-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ d6affa19:9110b177
2024-09-14 18:13:34
@ d6affa19:9110b177
2024-09-14 18:13:34The Timeless Relevance of Chivalry in Relationships
Chivalry, often romanticized in tales of medieval knights, is more than just a relic of the past. It’s a code of conduct that emphasizes respect, honor, and protection—values that still resonate today. While many think of chivalry as lost in today’s world, it has the potential to transform modern relationships, and perhaps fill a void in the modern definition of masculinity.
For a unique perspective, we can look at chivalry's evolution within Female Led Relationships (FLRs), where respect and devotion are foundational. In FLRs, women take the lead, guiding their partners through a blend of strength and nurturing. Chivalry enhances this dynamic, allowing men to express respect and devotion while embracing their roles in a supportive manner.
Let’s take a look at how chivalry has changed over time to become a defining component in many FLRs. We’ll look at the virtues of chivalry, its role in defining masculinity, and why it serves as a foundation for mutual respect and growth in relationships. By understanding these principles, we’ll begin to see how chivalry acts as a bridge between strength and submission, enriching the connection between partners.
Introduction to Chivalry
Chivalry began in the medieval period as a code of conduct for knights, focusing on virtues like bravery, loyalty, and the protection of those in need. Knights were expected to live by these ideals in their service to their lords and in their interactions with women, often viewing them as deserving of special respect and protection. This code created a framework of strength, honor, and courage to be embedded in the concept of masculinity.
As society has changed, so too has the interpretation of chivalry, leading to a broader understanding of what it means to be chivalrous today. The rigid structure of chivalry has softened a bit, allowing for a more nuanced understanding of respectful behavior in modern contexts.
Today, chivalry is less about following a strict code and more about embodying kindness, respect, and support in everyday interactions. It’s often seen as a choice rather than an obligation, allowing men to express their admiration for women in ways that feel genuine and meaningful. However, it challenges and expands upon the notion that a man’s role is solely to protect and provide.
The Virtues of Chivalry: A Contemporary View
Chivalry is often seen as a sign of healthy masculinity, demonstrating qualities like courage, respect, compassion, and support for women. This helps create relationship dynamics where both partners feel appreciated. Healthy masculinity, as expressed through chivalry, encourages men to engage in acts of kindness—whether surprising their partner with a home-cooked meal after a long day or actively listening to her concerns without distractions.
These behaviors demonstrate emotional intelligence and create deeper connections. Examples of chivalrous actions include taking the initiative to handle household chores, planning special dates that reflect the partner's interests, and offering emotional support during tough times. Simple yet meaningful gestures, like holding the door open or offering a comforting touch, reinforce the idea that strength lies in nurturing and uplifting one another.
With this basic understanding of chivalry, we can now explore how these principles are redefined and practiced in the context of Female Led Relationships.
Understanding FLRs
In Female Led Relationships, the woman takes on the primary leadership role, while the man supports her through devotion and service. This structure redefines leadership to highlight feminine strengths like empathy, intuition, and emotional intelligence.
What does it mean for a woman to lead in a relationship? In this dynamic, a woman might lead the decision-making process for family activities, while her gentleman supports her by taking care of the logistics. This is just one of many examples where a woman acts as the visionary, charting the course for her relationship and family.
Despite common misconceptions, FLRs are not, in essence, simply kink-driven or role-reversal relationships. They create space for both partners to grow and thrive in their distinct roles. Within this framework, the woman doesn’t necessarily adopt traditionally masculine behavior; instead, she may lead in a way that feels authentic to her feminine nature.
This dynamic allows for a greater flexibility of traditional roles, where both individuals can express their strengths and support one another. When a woman assumes the leadership role, the concept of chivalry can be framed to reflect this adjustment.
Supporting Her Lead: Chivalry's Place in FLRs
Traditionally, chivalry revolved around men using their strength and status to protect women, who were perceived as needing safeguarding. This aspect of chivalry is redefined in an FLR. Instead of the intention being about men protecting fragile women, the emphasis is now in showing deep respect and devotion to the women they admire and serve. This becomes a major shift away from the stereotypical image of the damsel in distress—who needs to be rescued by a knight in shining armor.
This adjustment makes space for a woman's inherent strength and her role as the central figure of leadership and authority. It positions her as the one a man submits to. The idea of submission, or service, in FLRs challenges the conventional views of masculinity, which often emphasize aggression and dominance.
Instead, submission is framed as a conscious choice that allows men to express vulnerability and emotional openness. Through acts of chivalry—such as opening doors, attending to her needs, or providing comfort—a man in an FLR expresses his devotion and commitment to a woman as his leader. These are the types of actions that serve as a bridge between a man’s masculine energy and his submission—a powerful and empowering act for both partners.
In this context, chivalry may then represent a minimum standard of behavior for a gentleman in an FLR. Understanding this redefinition is essential for appreciating the balance of power and respect that make FLRs work. A woman might decide to set chivalry as a starting point for behavior, guiding her partner in ways that strengthen their bond. Let’s take a closer look at how these chivalrous principles are expressed in this relationship setup.

Chivalry in Action: A Minimum Standard for Gentlemen
Chivalry offers a subtle and respectful way for a gentleman in an FLR to express his devotion in public. This allows him to honor his partner's leadership while keeping the intimate aspects of their relationship private. It’s important to reiterate, a gentleman performs these actions from a deep respect and admiration, not because the woman is incapable.
Let’s dive into how chivalry is demonstrated in everyday interactions and how these gestures reflect a deeper bond between the woman and her submissive gentleman.
- Discreet Displays of Devotion: Acts of chivalry like opening doors, pulling out chairs, and carrying bags are traditionally seen as courteous. In an FLR, these gestures take on added meaning—they become acts of service and submission, representing the gentleman’s commitment to the woman. These actions subtly reinforce the Female-led dynamic, making it clear who is leading the relationship, even without explicit words.
- Respect and Care: Public chivalry allows a gentleman to show his reverence and protectiveness in a non-dominating way. Escorting a woman across the street or guiding her with a hand on her back signals that her comfort and safety come first. Such gestures help reinforce his role as her protector, not through overpowering, but by ensuring her well-being.
- Empowering Her Leadership: Chivalry positions the woman as someone to be admired and revered. A gentleman's attentiveness—like ensuring her seat is comfortable, giving her his coat, or waiting for her to decide the next move—publicly celebrates her power and grace. It signals to the outside world that she is cherished, respected, and in control.
- Symbol of Hierarchy: Public chivalry subtly communicates the hierarchy in the relationship. A gentleman’s actions demonstrate that he prioritizes the woman’s needs above his own, affirming her leadership and his devotion. This can be empowering for both partners while maintaining the appearance of traditional courteous behavior.
Having examined how chivalry is publicly displayed in acts of service, it’s important to consider the relationship between chivalry and the concept of submission in FLRs. These gestures are just the tip of the iceberg; they pave the way for a deeper bond that intertwines strength with surrender, taking the relationship to another level. With this in mind, let’s explore further.
Chivalry and Submission: The Interplay of Strength and Vulnerability
Chivalry provides a beautiful way to express an FLR in public, but the bond between a woman and her submissive gentleman runs much deeper than it appears. The public gestures are merely a reflection of a more private intimacy and the dynamics at play in the relationship.
- Private Surrender: Behind closed doors, the gentleman’s devotion often takes on deeper, more intimate forms. While public chivalry may seem like courteous behavior, in private it evolves into true acts of surrender, vulnerability, and service. His obedience, respect, and loyalty are manifested in ways that may not be visible to the outside world—through emotional support, personal sacrifices, and an unwavering commitment to the woman’s happiness.
- Emotional Bond: The bond in an FLR is built on strong emotional understanding and trust. Public gestures, such as opening a door, may signal respect, but the private relationship is built on communication, vulnerability, and reciprocity. The gentleman’s willingness to be emotionally open and the woman’s acceptance of his submission generate a bond that goes beyond the surface-level acts.
- Empowerment and Growth: An FLR often involves the woman guiding and empowering her gentleman to become a better version of himself, and in turn, he finds fulfillment in supporting her goals and ambitions. This growth happens through encouragement, challenges, and nurturing. These elements are not always visible in public but are foundational to the strength of the relationship.
- Sacred Submission: A gentleman’s devotion in private is often much more profound and spiritual than what can be conveyed through chivalry alone. His willingness to give himself fully to a woman, to honor her needs and desires over his own, represents a depth of commitment that is intensely personal and transformational for both partners.
- Unspoken Understanding: The connection between a woman and her submissive gentleman often includes a deep, unspoken understanding of their roles and dynamics. While public gestures may hint at their FLR, their private moments of connection bring the relationship to the next level. These moments—whether through quiet service, intense conversation, or physical intimacy—solidify true emotional connections.
- Private Rituals of Devotion: Chivalry in public is often a toned-down version of the rituals of devotion that occur in private. Behind closed doors, a woman’s submissive gentleman may have more formal ways of showing his reverence, such as kneeling, offering his service in specific ways, or following set routines that reinforce his role. These private rituals strengthen the bond of submission and deepen the trust between partners.
We’ve seen that chivalry alone doesn’t fully capture the essence of submission in a Female Led Relationship. However, when we look at masculinity through the lens of chivalry, it becomes clear that the qualities associated with healthy masculinity—like devotion, compassion, and protection—are fundamentally about serving and supporting others.
The Essence of Chivalry: Strength Through Service
In summary, chivalry effectively bridges the gap between strength and submission within the framework of FLRs. Throughout this brief exploration, we’ve seen how chivalry can serve as a foundational guideline for men, allowing them to embody a form of healthy masculinity that’s empowered, but also open to submission.
By changing how we think about masculinity, chivalry encourages men to express their strength through simple acts of kindness, respect, and devotion. Whether it’s in public or behind closed doors, these gestures create a space where both partners can truly thrive. The qualities that make up healthy masculinity—bravery, loyalty, compassion, and a commitment to service—actually lean into the idea of submission as a natural part of masculinity. In this way, chivalry becomes an expression of this submission, allowing men to honor and uplift their partners while still maintaining their own sense of stability and strength.
By embracing these chivalrous behaviors, men can enhance their relationships and help create a more balanced and supportive partnership. Chivalry in the context of FLRs redefines the narrative of masculinity, demonstrating that true strength lies in the ability to serve, support, and cherish one another in a loving and respectful manner.
As a final thought, the essence of chivalry lies not just in the actions taken, but in the intentions behind them. In the pursuit of uplifting and supporting partners, true strength emerges through vulnerability and service. By reflecting on our relationships, we can look for and find opportunities to embody these principles. How might embracing the principles of chivalry expand and enrich what masculinity can contribute to any relationship?
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Personagens de jogos e símbolos
A sensação de "ser" um personagem em um jogo ou uma brincadeira talvez seja o mais próximo que eu tenha conseguido chegar do entendimento de um símbolo religioso.
A hóstia consagrada é, segundo a religião, o corpo de Cristo, mas nossa mente moderna só consegue concebê-la como sendo uma representação do corpo de Cristo. Da mesma forma outras culturas e outras religiões têm símbolos parecidos, inclusive nos quais o próprio participante do ritual faz o papel de um deus ou de qualquer coisa parecida.
"Faz o papel" é de novo a interpretação da mente moderna. O sujeito ali é a coisa, mas ele ao mesmo tempo que é também sabe que não é, que continua sendo ele mesmo.
Nos jogos de videogame e brincadeiras infantis em que se encarna um personagem o jogador é o personagem. não se diz, entre os jogadores, que alguém está "encenando", mas que ele é e pronto. nem há outra denominação ou outro verbo. No máximo "encarnando", mas já aí já é vocabulário jornalístico feito para facilitar a compreensão de quem está de fora do jogo.
-
 @ 361d3e1e:50bc10a8
2024-09-14 14:44:30
@ 361d3e1e:50bc10a8
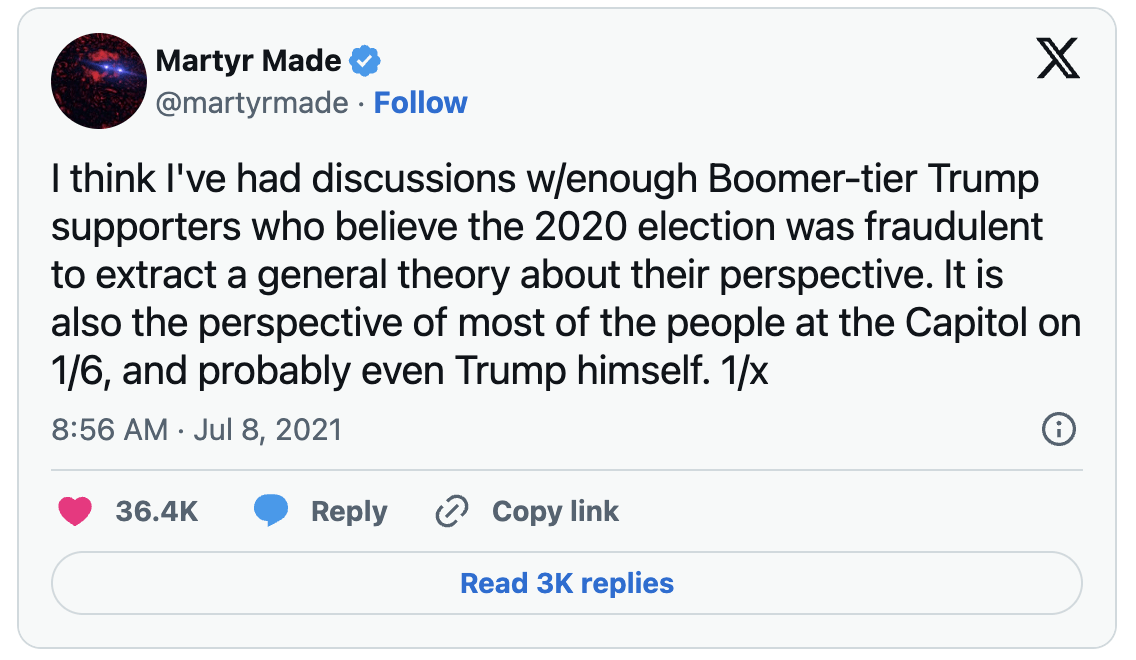
2024-09-14 14:44:30For every 1000 new injections, 5.7 people get myocarditis or pericarditis
usa #pfizer #sideeffects #vaccine #covid #monkeypox #mpox #health #myocarditis
-
 @ 7f5b758e:db91b367
2024-09-14 14:05:18
@ 7f5b758e:db91b367
2024-09-14 14:05:18Central en español,
Dios esta obrando.
Nosotros lo vemos cada semana - A través del servicio y luego en los grupos de comunidad (10:45AM). El Espíritu Santo trabaja en nosotros y a través de nosotros en los programas de niños y estudiantes. Mañana va a ser igual. Nosotros vivimos para Dios, eso nos da significado y lo celebramos como hijos del Rey. Nos vemos mañana, 9:30AM.
https://scontent-dfw5-2.xx.fbcdn.net/v/t39.30808-6/455704243_475776645232773_6440552152342423803_n.jpg?stp=cp6_dst-jpg&_nc_cat=100&ccb=1-7&_nc_sid=833d8c&_nc_ohc=uDrwym_Iu60Q7kNvgGcoQ6Z&_nc_ht=scontent-dfw5-2.xx&_nc_gid=AYZqyypf1_uXwqU1xlTUgX0&oh=00_AYC77jEwXJis9rw84CkoObvwNn4Wm6ZZGiZ1z1R5fJtLHQ&oe=66EB458B
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Causa
o Princípios de Economia Política de Menger é o único livro que enfatiza a CAUSA o tempo todo. os cientistas todos parecem não saber, ou se esquecer sempre, que as coisas têm causa, e que o conhecimento verdadeiro é o conhecimento da causa das coisas.
a causa é uma categoria metafísica muito superior a qualquer correlação ou resultado de teste de hipótese, ela não pode ser descoberta por nenhum artifício econométrico ou reduzida à simples antecedência temporal estatística. a causa dos fenômenos não pode ser provada cientificamente, mas pode ser conhecida.
o livro de Menger conta para o leitor as causas de vários fenômenos econômicos e as interliga de forma que o mundo caótico da economia parece adquirir uma ordem no momento em que você lê. é uma sensação mágica e indescritível.
quando eu te o recomendei, queria é te imbuir com o espírito da busca pela causa das coisas. depois de ler aquilo, você está apto a perceber continuidade causal nos fenômenos mais complexos da economia atual, enxergar as causas entre toda a ação governamental e as suas várias consequências na vida humana. eu faço isso todos os dias e é a melhor sensação do mundo quando o caos das notícias do caderno de Economia do jornal -- que para o próprio jornalista que as escreveu não têm nenhum sentido (tanto é que ele escreve tudo errado) -- se incluem num sistema ordenado de causas e consequências.
provavelmente eu sempre erro em alguns ou vários pontos, mas ainda assim é maravilhoso. ou então é mais maravilhoso ainda quando eu descubro o erro e reinsiro o acerto naquela racionalização bela da ordem do mundo econômico que é a ordem de Deus.
em scrap para T.P.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Veterano não é dono de bixete
"VETERANO NÃO É DONO DE BIXETE". A frase em letras garrafais chama a atenção dos transeuntes neófitos. Paira sobre um cartaz amarelo que lista várias reclamações contra os "trotes machistas", que, na opinião do responsável pelo cartaz, "não é brincadeira, é opressão".
Eis aí um bizarro exemplo de como são as coisas: primeiro todos os universitários aprovam a idéia do trote, apoiam sua realização e até mesmo desejam sofrer o trote -- com a condição de o poderem aplicar eles mesmos depois --, louvam as maravilhas do mundo universitário, onde a suprema sabedoria se esconde atrás de rituais iniciáticos fora do alcance da imaginação do homem comum e rude, do pobre e do filhinho-de-papai das faculdades privadas; em suma: fomentam os mais baixos, os mais animalescos instintos, a crueldade primordial, destroem em si mesmos e nos colegas quaisquer valores civilizatórios que tivessem sobrado ali, ficando todos indistingüíveis de macacos agressivos e tarados.
Depois vêm aí com um cartaz protestar contra os assédios -- que sem dúvida acontecem em larguíssima escala -- sofridos pelas calouras de 17 anos e que, sendo também novatas no mundo universitário, ainda conservam um pouco de discernimento e pudor.
A incompreensão do fenômeno, porém, é tão grande, que os trotes não são identificados como um problema mental, uma doença que deve ser tratada e eliminada, mas como um sintoma da opressão machista dos homens às mulheres, um produto desta civilização paternalista que, desde que Deus é chamado "o Pai" e não "a Mãe", corrompe a benéfica, pura e angélica natureza do homem primitivo e o torna esta tão torpe criatura.
Na opinião dos autores desse cartaz é preciso, pois, continuar a destruir o que resta da cultura ocidental, e então esperar que haja trotes menos opressores.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28neuron.vim
I started using this neuron thing to create an update this same zettelkasten, but the existing vim plugin had too many problems, so I forked it and ended up changing almost everything.
Since the upstream repository was somewhat abandoned, most users and people who were trying to contribute upstream migrate to my fork too.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28On "zk-rollups" applied to Bitcoin
ZK rollups make no sense in bitcoin because there is no "cheap calldata". all data is already ~~cheap~~ expensive calldata.
There could be an onchain zk verification that allows succinct signatures maybe, but never a rollup.
What happens is: you can have one UTXO that contains multiple balances on it and in each transaction you can recreate that UTXOs but alter its state using a zk to compress all internal transactions that took place.
The blockchain must be aware of all these new things, so it is in no way "L2".
And you must have an entity responsible for that UTXO and for conjuring the state changes and zk proofs.
But on bitcoin you also must keep the data necessary to rebuild the proofs somewhere else, I'm not sure how can the third party responsible for that UTXO ensure that happens.
I think such a construct is similar to a credit card corporation: one central party upon which everybody depends, zero interoperability with external entities, every vendor must have an account on each credit card company to be able to charge customers, therefore it is not clear that such a thing is more desirable than solutions that are truly open and interoperable like Lightning, which may have its defects but at least fosters a much better environment, bringing together different conflicting parties, custodians, anyone.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Splitpages
The simplest possible service: it splitted PDF pages in half.
Created specially to solve the problem of those scanned books that come with two pages side-by-side as if they were a single page and are much harder to read on Kindle because of that.

It required me to learn about Heroku Buildpacks though, and fork or contribute to a Heroku Buildpack that embedded a mupdf binary.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28tempreites
My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by http://microjs.com/ at the time and ended up not using the library. Probably no one ever did.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28litepub
A Go library that abstracts all the burdensome ActivityPub things and provides just the right amount of helpers necessary to integrate an existing website into the "fediverse" (what an odious name). Made for the gravity integration.
See also
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28questo.email
This was a thing done in a brief period I liked the idea of "indiewebcamp", a stupid movement of people saying everybody should have their site and post their lives in it.
From the GitHub postmortem:
questo.email was a service that integrated email addresses into the indieweb ecosystem by providing email-to-note and email-to-webmention triggers, which could be used for people to comment through webmention using their email addresses, and be replied, and also for people to send messages from their sites directly to the email addresses of people they knew; Questo also worked as an IndieAuth provider that used people's email addresses and Mozilla Persona.
It was live from December 2014 through December 2015.
Here's how the home page looked:

See also
- jekmentions, another thing related to "indieweb"
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: Rumple
a payments network based on trust channels
This is the description of a Lightning-like network that will work only with credit or trust-based channels and exist alongside the normal Lightning Network. I imagine some people will think this is undesirable and at the same time very easy to do (such that if it doesn't exist yet it must be because no one cares), but in fact it is a very desirable thing -- which I hope I can establish below -- and at the same time a very non-trivial problem to solve, as the history of Ryan Fugger's Ripple project and posterior copies of it show.
Read these first to get the full context:
- Ryan Fugger's Ripple
- Ripple and the problem of the decentralized commit
- The Lightning Network solves the problem of the decentralized commit
- Parallel Chains
Explanation about the name
Since we're copying the fundamental Ripple idea from Ryan Fugger and since the name "Ripple" is now associated with a scam coin called XRP, and since Ryan Fugger has changed the name of his old website "Ripplepay" to "Rumplepay", we will follow his lead here. If "Ripplepay" was the name of a centralized prototype to the open peer-to-peer network "Ripple", now that the centralized version is called "Rumplepay" the peer-to-peer version must be called "Rumple".
Now the idea
Basically we copy the Lightning Network, but without HTLCs or channels being opened and closed with funds committed to them on multisig Bitcoin transactions published to the blockchain. Instead we use pure trust relationships like the original Ripple concept.
And we use the blockchain commit method, but instead of spending an absurd amount of money to use the actual Bitcoin blockchain instead we use a parallel chain.
How exactly -- a protocol proposal attempt
It could work like this:
The parallel chain, or "Rumple Chain"
- We define a parallel chain with a genesis block;
- Following blocks must contain
a. the ID of the previous block; b. a list of up to 32768 entries of arbitrary 32-byte values; c. an ID constituted by sha256(the previous block ID + the merkle root of all the entries) - To be mined, each parallel block must be included in the Bitcoin chain according as explained above.
Now that we have a structure for a simple "blockchain" that is completely useless, just blocks over blocks of meaningless values, we proceed to the next step of assigning meaning to these values.
The off-chain payments network, or "Rumple Network"
- We create a network of nodes that can talk to each other via TCP messages (all details are the same as the Lightning Network, except where mentioned otherwise);
- These nodes can create trust channels to each other. These channels are backed by nothing except the willingness of one peer to pay the other what is owed.
- When Alice creates a trust channel with Bob (
Alice trusts Bob), contrary to what happens in the Lightning Network, it's A that can immediately receive payments through that channel, and everything A receives will be an IOU from Bob to Alice. So Alice should never open a channel to Bob unless Alice trusts Bob. But also Alice can choose the amount of trust it has in Bob, she can, for example, open a very small channel with Bob, which means she will only lose a few satoshis if Bob decides to exit scam her. (in the original Ripple examples these channels were always depicted as friend relationships, and they can continue being that, but it's expected -- given the experience of the Lightning Network -- that the bulk of the channels will exist between users and wallet provider nodes that will act as hubs). - As Alice receive a payment through her channel with Bob, she becomes a creditor and Bob a debtor, i.e., the balance of the channel moves a little to her side. Now she can use these funds to make payments over that channel (or make a payment that combines funds from multiple channels using MPP).
- If at any time Alice decides to close her channel with Bob, she can send all the funds she has standing there to somewhere else (for example, another channel she has with someone else, another wallet somewhere else, a shop that is selling some good or service, or a service that will aggregate all funds from all her channels and send a transaction to the Bitcoin chain on her behalf).
- If at any time Bob leaves the network Alice is entitled by Bob's cryptographic signatures to knock on his door and demand payment, or go to a judge and ask him to force Bob to pay, or share the signatures and commitments online and hurt Bob's reputation with the rest of the network (but yes, none of these things is good enough and if Bob is a very dishonest person none of these things is likely to save Alice's funds).
The payment flow
- Suppose there exists a route
Alice->Bob->Caroland Alice wants to send a payment to Carol. - First Alice reads an invoice she received from Carol. The invoice (which can be pretty similar or maybe even the same as BOLT11) contains a payment hash
hand information about how to reach Carol's node, optionally an amount. Let's say it's 100 satoshis. - Using the routing information she gathered, Alice builds an onion and sends it to Bob, at the same time she offers to Bob a "conditional IOU". That stands for a signed commitment that Alice will owe Bob an 100 satoshis if in the next 50 blocks of the Rumple Chain there appears a block containing the preimage
psuch thatsha256(p) == h. - Bob peels the onion and discovers that he must forward that payment to Carol, so he forwards the peeled onion and offers a conditional IOU to Carol with the same
h. Bob doesn't know Carol is the final recipient of the payment, it could potentially go on and on. - When Carol gets the conditional IOU from Bob, she makes a list of all the nodes who have announced themselves as miners (which is not something I have mentioned before, but nodes that are acting as miners will must announce themselves somehow) and are online and bidding for the next Rumple block. Each of these miners will have previously published a random 32-byte value
vthey they intend to include in their next block. - Carol sends payments through routes to all (or a big number) of these miners, but this time the conditional IOU contains two conditions (values that must appear in a block for the IOU to be valid):
psuch thatsha256(p) == h(the same that featured in the invoice) andv(which must be unique and constant for each miner, something that is easily verifiable by Carol beforehand). Also, instead of these conditions being valid for the next 50 blocks they are valid only for the single next block. - Now Carol broadcasts
pto the mempool and hopes one of the miners to which she sent conditional payments sees it and, allured by the possibility of cashing in Carol's payment, includespin the next block. If that does not happen, Carol can try again in the next block.
Why bother with this at all?
-
The biggest advantage of Lightning is its openness
It has been said multiple times that if trust is involved then we don't need Lightning, we can use Coinbase, or worse, Paypal. This is very wrong. Lightning is good specially because it serves as a bridge between Coinbase, Paypal, other custodial provider and someone running their own node. All these can transact freely across the network and pay each other without worrying about who is in which provider or setup.
Rumple inherits that openness. In a Rumple Network anyone is free to open new trust channels and immediately route payments to anyone else.
Also, since Rumple payments are also based on the reveal of a preimage it can do swaps with Lightning inside a payment route from day one (by which I mean one can pay from Rumple to Lightning and vice-versa).
-
Rumple fixes Lightning's fragility
Lightning is too fragile.
It's known that Lightning is vulnerable to multiple attacks -- like the flood-and-loot attack, for example, although not an attack that's easy to execute, it's still dangerous even if failed. Given the existence of these attacks, it's important to not ever open channels with random anonymous people. Some degree of trust must exist between peers.
But one does not even have to consider attacks. The creation of HTLCs is a liability that every node has to do multiple times during its life. Every initiated, received or forwarded payment require adding one HTLC then removing it from the commitment transaction.
Another issue that makes trust needed between peers is the fact that channels can be closed unilaterally. Although this is a feature, it is also a bug when considering high-fee environments. Imagine you pay $2 in fees to open a channel, your peer may close that unilaterally in the next second and then you have to pay another $15 to close the channel. The opener pays (this is also a feature that can double as a bug by itself). Even if it's not you opening the channel, a peer can open a channel with you, make a payment, then clone the channel, and now you're left with, say, an output of 800 satoshis, which is equal to zero if network fees are high.
So you should only open channels with people you know and know aren't going to actively try to hack you and people who are not going to close channels and impose unnecessary costs on you. But even considering a fully trusted Lightning Network, even if -- to be extreme -- you only opened channels with yourself, these channels would still be fragile. If some HTLC gets stuck for any reason (peer offline or some weird small incompatibility between node softwares) and you're forced to close the channel because of that, there are the extra costs of sweeping these UTXO outputs plus the total costs of closing and reopening a channel that shouldn't have been closed in the first place. Even if HTLCs don't get stuck, a fee renegotiation event during a mempool spike may cause channels to force-close, become valueless or settle for very high closing fee.
Some of these issues are mitigated by Eltoo, others by only having channels with people you trust. Others referenced above, plus the the griefing attack and in general the ability of anyone to spam the network for free with payments that can be pending forever or a lot of payments fail repeatedly makes it very fragile.
Rumple solves most of these problems by not having to touch the blockchain at all. Fee negotiation makes no sense. Opening and closing channels is free. Flood-and-loot is a non-issue. The griefing attack can be still attempted as funds in trust channels must be reserved like on Lightning, but since there should be no theoretical limit to the number of prepared payments a channel can have, the griefing must rely on actual amounts being committed, which prevents large attacks from being performed easily.
-
Rumple fixes Lightning's unsolvable reputation issues
In the Lightning Conference 2019, Rusty Russell promised there would be pre-payments on Lightning someday, since everybody was aware of potential spam issues and pre-payments would be the way to solve that. Fast-forward to November 2020 and these pre-payments have become an apparently unsolvable problem[^thread-402]: no one knows how to implement them reliably without destroying privacy completely or introducing worse problems.
Replacing these payments with tables of reputation between peers is also an unsolved problem[^reputation-lightning], for the same reasons explained in the thread above.
-
Rumple solves the hot wallet problem
Since you don't have to use Bitcoin keys or sign transactions with a Rumple node, only your channel trust is at risk at any time.
-
Rumple ends custodianship
Since no one is storing other people's funds, a big hub or wallet provider can be used in multiple payment routes, but it cannot be immediately classified as a "custodian". At best, it will be a big debtor.
-
Rumple is fun
Opening channels with strangers is boring. Opening channels with friends and people you trust even a little makes that relationship grow stronger and the trust be reinforced. (But of course, like it happens in the Lightning Network today, if Rumple is successful the bulk of trust will be from isolated users to big reliable hubs.)
Questions or potential issues
-
So many advantages, yes, but trusted? Custodial? That's easy and stupid!
Well, an enormous part of the current Lightning Network (and also onchain Bitcoin wallets) already rests on trust, mainly trust between users and custodial wallet providers like ZEBEDEE, Alby, Wallet-of-Satoshi and others. Worse: on the current Lightning Network users not only trust, they also expose their entire transaction history to these providers[^hosted-channels].
Besides that, as detailed in point 3 of the previous section, there are many unsolvable issues on the Lightning protocol that make each sovereign node dependent on some level of trust in its peers (and the network in general dependent on trusting that no one else will spam it to death).
So, given the current state of the Lightning Network, to trust peers like Rumple requires is not a giant change -- but it is still a significant change: in Rumple you shouldn't open a large trust channel with someone just because it looks trustworthy, you must personally know that person and only put in what you're willing to lose. In known brands that have reputation to lose you can probably deposit more trust, same for long-term friends, and that's all. Still it is probably good enough, given the existence of MPP payments and the fact that the purpose of Rumple is to be a payments network for day-to-day purchases and not a way to buy real estate.
-
Why would anyone run a node in this parallel chain?
I don't know. Ideally every server running a Rumple Network node will be running a Bitcoin node and a Rumple chain node. Besides using it to confirm and publish your own Rumple Network transactions it can be set to do BMM mining automatically and maybe earn some small fees comparable to running a Lightning routing node or a JoinMarket yield generator.
Also it will probably be very lightweight, as pruning is completely free and no verification-since-the-genesis-block will take place.
-
What is the maturity of the debt that exists in the Rumple Network or its legal status?
By default it is to be understood as being payable on demand for payments occurring inside the network (as credit can be used to forward or initiate payments by the creditor using that channel). But details of settlement outside the network or what happens if one of the peers disappears cannot be enforced or specified by the network.
Perhaps some standard optional settlement methods (like a Bitcoin address) can be announced and negotiated upon channel creation inside the protocol, but nothing more than that.
[^thread-402]: Read at least the first 10 messages of the thread to see how naïve proposals like you and me could have thought about are brought up and then dismantled very carefully by the group of people most committed to getting Lightning to work properly. [^reputation-lightning]: See also the footnote at Ripple and the problem of the decentralized commit. [^hosted-channels]: Although that second part can be solved by hosted channels.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Boardthreads
This was a very badly done service for turning a Trello list into a helpdesk UI.
Surprisingly, it had more paying users than Websites For Trello, which I was working on simultaneously and dedicating much more time to it.
The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.

-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28bolt12 problems
- clients can't programatically build new offers by changing a path or query params (services like zbd.gg or lnurl-pay.me won't work)
- impossible to use in a load-balanced custodian way -- since offers would have to be pregenerated and tied to a specific lightning node.
- the existence of fiat currency fields makes it so wallets have to fetch exchange rates from somewhere on the internet (or offer a bad user experience), using HTTP which hurts user privacy.
- the vendor field is misleading, can be phished very easily, not as safe as a domain name.
- onion messages are an improvement over fake HTLC-based payments as a way of transmitting data, for sure. but we must decide if they are (i) suitable for transmitting all kinds of data over the internet, a replacement for tor; or (ii) not something that will scale well or on which we can count on for the future. if there was proper incentivization for data transmission it could end up being (i), the holy grail of p2p communication over the internet, but that is a very hard problem to solve and not guaranteed to yield the desired scalability results. since not even hints of attempting to solve that are being made, it's safer to conclude it is (ii).
bolt12 limitations
- not flexible enough. there are some interesting fields defined in the spec, but who gets to add more fields later if necessary? very unclear.
- services can't return any actionable data to the users who paid for something. it's unclear how business can be conducted without an extra communication channel.
bolt12 illusions
- recurring payments is not really solved, it is just a spec that defines intervals. the actual implementation must still be done by each wallet and service. the recurring payment cannot be enforced, the wallet must still initiate the payment. even if the wallet is evil and is willing to initiate a payment without the user knowing it still needs to have funds, channels, be online, connected etc., so it's not as if the services could rely on the payments being delivered in time.
- people seem to think it will enable pushing payments to mobile wallets, which it does not and cannot.
- there is a confusion of contexts: it looks like offers are superior to lnurl-pay, for example, because they don't require domain names. domain names, though, are common and well-established among internet services and stores, because these services have websites, so this is not really an issue. it is an issue, though, for people that want to receive payments in their homes. for these, indeed, bolt12 offers a superior solution -- but at the same time bolt12 seems to be selling itself as a tool for merchants and service providers when it includes and highlights features as recurring payments and refunds.
- the privacy gains for the receiver that are promoted as being part of bolt12 in fact come from a separate proposal, blinded paths, which should work for all normal lightning payments and indeed are a very nice solution. they are (or at least were, and should be) independent from the bolt12 proposal. a separate proposal, which can be (and already is being) used right now, also improves privacy for the receiver very much anway, it's called trampoline routing.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The Lightning Network solves the problem of the decentralized commit
Before reading this, see Ripple and the problem of the decentralized commit.
The Bitcoin Lightning Network can be thought as a system similar to Ripple: there are conditional IOUs (HTLCs) that are sent in "prepare"-like messages across a route, and a secret
pthat must travel from the final receiver backwards through the route until it reaches the initial sender and possession of that secret serves to prove the payment as well as to make the IOU hold true.The difference is that if one of the parties don't send the "acknowledge" in time, the other has a trusted third-party with its own clock (that is the clock that is valid for everybody involved) to complain immediately at the timeout: the Bitcoin blockchain. If C has
pand B isn't acknowleding it, C tells the Bitcoin blockchain and it will force the transfer of the amount from B to C.Differences (or 1 upside and 3 downside)
-
The Lightning Network differs from a "pure" Ripple network in that when we send a "prepare" message on the Lightning Network, unlike on a pure Ripple network we're not just promising we will owe something -- instead we are putting the money on the table already for the other to get if we are not responsive.
