-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ b60c3e76:c9d0f46e
2024-05-27 13:50:24
@ b60c3e76:c9d0f46e
2024-05-27 13:50:24These inventions are straight out of science fiction.
1. Volkswagen RooBadge
Volkswagen has developed a clever VW badge that emits sounds to deter kangaroos from roads, thereby reducing collisions. With approximately 20,000 accidents involving these animals each year.
🔗 youtu.be/W9klRlKoEQk ← Full Video
https://video.nostr.build/219d3e2a7a3b21e5d485c7f2576e8b42fbbef661f35582e02090e03a2263cf92.mp4
2. Food Delivery Robot (Bullet Train)
A robot designed like a fast train delivers food efficiently, allowing customer customization. Created to address waiter shortages, it offers a low-cost delivery solution.
https://video.nostr.build/3a174aef12b2adf04470b43ffde99d287a4d3d695ebcde6d67f1b5efb20a0647.mp4
3. Astribot S1
China showcases the Astrobot S1, a fully autonomous humanoid robot, demonstrating remarkable speed and fluidity in completing tasks.
https://video.nostr.build/6475d93284a59a0853443337b42b1fbaa361612e5d7b94d50c49442735039344.mp4
4. Solskin
This new technology is highly efficient at harnessing the power of solar energy while also preventing rooms from overheating.
https://video.nostr.build/773a588b33f12da461c6b3867f31035c434f7efbd606d057131dee27c22ab6cb.mp4
5. Running Adwear
Imagine athletic clothing that doubles as an advertising platform, displaying dynamic ads while you run. You can even make some extra cash while generating more income just by running! 😅
https://video.nostr.build/8528ef90fbac3ef73fe038d0c892098a372dbf5608b894386ac3663b2d325b1d.mp4
6. Opula
World's first auto-adjustable coffee table featuring an AMD Ryzen 7 8845HS Mini-PC and a 27-inch HD screen. The table adjusts up to 75 degrees for optimal viewing, combining work and entertainment seamlessly - the future of smart home furniture.
https://video.nostr.build/acc6e34a8e2888a3d84a3a34e74f603bd6f76b6d8f329dc78c5598c104a4b86a.mp4
7. Ring Bot
This device is currently just a prototype. Hopefully, in the future, it will provide us with many benefits through its technology.
https://video.nostr.build/149aca79c79b59f2a5dfdff02b6d7935d7e113727f1bad9f0b81fdc1d0f8178e.mp4
8. Pininfarina Wind Tunnel
The Pininfarina Wind Tunnel sets new standards in vehicle performance and comfort through advanced aerodynamic testing.
https://video.nostr.build/7d7a2fb14c6c2ea41cdda5a939ee54ad83f85d83e4026913e023ded2c68583b8.mp4
I hope you've found this article helpful. What do you think?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-05-26 22:16:06
@ 3bf0c63f:aefa459d
2024-05-26 22:16:06 -
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 502ab02a:a2860397
2024-06-05 04:39:16
@ 502ab02a:a2860397
2024-06-05 04:39:16คิดว่า การไม่กินของ 0 แคล 0 คาร์บ จะทำให้คุณรอดพ้นจากสารให้ความหวานทดแทนไหมครับ โอเคบางคนอาจนึกถึง ไฮฟรุคโตสคอร์นไซรัป ซึ่งเป็นตัวพื้นฐานแล้วในยุคก่อน ไม่แปลกใจอะไร
แล้วถ้าผมถามถึงสารให้ความหวานที่มักมีข่าวที่ใช้ข้อมูลอิหยังวะ มานำเสนอหล่ะ เช่นพวก อิริท อะซิซัลเฟมเค ซูคราโลส หล่ะ หลายๆคนมั่นใจว่า ฉันไม่ซื้อของ 0แคล ไม่ซื้อของ no sugar มากิน ดังนั้นของพวกนี้ไม่ได้แอ้มฉันอยู่แล้ว น้ำตาลธรรมชาติดีกว่า ฉันกินน้ำตาลธรรมชาติ ดังนั้นฉันไม่กังวลเลยว่าฉันจะได้รับผลกระทบจากสารให้ความหวาน หรือ ที่เราเรียกบ้านๆว่า น้ำตาลเทียม
ผมบอกก่อนว่า ที่เขียนโพสนี้ ไม่ได้จะบอกว่า แบรนด์ไม่ดี ไม่ได้บอกว่าของพวกนี้ไม่ดี ไม่ได้บอกว่าหมกเม็ด ไม่ได้บอกหรือโน้มน้าวอะไรทั้งนั้น ไม่ได้เก่งกาจพอจะชี้สั่งได้ว่าอะไรกินได้กินไม่ได้ แบรนด์เขาแค่ผลิตสินค้ามาขายให้กับคนที่เป็นลูกค้าของเขา มันจบแค่นั้นไปแล้ว ส่วนใครจะซื้อหรือไม่ซื้ออะไร มันขึ้นอยู่กับแต่ละบุคคล โอเคนะ เข้าใจแล้วเราไปต่อ . . .
แต่ถ้าคุณเป็นคนหนึ่งที่ไม่อยากบริโภคสารให้ความหวาน ต้องขอแสดงความเสียใจด้วย มันใส่ในเครื่องดื่มปกติธรรมดาที่คุณดื่มอยู่มานานแล้วครับ ถ้าตกใจลองดูในรูปได้
สิ่งเดียวที่ผมบอกได้คือ จะบอกว่า ช่วยอ่านฉลากก่อนรับประทานกันเสียทีได้ไหม จะได้ไม่มาน้อยใจกันภายหลัง
รูปทั้งหมดที่ลงไว้ในโพสนี้ เป็นรูปฉลากโภชนาการที่ถ่ายมาจากร้านสะดวกซื้อ เป็นรูปสินค้าที่เป็นสินค้าปกติ ไม่ได้เน้นความพิเศษอะไร ไม่ได้ชูความแคลต่ำ ไม่ได้ชูความน้ำตาลต่ำ ไม่ได้ชูความเพื่อสุขภาพ ไม่ได้เสนอความเป็นรสหวานทางเลือก
เป็นสินค้าขายปกติทั่วไป ชูรสชาติ ชูยี่ห้อ ชูอะไรที่เขาชูอยู่เป็นปกติ แต่เขาได้ลดทอนปริมาณน้ำตาล แล้วเติมสารให้ความหวานต่างๆ ตามแต่ที่ R&D แต่ละบริษัทจะปรุงสุตรตัวเองขึ้นมา
คำถามที่เราควรตั้งกับตัวเองเช่น เขาทำเพื่ออะไร, เรารู้มาก่อนไหม, สูตรนี้มีมาตั้งแต่เมื่อไหร่ ที่สำคัญคือ ที่เคยมั่นใจมาก่อนหน้านี้ ยังมั่นใจอยู่ไหม ว่าเราไม่ได้บริโภคสารหวานทดแทนเหล่านี้
เรายังมั่นใจในอะไรที่เคยมั่นใจอยู่ไหม อย่างที่เคยพูดเสมอๆครับ เริ่มหัดอ่านฉลากโภชนาการได้แล้วหรือยัง#ฉลาก3รู้ มันสำคัญจริงๆนะครับ ไม่ได้เฉพาะเรื่องสุขภาพ มันไกลกว่านั้นครับ มันคือความรู้เท่าทันผู้ผลิต มันคือการปกป้องตัวเองของผู้บริโภค
ผู้ผลิตเล่นเกมส์นี้เสมอนะครับ เขาแจ้งให้ทราบในฉลากไม่เคยหมกเม็ด แค่เขาไม่ออกข่าวให้เราทราบว่า เห้ย ต่อไปนี้ฉันจะใช้สารให้ความหวานในสินค้ามาให้พวกคุณกินนะ เขาแค่ทำสิ่งที่ควรทำภายใต้ทั้งประกาศและกฎหมาย เรียกว่าทำตามหน้าที่เพื่อไม่ให้มีปัญหากับทางการนั่นแหละ ถ้ารู้สึกตกใจ เสียใจ น้อยใจ เลิกโทษคนอื่น แล้วกลับมาดูตัวเองครับ ว่าคุณจะเล่นเกมส์นี้ยังไง คุณอยู่ในโลกแห่งการตักตวงผลประโยชน์จากความหวาน
ในรูปเหล่านี้คือการไปสำรวจร้านสะดวกซื้อ โดยหยิบเฉพาะตัวสินค้าที่ “ไม่ได้เน้น” 0คาร์บ0แคล หรือ น้ำตาลน้อย เรียกได้ว่าหยิบเฉพาะตัวที่เป็นสินค้าปกติทั่วไปเลยครับ







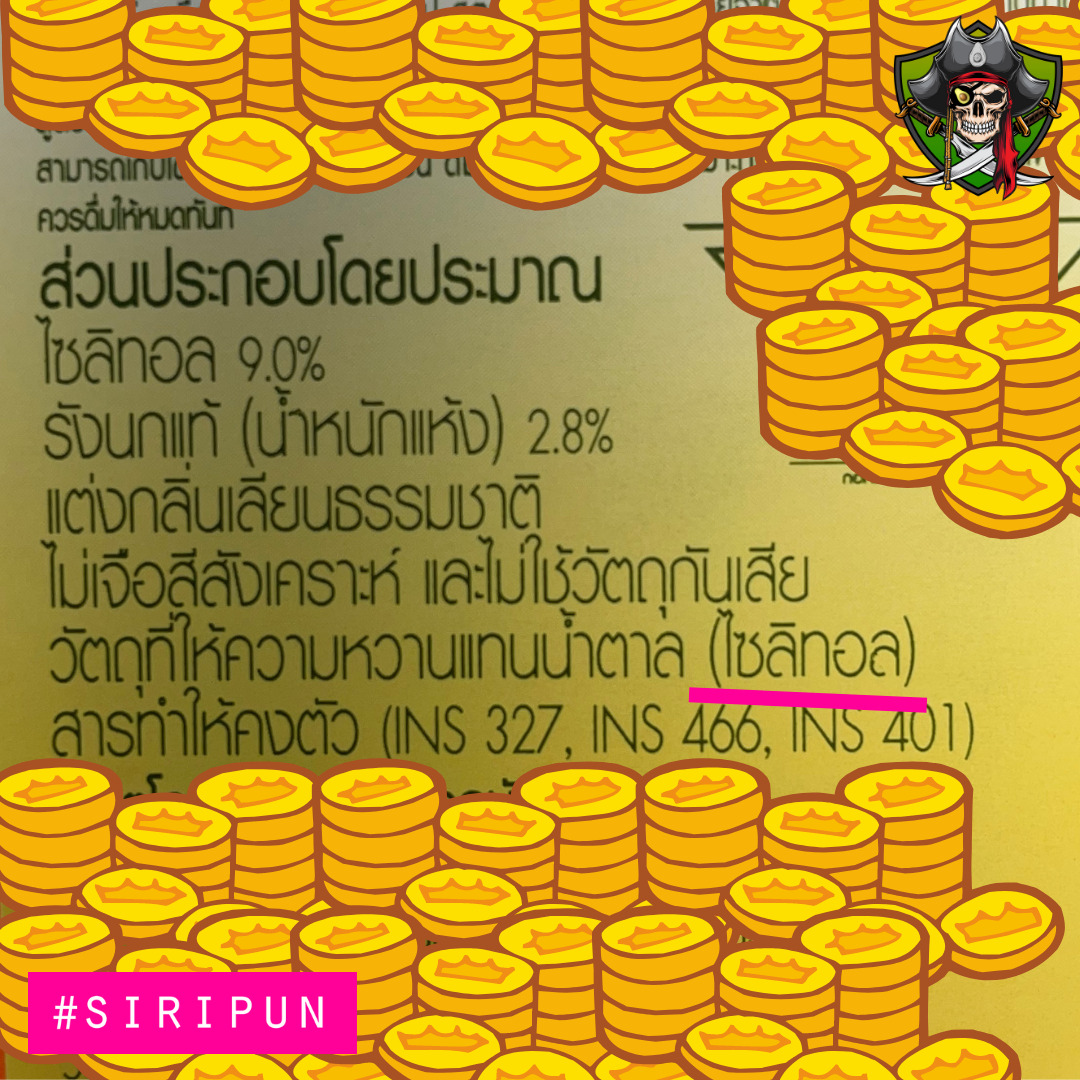
siamstr #pirateketo
-
 @ 7308f407:94057dcf
2024-06-04 22:47:27
@ 7308f407:94057dcf
2024-06-04 22:47:27Chef's notes
Telera bread, a beloved staple in Mexican cuisine, serves as the perfect foundation for sandwiches. I recently prepared this homemade Telera bread recipe for our local Nostr meetup group, Nostr Phx, where I crafted delicious ham sandwiches filled with a medley of flavors—Havarti cheese, seared Panela cheese, Butter Lettuce, Campari Tomatoes, Avocados, and a zesty Chipotle Mayonnaise. To add an extra kick, I also made Pickled Jalapenos as an optional topping for the Tortas. It was a joy to share these treats while immersing ourselves in discussions about Nostr, Bitcoin, and Nostr Product Marketing.
Details
- ⏲️ Prep time: 1 hour and 30 minutes to 2 hours
- 🍳 Cook time: 20 to 25 minutes
- 🍽️ Servings: 8 buns
Ingredients
- 1.5 cups water (about 115°F)
- 1 tablespoon sugar
- 1 tablespoon active dry yeast
- 3.5 cups all-purpose flour
- 1.5 teaspoons salt
Directions
- In a cup, add warm. (I place water without ingredients in the microwave for about 20-30 seconds to warm it, then I verify with a thermometer to be around 115 degrees Fahrenheit).
- Mix the water, sugar, and yeast then place them in a warm place to activate the yeast for about 10 minutes. The yeast will feed off the sugar, and the warm water environment will help the yeast expand to activate.
- In a bowl, mix to combine all dry ingredients: all-purpose flour, salt, and butter.
- After the activation time for the yeast liquid, start adding it to the dry ingredients in smaller splashes to combine. You will want the dough to be moist but not wet.
- Begin kneading the dough in the bowl, then transfer it to a countertop. Fold the dough in half towards you. Push the heel of your hand firmly into the dough, then fold it back over itself. Turn the dough 90 degrees and repeat steps 2 and 3. Continue kneading for 5-10 minutes, or until the dough is smooth and elastic.
- Place the smooth dough back into a lightly oiled bowl and cover it with a kitchen towel. Allow it to rise for about 40 minutes in a warm place. (I add a plastic wrap over the bowl then place the kitchen towel inside of the oven with the light on).
- After the resting time, remove the dough from the bowl onto the countertop to divide it into 8 parts.
- Round the 8 parts of dough into a ball shape. As you’re shaping each one, cover them with a kitchen towel to prevent them from drying out.
- Let the dough rest for about 5 minutes.
- Grab one of your pieces of dough and add flour to both sides, then lightly flatten it and place it on your countertop. Use your index finger to make two line indentations.
- After you shape your ball, place it back under your kitchen towel.
- Once all of them are shaped, bake at 380 degrees Fahrenheit for 21-25 minutes or until the bread is lightly golden brown. Optionally, add 2 cups of water in a separate oven-safe bowl to create steam.
- Remove from the oven, then place on a wire rack covered with a kitchen towel for a couple of minutes.
- Enjoy on its own, with butter, or make a delicious Torta.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 5d4b6c8d:8a1c1ee3
2024-05-21 17:45:14
@ 5d4b6c8d:8a1c1ee3
2024-05-21 17:45:14Previously, I wrote about my concerns surrounding the Keynesian Beauty Contest nature of Stacker News: https://stacker.news/items/473181/r/Undisciplined. Check that out for context.
Now, I'd like to add some thoughts about why I'm hopeful that we can sustain a culture of authenticity in the face of the perverse incentives those contests have.
Repeated games are different
The most important element that I didn't touch on in the previous post is that most of us don't just use Stacker News once and abscond with our rewards. We come back over and over again.
That matters for the incentives because we aren't just guessing today's beauty contest winner, we're signaling who tomorrow's contestants should be. If you're zapping posts that you don't like, just because you expect them to do well, then you're going to have more posts like that to look at in the future and fewer of the ones you do want to look at.
Eventually, I imagine inauthentic zappers will lose interest in a site that only offers content that's valuable to other people.
Authenticity optimizes global trust
Our votes in this beauty contest are weighted by our global trust score, which is something like our propensity to zap content that is valued by others. It's based on our individual trust scores with every other stacker, though, and this is what got me thinking about this post.
When you zap inauthentically, you may get more rewards today, but you are also increasing the trust scores of those who also zap that way and decreasing the scores of those who share your authentic preferences.
Alternatively, if you zap authentically, then you will elevate those who share your preferences and give more weight to their votes in the future. This incentivizes such people to be on Stacker News at all.
TLDR
Long-term, being authentic actually maximizes your voting power on Stacker News and will result in being maximally rewarded for zapping your favorite content.
That's in addition to the direct effect of incentivizing people to make more content that you like.
Zap true and Stacker News will become the place you want it to be.
Some other posts about using SN well
(Just hover over links to see the post titles)
From me https://stacker.news/items/287074/r/Undisciplined https://stacker.news/items/523858/r/Undisciplined https://stacker.news/items/488525/r/Undisciplined
From @Natalia https://stacker.news/items/252695 https://stacker.news/items/392551
From @cryotosensei https://stacker.news/items/400068/r/Undisciplined https://stacker.news/items/444755/r/Undisciplined https://stacker.news/items/393176/r/Undisciplined
As always, zap well.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ b804f68e:2fb0fa1f
2024-06-04 18:56:04
@ b804f68e:2fb0fa1f
2024-06-04 18:56:04In my travels, I've noticed profound differences in how people approach generosity. In Thailand, for instance, it's common to see people giving money to the homeless without hesitation. This is in stark contrast to what I observe back home in the States, where such acts of kindness are rare. This disparity made me reflect on the broader concept of change and how we often desire it without being willing to initiate it ourselves.
We frequently wish for change, hoping or even complaining about the need for it. However, we are rarely willing to take the first step toward making that change. The truth is, meaningful change always begins with us. We cannot expect the world to change on its own; change requires a conscious, deliberate decision to grow and improve.
Take my experience as a Bitcoiner, for example. I dream of a hyperbitcoinized world, yet I haven't fully committed to the changes necessary to move in that direction. I still use fiat currency, don't run a full node, and don't pay in sats regularly. This is a clear example of how our aspirations for change must be matched by our actions. Changing ourselves is the most effective way to begin transforming our environment. Even if the external world remains the same, our internal environment will have improved, and that's where the real impact lies.
We often talk about change but fail to follow through. I, too, desire a better world, yet I shy away from small gestures like saying hi to strangers. This simple act of acknowledgment can be the first step towards building a habit of kindness. The same goes for giving money to the homeless. It's not about whether they deserve it; it's about the act of kindness and the fulfillment it brings. These small, consistent actions can gradually transform our habits and, eventually, our environment.
Will giving a few dollars to a homeless person end homelessness or world hunger? Probably not. But it's a step in the right direction, much more so than doing nothing at all. Reflecting on the generosity I've witnessed in Thailand, I see that people there don't think twice about helping others, despite having less wealth than those in the West. They live in a developing country, yet their acts of kindness contribute to a generally happier society.
If we want the world to change, or even just a part of our lives to change, we must start with ourselves. Change always begins with us. If we are unwilling to change, nothing around us will ever change. By becoming the change we wish to see, we can gradually create a better world, one small act of kindness at a time.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-04 16:27:24
@ 5d4b6c8d:8a1c1ee3
2024-06-04 16:27:24We've had an impressive influx of new Stackers. Some have asked about various norms that have been established on SN. The one I want to talk about here is default zapping.
Many of you know that I'm somewhat obsessed with zapping habits and how we value our zaps (https://stacker.news/items/287074/r/Undisciplined, https://stacker.news/items/523858/r/Undisciplined, https://stacker.news/items/473181/r/Undisciplined, and https://stacker.news/items/221151/r/Undisciplined). This is the magic that makes Stacker News work so well, after all.
Why Zap?
Bitcoin is scarce and hodl'ing is deeply ingrained in us. I can read all of the content on Stacker News without zapping a single sat. Why should I buy the cow, when the milk is free?
- Maybe you're the rare person who really engages in V4V, even when you don't have to. That's great, but we can see from nostr that you're the exception.
- The SN rewards system will pay you back for zapping good content and it does so nonlinearly. Ranking higher in zapping can pay for itself, so you don't want to be shooting yourself in the foot by zapping less than everyone else out of ignorance.
Common Zaps
This is where knowing what other people are doing comes in handy. * Generally, people zap a comment between 10 and 100 sats. 21 is a very common choice for symbolic reasons. * Many people zap posts more, which I think is reasonable since posts generally take more creativity and cost the poster more than a comment does. Normal post zaps range up to 1000 sats.
So, if you're trying to think through what reasonable amounts are for yourself, think tens of sats for comments and hundreds for posts. However, there's tons of room for discretion in there.
My Numbers
One of the neat SN features is that the custom zap options store several of your recent values.
I set my default to 21, which lets me double tap to get 42. Then I have 69, 115, and 420 saved as custom zaps. Having numbers with symbolic meaning is just a bit of extra fun.
Generally, comments get one of the following from me * 21 (special btc number) * 42 (the answer to life, the universe, and everything) * 69 (nice)
while posts get * 115 (remember, remember) * 420 (hehe) * 1000 (1 kilosat)
Hopefully, it helps someone seeing this laid out.
As always, I'm curious to hear how you all think about this stuff. It's an ever moving target.
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 3c984938:2ec11289
2024-05-09 04:43:15
@ 3c984938:2ec11289
2024-05-09 04:43:15
It's been a journey from the Publishing Forest of Nostr to the open sea of web3. I've come across a beautiful chain of islands and thought. Why not take a break and explore this place? If I'm searching for devs and FOSS, I should search every nook and cranny inside the realm of Nostr. It is quite vast for little old me. I'm just a little hamster and I don't speak in code or binary numbers zeros and ones.

