-
 @ 42342239:1d80db24
2024-07-28 08:35:26
@ 42342239:1d80db24
2024-07-28 08:35:26Jerome Powell, Chairman of the US Federal Reserve, stated during a hearing in March that the central bank has no plans to introduce a central bank digital currency (CBDCs) or consider it necessary at present. He said this even though the material Fed staff presents to Congress suggests otherwise - that CBDCs are described as one of the Fed’s key duties .
A CBDC is a state-controlled and programmable currency that could allow the government or its intermediaries the possibility to monitor all transactions in detail and also to block payments based on certain conditions.
Critics argue that the introduction of CBDCs could undermine citizens’ constitutionally guaranteed freedoms and rights . Republican House Majority Leader Tom Emmer, the sponsor of a bill aimed at preventing the central bank from unilaterally introducing a CBDC, believes that if they do not mimic cash, they would only serve as a “CCP-style [Chinese Communist Party] surveillance tool” and could “undermine the American way of life”. Emmer’s proposed bill has garnered support from several US senators , including Republican Ted Cruz from Texas, who introduced the bill to the Senate. Similarly to how Swedish cash advocates risk missing the mark , Tom Emmer and the US senators risk the same outcome with their bill. If the central bank is prevented from introducing a central bank digital currency, nothing would stop major banks from implementing similar systems themselves, with similar consequences for citizens.
Indeed, the entity controlling your money becomes less significant once it is no longer you. Even if central bank digital currencies are halted in the US, a future administration could easily outsource financial censorship to the private banking system, similar to how the Biden administration is perceived by many to have circumvented the First Amendment by getting private companies to enforce censorship. A federal court in New Orleans ruled last fall against the Biden administration for compelling social media platforms to censor content. The Supreme Court has now begun hearing the case.
Deng Xiaoping, China’s paramount leader who played a vital role in China’s modernization, once said, “It does not matter if the cat is black or white. What matters is that it catches mice.” This statement reflected a pragmatic approach to economic policy, focusing on results foremost. China’s economic growth during his tenure was historic.
The discussion surrounding CBDCs and their negative impact on citizens’ freedoms and rights would benefit from a more practical and comprehensive perspective. Ultimately, it is the outcomes that matter above all. So too for our freedoms.
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b12b632c:d9e1ff79
2024-04-24 20:21:27
@ b12b632c:d9e1ff79
2024-04-24 20:21:27What's Blossom?
Blossom offers a bunch of HTTP endpoints that let Nostr users stash and fetch binary data on public servers using the SHA256 hash as a universal ID.
You can find more -precise- information about Blossom on the Nostr article published today by hzrd149, the developper behind it:
nostr:naddr1qqxkymr0wdek7mfdv3exjan9qgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgrqsqqqa28e4v8zy
You find the Blossom github repo here:
GitHub - hzrd149/blossom: Blobs stored simply on mediaservers https://github.com/hzrd149/blossom
Meet Blobs
Blobs are files with SHA256 hashes as IDs, making them unique and secure. You can compute these IDs from the files themselves using the sha256 hashing algorithm (when you run
sha256sum bitcoin.pdf).Meet Drives
Drives are like organized events on Nostr, mapping blobs to filenames and extra info. It's like setting up a roadmap for your data.
How do Servers Work?
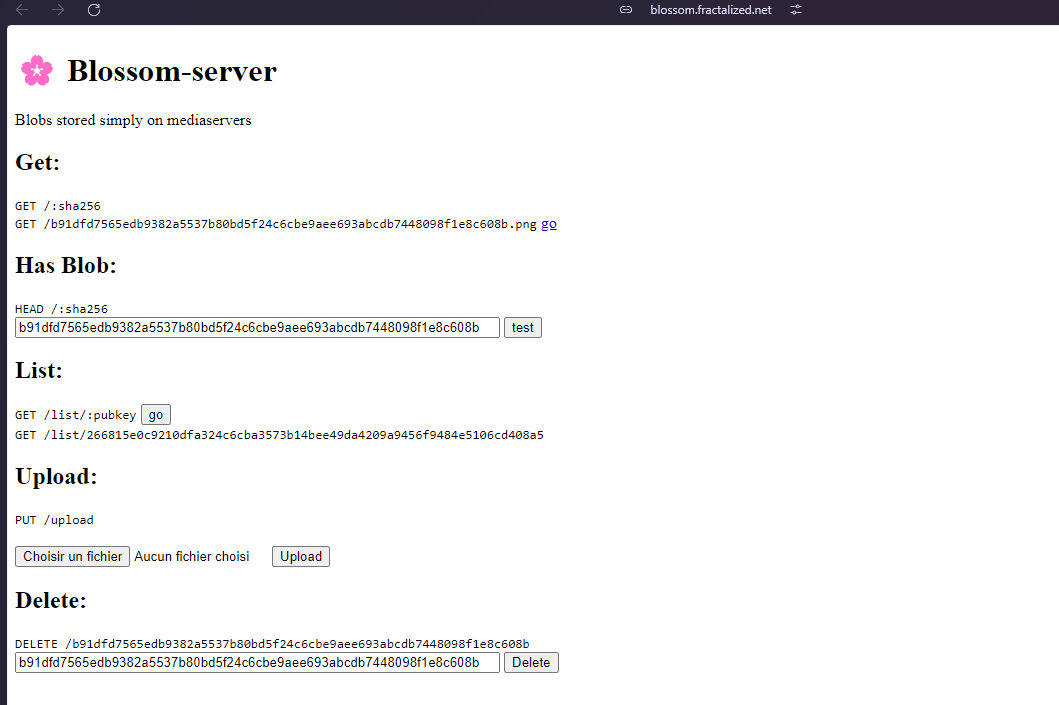
Blossom servers have four endpoints for users to upload and handle blobs:
GET /<sha256>: Get blobs by their SHA256 hash, maybe with a file extension. PUT /upload: Chuck your blobs onto the server, verified with signed Nostr events. GET /list/<pubkey>: Peek at a list of blobs tied to a specific public key for smooth management. DELETE /<sha256>: Trash blobs from the server when needed, keeping things tidy.Yon can find detailed information about the Blossom Server Implementation here..
https://github.com/hzrd149/blossom/blob/master/Server.md
..and the Blossom-server source code is here:
https://github.com/hzrd149/blossom-server
What's Blossom Drive?
Think of Blossom Drive as the "Front-End" (or a public cloud drive) of Blossom servers, letting you upload, manage, share your files/folders blobs.
Source code is available here:
https://github.com/hzrd149/blossom-drive
Developpers
If you want to add Blossom into your Nostr client/app, the blossom-client-sdk explaining how it works (with few examples 🙏) is published here:
https://github.com/hzrd149/blossom-client-sdk
How to self-host Blossom server & Blossom Drive
We'll use docker compose to setup Blossom server & drive. I included Nginx Proxy Manager because it's the Web Proxy I use for all the Fractalized self-hosted services :
Create a new docker-compose file:
~$ nano docker-compose.ymlInsert this content into the file:
``` version: '3.8' services:
blossom-drive: container_name: blossom-drive image: pastagringo/blossom-drive-docker
ports:
- '80:80'
blossom-server: container_name: blossom-server image: 'ghcr.io/hzrd149/blossom-server:master'
ports:
- '3000:3000'
volumes: - './blossom-server/config.yml:/app/config.yml' - 'blossom_data:/app/data'nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' - '81:81' - '443:443' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt - ./nginxproxymanager/_hsts_map.conf:/app/templates/_hsts_map.conf
volumes: blossom_data: ```
You now need to personalize the blossom-server config.yml:
bash ~$ mkdir blossom-server ~$ nano blossom-server/config.ymlInsert this content to the file (CTRL+X & Y to save/exit):
```yaml
Used when listing blobs
publicDomain: https://blossom.fractalized.net
databasePath: data/sqlite.db
discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.net # find files by asking upstream CDNs upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!
storage: # local or s3 backend: local local: dir: ./data # s3: # endpoint: https://s3.endpoint.com # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: # mime type of blob - type: text/ # time since last accessed expiration: 1 month - type: "image/" expiration: 1 week - type: "video/" expiration: 5 days - type: "model/" expiration: 1 week - type: "" expiration: 2 days
upload: # enable / disable uploads enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: false
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
You need to update few values with your own:
- Your own Blossom server public domain :
publicDomain: https://YourBlossomServer.YourDomain.tldand upstream domains where Nostr clients will also verify if the Blossom server own the file blob: :
upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!- The Nostr relays where you want to publish your Blossom events (I added my own Nostr relay):
yaml discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.netEverything is setup! You can now compose your docker-compose file:
~$ docker compose up -dI will let your check this article to know how to configure and use Nginx Proxy Manager.
You can check both Blossom containers logs with this command:
~$ docker compose logs -f blossom-drive blossom-serverRegarding the Nginx Proxy Manager settings for Blossom, here is the configuration I used:
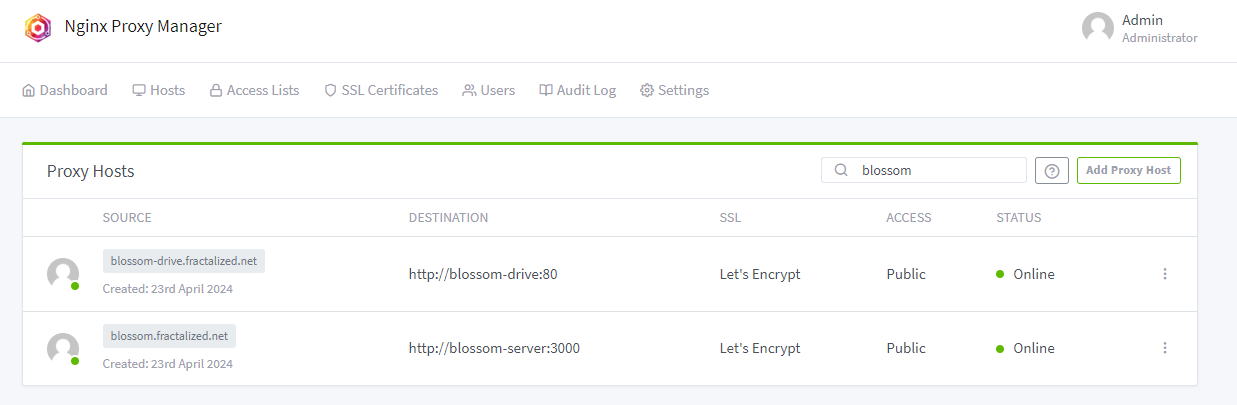
PS: it seems the naming convention for the kind of web service like Blossom is named "CDN" (for: "content delivery network"). It's not impossible in a near future I rename my subdomain blossom.fractalized.net to cdn.blossom.fractalized.net and blossom-drive.fractalized.net to blossom.fractalized.net 😅
Do what you prefer!
After having configured everything, you can now access Blossom server by going to your Blossom server subdomain. You should see a homepage as below:
Same thing for the Blossom Drive, you should see this homepage:
You can now login with your prefered method. In my case, I login on Blossom Drive with my NIP-07 Chrome extension.
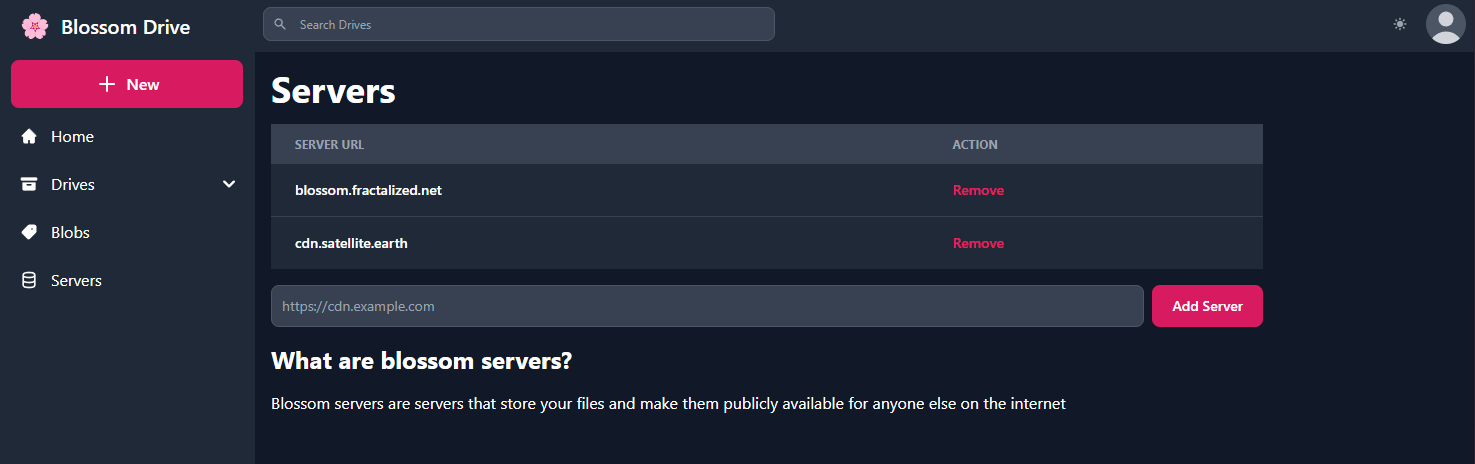
You now need to go the "Servers" tab to add some Blossom servers, including the fresh one you just installed.
