in it, Lightning connectivity, obviously FediMint for handling community custody. but it's also got Nostr support and any other freedom technology that's out there that's mature and reliable. We've taken the time to integrate into one simple to use app. So it allows you to have chat.</p> <p><strong>Obi:</strong> We use Matrix as this federated, decentralized, encrypted chat protocol. It has money with the combination of Lightning, Bitcoin, and Fediment and more. So it has a built in web browser inside it. And therefore you can access all of the Bitcoin ecosystem of apps from Bitrefill to Unleash. chat to BTCmaps and beyond.</p> <p><strong>Obi:</strong> All in one place. So you don't have to have this smorgasbord of different apps and tabs open one app to use them all. And the app itself, we announced as well, is now source available and will eventually be open source as well. So we're trying to make the best of it. portal into the freedom technology space.</p> <p><strong>Obi:</strong> So that's Fedi. And then Fedi the company builds the Fedi app. And we also have something we call the FedEye Order, which is, this selection of incredible people, FedEye Knights, who are on the ground and they, you can think of them as like a Decentralized genius bar. If you've got an iPhone, you have the genius bar that goes along with the phone.</p> <p><strong>Obi:</strong> The reason why the iPhone is so amazing is not just the phone, but it's also the incredible support you can get. If you can go to an Apple store and you go to the genius bar, they can help you. we have that instead of it being in, you know, Fifth Avenue or Oxford street in London or so on.</p> <p><strong>Obi:</strong> It's in, the capital of Togo or Uganda or. Guatemala, or so on. On the ground, they will locate communities, they will educate communities. and they will support communities on Bitcoin, on Lightning, on FediMent, on all of these different websites and services that are out there to provide that sort of support that's needed for the communities that are outside of the existing Bitcoin space.</p> <h1>How Federations Work</h1> <p><strong>Knut:</strong> Okay, great. so how does a federation work?</p> <p><strong>Obi:</strong> so the first thing you have to do, wherever you custody is where you transact and do and you live and so on, which is why. Banks try very much when you're young to get you to hold a bank account with them because they know that most people never leave and then all other services are provided. So how do you actually custody?</p> <p><strong>Obi:</strong> For many people they've had two choices. Either they do everything themselves and that's the best if you can do it just like it's the best to be able to build and fix your own car or house but not everybody can do that but that is always the best because no one's going to love you. And put as much care in as yourself.</p> <p><strong>Obi:</strong> The other extreme is to fully outsource it, fully give it to some private party, which is actually what ends up 95 percent plus people doing, and that's putting their money on a Coinbase or some other centralized service. and the same with communication. They would use some sort of centralized service.</p> <p><strong>Obi:</strong> They would use a WhatsApp, an X. com, a Telegram, a WeChat or so on. They would use some centralized chat. And if you think about it. Our lives are communication and money and value. So both those things, most people outsource, some people take it in house. If I want to set up a federation, which is to do with the custody of the money, where FedeMint is this middle, middle house, I can find within my community, a number of trusted parties.</p> <p><strong>Obi:</strong> We call them guardians. So let's say. You found us three plus, you know, your great t shirt, Greg Voss. The minimum we suggest is four for various Esoteric reasons From a cryptographic security point of view we suggest four, but you can have seven You can have you can keep growing you could have we've seen people have seen Federation stood up with as many as 40 people in them And it will get slower and slower if it gets beyond that, but, but technically you can.</p> <p><strong>Obi:</strong> It'll be this, it'll create this huge multisig, i. e. multiple people have to sign before you do a transaction on chain. And so multisig starts to get expensive of a certain size. But let's say us three plus Greg. We would FedeMint software. we would download the 30 minute software onto a machine that we have spare, and we would set up and run it.</p> <p><strong>Obi:</strong> The setup process will, part of it will enter the information about the other three. And we make that very simple, it's a web interface, you point and click and you get a code and you share that code with the other parties, everybody shares the code of each other. Maybe you go into a group chat and paste each other's code.</p> <p><strong>Obi:</strong> Everybody copies each other's, enters it into our own FediMint and then they connect to each other and they form a federation. As long as you keep that box, running, connected to the internet, and connected to electricity, the federation, for each, all the four, the federation are one.</p> <p><strong>Obi:</strong> But because it's a federation, if one of them, for example, had a power cut, or lost their internet, or had to change their domain name, or something like that, The other three will be able to continue and operate. Yep, so you've now created this community custody platform. Now, anyone with the FEDI app or any other app that supports the FEDIMINT protocol, Webimint, and we're hoping that many others will set up FEDIMINT wallets, like there are multiple Lightning wallets in future.</p> <p><strong>Obi:</strong> Any FDI min wallet compatible wallets like Fedie, can connect to your federation At the end of setting up the fed min server will show a QR code and the string that represents how to connect to your Federation. So you could take your Fed app, or the Mutiny wallet, or Web Mint, or any other, fed mint compatible wallet, and you'll scan that QR code.</p> <p><strong>Obi:</strong> And you've now connected to that federation and that federation becomes, you can now use it to custody. Now, what will happen is, if for example, someone wants to send money to you, you would, just as if you're using a Bitcoin wallet, let's say it's on chain. you would say, I want to receive, enter the amount and it'll show a QR code.</p> <p><strong>Obi:</strong> Someone else who's using a normal Bitcoin wallet will scan that code and send over the Bitcoin main chain money to you. But what's actually happening is your Fediap is communicating with the Federation. Your Federation is creating a Bitcoin address for you to send to and sends it back to you for you to display.</p> <p><strong>Obi:</strong> Okay. And then a user, someone else who's using a completely different wallet will send money to that address. Actually goes to the federation and they, the four of us combined will process that and create e cash, which is like a token representation of the</p> <p><strong>Obi:</strong> Bitcoin. And then the e cash will be sent to you. But the way it, the way it's sent is completely privacy preserving. So the guardians have no way of knowing who they are providing that service for, who's receiving the money.</p> <p><strong>Obi:</strong> There's full privacy.</p> <p><strong>Obi:</strong> All right, and neither does the sender, I assume, like the sender doesn't, that they sent Bitcoin to us and address. They have no idea who, so if there are, let's say we set this up and we're using it for our friends and extended family and in total, there are 40 of us or 50 of us</p> <p><strong>Obi:</strong> When you send to that address, there's no way to know out of those 40 or 50 people who received it or who requested it.</p> <p><strong>Knut:</strong> All right, so, a bit about the guardians and the multisig, that's obviously because you don't want to have a single point of attack for each, federation, right?</p> <p><strong>Obi:</strong> point of failure,</p> <p><strong>Knut:</strong> A single point of</p> <p><strong>Obi:</strong> the more likely thing is that someone's machine, if you had one machine, the most likely thing that will happen, almost guaranteed, at some point you'll have some sort of power cut or internet cut. Internet cut is probably the most likely you'll, you'll have a glitch on your internet for 30 minutes.</p> <p><strong>Obi:</strong> If you do, Everyone using your federation won't be able to use your system for 30 minutes.</p> <p><strong>Knut:</strong> but it's also an attack vector. Like if the, if the, if there's a lot of money in the federation and, so there's, there's an incentive to attack the guardians. Like, can you be completely sure that the guardians don't know each other's identities and stuff like that? Like how, I know you think a lot about the attack vector.</p> <p><strong>Knut:</strong> So I'm like, can you go into that a bit?</p> <p><strong>Obi:</strong> can't be completely sure of anything in life. So the answer to that is automatically no. Can you be completely sure of something? but, it depends on the Also, there's an assumption that you have, that the people don't know each other. Cause I think very often in, there's two types of scenarios.</p> <p><strong>Obi:</strong> It could be that each party completely doesn't know each other, or the more common scenario will be that you're some community or some group of friends. And within you, you've decided. Of the people who are my friends and family and so on, these four people are the ones who are consistently the most reliable, the most trusted and so on.</p> <p><strong>Obi:</strong> They do know each other, and you know who they are, and it's because you know who they are that you're comfortable with them holding. they're the Uncle Jims of the family. they're known to be reliable. They're known to be people who care about their friends and family.</p> <p><strong>Obi:</strong> that's very often actually what we're seeing is the more common scenario than the ones where people are completely, anonymous to each other. But as it matures, we may see the other scenario happen as well.</p> <h1>The Uncle Network</h1> <p><strong>Luke:</strong> It's a literal uncle network. I know Uncle Rockstar started the uncle network here on infinity day. Yeah, you got the brother Luke, and so that's four, so we're</p> <p><strong>Obi:</strong> are you an uncle?</p> <p><strong>Knut:</strong> am an uncle officially now.</p> <p><strong>Knut:</strong> an uncle as well, are like, but dubbed by Uncle Rockstar</p> <p><strong>Obi:</strong> I haven't been dubbed I, so</p> <p><strong>Obi:</strong> you are a good candidate. candidate, but I am biologically now, an</p> <p><strong>Knut:</strong> oh, congratulations,</p> <p><strong>Obi:</strong> Yeah,</p> <h1>How Fedi Launched</h1> <p><strong>Luke:</strong> Okay, well, I think we are looking just to dig in more about Fedi Fedi Mint and, what does your launch actually mean? Because the app has been in beta for quite a while, right? what's happened, to make it that you can launch?</p> <p><strong>Obi:</strong> Yeah, that's a very good question, because, we, the app from the, if you just focus on the app, from the previous version to the one we went live, there are only a few, changes. It was more about, did we have enough feedback from enough people on the ground that we thought that the product was stable enough, reliable enough?</p> <p><strong>Obi:</strong> behind the scenes, we've done a lot of internal plus from trusted friends, external security audits of different elements as well. I don't like to publicize it because it's just something we do. We don't think it's something you should promote to saying, Hey, look at what we're doing. We just try to build the best that we can.</p> <p><strong>Obi:</strong> and the really, big thing was to just say, a lot of people ask, is Fedi ready? And we wanted to get to a line where we thought it was good enough. And we got to that line. And then, we also wanted to have enough proof points in, the world. And again, we got to that line. So these things were separate things that were happening.</p> <p><strong>Obi:</strong> And finally, it was very clear to us that we wanted to make the software, Ultimately open source. And that was a big call because, you know, we raised 21 million and, normally you go two routes. You go, you raise a little bit and you stay open source and so on. Or you raise a lot and you stay closed source.</p> <p><strong>Obi:</strong> We believe that, over time, it's going to be considered, over the coming years, it's going to consider that you should always go open source no matter what you're doing, but we're in a transition. Five years ago, raising this much and going open source would be considered crazy, in five years time, raising this much and not being open source would be considered crazy.</p> <p><strong>Obi:</strong> And we wanted to be, afforded in that. So. We actually went source available. It's called a business source license. So it means you go source available and you set a date where you must go open source or earlier. and we set those. So we cannot change it now. We cannot say we're going to actually change our mind.</p> <p><strong>Obi:</strong> Well, the only thing we can say is that we're going to go open source earlier. that's the only thing we could do. Or if we decide to shut down, it's automatically open source as well. That's the sort of dead man's switch as well. Or we decide we're no longer going to develop the software.</p> <p><strong>Obi:</strong> we've added caveats like that, which are not optional, but actually add more restrictions. So no one's going to complain with us going open source earlier. that was agreed and put in place on May the 4th. So May the 4th we review of this year, 2024, just for posterity.</p> <p><strong>Obi:</strong> we, got enough proof points from different markets, that we felt that we're onto something here. Does that mean that we've finished? No, there's a lot of work to do, but enough to say that the idea of taking all of the best of freedom technologies out there. And putting them into one place and one app that's easy to use is something that's compelling to people.</p> <p><strong>Obi:</strong> And also we had enough to see the federation model. of this sort of really simple to use and privacy preserving multi sig is also a powerful model. So the model was proven out. And then finally the software, we got to a point where we thought, it's, of course, we've got years of more development, but it was good enough as well.</p> <p><strong>Obi:</strong> I think that was the final piece. And we thought, okay, we're ready to go. And we then set a date a few weeks after that. But even when we were getting close to it, we started the process of shooting a video because we just wanted to show people are wondering what were we doing for the last nearly two years and we wanted to show that as well.</p> <p><strong>Luke:</strong> what's the synopsis of the last two years? Like the big highlights?</p> <p><strong>Obi:</strong> so, I always say there's three phases in the business. There's initialization, of a startup, initialization, market product fit, in our case, not product market fit, I can go into why. And then, growth. And so, this phase that was, the end was finally, we crossed the line, on August the 6th, 2024, was the initialization phase.</p> <p><strong>Obi:</strong> And so, if you think about the analogy of, like you wanted to have A shop selling designer pet clothing, and you've decided you have this crazy idea and you have to first fund it, find the people to build it, and then find the place, set up the store, make the clothes and, open.</p> <p><strong>Obi:</strong> That's the initialization phase. And then once it's launched, you then. Start figuring out, okay, people come in, there's initial, interest, and then, you have this trickle of people coming in, you have to figure out what do they like, what do they not like, what do I have to adjust until it becomes this sort of regular viable business.</p> <p><strong>Luke:</strong> That's the market product fit phase. And then you start saying, okay, I've got something that's working fully and then I will repeat it, make more and more and more, Widgets?</p> <p><strong>Obi:</strong> Doggy fashion, Excel stores, whatever you want to call it. the last two years was our initialization phase.</p> <p><strong>Obi:</strong> we had this, amazing product with FediMint. we had this initial set of, crazy people with Erik, the inventor of FedEvent, Justin, who's, who was also incredible engineer, who was actually the one who suggested that we make a commercial enterprise. up until that, both myself and Erik just suggested it would be an open source project.</p> <p><strong>Obi:</strong> And then myself as well with my just, you know, only maybe six or seven months before we were finally finished selling. a Bitcoin exchange, the UK's longest running Bitcoin exchange. and so having that experience of building a company that was profitable and understanding what it meant to build something that custodies a large amount of money for people and provides them services is easy to use and all that sort of stuff.</p> <p><strong>Obi:</strong> and everything around that customer service, everything around that. So, we were there, I had a visit to the Oslo Freedom Forum, and that was the catalyst. we did one talk at, Bitcoin Miami, and, Alex Gladstein saw that, he suggested I go to Oslo Freedom Forum. I went, my mind was blown and I also realized whenever you're thinking about a business, you have to always think about chicken and the egg and how do you find your initial market for eventually this product is applicable to everybody everywhere, but who's the first use case that has a demand so high that they're going to willing to go through the really buggy early versions and help you.</p> <p><strong>Obi:</strong> Stabilize it to the point where it's something that people can click a button and it works everywhere. I realized that the community of human rights defenders and later on also humanitarian organizations fit that, need. We really cared about that need and we were concerned, we wanted to help, but we realized that this product could help in combination with the rest of the Bitcoin ecosystem.</p> <p><strong>Obi:</strong> That's what's quite cool. FediMint is the thing that handles the custody, but you still need to buy things, sell things, find things, and so on, and that's where the Fedi app also comes into play, but without FediMint as the core to handle the custody, the rest didn't make sense.</p> <p><strong>Obi:</strong> Then we started, it was, then you had this sort of scene from like the Magnificent Seven or so on where you're, you're finding your initial team members. So we found Renato Rodriguez, I chased her for like six months ago. She should have, you know, got a restraining order for six months trying to get her to join.</p> <p><strong>Obi:</strong> just if you look at the initial team, it was just everybody, the whole team is amazing. But it was just trying to find these incredible people. they tended to just immediately understand the value proposition and the market we were trying to help and were already doing incredibly well in their own careers, but there was something missing for them.</p> <p><strong>Obi:</strong> And when they saw this, it was like this fulfilled There's some other need that they had beyond the monetary need. The potential was amazing, but the mission side of it was what helped us bring on this incredible team. So I believe in philosophy, people, process, product. The philosophy was amazing, who we're helping, the potential, it's helping people and in so doing we're helping Bitcoin, in so doing we're helping the world.</p> <p><strong>Obi:</strong> And that's a powerful philosophy and mission and that attracted this incredible group of people. And if you've got the philosophy and you've got an incredible group of people, they will put in the processes that will lead to the right product.</p> <p><strong>Obi:</strong> It's like, let's say the video, for example. I said to Renata, I want a really powerful launch video and it should be like the best Apple keynote speech combined with a UNICEF or Save the Children commercial. That's it. That's the whole brief and that whole video. And somebody says, you need to go to Madeira.</p> <p><strong>Obi:</strong> You need to say this. And I just woke up and I say what she says. But the whole elements of it, all of it was her and her team, Mary and marketing and everybody building that over the following X months. and I didn't actually see the video myself. Until less than a month before we launched it for the first time as a rough draft.</p> <p><strong>Obi:</strong> And it was just basically perfect. My comments were like, I actually didn't have any significant comments, but that was the same for most of the team and the design of the product. We had this incredible designer, Skylar. I would give a brief and so as, Erik's brief was, I just want to be proud of something that I should be proud of, and that was it, you know?</p> <p><strong>Obi:</strong> And I was like, it just needs to be really simple. And that's the high level. And I might give comments on a little bit here or there, but in general, whenever he gave me it, I would say, well, he Skylarized it, like just Skylarize it. And he would just come up with something that was great. and I think that was the last two years.</p> <p><strong>Obi:</strong> We had the team we raised. again, the choice of investors was really, really key. I was very, very sure, especially from my previous experiences, that I only wanted Bitcoin on the investors, especially for the first couple of rounds. And when I've sometimes do talks on how to set up a Bitcoin company, my first slide says don't do it, but instead sort of a Bitcoin business, not a Bitcoin startup.</p> <p><strong>Obi:</strong> And I explain the difference between the two. but one part is, if you do want to raise capital, be really careful about your choice of investors. The wrong investors will, well, and they don't mean to, but they will kill your business without meaning to, but the right investors will. So, we were really, really careful about our choice of investors and the initial team and then the initial team brought on the rest of the team after that.</p> <p><strong>Obi:</strong> And that was the last, that's the last two years we've set ourself up very well. I did, being a classic entrepreneur, think it'll take six months, took two years. So I, so my estimation on that was a little bit off, but the end result, I'm really excited about. And now, now we're, now we're off to the races.</p> <p>Great news, everyone! Bitcoin, the inverse of clown world is out now. It's the successor to everything divided by 21 million. And it's based on the last two years of podcasts that we've done together. So if you like the show, you're going to love the book. Find the book on bitcoininfinitystore. com or on Amazon.</p> <p>That's right. We have our own store now. BitcoinInfinityStore. com. You can find not just books, but merchandise based on everything divided by 21 million, check out Bitcoin, the inverse of Clown World today and buy some other stuff while you're there too.</p> <p>This show is brought to you by Bit Box, our favorite hardware wallet. It's Swiss engineered and has all the most important security features to keep your Bitcoin safe while keeping a user experience that even your grandma can use. So visit Bit Box. Do Swiss slash Freedom to learn more, or use Code Freedom at checkout for 5% off.</p> <p>And remember, it's the Bit Box zero two Bitcoin only edition. Make sure to get that Bitcoin only firmware.</p> <h1>How does Fedi Make Money?</h1> <p><strong>Knut:</strong> How does the app make money?</p> <p><strong>Obi:</strong> Yeah.</p> <p><strong>Knut:</strong> For the company?</p> <p><strong>Obi:</strong> if you use the app, whenever you use the Freddie app. whenever a transaction happens, which would have occurred a fee. So it's a Bitcoin transaction, e cash or a lightning transaction. We add on an additional fee, 21, 21 basis points. So 0.</p> <p><strong>Knut:</strong> Oh, yeah,</p> <p><strong>Obi:</strong> And so, and the good thing is because we can charge in sats and I believe actually even fractions of a sat, it's a progressive tax, which a fee.</p> <p><strong>Obi:</strong> So what I mean by that is. If you're sending, let's say 100 through, then you would be charged on 100. 21, but if you're, worth of value, but if you're sending through 1, then you'll be charged 0. 21 cents. And if you're sending through 0. 10, you'll be charged 0. 20. 0 to 1 cents. So it'll always be a very small percentage of what you're sending.</p> <p><strong>Obi:</strong> Now, people might say in certain countries, don't they have mobile money and so on. But the problem is those mobile money systems have minimum fees. And it might be, 1%, which is not that bad, say. And it might be, even in some terms of scale, it could be half a percent, but with a minimum fee of 20 cents.</p> <p><strong>Obi:</strong> So if you're sending a hundred dollars, that's okay. But if you're sending, 1, that's 20%. And so if you have someone who has a monthly salary of. 10 in some of these markets, that 0. 20 fee starts becoming quite a significant per transaction hit. So therefore it becomes unaffordable for you to use mobile money.</p> <p><strong>Obi:</strong> So even though it's prolific above a certain wealth level, and so that leaves many people out, in the rain. But because this is progressive, if you're selling 10 cents, the, fee will actually round to zero. I mean it will be a fee, but you'll see it in sats, but if you were showing, trying to show it in local currency, it would basically be, it'll say about zero and then you click and you realize it's this small amount of sats.</p> <p><strong>Knut:</strong> so, yeah. the big thing that I'm thinking of if I'm like. Playing this out in my head with where this could be in 10 years, like you could run entire virtual nations on a federation, right? If you have the money and the communication and whatever other useful apps,</p> <p><strong>Obi:</strong> I think the big thing I think is, if you look at the internet, there are large organizations where, people use and they're highly centralized. You have a few people who may be wealthy enough to have their own direct connection to the internet, but the majority of people are connected on the internet.</p> <p><strong>Obi:</strong> I don't know at this stage, millions of intranets, like household intranets effectively, company intranets and school intranets and so on, where it's one connection to the internet shared by multiple people. That's actually the majority of people. And it's that middle ground between these huge mega organizations that people are connected to one mainframe.</p> <p><strong>Obi:</strong> With millions of users, I think there are very few of them now, but that was the denominant way at the beginning. It was these huge, centralized ways of connecting AOL, CompuServe, and so on. Now, they're actually relatively rare, but that was at the beginning. All of the internet was that. A few centralized parties, and I would liken them, conceptually in value terms, in value custody terms versus information custody terms, to, a coin basis.</p> <p><strong>Obi:</strong> And also there were a lot of hobbyists who had their own direct ISDN connection to the internet. but now most people connect through these intranets where they get one router, one connection, and they share with everybody in their household. That would be a criminal of the Uncle Jim federations or in their school or in their football club or in their office.</p> <p><strong>Obi:</strong> That's probably 95 percent of people and I think that this approach of federated model from the size from. Five or six people up to five or six hundred thousand, that range can cover 80, 90 percent of usage.</p> <h1>How to Use Fedi(Mint)</h1> <p><strong>Luke:</strong> Can we go back to the basics of how feint works in the perspective of someone actually using this thing? So, you explained to us last time how it works, but just for my own sanity, check that I got it. if you are sending e cash within the federation, that is just.</p> <p><strong>Luke:</strong> Direct between two users. There's not even a record outside of that. No one knows those transactions are even happening. Is that essentially correct?</p> <p><strong>Obi:</strong> Yeah. So the federation helps you mint technically, because actually the user creates their own e cash, they create their own e cash, but it's unstamped and then they give it to the federation and they stick in an envelope. And they give it to the federation with some carbon copy paper on the inside the envelope as well.</p> <p><strong>Obi:</strong> the federation collectively signs. So let's say all four people go stamp, stamp, stamp. And that makes it valid. then they give back the envelope to the user. The user then opens the envelope with the cache that they created, just some random piece of data.</p> <p><strong>Obi:</strong> And they now have this Ucash, but the Ucash they've created now has got the four stamps on it, say, for the four of us. And so anyone else in that federation, any other, person who's also connected to the federation. They can just literally, directly give them this, random set of data.</p> <p><strong>Obi:</strong> Let's say it's a picture of a fashionable dog and they can just give it to someone else. and the person will receive it and they don't really care what the data says. They just look, are the four stamps on it? Yes. Then it means it was stamped by the Federation, which means it's backed by a certain amount of information.</p> <p><strong>Obi:</strong> Actual Bitcoin. Yeah. So take the whole, the full path. Someone deposits some Bitcoin in return. They also, along with the Bitcoin, send them an envelope, give them an envelope with this random piece of data in it to the Federation and the Federation receives the Bitcoin. Okay. I've received the Bitcoin envelope.</p> <p><strong>Obi:</strong> Okay. I've received the Bitcoin. I will stamp. I received one, let's say. 10, 000 Satoshis. So I'm going to take my 10, 000 Satoshi stamp and stamp this envelope with 10, 000 Satoshis, pass it around to the other four, they all stamp the 10, 000 Satoshi stamp. And then give that back to the user.</p> <p><strong>Obi:</strong> User opens the envelope and says, I've got, okay, I've got an e cash note with, with, that's been proven that the, that it's been validated by the guardians. So as long as we all trust the guardians are holding that and that they will honor this and redeem. That's it. So now I can pass it to anyone in the Federation.</p> <p><strong>Obi:</strong> They receive it. They look at this picture of the cute dog, but what they're really looking at is, is it got the four stamps on it and it's 10, 000. So that means I've now received 10, 000 token. They can now at some point in the future, Often they do it immediately if they've gone into connection, but they don't have to.</p> <p><strong>Obi:</strong> They can give it back to the Federation. Federation will receive it and each one will check their own signature of the guardians. Okay, it's properly signed. Therefore, I'm willing to, and they might give them a Bitcoin address to send the money on chain to.</p> <p><strong>Obi:</strong> So they will receive it, it looks good, they will then, record that this, e cash note has been spent. But they don't know, of all the e cash they received, which one it was, because each one they received in the first place was in an envelope. So was it the first one they received, or the middle one they received?</p> <p><strong>Obi:</strong> They have no idea. It could have been received yesterday or a month ago. No way. All they know is, I must have stamped it, so it was one of the ones I stamped. And then they will look at the address the person's asking to send the Bitcoin to, and they will take some of the Bitcoin that they're holding in the multi sig that we're holding between the four of us and send it to that address.</p> <p><strong>Obi:</strong> So that's called Redeem versus Mint. Now, the user experience from a user, we can get onto Lightning, that's another level of complexity, but it's simple just for Bitcoin and eCash for now.</p> <p><strong>Obi:</strong> Someone sends me Bitcoin or I send it to myself from an outside wallet and I receive e cash. And then someone else in the, in the federation wants to, once I want to pay them some e cash, they will give me, they will give me a QR code to, to scan to pay and I will scan. And literally the e cash that's on my phone gets sent to them directly.</p> <p><strong>Obi:</strong> From me to them, one to one, that person when they receive it could keep it on their phone or they could say, you know what, I want to send that back to the federation and they can send it back to the federation and then the federation can destroy that, issue them new, fresh e cash in different denominations, maybe not 10, 000, but 10, 1, 000, you know, just like with notes, you could go and get change.</p> <p><strong>Obi:</strong> Yeah, because if someone transacts, if you're saying it gets sent from one computer, phone being a computer, whatever, one device to another, well, that original device would still</p> <p><strong>Obi:</strong> Yes,</p> <p><strong>Luke:</strong> copy of the thing on, right.</p> <p><strong>Obi:</strong> So they will still have a copy. Now you are in the same, this is where the community aspect works, you are in the same community, If you're in the same community, and the person, it's a merchant and you receive, and your phone will remember when you received what e cash, yeah?</p> <p><strong>Obi:</strong> Even though it's private, you do know this e cash was received at this time and this time for, and so, especially when you integrate with points of sale, it will say, well, you received this e cash for this purchase. You'll know that. so then if you go to redeem it, at the end of the day, and some of it doesn't match, you will know as the merchant, which e cash was involved in that.</p> <p><strong>Obi:</strong> You'll say, well, the e cash involved in this transaction. And that transaction was with John. So you've got proof of work. it's the same as if you have a merchant and you receive cash and then you finally got the end of the day to a bank.</p> <p><strong>Obi:</strong> And some of the notes are counterfeit. Now, you don't find high levels of counterfeit notes in a community where people know each other. It's normally in these widespread communities. But in those scenarios, what most people will do and how the default way the app works is the moment you receive it, it immediately goes off and redeems it and then issues itself back new, new change.</p> <p><strong>Obi:</strong> Yeah, that seems like a good default implementation. but if you have no internet connectivity, you can still use it and still receive. even if you can't send over the internet, you can create a QR code, which contains the e cash in the QR code, and the person can literally scan it and receive through the screen.</p> <p><strong>Obi:</strong> Because as long as it's the QR code, the e cash note is just some text. So a QR code can represent that text and you can scan it, even if you have no data. So for example, it could be you're in an area where you have no data, rural, Latin America or so on. But it could also be something more innocuous.</p> <p><strong>Obi:</strong> You could just be in a big sort of, But the thing is is that you might be at a Glastonbury like concert and there are a thousand phones and there's no data. Or you're in an indoor conference place underground and there's no data. But you can still take payments or the merchant has internet because they're the ones who really need it.</p> <p><strong>Obi:</strong> But the buyer doesn't and so in which case the merchant has internet because they're connected wired in because they're fixed, but the buyer doesn't need to have internet to pay and the merchant will just take a risk just like in most merchants in high streets they accept a certain amount of breakage and a certain amount of transactions are gonna be charged back by, credit card companies and so on.</p> <p><strong>Obi:</strong> I used to be a CTO for a major pan-European, online auction company. At the time I was competing with, eBay and so on. we were in a headliner, 300 hundred people working for me in technology. It was a very big technology offering. And we were doing millions of transactions a week.</p> <p><strong>Obi:</strong> It was very high volume. And in those e commerce sites, you just accept a certain amount of breakage, a certain amount of returns, and a certain amount of chargebacks, even if you do nothing wrong and you just factor it into your costs. For the benefit of the simplicity of the experience.</p> <h1>Fedi and Nostr</h1> <p><strong>Knut:</strong> you mentioned Nostr before, like, what's the marriage between Fedi and Nostr? Well, I would say right now, we are, because I think.</p> <p><strong>Knut:</strong> we're beyond dating. We're engaged. But we want to really take the two footed tackle of no return, to use a football euphemism. a web of trust thing, right?</p> <p><strong>Obi:</strong> Yeah, I think, whenever, from the first point I saw Nostr, a lot of people thought it was just social media and so on.</p> <p><strong>Obi:</strong> I think social media is Trojan horse is the wrong word, but it's the, initial vector by which it infiltrates communities. But what you're actually doing is building a simple, trust system and a simple discovery system. It's a form of decentralized search and it's a form decentralized identity.</p> <p><strong>Obi:</strong> Cause you, to search, you have to identify things to be able to search. So they're sort of two sides of the same coin. now the first thing you're using it for is identifying people who want to speak publicly and share their thoughts and so on and so forth and follow them and give feedback and like.</p> <p><strong>Obi:</strong> But it always seemed to me to, way more powerful than that. And I think now people, generally understand it that way. And so, What we've already done, in Fedi, and a lot of developers really like the way it works, if you sign up to Fedi, or if you download the Fedi app and start using it, you, first of all, you don't need to give your email, you don't need to give your phone number because it's not required, but, we do ask you to come up with some sort of Username for yourself.</p> <p><strong>Obi:</strong> That doesn't even have to be unique, by the way. We will add a unique element at the end, from it. But what we do is, whenever you create that label, which you can change the name, but we create, an NSEC, which is a Nostr, identity effectively. A unique identity and we automatically create that for you.</p> <p><strong>Obi:</strong> So again, for our users, we don't want to start educating them on the history of Austrian economics and Bitcoin and inflation at the beginning or a Nostr, et cetera, and how it works and relays. And we just want them to start using it. then subtly over time we expose certain features of it. So people become curious and then eventually.</p> <p><strong>Obi:</strong> You want to learn how this thing that's delivering value works, but we've put proof of work first, proof of talk second. So we educate through letting people see the benefits. And then there might be some people might say, well, how does this car thing work? Or how does this fridge thing work? But I don't need to know how refrigerant works to be able to use a fridge or how microwaves work to use a microwave.</p> <p><strong>Obi:</strong> When they want to know how all this stuff works, but we benefit first. So, and so and that's how it works with Nostr We immediately give you an NSEC.</p> <p><strong>Obi:</strong> And so because we've got that if you go and use unleash. chat, for example within the app It will go and you click login and there's one option login by Nostr You click that and it'll just within the app pop up something saying Nostr Do you want to log in with Nostr? And you click yes, and you're logged in and it just works and then you, and then also now you're logged in and then you can, and then you click, deposit money and instead of having to go to a different app, copy and paste the QR codes, it just, it pops up and says, do you, this, this, what the app's asking you to deposit this amount of money?</p> <p><strong>Obi:</strong> Do you want to go ahead? Yes. And then it's e cash. Is, is converted into lightning and then that you pay by lightning. But from your point of view, there's a circling key for three or four seconds. You have now credited your account. Do you want to withdraw the money back account? You click withdraw the amount.</p> <p><strong>Obi:</strong> Three or four seconds, it's been withdrawn to your account and, and it's all within the same app. so, but that only works because now if you, close the app or delete the mods, because you can delete these mods or these additional pieces of functionality, they're basically webpages, but the icon for them, and they have an app like experience, but they're actually just webpages.</p> <p><strong>Obi:</strong> and then you go away and then you delete the app from your service. Like six months later, you come back, you, you, you enter your 12 words, you're, you're re log on. And then if you scan to join a federation again, it will recognize that you were a member of the federation before, and it will reconstitute and recreate all your e cash and put it back on your phone.</p> <p><strong>Obi:</strong> And then if you click on, Unleash your chat or Stacker News or anyone that supports logging by Nostr. Your login with the same details and so on. So you basically, and we want to make that even more seamless. So from 12 words, your entire life can you think about moving from one mobile phone to another, where you have to move all your apps, your banking apps, your chat apps.</p> <p><strong>Obi:</strong> And now you could do that with just go and also try moving from an iPhone to an Android phone, Android to an iPhone. It's a nightmare. Here you could just download the Fedi app on your iPhone. this is some far point in the future. You don't have just chat, but you also have voice. You have video, all of that running from encrypted chat.</p> <h1>12 Magic Words</h1> <p><strong>Obi:</strong> you have access to money from, custody and payments. You have access to all these apps and then you back up 12 words. And there's something we call social backup, which is mind blowing, but, that's in beta. But let's just say backup 12 words, and then you delete that app, go to a different phone, could be an Android or an iPhone, and you just enter 12 words, and your entire thing comes back.</p> <p><strong>Obi:</strong> Not partially back, but it all will come back. based on just those 12 words and that's only made possible because of Nostr and we want it over time.</p> <p><strong>Knut:</strong> mean, when you think about it, it's insane. It's already insane with bitcoins, with the 12 magic words, because like every time I pass a security check at an airport, I think that go ahead, have my 200 milliliters of toothpaste. I'll, I have my 12 magic words, like it's the ultimate fuck you to, to anyone trying to meddle with your business, right?</p> <p><strong>Knut:</strong> that's the dream. I mean, we're not fully there, but it's, I would say it's like, we're like 90 percent there, but to extend beyond just your Bitcoin, Nostr is the protocol that allows us to do that because it's notes and other stuff and the other stuff can be, an encrypted version of the settings and so on that you have that we can store and be willing to pay for.</p> <p><strong>Obi:</strong> And then when you recover, you have your bitcoin, but then you can go off and send a request to say here, I'm willing to recover this file. Here's some zaps for the file and you get the file back and that additional file then contains the information. Okay, these are the federations you are a member of, you rejoin them.</p> <p><strong>Obi:</strong> These are the mods that you had, they're reset up. These are the settings you had, they're reset up. And then you log on them automatically using Nostr as well, the NSEC and Nostr login. from your point of view as the user, 12 words, it's back. I mean, you might have to drink a cup of coffee while it's happening, but 5, 10, 20 minutes later, it's back.</p> <p><strong>Knut:</strong> it's amazing, and it's an inheritance plan. Like, you can live forever by just letting your descendants, giving them the 12 words when you're on your deathbed.</p> <p><strong>Obi:</strong> backup also becomes really powerful, because social backup means that, cause the 12 words is still another thing to secure. And it's sort of one of these turtles all the way down type scenarios. Okay. We've got all this incredible security Fort Knox like, but behind them, but I walk around the back of the Fort Knox is these 12 words that's stored.</p> <p><strong>Obi:</strong> you also give one to your cousin and you say, look after this as a backup. And your cousin stores it on a fridge magnet. You know, you don't know, or you don't know your, your, your security is the lowest common denominator.</p> <p><strong>Obi:</strong> For your 12 words. And</p> <p><strong>Knut:</strong> is never stronger than the weakest</p> <p><strong>Obi:</strong> then the weakest link. And so with social backup, which is definitely an early beta. what we can do is use the power of the federation where we can take your 12 words, encrypt them and then split it up between the four guardians in this case, or seven guardians or 40 guardians or whatever.</p> <p><strong>Obi:</strong> For larger federations, and they all hold a piece of your encrypted piece of your, of</p> <p><strong>Knut:</strong> is important here.</p> <p><strong>Obi:</strong> Yeah.</p> <p>Knut, what are you doing over there? I'm stamping my seed. Everyone tells me I should, that it's good for bitcoin security and whatnot, and that I should go balls deep into bitcoin security, so I'm stamping. You don't do it like that, Knut. You don't stamp that seed. You stamp your seed phrase. What? Your seed phrase.</p> <p>Oh, so that's what these things are for. oh, I get it now. That's exactly right, Knut. And you can get everything you need to stamp your seed phrase at stampseed. com. And be sure to check out our limited edition Everything Divided by 21 Million Titanium Seed Plate.</p> <p>And use code INFINITY at checkout for 15 percent off. That's fantastic! And it hurts way less!</p> <h1>Redundancy in Fedi</h1> <p><strong>Luke:</strong> So this gets me back to what happens when one of the guardians drops off, and if it's like in a permanent way, if that one guardian is holding a piece of everyone else's 12 words, does everyone</p> <p><strong>Obi:</strong> Yeah. But it uses a prot, this is crypto, where cryptography comes in. So it's not like. We've taken your 12 words and split it up free between four guardians. Instead, you encrypt it using a scheme that allows each one of the four of us to have a cryptographic piece.</p> <p><strong>Obi:</strong> But as long as any three of us combine our piece together, we can recombine. It is, it's called, SHAIR Secret Sharing Scheme, but it's a way of cryptographically achieving that.</p> <p><strong>Luke:</strong> Excellent, I think you mentioned last time as well that if a guardian does go down, essentially you can replace that guardian, can you take us through that, adding or replacing a guardian if that ever were to need to happen?</p> <p><strong>Obi:</strong> replacing a garden is, probably one of the most complex things. And so you wouldn't necessarily replace a guardian, but what you would do is, some, if someone were to go down, there's two different things. The machine. Or the guardian, the actual person. So if the machine goes down, you can set up a new machine and you can recover the status of that.</p> <p><strong>Obi:</strong> You can, you can download the 30 minute software on that new machine. So that's the actual server that's running. And that will then connect to the rest of the federation and, and carry on. So as long as the guardian has a backup of their keys, they can recover that one machine and, and catch up and it'll automatically catch up.</p> <p><strong>Obi:</strong> Just like if you turn off a Bitcoin node and turn it on, it will reconnect to the Bitcoin network and catch up. It's a similar concept. so that's if a machine went down, if a machine was temporarily disconnected from the internet or, lost power, it would just restart and reconnect and you will have zero downtime as a user, as long as it's still running and active.</p> <p><strong>Obi:</strong> And this will all be, you'll notice that the performance will still be the same, but if you went into settings for that federation, you'll see that three of the four are running, so one is not running, but that won't affect your usage.</p> <p><strong>Obi:</strong> Is the N of M like a ratio, or is it always N 1, for example? It's a ratio. the number of guardians that, you need to have is dependent on how much redundancy. So if you want to be able to handle one guardian going down, then you'll need to have, one times by three plus one. So that's four. So that's why you need three or four.</p> <p><strong>Obi:</strong> if you want to handle two going down, then you need two times by three plus one, which is seven. So it's five of seven. 7 of 10, 9 of 13, and so on and so forth. You can have more than that, but the time that you get additional redundancy is every 3, but you can have, for example, 4 of 5, if you wanted to.</p> <p><strong>Obi:</strong> Anyway, so, yeah, in the event that someone goes down, that the machine goes down, you can recover. recently there was an issue where one machine, where two federations, had an issue with the domain name for one of those servers. And so if the domain name for someone is no longer available, you can now, with the update that came out a couple of weeks after that, you can modify, the domain name</p> <p><strong>Obi:</strong> for a Guardian 30 minute server, and it would communicate that securely with the other, Federation servers and then reconnect and, continue to operate. But it's important to, even in that scenario where the Federa Guardian, the domain name server went down, the Federation itself, Continue to operate because there was still at least free running.</p> <p><strong>Obi:</strong> So there was no downtime for the user. Whereas if, if we hadn't been federated, then for the one week or so where that was down, the users would have had no access at all, which would be the case where you're connecting to a centralized or a single server, offering. now, if one of the guardians, for some reason, the actual people who are running the Fedemyst server, for some reason, you no longer trusted them, they'd been helpful all their life and all of a sudden they decided, or they've been turned by some, malevolent nefarious actor.</p> <p><strong>Obi:</strong> Then you, if you could in theory pass to someone else, but in practice, you know, how do I know that the other person isn't still going to continue to operate it and so on and so forth. So what you actually want to do is set up a different federation and transfer people, the other three guardians and inform people with a different set of four people.</p> <p><strong>Obi:</strong> So those three, plus someone else. And just tell people to transfer their balances across. But transferring balances across is as easy as doing a lightning transaction from one server to another. You can, you know, within the FEDI app, be a member of multiple federations at the same time. I mean, right now, I mean, I'm a bit of a power user, but I'm a member of, over a dozen different federations from around the world.</p> <p><strong>Obi:</strong> I mean, well over a dozen, I think, yeah. and as we've, I'm sure there's people in the team with way more than that. but obviously I can't advertise the names because many of them are private federations. So, but there's a few public ones, but there's way more private ones.</p> <h1>Interoperability</h1> <p><strong>Luke:</strong> So is the e cash, if you're in multiple federations, is it interoperable there, or it's like a more like a, it's a lightning transaction between those two federations, but it's e cash that lives</p> <p><strong>Obi:</strong> You got it. It's, E cash lives within its federation, but the interoperability layer for most people is not on chain. It's for the vast majority of people, it's Lightning, so, but the user experience of sending e cash from one person to another in the same federation, sending e cash from one person to someone else receiving Lightning.</p> <p><strong>Obi:</strong> on a different wallet that's got nothing to do with Ferdie Mint. And finally sending e cash from one person in one federation. To someone else in another federation over the Lightning Network in between is exactly the same. From your point of view, QR code scan and the system will combination of the Fedi app and or whatever Fedi Mint compatible app you're using and Fedi Mint servers will make the experience</p> <p><strong>Obi:</strong> I just need to send the person the cash. In this case I can send e cash out over Lightning and that's my job is done. And then the other side would be a Lightning wallet and it will receive. And in this case, I will send e cash over Lightning to another federation, but I don't even know if it's another federation, it's just a Lightning address.</p> <p><strong>Obi:</strong> And then the other federation, receives the transaction and the other 30 minute server receives e cash on the other side. But from a user's point of view, this is the thing that also took the two years to make the experience the same. You just don't have to worry about which one is doing.</p> <p><strong>Obi:</strong> The fees will be slightly different. One won't have a Lightning component to the fee, e cash to e cash, but, the other two will because it will be like, in both cases, it will be e cash to Lightning, from your point of view.</p> <p><strong>Luke:</strong> So is there a fee to send e cash to someone else in the same federation? No, I guess. Right.</p> <p><strong>Obi:</strong> It depends on the federation. the federation, could choose not to charge a fee and many in these times choose not to because they're doing it for friends and family and so on and the fees are minimal. the Ferryman protocol does support, what we call a DDoS fee. So basically you're spending effort time</p> <p><strong>Obi:</strong> to sign these notes, the issuing is done by the user, but the stamping takes time. you're signing something cryptographically, that's effort. and you're also doing it in a federated manner, so you're coordinating and then you're all collectively signing.</p> <p><strong>Obi:</strong> So, to avoid DDoS, you can turn on a fee and, by our calculations, it doesn't need to be very large, one sat per note that issued is enough to prevent, because if someone really tried to DDoS you at scale, they could, but on normal sort of consumer laptops or hardware, they'll have to spend, hundreds of thousands a month at that sort of, one sat per note, and in which case you'll say, fine, you're giving me hundreds of thousands of dollars worth of Bitcoin to burn my, CPU.</p> <p><strong>Obi:</strong> Well, not to burn it, but just to heat my CPU. so you can charge a fee. And I think some will experiment with charging a DDoS fee, which is similar to Bitcoin. the fees in Bitcoin are a DDoS protection vector. So it's the same concept.</p> <h1>Fedi's Roadmap</h1> <p><strong>Knut:</strong> All right. So, what's on the roadmap? What's going on? How does the future look like? What will you be working on the next five years? And where do you see FedeMint going?</p> <p><strong>Obi:</strong> that's actually, the most, fun phase. up until now, we had a hypothesis and we had some early feedback, but a lot of it was based on, A hypothesis and theory as to what we thought people needed and we felt that freedom technology had got to a stage where they were good enough to provide this combined experience.</p> <p><strong>Obi:</strong> And that was a hypothesis. And we think we've got early validation, but we built that. Now it's life. And now it's the fun, but it's also the scary bit because we now actually see people using it and we test all our hypothesis. And this is the point where you have to be very detail oriented, very much listening to the users and listening to what they say</p> <p><strong>Obi:</strong> we cannot ignore if there are. Parts of our hypothesis that are incorrect, we have to adjust to support that. So it's going to be a lot of listening and we've already got hundreds of requests for feedback. and then working to rectify, or deal with the questions or feedback they've given us or the suggestions they've given us.</p> <p><strong>Obi:</strong> and we're going to continue to iterate and then we bring it back out to users and see what they think. And we keep in that loop. This is the market product fit loop until. The product that we produce, fits the requirements of the market. Now, again, I, I'm hoping that takes six months or less, just like I hoped it took six months or less</p> <p><strong>Obi:</strong> for the initialization phase, but it might take less. It might take a bit more, but it's fun. and that's the next phase. After that, we then go into the growth phase. Once we know we've got something that's repeatable, that really. is at the quality level that users need for it to be used a daily part of their life.</p> <p><strong>Obi:</strong> We'll then go into growth phase and that's where we'll really, you know, pull down, put our pedal to the metal and, and just repeat, repeat, repeat until. You know, billions of people are using this around the world, but that, that's phase three. And I'm, I'm very focused on this phase. You don't want to rush into phase three.</p> <p><strong>Obi:</strong> We're not going to rush to grow the numbers, until we are very sure that we've got something that's really slick, really reliable, and where we're meeting a clear demonstrable demand consistently. And that process is called human centered design. So it's not focused on this is my app, this is what I want, and I'm going to keep trying to make you agree with what I want.</p> <p><strong>Obi:</strong> this is what we've built. This is our first stab at it, but we're going to keep iterating until it serves your need properly. And that might require some, this is what makes this one very hard because it requires a very different mindset to the phase one. Phase one is like We can do everything and the impossible is possible phase two is really being pragmatic.</p> <p><strong>Obi:</strong> Or very self critical and being very open to killing your darlings, as the saying goes, you know, and saying this is not working or, or there's some fundamental issue. I mean, I don't think this will be the case at this stage, but if the feedback was from our market that we need to make some fundamental changes that would mean that 80 percent of the code we built has to be thrown away and have to start again.</p> <p><strong>Obi:</strong> Well, that's what we're being told. we've got far enough to think that's highly unlikely. cause most of the feedback, like some of the big pieces of feedback cause how can we make it easier to set up federations? So that's a really good sign because lots of people said there's only going to be a demand for like free federations and it's going to be very centralized.</p> <p><strong>Obi:</strong> Well, a very large percentage. I don't want to give it. These are the very large percentage of all our queries so far have been, how can I set my own federation up? So even based on those queries, there's not going to be free. You know, I can put it that way.</p> <p><strong>Luke:</strong> Super quick question on that, I guess, is it the Fetiman software? Is it on, for example, the note in a box, solutions, the umbrellas, start nines, et</p> <p><strong>Obi:</strong> Well, that's part of the feedback that we're getting. For example, can we set it up? Can you integrate with Umbro? Can you integrate with Start9? Can you integrate with RastyBlitz? can you make it simpler to set up? So, I think, a lot of that's done by the FediMint team.</p> <p><strong>Obi:</strong> Because remember, FediMint is an OpusSource project versus a different OpusSource project. At some point in the future, it will be two different open source projects. However, we are using them as the bedrock, because if you want to custody significant amounts of value We know that you want to go multisig.</p> <p><strong>Obi:</strong> Multisig for significant amounts of value is the best standard, and also you want privacy, so then privacy and multisig, that's FedEvent, basically. but, on the FedE side, we can do a lot as well. So we can provide, even though it's open source software, we can take it and provide it.</p> <p><strong>Obi:</strong> again, it will be open source, but tools to help you build it really easily or put efforts to integrate with people like Umbrell and Start9. we've already had an integration with an organization called Clover, which we've been working on, and you're going to see more on that. But from our point of view, that's a lot of where the work is.</p> <p><strong>Obi:</strong> Also you want to connect this to the Lightning Network. And connected to the Lightning Network and maintaining a reliable connection is not easy. it can be complicated for people, especially managing liquidity. And now again, over time, I could get easier, but right now it's not easy.</p> <p><strong>Obi:</strong> There are organizations like, Breeze and others who make that easy. and you just saw an announcement from Erik, where they've already started, showing connectivity and support for LDK, which is this cross, LSP standard. So, again, we at Fedi can provide tools for FediMint, or people who are using FediMint, whether it's with Fedi or someone else, that make it really easy.</p> <p><strong>Obi:</strong> And again, our aim is one click, and you have a connection. You can set up your own lightning node that's set up in a relatively good way, so it'd be relatively reliable, but you don't have to manage it yourself. Or, you can connect to one of these LSP's and for a fee, they'll just handle all the light and management, but you're still in a trust minimized way.</p> <p><strong>Obi:</strong> So there's, but given all the feedback we're getting, it's not, this is completely wrong. You need to go back to the drawing board, it's all, okay, I get it, but you need to go further. You need to integrate with more. You need to make it easier. so that's a good sign that we're on the right track.</p> <p><strong>Knut:</strong> Yeah. So, what about this date when you go open source? is that public or, when you have to go open source, it might be then or</p> <p><strong>Obi:</strong> in the, it's, it's, it's memorializing the business source license. In fact, we memorialized it. We actually have this memo memorializing when it happened. when we launched Freddy, we, we did this thing on the Bitcoin block. You can see it. We were established on a certain block.</p> <p><strong>Obi:</strong> And we said Fedi is here. When we, quietly on May the 4th, we also put something that said Fedi colon and it was a hash. That hash is a hash of a memo. And the memo, which is on our, Fedi's got an open source, you can see the link and you can verify it. Showed that on May the 4th, the code became business source license.</p> <p><strong>Obi:</strong> And by January the 3rd, 2026 or earlier, we must go, open source. And if we were to shut down or to stop development, we will instantly go open source. and so, so that, and we put it in block. I tried to find a core block. So it was block 8, 42069. It was actually was the block that was the core block as well.</p> <p><strong>Obi:</strong> so yeah, it's, it's there. And, that's the date. We, we cannot go open source later than that. And we may very well go open source a lot earlier than that.</p> <h1>Wrapping Up</h1> <p><strong>Luke:</strong> Hey Obi, I think we could keep on grilling you on this and that little detail, but this has been really enlightening, fantastic to see how far this has come, even since our last conversation back in October, and yeah, just looking forward to everything you guys are doing, and I guess just as a last thing, people can now grab the Fedi app and Public federations are available to start to try</p> <p><strong>Obi:</strong> federations and there are, and you can set up your own federation There's a lot, I don't like to talk too much about what's coming in future because we just work on everything in order of customer demands. So if customer demand comes in, that changes the order, but we're working really hard to make it, It's already easy for if you're quite technical, but we're going to make it easier and easier to set up a federation, so keep looking out because that's a very common request to set up a federation yourself, and we want to see what people do with it, create Fedi mods, create federations, use it, give us feedback, and we will continue to work on making an incredible, Open source interface portal to this freedom technology world.</p> <p><strong>Luke:</strong> Absolutely fantastic. We'll need to keep on having these conversations regularly, get updates because always fantastic to hear about this and good luck moving forward and I think we'll be trying some FETI stuff in our futures here. Lots of cool things have come out of Nostriga and Baltic. Honey Badger by</p> <p><strong>Luke:</strong> I'm exciting to see that. And anywhere else you want to direct our listeners and viewers.</p> <p><strong>Obi:</strong> So for Fedi, that's probably the best place because everything, that's a jumping off ground for everything else. And that's Fedi, F E D I dot X, Y, Z.</p> <p><strong>Luke:</strong> Fantastic.</p> <p><strong>Obi:</strong> One of the cooler things that came out in Nostriga and Honeybadger was of course, yes, the inverse of clown world, our new book, and we want to give you one. if you're not given one during this weekend, you'll find it on bitcoininfinitystore. com. Thank you very much.</p> <p><strong>Luke:</strong> and we need to sign it for you. Yeah, we'll do that offline. But Obi, thank you again. And this has been the Bitcoin Infinity Show. Thank you for listening.</p> <p><strong>Obi:</strong> Thanks.{\rtf1\adeflang1025\ansi\ansicpg1252\uc1\adeff0\deff0\stshfdbch0\stshfloch0\stshfhich0\stshfbi0\deflang1033\deflangfe1033\themelang1033\themelangfe0\themelangcs0{\fonttbl{\f0\fbidi \froman\fcharset0\fprq2{*\panose 02020603050405020304}Times New Roman;}{\f34\fbidi \froman\fcharset0\fprq2{*\panose 02040503050406030204}Cambria Math;} {\flomajor\f31500\fbidi \froman\fcharset0\fprq2{*\panose 02020603050405020304}Times New Roman;}{\fdbmajor\f31501\fbidi \froman\fcharset0\fprq2{*\panose 02020603050405020304}Times New Roman;}{\fhimajor\f31502\fbidi \fswiss\fcharset0\fprq2 Aptos Display;} {\fbimajor\f31503\fbidi \froman\fcharset0\fprq2{*\panose 02020603050405020304}Times New Roman;}{\flominor\f31504\fbidi \froman\fcharset0\fprq2{*\panose 02020603050405020304}Times New Roman;} {\fdbminor\f31505\fbidi \froman\fcharset0\fprq2{*\panose 02020603050405020304}Times New Roman;}{\fhiminor\f31506\fbidi \fswiss\fcharset0\fprq2 Aptos;}{\fbiminor\f31507\fbidi \froman\fcharset0\fprq2{*\panose 02020603050405020304}Times New Roman;} {\f1311\fbidi \froman\fcharset238\fprq2 Times New Roman CE;}{\f1312\fbidi \froman\fcharset204\fprq2 Times New Roman Cyr;}{\f1314\fbidi \froman\fcharset161\fprq2 Times New Roman Greek;}{\f1315\fbidi \froman\fcharset162\fprq2 Times New Roman Tur;} {\f1316\fbidi \froman\fcharset177\fprq2 Times New Roman (Hebrew);}{\f1317\fbidi \froman\fcharset178\fprq2 Times New Roman (Arabic);}{\f1318\fbidi \froman\fcharset186\fprq2 Times New Roman Baltic;} {\f1319\fbidi \froman\fcharset163\fprq2 Times New Roman (Vietnamese);}{\f1651\fbidi \froman\fcharset238\fprq2 Cambria Math CE;}{\f1652\fbidi \froman\fcharset204\fprq2 Cambria Math Cyr;}{\f1654\fbidi \froman\fcharset161\fprq2 Cambria Math Greek;} {\f1655\fbidi \froman\fcharset162\fprq2 Cambria Math Tur;}{\f1658\fbidi \froman\fcharset186\fprq2 Cambria Math Baltic;}{\f1659\fbidi \froman\fcharset163\fprq2 Cambria Math (Vietnamese);} {\flomajor\f31508\fbidi \froman\fcharset238\fprq2 Times New Roman CE;}{\flomajor\f31509\fbidi \froman\fcharset204\fprq2 Times New Roman Cyr;}{\flomajor\f31511\fbidi \froman\fcharset161\fprq2 Times New Roman Greek;} {\flomajor\f31512\fbidi \froman\fcharset162\fprq2 Times New Roman Tur;}{\flomajor\f31513\fbidi \froman\fcharset177\fprq2 Times New Roman (Hebrew);}{\flomajor\f31514\fbidi \froman\fcharset178\fprq2 Times New Roman (Arabic);} {\flomajor\f31515\fbidi \froman\fcharset186\fprq2 Times New Roman Baltic;}{\flomajor\f31516\fbidi \froman\fcharset163\fprq2 Times New Roman (Vietnamese);}{\fdbmajor\f31518\fbidi \froman\fcharset238\fprq2 Times New Roman CE;} {\fdbmajor\f31519\fbidi \froman\fcharset204\fprq2 Times New Roman Cyr;}{\fdbmajor\f31521\fbidi \froman\fcharset161\fprq2 Times New Roman Greek;}{\fdbmajor\f31522\fbidi \froman\fcharset162\fprq2 Times New Roman Tur;} {\fdbmajor\f31523\fbidi \froman\fcharset177\fprq2 Times New Roman (Hebrew);}{\fdbmajor\f31524\fbidi \froman\fcharset178\fprq2 Times New Roman (Arabic);}{\fdbmajor\f31525\fbidi \froman\fcharset186\fprq2 Times New Roman Baltic;} {\fdbmajor\f31526\fbidi \froman\fcharset163\fprq2 Times New Roman (Vietnamese);}{\fhimajor\f31528\fbidi \fswiss\fcharset238\fprq2 Aptos Display CE;}{\fhimajor\f31529\fbidi \fswiss\fcharset204\fprq2 Aptos Display Cyr;} {\fhimajor\f31531\fbidi \fswiss\fcharset161\fprq2 Aptos Display Greek;}{\fhimajor\f31532\fbidi \fswiss\fcharset162\fprq2 Aptos Display Tur;}{\fhimajor\f31535\fbidi \fswiss\fcharset186\fprq2 Aptos Display Baltic;} {\fhimajor\f31536\fbidi \fswiss\fcharset163\fprq2 Aptos Display (Vietnamese);}{\fbimajor\f31538\fbidi \froman\fcharset238\fprq2 Times New Roman CE;}{\fbimajor\f31539\fbidi \froman\fcharset204\fprq2 Times New Roman Cyr;} {\fbimajor\f31541\fbidi \froman\fcharset161\fprq2 Times New Roman Greek;}{\fbimajor\f31542\fbidi \froman\fcharset162\fprq2 Times New Roman Tur;}{\fbimajor\f31543\fbidi \froman\fcharset177\fprq2 Times New Roman (Hebrew);} {\fbimajor\f31544\fbidi \froman\fcharset178\fprq2 Times New Roman (Arabic);}{\fbimajor\f31545\fbidi \froman\fcharset186\fprq2 Times New Roman Baltic;}{\fbimajor\f31546\fbidi \froman\fcharset163\fprq2 Times New Roman (Vietnamese);} {\flominor\f31548\fbidi \froman\fcharset238\fprq2 Times New Roman CE;}{\flominor\f31549\fbidi \froman\fcharset204\fprq2 Times New Roman Cyr;}{\flominor\f31551\fbidi \froman\fcharset161\fprq2 Times New Roman Greek;} {\flominor\f31552\fbidi \froman\fcharset162\fprq2 Times New Roman Tur;}{\flominor\f31553\fbidi \froman\fcharset177\fprq2 Times New Roman (Hebrew);}{\flominor\f31554\fbidi \froman\fcharset178\fprq2 Times New Roman (Arabic);} {\flominor\f31555\fbidi \froman\fcharset186\fprq2 Times New Roman Baltic;}{\flominor\f31556\fbidi \froman\fcharset163\fprq2 Times New Roman (Vietnamese);}{\fdbminor\f31558\fbidi \froman\fcharset238\fprq2 Times New Roman CE;} {\fdbminor\f31559\fbidi \froman\fcharset204\fprq2 Times New Roman Cyr;}{\fdbminor\f31561\fbidi \froman\fcharset161\fprq2 Times New Roman Greek;}{\fdbminor\f31562\fbidi \froman\fcharset162\fprq2 Times New Roman Tur;} {\fdbminor\f31563\fbidi \froman\fcharset177\fprq2 Times New Roman (Hebrew);}{\fdbminor\f31564\fbidi \froman\fcharset178\fprq2 Times New Roman (Arabic);}{\fdbminor\f31565\fbidi \froman\fcharset186\fprq2 Times New Roman Baltic;} {\fdbminor\f31566\fbidi \froman\fcharset163\fprq2 Times New Roman (Vietnamese);}{\fhiminor\f31568\fbidi \fswiss\fcharset238\fprq2 Aptos CE;}{\fhiminor\f31569\fbidi \fswiss\fcharset204\fprq2 Aptos Cyr;} {\fhiminor\f31571\fbidi \fswiss\fcharset161\fprq2 Aptos Greek;}{\fhiminor\f31572\fbidi \fswiss\fcharset162\fprq2 Aptos Tur;}{\fhiminor\f31575\fbidi \fswiss\fcharset186\fprq2 Aptos Baltic;} {\fhiminor\f31576\fbidi \fswiss\fcharset163\fprq2 Aptos (Vietnamese);}{\fbiminor\f31578\fbidi \froman\fcharset238\fprq2 Times New Roman CE;}{\fbiminor\f31579\fbidi \froman\fcharset204\fprq2 Times New Roman Cyr;} {\fbiminor\f31581\fbidi \froman\fcharset161\fprq2 Times New Roman Greek;}{\fbiminor\f31582\fbidi \froman\fcharset162\fprq2 Times New Roman Tur;}{\fbiminor\f31583\fbidi \froman\fcharset177\fprq2 Times New Roman (Hebrew);} {\fbiminor\f31584\fbidi \froman\fcharset178\fprq2 Times New Roman (Arabic);}{\fbiminor\f31585\fbidi \froman\fcharset186\fprq2 Times New Roman Baltic;}{\fbiminor\f31586\fbidi \froman\fcharset163\fprq2 Times New Roman (Vietnamese);}} {\colortbl;\red0\green0\blue0;\red0\green0\blue255;\red0\green255\blue255;\red0\green255\blue0;\red255\green0\blue255;\red255\green0\blue0;\red255\green255\blue0;\red255\green255\blue255;\red0\green0\blue128;\red0\green128\blue128;\red0\green128\blue0; \red128\green0\blue128;\red128\green0\blue0;\red128\green128\blue0;\red128\green128\blue128;\red192\green192\blue192;\red0\green0\blue0;\red0\green0\blue0;\red102\green0\blue204;\red114\green179\blue114;\red222\green74\blue29;}{*\defchp }{*\defpap \ql \li0\ri0\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0 }\noqfpromote {\stylesheet{\ql \li0\ri0\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0 \rtlch\fcs1 \af0\afs20\alang1025 \ltrch\fcs0 \fs20\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 \snext0 \sqformat \spriority0 \styrsid13517917 Normal;}{\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 \snext1 \slink15 \sqformat \spriority9 \styrsid13517917 heading 1;}{*\cs10 \additive \sunhideused \spriority1 \styrsid13517917 Default Paragraph Font;}{* \ts11\tsrowd\trftsWidthB3\trpaddl108\trpaddr108\trpaddfl3\trpaddft3\trpaddfb3\trpaddfr3\trcbpat1\trcfpat1\tblind0\tblindtype3\tsvertalt\tsbrdrt\tsbrdrl\tsbrdrb\tsbrdrr\tsbrdrdgl\tsbrdrdgr\tsbrdrh\tsbrdrv \ql \li0\ri0\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0 \rtlch\fcs1 \af0\afs20\alang1025 \ltrch\fcs0 \fs20\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 \snext11 \ssemihidden \sunhideused Normal Table;}{*\cs15 \additive \rtlch\fcs1 \ab\af0\afs48 \ltrch\fcs0 \b\fs48 \sbasedon10 \slink1 \spriority9 \styrsid13517917 Heading 1 Char;}{\s16\ql \li0\ri0\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0 \rtlch\fcs1 \ab\af0\afs56\alang1025 \ltrch\fcs0 \b\fs56\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 \snext16 \slink17 \sqformat \spriority10 \styrsid13517917 Title;}{*\cs17 \additive \rtlch\fcs1 \ab\af0\afs56 \ltrch\fcs0 \b\fs56 \sbasedon10 \slink16 \spriority10 \styrsid13517917 Title Char;}{\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 \snext18 \spriority0 \styrsid13517917 Script ;}}{*\rsidtbl \rsid3088390\rsid4943407\rsid13517917}{\mmathPr\mmathFont34\mbrkBin0\mbrkBinSub0\msmallFrac0\mdispDef1\mlMargin0\mrMargin0\mdefJc1\mwrapIndent1440\mintLim0\mnaryLim1}{*\xmlnstbl {\xmlns1 http://schemas.microsoft.com/office/word/2003/wordm l}}\paperw11906\paperh16838\margl1440\margr1440\margt1440\margb1440\gutter0\ltrsect \widowctrl\ftnbj\aenddoc\trackmoves0\trackformatting1\donotembedsysfont1\relyonvml0\donotembedlingdata0\grfdocevents0\validatexml1\showplaceholdtext0\ignoremixedcontent0\saveinvalidxml0\showxmlerrors1\noxlattoyen \expshrtn\noultrlspc\dntblnsbdb\nospaceforul\formshade\horzdoc\dgmargin\dghspace180\dgvspace180\dghorigin1701\dgvorigin1984\dghshow1\dgvshow1 \jexpand\pgbrdrhead\pgbrdrfoot\splytwnine\ftnlytwnine\htmautsp\nolnhtadjtbl\useltbaln\alntblind\lytcalctblwd\lyttblrtgr\lnbrkrule\nobrkwrptbl\snaptogridincell\allowfieldendsel\wrppunct\asianbrkrule\rsidroot13517917 \newtblstyruls\nogrowautofit\usenormstyforlist\noindnmbrts\felnbrelev\nocxsptable\indrlsweleven\noafcnsttbl\afelev\utinl\hwelev\spltpgpar\notcvasp\notbrkcnstfrctbl\notvatxbx\krnprsnet\cachedcolbal \nouicompat \fet0{*\wgrffmtfilter 2450} \nofeaturethrottle1\ilfomacatclnup0\ltrpar \sectd \ltrsect\linex0\headery708\footery708\colsx708\endnhere\sectlinegrid360\sectdefaultcl\sectrsid13517917\sftnbj {*\pnseclvl1\pnucrm\pnstart1\pnindent720\pnhang {\pntxta .}}{*\pnseclvl2 \pnucltr\pnstart1\pnindent720\pnhang {\pntxta .}}{*\pnseclvl3\pndec\pnstart1\pnindent720\pnhang {\pntxta .