After being in sea for awhile, my heart raced for excitement for what I could find. It seems I wasn't alone, there were others here like me! Let's help spread the message to others about this uncharted realm. See, look at the other sailboats, aren't they pretty? Thanks to some generous donation of SATs, I was able to afford the docking fee.

Ever feel like everyone was going to a party, and you were supposed to dress up, but you missed the memo? Or a comic-con? well, I felt completely underdressed and that's an understatement. Well, turns out there is a some knights around here. Take a peek!

A black cat with a knight passed by very quickly. He was moving too fast for me to track. Where was he going? Then I spotted a group of knights heading in the same direction, so I tagged along. The vibes from these guys was impossible to resist. They were just happy-go-lucky. 🥰They were heading to a tavern on a cliff off the island.

Ehh? a Tavern? Slightly confused, whatever could these knights be doing here? I guess when they're done with their rounds they would here to blow off steam. Things are looking curiouser and curiouser. But the black cat from earlier was here with its rider, whom was dismounting. So you can only guess, where I'm going.

The atmosphere in this pub, was lively and energetic. So many knights spoke among themselves. A group here, another there, but there was one that caught my eye. I went up to a group at a table, whose height towed well above me even when seated. Taking a deep breath, I asked, "Who manages this place?" They unanimous pointed to one waiting for ale at the bar. What was he doing? Watching others talk? How peculiar.

So I went up to him! And introduced myself.
"Hello I'm Onigirl"
"Hello Onigirl, Welcome to Gossip"
"Gossip, what is Gossip?" scratching my head and whiskers.
What is Gossip? Gossip is FOSS and a great client for privacy-centric minded nostriches. It avoids browser tech which by-passes several scripting languages such as JavaScript☕, HTML parsing, rendering, and CSS(Except HTTP GET and Websockets). Using OpenGL-style rendering. For Nostriches that wish to remain anonymous can use Gossip over TOR. Mike recommends using QubesOS, Whonix and or Tails. [FYI-Gossip does not natively support tor SOCKS5 proxy] Most helpful to spill the beans if you're a journalist.

On top of using your nsec or your encryption key, Gossip adds another layer of security over your account with a password login. There's nothing wrong with using the browser extensions (such as nos2x or Flamingo) which makes it super easy to log in to Nostr enable websites, apps, but it does expose you to browser vulnerabilities.
Mike Points out
"people have already had their private key stolen from other nostr clients,"
so it a concern if you value your account. I most certainly care for mine.

Gossip UI has a simple, and clean interface revolving around NIP-65 also called the “Outbox model." As posted from GitHub,
"This NIP allows Clients to connect directly with the most up-to-date relay set from each individual user, eliminating the need of broadcasting events to popular relays."
This eliminates clients that track only a specific set of relays which can congest those relays when you publish your note. Also this can be censored, by using Gossip you can publish notes to alternative relays that have not censored you to reach the same followers.
👉The easiest way to translate that is reducing redundancy to publish to popular relays or centralized relays for content reach to your followers.

Cool! What an awesome client, I mean Tavern! What else does this knight do? He reaches for something in his pocket. what is it? A Pocket is a database for storing and retrieving nostr events but mike's written it in Rust with a few extra kinks inspired by Will's nostrdb. Still in development, but it'll be another tool for you dear user! 💖💕💚
Onigirl is proud to present this knights to the community and honor them with kisu. 💋💋💋 Show some 💖💘💓🧡💙💚
👉💋💋Will - jb55 Lord of apples 💋 @npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
👉💋💋 Mike Knight - Lord of Security 💋 @npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c

Knights spend a lot of time behind the screen coding for the better of humanity. It is a tough job! Let's appreciate these knights, relay operators, that support this amazing realm of Nostr! FOSS for all!

This article was prompted for the need for privacy and security of your data. They're different, not to be confused.
Recently, Edward Snowden warns Bitcoin devs about the need for privacy, Quote:
“I've been warning Bitcoin developers for ten years that privacy needs to be provided for at the protocol level. This is the final warning. The clock is ticking.”
Snowden’s comments come after heavy actions of enforcement from Samarai Wallet, Roger Ver, Binance’s CZ, and now the closure of Wasabi Wallet. Additionally, according to CryptoBriefing, Trezor is ending it’s CoinJoin integration as well. Many are concerned over the new definition of a money transmitter, which includes even those who don’t touch the funds.
Help your favorite the hamster
 ^^Me drowning in notes on your feed. I can only eat so many notes to find you.
^^Me drowning in notes on your feed. I can only eat so many notes to find you. 👉If there are any XMPP fans on here. I'm open to the idea of opening a public channel, so you could follow me on that as a forum-like style. My server of choice would likely be a German server.😀You would be receiving my articles as njump.me style or website-like. GrapeneOS users, you can download Cheogram app from the F-Driod store for free to access. Apple and Andriod users are subjected to pay to download this app, an alternative is ntalk or conversations. If it interests the community, just FYI. Please comment or DM.
👉If you enjoyed this content, please consider reposting/sharing as my content is easily drowned by notes on your feed. You could also join my community under Children_Zone where I post my content.
An alternative is by following #onigirl Just FYI this feature is currently a little buggy.
Follow as I search for tools and awesome devs to help you dear user live a decentralized life as I explore the realm of Nostr.
Thank you Fren
-
 @ 0861144c:e68a1caf
2024-06-04 13:44:05
@ 0861144c:e68a1caf
2024-06-04 13:44:05I was astonished by the Gold Confiscation in Shanghai by @Signal312 and forgot that I read already about this but during the WWII, this is my the continuation of that saga and the monster in this story is also the reason why bitcoin is important. So let's start with our story.
What/who is BIS?
The Bank of International Settlements is a Swiss-based bank was formed in 1930 with one objective: manage the reparation payment by Germany forged in the Versailles Treaty; at first, that was his only job but everything changes in when Thomas McKittrick comes as Chairman. Now, for a long time there were some hypothesis about the role of McKittrick and the nazis because on one hand the BIS declared itslef as a neutral bank, meaning they won't take parts during the conflicts. They took sides. We know that since the BIS declassified all his documents during the war we know now some of the following facts:
- Between the Reichsbank and the BIS, they transfered more 13.5 tons of stolen gold
- The nazis stole the gold not only from central banks of other countries defeated but also remelted gold from labor and prison camps. The BIS took all of it. No question asked.
- They said they were neutrals. Well, so neutrals that in the Board of Directors we had: Walther Funk, Emil Puhl, Herman Schmitz. Yes, they were all pro-nazis.
- Montagu Norman, Head of the Bank of England considered Hjalmar Schacht, president of the Reichsbank a close friend and helped him to transfer over 2.5 millions kg worth of gold to Hitler. Two things here: the gold belonged to Czechoslovakia and the movement was made 6 months before Great Britain went to war. Bonus is that Schacht considered the BIS as an allied. So, how in the hell did this happen? Well, remember BIS was a neutral bank so the Czechoslovaks believed that the BIS’s legal immunities would protect them. But they were wrong.
- When in 1944 the State Department had some suspicious hypothesis about the confabulation between BIS and the Reichsbank so the wanted to disband. In the official site of the BIS, you can read as follow:
In July 1944, a United Nations conference met at Bretton Woods in the United States to discuss the postwar international monetary system. The Bretton Woods Conference adopted a resolution calling for the abolition of the BIS "at the earliest possible moment", because it considered that the BIS would have no useful role to play once the newly created World Bank and International Monetary Fund were operational. European central bankers held a different opinion, and successfully lobbied for maintaining the BIS. By early 1948, the BIS liquidation resolution had been put aside. It was understood that henceforth the BIS would focus foremost on European monetary and financial matters.
European calling for maintain this? Well, not quite. Today, we know who was the wizard and his name: John Maynard Keynes, head of the British delegation during the Bretton Woods Conference voted against the abolition. When you ask about why they voted against, take a look in the photo above, that's the why.
So, if you stomach is starting to roar because what you're reading, I leave you two sources: The BIS and their documents during the war and The Tower of Basel: The Shadowy History of the Secret Bank that Runs the World. After you finish read those two sources, the conclusion will be -I think- the same as I came at that time: we need bitcoin.
-
 @ c11cf5f8:4928464d
2024-05-05 14:22:20
@ c11cf5f8:4928464d
2024-05-05 14:22:20Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ a30cdfee:2d2f97ff
2024-06-04 13:20:22
@ a30cdfee:2d2f97ff
2024-06-04 13:20:22Bringin: Fast Offramp from Lightning to Fiat with a Personal IBAN Account
Bringin lets you trade bitcoin to euros only using IBAN accounts in your own personal name.
Don't Get "Debanked"!
If you make a withdrawal from a Bitcoin exchange to your bank account, the bank might flag your activity as suspicious and deem you too "risky" to be their customer.
But if the fiat payment is coming from another bank account in your own name? 😏
All Bringin customers get a dedicated Maltese IBAN account, and all conversions go through this account.
Bringin doesn't custody any bitcoin, it's just a tool to connect Bitcoin and traditional banking in a smooth way.
From Lightning to Fiat, Very Fast!
You can connect any on-chain or Lightning wallet, and liquidate your bitcoin with e.g. SEPA Instant.
From Lightning to fiat in less than a minute!
With many other exchanges, the withdrawal can take a day or two because they often use 3rd party providers.
Buy Bitcoin.. Or Spend With Single-Use Virtual Debit cards
You can also buy bitcoin on Bringin directly to your own Lightning wallet!
Bringin takes a 1% fee on all transactions.
Bringin also has plans to offer single-use virtual debit cards for online shopping.
On the backend, the Lightning invoice (or on-chain transaction) that you pay becomes a one-time spendable balance on a debit card!
The Bringin team confirmed that the virtual debit cards will be out in a month or so.
The first version of virtual debit cards will not support adding them to Apple Pay/Google Pay, but there are plans to add support in the future.
Only in Europe.. and KYC Required
Bringin is currently only available in Europe, and KYC is required to use the service.
But if you're fine with that major tradeoff, Bringin seems like a good offramp tool if you need to go back to the fiat side.
Bringin is only a web app, at least for now. No mobile app!
API for Companies
Bringin also offers an API for companies if they want to accept bitcoin without really accepting bitcoin.
In the backend, Bringin will automatically convert the bitcoin to euros, and also takes care off all the necessary compliance.
Are Offramps Good or Bad for Bitcoin Adoption?
But why build tools to go back to fiat?
Aren't we building a Bitcoin standard?
Well, many people are still not ready to take the leap and tools like Bringin exist for those people to eventually take that leap.
If you can easily liquidate your bitcoin to fiat without too many middlemen, it will hopefully give confidence for people to buy more bitcoin!
What do you think about Bringin? Have you tried it?
Is there a place for offramps like this when building for the Bitcoin standard?
Additional Resources
Bringin.xyz ⚡️ Quick Pitch Video! #Bitcoin Spending, Debit Cards, Pay Bills, IBANs, Live in the EU
Project Links
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 266815e0:6cd408a5
2024-04-24 23:02:21
@ 266815e0:6cd408a5
2024-04-24 23:02:21NOTE: this is just a quick technical guide. sorry for the lack of details
Install NodeJS
Download it from the official website https://nodejs.org/en/download
Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script
bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20Clone example config.yml
bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.ymlModify config.yml
```bash nano config.yml
or if your that type of person
vim config.yml ```
Run blossom-server
```bash npx blossom-server-ts
or install it locally and run using npm
npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ```
Now you can open http://localhost:3000 and see your blossom server
And if you set the
dashboard.enabledoption in theconfig.ymlyou can open http://localhost:3000/admin to see the admin dashboard -
 @ c11cf5f8:4928464d
2024-06-04 11:57:10
@ c11cf5f8:4928464d
2024-06-04 11:57:10Wrangle up your latest tech discoveries, reviews, and recommendations. Let's hear all about your favorite tech products, services, or projects!
Feel free to share any new tech you've heard about, bought for yourself, or technology that you just think other stackers should know about. Found any gadgets or gizmos that blew your mind? Don't be shy—share the pros and cons and help your fellow stackers in the ~AGORA stay ahead of the tech curve!
Send your best 👇
-
 @ 1f9e547c:8af216ed
2024-04-23 08:35:18
@ 1f9e547c:8af216ed
2024-04-23 08:35:18Hashtag testing
Plaintext
hashtag #again
NostrOpinion
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 256a7941:b828ba8d
2024-06-04 11:49:03
@ 256a7941:b828ba8d
2024-06-04 11:49:03 -
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 3bf0c63f:aefa459d
2024-03-06 13:04:06
@ 3bf0c63f:aefa459d
2024-03-06 13:04:06início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ 8ce092d8:950c24ad
2024-02-04 23:35:07
@ 8ce092d8:950c24ad
2024-02-04 23:35:07Overview
- Introduction
- Model Types
- Training (Data Collection and Config Settings)
- Probability Viewing: AI Inspector
- Match
- Cheat Sheet
I. Introduction
AI Arena is the first game that combines human and artificial intelligence collaboration.
AI learns your skills through "imitation learning."
Official Resources
- Official Documentation (Must Read): Everything You Need to Know About AI Arena
Watch the 2-minute video in the documentation to quickly understand the basic flow of the game. 2. Official Play-2-Airdrop competition FAQ Site https://aiarena.notion.site/aiarena/Gateway-to-the-Arena-52145e990925499d95f2fadb18a24ab0 3. Official Discord (Must Join): https://discord.gg/aiarenaplaytest for the latest announcements or seeking help. The team will also have a exclusive channel there. 4. Official YouTube: https://www.youtube.com/@aiarena because the game has built-in tutorials, you can choose to watch videos.
What is this game about?
- Although categorized as a platform fighting game, the core is a probability-based strategy game.
- Warriors take actions based on probabilities on the AI Inspector dashboard, competing against opponents.
- The game does not allow direct manual input of probabilities for each area but inputs information through data collection and establishes models by adjusting parameters.
- Data collection emulates fighting games, but training can be completed using a Dummy As long as you can complete the in-game tutorial, you can master the game controls.
II. Model Types
Before training, there are three model types to choose from: Simple Model Type, Original Model Type, and Advanced Model Type.
It is recommended to try the Advanced Model Type after completing at least one complete training with the Simple Model Type and gaining some understanding of the game.

Simple Model Type
The Simple Model is akin to completing a form, and the training session is comparable to filling various sections of that form.
This model has 30 buckets. Each bucket can be seen as telling the warrior what action to take in a specific situation. There are 30 buckets, meaning 30 different scenarios. Within the same bucket, the probabilities for direction or action are the same.
For example: What should I do when I'm off-stage — refer to the "Recovery (you off-stage)" bucket.
For all buckets, refer to this official documentation:
https://docs.aiarena.io/arenadex/game-mechanics/tabular-model-v2
Video (no sound): The entire training process for all buckets
https://youtu.be/1rfRa3WjWEA
Game version 2024.1.10. The method of saving is outdated. Please refer to the game updates.
Advanced Model Type
The "Original Model Type" and "Advanced Model Type" are based on Machine Learning, which is commonly referred to as combining with AI.
The Original Model Type consists of only one bucket, representing the entire map. If you want the AI to learn different scenarios, you need to choose a "Focus Area" to let the warrior know where to focus. A single bucket means that a slight modification can have a widespread impact on the entire model. This is where the "Advanced Model Type" comes in.
The "Advanced Model Type" can be seen as a combination of the "Original Model Type" and the "Simple Model Type". The Advanced Model Type divides the map into 8 buckets. Each bucket can use many "Focus Area." For a detailed explanation of the 8 buckets and different Focus Areas, please refer to the tutorial page (accessible in the Advanced Model Type, after completing a training session, at the top left of the Advanced Config, click on "Tutorial").

III. Training (Data Collection and Config Settings)
Training Process:
- Collect Data
- Set Parameters, Train, and Save
- Repeat Step 1 until the Model is Complete
Training the Simple Model Type is the easiest to start with; refer to the video above for a detailed process.
Training the Advanced Model Type offers more possibilities through the combination of "Focus Area" parameters, providing a higher upper limit. While the Original Model Type has great potential, it's harder to control. Therefore, this section focuses on the "Advanced Model Type."
1. What Kind of Data to Collect
- High-Quality Data: Collect purposeful data. Garbage in, garbage out. Only collect the necessary data; don't collect randomly. It's recommended to use Dummy to collect data. However, don't pursue perfection; through parameter adjustments, AI has a certain level of fault tolerance.
- Balanced Data: Balance your dataset. In simple terms, if you complete actions on the left side a certain number of times, also complete a similar number on the right side. While data imbalance can be addressed through parameter adjustments (see below), it's advised not to have this issue during data collection.
- Moderate Amount: A single training will include many individual actions. Collect data for each action 1-10 times. Personally, it's recommended to collect data 2-3 times for a single action. If the effect of a single training is not clear, conduct a second (or even third) training with the same content, but with different parameter settings.
2. What to Collect (and Focus Area Selection)
Game actions mimic fighting games, consisting of 4 directions + 6 states (Idle, Jump, Attack, Grab, Special, Shield). Directions can be combined into ↗, ↘, etc. These directions and states can then be combined into different actions.
To make "Focus Area" effective, you need to collect data in training that matches these parameters. For example, for "Distance to Opponent", you need to collect data when close to the opponent and also when far away. * Note: While you can split into multiple training sessions, it's most effective to cover different situations within a single training.
Refer to the Simple Config, categorize the actions you want to collect, and based on the game scenario, classify them into two categories: "Movement" and "Combat."
Movement-Based Actions
Action Collection
When the warrior is offstage, regardless of where the opponent is, we require the warrior to return to the stage to prevent self-destruction.
This involves 3 aerial buckets: 5 (Near Blast Zone), 7 (Under Stage), and 8 (Side Of Stage).