You can now create your first Blossom Drive by clicking on "+ New" > "Drive" on the top left button:
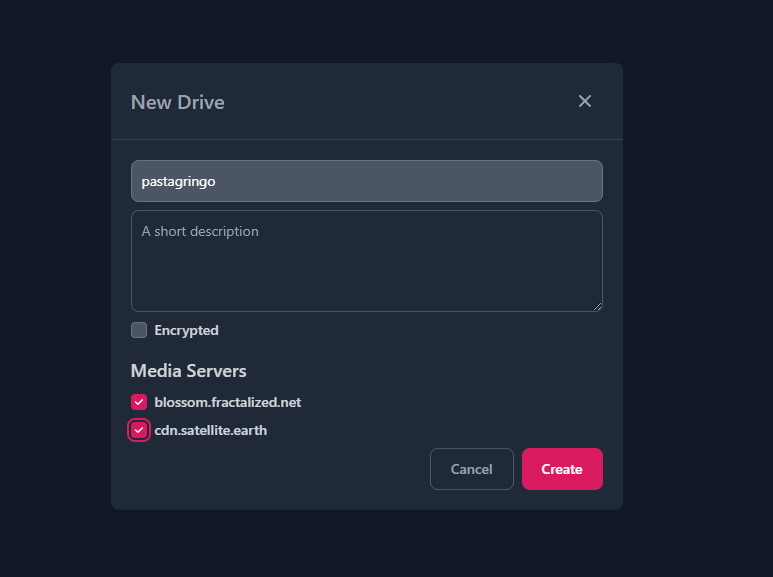
Fill your desired blossom drive name and select the media servers where you want to host your files and click on "Create":
PS: you can enable "Encrypted" option but as hzrd149 said on his Nostr note about Blossom:
"There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify"
You are now able to upload some files (a picture for instance):
And obtain the HTTP direct link by clicking on the "Copy Link" button:
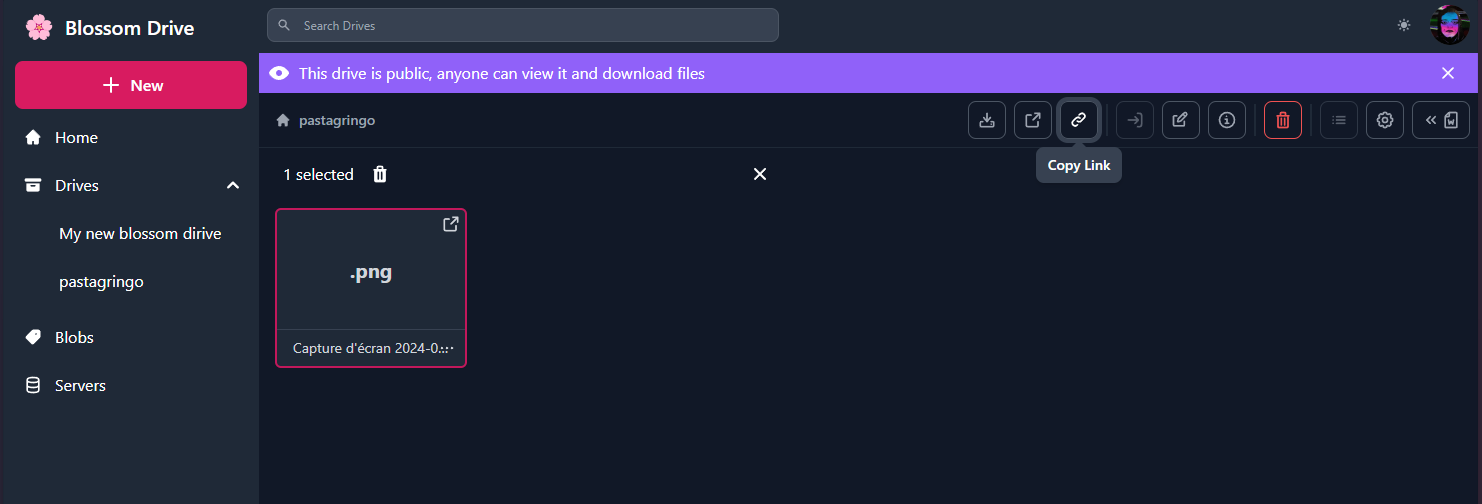
If you check URL image below, you'll see that it is served by Blossom:

It's done ! ✅
You can now upload your files to Blossom accross several Blossom servers to let them survive the future internet apocalypse.
Blossom has just been released few days ago, many news and features will come!
Don't hesisate to follow hzrd149 on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
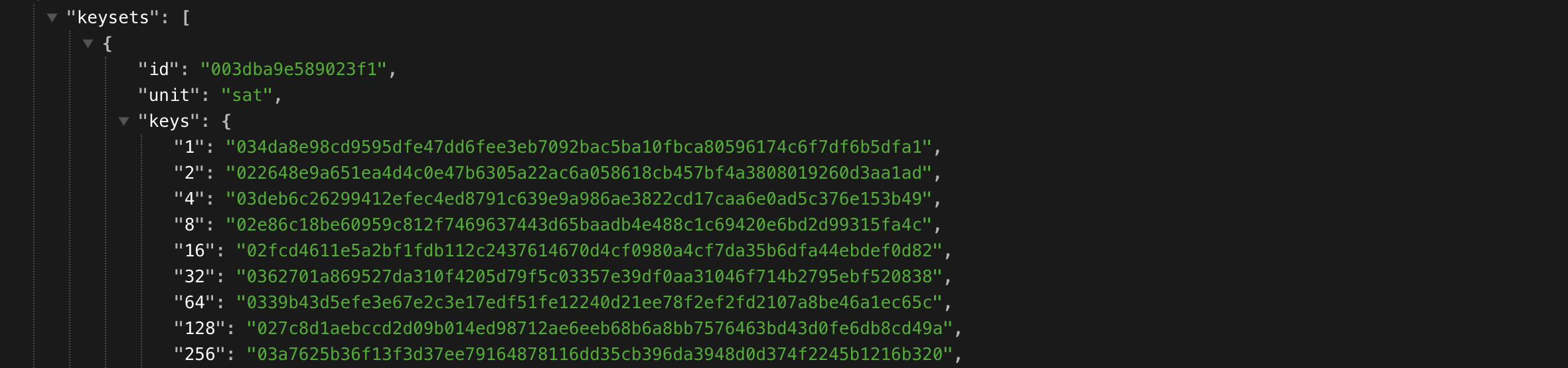
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
For instace, if we use wallet.cashu.me:
You can go into the "Settings" tab and add your mint :
If everything went find, you shoud see this :
You can now mint some ecash from your mint creating a sats invoice :
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
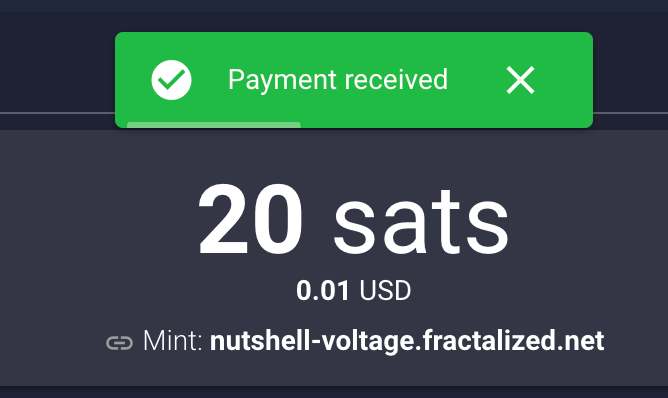
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
Add your mint again :
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
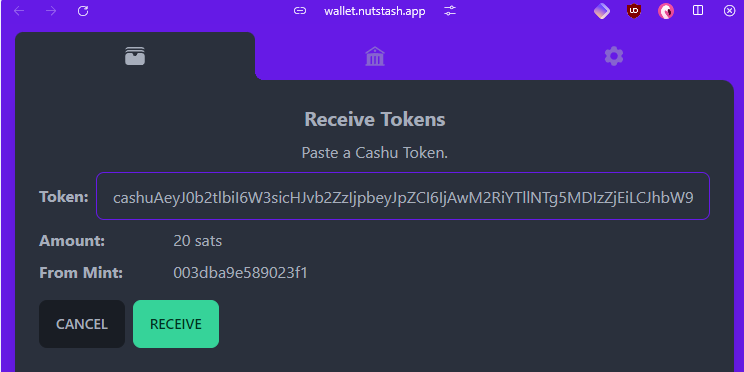
Click on "RECEIVE" again:
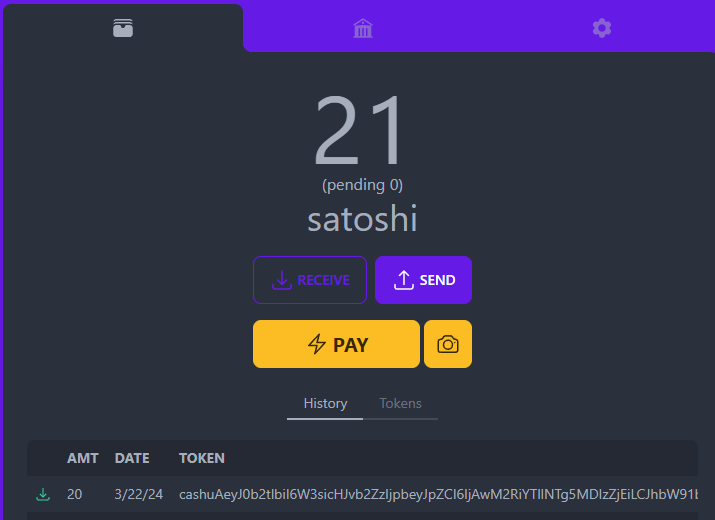
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
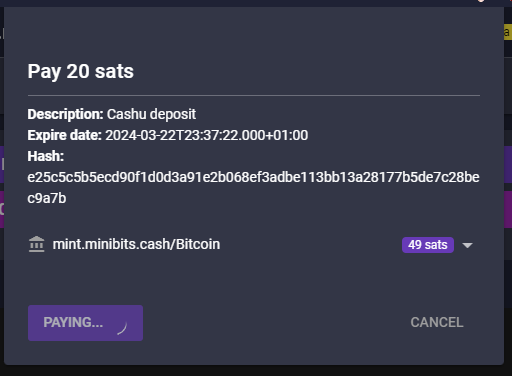
If everything is OK with the mints, the swap will be successful and the ecash received.
You can now see that the previous sats has been transfered (minus 2 fee sats).
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ 0176967e:1e6f471e
2024-07-28 15:31:13
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 8b85e487:532fa1b4
2024-07-28 14:00:29
@ 8b85e487:532fa1b4
2024-07-28 14:00:29|Portuguse|English| |---|---| |Quando eu era mais novo me diziam| When I was younger they told me| |que eu não batia muito bem da minha mente| I didn't hit my mind very well| |Me chama de louco ou de delinquente| Call me crazy or delinquent| |Mas é o flow que te deixa inconsciente| But it's the flow that makes you unconscious| |Toma hit, de repente| Take hit, all of a sudden| |Faz o drink, brinda com a gente| Drink, toast with us| ||| |E os moleque tá vivendo uma vida inconsequente| And the kids are living an inconsequent life| |Viajando pro fundo do futuro subconsciente| Traveling deep into the subconscious future| |Foi por causa dela que eu entrei na cena| It was because of her that I got into the scene| |Foi por ela mesmo que eu saí da cena| It's for herself that I left the scene| |Se eu tô em silêncio, quem ama é o sistema| If I'm silent, who loves is the system| |E sabe que eu sou moleque-problema, vai| And you know I'm a problem girl, go| ||| |Toma lá, toma cá| Here, here.| |Tenta vim pra trocar| Try to change.| |Se eu tiver sonhando, não precisa me acordar| If I'm dreaming, you don't have to wake me up| |Tô vendo meu passado no presente| I've seen my past in the present| |E o presente no futuro| And the present in the future| |E o futuro pisando no ar| And the future stepping on the air| ||| |O que tinha no meu copo, eu tô querendo saber?| What was in my glass, I'm trying to know?| |Elas querem meu corpo e eu querendo prazer| They want my body and I want pleasure| |Tô em todo lugar, não dá pra controlar| You're everywhere, you can't control|
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ b2caa9b3:9eab0fb5
2024-07-28 11:36:46
@ b2caa9b3:9eab0fb5
2024-07-28 11:36:46Yesterday was a bit of a rollercoaster. I started by diving into my digital past. Using Google Takeout, I extracted my photos and organized them into date-specific folders. It was a nostalgic trip down memory lane. After spending more time than expected organizing my digital life, I decided to take a break and grab a simple lunch at a local eatery. It's always interesting to experience the local vibe and enjoy affordable meals.

On my way back, I decided to finally get a SIM card. Much to my surprise, the price had doubled compared to just a few weeks ago. Is this the infamous "Mzungu" price? The price difference is making me reconsider my network provider. I might switch to avoid potential overcharges, but I haven't made a decision yet.
The eye problem, which has been bothering me for two days, put a damper on my plans for a relaxing video session at the evening. It was painful and blurry, so I opted for some soothing music instead.
Today, I started with a cold shower, hoping to alleviate the eye discomfort. It helped a bit, but the irritation persists. I suspect an infection and might need to visit a pharmacy. Given it's Sunday, I'm unsure about pharmacy hours and potential extra charges.
While I wait for my eye to improve, I've resumed downloading photos from Google and giving my public travel photo gallery another shot. Monetization through platforms is something I'm exploring seriously. The world of blockchain and cryptocurrencies has opened up new possibilities for generating income while traveling. Starting my journey in March 2017, I had no idea how to sustain myself financially while traveling. Generating income was a big question mark. Thanks to the people who've shared their knowledge, I've come a long way.
Speaking of travel, the weather here at the foot of Kilimanjaro is surprisingly chilly and cloudy. Who would have thought I'd need a fleece jacket in Africa? Google insists it's 27 degrees Celsius, but my body disagrees.
To add to my tech adventures, I installed the Ungoogled Chromium browser today. It's an interesting concept, but I'm still undecided about making the switch from Firefox. The world of open-source software has evolved significantly since my last deep dive, and I'm slowly rediscovering my way around. After years of using a Chromebook, I decided to switch back to Linux. I picked up a used ThinkPad and installed Fedora on it.
I'd love to hear your thoughts on the best Linux desktop environment – Gnome or KDE Plasma? And if you have any insights on platforms for generating income, please share them in the comments.
That's all for now. I'll keep you updated on my eye situation and my tech explorations. Until next time!
Unsure what photo to include, I decided to snap a quick shot of my workspace for today
Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
Fill a username and click on "Create account" :
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
To understand what happened, you need to inspect the web page to find the error :
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
Click on "Sign in" :
Click on "Show Advanced" :
Click on "Nostr connect / Bunker" :
Paste your bunker URL and click on "Connect" :
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ ee11a5df:b76c4e49
2023-11-09 05:20:37
@ ee11a5df:b76c4e49
2023-11-09 05:20:37A lot of terms have been bandied about regarding relay models: Gossip relay model, outbox relay model, and inbox relay model. But this term "relay model" bothers me. It sounds stuffy and formal and doesn't actually describe what we are talking about very well. Also, people have suggested maybe there are other relay models. So I thought maybe we should rethink this all from first principles. That is what this blog post attempts to do.
Nostr is notes and other stuff transmitted by relays. A client puts an event onto a relay, and subsequently another client reads that event. OK, strictly speaking it could be the same client. Strictly speaking it could even be that no other client reads the event, that the event was intended for the relay (think about nostr connect). But in general, the reason we put events on relays is for other clients to read them.
Given that fact, I see two ways this can occur:
1) The reader reads the event from the same relay that the writer wrote the event to (this I will call relay rendezvous), 2) The event was copied between relays by something.
This second solution is perfectly viable, but it less scalable and less immediate as it requires copies which means that resources will be consumed more rapidly than if we can come up with workable relay rendezvous solutions. That doesn't mean there aren't other considerations which could weigh heavily in favor of copying events. But I am not aware of them, so I will be discussing relay rendezvous.
