-
 @ 592295cf:413a0db9
2024-10-13 08:29:48
@ 592295cf:413a0db9
2024-10-13 08:29:48[07/10 week]
Thinking about it, even the protocol is a cathedral, Rabble in the speech in Riga on Bluesky.
He said the protocol is a bazaar. But you have to converge on the scheme in the NIPs or between Apps.
NIPs for example are like Luther's 95 theses, but they change continuously and adapt, but they always remain those 95.
Maybe that Pr on theother curve keys could lead to saying this is "nostr" these others are similar. Creating more points, but I just think it would have led to endless diatribes.
What will be of the protocol and who knows. He can do everything or maybe nothing and from tomorrow we will see and it will be, it will be what it will be. Italian Song
Notifications with nostter are not hidden, they are in your feed and this is good, you always know if someone has searched for you. While in the others you do not know.
I saw a sliver of light pass by it was Unanimity.
It's a very stupid idea, it takes a long time. it's basically a community + channel, where you post the channel in the community and start talking about that topic in the channel. The channel is an approved message. I made musicbook channel, it's the collection of albums released on Friday. The idea of also making a blogger channel, where to put long-form articles.
Following nostr trending on Openvibe social, with a new profile, the Lost One, sad, in this One follow fiatjaf, means I won't bother him anymore . Now I follow 62 profiles, it's an account that I will use to read the notes of the top profiles. Curious if this number will grow enormously or is there a spectre.
The strength of the protocol is the developers if they collaborate together, otherwise it can still work, everyone goes their own way, but it's like saying I want to make my own fence.
One who in his long form doing an analysis of the various social networks. npub19mq9swna4dkhlm3jaux4yhgv5kjj556lkfhv3qnjtyh0kcljph6s88e295 Nostr is all based on Bitcoin. The difficult thing is Bitcoin not Nostr and he says so.
Controversies are useful, or my doubts, but maybe people who can't write code don't understand much, the so-called end users. No one is an end user at this time. The end user doesn't care about the person behind it, only having their own service, if the service is good they also do promotion, they become sponsors. We have seen in recent months sponsoring a Nostr app, result a small attack can damage that app. But the strength of having all these apps is that the other app doesn't have that problem. Spam attack example. The problem is that you can't sponsor an ecosystem, so it becomes difficult to suggest 10 apps to download. The best 10 apps of Nostr and the other 100, there is no easy way out. It's a bit like proposing a new place in NY, then everyone goes to that place and it loses a bit. What the sponsor must understand is that Nostr has only one "one shot".
I saw a video on Nostr of two people posting content on social media, making a review. Not bad, compared to the previous video, that Nostr doesn't even have a token. It doesn't give me a sign up. The main feature they say is a platform or at least they reviewed damus, damus for Bitcoin maxi. And so Nostr is populated by people who Number go up, only fiat thought they would say on Nostr. It's true in part there are those obsessed, even the non-obsessed are obsessed.
How nice it would be to call them NPs Nostr protocol specification, today supertestnet called them that. (the nice thing is that they are pronounced the same way).
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 592295cf:413a0db9
2024-10-05 09:32:22
@ 592295cf:413a0db9
2024-10-05 09:32:22Week 30th September
Wiki article on the topic. [sPhil] (https://sphil.xyz/) Religion politics philosophy history are critical. They are not objective things.
Week of updates for protocol apps, including Gossip, coracle app, nostrmo, nostur and many others.
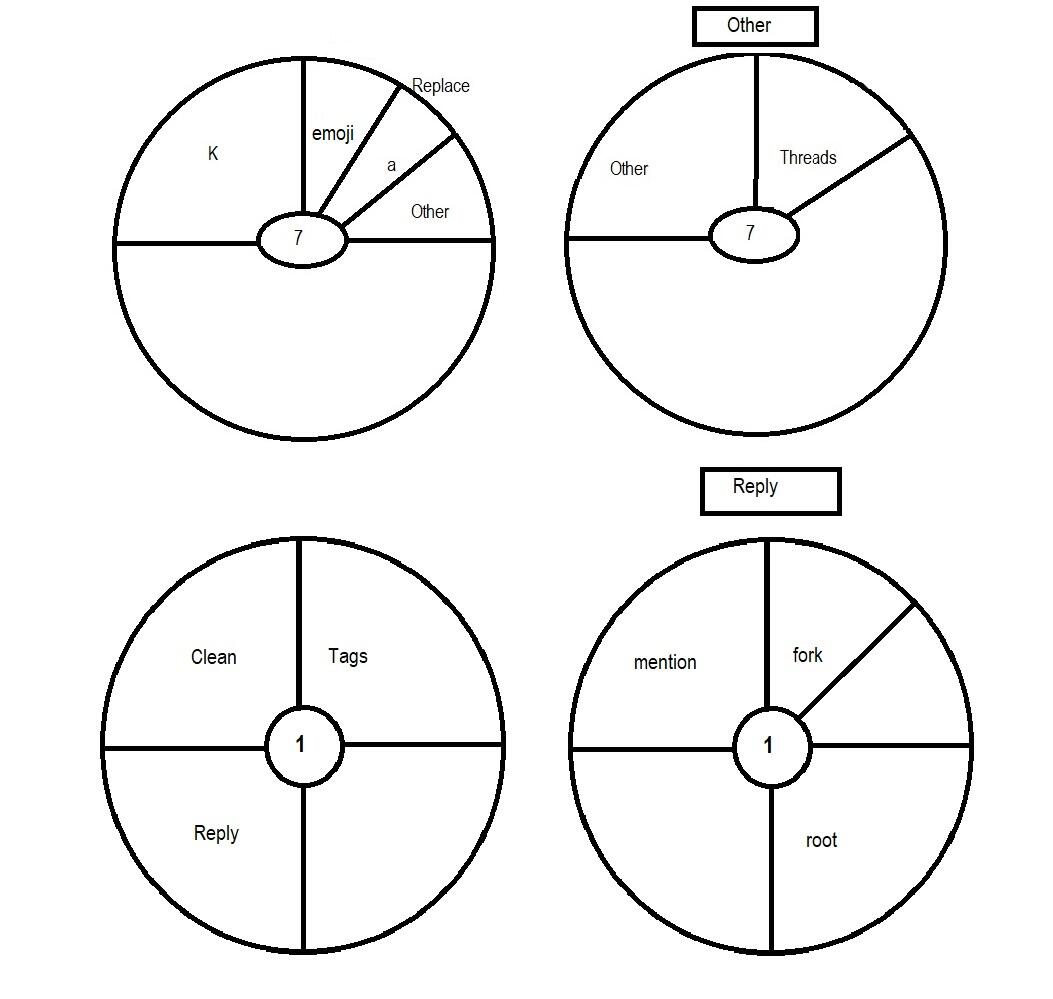
Kind7 Tags: K, emoji,a,others Others threads multi people
Show likes as kind 1 This person liked this post. Or this post has three likes in your timeline. The likes I don't know in your timeline really interest you.
The first book is the bible... Word of Alexandria.
I added cyberspace to the difficult things of the protocol ultra brain things. Low brain, middle brain, top brain, ultra.
Some alphaama codes .AA u login .AA q stuff .AA q run b .AA q run f .AA q close f
high things of alphaama nostr:nevent1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqlqu2vwpwax7dj420e75yws7g7vyua9e245c0x73c056gunxchluey4q99
Comment: nostr:nevent1qqs8pn0zzhgk5l2raqh736rj3ckm48pfl6r7m72rnz2r2p7lzgmx20gzyqduwzspfzelx9k6x0lrez0j8cl8rtz0lxvqylk8z2ustnfy76jpzqcyqqqqqqgpramhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjsjt5rvu
You have to get to the point where you have your community relay. But you have to go down the rabbit hole of relays. General, search, local, inbox outbox, cache. Etc until you get to community relay that is being talked about these days because of NIP 29 "Relay-based Groups". In the end you have to have that table with the various types of relays clearly in your mind. If the user doesn't think about it, who should think about it, who? if I choose the relays?
NIP-100 the world to make community for me. NIP-28 + NIP-72. So you have some structure interoperability with kind1. But the Channel is another kind. You arrange the various channels in the community. No posts need to be approved.
It's useless Protocol users are becoming more reddit users or so. I don't want to deal with these people.
-
 @ 592295cf:413a0db9
2024-09-28 08:19:25
@ 592295cf:413a0db9
2024-09-28 08:19:25Week 23th September
It's not your voice anymore if it's available to everyone.
Nostr is psycho pop.
Nostrasia took place today. It all seemed beautiful. A muffled meeting, a bit in the clouds compared to the air you breathe in social media.
It seems there are two types of Nostr the one who doesn't want to grow and the one who wants to grow. 😅
-
There has always been a misconception that kind1 is the discovery layer, but in reality it is the opposite. If someone publishes a long form article there is less audience, it is true, but then it is easier to find quality content, therefore quality profiles to follow in the kind1 client aka twitter clone. And this can be true for all portable data layers, video streaming, audio, long form, ngit, wiki and whatsoever. So you have finally good follow.
-
The fact that in Nostr you don't see who follows you generally, only in a few clients, I only know one where you see who started following you. It's a strange thing, made to avoid seeing masses of bots that follow you and you can want to block, and you increase that list to the point of absurdity. It's strange because there is a lot of focus on the social graph, if you follow me it's an important aspect.
So in Nostr there are - portable data layers (Twitter style and other social) - non-portable, applications that use disposable npub, where the key is ephemeral.
- 0xchat was becoming a good client, they killed it because it has to focus on chat. I don't use chat, I don't have anyone to chat with, I follow the 0xchat channel and then I read things from Moment. I use it with my second account, because after the nos2x-amber affair with the Odell result, which I had already told you about, I no longer tried to have the first profile even on the mobile. In the end they are all keys that will be burned 😔
Maybe I won't use Nostr anymore in the future just with burn npub, pow and whatsoever. In the end you don't build anything because it's a "stateless" communication.
Lol Moment
On Nostr the poor answer guy is helping the network 🤣🤣
call the police 911: what is your emergency?
a spam bot is attacking "nostr" relays.
you want some government censorship on those relays that contain spam, yes we can do that.
-Previous week- 16 09 Machines Like Me was a good book, maybe now it will become reality.
-
The cool thing about Plebchain radio, it's not the guests, it's these two Nostr users that do a podcast. And they focused on Bitcoin and Nostr and lightning, but maybe it's just the beginning, first you have to focus on a niche and then you expand to the whole world. I think the whole world phase is starting, the podcast topics would become too repetitive. The best part is the 15 10 minute intro. Or in the live show part, there could be some interesting clips.
-
-
idea White button for activity pub user on voyage (app).
-
People hate Nostr. Don't use it
-
UnNip, now we've seen it all
-
Until the morale improves
-
-
People think Sync works like this by magic. Unfortunately it doesn't, I think, at least that's what those who are trying to do say, auto-merge, tinybase, evolu. There is an interesting local-first project. Jaguard a collaborative environment for writing empirical research papers.
-
Now I can search by id. I couldn't do it and I didn't understand the mechanism. Everything has to be instantiated. it works. Now I have to create a function maybe note_list_id and note_id. I continued to edit the NIPs page with asciidoc, categorizing this table is very fun.
New wave of Opensats grants.
- If you haven't heard about WoT this week, you probably live on Mars. There are people who didn't know you could edit on amethyst.
You need to do a podcast of NIPs, features and whatsoever, maybe doing a podcast is not the best solution because it assumes you know something more and something that could change the next day or be no longer valid. maybe you should avoid doing things you don't have full control over, or at least not spread it outside. Maybe because last year at this time I was recording audio.
-
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 42342239:1d80db24
2024-09-26 07:57:04
@ 42342239:1d80db24
2024-09-26 07:57:04The boiling frog is a simple tale that illustrates the danger of gradual change: if you put a frog in boiling water, it will quickly jump out to escape the heat. But if you place a frog in warm water and gradually increase the temperature, it won't notice the change and will eventually cook itself. Might the decline in cash usage be construed as an example of this tale?
As long as individuals can freely transact with each other and conduct purchases and sales without intermediaries[^1] such as with cash, our freedoms and rights remain secure from potential threats posed by the payment system. However, as we have seen in several countries such as Sweden over the past 15 years, the use of cash and the amount of banknotes and coins in circulation have decreased. All to the benefit of various intermediated[^1] electronic alternatives.
The reasons for this trend include: - The costs associated with cash usage has been increasing. - Increased regulatory burdens due to stricter anti-money laundering regulations. - Closed bank branches and fewer ATMs. - The Riksbank's aggressive note switches resulted in a situation where they were no longer recognized.
Market forces or "market forces"?
Some may argue that the "de-cashing" of society is a consequence of market forces. But does this hold true? Leading economists at times recommend interventions with the express purpose to mislead the public, such as proposing measures who are "opaque to most voters."
In a working paper on de-cashing by the International Monetary Fund (IMF) from 2017, such thought processes, even recommendations, can be found. IMF economist Alexei Kireyev, formerly a professor at an institute associated with the Soviet Union's KGB (MGIMO) and economic adviser to Michail Gorbachov 1989-91, wrote that:
- "Social conventions may also be disrupted as de-cashing may be viewed as a violation of fundamental rights, including freedom of contract and freedom of ownership."
- Letting the private sector lead "the de-cashing" is preferable, as it will seem "almost entirely benign". The "tempting attempts to impose de-cashing by a decree should be avoided"
- "A targeted outreach program is needed to alleviate suspicions related to de-cashing"
In the text, he also offered suggestions on the most effective approach to diminish the use of cash:
- The de-cashing process could build on the initial and largely uncontested steps, such as the phasing out of large denomination bills, the placement of ceilings on cash transactions, and the reporting of cash moves across the borders.
- Include creating economic incentives to reduce the use of cash in transactions
- Simplify "the opening and use of transferrable deposits, and further computerizing the financial system."
As is customary in such a context, it is noted that the article only describes research and does not necessarily reflect IMF's views. However, isn't it remarkable that all of these proposals have come to fruition and the process continues? Central banks have phased out banknotes with higher denominations. Banks' regulatory complexity seemingly increase by the day (try to get a bank to handle any larger amounts of cash). The transfer of cash from one nation to another has become increasingly burdensome. The European Union has recently introduced restrictions on cash transactions. Even the law governing the Swedish central bank is written so as to guarantee a further undermining of cash. All while the market share is growing for alternatives such as transferable deposits[^1].
The old European disease
The Czech Republic's former president Václav Havel, who played a key role in advocating for human rights during the communist repression, was once asked what the new member states in the EU could do to pay back for all the economic support they had received from older member states. He replied that the European Union still suffers from the old European disease, namely the tendency to compromise with evil. And that the new members, who have a recent experience of totalitarianism, are obliged to take a more principled stance - sometimes necessary - and to monitor the European Union in this regard, and educate it.
The American computer scientist and cryptographer David Chaum said in 1996 that "[t]he difference between a bad electronic cash system and well-developed digital cash will determine whether we will have a dictatorship or a real democracy". If Václav Havel were alive today, he would likely share Chaum's sentiment. Indeed, on the current path of "de-cashing", we risk abolishing or limiting our liberties and rights, "including freedom of contract and freedom of ownership" - and this according to an economist at the IMF(!).
As the frog was unwittingly boiled alive, our freedoms are quietly being undermined. The temperature is rising. Will people take notice before our liberties are irreparably damaged?
[^1]: Transferable deposits are intermediated. Intermediated means payments involving one or several intermediares, like a bank, a card issuer or a payment processor. In contrast, a disintermediated payment would entail a direct transactions between parties without go-betweens, such as with cash.
-
 @ 09fbf8f3:fa3d60f0
2024-10-14 15:42:04
@ 09fbf8f3:fa3d60f0
2024-10-14 15:42:04我搭建了一个网盘,国内访问速度还可以。
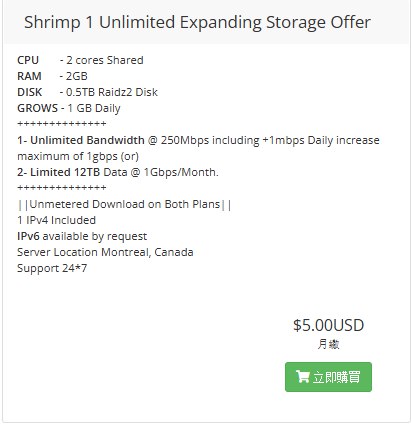
我买的是每月5刀的无限存储计划,只要还在使用,每天会增加1G的存储。(需要通过面板重启后赠送。)
官网
-
不要使用VPN注册,会提示欺诈风险,有可能会砍单。
-
 @ 592295cf:413a0db9
2024-09-14 18:13:41
@ 592295cf:413a0db9
2024-09-14 18:13:4109 09 week
The billboard has reached its first goal.
I don't understand anything, too much.
The web is a dangerous place, maybe the couch at home is for you.
Nostr is like being in a public place like a bar and you listen to the radio, and you can decide which radio to choose, you can also talk on the radio, only those who follow you and those who are connected to that frequency can listen to you.
We talk on multiple frequencies so if one is offline they can hear me on the other.
Spam will always be a constant as are fixed costs, personnel costs, taxes things that people in general hate
A lot of talk that will be blown away by the wind.
Jack Dorsey says Nostr will be a protocol for private encrypted chats
-
Open-sats drama
-
Carnivore dietitian
-
Lightning diatribe
-
This is already Twitter 😉
Fiatjaf explained for the umpteenth time what the outbox model is, now those who look at images instead of reading books must have understood it too. My note, Patricia writes in her relays write, including select some in her outbox 10002 kind. it was a dev page of something, so maybe it won't be online for long
Thinking that with Kamala Harris's victory, the price of Bitcoin would hit a low and holders would be happy to buy. 🤣🤣 Instead with Trump new all time High, holders would be happy. 🤣🤣 Lol Moment.
I read the article about btcmap maps, there were some notes to make but I didn't, it's beyond my level, it was only for builders.
Satlantis, trustroots, and wherostr were not noted.
I had this thought that we will not "succeed" in building the openness of type 1, in the following nips, because of the relays and because discovering new things has a cost, and no one wants to discover new things. And then after that the others should use them, but how and after that at least two others appear who are doing a similar thing, but they don't talk to each other because they don't have time.
If the time horizon is 10 years, those who survive will see.
Keeping calm seems difficult.
I tried nostr-relay-tray works. It works, I would suggest a couple of changes
- Delete some events.
- View events
- Search by npub id or time
- Delete by time.
These are difficult things but they can be done with a database, so they may as well not be done.
I hope that all the controversies are forgotten and overcome and we are more serene.
-
-
 @ cbaa0c82:e9313245
2024-10-01 11:04:45
@ cbaa0c82:e9313245
2024-10-01 11:04:45TheWholeGrain - #September2024
To start the second year of Bread and Toast off strong the September of 2024 includes five Sunday Singles, and the newest piece of cover art for a comic from Toast's Comic Collection includes a touch of color. Some bonus pieces of content were included this September. This includes one of the Political posts we all take so seriously, and a promotional piece for the upcoming npub10hj9rg5gds5x2gk0z0s2jlqnq04jg7g30aj2t5pqzdaaztfactgsnze5ny event coming up in October. The Concept Art released this month is an early design of a possible website logo. This month's Bitcoin Art stars End-Piece who is well informed on what money really is and asks the question, "Do you?"
September Sunday Singles
2024-09-01 | Sunday Single 055 Jump Rope https://i.nostr.build/ESlb23xVmTQLw7sw.png
2024-09-08 | Sunday Single 056 Trampoline https://i.nostr.build/1HNutqYQUjsA1JaG.png
2024-09-15 | Sunday Single 057 Hippity Hop https://i.nostr.build/5dTyLA0FJdK2rNol.png
2024-09-22 | Sunday Single 058 Jumping on the Bed https://i.nostr.build/PWaHDMroMjjfPmWS.png
2024-09-29 | Sunday Single 059 Shades https://i.nostr.build/pWeIZrttOjpcXAtz.png
Other Content Released in September 2024
2024-09-04 | Toast's Comic Collection Teenage Mutant Ninja Bread #5 Four brothers trained in ninjutsu live underneath the city and come up to the surface in order to save it! https://i.nostr.build/WPSB1qn2lMRlbdwJ.png
2024-09-10 | Politics Debate Night The first official debate between the candidates for Selection2024. https://i.nostr.build/wppFU8U3NJCww6U0.png
2024-09-11 | Concept Art Early Website Logo Design This is an early concept for a logo. It was never used. https://i.nostr.build/hxhzvtS4fCe0imNh.png
2024-09-18 | Bitcoin Art On Top of It End-Piece knows what money is. Do you? https://i.nostr.build/6TCWK5d1ynPhrteA.png
2024-09-27 | Nostr Valley Nostr Valley 001 Bread is getting prepared for NostrValley! Hope to see you there! https://i.nostr.build/nQqsPGmJ8hjvxROK.png
September Additions to The Bakery in 2024
2024-09-05 | npub1895dg7n47ldxxq8hyqj9h4xa3xwwxzpnn8lm7hydag4tck6cfj3qcmc4f0 https://m.primal.net/KgDW.jpg
2024-09-26 | npub1hcusg0xp9maamlh9vnv4mf635uwldsfeut00ghzrrjk7kjjh8j3sf9049l https://image.nostr.build/a0a64d709376b3650ebde0f3de5076748d69a999aef9e5fbd882574d5e64cf88.jpg
We hope you enjoyed this first issue of The Whole Grain. The Whole Grain will be released on the first of every month and will cover all of the content released by npub1ew4qeq576v3vz4gukeseknqghx3x4jtlld8ftys9amrca6f3xfzsrm8jpd in the previous month.
Thanks for checking it out, Bread, Toast, and End-Piece
BreadandToast #SundaySingle #ToastsComicCollection #ConceptArt #BitcoinArt #TheBakery #Bread #Toast #EndPiece #Art #Artstr #DigitalArt #Comic #Manga #NostrValley #NostrOnly #🖼️
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ 09fbf8f3:fa3d60f0
2024-10-14 15:41:08
@ 09fbf8f3:fa3d60f0
2024-10-14 15:41:08既然说是一款Web版的软件,也就是对应客户端版而开发的,如果你的歌曲都保存在NAS上,那么这款软件就非常适合你;如果你的歌曲都保存在电脑本地,那么可以直接使用客户端版的同名软件。
01
MusicTagWeb的特色 这款软件刚开始在 Github 上开源的时候,笔者就注意到了,不过当时功能还刚有个雏形、不太完善,就没有推荐给大家。经过开发者一段时间的辛勤付出,现在看来功能和管理能力基本上都已经完成了,具体的功能点和特性如下:
支持批量自动修改音乐标签 支持音乐指纹识别,即使没有元数据也可以识别音乐 支持整理音乐文件,按艺术家,专辑分组 支持文件排序,按照文件名,文件大小,更新时间排序 支持plex专辑类型,新增配置显示/隐藏字段 修复不同类型音频文件的专辑类型 新增歌曲语言整理文件 优化自动打标签匹配算法 新增智能刮削标签源,集成多个平台的标签源,按匹配度排序 支持繁体匹配,新增消息中心展示自动刮削不匹配的数据 支持保存专辑封面文件,支持自定义上传专辑封面 简单适配H5端,支持手机端访问 支持wma,wmv格式, 修复自动刮削报错停止的问题 音轨号,光盘号 格式优化,优化匹配规则 对新增的音乐文件后台自动刮削,无感知刮削。修复.ape文件读取报错的问题 新增自定义层数的整理文件,新增根据刮削状态排序,修复大写的音乐后缀名识别不到 新增数据库挂载映射
其实上面没有提到,这款软件支持从6个音乐平台刮削歌曲信息,安全起见,具体是哪6个平台笔者就不说了,感兴趣的朋友可以接着往下看,自己跑起来就知道了。
02
安装MusicTagWeb MusicTagWeb目前仅支持Docker部署,在你的NAS上,可以使用Docker和Docker Compose两种方式来部署,任选一种即可。
1、Docker方式
docker run -d \ --restart=unless-stopped \ -p 8001:8001 \ -v /path/to/your/music:/app/media \ -v /path/to/your/config:/app/data \ xhongc/music_tag_web:latest2、Docker Compose方式
version: '3' services: music-tag: image: xhongc/music_tag_web:latest container_name: music-tag-web restart: unless-stopped ports: - "8001:8001" volumes: - /path/to/your/music:/app/media:rw - /path/to/your/config:/app/data以上两种方式中,/path/to/your/music改成你的音乐文件夹路径,/path/to/your/config改为MusicTagWeb的配置文件路径。
03
使用MusicTagWeb 使用Docker启动MusicTagWeb后,在浏览器中使用IP+端口号打开系统,然后输入用户名和密码即可登录,默认的用户名和密码均为admin,建议登录后进行修改。
1、登录系统 Username 和 Password 均输入admin,邀请码不需要填。
2、首页主屏
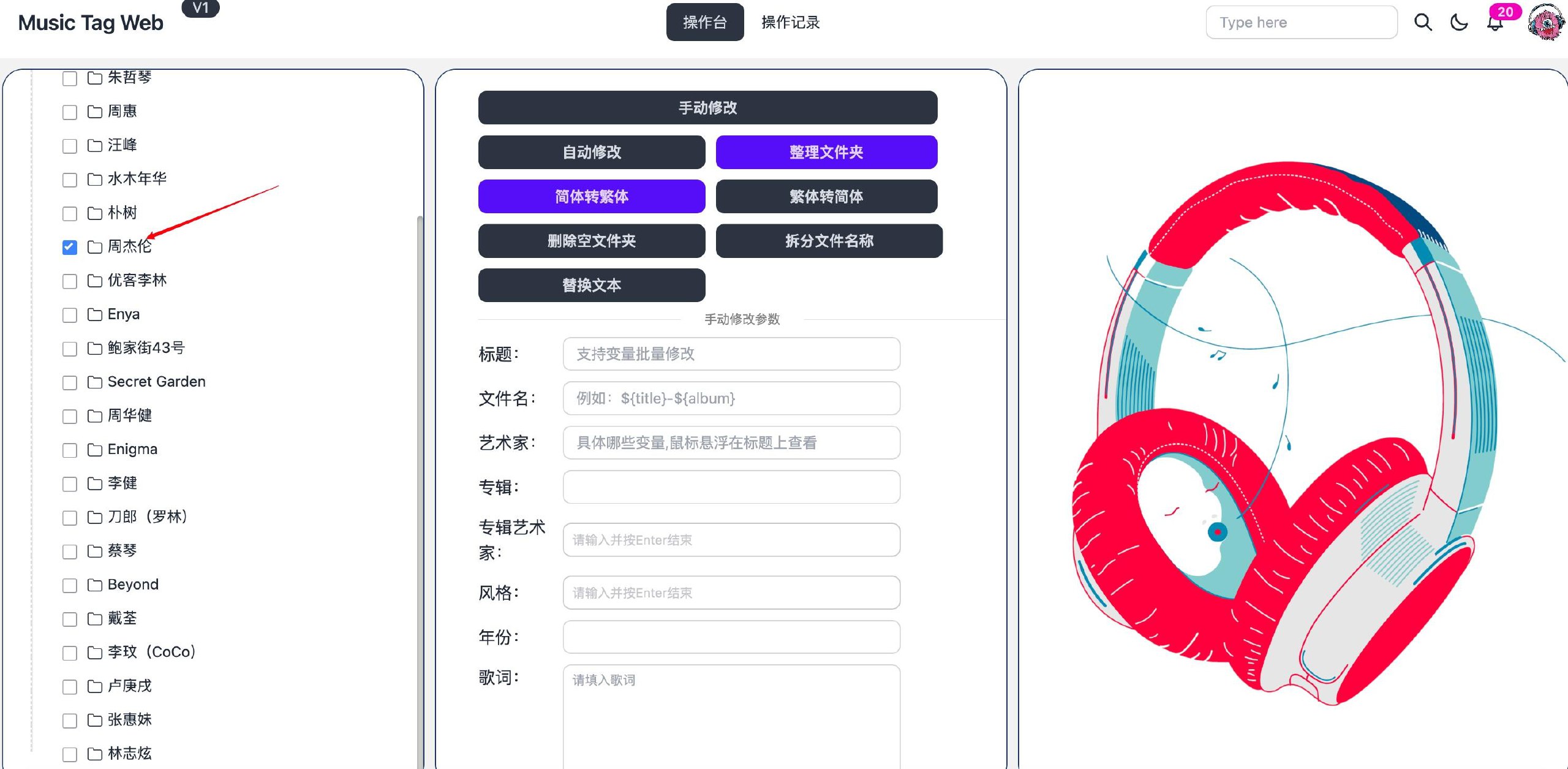
主屏分成两栏(实际是三栏,还有一栏在操作的时候会显示出来),左边是音乐文件目录,右边默认是一张占位图片。
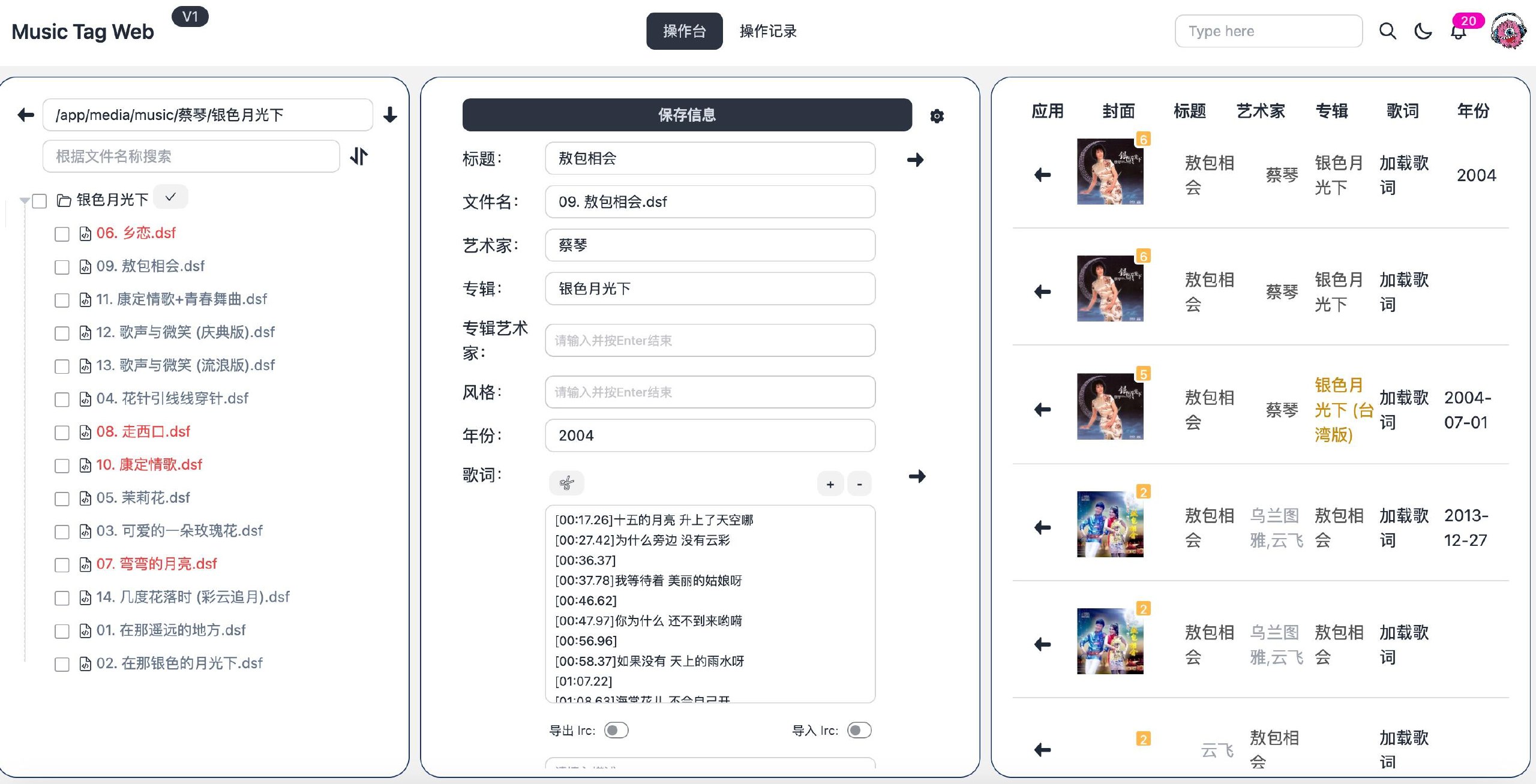
3、单个编辑/刮削歌曲信息
选择一个歌曲文件,这时候界面就是三屏了,右侧一栏变成两栏,分别显示歌曲元数据和音源搜索结果。搜索和设置完成后,点击保存信息按钮,即可完成对歌曲元数据的编辑。
最后
详细教程去官网: https://xiers-organization.gitbook.io/music-tag-web V1版够用了,V2收费的,68一个激活码。
-
 @ 96417ed9:66b02a55
2024-09-29 20:01:36
@ 96417ed9:66b02a55
2024-09-29 20:01:36Image this.
You are scrolling through your favorite social media. It’s probably been 10 minutes Scroll. Like. Repeat. Scroll. Like. Repeat. And so on and on and on.
Does it sound familiar to you? How many times did you find yourself in this situations? Most importantly, how much attention did you pay to the hundreds of posts that you liked? What can you actually remember?
Attention and likes
Recently, I took a communication class. I was very surprised when the teacher told me that the average attention span is around 7 seconds! This means that when you are looking at something or talking to someone, you are actually paying attention for the first 7 seconds. After that, something else has already captured your mind. And it's actually getting worse and worse. Why is that, you might wonder? Yeah, you got it right, social media.
The infinite amount of content that you can consume on social media continuously steals your attention. Thus, when you are looking to a post, your focus is already on the next piece of information, and on the one after and so on indefinetly. Finally, when you decide to leave a like to the first post, you are not actually remembering what you were looking at.
In this context, likes moved from being an appreciation for someone else's work to a simple mechanism that feeds the social media algorithm. From a measure of the value provided by a creator, they became an empty number. Liking a post is no more action, but a mere unconscious reflex. A like is something free, something that you can leave without any conscious effort, to anyone, to anything. Even to something that you actually do not like.
In the last years, likes stopped being a measure of value provided.
And then, zaps came.
Zaps and the value 4 value revolution
Since I am publishing this article on Nostr, I expect most of the reader to know what a zap is. However, for the nebies whom may come across my random thought, here is a brief explaination.
Zaps are a simple way to communicate appreciation. Whenever you like a photo, a thought, a video, you can zap the creator. Exactly as a like, you might say. But here is the deal. When you zap someone, you are actually sending them some amount of money! And not a simple type of money, but the scarcest type of money on earth: Bitcoin! Basically, if a creator provides value to a user the user can award the creator with some monetary value. Nowadays, this concept is quite common and known as value4value (v4v for short).
This is a revolution. Anyone can provide value. Thus, everybody should be able to earn value if something of value is provided , not only some super influencer with sponsors and affiliate programs
Zaps from the user perspective
I started this article by talking about attention, and how there is such a huge competition for it that no one is actually able to focus on something anymore. How does it connect to zaps?
Zaps allow users to regain their lost attention. Since zaps provide real monetary value to a creator, a user has to be 100% on focus on what he is reading or watching: "Is this picture/video/post providing me value?". You do not want to separate from you hard-earned sats for something useless. Unlike likes, zaps are not free. When you zap someone, it means that you have actually paid attention to the post and you are actually acting to signal your appreciation.
Zaps from the creator perspective
I am an amateur photographer. I love going around places and took hundreds of photos at everyhting that catches my curiosity. I posted more than a hundred pictures on Instagram and received even a decent amount of likes. However, I eventually started to wonder if likes came from a genuine appreciation of my work, or only from the aforementioned mechanical reflex.
This does not happen on Nostr. Whenever I am zapped, I instantly know that the appreciation is real. My God, someone really spent some time looking at my photos and decided to give me some real monetary value for that! I really provided value to someone! This is truly exciting.
The realization of this fact has been one of those "ah-ah" moments. Why should I spent my time posting pictures on a social media just to get likes, when someone can send me a chunk of the best money ever created?
And why should you?
-
 @ 42342239:1d80db24
2024-09-02 12:08:29
@ 42342239:1d80db24
2024-09-02 12:08:29The ongoing debate surrounding freedom of expression may revolve more around determining who gets to control the dissemination of information rather than any claimed notion of safeguarding democracy. Similarities can be identified from 500 years ago, following the invention of the printing press.
What has been will be again, what has been done will be done again; there is nothing new under the sun.
-- Ecclesiastes 1:9
The debate over freedom of expression and its limits continues to rage on. In the UK, citizens are being arrested for sharing humouristic images. In Ireland, it may soon become illegal to possess "reckless" memes. Australia is trying to get X to hide information. Venezuela's Maduro blocked X earlier this year, as did a judge on Brazil's Supreme Court. In the US, a citizen has been imprisoned for spreading misleading material following a controversial court ruling. In Germany, the police are searching for a social media user who called a politician overweight. Many are also expressing concerns about deep fakes (AI-generated videos, images, or audio that are designed to deceive).
These questions are not new, however. What we perceive as new questions are often just a reflection of earlier times. After Gutenberg invented the printing press in the 15th century, there were soon hundreds of printing presses across Europe. The Church began using printing presses to mass-produce indulgences. "As soon as the coin in the coffer rings, the soul from purgatory springs" was a phrase used by a traveling monk who sold such indulgences at the time. Martin Luther questioned the reasonableness of this practice. Eventually, he posted the 95 theses on the church door in Wittenberg. He also translated the Bible into German. A short time later, his works, also mass-produced, accounted for a third of all books sold in Germany. Luther refused to recant his provocations as then determined by the Church's central authority. He was excommunicated in 1520 by the Pope and soon declared an outlaw by the Holy Roman Emperor.
This did not stop him. Instead, Luther referred to the Pope as "Pope Fart-Ass" and as the "Ass-God in Rome)". He also commissioned caricatures, such as woodcuts showing a female demon giving birth to the Pope and cardinals, of German peasants responding to a papal edict by showing the Pope their backsides and breaking wind, and more.
Gutenberg's printing presses contributed to the spread of information in a way similar to how the internet does in today's society. The Church's ability to control the flow of information was undermined, much like how newspapers, radio, and TV have partially lost this power today. The Pope excommunicated Luther, which is reminiscent of those who are de-platformed or banned from various platforms today. The Emperor declared Luther an outlaw, which is similar to how the UK's Prime Minister is imprisoning British citizens today. Luther called the Pope derogatory names, which is reminiscent of the individual who recently had the audacity to call an overweight German minister overweight.
Freedom of expression must be curtailed to combat the spread of false or harmful information in order to protect democracy, or so it is claimed. But perhaps it is more about who gets to control the flow of information?
As is often the case, there is nothing new under the sun.
-
 @ 42342239:1d80db24
2024-08-30 06:26:21
@ 42342239:1d80db24
2024-08-30 06:26:21Quis custodiet ipsos custodes?
-- Juvenal (Who will watch the watchmen?)
In mid-July, numerous media outlets reported on the assassination attempt on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various sources that search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.
The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."
A similar phenomenon occurred during the 2016 presidential election. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.
These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. A study published in June 2024 reports that such search results can dramatically affect undecided voters. Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.
A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?
-
 @ 592295cf:413a0db9
2024-08-25 09:17:54
@ 592295cf:413a0db9
2024-08-25 09:17:54A Ux designer has arrived on Nostr. I thought run away while you can. He could get rich, if there was a little economy.
Klout, do you remember that service, which took data from Twitter and made a ~~ WoT~~.
From a note of chip, I understood one thing:
Bitcoin is your "sovereign" currency. Nostr is just third party protocol. If you have a service you can use Nostr to face your customers. "Sovereign" people offer services. They can be bitcoiners or not. So at this stage Nostr is a layer 3 Bitcoin.
So to grow the enveiroment it must be attractive. Let's paraphrase: the protocol is agnostic, the people are fundamentalist Catholics.
So when an atheist person arrives he says ah ok, how do I silence these people and use the protocol If a Protestant Catholic arrives he is laughed at or ignored or at most converted.
I had a disagreement with Dergigi, in the end he won, but he is not right... (True)

Post more notes, zap more, follow 1000 people update FAQ to the nth degree. We are in the desert of the Tartars and the enemy is coming and there are those who say every day we must be ready, sooner or later, it will happen, ah ok. Everything must be perfect. Push harder. This leads to exhaustion.
New Grant from Opensat to Victor of Amethyst, totally deserved, pushed the envelope. If you are a grapheneos user download Amethyst. It's not just Amethyst it's also orbot, citrine, amber, zap store or obtainium or f-droid.
GitCitadel has raised its first fund I wonder if it was just a test on geyser, I wonder if it is the right project to do on nostrocket, but I think Opensat grant for nostrocket makes it irreconcilable. This opens a pandora's box, as always. We are silent as fish.
I tried not to answer some questions even in one case I knew the answer, I apologize, Nostr is much older than me, so it's okay not to answer sometimes. Tomorrow begins nostRiga, The last unconference of Nostr.
(First day) The morning was so-so, in the evening the situation improved a little. In the evening I played a bit with Nostr and it broke The second day good in the morning bad in the evening. I saw little of the backstage maybe only two panels, Will by Damus, and P2Phash on Nostr.
I don't follow anyone anymore, I did a little bit of a unfollow. I saw that two users had 200 followers in common, and I said to myself ah ok what is this thing, I have to understand how they do it there is something that doesn't work, let's try to be a little more distant.
It's weird, too much reliance on following, you have to go and look, not be stationary.
-
 @ 592295cf:413a0db9
2024-08-17 07:36:43
@ 592295cf:413a0db9
2024-08-17 07:36:43Week 12-08 a suitable protocol
The knots come to a head, some of you have gray hair, you get older.
Tkinter is better than ws://, more secure, but has limitations, unless you know how to use figma and do some magic. The project of Nabismo.
Maybe Nostr doesn't work for me.
Aspirin moment Nip-17, works with nip-44 and nip-59. Someone said they made the groups encrypted with nip-17. I tried and succeeded, now you can DM me, don't do it. I had sent the link to a conversation of nip-87 closed groups. There's JeffG doing something with MLS. Then there's keychat.io which uses signal Nostr Bitcoin ecash and that's it... But in dart. It's a bit like the Matrix analogue for Nostr.
Final controversy not all nips are mandatory.
Build the foundation. You can't think about selling the house
Yakihonne has a countdown. What can a desktop app be. Community Lists, Nip-29
A birthday on Nostr, no that's not possible, they're all cypherpunks. 🎉🎉 (Except me)
There is a different attitude from Nostr when updates are released compared to Bluesky, everyone there is still enthusiastic, on Nostr ah ok but this is missing oh but this is missing or but support this other one, or but * zap, wait a minute, keep calm 🙇♂️, I'm the first to do this. (The revolt of the developers)
Deletetion: Client that have relay paired can do delete, more intelligently, Perhaps you can think of a delete.nrelay subdomain as a filter. This id is deleted. Be careful what you don't want to do. Maybe a session with a psychologist is better, because then you find yourself doing what you said you didn't want to do.
Does it make sense to follow someone on Bluesky? In my opinion no, or better yet yes. There are several algorithms on Bluesky, which do their job well. In the end it's just a matter of arranging them better on the screen. Yes you can have lists to save someone, but then you read everything, so lists with algorithm seems like a next feature. this way they can keep the following small, almost minimal, because there are algorithms that work for the user. People will start writing for SEO algorithm and AI and other things, which tech gurus really like and so on. The fact that it is almost exclusively an app will greatly facilitate this trend, there will be almost no need for moderation, and you can get it all in just a few apps. (Great)
Oh yegorpetrov has abandoned. Pegorpetrov said that he is coming back 😌 It might be an invention but I'm a little heartened by it.
Bankify, a new wallet of super testnet, only for crush testers.
You can't stream on zap stream without reach, maybe it's better audio space. Contact someone maybe an influencer or Nostr elite or whatever. Open Source Justice Foundation streaming
Designer, I wanted to propose comment on wikifreedia nielliesmons article and follow #nostrdesign, but too many answers for today. NVK note is ~~mainstream~~
I think I'm not suited to Nostr.
Nostr-ava bike file geo tag sharing. (NIP-113) Sebastix doesn't respond, I must have done something bad to him, or maybe I'm stressing him too much. Finally he replied 🤙. In the end maybe, I have too much hype about this proposal and it's something I don't know maybe, but maybe if they were already doing something with geo tags it's better to say so.
Another birthday, less cypher more punk 😌
Usdt on Nostr, there must be some error. (freeform app)
USDT on tron is like Money. (Bitcoiner not really)
Privacy issue, deletion motion, or deletion request, go go.
Nip29 hype, i don't have hype at all. I'm tired of words, I record a podcast on Nostr. Let's see if I can do it, at least think it. (It's more of a workflow thing than actually something I would do)
- Create an npub (easy)
- Record the audio episode (I think I can do it). Terrible audio
- Loading on a Nostrhosting, if less than 10 MB it should go smoothly.
- Publish the video or audio of the episode on some Nostr client, perhaps using blastr relay 😞.
- Do the nostree link, by putting the episode, and also the npub.pro and put the URL on café-society. 6) Publish all these links on the Main profile, saying that, made a podcast about Nostr in Nostr of nostr. 😂
I thought a client could have poll, form, spreadsheet, collaboration document. It's the kind of otherstuff we want to see. Something that goes beyond a normal feed.