* Note: The background comes from the Tutorial mentioned earlier. The arrows in the image indicate the direction of the action and are for reference only. * Note: Action collection should be clean; do not collect actions that involve leaving the stage.
Config Settings
In the Simple Config, you can directly choose "Movement" in it. However, for better customization, it's recommended to use the Advanced Config directly. - Intensity: The method for setting Intensity will be introduced separately later. - Buckets: As shown in the image, choose the bucket you are training. - Focus Area: Position-based parameters: - Your position (must) - Raycast Platform Distance, Raycast Platform Type (optional, generally choose these in Bucket 7)
Combat-Based Actions
The goal is to direct attacks quickly and effectively towards the opponent, which is the core of game strategy.
This involves 5 buckets: - 2 regular situations - In the air: 6 (Safe Zone) - On the ground: 4 (Opponent Active) - 3 special situations on the ground: - 1 Projectile Active - 2 Opponent Knockback - 3 Opponent Stunned
2 Regular Situations
In the in-game tutorial, we learned how to perform horizontal attacks. However, in the actual game, directions expand to 8 dimensions. Imagine having 8 relative positions available for launching hits against the opponent. Our task is to design what action to use for attack or defense at each relative position.
Focus Area - Basic (generally select all) - Angle to opponent
- Distance to opponent - Discrete Distance: Choosing this option helps better differentiate between closer and farther distances from the opponent. As shown in the image, red indicates a relatively close distance, and green indicates a relatively distant distance.- Advanced: Other commonly used parameters
- Direction: different facings to opponent
- Your Elemental Gauge and Discrete Elementals: Considering the special's charge
- Opponent action: The warrior will react based on the opponent's different actions.
- Your action: Your previous action. Choose this if teaching combos.
3 Special Situations on the Ground
Projectile Active, Opponent Stunned, Opponent Knockback These three buckets can be referenced in the Simple Model Type video. The parameter settings approach is the same as Opponent Active/Safe Zone.
For Projectile Active, in addition to the parameters based on combat, to track the projectile, you also need to select "Raycast Projectile Distance" and "Raycast Projectile On Target."
3. Setting "Intensity"
Resources
- The "Tutorial" mentioned earlier explains these parameters.
- Official Config Document (2022.12.24): https://docs.google.com/document/d/1adXwvDHEnrVZ5bUClWQoBQ8ETrSSKgG5q48YrogaFJs/edit
TL;DR:
Epochs: - Adjust to fewer epochs if learning is insufficient, increase for more learning.
Batch Size: - Set to the minimum (16) if data is precise but unbalanced, or just want it to learn fast - Increase (e.g., 64) if data is slightly imprecise but balanced. - If both imprecise and unbalanced, consider retraining.
Learning Rate: - Maximize (0.01) for more learning but a risk of forgetting past knowledge. - Minimize for more accurate learning with less impact on previous knowledge.
Lambda: - Reduce for prioritizing learning new things.
Data Cleaning: - Enable "Remove Sparsity" unless you want AI to learn idleness. - For special cases, like teaching the warrior to use special moves when idle, refer to this tutorial video: https://discord.com/channels/1140682688651612291/1140683283626201098/1195467295913431111
Personal Experience: - Initial training with settings: 125 epochs, batch size 16, learning rate 0.01, lambda 0, data cleaning enabled. - Prioritize Multistream, sometimes use Oversampling. - Fine-tune subsequent training based on the mentioned theories.
IV. Probability Viewing: AI Inspector
The dashboard consists of "Direction + Action." Above the dashboard, you can see the "Next Action" – the action the warrior will take in its current state. The higher the probability, the more likely the warrior is to perform that action, indicating a quicker reaction. It's essential to note that when checking the Direction, the one with the highest visual representation may not have the highest numerical value. To determine the actual value, hover the mouse over the graphical representation, as shown below, where the highest direction is "Idle."

In the map, you can drag the warrior to view the probabilities of the warrior in different positions. Right-click on the warrior with the mouse to change the warrior's facing. The status bar below can change the warrior's state on the map.

When training the "Opponent Stunned, Opponent Knockback" bucket, you need to select the status below the opponent's status bar. If you are focusing on "Opponent action" in the Focus Zone, choose the action in the opponent's status bar. If you are focusing on "Your action" in the Focus Zone, choose the action in your own status bar. When training the "Projectile Active" Bucket, drag the projectile on the right side of the dashboard to check the status.
Next
The higher the probability, the faster the reaction. However, be cautious when the action probability reaches 100%. This may cause the warrior to be in a special case of "State Transition," resulting in unnecessary "Idle" states.
Explanation: In each state a fighter is in, there are different "possible transitions". For example, from falling state you cannot do low sweep because low sweep requires you to be on the ground. For the shield state, we do not allow you to directly transition to headbutt. So to do headbutt you have to first exit to another state and then do it from there (assuming that state allows you to do headbutt). This is the reason the fighter runs because "run" action is a valid state transition from shield. Source
V. Learn from Matches
After completing all the training, your model is preliminarily finished—congratulations! The warrior will step onto the arena alone and embark on its debut!
Next, we will learn about the strengths and weaknesses of the warrior from battles to continue refining the warrior's model.
In matches, besides appreciating the performance, pay attention to the following:
-
Movement, i.e., Off the Stage: Observe how the warrior gets eliminated. Is it due to issues in the action settings at a certain position, or is it a normal death caused by a high percentage? The former is what we need to avoid and optimize.
-
Combat: Analyze both sides' actions carefully. Observe which actions you and the opponent used in different states. Check which of your hits are less effective, and how does the opponent handle different actions, etc.
The approach to battle analysis is similar to the thought process in the "Training", helping to have a more comprehensive understanding of the warrior's performance and making targeted improvements.
VI. Cheat Sheet
Training 1. Click "Collect" to collect actions. 2. "Map - Data Limit" is more user-friendly. Most players perform initial training on the "Arena" map. 3. Switch between the warrior and the dummy: Tab key (keyboard) / Home key (controller). 4. Use "Collect" to make the opponent loop a set of actions. 5. Instantly move the warrior to a specific location: Click "Settings" - SPAWN - Choose the desired location on the map - On. Press the Enter key (keyboard) / Start key (controller) during training.
Inspector 1. Right-click on the fighter to change their direction. Drag the fighter and observe the changes in different positions and directions. 2. When satisfied with the training, click "Save." 3. In "Sparring" and "Simulation," use "Current Working Model." 4. If satisfied with a model, then click "compete." The model used in the rankings is the one marked as "competing."
Sparring / Ranked 1. Use the Throneroom map only for the top 2 or top 10 rankings. 2. There is a 30-second cooldown between matches. The replays are played for any match. Once the battle begins, you can see the winner on the leaderboard or by right-clicking the page - Inspect - Console. Also, if you encounter any errors or bugs, please send screenshots of the console to the Discord server.
Good luck! See you on the arena!
-
 @ b804f68e:2fb0fa1f
2024-06-03 18:08:03
@ b804f68e:2fb0fa1f
2024-06-03 18:08:03Initially, I was turned off by the idea of subscribing and having to pay monthly or annually for a service or product, but lately my perspective has changed. Currently, I use two products that require no subscription and two that do for football training and development. All four require a hardware device and a software app. At first, the non-subscription products seemed better because you pay once and that's it. But over time, it has become obvious that for software-dependent products, you're probably better off with the subscription option.
The main reason subscription-based products are better, in my experience, is that the company continues to update and improve their software. One of the products I use without a subscription is a GPS tracker for metrics like top sprinting speed and total running distance. While it still works, it has become increasingly frustrating because 1) the app hasn't had a proper, useful update since I first got it three years ago, and 2) the app is getting buggier over time. In contrast, another wearable I use called Whoop (subscription-based) is constantly updated and improved. This makes sense, given that the non-subscription company only makes money when their hardware is sold, limiting their ability to continue software development. In contrast, a subscription-based company has regular revenue, allowing them to continuously enhance the software.
All in all, I've learned that there is a significant advantage in opting for the subscription model, especially when the product relies heavily on software.
What are stackers thoughts and experiences on the subscription model? Yay or nay? Any alternatives?
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 0861144c:e68a1caf
2024-06-03 15:46:35
@ 0861144c:e68a1caf
2024-06-03 15:46:35Last weekend, I was amazed of how the debates were taken in the past. More of this, I was reading the Lincoln-Douglas debate about slavery mostly. Imagine being in one of those debates where each one spoke for ~2.5 hours and people gathered all the concepts about that, being documented as we know so far is evidence enough to state that people listened each other.
No more books
The main node of democracy is the book, not one book but books, about everything. People these days don't read anymore, we're fewer readers, people prefer their 1-minute-resume of news with his favorite influencer. In the modern era, democracy didn't upgrade well because technology is faster, algorithms now close each other with their political preferences. We don't talk about anything, we share each other our visions just for ensure that we believe the right choice.
The ideas in other days borned from creativity. They stopped working, bored themselfs and then..a new fresh idea. In those days, when you had a new dangerous idea, the state will come for you and your idea. Everything is censored and our ancestor had to fight in order to gain some terrain in human rights. Now? Politics confuse the free speech with speech that's free..of everything. Democracy gave them the power and will to say something with no danger of being censored, today the censorship comes in different ways: consumer protection, macroeconomic BS to balance the economy and my favorite one: speak.
Most people just talk and create nonsense in social media. Since Facebook, X, Reddit, Snapchat and other social media posts need you to create something, they're on the mission of telling you: what's happening?, tell something... and other ads; they don't care about freedom, that's blatantly BS, they need to sell ads and how can they sell if you're not talking? The speech is a product, you words are keywords in order to place this new thing that's good for you.
The politic is the product
The political speech right now has a new brand: political marketing. See the difference? The objective of marketing according to dictionary is individuals and groups obtain what they need and want by exchanging products and services with other parties. And what's wrong to obtain what I want? Politics is talk with people you disagree, mostly you don't get what you want which should be normal, should be fine but we don't do that anymore because algorithms tought us to create content that won't offend anything or anyone. Don't get me wrong, I'm not telling you to tell everyone to offend. Otherwise, I encourage people to read the other part and try to understand from their point of view and offer alternatives with quality content, today the political debate ends with ad hominem attacks and communities reinforcing their visions without even consider if their ideas are wrong.
One reason I find Stacker News as a way to protect free speech is because authors can earn money for their content. And yes, people can come, disagree with what they're reading but in order to put your perspective, there's economic motivation of state something rational. This is why most users here don't like shitcoins and altcoins. These kind of shitcoinery don't attach with this place because here, your words have consequences.
Political instrumentation of bitcoin is normal. As a matter of fact, the whole internet is a political state. I'm not talking about your political-party-party bs that you watch in your deceased-state-supported TV station, I'm talking about real fighters, our community. They recently tried to censor Samourai for writing code through some money-laundering-scheme. And they can't, Ginger Wallet is the proof that our community will fight every inch of illogical prosecution.
I can go further but my main message to you is: fren, remember you're not a democracy anymore, social media companies and their grandparents (crap TV and radio shows) killed that long time ago. Now, where data is oil, for them you're just a tiny excell cell, a drop in the ocean. This is the infocracy, this enemy is fought with knowledge, real knowledge that come from books and forums where think is the rule, not the optionality. Social medias companies put the what do you think? in the end of each post just for the numbers, they want to sell that people put words in their news. They don't listen, they don't see you.
Stacker News against infocracy
Stacker News is the antidote (I hope) against that marketing instrumentation. Here you can post share your agreement/disagreement and these words will have consequences. It's not free (accountability) to say stupid things but it's free (speech) to write. Keep writing folks, we need more signals and less noise.
Make long format great again!
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-03 15:03:42
@ 5d4b6c8d:8a1c1ee3
2024-06-03 15:03:42The GOAT of the Raiders' franchise, Jim Otto, died a couple of weeks ago. He's unquestionably the greatest center in NFL history and he played every single game for the first 15 years of Raiders history.
He's not as well known as he ought to be although his jersey number "00" is iconic.
It got me thinking about the most impactful people in our team's history. Going with the Mt. Rushmore gimmick, here are the four most important Raiders of all-time.
Al Davis
Al Davis is the Raiders, as much as one man can be. He rose from head coach and general manager of the team to the majority owner (which is wild!). He's probably the most important owner in NFL history, because of his role in merging the AFL and NFL, as well as being a trailblazer in team relocations and hiring minorities for important roles.
Many of the famous phrases associated with the Raiders - "Just win baby!", "Commitment to excellence", "Once a Raider, always a Raider" - originated with Davis.
John Madden
The most famous figure in NFL history was also the youngest coach to win a Super Bowl, which was also the Raiders first. His coaching career was relatively short, but he holds the best winning percentage ever for an NFL head coach.
Jim Otto
The ten time All-Pro 1st Team center is the only player other than Jerry Rice to have accomplished that feat. Unlike Rice, Otto went undrafted by the NFL, which is why he was available to play in the newly founded AFL.
Technically he was drafted by the Raiders, after being passed over by the entirety of the NFL, so he might not count as an undrafted player. However, he still has a claim as being the greatest player ever who wasn't taken in the NFL draft.
Kenny "The Snake" Stabler
The near mythological status of Ken Stabler can hardly be overstated. He was the central figure of sseveral of the most iconic moments in NFL history: The Holy Roller, Sea of Hands, Ghost to the Post. Seldom thought of as the best QB in the league, he struck fear into the hearts of rival fans like no other player from that era.
The Snake embodied the Raiders motto "Just Win Baby!"
Your Mt. Rushmore
Who's on your team's Mt. Rushmore?
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-03 13:41:24
@ 5d4b6c8d:8a1c1ee3
2024-06-03 13:41:24This weekend, I was rushing to finish the fifth book of The Wheel of Time series, because I needed to give it to my mom before she left on a trip. We've been reading the saga together, which is pretty fun.
Anyway, over coffee, I was regaling my wife with the latest twists and turns of the story (which she found riveting, no doubt).
Our daughter overheard me talking about "Darkfriends" and wanted to know what they are. I told her that they were bad guys from the book I'm reading with Grandma. To which she said "I want to read it, too."
I told her it wasn't like her books with pictures and that she would have to learn how to read first. She replied "Ok!" and sprinted off to her room, presumably to learn how to read.
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28On "zk-rollups" applied to Bitcoin
ZK rollups make no sense in bitcoin because there is no "cheap calldata". all data is already ~~cheap~~ expensive calldata.
There could be an onchain zk verification that allows succinct signatures maybe, but never a rollup.
What happens is: you can have one UTXO that contains multiple balances on it and in each transaction you can recreate that UTXOs but alter its state using a zk to compress all internal transactions that took place.
The blockchain must be aware of all these new things, so it is in no way "L2".
And you must have an entity responsible for that UTXO and for conjuring the state changes and zk proofs.
But on bitcoin you also must keep the data necessary to rebuild the proofs somewhere else, I'm not sure how can the third party responsible for that UTXO ensure that happens.
I think such a construct is similar to a credit card corporation: one central party upon which everybody depends, zero interoperability with external entities, every vendor must have an account on each credit card company to be able to charge customers, therefore it is not clear that such a thing is more desirable than solutions that are truly open and interoperable like Lightning, which may have its defects but at least fosters a much better environment, bringing together different conflicting parties, custodians, anyone.
-
 @ 3c984938:2ec11289
2024-06-03 13:40:52
@ 3c984938:2ec11289
2024-06-03 13:40:52
Greetings!
Salutations, User! Ever wanted to publish articles or launch your own blog just for the sake of writing or imparting your knowledge? You can, right here in Nostr Wonderland! Let censorship, DE-platforming, shadow-banning be gone! You are the one that holds the keys to your empire here in NostrLand.
👉I'm here to help you OVERCOME the learning curve and take the plunge to SWITCH from conventional to Nostr Social media. If this is your first time, please read my Beginner's Guide here or on the web. Otherwise, let's 💃dance.

Why am I doing this?
I want to be your 🕯guiding light, dear user, to guide you when things get murky or confusing to find information. You probably have a ton of knowledge that you'd like to share with the world, but you haven't because you're afraid of the consequences or don't know where to begin. I'm here to help you along the road by using this tutorial. So you may confidently share your knowledge with the rest of the world using Nostr. If you'd like, you can use long-form notes (Nip-23) to accomplish this.
📩P.S. Elon Musk should blush, because this is also one of the most modest ways, to stack SATs in a den full of sovereign Bitcoin lions.

The Tools of the Trade
As a writer, it's important to learn new skills of the trade and add it to your arsenal. These are the current tools, which I utilize at my discretion. The list covers long form clients with random relays, NIP-65 compatible clients, communities, hashtags, Ai (optional), and finally 🌋 Obsidian. Obsidian is an excellent solution if you don't want to log into a long form client to send your content. Just one shot into the ether.
The Nostr Bell Ringers: Choosing a Long Form Client to Distribute Your Content
Long form content is distinct, with its own NIP. The notes you usually see on your client are microblogging notes with NIP-01 or Kind-01 (which include hashtags). To the best of my knowledge, the following platforms currently support NIP-23: Stacker.news (via cross posting), Habla.news, Yakihonne.com, flycat.club, and highlighter.com.
✨Yakihonne.com is my preferred medium because of their support for curation and additional relays for long-form on their site. I'd like to add that Highlighter.com (which also has its own dedicated relay) is free and open source, putting content creators in the driver's seat. They're fulfilling this through the integration of subscription services for premium content powered by Bitcoin Lightning.💡🚨 Isn't that awesome?

👉You can learn more about the Bell Ringers in my previous articles, The Publishing Forest of Nostr ✨Part One and ✨Part Two here.
Be a Relay anomaly; knowing what arena you're in is half the battle.
Not all relays are identical. Some relays support specific NIPs, (Nostr Implementation Possibilities) more than others, while others are paid relays. This is where you can try out unconventional relays to discover your following. I encourage using odd ball relays to reach followers from all corners, rather than the "popular relays" that clients automatically push and 💥jam users to utilize. This is known as the 🦜Gossip method, which can be noisy and active with constant Notes. I've literally seen my articles buried in notes, memes, and everything in between. Another alternative is to run your own relay.
👉Publish to random relays using Bell Ringers clients. Please refer to the image above. What's the reason? Because they don't currently support NIP-65. So go ahead and publish to weird relays!
🚨This doesn't mean to publish to 50+ relays, go somewhere in between 10-25.
👉It's also typical (at least for me) to have failed attempts to publish onto relays so don't get discouraged and try others. Click this link to see the relays list. Personally, I prefer German relays, but select any at your discretion.
✨Eventually, you will meet other users that will grant you access to their relays, this is through discovery. Just be patient, kind, and humble to receive these invites from other users that whitelist your npub to enable you to "write" onto their relays. These will become your "home" relays. Go where you're treated best and support each other. Pura Vida!
Using clients with NIP-65 support.

👉Since, everyone doesn't use the same relays, sometimes posts get delayed responses. To counteract this, I utilize Sir Mike Knight's Gossip Desktop Nostr Client. Gossip facilitates the application of "NIP-65," or "The Outbox Model." You can read more about it online or within your app. Great client to cut out the excessive programming language on browsers which does slow you.
⛔The way this works is if other (N)ostriches use a client that also supports NIP-65 as well. Even if other nostriches don't use supported clients, you're still able to pull from their relays.

✨👉Another client you could use is knight hzrd146's web client nostrudel which handles TOR quite lovely. NoStrudel also uses NIP-65 so you'll never miss an article.

🚨Amethyst v0.87+ the app is currently working to integrate NIP-65(at the time of this publication). This is a win for the De-googled Android community!
Use Communities to expand reach within Nostr for a forum like style or for conversations
👉I use NoStrudel mostly to manage my community, "Children_Zone," where I post all my articles and stories. It would be beneficial for you to look into communities where you might be able to share your articles, or stories, provided they are relevant. 🚨 Communities have moderators, so when you post to their board be mindful that it could get declined. You could build a relationship with the respective owners, or maybe even volunteer to manage postings. The last options is to create your own community.
⭐Tip⭐ ✨When you publish your long form content or NIP-23, at the same time you can create an njump.me link. The njump.me links are super easy to create and bridge the gap from Nostr back to web. To get the maximum coverage to all your followers, make a separate post with your njump.me link for users that are using clients that don't support NIP-23.
👉To create njump.me links Simply Copy Note ID on your client, https://njump.me/ + paste note ID = shareable URL ✨Add a cute message to your new post with your shareable link.
⭐note⭐ For long form content you should get naddr1 and for regular notes you normally get nevents.
❗Example for clarification: If you're reading this article within Amethyst, Damus, or Nos you can tap here to access my beginner's guide within the app or click here for the web version. Both contain the same information, but the experience is slightly different.
🚨The important part is to do both. This creates unity among users between different clients. Yes, it is an additional step, but the reward is well worth it in unexpected ways.
 ^^Created by cryptowolf. If your not on an app you can view the event here on the web. Another artists you can check out is M. My friends in NostrLand are welcoming, so what are you waiting for? Nostr is permission-less. Just go for it!
^^Created by cryptowolf. If your not on an app you can view the event here on the web. Another artists you can check out is M. My friends in NostrLand are welcoming, so what are you waiting for? Nostr is permission-less. Just go for it!Adding # Hashtags; 🍾the secret sauce
Similarly to X, you can use hashtags to search and scan for content. By using hashtags you can increase your visibility to the masses so don't skip on step. I, occasionally try to squeeze myself into the coffeechain, gm, plebchain, zaps, art, ai, nostr, bitcoin, and catstr arena. For the purpose of this article I will squeeze myself into introductions and obsidian. Because I think there's a possible chance, that a newbie may be interested in creating content. And with some 🍀luck they decide to🔖bookmark my article after getting acquainted with the Nostr.
🌟It would be the highest honor for me as a 🐹content creator, if you bookmarked this, and shared it with future nostriches, writers, and creators. Let's fill Nostr with a vibrant community with creators that make other platforms look dismally disappointing.
🤖To Ai or not to Ai
Ai is what you make it. For me, it's to create the beautiful art that you see in my articles. I engineer the prompts with the hope that the reader such as yourself might enjoy. I wouldn't be surprised if I had followers that just scroll through to look at my Ai images. Furthermore, I use Canva.com to produce these. However, I have dabbled with others. I do think Sats4ai is worth a go because it's open source and doesn't record data as a possible Midjourney replacement for images. Another AI, that I dabble with is ~Openagents (FOSS, and crowdsourced) that is fun to play with.