We can then divide the relay rendezvous situation into several cases: one-to-one, one-to-many, and one-to-all, where the many are a known set, and the all are an unbounded unknown set. I cannot conceive of many-to-anything for nostr so we will speak no further of it.
For a rendezvous to take place, not only do the parties need to agree on a relay (or many relays), but there needs to be some way that readers can become aware that the writer has written something.
So the one-to-one situation works out well by the writer putting the message onto a relay that they know the reader checks for messages on. This we call the INBOX model. It is akin to sending them an email into their inbox where the reader checks for messages addressed to them.
The one-to-(known)-many model is very similar, except the writer has to write to many people's inboxes. Still we are dealing with the INBOX model.
The final case, one-to-(unknown)-all, there is no way the writer can place the message into every person's inbox because they are unknown. So in this case, the writer can write to their own OUTBOX, and anybody interested in these kinds of messages can subscribe to the writer's OUTBOX.
Notice that I have covered every case already, and that I have not even specified what particular types of scenarios call for one-to-one or one-to-many or one-to-all, but that every scenario must fit into one of those models.
So that is basically it. People need INBOX and OUTBOX relays and nothing else for relay rendezvous to cover all the possible scenarios.
That is not to say that other kinds of concerns might not modulate this. There is a suggestion for a DM relay (which is really an INBOX but with a special associated understanding), which is perfectly fine by me. But I don't think there are any other relay models. There is also the case of a live event where two parties are interacting over the same relay, but in terms of rendezvous this isn't a new case, it is just that the shared relay is serving as both parties' INBOX (in the case of a closed chat) and/or both parties' OUTBOX (in the case of an open one) at the same time.
So anyhow that's my thinking on the topic. It has become a fairly concise and complete set of concepts, and this makes me happy. Most things aren't this easy.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ ee11a5df:b76c4e49
2023-07-29 03:27:23
@ ee11a5df:b76c4e49
2023-07-29 03:27:23Gossip: The HTTP Fetcher
Gossip is a desktop nostr client. This post is about the code that fetches HTTP resources.
Gossip fetches HTTP resources. This includes images, videos, nip05 json files, etc. The part of gossip that does this is called the fetcher.
We have had a fetcher for some time, but it was poorly designed and had problems. For example, it was never expiring items in the cache.
We've made a lot of improvements to the fetcher recently. It's pretty good now, but there is still room for improvement.
Caching
Our fetcher caches data. Each URL that is fetched is hashed, and the content is stored under a file in the cache named by that hash.
If a request is in the cache, we don't do an HTTP request, we serve it directly from the cache.
But cached data gets stale. Sometimes resources at a URL change. We generally check resources again after three days.
We save the server's ETag value for content, and when we check the content again we supply an If-None-Match header with the ETag so the server could respond with 304 Not Modified in which case we don't need to download the resource again, we just bump the filetime to now.
In the event that our cache data is stale, but the server gives us an error, we serve up the stale data (stale is better than nothing).
Queueing
We used to fire off HTTP GET requests as soon as we knew that we needed a resource. This was not looked on too kindly by servers and CDNs who were giving us either 403 Forbidden or 429 Too Many Requests.
So we moved into a queue system. The host is extracted from each URL, and each host is only given up to 3 requests at a time. If we want 29 images from the same host, we only ask for three, and the remaining 26 remain in the queue for next time. When one of those requests completes, we decrement the host load so we know that we can send it another request later.
We process the queue in an infinite loop where we wait 1200 milliseconds between passes. Passes take time themselves and sometimes must wait for a timeout. Each pass fetches potentially multiple HTTP resources in parallel, asynchronously. If we have 300 resources at 100 different hosts, three per host, we could get them all in a single pass. More likely a bunch of resources are at the same host, and we make multiple passes at it.
Timeouts
When we fetch URLs in parallel asynchronously, we wait until all of the fetches complete before waiting another 1200 ms and doing another loop. Sometimes one of the fetches times out. In order to keep things moving, we use short timeouts of 10 seconds for a connect, and 15 seconds for a response.
Handling Errors
Some kinds of errors are more serious than others. When we encounter these, we sin bin the server for a period of time where we don't try fetching from it until a specified period elapses.
-
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ ee11a5df:b76c4e49
2023-07-29 02:52:13
@ ee11a5df:b76c4e49
2023-07-29 02:52:13Gossip: Zaps
Gossip is a desktop nostr client. This post is about the code that lets users send lightning zaps to each other (NIP-57).
Gossip implemented Zaps initially on 20th of June, 2023.
Gossip maintains a state of where zapping is at, one of: None, CheckingLnurl, SeekingAmount, LoadingInvoice, and ReadyToPay.
When you click the zap lightning bolt icon, Gossip moves to the CheckingLnurl state while it looks up the LN URL of the user.
If this is successful, it moves to the SeekingAmount state and presents amount options to the user.
Once a user chooses an amount, it moves to the LoadingInvoice state where it interacts with the lightning node and receives and checks an invoice.
Once that is complete, it moves to the ReadyToPay state, where it presents the invoice as a QR code for the user to scan with their phone. There is also a copy button so they can pay it from their desktop computer too.
Gossip also loads zap receipt events and associates them with the event that was zapped, tallying a zap total on that event. Gossip is unfortunately not validating these receipts very well currently, so fake zap receipts can cause an incorrect total to show. This remains an open issue.
Another open issue is the implementation of NIP-46 Nostr Connect and NIP-47 Wallet Connect.
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ 41fa852b:af7b7706
2024-07-28 10:19:34
@ 41fa852b:af7b7706
2024-07-28 10:19:34“Nothing is so painful to the human mind as a great and sudden change.” — Mary Shelley
Things are getting very interesting.
If you've managed to watch any of the Nashville Bitcoin conferences it would be very difficult not to be feeling incredibly bullish right now. Are we hitting the 'suddenly' stage of the 'gradually, then suddenly' saying? The political interest of Bitcoin in the US is miles ahead of where the UK is, but we do seem to follow them here for better or worse (mostly worse). Will we see a future Keir Starmer at a UK Bitcoin conference begging for your vote with promises of greater state adoption?
The truth is we don't need government approval, we're doing just fine without them. In fact we are doing fine despite their continued opposition. And why wouldn't they oppose Bitcoin, after all, 'turkeys don't vote for Christmas'. I have a feeling Christmas is just around the corner.
Upcoming Bitcoin Meetups
Happening this week...
- Gloucestershire Bitcoin: This months meetup focuses on those new to Bitcoin and will introduce local businesses to the future of digital payments. Click the link for more details and to book a free ticket. Tuesday 30th 18:30.
- Canterbury Bitcoin: Meeting this month at the Millers Arms in Canterbury at 7 PM on Tuesday the 30th of July. An informal meetup to discuss Bitcoin and chat.
- Leamington Spa: Meetups on the last Tuesday of each month at 7 PM. You'll find them this month at the White Horse, CV32 5PZ on the 30th.
- BitDevs - London: London BitDevs is a community of Bitcoin enthusiasts and professionals interested in discussing and participating in the research and development of Bitcoin and related protocols. Socratic seminars in Westminster, London. Doors open at 6:45 PM. This month on the 31st. More info here.
- Brighton Bitcoin: Building a bitcoin community in the Brighton & Hove area. A regular informal meetup happens every last Wednesday of the month. This month on the 31st.
- Berkshire Bitcoiners: Berkshire Bitcoiner's next meetup is on Thursday 1st August at 7.00 pm, at The Volunteer, Church St, Theale, Reading RG7 5BX. Feedback on the recent film night showing of Dirty Coin, and discussion of a plan to screen God Bless Bitcoin—also some feedback from Nashville.
- Lincolnshire Bitcoin: Lincolnshire Bitcoin meets on the first Thursday of each month at 7:30 PM in the Treaty of Commerce, Lincoln, LN5 7AF. Open to all, from OG's to newcomers.
- Bitcoin Walk - Edinburgh**: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit.
- Leeds Bitcoin Network: The first Sunday of every month the Leeds Bitcoin Network meet at the Global Tribe Cafe, LS1 6LG at 1 PM.
New Businesses Accepting Bitcoin
Two new businesses are now set up and ready to go in Tooting Market and loads more to come there.
- Greek Mama's Bakery: Hand-made artisan greek pies. Baked fresh to order, perfect finger food for parties, or ideal for a nutritious and wholesome weeknight meal. Now available for bitcoin at Tooting Market
- Get Juiced!: A super-popular juice bar and vegan cafe, serving cold pressed juices, vegan food and vegan cakes.Find them on Instagram here and right in the center of Tooting Market.
Upcoming Special Events
- Tooting Market Bitcoin Event: Get your tickets now for this free event. The lineup is looking good with some great talks throughout the evening and plenty of merchants now accepting bitcoin. Guest speakers included Ray Youssef, Jordan Walker, Nicholas Gregory, Hashley Giles, Bridge2Bitcoin and many more. It all starts at 6 PM on the 7th August.
- Bitcoin - The change you've been waiting for: Mark your calendars for August 31 at 10:30 am for "The Change You’ve Been Waiting For" at Glasgow University Union. This seminar, costing £10, focuses on Bitcoin's transformative potential. With Bitcoin impacting individuals and businesses globally, understanding it is crucial. Guest speaker Allen Farrington will share his expertise, making this event perfect for both seasoned investors and the Bitcoin-curious. Don't miss this opportunity to explore how Bitcoin can shape your financial future.
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We’re here to support you every step of the way. We’ve assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Please share your ideas on how we can enhance this newsletter.
Consider subscribing on Substack HERE
Get out and support the meetups where you can and stay tuned for more updates next week!
Simon.
-
 @ 0176967e:1e6f471e
2024-07-28 09:16:10
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
Podcast Bandcamp Punk Nostr website alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-
 @ b12b632c:d9e1ff79
2023-07-19 00:17:02
@ b12b632c:d9e1ff79
2023-07-19 00:17:02Welcome to a new Fractalized episode of "it works but I can do better"!
Original blog post from : https://fractalized.ovh/use-ghost-blog-to-serve-your-nostr-nip05-and-lnurl/
Few day ago, I wanted to set my Ghost blog (this one) as root domain for Fractalized instead of the old basic Nginx container that served my NIP05. I succeed to do it with Nginx Proxy Manager (I need to create a blog post because NPM is really awesome) but my NIP05 was down.
Having a bad NIP05 on Amethyst is now in the top tier list of my worst nightmares.
As a reminder, to have a valid NIP05 on your prefered Nostr client, you need to have a file named "nostr.json" in a folder ".well-known" located in the web server root path (subdomain or domain). The URL shoud look like this http://domain.tld/.well-known/nostr.json
PS : this doesn't work with Ghost as explained later. If you are here for Ghost, skip this and go directly to 1).
You should have these info inside the nostr.json file (JSON format) :
{ "names": { "YourUsername": "YourNPUBkey" } }You can test it directly by going to the nostr.json URL, it should show you the JSON.
It was working like a charm on my previous Nginx and I needed to do it on my new Ghost. I saw on Google that I need to have the .well-known folder into the Ghost theme root folder (In my case I choosed the Solo theme). I created the folder, put my nostr.json file inside it and crossed my fingers. Result : 404 error.
I had to search a lot but it seems that Ghost forbid to server json file from its theme folders. Maybe for security reasons, I don't know. Nevertheless Ghost provide a method to do it (but it requires more than copy/paste some files in some folders) => routes
In the same time that configuring your NIP05, I also wanted to setup an LNURL to be zapped to pastagringo@fractalized.ovh (configured into my Amethyst profile). If you want more infromation on LNURL, it's very well explained here.
Because I want to use my Wallet of Satoshi sats wallet "behind" my LNURL, you'll have to read carefuly the EzoFox's blog post that explains how to retrieve your infos from Alby or WoS.
1) Configuring Ghost routes
Add the new route into the routes.yaml (accessible from "Settings" > "Labs" > "Beta features" > "Routes" ; you need to download the file, modify it and upload it again) to let him know where to look for the nostr.json file.
Here is the content of my routes.yaml file :
``` routes: /.well-known/nostr.json/: template: _nostr-json content_type: application/json /.well-known/lnurlp/YourUsername/: template: _lnurlp-YourUsername content_type: application/json collections: /: permalink: /{slug}/ template: index
taxonomies: tag: /tag/{slug}/ author: /author/{slug}/ ```
=> template : name of the file that ghost will search localy
=> content_type : file type (JSON is required for the NIP05)
The first route is about my NIP05 and the second route is about my LNURL.
2) Creating Ghost route .hbs files
To let Ghost serve our JSON content, I needed to create the two .hbs file filled into the routes.yaml file. These files need to be located into the root directory of the Ghost theme used. For me, it was Solo.
Here is there content of both files :
"_nostr-json.hbs"
{ "names": { "YourUsername": "YourNPUBkey" } }"_lnurlp-pastagringo.hbs" (in your case, _lnurlp-YourUsername.hbs)
{ "callback":"https://livingroomofsatoshi.com/api/v1/lnurl/payreq/XXXXX", "maxSendable":100000000000, "minSendable":1000, "metadata":"[[\"text/plain\",\"Pay to Wallet of Satoshi user: burlyring39\"],[\"text/identifier\",\"YourUsername@walletofsatoshi.com\"]]", "commentAllowed":32, "tag":"payRequest", "allowsNostr":true, "nostrPubkey":"YourNPUBkey" }After doing that, you almost finished, you just have to restart your Ghost blog. As I use Ghost from docker container, I just had to restart the container.
To verify if everything is working, you have to go in the routes URL created earlier:
https://YourDomain.tld/.well-known/nostr.jsonand
https://YourDomain.tld/.well-known/lnurlp/YourUsernameBoth URL should display JSON files from .hbs created ealier.
If it's the case, you can add your NIP05 and LNURL into your Nostr profile client and you should be able to see a valid tick from your domain and to be zapped on your LNURL (sending zaps to your WoS or Alby backend wallet).
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-17 22:09:53
@ b12b632c:d9e1ff79
2023-07-17 22:09:53Today I created a new item (NIP05) to sell into my BTCpayserver store and everything was OK. The only thing that annoyed me a bit is that when a user pay the invoice to get his NIP on my Nostr Paid Relay, I need to warn him that he needs to fill his npub in the email info required by BTCpayserver before paying. Was not so user friendly. Not at all.
So I checked if BTCpayserver is able to create custom input before paying the invoice and at my big surprise, it's possible ! => release version v1.8
They even use as example my need from Nostr to get the user npub.
So it's possible, yes, but with at least the version 1.8.0. I checked immediately my BTCpayserver version on my Umbrel node and... damn... I'm in 1.7.2. I need to update my local BTCpayserver through Umbrel to access my so wanted BTCpayserver feature. I checked the local App Store but I can't see any "Update" button or something. I can see that the version installed is well the v1.7.2 but when I check the latest version available from the online Umbrel App Store. I can see v1.9.2. Damn bis.