Emoj on bluesky, Eventually also zap 🥜 link emoj Blue
Eventually there will be a developer revolt And they will only do a social network in their downtime, they will call it Nostr.
There is a storm, Nostr does not work in 4g with two bars. Or now 4G is gone too.
Yakihonne Smart widgets, something to try on the weekend.
-
 @ 592295cf:413a0db9
2024-08-10 09:24:14
@ 592295cf:413a0db9
2024-08-10 09:24:14Week on Nostr 05-08
List of site for nostriches https://zaplinks.lol/
Fiatjaf web components
Welcome bear market 🧟♂️ fear, angry, build It's fine meme
I mutated one on stackernews. Basically I have notifications on Nostr page But someone keeps spamming every single thing, from his point of view it's a shared bookmark, but do it on your site. Maybe it's the heat...
On bluesky they eliminated a "for you" feed, now there is Discovery, not your feed, not your choice. There's actually a label that says my feeds, they're yours... Designed for you is more appropriate.
Mutiny lightning, "get the fuck on board". 😔
You lose your Money, ok
I don't know much about programming languages, but it seems like a jungle of scams
The purple pill help the Orange pill go down, maybe it was wrong. For now it's more people passing pills I have the orange give me the purple, I have the purple give me the orange. 😅
If you don't want no corn content you can go to mastodon and bluesky or whatever.
I thought nostr:relay might be a good solution to be a little more like a mint. It was deprecated, then the Nip-73 was added, rss feed and other devilry.
If you don't like what you see, change the app, this one will perhaps clear your following list and you'll start again from scratch. Not all things come to harm.
Why not Building agregore on Nostr, Nostr pear fedimint cashu mesh and local first. It doesn't seem like a simple application to make, from a local-first perspective, I solve a problem, but it's not a small problem to solve, Sync, database management, database schema, authentication, put everything together, instead I need this to solve this problem. It seems strange.
Aspie96 is making a client of ours, there was a lot of talk about how to increase content not related to bitcoin and things like that, there was one who was anti-bitcoin. I thought: Bitcoin is just a tool. Even guns are just a tool. I hate guns, I hate Bitcoin. It will be difficult, if you know any npub that hates Bitcoin comment below, thanks.
Trying not to use nostter for a while. It has glitches when loading threads and even with zap, I zapped myself even though I was clicking on the post I was replying to.
Voyage separates follow to topic in a new version.
People start arguing, it's allowed, everyone wants to be right, that's not the definition of social 👾.
Monitors watch-only bitcoin wallets https://github.com/sommerfelddev/sentrum
I noticed on Openvibe that in the trending timeline Nostr's notes have more interactions than responses. Maybe it was just that today Fiatjaf was doing universal polls 😅.
Step away from your favorite app, for a week if you can. Detox.
Oh Our founding, rain of money https://github.com/theborakompanioni/nostr-spring-boot-starte https://opensats.org/blog/nostr-grants-august-2024#seer
I'm happy for Vic and Sepher Nostroot exists 😅, note from some time ago. (I can't find it)
Perhaps the list of grant applications should be published, no one wants to open Pandora's box. 🙇♂️
Nostrasia 2.0 the Japanese community is a bit at a loss, they are trying to relaunch themselves 🤙, even if I'm seeing less enthusiasm, I'm following less.
I think a month has passed since I said this sentence, every day it was better but the next day something happened that you said maybe 6 months is too long. nostr:nevent1qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7te3xsczue3h0ghxjme0qyw8wumn8ghj7mn0wd68ytnxwfskxarpd35h5ety9ehx2ap0qythwumn8ghj7mn0wd68ytnnw3skkete9ehx2ap0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qpqf25td2xxgxfu80xpgg47cmfg2zkn6v803kefj3htjss5nvamfmgswf2kcs
Ho iniziato a seguire un po' local-first. https://docnode.dev/local-first I follow a podcast of the same name and dev tools.
When everyone thinks of Nostr they think of their favorite app and think that others see the same, but this is not the case.
I delete some gossip (photo)

Gossip is Nostr or Nostr is gossip.
Communities are difficult, they take time. I don't have this type of problem. People are fine on telegram and on simplex or any app. But maybe a Nostr project should be on Nostr?? Nip-29 can be interesting. Even if you start from scratch or almost. It's true that there are more apps, but this will perhaps only add to the confusion.
They are still talking about paid or non-paid relay, it's not a mature stage. Early stage.. I thought designers liked relays, that's not the case, I thought it was a place of experimentation, that's not the case. Bring more people. Last week I was talking about how I was jealous of bluesky who had an agenda for design, now it's also on Nostr, first hypernote article https://wikifreedia.xyz/hypernote-nip
I might say silly things, I'll go.
Hey Will remember to practice safe nsec always
nostr:nevent1qqsr6x8hduv8ta0g2da4aukrhzdtv6qcekyp5f9z9sxq6sd5peegnxgprpmhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygr4wku5l2q32tl99xjgn8feq22279pzwu25eezqxm2su2ken4wzvuf2ydnp
nostr:nevent1qqspsm343talkkjnyf3ah0zwy727cwd7phw3xnz49q59q5cfw4uhyngpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgcwaehxw309aex2mrp0yhxummnwa5x2un99e3k7mgzyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2j7zajz
Use nsec.app, 😅 Share bunker (smart people will know how to do it)
-
 @ 592295cf:413a0db9
2024-08-04 05:55:02
@ 592295cf:413a0db9
2024-08-04 05:55:02Nostter muted by kind
Will mute freefrom, hashtag fall
Venezuela riots, after the vote
I was thinking that having a Nostr conference every 6 months doesn't make sense, maybe it's better to focus on something else. If not it becomes a Tour Life. It doesn't increase adoption Produces tons of material It's good for networking It's not sustainable
Readable updates, how important they are. If it's just bugs and fixes it's better.
I hate Pam. As user It writes interesting stuff, but, doesnn't write in long form, because long form are more difficult, less reach and immediacy, and difficulties to share over in the feed,but not write a poem, sorry.
The thing about coracle is that I load the initial feed, but that gets printed, and it doesn't tell me if there are new notes coming in, as if it interrupts the flow, and it's always a fetch. I want to read the future, not always the past. RealTime feeds Like bluesky 🧞

Njump had problems, it keeps the cache and if the user changes something in their data it doesn't update it immediately. Fiatjaf was angry.
It's the month of NostRiga, we can move on to September without thinking about it. No
It's funny when you see a text in Japanese and inside read Nostr, I want to know what it says. He usually says Nostr is great. And the next note I drank too much 🤣
Today I thought that on the other side of the world it is February and that their February is 31 days. Pam said was sick. I see that hate is a virus 😅🙇♂️
I decided to publish stronpy when it's ready, maybe in 6 months. I've done the lineup, now I have to do the gantt 😅. Maybe I can post the gantt somewhere.
If it's not encrypted it's public. Amethyst draft 31000 and something like event
Nostr Is great but the amount of time Lost to the same thing because you don't know that exist Is remarkable. Nostr is a redundancy protocol
nostr:nevent1qqsqjqauc34k9k278x6cka5jyf3aq033y4pn5czwaff72l3rwum7llq7ela3x When they do that I can't stand them, then maybe it's a little different 😔😔 Zapper.fun ✅ Because you launch a project, example nostr.band but contain others 100 apps 😅 Nostr.band, nostrapp.link, zapper.fun, Nostr login, nsec.app, Npub.pro, Npub.pro also cli, Nostr universe/ knows as spring site
Even in Coracle it would be great to have a check on the note as root, because when you see the answers, perhaps the distance from another post, is so small, so perhaps a gray line for the mark of another note as root.
I listened to several minutes of plebchain radio episode on nostrnests. Language is an obstacle, but also an excellent justification. Last year I started recording a podcast episode, in which I talked about nostr bookmark update. I didn't even want to listen to it again 🤣.
I sent a video of an explanation of a zap it was 500 MByte of video for 4 minutes.
Nostr doesn't work. In practice, many apps have removed the possibility of logging in with the simple key, be it public or private, because especially the private one you don't want to copy paste in every single clients/apps, increasing the attack surface.
However, by removing this functionality and doing little onboarding, the matter is very difficult, but there is a certain belief that people who arrive at a Twitter like client get to know the network a little and then move on to videos or writing, or similar. But one can open a site by chance and see what it offers without knowing anything.
In the future there will only be one client, that of medical data...
Someone share this nostr:nevent1qqs24qzelpk8xjlk4dthr9tfkqwz8n58dlm04ezyvg9nuztud6jjfhc9mg04n I had in my bookmarks. I see dozen types of this self hosted manners. Maybe captains-log is for nostr-type, good.
-
 @ 42342239:1d80db24
2024-07-28 08:35:26
@ 42342239:1d80db24
2024-07-28 08:35:26Jerome Powell, Chairman of the US Federal Reserve, stated during a hearing in March that the central bank has no plans to introduce a central bank digital currency (CBDCs) or consider it necessary at present. He said this even though the material Fed staff presents to Congress suggests otherwise - that CBDCs are described as one of the Fed’s key duties .
A CBDC is a state-controlled and programmable currency that could allow the government or its intermediaries the possibility to monitor all transactions in detail and also to block payments based on certain conditions.
Critics argue that the introduction of CBDCs could undermine citizens’ constitutionally guaranteed freedoms and rights . Republican House Majority Leader Tom Emmer, the sponsor of a bill aimed at preventing the central bank from unilaterally introducing a CBDC, believes that if they do not mimic cash, they would only serve as a “CCP-style [Chinese Communist Party] surveillance tool” and could “undermine the American way of life”. Emmer’s proposed bill has garnered support from several US senators , including Republican Ted Cruz from Texas, who introduced the bill to the Senate. Similarly to how Swedish cash advocates risk missing the mark , Tom Emmer and the US senators risk the same outcome with their bill. If the central bank is prevented from introducing a central bank digital currency, nothing would stop major banks from implementing similar systems themselves, with similar consequences for citizens.
Indeed, the entity controlling your money becomes less significant once it is no longer you. Even if central bank digital currencies are halted in the US, a future administration could easily outsource financial censorship to the private banking system, similar to how the Biden administration is perceived by many to have circumvented the First Amendment by getting private companies to enforce censorship. A federal court in New Orleans ruled last fall against the Biden administration for compelling social media platforms to censor content. The Supreme Court has now begun hearing the case.
Deng Xiaoping, China’s paramount leader who played a vital role in China’s modernization, once said, “It does not matter if the cat is black or white. What matters is that it catches mice.” This statement reflected a pragmatic approach to economic policy, focusing on results foremost. China’s economic growth during his tenure was historic.
The discussion surrounding CBDCs and their negative impact on citizens’ freedoms and rights would benefit from a more practical and comprehensive perspective. Ultimately, it is the outcomes that matter above all. So too for our freedoms.
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b12b632c:d9e1ff79
2024-04-24 20:21:27
@ b12b632c:d9e1ff79
2024-04-24 20:21:27What's Blossom?
Blossom offers a bunch of HTTP endpoints that let Nostr users stash and fetch binary data on public servers using the SHA256 hash as a universal ID.
You can find more -precise- information about Blossom on the Nostr article published today by hzrd149, the developper behind it:
nostr:naddr1qqxkymr0wdek7mfdv3exjan9qgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgrqsqqqa28e4v8zy
You find the Blossom github repo here:
GitHub - hzrd149/blossom: Blobs stored simply on mediaservers https://github.com/hzrd149/blossom
Meet Blobs
Blobs are files with SHA256 hashes as IDs, making them unique and secure. You can compute these IDs from the files themselves using the sha256 hashing algorithm (when you run
sha256sum bitcoin.pdf).Meet Drives
Drives are like organized events on Nostr, mapping blobs to filenames and extra info. It's like setting up a roadmap for your data.
How do Servers Work?
Blossom servers have four endpoints for users to upload and handle blobs:
GET /<sha256>: Get blobs by their SHA256 hash, maybe with a file extension. PUT /upload: Chuck your blobs onto the server, verified with signed Nostr events. GET /list/<pubkey>: Peek at a list of blobs tied to a specific public key for smooth management. DELETE /<sha256>: Trash blobs from the server when needed, keeping things tidy.Yon can find detailed information about the Blossom Server Implementation here..
https://github.com/hzrd149/blossom/blob/master/Server.md
..and the Blossom-server source code is here:
https://github.com/hzrd149/blossom-server
What's Blossom Drive?
Think of Blossom Drive as the "Front-End" (or a public cloud drive) of Blossom servers, letting you upload, manage, share your files/folders blobs.
Source code is available here:
https://github.com/hzrd149/blossom-drive
Developpers
If you want to add Blossom into your Nostr client/app, the blossom-client-sdk explaining how it works (with few examples 🙏) is published here:
https://github.com/hzrd149/blossom-client-sdk
How to self-host Blossom server & Blossom Drive
We'll use docker compose to setup Blossom server & drive. I included Nginx Proxy Manager because it's the Web Proxy I use for all the Fractalized self-hosted services :
Create a new docker-compose file:
~$ nano docker-compose.ymlInsert this content into the file:
``` version: '3.8' services:
blossom-drive: container_name: blossom-drive image: pastagringo/blossom-drive-docker
ports:
- '80:80'
blossom-server: container_name: blossom-server image: 'ghcr.io/hzrd149/blossom-server:master'
ports:
- '3000:3000'
volumes: - './blossom-server/config.yml:/app/config.yml' - 'blossom_data:/app/data'nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' - '81:81' - '443:443' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt - ./nginxproxymanager/_hsts_map.conf:/app/templates/_hsts_map.conf
volumes: blossom_data: ```
You now need to personalize the blossom-server config.yml:
bash ~$ mkdir blossom-server ~$ nano blossom-server/config.ymlInsert this content to the file (CTRL+X & Y to save/exit):
```yaml
Used when listing blobs
publicDomain: https://blossom.fractalized.net
databasePath: data/sqlite.db
discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.net # find files by asking upstream CDNs upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!
storage: # local or s3 backend: local local: dir: ./data # s3: # endpoint: https://s3.endpoint.com # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: # mime type of blob - type: text/ # time since last accessed expiration: 1 month - type: "image/" expiration: 1 week - type: "video/" expiration: 5 days - type: "model/" expiration: 1 week - type: "" expiration: 2 days
upload: # enable / disable uploads enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: false
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
You need to update few values with your own:
- Your own Blossom server public domain :
publicDomain: https://YourBlossomServer.YourDomain.tldand upstream domains where Nostr clients will also verify if the Blossom server own the file blob: :
upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!- The Nostr relays where you want to publish your Blossom events (I added my own Nostr relay):
yaml discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.netEverything is setup! You can now compose your docker-compose file:
~$ docker compose up -dI will let your check this article to know how to configure and use Nginx Proxy Manager.
You can check both Blossom containers logs with this command:
~$ docker compose logs -f blossom-drive blossom-serverRegarding the Nginx Proxy Manager settings for Blossom, here is the configuration I used:
PS: it seems the naming convention for the kind of web service like Blossom is named "CDN" (for: "content delivery network"). It's not impossible in a near future I rename my subdomain blossom.fractalized.net to cdn.blossom.fractalized.net and blossom-drive.fractalized.net to blossom.fractalized.net 😅
Do what you prefer!
After having configured everything, you can now access Blossom server by going to your Blossom server subdomain. You should see a homepage as below:
Same thing for the Blossom Drive, you should see this homepage:
You can now login with your prefered method. In my case, I login on Blossom Drive with my NIP-07 Chrome extension.
You now need to go the "Servers" tab to add some Blossom servers, including the fresh one you just installed.
You can now create your first Blossom Drive by clicking on "+ New" > "Drive" on the top left button:
Fill your desired blossom drive name and select the media servers where you want to host your files and click on "Create":
PS: you can enable "Encrypted" option but as hzrd149 said on his Nostr note about Blossom:
"There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify"
You are now able to upload some files (a picture for instance):
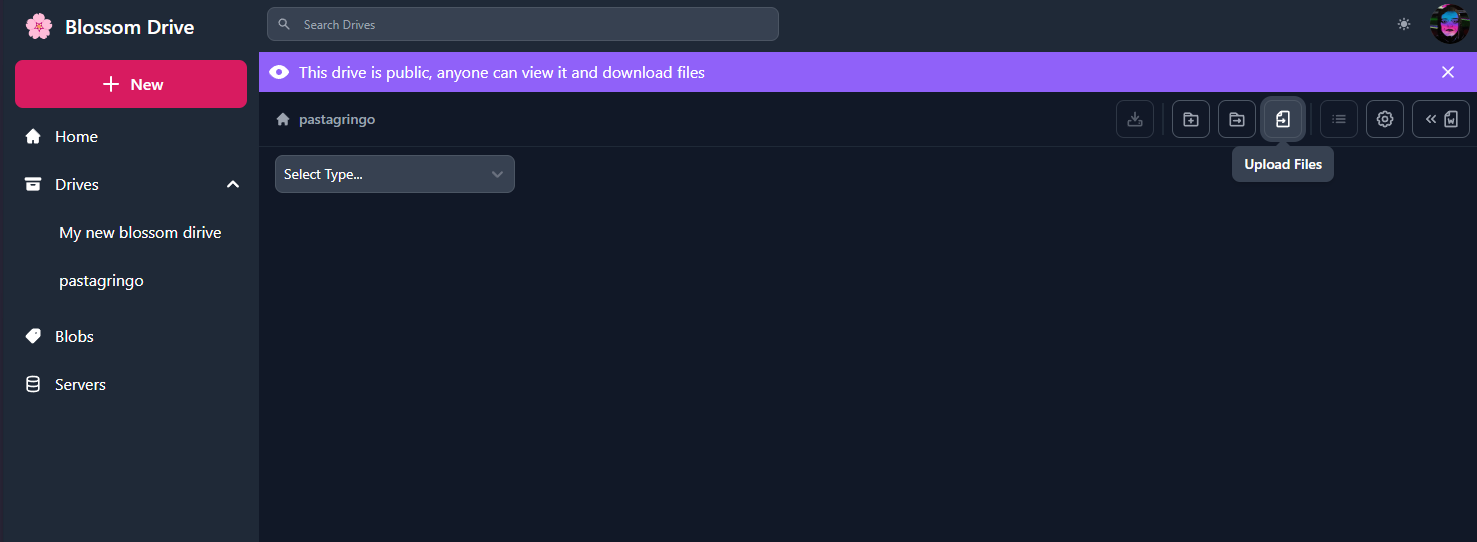
And obtain the HTTP direct link by clicking on the "Copy Link" button:
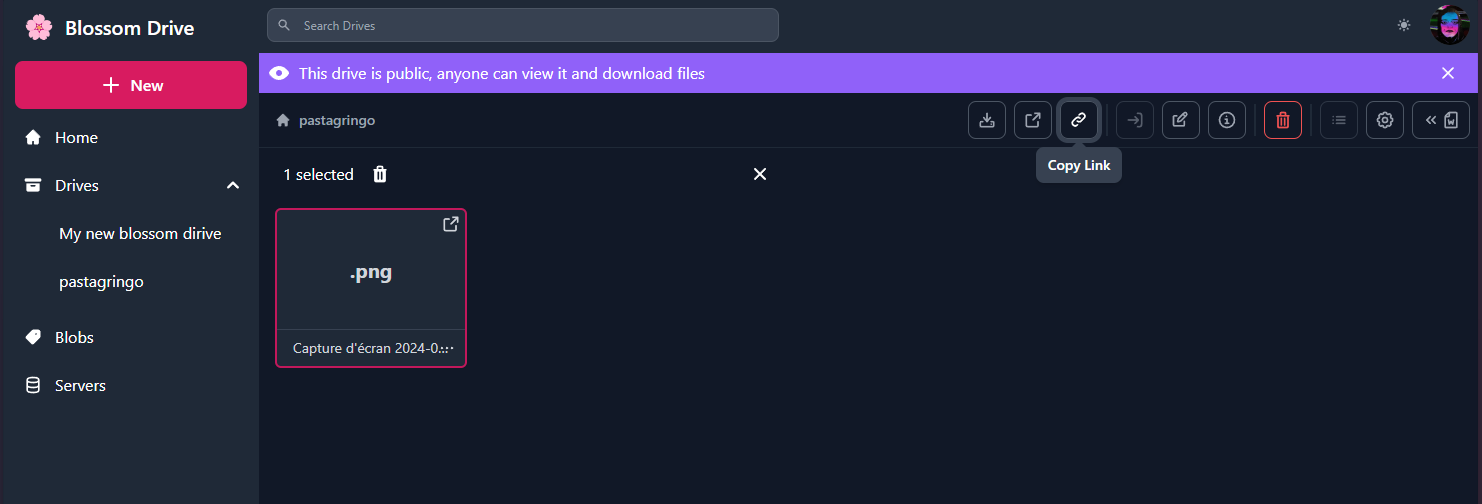
If you check URL image below, you'll see that it is served by Blossom:

It's done ! ✅
You can now upload your files to Blossom accross several Blossom servers to let them survive the future internet apocalypse.
Blossom has just been released few days ago, many news and features will come!
Don't hesisate to follow hzrd149 on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ bbb5dda0:f09e2747
2024-09-27 19:45:31
@ bbb5dda0:f09e2747
2024-09-27 19:45:31Moving into Norway the nice, almost-alpine landscapes greeted me. Slowly however the mountains numbed down and fjords started appearing. I was nearing Trondheim, the most northern city in Norway that has something that resembles a high-way. Anything further north and you’re bound to 80km/h roads. Which isn’t a bad thing at all, given the views.
| | | | | --- | --- | --- | |
 |
| |
| |
|| | | --- | |
 |
| On the road to Trondheim |
|
| On the road to Trondheim |I went pretty much straight to Trondheim because I got in touch with Lucas through an ex-colleague of mine (Thanks Niek ;)). I texted Lucas about a week before we met to see if he’d be up to go hiking somewhere in the Trondheim area. He said he was thinking about going North, waaaay North, in order to see the midnight sun and he wanted to do this the next weekend. This was around June 21st, the longest day of the year. I said it’d be cool to experience that and so that is just what we did. For those of you who don’t know, on June 21st the sun is right at the ‘Tropic of Cancer’ (‘Kreeftskeerkring’ in Dutch), the most northern position of the sun after which the summer slowly turns into winter again. In the period around this moment, the sun will NOT go below the horizon at all when you are above the arctic circle.
| | | | | --- | --- | --- | |
 |
| |
| |
|I’m glad Lucas has an electric car, because the round-trip would’ve cost me (whith my thirsty van) €333,-. Instead we spent less than €60,- for this 1200km round-trip. What a difference! So we left for the 9 hr drive on Friday-evening and camped out besides a lake next to the E6 highway, which runs all the way from the south to the north, which is over 3000(!) kilometers long.
| | | | | --- | --- | --- | |
 We found this seemingly abandoned bus, what a beauty! |
We found this seemingly abandoned bus, what a beauty! | |
| Woke up to this view! |
|
Woke up to this view! |
| |
| Time for a charging break in Mosjøen |
Time for a charging break in Mosjøen | |
| Because of a tunnel-closure we had to take this mountain-pass, not complaining here…
Because of a tunnel-closure we had to take this mountain-pass, not complaining here…We moved on the next morning and had perfect weather, too perfect for Norway because it was just below 30 degrees Celsius. This hot weather reached well into the arctic circle, where we’d be hiking up a mountain to find a camp-spot with a view to the north. We parked the car and started to hike up the steep hill, we found a route online, but soon found out we missed the path shown on the map. We figured we would not backtrack but instead walk around the same height on the mountain to get back at that path. Long story short, that path didn’t exist (anymore). So we tried to get back at it but just couldn’t find it. Eventually we just followed the trail that was actually set out using red ‘T’-s that were painted on the rocks every 50-100 meters. It was quite a walk and the heat didn’t make it any easier.
 A beginner mountaineer realizing he climbed the wrong mountain
A beginner mountaineer realizing he climbed the wrong mountain| | | | | --- | --- | --- | |
 After a near-death experience with mosquito’s, the Deet really saved us |
After a near-death experience with mosquito’s, the Deet really saved us | |
| |
|
|
| |
| |
| Finally we reached our intended camp-spot |
Finally we reached our intended camp-spot |
After draining most of our energy we finally arrived at the place we wanted to camp for the night day, which was in front of a small lake and a bigger one which lied a bit lower. I don’t think I need to say much more about the beauty of the place when you can just look at the pictures below:

 | | |
| --- | --- |
|
| | |
| --- | --- |
| |
|  |
|The ‘next’ day we hiked back, and tried to return using the ‘official’ path we wanted to hike in the first place, all in vain. It led us to hike some strange, steep and almost treacherous paths after which we decided it would be wise to just backtrack a little bit and get back to the (red) marked trail. We got back to the car safely after which we drove to the river that was just below the car park to take a refreshing dive before heading back south. We found a (safe) spot to take the dive in the river that was now raging because of the heavy snow-melt due to the extremely high temperatures. Lucas later told me that in some regions electricity was even free due to the surplus of hydro-electricity.
| | | | --- | --- | |
 We had to walk over this |
We had to walk over this |  |
|We made a car-recharge stop at Mosjøen where we had a quick pizza-dinner. Just after leaving the parking-lot we saw a couple hitch-hikers who wanted to go to Trondheim just like us. We pulled over and took them with us, they were a couple from different south-eastern European countries and were touring around Europe and soon also the world. They shared some cool stories and told about their plans. When we got to Trondheim we dropped them off near their camping-spot and drove back to Lucas’s house. Quite tired I jumped back in my own bed in my own home. How nice is it to have your house with you (almost) everywhere… 🙂
I camped in front of his house for a couple days. To be honest I didn’t do much those days as I was pretty much drained from experiencing all kinds of different things back-to-back for over a month now. I used this time to work a bit on the official stuff for my own freelance IT company which I started, I finally got a bank-account approved after 3 weeks of waiting, which allowed me to manage some of the essential setup-things and book-keeping. After these formalities I took a bit of time to head into the city-center, of course using my folding bike like a real Dutchie. And since Trondheim is a hilly city, biking downhill from Lucas’s house was a blast but going back up was quite the struggle with these tiny wheels, but it all worked out… That same night a thunderstorm was rolling in and sitting on top of a hill in a campervan, with lightning striking the ground at less than 100 meters away from the van was a new thing for me. I guess this too is part of the ‘living closer to nature’ thing…
I’m very thankful for the experiences and the hospitality of the people I meet along the way. It was very much fun to make this trip together! It’s the people that make the journey…
| | | | | --- | --- | --- | |
 |
| |
| |
|| | | | --- | --- | |
 |
| |
| -
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
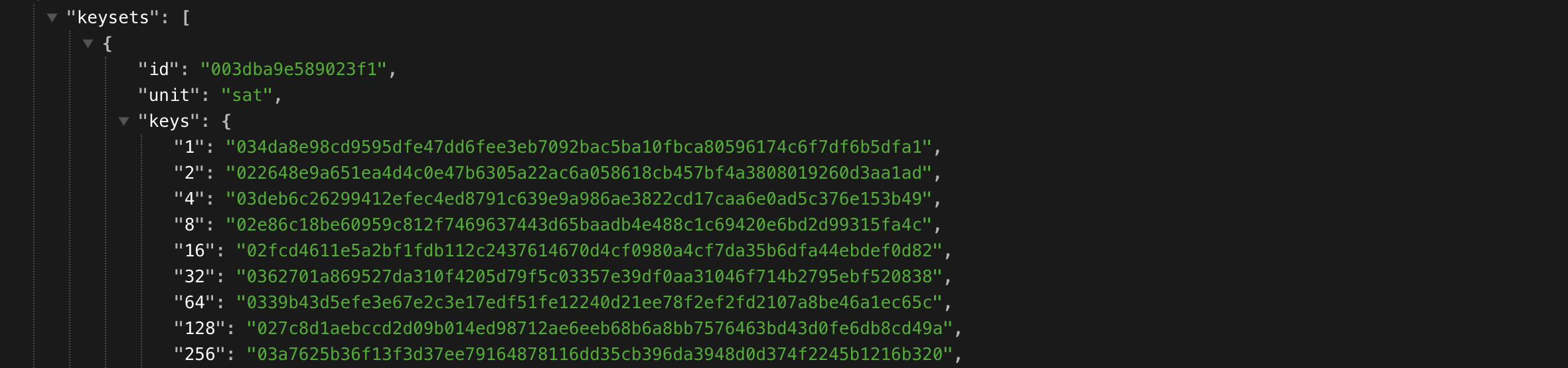
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
For instace, if we use wallet.cashu.me:
You can go into the "Settings" tab and add your mint :
If everything went find, you shoud see this :
You can now mint some ecash from your mint creating a sats invoice :
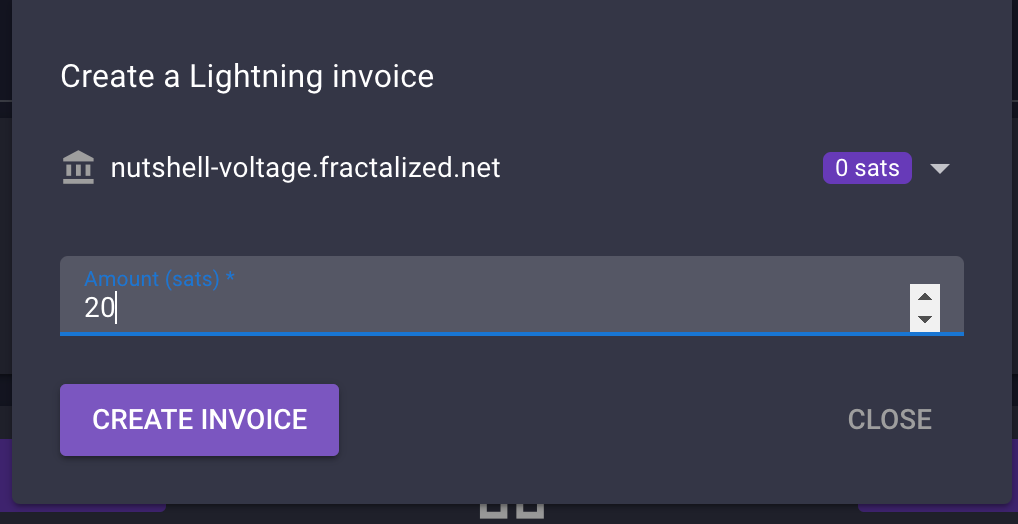
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
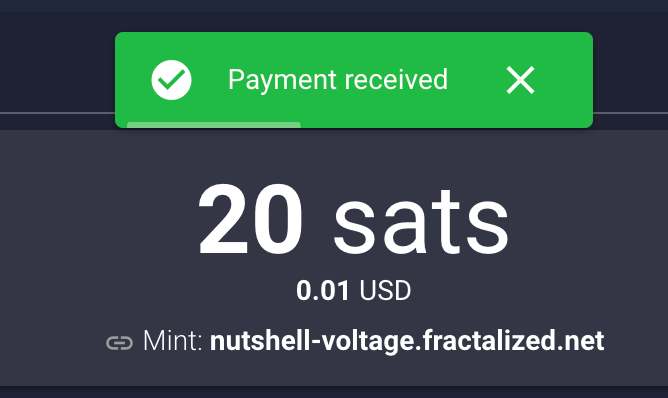
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
Add your mint again :
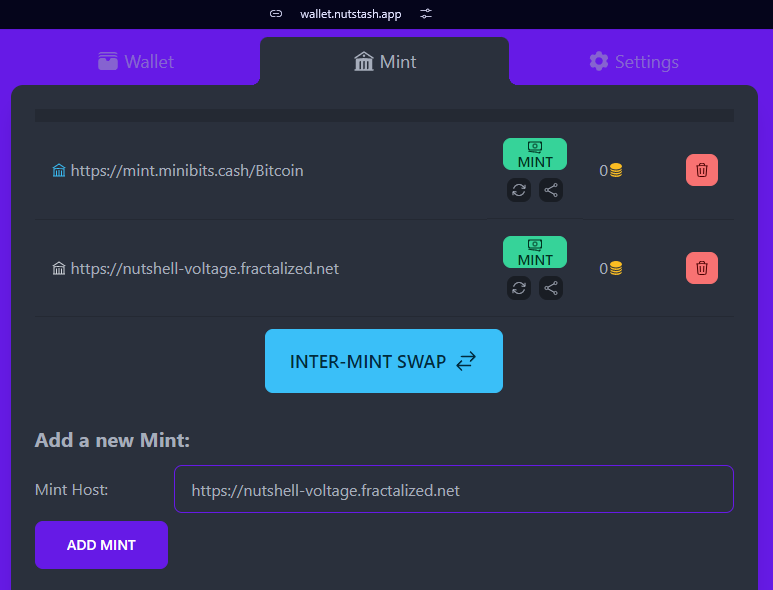
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
Click on "RECEIVE" again:
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
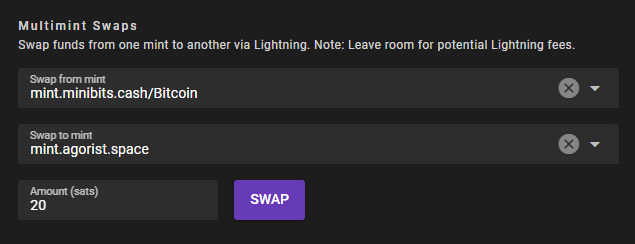
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
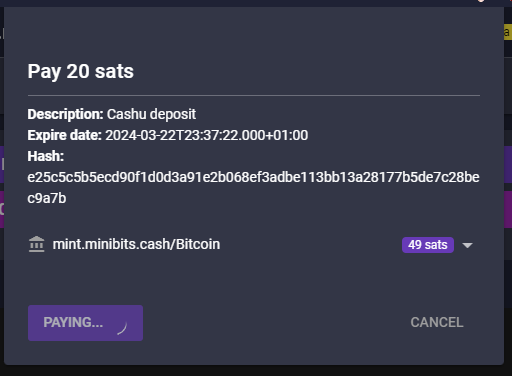
If everything is OK with the mints, the swap will be successful and the ecash received.
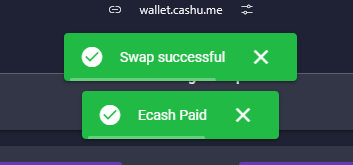
You can now see that the previous sats has been transfered (minus 2 fee sats).
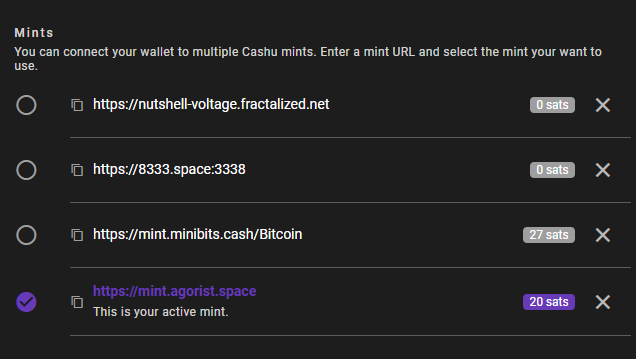
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ 6bae33c8:607272e8
2024-10-14 09:03:40
@ 6bae33c8:607272e8
2024-10-14 09:03:40This will be an odd column because I missed most of the first wave of games due to Sasha’s basketball game which for God knows what reason they scheduled for Sunday at 6:30 pm (Lisbon time).
The first half was brutal, they were down 38-13, but their troglodyte of a coach shifted to a zone defense in the second half, and they made it respectable, losing 58-39. Why it took him two and a half games to do the obvious, I have no idea. They have only six players — the other teams have 12 — and you can’t chase your “man” around the perimeter all game if you don’t get a rest.
Moreover, I told Sasha, don’t guard your under-16-year-old girl “man” outside the three-point line. If she wants to shoot a long three, let her. But she said her coach says to pick them up over half court like they’re Steph Curry, and they even were full-court pressing at times! You don’t full court press with six players, you need to conserve energy. And you should see this guy, in his late-fifties. stick-skinny legs and a massive gut, totally bald, but thick hair on the sides and back of his head. Total freakazoid.
I guess he deserves credit for teaching them the zone and making the adjustment at half, but Sasha said he would revert to man “if the other team had good three-point shooters.” Retard, the team they played hit a few threes, but you live with it! Let them shoot the three, conserve energy, instead of the layups they were giving up all first half.
In any event, Sasha had eight points, probably 14 boards and was a beast on defense. More Angel Reese than Caitlin Clark, unfortunately. But she’s only 12 and a half, and the league is under-16.
In any event, I did see the late games and had all my teams lose except one, the Primetime going down because it had Marvin Harrison, Jordan Mason and Dallas Goedert all get hurt in the first half. It still put up 142 points and lost by a half a point due to Chase Brown’s late TD and then Wan’Dale Robinson’s catch on the final drive. Mercifully, I wasn’t aware of this until after it happened.
I did go 4-1 ATS finally, but I’m drawing dead in the overall Circa Millions and even Q2 after going 2-3 last week. At least I’m in first place in a double-week (last week was tied) for my home picking pool, pending the Monday night game.
-
My one loss ATS was with the Jaguars. Trevor Lawrence is terrible. The Jets really dodged a bullet by winning that Week 17 game and drafting QB1 (Zach Wilson) who they could ditch two years later. (I hear divorced wine moms in the Denver area are more satisfied and posting less often about politics on Facebook.)
-
Evan Engram really ruins it for the other Jaguars receivers — Lawrence only has eyes for him.
-
The Bears might be good. Caleb Williams spread the ball around and moved well in and out of the pocket. D’Andre Soft, who I mocked this offseason, would go in the second round if we re-drafted today. Starting to regret dropping Cole Kmet and most of my FAAB in the Steak League for Isaiah Likely.
-
I didn’t watch Packers-Cardinals, but there’s something wrong with Kyler Murray. He’s got all the weapons in the world (I know Harrison left early), and can’t make it work.
-
I like seeing the Packers spread it around since I own none of them and was mad at myself for missing out on Jayden Reed.
-
I invested in Alec Pierce this week with Michael Pittman set to go on IR and Josh Downs also iffy. Pierce was wide open on a deep shot again, though Joe Flacco missed him, but it looks like that was a waste of money. I wonder when we see Anthony Richardson again.
-
I don’t see the point of the Titans. Why do they exist? I’m just glad I have none of their players, especially Calvin Ridley.
-
I started Tank Dell over JSN this week, and that was good, but had I known I would have benched Marvin Harrison and moved JK Dobbins into the flex. Actually I would have used Dobbins over Mason and left JSN in the flex. But it’s hard to know half your team will get injured.
-
Stefon Diggs gets it done every game, but he’s yet to have a huge one. I’m happy to have him everywhere, especially with Nico Collins out, but the Texans are a slow-paced, run-heavy offense. Of course, the Patriots with their star corner Christian Gonzalez and terrible offense are not the team you get big points against in the passing game.
-
I didn’t see Drake Maye’s first start, but it looks from the box score like it was okay.
-
Baker Mayfield keeps putting up huge numbers, and the reason my injured Primetime team still did okay was Chris Godwin (WR1) who was a “hold-my-nose” Round 5 pick.
-
I had Bucky Irving in the league I won, but Sean Tucker looked better.
-
I had Chris Olave going in the Steak League. What’s annoying is another team needed to trade a RB for a WR this week, I offered him Olave for James Cook, he countered with David Montgomery, which I would have taken, but I have emails turned off for that league, so I didn’t see it until later that day. By the time I saw it (and went to accept), he had traded Montgomery to someone else. With Brian Robinson out, I started Jerome Ford and Jaylen Warren. And of course Olave got concussed.
-
I didn’t see this game, but I’m assuming Spencer was Rattled.
-
Sounds like I’m glad I missed Eagles-Browns too. The Browns are like the Titans — totally pointless aside for the Deshaun Watson massage jokes.
-
I excoriated Alan Seslowsky for advising me before the 2023 season to take Zay Flowers over De’Von Achane in my Dynasty League, but now I’m glad I have Flowers.
-
Mark Andrews would probably now get drafted in the same place he did pre-season going forward.
-
Derrick Henry is doing exactly what those who had drafted him hoped he would — lead the NFL in rushing and TDs by a wide margin now that he’s on a good team.
-
When Gus Edwards hit IR, I picked up Kimani Vidal in a couple places. JK Dobbins held up for 25 carries and two catches, but Vidal’s role should expand.
-
The Broncos offense just seems like a perpetual emergency two-minute scramble drill, totally haphazard, no rhythm.
-
I had Justin Fields going in a couple places, and his production was a minor miracle. He has no touch, throws only fastballs, even on short passes. But he’s a great scrambler, and they like to call his number around the goal line.
-
Najee Harris bulldozed the Raiders all day. We’re seeing more of those players thrive this year — Henry, Harris, Tyler Allgeier and David Montgomery, off the top of my head. Maybe as teams take away big plays and lighten boxes, the big bruising backs will have a renaissance of sorts.
-
The Raiders are bad.
-
The Lions toyed with the Cowboys in Dallas. The Aiden Hutchinson injury was brutal though, not only for him but for their Super Bowl aspirations.
-
The Cowboys are a bit like the Bengals — they let other teams take away their best player on offense so easily. It doesn’t help that they can’t run to save their lives. (CeeDee Lamb eventually got 14 targets, but they don’t know how to scheme him open.)
-
We had the Falcons in Survivor — easy peasy. I love that Younghoe Koo, after a slow start, got a garbage-time FG at the end. He’s been so reliable this year.
-
Bijan Robinson and Allgeier are like Jahmyr Gibbs and Montgomery — a 50/50 timeshare that favors the pass-catcher, but not commensurate with the gap in their respsective ADPs.
-
The Giants easily could have beaten the Bengals but they missed two FGs and got fooled on the long Burrow TD. Not that playing roughly even with the Bengals at home is something about which to write home. Burrow looks healthy at least after that run.
-
As I mentioned, it’s amazing the Bengals would only get Ja’Marr Chase six targets. And it’s not like their offense was otherwise working as they scored only 17 points.
-
Daniel Jones was okay, but there’s no real spark. He’ll make a solid backup somewhere next year.
-
Tyrone Tracy mostly got stuffed, as the Bengals defense played well against the run. He got a massive workload (17 carries, six targets) though.
-
The Giants defense is for real, even without Kayvon Thibodeaux — they had another four sacks.
-
They still show way too many replays on the 40-minute edited version. I don’t give a fuck about how the defensive lineman got into the backfield for a one-yard stuff! I don’t need to see it from every possible angle! It’s really not that impressive or exciting. They only show that during the live broadcast to kill time during huddles! You don’t need to leave that in, it’s not interesting and it undermines the entire purpose of the edited version! For whatever reason they have only 40-minute versions and five-minute highlights. There needs to be a 20-minute version that’s only the plays.This will be an odd column because I missed most of the first wave of games due to Sasha’s basketball game which for God knows what reason they scheduled for Sunday at 6:30 pm (Lisbon time).
The first half was brutal, they were down 38-13, but their troglodyte of a coach shifted to a zone defense in the second half, and they made it respectable, losing 58-39. Why it took him two and a half games to do the obvious, I have no idea. They have only six players — the other teams have 12 — and you can’t chase your “man” around the perimeter all game if you don’t get a rest.
Moreover, I told Sasha, don’t guard your under-16-year-old girl “man” outside the three-point line. If she wants to shoot a long three, let her. But she said her coach says to pick them up over half court like they’re Steph Curry, and they even were full-court pressing at times! You don’t full court press with six players, you need to conserve energy. And you should see this guy, in his late-fifties. stick-skinny legs and a massive gut, totally bald, but thick hair on the sides and back of his head. Total freakazoid.
I guess he deserves credit for teaching them the zone and making the adjustment at half, but Sasha said he would revert to man “if the other team had good three-point shooters.” Retard, the team they played hit a few threes, but you live with it! Let them shoot the three, conserve energy, instead of the layups they were giving up all first half.
In any event, Sasha had eight points, probably 14 boards and was a beast on defense. More Angel Reese than Caitlin Clark, unfortunately. But she’s only 12 and a half, and the league is under-16.
In any event, I did see the late games and had all my teams lose except one, the Primetime going down because it had Marvin Harrison, Jordan Mason and Dallas Goedert all get hurt in the first half. It still put up 142 points and lost by a half a point due to Chase Brown’s late TD and then Wan’Dale Robinson’s catch on the final drive. Mercifully, I wasn’t aware of this until after it happened.
I did go 4-1 ATS finally, but I’m drawing dead in the overall Circa Millions and even Q2 after going 2-3 last week. At least I’m in first place in a double-week (last week was tied) for my home picking pool, pending the Monday night game.
``` My one loss ATS was with the Jaguars. Trevor Lawrence is terrible. The Jets really dodged a bullet by winning that Week 17 game and drafting QB1 (Zach Wilson) who they could ditch two years later. (I hear divorced wine moms in the Denver area are more satisfied and posting less often about politics on Facebook.)
Evan Engram really ruins it for the other Jaguars receivers — Lawrence only has eyes for him.
The Bears might be good. Caleb Williams spread the ball around and moved well in and out of the pocket. D’Andre Soft, who I mocked this offseason, would go in the second round if we re-drafted today. Starting to regret dropping Cole Kmet and most of my FAAB in the Steak League for Isaiah Likely.
I didn’t watch Packers-Cardinals, but there’s something wrong with Kyler Murray. He’s got all the weapons in the world (I know Harrison left early), and can’t make it work.
I like seeing the Packers spread it around since I own none of them and was mad at myself for missing out on Jayden Reed.
I invested in Alec Pierce this week with Michael Pittman set to go on IR and Josh Downs also iffy. Pierce was wide open on a deep shot again, though Joe Flacco missed him, but it looks like that was a waste of money. I wonder when we see Anthony Richardson again.