Obsidian; A powerful markdown editor for Writers or just to write notes.
Did you notice the 💎🌋Obsidian earring my Hamster is wearing? I put it on intentionally on my character to symbolize the tool I'm using. Obsidian is a beautiful markdown editor, that you can download on iOs, Android, Windows, Mac, Linux, and even through the Zap.store. If you want to just publish without any clients, then Obsidian does the job.
✨I discovered Obsidian from James when he mentioned a plugin tool in an article, that would let users "Publish to Nostr" on 🐇yakihonne.
✨An awesome feature that the plugin does is pasting an image and automatically getting hosted via nostr.build, so you don't have to manually upload it. The plugin supports short(NIP-01) and long form(NIP-23), and draft.
🚨Obsidian is a powerful tool, you can benefit by watching a few YouTube videos. Learn about the various tasks like RSS feeds, image converter, dictionary, and LanguageTool (for spell-check). 💋It has over 1,000 community plugins, so go 🎈play.
☠The developers of Obsidian have zero interest into turning this editor into FOSS. Don't bother trying to pitch idea, they will dismiss and delete your request.
🌋💎Setting up Obsidian with Nostr.
Are you excited to use this amazing markdown editor? Here's a quick guide to help get you rolling. Create breathtaking markdowns (for Long form) and distribute them like a beast to Nostr via Obsidian.
- Download for your preferred platform.
- Create a Vault, location, and name. Or open within an existing folder with other markdown(.md) files prior from using obsidian.
- Wait for the editor to load and open. Go to ⚙Settings on the bottom left.
- Locate Options on the top left window, select “Community plugins” and click "Browse."
- In the search bar, type "nostr," and select "Nostr Writer" by James McGauran. Install and enable.
- Read the mini guide, it should look similarly to this:

- Done. Now, show the world what you're made of❗
👉If you felt this article brought you value, please consider adding it to your bookmarks so you can easily share it with an aspiring creator that you may come across in chat. 💋
🧧⚡Zaps⚡ are always appreciated, but aren't required.
💜🧡Thank you💖💋
📢Special Shout-outs 📝James - Introducing me to Obsidian that I've made it my own. I wear on as an earring on my character.
npub10a8kw2hsevhfycl4yhtg7vzrcpwpu7s6med27juf4lzqpsvy270qrh8zkw -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A biblioteca infinita
Agora esqueci o nome do conto de Jorge Luis Borges em que a tal biblioteca é descrita, ou seus detalhes específicos. Eu tinha lido o conto e nunca havia percebido que ele matava a questão da aleatoriedade ser capaz de produzir coisas valiosas. Precisei mesmo da Wikipédia me dizer isso.
Alguns anos atrás levantei essa questão para um grupo de amigos sem saber que era uma questão tão batida e baixa. No meu exemplo era um cachorro andando sobre letras desenhadas e não um macaco numa máquina de escrever. A minha conclusão da discussão foi que não importa o que o cachorro escrevesse, sem uma inteligência capaz de compreender aquilo nada passaria de letras aleatórias.
Borges resolve tudo imaginando uma biblioteca que contém tudo o que o cachorro havia escrito durante todo o infinito em que fez o experimento, e portanto contém todo o conhecimento sobre tudo e todas as obras literárias possíveis -- mas entre cada página ou frase muito boa ou pelo menos legívei há toneladas de livros completamente aleatórios e uma pessoa pode passar a vida dentro dessa biblioteca que contém tanto conhecimento importante e mesmo assim não aprender nada porque nunca vai achar os livros certos.
Everything would be in its blind volumes. Everything: the detailed history of the future, Aeschylus' The Egyptians, the exact number of times that the waters of the Ganges have reflected the flight of a falcon, the secret and true nature of Rome, the encyclopedia Novalis would have constructed, my dreams and half-dreams at dawn on August 14, 1934, the proof of Pierre Fermat's theorem, the unwritten chapters of Edwin Drood, those same chapters translated into the language spoken by the Garamantes, the paradoxes Berkeley invented concerning Time but didn't publish, Urizen's books of iron, the premature epiphanies of Stephen Dedalus, which would be meaningless before a cycle of a thousand years, the Gnostic Gospel of Basilides, the song the sirens sang, the complete catalog of the Library, the proof of the inaccuracy of that catalog. Everything: but for every sensible line or accurate fact there would be millions of meaningless cacophonies, verbal farragoes, and babblings. Everything: but all the generations of mankind could pass before the dizzying shelves – shelves that obliterate the day and on which chaos lies – ever reward them with a tolerable page.
Tenho a impressão de que a publicação gigantesca de artigos, posts, livros e tudo o mais está transformando o mundo nessa biblioteca. Há tanta coisa pra ler que é difícil achar o que presta. As pessoas precisam parar de escrever.
-
 @ c11cf5f8:4928464d
2024-06-03 12:18:30
@ c11cf5f8:4928464d
2024-06-03 12:18:30Time to brush off the spurs and saddle up for a ride into the exciting ad-ventures ahead! What innovative goods or services are y'all bringin' on the wagon this week? Give us a sneak peek and let that entrepreneurial spirit get out.
Take some pics and start posting your items now!
[⚖️ SELL] - [🛒 BUY] - [🧑💻 HIRE] - [🖇 OFFER] - [🧑⚖️ AUCTION] - [🤝 SWAP] - [🆓 FREE] - [⭐ REVIEW]
Stay humble, stack sats!
-
 @ 57d1a264:69f1fee1
2024-06-03 05:48:25
@ 57d1a264:69f1fee1
2024-06-03 05:48:25
ODC #000019 - UX > IMPLEMENTDesign System for a recipies website using LightningIf you miss it, please read our WTF is ODC (Open Design Challenge) intro post from more details.
Scenario
You work at an agency that was hired by a Culinary Design company (competitors are Allrecipes and Yummly) to redesign their web portal that enable aloe to share recipes and get rewarded with bitcoin.
One of the main tasks is to build out a new design system and you've been put in charge of starting that process.
Task
Design specific elements (below) of a style guide for this fictional recipes website using your favorite design tool (using your tool's design system features) or HTML/CSS. Make sure all elements are responsive. Document and organize the design system and include a summary at the beginning with the overall goals. Elements: * Colors * Typography (headings, body, links) * Forms (text input, buttons, checkboxes, radios) * Icons * Grid * Recipe card
Extra Credit: Design more elements for the style guide, or add variants of the elements you've already created. Make a few mockups using the design system in practice to show how it all works together.
Guides
If you need help with this challenge, check out our hand-picked tutorial recommendations.
-
Design Systems 101 on nngroup.com
-
List of analyzed design systems on open-ui.org
-
Starting a Design System in a Start-up on uxdesign.cc
-
Design Systems Handbook on designbetter.co
-
Design Systems: What are They and How to Get Started on piped.video
Tools
Not sure which tools to use? Try something new, go 💯% FOSS!
For youPenPot by kaleidos
Bootstrap by twitter
Catalog.Style by Interactive Things
StoryBook by chromatic
VueDS by Ariel Salminen
For professional gurusSupernova (freemium) by supernova.io
ZeroHeight (freemium) by zeroheight.com
Share Your Results
When you finish the challenge, post your work including anonymized collected data and results on this thread! If you also share it on
nostr, be sure to use the hashtag #opendesigner and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Check our previous ODC and support this community for creative minds, where you'll be able to get open and constructive feedback on your PoW. Ask anything in the ~Design territory and get some ⚡sats for the value you provide!
```
Bitcoin #Design #BitcoinDesign #NostrDesign #Nostr #OpenDesign #DesignChallenge #OpenDesignChallenge
```
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Causa
o Princípios de Economia Política de Menger é o único livro que enfatiza a CAUSA o tempo todo. os cientistas todos parecem não saber, ou se esquecer sempre, que as coisas têm causa, e que o conhecimento verdadeiro é o conhecimento da causa das coisas.
a causa é uma categoria metafísica muito superior a qualquer correlação ou resultado de teste de hipótese, ela não pode ser descoberta por nenhum artifício econométrico ou reduzida à simples antecedência temporal estatística. a causa dos fenômenos não pode ser provada cientificamente, mas pode ser conhecida.
o livro de Menger conta para o leitor as causas de vários fenômenos econômicos e as interliga de forma que o mundo caótico da economia parece adquirir uma ordem no momento em que você lê. é uma sensação mágica e indescritível.
quando eu te o recomendei, queria é te imbuir com o espírito da busca pela causa das coisas. depois de ler aquilo, você está apto a perceber continuidade causal nos fenômenos mais complexos da economia atual, enxergar as causas entre toda a ação governamental e as suas várias consequências na vida humana. eu faço isso todos os dias e é a melhor sensação do mundo quando o caos das notícias do caderno de Economia do jornal -- que para o próprio jornalista que as escreveu não têm nenhum sentido (tanto é que ele escreve tudo errado) -- se incluem num sistema ordenado de causas e consequências.
provavelmente eu sempre erro em alguns ou vários pontos, mas ainda assim é maravilhoso. ou então é mais maravilhoso ainda quando eu descubro o erro e reinsiro o acerto naquela racionalização bela da ordem do mundo econômico que é a ordem de Deus.
em scrap para T.P.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Shitcoinery
IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.
The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.
Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.
See also
- Bitcoin, the only non-shitcoin
-
 @ 502ab02a:a2860397
2024-06-03 04:25:23
@ 502ab02a:a2860397
2024-06-03 04:25:23ต่อเนื่องจากเรื่องวุ้นเส้น ก็มีคำถามว่า ถ้าอย่างนั้นเส้นแก้ว ทำมาจากสาหร่ายจริงไหม ? เราลองเอา trust จากคำว่า เส้นแก้วคือสาหร่ายทิ้งไป แล้วมา verify คำพูดนี้กัน
ถ้าใช้ชุดความรู้เดียวกันกับวุ้นเส้น คำตอบสามารถเดาเบื้องต้นได้แล้วเลยว่า ไม่ได้เชิงว่าทำมาจากสาหร่ายซะทีเดียว เพราะทำมาจากสารสกัดบางอย่างในสาหร่าย พูดแบบง่ายๆคือ เส้นแก้ว คือ สารที่สกัดออกมาจากสาหร่าย ไม่ได้เกิดจากการเอาสาหร่ายมาใช้การปรุง (เช่น ต้ม ปั่น) ไอ้เจ้าผงๆที่ว่านั่นคือ โซเดียมอัลจิเนต นั่นเอง สำหรับสายขนมน่าจะคุ้นเคยกันดีในการทำ โมจิหยดน้ำ ที่เคยนิยมอยู่พักนึง และเจ้าโซเดียมอัลจิเนตนี้เขานับเป็น วัตถุเจือปนอาหาร ชนิดนึงในรหัส INS 401

เรามาทำความรู้จักกับ โซเดียมอัลจิเนตกัน
โซเดียมอัลจิเนต (Sodium Alginate) เป็นสารประเภทไฮโดรคอลลอยด์ (hydrocolloid) หรือสารแขวนลอยประเภทนึง ที่มีคุณสมบัติทำให้อาหารที่ถูกผสมเจ้าสิ่งนี้มีลักษณะข้นและหนืดขึ้น จนถึงเป็นเจล เป็นเจลประเภททนต่อความร้อน (Thermoirreversible gel) ไม่เปลี่ยนสภาพไปมาเมื่อได้รับความร้อน และสามารถคงรูปได้ได้เมื่อเจอกับแคลเซียม
โซเดียมอัลจิเนต จัดอยู่ในสารประเภทเดียวกับพวกผงวุ้น เจลาติน คาร์ราจีแนน และกัวกัม มีบางอุตสาหกรรมใช้ในการเคลือบผิวเนื้อปลาก่อนนำไปแช่แข็ง เพื่อป้องกันไม่ให้ปลาเกิด freeze burn นอกจากนี้ยังมีการใช้เป็นสารเพิ่มความคงตัวให้กับไอศครีม น้ำสลัด ด้วย
โซเดียมอัลจิเนตนั้น เป็นการนำสาหร่ายสีน้ำตาล (brown algae) มาผ่านกระบวนการสกัดสารที่อยู่บริเวณผนังเซลล์ของมันออกมา แล้วผ่านกระบวนการทำแห้ง มีลักษณะเป็นผง สามารถละลายน้ำได้
ด้วยความที่ โซเดียมอัลจิเนต เป็นอนุพันธ์โพลีแซ็กคาไรด์เชิงเส้นของกรดอัลจินิก อย่างที่เรารู้กันว่า โพลีแซ็กคาไรด์ มันก็คือ เซลลูโลสชนิดนึง ที่เรามักคุ้นกันในนาม ไฟเบอร์ นั่นเอง นี่เป็นเหตุผลที่ทำให้เส้นแก้วแตกต่างกับวุ้นเส้น คือตัวมันทำมาจากไฟเบอร์สกัดออกมาจากผนังสาหร่าย ในขณะที่วุ้นเส้นทำมาจากคาร์บ(starch)ที่สกัดออกมาจากถั่วเขียว แต่ในอีกทางนึง โซเดียมอัลจิเนตของเส้นแก้วจัดในหมวด วัตถุเจือปนอาหาร แต่แป้งจากวุ้นเส้นยังจัดเป็นส่วนประกอบในการทำอาหาร โดยที่ทั้ง 2 เส้น ไม่สามารถเรียกตัวไหนว่าเป็น อาหารธรรมชาติได้เลย
กระบวนการทำเส้นแก้ว
ถ้าดูรายการทำอาหารสมัยนี้ จะเข้าใจภาพกว้างได้ง่ายๆ เพราะมันคือการใช้เทคนิค โมลิคูลา (molecular) ที่นิยมมากในช่วง 10ปีที่ผ่านมา อย่างที่เชฟเอียนขึ้นชื่อว่าถนัดเทคนิคนี้คนนึงเลยทีเดียว เราจะคุ้นเคยกับ คาเวียร์ต่างๆ เช่นคาเวียร์ซอสต้มยำ หรือ สเฟียร์ผลไม้ โอยยย เยอะแยะตาแป๊ะครับ ดูจากในรูปเป็นตัวอย่างได้


เราสามารถทำเองที่บ้านได้ ด้วยการนำผงโซเดียมอัลจิเนตมาปั่นกับน้ำจนเกิดความเจล จากนั้นก็พักให้อิ่มตัว ก่อนจะบีบเป็นเส้น เป็นเม็ด หรือรูปทรงใดๆก็ได้ตามที่อยากทำและทำเป็น ลงในสารละลายแคลเซียมคลอไรด์ กับ แคลเซียมแลคเตต เพื่อทำให้เกิดการคงรูปร่างที่เราต้องการไว้ แค่นี้ก็เสร็จสิ้นกระบวนการครับ
สูตรคร่าวๆคือ น้ำเปล่า 700g ผง kelp 11g ในส่วนการทำ calcium bath ก็ลองดูแค่ว่าบีบแล้วจับตัวก็พอครับ อาจเริ่มลองจาก แคลเซียมคลอไรด์กับแคลเซียมแลคเตต อย่างละ 1ชอนโต๊ะ ต่อน้ำ 1.5ลิตร




มาถึงจุดนี้แล้ว ถ้าถามว่าเส้นแก้ว ดีต่อสุขภาพไหม ก็ต้องเกิดประเด็นในมุมมองที่ต่างกันครับ ถ้าคุณจะโฟกัสแค่ที่ คาร์บ เจ้าเส้นแก้วนี่ก็ไม่มีคาร์บ แต่ถ้าคุณโฟกัสที่สุขภาพองค์รวม เจ้าเส้นแก้วนี้นอกจากจะไม่ใช่อาหารธรรมชาติแล้ว ยังจัดในหมวดของ สารที่ก่อให้เกิดเจล ซึ่งเป็นวัตถุเจือปนอาหารชนิดนึงที่มันกินได้ ในรหัส ins401 นั่นหละครับ ดังนั้นคำตอบจึงต้องบอกว่า depend on อีกแล้วว่าคุณมองที่จุดใด สองคนยลตามช่องครับ เอาที่สบายใจ ผมได้แต่บอกที่มาที่ไปและอธิบายกรรมวิธีการว่ามันเกิดขึ้นได้อย่างไร เพื่อเป็นข้อมูลประกอบการเรียนรู้เทคโนโลยี