I searched into the Umbrel Community forum, Telegram group, Google posts, asked the question on Nostr and didn't have any clue.
I finally found the answer from the Umbrel App Framework documention :
sudo ./scripts/repo checkout https://github.com/getumbrel/umbrel-apps.gitSo I did it and it updated my local Umbrel App Store to the latest version available and my BTCpayserver.
After few seconds, the BTCpaysever local URL is available and I'm allowed to login => everything is OK! \o/
See you soon in another Fractalized story!
-
 @ 94204d73:1a9bfecc
2024-07-28 08:29:37
@ 94204d73:1a9bfecc
2024-07-28 08:29:37In the world of interior design, modern sofas have become a staple for creating chic and comfortable living spaces. With sleek lines, innovative designs, and a focus on both aesthetics and functionality, modern sofas have evolved to meet the needs of today's homeowners seeking a perfect balance between style and comfort.

Sleek Designs for Every Taste
Modern sofas come in a variety of designs to suit different tastes and preferences. From minimalist Scandinavian-inspired pieces to bold and luxurious statement sofas, there is a modern sofa to complement any interior style. Clean lines, geometric shapes, and a mix of materials like leather, velvet, and fabric are common features of modern sofa designs, adding a touch of sophistication to any room.

Functionality Meets Comfort
One of the key characteristics of modern sofas is their focus on functionality and comfort without compromising on style. Many modern sofas are designed with features like adjustable headrests, reclining mechanisms, built-in storage, and convertible options to maximize comfort and usability. Whether you're looking for a cozy spot to relax or a versatile piece of furniture for entertaining guests, modern sofas offer a perfect blend of style and functionality.

Customization and Personalization
Another trend in modern sofa design is the emphasis on customization and personalization. Many furniture manufacturers and retailers offer a wide range of options for customizing modern sofas, including choice of fabric, color, size, and configuration. This allows homeowners to create a sofa that fits their specific needs and reflects their personal style, making it a unique focal point in their living space.

Durability and Sustainability
In addition to style and comfort, modern sofas are also designed with durability and sustainability in mind. High-quality materials, sturdy construction, and eco-friendly practices are key considerations in the production of modern sofas, ensuring that they not only look good but also stand the test of time. Sustainable materials like FSC-certified wood, recycled fabrics, and non-toxic finishes are increasingly being used in the manufacturing of modern sofas, reflecting a growing awareness of environmental responsibility in the furniture industry.

Modern sofas have become more than just a piece of furniture – they are a reflection of contemporary design trends, lifestyle preferences, and individual personalities. With their sleek designs, functional features, customization options, and commitment to sustainability, modern sofas continue to be a popular choice for homeowners looking to elevate their living spaces with style and comfort. Whether you prefer a classic mid-century modern sofa or a cutting-edge modular design, there is a modern sofa out there to suit your taste and transform your home into a stylish haven of relaxation and sophistication.
-
 @ 8947a945:9bfcf626
2024-07-28 02:53:20
@ 8947a945:9bfcf626
2024-07-28 02:53:2027 มกราคม 2017 เป็นวันเกิดลูกชายของผม และเป็นวันที่ครอบครัวของผมย้ายเข้ามาอาศัยบ้านหลังแรกที่ซื้อ เพื่อลงหลักปักฐานที่จังหวัดนนทบุรี บ้านหลังนี้เป็น “หนี้ธนาคาร” ก้อนแรกในชีวิตของผม ถ้าผมไม่คิดมาก ลำพังรายได้จากงานประจำของผมก็เพียงพอกับการผ่อนธนาคารและได้บ้านเป็นของตัวเอง เพียงแต่ต้องใช้ระยะเวลาประมาณ 20 ปี ผมมีความคิดไม่อยากเป็นหนี้นานขนาดนั้น เลยมองหาโอกาสในการสร้างรายได้ทางอื่นๆนอกจากงานประจำ เหตุการณ์นี้เป็นจุดเริ่มต้นของผมในการศึกษาหาความรู้ใหม่ๆเรื่องการเงินครับ

“เป็นหนี้(บ้าน) ทำให้มีไฟในการหารายได้เพิ่มนั่นเอง”
ผมมีโอกาสได้ศึกษาวิชาการลงทุนในตลาดหุ้น , การเทรดเก็งกำไรสินค้าต่างๆของต่างประเทศ , กองทุนรวม + ตราสารหนี้ รวมถึงบิตคอยน์และเหรียญคริปโตอื่นๆ ใช้เวลาหลายปีกว่าจะเข้าใจและอยู่รอดได้ แต่ก็ยังไม่ประสบความสำเร็จตามเป้าหมาย
ในช่วงปีนั้นเป็นช่วงเวลาที่มีการสร้างคอนโดตามแนวรถไฟฟ้า BTS บริเวณพญาไท สุขุมวิทย์จำนวนมาก มีการซื้อขายกันอย่างคึกคักทำให้หลายๆคนประสบความสำเร็จในการลงทุนอสังหา ขณะเดียวกันรถไฟฟ้าสายสีม่วงในจังหวัดนนทบุรีได้เปิดใช้เป็นทางการ เป็นเส้นทางรถไฟฟ้าสายแรกที่เชื่อมจังหวัดนนทบุรีเข้ากับกรุงเทพ มีคอนโดสร้างใหม่ตลอดแนวรถไฟฟ้าสายสีม่วงเป็นจำนวนมาก ดึงดูดนักลงทุนในแวดวงอสังหาอยู่ไม่น้อย

“รีบซื้อคอนโดตามแนวรถไฟฟ้าสายสีม่วงจังหวัดนนทบุรี จะได้สำเร็จเหมือนการครอบครองคอนโดตามแนว BTS ในกรุงเทพ ” หรือ “ซื้อคอนโดจังหวัดนนทบุรี ใกล้แหล่งงาน เดินทางเข้าออกตัวเมืองสะดวก รวดเร็ว”
แต่ความจริงจังหวัดนนทบุรี มีระบบขนส่งสาธารณะที่ครอบคลุมมากเพียงพออยู่แล้ว ได้แก่
รถเมล์รถประจำทาง รถสองแถว พี่วินมอเตอร์ไซค์ เรือด่วนแม่น้ำเจ้าพระยา

การขนส่งสาธารณะในจังหวัดนนทบุรี ครอบคลุม สะดวกสบาย ดีอยู่แล้ว
การเดินทางภายในตัวนนทบุรีก็ดี การเดินทางไป-กลับกรุงเทพก็ดี มันไม่ได้ยากขนาดนั้น ค่าเดินทางก็ถูกกว่าการขึ้นรถไฟฟ้ามากอยู่ ผมได้แต่คิดว่าคอนโดที่สร้างใหม่เหล่านี้มันจำเป็นจริงๆหรือเปล่า จะมีความต้องการในการซื้อ (demand) มากตามการคาดการณ์จริงหรือเปล่า เป็นการลงทุนที่คุ้มค่าจริงหรือเปล่า ในวันนี้ที่ผมกำลังเขียนบทความคือเดือนสิงหาคมปี 2024 ผมคิดว่าใครที่ติดตามข่าวสารการลงทุนและแวดวงอสังหาริมทรัพย์ก็คงจะทราบดีว่าความจริงเป็นยังไง
มุมมองของผมต่อการลงทุนอสังหาริมทรัพย์
จากที่ผมศึกษาด้วยตัวเอง การลงทุนอสังหาฯ สามารถแบ่งได้หลักๆ 2 แบบคือ
ซื้อขายเก็งกำไร (Flip) ตรงตัวเลยครับ เป็นการเก็งกำไรมูลค่าในอนาคต ซื้อวันนี้ขายวันหน้า เพื่อหวังกำไรส่วนต่าง (capital gain)
ซื้อและถือระยะยาว (Hold) เป็นการซื้อแล้วถือเก็บไว้ แล้วทำให้มันสร้างค่าเช่ารายเดือนเป็นกระแสเงินสด

สาย hold เป็นการลงทุนที่ปลอดภัยกว่า ผลตอบแทนไม่ได้โลดโผน ไม่ได้ตื่นเต้นมาก แต่มันมีข้อดีคือสามารถสร้างผลตอบแทนนิ่งๆได้ในทุกสภาวะเศรษฐกิจ ที่อยู่อาศัยเป็นหนึ่งในปัจจัยสี่ที่มนุษย์ต้องมี ยกเว้นเสียแต่ว่ามนุษย์จะย้ายไปอาศัยอยู่ในถ้ำหรือบนต้นไม้ อันนั้นอีกเรื่องนึง
แต่อุปสรรคที่สำคัญของการเข้ามาสู่วงการอสังหาที่หลายๆคนทราบกันดีก็คือต้องมีทุนที่มากพอ เริ่มต้นหลักล้านในครอบครองคอนโดซักห้องนึง ถ้าหากว่าไม่ได้มีเงินสดมากพอก็ต้องยอมเป็นหนี้ธนาคารในการกู้ ตอนนั้นเองสถานการณ์ครอบครัวของผมยังไม่ได้วางแผนเผื่อการเอาตัวเข้าไปในวงการนี้ ผมเข้าใจดีว่ามันเป็นลงทุนที่น่าสนใจ เพียงแต่ “มันยังไม่ใช่สำหรับเรา ในตอนนั้น”
แต่ทำความเข้าใจก่อนนะครับ คำว่าอสังหาริมทรัพย์ มันไม่ได้หมายถึงคอนโดอย่างเดียว มันยังมีอย่างอื่นอีกได้แก่
อาคารชุด (คอนโด) - ตึกแถว - ทาวโฮม - บ้านเดี่ยว - อาคารพานิชย์ - ที่ดิน - โกดังสินค้า - อพาร์ตเม้นท์ ห้องเช่า - โรงแรม - รีสอร์ท

อสังหาริมทรัพย์ = ทรัพย์สินที่เดินไปไหนไม่ได้ เอาติดตัวไปด้วยไม่ได้
วิกฤตครอบครัว และ การได้เป็นเจ้าของคอนโดห้องแรก
จากที่ผมเกริ่นไว้ตอนแรก “เป็นหนี้(บ้าน) ทำให้มีไฟในการหารายได้เพิ่ม” มันเกิดดาบสองคมที่หันมาฆ่าผมเอง ผมเก็งกำไรในตลาด futures แล้วพอร์ตระเบิด มูลค่าความเสียหายประมาณ 1,500,000 บาทครับ
มันเกิดจาก “กับดักของเทรดเดอร์หน้าใหม่” ที่คิดว่าตัวเองเข้าใจการเทรดแล้ว อ่านตลาดออกแล้ว นั่นเองครับ มาลองดูนะครับว่ามันเหมือนกระสบการณ์ของเพื่อนๆมั้ย
เรียนการเทรดเอง คิดว่าเข้าใจแล้ว แล้วก็ไปไม่รอด
ผมศึกษาจาก Youtube ครับ ดูคลิปไป 3–4 คลิป ก็เข้าใจว่า “ตัวเองเข้าใจแล้ว” ง่ายแค่นี้เอง แต่พอไปเทรดเอง เจอของจริงหน้างาน กลับขาดทุน
ตามหาระบบเทพในการเทรด
ไปหาตามเวบบอร์ดทั้งไทย ทั้งของต่างชาติ ทั้งระบบฟรีและเสียตังค์ ไปลองมาหมดครับ แล้วก็ขาดทุน
ไปซื้อคอร์สเรียน
ทั้งเรียนออนไลน์และเรียนตัวต่อตัวกับครูผู้เชี่ยวชาญในวิธีการของเขา ผมไปเรียนคอร์สตัวต่อตัวกับครูสองท่าน ปัจจุบันนี้ครูทั้งสองท่านทำกำไรได้สม่ำเสมอจนลาออกจากงานประจำมาเลี้ยงชีพเลี้ยงครอบครัว ส่งลูกเรียนโรงเรียนนานาชาติได้จากรายได้จากการเทรด มันฟังดูยิ่งใหญ่และน่าชื่นชมมาก แต่ด้วยวิธีการเทรดและเงื่อนไขทางด้านเวลาของผม ทำให้ไม่สามารถทำเหมือนครู่ทั้งสองท่านได้ ก็ขาดทุนครับ แต่ขาดทุนไม่มาก เพราะเป็นการเทรดที่ทำตามระบบ
จ้างโปรแกรมเมอร์เขียนบอทเทรด แต่ไม่รอบคอบ
ความรู้ที่ผมได้จากครูท่านแรก มันคือการสร้างระบบเทรดและทดสอบย้อนหลังด้วยตัวเอง (systematic and back test) เป็นการเทรดที่มีเงื่อนไขการเข้าและออกออเดอร์ชัดเจน แต่ว่ามันต้องเฝ้าจอใน timeframe 15 นาที มันทำให้ชีวิตผมไม่อันเป็นทำอะไรครับ เวลาไปเดินห้างซื้อของกับครอบครัว พอมีเสียง alert เตือนว่าถึงจุดเฝ้าระวังในการเปิดออเดอร์ ผมต้องขอเวลาครอบครัว หาที่นั่งแปปนึงแล้วบริหารจัดการการเทรด บางครั้ง alert ดังตอนกำลังขับรถ ผมก็ต้องเอามือข้างนึงมาจัดการการเทรด โชคดีที่เป็นช่วงรถติดแถวๆปิ่นเกล้า เลยรอดจากอุบัติเหตุ ผมมองว่ามันไม่เวิคละ เลยว่าจ้างฟรีแลนซ์จาก “fastwork” ของคุณ “ซีเค เจิง”ในการ code บอทเทรดให้ครับ มันทำงานได้ดีมาก แต่พี่ฟรีแลนซ์ท่านนั้นก็เตือนผมด้วยความหวังดีว่า
“อย่าพึ่ง” เอาไปลองกับบัญชีจริงนะ ไปลองในเดโม่ก่อน เอาให้แน่ใจก่อน เพราะเงื่อนไขการเทรดระบบของผมมันสุดยอดแห่งความซับซ้อนเลย
พี่เขากลัวว่าจะเขียนโค้ดผิดซักที่นึง ผมก็ลองบอทในบัญชีเดโม่อยู่ 1–2 สัปดาห์แล้วเห็นว่ามันใช้ได้ ก็เลยเอามาเปิดในบัญชีจริงครับ นี่คือข้อผิดพลาดอย่างนึงของผมก็คือ ในช่วงเวลาที่ทดสอบกับบัญชีเดโม่ มันชนะตลอด ไม่มีช่วงแพ้
อธิบายแบบนี้ครับ ระบบเทรดของผมเป็นการเทรดแบบ grid ระยะในการวิ่งของราคาที่จะปิดออเดอร์ไม่ว่าจะเป็น take profit หรือ stop loss มันแคบมาก มันเทรดไปประมาณ 10 ครั้ง มันจะแพ้ 1–2 ครั้ง แต่เวลาแพ้ครั้งนึงมูลค่าความเสียหายคือ ขาดทุน 15%
ไม่มีอะไรได้มาฟรีๆครับ ระบบเทรดที่อัตราชนะสูงถึง 90–95% เวลาเจอ 5–10% ที่เป็นการแพ้ แพ้ทีนึงจุก ครูผมเรียกว่า “inverted martingale” แต่มันแก้ด้วยการ money management ดีๆ
วันที่เกิดเรื่องผ่านไป 3 เดือนหลังจากเริ่มให้บิททำงานเทรดบนบัญชีจริง แล้วเจอวันที่มันแพ้พอดี วันนั้นบอทมันไม่ได้ stop loss แต่ปล่อยให้การขาดทุนไหลยาวไปเรื่อยๆ พอผมมาดูพบว่าพอร์ตมูลค่าเกือบๆหนึ่งล้านบาท ขาดทุนอยู่ 50–60% ผมเลยโทรปรึกษาพี่ที่เขียนบอทให้ ปรากฏว่ามันมีโค้ดที่ผิดพลาดในคำสั่ง stop loss ครับ สุดท้ายพอร์ตก็เสียหายหนัก
เอาเงินไปลงในเวบพนัน
ในเมื่อการเทรดเองมันยาก ไปลองหาช่องทางลัดก็แล้วกัน ชนิดที่ว่ารีบเข้ารีบออก ลุกช้าจ่ายรอบวง ผลลัพธ์คือขาดทุนครับ
เหตุการณ์ทั้งหมดนี้เกิดขึ้นในปี 2017–2018
ผลที่ตามมาก็คือบ้านแตก ภรรยาผมโมโหที่ผมทำอะไรไม่บอกและโมโหที่ผมแบกรับทุกอย่างไว้คนเดียวไม่ให้เขาเข้ามาช่วย ไม่ได้โกรธที่เทรดขาดทุน ภรรยาผมบอกว่าหากอยู่บ้านเดียวกันต่อไปมีความเป็นไปได้มากที่เขาจะขอหย่ากับผม (ก็เขาเคืองผมมาก) มีช่วงนึงที่เขาพาลูกไปเที่ยวไปค้างที่ต่างจังหวัด ตัดขาดการติดต่อกับผม เพื่อพักสมองพักความคิด จนสุดท้ายก็กลับมาคุยกัน แต่แก้วที่มันร้าวไปแล้วการคุยมันไม่ได้ราบรื่นหรอกครับ ภรรยาผมให้แยกกันอยู่คนละบ้าน ผมยอมรับข้อเสนอนี้ด้วยเหตุผลว่าให้สองแม่ลูกอยู่เป็นหลักแหล่งที่บ้าน ให้ทั้งคู่มีความปลอดภัย ส่วนผมออกไปตะลอนๆคนเดียวได้ไม่เป็นไร เพราะผมก่อเรื่องไว้ ก้มหน้าก้มตายอมรับผิดในสิ่งที่ตัวเองทำไป มันดีแล้ว

แต่ก็แปลกนะครับ กลายเป็นว่าสองคนสามีภรรยานั่งดูกันว่าจะหาห้องเช่าให้ผมอยู่ใกล้ๆที่ทำงาน มันจะได้ไม่ต้องเหนื่อยกับการเดินทางมาก พอจะรู้ราคาค่าเช่าบ้างแล้ว แต่ก็พบว่าบริเวณใกล้เคียงก็มีคอนโดที่พึ่งสร้างเสร็จ ราคาเช่าก็ไม่ได้ต่างจากห้องเช่ามาก เลยพากันเข้าไปดูครับ
“ตั้งใจว่าจะไปหาห้องคอนโดเช่า แต่ดันได้เป็นเจ้าของกรรมสิทธิ์คอนโดซะเอง”
คอนโดหลังนี้คือโครงการ Zeen condo อยู่ซอยงามวงศ์วาน 31 ห้องที่ผมได้ครอบครองเป็นห้องชั้น 6 ห้องริมที่หันหลังเข้าซอยชุมชนดั้งเดิม ไม่มีตึกสูงบังวิว ลมพัดเข้าทั้งวัน เงียบ ขนาด 28.xx ตารางเมตร เป็นห้องที่หลุดมาจากผู้ยื่นกู้ซื้อ 2 ท่านก่อนหน้านี้