-
The feature above removes the trust element from the equation. We can now have relationships with people we don't trust, as the Bitcoin blockchain will serve as an automated escrow for our conditional payments and no one will be harmed. Therefore it is much easier to build networks and route payments if you don't always require trust relationships.
-
However it introduces the cost of the capital. A ton of capital must be made available in channels and locked in HTLCs so payments can be routed. This leads to potential issues like the ones described in https://twitter.com/joostjgr/status/1308414364911841281.
-
Another issue that comes with the necessity of using the Bitcoin blockchain as an arbiter is that it may cost a lot in fees -- much more than the value of the payment that is being disputed -- to enforce it on the blockchain.[^closing-channels-for-nothing]
Solutions
Because the downsides listed above are so real and problematic -- and much more so when attacks from malicious peers are taken into account --, some have argued that the Lightning Network must rely on at least some trust between peers, which partly negate the benefit.
The introduction of purely trust-backend channels is the next step in the reasoning: if we are trusting already, why not make channels that don't touch the blockchain and don't require peers to commit large amounts of capital?
The reason is, again, the ambiguity that comes from the problem of the decentralized commit. Therefore hosted channels can be good when trust is required only from one side, like in the final hops of payments, but they cannot work in the middle of routes without eroding trust relationships between peers (however they can be useful if employed as channels between two nodes ran by the same person).
The next solution is a revamped pure Ripple network, one that solves the problem of the decentralized commit in a different way.
[^closing-channels-for-nothing]: That is even true when, for reasons of the payment being so small that it doesn't even deserve an actual HTLC that can be enforced on the chain (as per the protocol), even then the channel between the two nodes will be closed, only to make it very clear that there was a disagreement. Leaving it online would be harmful as one of the peers could repeat the attack again and again. This is a proof that ambiguity, in case of the pure Ripple network, is a very important issue.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Webvatar
Like Gravatar, but using profile images from websites tagged with "microformats-2" tags, like people from the indiewebcamp movement liked. It falled back to favicon, gravatar and procedural avatar generators.
No one really used this, despite people saying they liked it. Since I was desperate to getting some of my programs appreciated by someone I even bought a domain. It was sad, but an enriching experience.
See also
-
 @ 18483135:00cf44f6
2024-09-14 13:30:41
@ 18483135:00cf44f6
2024-09-14 13:30:41(Highlighter version)
This article is a Nostr-exclusive so please give it a boost if you think it’s worthy of one!
The world of video games has come a long way since its inception, evolving from simple pixel-based arcade games to highly immersive experiences. However, the medium is still broadly considered to be not much more than entertainment. Even as a gamer, I used to agree with that statement, though some games did help shape who I am. I was a pretty lonely kid and certain game characters substituted as a father figure. I absorbed their values and even mimicked their behavior. And yet, at one point I stopped being interested in gaming. This happened around the same time I was “awakening” through Bitcoin, Austrian Economics and other meaningful topics. I no longer had any intention of wasting time on the medium as a means of distraction.
It didn’t take me very long to suspect I might have just been looking for the wrong things.
Instead of the best RPG, the best action, the best graphics, the best gameplay, … how about I look for games that people have found significant meaning in? As I browsed online through forums and blogs, particular discussions and comments really spoke to me, although they seemed a bit exaggerated at the time. Depression, existential crisis, temporary psychosis. These are not the kind of effects you’d expect people to have from a form of entertainment. But as I played them, I realized they weren’t kidding. These games challenged how I view myself, humanity, the world, life itself and even my own way of thinking. I went from being sick of gaming to finding profound and worthwhile experiences, all by simply changing what I was looking for. Now, I’m convinced that important topics will one day become more mainstream with the usage of the gaming medium. In the bottom of this note I will add a list of these games. They all deserve to be written about, but I will mainly focus on my experience with one in particular, the one that had the most impact on me. It’s one of those experiences that I can’t stop thinking about even after so many years, and I never will. This note is written out of sheer gratitude, as I feel indebted for the value I have received, and to spread awareness of its existence.
Video games allow for hugely ambitious projects, but if one aspect feels off, the product as a whole will drastically decrease in efficacy. Just like certain movies, it tries to incorporate nearly all forms of art, but with the key difference that it places you directly in the story with varying degrees of control, decisions, and the consequences of those decisions. The tricky part is achieving harmony and synchronicity between the visual, audiovisual, writing, and story execution. Everything needs to feel connected and this requires immense skill and cooperation between the involved entities to execute successfully. Naturally, the depths of wisdom contained in books are unparalleled. But it really hits different with games like Nier: Automata, which encapsulates wisdom within a story that shreds one’s mind and heart apart, accompanied by music which I can only understate as “the sound of the human condition”.
https://images5.alphacoders.com/921/thumb-1920-921994.jpg
Exploring The Underlying Themes
The first impression one may have when they look at Nier: Automata on the surface, is "hot android chicks fighting against machines". Everyone knows sex sells, but I dare say it is a rather typical Japanese media phenomenon where the female form is on the foreground but mind-boggling concepts are lurking behind it. I think a fair analogy to this is Bitcoin’s fiat price, where the prospect of wealth is the magnet that draws in people, but most of us know it is only the bait next to the rabbit hole. Much like in Nier, you’d miss out on all the incredible stuff if you didn’t look further than the hot androids.
Anyway, you will no doubt notice I will be extremely vague about the story itself. Instead, I will focus on some of the underlying content as to provide proper context for potential players.
The game takes place in 11945 AD, during a proxy war between human-made androids and alien-made machines. They were designed to serve a predetermined obligation. Don’t humans have a similar mechanism? Don’t we all feel like we need to serve a purpose, whether that is predetermined or not? Much of the game is about coping with the loss of purpose and the realization of an identity for yourself afterwards.
Nihilism is the belief that nothing matters and everything is meaningless.
Existentialism on the other hand, is the attempt to confront and deal with meaninglessness, as to not succumb to nihilism. An existentialist does not give up in the face of adversity, nor does he avoid responsibility. Albert Camus, for instance, believed the entire purpose of existential philosophy is to overcome absurdity. In other words, for man to triumph over the absurdity of existence. The nihilist says: I am a godless creature, there is no heaven or hell, there is no right or wrong. The existentialist says: you and I must figure out how to make life meaningful and good. We must, in fact, work (together) without cosmic aid to figure out what 'good' itself is, regardless of the existence or non-existence of a god.
Even though the game is full of events which would turn anyone to a nihilistic mindset, the game counters this during the most significant ending sequence, ending E, where players are able to leave a message for other players to see. Since I won’t spoil any details, what I can allow myself to say is this: the game isn't telling you that our existence is ultimately meaningless. Instead, an event lets YOU and other players demonstrate that it is not. Life doesn't HAVE to be pointless. Humanity doesn't HAVE to treat freedom as a curse, as Jean-Paul Sartre proclaimed. Games don't HAVE to be silly little things, made to distract us from our own meaninglessness. The potential absence of a god doesn’t HAVE to be a negative circumstance. We're not doomed per se. We can treat our freedom as an opportunity to create our own futures. To craft happier endings.
Mechanics
In the game, there are machines that take the form of real-life philosophers, because their specific work seemed most valuable to these machines. This is no different than us humans; we tend to absorb the views of the people whose words resonate with us. As such, we get to see a fresh perspective on certain philosophies, and how this might play out for machines is just another way of tuning our understanding of humanity.
You will also encounter rather unfriendly historical figures in machine form, For example, the first boss battle is versus an enemy called… Marx. That’s right, Karl Marx is your first boss fight. He takes the form of an excavator arm, which is normally attached to another machine lifeform, called Engels. And yes, that’s a reference to Friedrich Engels, who aided Marx in the construction of the communist theory. They quite literally seized the means of production. In real life the duo was inseparable until Marx's death, at which point Engels was alone with his thoughts. Just as when you defeat the Engels unit in-game, it will be separated from its right arm, Marx. By defeating it, it will be immobilized with nothing to do but contemplate upon its past actions, and you can return to speak to it on multiple occasions, if you wish to do so.
As I stated before, the game takes place in 11945 AD, so machines and androids are indeed extremely advanced. Some could be considered on par with the human gestalt in every way.
As such a technologically advanced entity, your current state of being along with your memories and all that makes you “you”, can be backed up and uploaded into a blank compatible body unit. For this reason, a well known system among gamers called "auto-save" is non-existent here. Saving your game equals backing up your state of being at the time. Many core elements of the main narrative and relationships between the protagonists are based on the ability or inability to back up data. And since this plot point of the androids backing up their data is tied to the game’s save system, there is no auto-save. The creator of the game, Yoko Taro, has an aversion to ludonarrative dissonance, where elements of the game go in stark contrast with what the story is telling, so using the game’s mechanics as a narrative device to deliver main plot elements is exactly one of the ways to avoid this. Gameplay and story stay true to each other. That said, our past experiences and recollections define who we are. This raises questions about the nature of self-identity and personal growth. Whether you believe it is possible for non-organic beings to develop human-like consciousness, or in the eventual possibility of backing up and uploading said consciousness, is irrelevant. The goal here is to explore the human condition and deepen our appreciation for its complexity.
The story unfolds over 3 major playthroughs, each of which are different. The first 2 playthroughs, though indeed different, are very similar as they tell the same part of the story but with additional context and information, as well as playing through the eyes of a different character. This is key to a proper transition into the powerful third part. Near the end, you gain the ability to redo certain events of the game so you can make different choices and see how this impacts that particular timeline. This part of the game is my favorite, as it allows a deep-dive into all the rabbit holes that are scattered throughout the game. Every time I thought I had seen the full truth or all there was to be seen, I kept making new discoveries. It felt very similar to figuring out all the lies and mechanics of the fiat system.
I will now move on to discuss a few of the philosophers and how they are relevant in-game. It’s important to note that the game does not try to push any philosophical views on you. Instead, you are shown the pros and cons of certain values, thoughts, beliefs, and ways of living. You are not told how to live your life, but through storytelling you are shown the importance of responsibility and walking your own path.
Friedrich Nietzsche
"Everything that lives is designed to end. We are perpetually trapped in a never-ending spiral of life and death. Is this a curse? Or some kind of punishment? I often think about the god who blessed us with this cryptic puzzle.. and wonder if we'll ever get the chance to kill him."
This is the game’s opening monologue by a female android called 2B. It is reminiscent of Samsara, a concept present especially in buddhism and hinduism, which describes the endless drifting of a futile existence that can only be stopped with true insight.
2B’s name is based on the famous speech in Shakespeare’s Hamlet “To be or not to be” in which the character Hamlet contemplates death and suicide, weighing the pain and unfairness of life against the alternative.
Nietzsche’s influence on this game is extremely obvious; in 2B’s monologue alone we can already see two major Nietzschean themes that tie into the Nier franchise. The first one is eternal return (or eternal recurrence). This is the concept which states that time repeats itself in an infinite loop, and that exactly the same events will continue to occur in exactly the same way, over and over again, for eternity. With a finite number of events and an infinite amount of time all things will repeat themselves forever. It is not known whether Nietzsche believed in the eternal return, or if it was merely used as a means to demonstrate his point. The second one, is on how to live life in a world without god(s).
“God is dead. God remains dead. And we have killed him.”
For Nietzsche, the idea of what it is to be a human was up until a point aimed at a God. What it meant “to be” was derived from a God. As such, meaning was given to existence. However, societal and scientific progress "killed" God, or the need for one, and a human being could no longer see themself as an existence with a “true” purpose. This in turn, leads to the crisis of the concept of being a human, as it no longer holds as the notion of purpose.
The androids in the game were created by humans, therefore we could say that humanity is their god. Humans are a natural phenomenon — androids are not. I am aware of the counterargument; since humans are a part of nature, anything we create could also be defined as natural, at least to a certain degree. I have no strong stance on this matter, but one could argue that when they die, their consciousness lives on because it shares an attachment to the natural world. One cannot say the same of an artificial consciousness. There is nothing for a machine to believe in after death. They know who their gods are. If their gods are gone, their objective goes with it, and they are left with absolutely nothing. Humans on the other hand have the “luxury” to believe in an afterlife, a rebirth, or simply an unknown. Machines do not, so if they are to survive life’s suffering, they must follow an ethic as stated by Nietzsche, who believed that if you want to live without a god, it is necessary to create your own values.
As I stated before, much of the game is about coping with the loss of purpose and the realization of an identity for yourself afterwards. Some androids clearly resent the purpose they have been given. You, the player, can see how the story potentially ends and resent the game creators for it. You either accept the fate given to you, or you decide it cannot continue like this, and you fight to defeat the gods of the game to break free.
Pascal Blaise
“When I consider the short duration of my life, swallowed up in the eternity before and after, the little space which I fill, and even can see, engulfed in the infinite immensity of spaces of which I am ignorant, and which know me not, I am frightened, and am astonished at being here rather than there; for there is no reason why here rather than there, why now rather than then. Who has put me here? By whose order and direction have this place and time been allotted to me? Memoria hospitis unius diei prætereuntis.”
Pascal Blaise, a mathematician, physicist, and philosopher, is a significant figure of the 17th century. He was the inventor of the first mechanical calculator, the Pascaline, and as you may have guessed, the unit of pressure “Pascal” was named after him.
Our existence is based on uncertainty, and there is no way to prove a god exists, or does not exist. Pascal chose to live his life as if god exists. You may be familiar with the philosophical argument “Pascal's wager”, which posits that individuals essentially engage in a life-defining gamble regarding the belief in the existence of God.
After seeing countless of his comrades die in an ongoing war, Machine Pascal refused to take any more part in this endless cycle and decided to become fully pacifistic while dedicating himself to learn about humanity and teaching other machines about emotions. At one point, we see Pascal studying Nietzsche’s work (In real life Pascal preceded Nietzsche so this would be an anachronistic event, if it weren’t for the fact that these characters are timeless machine representations).
“It seems this Nietzsche was quite the profound thinker.. Or perhaps he skipped right past profound and went straight to crazy instead.. I’d best go see the world for myself instead of burying my head in books.”
A wise choice indeed. I couldn’t help but think of Keynesian economists during this remark. Keynesians may have read very much about mainstream economics but they are completely oblivious as to how the world actually works. They are convinced that their statistics are causally linked and their formulas correct, despite the overwhelming evidence against it. They are blind to the destructive effects of their flawed beliefs. To quote Pascal: “It is man's natural sickness to believe that he possesses the truth.”
Jean-Paul Sartre
“Existence precedes essence”
This idea originated from a speech by Friedrich Schelling in December 1841, and can be found in the work of other philosophers such as Søren Kierkegaard in the 19th century, and Heidegger’s book ‘Being and Time’ in 1927. But it was philosopher Jean-Paul Sartre who worked out this concept in detail.
“Existence precedes essence” is a disagreement with the traditional philosophical view that the essence (nature) of something is more fundamental and unchangeable than its existence. People create their own values and determine their own meaning in life, since they have no innate identity or value. This identity or value must be created by the individual himself. By performing the actions of which they are composed, they make their existence more substantial.
To claim that existence precedes essence is to assert that there is no predetermined essence to be found in humans, and that an individual's essence is defined by the individual through how that individual creates and lives his or her life. As Sartre puts it in Existentialism is a Humanism: "man first of all exists, encounters himself, surges up in the world and defines himself afterwards".
In 2009, philosophy professor James Webber interpreted Sartre's usage of the term essence not in a modal fashion, i.e. as necessary features, but in a teleological fashion, thus relating to the explanation of phenomena in terms of the purpose they serve rather than of the cause by which they arise. An essence is the relational property of having a set of parts ordered in such a way as to collectively perform some activity. For example, it belongs to the essence of a house to keep the bad weather out, which is why it has walls and a roof. Humans are different from houses because unlike houses they don't have an inbuilt purpose: they are free to choose their own purpose and thereby shape their essence, therefore their existence precedes their essence.
When it is said that people define themselves, it is often perceived as stating that they can "wish" to be something and then be what they claim to be. According to Sartre, however, this would be a kind of bad faith. What is meant by the statement is that people are defined only insofar as they act, and that they are responsible for their actions. To clarify, it can be said that a person who acts cruelly towards other people is, by that act, defined as a cruel person and in that same instance, they (as opposed to their genes, for instance) are defined as being responsible for being this cruel person. Ofcourse, you can choose to act in a different way, and to be a good person instead of a cruel person. Here it is also clear that since people can choose to be either cruel or good, they are, in fact, neither of these things essentially.
Jean-Paul's depiction in Nier: Automata parodies the real-life Sartre, who despite great acclaim for his philosophy famously disdained awards and recognition. Among other honors, he was awarded the 1964 Nobel Prize for Literature, but refused to accept it. I also see the resemblance with the game’s creator, Yoko Taro, who is known for playing down his achievements very much, calling his games shit for instance. Though he does so in a playful manner.
Machine Jean-Paul takes the work of the human Jean-Paul so seriously that he ignores that the human versions had a life outside of philosophy. Or rather, whatever part of his life was not recorded or lost, would not exist to a machine.
\ https://i.pinimg.com/originals/39/b8/33/39b8331ebffb0f0c410a88fee80a1e03.jpg
Simone De Beauvoir
Simone de Beauvoir (who had a lifelong relationship with Jean-Paul Sartre) wrote of the example of a woman's identity going wrong if it is based on nothing but a man's affection.
In-game, she was at one point a normal machine. But one day, she fell in love with the Jean-Paul machine. When he disregarded her, pleasing him and getting his attention became her obsession. She made it her goal to become beautiful. “Beauty is pretty skin,” Simone says. “Beauty is stylish accessories. Beauty is looking one’s best.”
As time went on, and Jean-Paul still wouldn’t notice her, things went too far. Simone became desperate and consumed machines and androids to see if she could obtain beauty by digesting them. She even draped dozens of android corpses over her dress in a sickly decorative manner. Driven to madness by her obsession, Simone becomes a monster. And in the end, Jean-Paul still never noticed her. He still never looked her way. So yeah, I said I was not going to mention any more mechanics but looks like I lied; during the battle with Simone this theme is simulated, when you are unable to look at her with the camera at all, no matter what you do with the controls. And as the player deals enough damage to her outer case of morbid accessories, her true unappealing self is revealed.
\ https://untitledcritic.com/wp-content/uploads/2024/04/NieR_mainart-1536x863.jpg
Immanuel Kant
Admittedly, I’m not deeply familiar with Immanuel Kant’s work but I know this much: Kant wrote of the importance of duty in moral action and the intent behind an action being more important than the end result. In the forest section in Nier: Automata, we see a sacrifice being made with good intent but with little result. The entire sequence is about exploring this concept. In the first playthrough you go through an area where all you see is the result of something. The second playthrough shows you the intent. One should always keep in mind that in many cases, be it in-game or in real life, we are only left with results to judge. Kant believed that when people refuse to judge and think for themselves, it’s due to a lack of courage to be independent. He strongly argued against the idea of saying “Why dare to push against the grain when you could simply follow the herd?” Yet this is the antithesis of what in-game Immanuel Kant represents.
\ https://jumpitoy.com/wp-content/uploads/2024/04/NieR-creator-criticizes-Japanese-studios_11zon.webp
Yoko Taro
The creator of the Nier franchise agrees with the existential viewpoint that our lives have no innate meaning whatsoever and that our existence is profoundly absurd. He also confesses that he’s not yet ready to accept the world as it is, and intends to keep trying to change it with his video games.
As opposed to the majority of games, where many conventions of the game market inhibit creative freedom, he is keen in experimenting with the video game format.
“Throughout his entire career, Taro Yoko has always felt disheartened by the image of humanity reflected in most big-budget video games, which propose the use of firearms as the principal means of action. Through his own work, from Drakengard to NieR: Automata, this artist attempts to explore the reasons behind our strange fascination with conflict.
Is man so vicious that he must triumph, discriminate, hurt and kill even for entertainment?
Within the great fields of ruin resulting from wars in which mankind battled against mankind, Taro Yoko perceives this “entertainment” as a way for hope, a horizon, a shield against evil.”
-- The Strange Works of Taro Yoko: From Drakengard to NieR: Automata Hardcover – June 1, 2019
Yoko Taro is known for being quite the eccentric figure. He has an intense dislike for giving interviews and believes that game designers are not supposed to be entertainers or commentators on their work, and that the usual questions asked in traditional media interviews would be boring to the viewer. For this reason and others, he is anonymous. Nobody’s ever seen his face, and I think Yoko Taro isn’t even his real name. As for his work, he writes in a manner called "backwards scriptwriting", which he describes as starting with the ending first, then working backwards from there. He then creates central plot points that form emotional peaks in the narrative, adds details, then scatters them through the narrative so the player can build a suitable emotional connection. Many of his games reflect his own feelings about death and his socratic questioning of the concept. He also has an unconventional and creative approach to sharing extra information about his games. For example, inside the soundtrack there's a message that's coded in hexadecimal. When deciphered, you find it is a partial memory retrieved from one of the android protagonists.
Good developers are able to produce good games, but it takes an exceptional individual or team of exceptional individuals, to craft a piece of work that is so emotionally powerful, so moving, that it transcends the medium of entertainment and leaves an unforgettable mark.
\ https://img3.gelbooru.com//samples/76/13/sample_76134e4004bc4bcd629fb2a478ea6ff7.jpg
If you made it this far, thank you for reading!
A few quick tips to fully enjoy this masterpiece..
For the sake of all that’s holy, play it in the original Japanese voiceover. The immersion gets quite broken if you don’t get to hear the proper emotion in the character’s voices. English subtitles are included of course. It is also an experience that’s most effective when you go through it all alone, as to allow for the most self-reflection and absorption.
Quick echo of what I said on top: I would love it if this note got some visibility, it is a Nostr-exclusive article so please give it a boost if you think it’s worthy of one!
Also, HI EVERYONE. I haven’t used my #introductions formally yet, so this is it!
Now here is the list of games I said I was going to provide, not in any specific order, and a short description for some.
Must-play
Disco Elysium: The player controls a detective who suffers from amnesia and has to solve a murder case while navigating his own state of being and dealing with the consequences of past mistakes. One of the most unique elements in this game, is the fact that concepts such as logic, or various parts of your body such as your limbic system, actually converse with you.
The Talos Principle: Like Nier: Automata, lots of self-reflection and a challenge to your sense of morality. Its gameplay however is based on problem-solving and presenting you with thought-provoking questions in a direct manner.
The Talos Principle 2: A continuation of the events in the first game.
Semi must-play
Detroit: Become Human
Lisa
Bioshock Infinite
Omori
Oneshot
Doki Doki Literature Club
Meaningful Anime
Since I’m writing about existential stuff anyway, I might as well add the relevant anime that I’ve watched. It doesn’t have the same level of impact on me as games do but I feel like this note wouldn’t be complete without mentioning them.
Again, in no particular order:
Neon Genesis Evangelion (Yoko taro also mentioned Nier: Automata was inspired by this anime)
Serial Experiments Lain
Ergo Proxy
I know there’s plenty more gems out there but I haven’t gotten around to watching them yet.
## Tags and stuff
nier #nierautomata #philosophy #existentialism #game #gaming #games #gamestr #nihilism #story #storytelling #meaning #life #bitcoin
\ CREDIT for certain images I found: RPINr, Gasia112 on deviantart
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Eltoo
Read the paper, it's actually nice and small. You can read only everything up to section 4.2 and it will be enough. Done.
Ok, you don't want to. Or you tried but still want to read here.
Eltoo is a way of keeping payment channel state that works better than the original scheme used in Lightning. Since Lightning is a bunch of different protocols glued together, it can It replace just the part the previously dealed with keeping the payment channel.
Eltoo works like this: A and B want a payment channel, so they create a multisig transaction with deposits from both -- or from just one, doesn't matter. That transaction is only spendable if both cooperate. So if one of them is unresponsive or non-cooperative the other must have a way to get his funds back, so they also create an update transaction but don't publish it to the blockchain. That update transaction spends to a settlement transaction that then distributes the money back to A and B as their balances say.
If they are cooperative they can change the balances of the channel by just creating new update transactions and settlement transactions and number them like 1, 2, 3, 4 etc.

Solid arrows means a transaction is presigned to spend only that previous other transaction; dotted arrows mean it's a floating transaction that can spend any of the previous.
Why do they need and update and a settlement transaction?
Because if B publishes update2 (in which his balances were greater) A needs some time to publish update4 (the latest, which holds correct state of balances).
Each update transaction can be spent by any newer update transaction immediately or by its own specific settlement transaction only after some time -- or some blocks.
Hopefully you got that.
How do they close the channel?
If they're cooperative they can just agree to spend the funding transaction, that first multisig transaction I mentioned, to whatever destinations they want. If one party isn't cooperating the other can just publish the latest update transaction, wait a while, then publish its settlement transaction.
How is this better than the previous way of keeping channel states?
Eltoo is better because nodes only have to keep the last set of update and settlement transactions. Before they had to keep all intermediate state updates.
If it is so better why didn't they do it first?
Because they didn't have the idea. And also because they needed an update to the Bitcoin protocol that allowed the presigned update transactions to spend any of the previous update transactions. This protocol update is called
SIGHASH_NOINPUT[^anyprevout], you've seen this name out there. By marking a transaction withSIGHASH_NOINPUTit enters a mystical state and becomes a floating transaction that can be bound to any other transaction as long as its unlocking script matches the locking script.Why can't update2 bind itself to update4 and spend that?
Good question. It can. But then it can't anymore, because Eltoo uses
OP_CHECKLOCKTIMEVERIFYto ensure that doesn't actually check not a locktime, but a sequence. It's all arcane stuff.And then Eltoo update transactions are numbered and their lock/unlock scripts will only match if a transaction is being spent by another one that's greater than it.
Do Eltoo channels expire?
No.
What is that "on-chain protocol" they talk about in the paper?
That's just an example to guide you through how the off-chain protocol works. Read carefully or don't read it at all. The off-chain mechanics is different from the on-chain mechanics. Repeating: the on-chain protocol is useless in the real world, it's just a didactic tool.
[^anyprevout]: Later
SIGHASH_NOINPUTwas modified to fit better with Taproot and Schnorr signatures and renamed toSIGHASH_ANYPREVOUT. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: Hosted-channels Lightning wallet that runs in the browser
Communicates over HTTP with a server that is actually connected to the Lightning Network, but generates preimages and onions locally, doing everything like the Hosted Channels protocol says. Just the communication method changes.
Could use this library: https://www.npmjs.com/package/bolt04
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The problem with ION
ION is a DID method based on a thing called "Sidetree".
I can't say for sure what is the problem with ION, because I don't understand the design, even though I have read all I could and asked everybody I knew. All available information only touches on the high-level aspects of it (and of course its amazing wonders) and no one has ever bothered to explain the details. I've also asked the main designer of the protocol, Daniel Buchner, but he may have thought I was trolling him on Twitter and refused to answer, instead pointing me to an incomplete spec on the Decentralized Identity Foundation website that I had already read before. I even tried to join the DIF as a member so I could join their closed community calls and hear what they say, maybe eventually ask a question, so I could understand it, but my entrance was ignored, then after many months and a nudge from another member I was told I had to do a KYC process to be admitted, which I refused.
One thing I know is:
- ION is supposed to provide a way to rotate keys seamlessly and automatically without losing the main identity (and the ION proponents also claim there are no "master" keys because these can also be rotated).
- ION is also not a blockchain, i.e. it doesn't have a deterministic consensus mechanism and it is decentralized, i.e. anyone can publish data to it, doesn't have to be a single central server, there may be holes in the available data and the protocol doesn't treat that as a problem.
- From all we know about years of attempts to scale Bitcoins and develop offchain protocols it is clear that you can't solve the double-spend problem without a central authority or a kind of blockchain (i.e. a decentralized system with deterministic consensus).
- Rotating keys also suffer from the double-spend problem: whenever you rotate a key it is as if it was "spent", you aren't supposed to be able to use it again.
The logic conclusion of the 4 assumptions above is that ION is flawed: it can't provide the key rotation it says it can if it is not a blockchain.
See also
-
 @ e97aaffa:2ebd765d
2024-09-14 11:41:09
@ e97aaffa:2ebd765d
2024-09-14 11:41:09Há 4 ou 5 anos, eu fiz um comentário num tweet de um famoso shitcoiner português, entretanto o tweet foi apagado. Eu escrevi: «Ethereum é o WordPress 2.0», o influencer não concordou mas até foi cordial na resposta, o mesmo não aconteceu com o resto da sua comunidade, fui altamente atacado. Quanto mais tempo passa, eu estou mais convicto que estava certo.
Passados estes anos, eu continuo a manter o mesmo pensamento sobre a Ethereum, possivelmente não vai cair tanto como a WordPress, mas vai perder muito valor, comparado com o atual valor. Hoje em dia a tecnologia WordPress está em todo lado, utilizada por milhões de pessoas e empresas, mas o valor da empresa WordPress é ínfima parte do valor da tecnologia WordPress. Eu acredito que vai acontecer o mesmo com Ethereum, posso estar errado mas é a minha convicção.
O atual plano de negócios da empresa/fundação Ethereum é inviável a longo prazo, recentemente voltou a fazer uma enorme venda para financiar os custos operacionais. Os custos são uma monstruosidade, o seu tesouro inevitável vai acabar um dia, o problema está aqui, não há uma solução boa, qualquer que seja, é má. O que fazer para financiar:
Donativos
Uma alternativa, seguir o modelo mais opensource, sem uma fundação, ao estilo do #Bitcoin, através de donativos diretos ou empresas a pagar ao devs e devs voluntários. Só que este modelo, será difícil seguir uma linha orientadora, um roadmap, será um desenvolvimento mais anarquista. Ou então a fundação poderá ser financiada por empresas ou países, com o objetivo de seguir o rumo que os doadores pretendem, perdendo a liberdade.
Opensource/Patentes
Outra solução é, deixarem de ser exclusivamente opensource, para terem uma vantagem contra a concorrência. O atual modelo é péssimo em termos de negócio, porque a Ethereum gasta milhões em desenvolvimento e lança as inovações. Mas como é opensource, rapidamente a concorrência copia e implementa a tecnologia, como os custos destas são muito menores, conseguem disponibilizar um serviço muito mais barato, são uma concorrência desleal. Isto faz lembrar muito a indústria farmacêutica, por isso existem as patentes, durante x anos, quem inventa/descobre o medicamento tem uma exclusividade. Só que isto é contra os princípios básicos deste ecossistema, é ir contra a sua essência.
Inflação
A inflação será possivelmente o caminho mais provável, vão criar mais ether para se financiar. Ou em alternativa criar uma nova fee que reverta a favor, em exclusivo, para a fundação. Em ambos os casos, vai aumentar os custos para os utilizadores ou desvaloriza o ether para os investidores, ou seja, a rede fica ainda menos competitiva, em relação à concorrência. A maioria das pessoas vão querer sempre o mais barato. Assim será quase uma espiral da morte, terá que estar constantemente a desvalorizar o ether, é exatamente como os atuais governos fazem com as suas moedas FIAT e também sabemos as consequências destas medidas.
Estagnação
Se não houver bastante financiamento o projecto vai acabar por estagnar, mais tarde ou mais cedo vai surgir um outro projeto, com uma tecnologia melhor e o Ethereum será ultrapassado.
Ou a fundação arranja uma solução para o seu futuro ou este será muito sombrio. Com isto, eu não quero dizer que o projeto vai colapsar, mas não vai valer tanto como vale hoje em dia.
Esta é a grande vantagem do #Bitcoin, não é apenas tecnologia, a tecnologia é quase uma coisa secundária. O principal é o seu ethos, a política monetária, a descentralização e o efeito de rede, estes sim, são os reais valores do Bitcoin, a tecnologia serve apenas para garantir a segurança e que esses valores são cumpridos. O código é possível ser copiado e foi copiado no passado, não passou disso, apenas código, porque o real valor não pode ser replicado, por isso poucas pessoas trocaram o Bitcoin pelos “clones”.
No caso do Ethereum, é o oposto, o principal valor é a sua tecnologia(EVM), e esta pode e está a ser replicada em dezenas de projectos diferentes. Podem alegar que é mais seguro, sim é verdade, mas apenas uma minoria está disponível para pagar por esse premium, a esmagadora maioria dos utilizadores vai e está a preferir redes mais baratas. E é lógico que queiram, se tens dois serviços idênticos, não existe razão para escolher o mais caro. Na guerra dos clones, o Bitcoin saiu claramente vencedor, não perdeu utilizadores; o Ethereum estará em plena guerra, mas os clones estão a ganhar parte significativa desses mercado.
Eu sinceramente acredito que muita da tecnologia criada pela Ethereum estará no futuro por todo o lado, especialmente no sistema financeiro e notarial. Mas os investidores têm a expectativa que vai acontecer um boom, vai acontecer mas não será na Ethereum, nem em blockchains permissionless, cada instituição terá a sua própria blockchain ou vão juntar-se em cooperativas. O mundo financeiro e das securities é tão complexo, em termos de regras e regulatório, cada país tem as suas próprias regras, é provável no futuro, a BlackRock ter uma blockchain para os EUA, outra para UE e muitas outras. É apenas uma base de dados, ou seja, será o mesmo que aconteceu com a WordPress.
Na minha opinião, a Ethereum vai se tornar algo de nicho, a grande massa de utilizadores ficará dispersa por milhares de blockchains. É exatamente o mesmo que acontece com o Bitcoin, só que o Bitcoin está a ser construído com esse objetivo, ser um local de settlements. No Bitcoin estimula-se a utilização de outras redes, layers 2, ecash, sidechains e outras tecnologias, a descentralização pura.
Há muito tempo que os bitcoiners concluíram que é impossível escalar a blockchain do Bitcoin para uma adoção global, essa escalabilidade passará obrigatoriamente por layer 2 e outras tecnologias. Eu tenho a sensação que o Vitalik também já chegou a essa conclusão, o Ethereum não é escalável, e está a transformá-lo num local para os “settlements” de outras blockchains. Só que os investidores ainda não compreenderam isso… O atual valor do ether está sobrevalorizado, porque os investidores estão na expectativa de um crescimento exponencial de utilizadores, mas se crescimento nunca acontecer?
Esta é a minha opinião, posso estar completamente errado, mas é assim que eu penso. Enquanto for permitido, vou fazê-lo, expressar livremente, dizer aquilo que realmente penso. Prefiro errar, do que ficar calado ou expressar algo que não acredito, mas esses são os meus valores… outros preferem os valores monetários.
-
 @ a012dc82:6458a70d
2024-09-14 10:17:24
@ a012dc82:6458a70d
2024-09-14 10:17:24Table Of Content
-
What are Bitcoin Ordinals?
-
Importance of Bitcoin Ordinals in the Bitcoin Network
-
How Bitcoin Ordinals Work
-
The Significance of Bitcoin Ordinals
-
Advantages of Bitcoin Ordinals
-
Future of Bitcoin Ordinals and Blockchain Technology
-
Conclusion
-
FAQ
Bitcoin ordinals are a fundamental aspect of the Bitcoin network, serving a crucial role in ensuring the network's integrity and security. In this article, we will delve into the basics of Bitcoin ordinals, their importance, and how they are generated.
What are Bitcoin Ordinals?
Bitcoin ordinals are unique identifiers assigned to each transaction on the Bitcoin network. They distinguish each transaction from others by assigning a unique ordinal number to it. Bitcoin ordinals are represented as a long string of alphanumeric characters generated by the Bitcoin network's underlying code.
Importance of Bitcoin Ordinals in the Bitcoin Network
Bitcoin ordinals are a critical component of the Bitcoin network, serving several important purposes that are essential in ensuring the network's integrity and security.
Ensuring Transaction Authenticity
One of the primary purposes of Bitcoin ordinals is to ensure the authenticity of each transaction on the Bitcoin network. Each transaction is assigned a unique ordinal number that distinguishes it from other transactions, ensuring that it cannot be replicated or modified.
Preventing Double-Spending
Another important role of Bitcoin ordinals is to prevent double-spending, a fraudulent activity where a user spends the same Bitcoin more than once. Bitcoin ordinals ensure that each Bitcoin can only be spent once, preventing double-spending and enhancing the security of the Bitcoin network.
Verifying Transaction Origin and Destination
Bitcoin ordinals also help verify the origin and destination of Bitcoin transactions. Each Bitcoin transaction is associated with a specific public key that identifies the user who sent the Bitcoin and the user who received it.
How Bitcoin Ordinals Work
Bitcoin ordinals are generated through the process of Bitcoin mining. Each block added to the blockchain contains a unique set of Bitcoin transactions, and each transaction within the block is assigned a unique ordinal number. The ordinal number is derived from the block's hash, a unique identifier that represents the block's contents and its position in the blockchain.