pirateketo
siripun
siamstr
foodstr
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Why IPFS cannot work, again
Imagine someone comes up with a solution for P2P content-addressed data-sharing that involves storing all the files' contents in all computers of the network. That wouldn't work, right? Too much data, if you think this can work then you're a BSV enthusiast.
Then someone comes up with the idea of not storing everything in all computers, but only some things on some computers, based on some algorithm to determine what data a node would store given its pubkey or something like that. Still wouldn't work, right? Still too much data no matter how much you spread it, but mostly incentives not aligned, would implode in the first day.
Now imagine someone says they will do the same thing, but instead of storing the full contents each node would only store a pointer to where each data is actually available. Does that make it better? Hardly so. Still, you're just moving the problem.
This is IPFS.
Now you have less data on each computer, but on a global scale that is still a lot of data.
No incentives.
And now you have the problem of finding the data. First if you have some data you want the world to access you have to broadcast information about that, flooding the network -- and everybody has to keep doing this continuously for every single file (or shard of file) that is available.
And then whenever someone wants some data they must find the people who know about that, which means they will flood the network with requests that get passed from peer to peer until they get to the correct peer.
The more you force each peer to store the worse it becomes to run a node and to store data on behalf of others -- but the less your force each peer to store the more flooding you'll have on the global network, and the slower will be for anyone to actually get any file.
But if everybody just saves everything to Infura or Cloudflare then it works, magic decentralized technology.
Related
-
 @ 30ceb64e:7f08bdf5
2024-06-03 04:14:09
@ 30ceb64e:7f08bdf5
2024-06-03 04:14:09Hey Freaks,
TheWildHustle is about 3 seconds away from ditching his ifoan
Instead of opting for graphene, Hustle is thinking about ditching the phone all together, and using a VOIP provider with his laptop.
Hustle understands that calls and texts will be seen and heard by the looters regardless, and doesnt understand what threat model he's solving for.......but wants to explore life without a cell phone anyway.
He's sure there might be some privacy and security benefits, but it seems as though he's mainly just focused on sticking it to "the man".
Any good/cool resources will be handsomely zapped.
Much Appreciated, Hustle
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Who will build the roads?
Who will build the roads? Em Lagoa Santa, as mais novas e melhores ruas -- que na verdade acabam por formar enormes teias de bairros que se interligam -- são construídas pelos loteadores que querem as ruas para que seus lotes valham mais -- e querem que outras pessoas usem as ruas também. Também são esses mesmos loteadores que colocam os postes de luz e os encanamentos de água, não sem antes terem que se submeter a extorsões de praxe praticadas por COPASA e CEMIG.
Se ao abrir um loteamento, condomínio, prédio um indivíduo ou uma empresa consegue sem muito problema passar rua, eletricidade, água e esgoto, por que não seria possível existir livre-concorrência nesses mercados? Mesmo aquela velha estória de que é ineficiente passar cabos de luz duplicados para que companhias elétricas possam competir já me parece bobagem.
-
 @ 05b116ff:8e08606a
2024-06-02 23:37:40
@ 05b116ff:8e08606a
2024-06-02 23:37:40Is the following easily achievable currently? Or on anyone's roadmap?- Run your own Cashu or Fedi mint on SartOS, Raspiblitz, Umbral, etc.
- Generate a link for a friend/family member to a web wallet that comes pre-funded with 10,000 sats of eCash from your own mint
- Ideally this would be quick to do on the fly, and they would get a link that would just open up with a balance and be useable
- A blatent reminder to back-up would be nice, but also important for demo purposes to just work off the bat
- They’re able to spend those sats anywhere in an Uncle Jim scenario without having to learn about channel management
- If they want, they can move funds to a different eCash/Fedi mint, send to a lightning wallet of theirs, etc.
I saw this LNBits extension, but it seems no longer maintained: https://github.com/cashubtc/lnbits-cashu?tab=readme-ov-file
Mutiny used to have a gifting feature to gift funded lightning wallets, but, it would take the channel opening fee off the gift amount right off the bat, which always led to questions about where that fee went. Doing the same with eCash sounds much better for small value demos.
-
 @ c11cf5f8:4928464d
2024-06-02 18:25:48
@ c11cf5f8:4928464d
2024-06-02 18:25:48Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28How IPFS is broken
I once fell for this talk about "content-addressing". It sounds very nice. You know a certain file exists, you know there are probably people who have it, but you don't know where or if it is hosted on a domain somewhere. With content-addressing you can just say "start" and the download will start. You don't have to care.
Other magic properties that address common frustrations: webpages don't go offline, links don't break, valuable content always finds its way, other people will distribute your website for you, any content can be transmitted easily to people near you without anyone having to rely on third-party centralized servers.
But you know what? Saying a thing is good doesn't automatically make it possible and working. For example: saying stuff is addressed by their content doesn't change the fact that the internet is "location-addressed" and you still have to know where peers that have the data you want are and connect to them.
And what is the solution for that? A DHT!
DHT?
Turns out DHTs have terrible incentive structure (as you would expect, no one wants to hold and serve data they don't care about to others for free) and the IPFS experience proves it doesn't work even in a small network like the IPFS of today.
If you have run an IPFS client you'll notice how much it clogs your computer. Or maybe you don't, if you are very rich and have a really powerful computer, but still, it's not something suitable to be run on the entire world, and on web pages, and servers, and mobile devices. I imagine there may be a lot of unoptimized code and technical debt responsible for these and other problems, but the DHT is certainly the biggest part of it. IPFS can open up to 1000 connections by default and suck up all your bandwidth -- and that's just for exchanging keys with other DHT peers.
Even if you're in the "client" mode and limit your connections you'll still get overwhelmed by connections that do stuff I don't understand -- and it makes no sense to run an IPFS node as a client, that defeats the entire purpose of making every person host files they have and content-addressability in general, centralizes the network and brings back the dichotomy client/server that IPFS was created to replace.
Connections?
So, DHTs are a fatal flaw for a network that plans to be big and interplanetary. But that's not the only problem.
Finding content on IPFS is the most slow experience ever and for some reason I don't understand downloading is even slower. Even if you are in the same LAN of another machine that has the content you need it will still take hours to download some small file you would do in seconds with
scp-- that's considering that IPFS managed to find the other machine, otherwise your command will just be stuck for days.Now even if you ignore that IPFS objects should be content-addressable and not location-addressable and, knowing which peer has the content you want, you go there and explicitly tell IPFS to connect to the peer directly, maybe you can get some seconds of (slow) download, but then IPFS will drop the connection and the download will stop. Sometimes -- but not always -- it helps to add the peer address to your bootstrap nodes list (but notice this isn't something you should be doing at all).
IPFS Apps?
Now consider the kind of marketing IPFS does: it tells people to build "apps" on IPFS. It sponsors "databases" on top of IPFS. It basically advertises itself as a place where developers can just connect their apps to and all users will automatically be connected to each other, data will be saved somewhere between them all and immediately available, everything will work in a peer-to-peer manner.
Except it doesn't work that way at all. "libp2p", the IPFS library for connecting people, is broken and is rewritten every 6 months, but they keep their beautiful landing pages that say everything works magically and you can just plug it in. I'm not saying they should have everything perfect, but at least they should be honest about what they truly have in place.
It's impossible to connect to other people, after years there's no js-ipfs and go-ipfs interoperability (and yet they advertise there will be python-ipfs, haskell-ipfs, whoknowswhat-ipfs), connections get dropped and many other problems.
So basically all IPFS "apps" out there are just apps that want to connect two peers but can't do it manually because browsers and the IPv4/NAT network don't provide easy ways to do it and WebRTC is hard and requires servers. They have nothing to do with "content-addressing" anything, they are not trying to build "a forest of merkle trees" nor to distribute or archive content so it can be accessed by all. I don't understand why IPFS has changed its core message to this "full-stack p2p network" thing instead of the basic content-addressable idea.
IPNS?
And what about the database stuff? How can you "content-address" a database with values that are supposed to change? Their approach is to just save all values, past and present, and then use new DHT entries to communicate what are the newest value. This is the IPNS thing.
Apparently just after coming up with the idea of content-addressability IPFS folks realized this would never be able to replace the normal internet as no one would even know what kinds of content existed or when some content was updated -- and they didn't want to coexist with the normal internet, they wanted to replace it all because this message is more bold and gets more funding, maybe?
So they invented IPNS, the name system that introduces location-addressability back into the system that was supposed to be only content-addressable.
And how do they manage to do it? Again, DHTs. And does it work? Not really. It's limited, slow, much slower than normal content-addressing fetches, most of the times it doesn't even work after hours. But still although developers will tell it is not working yet the IPFS marketing will talk about it as if it was a thing.
Archiving content?
The main use case I had for IPFS was to store content that I personally cared about and that other people might care too, like old articles from dead websites, and videos, sometimes entire websites before they're taken down.
So I did that. Over many months I've archived stuff on IPFS. The IPFS API and CLI don't make it easy to track where stuff are. The
pincommand doesn't help as it just throws your pinned hash in a sea of hashes and subhashes and you're never able to find again what you have pinned.The IPFS daemon has a fake filesystem that is half-baked in functionality but allows you to locally address things by names in a tree structure. Very hard to update or add new things to it, but still doable. It allows you to give names to hashes, basically. I even began to write a wrapper for it, but suddenly after many weeks of careful content curation and distribution all my entries in the fake filesystem were gone.
Despite not having lost any of the files I did lose everything, as I couldn't find them in the sea of hashes I had in my own computer. After some digging and help from IPFS developers I managed to recover a part of it, but it involved hacks. My things vanished because of a bug at the fake filesystem. The bug was fixed, but soon after I experienced a similar (new) bug. After that I even tried to build a service for hash archival and discovery, but as all the problems listed above began to pile up I eventually gave up. There were also problems of content canonicalization, the code the IPFS daemon use to serve default HTML content over HTTP, problems with the IPFS browser extension and others.
Future-proof?
One of the core advertised features of IPFS was that it made content future-proof. I'm not sure they used this expression, but basically you have content, you hash that, you get an address that never expires for that content, now everybody can refer to the same thing by the same name. Actually, it's better: content is split and hashed in a merkle-tree, so there's fine-grained deduplication, people can store only chunks of files and when a file is to be downloaded lots of people can serve it at the same time, like torrents.
But then come the protocol upgrades. IPFS has used different kinds of hashing algorithms, different ways to format the hashes, and will change the default algorithm for building the merkle-trees, so basically the same content now has a gigantic number of possible names/addresses, which defeats the entire purpose, and yes, files hashed using different strategies aren't automagically compatible.
Actually, the merkle algorithm could have been changed by each person on a file-by-file basis since the beginning (you could for example split a book file by chapter or page instead of by chunks of bytes) -- although probably no one ever did that. I know it's not easy to come up with the perfect hashing strategy in the first go, but the way these matters are being approached make me wonder that IPFS promoters aren't really worried about future-proof, or maybe we're just in Beta phase forever.
Ethereum?
This is also a big problem. IPFS is built by Ethereum enthusiasts. I can't read the mind of people behind IPFS, but I would imagine they have a poor understanding of incentives like the Ethereum people, and they tend towards scammer-like behavior like getting a ton of funds for investors in exchange for promises they don't know they can fulfill (like Filecoin and IPFS itself) based on half-truths, changing stuff in the middle of the road because some top-managers decided they wanted to change (move fast and break things) and squatting fancy names like "distributed web".
The way they market IPFS (which is not the main thing IPFS was initially designed to do) as a "peer-to-peer cloud" is very seductive for Ethereum developers just like Ethereum itself is: as a place somewhere that will run your code for you so you don't have to host a server or have any responsibility, and then Infura will serve the content to everybody. In the same vein, Infura is also hosting and serving IPFS content for Ethereum developers these days for free. Ironically, just like the Ethereum hoax peer-to-peer money, IPFS peer-to-peer network may begin to work better for end users as things get more and more centralized.
More about IPFS problems:
- IPFS problems: Too much immutability
- IPFS problems: General confusion
- IPFS problems: Shitcoinery
- IPFS problems: Community
- IPFS problems: Pinning
- IPFS problems: Conceit
- IPFS problems: Inefficiency
- IPFS problems: Dynamic links
See also
- A crappy course on torrents, on the protocol that has done most things right
- The Tragedy of IPFS in a series of links, an ongoing Twitter thread.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The flaw of "just use paypal/coinbase" arguments
For the millionth time I read somewhere that "custodial bitcoin is not bitcoin" and that "if you're going to use custodial, better use Paypal". No, actually it was "better use Coinbase", but I had heard the "PayPal" version in the past.
There are many reasons why using PayPal is not the same as using a custodial Bitcoin service or wallet that are obvious and not relevant here, such as the fact that you can't have Bitcoin balances on Bitcoin (or maybe now you can? but you can't send it around); plus all the reasons that are also valid for Coinbase such as you having to give all your data and selfies of yourself and your government documents and so on -- but let's ignore these reasons for now.
The most important reason why it isn't the same thing is that when you're using Coinbase you are stuck in Coinbase. Your Coinbase coins cannot be used to pay anyone that isn't in Coinbase. So Coinbase-style custodianship doesn't help Bitcoin. If you want to move out of Coinbase you have to withdraw from Coinbase.
Custodianship on Lightning is of a very different nature. You can pay people from other custodial platforms and people that are hosting their own Lightning nodes and so on.
That kind of custodianship doesn't do any harm to anyone, doesn't fracture the network, doesn't reduce the network effect of Lightning, in fact it increases it.
-
 @ 7361ca91:252fce6d
2024-06-02 18:21:36
@ 7361ca91:252fce6d
2024-06-02 18:21:36日本は貧しい。 どうして日本が貧しいと言えるのでしょうか?多くの点で豊かであることは確かです。例えば、一人当たりのGDPでは、日本は世界で38位で、平均の221%の富があります。また、日本を訪れた人は誰でも、その都市や活動、そして豊かさと幸福感を感じるでしょう。鹿が安全に歩き回る公園さえあります。さらに、文化的にも非常に豊かです。日本文化が嫌いな人はいないでしょう。日本は貧困ランキングでは多くの国よりもずっと上位にあります。そして、これらすべては、第二次世界大戦後の非常に厳しい状況から達成されたものであり、アメリカの要求に従うことによって実現しました。
それでは、なぜ日本が貧しいと言えるのでしょうか?それは、日本がアメリカの要求に従い始めた時点でのことです。日本の真の富が少ない状況を探ってみましょう。そして、その危機的な状況が他の国々にどのような信号を送っているか。この信号を読むことができれば、「Buy Bitcoin」と示していることがわかるでしょう。
日本の10年国債は先日5%下落し、金利は1.08%に達しました。あなたは言うかもしれません、「1.08%?それほど危険には見えない」と。しかし、この水準は10年以上達成されていなかったものであり、その間に日本は大いに借金を増やしました。日本は世界経済の主要な役割を果たしており、アメリカの国債を持つ第二位の保有国であり、その通貨は誰もが安く資金を調達するために利用します。つまり、円を買い、低い利息(約1%)で借りて、もっと高い利息が得られる他の場所に投資します。これらの理由から、日本は特に安い資金を見つけたい人々にとって非常に訪れる場所です。
しかし、もちろん、先日のように国債の金利が上昇すると、この取引に悪影響を及ぼします。10年国債の金利が上昇すれば、円で借りる金利と、他の場所で得られる金利との差が縮小します。例えば、アメリカやオーストラリアの国債、あるいは他の場所の国債です。これは確かに真実であり、国債の金利が上昇するたびにその魅力は減りますが、同時に国債の金利が上昇するたびに、負債のコストも大幅に増加します。
日本は多額の借金を抱えています:9.2兆ドルの負債です。負債の金利が0.01%上昇するたびに、それは920億ドルの利息が追加されることを意味します。
状況を想像してみてください。火曜日に日本は1.02%の金利を支払っていて、水曜日の終わりには1.08%を支払っています。これは途方もない衝撃を与えるでしょう。一度にすべてを再資金調達する必要はありませんが、それでも紙の上ではほぼ60億ドルの影響があります。再資金調達が昨日よりも60億ドル多くかかることを知っている一日を想像してみてください。その日は良い日ではなく、いくら寿司を食べて気分を上げようとしても無駄でしょう。そのため、通貨はドルに対して下落し続けます。
しかし、日本は豊かです。何十年もの間、日本は大量の魚やその他の製品を世界中に輸出してきました。日本はこれまでに得たすべての利益をうまく投資してきたに違いありません。そして、今、困難な時期が来て、日本の状況が微妙な時に、貯蓄を使って円を買い、通貨を守り、次の日に向けて戦い続けることができるでしょう。
日本はアメリカの言うことに従うようになりました。アメリカが大好きなのは、自分の国債を買ってもらうことです。アメリカ人が最も喜ぶのは、自分たちの債務を買ってもらうことです。アメリカ人に気に入られたいなら、国債を買ってあげるといいでしょう。日本は第二次世界大戦以来、アメリカに従順であり、基本的に外国為替の準備としての国債のアイデアを発明しました。これはどういう意味でしょうか?つまり、アメリカの国債に貯蓄するというアイデアを発明したのです。「お金を稼いで貯蓄するなら、他の国の国債や債務として持っておけばいい」という考えです。
全国民の努力と、世界中への商品やサービスの輸出によって得られたすべての貯蓄をアメリカの国債に投資し始めました。日本と他の国々の金の保有量を総準備高の割合で見ると、日本はそのうちのわずか4.3%しか金を保有していない一方で、ドイツ、アメリカ、イタリア、フランスなどの他の国々は60%以上の準備高を金で保有しています。
日本が貧しいと言うとき、それは実質的な富がないことを意味します。すべての貯蓄がアメリカの国債に投資されています。日本は、アメリカの都合に合わせて、そしてある程度は日本自身もそれが良い考えだと思って、これらの国債を購入してきました。日本には多くのアメリカ国債がありますが、今の危機を解決する役には立ちません。
日本は、その通貨の価値を守り、通貨の価値が下落するのを防ぎ、市民の生活費が上昇しないようにする必要があります。市場で円を購入するために、その貯蓄を使って準備金を売却し、通貨を保護するべきです。しかし、その準備金はアメリカの国債にあるため、それらを売ることは現実的ではありません。アメリカの国債を売ると、その価格が下がり、市場での供給が増えて、国債の金利が上昇します。国債の価格が下がるほど、支払う金利は高くなります。
たとえば、100の価格で5%の利息を支払う国債を持っているとします。その国債が市場で売られ始めて価格が95に下がった場合、依然として5%の利息を支払います。しかし、95に対する5%は、100に対する5%よりも多いです。したがって、国債の価格が下がるたびに、利息が上がります。これにより、さらに多くの人々が日本に行き、低利で円を借りて(少ない利息を支払って)、高利を支払うアメリカの国債を購入することを奨励します。これが通貨をさらに下落させることになります。そのため、日本の準備金は役に立ちません。アメリカの国債を売却することなく、自国の通貨の価値をさらに低下させることはできません。このような困難な時期に日本を救うはずのものが、何の役にも立たないのです。
その結果、日本は多くの貯蓄があっても抜け出せない悪循環に陥っています。状況の深刻さは、円と金のチャートを見るとよくわかります。本来なら多くの馬鹿な国債の代わりに準備資産として購入すべきだったものです。円と金のチャートを見ると、過去15年で75%も下落していることがわかります。「日本は貧しい」と言うとき、それは実質的な富が欠如しているという意味で、この貧困は他の分野にも現れ始めています。通貨の価値を守ることができないことが、日本の成長と市民の生産能力を阻害しています。
日本は1人当たりのGDPが高いため、貧しくはないと言いました。しかし、1人当たりのGDPを見てみると、1990年以来停滞しています。また、実質的な貧困のレベルを見ると、日本の実質的な貧困が増加しており、間違った方向に進んでいることがわかります。日本の相対的貧困率は、G7諸国の中でアメリカに次いで2番目に高いです。
要するに、誰の負債でもなく、必要なときに売ることができる資産がなければ、富を持っているとは言えません。困難な時期に対応するために売却できる、他人の債務に依存しない資産が必要です。それが富であり、他のすべてはただの煙に過ぎません。
数年前、ロシアはアメリカの国債ではなく、自国の貯蓄を失いました。アメリカがそれらの債券を没収したのです。今日の日本も同様に、国債を持っていますが、売却することができず、実質的には役に立ちません。まるでそれが奪われたかのようです。これらの状況は、非常に明るくカラフルなネオンサインのように、国であれば固い資産に貯蓄するべきだという明確なシグナルです。
そのため、最近ではすべての中央銀行が記録的なレベルで金を購入しているのでしょう。そして、同様にビットコインも購入することになるでしょう。ビットコインは、金よりも没収されにくく、金よりも移動が容易で、金よりも価値が上昇する可能性が高いという追加の利点を持っています。日本は、これを今、教えてくれているのです。
コラボw @alberto_mera (X、文)& nostr:npub1wdsu4yfj6s5vkcktfx2l7y9tvprfsmwp55e2gj5xp266gff0eeks9cjda5 (Nostr、訳)
-
 @ 256a7941:b828ba8d
2024-06-02 14:02:07
@ 256a7941:b828ba8d
2024-06-02 14:02:07 -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28SummaDB
This was a hierarchical database server similar to the original Firebase. Records were stored on a LevelDB on different paths, like:
/fruits/banana/color:yellow/fruits/banana/flavor:sweet
And could be queried by path too, using HTTP, for example, a call to
http://hostname:port/fruits/banana, for example, would return a JSON document likejson { "color": "yellow", "flavor": "sweet" }While a call to
/fruitswould returnjson { "banana": { "color": "yellow", "flavor": "sweet" } }POST,PUTandPATCHrequests also worked.In some cases the values would be under a special
"_val"property to disambiguate them from paths. (I may be missing some other details that I forgot.)GraphQL was also supported as a query language, so a query like
graphql query { fruits { banana { color } } }would return
{"fruits": {"banana": {"color": "yellow"}}}.SummulaDB
SummulaDB was a browser/JavaScript build of SummaDB. It ran on the same Go code compiled with GopherJS, and using PouchDB as the storage backend, if I remember correctly.
It had replication between browser and server built-in, and one could replicate just subtrees of the main tree, so you could have stuff like this in the server:
json { "users": { "bob": {}, "alice": {} } }And then only allow Bob to replicate
/users/boband Alice to replicate/users/alice. I am sure the require auth stuff was also built in.There was also a PouchDB plugin to make this process smoother and data access more intuitive (it would hide the
_valstuff and allow properties to be accessed directly, today I wouldn't waste time working on these hidden magic things).The computed properties complexity
The next step, which I never managed to get fully working and caused me to give it up because of the complexity, was the ability to automatically and dynamically compute materialized properties based on data in the tree.
The idea was partly inspired on CouchDB computed views and how limited they were, I wanted a thing that would be super powerful, like, given
json { "matches": { "1": { "team1": "A", "team2": "B", "score": "2x1", "date": "2020-01-02" }, "1": { "team1": "D", "team2": "C", "score": "3x2", "date": "2020-01-07" } } }One should be able to add a computed property at
/matches/standingsthat computed the scores of all teams after all matches, for example.I tried to complete this in multiple ways but they were all adding much more complexity I could handle. Maybe it would have worked better on a more flexible and powerful and functional language, or if I had more time and patience, or more people.
Screenshots
This is just one very simple unfinished admin frontend client view of the hierarchical dataset.