ส่วนกระบวนการการคิดการตัดสินใจ กู้เพิ่มภาระหนี้ ตอนนั้นผมและภรรยาคิดอะไรอยู่ เดี๋ยวมาเล่าให้ฟังต่อตอนต่อไปนะครับ
-
 @ a619eb76:11d75935
2024-07-27 19:32:27
@ a619eb76:11d75935
2024-07-27 19:32:27II. Quantity, Quality, Morality
In the Brave New World of my fantasy eugenics and dysgenics were practiced systematically. In one set of bottles biologically superior ova, fertilized by biologically superior sperm, were given the best possible prenatal treatment and were finally decanted as Betas, Alphas and even Alpha Pluses. In another, much more numerous set of bottles, biologically inferior ova, fertilized by biologically inferior sperm, were subjected to the Bokanovsky Process (ninety-six identical twins out of a single egg) and treated prenatally with alcohol and other protein poisons. The creatures finally decanted were almost subhuman; but they were capable of performing unskilled work and, when properly conditioned, detensioned by free and frequent access to the opposite sex, constantly distracted by gratuitous entertainment and reinforced in their good behavior patterns by daily doses of soma, could be counted on to give no trouble to their superiors.
In this second half of the twentieth century we do nothing systematic about our breeding; but in our random and unregulated way we are not only over-populating our planet, we are also, it would seem, making sure that these greater numbers shall be of biologically poorer quality. In the bad old days children with considerable, or even with slight, hereditary defects rarely survived. Today, thanks to sanitation, modern pharmacology and the social conscience, most of the children born with hereditary defects reach maturity and multiply their kind. Under the conditions now prevailing, every advance in medicine will tend to be offset by a corresponding advance in the survival rate of individuals cursed by some genetic insufficiency. In spite of new wonder drugs and better treatment (indeed, in a certain sense, precisely because of these things), the physical health of the general population will show no improvement, and may even deteriorate. And along with a decline of average healthiness there may well go a decline in average intelligence. Indeed, some competent authorities are convinced that such a decline has already taken place and is continuing. "Under conditions that are both soft and unregulated," writes Dr. W. H. Sheldon, "our best stock tends to be outbred by stock that is inferior to it in every respect. . . . It is the fashion in some academic circles to assure students that the alarm over differential birthrates is unfounded; that these problems are merely economic, or merely educational, or merely religious, or merely cultural or something of the sort. This is Pollyanna optimism. Reproductive delinquency is biological and basic." And he adds that "nobody knows just how far the average IQ in this country [the U.S.A.] has declined since 1916, when Terman attempted to standardize the meaning of IQ 100."
In an underdeveloped and over-populated country, where four-fifths of the people get less than two thousand calories a day and one-fifth enjoys an adequate diet, can democratic institutions arise spontaneously? Or if they should be imposed from outside or from above, can they possibly survive?
And now let us consider the case of the rich, industrialized and democratic society, in which, owing to the random but effective practice of dysgenics, IQ's and physical vigor are on the decline. For how long can such a society maintain its traditions of individual liberty and democratic government? Fifty or a hundred years from now our children will learn the answer to this question.
Meanwhile we find ourselves confronted by a most disturbing moral problem. We know that the pursuit of good ends does not justify the employment of bad means. But what about those situations, now of such frequent occurrence, in which good means have end results which turn out to be bad?
For example, we go to a tropical island and with the aid of DDT we stamp out malaria and, in two or three years, save hundreds of thousands of lives. This is obviously good. But the hundreds of thousands of human beings thus saved, and the millions whom they beget and bring to birth, cannot be adequately clothed, housed, educated or even fed out of the island's available resources. Quick death by malaria has been abolished; but life made miserable by undernourishment and over-crowding is now the rule, and slow death by outright starvation threatens ever greater numbers.
And what about the congenitally insufficient organisms, whom our medicine and our social services now preserve so that they may propagate their kind? To help the unfortunate is obviously good. But the wholesale transmission to our descendants of the results of unfavorable mutations, and the progressive contamination of the genetic pool from which the members of our species will have to draw, are no less obviously bad. We are on the horns of an ethical dilemma, and to find the middle way will require all our intelligence and all our good will.
originally posted at https://stacker.news/items/624998
-
 @ 700c6cbf:a92816fd
2024-07-27 17:02:42
@ 700c6cbf:a92816fd
2024-07-27 17:02:42Hello Nostr-verse,
I have now fiddled so much with the photos and table, so, enjoy the photos!
https://cdn.satellite.earth/b24577e9162d7a313f703bef22b169f33945b9314d70561c953f01e96011776a.jpg
The first set of photos shows the progress from a nice, ripe and bubbly sourdough starter to mixing the dough and putting it in the fridge for overnight cool proofing.
| | | | --- | --- | | https://cdn.satellite.earth/b505474eeadfc64e1874162ac57dab05b8ba0926c0361442b0c462887af21026.jpg | https://cdn.satellite.earth/6d7c8faac003a3937e0dc35ef2ee1d230e1e3e781e5fa6aae9dbc9e58140f30e.jpg | | https://cdn.satellite.earth/7ac5dbc578074c0ab101fdb45c4e9ea158da060aaac7bfe09071ed9cdae58de6.jpg | https://cdn.satellite.earth/40429d73a05dfe7437656d6d26ab12ce506b1d519732a65302f1c6a07df384da.jpg | | https://cdn.satellite.earth/b594cf669967bf944f94e23112f4518318752574f2264a2c7a121cf03de46313.jpg | https://cdn.satellite.earth/4d4fc89a986b25bb8bcb135fae8c5358aaaf3b34affbbc79bc44722bcf60aeb6.jpg | | https://cdn.satellite.earth/9a25fde6fb761a52ca7d669f2a26b6c95536fcf01c5e22eeeff05a611af8fe60.jpg | https://cdn.satellite.earth/af9d0f9a48e6d3e76c33a88ce4cefd87125a26bd9e2f1ec1f01ae40fe9cdc611.jpg |
You can see quite nicely how the dough kept on developing overnight. I knew last night that I didn't want to make bread otherwise I would have shaped a bread loaf and stored it in a banneton overnight. This time I was going to make
Breadlings
a.k.a. rolls or dinner rolls. There wasn't much shaping involved, none actually. I took the dough out of the bowl, put it on a floured surface and divided it into 12 (?) differently shaped little dough pieces.
I placed them on a baking paper into my Dutch oven and baked each batch for about 30 - 35 minutes, 10 minutes on high heat and the remaining time on moderate heat.
| | | | --- | --- | | https://cdn.satellite.earth/b786ddc52895468ee47d59cca7a8bb0361a4cac1a59d06721232264edd510eb0.jpg | https://cdn.satellite.earth/0ef42689e0b0b5647abbd5111cabb69a40b4d47c23b443cb51a2f89b80c61b04.jpg | | https://cdn.satellite.earth/184c7dc2e23ec939ebbc7f6d11d80acf3789af9fe58ce4485c1d7069d9e52bdc.jpg | https://cdn.satellite.earth/1f5df9aa5be31bb80c2ac61185db3f9b755b5d0baa51c477e8ae9ac533d40db5.jpg | | https://cdn.satellite.earth/4617bea30796b81fddc1ecde6a354bd975c0e1628c6de54f0792ba2b88c62ffb.jpg | https://cdn.satellite.earth/ec0aa6496b521285ccf0c206e9e8776980922518e1789796f267388c31f83845.jpg | | https://cdn.satellite.earth/8ac7a1cb4b621c803ef42bb98d9d7c079f5723a632d9be6b105c048db44e123a.jpg | https://cdn.satellite.earth/9287253cd388f00b3083e713695c7de86a7e8ec2cdb4271db39da8b9da003740.jpg |
Then they had to cool down before, finally, two of them found their way onto our breakfast table and into our tummies.
The verdict: Awesome! They were slightly crusty on the outside, chewy but airy on the inside - perfect! https://cdn.satellite.earth/d239a280f8a23fe6d68657201d5000da074b963d1f9eba423f50f9337416bb67.jpg
Happy Weekend! OceanBee
-
 @ 4f7bd9c0:d530c5ce
2024-07-27 15:45:50
@ 4f7bd9c0:d530c5ce
2024-07-27 15:45:50The first is about how to ace your Y Combinator interview. There has been so much nonsense written about this topic that I've been meaning for years to write something telling founders the truth.
The second is about something politicians sometimes say — that the only way to become a billionaire is by exploiting people — and why this is mistaken.
Keep reading, and you'll learn both simultaneously.
I know the politicians are mistaken because it was my job to predict which people will become billionaires. I think I can truthfully say that I know as much about how to do this as anyone. If the key to becoming a billionaire — the defining feature of billionaires — was to exploit people, then I, as a professional billionaire scout, would surely realize this and look for people who would be good at it, just as an NFL scout looks for speed in wide receivers.
But aptitude for exploiting people is not what Y Combinator looks for at all. In fact, it's the opposite of what they look for. I'll tell you what they do look for, by explaining how to convince Y Combinator to fund you, and you can see for yourself.
What YC looks for, above all, is founders who understand some group of users and can make what they want. This is so important that it's YC's motto: "Make something people want."
A big company can to some extent force unsuitable products on unwilling customers, but a startup doesn't have the power to do that. A startup must sing for its supper, by making things that genuinely delight its customers. Otherwise it will never get off the ground.
Here's where things get difficult, both for you as a founder and for the YC partners trying to decide whether to fund you. In a market economy, it's hard to make something people want that they don't already have. That's the great thing about market economies. If other people both knew about this need and were able to satisfy it, they already would be, and there would be no room for your startup.
Which means the conversation during your YC interview will have to be about something new: either a new need, or a new way to satisfy one. And not just new, but uncertain. If it were certain that the need existed and that you could satisfy it, that certainty would be reflected in large and rapidly growing revenues, and you wouldn't be seeking seed funding.
So the YC partners have to guess both whether you've discovered a real need, and whether you'll be able to satisfy it. That's what they are, at least in this part of their job: professional guessers. They have 1001 heuristics for doing this, and I'm not going to tell you all of them, but I'm happy to tell you the most important ones, because these can't be faked; the only way to "hack" them would be to do what you should be doing anyway as a founder.