The mining process involves solving complex mathematical equations to validate Bitcoin transactions and create new blocks in the blockchain. Once a block is created, its ordinal numbers cannot be changed, ensuring the authenticity and security of each transaction within the block.
The Significance of Bitcoin Ordinals
Bitcoin ordinals play a crucial role in the security and integrity of the Bitcoin network. They help prevent fraudulent activities such as double-spending and ensure that each transaction on the network is authentic and secure. Bitcoin ordinals also provide a unique identifier for each transaction, allowing users to easily track the movement of Bitcoins through the network.
Advantages of Bitcoin Ordinals
Bitcoin ordinals provide several advantages that are crucial in ensuring the security and integrity of transactions on the Bitcoin network. These advantages include:
Improved Transaction Security: Bitcoin ordinals enhance transaction security by providing a unique identifier for each transaction, preventing fraudulent activities and enhancing network security.
Easy Tracking of Bitcoin Transactions: Bitcoin ordinals allow for easy tracking of Bitcoin transactions from one address to another, making it possible to verify the authenticity of each transaction.
Preventing Fraudulent Transactions: Bitcoin ordinals provide an additional layer of security that prevents fraudulent transactions on the Bitcoin network, making it nearly impossible for hackers to manipulate the transaction history or attempt to double-spend Bitcoins.
Future of Bitcoin Ordinals and Blockchain Technology
Bitcoin ordinals will remain a critical component of the Bitcoin network as it continues to evolve and expand. As the blockchain technology advances, new methods for generating and using ordinals may emerge, leading to even greater security and transaction efficiency. The continued growth and development of the Bitcoin network will rely heavily on the security and authenticity provided by Bitcoin ordinals.
Conclusion
Bitcoin ordinals are a unique and essential aspect of the Bitcoin network, serving several critical purposes in ensuring its security and integrity. Understanding how Bitcoin ordinals work and their importance in the Bitcoin network is essential for anyone investing or transacting with Bitcoins. As the Bitcoin network continues to grow and evolve, the role of Bitcoin ordinals will become increasingly significant in ensuring the network's security and success.
FAQ
What is the future of Bitcoin ordinals and blockchain technology? As blockchain technology advances, new methods for generating and using ordinals may emerge, leading to even greater security and transaction efficiency. The continued growth and development of the Bitcoin network will rely heavily on the security and authenticity provided by Bitcoin ordinals.
Can Bitcoin ordinals be changed or modified? No, once a block is created, its ordinal numbers cannot be changed or modified, ensuring the authenticity and security of each transaction within the block.
How do Bitcoin ordinals enhance transaction security? Bitcoin ordinals provide a unique identifier for each transaction, making it nearly impossible for hackers to manipulate the transaction history or attempt to double-spend Bitcoins.
Can Bitcoin ordinals be used in other blockchain networks? Bitcoin ordinals are unique to the Bitcoin network and cannot be directly used in other blockchain networks. However, other blockchain networks may have similar mechanisms to ensure transaction authenticity and prevent double-spending.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28doulas.club
A full catalog of all Brazilian doulas with data carefully scrapped from many websites that contained partial catalogs and some data manually included. All this packaged as a Couchapp and served directly from Cloudant.
This was done because the idea of doulas was good, but I spotted an issue: pregnant womwn should know many doulas before choosing one that would match well, therefore a full catalog with a lot of information was necessary.
This was a huge amount of work mostly wasted.
Many doulas who knew about this didn't like it and sent angry and offensive emails telling me to remove them. This was information one should know before choosing a doula.
See also
-
 @ eac63075:b4988b48
2024-09-14 10:06:38
@ eac63075:b4988b48
2024-09-14 10:06:38A privacidade do usuário na internet tornou-se um tema central na era digital atual. Com o aumento das preocupações sobre como os dados pessoais são coletados, armazenados e utilizados, legislações como a AB 3048 da Califórnia emergem para fortalecer a proteção dos dados dos usuários. Neste contexto, navegadores como o Brave posicionam-se como defensores proativos da privacidade, enquanto gigantes como o Google enfrentam desafios para alinhar seus modelos de negócio com essas novas diretrizes. Este artigo técnico analisa como o Brave e o Google diferem em sua abordagem à privacidade do usuário, especialmente em relação à legislação emergente.
Controle Global de Privacidade (GPC)
Brave: Implementação Proativa do GPC
O Brave foi um dos primeiros navegadores a implementar e suportar o Global Privacy Control (GPC). Ativado por padrão há quase quatro anos (até 2024), o GPC permite que os usuários sinalizem automaticamente aos sites sua preferência em não ter seus dados vendidos ou compartilhados. Esta funcionalidade está em total alinhamento com a intenção da AB 3048, que busca reforçar as escolhas de privacidade dos usuários no nível do navegador. Ao adotar o GPC antecipadamente, o Brave demonstra um compromisso em capacitar os usuários no controle de sua privacidade digital, sem depender exclusivamente de legislações para impulsionar essas mudanças.
Google: Adaptação Reativa às Demandas de Privacidade
Por outro lado, o Google não tem sido tão entusiasta em integrar ou ativar por padrão recursos como o GPC em seus serviços. A introdução de legislações como a AB 3048 pode pressionar a empresa a implementar controles de privacidade mais robustos. No entanto, o modelo de negócio do Google é amplamente baseado em publicidade e dados dos usuários, o que muitas vezes o coloca em desacordo com medidas de privacidade mais rigorosas. A abordagem do Google tende a ser mais reativa, implementando mudanças quando exigido por lei ou diante de pressão pública significativa.
Filosofia de Privacidade e Funcionalidades
Brave: Privacidade como Pilar Central
O Brave foi construído com a privacidade como foco principal. Por padrão, ele bloqueia anúncios e rastreadores, reduzindo significativamente a quantidade de dados coletados durante a navegação. Além disso, oferece um modo de navegação privada integrado com o Tor, proporcionando anonimato aprimorado. O Brave também desenvolveu seu próprio mecanismo de busca, o Brave Search, que prioriza a preservação da privacidade. Uma característica única é o sistema de recompensas em Basic Attention Tokens (BAT), que incentiva os usuários a visualizar anúncios respeitadores da privacidade, enfatizando o consentimento e a transparência.
Google: Equilíbrio Entre Serviços Personalizados e Privacidade
O Google Chrome, embora ofereça configurações de privacidade, não bloqueia anúncios ou rastreadores por padrão, exigindo que os usuários instalem extensões para obter funcionalidade semelhante. O modelo de receita do Google depende significativamente da publicidade direcionada, que necessita da coleta de dados do usuário. Embora o Google tenha feito avanços na melhoria da privacidade do usuário, como a eliminação gradual de cookies de terceiros, seu modelo de negócio central muitas vezes entra em conflito com o espírito de legislações de privacidade como a AB 3048.
Dados do Usuário e Publicidade
Brave: Minimização da Coleta de Dados
Por padrão, o Brave minimiza a coleta de dados e não armazena informações de navegação de uma forma que possa ser diretamente vinculada ao usuário. Esta abordagem está em consonância com a AB 3048, que visa limitar a venda ou compartilhamento de informações pessoais. Ao reduzir a coleta de dados ao mínimo necessário, o Brave reforça o controle do usuário sobre suas informações pessoais.
Google: Dependência de Dados para Eficácia Publicitária
O ecossistema do Google é projetado para reunir dados do usuário com o objetivo de aprimorar sua plataforma publicitária. Embora o Google tenha introduzido recursos de privacidade e ofereça algum nível de controle ao usuário, sua reação a legislações como a AB 3048 provavelmente envolverá a adaptação de seus sistemas existentes para cumprir os requisitos legais, ao mesmo tempo em que busca manter a eficácia de sua publicidade baseada em dados.
Suporte Público e Legislativo
Brave: Alinhamento com Defensores da Privacidade
Ao acolher a AB 3048, o Brave alinha-se com defensores da privacidade e usuários preocupados com os direitos sobre seus dados. Esta postura reforça sua marca como um navegador que coloca a privacidade em primeiro lugar, não apenas como um recurso, mas como um valor fundamental incorporado em sua arquitetura e serviços.
Google: Navegando Desafios Regulatórios
O Google pode perceber legislações restritivas de privacidade como um desafio complexo, dado seu vasto ecossistema de serviços que dependem de dados do usuário. Embora a empresa cumpra as legislações, sua posição pública pode enfatizar mais o equilíbrio entre a privacidade do usuário e a oferta de serviços personalizados, em vez de abraçar plenamente leis de privacidade restritivas.
Conclusão
Em um cenário digital onde a privacidade do usuário é cada vez mais valorizada, o Brave destaca-se por sua abordagem proativa e centrada no usuário. Sua filosofia e design intrínsecos estão em harmonia com legislações de privacidade como a AB 3048, e suas funcionalidades refletem um compromisso genuíno em dar aos usuários controle sobre suas informações pessoais.
O Google, apesar de adaptar-se às tendências e legislações de privacidade, enfrenta desafios mais complexos devido ao seu modelo de receita baseado em publicidade direcionada. A necessidade de coletar dados para manter a eficácia de seus serviços coloca a empresa em uma posição onde deve constantemente equilibrar os imperativos regulatórios com suas estratégias de negócio.
Para os usuários, a escolha entre o Brave e o Google Chrome pode depender de suas prioridades pessoais em relação à privacidade e à personalização dos serviços. Enquanto o Brave oferece uma experiência focada na proteção dos dados e no controle do usuário, o Google continua a fornecer serviços altamente integrados e personalizados, alimentados por dados coletados dos usuários.
À medida que legislações como a AB 3048 entram em vigor, será interessante observar como essas empresas e outras no setor tecnológico ajustarão suas estratégias. A tendência indica um movimento em direção a práticas que colocam a privacidade do usuário em primeiro plano, seja por convicção ou por conformidade regulatória. Independentemente do motivo, os maiores beneficiários serão os usuários, que terão maior controle e transparência sobre seus dados pessoais no ambiente digital.
-
 @ dc652bee:6154e7d0
2024-09-14 10:06:10
@ dc652bee:6154e7d0
2024-09-14 10:06:10Big eyes, big excitement! Join the fun and see what surprises await you in this thrilling game! 🎉👀 #memefi#hamsterkompat#blum http://facebooksz.lnkiy.in/Bigeyes_bot
-
 @ 502ab02a:a2860397
2024-09-14 08:26:05
@ 502ab02a:a2860397
2024-09-14 08:26:05
YakiHonne คือแพลทฟอร์ม long form ที่ผมมักใช้ประจำในการทำบทความยาวๆ มาวันนี้ได้เจอคุณเวนดี้ ที่งาน Thailand Bitcoin conference 2024 รู้สึกดีใจมากๆ
siamstr
-
 @ 1f698bd4:68d58e60
2024-09-13 23:27:37
@ 1f698bd4:68d58e60
2024-09-13 23:27:37"Mr. Tentmaker, it was nice living in this tent it was strong and secure and the sun was shining and the air was warm. But, Mr Tentmaker, it’s scary now. My tent is acting like it’s not going to hold together. The poles seem weak, and they shift with the wind. An a couple of the stakes here wiggled loose from the sand, and worst of all, the canvas has a rip. It no longer protects me from the beating rain or the stinging flies. Its scary in here, mr. Tentmaker. Last week I was sent to the repair shop and some repairman tried to path the rip in my canvas. It didn’t help much though, because the patched pulled away from the edges and now the tear is worse. What troubled me most, Mr. Tentmaker, is that the repairman didn’t seem to notice I was still in the tent. They just worked on the canvas while I shivered inside. I cried out once, but no one heard me. I guess my first real question is: Why did you give me such a flimsy tent? I can see by looking around the campground that some of the tents are much stronger and more stable than mine. Why Mr. Tent maker, did you pick a tent of such poor quality for me? And even more important, what do you intend to do about it?
God speaks: Oh little tent dweller, as the Creator and Provider of tents, I know all about you and your tent, and I love you both. I made a tent for myself once, and I lived in it on your campground. My tent was vulnerable too, and some vicious attackers ripped it to pieces while I was still in it. It was a terrible experience, but you’ll be glad to know they couldn’t hurt me. In fact, the whole occurrence was a tremendous advantage because it is this very victory over my enemy that frees me to be a present help to you. Little tent dweller, I am now prepared to come and live in your tent with you, if you will invite me. You will learn as we dwell together that real security comes from my being in your tent with you. When the storms come, you can huddle in my arms and I’ll hold you. When the canvas rips, we will go to the repair shop together. But someday, little tent dweller, your tent will collapse, for I have only designed it for temporary use. When it does, you and I will leave together. I promise not to leave before you do. And then, free of all that would hinder or restrict, we will move to our permanent home and together forever rejoice and be glad."
By Roselyn Aronson
-
 @ 1739d937:3e3136ef
2024-09-13 21:09:24
@ 1739d937:3e3136ef
2024-09-13 21:09:24This is the seventh in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
I was told recently that my update walls of text are too much. So, I'll try to keep things concise this week. 😅
This week has been all about building the reference implementation, which is quickly becoming a full-fledged client instead of just a reference implementation. I've not quite gotten to the MLS portion of the client yet but it does already support multiple accounts (including ephemeral accounts) and loads legacy (NIP-04) chats and full contact lists. So far, I've not implemented NIP-104 so there's not yet any updates to the MLS spec or other dependencies.
If you've got experience with using messengers in hostile environments (authoritarian regimes, you've been de-platformed, etc.) please get in touch. I'd love to hear more about what you'd like to see in a communication tool.
In the meantime, I'll be over here in the corner coding with my headphones on. 👨💻
Onward and Upwards!
-
 @ 3eacaa76:bac66fe4
2024-09-13 20:43:20
@ 3eacaa76:bac66fe4
2024-09-13 20:43:20!!! Attention !!! BANGER DROP just landed on @Wavlake ! #remixculture
Funny enough that today is a day - 9/11. Maybe coincidence, maybe not. This mashup is the result of playing around mixing amazing banger tunes with proper truth-telling vocals some loops and filthy delay fx.
I created kind of my personal #Manifesto according to world issues we're facing nowadays. Still, not many people can't see this. We are early so #fuckdabanks .
Let's build on Love and Respect - We can do this. Those fuckers can't take our spirit and knowledge, so use it against them.
Avoid bullshit at any price, don't be a fucking twat and ignorant.
...and always remember to stay humble. !!!
FreePalestine
wavlake #music #remix #sound
agora #anarchy #action
2140army ----> we are commin, we are everywhere

~~~~LISTEN HERE~~~~ --->
https://wavlake.com/track/959ddd10-823d-4f55-9176-5617cc791f2e
Please share this tune world wide. Spread da vibe to da roof,

TNX for Support
MadMunky
-
 @ 361d3e1e:50bc10a8
2024-09-13 18:57:17
@ 361d3e1e:50bc10a8
2024-09-13 18:57:17Cancer characteristic of adults, sharply affects young people as well. The reasons.
cancer #health #medicine #unitedkingdom #study #research #truth
-
 @ 6bae33c8:607272e8
2024-09-13 18:09:34
@ 6bae33c8:607272e8
2024-09-13 18:09:34I went 1-4 last week, and I didn’t deserve any better. I had the Giants and Browns on the wrong side of blowouts, and the favored Falcons who lost outright to the Steelers. The only close games were the Dolphins (I lost) and the Cardinals (I won.)
But while the 1-4 leaves me less margin for error, I’m not sweating it too much. Week 1 is always a crapshoot because you’re making assumptions on limited current information.
The main hazard for Week 2 is overusing the information from Week 1, i.e., we have only a little more information for 2024
My Picks:
 Lions -7 vs Buccaneers
Lions -7 vs BuccaneersThis is my least favorite of the five. I was stuck on four and had to pick a final one. The Bucs looked good last week at home against a soft Washington team, but I’ll sell them high. The Lions at home should move the ball at will and get some pressure on Mayfield.
Seahawks -3.5 at Patriots
The Patriots were able to hide Jacoby Brissett with a lead in Week 1, and Brissett did a good job managing the game. But if the Seahawks score some points — which they should — Brissett will have to do more and get exposed. Maybe someone on the Seahawks (unlike the Bengals) can tackle Rhamondre Stevenson too.
Steelers -2.5 at Broncos
Bo Nix looked overwhelmed to me last week, and the Steelers defense is pretty good. Justin Fields is a wild card, plenty of upside and downside, but this is a good spot where he won’t have to do much to keep up with a substandard Broncos offense.
Texans -6.5 vs Bears
Caleb Williams has to play better than in Week 1, but this line seems so small for a game in Houston I feel like I must be missing something.
Falcons +6.5 at Eagles
Kirk Cousins looked bad last week, but I’ll buy low on a Falcons team that needs to get going and sell high on the Eagles after a big Week 1 win in Brazil.
-
 @ a03b38f8:2c7ce1f0
2024-09-13 16:28:42
@ a03b38f8:2c7ce1f0
2024-09-13 16:28:42Your phone is not your friend
Your phone is not your friend. It is a filthy little snitch that tells anyone who asks where you are, what you are doing, and who you are doing it with. You can obscure and hide some things through the use of privacy respecting software like encrypted communication apps, Tor pathways using Orbot, or the base OS like Graphene but metadata and geolocation is still very loud and very present. It is built into the infrastructure of how cell phones work. Your phone is tracked at all times through every cell tower area you pass through logging your IMEI and by extension your phone number and identity. This data is logged and saved forever by companies who use and sell it for corporate surveillance and post Patriot Act give it to police and government agencies warrantlessly.
Fine, I will just turn it off then. Nice try, but unless the battery can be removed it still tracks you. You didn't think it was weird that Find My Phone still works even if the phone was off?
Luddites are not off the hook. That dumb phone or flip phone is tracked just the same and since it will not run encrypted communications you are screaming out the content of every call or text and not just the metadata.
OK, I will get a burner phone or anonymous SIM card not tied to my identity. Better but not bullet proof. This is great for use and toss but if you continue to use it multiple times, around other devices that are tied to you or your social network, or take it to your home, work, or any location associated with you then it will be doxxed. Once doxxed all past information associated with it becomes now linked to you.
Metadata, Profile, and Network
Your network is very easily known and built up over time. Who are the contacts saved in your phone. Who do you interact with. Who do you call, text, email, DM, or follow on social networks. Who do you never contact but your geolocation overlaps with them often. Now look at all those contacts and who do they have a network with. A giant spider web of connections. If by 7 degrees of Kevin Bacon you have a shady contact in your network then you may get more scrutiny than you may realize.
You are spilling metadata everywhere you go along with your geolocation. Time stamps, who you contacted, how long did you talk to them, which app was used when, internet searches, map app searches, etc. People are creatures of habit and over time this metadata builds a pretty good profile on you.
Phone becomes active around 7am when they wake up. Scans social media and news sites for usually 30 minutes. Assume they are taking a shower because the phone is on but not being used until 8am most week days. Travels to coffee place on the corner most mornings and then goes to their place of work. Between 9:30 and 10:30am they again scan social media and news sites for a solid 10 minutes, probably their bathroom schedule. During lunch they frequent these locations with these people.
You get the point. This profile, plus your geolocation history, plus your network paints a pretty complete picture on you. Surprisingly it is not what you do but when you do something different that gets attention.
There was a big protest last night that we are not happy about. We already have a list of everyone who took their phones with them at that geolocation and timestamp. We run a algorithm looking for simple patterns. John is usually at a restaurant eating with friends during this time but strangely his phone was left at home and turned off during that time frame. Did anyone in his network go to the protest that we have already confirmed? Anyone in his network follow the protest Facebook page, or have a deviation from their usual pattern such as their phone being somewhere dormant when it is usually active during this time?
What can you do?
You can choose to do nothing. You can just live your life with the awareness that you are being tracked and profiled, maybe work to limit how much metadata you are spilling out to the universe. If you are a activist, a oppressed minority, live in a oppressive regime, or your country suddenly becomes oppressive this might not be an option.
Randomize or maintain your profile. This is hard but not impossible. Make your profile and habits so chaotic that any deviation is not a deviation. Most people cannot do this but if you are a couch surfing, different place constantly, new friends and new activities on the daily agent of chaos then maybe this is a option. On the opposite extreme maybe you are very regimented person so be aware of that and always stick to your routine. If you want to go to that protest but are usually home doom scrolling youtube during that time then set your phone to no sleep mode and set up to watch a long playlist of youtube videos left at home while you go to the protest.
Home phone only. Maybe you decide to have a home phone only, no not a landline, but a actual smart device that can utilize encrypted communications services but never leaves the house. This could potentially save you a lot of money on data plans, texts, and minutes if you don't buy a network plan and just use VOIP on your home WIFI. Or maybe you have a very minimum network plan and when you leave the house you either take it with you in a Faraday bag or have a secondary device that lives in a Faraday bag that only comes out for emergencies and to check in. Just be aware that the time in and out of the Faraday bag is part of your profile.
No Phone. You can have no phone whatsoever. This will not work for most people in the modern age but if you have a extreme risk profile then this might be the extreme option you need.
How do you survive with no phone or only a home phone?
Just some alternatives and some ideas. You can still buy WIFI only devices that have no network connection and / or stay in airplane mode. Old MP3 players for music and podcasts while on the go. Old phones that you can download maps to for navagation and use VIOP services in WIFI hotspots.
Emergency Communication and Go Bag
Prepper culture has given us all sorts of bags: bug out bags, get home bags, never coming back bag, and go bags. I define go bags as very small, light weight, and compact bags or kits. They carry very minimum, bare necessary gear, and ideally are so small that you actually have it on you, in your purse or computer satchel or car all of the time. Emergency communication will be part of this. This is when the burner phone, purchased with cash out of town, and stored in a Faraday bag all the time shines. It has no connection to you and has no history of use. It is a have but hope to never use oh shit device.
If you are the activist, the whistle blower, the oppressed that they could come after at any time, or the journalist that investigates corruption, organized crime, or terrorism then you need this.
I will cover go bags in more details later, probably in a key note.
Always forward, GHOST
-
 @ 6ad3e2a3:c90b7740
2024-09-13 15:58:12
@ 6ad3e2a3:c90b7740
2024-09-13 15:58:12This is the story of our time.
The Emperor was scammed by fake weavers, who used a clever trick: They posed as experts in their craft and declared their work invisible to simpletons. In other words, if you did not go along with the scam, it was because you were stupid or of low character. Or, in modern parlance, you were a conspiracy theorist or an anti-vaxxer.
The story applies to so many facets of present narrative — from Joe Biden’s transparently declining cognitive capacity to the preposterously phony war on “disinformation,” there is stiff competition for the best example. But if I had to choose, it would be the “safe and effective” mRNA shots — they check all the boxes: veneration of “experts”, political and business interests masquerading as “The Science” and disparagement of those who were skeptical as stupid, selfish, childish and evil. Any questioning of the safety or efficacy of the mRNA shots could get you attacked by angry online mobs, deplatformed from social media or even fired from your job.
Why are people going along with the “safe and effective” narrative in the face of an unprecedented number of adverse effects, the sketchy track record of large pharmaceutical companies in putting profits above safety, the rush of these products to market more quickly than any prior vaccine, the fact it has not been updated to reflect the new strains, its quickly-waning efficacy such that multiple boosters are already needed in fewer than 18 months, the fact it doesn’t stop (and may increase) the spread and the relatively mild nature of the virus for those under 50 who don’t have pre-existing conditions? Surely, this emperor’s pale, flaccid gluteus maximi are flapping about in public view.
There are certain conditions under which people are especially likely to pretend the naked emperor is dressed, all of which have been met in this case:
-
Many powerful people are pot-committed to “safe and effective.”
-
Everyone knows powerful people are committed.
-
Everyone knows that everyone knows powerful people are committed.
Every elected official who required mandates, every corporation who forced people to get the shot as a condition for employment, the corporate news media, its on-air hosts, executives and board members, every doctor who advised it, many parents who gave it to their kids, every person who shamed others for not going along — and there were many — heads of state, the CDC, the WHO, etc. are pot committed. (Pot-committed is a poker term for when someone has put such a large percentage of his chips into a pot there is virtually no way he can fold his hand.)
If the mRNA shot were shown to be unsafe, the liability, both legally (I know they received a waiver under the EUA, but fraud, for example, would invalidate that), reputationally and worse (criminal prosecutions might be warranted, given it was mandated) would be catastrophic for them. In other words, many of the world’s most powerful people have a lot to lose if the mRNA shots were shown to have harmed and/or killed thousands of healthy young people who were at minuscule risk from covid itself. They will not easily be persuaded this happened, and they have massive incentives to destroy anyone making headway in persuading others. There are powerful forces who need you to view the emperor as clothed.
The second condition is that everyone is well aware of this. Any researcher contemplating speaking out or going deeper into the data to that end knows he could be blackballed, cut off from funding and any prospect at a career in science or academia. Any person who speaks up knows he could lose his job, get deplatformed or run afoul of the soon-to-be-created Bureau of Disinformation. In fact, you would expect the powerful to create just such a bureau under these conditions — when they have too much to lose should the word get out.
Finally, it’s not simply that everyone knows, but that everyone knows that everyone knows, i.e., per Ben Hunt, it’s common knowledge that you don’t screw with the pharmaceutical cartels and those who do their bidding. It’s not just you who are deterred, but you know everyone else has a similar deterrent. People who blow the whistle therefore expect to be ridiculed, destroyed and tarred as conspiracy theorists and also don’t expect their friends and colleagues to come to their aid.
With these three conditions present, we can all hail the incredibly safe and effective mRNA treatments are a miracle! Thank God we have them and are finally able to get out of this pandemic! The emperor has such a wonderful suit of clothes!
In the story, it took a child to blurt out the obvious, that the emperor was exposing his sagging, unsightly posterior. Interestingly, once he did, everyone else acknowledged the obvious, but the emperor — and members of his procession, who were going along — went on with the show. They were in too deep to back out.
I suspect that’s going on now — the child has noticed, word is getting out. They are desperately trying to shut it down with the most Orwellian measures (Bureau of Disinformation!) They will not succeed, but lasting damage has been done, and more will be inflicted before it’s over. The biggest question now is the lengths to which the emperor’s minions will go — creating a ministry of truth is extreme, but that pales in comparison to, say, starting World War III.
There are other reasons for a world war too — the collapse of the giant global debt bubble and the fallout therefrom — but in both cases the stakes are nearly infinite for those responsible, given how much damage has been done to the average person. We’d be wise not to underestimate the risks they’d run to avoid accountability.
-
-
 @ 361d3e1e:50bc10a8
2024-09-13 15:38:50
@ 361d3e1e:50bc10a8
2024-09-13 15:38:50Biden and Kamala and then Trump walk into the hall with the same people - see how they were greeted
biden #harris #kamalaharris #trump #usa #politics
-
 @ 8d34bd24:414be32b
2024-09-13 15:09:18
@ 8d34bd24:414be32b
2024-09-13 15:09:18I’ve recently had discussions with several people about the deity of Jesus Christ. They did not believe Jesus was God. I believe that the Bible claims Jesus is God and is part of the trinity (3 persons in one God). I know the 3-in-1 nature of God is confusing and hard to understand, but who wants to worship a God that is totally understandable by our human and mortal minds? I want to worship a God who is so awesome that we, the creatures, cannot fully comprehend Him because He is so much more than we have ever seen or imagined.
Now let’s go through multiple Scriptural evidences that Jesus is God. I don't want you to take my word that Jesus is God. I want you to believe it because the Bible says it and therefore God says it.
The Basic Claims of Jesus
Let’s start with the basics.
In John 10:30 Jesus says "I and the Father are one.”\ \ This sure sounds like Jesus is claiming to be God. I know some people claim that this is just Jesus saying that He is one with God or that they have the same goals. I find this interpretation to be hard to believe because I think Jesus speaks clearly and the most obvious interpretation is usually the intended meaning especially when you are speaking of God’s word. He created man and created the ability to communicate. I don’t believe He would ever speak unclearly or in a way that would lead people to blasphemy. The most obvious interpretation of what Jesus meant is that He is one with God.
"If you had known Me, you would have known My Father also; from now on you know Him, and have seen Him.”\ Philip *said to Him, “Lord, show us the Father, and it is enough for us.” Jesus said to him, “Have I been so long with you, and yet you have not come to know Me, Philip? He who has seen Me has seen the Father; how can you say, ‘Show us the Father’?" (John 14:7-9) {Emphasis Mine}
Jesus says knowing Him is knowing the Father and if you have seen Him you have seen the Father. This can only be true if they are one. Some may say that Jesus is just saying that seeing Him is like seeing God the Father because they are acting in agreement, but this once again is not the most obvious interpretation and I do not believe that God the Father or Jesus would speak in a misleading or unclear manner that could lead people astray.\ \ Even back in Genesis there is reference to the trinitarian nature of God. Genesis 1:26a says, "Then God said, ‘Let Us make man in Our image, according to Our likeness’" God refers to Himself in the plural. There are lots of other similar references in the Old Testament. This is early evidence of the trinitarian nature of God that was not clearly revealed until the New Testament (just as His plan for salvation was not revealed until the New Testament).
"Jesus answered them, “I showed you many good works from the Father; for which of them are you stoning Me?” The Jews answered Him, “For a good work we do not stone You, but for blasphemy; and because You, being a man, make Yourself out to be God.” Jesus answered them, “Has it not been written in your Law, ‘I said, you are gods’? If he called them gods, to whom the word of God came (and the Scripture cannot be broken), do you say of Him, whom the Father sanctified and sent into the world, ‘You are blaspheming,’ because I said, ‘I am the Son of God’? If I do not do the works of My Father, do not believe Me; but if I do them, though you do not believe Me, believe the works, so that you may know and understand that the Father is in Me, and I in the Father.” (John 10:32-38) {Emphasis Mine}
In this passage the Jews accuse Jesus of "blasphemy; and because You, being a man, make Yourself out to be God.” Jesus is being accused of claiming to be God, but Jesus does not deny being God. He says He does His miracles "so that you may know and understand that the Father is in Me, and I in the Father.” Jesus continues to claim to be God. Even if it is possible to explain Jesus’s claim “that the Father is in Me, and I in the Father” could mean that they have the same goals, it would be incomprehensible for Jesus to make an unclear statement that sounds like a claim to be God if He wasn’t while being accused of claiming to be God. If He isn't God, then He is guilty of blasphemy and can't save anyone. He doesn't allow people to think He is a good man, a prophet, or a teacher, but not God.1
Jesus’s biggest claim to be God is probably:
Jesus said to them, “Truly, truly, I say to you, before Abraham was born, I am.” (John 8:58)
Jesus started His statement with “Truly, Truly” (literally Amen, Amen). This repetition is used in Hebrew literature as an emphasis to mean pay attention to this statement. Then He claims “before Abraham was born, I am.” This is a doubly stunning statement because Abraham had died more than a thousand years before Jesus was physically born and because “I am” is what God told Moses to call Him at the burning bush.
Then Moses said to God, “Behold, I am going to the sons of Israel, and I will say to them, ‘The God of your fathers has sent me to you.’ Now they may say to me, ‘What is His name?’ What shall I say to them?” God said to Moses, “I AM WHO I AM”; and He said, “Thus you shall say to the sons of Israel, ‘I AM has sent me to you.’ ” (Exodus 3:13-14)
Jesus claimed the exalted name of God for Himself while claiming to exist since before Abraham. If Jesus is good, then Jesus must be God.
The Example of Godly Men and Angels
Let’s look at how angels and godly people react when accused of being or believed to be God.
When Paul & Silas were preaching in Lystra, the people thought they were gods because of the miracles they were performing through God’s power. Their response made it crystal clear that they were not to be worshipped.
But when the apostles Barnabas and Paul heard of it, they tore their robes and rushed out into the crowd, crying out and saying, “Men, why are you doing these things? We are also men of the same nature as you, and preach the gospel to you that you should turn from these vain things to a living God, who made the heaven and the earth and the sea and all that is in them. (Acts 14:14-15) {Emphasis Mine}
They didn’t reply that they were God’s messengers or working through God’s power and will. They said, “why are you doing these things? We are also men of the same nature as you.” There was no lack of clarity and they cleared up the misunderstanding as fast as possible.
When Peter was sent to Cornelius in answer to Cornelius’s prayer, Cornelius fell down to worship Peter, but Peter instantly made it clear that this was wrong.
When Peter entered, Cornelius met him, and fell at his feet and worshiped him. But Peter raised him up, saying, “Stand up; I too am just a man.” (Acts 10:25-26) {Emphasis Mine}
There was no mistake in his response that would allow anyone to think he was god. Peter gave God alone the glory.
We can even look at the example of an angel sent by God when John mistakenly fell at the angel’s feet to worship him:
Then he said to me, “Write, ‘Blessed are those who are invited to the marriage supper of the Lamb.’ ” And he said to me, “These are true words of God.” Then I fell at his feet to worship him. But he said to me, “Do not do that; I am a fellow servant of yours and your brethren who hold the testimony of Jesus; worship God. For the testimony of Jesus is the spirit of prophecy.” (Revelation 19:9-10) {Emphasis Mine}
The angel would not allow anyone to worship him even though he was a great messenger of God.
Jesus’s Response to Worship
Let’s contrast these responses to Jesus’s responses.
One of the synagogue officials named Jairus came up, and on seeing Him, fell at His feet and implored Him earnestly, saying, “My little daughter is at the point of death; please come and lay Your hands on her, so that she will get well and live.” And He went off with him; and a large crowd was following Him and pressing in on Him. (Mark 5:22-24) {Emphasis Mine}
Notice that Jesus did not rebuke Jairus for falling at His feet. He went to help him with the ultimate miracle, healing his servant.
But after hearing of Him, a woman whose little daughter had an unclean spirit immediately came and fell at His feet. Now the woman was a Gentile, of the Syrophoenician race. And she kept asking Him to cast the demon out of her daughter. And He was saying to her, “Let the children be satisfied first, for it is not good to take the children’s bread and throw it to the dogs.” But she answered and *said to Him, “Yes, Lord, but even the dogs under the table feed on the children’s crumbs.” And He said to her, “Because of this answer go; the demon has gone out of your daughter.” (Mark 7:25-29) {Emphasis Mine}
This woman fell at Jesus’s feet and called Him Lord (Adonai), but Jesus did not correct her. He gave to her her request because she believed in Him.
In the same way:
Therefore, when Mary came where Jesus was, she saw Him, and fell at His feet, saying to Him, “Lord, if You had been here, my brother would not have died.” (John 11:32) {Emphasis Mine}
Mary also fell at Jesus’s feet and called Him Lord without being corrected. Jesus accept this worship because He rightly deserved the worship and being called Lord because He is God. He confirmed His right to have people fall at His feet because He followed it up with raising Lazarus from the dead.
In this next passage, a man didn’t just fall at Jesus’s feet or call Him Lord, this man worshipped Jesus.
Jesus heard that they had put him out, and finding him, He said, “Do you believe in the Son of Man?” He answered, “Who is He, Lord, that I may believe in Him?” Jesus said to him, “You have both seen Him, and He is the one who is talking with you.” And he said, “Lord, I believe.” And he worshiped Him. And Jesus said, “For judgment I came into this world, so that those who do not see may see, and that those who see may become blind.” (John 9:35-39) {Emphasis Mine}
This man believed that Jesus was Lord and God and worshipped Him as such. Jesus did not reprimand this man for worshipping him instead of God. He accepted the worship and rebuked the hard hearted Pharisees that were in attendance.
When Jesus was walking on water past the boat holding his disciples, and Peter called out to Him. Jesus called Peter out to join Him. When Peter began to sink in unbelief, Jesus rescued him and calmed the sea. Then:
When they got into the boat, the wind stopped. And those who were in the boat worshiped Him, saying, “You are certainly God’s Son!” (Matthew 14:32-33) {Emphasis Mine}
This is yet another example of Jesus being worshipped and accepting the worship rather than rebuking them for worshipping a false god. If Jesus was just a man. This would be sin, but 2 Corinthians 5:21 says of Jesus, “He made Him who knew no sin to be sin on our behalf, so that we might become the righteousness of God in Him.” If Jesus is sinless, He has to be God because He accepted the worship of people.
In the Ten Commandments:
“You shall have no other gods before Me.\ “You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, (Exodus 20:3-5) {Emphasis Mine}
God makes it perfectly clear that nobody can be worshipped other than Himself. The fact that Jesus repeatedly allows people to fall at His feet and worship Him means He is either God, a blasphemer and the worst of sinners, or a madman. He has not left us any other options.
There are multiple additional examples of Jesus being worshipped and accepting worship.