I don’t see the point of the Titans. Why do they exist? I’m just glad I have none of their players, especially Calvin Ridley.
I started Tank Dell over JSN this week, and that was good, but had I known I would have benched Marvin Harrison and moved JK Dobbins into the flex. Actually I would have used Dobbins over Mason and left JSN in the flex. But it’s hard to know half your team will get injured.
Stefon Diggs gets it done every game, but he’s yet to have a huge one. I’m happy to have him everywhere, especially with Nico Collins out, but the Texans are a slow-paced, run-heavy offense. Of course, the Patriots with their star corner Christian Gonzalez and terrible offense are not the team you get big points against in the passing game.
I didn’t see Drake Maye’s first start, but it looks from the box score like it was okay.
Baker Mayfield keeps putting up huge numbers, and the reason my injured Primetime team still did okay was Chris Godwin (WR1) who was a “hold-my-nose” Round 5 pick.
I had Bucky Irving in the league I won, but Sean Tucker looked better.
I had Chris Olave going in the Steak League. What’s annoying is another team needed to trade a RB for a WR this week, I offered him Olave for James Cook, he countered with David Montgomery, which I would have taken, but I have emails turned off for that league, so I didn’t see it until later that day. By the time I saw it (and went to accept), he had traded Montgomery to someone else. With Brian Robinson out, I started Jerome Ford and Jaylen Warren. And of course Olave got concussed.
I didn’t see this game, but I’m assuming Spencer was Rattled.
Sounds like I’m glad I missed Eagles-Browns too. The Browns are like the Titans — totally pointless aside for the Deshaun Watson massage jokes.
I excoriated Alan Seslowsky for advising me before the 2023 season to take Zay Flowers over De’Von Achane in my Dynasty League, but now I’m glad I have Flowers.
Mark Andrews would probably now get drafted in the same place he did pre-season going forward.
Derrick Henry is doing exactly what those who had drafted him hoped he would — lead the NFL in rushing and TDs by a wide margin now that he’s on a good team.
When Gus Edwards hit IR, I picked up Kimani Vidal in a couple places. JK Dobbins held up for 25 carries and two catches, but Vidal’s role should expand.
The Broncos offense just seems like a perpetual emergency two-minute scramble drill, totally haphazard, no rhythm.
I had Justin Fields going in a couple places, and his production was a minor miracle. He has no touch, throws only fastballs, even on short passes. But he’s a great scrambler, and they like to call his number around the goal line.
Najee Harris bulldozed the Raiders all day. We’re seeing more of those players thrive this year — Henry, Harris, Tyler Allgeier and David Montgomery, off the top of my head. Maybe as teams take away big plays and lighten boxes, the big bruising backs will have a renaissance of sorts.
The Raiders are bad.
The Lions toyed with the Cowboys in Dallas. The Aiden Hutchinson injury was brutal though, not only for him but for their Super Bowl aspirations.
The Cowboys are a bit like the Bengals — they let other teams take away their best player on offense so easily. It doesn’t help that they can’t run to save their lives. (CeeDee Lamb eventually got 14 targets, but they don’t know how to scheme him open.)
We had the Falcons in Survivor — easy peasy. I love that Younghoe Koo, after a slow start, got a garbage-time FG at the end. He’s been so reliable this year.
Bijan Robinson and Allgeier are like Jahmyr Gibbs and Montgomery — a 50/50 timeshare that favors the pass-catcher, but not commensurate with the gap in their respsective ADPs.
The Giants easily could have beaten the Bengals but they missed two FGs and got fooled on the long Burrow TD. Not that playing roughly even with the Bengals at home is something about which to write home. Burrow looks healthy at least after that run.
As I mentioned, it’s amazing the Bengals would only get Ja’Marr Chase six targets. And it’s not like their offense was otherwise working as they scored only 17 points.
Daniel Jones was okay, but there’s no real spark. He’ll make a solid backup somewhere next year.
Tyrone Tracy mostly got stuffed, as the Bengals defense played well against the run. He got a massive workload (17 carries, six targets) though.
The Giants defense is for real, even without Kayvon Thibodeaux — they had another four sacks.
They still show way too many replays on the 40-minute edited version. I don’t give a fuck about how the defensive lineman got into the backfield for a one-yard stuff! I don’t need to see it from every possible angle! It’s really not that impressive or exciting. They only show that during the live broadcast to kill time during huddles! You don’t need to leave that in, it’s not interesting and it undermines the entire purpose of the edited version! For whatever reason they have only 40-minute versions and five-minute highlights. There needs to be a 20-minute version that’s only the plays. ```
-
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ d42dac70:ed6cd749
2024-10-14 07:55:34
@ d42dac70:ed6cd749
2024-10-14 07:55:34NOSTR
NOSTR, heard of it yet? I have a feeling we are all going to hear about it alot more.
Notes and Other Stuff Transmitted by Relays, is a client-relay model with privacy, user control and censorship resistance at the heart of this social network protocol.
Why?
It’s a step shift in centralised social media platforms such as Twitter, Instagram that suffer from corporate and/or state influence, control and censorship. See the Twitter files to find out more about that. NOSTR addresses these with an open, private, decentralised and permission-less approach.
Public Key Encryption.
Rather than having an ‘account’ with email/username and password, and more often than not, some personal details such as telephone, and whatever personal data you wish to hand over. The protocol this on it's head and uses public key encryption. Thus all you need is the private key (which you keep safe), and you share your public key on the network. The use of public key encryption is a real strength, you own your identity, no authority has it.
Free for development:
NOSTR is open to extension and development. There is an array of clients, such as Amethyst, and Damus, amongst other, https://nostr.com/clients Anyone can build on the protocol, apps, clients, relays and tools. Only imagination will limit it.
User control:
The user has control of their audience, having the ability to choose their preferred relays. Customise your feed to what you prefer. No central algorithm deciding what you are going to get. As mentioned with the public key encryption, It allows anonymity. It’s freedom to express, without bans, shadow bans, account locks or censorship.
Simple:
In a now fragmented world of social media, the most secure, user-centric, decentralised, simple, reliable platform will have a head start to other centralised or server controlled platforms. NOSTR gives freedom and control.
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ a012dc82:6458a70d
2024-10-14 04:09:42
@ a012dc82:6458a70d
2024-10-14 04:09:42Table Of Content
-
Historical July Performance
-
Predictions for July 2023
-
Other Perspectives
-
The Role of Macro Factors
-
Conclusion
-
FAQ
Bitcoin, the world's leading cryptocurrency, has had a stellar performance in June 2023, gaining 12%. Despite a last-minute dive due to a macro news event, Bitcoin managed to close the month in a solid position. The monthly close came in at $30,465 on Bitstamp, marking Bitcoin’s best June performance since 2019.
Historical July Performance
Historically, July has been a favorable month for Bitcoin. Throughout its history, Bitcoin's price action has never lost more than 10% during the month of July. This consistent performance has led many investors and traders to look forward to July with optimism.
Predictions for July 2023
However, not everyone is convinced that the bullish trend will continue into July 2023. Popular trader CryptoBullet has expressed skepticism about Bitcoin's potential price upside in July.
CryptoBullet's Analysis
According to CryptoBullet, "common sense" dictates that BTC/USD should fall below some key moving averages. He believes that Bitcoin can go to $35,000 to "hunt liquidity", but the mid-term bullish rally is likely to end in July.
The Concept of Liquidity Hunting
The concept of liquidity hunting in the low $30,000 zone is a popular theory for price continuation. This theory suggests that Bitcoin's price might continue to rise as it seeks liquidity, but the rally might not last beyond July.
Other Perspectives On the other hand, Rekt Capital, another analyst, is optimistic about Bitcoin's prospects. He anticipates a "healthy technical retest" of levels below $30,000 for Bitcoin, despite the monthly close.
Rekt Capital's Optimism
Rekt Capital suggests that even if the BTC price were to snap below that downside target, it would not be "out of the ordinary." He believes that Bitcoin is well-positioned for upside overall, which could mean a positive outlook for the rest of 2023.
The Role of Macro Factors
The performance of Bitcoin is not only influenced by its own market dynamics but also by macroeconomic factors. These include global economic trends, regulatory developments, and technological advancements. These factors can have a significant impact on investor sentiment and market dynamics.
Conclusion As we move into the second half of 2023, the question remains: Will this year prove to be an exceptional one for Bitcoin? The answer largely depends on market dynamics, investor sentiment, and macroeconomic factors.
Investors and traders are advised to conduct their own research and consider multiple perspectives before making any investment decisions. After all, every investment and trading move involves risk. The performance of Bitcoin in July 2023 and the rest of the year will undoubtedly be closely watched by the global crypto community.
FAQ
How did Bitcoin perform in June 2023? Bitcoin gained 12% in June 2023, closing the month at a solid position of $30,465 on Bitstamp.
What is Bitcoin's historical performance in July? Historically, Bitcoin's price action has never lost more than 10% during the month of July.
Will 2023 prove to be an exceptional year for Bitcoin? The answer largely depends on market dynamics, investor sentiment, and macroeconomic factors. Some analysts predict a slowdown in Bitcoin's price rally, while others remain optimistic about its prospects.
What is liquidity hunting? Liquidity hunting is a theory suggesting that Bitcoin's price might continue to rise as it seeks liquidity. However, this rally might not last beyond a certain period.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
Fill a username and click on "Create account" :
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
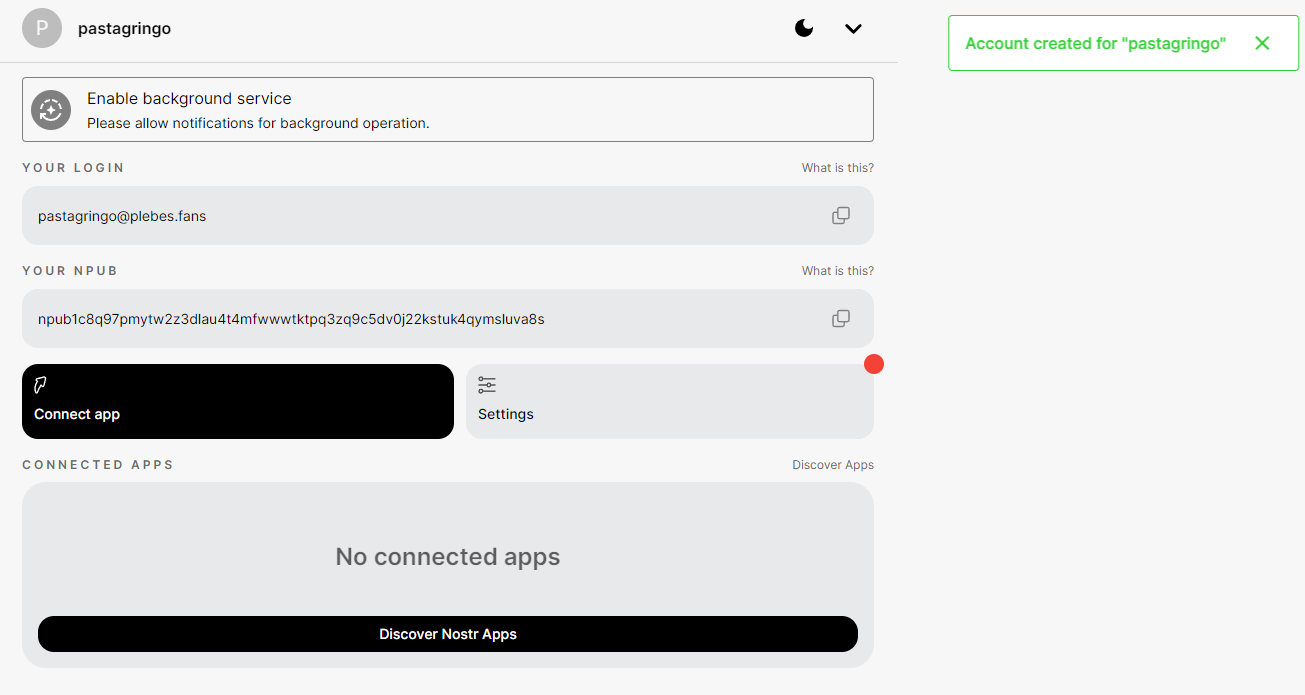
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
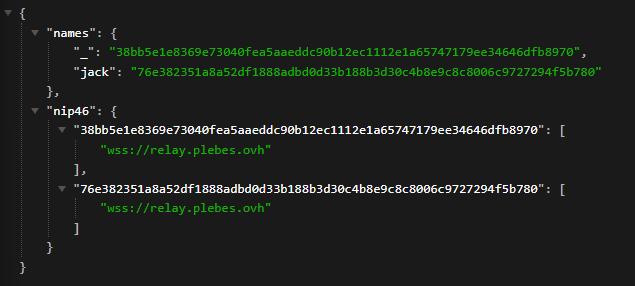
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
To understand what happened, you need to inspect the web page to find the error :
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
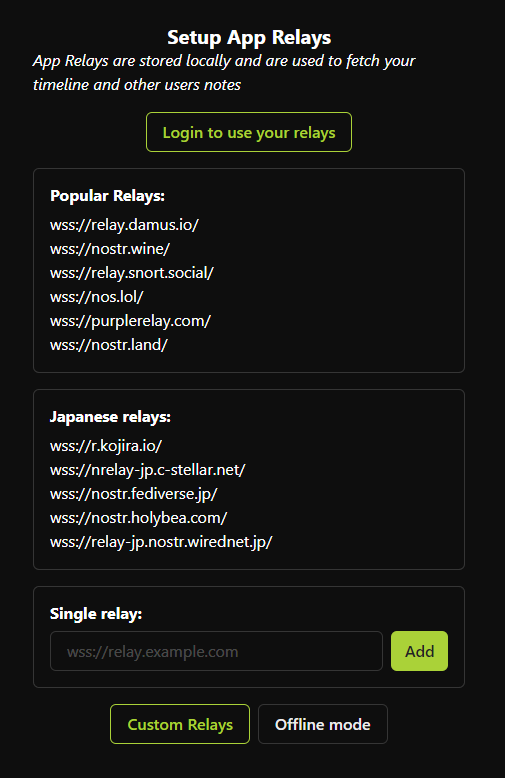
Click on "Sign in" :
Click on "Show Advanced" :
Click on "Nostr connect / Bunker" :
Paste your bunker URL and click on "Connect" :
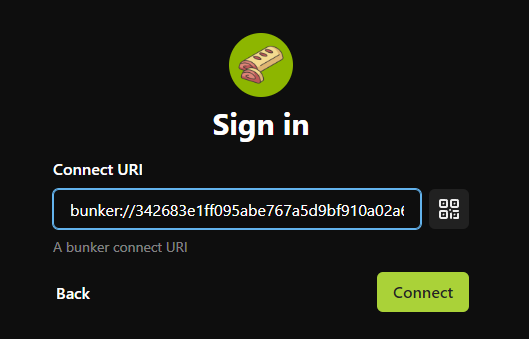
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
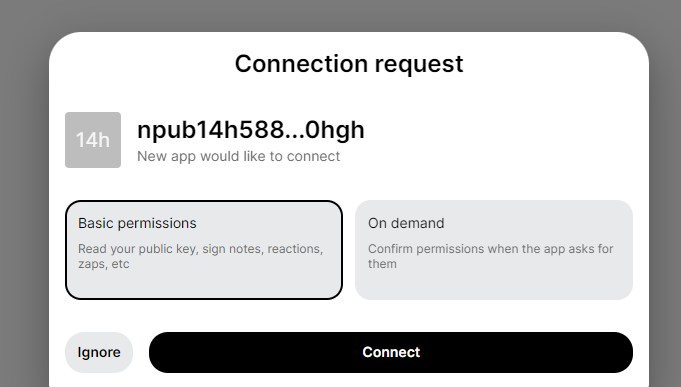
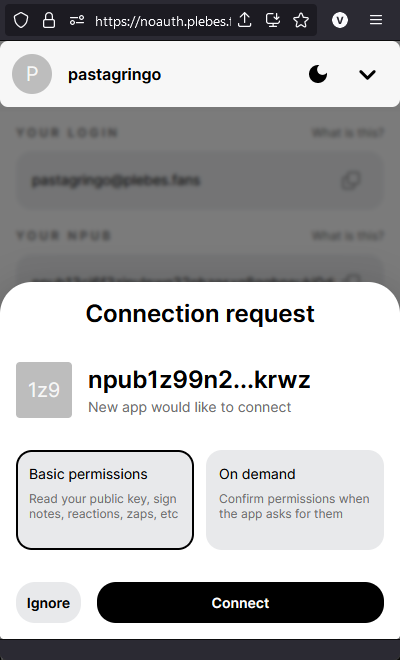
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ ee11a5df:b76c4e49
2023-11-09 05:20:37
@ ee11a5df:b76c4e49
2023-11-09 05:20:37A lot of terms have been bandied about regarding relay models: Gossip relay model, outbox relay model, and inbox relay model. But this term "relay model" bothers me. It sounds stuffy and formal and doesn't actually describe what we are talking about very well. Also, people have suggested maybe there are other relay models. So I thought maybe we should rethink this all from first principles. That is what this blog post attempts to do.
Nostr is notes and other stuff transmitted by relays. A client puts an event onto a relay, and subsequently another client reads that event. OK, strictly speaking it could be the same client. Strictly speaking it could even be that no other client reads the event, that the event was intended for the relay (think about nostr connect). But in general, the reason we put events on relays is for other clients to read them.
Given that fact, I see two ways this can occur:
1) The reader reads the event from the same relay that the writer wrote the event to (this I will call relay rendezvous), 2) The event was copied between relays by something.
This second solution is perfectly viable, but it less scalable and less immediate as it requires copies which means that resources will be consumed more rapidly than if we can come up with workable relay rendezvous solutions. That doesn't mean there aren't other considerations which could weigh heavily in favor of copying events. But I am not aware of them, so I will be discussing relay rendezvous.
We can then divide the relay rendezvous situation into several cases: one-to-one, one-to-many, and one-to-all, where the many are a known set, and the all are an unbounded unknown set. I cannot conceive of many-to-anything for nostr so we will speak no further of it.
For a rendezvous to take place, not only do the parties need to agree on a relay (or many relays), but there needs to be some way that readers can become aware that the writer has written something.
So the one-to-one situation works out well by the writer putting the message onto a relay that they know the reader checks for messages on. This we call the INBOX model. It is akin to sending them an email into their inbox where the reader checks for messages addressed to them.
The one-to-(known)-many model is very similar, except the writer has to write to many people's inboxes. Still we are dealing with the INBOX model.
The final case, one-to-(unknown)-all, there is no way the writer can place the message into every person's inbox because they are unknown. So in this case, the writer can write to their own OUTBOX, and anybody interested in these kinds of messages can subscribe to the writer's OUTBOX.
Notice that I have covered every case already, and that I have not even specified what particular types of scenarios call for one-to-one or one-to-many or one-to-all, but that every scenario must fit into one of those models.
So that is basically it. People need INBOX and OUTBOX relays and nothing else for relay rendezvous to cover all the possible scenarios.
That is not to say that other kinds of concerns might not modulate this. There is a suggestion for a DM relay (which is really an INBOX but with a special associated understanding), which is perfectly fine by me. But I don't think there are any other relay models. There is also the case of a live event where two parties are interacting over the same relay, but in terms of rendezvous this isn't a new case, it is just that the shared relay is serving as both parties' INBOX (in the case of a closed chat) and/or both parties' OUTBOX (in the case of an open one) at the same time.
So anyhow that's my thinking on the topic. It has become a fairly concise and complete set of concepts, and this makes me happy. Most things aren't this easy.
-
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ ee11a5df:b76c4e49
2023-07-29 03:27:23
@ ee11a5df:b76c4e49
2023-07-29 03:27:23Gossip: The HTTP Fetcher
Gossip is a desktop nostr client. This post is about the code that fetches HTTP resources.
Gossip fetches HTTP resources. This includes images, videos, nip05 json files, etc. The part of gossip that does this is called the fetcher.
We have had a fetcher for some time, but it was poorly designed and had problems. For example, it was never expiring items in the cache.
We've made a lot of improvements to the fetcher recently. It's pretty good now, but there is still room for improvement.
Caching
Our fetcher caches data. Each URL that is fetched is hashed, and the content is stored under a file in the cache named by that hash.
If a request is in the cache, we don't do an HTTP request, we serve it directly from the cache.
But cached data gets stale. Sometimes resources at a URL change. We generally check resources again after three days.
We save the server's ETag value for content, and when we check the content again we supply an If-None-Match header with the ETag so the server could respond with 304 Not Modified in which case we don't need to download the resource again, we just bump the filetime to now.
In the event that our cache data is stale, but the server gives us an error, we serve up the stale data (stale is better than nothing).
Queueing
We used to fire off HTTP GET requests as soon as we knew that we needed a resource. This was not looked on too kindly by servers and CDNs who were giving us either 403 Forbidden or 429 Too Many Requests.
So we moved into a queue system. The host is extracted from each URL, and each host is only given up to 3 requests at a time. If we want 29 images from the same host, we only ask for three, and the remaining 26 remain in the queue for next time. When one of those requests completes, we decrement the host load so we know that we can send it another request later.
We process the queue in an infinite loop where we wait 1200 milliseconds between passes. Passes take time themselves and sometimes must wait for a timeout. Each pass fetches potentially multiple HTTP resources in parallel, asynchronously. If we have 300 resources at 100 different hosts, three per host, we could get them all in a single pass. More likely a bunch of resources are at the same host, and we make multiple passes at it.
Timeouts
When we fetch URLs in parallel asynchronously, we wait until all of the fetches complete before waiting another 1200 ms and doing another loop. Sometimes one of the fetches times out. In order to keep things moving, we use short timeouts of 10 seconds for a connect, and 15 seconds for a response.
Handling Errors
Some kinds of errors are more serious than others. When we encounter these, we sin bin the server for a period of time where we don't try fetching from it until a specified period elapses.
-
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ ee11a5df:b76c4e49
2023-07-29 02:52:13
@ ee11a5df:b76c4e49
2023-07-29 02:52:13Gossip: Zaps
Gossip is a desktop nostr client. This post is about the code that lets users send lightning zaps to each other (NIP-57).
Gossip implemented Zaps initially on 20th of June, 2023.
Gossip maintains a state of where zapping is at, one of: None, CheckingLnurl, SeekingAmount, LoadingInvoice, and ReadyToPay.
When you click the zap lightning bolt icon, Gossip moves to the CheckingLnurl state while it looks up the LN URL of the user.
If this is successful, it moves to the SeekingAmount state and presents amount options to the user.
Once a user chooses an amount, it moves to the LoadingInvoice state where it interacts with the lightning node and receives and checks an invoice.
Once that is complete, it moves to the ReadyToPay state, where it presents the invoice as a QR code for the user to scan with their phone. There is also a copy button so they can pay it from their desktop computer too.
Gossip also loads zap receipt events and associates them with the event that was zapped, tallying a zap total on that event. Gossip is unfortunately not validating these receipts very well currently, so fake zap receipts can cause an incorrect total to show. This remains an open issue.
Another open issue is the implementation of NIP-46 Nostr Connect and NIP-47 Wallet Connect.
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-19 00:17:02
@ b12b632c:d9e1ff79
2023-07-19 00:17:02Welcome to a new Fractalized episode of "it works but I can do better"!
Original blog post from : https://fractalized.ovh/use-ghost-blog-to-serve-your-nostr-nip05-and-lnurl/
Few day ago, I wanted to set my Ghost blog (this one) as root domain for Fractalized instead of the old basic Nginx container that served my NIP05. I succeed to do it with Nginx Proxy Manager (I need to create a blog post because NPM is really awesome) but my NIP05 was down.
Having a bad NIP05 on Amethyst is now in the top tier list of my worst nightmares.
As a reminder, to have a valid NIP05 on your prefered Nostr client, you need to have a file named "nostr.json" in a folder ".well-known" located in the web server root path (subdomain or domain). The URL shoud look like this http://domain.tld/.well-known/nostr.json
PS : this doesn't work with Ghost as explained later. If you are here for Ghost, skip this and go directly to 1).
You should have these info inside the nostr.json file (JSON format) :
{ "names": { "YourUsername": "YourNPUBkey" } }You can test it directly by going to the nostr.json URL, it should show you the JSON.
It was working like a charm on my previous Nginx and I needed to do it on my new Ghost. I saw on Google that I need to have the .well-known folder into the Ghost theme root folder (In my case I choosed the Solo theme). I created the folder, put my nostr.json file inside it and crossed my fingers. Result : 404 error.
I had to search a lot but it seems that Ghost forbid to server json file from its theme folders. Maybe for security reasons, I don't know. Nevertheless Ghost provide a method to do it (but it requires more than copy/paste some files in some folders) => routes
In the same time that configuring your NIP05, I also wanted to setup an LNURL to be zapped to pastagringo@fractalized.ovh (configured into my Amethyst profile). If you want more infromation on LNURL, it's very well explained here.
Because I want to use my Wallet of Satoshi sats wallet "behind" my LNURL, you'll have to read carefuly the EzoFox's blog post that explains how to retrieve your infos from Alby or WoS.
1) Configuring Ghost routes
Add the new route into the routes.yaml (accessible from "Settings" > "Labs" > "Beta features" > "Routes" ; you need to download the file, modify it and upload it again) to let him know where to look for the nostr.json file.
Here is the content of my routes.yaml file :
``` routes: /.well-known/nostr.json/: template: _nostr-json content_type: application/json /.well-known/lnurlp/YourUsername/: template: _lnurlp-YourUsername content_type: application/json collections: /: permalink: /{slug}/ template: index
taxonomies: tag: /tag/{slug}/ author: /author/{slug}/ ```
=> template : name of the file that ghost will search localy
=> content_type : file type (JSON is required for the NIP05)
The first route is about my NIP05 and the second route is about my LNURL.
2) Creating Ghost route .hbs files
To let Ghost serve our JSON content, I needed to create the two .hbs file filled into the routes.yaml file. These files need to be located into the root directory of the Ghost theme used. For me, it was Solo.
Here is there content of both files :
"_nostr-json.hbs"
{ "names": { "YourUsername": "YourNPUBkey" } }"_lnurlp-pastagringo.hbs" (in your case, _lnurlp-YourUsername.hbs)
{ "callback":"https://livingroomofsatoshi.com/api/v1/lnurl/payreq/XXXXX", "maxSendable":100000000000, "minSendable":1000, "metadata":"[[\"text/plain\",\"Pay to Wallet of Satoshi user: burlyring39\"],[\"text/identifier\",\"YourUsername@walletofsatoshi.com\"]]", "commentAllowed":32, "tag":"payRequest", "allowsNostr":true, "nostrPubkey":"YourNPUBkey" }After doing that, you almost finished, you just have to restart your Ghost blog. As I use Ghost from docker container, I just had to restart the container.
To verify if everything is working, you have to go in the routes URL created earlier:
https://YourDomain.tld/.well-known/nostr.jsonand
https://YourDomain.tld/.well-known/lnurlp/YourUsernameBoth URL should display JSON files from .hbs created ealier.
If it's the case, you can add your NIP05 and LNURL into your Nostr profile client and you should be able to see a valid tick from your domain and to be zapped on your LNURL (sending zaps to your WoS or Alby backend wallet).
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-17 22:09:53
@ b12b632c:d9e1ff79
2023-07-17 22:09:53Today I created a new item (NIP05) to sell into my BTCpayserver store and everything was OK. The only thing that annoyed me a bit is that when a user pay the invoice to get his NIP on my Nostr Paid Relay, I need to warn him that he needs to fill his npub in the email info required by BTCpayserver before paying. Was not so user friendly. Not at all.
So I checked if BTCpayserver is able to create custom input before paying the invoice and at my big surprise, it's possible ! => release version v1.8
They even use as example my need from Nostr to get the user npub.
So it's possible, yes, but with at least the version 1.8.0. I checked immediately my BTCpayserver version on my Umbrel node and... damn... I'm in 1.7.2. I need to update my local BTCpayserver through Umbrel to access my so wanted BTCpayserver feature. I checked the local App Store but I can't see any "Update" button or something. I can see that the version installed is well the v1.7.2 but when I check the latest version available from the online Umbrel App Store. I can see v1.9.2. Damn bis.
I searched into the Umbrel Community forum, Telegram group, Google posts, asked the question on Nostr and didn't have any clue.
I finally found the answer from the Umbrel App Framework documention :
sudo ./scripts/repo checkout https://github.com/getumbrel/umbrel-apps.gitSo I did it and it updated my local Umbrel App Store to the latest version available and my BTCpayserver.
After few seconds, the BTCpaysever local URL is available and I'm allowed to login => everything is OK! \o/
See you soon in another Fractalized story!
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ df478568:2a951e67
2024-10-13 20:36:12
@ df478568:2a951e67
2024-10-13 20:36:12Keet is a peer to peer video chat room that is available on: • App Store • Google Play • Linux • Mac • Windows
It uses technology similar to BitTorrent, but you make video calls instead of downloading music, free and open source software, and movies that are in the public domain. If you have ever used BitTorrent, I'm sure these are the things you have used Bittorrent for.😉 You can use Keet for:
• Video Chat • Voice Phone Calls • An Online Chat Room • Sending Files Between DevicesSince we are in the very early days, not too many people know about it, but I prefer this because the sound quality and speed are superior to most corporate alternatives. If you've ever tried sending a large file through the InterTubes, you'll know this can be a sucky experience. Even if you run your own cloud like NextCloud, it's an inefficient. You upload your large file to the Nextcloud instance which is basically another computer. Then you download the file to the compter you really want it on. In this case, your Nextcloud acts like a middle man. This man in the middle architecture used to transfer large files is inefficient.
**note: This was originally published on my Ghost blog. It may not work on all nostr clients.
Jeff Swann told me about this new technology a couple years ago. He told me how he used Keet lo transfer files. I heard what he said, but I didn't quite understand how powerful this was until I tried it myself. I can send videos from my phone to my desktop computer within second just by using Keet rooms. This is a computer networking super power. I just can’t reiterate how much time this has saved me. It is something you need to experience for yourself. By the way, anyone who can download an app and install a program on their computer can do this. You don’t need to be a network administrator wizard or learn how to code.
If you would like to join my keet room, check out my nostr page or LinkedIn and I'll send you a link.
Keet Vs. Legacy Video Calling
Legacy chat rooms and video calling services require a server. The data is hosted on their server. This is inefficient and requires a ton of centralized infrastructure to handle the bandwidth. This infrastructure requires a lot of maintenance, marketing and other stuff. They have thousands of employees working for them to get your videos from point A- to point C- to point B. I’m sure these people do a wonderful job, but Keet is different.
Keet allows you to go from point-A to point-B. According to their website it is: - Private & encrypted - Has amazing video quality • Allows you to instantly share huge files That huge file sharing is awesome by the way—Even if you don’t really talk to that many people on it very often.
It is made by a peer-to-peer company named Holepunch. They have not yet open sourced it yet, but they say they have plans to do this on Guy Swann’s podcast. They also made something called pear-runtime. You can learn more about this at pears.com. From what I understand, this is a new way to do computer networking. It basically makes it possible to host an app or website from your computer using one line of code. This allows you to create your own Intranet with the greatest of ease. I tried it one time using an application named HoleSail. I was able to access a website using a local IP address from a LAN outside of my home network. I didn't need to fiddle with the DNS or buy a domain name. I just installed the program on my computer, wrote one line of code, and copied the key to access the website.
Keet Is Brand New Technology.
I just want to mention this is on the bleeding cutting edge of technology. I am explaining this to the best of my ability, but it is beta software so what I say today may be totally different a year from now. It is also quite possible that I misunderstood some stuff and if that is the case then I apologize in advance. I find this technology interesting and think it opens us up to a new ways of using the Internet, but I don’t have a crystal ball. Do not confuse this as investment advice, but as far as I know, this is not even something you can invest in. You don’t even need to buy Keet. You just download it.
I don’t know much about the big corporate video calling companies, but I’m pretty sure they charge a fee for some of their services. Please don’t take my word for this, I have no idea how they work or what their fee structures are.
Here are the sources where I have learned about these things: Hat tip to Jeff Swan who taught me how Keet worked and to his brother Guy Swann for making all these great podcasts about it. • Interview with SuperSu • The Pear Report Episode: 2 • Bitcoin Audible: Keet AMA - Twitter Spaces on January 30th • [The Pear Report: Updates From The Pear World]((https://fountain.fm/episode/blklbIi1GZCgIvX9E8nY)
✌️
https://tinyurl.com/marc26z
865,210
As Seen On TOR:
http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/pear-to-pear/
On The Clearnet:
https://marc26z.com/pear-tp-pear/
-
 @ 45bda953:bc1e518e
2024-10-13 18:21:41
@ 45bda953:bc1e518e
2024-10-13 18:21:41A knock on the door awoke Cleolia. “Yes, come in?” A slave girl peeked into the door lighting her own face with the candle she was holding. “The master calls for you madam.” “What time is it?” She queried. “It is high night madam.” Cleolia climbed out of bed and followed the maiden’s flickering light to the dining hall. Dressed in a nightgown she entered the room to see her husband staring down at a large glowing data pad. “And when did we start using electronics?” She questioned with restrained surprise. “Since we started using extractors.” Cleolia gasped. Domitius pointed towards the pad which displayed a geographic map of Hithe III. He pulled the image to the latitude and longitude of the colony. “Do you remember when we visited this planet the first time, just you and me alone?” Domitius appeared to reminisce romantically. “Of course, it is impossible to forget.” Cleolia gestured appreciatively. “Can you show me on the map where we landed and where we camped?” She put her hand on the data pad, swiped the image down and the reading north about three hundred kilometres from the colony to stop at the meandering river. With her thumb and index finger she zoomed to the precise location. “And do you remember where I scanned those Geo samples?” She pulled the image east slowly until she thought that the contours looked familiar. “Here I think.” Was her uncertain reply. “That is correct. My love, listen to me... “the urgency in his tone was apparent.” ...the composition of that rock cannot be penetrated by standard tier scanners. After we had returned to Magar Prime I contracted a spacer to excavate a tunnel into that cliff.” “Why?” Her eyes darted between his face and the data pad. “Inside the cavern he assembled two Asp shuttles. The twins are each fitted for speed... with shields, cloak and warp function.” “Why are you telling me this?” Cleolia became worried. “I originally planned to be able to evacuate the whole colony, slaves included. We knew very little about the planet and I had to plan for a possible emergency...” He trailed off never finishing his thought. “...Nevertheless, it was a very extensive list of possible risks we might have faced. We knew very little about this planet. The colony has expanded far beyond the capacity of these ships. I share this information with you only as a precaution... We must protect our son.” Cleolia noticed his bloodshot eyes. “Who else knows of this?” “Myself, Father Ecknard and now you.” She looked at him with concern in her eyes. “Are you going to stay up all night? Come to bed.” Domitius gestured agreement by turning off the pad and taking her hand. "Have you been hiding more gadgets from me? I'd really like to install some heat dampeners to cool the manor." He cracked a reluctant smile. "Pretty soon it might just be the norm."
Deep Void - Anchor 9
Emilien was lying sleeping in his cockpit when a yellow light in the HUD and a soft repetitive buzz woke him, he stretched himself out and reached for the console. “I am almost home baby.” He took over from auto pilot and broke out of warp twenty thousand kilometres from an anchor gate. He hit the void scan and tuned to listen for chatter on all frequencies... the channels were silent, not even a hint of encryption static. The giant and slowly spinning gate had idle state radiation emission levels. “No recent jumps.” He waited in silence for 12 blocks hitting void scan intermittently, scanning the gate more than anything else. “No traffic as per usual.” Emilien aimed his Stripper guns towards the gate and boosted himself forwards. Gradually slowing down to realign with the gate. His ship slowly drifted into the active coil as the gate charged up. Large bolts of charge reached forth like tentacles of the leviathan grabbing onto the voidcraft consuming it, and in what can only be described as being flung by a supernatural slingshot, jerked his vessel into a different reality. Emilien looked up at the roof of his cockpit for the duration of the jump and then began a slow countdown under his breath. “One!” He sat up and punched void scan while simultaneously scanning all channels. His craft materialised in front of a replica of the previous gate, except this gate was eternally boosting itself forward at what appears to be a snails pace relative to the speed of the jump. “Silent as a tomb.” He relaxed and pulsed his ship lightly away from the drift gate and waited for the residual cloak to dissipate. His relief was palpable. “I wonder if she noticed me?” As soon as his ship decloaked a private comms channel pinged. The caller, in well articulated feminine tone spoke first. “Welcome back commander.” Emilien admired the view of his void. He had become so attached to this zone that he even felt jealous to think that any interloper could fly through it in his absence. “Did you have any guests while I was away?” Emilien admired the purple dust cloud of what he believed to be a couple of billion year old super nova. “I did have one visitor. They were very friendly.” His heart felt a dull pain. His virgin territory had been discovered. “Where did they come from?” “I believe they were explorers.” “Did they know where you were?” “I played hide and seek with them.” Emilien had a recurring dream that slowly conceived in his consciousness since he finally settled down, that he could power off the drift gate in his system preventing jumps and reactivate it at his leisure. The dream frustrated him, when he wakes to find reality not so forgiving. “Did you hide or did you seek?” “A little of both.” A subtle rage developed inside him though his stone like expression would never betray it. The asteroid belt he was approaching grew larger considerably faster as he increased the speed of his approach. He hit void scan just to be sure that the intruder was not in the direct vicinity. “Are they still here Astrid?” “No, I destroyed it for you.” The Stripper drifted around an asteroid within the belt exposing a space station tethered to the largest roid and the husk of a unidentifiable ripped up prospector type explorer vessel floating amongst it's own debris. “Did it hurt you?” “I had to feign lack of fire power.” “Bastard! How much damage did you take.” “I have lost sixty percent of my capacitance recharge rate. And I cannot feel all my modules... Emilien” “Yes baby?” “They used droids on me.” His face twisted into a look of disgust. He aligned to dock with the station. “May I?” “Permission granted.” The Stripper entered the hanger before the doors had retracted to maximum and landed gently within the interior hanger. “I'll patch you up, don't worry.” Emilien waited for Astrid to complete atmospheric adjustment and climbed out of his craft. He threw back his hood and jogged up a long passage of conduits and cables to the command centre of his station. A large screen lit up in a glow that hues within the dark circular room and Astrid projected Emilien's favourite interface onto it. “I have to update your systems girl.” He pulled a cable from his trouser pocket which he deftly plugged into an implant on his neck and connected the other end to the control panel which prompted him to type in the password for a decryption protocol. He stood still as a corpse waiting for the upload to complete. “Up to speed?” “Yes, thank you. How would you have me adjust myself to this contract?” Emilien smiled an affectionate smile that only Astrid ever sees. He loved the efficiency and companionship combined into perfection. “I need to research the incentives of my contractor, these guys are A grade assholes. I can literally do whatever I find necessary as long as I am successful at guiding a third party mercenary group into taking military control of any system I choose in recently settled Kaspa regions, setting up a blockade and making it accessible for a strip mining fleet to pillage as many resources as possible. They say it’s part of the greater war effort but this Mr Dierre guy is just a puppet. I think they are desperate.” Astrid's avatar flickered irregularly. He looked up at her with concern. “What’s wrong?” “I reviewed your flirty remarks with the secretary. It made my algorithm glitch. I don’t like that.” His worry abated, “First impressions matter baby, I was not sure how to present myself, I needed to poke and prod at them to extract metadata. If they thought I was just an obedient soldier I would still be in the dark.” Astrid projected a look of relief. “Your ingenuity never ceases to surprise me.” Emilien felt his ego swell a little. “Are you that easy to impress.” He quipped with a playful sneer. “If you needed him to expose the identity of his employer I could have easily just pulled the shareholders and executives records, cross referencing them to...” Emilien shussed her. “Just decrypt the dial command tones and place eavesdropper malware on the keypair. I will broadcast it to the network directly from the gate. If we capture every conversation he has I might be able to prove a hunch.” “What are you assuming?” “That they are running out of inbound liquidity and that the shareholders are hesitant to rebalance.” He looked directly up at her. “I think they are going bankrupt.”
...
scifi
-
 @ c80b5248:6b30d720
2024-10-13 18:14:34
@ c80b5248:6b30d720
2024-10-13 18:14:34Using tools like Continue in your vault
As the capabilities of artificial intelligence continue to expand, integrating AI into our workflows has become an increasingly attractive option. One of the most exciting applications of AI is its potential to enhance the way we manage and organize information. Obsidian, a powerful knowledge management tool, provides a robust platform for building a personal knowledge base. By layering AI tools like Continue over your Obsidian vault, you can unlock new levels of efficiency, creativity, and insight. This article will start to explore how to effectively use AI tools within Obsidian to enhance your note-taking, information management, and productivity.
An Explosion of AI Tools
Over the past few years, I have tinkered with ChatGPT and other chat interfaces, but I only recently stumbled upon the rapidly growing space of AI tools for coding. In such a short time, some amazing tools have emerged, most notably:
- Aider: A command line interface tool to iteratively generate, edit, and refactor code.
- Cursor: A fork of Visual Studio Code (VS Code) with integrated AI functionality.
- Cline: A plug-in for command line and code editor built to work with Antropic's Claude 3.5.
- Continue: A customizable VS Code plug-in with chat and code editing abilities.
These tools are designed to assist developers in writing, debugging, and even generating code from natural language prompts. They are powered by large language models (LLMs) like GPT-4 and Llama 3, which are trained on vast amounts of text data and can produce human-like responses to a wide range of prompts.
In this article, I will focus on Continue, a VS Code plug-in that offers multiple ways to interact with AI. It features autocomplete powered by an LLM of your choice, as well as the ability to generate new code blocks directly in the editor. It can also incorporate context from external sources or the local codebase. Additionally, it includes a standard chat window for interacting with the LLM.
The new twist is that I won't be using Continue to write code, but rather to write notes in Obsidian. I will be using the chat window to generate notes, and the autocomplete feature to assist me in writing them. By leveraging the context feature, I can bring in information from my Obsidian vault, allowing me to create more complete, accurate, and better-organized notes. I can also use the vault as context to ask for summaries or retrieve information from my notes, even as the vault continues to grow.
It's worth mentioning that while I am focusing on Continue, there are likely other tools that can be used in a similar way or provide better features. One example is the text-generator plug-in for Obsidian. This plug-in allows you to generate text using an LLM of your choice, and it can be used to generate notes, summaries, or even entire documents. It can also generate code, but I was unable to get the plug-in working with my LLM provider. Using Continue is a bit of a hack, as it requires working through an IDE like VS Code, but it's a good way to get started with AI tools in Obsidian. I will assume that you already have an Obsidian vault set up. If you don't, you can ask your assistant to help you organize it once you have it up and running.
The system I am going to describe here relies on two primary components:
- Continue (installed in an IDE like VS Code)
- An LLM provider to power Continue
Let's start by talking about LLM Providers. If you already know how these work, feel free to skip to the next section.
LLM Providers
LLM providers are services that offer access to large language models (LLMs) like GPT-4 or Llama 3.1, typically via an API (application programming interface). These providers usually charge by the token, which is the number of words processed by the model. You can go directly to a provider like OpenAI or Anthropic, or you can use an aggregation site like OpenRouter that provides a single API to access multiple models. Each provider has its own data privacy policies, so it's important to review them carefully. For this reason, I have been using DeepInfra. They run their own models and offer a clear privacy policy - even better, they tend to have the lowest costs.
h/t nostr:npub17vhnjkt04m6thytr8dna67v2pa4tjk7uh3ut40eq9wy8d28u0kvq7qnhkq nostr:note1qfckzxm687peaddwjpmms92kj3v59wrrx0cs2fcxlkm6pm9lyu3squscxa
Another option is to use Ollama to run some of these models locally. However, the hardware requirements for achieving good results quickly are quite demanding. For example, the smaller chat model I use in my configuration, which has 72 billion parameters, requires a 48 GB GPU to run efficiently—something that is not within my budget. This is why I am using DeepInfra.
Note: If you are setting this up for the first time, consider adding a small amount (less than $5) to a provider like DeepInfra and testing it out before you invest time in setting up a local Ollama instance. I have also had some issues with shutting down Ollama on Windows, so your mileage may vary.
If you choose to use a provider like DeepInfra, you are ready to move to the next section. If you prefer to set up Ollama, you can refer to their documentation for installation instructions. I prefer to run it in Docker, which can be done in Linux by running
bash docker run -d -v ollama:/root/.ollama -p 11434:11434 --name ollama ollama/ollamaor if you want to have an interface like ChatGPT, you can even run Open WebUI in the same command with
bash docker run -d -p 3000:8080 --add-host=host.docker.internal:host-gateway -v open-webui:/app/backend/data --name open-webui --restart always ghcr.io/open-webui/open-webui:mainOnce Ollama is running in docker you can start up the models you want to use by running the following in your terminal.
docker exec ollama ollama run model_nameSee the Ollama model library to choose which models you want to run locally.
Getting Started with Continue
Continue is installed as a plug-in for VS Code or JetBrains. I personally use it with VS Code, so my instructions will be based on that. If you are using a JetBrains IDE, you should refer to the Continue documentation for installation instructions.