The first thing the partners will try to figure out, usually, is whether what you're making will ever be something a lot of people want. It doesn't have to be something a lot of people want now. The product and the market will both evolve, and will influence each other's evolution. But in the end there has to be something with a huge market. That's what the partners will be trying to figure out: is there a path to a huge market? [1]
Sometimes it's obvious there will be a huge market. If Boom manages to ship an airliner at all, international airlines will have to buy it. But usually it's not obvious. Usually the path to a huge market is by growing a small market. This idea is important enough that it's worth coining a phrase for, so let's call one of these small but growable markets a "larval market."
The perfect example of a larval market might be Apple's market when they were founded in 1976. In 1976, not many people wanted their own computer. But more and more started to want one, till now every 10 year old on the planet wants a computer (but calls it a "phone").
The ideal combination is the group of founders who are "living in the future" in the sense of being at the leading edge of some kind of change, and who are building something they themselves want. Most super-successful startups are of this type. Steve Wozniak wanted a computer. Mark Zuckerberg wanted to engage online with his college friends. Larry and Sergey wanted to find things on the web. All these founders were building things they and their peers wanted, and the fact that they were at the leading edge of change meant that more people would want these things in the future.
But although the ideal larval market is oneself and one's peers, that's not the only kind. A larval market might also be regional, for example. You build something to serve one location, and then expand to others.
The crucial feature of the initial market is that it exist. That may seem like an obvious point, but the lack of it is the biggest flaw in most startup ideas. There have to be some people who want what you're building right now, and want it so urgently that they're willing to use it, bugs and all, even though you're a small company they've never heard of. There don't have to be many, but there have to be some. As long as you have some users, there are straightforward ways to get more: build new features they want, seek out more people like them, get them to refer you to their friends, and so on. But these techniques all require some initial seed group of users.
So this is one thing the YC partners will almost certainly dig into during your interview. Who are your first users going to be, and how do you know they want this? If I had to decide whether to fund startups based on a single question, it would be "How do you know people want this?"
The most convincing answer is "Because we and our friends want it." It's even better when this is followed by the news that you've already built a prototype, and even though it's very crude, your friends are using it, and it's spreading by word of mouth. If you can say that and you're not lying, the partners will switch from default no to default yes. Meaning you're in unless there's some other disqualifying flaw.
That is a hard standard to meet, though. Airbnb didn't meet it. They had the first part. They had made something they themselves wanted. But it wasn't spreading. So don't feel bad if you don't hit this gold standard of convincingness. If Airbnb didn't hit it, it must be too high.
In practice, the YC partners will be satisfied if they feel that you have a deep understanding of your users' needs. And the Airbnbs did have that. They were able to tell us all about what motivated hosts and guests. They knew from first-hand experience, because they'd been the first hosts. We couldn't ask them a question they didn't know the answer to. We ourselves were not very excited about the idea as users, but we knew this didn't prove anything, because there were lots of successful startups we hadn't been excited about as users. We were able to say to ourselves "They seem to know what they're talking about. Maybe they're onto something. It's not growing yet, but maybe they can figure out how to make it grow during YC." Which they did, about three weeks into the batch.
The best thing you can do in a YC interview is to teach the partners about your users. So if you want to prepare for your interview, one of the best ways to do it is to go talk to your users and find out exactly what they're thinking. Which is what you should be doing anyway.
This may sound strangely credulous, but the YC partners want to rely on the founders to tell them about the market. Think about how VCs typically judge the potential market for an idea. They're not ordinarily domain experts themselves, so they forward the idea to someone who is, and ask for their opinion. YC doesn't have time to do this, but if the YC partners can convince themselves that the founders both (a) know what they're talking about and (b) aren't lying, they don't need outside domain experts. They can use the founders themselves as domain experts when evaluating their own idea.
This is why YC interviews aren't pitches. To give as many founders as possible a chance to get funded, we made interviews as short as we could: 10 minutes. That is not enough time for the partners to figure out, through the indirect evidence in a pitch, whether you know what you're talking about and aren't lying. They need to dig in and ask you questions. There's not enough time for sequential access. They need random access. [2]
The worst advice I ever heard about how to succeed in a YC interview is that you should take control of the interview and make sure to deliver the message you want to. In other words, turn the interview into a pitch. ⟨elaborate expletive⟩. It is so annoying when people try to do that. You ask them a question, and instead of answering it, they deliver some obviously prefabricated blob of pitch. It eats up 10 minutes really fast.
There is no one who can give you accurate advice about what to do in a YC interview except a current or former YC partner. People who've merely been interviewed, even successfully, have no idea of this, but interviews take all sorts of different forms depending on what the partners want to know about most. Sometimes they're all about the founders, other times they're all about the idea. Sometimes some very narrow aspect of the idea. Founders sometimes walk away from interviews complaining that they didn't get to explain their idea completely. True, but they explained enough.
Since a YC interview consists of questions, the way to do it well is to answer them well. Part of that is answering them candidly. The partners don't expect you to know everything. But if you don't know the answer to a question, don't try to bullshit your way out of it. The partners, like most experienced investors, are professional bullshit detectors, and you are (hopefully) an amateur bullshitter. And if you try to bullshit them and fail, they may not even tell you that you failed. So it's better to be honest than to try to sell them. If you don't know the answer to a question, say you don't, and tell them how you'd go about finding it, or tell them the answer to some related question.
If you're asked, for example, what could go wrong, the worst possible answer is "nothing." Instead of convincing them that your idea is bullet-proof, this will convince them that you're a fool or a liar. Far better to go into gruesome detail. That's what experts do when you ask what could go wrong. The partners know that your idea is risky. That's what a good bet looks like at this stage: a tiny probability of a huge outcome.
Ditto if they ask about competitors. Competitors are rarely what kills startups. Poor execution does. But you should know who your competitors are, and tell the YC partners candidly what your relative strengths and weaknesses are. Because the YC partners know that competitors don't kill startups, they won't hold competitors against you too much. They will, however, hold it against you if you seem either to be unaware of competitors, or to be minimizing the threat they pose. They may not be sure whether you're clueless or lying, but they don't need to be.
The partners don't expect your idea to be perfect. This is seed investing. At this stage, all they can expect are promising hypotheses. But they do expect you to be thoughtful and honest. So if trying to make your idea seem perfect causes you to come off as glib or clueless, you've sacrificed something you needed for something you didn't.
If the partners are sufficiently convinced that there's a path to a big market, the next question is whether you'll be able to find it. That in turn depends on three things: the general qualities of the founders, their specific expertise in this domain, and the relationship between them. How determined are the founders? Are they good at building things? Are they resilient enough to keep going when things go wrong? How strong is their friendship?
Though the Airbnbs only did ok in the idea department, they did spectacularly well in this department. The story of how they'd funded themselves by making Obama- and McCain-themed breakfast cereal was the single most important factor in our decision to fund them. They didn't realize it at the time, but what seemed to them an irrelevant story was in fact fabulously good evidence of their qualities as founders. It showed they were resourceful and determined, and could work together.
It wasn't just the cereal story that showed that, though. The whole interview showed that they cared. They weren't doing this just for the money, or because startups were cool. The reason they were working so hard on this company was because it was their project. They had discovered an interesting new idea, and they just couldn't let it go.
Mundane as it sounds, that's the most powerful motivator of all, not just in startups, but in most ambitious undertakings: to be genuinely interested in what you're building. This is what really drives billionaires, or at least the ones who become billionaires from starting companies. The company is their project.
One thing few people realize about billionaires is that all of them could have stopped sooner. They could have gotten acquired, or found someone else to run the company. Many founders do. The ones who become really rich are the ones who keep working. And what makes them keep working is not just money. What keeps them working is the same thing that keeps anyone else working when they could stop if they wanted to: that there's nothing else they'd rather do.
That, not exploiting people, is the defining quality of people who become billionaires from starting companies. So that's what YC looks for in founders: authenticity. People's motives for starting startups are usually mixed. They're usually doing it from some combination of the desire to make money, the desire to seem cool, genuine interest in the problem, and unwillingness to work for someone else. The last two are more powerful motivators than the first two. It's ok for founders to want to make money or to seem cool. Most do. But if the founders seem like they're doing it just to make money or just to seem cool, they're not likely to succeed on a big scale. The founders who are doing it for the money will take the first sufficiently large acquisition offer, and the ones who are doing it to seem cool will rapidly discover that there are much less painful ways of seeming cool. [3]
Y Combinator certainly sees founders whose m.o. is to exploit people. YC is a magnet for them, because they want the YC brand. But when the YC partners detect someone like that, they reject them. If bad people made good founders, the YC partners would face a moral dilemma. Fortunately they don't, because bad people make bad founders. This exploitative type of founder is not going to succeed on a large scale, and in fact probably won't even succeed on a small one, because they're always going to be taking shortcuts. They see YC itself as a shortcut.
Their exploitation usually begins with their own cofounders, which is disastrous, since the cofounders' relationship is the foundation of the company. Then it moves on to the users, which is also disastrous, because the sort of early adopters a successful startup wants as its initial users are the hardest to fool. The best this kind of founder can hope for is to keep the edifice of deception tottering along until some acquirer can be tricked into buying it. But that kind of acquisition is never very big. [4]
If professional billionaire scouts know that exploiting people is not the skill to look for, why do some politicians think this is the defining quality of billionaires?
I think they start from the feeling that it's wrong that one person could have so much more money than another. It's understandable where that feeling comes from. It's in our DNA, and even in the DNA of other species.
If they limited themselves to saying that it made them feel bad when one person had so much more money than other people, who would disagree? It makes me feel bad too, and I think people who make a lot of money have a moral obligation to use it for the common good. The mistake they make is to jump from feeling bad that some people are much richer than others to the conclusion that there's no legitimate way to make a very large amount of money. Now we're getting into statements that are not only falsifiable, but false.
There are certainly some people who become rich by doing bad things. But there are also plenty of people who behave badly and don't make that much from it. There is no correlation — in fact, probably an inverse correlation — between how badly you behave and how much money you make.
The greatest danger of this nonsense may not even be that it sends policy astray, but that it misleads ambitious people. Can you imagine a better way to destroy social mobility than by telling poor kids that the way to get rich is by exploiting people, while the rich kids know, from having watched the preceding generation do it, how it's really done?
I'll tell you how it's really done, so you can at least tell your own kids the truth. It's all about users. The most reliable way to become a billionaire is to start a company that grows fast, and the way to grow fast is to make what users want. Newly started startups have no choice but to delight users, or they'll never even get rolling. But this never stops being the lodestar, and bigger companies take their eye off it at their peril. Stop delighting users, and eventually someone else will.
Users are what the partners want to know about in YC interviews, and what I want to know about when I talk to founders that we funded ten years ago and who are billionaires now. What do users want? What new things could you build for them? Founders who've become billionaires are always eager to talk about that topic. That's how they became billionaires.
-
 @ 4f7bd9c0:d530c5ce
2024-07-27 15:42:52
@ 4f7bd9c0:d530c5ce
2024-07-27 15:42:52The first is about how to ace your Y Combinator interview. There has been so much nonsense written about this topic that I've been meaning for years to write something telling founders the truth.
The second is about something politicians sometimes say — that the only way to become a billionaire is by exploiting people — and why this is mistaken.
Keep reading, and you'll learn both simultaneously.
I know the politicians are mistaken because it was my job to predict which people will become billionaires. I think I can truthfully say that I know as much about how to do this as anyone. If the key to becoming a billionaire — the defining feature of billionaires — was to exploit people, then I, as a professional billionaire scout, would surely realize this and look for people who would be good at it, just as an NFL scout looks for speed in wide receivers.
But aptitude for exploiting people is not what Y Combinator looks for at all. In fact, it's the opposite of what they look for. I'll tell you what they do look for, by explaining how to convince Y Combinator to fund you, and you can see for yourself.
What YC looks for, above all, is founders who understand some group of users and can make what they want. This is so important that it's YC's motto: "Make something people want."
A big company can to some extent force unsuitable products on unwilling customers, but a startup doesn't have the power to do that. A startup must sing for its supper, by making things that genuinely delight its customers. Otherwise it will never get off the ground.
Here's where things get difficult, both for you as a founder and for the YC partners trying to decide whether to fund you. In a market economy, it's hard to make something people want that they don't already have. That's the great thing about market economies. If other people both knew about this need and were able to satisfy it, they already would be, and there would be no room for your startup.
Which means the conversation during your YC interview will have to be about something new: either a new need, or a new way to satisfy one. And not just new, but uncertain. If it were certain that the need existed and that you could satisfy it, that certainty would be reflected in large and rapidly growing revenues, and you wouldn't be seeking seed funding.
So the YC partners have to guess both whether you've discovered a real need, and whether you'll be able to satisfy it. That's what they are, at least in this part of their job: professional guessers. They have 1001 heuristics for doing this, and I'm not going to tell you all of them, but I'm happy to tell you the most important ones, because these can't be faked; the only way to "hack" them would be to do what you should be doing anyway as a founder.
The first thing the partners will try to figure out, usually, is whether what you're making will ever be something a lot of people want. It doesn't have to be something a lot of people want now. The product and the market will both evolve, and will influence each other's evolution. But in the end there has to be something with a huge market. That's what the partners will be trying to figure out: is there a path to a huge market? [1]
Sometimes it's obvious there will be a huge market. If Boom manages to ship an airliner at all, international airlines will have to buy it. But usually it's not obvious. Usually the path to a huge market is by growing a small market. This idea is important enough that it's worth coining a phrase for, so let's call one of these small but growable markets a "larval market."
The perfect example of a larval market might be Apple's market when they were founded in 1976. In 1976, not many people wanted their own computer. But more and more started to want one, till now every 10 year old on the planet wants a computer (but calls it a "phone").
The ideal combination is the group of founders who are "living in the future" in the sense of being at the leading edge of some kind of change, and who are building something they themselves want. Most super-successful startups are of this type. Steve Wozniak wanted a computer. Mark Zuckerberg wanted to engage online with his college friends. Larry and Sergey wanted to find things on the web. All these founders were building things they and their peers wanted, and the fact that they were at the leading edge of change meant that more people would want these things in the future.
But although the ideal larval market is oneself and one's peers, that's not the only kind. A larval market might also be regional, for example. You build something to serve one location, and then expand to others.
The crucial feature of the initial market is that it exist. That may seem like an obvious point, but the lack of it is the biggest flaw in most startup ideas. There have to be some people who want what you're building right now, and want it so urgently that they're willing to use it, bugs and all, even though you're a small company they've never heard of. There don't have to be many, but there have to be some. As long as you have some users, there are straightforward ways to get more: build new features they want, seek out more people like them, get them to refer you to their friends, and so on. But these techniques all require some initial seed group of users.