}}{*\pnseclvl4\pnlcltr\pnstart1\pnindent720\pnhang {\pntxta )}}{*\pnseclvl5\pndec\pnstart1\pnindent720\pnhang {\pntxtb (}{\pntxta )}}{*\pnseclvl6 \pnlcltr\pnstart1\pnindent720\pnhang {\pntxtb (}{\pntxta )}}{*\pnseclvl7\pnlcrm\pnstart1\pnindent720\pnhang {\pntxtb (}{\pntxta )}}{*\pnseclvl8\pnlcltr\pnstart1\pnindent720\pnhang {\pntxtb (}{\pntxta )}}{*\pnseclvl9\pnlcrm\pnstart1\pnindent720\pnhang {\pntxtb (}{\pntxta )}}\pard\plain \ltrpar\s16\ql \li0\ri0\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs56\alang1025 \ltrch\fcs0 \b\fs56\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 BIS130 - Transcript \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Welcome to the Bitcoin Infinity Show, brought to you by BitBox Stampseed, the Bitcoin Advisor and ShopInBit. Enjoy the conversation. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Welcoming Obi Nwosu \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Obi, welcome for the first time to the Bitcoin Infinity Show. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 well, \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 We rebranded. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 what is time in infinity? No, no, it's the second time, great to have you back. yeah, we have, it's been a wild ride and the journey is just beginning. So yeah, thank you. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 The Launch of Fedi \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917\ \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 so Fedimin launched, two weeks ago. Is it the Fedi \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Fedi, launched? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 launched? Yeah. These terms. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 no, no, Fedi Mint launched, effectively Fedi Mint launched nearly five years ago. FediMint is a very old technology, very, you know, the first, the first FediMint transaction, where someone used FediMint e cash over Lightning to buy a cup of coffee, whic h was after, you know, a year plus of development was on, I believe it was the 3rd of the 8th, 3rd of August, 2021. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And so we're trying to, like you have a Bitcoin Infinity Day, we're suggesting, that was actually Erik, my, the inventor of Fedi Mint. from Parinelli Police, just actually, and so I like to think of that as e cash coffee day. Cause actually it was like, you actually bought the cup of coffee with e cash. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 so yeah, but yeah, Fedi finally launched two weeks ago. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 All right. so I think, for those who haven't seen the previous episode with you, if they want to know more about you, we should probably go back to that episode, but I think you're going to have to do the TLDR on what Fedi is for our listeners. Like that 's a good start, I think. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So yeah, and now we can be clear about what Fedi is. And so Fedi, is two things still. Even Fedi is two things. One is the company called Fedi and the other is this product called Fedi. So if we talk about the product that people have on their phone, Fed i is a community super app. And so it's an app that takes the best of freedom technology. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 it's got Bitcoin functionality in it, Lightning connectivity, obviously FediMint for handling community custody. but it's also got Nostr support and any other freedom technology that's out there that's mature and reliable. We've taken the time to integra te into one simple to use app. So it allows you to have chat. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 We use Matrix as this federated, decentralized, encrypted chat protocol. It has money with the combination of Lightning, Bitcoin, and Fediment and more. So it has a built in web browser inside it. And therefore you can access all of the Bitcoin ecosystem of apps from Bitrefill to Unleash. chat to BTCmaps and beyond. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 All in one place. So you don't have to have this smorgasbord of different apps and tabs open one app to use them all. And the app itself, we announced as well, is now source available and will eventually be open source as well. So we're trying to make th e best of it. portal into the freedom technology space. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So that's Fedi. And then Fedi the company builds the Fedi app. And we also have something we call the FedEye Order, which is, this selection of incredible people, FedEye Knights, who are on the ground and they, you can think of them as like a Decentraliz ed genius bar. If you've got an iPhone, you have the genius bar that goes along with the phone. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 The reason why the iPhone is so amazing is not just the phone, but it's also the incredible support you can get. If you can go to an Apple store and you go to the genius bar, they can help you. we have that instead of it being in, you know, Fifth Avenue or Oxford street in London or so on. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 It's in, the capital of Togo or Uganda or. Guatemala, or so on. On the ground, they will locate communities, they will educate communities. and they will support communities on Bitcoin, on Lightning, on FediMent, on all of these different websites and se rvices that are out there to provide that sort of support that's needed for the communities that are outside of the existing Bitcoin space. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 How Federations Work \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Okay, great. so how does a federation work? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 so the first thing you have to do, wherever you custody is where you transact and do and you live and so on, which is why. Banks try very much when you're young to get you to hold a bank account with them because they know that most people never leave an d then all other services are provided. So how do you actually custody? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 For many people they've had two choices. Either they do everything themselves and that's the best if you can do it just like it's the best to be able to build and fix your own car or house but not everybody can do that but that is always the best because no one's going to love you. And put as much care in as yourself. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 The other extreme is to fully outsource it, fully give it to some private party, which is actually what ends up 95 percent plus people doing, and that's putting their money on a Coinbase or some other centralized service. and the same with communication. They would use some sort of centralized service. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 They would use a WhatsApp, an X. com, a Telegram, a WeChat or so on. They would use some centralized chat. And if you think about it. Our lives are communication and money and value. So both those things, most people outsource, some people take it in hou se. If I want to set up a federation, which is to do with the custody of the money, where FedeMint is this middle, middle house, I can find within my community, a number of trusted parties. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 We call them guardians. So let's say. You found us three plus, you know, your great t shirt, Greg Voss. The minimum we suggest is four for various Esoteric reasons From a cryptographic security point of view we suggest four, but you can have seven You ca n have you can keep growing you could have we've seen people have seen Federation stood up with as many as 40 people in them And it will get slower and slower if it gets beyond that, but, but technically you can. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 It'll be this, it'll create this huge multisig, i. e. multiple people have to sign before you do a transaction on chain. And so multisig starts to get expensive of a certain size. But let's say us three plus Greg. We would FedeMint software. we would dow nload the 30 minute software onto a machine that we have spare, and we would set up and run it. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 The setup process will, part of it will enter the information about the other three. And we make that very simple, it's a web interface, you point and click and you get a code and you share that code with the other parties, everybody shares the code of e ach other. Maybe you go into a group chat and paste each other's code. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Everybody copies each other's, enters it into our own FediMint and then they connect to each other and they form a federation. As long as you keep that box, running, connected to the internet, and connected to electricity, the federation, for each, all t he four, the federation are one. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 But because it's a federation, if one of them, for example, had a power cut, or lost their internet, or had to change their domain name, or something like that, The other three will be able to continue and operate. Yep, so you've now created this communi ty custody platform. Now, anyone with the FEDI app or any other app that supports the FEDIMINT protocol, Webimint, and we're hoping that many others will set up FEDIMINT wallets, like there are multiple Lightning wallets in future. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Any FDI min wallet compatible wallets like Fedie, can connect to your federation At the end of setting up the fed min server will show a QR code and the string that represents how to connect to your Federation. So you could take your Fed app, or the Muti ny wallet, or Web Mint, or any other, fed mint compatible wallet, and you'll scan that QR code. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And you've now connected to that federation and that federation becomes, you can now use it to custody. Now, what will happen is, if for example, someone wants to send money to you, you would, just as if you're using a Bitcoin wallet, let's say it's on c hain. you would say, I want to receive, enter the amount and it'll show a QR code. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Someone else who's using a normal Bitcoin wallet will scan that code and send over the Bitcoin main chain money to you. But what's actually happening is your Fediap is communicating with the Federation. Your Federation is creating a Bitcoin address for y ou to send to and sends it back to you for you to display. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Okay. And then a user, someone else who's using a completely different wallet will send money to that address. Actually goes to the federation and they, the four of us combined will process that and create e cash, which is like a token representation of the \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Bitcoin. And then the e cash will be sent to you. But the way it, the way it's sent is completely privacy preserving. So the guardians have no way of knowing who they are providing that service for, who's receiving the money. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 There's full privacy. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 All right, and neither does the sender, I assume, like the sender doesn't, that they sent Bitcoin to us and address. They have no idea who, so if there are, let's say we set this up and we're using it for our friends and extended family and in total, the re are 40 of us or 50 of us \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 When you send to that address, there's no way to know out of those 40 or 50 people who received it or who requested it. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 All right, so, a bit about the guardians and the multisig, that's obviously because you don't want to have a single point of attack for each, federation, right? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 point of failure, \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 A single point of \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 the more likely thing is that someone's machine, if you had one machine, the most likely thing that will happen, almost guaranteed, at some point you'll have some sort of power cut or internet cut. Internet cut is probably the most likely you'll, you'll have a glitch on your internet for 30 minutes. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 If you do, Everyone using your federation won't be able to use your system for 30 minutes. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 but it's also an attack vector. Like if the, if the, if there's a lot of money in the federation and, so there's, there's an incentive to attack the guardians. Like, can you be completely sure that the guardians don't know each other's identities and stu ff like that? Like how, I know you think a lot about the attack vector. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So I'm like, can you go into that a bit? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 can't be completely sure of anything in life. So the answer to that is automatically no. Can you be completely sure of something? but, it depends on the Also, there's an assumption that you have, that the people don't know each other. Cause I think very often in, there's two types of scenarios. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 It could be that each party completely doesn't know each other, or the more common scenario will be that you're some community or some group of friends. And within you, you've decided. Of the people who are my friends and family and so on, these four peo ple are the ones who are consistently the most reliable, the most trusted and so on. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 They do know each other, and you know who they are, and it's because you know who they are that you're comfortable with them holding. they're the Uncle Jims of the family. they're known to be reliable. They're known to be people who care about their frie nds and family. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 that's very often actually what we're seeing is the more common scenario than the ones where people are completely, anonymous to each other. But as it matures, we may see the other scenario happen as well. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 The Uncle Network \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 It's a literal uncle network. I know Uncle Rockstar started the uncle network here on infinity day. Yeah, you got the brother Luke, and so that's four, so we're</p> <p>\par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 are you an uncle? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 am an uncle officially now. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 an uncle as well, are like, but dubbed by Uncle Rockstar \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I haven't been dubbed I, so \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 you are a good candidate. candidate, but I am biologically now, an \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 oh, congratulations, \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah, \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 How Fedi Launched \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Okay, well, I think we are looking just to dig in more about Fedi Fedi Mint and, what does your launch actually mean? Because the app has been in beta for quite a while, right? what's happened, to make it that you can launch? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah, that's a very good question, because, we, the app from the, if you just focus on the app, from the previous version to the one we went live, there are only a few, changes. It was more about, did we have enough feedback from enough people on the gro und that we thought that the product was stable enough, reliable enough? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 behind the scenes, we've done a lot of internal plus from trusted friends, external security audits of different elements as well. I don't like to publicize it because it's just something we do. We don't think it's something you should promote to saying, Hey, look at what we're doing. We just try to build the best that we can. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 and the really, big thing was to just say, a lot of people ask, is Fedi ready? And we wanted to get to a line where we thought it was good enough. And we got to that line. And then, we also wanted to have enough proof points in, the world. And again, we got to that line. So these things were separate things that were happening. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And finally, it was very clear to us that we wanted to make the software, Ultimately open source. And that was a big call because, you know, we raised 21 million and, normally you go two routes. You go, you raise a little bit and you stay open source and so on. Or you raise a lot and you stay closed source. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 We believe that, over time, it's going to be considered, over the coming years, it's going to consider that you should always go open source no matter what you're doing, but we're in a transition. Five years ago, raising this much and going open source w ould be considered crazy, in five years time, raising this much and not being open source would be considered crazy. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And we wanted to be, afforded in that. So. We actually went source available. It's called a business source license. So it means you go source available and you set a date where you must go open source or earlier. and we set those. So we cannot change it now. We cannot say we're going to actually change our mind. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Well, the only thing we can say is that we're going to go open source earlier. that's the only thing we could do. Or if we decide to shut down, it's automatically open source as well. That's the sort of dead man's switch as well. Or we decide we're no lo nger going to develop the software. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 we've added caveats like that, which are not optional, but actually add more restrictions. So no one's going to complain with us going open source earlier. that was agreed and put in place on May the 4th. So May the 4th we review of this year, 2024, just for posterity. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 we, got enough proof points from different markets, that we felt that we're onto something here. Does that mean that we've finished? No, there's a lot of work to do, but enough to say that the idea of taking all of the best of freedom technologies out th ere. And putting them into one place and one app that's easy to use is something that's compelling to people. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And also we had enough to see the federation model. of this sort of really simple to use and privacy preserving multi sig is also a powerful model. So the model was proven out. And then finally the software, we got to a point where we thought, it's, of c ourse, we've got years of more development, but it was good enough as well. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I think that was the final piece. And we thought, okay, we're ready to go. And we then set a date a few weeks after that. But even when we were getting close to it, we started the process of shooting a video because we just wanted to show people are wond ering what were we doing for the last nearly two years and we wanted to show that as well. \par\ \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 what's the synopsis of the last two years? Like the big highlights? \par\ \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 so, I always say there's three phases in the business. There's initialization, of a startup, initialization, market product fit, in our case, not product market fit, I can go into why. And then, growth. And so, this phase that was, the end was finally, w e crossed the line, on August the 6th, 2024, was the initialization phase. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And so, if you think about the analogy of, like you wanted to have A shop selling designer pet clothing, and you've decided you have this crazy idea and you have to first fund it, find the people to build it, and then find the place, set up the store, ma ke the clothes and, open. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 That's the initialization phase. And then once it's launched, you then. Start figuring out, okay, people come in, there's initial, interest, and then, you have this trickle of people coming in, you have to figure out what do they like, what do they not l ike, what do I have to adjust until it becomes this sort of regular viable business. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 That's the market product fit phase. And then you start saying, okay, I've got something that's working fully and then I will repeat it, make more and more and more, Widgets? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Doggy fashion, Excel stores, whatever you want to call it. the last two years was our initialization phase. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 we had this, amazing product with FediMint. we had this initial set of, crazy people with Erik, the inventor of FedEvent, Justin, who's, who was also incredible engineer, who was actually the one who suggested that we make a commercial enterprise. up unt il that, both myself and Erik just suggested it would be an open source project. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And then myself as well with my just, you know, only maybe six or seven months before we were finally finished selling. a Bitcoin exchange, the UK's longest running Bitcoin exchange. and so having that experience of building a company that was profitable and understanding what it meant to build something that custodies a large amount of money for people and provides them services is easy to use and all that sort of stuff. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 and everything around that customer service, everything around that. So, we were there, I had a visit to the Oslo Freedom Forum, and that was the catalyst. we did one talk at, Bitcoin Miami, and, Alex Gladstein saw that, he suggested I go to Oslo Freedom Forum. I went, my mind was blown and I also realized whenever you're thinking about a business, you have to always think about chicken and the egg and how do you find your initial market for eventually this product is applicable to everybody everywhere , but who's the first use case that has a demand so high that they're going to willing to go through the really buggy early versions and help you. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Stabilize it to the point where it's something that people can click a button and it works everywhere. I realized that the community of human rights defenders and later on also humanitarian organizations fit that, need. We really cared about that need an d we were concerned, we wanted to help, but we realized that this product could help in combination with the rest of the Bitcoin ecosystem. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 That's what's quite cool. FediMint is the thing that handles the custody, but you still need to buy things, sell things, find things, and so on, and that's where the Fedi app also comes into play, but without FediMint as the core to handle the custody, t he rest didn't make sense. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Then we started, it was, then you had this sort of scene from like the Magnificent Seven or so on where you're, you're finding your initial team members. So we found Renato Rodriguez, I chased her for like six months ago. She should have, you know, got a restraining order for six months trying to get her to join. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 just if you look at the initial team, it was just everybody, the whole team is amazing. But it was just trying to find these incredible people. they tended to just immediately understand the value proposition and the market we were trying to help and wer e already doing incredibly well in their own careers, but there was something missing for them. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And when they saw this, it was like this fulfilled There's some other need that they had beyond the monetary need. The potential was amazing, but the mission side of it was what helped us bring on this incredible team. So I believe in philosophy, people, process, product. The philosophy was amazing, who we're helping, the potential, it's helping people and in so doing we're helping Bitcoin, in so doing we're helping the world. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And that's a powerful philosophy and mission and that attracted this incredible group of people. And if you've got the philosophy and you've got an incredible group of people, they will put in the processes that will lead to the right product. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 It's like, let's say the video, for example. I said to Renata, I want a really powerful launch video and it should be like the best Apple keynote speech combined with a UNICEF or Save the Children commercial. That's it. That's the whole brief and that wh ole video. And somebody says, you need to go to Madeira. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 You need to say this. And I just woke up and I say what she says. But the whole elements of it, all of it was her and her team, Mary and marketing and everybody building that over the following X months. and I didn't actually see the video myself. Until less than a month before we launched it for the first time as a rough draft. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And it was just basically perfect. My comments were like, I actually didn't have any significant comments, but that was the same for most of the team and the design of the product. We had this incredible designer, Skylar. I would give a brief and so as, Erik's brief was, I just want to be proud of something that I should be proud of, and that was it, you know? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And I was like, it just needs to be really simple. And that's the high level. And I might give comments on a little bit here or there, but in general, whenever he gave me it, I would say, well, he Skylarized it, like just Skylarize it. And he would just come up with something that was great. and I think that was the last two years. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 We had the team we raised. again, the choice of investors was really, really key. I was very, very sure, especially from my previous experiences, that I only wanted Bitcoin on the investors, especially for the first couple of rounds. And when I've someti mes do talks on how to set up a Bitcoin company, my first slide says don't do it, but instead sort of a Bitcoin business, not a Bitcoin startup. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And I explain the difference between the two. but one part is, if you do want to raise capital, be really careful about your choice of investors. The wrong investors will, well, and they don't mean to, but they will kill your business without meaning to, but the right investors will. So, we were really, really careful about our choice of investors and the initial team and then the initial team brought on the rest of the team after that. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And that was the last, that's the last two years we've set ourself up very well. I did, being a classic entrepreneur, think it'll take six months, took two years. So I, so my estimation on that was a little bit off, but the end result, I'm really excited about. And now, now we're, now we're off to the races. \par Great news, everyone! Bitcoin, the inverse of clown world is out now. It's the successor to everything divided by 21 million. And it's based on the last two years of podcasts that we've done together. So if you like the show, you're going to love the book . Find the book on bitcoininfinitystore. com or on Amazon. \par That's right. We have our own store now. BitcoinInfinityStore. com. You can find not just books, but merchandise based on everything divided by 21 million, check out Bitcoin, the inverse of Clown World today and buy some other stuff while you're there too . \par This show is brought to you by Bit Box, our favorite hardware wallet. It's Swiss engineered and has all the most important security features to keep your Bitcoin safe while keeping a user experience that even your grandma can use. So visit Bit Box. Do Swi ss slash Freedom to learn more, or use Code Freedom at checkout for 5% off. \par And remember, it's the Bit Box zero two Bitcoin only edition. Make sure to get that Bitcoin only firmware. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 How does Fedi Make Money? \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 How does the app make money? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 For the company? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 if you use the app, whenever you use the Freddie app. whenever a transaction happens, which would have occurred a fee. So it's a Bitcoin transaction, e cash or a lightning transaction. We add on an additional fee, 21, 21 basis points. So 0. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Oh, yeah, \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And so, and the good thing is because we can charge in sats and I believe actually even fractions of a sat, it's a progressive tax, which a fee.</p> <p>\par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So what I mean by that is. If you're sending, let's say 100 through, then you would be charged on 100. 21, but if you're, worth of value, but if you're sending through 1, then you'll be charged 0. 21 cents. And if you're sending through 0. 10, you'll be charged 0. 20. 0 to 1 cents. So it'll always be a very small percentage of what you're sending. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Now, people might say in certain countries, don't they have mobile money and so on. But the problem is those mobile money systems have minimum fees. And it might be, 1%, which is not that bad, say. And it might be, even in some terms of scale, it could b e half a percent, but with a minimum fee of 20 cents. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So if you're sending a hundred dollars, that's okay. But if you're sending, 1, that's 20%. And so if you have someone who has a monthly salary of. 10 in some of these markets, that 0. 20 fee starts becoming quite a significant per transaction hit. So the refore it becomes unaffordable for you to use mobile money. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So even though it's prolific above a certain wealth level, and so that leaves many people out, in the rain. But because this is progressive, if you're selling 10 cents, the, fee will actually round to zero. I mean it will be a fee, but you'll see it in s ats, but if you were showing, trying to show it in local currency, it would basically be, it'll say about zero and then you click and you realize it's this small amount of sats. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 so, yeah. the big thing that I'm thinking of if I'm like. Playing this out in my head with where this could be in 10 years, like you could run entire virtual nations on a federation, right? If you have the money and the communication and whatever other u seful apps, \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I think the big thing I think is, if you look at the internet, there are large organizations where, people use and they're highly centralized. You have a few people who may be wealthy enough to have their own direct connection to the internet, but the ma jority of people are connected on the internet. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I don't know at this stage, millions of intranets, like household intranets effectively, company intranets and school intranets and so on, where it's one connection to the internet shared by multiple people. That's actually the majority of people. And it 's that middle ground between these huge mega organizations that people are connected to one mainframe. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 With millions of users, I think there are very few of them now, but that was the denominant way at the beginning. It was these huge, centralized ways of connecting AOL, CompuServe, and so on. Now, they're actually relatively rare, but that was at the beg inning. All of the internet was that. A few centralized parties, and I would liken them, conceptually in value terms, in value custody terms versus information custody terms, to, a coin basis. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And also there were a lot of hobbyists who had their own direct ISDN connection to the internet. but now most people connect through these intranets where they get one router, one connection, and they share with everybody in their household. That would b e a criminal of the Uncle Jim federations or in their school or in their football club or in their office. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 That's probably 95 percent of people and I think that this approach of federated model from the size from. Five or six people up to five or six hundred thousand, that range can cover 80, 90 percent of usage. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 How to Use Fedi(Mint) \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Can we go back to the basics of how feint works in the perspective of someone actually using this thing? So, you explained to us last time how it works, but just for my own sanity, check that I got it. if you are sending e cash within the federation, tha t is just. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Direct between two users. There's not even a record outside of that. No one knows those transactions are even happening. Is that essentially correct? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah. So the federation helps you mint technically, because actually the user creates their own e cash, they create their own e cash, but it's unstamped and then they give it to the federation and they stick in an envelope. And they give it to the federa tion with some carbon copy paper on the inside the envelope as well. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 the federation collectively signs. So let's say all four people go stamp, stamp, stamp. And that makes it valid. then they give back the envelope to the user. The user then opens the envelope with the cache that they created, just some random piece of da ta. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And they now have this Ucash, but the Ucash they've created now has got the four stamps on it, say, for the four of us. And so anyone else in that federation, any other, person who's also connected to the federation. They can just literally, directly giv e them this, random set of data. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Let's say it's a picture of a fashionable dog and they can just give it to someone else. and the person will receive it and they don't really care what the data says. They just look, are the four stamps on it? Yes. Then it means it was stamped by the Fed eration, which means it's backed by a certain amount of information. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Actual Bitcoin. Yeah. So take the whole, the full path. Someone deposits some Bitcoin in return. They also, along with the Bitcoin, send them an envelope, give them an envelope with this random piece of data in it to the Federation and the Federation rec eives the Bitcoin. Okay. I've received the Bitcoin envelope. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Okay. I've received the Bitcoin. I will stamp. I received one, let's say. 10, 000 Satoshis. So I'm going to take my 10, 000 Satoshi stamp and stamp this envelope with 10, 000 Satoshis, pass it around to the other four, they all stamp the 10, 000 Satoshi stamp. And then give that back to the user. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 User opens the envelope and says, I've got, okay, I've got an e cash note with, with, that's been proven that the, that it's been validated by the guardians. So as long as we all trust the guardians are holding that and that they will honor this and rede em. That's it. So now I can pass it to anyone in the Federation. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 They receive it. They look at this picture of the cute dog, but what they're really looking at is, is it got the four stamps on it and it's 10, 000. So that means I've now received 10, 000 token. They can now at some point in the future, Often they do it immediately if they've gone into connection, but they don't have to. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 They can give it back to the Federation. Federation will receive it and each one will check their own signature of the guardians. Okay, it's properly signed. Therefore, I'm willing to, and they might give them a Bitcoin address to send the money on chain to. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So they will receive it, it looks good, they will then, record that this, e cash note has been spent. But they don't know, of all the e cash they received, which one it was, because each one they received in the first place was in an envelope. So was it the first one they received, or the middle one they received? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 They have no idea. It could have been received yesterday or a month ago. No way. All they know is, I must have stamped it, so it was one of the ones I stamped. And then they will look at the address the person's asking to send the Bitcoin to, and they wi ll take some of the Bitcoin that they're holding in the multi sig that we're holding between the four of us and send it to that address. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So that's called Redeem versus Mint. Now, the user experience from a user, we can get onto Lightning, that's another level of complexity, but it's simple just for Bitcoin and eCash for now. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Someone sends me Bitcoin or I send it to myself from an outside wallet and I receive e cash. And then someone else in the, in the federation wants to, once I want to pay them some e cash, they will give me, they will give me a QR code to, to scan to pay and I will scan. And literally the e cash that's on my phone gets sent to them directly. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 From me to them, one to one, that person when they receive it could keep it on their phone or they could say, you know what, I want to send that back to the federation and they can send it back to the federation and then the federation can destroy that, issue them new, fresh e cash in different denominations, maybe not 10, 000, but 10, 1, 000, you know, just like with notes, you could go and get change. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah, because if someone transacts, if you're saying it gets sent from one computer, phone being a computer, whatever, one device to another, well, that original device would still \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yes, \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 copy of the thing on, right. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So they will still have a copy. Now you are in the same, this is where the community aspect works, you are in the same community, If you're in the same community, and the person, it's a merchant and you receive, and your phone will remember when you rece ived what e cash, yeah? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Even though it's private, you do know this e cash was received at this time and this time for, and so, especially when you integrate with points of sale, it will say, well, you received this e cash for this purchase. You'll know that. so then if you go t o redeem it, at the end of the day, and some of it doesn't match, you will know as the merchant, which e cash was involved in that. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 You'll say, well, the e cash involved in this transaction. And that transaction was with John. So you've got proof of work. it's the same as if you have a merchant and you receive cash and then you finally got the end of the day to a bank. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And some of the notes are counterfeit. Now, you don't find high levels of counterfeit notes in a community where people know each other. It's normally in these widespread communities. But in those scenarios, what most people will do and how the default w ay the app works is the moment you receive it, it immediately goes off and redeems it and then issues itself back new, new change. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah, that seems like a good default implementation. but if you have no internet connectivity, you can still use it and still receive. even if you can't send over the internet, you can create a QR code, which contains the e cash in the QR code, and the p erson can literally scan it and receive through the screen. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Because as long as it's the QR code, the e cash note is just some text. So a QR code can represent that text and you can scan it, even if you have no data. So for example, it could be you're in an area where you have no data, rural, Latin America or so o n. But it could also be something more innocuous. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 You could just be in a big sort of, But the thing is is that you might be at a Glastonbury like concert and there are a thousand phones and there's no data. Or you're in an indoor conference place underground and there's no data. But you can still take p ayments or the merchant has internet because they're the ones who really need it. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 But the buyer doesn't and so in which case the merchant has internet because they're connected wired in because they're fixed, but the buyer doesn't need to have internet to pay and the merchant will just take a risk just like in most merchants in high s treets they accept a certain amount of breakage and a certain amount of transactions are gonna be charged back by, credit card companies and so on. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I used to be a CTO for a major pan-European, online auction company. At the time I was competing with, eBay and so on. we were in a headliner, 300 hundred people working for me in technology. It was a very big technology offering. And we were doing milli ons of transactions a week. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 It was very high volume. And in those e commerce sites, you just accept a certain amount of breakage, a certain amount of returns, and a certain amount of chargebacks, even if you do nothing wrong and you just factor it into your costs. For the benefit o f the simplicity of the experience. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Fedi and Nostr \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 you mentioned Nostr before, like, what's the marriage between Fedi and Nostr? Well, I would say right now, we are, because I think. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 we're beyond dating. We're engaged. But we want to really take the two footed tackle of no return, to use a football euphemism. a web of trust thing, right? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah, I think, whenever, from the first point I saw Nostr, a lot of people thought it was just social media and so on. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I think social media is Trojan horse is the wrong word, but it's the, initial vector by which it infiltrates communities. But what you're actually doing is building a simple, trust system and a simple discovery system. It's a form of decentralized search and it's a form decentralized identity. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Cause you, to search, you have to identify things to be able to search. So they're sort of two sides of the same coin. now the first thing you're using it for is identifying people who want to speak publicly and share their thoughts and so on and so fort h and follow them and give feedback and like. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 But it always seemed to me to, way more powerful than that. And I think now people, generally understand it that way. And so, What we've already done, in Fedi, and a lot of developers really like the way it works, if you sign up to Fedi, or if you downlo ad the Fedi app and start using it, you, first of all, you don't need to give your email, you don't need to give your phone number because it's not required, but, we do ask you to come up with some sort of Username for yourself. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 That doesn't even have to be unique, by the way. We will add a unique element at the end, from it. But what we do is, whenever you create that label, which you can change the name, but we create, an NSEC, which is a Nostr, identity effectively. A unique identity and we automatically create that for you. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So again, for our users, we don't want to start educating them on the history of Austrian economics and Bitcoin and inflation at the beginning or a Nostr, et cetera, and how it works and relays. And we just want them to start using it. then subtly over t ime we expose certain features of it. So people become curious and then eventually. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 You want to learn how this thing that's delivering value works, but we've put proof of work first, proof of talk second. So we educate through letting people see the benefits. And then there might be some people might say, well, how does this car thing w ork? Or how does this fridge thing work? But I don't need to know how refrigerant works to be able to use a fridge or how microwaves work to use a microwave. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 When they want to know how all this stuff works, but we benefit first. So, and so and that's how it works with Nostr We immediately give you an NSEC. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And so because we've got that if you go and use unleash. chat, for example within the app It will go and you click login and there's one option login by Nostr You click that and it'll just within the app pop up something saying Nostr Do you want to log i n with Nostr? And you click yes, and you're logged in and it just works and then you, and then also now you're logged in and then you can, and then you click, deposit money and instead of having to go to a different app, copy and paste the QR codes, it just, it pops up and says, do you, this, this, what the app's asking you to deposit this amount of money? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Do you want to go ahead? Yes. And then it's e cash. Is, is converted into lightning and then that you pay by lightning. But from your point of view, there's a circling key for three or four seconds. You have now credited your account. Do you want to with draw the money back account? You click withdraw the amount. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Three or four seconds, it's been withdrawn to your account and, and it's all within the same app. so, but that only works because now if you, close the app or delete the mods, because you can delete these mods or these additional pieces of functionality, they're basically webpages, but the icon for them, and they have an app like experience, but they're actually just webpages. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 and then you go away and then you delete the app from your service. Like six months later, you come back, you, you, you enter your 12 words, you're, you're re log on. And then if you scan to join a federation again, it will recognize that you were a memb er of the federation before, and it will reconstitute and recreate all your e cash and put it back on your phone. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And then if you click on, Unleash your chat or Stacker News or anyone that supports logging by Nostr. Your login with the same details and so on. So you basically, and we want to make that even more seamless. So from 12 words, your entire life can you th ink about moving from one mobile phone to another, where you have to move all your apps, your banking apps, your chat apps. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And now you could do that with just go and also try moving from an iPhone to an Android phone, Android to an iPhone. It's a nightmare. Here you could just download the Fedi app on your iPhone. this is some far point in the future. You don't have just cha t, but you also have voice. You have video, all of that running from encrypted chat. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 12 Magic Words \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 you have access to money from, custody and payments. You have access to all these apps and then you back up 12 words. And there's something we call social backup, which is mind blowing, but, that's in beta. But let's just say backup 12 words, and then yo u delete that app, go to a different phone, could be an Android or an iPhone, and you just enter 12 words, and your entire thing comes back. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Not partially back, but it all will come back. based on just those 12 words and that's only made possible because of Nostr and we want it over time. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 mean, when you think about it, it's insane. It's already insane with bitcoins, with the 12 magic words, because like every time I pass a security check at an airport, I think that go ahead, have my 200 milliliters of toothpaste. I'll, I have my 12 magic words, like it's the ultimate fuck you to, to anyone trying to meddle with your business, right? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 that's the dream. I mean, we're not fully there, but it's, I would say it's like, we're like 90 percent there, but to extend beyond just your Bitcoin, Nostr is the protocol that allows us to do that because it's notes and other stuff and the other stuff can be, an encrypted version of the settings and so on that you have that we can store and be willing to pay for. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And then when you recover, you have your bitcoin, but then you can go off and send a request to say here, I'm willing to recover this file. Here's some zaps for the file and you get the file back and that additional file then contains the information. Ok ay, these are the federations you are a member of, you rejoin them. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 These are the mods that you had, they're reset up. These are the settings you had, they're reset up. And then you log on them automatically using Nostr as well, the NSEC and Nostr login. from your point of view as the user, 12 words, it's back. I mean, y ou might have to drink a cup of coffee while it's happening, but 5, 10, 20 minutes later, it's back. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 it's amazing, and it's an inheritance plan. Like, you can live forever by just letting your descendants, giving them the 12 words when you're on your deathbed. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 backup also becomes really powerful, because social backup means that, cause the 12 words is still another thing to secure. And it's sort of one of these turtles all the way down type scenarios. Okay. We've got all this incredible security Fort Knox like , but behind them, but I walk around the back of the Fort Knox is these 12 words that's stored. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 you also give one to your cousin and you say, look after this as a backup. And your cousin stores it on a fridge magnet. You know, you don't know, or you don't know your, your, your security is the lowest common denominator. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 For your 12 words. And \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 is never stronger than the weakest \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 then the weakest link. And so with social backup, which is definitely an early beta. what we can do is use the power of the federation where we can take your 12 words, encrypt them and then split it up between the four guardians in this case, or seven gu ardians or 40 guardians or whatever. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 For larger federations, and they all hold a piece of your encrypted piece of your, of \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 is important here. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah. \par Knut, what are you doing over there? I'm stamping my seed. Everyone tells me I should, that it's good for bitcoin security and whatnot, and that I should go balls deep into bitcoin security, so I'm stamping. You don't do it like that, Knut. You don't stam p that seed. You stamp your seed phrase. What? Your seed phrase. \par Oh, so that's what these things are for. oh, I get it now. That's exactly right, Knut. And you can get everything you need to stamp your seed phrase at stampseed. com. And be sure to check out our limited edition Everything Divided by 21 Million Titanium Seed Plate. \par And use code INFINITY at checkout for 15 percent off. That's fantastic! And it hurts way less! \par\ \par\ \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Redundancy in Fedi \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So this gets me back to what happens when one of the guardians drops off, and if it's like in a permanent way, if that one guardian is holding a piece of everyone else's 12 words, does everyone \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah. But it uses a prot, this is crypto, where cryptography comes in. So it's not like. We've taken your 12 words and split it up free between four guardians. Instead, you encrypt it using a scheme that allows each one of the four of us to have a crypto graphic piece. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 But as long as any three of us combine our piece together, we can recombine. It is, it's called, SHAIR Secret Sharing Scheme, but it's a way of cryptographically achieving that. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Excellent, I think you mentioned last time as well that if a guardian does go down, essentially you can replace that guardian, can you take us through that, adding or replacing a guardian if that ever were to need to happen? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 replacing a garden is, probably one of the most complex things. And so you wouldn't necessarily replace a guardian, but what you would do is, some, if someone were to go down, there's two different things. The machine. Or the guardian, the actual person. So if the machine goes down, you can set up a new machine and you can recover the status of that. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 You can, you can download the 30 minute software on that new machine. So that's the actual server that's running. And that will then connect to the rest of the federation and, and carry on. So as long as the guardian has a backup of their keys, they can recover that one machine and, and catch up and it'll automatically catch up. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Just like if you turn off a Bitcoin node and turn it on, it will reconnect to the Bitcoin network and catch up. It's a similar concept. so that's if a machine went down, if a machine was temporarily disconnected from the internet or, lost power, it would just restart and reconnect and you will have zero downtime as a user, as long as it's still running and active. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And this will all be, you'll notice that the performance will still be the same, but if you went into settings for that federation, you'll see that three of the four are running, so one is not running, but that won't affect your usage. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Is the N of M like a ratio, or is it always N 1, for example? It's a ratio. the number of guardians that, you need to have is dependent on how much redundancy. So if you want to be able to handle one guardian going down, then you'll need to have, one tim es by three plus one. So that's four. So that's why you need three or four. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 if you want to handle two going down, then you need two times by three plus one, which is seven. So it's five of seven. 7 of 10, 9 of 13, and so on and so forth. You can have more than that, but the time that you get additional redundancy is every 3, but you can have, for example, 4 of 5, if you wanted to. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Anyway, so, yeah, in the event that someone goes down, that the machine goes down, you can recover. recently there was an issue where one machine, where two federations, had an issue with the domain name for one of those servers. And so if the domain nam e for someone is no longer available, you can now, with the update that came out a couple of weeks after that, you can modify, the domain name \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 for a Guardian 30 minute server, and it would communicate that securely with the other, Federation servers and then reconnect and, continue to operate. But it's important to, even in that scenario where the Federa Guardian, the domain name server went do wn, the Federation itself, Continue to operate because there was still at least free running. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So there was no downtime for the user. Whereas if, if we hadn't been federated, then for the one week or so where that was down, the users would have had no access at all, which would be the case where you're connecting to a centralized or a single serve r, offering. now, if one of the guardians, for some reason, the actual people who are running the Fedemyst server, for some reason, you no longer trusted them, they'd been helpful all their life and all of a sudden they decided, or they've been turned b y some, malevolent nefarious actor. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Then you, if you could in theory pass to someone else, but in practice, you know, how do I know that the other person isn't still going to continue to operate it and so on and so forth. So what you actually want to do is set up a different federation and transfer people, the other three guardians and inform people with a different set of four people. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So those three, plus someone else. And just tell people to transfer their balances across. But transferring balances across is as easy as doing a lightning transaction from one server to another. You can, you know, within the FEDI app, be a member of mul tiple federations at the same time. I mean, right now, I mean, I'm a bit of a power user, but I'm a member of, over a dozen different federations from around the world. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I mean, well over a dozen, I think, yeah. and as we've, I'm sure there's people in the team with way more than that. but obviously I can't advertise the names because many of them are private federations. So, but there's a few public ones, but there's wa y more private ones. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Interoperability \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So is the e cash, if you're in multiple federations, is it interoperable there, or it's like a more like a, it's a lightning transaction between those two federations, but it's e cash that lives \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 You got it. It's, E cash lives within its federation, but the interoperability layer for most people is not on chain. It's for the vast majority of people, it's Lightning, so, but the user experience of sending e cash from one person to another in the sa me federation, sending e cash from one person to someone else receiving Lightning. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 on a different wallet that's got nothing to do with Ferdie Mint. And finally sending e cash from one person in one federation. To someone else in another federation over the Lightning Network in between is exactly the same. From your point of view, QR co de scan and the system will combination of the Fedi app and or whatever Fedi Mint compatible app you're using and Fedi Mint servers will make the experience \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I just need to send the person the cash. In this case I can send e cash out over Lightning and that's my job is done. And then the other side would be a Lightning wallet and it will receive. And in this case, I will send e cash over Lightning to another federation, but I don't even know if it's another federation, it's just a Lightning address. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And then the other federation, receives the transaction and the other 30 minute server receives e cash on the other side. But from a user's point of view, this is the thing that also took the two years to make the experience the same. You just don't have to worry about which one is doing. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 The fees will be slightly different. One won't have a Lightning component to the fee, e cash to e cash, but, the other two will because it will be like, in both cases, it will be e cash to Lightning, from your point of view. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So is there a fee to send e cash to someone else in the same federation? No, I guess. Right. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 It depends on the federation. the federation, could choose not to charge a fee and many in these times choose not to because they're doing it for friends and family and so on and the fees are minimal. the Ferryman protocol does support, what we call a DD oS fee. So basically you're spending effort time \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 to sign these notes, the issuing is done by the user, but the stamping takes time. you're signing something cryptographically, that's effort. and you're also doing it in a federated manner, so you're coordinating and then you're all collectively signing.</p> <p>\par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So, to avoid DDoS, you can turn on a fee and, by our calculations, it doesn't need to be very large, one sat per note that issued is enough to prevent, because if someone really tried to DDoS you at scale, they could, but on normal sort of consumer lapto ps or hardware, they'll have to spend, hundreds of thousands a month at that sort of, one sat per note, and in which case you'll say, fine, you're giving me hundreds of thousands of dollars worth of Bitcoin to burn my, CPU. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Well, not to burn it, but just to heat my CPU. so you can charge a fee. And I think some will experiment with charging a DDoS fee, which is similar to Bitcoin. the fees in Bitcoin are a DDoS protection vector. So it's the same concept. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Fedi's Roadmap \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 All right. So, what's on the roadmap? What's going on? How does the future look like? What will you be working on the next five years? And where do you see FedeMint going? \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 that's actually, the most, fun phase. up until now, we had a hypothesis and we had some early feedback, but a lot of it was based on, A hypothesis and theory as to what we thought people needed and we felt that freedom technology had got to a stage where they were good enough to provide this combined experience. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And that was a hypothesis. And we think we've got early validation, but we built that. Now it's life. And now it's the fun, but it's also the scary bit because we now actually see people using it and we test all our hypothesis. And this is the point wher e you have to be very detail oriented, very much listening to the users and listening to what they say \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 we cannot ignore if there are. Parts of our hypothesis that are incorrect, we have to adjust to support that. So it's going to be a lot of listening and we've already got hundreds of requests for feedback. and then working to rectify, or deal with the qu estions or feedback they've given us or the suggestions they've given us. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 and we're going to continue to iterate and then we bring it back out to users and see what they think. And we keep in that loop. This is the market product fit loop until. The product that we produce, fits the requirements of the market. Now, again, I, I 'm hoping that takes six months or less, just like I hoped it took six months or less \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 for the initialization phase, but it might take less. It might take a bit more, but it's fun. and that's the next phase. After that, we then go into the growth phase. Once we know we've got something that's repeatable, that really. is at the quality leve l that users need for it to be used a daily part of their life. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 We'll then go into growth phase and that's where we'll really, you know, pull down, put our pedal to the metal and, and just repeat, repeat, repeat until. You know, billions of people are using this around the world, but that, that's phase three. And I'm , I'm very focused on this phase. You don't want to rush into phase three. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 We're not going to rush to grow the numbers, until we are very sure that we've got something that's really slick, really reliable, and where we're meeting a clear demonstrable demand consistently. And that process is called human centered design. So it's not focused on this is my app, this is what I want, and I'm going to keep trying to make you agree with what I want. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 this is what we've built. This is our first stab at it, but we're going to keep iterating until it serves your need properly. And that might require some, this is what makes this one very hard because it requires a very different mindset to the phase one . Phase one is like We can do everything and the impossible is possible phase two is really being pragmatic. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Or very self critical and being very open to killing your darlings, as the saying goes, you know, and saying this is not working or, or there's some fundamental issue. I mean, I don't think this will be the case at this stage, but if the feedback was fro m our market that we need to make some fundamental changes that would mean that 80 percent of the code we built has to be thrown away and have to start again. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Well, that's what we're being told. we've got far enough to think that's highly unlikely. cause most of the feedback, like some of the big pieces of feedback cause how can we make it easier to set up federations? So that's a really good sign because lots of people said there's only going to be a demand for like free federations and it's going to be very centralized. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Well, a very large percentage. I don't want to give it. These are the very large percentage of all our queries so far have been, how can I set my own federation up? So even based on those queries, there's not going to be free. You know, I can put it that way. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Super quick question on that, I guess, is it the Fetiman software? Is it on, for example, the note in a box, solutions, the umbrellas, start nines, et \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Well, that's part of the feedback that we're getting. For example, can we set it up? Can you integrate with Umbro? Can you integrate with Start9? Can you integrate with RastyBlitz? can you make it simpler to set up? So, I think, a lot of that's done by t he FediMint team. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Because remember, FediMint is an OpusSource project versus a different OpusSource project. At some point in the future, it will be two different open source projects. However, we are using them as the bedrock, because if you want to custody significant a mounts of value We know that you want to go multisig. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Multisig for significant amounts of value is the best standard, and also you want privacy, so then privacy and multisig, that's FedEvent, basically. but, on the FedE side, we can do a lot as well. So we can provide, even though it's open source software, we can take it and provide it. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 again, it will be open source, but tools to help you build it really easily or put efforts to integrate with people like Umbrell and Start9. we've already had an integration with an organization called Clover, which we've been working on, and you're goin g to see more on that. But from our point of view, that's a lot of where the work is. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Also you want to connect this to the Lightning Network. And connected to the Lightning Network and maintaining a reliable connection is not easy. it can be complicated for people, especially managing liquidity. And now again, over time, I could get easie r, but right now it's not easy. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 There are organizations like, Breeze and others who make that easy. and you just saw an announcement from Erik, where they've already started, showing connectivity and support for LDK, which is this cross, LSP standard. So, again, we at Fedi can provide tools for FediMint, or people who are using FediMint, whether it's with Fedi or someone else, that make it really easy. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And again, our aim is one click, and you have a connection. You can set up your own lightning node that's set up in a relatively good way, so it'd be relatively reliable, but you don't have to manage it yourself. Or, you can connect to one of these LSP's and for a fee, they'll just handle all the light and management, but you're still in a trust minimized way. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So there's, but given all the feedback we're getting, it's not, this is completely wrong. You need to go back to the drawing board, it's all, okay, I get it, but you need to go further. You need to integrate with more. You need to make it easier. so that 's a good sign that we're on the right track. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf19\insrsid13517917 Knut:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Yeah. So, what about this date when you go open source? is that public or, when you have to go open source, it might be then or \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 in the, it's, it's, it's memorializing the business source license. In fact, we memorialized it. We actually have this memo memorializing when it happened. when we launched Freddy, we, we did this thing on the Bitcoin block. You can see it. We were estab lished on a certain block. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And we said Fedi is here. When we, quietly on May the 4th, we also put something that said Fedi colon and it was a hash. That hash is a hash of a memo. And the memo, which is on our, Fedi's got an open source, you can see the link and you can verify it. Showed that on May the 4th, the code became business source license. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 And by January the 3rd, 2026 or earlier, we must go, open source. And if we were to shut down or to stop development, we will instantly go open source. and so, so that, and we put it in block. I tried to find a core block. So it was block 8, 42069. It wa s actually was the block that was the core block as well. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 so yeah, it's, it's there. And, that's the date. We, we cannot go open source later than that. And we may very well go open source a lot earlier than that. \par }\pard\plain \ltrpar\s1\ql \li0\ri0\sb120\sa260\widctlpar\wrapdefault\aspalpha\aspnum\faauto\outlinelevel0\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \ab\af0\afs48\alang1025 \ltrch\fcs0 \b\fs48\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Wrapping Up \par }\pard\plain \ltrpar\s18\ql \li0\ri0\sa360\widctlpar\wrapdefault\aspalpha\aspnum\faauto\adjustright\rin0\lin0\itap0\pararsid13517917 \rtlch\fcs1 \af0\afs28\alang1025 \ltrch\fcs0 \fs28\lang1033\langfe1033\cgrid\langnp1033\langfenp1033 {\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Hey Obi, I think we could keep on grilling you on this and that little detail, but this has been really enlightening, fantastic to see how far this has come, even since our last conversation back in October, and yeah, just looking forward to everything y ou guys are doing, and I guess just as a last thing, people can now grab the Fedi app and Public federations are available to start to try \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 federations and there are, and you can set up your own federation There's a lot, I don't like to talk too much about what's coming in future because we just work on everything in order of customer demands. So if customer demand comes in, that changes the order, but we're working really hard to make it, It's already easy for if you're quite technical, but we're going to make it easier and easier to set up a federation, so keep looking out because that's a very common request to set up a federation yours elf, and we want to see what people do with it, create Fedi mods, create federations, use it, give us feedback, and we will continue to work on making an incredible, Open source interface portal to this freedom technology world. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Absolutely fantastic. We'll need to keep on having these conversations regularly, get updates because always fantastic to hear about this and good luck moving forward and I think we'll be trying some FETI stuff in our futures here. Lots of cool things ha ve come out of Nostriga and Baltic. Honey Badger by \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 I'm exciting to see that. And anywhere else you want to direct our listeners and viewers. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 So for Fedi, that's probably the best place because everything, that's a jumping off ground for everything else. And that's Fedi, F E D I dot X, Y, Z. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Fantastic. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 One of the cooler things that came out in Nostriga and Honeybadger was of course, yes, the inverse of clown world, our new book, and we want to give you one. if you're not given one during this weekend, you'll find it on bitcoininfinitystore. com. Thank you very much. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf20\insrsid13517917 Luke:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 and we need to sign it for you. Yeah, we'll do that offline. But Obi, thank you again. And this has been the Bitcoin Infinity Show. Thank you for listening. \par }{\rtlch\fcs1 \ab\af0 \ltrch\fcs0 \b\cf21\insrsid13517917 Obi:}{\rtlch\fcs1 \af0 \ltrch\fcs0 \insrsid13517917 Thanks. \par }{*\themedata 504b030414000600080000002100e9de0fbfff0000001c020000130000005b436f6e74656e745f54797065735d2e786d6cac91cb4ec3301045f748fc83e52d4a 9cb2400825e982c78ec7a27cc0c8992416c9d8b2a755fbf74cd25442a820166c2cd933f79e3be372bd1f07b5c3989ca74aaff2422b24eb1b475da5df374fd9ad 5689811a183c61a50f98f4babebc2837878049899a52a57be670674cb23d8e90721f90a4d2fa3802cb35762680fd800ecd7551dc18eb899138e3c943d7e503b6 b01d583deee5f99824e290b4ba3f364eac4a430883b3c092d4eca8f946c916422ecab927f52ea42b89a1cd59c254f919b0e85e6535d135a8de20f20b8c12c3b0 0c895fcf6720192de6bf3b9e89ecdbd6596cbcdd8eb28e7c365ecc4ec1ff1460f53fe813d3cc7f5b7f020000ffff0300504b030414000600080000002100a5d6 a7e7c0000000360100000b0000005f72656c732f2e72656c73848fcf6ac3300c87ef85bd83d17d51d2c31825762fa590432fa37d00e1287f68221bdb1bebdb4f c7060abb0884a4eff7a93dfeae8bf9e194e720169aaa06c3e2433fcb68e1763dbf7f82c985a4a725085b787086a37bdbb55fbc50d1a33ccd311ba548b6309512 0f88d94fbc52ae4264d1c910d24a45db3462247fa791715fd71f989e19e0364cd3f51652d73760ae8fa8c9ffb3c330cc9e4fc17faf2ce545046e37944c69e462 a1a82fe353bd90a865aad41ed0b5b8f9d6fd010000ffff0300504b0304140006000800000021006b799616830000008a0000001c0000007468656d652f746865 6d652f7468656d654d616e616765722e786d6c0ccc4d0ac3201040e17da17790d93763bb284562b2cbaebbf600439c1a41c7a0d29fdbd7e5e38337cedf14d59b 4b0d592c9c070d8a65cd2e88b7f07c2ca71ba8da481cc52c6ce1c715e6e97818c9b48d13df49c873517d23d59085adb5dd20d6b52bd521ef2cdd5eb9246a3d8b 4757e8d3f729e245eb2b260a0238fd010000ffff0300504b03041400060008000000210094a9528694070000c7200000160000007468656d652f7468656d652f 7468656d65312e786d6cec595f8b1bc9117f0fe43b0cf32e6b66248da4c5f2a1bfdeb3776d63c90ef7d82bb566dadb333d4cb7762d8e83e07bca4b207077e421 0779cb430839c8418ebce4c3186c92cb874875cf68d42db5bc7f30c184dd7dd1b47e55fd9baaeaaa52f5fdcf5e27d4b9c039272cedb9fe3dcf75703a670b9246 3df7c56c52ebb80e17285d20ca52dc73d798bb9f3df8e52feea32311e3043b209ff223d4736321b2a37a9dcf6119f17b2cc3297cb7647982043ce6517d91a34b d09bd07ae079613d4124759d1425a0f6e97249e6d8994995ee838df23185c75470b930a7f954aac68684c22ece7d89e06b3ea4b9738168cf857d16ec72865f0b d7a1880bf8a2e77aeacfad3fb85f4747a51015076435b989fa2be54a81c579a0f6cca3b36a536f1c749a7ea55f01a8d8c78d3bf2bfd2a700683e87372db8e83a fd56e8758212ab818a8f16ddddb6df30f19afec61e67bf1b0e82a6a15f810afdcd3dbc37e98e472d03af4005beb587ef7bc1a0db30f00a54e0c33d7c73dc6f07 6303af403125e9f93e3a6c773a6189ae204b468fadf06e187aed5109dfa2201aaae8925b2c592a0ec55a825eb17c020009a44890d411eb0c2fd11ca2b89f09c6 9d11e119456bd7c950ca382c7b81ef43e835bda0fa571647471869d2921730e17b4b928fc3e739c944cf7d045a5d0df2eea79fdebef9f1ed9bbfbffdfaebb76f feea9c902816852a43ee18a5912ef7f39f7ef79fef7fedfcfb6f7ffcf99b6fed78aee3dfffe537effff1cf0fa987a3b635c5bbef7e78ffe30fef7effdb7ffdf9 1b8bf67e8ece74f88c24983b4ff0a5f39c25f082ca14267f7c96df4c621623a24bf4d388a314c95d2cfac72236d04fd688220b6e804d3bbecc21d5d8800f57af 0cc2d3385f0962d1f8384e0ce0296374c072ab151ecbbd3433cf566964df3c5fe9b8e7085dd8f61ea2d4f0f27895418e253695c3181b349f51940a14e1140b47 7ec7ce31b6bcdd178418763d25f39c71b614ce17c419206235c98c9c19d1b4153a2609f8656d2308fe366c73fad219306a7beb11be3091703610b5909f616a98 f1215a0994d854ce504275839f2011db484ed7f95cc78db9004f47983267bcc09cdb649ee6f0be9ad31f23c86e56b79fd27562227341ce6d3a4f10633a72c4ce 87314a321b764ad258c77ececf214491f38c091bfc949927443e831f507ad0dd2f0936dc7d75367801594ea7b40d10f9cd2ab7f8f2216646fc4ed77489b02dd5 f4f3c448b1fd9c58a363b08a8cd03ec198a24bb4c0d879f1b985c1806586cdb7a41fc590558eb12db01e213356e5738a39f44ab2b9d9cf9327841b213bc5113b c0e774bd9378d6284d507e48f313f0ba6ef3f1590e87d142e1299d9febc027047a408817ab519e72d0a105f741adcf62641430f9ccedf1bace0dff5de78cc1b9 7c65d0b8c6b904197c631948ecbacc076d3343d4d8601b3033449c135bba0511c3fd5b11595c95d8ca2ab7340fedd60dd01d194d4f42d22b3aa0ff5de703fdc5 bb3f7c6f09c18fd3edd8151ba9ea867dcea15472bcd3dd1cc2edf63443962fc8a7dfd28cd02a7d86a18aece7abbb8ee6aea371ffef3b9a43e7f9ae8f39d46ddc f5312ef417777d4c395af9387dccb67581ae468e178a318f1afa2407673e4b42e954ac293ee16aecc3e1d7cc62028b524ecd3b713503cc62f828cb1c6c60e0a2 1c29192767e25744c4d31865301bf25da924e2a5ea883b19e3303252cb56dd124f57c9295b14a34e355bf28acaca91d8ae7b2d183a15eb30a612053a6c978b92 9f9aa7025fc5365263d60d01297b1312da6626898685447bb37805093935fb382cba16161da97ee3aa3d5300b5ca2bf073db811fe93db7d594846046cee7d09a 2fa49f0a576fbcab9cf9313d7dc8984604c058b1781318ca579eee4aae075f4fbe5d116ad7f0b4414239a5082b9384b28c6af0780c3f82cbe894abd7a171535f 77b72e35e84953a8fd20beb734da9d0fb1b8adaf416e3737d054cf1434752e7b6ed86841c8cc51d673973032868f4906b1c3e52f2e4423b877998bbc38f0b7c9 2c59cec508f1b830b84a3a857b122270ee5092f45cf9fa951b68aa7288e2e60790103e59725d482b9f1a3970bae964bc5ce2b9d0ddaead484b178f90e18b5c61 fd5689df1e2c25d90adc3d8d1797ce195de5cf118458abed4b032e08879b03bfb0e682c0555895c8b6f1b75398cae4afdf45a9182ad611cd625456143d991770 554f2a3aeaa9b281f654be33185433495908cf22596075a31ad5b42a5d05878355f76a2169392d696e6ba6915564d5b4673163874d19d8b1e5ed8abcc66a6362 c8697a852f52f76ecaed6e72dd4e9f505509307865bfdb957e8dda7633839a64bc9f8665ce2e57cddab179c12ba85da74868593fdca8ddb15b5523acdbc1e2ad 2a3fc8ed462d2c2d377da5b2b4ba33d7afb5d9d92b481e23e872575470e54a98ebe608bab2a9ea498ab40147e4b5288f067c725639e9b95f7aad7e7318b48635 afd31ad79a8da657ebb4fa8d5abfd56af8e396ef8d06c1575058449cf8ade2be7e02d717745ddedaabf5bd9bfb647343736fce923a5337f375455cdddcfbc1e1 9b7b8740d2f93218fbcda01f0c6bc3911fd69ac128ac75da8d7e6d1884a3a00f293d9cf4bf729d0b05f607a3d164d20a6ae110704dafdfaaf5078d612dec8c07 c1c41f37471e80cbccf91afa6fb0e9c616f051f17af05f000000ffff0300504b0304140006000800000021000dd1909fb60000001b010000270000007468656d 652f7468656d652f5f72656c732f7468656d654d616e616765722e786d6c2e72656c73848f4d0ac2301484f78277086f6fd3ba109126dd88d0add40384e4350d 363f2451eced0dae2c082e8761be9969bb979dc9136332de3168aa1a083ae995719ac16db8ec8e4052164e89d93b64b060828e6f37ed1567914b284d26245228 2e3198720e274a939cd08a54f980ae38a38f56e422a3a641c8bbd048f7757da0f19b017cc524bd62107bd5001996509affb3fd381a89672f1f165dfe514173d9 850528a2c6cce0239baa4c04ca5bbabac4df000000ffff0300504b01022d0014000600080000002100e9de0fbfff0000001c0200001300000000000000000000 000000000000005b436f6e74656e745f54797065735d2e786d6c504b01022d0014000600080000002100a5d6a7e7c0000000360100000b000000000000000000 00000000300100005f72656c732f2e72656c73504b01022d00140006000800000021006b799616830000008a0000001c00000000000000000000000000190200 007468656d652f7468656d652f7468656d654d616e616765722e786d6c504b01022d001400060008000000210094a9528694070000c720000016000000000000 00000000000000d60200007468656d652f7468656d652f7468656d65312e786d6c504b01022d00140006000800000021000dd1909fb60000001b010000270000 00000000000000000000009e0a00007468656d652f7468656d652f5f72656c732f7468656d654d616e616765722e786d6c2e72656c73504b050600000000050005005d010000990b00000000} {*\colorschememapping 3c3f786d6c2076657273696f6e3d22312e302220656e636f64696e673d225554462d3822207374616e64616c6f6e653d22796573223f3e0d0a3c613a636c724d 617020786d6c6e733a613d22687474703a2f2f736368656d61732e6f70656e786d6c666f726d6174732e6f72672f64726177696e676d6c2f323030362f6d6169 6e22206267313d226c743122207478313d22646b3122206267323d226c743222207478323d22646b322220616363656e74313d22616363656e74312220616363 656e74323d22616363656e74322220616363656e74333d22616363656e74332220616363656e74343d22616363656e74342220616363656e74353d22616363656e74352220616363656e74363d22616363656e74362220686c696e6b3d22686c696e6b2220666f6c486c696e6b3d22666f6c486c696e6b222f3e} {*\latentstyles\lsdstimax376\lsdlockeddef0\lsdsemihiddendef0\lsdunhideuseddef0\lsdqformatdef0\lsdprioritydef99{\lsdlockedexcept \lsdqformat1 \lsdpriority0 \lsdlocked0 Normal;\lsdqformat1 \lsdpriority9 \lsdlocked0 heading 1; \lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority9 \lsdlocked0 heading 2;\lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority9 \lsdlocked0 heading 3;\lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority9 \lsdlocked0 heading 4; \lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority9 \lsdlocked0 heading 5;\lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority9 \lsdlocked0 heading 6;\lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority9 \lsdlocked0 heading 7; \lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority9 \lsdlocked0 heading 8;\lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority9 \lsdlocked0 heading 9;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 1; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 4;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 5; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 6;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 7;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 8;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index 9; \lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 1;\lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 2;\lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 3; \lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 4;\lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 5;\lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 6; \lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 7;\lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 8;\lsdsemihidden1 \lsdunhideused1 \lsdpriority39 \lsdlocked0 toc 9;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Normal Indent; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 footnote text;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 annotation text;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 header;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 footer; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 index heading;\lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority35 \lsdlocked0 caption;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 table of figures; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 envelope address;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 envelope return;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 footnote reference;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 annotation reference; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 line number;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 page number;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 endnote reference;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 endnote text; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 table of authorities;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 macro;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 toa heading;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Bullet;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Number;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List 3; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List 4;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List 5;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Bullet 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Bullet 3; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Bullet 4;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Bullet 5;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Number 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Number 3; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Number 4;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Number 5;\lsdqformat1 \lsdpriority10 \lsdlocked0 Title;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Closing; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Signature;\lsdsemihidden1 \lsdunhideused1 \lsdpriority1 \lsdlocked0 Default Paragraph Font;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Body Text;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Body Text Indent; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Continue;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Continue 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Continue 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Continue 4; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 List Continue 5;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Message Header;\lsdqformat1 \lsdpriority11 \lsdlocked0 Subtitle;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Salutation; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Date;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Body Text First Indent;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Body Text First Indent 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Note Heading; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Body Text 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Body Text 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Body Text Indent 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Body Text Indent 3; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Block Text;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Hyperlink;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 FollowedHyperlink;\lsdqformat1 \lsdpriority22 \lsdlocked0 Strong; \lsdqformat1 \lsdpriority20 \lsdlocked0 Emphasis;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Document Map;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Plain Text;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 E-mail Signature; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Top of Form;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Bottom of Form;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Normal (Web);\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Acronym; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Address;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Cite;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Code;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Definition; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Keyboard;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Preformatted;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Sample;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Typewriter; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 HTML Variable;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Normal Table;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 annotation subject;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 No List; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Outline List 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Outline List 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Outline List 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Simple 1; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Simple 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Simple 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Classic 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Classic 2; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Classic 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Classic 4;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Colorful 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Colorful 2; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Colorful 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Columns 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Columns 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Columns 3; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Columns 4;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Columns 5;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Grid 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Grid 2; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Grid 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Grid 4;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Grid 5;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Grid 6; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Grid 7;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Grid 8;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table List 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table List 2; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table List 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table List 4;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table List 5;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table List 6; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table List 7;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table List 8;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table 3D effects 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table 3D effects 2; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table 3D effects 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Contemporary;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Elegant;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Professional; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Subtle 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Subtle 2;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Web 1;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Web 2; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Web 3;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Balloon Text;\lsdpriority39 \lsdlocked0 Table Grid;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Table Theme;\lsdsemihidden1 \lsdlocked0 Placeholder Text; \lsdqformat1 \lsdpriority1 \lsdlocked0 No Spacing;\lsdpriority60 \lsdlocked0 Light Shading;\lsdpriority61 \lsdlocked0 Light List;\lsdpriority62 \lsdlocked0 Light Grid;\lsdpriority63 \lsdlocked0 Medium Shading 1;\lsdpriority64 \lsdlocked0 Medium Shading 2; \lsdpriority65 \lsdlocked0 Medium List 1;\lsdpriority66 \lsdlocked0 Medium List 2;\lsdpriority67 \lsdlocked0 Medium Grid 1;\lsdpriority68 \lsdlocked0 Medium Grid 2;\lsdpriority69 \lsdlocked0 Medium Grid 3;\lsdpriority70 \lsdlocked0 Dark List; \lsdpriority71 \lsdlocked0 Colorful Shading;\lsdpriority72 \lsdlocked0 Colorful List;\lsdpriority73 \lsdlocked0 Colorful Grid;\lsdpriority60 \lsdlocked0 Light Shading Accent 1;\lsdpriority61 \lsdlocked0 Light List Accent 1; \lsdpriority62 \lsdlocked0 Light Grid Accent 1;\lsdpriority63 \lsdlocked0 Medium Shading 1 Accent 1;\lsdpriority64 \lsdlocked0 Medium Shading 2 Accent 1;\lsdpriority65 \lsdlocked0 Medium List 1 Accent 1;\lsdsemihidden1 \lsdlocked0 Revision; \lsdqformat1 \lsdpriority34 \lsdlocked0 List Paragraph;\lsdqformat1 \lsdpriority29 \lsdlocked0 Quote;\lsdqformat1 \lsdpriority30 \lsdlocked0 Intense Quote;\lsdpriority66 \lsdlocked0 Medium List 2 Accent 1;\lsdpriority67 \lsdlocked0 Medium Grid 1 Accent 1; \lsdpriority68 \lsdlocked0 Medium Grid 2 Accent 1;\lsdpriority69 \lsdlocked0 Medium Grid 3 Accent 1;\lsdpriority70 \lsdlocked0 Dark List Accent 1;\lsdpriority71 \lsdlocked0 Colorful Shading Accent 1;\lsdpriority72 \lsdlocked0 Colorful List Accent 1; \lsdpriority73 \lsdlocked0 Colorful Grid Accent 1;\lsdpriority60 \lsdlocked0 Light Shading Accent 2;\lsdpriority61 \lsdlocked0 Light List Accent 2;\lsdpriority62 \lsdlocked0 Light Grid Accent 2;\lsdpriority63 \lsdlocked0 Medium Shading 1 Accent 2; \lsdpriority64 \lsdlocked0 Medium Shading 2 Accent 2;\lsdpriority65 \lsdlocked0 Medium List 1 Accent 2;\lsdpriority66 \lsdlocked0 Medium List 2 Accent 2;\lsdpriority67 \lsdlocked0 Medium Grid 1 Accent 2;\lsdpriority68 \lsdlocked0 Medium Grid 2 Accent 2; \lsdpriority69 \lsdlocked0 Medium Grid 3 Accent 2;\lsdpriority70 \lsdlocked0 Dark List Accent 2;\lsdpriority71 \lsdlocked0 Colorful Shading Accent 2;\lsdpriority72 \lsdlocked0 Colorful List Accent 2;\lsdpriority73 \lsdlocked0 Colorful Grid Accent 2; \lsdpriority60 \lsdlocked0 Light Shading Accent 3;\lsdpriority61 \lsdlocked0 Light List Accent 3;\lsdpriority62 \lsdlocked0 Light Grid Accent 3;\lsdpriority63 \lsdlocked0 Medium Shading 1 Accent 3;\lsdpriority64 \lsdlocked0 Medium Shading 2 Accent 3; \lsdpriority65 \lsdlocked0 Medium List 1 Accent 3;\lsdpriority66 \lsdlocked0 Medium List 2 Accent 3;\lsdpriority67 \lsdlocked0 Medium Grid 1 Accent 3;\lsdpriority68 \lsdlocked0 Medium Grid 2 Accent 3;\lsdpriority69 \lsdlocked0 Medium Grid 3 Accent 3; \lsdpriority70 \lsdlocked0 Dark List Accent 3;\lsdpriority71 \lsdlocked0 Colorful Shading Accent 3;\lsdpriority72 \lsdlocked0 Colorful List Accent 3;\lsdpriority73 \lsdlocked0 Colorful Grid Accent 3;\lsdpriority60 \lsdlocked0 Light Shading Accent 4; \lsdpriority61 \lsdlocked0 Light List Accent 4;\lsdpriority62 \lsdlocked0 Light Grid Accent 4;\lsdpriority63 \lsdlocked0 Medium Shading 1 Accent 4;\lsdpriority64 \lsdlocked0 Medium Shading 2 Accent 4;\lsdpriority65 \lsdlocked0 Medium List 1 Accent 4; \lsdpriority66 \lsdlocked0 Medium List 2 Accent 4;\lsdpriority67 \lsdlocked0 Medium Grid 1 Accent 4;\lsdpriority68 \lsdlocked0 Medium Grid 2 Accent 4;\lsdpriority69 \lsdlocked0 Medium Grid 3 Accent 4;\lsdpriority70 \lsdlocked0 Dark List Accent 4; \lsdpriority71 \lsdlocked0 Colorful Shading Accent 4;\lsdpriority72 \lsdlocked0 Colorful List Accent 4;\lsdpriority73 \lsdlocked0 Colorful Grid Accent 4;\lsdpriority60 \lsdlocked0 Light Shading Accent 5;\lsdpriority61 \lsdlocked0 Light List Accent 5; \lsdpriority62 \lsdlocked0 Light Grid Accent 5;\lsdpriority63 \lsdlocked0 Medium Shading 1 Accent 5;\lsdpriority64 \lsdlocked0 Medium Shading 2 Accent 5;\lsdpriority65 \lsdlocked0 Medium List 1 Accent 5;\lsdpriority66 \lsdlocked0 Medium List 2 Accent 5; \lsdpriority67 \lsdlocked0 Medium Grid 1 Accent 5;\lsdpriority68 \lsdlocked0 Medium Grid 2 Accent 5;\lsdpriority69 \lsdlocked0 Medium Grid 3 Accent 5;\lsdpriority70 \lsdlocked0 Dark List Accent 5;\lsdpriority71 \lsdlocked0 Colorful Shading Accent 5; \lsdpriority72 \lsdlocked0 Colorful List Accent 5;\lsdpriority73 \lsdlocked0 Colorful Grid Accent 5;\lsdpriority60 \lsdlocked0 Light Shading Accent 6;\lsdpriority61 \lsdlocked0 Light List Accent 6;\lsdpriority62 \lsdlocked0 Light Grid Accent 6; \lsdpriority63 \lsdlocked0 Medium Shading 1 Accent 6;\lsdpriority64 \lsdlocked0 Medium Shading 2 Accent 6;\lsdpriority65 \lsdlocked0 Medium List 1 Accent 6;\lsdpriority66 \lsdlocked0 Medium List 2 Accent 6; \lsdpriority67 \lsdlocked0 Medium Grid 1 Accent 6;\lsdpriority68 \lsdlocked0 Medium Grid 2 Accent 6;\lsdpriority69 \lsdlocked0 Medium Grid 3 Accent 6;\lsdpriority70 \lsdlocked0 Dark List Accent 6;\lsdpriority71 \lsdlocked0 Colorful Shading Accent 6; \lsdpriority72 \lsdlocked0 Colorful List Accent 6;\lsdpriority73 \lsdlocked0 Colorful Grid Accent 6;\lsdqformat1 \lsdpriority19 \lsdlocked0 Subtle Emphasis;\lsdqformat1 \lsdpriority21 \lsdlocked0 Intense Emphasis; \lsdqformat1 \lsdpriority31 \lsdlocked0 Subtle Reference;\lsdqformat1 \lsdpriority32 \lsdlocked0 Intense Reference;\lsdqformat1 \lsdpriority33 \lsdlocked0 Book Title;\lsdsemihidden1 \lsdunhideused1 \lsdpriority37 \lsdlocked0 Bibliography; \lsdsemihidden1 \lsdunhideused1 \lsdqformat1 \lsdpriority39 \lsdlocked0 TOC Heading;\lsdpriority41 \lsdlocked0 Plain Table 1;\lsdpriority42 \lsdlocked0 Plain Table 2;\lsdpriority43 \lsdlocked0 Plain Table 3;\lsdpriority44 \lsdlocked0 Plain Table 4; \lsdpriority45 \lsdlocked0 Plain Table 5;\lsdpriority40 \lsdlocked0 Grid Table Light;\lsdpriority46 \lsdlocked0 Grid Table 1 Light;\lsdpriority47 \lsdlocked0 Grid Table 2;\lsdpriority48 \lsdlocked0 Grid Table 3;\lsdpriority49 \lsdlocked0 Grid Table 4; \lsdpriority50 \lsdlocked0 Grid Table 5 Dark;\lsdpriority51 \lsdlocked0 Grid Table 6 Colorful;\lsdpriority52 \lsdlocked0 Grid Table 7 Colorful;\lsdpriority46 \lsdlocked0 Grid Table 1 Light Accent 1;\lsdpriority47 \lsdlocked0 Grid Table 2 Accent 1; \lsdpriority48 \lsdlocked0 Grid Table 3 Accent 1;\lsdpriority49 \lsdlocked0 Grid Table 4 Accent 1;\lsdpriority50 \lsdlocked0 Grid Table 5 Dark Accent 1;\lsdpriority51 \lsdlocked0 Grid Table 6 Colorful Accent 1; \lsdpriority52 \lsdlocked0 Grid Table 7 Colorful Accent 1;\lsdpriority46 \lsdlocked0 Grid Table 1 Light Accent 2;\lsdpriority47 \lsdlocked0 Grid Table 2 Accent 2;\lsdpriority48 \lsdlocked0 Grid Table 3 Accent 2; \lsdpriority49 \lsdlocked0 Grid Table 4 Accent 2;\lsdpriority50 \lsdlocked0 Grid Table 5 Dark Accent 2;\lsdpriority51 \lsdlocked0 Grid Table 6 Colorful Accent 2;\lsdpriority52 \lsdlocked0 Grid Table 7 Colorful Accent 2; \lsdpriority46 \lsdlocked0 Grid Table 1 Light Accent 3;\lsdpriority47 \lsdlocked0 Grid Table 2 Accent 3;\lsdpriority48 \lsdlocked0 Grid Table 3 Accent 3;\lsdpriority49 \lsdlocked0 Grid Table 4 Accent 3; \lsdpriority50 \lsdlocked0 Grid Table 5 Dark Accent 3;\lsdpriority51 \lsdlocked0 Grid Table 6 Colorful Accent 3;\lsdpriority52 \lsdlocked0 Grid Table 7 Colorful Accent 3;\lsdpriority46 \lsdlocked0 Grid Table 1 Light Accent 4; \lsdpriority47 \lsdlocked0 Grid Table 2 Accent 4;\lsdpriority48 \lsdlocked0 Grid Table 3 Accent 4;\lsdpriority49 \lsdlocked0 Grid Table 4 Accent 4;\lsdpriority50 \lsdlocked0 Grid Table 5 Dark Accent 4; \lsdpriority51 \lsdlocked0 Grid Table 6 Colorful Accent 4;\lsdpriority52 \lsdlocked0 Grid Table 7 Colorful Accent 4;\lsdpriority46 \lsdlocked0 Grid Table 1 Light Accent 5;\lsdpriority47 \lsdlocked0 Grid Table 2 Accent 5; \lsdpriority48 \lsdlocked0 Grid Table 3 Accent 5;\lsdpriority49 \lsdlocked0 Grid Table 4 Accent 5;\lsdpriority50 \lsdlocked0 Grid Table 5 Dark Accent 5;\lsdpriority51 \lsdlocked0 Grid Table 6 Colorful Accent 5; \lsdpriority52 \lsdlocked0 Grid Table 7 Colorful Accent 5;\lsdpriority46 \lsdlocked0 Grid Table 1 Light Accent 6;\lsdpriority47 \lsdlocked0 Grid Table 2 Accent 6;\lsdpriority48 \lsdlocked0 Grid Table 3 Accent 6; \lsdpriority49 \lsdlocked0 Grid Table 4 Accent 6;\lsdpriority50 \lsdlocked0 Grid Table 5 Dark Accent 6;\lsdpriority51 \lsdlocked0 Grid Table 6 Colorful Accent 6;\lsdpriority52 \lsdlocked0 Grid Table 7 Colorful Accent 6; \lsdpriority46 \lsdlocked0 List Table 1 Light;\lsdpriority47 \lsdlocked0 List Table 2;\lsdpriority48 \lsdlocked0 List Table 3;\lsdpriority49 \lsdlocked0 List Table 4;\lsdpriority50 \lsdlocked0 List Table 5 Dark; \lsdpriority51 \lsdlocked0 List Table 6 Colorful;\lsdpriority52 \lsdlocked0 List Table 7 Colorful;\lsdpriority46 \lsdlocked0 List Table 1 Light Accent 1;\lsdpriority47 \lsdlocked0 List Table 2 Accent 1;\lsdpriority48 \lsdlocked0 List Table 3 Accent 1; \lsdpriority49 \lsdlocked0 List Table 4 Accent 1;\lsdpriority50 \lsdlocked0 List Table 5 Dark Accent 1;\lsdpriority51 \lsdlocked0 List Table 6 Colorful Accent 1;\lsdpriority52 \lsdlocked0 List Table 7 Colorful Accent 1; \lsdpriority46 \lsdlocked0 List Table 1 Light Accent 2;\lsdpriority47 \lsdlocked0 List Table 2 Accent 2;\lsdpriority48 \lsdlocked0 List Table 3 Accent 2;\lsdpriority49 \lsdlocked0 List Table 4 Accent 2; \lsdpriority50 \lsdlocked0 List Table 5 Dark Accent 2;\lsdpriority51 \lsdlocked0 List Table 6 Colorful Accent 2;\lsdpriority52 \lsdlocked0 List Table 7 Colorful Accent 2;\lsdpriority46 \lsdlocked0 List Table 1 Light Accent 3; \lsdpriority47 \lsdlocked0 List Table 2 Accent 3;\lsdpriority48 \lsdlocked0 List Table 3 Accent 3;\lsdpriority49 \lsdlocked0 List Table 4 Accent 3;\lsdpriority50 \lsdlocked0 List Table 5 Dark Accent 3; \lsdpriority51 \lsdlocked0 List Table 6 Colorful Accent 3;\lsdpriority52 \lsdlocked0 List Table 7 Colorful Accent 3;\lsdpriority46 \lsdlocked0 List Table 1 Light Accent 4;\lsdpriority47 \lsdlocked0 List Table 2 Accent 4; \lsdpriority48 \lsdlocked0 List Table 3 Accent 4;\lsdpriority49 \lsdlocked0 List Table 4 Accent 4;\lsdpriority50 \lsdlocked0 List Table 5 Dark Accent 4;\lsdpriority51 \lsdlocked0 List Table 6 Colorful Accent 4; \lsdpriority52 \lsdlocked0 List Table 7 Colorful Accent 4;\lsdpriority46 \lsdlocked0 List Table 1 Light Accent 5;\lsdpriority47 \lsdlocked0 List Table 2 Accent 5;\lsdpriority48 \lsdlocked0 List Table 3 Accent 5; \lsdpriority49 \lsdlocked0 List Table 4 Accent 5;\lsdpriority50 \lsdlocked0 List Table 5 Dark Accent 5;\lsdpriority51 \lsdlocked0 List Table 6 Colorful Accent 5;\lsdpriority52 \lsdlocked0 List Table 7 Colorful Accent 5; \lsdpriority46 \lsdlocked0 List Table 1 Light Accent 6;\lsdpriority47 \lsdlocked0 List Table 2 Accent 6;\lsdpriority48 \lsdlocked0 List Table 3 Accent 6;\lsdpriority49 \lsdlocked0 List Table 4 Accent 6; \lsdpriority50 \lsdlocked0 List Table 5 Dark Accent 6;\lsdpriority51 \lsdlocked0 List Table 6 Colorful Accent 6;\lsdpriority52 \lsdlocked0 List Table 7 Colorful Accent 6;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Mention; \lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Smart Hyperlink;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Hashtag;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Unresolved Mention;\lsdsemihidden1 \lsdunhideused1 \lsdlocked0 Smart Link;}}{*\datastore 01050000 02000000180000004d73786d6c322e534158584d4c5265616465722e362e3000000000000000000000060000 d0cf11e0a1b11ae1000000000000000000000000000000003e000300feff090006000000000000000000000001000000010000000000000000100000feffffff00000000feffffff0000000000000000ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff fffffffffffffffffdfffffffeffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff ffffffffffffffffffffffffffffffff52006f006f007400200045006e00740072007900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000016000500ffffffffffffffffffffffff0c6ad98892f1d411a65f0040963251e500000000000000000000000040b2 e529fd1edb01feffffff00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000ffffffffffffffffffffffff00000000000000000000000000000000000000000000000000000000 00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000ffffffffffffffffffffffff0000000000000000000000000000000000000000000000000000 000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000ffffffffffffffffffffffff000000000000000000000000000000000000000000000000 0000000000000000000000000000000000000000000000000105000000000000}}BIS130 - Transcript Knut: Welcome to the Bitcoin Infinity Show, brought to you by BitBox Stampseed, the Bitcoin Advisor and ShopInBit. Enjoy the conversation. Welcoming Obi Nwosu Luke: Obi, welcome for the first time to the Bitcoin Infinity Show. Obi: well, Knut: We rebranded. Obi: what is time in infinity? No, no, it's the second time, great to have you back. yeah, we have, it's been a wild ride and the journey is just beginning. So yeah, thank you. The Launch of Fedi</p> <p>Knut: so Fedimin launched, two weeks ago. Is it the Fedi Obi: Fedi, launched? Knut: launched? Yeah. These terms. Obi: no, no, Fedi Mint launched, effectively Fedi Mint launched nearly five years ago. FediMint is a very old technology, very, you know, the first, the first FediMint transaction, where someone used FediMint e cash over Lightning to buy a cup of coffee, which was after, you know, a year plus of development was on, I believe it was the 3rd of the 8th, 3rd of August, 2021. Obi: And so we're trying to, like you have a Bitcoin Infinity Day, we're suggesting, that was actually Erik, my, the inventor of Fedi Mint. from Parinelli Police, just actually, and so I like to think of that as e cash coffee day. Cause actually it was like, you actually bought the cup of coffee with e cash. Obi: so yeah, but yeah, Fedi finally launched two weeks ago. Knut: All right. so I think, for those who haven't seen the previous episode with you, if they want to know more about you, we should probably go back to that episode, but I think you're going to have to do the TLDR on what Fedi is for our listeners. Like that's a good start, I think. Obi: So yeah, and now we can be clear about what Fedi is. And so Fedi, is two things still. Even Fedi is two things. One is the company called Fedi and the other is this product called Fedi. So if we talk about the product that people have on their phone, Fedi is a community super app. And so it's an app that takes the best of freedom technology. Obi: it's got Bitcoin functionality in it, Lightning connectivity, obviously FediMint for handling community custody. but it's also got Nostr support and any other freedom technology that's out there that's mature and reliable. We've taken the time to integrate into one simple to use app. So it allows you to have chat. Obi: We use Matrix as this federated, decentralized, encrypted chat protocol. It has money with the combination of Lightning, Bitcoin, and Fediment and more. So it has a built in web browser inside it. And therefore you can access all of the Bitcoin ecosystem of apps from Bitrefill to Unleash. chat to BTCmaps and beyond. Obi: All in one place. So you don't have to have this smorgasbord of different apps and tabs open one app to use them all. And the app itself, we announced as well, is now source available and will eventually be open source as well. So we're trying to make the best of it. portal into the freedom technology space. Obi: So that's Fedi. And then Fedi the company builds the Fedi app. And we also have something we call the FedEye Order, which is, this selection of incredible people, FedEye Knights, who are on the ground and they, you can think of them as like a Decentralized genius bar. If you've got an iPhone, you have the genius bar that goes along with the phone. Obi: The reason why the iPhone is so amazing is not just the phone, but it's also the incredible support you can get. If you can go to an Apple store and you go to the genius bar, they can help you. we have that instead of it being in, you know, Fifth Avenue or Oxford street in London or so on. Obi: It's in, the capital of Togo or Uganda or. Guatemala, or so on. On the ground, they will locate communities, they will educate communities. and they will support communities on Bitcoin, on Lightning, on FediMent, on all of these different websites and services that are out there to provide that sort of support that's needed for the communities that are outside of the existing Bitcoin space. How Federations Work Knut: Okay, great. so how does a federation work? Obi: so the first thing you have to do, wherever you custody is where you transact and do and you live and so on, which is why. Banks try very much when you're young to get you to hold a bank account with them because they know that most people never leave and then all other services are provided. So how do you actually custody? Obi: For many people they've had two choices. Either they do everything themselves and that's the best if you can do it just like it's the best to be able to build and fix your own car or house but not everybody can do that but that is always the best because no one's going to love you. And put as much care in as yourself. Obi: The other extreme is to fully outsource it, fully give it to some private party, which is actually what ends up 95 percent plus people doing, and that's putting their money on a Coinbase or some other centralized service. and the same with communication. They would use some sort of centralized service. Obi: They would use a WhatsApp, an X. com, a Telegram, a WeChat or so on. They would use some centralized chat. And if you think about it. Our lives are communication and money and value. So both those things, most people outsource, some people take it in house. If I want to set up a federation, which is to do with the custody of the money, where FedeMint is this middle, middle house, I can find within my community, a number of trusted parties. Obi: We call them guardians. So let's say. You found us three plus, you know, your great t shirt, Greg Voss. The minimum we suggest is four for various Esoteric reasons From a cryptographic security point of view we suggest four, but you can have seven You can have you can keep growing you could have we've seen people have seen Federation stood up with as many as 40 people in them And it will get slower and slower if it gets beyond that, but, but technically you can. Obi: It'll be this, it'll create this huge multisig, i. e. multiple people have to sign before you do a transaction on chain. And so multisig starts to get expensive of a certain size. But let's say us three plus Greg. We would FedeMint software. we would download the 30 minute software onto a machine that we have spare, and we would set up and run it. Obi: The setup process will, part of it will enter the information about the other three. And we make that very simple, it's a web interface, you point and click and you get a code and you share that code with the other parties, everybody shares the code of each other. Maybe you go into a group chat and paste each other's code. Obi: Everybody copies each other's, enters it into our own FediMint and then they connect to each other and they form a federation. As long as you keep that box, running, connected to the internet, and connected to electricity, the federation, for each, all the four, the federation are one. Obi: But because it's a federation, if one of them, for example, had a power cut, or lost their internet, or had to change their domain name, or something like that, The other three will be able to continue and operate. Yep, so you've now created this community custody platform. Now, anyone with the FEDI app or any other app that supports the FEDIMINT protocol, Webimint, and we're hoping that many others will set up FEDIMINT wallets, like there are multiple Lightning wallets in future. Obi: Any FDI min wallet compatible wallets like Fedie, can connect to your federation At the end of setting up the fed min server will show a QR code and the string that represents how to connect to your Federation. So you could take your Fed app, or the Mutiny wallet, or Web Mint, or any other, fed mint compatible wallet, and you'll scan that QR code. Obi: And you've now connected to that federation and that federation becomes, you can now use it to custody. Now, what will happen is, if for example, someone wants to send money to you, you would, just as if you're using a Bitcoin wallet, let's say it's on chain. you would say, I want to receive, enter the amount and it'll show a QR code. Obi: Someone else who's using a normal Bitcoin wallet will scan that code and send over the Bitcoin main chain money to you. But what's actually happening is your Fediap is communicating with the Federation. Your Federation is creating a Bitcoin address for you to send to and sends it back to you for you to display. Obi: Okay. And then a user, someone else who's using a completely different wallet will send money to that address. Actually goes to the federation and they, the four of us combined will process that and create e cash, which is like a token representation of the Obi: Bitcoin. And then the e cash will be sent to you. But the way it, the way it's sent is completely privacy preserving. So the guardians have no way of knowing who they are providing that service for, who's receiving the money. Obi: There's full privacy. Obi: All right, and neither does the sender, I assume, like the sender doesn't, that they sent Bitcoin to us and address. They have no idea who, so if there are, let's say we set this up and we're using it for our friends and extended family and in total, there are 40 of us or 50 of us Obi: When you send to that address, there's no way to know out of those 40 or 50 people who received it or who requested it. Knut: All right, so, a bit about the guardians and the multisig, that's obviously because you don't want to have a single point of attack for each, federation, right? Obi: point of failure, Knut: A single point of Obi: the more likely thing is that someone's machine, if you had one machine, the most likely thing that will happen, almost guaranteed, at some point you'll have some sort of power cut or internet cut. Internet cut is probably the most likely you'll, you'll have a glitch on your internet for 30 minutes. Obi: If you do, Everyone using your federation won't be able to use your system for 30 minutes. Knut: but it's also an attack vector. Like if the, if the, if there's a lot of money in the federation and, so there's, there's an incentive to attack the guardians. Like, can you be completely sure that the guardians don't know each other's identities and stuff like that? Like how, I know you think a lot about the attack vector. Knut: So I'm like, can you go into that a bit? Obi: can't be completely sure of anything in life. So the answer to that is automatically no. Can you be completely sure of something? but, it depends on the Also, there's an assumption that you have, that the people don't know each other. Cause I think very often in, there's two types of scenarios. Obi: It could be that each party completely doesn't know each other, or the more common scenario will be that you're some community or some group of friends. And within you, you've decided. Of the people who are my friends and family and so on, these four people are the ones who are consistently the most reliable, the most trusted and so on. Obi: They do know each other, and you know who they are, and it's because you know who they are that you're comfortable with them holding. they're the Uncle Jims of the family. they're known to be reliable. They're known to be people who care about their friends and family. Obi: that's very often actually what we're seeing is the more common scenario than the ones where people are completely, anonymous to each other. But as it matures, we may see the other scenario happen as well. The Uncle Network Luke: It's a literal uncle network. I know Uncle Rockstar started the uncle network here on infinity day. Yeah, you got the brother Luke, and so that's four, so we're Obi: are you an uncle? Knut: am an uncle officially now. Knut: an uncle as well, are like, but dubbed by Uncle Rockstar Obi: I haven't been dubbed I, so Obi: you are a good candidate. candidate, but I am biologically now, an Knut: oh, congratulations, Obi: Yeah, How Fedi Launched Luke: Okay, well, I think we are looking just to dig in more about Fedi Fedi Mint and, what does your launch actually mean? Because the app has been in beta for quite a while, right? what's happened, to make it that you can launch? Obi: Yeah, that's a very good question, because, we, the app from the, if you just focus on the app, from the previous version to the one we went live, there are only a few, changes. It was more about, did we have enough feedback from enough people on the ground that we thought that the product was stable enough, reliable enough? Obi: behind the scenes, we've done a lot of internal plus from trusted friends, external security audits of different elements as well. I don't like to publicize it because it's just something we do. We don't think it's something you should promote to saying, Hey, look at what we're doing. We just try to build the best that we can. Obi: and the really, big thing was to just say, a lot of people ask, is Fedi ready? And we wanted to get to a line where we thought it was good enough. And we got to that line. And then, we also wanted to have enough proof points in, the world. And again, we got to that line. So these things were separate things that were happening. Obi: And finally, it was very clear to us that we wanted to make the software, Ultimately open source. And that was a big call because, you know, we raised 21 million and, normally you go two routes. You go, you raise a little bit and you stay open source and so on. Or you raise a lot and you stay closed source. Obi: We believe that, over time, it's going to be considered, over the coming years, it's going to consider that you should always go open source no matter what you're doing, but we're in a transition. Five years ago, raising this much and going open source would be considered crazy, in five years time, raising this much and not being open source would be considered crazy. Obi: And we wanted to be, afforded in that. So. We actually went source available. It's called a business source license. So it means you go source available and you set a date where you must go open source or earlier. and we set those. So we cannot change it now. We cannot say we're going to actually change our mind. Obi: Well, the only thing we can say is that we're going to go open source earlier. that's the only thing we could do. Or if we decide to shut down, it's automatically open source as well. That's the sort of dead man's switch as well. Or we decide we're no longer going to develop the software. Obi: we've added caveats like that, which are not optional, but actually add more restrictions. So no one's going to complain with us going open source earlier. that was agreed and put in place on May the 4th. So May the 4th we review of this year, 2024, just for posterity. Obi: we, got enough proof points from different markets, that we felt that we're onto something here. Does that mean that we've finished? No, there's a lot of work to do, but enough to say that the idea of taking all of the best of freedom technologies out there. And putting them into one place and one app that's easy to use is something that's compelling to people. Obi: And also we had enough to see the federation model. of this sort of really simple to use and privacy preserving multi sig is also a powerful model. So the model was proven out. And then finally the software, we got to a point where we thought, it's, of course, we've got years of more development, but it was good enough as well. Obi: I think that was the final piece. And we thought, okay, we're ready to go. And we then set a date a few weeks after that. But even when we were getting close to it, we started the process of shooting a video because we just wanted to show people are wondering what were we doing for the last nearly two years and we wanted to show that as well.</p> <p>Luke: what's the synopsis of the last two years? Like the big highlights?</p> <p>Obi: so, I always say there's three phases in the business. There's initialization, of a startup, initialization, market product fit, in our case, not product market fit, I can go into why. And then, growth. And so, this phase that was, the end was finally, we crossed the line, on August the 6th, 2024, was the initialization phase. Obi: And so, if you think about the analogy of, like you wanted to have A shop selling designer pet clothing, and you've decided you have this crazy idea and you have to first fund it, find the people to build it, and then find the place, set up the store, make the clothes and, open. Obi: That's the initialization phase. And then once it's launched, you then. Start figuring out, okay, people come in, there's initial, interest, and then, you have this trickle of people coming in, you have to figure out what do they like, what do they not like, what do I have to adjust until it becomes this sort of regular viable business. Luke: That's the market product fit phase. And then you start saying, okay, I've got something that's working fully and then I will repeat it, make more and more and more, Widgets? Obi: Doggy fashion, Excel stores, whatever you want to call it. the last two years was our initialization phase. Obi: we had this, amazing product with FediMint. we had this initial set of, crazy people with Erik, the inventor of FedEvent, Justin, who's, who was also incredible engineer, who was actually the one who suggested that we make a commercial enterprise. up until that, both myself and Erik just suggested it would be an open source project. Obi: And then myself as well with my just, you know, only maybe six or seven months before we were finally finished selling. a Bitcoin exchange, the UK's longest running Bitcoin exchange. and so having that experience of building a company that was profitable and understanding what it meant to build something that custodies a large amount of money for people and provides them services is easy to use and all that sort of stuff. Obi: and everything around that customer service, everything around that. So, we were there, I had a visit to the Oslo Freedom Forum, and that was the catalyst. we did one talk at, Bitcoin Miami, and, Alex Gladstein saw that, he suggested I go to Oslo Freedom Forum. I went, my mind was blown and I also realized whenever you're thinking about a business, you have to always think about chicken and the egg and how do you find your initial market for eventually this product is applicable to everybody everywhere, but who's the first use case that has a demand so high that they're going to willing to go through the really buggy early versions and help you. Obi: Stabilize it to the point where it's something that people can click a button and it works everywhere. I realized that the community of human rights defenders and later on also humanitarian organizations fit that, need. We really cared about that need and we were concerned, we wanted to help, but we realized that this product could help in combination with the rest of the Bitcoin ecosystem. Obi: That's what's quite cool. FediMint is the thing that handles the custody, but you still need to buy things, sell things, find things, and so on, and that's where the Fedi app also comes into play, but without FediMint as the core to handle the custody, the rest didn't make sense. Obi: Then we started, it was, then you had this sort of scene from like the Magnificent Seven or so on where you're, you're finding your initial team members. So we found Renato Rodriguez, I chased her for like six months ago. She should have, you know, got a restraining order for six months trying to get her to join. Obi: just if you look at the initial team, it was just everybody, the whole team is amazing. But it was just trying to find these incredible people. they tended to just immediately understand the value proposition and the market we were trying to help and were already doing incredibly well in their own careers, but there was something missing for them. Obi: And when they saw this, it was like this fulfilled There's some other need that they had beyond the monetary need. The potential was amazing, but the mission side of it was what helped us bring on this incredible team. So I believe in philosophy, people, process, product. The philosophy was amazing, who we're helping, the potential, it's helping people and in so doing we're helping Bitcoin, in so doing we're helping the world. Obi: And that's a powerful philosophy and mission and that attracted this incredible group of people. And if you've got the philosophy and you've got an incredible group of people, they will put in the processes that will lead to the right product. Obi: It's like, let's say the video, for example. I said to Renata, I want a really powerful launch video and it should be like the best Apple keynote speech combined with a UNICEF or Save the Children commercial. That's it. That's the whole brief and that whole video. And somebody says, you need to go to Madeira. Obi: You need to say this. And I just woke up and I say what she says. But the whole elements of it, all of it was her and her team, Mary and marketing and everybody building that over the following X months. and I didn't actually see the video myself. Until less than a month before we launched it for the first time as a rough draft. Obi: And it was just basically perfect. My comments were like, I actually didn't have any significant comments, but that was the same for most of the team and the design of the product. We had this incredible designer, Skylar. I would give a brief and so as, Erik's brief was, I just want to be proud of something that I should be proud of, and that was it, you know? Obi: And I was like, it just needs to be really simple. And that's the high level. And I might give comments on a little bit here or there, but in general, whenever he gave me it, I would say, well, he Skylarized it, like just Skylarize it. And he would just come up with something that was great. and I think that was the last two years. Obi: We had the team we raised. again, the choice of investors was really, really key. I was very, very sure, especially from my previous experiences, that I only wanted Bitcoin on the investors, especially for the first couple of rounds. And when I've sometimes do talks on how to set up a Bitcoin company, my first slide says don't do it, but instead sort of a Bitcoin business, not a Bitcoin startup. Obi: And I explain the difference between the two. but one part is, if you do want to raise capital, be really careful about your choice of investors. The wrong investors will, well, and they don't mean to, but they will kill your business without meaning to, but the right investors will. So, we were really, really careful about our choice of investors and the initial team and then the initial team brought on the rest of the team after that. Obi: And that was the last, that's the last two years we've set ourself up very well. I did, being a classic entrepreneur, think it'll take six months, took two years. So I, so my estimation on that was a little bit off, but the end result, I'm really excited about. And now, now we're, now we're off to the races. Great news, everyone! Bitcoin, the inverse of clown world is out now. It's the successor to everything divided by 21 million. And it's based on the last two years of podcasts that we've done together. So if you like the show, you're going to love the book. Find the book on bitcoininfinitystore. com or on Amazon. That's right. We have our own store now. BitcoinInfinityStore. com. You can find not just books, but merchandise based on everything divided by 21 million, check out Bitcoin, the inverse of Clown World today and buy some other stuff while you're there too. This show is brought to you by Bit Box, our favorite hardware wallet. It's Swiss engineered and has all the most important security features to keep your Bitcoin safe while keeping a user experience that even your grandma can use. So visit Bit Box. Do Swiss slash Freedom to learn more, or use Code Freedom at checkout for 5% off. And remember, it's the Bit Box zero two Bitcoin only edition. Make sure to get that Bitcoin only firmware. How does Fedi Make Money? Knut: How does the app make money? Obi: Yeah. Knut: For the company? Obi: if you use the app, whenever you use the Freddie app. whenever a transaction happens, which would have occurred a fee. So it's a Bitcoin transaction, e cash or a lightning transaction. We add on an additional fee, 21, 21 basis points. So 0. Knut: Oh, yeah, Obi: And so, and the good thing is because we can charge in sats and I believe actually even fractions of a sat, it's a progressive tax, which a fee. Obi: So what I mean by that is. If you're sending, let's say 100 through, then you would be charged on 100. 21, but if you're, worth of value, but if you're sending through 1, then you'll be charged 0. 21 cents. And if you're sending through 0. 10, you'll be charged 0. 20. 0 to 1 cents. So it'll always be a very small percentage of what you're sending. Obi: Now, people might say in certain countries, don't they have mobile money and so on. But the problem is those mobile money systems have minimum fees. And it might be, 1%, which is not that bad, say. And it might be, even in some terms of scale, it could be half a percent, but with a minimum fee of 20 cents. Obi: So if you're sending a hundred dollars, that's okay. But if you're sending, 1, that's 20%. And so if you have someone who has a monthly salary of. 10 in some of these markets, that 0. 20 fee starts becoming quite a significant per transaction hit. So therefore it becomes unaffordable for you to use mobile money. Obi: So even though it's prolific above a certain wealth level, and so that leaves many people out, in the rain. But because this is progressive, if you're selling 10 cents, the, fee will actually round to zero. I mean it will be a fee, but you'll see it in sats, but if you were showing, trying to show it in local currency, it would basically be, it'll say about zero and then you click and you realize it's this small amount of sats. Knut: so, yeah. the big thing that I'm thinking of if I'm like. Playing this out in my head with where this could be in 10 years, like you could run entire virtual nations on a federation, right? If you have the money and the communication and whatever other useful apps, Obi: I think the big thing I think is, if you look at the internet, there are large organizations where, people use and they're highly centralized. You have a few people who may be wealthy enough to have their own direct connection to the internet, but the majority of people are connected on the internet. Obi: I don't know at this stage, millions of intranets, like household intranets effectively, company intranets and school intranets and so on, where it's one connection to the internet shared by multiple people. That's actually the majority of people. And it's that middle ground between these huge mega organizations that people are connected to one mainframe. Obi: With millions of users, I think there are very few of them now, but that was the denominant way at the beginning. It was these huge, centralized ways of connecting AOL, CompuServe, and so on. Now, they're actually relatively rare, but that was at the beginning. All of the internet was that. A few centralized parties, and I would liken them, conceptually in value terms, in value custody terms versus information custody terms, to, a coin basis. Obi: And also there were a lot of hobbyists who had their own direct ISDN connection to the internet. but now most people connect through these intranets where they get one router, one connection, and they share with everybody in their household. That would be a criminal of the Uncle Jim federations or in their school or in their football club or in their office. Obi: That's probably 95 percent of people and I think that this approach of federated model from the size from. Five or six people up to five or six hundred thousand, that range can cover 80, 90 percent of usage. How to Use Fedi(Mint) Luke: Can we go back to the basics of how feint works in the perspective of someone actually using this thing? So, you explained to us last time how it works, but just for my own sanity, check that I got it. if you are sending e cash within the federation, that is just. Luke: Direct between two users. There's not even a record outside of that. No one knows those transactions are even happening. Is that essentially correct? Obi: Yeah. So the federation helps you mint technically, because actually the user creates their own e cash, they create their own e cash, but it's unstamped and then they give it to the federation and they stick in an envelope. And they give it to the federation with some carbon copy paper on the inside the envelope as well. Obi: the federation collectively signs. So let's say all four people go stamp, stamp, stamp. And that makes it valid. then they give back the envelope to the user. The user then opens the envelope with the cache that they created, just some random piece of data. Obi: And they now have this Ucash, but the Ucash they've created now has got the four stamps on it, say, for the four of us. And so anyone else in that federation, any other, person who's also connected to the federation. They can just literally, directly give them this, random set of data. Obi: Let's say it's a picture of a fashionable dog and they can just give it to someone else. and the person will receive it and they don't really care what the data says. They just look, are the four stamps on it? Yes. Then it means it was stamped by the Federation, which means it's backed by a certain amount of information. Obi: Actual Bitcoin. Yeah. So take the whole, the full path. Someone deposits some Bitcoin in return. They also, along with the Bitcoin, send them an envelope, give them an envelope with this random piece of data in it to the Federation and the Federation receives the Bitcoin. Okay. I've received the Bitcoin envelope. Obi: Okay. I've received the Bitcoin. I will stamp. I received one, let's say. 10, 000 Satoshis. So I'm going to take my 10, 000 Satoshi stamp and stamp this envelope with 10, 000 Satoshis, pass it around to the other four, they all stamp the 10, 000 Satoshi stamp. And then give that back to the user. Obi: User opens the envelope and says, I've got, okay, I've got an e cash note with, with, that's been proven that the, that it's been validated by the guardians. So as long as we all trust the guardians are holding that and that they will honor this and redeem. That's it. So now I can pass it to anyone in the Federation. Obi: They receive it. They look at this picture of the cute dog, but what they're really looking at is, is it got the four stamps on it and it's 10, 000. So that means I've now received 10, 000 token. They can now at some point in the future, Often they do it immediately if they've gone into connection, but they don't have to. Obi: They can give it back to the Federation. Federation will receive it and each one will check their own signature of the guardians. Okay, it's properly signed. Therefore, I'm willing to, and they might give them a Bitcoin address to send the money on chain to. Obi: So they will receive it, it looks good, they will then, record that this, e cash note has been spent. But they don't know, of all the e cash they received, which one it was, because each one they received in the first place was in an envelope. So was it the first one they received, or the middle one they received? Obi: They have no idea. It could have been received yesterday or a month ago. No way. All they know is, I must have stamped it, so it was one of the ones I stamped. And then they will look at the address the person's asking to send the Bitcoin to, and they will take some of the Bitcoin that they're holding in the multi sig that we're holding between the four of us and send it to that address. Obi: So that's called Redeem versus Mint. Now, the user experience from a user, we can get onto Lightning, that's another level of complexity, but it's simple just for Bitcoin and eCash for now. Obi: Someone sends me Bitcoin or I send it to myself from an outside wallet and I receive e cash. And then someone else in the, in the federation wants to, once I want to pay them some e cash, they will give me, they will give me a QR code to, to scan to pay and I will scan. And literally the e cash that's on my phone gets sent to them directly. Obi: From me to them, one to one, that person when they receive it could keep it on their phone or they could say, you know what, I want to send that back to the federation and they can send it back to the federation and then the federation can destroy that, issue them new, fresh e cash in different denominations, maybe not 10, 000, but 10, 1, 000, you know, just like with notes, you could go and get change. Obi: Yeah, because if someone transacts, if you're saying it gets sent from one computer, phone being a computer, whatever, one device to another, well, that original device would still Obi: Yes, Luke: copy of the thing on, right. Obi: So they will still have a copy. Now you are in the same, this is where the community aspect works, you are in the same community, If you're in the same community, and the person, it's a merchant and you receive, and your phone will remember when you received what e cash, yeah? Obi: Even though it's private, you do know this e cash was received at this time and this time for, and so, especially when you integrate with points of sale, it will say, well, you received this e cash for this purchase. You'll know that. so then if you go to redeem it, at the end of the day, and some of it doesn't match, you will know as the merchant, which e cash was involved in that. Obi: You'll say, well, the e cash involved in this transaction. And that transaction was with John. So you've got proof of work. it's the same as if you have a merchant and you receive cash and then you finally got the end of the day to a bank. Obi: And some of the notes are counterfeit. Now, you don't find high levels of counterfeit notes in a community where people know each other. It's normally in these widespread communities. But in those scenarios, what most people will do and how the default way the app works is the moment you receive it, it immediately goes off and redeems it and then issues itself back new, new change. Obi: Yeah, that seems like a good default implementation. but if you have no internet connectivity, you can still use it and still receive. even if you can't send over the internet, you can create a QR code, which contains the e cash in the QR code, and the person can literally scan it and receive through the screen. Obi: Because as long as it's the QR code, the e cash note is just some text. So a QR code can represent that text and you can scan it, even if you have no data. So for example, it could be you're in an area where you have no data, rural, Latin America or so on. But it could also be something more innocuous. Obi: You could just be in a big sort of, But the thing is is that you might be at a Glastonbury like concert and there are a thousand phones and there's no data. Or you're in an indoor conference place underground and there's no data. But you can still take payments or the merchant has internet because they're the ones who really need it. Obi: But the buyer doesn't and so in which case the merchant has internet because they're connected wired in because they're fixed, but the buyer doesn't need to have internet to pay and the merchant will just take a risk just like in most merchants in high streets they accept a certain amount of breakage and a certain amount of transactions are gonna be charged back by, credit card companies and so on. Obi: I used to be a CTO for a major pan-European, online auction company. At the time I was competing with, eBay and so on. we were in a headliner, 300 hundred people working for me in technology. It was a very big technology offering. And we were doing millions of transactions a week. Obi: It was very high volume. And in those e commerce sites, you just accept a certain amount of breakage, a certain amount of returns, and a certain amount of chargebacks, even if you do nothing wrong and you just factor it into your costs. For the benefit of the simplicity of the experience. Fedi and Nostr Knut: you mentioned Nostr before, like, what's the marriage between Fedi and Nostr? Well, I would say right now, we are, because I think. Knut: we're beyond dating. We're engaged. But we want to really take the two footed tackle of no return, to use a football euphemism. a web of trust thing, right? Obi: Yeah, I think, whenever, from the first point I saw Nostr, a lot of people thought it was just social media and so on. Obi: I think social media is Trojan horse is the wrong word, but it's the, initial vector by which it infiltrates communities. But what you're actually doing is building a simple, trust system and a simple discovery system. It's a form of decentralized search and it's a form decentralized identity. Obi: Cause you, to search, you have to identify things to be able to search. So they're sort of two sides of the same coin. now the first thing you're using it for is identifying people who want to speak publicly and share their thoughts and so on and so forth and follow them and give feedback and like. Obi: But it always seemed to me to, way more powerful than that. And I think now people, generally understand it that way. And so, What we've already done, in Fedi, and a lot of developers really like the way it works, if you sign up to Fedi, or if you download the Fedi app and start using it, you, first of all, you don't need to give your email, you don't need to give your phone number because it's not required, but, we do ask you to come up with some sort of Username for yourself. Obi: That doesn't even have to be unique, by the way. We will add a unique element at the end, from it. But what we do is, whenever you create that label, which you can change the name, but we create, an NSEC, which is a Nostr, identity effectively. A unique identity and we automatically create that for you. Obi: So again, for our users, we don't want to start educating them on the history of Austrian economics and Bitcoin and inflation at the beginning or a Nostr, et cetera, and how it works and relays. And we just want them to start using it. then subtly over time we expose certain features of it. So people become curious and then eventually. Obi: You want to learn how this thing that's delivering value works, but we've put proof of work first, proof of talk second. So we educate through letting people see the benefits. And then there might be some people might say, well, how does this car thing work? Or how does this fridge thing work? But I don't need to know how refrigerant works to be able to use a fridge or how microwaves work to use a microwave. Obi: When they want to know how all this stuff works, but we benefit first. So, and so and that's how it works with Nostr We immediately give you an NSEC. Obi: And so because we've got that if you go and use unleash. chat, for example within the app It will go and you click login and there's one option login by Nostr You click that and it'll just within the app pop up something saying Nostr Do you want to log in with Nostr? And you click yes, and you're logged in and it just works and then you, and then also now you're logged in and then you can, and then you click, deposit money and instead of having to go to a different app, copy and paste the QR codes, it just, it pops up and says, do you, this, this, what the app's asking you to deposit this amount of money? Obi: Do you want to go ahead? Yes. And then it's e cash. Is, is converted into lightning and then that you pay by lightning. But from your point of view, there's a circling key for three or four seconds. You have now credited your account. Do you want to withdraw the money back account? You click withdraw the amount. Obi: Three or four seconds, it's been withdrawn to your account and, and it's all within the same app. so, but that only works because now if you, close the app or delete the mods, because you can delete these mods or these additional pieces of functionality, they're basically webpages, but the icon for them, and they have an app like experience, but they're actually just webpages. Obi: and then you go away and then you delete the app from your service. Like six months later, you come back, you, you, you enter your 12 words, you're, you're re log on. And then if you scan to join a federation again, it will recognize that you were a member of the federation before, and it will reconstitute and recreate all your e cash and put it back on your phone. Obi: And then if you click on, Unleash your chat or Stacker News or anyone that supports logging by Nostr. Your login with the same details and so on. So you basically, and we want to make that even more seamless. So from 12 words, your entire life can you think about moving from one mobile phone to another, where you have to move all your apps, your banking apps, your chat apps. Obi: And now you could do that with just go and also try moving from an iPhone to an Android phone, Android to an iPhone. It's a nightmare. Here you could just download the Fedi app on your iPhone. this is some far point in the future. You don't have just chat, but you also have voice. You have video, all of that running from encrypted chat. 12 Magic Words Obi: you have access to money from, custody and payments. You have access to all these apps and then you back up 12 words. And there's something we call social backup, which is mind blowing, but, that's in beta. But let's just say backup 12 words, and then you delete that app, go to a different phone, could be an Android or an iPhone, and you just enter 12 words, and your entire thing comes back. Obi: Not partially back, but it all will come back. based on just those 12 words and that's only made possible because of Nostr and we want it over time. Knut: mean, when you think about it, it's insane. It's already insane with bitcoins, with the 12 magic words, because like every time I pass a security check at an airport, I think that go ahead, have my 200 milliliters of toothpaste. I'll, I have my 12 magic words, like it's the ultimate fuck you to, to anyone trying to meddle with your business, right? Knut: that's the dream. I mean, we're not fully there, but it's, I would say it's like, we're like 90 percent there, but to extend beyond just your Bitcoin, Nostr is the protocol that allows us to do that because it's notes and other stuff and the other stuff can be, an encrypted version of the settings and so on that you have that we can store and be willing to pay for. Obi: And then when you recover, you have your bitcoin, but then you can go off and send a request to say here, I'm willing to recover this file. Here's some zaps for the file and you get the file back and that additional file then contains the information. Okay, these are the federations you are a member of, you rejoin them. Obi: These are the mods that you had, they're reset up. These are the settings you had, they're reset up. And then you log on them automatically using Nostr as well, the NSEC and Nostr login. from your point of view as the user, 12 words, it's back. I mean, you might have to drink a cup of coffee while it's happening, but 5, 10, 20 minutes later, it's back. Knut: it's amazing, and it's an inheritance plan. Like, you can live forever by just letting your descendants, giving them the 12 words when you're on your deathbed. Obi: backup also becomes really powerful, because social backup means that, cause the 12 words is still another thing to secure. And it's sort of one of these turtles all the way down type scenarios. Okay. We've got all this incredible security Fort Knox like, but behind them, but I walk around the back of the Fort Knox is these 12 words that's stored. Obi: you also give one to your cousin and you say, look after this as a backup. And your cousin stores it on a fridge magnet. You know, you don't know, or you don't know your, your, your security is the lowest common denominator. Obi: For your 12 words. And Knut: is never stronger than the weakest Obi: then the weakest link. And so with social backup, which is definitely an early beta. what we can do is use the power of the federation where we can take your 12 words, encrypt them and then split it up between the four guardians in this case, or seven guardians or 40 guardians or whatever. Obi: For larger federations, and they all hold a piece of your encrypted piece of your, of Knut: is important here. Obi: Yeah. Knut, what are you doing over there? I'm stamping my seed. Everyone tells me I should, that it's good for bitcoin security and whatnot, and that I should go balls deep into bitcoin security, so I'm stamping. You don't do it like that, Knut. You don't stamp that seed. You stamp your seed phrase. What? Your seed phrase. Oh, so that's what these things are for. oh, I get it now. That's exactly right, Knut. And you can get everything you need to stamp your seed phrase at stampseed. com. And be sure to check out our limited edition Everything Divided by 21 Million Titanium Seed Plate. And use code INFINITY at checkout for 15 percent off. That's fantastic! And it hurts way less!</p> <p>Redundancy in Fedi Luke: So this gets me back to what happens when one of the guardians drops off, and if it's like in a permanent way, if that one guardian is holding a piece of everyone else's 12 words, does everyone Obi: Yeah. But it uses a prot, this is crypto, where cryptography comes in. So it's not like. We've taken your 12 words and split it up free between four guardians. Instead, you encrypt it using a scheme that allows each one of the four of us to have a cryptographic piece. Obi: But as long as any three of us combine our piece together, we can recombine. It is, it's called, SHAIR Secret Sharing Scheme, but it's a way of cryptographically achieving that. Luke: Excellent, I think you mentioned last time as well that if a guardian does go down, essentially you can replace that guardian, can you take us through that, adding or replacing a guardian if that ever were to need to happen? Obi: replacing a garden is, probably one of the most complex things. And so you wouldn't necessarily replace a guardian, but what you would do is, some, if someone were to go down, there's two different things. The machine. Or the guardian, the actual person. So if the machine goes down, you can set up a new machine and you can recover the status of that. Obi: You can, you can download the 30 minute software on that new machine. So that's the actual server that's running. And that will then connect to the rest of the federation and, and carry on. So as long as the guardian has a backup of their keys, they can recover that one machine and, and catch up and it'll automatically catch up. Obi: Just like if you turn off a Bitcoin node and turn it on, it will reconnect to the Bitcoin network and catch up. It's a similar concept. so that's if a machine went down, if a machine was temporarily disconnected from the internet or, lost power, it would just restart and reconnect and you will have zero downtime as a user, as long as it's still running and active. Obi: And this will all be, you'll notice that the performance will still be the same, but if you went into settings for that federation, you'll see that three of the four are running, so one is not running, but that won't affect your usage. Obi: Is the N of M like a ratio, or is it always N 1, for example? It's a ratio. the number of guardians that, you need to have is dependent on how much redundancy. So if you want to be able to handle one guardian going down, then you'll need to have, one times by three plus one. So that's four. So that's why you need three or four. Obi: if you want to handle two going down, then you need two times by three plus one, which is seven. So it's five of seven. 