- https://github.com/fiatjaf/summadb
- https://github.com/fiatjaf/summuladb
- https://github.com/fiatjaf/pouch-summa
-
 @ a30cdfee:2d2f97ff
2024-06-01 17:47:43
@ a30cdfee:2d2f97ff
2024-06-01 17:47:43Nostr: Decentralized Identity for the Internet
Nostr is a protocol enabling censorship-resistant social media.
Bring your audience seamlessly from one app to another.
And earn bitcoin for the content you create!
Why Do We Need Nostr?
Because.. social media is broken. Centralized oligopolies control the public square of free speech. These companies control (often in ways they don't even understand) what we read, who we talk to, and what ideas gain traction in our culture.
Social media as we mostly know it today:
⚠️ uses your attention to sell ads
⚠️ uses psychological tricks to keep you addicted
⚠️ decides what content to show you based on a secret profit algorithm you can't inspect
⚠️ can ban you
⚠️ is filled with bots and spam
Traditional social media thrives on engagement, attention and outrage. This has had negative effects on society. Trust in media (and institutions) has plummeted, and people are increasingly valuing free speech, something which centralized platforms can't provide.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) fixes this! It's a simple protocol that allows users to sign and share notes (passed around as plain JSON text).
Using websockets, a client software relays these notes to a distributed set of servers (relays). Or to define Nostr even more simply: "Signed messages relayed".
Clients, Relays, Public/Private Key Pairs
Nostr is a protocol that you access via a client. A client can be a web, mobile, or desktop app. Some popular clients are e.g. nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg and nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955 .
Users have cryptographic key pairs (public and private key) to sign notes and to verify a note source. The public key is presented as a string with a prefix "npub", and the private key with a prefix "nsec". You can also think of your "npub" as a username and "nsec" as a password.
But on Nostr, there is no tech support to recover your password, so you have to take good care of it either with a password manager, browser extension such as e.g. nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm or write it down on a piece of paper.
"Npub" looks like this and you can follow users on Nostr on any client by searching for their npub:
"npub15vxdlmhftkh452a06vnr3mmks2dy8hqejeuxuv6sgy5rgtf0jllsccfzg7"
You can also search users by a more readable "NIP-05 identifier", such as "teemupleb_at_getalby.com"
For a step-by-step guide on how to create an account on Nostr, you can watch this tutorial by nostr:npub1rxysxnjkhrmqd3ey73dp9n5y5yvyzcs64acc9g0k2epcpwwyya4spvhnp8 .
Permissionless, Interoperable and Open-Source
Using Nostr and building on it is completely permissionless. No need to provide phone number, email, ID card etc.
Cool thing about Nostr is that your private key (and your audience) follows you from one client to another. E.g. if you have built a large following on a microblogging client built on Nostr, you can bring that following to the new video streaming client that just launched.
Nostr is not an app that you sign up for, but an open standard on which anybody can build! This takes the power of "walled gardens" away from centralized web behemoths! Also devs can access an existing user base easier in order to bootstrap new apps.
Relays Receive and Send Data
Relays are like back-end servers for Nostr. They allow Nostr clients to send them messages, and then broadcast those messages to all other connected clients.
Relays are very simple and "dumb". Their only job is to receive and send Nostr data. For this reason, you can easily run your own relay with e.g. a Raspberry Pi single-board computer (but of course, you don't have to run your own relay to use Nostr).
Relays don't have to be trusted. Signatures are verified on the client side. Because Nostr doesn't rely on a small number of trusted servers to relay data, it's very resilient. The protocol assumes that relays will disappear and allows users to connect to multiple relays that they can change over time. If you notice that your Nostr client feels slow, try adding more relays.
Notes
Notes can be text, links and other media types. They are digitally signed and timestamped. You can also like, repost, reply etc.
There is no character limit on notes or replies, but if you upload videos, there might be limits (then you can just host the video somewhere else and link to it on Nostr). Notes can't be edited (encourages accountability!)
NIPs for Interoperability
The Nostr protocol is defined in a set of NIPs (Nostr Implementation Possibilities). These standards allow different clients to communicate with each other. Only NIP-01 is mandatory (describes the basic protocol), and others are optional.
NIPs exist to promote interoperability. It's not a good idea for developers to implement ideas only in their own client app. It's better to come up with compatible solutions, and NIPs coordinate this process.
Bitcoin Lightning Network to Monetize Content
Nostr uses Bitcoin's Lightning Network to monetize content value. Users can instantly tip (zap) small micropayments in bitcoin to creators, and their npub works as a Lightning address.
Great idea: let's pay with sats instead than with our personal data and attention!
This value4value model is a revolutionary concept. Creators don't have to rely on advertising, subscriptions and paywalls, and followers can only pay for the content they like. Most followers won't tip anything, but some tip a little and the hardest fans tip a lot.
For the first time in history, we can link information to value. As the volume of information becomes infinite, the supply of bitcoin (value) remains scarce. Attaching this value to information will highlight the highest quality information (web of trust).
Nostr + Bitcoin search engine that indexes all information on a decentralized internet could be a real Google killer.
nostr:npub1sx9rnd03vs34lp39fvfv5krwlnxpl90f3dzuk8y3cuwutk2gdhdqjz6g8m is trying to do something along those lines, indexing the entirety of Nostr and making it searchable.
https://twitter.com/MaxAWebster/status/1614003577730760704
Nostr infrastructure providers can also monetize their services via Lightning payments. When Nostr gets more users, relays may have to scale up their infra and charge clients for usage (worry not, there would most likely still be free relays and clients for the end user).
Orange Honeybadger and Purple Ostrich
Nostr doesn't need Bitcoin, and Bitcoin doesn't need Nostr. They're completely independent protocols. However, each one makes the other one better.
Bitcoin decentralizes money, and Nostr decentralizes free speech. With Nostr npub as a Lightning address, Nostr can become a directory for Lightning payments.
The creator of Nostr, nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 and many early Nostr developers are also Lightning developers, which seems to make the synergistic relationship inevitable.
Bitcoin Lightning payments could be integrated to ANY app with nostr:npub19hg5pj5qmd3teumh6ld7drfz49d65sw3n3d5jud8sgz27avkq5dqm7yv9p . Once an app connection is created, the app can request bitcoin payments through a Nostr relay! 🤯 Open-source and non-custodial!
With Nostr, all messages and commerce could be done in an open-source and self-custodial super app. Send remittances as an instant message! Sell goods via a tweet!
Crowdsourced Content Moderation?
What about content moderation? All humans should have the right to free speech, but no one should be obliged to listen.
Nostr relays can ban users, but these users can always find another relay to publish, or host their own. Since users are identified by their public key, they don't lose their followers if they get banned from a relay.
Bitcoin tips can also work as a crowdsourced content moderation tool. If a wide majority of users think that e.g. posting some images is unacceptable, maybe users wouldn't even see those posts because the web of trust doesn't grant them any tips.
Lacking Privacy Features
The downside of Nostr currently is the lack of privacy features. DMs on Nostr are encrypted, but the metadata (who you DM with and when) is public. This obviously currently hinders the prospect of secure bitcoin payments on apps using Nostr.
Also, relays and clients can collect users' IP addresses. The intention of this feature was to tackle spammers and bots (if enough spammy data comes from a single IP address, that address can be blocked.) Maybe best to normalize using VPN with Nostr?
Not Just Social Media
Decentralized social media is just the first instance: there are many Nostr-based competitors to established web2 corporate platforms: Twitch-alternative, GitHub-alternative, Meetup-alternative.. even a P2P bitcoin exchange nostr:npub1m0str0d7z2ww8rdh20t2n9lx520xjwhaq24p68umqp06wwrwtsnqen40un!
X (Twitter) could also benefit from becoming a Nostr client. It could partially solve the content moderation problems it is having:
→ If the user-generated content was on Nostr, maybe X wouldn't have to resort to censorship when facing government pressure?
Easy for Developers
Are you a developer? Starting out with Nostr is easy. Any junior dev can build a functioning simple client in a couple of hours.
Here's a great website called Nostr Apps to discover the world of Nostr:
What do you think about Nostr?
Will it replace the internet as we know it today?
Additional Resources
nostr - Notes and Other Stuff Transmitted by Relays by Nostr's Creator fiatjaf nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
A 2-Minute Video Introduction to Nostr by LNbits
Why I'm Betting Big on Nostr by Max Webster from Hivemind Ventures nostr:npub18lzls4f6h46n43revlzvg6x06z8geww7uudhncfdttdtypduqnfsagugm3
Why Nostr Matters by Jameson Lopp nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp
The NOSTR Protocol: Social Media 3.0 by Jessica Chasteen nostr:npub1r8wdfruydenz84fxfespcswuhcvyatx6umtd5xguexup49u500xskf50hn
Nostr Resources by Dollar Parity
Project Information
-
 @ 256a7941:b828ba8d
2024-06-01 17:30:59
@ 256a7941:b828ba8d
2024-06-01 17:30:59What if we got 1 sat for every kill in multiplayer mode
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Parallel Chains
We want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).
On the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.
It's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.
Luckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.
How does it work
With the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.Then you create a long sequence of transactions (sufficient to last for many many years), each with an
nLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".With the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.
Then you combine it with
RBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.See also
[^eltoo]: The same thing used in Eltoo.
-
 @ 256a7941:b828ba8d
2024-06-01 17:29:19
@ 256a7941:b828ba8d
2024-06-01 17:29:19 -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Comprimido desodorante
No episódio sei-lá-qual de Aleixo FM Bruno Aleixo diz que os bêbados sempre têm as melhores idéias e daí conta uma idéia que ele teve quando estava bêbado: um comprimido que funciona como desodorante. Ao invés de passar o desodorante spray ou roll-on a pessoa pode só tomar o comprimido e pronto, é muito mais prático e no tempo de frio a pessoa pode vestir a roupa mais rápido, sem precisar ficar passando nada com o tronco todo nu. Quando o Busto lhe pergunta sobre a possibilidade de algo assim ser fabricado ele diz que não sabe, que não é cientista, só tem as idéias.
Essa passagem tão boba de um programa de humor esconde uma verdade sobre a doutrina cientística que permeia a sociedade. A doutrina segundo a qual é da ciência que vêm as inovações tecnológicas e de todos os tipos, e por isso é preciso que o Estado tire dinheiro das pessoas trabalhadoras e dê para os cientistas. Nesse ponto ninguém mais sabe o que é um cientista, foi-se toda a concretude, ficou só o nome: "cientista". Daí vão procurar o tal cientista, é um cara que se formou numa universidade e está fazendo um mestrado. Pronto, é só dar dinheiro pra esse cara e tudo vai ficar bom.
Tirando o problema da desconexão entre realidade e a tese, existe também, é claro, o problema da tese: não faz sentido, que um cientista fique procurando formas de realizar uma idéia, que não se sabe nem se é possível nem se é desejável, que ele ou outra pessoa tiveram, muito pelo contrário (mas não vou dizer aqui o que é que era para o cientista fazer porque isso seria contraditório e eu não acho que devam nem existir cientistas).
O que eu queria dizer mesmo era: todo o aparato científico da nossa sociedade, todos os departamentos, universidades, orçamentos e bolsas e revistas, tudo se resume a um monte de gente tentando descobrir como fazer um comprimido desodorante.
-
 @ 577781c0:fdc71ebd
2024-06-01 17:26:52
@ 577781c0:fdc71ebd
2024-06-01 17:26:52Often something like "get outside and touch grass" is posted online encouraging folks to, well, get outside, get offline, touch nature, and live. Essentially, it's a shortened version of Thoreau's Walden.
 Henry David Thoreau on touching grass.
Henry David Thoreau on touching grass.Source: https://forestnation.com/blog/transcendentalist-walk-woods-ecology-lesson-plan/ and the broader quote from https://www.goodreads.com/quotes/2690-i-went-to-the-woods-because-i-wished-to-live:
“I went to the woods because I wished to live deliberately, to front only the essential facts of life, and see if I could not learn what it had to teach, and not, when I came to die, discover that I had not lived. I did not wish to live what was not life, living is so dear; nor did I wish to practise resignation, unless it was quite necessary. I wanted to live deep and suck out all the marrow of life, to live so sturdily and Spartan-like as to put to rout all that was not life, to cut a broad swath and shave close, to drive life into a corner, and reduce it to its lowest terms...”
Anyway, this is essentially what my wife and I did yesterday. We loaded the kayaks, drove, got a little lost, got found, launched, paddled, found a remote spot, picnicked. Skinny dipping was considered, but that is unconfirmed.




-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28OP_CHECKTEMPLATEVERIFYand the "covenants" dramaThere are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-
 @ 256a7941:b828ba8d
2024-06-01 15:14:01
@ 256a7941:b828ba8d
2024-06-01 15:14:01My buttons aren't woking on the app or web. I can't sell or touch the Bitcoin in my wallet
-
 @ 256a7941:b828ba8d
2024-06-01 13:01:30
@ 256a7941:b828ba8d
2024-06-01 13:01:30I believe we need the White House on the Lightning Network to survive as a country.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Flowi.es
At the time I thought Workflowy had the ideal UI for everything. I wanted to implement my custom app maker on it, but ended up doing this: a platform for enhancing Workflowy with extra features:
- An email reminder based on dates input in items
- A website generator, similar to Websites For Trello, also based on Classless Templates
Also, I didn't remember this was also based on CouchDB and had some couchapp functionalities.
-
 @ c11cf5f8:4928464d
2024-06-01 11:11:38
@ c11cf5f8:4928464d
2024-06-01 11:11:38Let's hear some of your latest Bitcoin trades, feel free to include links to your shops or sites you sold it from or the pic of the sold item.
If you missed our last thread, here are some of the items stackers recently spent their sats on the ~AGORA territory.
-
 @ 21b41910:91f41a5e
2024-06-01 03:45:44
@ 21b41910:91f41a5e
2024-06-01 03:45:44May 2024 release of Corny Chat has been tagged at https://github.com/vicariousdrama/cornychat/releases/tag/v2024.05
🌽 Corny Chat is an open source audio space built on Jam that integrates Nostr and Lightning. A publicly running instance of Corny Chat is accessible at https://cornychat.com. The following enhancements were made during May 2024.
UI
Start page now has tabs for live rooms, users rooms (My Rooms) and scheduled events Start new Room will now initialize with Tutorial slides as guidance New My Rooms page added User can see a list of all rooms they are a member of by deviceid and npub User can remove themself from any room they are in A room left without an owner will promote the first moderator as owner A room left without any owners or moderators will be hard deleted Enter Room ads are now smaller and centered Personal settings Refactored into expandable/collapsable groups Add additional doorbells and preview playback Add toggle for displaying peer avatar or name in text chat Added support for Nostr Wallet Connect (NWC) NWC enabled users may opt in to support the service to forego ads NWC enabled users may opt in to auto-tip the room they are in if enabled Avatar cards Now check nostr npub for room role level Fix image URI of mature accounts that used legacy paths User Profile display Nostr users can now assign custom petnames (NIP81) to other users Fix for list cache invalidating prematurely, forcing data fetch on view Zap/Lightning button is now only depicted if the user has a lightning address Maintenance Message Can now appear on screen to inform users of planned maintenance Text Chat enhancements Unread indicator when the chat is not open and message received An ad may appear every 15 minutes, unless user opts to support Ads that appear may now have hyperlinks V4V payments are now reported to the text chat in an orange color Room settings enhancement Owner can set room to announce as nostr live activity Owners, Moderators, and Speakers may now be assigned via npub Corny Chat Slide set may now be deleted on the import screen Corny Chat Link set may now be deleted on the import screen Room Tips Fix: Private rooms with a lightning address no longer crash on tippingServer/Backend
Nostr Npub supported in revamped access control checks Nostr Live Events are published/updated periodically for enabled rooms Restriction added to room definition and required fields Support for smaller ad size retrieval, and denoting if it has a link Integrated Announcement Bot into the backend to announce rooms Add endpoint to return ad report Add endpoint to return list of rooms a user is in, and their role Fixed server crash bug when a public room was emptied of all usersDocumentation
Documented use of more kinds on data types page Additional known supporters added to the about page Fixed image tag names for the pantry-sfu in the install and update guidanceSpecial Thanks to all the Corny Chat regulars to help test, find bugs and provide feedback.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A big Ethereum problem that is fixed by Drivechain
While reading the following paragraphs, assume Drivechain itself will be a "smart contract platform", like Ethereum. And that it won't be used to launch an Ethereum blockchain copy, but instead each different Ethereum contract could be turned into a different sidechain under BIP300 rules.
A big Ethereum problem
Anyone can publish any "contract" to Ethereum. Often people will come up with somewhat interesting ideas and publish them. Since they want money they will add an unnecessary token and use that to bring revenue to themselves, gamify the usage of their contract somehow, and keep some control over the supposedly open protocol they've created by keeping a majority of the tokens. They will use the profits on marketing and branding, have a visual identity, a central website and a forum with support personnel and so on: their somewhat interesting idea have become a full-fledged company.
If they have success then another company will appear in the space and copy the idea, launch it using exactly the same strategy with a tweak, then try to capture the customers of the first company and new people. And then another, and another, and another. Very often these contracts require some network effect to work, i.e., they require people to be using it so others will use it. The fact that the market is now split into multiple companies offering roughly the same product hurts that, such that none of these protocols get ever enough usage to become really useful in the way they were first conceived. At this point it doesn't matter though, they get some usage, and they use that in their marketing material. It becomes a race to pump the value of the tokens and the current usage is just another point used for that purpose. The company will even start giving out money to attract new users and other weird moves that have no relationship with the initial somewhat intereting idea.
Once in a lifetime it happens that the first implementer of these things is not a company seeking profits, but some altruistic developer or company that believes in Ethereum and wants to see it grow -- or more likely someone financed by the Ethereum Foundation, which allegedly doesn't like these token schemes and would prefer everybody to use the token they issued first, the ETH --, but that's a fruitless enterprise because someone else will copy that idea anyway and turn it into a company as described above.
How Drivechain fixes it
In the Drivechain world, if someone had an idea, they would -- as it happens all the time with Bitcoin things -- publish it in a public forum. Other members of the community would evaluate that idea, add or remove things, all interested parties would contribute to make it the best possible incarnation of that idea. Once the design was settled, someone would volunteer to start writing the code to turn that idea into a sidechain. Maybe some company would fund those efforts and then more people would join. It's not a perfect process and one that often involves altruism, but Bitcoin inspires people to do these things.
Slowly, the thing would get built, tested, activated as a sidechain on testnet, tested more, and at this point luckily the entire community of interested Bitcoin users and miners would have grown to like that idea and see its benefits. It could then be proposed to be activated according to BIP300 rules.
Once it was activated, the entire pool of interested users would join it. And it would be impossible for someone else to create a copy of that because everybody would instantly notice it was a copy. There would be no token, no one profiting directly from the operations of that "smart contract". And everybody would be incentivized to join and tell others to join that same sidechain since the network effect was already the biggest there, they will know more network effect would only be good for everybody involved, and there would be no competing marketing and free token giveaways from competing entities.
See also
-
 @ 0f1b5961:868242bd
2024-05-31 14:26:24
@ 0f1b5961:868242bd
2024-05-31 14:26:24Ever since reading Darwin's Origin of Species a couple years ago, one part of the book has always stuck with me. In the seventh chapter, Instinct, Darwin says that certain species of ants appeared "fatal" to his entire theory. Here is a longer quote from the section:
I will ... here ... confine myself to one special difficulty, which at first appeared to me insuperable, and actually fatal to my whole theory. ...neuters or sterile females in insect-communities: for these neuters often differ widely in instinct and in structure from both the males and fertile females, and yet, from being sterile, they cannot propagate their kind. — Origin of Species, Chapter VII, Page 236
The idea that all of the genetic information of these sterile ants had to be passed along, but not expressed, by the breeding males and females was a difficult challenge. Darwin had been focusing on natural selection at the level of the individual organism, but a sterile ant has exactly zero fitness when analyzed at this level. As an individual organism, it can't pass on its genes!
This led Darwin to expand his concept of natural selection in the following way:
This difficulty, though appearing insuperable, is lessened, or, as I believe, disappears, when it is remembered that selection may be applied to the family, as well as to the individual, and may thus gain the desired end. — Origin of Species, Chapter VII, Page 237
I think this example really stuck with me because it represents one of the main biases of the conventional Darwinian approach. It seems like the more intuitive a form of natural selection is the more its power is overestimated. Darwin was overcommitted to natural selection at the level of the individual organism and didn’t really consider selection at the level of the family until forced by a real world example.
I said “intuitive” forms of natural selection are overestimated, but I think these could also be described as “low order”, “tangible”, “concrete”, or “basic”. It’s part and parcel with the dawning insight that the enlightenment project overcommitted to bottom-up explanations and neglected top-down ones.
I think this is important because we stand at a moment where the popularized mathematical explanations of how life develops are breaking down. It becoming clear that life has the ability to move through the combinatorial genetic space staggeringly fast in a way that simply must deny a blind search through random mutation.
Perhaps a top-down natural selection can cover some of the distance present by this obstacle that is coming into focus.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28contratos.alhur.es
A website that allowed people to fill a form and get a standard Contrato de Locação.
Better than all the other "templates" that float around the internet, which are badly formatted
.docfiles.It was fully programmable so other templates could be added later, but I never did. This website made maybe one dollar in Google Ads (and Google has probably stolen these like so many other dollars they did with their bizarre requirements).
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28neuron.vim
I started using this neuron thing to create an update this same zettelkasten, but the existing vim plugin had too many problems, so I forked it and ended up changing almost everything.
Since the upstream repository was somewhat abandoned, most users and people who were trying to contribute upstream migrate to my fork too.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Multi-service Graph Reputation protocol
The problem
- Users inside centralized services need to know reputations of other users they're interacting with;
- Building reputation with ratings imposes a big burden on the user and still accomplishes nothing, can be faked, no one cares about these ratings etc.
The ideal solution
Subjective reputation: reputation based on how you rated that person previously, and how other people you trust rated that person, and how other people trusted by people you trust rated that person and so on, in a web-of-trust that actually can give you some insight on the trustworthiness of someone you never met or interacted with.
The problem with the ideal solution
- Most of the times the service that wants to implement this is not as big as Facebook, so it won't have enough people in it for such graphs of reputation to be constructed.
- It is not trivial to build.
My proposed solution:
I've drafted a protocol for an open system based on services publishing their internal reputation records and indexers using these to build graphs, and then serving the graphs back to the services so they can show them to users when it is needed (as HTTP APIs that can be called directly from the user client app or browser).
Crucially, these indexers will gather data from multiple services and cross-link users from these services so the graph is better.
https://github.com/fiatjaf/multi-service-reputation-rfc
The first and single actionable and useful feedback I got, from @bootstrapbandit was that services shouldn't share email addresses in plain text (email addresses and other external relationships users of a service may have are necessary to establish links from users accross services), but I think it is ok if services publish hashes of these email addresses instead. At some point I will update the spec draft and that may have been before the time you're reading this.
Another issue is that services may lie about their reputation records and that will hurt other services and users in these other services that are relying on that data. Maybe indexers will have to do some investigative job here to assert service honesty. Or maybe this entire protocol is just failed and we will actually need a system in which users themselves will publish their own records.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28doulas.club
A full catalog of all Brazilian doulas with data carefully scrapped from many websites that contained partial catalogs and some data manually included. All this packaged as a Couchapp and served directly from Cloudant.
This was done because the idea of doulas was good, but I spotted an issue: pregnant womwn should know many doulas before choosing one that would match well, therefore a full catalog with a lot of information was necessary.
This was a huge amount of work mostly wasted.
Many doulas who knew about this didn't like it and sent angry and offensive emails telling me to remove them. This was information one should know before choosing a doula.
See also
-
 @ 5d4b6c8d:8a1c1ee3
2024-05-31 13:41:07
@ 5d4b6c8d:8a1c1ee3
2024-05-31 13:41:07The darlings of the post-season, the Timberwolves and Anthony Edwards' ascension were an absolute delight. Watching their rabid defense discombobulate the defending champs harkened back to the '04 Pistons demolition of Shaq and Kobe.
This is a special team and I fully expect them to be back approaching the mountain top in the near future.
They do have one glaring problem, but fortunately it should be solvable.
KAT, the opposite of basketball Viagra
There's no turnoff in sports quite like Karl Anthony Towns. He's a graceless ox with absolutely no feel for the game. He makes two or three of the dumbest decisions you've ever seen, on a nightly basis. The kicker is that he possesses more skill than 99% of other centers, so he's perpetually letting everyone down by falling so short of his potential.
He is the antithesis of this young Timberwolves squad and they need to turn him into someone who belongs in this pack.
I don't even think he's part of the best 5-man lineup on this current team. The group that played the best, by my eye test, was - Gobert - Reid - Anderson - Edwards - Conley
They should try to build on the dynamic of that group.
Offseason options
KAT should still be easily tradeable. For all of his shortcomings, he is still in his 20's and he possesses skills that all 30 teams are constantly looking for. Plus, there may be some superstars demanding trades this summer and KAT may be the best their teams can do.
Here are some of my favorite KAT possibilities:
KAT->KD->Jimmy
After the Phoenix collapse, combined with KD's history, I don't think anyone will be surprised if he asks to be traded. Last time he asked to be traded he had two destinations on his list: Phoenix and Miami.
Meanwhile, Miami is in a tense contract situation with Jimmy Butler and Pat Riley has a long track record of shipping of his star players before it's too late to do so.
KAT for Jimmy in a straight swap would be the funniest trade possible. However, for all the reasons he has to leave Minnesota, he can't go to Miami. Phoenix, on the other hand, needs a skilled big and they have very few prospects of acquiring one.
These guys all make basically the same money and the new trade rules are confusing, so let's just say the trade is Jimmy back to Minnesota, KAT to Phoenix, KD to Miami, plus some draft picks to Phoenix from the other two.
On paper, I think that makes all three teams make more sense. Jimmy seems like an ideal fit for that SF spot, with the mentality and skill set this team needs.
KAT to Orlando
Doesn't KAT just seem like an Orlando guy?
Orlando has tons of cap space and they need floor spacing desperately. You might be saying "Doesn't Orlando already have ten centers on their roster?" And, yes, they do. So clearly KAT is right on brand for them.
The trade I'm imagining is KAT for Jonathan Isaac and Joe Ingles. Isaac can solve the defensive issues they've run into in this Dallas series, as he's athletic enough to put on Luka and/or defend against those lob passes. Joe Ingles is a smart vet who can help settle down the offense and space the floor.
KAT goes home
Here's my last one: KAT to the Nets for Mikal Bridges. KAT's a Jersey kid, so maybe they can do him a solid and let him play for his childhood team. Also, don't he and Ben Simmons belong together?
Mikal proved in Phoenix that he is an excellent 3-and-D wing. Minnesota really suffered for not having reliable 3-point shooting in this Dallas series.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Why I don't like NIP-26 as a solution for key management
NIP-26 was created out of the needs of the Nostr integration at https://minds.com/. They wanted Minds users to be able to associate their "custodial" Nostr key with an external self-owned key. NIP-26 looked like a nice fit for the job, because it would allow supporting clients to associate the two identities statelessly (i.e. by just seeing one event published by Minds but with a delegation tag on it the client would be able to associate that with the self-owned external key without anything else[^1]).
The big selling point of NIP-26 (to me) was that it was fully optional. Clients were free to not implement it and they would not suffer much. They would just see "bob@minds.com" published this, and "bob-self-owned" published that. They would probably know intuitively that these two were the same person, or not, but it wouldn't be an issue. Both would still be identified as Bob and have a picture, a history and so on. Moreover, this wasn't expected to happen a lot, it would be mostly for the small intersection of people that wanted to have their own keys and also happened to be using one of these "custodial Nostr" platforms like Minds.
At some point, though, NIP-26 started to be seen as the solution for key management on Nostr. The idea is that someone will generate a very safe key on a hardware device and guard it as their most precious treasure without it ever touching the internet, and use it just to sign delegation tags. Then use multiple of these delegation tags, one for each different Nostr app, and maybe rotate them every month or so, details are unclear.
This breaks the previous expectations I had for NIP-26 entirely, as now these keys become faceless entities that can't be associated with anything except their "master" key (the one that is in cold storage). So in a world in which most Nostr users are using NIP-26 for everything, clients that do not implement NIP-26 become completely useless, as all they will see is a constant stream of random keys. They won't be able to follow anyone or interact with anyone, as these keys will not identify any concrete person on their back, they will vanish all the time and new keys will show up and the world will be chaotic. So now every client must implement NIP-26 to become usable at all, it is not optional anymore.
You may argue that making NIP-26 a de facto mandatory NIP isn't a bad thing and is worth the cost, but I think it breaks a lot of the simplicity of the protocol. It would probably be worth the cost if we knew NIP-26 was an actual complete solution, but it definitely is not, it is partial, and not the most elegant thing in the world. I think key management can be solved in multiple different ways that can all work together or not, but most importantly they can all remain optional.
More thoughts on these multiple ways can be found at Thoughts on Nostr key management.
If I am wrong about all this and we really come to the conclusion that we need a de facto mandatory key delegation method for Nostr, so be it -- but in that case, considering that we will break backwards-compatibility anyway, I think there might be a better design than NIP-26, more optimized and easier to implement, I don't know how exactly. But I really think we shouldn't rush that.
[^1]: as opposed to other suggestions that would also work, but that would require dealing with multiple events -- for example, the external user could publish a new replaceable event -- or use
kind:0-- to say they wanted to grandfather the Minds key into their umbrella, while the Minds key would also need to signal its acceptance of that. This also had the problem of requiring changes every time a new replaceable event of such kind was found. Although I am unsure now, at the time me and William agreed this was worse than NIP-26 with the delegation tag. -
 @ c11cf5f8:4928464d
2024-05-31 13:38:19
@ c11cf5f8:4928464d
2024-05-31 13:38:19Cowboys and cowgirls, it's time to shine! Spotlight your preferred product or service in the ~AGORA.
Tell us why you love it so much.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Splitpages
The simplest possible service: it splitted PDF pages in half.
Created specially to solve the problem of those scanned books that come with two pages side-by-side as if they were a single page and are much harder to read on Kindle because of that.