So this is one thing the YC partners will almost certainly dig into during your interview. Who are your first users going to be, and how do you know they want this? If I had to decide whether to fund startups based on a single question, it would be "How do you know people want this?"
The most convincing answer is "Because we and our friends want it." It's even better when this is followed by the news that you've already built a prototype, and even though it's very crude, your friends are using it, and it's spreading by word of mouth. If you can say that and you're not lying, the partners will switch from default no to default yes. Meaning you're in unless there's some other disqualifying flaw.
That is a hard standard to meet, though. Airbnb didn't meet it. They had the first part. They had made something they themselves wanted. But it wasn't spreading. So don't feel bad if you don't hit this gold standard of convincingness. If Airbnb didn't hit it, it must be too high.
In practice, the YC partners will be satisfied if they feel that you have a deep understanding of your users' needs. And the Airbnbs did have that. They were able to tell us all about what motivated hosts and guests. They knew from first-hand experience, because they'd been the first hosts. We couldn't ask them a question they didn't know the answer to. We ourselves were not very excited about the idea as users, but we knew this didn't prove anything, because there were lots of successful startups we hadn't been excited about as users. We were able to say to ourselves "They seem to know what they're talking about. Maybe they're onto something. It's not growing yet, but maybe they can figure out how to make it grow during YC." Which they did, about three weeks into the batch.
The best thing you can do in a YC interview is to teach the partners about your users. So if you want to prepare for your interview, one of the best ways to do it is to go talk to your users and find out exactly what they're thinking. Which is what you should be doing anyway.
This may sound strangely credulous, but the YC partners want to rely on the founders to tell them about the market. Think about how VCs typically judge the potential market for an idea. They're not ordinarily domain experts themselves, so they forward the idea to someone who is, and ask for their opinion. YC doesn't have time to do this, but if the YC partners can convince themselves that the founders both (a) know what they're talking about and (b) aren't lying, they don't need outside domain experts. They can use the founders themselves as domain experts when evaluating their own idea.
This is why YC interviews aren't pitches. To give as many founders as possible a chance to get funded, we made interviews as short as we could: 10 minutes. That is not enough time for the partners to figure out, through the indirect evidence in a pitch, whether you know what you're talking about and aren't lying. They need to dig in and ask you questions. There's not enough time for sequential access. They need random access. [2]
The worst advice I ever heard about how to succeed in a YC interview is that you should take control of the interview and make sure to deliver the message you want to. In other words, turn the interview into a pitch. ⟨elaborate expletive⟩. It is so annoying when people try to do that. You ask them a question, and instead of answering it, they deliver some obviously prefabricated blob of pitch. It eats up 10 minutes really fast.
There is no one who can give you accurate advice about what to do in a YC interview except a current or former YC partner. People who've merely been interviewed, even successfully, have no idea of this, but interviews take all sorts of different forms depending on what the partners want to know about most. Sometimes they're all about the founders, other times they're all about the idea. Sometimes some very narrow aspect of the idea. Founders sometimes walk away from interviews complaining that they didn't get to explain their idea completely. True, but they explained enough.
Since a YC interview consists of questions, the way to do it well is to answer them well. Part of that is answering them candidly. The partners don't expect you to know everything. But if you don't know the answer to a question, don't try to bullshit your way out of it. The partners, like most experienced investors, are professional bullshit detectors, and you are (hopefully) an amateur bullshitter. And if you try to bullshit them and fail, they may not even tell you that you failed. So it's better to be honest than to try to sell them. If you don't know the answer to a question, say you don't, and tell them how you'd go about finding it, or tell them the answer to some related question.
If you're asked, for example, what could go wrong, the worst possible answer is "nothing." Instead of convincing them that your idea is bullet-proof, this will convince them that you're a fool or a liar. Far better to go into gruesome detail. That's what experts do when you ask what could go wrong. The partners know that your idea is risky. That's what a good bet looks like at this stage: a tiny probability of a huge outcome.
Ditto if they ask about competitors. Competitors are rarely what kills startups. Poor execution does. But you should know who your competitors are, and tell the YC partners candidly what your relative strengths and weaknesses are. Because the YC partners know that competitors don't kill startups, they won't hold competitors against you too much. They will, however, hold it against you if you seem either to be unaware of competitors, or to be minimizing the threat they pose. They may not be sure whether you're clueless or lying, but they don't need to be.
The partners don't expect your idea to be perfect. This is seed investing. At this stage, all they can expect are promising hypotheses. But they do expect you to be thoughtful and honest. So if trying to make your idea seem perfect causes you to come off as glib or clueless, you've sacrificed something you needed for something you didn't.
If the partners are sufficiently convinced that there's a path to a big market, the next question is whether you'll be able to find it. That in turn depends on three things: the general qualities of the founders, their specific expertise in this domain, and the relationship between them. How determined are the founders? Are they good at building things? Are they resilient enough to keep going when things go wrong? How strong is their friendship?
Though the Airbnbs only did ok in the idea department, they did spectacularly well in this department. The story of how they'd funded themselves by making Obama- and McCain-themed breakfast cereal was the single most important factor in our decision to fund them. They didn't realize it at the time, but what seemed to them an irrelevant story was in fact fabulously good evidence of their qualities as founders. It showed they were resourceful and determined, and could work together.
It wasn't just the cereal story that showed that, though. The whole interview showed that they cared. They weren't doing this just for the money, or because startups were cool. The reason they were working so hard on this company was because it was their project. They had discovered an interesting new idea, and they just couldn't let it go.
Mundane as it sounds, that's the most powerful motivator of all, not just in startups, but in most ambitious undertakings: to be genuinely interested in what you're building. This is what really drives billionaires, or at least the ones who become billionaires from starting companies. The company is their project.
One thing few people realize about billionaires is that all of them could have stopped sooner. They could have gotten acquired, or found someone else to run the company. Many founders do. The ones who become really rich are the ones who keep working. And what makes them keep working is not just money. What keeps them working is the same thing that keeps anyone else working when they could stop if they wanted to: that there's nothing else they'd rather do.
That, not exploiting people, is the defining quality of people who become billionaires from starting companies. So that's what YC looks for in founders: authenticity. People's motives for starting startups are usually mixed. They're usually doing it from some combination of the desire to make money, the desire to seem cool, genuine interest in the problem, and unwillingness to work for someone else. The last two are more powerful motivators than the first two. It's ok for founders to want to make money or to seem cool. Most do. But if the founders seem like they're doing it just to make money or just to seem cool, they're not likely to succeed on a big scale. The founders who are doing it for the money will take the first sufficiently large acquisition offer, and the ones who are doing it to seem cool will rapidly discover that there are much less painful ways of seeming cool. [3]
Y Combinator certainly sees founders whose m.o. is to exploit people. YC is a magnet for them, because they want the YC brand. But when the YC partners detect someone like that, they reject them. If bad people made good founders, the YC partners would face a moral dilemma. Fortunately they don't, because bad people make bad founders. This exploitative type of founder is not going to succeed on a large scale, and in fact probably won't even succeed on a small one, because they're always going to be taking shortcuts. They see YC itself as a shortcut.
Their exploitation usually begins with their own cofounders, which is disastrous, since the cofounders' relationship is the foundation of the company. Then it moves on to the users, which is also disastrous, because the sort of early adopters a successful startup wants as its initial users are the hardest to fool. The best this kind of founder can hope for is to keep the edifice of deception tottering along until some acquirer can be tricked into buying it. But that kind of acquisition is never very big. [4]
If professional billionaire scouts know that exploiting people is not the skill to look for, why do some politicians think this is the defining quality of billionaires?
I think they start from the feeling that it's wrong that one person could have so much more money than another. It's understandable where that feeling comes from. It's in our DNA, and even in the DNA of other species.
If they limited themselves to saying that it made them feel bad when one person had so much more money than other people, who would disagree? It makes me feel bad too, and I think people who make a lot of money have a moral obligation to use it for the common good. The mistake they make is to jump from feeling bad that some people are much richer than others to the conclusion that there's no legitimate way to make a very large amount of money. Now we're getting into statements that are not only falsifiable, but false.
There are certainly some people who become rich by doing bad things. But there are also plenty of people who behave badly and don't make that much from it. There is no correlation — in fact, probably an inverse correlation — between how badly you behave and how much money you make.
The greatest danger of this nonsense may not even be that it sends policy astray, but that it misleads ambitious people. Can you imagine a better way to destroy social mobility than by telling poor kids that the way to get rich is by exploiting people, while the rich kids know, from having watched the preceding generation do it, how it's really done?
I'll tell you how it's really done, so you can at least tell your own kids the truth. It's all about users. The most reliable way to become a billionaire is to start a company that grows fast, and the way to grow fast is to make what users want. Newly started startups have no choice but to delight users, or they'll never even get rolling. But this never stops being the lodestar, and bigger companies take their eye off it at their peril. Stop delighting users, and eventually someone else will.
Users are what the partners want to know about in YC interviews, and what I want to know about when I talk to founders that we funded ten years ago and who are billionaires now. What do users want? What new things could you build for them? Founders who've become billionaires are always eager to talk about that topic. That's how they became billionaires.
-
 @ c0cb8a44:d87d4363
2024-07-27 14:35:12
@ c0cb8a44:d87d4363
2024-07-27 14:35:12I was talking recently to a friend who teaches at MIT. His field is hot now and every year he is inundated by applications from would-be graduate students. "A lot of them seem smart," he said. "What I can't tell is whether they have any kind of taste."
Taste. You don't hear that word much now. And yet we still need the underlying concept, whatever we call it. What my friend meant was that he wanted students who were not just good technicians, but who could use their technical knowledge to design beautiful things.
Mathematicians call good work "beautiful," and so, either now or in the past, have scientists, engineers, musicians, architects, designers, writers, and painters. Is it just a coincidence that they used the same word, or is there some overlap in what they meant? If there is an overlap, can we use one field's discoveries about beauty to help us in another?
For those of us who design things, these are not just theoretical questions. If there is such a thing as beauty, we need to be able to recognize it. We need good taste to make good things. Instead of treating beauty as an airy abstraction, to be either blathered about or avoided depending on how one feels about airy abstractions, let's try considering it as a practical question: how do you make good stuff?
If you mention taste nowadays, a lot of people will tell you that "taste is subjective." They believe this because it really feels that way to them. When they like something, they have no idea why. It could be because it's beautiful, or because their mother had one, or because they saw a movie star with one in a magazine, or because they know it's expensive. Their thoughts are a tangle of unexamined impulses.
Most of us are encouraged, as children, to leave this tangle unexamined. If you make fun of your little brother for coloring people green in his coloring book, your mother is likely to tell you something like "you like to do it your way and he likes to do it his way."
Your mother at this point is not trying to teach you important truths about aesthetics. She's trying to get the two of you to stop bickering.
Like many of the half-truths adults tell us, this one contradicts other things they tell us. After dinning into you that taste is merely a matter of personal preference, they take you to the museum and tell you that you should pay attention because Leonardo is a great artist.
What goes through the kid's head at this point? What does he think "great artist" means? After having been told for years that everyone just likes to do things their own way, he is unlikely to head straight for the conclusion that a great artist is someone whose work is better than the others'. A far more likely theory, in his Ptolemaic model of the universe, is that a great artist is something that's good for you, like broccoli, because someone said so in a book.
Saying that taste is just personal preference is a good way to prevent disputes. The trouble is, it's not true. You feel this when you start to design things.
Whatever job people do, they naturally want to do better. Football players like to win games. CEOs like to increase earnings. It's a matter of pride, and a real pleasure, to get better at your job. But if your job is to design things, and there is no such thing as beauty, then there is no way to get better at your job. If taste is just personal preference, then everyone's is already perfect: you like whatever you like, and that's it.
As in any job, as you continue to design things, you'll get better at it. Your tastes will change. And, like anyone who gets better at their job, you'll know you're getting better. If so, your old tastes were not merely different, but worse. Poof goes the axiom that taste can't be wrong.
Relativism is fashionable at the moment, and that may hamper you from thinking about taste, even as yours grows. But if you come out of the closet and admit, at least to yourself, that there is such a thing as good and bad design, then you can start to study good design in detail. How has your taste changed? When you made mistakes, what caused you to make them? What have other people learned about design?
Once you start to examine the question, it's surprising how much different fields' ideas of beauty have in common. The same principles of good design crop up again and again.
Good design is simple. You hear this from math to painting. In math it means that a shorter proof tends to be a better one. Where axioms are concerned, especially, less is more. It means much the same thing in programming. For architects and designers it means that beauty should depend on a few carefully chosen structural elements rather than a profusion of superficial ornament. (Ornament is not in itself bad, only when it's camouflage on insipid form.) Similarly, in painting, a still life of a few carefully observed and solidly modelled objects will tend to be more interesting than a stretch of flashy but mindlessly repetitive painting of, say, a lace collar. In writing it means: say what you mean and say it briefly.
It seems strange to have to emphasize simplicity. You'd think simple would be the default. Ornate is more work. But something seems to come over people when they try to be creative. Beginning writers adopt a pompous tone that doesn't sound anything like the way they speak. Designers trying to be artistic resort to swooshes and curlicues. Painters discover that they're expressionists. It's all evasion. Underneath the long words or the "expressive" brush strokes, there is not much going on, and that's frightening.
When you're forced to be simple, you're forced to face the real problem. When you can't deliver ornament, you have to deliver substance.
Good design is timeless. In math, every proof is timeless unless it contains a mistake. So what does Hardy mean when he says there is no permanent place for ugly mathematics? He means the same thing Kelly Johnson did: if something is ugly, it can't be the best solution. There must be a better one, and eventually someone will discover it.
Aiming at timelessness is a way to make yourself find the best answer: if you can imagine someone surpassing you, you should do it yourself. Some of the greatest masters did this so well that they left little room for those who came after. Every engraver since Durer has had to live in his shadow.
Aiming at timelessness is also a way to evade the grip of fashion. Fashions almost by definition change with time, so if you can make something that will still look good far into the future, then its appeal must derive more from merit and less from fashion.
Strangely enough, if you want to make something that will appeal to future generations, one way to do it is to try to appeal to past generations. It's hard to guess what the future will be like, but we can be sure it will be like the past in caring nothing for present fashions. So if you can make something that appeals to people today and would also have appealed to people in 1500, there is a good chance it will appeal to people in 2500.
Good design solves the right problem. The typical stove has four burners arranged in a square, and a dial to control each. How do you arrange the dials? The simplest answer is to put them in a row. But this is a simple answer to the wrong question. The dials are for humans to use, and if you put them in a row, the unlucky human will have to stop and think each time about which dial matches which burner. Better to arrange the dials in a square like the burners.