7 of 10, 9 of 13, and so on and so forth. You can have more than that, but the time that you get additional redundancy is every 3, but you can have, for example, 4 of 5, if you wanted to. Obi: Anyway, so, yeah, in the event that someone goes down, that the machine goes down, you can recover. recently there was an issue where one machine, where two federations, had an issue with the domain name for one of those servers. And so if the domain name for someone is no longer available, you can now, with the update that came out a couple of weeks after that, you can modify, the domain name Obi: for a Guardian 30 minute server, and it would communicate that securely with the other, Federation servers and then reconnect and, continue to operate. But it's important to, even in that scenario where the Federa Guardian, the domain name server went down, the Federation itself, Continue to operate because there was still at least free running. Obi: So there was no downtime for the user. Whereas if, if we hadn't been federated, then for the one week or so where that was down, the users would have had no access at all, which would be the case where you're connecting to a centralized or a single server, offering. now, if one of the guardians, for some reason, the actual people who are running the Fedemyst server, for some reason, you no longer trusted them, they'd been helpful all their life and all of a sudden they decided, or they've been turned by some, malevolent nefarious actor. Obi: Then you, if you could in theory pass to someone else, but in practice, you know, how do I know that the other person isn't still going to continue to operate it and so on and so forth. So what you actually want to do is set up a different federation and transfer people, the other three guardians and inform people with a different set of four people. Obi: So those three, plus someone else. And just tell people to transfer their balances across. But transferring balances across is as easy as doing a lightning transaction from one server to another. You can, you know, within the FEDI app, be a member of multiple federations at the same time. I mean, right now, I mean, I'm a bit of a power user, but I'm a member of, over a dozen different federations from around the world. Obi: I mean, well over a dozen, I think, yeah. and as we've, I'm sure there's people in the team with way more than that. but obviously I can't advertise the names because many of them are private federations. So, but there's a few public ones, but there's way more private ones. Interoperability Luke: So is the e cash, if you're in multiple federations, is it interoperable there, or it's like a more like a, it's a lightning transaction between those two federations, but it's e cash that lives Obi: You got it. It's, E cash lives within its federation, but the interoperability layer for most people is not on chain. It's for the vast majority of people, it's Lightning, so, but the user experience of sending e cash from one person to another in the same federation, sending e cash from one person to someone else receiving Lightning. Obi: on a different wallet that's got nothing to do with Ferdie Mint. And finally sending e cash from one person in one federation. To someone else in another federation over the Lightning Network in between is exactly the same. From your point of view, QR code scan and the system will combination of the Fedi app and or whatever Fedi Mint compatible app you're using and Fedi Mint servers will make the experience Obi: I just need to send the person the cash. In this case I can send e cash out over Lightning and that's my job is done. And then the other side would be a Lightning wallet and it will receive. And in this case, I will send e cash over Lightning to another federation, but I don't even know if it's another federation, it's just a Lightning address. Obi: And then the other federation, receives the transaction and the other 30 minute server receives e cash on the other side. But from a user's point of view, this is the thing that also took the two years to make the experience the same. You just don't have to worry about which one is doing. Obi: The fees will be slightly different. One won't have a Lightning component to the fee, e cash to e cash, but, the other two will because it will be like, in both cases, it will be e cash to Lightning, from your point of view. Luke: So is there a fee to send e cash to someone else in the same federation? No, I guess. Right. Obi: It depends on the federation. the federation, could choose not to charge a fee and many in these times choose not to because they're doing it for friends and family and so on and the fees are minimal. the Ferryman protocol does support, what we call a DDoS fee. So basically you're spending effort time Obi: to sign these notes, the issuing is done by the user, but the stamping takes time. you're signing something cryptographically, that's effort. and you're also doing it in a federated manner, so you're coordinating and then you're all collectively signing. Obi: So, to avoid DDoS, you can turn on a fee and, by our calculations, it doesn't need to be very large, one sat per note that issued is enough to prevent, because if someone really tried to DDoS you at scale, they could, but on normal sort of consumer laptops or hardware, they'll have to spend, hundreds of thousands a month at that sort of, one sat per note, and in which case you'll say, fine, you're giving me hundreds of thousands of dollars worth of Bitcoin to burn my, CPU. Obi: Well, not to burn it, but just to heat my CPU. so you can charge a fee. And I think some will experiment with charging a DDoS fee, which is similar to Bitcoin. the fees in Bitcoin are a DDoS protection vector. So it's the same concept. Fedi's Roadmap Knut: All right. So, what's on the roadmap? What's going on? How does the future look like? What will you be working on the next five years? And where do you see FedeMint going? Obi: that's actually, the most, fun phase. up until now, we had a hypothesis and we had some early feedback, but a lot of it was based on, A hypothesis and theory as to what we thought people needed and we felt that freedom technology had got to a stage where they were good enough to provide this combined experience. Obi: And that was a hypothesis. And we think we've got early validation, but we built that. Now it's life. And now it's the fun, but it's also the scary bit because we now actually see people using it and we test all our hypothesis. And this is the point where you have to be very detail oriented, very much listening to the users and listening to what they say Obi: we cannot ignore if there are. Parts of our hypothesis that are incorrect, we have to adjust to support that. So it's going to be a lot of listening and we've already got hundreds of requests for feedback. and then working to rectify, or deal with the questions or feedback they've given us or the suggestions they've given us. Obi: and we're going to continue to iterate and then we bring it back out to users and see what they think. And we keep in that loop. This is the market product fit loop until. The product that we produce, fits the requirements of the market. Now, again, I, I'm hoping that takes six months or less, just like I hoped it took six months or less Obi: for the initialization phase, but it might take less. It might take a bit more, but it's fun. and that's the next phase. After that, we then go into the growth phase. Once we know we've got something that's repeatable, that really. is at the quality level that users need for it to be used a daily part of their life. Obi: We'll then go into growth phase and that's where we'll really, you know, pull down, put our pedal to the metal and, and just repeat, repeat, repeat until. You know, billions of people are using this around the world, but that, that's phase three. And I'm, I'm very focused on this phase. You don't want to rush into phase three. Obi: We're not going to rush to grow the numbers, until we are very sure that we've got something that's really slick, really reliable, and where we're meeting a clear demonstrable demand consistently. And that process is called human centered design. So it's not focused on this is my app, this is what I want, and I'm going to keep trying to make you agree with what I want. Obi: this is what we've built. This is our first stab at it, but we're going to keep iterating until it serves your need properly. And that might require some, this is what makes this one very hard because it requires a very different mindset to the phase one. Phase one is like We can do everything and the impossible is possible phase two is really being pragmatic. Obi: Or very self critical and being very open to killing your darlings, as the saying goes, you know, and saying this is not working or, or there's some fundamental issue. I mean, I don't think this will be the case at this stage, but if the feedback was from our market that we need to make some fundamental changes that would mean that 80 percent of the code we built has to be thrown away and have to start again. Obi: Well, that's what we're being told. we've got far enough to think that's highly unlikely. cause most of the feedback, like some of the big pieces of feedback cause how can we make it easier to set up federations? So that's a really good sign because lots of people said there's only going to be a demand for like free federations and it's going to be very centralized. Obi: Well, a very large percentage. I don't want to give it. These are the very large percentage of all our queries so far have been, how can I set my own federation up? So even based on those queries, there's not going to be free. You know, I can put it that way. Luke: Super quick question on that, I guess, is it the Fetiman software? Is it on, for example, the note in a box, solutions, the umbrellas, start nines, et Obi: Well, that's part of the feedback that we're getting. For example, can we set it up? Can you integrate with Umbro? Can you integrate with Start9? Can you integrate with RastyBlitz? can you make it simpler to set up? So, I think, a lot of that's done by the FediMint team. Obi: Because remember, FediMint is an OpusSource project versus a different OpusSource project. At some point in the future, it will be two different open source projects. However, we are using them as the bedrock, because if you want to custody significant amounts of value We know that you want to go multisig. Obi: Multisig for significant amounts of value is the best standard, and also you want privacy, so then privacy and multisig, that's FedEvent, basically. but, on the FedE side, we can do a lot as well. So we can provide, even though it's open source software, we can take it and provide it. Obi: again, it will be open source, but tools to help you build it really easily or put efforts to integrate with people like Umbrell and Start9. we've already had an integration with an organization called Clover, which we've been working on, and you're going to see more on that. But from our point of view, that's a lot of where the work is. Obi: Also you want to connect this to the Lightning Network. And connected to the Lightning Network and maintaining a reliable connection is not easy. it can be complicated for people, especially managing liquidity. And now again, over time, I could get easier, but right now it's not easy. Obi: There are organizations like, Breeze and others who make that easy. and you just saw an announcement from Erik, where they've already started, showing connectivity and support for LDK, which is this cross, LSP standard. So, again, we at Fedi can provide tools for FediMint, or people who are using FediMint, whether it's with Fedi or someone else, that make it really easy. Obi: And again, our aim is one click, and you have a connection. You can set up your own lightning node that's set up in a relatively good way, so it'd be relatively reliable, but you don't have to manage it yourself. Or, you can connect to one of these LSP's and for a fee, they'll just handle all the light and management, but you're still in a trust minimized way. Obi: So there's, but given all the feedback we're getting, it's not, this is completely wrong. You need to go back to the drawing board, it's all, okay, I get it, but you need to go further. You need to integrate with more. You need to make it easier. so that's a good sign that we're on the right track. Knut: Yeah. So, what about this date when you go open source? is that public or, when you have to go open source, it might be then or Obi: in the, it's, it's, it's memorializing the business source license. In fact, we memorialized it. We actually have this memo memorializing when it happened. when we launched Freddy, we, we did this thing on the Bitcoin block. You can see it. We were established on a certain block. Obi: And we said Fedi is here. When we, quietly on May the 4th, we also put something that said Fedi colon and it was a hash. That hash is a hash of a memo. And the memo, which is on our, Fedi's got an open source, you can see the link and you can verify it. Showed that on May the 4th, the code became business source license. Obi: And by January the 3rd, 2026 or earlier, we must go, open source. And if we were to shut down or to stop development, we will instantly go open source. and so, so that, and we put it in block. I tried to find a core block. So it was block 8, 42069. It was actually was the block that was the core block as well. Obi: so yeah, it's, it's there. And, that's the date. We, we cannot go open source later than that. And we may very well go open source a lot earlier than that. Wrapping Up Luke: Hey Obi, I think we could keep on grilling you on this and that little detail, but this has been really enlightening, fantastic to see how far this has come, even since our last conversation back in October, and yeah, just looking forward to everything you guys are doing, and I guess just as a last thing, people can now grab the Fedi app and Public federations are available to start to try Obi: federations and there are, and you can set up your own federation There's a lot, I don't like to talk too much about what's coming in future because we just work on everything in order of customer demands. So if customer demand comes in, that changes the order, but we're working really hard to make it, It's already easy for if you're quite technical, but we're going to make it easier and easier to set up a federation, so keep looking out because that's a very common request to set up a federation yourself, and we want to see what people do with it, create Fedi mods, create federations, use it, give us feedback, and we will continue to work on making an incredible, Open source interface portal to this freedom technology world. Luke: Absolutely fantastic. We'll need to keep on having these conversations regularly, get updates because always fantastic to hear about this and good luck moving forward and I think we'll be trying some FETI stuff in our futures here. Lots of cool things have come out of Nostriga and Baltic. Honey Badger by Luke: I'm exciting to see that. And anywhere else you want to direct our listeners and viewers. Obi: So for Fedi, that's probably the best place because everything, that's a jumping off ground for everything else. And that's Fedi, F E D I dot X, Y, Z. Luke: Fantastic. Obi: One of the cooler things that came out in Nostriga and Honeybadger was of course, yes, the inverse of clown world, our new book, and we want to give you one. if you're not given one during this weekend, you'll find it on bitcoininfinitystore. com. Thank you very much. Luke: and we need to sign it for you. Yeah, we'll do that offline. But Obi, thank you again. And this has been the Bitcoin Infinity Show. Thank you for listening. Obi: Thanks.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsrcn3vt2qdxxl6wxxf794ya8ufgl6g0feack39f204gkp8zmhpnzszyzletcdyt027ch9q6ss0fa2u6qtyt3uynatlm5fm33d0a38tmnyysterm20" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsrcn3vt2qdxxl6wxxf794ya8ufgl6g0feack39f204gkp8zmhpnzszyzletcdyt027ch9q6ss0fa2u6qtyt3uynatlm5fm33d0a38tmnyysterm20" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsrcn3vt2qdxxl6wxxf794ya8ufgl6g0feack39f204gkp8zmhpnzszyzletcdyt027ch9q6ss0fa2u6qtyt3uynatlm5fm33d0a38tmnyysterm20" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsrcn3vt2qdxxl6wxxf794ya8ufgl6g0feack39f204gkp8zmhpnzszyzletcdyt027ch9q6ss0fa2u6qtyt3uynatlm5fm33d0a38tmnyysterm20" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 472f440f:5669301e <div class="time" style="margin-left: auto;">2024-08-27 22:36:32</div> </div> <div> <p>I'm sure you are all well aware of the news out of France. The French government has made the bold move of arresting the founder of Telegram, Pavel Durov, after charging him with 12 criminal counts ranging from "complicity in web-mastering an online platform in order to enable an illegal transaction in organized group" to "importing a cryptology tool ensuring authentication or integrity monitoring without prior declaration".</p> <p>Telegram is an extremely popular messaging app that is used by almost 1 billion people from around the world. I have personally been a user for seven years and it is very dismaying to see the French government attack an entrepreneur who has built a widely used and loved app. We've said it many times over the years in this rag, governments need to stop throwing the baby out with the bath water by attacking successful businesses for the crimes their users commit and begin doing better law enforcement. It makes no sense to demonize a technology for the crimes that are committed by a small minority of users of that tool. Is the French government going to go after the CEO of Bic, the largest producer of pens in the world, because there are pen pals out there who use their pens to write letters in which they coordinate criminal activity? If we apply the same logic behind the decision to arrest Pavel it would seem that the Bic CEO should be a bit worried. </p> <p>Who knows what evidence the French government has against Pavel. Maybe he is directly involved in the coordination of crimes that were committed on his app. I highly doubt it, but who knows. We'll have to wait and see what evidence the French courts put forth once a trial gets under way. As of yesterday, we know that this seems like a classic case of "You refuse to cooperate with deep state actors who want access to your users' data, so we're going to accuse you of all of the crimes."</p> <p>The fact of the matter is, we shouldn't have to worry about the actions of a founder dictating the accessibility of a novel technology that they bring to market. Especially technologies that enable people to connect in the digital world to exercise their God given right to free speech.</p> <p>It's a bit poetic that this happened on Saturday night in Europe. Just one day after the Nostriga conference in Riga, Latvia wrapped up. Nostriga was a two-day event which attracted people from all over the world so that they could meet to discuss how to push the Nostr protocol forward. For those who are unaware of what Nostr is, it is an open source communications protocol with no leaders that enables individuals to publish their thoughts to the world is a distributed, censorship resistant fashion. User profiles are created via a private-public key pair. The public key makes it easy for others to follow and the private key enables a user to sign notes with certain data that get broadcasted to relays. App developers can then pull the user generated data from those relays and present the data in unique ways using front-end interfaces known as clients. Users can port their private keys (commonly known as nsecs) into any client they like and have all of the data they've published to the protocol automatically show up. Said another way, since Nostr is a protocol and not a platform, users have way more optionality when it comes to the applications that present the data they publish. If one client decides to censor or simply has a bad UX, they can plop their magic string (private key) into another client and see everything they've ever posted while still being connected to everyone they added to their social graph historically. This is extremely powerful on many fronts. </p> <p>Gone are the days of having to worry about building an audience on a platform, making that a critical part of your brand and livelihood, and having to self-censor because of the fear of being deplatformed. You own your private key and that gives you access to your data. Not the platform.</p> <p>For app developers, the network effect of Nostr produces an incredible and truly unique bootstrapping mechanism. Instead of having to start from scratch and hope that users find your app, fill it with data, and begin spreading the word to more users you adopt the social graph of Nostr from day one. Every user of the protocol is already feeding your application data. If you can build an appealing product that provides users of the protocol with value, they will find it and immediately be able to leverage it. There will be no need for them to build up a reputation or find their social connections on the app. They will be ported into the client.</p> <p>Nostr can be additive to seemingly unrelated applications that aren't built directly on Nostr. We've already seen this with bitcoin wallets that have enabled users to port their Nostr social graphs directly into their wallet. Making it easy for individuals to find their friend's Nostr account and send bitcoin directly to the lightning address they've associated with it. No need for an invoice. Just find your friend and send them money like you would on an app like Venmo.</p> <p>The number of added benefits users and app developers get from Nostr beyond those I just explained are too long to list. Long story short, this protocol is a massive deal.</p> <p>It is still very early for Nostr, but the progress that has been made in the last couple of years has been nothing short of awe inspiring. If you squint into the future, it isn't hard to see how Nostr becomes mainstream by the end of the decade. The compounding network effects are stronger than anything I've seen since bitcoin.</p> <p>All of this is to say that this will be one of the only ways to build truly robust communications-based applications moving forward. As we've seen with TikTok and now Telegram, if the state doesn't like the owner of a particular platform they will either kick the platform out of their country or arrest the founder and do their best to corrupt the platform itself once he is in custody. This hasn't happened yet with Telegram, but you can bet your ass that the deep state will try to corrupt Telegram if they successfully remove him from the picture.</p> <p>To be clear, this doesn't make the founders of particular Nostr clients immune to this type of overt overreach by governments. However, the design of Nostr is such that governments would have an exponentially harder time achieving their end goal, suppressing and controlling speech that's expressed on these platforms, because the protocol has hundreds of competing clients serving customers the data stored in relays. They could even attempt to go after the relays, but that task may prove to be impossible as well. </p> <p>Make no mistake, we live in very trying times. The world's governments are losing control and they are doing the best they can to suppress freedom of speech in anyway they can to prevent people from spreading information that makes the Regime to look like the evil fools that they are. The best we can do is to build robust systems that make their attempts at suppressing speech as close to impossible as is possible. The efforts to build out robust systems like bitcoin and Nostr should be complemented with pushing back against the Regime via the courts. But as we all know, we can't always depend on the courts to actually deliver justice. There are times where freedom must be taken and defended. We are certainly living through one of those times right now.</p> <p>Despite the insanity of the world and the governments who would like to rule it, the momentum of the light is building. People are taking action and solutions are being built slowly but surely. It is our job to keep the momentum up and make sure the lifeboats of bitcoin, Nostr and similar protocols are ready to go once the Deep State begins attacking others. They came for TikTok and Telegram. Don't think that platforms like X, Rumble and Gab aren't in their crosshairs as well.</p> <p>Here are four videos from Nostriga that I think you all should watch.</p> <p>https://youtu.be/XUsk7cqZyKU?si=2vUl01azeFJQjczZ</p> <p>https://youtu.be/qUwXRDrfJU0?si=np3vyTDddoQKuPJK</p> <p>https://youtu.be/OHqxp-Hrx9k?si=K7vhVBWtFQwB68Tr</p> <p>https://youtu.be/iZyqVGHjDGo?si=CjJCbAlNBa06qcwV</p> <p>And a panel I hosted about funding Nostr if you're interested in that.</p> <p>https://youtu.be/qD-Y0fq5KiA?si=L81sFCPGw2ayXXzw</p> <p>We're going to win.</p> <hr /> <p>Final thought... Jet lag sucks.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsf6h769agy2hzm4vzn6aa3ks9e8xxfcc2g5pewsygdf5zq3ew34yszyprj73q098hejm5j5xrt35eqluvqep2eqwyzukw4phsm302kdycpu6trkfa" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsf6h769agy2hzm4vzn6aa3ks9e8xxfcc2g5pewsygdf5zq3ew34yszyprj73q098hejm5j5xrt35eqluvqep2eqwyzukw4phsm302kdycpu6trkfa" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsf6h769agy2hzm4vzn6aa3ks9e8xxfcc2g5pewsygdf5zq3ew34yszyprj73q098hejm5j5xrt35eqluvqep2eqwyzukw4phsm302kdycpu6trkfa" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsf6h769agy2hzm4vzn6aa3ks9e8xxfcc2g5pewsygdf5zq3ew34yszyprj73q098hejm5j5xrt35eqluvqep2eqwyzukw4phsm302kdycpu6trkfa" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 91687725:a0de48ea <div class="time" style="margin-left: auto;">2024-08-24 05:40:14</div> </div> <div> <p>こんにちは。Kateです。</p> <p>最近ちょっとお休みしていますが、日本でビットコインを専門に扱う<a href="https://diamondhandscommunity.substack.com/">Diamond Hands Magazine</a>に寄稿したりしてます。</p> <p>私がビットコインと出会ったのは2011年、まだビットコイン利用者はとても少なかった時代です。たまたま身内にビットコイン界隈の人がいました。もしかしたら今でいうビト妻だったかも?</p> <p>まだビットコインが1ドル以下でおもちゃみたいな存在だった頃に知ったわけですが、その後勢いづいて、100ドル、1000ドルと価値が上がっていきました。</p> <p>それを見て、ビットコインを少しずつ買って貯めておけば、将来リタイヤの蓄えになるかもと思ってお小遣い程度のビットコインを積立してました。でも、アクシデントで失くしちゃったんですよね。</p> <p>その後、身内のごたごたで自分の生活が天地がひっくり返るように一変し、気がつけばカナダでただお金がないアジア系移民シングルマザー、しかも周りに家族が誰もいないという、非常にマイノリティな立場になりました。</p> <p>人生、何事も経験。一度ビットコインを失くし、傷心もあり、数年はビットコインから離れました。でも気がつけばビットコインは冬の時代を終えて、また元気になっていたんですね。自分は海外でひとり子育てに追われ、なんとか生きてた感じですが!</p> <p>ビットコインが500ドルくらいになっていた時に困窮していた私は、ふとペーパーウォレットと呼ばれた当時の携帯可能ウォレット?に0.5btc 残っていたのを発見して速攻換金しましたね。悔やまれます。</p> <p>その後、2017年頃、カナダで当時大手の割と使い勝手のいい取引所があることを知って、再度ビットコイン貯蓄にチャレンジしました。2年ほどで、ほぼ1ビットコインと10ETHくらいあったんですけどね、今度は取引所の代表者が行方不明になり、またもやビットコインを失くしました。</p> <p>ふつうだったら、もうやめますよね。2回もなくしたら。</p> <p>けれど、自分はかつてインターネットが始まったころのワクワクを経験していました。90年代半ば、新宿にできたばかりのインターネットカフェで、GIFがかろうじて表示できるグレーのブラウザ画面と対面しました。世界を変える技術を体験した時の感動は今でも忘れられません。</p> <p>(こう書くと立派なオバサンなのがバレちゃいますね。ビットコインネイティブ世代の中では年長者)</p> <p>それから15年以上たって、初めてサトシナカモトのホワイトペーパーを読んだ時に、同じ衝撃を受けたのです。初めて実用化されたインターネット上で世界の誰とでも送り合えるマネー。その可能性は無限∞。</p> <p>そのビットコインの進化を、実際に買ってみたり、使ってみたり、なくしたりしつつ、より深く知ろうと付き合ってきた自分は、いつの間にかビットコインを通して世の中のいろいろを見て考えるようになりました。</p> <p>ビットコインが生まれ、実験段階を経て、すでに15年が経ちます。けれども、ビットコインは今でも多くの人から最も誤解されている技術・発明のように見えます。ここまで来たら、自分が生きている間に、ビットコインが世界とどう関わっていくのか見届けたいと思います!</p> <p>そして、私自身がビットコインを知ることで発見した世界や新しい価値観を、誰かに伝えられたらいいなと願って、このブログをスタートすることにしました。</p> <p>今回は自己紹介という形になりましたが、私がビットコインを通して学んだことや気づいたことをこれから少しづつアップしてみます!</p> <p>週1くらいのペースで投稿が目標です。よろしくお願いします。</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsda88st3zhaal58nq77da6wmtrsxfcfdthzsycf7092uysw097jqgzyzgksae9vnnxcpa8w6379pymqtg6ptyg5luwvgtqp32yj09qmeyw5gma7e9" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsda88st3zhaal58nq77da6wmtrsxfcfdthzsycf7092uysw097jqgzyzgksae9vnnxcpa8w6379pymqtg6ptyg5luwvgtqp32yj09qmeyw5gma7e9" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsda88st3zhaal58nq77da6wmtrsxfcfdthzsycf7092uysw097jqgzyzgksae9vnnxcpa8w6379pymqtg6ptyg5luwvgtqp32yj09qmeyw5gma7e9" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsda88st3zhaal58nq77da6wmtrsxfcfdthzsycf7092uysw097jqgzyzgksae9vnnxcpa8w6379pymqtg6ptyg5luwvgtqp32yj09qmeyw5gma7e9" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 6ad08392:ea301584 <div class="time" style="margin-left: auto;">2024-10-19 18:02:21</div> </div> <div> <p><em>Prediction: Social Networks of the 2030s, will be different to Social Networks of the 2020s, and in some ways, will come to slowly resemble the Social Networks of the mid 2000s and early 2010s.</em></p> <p>In the last decade - the past five years especially - social apps have become more social media than social network. They’ve become more about discovery, and less about relationship. More about size, and less about connection. More about the algorithms, and less about the social graph.</p> <p>Jack Conte, CEO of Patreon, gave a fantastic talk on a similar thread at SXSW 2024, called “The Death of the Follower”</p> <p><a href="https://youtu.be/hwn6-8XpIuE">https://youtu.be/hwn6-8XpIuE</a></p> <p>I believe this will change over the coming decade, as people begin to crave community and connection again, and not just content consumption.</p> <p>This doesn’t mean the multi billion user platforms run by algorithms will disappear. In fact, they will probably be larger and stronger than ever.</p> <p>BUT…I predict that we will also see the rise of many, many niche and micro-social networks with a focus on relationships, communities and the social graph.</p> <p>In fact, there will also be applications that do a mixture of both media/content/algorithm and network/community/social.</p> <p>In this essay, I’d like to look at the history of Social Networks, how they started, how they’re going, what the evolution looked like and what the future will hold.</p> <h1>Social 1.0?</h1> <p>Social 1.0 has been about massive, billion+ user platforms. Think Facebook, Twitter, Instagram, TikTok, LinkedIn.</p> <p>While there is certainly a variance in the kinds of users attracted to each, and also how they work, there are some underlying commonalities among them.</p> <p>First of all, each of these Social 1.0 networks are platforms.</p> <p>They are built in such a way that they own not only the content and data, but also the user’s identity (eg: your handle), the social graphs and connections (follows/following), and the algorithms that serve up the content (or censor it).</p> <p>This is not a problem in and of itself. In fact, it worked extraordinarily well for the teams who built sticky-enough applications that fostered network effects and reached scale.</p> <p>The problem however, arises later, when the platforms who basically own everything, lose the incentive to provide value, and instead need to find ways to keep people “locked in.” Turns out, the best way to lock people in is to push their dopamine buttons and hook them on content. In other words, when social-networks reach saturation, the only thing left to do is drive consumption.</p> <p>This of course creates some perverse incentives. And since we are creative human beings after all, we find ways to game the incentives, resulting in the problematic state that social media finds itself in today: a big digital dopamine-dispenser, where the user, instead of being a client, becomes the product, and a slave to the algorithm.</p> <blockquote> <p><em>“If you’re not paying for the product, you are the product. It’s the gradual, slight, imperceptible change in your own behavior and perception that is the product.”</em></p> <p><strong><em>-Tristan Harris, The Social Dilemma Documentary</em></strong></p> </blockquote> <p><strong>The second issue is the converging nature of all these social networks.</strong></p> <p>Because they are siloed platforms, they cannot leverage content between each other. In the early days of social (pre-2010), there were open APIs all over the place and each social network bootstrapped off the other. Instagram bootstrapped both off Twitter and Facebook!</p> <p>But, as the realisation dawned on each of them that their key asset was their users, they had to - economically-speaking - <strong><em>cut off</em></strong> <strong><em>access</em></strong> to others that might leech their user base. This is perfectly rational market behaviour, given the constraints they were working with. <strong>Your</strong> social network is valuable insofar as <strong>you</strong> have enough connections there to sustain it. If someone starts to suck your users away, it could destroy you. See MySpace and many others along the way.</p> <p>So what happens here in time, is that all the feature set of all these platforms begin to, slowly by slowly, inch toward each other.</p> <p>Instagram created the first real “influencers,” and since then every other social network copied. SnapChat created stories, basically everyone followed. TikTok came out and has since pushed almost every social network towards being more ‘social media’ by implicitly incentivising video. Now, almost every platform is doing some sort of video short.</p> <p>Of course, the increase in internet bandwidth and device quality has gone hand in hand with this. Video is far more engaging and close to “real life” than simple photos or text are. But there’s something else that came with this. And that’s the more from being networks with a social graph, toward being essentially content engines. I will elaborate on this in a future essay.</p> <p>The result of all this is a strange blend of excess redundancy and dependence on platforms which own your digital footprint.</p> <p>I find myself these days, posting basically the same shit, across multiple social apps. Sure, there is some variance, but since everyone is increasingly getting on all of them, the audiences, while quite different in the early days, are slowly becoming the same.</p> <p>This redundancy part, is something that platforms like Buffer and Hootsuite have taken full advantage of.</p> <p>Other than the annoying redundancy, the dependence side of things involves me as a creator, trying to optimise all of my content for the algorithms, ie": for maximum engagement instead of maximum value, across all of these platforms. And worse, trying to do it such a way that doesn't get me banned, because my content, my social graph and my identity are owned by the platform, not by me.</p> <p>Long term, what this does is both (a) waste a lot of time, and (b) make creators less interested in producing for their niche, and instead producing for a bunch of algorithms that are increasingly converging around appeal to a lowest-common-denominator of consooomer.</p> <p>It’s a strange situation, that almost had to happen, but which we can change.</p> <h2>How and why did this happen?</h2> <p>Despite what the conspiracy theorists might believe, this was not all part of some premeditated agenda. These things are complex and emergent. Nobody had any clue what these platforms would come to be in the early days. Nobody had any idea Facebook would be used for marketplaces or that Instagram would change the very nature of travel, food and fashion. But they did, because they evolved, and did so in such a way that conspiring to use them became necessary.</p> <p>Because Social 1.0 platforms are all companies, they are able to be “captured” - especially if they’re public. This is part of why Elon is such an important figure. He’s rich enough to not be entirely captured and he acts as somewhat of a bastion against the rot. That being said, this is not a viable long term solution to the problem, because one man is fragile, and the nature of the current paradigm and available building blocks is such that it will trend once more to centralisation, censorship and co-opting.</p> <p>So if you want to know the real reason as to why we got here, it pretty much boils down to the building blocks that we had available. If you have mud all around you, don’t be surprised that the best structure you can build is a mud-hut.</p> <p>This first round of social networks saw humans and human nature collide with an ‘internet’ that fundamentally lacked an identity layer, something the early pioneers were not ignorant about. The issue was that a viable implementation was never conceived - or at least, never broadly adopted. The internet stack only made it four layers deep:</p> <p><img src="https://blossom.primal.net/ff0da099c9938d347089a4adb2e34f53667ca95f9382f2820e63bf0f4ed28a91.jpg"></p> <p>What happened instead of a native digital identity for the web, was the creation of many identities owned by the actual applications built ON the internet. Instead of a protocol like TCP or IP, identity became a feature inside of a product. In fact, “logging in” is basically a feature, and your profile or identity are simply a database entry owned by whichever online product / service you signed up for. You have an identity with Amazon, with your bank, with your sales software, with Facebook, with Google and with every other online service.</p> <p>This of course got very messy in time. We all ended up with a million and one identities, each requiring their own username and password. Not only that, but each online service became a honeypot full of private, identifying data that hackers love to exploit.</p> <p>Some bandaid solutions arose to solve this problem. One was password managers (which we all hate). The other was SSO. Companies like Google and Facebook saw an opportunity here and being so broadly used developed Single Sign On (SSO) - and to some degree, they solved a big issue. It’s much easier to have a secure email set up with Google and just log in using SSO. The solution of course, comes with its very own problem, namely; Google/Facebook (insert SSO provider) ends up owning your identity, making you increasingly dependent on them.</p> <p>This might be ok in a perfect world, but as you know, we live in an imperfect one. It’s very easy for Google to not only use that information to exploit you (selling your data, selling you shit, etc), but you can very easily get ‘cancelled’ or deplatformed.</p> <p>While this is problematic with an email account, it even worse with a social account on a platform like Facebook or Twitter, because at least with your emails, you can own the list. On a social network, you could spend years building a following, an audience, a treasure trove of data and content - and then one day, be cancelled for saying or believing the wrong thing. Or perhaps even worse: become algorithmically irrelevant.</p> <p>This is clearly a problem and one that has only become more prevalent since 2020. Celebrity chef Pete Evans, was de-platformed from Facebook and Instagram in 2020 after his public support for Trump and his opinion on the Covid-19 situation. Almost 2 million followers, gone overnight. The same has happened to countless other creators and online personalities who dared have an opinion in conflict with the mainstream narrative - I was one of them. My personal twitter account was perma-banned in 2021, right as my public profile began to take off because I dared question official narratives (although I created a new one).</p> <p>So ultimately, we have a web stack that is ok, and got us quite far over the last 30-40 years - but comes with a unique set of problems, that are a function of the building blocks we’ve had to work with. I don’t believe there was a ‘master plan’ to get here, but there was no other option consider the ingredients we had. The only way to really handle identity, and later social, at scale, has thus far been with these constraints.</p> <p>Hence why I call it Social 1.0, and why now, with the emergence of new technologies and new ways of managing your digital identity and footprint, we have an opportunity to build a <strong><em>new</em></strong> Social Web that doesn’t fall into the same trap as the first one did. We understand how people behave online much better than we did a decade or two ago. If we learn from the past, we can do things differently in the future. We can build something fundamentally new, and more importantly, <strong><em>better</em></strong>.</p> <h1>What is Social 2.0?</h1> <p>Social 2.0 is the term I’m giving to this very nascent but emerging new field of social networks that are smaller and more niche, and that are once again focusing on the connection between people, as opposed to the algorithmic content-recommendation engines. Some (not all) are leveraging the new building blocks that have emerged over the last five years.</p> <p>In general, they are smaller, more community focused, and concentrate around a particular domain. This is a trend that is gaining traction, with a number of strong examples in various domains:</p> <ul> <li>Cara: Basically an Instagram for artists</li> <li>BlueSky: Basically Twitter for the Left</li> <li>TruthSocial: Like Twitter for MAGA</li> <li>New Public: Pluralist digital public spaces</li> <li>Dribble: A social network for designers and digital artists</li> <li>Primal: Like a Twitter meets Venmo that appeals to Bitcoiners</li> <li>Farcaster: Kind of like Twitter, but for Crypto Degens, built on ETH</li> <li>Ditto: Decentralised, self hosted, community-social networks</li> <li>Highlighter: Like Patreon meets Substack for digital creators that want censorship resistance.</li> </ul> <p>And of course there is <a href="Satlantis.io">Satlantis</a>, which is essentially a Social Network for Sovereign Individuals. We are interested in the global community of people who live at the nexus of the following interests and domains:</p> <p><img src="https://blossom.primal.net/5014f71582a77ad4eb7716e5f6a51d7036389f0c4ff7284b4aac3c3a72535d15.jpg"></p> <p>Beyond their size and focus, the most interesting commonality, which in my opinion will become an ever-increasingly defining characteristic for Social 2.0 platforms, is that some of these (eg: Highlighter, Primal, Ditto and Satlantis) are all built atop a <strong><em>common social protocol</em></strong>: Nostr.</p> <p>This is important because the identity and social graph do not live on the platform, but instead live on an underlying protocol - a bit like how your email lives on and is transmitted on the SMTP protocol.</p> <p>This approach and what it implies could be the most significant upgrade to the web, perhaps since Web 2.0 really became a thing. If a robust, user-owned identity layer is adopted across the web, the entire topography of the internet will change, and so will the design space and the kinds of products which can be built.</p> <p>Of course, the benefits it comes with, also bring some drawbacks, but in my opinion, they far outweigh the downsides. This is why I am so interested in the future of the social web, and the role Nostr in particular can play.</p> <h2>What is Nostr?</h2> <p>An explanation of Nostr is probably not necessary for anyone reading this essay here, but I'll summarise how I explained it over on Substack for normies and non-Nostr people. Hopefully it's useful when you're doing some Purple-pilling.</p> <ul> <li>Nostr is a rich identity layer for the internet.</li> <li>This identity is rich because you can append meta-data to it, for example, a profile photo, a description and perhaps most importantly, a list of follows and followers. This is what makes it a ‘social protocol,’ and not just native identity for the web.</li> <li>This identity is also sovereign, meaning that it’s not “issued” by some platform or entity, but instead mathematically derived as a crypto-graphic key pair. Your private key is your ID, and your public key is your public address / username (how people find you). So long as you control the private key, you fully control your ID.</li> <li>Unlike a blockchain, Nostr is stateless (like the internet) so it has the capacity to scale, and because it’s not money, it doesn’t need consensus. This avoids all the extra bloat that kills the usage of all other “crypto” and “blockchain” networks.</li> <li>Storage is solved by the market. If you are posting data that might be censored, you can run your own relay (like a database) and ensure that it’s never taken down. If you’re posting non-sensitive content, you can very easily rely on the network of relays that the apps you’re using use. This is fine for 99% of use cases, and is abstracted away so nobody is impacted or annoyed.</li> <li>It is very tightly linked to Bitcoin, the lightning network and other e-cash solutions, which make it “internet money native.” This is a huge benefit because commerce on the web will only want to grow, while the legacy digital banking infrastructure gets more stringent and draconian - so we need a plan B. Bitcoin solves that, and Nostr can scale without needing to shoehorn a token into it.</li> <li>Like TCP/IP and SMTP, it is a protocol. This means it’s not owned by a single entity or company - making it much harder to capture.</li> <li>As a new protocol layer, it upgrades the topography of the web, and opens up a design space that was not possible before. It’s a significant new building block for the web. Recall the earlier diagram depicting the current “internet stack.” With Nostr and Bitcoin, the internet stack gets a serious upgrade:</li> </ul> <p><img src="https://blossom.primal.net/2af1b7e7e19bde55aceab72b4c0eb5f82a92539f34380a1c2bb8a7fbdeca24ac.jpg"></p> <p>Of ocurse, if you haven't read <span data-type="mention" data-id="eab0e756d32b80bcd464f3d844b8040303075a13eabc3599a762c9ac7ab91f4f" data-label="nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a">@nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a</span> 's peice on Nostr it's worth doing so: <a href="https://www.lynalden.com/the-power-of-nostr/">https://www.lynalden.com/the-power-of-nostr/</a></p> <p>I also did a thorough X post explaining it here: <a href="https://x.com/SvetskiWrites/status/1828403019081269661">https://x.com/SvetskiWrites/status/1828403019081269661</a></p> <p>There’s also a great post from my other Substack called Reviewing Reviews:</p> <p><a href="https://remnantchronicles.substack.com/p/reviewing-reviews">https://remnantchronicles.substack.com/p/reviewing-reviews</a></p> <h1>Comparing Social 1.0 and 2.0</h1> <p>Now that you have all of this context, let’s close out this essay with a quick comparison table between the two social paradigms:</p> <p><img alt="" src="blob:https://highlighter.com/8263e97b-37e8-4e5d-80be-034dea93ed30" /></p> <p>As you can see, there are some general differences. And while I don’t show it to make the claim that one is good or the other is evil, I personally believe that Social 2.0 is technically and socially superior. It has better building blocks, and it’s the best shot we have at making the web more sovereign, independent and useful.</p> <p>Also note:</p> <ol> <li>These dichotomies are not hard rules. There’s a lot of both elements across all kinds of social networks, but broadly speaking Social 1.0 is larger, more about discovery than relationships, more about content consumption and more algorithmically driven than Social 2.0 will be.</li> <li>The rise of Social 2.0 doesn’t mean social 1.0 will entirely disappear. In fact, part of the 2.0 movement implies that there will be both big and large social networks, and both protocol-connected and independent platform-enclosed social networks. In fact, there will also be blends of the two. I wouldn’t be surprised to see Threads, or maybe even X one day, leverage something like Nostr. Maybe they become “Nostr-compatible” so that people who have built profiles and audiences on Nostr, can easily port them over to X, while maintaining control.</li> </ol> <p>It will be interesting to see how the future evolves, now that we have some new and unique building blocks. One thing I am certain of, is that the future will look different to the present, and I look forward to helping built it with Satlantis.</p> <p>Thankyou for reading the first full essay on Social 2.0. If you're interested in checking out Satlantis, go here: <a href="Satlantis.io">Satlantis.io</a></p> <h3>Aleksandar Svetski</h3> <p><img alt="" src="https://substackcdn.com/image/fetch/w_1456,c_limit,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F960aa20e-a4d5-4f4b-847f-89bbf2e2ed46_1344x256.png" /></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs07en9knjclqds3ad2hvnstt8z8hatl4rw30ylvwedlxae23vxqmszyp4dpquj6xa28ahl022qnc4vte2yxkrjvhvtffvpccr8mz82xq2cgjk7gce" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs07en9knjclqds3ad2hvnstt8z8hatl4rw30ylvwedlxae23vxqmszyp4dpquj6xa28ahl022qnc4vte2yxkrjvhvtffvpccr8mz82xq2cgjk7gce" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs07en9knjclqds3ad2hvnstt8z8hatl4rw30ylvwedlxae23vxqmszyp4dpquj6xa28ahl022qnc4vte2yxkrjvhvtffvpccr8mz82xq2cgjk7gce" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs07en9knjclqds3ad2hvnstt8z8hatl4rw30ylvwedlxae23vxqmszyp4dpquj6xa28ahl022qnc4vte2yxkrjvhvtffvpccr8mz82xq2cgjk7gce" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 83794dfe:e46c6636 <div class="time" style="margin-left: auto;">2024-10-14 19:40:37</div> </div> <div> <p>BRM 200 km – Samstag, 28.09.2024 05:30 – 09:30 Uhr</p> <p>We left on Saturday morning and enjoyed a great day on the bike, meeting some friends along the way and dropped some.</p> <p>with an average speed of 26.5 we needed around 7.3 hours to complete the track.</p> <p>It was a sunny but windy day at the end we even ended up with some cold shower at the end.</p> <p>A Brevet is not a race along the way we had to pick up some proof that we visited certain points like gas stations.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0yzgd597up6hyn2hgegc8f7cf3u3mmly03uesa3yukjmz56jzx3gzyzphjn0728ftyasp39lcku66hmc2lswap9g4l9a9lcsr9s0yd3nrv0evy59" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0yzgd597up6hyn2hgegc8f7cf3u3mmly03uesa3yukjmz56jzx3gzyzphjn0728ftyasp39lcku66hmc2lswap9g4l9a9lcsr9s0yd3nrv0evy59" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0yzgd597up6hyn2hgegc8f7cf3u3mmly03uesa3yukjmz56jzx3gzyzphjn0728ftyasp39lcku66hmc2lswap9g4l9a9lcsr9s0yd3nrv0evy59" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0yzgd597up6hyn2hgegc8f7cf3u3mmly03uesa3yukjmz56jzx3gzyzphjn0728ftyasp39lcku66hmc2lswap9g4l9a9lcsr9s0yd3nrv0evy59" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 599f67f7:21fb3ea9 <div class="time" style="margin-left: auto;">2024-10-14 19:36:50</div> </div> <div> <p>Inoiz pentsatu al duzu norbaiti satoshiak modu originalean oparitzea, Bitcoin mundura hurbiltzeko? LNbits zorro batekin NFC opari txartel bat erraz sor dezakezu. Honek LNURLw esteka bat NFC txartelean idatziz funtzionatzen du, eta jasotzaileak bere satoshiak erabili ditzake LNURL gaitutako zorro batekin.</p> <h3>Zer behar dut?</h3> <ul> <li>LNbits zorroa</li> <li>Android telefono bat</li> <li>NTAG2* gaitasunak dituen NFC txartela, adibidez NTAG216.</li> </ul> <p>💡 NTAG2<em> txartelek esteka </em><em>bat</em>* idazteko aukera ematen dute. Adibidez, enpresaren webgunerako URLa duen bisita-txartel gisa joka dezakete. NTAG424 txartelek ez dute memoria handiagoa bakarrik, baizik eta SUN parametro deitzen den zerbait ere badute, zerbitzariaren autentifikazioa ahalbidetzen duena, eta horrek segurtasun gehiago ematen die zure ordainketei. Azkenean txartel mota hau <a href="https://boltcard.org/">BoltCard</a> bat bihur daiteke.</p> <h3>1. Hedapena aktibatu</h3> <p>Ireki zure LNbits zorroa. Tresna-barran, aktibatu <code>Withdraw Links</code> hedapena eta ondoren joan hedapenera.</p> <h3>2. Erretiratzeko esteka sortu</h3> <p><code>Withdraw Links</code> hedapen orrian, aukeratu <code>Advanced Withdraw Link(s)</code> aukera. </p> <p>Ondoren, aukeratu satoshiak ateratzeko erabiliko duzun zorroa. Ziurrenik, hori zure LNbits zorro nagusitik bereizi nahi izango duzu. Horretarako, LNbits zorro berri bat sor dezakezu tresna-barratik, <code>+ Add a new wallet</code> aukera hautatuz. Behin zorro berria sortuta, sartu satoshi batzuk bertan.</p> <p><img alt="configure" src="https://cdn.satellite.earth/9eefb0bcc03e218aac55a5c3bfa06f0cdd59d3b36959c58e3f2f88941cca0d01.webp" /></p> <p>Eman izenburu bat erretiratzeko estekari. </p> <p>Ezarri erreskatatu daitezkeen gutxieneko eta gehienezko zenbatekoak.</p> <p>Ezarri esteka zenbat aldiz erabil daitekeen eta erretiratze saiakeren arteko denbora.</p> <p>Aukeran, argazki pertsonalizatu bat gehi dezakezu <code>Use a custom voucher design</code> laukitxoa markatuz, eta .png irudi baten URL-a sartuz.</p> <p>Gogoan izan “assmilking” laukitxoa ez markatzea.</p> <p>Konfigurazioa amaitu ondoren, jarraitu erretiratzeko esteka sortzera.</p> <h3>3. Idatzi esteka NFC txartelean</h3> <p>Zure erretiratzeko esteka berrian, klikatu <code>View LNURL</code> estekan. Ondoren, sakatu <code>Write to NFC</code> botoia eta eutsi NFC txartela telefonoaren aurrean idazketa-prozesua burutzeko.</p> <p><img alt="write" src="https://cdn.satellite.earth/7d290d0c076c724af88089f3ad2bdc7c22cac5bc7bb521e5f28c5646a4fe350d.webp" /></p> <p>✔️ <strong>EGINDA</strong></p> <p>💡 Esan txartelaren jasotzaileari satoshi saldoari buruz, denbora ez dezan galdu azkeneko satoshia lortzen saiatzeko.</p> <p>💡 Jasotzaileak txartelaren satoshiak atera ondoren, bere zorroan berridatzi dezake eta berrerabili. Gainera, eman diozun txartela NTAG424 bada, aurreko gidako (nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65whwqrr5) bezala Lightning "zor txartela" bihur dezake. Baina txartela NTAG2* bakarrik bada, beste opari txartel bat bihur dezake soilik.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqspu0zu8xrdsd5s476vv4hujggedmmzgef5ydxkqvu5c47swat0gpgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jk3h28v" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqspu0zu8xrdsd5s476vv4hujggedmmzgef5ydxkqvu5c47swat0gpgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jk3h28v" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqspu0zu8xrdsd5s476vv4hujggedmmzgef5ydxkqvu5c47swat0gpgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jk3h28v" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqspu0zu8xrdsd5s476vv4hujggedmmzgef5ydxkqvu5c47swat0gpgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jk3h28v" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ f33c8a96:5ec6f741 <div class="time" style="margin-left: auto;">2024-10-19 16:28:32</div> </div> <div> <div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/rbqY19UwyLw?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsya64qzjprjlyetc362kgdsyk5v2v4fymgaywlk4evv2xp9u2wcagzyrenez5kzl93tac9l3cv63sul4h27gheufxr8646mxqkfrj7cmm5z2qdcy4" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsya64qzjprjlyetc362kgdsyk5v2v4fymgaywlk4evv2xp9u2wcagzyrenez5kzl93tac9l3cv63sul4h27gheufxr8646mxqkfrj7cmm5z2qdcy4" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsya64qzjprjlyetc362kgdsyk5v2v4fymgaywlk4evv2xp9u2wcagzyrenez5kzl93tac9l3cv63sul4h27gheufxr8646mxqkfrj7cmm5z2qdcy4" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsya64qzjprjlyetc362kgdsyk5v2v4fymgaywlk4evv2xp9u2wcagzyrenez5kzl93tac9l3cv63sul4h27gheufxr8646mxqkfrj7cmm5z2qdcy4" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 45bda953:bc1e518e <div class="time" style="margin-left: auto;">2024-10-14 16:47:18</div> </div> <div> <p>Kaspa Empire - Ceb System - Planet Hithe III</p> <p>The day was hot and the manor sounded eerily quiet compared to the hustle and commotion of the hours prior. On the estate and in the master bedroom specifically, a married pair had become parents. “He looks so much like you Domitius.” Cleolia remarked while stroking the newborn's tiny arms. “He has strong blood.” The father responded smiling fondly sitting on the bedside. A silent nurse was tidying up the apparel and instruments of labour while the couple waited patiently for her exit to have more private discourse. “I am so glad to have born you an heir my love.” Domitius stared intently at his offspring. He had no qualms neglecting obligations to his property and recessed momentarily to celebrate the occasion with his wife. “I will send for the priest, register the child as an Imperial citizen and have him scribed into our family archives, but in the meantime, you must recover. Let a servant girl take our son for a while.” She pouted a playful but exhausted look of non compliance. “You must rest.” He insisted. “How can I let him go when I only just met him? Who are you little man?” She smiled faintly and nodded. “You are right, Domitius, where are you going?” “To the fields, the slaves are behind schedule, our harvest is big and taxes are high. This war is taking it's toll, we must excel to adequately serve the Empire in these pressing times. If the tamed Osteri could only comprehend what is at stake.” Cleolia peered cautiously at the embellishment and carvings on the wooden door knowing that Sethari was standing just beyond. Domitius trailed her gaze. “Don't worry my love, he means well, at least he tries to understand the urgency of my affairs.” He stood up straitening his vest and prepared to leave the room. “Domitius, wait...” He stopped at the door. “What will you tell the priest?” Domitius paused. “I will tell him Albin... Albin Domitius Chevalier.”</p> <p>He left the room and it was quiet, the help entered and swaddled the baby rocking him while Cleolia drifted between sleep and conciousness. “Albin.” She repeated to herself as deep slumber enveloped her.</p> <p>Domitius and his overseer walked briskly out of the manor towards the grain fields squinting as blue Ceb light reflected off the lanscape. “I honour you on the spawn of your son my lord, I hope for a good strong boy, you will be a happy father. I am happy with Seth.” He pounded his chest softly and proudly. “Thank you Sethari, is your son walking yet?” Domitius queried. “No my lord, still crawling on his belly like a beast.” The headman was trying to make his master laugh though Domitius was in a sterner mood having a weight on conscience. “I am in no mood to jest Sethari.” Domitius suddenly clenched his fists. “Get those slaves to work, I cannot have them idling when they should be harvesting.” Sethari made a small bow to his master and started yelling at his Osteri kinsmen, threatening them with a rolled up whip he procured from somewhere inside his tunic, waving it about and cracking it in the air every so often. Domitius picked up a scythe and proceeded to cleave down large swathes of grain. This had a more compelling effect of rallying the straggling workers to action than did the whip. They all toiled together in the pale light of Ceb.</p> <p>Domitius was sweating, sweating and praying for a swift victory over the Jeula Federation. Fighting his small part in a increasingly complicated war, loyal to his Empire in his own unique way even though the conflict was far from home. A powerful loyalty that cannot be bought with riches or broken by coercion. A loyalty born through inheritance and blood.</p> <p>...</p> <p>The priest was in a more jovial mood than usual. The break of routine was a welcome one. The birth was indeed a momentous occasion. Few things seem of much report in a small planetary expansion program. He did not even seem to mind carrying a keg full of honey mead over the rolling hills of the plantation colony. “Domitius comes to church submissions far to infrequently.” The portly man mumbled to himself while wiping the accumulated sweat from his brow. “I eat too well among all these farmers.” The habit of speaking to himself was ordinary for this man of the cloth who always felt socially disconnected from his flock, caring for their souls, protecting their dignity and general well being like a responsible patron. “I feed their spirits, they feed my body, Hahaha. Tonight I will share my good spirits! Hahahaha.” Impressed by his own sense of humour he turned to witness the majestic blue star set over the skyline. Everything turned a silvery gray hue, and then the stars broke through the atmosphere lighting his way. “Clear skies, the blessed stars guide me.” He continued on the path approaching the Domitian manor and rapped a quick knock on the side of the root cellar doors. It creaked open upwards and a tall muscular Osteri took his baggage and let him in. “Thank you Setharis, my arms are weary, ready to fall off, bless you.” Domitius looked up from his bench seat below a glowing lantern. “Good to see you Father Ecknard.” “Dispense with the formalities and bring the dispenser.” He motioned to Setharis who placed the heavy keg on a table next to an assortment of documents, quill and sealed inkpot. “You pour Setharis and I will write. Name?” Ecknard scratches his chin with the quill contemplating his seat and it’s adequacy for the prolonged exercise of scribble. “Name?” Domitius paused. “Albin Domitius Chevalier.” The priest focused, started with his calligraphic art and fashioned the name and ASN standard block height beautifully onto the family records all the while biting his tongue. “He will inherit the colonial estates, all your assets in Kaspa Prime and the parochial offices at Magar Prime. Correct?” “Yes.” Replied Domitius solemnly. “I'll soon have to amend your will and testament. I'd have to make a registry at the parish and send correspondence to Magar Prime. There would be many from the royal courts who'll send their best regards from afar when this news becomes public.” Domitius did not seem as enthusiastic as Ecknard would have liked. “What ails you Domitius?” The priest could not help but make the pun and restrained a grunted laugh inside himself.</p> <p>“I wonder if we should wait before registering and announcing him to Empire.” Ecknard’s expression slowly changed to puzzlement sitting up straight, his belly pushing on the heavy table. “In the voids name why?” “I am concerned... about this war...” “It is on the other side of Magar space!” The priest interjected in astonished retort. “I know father, maybe I am just being overly cautious, but with the Magar Dominus fleet occupied at the divide I am worried about the colonies in the isolated regions.” “Surely Kaspa prime will spare no expense to our defence in the improbable event of an invasion.” “The core keepers will not allow foul play from the Jeul.” “Yes Ecknard, but the fleet is not capable because most of our ships are at the aforementioned objective!” “No, no, no. Suggesting that conflict would happen outside of the divide is practically blasphemy. I cannot imagine insubordination to the Core mandates and the Accords." Domitius remained silently astute and father Ecknard decided to not argue further with the lord. His shoulders sagged. “I will not register the boy in the Imperial records.” “Thank you father.” “What do you know that I fail to see Domitius.” The two men stared at each other from across the table. The hulking bodyguard ever present in body but semi ignorant in mind silently and intriguingly observing the discussion.</p> <p>“The value of sat. It is not calculated well by the common people, no offence father.” The priest piously lifted his hand and with tilted brow motioned. “None taken.” “My son and our blood line is invested with empiric power, if opportunists become aware of his existence and being outside the Magar prime void, we might have problems here on Hithe III.” Cumbersome thoughts and machinations of the mind darkened the mood of the party. Not at all what Father Ecknard was projecting in his minds eye during his arduous walk to what he was hoping, a celebration and getting drunk with an old friend. “The war does not seem to be ending any time soon, how long shall we stall his registration?” The priest reasoned on. “Think of the rites he will not be allowed to partake in at the church. He will be like Osteri.” Ecknard gestured towards Sethari. “This is a small colony Ecknard. My son will be educated as a member of royalty, all on Hithe III will acknowledge his social standing, I am only concerned that the secret be kept from the outside worlds. He will never be considered Osteri, he will know who he is and what his position is in the greater void. When the war is over we will properly introduce him to the families, currently they would be too occupied with politic as it is, and might not offer him due ceremony as they would under more peaceable circumstances.” The priest capitulated and grabbed a mug. “Your secret is safe with me Domitius, the lack of technology on this forsaken planet is good for your purposes, seeing as the only comms service on the planet is in the church tower. That blinking comms station hounds me daily with requests for your return to Magar Prime. The high counsel want to rebalance and need your signature.” Domitius sighed and looked away as if some spectre loomed in front of him.</p> <p>I swear silence on the birth my lord, though let me make a final amendment to your proposal. A bit of extra security shall I say.” Domitius filled a cup of mead for Sethari and himself, becoming more relaxed and hospitable. “I am listening.” “If the risks are as great as you assume, let us pretend for the child's sake that he is Kaspian royalty only, and not true Magar. We then continue his education to the full and not put him in a position where he could compromise himself should he be... void forbid, captured by some opportunistic prospector.” Domitius looked ponderously into his cup. “Ecknard, my son is an infant... If we have to keep the boy in the dark about the true nature of his identity, how long do you predict this war to continue?” Father Ecknard leaned forward... “I sit at the comms desk every night and listen to the chatter. This war... is going to be a long one.”</p> <p>...</p> <h1>scifi</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqswq2xahfm2uss6r92cdejwt4j3yzeya899u8vjfd59neye9eese3qzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcugzz2sq" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqswq2xahfm2uss6r92cdejwt4j3yzeya899u8vjfd59neye9eese3qzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcugzz2sq" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqswq2xahfm2uss6r92cdejwt4j3yzeya899u8vjfd59neye9eese3qzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcugzz2sq" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqswq2xahfm2uss6r92cdejwt4j3yzeya899u8vjfd59neye9eese3qzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcugzz2sq" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ b0510a0c:12716ced <div class="time" style="margin-left: auto;">2024-08-21 06:03:43</div> </div> <div> <h1>On April 24, 2012, Erik Voorhees changed everything about Bitcoin with the launch of Satoshi Dice:</h1> <p>a game that captivated users and intensified debates about Bitcoin's evolution and the network's ability to handle an increasing volume of transactions.</p> <p>At that time, Satoshi Dice allowed thousands of players to bet on digital dice rolls, leading to a <strong>MASSIVE</strong> influx of transactions that filled the blocks of the blockchain. <img alt="" src="https://m.stacker.news/47060" /></p> <h2>📈 Success of Satoshi Dice:</h2> <p>Satoshi Dice achieved phenomenal success, attracting millions of users with its simplicity. Players flocked in, bets piled up, and blocks filled up. <img alt="" src="https://m.stacker.news/47066" /></p> <p>Erik Voorhees effectively leveraged Bitcoin's microtransactions, quickly saturating the blocks with these. This was a testament to the game's popularity, but also a source of tension within the community.</p> <p>Within months, Satoshi Dice became the most popular service on the Bitcoin network, boosting its usage and virality.</p> <p>Players appreciated the "provable fairness" aspect of the game, where they could verify the transparency and fairness of each bet.</p> <h2>🚫 Criticism and Controversy:</h2> <p>However, this success was not without criticism.</p> <p>Many Bitcoin enthusiasts viewed the massive influx of transactions generated by the game unfavorably. For them, these sometimes trivial transactions "spammed" the blockchain, clogging the blocks and increasing transaction fees for all users. Does this sound familiar?</p> <p>The network, designed to handle about seven transactions per second, quickly reached its maximum capacity, causing validation delays and "high" fees. <img alt="" src="https://m.stacker.news/47067" /></p> <h2>⚔️ BlockSize Wars:</h2> <p>The BlockSize wars, which took place mainly between 2016 and 2017, were a technical and ideological conflict centered on block size and scalability solutions.</p> <p>While Satoshi Dice was not the sole cause, the game significantly contributed to the emergence of this event by helping to popularize Bitcoin among new users and generating substantial transaction volume.</p> <p>As Bitcoin adoption grew, the network faced intense pressure, leading to block saturation and rising transaction fees. On one side, some advocated for increasing block size to allow more transactions, leading to the creation of Bitcoin Cash in August 2017. On the other, proponents of solutions like SegWit pushed for improvements without compromising decentralization.</p> <h2>🔧 Adoption of SegWit:</h2> <p>Erik Voorhees expressed his support for the SegWit2x proposal, which aimed to improve network scalability by combining the implementation of SegWit with an increase in block size.</p> <p>Segregated Witness (SegWit) was adopted in August 2017, allowing transaction data to be separated from signatures. This reorganization not only increased transaction processing capacity but also paved the way for the development of the Lightning Network, a layer 2 solution enabling instant and low-cost transactions.</p> <p>SegWit was a crucial response to the challenges posed by network congestion, which had been exacerbated by Bitcoin's growing adoption and the emergence of popular applications like Satoshi Dice.</p> <h2>⚡ SegWit and Lightning:</h2> <p>The adoption of SegWit helped resolve blockchain congestion issues, while the Lightning Network, a layer 2 solution, facilitated fast and low-cost transactions.</p> <p>Together, these innovations not only addressed technical challenges but also renewed enthusiasm for games and other applications on Bitcoin, paving the way for a new wave of development. <img alt="" src="https://m.stacker.news/47068" /></p> <h2>🎲 Nostr Dice:</h2> <p>Today, as we reflect on the impact of Satoshi Dice, a new project emerges: nostr:npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84</p> <p>This modern clone of the original game is built on Nostr, a decentralized communication protocol, and Lightning, paying homage to the past while offering an enhanced gaming experience that does not impact layer 1 congestion!</p> <p>From a game that caused Bitcoin congestion to its rebirth on Lightning, which it helped to bring about, the circle is complete! <img alt="" src="https://m.stacker.news/47069" /></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvwjcdr6s8nms5qtkkl49yq97jjextn9vz5lah7lyqcvz4vfgp8nszyzc9zzsvyw8u7safhnq9nnsvytdhglhu22wwe90jgccz5wsjw9kw6fyy7uk" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvwjcdr6s8nms5qtkkl49yq97jjextn9vz5lah7lyqcvz4vfgp8nszyzc9zzsvyw8u7safhnq9nnsvytdhglhu22wwe90jgccz5wsjw9kw6fyy7uk" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvwjcdr6s8nms5qtkkl49yq97jjextn9vz5lah7lyqcvz4vfgp8nszyzc9zzsvyw8u7safhnq9nnsvytdhglhu22wwe90jgccz5wsjw9kw6fyy7uk" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvwjcdr6s8nms5qtkkl49yq97jjextn9vz5lah7lyqcvz4vfgp8nszyzc9zzsvyw8u7safhnq9nnsvytdhglhu22wwe90jgccz5wsjw9kw6fyy7uk" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 45bda953:bc1e518e <div class="time" style="margin-left: auto;">2024-10-19 15:24:18</div> </div> <div> <p>This post will be edited and refined over time.</p> <p>Eschatology is the study of Biblical prophecy pertaining to what is commonly referred to as the end times. Bitcoin is the transformation of Austrian school economics theory into an efficient and applicable method driven by natural incentives and free market consensus mechanisms.</p> <p>What happens when eschatology is viewed through a Bitcoin inspired world view?</p> <p>In this thesis I contend that it is possible and very probable that the consequences of what Satoshi Nakamoto created in Bitcoin and the prophecies surrounding Jesus Christ with regards to the second coming and a thousand year kingdom of peace and prosperity convalesce into a very compelling argument for Biblical prophecy fulfilment.</p> <p>...</p> <p>No one would argue that modern major banks are today more powerful than kings of old and governments are mere puppets to the sway that the banking empires hold over them.</p> <p>In Biblical prophecy when kings and powers are mentioned people rarely think of banking but nothing is comparable to the immense scale of wealth, power and territory controlled directly or indirectly by banks.</p> <p>IMF, BIS, the FED and Blackrock are where the levers of power are pulled in the current dispensation. Governments restructure more frequently than these institutions whom endure and exercise unmerited influence over said governments and the public interests they claim to represent.</p> <p>An excerpt from the King James Bible, Daniel chapter 2 describes prophetically the ages of man and its rotations of power.</p> <p>Interesting to note that it is symbolically portrayed in monetary/industrial metals. All used as tokens for trade, symbols of wealth and manufacture.</p> <p>Gold, silver, bronze, iron and clay. Gold has been a dominant symbol of power and wealth through millennia. Silver, brass and iron ores are mainly industrial metals although they all had prominent turns as coinage. Due to the debasement and concentration of gold specifically.</p> <p>Clay on the other hand is only a symbol of power in construction and iron has never been used in construction to the extent it is in the 20th and 21st century. Skyscrapers are the symbols of money and power today, i.e. big bank and government buildings.</p> <p>Daniel Chapter 2:24–45</p> <p><strong>24Therefore Daniel went to Arioch, whom the king had appointed to destroy the wise <em>men</em> of Babylon. He went and said thus to him: “Do not destroy the wise <em>men</em> of Babylon; take me before the king, and I will tell the king the interpretation.”</strong></p> <p>25Then Arioch quickly brought Daniel before the king, and said thus to him, “I have found a man of the captives of Judah, who will make known to the king the interpretation.”</p> <p>26The king answered and said to Daniel, whose name <em>was</em> Belteshazzar, “Are you able to make known to me the dream which I have seen, and its interpretation?”</p> <p>27Daniel answered in the presence of the king, and said, “The secret which the king has demanded, the wise <em>men,</em> the astrologers, the magicians, and the soothsayers cannot declare to the king. 28But there is a God in heaven who reveals secrets, and He has made known to King Nebuchadnezzar what will be in the latter days. Your dream, and the visions of your head upon your bed, were these: 29As for you, O king, thoughts came <em>to</em> your <em>mind while</em> on your bed, <em>about</em> what would come to pass after this; and He who reveals secrets has made known to you what will be. 30But as for me, this secret has not been revealed to me because I have more wisdom than anyone living, but for <em>our</em> sakes who make known the interpretation to the king, and that you may know the thoughts of your heart.</p> <p>31“You, O king, were watching; and behold, a great image! This great image, whose splendor <em>was</em> excellent, stood before you; and its form <em>was</em> awesome. 32This image’s head <em>was</em> of fine gold, its chest and arms of silver, its belly and thighs of bronze, 33its legs of iron, its feet partly of iron and partly of clay. 34You watched while a stone was cut out without hands, which struck the image on its feet of iron and clay, and broke them in pieces. 35Then the iron, the clay, the bronze, the silver, and the gold were crushed together, and became like chaff from the summer threshing floors; the wind carried them away so that no trace of them was found. And the stone that struck the image became a great mountain and filled the whole earth.</p> <p>36“This <em>is</em> the dream. Now we will tell the interpretation of it before the king. 37You, O king, <em>are</em> a king of kings. For the God of heaven has given you a kingdom, power, strength, and glory; 38and wherever the children of men dwell, or the beasts of the field and the birds of the heaven, He has given <em>them</em> into your hand, and has made you ruler over them all — you <em>are</em> this head of gold. 39But after you shall arise another kingdom inferior to yours; then another, a third kingdom of bronze, which shall rule over all the earth. 40And the fourth kingdom shall be as strong as iron, inasmuch as iron breaks in pieces and shatters everything; and like iron that crushes, <em>that kingdom</em> will break in pieces and crush all the others. 41Whereas you saw the feet and toes, partly of potter’s clay and partly of iron, the kingdom shall be divided; yet the strength of the iron shall be in it, just as you saw the iron mixed with ceramic clay. 42And <em>as</em> the toes of the feet <em>were</em> partly of iron and partly of clay, <em>so</em> the kingdom shall be partly strong and partly fragile. 