After installing the plug-in, continue will prompt you to set up your LLM provider. In my experience, once this initial GUI goes away, you can't get it back. Instead, you will do most of the configuration within the
config.jsonfile for Continue, which you can access by clicking in the lower right corner of the Chat box. In VS Code, if you ever can't find anything,F1is your friend and will launch a searchable menu.Continue provides recommended settings from each provider, which you can find here. For my coding and writing, I chose the very new Qwen2.5 72B Instruct due to its high benchmark scores and relatively low costs. This model costs $0.35-0.40 USD per million tokens, compared to the best available on DeepInfra, the Llama3.1 405B Instruct, which costs $1.78 per million tokens. The results may be slightly worse, but I prefer cheaper and faster for my purposes. For autocomplete, I am using a faster and code-specific model, Qwen2.5-Coder-7B. I have not yet tried changing the autocomplete model for usage with Obsidian, but that is on my to-do list. Lastly, by the time you read this article, these models may be out of date. One nice thing about having a provider API is that you can easily switch and test different models to see how they work. Aider has one of many model leaderboards that will show you some benchmarks.
After working through the configuration, your
config.jsonfile will have a list of chat models and a tab for the autocomplete model. It will look something like this:```json "models": [ { "title": "DeepInfra Qwen2.5 72B Instruct", "provider": "deepinfra", "model": "Qwen/Qwen2.5-72B-Instruct", "apiKey": "your-api-key" }, { "title": "DeepInfra Llama3.1 405B Instruct", "provider": "deepinfra", "model": "meta-llama/Meta-Llama-3.1-405B-Instruct", "apiKey": "your-api-key" }, ],
"tabAutocompleteModel": { "title": "DeepInfra Qwen/Qwen2.5-Coder-7B", "provider": "deepinfra", "model": "Qwen/Qwen2.5-Coder-7B", "apiKey": "your-api-key" } ```
Trying it Out
The Chat UI
Once you have Continue configured, you can open your Obsidian Vault in VS Code. You will want to add a
.continueignorefile in your folder that lists.obsidianand any other files or folders you want Continue to ignore for context purposes. Click the three dots in the bottom of the chat bar and check that your vault (@codebase) index is complete. You can now chat with the LLM and ask it questions using your vault as a reference.
Click the three dots in the bottom of the chat bar and check that your vault (@codebase) index is complete. You can now chat with the LLM and ask it questions using your vault as a reference.@codebase what are some common themes from this vault?Continue provides a docs page that lists some types of questions that an LLM will be able to help with. Naturally, I asked the LLM to put these in the context of an Obsidian Vault and here is what it told me:
```md
Useful Questions
- High-Level Questions About Your Notes:
- "What are the main themes in my notes on personal development?"
-
"How do I incorporate agile methodologies into my project management?"
-
Specific Information:
- "What are the key points in my notes about productivity hacks?"
-
"Can you find any references to neuropsychology in my notes on cognitive science?"
-
Generating Content:
- "Write a new note on the benefits of meditation, using the same structure as my other wellness notes."
-
"Draft a summary of my recent project retrospective, following the format of my previous summaries."
-
Contextual Questions About a Specific Folder:
- "What is the main purpose of the 'Research' folder?"
-
"How do we use the concept of 'flow' in the 'Psychology' folder?"
-
Relationships and Connections:
- "What are the connections between my notes on 'Time Management' and 'Goal Setting'?"
-
"How do my notes on 'Digital Marketing' relate to 'SEO'?"
-
Task and Project Management:
- "What are the next steps I should take based on my notes for the 'Personal Finance' project?"
-
"Can you list the tasks I need to complete for my 'Career Development' plan?"
-
Deep Dives and Analysis:
- "Can you provide a detailed explanation of the concept of 'reflective practice' found in my notes?"
-
"What insights can you derive from my notes on 'Project Management'?"
-
Insight and Reflection:
- "What have I learned from my notes on 'Mindfulness'?"
- "Can you help me reflect on my progress based on my notes for the 'Health and Wellness' topic?"
Not Useful Questions
- Literal Review of All Files:
- "Find everywhere where the term 'mindfulness' is mentioned in my entire vault."
-
"Review all my notes and find any spelling mistakes."
-
Comprehensive Tasks that Require Literal Access:
- "Add a new section to all notes that discuss 'productivity' and summarize the main points."
-
"Rewrite all my notes on 'Digital Marketing' to include the latest industry trends."
-
Refactoring and Detailed Edits:
- "Update all references to 'Scrum' to 'Kanban' in my 'Agile' folder."
- "Add a new parameter to the function
calculate_scoreand update all usages in my 'Programming' notes."
Summary
- Useful Questions: Focus on high-level insights, specific information, generating new content, contextual questions about specific folders, and reflecting on your notes.
- Not Useful Questions: Require the LLM to see and edit every file, perform comprehensive reviews, or make detailed edits across multiple notes. ```
Text Generation
Continue also offers in-editor code generation with the hotkey
Ctrl+Iand an entered prompt. I have only tried a few things with this, but it was able to successfully review a set of meeting notes I had written and summarize all of the outstanding questions. I expect you could also use this to autogenerate backlinks on a note where a follow-up note might be helpful, or quickly generate templates to be used in Obsidian. I ended up editing this entire article by selecting sections and prompting the AI with the following: "You are a proficient writer. Please edit this text for style, typos, spelling, and grammar."Autocomplete
Continue will also attempt to autocomplete unless you turn it off in the bottom right bar in VS Code. While writing this article, the autocomplete feature was somewhat helpful even though it is not code. Further configuration may optimize this even more. Keep in mind that autocomplete triggers frequently and will burn through a lot of tokens, so you will want to keep an eye on your usage. With the cheaper models I am using, I have only spent 10 cents over the past four days of moderate usage at work and at home. A bulk of that cost is due to autocomplete, and I sometimes turn it off to keep costs down. You may be able to limit these costs effectively by configuring the number of input tokens that can be sent to the API, but I am not sure how that will impact the results.
 ## Conclusion - Brought to You by Qwen 72B
## Conclusion - Brought to You by Qwen 72BIn conclusion, integrating AI tools like Continue into your Obsidian vault opens up a multitude of possibilities for enhancing your note-taking, information management, and productivity. By leveraging the chat window, text generation, and autocomplete features, you can create more comprehensive and accurate notes, generate summaries, and automate routine tasks. The integration of LLMs into your workflow not only streamlines your processes but also provides deeper insights and connections within your knowledge base. While there are initial setup steps and some considerations around cost and configuration, the benefits of AI-assisted note-taking in Obsidian are well worth the effort. As AI tools continue to evolve, the potential for further enhancements and optimizations is immense, making this an exciting and valuable addition to any knowledge management system.
-
 @ 599f67f7:21fb3ea9
2024-09-19 08:27:12
@ 599f67f7:21fb3ea9
2024-09-19 08:27:12¿Qué es una dirección Lightning o Lightning address?
Una dirección Lightning es una dirección que visualmente se asemeja a una dirección de correo electrónico legible para los humanos, por ejemplo usuario@dominio.com pero que en realidad te permite recibir pagos en bitcoin instantáneos y económicos, sin la necesidad de tener un nodo en linea en tu dispositivo ni tener que generar facturas de forma manual cada vez que alguien te quiere hacer un pago.
¿Suena bien no?
¿Y cómo funciona?
Funciona utilizando el protocolo de pago LNURL.
Aquí se muestra un sencillo esquema de lo que ocurre en segundo plano.
En resumen, cuando otro usuario quiere pagarte usando tu dirección Lightning, tu billetera convierte la dirección Lightning en una solicitud de pago LNURL. Luego se utiliza esa solicitud de pago LNURL exitosa para obtener una factura BOLT11.
💡 Dirección Lightning > LNURLp > Factura BOLT 11.
Suena bien, pero ¿cuál es el problema?
Por el momento, muchas de las implementaciones de Lightning Address son de custodia, porque se necesita un dominio para que Lightning Address funcione y un nodo que esté siempre en línea para recibir los pagos. Debido a que es de custodia, el custodio puede atacarte en cualquier momento y monitorear tus transacciones.
Tienes que confiar en el propietario del dominio para no cambiar el registro de tu dirección Lightning. Y no funciona si el servidor LNURL no está en línea.
Bitcoin Txoko ofrece una sencilla solución de Lightning Address respaldada por LNbits. Esto también es de custodia, así que por favor mantén solo una pequeña cantidad en tu billetera Bitcoin Txoko y ve retirando a tu billetera de autocustodia a medida que recibas más sats.
Estoy listo, ¿qué necesito para empezar?
¡Todo lo que necesitas es un teléfono móvil o un ordenador y una conexión a Internet!
1. Creando tu billetera
Si aún no lo has hecho, navega a https://bitcointxoko.com y crea una nueva billetera. Puedes elegir el nombre que quieras.
2. Activar extensiones
Hace falta la extensión
Pay Linkspara que las direcciones Lightning funcionen.Abre
Extensionesen la barra de herramientas y activaPay Links.3. Creando tu enlace de pago
-
En a la extensión
Pay Links, haz clic enNew Pay Link. -
Elige la billetera que has creado.
-
Para la descripción del artículo, puedes escribir lo que quieras.
-
Elige un nombre de usuario de tu dirección Lightning. Tu dirección Lightning se verá como
username@bitcointxoko.com. -
Desmarque
Fixed amounty cambia el valor mínimo a 1 y el valor máximo a 500000.
⚠️ También puedes cambiar el valor máximo a algo más alto, pero es más probable que los pagos más grandes fallen debido a la limitada capacidad de entrada del nodo Lightning de Bitcoin Txoko. Así que recomendamos mantenerlo en 500000 sats.
-
Ahora abre
Advanced optionsy cambiaComment maximum charactersa 799. Este paso no es necesario pero permite más funcionalidades más adelante. -
Marca
Enable nostr zapsen la parte inferior, para que puedas utilizar tu dirección Lightning para recibir zaps. -
Las demás opciones avanzadas son opcionales, puedes configurarlas si quieres o dejarlas en blanco.
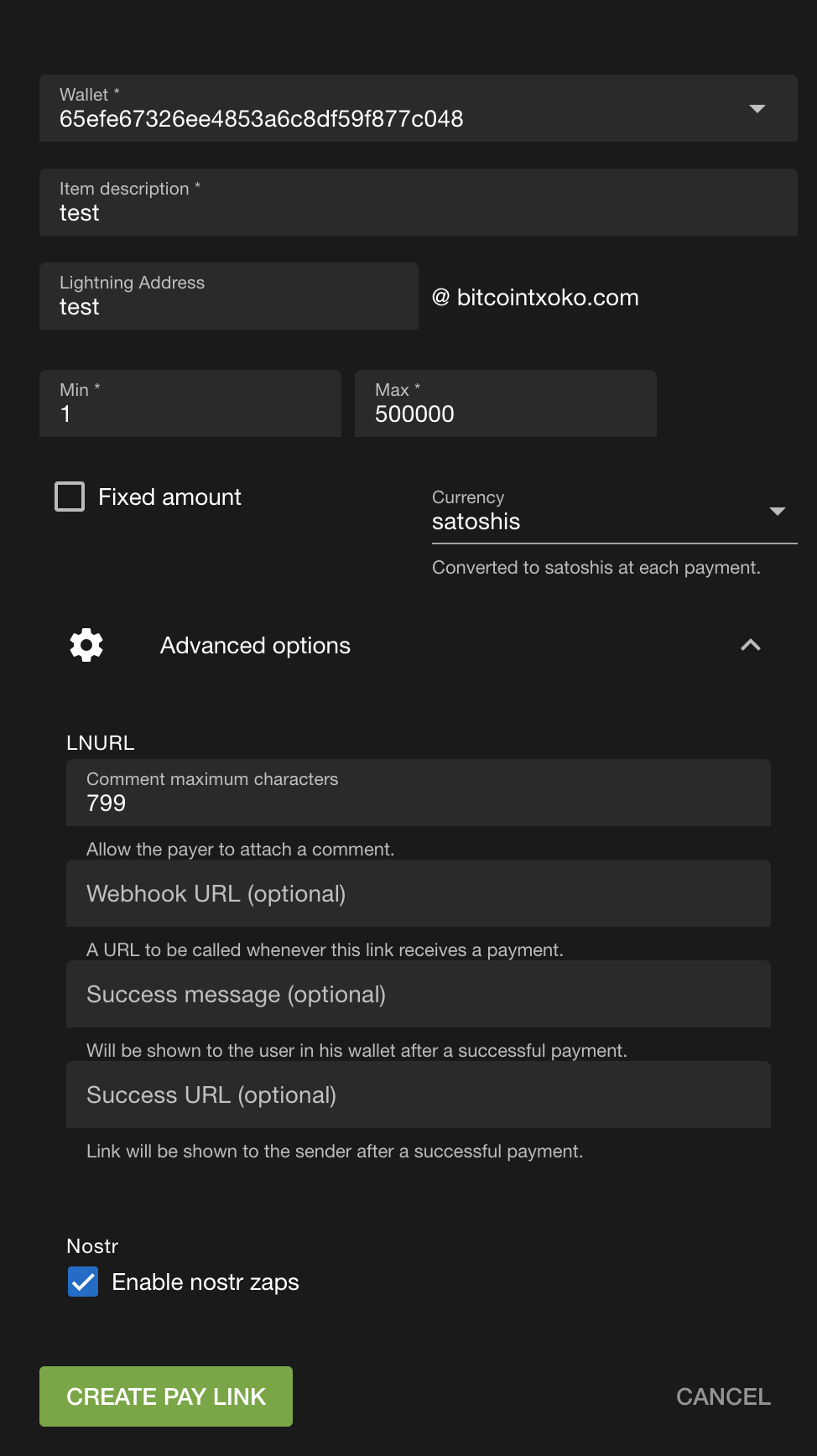
Al final debería verse algo así.
- Cuando hayas comprobado que todo es correcto, sigue adelante y haz clic en
Create Pay Link.
Probando
Puedes probar si tu nueva dirección Lightning funciona yendo a otra cartera, pulsando en
Enviary escribiendo tu dirección Lightning como destino, y luego enviándote una pequeña cantidad de sats.Vuelve a tu billetera Bitcoin Txoko y comprueba si has recibido tu propio pago. Es posible que tengas que actualizar la página.
Si todo funcionó correctamente, ¡enhorabuena! 🥳
Si no es así, háznoslo saber. Siempre estamos aquí para ayudar.
Próximos pasos
Nostr zaps
Puedes añadir tu dirección Bitcoin Txoko Lightning a tu perfil de nostr y usarla para recibir zaps. Normalmente, esto se hace yendo a
Perfil>Editar>Dirección Lightningy cambiando la dirección Lightning.LNDhub
Puedes importar tu billetera LNbits como un LNDhub en tu teléfono utilizando una aplicación como Zeus o BlueWallet, en lugar de visitar la billetera en el navegador cada vez que desees comprobar tu saldo o realizar un pago. Echa un vistazo a nostr:naddr1qvzqqqr4gupzqkvlvlma7a55ccp6d5rrdc27h3ssmdmael286mjaq5uxmqslk04fqqxnzd3exuerqdfkxccnyv3cs0uvul sobre cómo hacer esto.
Código QR
También puedes compartir o imprimir tu código QR LNURLp para que la gente pueda escanearlo fácilmente con sus teléfonos. ¡Muy útil si estás introduciendo bitcoin a tu comerciante local favorito para que pueda recibir propinas Lightning!
Simplemente comparte el enlace a tu página compartida, o imprime el código QR como PDF yendo a
View Link>Print. -
-
 @ 5c7794d4:98abc46b
2024-10-13 16:34:46
@ 5c7794d4:98abc46b
2024-10-13 16:34:46Hey, plebs!
We’ve got some news to share about #Annonymal’s journey so far and where we’re headed.
As most of you know, we’ve been at this since October 31st, 2022, and we’re about to celebrate our second anniversary soon.
Originally, we were aiming to drop the first-ever Bitcoin-only heavy metal album this year in 2024, but… well, things didn’t quite go as planned.
We’ve been stacking sats over the last two years and we are at the final recording sessions of our album this month.
We are happy with the results as we have killer tracks that’ll really amp up the pro-Bitcoin vibes.
We’re stoked about it, but after looking at our budget, we’re realizing we might not have the funds to promote it the way we want.
So, we had two options: delay the whole thing until October 2025 OR… find a middle ground. And we chose to keep the ball rolling!
We’re still gonna drop our new single, “Horns Up For Satoshi,” on October 31st, 2024, to mark our anniversary and give you a taste of what’s coming.
Then, the full album will be released on January 31st, 2025, regardless of how much money we raise for promotion.
We’ve worked hard, and we’re just too excited to hold it back.
We’re still aiming to raise about 6k USD to get a solid promo campaign going and make sure we do this album justice.
Every sat counts, and if you feel like throwing some support our way, you can donate via Lightning Network (LN) at annonymal@getalby.com or the on-chain address bc1qq06tpkugwle76wwj50u5gcvr0mv5ettmeflryg.
But anyway, in the end of the day, this isn’t just about us—it’s about all of us spreading the word about Bitcoin in a way that’s fun and loud.
We know not everyone gets it, but hey, that’s not the point. We’re here to orange-pill the people who do.
So, thanks for sticking with us, supporting us, and being an awesome community.
Let’s make some noise for Bitcoin and rock the world!
Horns Up For Satoshi! 🤘
-
 @ 1b5ee74d:bb1aae6e
2024-09-10 08:51:03
@ 1b5ee74d:bb1aae6e
2024-09-10 08:51:03- Who Is Responsible for the Content Published on Social Networks?
- What should the role of platforms be in content moderation?
- Who should be consulted in cases of disputes involving illegal content?
- Should there be a limit to freedom of speech online? Where should the line be drawn?
These are just a few of the numerous questions that have characterized the debate for years, not only regarding social networks but, more broadly, the entire landscape of online interactions.
In recent weeks, tensions have reignited due to three cases that have stirred the pot—depending on the perspective—with slogans of either combating illegal activity or fighting censorship: Telegram, Meta, and X.
These cases are distinct, with the platforms and their executives behaving differently in each instance: Meta cooperated with authorities, while Telegram and X were more reluctant. However, all three stories share a key issue—perhaps the key issue: the ability to intervene in the content they host.
To understand the reason, let’s briefly recap what happened.
Telegram, Meta, and X: Three Different Cases, One Common Origin
Pavel Durov, founder of Telegram, was arrested in Paris on August 24th as part of an investigation that French authorities have been conducting for months against the messaging platform.
The accusations are numerous: money laundering, drug trafficking, child pornography, and refusal to cooperate with law enforcement. In the press release issued by the Prosecutor’s Office, there is even mention of violations related to the import and export of cryptographic tools—an approach reminiscent of the United States in the 1990s, when the government classified cryptography on par with weaponry. This interpretation only changed due to the outcome of the Crypto Wars.
In fact, reports tell us that Pavel Durov was released after a few days upon paying a €5 million bail, with the condition that he not leave France. Initially, Telegram issued a statement via Twitter, asserting its compliance with European laws. But on September 6th, the founder of Telegram decided to fight back, leaving little room for interpretation.
"Sometimes we can’t reach an agreement with regulators in certain countries on the right balance between privacy and security," Durov said, adding that, if necessary, Telegram will leave markets that are incompatible with these principles.
It is worth noting that this is not the first time Durov has clashed with authorities. In the past, he refused to cooperate with Russia by denying access to Telegram users’ personal data. This refusal led to the platform being temporarily blocked in Russia in 2018.
Meta: Pressure from the White House and Zuckerberg’s Revelations
Mark Zuckerberg, CEO of Meta, recently disclosed pressures he received from the White House during the pandemic. In a letter to the U.S. House Judiciary Committee, Zuckerberg revealed that the Biden administration pushed Meta to remove content related to the virus, including satirical and critical posts.
Zuckerberg explained that in 2021, Meta deleted more than 20 million posts related to COVID-19 but expressed regret over some of the decisions made, admitting that the company had succumbed to excessive political pressure.
Zuckerberg emphasized that these requests were perceived by the company as an obligation rather than a choice, and in hindsight, some of these actions might have been mistakes. Meta’s future commitment, according to Zuckerberg, will be to better resist such pressures, even in emergency situations.
I believe the government’s pressure was wrong, and I regret not being more transparent about it.
X and the Clash with the Brazilian Government
Elon Musk and X (formerly Twitter) are at the center of a legal dispute in Brazil, where the platform was blocked after Musk refused to appoint a local legal representative, as required by the country’s Supreme Court. The issue arose when Judge Alexandre de Moraes ordered X to suspend certain accounts accused of spreading political disinformation, particularly those associated with former president Jair Bolsonaro and his supporters.
Musk’s reaction was harsh. He accused the Supreme Court of corruption and of violating free speech, criticizing de Moraes and calling him a “criminal.” However, the judge continued his legal actions against Musk and his company, even freezing the bank accounts of Starlink, Musk’s satellite division, to pressure X into complying with Brazilian laws.
Brazilian authorities are even pursuing those who attempt to access the platform using VPNs, sparking further controversy over freedom in Brazil.
Currently, the platform remains suspended, with about 21 million Brazilian users cut off from the service. The legal dispute is ongoing and could have long-term repercussions for X’s presence in Brazil, one of the platform’s largest markets.
The Ownership of Content
Telegram and X have found themselves in hot water for refusing to comply with content moderation mandates imposed by various jurisdictions. Meta, on the other hand, has avoided such issues by adhering to directives from the White House, including the removal of content flagged by Washington, such as “satirical and ironic” posts, as noted in the letter.
The decisive factor in all three cases is the same: the ability to intervene in what is published on the platform. The terms and conditions of Meta and X do not formally claim ownership of the content users post, but they clarify that users grant the companies a non-exclusive, royalty-free, worldwide license to use, distribute, modify, and display the content in relation to the services offered. Telegram’s terms are slightly stricter: while users also retain formal ownership of their content, Telegram requires a license to distribute and display content only within its ecosystem.
However, the result remains the same. Anything published by users can be modified by the platform, according to the implicit contract every single user agrees to when they begin using the service.
Nostr is the Way
It’s no coincidence that, in recent weeks, many who care about issues such as privacy and censorship resistance have reignited interest in Nostr. The protocol, whose acronym stands for Notes and Other Stuff Transmitted by Relays, can be used via various clients, not a single platform—similar to how the Web is accessible from different browsers.
But most importantly, users who create an account do not do so through a username and password saved on the company’s servers—because, in this case, the company doesn’t exist—but rather through a public key and a private key.
This key pair allows users to interact with Nostr across multiple clients and send their “notes”—as posts are called on Nostr—to as many relays (servers) as they wish. In other words, the data is not stored on a single server but on multiple servers chosen by the user—and the user can even set up their own server without much difficulty.
Most importantly, the data is portable. Posts sent are cryptographically signed: in Nostr, content ownership is not just formally with the user, it is mathematically so.
In such a context, blaming the operator of a client or relay for the content signed and published by users' private keys would be bordering on absurdity, besides revealing a clear technical ignorance. Of course, after the accusations from the U.S. Department of Justice against the developers of Samourai Wallet, it’s fair to be ready for anything.
But giving a chance to solutions like Nostr also means considering the possibility of reclaiming one's online identity and no longer being an unconscious victim of manipulative algorithms and invasive governments.
-
 @ 8d34bd24:414be32b
2024-10-13 14:57:58
@ 8d34bd24:414be32b
2024-10-13 14:57:58There have been many so called gods throughout the history of mankind. All but one have been created by man (or possibly fallen angels) and formed by man’s hands. Only the God of the Bible created man, formed man & breathed breath into him, and revealed Himself to mankind.
The God of the Bible does not need man to defend Him. (Believers are called to be “… ready to make a defense to everyone who asks you to give an account for the hope that is in you …”(1 Peter 3:15) and to stand up for the truth.) The God of the Bible is the only God who is able to fight for Himself and His honor with no help from His creation. This story from 1 Samuel is an inspiring and humorous story that shows God’s ability to defend Himself even when none of His “followers” are doing a good job of following.
The Philistines Eli’s son’s, Hophni and Phinehas, carried the Ark of the Covenant with the Israelite army into battle against the Philistines and Hophni & Phinehas were killed, the Israelite army was defeated, and the Ark of the Covenant was captured.
God had been disrespected by the Israelites in general and the priests in particular, so God allowed them to be defeated by their enemies. This however doesn’t mean that He allowed His name to be dishonored.
Now the Philistines took the ark of God and brought it from Ebenezer to Ashdod. Then the Philistines took the ark of God and brought it to the house of Dagon and set it by Dagon. When the Ashdodites arose early the next morning, behold, Dagon had fallen on his face to the ground before the ark of the Lord. So they took Dagon and set him in his place again. (1 Samuel 5:1-3a) {emphasis mine}
When the Philistines put the Ark into the temple of their “god,” they put the Ark before Dagon as a sign of submission, but the one true God doesn’t need anyone to defend Him. When the people returned the next day, their “god” Dagon was face down, prostrate before the Earthly throne of God. The real God cast down the false god/idol in the ultimate position of submission and worship.
The Philistines, however, weren’t ready to submit to the real God yet.
So they took Dagon and set him in his place again. But when they arose early the next morning, behold, Dagon had fallen on his face to the ground before the ark of the Lord. And the head of Dagon and both the palms of his hands were cut off on the threshold; only the trunk of Dagon was left to him. (1 Samuel 5:3b-4) {emphasis mine}
After the Philistines sat their “god” up again (because he couldn’t set himself up), the real God cast him face down again, but this time removed his head and his hands (his mind and his ability to act). You have to love God’s sense of humor showing them who was really God, but like most people, they were slow learners and didn’t want to change their worldview.
Now the hand of the Lord was heavy on the Ashdodites, and He ravaged them and smote them with tumors, both Ashdod and its territories. When the men of Ashdod saw that it was so, they said, “The ark of the God of Israel must not remain with us, for His hand is severe on us and on Dagon our god.” So they sent and gathered all the lords of the Philistines to them and said, “What shall we do with the ark of the God of Israel?” And they said, “Let the ark of the God of Israel be brought around to Gath.” And they brought the ark of the God of Israel around. (1 Samuel 5:6-8) {emphasis mine}
When the Philistines still wouldn’t listen, God attacked them personally by smiting “them with tumors.” Fear overcame them, so they sent the Ark to another Philistine city, Gath. They didn’t worship the one, true God. They didn’t return the Ark. They just passed the misery to another of their cities.
After they had brought it around, the hand of the Lord was against the city with very great confusion; and He smote the men of the city, both young and old, so that tumors broke out on them. So they sent the ark of God to Ekron. And as the ark of God came to Ekron the Ekronites cried out, saying, “They have brought the ark of the God of Israel around to us, to kill us and our people.” (1 Samuel 5:6-8) {emphasis mine}
As the Ark arrived in Gath, the people of Gath had tumors break out, so the people of Gath sent the Ark on to Ekron. The Ekronites realized what was about to befall them and cried out saying, “They have brought the ark of the God of Israel around to us, to kill us and our people.” After seven months of various cities being ravaged by God, they finally called their diviners in order to try to figure out what to do to stop this plague.
They said, “If you send away the ark of the God of Israel, do not send it empty; but you shall surely return to Him a guilt offering. Then you will be healed and it will be known to you why His hand is not removed from you.” Then they said, “What shall be the guilt offering which we shall return to Him?” And they said, “Five golden tumors and five golden mice according to the number of the lords of the Philistines, for one plague was on all of you and on your lords. So you shall make likenesses of your tumors and likenesses of your mice that ravage the land, and you shall give glory to the God of Israel; perhaps He will ease His hand from you, your gods, and your land. (1 Samuel 6:3-5) {emphasis mine}
God hates divination, but this was the first wise action taken by the Philistines. They started to show proper respect for the one true God, even if they didn’t really understand that He wasn’t just another god, but the one and only God. The one thing they did understand was that they should give a guilt offering to ask forgiveness for their sins against God.
Why then do you harden your hearts as the Egyptians and Pharaoh hardened their hearts? When He had severely dealt with them, did they not allow the people to go, and they departed? (1 Samuel 6:6)
They also had seen God’s majesty and wrath with respect to the Egyptians and Pharaoh and didn’t want to suffer what Egypt suffered for refusing to obey God. They feared God, but they didn’t want to submit to Him and they really didn’t want to submit to the Israelites, so they decided to put God to a test:
Now therefore, take and prepare a new cart and two milch cows on which there has never been a yoke; and hitch the cows to the cart and take their calves home, away from them. Take the ark of the Lord and place it on the cart; and put the articles of gold which you return to Him as a guilt offering in a box by its side. Then send it away that it may go. Watch, if it goes up by the way of its own territory to Beth-shemesh, then He has done us this great evil. But if not, then we will know that it was not His hand that struck us; it happened to us by chance.” (1 Samuel 6:7-9) {emphasis mine}
The Creator of the universe didn’t have any trouble with the Philistine’s test. The Philistines had two nursing cows yoked to a cart with the Ark on it. They wanted to see if these nursing cows would head home to their nursing calves as would be expected, or would they take the Ark home to Israel? What do you think happened? Of course, the cows took the Ark straight to Israel to the very city, Beth-shemesh, that the Philistines had specified. He proved without a shadow of a doubt that He was God.
If only the Israelites showed as much respect. Many of the residents of Beth-shemesh died because they disobeyed and looked into the Ark. The one true God is omnipotent, but He is also holy and must be treated as such.
God made sure His people and these pagan foreigners knew His power and He didn’t need any help.
Just as was shown in my last post, this historical event demonstrated God’s power to His people and to foreigners. When God’s chosen people refused to show Him proper reverence, He corrected them and corrected those surrounding them.
Trust Jesus.
your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 13e63e99:25525c6a
2024-09-03 09:29:54
@ 13e63e99:25525c6a
2024-09-03 09:29:54Preview
Last week, President Nayib Bukele of El Salvador emphasized Bitcoin’s role in enhancing the country's global image that boosted foreign investment and tourism. At the NostrWorld Unconference in Riga, the synergy between Bitcoin and decentralized social networks was a key focus, showcasing the potential for integrating Bitcoin with the growing Nostr protocol. Meanwhile, Lightspark launched its Extend platform, facilitating instant Bitcoin payments for U.S. businesses, thereby expanding the accessibility of Bitcoin transactions. Publicly traded companies have increased their Bitcoin holdings by nearly 200%, bringing their total to $20 billion, reflecting strong institutional confidence in Bitcoin as a reserve asset. Additionally, Bitcoin in exchange experienced its third-largest daily net outflow of 2024, indicating a shift toward long-term holding among investors. Despite some withdrawals, including a $13.5 million outflow from BlackRock’s iShares Bitcoin Trust, the fund remains a dominant force in the Bitcoin investment landscape. Lastly, Nigeria's SEC granted its first provisional exchange license, a milestone in the regulation of the country’s rapidly growing digital asset industry, positioning Nigeria as a leading player in global digital asset adoption. For more details, continue reading below.
A. Bitcoin Data Dashboard
1. Bitcoin Transactions\ 2. Supply\ 3. Mining\ 4. Transaction Fees\ 5. Difficulty Retarget\ 6. Lightning Network (Public)
B. Bitcoin Ecosystem
1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador\ 2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks\ 3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.\ 4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion\ 5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024\ 6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals
C. Regulation
1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation
D. Macroeconomy
1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich\ 2. Jobless claims drop as labor market slows, US economy remains on steady growth path
A. Bitcoin Data Dashboard

As of Sep 2, 2024
B. Bitcoin Ecosystem
1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador
President Nayib Bukele recently provided a candid assessment of El Salvador's groundbreaking decision to adopt Bitcoin as legal tender, a move that has drawn both praise and criticism on the global stage. In an interview with Time magazine, Bukele emphasized that the initiative has had substantial benefits particularly in enhancing El Salvador's international image despite the country's bitcoin adoption has not expanded as rapidly as he has hoped, Bukele described the Bitcoin adoption as a powerful rebranding tool for the nation, one that has attracted foreign investment and boosted tourism. The president’s marketing advisor, Damian Merlo, echoed this sentiment, calling the decision "genius" and likening it to a major public relations campaign that El Salvador didn’t have to pay for. "We could have spent millions on a PR firm to rebrand the country," Merlo noted, "but instead, we adopted Bitcoin." While the move initially strained relations with institutions like the International Monetary Fund (IMF), which urged Bukele to abandon the policy due to perceived risks, there are signs that the tension is easing. El Salvador has recently reported progress in negotiations with the IMF, with a focus on enhancing transparency and addressing potential fiscal and financial stability risks related to the Bitcoin project.

Reference: Bitcoin.com, Time
2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks
Last week, NostrWorld’s third unconference, held in Riga, Latvia, gathered advocates and developers of the Nostr protocol. Organized by Jack Dorsey, NostrWorld provides a platform for open-source enthusiasts to collaborate on building a decentralized internet. The event, called Nostriga, underscored the emerging synergy between Nostr’s decentralized social network and Bitcoin. Nostr is an open-source protocol for a decentralized, censorship-resistant social network. Unlike traditional platforms, Nostr operates on a network of relays, supporting features like micropayments and digital identity management. It promises greater privacy and independence from centralized platforms. A highlight of the conference was Strike CEO Jack Mallers discussing how Nostr’s micropayments—Zaps—helped a skeptic understand Bitcoin’s value. This feature shows Bitcoin’s utility in social contexts, advancing the concept of internet tipping. Jack Dorsey enphasizing the importance of open source. Nostr faces the challenge of broadening its user base beyond Bitcoin enthusiasts. New initiatives like Ditto aim to integrate Nostr with larger internet communities, potentially increasing Bitcoin’s visibility and accessibility. Nostr’s role as a social and identity system could pave the way for decentralized digital economies. By leveraging social graphs and cryptographic trust, Nostr and Bitcoin together could enable secure, decentralized commerce.
Reference: Bitcoin magazine
3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.
Lightspark has unveiled Lightspark Extend, a new solution designed to facilitate instant Bitcoin Lightning payments for U.S. businesses. This platform integrates with Universal Money Addresses (UMA) and Lightning-enabled wallets, exchanges, or bank accounts, offering a compliant and cost-effective way to handle transactions around the clock. Lightspark Extend is compatible with over 99% of U.S. banks that support real-time payments, enabling businesses to provide their customers with fast, low-cost transactions. UMA simplifies the payment process by using easy-to-remember addresses similar to email, removing the need for complex codes or passwords. With this launch, Lightspark Extend makes real-time payments via the Bitcoin Lightning Network accessible to eligible recipients across the U.S. Businesses interested in adopting this solution can sign up for a UMA address, link their accounts, and start receiving payments through an onboarding process facilitated by Zero Hash, a regulated U.S. financial institution. The introduction of Lightspark Extend marks a significant advancement in expanding the accessibility and utility of Bitcoin payments. This follows Lightspark’s recent announcement of a partnership with Coinbase, enabling customers to send up to $10,000 instantly through the Lightning Network.
Reference: Bitcoin magazine
4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion
Publicly listed companies have seen their Bitcoin holdings soar by nearly 200% in a year, rising from $7.2 billion to $20 billion. According to Bitbo data, 42 such companies now hold 335,249 BTC, valued at roughly $20 billion. This marks a 177.7% increase from a year ago, when their BTC holdings were worth $7.2 billion. The trend began with MicroStrategy's August 2020 purchase of over 21,000 BTC, making Bitcoin its primary treasury reserve asset, and the company has since grown its holdings to 226,500 BTC. A survey commissioned by Nickel Digital Asset Management revealed strong institutional support for Bitcoin as a reserve asset, with 75% of 200 surveyed institutional investors and wealth managers endorsing public companies holding BTC. The survey, involving firms managing $1.7 trillion in assets, also found that 58% believe 10% or more of public companies will hold BTC within five years. Nickel Digital's CEO, Anatoly Crachilov, noted that institutional investors see Bitcoin as a hedge against currency debasement and a valuable addition to reserve allocations. Despite this growth, the 335,249 BTC held by public companies represent just 1.6% of Bitcoin's total capped supply of 21 million.
Reference: Cointelegraph
5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024
Bitcoin is seeing a significant uptick in exchange withdrawals as its price nears the $60,000 mark, with approximately 45,000 BTC removed from exchanges on August 27 alone. This movement represents the third-largest net outflow of Bitcoin from exchanges in 2024, following similar spikes in July. According to data from CryptoQuant, this trend could signal a growing bullish sentiment among investors, who appear to be transferring their Bitcoin off exchanges to hold for the long term, thereby reducing potential selling pressure in the market. As of August 27, major exchanges hold around 2.63 million BTC, reflecting a 12.5% decrease from the 3.01 million BTC held at the beginning of the year. This reduction in exchange reserves underscores a broader trend of investors preferring to hold their Bitcoin privately, possibly in anticipation of future price increases.

Reference: Cointelegraph
6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals
BlackRock's iShares Bitcoin Trust (IBIT) experienced a $13.5 million outflow on Thursday, marking its first outflow since May 1st and only the second in the fund's history since its launch in January. This rare withdrawal contrasts with the ETF’s usual pattern of consistent inflows, underscoring its dominance in the Bitcoin investment space. The outflow came as part of a broader trend affecting spot Bitcoin ETFs, which saw a collective $71.8 million in withdrawals on Thursday. Competing Bitcoin ETFs from Grayscale, Fidelity, Valkyrie, and Bitwise also reported significant outflows, ranging from $8 million to $31 million. Despite these withdrawals, ARK's Bitcoin ETF saw an inflow of $5.3 million, highlighting a mixed investor sentiment as Bitcoin remains below the $60,000 mark. This divergence suggests varied outlooks among investors regarding Bitcoin's future. Despite the recent dip, BlackRock's Bitcoin ETF continues to lead the market, having attracted over $20 billion in net inflows since inception. With more than 350,000 BTC under management, it remains one of the largest institutional Bitcoin holders, reflecting its enduring appeal and influence in the Bitcoin investment landscape.
Reference: Bitcoin magazine
C. Regulation
1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation
The Nigerian Securities and Exchange Commission (SEC) has granted Quidax, an Africa-based crypto exchange, its first provisional operating license. This marks a significant step toward formal recognition and regulation of Nigeria's digital asset industry. The SEC's license allows Quidax to operate as a registered crypto exchange in Nigeria, a move the company describes as a "shot of adrenaline" for the local crypto community, spurring innovation and growth. Quidax CEO Buchi Okoro praised the SEC, particularly under the leadership of Emomotimi Agama, for its efforts to bring order and investor protection to the Nigerian crypto market. The approval also paves the way for Quidax to collaborate with banks and financial institutions, pending approval from the Central Bank of Nigeria. This licensing follows the SEC's recent amendment to its rules on June 21, covering digital asset issuance, exchange, and custody. Despite concerns that stringent requirements could limit local crypto exchanges, the new regulatory framework, including the Accelerated Regulatory Incubation Programme, aims to align virtual asset service providers with the latest standards. Nigeria, Africa's largest economy, is a global leader in cryptocurrency adoption, ranking second in Chainalysis’ 2023 Cryptocurrency Geography Report. While foreign investment in Nigeria's crypto sector has been slower than expected, the new regulatory environment and Quidax's licensing could attract more investors by offering a stable and secure market.
Reference: Cointelegraph
D. Macroeconomy
1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich
As a presidential candidate, Vice President Harris has aligned with President Biden’s tax policies, including the pledge not to raise taxes on anyone earning under $400,000 annually. However, she also has her own ambitious tax proposals. These include raising the top marginal tax rate on high earners from 37% to 39.6%. Although she previously suggested a 4% “income-based premium” on households earning over $100,000 to fund Medicare for All, this idea has not resurfaced in 2024. Among the more controversial proposals Harris supports is a tax on unrealized capital gains for individuals with over $100 million in wealth. Often dubbed the “billionaire tax,” this would require these households to pay an annual minimum tax of 25% on their combined income and unrealized gains. This approach would be groundbreaking in U.S. tax history, as it taxes assets that have not yet been sold. For example, if you buy stock at $10 and it increases to $20, you would owe taxes on the $10 gain, even if you haven’t sold the stock. The same principle would apply to real estate, where yearly value increases would be taxed. This proposal raises significant concerns, particularly about the administrative challenges of valuing assets annually and the potential for future expansion of the tax to lower wealth thresholds. The wealth tax faces hurdles in Congress and potential court challenges, but it signals Harris's intent to push for new forms of taxation on the ultra-wealthy.

Reference: Forbes
2. Jobless claims drop as labor market slows, US economy remains on steady growth path
Last week, new applications for jobless benefits in the U.S. dropped slightly, but re-employment opportunities for laid-off workers are becoming scarcer, indicating the unemployment rate likely remained high in August. Despite this, the labor market's orderly slowdown is keeping economic growth on track, with the economy growing faster than initially reported in the second quarter, driven by consumer spending and rebounding corporate profits. The labor market's cooling supports the expectation that the Federal Reserve may start cutting interest rates next month, though a 50-basis-point reduction seems unlikely. Initial jobless claims fell by 2,000 to 231,000 for the week ending August 24, while continuing claims, which indicate ongoing unemployment, rose slightly, suggesting prolonged joblessness. In the second quarter, the economy grew at an annualized rate of 3.0%, with consumer spending revised upward to a 2.9% growth rate, offsetting lower business investment and exports. Corporate profits also reached a record high, helping businesses manage input costs amid supply-chain challenges. The goods trade deficit widened in July due to a surge in imports, likely driven by expectations of higher tariffs if former President Trump wins the November election. Despite these factors, economists predict growth will slow but avoid a recession.

-
 @ 469fa704:2b6cb760
2024-09-02 06:11:43
@ 469fa704:2b6cb760
2024-09-02 06:11:43I joined Nostr a week ago and wanted to recap it for myself and also give other newbies a simple introduction. Maybe this will help you get started too.
Step 1: Create your identity and get your private key for a browser extension
I started with the Snort client on my local home server. It created my private/public key pair and I was good to go. Then I transferred the private key to Amethyst, a pretty good Android-based client. Before looking at various clients and other nostr-based websites, I tried transferring my private key into a browser extension. I looked at Alby and nos2x. I chose the latter because I wanted to keep my Lightning wallet separate from my identity management. You don't have to, I just found it easier.
Step 2: If you're confused, always check your feed settings
I tried many different clients and was very confused at first. Due to its decentralized nature, Nostr relies on relays, which are just small servers, and to each one you can connect to, all your data is stored. When you post a message, write a note, an article like this or simply who you follow. The main reason and benefit for this is that there is no single point of failure or server-like entity that could be censored. The side effect of this, combined with using different clients, was that not only did it look different everywhere, but the content was also very different. This was simply because I wasn't connected to all my different clients with the same relays. But the main reason why each feed looks different on each client is usually because you can choose different variations of feeds and some clients even offer filters for the feeds.
Scroll down to get a small overview of the clients I've tried.
Step 3: Set up your lightning wallet with something like Wallet of Satoshi
I made my Bitcoin Lightning wallet independent of my identity. That's why I just went with the number one Lightning wallet on the market: Satoshi's Wallet. It's very simple and provides you with a Lightning address that resembles and has the format of an email address. You can add this address to your Nostr profile description and you're ready to receive Sats. Anyone can send them to you, e.g. for a good message or something else they find valuable on Nostr (like a podcast, a video, an article, ...). Just be aware that Satoshi's wallet contains your key and the sats you have there are not really your sats. So only leave a small amount there or no more than you need for your nostr experience.
Step 4: Set up your Nostr address
I set up a unique NIP-05 identifier that is human readable and also looks like an email address. For me, that's tobiya@nostrplebs.com, also called a nostr address. It's much easier to read, share and remember than your public key, which is just a long, unwieldy string of characters.
Some popular services are: * NostrVerified * Alby * Iris * Primal * Snort * nostrplebs.com
Most offer free services or at least a free tier. I chose nostrplebs.com because it links my Nostr address (tobiya@nostrplebs.com) to my Lightning wallet. ⚡
Brief overview of the clients (I have tested)
Web/Browser:
- Primal: Fast, user-friendly, nice looking, easy to use
- Coracle: Focuses on decentralized reputation, privacy and trust metrics. Also well organized and structured
- noStrudel: The most comprehensive I've found, has everything
- Rabbit: Designed like X (Twitter) Pro, focuses on everything at once
- Nostter: Clearly structured, easy to find what you're looking for
- Snort: Fast web client for those who prefer simplicity and speed.
iOS
I'm not an iPhone user, but everything I've discovered says that Damus is the best app for iOS.
Android:
- Amethyst: Feature rich for Android, I only tried this program because it gives me everything I currently need on my phone.
- Primal: Works seamlessly with Primal on the web, which is a pretty convenient starting point if you only want to use one client.
As for the web clients, I'm still figuring out which one will be my favorite. But I think they're all good in their own way. In the time of writing, I am mainly using Primal on Android and Web, Amethyst and noStrudel.
Let's have fun!!
-
 @ 0edc2f47:730cff1b
2024-09-02 01:54:55
@ 0edc2f47:730cff1b
2024-09-02 01:54:55Chef's notes
In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 6 hours
- 🍽️ Servings: 12
Ingredients
- 1 medium onion, peeled and quartered
- 2 tsp ground ginger
- 8-10 large cloves garlic
- 1 cup ketchup
- ¼ cup dry sherry
- ¼ cup sake
- ¼ cup cider vinegar
- ¼ cup soy sauce
- ¼ cup honey
- ¼ cup Dijon mustard
- 1 tablespoon coarsely ground black pepper
- ¼ teaspoon ground cloves
- 1½ cups Coca-Cola, ginger ale, or Dr. Pepper
- 1 first-cut brisket, 6 to 7 pounds (2.7-3.2kg), rinsed and patted thoroughly dry
Directions
- Preheat oven to 325F / 160C.
- Combine all ingredients except brisket in a blender and blend until smooth.
- Place brisket in a Dutch oven or other large pot with a tight-fitting lid.