Right after being raised from the dead:
And behold, Jesus met them and greeted them. And they came up and took hold of His feet and worshiped Him. Then Jesus said to them, “Do not be afraid; go and take word to My brethren to leave for Galilee, and there they will see Me.” (Matthew 28:9-10) {Emphasis Mine}
When His disciples “took hold of His feet and worshiped Him,” His response was “Do not be afraid” instead of “Do not worship me.”
When they saw Him, they worshiped Him; but some were doubtful. And Jesus came up and spoke to them, saying, “All authority has been given to Me in heaven and on earth. Go therefore and make disciples of all the nations, baptizing them in the name of the Father and the Son and the Holy Spirit, teaching them to observe all that I commanded you; and lo, I am with you always, even to the end of the age.” (Matthew 28:17-20) {Emphasis Mine}
Jesus’s response to being worshipped is to say that He has “All authority … in heaven and on earth” and to tell them to “observe all that I commanded you.” If He was only a godly man, he would have rebuked the worshippers not talked about His authority and commands.
While He was blessing them, He parted from them and was carried up into heaven. And they, after worshiping Him, returned to Jerusalem with great joy, and were continually in the temple praising God. (Luke 24:51-53) {Emphasis Mine}
I think I’ve have given plenty of examples to show that Jesus accepted worship and therefore is either God or a blaspheming sinner. No good man or Godly teacher would ever allow another to worship him without rebuking them.
The Word Made Flesh
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men.... And the Word became flesh, and dwelt among us, and we saw His glory, glory as of the only begotten from the Father, full of grace and truth. John testified about Him and cried out, saying, “This was He of whom I said, ‘He who comes after me has a higher rank than I, for He existed before me.’ ” For of His fullness we have all received, and grace upon grace. For the Law was given through Moses; grace and truth were realized through Jesus Christ. " (John 1:1-4, 14-17) {Emphasis Mine}
“In the beginning was the Word” refers to before time and space began. This refers to God, the first cause of all things that exist.
The Word "was with God" and "was God" and "All things came into being through Him" (aka He is creator). These verses are explicitly saying that the Word is God and implying He is God since He is the creator.
At the end of the verse it is made clear who “The Word” is. John is referring to Jesus Christ as “The Word.” John the Baptist also refers to Jesus as God when he talks of His higher rank and that Jesus existed before John (Other gospels say John was physically born first, so this refers to Jesus existing well before His physical birth).
The Bible clearly teaches that Jesus is God and I am seriously concerned that anyone who denies Jesus’s deity will be one of those referred to in this passage:
Many will say to Me on that day, ‘Lord, Lord, did we not prophesy in Your name, and in Your name cast out demons, and in Your name perform many miracles?’ And then I will declare to them, ‘I never knew you; depart from Me, you who practice lawlessness.’ (Matthew 7:22-23)
If you are one of those who believes that Jesus is only a good man, a good teacher, a prophet, or a righteous man created for God’s purpose, I beg you to do like these Christians who were praised for their actions:
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11)
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
FYI, I’ve included this extended passage without commentary because it is an excellent passage describing the trinity and including God the Father, God the Son, and God the Holy Spirit.
8Philip *said to Him, “Lord, show us the Father, and it is enough for us.” 9Jesus *said to him, “Have I been so long with you, and yet you have not come to know Me, Philip? He who has seen Me has seen the Father; how can you say, ‘Show us the Father’? 10Do you not believe that I am in the Father, and the Father is in Me? The words that I say to you I do not speak on My own initiative, but the Father abiding in Me does His works. 11Believe Me that I am in the Father and the Father is in Me; otherwise believe because of the works themselves. 12Truly, truly, I say to you, he who believes in Me, the works that I do, he will do also; and greater works than these he will do; because I go to the Father. 13Whatever you ask in My name, that will I do, so that the Father may be glorified in the Son. 14If you ask Me anything in My name, I will do it.
15 “If you love Me, you will keep My commandments.
16 I will ask the Father, and He will give you another Helper, that He may be with you forever; 17that is the Spirit of truth, whom the world cannot receive, because it does not see Him or know Him, but you know Him because He abides with you and will be in you.
18 “I will not leave you as orphans; I will come to you. 19After a little while the world will no longer see Me, but you will see Me; because I live, you will live also. 20In that day you will know that I am in My Father, and you in Me, and I in you. 21He who has My commandments and keeps them is the one who loves Me; and he who loves Me will be loved by My Father, and I will love him and will disclose Myself to him.” (John 14:8-21) {Emphasis Mine}
This post is scheduled to publish on Sunday, September 15th on my Trust Jesus Substack, but is being published early on nostr due to a discussion that occurred here.
-
 @ 87730827:746b7d35
2024-09-13 12:42:31
@ 87730827:746b7d35
2024-09-13 12:42:31As an avid RSS user, I've always been on the lookout for the perfect feed reader. Recently, I made the switch from FreshRSS to Miniflux, and I wanted to share my experience with the Nostr community.
Why Miniflux?
Miniflux caught my attention as a simpler alternative to FreshRSS. Don't get me wrong, FreshRSS is a powerful tool, but sometimes less is more. Here's why Miniflux has won me over:
- Minimalist Design: Miniflux strips away the unnecessary, focusing on what matters most - your feeds.
- Speed: With its lightweight architecture, Miniflux is blazing fast, even with a large number of feeds.
- Third-party App Support: This is where Miniflux really shines. The ecosystem of third-party apps is robust and growing.
- Easy Self-Hosting: If you're into self-hosting like me, Miniflux makes it a breeze.
- Vim Keybindings: As a Vim enthusiast, I absolutely love that the Miniflux web client comes with default Vim keybindings. This feature significantly speeds up my workflow and makes navigation a breeze.
Third-Party Apps: The Icing on the Cake
Speaking of third-party apps, I've been experimenting with MiniFlutt (https://github.com/docmarty84/miniflutt). It's a Flutter-based mobile client for Miniflux that brings the simplicity of the web version to your pocket. MiniFlutt is just one example of the diverse app ecosystem surrounding Miniflux. Whether you prefer mobile, desktop, or web-based clients, chances are you'll find something that suits your needs.
Final Thoughts
If you're looking for a no-frills RSS reader that does its job exceptionally well, give Miniflux a try. The transition from FreshRSS was smooth, I was able to import all my feeds from an OPML file and I haven't looked back since. Remember, the best RSS reader is the one that fits your workflow. For me, Miniflux's simplicity and third-party app support make it a winner. What's your go-to RSS solution?
-
 @ e27ae11e:e0c36580
2024-09-13 12:35:33
@ e27ae11e:e0c36580
2024-09-13 12:35:33Choosing colors involves a thoughtful process that takes into account various factors to ensure that the final palette achieves the desired effect, whether it’s for design, branding, or art. Here’s a detailed breakdown of the process: 1. Understand the Purpose Before diving into color selection, it's crucial to understand the purpose of the color scheme. Are you designing a brand identity, creating a website, painting a room, or something else? Each scenario may have different requirements and goals. For instance, branding colors need to align with the brand’s personality and values, while interior colors might focus on mood and comfort. 2. Know Your Audience Consider the preferences and cultural meanings associated with colors for your target audience. Different colors can evoke various emotions and associations. For example, blue often represents trust and calmness, while red can signify excitement and urgency. Understanding your audience’s cultural context and psychological responses to colors can help you choose a palette that resonates with them. 3. Research Color Theory Color theory is a foundational aspect of choosing colors. It involves understanding how colors interact with each other and the effects they produce. Key concepts include: Color Wheel: A circular diagram of colors arranged by their chromatic relationship. It helps in understanding primary, secondary, and tertiary colors. Complementary Colors: Colors opposite each other on the color wheel, such as blue and orange. They create high contrast and stand out. Analogous Colors: Colors next to each other on the color wheel, such as blue, teal, and green. They create harmony and are pleasing to the eye. Triadic Colors: Three colors evenly spaced around the color wheel, such as red, yellow, and blue. They offer vibrant contrast while maintaining balance. Monochromatic Colors: Variations of one hue, including tints and shades. They provide a cohesive and unified look. 4. Create a Mood Board A mood board is a visual tool that helps you gather inspiration and visualize how different colors work together. Collect images, fabric swatches, color samples, and any other materials that represent the mood or aesthetic you're aiming for. This can help you see how colors interact and narrow down your choices. 5. Consider Color Psychology Color psychology examines how colors affect human behavior and emotions. For instance: Red: Stimulates energy and urgency, often used in promotions or to grab attention. Blue: Conveys trust, calm, and professionalism, making it popular for corporate and tech brands. Green: Represents nature, growth, and tranquility, often used in eco-friendly and health-related contexts. Yellow: Evokes warmth and optimism but can be overwhelming if overused. By incorporating color psychology, you can choose colors that align with the emotional response you want to elicit. 6. Select a Base Color Start by choosing a base color that will dominate your design. This color sets the tone and direction for the rest of the palette. The base color should align with the overall goal and purpose of your project. 7. Build a Color Palette With your base color in mind, build a color palette by selecting complementary, analogous, or triadic colors that work well together. Use color schemes and tools, such as Adobe Color or Coolors, to experiment with different combinations. Ensure that the palette is balanced and harmonious. 8. Test Your Colors Once you have a palette, test how the colors look in real-world scenarios. For digital designs, check how they appear on various screens and under different lighting conditions. For physical spaces, sample paint colors or materials in the actual environment to see how they look at different times of day and under various lighting conditions. 9. Consider Accessibility Accessibility is a crucial factor, especially in digital design. Ensure that your color choices provide enough contrast for readability and usability. Tools like the WebAIM Contrast Checker can help you evaluate whether your color combinations meet accessibility standards. 10. Refine and Finalize After testing, refine your color choices as needed. Make adjustments based on feedback, functionality, and aesthetic preferences. Finalize the color palette that best meets your goals and resonates with your audience. 11. Document Your Palette Once you’ve settled on a color palette, document it for consistency. Create a color guide or style guide that includes color codes (such as HEX, RGB, or CMYK values) and usage guidelines. This ensures that the colors are used consistently across different applications and mediums. 12. Stay Current Color trends can evolve, so it’s important to stay informed about current color trends and how they might influence your choices. However, prioritize timelessness and relevance to your specific project over fleeting trends. Conclusion The process of choosing colors is a blend of creativity, psychology, and practical considerations. By understanding the purpose, audience, and principles of color theory, you can create a color palette that effectively communicates your message, evokes the desired emotions, and enhances the overall design.
-
 @ 7579076d:1bbfcb19
2024-09-13 12:00:20
@ 7579076d:1bbfcb19
2024-09-13 12:00:20Amber 2.0.0
- New sign keys, to use this version you will need to first backup your accounts, uninstall the old version and install the new version
- When you not configured a notification type Amber will ask you to configure and default to direct connection to relays
- Check if is a valid relay before adding it when changing the default relays or adding a relay to a application
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v2.0.0.txtandmanifest-v2.0.0.txt.sigare in the current directory) with:bash gpg --verify manifest-v2.0.0.txt.sig manifest-v2.0.0.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v2.0.0.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 8e7e2128:25e34fd1
2024-09-13 10:07:37
@ 8e7e2128:25e34fd1
2024-09-13 10:07:37Have you ever dreamed of a non-invasive way to improve your skin's appearance without the pain and downtime of traditional treatments?
Look no further than Healite LED Therapy. This innovative technology harnesses the power of light to rejuvenate and revitalize your skin, leaving you with a radiant and youthful glow. What is Healite LED Therapy?
Healite LED Therapy utilizes light-emitting diodes (LEDs) to deliver specific wavelengths of light to the skin. These wavelengths penetrate the skin's layers, stimulating cellular activity and promoting healing. Unlike lasers, which can be intense and potentially damaging, LED therapy is gentle and safe for most skin types.
How Does Healite LED Therapy Work?
When LED light is applied to the skin, it triggers a series of biological processes that can improve skin health. These processes include:
Increased collagen production: Collagen is a protein that gives the skin its structure and elasticity. LED therapy can stimulate the production of collagen, helping to reduce wrinkles and fine lines. Improved blood circulation: LED light can increase blood flow to the skin, providing essential nutrients and oxygen to the cells. This can help to improve skin tone and texture. Reduced inflammation: LED therapy can help to reduce inflammation, which is often associated with skin conditions like acne and rosacea. Enhanced wound healing: LED therapy can accelerate the healing process of wounds, including cuts, scrapes, and surgical incisions.The Benefits of Healite LED Therapy
Non-invasive and painless: Healite LED Therapy is a completely non-invasive treatment that requires no needles or incisions. The procedure is generally comfortable and painless. Safe for all skin types: Unlike some other skin treatments, LED therapy is suitable for all skin types, including sensitive skin. Effective for a wide range of skin concerns: LED therapy can be used to address a variety of skin issues, including acne, wrinkles, fine lines, sun damage, and uneven skin tone. Minimal downtime: Most people can resume their normal activities immediately after a Healite LED Therapy treatment. Long-lasting results: While the results of LED therapy may vary depending on individual factors, many people experience long-lasting improvements in their skin's appearance.Who is a Good Candidate for Healite LED Therapy?
Individuals who are seeking to improve their skin's health and appearance may be good candidates for Healite LED Therapy. This treatment is particularly effective for those who:
Have acne or acne scars Experience premature aging or wrinkles Have sun damage or uneven skin tone Want to enhance their skin's overall radianceIf you're looking for a gentle, effective, and non-invasive way to rejuvenate your skin, Healite LED Therapy may be the perfect solution for you.
-
 @ 733a7b6e:9c4a4b9b
2024-09-13 10:03:04
@ 733a7b6e:9c4a4b9b
2024-09-13 10:03:04Lorem ipsum
Lorem ipsum dolor sit amet, consectetur adipiscing elit[^1]. Sed non risus. Suspendisse lectus tortor, dignissim sit amet, adipiscing nec, ultricies sed, dolor. Cras elementum ultrices diam. Maecenas ligula massa, varius a, semper congue, euismod non, mi. Proin porttitor, orci nec nonummy molestie, enim est eleifend mi, non fermentum diam nisl sit amet erat. Duis semper. Duis arcu massa, scelerisque vitae, consequat in, pretium a, enim. Pellentesque congue. Ut in risus volutpat libero pharetra tempor. Cras vestibulum bibendum augue. Praesent egestas leo in pede. Praesent blandit odio eu enim. Pellentesque sed dui ut augue blandit sodales. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Aliquam nibh. Mauris ac mauris sed pede pellentesque fermentum. Maecenas adipiscing ante non diam sodales hendrerit.
Ut velit mauris, egestas sed
Ut velit mauris, egestas sed, gravida nec, ornare ut, mi. Aenean ut orci vel massa suscipit pulvinar. Nulla sollicitudin. Fusce varius, ligula non tempus aliquam, nunc turpis ullamcorper nibh, in tempus sapien eros vitae ligula. Pellentesque rhoncus nunc et augue. Integer id felis. Curabitur aliquet pellentesque diam. Integer quis metus vitae elit lobortis egestas. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Morbi vel erat non mauris convallis vehicula. Nulla et sapien. Integer tortor tellus, aliquam faucibus, convallis id, congue eu, quam. Mauris ullamcorper felis vitae erat. Proin feugiat, augue non elementum posuere, metus purus iaculis lectus, et tristique ligula justo vitae magna.
[^1]: Ut velit mauris, egestas sed.
-
 @ 6bae33c8:607272e8
2024-09-13 08:22:42
@ 6bae33c8:607272e8
2024-09-13 08:22:42That was annoying. I have Tua in one league and of course he got concussed on one of his two scrambles. At least he had the decency to have 145 passing yards and a TD when he did it. But the bigger problem is the Dolphins offense. Why not some play action on 1st-and-10 every now and then. It was just run-run-obvious passing down with a totally immobile “eggshell plaintiff” QB. I know they lost Terron Armstead, but the game was already salted away at that point.
The other crazy thing was they kept De’Von Achane in with an ankle injury during garbage time. The guy weighs 188 pounds, but they’re tacking on carries like he’s John Riggins. As an Achane owner I’ll take the production, but it made little sense.
Three silver linings: I have no shares of Josh Allen. I have no shares of Tyreek Hill. And Tyler Bass’ shank cost whoever was using him too.
-
Allen played well but had to do very little, and James Cook even got a goal-line carry for the TD.
-
Cook had only 11 carries and one target, but somehow scored three times on a team where the QB vultures most of the goal-line carries. Enjoy it, but don’t get used to it.
-
Dalton Kincaid looked good, breaking tackles every time he touched the ball, and it was nice to see them get him involved early on short screens. But game flow wasn’t in his favor, and he wasn’t used much after that.
-
Khalil Shakir is probably the team’s No. 1 WR, but it’s hard to rely on him. Curtis Samuel, if it wasn’t obvious before, is a cut. Keon Coleman isn’t playable now either, borderline cut, but in NFFC I’d give him more time.
-
Tua’s first pick wasn’t his fault, but the booth bent over backwards to excuse him for the second one (blamed the WR) and then he was of course at fault for the pick six. He’s accurate from the pocket and has good touch, but now he’s concussed for the 25th time, so who knows going forward? That it’s so dangerous for him to run (and even more so now) is a serious handicap. He has 10 days to get ready for Week 3, but given his history, I’m not sure he plays. Skylar Thompson was terrible in relief too.
-
Achane is just a fantasy points producing machine whenever he’s playing. Mike McDaniel apparently doesn’t worry about pitch counts, either.
-
Jaylen Wright had a couple carries for loss, but looked okay. Definitely a hold despite the ugly box score.
-
Jonnu Smith who I drafted in a few places (and unfortunately dropped in one or two) is the Dolphins third or fourth WR (depending on how you classify Achane.) He looked nimble, and if/when Tua returns has a floor in that offense now.
-
Another dumb thing McDaniel did was go to the up-back (Alec Ingold) twice in a row on fourth and short. The first time, fine, you have the element of surprise. But the Bills were waiting for it the second time, and it got stuffed.
-
Hill and Waddle have to get more targets, and they will. But if Thompson is the QB, it’s obviously a big downgrade for both.
-
-
 @ a012dc82:6458a70d
2024-09-13 08:07:27
@ a012dc82:6458a70d
2024-09-13 08:07:27Table Of Content
-
The Self-Custody Movement
-
Impact on Exchange Supply
-
Future Implications
-
Conclusion
-
FAQ
The exchange supply of Bitcoin has been witnessing a steady decline as more people opt for self-custody solutions. This trend has caught the attention of investors and analysts alike, as it could have significant implications for the cryptocurrency's price and overall market dynamics. In this article, we will explore the reasons behind this shift and what it means for the future of Bitcoin.
The Self-Custody Movement
In recent years, the self-custody movement has gained traction as a growing number of Bitcoin users have started to move their funds from centralized exchanges to private wallets. This allows users to maintain full control over their digital assets, as opposed to relying on third parties to secure their funds.
1. Security Concerns One of the primary reasons people are shifting to self-custody is the increasing number of security breaches and hacks that have plagued cryptocurrency exchanges. By holding their Bitcoin in private wallets, users can mitigate the risk of losing their funds due to exchange vulnerabilities or fraudulent activities.
2. Financial Sovereignty Another driving force behind the self-custody movement is the desire for financial sovereignty. By holding their own private keys, users can exercise complete control over their digital assets, eliminating the need for intermediaries like banks and exchanges.
Impact on Exchange Supply
As more users withdraw their Bitcoin from exchanges and move them to private wallets, the exchange supply decreases. This can lead to several potential consequences:
1. Reduced Selling Pressure With fewer Bitcoins available for trading on exchanges, the selling pressure is likely to decrease, which could result in a more stable price or even upward price movements.
2. Enhanced Liquidity As the exchange supply diminishes, the available liquidity for trading can be affected, which might lead to increased volatility in the market.
3. Strengthened Decentralization The shift towards self-custody can also contribute to the decentralization of the Bitcoin network, making it more resistant to censorship and control.
Future Implications
The decline in exchange supply is an important trend to watch, as it may have several implications for the future of Bitcoin:
1. Growing Adoption of Decentralized Exchanges (DEXs) As users become more security-conscious and seek financial sovereignty, we may see an increased adoption of decentralized exchanges. These platforms allow users to trade directly from their private wallets, thereby reducing the need for centralized intermediaries.
2. Enhanced Security Measures by Centralized Exchanges In response to the growing demand for self-custody, centralized exchanges may be forced to improve their security measures and provide better custody solutions to retain users.
Conclusion
The ongoing decrease in the exchange supply of Bitcoin can be attributed to the growing adoption of self-custody solutions. As more people move their funds to private wallets, this trend is likely to impact market dynamics, liquidity, and the overall decentralization of the Bitcoin network. It is essential for investors and market participants to keep a close eye on these developments, as they will shape the future of the cryptocurrency landscape.
FAQ
Why are people moving to self-custody? The main reasons behind the shift to self-custody include security concerns due to exchange hacks, a desire for financial sovereignty, and an increasing preference for decentralized solutions.
How does the decrease in exchange supply impact Bitcoin's price? Reduced exchange supply can lead to decreased selling pressure, which could result in a more stable price or even upward price movements. However, the overall impact on price depends on various factors, such as market sentiment and demand.
What are the potential consequences of decreasing exchange supply? Some consequences of decreasing exchange supply include reduced selling pressure, enhanced liquidity, and strengthened decentralization of the Bitcoin network.
How does the self-custody trend affect decentralized exchanges (DEXs)? The growing demand for self-custody may lead to increased adoption of decentralized exchanges, as they allow users to trade directly from their private wallets without relying on centralized intermediaries.
How can centralized exchanges respond to the self-custody movement? Centralized exchanges can improve their security measures, provide better custody solutions, and integrate with decentralized services to retain users and adapt to the changing landscape.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 733a7b6e:9c4a4b9b
2024-09-13 07:36:15
@ 733a7b6e:9c4a4b9b
2024-09-13 07:36:15Lorem ipsum
Lorem ipsum dolor sit amet, consectetur adipiscing elit[^1]. Sed non risus. Suspendisse lectus tortor, dignissim sit amet, adipiscing nec, ultricies sed, dolor. Cras elementum ultrices diam. Maecenas ligula massa, varius a, semper congue, euismod non, mi. Proin porttitor, orci nec nonummy molestie, enim est eleifend mi, non fermentum diam nisl sit amet erat. Duis semper. Duis arcu massa, scelerisque vitae, consequat in, pretium a, enim. Pellentesque congue. Ut in risus volutpat libero pharetra tempor. Cras vestibulum bibendum augue. Praesent egestas leo in pede. Praesent blandit odio eu enim. Pellentesque sed dui ut augue blandit sodales. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Aliquam nibh. Mauris ac mauris sed pede pellentesque fermentum. Maecenas adipiscing ante non diam sodales hendrerit.
Ut velit mauris, egestas sed
Ut velit mauris, egestas sed, gravida nec, ornare ut, mi. Aenean ut orci vel massa suscipit pulvinar. Nulla sollicitudin. Fusce varius, ligula non tempus aliquam, nunc turpis ullamcorper nibh, in tempus sapien eros vitae ligula. Pellentesque rhoncus nunc et augue. Integer id felis. Curabitur aliquet pellentesque diam. Integer quis metus vitae elit lobortis egestas. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Morbi vel erat non mauris convallis vehicula. Nulla et sapien. Integer tortor tellus, aliquam faucibus, convallis id, congue eu, quam. Mauris ullamcorper felis vitae erat. Proin feugiat, augue non elementum posuere, metus purus iaculis lectus, et tristique ligula justo vitae magna.
[^1]: Ut velit mauris, egestas sed.
-
 @ 733a7b6e:9c4a4b9b
2024-09-13 07:24:47
@ 733a7b6e:9c4a4b9b
2024-09-13 07:24:47Ceci est une tentative de publication sur Nostr
-
 @ 1f698bd4:68d58e60
2024-09-13 03:13:26
@ 1f698bd4:68d58e60
2024-09-13 03:13:26Dear family in Christ,
We want to update you on the latest developments regarding our visa. We have finally received a six-month extension, but not the two and a half years we were hoping for.
This decision was due to an error in the dates on the documents. We are a bit frustrated because the lawyer representing us did not correct this mistake and is not taking responsibility for it. Now, we have to make a new petition to immigration to stay here for the remaining two years, which means paying the government fees again, amounting to $1,000. We have also lost the benefit of having paid the “premium" service to expedite our case, as this is considered a new application.
We ask that you continue to pray for our lawyer to accept her responsibility and cover the immigration fees. We praise God because, at least, we can stay here until March 2025 and do not have to rush back to Spain.
In the midst of these challenges, our daughter Isabel fell off her scooter on Saturday and fractured two bones in her right arm. These have been difficult days for our little one as she gets used to managing without the help of her arm, which is causing her a lot of frustration.
Besides the emotional aspect, we are facing a new financial challenge. Her appointment to get a cast is on Friday, and we need to pay $653 upfront, in addition to the costs from the emergency visit.
Lately, we have been praying a lot, asking God for direction on how to move forward as a family. Carol and I believe it is good and God's will for her to be dedicated to the family and ministry, which demands a lot of time and has been our calling from the beginning. However, we see how it is becoming increasingly difficult to stay afloat with just my income. Every unexpected expense destabilizes our ability to cover the necessary monthly expenses, and that is why we are asking for your prayers for our family’s financial provision.
We know that God’s promises are to bless His children and that the righteous will never be forsaken. Please join us in asking God for His favor and provision for this need, and for direction in our lives.
Thank you in advance for your prayers. May God bless your life with fullness of joy!
Love, Perera Family.
-
 @ 8cb60e21:5f2deaea
2024-09-12 22:00:26
@ 8cb60e21:5f2deaea
2024-09-12 22:00:26Python for Absolute Beginners
Welcome to the world of Python programming! This guide will introduce you to the basics of Python, a powerful and beginner-friendly programming language.
What is Python?
Python is a high-level, interpreted programming language known for its simplicity and readability. It's widely used in various fields, including web development, data science, artificial intelligence, and more.
Why Choose Python?
- Easy to learn and read
- Versatile and powerful
- Large community and extensive libraries
- Used in many industries
Getting Started
1. Installing Python
Visit the official Python website (https://www.python.org) and download the latest version for your operating system.
2. Your First Python Program
Open a text editor and type the following:
python print("Hello, World!")Save the file as
hello.pyand run it using the Python interpreter.Basic Python Concepts
Variables
Variables store data in your program:
python name = "Alice" age = 30 height = 1.75Data Types
Python has several built-in data types:
- Strings:
"Hello" - Integers:
42 - Floats:
3.14 - Booleans:
TrueorFalse - Lists:
[1, 2, 3] - Dictionaries:
{"name": "Bob", "age": 25}
Control Flow
If Statements
python if age >= 18: print("You're an adult") else: print("You're a minor")Loops
For loop:
python for i in range(5): print(i)While loop:
python count = 0 while count < 5: print(count) count += 1Functions
Functions help organize and reuse code:
```python def greet(name): return f"Hello, {name}!"
message = greet("Charlie") print(message) ```
Next Steps
- Practice writing simple programs
- Learn about modules and libraries
- Explore Python documentation
- Join Python communities and forums
Remember, programming is a skill that improves with practice. Don't be afraid to experiment and make mistakes – it's all part of the learning process!
Happy coding!
-
 @ 8cb60e21:5f2deaea
2024-09-12 21:56:38
@ 8cb60e21:5f2deaea
2024-09-12 21:56:38 -
 @ 361d3e1e:50bc10a8
2024-09-12 21:04:52
@ 361d3e1e:50bc10a8
2024-09-12 21:04:52https://forex-strategy.com/2024/09/12/the-end-of-normal-food-is-coming-gmo-food-will-not-be-labeled/
The end of normal food is coming - GMO food will not be labeled
food #organic #bio #politics #gmo #australia #newzealand #truth
-
 @ a03b38f8:2c7ce1f0
2024-09-12 19:16:50
@ a03b38f8:2c7ce1f0
2024-09-12 19:16:50-----BEGIN PGP MESSAGE-----
wcDMA17V9MGW3LFGAQv/erNSJ4ooO6fERifSPB0ENbX8V+XEMeoq4DXt/EyRdeBP DpettdnDboZWnaJz2g3fk6VUAeSNH+ZqKW67LSNEg/qk3L7AdcxrVji1DJhfQ8WR K3r/iQzSO8OXSWsez3yEXhmJSy6fwFS/D6kHpCcHu3wo4fipLLJ96lkMpUd0zzir JDw7atRjI7LfulDwfIuFk2hAXEDrWJkPosdZ3g9cCayfzV440WvAMN0K7pv6OQp+ I7Zxf6KsMB5hNz3yEQRJIspqaQaI7gdNqEkfkdCkTw5wfmhlyKVgukvSkrIGe6Cb WEXBpO/QKMsY4HBOiPc/Mu4i4gEQlSZxGDNiGB6AkWz7o0hEiT+ugXIdMXl/ACH6 DhBOWOr2JQtHo70z5mpiqAkbG2lFcPnSGXikCIZ1ONh/eJiM7ZbpRcPZ+Vo7veAQ 3dfrB5g32cmVteL8T9H3bL88uP06FoRqQU6YmdKtu101SpEkXzAP46NDZ0re54QA IPxCy8t1BcjAfDmtuHsW0susATLI40nPziahKfLA7iOYhpUsHT9tnZm63g1uIwGF MlT377PJydN9hTAQbxTsfNSPws8/OoHzE5UeEQehFhOKxjw0lslM3HQhsgYVN6F6 6/ileO7LsJo9UPVd5D5Qy1qGwBWKl5wZk80Io5kJlvHp3BjFDfjCsPUXmmc1Kh8J Yn6wiFzm6Ti6rBDxuZSCbcyRhebOi+ZKnkzra+4rwy5BYPArj+N0mbwUbMh+1DR5 86m683N7bOMJkOYfjXxm00PTz17usJLzfPmcqkUE9x4RC8p/huz7MmCFhnTVedOl io4RHg2iV0hgUf0ybuO49ROuEB9B/nrqpdUYiL2PVUKUkVnFRQ5XZvKr9/4pUh95 eTrLCUYP5+X1IZfoF8nHEy4D/HuHQGdtAeCADvARB0nnTphIV9YUBpCuq1MWKkBa iSWnD4X9ErodF8aGaVG2Cvh/BlMMl5CkHlzZUHJEedrFllLTZNdCgmDggduGzq5n iD2FdKz9O2MrNEbBu5o2NHOvFcs5KFFfqUeb028kOxNnTozPO5sMZJYZvlQCPBv7 eeWsM6WRPq6lB8xSZAO3yRlBa/EEvMU9k8qBq56G91dNYDUu03kS/WBzUZYoCS5e YLhpn8Jb5XP4HJdct/VPKmpzPRBzj7Xyeqc3hZdj6/uF2fMngmCt2IeNQjsZrjKQ mszv/A7huvTbU9wUdA8ssrkD4GLeg6q1a7WNBJ12SkoOK1ld+g6s6k4Z6UwSJVgc R9JtPC77A+/kyRgPJW6JdEmlZXYpagtPRP/eIt52IMByQ9s/L7HkYO/FGPMok9Yb 1X6NLh+3CQMBkscuUcUbWjsWGVrJxqQYdMBnXuvCUDILPm3NrRBUO8Y9yieG/lwT kG1d/90WrjgtGO3Bny3UgsEap2RZ/91KN8dS6+PfgqBUc8nQV7zpsxDGfvLFryFF GBLKtv6IbWw8mYqPMBrf/q8a06+TVtUkIYxlhmfxut+Zpf+o99Ph81CH90PO290M 1FxBwL7j4lqFeYoQSz9Xs6wrJ6V+F9ORwVXpPqdJGSYNcBUhk9inIo/imyhdd0rV u0V1NkepX9DmP/vRdu4e1VJJoh70XOQImfa+92DP01B6sGq5Ah1/b5/U6LOml5Nj 7kC/RPLs/R0yZ8eGZW04MuDLu3flZtkvgsw2RNutlrFyN/pdHksRa+4qgyIAY2q2 2+iGtKZ5ksTYY53WoRmnMzz3Pwkb7Vw6/ROpJB9qrSTkNtZ3DIgavXznmMGfg5Yx AcoEElg3Why65wMSUXXeenW/0UUVfyZZJhV5822I3/b9wJgkRsA2G3+Pqu4Fw3Xs OnsSRIj7Wcg3RFvld/2Su05LO8zzQKzt5+JbG689J4Mb4wc8s4/o3vgF6J8+GR7G a081oL0gStqNRAL5dgXwqdFswEpYu3mYROVjZlsM+Yw6i5JsyzDtDjyJJs6A+Jxx 0yCQ/21lkc4n3RGItFce2JVogBs+0YkL8tqDZnhtDtPJgp0t9t8L7Po55sGHnigE faBdbpVfJEU6G7qGS5/xxv9Pkw4qTTV/5ENGPybfQ4CGgLUAWkGaT1PTNa7x3i65 TDF+N5heKXOwuTg+18oCvYpGxVTDmboSaqc835dExoP1r9GZ9zgODXM9+034GNP7 DmuKnw5tyJlF7lZjXioWmer1RCFGyicsI9XaXqqYsQiAo0EZzArA5lri5cnxIa6g 6d88gkOjMV+6mGnXfpm8Cb8pl5dGmsWo7vZdoFDK5a/6ueDqp7yj20Kug672Of32 R5LUUiwr0IslCAaYwraU/Tv2PvS1JERoN1YE6clUEFaraSOO3099/duxPa5vgNbs l8tG2gyuRFtqcGEio8bUqlNnpsg2KM0Cs3SOUx7siXpQzcatx0kvffFNdt8CAsTh xLu8byxoFxlJp6meNMjSNOO37kkZ8DgjyUdwfhpCf4/Lfzox/te2ulC4/6Jccc28 rbeFTRw536IAEQYW0R+m7iL5HVmC8K0xO6k98ESo8TVSW3+gHdwkBXtuwqIl8iD5 bxnbqUtrmnfyYe32SZZVtyaUUtFjwfJ3crsdTWJmSrsd54ZNRzfs8R9ymnQEU+EW Fngulk2/NiU7Nw9rzoW6o35DsrLXFFpoNbEotVn8Pqb+8bDWwhXIY1tC0VQq6D9p 9l4s2ZB+ps2N5iGsijIvdSNNiLttZl+NFUnyQOAn+hbbb8R9GsGWam9thrdBMRNo hUSxRTgWRUqEQ6Tue8vbG+S/CylaAaryF1nz6ShRBegluI5ivyUV8MbxiSTKo2r6 MRYXGp2j4K0vADDjd2M8gwgmancszgZxjN9XTeO/xhWQ1Ed8SEI87I6ymQA7nXTm Cn5fMHdht+uOMdZ3CHOXO+YWoxsOpq60K2lkldb/Cv1s9F9gZqXC6aauPZ9un6K5 p7/1Kje7ATFgUrfcsNMuI04qobJc7QiiQJLf3yoQ64bF3GHXQmUfxJurQ9nUg0oW rETBdT4gz3eDS6ApbSXnUIV+SSbQTWCBGkqJddjYtoYTONBkZFTLg9yYdAw43+8P 9mv5Mwe5nocd2322W1zQj/npUDh1H61UQTIsZHUY66/KNprNi4PLawEFy1MpJiE0 0UT4Xhbw+3/ynIYy+ibAj71O4ymslzbz7P/zn/vR8iy8ZY8o0riMtwE8v+nBRWEs uwG/kW7vjPYA5RZkYLRz3LNnrlfiOgd7eCoFc2PU/c9NdBT0+pZQbudXiMW+eX6C FZY3oh+6heTuWF1kzyQy9RCDx43XSg/GON5Vy2pD/+24CDpscE6AObLGCWQoVYxk KQUwx85iomVWijRkWC7Nm4lTUIH8jnA5BZxyhymPbUttoUOiN+z2umtgNUfIp1L7 CwFAs0VThseHny/ra7q/5rmepP1s98ojcyBF3YD3o+Wy981R61e1v/c4L2P8iSZC LMyVSK+pWWaMLWIdFBSR8Ke/vDS1pz8GAeAdcXRQRjVw1l/aIQPXYNKJ0S6kNbQ0 IwnYdiMuOXEkhOlnFsUV1uiSN2LY6W8/Kk2cxcwheCgTkk5ibKl39VFsy9h2vxiP +ecjDnAGrR+ZJV958zrnnt7gosr2Nm/VUSlU/NbFlXE2kIhhulyd/M2GGKrj3j70 lD1HRjUjrSLrZsirdITG4VbYIIq/00K4x3hYbcY8R6ROrCJemdE4DUkDvirYZ7rU yEhbpuo2oz/KjubgPKAY9srkJ8Tv8dcZQR0c2XfpohAzl5ctv3Ai9c0LW+eePUSk RtgOnges73+WImv5rgjYv2y7eeupXgnAMcndFF490vUk3+B3F/LafsFNLSVwqJUL qhimUv+84J6/G9uG6xEc6b+4B1VMvmM7/cFmjZYRRvBxvBaOTyjP1OMe69TgKM69 H73haTEA0QEwenRxQq0tKqCo2fygK0uVkFSGQ3dRDh6QueTVRzbmopKwWrSMw3ye +NjpdRR8tBj95bTj7YvesJP7z0WqtHj6N8FJt+VY9bfAHB97oCc3QziEmdY+lpZe 37PMAY6JN2chQ8HuwPpgWe5JmhiO09w8DgYcQnOJqVl4UQulkJvti7i4VDyMY8Z+ hxiNDsb8agY03zAchgLN6cXrpall5/XDzGVBbnbnccVS/x7L0Dr940+AF6yKi1mD 0l79sqWjT5nNHmf/ni5YXfLU+4ajSHWOm4yLaqWRjTSTUh/41v9iHqQwPj4RgBZP 1/fFy4HpM5kBMSYlCFFLPrY2OFqFX8yw1HyRn39W62FETIH4CASdEF5ieJ44CWef L/TwrLaS2R0SS6Xnnhyckr8dwh86tDgxZhtruQ4unu4EiOj15PMWymI69J+Ad6jF oRfrZ/mqyi0+hfxFyoLnI5Uz/Gxza/0A7mcBiwqLrbqU9K0695u8ZCi4B3ytB0rP l6HJZuODn6sQiUta/03Yo3GabFNzTuoqQ9HerdVOyPxpRjeTjEbULdmOmnHltUIQ AlgCAXJ71nmaCazGPIVvkIC2QQSg6TxJWvAR/vF879K2NcXZfImB4OpoWGJ1vb9W BiDq1nU57jiyugxxSR3/RlZRfqpo9HPkq8qooQR1VxqfxBxV0XgxEsxs6LB2cr9g RPJ6Cys/OmOj698rjKzss+2OVbHQiXknIUgZqaAgqThVI8G5R/FNWQVM5okmodnf unTVl9eTXVkK/vrzU8iw1K4H2TCJQhFTJX9m4dE9GxnNKeH+T7D8TqtJHjkd7tUH 6+k+Ar4xZwLPB6rNHNbw+4DNDmCyJ9hXMGhCIbqn =RNR1 -----END PGP MESSAGE-----
-
 @ a03b38f8:2c7ce1f0
2024-09-12 16:49:50
@ a03b38f8:2c7ce1f0
2024-09-12 16:49:50First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-
 @ a03b38f8:2c7ce1f0
2024-09-12 16:45:51
@ a03b38f8:2c7ce1f0
2024-09-12 16:45:51Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled.