It required me to learn about Heroku Buildpacks though, and fork or contribute to a Heroku Buildpack that embedded a mupdf binary.
-
 @ 72592ec9:ffa64d2c
2024-05-31 13:22:58
@ 72592ec9:ffa64d2c
2024-05-31 13:22:58Original Post by GrassFedBitcoin https://x.com/GrassFedBitcoin/status/1796311998466003418
Wow just figured out Bitmain's latest fuckery in real time.
I'll give you the back story...Once upon a time Bitmain was grinding merkle roots instead of nonces aka "covert ASICBOOST". This gave them an advantage over other miners who didn't know this was possible. One company went out of business - KNC - citing "the Chinese having some secret advantage we don't know about" - which turned out to be true precisely for this reason.
It's one of the reasons ASIC manufacture is so centralized today and this is correctly identified by many as being one of the most vulnerable aspects of the entire bitcoin ecosystem. The ASICBOOST issue came to a head when Bitmain used their influence to block the activation of SEGWIT (essential for Lightning) because it would break their ability to do it - at least covertly. Well, they would still be able to use asicboost, but just in an obvious way that would mean everyone else could do it too.
They had patented it so as to try and prevent this because that's the kind of people we're dealing with here but I digress... When asicboost was independently discovered by u/nullc aka Greg Maxwell.
Bitmain lied and said they weren't in fact using it. This was after years of bullshitting about segwit, with Bitmain pretending to be in favour of "alternative scaling solutions" or even doing segwit as a hard fork instead which would allow them to continue what they were doing.....
Absolutely nobody believed them thanks to GMax having reverse engineered one of their ASICs and demonstrating what they had built and tried to keep to themselves. This was a watershed moment in the fork wars where everyone suddenly understood why Bitmain had been making nonsensical arguments against segwit forever.
Wanting big/small blocks wasn't a related discussion. Segwit fixed TX malleability and was a no-brainer upgrade and in the end was combined with a block size increase anyway as a compromise. So we proceeded with segwit anyway, at which point Bitmain switched to overt asicboost which is actually even more powerful, it just requires grinding version bits instead of merkle roots but it's obvious if a miner is doing this.
Now everybody does it so essentially the net effect of it being possible is zero, except your node asking you wtf miners are doing signalling for upgrades your node knows nothing about (upgrade coordination is what version bits are actually supposed to be used for). Oh well, relatively little harm done. If you're happy to ignore the obvious dishonesty and effort to undermine what's arguably Bitcoin's most important ever upgrade.
Fun extra tidbit: Antbleed - an intentional backdoor with which Bitmain could remotely shutdown any Antminer in the world. They said it was for shutting down stolen ASICs but immediately patched it once it was discovered.
Anyway, this company now accounts for 25-30% of all blocks found, if you naively observe the blockchain. That's not enough to spook anyone, but unfortunately many smaller pools are in fact just fronts for Bitmain which we know for three reasons:
- The smaller pools are clearly using blocks constructed by, or for the benefit of, Antpool.
- They share the same custodian of their newly mined coins (Cobo).
- They have a lending program to bail out smaller pools who get in over their head due to FPPS.
And the trend is sadly in the wrong direction, given Braiins recently abandoning its old payout model and becoming just a simple proxy for Bitmain as result of switching to FPPS.
[Massive shoutout to @mononautical and @0xB10C for helping uncover how centralized pools have become.]Summary - Bitmain is not just Antpool, it probably accounts for >50% of block templates and manufactures >90% of the mining hardware in the world.
So where am I going with all this?
Amazingly, it's about empty blocks. What does that have to do with anything? Well, famously OCEAN has found 3 empty blocks in its short existence, causing many to wrongly make allegations of some sort of issue with the pool itself. This spurred on endless debate about why pools make empty templates in the first place and the actual reason so many of them get solved.
In short, pools send empty templates then immediately follow up with full templates. So quickly, that the interim period accounts for a tiny minority of the empty blocks that get found on the network, and none of ours.
In all three cases with OCEAN, the miner solved the empty block longer after already having a full template to work on - - leaving the pool in a position to either throw away a perfectly good (but empty) block or to broadcast it to the network and get miners >90% of the reward of a full block.
Obviously the latter makes sense and does zero harm to the network while still adding to the overall PoW necessary for any attacker. So why would an empty block happen a few seconds after the pool had already sent an updated job for a full block? Because Antminers suck.
What we didn't realize was that they intentionally sucked.
You can send an updated job to an Antminer and watch it continue to work on an old job for over 60 seconds in edge cases. This was something we assumed was due to design of the ASIC itself, and thus just poor engineering on the part of Bitmain. But it turns out we were wrong, it's due to Antminer firmware.
We know this because they just released a fix for it.So Bitmain watched, while people kept mining empty blocks, everyone would wrongly attribute it to pools, while explainers on popular websites like mempool(.)space would offer wrong explanations about it happening due to pools being slow to send proper templates and seemingly no one would understand even the motivation for sending empty templates, let alone the reason they get worked on for so long.
But the fix being something that gets released right after OCEAN starts explaining what's really going on here is beyond reasonable doubt. They had a fix for it, and have been using that fix for their own mining. Now they can't get away with it because increasingly people are realizing that Whatsminers and ASICs from other manufacturers aren't finding anything like the amount of empty blocks because they switch jobs far more quickly.
An Antminer has a far greater likelihood of finding an empty block because it spends longer working on old jobs. We've been out here yelling that the issue is with the ASIC NOT the pool.
The fact that Bitmain intentionally crippled the firmware on the Antminers they would sell to the world, while keeping more functional units for their own mining is typical of everything Bitmain.
Sure it can be incompetence and coincidental timing on the fix, but I sincerely doubt it. The conversation around empty blocks reached the point where people were beginning to realize something was broken with Antminers and then they just happen to release a fix for it right after people finally start catching wind of what's really going on.
So imagine this - You sell shovels to gold miners, and as we all know, the people who make money during a gold rush are the people who sell the shovels. But in this case the shovel seller is digging for gold himself too. And he has intentionally sold crappy shovels to all of his customers so as give himself an advantage.
Empty blocks kept happening, people kept blaming pools.OCEAN got attacked over it. We explained the real reason they happen so much, and Bitmain releases a fix right after. Insane. This goes further than empty blocks. It's not just empty templates that take forever to work their way out of an Antminer, it's all templates and pools are constantly updating work as new transactions show up.
A super lucrative transaction shows up in your mempool? All other pools are sending an updated job to hundreds of thousands of Antminers who will ignore it for a while, while Antpool has their miners working on it more quickly. It's not hard to see the motivation for all this, especially going forward as TX fees become more and more important. Again, insane.
If you want to watch @wk057 and I figure this all out in real time, watch the video below which was just intended to be a discussion on why empty blocks happen. I'll post it shortly so tweeter doesn't kill this post like it always does with external links. https://www.youtube.com/watch?v=4BkyhdxnDrM
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Criteria for activating Drivechain on Bitcoin
Drivechain is, in essence, just a way to give Bitcoin users the option to deposit their coins in a hashrate escrow. If Bitcoin is about coin ownership, in theory there should be no objection from anyone on users having the option to do that: my keys, my coins etc. In other words: even if you think hashrate escrows are a terrible idea and miners will steal all coins from that, you shouldn't care about what other people do with their own money.
There are only two reasonable objections that could be raised by normal Bitcoin users against Drivechain:
- Drivechain adds code complexity to
bitcoind - Drivechain perverts miner incentives of the Bitcoin chain
If these two objections can be reasonably answered there remains no reason for not activating the Drivechain soft-fork.
1
To address 1 we can just take a look at the code once it's done (which I haven't) but from my understanding the extra validation steps needed for ensuring hashrate escrows work are very minimal and self-contained, they shouldn't affect anything else and the risks of introducing some catastrophic bug are roughly zero (or the same as the risks of any of the dozens of refactors that happen every week on Bitcoin Core).
For the BMM/BIP-301 part, again the surface is very small, but we arguably do not need that at all, since anyprevout (once that is merged) enables blind merge-mining in way that is probably better than BIP-301, and that soft-fork is also very simple, plus already loved and accepted by most of the Bitcoin community, implemented and reviewed on Bitcoin Inquisition and is live on the official Bitcoin Core signet.
2
To address 2 we must only point that BMM ensures that Bitcoin miners don't have to do any extra work to earn basically all the fees that would come from the sidechain, as competition for mining sidechain blocks would bid the fee paid to Bitcoin miners up to the maximum economical amount. It is irrelevant if there is MEV on the sidechain or not, everything that reaches the Bitcoin chain does that in form of fees paid in a single high-fee transaction paid to any Bitcoin miner, regardless of them knowing about the sidechain or not. Therefore, there are no centralization pressure or pervert mining incentives that can affect Bitcoin land.
Sometimes it's argued that Drivechain may facilitate the ocurrence of a transaction paying a fee so high it would create incentives for reorging the Bitcoin chain. There is no reason to believe Drivechain would make this more likely than an actual attack than anyone can already do today or, as has happened, some rich person typing numbers wrong on his wallet. In fact, if a drivechain is consistently paying high fees on its BMM transactions that is an incentive for Bitcoin miners to keep mining those transactions one after the other and not harm the users of sidechain by reorging Bitcoin.
Moreover, there are many factors that exist today that can be seen as centralization vectors for Bitcoin mining: arguably one of them is non-blind merge mining, of which we have a (very convoluted) example on the Stacks shitcoin, and introducing the possibility of blind merge-mining on Bitcoin would basically remove any reasonable argument for having such schemes, therefore reducing the centralizing factor of them.
- Drivechain adds code complexity to
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28"Você só aprendeu mesmo uma coisa quando consegue explicar para os outros"
Mentira. Tá certo que existe um ponto em que você acha que sabe algo mas não consegue explicar, mas não necessariamente isso significa não saber. Conseguir explicar não depende de saber, mas de verbalizar. Podemos saber muitas coisas sem as conseguir verbalizar. Aliás, para a maior parte das experiências humanas verbalizar é que é a parte difícil. Por último, é importante dizer que a verbalização é uma abstração e portanto quando alguém tenta explicar algo e se força a fazer uma abstração está arriscando substituir a experiência concreta ou mesmo o conhecimento difuso de algo por aquela abstração e com isso ficar mais burro -- me parece que esse é risco é maior quanto mais prematura for a tentativa de explicação e quando mais sucesso a abstração improvisada fizer.
-
 @ 0861144c:e68a1caf
2024-05-31 13:02:40
@ 0861144c:e68a1caf
2024-05-31 13:02:40Lot of debates has been surrounding the Donald Trump veredict and how can affect our markets a decision of one running president[^1] who support openly cryptocurrencies in general and my friends...the answer is the same we give each time these kind of topic is opened:
Bitcoin is for me Bitcoin is for my family Bitcoin is for my friends Bitcoin is for terrorists Bitcoin is for help Gaza citizens Bitcoin is for Israel Bitcoin is for my enemies
Why?
- Bitcoin is for me, it helps my economy and prevents that inflation come and eat all my savings. As a said in other posts, I don't invest but save money with bitcoin. It's the best.
- Bitcoin is for my family, I teach them about hard money and the inflation. It's an ongoing work and I want the security I have with bitcoin for theirs.
- Bitcoin is for my friends, each time they approach to me asking me the basic stuff of crypto, I ask them not to see rainbows and fall in the charm of buzzwords; I don't have control over their actions but I try my best with them.
- Bitcoin is for terrorists...well, what your government call terrorism. Imagine being arrested for money laundering, imagine you're helping terrorism because you...write code.
- Bitcoin is for all Gaza citizens who needs your help, people suffering and right now a piece of hope in form of sats comes handy.
- Bitcoin is for Israel, who is struggling since always their right to have a piece of land[^2] and fought inflation in the past.
- Bitcoin is for my enemies, for the Lazarus Group and Donald Trump[^3]
Oh, you don't like that way? Well my dear friend, the exit is called fiat money, supported by high centralized moral standards.
[^1]: I'm not too much political guy but I think he'll win, I'll bet later on that with my sats. Democracy is overrated :) [^2]: I know you don't like what you're reading, I smell it from here [^3]: Did you consider it that, from now on, he's a criminal using bitcoin? It's funny now that I'm writing. BTW, I consider Trump a threat to democracy but hey!...that's the beauty of the systerm, you can disagree.
-
 @ 3c984938:2ec11289
2024-05-31 07:53:10
@ 3c984938:2ec11289
2024-05-31 07:53:10For laughs and giggles(plus part education) here's a simple explanation of different economic models.
👉Capitalism: You have two cows. You sell one cow and buy a bull. This represents the concept of private ownership and the idea that individuals can buy and sell goods and services to earn a profit.
👉Socialism: You have two cows. You give one cow to your neighbor. This represents the idea of sharing resources and wealth with others, and the government playing a role in redistributing wealth and resources. ^^Does this sound like the U.S. or Canada right now?
👉Communism: You have two cows. The government takes both cows and gives you some milk. This represents the idea of the government owning and controlling all resources, and distributing them equally among the population.
👉Fascism: You have two cows. The government takes both cows and sells you some milk. This represents the idea of the government controlling all aspects of the economy, including production and distribution, and using the profits for its own benefit.
👉Bureaucratism: You have two cows. The government takes both, shoots one, milks the other, and then throws the milk away. This represents the idea of government inefficiency and waste, as well as the lack of accountability and transparency.
👉Anarchism: You have two cows. You keep both cows, shoot the government agent, and steal another cow. This represents the idea of individual freedom and the rejection of government control and authority.
👉Traditional Capitalism: You have two cows. You sell one cow and use the money to buy a new cow. This represents the idea of private ownership and the concept of profit and loss.
👉Venture Capitalism: You have two cows. You sell three of them to your publicly listed company, using letters of credit opened by your brother-in-law at the bank, then execute a debt/equity swap with an associated general offer so that you get all four cows back, with a tax exemption for five cows. This represents the idea of complex financial transactions and the use of financial instruments to manipulate the market.
👉New Dealism: You have two cows. The government takes both, shoots one, buys milk from the other, and then pours the milk down the drain. This represents the idea of government intervention in the economy and the use of government programs to redistribute wealth and resources.
👉A GREEK CORPORTATION You have two cows borrowed from French and German banks. You eat both of them. The banks call to collect their milk, but you cannot deliver, so you call the IMF. The IMF loans you two cows. You eat both of them. The and the IMF call to collect their cows/milk. You are out getting a harcut.
👉AN IRISH CORPORATION You have two cows. One of them is a horse.
⭐⭐For additional fun; I pulled this from here.
👉A FRENCH CORPORATION You have two cows. You go on strike, organise a riot, and block the roads, because you want three cows.
👉A JAPANESE CORPORATION You have two cows. You redesign them so they are one-tenth the size of an ordinary cow and produce twenty times the milk. You then create a clever cow cartoon image called 'Cowkimon' and market it worldwide.
👉A GERMAN CORPORATION You have two cows. You re-engineer them so they live for 100 years, eat once a month, and milk themselves.
👉AN ITALIAN CORPORATION You have two cows, but you don't know where they are. You decide to have lunch.
👉A RUSSIAN CORPORATION You have two cows. You count them and learn you have five cows. You count them again and learn you have 42 cows. You count them again and learn you have 2 cows. You stop counting cows and open another bottle of vodka.
👉A SWISS CORPORATION You have 5000 cows. None of them belong to you. You charge the owners for storing them.
👉A CHINESE CORPORATION You have two cows. You have 300 people milking them. You claim that you have full employment, and high bovine productivity. You arrest the newsman who reported the real situation.
👉AN INDIAN CORPORATION You have two cows. You worship them.
👉A BRITISH CORPORATION You have two cows. Both are mad.
👉AN IRAQI CORPORATION Everyone thinks you have lots of cows. You tell them that you have none. No-one believes you, so they bomb the sh#t out of you and invade your country. You still have no cows, but at least now you are part of a Democracy...
👉AN AUSTRALIAN CORPORATION You have two cows. Business seems pretty good. You close the office and go for a few beers to celebrate.
👉A NEW ZEALAND CORPORATION You have two cows. The one on the left looks very attractive.