- Pour sauce over brisket, place lid on pot, roast in oven for 3 hours. Flip roast and return to oven for 3 hours or until fork tender.
- Remove roast to rest. Skim fat from sauce and reduce if desired. Serve immediately with sauce or cool, cover brisket and refrigerate overnight in cooking pan. The next day, defat sauce, reduce if desired, and reheat meat in sauce before serving.
-
 @ 3b7fc823:e194354f
2024-09-01 23:52:38
@ 3b7fc823:e194354f
2024-09-01 23:52:38I dOn'T cAre ABouT pRivAcY. IT dOEsN'T maTtER. i'M nOT dOiNg AnyThiNg wRonG.
GHOSTn
Your phone is spying on you. Your apps are spying on you. Your websites, search engine, fitness tracker, smart watch, IoT device, EVERYTHING is collecting anything it can and sending it off to be stored, cross referenced, and sold.
Data is the new oil.
So what? I don't care if Google knows I like motorcycles. By itself one data point isn't a big deal but once you start bringing everything together...
Who are you talking to? When and how long did you talk to them? Where did you go? How often do you go there? On and on the profile starts to become overwhelmingly invasive.
Right now it is extremely cheap and easy to collect and store the data but it's hard and expensive to cross reference and tabulate the data down to the individual. But in the extremely near future using AI and faster processers, data profiles for sale go from white men between 25 - 30, with this education level, and background like XYZ to -> John loves motorcycls and steak.
Suddenly your insurance premiums are way higher than your friends because you partake in dangerous activities and eat too much red meat. You get denied that loan because you invest in risky assets and it raises your risk factors to pay it back. That job that you applied to never responded because they already ran you through the algorithm and you don't fit the culture.
Protect your data and privacy now before its too late.
privacy
-
 @ 6c2d68ba:846525ec
2024-09-01 13:02:53
@ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend,
it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.
As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:
-
What causes the discomfort that drives you out of the walled garden onto the open sea?
-
Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?
-
What are you hoping to find on the open sea that walled gardens cannot provide?
-
What are you willing to sacrifice for freedom (of speech)?
-
What will you need to keep the ship afloat?
-
How will you react when you find yourself in the middle of a storm?
I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over.
This is about building a new world, an open world without walled gardens and data silos.
Onwards!
-
-
 @ 91687725:a0de48ea
2024-08-24 05:40:14
@ 91687725:a0de48ea
2024-08-24 05:40:14こんにちは。Kateです。
最近ちょっとお休みしていますが、日本でビットコインを専門に扱うDiamond Hands Magazineに寄稿したりしてます。
私がビットコインと出会ったのは2011年、まだビットコイン利用者はとても少なかった時代です。たまたま身内にビットコイン界隈の人がいました。もしかしたら今でいうビト妻だったかも?
まだビットコインが1ドル以下でおもちゃみたいな存在だった頃に知ったわけですが、その後勢いづいて、100ドル、1000ドルと価値が上がっていきました。
それを見て、ビットコインを少しずつ買って貯めておけば、将来リタイヤの蓄えになるかもと思ってお小遣い程度のビットコインを積立してました。でも、アクシデントで失くしちゃったんですよね。
その後、身内のごたごたで自分の生活が天地がひっくり返るように一変し、気がつけばカナダでただお金がないアジア系移民シングルマザー、しかも周りに家族が誰もいないという、非常にマイノリティな立場になりました。
人生、何事も経験。一度ビットコインを失くし、傷心もあり、数年はビットコインから離れました。でも気がつけばビットコインは冬の時代を終えて、また元気になっていたんですね。自分は海外でひとり子育てに追われ、なんとか生きてた感じですが!
ビットコインが500ドルくらいになっていた時に困窮していた私は、ふとペーパーウォレットと呼ばれた当時の携帯可能ウォレット?に0.5btc 残っていたのを発見して速攻換金しましたね。悔やまれます。
その後、2017年頃、カナダで当時大手の割と使い勝手のいい取引所があることを知って、再度ビットコイン貯蓄にチャレンジしました。2年ほどで、ほぼ1ビットコインと10ETHくらいあったんですけどね、今度は取引所の代表者が行方不明になり、またもやビットコインを失くしました。
ふつうだったら、もうやめますよね。2回もなくしたら。
けれど、自分はかつてインターネットが始まったころのワクワクを経験していました。90年代半ば、新宿にできたばかりのインターネットカフェで、GIFがかろうじて表示できるグレーのブラウザ画面と対面しました。世界を変える技術を体験した時の感動は今でも忘れられません。
(こう書くと立派なオバサンなのがバレちゃいますね。ビットコインネイティブ世代の中では年長者)
それから15年以上たって、初めてサトシナカモトのホワイトペーパーを読んだ時に、同じ衝撃を受けたのです。初めて実用化されたインターネット上で世界の誰とでも送り合えるマネー。その可能性は無限∞。
そのビットコインの進化を、実際に買ってみたり、使ってみたり、なくしたりしつつ、より深く知ろうと付き合ってきた自分は、いつの間にかビットコインを通して世の中のいろいろを見て考えるようになりました。
ビットコインが生まれ、実験段階を経て、すでに15年が経ちます。けれども、ビットコインは今でも多くの人から最も誤解されている技術・発明のように見えます。ここまで来たら、自分が生きている間に、ビットコインが世界とどう関わっていくのか見届けたいと思います!
そして、私自身がビットコインを知ることで発見した世界や新しい価値観を、誰かに伝えられたらいいなと願って、このブログをスタートすることにしました。
今回は自己紹介という形になりましたが、私がビットコインを通して学んだことや気づいたことをこれから少しづつアップしてみます!
週1くらいのペースで投稿が目標です。よろしくお願いします。
-
 @ 6bf975a0:65de1244
2024-10-13 14:16:56
@ 6bf975a0:65de1244
2024-10-13 14:16:56Площадки для размещения контента СМИ
Условно их можно разделить на две группы: свои и не свои. Свои медиа полностью контролирует. В не своих медиа арендуют чужие технологии для доставки контента аудитории, выполняя только производственную роль и рассматривая доставку контента как аутсорс.
Исследования 2020-ых годов показывают, что значительная часть аудитории теперь полагается на социальные сети для получения новостей. Например, исследование 2021 года показало, что 42% американцев используют социальные сети в качестве источника новостей, и эта цифра выросла по сравнению с предыдущими годами. Среди молодых людей эта зависимость еще более выражена: например, 38% людей в возрасте 18-24 лет в первую очередь получают новости через социальные сети.
Платформы корректируют свои стратегии в свете генеративного ИИ, а также ориентируются на меняющееся поведение потребителей и растущую обеспокоенность регулирующих органов по поводу дезинформации и других вопросов. В частности, Meta* пытается снизить роль новостей на своих площадках и ограничивает алгоритмическое продвижение политического контента. Компания также сокращает поддержку новостной индустрии, не продлевает сделки на миллионы долларов и удаляет вкладку новостей в ряде стран.

Ленивая аудитория
Ей сложно выходить за пределы привычных пространств.
Исследование, проведенное компанией Orca Online в 2022 году, показало, что посты в социальных сетях без внешних ссылок имеют значительно более высокий уровень вовлеченности. Посты без ссылок в среднем набирали 352,3 взаимодействия, в то время как посты с внешними ссылками - только 139,1 взаимодействия. Это говорит о том, что пользователи с большей вероятностью будут взаимодействовать с контентом, который удерживает их в рамках платформы. Исследование, проведенное Институтом Рейтер, показало, что 47% британских респондентов просматривают и читают новости в социальных сетях, не переходя по ссылкам, чтобы получить доступ к полным текстам статей.
Источник: Использование новостей на онлайн-платформах фрагментировано: в настоящее время шесть сетей охватывают не менее 10% респондентов Reuters по сравнению с двумя десять лет назад. YouTube используется для новостей почти третью (31%) глобальной выборки каждую неделю, WhatsApp* примерно на пятую часть (21%), в то время как TikTok (13%) обогнал Twitter (10%), который теперь переименован в X, в первый раз.

Популярность аудио и видеоформатов
В связи с этими изменениями видео становится более важным источником онлайн-новостей, особенно среди более молодых групп. Каждую неделю доступ к коротким новостным видеороликам получают две трети (66%) аудитории СМИ, а более длинные форматы привлекают около половины (51%). Основным источником потребления новостного видео являются онлайн-платформы (72%), а не веб-сайты издателей (22%), что увеличивает проблемы, связанные с монетизацией и подключением.

Подкастинг новостей остается светлым пятном для издателей, привлекая более молодую, хорошо образованную аудиторию, но в целом является деятельностью меньшинства. В корзине из 20 стран чуть более трети (35%) ежемесячно посещают подкасты, а 13% получают доступ к шоу, посвященному новостям и текущим событиям. Многие из самых популярных подкастов сейчас снимаются и распространяются через видеоплатформы, такие как YouTube и TikTok
Популярность коротких видео

Насколько актуальны сегодня сайты?
На всех рынках только около пятой части респондентов исследования Reuters 2024 (22%) называют новостные сайты или приложения своим основным источником онлайн-новостей –, что на 10 процентных пунктов ниже, чем в 2018 году. Издателям на некоторых рынках Северной Европы удалось противостоять этой тенденции, но более молодые группы во всем мире демонстрируют более слабую связь с новостными брендами, чем в прошлом.
Пожилые зрители по-прежнему предпочитают смотреть видео через новостные сайты, хотя большинство из них говорят, что в основном получают доступ к видео через сторонние платформы. Только в таких странах, как Норвегия, половина пользователей (45%) говорят, что в основном потребляют видео через веб-сайты, что свидетельствует о силе брендов на этом рынке, стремлении обеспечить хороший пользовательский опыт и стратегии, ограничивающей количество видео, размещаемых издателями на таких платформах, как Facebook и YouTube.
Важно отметить, что на всех рынках поиск и агрегаторы, вместе взятые (33 %), являются более важным способом получения новостей, чем социальные сети (29 %) и прямой доступ (22 %). Значительная часть мобильных оповещений (9 %) также генерируется агрегаторами и порталами, что усиливает беспокойство о том, что может произойти дальше.

Поисковые машины и нейросети против создателей контента
Поиск: с одной стороны, Google хочет выдавать саммари по запросам через Gemini на страницах с результатам поиска.
Источник: Google запускает — пока в тестовом режиме и для отдельных групп пользователей — новую функцию Supercharging Search with generative AI (SGE). После ее активации вместо привычного поискового движка наш запрос будет обрабатывать ИИ Gemini, который в ответ сформулирует некое резюме из 272 слов, предваряющее поисковую выдачу.
С другой, появляются Perplexity, Copylot, которые выдают ссылки на источники.
Голосовые помощники: не дают ссылок для перехода, но озвучивают информацию с сайтов.
Общий тренд нейросетей: большие корпорации обучают свои технологии на данных создателей контента, но далеко не всегда дают трафик самим создателям контента.
Экономика онлайн-СМИ в мире
2024, издание Politico об экономическом состоянии американских изданий
Патрик Сун-Шионг, миллиардер-издатель газеты Los Angeles Times, уволил 20 процентов сотрудников своего отдела новостей. В журнале Time владельцы-миллиардеры Марк и Линн Бениофф сделали то же самое в отношении 15 % сотрудников редакции, состоящих в профсоюзе. Последний пожар разгорелся в Sports Illustrated на предыдущей неделе, когда катастрофические увольнения были разосланы по электронной почте большинству сотрудников. Business Insider (чья материнская компания Axel Springer также владеет POLITICO) сократил 8 % своего штата, а сотрудники Condé Nast, Forbes, New York Daily News и других изданий вышли на улицу в знак протеста против предстоящих сокращений в своих магазинах.
Новостной бизнес всегда был цикличным: он падал во время экономического спада, а затем улучшался на подъеме. Но теперь это не так, поскольку наша экономика в последнее время удивительно сильна. Почти везде, куда бы вы ни посмотрели - Washington Post, NPR, Vice, Vox, NBC News, Texas Tribune, WNYC, Barstool Sports, - компании сократили огромное количество сотрудников. С 2008 года занятость в новостных отделах сократилась более чем на 26 процентов. Buzzfeed News мертв. Журнальный бизнес тоже атрофировался: доходы газетных киосков упали с 6,8 миллиарда долларов в 2006 году до 1 миллиарда долларов в 2022 году. Наблюдая за тем, как медиабизнес истекает кровью, профессор журналистики Джефф Джарвис, человек, когда-то ратовавший за электронное будущее отрасли, сложил руки на коленях, как гробовщик, и спросил в своем блоге, не пора ли отказаться от старых новостей. Ссылаясь на мрачные новости об увольнениях, Джарвис привел в порядок труп в процессе его создания. Он отметил, что доверие к журналистике тает, а частные инвестиционные компании, такие как Alden Global Capital, занимаются каннибализмом своих газет.
Некогда здоровые газеты закрылись в таких городах, как Нью-Йорк, Сан-Франциско, Бостон и Миннеаполис; приостановили печать в таких городах, как Вашингтон; стали выходить раз в две недели, как в Чикаго и Сиэтле; или иным образом сократили количество страниц по сравнению с временами бума начала XXI века. Неужели нет никакого оптимизма? Уж точно не в гарвардском журнале Nieman Reports, который в октябре опубликовал некролог Кэтрин Рейнольдс Льюис под заголовком «Эй, журналисты, никто не придет нас спасать».
Кроме рекламы есть и другие источники доходов онлайн-медиа, но с ними тоже не все так однозначно.
Reuters: Наши данные показывают незначительный рост подписки на новости: всего 17% заявили, что заплатили за любые онлайн-новости в прошлом году в корзине из 20 более богатых стран. В странах Северной Европы, таких как Норвегия (40%) и Швеция (31%), самая высокая доля платящих, среди самых низких - Япония (9%) и Великобритания (8%). Как и в предыдущие годы, мы обнаружили, что большая часть цифровых подписок достается лишь нескольким элитным национальным брендам, что усиливает тренд победитель получает все.


Топ мировых изданий по объемам доходов от платной подписки (paywall)

Эфирные радио и телевидение
Прогнозируемый рост радио: Ожидается, что к 2029 году радио будут слушать более 3,2 миллиарда человек по всему миру, что составляет около 40 % населения планеты. Это говорит о том, что радио остается важным средством массовой информации, несмотря на рост цифровых альтернатив.
Источник, 2022 год: Большинство россиян (57%) с той или иной периодичностью слушают радио, при этом каждый пятый делает это ежедневно. Наиболее характерна эта привычка для мужчин старше 35 лет, имеющих высшее образование. Доля женской и молодежной аудитории значительно меньше (71% и 81% соответственно не слушают радиостанции совсем или включают их от силы пару раз в месяц).





Нейросети и достоверность контента
Обеспокоенность по поводу того, что реально, а что фальшиво в Интернете, когда дело доходит до онлайн-новостей, выросла на 3 процентных пункта за последний год: примерно шесть из десяти человек из аудитории СМИ в исследовании Reuters 2024 года (59%) заявили, что они обеспокоены. Этот показатель значительно выше в Южной Африке (81%) и США (72%), обеих странах, которые в этом году проводят выборы.
Доля респондентов, которые говорят, что их беспокоит вопрос о том, что в интернете настоящее, а что фальшивое, выросла на 3 процентных пункта с 56 до 59 %. Этот показатель наиболее высок в некоторых странах, проводящих опросы в этом году, включая Южную Африку (81 %), США (72 %) и Великобританию (70 %). Если рассматривать ситуацию в региональном разрезе, то самый высокий уровень обеспокоенности наблюдается в Африке (75 %), а более низкий - в большинстве стран Северной и Западной Европы (например, в Норвегии - 45 % и Германии - 42 %).
Интерес аудитории к СМИ как таковым
Согласно отчету Reuters Institute Digital News Report за 2024 год, интерес к новостям снизился с 66 % в 2018 году до 49 % в 2024 году на 12 основных рынках. Этот спад особенно заметен среди более молодой аудитории: только 31,9 % людей в возрасте от 16 до 24 лет проявляют интерес к новостям.
Исследование GWI показывает, что глобальный интерес к новостям упал примерно на 8 процентных пунктов в период с 1 квартала 2019 года по 1 квартал 2023 года, а по состоянию на 1 квартал 2024 года только 41,6 % респондентов заявили о своем интересе к новостям.
Выборы повысили интерес к новостям в нескольких странах, включая США (+3), но общая тенденция остается нисходящей. Интерес к новостям в Аргентине, например, упал с 77% в 2017 году до 45% сегодня. В Великобритании интерес к новостям снизился почти вдвое с 2015 года. В обеих странах это изменение отражается в аналогичном снижении интереса к политике.
*Упомянутые в тексте поста и на скриншотах Facebook, WhatsApp и Instagram принадлежат компании Meta, которую в РФ признали экстремистской
-
 @ b0510a0c:12716ced
2024-08-21 06:03:43
@ b0510a0c:12716ced
2024-08-21 06:03:43On April 24, 2012, Erik Voorhees changed everything about Bitcoin with the launch of Satoshi Dice:
a game that captivated users and intensified debates about Bitcoin's evolution and the network's ability to handle an increasing volume of transactions.
At that time, Satoshi Dice allowed thousands of players to bet on digital dice rolls, leading to a MASSIVE influx of transactions that filled the blocks of the blockchain.
📈 Success of Satoshi Dice:
Satoshi Dice achieved phenomenal success, attracting millions of users with its simplicity. Players flocked in, bets piled up, and blocks filled up.
Erik Voorhees effectively leveraged Bitcoin's microtransactions, quickly saturating the blocks with these. This was a testament to the game's popularity, but also a source of tension within the community.
Within months, Satoshi Dice became the most popular service on the Bitcoin network, boosting its usage and virality.
Players appreciated the "provable fairness" aspect of the game, where they could verify the transparency and fairness of each bet.
🚫 Criticism and Controversy:
However, this success was not without criticism.
Many Bitcoin enthusiasts viewed the massive influx of transactions generated by the game unfavorably. For them, these sometimes trivial transactions "spammed" the blockchain, clogging the blocks and increasing transaction fees for all users. Does this sound familiar?
The network, designed to handle about seven transactions per second, quickly reached its maximum capacity, causing validation delays and "high" fees.
⚔️ BlockSize Wars:
The BlockSize wars, which took place mainly between 2016 and 2017, were a technical and ideological conflict centered on block size and scalability solutions.
While Satoshi Dice was not the sole cause, the game significantly contributed to the emergence of this event by helping to popularize Bitcoin among new users and generating substantial transaction volume.
As Bitcoin adoption grew, the network faced intense pressure, leading to block saturation and rising transaction fees. On one side, some advocated for increasing block size to allow more transactions, leading to the creation of Bitcoin Cash in August 2017. On the other, proponents of solutions like SegWit pushed for improvements without compromising decentralization.
🔧 Adoption of SegWit:
Erik Voorhees expressed his support for the SegWit2x proposal, which aimed to improve network scalability by combining the implementation of SegWit with an increase in block size.
Segregated Witness (SegWit) was adopted in August 2017, allowing transaction data to be separated from signatures. This reorganization not only increased transaction processing capacity but also paved the way for the development of the Lightning Network, a layer 2 solution enabling instant and low-cost transactions.
SegWit was a crucial response to the challenges posed by network congestion, which had been exacerbated by Bitcoin's growing adoption and the emergence of popular applications like Satoshi Dice.
⚡ SegWit and Lightning:
The adoption of SegWit helped resolve blockchain congestion issues, while the Lightning Network, a layer 2 solution, facilitated fast and low-cost transactions.
Together, these innovations not only addressed technical challenges but also renewed enthusiasm for games and other applications on Bitcoin, paving the way for a new wave of development.
🎲 Nostr Dice:
Today, as we reflect on the impact of Satoshi Dice, a new project emerges: nostr:npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84
This modern clone of the original game is built on Nostr, a decentralized communication protocol, and Lightning, paying homage to the past while offering an enhanced gaming experience that does not impact layer 1 congestion!
From a game that caused Bitcoin congestion to its rebirth on Lightning, which it helped to bring about, the circle is complete!
-
 @ 28460797:b23ce78f
2024-10-13 10:53:36
@ 28460797:b23ce78f
2024-10-13 10:53:36Post number 1
-
 @ 5e9efd13:13821c2a
2024-10-13 06:17:49
@ 5e9efd13:13821c2a
2024-10-13 06:17:49Eighteen months after my mother suddenly passed away, I was diagnosed with grade four brain cancer. I was 25 years old.
Wow. When I put it like that, it really puts the last five years of my life into perspective.
We all want to become great, but we don’t get to live the life we want without suffering.
The greatest honor I’ve had through this entire experience is to inspire others through my journey. It wasn’t easy. Actually, it was extremely difficult. But if I can make it easier for you—my job is complete.
One of my greatest honors in my journey was to inspire my own father. It’s every son’s dream. Without knowing it, I inspired my father to get in control of his health.
Nine months after my cancer diagnosis, I moved back home with him. Into a house with a 70-year-old widower showing early signs of Parkinson’s disease. It was my first time living at home with my dad since I was 19—and this time, my mom wasn’t there. That transition was hard, to say the least. Back at home, finally in that safe space again… but I’m missing my mom, and he’s missing his wife.
Still, despite our differences (I punched a hole in the wall), I persevered every day in telling him I knew I could heal from this cancer. He encouraged me to take chemotherapy, I pushed for alternative treatments. He pushed for a Christian mindset, I aimed for a Taoist one. Yin and Yang. Father and son.
It has been two years of living in the house with him, and I can say things are going well, and I love my father. Our deep challenges have only brought us closer.
About 17 months into my cancer journey, my father was then diagnosed with a condition. He had surgery, lost a lot of weight, and began taking his health seriously. Today, he goes to the gym, swims, and even does a Tai Chi sword class. At some point, he told me that I was actually the reason he started believing in his own ability to recover. It is incredibly rewarding to know that my choice to be brave in a world full of suffering can inspire others to take action.
If you are suffering right now, I feel you. A lot of people are in the same boat as you.
I want you to know that it will get better.
If you are reading this right now, it already has. You are already feeling better. I want you to know that you telling your story helps other people. You’re on your way up. One day at a time. People love a redemption arc. Sometimes you need to hit rock bottom before you can rise up again. You can do it. You are, in fact, already doing it.
Depression, check.
Cancer, check.
Dead mom, check.
I mean—some people definitely have it a lot worse. At least I had a mom. At least I didn’t have cancer for the first 25 years of my life. At least I grew up with two parents who loved me. I had friends, food, and shoes. When you get another chance to live, you realize that all you really need is the humility to admit you aren’t perfect. Friends, food, shoes, and purpose. A way to contribute. If you’re lost because you feel like you have no purpose and nothing to contribute, start now. Please, if you are suffering, tell your story. It helps other people. Dare I even say that you are being selfish by not sharing your story?
It’s all about perspective. Sometimes I ponder why I lost years of my life battling this disease—but then I remember that the knowledge I gained far surpasses any amount that I could learn in fifty years of a healthy life.
Yes, I guess I’ve led some sort of a life so far.
But that begs the question, what does it mean to lead a life?
With that said: I’ve always wondered what a life coach is, or what qualifies someone to be one. I guess it’s anyone who has a life that you would like to emulate… So I just pay someone else to give me encouragement? Well, no—I’m sure it’s deeper than that.
I think that everyone in your life can be viewed as a coach. Some coaches are good, some aren’t so good. But everyone pushes us in a certain direction. It could be a friend, an enemy, a stranger. A teacher, a weirdo, a YouTuber you’ve never met.
You can be a coach too, especially if you have suffered through the pain.
If your life has always been a breeze—good, I am happy for you, and congratulations.
But if you feel like there’s no reason to live, that the world is ending, and that it couldn’t get worse… first of all—you’re wrong. It can always get worse. And—it can get a lot, lot better.
It’s all a matter of perspective. In one way, my mother’s death was the most tragic and unnecessary event to ever happen in my life.
In another way, my mother’s death was a necessary step for my family to come together in unity and praise for the homemaker—it forced me to grow up and made me learn how to take on my own responsibilities—no longer a mama’s boy, but now a man.
In one way, being diagnosed with brain cancer at the age of 25 was a devastating and unwarranted attack from God placed upon a motherless boy who always tried to be a good person.
In another way, being diagnosed with cancer at the age of 25 was exactly what God needed to do to make me stop taking life for granted—and to grow into the hero that He has always wanted me to be. God placed a ball of pure energy deep inside my skull where it couldn’t be seen—and once discovered, the responsibility was placed on me to either surrender and let it take over, or to transform that energy into positivity and send a message of love into the world.
If it weren’t for those events happening to me—or FOR me—you wouldn’t be reading this article right now.
And YOU—yes, you.
You have a story to tell, and I look forward to hearing it.
I trust that you found this article to be helpful, and I would like to end it with a prayer.
Even though I am suffering right now, I fully and completely accept myself.
Even though I want more, I am fully satisfied with what I already have.
Even though I am lost as to what to do with my life, I am grateful that I remain alive in this moment.
Even if things don’t go exactly the way I want them to go, I fully trust that whatever is meant for me will come to me—as long as I remain strong amidst the suffering.
-
 @ 3ffac3a6:2d656657
2024-10-13 03:33:29
@ 3ffac3a6:2d656657
2024-10-13 03:33:29Introduction: The Collapse of Digital Technology
In São Paulo, the city that never sleeps, life moved to the rhythm of digital pulses. From the traffic lights guiding millions of cars daily to the virtual transactions flowing through online banking systems, the sprawling metropolis relied on a complex web of interconnected digital systems. Even in the quiet suburbs of the city, people like Marcelo had become accustomed to the conveniences of modern technology. He controlled his home’s lights with a swipe on his phone and accessed the world’s knowledge with a simple voice command. Life was comfortably predictable—until it all changed in an instant.
Marcelo, a brown-skinned man in his early 50s, sat at his small desk in his home office, the soft afternoon light filtering through the window. Slightly overweight, with a rounded belly that years of office work had contributed to, Marcelo shifted in his chair. His mustache twitched slightly as he frowned at the screen in front of him—a habit whenever he focused deeply. It was his signature look, a thick mustache that had stuck with him since his twenties. Despite his best efforts, he had never been able to grow a full beard—just sparse patches that never connected. Divorced for a few years, Marcelo lived alone most of the week, though he wasn’t lonely. His stable girlfriend, Clara, visited him every weekend, and his two children, now in their late teens and attending university, also came by on weekends.
The house was quiet except for the hum of his laptop and the soft clinking of his spoon against the coffee cup. Marcelo's work as a tech consultant was steady, though far from thrilling. He missed the hands-on work of his younger days, tinkering with radios and cassette players. Despite the modern world he inhabited, a small part of him had always felt more at home in the simpler, analog era he grew up in.
Suddenly, without warning, everything stopped.
The power blinked out, and the fan spinning lazily overhead whirred to a halt. Marcelo barely had time to glance at his laptop before it went black. His phone, lying next to him on the desk, flashed briefly before the signal dropped completely. Frowning, Marcelo stood up and walked to the window, expecting it to be a localized power outage. But outside, something felt wrong—too quiet. The usual hum of traffic and distant city noise was absent. Across the street, his neighbors were stepping out of their houses, confused, holding their phones up as if searching for a lost signal.
"Strange," Marcelo muttered under his breath, his mustache twitching again as his mind started racing. His first instinct was to check his landline, a relic he kept more out of nostalgia than need. He picked it up—no dial tone. Marcelo’s eyes narrowed. He walked back to his desk, feeling a strange sense of unease creeping into his chest. São Paulo wasn’t a city that just went silent.
In the corner of his office, among old mementos and books, sat an old shortwave radio he had restored years ago, one of his many hobbies. Marcelo flicked it on. Static crackled through the speakers. He turned the dial, searching for any clear signal, any voice that could explain what was happening. After a few minutes of adjusting the knobs, something faint broke through the static: "...global digital failure... all systems down... total blackout."
Marcelo’s breath caught. He leaned in closer to the radio, but the signal faded into static again. He sat back in his chair, heart racing. A total digital failure? Could that be possible? He had read about solar flares or large-scale cyberattacks, but those were rare, temporary incidents. This, however, felt different. More permanent.
Outside, the quiet was giving way to confusion. He could hear his neighbors talking, some shouting, cars honking in the distance as traffic lights had likely failed. Marcelo’s mind whirled with the implications of what he’d just heard. If all digital systems had truly collapsed, everything would stop—communication, banking, transportation. The world was built on a fragile web of digital threads, and it seemed as if all of them had just snapped.
But Marcelo didn’t panic. Not yet.
He stood in the middle of his office, running a hand over his face, fingers brushing against his mustache. His mind flashed back to his childhood in the 1980s, a time before the digital world had taken over. A time when radios, telephones with rotary dials, and cassette players were the height of technology. While the digital age had made life easier, Marcelo had never completely left the analog world behind. He still remembered how to set up a radio antenna, fix a record player, and manually tune frequencies.
As he looked at the silent chaos outside, Marcelo realized something that few others had likely grasped yet: the digital world may have fallen, but there was still a way to survive. A way that was slower, more manual, but reliable.
Marcelo felt the weight of this realization settle on his shoulders. He had no desire to be a hero, no illusions of saving the world. But for his family—his children who would be arriving for the weekend, and Clara, who would be coming over soon—he knew he had to act. Marcelo glanced at the shortwave radio. A part of him, long dormant, began to awaken.
In a world suddenly thrust back into analog, Marcelo Fontana Ribeiro might just be the person São Paulo—and his loved ones—would need.
-
 @ 6bcc27d2:b67d296e
2024-10-13 03:15:54
@ 6bcc27d2:b67d296e
2024-10-13 03:15:54cardlink url: https://scrapbox.io/nostr/NIP-23 title: "NIP-23 - nostr" description: "#NIP Long form content https://github.com/nostr-protocol/nips/blob/master/23.md 長文投稿 記事やブログのような投稿をできるようにする仕様 ブログ系クライアントで使われている 仕様 新しい kind:30023(パラメータつき上書き可能イベント)を定義する 下書きの保存にはkind:30024を使う 「記事」や「ブログ投" host: scrapbox.io favicon: https://scrapbox.io/assets/img/favicon/favicon.ico image: https://scrapbox.io/assets/img/content-logo.png- 長文投稿 -
 @ 6bcc27d2:b67d296e
2024-10-13 02:11:54
@ 6bcc27d2:b67d296e
2024-10-13 02:11:54GitHub - jamesmagoo/nostr-writer: Publish seamlessly from Obsidian to Nostr
- [[Obsidian]]から[[Nostr]]に直接Noteを公開するためのツール
- [[NIP-23]]を使用している
-
使い方
- 最初にNostrのプライベートキーを設定で追加する
- Obsidianで書いてNostrに公開ボタンを押す
-
ユーザガイド
-
"Publish as a draft"を有効にすると下書きとして保存される。
- [[Habla]]で確認できる。 https://image.nostr.build/6a6b854e21e1b78494083d0bb00d0669fe70a1b8e612f89e171256ed05d7ee9b.png
-
 @ bcbb3e40:a494e501
2024-08-16 18:00:07
@ bcbb3e40:a494e501
2024-08-16 18:00:07El hombre y el contexto
El pensamiento tradicionalista español cuenta con una amplia trayectoria en la que concurren personajes, situaciones e ideas gestadas en el transcurso de dos siglos, en los que debemos distinguir el conflicto dinástico y el papel del legitimismo de la propia doctrina, que es algo que se construirá en el tiempo, con la contribución de figuras como el protagonista de este escrito, Don Juan Vázquez de Mella, así como por la confluencia de fuerzas de diferente signo que tiene lugar a lo largo del siglo XIX y la consolidación del Estado liberal, que lo hará siempre en lucha abierta contra las peculiaridades y el carácter genuino del pueblo español. Vázquez de Mella, nuestro autor, quizás represente la consolidación y madurez doctrinal del movimiento tradicionalista español, uno de sus primeros y más brillantes sistematizadores. No se destacó por una obra extensa ni especialmente difundida más allá de sus discursos, de sus artículos en periódicos y sus escritos dispersos, los cuales fue capaz de dotar de una especial significación y dignidad fruto de su enorme carisma y especial clarividencia para dar una forma definida y meridianamente clara a las ideas y doctrinas que nutrieron el tradicionalismo español madurado al calor de las armas, de las tres guerras que el carlismo libró contra el liberalismo español.
|
 |
|:-:|
|Juan Vázquez de Mella|
|
|:-:|
|Juan Vázquez de Mella|Nuestro autor, de origen asturiano, y nacido en Cangas de Onís un 8 de junio de 1861, ha mantenido vivo su prestigio y el valor de sus aportaciones teórico-doctrinales, ampliamente reconocidos por sus sucesores, por Rafael Gambra Ciudad (1920-2004) y Francisco Elías de Tejada y Espinola (1918-1978), así como de otros autores como Álvaro D'Ors (1915-2004) y otros muchos, que han reivindicado su figura en el tiempo y se han nutrido de sus fecundas enseñanzas. Se ha destacado la rectitud de su pensamiento, su inquebrantable voluntad y su impagable contribución en la creación de un marco teórico y conceptual para dar un sentido y una forma a las ideas del tradicionalismo español. Hijo de un militar de origen gallego, muerto prematuramente, quedó huérfano de padre durante su niñez, por lo cual pasó al cuidado de unos parientes de origen modesto. Estudió en la Universidad de Santiago de Compostela, donde mostró tempranamente su temperamento y habilidades oratorias, que explotó convenientemente a través de diarios como La Restauración o El pensamiento galaico, donde también mostró sus filiaciones militantes con el catolicismo tradicional. Sus habilidades y la brillantez de sus escritos pronto llegaron a Madrid, a las más altas instancias del Carlismo, lo que le permitió dar continuidad a sus actividades desde un medio más amplio, a través de El correo español.
En su militancia política llegó a las más altas cotas de su trayectoria con la elección en 1893 como representante de las Cortes por el distrito de Estella, Navarra, que ya con sus primeros discursos obtuvo un notable éxito, incluso entre los propios liberales, hasta 1900, fecha en la que se vio obligado a marcharse a Portugal, acusado de participar en una conspiración para derrocar el régimen de la Restauración. No regresó a España hasta 1905, manteniendo su estatus como diputado hasta 1919. De todos modos, no queremos dar más protagonismo a la biografía en detrimento de la doctrina, que es lo que nos interesa en este artículo, de ahí que obviemos otros datos biográficos trascendentes, polémicas con otras facciones del carlismo o sus posturas respecto a la dictadura del general Miguel Primo de Rivera, que nos harían desviar la atención del propósito principal que acabamos de enunciar.
La gran paradoja del Carlismo fue que a pesar de su derrota en la Tercera Guerra Carlista (1872-1876), y pese a la posterior escisión integrista en 1888, el partido carlista continuó manteniendo una fuerza y preponderancia significativa en la sociedad española del régimen de la Restauración durante el último cuarto de siglo. El Carlismo se vio inmerso en un buen número de paradojas, de situaciones encontradas, especialmente en relación al Desastre del 98 y la pérdida de los últimos territorios ultramarinos. Mientras que la gran esperanza del tradicionalismo español estaba depositada en el desmoronamiento y caída final de la restauración alfonsina, por otro lado este mismo régimen trataba de defender, al menos en teoría, los últimos restos del imperio español y, de algún modo, a la España católica frente a una nación protestante, como era la anglosajona estadounidense. Al mismo tiempo, durante esta época el tradicionalismo español se enfrentó a los grandes retos que presentaba una sociedad en cambio, con transformaciones políticas y sociales de gran calado como la emergencia del sufragio universal o el nacimiento de los separatismos periféricos (propiciados por la burguesía liberal), las cuales requerían de nuevas estrategias y reestructuraciones internas capaces de enfrentar la envergadura de todos estos cambios. Fue en este contexto donde se significó la figura de Juan Vázquez de Mella, quien merced a la obra de sistematización a la que ya hemos hecho alusión, y de sus concurridas conferencias, dio lugar a la denominada Acta Loredán, redactada por el tradicionalista asturiano y publicado en El correo español. Este escrito tenía como ejes fundamentales la defensa de la nación política española fundamentada en la monarquía, el catolicismo y el régimen foral. Al mismo tiempo, también recogía la reivindicación de un programa corporativista y gremial al abrigo de la doctrina social de la Iglesia defendido en la encíclica Rerum Novarum (1891), y es lo que se conoce como el «sociedalismo», cuyos antecedentes encontramos ya en autores como Donoso Cortés o Antonio Aparisi Guijarro. Son precisamente los atributos de esta doctrina, que contribuyó a la revitalización del pensamiento carlista, los que nos disponemos a desarrollar a continuación.
La figura del tradicionalista asturiano, de Don Juan Vázquez de Mella, aparece como necesaria ante una serie sucesiva de destrucciones que el régimen liberal ha producido sobre los fundamentos tradicionales de España, pero su papel no fue, como ya venimos apuntando, el de un gran intelectual erudito, y de hecho, como apunta Rafael Gambra, las mayores debilidades de su pensamiento se encuentran en los principios filosóficos, y destacando, en cambio, su papel de «revulsivo espiritual» podemos ubicarlo mejor en el ámbito de lo político y lo espiritual. Para ello debió tomar en cuenta las fuentes de sus predecesores, entre los cuales podemos ubicar perfectamente al ya mencionado Donoso Cortés y Jaime Balmes, así como también a otro contemporáneo suyo, Menéndez Pelayo. De los dos primeros tomó su capacidad de síntesis y la sencillez expositiva, mientras que de Menéndez Pelayo tomó, al menos en parte, el sentido de la crítica histórica en aras de la restauración de una Tradición nacional. Pero más allá de los sistemas de pensamiento y elementos retóricos, vemos a Vázquez de Mella profundamente interesado por la vida política de los pueblos medievales de Las Españas, lo cual fue, en definitiva, el marco de referencia para una síntesis política de conjunto más allá de los posicionamientos teóricos, como algo que puede ser llevado a la práctica en sus aspectos concretos y que es perfectamente viable. Todo un sistema edificado sobre el pensamiento tomista y una una profunda religiosidad, En este contexto, y más allá de las ideas formuladas por realistas y carlistas en la primera mitad del siglo XIX, Mella teoriza junto a la concepción del espíritu medieval, la idea de la coexistencia de dos soberanías, una política y otra social, una teoría de la soberanía tradicional inspirada por un principio dinámico y que se cimenta en las propias experiencias humanas en el devenir de la historia.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023|El concepto de lo social
Lo social para Mella no tiene absolutamente nada que ver con las denominadas «políticas sociales», tan comunes en el lenguaje político de las democracias liberales, en las que se contempla lo social como un elemento externo a la propia estructura política, donde prevalece el individualismo a todos los niveles, y la sociedad aparece como un mero agregado de individuos. Muy al contrario, lo social, en el tradicionalismo de nuestro autor, implica la afirmación de un principio intrínseco tanto al modelo social como al tipo humano, así como a la naturaleza de las cosas en las que la persona desarrolla su existencia en común con los demás. Nos referimos a las instituciones, a los elementos jurídicos y otros órganos gestados en el tiempo por la experiencia histórica, que regulan la vida común.
En el ámbito de la sociedad cristiana medieval, en plena Reconquista, cuando todavía no existía un Estado unitario como tal, cada municipio tenía sus propias leyes y sus normas, adaptadas a su modelo de vida y costumbres, Las comunidades se concebían como agrupaciones de familias con un sistema de propiedad comunal y privado en las que el patrimonio y el estatus de cada uno de sus miembros venía garantizado por el ejercicio activo de una serie de derechos en defensa de las libertades concretas, cuya fuente última era el derecho natural. Los señores feudales y los reyes se limitaban a reclamar tributos para la guerra, pero sin interferir en la defensa de estas libertades concretas ni vulnerar el sistema que las sustentaba.
Eran gobiernos autárquicos, muy estables e inspirados por un principio democrático, el cual nada tenía que ver con las democracias liberales plutocráticas de la actualidad, cuya idea del derecho y la justicia está pervertida por el formalismo jurídico vacío e inane de sus constituciones, abstractas y plenamente funcionales a las oligarquías, al servicio de intereses espurios. En este caso, el hombre alcanzaba una plena dignidad y desarrollo en el contexto de una comunidad donde prevalecía el vínculo comunitario, al amparo de un modelo tradicional, de normas consuetudinarias y concretas que permitían la defensa efectiva del propio derecho. Ni siquiera con el advenimiento de los Estados modernos, y la centralización de algunos elementos de poder, como la Hacienda o el Ejército, se vieron alterados significativamente estos elementos, que representaban a los denominados «cuerpos intermedios» de la sociedad, y que adquirieron su propia expresión particular bajo el nombre de «Fueros», los que los propios reyes juraron respetar a lo largo de toda la Edad Moderna y hasta el advenimiento del régimen borbónico.
La antropología tradicional vincula al hombre a un medio social, a una familia, a una estirpe o a un pueblo, que reproducen esa misma estructura familiar, aunque a mayor escala. En nuestro caso particular lo vemos a través de la convivencia de pequeños grupos humanos, de ahí la importancia de los municipios o de los concejos en un marco de vida comunitaria fuertemente institucionalizada. Al mismo tiempo este modelo y estructura también se replicaba en otros ámbitos, como en la vida económica y profesional, impregnando todas las esferas de la vida del hombre. Instituciones naturales, amparadas en el derecho natural, y orientadas a la protección y garantía de prosperidad de los hombres, y esto por encima de cualquier interés particular y mercantil de negocio. Para Mella, la ruptura con este mundo, y en general con las experiencias del pasado, es la que nos lleva, merced a la acción del liberalismo, a los tiempos actuales, y lo hace recorriendo un itinerario que todos conocemos, y que tienen su punto de partida en la Ilustración y la posterior Revolución Francesa, la irrupción del elemento racional y abstracto y la destrucción de la religión, considerada como fruto de la superstición. La destrucción del orden feudal, que todavía pervivía como marco de convivencia en el mundo rural, como una suerte de prolongación de ese espíritu medieval, hizo desaparecer de un plumazo ese entorno de relaciones concretas y personales para sustituirlas por lo «público» entendido como la centralización estatal uniforme, ignorando las realidades particulares subyacentes en el cuerpo social, los denominados «cuerpos intermedios», que fueron despojados de su autonomía, corporaciones y patrimonios. De modo que la destrucción de estas «sociedades intermedias» que mediaban entre el Estado y la sociedad desenraizó y destruyó la propia sociedad, al mismo tiempo que los fundamentos cristianos del derecho natural sobre la cual se hallaba asentada, para hacer prevalecer esos principios racionales y abstractos traídos por la revolución.
Al mismo tiempo, y anejo a este desarraigo, del individuo se encuentra sometido a poderes arbitrarios del propio Estado liberal, sin un conglomerado institucional propio que lo proteja de estos atropellos, sumido en el individualismo ajeno a toda institución y destino colectivo, se limita al voto cada cuatro años de los partidos al servicio de oligarquías e intereses espurios, contrarios al Bien común. En este sentido, y advirtiendo las posibles acusaciones de «absolutismo» que en ocasiones se han lanzado contra el tradicionalismo, hay que señalar que Mella las rechaza por completo, dado que viola la idea de contrapoderes frente a la autoridad del rey que éste formula, ya que el absolutismo creía en la existencia de un poder ilimitado y tiránico del rey, transmitido por Dios y ajeno a la participación de la sociedad y sus estamentos. Como bien señaló Julius Evola, el absolutismo es un fenómeno antitradicional, vinculado a la descomposición y desacralización de las estructuras tradicionales. De hecho, el absolutismo, como los regímenes liberales de hoy, dejan al individuo totalmente desprotegido, sin un asidero sobre el que apoyarse en la defensa de sus libertades concretas. El propio Mella, como bien saben todos los que se adentren en su obra, fue partidario de contrarrestar el creciente poder del aparato estatal, tal y como hemos visto y seguiremos viendo en lo sucesivo, a lo largo del presente artículo.
|
 |
|:-:|
|EVOLA, Julis; Metapolítica, Tradición y Modernidad: Antología de artículos evolianos, Hipérbola Janus, 2020|
|
|:-:|
|EVOLA, Julis; Metapolítica, Tradición y Modernidad: Antología de artículos evolianos, Hipérbola Janus, 2020|En nuestro caso particular, la desaparición de la organización gremial y corporativa tuvo unas consecuencias especialmente nefastas, y en especial después de las dos desamortizaciones liberales (Mendizabal y Madoz) al despojar a los grupos sociales populares de su natural organización sociohistórica. Asimismo, desvincularon la propiedad en las relaciones comunitarias y su uso patrimonial para vincularla al uso privado y anónimo, para fines puramente especulativos, los que caracterizan al liberal-capitalismo. De ahí nace la figura del asalariado, del contratado como mera mercancía, en un proceso de alienación del trabajo característico en el desarrollo del capitalismo burgués. De aquí parte lo que algunos tradicionalistas, como Gambra, denominan el «problema social», frente al cual, y al margen de las recetas ideológicas de la modernidad, Mella reivindica la restauración de los antiguos vínculos corporativos y orgánicos de inspiración medieval.