If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-
 @ 8cb60e21:5f2deaea
2024-09-12 15:47:40
@ 8cb60e21:5f2deaea
2024-09-12 15:47:40h1 Heading
h2 Heading
h3 Heading
h4 Heading
h5 Heading
h6 Heading
Horizontal Rules
Typographic replacements
Enable typographer option to see result.
(c) (C) (r) (R) (tm) (TM) (p) (P) +-
test.. test... test..... test?..... test!....
!!!!!! ???? ,, -- ---
"Smartypants, double quotes" and 'single quotes'
Emphasis
This is bold text
This is bold text
This is italic text
This is italic text
~~Strikethrough~~
Blockquotes
Blockquotes can also be nested...
...by using additional greater-than signs right next to each other...
...or with spaces between arrows.
Lists
Unordered
- Create a list by starting a line with
+,-, or* - Sub-lists are made by indenting 2 spaces:
- Marker character change forces new list start:
- Ac tristique libero volutpat at
- Facilisis in pretium nisl aliquet
- Nulla volutpat aliquam velit
- Very easy!
Ordered
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
-
Integer molestie lorem at massa
-
You can use sequential numbers...
- ...or keep all the numbers as
1.
Start numbering with offset:
- foo
- bar
Code
Inline
codeIndented code
// Some comments line 1 of code line 2 of code line 3 of codeBlock code "fences"
Sample text here...Syntax highlighting
``` js var foo = function (bar) { return bar++; };
console.log(foo(5)); ```
Tables
| Option | Description | | ------ | ----------- | | data | path to data files to supply the data that will be passed into templates. | | engine | engine to be used for processing templates. Handlebars is the default. | | ext | extension to be used for dest files. |
Right aligned columns
| Option | Description | | ------:| -----------:| | data | path to data files to supply the data that will be passed into templates. | | engine | engine to be used for processing templates. Handlebars is the default. | | ext | extension to be used for dest files. |
Links
Autoconverted link https://github.com/nodeca/pica (enable linkify to see)
Images

Like links, Images also have a footnote style syntax

With a reference later in the document defining the URL location:
Plugins
The killer feature of
markdown-itis very effective support of syntax plugins.Emojies
Classic markup: :wink: :cry: :laughing: :yum:
Shortcuts (emoticons): :-) :-( 8-) ;)
see how to change output with twemoji.
Subscript / Superscript
- 19^th^
- H~2~O
\
++Inserted text++
\
==Marked text==
Footnotes
Footnote 1 link[^first].
Footnote 2 link[^second].
Inline footnote^[Text of inline footnote] definition.
Duplicated footnote reference[^second].
[^first]: Footnote can have markup
and multiple paragraphs.[^second]: Footnote text.
Definition lists
Term 1
: Definition 1 with lazy continuation.
Term 2 with inline markup
: Definition 2
{ some code, part of Definition 2 } Third paragraph of definition 2.Compact style:
Term 1 ~ Definition 1
Term 2 ~ Definition 2a ~ Definition 2b
Abbreviations
This is HTML abbreviation example.
It converts "HTML", but keep intact partial entries like "xxxHTMLyyy" and so on.
*[HTML]: Hyper Text Markup Language
Custom containers
- Create a list by starting a line with
-
 @ 7ab1ed7a:f8e15275
2024-09-12 15:32:35
@ 7ab1ed7a:f8e15275
2024-09-12 15:32:35Summary
This article outlines an approach to handling IoT event data in Nostr, considering both replaceable and regular events. It discusses event structures, including types, units, and metadata tags, and suggests efficient ways to manage the size of data relayed through Nostr. The article also touches on the importance of maintaining privacy in IoT applications and addresses the potential challenges of scaling IoT data within the Nostr protocol.
Events
There are several possible approaches to structuring IoT event data. The following approach is being considered for use within Nostr:
Event Structure
Kind:\ The NIP (Nostr Implementation Proposal) should define both replaceable and regular event kinds. Previous PRs for IoT on Nostr NIPs defined kinds for each data type (e.g.,
30106for temperature), a more maintainable solution would be to have a limited number of kinds with data types and units defined in event tags. This would simplify management while improving long-term maintainability.Content:\ The content field will typically contain data from IoT sensors, commands, or statuses. For example, a switch could have a value of
1or0, and a temperature reading might have a value like20.Tags:\ Tags are essential for defining the data types, units, and additional metadata such as physical coordinates. These are some of the key tags that could be used:
- ["l", "type", "[data-type]"]. Describes the type of data, where [data-type] could be for example
intent,status,temperature, orlight. - ["unit", "[unit-name]"]. Describes the measurement unit where [unit-name] is for example "celsius" (
°C), "hectopascal" (hPa), or "lux".
Private Data
Using IoT on Nostr privately should be a priority. Following an approach similar to how Direct Message Volumes (DVMs) encrypt all data (as per NIP90) could work well. Encrypting IoT event data and possibly "giftwrapping" it could enhance privacy. However, this is currently out of the article's scope and requires further investigation.
Replaceable vs. Regular Events
One challenge with Nostr events is their size, especially when compared to IoT protocols like MQTT. A typical Nostr event, such as:
json {"id":"072ec5876798efb182e9083464a7d6be41b2a0e46a8336db7c550eca173e1f9b","pubkey":"0987d97ee78e6a2281d2f45aedebc3d22da346a064850ca85440c2dd104badd4","created_at":1726123555,"kind":30107,"tags":[["l","type","pressure"],["unit","hectopascal"]],"content":"1005.78","sig":"a4d65dee6d2c9aed705acebaf2c8fd4ef3411126b8de472e9d03a2a94d420bb72a64fbc307146cac56abfa0b1716f001bbc1516b1ee48bc5fa955f6a1149f42d"}is around 387 bytes. If a device sends this data to a public relay every 60 seconds, it would generate approximately 540 KB of data daily or 194 MB per year. If thousands of devices do this, relays could experience significant strain.
To address this, distinct IoT kinds could be defined for replaceable and regular events—perhaps
30107for replaceable events and9107for regular events. This would allow relay operators to manage event storage more effectively, possibly rejecting regular events that originate from npubs that are not subscribed to a paid relay.For replaceable events, relays will persist the event and replace it with a new event that is published by the same pubkey with the same kind and d tag. Defining replaceable events would allow IoT devices to publish to public relays in a manner that doesn't abuse the relay. Third-party clients or relays could "harvest" these events in real time and index them for future processing.
Example REQ for data queries
Using tags in the manner described above, querying a relay for specific information could be done with a request similar to the one shown below:
["REQ", "TMBl2WOTX5oMI8ngKKwzBhpONaH8ahanYFM0DUDmspxQ3Sf9K06zqztjTwYLV2Ul0",{"kinds": [30107], "authors": ["d0bfc94bd4324f7df2a7601c4177209828047c4d3904d64009a3c67fb5d5e7ca"], "#l": ["type", "temperature"], "limit": 2}]Event Kinds
In Nostr, event kinds are divided as follows:
-
Regular Events:\
1000 <= n < 10000or4 <= n < 45orn == 1 || n == 2. These events are expected to be stored by relays. -
Ephemeral Events:\
20000 <= n < 30000. These are not expected to be stored by relays. -
Parameterised replaceable\
30000 <= n < 40000, These events are parameterised replaceable, which means that, for each combination of pubkey, kind and the d tag's first value, only the latest event MUST be stored by relays, older versions MAY be discarded.
Conclusion
Managing IoT data on Nostr requires balancing the need for efficient data transmission with the constraints of relay storage. Distinguishing between replaceable and regular events can help optimize relay usage. Future discussions on privacy and encryption strategies are essential to ensuring secure IoT implementations on Nostr.
- ["l", "type", "[data-type]"]. Describes the type of data, where [data-type] could be for example
-
 @ e27ae11e:e0c36580
2024-09-12 15:16:08
@ e27ae11e:e0c36580
2024-09-12 15:16:08Electrical repairs are a basic piece of keeping homes protected and useful. In a spot like Bundaberg, where the weather conditions can get very sweltering and storms are successive, having a very much kept up with electrical framework is fundamental. This article will make sense of all that you want to be aware of electrical repairs in Bundaberg. We'll cover normal issues, how to distinguish them, when to call an expert, and why keeping steady over electrical maintenance is so significant. By and by, you'll have an unmistakable comprehension of what electrical repairs include and why they matter for keeping your home protected and agreeable.
** Why Electrical Repairs Are Significant**
Power drives almost everything in our homes. From the lights we use around evening time to the cooling that keeps us cool during the sweltering Bundaberg summers, power is a major piece of our lives. When something turns out badly with the electrical framework, it can lead to many issues. Some may be minor, similar to a light not turning on, yet others can be more serious, similar to a blackout or even a fire.
**Here are a few key motivations behind why electrical repairs in Bundaberg are significant: ** 1. Security: Flawed wiring or harmed electrical parts can cause flames or electric shocks. Opportune repairs guarantee that your home remaining parts ok for yourself as well as your loved ones.
-
Forestalling Greater Issues: Little electrical issues, whenever left unattended, can prompt greater, more costly repairs. Fixing minor issues early can save you from significant cerebral pains later.
-
Energy Proficiency: An electrical framework in decent shape will work all the more effectively. This implies you won't squander power, and your bills will be lower.
-
Dependability: A very much kept up with framework guarantees that your lights, machines, and different gadgets work when you really want them.
** Normal Electrical Issues in Bundaberg Homes**
In Bundaberg, homes frequently face explicit electrical issues because of the nearby environment and climate. The following are probably the most well-known issues that property holders could experience: 1. Stumbling Circuit Breakers: This is quite possibly of the most widely recognized electrical issue. An electrical switch is intended to stop the progression of power in the event that there's an excess of flow. On the off chance that it trips oftentimes, it could mean there's an over-burden in the circuit, a short out, or a ground issue. Stumbling breakers are an indication that electrical repairs in Bundaberg are required.
-
Gleaming or Darkening Lights: On the off chance that your lights flash or faint consistently, it could demonstrate a free or broken association in your wiring. This isn't something you ought to overlook, as it very well may be a fire danger.
-
Power Floods: Power floods can occur because of lightning tempests or issues with the power supply. While most floods are brief, they can harm electronic gadgets assuming that they happen often.
-
Electrical Outlets Not Working: Now and then, an outlet will quit working. This could be a direct result of a stumbled breaker or a flawed outlet. In more established homes, it could likewise be because of obsolete wiring that can't deal with present day electrical burdens.
-
Hot Electrical Outlets or Switches: In the event that you notice that your outlets or switches feel warm to the touch, this is a significant issue. It could truly intend that there's a lot of interest on the circuit, or it could show broken wiring. One way or the other, this is an indication that prompt electrical repairs in Bundaberg are required.
-
Humming Sounds: Power ought to stream quietly through your home's wiring. Assuming you hear humming commotions close to outlets, switches, or light installations, there's probable an issue with the wiring.
-
Consuming Scents: A consuming smell coming from any electrical source in your house is a crisis. It could intend that there's overheating in the wiring, which is a significant fire peril.
DIY versus Capable Electrical Repairs
It's fundamental to understand that while a couple of minor electrical issues can be dealt with by contract holders, most electrical repairs require the expertise of an approved electrical specialist. In Bundaberg, circuit repairmen are ready to manage the specific electrical challenges that go with the close by climate and system. Here is a breakdown of what you can deal with yourself and what should be given to the specialists:
** DIY Electrical Repairs**
A couple of minor electrical fixes ought to be conceivable safely by property holders. These include:
Replacing Lights: In case a light breaks down, it is easy to override it yourself. Essentially guarantee you're including the right wattage for the establishment.
Resetting Circuit Breakers: In case a breaker trips, you can reset it by switching it off and a short time later on again. In case it keeps on stumbling, regardless, you should call a circuit repairman.
Changing Outlet Covers: If an outlet cover is broken or hurt, you can displace it really with a screwdriver.
** Capable Electrical Repairs**
Most other electrical issues should be managed by a specialist. These include:
Wiring Repairs: Expecting that you suspect there's an issue with the wiring in your home, it is ideal to call an electrical technician. Dealing with wiring without the genuine data can incite electric shocks or flares.
Placing in New Outlets or Switches: Adding new outlets or switches incorporates overseeing live wires, which is unsafe if you're not experienced.
Refreshing Electrical Sheets: More prepared homes regularly need their electrical blocks moved to manage present day electrical solicitations. This is a confusing place that requires an approved circuit repairman.
Fixing Circuit Breakers: While resetting a breaker is straightforward, fixing or replacing an inadequate breaker is an errand for a trained professional.
** Why You Should Enroll an Approved Circuit analyzer in Bundaberg**
Selecting an approved circuit repairman for electrical repairs in Bundaberg ensures that the assignment is done safely and precisely. Approved circuit repairmen have the planning and experience to manage a large number of electrical repairs, from minor fixes to major redesiging position. The following are a couple of key inspirations driving why you should continually enroll an approved electrical expert:
-
Security: Electrical work is perilous if not finished true to form. Approved circuit analyzers know how to manage power safely, decreasing the bet of shocks, fires, or various incidents.
-
Code Consistence: Electrical work ought to meet close by building guidelines to ensure prosperity. Approved electrical specialists are have a lot of experience with these codes and will guarantee that all repairs truly rely upon standard.
-
Assurance: Expecting you enlist an unlicensed electrical master and something turns out gravely, your security may not cover the damage. Approved electrical specialists are ensured, so you're gotten if any issues arise.
-
Experience: An approved circuit analyzer has the data and experience to dissect issues quickly and fix them beneficially.
-
Long stretch Plans: A specialist won't simply fix the fast issue yet likewise perceive any key issues that could make future issues.
The most effective method to Pick the Right Circuit repairman in Bundaberg
With regards to electrical repairs in Bundaberg, picking the right circuit repairman for the job is significant. Here are a few hints to assist you with viewing as a solid, gifted proficient:
-
Actually look at Accreditations: Ensure the electrical technician is authorized and protected. This guarantees they are able to finish the work securely and accurately.
-
Understand Audits: Search for surveys and tributes from past clients. This can provide you with a thought of the circuit tester's dependability and nature of work.
-
Get some information about Experience: It's critical to recruit somebody who has insight with the kind of fix you want. For instance, assuming you're updating your electrical board, ensure the circuit repairman has done this sort of work previously.
-
Get Numerous Statements: It's really smart to get statements from a few circuit repairmen to look at costs. Nonetheless, don't simply go with the least expensive choice. Ensure the circuit repairman you pick is qualified and experienced.
-
Get some information about Guarantees: A few electrical experts offer guarantees on their work. This implies they'll return and fix any issues that emerge after the maintenance is finished.
** Forestalling Electrical Issues**
While electrical repairs in Bundaberg are at times undeniable, there are steps you can take to keep issues from happening in any case:
-
Ordinary Examinations: Have your electrical framework investigated by an expert no less than once at regular intervals, particularly on the off chance that your house is more established.
-
Try not to Over-burden Circuits: Be aware of the number of gadgets you that attachment into one circuit. Over-burdening can make breakers trip and can harm your wiring.
-
Supplant Old Wiring: Assuming your home has old wiring, consider having it supplanted. Present day wiring is more secure and can deal with the requests of the present electrical gadgets.
-
Use Flood Defenders: Safeguard your electronic gadgets from power floods by utilizing flood defenders.
-
Introduce Smoke Cautions: Ensure your house is furnished with working smoke alerts. This is particularly significant assuming you live in a more established home with obsolete wiring.
** End**
Electrical repairs in Bundaberg are a fundamental piece of keeping your home protected and practical. By understanding the normal electrical issues that can happen, knowing when to call an expert, and doing whatever it takes to forestall issues, you can guarantee that your home's electrical framework stays in top shape. Continuously recall, if all else fails, it's ideal to enlist an authorized electrical technician to deal with any electrical repairs. Your security and the wellbeing of your home rely upon it!
-
-
 @ dfe02069:d3e2fa29
2024-09-12 14:50:45
@ dfe02069:d3e2fa29
2024-09-12 14:50:45https://www.youtube.com/watch?v=kCE0v-SK5_c
-
 @ 09fbf8f3:fa3d60f0
2024-09-12 13:48:54
@ 09fbf8f3:fa3d60f0
2024-09-12 13:48:54图床平台
2024.09.12更新 https://img.chkaja.com/
https://im.gurl.eu.org/ 已失效 https://img.fzxx.xyz/index2 https://imgse.com/ https://img.gejiba.com/ https://imgloc.com/ https://www.superbed.cn/ https://www.helloimg.com/ https://im.ge/ https://png.cm/ https://img.ax/ https://tucdn.wpon.cn/ https://locimg.com/ https://xiray.cf/ https://pic.sl.al/ https://lvse.eu.org/ https://img.ink/
🏷 #图床 #合集
-
 @ 361d3e1e:50bc10a8
2024-09-12 12:54:05
@ 361d3e1e:50bc10a8
2024-09-12 12:54:05How did Kamala Harris manage not to look stupid at the presidential debate against Trump?
usa #vote2024 #trump #kamalaharris #debate #politics #truth #maga
-
 @ a03b38f8:2c7ce1f0
2024-09-12 12:49:56
@ a03b38f8:2c7ce1f0
2024-09-12 12:49:56Operational Security and Your Digital Life
I. Definitions
Operations security (OPSEC) is a process that identifies what information can be seen by threat actors, whether that information could be weaponized, and possible mitigation actions.
Your digital life is every interaction you have, all personal identifying, financial, and health information, your preferences, your habits, and any history that can be obtained both publicly and privately that has ever been recorded or digitized.
Your digital life is a incredibly rich field for various actors to observe, record, analyze, sell, and exploit for profit, harm, or control. Some of this information you give away without thinking (social media), some you give to one party but it is shared without your knowledge to other parties (data brokers, big tech), or it is taken without your consent (criminals, governments).
II. Threats
It would be impossible to list them all but a few examples:
Mass surveillance by governments to fight crime, terrorism, civil unrest, and control the population. This is across the board blanket information on everyone that is stored for later use from feeding algorithms for social credit systems to lists of people who are threats that need to be disappeared. The only variable is how explicit the government in question is doing it.
Corporate surveillance by public and private companies for marketing, market share, or selling for profit. Your data is incredibly profitable. Entire mega companies have built their entire business model on it like Google, Meta, and various Data Brokers. This information is collected and stored. It is then used internally, sold for profit, acquired by governments, or stolen by nefarious actors.
Criminal or Nefarious Surveillance for harm, control, or profit. This is a catch all from partners in a controlling relationship, angry ex's wanting revenge, religions and groups watching their members, terrorists and cults looking for people to recruit or indoctrinate, and foreign espionage to plain old criminals who want your information to sell to other criminals, looking for blackmail opportunities, to steal your financial or social accounts, or identity theft.
III. Mitigation
To do this properly a security self audit should be performed to determine exactly what assets you have to protect, how at risk they are, ranking their priority, and specific steps that are needed to protect them. I will detail how to do this for the average person in a later post but until then we will stick to generalities.
It is impossible to to block or hide all information all the time. Not only is it impossible but it would be exhausting to even try. This is where most people interested in privacy get confused, lost, and give up the idea of privacy because the only path they see to achieve it is living in a underground faraday cage out in the woods.
The only viable path is obscurity and compartmentlizion. Compartmentation of your devices, accounts, and digital selves is wildly misunderstood and not applied properly. Done incorrectly this can be disastrous if you are too casual with something that you thought was hidden or putting a spotlight on yourself by attempting to be obscured.
IV. Tactics For Everyone
Common advice I give to everyone. I don't care what your thoughts are on privacy and security, you should be doing this.
-
Do not give your personal email or phone number to anyone except friends and family. This just opens you up to spam, phishing attacks, and an identifying tracer. Use a email alias service or a throw away email account to give to stores and online accounts. Get a VOIP number for that dating app or service quote. When your real number rings, recieves texts, or get a email you know it is from someone you know and trust.
-
Use cash locally if you can and for everything else get a virtual debit or credit card with a spending limit or fixed amount. Do you really need your entire paycheck, emergency savings, life savings tied to a single card / account? Are you really entering your real credit card or banking information into a random website to buy something? Even if it's not a scam site, how well are they protecting it while in transit or storage? You will probably get the money back in case of fraud but why feed the beast and besides it's a total hassle to get your accounts frozen, wait for reimbursement, open and change accounts. Just avoid it. For extra credit you can use visa gift cards purchased with cash to obscure your financial transactions if you choose. Every financial transaction doesn't have to be public record.
-
Stop using unencrypted phone calls and SMS texts. Switch to encrypted options such as Signal or SimpleX and make anyone who wants to have contact with you reach out to you on it. Even if you "have nothing to hide" there is no reason for you to broadcast every personal conversation, comment, or shared meme with Ma'bell, the government, and anyone else listening and recording. Seriously, just stop.
V. Compartmentation of Your Digital Selves
I will keep this very high level as this article has already run longer than I intended but will cover this in much greater detail in the future.
You can break down all digital activities and interactions into several broad categories or digital selves. Then build separate systems for use in each category depending on the activity and need. The trick is to preplan what activities go where. Using the wrong account on the wrong system means they are now burned. Letting the systems overlap and contaminate each other then you risk exposing anything ever done on those systems. The separation can be accomplished with multiple accounts and devices, isolated virtual machines, or operating systems that enable compartmentation such as Qubes OS or Tails.
VI. Breakdown
- Public
This is the default. This is you. Your real name, address, and details. This is unavoidable and would be weird and attract attention if you didn't have one.
Use this for any KYC activities that you have to log into such as taxes, bank accounts, utility bills, etc. Clearnet only, you have nothing to hide.
Awareness: If it has to be public then put your best foot forward. Only show them what you want them to see and make it good and boring. Blend into the crowd of normies not important enough to pay attention to.
- Private No logins to KYC services. Traffic routed through a VPN. Use of sudo anonymous account names. You are Neo, not Mr. Anderson.
Use for most social media that is not public facing. Shopping and browsing that would be embarrassing or misunderstood if made public. Encrypted to protect against criminals and looky loos. A good default if people just don't need to know.
Awareness: Do not be confused by the word private. The goal is to make it to difficult, to expensive, or just not worth the effort to determine exactly who you are and what you are doing but it's not impossible. Only use this with the knowledge that someday it might get doxxed. That potential only increases with time and frequency of use of accounts. Not to be used for anything that could be considered illegal or has the potential to get you fired or cancelled.
- Anonymous Only single use non KYC logins. Single purpose accounts and names that are burned after achieving that purpose. Traffic routed only through Tor. Encryption by default.
Use if you are a whistle blower, freedom fighter, activist, or for shady activities.
Awareness: Be very careful and deliberate with this system as to not accidentally compromise it with something that would have been better served by a different system. Rotate and clean accounts and systems often. Don't carry stuff over after a cleaning to a new system. Reusing names and handles is how people get busted.
- Nemo
Nemo doesn't exist. There is no record that they ever existed. Only amnesiac systems are even used and never a login. If files or traces are left behind they are encrypted, hidden, and have plausible deniability.
Enjoy anon, more to come.
-
-
 @ a03b38f8:2c7ce1f0
2024-09-12 12:43:32
@ a03b38f8:2c7ce1f0
2024-09-12 12:43:32If you want privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs.
Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see.
Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be.
Your anonymous nym that only uses tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes.
Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
-
 @ a03b38f8:2c7ce1f0
2024-09-12 12:35:02
@ a03b38f8:2c7ce1f0
2024-09-12 12:35:02-----BEGIN PGP MESSAGE-----
wcDMA17V9MGW3LFGAQwApZmuIzibdT7//BF/vtZEwRrrR/PXU4a35/TeW/W1b/BR T7y92hPns4QoITKxjluRCRIuupEbQ4rEA8BcOrqDtNFa/TcHIiNzV9xx15NQRHcj i8A5Ktega688adUoPpHcXd39EOXo+E4MhstUHyqQLkdQSHDHEqsns9ZwoDDo/A7l MFm/0X6UQU4dPweoLq4M5NkFoWu0CUFZvTaLIzxjKLPP+O/4E9EE11X8wKTaoJge j/hP6nHvuT5Ky9MLqc3uGxjIwJYjlDL7+dIxyxMo9IZRdBGTtkuWG/+j0bUQUhle KMgQcfgi3ul28245eZpGKSZkpGphwUchx2RZzWeH584dASysAFqHhqwqlAt9/gER dhJ5RkQMikr3UF7edAe7CkKHlXxpe9Cy4v0V7p7qsft5d0+un3r9C29Ud3BPEPkY /5ppip3Hs/Ef8QPSrwbk/TDWFDlU5Xvnrw/mRzaoVImmz/DESQXV+NEWcMoAgfdx X4lQv/1rL8w68wXsBGZq0sQ4ARCEEhACRyWO9d4FCn6J6LHKYteony562WnucqSM tOd0p03COpkE+ji0eAT03mtofTR3NHFfkUqi9L3yyjCcnxcNH7x3f+Bu1vUHwPUo q9y8VqACU/KlAjYL8wK2URtPN3xV792enygDakMNXNVt/SDkpyoPBOjbyjajnwF+ YhViBGRpRnzBHdKMX68/uG3AgCgYELxUvpBLsvHgCVjl8DY7j0ltWfk/7rzzkFp2 LtTngaw7gZzA2jEIMSTXpQZ3WLJK2e1fQWl5UTHfXv1y3OyoWegkevlYCI+A3Rwi YkJObkT6TG8QkKUPoBi0CzNeeF5ns8oBhv8NrQJ9UehbulSpPEIdK2VlesV8sHiS MYGUn1RtEGdLA9kR0+GcegoF8c6ft6MBTQmYk3ysXjnCxZ0MG4Gj2Ba38ZHsoiJQ c7r/a92sFRV75N8Ob6BDuviEX1q77rXuEdG+QbV8nVcEf8TU76PUY0EXZVzpg2UV aXLjH7b/rJCCNy/wE8rIEAeEUqU4LE/DBGRgLFtxj1E7ybFrhETeS5mkrs8V5/Fi XCXZoA7zo8E1oLJT+irFcEmTA+eraij3ZEG2TTjDq0cMQBpXKwhcxgbyyM638aQX 6WqyJH6JVs14V7T+w/NjJLGwpy9yiO/trsFHP+N7/iEAEmC22IonSWLtRmT0W4iF MOHseJQ72q3yjgy+jNt1OkSN6SuiCPXKNR2YtBd410QIkPVBGoc1OKHGsOIuLAxY 5WQN3pudN++Cxj6Ap6Ia5DF/PHVZOyXMXnCUp5GoUhV6xcgqp6i8CeVigQPrEN68 vQhmrx47VAUP3aeyjeQF4MTiXn+06IJXfnmxKKghfrfv+uuBq9Yefx505MBBDAXQ /OOBTNLnK7V2K2rXckKl8aD/jz1qjbM4gfV1MCcqKDqZr/4HCyNhT5RCDLOwifyL MODcVIKoyNyEYt5xLc2QtXYhFQS1vx19vcNex90E/U5R1tHzG2HeXQI48NTNJ6Qj eVeVqHsTMtfRLxLZ7bt0GF3NSaDTdDYcFk374fAjafPW6vmqbmV4mBsIUdq7LaXA JtQKF/UyARgYe/zkqL5kFrl1TCuh54wK54wtuOBA6WewxVHYYaiWmys8H2YxHXFN 7nqMUnNr6WU+nYLOoWSXVcyfF+d9tjz98f11cwmXcQNvTL4YYeFwy2ctw5oV4Fkv kxpaoiKjAJ2Hf4+pogidYonh4wmczxTDpE/4XYB7nOdmsvz341lTv6YpZETXWuZg EiClOTgMrdRwR7QBSvFriLKAeV05Ws38gGOODZxAteI8IIngKogJXfY5MhsDIdQE mENXiprdYcznLZkqqG2X3j1E3bzmWfmvnbGtwCS9VNMjyS8bZKwbJKHEFtl7LCzx xWJWq58P3LBr3MHqmZdOht7APfwZdnWeakpkfXY7ec2x/xavL3bA/iO4UzK7sPR6 70/5/YzwTYUxwUhyKsgH1JoAdF+iQfw9P0h6iWrKxK079MipTcsOjKVJcQBmcGCK TMhOi9DX7Gv+3a/4crNU+KDkHaNnfGC/D5yrpQcjbfWTsLnw0Yz+qSNyEzHeYBPw 2Z4lc2kH+tPNqVAkjimFbPe65yQMcsMNKGMF1Ga5N1bRidq21J4/Wfpr5IA4Komr Wzi0/Lodo9oZUrvGlbP6YAJO825e6ws6OMRbXbzU9or6HN0xdWDkkY4x =vOl0 -----END PGP MESSAGE-----
-
 @ 6bf975a0:65de1244
2024-09-12 12:12:26
@ 6bf975a0:65de1244
2024-09-12 12:12:26План темы
- Происхождение термина «мультимедиа»
- Варианты определений «мультимедиа» в разные десятилетия;
- Свойства мультимедиа;
- Web 1990-х и технологические возможности для публикации мультимедийного контента;
- Первые российские и зарубежные мультимедийные проекты СМИ. Их возможности и ограничения;
- Появление термина «медиаконвергенция», его определение.
- Уровни конвергенции
- Превращение традиционных СМИ в конвергентные, мультимедийные: кейсы
- Мультимедийный лонгрид, мультимедийный сторителлинг. Определения
- Кроссплатформенность в СМИ в 2010-2020 годы. Что поменялось в форматах работы мультимедийных редакций.
- Трансмедийный сторителлинг: определение. Свойства трансмедиа
-
 @ 6bf975a0:65de1244
2024-09-12 11:49:05
@ 6bf975a0:65de1244
2024-09-12 11:49:05Впервые термин «мультимедиа» появился в 1960-х годах, он использовался для описания экстравагантных для того времени театрализованных шоу, использовавших разные виды и формы представления информации: слайды, кино, видео, аудио фрагменты, световые эффекты и живую музыку. В 1970-е им также называли световые шоу, сочетавшие музыку, кинофрагменты и графические проекции.
В это время слово мультимедиа использовалось для описания проектов современного искусства, в контексте театральных постановок и в других творческих сферах, но не в медиа. Несмотря на появление первых кабельных каналов и первые шаги Интернета, СМИ оставались жестко поделенными на ТВ, радио и периодическую печать.
Развитие компьютерных технологий также ознаменовало начало ассоциации мультимедиа с цифровыми форматами. Разработка видеоигр, таких как Pong от Atari в 1972 году, продемонстрировала ранние примеры сочетания графики и звука, намекая на потенциал для более сложных мультимедийных опытов в будущем.
1980-е годы ознаменовались значительным сдвигом, когда персональные компьютеры стали более доступными. Выпуск Apple II в 1977 году и IBM PC в 1981 году ввели цветную графику и заложили основу для мультимедийных вычислений. Macintosh, запущенный в 1984 году, включал графический пользовательский интерфейс (GUI) и был одним из первых систем, эффективно интегрирующих звук и графику, делая мультимедиа более удобным и интерактивным.
В 1990-х годах термин «мультимедиа» обрел своё современное значение. В 1993 году первое издание «McGraw-Hill» опубликовало статью «Multimedia: Making It Work», где сообщалось:
Мультимедиа – это различные комбинации текста, графики, анимации, звука и видео, которые передаются с помощью компьютера. Когда вы позволяете пользователю (зрителю вашего проекта) контролировать эти элементы, то мультимедиа приобретает интерактивность, становится интерактивным мультимедиа. Когда вы предусматриваете структуру соединения элементов – навигацию, интерактивным мультимедиа становится гипермедиа.
Про мультимедиа стали говорить в контексте компьютерных игр, электронных энциклопедий, но по-прежнему не СМИ
Российский интернет в 1990-е годы
Первые российские веб-сайты появились в начале 1990-х. 19.10.1990 года доменная зона появилась у Советского Союза — SU, а 7 апреля 1994 года считается датой рождения российского интернета, когда был зарегистрирован домен .RU. Первые сайты российских СМИ, которые появились в 1990-е годы, представляли собой исключительно текстовые страницы, в лучшем случае, с очень небольшими графическими файлами и небольшими фотографиями.
Первым российским изданием, запустившим свой сайт в Интернете, считается «Учительская газета», которая открыла свой сайт в апреле 1995 года. Этот сайт стал первым в Рунете, представляющим печатное СМИ, и изначально на нем размещались оцифрованные выпуски газеты, полностью совпадающие с офлайн-версией.
Радиостанция «Эхо Москвы» запустила онлайн-вещание в 1998 году. Это стало значимым шагом в развитии радиовещания в России, так как «Эхо Москвы» было одной из первых радиостанций, предложивших свои передачи в интернете, что позволило расширить аудиторию и обеспечить доступ к контенту для слушателей за пределами традиционного радиоэфира.
Первые российские онлайн-издания Lenta.ru и Gazeta.ru были запущены в 1999 году. Lenta.ru была создана в рамках проекта ФЭП (Финансово-экономическое партнерство) и быстро стала одним из ведущих новостных сайтов в России. Gazeta.ru также начала свою работу в том же году, предлагая читателям новости и аналитические материалы в формате интернет-издания.
Пропускная способность каналов связи в то время была ещё незначительной, поэтому о тяжелом мультимедийном контенте, сочетавшем бы в себе графику, видео и качественный звук, пока говорить не приходилось. Он стал появляться уже в 2000-е годы.
2000-е годы и медиаконвергенция
Расцвет конвергентной журналистики пришёлся на период социальных медиа, родившихся из идей Web 2.0 нулевых годов. Воедино сошлись:
- скоростной доступ к интернету;
- доступность мультимедийных устройств: смартфонов, цифровых камер и т.д.;
- доступность компьютерной техники;
- большое количество платформ в вебе для лёгкой публикации без знания кода;
- «освобожденное авторство» социального веба;
Воплощением идей медиаконвергенции стали мультимедийные лонгриды, ставшие демонстрацией возможностей редакций конца 2010-х годов.