43As you saw iron mixed with ceramic clay, they will mingle with the seed of men; but they will not adhere to one another, just as iron does not mix with clay. 44And in the days of these kings the God of heaven will set up a kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. 45Inasmuch as you saw that the stone was cut out of the mountain without hands, and that it broke in pieces the iron, the bronze, the clay, the silver, and the gold — the great God has made known to the king what will come to pass after this. The dream is certain, and its interpretation is sure.”</p> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:700/1*4I01kq4ybEruX9dD0tZs4w.png" />I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time, resources and energy.</p> <p>Skyscrapers and large construction are the modern symbols of money and power. Not so much kings, palaces and temples. The stone breaking the power of the statue has to break something contemporary other than kings and palaces if it is to be eschatological prophecy fulfilled in our time.</p> <p><a href="https://www.britannica.com/technology/cement-building-material/History-of-cement"><strong>https://www.britannica.com/technology/cement-building-material/History-of-cement</strong></a></p> <p>The invention of <a href="https://www.britannica.com/technology/portland-cement">portland cement </a>usually is attributed to <a href="https://www.britannica.com/biography/Joseph-Aspdin">Joseph Aspdin </a>of <a href="https://www.britannica.com/place/Leeds-England">Leeds</a>, <a href="https://www.britannica.com/place/Yorkshire-former-county-England">Yorkshire</a>, England, who in <strong>1824</strong> took out a patent for a material that was produced from a <a href="https://www.merriam-webster.com/dictionary/synthetic">synthetic </a>mixture of <a href="https://www.britannica.com/science/limestone">limestone </a>and <a href="https://www.britannica.com/science/clay-mineral">clay</a>.</p> <p><a href="https://www.thoughtco.com/how-skyscrapers-became-possible-1991649"><strong>https://www.thoughtco.com/how-skyscrapers-became-possible-1991649</strong></a></p> <p>Later, taller and taller buildings were made possible through a series of architectural and engineering innovations, including the invention of the first process to mass-produce steel.</p> <p>Construction of skyscrapers was made possible thanks to Englishman <a href="https://www.thoughtco.com/henry-bessemer-the-steel-man-4075538">Henry Bessemer</a>, (<strong>1856 to 1950</strong>) who invented the first process to mass-produce steel inexpensively.</p> <p><strong>You watched while a stone was cut out without hands,</strong></p> <p>No hands needed when the stone is an idea.</p> <p>As a thought experiment, imagine there was a base metal as scarce as gold but with the following properties:\ — boring grey in colour\ — not a good conductor of electricity\ — not particularly strong, but not ductile or easily malleable either\ — not useful for any practical or ornamental purpose\ \ and one special, magical property:\ — can be transported over a communications channel</p> <p><strong>Greshams Law illustrated in slow motion picture.</strong></p> <p><strong>1: The banks collapse. Being fundamentally weak because of zero reserve lending, any student of Austrian economics has been correctly predicting banking collapse, and have incorrectly been advocating gold as the solution to this collapse. Many of the big economies are valued through their housing market. Housing will be demonetised (Iron and clay economy) meaning shelter and property will become affordable to the average wage earner again. The large cement and iron structures become redundant. Everyone will work from home and a value to value economy will make banks seem like relics from an age of stupidity and evil.</strong></p> <p><strong>2: Industrial metal iron will not be for mega structures that contain speculators and bookkeepers who have fiat jobs slaving for fiat money. Iron will be used to improve the lives of individuals. Iron as coinage is already demonetised.</strong></p> <p><strong>3: Brass is demonetised as coinage and only valuable in industry. Ammunition, music, plumbing etcetera.</strong></p> <p><strong>4: Silver has been a terrible money throughout history and when the silver investors wake up to the fact that they are holding onto a redundant asset with zero monetary properties compared to the alternative they will dump their holdings, crashing the silver market and subsequently reducing the prices of producing -</strong></p> <p>solder and brazing alloys, batteries, dentistry, TV screens, smart phones microwave ovens, ad infinitum. To quote Jeff Booth. "Prices always fall to the marginal cost of production."</p> <p><strong>5: The final Rubicon is gold, people get excited about the Bitcoin exchange traded funds but it is nothing compared to the value proposition when gold pundits, large investment funds, governments pension funds and reserve banks finally realise that gold is worthless as money in this new dispensation.</strong></p> <p><strong>To illustrate the point more vividly.</strong></p> <p><strong>Ezekiel 7:19</strong></p> <p><strong>They shall cast their silver in the streets, and their gold shall be removed: their silver and their gold shall not be able to deliver them in the day of the wrath of the LORD: they shall not satisfy their souls, neither fill their bowels: because it is the stumbling block of their iniquity.</strong></p> <p><strong>What we are witnessing is the biggest rug pull the world has ever seen. In this future metals will exclusively be used for industrial use cases after being stripped of their monetary premium.</strong></p> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:700/1*a-S251iw1_D6onntqxRLug.png" />This collapse is something that happens slowly over a long period of time. More or less one hour.</p> <p>Revelation 18 verse 11–19 (The fall of Babylon)</p> <p>And the merchants of the earth shall weep and mourn over her; for no man buyeth their merchandise any more: The merchandise of gold, and silver, and precious stones, and of pearls, and fine linen, and purple, and silk, and scarlet, and all thyine wood, and all manner vessels of ivory, and all manner vessels of most precious wood, and of brass, and iron, and marble, And cinnamon, and odours, and ointments, and frankincense, and wine, and oil, and fine flour, and wheat, and beasts, and sheep, and horses, and chariots, and slaves, and souls of men. And the fruits that thy soul lusted after are departed from thee, and all things which were dainty and goodly are departed from thee, and thou shalt find them no more at all. The merchants of these things, which were made rich by her, shall stand afar off for the fear of her torment, weeping and wailing, And saying, Alas, alas, that great city, that was clothed in fine linen, and purple, and scarlet, and decked with gold, and precious stones, and pearls! For in one hour so great riches is come to nought. And every shipmaster, and all the company in ships, and sailors, and as many as trade by sea, stood afar off, And cried when they saw the smoke of her burning, saying, What <em>city is</em> like unto this great city! And they cast dust on their heads, and cried, weeping and wailing, saying, Alas, alas, that great city, wherein were made rich all that had ships in the sea by reason of her costliness! for in <strong>one hour</strong> is she made desolate.</p> <p>TLDR - No more money printer go BRRR. means death to the bourgeoisie cantillionaire class.**</p> <p><strong>Is it realistic to assume that all the worlds monetised industries collapse to fair value in one hour?</strong></p> <p>Coming back to eschatology, 2 Peter 3:8</p> <p>But, beloved, be not ignorant of this one thing, that one day <em>is</em> with the Lord as a thousand years, and a thousand years as one day.</p> <p>Eschatology students use this verse to speculatively project the fulfilment of Biblical prophecies with regards to their predicted time of occurrence. Now let’s apply this to Babylon falling in one hour.</p> <p>1000 (one day) divided by 24 (hours) equals 41,6 years (one hour)</p> <p>Since the first block was mined in January 2009 you add 41,6 years you get a completion date of 2050 a.d</p> <p>Remember, this stone (Bitcoin) becomes a great mountain and fills the whole earth. A kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. The dream is certain, and its interpretation is sure.</p> <p>But contemporary sources must reflect this probability if it is a good theory. https://www.newsbtc.com/news/50-of-population-to-use-bitcoin-by-2043-if-crypto-follows-internet-adoption/</p> <p>If the banking system is first to collapse we can give it +- 10 years and we are already 14 years in since (<strong>Genesis Block</strong>) the stone struck the feet. People are slow to see the reality of the world they are living in. If all this is accurate then the world banking system is doomed.</p> <p><a href="https://www.youtube.com/watch?v=exK5yFEuBsk">https://www.youtube.com/watch?v=exK5yFEuBsk</a></p> <p>Regards</p> <p>Echo Delta</p> <h1>bitbib</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsr0vyvsh9e34eldu8rt4alxmdjg8cc6d5c9s6ccw67ssajtr73w2czypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcurtmy0w" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsr0vyvsh9e34eldu8rt4alxmdjg8cc6d5c9s6ccw67ssajtr73w2czypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcurtmy0w" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsr0vyvsh9e34eldu8rt4alxmdjg8cc6d5c9s6ccw67ssajtr73w2czypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcurtmy0w" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsr0vyvsh9e34eldu8rt4alxmdjg8cc6d5c9s6ccw67ssajtr73w2czypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcurtmy0w" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ df478568:2a951e67 <div class="time" style="margin-left: auto;">2024-10-13 20:36:12</div> </div> <div> <p>Keet is a peer to peer video chat room that is available on: • App Store • Google Play • Linux • Mac • Windows </p> <p>It uses technology similar to BitTorrent, but you make video calls instead of downloading music, free and open source software, and movies that are in the public domain. If you have ever used BitTorrent, I'm sure these are the things you have used Bittorrent for.😉 You can use Keet for:</p> <pre><code>• Video Chat • Voice Phone Calls • An Online Chat Room • Sending Files Between Devices </code></pre> <p>Since we are in the very early days, not too many people know about it, but I prefer this because the sound quality and speed are superior to most corporate alternatives. If you've ever tried sending a large file through the InterTubes, you'll know this can be a sucky experience. Even if you run your own cloud like NextCloud, it's an inefficient. You upload your large file to the Nextcloud instance which is basically another computer. Then you download the file to the compter you really want it on. In this case, your Nextcloud acts like a middle man. This man in the middle architecture used to transfer large files is inefficient.</p> <video src="https://keet.io/videos/keet-explainer.mp4" width="320" height="240" controls></video> <p>**note: This was originally published on my <a href="https://marc26z.com/">Ghost blog.</a> It may not work on all nostr clients.</p> <p>Jeff Swann told me about this new technology a couple years ago. He told me how he used Keet lo transfer files. I heard what he said, but I didn't quite understand how powerful this was until I tried it myself. I can send videos from my phone to my desktop computer within second just by using Keet rooms. This is a computer networking super power. I just can’t reiterate how much time this has saved me. It is something you need to experience for yourself. By the way, anyone who can download an app and install a program on their computer can do this. You don’t need to be a network administrator wizard or learn how to code.</p> <p>If you would like to join my keet room, check out my nostr page or LinkedIn and I'll send you a link.</p> <h2>Keet Vs. Legacy Video Calling</h2> <p>Legacy chat rooms and video calling services require a server. The data is hosted on their server. This is inefficient and requires a ton of centralized infrastructure to handle the bandwidth. This infrastructure requires a lot of maintenance, marketing and other stuff. They have thousands of employees working for them to get your videos from point A- to point C- to point B. I’m sure these people do a wonderful job, but Keet is different.</p> <p>Keet allows you to go from point-A to point-B. According to their website it is: - Private & encrypted - Has amazing video quality • Allows you to instantly share huge files That huge file sharing is awesome by the way—Even if you don’t really talk to that many people on it very often.</p> <p>It is made by a peer-to-peer company named Holepunch. They have not yet open sourced it yet, but they say they have plans to do this on Guy Swann’s podcast. They also made something called pear-runtime. You can learn more about this at pears.com. From what I understand, this is a new way to do computer networking. It basically makes it possible to host an app or website from your computer using one line of code. This allows you to create your own Intranet with the greatest of ease. I tried it one time using an application named HoleSail. I was able to access a website using a local IP address from a LAN outside of my home network. I didn't need to fiddle with the DNS or buy a domain name. I just installed the program on my computer, wrote one line of code, and copied the key to access the website.</p> <h3>Keet Is Brand New Technology.</h3> <p>I just want to mention this is on the bleeding cutting edge of technology. I am explaining this to the best of my ability, but it is beta software so what I say today may be totally different a year from now. It is also quite possible that I misunderstood some stuff and if that is the case then I apologize in advance. I find this technology interesting and think it opens us up to a new ways of using the Internet, but I don’t have a crystal ball. Do not confuse this as investment advice, but as far as I know, this is not even something you can invest in. You don’t even need to buy Keet. You just download it.</p> <p>I don’t know much about the big corporate video calling companies, but I’m pretty sure they charge a fee for some of their services. Please don’t take my word for this, I have no idea how they work or what their fee structures are.</p> <p>Here are the sources where I have learned about these things: Hat tip to Jeff Swan who taught me how Keet worked and to his brother Guy Swann for making all these great podcasts about it. • Interview with SuperSu • The Pear Report Episode: 2 • Bitcoin Audible: Keet AMA - Twitter Spaces on January 30th • [The Pear Report: Updates From The Pear World]((https://fountain.fm/episode/blklbIi1GZCgIvX9E8nY)</p> <p>✌️</p> <p>https://tinyurl.com/marc26z</p> <p>865,210</p> <p>As Seen On TOR:</p> <p>http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/pear-to-pear/</p> <p>On The Clearnet:</p> <p>https://marc26z.com/pear-tp-pear/</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsv7argydee0ast5x9q07r52nrzxldlwpma0ss3gu5laf7xhym0lkczyr050ptgg7w7y662s0qmm3xm4dsmtnyzux339c4j30yptgf2j50xwy2w2ar" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsv7argydee0ast5x9q07r52nrzxldlwpma0ss3gu5laf7xhym0lkczyr050ptgg7w7y662s0qmm3xm4dsmtnyzux339c4j30yptgf2j50xwy2w2ar" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsv7argydee0ast5x9q07r52nrzxldlwpma0ss3gu5laf7xhym0lkczyr050ptgg7w7y662s0qmm3xm4dsmtnyzux339c4j30yptgf2j50xwy2w2ar" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsv7argydee0ast5x9q07r52nrzxldlwpma0ss3gu5laf7xhym0lkczyr050ptgg7w7y662s0qmm3xm4dsmtnyzux339c4j30yptgf2j50xwy2w2ar" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ c80b5248:6b30d720 <div class="time" style="margin-left: auto;">2024-10-13 18:14:34</div> </div> <div> <h2>Using tools like Continue in your vault</h2> <p>As the capabilities of artificial intelligence continue to expand, integrating AI into our workflows has become an increasingly attractive option. One of the most exciting applications of AI is its potential to enhance the way we manage and organize information. Obsidian, a powerful knowledge management tool, provides a robust platform for building a personal knowledge base. By layering AI tools like Continue over your Obsidian vault, you can unlock new levels of efficiency, creativity, and insight. This article will start to explore how to effectively use AI tools within Obsidian to enhance your note-taking, information management, and productivity.</p> <h2>An Explosion of AI Tools</h2> <p>Over the past few years, I have tinkered with ChatGPT and other chat interfaces, but I only recently stumbled upon the rapidly growing space of AI tools for coding. In such a short time, some amazing tools have emerged, most notably:</p> <ul> <li><a href="https://aider.chat/">Aider</a>: A command line interface tool to iteratively generate, edit, and refactor code.</li> <li><a href="https://cursor.sh/">Cursor</a>: A fork of Visual Studio Code (VS Code) with integrated AI functionality.</li> <li><a href="https://github.com/cline/cline">Cline</a>: A plug-in for command line and code editor built to work with Antropic's Claude 3.5.</li> <li><a href="https://continue.dev/">Continue</a>: A customizable VS Code plug-in with chat and code editing abilities.</li> </ul> <p>These tools are designed to assist developers in writing, debugging, and even generating code from natural language prompts. They are powered by large language models (LLMs) like GPT-4 and Llama 3, which are trained on vast amounts of text data and can produce human-like responses to a wide range of prompts.</p> <p>In this article, I will focus on <a href="continue.dev">Continue</a>, a <a href="https://code.visualstudio.com/">VS Code</a> plug-in that offers multiple ways to interact with AI. It features autocomplete powered by an LLM of your choice, as well as the ability to generate new code blocks directly in the editor. It can also incorporate context from external sources or the local codebase. Additionally, it includes a standard chat window for interacting with the LLM.</p> <p>The new twist is that I won't be using Continue to write code, but rather to write notes in Obsidian. I will be using the chat window to generate notes, and the autocomplete feature to assist me in writing them. By leveraging the context feature, I can bring in information from my Obsidian vault, allowing me to create more complete, accurate, and better-organized notes. I can also use the vault as context to ask for summaries or retrieve information from my notes, even as the vault continues to grow.</p> <p>It's worth mentioning that while I am focusing on Continue, there are likely other tools that can be used in a similar way or provide better features. One example is the <a href="https://docs.text-gen.com/">text-generator plug-in</a> for Obsidian. This plug-in allows you to generate text using an LLM of your choice, and it can be used to generate notes, summaries, or even entire documents. It can also generate code, but I was unable to get the plug-in working with my LLM provider. Using Continue is a bit of a hack, as it requires working through an IDE like VS Code, but it's a good way to get started with AI tools in Obsidian. I will assume that you already have an Obsidian vault set up. If you don't, you can ask your assistant to help you organize it once you have it up and running.</p> <p>The system I am going to describe here relies on two primary components:</p> <ol> <li><strong>Continue</strong> (installed in an IDE like VS Code)</li> <li><strong>An LLM provider</strong> to power Continue</li> </ol> <p>Let's start by talking about LLM Providers. If you already know how these work, feel free to skip to the next section.</p> <h2>LLM Providers</h2> <p>LLM providers are services that offer access to large language models (LLMs) like GPT-4 or Llama 3.1, typically via an API (application programming interface). These providers usually charge by the token, which is the number of words processed by the model. You can go directly to a provider like OpenAI or Anthropic, or you can use an aggregation site like <a href="https://openrouter.ai/">OpenRouter</a> that provides a single API to access multiple models. Each provider has its own data privacy policies, so it's important to review them carefully. For this reason, I have been using <a href="https://deepinfra.com/">DeepInfra</a>. They run their own models and offer a clear privacy policy - even better, they tend to have the lowest costs.</p> <p>h/t nostr:npub17vhnjkt04m6thytr8dna67v2pa4tjk7uh3ut40eq9wy8d28u0kvq7qnhkq nostr:note1qfckzxm687peaddwjpmms92kj3v59wrrx0cs2fcxlkm6pm9lyu3squscxa</p> <p>Another option is to use Ollama to run some of these models locally. However, the hardware requirements for achieving good results quickly are quite demanding. For example, the smaller chat model I use in my configuration, which has 72 billion parameters, requires a 48 GB GPU to run efficiently—something that is not within my budget. This is why I am using DeepInfra.</p> <blockquote> <p>Note: If you are setting this up for the first time, consider adding a small amount (less than $5) to a provider like DeepInfra and testing it out before you invest time in setting up a local Ollama instance. I have also had some issues with shutting down Ollama on Windows, so your mileage may vary.</p> </blockquote> <p>If you choose to use a provider like DeepInfra, you are ready to move to the next section. If you prefer to set up Ollama, you can refer to their documentation for installation instructions. I prefer to run it in Docker, which can be done in Linux by running</p> <p><code>bash docker run -d -v ollama:/root/.ollama -p 11434:11434 --name ollama ollama/ollama</code></p> <p>or if you want to have an interface like ChatGPT, you can even run <a href="https://github.com/open-webui/open-webui">Open WebUI</a> in the same command with</p> <p><code>bash docker run -d -p 3000:8080 --add-host=host.docker.internal:host-gateway -v open-webui:/app/backend/data --name open-webui --restart always ghcr.io/open-webui/open-webui:main</code></p> <p>Once Ollama is running in docker you can start up the models you want to use by running the following in your terminal.</p> <p><code>docker exec ollama ollama run model_name</code></p> <p>See the <a href="https://ollama.com/library">Ollama model library</a> to choose which models you want to run locally.</p> <h2>Getting Started with Continue</h2> <p>Continue is installed as a plug-in for VS Code or JetBrains. I personally use it with VS Code, so my instructions will be based on that. If you are using a JetBrains IDE, you should refer to the <a href="https://docs.continue.dev/">Continue documentation</a> for installation instructions.</p> <p>After installing the plug-in, continue will prompt you to set up your LLM provider. In my experience, once this initial GUI goes away, you can't get it back. Instead, you will do most of the configuration within the <code>config.json</code> file for Continue, which you can access by clicking in the lower right corner of the Chat box. In VS Code, if you ever can't find anything, <code>F1</code> is your friend and will launch a searchable menu.</p> <p>Continue provides recommended settings from each provider, which you can find <a href="https://docs.continue.dev/customize/model-providers">here</a>. For my coding and writing, I chose the very new <a href="https://deepinfra.com/Qwen/Qwen2.5-72B-Instruct">Qwen2.5 72B Instruct</a> due to its high benchmark scores and relatively low costs. This model costs $0.35-0.40 USD per million tokens, compared to the best available on DeepInfra, the <a href="https://deepinfra.com/meta-llama/Meta-Llama-3.1-405B-Instruct">Llama3.1 405B Instruct</a>, which costs $1.78 per million tokens. The results may be slightly worse, but I prefer cheaper and faster for my purposes. For autocomplete, I am using a faster and code-specific model, <a href="https://deepinfra.com/Qwen/Qwen2.5-Coder-7B">Qwen2.5-Coder-7B</a>. I have not yet tried changing the autocomplete model for usage with Obsidian, but that is on my to-do list. Lastly, by the time you read this article, these models may be out of date. One nice thing about having a provider API is that you can easily switch and test different models to see how they work. Aider has <a href="https://aider.chat/docs/leaderboards/">one of many model leaderboards that will show you some benchmarks</a>.</p> <p>After working through the configuration, your <code>config.json</code> file will have a list of chat models and a tab for the autocomplete model. It will look something like this:</p> <p>```json "models": [ { "title": "DeepInfra Qwen2.5 72B Instruct", "provider": "deepinfra", "model": "Qwen/Qwen2.5-72B-Instruct", "apiKey": "your-api-key" }, { "title": "DeepInfra Llama3.1 405B Instruct", "provider": "deepinfra", "model": "meta-llama/Meta-Llama-3.1-405B-Instruct", "apiKey": "your-api-key" }, ],</p> <p>"tabAutocompleteModel": { "title": "DeepInfra Qwen/Qwen2.5-Coder-7B", "provider": "deepinfra", "model": "Qwen/Qwen2.5-Coder-7B", "apiKey": "your-api-key" } ```</p> <h2>Trying it Out</h2> <h3>The Chat UI</h3> <p>Once you have Continue configured, you can open your Obsidian Vault in VS Code. You will want to add a <code>.continueignore</code> file in your folder that lists <code>.obsidian</code> and any other files or folders you want Continue to ignore for context purposes.</p> <p><img alt="chat in vscode" src="https://image.nostr.build/87c3863853c9b547653ea0dcb034eb91afea76a48a4db67f441512832d41ad07.png" />Click the three dots in the bottom of the chat bar and check that your vault (@codebase) index is complete. You can now chat with the LLM and ask it questions using your vault as a reference.</p> <p><code>@codebase what are some common themes from this vault?</code></p> <p>Continue provides a <a href="https://docs.continue.dev/customize/deep-dives/codebase">docs page</a> that lists some types of questions that an LLM will be able to help with. Naturally, I asked the LLM to put these in the context of an Obsidian Vault and here is what it told me:</p> <p>```md</p> <h3>Useful Questions</h3> <ol> <li><strong>High-Level Questions About Your Notes:</strong></li> <li>"What are the main themes in my notes on personal development?"</li> <li> <p>"How do I incorporate agile methodologies into my project management?"</p> </li> <li> <p><strong>Specific Information:</strong></p> </li> <li>"What are the key points in my notes about productivity hacks?"</li> <li> <p>"Can you find any references to neuropsychology in my notes on cognitive science?"</p> </li> <li> <p><strong>Generating Content:</strong></p> </li> <li>"Write a new note on the benefits of meditation, using the same structure as my other wellness notes."</li> <li> <p>"Draft a summary of my recent project retrospective, following the format of my previous summaries."</p> </li> <li> <p><strong>Contextual Questions About a Specific Folder:</strong></p> </li> <li>"What is the main purpose of the 'Research' folder?"</li> <li> <p>"How do we use the concept of 'flow' in the 'Psychology' folder?"</p> </li> <li> <p><strong>Relationships and Connections:</strong></p> </li> <li>"What are the connections between my notes on 'Time Management' and 'Goal Setting'?"</li> <li> <p>"How do my notes on 'Digital Marketing' relate to 'SEO'?"</p> </li> <li> <p><strong>Task and Project Management:</strong></p> </li> <li>"What are the next steps I should take based on my notes for the 'Personal Finance' project?"</li> <li> <p>"Can you list the tasks I need to complete for my 'Career Development' plan?"</p> </li> <li> <p><strong>Deep Dives and Analysis:</strong></p> </li> <li>"Can you provide a detailed explanation of the concept of 'reflective practice' found in my notes?"</li> <li> <p>"What insights can you derive from my notes on 'Project Management'?"</p> </li> <li> <p><strong>Insight and Reflection:</strong></p> </li> <li>"What have I learned from my notes on 'Mindfulness'?"</li> <li>"Can you help me reflect on my progress based on my notes for the 'Health and Wellness' topic?"</li> </ol> <h3>Not Useful Questions</h3> <ol> <li><strong>Literal Review of All Files:</strong></li> <li>"Find everywhere where the term 'mindfulness' is mentioned in my entire vault."</li> <li> <p>"Review all my notes and find any spelling mistakes."</p> </li> <li> <p><strong>Comprehensive Tasks that Require Literal Access:</strong></p> </li> <li>"Add a new section to all notes that discuss 'productivity' and summarize the main points."</li> <li> <p>"Rewrite all my notes on 'Digital Marketing' to include the latest industry trends."</p> </li> <li> <p><strong>Refactoring and Detailed Edits:</strong></p> </li> <li>"Update all references to 'Scrum' to 'Kanban' in my 'Agile' folder."</li> <li>"Add a new parameter to the function <code>calculate_score</code> and update all usages in my 'Programming' notes."</li> </ol> <h3>Summary</h3> <ul> <li><strong>Useful Questions</strong>: Focus on high-level insights, specific information, generating new content, contextual questions about specific folders, and reflecting on your notes.</li> <li><strong>Not Useful Questions</strong>: Require the LLM to see and edit every file, perform comprehensive reviews, or make detailed edits across multiple notes. ```</li> </ul> <h3>Text Generation</h3> <p>Continue also offers in-editor code generation with the hotkey <code>Ctrl+I</code> and an entered prompt. I have only tried a few things with this, but it was able to successfully review a set of meeting notes I had written and summarize all of the outstanding questions. I expect you could also use this to autogenerate backlinks on a note where a follow-up note might be helpful, or quickly generate templates to be used in Obsidian. I ended up editing this entire article by selecting sections and prompting the AI with the following: "You are a proficient writer. Please edit this text for style, typos, spelling, and grammar."</p> <h3>Autocomplete</h3> <p>Continue will also attempt to autocomplete unless you turn it off in the bottom right bar in VS Code. While writing this article, the autocomplete feature was somewhat helpful even though it is not code. Further configuration may optimize this even more. Keep in mind that autocomplete triggers frequently and will burn through a lot of tokens, so you will want to keep an eye on your usage. With the cheaper models I am using, I have only spent 10 cents over the past four days of moderate usage at work and at home. A bulk of that cost is due to autocomplete, and I sometimes turn it off to keep costs down. You may be able to limit these costs effectively by configuring the number of input tokens that can be sent to the API, but I am not sure how that will impact the results.</p> <p><img alt="autocomplete in action" src="https://image.nostr.build/2e1b733a95ec0b2efa31a157a19cbab4529d0d5bb253a4fadd1db5954d7a1727.png" />## Conclusion - Brought to You by Qwen 72B</p> <p>In conclusion, integrating AI tools like Continue into your Obsidian vault opens up a multitude of possibilities for enhancing your note-taking, information management, and productivity. By leveraging the chat window, text generation, and autocomplete features, you can create more comprehensive and accurate notes, generate summaries, and automate routine tasks. The integration of LLMs into your workflow not only streamlines your processes but also provides deeper insights and connections within your knowledge base. While there are initial setup steps and some considerations around cost and configuration, the benefits of AI-assisted note-taking in Obsidian are well worth the effort. As AI tools continue to evolve, the potential for further enhancements and optimizations is immense, making this an exciting and valuable addition to any knowledge management system.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsyjulwlzyhz6gxl0xf36k2k772qecvean0j5natnntp0psszazzaczyryqk5jgl0508y4u8wj9py0mfehzkkrj8pmqr0us75ueydntxrtjq7xja22" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsyjulwlzyhz6gxl0xf36k2k772qecvean0j5natnntp0psszazzaczyryqk5jgl0508y4u8wj9py0mfehzkkrj8pmqr0us75ueydntxrtjq7xja22" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsyjulwlzyhz6gxl0xf36k2k772qecvean0j5natnntp0psszazzaczyryqk5jgl0508y4u8wj9py0mfehzkkrj8pmqr0us75ueydntxrtjq7xja22" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsyjulwlzyhz6gxl0xf36k2k772qecvean0j5natnntp0psszazzaczyryqk5jgl0508y4u8wj9py0mfehzkkrj8pmqr0us75ueydntxrtjq7xja22" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 7cc328a0:2a247c0e <div class="time" style="margin-left: auto;">2024-10-12 15:54:42</div> </div> <div> <h1>relay.tools quarterly report</h1> <p>October, 2024</p> <h1>Project Updates</h1> <p>Milestone: Relay.tools is celebrating 1 year of OpenSats! Cheers to everyone that made this possible.</p> <p>Relays were very popular this quarter. Scaling efforts were prioritized! This is a good indicator for relay.tools as it means that it's healthily growing. Development was executed well, completing one project at a time across the whole stack.</p> <h1>Relay Discovery</h1> <p>I've been working with @sandwich from nostr.watch on NIP66.</p> <p>NIP66 will be an ABSOLUTE GAMECHANGER for clients in finding of their relays. This was always a vision for relay.tools and I am honored to be working with @sandwich on what is a pretty amazing solution. We are now in a phase of client outreach, to gather client feedback and help them implement/understand the overall goal of the NIP.</p> <p>TLDR: the goal is to create a distributed version of the nostr.watch data, using nostr events.</p> <ul> <li>[x] implemented NIP66 draft7 (the 'final' design) in monitorlizard</li> <li>[x] started shipping events to the monitor relay(s) in collab with nostr.watch backends and relay.tools backends.</li> <li>[x] fixed bugs and released new binaries for monitorlizard (a NIP66 data reporting tool)</li> </ul> <h1>Auth Proxy Rollout</h1> <p>The NIP42 Auth Proxy project went really well this quarter. It's now serving tons of traffic and most bugs with clients have been squashed and the proxy hardened. This has become a very popular feature on the relays, as AUTH has many benefits beyond protecting of DMs.</p> <ul> <li>[x] testing vs. NIP17 and bugs fixed</li> <li>[x] cluster operations (multiple proxies)</li> </ul> <h1>UI/UX</h1> <p>A huge milestone this quarter was the release of the settings wizard. This is a walkthrough for new (and current) users of all the available settings for different 'relay types'. A lot of work over the last year has gone into the culmination of these settings and the wizard was a major step forward to help users understand what their options are when running a relay.</p> <p>Another major UI change was the introduction of a relay feed to the landing page for a relay. This is called the relay explorer. The idea was to move to a single page app, and re-do navigation for easy relay browsing and discovery.</p> <ul> <li>[x] settings wizard released</li> <li>[x] relay explorer v2</li> </ul> <h1>Installer</h1> <p>The installer had lots of good effort put in by me and some nice contributors. We did a couple iterations on documentation and facilitated in the creation of 2-3 new relay hubs that are using this installer infrastructure.</p> <p>Some additions to the installer were:</p> <ul> <li>[x] docs for building self-hosted machine images and installing on a VPS</li> <li>[x] FULLY AUTOMATIC SSL certificate handling for multiple domains with certbot</li> <li>[x] self-hosted influxDB (for relay metrics)</li> <li>[x] fix bugs with auto-deploy upgrade</li> </ul> <h1>Billing/Invoicing/Support</h1> <p>The billing system had some improvements this quarter and many invoices were sent. :) It now has better super-admin tools to notify users of past-due balances via nostr (With NDK). This took a few iterations of deciding the best way to contact users of nostr and figuring out why they don't respond to messages. It's a learning experience all the way around and the billing system will evolve over time in ways that are conducive to remaining 100% nostr for user communication and support.</p> <p>The support system also showed signs of life, and people were able to use it to contact me with their questions via the various help-desk methods that I've been rolling out. (A relay, a support npub, DMs, NIP17 DMs, simplex)</p> <h1>Scaling!</h1> <p>Relay.tools successfully completed the first scale-out event. This is HUGE. Relays take more and more bandwidth and resources as they establish themselves, while at the same time needing a reasonable low-cost environment to grow in. To meet their demands the horizontal scaling is important. This will scale on commodity hardware or VPSs with ZERO vendor lock-in.</p> <p><img alt="invoices page" src="https://d.nostr.build/jp2oyiTBA38QFarD.svg" /></p> <ul> <li>[x] multi-server clustering with ZERO cloud vendor lock-in</li> <li>[x] deployment pipeline and capacity planning</li> <li>[x] HAproxy and additional AUTH proxies fronting all services</li> <li>[x] internal/external network support</li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsz40gpjmqlaz07dd7keyr8p9qqysv6w000n3dn229p57pelk370cqzyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37quwzk8jr" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsz40gpjmqlaz07dd7keyr8p9qqysv6w000n3dn229p57pelk370cqzyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37quwzk8jr" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsz40gpjmqlaz07dd7keyr8p9qqysv6w000n3dn229p57pelk370cqzyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37quwzk8jr" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsz40gpjmqlaz07dd7keyr8p9qqysv6w000n3dn229p57pelk370cqzyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37quwzk8jr" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ bcbb3e40:a494e501 <div class="time" style="margin-left: auto;">2024-08-16 18:00:07</div> </div> <div> <h2>El hombre y el contexto</h2> <p>El pensamiento tradicionalista español cuenta con una amplia trayectoria en la que concurren personajes, situaciones e ideas gestadas en el transcurso de dos siglos, en los que debemos distinguir el conflicto dinástico y el papel del legitimismo de la propia doctrina, que es algo que se construirá en el tiempo, con la contribución de figuras como el protagonista de este escrito, Don Juan Vázquez de Mella, así como por la confluencia de fuerzas de diferente signo que tiene lugar a lo largo del siglo XIX y la consolidación del Estado liberal, que lo hará siempre en lucha abierta contra las peculiaridades y el carácter genuino del pueblo español. Vázquez de Mella, nuestro autor, quizás represente la consolidación y madurez doctrinal del movimiento tradicionalista español, uno de sus primeros y más brillantes sistematizadores. No se destacó por una obra extensa ni especialmente difundida más allá de sus discursos, de sus artículos en periódicos y sus escritos dispersos, los cuales fue capaz de dotar de una especial significación y dignidad fruto de su enorme carisma y especial clarividencia para dar una forma definida y meridianamente clara a las ideas y doctrinas que nutrieron el tradicionalismo español madurado al calor de las armas, de las tres guerras que el carlismo libró contra el liberalismo español.</p> <p>|<img alt="Juan Vázquez de Mella" src="https://hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/imgs/juan_vazquez_mella_hu8063713700756101955.webp" />| |:-:| |Juan Vázquez de Mella|</p> <p>Nuestro autor, de origen asturiano, y nacido en Cangas de Onís un 8 de junio de 1861, ha mantenido vivo su prestigio y el valor de sus aportaciones teórico-doctrinales, ampliamente reconocidos por sus sucesores, por <a href="https://hiperbolajanus.com/posts/la-sociedad-tradicional-y-sus-enemigos/"><strong>Rafael Gambra Ciudad</strong></a> (1920-2004) y <a href="https://hiperbolajanus.com/libros/mos-maiorum-1/"><strong>Francisco Elías de Tejada y Espinola</strong></a> (1918-1978), así como de otros autores como <strong>Álvaro D'Ors</strong> (1915-2004) y otros muchos, que han reivindicado su figura en el tiempo y se han nutrido de sus fecundas enseñanzas. Se ha destacado la rectitud de su pensamiento, su inquebrantable voluntad y su impagable contribución en la creación de un marco teórico y conceptual para dar un sentido y una forma a las ideas del tradicionalismo español. Hijo de un militar de origen gallego, muerto prematuramente, quedó huérfano de padre durante su niñez, por lo cual pasó al cuidado de unos parientes de origen modesto. Estudió en la Universidad de Santiago de Compostela, donde mostró tempranamente su temperamento y habilidades oratorias, que explotó convenientemente a través de diarios como <em>La Restauración</em> o <em>El pensamiento galaico</em>, donde también mostró sus filiaciones militantes con el catolicismo tradicional. Sus habilidades y la brillantez de sus escritos pronto llegaron a Madrid, a las más altas instancias del Carlismo, lo que le permitió dar continuidad a sus actividades desde un medio más amplio, a través de <em>El correo español</em>.</p> <p>En su militancia política llegó a las más altas cotas de su trayectoria con la elección en 1893 como representante de las Cortes por el distrito de Estella, Navarra, que ya con sus primeros discursos obtuvo un notable éxito, incluso entre los propios liberales, hasta 1900, fecha en la que se vio obligado a marcharse a Portugal, acusado de participar en una conspiración para derrocar el régimen de la Restauración. No regresó a España hasta 1905, manteniendo su estatus como diputado hasta 1919. De todos modos, no queremos dar más protagonismo a la biografía en detrimento de la doctrina, que es lo que nos interesa en este artículo, de ahí que obviemos otros datos biográficos trascendentes, polémicas con otras facciones del carlismo o sus posturas respecto a la dictadura del general Miguel Primo de Rivera, que nos harían desviar la atención del propósito principal que acabamos de enunciar.</p> <p>La gran paradoja del Carlismo fue que a pesar de su derrota en la Tercera Guerra Carlista (1872-1876), y pese a la posterior escisión integrista en 1888, el partido carlista continuó manteniendo una fuerza y preponderancia significativa en la sociedad española del régimen de la Restauración durante el último cuarto de siglo. El Carlismo se vio inmerso en un buen número de paradojas, de situaciones encontradas, especialmente en relación al Desastre del 98 y la pérdida de los últimos territorios ultramarinos. Mientras que la gran esperanza del tradicionalismo español estaba depositada en el desmoronamiento y caída final de la restauración alfonsina, por otro lado este mismo régimen trataba de defender, al menos en teoría, los últimos restos del imperio español y, de algún modo, a la España católica frente a una nación protestante, como era la anglosajona estadounidense. Al mismo tiempo, durante esta época el tradicionalismo español se enfrentó a los grandes retos que presentaba una sociedad en cambio, con transformaciones políticas y sociales de gran calado como la emergencia del sufragio universal o el nacimiento de los separatismos periféricos (propiciados por la burguesía liberal), las cuales requerían de nuevas estrategias y reestructuraciones internas capaces de enfrentar la envergadura de todos estos cambios. Fue en este contexto donde se significó la figura de Juan Vázquez de Mella, quien merced a la obra de sistematización a la que ya hemos hecho alusión, y de sus concurridas conferencias, dio lugar a la denominada <em>Acta Loredán</em>, redactada por el tradicionalista asturiano y publicado en <em>El correo español</em>. Este escrito tenía como ejes fundamentales la defensa de la nación política española fundamentada en la monarquía, el catolicismo y el régimen foral. Al mismo tiempo, también recogía la reivindicación de un programa corporativista y gremial al abrigo de la doctrina social de la Iglesia defendido en la encíclica <em>Rerum Novarum</em> (1891), y es lo que se conoce como el «sociedalismo», cuyos antecedentes encontramos ya <a href="https://hiperbolajanus.com/posts/resena-de-los-fundamentos-historicos/">en autores como <strong>Donoso Cortés</strong></a> o <strong>Antonio Aparisi Guijarro</strong>. Son precisamente los atributos de esta doctrina, que contribuyó a la revitalización del pensamiento carlista, los que nos disponemos a desarrollar a continuación.</p> <p>La figura del tradicionalista asturiano, de Don Juan Vázquez de Mella, aparece como necesaria ante una serie sucesiva de destrucciones que el régimen liberal ha producido sobre los fundamentos tradicionales de España, pero su papel no fue, como ya venimos apuntando, el de un gran intelectual erudito, y de hecho, como apunta Rafael Gambra, las mayores debilidades de su pensamiento se encuentran en los principios filosóficos, y destacando, en cambio, su papel de «revulsivo espiritual» podemos ubicarlo mejor en el ámbito de lo político y lo espiritual. Para ello debió tomar en cuenta las fuentes de sus predecesores, entre los cuales podemos ubicar perfectamente al ya mencionado Donoso Cortés y <strong>Jaime Balmes</strong>, así como también a otro contemporáneo suyo, <strong>Menéndez Pelayo</strong>. De los dos primeros tomó su capacidad de síntesis y la sencillez expositiva, mientras que de Menéndez Pelayo tomó, al menos en parte, el sentido de la crítica histórica en aras de la restauración de una Tradición nacional. Pero más allá de los sistemas de pensamiento y elementos retóricos, vemos a Vázquez de Mella profundamente interesado por la vida política de los pueblos medievales de Las Españas, lo cual fue, en definitiva, el marco de referencia para una síntesis política de conjunto más allá de los posicionamientos teóricos, como algo que puede ser llevado a la práctica en sus aspectos concretos y que es perfectamente viable. Todo un sistema <a href="https://hiperbolajanus.com/posts/en-el-mar-de-la-nada-curzio-nitoglia/">edificado sobre el pensamiento tomista</a> y una una profunda religiosidad, En este contexto, y más allá de las ideas formuladas por realistas y carlistas en la primera mitad del siglo XIX, Mella teoriza junto a la concepción del espíritu medieval, la idea de la coexistencia de dos soberanías, una política y otra social, una teoría de la soberanía tradicional inspirada por un principio dinámico y que se cimenta en las propias experiencias humanas en el devenir de la historia.</p> <p>|<a href="https://amzn.to/3W6ymTM"><img alt="En el mar de la nada" src="https://www.hiperbolajanus.com/libros/mar-nada-curzio-nitoglia/imgs/En_el_mar_de_la_nada_curzio_nitoglia_hu15262713016003388470.webp" /></a>| |:-:| |<a href="https://amzn.to/3W6ymTM">NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023</a>|</p> <h2>El concepto de lo social</h2> <p>Lo social para Mella no tiene absolutamente nada que ver con las denominadas «políticas sociales», tan comunes en el lenguaje político de las democracias liberales, en las que se contempla lo social como un elemento externo a la propia estructura política, donde prevalece el individualismo a todos los niveles, y la sociedad aparece como un mero agregado de individuos. Muy al contrario, lo social, en el tradicionalismo de nuestro autor, implica la afirmación de un principio intrínseco tanto al modelo social como al tipo humano, así como a la naturaleza de las cosas en las que la persona desarrolla su existencia en común con los demás. Nos referimos a las instituciones, a los elementos jurídicos y otros órganos gestados en el tiempo por la experiencia histórica, que regulan la vida común.</p> <p>En el ámbito de la sociedad cristiana medieval, en plena Reconquista, cuando todavía no existía un Estado unitario como tal, cada municipio tenía sus propias leyes y sus normas, adaptadas a su modelo de vida y costumbres, Las comunidades se concebían como agrupaciones de familias con un sistema de propiedad comunal y privado en las que el patrimonio y el estatus de cada uno de sus miembros venía garantizado por el ejercicio activo de una serie de derechos en defensa de las libertades concretas, cuya fuente última era el derecho natural. Los señores feudales y los reyes se limitaban a reclamar tributos para la guerra, pero sin interferir en la defensa de estas libertades concretas ni vulnerar el sistema que las sustentaba.</p> <p>Eran gobiernos autárquicos, muy estables e inspirados por un principio democrático, el cual nada tenía que ver con las democracias liberales plutocráticas de la actualidad, cuya idea del derecho y la justicia está pervertida por el formalismo jurídico vacío e inane de sus constituciones, abstractas y plenamente funcionales a las oligarquías, al servicio de intereses espurios. En este caso, el hombre alcanzaba una plena dignidad y desarrollo en el contexto de una comunidad donde prevalecía el vínculo comunitario, al amparo de un modelo tradicional, de normas consuetudinarias y concretas que permitían la defensa efectiva del propio derecho. Ni siquiera con el advenimiento de los Estados modernos, y la centralización de algunos elementos de poder, como la Hacienda o el Ejército, se vieron alterados significativamente estos elementos, que representaban a los denominados «cuerpos intermedios» de la sociedad, y que adquirieron su propia expresión particular bajo el nombre de «Fueros», los que los propios reyes juraron respetar a lo largo de toda la Edad Moderna y hasta el advenimiento del régimen borbónico.</p> <p>La antropología tradicional vincula al hombre a un medio social, a una familia, a una estirpe o a un pueblo, que reproducen esa misma estructura familiar, aunque a mayor escala. En nuestro caso particular lo vemos a través de la convivencia de pequeños grupos humanos, de ahí la importancia de los municipios o de los concejos en un marco de vida comunitaria fuertemente institucionalizada. Al mismo tiempo este modelo y estructura también se replicaba en otros ámbitos, como en la vida económica y profesional, impregnando todas las esferas de la vida del hombre. Instituciones naturales, amparadas en el derecho natural, y orientadas a la protección y garantía de prosperidad de los hombres, y esto por encima de cualquier interés particular y mercantil de negocio. Para Mella, la ruptura con este mundo, y en general con las experiencias del pasado, es la que nos lleva, <a href="https://hiperbolajanus.com/posts/mos-maiorum-7/">merced a la acción del liberalismo, a los tiempos actuales</a>, y lo hace recorriendo un itinerario que todos conocemos, y que tienen su punto de partida <a href="https://hiperbolajanus.com/posts/joseph-de-maistre/">en la Ilustración y la posterior Revolución Francesa</a>, la irrupción del elemento racional y abstracto y la destrucción de la religión, considerada como fruto de la superstición. La destrucción del orden feudal, que todavía pervivía como marco de convivencia en el mundo rural, como una suerte de prolongación de ese espíritu medieval, hizo desaparecer de un plumazo ese entorno de relaciones concretas y personales para sustituirlas por lo «público» entendido como la centralización estatal uniforme, ignorando las realidades particulares subyacentes en el cuerpo social, los denominados «cuerpos intermedios», que fueron despojados de su autonomía, corporaciones y patrimonios. De modo que la destrucción de estas «sociedades intermedias» que mediaban entre el Estado y la sociedad desenraizó y destruyó la propia sociedad, al mismo tiempo que los fundamentos cristianos del derecho natural sobre la cual se hallaba asentada, para hacer prevalecer esos principios racionales y abstractos traídos por la revolución.</p> <p>Al mismo tiempo, y anejo a este desarraigo, del individuo se encuentra sometido a poderes arbitrarios del propio Estado liberal, sin un conglomerado institucional propio que lo proteja de estos atropellos, sumido en el individualismo ajeno a toda institución y destino colectivo, se limita al voto cada cuatro años de los partidos al servicio de oligarquías e intereses espurios, contrarios al Bien común. En este sentido, y advirtiendo las posibles acusaciones de «absolutismo» que en ocasiones se han lanzado contra el tradicionalismo, hay que señalar que Mella las rechaza por completo, dado que viola la idea de contrapoderes frente a la autoridad del rey que éste formula, ya que el absolutismo creía en la existencia de un poder ilimitado y tiránico del rey, transmitido por Dios y ajeno a la participación de la sociedad y sus estamentos. Como bien señaló <a href="https://hiperbolajanus.com/libros/metapolitica-tradicion-modernidad-julius-evola/"><strong>Julius Evola</strong></a>, el absolutismo es un fenómeno antitradicional, vinculado a la descomposición y desacralización de las estructuras tradicionales. De hecho, el absolutismo, como los regímenes liberales de hoy, dejan al individuo totalmente desprotegido, sin un asidero sobre el que apoyarse en la defensa de sus libertades concretas. El propio Mella, como bien saben todos los que se adentren en su obra, fue partidario de contrarrestar el creciente poder del aparato estatal, tal y como hemos visto y seguiremos viendo en lo sucesivo, a lo largo del presente artículo.</p> <p>|<a href="https://amzn.to/2LqITcb"><img alt="Metapolítica, Tradición y Modernidad" src="https://www.hiperbolajanus.com/libros/metapolitica-tradicion-modernidad-julius-evola/imgs/Metapolitica_Tradicion_Modernidad_Julius_Evola_hu17040587065044950472.webp" /></a>| |:-:| |<a href="https://amzn.to/2LqITcb">EVOLA, Julis; <em>Metapolítica, Tradición y Modernidad: Antología de artículos evolianos</em>, Hipérbola Janus, 2020</a>|</p> <p>En nuestro caso particular, la desaparición de la organización gremial y corporativa tuvo unas consecuencias especialmente nefastas, y en especial después de las dos desamortizaciones liberales (Mendizabal y Madoz) al despojar a los grupos sociales populares de su natural organización sociohistórica. Asimismo, desvincularon la propiedad en las relaciones comunitarias y su uso patrimonial para vincularla al uso privado y anónimo, para fines puramente especulativos, los que caracterizan al liberal-capitalismo. De ahí nace la figura del asalariado, del contratado como mera mercancía, en un proceso de alienación del trabajo característico en el desarrollo del capitalismo burgués. De aquí parte lo que algunos tradicionalistas, como Gambra, denominan el «problema social», frente al cual, y al margen de las recetas ideológicas de la modernidad, Mella reivindica la restauración de los antiguos vínculos corporativos y orgánicos de inspiración medieval.</p> <h2>La idea de soberanía social</h2> <p>Todos los procesos disolutivos que conducen a la Modernidad liberal tienen su punto de inicio con el Renacimiento, con la afirmación del individualismo y la ruptura definitiva del ecumene cristiano medieval, algo que aparece indefectiblemente unido a la Reforma luterana, así como la «valorización» del mundo clásico, con la reemergencia de teorías de tipo hedonista, como las de Epicuro, por ejemplo, generando una disolución de los vínculos con el medio concreto. Esto supone la aparición de un nuevo tipo, que es el hombre abstracto que escapa cada vez más al entorno inmediato y vital, esto al tiempo que el poder del Estado se robustece y se vuelve omnipotente. Es por ese motivo que en lo sucesivo se ha impuesto en nuestras sociedades la falta de concreción, tanto en lo teórico como en lo político, lo cual ha propiciado el triunfo del contrato social roussoniano y la justificación del orden social en virtud de componendas voluntarias y totalmente artificiales. Estas construcciones político-ideológicas son las que contribuyen a la construcción de la sociedad liberal, asentada sobre patrones puramente racionales, individualistas y mercantilistas.</p> <p>De hecho, la mayor preocupación de Mella es la destrucción de las instituciones locales y ese vínculo afectivo del hombre con su realidad inmediata, algo que impregnaba su relación con el trabajo, con su obra, con su impronta vocacional y devota, imprimiéndole, como en el caso del artesano, un sello propio y particular a su trabajo.</p> <p>Y en este sentido, Mella afirma que la sociedad moderna ha perdido su sentido institucional como base estable de la sociabilidad. A través del elemento jurídico y la participación en las instituciones es el medio a partir del cual la comunidad se cohesiona y construye sus vínculos y su particular autonomía, que le hace tener una vida propia e interna, y con la institución nos podemos referir desde una asociación profesional, a la universidad o una cofradía etc. El individualismo ha representado el factor disolutivo y corrosivo que ha destruido este vínculo social fundado en múltiples solidaridades que han enfrentado y polarizado al cuerpo social, con el enfrentamiento entre «clases sociales» y la negación de las jerarquías naturales.</p> <p>Ante todo lo relatado, y como consecuencia de las destrucciones provocadas por la revolución, Mella plantea su teoría de la soberanía social. Esta teoría consiste básicamente en encuadrar de nuevo a la sociedad en sus raíces naturales, concebida en todos sus órdenes como portadora de un dinamismo propio en una suerte de organización geométrica en la que conviven objetivos y finalidades variadas y concretas con su propia legitimidad y autonomía. Estas finalidades, amparadas en el derecho natural, son junto al poder del propio Estado las únicas formas de limitación del poder. La particularidad de esta idea de soberanía social está en el hecho de que la formación de la jerarquía social tiene una dirección ascendente, que tiene como punto de partida a las personas colectivas y concretas, pasando por una serie de instituciones, hasta llegar al Estado central, de forma escalonada y plenamente conscientes de sus funciones. Así lo expresa Mella en su propio lenguaje: «<em>la jerarquía de personas colectivas, de poderes organizados, de clases, que suben desde la familia hasta la soberanía que llamo política concretada en el Estado, que deben auxiliar, pero también contener</em>». Es lo que Mella concibe como el sociedalismo, que supone la reintegración de la sociedad en la vida concreta de los hombres, con el desarrollo de una vida política común y estable en el marco de instituciones naturales que potencien las relaciones humanas y sociales, estimulando la sociabilidad. Y hablamos, desde la perspectiva de la integración de distintas sociedades, fuertemente institucionalizadas con funciones y finalidades concretas, más allá del sentido democrático y pactista que pueda entenderse en términos modernos o de cualquier asociación u organización relacionada con el «problema social».</p> <h2>¿Qué es la Tradición?</h2> <p>De este modo quedan formuladas las dos soberanías, la política y la social, que coexisten en un mismo espacio limitándose y apoyándose recíprocamente en lo que es uno de los fundamentos del sociedalismo de Mella. No obstante, esta doble soberanía no explica todavía la concreción política de cada pueblo y el vínculo superior que lo lleva a federarse con las diferentes sociedades y a mantenerse unido en una historia y espíritu comunes. Los vínculos que las mantienen unidas en el tiempo tienen que ver con un orden histórico concreto, con un vínculo espiritual que las entrelaza interiormente de una generación a otra, y en última instancia de <a href="https://hiperbolajanus.com/posts/comprendiendo-la-tradicion/">ese orden tradicional</a> que lo engloba todo, y que al mismo tiempo se asienta en la monarquía y la religión católica. La lealtad a Dios y a un solo rey en torno a los cuales se aglutina la fe, viene a coronar todas estas estructuras y lazos forjados en el fermento de la historia.</p> <p>No se trata de la Tradición en términos de un «ultraconservadurismo», que ya sabemos que el prefijo «ultra» (lo que sea) es muy recurrente en nuestros días, con la idea de un medio social y político petrificado e invariable, sino que es el producto de un proceso de maduración y evolución histórica, de carácter dinámico y nutrido de experiencias humanas. Nada que ver con las monstruosas ideologías progresistas y modernas, nacidas de lo abstracto e impulsadas por un desbocado «ir hacia delante», desarraigado y que tiende siempre hacia la deshumanización y la destrucción de toda creación humana natural forjada en el devenir de los siglos. Este mismo dinamismo, planteado por Mella, en torno al concepto e idea de Tradición tiene continuidad y adquiere fuerza en sus sucesores y depositarios. Y al fin y al cabo, Mella no hace más que partir de la propia etimología del término, que viene del latín <em>tradere</em>, entregar, de la generación que entrega los frutos de su experiencia a la siguiente, perfeccionándola, haciéndola más estable y segura.</p> <p>Podríamos seguir extrayendo más conclusiones del pensamiento tradicional de Vázquez de Mella, pero probablemente excedería, y por mucho, el modesto propósito de este escrito, de modo que nos quedaremos aquí, no sin advertir a nuestros lectores de la posibilidad de que en un futuro volvamos a retomar nuevamente el tema.</p> <p>Antes de acabar queremos llamar la atención sobre <a href="https://www.lavozdigital.es/madrid/20150723/abci-quien-vazquez-mella-201507221907.html">una polémica acontecida hace unos años en torno a una Plaza en Madrid</a> que llevaba el nombre de nuestro autor y que se cambio para dedicársela a un sujeto cuyos méritos eran, por decirlo suavemente, más que discutibles, concretamente a Pedro Zerolo, miembro del PSOE y activista al servicio del lobby homosexualista. Durante aquella época, en 2019, muchos miembros de la izquierda globalista trataron de identificar a Vázquez de Mella como un «pensador franquista», cuando en realidad ni cronológica ni ideológicamente tuvo nunca nada que ver con el franquismo. Recordemos que murió en 1928, y la impronta de su pensamiento ha tenido como continuadores a sus propios correligionarios dentro del ámbito tradicional, aunque en su tiempo llegó a ser muy respetado también por sus adversarios, los liberales. Aunque la retirada del nombre de una calle pueda resultar algo banal, o carente de una importancia excesiva, también contribuye, a su modo, a una forma de <em>damnatio memoriae</em> que condena al olvido y al ostracismo a grandes autores de la Tradición, portadores de un Patriotismo sano y capaz de entender las peculiaridades y el <em>Dasein</em> profundo de España, que si bien no nació invertebrada, como pretendían los Orteguianos, su esencia y naturaleza es mucho más compleja que cualquiera de las grandes naciones de Europa.</p> <hr /> <p><strong>Artículo original</strong>: Hipérbola Janus, <a href="https://www.hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/"><em>Juan Vázquez de Mella y el tradicionalismo español</em></a>, 16/Ago/2024</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs27v366m0se75uknpftctsflmay0tnlx7tu3szhw9hq3hyakcc6zczyz7tk0jqcwl4ugellca6c0fm5z3gv8tcc2gn4rl5dyg6ue9yjnjszd0sd38" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs27v366m0se75uknpftctsflmay0tnlx7tu3szhw9hq3hyakcc6zczyz7tk0jqcwl4ugellca6c0fm5z3gv8tcc2gn4rl5dyg6ue9yjnjszd0sd38" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs27v366m0se75uknpftctsflmay0tnlx7tu3szhw9hq3hyakcc6zczyz7tk0jqcwl4ugellca6c0fm5z3gv8tcc2gn4rl5dyg6ue9yjnjszd0sd38" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs27v366m0se75uknpftctsflmay0tnlx7tu3szhw9hq3hyakcc6zczyz7tk0jqcwl4ugellca6c0fm5z3gv8tcc2gn4rl5dyg6ue9yjnjszd0sd38" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 5afdec5b:2d631be1 <div class="time" style="margin-left: auto;">2024-08-14 09:42:29</div> </div> <div> <h1>Introducing Our New Whitepaper on Escrow-Less Bitcoin-Collateralized Lending</h1> <p>We are thrilled to release our latest whitepaper, elaborating on our innovative Escrow-Less Bitcoin-Collateralized Lending protocol. This pioneering system leverages the power of Discreet Log Contracts (DLCs) and Hash Time Lock Contracts (HTLCs) to create a trustless, peer-to-peer lending environment that aligns with the ethos of decentralization and user empowerment.</p> <p><a href="http://whitepaper.lendasat.com/lendasat-whitepaper.pdf">Read the full whitepaper here</a> <img alt="" src="https://m.stacker.news/45722" /></p> <h2>Empowering Users with Our Architecture</h2> <p>Our protocol is meticulously designed to empower users by allowing them to borrow against their Bitcoin while retaining full control over it. We believe that this is not just a technological advancement, but a crucial step towards crafting a more decentralized, trust-minimized, and secure financial ecosystem. By eliminating the need for intermediaries, we aim to give users greater autonomy and flexibility, freeing them from traditional constraints.</p> <h2>Addressing Market Needs for Peer-to-Peer, Trustless Lending</h2> <p>Extensive market research highlights a significant, growing demand for peer-to-peer, trustless lending solutions. Users consistently expressed a desire for more control over their assets and greater flexibility in their lending options. Our Escrow-Less Lending protocol directly addresses these needs, providing a robust framework that enhances user control while maintaining the integrity and security of the lending process.</p> <h2>Exploring the Potential of Ark for Microloan Liquidity Management</h2> <p>Initially, our focus was predominantly on micro-loans. However, user interviews revealed a relatively limited demand for such products at this time. Nonetheless, we identified Ark as good solution in the context of Bitcoin microloans. Ark's capabilities could unlock new possibilities and efficiencies, making microloans more viable and attractive.</p> <h2>Remaining Flexible and Adaptable</h2> <p>Even as our primary focus shifts, the potential of Ark continues to intrigue us. Our protocol's design is inherently flexible and adaptable, allowing for continuous refinement and adjustments based on user interest and feedback. Should there be sufficient interest in the future, we are open and ready to explore Ark's integration once again to better serve our users’ needs.</p> <h2>Revolutionizing Bitcoin Borrowing and Lending</h2> <p>We firmly believe that our Escrow-Less Bitcoin-Collateralized Lending protocol has the potential to revolutionize the borrowing and lending landscape within the Bitcoin ecosystem. Our commitment is steadfast; we aim to make this innovative protocol a reality and will diligently work to iterate and improve based on user feedback. Together, let’s shape the future of decentralized lending.</p> <h2>Your Feedback Matters</h2> <p>We invite you to delve into our whitepaper and share your thoughts and feedback on this groundbreaking approach. Your insights are invaluable as we strive to create a more user-centric, flexible, and secure lending protocol. <a href="http://whitepaper.lendasat.com/lendasat-whitepaper.pdf">Read the full whitepaper here</a></p> <hr /> <p>Feel free to reach out with your thoughts, questions, or suggestions. We’re eager to engage with you and iterate based on your valuable input.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsw355wt4xnr7lxnsw9lmesp5mfjh39ks0qagrrdqrw82sl87mcg5szypd0mmzm5sx5cprhjqte2r53qce2n656avha80e90d647mpdvvd7zmkw2a9" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsw355wt4xnr7lxnsw9lmesp5mfjh39ks0qagrrdqrw82sl87mcg5szypd0mmzm5sx5cprhjqte2r53qce2n656avha80e90d647mpdvvd7zmkw2a9" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsw355wt4xnr7lxnsw9lmesp5mfjh39ks0qagrrdqrw82sl87mcg5szypd0mmzm5sx5cprhjqte2r53qce2n656avha80e90d647mpdvvd7zmkw2a9" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsw355wt4xnr7lxnsw9lmesp5mfjh39ks0qagrrdqrw82sl87mcg5szypd0mmzm5sx5cprhjqte2r53qce2n656avha80e90d647mpdvvd7zmkw2a9" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 7cc328a0:2a247c0e <div class="time" style="margin-left: auto;">2024-10-12 15:33:58</div> </div> <div> <h1>relay.tools quarterly report</h1> <p>January, 2024</p> <h2>Project updates</h2> <h2>UI design</h2> <p><a href="https://relay.tools">Relay.tools</a> spent quite a bit of time working on UI design this quarter. Since UI is time intensive and there are many other aspects of the project that need work, I time-boxed this work to 3-4 weeks total.</p> <p>I engaged with @Daniel from #nostrdesign and a freelance UI developer @freecritter. We setup a penpot instance for relay.tools and practiced using that instead of closed-source figma. We learned that penpot is not as friendly as figma from a designers point of view, but is workable. From the perspective of a frontend engineer it is no different than figma and using penpot is a big opensource win.</p> <p>The following designs were implemented this quarter. There is still much to do in this area and some aspects have been brainstormed but put on hold due to other priorities.</p> <h3>Relay branding and directory</h3> <p>I wanted to give the relays personality and branding, here is a list of improvements in this area:</p> <ul> <li>[x] The home page now prominently displays the public relays that have chosen to advertise.</li> <li>[x] Relay 'Badges' were re-designed to have better contrast and fit.</li> </ul> <p><img alt="explore relays" src="https://i.nostr.build/KDq3.png" /></p> <ul> <li>[x] Relays have a custom direct landing page at their domain. eg. <a href="https://frogathon.nostr1.com">frogathon.nostr1.com</a></li> </ul> <p>### 'Paid relay' support</p> <p>Relays now support lightning payments to the relay.tools operator. This helps with combating spam and allowing the relay owners to subsidize their monthly cost.</p> <p><img alt="landing page" src="https://i.nostr.build/5PMK.png" /></p> <h3>Layout / theme</h3> <p>The frontend code has been modified so that it is responsive on mobile/desktop using columns. The menu was re-designed to be responsive on mobile and shows user hints for login as well as additional links (explore, FAQ). Theme switcher bugs for light/dark modes have been fixed. (Nextjs bleeding edge workaround was required).</p> <h3>Relay Explorer Alpha</h3> <p>The Relay Explorer Alpha is a mini-client for interacting with a single relay. The following improvements were made:</p> <ul> <li>[x] Moderation capabilities added: Mods can delete messages, block pubkeys, and delete+block directly from the explorer.</li> <li>[x] Image and Link parsing / optional loading.</li> <li>[x] Replies implemented.</li> </ul> <p>Example screenshot showing these features: <img alt="mod capabilities" src="https://i.nostr.build/gVrG.png" /></p> <h2>Installer</h2> <p>Another main focus this quarter was to implement an installer for the relay.tools software so that anyone can easily self-host this on a generic VPS.</p> <p>The installer will be a simple shell script that asks the user a few questions (like their domain name) and then automatically installs the entire stack.</p> <p>A new code repository was created for this called <a href="https://github.com/relaytools/relay-tools-images">relay-tools-images</a></p> <ul> <li>[x] Main architecture to match production (systemd and nspawn).</li> <li>[x] Common Base OS image builds (Debian).</li> <li>[x] Haproxy, Strfry, Relaycreator and Mysql image builds.</li> <li>[x] Auto-updating of application code (including database migrations).</li> </ul> <p>This is still in-progress and will be part of next quarter's priorities to finish the first stage. (described in plans for next quarter)</p> <h2>Lightning Node</h2> <p>A decent amount of time was spent managing a Bitcoin+Lightning+LnBits node and building a second node for testing and standby purposes.</p> <p>I had some node issues this quarter and have been learning, re-building the node, upgrading, and aquiring more inbound liquidity to support relay operations.</p> <h2>Relay Management / daily operations</h2> <p>Relay.tools growth last quarter exceeded expectations and lots of work in the ladder part of this quarter went into daily operations.</p> <p>It grew so fast that I have paused any advertising so that I have time to implement some important growth related features (as described in the plans for next quarter).</p> <ul> <li>number of relays currently running: 63</li> <li>number of unique admins/mods: 207 </li> <li>events processed in last 30d: 5,091,724</li> <li>gigabytes sent/received in last 30d: 1,651GB / 175GB</li> </ul> <h3>Monitoring</h3> <p>Daily operations include checking in on the relay activity to get a feel for what's going on. I've implemented an InfluxDB integration for the strfry plugin, which helps with daily operations and in the future will provide owners, mods, and users with stats showing relay performance and event counts. This greatly improves visibility into the relays and is the backbone of data analysis for the platform.</p> <h4>Events by Kind (7d)</h4> <p><img alt="Events by Kind (7d)" src="https://i.nostr.build/6WgO.png" /></p> <h4>Events by Relay (7d)</h4> <p><img alt="Events by Relay (7d)" src="https://i.nostr.build/B46w.png" /></p> <h4>Data Explorer View (single relay, kind 3)</h4> <p><img alt="Data Explorer view" src="https://i.nostr.build/zWx0.png" /></p> <h3>Moderation</h3> <p>Daily operations time is also spent ensuring relays meet our TOS. That includes browsing the relays content for anything that does not meet the TOS and performing mitigation when necessary. This can be time consuming. I will be adding super-moderator capability so that others can assist as we grow (as described in the plans for next quarter).</p> <h3>Training / Feedback / Community</h3> <p>I promoted the use of event specific relays for nostr community events. Feedback was very positive and showed that people enjoy having event specific relays even if client support is minimal. * Nostrasia * Frogathon</p> <p><img alt="nostrasia feedback" src="https://i.nostr.build/YQX7.png" /></p> <h2>Plans for next Quarter</h2> <p>Finish the installer - [ ] SSL certificate management with certbot. - [ ] Nostr key generation for API credentials. - [ ] install.sh script for interactive -and- config file based one-shot installation. - [ ] Publish pre-built images and integrate their use with the installer.</p> <p>Re-Occuring Billing (+ tools for interacting with community of relay runners) - [ ] Implement re-occuring billing using a credits system and lightning payments. - [ ] Implement user notification(s) for billing cycle notifications. - [ ] Implement user feedback / support channel.</p> <p>Additional visibility and moderation tools - [ ] Implement super-moderator capability for TOS violations. - [ ] Engage with community to help support moderation</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsghj06lhdvmfq6txefm7tv64y85pqtdwx7d5905pdm4ssw2vm6xlszyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37qurpu6mr" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsghj06lhdvmfq6txefm7tv64y85pqtdwx7d5905pdm4ssw2vm6xlszyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37qurpu6mr" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsghj06lhdvmfq6txefm7tv64y85pqtdwx7d5905pdm4ssw2vm6xlszyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37qurpu6mr" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsghj06lhdvmfq6txefm7tv64y85pqtdwx7d5905pdm4ssw2vm6xlszyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37qurpu6mr" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 06830f6c:34da40c5 <div class="time" style="margin-left: auto;">2024-08-11 20:13:46</div> </div> <div> <p>On August 10, 2024, the vibrant Sarit Expo was alive with energy as Bitcoin Dada celebrated the graduation of its seventh cohort. This momentous event, dedicated to advancing the understanding and application of cryptocurrency, showcased the dynamism and innovation of the Bitcoin Dada community. <img alt="image" src="https://image.nostr.build/11e279544c08643edf301496a0b631f402af124474d75d1f7afa01750bc09d44.jpg" /> The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts. <img alt="image" src="https://image.nostr.build/ceb61cd696ea9ac8d9498e80ce8d141e493acdccd738d2e1668c3d706b18f533.jpg" /></p> <p>As the MC continued, participants were asked for their impressions of the event space and suggestions for improvement. Comments ranged from critiques of overly bright lighting to discussions about the relevance of Bitcoin. One participant proposed an intriguing app idea that combined Eventbrite and WhatsApp, reflecting the innovative spirit of the audience.</p> <p>The highlight of the evening was the inspiring opening speech by the CEO of Bitcoin Dada. <img alt="image" src="https://image.nostr.build/70f71c83b4c9077a94ab137ae9d5f3a383fa128efe7bc2a8a3abcbb197fbbd8f.jpg" /> She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team <img alt="image" src="https://image.nostr.build/294c48a2ff09816c78217488f388855597df189c87644ae89f1aa4b8b5d92d83.jpg" /></p> <p>each member contributing uniquely: Edith, the community lead from Uganda; Sabina, the recruiter who found a sense of belonging; and Memelord, the project manager with a flair for comedy. <img alt="image" src="https://image.nostr.build/2485959b39e21b152fa92d451d50901919b4ec63438c8592fe6be8aaa62653e6.jpg" /></p> <p>The ideathon segment was particularly thrilling. Debra’s third-place pitch proposed a Bitcoin-powered marketplace aimed at reducing youth unemployment by showcasing skills. Shantelle’s second-place idea focused on using Bitcoin to address global issues, such as helping refugees find safe zones with GPS technology. The top prize went to Meg, with her solution promising a significant impact—though the specifics were left as a tantalizing cliffhanger. 