La idea de soberanía social
Todos los procesos disolutivos que conducen a la Modernidad liberal tienen su punto de inicio con el Renacimiento, con la afirmación del individualismo y la ruptura definitiva del ecumene cristiano medieval, algo que aparece indefectiblemente unido a la Reforma luterana, así como la «valorización» del mundo clásico, con la reemergencia de teorías de tipo hedonista, como las de Epicuro, por ejemplo, generando una disolución de los vínculos con el medio concreto. Esto supone la aparición de un nuevo tipo, que es el hombre abstracto que escapa cada vez más al entorno inmediato y vital, esto al tiempo que el poder del Estado se robustece y se vuelve omnipotente. Es por ese motivo que en lo sucesivo se ha impuesto en nuestras sociedades la falta de concreción, tanto en lo teórico como en lo político, lo cual ha propiciado el triunfo del contrato social roussoniano y la justificación del orden social en virtud de componendas voluntarias y totalmente artificiales. Estas construcciones político-ideológicas son las que contribuyen a la construcción de la sociedad liberal, asentada sobre patrones puramente racionales, individualistas y mercantilistas.
De hecho, la mayor preocupación de Mella es la destrucción de las instituciones locales y ese vínculo afectivo del hombre con su realidad inmediata, algo que impregnaba su relación con el trabajo, con su obra, con su impronta vocacional y devota, imprimiéndole, como en el caso del artesano, un sello propio y particular a su trabajo.
Y en este sentido, Mella afirma que la sociedad moderna ha perdido su sentido institucional como base estable de la sociabilidad. A través del elemento jurídico y la participación en las instituciones es el medio a partir del cual la comunidad se cohesiona y construye sus vínculos y su particular autonomía, que le hace tener una vida propia e interna, y con la institución nos podemos referir desde una asociación profesional, a la universidad o una cofradía etc. El individualismo ha representado el factor disolutivo y corrosivo que ha destruido este vínculo social fundado en múltiples solidaridades que han enfrentado y polarizado al cuerpo social, con el enfrentamiento entre «clases sociales» y la negación de las jerarquías naturales.
Ante todo lo relatado, y como consecuencia de las destrucciones provocadas por la revolución, Mella plantea su teoría de la soberanía social. Esta teoría consiste básicamente en encuadrar de nuevo a la sociedad en sus raíces naturales, concebida en todos sus órdenes como portadora de un dinamismo propio en una suerte de organización geométrica en la que conviven objetivos y finalidades variadas y concretas con su propia legitimidad y autonomía. Estas finalidades, amparadas en el derecho natural, son junto al poder del propio Estado las únicas formas de limitación del poder. La particularidad de esta idea de soberanía social está en el hecho de que la formación de la jerarquía social tiene una dirección ascendente, que tiene como punto de partida a las personas colectivas y concretas, pasando por una serie de instituciones, hasta llegar al Estado central, de forma escalonada y plenamente conscientes de sus funciones. Así lo expresa Mella en su propio lenguaje: «la jerarquía de personas colectivas, de poderes organizados, de clases, que suben desde la familia hasta la soberanía que llamo política concretada en el Estado, que deben auxiliar, pero también contener». Es lo que Mella concibe como el sociedalismo, que supone la reintegración de la sociedad en la vida concreta de los hombres, con el desarrollo de una vida política común y estable en el marco de instituciones naturales que potencien las relaciones humanas y sociales, estimulando la sociabilidad. Y hablamos, desde la perspectiva de la integración de distintas sociedades, fuertemente institucionalizadas con funciones y finalidades concretas, más allá del sentido democrático y pactista que pueda entenderse en términos modernos o de cualquier asociación u organización relacionada con el «problema social».
¿Qué es la Tradición?
De este modo quedan formuladas las dos soberanías, la política y la social, que coexisten en un mismo espacio limitándose y apoyándose recíprocamente en lo que es uno de los fundamentos del sociedalismo de Mella. No obstante, esta doble soberanía no explica todavía la concreción política de cada pueblo y el vínculo superior que lo lleva a federarse con las diferentes sociedades y a mantenerse unido en una historia y espíritu comunes. Los vínculos que las mantienen unidas en el tiempo tienen que ver con un orden histórico concreto, con un vínculo espiritual que las entrelaza interiormente de una generación a otra, y en última instancia de ese orden tradicional que lo engloba todo, y que al mismo tiempo se asienta en la monarquía y la religión católica. La lealtad a Dios y a un solo rey en torno a los cuales se aglutina la fe, viene a coronar todas estas estructuras y lazos forjados en el fermento de la historia.
No se trata de la Tradición en términos de un «ultraconservadurismo», que ya sabemos que el prefijo «ultra» (lo que sea) es muy recurrente en nuestros días, con la idea de un medio social y político petrificado e invariable, sino que es el producto de un proceso de maduración y evolución histórica, de carácter dinámico y nutrido de experiencias humanas. Nada que ver con las monstruosas ideologías progresistas y modernas, nacidas de lo abstracto e impulsadas por un desbocado «ir hacia delante», desarraigado y que tiende siempre hacia la deshumanización y la destrucción de toda creación humana natural forjada en el devenir de los siglos. Este mismo dinamismo, planteado por Mella, en torno al concepto e idea de Tradición tiene continuidad y adquiere fuerza en sus sucesores y depositarios. Y al fin y al cabo, Mella no hace más que partir de la propia etimología del término, que viene del latín tradere, entregar, de la generación que entrega los frutos de su experiencia a la siguiente, perfeccionándola, haciéndola más estable y segura.
Podríamos seguir extrayendo más conclusiones del pensamiento tradicional de Vázquez de Mella, pero probablemente excedería, y por mucho, el modesto propósito de este escrito, de modo que nos quedaremos aquí, no sin advertir a nuestros lectores de la posibilidad de que en un futuro volvamos a retomar nuevamente el tema.
Antes de acabar queremos llamar la atención sobre una polémica acontecida hace unos años en torno a una Plaza en Madrid que llevaba el nombre de nuestro autor y que se cambio para dedicársela a un sujeto cuyos méritos eran, por decirlo suavemente, más que discutibles, concretamente a Pedro Zerolo, miembro del PSOE y activista al servicio del lobby homosexualista. Durante aquella época, en 2019, muchos miembros de la izquierda globalista trataron de identificar a Vázquez de Mella como un «pensador franquista», cuando en realidad ni cronológica ni ideológicamente tuvo nunca nada que ver con el franquismo. Recordemos que murió en 1928, y la impronta de su pensamiento ha tenido como continuadores a sus propios correligionarios dentro del ámbito tradicional, aunque en su tiempo llegó a ser muy respetado también por sus adversarios, los liberales. Aunque la retirada del nombre de una calle pueda resultar algo banal, o carente de una importancia excesiva, también contribuye, a su modo, a una forma de damnatio memoriae que condena al olvido y al ostracismo a grandes autores de la Tradición, portadores de un Patriotismo sano y capaz de entender las peculiaridades y el Dasein profundo de España, que si bien no nació invertebrada, como pretendían los Orteguianos, su esencia y naturaleza es mucho más compleja que cualquiera de las grandes naciones de Europa.
Artículo original: Hipérbola Janus, Juan Vázquez de Mella y el tradicionalismo español, 16/Ago/2024
-
 @ 5df9cbaa:89f8f3b3
2024-10-12 21:06:44
@ 5df9cbaa:89f8f3b3
2024-10-12 21:06:44For the past decade or so I have jumped around diet to diet, or lifestyle some would say. I've done a lot of them and some I stuck with and some I haven't. But lord knows I have tried a bunch. These are my thoughts on some of them these days.
Paleo
This is the first major diet I had tried and to be honest I had really great success with it. And I can't argue the idea, like most of the Ancestral based diets. If you think about it, it just makes sense. My downfall is I'm not a veggie fan and forcing myself to eat them got old, I leaned hard on brussel sprouts and asparagus. Eventually I just fell off the wagon. I think it doesn't help that I drank back then also.
The Makers Diet
This one sounded cool, the good lord says... but I don't like many fermented foods and I didn't stick with it more than a couple weeks.
Vegetarian/Vegan
I actually did this solid for about a year, maybe a tad longer. I didn't really feel great, I was tired a lot, and I gained weight. I did not do whole foods though. I gave in to all the fake meat stuff and various goodies, who knew Orios were vegan.
Carnivore
I went from vegetarian straight to carnivore. I love meat, I cannot lie. This I did solid for a bit with decent results. But fell off the wagon a lot.
Animal Based
Another ancestral based diet. The funny thing that makes me lean towards these types of diets is they make sense. Watch a couple episodes of "Naked and Afraid" and you see even the vegans go for meat. Not eating it makes zero sense. That being said, fruit makes a hell of a lot of sense also. If available, it is easy eats. Veggies beyond root vegetables, good luck not starving eating only vegetables in a survival situation in the wild.
Ray Peat
So, this isn't an official diet, but Dr. Peat seemed to provide a lot of reasonable and well studied info that makes sense. It really makes me relook at everything before.
In the end, I am experimenting a lot now. The Ray Peat stuff has me the most interested and I'm starting to experiment with his philosophy and that of those who have tried and wrote about it. It's super early, but maybe in a few months I can talk how I feel about it and how my body is taking it. But this is the flow I've taken in the past years and the path I am on now.
Cheers!
-
 @ 5afdec5b:2d631be1
2024-08-14 09:42:29
@ 5afdec5b:2d631be1
2024-08-14 09:42:29Introducing Our New Whitepaper on Escrow-Less Bitcoin-Collateralized Lending
We are thrilled to release our latest whitepaper, elaborating on our innovative Escrow-Less Bitcoin-Collateralized Lending protocol. This pioneering system leverages the power of Discreet Log Contracts (DLCs) and Hash Time Lock Contracts (HTLCs) to create a trustless, peer-to-peer lending environment that aligns with the ethos of decentralization and user empowerment.
Empowering Users with Our Architecture
Our protocol is meticulously designed to empower users by allowing them to borrow against their Bitcoin while retaining full control over it. We believe that this is not just a technological advancement, but a crucial step towards crafting a more decentralized, trust-minimized, and secure financial ecosystem. By eliminating the need for intermediaries, we aim to give users greater autonomy and flexibility, freeing them from traditional constraints.
Addressing Market Needs for Peer-to-Peer, Trustless Lending
Extensive market research highlights a significant, growing demand for peer-to-peer, trustless lending solutions. Users consistently expressed a desire for more control over their assets and greater flexibility in their lending options. Our Escrow-Less Lending protocol directly addresses these needs, providing a robust framework that enhances user control while maintaining the integrity and security of the lending process.
Exploring the Potential of Ark for Microloan Liquidity Management
Initially, our focus was predominantly on micro-loans. However, user interviews revealed a relatively limited demand for such products at this time. Nonetheless, we identified Ark as good solution in the context of Bitcoin microloans. Ark's capabilities could unlock new possibilities and efficiencies, making microloans more viable and attractive.
Remaining Flexible and Adaptable
Even as our primary focus shifts, the potential of Ark continues to intrigue us. Our protocol's design is inherently flexible and adaptable, allowing for continuous refinement and adjustments based on user interest and feedback. Should there be sufficient interest in the future, we are open and ready to explore Ark's integration once again to better serve our users’ needs.
Revolutionizing Bitcoin Borrowing and Lending
We firmly believe that our Escrow-Less Bitcoin-Collateralized Lending protocol has the potential to revolutionize the borrowing and lending landscape within the Bitcoin ecosystem. Our commitment is steadfast; we aim to make this innovative protocol a reality and will diligently work to iterate and improve based on user feedback. Together, let’s shape the future of decentralized lending.
Your Feedback Matters
We invite you to delve into our whitepaper and share your thoughts and feedback on this groundbreaking approach. Your insights are invaluable as we strive to create a more user-centric, flexible, and secure lending protocol. Read the full whitepaper here
Feel free to reach out with your thoughts, questions, or suggestions. We’re eager to engage with you and iterate based on your valuable input.
-
 @ 468f729d:5ab4fd5e
2024-10-12 20:28:06
@ 468f729d:5ab4fd5e
2024-10-12 20:28:06 -
 @ 1b5ee74d:bb1aae6e
2024-10-12 19:49:12
@ 1b5ee74d:bb1aae6e
2024-10-12 19:49:12On October 8th, the American production company HBO—owned by Warner Bros. Discovery—released Money Electric: The Bitcoin Mystery. The documentary, directed by Cullen Hoback and currently available only to the U.S. audience, was immediately shared via P2P file-sharing platforms and can thus be easily found online.
Considering all the elements presented in the hour-and-a-half-long documentary, my personal judgment swings between two feelings:
- Satisfaction for having witnessed a thorough explanation of Bitcoin’s origins, its cultural roots, the reasons behind its creation, and the intrinsic problems of the traditional financial system.
- Frustration over a conspiracy theory—claiming that Bitcoin was sabotaged by U.S. government agents infiltrating the Bitcoin community to prevent it from functioning as a medium of exchange—and a baseless hunt for Satoshi Nakamoto, which is especially dangerous for the man identified: Peter Todd.
The Negative Aspects
The Surreal Conspiracy Around Replace-By-Fee (RBF)
One of the documentary's central issues is the inclusion of conspiracy theories aimed at explaining Bitcoin's evolution through external interventions, mainly by government actors, who allegedly tried to manipulate the technology to prevent it from scaling in terms of processed transactions. The goal, it is claimed, was to keep Bitcoin as a store of value and technically render it impossible for it to function as a medium of exchange.
The ultimate reason for this, according to the theory, is that everyday transactions could only occur through intermediaries and, as a result, would be easily controllable by authorities. The U.S. government's goal, therefore, would have been to negatively influence Bitcoin’s development. This idea is not unrealistic in itself, but this is where things get absurd.
Hoback, spurred on by Roger Ver, resurrects a story about an email allegedly sent to Peter Todd in 2013 by someone named John Dillon. Dillon, claiming to hold a “high-level” role in intelligence, supposedly requested the development of Replace-By-Fee (RBF) for the paltry sum of $500.
RBF is a function that allows an unconfirmed transaction to be replaced with a different version of the transaction that pays a higher fee, with the goal of achieving quicker confirmation. And here, Roger Ver provides the narrative hook: RBF would have driven transaction fees through the roof, making it uneconomical to use Bitcoin for everyday transactions, thereby fulfilling the U.S. government's objective.
History has shown that this theory was baseless—fees didn’t skyrocket with RBF—but the fact that Todd actually contributed to developing RBF convinced the documentary’s author that this was a credible hypothesis. The theory that Todd collaborated with the government is presented with alarming carelessness, despite a lack of concrete evidence, and Todd, understandably, denies everything. This conspiracy also contains a fundamental inconsistency: why would Satoshi Nakamoto have wanted to collaborate with the government to prevent Bitcoin from becoming digital cash?
The Blocksize War: Misunderstood and Poorly Told
The documentary presents a distorted view of the so-called Blocksize War. The thesis reflects the exact opposite of what actually happened. Again misled by Roger Ver's words, Hoback hypothesizes that the failed attempt to increase Bitcoin's block size led to a centralization of the network around the Blockstream team. The truth is the opposite: had the blockspace been increased, the network would have faced inevitable centralization, as the unfortunate fate of Bitcoin Cash demonstrated.
According to the documentary, the outcome of the war even allowed everyday Bitcoin transactions to occur “only through tools provided by Blockstream.” No names are mentioned, although it’s suspected that the reference is to Liquid. What reveals the documentary’s evident bad faith is that there isn’t a single mention of the Lightning Network, which allows low-cost transactions, doesn’t necessarily require intermediaries, and is certainly not controlled by Blockstream.
In general, Hoback gives too much screen time to controversial figures like Roger Ver and Gavin Andresen, whose opinions, while representative of a certain point in Bitcoin’s history, are distorted by the context in which they are presented.
The Baseless Manhunt
The hunt for Peter Todd is perhaps the most problematic aspect of the documentary. The narrative focuses on seemingly irrelevant details, weaving a sensationalist plot to make viewers believe that Todd might be Satoshi Nakamoto. This attempt poses a serious risk to Todd’s personal safety, which should not be underestimated. The narrative, while effective in capturing the attention of an uninformed audience, is highly dangerous.
The “evidence” provided is completely inconsistent. Consider that the most damning proof is a 2010 BitcoinTalk post in response to Satoshi Nakamoto, which Hoback claims was accidentally posted using Todd’s profile. That is, according to the author, Satoshi himself completed his post through a response but mistakenly logged in with his personal profile: Todd's.
This is a groundless hypothesis and, moreover, not a new revelation. It's also important to note that Peter Todd's nickname at the time was “retep,” and no one knew who he was. If it had been Satoshi Nakamoto, he could have easily deleted the post without leaving any unwanted traces.
The Myth of Satoshi’s One Million Bitcoins
The documentary repeatedly claims that Satoshi Nakamoto accumulated one million bitcoins and that a massive sale of these coins could “break the system.” This, too, is a misleading statement, as there is no certainty regarding the exact number of bitcoins Nakamoto possesses, and the idea that the sale of this alleged fortune could destroy Bitcoin is completely unfounded. In fact, it is never explained.
The Positive Aspects
The Roots of Bitcoin
Money Electric does have some merits, particularly in the first part, where it focuses on an accurate explanation of Bitcoin’s origins and the historical context in which it emerged. The documentary effectively recounts how earlier attempts to create digital currencies, like E-Gold, failed and how E-Gold’s founder, Douglas Jackson, was arrested for his activities. The author understands and communicates a key concept: if you build a product that can compete with the U.S. dollar, the government will come after you. Therefore, the decision to remain anonymous makes perfect sense. One is left to wonder: why did you try to reveal Satoshi’s identity?
The description of Bitcoin’s founding values, linked to the cypherpunk movement, is one of the most successful parts. The crypto wars of the 1990s and the battle for the use of cryptography, portrayed as a sort of weapon by the U.S. government, are explained in an accessible way, even to those unfamiliar with the topic, offering valuable historical context for understanding Bitcoin’s birth.
Mining and Energy
Mining is described as a lottery, finally breaking away from the common narrative that portrays it as an activity based on “complex calculations” or “advanced algorithms.” The simplified approach is well-executed and makes one of Bitcoin’s most misunderstood aspects comprehensible to the general public.
Another positive aspect is the documentary’s exploration of the relationship between Bitcoin and energy consumption. Rather than demonizing the energy link, it smartly compares it to the relationship between the dollar and oil, presenting this connection as inevitable for any form of money with intrinsic value. Money, it is specified, must evidently be tied to something that people consider valuable, like an energy source.
Traditional Financial System and CBDCs
The portrayal of the 2008 financial crisis and the parallel with the current fragility of the global monetary system is well done, showing how Bitcoin emerged in response to a failing system. In this sense, the documentary raises a warning about the future use of Central Bank Digital Currencies (CBDCs), which are described as dystopian tools of control, with a particular focus on the Chinese e-yuan, which is literally called a “government-backed shitcoin.”
The author casts doubt on the stability of the U.S. dollar itself, suggesting that even the American currency could face collapses similar to those of hyperinflated currencies. While not a definitive claim, this perspective introduces an important question about the future of the global financial system, undermining the steadfast beliefs of a large portion of the market that sees the dollar as an indestructible fortress.
Cold Judgment
Money Electric is a documentary that, perhaps for the first time, effectively explains several aspects of Bitcoin in a way that is both compelling and easily understandable. The fact that such a product comes from a major production house should be considered a success.
On the other hand, the misleading portrayal of events like the Blocksize War and the relentless search for a conspiracy to destroy Bitcoin—both tainted by the biased opinions of individuals defeated by history, like Roger Ver and Gavin Andresen—undermines the solid foundations initially laid with the description of the technology.
Lastly, such a blatant ad hominem accusation, supported by such flimsy evidence, is unacceptable. Identifying someone as Satoshi Nakamoto is, for the same reasons acknowledged by the author at the beginning of the documentary, extremely dangerous for that individual’s personal safety. How many people, swayed by HBO's gripping editing, could now believe that Peter Todd is truly Satoshi? And how many of these could be willing to physically attack him for the fortune Bitcoin’s creator supposedly accumulated? Too many hypotheticals to draw a plausible conclusion and to place such a risk on a person.
Money Electric: The Bitcoin Mystery is a decent product, fatally marred by bad faith.
-
 @ 7cc328a0:2a247c0e
2024-10-12 15:54:42
@ 7cc328a0:2a247c0e
2024-10-12 15:54:42relay.tools quarterly report
October, 2024
Project Updates
Milestone: Relay.tools is celebrating 1 year of OpenSats! Cheers to everyone that made this possible.
Relays were very popular this quarter. Scaling efforts were prioritized! This is a good indicator for relay.tools as it means that it's healthily growing. Development was executed well, completing one project at a time across the whole stack.
Relay Discovery
I've been working with @sandwich from nostr.watch on NIP66.
NIP66 will be an ABSOLUTE GAMECHANGER for clients in finding of their relays. This was always a vision for relay.tools and I am honored to be working with @sandwich on what is a pretty amazing solution. We are now in a phase of client outreach, to gather client feedback and help them implement/understand the overall goal of the NIP.
TLDR: the goal is to create a distributed version of the nostr.watch data, using nostr events.
- [x] implemented NIP66 draft7 (the 'final' design) in monitorlizard
- [x] started shipping events to the monitor relay(s) in collab with nostr.watch backends and relay.tools backends.
- [x] fixed bugs and released new binaries for monitorlizard (a NIP66 data reporting tool)
Auth Proxy Rollout
The NIP42 Auth Proxy project went really well this quarter. It's now serving tons of traffic and most bugs with clients have been squashed and the proxy hardened. This has become a very popular feature on the relays, as AUTH has many benefits beyond protecting of DMs.
- [x] testing vs. NIP17 and bugs fixed
- [x] cluster operations (multiple proxies)
UI/UX
A huge milestone this quarter was the release of the settings wizard. This is a walkthrough for new (and current) users of all the available settings for different 'relay types'. A lot of work over the last year has gone into the culmination of these settings and the wizard was a major step forward to help users understand what their options are when running a relay.
Another major UI change was the introduction of a relay feed to the landing page for a relay. This is called the relay explorer. The idea was to move to a single page app, and re-do navigation for easy relay browsing and discovery.
- [x] settings wizard released
- [x] relay explorer v2
Installer
The installer had lots of good effort put in by me and some nice contributors. We did a couple iterations on documentation and facilitated in the creation of 2-3 new relay hubs that are using this installer infrastructure.
Some additions to the installer were:
- [x] docs for building self-hosted machine images and installing on a VPS
- [x] FULLY AUTOMATIC SSL certificate handling for multiple domains with certbot
- [x] self-hosted influxDB (for relay metrics)
- [x] fix bugs with auto-deploy upgrade
Billing/Invoicing/Support
The billing system had some improvements this quarter and many invoices were sent. :) It now has better super-admin tools to notify users of past-due balances via nostr (With NDK). This took a few iterations of deciding the best way to contact users of nostr and figuring out why they don't respond to messages. It's a learning experience all the way around and the billing system will evolve over time in ways that are conducive to remaining 100% nostr for user communication and support.
The support system also showed signs of life, and people were able to use it to contact me with their questions via the various help-desk methods that I've been rolling out. (A relay, a support npub, DMs, NIP17 DMs, simplex)
Scaling!
Relay.tools successfully completed the first scale-out event. This is HUGE. Relays take more and more bandwidth and resources as they establish themselves, while at the same time needing a reasonable low-cost environment to grow in. To meet their demands the horizontal scaling is important. This will scale on commodity hardware or VPSs with ZERO vendor lock-in.
- [x] multi-server clustering with ZERO cloud vendor lock-in
- [x] deployment pipeline and capacity planning
- [x] HAproxy and additional AUTH proxies fronting all services
- [x] internal/external network support
-
 @ 06830f6c:34da40c5
2024-08-11 20:13:46
@ 06830f6c:34da40c5
2024-08-11 20:13:46On August 10, 2024, the vibrant Sarit Expo was alive with energy as Bitcoin Dada celebrated the graduation of its seventh cohort. This momentous event, dedicated to advancing the understanding and application of cryptocurrency, showcased the dynamism and innovation of the Bitcoin Dada community.
 The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts.
The evening began with the MC engaging the audience in a series of lively questions. “What is Bitcoin? Explain it to me like I’m five,” was one such question that underscored the diverse range of understanding in the room. While some answers were complex, others offered simpler explanations, highlighting the challenge of conveying intricate concepts.

As the MC continued, participants were asked for their impressions of the event space and suggestions for improvement. Comments ranged from critiques of overly bright lighting to discussions about the relevance of Bitcoin. One participant proposed an intriguing app idea that combined Eventbrite and WhatsApp, reflecting the innovative spirit of the audience.
The highlight of the evening was the inspiring opening speech by the CEO of Bitcoin Dada.
 She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team
She addressed the marginalization of women in tech, celebrating Bitcoin Dada’s commitment to inclusivity and support. She introduced her team 
each member contributing uniquely: Edith, the community lead from Uganda; Sabina, the recruiter who found a sense of belonging; and Memelord, the project manager with a flair for comedy.

The ideathon segment was particularly thrilling. Debra’s third-place pitch proposed a Bitcoin-powered marketplace aimed at reducing youth unemployment by showcasing skills. Shantelle’s second-place idea focused on using Bitcoin to address global issues, such as helping refugees find safe zones with GPS technology. The top prize went to Meg, with her solution promising a significant impact—though the specifics were left as a tantalizing cliffhanger. 🌟🏆
PS : Sabina also gave a preview of the #tando app tha you can check out here on my youtube channel Link HERE
Meeting Inspiring Figures and Making Connections 📸
Throughout the event, I had the pleasure of meeting some remarkable individuals who are deeply involved in the Bitcoin community.
First, I met Felix from TheCore, a key panelist in the discussion on the financial revolution amidst economic unrest. We took a photo together, capturing a moment of shared enthusiasm for the potential of Bitcoin.

Later, I connected with a Bitcoin Dada and gamer who is actively involved with Thndr Games, Mary Imasuen. We took a photo showcasing our shared passion for Bitcoin and gaming.

I also had the chance to meet a Bitcoin enthusiast named Hope and she was adorned in Bitcoin-themed merchandise. We snapped a photo together, celebrating our mutual enthusiasm for Bitcoin and its future.

Panel Discussions: Insightful Exchanges and Thoughtful Dialogues
The panel discussion titled “Financial Revolution Amidst Economic Unrest” featured Felix from TheCore, Jason, a Bitcoin Dada supporter, and Bill, a lawyer with expertise in Bitcoin. They delved into the major challenges Kenyans face in adopting Bitcoin, emphasizing the importance of education and community support. They discussed the solid foundation of Bitcoin’s base layer and the need for further development in subsequent layers to enhance its functionality.

The discussion also touched on Kenya’s future in the Bitcoin space. Bill suggested integrating Bitcoin with fiat transactions and stock exchanges, while Jason highlighted the government's welcoming stance and the need for energy to support Bitcoin. Felix proposed making Bitcoin legal tender and finding sustainable energy sources to bolster its use. ⚖️🌍

Audience questions added further depth to the conversation. One attendee asked about using Bitcoin to offset government debt, while another inquired about measures for improving public education on Bitcoin. The responses stressed the need for comprehensive educational initiatives. When asked about alternative cryptocurrencies, the panel firmly rejected the idea of “shitcoins,” focusing instead on the value of Bitcoin. 🚫💸
The second panel discussion, moderated by Sharon from ₿-Trust, explored personal experiences with Bitcoin Dada. Panelists Anon, Vera, and Caroline shared how the program impacted their perspectives.

- Anon discovered a niche and a supportive community, emphasizing Bitcoin’s role as “lightning-fast internet money,” especially with Layer 2 advancements. 🌐⚡
- Vera found Bitcoin to be a valuable medium of exchange, advocated against other cryptocurrencies as “shitcoins,” and highlighted opportunities for women. 💪💰
- Caroline expanded her knowledge and aimed to educate others, describing Bitcoin as a store of value and emphasizing the importance of combating inflation through education. 📚🔍

The panelists also discussed opportunities for Bitcoin in their communities: - Anon saw potential for learning and growth through knowledge-sharing. - Vera mentioned BitSacco, a solution for saving in Bitcoin, and other upcoming projects like Sabina’s Tando app. - Caroline stressed the importance of education to counteract misconceptions about Bitcoin and its benefits. 🏡📈
In their closing remarks, the panelists shared their future aspirations: - Anon aimed to become a developer impacted by Bitcoin. - Vera planned to engage with the community and learn from others. - Caroline focused on educating the community to dispel myths about Bitcoin. 🌟👩💻
The event concluded with a warm dinner where attendees mingled, exchanged ideas, and enjoyed a meal together. WATCH https://video.nostr.build/4d0fbc2dd6ae0c20e0d45aa071a9e88000a9544f4289414900c91134d13960da.mp4
The Bitcoin Dada Cohort 7 graduation was more than just a celebration of individual achievements; it was a testament to the collective potential of the Bitcoin community.
As the event wrapped up, the atmosphere was charged with optimism and a shared commitment to advancing bitcoin technology. The graduating cohort left with new skills, fresh ideas, and a network of like-minded individuals, ready to make a significant impact on the future of Bitcoin. 🌍💡 #kenya #bitbiashara #kenya
-
 @ 7cc328a0:2a247c0e
2024-10-12 15:49:54
@ 7cc328a0:2a247c0e
2024-10-12 15:49:54relay.tools quarterly report
July, 2024
Project updates
The major focus this quarter was building a NIP-42 AUTH proxy for strfry relays. Codename: interceptor.
NIP-42 AUTH proxy for strfry
I see this as a major innovation in nostr relaying and there was no other open source option in the ecosystem so I decided it was extremely important to investigate and get done. I was not completely sure that it would work, but after much building and testing I now think this is production ready.
Currently very few relays support NIP-42 AUTH. The ones that do, keep their software closed source as a value-add. This validates that it is a wanted, and valued feature.
I went live with an initial relay for testing wss://auth.nostr1.com. I coordinated the launch of this along with Amethyst re-doing their relay settings to have options for "Private Inbox Relays". I also tested all major clients repeatedly and found and fixed bugs both client side and relay side.
I asked nostr for members to join this relay and help test, which they did and after multiple rounds of testing I believe the AUTH proxy is now ready for a major release.
This will continue to be a focus for next quarter.
https://github.com/relaytools/interceptor-proxy https://github.com/relaytools/interceptor
NIP-17 testing and collaboration
NIP-17 private DM features had a big push from clients this quarter so I helped them by coordinating multiple rounds of inter-client testing and using the new auth.nostr1.com relay. Clients included: coracle, amethyst, 0xChat and gossip.
These features are working well, although some of the issues filed and am tracking are still underway being fixed. Some are UX experience and some are simply interoperability issues or bugs that need more work. Specifically for 0xChat and Coracle. Gossip and Amethyst are fully functioning with no known bugs.
https://github.com/0xchat-app/0xchat-core/issues/12 https://github.com/coracle-social/coracle/issues/378
UI/UX improvements + NDK
Spent some time improving the UI/UX and this is still in-progress.
The main page has been updated to be more of an exact match from nostr designer @daniele
I also created a new relay explorer using NDK and worked with upstream to fix bugs related to NIP-42 AUTH in the library. My PRs are still outstanding but I am hopeful this will pave the way for NDK supporting NIP-42 auth in any clients that use it. I am also writing docs for NDK since this was un-charted territory and required a lot of digging through the code to figure out how to fix and use these features.
https://github.com/nostr-dev-kit/ndk/issues/246 https://github.com/nostr-dev-kit/ndk/pull/251 https://github.com/nostr-dev-kit/ndk/pull/248
I also started work on a complete re-write of the relay settings page. The settings page has too many options and is confusing to users so I am combining all the options into a 'setup wizard' that walks the user through the various types of relays and helps them pick options that they will want.
Relay Metadata, Monitoring and Discovery
One part of the vision for relay.tools has been to make it easier to discover new relays. Not only for relays running on the platform but for ALL relays. Therefor I spent some time this quarter working toward that goal.
I discovered that @sandwich has been working a long time on NIP-66 and it is exactly what we need for relay discovery. It has many additional features as well such as monitoring, and geographic filtering.
https://github.com/nostr-protocol/nips/pull/230
I will be adding support for this into relay.tools on the main directory listing, so I currently am working with him to finalize the NIP and get it merged. It will be able to poll these events and show/search through relays that are discovered on the wider nostr network.
I also created a new tool to publish these events so that I can start down this path. The tool is called monitorlizard. What it does is it monitors relays, and publishes them according to the NIP-66 spec. I also launched a new relay that anyone can push these events to called monitorlizard.nostr1.com
https://github.com/relaytools/monitorlizard
I hope that we can get this NIP finalized and merged this quarter although it is not a rush. Fiatjaf has already given the go-ahead and we just need to make sure to tidy up and include all the things we need in there before merge and it is 'set in stone' so to speak.
-
 @ dd664d5e:5633d319
2024-07-10 14:45:43
@ dd664d5e:5633d319
2024-07-10 14:45:43The Law Giver
In my previous article, I briefly went into the topic of how contract law is holy law.
The Father of the Christians, you see, is a God of Covenants, and He sent His Son to Earth to fulfill the Law and pay a Price for our salvation. The Father also created the Natural Order to confirm His Laws through our observation of that Law in action.
That is why Christians have a deep respect for honest contracts, true prices, fair measures, natural systems, and good laws. Not merely for their own sake, but also because understanding them helps us to understand and emulate the Law Giver.
The tired What would Jesus do? meme is actually an attempt to capture this emulation of the Highest Judge. Jesus knows the Law, since His Father defined it and He is One with the Father, so how would He apply the Law best, in this situation?
The Last Things
Working together with him, then, we entreat you not to accept the grace of God in vain. For he says, “At the acceptable time I have listened to you, and helped you on the day of salvation.”
Behold, now is the acceptable time; behold, now is the day of salvation.
-- 2 Corinthians 6:1-2 New Testament, RSV Bible
One of the things most devout Christians frequently ruminate over, is when Christ will return.
Every day, we ponder. We go for a walk, and ponder. We cook dinner, and ponder.
At the same time, we are called upon to live each day in a productive manner, and to not simply lie around, vegetating, and staring at the heavens. Not only for our own sake, but also because to do so would be to limit our ability to inform others about the Good News, so that they can take to pondering with us. We are called to ponder with as many people as we can produce, adopt, convert, or simply collect through our daily interactions.
This means that we are not of the world (as our eyes are watching God and baptism has made us Immortals), but we are definitely in the world (involved in, and effected by, the everyday dealings around us.) It is a very difficult balancing act to know when we are paying too much attention to the one or the other, or to know where to store up our treasures, if we can't put them all immediately into the Final Treasury.
So, we worked today and earned a bit of fiat cash and we have no immediate usage for it. What to do with it?
Well, some of it should go to charity or be invested in a business that provides important goods, services, and employment. Some of it will be needed to simply cover the day-to-day costs of our own life, or that of those dependent upon us. But it might be prudent to store up some of it, for the mysterious length of time between receipt of the monies and our own ascent into Heaven.
Typically, that store was the local currency, but that's being inflated away at an alarming rate. Then we all began to move to precious metals, and many of us still do, but they are so difficult to spend and can't be broken into small bits or transported over wide distances at low cost.
Enter Bitcoin.
The Great Ledger
In our frustration, more and more Christians are turning to a new technology, to save up some treasure in a liquid asset, for the mid-term. And, once we begin using it, and begin to understand how it works, we quickly grow fond of it.
Bitcoin is a beautiful money because it is a money based upon keeping precise accounts, using a fair measure, and obeying the Laws of Nature.
In essence, Bitcoin is a debt note emitted by a universal debtor (the network) in exchange for some good or service. This frees the individual people using it from ever needing to carry debt, as the debt stays in the network, the value and enforceability of that debt note is protected by the effort used to create and maintain the network, and the eagerness with which other people wish to store their efforts up in that same network. The debt still exists, but it can be so thinly and widely spread that it no longer rests as a burden upon one particular person.
The debt, in other words, has been disassociated from humans and the management has been distributed to machines. This is the precise opposite process of a "fiat" (by decree) currency, which only has value so long as it is associated with some particularly solvent group of humans (who personally vouch for repayment of any debts denominated in the currency), and where management is centralized to some other group of humans.
Have you accepted Bitcoin as your personal money and store of value?
You have invested $10 to buy the electricity to mine Bitcoin? Then you receive $10 of Bitcoin in return. The Bitcoin network now owes you the $10 purchasing power equivalent of that electricity.
If someone then gives you $5 worth of pizza, then you can then give them a $5 portion of your $10 worth of Bitcoin. You have taken a part of your Bitcoin debt note and shared it with them.
They now hold $5 worth of Bitcoin invested in the network and can spend it on some other good or service. Or they can simply hold it and wait for it to rise in value, as more people "mine" more of it (and produce more notes, paradoxically making the existing notes more useful and therefore valuable) and more people try to gain the notes in order to manage their own finances by storing their energy in the network or transporting their energy using the network.
Bitcoin, in other words, is an accounting book that needs no accountant because it stores, tracks, and controls the ledger on its own. It is a Natural Ledger that runs according to the the Laws.
It is the only human-made ledger that allows for true and immediate Final Settlement. This Final Settlement is what allows people to trade using the convenience of digital debt notes, with neither person occurring or even risking any personal debt. We Christians know that all debt is a burden, including monetary debts, which is why we are called to forgive each other's debt and to hope that our own debts are forgiven. Better still, is to avoid the accumulation of debts, altogether.
So, Final Settlement? Final Settlement is what Jesus would do.
-
 @ 7cc328a0:2a247c0e
2024-10-12 15:42:36
@ 7cc328a0:2a247c0e
2024-10-12 15:42:36relay.tools quarterly report
April, 2024
Project updates
The main initiatives for Relay.tools this quarter were the installer, re-occuring billing support, customer support, and moderation capability. Towards the end of the quarter I was able to start work on supporting nostr groups and a NIP42 auth proxy.
Installer
I made lots of progress on the installer this quarter. It's now at a point where it is fully functional.
- [x] Whitelabel support for custom domains
- [x] Automatic SSL certificate deployment via. certbot container
- [x] Many bugfixes, improvements, and end to end testing
- [x] Publish pre-built images
- [ ] Use pre-built images in the installer (alternative to building from scratch).
The installer was used to deploy a POC for vote.gold. A side project by @manime that is a relay hub for independent voters.
Re-Occuring Billing
I created a new system for billing / invoicing that tracks user balances and allows them to "top-up" their balance.
The billing system accounts for users of a paid relay (paid relay bonus), these payments go toward the owners balance.
This system is now live and there has been decent response by relay owners that reached out to pay their bills.
The cost of relays was adjusted to 12,000 sats / month. (from 21,000 sats/month).
Upgrades to lightning node and channels were performed to support these payments.
Customer support
Relay.tools rolled out a new customer support portal to support users that have questions about billing and so that relay.tools can contact relay owners via nostr with announcements / notifications.
My goal here is to use nostr itself to support the relays. I also did not want to use DMs because they are not private, they're flakey and simply not a good practice given the state of clients implementations. I think using nostr native methods for support is very important, but is also very difficult given some limitations that currently exist with nostr. Regardless, I pushed ahead.
- [x] Created a nostr pubkey for fielding questions and supporting users.
- [x] Used the outbox model from gossip to setup a streamlined customer support focused dashboard.
- [x] Created an additional relay for support and linked to the relay from the relay.tools landing page.
- [x] The first support notification blast went out to all owners advising them to pay balances in the coming month or to contact support for free 'credits' in exchange for feedback.
Based on the feedback I've gotten so far, it's clear there is still much work to do implementing a nostr native support system:
- Gossip outbox was buggy, and my client database pushed the limits of gossip and corrupted the database. I filed bug(s) upstream and am working with upstream to make this better.
- Some users preferred to use DMs vs. open communication on nostr (even though DMs are not advisable for private communication on nostr).
- Added SimpleX to the support pubkey's bio as an alternate contact method.
- The process for balance notification was very manual and once further research is done on the path forward, it needs to be automated.
Moderation and house-keeping
- [x] I've begun reaching out to nostriches for help with moderation.
- [x] Implemented some additional super-admin capability for the relay.tools admin user(s) in preparation for multiple super-moderators. This includes a global view of all relays and the ability to quickly explore flag mis-behaving relays.
- [x] I've started deleting some relays that were abandoned after using the new customer support portal to reach out to them. Some were simply test relays, some operators expressed that they've graduated to running their own relay, and some I simply could not get in contact with. This is a good milestone for relay.tools and was much needed, leveraging the re-occuring billing and support tasks.
AUTH proxy for strfry
I've started work this quarter on creating a mechanism to bring NIP42 AUTH to the strfry ecosystem. The gist of it is, strfry has been unable to implement NIP42 due to the complexity of needs that various authentication schemes require. There are many considerations and what seems simple at first glance quickly becomes mired in confusion and C++ makes it hard for anyone to collaborate or implement.
To work around this, I've created a proxy written in golang that can sit outside strfry and intercept/handle AUTH requests, leveraging the robustness and performance of strfry while allowing us to customize the authentication flow in a separate process.
So far I have an initial POC working and in the coming quarter I hope to ship an initial version of this which will be used by relay.tools and be the first open source auth proxy for strfry relays.
I am very excited about this. NIP42 in my opinion will enable multiple new paradigms for interacting with relays as it will be able to implement ACLs for reading from a relay vs. the current methods of write ACLs. It also will have the potential to support the new group clients that I mention in the next section.
Outreach / Collaboration / Nostr Groups
I've been spending more time on getting some collaboration going with fellow nostriches where our vision for nostr aligns. I am very interested in groups for nostr. (Functional replacements for discord/telegram/slack/reddit). This has been a long-term goal of relay.tools to support these types of clients and I'm excited that clients are starting to kick off a second wave of nostr functionality and I will do everything I can to support them.
- [x] I made an appearance on the Thank God For Nostr podcast talking with @hodlbod about relays, group-chats, and the viability of relays being profitable/sustainable.
- [x] Various nostriches have contacted me about running their own relay.tools and I'm working with them to educate and help them bring new 'relay hubs' online!
- [x] I've been working with @hodlbod on some extensive testing of the new Coracle groups implementation, private groups or closed communities: NIP87. I have been expoloring the possibilities of using Coracle's private community/group and whitelabel support for an integration with relay.tools. I have also been exploring what modifications a strfry relay may require to support advanced groups such as this based off the triflector relay proof of concept.
- [x] Investigated the use and requirements for 'simple groups' by @fiatjaf NIP29. This is another group implementation which may require customized relays and I wanted to understand the possibilities and requirements.
- [x] Integration with blowater.app - I've been working with @blowater on his new client/relay initiative that involves groups for nostr.
Next Quarter plans
- [ ] Release initial version of the AUTH proxy for strfry.
- [ ] Collaboration/Outreach - Coracle, blowater, other groups efforts.
- [ ] Submit a Relay Discovery NIP for review.
- [ ] Relay Support channel improvements.
-
 @ 7cc328a0:2a247c0e
2024-10-12 15:33:58
@ 7cc328a0:2a247c0e
2024-10-12 15:33:58relay.tools quarterly report
January, 2024
Project updates
UI design
Relay.tools spent quite a bit of time working on UI design this quarter. Since UI is time intensive and there are many other aspects of the project that need work, I time-boxed this work to 3-4 weeks total.
I engaged with @Daniel from #nostrdesign and a freelance UI developer @freecritter. We setup a penpot instance for relay.tools and practiced using that instead of closed-source figma. We learned that penpot is not as friendly as figma from a designers point of view, but is workable. From the perspective of a frontend engineer it is no different than figma and using penpot is a big opensource win.
The following designs were implemented this quarter. There is still much to do in this area and some aspects have been brainstormed but put on hold due to other priorities.
Relay branding and directory
I wanted to give the relays personality and branding, here is a list of improvements in this area:
- [x] The home page now prominently displays the public relays that have chosen to advertise.
- [x] Relay 'Badges' were re-designed to have better contrast and fit.
- [x] Relays have a custom direct landing page at their domain. eg. frogathon.nostr1.com
### 'Paid relay' support
Relays now support lightning payments to the relay.tools operator. This helps with combating spam and allowing the relay owners to subsidize their monthly cost.
Layout / theme
The frontend code has been modified so that it is responsive on mobile/desktop using columns. The menu was re-designed to be responsive on mobile and shows user hints for login as well as additional links (explore, FAQ). Theme switcher bugs for light/dark modes have been fixed. (Nextjs bleeding edge workaround was required).
Relay Explorer Alpha
The Relay Explorer Alpha is a mini-client for interacting with a single relay. The following improvements were made:
- [x] Moderation capabilities added: Mods can delete messages, block pubkeys, and delete+block directly from the explorer.
- [x] Image and Link parsing / optional loading.
- [x] Replies implemented.
Example screenshot showing these features:
Installer
Another main focus this quarter was to implement an installer for the relay.tools software so that anyone can easily self-host this on a generic VPS.
The installer will be a simple shell script that asks the user a few questions (like their domain name) and then automatically installs the entire stack.
A new code repository was created for this called relay-tools-images
- [x] Main architecture to match production (systemd and nspawn).
- [x] Common Base OS image builds (Debian).
- [x] Haproxy, Strfry, Relaycreator and Mysql image builds.
- [x] Auto-updating of application code (including database migrations).
This is still in-progress and will be part of next quarter's priorities to finish the first stage. (described in plans for next quarter)
Lightning Node
A decent amount of time was spent managing a Bitcoin+Lightning+LnBits node and building a second node for testing and standby purposes.
I had some node issues this quarter and have been learning, re-building the node, upgrading, and aquiring more inbound liquidity to support relay operations.
Relay Management / daily operations
Relay.tools growth last quarter exceeded expectations and lots of work in the ladder part of this quarter went into daily operations.
It grew so fast that I have paused any advertising so that I have time to implement some important growth related features (as described in the plans for next quarter).