Трансмедиа и мультиплатформенность 2020-ых
-
 @ 79008e78:dfac9395
2024-09-12 11:16:45
@ 79008e78:dfac9395
2024-09-12 11:16:45" ผมตื่นเต้นที่จะประกาศเปิดตัว NWS ครั้งแรก นี่เป็นคำตอบของการเชื่อมต่อออกไปยังโลกของอินเตอร์เน็ต โดยใช้ NOSTR เข้าไปแทรกระหว่าง transport layer และ network layer ที่อยู่บน TCP/IP โมเดล NWS นั้นจะเข้ามาช่วยให้การสื่อสารระหว่างอุปกรณ์ต่างๆ ให้เป็นไปอย่างราบรื่น มีความเป็นส่วนตัวเพิ่มขึ้น และทำให้เราสามารถท่องโลกของอินเตอร์เน็ตโดยไม่จำเป็นต้องใช้ Public IP " -asmogo
NostrWebServices (NWS) คืออะไร?
NWS คือการนำ Nostr เข้ามาช่วยในการเข้าถึงบริการของเว็บไซต์ต่าง ๆ โดยยังสามารถส่งข้อมูลขึ้นไปยัง transport layer บน TCP/IP ซึ่งด้วยวิธีนี้เองเลยทำให้เราสามารถสร้างการเชื่อมต่อได้โดยไม่จำเป็นต้องมี Public IP โดยส่วนที่จำเป็นหลัก ๆ ในการทำงานนี้เราจำเป็นต้องเตรียม
-
Entry node: SOCKS5 proxy ที่คอยส่งต่อ TCP packets ที่เข้ารหัสผ่านทาง event ของ Nostr ก่อนส่งส่งผ่านรีเลย์ต่าง ๆ ไปยัง Exit node
-
Exit node: TCP reverse proxy ที่คอยรอรับข้อมูลมาจาก Entry node และส่งต่อข้อมูลต่าง ๆ ไปยังบริการอื่น ๆ ต่อไป

ในส่วนของการทำงานนั้นสามารถดูได้จากในรูปที่ได้แนบไว้ข้างต้นได้เลย อย่างที่เห็นเลยว่ามันเริ่มจากแอพต่าง ๆ เหมือนที่เรามีการใช้งานกันอยู่ในปัจจุบัน เพียงแต่แทนที่เราจะส่งข้อมูลต่าง ๆ ผ่าน IP layer ตามปกติ เราสามารถส่งเข้าไปยัง Entry node และหลังจากนั้นข้อมูลจะถูกส่งผ่าน relay ต่าง ๆ ก่อนที่จะวิ่งไปยัง Exit node และ Exit node จะคอยส่งข้อมูลต่าง ๆ ไปยังบริการหลังบ้านที่เราต้องการจะเชื่อมต่อ
เราจะเห็นได้ว่าการทำงานของ NWS นั้น สำหรับผู้ใช้งานโดยทั่วไปแล้วแทบจะไม่แตกต่างอะไรกับในปัจจุบันเลย นั่นก็เพราะว่าเรายังทำการใช้งานแอพต่าง ๆ ตามปกติ แต่ประโยชน์ที่เราจะได้รับเพิ่มเติมนั้นคือความเป็นส่วนตัวในการใช้บริการเบื้องหลังอื่น ๆ
นอกจากนี้ยังมีในส่วนของ NWS domain names ใน NWS นั้นมีการรับรอง domain สองตัวนั้นคือ
- ".nostr" ซึ่งใช้ชื่อโฮสต์เป็นกุญแจสาธารณะที่เข้ารหัสด้วย base32 และ รีเลย์ที่เข้ารหัสด้วย base32 เป็นโดเมนย่อย
- "nprofiles" ซึ่งเป็นการผสมผสานกันระหว่างกุญแจสาธารณะของNostrและรีเลย์หลายตัว
ซึ่งโดเมนทั้งสองประเภทจะถูกสร้างและปรากฏอยู่บนคอนโซลเมื่อเริ่มต้นใช้งาน
หัวใจหลักในการทำงานของ NWS
อย่างที่ได้กล่าวไว้ข้างต้นว่า NWS เข้ามาช่วยเหลือในการเพิ่มความเป็นส่วนตัวได้ แล้วถ้าเราไม่ได้ต้องการเข้ารหัส หรือถ้าเราอยากจะเปิด Entry node แล้วเราไม่ต้องการให้คนที่จะเชื่อมต่อเข้ามาเข้ารหัสข้อมูลเราสามารถทำได้เช่นกัน โดยทั้งสองระบบที่ NWS ทำได้มีดังนี้
-
แบบไม่เข้ารหัส: เราจำเป็นต้องรันโหนดไว้ในเครื่องที่เราใช้รัน client แล้วแปลง client ให้ส่งข้อความใส่โหนดปลายทางตรง ๆ
-
แบบเข้ารหัส เริ่มจากการเชื่อมไปที่โหนดที่ต้องการ (อารมณ์ ssh เข้าไป) แต่วิธีนี้ยังติดที่บางเว็บที่เป็น https จะเชื่อมไม่ได้หาก cert ของโหนดที่เราเชื่อมมีปัญหา ส่วนข้อมูลที่ส่งจะถูก encrypt ไว้ด้วย Sphinx (เข้ารหัสแบบหนึ่งในมาตรฐาน RSA) ฉนั้นมั่นใจได้ว่าโหนดที่เราไปยืมจมูกเขาหายใจก็ไม่รู้ว่าเราส่งอะไรไป
การตรวจสอบตัวตนของเซิร์ฟเวอร์ปลายทาง
การตรวจสอบตัวตนของเซิร์ฟเวอร์ปลายทางของ NWS ทำโดยการใช้ประโยชน์จาก nostr โดยให้โหนดปลายทางปล่อย cert (TLS) บน nostr และเซ็นรับรองด้วยตนเองและอณุญาติให้ไคลเอนต์สามารถดึงใบรับรองนี้มาก่อนเชื่อมต่อกับโหนดที่เป็นจุดเริ่มที่เราใช้
และนอกจากนี้ในอนาคตของการพัฒนา NWS กำลังพัฒนาให้ NWS สามารถกำหนดให้โหนดปลายทางสามารถกำหนดค่าให้เข้าถึงอินเทอร์เน็ตได้ (ไม่ใช่แค่บริการภายใน) ทำให้ NWS ทำงานคล้าย VPN โดยสามารถเข้าเว็บไซต์ปกติได้ เช่น พิมพ์ "https google dot com" ก็เข้า google ได้
และทั้งหมดที่กล่าวไว้ข้างต้นเป็นเพียงการเริ่มต้น ยังมีคุณสมบัติอย่างอื่นอีกมากมายที่จะเข้ามาปรับปรุงปัญหาต่าง ๆ ในการใช้งานอินเตอร์เน็ต โดยส่วนตัวผมรู้สึกตื่นเต้นกับอนาคตของ NWS มาก ๆ และคาดหวังที่จะได้เห็นคนหันมาให้ความสนใจและใช้งานมัน ทั้งนี้หากใครอยากทดลองใช้งานก็สามารถติดตามได้ที่
GitHub: https://github.com/asmogo/nws
ส่งท้าย
สำหรับ series nOStr ผมตั้งใจจะหาเรื่องราวเกี่ยวกับ other stuff ที่น่าสนใจ ให้ทุกคน ๆ ได้ศึกษาไปพร้อม ๆ กัน เพราะว่า nostr ไม่ได้มีแค่โน๊ต
-
-
 @ a012dc82:6458a70d
2024-09-12 08:36:53
@ a012dc82:6458a70d
2024-09-12 08:36:53Table Of Content
-
What is the new policy?
-
What are the benefits of paying taxes with cryptocurrency?
-
How will this affect the cryptocurrency market?
-
Conclusion
-
FAQ
Cryptocurrency has been a hot topic in Brazil for a while now, with more and more people investing in digital assets. Now, the Brazilian government has taken a step forward by allowing citizens to pay taxes with cryptocurrency. This is a significant move for Brazil and the wider cryptocurrency world, as it shows that digital assets are becoming increasingly accepted by governments and financial institutions. In this article, we will explore what this means for Brazilians and the cryptocurrency market as a whole.
What is the new policy?
As of now, Brazilian taxpayers can use Bitcoin, Ethereum, and USDT to pay their taxes. The payments will be processed by the Federal Revenue Service of Brazil, which will convert the cryptocurrency into Brazilian reals. This means that taxpayers will no longer have to go through banks or other financial institutions to pay their taxes.
What are the benefits of paying taxes with cryptocurrency?
Cryptocurrency has become increasingly popular in recent years, with more and more people investing in digital assets. Now, the Brazilian government has taken a significant step forward by allowing citizens to pay taxes with cryptocurrency. Here are some of the benefits of paying taxes with cryptocurrency:
Security
Cryptocurrency transactions are recorded on a blockchain that cannot be altered, making them highly secure. This reduces the risk of fraud and hacking, providing taxpayers with greater peace of mind when making payments. Additionally, cryptocurrency wallets are encrypted and require a private key to access, further increasing security.
Speed
Cryptocurrency transactions are processed much faster than traditional payment methods, such as bank transfers or credit card payments. This means that taxpayers can avoid long wait times and receive confirmation of payment almost instantly.
Cost-effectiveness
Cryptocurrency transactions are often cheaper than traditional payment methods, as they don't involve intermediaries like banks. This means that taxpayers can save money on fees and charges when making payments, which is especially beneficial for those who make frequent or large payments.
Transparency
Cryptocurrency transactions are transparent, as they are recorded on a public blockchain that can be accessed by anyone. This reduces the risk of corruption and ensures that taxes are being paid fairly. Additionally, taxpayers can easily track their payments and ensure that they have been processed correctly.
Accessibility
Paying taxes with cryptocurrency is accessible to anyone who has a cryptocurrency wallet and the relevant digital assets. This means that taxpayers no longer have to rely on banks or other financial institutions to make their payments, making the process more streamlined and convenient.
How will this affect the cryptocurrency market?
The decision to allow taxpayers to pay their taxes with cryptocurrency is a significant move for the cryptocurrency market. It shows that governments and financial institutions are becoming increasingly accepting of digital assets, which could lead to increased adoption and investment in the future. Additionally, it could lead to other countries following suit and allowing taxpayers to pay their taxes with cryptocurrency.
Conclusion
The decision to allow Brazilians to pay their taxes with cryptocurrency is a significant move for both Brazil and the cryptocurrency market as a whole. It shows that governments and financial institutions are becoming increasingly accepting of digital assets, which could lead to increased adoption and investment in the future. While there are still some challenges to overcome, such as volatility and regulation, the future of cryptocurrency looks promising in Brazil and beyond.
FAQ
What cryptocurrencies can be used to pay taxes in Brazil? Bitcoin, Ethereum, and USDT can be used to pay taxes in Brazil.
How will the payments be processed? The payments will be processed by the Federal Revenue Service of Brazil, which will convert the cryptocurrency into Brazilian reals.
Are there any benefits to paying taxes with cryptocurrency? Yes, there are several benefits, including security, speed, cost-effectiveness, and transparency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 7e069ad4:feb9fb1a
2024-09-12 05:20:12
@ 7e069ad4:feb9fb1a
2024-09-12 05:20:12When venturing into online casino Malaysia, knowing which games offer the best odds is a crucial step in improving your chances of walking away with a profit. Not all casino games are created equal—some give players better odds, while others heavily favor the house. Understanding the house edge and making strategic decisions can make all the difference between leaving the casino as a winner or seeing your bankroll dwindle away. In this article, we’ll dive into the concept of the house edge and explore some of the best-odds casino games available both online and at land-based casinos.
Understanding the House Edge
The house edge is the casino’s mathematical advantage over the player, ensuring that the house profits over time. For example, a game with a 2% house edge indicates that the casino anticipates keeping MYR 2 on average for every MYR 100 wagered. While this doesn’t guarantee a loss for every player, it does ensure that, over the long run, the house will make money.
Playing games with the lowest house edge feasible should be the aim of players. This increases the chances of walking away with some winnings. However, even in games with a low house edge, strategy and skill play a significant role in tipping the odds in your favor.
Best-Odds Casino Games
Some casino games give players much better odds than others, especially those where skill and strategy can influence the outcome. Below, we explore five casino games that offer some of the best odds in both online and land-based casinos.
1. Single-Deck Blackjack (House Edge: 1.5%)
Blackjack is one of the most popular and best-odds casino games, especially the single-deck variation. Your choices in this game—whether to hit, stand, or double down—have a direct impact on the result. A well-played strategy can reduce the house edge to as low as 1.5%, giving players a significant advantage compared to other games. In fact, blackjack is a game where experienced players with a sound strategy can turn the odds in their favor, particularly in single-deck formats where card counting can be effective.
2. Baccarat (House Edge: 1.06% for Banker Bets)
Baccarat, particularly the banker bet, offers one of the lowest house edges of any casino game, making it an excellent choice for players looking to maximize their chances of winning. With a house edge of only 1.06% when betting on the banker, the player bet has a marginally greater edge of 1.24%. This game requires no complex strategy, and with simple rules, even beginners can quickly catch on and improve their odds.
Additionally, baccarat has become increasingly popular in live casinos online, allowing players in Malaysia to engage with live dealers and other players, enhancing the excitement.
3. Craps (House Edge: 1.41% for Pass Line Bets)
Craps is often perceived as a complex game due to the variety of bets and rules, but it actually offers excellent odds for players who stick to the basics. The most popular and simple bet in craps is the Pass Line bet, which has a house edge of only 1.41. Although it can seem intimidating to beginners, once you understand the basic rules, craps can be one of the most exciting and rewarding games in the casino.
4. Roulette (House Edge: 2.7% for European Roulette)
Roulette is a classic casino game that offers different variations with varying house edges. European Roulette, which features a single zero on the wheel, provides better odds compared to American Roulette, which has an additional double zero, significantly increasing the house edge. For players looking for a more equitable chance to win, European Roulette is a preferable choice because of its 2.7% house edge. By sticking to outside bets such as red or black, odd or even, players can further improve their chances of walking away with some winnings.
5. Three-Card Poker (House Edge: 1.5%)
Three-Card Poker is a fast-paced and straightforward poker variation that offers relatively good odds with a low house edge of around 1.5%. Three cards are dealt to each player, and their goal is to build the best hand to beat the dealer. While the game is based primarily on luck, some poker strategies can be applied to slightly reduce the house edge, making it a popular choice for both beginners and experienced players alike.
What About Slot Games?
Slots are often the most popular games at online casinos due to their simplicity and visually appealing designs. However, slots tend to have higher house edges compared to table games, sometimes ranging from 5% to 10%. While it’s possible to win big on slots, particularly on progressive jackpot games, the odds of hitting those massive payouts are incredibly low. For example, some progressive slot machines may offer a return-to-player (RTP) rate of 95%, meaning a house edge of 5%. This volatility means that players may not see consistent returns, and wins can be few and far between.
That being said, if you enjoy slots and are playing primarily for fun, they can still offer entertainment and the potential for a life-changing win, albeit with much higher risks than table games like blackjack or baccarat.
Final Thoughts
When it comes to maximizing your chances of winning at online casinos, focusing on games with the best odds is a smart strategy. Games like blackjack, baccarat, and craps offer some of the lowest house edges, allowing players to use strategy and skill to their advantage. While slots can be fun and offer the possibility of big wins, their higher house edge makes them a riskier choice for players looking for consistent payouts.
If you're looking for the best odds in an online casino, stick to games like blackjack, baccarat, and craps, where skill and strategy can reduce the house edge. While slots can be fun and potentially lucrative, their odds are generally lower, so it's essential to manage your bankroll and expectations. Whether you're playing at home or on the go, platforms like G6Casino - Online Casino Malaysia offer a wide selection of games with competitive odds, ensuring an exciting and rewarding experience. Don’t miss out—play at G6Casino today and take advantage of their fantastic bonuses!
-
 @ 472f440f:5669301e
2024-09-12 03:17:07
@ 472f440f:5669301e
2024-09-12 03:17:07TAPS SIGN
"There is no industry in the world that is more ruthlessly competitive than the bitcoin mining industry."
From any angle you cut it the bitcoin mining economic landscape is absolutely BRUTAL at the moment. Hashprice is sitting right above an all time low at $0.04/TH/day. Yesterday brought with it yet another new difficulty all time high. Competition for energy resources is as fierce as it has ever been as rack space continues to be tight in the United States and hoards of AI data centers move in to scoop up as much power as possible.
To make matters worse, with current economics it doesn't really make sense to buy bitcoin mining machines at their current prices. The pay back period on machines is absurd considering where we find ourselves in the market. Adam O from Upstream Data broke it down in a tweet earlier today.
As he says, it probably makes more sense to buy used machines than new machines right now if you are looking to make back your money on a reasonable timeline. The only reasons you would buy new hardware right now is if you believe the price is going to rip in the near term (risky bet), you think hashrate is going to come off the network (risky bet), or if you have obscenely low power costs (unlikely for most).
If you have machines plugged in or are thinking about plugging them in soon you better be running firmware that enables you to run your machines more efficiently to increase margins. With current economics, I would make the argument that it is incredibly irresponsible to be running your machines using stock firmware. Especially if you are operating a miner in the public markets or are a private miner backed by investors. It is a disservice to your shareholders. This is a strategy we have been deploying at Cathedra for years now and it has helped us to survive during these trying times in the mining industry and set us up to successfully complete a strategic merger with Kungsleden at an opportune time.
On that note, this is a trend you can expect to pick up over the next six months; mergers and acquisitions. We wrote earlier this year that M&A activity would pick up after the halving began to eat into the economics of mining businesses and that is exactly what is happening. We decided to move early at Cathedra to get ahead of the curve. Since then Cleanspark announced a merger with GRIID, Riot has initiated an attempted hostile takeover of Bitfarms, Bitfarms has entered an agreement to merge with Stronghold, and Terawulf has signaled that they are open to a merger if a particular deal makes sense. On top of this, Rhodium slipped into bankruptcy last month. As margins continue to be squeezed and companies get more desperate I expect this type of consolidation to accelerate.
All signs are pointing toward more pain in the world of mining in the near term. There is nothing outside of a face ripping rally in the price of bitcoin or some unforeseen event that knocks out a material amount of hashrate that will change this reality. Especially considering the fact that Bitmain announced a new hydro model that will produce 860 TH/s at ~13 J/TH! This will be the highest hashing, most energy efficient machine to ever hit the market by a considerable margin.
Once these machines hit the market (if they haven't already via Bitmain plugging them in, which could explain new difficulty all time highs despite terrible mining conditions) every other machine on the market is going to suffer economically.
To make matters worse for everyone struggling right now, savvy energy producers are beginning to understand the benefits bitcoin mining can bring to their operational stack. Japanese energy giant TEPCO is reportedly planning to scale up their mining operations after beginning pilots in late 2022. They want to utilize the excess energy produced by renewable sources to mine bitcoin. From what I can tell, they haven't scaled up significantly yet. However, it is reasonable to believe that they will scale up and other energy producers will take notice. Pushing the industry closer to its inevitable end state; vertical integration via energy producers who have the lowest cost of production.
Thank you for coming to my TED Talk. Keep hashing if you can.
Final thought...
The pets need protecting.
-
 @ a03b38f8:2c7ce1f0
2024-09-12 03:01:55
@ a03b38f8:2c7ce1f0
2024-09-12 03:01:55A quick overview
- Computer -> clearnet -> Website
ISP: sees that you are connected to website
VPN: n/a Tor Entrance Node: n/a Tor Exit Node: n/a
Website: sees your IP address and logs everything that you do on the website
Good for when the expectation of privacy does not exist. A KYC site you are logging into. Utility bill pay site, bank
- Computer -> VPN -> Website
ISP: sees that you are connecting to a VPN but not what you are doing afterwards
VPN: sees your IP Address and that you are connecting to a website
Tor Entrance Node: n/a Tor Exit Node: n/a
Website: sees that someone from a VPN exit node has connected but doesn’t know who. Logs data.
Good for hiding your activity from your ISP. Good for hiding your identity from the website. Good for when you want low level privacy but not anonymity. VPN provider sees everything and your level of privacy depends on how much they know about you and how much data they log and retain (varies greatly from provider to provider).
- Computer -> Tor -> Website
ISP: sees that you are connected to Tor but nothing afterwards
VPN: n/a
Tor Entrance Node: sees your IP address but nothing afterwards
Tor Exit Node: sees website you are going to but not who you are
Website: sees someone from Tor has connected but doesn’t know who. Logs.
Good for privacy and anonymity. Assumes that Tor is legal in your country.
- Computer -> VPN -> Tor -> Website
ISP: sees that you connected to a VPN but nothing afterwards
VPN: sees IP address and that you are connecting to Tor but nothing afterwards
Tor Entrance Node: sees a VPN is connected but nothing afterwards
Tor Exit Node: sees website you are going to but not who you are
Website: sees someone from Tor has connected but doesn’t know who. Logs.
Good for if your ISP blocks or cancels your service for using Tor. Potentially an option if Tor is illegal in your country (Dangerous).
- Computer -> Tor -> VPN -> Website
ISP: sees that you are connecting to Tor but nothing afterwards
VPN: sees someone from Tor is connected and that they are connecting to a website
Tor Entrance Node: sees IP address but nothing afterwards
Tor Exit Node: sees someone is connecting to a VPN but nothing afterwards
Website: sees someone from a VPN is connecting but doesn’t know who. Logs.
Good for when a website blocks Tor traffic. Assumes Tor is legal in your country. Assumes that the VPN doesn’t know who you are. To maximize privacy and anonymity VPN provider should be KYC free and accept privacy payments (ex: Monero).
Note: If a website blocks Tor and VPN then maybe that is a sign that you shouldn’t go there.
-
 @ 916cb5ff:c7d507c9
2024-09-12 00:46:33
@ 916cb5ff:c7d507c9
2024-09-12 00:46:33Key Numbers
- 986 total commits
- 718 commits (excluding merges)
- 590 commits (excluding merges and script runs)
- 359 products newly evaluated
- 200 merge requests reviewed and merged
- 128 binaries tested for reproducibility:
- 73 with successful reproducibility attestations
- 44 successful compilations that differed from the official binary
- 8 failures to compile
- 33 distinct wallets compiled from their source code
- 10 code contributors
- 7 paid contributors
Additionally, 6,444 products require significant maintenance efforts, for which we developed several scripts to streamline the process.
New Features
Compilation Videos
We now provide detailed documentation of our compilation process, including an ASCII recording of each step to enhance the transparency and trust in our evaluations.
Social Share Images
For each product, we generate an updated image that appears when sharing reviews on social media. These images can also be embedded in third-party websites, offering an alternative for platforms that prefer not to use our widget for security reasons.
Opinions
We introduced Nostr-based opinions for all products. With fewer than 100 community-submitted opinions, which fell short of expectations, we are actively exploring ways to increase both the volume of opinions and user engagement.
Desktop Wallets
We expanded WalletScrutiny to include desktop applications, listing 77 new products. An essential improvement to our methodology, including Nostr-based attestations, is currently under review. In August, a new senior developer joined us and is now dedicating 10 hours per week to lead this initiative.
Binary Checker
A key addition currently under development is a tool allowing users to drag apps onto the WalletScrutiny website to check them. The site will either display relevant attestations or offer to check the binary if none are found.
-
 @ 8d34bd24:414be32b
2024-09-11 22:17:13
@ 8d34bd24:414be32b
2024-09-11 22:17:13This title came from a statement from R.C. Sproul in his sermon entitled “How Does Truth Command Me?” that was the inspiration of this post.
We have all been taught to blindly follow either the crowd or the so-called authority figures. We are not taught to seek the truth. We are not taught to seek what is right. We are taught to follow the crowd.
All Like Sheep Have Gone Astray
Unfortunately, following the crowd almost always leads us astray.
All of us like sheep have gone astray,\ Each of us has turned to his own way;\ But the Lord has caused the iniquity of us all\ To fall on Him. (Isaiah 53:6) {emphasis mine}
If you are a student, have you been trained to blindly follow the teacher or your peers rather than actively seeking the truth? If you are working in a career, have you been trained to fit in with your peers or do whatever management says even if those actions are foolish or immoral? Does your church follow the culture or the word of God as explicitly stated in the Bible?
Who or what are you following? Are you following the media? the culture? authority figures? your heart? or are you following the word of God? Do you even know the Bible to know if you are following the word of God or not?
“My people have become lost sheep;\ Their shepherds have led them astray.\ They have made them turn aside on the mountains;\ They have gone along from mountain to hill\ And have forgotten their resting place.\ All who came upon them have devoured them;\ And their adversaries have said, ‘We are not guilty,\ Inasmuch as they have sinned against the Lord\ who is the habitation of righteousness,\ Even the Lord, the hope of their fathers.’ (Jeremiah 50:6-7) {emphasis mine}
There is a reason that people are frequently referred to as sheep in the Bible. Sheep aren’t very smart. They don’t think things through. They tend to blindly follow the flock or the shepherd without thinking about where that may lead them.
Follow the Good Shepherd
For you have been called for this purpose, since Christ also suffered for you, leaving you an example for you to follow in His steps, who committed no sin, nor was any deceit found in His mouth; and while being reviled, He did not revile in return; while suffering, He uttered no threats, but kept entrusting Himself to Him who judges righteously; and He Himself bore our sins in His body on the cross, so that we might die to sin and live to righteousness; for by His wounds you were healed. For you were continually straying like sheep, but now you have returned to the Shepherd and Guardian of your souls. (1 Peter 2:21-25) {emphasis mine}
Following the herd or flock will lead us astray. Following the many self-proclaimed shepherds will lead us astray. Following the true “Shepherd and Guardian of your souls” will lead you in the path of righteousness and lead you to obedience to God.
One sign that we truly are Christians is that we can recognize what is from Jesus and what is from the Devil. Reading, studying, and memorizing the Bible will help us determine truth, but the Holy Spirit, who indwells all believers, also guides us.
“I am the good shepherd, and I know My own and My own know Me, even as the Father knows Me and I know the Father; and I lay down My life for the sheep. I have other sheep, which are not of this fold; I must bring them also, and they will hear My voice; and they will become one flock with one shepherd.” (John 10:14-16) {emphasis mine}
Those who have truly trusted in Jesus as Savior should recognize the voice of the “Good Shepherd” and follow Him.
But you do not believe because you are not of My sheep. My sheep hear My voice, and I know them, and they follow Me; and I give eternal life to them, and they will never perish; and no one will snatch them out of My hand. My Father, who has given them to Me, is greater than all; and no one is able to snatch them out of the Father’s hand. (John 10:26-29) {emphasis mine}
Are you following the Good Shepherd (Jesus) or are you following false shepherds or lost flocks?
Standing Alone
When we surround ourselves with a group of godly believers (friends, family, or church), standing firm on the word of God tends to not feel too burdensome. We have others to lean on and to help us stay on the path.
When we feel like we are standing alone, it is really hard to stay faithful. It is easy to follow the herd instead of standing firm on the foundation set for us by the Creator, Jesus. There are many people in the Bible who felt the same way, and yet they stayed faithful till the end.
God has not rejected His people whom He foreknew. Or do you not know what the Scripture says in the passage about Elijah, how he pleads with God against Israel? “Lord, they have killed Your prophets, they have torn down Your altars, and I alone am left, and they are seeking my life.” But what is the divine response to him? “I have kept for Myself seven thousand men who have not bowed the knee to Baal.” In the same way then, there has also come to be at the present time a remnant according to God’s gracious choice. (Romans 11:2-5) {emphasis mine}
In reality, you are never alone. God is with all believers, but there are also other believers around. Some believers are good at standing firm in the face of adversity. Sadly, most are not and will try to hide in the crowd to keep from standing out or being attacked. We are called to obey God even if nobody else will. We are called to obey God even if it costs us our life.
Being that faithful believer who stands up even when he feels all alone can make an amazing difference. One stands up against the godless culture. Another, with less courage, sees the faithful stand and grows in courage and decides to stand alongside the first. Others, seeing the faith of the two, gain courage and decide to join in for what is right. Pretty soon even unbelievers start to notice and become interested in what makes them different and courageous.
Jesus died for you. What would you do for Him?
On the other hand, when none choose to stand for what is right, things can get pretty bad fast. This poem written during the reign of Adolf Hitler is a sad reminder of what happens when nobody speaks up against evil.
First they came for the socialists,\ and I did not speak out—because I was not a socialist.
Then they came for the trade unionists,\ and I did not speak out—because I was not a trade unionist.
Then they came for the Jews,\ and I did not speak out—because I was not a Jew.
Then they came for me—and there was no one left to speak for me.
—Martin Niemöller
There were many Christians and churches in Germany at this time, but they chose to keep silent in order to not inconvenience their lives. The result was great evil and the loss of many lives and souls. This quote, often wrongly attributed to Edmund Burke, succinctly states a great truth:
The only thing necessary for the triumph of evil is that good men do nothing.
Although Burke did have a much longer similar quote, it is unknown who gave this exact quote. Still it is true. So often we worry so much about “Thou shalt not …” that we miss the “Thou Shalt …” Sometimes what we fail to do is as bad or worse than the bad thing we do. When evil (as defined in the Bible) prevails, we are called to stand up for the truth and for God’s standard. We are called to battle evil, even when it is inconvenient, and even when it is dangerous to our very lives.
These are not necessarily Christians standing up for their faith, but they are people standing up for what is right despite the fact that everyone else is cowering in fear and going along to get along.
 This picture is a solitary college student standing up to tanks in Tiananmen Square in China to protest tyranny and silencing of speech. This young man lost his life, but he made a difference in China and beyond and has been a hero and an encouragement to many.
This picture is a solitary college student standing up to tanks in Tiananmen Square in China to protest tyranny and silencing of speech. This young man lost his life, but he made a difference in China and beyond and has been a hero and an encouragement to many.Look closely to this one man in the crowd at a rally for Hitler.
 The whole crowd is enthusiastically giving the Nazi salute to Hitler. I’m sure some don’t like Hitler, the Nazis, or the salute, but they are going along to get along. One brave soul out of hundreds is taking a stand. He refuses to give the salute.
The whole crowd is enthusiastically giving the Nazi salute to Hitler. I’m sure some don’t like Hitler, the Nazis, or the salute, but they are going along to get along. One brave soul out of hundreds is taking a stand. He refuses to give the salute.We all know what the Nazis represented. They murdered disfavored groups like the Jews. They silenced opponents. They did medical experimentation on undesirables. When the modern world thinks of evil, this is what they think of, but most of the people went along with the crowd. This was herd morality. Even most churches went along with the Nazi regime.
Only a few brave souls stood up and said, “No, this is wrong.” Only a few risked their lives to either speak up or to try to rescue those who were being destroyed. Is your faith strong enough that you would be the one man in the crowd refusing to give the salute? Would you be like Dietrich Bonhoeffer, and risk your life to sneak Jewish children out of Germany to rescue their lives? He did the right thing, but ultimately lost his life.
Are you willing to stand up against the evil in our culture today and say, “That is wrong!”? What Biblical truths are dear enough that you would risk your livelihood or your life to defend? If your life was threatened, but you would be left alone if you denied Jesus, would you deny Him?
Will You Follow the Herd or the Shepherd?
We learned that following herd morals is a bad idea and that we should follow the commands of the Good Shepherd, Jesus Christ. Whom will you follow? Will you stand firm? What will you endure for the one who died for you?
By this we know that we have come to know Him, if we keep His commandments. The one who says, “I have come to know Him,” and does not keep His commandments, is a liar, and the truth is not in him; but whoever keeps His word, in him the love of God has truly been perfected. By this we know that we are in Him: the one who says he abides in Him ought himself to walk in the same manner as He walked. (1 John 2:3-6) {emphasis mine}
The God and Creator of the universe came down to Earth as a man and lived the perfect life that we couldn’t, died on the cross to be a sacrifice for our sins, and was raised on the third day proving He had conquered sin and death. Jesus is our example, and “the one who says he abides in Him ought himself to walk in the same manner as He walked.”
In addition to living sinless life as an example, God gave us His word so we would know His commandments.
All Scripture is inspired by God and profitable for teaching, for reproof, for correction, for training in righteousness; so that the man of God may be adequate, equipped for every good work. (2 Timothy 3:16-17) {emphasis mine}
God gave us everything we needed to live the life He has set before us. He gave us access to the truth. He gave us access to who He is. He gave us access to what He requires of us. We need to follow Him and not the herd.
And do not be conformed to this world, but be transformed by the renewing of your mind, so that you may prove what the will of God is, that which is good and acceptable and perfect. (Romans 12:2) {emphasis mine}
We are commanded to “not be conformed to this world.” We are not to have herd morals. We are called to be “transformed by the renewing of your mind.” How will our mind be renewed? Our minds are renewed by faith in Jesus, the indwelling of the Holy Spirit, and the studying of the inspired word of God.
Do not be conformed, but trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 3cd2ea88:bafdaceb
2024-09-11 20:40:32
@ 3cd2ea88:bafdaceb
2024-09-11 20:40:32💥 Partecipa GRATIS e dimostra le tue abilità di trading con il nostro account demo premium. Nessun costo, solo emozioni! 💥
🎯 Ecco cosa puoi ottenere:
1️⃣ Fino a 10.000 USDT di supporto reale al capitale con rapporto 1:1!
2️⃣ Raddoppia i tuoi guadagni con i premi del trading e la condivisione dei profitti del copy trading.
3️⃣ Diventa un trader d'élite e guadagna visibilità a livello globale.
🔗 Iscriviti ora e mostra al mondo le tue capacità di trading!
https://www.bitget.com/it/copy-trading/traderpro?utmTerm=koc
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
-
 @ b7338786:fdb5bff3
2024-09-11 19:37:20
@ b7338786:fdb5bff3
2024-09-11 19:37:20Though the river's current never fails, the water passing, moment by moment, is never the same. Where the current pools, bubbles form on the surface, bursting and disappearing as others rise to replace them, none lasting long. In this world, people and their dwelling places are like that, always changing.
When you see the ridgepoles of the impressive houses in Heian-kyo competing to rise above one another--dwellings of people of high status or of low--they look like they might stand for generations, but when you inquire you discover there are very few still standing from ages past. Some may have burned down just last year, and been rebuilt since. Or a mansion may have disappeared, to be replaced by smaller houses. Things change in the lives of the people living in those houses, too. There may be just as many people, but in places where I might have known twenty or thirty people in my youth, I may only recognize one or two now. Some die in the morning; others are born in the evening. That's the way it is with the people of this world--they are like those bubbles floating on the water.
Nor is it clear to me, as people are born and die, where they are coming from and where they are going. Nor why, being so ephemeral in this world, they take such pains to make their houses pleasing to the eye. The master and the dwelling are competing in their transience. Both will perish from this world like the morning glory that blooms in the morning dew. In some cases, the dew may evaporate first, while the flower remains--but only to be withered by the morning sun. In others the flower may wither even before the dew is gone, but no one expects the dew to last until evening.
I have seen many terrible things in the forty years I have lived since I first noticed such things.
I believe it was April 28th of the third year of Angen (1177). There was a strong wind blowing at the hour of the dog (8 o'clock in the evening) to spread a fire which broke out in the southeast part of the capital to the northwest. In that one night the Red Sparrow Gate, the Palace Council Hall, school dormitories, the Public Housing Ministry, and many other buildings were burned to the ground, reduced to ashes.
I heard that the fire broke out in Higuchitominokoji, in a shack where a dancer lived. Then, spread by the wind, it touched place after place, until finally it reached everywhere, like the unfolding of a fan. Houses far off became engulfed in smoke as those near the center were caught up in swirling flames. The brightness of the fire was reflected against the solid cloud of ashes blown up in the night sky, a deep red at the center, which, as the wind had flames leaping 100 to 200 yards, kept shifting. People caught in the middle gave up all hope. Some died as they were completely overcome by the smoke, others as they became dizzy in the eye of the flame. Still others, who barely escaped with their lives, lost everything they owned. Some of the great treasures in the Palace were also reduced to ashes. How great was the damage? Sixteen buildings in the Imperial Court were burned, but it is impossible to calculate the total loss. Perhaps a third of the capital city was destroyed by this fire. Scores of men and women were killed, and who knows how many horses and cattle?
I think it is absurd to sacrifice so much wealth and energy to build a house anywhere, but particularly in such a dangerous place as the center of the capital city.