A lot of bad design is industrious, but misguided. In the mid twentieth century there was a vogue for setting text in sans-serif fonts. These fonts are closer to the pure, underlying letterforms. But in text that's not the problem you're trying to solve. For legibility it's more important that letters be easy to tell apart. It may look Victorian, but a Times Roman lowercase g is easy to tell from a lowercase y.
Problems can be improved as well as solutions. In software, an intractable problem can usually be replaced by an equivalent one that's easy to solve. Physics progressed faster as the problem became predicting observable behavior, instead of reconciling it with scripture.
Good design is suggestive. Jane Austen's novels contain almost no description; instead of telling you how everything looks, she tells her story so well that you envision the scene for yourself. Likewise, a painting that suggests is usually more engaging than one that tells. Everyone makes up their own story about the Mona Lisa.
In architecture and design, this principle means that a building or object should let you use it how you want: a good building, for example, will serve as a backdrop for whatever life people want to lead in it, instead of making them live as if they were executing a program written by the architect.
In software, it means you should give users a few basic elements that they can combine as they wish, like Lego. In math it means a proof that becomes the basis for a lot of new work is preferable to a proof that was difficult, but doesn't lead to future discoveries; in the sciences generally, citation is considered a rough indicator of merit.
Good design is often slightly funny. This one may not always be true. But Durer's engravings and Saarinen's womb chair and the Pantheon and the original Porsche 911 all seem to me slightly funny. Godel's incompleteness theorem seems like a practical joke.
I think it's because humor is related to strength. To have a sense of humor is to be strong: to keep one's sense of humor is to shrug off misfortunes, and to lose one's sense of humor is to be wounded by them. And so the mark-- or at least the prerogative-- of strength is not to take oneself too seriously. The confident will often, like swallows, seem to be making fun of the whole process slightly, as Hitchcock does in his films or Bruegel in his paintings-- or Shakespeare, for that matter.
Good design may not have to be funny, but it's hard to imagine something that could be called humorless also being good design.
Good design is hard. If you look at the people who've done great work, one thing they all seem to have in common is that they worked very hard. If you're not working hard, you're probably wasting your time.
Hard problems call for great efforts. In math, difficult proofs require ingenious solutions, and those tend to be interesting. Ditto in engineering.
When you have to climb a mountain you toss everything unnecessary out of your pack. And so an architect who has to build on a difficult site, or a small budget, will find that he is forced to produce an elegant design. Fashions and flourishes get knocked aside by the difficult business of solving the problem at all.
Not every kind of hard is good. There is good pain and bad pain. You want the kind of pain you get from going running, not the kind you get from stepping on a nail. A difficult problem could be good for a designer, but a fickle client or unreliable materials would not be.
In art, the highest place has traditionally been given to paintings of people. There is something to this tradition, and not just because pictures of faces get to press buttons in our brains that other pictures don't. We are so good at looking at faces that we force anyone who draws them to work hard to satisfy us. If you draw a tree and you change the angle of a branch five degrees, no one will know. When you change the angle of someone's eye five degrees, people notice.
When Bauhaus designers adopted Sullivan's "form follows function," what they meant was, form should follow function. And if function is hard enough, form is forced to follow it, because there is no effort to spare for error. Wild animals are beautiful because they have hard lives.
Good design looks easy. Like great athletes, great designers make it look easy. Mostly this is an illusion. The easy, conversational tone of good writing comes only on the eighth rewrite.
In science and engineering, some of the greatest discoveries seem so simple that you say to yourself, I could have thought of that. The discoverer is entitled to reply, why didn't you?
Some Leonardo heads are just a few lines. You look at them and you think, all you have to do is get eight or ten lines in the right place and you've made this beautiful portrait. Well, yes, but you have to get them in exactly the right place. The slightest error will make the whole thing collapse.
Line drawings are in fact the most difficult visual medium, because they demand near perfection. In math terms, they are a closed-form solution; lesser artists literally solve the same problems by successive approximation. One of the reasons kids give up drawing at ten or so is that they decide to start drawing like grownups, and one of the first things they try is a line drawing of a face. Smack!
In most fields the appearance of ease seems to come with practice. Perhaps what practice does is train your unconscious mind to handle tasks that used to require conscious thought. In some cases you literally train your body. An expert pianist can play notes faster than the brain can send signals to his hand. Likewise an artist, after a while, can make visual perception flow in through his eye and out through his hand as automatically as someone tapping his foot to a beat.
When people talk about being in "the zone," I think what they mean is that the spinal cord has the situation under control. Your spinal cord is less hesitant, and it frees conscious thought for the hard problems.
Good design uses symmetry. I think symmetry may just be one way to achieve simplicity, but it's important enough to be mentioned on its own. Nature uses it a lot, which is a good sign.
There are two kinds of symmetry, repetition and recursion. Recursion means repetition in subelements, like the pattern of veins in a leaf.
Symmetry is unfashionable in some fields now, in reaction to excesses in the past. Architects started consciously making buildings asymmetric in Victorian times and by the 1920s asymmetry was an explicit premise of modernist architecture. Even these buildings only tended to be asymmetric about major axes, though; there were hundreds of minor symmetries.
In writing you find symmetry at every level, from the phrases in a sentence to the plot of a novel. You find the same in music and art. Mosaics (and some Cezannes) get extra visual punch by making the whole picture out of the same atoms. Compositional symmetry yields some of the most memorable paintings, especially when two halves react to one another, as in the Creation of Adam or American Gothic.
In math and engineering, recursion, especially, is a big win. Inductive proofs are wonderfully short. In software, a problem that can be solved by recursion is nearly always best solved that way. The Eiffel Tower looks striking partly because it is a recursive solution, a tower on a tower.
The danger of symmetry, and repetition especially, is that it can be used as a substitute for thought.
Good design resembles nature. It's not so much that resembling nature is intrinsically good as that nature has had a long time to work on the problem. It's a good sign when your answer resembles nature's.
It's not cheating to copy. Few would deny that a story should be like life. Working from life is a valuable tool in painting too, though its role has often been misunderstood. The aim is not simply to make a record. The point of painting from life is that it gives your mind something to chew on: when your eyes are looking at something, your hand will do more interesting work.
Imitating nature also works in engineering. Boats have long had spines and ribs like an animal's ribcage. In some cases we may have to wait for better technology: early aircraft designers were mistaken to design aircraft that looked like birds, because they didn't have materials or power sources light enough (the Wrights' engine weighed 152 lbs. and generated only 12 hp.) or control systems sophisticated enough for machines that flew like birds, but I could imagine little unmanned reconnaissance planes flying like birds in fifty years.
Now that we have enough computer power, we can imitate nature's method as well as its results. Genetic algorithms may let us create things too complex to design in the ordinary sense.
Good design is redesign. It's rare to get things right the first time. Experts expect to throw away some early work. They plan for plans to change.
It takes confidence to throw work away. You have to be able to think, there's more where that came from. When people first start drawing, for example, they're often reluctant to redo parts that aren't right; they feel they've been lucky to get that far, and if they try to redo something, it will turn out worse. Instead they convince themselves that the drawing is not that bad, really-- in fact, maybe they meant it to look that way.
Dangerous territory, that; if anything you should cultivate dissatisfaction. In Leonardo's drawings there are often five or six attempts to get a line right. The distinctive back of the Porsche 911 only appeared in the redesign of an awkward prototype. In Wright's early plans for the Guggenheim, the right half was a ziggurat; he inverted it to get the present shape.
Mistakes are natural. Instead of treating them as disasters, make them easy to acknowledge and easy to fix. Leonardo more or less invented the sketch, as a way to make drawing bear a greater weight of exploration. Open-source software has fewer bugs because it admits the possibility of bugs.
It helps to have a medium that makes change easy. When oil paint replaced tempera in the fifteenth century, it helped painters to deal with difficult subjects like the human figure because, unlike tempera, oil can be blended and overpainted.
Good design can copy. Attitudes to copying often make a round trip. A novice imitates without knowing it; next he tries consciously to be original; finally, he decides it's more important to be right than original.
Unknowing imitation is almost a recipe for bad design. If you don't know where your ideas are coming from, you're probably imitating an imitator. Raphael so pervaded mid-nineteenth century taste that almost anyone who tried to draw was imitating him, often at several removes. It was this, more than Raphael's own work, that bothered the Pre-Raphaelites.
The ambitious are not content to imitate. The second phase in the growth of taste is a conscious attempt at originality.
I think the greatest masters go on to achieve a kind of selflessness. They just want to get the right answer, and if part of the right answer has already been discovered by someone else, that's no reason not to use it. They're confident enough to take from anyone without feeling that their own vision will be lost in the process.
Good design is often strange. Some of the very best work has an uncanny quality: Euler's Formula, Bruegel's Hunters in the Snow, the SR-71, Lisp. They're not just beautiful, but strangely beautiful.
I'm not sure why. It may just be my own stupidity. A can-opener must seem miraculous to a dog. Maybe if I were smart enough it would seem the most natural thing in the world that ei*pi = -1. It is after all necessarily true.
Most of the qualities I've mentioned are things that can be cultivated, but I don't think it works to cultivate strangeness. The best you can do is not squash it if it starts to appear. Einstein didn't try to make relativity strange. He tried to make it true, and the truth turned out to be strange.
At an art school where I once studied, the students wanted most of all to develop a personal style. But if you just try to make good things, you'll inevitably do it in a distinctive way, just as each person walks in a distinctive way. Michelangelo was not trying to paint like Michelangelo. He was just trying to paint well; he couldn't help painting like Michelangelo.
The only style worth having is the one you can't help. And this is especially true for strangeness. There is no shortcut to it. The Northwest Passage that the Mannerists, the Romantics, and two generations of American high school students have searched for does not seem to exist. The only way to get there is to go through good and come out the other side.
Good design happens in chunks. The inhabitants of fifteenth century Florence included Brunelleschi, Ghiberti, Donatello, Masaccio, Filippo Lippi, Fra Angelico, Verrocchio, Botticelli, Leonardo, and Michelangelo. Milan at the time was as big as Florence. How many fifteenth century Milanese artists can you name?
Something was happening in Florence in the fifteenth century. And it can't have been heredity, because it isn't happening now. You have to assume that whatever inborn ability Leonardo and Michelangelo had, there were people born in Milan with just as much. What happened to the Milanese Leonardo?
There are roughly a thousand times as many people alive in the US right now as lived in Florence during the fifteenth century. A thousand Leonardos and a thousand Michelangelos walk among us. If DNA ruled, we should be greeted daily by artistic marvels. We aren't, and the reason is that to make Leonardo you need more than his innate ability. You also need Florence in 1450.
Nothing is more powerful than a community of talented people working on related problems. Genes count for little by comparison: being a genetic Leonardo was not enough to compensate for having been born near Milan instead of Florence. Today we move around more, but great work still comes disproportionately from a few hotspots: the Bauhaus, the Manhattan Project, the New Yorker, Lockheed's Skunk Works, Xerox Parc.
At any given time there are a few hot topics and a few groups doing great work on them, and it's nearly impossible to do good work yourself if you're too far removed from one of these centers. You can push or pull these trends to some extent, but you can't break away from them. (Maybe you can, but the Milanese Leonardo couldn't.)
Good design is often daring. At every period of history, people have believed things that were just ridiculous, and believed them so strongly that you risked ostracism or even violence by saying otherwise.
If our own time were any different, that would be remarkable. As far as I can tell it isn't.
This problem afflicts not just every era, but in some degree every field. Much Renaissance art was in its time considered shockingly secular: according to Vasari, Botticelli repented and gave up painting, and Fra Bartolommeo and Lorenzo di Credi actually burned some of their work. Einstein's theory of relativity offended many contemporary physicists, and was not fully accepted for decades-- in France, not until the 1950s.
Today's experimental error is tomorrow's new theory. If you want to discover great new things, then instead of turning a blind eye to the places where conventional wisdom and truth don't quite meet, you should pay particular attention to them.
As a practical matter, I think it's easier to see ugliness than to imagine beauty. Most of the people who've made beautiful things seem to have done it by fixing something that they thought ugly. Great work usually seems to happen because someone sees something and thinks, I could do better than that. Giotto saw traditional Byzantine madonnas painted according to a formula that had satisfied everyone for centuries, and to him they looked wooden and unnatural. Copernicus was so troubled by a hack that all his contemporaries could tolerate that he felt there must be a better solution.
Intolerance for ugliness is not in itself enough. You have to understand a field well before you develop a good nose for what needs fixing. You have to do your homework. But as you become expert in a field, you'll start to hear little voices saying, What a hack! There must be a better way. Don't ignore those voices. Cultivate them. The recipe for great work is: very exacting taste, plus the ability to gratify it.
-
 @ 4b20a602:b57153f5
2024-07-27 12:26:02
@ 4b20a602:b57153f5
2024-07-27 12:26:02We're back with another masterclass, this time bringing you insights from Michael Saylor's most recent presentation at the Bitcoin 2024 conference in Nashville. Prepare for another thought provoking lecture about the impact and the benefitsof Bitcoin!
Saylor's vision of Bitcoin as the ultimate "digital capital" is more compelling than ever. Here are the key takeaways:
-
Immortal Capital: Saylor argues that Bitcoin represents a leap in capital preservation, potentially lasting thousands of years compared to traditional assets' 30-50 year lifespan.
-
$270 Trillion Opportunity: The potential market for digital capital is estimated at $270 trillion, based on current global wealth and preservation costs.
-
2045 Bitcoin Forecast: Saylor projects Bitcoin could reach $13 million per coin by 2045 in his base case, representing about 7% of global assets.
-
Tiered Investment Strategies: From "Normie" to "Triple Maxi," Saylor outlines Bitcoin strategies for individuals, corporations, and even nations.
-
National Bitcoin Adoption: Countries embracing Bitcoin aggressively could potentially turn national debts into surpluses.
-
U.S. Economic Impact: Saylor demonstrates how various levels of Bitcoin adoption could reshape the U.S. economy, potentially solving "half our problems."
-
Cyber Manhattan: Bitcoin is likened to "cyber Manhattan," with Saylor predicting a massive capital influx and demonetization of less efficient value stores.
While Saylor's optimism is infectious, we encourage critical thinking and thorough research. If even a fraction of his vision materializes, we're witnessing the dawn of an economic revolution.
What's your take on Saylor's predictions? Hit reply and share your thoughts!
Stay sovereign, The Bitcoin Blok Team
P.S. Recall Satoshi's words: "It might make sense just to get some in case it catches on." Saylor argues we're now staring at a trillion dollars of proof that it has.
P.P.S. Don't miss Saylor's full Bitcoin 2024 presentation here: https://youtu.be/O9KnBcWMkpw?si=7Szn-pvBMgR5Pw8S. It's a masterclass in Bitcoin strategy you'll want to watch!
-
-
 @ 0176967e:1e6f471e
2024-07-27 11:10:06
@ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.