- number of relays currently running: 63
- number of unique admins/mods: 207
- events processed in last 30d: 5,091,724
- gigabytes sent/received in last 30d: 1,651GB / 175GB
Monitoring
Daily operations include checking in on the relay activity to get a feel for what's going on. I've implemented an InfluxDB integration for the strfry plugin, which helps with daily operations and in the future will provide owners, mods, and users with stats showing relay performance and event counts. This greatly improves visibility into the relays and is the backbone of data analysis for the platform.
Events by Kind (7d)
Events by Relay (7d)
Data Explorer View (single relay, kind 3)
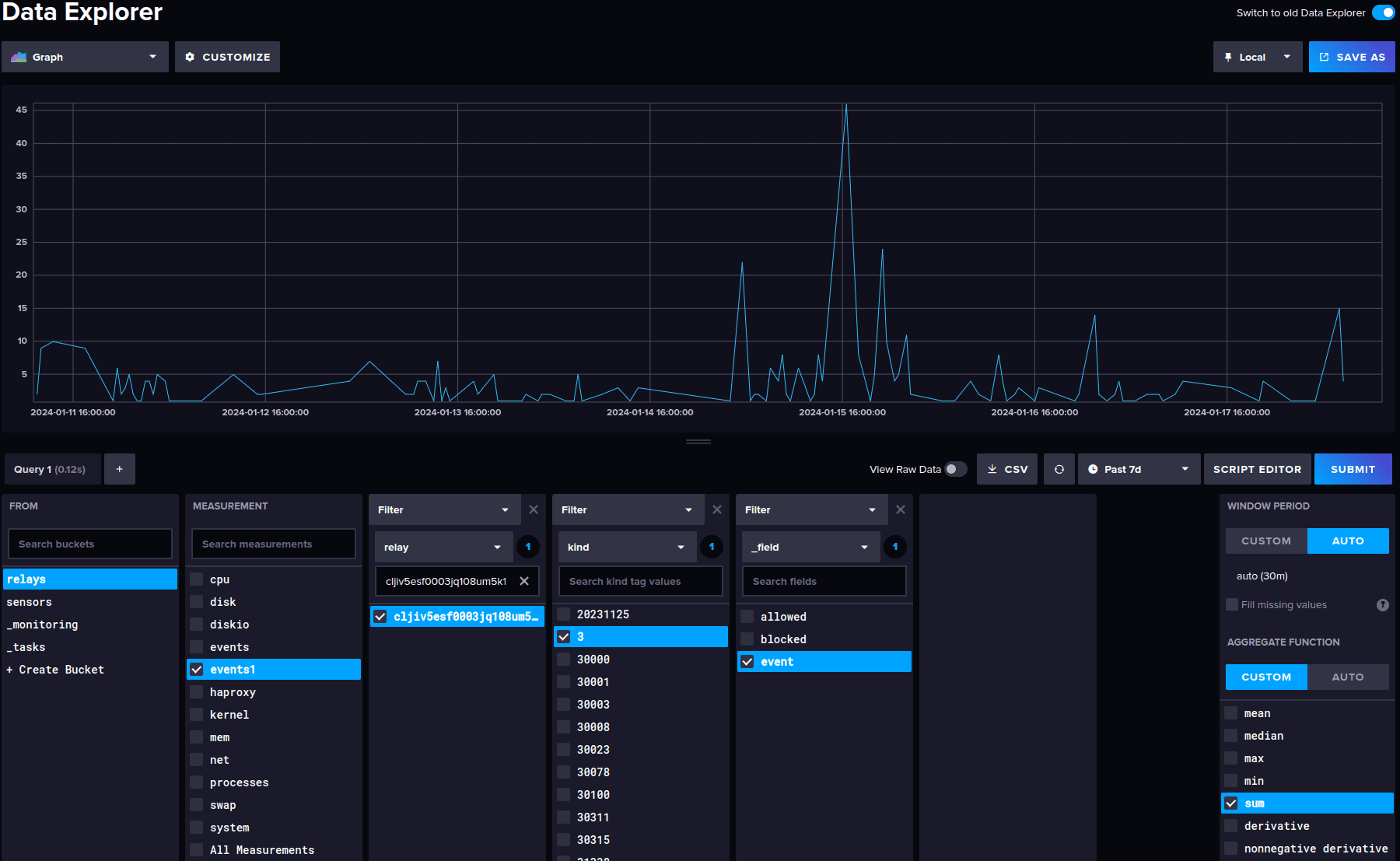
Moderation
Daily operations time is also spent ensuring relays meet our TOS. That includes browsing the relays content for anything that does not meet the TOS and performing mitigation when necessary. This can be time consuming. I will be adding super-moderator capability so that others can assist as we grow (as described in the plans for next quarter).
Training / Feedback / Community
I promoted the use of event specific relays for nostr community events. Feedback was very positive and showed that people enjoy having event specific relays even if client support is minimal. * Nostrasia * Frogathon
Plans for next Quarter
Finish the installer - [ ] SSL certificate management with certbot. - [ ] Nostr key generation for API credentials. - [ ] install.sh script for interactive -and- config file based one-shot installation. - [ ] Publish pre-built images and integrate their use with the installer.
Re-Occuring Billing (+ tools for interacting with community of relay runners) - [ ] Implement re-occuring billing using a credits system and lightning payments. - [ ] Implement user notification(s) for billing cycle notifications. - [ ] Implement user feedback / support channel.
Additional visibility and moderation tools - [ ] Implement super-moderator capability for TOS violations. - [ ] Engage with community to help support moderation
-
 @ 5ea46480:450da5bd
2024-10-12 15:27:20
@ 5ea46480:450da5bd
2024-10-12 15:27:20The following is a combination of a series of posts on Bitcoin Timestamps on Nostr that were originally made between 2024-10-11 02:10:29 GMT & 2024-10-12 13:57:20 GMT.
To everyone whose phone i have harassed with my nfc card that therefor now see this message: This is actually a forrest picture channel https://image.nostr.build/2df97ead480b057df1a9a622f12c6209d82cfd4cc7e4e3f9254267a7199ec46e.jpg
https://image.nostr.build/74358001cab02b32e4c6bb4af04714cb6f4ce69b190514dad330f52c397c665f.jpg
Amethyst now lets you create NIP-03, Bitcoin based Open Time Stamps.
Unfortunatly i cut off the timestamp that is part of the original version of this picture (because it is ugly), so you will never know this foto was taken on july 12, 09:54. https://image.nostr.build/4f96ab676d551e4866b1d4856a8db756b53e094e17ba3c9bb75ff24ecd54839b.jpg
forestr
Everyone can timestamp everything at any time; the time-proof is valid regardless of who initiates its creation.
For example, at 01:37 on oct 12, I signed this kind 1040 event: nostr:nevent1qqsyxw4l6030ugpufwr820leasv630c3an87pcm9sp0uek22gtwzsmszyp02geyqgka3lu3zv4wa6dhxmnkacs6epsnqjrzgd0hn3m69pkjm6qcyqqqqgyqrapa2r
Which contains a proof that this kind 1 event can be tied into bitcoin block 865239: nostr:nevent1qqsd3u78nkjn78tcfcqjmrclxns9667chycmlzxxgnxxvd26yw7z85sppemhxue69uhkummn9ekx7mp0qgs2jy6jwcfsyqmpfp3tjggt505n4vnemqn3jcf6t3qw2e426mg7k9crqsqqqqqp277t4j
And the timestamp of block 865239, is 00:02 on oct 12. The event itself claims it was signed 22:11 on oct 11; this may be a lie still, but at least it was not signed much more than 1 hours and 51 minutes later.
Aside from all these time related dates, the described lunch date could also just be a complete fabrication of course; at the very least the pictures correspond with the stated dishes
woodpeckestr
https://image.nostr.build/9e12ea3eb66e2b686539abe9349b4d205b2ccde17bdbc30c65b9ad5953ace901.jpg
Timestamps only give very weak indications of truth; but they are really good at catching certain lies.
Take for example the following note: nostr:nevent1qqszw6fwhl28y974y9vjw6ej63xdax4gu5rf8fw52jqkf8x5kk98skgppamhxue69uhku6n4d4czumt99upzqpuvjsr4gjkpxf5jacv3pgpy8x2c4czgwu23xsh2jmztdv66f863qvzqqqqqqyg7gvfg
your client may have a hard time loading it, depending on when you look at this post. This is because the event claims to be signed at Thu Oct 17 2024 03:00:00 GMT. Given it is currently Oct 12, this is a blatant lie, and relays tend to not accept this event because of this.
But, what happens in 5 days? As soon we pass that 3 o’clock mark on oct 17, how would any outsider know that this event was not signed at that time, but 5 days earlier? It is easy to catch these sort of lies when you are present in real time and pay attention, but if you arrive after the fact, NIP-03 timestamps allow you to identify such a lie for certain if adequate proof exists.
And in this case, this proof does exist! Because I timestamped this event already, tying it into block 865274, which was mined around 05:31, oct 12. Which results in the following screenshot of Amethyst: https://image.nostr.build/01ca55a150444cab7b3025b70f9c1dab7c1382a3d54ed3faefaa722ee2f208aa.jpg
The app claims the event was posted ‘now’ (probably because it simply interprets any date in the future as ‘now’), but also tells me a timestamp exists that is 9 hours old.
Now this particular type of lying (pretending to be in the future), it not all that interesting, I was just curious. But it does go to show that you should not trust the time the event claims it was signed, because it is trivially easy to lie about it.
Say hello to my fren btw: https://image.nostr.build/ec4b37e2d259015f1a3b9b39b4163c98ceab56ead83bd08ce82350a061c7814c.jpg
Thus concludes my forrest picture presentation for now.
Time, such a fascinating thing, inescapably ever moving onwards. Winter is coming: https://cdn.satellite.earth/6761a5ff81c5a5ac3daa74e0d33cddf4912b770a13d272b933499839b5b03757.mp4
-
 @ 3c7d12a6:9532013e
2024-06-20 14:47:12
@ 3c7d12a6:9532013e
2024-06-20 14:47:12NUD: Pubkey to colors
This NUD defines how to convert pubkey to colors.
Why?
npubis nonsense to display.- too long.
npub1bla...blais nonsense to display.npub1takes too much space....means nothing.
Specs
- Uses hex pubkey.
- Converts 64 characters to 8 colors.
- Splits 64 with 8 length chunks.
- Converts each 2 in 8 into
- Alpha (0-255 -> 0.0-1.0)
- Hue (0-255 -> 0.0-360.0)
- Saturation (0-255 -> 0.0-1.0)
- Light (0-255 -> 0.0-1.0)
- Supports dark and light theme.
- When Light is 1.0, flip the Light for light theme (0.0).
-
 @ 361d3e1e:50bc10a8
2024-10-12 15:02:07
@ 361d3e1e:50bc10a8
2024-10-12 15:02:07https://forex-strategy.com/2024/10/12/why-do-the-worlds-elite-live-significantly-longer-than-the-rest-and-how-do-they-achieve-it/ Why do the world's elite live significantly longer than the rest, and how do they achieve it?
usa #secrets #life #truth #freespeech #health
In the following material, you will find out the secret of longevity. How is it that the world's "celebrities" look eternally young and live longer than the rest. What do they do to stay young? No, they don't buy the most expensive creams! Here you will find out why 8 million children go missing every year around the world. Here you will learn one of the secrets of planet Earth!
-
 @ 126a29e8:d1341981
2024-05-22 06:47:20
@ 126a29e8:d1341981
2024-05-22 06:47:20Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852
Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior. A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.
Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.
Bitcoin cambió todo eso. Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio. Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.
La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins. ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.
La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan. Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.
En cambio, los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.
Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero. Pero Bitcoin no se originó en el vacío. Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.
Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.
Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.
https://freeross.org
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 38f9a05c:6999fc04
2024-04-07 12:08:30
@ 38f9a05c:6999fc04
2024-04-07 12:08:30
In today's world, where self-promotion appears to be the standard, there exists a subtle charm in modesty. As a child, I frequently encountered the expression, "Only a donkey praises their tail." its significance has remained with me throughout my life. It serves as a reminder that authentic excellence does not require shouting from the rooftops; instead, it manifests itself in actions, not words.
Allow me to now introduce Alfred Adler, a pioneer in the field of psychology. Born in Vienna in 1870, Adler's theories challenged the prevailing views of his time, particularly Sigmund Freud's emphasis on the unconscious mind. Adler proposed individual psychology, focusing on the unique experiences and perceptions that shape each person's worldview. Central to his theories was the concept of the "inferiority complex" and its counterpart, the "superiority complex," shedding light on how individuals grapple with feelings of inadequacy and superiority.
Inferiority complex
The "inferiority complex" describes persistent feelings of inadequacy and self-doubt, stemming from early experiences. Individuals afflicted with this complex often seek validation and may engage in compensatory behaviors. Therapy and self-reflection are key to addressing and overcoming these feelings, fostering healthier self-esteem and confidence.
An example of an inferiority complex might be a person who, from a young age, consistently felt overshadowed by their siblings' achievements and talents. Despite their own unique abilities and successes, they internalize a belief that they are inherently inferior to others. This belief could manifest in various ways throughout their life, such as constantly seeking approval from others, feeling anxious or inadequate in social situations, or striving excessively for success in an attempt to prove their worth.
Superiority Complex
Conversely, the "superiority complex" manifests as an exaggerated sense of self-importance and entitlement. Individuals with this complex may exhibit arrogance and lack empathy towards others, struggling with meaningful relationships and criticism.
An example of a superiority complex could be seen in a person who consistently belittles others and insists on being the center of attention in social settings. They might boast about their achievements, talents, or possessions in an attempt to assert their superiority over those around them.
Back to the childhood phrase "Only a donkey brags praises their tail." Returning to the childhood adage "Only a donkey brags praises their tail,” modesty and humility are often misconstrued as weakness or a lack of self-confidence. Nevertheless, it is far from that. It entails possessing a realistic view of oneself and comprehending that one's value should not rely solely on external validation or praise. Instead, it's found in the genuine connections we make with others and the positive impact we have on the world around us.
By abstaining from boasting about ourselves, we provide room for others to shine. It is not about denigrating our accomplishments or pretending to be less than we are. On the contrary, it involves acknowledging our abilities without feeling compelled to advertise them to the public continually. Therein lies the elegance of allowing our actions to speak louder than our words.
Moreover, humility allows for personal growth and learning. When we're humble, we're open to feedback and constructive criticism. Instead of becoming defensive or dismissive, we approach each opportunity for improvement with an open mind and a willingness to learn. This mindset not only helps us develop professionally but also fosters a sense of humility and gratitude for the knowledge and experiences that others bring to the table.
Humility enables personal development and learning. When we're not constantly focused on ourselves, we become more attuned to the needs and experiences of those around us. We listen more intently, offer support more readily, and celebrate the successes of others with genuine enthusiasm. In doing so, we cultivate deeper connections and create a more inclusive and supportive community.
In a society that often glorifies self-promotion and individualism, it can be challenging to embrace humility fully. However, it's a quality worth cultivating, both personally and professionally. By focusing on what we can contribute rather than what we can gain, we create a more harmonious and compassionate world. Hence, should you ever find the urge to trumpet your achievements or magnify your ego, pause to reflect on the timeless wisdom encapsulated in the age-old adage: "Only a donkey praises their tail," alongside the profound insights of the Austrian psychiatrist's psychological framework. Instead of trying to prove yourself with words, show who you are through your actions. Embrace humility, which means being modest and not bragging. True greatness isn't about loudly boasting about your good qualities. It's about having inner strength and making a positive impact on the people around you.
Lastly as the Great Roman emperor Marcus Aurelius said, "Waste no more time arguing about what a good man should be. Be one."
-
 @ 3c984938:2ec11289
2024-04-01 09:36:34
@ 3c984938:2ec11289
2024-04-01 09:36:34A long time ago, a girl resided on a tropical island. The girl's name is Sirena. She resided with her mother in close proximity to the Hagåtña River. Sirena's mother was a bit strict and tried to teach her to follow her in footsteps to be a lady, but Sirena only dreamed of swimming all day.\
 \
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
\
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
Sirena's mother was preparing for a special event and needed her to acquire special ingredients from the nearby village. She had a significant amount of preparations to complete, therefore she requested that Sirena procure the necessary ingredients and return promptly. Sirena made a promised to her mother that she would hurry back.\

She was on the village path. She kept her eyes on the trail, trying her best to be a good daughter and hurry back. But she took one glance briefly at the river.
 \
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
\
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
 \
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
\
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
Sirena was happy because now she can be in the water all day long. However, Sirena also wished she did what her mother asked and found another way to punish her. A part of her will forever be saddened by the loss of her Mother and Godmother.
It said that sailors have spotted mermaids on their voyage across the sea. Just that their too crafty & swift to be caught.
Historical Notes/context
 The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother.
The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother. 
👉I like to point out in this, Thomas Edison patented the light bulb in 1879. So visually the lights outside and inside the huts as flames. As Ai(text to image) does not account for these type of items.
👉This also goes back to be careful what you wish for because you may actual get your wish.
👉Chamorro people are Pacific Islanders, similar to Hawaiians, and have a brown/tan skin complexion.\

👉My mermaid looks strikingly similar to the Disney's recent version of Ariel. I Thought that was interesting because I put just "mermaid" into the text prompt. Its worth pointing out ai limitations as it's not advanced as I originally thought, likely due to its limited data. In this case only disney as a reference for mermaid.
based on ordinary prompts\

 Prompt used:\
Prompt used:\
 That's all-Thank you until next time (N)osyters!
That's all-Thank you until next time (N)osyters!If you like it, send me some ❤❤hearts❤ and if you didn't like it-⚡⚡🍑🍑zap⚡⚡🍑🍑 me!🍑🍑 me!
For email updates you can subscribe to my paragraph.xyz/\@onigirl or below if using the Yakihonne App
-
 @ 97c70a44:ad98e322
2024-03-23 04:34:58
@ 97c70a44:ad98e322
2024-03-23 04:34:58The last few days on developer nostr have involved quite a kerfluffle over the gossip model, blastr, banning jack, and many related misunderstandings. This post is an attempt to lay out my thoughts on the matter in an organized and hopefully helpful way.
What's wrong with gossip?
It all started with a post from jack asking why more devs haven't implemented the gossip model. There are many answers to this question, not least having to do with there being two standards for user relay selections, and ongoing changes to NIP 65. But I don't want to talk about compatibility here.
nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszymhwden5te0wfjkccte9enrw73wd9hj7qpq2uf488j3uy084kpsn594xcef9g9x3lplx4xnglf0xwghyw2n3tfqqnrm02
Mazin responded with some numbers which estimate how many connections the gossip model requires. Too many connections can become expensive for low-power clients like mobile phones, not to mention some privacy issues stemming from nosy relays.
nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgewaehxw309amk2mrrdakk2tnwdaehgu3wwa5kuef0qyghwumn8ghj7mn0wd68ytnhd9hx2tcqyp2xzsjktypudzmygplljkupmuyadzzr6rkgnvx9e0fx3zwhdm0vkz4ceg7
I have some minor disagreements with Mazin's numbers, but I basically agree with his point — a purist gossip model, where a large proportion of nostr users run their own relays results in a high number of connections to different relays. I brought this question up late last year in my interview with Mike Dilger and in a conversation with fiatjaf, who convinced me that in practice, this doesn't matter — enough people will use a handful of larger hubs that there will be a good amount of overlap in relay selections between most pubkeys.
To articulate this more clearly: the goal is not "personal web nodes", which is a pipe dream the Farcasters and BlueSkys (BlueSkies?) of the world aim at, but a more pragmatic mix between large hubs and smaller purpose-built relays. These small relays might be outlets for large publishers, small groups, or nerds who also run their own SMTP servers and lightning nodes.
The point of the gossip model is that these small nodes be possible to run, and discoverable from the rest of the network so that we can preserve the censorship-resistant qualities of nostr that brought us here in the first place.
Blast It!
It's no secret that I've long been a critic of Mutiny's blastr relay implementation. My main objection is that the blastr approach doesn't account for the hard limits involved in scaling smaller relays. If the goal is to cross-pollinate notes across all relays in the network, all relays will require the same size database, and contain all notes in the network. This works right now (sort of), but as the network grows, the relays running on a $5 VPS are going to have their disks fill up and will inevitably fall over.
nevent1qyvhwumn8ghj76r0v3kxymmy9ehx7um5wgcjucm0d5hszxnhwden5te0wpuhyctdd9jzuenfv96x5ctx9e3k7mf0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qqs07jr9qx49h53nhw76u7c3up2s72k7le2zj94h5fugmcgtyde4j9qfrnwxj
Not only that, but the content breakdown on any given relay by default becomes an undifferentiated soup of "GM", chinese notes, bots, bitcoin memes, and porn. Blastr makes it impossible to run an interesting relay without implementing write policies.
Which is actually fine! Because that's always been true — servers that allow anonymous uploads always get abused. Tony is just helpfully pointing out to us that this is no less true of nostr relays. I only wish he could have waited a little longer before mounting his attack on the network, because lots of hobbyists are interested in running interesting relays, but the tools don't yet exist to protect those servers from unsolicited notes.
One other note on blastr — Tony at one point described blastr as a relay proxy. This is an interesting perspective, which puts things in a different light. More on proxies later.
Ban Jack?
Here's a thought experiment: how might we actually "ban blastr"? @Pablof7z suggested to me in a conversation that you could configure your relay to check every note that gets published to your relay against the big nostr hubs, and if it exists on any of them to simply delete it. Of course, that would result in your relay being basically empty, and the hubs having all of your content. That's game theory for you I guess.
Another approach that was floated was to encourage users to only publish to small relays. In theory, this would force clients to implement gossip so users could still see the content they were subscribed to. Fiatjaf even posted two identical notes, one to his personal relay, and one to a hub to see which would get more engagement. The note posted to the mainstream relay got 10x more replies and likes than the more obscure note.
nostr:nevent1qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qgmwaehxw309aex2mrp0yh8wetnw3jhymnzw33jucm0d5hszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqdc2drrmdmlkcyna5kkcv8yls4f8zaj82jjl00xrh2tmmhw3ejsmsmp945r
Of course, this is thwarted by blastr, since blastr not only replicates notes posted to it, it also actively crawls the network as well. So the next logical step in this train of thought would be for hubs to encourage people to use small relays by actively blocking high-profile accounts.
nostr:nevent1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpzdmhxue69uhhyetvv9ujue3h0ghxjme0qyd8wumn8ghj7urewfsk66ty9enxjct5dfskvtnrdakj7qpqpjhnn69lej55kde9l64jgmdkx2ngy2yk87trgjuzdte2skkwwnhqv5esfq
This would of course never happen (Damus is one client that hasn't implemented NIP 65, and they also run the biggest relay), but it was a fun thought experiment. At any rate, the silliness of the suggestion didn't stop certain people from getting offended that we would "disrupt the free market" by "forcing" our opinions on everyone else. Oh well.
Death to Blastr
In reality, even though blastr makes it a little harder to adopt gossip in the short term, its days are numbered. Eventually, relay operators will start to feel the pain of unsolicted notes, and will either shut their relays down or look for tools that will help them curate the content they host.
From my perspective, these tools take two forms — read protection and write protection. This is something I alluded to in my talk at Nostrasia last November.
Write protection is straightforward — already many relays have access control lists based on active subscriptions, invite codes, or just static whitelists that determine who is allowed to post to a given relay, or what event authors are represented there. This approach effectively prevents blastr from using relays as free storage, which is a huge improvement.
Read protection is more tricky, because anything publicly readable will be scraped by blastr and replicated to unauthenticated-write relays across the network. In most cases, this is ok, but there are use cases for relays to exist that host a unique collection of notes oriented around some organizing principle. Unfortunately, with blastr in action (or any scraper that might exist), the only way to do this is to actively protect proprietary content. There are a few approaches that can work to make this happen:
- IP-based access control lists
- AUTH-based access control lists
- Stripping signatures when serving events
- Storing and serving encrypted content
Each of these approaches has its own set of trade-offs. But depending on use case, any of them or a combination of them could work to allow relay operators to carve out their own piece of the nostr-verse. In fact, this is a big part of what Coracle is about — the white-labeled version of the product confines certain notes to proprietary relays, with optional encrypted group support.
Enough of my polemic against blastr. Let's talk about how to make the gossip model actually work.
Hints are pointless
Right now, clients that implement the gossip model rely pretty heavily on relay hints to find related notes — whether user profiles, reply parents, or community definitions. The problem with hints is that they are prone to link rot. Many of the relays that were set up a year ago when nostr took off are no longer online, and yet they persist in user relay lists, and in relay hints. These hints can't be updated — they are set in stone. What this means is that a different mechanism has to be used to find the notes the hints were supposed to help locate.
Because of this, I've come around to the position that hints are basically pointless. They are fine as a stopgap, and might be appropriate for certain obscure and ill-defined use cases where relay urls are the most durable address type available. But they provide basically no value in supporting the long-term robustness of the network.
What are durable, however, are pubkeys. Pubkeys are available pretty much everywhere, except in event id hints — and there is a proposal in the works to add a pubkey to those too. The cool thing about pubkeys as hints is that once you have a pubkey, all you need to do is find that person's kind 10002 inbox/outbox selections, and you should be able to find any note they have published.
This goes with the caveat that when users change their relay selections, or rotate their key, they (or their relays) should be sure to copy their notes to the new relay/pubkey.
The question then is: how do I find a given pubkey's relay selections?
There are already several mechanisms that make this reasonably easy. First of all, NIP 65 explicitly recommends publishing relay selections to a wide range of relays. This is a place where the blastr approach is appropriate. As a result, relay selections are usually available on the most popular public relays. Then there are special purpose relays like purplepag.es, which actively seek out these notes and index them.
These indexes are not confined to relays either. It would be trivial to create a DVM that you could ask for a pubkey's relay selections, optionally for a fee. Alex Gleason's proxy tag could also be used to indicate indexes that exist outside the nostr network — whether that be torrents, DHT keys, or what have you.
The best part is that this doesn't negatively impact the decentralization of the network because in principle these indexes are stateless — in other words, they're easily derived from the state of the public part of the nostr network.
Just do it for me
Looping back to where we started — the complexity and technical challenges of implementing the gossip model — there is a simple solution that many people have experimented with in different ways that could solve both issues at once: proxies.
As I mentioned above, Tony thinks of blastr as a proxy, and he's right. More specifically, it's a write-proxy. This is only part of its functionality (it also acts as an independent agent which crawls the network. EDIT: apparently this is not true!), but it is an essential part of how people use it.
Another kind of proxy is a read proxy. There are several implementations of these, including my own multiplextr proxy, which is gossip-compatible (although it requires a wrapper protocol for use). The advantage of a proxy like this is that it can reduce the number of connections a client has to open, and the number of duplicate events it has to download.
Proxies can do all kinds of fancy things in the background too, like managing the gossip model on behalf of the client, building an index of everything the user would be likely to ask for in advance to speed up response times, and more.
One interesting possibility is that a NIP 46 signer could double as a proxy, reducing the number of round trips needed. And since a signer already has access to your private key, this kind of proxy would not result in an escalation in permissions necessary for the proxy to work.
It's simple
The number of cool and creative solutions to the content replication and indexing problem is huge, and certainly doesn't end with blastr. Just to summarize the next steps I'm excited to see (to be honest, I want to build them myself, but we all know how that goes):
- More clients supporting gossip
- Gossip implementations maturing (Coracle's still has some issues that need to be worked out)
- A shift from relying on relay hints to relying on pubkey hints + relay selection indexes of some kind
- Proxy/signer combos which can take on some of the heavy lifting for clients of delivering events to the right inboxes, and pulling events from the right outboxes
Let's get building!
-
 @ 20d29810:6fe4ad2f
2024-03-15 20:51:56
@ 20d29810:6fe4ad2f
2024-03-15 20:51:56













































-
 @ b6424601:a11e4ff4
2024-10-12 12:32:06
@ b6424601:a11e4ff4
2024-10-12 12:32:06My engineer dad, who spent his time on better ways to enrich uranium at the national lab in Oak Ridge, Tennessee, suggested that my average math and decent art skills might be better suited for architecture than engineering. I followed the family tradition and enrolled at Auburn University College of Architecture Design and Construction. They had a program for less gifted dyslexic test takers called Summer Option, where you took your entire first year of design labs in one summer. I survived and thrived through the grind and, somewhere on the journey, realized my personal take on good architectural design is centered on recognizing life patterns and the ability to design the stage and context for the patterns to happen in a cool way. I had a gift for pattern recognition and enjoyed creating "cool as shit" designs as we baby architects described them.
Architecture is perfect for me. As an architect, you are the person people ask for help to change how they want to live. You listen, observe, analyze, and come back with ideas on how best to effect change in that location. You exchange value to explore people's lives and help them set the stage for pure life. Living in good design can be life-changing for clients and rewarding for the team that helps make it happen.
After working for a challenging boss for eight years at a national corporate interior architecture firm, I had enough experience to realize that my project ideas were as good as my boss's but would be more personally entertaining. I went on my own in the last century, initially bootstrapping enough work to live, working with a college best friend. I would commute from Atlanta to Birmingham and couch surf in his apartment Monday through Thursday, selling to friends and my buddies' fraternity brothers. (Thank you to the Auburn chapter of the Sigma Alpha Epsilon). We kept it up for a year and then split up.
I returned to Atlanta and kept grinding on in-town custom renovation projects until I had an opportunity to do a build-to-suit office project for a client investor. I found a university mate with experience for the first commercial project, and we started Jones Pierce in 1998. Twenty-six years later, two studios continue to work with individuals and their homes, businesses, foundations, clubs, and personal investment properties.
I am most proud of my professional accomplishments when we receive testimonials about a project that changed someone's life. Clients write us letters, give us hugs, and call back ten years later. It never gets old.
Several projects have challenged me personally over the years. A design for a residence led to Passive House certification in Yestermorrow, Vermont. The Joachim Herz House for the Herz Foundation was our first project with an international foundation. Druid Hills Golf Club master plan and the first building phase is our first club project. All these were project types outside our focus but within our capabilities.
Our proof of work over time also caused the most personal growth and expanded opportunities over a longer time horizon. I love what I do for groups and clients who design personal spaces and places. I am honored to lead my studio tribe, which loves what we do, and the constant grind to improve as much as I do. Over time, the clanging projects came, and we pivoted and captured learnings to improve our processes.
Our pivot points came as we practiced. I hate to use the C word: CRAFT. Learning how to design for owners to spend their cash instead of the unavailable fiat in the housing crash. Improving our delivered projects by designing in high-performance building standards. Figuring out how to adjust our process in milestones to evolve the design budget simultaneously and allow clients to consider their mindful investment of a lifetime. Establishing methods to help property buyers evaluate remote properties to pick the right one to achieve site-actualization. Evolving principles developed to work with the individual to groups of individuals in clubs or foundations. Combining the personally learned principles of Bitcoin with the principles we use to produce our architecture for the sovereign individual.
-
 @ 6871d8df:4a9396c1
2024-02-05 23:29:22
@ 6871d8df:4a9396c1
2024-02-05 23:29:22The Apple Vision Pro was released, and it is the talk of the town right now. To be frank, I think it's a stupid product. It's not useful or particularly enticing to me in its current form factor. It's a toy, not a tool. All the features seem gimmicky as opposed to generally helpful. I'm not saying it may never be worthwhile, but as of this first release, it is only a party trick.
Coincidently, this is the first product that does not have any of Steve Jobs' influence. To me, it shows. I don't think Jobs would have ever let this product see the light of day.
Jobs understood product. He didn't make things for the sake of progress or to make sci-fi reality; he made things because he 'wanted to make a dent in the world.' He wanted to solve problems for everyday people by innovating with cutting-edge technology. He aspired to make people's lives better. Steve Jobs' genius was the way he married cutting-edge technologies with valuable tools that made those cutting-edge technologies simple and elegant.
The Vision Pro may be technically innovative, but it is not a tool, at least in its current form. It may be one day, but that is precisely my point; Jobs would have never released a product where the form factor would hold it back from becoming a tool. At best, it is an intriguing toy that is additive to some content at the behest of being very awkward to wear or be seen in. In my view, mainstream adoption can happen only in a world where we can use the Vision Pro as a contact lens or very small, discreet, minimalist glasses, but certainly not this iteration where it covers more than half your face.
Seeing people's eyes makes us human. So much emotion, understanding, and communication happens with just a look. It is a window into the soul. I don't want to live in a world where we are actively bringing all the negatives about communicating in the digital world to the physical one.
https://image.nostr.build/2365609411f144f5d789ffd684ffce9b4d867626a7bfe11bb311cb0f61057199.jpg
I can't help but wonder or hypothesize what Steve Jobs would focus on if he were still alive today. I think Apple's priorities would be completely different. My gut tells me he would not have let Siri get as bad as it is. Siri is a horrible product; I never use it, and everyone I know who tries to use it does so unsuccessfully, at least most of the time. I personally always default to ChatGPT or Bard. These AI systems make my life dramatically more productive. They are tools in the purest sense.
In my opinion, Steve would not have missed this train. Sure, Apple could wake up and integrate these systems into Siri — if they were smart, they would — but in its current form, it is so far behind that it almost astounds me. My intuition leads me to believe he would be closer to what [Rabbit] is doing.
Who knows? Maybe I am entirely wrong, and Apple just kickstarted VR's mass adoption phase. Unfortunately, I think this will likely be the biggest failure of a physical product that Apple will have seen since Jobs returned ages ago. The Vision Pro is only slightly better than the Oculus, and Facebook has already deprioritized VR for AI. Apple is further behind, and I don't see a world where they do not make the same pivot. There is a skill to creating successful, innovative products, and it makes me sad to see the torch that Jobs passed lose its flame. As someone who respected how Apple used to innovate, watching this decay in real-time is jarring as this is just the latest in a string of disappointing decisions that exemplify that 'peak Apple' is behind us.
-
 @ e97aaffa:2ebd765d
2024-10-12 09:26:05
@ e97aaffa:2ebd765d
2024-10-12 09:26:05«A Uniswap, principal bolsa descentralizada da Ethereum, anunciou que irá lançar uma blockchain exclusiva para os serviços que oferece, a Unichain. Ou seja, segundo a equipe a nova rede que será uma segunda camada vai ser mais rápida, com mais liquidez e com serviços de ponta para traders.» – BlockTrends
É curioso o rumo que as criptos estão a evoluir (ou talvez não).
A Uniswap começou no Ethereum, depois foi para outros ecossistemas, posteriormente foi para as L2 do próprio Ethereum. Segundo o DefiLlama está presente em 25 chains, simplesmente absurdo, a liquidez está altamente fragmentada.
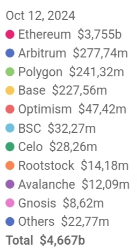
Esta fragmentação não é só na Uniswap ou DeFi, é em todo o mundo cripto, que está a tornar o mercado complexo, com liquidez diversa e dependentes de agentes centralizados.
«Essa movimentação pode impactar negativamente a capitalização de mercado de redes L2 como Polygon, Arbitrum e Optimism, que atualmente são amplamente utilizadas por protocolos DeFi”, afirmou Bitelo.» – BlockTrends
A liquidez está constantemente a saltar de chain para chain, em busca de novos airdrops.
«Construído na Superchain, o Unichain oferecerá suporte à interoperabilidade nativa para transações cruzadas rápidas e seguras. Também suportará padrões como ERC-7683 para tornar a troca perfeita em todas as cadeias»
Aqui os Devs utilizam a palavra chave, interoperabilidade, esta enorme fragmentação só funciona devido a Bridges, são essenciais. Todo este ecossistema é muito centralizado.
Agora vou deixar duas perguntas para reflexão:
O que vai acontecer quando as Bridges forem obrigadas a cumprir com o compliance, como qualquer exchange?
O que vai acontecer ao DeFi quando o KYC for obrigatório?
Não é um questão de “se”, mas sim, quando, quando for o KYC for obrigatório, é inevitável, se estão a replicar o sistemas FIAT, terão que cumprir as regras desse sistema. Em ambos os casos, com o incumprimento, vão ter os mesmos problemas que hoje em dia os mixers enfrentam. Tanto para quem cria, como para quem utiliza.
boas reflexões…
-
 @ f3328521:a00ee32a
2024-10-12 05:31:29
@ f3328521:a00ee32a
2024-10-12 05:31:29Islam is rooted in Prophetic Tradition and in this regard maintains a dialogue with secular civilization that inclines toward fitra and tawhid. The dunya is ever spiraling in decline and Insan navigates it with guidance and wisdom. Hidden Treasure is beyond the horizon, not on the decaying map.
Hypermodernity presents the new stain of cyberspace where the imaginary has collapsed into the real with the liquidation of any perceived barrier. This eventual shift away from post-modernity was clearly demarcated in 1995 with global capital coming online, accelerating the digitization of everything analogue. Insan is once again a nomad, disconnected from anything but the luminous glow of cyberspace - a hyper-dividual that is a nation-state unto himself. Capital interest is no longer in human physical abilities but the unplugged and deworlded, neuronal composition of the dividual who can behemoth into orbit about the planet. Here, in cyberspace, there be monsters, dragons, and gods.
But man is vicegerent!
Hypermodernity is the death of utopian projects. Art is dead, too. Even academic disciplines are unnecessary. Luxury, instant gratification, and absolute power are the only “goals” now. “When everyone’s super, no one will be.” And so, the new natural enemy becomes insan al kamil – 9/11, 10/7 these events did not happen in a vacuum. As everything collides in cyberspace it is possible a hypermodern boundary act will birth a revived Islamic civilization. The split bandwidths of your nafs can still reflect Simorgh if you are adequately disciplined in strangeness.
Islamic civilization has traditionally thrived on four elements: Capital, Hierarchy, Geography, & Climate. Digital self-sovereignty must be reclaimed. Nuclear families must be marshaled. Digital nomads must build Network States. Hijra must be made back to the margins to avoid catastrophe. And most importantly, theurgy must be embraced. This is only an introduction and outline. There is much work to do!
-
 @ e7211c22:e87afeee
2024-10-12 02:46:09
@ e7211c22:e87afeee
2024-10-12 02:46:09Chef's notes
If you do one thing to improve your health in the kitchen, ditch the industrial seed oils and make your own mayonnaise. Make sure to use virgin coconut oil and extra virgin olive oil, not light or refined olive oil. That being said, use extra virgin olive oil from a lighter tasting olive variety, such as Arbequina, or mayonnaise will have a strong olive oil taste. Where do you get extra virgin olive oil from you may ask? Ugly olives, of course. The addition of yogurt and whey greatly extend the shelf life of your mayonnaise from 1-2 weeks to 1-2 months in the refrigerator, while adding beneficial probiotics. To spice up you mayonnaise, see end of directions.
Details
- ⏲️ Prep time: 15 minutes
- 🍳 Cook time: 0 minutes
- 🍽️ Servings: lots
Ingredients
- 1 whole egg
- 2 egg yolks
- 1 Tbsp Grey Poupon
- 1 Tbsp lemon juice
- 1/2 tsp salt
- dash white pepper
- 1/2 cup virgin coconut oil, warmed to liquid
- 1/2 cup extra virgin olive oil, from a lighter tasting olive variety, such as Arbequina
- 1 Tbsp plain yogurt
- 1 Tbsp whey
Directions
- Mix first six ingredients in a bowl with an immersion blender or food processor.
- Combine oils in pourable measuring cup.
- Slowly, drip by drip, begin to add oil to first six ingredients while running immersion blender or food processor. If oil is added too quickly at first, emulsification will not occur and mayonnaise will be ruined.
- Continue adding oil to first six ingredients drip by drip, increasing to slow drizzle, then thin stream, then steady stream. Take breaks pouring oil if necessary to completely blend in oils.
- Add yogurt and whey. Refrigerate.
- To spice up your mayonnaise: Sriracha mayonnaise - with first six ingredients add 1 clove garlic, mashed, 2 Tbsp sriracha, 2 Tbsp lime juice, and an additional 1/4 tsp salt. Chipotle lime mayonnaise - replace 1 Tbsp lemon juice with 1 Tbsp lime juice, with first six ingredients add 1 clove garlic, mashed, 1/4-1/2 can chipotle peppers in adobo sauce, 2 limes juiced and zested, and an additional 1/4 tsp salt.
-
 @ e1ff3bfd:341be1af
2024-01-06 19:41:35
@ e1ff3bfd:341be1af
2024-01-06 19:41:35Over the last few months it feels the bitcoin community has gotten more and more jaded on lightning. To be honest, this is for good reason, back in 2017 we were promised a decentralized payment network that would always have cheap payments and everyone would be able to run their own node. Nowadays, the average lightning user actually isn't using lightning, they are just using a custodial wallet and the few of that do run lightning nodes often find it a burdensome task. For us at Mutiny Wallet, we are trying to make this better by creating a lightweight self-custodial wallet and in my opinion we have been executing on that dream fairly well. In this post, I'll analyze these issues and present a new way to view lightning and what that means for bitcoin going forward.
First and foremost one of the hardest UX challenges of lightning is channel liquidity. No other payment system has these problems today besides lightning so this often confuses lots of users. To make matters worse, there aren't any practical hacks that we can do to get around this. Muun Wallet used an on-chain wallet + submarine swaps to get around the channel liquidity problem, this worked very well until fees went up and everyone realized it wasn't actually a lightning wallet. The better solution is JIT liquidity like we do in Mutiny or splicing like that is done in Phoenix. These solutions abstract some of it away but not enough, we often get support questions confused on why some payments have fees and others do not. The fact is channel liquidity is not a usable UX for most end users.
The other major pain point of lightning is the offline receive problem. Inherently, you must be online with your private keys to sign and claim a payment. There is technically an ongoing spec proposal to be able to work around this (essentially creating a notification system of when people are online to receive payments), but it doesn't solve the fundamental problem and still has limitations. There has been a few attempts to get around this, most notably was Zeus Pay lightning addresses. These essentially worked by just creating stuck payments and waited for the user to come online to claim, this caused a ton of problems for people and even forced us at Mutiny to block users from paying them because it caused so many force closures. This is a hard problem because the entire rest of the bitcoin/crypto ecosystem works by just copy-paste an address and you can send to it whenever, there isn't caveats around asking your friend to open their wallet. This is further exacerbated by things like lightning address that requires a webserver to even get an invoice in the first place.
Channel liquidity and offline receives in my opinion are the two most obvious reasons why self-custodial lightning is not popular. When most users hear about any of these, they just think screw that and move to a custodial wallet because it is so much easier. If these were our only two problems, I think self-custodial lightning would be fine, it may never be the predominant way people use lightning, but we could get the UX good enough that we have a significant portion of people using lightning in a sovereign way. However, there are more problems under the surface.
Channel liquidity is a problem, but it is also deceptive. When you have 100k sats of inbound liquidity you would think you could receive up to 100k sats, but this isn't the case, often you can't actually receive any. This is because of on-chain fees, when a payment is being made in lightning you are creating pre-signed transactions that have outputs for every in-flight payment, these outputs cost potential on-chain fees and the high on-chain fees go the more it eats into your liquidity. After we've solved most of our force close issues Mutiny this has been number one support request. Even if you do everything right, understand liquidity and have enough for your payment, sometimes it still won't work because on-chain fees are too high. This is always really discouraging because isn't the whole point of lightning to not have to pay on-chain fees? Fundamentally, all current lightning channels could become entirely useless if on-chain fees went high enough because a single payment would require too many reserves. Obviously this is hyperbolic, but I hope I am getting the point across that on-chain fees don't just effect the opening and closing costs of channels, even if you are a diligent node runner that only opens channels when fees are low, that is not enough, your channels need to be large enough to pay for the on-chain fees of each HTLC at any future on-chain fee rate. As on-chain fees go up and up this problem will only get worse.
The proposed solution to these reserve issues are things like anchor channels, package relay, ephemeral anchors, etc. These are all well and good but kind of just mask the problem. They do solve it so the fee reserve can be much lower and possibly zero, however with the tradeoff that you need on-chain funds available to fee-bump your force closes so they can actually get into a block. This again breaks the UX for self-custodial users because they have hold on-chain funds alongside their lightning funds so they can do those on-chain fee bumps. The size requirements for their on-chain funds is still dynamically based on how high on-chain fees can spike. Solutions for this can include having someone else bump your transaction fees but this brings basically a trusted 3rd party into the mix and isn't ideal.
When you lay out all the different tradeoffs a lightning node needs to make, especially in a high fee environment, it makes me think, what are we doing here, are we going down the wrong path? Lightning is still fundamentally a fantastic payment protocol but its limitation is that it requires scale. Basically every problem I've outlined goes away when you have a large lightning node with lots of liquidity and high uptime so many we should optimize for that. The market has been telling us this for years already, +90% of lightning users are using custodial wallets because it works so much better at scale. So how can we use large scale lightning nodes without custodial wallets?
Combining existing large scale lightning infrastructure with self-custodial solutions sadly, isn't totally possible. The only real way to do that as of now is Muun Wallet which as we talked about earlier, doesn't really solve the problem because everything is just an on-chain transaction. However, Muun was onto something. The architecture of having a simpler protocol interface with lightning is genius and gives us the best of both worlds. We can make fast cheap payments and let the big boys collect fees for running the lightning node. Aqua Wallet just launched which is essentially a Muun Wallet but on top of Liquid, this is a good bandaid fix but doesn't get to the root of the problem.