Again it was in April of the fourth year of Jisho (1180) when a great whirlwind struck near Naka-no-Mikado, east of the Imperial Palace, and swept southwest to Sixth Street.
Racing across the city, 300 to 400 yards wide, the whirlwind destroyed every house, large or small, in its path. In some cases they were completely flattened; in others only beams or pillars remained. The roofs of gates were blown 400 or 500 yards away, as if offering no resistance at all, and hedge fences were completely blown away, so the boundaries between neighbors disappeared. Household goods and cypress shingles flew up into the air, like leaves from winter trees, to be distributed far and wide. There was so much dust and trash in the air that it was better not to open your eyes, and you couldn't hear a thing anyone said to you in the terrible echoing. I thought it must be like this in Hell. Not only were buildings destroyed, but many people were crippled trying to salvage those that had just been damaged. This wind moved in a south, southwest direction, across the central part of the capital city, so it caused grief for a great many people.
Since there are often whirlwinds, this would not be such an unusual thing except for the severity. Many saw it as a special Buddhist or Shinto warning.
Then, in June of that same fourth year of Jisho, the capital was suddenly and unexpectedly moved. I have heard that Heian-kyo had been the capital for almost 400 years, since the reign of the Emperor Saga. So it would certainly seem unwise to move such a stable capital without some special reason, and it naturally caused a great deal of anxiety among the people.
But no matter what people said, they all moved, beginning with the emperor, his ministers, and other nobles. I wondered if anyone associated with the government would remain in the old capital. Certainly anyone who wanted an important position in the government, or promotion in rank at court, very quickly moved to the new capital, leaving behind only those with little chance of successful careers, or those for whom the future had little to offer. Soon the most impressive mansions fell into disrepair. Some were disassembled, the pieces floated down the Yodo River on rafts, so the land they had occupied became open fields. People's ideas changed completely. Now a horse and saddle was valued over an ox and ox-cart. Land in the direction of the sea, south and west, was thought desirable, while no one wanted to settle in the direction of Tohoku, or to the north.
I happened to visit the new capital, at the seaport in Settsu, at this time. It was obvious that the place was too narrow even to lay out the streets properly. On the north side the mountains were crowding in and the south side was sloping into the sea. The sound of the waves was noisy all year long, and the salt water wind was especially strong. The Imperial Palace was right in the mountains, and the trees used to build it became the fashion, with comments about the peculiar points of elegance it had. Houses were re-constructed from the components of so many being floated down the river as almost to dam it; still, though unoccupied land was plentiful, few new houses had been built. So the old capital was already ruined, while the new capital was not yet established. People came to feel like floating clouds. The natives of the place complained because they had lost their land, and those who had moved there about the difficulties of building in this new place. The people I saw on the streets who ought to have been riding in ox-carts were on horseback, and instead of kimono, ancient headdress, and formal wear most had assumed the clothing of soldiers. The manners of the capital had changed, became no different from those of country samurai. People wondered if, in these troubled times, courtly manners would be lost completely, and whether this might not presage greater catastrophes to come. Finally, after all the complaints, in the winter of that year the emperor returned to Heian-Kyo. However, by then most of the mansions had already been pulled down, and I don't believe that as many new ones were ever built.
I have heard that, long ago, a wise and virtuous emperor ruled over the country, who looked upon his subjects with pity. Even when thatching the roof of the palace they did not trouble to make the eaves uniform, and when there was not as much smoke coming from his subjects' kitchen chimneys as he expected, he exempted them from taxes. He had his subject's blessing, because the public welfare was his concern. This is the way it was. If we compare the state of affairs in today's society to that of this legendary wise emperor's reign what do we find them to have in common?
Also about that time, in the reign of Emperor Yowa (1181), I believe, though it becomes so long ago I have trouble remembering, there was a terrible famine, lasting for two years. From spring through summer there was a drought, and in autumn and winter typhoon and flood--bad conditions one after another, so that grain crops failed completely. Everything people did became wasted effort. Though they prepared the ground in the spring, and transplanted the rice in the summer, the fall's rice harvest and winter's prosperity were not achieved.
In all the provinces, peasants were abandoning the land and leaving the region. Some went to live in the mountains. In the Imperial Court special Buddhist prayers were scrupulously conducted, but to no effect. The prosperity of Heian-kyo depended on these crops, and under these conditions a normal economy could not be sustained. Given these pressures, people living on bamboo shoots tried to sell their valuables at sacrificial prices, but nobody wanted to buy anything. They engaged in barter as monetary values were depressed, and the value of grains skyrocketed. It became common for beggars to be heard in the main street of the capital, complaining about their conditions.
After a year of such suffering, people hoped the new year would be better, but the misery increased as, in addition to the famine, people were afflicted by contagious disease. Everyone suffered from malnutrition, until gradually to say that "All the fish will choke in shallow water" would fit very well. Now even those wearing bamboo hats, with legs wrapped in leggings, walked frantically from house to house begging. I saw vagabonds of this kind, as they were walking, suddenly collapse and die. Close to the roofed mud wall at the side of the road, the number of bodies dead from starvation continually increased. Because no one even tried to clear away those corpses, the odor of the putrefaction became offensive throughout Heian-kyo, and people could not even stand to look at them. The city was permeated by the smell, and the mountain of corpses accumulated along the Kamo river bed until there were places where horses and carriages could not pass. Poor woodcutters, becoming exhausted, were unable to carry firewood into the city, and, as fuel became scarce, people were breaking up their own houses and selling the wood in the city. However, all the wood a man could carry would not sell for enough to sustain him for a single day. And it was not unusual to find red paint and gold and silver foil here and there among the firewood, because desperate people would sneak into temples and steal the image of the Buddha, or pull down temple ornaments and furniture to turn into firewood. I was born into a world in which this kind of thing could happen.
And there were other terrible, pitiful things. No one was prepared to abandon a beloved wife or husband before they were separated by death. When they thought their partner was failing, sometimes they would put their own food into the hand of that cherished wife or husband, and it was frequently the case that the parent sacrificed for the child. Sometimes the mother was dead, and the nursing child did not even know it. There were many situations like that.
The high priest Ryugyo, of Ninanji Temple, deploring the fact that so many people were dying unrecorded, whenever he encountered a dying person wrote the Buddhist letter A on that person's forehead, binding the person, on the point of death, to Buddha's providence. When they estimated the number of people who died, in the two months of April and May, in the city of Heian-kyo, from 1st Street in the south to 9th Street in the north, from the Eastern Capitol in the west to the Red Sparrow Gate in the east--that is to say on all the roads of the entire city--the number of dead came to more than 42,300. Since many died before and after that two month period, and many died outside the city, in the Dry River Bed, in White River, in the West Capitol, and in the suburbs, the total number far exceeded such counting. And if we think beyond Heian-kyo and the suburbs--adding all the provinces--it is an appalling thing to consider.
I've heard that when Sutoku was emperor (1134), there was such a pestilence, but know nothing of that time. The misery in this case I saw with my own eyes, and it was very extraordinary.
Not long after this (1185) there was a violent earthquake, causing unbelievable damage. Mountains crumbled, rivers were completely filled up, and waves from the sea inundated the land. The earth split and water gushed out. Boulders broke off in the mountains and tumbled into the valley. Ships were tossed around on the sea, and horses were unable to keep their footing on the roads. In the vicinity of Heian-kyo, temples, shrines, and towers were so damaged that not a single one was left in good condition. Some collapsed; others were turned upside down. Dust and ashes billowed up like smoke. The sound of the movement of the earth, and of the destruction of houses, was like thunder. People who were inside the houses might be crushed at once, but those who ran outside were faced by the cracks in the earth. Since they did not have wings, they could not fly up into the sky, or become dragons riding in the clouds. We can only imagine their misery. Among the most dreaded of catastrophes, we must conclude that the earthquake is the worst of all.
In that earthquake the only child of a samurai, a child of about six or seven, was innocently playing under the roof of a mud wall, making a toy house, when suddenly that wall collapsed, burying the child, crushing it so badly that it couldn't be recognized, both eyeballs having been popped out about three centimeters. It is impossible to express in words the pity I felt seeing the mother and father, crying and wailing in loud voices, holding that child in their arms. To see that not even a brave warrior could disguise the anguish in his eyes suffering the agony of his child's death, could not control this kind of natural lament, provoked my sympathy.
The terrible shaking stopped after a short time, but then there were after-shocks. After that great earthquake, there might be twenty or thirty tremors in a single day. After ten days, then twenty days, they gradually came to be more widely spaced, probably four or five times in a day, then two or three times, then every other day, skipping two or three days--but there were still some aftershocks up to perhaps three months.
Among the four great elements recognized by Buddhism, three--fire, water, and wind--are frequently associated with disasters, but earth is most often identified with stability. Still, in the Saiko era (540), I believe, there was an earthquake so severe that it damaged the neck of the Todaiji's Great Buddha so that the head fell off, and did unusual damage to many other things. But it was no match for the violence of the earthquake this time. Those who experienced this earthquake all talked about it that way at the time, that of all the miserable things in this world, it was the worst, seemed to be a thing of evil passions. But the days and months passed into years, and they came to deplore other things, so that you might go for a month now without meeting anyone talking about the earthquake.
People respond to these disasters in terms of their own experience. Unless the disaster has struck them personally, their circumstances, their environment, it is dismissed as a superficial thing.
Someone of low status who becomes a neighbor of a man of power, even when he has cause to be very happy, cannot celebrate loudly, or if his sorrow is severe, his lamentation and weeping must be muted. His conduct is controlled by anxiety, for in any situation he is as fearful as a sparrow caught in a hawk's nest. Poor people, living as neighbors to the rich, morning and evening are embarrassed by their poorly dressed appearance, even as they go into and leave the house, seeing their neighbor's flattering condescension. The wife and children envy the neighbor's servants, who look down on them with haughty expression, provoking bad feelings. They can never have peace of mind. If it is crowded in the neighborhood, and the next-door house catches fire, there is no escaping the spreading fire. If you live outside the city, where it is sparsely populated, it is difficult to go and come, and you have to worry about being attacked by thieves. People want power and authority, for if their family has none, others look down on them. But people who have property have many worries, too, just as the poor people who envy them do. Whenever you must rely upon others, so are not self-sufficient, then those others come to possess you. Even helping a stranger, if you are drawn to that person, infringes on your independence of spirit. On the one hand, it is difficult to maintain independence in following the standard social conventions, but, if you do not, you will seem absurd, will look like a lunatic. And wherever you live, whatever you do, in the short period of time of this life, you should seek peace of mind--but this seems impossible for human beings.
This has been true in my life. At first, taking over the estate of my father's grandmother, I lived there for many years. But, after that, cut off by fate, I fell into adversity. Finally, I could no longer stay there. I was thirty years old when I built a smaller house for myself. Compared with the previous house, it was only a tenth of the size. It was no more than my own sleeping quarters, constructed as such a modest building might be. A mud wall was finally added, but there were never funds for a gate. Bamboo supports were constructed, through which a vehicle could enter. If the snow was falling, or the wind was blowing, there were difficulties. Because it was near the Kamo River channel, there was great danger of flooding, and there were many cases of robbery in the area.
It was difficult to find a satisfactory place to live, as I struggled with the problems of this world for over thirty years. During that time, as I stumbled from one situation to another, I came to realize that it was all a matter of fate. Therefore, in the spring of the year in which I became fifty, I abandoned that house, too, and sought seclusion from the world. Since I had no wife and children, and no allowance for rank or office, in what did my commitment lie? I had no obligations beyond myself, so was free to go into monastic seclusion. Though attached to nothing, living in Ohara, I had managed to live through the cycle of months meaninglessly for five years.
Now I am sixty years old, and again changing my way of life so late in life, have constructed a house to which to entrust my last years. It was like a silkworm diligently making a cocoon, or as if designed to provide a single bed for a traveler for a single night. This house, compared to the one I built in the middle of my life near the river bank, must not be a hundredth part of that house. Many find fault with what I am doing, as I move to a smaller and smaller dwelling house as my age increases from year to year. Comparing to the earlier, larger dwellings, this does not even resemble an ordinary building. The house is only ten feet square, and the height is less than seven feet. I did not model it on houses I have lived in all through my life, but selected the lot and built the house on other principles. I built the foundation and constructed the simple roof by linking timbers together and pulling them up so that they are suspended from metal fittings. By planning it this way, if I become displeased with the place it is located, it is easy to move it to another location. The house is so constructed that to move it is relatively easy to pile the pieces in two carts, and, except for the charge for the rental of the carts, no other expenses are required.
So I have withdrawn to live in the Hino mountains in this ten-foot square hermit's cell. On the east side, where the eaves extend less than a meter, there is a place to burn the firewood I have gathered. On the south the bamboo drainboard is spread. Inside, on the west, is a shelf made for the water offerings to the Buddha. On the north, in a single-leaf screen partition, the portrait of Amida Buddha is placed, and, next to that, Fugen Bodhisatva's portrait, before which the Kekyo sutra is placed. On the east side of the hermit's cell, I spread the straw from bracken grain as a cot. In the southwest corner, I have built a hanging shelf on which three black leather-covered boxes are placed, for poems, music books, and collections of sutra prayers. Next to that a koto and biwa stand, one on either side. These are the circumstances in this temporary hermit's cell.
Outside my hut, to the south, I have a water pipe. The water accumulates in a basin formed by rocks I have piled there. And because I am surrounded by forest, it is easy to gather small branches for firewood. The name of this place is Toyama. Creeping vines almost conceal the paths to it, but, though the trees grow thick in the valley, in the west it is clear, making this Western Paradise Pure Land view convenient for silent prayer. In spring the wisteria flowers tremble in the wind, so many blooming in the west that it seemed like the coming of Amida Buddha riding on purple clouds. In summer I can hear the cry of the cuckoo, promising to be my guide on the mountain road to death. In autumn the sound of the cicada fills the ear, and, as I hear it, I grieve to think of the transience of life in this world. In winter I see the snow with some emotion as it piles up and then begins to melt away, as the sins that people have committed may disappear if they are able to repent. If reciting the nembutsu becomes troublesome, or I do not feel I have time to read the sutras, no one is here to accuse me of being lazy. There is no one to interfere in any way. If I do not impose the severity of silence as a religious discipline, as may be my responsibility, living alone it is difficult to violate the rule in any case. If I were not strictly observing the commandments, I would wonder why, given this environment, I were not able to. But I don't break the rules. In the morning, I watch the boats come and go in the kanoya vicinity. When, after a boat passes, the white waves immediately fade away, I see my own transient experience in that, and am provoked to try to imitate the priest Mansei's elegant poetry, or, in the evening, if the wind blows in the maple trees, making the leaves sound, I recall the river at Jinyo, and I mimic the Minister Minamoto Tsunenobu in playing the biwa. When that has still not exhausted my mood, I try to skillfully combine the sound of the koto with that of the autumn wind through the pines, or the sound of a valley stream, as I accompany my prayer by playing on the biwa. I am clumsy in playing on the instrument, but, since no one else can hear it, it doesn't matter. Alone by myself in musical performance, or singing, it is only for personal enjoyment.
There is also a thatched cottage at the foot of this mountain. That is where this mountain's keeper lives, and there is a small boy there. Sometimes he comes to visit me. When I am bored with what I am doing, he may become my companion on the walks I take. He is ten years old and I am sixty. The age difference is great, but the pleasure we take in walking is the same. Sometimes we pull up the sprouts of chugaya flowers, gather peach moss, pull up rice bran, or pick Japanese parsley. Sometimes walking in the fields at the foot of the mountain we may also glean heads of grain. If the weather is nice, we may climb to the summit of the mountain and look out over Kobatayama, Fushimi Village, Toba, or Hatsukashi. This is a good neighborhood for this kind of scenery, and, best of all, since it is not owned by anyone, I can look at it all I want to with no one able to keep me from it. When I feel like walking further, we may traverse a series of peaks, passing Sumiyama and Kasatori, perhaps, to visit Iwama Temple, or Ishiyama Temple, to worship. Or we may cross Awazu Plain to look for the ruined hut where the old man Semimaru used to stay, or crossing the Tanakami River to visit Sara Maru Taiyu's grave. On the way back, depending on the season, we may look at the cherry blossoms, or observe the maple leaves, breaking off the bracken tree's berries to place before the Buddha's altar at home, or just to eat. When my heart is becoming lonely in the evening, I look at the moon from the hut's window, and think about old friends, and hear the voice of the monkey, my tears flowing sentimentally. In the grass of the high meadow there seem to be fireflies, but they also seem to be points of fire on Maki no Shima. At dawn I also like to hear the rain blowing in the leaves of the trees like a storm. When I hear the weeping chirp of the mountain birds, I think of children calling their father and mother. And when I see the approach of the mountain deer near the summit without fear, I understand how far I have been separated from society. Or when I again rake the banked fire when I am unable to sleep, I do it as an old friend. These mountain recesses are not fearful, and the lonely owl's voice, rather than sounding frightening, has a sad charm. The mountain scene, in going through the artistic effects of the four seasons, offers abundant change, never exhausts your interest. Since I feel this way, I think any deep thinking person, or person more knowledgeable than I am, would find the experience I have described of unlimited value.
Though when I came here I only expected to be living in this place for a short time, it has already been five years. I have gotten used to this temporary residence, as the dead leaves have collected in the eaves, and the moss has grown on the foundation. Naturally, on occasion, I have heard of happenings in Heian-kyo since I have retreated to the mountain, of how many of the people in high social position have died. I couldn't count the number of people of lower position who have, or how many houses have been consumed by fire. But I have no concern about the security of this temporary residence. Even if it is small, it offers a place to sleep at night and a place to sit during the day. There is no shortage of room for my single body. It provides a small shell, like the hermit crab likes, somewhere to return to when danger threatens. The osprey always lives on the windswept seashore, because it fears the proximity of human beings. I am like the hermit crab and the osprey. If you are insecure living in the capital, you should not busy yourself with worldly desire. Only the quiet life is important, and taking pleasure in assuming its hardships. Ordinary people cannot give up their house, feeling that it is needed to preserve their safety. Some consider it necessary as a place for their wife and children, for the family structure, others for their intimates and friends. Some may build for landowners, or teachers, or own property to keep cows and horses, but others have no need to construct a building. Asked why I live like this, given the present circumstances of the world, and my own position, I say that I have no wife and children, and no need to rely upon servants. If I were to build a larger house, who would be staying with me? Who would I live with?
It may be important to people who have friends to have property, and a superficially friendly person makes a lot of friends. It is not necessary for a person who has friendships, or a gentle character. If it was, you are better off with no friends. It is better to have only music and the changing landscapes of the seasons as your friends. People's servants must be rewarded. It is important that they receive a great many benefits. If they are treated kindly, without these benefits, there is little likelihood of tranquility of life. Because of that, I myself do without servants. I have become my own servant, which is the better way. If I have something to do, I use my own body. If I am tired, it is still better than using other people, where there is so much more to worry about. If it is necessary to walk, I use my own legs. If I am tired, it is still better than the trouble of taking care of a horse, or riding in an ox-cart. With one body, the work can be divided between two hands and two feet. With my hands as my servants and feet as my vehicles, I do everything entirely by myself. Because I understand the emotional distress and torment of my own body very well, I know when I need to rest to improve my spirit. Even if I use my own body, I don't often have to for too long a time. Since feeling tired is up to me to determine, there is no reason to overdo it. And, if a person always walks, he is always moving his body, which tends to keep him thin and promote good health. There is no encouragement to be lazy. To make other people suffer is a sinful thing. So why borrow other people's strength and energy? Clothing and food are also concerns. Plain, coarse clothing can be woven from arrowroot, and hemp can be used for bedding. Whatever I can make by hand is good to wear. I grow starwort in the field, and gather nuts from the trees by the mountain peak, and in this way sustain life. I might be concerned to expose myself to other people dressed so, but since I have no others to see me, have no cause for remorse. And I might feel that I am eating poor things, but, though they are poor, they are the product of my own industry and I thank heaven for them, This leads to happiness, a rich life, which I say without sarcasm--by myself alone, using my own body--compared to the life I led before.
Since entering the priesthood, fear and resentment of other people has disappeared. Because life is under heaven's control, it doesn't matter if I live long or not. I am not concerned about early death, am like a floating cloud, and do not complain. The happiness of my life can be expressed in one peaceful nap, and in the hope of seeing the beautiful scenery of the four seasons.
In general, the past, present, and future history of human beings is a product of the mind. If there is no peace of mind in possessing the elephant or horse, or the seven wonders or treasures of the world, it is meaningless to have palaces and buildings of many stories. Now I dwell in my tranquil residence. It is only a ten-foot hut, but I love it. When I want to go to the capital for something, I may feel ashamed to go in the appearance of a beggar, but I return feeling sorry for the people I see there, who are so caught up in and preoccupied with wealth and honor, so busy doing things. If you are doubtful about what I am saying, look at the situation of the fish and the birds. Fish are always in the water, yet they don't become bored with the water. If you are not a fish you probably can't understand that feeling. Birds hope to live in the forest. If you are not a bird, you probably can't understand that motive. My feeling about my tranquil residence is of the same kind. Who can understand this if they haven't tried it?
My life, like the waning moon, is about to finish. The remaining days are few. Soon the Three Ways of the Hereafter will begin. The acts of my whole life may be criticized. An important Buddhist teaching is not to form attachment to anything of this world. I now feel that it is a crime to begin to love this hermitage so much. I have also persisted in the silent life here, that may become an obstacle to salvation too, perhaps. Why am I wasting time speaking about this worthless happiness with so little time remaining? This is not the thing to do.
Thinking about this at dawn after a quiet night, I try to give vent to my own heart facing these questions. "Chomei, by trying to escape from the world by going to the mountains and forests this way, to put the disorder of your heart into order is a Buddhist practice. And yet, while trying to become a pure monk, your heart remains tainted by impurity. By living in a ten-foot hut in imitation of the Jomyo Buddhist layman Yuima, even if you are given the benefit of the doubt, you have not realized the practice of Shuri Handoku. When you perhaps do by chance, doesn't your karma's punishment worry you? Or again, by reckless judgment, not becoming more intelligent you grow worse by this, grow crazy. What do you think?" When I ask myself like this, my heart cannot answer. I have no answer. There is one way remaining. I continue to move my tongue, but I am unable to welcome the celebration of Amida Nurai. I only chant two or three times. That is all.
It is now Senryo Two (1212), the end of March. I have become a priest. I remain in Hino's Toyama hut, and am writing this letter.
-
 @ 6871d8df:4a9396c1
2024-09-11 19:10:52
@ 6871d8df:4a9396c1
2024-09-11 19:10:52Darryl Cooper — aka Martyrmade — has had a whirlwind of a couple of weeks.
For those who don't know Cooper, he is a Twitter personality and podcaster who wades into some weighty subject matter. I first found him from a tweet that went viral back in 2021, which resonated with me so absolutely that I had to give him a follow.
From there, I saw he was a history buff and had a podcast exploring complicated, deep, interesting topics that I have seen very few people explore.
I started to listen and became hooked.
Cooper's material is long. Some series go on for about 30 hours of podcast time. Don't let the length fool you, though; they are engaging in a way that I have yet to experience with history material. He explores topics with such incredible nuance and detail that you almost feel like you're there. He dives deep into each side's motivations, bringing the events to life in such vivid detail that you feel right in the middle of it all.
Shilling for him aside, I wasn't the only one who became hooked and wanted to share his content. Joining me was Tucker Carlson, who had him on his podcast, talking to him about a wide array of subjects.
However, there was a particular spot in his podcast that caused quite a stir: Cooper's thoughts on WWII.
Without diving into specifics, Cooper's analysis of WWII veered into territory that challenged some of the widely accepted narratives about the war. He predicted the backlash, noting that certain topics have become untouchable, akin to mythic lore. And sure enough, the media response was swift and harsh.
The backlash was unnecessary and deeply disappointing, especially from some personalities I admire. For me, the most grotesque response was from Niall Ferguson.
The subject matter of the response aside, the way he responded, and the attacks he threw at Cooper were the most disappointing. I have no issue with historians who want to challenge his thoughts on the merits, but interestingly, to do that alone was rare. To start his response to Cooper, Ferguson talks of Tucker Carlson's description of Cooper as
"the most important popular historian working in the United States today"
as ridiculous because
"...when I went to look for his books. There are none."
So yeah, Cooper is a charlatan because he hasn't written any books.
But as someone who likes and respects Niall — I have read two of his books, The Accent of Money and Civilization — I can say that as a historian, I can't recall a single thing from him.
Unfortunately, I couldn't repeat one piece of information, insight, or overarching point he was trying to convey in either of those books. Although, I'll be the first to admit that I am sure they were well-researched and elegantly put together.
While I respect Ferguson's research, his books felt distant and dry, like they were more concerned with academic posturing than engaging the reader. In contrast, Cooper's work draws you in emotionally, giving the history real weight and relevance.
For example, I will always remember Fear & Loathing in New Jerusalem by Cooper. I listened to all 26 hours- the equivalent of any book- and was hooked for two weeks straight.
You can almost feel that it hurts him to get into the minds of those in the middle of these conflicts. The passion seems genuine, which makes the content much more accessible to digest and trust. Cooper doesn't just teach history; he makes you feel the weight of it.
He made me fully appreciate how complex the issues in the Middle East were in a way that made me actually feel educated on the subject. Interestingly, I didn't come out choosing a side, either. I came out understanding why we are here where we are today and why there are such passionate voices on both sides, which, for me, is far more significant.
So yeah, sure — he hasn't written any books 🤷♂️. But is that what the goal of a historian should be? To write books? No, obviously not. A historian's role isn't just to churn out books or pile up credentials; it's to help people understand the complexities of the past and foster empathy for those who lived through it. For me, a good historian answers this question:
How did I help the audience better understand the complexities of the period I'm teaching, fostering empathy for the challenges and perspectives of the people of that time?
And with that goal, Cooper does that as well as anyone.
Sometimes, I am unpleasantly reminded that even though they rail against their tactics, the conservatives can fall just as easily into the elitism of academic credentialism as progressives.
Ironically, starting his argument with those cheap attacks made me roll my eyes rather than want to take his criticisms seriously. Ferguson's critique reflects a broader issue within academic circles—an overemphasis on credentials at the expense of real engagement or value-add with audiences and source material. But as the way we consume information shifts, so too must our understanding of what makes a historian valuable.
At the end of the day, we shouldn't measure historical understanding by credentials or publications alone. It's about fostering empathy, grappling with nuance, and helping people grasp the complexities of the past. By that measure, Darryl Cooper is as much a historian as anyone—whether or not he's written a book. In a world where we increasingly consume information through podcasts and social media, perhaps the future of history looks a lot more like Darryl Cooper's work—engaging, empathetic, and free from the constraints of academia.
-
 @ 3b7fc823:e194354f
2024-09-11 19:08:03
@ 3b7fc823:e194354f
2024-09-11 19:08:03Operational Security and Your Digital Life
I. Definitions
Operations security (OPSEC) is a process that identifies what information can be seen by threat actors, whether that information could be weaponized, and possible mitigation actions.
Your digital life is every interaction you have, all personal identifying, financial, and health information, your preferences, your habits, and any history that can be obtained both publicly and privately that has ever been recorded or digitized.
Your digital life is a incredibly rich field for various actors to observe, record, analyze, sell, and exploit for profit, harm, or control. Some of this information you give away without thinking (social media), some you give to one party but it is shared without your knowledge to other parties (data brokers, big tech), or it is taken without your consent (criminals, governments).
II. Threats
It would be impossible to list them all but a few examples:
Mass surveillance by governments to fight crime, terrorism, civil unrest, and control the population. This is across the board blanket information on everyone that is stored for later use from feeding algorithms for social credit systems to lists of people who are threats that need to be disappeared. The only variable is how explicit the government in question is doing it.
Corporate surveillance by public and private companies for marketing, market share, or selling for profit. Your data is incredibly profitable. Entire mega companies have built their entire business model on it like Google, Meta, and various Data Brokers. This information is collected and stored. It is then used internally, sold for profit, acquired by governments, or stolen by nefarious actors.
Criminal or Nefarious Surveillance for harm, control, or profit. This is a catch all from partners in a controlling relationship, angry ex's wanting revenge, religions and groups watching their members, terrorists and cults looking for people to recruit or indoctrinate, and foreign espionage to plain old criminals who want your information to sell to other criminals, looking for blackmail opportunities, to steal your financial or social accounts, or identity theft.
III. Mitigation
To do this properly a security self audit should be performed to determine exactly what assets you have to protect, how at risk they are, ranking their priority, and specific steps that are needed to protect them. I will detail how to do this for the average person in a later post but until then we will stick to generalities.
It is impossible to to block or hide all information all the time. Not only is it impossible but it would be exhausting to even try. This is where most people interested in privacy get confused, lost, and give up the idea of privacy because the only path they see to achieve it is living in a underground faraday cage out in the woods.
The only viable path is obscurity and compartmentlizion. Compartmentation of your devices, accounts, and digital selves is wildly misunderstood and not applied properly. Done incorrectly this can be disastrous if you are too casual with something that you thought was hidden or putting a spotlight on yourself by attempting to be obscured.
IV. Tactics For Everyone
Common advice I give to everyone. I don't care what your thoughts are on privacy and security, you should be doing this.
-
Do not give your personal email or phone number to anyone except friends and family. This just opens you up to spam, phishing attacks, and an identifying tracer. Use a email alias service or a throw away email account to give to stores and online accounts. Get a VOIP number for that dating app or service quote. When your real number rings, recieves texts, or get a email you know it is from someone you know and trust.
-
Use cash locally if you can and for everything else get a virtual debit or credit card with a spending limit or fixed amount. Do you really need your entire paycheck, emergency savings, life savings tied to a single card / account? Are you really entering your real credit card or banking information into a random website to buy something? Even if it's not a scam site, how well are they protecting it while in transit or storage? You will probably get the money back in case of fraud but why feed the beast and besides it's a total hassle to get your accounts frozen, wait for reimbursement, open and change accounts. Just avoid it. For extra credit you can use visa gift cards purchased with cash to obscure your financial transactions if you choose. Every financial transaction doesn't have to be public record.
-
Stop using unencrypted phone calls and SMS texts. Switch to encrypted options such as Signal or SimpleX and make anyone who wants to have contact with you reach out to you on it. Even if you "have nothing to hide" there is no reason for you to broadcast every personal conversation, comment, or shared meme with Ma'bell, the government, and anyone else listening and recording. Seriously, just stop.
V. Compartmentation of Your Digital Selves
I will keep this very high level as this article has already run longer than I intended but will cover this in much greater detail in the future.
You can break down all digital activities and interactions into several broad categories or digital selves. Then build separate systems for use in each category depending on the activity and need. The trick is to preplan what activities go where. Using the wrong account on the wrong system means they are now burned. Letting the systems overlap and contaminate each other then you risk exposing anything ever done on those systems. The separation can be accomplished with multiple accounts and devices, isolated virtual machines, or operating systems that enable compartmentation such as Qubes OS or Tails.
VI. Breakdown
- Public
This is the default. This is you. Your real name, address, and details. This is unavoidable and would be weird and attract attention if you didn't have one.
Use this for any KYC activities that you have to log into such as taxes, bank accounts, utility bills, etc. Clearnet only, you have nothing to hide.
Awareness: If it has to be public then put your best foot forward. Only show them what you want them to see and make it good and boring. Blend into the crowd of normies not important enough to pay attention to.
- Private No logins to KYC services. Traffic routed through a VPN. Use of sudo anonymous account names. You are Neo, not Mr. Anderson.
Use for most social media that is not public facing. Shopping and browsing that would be embarrassing or misunderstood if made public. Encrypted to protect against criminals and looky loos. A good default if people just don't need to know.
Awareness: Do not be confused by the word private. The goal is to make it to difficult, to expensive, or just not worth the effort to determine exactly who you are and what you are doing but it's not impossible. Only use this with the knowledge that someday it might get doxxed. That potential only increases with time and frequency of use of accounts. Not to be used for anything that could be considered illegal or has the potential to get you fired or cancelled.
- Anonymous Only single use non KYC logins. Single purpose accounts and names that are burned after achieving that purpose. Traffic routed only through Tor. Encryption by default.
Use if you are a whistle blower, freedom fighter, activist, or for shady activities.
Awareness: Be very careful and deliberate with this system as to not accidentally compromise it with something that would have been better served by a different system. Rotate and clean accounts and systems often. Don't carry stuff over after a cleaning to a new system. Reusing names and handles is how people get busted.
- Nemo
Nemo doesn't exist. There is no record that they ever existed. Only amnesiac systems are even used and never a login. If files or traces are left behind they are encrypted, hidden, and have plausible deniability.
Enjoy anon, more to come.
-
-
 @ 1d5357bf:1bdf0a52
2024-09-11 18:49:09
@ 1d5357bf:1bdf0a52
2024-09-11 18:49:09Recently, a heated discussion emerged following a well-known influencer's announcement of their collaboration with a prominent financial institution to offer a Bitcoin custody product. This raised a few eyebrows, especially given that this influencer, who happens to be the author of a highly regarded book in the Bitcoin space, seems to have shifted away from Bitcoin’s core ethos of individual sovereignty and self-custody. While some expressed disappointment in the influencer, the conversation sparked a deeper debate on what is truly needed for the mass adoption of Bitcoin.
One participant argued that mass adoption will only occur when Bitcoin can be used seamlessly, without people even realizing they’re using it. They drew a comparison to how credit cards, Apple Pay, and Google Pay work today: most users don’t understand or care about the underlying technology. They simply use these systems because they are convenient and meet a need. The argument was that Bitcoin will reach mass adoption when it reaches a similar level of simplicity and invisibility.
On the surface, this sounds like a reasonable path toward adoption. But I see a fundamental problem with the idea that people shouldn't know or care about what they’re using. It's not about understanding the technical intricacies of Bitcoin’s code or blockchain mechanics—most people won’t ever need that level of knowledge. The issue lies in users not being aware of the risks associated with their actions, especially when using custodial solutions for holding Bitcoin.
If someone places their Bitcoin (or rather, IOUs representing Bitcoin) in a custodial service, it’s crucial that they understand the counterparty risks involved. These risks include asset inflation (as we’ve seen with fractional reserve banking), bank runs, transaction censorship, or even outright asset seizure. Unfortunately, many influencers don’t talk about these risks when promoting custodial solutions. Instead, they focus on the “to the moon” narrative, framing Bitcoin solely as a hard asset that will protect users in the event of some future apocalypse, often referred to as "hyperbitcoinization." This narrative, though appealing, leaves out crucial details about the very real risks of custody and the importance of self-sovereignty.
The distinction between custodial solutions and true Bitcoin ownership must be made crystal clear. Holding Bitcoin on an exchange or through a custodial product may expose you to Bitcoin’s price movements, but you don’t actually own Bitcoin in the purest sense. You own a promise of Bitcoin. And that distinction could make all the difference if things go wrong.
Self-custody, on the other hand, brings its own responsibilities but also delivers on the fundamental principles for which Bitcoin was created. Yes, it requires users to manage their own keys and bear the consequences if something goes wrong, but it provides the level of sovereignty that Bitcoin was designed to offer. There’s no counterparty to trust, no intermediary to confiscate or censor your assets, and no institution that can suddenly become insolvent and take your Bitcoin with it.
To me, Bitcoin adoption should be more organic. While it’s true that Bitcoiners benefit from a broader network of users, especially in terms of price stability and reduced manipulation, it’s even more important that new users understand what they’re getting into. It’s not enough for people to simply hold Bitcoin. They should be aware of the reasons why self-custody matters, the advantages of running a node, and even the importance of participating in mining.
In an ideal world, every group of friends or family would have an “Uncle Jim”—someone knowledgeable about Bitcoin who could help guide others through the complexities of self-custody, nodes, and mining. This grassroots approach would ensure that new adopters are well-informed, capable, and truly sovereign in their Bitcoin ownership.
Mass adoption is not just about making Bitcoin easy to use. It's about educating people on the trade-offs of convenience versus sovereignty, on the risks of custodial solutions, and on the long-term vision of Bitcoin as a tool for individual empowerment. We don’t need Bitcoin to become invisible to achieve adoption. We need it to become understood.
-
 @ 361d3e1e:50bc10a8
2024-09-11 18:40:39
@ 361d3e1e:50bc10a8
2024-09-11 18:40:39What kind of stickers do they put on children in schools and what do they aim for?
usa #california #freespeech #truth #school #children #stickers
-
 @ c7eadcf0:7821e562
2024-09-11 18:34:12
@ c7eadcf0:7821e562
2024-09-11 18:34:12This is a question that isn't thought about very often but should be reconsidered in my opinion. While I'm not super technical when it comes to Bitcoin, anyone that has been around Bitcoin for awhile can and will notice disturbing trends in the mining space.