🌟🏆 </p> <p>PS : Sabina also gave a preview of the #tando app tha you can check out here on my youtube channel Link <a href="https://youtu.be/SO76X8-FkKg">HERE</a></p> <p><strong>Meeting Inspiring Figures and Making Connections 📸</strong></p> <p>Throughout the event, I had the pleasure of meeting some remarkable individuals who are deeply involved in the Bitcoin community. </p> <p>First, I met Felix from TheCore, a key panelist in the discussion on the financial revolution amidst economic unrest. We took a photo together, capturing a moment of shared enthusiasm for the potential of Bitcoin. </p> <p><img alt="image" src="https://image.nostr.build/6cd85793c7c3e50b6b7a67edc43c8425ca8f8822251eaead2c625825f5bfea2e.jpg" /></p> <p>Later, I connected with a Bitcoin Dada and gamer who is actively involved with Thndr Games, Mary Imasuen. We took a photo showcasing our shared passion for Bitcoin and gaming. </p> <p><img alt="image" src="https://image.nostr.build/5a15c07f021a80621a7f36f1a1d4b0a0416402c25740ab850ddae9466d0e778e.jpg" /></p> <p>I also had the chance to meet a Bitcoin enthusiast named Hope and she was adorned in Bitcoin-themed merchandise. We snapped a photo together, celebrating our mutual enthusiasm for Bitcoin and its future. <img alt="image" src="https://image.nostr.build/94d3f06f6035fe1be8c0e0cd711c95ba3d071d4303574bd38327c5ec36ef0f2c.jpg" /></p> <p><strong>Panel Discussions: Insightful Exchanges and Thoughtful Dialogues</strong></p> <p>The panel discussion titled “Financial Revolution Amidst Economic Unrest” featured Felix from TheCore, Jason, a Bitcoin Dada supporter, and Bill, a lawyer with expertise in Bitcoin. They delved into the major challenges Kenyans face in adopting Bitcoin, emphasizing the importance of education and community support. They discussed the solid foundation of Bitcoin’s base layer and the need for further development in subsequent layers to enhance its functionality. </p> <p><img alt="image" src="https://image.nostr.build/c68afd9248f6b5aaa9821470ef7ed982734be77d5918a5af785977fc9ab3dcd3.jpg" /></p> <p>The discussion also touched on Kenya’s future in the Bitcoin space. Bill suggested integrating Bitcoin with fiat transactions and stock exchanges, while Jason highlighted the government's welcoming stance and the need for energy to support Bitcoin. Felix proposed making Bitcoin legal tender and finding sustainable energy sources to bolster its use. ⚖️🌍 <img alt="image" src="https://image.nostr.build/cf731d0692ebcc12bd0e73bd8c315b34eff0fb3625d6e1642c3e948d0a32138d.jpg" /></p> <p>Audience questions added further depth to the conversation. One attendee asked about using Bitcoin to offset government debt, while another inquired about measures for improving public education on Bitcoin. The responses stressed the need for comprehensive educational initiatives. When asked about alternative cryptocurrencies, the panel firmly rejected the idea of “shitcoins,” focusing instead on the value of Bitcoin. 🚫💸</p> <p>The second panel discussion, moderated by Sharon from ₿-Trust, explored personal experiences with Bitcoin Dada. Panelists Anon, Vera, and Caroline shared how the program impacted their perspectives. <img alt="image" src="https://image.nostr.build/4a803cb1d1d2360c4ae469933621f509697c20a63307b3ab9ffeeda2ca2e522d.jpg" /></p> <ul> <li><strong>Anon</strong> discovered a niche and a supportive community, emphasizing Bitcoin’s role as “lightning-fast internet money,” especially with Layer 2 advancements. 🌐⚡</li> <li><strong>Vera</strong> found Bitcoin to be a valuable medium of exchange, advocated against other cryptocurrencies as “shitcoins,” and highlighted opportunities for women. 💪💰</li> <li><strong>Caroline</strong> expanded her knowledge and aimed to educate others, describing Bitcoin as a store of value and emphasizing the importance of combating inflation through education. 📚🔍</li> </ul> <p><img alt="image" src="https://image.nostr.build/23ee874bac66e35abb5eb4ef76976c3874e0d35bfecddb05446d2d9a113e667e.jpg" /></p> <p>The panelists also discussed opportunities for Bitcoin in their communities: - <strong>Anon</strong> saw potential for learning and growth through knowledge-sharing. - <strong>Vera</strong> mentioned BitSacco, a solution for saving in Bitcoin, and other upcoming projects like Sabina’s Tando app. - <strong>Caroline</strong> stressed the importance of education to counteract misconceptions about Bitcoin and its benefits. 🏡📈</p> <p>In their closing remarks, the panelists shared their future aspirations: - <strong>Anon</strong> aimed to become a developer impacted by Bitcoin. - <strong>Vera</strong> planned to engage with the community and learn from others. - <strong>Caroline</strong> focused on educating the community to dispel myths about Bitcoin. 🌟👩💻</p> <p>The event concluded with a warm dinner where attendees mingled, exchanged ideas, and enjoyed a meal together. WATCH https://video.nostr.build/4d0fbc2dd6ae0c20e0d45aa071a9e88000a9544f4289414900c91134d13960da.mp4 </p> <p>The Bitcoin Dada Cohort 7 graduation was more than just a celebration of individual achievements; it was a testament to the collective potential of the Bitcoin community.</p> <p>As the event wrapped up, the atmosphere was charged with optimism and a shared commitment to advancing bitcoin technology. The graduating cohort left with new skills, fresh ideas, and a network of like-minded individuals, ready to make a significant impact on the future of Bitcoin. 🌍💡 #kenya #bitbiashara #kenya</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs8jq6x8jxa6uf6asm3w9ldp06xsctnwxgfhngasvuan6k8kadky3szyqrgxrmvkkf9hkpvefvmm2zg7qzkvekl7prv2wpfvw5e0g35mfqv2q2ajyj" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs8jq6x8jxa6uf6asm3w9ldp06xsctnwxgfhngasvuan6k8kadky3szyqrgxrmvkkf9hkpvefvmm2zg7qzkvekl7prv2wpfvw5e0g35mfqv2q2ajyj" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs8jq6x8jxa6uf6asm3w9ldp06xsctnwxgfhngasvuan6k8kadky3szyqrgxrmvkkf9hkpvefvmm2zg7qzkvekl7prv2wpfvw5e0g35mfqv2q2ajyj" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs8jq6x8jxa6uf6asm3w9ldp06xsctnwxgfhngasvuan6k8kadky3szyqrgxrmvkkf9hkpvefvmm2zg7qzkvekl7prv2wpfvw5e0g35mfqv2q2ajyj" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 45bda953:bc1e518e <div class="time" style="margin-left: auto;">2024-10-12 14:35:33</div> </div> <div> <p>This post will be edited and refined over time.</p> <p>Eschatology is the study of Biblical prophecy pertaining to what is commonly referred to as the end times. Bitcoin is the transformation of Austrian school economics theory into an efficient and applicable method driven by natural incentives and free market consensus mechanisms.</p> <p>What happens when eschatology is viewed through a Bitcoin inspired world view?</p> <p>In this thesis I contend that it is possible and very probable that the consequences of what Satoshi Nakamoto created in Bitcoin and the prophecies surrounding Jesus Christ with regards to the second coming and a thousand year kingdom of peace and prosperity convalesce into a very compelling argument for Biblical prophecy fulfilment.</p> <p>...</p> <p>No one would argue that modern major banks are today more powerful than kings of old and governments are mere puppets to the sway that the banking empires hold over them.</p> <p>In Biblical prophecy when kings and powers are mentioned people rarely think of banking but nothing is comparable to the immense scale of wealth, power and territory controlled directly or indirectly by banks.</p> <p>IMF, BIS, the FED and Blackrock are where the levers of power are pulled in the current dispensation. Governments restructure more frequently than these institutions whom endure and exercise unmerited influence over said governments and the public interests they claim to represent.</p> <p>An excerpt from the King James Bible, Daniel chapter 2 describes prophetically the ages of man and its rotations of power.</p> <p>Interesting to note that it is symbolically portrayed in monetary/industrial metals. All used as tokens for trade, symbols of wealth and manufacture.</p> <p>Gold, silver, bronze, iron and clay. Gold has been a dominant symbol of power and wealth through millennia. Silver, brass and iron ores are mainly industrial metals although they all had prominent turns as coinage. Due to the debasement and concentration of gold specifically.</p> <p>Clay on the other hand is only a symbol of power in construction and iron has never been used in construction to the extent it is in the 20th and 21st century. Skyscrapers are the symbols of money and power today, i.e. big bank and government buildings.</p> <p>Daniel Chapter 2:24–45</p> <p><strong>24Therefore Daniel went to Arioch, whom the king had appointed to destroy the wise <em>men</em> of Babylon. He went and said thus to him: “Do not destroy the wise <em>men</em> of Babylon; take me before the king, and I will tell the king the interpretation.”</strong></p> <p>25Then Arioch quickly brought Daniel before the king, and said thus to him, “I have found a man of the captives of Judah, who will make known to the king the interpretation.”</p> <p>26The king answered and said to Daniel, whose name <em>was</em> Belteshazzar, “Are you able to make known to me the dream which I have seen, and its interpretation?”</p> <p>27Daniel answered in the presence of the king, and said, “The secret which the king has demanded, the wise <em>men,</em> the astrologers, the magicians, and the soothsayers cannot declare to the king. 28But there is a God in heaven who reveals secrets, and He has made known to King Nebuchadnezzar what will be in the latter days. Your dream, and the visions of your head upon your bed, were these: 29As for you, O king, thoughts came <em>to</em> your <em>mind while</em> on your bed, <em>about</em> what would come to pass after this; and He who reveals secrets has made known to you what will be. 30But as for me, this secret has not been revealed to me because I have more wisdom than anyone living, but for <em>our</em> sakes who make known the interpretation to the king, and that you may know the thoughts of your heart.</p> <p>31“You, O king, were watching; and behold, a great image! This great image, whose splendor <em>was</em> excellent, stood before you; and its form <em>was</em> awesome. 32This image’s head <em>was</em> of fine gold, its chest and arms of silver, its belly and thighs of bronze, 33its legs of iron, its feet partly of iron and partly of clay. 34You watched while a stone was cut out without hands, which struck the image on its feet of iron and clay, and broke them in pieces. 35Then the iron, the clay, the bronze, the silver, and the gold were crushed together, and became like chaff from the summer threshing floors; the wind carried them away so that no trace of them was found. And the stone that struck the image became a great mountain and filled the whole earth.</p> <p>36“This <em>is</em> the dream. Now we will tell the interpretation of it before the king. 37You, O king, <em>are</em> a king of kings. For the God of heaven has given you a kingdom, power, strength, and glory; 38and wherever the children of men dwell, or the beasts of the field and the birds of the heaven, He has given <em>them</em> into your hand, and has made you ruler over them all — you <em>are</em> this head of gold. 39But after you shall arise another kingdom inferior to yours; then another, a third kingdom of bronze, which shall rule over all the earth. 40And the fourth kingdom shall be as strong as iron, inasmuch as iron breaks in pieces and shatters everything; and like iron that crushes, <em>that kingdom</em> will break in pieces and crush all the others. 41Whereas you saw the feet and toes, partly of potter’s clay and partly of iron, the kingdom shall be divided; yet the strength of the iron shall be in it, just as you saw the iron mixed with ceramic clay. 42And <em>as</em> the toes of the feet <em>were</em> partly of iron and partly of clay, <em>so</em> the kingdom shall be partly strong and partly fragile. 43As you saw iron mixed with ceramic clay, they will mingle with the seed of men; but they will not adhere to one another, just as iron does not mix with clay. 44And in the days of these kings the God of heaven will set up a kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. 45Inasmuch as you saw that the stone was cut out of the mountain without hands, and that it broke in pieces the iron, the bronze, the clay, the silver, and the gold — the great God has made known to the king what will come to pass after this. The dream is certain, and its interpretation is sure.”</p> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:700/1*4I01kq4ybEruX9dD0tZs4w.png" />I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time, resources and energy.</p> <p>Skyscrapers and large construction are the modern symbols of money and power. Not so much kings, palaces and temples. The stone breaking the power of the statue has to break something contemporary other than kings and palaces if it is to be eschatological prophecy fulfilled in our time.</p> <p><a href="https://www.britannica.com/technology/cement-building-material/History-of-cement"><strong>https://www.britannica.com/technology/cement-building-material/History-of-cement</strong></a></p> <p>The invention of <a href="https://www.britannica.com/technology/portland-cement">portland cement </a>usually is attributed to <a href="https://www.britannica.com/biography/Joseph-Aspdin">Joseph Aspdin </a>of <a href="https://www.britannica.com/place/Leeds-England">Leeds</a>, <a href="https://www.britannica.com/place/Yorkshire-former-county-England">Yorkshire</a>, England, who in <strong>1824</strong> took out a patent for a material that was produced from a <a href="https://www.merriam-webster.com/dictionary/synthetic">synthetic </a>mixture of <a href="https://www.britannica.com/science/limestone">limestone </a>and <a href="https://www.britannica.com/science/clay-mineral">clay</a>.</p> <p><a href="https://www.thoughtco.com/how-skyscrapers-became-possible-1991649"><strong>https://www.thoughtco.com/how-skyscrapers-became-possible-1991649</strong></a></p> <p>Later, taller and taller buildings were made possible through a series of architectural and engineering innovations, including the invention of the first process to mass-produce steel.</p> <p>Construction of skyscrapers was made possible thanks to Englishman <a href="https://www.thoughtco.com/henry-bessemer-the-steel-man-4075538">Henry Bessemer</a>, (<strong>1856 to 1950</strong>) who invented the first process to mass-produce steel inexpensively.</p> <p><strong>You watched while a stone was cut out without hands,</strong></p> <p>No hands needed when the stone is an idea.</p> <p>As a thought experiment, imagine there was a base metal as scarce as gold but with the following properties:\ — boring grey in colour\ — not a good conductor of electricity\ — not particularly strong, but not ductile or easily malleable either\ — not useful for any practical or ornamental purpose\ \ and one special, magical property:\ — can be transported over a communications channel</p> <p><strong>Greshams Law illustrated in slow motion picture.</strong></p> <p><strong>1: The banks collapse. Being fundamentally weak because of zero reserve lending, any student of Austrian economics has been correctly predicting banking collapse, and have incorrectly been advocating gold as the solution to this collapse. Many of the big economies are valued through their housing market. Housing will be demonetised (Iron and clay economy) meaning shelter and property will become affordable to the average wage earner again. The large cement and iron structures become redundant. Everyone will work from home and a value to value economy will make banks seem like relics from an age of stupidity and evil.</strong></p> <p><strong>2: Industrial metal iron will not be for mega structures that contain speculators and bookkeepers who have fiat jobs slaving for fiat money. Iron will be used to improve the lives of individuals. Iron as coinage is already demonetised.</strong></p> <p><strong>3: Brass is demonetised as coinage and only valuable in industry. Ammunition, music, plumbing etcetera.</strong></p> <p><strong>4: Silver has been a terrible money throughout history and when the silver investors wake up to the fact that they are holding onto a redundant asset with zero monetary properties compared to the alternative they will dump their holdings, crashing the silver market and subsequently reducing the prices of producing -</strong></p> <p>solder and brazing alloys, batteries, dentistry, TV screens, smart phones microwave ovens, ad infinitum. To quote Jeff Booth. "Prices always fall to the marginal cost of production."</p> <p><strong>5: The final Rubicon is gold, people get excited about the Bitcoin exchange traded funds but it is nothing compared to the value proposition when gold pundits, large investment funds, governments pension funds and reserve banks finally realise that gold is worthless as money in this new dispensation.</strong></p> <p><strong>To illustrate the point more vividly.</strong></p> <p><strong>Ezekiel 7:19</strong></p> <p><strong>They shall cast their silver in the streets, and their gold shall be removed: their silver and their gold shall not be able to deliver them in the day of the wrath of the LORD: they shall not satisfy their souls, neither fill their bowels: because it is the stumbling block of their iniquity.</strong></p> <p><strong>What we are witnessing is the biggest rug pull the world has ever seen. In this future metals will exclusively be used for industrial use cases after being stripped of their monetary premium.</strong></p> <p><img alt="" src="https://miro.medium.com/v2/resize:fit:700/1*a-S251iw1_D6onntqxRLug.png" />This collapse is something that happens slowly over a long period of time. More or less one hour.</p> <p>Revelation 18 verse 11–19 (The fall of Babylon)</p> <p>And the merchants of the earth shall weep and mourn over her; for no man buyeth their merchandise any more: The merchandise of gold, and silver, and precious stones, and of pearls, and fine linen, and purple, and silk, and scarlet, and all thyine wood, and all manner vessels of ivory, and all manner vessels of most precious wood, and of brass, and iron, and marble, And cinnamon, and odours, and ointments, and frankincense, and wine, and oil, and fine flour, and wheat, and beasts, and sheep, and horses, and chariots, and slaves, and souls of men. And the fruits that thy soul lusted after are departed from thee, and all things which were dainty and goodly are departed from thee, and thou shalt find them no more at all. The merchants of these things, which were made rich by her, shall stand afar off for the fear of her torment, weeping and wailing, And saying, Alas, alas, that great city, that was clothed in fine linen, and purple, and scarlet, and decked with gold, and precious stones, and pearls! For in one hour so great riches is come to nought. And every shipmaster, and all the company in ships, and sailors, and as many as trade by sea, stood afar off, And cried when they saw the smoke of her burning, saying, What <em>city is</em> like unto this great city! And they cast dust on their heads, and cried, weeping and wailing, saying, Alas, alas, that great city, wherein were made rich all that had ships in the sea by reason of her costliness! for in <strong>one hour</strong> is she made desolate.</p> <p>TLDR - No more money printer go BRRR. means death to the bourgeoisie cantillionaire class.**</p> <p><strong>Is it realistic to assume that all the worlds monetised industries collapse to fair value in one hour?</strong></p> <p>Coming back to eschatology, 2 Peter 3:8</p> <p>But, beloved, be not ignorant of this one thing, that one day <em>is</em> with the Lord as a thousand years, and a thousand years as one day.</p> <p>Eschatology students use this verse to speculatively project the fulfilment of Biblical prophecies with regards to their predicted time of occurrence. Now let’s apply this to Babylon falling in one hour.</p> <p>1000 (one day) divided by 24 (hours) equals 41,6 years (one hour)</p> <p>Since the first block was mined in January 2009 you add 41,6 years you get a completion date of 2050 a.d</p> <p>Remember, this stone (Bitcoin) becomes a great mountain and fills the whole earth. A kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. The dream is certain, and its interpretation is sure.</p> <p>But contemporary sources must reflect this probability if it is a good theory. https://www.newsbtc.com/news/50-of-population-to-use-bitcoin-by-2043-if-crypto-follows-internet-adoption/</p> <p>If the banking system is first to collapse we can give it +- 10 years and we are already 14 years in since (<strong>Genesis Block</strong>) the stone struck the feet. People are slow to see the reality of the world they are living in. If all this is accurate then the world banking system is doomed.</p> <p><a href="https://www.youtube.com/watch?v=exK5yFEuBsk">https://www.youtube.com/watch?v=exK5yFEuBsk</a></p> <p>Regards</p> <p>Echo Delta</p> <h1>bitbib</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvhajhrxylnvklz60weklfhyjx6fu9n9g063zsf5zc5wsltejv9hqzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcu2kqzt2" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvhajhrxylnvklz60weklfhyjx6fu9n9g063zsf5zc5wsltejv9hqzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcu2kqzt2" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvhajhrxylnvklz60weklfhyjx6fu9n9g063zsf5zc5wsltejv9hqzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcu2kqzt2" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvhajhrxylnvklz60weklfhyjx6fu9n9g063zsf5zc5wsltejv9hqzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcu2kqzt2" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ dd664d5e:5633d319 <div class="time" style="margin-left: auto;">2024-07-10 14:45:43</div> </div> <div> <h2>The Law Giver</h2> <p>In my <a href="https://habla.news/u/laeserin@getalby.com/1720611419942">previous article</a>, I briefly went into the topic of how contract law is holy law.</p> <p>The Father of the Christians, you see, is a God of Covenants, and He sent His Son to Earth to fulfill the Law and pay a Price for our salvation. The Father also created the Natural Order to confirm His Laws through our observation of that Law in action.</p> <p>That is why Christians have a deep respect for honest contracts, true prices, fair measures, natural systems, and good laws. Not merely for their own sake, but also because understanding them helps us to understand and emulate the Law Giver.</p> <p>The tired <em>What would Jesus do?</em> meme is actually an attempt to capture this emulation of the Highest Judge. Jesus knows the Law, since His Father defined it and He is One with the Father, so how would He apply the Law best, in this situation?</p> <h2>The Last Things</h2> <blockquote> <p>Working together with him, then, we entreat you not to accept the grace of God in vain. For he says, “At the acceptable time I have listened to you, and helped you on the day of salvation.”</p> <p><strong>Behold, now is the acceptable time; behold, now is the day of salvation.</strong></p> </blockquote> <p>-- <a href="https://www.biblegateway.com/passage/?search=2+Corinthians+6%3A1-2&version=RSVCE">2 Corinthians 6:1-2</a> New Testament, RSV Bible</p> <p>One of the things most devout Christians frequently ruminate over, is when Christ will return.</p> <p>Every day, we ponder. We go for a walk, and ponder. We cook dinner, and ponder.</p> <p>At the same time, we are called upon to live each day in a productive manner, and to not simply lie around, vegetating, and staring at the heavens. Not only for our own sake, but also because to do so would be to limit our ability to inform others about the Good News, so that they can take to pondering with us. We are called to ponder with as many people as we can produce, adopt, convert, or simply collect through our daily interactions.</p> <p>This means that we are not <em>of</em> the world (as our eyes are watching God and baptism has made us Immortals), but we are definitely <em>in</em> the world (involved in, and effected by, the everyday dealings around us.) It is a very difficult balancing act to know when we are paying too much attention to the one or the other, or to know where to store up our treasures, if we can't put them all immediately into the Final Treasury.</p> <p>So, we worked today and earned a bit of fiat cash and we have no immediate usage for it. What to do with it?</p> <p>Well, some of it should go to charity or be invested in a business that provides important goods, services, and employment. Some of it will be needed to simply cover the day-to-day costs of our own life, or that of those dependent upon us. But it might be prudent to store up some of it, for the mysterious length of time between receipt of the monies and our own ascent into Heaven.</p> <p>Typically, that store was the local currency, but that's being inflated away at an alarming rate. Then we all began to move to precious metals, and many of us still do, but they are so difficult to spend and can't be broken into small bits or transported over wide distances at low cost.</p> <p>Enter Bitcoin.</p> <h2>The Great Ledger</h2> <p>In our frustration, more and more Christians are turning to a new technology, to save up some treasure in a liquid asset, for the mid-term. And, once we begin using it, and begin to understand how it works, we quickly grow fond of it.</p> <p>Bitcoin is a beautiful money because it is a money based upon keeping precise accounts, using a fair measure, and obeying the Laws of Nature.</p> <p>In essence, Bitcoin is a debt note emitted by a universal debtor (the network) in exchange for some good or service. This frees the individual people using it from ever needing to carry debt, as the debt stays in the network, the value and enforceability of that debt note is protected by the effort used to create and maintain the network, and the eagerness with which other people wish to store their efforts up in that same network. The debt still exists, but it can be so thinly and widely spread that it no longer rests as a burden upon one particular person.</p> <p>The debt, in other words, has been <em>disassociated</em> from humans and the management has been <em>distributed</em> to machines. This is the precise opposite process of a "fiat" (by decree) currency, which only has value so long as it is <em>associated</em> with some particularly solvent group of humans (who personally vouch for repayment of any debts denominated in the currency), and where management is <em>centralized</em> to some other group of humans.</p> <h2>Have you accepted Bitcoin as your personal money and store of value?</h2> <p>You have invested $10 to buy the electricity to mine Bitcoin? Then you receive $10 of Bitcoin in return. The Bitcoin network now owes you the $10 purchasing power equivalent of that electricity.</p> <p>If someone then gives you $5 worth of pizza, then you can then give them a $5 portion of your $10 worth of Bitcoin. You have taken a part of your Bitcoin debt note and shared it with them.</p> <p>They now hold $5 worth of Bitcoin invested in the network and can spend it on some other good or service. Or they can simply hold it and wait for it to rise in value, as more people "mine" more of it (and produce more notes, paradoxically making the existing notes more useful and therefore valuable) and more people try to gain the notes in order to manage their own finances by storing their energy in the network or transporting their energy using the network.</p> <p>Bitcoin, in other words, is an accounting book that needs no accountant because it stores, tracks, and controls the ledger on its own. It is a Natural Ledger that runs according to the the Laws.</p> <p>It is the only human-made ledger that allows for true and immediate Final Settlement. This Final Settlement is what allows people to trade using the convenience of digital debt notes, with neither person occurring or even risking any personal debt. We Christians know that all debt is a burden, including monetary debts, which is why we are called to forgive each other's debt and to hope that our own debts are forgiven. Better still, is to avoid the accumulation of debts, altogether.</p> <p>So, Final Settlement? Final Settlement is what Jesus would do.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsr8t49mnpj5qgzz6lpd0xn2e2dww5eag5g0gl2zqzm0a07yrtwqxgzyrwkvn27gqtyxw5v660sqkhpfqyqgdgh3x6emed0qcnkmejkx0f3jar7u09" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsr8t49mnpj5qgzz6lpd0xn2e2dww5eag5g0gl2zqzm0a07yrtwqxgzyrwkvn27gqtyxw5v660sqkhpfqyqgdgh3x6emed0qcnkmejkx0f3jar7u09" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsr8t49mnpj5qgzz6lpd0xn2e2dww5eag5g0gl2zqzm0a07yrtwqxgzyrwkvn27gqtyxw5v660sqkhpfqyqgdgh3x6emed0qcnkmejkx0f3jar7u09" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsr8t49mnpj5qgzz6lpd0xn2e2dww5eag5g0gl2zqzm0a07yrtwqxgzyrwkvn27gqtyxw5v660sqkhpfqyqgdgh3x6emed0qcnkmejkx0f3jar7u09" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 2c7cc62a:622a5cdc <div class="time" style="margin-left: auto;">2024-07-08 10:24:56</div> </div> <div> <p>Nostr で見掛けた焼肉店情報。いつか見返す。</p> <h1>ちょうしゅう</h1> <p>石垣島</p> <p>http://yugafu-llc.com/</p> <p>nostr:note1tgnt39hgyvn4lskp5s684czgsce9y55xm8ysfrfdj4mp3gguhhvsu6jtjw</p> <h1>とらじ</h1> <p>http://www.toraji.net/</p> <p>大阪上新庄</p> <p>nostr:note1x3fhl9w0wf5r7e75aem3n4ffcqcuqggp3uda6cj8p3ewg4hgrrjqwye9lc</p> <h1>瑞園</h1> <p>https://tabelog.com/osaka/A2701/A270307/27001977/</p> <p>大阪上新庄</p> <p>nostr:note1whjkp27hztcy5yey5r7nvc23yjcavpu322q5xyp8grua98rshz7stz9grh</p> <h1>たん清</h1> <p>https://www.tankiyo.com/</p> <p>東京秋葉原</p> <p>nostr:note1ke9ekpe3h92nq7qgjg4w4nmz4u7s4wyn753gagsf49pam4h6aefsddwr0k</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvhddkat2fgpmtfh8rg063lgn8a3knz588vncmju0segq98j2832gzyqk8e332d9l28fuzv5sl8lf57r9jwd5ne0j7jvg0x4zf7smz9fwdc7htj5w" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvhddkat2fgpmtfh8rg063lgn8a3knz588vncmju0segq98j2832gzyqk8e332d9l28fuzv5sl8lf57r9jwd5ne0j7jvg0x4zf7smz9fwdc7htj5w" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvhddkat2fgpmtfh8rg063lgn8a3knz588vncmju0segq98j2832gzyqk8e332d9l28fuzv5sl8lf57r9jwd5ne0j7jvg0x4zf7smz9fwdc7htj5w" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvhddkat2fgpmtfh8rg063lgn8a3knz588vncmju0segq98j2832gzyqk8e332d9l28fuzv5sl8lf57r9jwd5ne0j7jvg0x4zf7smz9fwdc7htj5w" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 5e5fc143:393d5a2c <div class="time" style="margin-left: auto;">2024-10-11 22:26:08</div> </div> <div> <p>Just revisiting some quick tips for #newbies #pow #public #blockchain users only.</p> <p>if you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.</p> <p>Hot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process</p> <p>Cold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts Paper wallets are best n cheapest form of cold wallet that can used once n thrown away.</p> <h1>Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/</h1> <p><img alt="https://nostr.build/i/nostr.build_410ff11cd83aadbcdb8f96427a21bff29b5a2d0278482b70bbe46d9fb7144bf5.png " src="https://nostr.build/i/nostr.build_410ff11cd83aadbcdb8f96427a21bff29b5a2d0278482b70bbe46d9fb7144bf5.png" /></p> <p>Any thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.</p> <p>Beginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet</p> <p>Almost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value</p> <p>You can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !</p> <p>Always delete hot wallet to test practice restoration before sending any large refunds to it to be safe. </p> <p>Large funds are always best to keep in self custody node wallets rare n occasional use</p> <p>Final word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲</p> <p>Use wallet which u learn or understand best only</p> <p>That’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️</p> <p>Some Cold wallet nostr posts nostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2 nostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw nostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q</p> <p>some nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option nostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8 related blog post nostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsyrke8ajvu5k02elq2y5q0uaszetqr69vrvs6uxkjx8cx5yq28jqszyp09ls2rfjfghnwt5muqrpva2gurgyyn9yvcplfkuvahg93e84dzc62ahqa" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsyrke8ajvu5k02elq2y5q0uaszetqr69vrvs6uxkjx8cx5yq28jqszyp09ls2rfjfghnwt5muqrpva2gurgyyn9yvcplfkuvahg93e84dzc62ahqa" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsyrke8ajvu5k02elq2y5q0uaszetqr69vrvs6uxkjx8cx5yq28jqszyp09ls2rfjfghnwt5muqrpva2gurgyyn9yvcplfkuvahg93e84dzc62ahqa" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsyrke8ajvu5k02elq2y5q0uaszetqr69vrvs6uxkjx8cx5yq28jqszyp09ls2rfjfghnwt5muqrpva2gurgyyn9yvcplfkuvahg93e84dzc62ahqa" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3c7d12a6:9532013e <div class="time" style="margin-left: auto;">2024-06-20 14:47:12</div> </div> <div> <h1>NUD: Pubkey to colors</h1> <p>This NUD defines how to convert pubkey to colors.</p> <p><a href="https://1l0.github.io/hexpattern/">Live demo</a></p> <h2>Why?</h2> <ul> <li><code>npub</code> is nonsense to display.</li> <li>too long.</li> <li><code>npub1bla...bla</code> is nonsense to display.</li> <li><code>npub1</code> takes too much space.</li> <li><code>...</code> means nothing.</li> </ul> <h2>Specs</h2> <ul> <li>Uses hex pubkey.</li> <li>Converts 64 characters to 8 colors.</li> <li>Splits 64 with 8 length chunks.</li> <li>Converts each 2 in 8 into<ul> <li>Alpha (0-255 -> 0.0-1.0)</li> <li>Hue (0-255 -> 0.0-360.0)</li> <li>Saturation (0-255 -> 0.0-1.0)</li> <li>Light (0-255 -> 0.0-1.0)</li> </ul> </li> <li>Supports dark and light theme.</li> <li>When Light is 1.0, flip the Light for light theme (0.0).</li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvj37pgd4f5m5ejtwscp87aagj9mlvgea82f0aew7fj64rfu24jcgzyq786y4xctm3l6w2y5njzm6jngfhhv8javqckx8nqqpexwu4xgqnumz8ngd" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvj37pgd4f5m5ejtwscp87aagj9mlvgea82f0aew7fj64rfu24jcgzyq786y4xctm3l6w2y5njzm6jngfhhv8javqckx8nqqpexwu4xgqnumz8ngd" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvj37pgd4f5m5ejtwscp87aagj9mlvgea82f0aew7fj64rfu24jcgzyq786y4xctm3l6w2y5njzm6jngfhhv8javqckx8nqqpexwu4xgqnumz8ngd" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvj37pgd4f5m5ejtwscp87aagj9mlvgea82f0aew7fj64rfu24jcgzyq786y4xctm3l6w2y5njzm6jngfhhv8javqckx8nqqpexwu4xgqnumz8ngd" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d830ee7b:4e61cd62 <div class="time" style="margin-left: auto;">2024-06-02 05:44:01</div> </div> <div> <p><em>This article is a translation of my original Thai-language article, which will be published as a long-form piece in the coming days.</em></p> <p>.........................</p> <p>After listening to these two masters go back and forth, circling each other like intellectual gladiators, I gotta say… the lines between the "<strong>real world</strong>" and the "<strong>virtual world</strong>" are getting seriously blurry. </p> <p>Watch more > <a href="https://youtu.be/xxNk-hE0MaQ?si=oKOnyoZ1_ZdJrm72">Alt+Tab Season 2 EP4 : "พี่ชิต" ดร.วิชิต ซ้ายเกล้า</a></p> <p>The battle for power is changing, man. </p> <p>Forget tanks and explosions, the most powerful weapon now is invisible, hiding in plain sight. It's woven into the fabric of society. We call it "<strong>Soft Power</strong>", the unseen influence that slowly consumes us, manipulates us... without us even realizing it.</p> <p>"The wars we see today..." Wichit says with a voice that sends shivers down your spine, "It's just throwing percentages at each other in the air."</p> <p>Piriya nods in agreement. "Like you said, humans are getting smarter, more cunning. Those old-school, head-on confrontations? They just lead to destruction. Waste of resources, waste of life..."</p> <p>They're right, you know... Back in the day, if you wanted something, you just sent an army to take it. Conquered land, plundered resources. It was all about "<strong>Hard Power.</strong>" </p> <p>Direct, brutal, effective... but the scars ran deep. </p> <p>The world today is way more complex. Humans have learned to use "<strong>influence</strong>" to infiltrate every aspect of life.. individuals, societies, even international relations. No bloodshed, but the results are even more potent...</p> <blockquote> <p>That's why "<strong>Soft Power</strong>" has become the most powerful weapon in this new age.</p> </blockquote> <p>Imagine...</p> <p>A world where information is the new crude oil... Where attention is the currency... And beliefs are weapons... Used cunningly in this invisible battlefield...</p> <p>"<strong>Influence</strong>" is the real victory. Not about conquering land anymore. It's about controlling minds, hearts, and actions...</p> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1717306829673-YAKIHONNES3.png" /></p> <p>Here are some prime examples of "<strong>Soft Power</strong>" playing out in our everyday lives.</p> <p><strong>Online Warfare</strong> - Fake news, twisted facts, everyone's sharing it like crazy on social media. A few taps on a screen can destroy reputations, incite hatred, and control people's thoughts without breaking a sweat. (Wichit calls it "<strong>promiscuous bits</strong>" in his lectures.)</p> <p>Have you ever... almost made a bad decision because you believed a rumor or fake news? Have you ever... fallen prey to manipulation, been tricked into hating or opposing someone without even knowing why?</p> <p>That, my friend, is Soft Power working its magic... behind the scenes...</p> <p><strong>Economic Control</strong> - Think about those skyrocketing interest rates, inflation… everything's getting more expensive by the day while our wallets get thinner.</p> <p>That's the consequence of Soft Power wielded by a handful of people who control the global economy.</p> <p>Ever wonder... why your money seems to be worth less and less each day? Why you work harder, but life doesn't get any better?</p> <p>The "<strong>money</strong>" system, controlled by the few… that's the culprit...</p> <p><strong>Cultural Domination</strong> - Movies, TV shows, music, fashion… We consume it all every day, and it slowly seeps in, shaping our thoughts, values, and behavior without us even realizing it. It's a tool used by certain groups to manipulate and steer society...</p> <p>Have you ever… wanted to be, have, or act like what you see in the media? Ever gone along with trends or fads, even if they didn't really reflect who you are?</p> <p>That's the power of "<strong>Cultural Domination</strong>"...</p> <p>"The scary part is… most people don't even realize they're being manipulated." Piriya shakes his head.</p> <p>"It's like a frog being boiled alive. By the time they realize it, it's too late..."</p> <p>Wichit sighs...</p> <p>"The system is broken, slowly eroding us from the inside... God knows where it'll all end, but it's not gonna be pretty."</p> <p>...</p> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1717306852118-YAKIHONNES3.png" /></p> <h3>Wait, what about "Money"? Isn't that Soft Power too?</h3> <p>Money used to be a mirror, reflecting the "<strong>value</strong>" of work, of resources. It was a tool for exchanging, saving, building wealth...</p> <p>But today... the "<strong>money</strong>" system is designed to be conjured up out of thin air. No real cost, no sweat. Just print more bills, and suddenly its value is distorted. Leading to "<strong>bubbles of inequality</strong>" and a crisis of faith in money itself...</p> <p>It's like sand… the tighter you grip it, the more it slips away…</p> <p>"Like when America ditched the Bretton Woods system and embraced Fiat currency, which they can print endlessly… It's how they became the world's financial superpower." Wichit explains.</p> <p>"Countries that used to hoard gold, like Europe, China, Russia… they lost power because the money they held wasn't worth as much anymore."</p> <p>"So what about Thailand? We're just a small country. How can we survive?" Piriya asks, worried.</p> <p>"We can't just print our own money. We have no control over the global economy..."</p> <p>"That's the million-dollar question…" Wichit says with a serious tone. </p> <p>"If we don't wake up, if we're not prepared, Thailand could become a victim in this power struggle."</p> <p>"We need to build up our "<strong>immunity,</strong>" man..."</p> <p>...</p> <h3>Bitcoin.. Hope or Menace?</h3> <p>In the midst of this Soft Power battleground, filled with deception and distorted truths, Bitcoin emerges… like a beacon of light piercing through the darkness. A glimmer of hope for a fairer world, a chance to reshape the global economy...</p> <p>"Weapons should be used for self-defense, not to attack others." Wichit says, implying that Bitcoin is no different.</p> <blockquote> <p>"It's a tool that can be used for good or for evil. It all depends on who's wielding it."</p> </blockquote> <p>Bitcoin is presented as a symbol of "<strong>Truth</strong>" in the digital realm. </p> <p>No one can counterfeit it or control it. It's finite, requiring energy to "<strong>mine</strong>." It's like applying the laws of physics to the financial system, creating honesty and transparency that traditional money can't achieve.</p> <blockquote> <p>Imagine… a public ledger that everyone can see, transparent, unchangeable... That's Bitcoin.</p> </blockquote> <p>"It's like a monetary revolution, creating a new system that's fair, transparent, and accessible to everyone." Piriya says excitedly.</p> <p>"No one can print more Bitcoin on a whim. No one controls it."</p> <p>"Exactly." Wichit adds. </p> <p>"If people understand and accept it, Bitcoin can change the world. Bring balance, reduce inequality, and return power to the people."</p> <p>"Imagine… a world where money belongs to the people, not the government or banks..."</p> <p>But Bitcoin is a double-edged sword... In the hands of the righteous, it's a beacon of hope. A chance to create a fairer world. </p> <p>*But in the wrong hands? *</p> <p>It could become a menace, a tool for money laundering, crime, even a "<strong>weapon</strong>" for cyber warfare…</p> <p>...</p> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1717306874995-YAKIHONNES3.png" /></p> <h3>Where Does Thailand Stand?</h3> <p>"The question is… with Bitcoin challenging the old powers, how should Thailand respond?" Piriya asks seriously.</p> <p>"Do we embrace it? Resist it? Or just ignore it?"</p> <p>"Doing nothing is not an option, just like when we missed the boat on the gold standard." Wichit emphasizes.</p> <p>"Back then, England pushed for the gold standard, but Thailand clung to the old way. We ended up losing out, trade deficits, economic downturn... We can't let history repeat itself."</p> <p>"I agree." Piriya nods.</p> <p>"We need to learn from the past and prepare for the future."</p> <p>"The government and the people need to wake up, study, and truly understand Bitcoin." Wichit continues.</p> <p>"Not just knowing what it is… but understanding its mechanisms, its potential, its risks."</p> <p>"You mean… we should push for Bitcoin to be the main currency of Thailand?" Piriya asks.</p> <p>"Whoa, hold your horses, Professor." Wichit smiles.</p> <p>"No need to rush things. I think we should start by creating a space for people to learn and experiment with Bitcoin. Promote innovation and businesses related to blockchain. Maybe the government could set up a "<strong>regulatory sandbox</strong>" to control and mitigate risks along the way."</p> <p>"But will the government be willing to relinquish control over money and embrace Bitcoin?" Piriya asks skeptically.</p> <p>"It won't be easy." Wichit sighs…</p> <p>"Power is seductive. Everyone wants to hold on to it. But if we see Bitcoin as an opportunity for Thailand to develop, to create stability and prosperity for the people, I believe the government will see the benefits and eventually embrace it."</p> <p>"So what can we, the people, do?" Piriya asks.</p> <p>"We need to be aware of Soft Power." Wichit answers.</p> <p>"Question the information we receive, be savvy about media tactics, don't fall prey to anyone's agenda. And most importantly, use Soft Power constructively, for the betterment of society."</p> <p>"Absolutely." Piriya agrees wholeheartedly.</p> <p>"We need to be informed citizens, not manipulated victims."</p> <p>"And remember… Bitcoin is not some far-off concept anymore. We need to learn, stay informed, and be prepared because the future is in our hands." Wichit concludes. "The future of money, the future of our country, the future of the world…"</p> <p>The conversation ends… but the crucial question lingers.</p> <p><strong><em>Will Thailand keep up and be ready for the world's seismic shift?</em></strong></p> <p>The answer… lies with each and every one of us...</p> <p>...</p> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1717306891402-YAKIHONNES3.png" /></p> <p>This conversation between Wichit and Piriya is like a doorway to another dimension. </p> <p>A dimension we're familiar with, but never truly see clearly. A world teeming with games, power struggles, and manipulations happening all around us… often without us even realizing it.</p> <p>They're trying to show us the "<strong>Soft Power,</strong>" the formless force that lurks in every corner of our lives. From the news we consume, the economic systems we rely on, to the culture and values that shape our thoughts and actions. </p> <p>They're not trying to scare us, but to "<strong>wake us up,</strong>" make us aware, so we don't become victims in this game.</p> <p>The things they emphasize most is the "<strong>importance of education.</strong>" We need to understand Bitcoin, blockchain, and all these new technologies transforming our world. Not just "<strong>knowing</strong>" what they are, but "<strong>understanding</strong>" their mechanisms, their potential, their risks. </p> <p>So we can decide how to use them, "<strong>for what</strong>," and "<strong>how.</strong>"</p> <p>Where does Thailand stand in this world where "<strong>Soft Power</strong>" is thriving? </p> <p>Wichit and Piriya don't offer a clear-cut answer. Instead, they "<strong>invite</strong>" us to "<strong>ask questions,</strong>" "<strong>think critically,</strong>" and find our own answers.</p> <p>We… as "<strong>citizens</strong>" of this new world… must be aware, learn, and adapt wisely to the changes. "<strong>Soft Power</strong>" isn't scary if we understand it and use it constructively. </p> <blockquote> <p>We can turn "<strong>threats</strong>" into "<strong>opportunities.</strong>"</p> </blockquote> <p>The lessons from this conversation aren't just about "<strong>Soft Power</strong>" or "<strong>Bitcoin.</strong>" They're about "<strong>awareness,</strong>" "<strong>questioning,</strong>" "<strong>critical thinking,</strong>" and "<strong>taking responsibility</strong>" for the future of ourselves, our society, and our nation.</p> <p>It's a wake-up call, revealing the "<strong>truth" of the world hidden beneath the "illusion" of "Soft Power.</strong>" And it reminds us of the true "power" that lies in our hands… </p> <p>the power to "<strong>choose,</strong>" "<strong>decide,</strong>" and "<strong>create</strong>" the future we want...</p> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1717306911094-YAKIHONNES3.png" /></p> <h2>Decoding Wichit's Thoughts. "Soft Power" vs. "Hard Power" - The Game of Power in the Modern World</h2> <p>From the conversation, we see that Wichit views "<strong>power</strong>" beyond just weapons and military force. He defines it as the <em>"</em><em>ability to influence, persuade, control, or direct the behavior, thoughts, and decisions of others</em><em>"</em> without resorting to physical force or coercion.</p> <p>Wichit sees a fascinating connection between Soft Power, Bitcoin, and national security in the digital age. Imagine a "<strong>power triangle</strong>" where each side influences and is intertwined with the others.</p> <p>He divides "<strong>power</strong>" into two main forms..</p> <p>First, there's "<strong>Hard Power,</strong>" the traditional approach focused on using force, coercion, and direct control. It relies on tangible resources like military might, weapons, economic clout, or sanctions.</p> <p>Think of examples like waging war, military occupation, controlling trade routes, or imposing economic sanctions.</p> <p>Then there's "<strong>Soft Power.</strong>" This new form of power emphasizes influence, persuasion, and attraction, making others "<strong>want</strong>" to follow without force or coercion.</p> <p>Examples include using information to shape narratives and guide thinking, employing culture and entertainment to create values and trends that influence behavior, or using economic systems to incentivize desired actions.</p> <blockquote> <p>Wichit believes that in today's world, Soft Power is gaining more influence and impact than Hard Power.</p> </blockquote> <p>Why? </p> <p>Because beliefs, values, and information can spread and penetrate people's minds easier and faster than brute force or coercion.</p> <p>He compares modern warfare to "<strong>throwing percentages at each other in the air.</strong>" Meaning that the fight for dominance in this era is no longer about physical destruction like in the past. It's a battle on an invisible battlefield, where the stakes are "<strong>information,</strong>" "<strong>beliefs,</strong>" and "<strong>influence.</strong>"</p> <p>In Wichit's view, Bitcoin can be both a "<strong>tool</strong>" and a "<strong>weapon</strong>" in the game of Soft Power.</p> <p>And ultimately, "<strong>power,</strong>" in any form, has both light and dark sides. It depends on the user, whether they choose to use it for creation or destruction...</p> <h2>When "<strong>Influence</strong>" Becomes a "<strong>Chain</strong>" on Thai Society</h2> <p>Yes, Soft Power has a glamorous, alluring side, evident in movies, music, TV shows, food, fashion, and tourism, all of which contribute to Thailand's income and image.</p> <p>But there's a dark side... one that slowly erodes our thoughts, values, and identity... without us even noticing.</p> <p>Look around… Is our younger generation today more obsessed with Korean dramas, Western series, K-pop, and designer brands than Thai movies, music, fabrics, or cuisine?</p> <p>Do they dream of living like idols, celebrities, rather than ordinary Thais?</p> <p>This is the consequence of Soft Power, influencing us to want to "<strong>be</strong>" and "<strong>have</strong>" like others, forgetting our roots, our identity, and our own values.</p> <p>The Government Uses Soft Power to Control the People Too!</p> <p>Ever wonder… why people believe government pronouncements more than news from fellow citizens? Why we accept unfair policies without much resistance?</p> <p>Is Soft Power in the hands of the government used to craft an image, hide the truth, distract, and control people's thoughts? </p> <p>I don't know... We need to observe and find the answers.</p> <h3>Are Today's Youth "Victims" or "Awakened"?</h3> <p>The younger generation, raised with the internet, social media, and global entertainment, is more susceptible to Soft Power's influence. But... they also have the potential to be aware, to question, to analyze, and to break free from the chains of manipulation.</p> <p>Don't let influence become your prison…</p> <blockquote> <p>Be "<strong>aware,</strong>" "<strong>question everything,</strong>" and "<strong>be yourself</strong>"</p> </blockquote> <hr /> <p>This is just a taste of what's discussed in the full video. To truly savor the "<strong>flavor</strong>" of "<strong>Soft Power</strong>" and "<strong>Bitcoin,</strong>" you gotta watch the whole thing. </p> <p>Watch more > <a href="https://youtu.be/xxNk-hE0MaQ?si=oKOnyoZ1_ZdJrm72">Alt+Tab Season 2 EP4 : "พี่ชิต" ดร.วิชิต ซ้ายเกล้า</a></p> <p>Trust me... you'll be blown away by the depth and intensity of the conversation. </p> <p>"One listen is not enough."</p> <p>Let me tell you… This video is "<strong>heavy,</strong>" "<strong>dense,</strong>" and "<strong>intense.</strong>" Even me had to rewind several times to let it all sink in.</p> <p>But it's "<strong>worth it,</strong>" I promise. You'll "<strong>decode</strong>" the world today, understand the mechanics of "<strong>power</strong>" and "<strong>money</strong>" in a way no one's ever explained before.</p> <h3>So why share it?</h3> <p>Because "<strong>truths</strong>" like these shouldn't be hidden. "<strong>Knowledge</strong>" like this should be "<strong>spread</strong>" to "<strong>everyone.</strong>"</p> <p>But… to be honest, this video is "<strong>deep,</strong>" "<strong>complex,</strong>" and "<strong>hard to grasp</strong>" for the average person. So we have to transform ourselves into "interpreters," <strong>"translating</strong>" the "<strong>divine language</strong>" into "<strong>human language.</strong>" Explain it simply, clearly, and visually.</p> <p>Remember… sharing is not just "<strong>talking,</strong>" it's about communication that's easy to understand, relatable, and resonates with the listener.</p> <p>Because knowledge is precious… if it's "<strong>shared.</strong>"</p> <hr /> <p><strong>PS.</strong> Wichit's ideas and concepts regarding Soft War are heavily influenced and inspired by the book "Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin" by Major Jason P. Lowery. (2023)</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0mdw7tpm3eree0mkdwlmerwg9phsx673a8f29kdjrdy5ux3rl99gzyrvrpmnm0sc2xe93y39h0xhmknc4vuellwxgwg6ssm3xkz6wv8xky8677wg" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0mdw7tpm3eree0mkdwlmerwg9phsx673a8f29kdjrdy5ux3rl99gzyrvrpmnm0sc2xe93y39h0xhmknc4vuellwxgwg6ssm3xkz6wv8xky8677wg" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0mdw7tpm3eree0mkdwlmerwg9phsx673a8f29kdjrdy5ux3rl99gzyrvrpmnm0sc2xe93y39h0xhmknc4vuellwxgwg6ssm3xkz6wv8xky8677wg" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0mdw7tpm3eree0mkdwlmerwg9phsx673a8f29kdjrdy5ux3rl99gzyrvrpmnm0sc2xe93y39h0xhmknc4vuellwxgwg6ssm3xkz6wv8xky8677wg" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 5e5fc143:393d5a2c <div class="time" style="margin-left: auto;">2024-10-11 22:15:54</div> </div> <div> <p>We are now given a choice of digital freedom #nostr .</p> <p>Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document. </p> <p>Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too.</p> <p>New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management.</p> <p>Relay management is an active regular task based on where when n how you are using.</p> <p>Relay list are saved within you npub profile backup file which can edited and broadcast anytime.</p> <p>Relay management is an active regular task based on where when and how you are using. </p> <p>Relay list always need to be updated time to time as and when needed. </p> <p>2 Users MUST a common RELAY between them even if one only need to follow another. Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay</p> <p>Most nostr client applications has SETTINGS where user choose add/remove relays Also user choose which function to enable - READ or WRITE </p> <p>Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling.</p> <p>Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage.</p> <p>Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected.</p> <p>Relay types: They can be categorized by various features or policy or technologies.</p> <p>FREE PUBLIC Relays vs PAID PUBLIC Relays</p> <p>PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly.</p> <p>Private Replay or Tor Relays – normally not easily visible until unless someone tell you. You can also host own private relay not opened to internet of archive and back of your own notes.</p> <p>The technical landscape in nostr can be fast changing as more NIPs get proposed or updated. Relays admin can choose implement certain NIPs or not based on policy or technical limitations.</p> <p>Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this. NIP07 is used for client authentication like nos2x and is implemented by all relays in fact. Nostr is so fasting changing-hence many links many broken Pushing long note again.</p> <p>To be continued again ... reference pics will added later also Hope this help you understand "why when what" to tune and maintain active set of proper relays. Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙</p> <p>References: https://habla.news/relays https://relay.exchange/ https://relays.vercel.app/ https://nostr.info/relays/ https://nostrudel.ninja/#/relays</p> <p>Related Articles: https://thebitcoinmanual.com/articles/types-nostr-relays/ nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98 https://habla.news/u/current@getcurrent.io/1694434022411</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9gwepmvqpsuta3808gy7csc6hvtjavupkt3zxmq37qa76maslk0gzyp09ls2rfjfghnwt5muqrpva2gurgyyn9yvcplfkuvahg93e84dzcu8hpvg" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9gwepmvqpsuta3808gy7csc6hvtjavupkt3zxmq37qa76maslk0gzyp09ls2rfjfghnwt5muqrpva2gurgyyn9yvcplfkuvahg93e84dzcu8hpvg" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9gwepmvqpsuta3808gy7csc6hvtjavupkt3zxmq37qa76maslk0gzyp09ls2rfjfghnwt5muqrpva2gurgyyn9yvcplfkuvahg93e84dzcu8hpvg" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9gwepmvqpsuta3808gy7csc6hvtjavupkt3zxmq37qa76maslk0gzyp09ls2rfjfghnwt5muqrpva2gurgyyn9yvcplfkuvahg93e84dzcu8hpvg" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 9e69e420:d12360c2 <div class="time" style="margin-left: auto;">2024-10-19 12:52:02</div> </div> <div> <h1>Joe Biden and Senator Lindsey Graham about securing a U.S.-Saudi defense treaty, as revealed in Bob Woodward's new book "War".</h1> <h2>The Proposed "Megadeal"</h2> <p>The conversation took place in the context of Biden's attempts to negotiate a "megadeal" between the United States, Saudi Arabia, and Israel[1]. The goal was to create a permanent, U.S.-led security alliance in the Middle East[1].</p> <h2>Bipartisan Collaboration</h2> <p>Graham reportedly told Biden that only a Democratic president could convince Democrats to "vote to go to war for Saudi Arabia," to which Biden responded, "Let's do it"[1]. This exchange highlights the bipartisan willingness to consider military commitments in the Middle East[2].</p> <h2>Political Calculations</h2> <p>Graham suggested that: - A Republican administration wouldn't be able to secure such a deal - Democrats wouldn't support it if introduced by Trump - Republicans could provide 45 votes if Israel encouraged it Biden assured Graham he could secure the remaining Democratic votes[1].</p> <h2>Saudi Arabia's Perspective</h2> <p>Crown Prince Mohammed bin Salman was reportedly interested in the deal to gain protection under the U.S. nuclear umbrella[1]. However, after the October 7, 2023 attacks on Israel, bin Salman became hesitant, fearing potential assassination if he didn't stand up for Palestinian rights[1].</p> <h2>Current Status</h2> <p>The deal is currently in suspended animation due to bin Salman's concerns and changing regional dynamics. The Biden administration continues to pursue negotiations, urging Israel to make concessions on Palestinian rights to facilitate the agreement.</p> <p>The article concludes by noting that if Woodward's reporting is accurate, both Biden and Graham seemed willing to commit American troops to potential conflict with relative ease.</p> <p>Sauce: <a href="">https://reason.com/2024/10/18/biden-and-graham-reportedly-schemed-on-how-to-go-to-war-for-saudi-arabia/</a></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqszk0qlksvatwxjslrenfndmp5k7wuy5x4mpdxva6n5kah54j6exfczyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyd0449c" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqszk0qlksvatwxjslrenfndmp5k7wuy5x4mpdxva6n5kah54j6exfczyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyd0449c" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqszk0qlksvatwxjslrenfndmp5k7wuy5x4mpdxva6n5kah54j6exfczyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyd0449c" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqszk0qlksvatwxjslrenfndmp5k7wuy5x4mpdxva6n5kah54j6exfczyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyd0449c" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 126a29e8:d1341981 <div class="time" style="margin-left: auto;">2024-05-22 06:47:20</div> </div> <div> <blockquote> <p>Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: <a href="https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852">https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852</a></p> </blockquote> <p>Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. <strong>Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior.</strong> A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.</p> <p>Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.</p> <p>Bitcoin cambió todo eso. <strong>Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio.</strong> Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.</p> <p><strong>La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins.</strong> ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.</p> <p><strong>La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan.</strong> Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.</p> <p>En cambio, <strong>los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente</strong> para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.</p> <p>Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. <strong>Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero.</strong> Pero Bitcoin no se originó en el vacío. <strong>Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.</strong></p> <p>Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.</p> <p>Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.</p> <p>https://freeross.org</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsdeu7p4nny8rytnu9x6uxjqjytupv8ahhdtn02jayeahlk527hu0czyqfx520grqwpvcawvyww9pt43vytgaw0sxekxnwjx7uzxnx3xsvcz7nuaqn" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsdeu7p4nny8rytnu9x6uxjqjytupv8ahhdtn02jayeahlk527hu0czyqfx520grqwpvcawvyww9pt43vytgaw0sxekxnwjx7uzxnx3xsvcz7nuaqn" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsdeu7p4nny8rytnu9x6uxjqjytupv8ahhdtn02jayeahlk527hu0czyqfx520grqwpvcawvyww9pt43vytgaw0sxekxnwjx7uzxnx3xsvcz7nuaqn" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsdeu7p4nny8rytnu9x6uxjqjytupv8ahhdtn02jayeahlk527hu0czyqfx520grqwpvcawvyww9pt43vytgaw0sxekxnwjx7uzxnx3xsvcz7nuaqn" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ a012dc82:6458a70d <div class="time" style="margin-left: auto;">2024-10-19 12:51:04</div> </div> <div> <p><strong>Table Of Content</strong></p> <ul> <li> <p>The Current State of Bitcoin ETFs</p> </li> <li> <p>The 'Silver Bullet' Solution</p> </li> <li> <p>The Role of ARK Invest</p> </li> <li> <p>Implications for the Future</p> </li> <li> <p>Conclusion</p> </li> <li> <p>FAQ</p> </li> </ul> <p>In the dynamic and rapidly changing landscape of cryptocurrencies, Cathie Wood's ARK Invest has consistently been a pioneer, leading the charge with innovative strategies and investment products. The latest development from the firm is a groundbreaking strategy for their Bitcoin ETF filing, a solution they have intriguingly dubbed the 'Silver Bullet'. This approach, while shrouded in some degree of mystery, aims to address regulatory concerns that have long plagued the cryptocurrency sector. It promises to pave the way for a more secure, transparent, and efficient future for Bitcoin investments, potentially revolutionizing the way we perceive and interact with this digital asset.</p> <p><strong>The Current State of Bitcoin ETFs</strong></p> <p>Exchange-Traded Funds (ETFs) have become a popular investment vehicle in the financial world. They offer diversified exposure to a particular asset class or sector, allowing investors to mitigate risk while capitalizing on market trends. However, the creation of a Bitcoin ETF has been a contentious issue. Regulatory bodies, particularly the U.S. Securities and Exchange Commission (SEC), have expressed concerns over the potential for market manipulation and the need for robust investor protection measures. This has led to a stalemate, with several Bitcoin ETF proposals being rejected or left in regulatory limbo.</p> <p><strong>The 'Silver Bullet' Solution</strong></p> <p>ARK Invest's 'Silver Bullet' solution is a novel and ambitious approach designed to address these regulatory concerns head-on. While the specifics of this strategy remain undisclosed due to confidentiality and strategic reasons, it is believed to involve a blend of advanced technology and stringent compliance measures. The 'Silver Bullet' is not just a solution; it's a statement of intent, a commitment to providing greater transparency, reducing the risk of market manipulation, and ensuring robust investor protection. It's a testament to ARK's belief in the potential of Bitcoin and their determination to overcome the regulatory hurdles that stand in its path.</p> <p><strong>The Role of ARK Invest</strong></p> <p>Under the visionary leadership of Cathie Wood, ARK Invest has emerged as a strong advocate for cryptocurrencies and the transformative potential of blockchain technology. The firm's active management style, combined with its unwavering focus on disruptive innovation, has led to significant returns for their investors and cemented their reputation as trailblazers in the investment world. The introduction of the 'Silver Bullet' solution is another testament to ARK's commitment to pushing the boundaries of traditional finance, challenging the status quo, and driving the adoption of innovative financial products.</p> <p><strong>Implications for the Future</strong></p> <p>If successful, the 'Silver Bullet' solution could have far-reaching implications for the future of Bitcoin and the broader cryptocurrency sector. It could revolutionize the way Bitcoin ETFs are viewed by regulatory bodies, potentially leading to a shift in perception and a softening of the regulatory stance. This could pave the way for more widespread acceptance of Bitcoin as a legitimate and regulated asset class. The potential impact of this cannot be overstated. It could lead to an influx of institutional investors into the Bitcoin market, further driving its growth, increasing its liquidity, and promoting its adoption on a global scale.</p> <p><strong>Conclusion</strong></p> <p>The 'Silver Bullet' solution introduced by ARK Invest represents a significant and potentially game-changing step forward in the quest for a Bitcoin ETF. While the road to regulatory approval may still be fraught with challenges and uncertainties, this innovative approach offers a promising glimpse into the future of Bitcoin investments. As we continue to navigate the uncharted waters of cryptocurrency regulation, it is clear that firms like ARK Invest are not just observers but active participants, leading the charge towards a more secure, transparent, and inclusive financial future.</p> <p><strong>FAQ</strong></p> <p><strong>What is the 'Silver Bullet' solution by ARK Invest?</strong> The 'Silver Bullet' is a novel strategy introduced by ARK Invest for their Bitcoin ETF filing. While specific details are confidential, it's designed to address regulatory concerns, aiming to provide greater transparency, reduce market manipulation risk, and ensure investor protection.</p> <p><strong>Why is the 'Silver Bullet' solution significant?</strong> If successful, the 'Silver Bullet' could revolutionize how Bitcoin ETFs are viewed by regulatory bodies, potentially leading to more widespread acceptance of Bitcoin as a regulated asset class. This could attract more institutional investors into the Bitcoin market, driving its growth and adoption.</p> <p><strong>What is ARK Invest's role in the cryptocurrency market?</strong> Led by Cathie Wood, ARK Invest is a strong advocate for cryptocurrencies and blockchain technology. The firm's focus on disruptive innovation has led to significant returns for investors and the introduction of the 'Silver Bullet' solution is another testament to ARK's commitment to pushing the boundaries of traditional finance.</p> <p><strong>That's all for today</strong></p> <p><strong>If you want more, be sure to follow us on:</strong></p> <p><strong>NOSTR: croxroad@getalby.com</strong></p> <p><strong>X: <a href="https://x.com/croxroadnewsco">@croxroadnews</a></strong></p> <p><strong>Instagram: <a href="https://www.instagram.com/croxroadnews.co/">@croxroadnews.co</a></strong></p> <p><strong>Youtube: <a href="https://www.youtube.com/@croxroadnews">@croxroadnews</a></strong></p> <p><strong>Store: https://croxroad.store</strong></p> <p><strong>Subscribe to CROX ROAD Bitcoin Only Daily Newsletter</strong></p> <p><strong>https://www.croxroad.co/subscribe</strong></p> <p><em>DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.</em></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqswpmxmw0hxqlvh00rv6xfr6l8xv9734e8nwzx6fd3w375xkvx64mczyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns64q7rxh" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqswpmxmw0hxqlvh00rv6xfr6l8xv9734e8nwzx6fd3w375xkvx64mczyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns64q7rxh" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqswpmxmw0hxqlvh00rv6xfr6l8xv9734e8nwzx6fd3w375xkvx64mczyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns64q7rxh" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqswpmxmw0hxqlvh00rv6xfr6l8xv9734e8nwzx6fd3w375xkvx64mczyzsp9hyz808cp402ma9kdqcr2c6tcs83kzjjh9vz0zmthjtytzns64q7rxh" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 75da9402:77a65b5c <div class="time" style="margin-left: auto;">2024-05-19 00:07:36</div> </div> <div> <p>Empezare este articulo indicando que iba hacer publicado como un hilo en <strong>Twitter o X</strong> o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje <strong>"no se puede enviar"</strong> usted debe <strong>UPDATE TO PREMIUM</strong> para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.</p> <hr /> <h2>Te cuento una pequeňa historia.</h2> <p>Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: <em>Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial</em> y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: <strong>AL FINNN...</strong> volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. <strong>HASTA AHORA..</strong></p> <h2>Te gusta twitter pero a la vez estás arto de lo mismo?</h2> <p>Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.</p> <p>Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de <strong>BUENOS DIAS</strong> todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA <em>(grupo familiar que pasa silenciado por siempre)</em> y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, <strong>NO lo que TÚ quieres</strong>. Ellos dictan y te <strong>“Sugieren el contenido que puedes ver”</strong> pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente <em>mentira....</em></p> <p>Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés: </p> <p>https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana</p> <p>Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr. </p> <h2>Pero que son Mastodon, Bluesky y Nostr?</h2> <p>Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....</p> <p>Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.</p> <p><strong>-Y por qué sucede esto con Nostr?</strong></p> <p>Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.</p> <p><strong>-Y que ganamos los usuarios?</strong></p> <p>Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que <strong>NO</strong> encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:</p> <p>https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR</p> <h2>Te interesa usar y aprender que puedes hacer con Nostr?</h2> <p>Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.</p> <ul> <li>Lives: https://zap.stream/</li> <li>Música: https://wavlake.com/</li> <li>Blogs: https://yakihonne.com/</li> <li>Podcast: https://www.fountain.fm/</li> </ul> <p>Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/</p> <p>Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:</p> <p><strong>En iOS:</strong> - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/</p> <p><strong>En ANDROID:</strong> - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en</p> <p><strong>En WEB:</strong> - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/</p> <p>Debes saber que puedes con el mismo usuario y contraseña <strong>(en #Nostr se dicen llaves)</strong> puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.</p> <p>Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.</p> <p>Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.</p> <p>https://nostr.com/ https://nostr.how/</p> <h2>Para terminar con este pequeño hilo... (te odio Elon) jajaja</h2> <p>Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.</p> <p>Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar <strong>NOSTR</strong> como <strong>TU</strong> quieras. Solo haz lo siguiente:</p> <ol> <li>Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.</li> <li>Crea el Usuario <strong>(npub....)</strong> llave 1</li> <li>Crea la contraseña <strong>(nsec....)</strong> llave 2</li> <li>Guarda tus llaves, <strong>que no se te olviden</strong>. (anótalas) </li> <li>Envia tu primer post colocando al final el hashtag <strong>#introductions</strong></li> <li>Y a disfrutar de #nostr </li> </ol> <p>Si te gustó este hilo <strong>(Elon de >:{ #$%&)</strong> dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.</p> <p>Si deseas seguirme en #Nostr •𓅦 </p> <p>primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60</p> <p>Alla nos vemos...escríbeme y pregunta lo que quieras.</p> <p>Saludos, johnny</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsdzz50r0cu4gm84l49xuyzkyflawgepccjeh6h37ufttss6409g7qzyp6a49qz0t2q30p04lltrenawxatartcmzwrvgx6yy3s8wrh5ed4c09cnrg" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsdzz50r0cu4gm84l49xuyzkyflawgepccjeh6h37ufttss6409g7qzyp6a49qz0t2q30p04lltrenawxatartcmzwrvgx6yy3s8wrh5ed4c09cnrg" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsdzz50r0cu4gm84l49xuyzkyflawgepccjeh6h37ufttss6409g7qzyp6a49qz0t2q30p04lltrenawxatartcmzwrvgx6yy3s8wrh5ed4c09cnrg" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsdzz50r0cu4gm84l49xuyzkyflawgepccjeh6h37ufttss6409g7qzyp6a49qz0t2q30p04lltrenawxatartcmzwrvgx6yy3s8wrh5ed4c09cnrg" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 9e69e420:d12360c2 <div class="time" style="margin-left: auto;">2024-10-19 12:06:34</div> </div> <div> <h1>Cancer cases in England hit record high - with almost 1,000 people diagnosed every day</h1> <p>Cancer cases in England have reached a new high, with nearly 1,000 diagnoses made every day, according to NHS data. In 2022, there were 346,217 cancer diagnoses, a 5% increase from 2021. The rise largely stems from a significant increase in prostate cancer cases, which rose by over 25%.</p> <p>While the incidence of cancer has increased, death rates are falling. Dame Cally Palmer of NHS England stated, "Our work is leading to more people starting treatment promptly – potentially saving lives." Current initiatives are encouraging earlier cancer checks post-pandemic, aiming for quicker diagnoses and better care for patients.</p> <p>Sauce: <a href="">https://www.dailymail.co.uk/news/cancer/index.html</a></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs2u95f3fh8v2807vht667g0vuuty4dewz5y5czsxutym3c3xrthkqzyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyuw5wn0" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs2u95f3fh8v2807vht667g0vuuty4dewz5y5czsxutym3c3xrthkqzyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyuw5wn0" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs2u95f3fh8v2807vht667g0vuuty4dewz5y5czsxutym3c3xrthkqzyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyuw5wn0" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs2u95f3fh8v2807vht667g0vuuty4dewz5y5czsxutym3c3xrthkqzyz0xnepqucxld8xeg4gs3qk0u3xezat693vdrssuqfa8ja73ydsvyuw5wn0" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3c984938:2ec11289 <div class="time" style="margin-left: auto;">2024-05-11 12:21:43</div> </div> <div> <p>👉play the audio to listen to the article. https://media.nostr.build/av/749a03816c328c599054f31113588f9f5a47b5e67681e3a1eb9ee97c8f2e0dd3.mp3</p> <h2>Welcome to Nostr!