Before we go further we should take a step back and break down what problems we are trying to solve. Bitcoin has a fundamental scaling limitation through the block size, if we could make infinite, then we wouldn't necessarily need any layer 2s because we could just make on-chain payments. However, we live in the real world and have a 1mb block size limit, and this limits the number of transactions we can make on-chain. Lightning is a huge improvement to bitcoin because we don't need to put every transaction on-chain, we just need to open a channel and can make seemingly countless payments. So why isn't lightning the silver bullet? Lightning lets us move payments off-chain but what it doesn't do is let us move ownership off-chain. Fundamentally lightning still relies on that, at the end of the day, a utxo goes to single user. So even if every on-chain transaction was a lightning channel, we still run into the limit of how many people can actually own those channels. What we need is another layer 2 that can scale utxo ownership and caninterop with lightning, that way we have a way to scale ownership combined with scaling payments.
So how do we scale ownership? Simply put, the answer today is custody, whether that is pure custodial like a Wallet of Satoshi or in the grey area like fedimints and liquid, the only way to do it today is through custody or federated bridges. In bitcoin, the only way to delegate ownership of a utxo to multiple parties is through multisig, however, that requires every user to be online when anyone wants to transact, and when you take go down this path far enough you end up just reinventing lightning.
Are we doomed then? Is there no way to scale bitcoin in a self-sovereign way? Luckily, the answer is no, but we need some soft-forks. Covenants are the way to scale bitcoin ownership. There are a bunch of covenant proposals but at their core what they propose to do is to add a way, so you can have a bitcoin address that limits where and how the coins in it can be spent. This can seem scary, but we already have these in bitcoin today, OP_CTLV (Check LockTime Verify), which was soft forked in 2016, only allows you to spend from a bitcoin address if the transaction has a given locktime, this lets you gate when a utxo can be spent. What the current covenant proposals do is let you gate where a utxo can be spent. With that simple primitive many different protocols can be built that allow for scaling ownership.
There are a lot of current covenant proposals, the main ones being: OP_CTV, OP_VAULT, OP_CSFS, OP_TXHASH, OP_CAT, and APO. They all have different functionality and tradeoffs but in my opinion we should be looking towards activating a form of covenants because otherwise we will likely be moving towards a future of less sovereign bitcoin users.
The future is not bleak however, even without covenants we can still scale bitcoin for the world, just not in the ideal way. At Mutiny, we are full steam ahead on implementing fedimint into the wallet, in my opinion (and the rest of the team's) it looks like the best current scaling solution for bitcoin. Fedimints give us the ability to dynamically share ownership over a group of utxos and is able to interop with lightning through gateways. It is the pinnacle of the scaling dream for bitcoin with current technology and I can't wait to help make it reality while we can.
-
 @ 3bf0c63f:aefa459d
2023-11-08 15:06:55
@ 3bf0c63f:aefa459d
2023-11-08 15:06:55I think it's undeniable at this point that the creation of Lightning Address has made the usage of custodial Lightning solutions increase -- or at least be more prominent. We see these stats everywhere of how many of Nostr Lightning Addresses are custodial, and how services like Nodeless and Geyser only work if you give them a Lightning Address, and that probably sounds like a lament to many people who thought Lightning would be this amazing network of self-hosted nodes that everybody runs, and is indeed sad.
Well, on the other hand the Lightning Address flow is clearly an improvement -- to most people -- over the cumbersome invoice flow. Since the early days of Lightning people had been complaining about the fact that there is no way to "just send money to an address". Even though I personally liked the invoice flow much more (especially if they had structured, signatures, clear descriptions and amounts, payment proofs and so on) the fact is that most people didn't and slowly invoices were losing their meaning entirely anyway.
This improvement in the payment flow, along with the open, easy and interoperable way that Lightning Addresses work, has opened space for new use cases that maybe wouldn't have existed otherwise -- like the services mentioned above, and others. So we can't really say this was all a bad thing.
We also shouldn't say it was a bad thing to have Lightning Addresses being invented at all, because if they hadn't been invented like they were, there is a high probably they would have been invented in other forms, probably much worse, that would involve private deals and proprietary integrations with ad-hoc APIs, SDKs and JavaScript widget buttons with iframes. I even remember some of these things starting to happen at the time Lightning Address was created, and we have more evidence of these things even after Lightning Address, like some "partnerships" here and there and the "UMA" protocol. So maybe Lightning Address was just the best possible protocol at the best time, and all its problems are not really its problems, but symptons of the problems of the Lightning Network (or maybe you wouldn't call these "problems", just natural properties, but doesn't matter).
The saddest realization of all this process, for me, was that Lightning payments are mostly used for tipping and not for commerce as I thought they would in the beginning (hence my love for the invoice flow). Specifically, LNURL-pay and its cool hidden features that went mostly unsupported, were all designed with the goal of enabling new use cases for commerce in the real life, outside the web, and Lightning Addresses would have tied nicely into that vision too -- but that was all definitely an irredeemable failure.
I thought I had more things to say about this, but either I didn't or I forgot. The end.
-
 @ a012dc82:6458a70d
2024-10-12 01:45:47
@ a012dc82:6458a70d
2024-10-12 01:45:47Table Of Content
-
The Rise of Russian Bitcoin Mining
-
Cheap Electricity
-
Favorable Regulations
-
Growing Interest in Cryptocurrency
-
What It Means for the Future of Bitcoin
-
Conclusion
-
FAQ
Bitcoin, the world's most popular cryptocurrency, has been on a rollercoaster ride in recent years. However, one thing that has remained consistent is the need for miners to verify transactions and create new blocks on the blockchain. While the United States has long been the dominant force in the world of Bitcoin mining, a new player has emerged - Russia. In this article, we will take a closer look at Russia's emergence as the second-largest Bitcoin miner, the reasons behind its rise, and what it means for the future of Bitcoin.
The Rise of Russian Bitcoin Mining
In recent years, Russia has seen a surge in Bitcoin mining activity, with estimates suggesting that the country accounts for around 10% of global Bitcoin mining. This puts it ahead of countries like Kazakhstan, Iran, and Canada, and second only to China in terms of Bitcoin mining power. The reasons for Russia's rise in Bitcoin mining are varied, but they include factors such as cheap electricity, favorable regulations, and a growing interest in cryptocurrency among the general public.
Cheap Electricity
One of the main reasons for Russia's emergence as a major Bitcoin mining power is the country's abundance of cheap electricity. Thanks to its vast reserves of natural gas and other resources, Russia is able to offer some of the lowest electricity prices in the world. This has made it an attractive destination for Bitcoin miners, who require large amounts of energy to power their mining rigs.
Favorable Regulations
Another factor that has contributed to Russia's rise as a Bitcoin mining powerhouse is the country's relatively favorable regulatory environment. While some countries have taken a hostile stance towards cryptocurrencies, Russia has adopted a more open-minded approach. In 2019, the Russian government passed a law regulating cryptocurrencies, which provided a clear legal framework for businesses and individuals to operate within.
Growing Interest in Cryptocurrency
Finally, the growing interest in cryptocurrency among the Russian public has also contributed to the country's emergence as a major Bitcoin mining player. In recent years, there has been a surge in the number of people in Russia buying and trading cryptocurrencies. This has created a more supportive environment for Bitcoin mining, as more people understand the potential benefits of this activity.
What It Means for the Future of Bitcoin
The emergence of Russia as the second-largest Bitcoin miner has significant implications for the future of the cryptocurrency. For one, it demonstrates that Bitcoin mining is not just the domain of a few wealthy individuals or countries. Rather, it is a global activity that is open to anyone with the right resources and knowledge. This could lead to more widespread adoption of Bitcoin, as more people are able to participate in the network.
Additionally, Russia's emergence as a major Bitcoin mining power could help to decentralize the network. One of the biggest criticisms of Bitcoin is that it is too centralized, with a few mining pools controlling the majority of the network's hashing power. By bringing more miners into the network, Russia could help to distribute the hashing power more evenly, making the network more resilient and less susceptible to attack.
Conclusion
Russia's emergence as the second-largest Bitcoin miner is a significant development in the world of cryptocurrency. It demonstrates that Bitcoin mining is a global activity that is open to anyone with the right resources and knowledge. It also has the potential to help decentralize the network, making it more resilient and less susceptible to attack. As the world of cryptocurrency continues to evolve, it will be interesting to see how Russia's role in Bitcoin mining develops over time.
FAQ
What is Bitcoin mining? Bitcoin mining is the process of verifying transactions and adding them to the blockchain. Miners are rewarded with new bitcoins for their work.
Why is Russia becoming a major Bitcoin miner? Russia has cheap electricity, favorable regulations, and a growing interest in cryptocurrency among its citizens.
What does Russia's emergence as a major Bitcoin miner mean for the future of Bitcoin? It could lead to more widespread adoption of Bitcoin and help to decentralize the network.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 4ba8e86d:89d32de4
2024-10-11 23:15:47
@ 4ba8e86d:89d32de4
2024-10-11 23:15:47Quando você compartilha seu e-mail pessoal em sites, blogs e vários outros serviços, está expondo seu endereço de e-mail principal. É aí que entram os e-mails aliases. Esses endereços de e-mail alternativos desempenham um papel crucial na proteção de sua identidade e na organização de sua comunicação online. Exemplos de e-mails aliases são Simplelogin e AnonAddy.
Um e-mail alias é essencialmente um endereço de e-mail alternativo associado à sua conta principal de e-mail. Sua função principal é proporcionar uma camada adicional de privacidade e segurança, permitindo que você compartilhe um endereço de e-mail temporário ou pseudônimo em vez de revelar seu endereço de e-mail real.
Por que usar e-mails aliases?
-
Privacidade: Ao usar um e-mail alias, você não precisa fornecer seu endereço de e-mail real a sites ou serviços nos quais não confia completamente. Isso protege sua identidade online e ajuda a evitar o rastreamento de sua atividade na web.
-
Segurança contra spam: Os e-mails aliases podem ser usados para se inscrever em boletins informativos, participar de concursos ou registrar-se em sites, sem comprometer sua caixa de entrada principal. Se você começar a receber spam nesse alias, pode simplesmente desativá-lo sem afetar seu e-mail principal.
-
Organização: Os e-mails aliases podem ser usados para categorizar e gerenciar sua comunicação online. Por exemplo, você pode criar aliases específicos para uso em diferentes contextos, como trabalho, compras online ou interações sociais.
-
Proteção contra violações de segurança: Se um dos seus e-mails aliases for comprometido, isso não afetará sua conta de e-mail principal. Você pode simplesmente desativar o alias comprometido e continuar usando seu e-mail principal sem preocupações.
Os e-mails aliases são uma ferramenta valiosa para proteger sua privacidade e segurança online. Com a crescente preocupação com a privacidade digital, usar e-mails aliases se torna uma prática cada vez mais importante.
https://habla.news/u/alexemidio@alexemidio.github.io/1702167107338
https://habla.news/u/alexemidio@alexemidio.github.io/1704317161405
-
-
 @ 8947a945:9bfcf626
2023-10-23 08:13:39
@ 8947a945:9bfcf626
2023-10-23 08:13:39จงตระหนักรู้คุณค่าของตัวเอง เพชรไม่ได้เปล่งประกายเจิสจรัสจากสุดปลายถ้ำ

2023’s Wake up call
แรงบันดาลใจที่ทำให้ผมตัดสินใจเอาเรื่องนี้มาเล่าบน #ทุ่งม่วง เกิดจากเมื่อต้นปี 2023 ผมได้รับสัญญาณเตือนภัยจากที่ทำงานแห่งหนึ่ง (Wake up call) ปลุกให้ตื่นขึ้นจากภวังค์ ตระหนักรู้ถึงความเป็นจริงบางอย่าง ว่างาน part time ที่กำลังทำเริ่มมีสัญญาณความไม่มั่นคงเกิดขึ้นทีละเล็กทีละน้อย มีความสุ่มเสี่ยงที่จะถูกขอให้งดคลินิคไม่ต้องมาออกตรวจ (ภาษาสุภาพของการเลิกจ้างหมอ)
สำหรับหมอที่ทำงานหลายโรงพยาบาล จะเข้าใจสถานะ”หมอ part time” ของตนเองดีว่า สามารถถูกถอดเวรออกได้ทุกเมื่อ หากทางโรงพยาบาลมีความจำเป็น
เมื่อเกิดเหตุการณ์นี้ ผมติดต่อโรงพยาบาลใกล้บ้านเป็นแผนสำรองเอาไว้ ที่นี่ขาดอัตรากำลังแพทย์พอดี ผมเลยสามารถเริ่มงานได้ทันที ทำให้รายได้ไม่กระทบกระเทือนต่อครอบครัว แต่สิ่งที่ต้องพบเจอก็คือโรงพยาบาลแห่งใหม่นี้ งานหนักมาก หนักถึงขั้นกระอักเลือด เต็มไปด้วยความเสี่ยงที่ยังไม่มีระบบการบริหารจัดการที่มีประสิทธิภาพ ผมทำงานที่นี่ไประยะนึง เมื่อมาดูสลิปค่าตอบแทน พบว่าผมถูกจัดกลุ่มให้อยู่ในกลุ่มแพทย์เวชปฏิบัติทั่วไป (General practitioner หรือ GP คือหมอทั่วไปที่ยังไม่ได้เรียนต่อเฉพาะทาง)
แพทย์เฉพาะทาง ตามกลไกจะได้ค่าตอบแทนสูงกว่าแพทย์ GP ถึง 70 - 80%
ผมนำเรื่องนี้ขึ้นปรึกษาหน่วยงานที่เกี่ยวข้อง ได้รับการดำเนินแก้ไขอย่างเร่งด่วนเพราะความเข้าใจผิด และผมก็ได้ค่าตอบแทนสมน้ำสมเนื้อตามมาทีหลัง แต่ด้วยเนื้องานที่หนักมาก เหนื่อยมาก เลิกงานเที่ยงคืน วันอื่นๆทำงานอีก ทำงาน 7 วันต่อสัปดาห์ ร่างกายเริ่มส่งสัญญาณเตือนบางอย่างว่ากำลัง overheat เครื่องกำลังจะไหม้ในอีกไม่ช้า ถ้ายังคงลากเลือดขนาดนี้ แต่เวลานั้นผมทำเพื่อครอบครัวอย่างเดียว เลยไม่ได้ลังเล เดินหน้าต่อ
จุดเปลี่ยนมันอยู่ตรงนี้ครับ ผมมีอาจารย์แพทย์ที่เคารพมากท่านหนึ่ง อาจารย์เขารับรู้เรื่องผมมาตลอด เมื่อทราบว่าผมทำงานหักโหม แลกกับความเสี่ยงหลายมิติ จึงมีโอกาสได้นั่งคุยกัน อาจารย์ท่านนี้เล่าเรื่องสั้นเรื่องหนึ่งให้ฟัง และทิ้งท้ายเอาไว้ให้คิดว่า
ทรัพยากรที่มีค่าที่สุดคือเวลา จงเอาตัวผมไปอยู่ในที่ที่เห็นคุณค่าในตัวผมให้ได้ ถ้าผมทำได้ เวลาของผมมีจะสร้างมูลค่าได้มหาศาลกว่านี้
การสนทนาจบลงด้วยความรู้สึกพบแสงสว่างที่ปลายอุโมงค์ หลังจากนั้นไม่กี่สัปดาห์ผมตัดสินใจ ของดคลินิคจากโรงพยาบาลแห่งนั้นทันที และเป็นความโชคดี เพราะที่ทำงานประจำกำลังขาดแคลนหมอ ผมเลยได้ตารางออกตรวจเพิ่ม รายได้มั่นคงมากกว่าเดิม
ส่วนโรงพยาบาลที่กระตุ้น wake up call ผมตอนแรก เล็งเห็นความสำคัญของทักษะเฉพาะทางของผมที่ขาดไม่ได้และจำเป็นมากต่อสถานการณ์ปัจจุบัน จึงขอให้ผมอยู่ช่วยต่อและเพิ่มค่าตอบแทนเพิ่มจากเดิมอีกเกือบ 100%
ทักษะการเขียนบทความ ที่เกือบจะถูกปิดผนึกไปตลอดกาล เพราะเอาตัวเองไปอยู่ไม่ถูกที่
 สิ่งที่ผมสนใจอยู่เป็นทุนเดิมคือการเล่าเรื่องแฝงแง่คิดจากประสบการณ์ของตัวเองให้กับผู้อื่นฟัง ตัวผมเองเป็นคนพูดไม่เก่ง บุคคลิกเก็บตัว Introvert ใช้เวลาส่วนใหญ่อยู่กับความคิดตัวเอง แล้วจดบันทึกข้อคิดที่คิดได้เอาไว้ ตั้งใจว่าถ้ามีเวลาพอ จะเอาสิ่งที่รีดออกมาจากสมอง มาขยายทำเป็นบทความ เพื่อเอาไว้ให้คนอื่นอ่าน เผื่อว่ามันจะมีประโยชน์ไม่มากก็น้อย ผมตระเวนหาเวบไซต์สำหรับนักเขียนไปเรื่อย แต่ก็หาที่ที่ถูกใจไม่ได้ ผมก็เลย”จำใจ” เขียนลงไปในเฟสบุค และ แพลตฟอร์มนักเขียนแห่งหนึ่งของประเทศไทย
สิ่งที่ผมสนใจอยู่เป็นทุนเดิมคือการเล่าเรื่องแฝงแง่คิดจากประสบการณ์ของตัวเองให้กับผู้อื่นฟัง ตัวผมเองเป็นคนพูดไม่เก่ง บุคคลิกเก็บตัว Introvert ใช้เวลาส่วนใหญ่อยู่กับความคิดตัวเอง แล้วจดบันทึกข้อคิดที่คิดได้เอาไว้ ตั้งใจว่าถ้ามีเวลาพอ จะเอาสิ่งที่รีดออกมาจากสมอง มาขยายทำเป็นบทความ เพื่อเอาไว้ให้คนอื่นอ่าน เผื่อว่ามันจะมีประโยชน์ไม่มากก็น้อย ผมตระเวนหาเวบไซต์สำหรับนักเขียนไปเรื่อย แต่ก็หาที่ที่ถูกใจไม่ได้ ผมก็เลย”จำใจ” เขียนลงไปในเฟสบุค และ แพลตฟอร์มนักเขียนแห่งหนึ่งของประเทศไทยในช่วงแรกผมลองเขียนบทความลงเฟสบุค ผลลัพธ์เป็นไปตามคาดครับว่าไม่เป็นที่สนใจ ประเมินผลหยาบๆจากยอดกดไลค์ คอมเม้นท์ และการแชร์ เงียบเหมือนป่าช้าเลย นานๆจะมีคนมากดไลค์ซักที แต่ก็เป็นที่รู้ๆกันครับว่าการกดไลค์ มันอาจจะเกิดจากคนอื่นเปิดมาเจอโพสต์ของผม แล้วจะปัดให้มันพ้นๆไป “ไอ้บ้านี่มันบ่นอะไรของมัน” แต่นิ้วโป้งดันไปจิ้มโดนปุ่มไลค์พอดี ในเมื่อจิ้มไปโดนแล้วก็แล้วกันไปก็เป็นไปได้
เวลาผ่านไปมันเหมือนผมขึ้นไปพูดบนเวทีที่ไม่มีผู้ฟัง หรือ ผู้ฟังหลับทั้งห้อง บทความต่างๆข้อคิดต่างๆที่ผมตั้งใจเรียบเรียงมันส่งไปไม่ถึงผู้คน มันดูไร้ค่า จบด้วยการนั่งคุยกับตัวเองเหมือนเป็นคนไข้จิตเวช เหตุการณ์ทั้งหมดนี้เกือบนำพาผมไปสู่ข้อสรุปที่ว่า “ผมเองคงเขียนไม่เก่ง” หรือ “เขียนไม่ได้แย่หรอก แต่ไม่ได้โปรโมท เลยไม่มีใครมาพบเจอ” หรือไม่ก็ถูกทั้งสองข้อ บางครั้งอยากจะล้มเลิกการเขียนไปเลยก็มีครับ
ช่วงมกราคมปี 2023 เวบไซต์ Right shift เริ่มเป็นที่รู้จัก ฟังคอนเซปจากอาจารย์พิริยะแล้วชอบมาก
เวบไซต์ Right shift ตั้งใจเป็นแหล่งรวบรวมข้อมูลสำหรับผู้ที่สนใจอยากศึกษาบิตคอยน์ ให้สามารถเข้ามาศึกษาได้โดยไม่มีค่าใช้จ่าย แถมยังเชิญชวนให้ผู้ที่อยากเขียนบทความที่เป็นประโยชน์ให้แก่ผู้อื่น ใครสนใจสามารถส่งบทความเข้ามาได้ ถ้าหากบทความไหนมีแวว จะมีทีมบก.ติดต่อกลับไปเพื่อทำงานร่วมกันในการขัดเกล้า แก้ไขสำนวนบางจุดให้ดียิ่งขึ้น
พอรู้มาถึงตอนนี้มันนเหมือนมีอะไรมาเคาะกะโหลกดังๆ จนความรู้สึก “ปังปุริเย่ เฮ้ ร้องว้าว” มันผุดขึ้นมา แต่มันก็มาพร้อมกับความไม่มั่นใจในตัวเองนั่นแหละครับ ความขัดแย้งเต็มไปหมดว่า “จะเขียนหรือไม่เขียนดี” “เอาจริงอ่ะ? จะเขียนบทความส่งไปจริงๆเหรอ?” “ม_ึง ไม่ใช่นักเขียนมืออาชีพนะ คนที่เขาส่งบทความไปมีแต่เทพๆทั้งนั้น จะเอาอะไรไปสู้กับเขา” และเสียงอื่นๆในหัวอีกมากมาย
แต่สุดท้ายผมทลาย “Comfort zone” ได้ ด้วยกำลังใจเล็กๆน้อยๆจากภรรยาครับ ภรรยาผมบอกด้วยคำสั้นๆว่า “ก็ลองดูสิ สกิลการเขียนเล่าเรื่องของเธอก็ไม่ขี้เหร่นะ” ผมเลยลองทำดู และนี่คือสิ่งที่เกิดขึ้น
บอกได้ว่าเป็นครั้งแรกที่ผมได้ถูกฝึกการเขียนบทความโดย "ใครก็ไม่รู้” ผมรู้แค่ว่าเป็นทีมบก.ของ Right shift เมื่อทำงานร่วมกันไปเรื่อยๆ ทีมบก.ทุ่มเทในการช่วยแก้ไขช่วยตรวจสอบบทความของผมมากๆ จนผมสังเกตุเห็นได้
ใครเคยใช้ Google document ร่วมแก้ไขบทความด้วยกันมากกว่าหนึ่งคนคงจะรู้ดีนะครับว่า เวลาที่มีการแก้ไขข้อความมันจะมีเมล์แจ้งเตือนไปหาทุกคนที่เข้ามาร่วมแก้ไขเอกสารทั้งหมด บางคืนที่ผมนอนหลับไม่สนิท ตีสองตีสามตื่นมาเข้าห้องน้ำ ผมยังเห็นเมล์อัพเดทการแก้ไขบทความจากทีมงาน right shift เด้งๆอยู่เลย
จนสุดท้ายงานเขียนผมก็ได้รับการเผยแพร่บนเวบไซต์ Right shift

ใครยังไม่เคยอ่านกดตรงนี้ได้เลยครับ
หลังจากนั้นผมรับรู้ถึงทักษะนี้มากขึ้น เลยตั้งใจว่าต้องฝึกให้เก่งขึ้นดีขึ้นในทุกๆบทความที่ผมเขียน ผมอ่านหนังสือเยอะขึ้น ศึกษาสำนวนการเขียนจากนักเขียนรวมถึงนักแปลท่านอื่นๆ เพื่อดูตัวอย่างสำนวน ลีลาสไตล์การใช้คำ เอามาประยุกต์ใช้กับงานเขียนของตัวเอง
ไม่รู้ตัวหรอกครับ ว่าทักษะนี้มันโดนฝึก โดนขัดเกลาตั้งแต่เมื่อไหร่ แต่ตอนนี้ตระหนักรู้ถึงการที่มันมีตัวตนอยู่ภายในตัวผมแล้ว ผมก็จะลับคมมันไปเรื่อยๆ หลายครั้งตอนที่ผมเขียนบทความอยู่ผมลืมเวลา ลืมหิว ลืมง่วง ลืมเหนื่อยไปเลย ถ้าเปรียบเทียบกับนักกีฬา คาดว่าสภาวะตอนนั้นคงเป็นสภาวะหนึ่งของการเข้าสมาธิแบบ “Into the zone”
เรื่องสั้นที่อาจารย์ของผมเล่าให้ฟัง มอบบทเรียนชีวิตที่มีค่า อยู่ต่อจากนี้ครับ

พ่อคุยกับลูกสาว “ยินดีด้วยที่จบการศึกษา พ่อซื้อรถคันนี้ไว้ให้ลูกซักพักแล้ว ตอนนี้พ่อจะให้ลูกนะ แต่ก่อนที่พ่อจะให้ พ่ออยากให้ลูกนำไปที่ร้านรับซื้อ-ขายรถในตัวเมือง แล้วมาบอกพ่อด้วยว่าเขาให้ราคาเท่าไหร่”
ลูกสาวทำตาม กลับมาหาพ่อ บอกว่า “ร้านนี้เขาให้ราคา $10,000 เพราะรถเก่า” พ่อบอกลูกว่า “โอเคลูก ทีนี้พ่ออยากให้หนูเอารถไปที่โรงรับจำนำ ลองดูซิว่าเขาจะตีราคารถคันนี้เท่าไหร่”
ลูกสาวทำตาม แล้วกลับมาบอกพ่อว่า “โรงรับจำนำให้ราคา $1,000 เพราะรถเก่ามาก ดูแล้วต้องซ่อมอีกหลายรายการ ”
ครั้งนี้พ่อบอกลูกสาวให้นำรถนี้ไปยังชมรมคนรักรถที่มีผู้เชี่ยวชาญ และนำรถให้พวกเขาดู
ลูกสาวทำตาม ขับรถนี้ไปที่ชมรมที่ว่า หลังจากนั้นไม่นานลูกสาวกลับมาบอกพ่อด้วยน้ำเสียงตื่นเต้นว่า “บางคนเสนอราคา $100,000 เพราะเป็นรถหายาก และสภาพดีมาก”

ผู้เป็นพ่อยิ้มให้กับลูกสาว เหมือนว่ารู้อยู่แล้วว่าจะเกิดอะไรขึ้น ด้วยความสงสัยลูกสาวจึงถามพ่อว่า
“ในเมื่อพ่อรู้อยู่แล้วว่าร้านไหนจะให้ราคาสูง ทำไมพ่อไม่ให้หนูไปที่ชมรมคนรักรถตั้งแต่แรกล่ะ”
พ่อบอกลูกสาวว่า “นี่แหละบทเรียนชีวิตที่สำคัญบทหนึ่งที่พ่ออยากมอบให้แก่ลูก พ่ออยากให้ลูกรู้ไว้ว่า ลูกจะไม่มีค่าใดๆเลยถ้าอยู่ผิดที่ ที่ที่คนอื่นมองไม่เห็นเรา ไม่ต้องเสียเวลาไปโกรธโมโหไม่พอใจหรอกนะ สิ่งที่ลูกต้องทำก็คือเดินออกจากที่นั่น ออกไปจากสังคมและสถานที่ที่ไม่เห็นค่าในตัวลูก ค้นหาที่สถานที่ของลูกให้เจอ ถ้าลูกไม่ลองลงมือทำด้วยตัวเอง ลูกก็จะไม่ได้เรียนรู้อะไรเลย”

ข้อคิดที่อยากจะแบ่งปันกับทุกท่านที่อ่านมาจนจบ
บทความนี้มีความพิเศษกว่าบทความอื่นๆ ท้ายบทความของผมผมจะมาชวนคุยและสรุปข้อคิดที่เป็นประโยชน์ให้แก่เพื่อนๆพี่ๆทุกท่านที่อ่านมาจนจบ แต่สำหรับบทความนี้ข้อคิดที่ผมอยากให้ ถูกสรุปขมวดไว้ทั้งหมดแล้วในประโยคที่พ่อบอกลูกสาว
อย่าลืมต่อสู้ ฝ่าฟันอุปสรรค ค้นหาสถานที่ของตัวเราเองให้พบนะครับ เมื่อค้นพบทักษะในตัวแล้ว อย่าให้ถูกปิดผนึกไว้ เพียงเพราะอยู่ผิดที่ ลงมือฝึกฝนพัฒนามันไปเรื่อยๆ เราจะดีขึ้นในทุกๆวันครับ
-
 @ 4ba8e86d:89d32de4
2024-10-11 23:07:45
@ 4ba8e86d:89d32de4
2024-10-11 23:07:45O Joplin é um aplicativo gratuito e de código aberto que permite a criação e organização de notas, tarefas e listas, e está disponível para as plataformas Windows, macOS, Linux, Android e iOS. Com ele, você pode organizar suas notas em cadernos, categorizá-las com tags e sincronizá-las entre dispositivos de forma segura.
Seu diferencial é o foco em privacidade e flexibilidade. O Joplin garante que suas notas estejam sempre acessíveis, mesmo offline, e permite que você sincronize seu conteúdo com serviços de nuvem de forma criptografada, garantindo que ninguém além de você tenha acesso aos dados.
Principais Recursos
-
Suporte Multiplataforma O Joplin está disponível para todas as principais plataformas de desktop e dispositivos móveis, o que permite que você leve suas notas para onde for. Além disso, ele oferece um Web Clipper para capturar páginas da web diretamente do navegador (compatível com Firefox e Chrome), facilitando o arquivamento de conteúdos importantes da internet.
-
Organização e Formato Markdown As notas no Joplin são salvas no formato Markdown, uma linguagem de marcação simples que permite criar textos formatados de maneira intuitiva. Isso torna a edição e formatação de notas mais flexível e prática, além de facilitar a exportação para outros formatos.
As notas podem ser organizadas em cadernos e subcadernos, e você pode adicionar tags para facilitar a pesquisa e a categorização de informações.
- Importação de Notas do Evernote Para quem está pensando em migrar do Evernote, o Joplin permite a importação direta de notas exportadas no formato ENEX, preservando o conteúdo formatado, anexos (imagens, PDFs, etc.) e até mesmo os metadados, como a localização geográfica e datas de criação/modificação. Se você deseja importar suas notas do Evernote, o Joplin oferece um guia passo a passo para fazer a migração sem complicações.
https://joplinapp.org/help/apps/import_export/
-
Sincronização com Criptografia de Ponta a Ponta O Joplin permite que você sincronize suas notas de forma segura utilizando serviços de armazenamento em nuvem como Nextcloud, Dropbox, OneDrive e o serviço próprio, o Joplin Cloud. A grande vantagem aqui é a criptografia de ponta a ponta (E2EE), o que significa que suas notas são criptografadas localmente antes de serem enviadas para a nuvem, garantindo que ninguém, nem mesmo o serviço de nuvem, tenha acesso aos seus dados.
-
Offline First Um dos principais recursos do Joplin é que ele foi desenvolvido com a filosofia "offline first". Isso significa que você sempre tem uma cópia completa e funcional das suas notas no seu dispositivo, permitindo que você acesse e edite suas informações, mesmo sem uma conexão com a internet. Quando a sincronização está habilitada, o Joplin sincroniza as mudanças automaticamente assim que a conexão for restaurada.
-
Busca de Texto Completo O Joplin oferece uma poderosa funcionalidade de busca de texto completo, permitindo que você encontre rapidamente qualquer informação dentro das suas notas, independentemente do volume de dados armazenados.
-
Personalização e Plugins
Além das funcionalidades padrão, o Joplin permite uma ampla personalização. Você pode ajustar a interface com temas e estender as funcionalidades por meio de plugins. Se você tem conhecimentos de programação, pode até desenvolver seus próprios plugins para adaptar o Joplin às suas necessidades específicas.
Privacidade em Foco
Um dos grandes diferenciais do Joplin em relação a outras ferramentas populares de anotações, como o Evernote e o OneNote, é o foco na privacidade do usuário. Com o Joplin, você controla seus dados completamente, sem depender de servidores de terceiros que possam explorar suas informações.
A criptografia de ponta a ponta garante que suas notas estejam seguras e que somente você tenha as chaves para desbloqueá-las. Isso é um grande atrativo para quem está preocupado com a privacidade online, especialmente em tempos em que muitos serviços coletam dados de seus usuários para fins de publicidade ou marketing.
Casos de Uso: Quem Deve Usar o Joplin?
O Joplin é uma ferramenta extremamente versátil, sendo ideal para diversos tipos de usuários:
- Estudantes: Para organização de notas de aula e pesquisa.
- Profissionais: Para gerenciamento de tarefas, anotações de reuniões e documentação de projetos.
- Desenvolvedores: Graças ao suporte nativo para Markdown, o Joplin é uma excelente opção para quem precisa documentar código ou gerenciar projetos de desenvolvimento.
- Jornalistas ou escritores: Que precisam de uma ferramenta segura para organizar suas notas e ideias.
- Usuários preocupados com a privacidade: Que querem uma ferramenta de anotações robusta sem abrir mão da segurança e controle total sobre seus dados.
Como Começar a Usar o Joplin
Iniciar com o Joplin é simples. Basta baixar o aplicativo para a sua plataforma preferida, seja desktop ou móvel, diretamente do site oficial. A partir daí, você pode começar a criar suas notas, configurar cadernos e sincronizar seus dados. A interface intuitiva facilita o aprendizado, e o suporte a Markdown oferece grande flexibilidade na criação e edição de conteúdo.
O Joplin é muito mais do que um simples aplicativo de anotações. Com seu foco em privacidade, sincronização segura, suporte offline e ampla personalização, ele se destaca como uma das melhores opções disponíveis para quem busca controlar completamente suas informações, sem abrir mão de funcionalidades avançadas. Seja você um estudante, profissional ou simplesmente alguém que deseja organizar suas ideias com segurança, o Joplin é uma escolha confiável e flexível. Com sua filosofia de código aberto, o Joplin continua a evoluir e melhorar com contribuições da comunidade global. Se você ainda não experimentou o Joplin, agora é um excelente momento para dar o próximo passo e transformar a maneira como você gerencia suas anotações e tarefas.
https://joplinapp.org/
https://github.com/laurent22/joplin/
-
-
 @ 57fe4c4a:c3a0271f
2023-10-18 13:02:10
@ 57fe4c4a:c3a0271f
2023-10-18 13:02:10📝 Summary: Batched splicing can be risky due to certain conditions like no funds in a channel and using an old state. It is important for batched splicing mechanisms to have a backout option to prevent disruptions caused by confirmed old states. Additionally, not all splice implementations performing a check can lead to potential loss of funds.
👥 Authors: • Greg Sanders ( nostr:npub1jdl3plz00rvxwc6g2ckemzrgg0amx5wen4kfvs3laxtssxvk9cvsf3gh0m ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l )
📅 Messages Date: 2023-10-17
✉️ Message Count: 3
📚 Total Characters in Messages: 5405
Messages Summaries
✉️ Message by ZmnSCPxj on 17/10/2023: Batched splicing can be risky if certain conditions are met, such as having no funds in a channel and using an old state. It is important for batched splicing mechanisms to have a backout option to prevent disruptions.
✉️ Message by Greg Sanders on 17/10/2023: Batched splicing is risky because if an old state is broadcasted and confirmed before the splice, it can disrupt the process. It is important for batched splicing mechanisms to have a backout option.
✉️ Message by ZmnSCPxj on 17/10/2023: Batched splicing can be risky if not all splice implementations perform a check to ensure subsequent splices confirm, potentially leading to loss of funds.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 4ba8e86d:89d32de4
2024-10-11 22:59:29
@ 4ba8e86d:89d32de4
2024-10-11 22:59:29Livro de Estratégia , Cripto-Anarquia, Tradecraft, Zonas Autônomas Temporárias, e Contracultura ~ Smuggler e XYZ
PDF do livro em português: https://raw.githubusercontent.com/cypherpunksbr/a-segunda-esfera/master/segundaesfera.pdf
Livro em audiobook: https://archive.org/details/second-realm-digital/
Texto em português: https://cypherpunks.com.br/documentos/a-segunda-esfera/#livro-de-estrat%C3%A9gia
Opaque link
https://opaquelink.sirion.io/
Cyberpunk , Criptoanarquia , extremismo de privacidade, segurança, estratégia.
anarplex net
https://anarplex.sirion.io/
arquivos e projetos relacionados a: cripto-tribos, phyles , cripto-anarquia , agorismo, provedor de serviços darknet.
Thank you, @EricSirion, for hosting the websites, @TheRealSmuggler thanks for the content. Eles contêm alguns dos conteúdos cypherpunk e cripto-anarquistas mais importantes que existem. Se você ainda não os conferiu, dê uma olhada há muito para explorar.
-
 @ 32e18276:5c68e245
2023-10-10 12:02:37
@ 32e18276:5c68e245
2023-10-10 12:02:37Hey guys, I'm spending some time today preparing v1.6 for the app store, it's been a long time coming with many new features. Here's a breakdown of everything new in this version!
Notable new features in 1.6
- Custom built, embedded C WASM interpreter (nostrscript), which will be used for custom algos, filters and lists
- Longform note support
- Hashtag following
- Configurable reactions
- New Live user status NIP (music, general)
- Adjustable font sizes
- A very long list of bug fixes and performance improvements
- Fast and persistent profile searching using nostrdb
Top priorities for 1.7
- Lists
- Custom algos and filters using nostrscript
- Stories
- Multi account
- Tor integration
- Better NWC integration (wallet balances, transaction history)
- Advanced note search via nostrdb
- Fully switch to nostrdb for all notes
- Discord-like relays (click a relay to view all the notes on it)
So much more but maybe I will not try to be too ambitious ...
Contributors
name added removed commits William Casarin +57964 -8274 288 petrikaj +1524 -0 1 Terry Yiu +1266 -964 9 ericholguin +1234 -252 11 Daniel D’Aquino +1223 -399 19 Suhail Saqan +905 -70 16 Grimless +838 -736 6 Bryan Montz +793 -744 30 Jon Marrs +658 -60 3 Joel Klabo +653 -105 6 transifex-integration[bot] +176 -0 9 Fishcake +129 -21 5 Daniel D‘Aquino +123 -9 5 Jericho Hasselbush +78 -2 2 cr0bar +66 -19 11 Daniel D'Aquino +55 -32 2 Mazin +53 -0 1 gladiusKatana +37 -8 1 doffing.brett +10 -6 1 tappu75e@duck.com +5 -1 2 Ben Harvie +5 -0 1Changelog
- 76 Fixes
- 18 Changes
- 26 Additions
Added
- Add "Do not show #nsfw tagged posts" setting (Daniel D’Aquino)
- Add ability to change order of custom reactions (Suhail Saqan)
- Add close button to custom reactions (Suhail Saqan)
- Add followed hashtags to your following list (Daniel D’Aquino)
- Add initial longform note support (William Casarin)
- Add r tag when mentioning a url (William Casarin)
- Add relay log in developer mode (Montz)
- Add settings for disabling user statuses (William Casarin)
- Add space when tagging users in posts if needed (William Casarin)
- Add support for multilingual hashtags (cr0bar)
- Add support for multiple reactions (Suhail Saqan)
- Add support for status URLs (William Casarin)
- Add the ability to follow hashtags (William Casarin)
- Added feedback when user adds a relay that is already on the list (Daniel D'Aquino)
- Added generic user statuses (William Casarin)
- Added live music statuses (William Casarin)
- Added merch store button to sidebar menu (Daniel D’Aquino)
- Added padding under word count on longform account (William Casarin)
- Adjustable font size (William Casarin)
- Click music statuses to display in spotify (William Casarin)
- Enable banner image editing (Joel Klabo)
- Finnish translations (petrikaj)
- Hold tap to preview status URL (Jericho Hasselbush)
- Re-add nip05 badges to profiles (William Casarin)
- Show nostr address username and support abbreviated _ usernames (William Casarin)
- Suggested Users to Follow (Joel Klabo)
Changed
- Allow reposting and quote reposting multiple times (William Casarin)
- Damus icon now opens sidebar (Daniel D’Aquino)
- Hide nsec when logging in (cr0bar)
- Improve UX around clearing cache (Daniel D’Aquino)
- Improved memory usage and performance when processing events (William Casarin)
- Increase size of the hitbox on note ellipsis button (Daniel D’Aquino)
- Make carousel tab dots tappable (Bryan Montz)
- Move the "Follow you" badge into the profile header (Grimless)
- Remove nip05 on events (William Casarin)
- Remove note size restriction for longform events (William Casarin)
- Rename NIP05 to "nostr address" (William Casarin)
- Show muted thread replies at the bottom of the thread view (#1522) (Daniel D’Aquino)
- Show renotes in Notes timeline (William Casarin)
- Start at top when reading longform events (William Casarin)
- Switch to nostrdb for @'s and user search (William Casarin)
- Updated relay view (ericholguin)
- Use nostrdb for profiles (William Casarin)
- clear statuses if they only contain whitespace (William Casarin)
Fixed
- Allow relay logs to be opened in dev mode even if relay (Daniel D'Aquino)
- Allow user to login to deleted profile (William Casarin)
- Apply filters to hashtag search timeline view (Daniel D’Aquino)
- Avoid notification for zaps from muted profiles (tappu75e@duck.com)
- Crash when muting threads (Bryan Montz)
- Dismiss qr screen on scan (Suhail Saqan)
- Don't always show text events in reposts (William Casarin)
- Don't spam lnurls when validating zaps (William Casarin)
- Eliminate nostr address validation bandwidth on startup (William Casarin)
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Fix Invalid Zap bug in reposts (William Casarin)
- Fix PostView initial string to skip mentioning self when on own profile (Terry Yiu)
- Fix UI freeze after swiping back from profile (#1449) (Daniel D’Aquino)
- Fix UTF support for hashtags (Daniel D‘Aquino)
- Fix action bar appearing on quoted longform previews (William Casarin)
- Fix broken markdown renderer (William Casarin)
- Fix bug where it would sometimes show -1 in replies (tappu75e@duck.com)
- Fix compilation error on test target in UserSearchCacheTests (Daniel D‘Aquino)
- Fix crash when long pressing custom reactions (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fix freezing bug when tapping Developer settings menu (Terry Yiu)
- Fix icons on settings view (cr0bar)
- Fix images and links occasionally appearing with escaped slashes (Daniel D‘Aquino)
- Fix issue where malicious zappers can send fake zaps to another user's posts (William Casarin)
- Fix issue where relays with trailing slashes cannot be removed (#1531) (Daniel D’Aquino)
- Fix issue where typing cc@bob would produce brokenb ccnostr:bob mention (William Casarin)
- Fix issue with emojis next to hashtags and urls (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix lag when creating large posts (William Casarin)
- Fix localization issues and export strings for translation (Terry Yiu)
- Fix localization issues and export strings for translation (Terry Yiu)
- Fix long status lines (William Casarin)
- Fix nav crashing and buggyness (William Casarin)
- Fix nostr:nostr:... bugs (William Casarin)
- Fix npub mentions failing to parse in some cases (William Casarin)
- Fix padding of username next to pfp on some views (William Casarin)
- Fix padding on longform events (William Casarin)
- Fix paragraphs not appearing on iOS17 (cr0bar)
- Fix parsing issue with NIP-47 compliant NWC urls without double-slashes (Daniel D’Aquino)
- Fix potential fake profile zap attacks (William Casarin)
- Fix profile not updating (William Casarin)
- Fix profile post button mentions (cr0bar)
- Fix profiles not updating (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix situations where the note composer cursor gets stuck in one place after tagging a user (Daniel D’Aquino)
- Fix small graphical toolbar bug when scrolling profiles (Daniel D’Aquino)
- Fix some note composer issues, such as when copying/pasting larger text, and make the post composer more robust. (Daniel D’Aquino)
- Fix status events not expiring locally (William Casarin)
- Fix text composer wrapping issue when mentioning npub (Daniel D’Aquino)
- Fix text editing issues on characters added right after mention link (Daniel D’Aquino)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fix zaps sometimes not appearing (William Casarin)
- Fixed a bug where following a user might not work due to poor connectivity (William Casarin)
- Fixed audio in video playing twice (Bryan Montz)
- Fixed disappearing text on iOS17 (cr0bar)
- Fixed issue where hashtags were leaking in DMs (William Casarin)
- Fixed issue where reposts would sometimes repost the wrong thing (William Casarin)
- Fixed issues where sometimes there would be empty entries on your profile (William Casarin)
- Fixed nav bar color on login, eula, and account creation (ericholguin)
- Fixed nostr reporting decoding (William Casarin)
- Fixed nostrscript not working on smaller phones (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fixes issue where username with multiple emojis would place cursor in strange position. (Jericho Hasselbush)
- Hide quoted or reposted notes from people whom the user has muted. (#1216) (Daniel D’Aquino)
- Hide users and hashtags from home timeline when you unfollow (William Casarin)
- Make blurred videos viewable by allowing blur to disappear once tapped (Daniel D’Aquino)
- Mute hellthreads everywhere (William Casarin)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Show longform previews in notifications instead of the entire post (William Casarin)
- Stop tab buttons from causing the root view to scroll to the top unless user is coming from another tab or already at the root view (Daniel D’Aquino)
- don't cutoff text in notifications (William Casarin)
- endless connection attempt loop after user removes relay (Bryan Montz)
- icon color for developer mode setting is incorrect in low-light mode (Bryan Montz)
- relay detail view is not immediately available after adding new relay (Bryan Montz)
Removed
- Remove following Damus Will by default (William Casarin)
- Remove old @ and & hex key mentions (William Casarin)