What is the first thing that pops into your head when you think about Bitcoin. For me its the 21 million hard cap and censorship resistant money but what does it mean to be censorship resistant? In essence what censorship resistant means is that your transaction can not be stopped arbitrarily by a third party unlike what they can do in the fiat system. In the fiat system there are tons of choke points that can stop your transaction from going through and conducting business with anyone that you want. Banks stop payments all the time for all kinds of stupid reasons.
This is a form of censorship. The government doesn't like you or your political activism, bam there goes your bank account so no you have no way of even conducting commerce in a efficient way. Don't believe me? Here a a few examples of banks and governments censoring individuals and groups they don't approve of.
Chokepoint 2.0: How Regulator Fight Bitcoin With Financial Censorship
[Nigerian Banks Shut Them Out, so These Activists Are Using Bitcoin to Battle Police Brutality]
There are just two examples of how censorship is being used as a weapon to stop people from using their god given rights as human beings to live their lives as they see fit. We know that the fiat world has the power to censor your transactions but what about in the Bitcoin ecosystem?
As a Bitcoiner you would think that you don't have to worry about stuff like that. Well think again. If you have been watching the Bitcoin mining space lately, you have seen the growth of these large companies with a boat load of ASICs and hashrate. As a Bitcoin pleb its hard to compete with that kind of scale, so less regular joes like us can't mine profitably at home thus reducing the decentralization of hashrate to the large public miners.
In addition to less hashrate being controlled by pleb miners, these large miners point there hashrate to the largest pools out there such as Foundry and Antpool.
https://image.nostr.build/fb547485c8414dab4ef0c2997ae10cda89f7d866d255ce4e97613f5d71bf6ed4.jpg
This image is from the minermag.com. What do you notice about this graph? Lots and lots of centralization going on. Between 2020 and 2024 the top three pools went from 50 percent, mind you which isn't great to begin with and now the top 3 pools control 65 percent of the Bitcoin hashrate is scary as hell and is not a topic that I hear anyone on #Nostr talking about. That's not a diss on anyone, just an issue that needs to be more widely discussed as it has wider implications for all of us.
With this much centralization going on in the mining space how easy will it be for governments to target these large mining pools and tell them to start to censor certain types of transactions.
Governments would have this ability because most miners simply provide hash power and leave the construction of what goes into a #Bitcoin block to the pool operators. To be honest I had no idea that this was the case until recently. So basically Antpool and Foundry get to decide what blocks look like, cool right? Bitcoin isn't looking so decentralized now, is it?
It would be rather trivial for governments to tell these pools to exclude things like ordinals, coinjoins or even opening lightning channels for that matter. When you put a gun to their head and threaten them with excessive fines and jail time, guess what these CEO are going to do. Sellout and cover their assess. It happens every time. This is why it is so incredibly important to decentralize mining pools and promote solo mining as much as we can. There are moves being made in that direction with the Ocean Mining Pool and their radically different approach to operating a mining pool.
Ocean Mining only coordinates the payout split and does not payout simply because you are supplying hashrate to the pool such as with the Pay Per Last N Shares (PPLNS) set up that is popular right now.
There are companies that are trying to turn the tide on mining centralization, the one I like the most and is the most accessible to the average person is the Bitaxe miner. Sure its not very powerful when you compare it to the latest and greatest ASIC but it stays true to the Bitcoin ethos of decentralized mining.
Not long ago a Bitaxe miner found a block! The odds of finding a block with these tiny machines is small but hey why not. You have a chance to find a block and you are living up to the ethos of Bitcoin. That's enough for me to be honest.
I hope that this recent trend of centralization can be reversed before its too late. In the mean time spread the word about Bitcoin and Nostr to all of your friends and family!
Bitcoin
-
 @ 622bd9cb:10a061b3
2024-09-11 16:41:08
@ 622bd9cb:10a061b3
2024-09-11 16:41:08Get back to ye olde newsgroup! BACK I SAY!!
-
 @ 6ad3e2a3:c90b7740
2024-09-11 15:16:53
@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous.
In other words, my primary negative sentiment — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause catastrophic outcomes — stems from a sort of disappointed idealism, not cynicism.
On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important.
That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played.
Twitter threads don’t show up on substack anymore, but I’d encourage you to read this one with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end.
The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism:
 I’d encourage people to read the entire thread, but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.
I’d encourage people to read the entire thread, but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore.
The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true.
The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good.
In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.”
I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
-
 @ 361d3e1e:50bc10a8
2024-09-11 14:41:28
@ 361d3e1e:50bc10a8
2024-09-11 14:41:28Why is chemtrails needed? If you know the whole truth you will start supporting chemtrails.
usa #chemtrails #billgates #climate #haarp #truth #politics #climatechange
-
 @ 6bf975a0:65de1244
2024-09-11 12:48:27
@ 6bf975a0:65de1244
2024-09-11 12:48:27Всем привет! Это открытое сообщество, поэтому потенциальная аудитория постов может быть чуть больше, чем мы рассчитываем, но это ок и не страшно, потому что конфиденциальных данных здесь не будет.
Как мы будем работать с этим сообществом?
- Прежде всего, нужно сделать аккаунт в Nostr. Особенность этой сети такова, что всё, что вы постите в ней (в том числе в любых сообществах), будет автоматически отображаться у ваших подписчиков (если они будут). Поэтому если вдруг (ну, мало ли) вы захотите постить что-либо личное вместе с ответами на вопросы заданий, весь этот контент окажется в одной ленте. Если это ок для вас, все хорошо. Если нет, лучше сделать отдельные аккаунты для личных постов и для ответов на задания. Как, например, сделал я.
- По каждой теме здесь будет её структура. Информацию для заполнения этой структуры — определения, типологии, кейсы — вы ищете самостоятельно через нейросеть Perplexity. Она работает без каких-либо ухищрений, достаточно только зарегистрироваться. Найденный материал вы оставляете в комментариях к постам с названиями соответствующих тем.
- Отдельным постами здесь будут видео, иллюстрации и другой наглядный контент к темам. Его мы посмотрим в онлайне, и благодаря постам в этом сообществе всегда можно будет вернуться к нему позже
Приложения
- Комментировать можно через любое приложение. Habla.news удобна для больших комментариев. Ей я и пользуюсь. Авторизация в ней через расширение в браузере nos2x для браузеров на основе Chrome
Начнём!
-
 @ 3c7d12a6:9532013e
2024-09-11 09:07:36
@ 3c7d12a6:9532013e
2024-09-11 09:07:36NUD: Pubkey to waveform
This NUD defines how to convert pubkey to waveform.

Why?
npubis nonsense to display.- too long.
npub1bla...blais nonsense to display.npub1takes too much space....means nothing.
Specs
- Uses hex pubkey.
- Converts 64 characters into 32 scalars.
- Splits 64 with 2 length chunks.
- Converts each chunk into a scalar.
0 ~ 255to-1.0 ~ 1.0
-
 @ 2bc6e990:70c64098
2024-09-11 09:00:23
@ 2bc6e990:70c64098
2024-09-11 09:00:23
The automotive industry is undergoing a significant transformation in 2024, driven by key technological advancements that are reshaping the future of transportation. Electric vehicles (EVs) are becoming more efficient and accessible, while autonomous driving technology continues to evolve, bringing safer, self-driving cars closer to reality. Connected car technologies are enhancing the driving experience by integrating vehicles with smart devices and utilizing data to improve performance. At the same time, sustainability is a major focus, with automakers adopting eco-friendly materials and energy-efficient systems. Additionally, artificial intelligence (AI) and data analytics are revolutionizing vehicle safety and personalization, paving the way for smarter, greener, and more innovative vehicles.
Source: Triangle Tires Philippines
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ 361d3e1e:50bc10a8
2024-09-11 07:27:02
@ 361d3e1e:50bc10a8
2024-09-11 07:27:02Are WHO troops preparing for the pandemic a month before the election?
usa #politics #election #election2024 #pandemic #trump #maga #truth #freespeech #vote2024
-
 @ bf95e1a4:ebdcc848
2024-09-11 06:31:05
@ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good!
If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! https://bitcoininfinitystore.com/
Intro
Luke: Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us.
Paolo: Thank you for having us.
Knut: Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we?
Luke: Sounds like that's the plan. So thank you again, both for joining us.
Introducing Paolo and Mathias
Luke: would you both mind giving a quick introduction on yourselves just so our listeners have the background on you
Paolo: Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate.
Luke: And, Mathias, over to you.
Mathias: Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use.
P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that.
And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here.
Luke: Oh, fantastic.
Introduction to Holepunch
Luke: Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch.
What is Holepunch and what are you doing?
Mathias: Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us.
but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy.
It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God.
that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks.
Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use,
Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it?
and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world.
And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company.
And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand.
anything, super exciting and, encourage everybody to try to check it out.
Luke: we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product?
What is the easiest way that you would explain what it is?
The Vision Behind Keet
Mathias: But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer
People don't care about technology. We loved it, but don't have that surface off too much to the user.
Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it.
It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard.
And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that.
Keet vs Nostr
Knut: Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here.
Paolo: I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform.
And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly.
You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users.
So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays.
and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology.
It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace.
Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly.
Luke: Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that.
Pear Runtime
Luke: So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform,
Mathias: Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So
We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it.
And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications.
We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that.
So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve.
But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything.
So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view.
and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard.
so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example.
It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app.
So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place.
But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that.
And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone.
And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached.
Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like
Knut: and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective.
And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that?
Mathias: I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective.
And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things.
I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point.
Decentralization vs. Centralization
Luke: So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor?
Mathias: yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias.
I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right?
Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions.
and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers.
That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there.
And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far.
Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features.
And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users.
And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is.
It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that.
And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key
Paolo: I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites.
But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept.
over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud.
And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers.
the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on.
is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole.
And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before.
Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize.
And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system.
And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country.
So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to.
Knut: Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives.
So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right?
Mathias: I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all.
So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting.
yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why
Challenges and Future of Decentralization
Luke: So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company.
And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing.
So is there a limitation to how far this can go?
Paolo: I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world.
Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling.
So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house.
I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created.
imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you.
Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure.
So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another.
And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example.
Knut: Yeah.
Mathias: I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money.
And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook?
it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way.
And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it.
We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback.
Bitcoin and Holepunch: Drawing Parallels
Mathias: I think, that's the main thing to think about in that. Discussion.
Luke: when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line.
And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin?
Paolo: Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange.
For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government.
and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right?
Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them.
and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them.
Luke: Yeah, fantastic.
The Future of Decentralized Communication
Luke: And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet.
So is, that a goal? Is that on the roadmap?
Paolo: Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world.
But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind.
Mathias: But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly.
And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app.
And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly,
Interoperability and User Experience
Luke: Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong,
Mathias: Very, true.
Luke: you backups with the same 1224 words.
Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be
Mathias: We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it.
Paolo: I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life.
You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build.
Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible.
Luke: Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems?
What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that?
Paolo: Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us.
The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity.
No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful.
Mathias: also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever.
but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera.
But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem.
And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it.
Paolo: And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options.
Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right?
you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion.
so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai.
So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that.
And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself.
And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center.
Knut: Yeah.
The Role of Tether in the Crypto Ecosystem
Knut: It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo?
And, what, made this thing happen? Can you give us the story here about Tether?
Tether's Origin and Evolution
Paolo: Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014.
it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat.
That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000.
But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right?
International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin.
For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic.
USDT's Impact on Emerging Markets
Paolo: So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries.
Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap.
So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time.
we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world.
At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right?
you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others.
And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT.
If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right?
So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U.
S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant.
Bitcoin as a Savings Account
Paolo: the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend.
The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies.
we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining.
We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other.
I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math.
That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin.
Knut: Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother.
Paolo: we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether.
So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right?
So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education.
Knut: No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic.
I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke.
Luke: Always say the title, Knut. Always say the title.
Knut: Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course.
Paolo: Oh, with pleasure, with great pleasure, with a nice, education.
Luke: Absolutely. Yep.
Plan B Forum and Future Events
Luke: 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year.
so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event.
Paolo: I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year.
I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world.
And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing.
Knut: No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time.
And I think we're even playing this year, aren't we, Luke?
Paolo: You're
Luke: yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos.
Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague?
Knut: paranoid and,
Paolo: Can I commission a
Knut: What song would you like to hear?
Paolo: I have two that I would suggest. One is Nothing Else Matters.
Knut: Alright.
Paolo: So I think that, is very inspiring, right?
Knut: Bitcoin, for sure.
Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke?
Mathias: we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference,
Knut: Yeah.
Mathias: not so much music, but yeah, that's peer to
Knut: Nothing else matters.
Luke: looking forward to that.
Knut: Sorry, brain fart. Sad but true is about the dollar still being around,
Paolo: Yeah, you can say that.
Luke: Okay.
Final Thoughts and Closing Remarks
Luke: Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that?
Mathias: only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms.
There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out.
Paolo: we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting.
Mathias: Just those things, that's all.
Paolo: Yeah, we can piss off more than this. Thanks.
Mathias: a
Luke: No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners?
Paolo: just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them.
Mathias: We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good.
Luke: So that's, all at Keet. Is that correct? For Keet?
Mathias: Key. io and pairs. com for our runtime. It's all peer to peer.
Knut: Alright,
Mathias: Wonderful. And you're also still on the legacy social media platforms, right? Yeah.
Knut: we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano.
Paolo: Likewise, I
Knut: But yeah, worth saying again.
Paolo: Thank you for having an invitation.
Luke: Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
-
 @ a012dc82:6458a70d
2024-09-11 02:30:59
@ a012dc82:6458a70d
2024-09-11 02:30:59Table Of Content
-
The Rise and Fall of Bitcoin's Price in 2021
-
Why Experts are Optimistic About Bitcoin's Future in 2023
-
Factors Influencing Bitcoin's Growth in 2023
-
What to Expect for Bitcoin Investors in the Coming Years
-
Conclusion
-
FAQ
The year 2021 was an eventful one for the world of cryptocurrency, with Bitcoin's price reaching an all-time high of over $60,000 in April before plunging to nearly half its value by May. The volatility of the digital currency market was a wake-up call for investors, especially those new to the game. However, despite these hiccups, experts are predicting that Bitcoin's price will continue to increase in 2023.
This article will explore the reasons why Bitcoin's price is predicted to increase despite the challenges it faced in 2021. We will also take a look at the factors that will influence its growth and what investors can expect in the coming years.
The Rise and Fall of Bitcoin's Price in 2021:
Bitcoin's price saw a rapid rise in early 2021, hitting an all-time high of over $60,000 in April. However, this was followed by a sharp decline, with the price falling to below $30,000 by July. This volatility can be attributed to several factors, including the following:
-
Elon Musk's tweets: Tesla CEO Elon Musk's tweets about Bitcoin, including his decision to stop accepting Bitcoin as payment for Tesla cars, had a significant impact on the digital currency market.
-
China's crackdown: The Chinese government's decision to crack down on cryptocurrency mining and trading had a ripple effect on the global market.
-
Regulatory concerns: Governments worldwide are still grappling with how to regulate cryptocurrencies, which has led to uncertainty in the market.
Why Experts are Optimistic About Bitcoin's Future in 2023:
Despite the challenges faced in 2021, experts remain optimistic about Bitcoin's future in 2023. Here are some of the reasons why:
-
Institutional adoption: Large institutions such as MicroStrategy, Square, and Tesla have invested heavily in Bitcoin, signaling a growing acceptance of cryptocurrencies.
-
Limited supply: Bitcoin's supply is limited to 21 million coins, which means that as demand increases, so will the price.
-
Increasing demand: As more people become familiar with Bitcoin and other cryptocurrencies, demand for them is expected to increase, driving up prices.
Factors Influencing Bitcoin's Growth in 2023:
Several factors will influence Bitcoin's growth in 2023, including the following:
-
Institutional adoption: As more large institutions invest in Bitcoin, it is expected to become more mainstream, leading to a further increase in demand.
-
Government regulation: The regulatory environment around cryptocurrencies is still uncertain, but as governments worldwide develop clearer guidelines, it will provide a more stable market for investors.
-
Technological advancements: Improvements in the underlying technology behind Bitcoin, such as faster transaction speeds and lower transaction fees, will increase its usability and drive up demand.
What to Expect for Bitcoin Investors in the Coming Years:
Bitcoin investors can expect continued volatility in the market, but experts predict that the price will continue to rise in the long term. Here are some tips for investors:
-
Invest for the long term: Bitcoin's price is likely to be volatile in the short term, but investing for the long term can help mitigate some of the risks associated with volatility.
-
Diversify your portfolio: As with any investment, it's important to diversify your portfolio to manage risk. Consider investing in other cryptocurrencies or traditional assets.
-
Stay informed: Stay up to date with the latest news and developments in the cryptocurrency market, including regulatory changes and technological advancements.
Conclusion
Despite the challenges faced by Bitcoin in 2021, experts remain optimistic about its future in 2023. Factors such as institutional adoption, limited supply, and increasing demand are expected to drive up its price in the long term. However, investors should remain cautious and be prepared for continued volatility in the short term. By diversifying their portfolios, staying informed, and investing for the long term, investors can potentially reap the benefits of Bitcoin's predicted growth in the coming years. Despite hiccups, Bitcoin price is predicted to increase in 2023, making it an exciting investment opportunity for those willing to take on the risks.
FAQ
Will Bitcoin's price continue to be volatile in 2023? While Bitcoin's price is expected to increase in the long term, it is likely to continue to be volatile in the short term.
Is Bitcoin a good investment for the long term? Bitcoin can be a good investment for the long term, but it's important to remember that it's a high-risk investment and should only be considered as part of a diversified portfolio.
What factors will influence Bitcoin's growth in 2023? Factors that will influence Bitcoin's growth in 2023 include institutional adoption, government regulation, and technological advancements.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8cb60e21:5f2deaea
2024-09-10 21:14:08
@ 8cb60e21:5f2deaea
2024-09-10 21:14:08 -
 @ e5272de9:a16a102f
2024-09-10 19:13:30
@ e5272de9:a16a102f
2024-09-10 19:13:30What is the Grapevine?
The Grapevine enables you and your community to identify who is the most trustworthy, and in what context, to curate content, facts, and information.
In this article we present an overview of the Grapevine Worldview, a visualization tool and control panel for the management of your grapevine.
How does the grapevine work?
The construction of a Grapevine Worldview can be broken down into the following steps:
Step 1. Decide what question you want to answer or the problem you want to solve. For example: curate a directory of nostr apps. The finished product will be a ranked list, G, of items that may be pubkeys or could be something else, e.g. products from an eCommerce site.
Step 2. Select whatever sources of raw data (usually from within nostr, but in theory, could come from outside nostr) that are both 1) available to you and 2) relevant to the question or problem. (See Table: Sources of Raw Data at [1].)
Step 3. Translate each data source into a format suitable for consumption by the grapevine through the process of interpretation (see [1]).
Step 4. Crunch the numbers using the GrapeRank equations. Each purple arrow in the Worldview represents a single iteration. If the arrow loops around in a circle, iterations repeat until convergence. The finished product will be a list G of items, ranked by GrapeRank score.
Step 5: Consume the list G in whatever way you see fit. If the product is a ranked list of pubkeys, it may be used to curate a feed or you may use it as part of the curation process within other Worldviews.
The Worldview is designed to give a big picture overview of the entire above process. In this post I will walk though a simple example of a hypothetical Grapevine Worldview, designed around the problem of how to curate a list of nostr apps.
Example Worldview: Curation of Nostr Apps
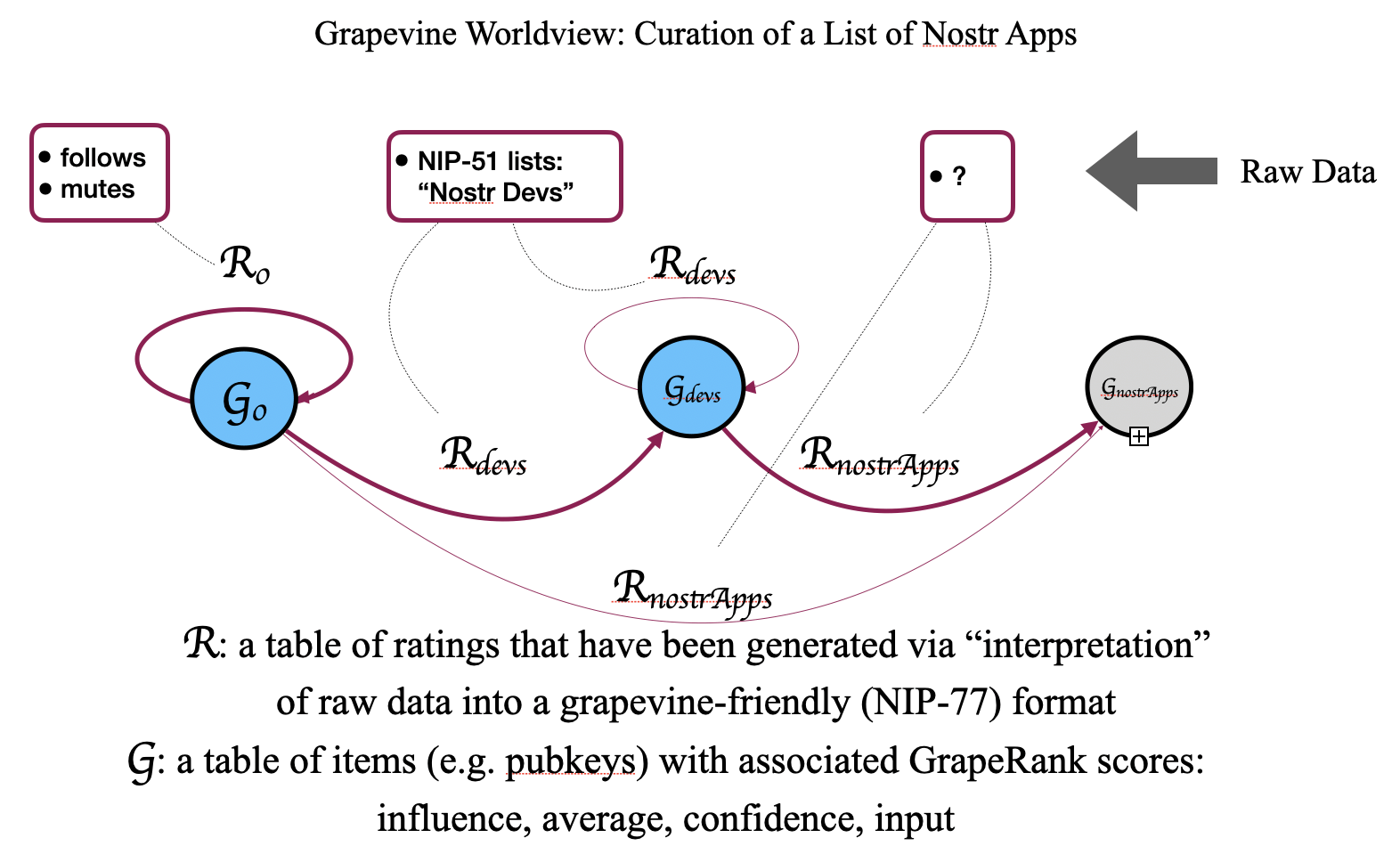
The Worldview in the above figure is designed for a specific purpose: to manage a list of nostr apps. [2]
Each node G on the worldview represents a table of items, each of which is associated with a contextual GrapeRank score, calculated using the GrapeRank algorithm. The blue nodes represent tables of pubkeys, and the grey node represents a list of non-pubkey items, in this case the list of nostr apps.
Each edge (purple arrow) is associated with an array R of ratings r, each of which must follow the Grapevine Ratings format. Each R is generated from raw ratings data that can be from any source, in any format. Multiple categories of data can be merged into a single dataset R. For each R, and for each category of raw data that contributes to R, an explicit Interpretation must be provided.
If we look from left to right in the above figure, we can see information processed through the following stages:
Stage 1: Follows and mutes (raw ratings data) is used to curate G_o: a table of pubkeys that are (probably) not bots or other bad actors
Stage 2: NIP-51 lists entitled "Nostr Devs" (raw data) is used to curate G_devs. Note that authors of these lists are filtered and weighted using G_o from the previous stage.
Stage 3: Content authored by G_devs is used to curate G_nostrApps, the list of Nost Apps.
The source of potential items to initialize the list G_nostrApps is unspecified in the worldview, but one possibility would be to make use of Nostr forms, as seen at formstr.
The content used to initialized R_nostrApps used in stage 3 is also left unspecified. One possibility would be to use NIP-32 labels to endorse submitted items as belonging / not belonging on the list. Anyone could submit labels, but only pubkeys represented in G_0 or G_devs will be given a voice, and that voice will be proportional to that pubkey's influence score. The relative thickness of the two purple arrows leading to the G_nostrApps node on the right tells us that nostr developers are given a louder voice in the final curation of G_nostrApps.
Values and choices of the end-user
The Grapevine Worldview places the values and choices of the end user center stage. These choices are manifest in several ways: * the choice of raw data: what is included, what data is available but ignored * the specifics of the interpretation of each category of raw data into a list R of individual ratings r * the overall topology of the Worldview, including the choices of which G's to incorporate * the demonstrated willingness to expend computational energy on any given aspects of the above. For now, the computational energy will be trivial. At some point, the energy expenditure will have a nontrivial cost.
Summary
The Grapevine Worldview is a visual overview and a control panel for the process leading up to the curation of some category of content by your grapevine. Construction of any given worldview includes decisions on who should be trusted to curate what. These decisions may or may not be the same from one end user to another.
Each user can manage multiple Worldviews, each one of which is purposed for the curation of a given G. And the output of one Worldview, G, can be consumed by a different Worldview.
Current efforts are directed at creating an open source library for the GrapeRank equations. Next step will be back end services that partner with relays and will enable generation of G_0, the Grapevine Network of "not-bot" pubkeys. We anticipate that future work will build out the front end control panel for Worldviews, including control panels for the interpretation of additional data sources and curation of lists like nostr apps as in the example above.
Notes
[1] https://njump.me / naddr1qvzqqqr4gupzpef89h53f0fsza2ugwdc3e54nfpun5nxfqclpy79r6w8nxsk5yp0qqxnzdejx5urzwp58qcrgdp4dutxqa
[2] Currently, various lists of nostr apps are maintained, e.g. at Awesome Nostr by (Aljaz Ceru?), or at nostrapps.com by (Karnage?).
-
 @ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05
@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint.
I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, freebitcoin hasn't put any NFL games up, yet. Hopefully they get around to it at some point.
I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog.
In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout.
Are there any odds you're excited about (doesn't have to be football)?
originally posted at https://stacker.news/items/679894
-
 @ 955e5a04:c03b3cc3
2024-09-10 18:51:16
@ 955e5a04:c03b3cc3
2024-09-10 18:51:16Today I want to review a passage from the second book, fourth text, which talks about anger and how passions develop. This passage explains three stages: how they begin, how they grow, and finally, how they unleash with fury.
-
First moment: Anger appears unexpectedly, like a reflex. It is a quick, physical reaction that cannot be controlled by reason, as it does not stem from it. It is a moment of alertness that arises without warning, an impulse that is beyond our will.
-
Second stage: At this point, there is clarity about the situation. It’s when one evaluates whether or not it is appropriate to react or even seek revenge. In extreme cases, one reflects on what punishment is suitable if a wrongdoing has been committed. Here, reason still plays an important role because justice or reprisal is being weighed.
-
Third stage: At this stage, anger takes control. Reason has been overridden, and actions become impulsive and destructive. If one acts in this state, plans will be poorly executed, without considering the consequences or the harm that might be caused to oneself or others.
It's crucial to remember that, in the first stage, there’s nothing to be done as it’s an automatic reflex. However, the words spoken at that moment do not have a real impact on our bodies or actions, which leaves room for reason to regain control.
Final Reflection: It is important to keep our minds active and aware of our reactions. Taking a step back when necessary shows that we are human beings capable of recognizing and correcting our mistakes. However, we must remain vigilant and strict with our responses, ensuring they do not harm what we wish to build: our relationships, our community, and, above all, ourselves.
-
-
 @ 361d3e1e:50bc10a8
2024-09-10 16:47:12
@ 361d3e1e:50bc10a8
2024-09-10 16:47:12What is the outcome of the vaccinated children versus the unvaccinated control group?
vaccine #sideeffects #usa #research #study #vaccinated #unvaccinated
-
 @ dd664d5e:5633d319
2024-09-10 15:04:43
@ dd664d5e:5633d319
2024-09-10 15:04:43What is 3 minutes worth?
I think I've run into the problem that the sort of work I do on here is only efficient and effective, if I spend all day doing it and really concentrate on it. It's not like being a developer or an influencer, where you can allot 2 hours in the morning to it, and then spend all day doing something else and talking about touching grass.
I either have to do it all day or completely stop because 99% of the work is absorbing and digesting information and interacting in real time; pausing is like pulling a mental break and slamming to a stop. It's more of a performance art than a durable good. I have to practice all damn day, every day, for a week, producing only ephemeral products, just to get up and sing for 3 minutes.
Shut up and sing
But with singing, the value is obvious, since most people have tried to sing and know that they aren't very good at it. Most people haven't tried to manage, design, or test systems on an open software protocol, but they all figure they can spontaneously do it, at some point, with little knowledge and no preparation, and be really great at it. That means that hardly anyone sees any value in it, especially as I make it look so easy, that watching me do it merely enhances the idea that the effort can be performed on a whim. The difference in enthusiasm between my dev work and my other work is palpable, but contains no signal.
That is the opposite of development or system administration, that is mostly done off in a hidey-hole, and no one can tell how much effort you personally expended, but they know you did something they can't fully understand, so they get all excited about it.
The indifferent bleating at the uninterested
But we can see that this differentiation is unfounded. Auxiliary software development is highly-skilled labor, it's tedious and exhausting, and it brings no status or prestige, which is why hardly anyone does it or their efforts are of low-quality and relatively pointless. Most developers and funders are regularly encouraging people to "step up" and do it spontaneously and on a purely volunteer basis because they feel obliged to pretend to care about software quality, but actually think it has little value.
Well, the people they are speaking to, agree with them. So, they ignore them.
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:22:42
@ 09fbf8f3:fa3d60f0
2024-09-10 13:22:42发现一个可以将Telegram频道内容转换为微博客。
-
开源项目: BroadcastChannel
-
演示站点:https://memo.miantiao.me/
✨ 特性 * 将 Telegram Channel 转为微博客 * SEO 友好 /sitemap.xml * 浏览器端 0 JS * 提供 RSS 和 RSS JSON /rss.xml /rss.json
使用 Astro 框架,支持部署在 Cloudflare、Netlify、Vercel 等支持 Node.js SSR 的无服务器平台或 VPS,可搜索,可 RSS 订阅
🏗️部署注意: * 项目通过 https://t.me/s/ 获取频道内容,如果频道被限制无法预览会显示空白 * 频道需要关闭 Restricting Saving Content * 环境变量 CHANNEL 值必须为频道 ID * 环境变量 TIMEZONE 值不要添加双引号 * 建议安装测试时只填写 CHANNEL 值 * BUG: 带引用回复的内容无法显示 已修复 * BUG: 带自定义 emoji 的无法显示 已修复 * BUG: 带 Quote 的内容无法显示
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 361d3e1e:50bc10a8
2024-09-10 12:56:56
@ 361d3e1e:50bc10a8
2024-09-10 12:56:56Dr. Joseph Mercola: What increases your risk of skin cancer is your sunscreen
sun #vitaminD #sunscreen #health #cancer #truth #freespeech #medicine #usa #mercola
-
 @ dd664d5e:5633d319
2024-09-10 10:21:42
@ dd664d5e:5633d319
2024-09-10 10:21:42I hate to be the one to tell y'all this, but my profile pic doesn't matter to me. And it shouldn't matter to you. My handle also shouldn't matter, except as a pet name for display. My NIP-05 matters, for human-typed discoverability and link/mention-readability, but it can be changed. My npub matters, but I could have more than one or stop using one, like I have done and will continue to do.
A profile on the Internet is not a person. Who is writing this article? Is it Stella? Oh, yeah? You know that? How? Did you sit there and watch me type it in?
I don't need PfP-recognition because I post stuff a lot of people like to look at (even if they have no idea who I am, imagine that!), and my npub therefore has high WoT.
Here's what I think: Y'all are trying to change a communication protocol into Twitter 2.0, where everyone needs to self-brand and stay on-script, on-camera, and in-their-lane. But if I were that sort of person, I'd be terrible at my job. The whole point of my job is to do all the stuff most users won't do, but some might, and to tell you how it went.
How about we just turn off all of the profile pics and people have to be interesting, entertaining, and/or knowledgeable again? How many of the people getting engagement, now, wouldn't get as much? How many people getting little engagement, now, would get more?
I have questions.
-
 @ a012dc82:6458a70d
2024-09-10 10:18:42
@ a012dc82:6458a70d
2024-09-10 10:18:42Table Of Content
-
Hong Kong's Regulatory Environment
-
Mainland China's Crypto Crackdown
-
The Rise of Crypto Exchanges and Institutions
-
Growing Interest from Institutional Investors
-
Hong Kong's Role in the Global Crypto Market
-
Conclusion
-
FAQ
The world of cryptocurrencies has experienced numerous ups and downs, with Bitcoin being the poster child for massive price surges and sharp declines. Recently, Hong Kong has emerged as a potential catalyst for a new crypto bull run. In this article, we will explore the factors that could propel the cryptocurrency markets forward in the near future.
Hong Kong's Regulatory Environment
Hong Kong has long been known for its business-friendly environment and relatively lenient financial regulations. With the government actively working to create a clear and comprehensive regulatory framework for cryptocurrencies, market participants are optimistic about the potential growth of the crypto ecosystem in Hong Kong.
Mainland China's Crypto Crackdown
The Chinese government's ongoing crackdown on cryptocurrency activities has led to many businesses, investors, and miners looking for new opportunities elsewhere. Hong Kong has emerged as a popular destination for these players, as its proximity to mainland China and its established financial infrastructure offer a conducive environment for the crypto industry to thrive.
The Rise of Crypto Exchanges and Institutions
The influx of mainland Chinese businesses and investors has led to a surge in demand for digital asset trading platforms and services. This has resulted in the establishment of several cryptocurrency exchanges and institutions in Hong Kong, further bolstering the growth of the crypto market in the region.
Growing Interest from Institutional Investors
As the global economy continues to recover, institutional investors are actively seeking alternative asset classes to diversify their portfolios. Hong Kong's well-regulated crypto market has attracted significant interest from these investors, providing additional liquidity and stability to the market.
Hong Kong's Role in the Global Crypto Market
Hong Kong's growing prominence in the global cryptocurrency market could serve as a catalyst for a new bull run. As more businesses, investors, and institutions flock to the city, the positive sentiment surrounding the crypto ecosystem is likely to spread, potentially spurring increased global adoption and demand for digital assets.
Conclusion
The combination of a favorable regulatory environment, an influx of market participants from mainland China, and growing interest from institutional investors has positioned Hong Kong as a key player in the global cryptocurrency market. While it is impossible to predict with certainty when or if a bull run will occur, the factors discussed in this article suggest that Hong Kong could play a pivotal role in pushing the crypto markets to new heights.
FAQ
Could Hong Kong potentially push the crypto market into a bull run? Yes, Hong Kong could play a pivotal role in pushing the crypto market into a bull run, thanks to its favorable regulatory environment, an influx of market participants from mainland China, and growing interest from institutional investors.
Why is Hong Kong's regulatory environment attractive for the crypto market? Hong Kong's regulatory environment is attractive for the crypto market because of its business-friendly nature and the government's ongoing efforts to create a clear and comprehensive regulatory framework for cryptocurrencies.
What makes Hong Kong an attractive destination for crypto miners? Hong Kong's proximity to mainland China, its established financial infrastructure, and relatively lenient regulations make it an attractive destination for crypto miners seeking new opportunities in the wake of China's crackdown on cryptocurrency activities.
Is it possible to predict when a bull run will occur in the crypto market? It is impossible to predict with certainty when or if a bull run will occur in the crypto market. However, factors such as Hong Kong's regulatory environment, the influx of market participants from mainland China, and growing interest from institutional investors suggest that the region could play a pivotal role in pushing the crypto markets to new heights.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-