</h2> <p><strong>Introduction.</strong> Is this your first time here in Nostr? Welcome! Nostr has a oddball acronym for "<strong>N</strong>otes and <strong>O</strong>ther <strong>S</strong>tuff <strong>T</strong>ransmitted by <strong>R</strong>elays" with a simple goal, to be censorship-resistance. An alternative to traditional social media, communications, blogging, streaming, podcasting and eventually email (<em>in development</em>) with decentralization that empowers you, dear user. No more will you have to be plagued by ads, held by centralized entities and data hungry algorithms that monetizes you.</p> <p>Allow me to be your host! I'm <strong>Onigirl!</strong> I'm on a quest to explore the world of Nostr, a decentralized communication protocol. I write about the tools, and the <em>awesome</em> developers within Nostr that bring this realm roaring with life. </p> <p><img alt="" src="https://image.nostr.build/130e25ce8e83136e69732b6b37e503541fbd82b7598d58ba64e504e19402d297.jpg" /></p> <h3>Welcome to Nostr Wonderland</h3> <p>You're about to step into another world that will explode your mind from all the decentralized apps, clients, web3 enabled sites that you can use. You're never going to look at communications, logging in, 2FA, and social media the same way ever again. All thanks to Nostr's cryptographic nature inspired by Bitcoin blockchain technology. Each user, when they create a Nostr account, they get two keys, a private and a public key. These are your keys to your very own kingdom. Whatever you write, sing, podcast, stream, anything you create --all of it belongs to you. The sky is literally the limit!</p> <p><img alt="" src="https://image.nostr.build/6f262291ddd72e45350d360f6e45fc9dd38740074de000ff4e48924bb838bf9c.jpg" /></p> <h3>A Gold and Silver Key</h3> <p>A friend of mine and I, call this "<strong>Identity by Encryption</strong>" because your Identity is encrypted. You can share your <strong><em>silver key</em></strong>, "<strong><em>npub</em></strong>" to other users to connect and follow. Use your <strong><em>gold key,</em></strong> "<strong><em>nsec</em></strong>" to unlock your account to plugin into a plethora of applications. Keep this key safe at all times. <strong>There is no reason to be caged ever again by social platforms TOS henceforth!</strong></p> <p>👉Give it a whirl, you can follow me by <em>copying and pasting my public key</em> into your search bar on any client that you decide to use.</p> <p>Onigirl <code>npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3</code></p> <h3>Don't have a client yet? Select the best option</h3> <p>Find the right App for you! This is where you can use your gold key, "<strong>nsec</strong>" to login into these wonderful tools. You can also visit Nostr's app <a href="https://www.nostrapps.com/">page here.</a> Before you start pasting your gold key everywhere on apps, consider using a signers (for web3 enabled sites) please look at the next image for details, also refer to the legend. </p> <p><img alt="" src="https://image.nostr.build/0db9d3efe15c3a02d40c3a5e65e7f6a64d50c6738dfe83c37330194d1b85059f.jpg" /></p> <h3>Get a Signer extension via chrome webstore</h3> <p>A signer is an extension in the chrome webstore on Google. <em>Nos2x</em> and <em>NostrConnect</em> are widely accepted extension for logins. This simplifies the process of logging into web3 sites instead of copying and pasting your gold key, "nsec" each and every time, you keep it within the extension and give it permission(s) to sign you in. </p> <p><img alt="" src="https://image.nostr.build/ff751710a0e3c808355a8d03721b633da7a8926a16f7e91b6e5d451fecc5d887.jpg" /></p> <h3>👉⚡⚡Get a Bitcoin lightning wallet to send/receive Zaps⚡⚡ (This is optional)</h3> <p><img alt="" src="https://image.nostr.build/cde06896707080ed92fff2cce1c4dd50b0095f371b8d2762fce7eeebf3696cd4.jpg" /></p> <p>Here on Nostr, we use the Bitcoin Lightning network (L2). You will need to get a lightning wallet in order to send/receive Satoshi. These are the smallest denominations of a Bitcoin. It is a one hundred millionth of a single bitcoin (0.00000001 BTC). Zaps are a form of "micropayment with sats" here on Nostr. If you enjoy a user content, it is the norm to <strong>"⚡zap⚡"</strong> a.k.a <strong>"tip"</strong> for their content. For example, If you like my content, you can zap me with SATs to reward my work. But you just arrived, you don't have a wallet yet. No worries! I got you covered!</p> <p>"<a href="https://stacker.news/r/Hamstr">Stacker.News</a>" is a platform where users can earn SATs by writing articles and engaging with other users. You.</p> <p><img alt="" src="https://image.nostr.build/91198aba183890b479629ee346ba1aa3c9565ab863c665d91d24b0260917a131.jpg" /></p> <p>👉Stacker.News is also the easiest place to get a Bitcoin Lighting wallet address. </p> <ol> <li>Log in with your "Signer" extension either "Nos2x or NostrConnect" click your <strong>profile</strong> which will be random letters and numbers in the upper right corner. You will see something like this: <img alt="" src="https://image.nostr.build/9d03196a588fc2936538803ae27a2cf057b1efaf4eff5558b9612b9fabc7bd31.png" /></li> <li>Click <strong>"edit"</strong> and choose a name that you like, and if you don't like it. You can change again later. <img alt="" src="https://image.nostr.build/34e9b0088dd5c12d4b9893e7818f0bee59f918699103ec0c45c01c384eb94164.jpg" /></li> <li>Click <strong>"save"</strong></li> <li>Create a bio and the SN community are very welcoming and will zap you some sats to welcome you.</li> <li>You new Bitcoin Lightning Wallet address will appear like this: <img alt="" src="https://image.nostr.build/8a3f373cedcebd967aef3ba0fba1504446f3e2b4bb497f7405a05ef3e145aca2.png" /> #### ^^<strong>Do not zap this address; this is purely for educational purposes!</strong></li> <li>With your <strong>New</strong> Bitcoin Lightning wallet address you can put this into any client or app of your choice. To do this, go to your <strong>profile page</strong> and under your wallet address under "<strong>LN Address,</strong>" enter your new address and hit <strong>"save"</strong> and there ya go. Congratulations!</li> </ol> <p>👉✨Eventually, you may want to move to self custodial options and maybe consider to even self-host your own LN node for better privacy. Good news is stacker.news is also moving away from being a custodian wallet. </p> <h3>Nostr, the maverick of Servers</h3> <p><img alt="" src="https://image.nostr.build/2cf428a02cfc94365150112e12e541ff338390faf0718ed65957098123ca5016.jpg" /> Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.</p> <h3>My friends in Nostr welcome you!</h3> <p>Welcome to the tea Party, would you like a spot of tea?🍵 <img alt="" src="https://image.nostr.build/03c85e38f0b8a5ed0721281ae23aca4f7d217bef5b12c8d8c2c127c6bb3189f6.jpg" /></p> <h3>There's so much more!</h3> <p>This is just the tip of the iceberg. Follow me as I continue to explore new lands and the developers, called "knights" behind this ever-growing ecosystem. Meet me here for more content like this and share this with future nostr users. Learn about the knights fighting for freedomTech within Nostr and the projects that are contributing to make it happen. Make your life more decentralized with Nostr. 💋</p> <p>Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsgq8597dgpra6zsfv7wpqf3z84kv85z9x9r07waszvdstx8c0gx6czyq7fsjfc80023qash5t0ans76dkn0cmumh3uusa306jwjxfwcyfgjypxhxs" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsgq8597dgpra6zsfv7wpqf3z84kv85z9x9r07waszvdstx8c0gx6czyq7fsjfc80023qash5t0ans76dkn0cmumh3uusa306jwjxfwcyfgjypxhxs" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsgq8597dgpra6zsfv7wpqf3z84kv85z9x9r07waszvdstx8c0gx6czyq7fsjfc80023qash5t0ans76dkn0cmumh3uusa306jwjxfwcyfgjypxhxs" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsgq8597dgpra6zsfv7wpqf3z84kv85z9x9r07waszvdstx8c0gx6czyq7fsjfc80023qash5t0ans76dkn0cmumh3uusa306jwjxfwcyfgjypxhxs" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ e88a691e:27850411 <div class="time" style="margin-left: auto;">2024-10-11 13:17:16</div> </div> <div> <h1>An opinionated guide to Sauna.</h1> <p>By NVK <a href="https://primal.net/nvk">🌐</a> <a href="https://twitter.com/nvk">🐦</a></p> <h2>Introduction</h2> <p>Updated from the Sauna, October 7th 2024</p> <p>After years of experimenting with different sauna types, I’ve developed strong opinions on the subject. The purpose of this article is to share these opinions with anyone who is interested in them and, hopefully, help others get more out of their sauna experience.</p> <p>I’m certain my opinions will offend some, including all the people who (in my view) are doing it wrong. I know that saunas are important to many cultures around the world and that my strongly held opinions may offend some of those cultures.</p> <p>Mind you, although I grew up in South America, I do have a fair amount of slavic blood in me. When I was a child, my grandfather regularly took me with him to the shvitz. One of my fondest memories from this time was the “Scottish Bath”, which involves standing against the sauna wall, execution-style, so that someone can spray you with freezing water from a high pressure hose. I’ve never heard of this outside of South American and can’t attest to whether it has any real Scottish origins.</p> <p>The various health claims about using a sauna are beyond the scope of this article. All I have to say is that, like many things in my life, like Bitcoin, the meat/keto diet, and fasting, I find sauna to be yet another cheat code to life: it’s a simple thing that just makes life a lot better. If you want a good primer on scientific health benefits of sauna, I recommend starting with <a href="https://www.foundmyfitness.com/topics/sauna">this article by Rhonda Patric</a>. She goes in depth.</p> <p>To be clear, it should go without saying that I am not a medical expert or professional. None of the opinions below are, or should be interpreted as, medical advice. There are many people for whom sauna use is not recommended. It would be prudent for any sauna user to consult with his or her doctor before entering a sauna.</p> <p><em>Thanks to S. for taking the time to do a very helpful first review of this article. And thanks to The Wife for helping make my words legible and helping me make time to sauna–I don’t know which sacrifice was bigger.</em></p> <h2>Banya or Nothing</h2> <p>When I talk about saunas, I’m talking about a sauna with a stove, either wood or electric, that allows for steam. I call this “Banya style”. To be clear, I’m distinguishing between saunas and steam baths. Steam baths have their own place, but they aren’t my thing and I don’t consider them saunas.</p> <p>A breakdown of the main types of saunas may be helpful, so you know which to avoid:</p> <ol> <li>Wet saunas, which are typically cedar rooms with wood burning or electric stoves onto which you throw liquid to create steam (I call this “Banya style”);</li> <li>Dry saunas, which are typically cedar rooms with wood burning or electric stoves without added steam (like Korean style saunas); and</li> <li>Infrared saunas, which, unlike traditional saunas, don’t heat the surrounding air. Instead, they use infrared panels to warm your body directly.</li> </ol> <p>In my opinion, it’s Banya style or nothing. I’m not a huge fan of dry saunas, and I don’t even bother with infrared saunas. Infrared is a fiat-shitcoin. I want steam!</p> <h2>How to Sauna</h2> <h3>Sauna Etiquette</h3> <p>If you read no other part of this already-too-long-article, read this.</p> <p>Saunas are social places. There are proper ways of being in a sauna with others, and there are ways to do it wrong. You don’t want to be the person who ruins it for everyone. Here are some important etiquette tips:</p> <p><strong>Silence vs. Chatting:</strong> It’s not a question of whether you have to stay silent in a sauna or if it’s ok to talk. It depends on the circumstances and who else is around. If you’re using a sauna that isn’t your own, ask the staff about the preferred custom. The noise level in a sauna differs depending on the group in the sauna at a particular time. If you do want to chat with others, there’s nothing wrong with that. But, pay attention to whether there are others in the sauna who'd prefer it quiet. And definitely do NOT be obnoxiously loud – yes, I’m looking at you bachelor(ette) group who just discovered the Russian Banya.</p> <p><strong>Coming and Going:</strong> People rotate in and out of the sauna at different paces, so there will be people coming and going during your shvitz. But there are ways to come and go that are considerate and proper.</p> <p>Keep the f-ing door closed (which was the working title of this article). Once you leave, don’t come back inside moments later. Doing so disturbs your fellow sauna users, lets out the all-important steam, and prevents the sauna from reaching an appropriate temperature.</p> <p>If you’re in the sauna with a group of friends, try to coordinate your comings and goings so you’re all on the same cycle.</p> <p>If you can only last 5 min at a sauna, don’t go in too often at the risk of ruining it for others (assuming it’s not your own private sauna).</p> <p>Be fast when closing the sauna door when you come or leave. Otherwise, you will get dirty looks from others and may even hear mumbles of “quick quick, fast fast” from a Gray Beard. And you will deserve it.</p> <p>Never open the door right after someone puts water on the stove to make steam. It’s all about the steam. Don’t waste it.</p> <p><strong>Controlling the heat:</strong> if you can’t handle the heat in the sauna, don’t just turn the heat down, because it ruins it for others. Instead, go to a lower bench or get out and take your break. Saunas are meant to be hot. That’s the whole point.</p> <p><strong>Personal Hygiene:</strong> Shower before you go into the sauna. Don’t wear perfume, smelly deodorant, or fragrant lotions. Smells get amplified in a sauna. Have a towel under you, don't leave your drippings behind. Best yet, make a Z with your towel, this covers your butt and down under your feet.</p> <p><strong>Clothing:</strong> sauna is not a place for wearing clothing. It is a place to get back to nature. If you are shy, just wrap a towel around yourself. People ask if I don't feel awkward, the answer is no. Who cares, humans naked is not novel. In many countries, it is strictly forbidden to wear clothing or bring anything but a towel into the sauna. It's understandable that may not be possible in North American public saunas on mix gender "family" days. If you have to wear something, then wear something 100% cotton or marino wool. You don't want plastic being backed into your genitals. One more thing, leave the watch out as it gets hot and will burn you. Also, flip-flops/sandals, stay outside.</p> <p>Some saunas sell body scrubs and masks for you to apply before or in the sauna. Note that once in the heat, these can get goopy and drippy and may melt into your eyes and mouth. So (in this opinionated guides’ wife’s opinion), they are better in theory than reality.</p> <p><strong>Adding Oils and scents:</strong> As discussed below, it can be nice to add certain oils and other scents to the steam. But if there are others in the sauna, ask first before you do.</p> <p><strong>Where and how to sit:</strong> Hot air rises. So, the higher benches are hotter and the lower benches are cooler. If you are a newbie, pick a lower bench so you don’t have to leave as quickly and open the door unnecessarily.</p> <p>It’s great to lay down in the sauna, but if it gets crowded, sit up to make room for others.</p> <p>When moving around to find your seat, don’t walk on the benches in your sandals. Leave your sandals outside the sauna or on the sauna floor.</p> <h3>Sauna Temperature</h3> <p>In most proper Russian style Banyas you will find temperatures of 80-95 degrees celsius, which, in my opinion, is the best range. Thats near your body. "Offical" on the dial will he 100-120C. But sometimes you want to take it a little easier or last a little longer in the sauna. In these cases, 65-85 at body, dial at 80-100. degrees celsius will do.</p> <p>However, if your sauna is below 85 degrees celsius on the dial, you might as well just go hide under your bed sheets and not waste your time.</p> <p>At some saunas in hotels, gyms, or spas, you may not be allowed to set the sauna as high as you’d like (see below). There are many tricks to circumvent these frustrating restrictions, but my legal counsel has advised me not to go into any details here.</p> <h3>Sauna Duration</h3> <p>The amount of time you spend in the sauna is a matter of personal preference and depends on the number of cycles you do (more on cycles, below).</p> <p>For your first round, my opinion is that most people should try to last 15 minutes in the sauna. If a sauna is at the proper temperature, most people will struggle to stay inside any longer. If you can stay inside for 20-30 minutes, your sauna is probably too cold and/or there is not enough steam. Many saunas have hourglasses inside to keep time, and I’ve never seen a sauna hourglass with more than 15 minutes, which should be a good hint.</p> <p>My preferred is; </p> <p>Cold Plunge => Sauna 15 min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest </p> <p>if you can rest in the sun even better (no sunscreen poison please). You can add alcohol drinks to the hydration if you feel comfortable with that. But only add food after the last cycle.</p> <p>For subsequent rounds, hydration starts to play a bigger role in how long you stay inside. Most people seem to last longer on their first round than on their second or third. If you can do 15 minutes on your second round, great. But 5-10 minutes is also fine.</p> <h3>Sauna Cycles</h3> <p>The traditional Russian Banya method (and in this writer’s opinion, the best method) is to do sauna cycles. Go into the sauna and just stay as long as you can take it (up to 15 minutes or so). Then take a cold shower and/or cold plunge (see below). Then robe-up and go relax with water, tea or beer. Once you start feeling “normal” again, repeat. For me, three cycles is the sweet spot. I’ll do more cycles if I’m spending the day at the Banya facility. If I’m at home, where I often sauna every other day, I find just one or two cycles does the trick. Sometimes I add a cycle or two on the weekend.</p> <p>Occasionally, I like to go into the sauna as it’s warming up and before it reaches optimum heat (i.e. at around 60 degree celsius). This way, I can stay longer in the sauna for my first round (about 30-40 minutes). If I take this approach, I generally only do one more short round after my cold plunge.</p> <h3>Cold showers and plunges</h3> <p>In my experience, you want to take a cold shower or a cold plunge (or both, plunge is better) after the sauna cycle.After you come out of the sauna, immediately jump into cold plunge for a bit, i don't like to stay too long. Some Banya facilities will have a bucket filled with cold water that you can pull with a string to let the water pour over you, pull a couple times. The banyas may also have a cold pool of water into which you can plunge for a bit.</p> <p><img alt="" src="https://banya.lol/nvk-coldwater.jpg" /></p> <p>If I’m at my country place, after I get out of the sauna I jump into the cold lake. If it’s winter, I like to roll in the snow, which is satisfying. Some cultures would say that it’s not a real sauna experience unless you roll in at least one foot of snow.</p> <p>After your cold shower or plunge, put on a warm robe and go relax before going back into the sauna. I like to relax for 5-20 minutes, depending on how much time I have. This allows the body’s temperature to decrease slowly. I do not recommend going directly back into the sauna after your cold plunge. If you don’t give yourself enough time after the cold plunge, you will overheat and won’t last very long when you return to the sauna.</p> <h3>Position</h3> <p>There really are no rules here. The way you position yourself in the sauna depends on your mood and preference, and there are many options. For example, you can sauna seated with your legs hanging down or with your knees up. You can lie down if there’s room. My favorite position is to lie down on my back with my legs up against the wall and, assuming the ceiling is low enough, with my feet stretched against the ceiling. This is a great way to stretch the hamstrings (check out stretching under “Sauna Activities”, below).</p> <p>Choosing whether to sit on a higher bencher or lower bench is the best way to control the temperature you experience without adjusting the room temperature itself. You will notice the heat in the sauna increases exponentially every inch you go up. If you are struggling to stay in the sauna but don’t want to get out just yet, try moving down to a lower bench to last a little longer. Lying on the floor is the coolest spot and a great place for kids to start getting exposed to saunas.</p> <hr /> <h4>There is no shame in going to lower benches or even the floor, there is only shame in opening the door before 15min</h4> <hr /> <h3>Getting Steamy</h3> <p>Without steam, the sauna would just be a sad, hot oven (I’m looking at you, infrared sauna).</p> <p>The steam in the sauna has many benefits but most importantly it increases the thermal coupling of your body to the air and it feels great.</p> <p>The amount of steam in the sauna is a matter of personal taste. You don’t want to make it into a steam room (remember, steam rooms are NOT saunas). But, you do want the sauna to be very moist. I find that two to four ladles of water in a mid-size sauna every five to seven minutes does the trick. Keep it between 50-60% humidity.</p> <p>I keep a bucket of water in the sauna at all times so that I can continue to ladle water as I shvitz. Make sure to get a wood bucket and a metal ladle with a wooden handle. Wood ladles will crack, and if the handle is metal, it’ll burn you when you grab it.</p> <p>If, when you enter the sauna, it’s already been on for a while, the wood is likely to already be wet and the sauna full of steam, so you may not need to add too much water. However, if you’ve just turned on the sauna and the wood walls are dry, you will need to ladle more water to make the air moist enough. If the sauna is too moist for comfort, open the door and let it dry out a bit (obviously, only do this in a private sauna).</p> <p>Essential oils and even beer can all be added to the water to create scented steam. I recommend starting your sauna with just water, and add the scent as you get going.</p> <p>You can try all sorts of different essential oils. I’ve tried everything from oak and cedar to tangerine and cinnamon (gag) essential oil. In the end, there are really only two oils that are worth it, in my opinion. The first is eucalyptus. I’ve experimented with different types of eucalyptus oil, and the variety you use makes a difference. My favorite is eucalyptus globulus. I also like diluted pine tar oil.</p> <p>When you settle on your essential oil, add a healthy dose of the oil to the ladle filled with water. Never put the oil onto the oven directly. It’ll just burn.</p> <p>In a few Russian facilities, I’ve seen Gray Beards pour Russian beer onto the oven and it was actually quite nice. It’s almost like being in a cozy bakery while you sweat</p> <p>Some people like to place a salt brick or compressed solid blocks in their sauna from time to time. Put the salt block on the stove and pour water over it. The steam takes on a saltiness that feels nice. If a salt block is not available, you can get a cast iron teapot, fill it up with salt water, and place it on top of the stove.</p> <p>And for my most important steam tip, I recommend using the “towel spin”. This is an effective and underrated technique to help circulate steam in the sauna. After creating steam, take your towel above your head and spin it around hard, like a ceiling fan. This movement works like a convection oven and spreads and equalizes the heat and steam throughout the room. It might make the folks sitting lower down in the sauna a little hotter, but that's what they’re there for, isn’t it?</p> <h3>Hydration</h3> <p>Being hydrated is important to having a positive sauna experience. You will lose a lot of your body’s water in the sauna. Ideally, start to hydrate well up to an hour before your sauna. I like to add a pinch of salt to my water to encourage water retention.</p> <p>Do not bring any drinks into the sauna (the exception being a dedicated steam-beer, see above). Have your water or beverage when you’re outside the sauna, resting. If you find you need to drink water inside the sauna in order to cool yourself down, then it’s time for you to get out and allow your body a cool-down.</p> <p>When you’re outside the sauna, don’t immediately down a glass of super cold water because you will cool down your internal body too fast. Personally, I like to drink warm tea after my first two cycles. After my second cycle, I enjoy a beer (pre-keto days), soup, or vodka drink. When non-keto, I do enjoy adult drinks in the cycles.</p> <p>If you are doing a sauna while on a multi-day fast, you need to have water and salt, at a minimum. Otherwise, you will deplete your natural reserve of electrolytes and not be able to think straight.</p> <h3>Sauna Frequency</h3> <p>When it comes to frequency, if you are not in the equatorial heat do it every day. I now do mornings and end of day if I can. so 2x 2-3x cycles. In the summer, living in a hot & humid location, I sauna a lot less frequently. My desire to sauna is greatly diminished because I spend a lot of time in the sun and heat.</p> <h3>What to wear</h3> <p><strong>Sauna Hat:</strong> I highly recommend wearing a Russian/Finish style wool hat when you’re inside the sauna. It may seem counterintuitive, but wearing a hat keeps your head cooler. An overheated head is not good for your brain. Wearing the hat stops you from overheating and lets you stay longer in the sauna. The temperature in a sauna is significantly hotter the higher in the room you are, and one’s head is at the top of the body (for most people). So protect your brain in style with a felt sauna hat. If you don’t have a felt sauna hat, buy one. They are easily found online. But in the meantime, you can wrap a dry towel around your head. Don’t forget to take your sauna hat off as you relax between cycles so your head can cool down.</p> <p><img alt="" src="https://banya.lol/nvk-hat.jpg" /></p> <p><strong>Clothing:</strong> These days, many public saunas will have family days, men-only days, and women-only days. For obvious reasons, you’re only allowed to sauna naked if you’re attending one of the single-sex days.</p> <p>If you’re at home, there’s no good reason to wear shorts or a bathing suit. Sauna naked. It's a lot more pleasant.</p> <p>If you do wear clothing in the sauna, be careful with items with materials like metal or plastic attached. Things like pins, buttons, or string-ends will get very hot and probably burn you. Remember to take off any heat-conductive jewelry and leave your smart watch outside, as the heat will ruin its battery.</p> <p>Don’t wear your robe inside the sauna. A robe is what you wear outside when relaxing or eating. If you wear it inside, you’ll overheat (and look like an idiot). Go ahead and sweat out that body shame robe-free. You can bring a towel into the sauna to sit on, if you want.</p> <p>Shoes or sandals are highly recommended in public facilities. I mean, there are many people walking around wet. Ew. But keep your sandals outside the sauna itself, or on the sauna floor.</p> <h3>Sauna activities.</h3> <p>Don’t overthink it. Sitting in a sauna is activity enough, in my opinion. But there are some sauna activities you can do:</p> <p><strong>Veniks/Viht beating:</strong> these are bundles of leaves (commonly birch, oak, or eucalyptus) that are pre-soaked in hot water. Someone with both strength and capacity to exert themselves in the heat will beat your whole body with the leaves. This exfoliates your skin and also gets the plant oils to permeate your skin. And it’s very relaxing. If you’re at a sauna facility, don’t just grab any bundle you see lying around - that belongs to someone else and veniks aren’t shared. You have to bring your own or buy them at the front desk.</p> <p><strong>Stretching:</strong> this is a great activity to do in the sauna, but make sure to go very easy. Your muscles will be super warm and you don’t want to overdo it and hurt yourself.</p> <p><strong>Exercise or Sex:</strong> your heart better be in good shape if you try out these high intensity activities in the sauna. If you engage in the latter, you better be in your own home sauna. With respect to the former, I think doing some leg-ups can be very satisfying.</p> <p><strong>Phone use:</strong> If you’re at home, it’s nice to use your sauna time to shit-post on Twitter or read an article, if you feel like it. Just keep your phone close to the colder, lower parts near the floor or it’ll overheat and shut down. You can also place the phone outside of the air vent and play a <a href="https://bitcoin.review">podcast! The Bitcoin.review is great ;)</a></p> <p><strong>Napping:</strong> I don’t recommend this. If you fall asleep or pass out, you will probably die due to overheating or dehydration.</p> <p><strong>Chatting:</strong> Saunas are great places for conversations (subject to the caveats I address above). Note that nowadays, microphone modules are both very tiny and can withstand high temperatures, so it’s no longer recommended to reenact mafia movie sauna scenes.</p> <p><strong>Eating and Drinking:</strong> As discussed above, never have food or drink inside the sauna. But when you finish your sauna, take advantage of whatever snacks the facility offers. For Russian joints, the soups, fish roe and dry salty fish snacks are great. Again, don’t eat before your sauna; wait until you’re done. Some places will have bottled salty-ish lake water, and beer seems to be a good source of salts and re-hydration. Vodka drinks are nice sometimes, too. My favorites are vodka with beet juice and horseradish, vodka with pickle juice, or just a chilled shot of Zubrowka (vodka infused with bison grass). Teas are also very enjoyable post-sauna. I prefer non-caffeinated berry teas. Some Banyas even offer free tea to patrons.</p> <p><img alt="" src="https://banya.lol/nvk-food.jpg" /></p> <h2>Ready to Sweat It Out?</h2> <p>Thanks to this fantastic guide to sauna, you’re now feeling confident and excited to seek out a solid sauna. So where do you go?</p> <h2>Where to Find a Sauna</h2> <p><strong>Spas:</strong> Spas are not the best place to have an optimal sauna experience. Saunas at spas are typically not hot enough and spas have annoying staff whose job it is to enforce idiotic rules and practices that prevent you from having a real sauna experience.</p> <p><strong>Gyms & Hotels:</strong> These are some of the worst places to sauna. For liability reasons, these saunas tend to be too cold and there are often mechanisms that prevent you from raising the temperature. Here, you’ll often see saunas with glass doors, which may look chic, but are inefficient and stupid because they don’t seal properly and leak steam. Gyms and hotels are high traffic areas, so people who don’t know what they are doing are constantly coming and going from the sauna, which, as we discussed, is a sauna no-no. If you still want to try the sauna at your gym or hotel, I recommend going in naked. It’ll deter people from joining you and ruining the little steam you managed to get going.</p> <p><strong>Traditional bath houses (Banyas):</strong> These usually offer a great experience because they deliver a super hot sauna, good cold baths and plunges, delicious food and drinks, and knowledgeable staff.</p> <p><strong>Home:</strong> Yes, you can build a great sauna in your own home! You can create a small space in your basement, turn a closet or cold room into a sauna, or just add an outdoor hut or barrel sauna in your backyard. This is the best way for you to control the whole experience and do it often. As with anything, the easier it is to access, the more you will do it.</p> <p><em>Build it. They will Come</em></p> <p>Many people have asked me for details about sauna building. If you’re ready to build your own personal home sauna, here are some important considerations.</p> <h4>Materials</h4> <p>Saunas are insulated rooms, most commonly finished with cedar tung and groove slats. Cedar is used because it doesn’t rot with moisture. You don’t want treated wood as it will release all the bad stuff that keeps the wood from rotting into the air when heated. Cedar interior is often placed over a vapor barrier, followed by insulation and then the outer wall. Many outdoor saunas are not insulated. They simply have a single layer of cedar 2x6 planks functioning as both the interior and exterior. Non-insulated saunas need much more heating power in the winter.</p> <h4>Structure</h4> <p>For indoor saunas, you may want to find a bricklayer to build something for you. Traditional facilities often have brick-lined rooms and very large wood-burning stoves.</p> <p>You can buy prefab outdoor saunas, which are often sheds or barrels. After experimenting with both, I’ve concluded that barrel saunas are inferior, even though that’s what I have at my country property. This is because barrels have concave ceilings and inner walls. This means the benches are lower and the curve makes the topmost part of the ceiling (and the hottest part) the furthest from you, or inaccessible. The spinning towel trick really helps in the barrel.</p> <p>When it comes to buying a sauna, go with the most traditional structure possible. They are based on thousands of years of evolution and knowledge.</p> <p>Portable tent saunas are fun, but impractical because you have to set them up before each use.</p> <p>Bench height inside the sauna is important. I think the top-most bench should be very near the ceiling. This way, when you’re lying down, you can use the ceiling to stretch the hamstrings. As a rule of thumb, bench length should allow you to lie down completely. It is also nice to have at least one lower bench for visitors or less intense sauna days.</p> <p><img alt="" src="https://banya.lol/nvk-feetup.jpg" /></p> <h4>Sauna Ovens</h4> <p>There are two main types of sauna ovens: wood burning and electrical (with gas heating being available, but not common). If the location you are building allows for it, go with electrical. It’s practical and easy to get going quickly. This means you will use it more often. Wood burning saunas are romantic and smell great, but it is a lot more work to get a fire going, especially in the winter.</p> <p>Opt for oven sizes that are recommended or above recommended for the size of the sauna. A larger oven means more thermic inertia, more rocks for steam, and therefore less time to warm up the room. Bigger is better. The Scandinavians make the best quality ovens.</p> <h4>Oven controllers</h4> <p>There are two types of temperature control devices: the analog cooking-style or the digital type. I think, due to liability and safety, all ovens have a timer that max out at one hour.</p> <p>The digital oven controllers are fantastic and I have one in the city in my basement sauna.</p> <p>However, you have to consider your environment. For me, temperatures in the winter can reach below -30C and in the summer, over 40C. This massive range can take a toll on outdoor equipment and materials. For this reason, I opted for an analog controller for my outdoor sauna in the country, since the weather will likely ruin the electronics of the digital controller.</p> <p>I would avoid ovens with analog pre-heat timers. They are great in theory, but the implementation is utter garbage. The timer won’t be precise and it’ll just lead to frustration, for example, when you thought you set the oven to start in three hours, but it actually started in two hours and already turned off.</p> <h4>Important Sauna Gear</h4> <p>Windows are nice to have, especially if you have a view to enjoy. Opt for at least a cedar door with a little window. Do not go with modern glass door styles. They are crap. They have gaps, no insulation, and let in too much light.</p> <p>Saunas need thermometers and hygrometers (to measure humidity). The thermometers should be rated for saunas and be visible inside. This is both for safety and bragging rights.</p> <p>I think having an hourglass inside your sauna is a must. Being able to know for sure how long you’ve been inside is important, since your sense of timing inside the sauna may be off depending on the state of your mind and body on a given day. You shouldn’t wear a watch inside the sauna, since it’ll overheat or break. Having a clock visible from the inside is also a good idea, especially if you sauna often and have a wife and kids who you don’t want to leave you.</p> <p>Air circulation is an often-overlooked but important part of a sauna design. Saunas should not have stale air. The best sauna design creates natural “real convection” by placing an air intake under the oven wall and another at the top opposite wall. This allows fresh air to enter the sauna while in use. Be sure to add regulators, since you don’t want to cool the sauna or expel all steam. Without regulators you may get too much or too little air in. With too much air, you may cool the sauna down too much and/or lose too much steam.</p> <h4>Nice Things to Have</h4> <p>Lights are optional but welcome additions. It can be unpleasant to have no lighting at all, especially in an outdoor sauna on a cold, dark night. Lights should be warm-temperature and low power. I recommend an oven light, since they don’t sweat the heat (get it?) and are often low power.</p> <p>Put a baking tray under your oven–thank me later.</p> <p>Wood “pillows” for your head are nice and don’t get sweat-stained and stinky, like a fabric pillow.</p> <p>Keep some extra felt hats near your sauna so when you or your guests forget their hat, you still have easy access to one.</p> <p>I like to keep a couple of essential oils on the floor of the sauna, for easy access. If you keep the oils too high in the sauna, they’ll get too hot and spoil.</p> <p>I place some duck boards over floor tiles in the sauna to prevent cold feet.</p> <p>I also like to keep a small, natural broom inside the sauna to sweep up any dirt or leaves that come into the sauna on people’s feet.</p> <h2>Final words</h2> <p>As you can tell, I have some strong opinions when it comes to the proper way to enjoy a sauna. My hope is that my musings will help you to maximize your own sauna experience.. If you follow this guide, I’m certain you will benefit from and enjoy the sauna as much as I do and, just maybe, you too will develop your own strongly held opinions that will most definitely offend me.</p> <h3>Thanks for reading, please close the F-ing door.</h3> <p>ps, you can get a Bitcoin Honey Badger Sauna Hat <a href="https://store.coinkite.com/store/ht-sauna">here</a></p> <ul> <li>EOF</li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs02w3g64yz8ekyxm320jy460lny5yzcldw6j6j4zf6907240atnmgzyr5g56g7nrveslykg5salasqyhmqwqph3fy8jxqdewa555p8s5zpzwhwu5a" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs02w3g64yz8ekyxm320jy460lny5yzcldw6j6j4zf6907240atnmgzyr5g56g7nrveslykg5salasqyhmqwqph3fy8jxqdewa555p8s5zpzwhwu5a" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs02w3g64yz8ekyxm320jy460lny5yzcldw6j6j4zf6907240atnmgzyr5g56g7nrveslykg5salasqyhmqwqph3fy8jxqdewa555p8s5zpzwhwu5a" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs02w3g64yz8ekyxm320jy460lny5yzcldw6j6j4zf6907240atnmgzyr5g56g7nrveslykg5salasqyhmqwqph3fy8jxqdewa555p8s5zpzwhwu5a" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ e97aaffa:2ebd765d <div class="time" style="margin-left: auto;">2024-10-19 10:07:46</div> </div> <div> <p>As eleições nos países democráticos, são uma espécie de um concurso de popularidade, vence o mais popular. Os governos, como querem vencer as próximas eleições, tendem a tomar medidas com execução curtas, que apresente resultados num curto espaço de tempo. Os governos deixaram de fazer reformas estruturais, que teriam bons resultados daqui a 10 a 20 anos, pensam apenas a curto prazo, com uma alta preferência temporal e que sejam populares. Os incentivos estão completamente desalinhados.</p> <p>Isto coloca os partidos políticos, um pouco refém da opinião pública, dificilmente fazem algo contra a opinião da maioria dos cidadãos. Se executar medidas muito impopulares, existe uma forte probabilidade de perder a próxima eleição.</p> <p>Assim os governos só aprovam propostas que tenham uma “aprovação” parcial da população, poderá não existir uma maioria, mas uma parte terá que compreender essa proposta.</p> <p>Muitas das vezes, os governos querem aprovar uma nova lei, mas sabem de antemão que é extremamente impopular, por isso, primeiro manipulam a opinião pública para ganhar apoio popular, depois sim aprovam a lei. Ou seja, cria uma narrativa, um motivo que justifique aquele ato.</p> <p>Vamos um exemplo prático, dificilmente um governo aprova um aumento de impostos com o único objetivo de aumentar o salário dos deputados, seria extremamente impopular.</p> <p>Os governos acabam por manipular a população, criam uma narrativa, prometem que o aumento dos impostos é para ajudar os mais pobres. É algo popular, mas depois de aprovada, uma parte do dinheiro vai para os pobres, a outra parte vai para os bolsos dos deputados. Assim conseguiram realizar a ideia inicial com o apoio popular.</p> <p>Em suma, os incentivos levam os governos a tomar medidas que tenham uma parte de apoio popular. Terá que existir sempre um motivo que justifique. É uma espécie de <a href="https://pt.wikipedia.org/wiki/Equil%C3%ADbrio_de_Nash">equilíbrio de Nash</a>, tem que existir um equilíbrio entre a opinião do governo e a opinião da população. Se existir uma enorme divergência, as perdas são muito superiores aos benefícios para o governo.</p> <h1>Bitcoin</h1> <p>A grande herança/legado do Satoshi não foi a tecnologia (até tinha muitos bugs) mas sim a política económica e protocolo de consenso, as suas múltiplas teorias dos jogos coexistentes, é uma verdadeira obra prima.</p> <p>Já foram realizados inúmeros melhoramentos no código (tecnologia), talvez daqui a 20 anos, pouco restará do código inicial, mas a sua política está inalterada e está completamente atual e possivelmente nunca será alterada.</p> <p>O Satoshi ao criar um novo sistema monetário alternativo, sabia que mais cedo ou mais tarde, o bitcoin seria atacado pelos governos. Como aconteceu em todas as tentativas anteriores ao bitcoin.</p> <p>Após este comentário de um anónimo:</p> <blockquote> <p>Você não encontrará uma solução para problemas políticos na criptografia</p> </blockquote> <p>Satoshi respondeu:</p> <blockquote> <p>Sim, mas podemos vencer uma grande batalha na corrida armamentista e conquistar novos caminhos para a liberdade por alguns anos. Os governos são bons em cortar cabeças de redes gerenciadas centralmente, como a Napster, mas redes P2P puras, como Gnutella e Tor, parecem estar se mantendo funcionando.</p> </blockquote> <p>Assim quanto mais tarde, melhor, permitindo o desenvolvimento tecnológico e um maior crescimento da adoção. A adoção é o melhor escudo, um escudo humano sem armas mas com o poder no voto, de poder eleger ou derrubar o governo.</p> <p>A diferença de poderes entre o estado e o Bitcoin é desproporcional, num confronto direto, o pequeno nunca vencerá essa guerra. O pequeno nunca conseguirá explodir o grande, mas poderá implodi-lo, ou seja, entrar dentro do sistema como um cavalo de Troia e depois implodi-lo.</p> <p>A minha convicção, é que Satoshi não cria destruir o sistema Fiat, mas sim construir uma alternativa, com diversos casos de uso.</p> <blockquote> <p>Bitcoin seria conveniente para pessoas que não têm cartão de crédito ou não querem usar os cartões que possuem, não querem que o cônjuge o veja na conta ou não confiam em fornecer seu número para “caras da por”, ou com medo de cobrança recorrente.</p> </blockquote> <p>Se pensarmos bem, até é importante manter o sistema FIAT, nem que seja como uma referência (a não seguir). Nós, só sabemos que a refeição A é deliciosa, porque já provamos a refeição B (que é uma porcaria). Se perdermos a referência da B, deixamos de saber que A é deliciosa.</p> <p>É claro que em última instância, se o sistema alternativo tiver uma adoção de 100%, acabaria por destruir o sistema FIAT. O essencial é existir liberdade monetária, o poder de escolha fica em exclusivo no indivíduo.</p> <p>Como é lógico, o estado não quer perder o monopólio da moeda. Como expliquei na introdução, os governos democráticos necessitam de uma motivo plausível ou uma razão moral para proibir, parte da população tem que compreender. Se não compreender, vão questionar o porquê, isto pode gerar um efeito oposto, o chamado <a href="https://pt.wikipedia.org/wiki/Efeito_Streisand">efeito Barbra Streisand</a>. Ao proibir sem motivo aparente pode gerar um movimento de adoção em massa, porque somos humanos e o fruto proibido é sempre o mais apetecível.</p> <p>O Bitcoin ao ser construído num limbo, repleto de teoria dos jogos, sem violar qualquer lei vigente, sem nunca bater de frente com os governos, é uma revolução pacífica e silenciosa. Como nunca pisou linhas vermelhas, coube aos governos encontrar um motivo para proibir, durante toda a história, os políticos bem tentaram mas nunca encontraram o motivo plausível.</p> <p>Bitcoin vive nesse limbo, não viola qualquer lei, mas ao mesmo tempo, não compactua com os governos, apenas está a criar um sistema monetário paralelo. É como os bons advogados trabalham, aproveitam os buracos das leis ou contornam as leis sem nunca as violar.</p> <p>Para que a adopção seja rápida, é importante tem de estar dentro da lei.</p> <p>Quando os governos/procuradores não encontram provas diretas para condenar, adoram encontrar motivos circunstanciais, subterfúgios. Um bom exemplo foi Al Capone, apenas conseguiram encarcerar por sonegação de impostos, ele nunca foi condenado por crimes mais graves, de sangue.</p> <p>Um bom exemplo foi o algoritmo de assinaturas Schnorr, que só foi adicionado ao Bitcoin na atualização Taproot, não foi adicionado anteriormente devido as pendentes, que estaria em vigor à data do bloco gênesis. Satoshi era rigoroso e calculista.</p> <p>Em Dezembro de 2010, Satoshi demonstrou que não queria um conflito com os governos, ainda era muito cedo. Após o bloqueio das contas bancárias dos Wikileaks, Assange queria receber doações em bitcoin, mas Satoshi tentou dissuadi-lo, ainda era cedo, a descentralização ainda não era suficientemente robusta.</p> <blockquote> <p>Não, não faça isso. O Bitcoin é uma pequena comunidade beta em sua infância. Você não arrecadaria mais do que alguns trocados, e a pressão que você traria provavelmente nos destruiria (a rede do Bitcoin) nesta fase.</p> <p>O Wikileaks chutou o ninho de vespas e o enxame está vindo em nossa direção.»</p> </blockquote> <p>Após estes acontecimentos, Satoshi afastou-se.</p> <h1>Transparência</h1> <p>Muitos apoiantes do Monero, criticam o Bitcoin devido à falta de privacidade, mas Satoshi optou por uma transparência total e por um pseudo anonimato.</p> <blockquote> <p>O problema fundamental com a moeda convencional é toda a confiança necessária para fazê-la funcionar. Precisamos confiar que o banco central não vai desvalorizar a moeda, mas a história das moedas fiduciárias está repleta de violações dessa confiança. Deve-se confiar nos bancos para reter o nosso dinheiro e transferi-lo eletronicamente, mas eles emprestam-no em ondas de bolhas de crédito com apenas uma fração de reserva. Temos que confiar-lhes a nossa privacidade, confiar que não permitirão que ladrões de identidade drenem as nossas contas. – Satoshi</p> </blockquote> <p>Satoshi descreve magistralmente os problemas do sistema financeiro, o ter que confiar, a falta de transparência e a reserva fracionária. Bitcoin é exatamente a resposta a isso, um sistema totalmente transparente, onde tudo é visível, tudo é auditável e sem a necessidade de confiar em terceiros.</p> <p>Assim, garantiu a segurança e a integridade do sistema, promoveu a confiança e incentivou a verificação e não confiar em informações de terceiros. A qualquer momento, qualquer pessoa consegue verificar todas as transações e saber o supply total do bitcoin, isto é incrível.</p> <p>Don’t Trust, Verify!</p> <p>É claro que essa total transparência gera “efeitos secundários”, uma menor privacidade. Temos que saber viver com isso, é um mal menor, para garantir um bem muito superior, uma moeda justa.</p> <p>A transparência é a prioridade, privacidade fica parcialmente garantida através do pseudo anonimato, tem algumas limitações, mas bem utilizado, pode garantir uma certa privacidade, basta fazer uma boa gestão de chaves e uma utilização de endereços descartáveis.</p> <blockquote> <p>Como uma camada de segurança adicional, um novo par de chaves deve ser usado para cada transação para evitar que elas sejam vinculadas a um proprietário comum. – Satoshi</p> </blockquote> <p>O problema do pseudo anonimato é agravado devido ao mau comportamento das pessoas, que utilizam exchanges e vinculam os endereços à identidade real.</p> <blockquote> <p>A possibilidade de ser anônimo ou pseudônimo depende de você não revelar nenhuma informação de identificação sobre você em relação aos endereços bitcoin que você usa. Se você publicar seu endereço bitcoin na web, estará associando esse endereço e quaisquer transações com o nome com o qual você postou. Se você postou com um identificador que não associou à sua identidade real, ainda é um pseudônimo. – Satoshi</p> </blockquote> <p>Não é possível querer os dois mundos em simultâneo, quem quer privacidade não poderá utilizar exchanges, apenas p2p.</p> <p>E Satoshi tinha razão, atraíram as “vespas”, em 2011, o Gavin Andresen foi convocado pela CIA, o serviço de inteligência dos Estados Unidos, para falar sobre o Bitcoin.</p> <p>Comunicado de Gavin Andresen:</p> <blockquote> <p>Aceitei o convite para falar porque o fato de ter sido convidado significa que o Bitcoin já está no radar deles, e acho que pode ser uma boa chance de falar sobre por que acho que o Bitcoin tornará o mundo um lugar melhor. Acho que os objetivos deste projeto são criar uma moeda melhor, criar um sistema de pagamento internacional mais competitivo e eficiente e dar às pessoas um controle mais direto sobre suas finanças. E não acho que nenhum desses objetivos seja incompatível com os objetivos do governo. Estou apenas um pouco preocupado que falar sobre bitcoin na CIA aumente as chances de que eles tentem fazer algo que não queremos que eles façam. Acho que aceitar o convite deles e ser aberto sobre exatamente o que é o bitcoin tornará menos provável que eles o vejam como uma ameaça.</p> </blockquote> <p>Como no Bitcoin não existe uma privacidade total e as transações são rastreáveis, não representava uma ameaça para a segurança nacional dos estados. Assim não existe um motivo plausível para o governo o proibirem.</p> <p>A total privacidade é claramente uma linha vermelha para os governos.</p> <p>A generalidade das pessoas tem dificuldade em compreender o verdadeiro valor da privacidade, acreditam na ideia, “quem não tem nada a esconder, não tem nada a temer”. Na época, se o governo tivesse a intenção de atacar o Bitcoin, possivelmente teriam conseguido proibi-lo e as pessoas nem teriam contestado.</p> <p>Foi exatamente o que aconteceu agora com a Monero, a privacidade/anonimato foi utilizada como o motivo, está a ser ilegalizada em vários países, sem gerar alguma consternação na população. Infelizmente as pessoas não dão valor à privacidade, são demasiado ingénuas, acreditam que isto dará mais segurança.</p> <blockquote> <p>Qualquer sociedade que renuncie um pouco da sua liberdade para ter um pouco mais de segurança, não merece nem uma, nem outra, e acabará por perder ambas. – Benjamin Franklin</p> </blockquote> <p>Eu acredito que se o bitcoin tivesse o mesmo grau de privacidade da Monero, hoje em dia, ou já não existia ou seria apenas um micro nicho, nunca teria atingido a atual dimensão.</p> <p>É um equilíbrio, se houvesse um maior grau de privacidade a adoção seria baixa, se privacidade fosse nula (FIAT) a adoção seria elevadíssima. Satoshi optou por um pouco de equilíbrio, com o pseudo anonimato.</p> <p>O bitcoin sacrificou um pouco a privacidade, em prol de um bem muito superior, é o instituto de sobrevivência. Esse sacrifício era a única via, uma maior privacidade poderá ser garantida com outras soluções ou em segundas camadas.</p> <p>A camada base deve manter este nível de privacidade, como padrão, quem quiser uma maior privacidade terá que optar por sistemas alternativos, como mixers ou outras camadas.</p> <p>A tecnologia deve ser imparcial e genérica, é uma situação similar das facas, apenas uma tecnologia agnóstica. A responsabilidade não está na tecnologia, mas sim de quem a utiliza. Quem utiliza uma faca para cometer um crime, é quem deve ser condenado. Deve ser condenado quem faz mau uso da tecnologia e nunca deve ser condenado quem construiu a tecnologia e muito menos proibir a tecnologia.</p> <p>Num futuro longínquo, a camada base será um local de Settlements, apenas utilizado por liquidity provider(LP), bancos ou pessoas com bastante valor. A generalidade das pessoas utilizarão apenas camadas secundárias, onde existirá um maior grau de privacidade. Vão existir centenas de L2 ou sidechains que estarão ligadas à L1, onde a liquidez está colaterizada, por isso é essencial uma transparência total, para ser facilmente auditável a quantidade de fundos colaterizados, para garantir a segurança.</p> <p>Neste futuro, a maioria das transações na L1 serão de instituições ou estados, eu acredito que vão querer implementar maior privacidade, nesse momento, seremos nós a não querer. A verdade está na transparência.</p> <h1>Custódia</h1> <p>Como os políticos não fizeram nada durante anos, o Bitcoin cresceu na adoção, mas sobretudo na descentralização. A descentralização atingiu uma tal dimensão, que hoje em dia, é impossível proibir o Bitcoin e os políticos sabem disso. Como já não é possível proibir tecnicamente, agora a única via, é tornar ilegal a sua utilização.</p> <p>Os políticos durante anos tentaram fabricar motivos plausíveis, manipularam a opinião pública com FUDs e informações falsas, mas nunca conseguiram um forte apoio popular.</p> <p>O Bitcoin continuou a crescer, agora os governos ocidentais mudaram ligeiramente de estratégia, em vez de proibir, estão a direcionar/condicionar a sua utilização, ou seja, estão a aceitar o Bitcoin como um ativo, como o ouro, como reserva de valor, sobretudo em locais centralizados, como ETFs e em exchanges, bancos, tudo altamente regulamentado. Tudo por baixo da asa dos governos, onde os políticos podem controlar, confiscar o bitcoin e identificar facilmente.</p> <p>Mas ao mesmo tempo vão dificultar a auto-custódia e a utilização do Bitcoin como meio de troca. O grande medo dos governos é o Bitcoin ser utilizado como uma moeda, eles não querem concorrência às suas moedas FIAT, estão apenas a tolerar como reserva de valor.</p> <p>Agora o grande objetivo é ilegalizar/limitar a auto-custódia, mas aqui existe um enorme medo por parte dos governos ocidentais, ao fazê-lo, podem dar uma percepção à sua população que é um ataque às liberdades individuais, os governos não querem dar imagem de ser autoritários. Poderia também gerar o efeito Barbra Streisand, gerando uma adoção em massa, o tiro poderia sair pela culatra. Mesmo sem proibir, os governos vão utilizar os impostos para limitar a adoção e a utilização.</p> <p>Como o euro e o dólar tem uma volatilidade muito inferior ao Bitcoin, é natural que a utilização do Bitcoin como moeda seja baixa na União Europeia e nos EUA. Como o benefício é baixo, mas o risco é muito elevado, possivelmente os governos vão deixar andar, só vão proibir a auto-custódia em último caso, em desespero.</p> <p>Será pouca a utilização como moeda na Europa e nos EUA, mas a adoção vai ser grande como reserva de valor, vai permitir reduzir a volatilidade e ainda vai dar mais resiliência ao bitcoin. O aumento da adoção não será apenas pelo cidadão comum, mas também por políticos, empresários e investidores, criando um forte <em>lobby</em> pró-bitcoin. Este conflito de interesses dos políticos, vai dificultar a aprovação de medidas mais restritivas, porque haverá sempre algum <em>bitcoiner</em> dentro dos partidos políticos, haverá oposição interna.</p> <p>A entrada da BlackRock foi um divisor de água, podemos não gostar, mas a percepção geral mudou completamente, existe antes e depois do apoio BlackRock. Os ETFs que estavam há 10 anos num limbo, foram aprovados em meses, a narrativa negativa (que o bitcoin consumia muita energia e só era utilizado por criminosos) desvaneceu. </p> <p>Mas nem tudo poderá ser um mar de rosas, existe um dúvida no ar, de que lado está a BlackRock, sobre a auto-custódia, fará lobby para que lado?</p> <p>Em teoria, a proibição da auto-custódia faria crescer o número de clientes, mas provocaria um efeito secundário, como a soberania e a descentralização é fulcral, ao atacar esses pontos teria um forte impacto no preço, os clientes da BlackRock perderiam dinheiro e poderiam desistiriam dos EFTs. O que no início poderia resultar num aumento de clientes, poderia resultar numa perda de clientes, é a teoria dos jogos, o <a href="https://pt.wikipedia.org/wiki/Dilema_do_prisioneiro">Dilema do prisioneiro</a>. O melhor para ambos, é a coexistência dos serviços custodiais e não-custodiais, porque ambos geram procura, ambos serão beneficiados. Só o tempo dirá, de que lado está a BlackRock.</p> <p>Hoje em dia é visível a forte adoção dos EFTs, tanto por empresas/instituições, como por particulares, alguns milionários. Os ETFs são um produto simples, muito fácil de utilizar, sem necessidade de fazer a custódia, mas existe sempre o risco de confisco. As empresas e fundos de pensões, não terão outra alternativa, obrigatoriamente terão que estar sempre em serviço custodiais, mas no caso dos investidores particulares, estes vão pensar duas vezes.</p> <p>Numa fase inicial vão utilizar os ETFs, depois com tempo vão estudar e compreender como funciona o bitcoin. Possivelmente alguns vão mudar para auto-custódia ou para outros serviços mais resilientes ao confisco.</p> <p>Os particulares milionários como tem empresas ou outros ativos, como no mercado de capitais ou então imobiliário, já estão demasiado expostos aos poder do estado e há boa bondade dos políticos. Os milionários também têm medo dos governos, por isso, já colocam parte da sua riqueza em jurisdições mais amigáveis (<em>offshores</em>). Nas <em>offshores</em> só uma pequena parte do capital tem origem criminosa, a grande maioria do dinheiro tem uma origem lícita, as poupanças estão ali como uma proteção, uma segurança extra, porque também tem uma certa desconfiança do poder político.</p> <p>No futuro, alguns desses milhões de dólares que estão depositados na Suíça, Dubai, Caimão, Curaçau e entre outros, vão ser transformados em bitcoin, é inevitável. Alguns vão optar por serviço custodial nessas mesmas jurisdições, mas certamente alguns vão optar pela auto-custódia.</p> <p>As <em>offshores</em> dão segurança ao cidadão, mas apenas estava acessível aos mais ricos, mas agora existe o Bitcoin, que dá ainda mais soberania e está acessível para toda a gente, é universal.</p> <p>Até para o lado dos governos, é mais fácil rastrear as transações de Bitcoin do que as transações em certas <em>offshores</em>.</p> <h1>Meio de troca</h1> <p>São nos países onde as moedas perdem mais poder de compra, é onde existe uma maior adoção do Bitcoin. Assim, a forte adoção como reserva de valor, vai permitir reduzir bastante a volatilidade do Bitcoin, provocando uma forte adoção em países com moedas com inflação mais elevadas, sobretudo na América central e latina, na África e na Ásia.</p> <p>Hoje em dia, este “mercado”, das compras do dia-a-dia, foi dominado por <em>stablecoins</em>. Mas as <em>stablecoins</em> são uma CBDCs disfarçada, o FED tem um poder absoluto sobre elas, congela fundos a qualquer momento, sem qualquer limitação. Os EUA já utilizam as <em>stablecoins</em> como uma política expansionista, esse processo vai acelerar nos próximos anos, vão imprimir biliões/triliões de dólares para financiar o governo e vão distribuir essa inflação para o resto do mundo em forma de <em>stablecoins</em>.</p> <p>O forte crescimento da adoção das <em>stablecoins</em> de dólares, está a colocar em causa as políticas monetárias internas nos países subdesenvolvidos. Atualmente os políticos utilizam a moeda como uma arma contra o seu próprio povo, este refugia-se no dólar, como uma proteção contra as altas inflações e contra a tirania dos seus políticos.</p> <p>Não é o Bitcoin a principal ameaça às moedas FIAT, mas sim as <em>stablecoins</em> de dólares.</p> <p>Nestas economias sempre houve dólares, existem mercados paralelos de dólares, mas este mercado tinha uma limitação física que impedia o seu crescimento, é difícil entrar novas notas/cédulas de dólares em circulação. O digital resolveu esse problema, agora é fácil entrar “novos” dólares nessas economias, os governos mais austeros, com políticas de controle de capitais mais agressivas, não conseguem evitar a entrada.</p> <p>A utilização das <em>stablecoins</em> está a crescer rapidamente, mas em algum momento, existirá um ponto de inflexão, os governos não vão querer perder o poder da sua moeda FIAT, vão retaliar. Ao contrário do papel-moeda, as <em>stablecoins</em> são fáceis de confiscar/congelar fundos. Os governos vão retaliar e vão começar a obrigar a Tether (e os outros) a congelar fundos arbitrariamente, será congelamentos em massa.</p> <p>Haverá muitos conflitos diplomáticos, a Tether vai compactuar com grande parte dos governos, mas será que compactuará com o governo russo no congelamento de fundos?</p> <p>Só nesse preciso momento, as pessoas vão compreender o verdadeiro valor da descentralização do Bitcoin. Será um catalisador no aceleramento da adoção do Bitcoin, como moeda, nessas economias.</p> <p>Além disso, a política expansionista dos EUA não é imparável, nem inesgotável, um dia terá que afrouxar, quando colocarem o KYC como obrigatório, milhões de pessoas vão afastar-se das <em>stablecoins</em>.</p> <p>Mais tarde, os fluxos migratórios desses países subdesenvolvidos, serão uma forte contribuinte para eclodir os mercados p2p na Europa e para os EUA, vai gerar uma enorme utilização do Bitcoin como moeda.</p> <p>A “reserva de valor” vai alimentar o “meio de troca“ e por sua vez este vai alimentar ainda mais o “reserva de valor”. Se isto acontecer, os governos ocidentais poderão desesperar e vão tentar desesperadamente ilegalizar o bitcoin, especialmente os governos europeus, mas talvez seja tarde demais. O Bitcoin já estará disseminado em todo o lado, como um vírus.</p> <h1>Independência</h1> <p>Como disse em cima, quanto maior for a adoção, maior é o escudo humano. Apesar de existir milhões de <em>bitcoiners</em>, ainda somos uma gota num oceano, neste mundo com biliões de habitantes.</p> <p>Bitcoin é um sistema financeiro alternativo, mas ainda está altamente dependente do sistema FIAT, para crescer. Se os governos conseguirem cortar todas as rampas de entrada FIAT, a adoção ficaria muito mais lenta. Seria como em 2012, quando não existiam <em>exchanges</em>, a única maneira de comprar era através de p2p, os <em>scams</em> online eram imensos, não existia confiança, as pessoas tinham medo de comprar, não arriscavam. As <em>exchanges</em> facilitam imenso, foram fundamentais para acelerar o crescimento da adoção.</p> <p>Bitcoin necessita reduzir esta dependência e tornar-se totalmente independente, para isso é essencial uma adoção massiva. As economias circular vão desempenhar um papel fundamental, se em cada terra/cidade existirem várias pessoas disponíveis para p2p, já não será necessário ir online para trocar FIAT por Bitcoin, aí sim alcançarmos a independência.</p> <p>O Bitcoin tem que ser acessível, fácil, rápido e sem a necessidade de uma KYC.</p> <h1>Impacto Global e Social</h1> <p>Quanto maior for o impacto global, mais resiliente será o bitcoin, é a teoria de jogos na sua plenitude.</p> <p>Se houve um forte crescimento na adoção do Bitcoin como moeda em países em desenvolvimento, utilizada por grupos sociais perseguidos, pelos mais pobres, pelos mais necessitados e cidadãos em países sob regimes autoritários, todos eles serão um escudo humano e social no ocidente. Ou seja, haverá pressão social sobre os políticos ocidentais, porque qualquer coisa que prejudique o Bitcoin teriam um impacto tremendo no preço, consequentemente, vai destruir as poupanças dos mais necessitados em todo o mundo. O impacto seria global.</p> <p>Será que o governo terá coragem de prejudicar as populações mais necessitadas em todo o mundo?</p> <h1>Conclusão</h1> <p>Quanto maior a adoção, maior será o escudo humano. Tudo isto não passa de uma opinião pessoal, a minha interpretação. Não confie em nada aqui escrito, verifique!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvq3vn5a7v9edw5vhj0nsr7fk7jjp7djstz6jh52yffs4uhhafdpczyr5h4tl6gqqm5hdcde7xhlz0jlzz0pq47jra784nk5hdkj3wh4m96zprp7z" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvq3vn5a7v9edw5vhj0nsr7fk7jjp7djstz6jh52yffs4uhhafdpczyr5h4tl6gqqm5hdcde7xhlz0jlzz0pq47jra784nk5hdkj3wh4m96zprp7z" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvq3vn5a7v9edw5vhj0nsr7fk7jjp7djstz6jh52yffs4uhhafdpczyr5h4tl6gqqm5hdcde7xhlz0jlzz0pq47jra784nk5hdkj3wh4m96zprp7z" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvq3vn5a7v9edw5vhj0nsr7fk7jjp7djstz6jh52yffs4uhhafdpczyr5h4tl6gqqm5hdcde7xhlz0jlzz0pq47jra784nk5hdkj3wh4m96zprp7z" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ a95c6243:d345522c <div class="time" style="margin-left: auto;">2024-10-19 08:53:30</div> </div> <div> <p>Wünsche euch allen einen wunder<a href="https://denkbar.substack.com/">bar</a>en Tag, bald ist Wochenende!!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqszpn0m0392g73m9z9dnvhm7v9qc9nte9qpu98efkupzw6zgyh55yczyz54ccjrsnrqjq424jw7224sln3e485d4g7jk9prv4e6py7ng4fzca9mnrr" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqszpn0m0392g73m9z9dnvhm7v9qc9nte9qpu98efkupzw6zgyh55yczyz54ccjrsnrqjq424jw7224sln3e485d4g7jk9prv4e6py7ng4fzca9mnrr" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqszpn0m0392g73m9z9dnvhm7v9qc9nte9qpu98efkupzw6zgyh55yczyz54ccjrsnrqjq424jw7224sln3e485d4g7jk9prv4e6py7ng4fzca9mnrr" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqszpn0m0392g73m9z9dnvhm7v9qc9nte9qpu98efkupzw6zgyh55yczyz54ccjrsnrqjq424jw7224sln3e485d4g7jk9prv4e6py7ng4fzca9mnrr" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d830ee7b:4e61cd62 <div class="time" style="margin-left: auto;">2024-05-10 14:03:50</div> </div> <div> <h2>จุดเริ่มต้นของตำนาน</h2> <p>ท่ามกลางแสงแดดเจิดจ้าและลมทะเลเย็นสบายของหาดเมืองแกลง ชายหนุ่มรูปร่างกระทัดรัดนามว่า "ซุป" กำลังนั่งจดจ่ออยู่หน้าจอคอมพิวเตอร์ ดวงตาเป็นประกายฉายแววความสนใจขณะไล่อ่านบทความวิชาการทางด้านเศรษฐศาสตร์ ความรู้ไม่ได้เป็นเพียงแค่ตัวอักษรบนหน้าจอ แต่มันคือแรงบันดาลใจ เปรียบเสมือนขุมทรัพย์ที่รอการขุดค้นสำหรับเขา</p> <p>ซุป ไม่ใช่หนุ่มนักเรียนหัวกะทิหรือบัณฑิตจบใหม่จากรั้วมหาวิทยาลัยดัง แต่เป็นชายหนุ่มธรรมดาที่หลงใหลในศาสตร์แห่งการจัดสรรทรัพยากรอันหายาก เศรษฐศาสตร์ ไม่ว่าจะเป็นสำนักคลาสสิคหรือออสเตรียน ล้วนดึงดูดความสนใจของเขาให้เข้าไปสำรวจอย่างลึกซึ้ง ยิ่งเรียนรู้ ซุปยิ่งค้นพบความมหัศจรรย์ของศาสตร์นี้ มันไม่ใช่แค่ทฤษฎีบนหน้ากระดาษ แต่สะท้อนอยู่ในทุกๆ การกระทำของมนุษย์</p> <p>มันเหมือนเวลาที่เราไปเที่ยวทะเล.. เราไม่ได้แค่เห็นน้ำทะเลสีฟ้าสวยงาม แต่เราสัมผัสได้ถึงไอเย็นของลมทะเล ได้ยินเสียงคลื่นซัดสาด ได้กลิ่นอายของเกลือ ความรู้ด้านเศรษฐศาสตร์เองก็เช่นกัน เราจะมองเห็นมันได้ในทุกๆ การตัดสินใจ ทุกๆ การกระทำ ตั้งแต่การซื้อของในร้านสะดวกซื้อ ไปจนถึงการเลือกอาชีพ</p> <p>หนึ่งในขุมทรัพย์ความรู้ที่ซุปหลงใหลมากที่สุด คือ เศรษฐศาสตร์สำนักออสเตรียน โดยเฉพาะแนวคิดเรื่อง <strong>"มูลค่าอัตวิสัย"</strong> (Subjective Value) ทฤษฎีนี้สอนให้เขาเข้าใจว่ามูลค่าของสิ่งต่างๆ ไม่ได้ขึ้นอยู่กับต้นทุนการผลิต หรือแรงงานที่ใส่ลงไป แต่มันขึ้นอยู่กับการประเมินของแต่ละบุคคล สิ่งที่สำคัญสำหรับคนหนึ่ง อาจดูไร้ค่าสำหรับอีกคน และมูลค่าของสิ่งเดียวกันก็อาจเปลี่ยนแปลงไปตามกาลเวลาและสถานการณ์</p> <p>ซึ่งก็เหมือนกับตอนเรายังเด็กๆ ของเล่นชิ้นโปรดอาจเป็นตุ๊กตากันหมีตัวเก่าๆ แต่วันนี้ ตุ๊กตาตัวนั้นอาจถูกเก็บไว้ในกล่องใต้เตียงไปแล้ว เพราะความต้องการของเราเปลี่ยนไป เราให้คุณค่ากับสิ่งอื่นๆ มากกว่าเมื่อเวลาผ่านไป</p> <p>ความหลงใหลในเศรษฐศาสตร์สำนักออสเตรียนนำพาซุปไปรู้จักกับ อ.พิริยะ และทีมงาน Right Shift กลุ่มคนรุ่นใหม่ที่มุ่งมั่นเผยแพร่ความรู้ทางเศรษฐศาสตร์อย่างเข้าใจง่าย ซุปกลายเป็นแฟนตัวยง ติดตามผลงานแทบทุกชิ้น และใฝ่ฝันว่าสักวันหนึ่งจะได้มีโอกาสร่วมงานกับทีม แต่ด้วยความขี้อายและอ่อนน้อมถ่อมตน ซุปจึงไม่เคยกล้าเอ่ยปาก เขาเลือกที่จะเป็นผู้สนับสนุนอยู่ห่างๆ อย่างเงียบๆ</p> <blockquote> <p>บางครั้ง.. ความฝันก็เหมือนเมล็ดพันธุ์ เราต้องหมั่นรดน้ำ พรวนดิน และดูแลมันอย่างดี ถึงแม้จะไม่รู้ว่ามันจะเติบโตงอกงามเมื่อไร แต่ถ้าเรายังคงดูแลมันต่อไป สักวันหนึ่งมันจะผลิดอกออกผลให้เราได้ชื่นชม </p> </blockquote> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1715349542367-YAKIHONNES3.jpg" /></p> <h2>จุดเปลี่ยนแห่งโชคชะตา</h2> <p>ชีวิตของซุป.. เหมือนเรือเล็กที่ล่องลอยไปตามกระแสน้ำ มีความสุขกับการเรียนรู้ เสพย์ติดความรู้ด้านเศรษฐศาสตร์และมีความฝันเล็กๆ ที่อยากร่วมงานกับทีม Right Shift </p> <p>วันหนึ่ง.. โชคชะตาก็เล่นตลก เหมือนส่งคลื่นลูกใหญ่ซัดเข้ามาหาเรือลำน้อยของซุป</p> <p>Right Shift กำลังประสบปัญหาขาดแคลนนักตัดต่อวิดีโอคลิป จนกระทั่ง Jakk Goodday หนึ่งในผู้ก่อตั้ง ต้องลงมาทำเองแก้ขัดไปก่อน ข่าวนี้แพร่สะพัดไปถึงหูของซุป เขาถึงกับอุทานออกมาเบาๆ</p> <p>"เอ๊ะ.. นี่มันโอกาสของเราหรือเปล่านะ?"</p> <p>สถานการณ์แบบนี้มันเหมือนตอนเราเดินเล่นอยู่ริมชายหาด แล้วเจอขวดแก้วที่ถูกคลื่นซัดมาเกยตื้น ข้างในมีกระดาษเขียนข้อความลอยอยู่ เราจะเก็บมันขึ้นมาอ่านไหมหรือจะปล่อยให้คลื่นซัดมันกลับลงทะเลไป?</p> <p>ความคิดมากมายวนเวียนอยู่ในหัวของซุป เขาไม่ใช่มืออาชีพ แต่ก็พอมีฝีมือด้านการตัดต่ออยู่บ้าง จะลองเสี่ยงดูดีไหมนะ? ถ้าไม่ลอง.. ก็คงไม่มีโอกาส แต่ถ้าลองแล้วไม่สำเร็จล่ะ? จะกลายเป็นตัวตลกหรือเปล่านะ?</p> <p>ในที่สุด.. ซุปก็ตัดสินใจ "เอาวะ! ลองดูสักตั้ง อย่างน้อยก็ได้พิสูจน์ตัวเอง" </p> <p>เขาส่งข้อความไปหา Jakk บอกเล่าความสามารถและความตั้งใจ พร้อมกับยื่นมือเข้าช่วยเหลือ</p> <blockquote> <p>บางครั้ง.. โอกาสก็มาในรูปแบบของปัญหา คนที่มองเห็นโอกาสและกล้าที่จะคว้ามันไว้ ก็จะประสบความสำเร็จ</p> </blockquote> <p>สิ่งที่เกิดขึ้นหลังจากนั้นมันราวกับความฝัน Jakk ตอบรับและให้โอกาสซุปเข้ามาทดลองงาน ความกดดันถาโถมเข้ามาอย่างหนัก แต่ซุปก็พยายามอย่างเต็มที่ เขาใช้ความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนในการประเมินคุณค่าของโอกาสนี้ มันมีค่ามากกว่าความสบายใจในฐานะแฟนคลับ มากกว่าความกลัวที่จะล้มเหลว</p> <blockquote> <p>"ความกลัว คือ กำแพงที่กั้นระหว่าง ตัวเรา กับ ความฝัน" </p> </blockquote> <p>ซุปทุ่มเททุกอย่างให้กับงาน ไม่เคยเกี่ยงงอนหรือบ่นว่าเหนื่อย เพราะสำหรับเขา.. นี่คือโอกาสทอง มันคือการได้ทำงานที่รักร่วมกับทีมที่เขาชื่นชม</p> <blockquote> <p>ทฤษฎีมูลค่าอัตวิสัยสอนให้เรารู้ว่า มูลค่าของสิ่งต่างๆ ไม่ได้ขึ้นอยู่กับปัจจัยภายนอก เช่น ราคา หรือ ต้นทุนการผลิต แต่มันขึ้นอยู่กับ การประเมินของแต่ละบุคคล</p> </blockquote> <p>การตัดสินใจครั้งสำคัญของซุป นำพาเขาไปสู่เส้นทางใหม่ เส้นทางที่เต็มไปด้วยความท้าทาย แต่ก็เต็มไปด้วยโอกาสเช่นกัน เส้นทางที่เขาจะได้เรียนรู้ เติบโต และสร้างคุณค่าให้กับตัวเองและสังคม การตัดสินใจของซุปนั้นมันช่างสอดคล้องกับหลักการของเศรษฐศาสตร์สำนักออสเตรียนที่เน้นการกระทำของมนุษย์ การประเมินมูลค่า และการตัดสินใจ</p> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1715349569131-YAKIHONNES3.jpg" /></p> <h2>วันเวลาแห่งการสร้างคุณค่า</h2> <p>แสงไฟจากจอคอมพิวเตอร์ยังคงสาดส่องใบหน้าของซุป.. ดวงตาของเขาจดจ้องอยู่กับเส้นเวลา ตัดต่อ เรียบเรียง ประกอบร่าง วิดีโอคลิปแต่ละชิ้นให้สมบูรณ์ งานที่ได้รับมอบหมายไม่ใช่งานง่าย แต่ซุปไม่เคยปริปากบ่น เขาก้มหน้าก้มตาทำงานของตัวเองไปอย่างเต็มที่</p> <p>"นี่มันคือความฝันของเราเลยนะ จะมัวบ่นทำไมกัน" ซุปพึมพำกับตัวเอง</p> <p>ซุปในตอนนี้ก็เหมือนนักปีนเขาที่กำลังไต่ขึ้นสู่ยอดเขา เส้นทางอาจจะลำบาก ขรุขระ และเต็มไปด้วยอุปสรรค แต่ทุกย่างก้าวก็คือ ความท้าทาย และความภาคภูมิใจ</p> <p>แม้จะไม่ได้รับผลตอบแทนมากมาย แต่สำหรับซุป ความสุขที่ได้รับจากการทำงานมันมีค่ามากกว่าเงินทอง เขาได้เรียนรู้อะไรใหม่ๆ มากมาย ได้ฝึกฝนทักษะ ได้สร้างสรรค์ผลงาน และที่สำคัญที่สุด คือ ได้เป็นส่วนหนึ่งของทีมที่เขารัก</p> <p>ในทางเศรษฐศาสตร์สำนักออสเตรียน เราเรียกสิ่งนี้ว่า <strong>"การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด"</strong> (Valuation by the Least Valuable Use) หมายความว่า.. เมื่อคนเราต้องตัดสินใจ เราจะประเมินมูลค่าของสิ่งต่างๆ โดยพิจารณาจากประโยชน์ที่เราจะได้รับจากการใช้งานนั้นๆ</p> <p>ในกรณีของซุป.. การทำงานกับ Right Shift อาจไม่ได้ทำให้เขาร่ำรวย แต่เขาได้รับประสบการณ์ ความรู้ และความสุข ซึ่งสิ่งเหล่านี้มีมูลค่าสำหรับซุปมากกว่าเงินทอง</p> <blockquote> <p>บางครั้ง.. คุณค่าของสิ่งต่างๆ ก็ไม่สามารถวัดได้ด้วยเงิน</p> </blockquote> <p>นอกจากนี้.. การทำงานกับ Right Shift ยังเปิดโอกาสให้ซุปได้พบปะผู้คนมากมาย ทั้งคนดัง ผู้เชี่ยวชาญ และบุคคลที่น่าสนใจ ซึ่งเป็นเหมือน <strong>"อรรถประโยชน์ส่วนเพิ่ม"</strong> (Marginal Utility) ที่เติมเต็มความสุขในการทำงานของเขา</p> <p>เหมือนเวลาเรากินข้าวจานแรกอาจจะอร่อยมากเพราะเราหิว แต่พอจานที่สอง จานที่สาม ความอร่อยก็เริ่มลดลง จนกระทั่งเราอิ่ม จนไม่อยากกินอีกแล้ว</p> <p>ประสบการณ์ใหม่ๆ ก็เช่นกัน ครั้งแรกที่ได้เจออาจจะตื่นเต้น ประทับใจ แต่พอเจอบ่อยๆ ความตื่นเต้นก็จะลดลง แต่ความทรงจำและความรู้สึกดีๆ ยังคงอยู่</p> <p>แนวคิดเรื่อง "อรรถประโยชน์ส่วนเพิ่ม" ช่วยอธิบายว่า ทำไมคนเราถึงแสวงหาประสบการณ์ใหม่ๆ แม้ว่าความตื่นเต้นจะลดลงตามกาลเวลา</p> <p>ซุป ยังคงทำงานอย่างหนัก พัฒนาตัวเองและสร้างสรรค์ผลงาน เขาไม่รู้ว่าอนาคตจะเป็นอย่างไร แต่เขารู้ว่า.. เขาได้เลือกเส้นทางที่ถูกต้องแล้ว เส้นทางที่เขาได้สร้างคุณค่าให้กับตัวเองและสังคม</p> <blockquote> <p>"ความสุข ไม่ได้อยู่ที่ปลายทาง แต่อยู่ในระหว่างทาง" </p> </blockquote> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1715349584816-YAKIHONNES3.jpg" /></p> <h2>บทเพลงแห่งการแบ่งปัน</h2> <p>เวลาผ่านไป.. ซุปสั่งสมประสบการณ์และความรู้มากขึ้น จากชายหนุ่มขี้อาย เขากลายเป็นนักตัดต่อมือฉมัง และที่สำคัญคือความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนที่สั่งสมมาตลอดมันเริ่มผลิดอกออกผล</p> <p>ซุป อยากแบ่งปันความรู้ อยากให้คนอื่นๆ ได้สัมผัสความมหัศจรรย์ของศาสตร์นี้เหมือนที่เขาเคยสัมผัส เขาปรึกษากับ Jakk และ อิสระ (น้องเล็กในทีม) ซึ่งมีความสนใจในเรื่องเดียวกันและต่างก็มีแรงปรารถนาที่จะจะเผยแพร่มันเช่นกัน</p> <p>ซุป: "พี่ Jakk, อิส ผมอยากทำรายการเกี่ยวกับเศรษฐศาสตร์สำนักออสเตรียน พี่คิดว่าไงครับ"</p> <p>Jakk: "ไอเดียดีนะซุป แต่จะทำยังไงให้มันเข้าใจง่าย ไม่น่าเบื่อ ไม่เอาศัพท์แสงบ้าบอคอแตกนะ"</p> <p>อิสระ: "พี่ซุปเล่าเรื่องเก่ง เราทำเป็นนิทานก็ได้นี่ครับ"</p> <p>ซุป: "นิทานอิสซุป เหมือนที่ อ.