These examples are meant to be humorous and simplified, but they can help to illustrate the basic principles of each economic system.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28There's a problem with using Git concepts for everything
We've been seeing a surge in applications that use Git to store other things than code, or that are based on Git concepts and so enable "forking, merging and distributed collaboration" for things like blogs, recipes, literature, music composition, normal files in a filesystem, databases.
The problem with all this is they will either:
- assume the user will commit manually and expect that commit to be composed by a set of meaningful changes, and the commiter will also add a message to the commit, describing that set of meaningful, related changes; or
- try to make the committing process automatic and hide it from the user, so will producing meaningless commits, based on random changes in many different files (it's not "files" if we are talking about a recipe or rows in a table, but let's say "files" for the sake of clarity) that will probably not be related and not reduceable to a meaningful commit message, or maybe the commit will contain only the changes to a single file, and its commit message would be equivalent to "updated
<name of the file>".
Programmers, when using Git, think in Git, i.e., they work with version control in their minds. They try hard to commit together only sets of meaningful and related changes, even when they happen to make unrelated changes in the meantime, and that's why there are commands like
git add -pand many others.Normal people, to whom many of these git-based tools are intended to (and even programmers when out of their code-world), are much less prone to think in Git, and that's why another kind of abstraction for fork-merge-collaborate in non-code environments must be used.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Custom spreadsheets
The idea was to use it to make an app that would serve as custom database for everything and interact with the spreadsheet so people could play and calculate with their values after they were created by the custom app, something like an MS Access integrated with Excel?
My first attempt that worked (I believe there was an attempt before but I have probably deleted it from everywhere) was this
react-microspreadsheetthing (at the time calledreact-spreadsheetbefore I donated the npm name to someone who asked):This was a very good spreadsheet component that did many things current "react spreadsheet" components out there don't do. It had formulas; support for that handle thing that you pulled with the mouse and it autofilled cells with a pattern; it had keyboard navigation with Ctrl, Shift, Ctrl+Shift; it had that thing through which you copy-pasted formulas and they would change their parameters depending on where you pasted them (implemented in a very poor manner because I was using and thinking about Excel in baby mode at the time).
Then I tried to make it into "a small sheet you can share" kind of app through assemblymade.com, and eventually as I tried to add more things bugs began to appear.
Then there was
cycle6-spreadsheet:If I remember well this was very similar to the other one, although made almost 2 years after. Despite having the same initial goal of the other (the multi-app custom database thing) it only yielded:
- Sidesheet, a Chrome extension that opened a spreadsheet on the side of the screen that you could use to make calculations and so on. It worked, but had too many bugs that probably caused me to give up entirely.
I'm not sure which of the two spreadsheets above powers http://sheets.alhur.es.
-
 @ b804f68e:2fb0fa1f
2024-05-31 06:34:02
@ b804f68e:2fb0fa1f
2024-05-31 06:34:02The main reason you struggle to stop something you "know" is bad for you, or to continue something you "know" is good for you, is because you don't actually know. True knowledge goes beyond hearing it once, reading it somewhere, or being told it’s good or bad.
I used to be a sucker for sweet things. Luckily, my mom limited my access to sugary snacks when I was young. But as I grew older, I made up for lost time, indulging in sweets, particularly Japanese sodas. In England, I snacked on English sweets all the time. Oh, and those energy drink sodas called Lucozade—I was a complete sucker for them. I had so many that I ended up winning a Lucozade hoodie. Yeah I know, it was bad!
Even then, as an athlete, I thought, "I know it's bad for me, but I work out all the time, so it balances out, right?" Wrong!
Fast forward almost a decade, and I’m much fitter, stronger, and healthier than I was at 18. The difference? I took the time to learn, apply, and understand the actual knowledge about things labeled as good or bad for you. With sugar, once I understood what it is and why it could harm my body and brain, it was easier to lay off it. Now, I only eat sweets knowing the potential cons or I might consume sugar when I need immediate energy or to replenish my glycogen stores.
This approach applies to carbs as well, since sugars are a form of carbohydrate. Carbs consist of glucose, a monosaccharide that our body uses for energy. Sucrose, or table sugar, is a disaccharide composed of glucose and fructose. Glucose can be used immediately for energy but can cause harm if it stays in the bloodstream too long. High blood sugar levels can lead to insulin resistance and diabetes. Table sugar is often considered worse because fructose can only be metabolized by the liver, potentially causing issues like non-alcoholic fatty liver disease. Given our high sugar consumption today, it's easy to overdo it. Understanding why sugar is bad has turned me off from drinking soda completely, and I probably won't touch one again.
The same principle applies to maintaining good habits. You need to understand why something is good for you to find purpose and direction. I heard cold showers were beneficial, so I tried them. But without understanding their benefits, I lacked consistency. Once I learned and understood their purpose, I became consistent. Now, my body and brain know the benefits, urging me to take cold showers.
If you struggle to quit a bad habit or maintain a good one, it's because you just don't know. You might think you know it’s good or bad for you, but in reality you don't truly understand and that ultimately shows in your inability to stay consistent.
The great news though is that if I can do it, then absolutely so can you, and you, and even you! Choose one thing that you've been struggling to quit or wanting to start, and take the time to learn about it. The reason why Stackers are consistent with stacking sats is because we've all done our due diligence to learn about Bitcoin, about the fiat system, and about all the other subjects that we come across in the rabbit hole journey. Same goes with developing healthy habits and kicking bad ones to the curb for good, we have to know exactly why we are doing it.
Knowledge is power.
-
 @ 0271e1b9:ad8cff90
2024-05-31 05:54:12
@ 0271e1b9:ad8cff90
2024-05-31 05:54:12Separating money from state is the single most effective way to stop all wars from happening, everywhere, and that is something we can all actively participate in, right now.
Yelling at a problem won’t make it go away.
Some lessons and notable quotes from history:
 Source: "Hyperinflation in the Weimar Republic" Britannica article
Source: "Hyperinflation in the Weimar Republic" Britannica article“It is no coincidence that the century of total war coincided with the century of central banking.”
― Ron Paul
“It is the ability of governments to acquire money without direct taxation that makes modern warfare possible, and a central bank has become the preferred method of accomplishing that.”
― G. Edward Griffin
“The government created the national banking system during the Civil War.”
― Michael D. Bordo ("A Brief History of Central Banks," published on the Federal Reserve Bank of Cleveland website, 2007)
“Why did nations start central banks? To finance the materiel needs of the nation-state in time of war.”
― Brian Domitrovic (“Central Banking's Connection To Warfare Is Intimate,” published on Forbes, 2018)
“War... is harmful, not only to the conquered but to the conqueror.”
― Ludwig von Mises
“War is a profitable venture for the banking elite, as it allows them to finance both sides and profit from increased debt.”
― G. Edward Griffin (“The Creature From Jekyll Island,” 1994)
“Again, coinage saw its greatest debasement during times of war and uncertainty.”
― “Roman currency” Wikipedia article
“Nobody should have money but I, so that I may bestow it upon the soldiers."
― Caracalla (the Roman Emperor from 198 to 217 A.D., who raised his soldiers' pay by 50%, doubled the inheritance tax, admitted almost every inhabitant of the empire to Roman citizenship (for tax collection purposes, of course) and subsequently resorted to debasing both the silver and gold coins). Sources: Jeff Desjardins (“Currency and the Collapse of the Roman Empire,” The Money Project), “Caracalla” Wikipedia article
“To defeat the aggressors is not enough to make peace durable. The main thing is to discard the ideology that generates war.”
― Ludwig von Mises
“It’s a great business to be in - central banking. We print money and people believe it.”
― Adrian Orr (Governor of the Reserve Bank of New Zealand, February 2024)
“Politics can affect things temporarily and locally, but technology is what drives things forward globally and permanently.” ― Lyn Alden (“Broken Money,” 2023)
 Source: New York Tribune, December 4, 1921
Source: New York Tribune, December 4, 1921“The essential evil of gold in its relation to war is the fact that it can be controlled. Break the control and you stop war."
― Henry Ford
Study the history of money. Study Bitcoin.
Also, don’t buy government bonds, t-bills, t-notes or any other type of government debt, no matter what your financial advisor or favorite macroeconomics guru is telling you. It’s just another way of feeding the same beast.
And what we need to do is starve the beast.
This is just one of the many reasons why “separation of money and state” is such a critical issue at this point in history.
Stay safe and stay sane, my friends. Don’t succumb to the hate. ☮️ & ❤️, Kontext
///
May 29, 2024, published at block height 845,667
Edited May 31, 2024: added the New York Tribune headline + Henry Ford quote
-
 @ 80482e60:7cb71b78
2024-05-31 05:23:00
@ 80482e60:7cb71b78
2024-05-31 05:23:00El Tunco is dense enough that you can walk into every single restaurant, bar and shop and ask if they accept Bitcoin. Not all do, but there are enough to exclusively live on Bitcoin for one out of four days you are staying here, assuming you don't always want to eat the same things. There might have been far more places accepting Bitcoin at some point, judging from the "Acceptamos Bitcoin" stickers all around.
The absence of a local Bitcoin community becomes more notable. There is nobody here who can help local businesses use Bitcoin to their advantage. But the absence of such a community also gives the impression that Bitcoin adoption is a lot more organic, and there is a very high diversity of apps and services that businesses are using. Blink, which is the number one app in Berlin and El Zonte, is completely absent in El Tunco.
🐷 El Tunco: 🛏️ My hotel takes Bitcoin, but only in person, and only at the reception. So when paying at the adjacent bar and restaurant with its beautiful ocean view, the waiter has to print the bill and walk with me across the courtyard to the hotel reception, where I wait almost 10 minutes for the receptionist to find the tablet they use to process payments. They're using PaySea, and I encountered them in El Tunco before, but never anywhere else.
🥗 For my first dinner I head out to a restaurant serving salads, falafels and tacos. The staff seem a bit hesitant when I ask about Bitcoin, but eventually agree that yes, they take it. They're using Strike as a payment processor, but instead of using the checkout system, they are using the app, and are asking me for my help with requesting the payment.
🥤There are about four convenience stores in El Tunco, and one of them takes Bitcoin through the Chivo app. They are also a bit hesitant at first about whether they really want to accept it, but with some guidance we swiftly process the payment. The owner opts to convert the balance to USD and the next time I buy something here, he knows what to do.
👜Of the plenty souvenir stalls, only two accept Bitcoin payments. If we agree that Bitcoin serves largely as the payment method of choice for foreign tourists and surfers, this may make sense. I buy from one of these vendors, and they accept payments through Chivo and opt to convert the payment to USD.
🥡There's a local food court that seems very appealing. There are maybe 10 shops serving food here in total, and more than half of them have some indication they accept Bitcoin. Only two restaurants do, and one of these does not have a sign. The signs are primarily from Strike, and if you don't know that Strike is a Bitcoin/Lightning payment processor, you wouldn't be able to tell from the sign that you can pay with Lightning here.
🥯 I have a bagel at Point Break Cafe at the food court, where they confidently know how to use the Strike checkout to process my payment. From here, I can also see the Chivo ATM.
💸There are two Bitcoin ATMs in town, and both can both accept and dispense dollars. One machine is a General Bytes BATMThree from an unknown operator, and the machine is out of service. The other is a Genesis Coin Satoshi1 operated by Chivo. As I sit in the cafe, three people are using the ATM, all seemingly cashing. Chivo also seems to have an employee on standby, and I wonder what issues they typically have to help with. During my day here onchain fees dip to below 20 sat/vB, so I head over and buy $120 used dollar bills with nonsequential serial numbers (only invest in fiat currency what you can afford to lose!). To do that, I have to use the phone number of a friend. I make the onchain payment from my Muun wallet, and while for about two minutes nothing happens, to my surprise I'm given the cash right away, without waiting for confirmations. I do wonder how that works and how easy it would be for somebody to double-spend the transaction. The people in front of me did appear to have to wait for their onchain confirmations, as they all made two trips to the machine. One to deposit sats, another to retrieve the cash. Chivo's rate is incredibly competitive. I pay a 40 bip fee, far less than what I assume you would pay at any of the four bank ATMs in town. Even my onchain transaction only cost me 3000 sat (US$2.1), far below the typical bank ATM withdrawal fee. If you have access to an El Salvadorian number, maybe you can sign up for the Chivo wallet yourself, then you can deposit your sats over the Lightning network and withdraw instantly from the Chivo ATM. The rate is likely subsidized, but for the moment withdrawing cash from Chivo machines in El Salvador is far superior over using your bank card, and in my case did not take any longer. In the long run, what rates will the market converge to?
🥟There's a hip Asian fusion place nearby that I try out for dinner. They use Strike to process payments and know what they are doing. I may be eating too much on this trip, and I also notice how difficult it is in El Tunco to find the typical local foods that were so ubiquitous in Berlin. In El Tunco, everything is either branded as "American", "Healthy" of "Fusion", and most of all, it has to be hip.
🥞 There's one prominent papusa stand in El Tunco, and sadly I did not get to go. But as I walk past I do see two tourists settling their bill over Bitcoin.
💳 The only time a fiat payment had to be made since I left San Salvador was at a local restaurant that advertised Bitcoin payments at the door (through PaySea), but wasn't willing to accept it when it came to settling the bill. Luckily a friend was with me who could handle the blasphemous act of paying with card.
🍻 Michela is a small local bar that is very popular with foreign young tourists. They were the only business I encountered using Athena Pay, which has this odd "onchain," "lightning," "Chivo" or "Strike" prompt, as if these were four different payment methods. As a Lightning "maximalist" I found this unnecessary, and the staff found this very confusing. They also impose a minimum $5 spend when paying with Bitcoin, which they probably inherit from their card payments. When I passed it around 9pm, it was the only busy place in El Tunco, full of young foreign surfers and travellers. I don't think any of them paid with Bitcoin, though.
🌴 Sunzal: On the eastern bank of the small river demarking El Tunco lies Sunzal. On my previous visits it was not easily possible to cross over, but now the river has been artificially backed up and you can cross on dry foot via a sand dam. Walking along the beach is beautiful but also exhausting, even when the sun is low. Sunzal consits of a couple of walled beach resorts, but for the most part you walk past undeveloped land with cows and horses grazing right by the beach. Quite obviously there is enormous growth potential in this beach town, but unlike in El Tunco, there appears to be no construction here.
🌊 The Cafe Sunzal isn't quite a cafe, it's a full scale high-end restaurant with multiple floors that each have a magnificent view over the pacific, El Tunco and all the way to La Libertad. It's a great place to watch the surfers ride into the sunset. The place was last verified on BTCMap as accepting Bitcoin in November 2022, around the time of the second Adopting Bitcoin conference. I try my luck, and am informed by staff that they do not take Bitcoin. However upon paying, the card payment does not go through so I'm asked to come to the counter, where I ask about Bitcoin again and successfully make my payment through Chivo.
🗞️On the road between Sunzal and El Tunco are a couple of Ditobanx advertisments. I encountered the Ditobanx app once on my trip, but it has been pitched to me as a great local debit card that can handle Lightning deposits and withdrawals. The advertisment seems to focus on the Mastercard partnership, hinting that providing you access to debit cards may be more of a selling point than providing access to the Lightning Network.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Democracia na América
Alexis de Tocqueville escreveu um livro só elogiando o sistema político dos Estados Unidos. E mesmo tendo sido assim, e mesmo tendo escrito o seu livro quase 100 anos antes do mais precoce sinal de decadência da democracia na América, percebeu coisas que até hoje quase ninguém percebe: o mandato da suprema corte é um enorme poder, uma força centralizadora, imune ao voto popular e com poderes altamente indefinidos e por isso mesmo ilimitados.
Não sei se ele concluiu, porém, que não existe nem pode existir balanço perfeito entre poderes. Sempre haverá furos.
De qualquer maneira, o homem é um gênio apenas por ter percebido isso e outras coisas, como o fato da figura do presidente, também obviamente um elemento centralizador, não ser tão poderosa quanto a figura de um rei da França, por exemplo. Mas ao mesmo tempo, por entre o véu de elogios (sempre muito sóbrios) deixou escapar que provavelmente também achava que não poderia durar para sempre a fraqueza do cargo de presidente.