พิริยะ ตั้งให้อะหรอ เออ.. ชื่อนี้ เข้าท่าดีนะ"</p> <p>และแล้ว <strong>"นิทานอิสซุป"</strong> ก็ถือกำเนิดขึ้น รายการที่นำเสนอความรู้ด้านเศรษฐศาสตร์สำนักออสเตรียนในรูปแบบง่ายๆ สบายๆ เข้าใจง่าย เสียงนุ่มๆ ของซุป บวกกับลีลาการเล่าเรื่องที่เป็นเอกลักษณ์ของอิสระ ดึงดูดผู้ชมได้อย่างมากมาย </p> <p>เหมือนแม่น้ำที่ไหลรินลงจากยอดเขา นำพาธาตุอาหารไปหล่อเลี้ยง ต้นไม้ พืชพันธุ์และสัตว์น้อยใหญ่ ความรู้ก็เช่นกัน เมื่อถูกแบ่งปันมันจะสร้างคุณค่าให้กับผู้รับและผู้ให้ ซุปมีความสุขที่ได้แบ่งปันความรู้ และยิ่งแบ่งปันเขาก็ยิ่งได้รับความสุขและคุณค่ามากขึ้น</p> <p>นี่อาจคล้าย <strong>"กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง"</strong> (Law of Diminishing Marginal Utility) เมื่อเรามีบางสิ่งบางอย่างมากขึ้น ความพึงพอใจที่ได้รับจากหน่วย (Unit) ที่เพิ่มขึ้นจะค่อยๆ ลดลง</p> <p>แต่.. กฎนี้ใช้ไม่ได้กับ “ความรู้” และ “การแบ่งปัน” ยิ่งเรามีความรู้มากขึ้น ยิ่งเราแบ่งปันมากขึ้น ความสุขและ คุณค่าที่ได้รับก็จะยิ่งเพิ่มขึ้น ซึ่ง ซุป ก็เข้าใจหลักการนี้จึงเลือกที่จะแบ่งปันความรู้เพื่อสร้างคุณค่าให้กับสังคม และเติมเต็มความสุขให้กับตัวเอง</p> <p>"นิทานอิสซุป" ไม่ได้เป็นเพียงแค่รายการ แต่เป็นพื้นที่ ที่ซุปได้แสดงออกถึงความรักและความหลงใหลในเศรษฐศาสตร์สำนักออสเตรียน เขาไม่ได้ทำเพื่อชื่อเสียงหรือเงินทอง แต่ทำเพื่อแบ่งปันและสร้างคุณค่าให้กับสังคม</p> <blockquote> <p>การให้ คือ การได้รับ ที่ยิ่งใหญ่ที่สุด</p> </blockquote> <p>"นิทานอิสซุป" จึงเป็นมากกว่านิทานวิชาการ มันคือบทเพลงแห่งการแบ่งปัน บทเพลงที่ ซุป บรรจงแต่ง เพื่อส่งต่อความรู้และแรงบันดาลใจให้กับผู้คน</p> <blockquote> <p>"เพราะ.. ความรู้ คือ แสงสว่าง ที่ช่วยขับไล่ความมืดมน" </p> </blockquote> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1715349599508-YAKIHONNES3.jpg" /></p> <h2>ก้าวสู่แสงไฟ</h2> <p>นิทานอิสซุป กลายเป็นจุดเริ่มต้นของเส้นทางใหม่ เส้นทางที่นำพา ซุป ก้าวออกจากเงามืดไปสู่แสงไฟ เหมือนดอกไม้ที่เบ่งบานท่ามกลางแสงแดด อวดสีสันและกลิ่นหอม ดึงดูดผึ้งและผีเสื้อให้เข้ามาดอมดม</p> <p>ซุป ไม่ใช่แค่นักเล่านิทาน แต่เขาได้ค่อยๆ กลายเป็นหนึ่งในอินฟลูเอนเซอร์ในวงการบิตคอยน์ไทยอย่างช้าๆ ภายใต้ฉายา "ประธานซุป" เขาได้รับเชิญไปบรรยาย ออกรายการ และร่วมงานกับบุคคลที่มีชื่อเสียงมากมาย</p> <p>ความสำเร็จ มันก็มักจะมาพร้อมกับความรับผิดชอบและความคาดหวัง เส้นทางของ ซุป ไม่ได้ถูกโรยด้วยกลีบกุหลาบ เขาต้องตัดสินใจครั้งสำคัญหลายครั้ง เช่น การทิ้งรายได้จากงานฟรีแลนซ์, การสละโอกาสทางการเมือง เพื่อทุ่มเทให้กับ Right Shift</p> <blockquote> <p>“การตัดสินใจ” คือ กระบวนการเลือกทางเลือกหนึ่ง เหนือทางเลือกอื่นๆ โดยพิจารณาจาก การประเมินมูลค่าอัตวิสัย </p> </blockquote> <p>ซุป เลือกที่จะเสียสละสิ่งที่คนอื่นมองว่ามีค่า เพื่อสิ่งที่เขามองว่ามีค่ามากกว่า นั่นคือ.. ความฝัน ความสุข และ การสร้างคุณค่าให้กับสังคม</p> <blockquote> <p>"การเสียสละ คือ บทพิสูจน์ ของความมุ่งมั่น"</p> </blockquote> <p>ตลอดเส้นทาง ซุป ได้รับการสนับสนุนและคำแนะนำ จาก Jakk Goodday ผู้ที่เชื่อมั่นในศักยภาพของเขา ตั้งแต่วันแรก ความสัมพันธ์ระหว่าง ซุป และ Jakk สะท้อนให้เห็นถึงความสำคัญของ <strong>"การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกัน"</strong> (Mutually Beneficial Exchange) ซึ่งเป็นหัวใจสำคัญของ เศรษฐศาสตร์สำนักออสเตรียน</p> <p>Jakk เห็นคุณค่าในตัว ซุป จึงให้โอกาสและสนับสนุนเขา ในขณะที่ ซุป ก็ตอบแทนด้วยการทำงานอย่างเต็มที่ และ สร้างคุณค่าให้กับทีม Right Shift</p> <blockquote> <p>การให้ และ การรับ นั้นเป็นวัฏจักรที่สร้างสรรค์ และ ยั่งยืน</p> </blockquote> <p>เส้นทางของ "ซุป" จากแฟนคลับสู่ประธานซุป เป็นบทเรียนชีวิตที่สอนให้เรารู้ว่า.. ความฝัน ความมุ่งมั่น การเสียสละ และการสร้างคุณค่า คือ สิ่งสำคัญที่นำพาเราไปสู่ความสำเร็จ</p> <p>และทุกคน ก็มีศักยภาพที่จะสร้างคุณค่า และประสบความสำเร็จ ในแบบของตัวเอง</p> <h2>คุณค่าที่แท้จริง</h2> <p>เรื่องราวของ "ซุป" ไม่ได้เป็นเพียงแค่เรื่องราวของความสำเร็จ แต่เป็นบทเรียนชีวิตที่สอนให้เราเข้าใจถึงคุณค่าที่แท้จริง </p> <p>เหมือนต้นไม้ใหญ่ที่เติบโตแผ่กิ่งก้านสาขา ให้ร่มเงาและผลิดอกออกผล ซุป เปรียบเสมือนต้นไม้ต้นนั้น เขาเติบโต จากเมล็ดพันธุ์เล็กๆ ที่หลงใหลในความรู้ ด้วยการหมั่นรดน้ำ พรวนดิน ใส่ปุ๋ย คือความมุ่งมั่น ความอดทน และ การเสียสละ จนกระทั่งเติบใหญ่ แผ่กิ่งก้านสาขาให้ร่มเงา คือการแบ่งปันความรู้และผลิดอกออกผล คือความสำเร็จและการเป็นแรงบันดาลใจให้กับผู้อื่น</p> <p>หลักการของ <strong>ทฤษฎีมูลค่าอัตวิสัย</strong> (Subjective value) สะท้อนให้เห็นในทุกๆ การตัดสินใจของ ซุป</p> <p>การประเมินมูลค่า >> ซุป ประเมินคุณค่าของโอกาส ประสบการณ์ และความสุข มากกว่าเงินทองและชื่อเสียง การเสียสละ >> ซุป ยอมสละรายได้และโอกาสทางการเมือง เพื่อหันมาทำในสิ่งที่เขารักและเชื่อมั่น ความอดทน >> ซุป ทำงานหนัก พัฒนาตัวเองและอดทนรอคอย จนกระทั่งประสบความสำเร็จ การสร้างคุณค่า >> ซุป แบ่งปันความรู้และสร้างแรงบันดาลใจ ให้กับผู้อื่น</p> <p>เรื่องราวของ ซุป สะท้อนให้เห็นถึง <strong>"ปฏิทรรศน์น้ำ-เพชร"</strong> (Water-Diamond Paradox) ซึ่งเป็นแนวคิดใน เศรษฐศาสตร์สำนักออสเตรียน ที่อธิบายว่า.. ทำไมสิ่งที่จำเป็นอย่าง น้ำ ถึงมีราคาถูก ในขณะที่สิ่งฟุ่มเฟือยอย่าง เพชร ถึงมีราคาแพง</p> <p>ในชีวิตจริง.. สิ่งที่สำคัญสำหรับคนหนึ่ง อาจไม่ได้สลักสำคัญสำหรับอีกคน และมูลค่าของสิ่งต่างๆ ก็ขึ้นอยู่กับ บริบทและความต้องการของแต่ละบุคคล</p> <blockquote> <p>ความสุข และ ความสำเร็จ ไม่ได้มีสูตรสำเร็จตายตัว แต่ละคนต้องค้นหาและสร้างมันขึ้นมาเอง</p> </blockquote> <p>ซุป ค้นพบ “คุณค่าที่แท้จริง” ของชีวิต เขาไม่จำเป็นต้องมีเงินทองมากมาย หรือมีชื่อเสียงโด่งดัง แต่เขามีความสุขกับการได้ทำในสิ่งที่รักและสร้างคุณค่าให้กับสังคม</p> <p>“จงค้นหาคุณค่าที่แท้จริงของชีวิต และ ใช้ชีวิตให้มีความหมาย”</p> <blockquote> <p>"คุณค่าของคน อยู่ที่ผลของงาน"</p> </blockquote> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/d830ee7b7c30a364b1244b779afbb4f156733ffb8c87235086e26b0b4e61cd62/files/1715349489131-YAKIHONNES3.jpg" /></p> <p><em>11 พฤษภาคม เป็นวันคล้ายวันเกิดของ ซุป บทความนี้ผมจึงอุทิศน์ให้กับเขา และขอให้เจ้าตัวมีความสุขในการมุ่งมั่นสร้างคุณค่าในแบบของตัวเองสืบต่อไป ขอให้ทุกคนได้ร่วมอวยพรและให้กำลังใจเพื่อนคนเก่งของเราคนนี้กันด้วยครับ</em></p> <h1>ภาคผนวก</h1> <h2>Subjective Value มองคุณค่าผ่านเลนส์ของตัวเอง</h2> <p>ทฤษฎีมูลค่าอัตวิสัย (Subjective Value) เปรียบเสมือนแว่นตาพิเศษที่ช่วยให้เราเข้าใจว่าทำไมคนเราถึงมองเห็น "คุณค่า" ของสิ่งต่างๆ แตกต่างกัน</p> <p>ลองนึกภาพว่าเรากำลังดูภาพวาด abstract บางคนอาจมองว่ามันสวยงาม มีเอกลักษณ์ ในขณะที่บางคนอาจมองว่ามันดูยุ่งเหยิง ไม่มีความหมาย</p> <p>ทฤษฎีนี้บอกเราว่า "คุณค่า" ไม่ได้ติดมากับสิ่งของ หรือถูกกำหนดโดยปัจจัยภายนอก เช่น ต้นทุนการผลิตหรือแรงงานที่ใช้ แต่ "คุณค่า" เกิดขึ้นจากการประเมินของแต่ละบุคคล ขึ้นอยู่กับความต้องการ ความชอบ ประสบการณ์ และสถานการณ์ของแต่ละคน</p> <p>นักเศรษฐศาสตร์สำนักออสเตรียนเชื่อว่า "มนุษย์" เป็นศูนย์กลางของกิจกรรมทางเศรษฐกิจ และการตัดสินใจของมนุษย์นั้นขับเคลื่อนด้วย "มูลค่าอัตวิสัย" ที่พวกเขามีต่อสิ่งต่างๆ</p> <p>ยกตัวอย่างง่ายๆ</p> <p>คนที่กำลังหิวโหย อาจมองว่า "ข้าวเปล่า 1 จาน" มีค่ามาก แต่สำหรับคนที่เพิ่งกินอิ่มมา ข้าวเปล่าจานนั้นอาจไม่มีค่าเลย</p> <p>นักสะสมงานศิลปะ อาจยอมจ่ายเงินมหาศาลเพื่อซื้อภาพวาด แต่สำหรับคนที่ไม่เข้าใจศิลปะ ภาพวาดนั้นอาจดูไร้ค่า</p> <p>นักเรียนที่กำลังเตรียมสอบ อาจมองว่า "เวลา 1 ชั่วโมง" มีค่ามาก แต่สำหรับคนที่กำลังว่าง เวลา 1 ชั่วโมงอาจไม่มีค่าอะไรเลย</p> <p>การเข้าใจ "ทฤษฎีมูลค่าอัตวิสัย" ช่วยให้เรายอมรับความแตกต่างและเคารพการตัดสินใจของผู้อื่น เพราะสิ่งที่สำคัญสำหรับเราอาจไม่สำคัญสำหรับคนอื่น และที่สำคัญ "มูลค่า" ยังสามารถเปลี่ยนแปลงไปตามกาลเวลาและสถานการณ์</p> <p>โทรศัพท์มือถือรุ่นเก่า ที่เมื่อก่อนอาจมีมูลค่ามาก แต่ตอนนี้อาจกลายเป็นของสะสมหรือ ขยะอิเล็กทรอนิกส์</p> <p>บ้านหลังเก่า เมื่อก่อนอาจเคยเป็นบ้านในฝัน แต่ตอนนี้อาจทรุดโทรม จนต้องซ่อมแซม</p> <p>เรื่องราวของ "ซุป" สะท้อนให้เห็นถึงการเปลี่ยนแปลงของ "มูลค่า" เขาเคยให้คุณค่ากับความสบายใจในฐานะแฟนคลับ แต่เมื่อมีโอกาสเขาก็เปลี่ยนมาให้คุณค่ากับการทำงาน การสร้างคุณค่า และการแบ่งปันความรู้</p> <p>"ทฤษฎีมูลค่าอัตวิสัย" จึงเป็นเครื่องมือสำคัญที่ช่วยให้เราเข้าใจการตัดสินใจ พฤติกรรม และการกระทำของมนุษย์ ทั้งในชีวิตประจำวันและในระบบเศรษฐกิจ</p> <h2>เลือกสิ่งที่ดีที่สุด ณ เวลานั้น</h2> <p><strong>"การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด"</strong> (Valuation by the Least Valuable Use) ฟังดูอาจจะซับซ้อนทำความเข้าใจได้ยาก แต่จริงๆแล้วมันคือหลักการง่ายๆ ที่เราใช้ในการตัดสินใจในชีวิตประจำวัน</p> <p>เวลาเราเข้าไปในร้านขายเสื้อผ้าที่มีเสื้อผ้ามากมายหลากหลายแบบ เราจะเลือกซื้อ เสื้อผ้าตัวไหน?</p> <p>เราคงไม่เลือกซื้อเสื้อผ้าทุกตัวในร้าน แต่จะเลือกเสื้อผ้าที่ตอบโจทย์ความต้องการของเรามากที่สุด ณ เวลานั้น เช่น เสื้อผ้าที่ใส่ไปทำงาน เสื้อผ้าที่ใส่ไปเที่ยว หรือเสื้อผ้าที่ใส่ไปออกกำลังกาย</p> <p>ทฤษฎีนี้อธิบายว่า.. เมื่อคนเรามีสินค้าหรือบริการหลายอย่าง เราจะเลือกใช้สินค้าหรือ บริการที่ตอบสนองต่อความต้องการที่เร่งด่วนที่สุดก่อน</p> <p>ยกตัวอย่างเช่น..</p> <p>เราอาจจะมีการแบ่งเงินเป็นหลายก้อน แต่ก้อนที่เราจะใช้ก่อน คือก้อนที่เราต้องการใช้ มากที่สุด ณ เวลานั้น เช่น ค่าอาหาร ค่าเดินทางหรือค่าเช่าบ้าน การตัดสินใจของคนเรา จึงขึ้นอยู่กับความต้องการและสถานการณ์ ณ เวลานั้น</p> <p>ดังนั้น "การประเมินมูลค่าโดยการใช้ประโยชน์ที่มีค่าน้อยที่สุด" จึงเป็นหลักการที่ช่วยให้เราจัดลำดับความสำคัญ และเลือกสิ่งที่ดีที่สุดสำหรับตัวเรา ณ เวลานั้น</p> <p>ซุป ก็ใช้หลักการนี้ในการตัดสินใจ เช่น การเลือกทำงานกับ Right Shift แม้ว่า จะไม่ได้รับ ผลตอบแทนมากมายนัก แต่เขาได้รับความสุขและประสบการณ์ ซึ่งมีค่ามากกว่าสำหรับเขา </p> <h2>อิ่มเอม...แต่ไม่เท่าเดิม</h2> <p><strong>"กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง"</strong> (Law of Diminishing Marginal Utility) เป็นกฎพื้นฐานทางเศรษฐศาสตร์ที่อธิบายถึงความรู้สึก "อิ่มเอม" ที่ลดลง เมื่อเราบริโภคสินค้าหรือบริการมากขึ้น</p> <p>ลองนึกภาพว่าเรากำลังกินพิซซ่า ชิ้นแรกอร่อยมาก ชิ้นที่สองก็ยังอร่อยอยู่ แต่พอชิ้นที่สาม ชิ้นที่สี่ ความอร่อยก็เริ่มลดลง จนกระทั่งเราอิ่ม และไม่อยากกินอีกแล้ว</p> <p>นั่นเป็นเพราะ "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) หรือความพึงพอใจที่ได้รับ จากการบริโภค สินค้าหรือบริการ จากหน่วย (Unit) เพิ่มเติมนั้นลดลง</p> <p>กฎนี้อธิบายว่า ยิ่งเราบริโภคสินค้าหรือบริการมากขึ้น ความพึงพอใจที่ได้รับจากหน่วย เพิ่มเติมจะลดลง</p> <p>ยกตัวอย่างเช่น..</p> <p>เสื้อผ้าตัวใหม่อาจจะทำให้เรารู้สึกดี ตื่นเต้น แต่พอมีเสื้อผ้าเยอะๆ ความตื่นเต้นก็จะ ลดลง</p> <p>เงินก้อนแรกที่เราหามาได้ อาจจะมีค่ามาก แต่พอมั่งคั่งเงินก้อนต่อๆ ไปก็จะมีค่าน้อยลง</p> <p>กฎนี้สอนให้เรารู้จักพอเพียง และเห็นคุณค่าของสิ่งที่เรามี</p> <p>อย่างไรก็ตาม "กฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง" มีข้อยกเว้น เช่น ความรู้ และ การแบ่งปัน ตามที่ได้กล่าวถึงในบทความ</p> <h2>win-win situation</h2> <p><strong>"การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกัน"</strong> (Mutually Beneficial Exchange) เป็นหัวใจสำคัญของระบบเศรษฐกิจ และเป็นเหตุผลที่ทำให้คนเรา "ค้าขาย" กัน</p> <p>เวลาเราไปตลาด เราเอาเงินไปแลกกับอาหาร แม่ค้าได้เงิน เราก็ได้อาหาร ต่างคนต่างได้ประโยชน์ การแลกเปลี่ยนจะเกิดขึ้นก็ต่อเมื่อ ทั้งสองฝ่าย เชื่อว่า พวกเขาจะ "ได้" มากกว่า "เสีย"</p> <p>นักเศรษฐศาสตร์สำนักออสเตรียน เชื่อว่า การแลกเปลี่ยนที่เป็นประโยชน์ร่วมกันเกิดขึ้นได้ เพราะคนเรามี "มูลค่าอัตวิสัย" ที่แตกต่างกัน</p> <p>ยกตัวอย่างเช่น..</p> <p>ชาวนามีข้าวแต่ไม่มีปลา ชาวประมงมีปลาแต่ไม่มีข้าว ทั้งสองจึงแลกเปลี่ยนสินค้ากัน เพื่อ เพื่อตอบสนองความต้องการของตัวเอง</p> <p>นายจ้างต้องการคนทำงาน ลูกจ้างต้องการรายได้ ทั้งสองจึงทำสัญญาจ้าง เพื่อแลกเปลี่ยน แรงงานกับเงินเดือน</p> <p>การแลกเปลี่ยนช่วยให้คนเราได้สินค้าและบริการที่หลากหลาย มากกว่าที่จะผลิตเอง ทั้งหมด นอกจากนี้ การแลกเปลี่ยนยังกระตุ้นให้เกิดการพัฒนาและนวัตกรรม เพราะผู้ผลิตต้องแข่งขันกัน เพื่อตอบสนองความต้องการของผู้บริโภค</p> <blockquote> <p>"การค้า คือ การสร้างสรรค์ ความมั่งคั่ง ร่วมกัน"</p> </blockquote> <h2>แกะปริศนา "ปฏิทรรศน์น้ำ-เพชร"</h2> <p>มาถึงตรงนี้.. หลายคนอาจจะสงสัยว่าทำไม "น้ำ" ซึ่งเป็นสิ่งที่จำเป็นต่อการดำรงชีวิต ถึงมีราคาถูกหรือบางที่ก็ฟรี ในขณะที่ "เพชร" ซึ่งเป็นแค่เครื่องประดับกลับมีราคาแพงหูฉี่</p> <p>เหมือนเวลาเราไปร้านอาหาร เราสั่ง "ข้าวผัด" จานใหญ่ราคา 50 บาท แต่ "ไข่ดาว" ฟองเล็กๆ ราคา 10 บาท ทำไมข้าวผัดถึงถูกกว่า ไข่ดาว ทั้งที่ ข้าวผัดมี ข้าว ผัก เนื้อสัตว์ เครื่องปรุง ตั้งหลายอย่าง</p> <p>คำตอบอยู่ที่ "ความขาดแคลน" (Scarcity) และ "อรรถประโยชน์ส่วนเพิ่ม" (Marginal Utility) ซึ่งเป็นแนวคิดสำคัญในเศรษฐศาสตร์สำนักออสเตรียน</p> <p>น้ำ มีอยู่มากมาย ในขณะที่ เพชร นั้นหายาก น้ำ แก้วแรกอาจจะช่วยชีวิตเราได้ แต่ น้ำ แก้วที่ 10 อาจจะทำให้เราจุก</p> <p>"อรรถประโยชน์ส่วนเพิ่ม" หมายถึง ความพึงพอใจที่ได้รับจากการบริโภคสินค้าหรือ บริการในหน่วย (Unit) เพิ่มเติม (ในจำนวนมากขึ้น)</p> <p>เมื่อน้ำมีอยู่มาก เราจึงประเมินมูลค่าของน้ำแก้วที่ 10 ต่ำ เพราะมันไม่ได้ตอบสนองความต้องการที่เร่งด่วน แต่เพชรที่หายาก ทำให้แม้แต่เพชรเม็ดเล็กๆ ก็ยังมีมูลค่าสูง</p> <p>คุณค่า ไม่ได้ขึ้นอยู่กับความจำเป็นหรือความฟุ่มเฟือย แต่ขึ้นอยู่กับความขาดแคลนและ การประเมินมูลค่าของแต่ละบุคคล</p> <p>ดังนั้น ปฏิทรรศน์น้ำ-เพชร (Water-Diamond Paradox) จึงไม่ใช่ความขัดแย้ง แต่เป็น การสะท้อนให้เห็นถึงหลักการพื้นฐานของเศรษฐศาสตร์ นั่นคือ มูลค่า เป็นเรื่องส่วนบุคคล และขึ้นอยู่กับบริบท</p> <p>เรื่องราวของ "ซุป" ก็เช่นกัน.. เขาประเมินมูลค่าของ ความรู้ ความสุข และการสร้างคุณค่า สูงกว่าเงินทองและชื่อเสียง</p> <p>เขาเลือกที่จะเดินบนเส้นทางที่คนอื่นอาจมองว่า "ขาดแคลน" คือ เส้นทางที่ไม่ได้เต็มไปด้วยเงินทองหรือชื่อเสียง แต่เป็นเส้นทางที่เต็มไปด้วย ความสุข ความหมาย และคุณค่า</p> <blockquote> <p>"ความสุข ที่แท้จริง หาซื้อไม่ได้ ด้วยเงิน"</p> </blockquote> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsd2zewvpevejg85vgym595v4fczw96pxsxej9r5sxa5jgnj9csuwszyrvrpmnm0sc2xe93y39h0xhmknc4vuellwxgwg6ssm3xkz6wv8xky3m6hcn" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsd2zewvpevejg85vgym595v4fczw96pxsxej9r5sxa5jgnj9csuwszyrvrpmnm0sc2xe93y39h0xhmknc4vuellwxgwg6ssm3xkz6wv8xky3m6hcn" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsd2zewvpevejg85vgym595v4fczw96pxsxej9r5sxa5jgnj9csuwszyrvrpmnm0sc2xe93y39h0xhmknc4vuellwxgwg6ssm3xkz6wv8xky3m6hcn" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsd2zewvpevejg85vgym595v4fczw96pxsxej9r5sxa5jgnj9csuwszyrvrpmnm0sc2xe93y39h0xhmknc4vuellwxgwg6ssm3xkz6wv8xky3m6hcn" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ df8f0a64:057d87a5 <div class="time" style="margin-left: auto;">2024-10-10 15:18:39</div> </div> <div> <h2>書き散らす動機</h2> <p>残暑続きからの急な気温低下で鼻炎がひどくなる今日この頃、皆様お元気でしょうか</p> <p>株主への抗議のために退職してから2ヶ月半、流石に暇を持て余してきました 時間がある上に能動的に働く気も起きず、ひたすらボーッとしたりうねうね考え事をする日々です 幸いにして人生も折り返しにさしかかる頃になり、時折「今、人生が終わって構わないのでは?」というようなことも考えたりします (鬱病既往歴ありますが私は元気です)</p> <p>子どものお迎えを終えて、いつもどおり夕食をとり、またうねうねしているうちに ふと、6年前の年末に急死された、仕事でお世話になったTさんのことを思い出しました</p> <p>子を寝かしつけてもまだ頭の中をぐるぐるしていたので、ここに吐き出してすっきりしようという魂胆です</p> <h2>Tさんとの出会い</h2> <p>私のキャリアの(ほぼ)スタートはVC(ベンチャーキャピタル)でした 誰のせいでもないとある経緯もあり、周囲からは警戒され避けられ、わずか6年ではありますが、 インナーサークルに入り込めない時期を過ごし、当時の上司と二人、とにかくやれることをやり続ける毎日でした</p> <p>いつものようにピッチイベントに参加しているとき、近くの席にいたスーツ姿の3人組と目が一瞬合います</p> <p>「事業会社の人だ」</p> <p>協調投資やファンド出資のきっかけを掴むべく、その3人に話かけます</p> <p>「よろしければ弊社投資先のご紹介や御社の...」</p> <p>ひととおりの挨拶を済ませ、この人たちにも避けられるんだろうと思いながらも要件を切り出します</p> <p>「是非やりましょう」</p> <p>いつもとは違う嬉しい返事をくれたのがTさんでした</p> <h2>面倒見の良い他社の先輩</h2> <p>そのときの3人組であるMさん・Iさん・Tさんには、私の仕事人生の中で最もお世話になったと言っても過言ではありません</p> <p>ファンドの営業を受けていただき、協調投資を行い、VCからの転職後にも協業相手として他部署のキーマンをご紹介いただき...</p> <p>社会人になったばかりの私の、今思い返せば恥ずかしい(部下がこんな提案したら卒倒する)レベルの提案を、 誰もが知る一流企業の多忙な役職持ちであるにも関わらず、毎回一時間も割いて丁寧に対応してくださる心の広い方でした</p> <p>当時、VCと接点をもつような事業会社の対スタートアップ部隊は、本業でご活躍されている方が兼任で取り組むパターンが多く、Mさん・Iさん・Tさんももちろんそう</p> <p>その後も昇進され、最後には本社の取締役に。今年遂に退任され、所謂「あがり」でしょうか、子会社の取締役に異動 長い社会人人生をほぼ走りきり、有終の美を飾ろうとする時期にさしかかっています</p> <p>でもTさんはそこにはいません</p> <h2>残される側</h2> <p>冒頭触れたとおり、Tさんは6年前のこの時期に急死されました 死因については、Tさんのご友人がFBに投稿していた文章を読んでも、Iさんに聞いてもわからない</p> <p>悲しいかな、四十年近く生きていると、死因が明かされない理由がわかるようになる機会が一度や二度はあります Tさんもおそらくそうだったのでしょう</p> <p>直前まで、Iさんと一緒にベイエリアに出張され、楽しそうなコメントと共に写真を投稿されていたのに 晩婚なのか再婚なのか、とにかくご結婚されて一年ちょっと。お子様も生まれたばかりだったのに Tさんは近い人間に心中を隠して、静かにこの世を去りました</p> <p>あなたの快い返事に、どれほど私が救われたのか 転職後の提案のとき、受付で顔を出してすぐ「元気?」と声をかけてくださったことがどれほど私を安心させてくれたか あなたが声をかけてくれる度、私の社会人としての成果が生まれたことに、私は十分に感謝を伝えられていません</p> <h2>まだしばらく残る理由</h2> <p>振り返って、Tさんのように誰かの人生をenhanceできたのか?と自分に問うと、まだできたとは思えません。残念ですが</p> <p>今ここで死んでも私は構わないけど、まだもうちょっと頑張るべきかな、老いてから誰かに感謝をしてもらうまで生きてみてもいいかな</p> <p>そうふと思い直しているうちに日付が変わりました</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs9utd4lcvqzt9amh687un7a75fr0jev7xctskgtqgd3d6f5aq0srgzyr0c7znypsll6z0zjwve4narn8g9wny9q87d408v55rjacs90kr620q8zjv" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs9utd4lcvqzt9amh687un7a75fr0jev7xctskgtqgd3d6f5aq0srgzyr0c7znypsll6z0zjwve4narn8g9wny9q87d408v55rjacs90kr620q8zjv" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs9utd4lcvqzt9amh687un7a75fr0jev7xctskgtqgd3d6f5aq0srgzyr0c7znypsll6z0zjwve4narn8g9wny9q87d408v55rjacs90kr620q8zjv" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs9utd4lcvqzt9amh687un7a75fr0jev7xctskgtqgd3d6f5aq0srgzyr0c7znypsll6z0zjwve4narn8g9wny9q87d408v55rjacs90kr620q8zjv" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 266815e0:6cd408a5 <div class="time" style="margin-left: auto;">2024-04-22 22:20:47</div> </div> <div> <p>While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent</p> <p>I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS</p> <p>There were a few things I learned from all these conversations:</p> <ol> <li>All the existing solutions have one thing in common. A universal ID of some kind for files</li> <li>HTTP is still good. we don't have to throw the baby out with the bath water</li> <li>nostr could fix this... somehow</li> </ol> <p>Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...</p> <h2>An Identity system</h2> <p>An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files</p> <p>This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)</p> <h2>What is blossom?</h2> <p>Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id</p> <h2>What are Blobs?</h2> <p>blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names</p> <p>Instead blobs have a sha256 hash (like <code>b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553</code>) as an ID</p> <p>These IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using: <code>sha256sum bitcoin.pdf</code> )</p> <h2>How do the servers work?</h2> <p>Blossom servers expose four endpoints to let clients and users upload and manage blobs</p> <ul> <li><code>GET /<sha256></code> (optional file <code>.ext</code>)</li> <li><code>PUT /upload</code></li> <li><code>Authentication</code>: Signed <a href="https://github.com/hzrd149/blossom/blob/master/Server.md#upload-authorization-required">nostr event</a></li> <li>Returns a blob descriptor</li> <li><code>GET /list/<pubkey></code></li> <li>Returns an array of blob descriptors</li> <li><code>Authentication</code> <em>(optional)</em>: Signed <a href="https://github.com/hzrd149/blossom/blob/master/Server.md#list-authorization-optional">nostr event</a></li> <li><code>DELETE /<sha256></code></li> <li><code>Authentication</code>: Signed <a href="https://github.com/hzrd149/blossom/blob/master/Server.md#delete-authorization-required">nostr event</a></li> </ul> <h2>What is Blossom Drive?</h2> <p>Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs</p> <h2>What are Drives</h2> <p>Drives are just nostr events (kind <code>30563</code>) that store a map of blobs and what filename they should have along with some extra metadata</p> <p>An example drive event would be <code>json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }</code></p> <p>There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at</p> <p>If your interested, the full event definition is at <a href="https://github.com/hzrd149/blossom-drive/blob/master/docs/drive.md">github.com/hzrd149/blossom-drive</a></p> <h2>Getting started</h2> <p>Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started</p> <h3>1. Open the app</h3> <p>Open https://blossom.hzrd149.com</p> <h3>2. Login using extension</h3> <p><img alt="" src="https://cdn.hzrd149.com/de4a9fbf07eea796f166d6846aef7e1ffda2abb0b30c2390f02774253141c4c3.png" /></p> <p>You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an <code>ncryptsec</code> password protected private key - a <code>nsec</code> unprotected private key (please don't) - bunker:// URI from nsecbunker</p> <h3>3. Add a blossom server</h3> <p><img alt="" src="https://cdn.hzrd149.com/5f0497549d426dba5613abf52406a12a70d417688d4cda0e19cc20f98184593a.png" /></p> <p>Right now <code>https://cdn.satellite.earth</code> is the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript <a href="https://github.com/hzrd149/blossom-server">github.com/hzrd149/blossom-server</a></p> <h3>4. Start uploading your files</h3> <p><strong>NOTE: All files upload to blossom drive are public by default. DO NOT upload private files</strong></p> <p><img alt="" src="https://cdn.hzrd149.com/47d6b7716f582fa2bdebadc9e2bc4a336d445846c343d812c270086533580deb.png" /></p> <h3>5. Manage files</h3> <p><img alt="" src="https://cdn.hzrd149.com/63065794567112da49c9613c61ea392d520220e0fdedf15aa81d9da4145643c1.png" /></p> <h2>Encrypted drives</h2> <p>There is also the option to encrypt drives using <a href="https://github.com/nostr-protocol/nips/blob/master/49.md">NIP-49</a> password encryption. although its not tested at all so don't trust it, verify</p> <p><img alt="" src="https://cdn.hzrd149.com/1c073e7d7d378e6019529882a0ccff2f9c09de65d7aef7017f395307792cce51.png" /></p> <h2>Whats next?</h2> <p>I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything</p> <p>also all the images in this article are stored in one of my blossom drives <a href="nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka">here</a></p> <p>nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqspm5jtl3ksuqkxwg9u0ac8l4rvvy7l89ffr505acuw459l948z9hqzyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22nmgry8" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqspm5jtl3ksuqkxwg9u0ac8l4rvvy7l89ffr505acuw459l948z9hqzyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22nmgry8" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqspm5jtl3ksuqkxwg9u0ac8l4rvvy7l89ffr505acuw459l948z9hqzyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22nmgry8" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqspm5jtl3ksuqkxwg9u0ac8l4rvvy7l89ffr505acuw459l948z9hqzyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22nmgry8" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ fcc4252f:e9ec0d5d <div class="time" style="margin-left: auto;">2024-04-17 22:52:57</div> </div> <div> <p>Check out the <a href="https://plebeian.market/">latest auctions and products</a> below 👀</p> <p>Plebeian Market sees growth every week, with new merchants setting up stalls and showcasing their products and services. We are grateful to each and every one of you for your ongoing support! Thank you!</p> <h3>Latest Auctions on the Marketplace</h3> <h4><a href="https://plebeian.market/product/11324bdf-5ce1-4a4b-bc6c-b6e0f99f5a3c">MaxisClub - The Halving</a></h4> <p>Celebrate the next bitcoin epoch with another classic MaxisClub meme! <img alt="" src="https://image.nostr.build/e841d16587d502daf38292499efa6b4bac997865be88956987e5c7a1f22a01c6.png" /></p> <h4><a href="https://plebeian.market/product/e94a70dc-8e30-45a8-b10f-d159dbed6aca">Isabel Sydow Greeting Cards</a></h4> <p><img alt="" src="https://image.nostr.build/3b9c59dfce721443768a9719a91ef45b1a3521d23f72ab6604bbf01e2a6d30c4.png" /></p> <h3>Newest Merchants</h3> <h4><a href="https://plebeian.market/p/32a6f101ade75ffadcaf74a6ff4e58cde1c3aa30f41474f5658e6b0655864cc5/stall/d1da87bc12c9840b3a1a4f77a94bbeba63766bb27185c1427542587af4a51b63">Depbit - QR Code Kits</a></h4> <p><a href="https://plebeian.market/p/32a6f101ade75ffadcaf74a6ff4e58cde1c3aa30f41474f5658e6b0655864cc5/stall/d1da87bc12c9840b3a1a4f77a94bbeba63766bb27185c1427542587af4a51b63">Depbit</a> offers an alternative to metal plated backup QR seed. The problem is that metal ones are very expensive and very difficult to make. Generally people don't buy more than one metal backup plate and then it is the only one they keep which isn’t best practices for backing up your seed. With Depbit you can buy 15 plastics QR kits to use and discard them as needed.</p> <h5><a href="https://x.com/depbit/status/1780153077544169800">Watch Video Here</a></h5> <p>In principle, everyone prefers the metal option. But after fighting with the hammer and seeing how easy the plastic one is. Everyone who has tried it has loved it, so try it for yourself! </p> <h5><a href="https://plebeian.market/p/32a6f101ade75ffadcaf74a6ff4e58cde1c3aa30f41474f5658e6b0655864cc5/stall/d1da87bc12c9840b3a1a4f77a94bbeba63766bb27185c1427542587af4a51b63">Order Here</a></h5> <p><img alt="" src="https://image.nostr.build/27adaca94433287acd771003104157f7f3ebd6c1c487d3f620aea1bc1d5bdf49.png" /></p> <h3><a href="https://plebeian.market/">Join Us!</a></h3> <p>Plebeian Market is a commerce platform that supports open trade and communications while helping individuals and merchants transition onto a bitcoin standard.</p> <p>Let's Build Together </p> <p>Bekka</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0dfpdcjejap5vfvv65ekmd83fedsst8u2q63aqt7k26m80yr6rkqzyr7vgff03w4nvrq5a27lnxuvqr3nrtnftk6czx3r6nkjac0fasx46km79yd" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0dfpdcjejap5vfvv65ekmd83fedsst8u2q63aqt7k26m80yr6rkqzyr7vgff03w4nvrq5a27lnxuvqr3nrtnftk6czx3r6nkjac0fasx46km79yd" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0dfpdcjejap5vfvv65ekmd83fedsst8u2q63aqt7k26m80yr6rkqzyr7vgff03w4nvrq5a27lnxuvqr3nrtnftk6czx3r6nkjac0fasx46km79yd" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0dfpdcjejap5vfvv65ekmd83fedsst8u2q63aqt7k26m80yr6rkqzyr7vgff03w4nvrq5a27lnxuvqr3nrtnftk6czx3r6nkjac0fasx46km79yd" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 460c25e6:ef85065c <div class="time" style="margin-left: auto;">2024-10-10 13:22:06</div> </div> <div> <p>In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.</p> <p>nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees: </p> <p>nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp</p> <p>But how big is too big? How can we better understand the range of options available for devs out there?</p> <p>I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - <strong>Super Clients</strong>: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.</p> <ul> <li> <p><strong>Clients</strong>: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.</p> </li> <li> <p><strong>Mini Clients</strong>: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.</p> </li> <li> <p><strong>Micro Clients</strong>: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.</p> </li> </ul> <p>Based on my made-up categories described at the end, this is how I would split our most known apps. </p> <p><strong>Super Clients</strong> - <a href="https://amethyst.social">amethyst</a> - <a href="https://nostrudel.ninja">nostrudel</a> - <a href="https://coracle.social">coracle</a></p> <p><strong>Clients</strong> - <a href="https://damus.io">damus</a> - twitter - <a href="https://primal.net">primal</a> - twitter - <a href="https://snort.social">snort</a> - twitter - <a href="https://github.com/mikedilger/gossip">gossip</a> - twitter - <a href="https://lume.nu">lume</a> - twitter - <a href="https://soapbox.pub/ditto/">ditto</a> - twitter - <a href="https://rabbit.syusui.net">rabbit</a> - twitter - <a href="https://freefrom.space">freefrom</a> - twitter - <a href="https://nos.social">nos</a> - twitter - <a href="https://flycat.club">flycat</a> - twitter - <a href="https://straylight.cafe">straylight</a> - twitter - <a href="https://nostter.app">nostter</a> - twitter - <a href="https://iris.to">iris</a> - twitter - <a href="https://nostur.com">nostur</a> - twitter - <a href="https://apps.apple.com/us/app/nostrmo/id6447441761">nostrmo</a> - twitter - <a href="https://yana.do">yana</a> - twitter - <a href="https://openvibe.social">openvibe</a> - twitter - <a href="https://freerse.com">freerse</a> - twitter - <a href="https://0xchat.com">0xchat</a> - chats - <a href="https://cornychat.com">cornychat</a> - chats - <a href="https://github.com/lumehq/coop">coop</a> - chats - <a href="https://nostrchat.io">nostrchat</a> - chats - <a href="https://blowater.deno.dev">blowater</a> - chats - <a href="https://habla.news">habla</a> - blogs - <a href="https://yakihonne.com">yakihonne</a> - blogs - <a href="https://highlighter.com">highlighter</a> - blogs - <a href="https://blogstack.io">blogstack</a> - blogs - <a href="https://stemstr.app">stemstr</a> - music - <a href="https://wavlake.com">wavlake</a> - music - <a href="https://fountain.fm">fountain</a> - podcasts - <a href="https://zap.stream">zap.stream</a> - live streaming - <a href="https://shopstr.store">shopstr</a> - marketplace - <a href="https://plebeian.market">plebeian.market</a> - marketplace - <a href="https://flotilla.coracle.social">flotilla</a> - communities - <a href="https://satellite.earth">satellite</a> - communities - <a href="https://zapddit.com">zapddit</a> - communities - <a href="https://nostr.kiwi">nostr.kiwi</a> - communities - <a href="https://hivetalk.org">hivetalk</a> - video calls - <a href="https://flare.pub">flare</a> - long-form videos - <a href="https://nostrnests.com">nostrnests</a> - audio spaces - <a href="https://wherostr.social">wherostr</a> - location - <a href="https://go.yondar.me">yondar</a> - location - <a href="https://stacker.news">stacker.news</a> - news - <a href="https://flockstr.com">flockstr</a> - events - <a href="https://nostrocket.org">nostrocket</a> - issue tracker - <a href="https://docstr.app">docstr</a> - docs - <a href="https://satshoot.com">satshoot</a> - freelance - <a href="https://wikifreedia.xyz">wikifreedia</a> - wiki - <a href="https://formstr.app">formstr</a> - forms - <a href="https://chesstr.pages.dev">chesstr</a> - chess - <a href="https://memestr.app">memestr</a> - meme feed - <a href="https://npub.cash">npub.cash</a> - wallet - <a href="https://npub.pro">npub.pro</a> - websites - <a href="https://gitworkshop.dev">gitworkshop</a> - dev tools - <a href="https://onosendai.tech">onosendai</a> - metaverse - <a href="https://degmods.com">degmods</a> - games - <a href="https://turdsoup.com">turdsoup</a> - prompts</p> <p><strong>Mini Clients</strong> - <a href="https://github.com/greenart7c3/Amber">amber</a> - signer - <a href="https://getalby.com">alby</a> - signer - <a href="https://github.com/fiatjaf/nos2x">nos2x</a> - signer - <a href="https://nsec.app">nsec.app</a> - signer - <a href="https://keys.band">keys.band</a> - signer - <a href="https://github.com/Anderson-Juhasc/nostrame">nostrame</a> - signer - <a href="https://nokakoi.com">nokakoi</a> - anon - <a href="https://zap.cooking">zap.cooking</a> - recipes - <a href="https://anonostr.com">anonostr</a> - anon - <a href="https://getwired.app">getwired</a> - anon - <a href="https://lowent.xyz">lowent</a> - anon - <a href="https://creatr.nostr.wine">creatr</a> - exclusive content - <a href="https://lightning.video">lightning.video</a> - exclusive content - <a href="https://zaplinks.lol/slides">zaplinks</a> - slides - <a href="https://listr.lol">listr</a> - lists - <a href="https://zap.store">zap.store</a> - app store - <a href="https://badges.page">badges.page</a> - badges - <a href="https://oddbean.com">oddbean</a> - news - <a href="https://dtan.xyz">dtan</a> - torrents - <a href="https://nosta.me">nosta</a> - user pages - <a href="https://pinstr.app">pinstr</a> - pinterest - <a href="https://pollerama.fun">pollerama</a> - polls - <a href="https://swarmstr.com">swarmstr</a> - trending - <a href="https://nostrapp.link">nostrapp</a> - apps manager - <a href="https://noogle.lol">noogle</a> - search - <a href="https://ostrich.work">ostrich.work</a> - job postings - <a href="https://emojito.meme">emojito</a> - emoji manager - <a href="https://nostree.me">nostree</a> - links - <a href="https://github.com/greenart7c3/citrine">citrine</a> - local relay - <a href="https://joinstr.xyz">joinstr</a> - coinjoins - <a href="https://heya.fund">heya</a> - crowdfunding - <a href="https://zapplepay.com">zapplepay</a> - zaps - <a href="https://nosbin.com">nosbin</a> - clipboard - <a href="https://shipyard.pub">shipyard</a> - scheduler - <a href="https://tunestr.io">tunestr</a> - live streams - <a href="https://filestr.vercel.app">filestr</a> - files - <a href="https://nostrcheck.me/">nostrcheck.me</a> - media hosting - <a href="https://sheetstr.amethyst.social">sheetstr</a> - spreadsheets - <a href="https://crafters.amethyst.social">crafters</a> - curriculum vitae</p> <p><strong>Micro Clients</strong> - <a href="https://w3.do">w3</a> - url shortener - <a href="https://nosdrive.app">nosdrive</a> - backups - <a href="https://zaplife.lol">zaplife</a> - zaps dashboard - <a href="https://zapper.fun">zapper.fun</a> - payments - <a href="https://nostrends.vercel.app">nostrends</a> - trends - <a href="https://zephyr.coracle.social">zephyr</a> - trends - <a href="https://wavman.app">wavman</a> - music player - <a href="https://nostrrr.com">nostrrr</a> - relay info - <a href="https://github.com/jiftechnify/nosdump">nosdump</a> - relay info - <a href="https://notestack.com">notestack</a> - blogs - <a href="https://nostr.build">nostr.build</a> - media hosting - <a href="https://nostr.watch">nostr.watch</a> - relay info - <a href="https://snowcait.github.io/nostr-hours/">nostr hours</a> - use reports - <a href="https://lazereyes.nosfabrica.com">lazereyes</a> - vision prescriptions - <a href="https://satoshipuzzles.github.io/Snakestr">snakestr</a> - games - <a href="https://zaplinks.lol/deletestr">deletestr</a> - deletion requests - <a href="https://zaplinks.lol/2048str">2048str</a> - games - <a href="https://zaplinks.lol/nostrqr">nostrqr</a> - qr generator - <a href="https://zaplinks.lol/notanostrclient">notanostrclient</a> - anon </p> <p>Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more <strong>Mini</strong> and <strong>Micro</strong> clients. </p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqszj9hw9cqn5san9jyhu2lvhp5d8gdtpup0em2c2ermetucsjunwmszyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c6x55rh" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqszj9hw9cqn5san9jyhu2lvhp5d8gdtpup0em2c2ermetucsjunwmszyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c6x55rh" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqszj9hw9cqn5san9jyhu2lvhp5d8gdtpup0em2c2ermetucsjunwmszyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c6x55rh" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqszj9hw9cqn5san9jyhu2lvhp5d8gdtpup0em2c2ermetucsjunwmszyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c6x55rh" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3ad01248:962d8a07 <div class="time" style="margin-left: auto;">2024-10-19 02:11:09</div> </div> <div> <p>The 2024 US presidential election is less than a month out and many states have already sent out early ballots to their citizens. The time to decide is coming ever closer and have no idea who I am going to vote for or if at all. Well let me be clear, the Harris/Walz ticket is a no go for me as they represent more of the same policies of the Biden administration. As someone who takes a holistic view of things, what Biden did while in office wasn't 100 percent all bad. </p> <p><a href="https://www.cnn.com/2024/10/17/politics/biden-student-loan-forgiveness/index.html">I think trying to wipe away the debts for millions of Americans</a> struggling with college debt isn't bad policy because college education isn't what it used to be. I went to college and for some it is beneficial if you are going into a specific line of work such as education or law school. For the vast majority of people who go to these overpriced universities are going there to party and for the "experience". </p> <p>The propaganda of go to college, get a good job and buy a house has been crammed down everyone's throat for so long that it is considered normal to be in debt when you graduate. I see Biden trying to rectify some of this with his attempt to wipe away debt. Again not an endorsement but give credit when its due. </p> <p>I also like that fact that the Biden administration has made American manufacturing and green jobs a priority of his administration with his Inflation Reduction Act passed 2 years ago. It looks like it has benefitted Republicans states to the <a href="https://www.bloomberg.com/graphics/2024-opinion-biden-ira-sends-green-energy-investment-republican-districts/">tune of $161 billion</a>. </p> <p>I do like the fact that he stood by Ukraine and has provided weapons and resources to Ukraine to help it defend itself. I don't know if there is some conspiracy behind why the war was started or Russia geopolitical motivations for starting the war, all I know is innocent victims are being killed by Russian military hardware and that is not ok morally. </p> <p>If America or Americans are going to be known for something, let it be known that we stand by our friends. That's how I live my life and I'm yours as well. We don't abandon friends in need. Imagine if we were in Ukraine's situation, wouldn't we want a friend to come to our aid? </p> <p>Again this isn't a ringing endorsement of the Biden Administration as they have done significant harm to our creditworthiness and national debt crisis. The country is $35 trillion in debt and counting with no credible plan to get this under control. They are going to pass the buck to whoever gets elected in November. This is incredibly reckless and stupid on their part to not even attempt to reign in the debt. </p> <p>I know Trump or Harris will continue the big spending policies that is going to turn us into Argentina someday. This gravy train that we are on right now will not last forever. Mark my words. This is going to blow up in our face in spectacular fashion. Now on to Trump.</p> <h2>Trump Is More Of The Same</h2> <p>My value align more with the Republican party and I am torn between holding my nose and voting for Trump knowing his baggage, voting third party or not voting at all. I judge Trump the same way I do the Biden Administration. Trump did some good things while he was in office such as trying to curb illegal immigration by building a wall. </p> <p>I was very much in favor of that as I think uncontrolled immigration is horrible for the country and creates are false expectation from illegal immigrants that we will provide for them. So I give him kudos for trying but he wasn't ultimately successful because he didn't know how to play the game and keep his mouth shut. </p> <p>Honestly if he stayed off Twitter but his nose to the grindstone he could have got so much more done and gone down as one of the most successful presidents in modern times. He had that kind of potential but now that is all gone.</p> <p>Even if he is elected again in November, he will get hardly any help from Democrats to get anything done. They will be on their war path again of trying to stymie anything and everything he does, even if it is for the good of the American people. Do we really want to go through ANOTHER 4 years of this? I sure as hell don't. </p> <p>Also lets not forget 2020, Jan.6th and the whole COVID fiasco that was. Trump seems incredibly proud of the vaccines that have been known to cause irreparable vaccine injury or the fact that he supported unconstitutional lockdowns or let it passively happen state by state violating our freedoms as American citizens. </p> <p>Jan. 6th is another mark against him. If he knew he lost why the fuck did he push the election was stolen narrative? To soothe his ego? Fuck that shit. Multiple people died because he pushed this narrative that turned out to be false. This really gets under my skin. Case after case was thrown out in court and multi million dollar lawsuits against Tucker Carlson were settled out of court. This alone should disqualify Trump in my eyes. </p> <p>Throw in his support for the <a href="https://www.oxfam.org/en/press-releases/more-women-and-children-killed-gaza-israeli-military-any-other-recent-conflict">genocidal war in Gaza</a>, and this makes it incredibly hard to vote for him.</p> <p>Buuut there are two things that are making me reconsider voting for him. Trump's 180 on Bitcoin and freeing <a href="https://freeross.org/meet-ross/">Ross Ulbricht</a>. I don't know if Trump's change of heart on Bitcoin is genuine or not but it does seem that he is starting to understand how important Bitcoin is and can be for the future of the country. </p> <p>Even if he hasn't had a change of heart personally, as long as he puts people in his administration that will leave Bitcoin alone is a victory in itself. In addition to have a friendly regulatory environment, it has been stated numerous times that a Trump victory will cause the Bitcoin price to go up. Who doesn't want that right?</p> <p>This is the rub, do I vote for a person with his history or do I vote third party or not vote at all? My conscience is leaning towards voting third party or not voting at all. The deal breaker for is providing arms that are used to kill innocent people. This might be a naïve on my part but it really doesn't sit well with me at all. How do you guys feel about this?</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsx0eefytfpfm2f0me8evpzzg95fgq6mlpk73g9e8pgjtpesjm35qqzyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwrkfhmp" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsx0eefytfpfm2f0me8evpzzg95fgq6mlpk73g9e8pgjtpesjm35qqzyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwrkfhmp" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsx0eefytfpfm2f0me8evpzzg95fgq6mlpk73g9e8pgjtpesjm35qqzyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwrkfhmp" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsx0eefytfpfm2f0me8evpzzg95fgq6mlpk73g9e8pgjtpesjm35qqzyqadqyjgcehnc4kgguxuucls2ddrhemg7ws299n3n6pss5vk9k9qwrkfhmp" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 8d34bd24:414be32b <div class="time" style="margin-left: auto;">2024-10-18 21:59:23</div> </div> <div> <p>This was ready and went out on substack on Wednesday, October 16, 2024, but I missed posting on nostsr.</p> <p>Check out:</p> <ul> <li> <p><a href="https://trustjesus.substack.com/p/god-demonstrates-his-power">God Demonstrates His Power: </a>Part 1 (Egypt)</p> </li> <li> <p><a href="https://trustjesus.substack.com/p/god-defends-his-honor">God Defends His Honor</a>: Part 2 (Phillistines)</p> </li> </ul> <p>Many people today talk as if there are many ways to God or that all religions really worship the same god. This is not true. It is a lie from Satan. There is only one true God. There is only one way to God—through repentance and faith in Jesus Christ.</p> <p>Through this event in history, the God of the Bible made Himself known as the one true God, the God who answered with fire in an unfathomable way.</p> <h2>Elijah vs Baal</h2> <p>It isn’t just foreign people that need to know the power of God; it is also God’s own people, Israel.</p> <blockquote> <p>Ahab the son of Omri did evil in the sight of the Lord more than all who were before him. It came about, as though it had been a trivial thing for him to walk in the sins of Jeroboam the son of Nebat, that he married Jezebel the daughter of Ethbaal king of the Sidonians, and <strong>went to serve Baal and worshiped him. So he erected an altar for Baal in the house of Baal which he built in Samaria. Ahab also made the Asherah. Thus Ahab did more to provoke the Lord God of Israel than all the kings of Israel who were before him</strong>. (1 Kings 16:30-33) {emphasis mine}</p> </blockquote> <p>Ahab and his foreign wife, Jezebel, “<em>did more to provoke the Lord God of Israel than all the kings of Israel who were before him</em>.” They worshipped multiple false Gods and persecuted the believers in the one true God. Therefore God used Elijah to make clear who was really God.</p> <blockquote> <p>Now Elijah the Tishbite, who was of the settlers of Gilead, said to Ahab, “As the Lord, the God of Israel lives, before whom I stand, surely there shall be neither dew nor rain these years, except by my word.” (1 Kings 17:1)</p> </blockquote> <p>God’s first action was to stop the rain and cause a severe drought throughout the land. God provided for the needs of His servant and prophet Elijah. First He used Ravens to feed him. Then He used a Sidonian widow to provide for him. God also did a miracle to bring the Sidonian widow’s son back to life, but God had only begun to teach Ahab and the Israelites who the one, true God is.</p> <blockquote> <p>When Ahab saw Elijah, Ahab said to him, “Is this you, you troubler of Israel?” He said, “I have not troubled Israel, but you and your father’s house have, because <strong>you have forsaken the commandments of the Lord and you have followed the Baals. Now then send and gather to me all Israel at Mount Carmel, together with 450 prophets of Baal and 400 prophets of the Asherah</strong>, who eat at Jezebel’s table.” (1 Kings 18:17-19) {emphasis mine}</p> </blockquote> <p>Ahab accused Elijah of being the troubler of Israel when, in fact, it was Ahab who was the troubler because he was the one leading Israel astray. Do we see this today? We constantly see the people, whose sins cause trouble, accusing others of the very sin that they are guilty of committing.</p> <p>God was going to prove who was the real, true God. He was going to pit His single prophet, Elijah, against all 450 of the prophets of Baal.</p> <blockquote> <p>Elijah came near to all the people and said, “How long will you hesitate between two opinions? <strong>If the Lord is God, follow Him; but if Baal, follow him.” But the people did not answer him a word</strong>. (1 Kings 18:21) {emphasis mine}</p> </blockquote> <p>Elijah challenged the people to follow their God (the one, true God), but they stayed silent and wouldn’t stand up for the truth. How often today do we see believers who are afraid to speak up for the truth? They would rather please the people around them than their creator God. Our sinful, human nature never changes.</p> <blockquote> <p>Then Elijah said to the people, “I alone am left a prophet of the Lord, but Baal’s prophets are 450 men. Now let them give us two oxen; and let them choose one ox for themselves and cut it up, and place it on the wood, but put no fire under it; and I will prepare the other ox and lay it on the wood, and I will not put a fire under it. <strong>Then you call on the name of your god, and I will call on the name of the Lord, and the God who answers by fire, He is God</strong>.” And all the people said, “That is a good idea.” (1 Kings 18:21) {emphasis mine}</p> </blockquote> <p>I’m sure everyone, especially the prophets of Baal, were shocked when they were called upon to offer a sacrifice, but they had to rely on their god to provide the fire. They couldn’t light a fire themselves as they had always done. They all had to wait to see which god, if any, was powerful enough to create fire out of nothing, with no help from man.</p> <p>Being dramatic, Elijah and God, had the prophets of Baal go first. These prophets of the false god, Baal, picked their ox and their altar and started chanting.</p> <blockquote> <p>Then they took the ox which was given them and they prepared it and called on the name of Baal from morning until noon saying, “<strong>O Baal, answer us.” But there was no voice and no one answered</strong>. And they leaped about the altar which they made. It came about at noon, that <strong>Elijah mocked them and said, “Call out with a loud voice, for he is a god; either he is occupied or gone aside, or is on a journey, or perhaps he is asleep and needs to be awakened.”</strong> So they cried with a loud voice and cut themselves according to their custom with swords and lances until the blood gushed out on them. When midday was past, they raved until the time of the offering of the evening sacrifice; <strong>but there was no voice, no one answered, and no one paid attention.</strong> (1 Kings 18:26-29) {emphasis mine}</p> </blockquote> <p>This was a pathetic attempt to get a man-made idol to act. The prophets chanted; they cut themselves; they raved, “<em>but there was no voice, no one answered, and no one paid attention</em>.” There was nothing these people could do to make their false god do anything. With blood, sweat, and tears, they failed.</p> <p>I’ll admit I so enjoy Elijah’s mocking, “<em>Call out with a loud voice, for he is a god; either he is occupied or gone aside, or is on a journey, or perhaps he is asleep and needs to be awakened</em>.” A god that needs rest isn’t much of a god and Elijah makes his point clear to the prophets, but even more to the people watching and waiting for a response.</p> <p>By the end of the day, it says “<em>and no one paid attention</em>.” Which god to worship was everything, but back then, just as today, people lose interest quickly and don’t put the time and effort into important things like they should.</p> <blockquote> <p>Then <strong>Elijah said to all the people, “Come near to me</strong>.” So all the people came near to him. And he repaired the altar of the Lord which had been torn down. <strong>Elijah took twelve stones according to the number of the tribes of the sons of Jacob</strong>, to whom the word of the Lord had come, saying, “Israel shall be your name.” So with the stones he built an altar in the name of the Lord, and <strong>he made a trench around the altar</strong>, large enough to hold two measures of seed. Then he arranged the wood and cut the ox in pieces and laid it on the wood. And he said, “<strong>Fill four pitchers with water and pour it on the burnt offering and on the wood.</strong>” And he said, “Do it <strong>a second time</strong>,” and they did it a second time. And he said, “Do it <strong>a third time</strong>,” and they did it a third time. The <strong>water flowed around the altar and he also filled the trench with water</strong>. (1 Kings 18:26-29) {emphasis mine}</p> </blockquote> <p>When Elijah’s turn to call on God came, he was different. He called the people to come and pay attention. He rebuilt the altar of the Lord using 12 uncut stones for the 12 tribes of Israel as had been prescribed by God. Then, in order to make sure nobody could possibly believe anyone, except God, had brought fire, He poured four pitchers of water on the altar three times so the altar, the wood, and the sacrifice were sopping wet. It is unlikely any person could start a fire until this mess dried out, but a person didn’t need to start the fire. The omnipotent, creator God was going to bring fire and nothing could stop Him. When God acts, He acts in a big way.</p> <blockquote> <p>At the time of the offering of the evening sacrifice, Elijah the prophet came near and said, “O Lord, the God of Abraham, Isaac and Israel, <strong>today let it be known that You are God in Israel and that I am Your servant</strong> and I have done all these things at Your word. Answer me, O Lord, answer me, that this people may know that You, O Lord, are God, and that You have turned their heart back again.” Then <strong>the fire of the Lord fell and consumed the burnt offering and the wood and the stones and the dust, and licked up the water that was in the trench.</strong> (1 Kings 18:36-38) {emphasis mine}</p> </blockquote> <p>Elijah prayed that God would let the people know that there is a true God in Israel. Then “<em>the fire of the Lord fell and consumed the burnt offering and the wood and the stones and the dust, and licked up the water that was in the trench</em>.” The prophets of Baal had prayed, cried out, and cut themselves all day long with no hint of a response, but when Elijah gave a simple prayer asking God to reveal Himself fire instantly came down from heaven. It didn’t just light a fire; it didn’t just burn the offering; but the fire consumed the wood, offering, stones, dust, and water. God didn’t leave the option to not believe. He made His power immediately obvious to everyone in attendance.</p> <blockquote> <p>When all the people saw it, they fell on their faces; and they said, “The Lord, He is God; the Lord, He is God.” (1 Kings 18:36-38)</p> </blockquote> <p>The people, who had been silent and not said a word, now fell on their faces and repeated, “<em>The Lord, He is God; the Lord, He is God</em>!” They realized their sinfulness and they realized God’s awesomeness, so they worshipped — real worship. There was no more nonchalance. There was no more waffling between gods. They knew who was God and they fell down in worship.</p> <p>God was merciful to His people and displayed such power that they could do nothing except worship Him. For those who had led them astray, the prophets of Baal, there was no mercy and they were put to death.</p> <p>Shortly after, Elijah prayed, and it rained a torrential rain that watered the parched land.</p> <p>God once again led his chosen people back to Him. Unfortunately, they never stayed faithful. Even when one generation was mostly faithful, within a generation or two, they were back to worshipping false gods.</p> <p>It might make you wonder why an all-knowing God would pick a people who were so consistently unfaithful. I think it was to show His own faithfulness. He was showing the world that His word is true.</p> <blockquote> <p>If we are faithless, He remains faithful, for He cannot deny Himself. (2 Timothy 2:13)</p> </blockquote> <p>Trust Jesus.\ \ your sister in Christ,</p> <p>Christy</p> <p>Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsddps0xeyu8vxvuq9gtxttmvlqjd2skgp43f3xtk7fagl6fscewhczyzxnf0fyxgjqc43hza9rmvv3s79658qn8tk88xmy5fjzt86pf03jkx5ugy2" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsddps0xeyu8vxvuq9gtxttmvlqjd2skgp43f3xtk7fagl6fscewhczyzxnf0fyxgjqc43hza9rmvv3s79658qn8tk88xmy5fjzt86pf03jkx5ugy2" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsddps0xeyu8vxvuq9gtxttmvlqjd2skgp43f3xtk7fagl6fscewhczyzxnf0fyxgjqc43hza9rmvv3s79658qn8tk88xmy5fjzt86pf03jkx5ugy2" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsddps0xeyu8vxvuq9gtxttmvlqjd2skgp43f3xtk7fagl6fscewhczyzxnf0fyxgjqc43hza9rmvv3s79658qn8tk88xmy5fjzt86pf03jkx5ugy2" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 38f9a05c:6999fc04 <div class="time" style="margin-left: auto;">2024-04-07 12:08:30</div> </div> <div> <p><img alt="image" src="https://i.nostr.build/7Ge6g.png" /></p> <p>In today's world, where self-promotion appears to be the standard, there exists a subtle charm in modesty. As a child, I frequently encountered the expression, "Only a donkey praises their tail." its significance has remained with me throughout my life. It serves as a reminder that authentic excellence does not require shouting from the rooftops; instead, it manifests itself in actions, not words.</p> <p>Allow me to now introduce Alfred Adler, a pioneer in the field of psychology. Born in Vienna in 1870, Adler's theories challenged the prevailing views of his time, particularly Sigmund Freud's emphasis on the unconscious mind. Adler proposed individual psychology, focusing on the unique experiences and perceptions that shape each person's worldview. Central to his theories was the concept of the "inferiority complex" and its counterpart, the "superiority complex," shedding light on how individuals grapple with feelings of inadequacy and superiority.</p> <p><strong>Inferiority complex</strong></p> <p>The "inferiority complex" describes persistent feelings of inadequacy and self-doubt, stemming from early experiences. Individuals afflicted with this complex often seek validation and may engage in compensatory behaviors. Therapy and self-reflection are key to addressing and overcoming these feelings, fostering healthier self-esteem and confidence.</p> <p>An example of an inferiority complex might be a person who, from a young age, consistently felt overshadowed by their siblings' achievements and talents. Despite their own unique abilities and successes, they internalize a belief that they are inherently inferior to others. This belief could manifest in various ways throughout their life, such as constantly seeking approval from others, feeling anxious or inadequate in social situations, or striving excessively for success in an attempt to prove their worth.</p> <p><strong>Superiority Complex</strong></p> <p>Conversely, the "superiority complex" manifests as an exaggerated sense of self-importance and entitlement. Individuals with this complex may exhibit arrogance and lack empathy towards others, struggling with meaningful relationships and criticism.</p> <p>An example of a superiority complex could be seen in a person who consistently belittles others and insists on being the center of attention in social settings. They might boast about their achievements, talents, or possessions in an attempt to assert their superiority over those around them.</p> <p>Back to the childhood phrase "Only a donkey brags praises their tail." Returning to the childhood adage "Only a donkey brags praises their tail,” modesty and humility are often misconstrued as weakness or a lack of self-confidence. Nevertheless, it is far from that. It entails possessing a realistic view of oneself and comprehending that one's value should not rely solely on external validation or praise. Instead, it's found in the genuine connections we make with others and the positive impact we have on the world around us.</p> <p>By abstaining from boasting about ourselves, we provide room for others to shine. It is not about denigrating our accomplishments or pretending to be less than we are. On the contrary, it involves acknowledging our abilities without feeling compelled to advertise them to the public continually. Therein lies the elegance of allowing our actions to speak louder than our words.</p> <p>Moreover, humility allows for personal growth and learning. When we're humble, we're open to feedback and constructive criticism. Instead of becoming defensive or dismissive, we approach each opportunity for improvement with an open mind and a willingness to learn. This mindset not only helps us develop professionally but also fosters a sense of humility and gratitude for the knowledge and experiences that others bring to the table.</p> <p>Humility enables personal development and learning. When we're not constantly focused on ourselves, we become more attuned to the needs and experiences of those around us. We listen more intently, offer support more readily, and celebrate the successes of others with genuine enthusiasm. In doing so, we cultivate deeper connections and create a more inclusive and supportive community.</p> <p>In a society that often glorifies self-promotion and individualism, it can be challenging to embrace humility fully. However, it's a quality worth cultivating, both personally and professionally. By focusing on what we can contribute rather than what we can gain, we create a more harmonious and compassionate world. Hence, should you ever find the urge to trumpet your achievements or magnify your ego, pause to reflect on the timeless wisdom encapsulated in the age-old adage: "Only a donkey praises their tail," alongside the profound insights of the Austrian psychiatrist's psychological framework. Instead of trying to prove yourself with words, show who you are through your actions. Embrace humility, which means being modest and not bragging. True greatness isn't about loudly boasting about your good qualities. It's about having inner strength and making a positive impact on the people around you.</p> <blockquote> <p>Lastly as the Great Roman emperor Marcus Aurelius said, "Waste no more time arguing about what a good man should be. Be one."</p> </blockquote> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0qddlkaqe5f0axuxutt57ap2xnfcdkcnlpschnjw7mnc5xegrmpqzyqu0ngzurcvgqsg23x2rymu0y3z74u30nv4kcy7j7zgcmxtfn87qg5nj6s5" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0qddlkaqe5f0axuxutt57ap2xnfcdkcnlpschnjw7mnc5xegrmpqzyqu0ngzurcvgqsg23x2rymu0y3z74u30nv4kcy7j7zgcmxtfn87qg5nj6s5" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0qddlkaqe5f0axuxutt57ap2xnfcdkcnlpschnjw7mnc5xegrmpqzyqu0ngzurcvgqsg23x2rymu0y3z74u30nv4kcy7j7zgcmxtfn87qg5nj6s5" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0qddlkaqe5f0axuxutt57ap2xnfcdkcnlpschnjw7mnc5xegrmpqzyqu0ngzurcvgqsg23x2rymu0y3z74u30nv4kcy7j7zgcmxtfn87qg5nj6s5" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ bcea2b98:7ccef3c9 <div class="time" style="margin-left: auto;">2024-10-18 17:29:00</div> </div> <div> <p><img alt="" src="https://m.stacker.news/58340" /></p> <p>originally posted at https://stacker.news/items/729964</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsgdymz75acue7rwa33dqdt8648ragwkl5ryhse7zml7t4n88rzaygzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfuaxhh" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsgdymz75acue7rwa33dqdt8648ragwkl5ryhse7zml7t4n88rzaygzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfuaxhh" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsgdymz75acue7rwa33dqdt8648ragwkl5ryhse7zml7t4n88rzaygzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfuaxhh" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsgdymz75acue7rwa33dqdt8648ragwkl5ryhse7zml7t4n88rzaygzyz7w52uc2pk36hwjesz9tfqzwq0rgtrk6u85dcu88x4dmemuemeujfuaxhh" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 1bda7e1f:bb97c4d9 <div class="time" style="margin-left: auto;">2024-10-10 03:05:10</div> </div> <div> <h3>Tldr</h3> <ul> <li>Nostr identities can be linked to a third-party service</li> <li>You can set up that verification at your own domain, and</li> <li>You can also set up your own Lightning Address at your own domain</li> <li>These both require files in the .well-known directory on your domain</li> <li>You can set these up together, quickly and for free, with Sveltekit and Vercel</li> <li>Now I am identified and can receive payments with my username "rb" at my own domain "rodbishop.nz"</li> </ul> <h3>Getting .Well-Known</h3> <h5>For your npub</h5> <p>The first step in setting up a Nostr profile is to get your keys. I wrote about it in this article, <a href="nostr:naddr1qvzqqqr4gupzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyesvp3njy">Mining Your Vanity Pubkey</a>. </p> <p>These keys represent your identity and are issued by you, not a third-party issuer. This is good for personal ownership, but creates an issue around identification. </p> <p>If you have an ID issued by an issuer, I can ask the issuer to confirm that you are who you say you are. But with a Nostr npub, which has no issuer, how do I confirm that an npub which claims to be yours, is in fact yours?</p> <p>Nostr allows you to link your npub to a username and to a third-party service of your choice to help in confirming that your npub is really yours (It is <a href="https://github.com/nostr-protocol/nips/blob/master/05.md">documented in NIP-05</a>).</p> <p>Normal users can use a service like nostrplebs.com and to set up a username very quickly and easily. However, it is also possible to set up your own identification that relates your username to your npub using any domain you own. </p> <p>In my view having your username tied to your own domain is better branding, and more self-ownership, and so that's what I'll set up using my domain rodbishop.nz.</p> <h5>For your lightning address</h5> <p>Nostr has integrated payments which allow people to send you Bitcoin over the Lightning network the same way they would send you an email. I wrote about it in <a href="nostr:naddr1qvzqqqr4gupzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmscnxk5d">Setting up Payments on Nostr</a>.</p> <p>The path I took in setting up my lightning address was to use Alby, and with an Alby Account you automatically get a Lightning Address at getalby.com.</p> <p>Normal users can use that Lightning Address just fine. However, it is also possible to set up your own Lightning Address which will forward payments to your Lightning Wallet using any domain you own.</p> <p>Similar to with NIP-05, my view is having your Lightning Address tied to your own domain is better branding, and so again that's what I'll set up.</p> <p>Both of these tasks use the .well-known folder on your web server.</p> <h3>Preparing .Well-Known with Sveltekit</h3> <p>There are many ways to do this. NVK published a very simple method using Github pages which is free and which you can <a href="https://nvk.org/n00b-nip5">read about on his blog</a>.</p> <p>For me, I will set up .well-known using Sveltekit and Vercel. I have been learning Sveltekit and Nostr together, thanks to fantastic tutorials by <a href="https://www.youtube.com/channel/UCwjWOu_QJCjusHKlOo9_52w">Jeff G on his Youtube</a>.</p> <p>Using Sveltekit and Vercel to set up Nostr NIP-05 and Lightning URLs on your own domain is easy and free.</p> <h5>Create a new project</h5> <p>To start, create a new Sveltekit project with NodeJS and Node Package Manager using the code documented on the <a href="https://kit.svelte.dev/">Sveltekit website</a>.</p> <p><code>npm create svelte@latest my-app cd my-app npm install npm run dev -- --open</code></p> <p>Sveltekit contains many convenient short-cuts for web hosting, and one of them is the file structure. The structure contains an <code>/src</code> folder to contain javascript files to build complex applications, and a <code>/static</code> folder to contain other simple static files which need to be hosted at the domain. It is this <code>/static</code> folder you'll be using for now.</p> <h5>NIP-05 identification with nostr.json</h5> <p>For your NIP-05 identification, you need to create the folder and file for /.well-known/nostr.json as follows–</p> <p><code>static └── .well-known └── nostr.json</code></p> <p>In that file, you will use some JSON to link a username to a hex-format public key, which will enable Nostr apps to confirm that the username relates to the key. In my case, I create a link between the username "rb" and the public key formatted in hex format "1bda7e1..."–</p> <p><code>{ "names": { "rb": "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" } }</code></p> <p>That's it!</p> <h5>Lightning Address forwarding with lnurlp</h5> <p>For your Lightning Address, you need to create the folder and file for /.well-known/lnurlp/your-username as follows, replacing the "your-username" text with your username (in my case, "rb") –</p> <p><code>static └── .well-known └── lnurlp └── your-username</code></p> <p>In that file, you create a link between the username on your domain, and the provider of your Lightning service (in my case, Alby). Alby provides a helpful guide on how to do this, which you can <a href="https://guides.getalby.com/user-guide/alby-account-and-browser-extension/alby-account/use-your-lightning-address/own-domain">read on the Alby site</a>.</p> <ul> <li>Visit the Alby page for your Lightning Address which Alby hosts</li> <li>Copy that text across to the new file you have created</li> </ul> <p>That's it! These files are now ready and can be hosted anywhere.</p> <h3>Hosting .well-known with Vercel</h3> <p>I chose Vercel to host with because it was very easy to use, and provides all the hosting I need for free. To deploy, you first create a Github repository for my Sveltekit project, and then you set up Vercel to deploy every push by default.</p> <p>At a high level – </p> <ol> <li>Set up a Github repository</li> <li>Push your project to Github</li> <li>Sign up for Vercel </li> <li>Link your Vercel to your Github, and Vercel will then show all your Git repositories</li> <li>Import your project from Github, and Vercel will deploy it to a Vercel.com domain</li> </ol> <p>Once your project has deployed to Vercel, you will be given a deployment URL, and you can test to see that your static .well-known files are successfully online.</p> <ul> <li>E.g. I was given https://rodbishop-mw64m8ylx-rods-projects-c9b67f57.vercel.app</li> <li>I can add /.well-known/nostr.json or /.well-known/lnurlp/rb to the domain and view my files</li> </ul> <p>Now that the files are deployed, you need to link them to your domain. At a high level –</p> <ol> <li>Get your domain (buy one if you need to)</li> <li>In Vercel, navigate to your project’s settings and add your domain. Vercel will provide DNS records for you to add to your domain registrar</li> <li>In your domain's DNS settings add those records as an A record to your root domain</li> </ol> <p>Your .well-known files are now hosted in Vercel and pointed at your domain. </p> <h5>Setting up CORS in Vercel</h5> <p>You need to tell Vercel to allow third-party applications to access those files, by enabling CORS ("Cross-Origin Resource Sharing"). Vercel has good <a href="https://vercel.com/guides/how-to-enable-cors">CORS documentation on their website</a>. </p> <p>To set this up, return to your project, and in the root folder create a new file named vercel.json. This file will tell Vercel to allow third-party applications to access your nostr.json file. Add the following to it</p> <p><code>{ "headers": [ { "source": "/.well-known/nostr.json", "headers": [ { "key": "Access-Control-Allow-Origin", "value": "*" }, { "key": "Access-Control-Allow-Methods", "value": "GET, OPTIONS" }, { "key": "Access-Control-Allow-Headers", "value": "Content-Type" } ] } ] }</code></p> <p>Then– - Push to Github - Vercel will deploy the push automatically by default</p> <p>That's it. Your .well-known files are able to be reached by every Nostr app.</p> <h5>Testing it with your Nostr profile</h5> <p>Now that this is hosted at your domain, you can connect your Nostr profile. In any Nostr client, visit your profile page and edit, then update your NIP-05 and Lightning Address fields.</p> <p>Once your client has refreshed, give it a test</p> <ul> <li>Your NIP-05 identity should show a "success" type icon, rather than a "fail" type icon (what icons depends on the client you're using, but think "green tick" rather than "red cross")</li> <li>Your Lightning Address should simply work–get someone to send you a payment to your new Address and it should go through successfully and appear in your wallet.</li> </ul> <h3>Things I Did Wrong</h3> <p>Initially, my NIP-05 verification didn't work. I had done two things wrong.</p> <h5>Wrong form of pubkey</h5> <p>The first mistake I made was in the NIP-05 nostr.json file I used the wrong format of public key. The public key that you mostly use in clients is your "npub" which starts with "npub1..." However, the public key this file needs is formatted in hex and starts with "1...".</p> <p>If you don't have your hex formatted pubkey, you can use a site like https://nostrtool.com/ –enter your pubkey in npub format, and it will return it in hex format.</p> <h5>Redirects caused CORS issues</h5> <p>The second mistake was caused by a URL redirect. Your .well known files need to be served at the root of your domain, not at a www prefix (e.g. for me https://rodbishop.nz, not https://www.rodishop.nz). For this to work, you need to ensure that requests to your root domain aren’t redirected to www.</p> <p>In Vercel domain configuration, you can configure your redirects. By default, it will redirect traffic to www, and this is wrong for our purposes. To correct it, visit your domain settings, click "Edit" and look for "Redirect to". The correct setting is "No Redirect".</p> <p>The issue is caused because when applications go looking for your nostr.json, they need to receive a clean "Success" (200) response from your server prior to accessing the file. If you are redirecting to www, then the server gives a "Redirect" (300) response instead.</p> <p>In case you think your CORS is failing, take a look at the server http response code to see if there is a redirect. I used as follows–</p> <p><code>curl -X OPTIONS -i [https://rodbishop.nz/.well-known/nostr.json](https://rodbishop.nz/.well-known/nostr.json) \ -H "Origin: [https://anotherdomain.com](https://anotherdomain.com/)" \ -H "Access-Control-Request-Method: GET"</code></p> <ul> <li>Initially the response was "HTTP/2 308" which means a redirect was in place (and so the process was failing)</li> <li>Once I resolved the redirect issue at Vercel, the response was "HTTP/2 204" which means success, and from that point, Nostr apps recognised the NIP-05 successfully</li> </ul> <h3>What's Next</h3> <p>Over the last three blogs I have - Mined a Nostr pubkey and backed up the mnemonic - Set up Nostr payments with a Lightning wallet plus all the bells and whistles - Set up NIP-05 and Lighting Address at my own domain</p> <p>At this point I am up and running with a great Nostr profile and able to fully engage with the network. </p> <p>But there are still many rabbit holes to explore. The next place I will explore deeply is running my own relay, and if I have some success I will be back to blog about it soon.</p> <p>I'm looking forward to sharing what I learn as I explore what’s possible on Nostr.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqspfq4rgj3h0dyye0hr9tw7v505dph2sp98v6v9z6tc4gy4tf2eukszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjrpr2dy" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqspfq4rgj3h0dyye0hr9tw7v505dph2sp98v6v9z6tc4gy4tf2eukszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjrpr2dy" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqspfq4rgj3h0dyye0hr9tw7v505dph2sp98v6v9z6tc4gy4tf2eukszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjrpr2dy" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqspfq4rgj3h0dyye0hr9tw7v505dph2sp98v6v9z6tc4gy4tf2eukszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjrpr2dy" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ dc734347:5844239d <div class="time" style="margin-left: auto;">2024-10-18 15:59:28</div> </div> <div> <p>M2M SIMs come in every SIM form factor, so it’s easy to find one whose size and features best fit your device design and use case.</p> <p>Mini SIM (2FF) The Mini SIM is the largest removable SIM card currently in use. This SIM has been used since the mid-1990s. Today, the Mini SIM is still a good option for larger connected devices, like cars and vending machines.</p> <p>Micro SIM (3FF) The Micro SIM is significantly smaller than the Mini SIM. It’s large enough to be manageable for easy physical swapping of SIM cards, but it fits better in mid-size IoT devices like tablets and telehealth monitors.</p> <p>Nano SIM (4FF) The Nano SIM is smaller and slimmer than the Mini and Micro SIM. It’s an ideal solution for compact IoT devices. <a href="">https://uktelecomdistribution.co.uk/m2m-sims-html.html</a> is perfect for automotive, GPS trackers, telemetry, alarms, and point-of-sale terminals.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsppdgh0dse9w8sz5nlgg4923kurnn3q50ttkxxac5y6xe3337687szyrw8xs68s6qv5ax0rvcskxwlukrkgdf58ge2cerklft72ezcgs3e6awrmvx" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsppdgh0dse9w8sz5nlgg4923kurnn3q50ttkxxac5y6xe3337687szyrw8xs68s6qv5ax0rvcskxwlukrkgdf58ge2cerklft72ezcgs3e6awrmvx" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsppdgh0dse9w8sz5nlgg4923kurnn3q50ttkxxac5y6xe3337687szyrw8xs68s6qv5ax0rvcskxwlukrkgdf58ge2cerklft72ezcgs3e6awrmvx" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsppdgh0dse9w8sz5nlgg4923kurnn3q50ttkxxac5y6xe3337687szyrw8xs68s6qv5ax0rvcskxwlukrkgdf58ge2cerklft72ezcgs3e6awrmvx" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3c984938:2ec11289 <div class="time" style="margin-left: auto;">2024-04-01 09:36:34</div> </div> <div> <p>A long time ago, a girl resided on a tropical island. The girl's name is Sirena. She resided with her mother in close proximity to the Hagåtña River. Sirena's mother was a bit strict and tried to teach her to follow her in footsteps to be a lady, but Sirena only dreamed of swimming all day.\ <img alt="" src="https://image.nostr.build/ec6c9e6d1e67f67c711cdc1fe37ce57f1a0a273b311ce637ed960d7f8e6416be.jpg" />\ Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.</p> <p><img alt="" src="https://image.nostr.build/3fba90ec2e934f42ded7eb97673597a0f95270bf27135c990c1a643c5dc997a7.jpg" /></p> <p>Sirena's mother was preparing for a special event and needed her to acquire special ingredients from the nearby village. She had a significant amount of preparations to complete, therefore she requested that Sirena procure the necessary ingredients and return promptly. Sirena made a promised to her mother that she would hurry back.\ <img alt="" src="https://image.nostr.build/6e95f7b9bb9fbf22b62e9dc837f018d73b5aebc26bf399d5b96b29455e6f9f15.jpg" /></p> <p>She was on the village path. She kept her eyes on the trail, trying her best to be a good daughter and hurry back. But she took one glance briefly at the river.</p> <p><img alt="" src="https://image.nostr.build/6786326cdeca49b2dc1e8821cb5121144fb58a89993c26e54430310b99718175.jpg" />\ She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\ <img alt="" src="https://image.nostr.build/25e02b990f7716cc7e35ae55169e8864304618c2bce60aab200f77eaf16a6460.jpg" />\ In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.</p> <p><img alt="" src="https://image.nostr.build/607d32453e4fe65a2c13a917a2c9384debfcfc94b34ee8b28a905801003676c7.jpg" /></p> <p>Sirena was happy because now she can be in the water all day long. However, Sirena also wished she did what her mother asked and found another way to punish her. A part of her will forever be saddened by the loss of her Mother and Godmother.</p> <p>It said that sailors have spotted mermaids on their voyage across the sea. Just that their too crafty & swift to be caught.</p> <h1>Historical Notes/context</h1> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/3c9849383bdea883b0bd16fece1ed36d37e37cdde3ce43b17ea4e9192ec11289/files/1711796574428-YAKIHONNES3.png" /> The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother. <img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/3c9849383bdea883b0bd16fece1ed36d37e37cdde3ce43b17ea4e9192ec11289/files/1711801015624-YAKIHONNES3.jpg" /></p> <p>👉I like to point out in this, Thomas Edison patented the light bulb in 1879. So visually the lights outside and inside the huts as flames. As Ai(text to image) does not account for these type of items.</p> <p>👉This also goes back to be careful what you wish for because you may actual get your wish.</p> <p>👉Chamorro people are Pacific Islanders, similar to Hawaiians, and have a brown/tan skin complexion.\ <img alt="" src="https://image.nostr.build/2c31473205adb1a784c25a23688428efcd00f7a93e6aaeb5afa1e8e84f3fde0f.jpg" /></p> <p>👉My mermaid looks strikingly similar to the Disney's recent version of Ariel. I Thought that was interesting because I put just "mermaid" into the text prompt. Its worth pointing out ai limitations as it's not advanced as I originally thought, likely due to its limited data. In this case only disney as a reference for mermaid.</p> <p>based on ordinary prompts\ <img alt="" src="https://image.nostr.build/8a9a31b28bc02fdea6db1b17d3a45084836b23b56192ab002915315f337fa694.jpg" /> <img alt="" src="https://image.nostr.build/9ad05f33f4fe1055662ffb3135ce009c437803ebcc5059ae0d1eacef0b2e988b.jpg" /> Prompt used:\ <img alt="" src="https://image.nostr.build/994db2ec15393223c8f6e98ff88435e6066e9906c3ddf739fc9378600b030a30.jpg" /> That's all-Thank you until next time (N)osyters!</p> <p>If you like it, send me some ❤❤hearts❤ and if you didn't like it-⚡⚡🍑🍑zap⚡⚡🍑🍑 me!🍑🍑 me!</p> <p>For email updates you can subscribe to my <a href="paragraph.xyz/@onigirl">paragraph.xyz/\@onigirl</a> or below if using the Yakihonne App</p> <iframe src="https://paragraph.xyz/@onigirl/embed?minimal=true" width="480" height="45" style="border:1px solid #EEE; background:white;" frameborder="0" scrolling="no"> </iframe> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsdvu38qdxhvfxyfk35d9kuchhu7rys3shxdw2kel0yhrp85c6363qzyq7fsjfc80023qash5t0ans76dkn0cmumh3uusa306jwjxfwcyfgj2cj2s2" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsdvu38qdxhvfxyfk35d9kuchhu7rys3shxdw2kel0yhrp85c6363qzyq7fsjfc80023qash5t0ans76dkn0cmumh3uusa306jwjxfwcyfgj2cj2s2" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsdvu38qdxhvfxyfk35d9kuchhu7rys3shxdw2kel0yhrp85c6363qzyq7fsjfc80023qash5t0ans76dkn0cmumh3uusa306jwjxfwcyfgj2cj2s2" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsdvu38qdxhvfxyfk35d9kuchhu7rys3shxdw2kel0yhrp85c6363qzyq7fsjfc80023qash5t0ans76dkn0cmumh3uusa306jwjxfwcyfgj2cj2s2" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> </ul> </div> </div> <script> // 处理回车键 function handleKeyDown(event) { if (event.key === 'Enter') { handleSearch(); } } // 处理搜索 function handleSearch() { const keyword = document.getElementById('searchInput').value.trim(); if (keyword) { window.location.href = `/search?q=${encodeURIComponent(keyword)}`; } else { alert('请输入搜索关键词!'); } } </script> </body> </html>
















